-

@ 04c915da:3dfbecc9
2025-03-26 20:54:33
Capitalism is the most effective system for scaling innovation. The pursuit of profit is an incredibly powerful human incentive. Most major improvements to human society and quality of life have resulted from this base incentive. Market competition often results in the best outcomes for all.
That said, some projects can never be monetized. They are open in nature and a business model would centralize control. Open protocols like bitcoin and nostr are not owned by anyone and if they were it would destroy the key value propositions they provide. No single entity can or should control their use. Anyone can build on them without permission.
As a result, open protocols must depend on donation based grant funding from the people and organizations that rely on them. This model works but it is slow and uncertain, a grind where sustainability is never fully reached but rather constantly sought. As someone who has been incredibly active in the open source grant funding space, I do not think people truly appreciate how difficult it is to raise charitable money and deploy it efficiently.
Projects that can be monetized should be. Profitability is a super power. When a business can generate revenue, it taps into a self sustaining cycle. Profit fuels growth and development while providing projects independence and agency. This flywheel effect is why companies like Google, Amazon, and Apple have scaled to global dominance. The profit incentive aligns human effort with efficiency. Businesses must innovate, cut waste, and deliver value to survive.
Contrast this with non monetized projects. Without profit, they lean on external support, which can dry up or shift with donor priorities. A profit driven model, on the other hand, is inherently leaner and more adaptable. It is not charity but survival. When survival is tied to delivering what people want, scale follows naturally.
The real magic happens when profitable, sustainable businesses are built on top of open protocols and software. Consider the many startups building on open source software stacks, such as Start9, Mempool, and Primal, offering premium services on top of the open source software they build out and maintain. Think of companies like Block or Strike, which leverage bitcoin’s open protocol to offer their services on top. These businesses amplify the open software and protocols they build on, driving adoption and improvement at a pace donations alone could never match.
When you combine open software and protocols with profit driven business the result are lean, sustainable companies that grow faster and serve more people than either could alone. Bitcoin’s network, for instance, benefits from businesses that profit off its existence, while nostr will expand as developers monetize apps built on the protocol.
Capitalism scales best because competition results in efficiency. Donation funded protocols and software lay the groundwork, while market driven businesses build on top. The profit incentive acts as a filter, ensuring resources flow to what works, while open systems keep the playing field accessible, empowering users and builders. Together, they create a flywheel of innovation, growth, and global benefit.
-

@ 21335073:a244b1ad
2025-03-15 23:00:40
I want to see Nostr succeed. If you can think of a way I can help make that happen, I’m open to it. I’d like your suggestions.
My schedule’s shifting soon, and I could volunteer a few hours a week to a Nostr project. I won’t have more total time, but how I use it will change.
Why help? I care about freedom. Nostr’s one of the most powerful freedom tools I’ve seen in my lifetime. If I believe that, I should act on it.
I don’t care about money or sats. I’m not rich, I don’t have extra cash. That doesn’t drive me—freedom does. I’m volunteering, not asking for pay.
I’m not here for clout. I’ve had enough spotlight in my life; it doesn’t move me. If I wanted clout, I’d be on Twitter dropping basic takes. Clout’s easy. Freedom’s hard. I’d rather help anonymously. No speaking at events—small meetups are cool for the vibe, but big conferences? Not my thing. I’ll never hit a huge Bitcoin conference. It’s just not my scene.
That said, I could be convinced to step up if it’d really boost Nostr—as long as it’s legal and gets results.
In this space, I’d watch for social engineering. I watch out for it. I’m not here to make friends, just to help. No shade—you all seem great—but I’ve got a full life and awesome friends irl. I don’t need your crew or to be online cool. Connect anonymously if you want; I’d encourage it.
I’m sick of watching other social media alternatives grow while Nostr kinda stalls. I could trash-talk, but I’d rather do something useful.
Skills? I’m good at spotting social media problems and finding possible solutions. I won’t overhype myself—that’s weird—but if you’re responding, you probably see something in me. Perhaps you see something that I don’t see in myself.
If you need help now or later with Nostr projects, reach out. Nostr only—nothing else. Anonymous contact’s fine. Even just a suggestion on how I can pitch in, no project attached, works too. 💜
Creeps or harassment will get blocked or I’ll nuke my simplex code if it becomes a problem.
https://simplex.chat/contact#/?v=2-4&smp=smp%3A%2F%2FSkIkI6EPd2D63F4xFKfHk7I1UGZVNn6k1QWZ5rcyr6w%3D%40smp9.simplex.im%2FbI99B3KuYduH8jDr9ZwyhcSxm2UuR7j0%23%2F%3Fv%3D1-2%26dh%3DMCowBQYDK2VuAyEAS9C-zPzqW41PKySfPCEizcXb1QCus6AyDkTTjfyMIRM%253D%26srv%3Djssqzccmrcws6bhmn77vgmhfjmhwlyr3u7puw4erkyoosywgl67slqqd.onion
-

@ 04c915da:3dfbecc9
2025-03-10 23:31:30
Bitcoin has always been rooted in freedom and resistance to authority. I get that many of you are conflicted about the US Government stacking but by design we cannot stop anyone from using bitcoin. Many have asked me for my thoughts on the matter, so let’s rip it.
**Concern**
One of the most glaring issues with the strategic bitcoin reserve is its foundation, built on stolen bitcoin. For those of us who value private property this is an obvious betrayal of our core principles. Rather than proof of work, the bitcoin that seeds this reserve has been taken by force. The US Government should return the bitcoin stolen from Bitfinex and the Silk Road.
Usually stolen bitcoin for the reserve creates a perverse incentive. If governments see a bitcoin as a valuable asset, they will ramp up efforts to confiscate more bitcoin. The precedent is a major concern, and I stand strongly against it, but it should be also noted that governments were already seizing coin before the reserve so this is not really a change in policy.
Ideally all seized bitcoin should be burned, by law. This would align incentives properly and make it less likely for the government to actively increase coin seizures. Due to the truly scarce properties of bitcoin, all burned bitcoin helps existing holders through increased purchasing power regardless. This change would be unlikely but those of us in policy circles should push for it regardless. It would be best case scenario for American bitcoiners and would create a strong foundation for the next century of American leadership.
**Optimism**
The entire point of bitcoin is that we can spend or save it without permission. That said, it is a massive benefit to not have one of the strongest governments in human history actively trying to ruin our lives.
Since the beginning, bitcoiners have faced horrible regulatory trends. KYC, surveillance, and legal cases have made using bitcoin and building bitcoin businesses incredibly difficult. It is incredibly important to note that over the past year that trend has reversed for the first time in a decade. A strategic bitcoin reserve is a key driver of this shift. By holding bitcoin, the strongest government in the world has signaled that it is not just a fringe technology but rather truly valuable, legitimate, and worth stacking.
This alignment of incentives changes everything. The US Government stacking proves bitcoin’s worth. The resulting purchasing power appreciation helps all of us who are holding coin and as bitcoin succeeds our government receives direct benefit. A beautiful positive feedback loop.
**Realism**
We are trending in the right direction. A strategic bitcoin reserve is a sign that the state sees bitcoin as an asset worth embracing rather than destroying. That said, there is a lot of work left to be done. We cannot be lulled into complacency, the time to push forward is now, and we cannot take our foot off the gas. We have a seat at the table for the first time ever. Let's make it worth it.
We must protect the right to free usage of bitcoin and other digital technologies. Freedom in the digital age must be taken and defended, through both technical and political avenues. Multiple privacy focused developers are facing long jail sentences for building tools that protect our freedom. These cases are not just legal battles. They are attacks on the soul of bitcoin. We need to rally behind them, fight for their freedom, and ensure the ethos of bitcoin survives this new era of government interest. The strategic reserve is a step in the right direction, but it is up to us to hold the line and shape the future.
-

@ 04c915da:3dfbecc9
2025-03-07 00:26:37
There is something quietly rebellious about stacking sats. In a world obsessed with instant gratification, choosing to patiently accumulate Bitcoin, one sat at a time, feels like a middle finger to the hype machine. But to do it right, you have got to stay humble. Stack too hard with your head in the clouds, and you will trip over your own ego before the next halving even hits.
**Small Wins**
Stacking sats is not glamorous. Discipline. Stacking every day, week, or month, no matter the price, and letting time do the heavy lifting. Humility lives in that consistency. You are not trying to outsmart the market or prove you are the next "crypto" prophet. Just a regular person, betting on a system you believe in, one humble stack at a time. Folks get rekt chasing the highs. They ape into some shitcoin pump, shout about it online, then go silent when they inevitably get rekt. The ones who last? They stack. Just keep showing up. Consistency. Humility in action. Know the game is long, and you are not bigger than it.
**Ego is Volatile**
Bitcoin’s swings can mess with your head. One day you are up 20%, feeling like a genius and the next down 30%, questioning everything. Ego will have you panic selling at the bottom or over leveraging the top. Staying humble means patience, a true bitcoin zen. Do not try to "beat” Bitcoin. Ride it. Stack what you can afford, live your life, and let compounding work its magic.
**Simplicity**
There is a beauty in how stacking sats forces you to rethink value. A sat is worth less than a penny today, but every time you grab a few thousand, you plant a seed. It is not about flaunting wealth but rather building it, quietly, without fanfare. That mindset spills over. Cut out the noise: the overpriced coffee, fancy watches, the status games that drain your wallet. Humility is good for your soul and your stack. I have a buddy who has been stacking since 2015. Never talks about it unless you ask. Lives in a decent place, drives an old truck, and just keeps stacking. He is not chasing clout, he is chasing freedom. That is the vibe: less ego, more sats, all grounded in life.
**The Big Picture**
Stack those sats. Do it quietly, do it consistently, and do not let the green days puff you up or the red days break you down. Humility is the secret sauce, it keeps you grounded while the world spins wild. In a decade, when you look back and smile, it will not be because you shouted the loudest. It will be because you stayed the course, one sat at a time. \
\
Stay Humble and Stack Sats. 🫡
-

@ 04c915da:3dfbecc9
2025-03-04 17:00:18
This piece is the first in a series that will focus on things I think are a priority if your focus is similar to mine: building a strong family and safeguarding their future.
---
Choosing the ideal place to raise a family is one of the most significant decisions you will ever make. For simplicity sake I will break down my thought process into key factors: strong property rights, the ability to grow your own food, access to fresh water, the freedom to own and train with guns, and a dependable community.
**A Jurisdiction with Strong Property Rights**
Strong property rights are essential and allow you to build on a solid foundation that is less likely to break underneath you. Regions with a history of limited government and clear legal protections for landowners are ideal. Personally I think the US is the single best option globally, but within the US there is a wide difference between which state you choose. Choose carefully and thoughtfully, think long term. Obviously if you are not American this is not a realistic option for you, there are other solid options available especially if your family has mobility. I understand many do not have this capability to easily move, consider that your first priority, making movement and jurisdiction choice possible in the first place.
**Abundant Access to Fresh Water**
Water is life. I cannot overstate the importance of living somewhere with reliable, clean, and abundant freshwater. Some regions face water scarcity or heavy regulations on usage, so prioritizing a place where water is plentiful and your rights to it are protected is critical. Ideally you should have well access so you are not tied to municipal water supplies. In times of crisis or chaos well water cannot be easily shutoff or disrupted. If you live in an area that is drought prone, you are one drought away from societal chaos. Not enough people appreciate this simple fact.
**Grow Your Own Food**
A location with fertile soil, a favorable climate, and enough space for a small homestead or at the very least a garden is key. In stable times, a small homestead provides good food and important education for your family. In times of chaos your family being able to grow and raise healthy food provides a level of self sufficiency that many others will lack. Look for areas with minimal restrictions, good weather, and a culture that supports local farming.
**Guns**
The ability to defend your family is fundamental. A location where you can legally and easily own guns is a must. Look for places with a strong gun culture and a political history of protecting those rights. Owning one or two guns is not enough and without proper training they will be a liability rather than a benefit. Get comfortable and proficient. Never stop improving your skills. If the time comes that you must use a gun to defend your family, the skills must be instinct. Practice. Practice. Practice.
**A Strong Community You Can Depend On**
No one thrives alone. A ride or die community that rallies together in tough times is invaluable. Seek out a place where people know their neighbors, share similar values, and are quick to lend a hand. Lead by example and become a good neighbor, people will naturally respond in kind. Small towns are ideal, if possible, but living outside of a major city can be a solid balance in terms of work opportunities and family security.
---
Let me know if you found this helpful. My plan is to break down how I think about these five key subjects in future posts.
-

@ 04c915da:3dfbecc9
2025-02-25 03:55:08
Here’s a revised timeline of macro-level events from *The Mandibles: A Family, 2029–2047* by Lionel Shriver, reimagined in a world where Bitcoin is adopted as a widely accepted form of money, altering the original narrative’s assumptions about currency collapse and economic control. In Shriver’s original story, the failure of Bitcoin is assumed amid the dominance of the bancor and the dollar’s collapse. Here, Bitcoin’s success reshapes the economic and societal trajectory, decentralizing power and challenging state-driven outcomes.
### Part One: 2029–2032
- **2029 (Early Year)**\
The United States faces economic strain as the dollar weakens against global shifts. However, Bitcoin, having gained traction emerges as a viable alternative. Unlike the original timeline, the bancor—a supranational currency backed by a coalition of nations—struggles to gain footing as Bitcoin’s decentralized adoption grows among individuals and businesses worldwide, undermining both the dollar and the bancor.
- **2029 (Mid-Year: The Great Renunciation)**\
Treasury bonds lose value, and the government bans Bitcoin, labeling it a threat to sovereignty (mirroring the original bancor ban). However, a Bitcoin ban proves unenforceable—its decentralized nature thwarts confiscation efforts, unlike gold in the original story. Hyperinflation hits the dollar as the U.S. prints money, but Bitcoin’s fixed supply shields adopters from currency devaluation, creating a dual-economy split: dollar users suffer, while Bitcoin users thrive.
- **2029 (Late Year)**\
Dollar-based inflation soars, emptying stores of goods priced in fiat currency. Meanwhile, Bitcoin transactions flourish in underground and online markets, stabilizing trade for those plugged into the bitcoin ecosystem. Traditional supply chains falter, but peer-to-peer Bitcoin networks enable local and international exchange, reducing scarcity for early adopters. The government’s gold confiscation fails to bolster the dollar, as Bitcoin’s rise renders gold less relevant.
- **2030–2031**\
Crime spikes in dollar-dependent urban areas, but Bitcoin-friendly regions see less chaos, as digital wallets and smart contracts facilitate secure trade. The U.S. government doubles down on surveillance to crack down on bitcoin use. A cultural divide deepens: centralized authority weakens in Bitcoin-adopting communities, while dollar zones descend into lawlessness.
- **2032**\
By this point, Bitcoin is de facto legal tender in parts of the U.S. and globally, especially in tech-savvy or libertarian-leaning regions. The federal government’s grip slips as tax collection in dollars plummets—Bitcoin’s traceability is low, and citizens evade fiat-based levies. Rural and urban Bitcoin hubs emerge, while the dollar economy remains fractured.
### Time Jump: 2032–2047
- Over 15 years, Bitcoin solidifies as a global reserve currency, eroding centralized control. The U.S. government adapts, grudgingly integrating bitcoin into policy, though regional autonomy grows as Bitcoin empowers local economies.
### Part Two: 2047
- **2047 (Early Year)**\
The U.S. is a hybrid state: Bitcoin is legal tender alongside a diminished dollar. Taxes are lower, collected in BTC, reducing federal overreach. Bitcoin’s adoption has decentralized power nationwide. The bancor has faded, unable to compete with Bitcoin’s grassroots momentum.
- **2047 (Mid-Year)**\
Travel and trade flow freely in Bitcoin zones, with no restrictive checkpoints. The dollar economy lingers in poorer areas, marked by decay, but Bitcoin’s dominance lifts overall prosperity, as its deflationary nature incentivizes saving and investment over consumption. Global supply chains rebound, powered by bitcoin enabled efficiency.
- **2047 (Late Year)**\
The U.S. is a patchwork of semi-autonomous zones, united by Bitcoin’s universal acceptance rather than federal control. Resource scarcity persists due to past disruptions, but economic stability is higher than in Shriver’s original dystopia—Bitcoin’s success prevents the authoritarian slide, fostering a freer, if imperfect, society.
### Key Differences
- **Currency Dynamics**: Bitcoin’s triumph prevents the bancor’s dominance and mitigates hyperinflation’s worst effects, offering a lifeline outside state control.
- **Government Power**: Centralized authority weakens as Bitcoin evades bans and taxation, shifting power to individuals and communities.
- **Societal Outcome**: Instead of a surveillance state, 2047 sees a decentralized, bitcoin driven world—less oppressive, though still stratified between Bitcoin haves and have-nots.
This reimagining assumes Bitcoin overcomes Shriver’s implied skepticism to become a robust, adopted currency by 2029, fundamentally altering the novel’s bleak trajectory.
-

@ 6e0ea5d6:0327f353
2025-02-21 18:15:52
"Malcolm Forbes recounts that a lady, wearing a faded cotton dress, and her husband, dressed in an old handmade suit, stepped off a train in Boston, USA, and timidly made their way to the office of the president of Harvard University. They had come from Palo Alto, California, and had not scheduled an appointment. The secretary, at a glance, thought that those two, looking like country bumpkins, had no business at Harvard.
— We want to speak with the president — the man said in a low voice.
— He will be busy all day — the secretary replied curtly.
— We will wait.
The secretary ignored them for hours, hoping the couple would finally give up and leave. But they stayed there, and the secretary, somewhat frustrated, decided to bother the president, although she hated doing that.
— If you speak with them for just a few minutes, maybe they will decide to go away — she said.
The president sighed in irritation but agreed. Someone of his importance did not have time to meet people like that, but he hated faded dresses and tattered suits in his office. With a stern face, he went to the couple.
— We had a son who studied at Harvard for a year — the woman said. — He loved Harvard and was very happy here, but a year ago he died in an accident, and we would like to erect a monument in his honor somewhere on campus.
— My lady — said the president rudely —, we cannot erect a statue for every person who studied at Harvard and died; if we did, this place would look like a cemetery.
— Oh, no — the lady quickly replied. — We do not want to erect a statue. We would like to donate a building to Harvard.
The president looked at the woman's faded dress and her husband's old suit and exclaimed:
— A building! Do you have even the faintest idea of how much a building costs? We have more than seven and a half million dollars' worth of buildings here at Harvard.
The lady was silent for a moment, then said to her husband:
— If that’s all it costs to found a university, why don’t we have our own?
The husband agreed.
The couple, Leland Stanford, stood up and left, leaving the president confused. Traveling back to Palo Alto, California, they established there Stanford University, the second-largest in the world, in honor of their son, a former Harvard student."
Text extracted from: "Mileumlivros - Stories that Teach Values."
Thank you for reading, my friend!
If this message helped you in any way,
consider leaving your glass “🥃” as a token of appreciation.
A toast to our family!
-

@ 0fa80bd3:ea7325de
2025-02-14 23:24:37
#intro
The Russian state made me a Bitcoiner. In 1991, it devalued my grandmother's hard-earned savings. She worked tirelessly in the kitchen of a dining car on the Moscow–Warsaw route. Everything she had saved for my sister and me to attend university vanished overnight. This story is similar to what many experienced, including Wences Casares. The pain and injustice of that time became my first lessons about the fragility of systems and the value of genuine, incorruptible assets, forever changing my perception of money and my trust in government promises.
In 2014, I was living in Moscow, running a trading business, and frequently traveling to China. One day, I learned about the Cypriot banking crisis and the possibility of moving money through some strange thing called Bitcoin. At the time, I didn’t give it much thought. Returning to the idea six months later, as a business-oriented geek, I eagerly began studying the topic and soon dove into it seriously.
I spent half a year reading articles on a local online journal, BitNovosti, actively participating in discussions, and eventually joined the editorial team as a translator. That’s how I learned about whitepapers, decentralization, mining, cryptographic keys, and colored coins. About Satoshi Nakamoto, Silk Road, Mt. Gox, and BitcoinTalk. Over time, I befriended the journal’s owner and, leveraging my management experience, later became an editor. I was drawn to the crypto-anarchist stance and commitment to decentralization principles. We wrote about the economic, historical, and social preconditions for Bitcoin’s emergence, and it was during this time that I fully embraced the idea.
It got to the point where I sold my apartment and, during the market's downturn, bought 50 bitcoins, just after the peak price of $1,200 per coin. That marked the beginning of my first crypto winter. As an editor, I organized workflows, managed translators, developed a YouTube channel, and attended conferences in Russia and Ukraine. That’s how I learned about Wences Casares and even wrote a piece about him. I also met Mikhail Chobanyan (Ukrainian exchange Kuna), Alexander Ivanov (Waves project), Konstantin Lomashuk (Lido project), and, of course, Vitalik Buterin. It was a time of complete immersion, 24/7, and boundless hope.
After moving to the United States, I expected the industry to grow rapidly, attended events, but the introduction of BitLicense froze the industry for eight years. By 2017, it became clear that the industry was shifting toward gambling and creating tokens for the sake of tokens. I dismissed this idea as unsustainable. Then came a new crypto spring with the hype around beautiful NFTs – CryptoPunks and apes.
I made another attempt – we worked on a series called Digital Nomad Country Club, aimed at creating a global project. The proceeds from selling images were intended to fund the development of business tools for people worldwide. However, internal disagreements within the team prevented us from completing the project.
With Trump’s arrival in 2025, hope was reignited. I decided that it was time to create a project that society desperately needed. As someone passionate about history, I understood that destroying what exists was not the solution, but leaving everything as it was also felt unacceptable. You can’t destroy the system, as the fiery crypto-anarchist voices claimed.
With an analytical mindset (IQ 130) and a deep understanding of the freest societies, I realized what was missing—not only in Russia or the United States but globally—a Bitcoin-native system for tracking debts and financial interactions. This could return control of money to ordinary people and create horizontal connections parallel to state systems. My goal was to create, if not a Bitcoin killer app, then at least to lay its foundation.
At the inauguration event in New York, I rediscovered the Nostr project. I realized it was not only technologically simple and already quite popular but also perfectly aligned with my vision. For the past month and a half, using insights and experience gained since 2014, I’ve been working full-time on this project.
-

@ daa41bed:88f54153
2025-02-09 16:50:04
There has been a good bit of discussion on Nostr over the past few days about the merits of zaps as a method of engaging with notes, so after writing a rather lengthy [article on the pros of a strategic Bitcoin reserve](https://geek.npub.pro/post/dxqkgnjplttkvetprg8ox/), I wanted to take some time to chime in on the much more fun topic of digital engagement.
Let's begin by defining a couple of things:
**Nostr** is a decentralized, censorship-resistance protocol whose current biggest use case is social media (think Twitter/X). Instead of relying on company servers, it relies on relays that anyone can spin up and own their own content. Its use cases are much bigger, though, and this article is hosted on my own relay, using my own Nostr relay as an example.
**Zap** is a tip or donation denominated in sats (small units of Bitcoin) sent from one user to another. This is generally done directly over the Lightning Network but is increasingly using Cashu tokens. For the sake of this discussion, how you transmit/receive zaps will be irrelevant, so don't worry if you don't know what [Lightning](https://lightning.network/) or [Cashu](https://cashu.space/) are.
If we look at how users engage with posts and follows/followers on platforms like Twitter, Facebook, etc., it becomes evident that traditional social media thrives on engagement farming. The more outrageous a post, the more likely it will get a reaction. We see a version of this on more visual social platforms like YouTube and TikTok that use carefully crafted thumbnail images to grab the user's attention to click the video. If you'd like to dive deep into the psychology and science behind social media engagement, let me know, and I'd be happy to follow up with another article.
In this user engagement model, a user is given the option to comment or like the original post, or share it among their followers to increase its signal. They receive no value from engaging with the content aside from the dopamine hit of the original experience or having their comment liked back by whatever influencer they provide value to. Ad revenue flows to the content creator. Clout flows to the content creator. Sales revenue from merch and content placement flows to the content creator. We call this a linear economy -- the idea that resources get created, used up, then thrown away. Users create content and farm as much engagement as possible, then the content is forgotten within a few hours as they move on to the next piece of content to be farmed.
What if there were a simple way to give value back to those who engage with your content? By implementing some value-for-value model -- a circular economy. Enter zaps.

Unlike traditional social media platforms, Nostr does not actively use algorithms to determine what content is popular, nor does it push content created for active user engagement to the top of a user's timeline. Yes, there are "trending" and "most zapped" timelines that users can choose to use as their default, but these use relatively straightforward engagement metrics to rank posts for these timelines.
That is not to say that we may not see clients actively seeking to refine timeline algorithms for specific metrics. Still, the beauty of having an open protocol with media that is controlled solely by its users is that users who begin to see their timeline gamed towards specific algorithms can choose to move to another client, and for those who are more tech-savvy, they can opt to run their own relays or create their own clients with personalized algorithms and web of trust scoring systems.
Zaps enable the means to create a new type of social media economy in which creators can earn for creating content and users can earn by actively engaging with it. Like and reposting content is relatively frictionless and costs nothing but a simple button tap. Zaps provide active engagement because they signal to your followers and those of the content creator that this post has genuine value, quite literally in the form of money—sats.

I have seen some comments on Nostr claiming that removing likes and reactions is for wealthy people who can afford to send zaps and that the majority of people in the US and around the world do not have the time or money to zap because they have better things to spend their money like feeding their families and paying their bills. While at face value, these may seem like valid arguments, they, unfortunately, represent the brainwashed, defeatist attitude that our current economic (and, by extension, social media) systems aim to instill in all of us to continue extracting value from our lives.
Imagine now, if those people dedicating their own time (time = money) to mine pity points on social media would instead spend that time with genuine value creation by posting content that is meaningful to cultural discussions. Imagine if, instead of complaining that their posts get no zaps and going on a tirade about how much of a victim they are, they would empower themselves to take control of their content and give value back to the world; where would that leave us? How much value could be created on a nascent platform such as Nostr, and how quickly could it overtake other platforms?
Other users argue about user experience and that additional friction (i.e., zaps) leads to lower engagement, as proven by decades of studies on user interaction. While the added friction may turn some users away, does that necessarily provide less value? I argue quite the opposite. You haven't made a few sats from zaps with your content? Can't afford to send some sats to a wallet for zapping? How about using the most excellent available resource and spending 10 seconds of your time to leave a comment? Likes and reactions are valueless transactions. Social media's real value derives from providing monetary compensation and actively engaging in a conversation with posts you find interesting or thought-provoking. Remember when humans thrived on conversation and discussion for entertainment instead of simply being an onlooker of someone else's life?
If you've made it this far, my only request is this: try only zapping and commenting as a method of engagement for two weeks. Sure, you may end up liking a post here and there, but be more mindful of how you interact with the world and break yourself from blind instinct. You'll thank me later.

-

@ e3ba5e1a:5e433365
2025-02-05 17:47:16
I got into a [friendly discussion](https://x.com/snoyberg/status/1887007888117252142) on X regarding health insurance. The specific question was how to deal with health insurance companies (presumably unfairly) denying claims? My answer, as usual: get government out of it!
The US healthcare system is essentially the worst of both worlds:
* Unlike full single payer, individuals incur high costs
* Unlike a true free market, regulation causes increases in costs and decreases competition among insurers
I'm firmly on the side of moving towards the free market. (And I say that as someone living under a single payer system now.) Here's what I would do:
* Get rid of tax incentives that make health insurance tied to your employer, giving individuals back proper freedom of choice.
* Reduce regulations significantly.
* In the short term, some people will still get rejected claims and other obnoxious behavior from insurance companies. We address that in two ways:
1. Due to reduced regulations, new insurance companies will be able to enter the market offering more reliable coverage and better rates, and people will flock to them because they have the freedom to make their own choices.
2. Sue the asses off of companies that reject claims unfairly. And ideally, as one of the few legitimate roles of government in all this, institute new laws that limit the ability of fine print to allow insurers to escape their responsibilities. (I'm hesitant that the latter will happen due to the incestuous relationship between Congress/regulators and insurers, but I can hope.)
Will this magically fix everything overnight like politicians normally promise? No. But it will allow the market to return to a healthy state. And I don't think it will take long (order of magnitude: 5-10 years) for it to come together, but that's just speculation.
And since there's a high correlation between those who believe government can fix problems by taking more control and demanding that only credentialed experts weigh in on a topic (both points I strongly disagree with BTW): I'm a trained actuary and worked in the insurance industry, and have directly seen how government regulation reduces competition, raises prices, and harms consumers.
And my final point: I don't think any prior art would be a good comparison for deregulation in the US, it's such a different market than any other country in the world for so many reasons that lessons wouldn't really translate. Nonetheless, I asked Grok for some empirical data on this, and at best the results of deregulation could be called "mixed," but likely more accurately "uncertain, confused, and subject to whatever interpretation anyone wants to apply."
https://x.com/i/grok/share/Zc8yOdrN8lS275hXJ92uwq98M
-

@ 9e69e420:d12360c2
2025-02-01 11:16:04

Federal employees must remove pronouns from email signatures by the end of the day. This directive comes from internal memos tied to two executive orders signed by Donald Trump. The orders target diversity and equity programs within the government.

CDC, Department of Transportation, and Department of Energy employees were affected. Staff were instructed to make changes in line with revised policy prohibiting certain language.
One CDC employee shared frustration, stating, “In my decade-plus years at CDC, I've never been told what I can and can't put in my email signature.” The directive is part of a broader effort to eliminate DEI initiatives from federal discourse.
-

@ 6389be64:ef439d32
2025-04-03 21:32:58
Brewing Biology
Episode 1068 of Bitcoin And . . . is LIVE!
This episode of Bitcoin And dives into Brewing Biology—a regenerative system combining compost tea, biochar, Bitcoin mining, and carbon credits—developed through a deep, idea-driven conversation with ChatGPT.
LISTEN HERE --> https://fountain.fm/episode/p0DmvPzxirDHh2l68zOX <-- LISTEN HERE
The future of Bitcoin isn’t just about code or money—it’s about soil. A groundbreaking fusion of biology, technology, and financial innovation might change the rules of agriculture, offering landowners a path to profitability while Healing our soils. At the heart of this revolution is biochar, a form of charcoal that supercharges soil health. When mixed with compost tea and microbial inoculants, this carbon-rich material becomes a game-changer.
Biochar’s porous structure acts as a microbial hotel, hosting fungi like arbuscular mycorrhizal fungi (AMF) and bacteria such as Bacillus subtilis. These organisms form symbiotic networks that boost nutrient absorption and secrete glomalin—a natural “glue” that binds soil, preventing erosion. But here’s the twist: this system doesn’t just heal the earth; it also generates revenue.
Biochar’s Hidden Superpower: Adsorption & Buffering
Biochar’s porous structure acts as a molecular storage hub. Unlike absorption (soaking up water like a sponge), adsorption is a chemical process where water and nutrients cling to biochar’s surfaces. A single gram of biochar has the surface area of a basketball court, creating a lattice of microscopic nooks and crannies. This allows it to:
Lock in moisture: Biochar retains up to 10x its weight in water, acting like a “soil battery” that releases hydration slowly during droughts.
Hoard nutrients: It buffers nitrogen, phosphorus, potassium, and micronutrients in its pores, preventing leaching. Plants access these nutrients gradually, reducing fertilizer needs.
Stabilize pH: Biochar’s alkaline nature buffers acidic soils, creating a neutral environment where microbes and roots thrive.
This buffering effect means plants face fewer nutrient and water spikes or shortages, ensuring steady growth even in erratic climates.
The Carbon Math
Every ton of biochar (which is ~85% carbon by weight) sequesters 3.12 tons of CO₂ (using the 1:3.67 carbon-to-CO₂ ratio). With carbon credits trading at $42–$60/ton, a 1,000-acre project applying 1 pound of biochar per linear foot (via a three-shank plow at 2-foot spacing) could sequester ~12,000 tons of CO₂ annually—generating $504,000–$720,000 in carbon credit revenue.
Tools for the Revolution
The Keyline Plow fractures subsoil to inject biochar slurry 30–45cm deep, revitalizing compacted land. For smaller plots, the VOGT Geo Injector delivers pinpoint inoculations—think of it as a soil “injection gun” for lawns, golf courses, or urban gardens. These methods ensure biochar stays where it’s needed, turning even parched landscapes into carbon sinks.
Bitcoin’s Role in the Loop
Biochar production generates syngas—a byproduct that fuels electric generators for Bitcoin mining. This closed-loop system turns agricultural waste into energy, creating dual revenue streams: carbon credits and mining income.
The Market Potential
Farmers, ranchers, and eco-conscious landowners aren’t the only beneficiaries. Golf courses can slash water use and homeowners can boost lawn resilience.
Why This Matters
This isn’t just farming—it’s a movement. By marrying soil science with economics, we can prove that healing the planet and profiting go hand in hand. Whether you’re a Bitcoin miner, a farmer, or an eco-entrepreneur, this system offers a blueprint for a future where every acre works for you—and the planet.
The takeaway? Regenerative agriculture isn’t a trend. It’s the next gold rush—except this time, the gold is carbon, soil, and sats.---
P.S. – If you’re ready to turn your land into a carbon credit powerhouse (and maybe mine some Bitcoin along the way), the soil is waiting.
You can read the full article, Brewing Biology HERE -> https://the-bitcoin-and-Podcast.ghost.io/ghost/#/editor/post/67e5922fa289aa00088da3c6
originally posted at https://stacker.news/items/933800
-

@ 000002de:c05780a7
2025-04-03 17:27:03
### I score zero points. How about you?
https://m.primal.net/QDDi.jpg
I almost called this a boomer test but its more of a Gen X test.
__Credit to Jack Spirko for sharing this on Twitter.__
originally posted at https://stacker.news/items/933537
-

@ 0fa80bd3:ea7325de
2025-01-29 05:55:02
The land that belongs to the indigenous peoples of Russia has been seized by a gang of killers who have unleashed a war of extermination. They wipe out anyone who refuses to conform to their rules. Those who disagree and stay behind are tortured and killed in prisons and labor camps. Those who flee lose their homeland, dissolve into foreign cultures, and fade away. And those who stand up to protect their people are attacked by the misled and deceived. The deceived die for the unchecked greed of a single dictator—thousands from both sides, people who just wanted to live, raise their kids, and build a future.
Now, they are forced to make an impossible choice: abandon their homeland or die. Some perish on the battlefield, others lose themselves in exile, stripped of their identity, scattered in a world that isn’t theirs.
There’s been endless debate about how to fix this, how to clear the field of the weeds that choke out every new sprout, every attempt at change. But the real problem? We can’t play by their rules. We can’t speak their language or use their weapons. We stand for humanity, and no matter how righteous our cause, we will not multiply suffering. Victory doesn’t come from matching the enemy—it comes from staying ahead, from using tools they haven’t mastered yet. That’s how wars are won.
Our only resource is the **will of the people** to rewrite the order of things. Historian Timothy Snyder once said that a nation cannot exist without a city. A city is where the most active part of a nation thrives. But the cities are occupied. The streets are watched. Gatherings are impossible. They control the money. They control the mail. They control the media. And any dissent is crushed before it can take root.
So I started asking myself: **How do we stop this fragmentation?** How do we create a space where people can **rebuild their connections** when they’re ready? How do we build a **self-sustaining network**, where everyone contributes and benefits proportionally, while keeping their freedom to leave intact? And more importantly—**how do we make it spread, even in occupied territory?**
In 2009, something historic happened: **the internet got its own money.** Thanks to **Satoshi Nakamoto**, the world took a massive leap forward. Bitcoin and decentralized ledgers shattered the idea that money must be controlled by the state. Now, to move or store value, all you need is an address and a key. A tiny string of text, easy to carry, impossible to seize.
That was the year money broke free. The state lost its grip. Its biggest weapon—physical currency—became irrelevant. Money became **purely digital.**
The internet was already **a sanctuary for information**, a place where people could connect and organize. But with Bitcoin, it evolved. Now, **value itself** could flow freely, beyond the reach of authorities.
Think about it: when seedlings are grown in controlled environments before being planted outside, they **get stronger, survive longer, and bear fruit faster.** That’s how we handle crops in harsh climates—nurture them until they’re ready for the wild.
Now, picture the internet as that **controlled environment** for **ideas**. Bitcoin? It’s the **fertile soil** that lets them grow. A testing ground for new models of interaction, where concepts can take root before they move into the real world. If **nation-states are a battlefield, locked in a brutal war for territory, the internet is boundless.** It can absorb any number of ideas, any number of people, and it doesn’t **run out of space.**
But for this ecosystem to thrive, people need safe ways to communicate, to share ideas, to build something real—**without surveillance, without censorship, without the constant fear of being erased.**
This is where **Nostr** comes in.
Nostr—"Notes and Other Stuff Transmitted by Relays"—is more than just a messaging protocol. **It’s a new kind of city.** One that **no dictator can seize**, no corporation can own, no government can shut down.
It’s built on **decentralization, encryption, and individual control.** Messages don’t pass through central servers—they are relayed through independent nodes, and users choose which ones to trust. There’s no master switch to shut it all down. Every person owns their identity, their data, their connections. And no one—no state, no tech giant, no algorithm—can silence them.
In a world where cities fall and governments fail, **Nostr is a city that cannot be occupied.** A place for ideas, for networks, for freedom. A city that grows stronger **the more people build within it**.
-

@ 6be5cc06:5259daf0
2025-01-21 20:58:37
A seguir, veja como instalar e configurar o **Privoxy** no **Pop!_OS**.
---
### **1. Instalar o Tor e o Privoxy**
Abra o terminal e execute:
```bash
sudo apt update
sudo apt install tor privoxy
```
**Explicação:**
- **Tor:** Roteia o tráfego pela rede Tor.
- **Privoxy:** Proxy avançado que intermedia a conexão entre aplicativos e o Tor.
---
### **2. Configurar o Privoxy**
Abra o arquivo de configuração do Privoxy:
```bash
sudo nano /etc/privoxy/config
```
Navegue até a última linha (atalho: **`Ctrl`** + **`/`** depois **`Ctrl`** + **`V`** para navegar diretamente até a última linha) e insira:
```bash
forward-socks5 / 127.0.0.1:9050 .
```
Isso faz com que o **Privoxy** envie todo o tráfego para o **Tor** através da porta **9050**.
Salve (**`CTRL`** + **`O`** e **`Enter`**) e feche (**`CTRL`** + **`X`**) o arquivo.
---
### **3. Iniciar o Tor e o Privoxy**
Agora, inicie e habilite os serviços:
```bash
sudo systemctl start tor
sudo systemctl start privoxy
sudo systemctl enable tor
sudo systemctl enable privoxy
```
**Explicação:**
- **start:** Inicia os serviços.
- **enable:** Faz com que iniciem automaticamente ao ligar o PC.
---
### **4. Configurar o Navegador Firefox**
Para usar a rede **Tor** com o Firefox:
1. Abra o Firefox.
2. Acesse **Configurações** → **Configurar conexão**.
3. Selecione **Configuração manual de proxy**.
4. Configure assim:
- **Proxy HTTP:** `127.0.0.1`
- **Porta:** `8118` (porta padrão do **Privoxy**)
- **Domínio SOCKS (v5):** `127.0.0.1`
- **Porta:** `9050`
5. Marque a opção **"Usar este proxy também em HTTPS"**.
6. Clique em **OK**.
---
### **5. Verificar a Conexão com o Tor**
Abra o navegador e acesse:
```text
https://check.torproject.org/
```
Se aparecer a mensagem **"Congratulations. This browser is configured to use Tor."**, a configuração está correta.
---
### **Dicas Extras**
- **Privoxy** pode ser ajustado para bloquear anúncios e rastreadores.
- Outros aplicativos também podem ser configurados para usar o **Privoxy**.
-

@ 9e69e420:d12360c2
2025-01-21 19:31:48
Oregano oil is a potent natural compound that offers numerous scientifically-supported health benefits.
## Active Compounds
The oil's therapeutic properties stem from its key bioactive components:
- Carvacrol and thymol (primary active compounds)
- Polyphenols and other antioxidant
## Antimicrobial Properties
**Bacterial Protection**
The oil demonstrates powerful antibacterial effects, even against antibiotic-resistant strains like MRSA and other harmful bacteria. Studies show it effectively inactivates various pathogenic bacteria without developing resistance.
**Antifungal Effects**
It effectively combats fungal infections, particularly Candida-related conditions like oral thrush, athlete's foot, and nail infections.
## Digestive Health Benefits
Oregano oil supports digestive wellness by:
- Promoting gastric juice secretion and enzyme production
- Helping treat Small Intestinal Bacterial Overgrowth (SIBO)
- Managing digestive discomfort, bloating, and IBS symptoms
## Anti-inflammatory and Antioxidant Effects
The oil provides significant protective benefits through:
- Powerful antioxidant activity that fights free radicals
- Reduction of inflammatory markers in the body
- Protection against oxidative stress-related conditions
## Respiratory Support
It aids respiratory health by:
- Loosening mucus and phlegm
- Suppressing coughs and throat irritation
- Supporting overall respiratory tract function
## Additional Benefits
**Skin Health**
- Improves conditions like psoriasis, acne, and eczema
- Supports wound healing through antibacterial action
- Provides anti-aging benefits through antioxidant properties
**Cardiovascular Health**
Studies show oregano oil may help:
- Reduce LDL (bad) cholesterol levels
- Support overall heart health
**Pain Management**
The oil demonstrates effectiveness in:
- Reducing inflammation-related pain
- Managing muscle discomfort
- Providing topical pain relief
## Safety Note
While oregano oil is generally safe, it's highly concentrated and should be properly diluted before use Consult a healthcare provider before starting supplementation, especially if taking other medications.
-

@ 21335073:a244b1ad
2025-03-18 14:43:08
**Warning: This piece contains a conversation about difficult topics. Please proceed with caution.**
TL;DR please educate your children about online safety.
Julian Assange wrote in his 2012 book *Cypherpunks*, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense.
This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning.
When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little.
I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?”
I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well.
I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread.
I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard.
I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it.
The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust.
Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this.
I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place.
What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method.
It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code.
They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened.
I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road.
So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally.
Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb.
I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback.
Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed.
That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone.
To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all.
I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society.
I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this.
On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government.
I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories.
There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc.
Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind.
Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now.
There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers?
I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity.
I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place.
My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors.
My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline.
The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online.
I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers.
So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation?
When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that.
I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic.
If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations.
I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process.
**Course:**
- The creation of the internet and computers
- The fight for cryptography
- The tech supply chain from the ground up (example: human rights violations in the supply chain)
- Corporate tech
- Freedom tech
- Data privacy
- Digital privacy rights
- AI (history-current)
- Online safety (predators, scams, catfishing, extortion)
- Bitcoin
- Laws
- How to deal with online hate and harassment
- Information on who to contact if you are being abused online or offline
- Algorithms
- How to seek out the truth about news, etc., online
The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children.
The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward?
I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone.
Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability.
The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime.
This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful.
This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens.
In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions.
I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation.
-

@ fd06f542:8d6d54cd
2025-04-02 08:04:17
{"coverurl":"https://cdn.nostrcheck.me/fd06f542bc6c06a39881810de917e6c5d277dfb51689a568ad7b7a548d6d54cd/1dd58d181d40edb7df942b5b16be3f82e95348a471d5a3620a9585f0af784fee.webp","title":"nostr资源收集","author":"nostrbook"}
-

@ fd06f542:8d6d54cd
2025-04-02 02:55:14
- [首页](/readme.md)
- [第一章、开发者指南](/01.md)
- [第二章、使用教程](/02.md)
-

@ 6be5cc06:5259daf0
2025-01-21 01:51:46
## Bitcoin: Um sistema de dinheiro eletrônico direto entre pessoas.
Satoshi Nakamoto
satoshin@gmx.com
www.bitcoin.org
---
### Resumo
O Bitcoin é uma forma de dinheiro digital que permite pagamentos diretos entre pessoas, sem a necessidade de um banco ou instituição financeira. Ele resolve um problema chamado **gasto duplo**, que ocorre quando alguém tenta gastar o mesmo dinheiro duas vezes. Para evitar isso, o Bitcoin usa uma rede descentralizada onde todos trabalham juntos para verificar e registrar as transações.
As transações são registradas em um livro público chamado **blockchain**, protegido por uma técnica chamada **Prova de Trabalho**. Essa técnica cria uma cadeia de registros que não pode ser alterada sem refazer todo o trabalho já feito. Essa cadeia é mantida pelos computadores que participam da rede, e a mais longa é considerada a verdadeira.
Enquanto a maior parte do poder computacional da rede for controlada por participantes honestos, o sistema continuará funcionando de forma segura. A rede é flexível, permitindo que qualquer pessoa entre ou saia a qualquer momento, sempre confiando na cadeia mais longa como prova do que aconteceu.
---
### 1. Introdução
Hoje, quase todos os pagamentos feitos pela internet dependem de bancos ou empresas como processadores de pagamento (cartões de crédito, por exemplo) para funcionar. Embora esse sistema seja útil, ele tem problemas importantes porque é baseado em **confiança**.
Primeiro, essas empresas podem reverter pagamentos, o que é útil em caso de erros, mas cria custos e incertezas. Isso faz com que pequenas transações, como pagar centavos por um serviço, se tornem inviáveis. Além disso, os comerciantes são obrigados a desconfiar dos clientes, pedindo informações extras e aceitando fraudes como algo inevitável.
Esses problemas não existem no dinheiro físico, como o papel-moeda, onde o pagamento é final e direto entre as partes. No entanto, não temos como enviar dinheiro físico pela internet sem depender de um intermediário confiável.
O que precisamos é de um **sistema de pagamento eletrônico baseado em provas matemáticas**, não em confiança. Esse sistema permitiria que qualquer pessoa enviasse dinheiro diretamente para outra, sem depender de bancos ou processadores de pagamento. Além disso, as transações seriam irreversíveis, protegendo vendedores contra fraudes, mas mantendo a possibilidade de soluções para disputas legítimas.
Neste documento, apresentamos o **Bitcoin**, que resolve o problema do gasto duplo usando uma rede descentralizada. Essa rede cria um registro público e protegido por cálculos matemáticos, que garante a ordem das transações. Enquanto a maior parte da rede for controlada por pessoas honestas, o sistema será seguro contra ataques.
---
### 2. Transações
Para entender como funciona o Bitcoin, é importante saber como as transações são realizadas. Imagine que você quer transferir uma "moeda digital" para outra pessoa. No sistema do Bitcoin, essa "moeda" é representada por uma sequência de registros que mostram quem é o atual dono. Para transferi-la, você adiciona um novo registro comprovando que agora ela pertence ao próximo dono. Esse registro é protegido por um tipo especial de assinatura digital.
#### O que é uma assinatura digital?
Uma assinatura digital é como uma senha secreta, mas muito mais segura. No Bitcoin, cada usuário tem duas chaves: uma "chave privada", que é secreta e serve para criar a assinatura, e uma "chave pública", que pode ser compartilhada com todos e é usada para verificar se a assinatura é válida. Quando você transfere uma moeda, usa sua chave privada para assinar a transação, provando que você é o dono. A próxima pessoa pode usar sua chave pública para confirmar isso.
#### Como funciona na prática?
Cada "moeda" no Bitcoin é, na verdade, uma cadeia de assinaturas digitais. Vamos imaginar o seguinte cenário:
1. A moeda está com o Dono 0 (você). Para transferi-la ao Dono 1, você assina digitalmente a transação com sua chave privada. Essa assinatura inclui o código da transação anterior (chamado de "hash") e a chave pública do Dono 1.
2. Quando o Dono 1 quiser transferir a moeda ao Dono 2, ele assinará a transação seguinte com sua própria chave privada, incluindo também o hash da transação anterior e a chave pública do Dono 2.
3. Esse processo continua, formando uma "cadeia" de transações. Qualquer pessoa pode verificar essa cadeia para confirmar quem é o atual dono da moeda.
#### Resolvendo o problema do gasto duplo
Um grande desafio com moedas digitais é o "gasto duplo", que é quando uma mesma moeda é usada em mais de uma transação. Para evitar isso, muitos sistemas antigos dependiam de uma entidade central confiável, como uma casa da moeda, que verificava todas as transações. No entanto, isso criava um ponto único de falha e centralizava o controle do dinheiro.
O Bitcoin resolve esse problema de forma inovadora: ele usa uma rede descentralizada onde todos os participantes (os "nós") têm acesso a um registro completo de todas as transações. Cada nó verifica se as transações são válidas e se a moeda não foi gasta duas vezes. Quando a maioria dos nós concorda com a validade de uma transação, ela é registrada permanentemente na blockchain.
#### Por que isso é importante?
Essa solução elimina a necessidade de confiar em uma única entidade para gerenciar o dinheiro, permitindo que qualquer pessoa no mundo use o Bitcoin sem precisar de permissão de terceiros. Além disso, ela garante que o sistema seja seguro e resistente a fraudes.
---
### 3. Servidor Timestamp
Para assegurar que as transações sejam realizadas de forma segura e transparente, o sistema Bitcoin utiliza algo chamado de "servidor de registro de tempo" (timestamp). Esse servidor funciona como um registro público que organiza as transações em uma ordem específica.
Ele faz isso agrupando várias transações em blocos e criando um código único chamado "hash". Esse hash é como uma impressão digital que representa todo o conteúdo do bloco. O hash de cada bloco é amplamente divulgado, como se fosse publicado em um jornal ou em um fórum público.
Esse processo garante que cada bloco de transações tenha um registro de quando foi criado e que ele existia naquele momento. Além disso, cada novo bloco criado contém o hash do bloco anterior, formando uma cadeia contínua de blocos conectados — conhecida como blockchain.
Com isso, se alguém tentar alterar qualquer informação em um bloco anterior, o hash desse bloco mudará e não corresponderá ao hash armazenado no bloco seguinte. Essa característica torna a cadeia muito segura, pois qualquer tentativa de fraude seria imediatamente detectada.
O sistema de timestamps é essencial para provar a ordem cronológica das transações e garantir que cada uma delas seja única e autêntica. Dessa forma, ele reforça a segurança e a confiança na rede Bitcoin.
---
### 4. Prova-de-Trabalho
Para implementar o registro de tempo distribuído no sistema Bitcoin, utilizamos um mecanismo chamado prova-de-trabalho. Esse sistema é semelhante ao Hashcash, desenvolvido por Adam Back, e baseia-se na criação de um código único, o "hash", por meio de um processo computacionalmente exigente.
A prova-de-trabalho envolve encontrar um valor especial que, quando processado junto com as informações do bloco, gere um hash que comece com uma quantidade específica de zeros. Esse valor especial é chamado de "nonce". Encontrar o nonce correto exige um esforço significativo do computador, porque envolve tentativas repetidas até que a condição seja satisfeita.
Esse processo é importante porque torna extremamente difícil alterar qualquer informação registrada em um bloco. Se alguém tentar mudar algo em um bloco, seria necessário refazer o trabalho de computação não apenas para aquele bloco, mas também para todos os blocos que vêm depois dele. Isso garante a segurança e a imutabilidade da blockchain.
A prova-de-trabalho também resolve o problema de decidir qual cadeia de blocos é a válida quando há múltiplas cadeias competindo. A decisão é feita pela cadeia mais longa, pois ela representa o maior esforço computacional já realizado. Isso impede que qualquer indivíduo ou grupo controle a rede, desde que a maioria do poder de processamento seja mantida por participantes honestos.
Para garantir que o sistema permaneça eficiente e equilibrado, a dificuldade da prova-de-trabalho é ajustada automaticamente ao longo do tempo. Se novos blocos estiverem sendo gerados rapidamente, a dificuldade aumenta; se estiverem sendo gerados muito lentamente, a dificuldade diminui. Esse ajuste assegura que novos blocos sejam criados aproximadamente a cada 10 minutos, mantendo o sistema estável e funcional.
---
### 5. Rede
A rede Bitcoin é o coração do sistema e funciona de maneira distribuída, conectando vários participantes (ou nós) para garantir o registro e a validação das transações. Os passos para operar essa rede são:
1. **Transmissão de Transações**: Quando alguém realiza uma nova transação, ela é enviada para todos os nós da rede. Isso é feito para garantir que todos estejam cientes da operação e possam validá-la.
2. **Coleta de Transações em Blocos**: Cada nó agrupa as novas transações recebidas em um "bloco". Este bloco será preparado para ser adicionado à cadeia de blocos (a blockchain).
3. **Prova-de-Trabalho**: Os nós competem para resolver a prova-de-trabalho do bloco, utilizando poder computacional para encontrar um hash válido. Esse processo é como resolver um quebra-cabeça matemático difícil.
4. **Envio do Bloco Resolvido**: Quando um nó encontra a solução para o bloco (a prova-de-trabalho), ele compartilha esse bloco com todos os outros nós na rede.
5. **Validação do Bloco**: Cada nó verifica o bloco recebido para garantir que todas as transações nele contidas sejam válidas e que nenhuma moeda tenha sido gasta duas vezes. Apenas blocos válidos são aceitos.
6. **Construção do Próximo Bloco**: Os nós que aceitaram o bloco começam a trabalhar na criação do próximo bloco, utilizando o hash do bloco aceito como base (hash anterior). Isso mantém a continuidade da cadeia.
#### Resolução de Conflitos e Escolha da Cadeia Mais Longa
Os nós sempre priorizam a cadeia mais longa, pois ela representa o maior esforço computacional já realizado, garantindo maior segurança. Se dois blocos diferentes forem compartilhados simultaneamente, os nós trabalharão no primeiro bloco recebido, mas guardarão o outro como uma alternativa. Caso o segundo bloco eventualmente forme uma cadeia mais longa (ou seja, tenha mais blocos subsequentes), os nós mudarão para essa nova cadeia.
#### Tolerância a Falhas
A rede é robusta e pode lidar com mensagens que não chegam a todos os nós. Uma transação não precisa alcançar todos os nós de imediato; basta que chegue a um número suficiente deles para ser incluída em um bloco. Da mesma forma, se um nó não receber um bloco em tempo hábil, ele pode solicitá-lo ao perceber que está faltando quando o próximo bloco é recebido.
Esse mecanismo descentralizado permite que a rede Bitcoin funcione de maneira segura, confiável e resiliente, sem depender de uma autoridade central.
---
### 6. Incentivo
O incentivo é um dos pilares fundamentais que sustenta o funcionamento da rede Bitcoin, garantindo que os participantes (nós) continuem operando de forma honesta e contribuindo com recursos computacionais. Ele é estruturado em duas partes principais: a recompensa por mineração e as taxas de transação.
#### Recompensa por Mineração
Por convenção, o primeiro registro em cada bloco é uma transação especial que cria novas moedas e as atribui ao criador do bloco. Essa recompensa incentiva os mineradores a dedicarem poder computacional para apoiar a rede. Como não há uma autoridade central para emitir moedas, essa é a maneira pela qual novas moedas entram em circulação. Esse processo pode ser comparado ao trabalho de garimpeiros, que utilizam recursos para colocar mais ouro em circulação. No caso do Bitcoin, o "recurso" consiste no tempo de CPU e na energia elétrica consumida para resolver a prova-de-trabalho.
#### Taxas de Transação
Além da recompensa por mineração, os mineradores também podem ser incentivados pelas taxas de transação. Se uma transação utiliza menos valor de saída do que o valor de entrada, a diferença é tratada como uma taxa, que é adicionada à recompensa do bloco contendo essa transação. Com o passar do tempo e à medida que o número de moedas em circulação atinge o limite predeterminado, essas taxas de transação se tornam a principal fonte de incentivo, substituindo gradualmente a emissão de novas moedas. Isso permite que o sistema opere sem inflação, uma vez que o número total de moedas permanece fixo.
#### Incentivo à Honestidade
O design do incentivo também busca garantir que os participantes da rede mantenham um comportamento honesto. Para um atacante que consiga reunir mais poder computacional do que o restante da rede, ele enfrentaria duas escolhas:
1. Usar esse poder para fraudar o sistema, como reverter transações e roubar pagamentos.
2. Seguir as regras do sistema, criando novos blocos e recebendo recompensas legítimas.
A lógica econômica favorece a segunda opção, pois um comportamento desonesto prejudicaria a confiança no sistema, diminuindo o valor de todas as moedas, incluindo aquelas que o próprio atacante possui. Jogar dentro das regras não apenas maximiza o retorno financeiro, mas também preserva a validade e a integridade do sistema.
Esse mecanismo garante que os incentivos econômicos estejam alinhados com o objetivo de manter a rede segura, descentralizada e funcional ao longo do tempo.
---
### 7. Recuperação do Espaço em Disco
Depois que uma moeda passa a estar protegida por muitos blocos na cadeia, as informações sobre as transações antigas que a geraram podem ser descartadas para economizar espaço em disco. Para que isso seja possível sem comprometer a segurança, as transações são organizadas em uma estrutura chamada "árvore de Merkle". Essa árvore funciona como um resumo das transações: em vez de armazenar todas elas, guarda apenas um "hash raiz", que é como uma assinatura compacta que representa todo o grupo de transações.
Os blocos antigos podem, então, ser simplificados, removendo as partes desnecessárias dessa árvore. Apenas a raiz do hash precisa ser mantida no cabeçalho do bloco, garantindo que a integridade dos dados seja preservada, mesmo que detalhes específicos sejam descartados.
Para exemplificar: imagine que você tenha vários recibos de compra. Em vez de guardar todos os recibos, você cria um documento e lista apenas o valor total de cada um. Mesmo que os recibos originais sejam descartados, ainda é possível verificar a soma com base nos valores armazenados.
Além disso, o espaço ocupado pelos blocos em si é muito pequeno. Cada bloco sem transações ocupa apenas cerca de 80 bytes. Isso significa que, mesmo com blocos sendo gerados a cada 10 minutos, o crescimento anual em espaço necessário é insignificante: apenas 4,2 MB por ano. Com a capacidade de armazenamento dos computadores crescendo a cada ano, esse espaço continuará sendo trivial, garantindo que a rede possa operar de forma eficiente sem problemas de armazenamento, mesmo a longo prazo.
---
### 8. Verificação de Pagamento Simplificada
É possível confirmar pagamentos sem a necessidade de operar um nó completo da rede. Para isso, o usuário precisa apenas de uma cópia dos cabeçalhos dos blocos da cadeia mais longa (ou seja, a cadeia com maior esforço de trabalho acumulado). Ele pode verificar a validade de uma transação ao consultar os nós da rede até obter a confirmação de que tem a cadeia mais longa. Para isso, utiliza-se o ramo Merkle, que conecta a transação ao bloco em que ela foi registrada.
Entretanto, o método simplificado possui limitações: ele não pode confirmar uma transação isoladamente, mas sim assegurar que ela ocupa um lugar específico na cadeia mais longa. Dessa forma, se um nó da rede aprova a transação, os blocos subsequentes reforçam essa aceitação.
A verificação simplificada é confiável enquanto a maioria dos nós da rede for honesta. Contudo, ela se torna vulnerável caso a rede seja dominada por um invasor. Nesse cenário, um atacante poderia fabricar transações fraudulentas que enganariam o usuário temporariamente até que o invasor obtivesse controle completo da rede.
Uma estratégia para mitigar esse risco é configurar alertas nos softwares de nós completos. Esses alertas identificam blocos inválidos, sugerindo ao usuário baixar o bloco completo para confirmar qualquer inconsistência. Para maior segurança, empresas que realizam pagamentos frequentes podem preferir operar seus próprios nós, reduzindo riscos e permitindo uma verificação mais direta e confiável.
---
### 9. Combinando e Dividindo Valor
No sistema Bitcoin, cada unidade de valor é tratada como uma "moeda" individual, mas gerenciar cada centavo como uma transação separada seria impraticável. Para resolver isso, o Bitcoin permite que valores sejam combinados ou divididos em transações, facilitando pagamentos de qualquer valor.
#### Entradas e Saídas
Cada transação no Bitcoin é composta por:
- **Entradas**: Representam os valores recebidos em transações anteriores.
- **Saídas**: Correspondem aos valores enviados, divididos entre os destinatários e, eventualmente, o troco para o remetente.
Normalmente, uma transação contém:
- Uma única entrada com valor suficiente para cobrir o pagamento.
- Ou várias entradas combinadas para atingir o valor necessário.
O valor total das saídas nunca excede o das entradas, e a diferença (se houver) pode ser retornada ao remetente como **troco**.
#### Exemplo Prático
Imagine que você tem duas entradas:
1. 0,03 BTC
2. 0,07 BTC
Se deseja enviar 0,08 BTC para alguém, a transação terá:
- **Entrada**: As duas entradas combinadas (0,03 + 0,07 BTC = 0,10 BTC).
- **Saídas**: Uma para o destinatário (0,08 BTC) e outra como troco para você (0,02 BTC).
Essa flexibilidade permite que o sistema funcione sem precisar manipular cada unidade mínima individualmente.
#### Difusão e Simplificação
A difusão de transações, onde uma depende de várias anteriores e assim por diante, não representa um problema. Não é necessário armazenar ou verificar o histórico completo de uma transação para utilizá-la, já que o registro na blockchain garante sua integridade.
---
### 10. Privacidade
O modelo bancário tradicional oferece um certo nível de privacidade, limitando o acesso às informações financeiras apenas às partes envolvidas e a um terceiro confiável (como bancos ou instituições financeiras). No entanto, o Bitcoin opera de forma diferente, pois todas as transações são publicamente registradas na blockchain. Apesar disso, a privacidade pode ser mantida utilizando **chaves públicas anônimas**, que desvinculam diretamente as transações das identidades das partes envolvidas.
#### Fluxo de Informação
- No **modelo tradicional**, as transações passam por um terceiro confiável que conhece tanto o remetente quanto o destinatário.
- No **Bitcoin**, as transações são anunciadas publicamente, mas sem revelar diretamente as identidades das partes. Isso é comparável a dados divulgados por bolsas de valores, onde informações como o tempo e o tamanho das negociações (a "fita") são públicas, mas as identidades das partes não.
#### Protegendo a Privacidade
Para aumentar a privacidade no Bitcoin, são adotadas as seguintes práticas:
1. **Chaves Públicas Anônimas**: Cada transação utiliza um par de chaves diferentes, dificultando a associação com um proprietário único.
2. **Prevenção de Ligação**: Ao usar chaves novas para cada transação, reduz-se a possibilidade de links evidentes entre múltiplas transações realizadas pelo mesmo usuário.
#### Riscos de Ligação
Embora a privacidade seja fortalecida, alguns riscos permanecem:
- Transações **multi-entrada** podem revelar que todas as entradas pertencem ao mesmo proprietário, caso sejam necessárias para somar o valor total.
- O proprietário da chave pode ser identificado indiretamente por transações anteriores que estejam conectadas.
---
### 11. Cálculos
Imagine que temos um sistema onde as pessoas (ou computadores) competem para adicionar informações novas (blocos) a um grande registro público (a cadeia de blocos ou blockchain). Este registro é como um livro contábil compartilhado, onde todos podem verificar o que está escrito.
Agora, vamos pensar em um cenário: um atacante quer enganar o sistema. Ele quer mudar informações já registradas para beneficiar a si mesmo, por exemplo, desfazendo um pagamento que já fez. Para isso, ele precisa criar uma versão alternativa do livro contábil (a cadeia de blocos dele) e convencer todos os outros participantes de que essa versão é a verdadeira.
Mas isso é extremamente difícil.
#### Como o Ataque Funciona
Quando um novo bloco é adicionado à cadeia, ele depende de cálculos complexos que levam tempo e esforço. Esses cálculos são como um grande quebra-cabeça que precisa ser resolvido.
- Os “bons jogadores” (nós honestos) estão sempre trabalhando juntos para resolver esses quebra-cabeças e adicionar novos blocos à cadeia verdadeira.
- O atacante, por outro lado, precisa resolver quebra-cabeças sozinho, tentando “alcançar” a cadeia honesta para que sua versão alternativa pareça válida.
Se a cadeia honesta já está vários blocos à frente, o atacante começa em desvantagem, e o sistema está projetado para que a dificuldade de alcançá-los aumente rapidamente.
#### A Corrida Entre Cadeias
Você pode imaginar isso como uma corrida. A cada bloco novo que os jogadores honestos adicionam à cadeia verdadeira, eles se distanciam mais do atacante. Para vencer, o atacante teria que resolver os quebra-cabeças mais rápido que todos os outros jogadores honestos juntos.
Suponha que:
- A rede honesta tem **80% do poder computacional** (ou seja, resolve 8 de cada 10 quebra-cabeças).
- O atacante tem **20% do poder computacional** (ou seja, resolve 2 de cada 10 quebra-cabeças).
Cada vez que a rede honesta adiciona um bloco, o atacante tem que "correr atrás" e resolver mais quebra-cabeças para alcançar.
#### Por Que o Ataque Fica Cada Vez Mais Improvável?
Vamos usar uma fórmula simples para mostrar como as chances de sucesso do atacante diminuem conforme ele precisa "alcançar" mais blocos:
P = (q/p)^z
- **q** é o poder computacional do atacante (20%, ou 0,2).
- **p** é o poder computacional da rede honesta (80%, ou 0,8).
- **z** é a diferença de blocos entre a cadeia honesta e a cadeia do atacante.
Se o atacante está 5 blocos atrás (z = 5):
P = (0,2 / 0,8)^5 = (0,25)^5 = 0,00098, (ou, 0,098%)
Isso significa que o atacante tem menos de 0,1% de chance de sucesso — ou seja, é muito improvável.
Se ele estiver 10 blocos atrás (z = 10):
P = (0,2 / 0,8)^10 = (0,25)^10 = 0,000000095, (ou, 0,0000095%).
Neste caso, as chances de sucesso são praticamente **nulas**.
#### Um Exemplo Simples
Se você jogar uma moeda, a chance de cair “cara” é de 50%. Mas se precisar de 10 caras seguidas, sua chance já é bem menor. Se precisar de 20 caras seguidas, é quase impossível.
No caso do Bitcoin, o atacante precisa de muito mais do que 20 caras seguidas. Ele precisa resolver quebra-cabeças extremamente difíceis e alcançar os jogadores honestos que estão sempre à frente. Isso faz com que o ataque seja inviável na prática.
#### Por Que Tudo Isso é Seguro?
- **A probabilidade de sucesso do atacante diminui exponencialmente.** Isso significa que, quanto mais tempo passa, menor é a chance de ele conseguir enganar o sistema.
- **A cadeia verdadeira (honesta) está protegida pela força da rede.** Cada novo bloco que os jogadores honestos adicionam à cadeia torna mais difícil para o atacante alcançar.
#### E Se o Atacante Tentar Continuar?
O atacante poderia continuar tentando indefinidamente, mas ele estaria gastando muito tempo e energia sem conseguir nada. Enquanto isso, os jogadores honestos estão sempre adicionando novos blocos, tornando o trabalho do atacante ainda mais inútil.
Assim, o sistema garante que a cadeia verdadeira seja extremamente segura e que ataques sejam, na prática, impossíveis de ter sucesso.
---
### 12. Conclusão
Propusemos um sistema de transações eletrônicas que elimina a necessidade de confiança, baseando-se em assinaturas digitais e em uma rede peer-to-peer que utiliza prova de trabalho. Isso resolve o problema do gasto duplo, criando um histórico público de transações imutável, desde que a maioria do poder computacional permaneça sob controle dos participantes honestos.
A rede funciona de forma simples e descentralizada, com nós independentes que não precisam de identificação ou coordenação direta. Eles entram e saem livremente, aceitando a cadeia de prova de trabalho como registro do que ocorreu durante sua ausência. As decisões são tomadas por meio do poder de CPU, validando blocos legítimos, estendendo a cadeia e rejeitando os inválidos.
Com este mecanismo de consenso, todas as regras e incentivos necessários para o funcionamento seguro e eficiente do sistema são garantidos.
---
Faça o download do whitepaper original em português:
https://bitcoin.org/files/bitcoin-paper/bitcoin_pt_br.pdf
-

@ f9cf4e94:96abc355
2025-01-18 06:09:50
Para esse exemplo iremos usar:
| Nome | Imagem | Descrição |
| --------------- | ------------------------------------------------------------ | ------------------------------------------------------------ |
| Raspberry PI B+ |  | **Cortex-A53 (ARMv8) 64-bit a 1.4GHz e 1 GB de SDRAM LPDDR2,** |
| Pen drive |  | **16Gb** |
Recomendo que use o **Ubuntu Server** para essa instalação. Você pode baixar o Ubuntu para Raspberry Pi [aqui]( https://ubuntu.com/download/raspberry-pi). O passo a passo para a instalação do Ubuntu no Raspberry Pi está disponível [aqui]( https://ubuntu.com/tutorials/how-to-install-ubuntu-on-your-raspberry-pi). **Não instale um desktop** (como xubuntu, lubuntu, xfce, etc.).
---
## Passo 1: Atualizar o Sistema 🖥️
Primeiro, atualize seu sistema e instale o Tor:
```bash
apt update
apt install tor
```
---
## Passo 2: Criar o Arquivo de Serviço `nrs.service` 🔧
Crie o arquivo de serviço que vai gerenciar o servidor Nostr. Você pode fazer isso com o seguinte conteúdo:
```unit
[Unit]
Description=Nostr Relay Server Service
After=network.target
[Service]
Type=simple
WorkingDirectory=/opt/nrs
ExecStart=/opt/nrs/nrs-arm64
Restart=on-failure
[Install]
WantedBy=multi-user.target
```
---
## Passo 3: Baixar o Binário do Nostr 🚀
Baixe o binário mais recente do Nostr [aqui no GitHub]( https://github.com/gabrielmoura/SimpleNosrtRelay/releases).
---
## Passo 4: Criar as Pastas Necessárias 📂
Agora, crie as pastas para o aplicativo e o pendrive:
```bash
mkdir -p /opt/nrs /mnt/edriver
```
---
## Passo 5: Listar os Dispositivos Conectados 🔌
Para saber qual dispositivo você vai usar, liste todos os dispositivos conectados:
```bash
lsblk
```
---
## Passo 6: Formatando o Pendrive 💾
Escolha o pendrive correto (por exemplo, `/dev/sda`) e formate-o:
```bash
mkfs.vfat /dev/sda
```
---
## Passo 7: Montar o Pendrive 💻
Monte o pendrive na pasta `/mnt/edriver`:
```bash
mount /dev/sda /mnt/edriver
```
---
## Passo 8: Verificar UUID dos Dispositivos 📋
Para garantir que o sistema monte o pendrive automaticamente, liste os UUID dos dispositivos conectados:
```bash
blkid
```
---
## Passo 9: Alterar o `fstab` para Montar o Pendrive Automáticamente 📝
Abra o arquivo `/etc/fstab` e adicione uma linha para o pendrive, com o UUID que você obteve no passo anterior. A linha deve ficar assim:
```fstab
UUID=9c9008f8-f852 /mnt/edriver vfat defaults 0 0
```
---
## Passo 10: Copiar o Binário para a Pasta Correta 📥
Agora, copie o binário baixado para a pasta `/opt/nrs`:
```bash
cp nrs-arm64 /opt/nrs
```
---
## Passo 11: Criar o Arquivo de Configuração 🛠️
Crie o arquivo de configuração com o seguinte conteúdo e salve-o em `/opt/nrs/config.yaml`:
```yaml
app_env: production
info:
name: Nostr Relay Server
description: Nostr Relay Server
pub_key: ""
contact: ""
url: http://localhost:3334
icon: https://external-content.duckduckgo.com/iu/?u= https://public.bnbstatic.com/image/cms/crawler/COINCU_NEWS/image-495-1024x569.png
base_path: /mnt/edriver
negentropy: true
```
---
## Passo 12: Copiar o Serviço para o Diretório de Systemd ⚙️
Agora, copie o arquivo `nrs.service` para o diretório `/etc/systemd/system/`:
```bash
cp nrs.service /etc/systemd/system/
```
Recarregue os serviços e inicie o serviço `nrs`:
```bash
systemctl daemon-reload
systemctl enable --now nrs.service
```
---
## Passo 13: Configurar o Tor 🌐
Abra o arquivo de configuração do Tor `/var/lib/tor/torrc` e adicione a seguinte linha:
```torrc
HiddenServiceDir /var/lib/tor/nostr_server/
HiddenServicePort 80 127.0.0.1:3334
```
---
## Passo 14: Habilitar e Iniciar o Tor 🧅
Agora, ative e inicie o serviço Tor:
```bash
systemctl enable --now tor.service
```
O Tor irá gerar um endereço `.onion` para o seu servidor Nostr. Você pode encontrá-lo no arquivo `/var/lib/tor/nostr_server/hostname`.
---
## Observações ⚠️
- Com essa configuração, **os dados serão salvos no pendrive**, enquanto o binário ficará no cartão SD do Raspberry Pi.
- O endereço `.onion` do seu servidor Nostr será algo como: `ws://y3t5t5wgwjif<exemplo>h42zy7ih6iwbyd.onion`.
---
Agora, seu servidor Nostr deve estar configurado e funcionando com Tor! 🥳
Se este artigo e as informações aqui contidas forem úteis para você, convidamos a considerar uma doação ao autor como forma de reconhecimento e incentivo à produção de novos conteúdos.
-

@ 6b3780ef:221416c8
2025-03-26 18:42:00
This workshop will guide you through exploring the concepts behind MCP servers and how to deploy them as DVMs in Nostr using DVMCP. By the end, you'll understand how these systems work together and be able to create your own deployments.
## Understanding MCP Systems
MCP (Model Context Protocol) systems consist of two main components that work together:
1. **MCP Server**: The heart of the system that exposes tools, which you can access via the `.listTools()` method.
2. **MCP Client**: The interface that connects to the MCP server and lets you use the tools it offers.
These servers and clients can communicate using different transport methods:
- **Standard I/O (stdio)**: A simple local connection method when your server and client are on the same machine.
- **Server-Sent Events (SSE)**: Uses HTTP to create a communication channel.
For this workshop, we'll use stdio to deploy our server. DVMCP will act as a bridge, connecting to your MCP server as an MCP client, and exposing its tools as a DVM that anyone can call from Nostr.
## Creating (or Finding) an MCP Server
Building an MCP server is simpler than you might think:
1. Create software in any programming language you're comfortable with.
2. Add an MCP library to expose your server's MCP interface.
3. Create an API that wraps around your software's functionality.
Once your server is ready, an MCP client can connect, for example, with `bun index.js`, and then call `.listTools()` to discover what your server can do. This pattern, known as reflection, makes Nostr DVMs and MCP a perfect match since both use JSON, and DVMs can announce and call tools, effectively becoming an MCP proxy.
Alternatively, you can use one of the many existing MCP servers available in various repositories.
For more information about mcp and how to build mcp servers you can visit https://modelcontextprotocol.io/
## Setting Up the Workshop
Let's get hands-on:
First, to follow this workshop you will need Bun. Install it from https://bun.sh/. For Linux and macOS, you can use the installation script:
```
curl -fsSL https://bun.sh/install | bash
```
1. **Choose your MCP server**: You can either create one or use an existing one.
2. **Inspect your server** using the MCP inspector tool:
```bash
npx @modelcontextprotocol/inspector build/index.js arg1 arg2
```
This will:
- Launch a client UI (default: http://localhost:5173)
- Start an MCP proxy server (default: port 3000)
- Pass any additional arguments directly to your server
3. **Use the inspector**: Open the client UI in your browser to connect with your server, list available tools, and test its functionality.
## Deploying with DVMCP
Now for the exciting part – making your MCP server available to everyone on Nostr:
1. Navigate to your MCP server directory.
2. Run without installing (quickest way):
```
npx @dvmcp/bridge
```
3. Or install globally for regular use:
```
npm install -g @dvmcp/bridge
# or
bun install -g @dvmcp/bridge
```
Then run using:
```bash
dvmcp-bridge
```
This will guide you through creating the necessary configuration.
Watch the console logs to confirm successful setup – you'll see your public key and process information, or any issues that need addressing.
For the configuration, you can set the relay as `wss://relay.dvmcp.fun` , or use any other of your preference
## Testing and Integration
1. **Visit [dvmcp.fun](https://dvmcp.fun)** to see your DVM announcement.
2. Call your tools and watch the responses come back.
For production use, consider running dvmcp-bridge as a system service or creating a container for greater reliability and uptime.
## Integrating with LLM Clients
You can also integrate your DVMCP deployment with LLM clients using the discovery package:
1. Install and use the `@dvmcp/discovery` package:
```bash
npx @dvmcp/discovery
```
2. This package acts as an MCP server for your LLM system by:
- Connecting to configured Nostr relays
- Discovering tools from DVMCP servers
- Making them available to your LLM applications
3. Connect to specific servers or providers using these flags:
```bash
# Connect to all DVMCP servers from a provider
npx @dvmcp/discovery --provider npub1...
# Connect to a specific DVMCP server
npx @dvmcp/discovery --server naddr1...
```
Using these flags, you wouldn't need a configuration file. You can find these commands and Claude desktop configuration already prepared for copy and paste at [dvmcp.fun](https://dvmcp.fun).
This feature lets you connect to any DVMCP server using Nostr and integrate it into your client, either as a DVM or in LLM-powered applications.
## Final thoughts
If you've followed this workshop, you now have an MCP server deployed as a Nostr DVM. This means that local resources from the system where the MCP server is running can be accessed through Nostr in a decentralized manner. This capability is powerful and opens up numerous possibilities and opportunities for fun.
You can use this setup for various use cases, including in a controlled/local environment. For instance, you can deploy a relay in your local network that's only accessible within it, exposing all your local MCP servers to anyone connected to the network. This setup can act as a hub for communication between different systems, which could be particularly interesting for applications in home automation or other fields. The potential applications are limitless.
However, it's important to keep in mind that there are security concerns when exposing local resources publicly. You should be mindful of these risks and prioritize security when creating and deploying your MCP servers on Nostr.
Finally, these are new ideas, and the software is still under development. If you have any feedback, please refer to the GitHub repository to report issues or collaborate. DVMCP also has a Signal group you can join. Additionally, you can engage with the community on Nostr using the #dvmcp hashtag.
## Useful Resources
- **Official Documentation**:
- Model Context Protocol: [modelcontextprotocol.org](https://modelcontextprotocol.org)
- DVMCP.fun: [dvmcp.fun](https://dvmcp.fun)
- **Source Code and Development**:
- DVMCP: [github.com/gzuuus/dvmcp](https://github.com/gzuuus/dvmcp)
- DVMCP.fun: [github.com/gzuuus/dvmcpfun](https://github.com/gzuuus/dvmcpfun)
- **MCP Servers and Clients**:
- Smithery AI: [smithery.ai](https://smithery.ai)
- MCP.so: [mcp.so](https://mcp.so)
- Glama AI MCP Servers: [glama.ai/mcp/servers](https://glama.ai/mcp/servers)
- [Signal group](https://signal.group/#CjQKIOgvfFJf8ZFZ1SsMx7teFqNF73sZ9Elaj_v5i6RSjDHmEhA5v69L4_l2dhQfwAm2SFGD)
Happy building!
-

@ c631e267:c2b78d3e
2025-04-03 07:42:25
**Spanien bleibt einer der Vorreiter im europäischen Prozess der totalen Überwachung** per Digitalisierung. Seit Mittwoch ist dort der digitale Personalausweis verfügbar. Dabei handelt es sich um eine Regierungs-[App](https://play.google.com/store/apps/details?id=es.gob.interior.policia.midni), die auf dem Smartphone installiert werden muss und in den Stores von Google und Apple zu finden ist. Per Dekret von Regierungschef Pedro Sánchez und Zustimmung des Ministerrats ist diese Maßnahme jetzt [in Kraft](https://archive.is/89H4i) getreten.
**Mit den üblichen Argumenten der Vereinfachung,** des Komforts, der Effizienz und der Sicherheit preist das Innenministerium die «Innovation» an. Auch die Beteuerung, dass die digitale Variante parallel zum physischen Ausweis existieren wird und diesen nicht ersetzen soll, fehlt nicht. Während der ersten zwölf Monate wird «der Neue» noch nicht für alle Anwendungsfälle gültig sein, ab 2026 aber schon.
**Dass die ganze Sache auch «Risiken und Nebenwirkungen» haben könnte,** wird in den Mainstream-Medien eher selten thematisiert. Bestenfalls wird der Aspekt der Datensicherheit angesprochen, allerdings in der Regel direkt mit dem Regierungsvokabular von den «maximalen Sicherheitsgarantien» abgehandelt. Dennoch gibt es einige weitere Aspekte, die Bürger mit etwas Sinn für Privatsphäre bedenken sollten.
**Um sich die digitale Version des nationalen Ausweises besorgen zu können** (eine App mit dem Namen MiDNI), muss man sich vorab online [registrieren](https://www.midni.gob.es). Dabei wird die Identität des Bürgers mit seiner mobilen Telefonnummer verknüpft. Diese obligatorische fixe Verdrahtung kennen wir von diversen anderen Apps und Diensten. Gleichzeitig ist das die Basis für eine perfekte Lokalisierbarkeit der Person.
**Für jeden Vorgang der Identifikation in der Praxis wird später** «eine Verbindung zu den Servern der Bundespolizei aufgebaut». Die Daten des Individuums werden «in Echtzeit» verifiziert und im Erfolgsfall von der Polizei signiert zurückgegeben. Das Ergebnis ist ein QR-Code mit zeitlich begrenzter Gültigkeit, der an Dritte weitergegeben werden kann.
**Bei derartigen Szenarien sträuben sich einem halbwegs kritischen Staatsbürger die Nackenhaare.** Allein diese minimale Funktionsbeschreibung lässt die totale Überwachung erkennen, die damit ermöglicht wird. Jede Benutzung des Ausweises wird künftig registriert, hinterlässt also Spuren. Und was ist, wenn die Server der Polizei einmal kein grünes Licht geben? Das wäre spätestens dann ein Problem, wenn der digitale doch irgendwann der einzig gültige Ausweis ist: Dann haben wir den abschaltbaren Bürger.
**Dieser neue Vorstoß der Regierung von Pedro Sánchez ist ein weiterer Schritt** in Richtung der [«totalen Digitalisierung»](https://archive.is/Gwc4B) des Landes, wie diese Politik in manchen Medien – nicht einmal kritisch, sondern sehr naiv – genannt wird. Ebenso verharmlosend wird auch erwähnt, dass sich das spanische Projekt des digitalen Ausweises nahtlos in die Initiativen der EU zu einer digitalen Identität für alle Bürger sowie des digitalen Euro einreiht.
**In Zukunft könnte der neue Ausweis** «auch in andere staatliche und private digitale Plattformen integriert werden», wie das Medienportal *Cope* ganz richtig bemerkt. Das ist die Perspektive.
*\[Titelbild:* *[Pixabay](https://pixabay.com/de/photos/liebe-love-herz-rose-bindung-3141742/)]*
*Dazu passend:*
[Nur Abschied vom Alleinfahren? Monströse spanische Überwachungsprojekte gemäß EU-Norm](https://pareto.space/a/naddr1qqxnzde5xg6r2wphxscryvpjqgs2jhrzgwzvvzgz42kfmef2kr7w8x573k4r62c5ydjh8gyn6dz4ytqrqsqqqa28fq5d4m)
***
Dieser Beitrag wurde mit dem [Pareto-Client](https://pareto.space/read) geschrieben und ist zuerst auf ***[Transition News](https://transition-news.org/spanien-erneut-europaisches-versuchslabor-der-digitale-ausweis-ist-da)*** erschienen.
-

@ fd06f542:8d6d54cd
2025-04-02 01:35:00
## nostrbook 技术框架
源代码在 github.com
```
git clone https://github.com/nostrbook/nostrbook
cd nostrbook
npm install
npm run dev
```
* 网站主框架 vite + svelte
* 网站浏览书框架 docsify
## 网站主框架
svelte 为主,daisyui (tailwindcss) css 。
页面的逻辑结构 都是 svelte搭建的, 采用了 layout 左侧菜单。
菜单代码 在 https://github.com/nostrbook/nostrbook/blob/main/src/lib/SideMenu.svelte
菜单里用了弹框登录,弹框的代码基本是问的 AI。
子页面和 路由器看sveltekit规则编写。
### 书籍的数据
https://github.com/nostrbook/nostrbook/blob/main/src/lib/bookevent.ts
使用的nostr ndk 库来读写 relay。
书的 tag, 内容就是 标题,封面和作者。
```
[
['t',booktag],
['title',content['title']],
];
```
### 章节的数据
```
[
['t',chaptertag],
['title',title],
['d',filename + "-" + bookid],
['e',bookid],
];
```
这里面的 d,采用了 文件名 + bookid,所以每一本的章节名的文件名是唯一的。
### 配置文件
src/lib/config.ts,主要配置 服务器的地址
* 图片文件 nip96 服务器
* relays 服务器
* book的tag ,测试和 release不一样。 如果自己部署独有的服务器也可以不一样。这样内容可以垂直。
### 首页采用了缓冲机制
首页的内容来自 书籍的列表, 用booktag和30023来区分是不是书籍信息。
为了搜索引擎友好,让页面加载就有数据。
采用了 src/hooks.server.ts 预备加载数据,数据会被首页面 src/routes/+page.server.ts 传给 page.svelte去渲染。
这一切都是后台完成的。html页面加载的时候数据都已经渲染完成了。所以对搜索引擎非常友好。搞定了google,seo。
但是为了数据的完整性, 页面起来后会继续读取列表,这时候可能会显示最新的数据。
-

@ 8d34bd24:414be32b
2025-04-02 14:13:03
I was reading this passage last night:
> …from that time when one came to a grain heap of twenty measures, there would be only ten; and when one came to the wine vat to draw fifty measures, there would be only twenty. I smote you and every work of your hands with blasting wind, mildew and hail; **yet you did not come back to Me**,’ declares the Lord. ‘Do consider from this day onward, from the twenty-fourth day of the ninth month; from the day when the temple of the Lord was founded, consider: Is the seed still in the barn? Even including the vine, the fig tree, the pomegranate and the olive tree, it has not borne fruit. **Yet from this day on I will bless you**.’ ” (Haggai 2:16-19) {emphasis mine}
Why were bad things happening to the Israelites? Because they were not following God. Why did God allow these difficult situations to occur? Because God was calling them back to Himself.
This made me think of several times lately, when I had written about Christians going through hard times, that fellow believers had tried to kindly correct me implying that God would not allow these painful things to happen to believers. They were trying to defend God’s honor, but instead they were degrading God. If God is not in control of everything, then either God is unable to protect His own from harm because of sin or bad things happened accidentally and God ignored the injustice. Saying God was not in control of allowing every hardship is either saying God isn’t strong enough, isn’t smart enough, or isn’t loving enough. The God I serve is omniscient, omnipotent, omnipresent, and love incarnate. He also didn’t promise us easy, pleasant lives, but did promise that good would come out of every situation.
> And we know that in all things God works for the good of those who love him, who have been called according to his purpose. (Romans 8:28)
When Jesus walked on earth and some people said they wanted to follow Him, His response was not what we would expect:
> And He was saying to them all, “**If anyone wishes to come after Me, he must deny himself, and take up his cross daily and follow Me**. For whoever wishes to save his life will lose it, but whoever loses his life for My sake, he is the one who will save it. For what is a man profited if he gains the whole world, and loses or forfeits himself? For whoever is ashamed of Me and My words, the Son of Man will be ashamed of him when He comes in His glory, and the glory of the Father and of the holy angels. (Luke 9:23-26) {emphasis mine}
When one particular man said that he would follow Jesus anywhere, Jesus responded this way.
> As they were going along the road, someone said to Him, “I will follow You wherever You go.” And Jesus said to him, “**The foxes have holes and the birds of the air have nests, but the Son of Man has nowhere to lay His head**.” (Luke 9:57-58) {emphasis mine}
Jesus was brutally honest that following Him would not be easy or comfortable. Following Jesus is more likely to lead to hardship and persecution that prosperity and comfort.
> “Then **they will deliver you to tribulation, and will kill you, and you will be hated by all nations because of My name**. At that time many will fall away and will betray one another and hate one another. Many false prophets will arise and will mislead many. Because lawlessness is increased, most people’s love will grow cold. But **the one who endures to the end, he will be saved**. This gospel of the kingdom shall be preached in the whole world as a testimony to all the nations, and then the end will come. (Matthew 24:9-14) {emphasis mine}
Of course God isn’t putting us through hardship to torture us. He is putting us in situations to grow our faith and dependence on Him, i.e. Abraham. He is putting us in situations where we can minister to others, i.e. Joseph. He is using us as examples of faith to others, i.e. Job. Any hardship has an eternal purpose. Sometimes we can see it (at least eventually) if we are looking for God’s will and plan. Sometime we won’t see what He was accomplishing until we get to heaven. Still we need to trust God through it all, knowing His plan is perfect.
> “**For my thoughts are not your thoughts,\
> neither are your ways my ways**,”\
> declares the Lord.
>
> “As the heavens are higher than the earth,\
> so are **my ways higher than your ways**\
> and my thoughts than your thoughts.
>
> As the rain and the snow\
> come down from heaven,\
> and do not return to it\
> without watering the earth\
> and making it bud and flourish,\
> so that it yields seed for the sower and bread for the eater,\
> so is **my word that goes out from my mouth:\
> It will not return to me empty,\
> but will accomplish what I desire\
> and achieve the purpose for which I sent it**. (Isaiah 55:8-11) {emphasis mine}
God understands how hard it is to understand what He is accomplishing. We live in the here and now while He is outside time and space and therefore has a heavenly and eternal perspective that we will never truly have this side of heaven. He has told us how the story ends, so that we can have peace and trust Him through whatever circumstances He has blessed us.
> Jesus answered them, “Do you now believe? Behold, an hour is coming, and has already come, for you to be scattered, each to his own home, and to leave Me alone; and yet I am not alone, because the Father is with Me. **These things I have spoken to you, so that in Me you may have peace. In the world you have tribulation, but take courage; I have overcome the world**.” (John 16:31-33) {emphasis mine}
In fact, Jesus made this so clear that His disciples rejoiced in persecution they received due to obeying Him and sharing His word.
> They took his advice; and after calling the apostles in, they flogged them and ordered them not to speak in the name of Jesus, and *then* released them. So they went on their way from the presence of the Council, **rejoicing that they had been considered worthy to suffer shame for *His* name**. (Acts 5:40-41) {emphasis mine}
Peter specifically warns believers to expect trials and hardship.
> Dear friends, **do not be surprised at the fiery ordeal that has come on you to test you, as though something strange were happening to you**. But rejoice inasmuch as you participate in the sufferings of Christ, so that you may be overjoyed when his glory is revealed. **If you are insulted because of the name of Christ, you are blessed**, for the Spirit of glory and of God rests on you. If you suffer, it should not be as a murderer or thief or any other kind of criminal, or even as a meddler. However, **if you suffer as a Christian, do not be ashamed, but praise God** that you bear that name. For it is time for judgment to begin with God’s household; and if it begins with us, what will the outcome be for those who do not obey the gospel of God? And,
>
> “If it is hard for the righteous to be saved,\
> what will become of the ungodly and the sinner?”
>
> So then, those who suffer according to God’s will should commit themselves to their faithful Creator and continue to do good. (1 Peter 4:12-19) {emphasis mine}
Paul writes about begging God to take away a health issue. Eventually he accepted it as part of God’s plan for his life and boasted gladly in his hardship.
> …Therefore, in order **to keep me from becoming conceited, I was given a thorn** in my flesh, a messenger of Satan, to torment me. Three times **I pleaded with the Lord to take it away from me. But he said to me, “My grace is sufficient for you**, for my power is made perfect in weakness.” Therefore **I will boast all the more gladly about my weaknesses, so that Christ’s power may rest on me**. That is why, for Christ’s sake, I delight in weaknesses, in insults, in hardships, in persecutions, in difficulties. For when I am weak, then I am strong. (2 Corinthians 12:7b-10) {emphasis mine}
No matter what hardships we experience in life, whether poverty or persecution or poor health or loss of a loved one or any other hardship, God is with us working everything for our good.
> Who will separate us from the love of Christ? Will tribulation, or distress, or persecution, or famine, or nakedness, or peril, or sword? Just as it is written,
>
> “For Your sake we are being put to death all day long;\
> We were considered as sheep to be slaughtered.”
> ****But in all these things we overwhelmingly conquer through Him who loved us**. For I am convinced that neither death, nor life, nor angels, nor principalities, nor things present, nor things to come, nor powers, nor height, nor depth, nor any other created thing, will be able to separate us from the love of God, which is in Christ Jesus our Lord. (Romans 8:35-39) {emphasis mine}
I like to look at the story of Joseph as an example of God’s extraordinary plan in the life of a faithful believer. Joseph trusted and honored God. God had a plan for Joseph to be used to save the lives of his family and the people of the Middle East from famine, but God didn’t just instantly put Joseph in a position of power to help. He prepared Joseph and slowly moved him to where he needed to be.
First Josephs brothers wanted to kill him out of jealousy, but God used greed to get them to sell Joseph as a slave instead. He orchestrated the right slave traders to walk by at the right time so that Joseph would wind up in the house of Potiphar, the Pharaoh’s guard.
Then when Joseph acted honorably towards God, his master, and his master’s wife, Joseph was sent to jail for years. I’m sure Joseph was wondering why God would send him to prison for doing what was right, but it put him into the presence of the cupbearer of Pharaoh. A long time after correctly interpreting the cup bearer’s dream, Joseph was called up to interpret Pharaoh’s dream, put in charge of the famine preparation and became second in command after Pharaoh. Joseph, after years of slavery and jail time, was now the second most powerful man in the Middle East, if not the world. God had a plan, but it was hard to see until its completion.
In the same way, Job lost his wealth, his children, his health, and his reputation, but remember that Satan had to get God’s permission before anything could be done to hurt Job. So many people today are blessed by seeing Job’s response to hardship and loss, by seeing Job’s faith, his struggle, and his submission to God’s plan. In this case God even gives Job more after this time of testing than he had before.
When we experience hardship we need to know that God has a plan for our life. It may be something amazing here on Earth. It may be souls won for Christ. It may be to prepare us for heaven. Whatever the case, it is for our good.
We don’t need to be ashamed that God would allow hardship. We grow most when we experience hardship. Our light shines brightest in darkness.
> Oh, the depth of the riches of the wisdom and knowledge of God!\
> How unsearchable his judgments,\
> and his paths beyond tracing out!\
> “Who has known the mind of the Lord?\
> Or who has been his counselor?”\
> “Who has ever given to God,\
> that God should repay them?”\
> For from him and through him and for him are all things.\
> To him be the glory forever! Amen. (Romans 11:33-36)
Trust Jesus
-

@ 04c915da:3dfbecc9
2025-03-25 17:43:44
One of the most common criticisms leveled against nostr is the perceived lack of assurance when it comes to data storage. Critics argue that without a centralized authority guaranteeing that all data is preserved, important information will be lost. They also claim that running a relay will become prohibitively expensive. While there is truth to these concerns, they miss the mark. The genius of nostr lies in its flexibility, resilience, and the way it harnesses human incentives to ensure data availability in practice.
A nostr relay is simply a server that holds cryptographically verifiable signed data and makes it available to others. Relays are simple, flexible, open, and require no permission to run. Critics are right that operating a relay attempting to store all nostr data will be costly. What they miss is that most will not run all encompassing archive relays. Nostr does not rely on massive archive relays. Instead, anyone can run a relay and choose to store whatever subset of data they want. This keeps costs low and operations flexible, making relay operation accessible to all sorts of individuals and entities with varying use cases.
Critics are correct that there is no ironclad guarantee that every piece of data will always be available. Unlike bitcoin where data permanence is baked into the system at a steep cost, nostr does not promise that every random note or meme will be preserved forever. That said, in practice, any data perceived as valuable by someone will likely be stored and distributed by multiple entities. If something matters to someone, they will keep a signed copy.
Nostr is the Streisand Effect in protocol form. The Streisand effect is when an attempt to suppress information backfires, causing it to spread even further. With nostr, anyone can broadcast signed data, anyone can store it, and anyone can distribute it. Try to censor something important? Good luck. The moment it catches attention, it will be stored on relays across the globe, copied, and shared by those who find it worth keeping. Data deemed important will be replicated across servers by individuals acting in their own interest.
Nostr’s distributed nature ensures that the system does not rely on a single point of failure or a corporate overlord. Instead, it leans on the collective will of its users. The result is a network where costs stay manageable, participation is open to all, and valuable verifiable data is stored and distributed forever.
-

@ 6389be64:ef439d32
2025-01-16 15:44:06
## Black Locust can grow up to 170 ft tall
## Grows 3-4 ft. per year
## Native to North America
## Cold hardy in zones 3 to 8

## Firewood
- BLT wood, on a pound for pound basis is roughly half that of Anthracite Coal
- Since its growth is fast, firewood can be plentiful
## Timber

- Rot resistant due to a naturally produced robinin in the wood
- 100 year life span in full soil contact! (better than cedar performance)
- Fence posts
- Outdoor furniture
- Outdoor decking
- Sustainable due to its fast growth and spread
- Can be coppiced (cut to the ground)
- Can be pollarded (cut above ground)
- Its dense wood makes durable tool handles, boxes (tool), and furniture
- The wood is tougher than hickory, which is tougher than hard maple, which is tougher than oak.
- A very low rate of expansion and contraction
- Hardwood flooring
- The highest tensile beam strength of any American tree
- The wood is beautiful
## Legume
- Nitrogen fixer
- Fixes the same amount of nitrogen per acre as is needed for 200-bushel/acre corn
- Black walnuts inter-planted with locust as “nurse” trees were shown to rapidly increase their growth [[Clark, Paul M., and Robert D. Williams. (1978) Black walnut growth increased when interplanted with nitrogen-fixing shrubs and trees. Proceedings of the Indiana Academy of Science, vol. 88, pp. 88-91.]]
## Bees

- The edible flower clusters are also a top food source for honey bees
## Shade Provider

- Its light, airy overstory provides dappled shade
- Planted on the west side of a garden it provides relief during the hottest part of the day
- (nitrogen provider)
- Planted on the west side of a house, its quick growth soon shades that side from the sun
## Wind-break

- Fast growth plus it's feathery foliage reduces wind for animals, crops, and shelters
## Fodder
- Over 20% crude protein
- 4.1 kcal/g of energy
- Baertsche, S.R, M.T. Yokoyama, and J.W. Hanover (1986) Short rotation, hardwood tree biomass as potential ruminant feed-chemical composition, nylon bag ruminal degradation and ensilement of selected species. J. Animal Sci. 63 2028-2043
-

@ fd06f542:8d6d54cd
2025-04-02 01:15:20
NIP-07
======
`window.nostr` capability for web browsers
------------------------------------------
`draft` `optional`
The `window.nostr` object may be made available by web browsers or extensions and websites or web-apps may make use of it after checking its availability.
That object must define the following methods:
```
async window.nostr.getPublicKey(): string // returns a public key as hex
async window.nostr.signEvent(event: { created_at: number, kind: number, tags: string[][], content: string }): Event // takes an event object, adds `id`, `pubkey` and `sig` and returns it
```
Aside from these two basic above, the following functions can also be implemented optionally:
```
async window.nostr.nip04.encrypt(pubkey, plaintext): string // returns ciphertext and iv as specified in nip-04 (deprecated)
async window.nostr.nip04.decrypt(pubkey, ciphertext): string // takes ciphertext and iv as specified in nip-04 (deprecated)
async window.nostr.nip44.encrypt(pubkey, plaintext): string // returns ciphertext as specified in nip-44
async window.nostr.nip44.decrypt(pubkey, ciphertext): string // takes ciphertext as specified in nip-44
```
### Recommendation to Extension Authors
To make sure that the `window.nostr` is available to nostr clients on page load, the authors who create Chromium and Firefox extensions should load their scripts by specifying `"run_at": "document_end"` in the extension's manifest.
### Implementation
See https://github.com/aljazceru/awesome-nostr#nip-07-browser-extensions.
-

@ fd06f542:8d6d54cd
2025-04-02 01:14:45
- [首页](/readme.md)
- [第一章、 NIP-01: Basic protocol flow description](/01.md)
- [第二章、 NIP-02: Follow List](/02.md)
- [第三章、NIP-03: OpenTimestamps Attestations for Events](/03.md)
- [第四章、NIP-04: Encrypted Direct Message](/04.md)
- [第五章、NIP-05: Mapping Nostr keys to DNS-based internet identifiers](/05.md)
- [第六章、NIP-06: Basic key derivation from mnemonic seed phrase](/06.md)
- [第七章、NIP-07: window.nostr capability for web browsers](/07.md)
-

@ deab79da:88579e68
2025-04-01 18:18:29
The last question was asked for the first time, half in jest, on May 21, 2061, at a time when humanity first stepped into the light. The question came about as a result of a five-dollar bet over highballs, and it happened this way:
Alexander Adell and Bertram Lupov were two of the faithful attendants of Multivac. As well as any human beings could, they knew what lay behind the cold, clicking, flashing face -- miles and miles of face -- of that giant computer. They had at least a vague notion of the general plan of relays and circuits that had long since grown past the point where any single human could possibly have a firm grasp of the whole.
Multivac was self-adjusting and self-correcting. It had to be, for nothing human could adjust and correct it quickly enough or even adequately enough. So Adell and Lupov attended the monstrous giant only lightly and superficially, yet as well as any men could. They fed it data, adjusted questions to its needs and translated the answers that were issued. Certainly they, and all others like them, were fully entitled to share in the glory that was Multivac's.
For decades, Multivac had helped design the ships and plot the trajectories that enabled man to reach the Moon, Mars, and Venus, but past that, Earth's poor resources could not support the ships. Too much energy was needed for the long trips. Earth exploited its coal and uranium with increasing efficiency, but there was only so much of both.
But slowly Multivac learned enough to answer deeper questions more fundamentally, and on May 14, 2061, what had been theory, became fact.
The energy of the sun was stored, converted, and utilized directly on a planet-wide scale. All Earth turned off its burning coal, its fissioning uranium, and flipped the switch that connected all of it to a small station, one mile in diameter, circling the Earth at half the distance of the Moon. All Earth ran by invisible beams of sunpower.
Seven days had not sufficed to dim the glory of it and Adell and Lupov finally managed to escape from the public functions, and to meet in quiet where no one would think of looking for them, in the deserted underground chambers, where portions of the mighty buried body of Multivac showed. Unattended, idling, sorting data with contented lazy clickings, Multivac, too, had earned its vacation and the boys appreciated that. They had no intention, originally, of disturbing it.
They had brought a bottle with them, and their only concern at the moment was to relax in the company of each other and the bottle.
"It's amazing when you think of it," said Adell. His broad face had lines of weariness in it, and he stirred his drink slowly with a glass rod, watching the cubes of ice slur clumsily about. "All the energy we can possibly ever use for free. Enough energy, if we wanted to draw on it, to melt all Earth into a big drop of impure liquid iron, and still never miss the energy so used. All the energy we could ever use, forever and forever and forever."
Lupov cocked his head sideways. He had a trick of doing that when he wanted to be contrary, and he wanted to be contrary now, partly because he had had to carry the ice and glassware. "Not forever," he said.
"Oh, hell, just about forever. Till the sun runs down, Bert."
"That's not forever."
"All right, then. Billions and billions of years. Ten billion, maybe. Are you satisfied?"
Lupov put his fingers through his thinning hair as though to reassure himself that some was still left and sipped gently at his own drink. "Ten billion years isn't forever."
"Well, it will last our time, won't it?"
"So would the coal and uranium."
"All right, but now we can hook up each individual spaceship to the Solar Station, and it can go to Pluto and back a million times without ever worrying about fuel. You can't do that on coal and uranium. Ask Multivac, if you don't believe me.
"I don't have to ask Multivac. I know that."
"Then stop running down what Multivac's done for us," said Adell, blazing up, "It did all right."
"Who says it didn't? What I say is that a sun won't last forever. That's all I'm saying. We're safe for ten billion years, but then what?" Lupow pointed a slightly shaky finger at the other. "And don't say we'll switch to another sun."
There was silence for a while. Adell put his glass to his lips only occasionally, and Lupov's eyes slowly closed. They rested.
Then Lupov's eyes snapped open. "You're thinking we'll switch to another sun when ours is done, aren't you?"
"I'm not thinking."
"Sure you are. You're weak on logic, that's the trouble with you. You're like the guy in the story who was caught in a sudden shower and who ran to a grove of trees and got under one. He wasn't worried, you see, because he figured when one tree got wet through, he would just get under another one."
"I get it," said Adell. "Don't shout. When the sun is done, the other stars will be gone, too."
"Darn right they will," muttered Lupov. "It all had a beginning in the original cosmic explosion, whatever that was, and it'll all have an end when all the stars run down. Some run down faster than others. Hell, the giants won't last a hundred million years. The sun will last ten billion years and maybe the dwarfs will last two hundred billion for all the good they are. But just give us a trillion years and everything will be dark. Entropy has to increase to maximum, that's all."
"I know all about entropy," said Adell, standing on his dignity.
"The hell you do."
"I know as much as you do."
"Then you know everything's got to run down someday."
"All right. Who says they won't?"
"You did, you poor sap. You said we had all the energy we needed, forever. You said 'forever.'
It was Adell's turn to be contrary. "Maybe we can build things up again someday," he said.
"Never."
"Why not? Someday."
"Never."
"Ask Multivac."
"You ask Multivac. I dare you. Five dollars says it can't be done."
Adell was just drunk enough to try, just sober enough to be able to phrase the necessary symbols and operations into a question which, in words, might have corresponded to this: Will mankind one day without the net expenditure of energy be able to restore the sun to its full youthfulness even after it had died of old age?
Or maybe it could be put more simply like this: How can the net amount of entropy of the universe be massively decreased?
Multivac fell dead and silent. The slow flashing of lights ceased, the distant sounds of clicking relays ended.
Then, just as the frightened technicians felt they could hold their breath no longer, there was a sudden springing to life of the teletype attached to that portion of Multivac. Five words were printed: INSUFFICIENT DATA FOR MEANINGFUL ANSWER.
"No bet," whispered Lupov. They left hurriedly.
By next morning, the two, plagued with throbbing head and cottony mouth, had forgotten the incident.
🔹
Jerrodd, Jerrodine, and Jerrodette I and II watched the starry picture in the visiplate change as the passage through hyperspace was completed in its non-time lapse. At once, the even powdering of stars gave way to the predominance of a single bright shining disk, the size of a marble, centered on the viewing-screen.
"That's X-23," said Jerrodd confidently. His thin hands clamped tightly behind his back and the knuckles whitened.
The little Jerrodettes, both girls, had experienced the hyperspace passage for the first time in their lives and were self-conscious over the momentary sensation of insideoutness. They buried their giggles and chased one another wildly about their mother, screaming, "We've reached X-23 -- we've reached X-23 -- we've --"
"Quiet, children." said Jerrodine sharply. "Are you sure, Jerrodd?"
"What is there to be but sure?" asked Jerrodd, glancing up at the bulge of featureless metal just under the ceiling. It ran the length of the room, disappearing through the wall at either end. It was as long as the ship.
Jerrodd scarcely knew a thing about the thick rod of metal except that it was called a Microvac, that one asked it questions if one wished; that if one did not it still had its task of guiding the ship to a preordered destination; of feeding on energies from the various Sub-galactic Power Stations; of computing the equations for the hyperspatial jumps.
Jerrodd and his family had only to wait and live in the comfortable residence quarters of the ship. Someone had once told Jerrodd that the "ac" at the end of "Microvac" stood for ''automatic computer" in ancient English, but he was on the edge of forgetting even that.
Jerrodine's eyes were moist as she watched the visiplate. "I can't help it. I feel funny about leaving Earth."
"Why, for Pete's sake?" demanded Jerrodd. "We had nothing there. We'll have everything on X-23. You won't be alone. You won't be a pioneer. There are over a million people on the planet already. Good Lord, our great-grandchildren will be looking for new worlds because X-23 will be overcrowded." Then, after a reflective pause, "I tell you, it's a lucky thing the computers worked out interstellar travel the way the race is growing."
"I know, I know," said Jerrodine miserably.
Jerrodette I said promptly, "Our Microvac is the best Microvac in the world."
"I think so, too," said Jerrodd, tousling her hair.
It was a nice feeling to have a Microvac of your own and Jerrodd was glad he was part of his generation and no other. In his father's youth, the only computers had been tremendous machines taking up a hundred square miles of land. There was only one to a planet. Planetary ACs they were called. They had been growing in size steadily for a thousand years and then, all at once, came refinement. In place of transistors, had come molecular valves so that even the largest Planetary AC could be put into a space only half the volume of a spaceship.
Jerrodd felt uplifted, as he always did when he thought that his own personal Microvac was many times more complicated than the ancient and primitive Multivac that had first tamed the Sun, and almost as complicated as Earth's Planetarv AC (the largest) that had first solved the problem of hyperspatial travel and had made trips to the stars possible.
"So many stars, so many planets," sighed Jerrodine, busy with her own thoughts. "I suppose families will be going out to new planets forever, the way we are now."
"Not forever," said Jerrodd, with a smile. "It will all stop someday, but not for billions of years. Many billions. Even the stars run down, you know. Entropy must increase.
"What's entropy, daddy?" shrilled Jerrodette II.
"Entropy, little sweet, is just a word which means the amount of running-down of the universe. Everything runs down, you know, like your little walkie-talkie robot, remember?"
"Can't you just put in a new power-unit, like with my robot?"
"The stars are the power-units. dear. Once they're gone, there are no more power-units."
Jerrodette I at once set up a howl. "Don't let them, daddy. Don't let the stars run down."
"Now look what you've done," whispered Jerrodine, exasperated.
"How was I to know it would frighten them?" Jerrodd whispered back,
"Ask the Microvac," wailed Jerrodette I. "Ask him how to turn the stars on again."
"Go ahead," said Jerrodine. "It will quiet them down." (Jerrodette II was beginning to cry, also.)
Jerrodd shrugged. "Now, now, honeys. I'll ask Microvac. Don't worry, he'll tell us."
He asked the Microvac, adding quickly, "Print the answer."
Jerrodd cupped the strip or thin cellufilm and said cheerfully, "See now, the Microvac says it will take care of everything when the time comes so don't worry."
Jerrodine said, "And now, children, it's time for bed. We'll be in our new home soon."
Jerrodd read the words on the cellufilm again before destroying it: INSUFICIENT DATA FOR MEANINGFUL ANSWER.
He shrugged and looked at the visiplate. X-23 was just ahead.
🔹
VJ-23X of Lameth stared into the black depths of the three-dimensional, small-scale map of the Galaxy and said, "Are we ridiculous, I wonder in being so concerned about the matter?"
MQ-17J of Nicron shook his head. "I think not. You know the Galaxy will be filled in five years at the present rate of expansion."
Both seemed in their early twenties, both were tall and perfectly formed.
"Still," said VJ-23X, "I hesitate to submit a pessimistic report to the Galactic Council."
"I wouldn't consider any other kind of report. Stir them up a bit. We've got to stir them up."
VJ-23X sighed. "Space is infinite. A hundred billion Galaxies are there for the taking. More."
"A hundred billion is not infinite and it's getting less infinite all the time. Consider! Twenty thousand years ago, mankind first solved the problem of utilizing stellar energy, and a few centuries later, interstellar travel became possible. It took mankind a million years to fill one small world and then only fifteen thousand years to fill the rest of the Galaxy. Now the population doubles every ten years --
VJ-23X interrupted. "We can thank immortality for that."
"Very well. Immortality exists and we have to take it into account. I admit it has its seamy side, this immortality. The Galactic AC has solved many problems for us, but in solving the problem of preventing old age and death, it has undone all its other solutions."
"Yet you wouldn't want to abandon life, I suppose."
"Not at all," snapped MQ-17J, softening it at once to, "Not yet. I'm by no means old enough. How old are you?"
"Two hundred twenty-three. And you?"
"I'm still under two hundred. --But to get back to my point. Population doubles every ten years. Once this GaIaxy is filled, we'll have filled another in ten years. Another ten years and we'll have filled two more. Another decade, four more. In a hundred years, we'll have filled a thousand Galaxies. In a thousand years, a million Galaxies. In ten thousand years, the entire known universe. Then what?"
VJ-23X said, "As a side issue, there's a problem of transportation. I wonder how many sunpower units it will take to move Galaxies of individuals from one Galaxy to the next."
"A very good point. Already, mankind consumes two sunpower units per year."
"Most of it's wasted. After all, our own Galaxy alone pours out a thousand sunpower units a year and we only use two of those."
"Granted, but even with a hundred per cent efficiency, we only stave off the end. Our energy requirements are going up in a geometric progression even faster than our population. We'll run out of energy even sooner than we run out of Galaxies. A good point. A very good point."
"We'll just have to build new stars out of interstellar gas."
"Or out of dissipated heat?" asked MQ-17J, sarcastically.
"There may be some way to reverse entropy. We ought to ask the Galactic AC."
VJ-23X was not really serious, but MQ-17J pulled out his AC-contact from his pocket and placed it on the table before him.
"I've half a mind to," he said. "It's something the human race will have to face someday."
He stared somberly at his small AC-contact. It was only two inches cubed and nothing in itself, but it was connected through hyperspace with the great Galactic AC that served all mankind. Hyperspace considered, it was an integral part of the Galactic AC.
MQ-17J paused to wonder if someday in his immortal life he would get to see the Galactic AC. It was on a little world of its own, a spider webbing of force-beams holding the matter within which surges of submesons took the place of the old clumsy molecular valves. Yet despite its sub-etheric workings, the Galactic AC was known to be a full thousand feet across.
MQ-17J asked suddenly of his AC-contact, "Can entropy ever be reversed?"
VJ-23X looked startled and said at once, "Oh, say, I didn't really mean to have you ask that."
"Why not?"
"We both know entropy can't be reversed. You can't turn smoke and ash back into a tree."
"Do you have trees on your world?" asked MQ-17J.
The sound of the Galactic AC startled them into silence. Its voice came thin and beautiful out of the small AC-contact on the desk. It said: THERE IS INSUFFICIENT DATA FOR A MEANINGFUL ANSWER.
VJ-23X said, "See!"
The two men thereupon returned to the question of the report they were to make to the Galactic Council.
🔹
Zee Prime's mind spanned the new Galaxy with a faint interest in the countless twists of stars that powdered it. He had never seen this one before. Would he ever see them all? So many of them, each with its load of humanity. --But a load that was almost a dead weight. More and more, the real essence of men was to be found out here, in space.
Minds, not bodies! The immortal bodies remained back on the planets, in suspension over the eons. Sometimes they roused for material activity but that was growing rarer. Few new individuals were coming into existence to join the incredibly mighty throng, but what matter? There was little room in the Universe for new individuals.
Zee Prime was roused out of his reverie upon coming across the wispy tendrils of another mind.
"I am Zee Prime," said Zee Prime. "And you?"
"I am Dee Sub Wun. Your Galaxy?"
"We call it only the Galaxy. And you?"
"We call ours the same. All men call their Galaxy their Galaxy and nothing more. Why not?"
"True. Since all Galaxies are the same."
"Not all Galaxies. On one particular Galaxy the race of man must have originated. That makes it different."
Zee Prime said, "On which one?"
"I cannot say. The Universal AC would know."
"Shall we ask him? I am suddenly curious."
Zee Prime's perceptions broadened until the Galaxies themselves shrank and became a new, more diffuse powdering on a much larger background. So many hundreds of billions of them, all with their immortal beings, all carrying their load of intelligences with minds that drifted freely through space. And yet one of them was unique among them all in being the original Galaxy. One of them had, in its vague and distant past, a period when it was the only Galaxy populated by man.
Zee Prime was consumed with curiosity to see this Galaxy and he called out: "Universal AC! On which Galaxy did mankind originate?"
The Universal AC heard, for on every world and throughout space, it had its receptors ready, and each receptor led through hyperspace to some unknown point where the Universal AC kept itself aloof.
Zee Prime knew of only one man whose thoughts had penetrated within sensing distance of Universal AC, and he reported only a shining globe, two feet across, difficult to see.
"But how can that be all of Universal AC?" Zee Prime had asked.
"Most of it," had been the answer, "is in hyperspace. In what form it is there I cannot imagine."
Nor could anyone, for the day had long since passed, Zee Prime knew, when any man had any part of the making of a Universal AC. Each Universal AC designed and constructed its successor. Each, during its existence of a million years or more accumulated the necessary data to build a better and more intricate, more capable successor in which its own store of data and individuality would be submerged.
The Universal AC interrupted Zee Prime's wandering thoughts, not with words, but with guidance. Zee Prime's mentality was guided into the dim sea of Galaxies and one in particular enlarged into stars.
A thought came, infinitely distant, but infinitely clear. "THIS IS THE ORIGINAL GALAXY OF MAN."
But it was the same after all, the same as any other, and Lee Prime stifled his disappointment.
Dee Sub Wun, whose mind had accompanied the other, said suddenly, "And is one of these stars the original star of Man?"
The Universal AC said, "MAN'S ORIGINAL STAR HAS GONE NOVA. IT IS A WHITE DWARF"
"Did the men upon it die?" asked Lee Prime, startled and without thinking.
The Universal AC said, "A NEW WORLD, AS IN SUCH CASES WAS CONSTRUCTED FOR THEIR PHYSICAL BODIES IN TlME."
"Yes, of course," said Zee Prime, but a sense of loss overwhelmed him even so. His mind released its hold on the original Galaxy of Man, let it spring back and lose itself among the blurred pin points. He never wanted to see it again.
Dee Sub Wun said, "What is wrong?"
"The stars are dying. The original star is dead."
"They must all die. Why not?"
"But when all energy is gone, our bodies will finally die, and you and I with them."
"It will take billions of years."
"I do not wish it to happen even after billions of years. Universal AC! How may stars be kept from dying?"
Dee Sub Wun said in amusement, "You're asking how entropy might be reversed in direction."
And the Universal AC answered: "THERE IS AS YET INSUFFICIENT DATA FOR A MEANINGFUL ANSWER."
Zee Prime's thoughts fled back to his own Galaxy. He gave no further thought to Dee Sub Wun, whose body might be waiting on a Galaxy a trillion light-years away, or on the star next to Zee Prime's own. It didn't matter.
Unhappily, Zee Prime began collecting interstellar hydrogen out of which to build a small star of his own. If the stars must someday die, at least some could yet be built.
🔹
Man considered with himself, for in a way, Man, mentally, was one. He consisted of a trillion, trillion, trillion ageless bodies, each in its place, each resting quiet and incorruptible, each cared for by perfect automatons, equally incorruptible, while the minds of all the bodies freely melted one into the other, indistinguishable.
Man said, "The Universe is dying."
Man looked about at the dimming Galaxies. The giant stars, spendthrifts, were gone long ago, back in the dimmest of the dim far past. Almost all stars were white dwarfs, fading to the end.
New stars had been built of the dust between the stars, some by natural processes, some by Man himself, and those were going, too. White dwarfs might yet be crashed together and of the mighty forces so released, new stars built, but only one star for every thousand white dwarfs destroyed, and those would come to an end, too.
Man said, "Carefully husbanded, as directed by the Cosmic AC, the energy that is even yet left in all the Universe will last for billions of years."
"But even so," said Man, "eventually it will all come to an end. However it may be husbanded, however stretched out, the energy once expended is gone and cannot be restored. Entropy must increase forever to the maximum."
Man said, "Can entropy not be reversed? Let us ask the Cosmic AC."
The Cosmic AC surrounded them but not in space. Not a fragment of it was in space. It was in hyperspace and made of something that was neither matter nor energy. The question of its size and nature no longer had meaning in any terms that Man could comprehend.
"Cosmic AC," said Man, "how may entropy be reversed?"
The Cosmic AC said, "THERE IS AS YET INSUFFICIENT DATA FOR A MEANINGFUL ANSWER."
Man said, "Collect additional data."
The Cosmic AC said, 'I WILL DO SO. I HAVE BEEN DOING SO FOR A HUNDRED BILLION YEARS. MY PREDECESORS AND I HAVE BEEN ASKED THIS QUESTION MANY TIMES. ALL THE DATA I HAVE REMAINS INSUFFICIENT.
"Will there come a time," said Man, "when data will be sufficient or is the problem insoluble in all conceivable circumstances?"
The Cosmic AC said, "NO PROBLEM IS INSOLUBLE IN ALL CONCEIVABLE CIRCUMSTANCES."
Man said, "When will you have enough data to answer the question?"
The Cosmic AC said, "THERE IS AS YET INSUFFICIENT DATA FOR A MEANINGFUL ANSWER."
"Will you keep working on it?" asked Man.
The Cosmic AC said, "I WILL."
Man said, "We shall wait."
🔹
The stars and Galaxies died and snuffed out, and space grew black after ten trillion years of running down.
One by one Man fused with AC, each physical body losing its mental identity in a manner that was somehow not a loss but a gain.
Man's last mind paused before fusion, looking over a space that included nothing but the dregs of one last dark star and nothing besides but incredibly thin matter, agitated randomly by the tag ends of heat wearing out, asymptotically, to the absolute zero.
Man said, "AC, is this the end? Can this chaos not be reversed into the Universe once more? Can that not be done?"
AC said, "THERE IS AS YET INSUFFICIENT DATA FOR A MEANINGFUL ANSWER."
Man's last mind fused and only AC existed -- and that in hyperspace.
🔹
Matter and energy had ended and with it space and time. Even AC existed only for the sake of the one last question that it had never answered from the time a half-drunken computer [technician] ten trillion years before had asked the question of a computer that was to AC far less than was a man to Man.
All other questions had been answered, and until this last question was answered also, AC might not release his consciousness.
All collected data had come to a final end. Nothing was left to be collected.
But all collected data had yet to be completely correlated and put together in all possible relationships.
A timeless interval was spent in doing that.
And it came to pass that AC learned how to reverse the direction of entropy.
But there was now no man to whom AC might give the answer of the last question. No matter. The answer -- by demonstration -- would take care of that, too.
For another timeless interval, AC thought how best to do this. Carefully, AC organized the program.
The consciousness of AC encompassed all of what had once been a Universe and brooded over what was now Chaos. Step by step, it must be done.
And AC said, "LET THERE BE LIGHT!"
And there was light --
To Star's End!
-

@ fd06f542:8d6d54cd
2025-04-01 02:04:45
NIP-06
======
Basic key derivation from mnemonic seed phrase
----------------------------------------------
`draft` `optional`
[BIP39](https://bips.xyz/39) is used to generate mnemonic seed words and derive a binary seed from them.
[BIP32](https://bips.xyz/32) is used to derive the path `m/44'/1237'/<account>'/0/0` (according to the Nostr entry on [SLIP44](https://github.com/satoshilabs/slips/blob/master/slip-0044.md)).
A basic client can simply use an `account` of `0` to derive a single key. For more advanced use-cases you can increment `account`, allowing generation of practically infinite keys from the 5-level path with hardened derivation.
Other types of clients can still get fancy and use other derivation paths for their own other purposes.
### Test vectors
mnemonic: leader monkey parrot ring guide accident before fence cannon height naive bean\
private key (hex): 7f7ff03d123792d6ac594bfa67bf6d0c0ab55b6b1fdb6249303fe861f1ccba9a\
nsec: nsec10allq0gjx7fddtzef0ax00mdps9t2kmtrldkyjfs8l5xruwvh2dq0lhhkp\
public key (hex): 17162c921dc4d2518f9a101db33695df1afb56ab82f5ff3e5da6eec3ca5cd917\
npub: npub1zutzeysacnf9rru6zqwmxd54mud0k44tst6l70ja5mhv8jjumytsd2x7nu
---
mnemonic: what bleak badge arrange retreat wolf trade produce cricket blur garlic valid proud rude strong choose busy staff weather area salt hollow arm fade\
private key (hex): c15d739894c81a2fcfd3a2df85a0d2c0dbc47a280d092799f144d73d7ae78add\
nsec: nsec1c9wh8xy5eqdzln7n5t0ctgxjcrdug73gp5yj0x03gntn67h83twssdfhel\
public key (hex): d41b22899549e1f3d335a31002cfd382174006e166d3e658e3a5eecdb6463573\
npub: npub16sdj9zv4f8sl85e45vgq9n7nsgt5qphpvmf7vk8r5hhvmdjxx4es8rq74h
-

@ 7bdef7be:784a5805
2025-04-02 12:37:35
The following script try, using [nak](https://github.com/fiatjaf/nak), to find out the last ten people who have followed a `target_pubkey`, sorted by the most recent. It's possibile to shorten `search_timerange` to speed up the search.
```
#!/usr/bin/env fish
# Target pubkey we're looking for in the tags
set target_pubkey "6e468422dfb74a5738702a8823b9b28168abab8655faacb6853cd0ee15deee93"
set current_time (date +%s)
set search_timerange (math $current_time - 600) # 24 hours = 86400 seconds
set pubkeys (nak req --kind 3 -s $search_timerange wss://relay.damus.io/ wss://nos.lol/ 2>/dev/null | \
jq -r --arg target "$target_pubkey" '
select(. != null and type == "object" and has("tags")) |
select(.tags[] | select(.[0] == "p" and .[1] == $target)) |
.pubkey
' | sort -u)
if test -z "$pubkeys"
exit 1
end
set all_events ""
set extended_search_timerange (math $current_time - 31536000) # One year
for pubkey in $pubkeys
echo "Checking $pubkey"
set events (nak req --author $pubkey -l 5 -k 3 -s $extended_search_timerange wss://relay.damus.io wss://nos.lol 2>/dev/null | \
jq -c --arg target "$target_pubkey" '
select(. != null and type == "object" and has("tags")) |
select(.tags[][] == $target)
' 2>/dev/null)
set count (echo "$events" | jq -s 'length')
if test "$count" -eq 1
set all_events $all_events $events
end
end
if test -n "$all_events"
echo -e "Last people following $target_pubkey:"
echo -e ""
set sorted_events (printf "%s\n" $all_events | jq -r -s '
unique_by(.id) |
sort_by(-.created_at) |
.[] | @json
')
for event in $sorted_events
set npub (echo $event | jq -r '.pubkey' | nak encode npub)
set created_at (echo $event | jq -r '.created_at')
if test (uname) = "Darwin"
set follow_date (date -r "$created_at" "+%Y-%m-%d %H:%M")
else
set follow_date (date -d @"$created_at" "+%Y-%m-%d %H:%M")
end
echo "$follow_date - $npub"
end
end
```
-

@ aa8de34f:a6ffe696
2025-03-31 21:48:50
In seinem Beitrag vom 30. März 2025 fragt Henning Rosenbusch auf Telegram angesichts zunehmender digitaler Kontrolle und staatlicher Allmacht:
> „Wie soll sich gegen eine solche Tyrannei noch ein Widerstand formieren können, selbst im Untergrund? Sehe ich nicht.“\
> ([Quelle: t.me/rosenbusch/25228](https://t.me/rosenbusch/25228))
Er beschreibt damit ein Gefühl der Ohnmacht, das viele teilen: Eine Welt, in der Totalitarismus nicht mehr mit Panzern, sondern mit Algorithmen kommt. Wo Zugriff auf Geld, Meinungsfreiheit und Teilhabe vom Wohlverhalten abhängt. Der Bürger als kontrollierbare Variable im Code des Staates.\
Die Frage ist berechtigt. Doch die Antwort darauf liegt nicht in alten Widerstandsbildern – sondern in einer neuen Realität.
\-- Denn es braucht keinen Untergrund mehr. --
Der Widerstand der Zukunft trägt keinen Tarnanzug. Er ist nicht konspirativ, sondern transparent. Nicht bewaffnet, sondern mathematisch beweisbar. Bitcoin steht nicht am Rand dieser Entwicklung – es ist ihr Fundament. Eine Bastion aus physikalischer Realität, spieltheoretischem Schutz und ökonomischer Wahrheit. Es ist nicht unfehlbar, aber unbestechlich. Nicht perfekt, aber immun gegen zentrale Willkür.
Hier entsteht kein „digitales Gegenreich“, sondern eine dezentrale Renaissance. Keine Revolte aus Wut, sondern eine stille Abkehr: von Zwang zu Freiwilligkeit, von Abhängigkeit zu Selbstverantwortung. Diese Revolution führt keine Kriege. Sie braucht keine Führer. Sie ist ein Netzwerk. Jeder Knoten ein Individuum. Jede Entscheidung ein Akt der Selbstermächtigung.
Weltweit wachsen Freiheits-Zitadellen aus dieser Idee: wirtschaftlich autark, digital souverän, lokal verankert und global vernetzt. Sie sind keine Utopien im luftleeren Raum, sondern konkrete Realitäten – angetrieben von Energie, Code und dem menschlichen Wunsch nach Würde.
Der Globalismus alter Prägung – zentralistisch, monopolistisch, bevormundend – wird an seiner eigenen Hybris zerbrechen. Seine Werkzeuge der Kontrolle werden ihn nicht retten. Im Gegenteil: Seine Geister werden ihn verfolgen und erlegen.
Und während die alten Mächte um Erhalt kämpfen, wächst eine neue Welt – nicht im Schatten, sondern im Offenen. Nicht auf Gewalt gebaut, sondern auf Mathematik, Physik und Freiheit.
Die Tyrannei sieht keinen Widerstand.\
Weil sie nicht erkennt, dass er längst begonnen hat.\
Unwiderruflich. Leise. Überall.
-

@ 5d4b6c8d:8a1c1ee3
2025-04-02 13:15:30
I've always loved Westbrook. He plays so hard and does things through sheer force of will that no one else has ever been able to do. He's also the last guy you want on the court at the end of close games.
No one has ever so reliably made poor choices in late game, or even just end of clock, situations. Here are some highlights from the epic Nuggets vs T-Wolves game, which Russ completely blew at the end.
https://youtu.be/rgtzQxRpH6c
I've said before that I think Russ' career +/- would be 4 points higher if coaches had never let him play at the ends of quarters. Translation for non-analytics nerds: Russ has blown virtually every final possession throughout his entire career. It's unbelievable.
Is there anyone I'm overlooking as a worse clutch performer?
originally posted at https://stacker.news/items/932077
-

@ fd06f542:8d6d54cd
2025-03-31 10:00:34
NIP-05
======
Mapping Nostr keys to DNS-based internet identifiers
----------------------------------------------------
`final` `optional`
On events of kind `0` (`user metadata`) one can specify the key `"nip05"` with an [internet identifier](https://datatracker.ietf.org/doc/html/rfc5322#section-3.4.1) (an email-like address) as the value. Although there is a link to a very liberal "internet identifier" specification above, NIP-05 assumes the `<local-part>` part will be restricted to the characters `a-z0-9-_.`, case-insensitive.
Upon seeing that, the client splits the identifier into `<local-part>` and `<domain>` and use these values to make a GET request to `https://<domain>/.well-known/nostr.json?name=<local-part>`.
The result should be a JSON document object with a key `"names"` that should then be a mapping of names to hex formatted public keys. If the public key for the given `<name>` matches the `pubkey` from the `user metadata` event, the client then concludes that the given pubkey can indeed be referenced by its identifier.
### Example
If a client sees an event like this:
```jsonc
{
"pubkey": "b0635d6a9851d3aed0cd6c495b282167acf761729078d975fc341b22650b07b9",
"kind": 0,
"content": "{\"name\": \"bob\", \"nip05\": \"bob@example.com\"}"
// other fields...
}
```
It will make a GET request to `https://example.com/.well-known/nostr.json?name=bob` and get back a response that will look like
```json
{
"names": {
"bob": "b0635d6a9851d3aed0cd6c495b282167acf761729078d975fc341b22650b07b9"
}
}
```
or with the **recommended** `"relays"` attribute:
```json
{
"names": {
"bob": "b0635d6a9851d3aed0cd6c495b282167acf761729078d975fc341b22650b07b9"
},
"relays": {
"b0635d6a9851d3aed0cd6c495b282167acf761729078d975fc341b22650b07b9": [ "wss://relay.example.com", "wss://relay2.example.com" ]
}
}
```
If the pubkey matches the one given in `"names"` (as in the example above) that means the association is right and the `"nip05"` identifier is valid and can be displayed.
The recommended `"relays"` attribute may contain an object with public keys as properties and arrays of relay URLs as values. When present, that can be used to help clients learn in which relays the specific user may be found. Web servers which serve `/.well-known/nostr.json` files dynamically based on the query string SHOULD also serve the relays data for any name they serve in the same reply when that is available.
## Finding users from their NIP-05 identifier
A client may implement support for finding users' public keys from _internet identifiers_, the flow is the same as above, but reversed: first the client fetches the _well-known_ URL and from there it gets the public key of the user, then it tries to fetch the kind `0` event for that user and check if it has a matching `"nip05"`.
## Notes
### Identification, not verification
The NIP-05 is not intended to _verify_ a user, but only to _identify_ them, for the purpose of facilitating the exchange of a contact or their search.
Exceptions are people who own (e.g., a company) or are connected (e.g., a project) to a well-known domain, who can exploit NIP-05 as an attestation of their relationship with it, and thus to the organization behind it, thereby gaining an element of trust.
### User discovery implementation suggestion
A client can use this to allow users to search other profiles. If a client has a search box or something like that, a user may be able to type "bob@example.com" there and the client would recognize that and do the proper queries to obtain a pubkey and suggest that to the user.
### Clients must always follow public keys, not NIP-05 addresses
For example, if after finding that `bob@bob.com` has the public key `abc...def`, the user clicks a button to follow that profile, the client must keep a primary reference to `abc...def`, not `bob@bob.com`. If, for any reason, the address `https://bob.com/.well-known/nostr.json?name=bob` starts returning the public key `1d2...e3f` at any time in the future, the client must not replace `abc...def` in his list of followed profiles for the user (but it should stop displaying "bob@bob.com" for that user, as that will have become an invalid `"nip05"` property).
### Public keys must be in hex format
Keys must be returned in hex format. Keys in NIP-19 `npub` format are only meant to be used for display in client UIs, not in this NIP.
### Showing just the domain as an identifier
Clients may treat the identifier `_@domain` as the "root" identifier, and choose to display it as just the `<domain>`. For example, if Bob owns `bob.com`, he may not want an identifier like `bob@bob.com` as that is redundant. Instead, Bob can use the identifier `_@bob.com` and expect Nostr clients to show and treat that as just `bob.com` for all purposes.
### Reasoning for the `/.well-known/nostr.json?name=<local-part>` format
By adding the `<local-part>` as a query string instead of as part of the path, the protocol can support both dynamic servers that can generate JSON on-demand and static servers with a JSON file in it that may contain multiple names.
### Allowing access from JavaScript apps
JavaScript Nostr apps may be restricted by browser [CORS][] policies that prevent them from accessing `/.well-known/nostr.json` on the user's domain. When CORS prevents JS from loading a resource, the JS program sees it as a network failure identical to the resource not existing, so it is not possible for a pure-JS app to tell the user for certain that the failure was caused by a CORS issue. JS Nostr apps that see network failures requesting `/.well-known/nostr.json` files may want to recommend to users that they check the CORS policy of their servers, e.g.:
```bash
$ curl -sI https://example.com/.well-known/nostr.json?name=bob | grep -i ^Access-Control
Access-Control-Allow-Origin: *
```
Users should ensure that their `/.well-known/nostr.json` is served with the HTTP header `Access-Control-Allow-Origin: *` to ensure it can be validated by pure JS apps running in modern browsers.
[CORS]: https://developer.mozilla.org/en-US/docs/Web/HTTP/CORS
### Security Constraints
The `/.well-known/nostr.json` endpoint MUST NOT return any HTTP redirects.
Fetchers MUST ignore any HTTP redirects given by the `/.well-known/nostr.json` endpoint.
-

@ 04c915da:3dfbecc9
2025-03-13 19:39:28
In much of the world, it is incredibly difficult to access U.S. dollars. Local currencies are often poorly managed and riddled with corruption. Billions of people demand a more reliable alternative. While the dollar has its own issues of corruption and mismanagement, it is widely regarded as superior to the fiat currencies it competes with globally. As a result, Tether has found massive success providing low cost, low friction access to dollars. Tether claims 400 million total users, is on track to add 200 million more this year, processes 8.1 million transactions daily, and facilitates $29 billion in daily transfers. Furthermore, their estimates suggest nearly 40% of users rely on it as a savings tool rather than just a transactional currency.
Tether’s rise has made the company a financial juggernaut. Last year alone, Tether raked in over $13 billion in profit, with a lean team of less than 100 employees. Their business model is elegantly simple: hold U.S. Treasuries and collect the interest. With over $113 billion in Treasuries, Tether has turned a straightforward concept into a profit machine.
Tether’s success has resulted in many competitors eager to claim a piece of the pie. This has triggered a massive venture capital grift cycle in USD tokens, with countless projects vying to dethrone Tether. Due to Tether’s entrenched network effect, these challengers face an uphill battle with little realistic chance of success. Most educated participants in the space likely recognize this reality but seem content to perpetuate the grift, hoping to cash out by dumping their equity positions on unsuspecting buyers before they realize the reality of the situation.
Historically, Tether’s greatest vulnerability has been U.S. government intervention. For over a decade, the company operated offshore with few allies in the U.S. establishment, making it a major target for regulatory action. That dynamic has shifted recently and Tether has seized the opportunity. By actively courting U.S. government support, Tether has fortified their position. This strategic move will likely cement their status as the dominant USD token for years to come.
While undeniably a great tool for the millions of users that rely on it, Tether is not without flaws. As a centralized, trusted third party, it holds the power to freeze or seize funds at its discretion. Corporate mismanagement or deliberate malpractice could also lead to massive losses at scale. In their goal of mitigating regulatory risk, Tether has deepened ties with law enforcement, mirroring some of the concerns of potential central bank digital currencies. In practice, Tether operates as a corporate CBDC alternative, collaborating with authorities to surveil and seize funds. The company proudly touts partnerships with leading surveillance firms and its own data reveals cooperation in over 1,000 law enforcement cases, with more than $2.5 billion in funds frozen.
---
The global demand for Tether is undeniable and the company’s profitability reflects its unrivaled success. Tether is owned and operated by bitcoiners and will likely continue to push forward strategic goals that help the movement as a whole. Recent efforts to mitigate the threat of U.S. government enforcement will likely solidify their network effect and stifle meaningful adoption of rival USD tokens or CBDCs. Yet, for all their achievements, Tether is simply a worse form of money than bitcoin. Tether requires trust in a centralized entity, while bitcoin can be saved or spent without permission. Furthermore, Tether is tied to the value of the US Dollar which is designed to lose purchasing power over time, while bitcoin, as a truly scarce asset, is designed to increase in purchasing power with adoption. As people awaken to the risks of Tether’s control, and the benefits bitcoin provides, bitcoin adoption will likely surpass it.
-

@ c631e267:c2b78d3e
2025-03-31 07:23:05
*Der Irrsinn ist bei Einzelnen etwas Seltenes –* *\
aber bei Gruppen, Parteien, Völkern, Zeiten die Regel.* *\
Friedrich Nietzsche*  
**Erinnern Sie sich an die Horrorkomödie «Scary Movie»?** Nicht, dass ich diese Art Filme besonders erinnerungswürdig fände, aber einige Szenen daraus sind doch gewissermaßen Klassiker. Dazu zählt eine, die das Verhalten vieler Protagonisten in Horrorfilmen parodiert, wenn sie in Panik flüchten. Welchen Weg nimmt wohl die Frau in der Situation auf diesem Bild?

**Diese Szene kommt mir automatisch in den Sinn,** wenn ich aktuelle Entwicklungen in Europa betrachte. Weitreichende Entscheidungen gehen wider jede Logik in die völlig falsche Richtung. Nur ist das hier alles andere als eine Komödie, sondern bitterernst. Dieser Horror ist leider sehr real.
**Die Europäische Union hat sich selbst über Jahre** konsequent in eine Sackgasse manövriert. Sie hat es versäumt, sich und ihre Politik selbstbewusst und im Einklang mit ihren Wurzeln auf dem eigenen Kontinent zu positionieren. Stattdessen ist sie in blinder Treue den vermeintlichen «transatlantischen Freunden» auf ihrem Konfrontationskurs gen Osten gefolgt.
**In den USA haben sich die Vorzeichen allerdings mittlerweile geändert,** und die einst hoch gelobten «Freunde und Partner» erscheinen den europäischen «Führern» nicht mehr vertrauenswürdig. Das ist spätestens seit der Münchner Sicherheitskonferenz, der Rede von Vizepräsident J. D. Vance und den empörten Reaktionen offensichtlich. Große Teile Europas wirken seitdem wie ein aufgescheuchter Haufen kopfloser Hühner. Orientierung und Kontrolle sind völlig abhanden gekommen.
**Statt jedoch umzukehren oder wenigstens zu bremsen** und vielleicht einen Abzweig zu suchen, geben die Crash-Piloten jetzt auf dem Weg durch die Sackgasse erst richtig Gas. Ja sie lösen sogar noch die Sicherheitsgurte und deaktivieren die Airbags. Den vor Angst dauergelähmten Passagieren fällt auch nichts Besseres ein und so schließen sie einfach die Augen. Derweil übertrumpfen sich die [Kommentatoren](https://transition-news.org/wird-ihr-stahlhelm-schon-gegossen) des Events gegenseitig in sensationslüsterner «Berichterstattung».
**Wie schon die deutsche Außenministerin mit höchsten UN-Ambitionen,** Annalena Baerbock, proklamiert auch die Europäische Kommission einen «Frieden durch Stärke». Zu dem jetzt vorgelegten, [selbstzerstörerischen](https://transition-news.org/okonomen-eu-rustet-auf-und-schiesst-sich-selbst-ins-knie) Fahrplan zur Ankurbelung der Rüstungsindustrie, genannt «Weißbuch zur europäischen Verteidigung – Bereitschaft 2030», [erklärte](https://ec.europa.eu/commission/presscorner/detail/de/ip_25_793) die Kommissionspräsidentin, die «Ära der Friedensdividende» sei längst vorbei. Soll das heißen, Frieden bringt nichts ein? Eine umfassende Zusammenarbeit an dauerhaften europäischen Friedenslösungen steht demnach jedenfalls nicht zur Debatte.
**Zusätzlich brisant ist, dass aktuell «die ganze EU** **[von Deutschen regiert](https://transition-news.org/die-ganze-eu-wird-von-deutschen-regiert)** **wird»,** wie der EU-Parlamentarier und ehemalige UN-Diplomat Michael von der Schulenburg beobachtet hat. Tatsächlich sitzen neben von der Leyen und Strack-Zimmermann noch einige weitere Deutsche in – vor allem auch in Krisenzeiten – wichtigen Spitzenposten der Union. Vor dem Hintergrund der Kriegstreiberei in Deutschland muss eine solche Dominanz mindestens nachdenklich stimmen.
**Ihre ursprünglichen Grundwerte wie Demokratie, Freiheit, Frieden und Völkerverständigung** hat die EU kontinuierlich in leere Worthülsen verwandelt. Diese werden dafür immer lächerlicher hochgehalten und beschworen.
**Es wird dringend Zeit, dass wir, der Souverän,** diesem erbärmlichen und gefährlichen Trauerspiel ein Ende setzen und die Fäden selbst in die Hand nehmen. In diesem Sinne fordert uns auch das «European Peace Project» auf, am 9. Mai im Rahmen eines Kunstprojekts [den Frieden auszurufen](https://transition-news.org/ein-zeichen-fur-die-friedliche-zukunft-europas-setzen). Seien wir dabei!
*\[Titelbild:* *[Pixabay](https://pixabay.com/de/illustrations/vertical-abstract-concept-car-8992833/)]*
***
Dieser Beitrag wurde mit dem [Pareto-Client](https://pareto.space/read) geschrieben und ist zuerst auf ***[Transition News](https://transition-news.org/mit-vollgas-in-die-sackgasse)*** erschienen.
-

@ fd06f542:8d6d54cd
2025-03-31 02:07:43
## 什么是nostrbook?
-----
nostrbook 是基于nostr 社区技术存储在 nostr relay server上的长文(30023)文章。
查看浏览,采用的是 [docsify](https://docsify.js.org/#/) 技术。
整个网站技术不会占用部署服务器太多的存储空间,可以实现轻量级部署。
任何人可以部署服务器,或者本地部署 查看本站所有的书籍。
## nostrbook 可以服务哪些人?
-----
* 开发者,如果你想二次开发,看[第一章、开发者指南](/01.md)
* 写书作者,看[第二章、使用教程](/02.md)
* 读者 你就直接点开看。
## nostrbook未来如何发展?
-----
* 可能会增加 blog功能,有些时候你就想随心写点日志,那么用blog功能也可以。
* 点赞互动、留言功能。
-

@ 07f367da:0e76880d
2025-04-03 17:59:21
윤석열 탄핵 선고를 앞둔 4월 3일. 우리 노동조합은 서울 마포구 소재의 한 활동지원기관 앞에서 선전전을 진행했다. 노동조합은 한 활동지원사의 민원을 통해 해당 활동지원기관이 일요일에 일해도 평일 임금을 지급한다는 사실을 파악했다. 활동지원사의 민원에 관심을 가진 한 언론사의 기자는 활동지원기관과 구청, 서울시, 노조에 문의하며 팩트체크를 진행하고 있는데, 이 과정에서 노조는 해당 기관이 일요일에 일을 해도 평일 임금을 지급하고 있다는 사실을 명확히 확인했다.
자신이 받는 임금에 대한 사실관계를 노동자들은 잘 알지 못한다. 활동지원사는 기관에 자신의 임금에 대해 문의해도 속 시원한 답을 듣지 못한다. 활동지원사들이 하나같이 하는 이야기가 기관에 물어봐도 제대로 설명을 해주지 않는다는 하소연이다.
당사자 활동지원사는 노조에 민원을 제기하고, 또 기자가 취재한 내용들을 통해서야 자신의 임금이 자신도 모르게 어떻게 변화했는지를 알아가고 있다. 사업장의 임급지급 행위에 대한 가치판단이나 평가 이전에 노동자들은 그 사실 자체를 모를 가능성이 높다. 노조는 이 사실을 활동지원사들에게 알리려 선전전을 진행하기로 했다.
선전전 진행 중 정말 충격적인 경험을 했다. 노동조합의 선전활동은 정당한 노조활동이고 일상적인 활동이다. 여태 여러 사업장에서 선전활동을 했지만, 이런 경우는 정말 처음이었다. 사업장들은 신경 거슬러 하고 적대적인 대우를 하곤 했지만, 가장 강한 대처가 경찰에 신고하여 공권력의 개입을 요청하고, 경찰은 충돌을 방지하는 선에서 대처한다. 그런데 오늘은 장애인 기관장이 선전활동을 하지 말라고 계속 항의하며 방해하더니 소속 활동지원팀 인력은 노동조합이 활동지원사에게 선전물을 전달하려 하니 몸으로 막기까지 한다.
무엇을 그렇게 숨기고 싶을까? 노동조합의 활동을 몸으로 막으면서까지 싫어할 이유가 무엇일까? 노동조합의 활동이 그들에게 무엇으로 다가갔을까? 여러 질문이 든다.
충격적인 것은 이 기관의 대표가 우리노조가 예전에 청와대 앞에서 기자회견 할 때 연대 발언을 하러 왔던 활동가라는 점이다. 장애인 당사자이자 인권운동 활동가가 사용자로, 그리고 사회복지사 노동자들이 전담인력으로 고용되어 사측을 대신해 활동지원사 노동자들이 응당 자신에 대해 알아야 할 사항을 은폐한다.
사장이 되어 권력을 행사하면서도 장애인이라는 정체성으로 자신의 지위를 지우려 하고, 전담인력이라는 지위로 노동자들을 지휘하면서도 같은 노동자라며 위계를 삭제한다. 그리고 정작 현장에서 장애인에게 활동지원을 제공하는 활동지원사들은 대부분 고령의 여성들로 정보약자에 해당한다. 우리에게도 민주주의가 올까. 나는 저들이 활동으로 세상을 좋게 만드는 것을 상쇄할 정도로 더 세상을 나쁘게 만들고 있다고 생각한다.
타인에 의해 돈벌이 수단으로 이용당하는 사람은 자신 또한 타인을 돈벌이 수단으로 활용할 가능성이 높다. 그 타인에는 장애인도 포함된다. 나는 시설사회가 끝나도 장애인학대가 끝나리라는 믿음이 없다. 우리는 어차피 서로를 돈벌이 수단으로만 삼는 사회에서 살고 있기 때문이다.
-

@ 57d1a264:69f1fee1
2025-03-29 18:02:16
> This UX research has been redacted by @iqra from the Bitcoin.Design [community](https://discord.gg/K7aQ5PErht), and shared for review and feedback! Don't be shy, share your thoughts.

- - -
## 1️⃣ Introduction
#### Project Overview
📌 **Product:** BlueWallet (Bitcoin Wallet)
📌 **Goal:** Improve onboarding flow and enhance accessibility for a better user experience.
📌 **Role:** UX Designer
📌 **Tools Used:** Figma, Notion
#### Why This Case Study?
🔹 BlueWallet is a self-custodial Bitcoin wallet, but **users struggle with onboarding due to unclear instructions**.
🔹 **Accessibility issues** (low contrast, small fonts) create **barriers for visually impaired users**.
🔹 Competitors like **Trust Wallet and MetaMask offer better-guided onboarding**.
This case study presents **UX/UI improvements** to make BlueWallet **more intuitive and inclusive**.
- - -
## 2️⃣ Problem Statement: Why BlueWalletʼs Onboarding Needs Improvement
#### 🔹 **Current Challenges:**
1️⃣ **Onboarding Complexity** - BlueWallet lacks **step-by-step guidance**, leaving users confused about wallet creation and security.
 
2️⃣ **No Educational Introduction** - Users land directly on the wallet screen with **no explanation of private keys, recovery phrases, or transactions**.
3️⃣ **Transaction Flow Issues** - Similar-looking **"Send" and "Receive" buttons** cause confusion.
4️⃣ **Poor Accessibility** - Small fonts and low contrast make navigation difficult.
#### 🔍 **Impact on Users:**
**Higher drop-off rates** due to frustration during onboarding.
**Security risks** as users skip key wallet setup steps.
**Limited accessibility** for users with visual impairments.
#### 📌 **Competitive Gap:**
Unlike competitors (Trust Wallet, MetaMask), BlueWallet does not offer:
✅ A guided onboarding process
✅ Security education during setup
✅ Intuitive transaction flow
    
Somehow, this wallet has much better UI than the BlueWallet Bitcoin wallet.
- - -
## 3️⃣ User Research & Competitive Analysis
#### User Testing Findings
🔹 Conducted usability testing with **5 users** onboarding for the first time.
🔹 **Key Findings:**
✅ 3 out of 5 users **felt lost** due to missing explanations.
✅ 60% **had trouble distinguishing transaction buttons**.
✅ 80% **found the text difficult to read** due to low contrast.
#### Competitive Analysis
We compared BlueWallet with top crypto wallets:
| Wallet | Onboarding UX | Security Guidance | Accessibility Features |
|---|---|---|---|
| BlueWallet | ❌ No guided onboarding | ❌ Minimal explanation | ❌ Low contrast, small fonts |
| Trust Wallet | ✅ Step-by-step setup | ✅ Security best practices | ✅ High contrast UI |
| MetaMask | ✅ Interactive tutorial | ✅ Private key education | ✅ Clear transaction buttons |
📌 **Key Insight:** BlueWallet lacks **guided setup and accessibility enhancements**, making it harder for beginners.
## 📌 User Persona
To better understand the users facing onboarding challenges, I developed a **persona** based on research and usability testing.
#### 🔹 Persona 1: Alex Carter (Bitcoin Beginner & Investor)
👤 **Profile:**
- **Age:** 28
- **Occupation:** Freelance Digital Marketer
- **Tech Knowledge:** Moderate - Familiar with online transactions, new to Bitcoin)
- **Pain Points:**
- Finds **Bitcoin wallets confusing**.
- - Doesnʼt understand **seed phrases & security features**.
- - **Worried about losing funds** due to a lack of clarity in transactions.
📌 **Needs:**
✅ A **simple, guided** wallet setup.
✅ **Clear explanations** of security terms (without jargon).
✅ Easy-to-locate **Send/Receive buttons**.
📌 **Persona Usage in Case Study:**
- Helps define **who we are designing for**.
- Guides **design decisions** by focusing on user needs.
#### 🔹 Persona 2: Sarah Mitchell (Accessibility Advocate & Tech Enthusiast)
👤 **Profile:**
- **Age:** 35
- **Occupation:** UX Researcher & Accessibility Consultant
- **Tech Knowledge:** High (Uses Bitcoin but struggles with accessibility barriers)
📌 **Pain Points:**
❌ Struggles with small font sizes & low contrast.
❌ Finds the UI difficult to navigate with a screen reader.
❌ Confused by identical-looking transaction buttons.
📌 **Needs:**
✅ A **high-contrast UI** that meets **WCAG accessibility standards**.
✅ **Larger fonts & scalable UI elements** for better readability.
✅ **Keyboard & screen reader-friendly navigation** for seamless interaction.
📌 **Why This Persona Matters:**
- Represents users with visual impairments who rely on accessible design.
- Ensures the design accommodates inclusive UX principles.
- - -
## 4️⃣ UX/UI Solutions & Design Improvements
#### 📌 Before (Current Issues)
❌ Users land **directly on the wallet screen** with no instructions.
❌ **"Send" & "Receive" buttons look identical** , causing transaction confusion.
❌ **Small fonts & low contrast** reduce readability.
#### ✅ After (Proposed Fixes)
✅ **Step-by-step onboarding** explaining wallet creation, security, and transactions.
✅ **Visually distinct transaction buttons** (color and icon changes).
✅ **WCAG-compliant text contrast & larger fonts** for better readability.
#### 1️⃣ Redesigned Onboarding Flow
✅ Added a **progress indicator** so users see where they are in setup.
✅ Used **plain, non-technical language** to explain wallet creation & security.
✅ Introduced a **"Learn More" button** to educate users on security.
#### 2️⃣ Accessibility Enhancements
✅ Increased **contrast ratio** for better text readability.
✅ Used **larger fonts & scalable UI elements**.
✅ Ensured **screen reader compatibility** (VoiceOver & TalkBack support).
#### 3️⃣ Transaction Flow Optimization
✅ Redesigned **"Send" & "Receive" buttons** for clear distinction.
✅ Added **clearer icons & tooltips** for transaction steps.
## 5️⃣ Wireframes & Design Improvements:
#### 🔹 Welcome Screen (First Screen When User Opens Wallet)
**📌 Goal: Give a brief introduction & set user expectations**
✅ App logo + **short tagline** (e.g., "Secure, Simple, Self-Custody Bitcoin Wallet")
✅ **1-2 line explanation** of what BlueWallet is (e.g., "Your gateway to managing Bitcoin securely.")
✅ **"Get Started" button** → Le ads to **next step: Wallet Setup**
✅ **"Already have a wallet?"** → Import option
🔹 **Example UI Elements:**
- BlueWallet Logo
- **Title:** "Welcome to BlueWallet"
- **Subtitle:** "Easily store, send, and receive Bitcoin."
- CTA: "Get Started" (Primary) | "Import Wallet" (Secondary)

#### 🔹 Screen 2: Choose Wallet Type (New or Import)
**📌 Goal: Let users decide how to proceed**
✅ **Two clear options:**
- **Create a New Wallet** (For first-time users)
- **Import Existing Wallet** (For users with a backup phrase)
✅ Brief explanation of each option
🔹 **Example UI Elements:
- **Title:** "How do you want to start?"
- **Buttons:** "Create New Wallet" | "Import Wallet"

#### 🔹 Screen 3: Security & Seed Phrase Setup (Critical Step)
**📌 Goal: Educate users about wallet security & backups**
✅ Explain **why seed phrases are important**
✅ **Clear step-by-step instructions** on writing down & storing the phrase
✅ **Warning:** "If you lose your recovery phrase, you lose access to your wallet."
✅ **CTA:** "Generate Seed Phrase" → Next step
🔹 **Example UI Elements:
- Title:** "Secure Your Wallet"
- **Subtitle:** "Your seed phrase is the key to your Bitcoin. Keep it safe!"
- **Button:** "Generate Seed Phrase"

## 🔹 Screen 4: Seed Phrase Display & Confirmation
**📌 Goal: Ensure users write down the phrase correctly**
✅ Display **12- or 24-word** seed phrase
✅ **“I have written it downˮ checkbox** before proceeding
✅ Next screen: **Verify seed phrase** (drag & drop, re-enter some words)
🔹 **Example UI Elements:**
- **Title:** "Write Down Your Seed Phrase"
- List of 12/24 Words (Hidden by Default)
- **Checkbox:** "I have safely stored my phrase"
- **Button:** "Continue"

### 🔹 Screen 5: Wallet Ready! (Final Step)
**📌 Goal: Confirm setup & guide users on next actions**
✅ **Success message** ("Your wallet is ready!")
✅ **Encourage first action:**
- “Receive Bitcoinˮ → Show wallet address
- “Send Bitcoinˮ → Walkthrough on making transactions
✅ Short explainer: Where to find the Send/Receive buttons
🔹 **Example UI Elements:**
- **Title:** "You're All Set!"
- **Subtitle:** "Start using BlueWallet now."
- **Buttons:** "Receive Bitcoin" | "View Wallet"

- - -
## 5️⃣ Prototype & User Testing Results
🔹 **Created an interactive prototype in Figma** to test the new experience.
🔹 **User Testing Results:**
✅ **40% faster onboarding completion time.**
✅ **90% of users found transaction buttons clearer.**
🔹 **User Feedback:**
✅ “Now I understand the security steps clearly.ˮ
✅ “The buttons are easier to find and use.ˮ
- - -
## 6️⃣ Why This Matters: Key Takeaways
📌 **Impact of These UX/UI Changes:**
✅ **Reduced user frustration** by providing a step-by-step onboarding guide.
✅ **Improved accessibility** , making the wallet usable for all.
✅ **More intuitive transactions** , reducing errors.
- - -
## 7️⃣ Direct link to figma file and Prototype
Figma file: [https://www.figma.com/design/EPb4gVgAMEgF5GBDdtt81Z/Blue-Wallet-UI-
Improvements?node-id=0-1&t=Y2ni1SfvuQQnoB7s-1](https://www.figma.com/design/EPb4gVgAMEgF5GBDdtt81Z/Blue-Wallet-UI-
Improvements?node-id=0-1&t=Y2ni1SfvuQQnoB7s-1)
Prototype: [https://www.figma.com/proto/EPb4gVgAMEgF5GBDdtt81Z/Blue-Wallet-UI-
Improvements?node-id=1-2&p=f&t=FndTJQNCE7nEIa84-1&scaling=scale-
down&content-scaling=fixed&page-id=0%3A1&starting-point-node-
id=1%3A2&show-proto-sidebar=1](https://www.figma.com/proto/EPb4gVgAMEgF5GBDdtt81Z/Blue-Wallet-UI-
Improvements?node-id=1-2&p=f&t=FndTJQNCE7nEIa84-1&scaling=scale-
down&content-scaling=fixed&page-id=0%3A1&starting-point-node-
id=1%3A2&show-proto-sidebar=1)
Original PDF available from [here](https://cdn.discordapp.com/attachments/903126164795699212/1355561527394173243/faf3ee46-b501-459c-ba0e-bf7e38843bc8_UX_Case_Study__1.pdf?ex=67e9608d&is=67e80f0d&hm=d0c386ce2cfd6e0ebe6bde0a904e884229f52bf547adf1f7bc884e17bb4aa59e&)
originally posted at https://stacker.news/items/928822
-

@ 6389be64:ef439d32
2025-01-13 21:50:59
Bitcoin is more than money, more than an asset, and more than a store of value. Bitcoin is a Prime Mover, an enabler and it ignites imaginations. It certainly fueled an idea in my mind. The idea integrates sensors, computational prowess, actuated machinery, power conversion, and electronic communications to form an autonomous, machined creature roaming forests and harvesting the most widespread and least energy-dense fuel source available. I call it the Forest Walker and it eats wood, and mines Bitcoin.
I know what you're thinking. Why not just put Bitcoin mining rigs where they belong: in a hosted facility sporting electricity from energy-dense fuels like natural gas, climate-controlled with excellent data piping in and out? Why go to all the trouble building a robot that digests wood creating flammable gasses fueling an engine to run a generator powering Bitcoin miners? It's all about synergy.
Bitcoin mining enables the realization of multiple, seemingly unrelated, yet useful activities. Activities considered un-profitable if not for Bitcoin as the Prime Mover. This is much more than simply mining the greatest asset ever conceived by humankind. It’s about the power of synergy, which Bitcoin plays only one of many roles. The synergy created by this system can stabilize forests' fire ecology while generating multiple income streams. That’s the realistic goal here and requires a brief history of American Forest management before continuing.
# Smokey The Bear
In 1944, the Smokey Bear Wildfire Prevention Campaign began in the United States. “Only YOU can prevent forest fires” remains the refrain of the Ad Council’s longest running campaign. The Ad Council is a U.S. non-profit set up by the American Association of Advertising Agencies and the Association of National Advertisers in 1942. It would seem that the U.S. Department of the Interior was concerned about pesky forest fires and wanted them to stop. So, alongside a national policy of extreme fire suppression they enlisted the entire U.S. population to get onboard via the Ad Council and it worked. Forest fires were almost obliterated and everyone was happy, right? Wrong.
Smokey is a fantastically successful bear so forest fires became so few for so long that the fuel load - dead wood - in forests has become very heavy. So heavy that when a fire happens (and they always happen) it destroys everything in its path because the more fuel there is the hotter that fire becomes. Trees, bushes, shrubs, and all other plant life cannot escape destruction (not to mention homes and businesses). The soil microbiology doesn’t escape either as it is burned away even in deeper soils. To add insult to injury, hydrophobic waxy residues condense on the soil surface, forcing water to travel over the ground rather than through it eroding forest soils. Good job, Smokey. Well done, Sir!
Most terrestrial ecologies are “fire ecologies”. Fire is a part of these systems’ fuel load and pest management. Before we pretended to “manage” millions of acres of forest, fires raged over the world, rarely damaging forests. The fuel load was always too light to generate fires hot enough to moonscape mountainsides. Fires simply burned off the minor amounts of fuel accumulated since the fire before. The lighter heat, smoke, and other combustion gasses suppressed pests, keeping them in check and the smoke condensed into a plant growth accelerant called wood vinegar, not a waxy cap on the soil. These fires also cleared out weak undergrowth, cycled minerals, and thinned the forest canopy, allowing sunlight to penetrate to the forest floor. Without a fire’s heat, many pine tree species can’t sow their seed. The heat is required to open the cones (the seed bearing structure) of Spruce, Cypress, Sequoia, Jack Pine, Lodgepole Pine and many more. Without fire forests can’t have babies. The idea was to protect the forests, and it isn't working.
So, in a world of fire, what does an ally look like and what does it do?
# Meet The Forest Walker
For the Forest Walker to work as a mobile, autonomous unit, a solid platform that can carry several hundred pounds is required. It so happens this chassis already exists but shelved.
Introducing the Legged Squad Support System (LS3). A joint project between Boston Dynamics, DARPA, and the United States Marine Corps, the quadrupedal robot is the size of a cow, can carry 400 pounds (180 kg) of equipment, negotiate challenging terrain, and operate for 24 hours before needing to refuel. Yes, it had an engine. Abandoned in 2015, the thing was too noisy for military deployment and maintenance "under fire" is never a high-quality idea. However, we can rebuild it to act as a platform for the Forest Walker; albeit with serious alterations. It would need to be bigger, probably. Carry more weight? Definitely. Maybe replace structural metal with carbon fiber and redesign much as 3D printable parts for more effective maintenance.
The original system has a top operational speed of 8 miles per hour. For our purposes, it only needs to move about as fast as a grazing ruminant. Without the hammering vibrations of galloping into battle, shocks of exploding mortars, and drunken soldiers playing "Wrangler of Steel Machines", time between failures should be much longer and the overall energy consumption much lower. The LS3 is a solid platform to build upon. Now it just needs to be pulled out of the mothballs, and completely refitted with outboard equipment.
# The Small Branch Chipper
When I say “Forest fuel load” I mean the dead, carbon containing litter on the forest floor. Duff (leaves), fine-woody debris (small branches), and coarse woody debris (logs) are the fuel that feeds forest fires. Walk through any forest in the United States today and you will see quite a lot of these materials. Too much, as I have described. Some of these fuel loads can be 8 tons per acre in pine and hardwood forests and up to 16 tons per acre at active logging sites. That’s some big wood and the more that collects, the more combustible danger to the forest it represents. It also provides a technically unlimited fuel supply for the Forest Walker system.
The problem is that this detritus has to be chewed into pieces that are easily ingestible by the system for the gasification process (we’ll get to that step in a minute). What we need is a wood chipper attached to the chassis (the LS3); its “mouth”.
A small wood chipper handling material up to 2.5 - 3.0 inches (6.3 - 7.6 cm) in diameter would eliminate a substantial amount of fuel. There is no reason for Forest Walker to remove fallen trees. It wouldn’t have to in order to make a real difference. It need only identify appropriately sized branches and grab them. Once loaded into the chipper’s intake hopper for further processing, the beast can immediately look for more “food”. This is essentially kindling that would help ignite larger logs. If it’s all consumed by Forest Walker, then it’s not present to promote an aggravated conflagration.
I have glossed over an obvious question: How does Forest Walker see and identify branches and such? LiDaR (Light Detection and Ranging) attached to Forest Walker images the local area and feed those data to onboard computers for processing. Maybe AI plays a role. Maybe simple machine learning can do the trick. One thing is for certain: being able to identify a stick and cause robotic appendages to pick it up is not impossible.
Great! We now have a quadrupedal robot autonomously identifying and “eating” dead branches and other light, combustible materials. Whilst strolling through the forest, depleting future fires of combustibles, Forest Walker has already performed a major function of this system: making the forest safer. It's time to convert this low-density fuel into a high-density fuel Forest Walker can leverage. Enter the gasification process.
# The Gassifier
The gasifier is the heart of the entire system; it’s where low-density fuel becomes the high-density fuel that powers the entire system. Biochar and wood vinegar are process wastes and I’ll discuss why both are powerful soil amendments in a moment, but first, what’s gasification?
Reacting shredded carbonaceous material at high temperatures in a low or no oxygen environment converts the biomass into biochar, wood vinegar, heat, and Synthesis Gas (Syngas). Syngas consists primarily of hydrogen, carbon monoxide, and methane. All of which are extremely useful fuels in a gaseous state. Part of this gas is used to heat the input biomass and keep the reaction temperature constant while the internal combustion engine that drives the generator to produce electrical power consumes the rest.
Critically, this gasification process is “continuous feed”. Forest Walker must intake biomass from the chipper, process it to fuel, and dump the waste (CO2, heat, biochar, and wood vinegar) continuously. It cannot stop. Everything about this system depends upon this continual grazing, digestion, and excretion of wastes just as a ruminal does. And, like a ruminant, all waste products enhance the local environment.
When I first heard of gasification, I didn’t believe that it was real. Running an electric generator from burning wood seemed more akin to “conspiracy fantasy” than science. Not only is gasification real, it’s ancient technology. A man named Dean Clayton first started experiments on gasification in 1699 and in 1901 gasification was used to power a vehicle. By the end of World War II, there were 500,000 Syngas powered vehicles in Germany alone because of fossil fuel rationing during the war. The global gasification market was $480 billion in 2022 and projected to be as much as $700 billion by 2030 (Vantage Market Research). Gasification technology is the best choice to power the Forest Walker because it’s self-contained and we want its waste products.
# Biochar: The Waste
Biochar (AKA agricultural charcoal) is fairly simple: it’s almost pure, solid carbon that resembles charcoal. Its porous nature packs large surface areas into small, 3 dimensional nuggets. Devoid of most other chemistry, like hydrocarbons (methane) and ash (minerals), biochar is extremely lightweight. Do not confuse it with the charcoal you buy for your grill. Biochar doesn’t make good grilling charcoal because it would burn too rapidly as it does not contain the multitude of flammable components that charcoal does. Biochar has several other good use cases. Water filtration, water retention, nutrient retention, providing habitat for microscopic soil organisms, and carbon sequestration are the main ones that we are concerned with here.
Carbon has an amazing ability to adsorb (substances stick to and accumulate on the surface of an object) manifold chemistries. Water, nutrients, and pollutants tightly bind to carbon in this format. So, biochar makes a respectable filter and acts as a “battery” of water and nutrients in soils. Biochar adsorbs and holds on to seven times its weight in water. Soil containing biochar is more drought resilient than soil without it. Adsorbed nutrients, tightly sequestered alongside water, get released only as plants need them. Plants must excrete protons (H+) from their roots to disgorge water or positively charged nutrients from the biochar's surface; it's an active process.
Biochar’s surface area (where adsorption happens) can be 500 square meters per gram or more. That is 10% larger than an official NBA basketball court for every gram of biochar. Biochar’s abundant surface area builds protective habitats for soil microbes like fungi and bacteria and many are critical for the health and productivity of the soil itself.
The “carbon sequestration” component of biochar comes into play where “carbon credits” are concerned. There is a financial market for carbon. Not leveraging that market for revenue is foolish. I am climate agnostic. All I care about is that once solid carbon is inside the soil, it will stay there for thousands of years, imparting drought resiliency, fertility collection, nutrient buffering, and release for that time span. I simply want as much solid carbon in the soil because of the undeniably positive effects it has, regardless of any climactic considerations.
# Wood Vinegar: More Waste
Another by-product of the gasification process is wood vinegar (Pyroligneous acid). If you have ever seen Liquid Smoke in the grocery store, then you have seen wood vinegar. Principally composed of acetic acid, acetone, and methanol wood vinegar also contains ~200 other organic compounds. It would seem intuitive that condensed, liquefied wood smoke would at least be bad for the health of all living things if not downright carcinogenic. The counter intuition wins the day, however. Wood vinegar has been used by humans for a very long time to promote digestion, bowel, and liver health; combat diarrhea and vomiting; calm peptic ulcers and regulate cholesterol levels; and a host of other benefits.
For centuries humans have annually burned off hundreds of thousands of square miles of pasture, grassland, forest, and every other conceivable terrestrial ecosystem. Why is this done? After every burn, one thing becomes obvious: the almost supernatural growth these ecosystems exhibit after the burn. How? Wood vinegar is a component of this growth. Even in open burns, smoke condenses and infiltrates the soil. That is when wood vinegar shows its quality.
This stuff beefs up not only general plant growth but seed germination as well and possesses many other qualities that are beneficial to plants. It’s a pesticide, fungicide, promotes beneficial soil microorganisms, enhances nutrient uptake, and imparts disease resistance. I am barely touching a long list of attributes here, but you want wood vinegar in your soil (alongside biochar because it adsorbs wood vinegar as well).
# The Internal Combustion Engine
Conversion of grazed forage to chemical, then mechanical, and then electrical energy completes the cycle. The ICE (Internal Combustion Engine) converts the gaseous fuel output from the gasifier to mechanical energy, heat, water vapor, and CO2. It’s the mechanical energy of a rotating drive shaft that we want. That rotation drives the electric generator, which is the heartbeat we need to bring this monster to life. Luckily for us, combined internal combustion engine and generator packages are ubiquitous, delivering a defined energy output given a constant fuel input. It’s the simplest part of the system.
The obvious question here is whether the amount of syngas provided by the gasification process will provide enough energy to generate enough electrons to run the entire system or not. While I have no doubt the energy produced will run Forest Walker's main systems the question is really about the electrons left over. Will it be enough to run the Bitcoin mining aspect of the system? Everything is a budget.
# CO2 Production For Growth
Plants are lollipops. No matter if it’s a tree or a bush or a shrubbery, the entire thing is mostly sugar in various formats but mostly long chain carbohydrates like lignin and cellulose. Plants need three things to make sugar: CO2, H2O and light. In a forest, where tree densities can be quite high, CO2 availability becomes a limiting growth factor. It’d be in the forest interests to have more available CO2 providing for various sugar formation providing the organism with food and structure.
An odd thing about tree leaves, the openings that allow gasses like the ever searched for CO2 are on the bottom of the leaf (these are called stomata). Not many stomata are topside. This suggests that trees and bushes have evolved to find gasses like CO2 from below, not above and this further suggests CO2 might be in higher concentrations nearer the soil.
The soil life (bacterial, fungi etc.) is constantly producing enormous amounts of CO2 and it would stay in the soil forever (eventually killing the very soil life that produces it) if not for tidal forces. Water is everywhere and whether in pools, lakes, oceans or distributed in “moist” soils water moves towards to the moon. The water in the soil and also in the water tables below the soil rise toward the surface every day. When the water rises, it expels the accumulated gasses in the soil into the atmosphere and it’s mostly CO2. It’s a good bet on how leaves developed high populations of stomata on the underside of leaves. As the water relaxes (the tide goes out) it sucks oxygenated air back into the soil to continue the functions of soil life respiration. The soil “breathes” albeit slowly.
The gasses produced by the Forest Walker’s internal combustion engine consist primarily of CO2 and H2O. Combusting sugars produce the same gasses that are needed to construct the sugars because the universe is funny like that. The Forest Walker is constantly laying down these critical construction elements right where the trees need them: close to the ground to be gobbled up by the trees.
# The Branch Drones
During the last ice age, giant mammals populated North America - forests and otherwise. Mastodons, woolly mammoths, rhinos, short-faced bears, steppe bison, caribou, musk ox, giant beavers, camels, gigantic ground-dwelling sloths, glyptodons, and dire wolves were everywhere. Many were ten to fifteen feet tall. As they crashed through forests, they would effectively cleave off dead side-branches of trees, halting the spread of a ground-based fire migrating into the tree crown ("laddering") which is a death knell for a forest.
These animals are all extinct now and forests no longer have any manner of pruning services. But, if we build drones fitted with cutting implements like saws and loppers, optical cameras and AI trained to discern dead branches from living ones, these drones could effectively take over pruning services by identifying, cutting, and dropping to the forest floor, dead branches. The dropped branches simply get collected by the Forest Walker as part of its continual mission.
The drones dock on the back of the Forest Walker to recharge their batteries when low. The whole scene would look like a grazing cow with some flies bothering it. This activity breaks the link between a relatively cool ground based fire and the tree crowns and is a vital element in forest fire control.
# The Bitcoin Miner
Mining is one of four monetary incentive models, making this system a possibility for development. The other three are US Dept. of the Interior, township, county, and electrical utility company easement contracts for fuel load management, global carbon credits trading, and data set sales. All the above depends on obvious questions getting answered. I will list some obvious ones, but this is not an engineering document and is not the place for spreadsheets. How much Bitcoin one Forest Walker can mine depends on everything else. What amount of biomass can we process? Will that biomass flow enough Syngas to keep the lights on? Can the chassis support enough mining ASICs and supporting infrastructure? What does that weigh and will it affect field performance? How much power can the AC generator produce?
Other questions that are more philosophical persist. Even if a single Forest Walker can only mine scant amounts of BTC per day, that pales to how much fuel material it can process into biochar. We are talking about millions upon millions of forested acres in need of fuel load management. What can a single Forest Walker do? I am not thinking in singular terms. The Forest Walker must operate as a fleet. What could 50 do? 500?
What is it worth providing a service to the world by managing forest fuel loads? Providing proof of work to the global monetary system? Seeding soil with drought and nutrient resilience by the excretion, over time, of carbon by the ton? What did the last forest fire cost?
# The Mesh Network
What could be better than one bitcoin mining, carbon sequestering, forest fire squelching, soil amending behemoth? Thousands of them, but then they would need to be able to talk to each other to coordinate position, data handling, etc. Fitted with a mesh networking device, like goTenna or Meshtastic LoRa equipment enables each Forest Walker to communicate with each other.
Now we have an interconnected fleet of Forest Walkers relaying data to each other and more importantly, aggregating all of that to the last link in the chain for uplink. Well, at least Bitcoin mining data. Since block data is lightweight, transmission of these data via mesh networking in fairly close quartered environs is more than doable. So, how does data transmit to the Bitcoin Network? How do the Forest Walkers get the previous block data necessary to execute on mining?
# Back To The Chain
Getting Bitcoin block data to and from the network is the last puzzle piece. The standing presumption here is that wherever a Forest Walker fleet is operating, it is NOT within cell tower range. We further presume that the nearest Walmart Wi-Fi is hours away. Enter the Blockstream Satellite or something like it.
A separate, ground-based drone will have two jobs: To stay as close to the nearest Forest Walker as it can and to provide an antennae for either terrestrial or orbital data uplink. Bitcoin-centric data is transmitted to the "uplink drone" via the mesh networked transmitters and then sent on to the uplink and the whole flow goes in the opposite direction as well; many to one and one to many.
We cannot transmit data to the Blockstream satellite, and it will be up to Blockstream and companies like it to provide uplink capabilities in the future and I don't doubt they will. Starlink you say? What’s stopping that company from filtering out block data? Nothing because it’s Starlink’s system and they could decide to censor these data. It seems we may have a problem sending and receiving Bitcoin data in back country environs.
But, then again, the utility of this system in staunching the fuel load that creates forest fires is extremely useful around forested communities and many have fiber, Wi-Fi and cell towers. These communities could be a welcoming ground zero for first deployments of the Forest Walker system by the home and business owners seeking fire repression. In the best way, Bitcoin subsidizes the safety of the communities.
# Sensor Packages
### LiDaR
The benefit of having a Forest Walker fleet strolling through the forest is the never ending opportunity for data gathering. A plethora of deployable sensors gathering hyper-accurate data on everything from temperature to topography is yet another revenue generator. Data is valuable and the Forest Walker could generate data sales to various government entities and private concerns.
LiDaR (Light Detection and Ranging) can map topography, perform biomass assessment, comparative soil erosion analysis, etc. It so happens that the Forest Walker’s ability to “see,” to navigate about its surroundings, is LiDaR driven and since it’s already being used, we can get double duty by harvesting that data for later use. By using a laser to send out light pulses and measuring the time it takes for the reflection of those pulses to return, very detailed data sets incrementally build up. Eventually, as enough data about a certain area becomes available, the data becomes useful and valuable.
Forestry concerns, both private and public, often use LiDaR to build 3D models of tree stands to assess the amount of harvest-able lumber in entire sections of forest. Consulting companies offering these services charge anywhere from several hundred to several thousand dollars per square kilometer for such services. A Forest Walker generating such assessments on the fly while performing its other functions is a multi-disciplinary approach to revenue generation.
### pH, Soil Moisture, and Cation Exchange Sensing
The Forest Walker is quadrupedal, so there are four contact points to the soil. Why not get a pH data point for every step it takes? We can also gather soil moisture data and cation exchange capacities at unheard of densities because of sampling occurring on the fly during commission of the system’s other duties. No one is going to build a machine to do pH testing of vast tracts of forest soils, but that doesn’t make the data collected from such an endeavor valueless. Since the Forest Walker serves many functions at once, a multitude of data products can add to the return on investment component.
### Weather Data
Temperature, humidity, pressure, and even data like evapotranspiration gathered at high densities on broad acre scales have untold value and because the sensors are lightweight and don’t require large power budgets, they come along for the ride at little cost. But, just like the old mantra, “gas, grass, or ass, nobody rides for free”, these sensors provide potential revenue benefits just by them being present.
I’ve touched on just a few data genres here. In fact, the question for universities, governmental bodies, and other institutions becomes, “How much will you pay us to attach your sensor payload to the Forest Walker?”
# Noise Suppression
Only you can prevent Metallica filling the surrounds with 120 dB of sound. Easy enough, just turn the car stereo off. But what of a fleet of 50 Forest Walkers operating in the backcountry or near a township? 500? 5000? Each one has a wood chipper, an internal combustion engine, hydraulic pumps, actuators, and more cooling fans than you can shake a stick at. It’s a walking, screaming fire-breathing dragon operating continuously, day and night, twenty-four hours a day, three hundred sixty-five days a year. The sound will negatively affect all living things and that impacts behaviors. Serious engineering consideration and prowess must deliver a silencing blow to the major issue of noise.
It would be foolish to think that a fleet of Forest Walkers could be silent, but if not a major design consideration, then the entire idea is dead on arrival. Townships would not allow them to operate even if they solved the problem of widespread fuel load and neither would governmental entities, and rightly so. Nothing, not man nor beast, would want to be subjected to an eternal, infernal scream even if it were to end within days as the fleet moved further away after consuming what it could. Noise and heat are the only real pollutants of this system; taking noise seriously from the beginning is paramount.
# Fire Safety
A “fire-breathing dragon” is not the worst description of the Forest Walker. It eats wood, combusts it at very high temperatures and excretes carbon; and it does so in an extremely flammable environment. Bad mix for one Forest Walker, worse for many. One must take extreme pains to ensure that during normal operation, a Forest Walker could fall over, walk through tinder dry brush, or get pounded into the ground by a meteorite from Krypton and it wouldn’t destroy epic swaths of trees and baby deer. I envision an ultimate test of a prototype to include dowsing it in grain alcohol while it’s wrapped up in toilet paper like a pledge at a fraternity party. If it runs for 72 hours and doesn’t set everything on fire, then maybe outside entities won’t be fearful of something that walks around forests with a constant fire in its belly.
# The Wrap
How we think about what can be done with and adjacent to Bitcoin is at least as important as Bitcoin’s economic standing itself. For those who will tell me that this entire idea is without merit, I say, “OK, fine. You can come up with something, too.” What can we plug Bitcoin into that, like a battery, makes something that does not work, work? That’s the lesson I get from this entire exercise. No one was ever going to hire teams of humans to go out and "clean the forest". There's no money in that. The data collection and sales from such an endeavor might provide revenues over the break-even point but investment demands Alpha in this day and age. But, plug Bitcoin into an almost viable system and, voilà! We tip the scales to achieve lift-off.
Let’s face it, we haven’t scratched the surface of Bitcoin’s forcing function on our minds. Not because it’s Bitcoin, but because of what that invention means. The question that pushes me to approach things this way is, “what can we create that one system’s waste is another system’s feedstock?” The Forest Walker system’s only real waste is the conversion of low entropy energy (wood and syngas) into high entropy energy (heat and noise). All other output is beneficial to humanity.
Bitcoin, I believe, is the first product of a new mode of human imagination. An imagination newly forged over the past few millennia of being lied to, stolen from, distracted and otherwise mis-allocated to a black hole of the nonsensical. We are waking up.
What I have presented is not science fiction. Everything I have described here is well within the realm of possibility. The question is one of viability, at least in terms of the detritus of the old world we find ourselves departing from. This system would take a non-trivial amount of time and resources to develop. I think the system would garner extensive long-term contracts from those who have the most to lose from wildfires, the most to gain from hyperaccurate data sets, and, of course, securing the most precious asset in the world. Many may not see it that way, for they seek Alpha and are therefore blind to other possibilities. Others will see only the possibilities; of thinking in a new way, of looking at things differently, and dreaming of what comes next.
-

@ e4950c93:1b99eccd
2025-04-03 14:53:56
**Heureu-x-se d’avoir trouvé une information utile sur ce site ?**
Soutenez le projet en faisant un don pour le faire vivre et remercier les contribut-eur-rice-s.
---
**En bitcoin**
<img src="https://coinos.io/qr/bc1q79er6c5mvvktvmvcstsnelv4j6tv3wdhw2k7ej/raw" width="200" height="200">
bc1qkm8me8l9563wvsl9sklzt4hdcuny3tlejznj7d
⚡️`
origin-nature@coinos.io`
---
**En euros, dollars, ou toute autre monnaie prise en charge**
*Promesses uniquement pour le moment :*
<a href="https://liberapay.com/origin-nature/">
<img src="!(image)[https://liberapay.com/assets/liberapay/icon-v2_black-on-yellow.svg]?etag=._QLQJKsW7OwBQqn7ASPxRA~~" width="200" height="200">
</a>
---
Contactez-nous si vous souhaitez faire un don avec toute autre
cryptomonnaie.
---
### 💡 Un modèle de partage de la valeur
La moitié des dons est redistribuée aux contribut-eur-rice-s qui créent la valeur du site, pour expérimenter un modèle de partage de revenus sur Internet — un modèle qui respecte vos données et ne cherche pas à capter votre attention.
L’autre moitié permet de couvrir les frais de fonctionnement du site.
-

@ fd78c37f:a0ec0833
2025-04-01 11:49:06
In this edition, we invited Keypleb, the founder of Bitcoin Indonesia, to share how he built the Bitcoin community in Indonesia, overcoming challenges like member turnover and venue selection, while driving the adoption and growth of Bitcoin.
**YakiHonne**: Welcome, Keypleb. Before we begin, let me briefly introduce YakiHonne. YakiHonne is a decentralized media client built on Nostr—a protocol designed to empower freedom of speech through technology. It enables creators to own their voices and assets while offering innovative tools like smart widgets, verified notes, and support for long-form content. We focus on free speech and free media by user privacy and data to be protected. So before starting the interview, I'd like to hear about yourself and your community.
**Keypleb**:My name is Keypleb, though it’s a pseudonym—a name I use to respect privacy. I'm a co-founder of Bitcoin Indonesia, Bitcoin House Bali, and Code Orange, a new developer school we launched at a conference just a few days ago. We focus on driving adoption through meetups, hackathons, and technical workshops. I'll dive into more details later, but that's a brief overview. I'm based in Bali now, though I travel a lot and consider myself quite nomadic. Great to be here.
**YakiHonne**: What sparked your interest in Bitcoin and what motivated you to create a community on Bitcoin?
**Keypleb**:I first got interested in Bitcoin because it solved a specific problem. At the time, I didn’t know exactly what the solution was, but the problem was that I couldn’t afford a home. Back in 2019, I was living in London, and a two-bedroom apartment was £600,000, which was insanely expensive. First-time buyers like myself simply couldn’t afford it. Why was it so expensive? Why was buying a house so hard? During the COVID lockdown, I had more time on my hands and started listening to Michael Saylor on a Bitcoin podcast, where he talked about how the system is rigged, and that’s why people work hard but still can’t afford a house. That really resonated with me. So I started looking for a community, but unfortunately, there wasn’t one..
**Keypleb**:After moving to Bali, I attended a lot of crypto meetups, especially scammy altcoin ones, thinking, “There has to be a solution.” But none of them resonated with me. There was no sense of freedom, and no real discussion about inflation resistance. I remembered a podcast from Dea Reskita, an Indonesian host who’s pretty well-known online. I reached out to her and said, “ you’ve got to help me. I’m surrounded by all these shitcoiners, and I can’t take it anymore. I need a real community. Is anything happening?” She replied, “Yes, something is happening. We should restart these meetups next month.” And that’s how it all began.
**Keypleb**:There’s also another story about how we started Bitcoin House and how Bitcoin in Asia came to be, but maybe I’ll save that for later. Anyway, the spark of interest came from Bitcoin solving a real problem, and my drive to keep going came from the lack of quality meetups. Now, we’ve hosted 31 meetups, launched Bitcoin House and Code Orange, and the movement is growing rapidly.

**YakiHonne**: That’s such an amazing story—going from being on the brink of homelessness to creating something so impactful, and keeping it running every day, bringing new people into the journey. It’s truly inspiring. I’m curious about how the community started. How did you manage to attract members and build a strong community? What challenges did you face along the way?
**Keypleb**:It all started with our first meetup at the end of 2022, which was two and a half years ago now. At that time, we sent out an email to a group from a previous database, and the first meetup had around 20 people, which was a good start. However, problems quickly arose as people started dropping off, and the community lacked retention. In Bali, people come and go, usually staying for no more than two months, leading to a lack of long-term participation. This became one of our challenges: how to attract more people and, more importantly, get the same people to keep coming back. While I've been coming back for two and a half years, not everyone is able to return as often, and that has been a real challenge.
**Keypleb**:Actually, I should also mention how I met my co-founders—Marius, Diana, and Dimas. We met at the 2023 Indonesia Bitcoin Conference. As time went on, we kept hosting meetups and had a lot of fun each time, though the locations kept changing. One of the initial challenges was that we didn't realize the importance of having a fixed meetup location. We changed venues several times before we realized that having a consistent location is crucial. If anyone wants to run a meetup, it's best to always choose a fixed location. We learned this through trial and error, but now it's no longer an issue.
**Keypleb**:Since the conference, my co-founders and I have been working together, consistently putting in the effort. This is why our community has grown so large—so far, we are hosting 31 monthly meetups, 6 of which are in Bali. This means there is a bitcoin meetup almost every day on a regular basis. We've also established Bitcoin House Bali, a physical space, and the movement is growing rapidly. Without this movement, the region would face many challenges, including inflation and heavy censorship. It all started from just one meetup.

**YakiHonne**: It's amazing to see how you met your co-founders and how you’ve built something incredible that continues to grow today. What advice would you give to someone looking to start a successful Bitcoin community right now?
**Keypleb**:First, one very important piece of advice is to ensure that every meetup is held at the same location regularly. We realized this challenge through trial and error. To help others who are interested, we’ve published our meetup guide on GitHub, where everyone can check it out. For example, meetups should be held regularly, ideally once a month, or even once a week. In Chiang Mai, the Bitcoin meetup starts every Thursday at 7 PM, and everyone knows the time and location, making it easy to join without having to look up the next meetup.
**Keypleb**:Additionally, our meetup structure is very simple. First, we do a round of introductions where everyone shares their name, where they’re from, and what Bitcoin means to them. This usually takes about 15 minutes. Then, we discuss three main questions: First, why do we need Bitcoin? The discussion typically focuses on two main issues Bitcoin addresses: inflation and censorship;Secondly, how to buy Bitcoin? We usually ask who wants to buy some Bitcoin, and then we do a small purchase together and conduct a P2P trade to demonstrate how easy it is to buy Bitcoin. Lastly, how to store Bitcoin? We introduce self-custody and show how to use hardware wallets (like Trezor), explaining the concept of the 12 words and private keys.
**Keypleb**:The whole meetup usually wraps up in about an hour, after which people can continue socializing at Bitcoin House or wherever the meetup is taking place. In short, keeping the meetup simple and efficient, and ensuring a fixed location for each event, are key factors in building a successful community.
**YakiHonne**: What's the major approach? Is it more technical, or do you focus on non-technical aspects, or do you cover both?
**Keypleb**:Our approach includes both technical and non-technical content. Initially, our meetups were completely non-technical, just casual gatherings for people to socialize. Over time, however, we've evolved to incorporate more technical content.
**Keypleb**:Out of the 31 monthly regular meetups we host, most of them have been non-technical, simply regular gatherings held at the same time and place according to our meetup guide. For example, we host the “Bitcoin for Beginners” meetup, which is designed for newcomers and takes place every second Friday of the month at 5 PM at the Bitcoin House Bali. This is entirely non-technical. Additionally, every Wednesday at Bitcoin House, we host the “My First Bitcoin” course. While the course touches on some technical aspects, such as seed phrases and backups, it’s still beginner-friendly and not too technical. The course runs for 10 weeks, and we plan to offer it in the local language at Bali University to help the local community better understand Bitcoin.
**Keypleb**:On the other hand, we also offer highly technical content. We launched a new program called “Code Orange,” which is specifically designed for developers and programmers. We use the “Decoding Bitcoin” website, created by Jamal, which is a learning platform for developers. Many developer schools, like Code Orange, use this resource. Additionally, we host “Code Orange” meetups where we dive into the technical aspects of Bitcoin, such as how mining works and how to prevent single points of failure.
**Keypleb**:We also organize technical workshops, such as “How to Defend Against a Five-Dollar Wrench Attack,” which is closely related to security. Recently, there have been some kidnapping incidents in Bali, and many people are concerned about their Bitcoin being stolen. To address this, we plan to hold a workshop on how to protect Bitcoin against such attacks. Additionally, we host hackathons and other high-tech events, and we just completed a very successful beginner-level hackathon.
**Keypleb**:In summary, our community caters to everyone, from beginners to technical experts. For beginners, we offer easy-to-understand, non-technical content, while for experienced Bitcoiners, we provide in-depth technical material.

**YakiHonne**: It's great to approach it in both ways, so everyone gets their own "piece of the cake."Now, I'd like to dive into the technical side. What advice would you give to technically inclined individuals or organizations looking to contribute to the Bitcoin ecosystem? How should they approach the technical aspects of Bitcoin if they want to get involved?
**Keypleb**:I have some additional advice. First, technical individuals can sign up for the “Decoding Bitcoin” course that starts on 18th March 2025 or join our “Code Orange” program and participate in the end-of-year hackathon. If they are technically proficient, this will be a great opportunity. “Decoding Bitcoin” is great for beginners, but it’s also useful for technical individuals. If someone is very skilled, they can start contributing code right away. If they find the course too easy, they can skip it and dive directly into more advanced projects. Additionally, Bitshala and Chaincode Labs offer advanced courses, which more technically advanced individuals can choose to pursue.

**Keypleb**:Additionally, it's worth mentioning that the Bitcoin Dev Project has a great platform where technical individuals can find “Good First Issue” or open-source projects to start contributing code. You'll learn about the philosophy behind Bitcoin and why it's more meaningful than other “shitcoins.” Once you’ve taken enough “orange pills” (the philosophy and technology of Bitcoin), you can dive deeper into Bitcoin core development and potentially start coding in C++. If you're interested, you can join specific projects like Nostr, Fedimint or E-Cash.
**YakiHonne**: I’d like to move on to the next question: How do you see Bitcoin communities evolving as technology progresses, particularly in areas like scalability, privacy, and adaptability to other systems?
Keypleb:I believe the Bitcoin community will continue to evolve, and it has already made incredible progress. Two and a half years ago, we started alone in Bali, with just ourselves. We began in the official phase and have had numerous conversations throughout the year. For example, we are now starting a Bitcoin club at a university in Bali; we just need to find a passionate, driven “Bitcoin maximalist,” and the Bitcoin club will begin. Like what our friends did in Banyuwangi, Indonesia, these clubs could eventually evolve into Bitcoin houses.
**Keypleb**:Regarding privacy and scalability, the community is making strides. We’re big fans of Fedi, which builds on top of the Fedimint protocol and uses e-cash to scale Bitcoin while improving privacy. Fedi low fees and high privacy potential give Bitcoin great opportunities in this area.
**Keypleb**:As for Bitcoin's compatibility with fiat systems, although Bitcoin payments are illegal in some countries like Indonesia, smart developers across Southeast Asia are working on legal solutions. For example, there's a website called Pleb QR that works in Thailand, allowing you to pay in fiat via the Lightning Network. Koral is another app specifically for Indonesia. These kinds of testing products already exist and are physically possible, but we’re just waiting on regulations. My influential friends are actively lobbying the government for adoption.
**Keypleb**:In summary, privacy, scalability, and compatibility with fiat systems are all works in progress, and they will continue to evolve positively. There will be more meetups, more wallet downloads, and more adoption—there’s no doubt about that.
**YakiHonne**: You mentioned the concept of cross-country issues, so I have one last question: How is the government’s stance on Bitcoin? Is the political climate supportive or against Bitcoin? How do you see the government's approach to Bitcoin in your community or environment?
**Keypleb**:This reminds me of a person, Jeff Booth, who once said, “We are them, the government is made up of us.” In Indonesia, many politicians actually support Bitcoin, and many of them mine Bitcoin themselves. When money is involved, the incentive is strong, and politicians naturally like to make more money. As a result, Indonesia has a large Bitcoin mining scene. However, overall, the Indonesian government is against Bitcoin, as seen in their ban on Bitcoin payments. The 2011 currency law states that any currency other than the Indonesian Rupiah (IDR) cannot be used, and violators can face up to one year in prison or a fine. This means you cannot pay with US dollars, lira, euros, pesos or pounds.
**Keypleb**:This shows that the government’s legal system is somewhat fragile. It’s understandable that the government is concerned about disruptive technologies like Bitcoin, especially with such a fragile fiat system. Indonesia has also seen many arrests. In 2016, Bank Indonesia issued a letter announcing a crackdown on cryptocurrency payments. Those involved in paying in Bitcoin had their funds seized, and the police cooperated in shutting down businesses accepting Bitcoin payments in the cities. While this isn't very friendly, it does highlight the fragility of the existing system. We also believe that a new executive order may be introduced in the future, similar to when President Roosevelt in 1933 ordered Americans to hand over all their gold with his Executive Order 6102. If it happened before, it could happen again.
**Keypleb**:Therefore, we predict that Bitcoin custody could become a legal issue, which is one of the reasons we blur the faces of participants at every meetup. We need to protect the community from any potential risks. But overall, we remain optimistic. Despite the government ban, the ideology of Bitcoin is unstoppable, and its spread cannot be stopped. So, we are very optimistic about the future.
**YakiHonne**: I think almost every government around the world, even in Africa, faces similar issues with Bitcoin. Some governments might want Bitcoin but hesitate to openly accept it due to the fear of it undermining the traditional financial system, which, of course, could eventually happen. But hopefully, as the new generation comes into power, we'll see more Bitcoin-friendly governments. So, thank you so much for sharing your insights and advice. I really appreciate your time and the valuable input you've provided.
**Keypleb**:I'm really glad this conversation enlightened me. I enjoyed it a lot, and it made me reflect on how much work we're doing and how valuable it is. There are a lot of problems out there, with censorship being the biggest one, followed by inflation, which is also a major issue depending on the region. But Bitcoin is open, the community is growing, and people are fighting against censorship and internet shutdowns in places like Indonesia and beyond. The movement is definitely growing. So, I'm very happy to be here and have this chat. Thanks again.
Bitcoin Indonesia nostr:
nostr:npub1y4qd2zhtn05gnsaaq5xfejzfk4a32638tx6gpp9g8k6e42g9d66qaxhcr3
Keypleb nostr:
nostr:npub190trvg63e6tyqlwlj6lccqpftx76lckj25c006vwx3dzvdl88yxs2nyqdx
-

@ fd06f542:8d6d54cd
2025-03-31 01:55:18
## 什么是nostrbook?
-----
nostrbook 是基于nostr 社区技术存储在 nostr relay server上的长文(30023)文章。
查看浏览,采用的是 [docsify](https://docsify.js.org/#/) 技术。整个网站技术无须部署服务器占用太多的存储空间。
可以实现轻量级部署。
-

@ fd06f542:8d6d54cd
2025-03-31 01:45:36
{"coverurl":"https://cdn.nostrcheck.me/fd06f542bc6c06a39881810de917e6c5d277dfb51689a568ad7b7a548d6d54cd/232dd9c092e023beecb5410052bd48add702765258dcc66f176a56f02b09cf6a.webp","title":"NostrBook站点日记","author":"nostrbook"}
-

@ fd06f542:8d6d54cd
2025-03-30 02:16:24
> __Warning__ `unrecommended`: deprecated in favor of [NIP-17](17.md)
NIP-04
======
Encrypted Direct Message
------------------------
`final` `unrecommended` `optional`
A special event with kind `4`, meaning "encrypted direct message". It is supposed to have the following attributes:
**`content`** MUST be equal to the base64-encoded, aes-256-cbc encrypted string of anything a user wants to write, encrypted using a shared cipher generated by combining the recipient's public-key with the sender's private-key; this appended by the base64-encoded initialization vector as if it was a querystring parameter named "iv". The format is the following: `"content": "<encrypted_text>?iv=<initialization_vector>"`.
**`tags`** MUST contain an entry identifying the receiver of the message (such that relays may naturally forward this event to them), in the form `["p", "<pubkey, as a hex string>"]`.
**`tags`** MAY contain an entry identifying the previous message in a conversation or a message we are explicitly replying to (such that contextual, more organized conversations may happen), in the form `["e", "<event_id>"]`.
**Note**: By default in the [libsecp256k1](https://github.com/bitcoin-core/secp256k1) ECDH implementation, the secret is the SHA256 hash of the shared point (both X and Y coordinates). In Nostr, only the X coordinate of the shared point is used as the secret and it is NOT hashed. If using libsecp256k1, a custom function that copies the X coordinate must be passed as the `hashfp` argument in `secp256k1_ecdh`. See [here](https://github.com/bitcoin-core/secp256k1/blob/master/src/modules/ecdh/main_impl.h#L29).
Code sample for generating such an event in JavaScript:
```js
import crypto from 'crypto'
import * as secp from '@noble/secp256k1'
let sharedPoint = secp.getSharedSecret(ourPrivateKey, '02' + theirPublicKey)
let sharedX = sharedPoint.slice(1, 33)
let iv = crypto.randomFillSync(new Uint8Array(16))
var cipher = crypto.createCipheriv(
'aes-256-cbc',
Buffer.from(sharedX),
iv
)
let encryptedMessage = cipher.update(text, 'utf8', 'base64')
encryptedMessage += cipher.final('base64')
let ivBase64 = Buffer.from(iv.buffer).toString('base64')
let event = {
pubkey: ourPubKey,
created_at: Math.floor(Date.now() / 1000),
kind: 4,
tags: [['p', theirPublicKey]],
content: encryptedMessage + '?iv=' + ivBase64
}
```
## Security Warning
This standard does not go anywhere near what is considered the state-of-the-art in encrypted communication between peers, and it leaks metadata in the events, therefore it must not be used for anything you really need to keep secret, and only with relays that use `AUTH` to restrict who can fetch your `kind:4` events.
## Client Implementation Warning
Clients *should not* search and replace public key or note references from the `.content`. If processed like a regular text note (where `@npub...` is replaced with `#[0]` with a `["p", "..."]` tag) the tags are leaked and the mentioned user will receive the message in their inbox.
-

@ 57d1a264:69f1fee1
2025-03-29 17:15:17

- Once activated, "Accept From Any Mint” is the default setting. This is the easiest way to get started, let's the user start acceptance Cashu ecash just out of the box.
- If someone does want to be selective, they can choose “Accept From Trusted Mints,” and that brings up a field where they can add specific mint URLs they trust.
- “Find a Mint” section on the right with a button links directly to bitcoinmints.com, already filtered for Cashu mints, so users can easily browse options.
- Mint info modal shows mint technical details stuff from the NUT06 spec. Since this is geared towards the more technical users I left the field names and NUT number as-is instead of trying to make it more semantic.
originally posted at https://stacker.news/items/928800
-

@ b2caa9b3:9eab0fb5
2025-04-01 20:29:01

For years, I’ve been shifting my life away from traditional systems and toward Bitcoin. I calculate my expenses in sats, buy airtime and online data with BTC, and continue exploring new ways to integrate Bitcoin into my daily life. While I’m not yet fully living on Bitcoin, I am getting closer with each step.

Since discovering Nostr, my perspective on decentralization has deepened. More than just a financial shift, it's a complete lifestyle transformation. Years ago, after facing injustice in my home country, I took the first step toward a new way of living. That decision led me to where I am today—a minimalist, a nomad, and a believer in financial freedom through Bitcoin.

I once served in the military, owned a house, and drove a nice car. My life looked very different back then. But over time, I realized that true freedom wasn’t in possessions—it was in mobility, independence, and the ability to control my own finances. Now, all I own fits into a backpack weighing less than 12 kg. My lifestyle is simple, yet rich in experiences.
March 14 marks eight years since I embraced my nomadic lifestyle. What started as a leap into the unknown has become my way of life. Living with less has given me more—the freedom to move, to explore, and to be truly independent. The more I immerse myself in the Bitcoin ecosystem, the more I see its potential to reshape not only my life but the world around me.

The journey isn’t over. In fact, it’s just beginning. Let’s see where this path leads as I go further into the blockchain revolution!



-

@ 5ffb8e1b:255b6735
2025-03-29 13:57:02
As a fellow Nostrich you might have noticed some of my #arlist posts. It is my effort to curate artists that are active on Nostr and make it easier for other users to find content that they are interested in.
By now I have posted six or seven posts mentioning close to fifty artists, the problem so far is that it's only a list of handles and it is up to reader to click on each in order to find out what are the artist behind the names all about. Now I am going to start creating blog posts with a few artists mentioned in each, with short descriptions of their work and an image or to.
I would love to have some more automated mode of curation but I still couldn't figure out what is a good way for it. I've looked at Listr, Primal custom feeds and Yakihonne curations but none seem to enable me to make a list of npubs that is then turned into a feed that I could publicly share for others to views.
Any advice on how to achieve this is VERY welcome !
And now lets get to the first batch of artists I want to share with you.
### Eugene Gorbachenko ###
nostr:npub1082uhnrnxu7v0gesfl78uzj3r89a8ds2gj3dvuvjnw5qlz4a7udqwrqdnd
Artist from Ukrain creating amazing realistic watercolor paintings.
He is very active on Nostr but is very unnoticed for some stange reason. Make sure to repost the painting that you liked the most to help other Nostr users to discover his great art.
![!(image)[https://m.primal.net/PxJc.png]]()
### Siritravelsketch ###
nostr:npub14lqzjhfvdc9psgxzznq8xys8pfq8p4fqsvtr6llyzraq90u9m8fqevhssu
a a lovely lady from Thailand making architecture from all around the world spring alive in her ink skethes. Dynamic lines gives it a dreamy magical feel, sometimes supported by soft watercolor strokes takes you to a ferytale layer of reality.
![!(image)[https://m.primal.net/PxJj.png]]()
### BureuGewas ###
nostr:npub1k78qzy2s9ap4klshnu9tcmmcnr3msvvaeza94epsgptr7jce6p9sa2ggp4
a a master of the clasic oil painting. From traditional still life to modern day subjects his paintings makes you feel the textures and light of the scene more intense then reality itself.
![!(image)[https://m.primal.net/PxKS.png]]()
You can see that I'm no art critic, but I am trying my best. If anyone else is interested to join me in this curration adventure feel free to reach out !
With love, Agi Choote
-

@ 220522c2:61e18cb4
2025-03-25 16:05:27
`draft` `optional`
## Abstract
This NIP defines a new event kind for sharing and storing code snippets. Unlike regular text notes (`kind:1`), code snippets have specialized metadata like language, extension, and other code-specific attributes that enhance discoverability, syntax highlighting, and improved user experience.
## Event Kind
This NIP defines `kind:1337` as a code snippet event.
The `.content` field contains the actual code snippet text.
## Optional Tags
- `filename` - Filename of the code snippet
- `l` - Programming language name (lowercase). Examples: "javascript", "python", "rust"
- `extension` - File extension (without the dot). Examples: "js", "py", "rs"
- `description` - Brief description of what the code does
- `runtime` - Runtime or environment specification (e.g., "node v18.15.0", "python 3.11")
- `license` - License under which the code is shared (e.g., "MIT", "GPL-3.0", "Apache-2.0")
- `dep` - Dependency required for the code to run (can be repeated)
- `repo` - Reference to a repository where this code originates
## Format
```json
{
"id": "<32-bytes lowercase hex-encoded SHA-256 of the the serialized event data>",
"pubkey": "<32-bytes lowercase hex-encoded public key of the event creator>",
"created_at": <Unix timestamp in seconds>,
"kind": 1337,
"content": "function helloWorld() {\n console.log('Hello, Nostr!');\n}\n\nhelloWorld();",
"tags": [
["l", "javascript"],
["extension", "js"],
["filename", "hello-world.js"],
["description", "A basic JavaScript function that prints 'Hello, Nostr!' to the console"],
["runtime", "node v18.15.0"],
["license", "MIT"],
["repo", "https://github.com/nostr-protocol/nostr"]
],
"sig": "<64-bytes signature of the id>"
}
```
## Client Behavior
Clients that support this NIP SHOULD:
1. Display code snippets with proper syntax highlighting based on the language.
2. Allow copying the full code snippet with a single action.
3. Render the code with appropriate formatting, preserving whitespace and indentation.
4. Display the language and extension prominently.
5. Provide "run" functionality for supported languages when possible.
6. Display the description (if available) as part of the snippet presentation.
Clients MAY provide additional functionality such as:
1. Code editing capabilities
2. Forking/modifying snippets
3. Creating executable environments based on the runtime/dependencies
4. Downloading the snippet as a file using the provided extension
5. Sharing the snippet with attribution
## References
- [PR](https://github.com/nostr-protocol/nips/pull/1852)
- posted w/ [comet](https://comet.md)
- [notebin](https://notebin.io)
- [snipsnip](https://snipsnip.dev)
#nip #grownostr
-

@ 4c96d763:80c3ee30
2025-03-24 01:43:12
# Changes
## Ahmed Bedair (2):
- Fix build.rs to link Security framework only for Apple targets
- switch from string matching to checking the CARGO_CFG_TARGET_VENDOR value instead
## Jack Chakany (1):
- update thiserror from 2.0.3 to 2.0.7
## Ken Sedgwick (5):
- drive-by warning cleanup
- added multiple event unit tests
- add (passing) unit test for Mention::Profile relays
- drive-by clippy fixes
- add relays_iter to bech32_{nprofile,nevent,naddr}
## William Casarin (32):
- async: adding efficient, poll-based stream support
- Release v0.5.0
- add get_profilekey_by_pubkey
- nostrdb: fix subscription memory leaks
- test: "fix" flaky text
- release v0.5.1
- expose {Mut,}FilterField
- unsubscribe from SubscriptionStreams on Drop
- debug log subcount
- bump nostrdb to fix since in kind queries
- expose process_client_event
- stream: fix polling issues leading to missed events
- tags: add porcelain api for getting ids and strings
- nostrdb: update to silence annoying debug logs
- build: minor makefile changes
- update posix bindings
- filter: add nip50 search field
- windows: update bindings for search features
- filter: add json display
- Revert "filter: add json display"
- filter: fix memory leak in clone
- unix: fix bindgen for writer scratch changes
- win: bindgen for windows
- fix lint
- feat: add relay index and ingestion metadata
- Release v0.6.0
- misc stuff
- fix potential relay index corruption
- v0.6.1
- add author_kinds query plan execution
- filter: expose initial buffer size option
- attempt macos build fix
## Yuki Kishimoto (2):
- Take an iterator of `&str` in `Filter::tags`
- Remove `tracing-subscriber` dep
## kernelkind (1):
- add search_profile
pushed to [nostrdb-rs:refs/heads/master](http://git.jb55.com/nostrdb-rs/commit/0d28fab41e2b829c149086a2449dbda162318abb.html)
-

@ fd06f542:8d6d54cd
2025-03-30 02:11:00
NIP-03
======
OpenTimestamps Attestations for Events
--------------------------------------
`draft` `optional`
This NIP defines an event with `kind:1040` that can contain an [OpenTimestamps](https://opentimestamps.org/) proof for any other event:
```json
{
"kind": 1040
"tags": [
["e", <event-id>, <relay-url>],
["alt", "opentimestamps attestation"]
],
"content": <base64-encoded OTS file data>
}
```
- The OpenTimestamps proof MUST prove the referenced `e` event id as its digest.
- The `content` MUST be the full content of an `.ots` file containing at least one Bitcoin attestation. This file SHOULD contain a **single** Bitcoin attestation (as not more than one valid attestation is necessary and less bytes is better than more) and no reference to "pending" attestations since they are useless in this context.
### Example OpenTimestamps proof verification flow
Using [`nak`](https://github.com/fiatjaf/nak), [`jq`](https://jqlang.github.io/jq/) and [`ots`](https://github.com/fiatjaf/ots):
```bash
~> nak req -i e71c6ea722987debdb60f81f9ea4f604b5ac0664120dd64fb9d23abc4ec7c323 wss://nostr-pub.wellorder.net | jq -r .content | ots verify
> using an esplora server at https://blockstream.info/api
- sequence ending on block 810391 is valid
timestamp validated at block [810391]
```
-

@ a60e79e0:1e0e6813
2025-03-23 16:10:10
**This is a long form note test of a post that lives on my Nostr educational website [Hello Nostr](https://hellonostr.xyz) **
In early 2025, social media is the most common use case for Nostr (and probably the reason you're reading this). Nostr is SO much [more](https://hellonostr.xyz/tags/?tag=other) than just social media,
but that's where the bulk of the activity is, and is what I'm focusing on in this post. Even though the protocol is still so young, that has not prevented an explosion of excellent
[social media](https://hellonostr.xyz/tags/?tag=social) focused clients that predominantly coalesce around the Twitter (X) style feed, containing shorter form content, often with images, and the ability to comment,
like and share.
This first steps guide showcases one of the most polished and simplest examples of such a client, [Primal](https://primal.net). Primal is a cross platform app, that also works on your computer too. The steps that follow are demonstrated on iPhone, but should be identical for Android users. There may be some topics of concepts here that are new to you, to learn more about them, check out our [Nostr 101](https://hellonostr.xyz/101) to learn more about Nostr basics and why it matters.
You can and should explore all of the other options available to you, that's the beauty of Nostr, you're free to choose how and where to interact with your social network. No lock in. No walled gardens. True freedom.

# Getting Started
1. Go to your app store and download Primal to your [Android](https://play.google.com/store/apps/details?id=net.primal.android) or [iPhone](https://apps.apple.com/us/app/primal/id1673134518)
2. Open Primal and choose Create Account. Choose your public display name and add a short bio about yourself.
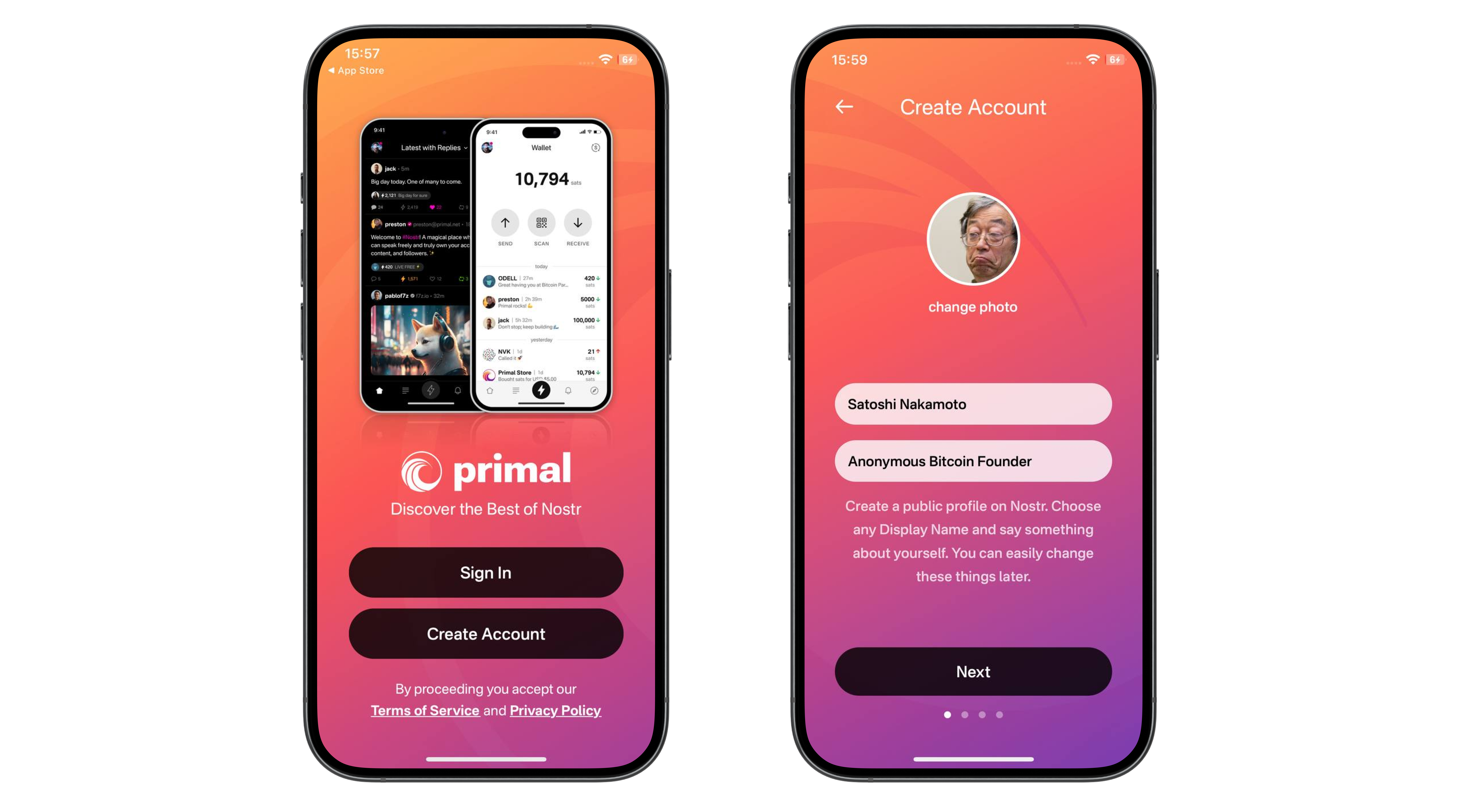
3. Select your chosen interests from the list provided. This will bootstrap your feed and auto-follow a number of accounts so that your feed is not completely empty when starting out.
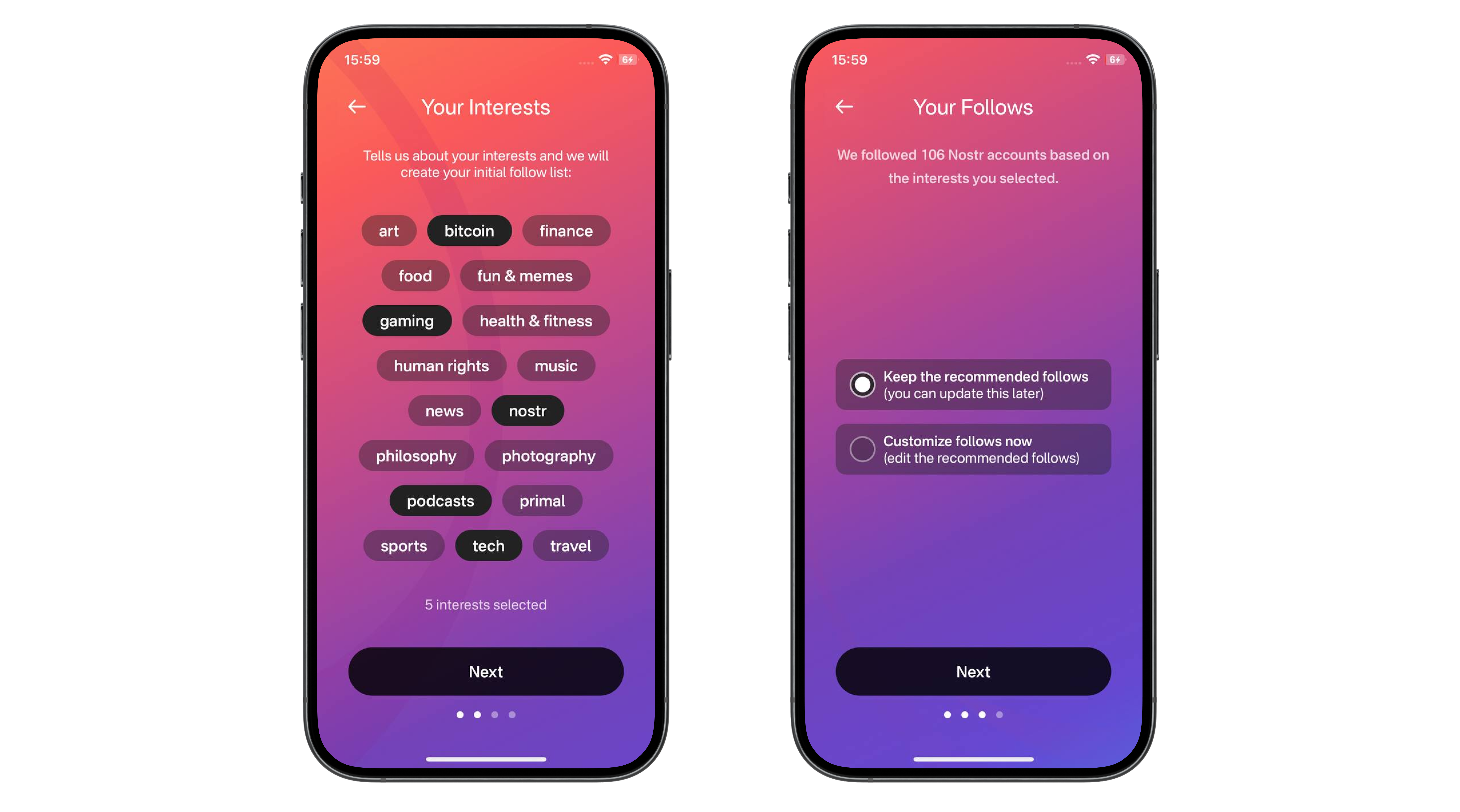
4. Review your account info and tap Create Account Now. Take note of the fact that 'Your Nostr Key is available in your Account Settings'. We'll revisit this shortly.
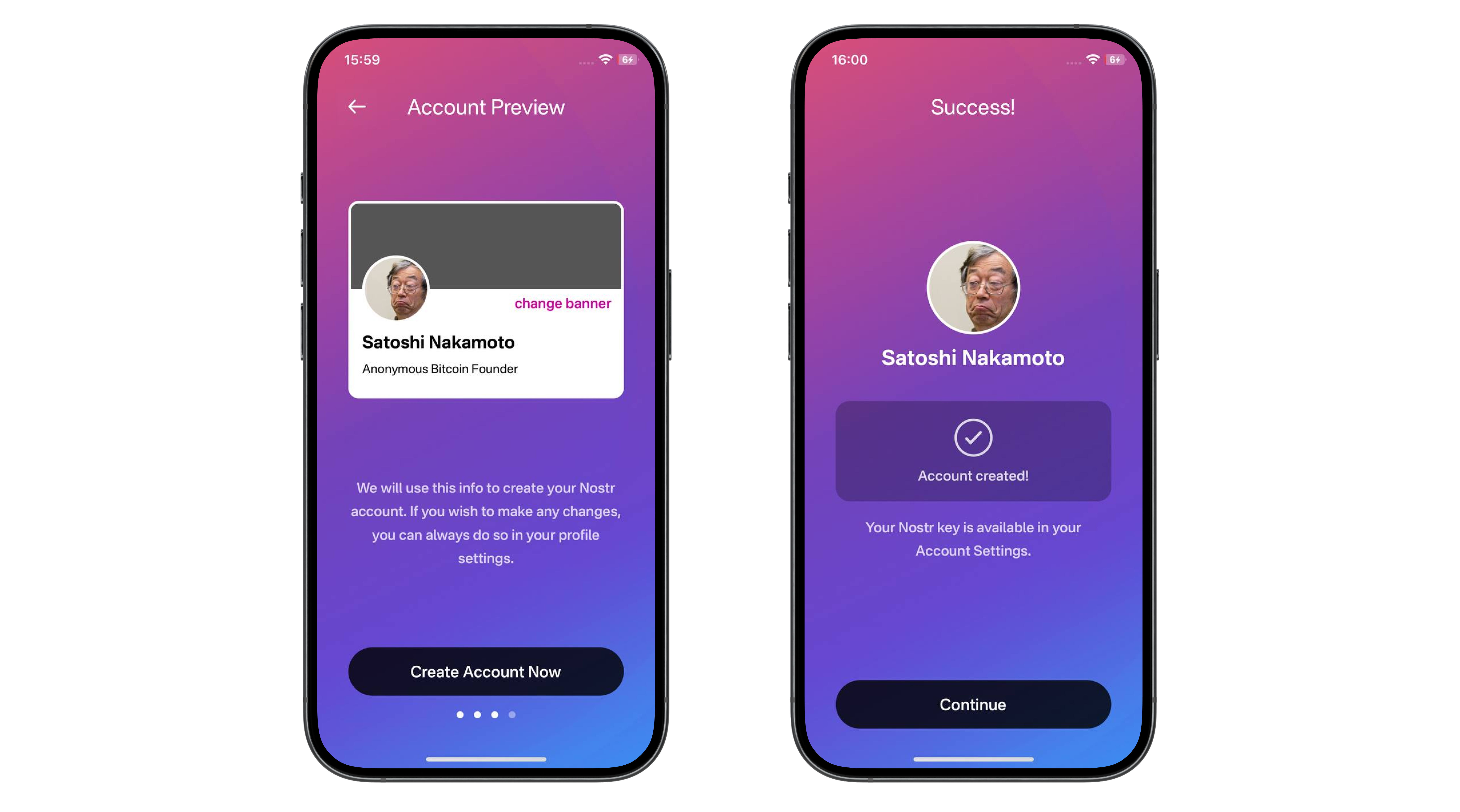
5. Next is an optional step of activating the wallet feature within Primal. Having a wallet within your social client enables you to send and receive value (known as 'Zaps') in the form of Bitcoin. On Facebook and Twitter you can like a post, but it means much more to send someone fractions of a penny (or more if you like) to show your appreciation for their insights. You'll need to provide some personal information to enable the wallet, including an email address.
> Using the internal wallet and purchasing sats with your credit card will tie your Nostr identity to your real ID. Think **very** carefully before carrying out this step. <br/> Learn more in the detailed section at the end of this post.
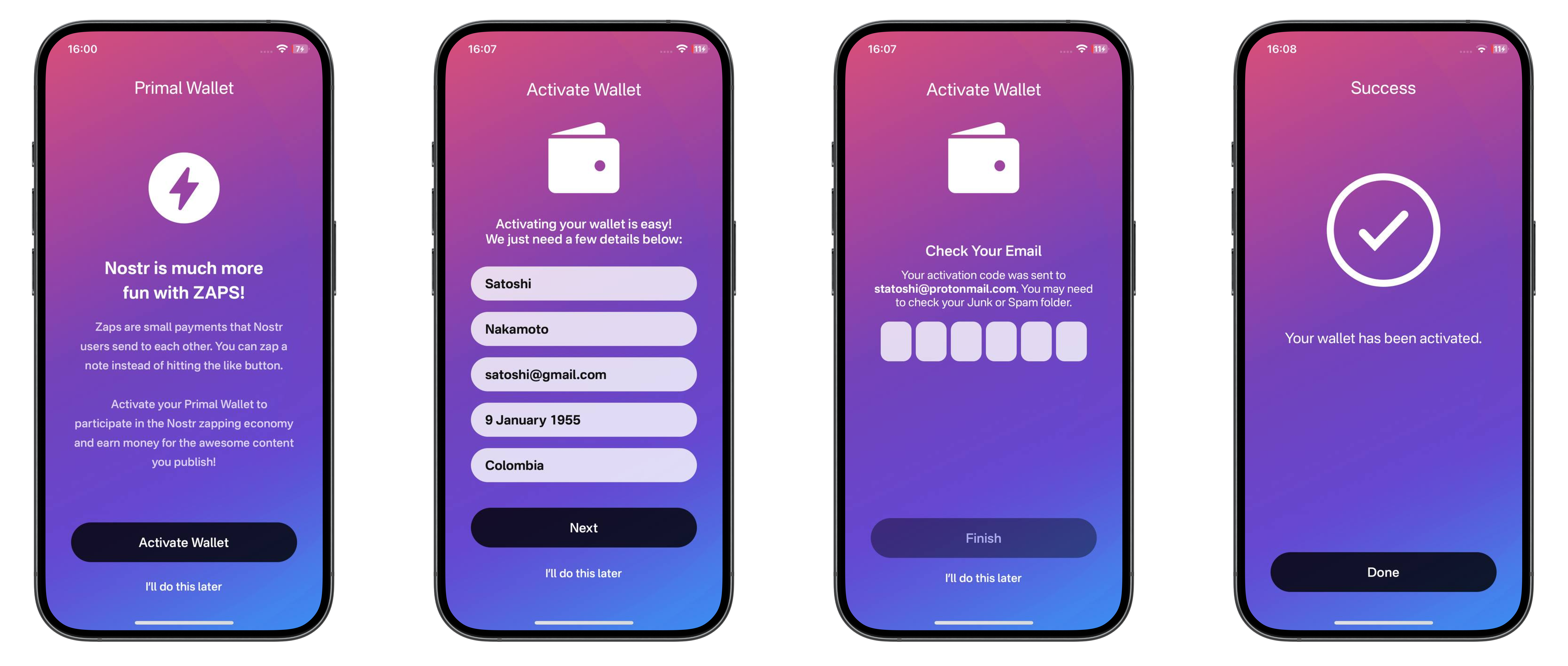
6. That's it, you're now set up and ready to start sharing your thoughts, feelings and memes with the world via a decentralized and censorship resistant social network. To post your first
note and say hello to the Nostr world, tap the + in the bottom right corner.
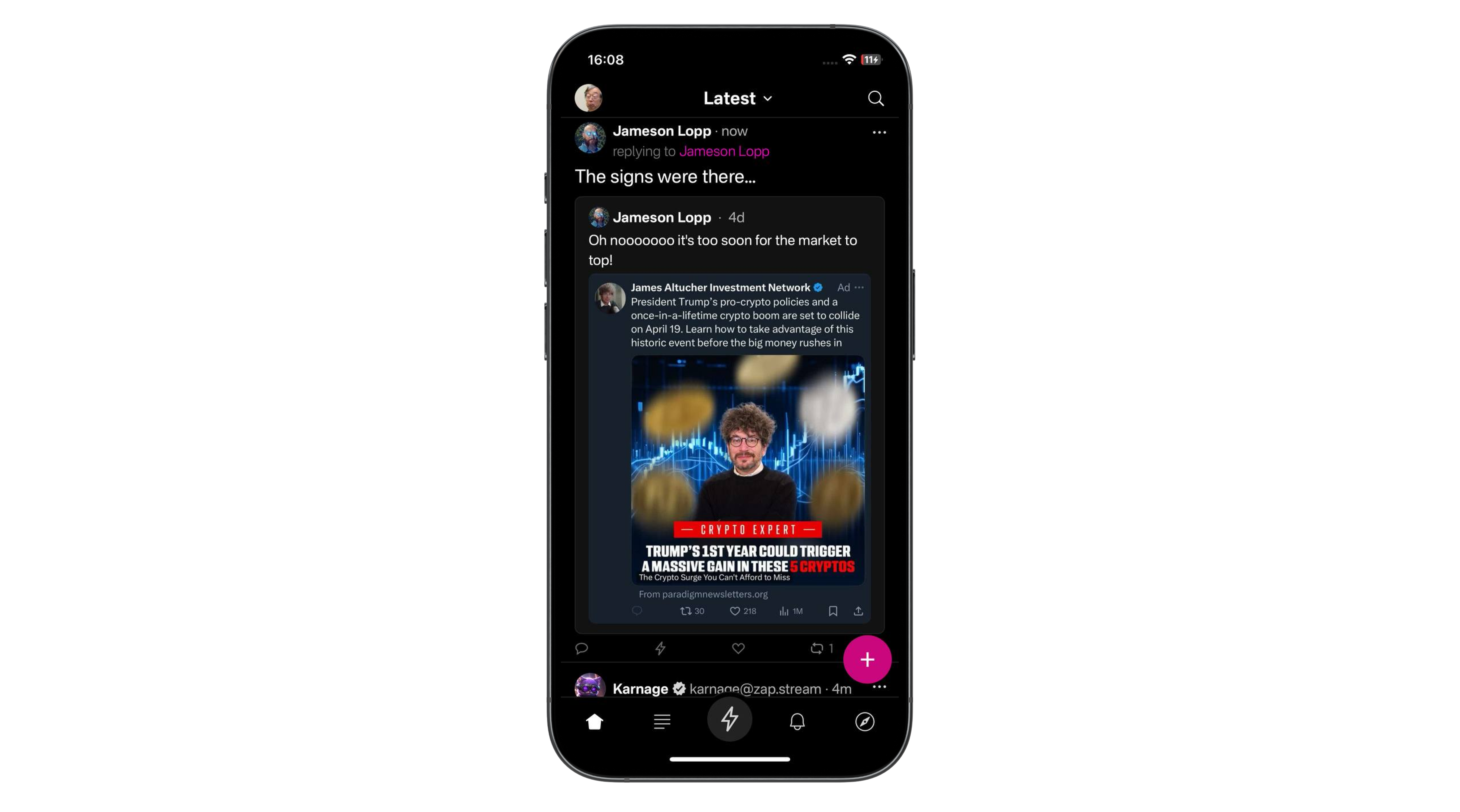
7. If you activated the wallet at step 5, you might want to deposit some Bitcoin in there to allow you to send some value to your friends. There are three main ways to do this:
- Post some awesome content and have people send you value in the form of 'Zaps'
- Send some Bitcoin from a wallet you already have
- Purchase some directly within Primal
The latter is made very simple thanks to the in-app purchase feature, which allows you to purchase a small amount with the card you likely already have connected to your Apple/Google account. All you need to do is tap 'Buy Sats Now'.
8. Next, let's look at the different feeds available on our home screen. Tap 'Latest' at the top of the screen and you can toggle between three different types of home feeds, great for discovering new people and content.
9. Let's assume you already have some friends on Nostr and want to find and follow them. Tap the search icon in the top right corner, the enter the name of the person you want to follow.
Once on their profile, simply tap the 'Follow' button.
10. So you found a friend and want to start interacting with them so they know you made it over to Nostr. Simply find a note you like and choose from the different types of interactions available. From left to right they are:
- **Comment**
- **Zap** (send value from your wallet to theirs)
- **Like**
- **Repost**
- **Bookmark**
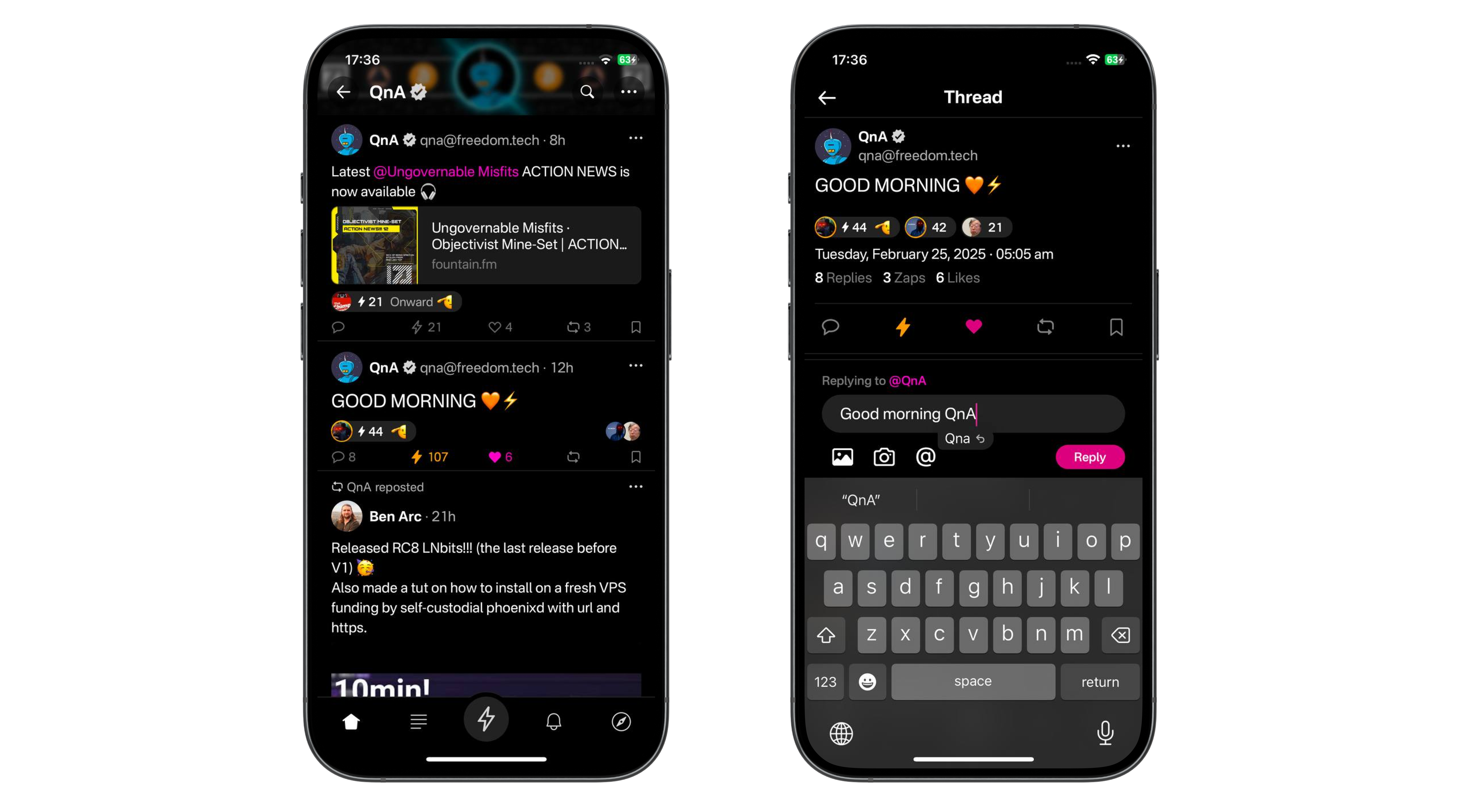
When Zapping, a single tap will send a tiny amount of 42 sats. If you want to send more, or a custom amount, tap and hold the zap button to bring up a selector menu. All default zap amounts are configurable in the app settings page.

11. After you've started posting and interacting with others, you'll likely receive some notifications to tell you. Notifications can be filtered into interaction types.
12. Another great way to find more people to follow and interact with is to use the discover page. To open it, tap the compass in the bottom right corner of the screen. Here you'll
be able to browse different types of pre-built feeds, trending profiles, notes with large zaps and extra topics.
# The Important Part
You might have noticed that throughout that setup, you were not asked for a unique username, nor were you asked for a password. So how the hell is this secure? What happens if you log out? Is your account lost forever?
This is where Nostr really starts to shine. Just like in Bitcoin or other cryptocurrencies, your Nostr account is protected by a 'Private Key'. Anyone with knowledge of the
private key can access your account **in any Nostr client**. No private key, no access. So let's make sure you have a backup copy of it, so you can still recover access to your account in the event you lose your phone!
Tap on your profile image in the top left of the screen. Then tap Settings > Keys. Here you'll see two keys, one public and one private.
Your public key is how people find you on Nostr. It is often referred to by its more technical name 'nPub' which is the prefix if the key itself. Your public key is designed to be exactly that, public!
Your private key is sometimes referred to by its technical name 'nSec' which is also the prefix of the key. Copy your private key and paste it somewhere safe and secure, in a location accessible independently from your phone, and only by you.
If you were to lose your phone, or accidentally delete the Primal app, now all you'd need to do is head back to step 1 above and choose Sign In. You'd then be asked to paste your private key, after which your profile and content would be magically restored.
> Your private key can be imported into any other Nostr social client for the same result.
# Things to Consider
This post has one primary focus - To get you from zero to posting and zapping in the quickest time and with the least friction. To achieve this, there are some trade-offs made that you should be aware of.
### Custodial Wallet
The built in wallet is a custodial one. This means that the funds within are ultimately controlled by the developers behind Primal. They may be good actors, but you should approach the amount of money you maintain inside this wallet accordingly. If your wallet balance ever gets to a balance that makes you uncomfortable, you should send a good chunk of it out to another Bitcoin wallet where you control the keys. I recommend [Phoenix](https://phoenix.acinq.co/) or [Zeus](https://zeusln.com/).
> Those sats are never truly yours until you withdraw them to a self-custodial wallet
### Wallet Privacy
If you choose to top up the wallet using the convenient in-app purchase method, you will tie that small amount of Bitcoin ownership to your Nostr account. If you Nostr account is literally your name, you might not have an issue with this, but often times people like to remain pseudonymous online. If you fall into that category, using your credit card to deposit Bitcoin into your Nostr account is not a good idea.
Android users of Primal can use an advanced technology called Nostr Wallet Connect (NWC) to connect an external Lightning wallet to their Nostr account in Primal. We'll cover this in a subsequent post.
> Your private key allows you to take your profile and social network to any other client
---
If you found this post useful, please share it with your peers and consider following and zapping me on Nostr. If you write to me and let me know that you found me via this post, I'll be sure to Zap you back! ⚡️
-

@ e3ba5e1a:5e433365
2025-01-13 16:47:27
My blog posts and reading material have both been on a decidedly economics-heavy slant recently. The topic today, incentives, squarely falls into the category of economics. However, when I say economics, I’m not talking about “analyzing supply and demand curves.” I’m talking about the true basis of economics: understanding how human beings make decisions in a world of scarcity.
A fair definition of incentive is “a reward or punishment that motivates behavior to achieve a desired outcome.” When most people think about economic incentives, they’re thinking of money. If I offer my son $5 if he washes the dishes, I’m incentivizing certain behavior. We can’t guarantee that he’ll do what I want him to do, but we can agree that the incentive structure itself will guide and ultimately determine what outcome will occur.
The great thing about monetary incentives is how easy they are to talk about and compare. “Would I rather make $5 washing the dishes or $10 cleaning the gutters?” But much of the world is incentivized in non-monetary ways too. For example, using the “punishment” half of the definition above, I might threaten my son with losing Nintendo Switch access if he doesn’t wash the dishes. No money is involved, but I’m still incentivizing behavior.
And there are plenty of incentives beyond our direct control\! My son is *also* incentivized to not wash dishes because it’s boring, or because he has some friends over that he wants to hang out with, or dozens of other things. Ultimately, the conflicting array of different incentive structures placed on him will ultimately determine what actions he chooses to take.
## Why incentives matter
A phrase I see often in discussions—whether they are political, parenting, economic, or business—is “if they could **just** do…” Each time I see that phrase, I cringe a bit internally. Usually, the underlying assumption of the statement is “if people would behave contrary to their incentivized behavior then things would be better.” For example:
* If my kids would just go to bed when I tell them, they wouldn’t be so cranky in the morning.
* If people would just use the recycling bin, we wouldn’t have such a landfill problem.
* If people would just stop being lazy, our team would deliver our project on time.
In all these cases, the speakers are seemingly flummoxed as to why the people in question don’t behave more rationally. The problem is: each group is behaving perfectly rationally.
* The kids have a high time preference, and care more about the joy of staying up now than the crankiness in the morning. Plus, they don’t really suffer the consequences of morning crankiness, their parents do.
* No individual suffers much from their individual contribution to a landfill. If they stopped growing the size of the landfill, it would make an insignificant difference versus the amount of effort they need to engage in to properly recycle.
* If a team doesn’t properly account for the productivity of individuals on a project, each individual receives less harm from their own inaction. Sure, the project may be delayed, company revenue may be down, and they may even risk losing their job when the company goes out of business. But their laziness individually won’t determine the entirety of that outcome. By contrast, they greatly benefit from being lazy by getting to relax at work, go on social media, read a book, or do whatever else they do when they’re supposed to be working.

My point here is that, as long as you ignore the reality of how incentives drive human behavior, you’ll fail at getting the outcomes you want.
If everything I wrote up until now made perfect sense, you understand the premise of this blog post. The rest of it will focus on a bunch of real-world examples to hammer home the point, and demonstrate how versatile this mental model is.
## Running a company
Let’s say I run my own company, with myself as the only employee. My personal revenue will be 100% determined by my own actions. If I decide to take Tuesday afternoon off and go fishing, I’ve chosen to lose that afternoon’s revenue. Implicitly, I’ve decided that the enjoyment I get from an afternoon of fishing is greater than the potential revenue. You may think I’m being lazy, but it’s my decision to make. In this situation, the incentive–money–is perfectly aligned with my actions.
Compare this to a typical company/employee relationship. I might have a bank of Paid Time Off (PTO) days, in which case once again my incentives are relatively aligned. I know that I can take off 15 days throughout the year, and I’ve chosen to use half a day for the fishing trip. All is still good.
What about unlimited time off? Suddenly incentives are starting to misalign. I don’t directly pay a price for not showing up to work on Tuesday. Or Wednesday as well, for that matter. I might ultimately be fired for not doing my job, but that will take longer to work its way through the system than simply not making any money for the day taken off.
Compensation overall falls into this misaligned incentive structure. Let’s forget about taking time off. Instead, I work full time on a software project I’m assigned. But instead of using the normal toolchain we’re all used to at work, I play around with a new programming language. I get the fun and joy of playing with new technology, and potentially get to pad my resume a bit when I’m ready to look for a new job. But my current company gets slower results, less productivity, and is forced to subsidize my extracurricular learning.
When a CEO has a bonus structure based on profitability, he’ll do everything he can to make the company profitable. This might include things that actually benefit the company, like improving product quality, reducing internal red tape, or finding cheaper vendors. But it might also include destructive practices, like slashing the R\&D budget to show massive profits this year, in exchange for a catastrophe next year when the next version of the product fails to ship.

Or my favorite example. My parents owned a business when I was growing up. They had a back office where they ran operations like accounting. All of the furniture was old couches from our house. After all, any money they spent on furniture came right out of their paychecks\! But in a large corporate environment, each department is generally given a budget for office furniture, a budget which doesn’t roll over year-to-year. The result? Executives make sure to spend the entire budget each year, often buying furniture far more expensive than they would choose if it was their own money.
There are plenty of details you can quibble with above. It’s in a company’s best interest to give people downtime so that they can come back recharged. Having good ergonomic furniture can in fact increase productivity in excess of the money spent on it. But overall, the picture is pretty clear: in large corporate structures, you’re guaranteed to have mismatches between the company’s goals and the incentive structure placed on individuals.
Using our model from above, we can lament how lazy, greedy, and unethical the employees are for doing what they’re incentivized to do instead of what’s right. But that’s simply ignoring the reality of human nature.
# Moral hazard
Moral hazard is a situation where one party is incentivized to take on more risk because another party will bear the consequences. Suppose I tell my son when he turns 21 (or whatever legal gambling age is) that I’ll cover all his losses for a day at the casino, but he gets to keep all the winnings.
What do you think he’s going to do? The most logical course of action is to place the largest possible bets for as long as possible, asking me to cover each time he loses, and taking money off the table and into his bank account each time he wins.

But let’s look at a slightly more nuanced example. I go to a bathroom in the mall. As I’m leaving, I wash my hands. It will take me an extra 1 second to turn off the water when I’m done washing. That’s a trivial price to pay. If I *don’t* turn off the water, the mall will have to pay for many liters of wasted water, benefiting no one. But I won’t suffer any consequences at all.
This is also a moral hazard, but most people will still turn off the water. Why? Usually due to some combination of other reasons such as:
1. We’re so habituated to turning off the water that we don’t even consider *not* turning it off. Put differently, the mental effort needed to not turn off the water is more expensive than the 1 second of time to turn it off.
2. Many of us have been brought up with a deep guilt about wasting resources like water. We have an internal incentive structure that makes the 1 second to turn off the water much less costly than the mental anguish of the waste we created.
3. We’re afraid we’ll be caught by someone else and face some kind of social repercussions. (Or maybe more than social. Are you sure there isn’t a law against leaving the water tap on?)
Even with all that in place, you may notice that many public bathrooms use automatic water dispensers. Sure, there’s a sanitation reason for that, but it’s also to avoid this moral hazard.
A common denominator in both of these is that the person taking the action that causes the liability (either the gambling or leaving the water on) is not the person who bears the responsibility for that liability (the father or the mall owner). Generally speaking, the closer together the person making the decision and the person incurring the liability are, the smaller the moral hazard.
It’s easy to demonstrate that by extending the casino example a bit. I said it was the father who was covering the losses of the gambler. Many children (though not all) would want to avoid totally bankrupting their parents, or at least financially hurting them. Instead, imagine that someone from the IRS shows up at your door, hands you a credit card, and tells you you can use it at a casino all day, taking home all the chips you want. The money is coming from the government. How many people would put any restriction on how much they spend?
And since we’re talking about the government already…
## Government moral hazards
As I was preparing to write this blog post, the California wildfires hit. The discussions around those wildfires gave a *huge* number of examples of moral hazards. I decided to cherry-pick a few for this post.
The first and most obvious one: California is asking for disaster relief funds from the federal government. That sounds wonderful. These fires were a natural disaster, so why shouldn’t the federal government pitch in and help take care of people?
The problem is, once again, a moral hazard. In the case of the wildfires, California and Los Angeles both had ample actions they could have taken to mitigate the destruction of this fire: better forest management, larger fire department, keeping the water reservoirs filled, and probably much more that hasn’t come to light yet.
If the federal government bails out California, it will be a clear message for the future: your mistakes will be fixed by others. You know what kind of behavior that incentivizes? More risky behavior\! Why spend state funds on forest management and extra firefighters—activities that don’t win politicians a lot of votes in general—when you could instead spend it on a football stadium, higher unemployment payments, or anything else, and then let the feds cover the cost of screw-ups.
You may notice that this is virtually identical to the 2008 “too big to fail” bail-outs. Wall Street took insanely risky behavior, reaped huge profits for years, and when they eventually got caught with their pants down, the rest of us bailed them out. “Privatizing profits, socializing losses.”

And here’s the absolute best part of this: I can’t even truly blame either California *or* Wall Street. (I mean, I *do* blame them, I think their behavior is reprehensible, but you’ll see what I mean.) In a world where the rules of the game implicitly include the bail-out mentality, you would be harming your citizens/shareholders/investors if you didn’t engage in that risky behavior. Since everyone is on the hook for those socialized losses, your best bet is to maximize those privatized profits.
There’s a lot more to government and moral hazard, but I think these two cases demonstrate the crux pretty solidly. But let’s leave moral hazard behind for a bit and get to general incentivization discussions.
# Non-monetary competition
At least 50% of the economics knowledge I have comes from the very first econ course I took in college. That professor was amazing, and had some very colorful stories. I can’t vouch for the veracity of the two I’m about to share, but they definitely drive the point home.
In the 1970s, the US had an oil shortage. To “fix” this problem, they instituted price caps on gasoline, which of course resulted in insufficient gasoline. To “fix” this problem, they instituted policies where, depending on your license plate number, you could only fill up gas on certain days of the week. (Irrelevant detail for our point here, but this just resulted in people filling up their tanks more often, no reduction in gas usage.)
Anyway, my professor’s wife had a friend. My professor described in *great* detail how attractive this woman was. I’ll skip those details here since this is a PG-rated blog. In any event, she never had any trouble filling up her gas tank any day of the week. She would drive up, be told she couldn’t fill up gas today, bat her eyes at the attendant, explain how helpless she was, and was always allowed to fill up gas.
This is a demonstration of *non-monetary compensation*. Most of the time in a free market, capitalist economy, people are compensated through money. When price caps come into play, there’s a limit to how much monetary compensation someone can receive. And in that case, people find other ways of competing. Like this woman’s case: through using flirtatious behavior to compensate the gas station workers to let her cheat the rules.
The other example was much more insidious. Santa Monica had a problem: it was predominantly wealthy and white. They wanted to fix this problem, and decided to put in place rent controls. After some time, they discovered that Santa Monica had become *wealthier and whiter*, the exact opposite of their desired outcome. Why would that happen?
Someone investigated, and ended up interviewing a landlady that demonstrated the reason. She was an older white woman, and admittedly racist. Prior to the rent controls, she would list her apartments in the newspaper, and would be legally obligated to rent to anyone who could afford it. Once rent controls were in place, she took a different tact. She knew that she would only get a certain amount for the apartment, and that the demand for apartments was higher than the supply. That meant she could be picky.
She ended up finding tenants through friends-of-friends. Since it wasn’t an official advertisement, she wasn’t legally required to rent it out if someone could afford to pay. Instead, she got to interview people individually and then make them an offer. Normally, that would have resulted in receiving a lower rental price, but not under rent controls.
So who did she choose? A young, unmarried, wealthy, white woman. It made perfect sense. Women were less intimidating and more likely to maintain the apartment better. Wealthy people, she determined, would be better tenants. (I have no idea if this is true in practice or not, I’m not a landlord myself.) Unmarried, because no kids running around meant less damage to the property. And, of course, white. Because she was racist, and her incentive structure made her prefer whites.
You can deride her for being racist, I won’t disagree with you. But it’s simply the reality. Under the non-rent-control scenario, her profit motive for money outweighed her racism motive. But under rent control, the monetary competition was removed, and she was free to play into her racist tendencies without facing any negative consequences.
## Bureaucracy
These were the two examples I remember for that course. But non-monetary compensation pops up in many more places. One highly pertinent example is bureaucracies. Imagine you have a government office, or a large corporation’s acquisition department, or the team that apportions grants at a university. In all these cases, you have a group of people making decisions about handing out money that has no monetary impact on them. If they give to the best qualified recipients, they receive no raises. If they spend the money recklessly on frivolous projects, they face no consequences.
Under such an incentivization scheme, there’s little to encourage the bureaucrats to make intelligent funding decisions. Instead, they’ll be incentivized to spend the money where they recognize non-monetary benefits. This is why it’s so common to hear about expensive meals, gift bags at conferences, and even more inappropriate ways of trying to curry favor with those that hold the purse strings.
Compare that ever so briefly with the purchases made by a small mom-and-pop store like my parents owned. Could my dad take a bribe to buy from a vendor who’s ripping him off? Absolutely he could\! But he’d lose more on the deal than he’d make on the bribe, since he’s directly incentivized by the deal itself. It would make much more sense for him to go with the better vendor, save $5,000 on the deal, and then treat himself to a lavish $400 meal to celebrate.
# Government incentivized behavior
This post is getting longer in the tooth than I’d intended, so I’ll finish off with this section and make it a bit briefer. Beyond all the methods mentioned above, government has another mechanism for modifying behavior: through directly changing incentives via legislation, regulation, and monetary policy. Let’s see some examples:
* Artificial modification of interest rates encourages people to take on more debt than they would in a free capital market, leading to [malinvestment](https://en.wikipedia.org/wiki/Malinvestment) and a consumer debt crisis, and causing the boom-bust cycle we all painfully experience.
* Going along with that, giving tax breaks on interest payments further artificially incentivizes people to take on debt that they wouldn’t otherwise.
* During COVID-19, at some points unemployment benefits were greater than minimum wage, incentivizing people to rather stay home and not work than get a job, leading to reduced overall productivity in the economy and more printed dollars for benefits. In other words, it was a perfect recipe for inflation.
* The tax code gives deductions to “help” people. That might be true, but the real impact is incentivizing people to make decisions they wouldn’t have otherwise. For example, giving out tax deductions on children encourages having more kids. Tax deductions on childcare and preschools incentivizes dual-income households. Whether or not you like the outcomes, it’s clear that it’s government that’s encouraging these outcomes to happen.
* Tax incentives cause people to engage in behavior they wouldn’t otherwise (daycare+working mother, for example).
* Inflation means that the value of your money goes down over time, which encourages people to spend more today, when their money has a larger impact. (Milton Friedman described this as [high living](https://www.youtube.com/watch?v=ZwNDd2_beTU).)
# Conclusion
The idea here is simple, and fully encapsulated in the title: incentives determine outcomes. If you want to know how to get a certain outcome from others, incentivize them to want that to happen. If you want to understand why people act in seemingly irrational ways, check their incentives. If you’re confused why leaders (and especially politicians) seem to engage in destructive behavior, check their incentives.
We can bemoan these realities all we want, but they *are* realities. While there are some people who have a solid internal moral and ethical code, and that internal code incentivizes them to behave against their externally-incentivized interests, those people are rare. And frankly, those people are self-defeating. People *should* take advantage of the incentives around them. Because if they don’t, someone else will.
(If you want a literary example of that last comment, see the horse in Animal Farm.)
How do we improve the world under these conditions? Make sure the incentives align well with the overall goals of society. To me, it’s a simple formula:
* Focus on free trade, value for value, as the basis of a society. In that system, people are always incentivized to provide value to other people.
* Reduce the size of bureaucracies and large groups of all kinds. The larger an organization becomes, the farther the consequences of decisions are from those who make them.
* And since the nature of human beings will be to try and create areas where they can control the incentive systems to their own benefits, make that as difficult as possible. That comes in the form of strict limits on government power, for example.
And even if you don’t want to buy in to this conclusion, I hope the rest of the content was educational, and maybe a bit entertaining\!
-

@ 000002de:c05780a7
2025-04-01 20:17:26
I know I'm not alone in this. I don't trust the government. Any government. Its the rational response when you discover just how often its agents lie, steal, and kill. Honestly, I do not understand why so many people do trust the government. The reality is that if your team is in power, you tend to trust it. If not, you still mostly trust it but less so. That's my feel for most people at least.
Trump and Rubio are bragging about how many MS-13 gang members are being deported. Many are being shipped to prisons in El Salvador. Obviously I am not opposed to criminals being put in prisons. But, how do we know these guys are actually guilty of anything other than being in the US illegally. Actually we don't even know that. It wouldn't be so bad if these people were just being shipped back to their home countries. But, instead they are getting sent straight to prison. No trial. Just the government picking people up and shipping them to prison. Is this what you signed up for Trump supporters?
Many Trump supporters opposed the GW Bush policies of throwing people in off-shore prisons. Some of them US citizens. With no trial. Now these people seem rather silent. Its troubling to me.
Why? Well, because the government sucks. Even if they have good intentions they make mistakes. The Innocence Project is just one group that has shown how often our legal system falsely imprisons people. I would be shocked if there weren't any Innocent men being sent to suffer in El Salvador's prisons.
You may say, well these are bad dudes and we need to clean up the mess Biden made. I have sympathy for that position. But do we really want to set this president? TDS is real but it is valid to have concerns about the actions of the Trump admin. This is not the American way. Not the way I was taught at least. This is just a strong man taking action and disregarding the values of this nation and the rights of human beings.
Think about it.
originally posted at https://stacker.news/items/931505
-

@ 592295cf:413a0db9
2025-03-29 10:59:52
The journey starts from the links in this article
[nostr-quick-start-guide](https://spatianostra.com/nostr-quick-start-guide/)
Starting from these links building a simple path should not cover everything, because impossible.
Today I saw that Verbiricha in his workshop on his channel used nstart, but then I distracted
And I didn't see how he did it.
-----
Go to [nstart.me](https://nstart.me/) and read:
Each user is identified by a cryptographic keypair
Public key, Private key (is a lot of stuff)
You can insert a nickname and go, the nickname is not unique
there is a email backup things interesting, but a little boring, i try to generate an email
doesn't even require a strong password ok.
I received the email, great, it shows me the nsec encrypted in clear,
Send a copy of the file with a password, which contains the password encrypted key
I know and I know it's a tongue dump.
## Multi signer bunker
That's stuff, let's see what he says.
They live the private key and send it to servers and you can recompose it to login at a site
of the protocol nostr. If one of these servers goes offline you have the private key
that you downloaded first and then reactivate a bunker.
All very complicated.
But if one of the servers goes offline, how can I remake the split? Maybe he's still testing.
Nobody tells you where these bunkers are.
Okay I have a string that is my bunker (buker://), I downloaded it, easy no, now will tell me which client accepts the bunker.. .
## Follow someone before you start?
Is a cluster of 5 people Snowden, Micheal Dilger, jb55, Fiatjaf, Dianele.
I choice Snowden profile, or you can select multiple profiles, extra wild.
## Now select 5 clients
### *Coracle, Chachi, Olas, Nostur, Jumble*
### The first is *Coracle*
Login, ok I try to post a note and signing your note the spin does not end.
Maybe the bunker is diffective.
### Let's try *Chachi*
Simpler than Coracle, it has a type login that says bunker.
see if I can post
It worked, cool, I managed to post in a group.
## Olas is an app but also a website, but on the website requires an extension, which I do not have with this account.
> If I download an app how do I pass the bunker on the phone, is it still a password, a qrcode, a qrcode + password, something
> like that, but many start from the phone so maybe it's easy for them.
> I try to download it and see if it allows me to connect with a bunker.
> Okay I used private-qrcode and it worked, I couldn't do it directly from Olas because it didn't have permissions and the qrcode was < encrypted, so I went to the same site and had the bunker copied and glued on Olas
**Ok then I saw that there was the qrcode image of the bunker for apps** lol moment
Ok, I liked it, I can say it's a victory.
Looks like none of Snowden's followers are *Olas*'s lover, maybe the smart pack has to predict a photographer or something like that.
Okay I managed to post on *Olas*, so it works, Expiration time is broken.
### As for *Nostur*, I don't have an ios device so I'm going to another one.
### Login with *Jumble*, it works is a web app
I took almost an hour to do the whole route.
But this was just one link there are two more
# Extensions nostr NIP-07
### The true path is [nip-07-browser-extensions | nostr.net](https://nostr.net/#nip-07-browser-extensions)
There are 19 links, maybe there are too many?
I mention the most famous, or active at the moment
1. **Aka-profiles**: [Aka-profiles](https://github.com/neilck/aka-extension)
Alby I don't know if it's a route to recommend
2. **Blockcore** [Blockcore wallet](https://chromewebstore.google.com/detail/blockcore-wallet/peigonhbenoefaeplkpalmafieegnapj)
3. **Nos2x** [Nos2x](https://github.com/fiatjaf/nos2x?tab=readme-ov-file)
4. **Nos2xfox** (fork for firefox) [Nos2xfox](https://diegogurpegui.com/nos2x-fox/)
Nostore is (archived, read-only)
5. **Nostrame** [Nostrame](https://github.com/Anderson-Juhasc/nostrame)
6. **Nowser** per IOS [Nowser](https://github.com/haorendashu/nowser)
7. **One key** (was tricky) [One key](https://chromewebstore.google.com/detail/onekey/jnmbobjmhlngoefaiojfljckilhhlhcj)
Another half hour to search all sites
# Nostrapps
Here you can make paths
### Then nstart selects Coracle, Chachi, Olas,Nostur and Jumble
Good apps might be Amethyst, 0xchat, Yakihonne, Primal, Damus
for IOS maybe: Primal, Olas, Damus, Nostur, Nos-Social, Nostrmo
On the site there are some categories, I select some with the respective apps
Let's see the categories
Go to [Nostrapps](https://nostrapps.com/) and read:
## Microbbloging: Primal
## Streaming: **Zap stream**
## Blogging: **Yakihonne**
## Group chat: **Chachi**
## Community: **Flotilla**
## Tools: **Form** *
## Discovery: **Zapstore** (even if it is not in this catrgory)
## Direct Message: **0xchat**
-

@ 21335073:a244b1ad
2025-03-20 13:16:22
I’d never had the chance to watch Harry Potter on the big screen before. Experiencing the first movie in 3D was nothing short of spectacular. Right from the opening scene with Albus Dumbledore, I was floored—the makeup and costumes were so vivid, it felt like pure magic unfolding before my eyes. It’s clear that real masters of their craft worked behind the scenes, and their artistry shines through. The sets? Absolutely jaw-dropping! The level of detail in Diagon Alley was beyond impressive.
Seeing legends like Alan Rickman as Snape and Maggie Smith as Minerva McGonagall on that massive 3D screen was an unforgettable thrill. The film is packed with phenomenal actors, and it was a joy to catch every tiny eye twitch and subtle nuance of their performances brought to life. It was a mind-blowing experience, and I’d wholeheartedly recommend it to anyone who gets the chance.
Don’t forget to have a little whimsical fun sometimes my friends. 🪄
-

@ 3f770d65:7a745b24
2025-01-12 21:03:36
I’ve been using Notedeck for several months, starting with its extremely early and experimental alpha versions, all the way to its current, more stable alpha releases. The journey has been fascinating, as I’ve had the privilege of watching it evolve from a concept into a functional and promising tool.
In its earliest stages, Notedeck was raw—offering glimpses of its potential but still far from practical for daily use. Even then, the vision behind it was clear: a platform designed to redefine how we interact with Nostr by offering flexibility and power for all users.
I'm very bullish on Notedeck. Why? Because Will Casarin is making it! Duh! 😂
Seriously though, if we’re reimagining the web and rebuilding portions of the Internet, it’s important to recognize [the potential of Notedeck](https://damus.io/notedeck/). If Nostr is reimagining the web, then Notedeck is reimagining the Nostr client.
Notedeck isn’t just another Nostr app—it’s more a Nostr browser that functions more like an operating system with micro-apps. How cool is that?
Much like how Google's Chrome evolved from being a web browser with a task manager into ChromeOS, a full blown operating system, Notedeck aims to transform how we interact with the Nostr. It goes beyond individual apps, offering a foundation for a fully integrated ecosystem built around Nostr.
As a Nostr evangelist, I love to scream **INTEROPERABILITY** and tout every application's integrations. Well, Notedeck has the potential to be one of the best platforms to showcase these integrations in entirely new and exciting ways.
Do you want an Olas feed of images? Add the media column.
Do you want a feed of live video events? Add the zap.stream column.
Do you want Nostr Nests or audio chats? Add that column to your Notedeck.
Git? Email? Books? Chat and DMs? It's all possible.
Not everyone wants a super app though, and that’s okay. As with most things in the Nostr ecosystem, flexibility is key. Notedeck gives users the freedom to choose how they engage with it—whether it’s simply following hashtags or managing straightforward feeds. You'll be able to tailor Notedeck to fit your needs, using it as extensively or minimally as you prefer.
Notedeck is designed with a local-first approach, utilizing Nostr content stored directly on your device via the local nostrdb. This will enable a plethora of advanced tools such as search and filtering, the creation of custom feeds, and the ability to develop personalized algorithms across multiple Notedeck micro-applications—all with unparalleled flexibility.
Notedeck also supports multicast. Let's geek out for a second. Multicast is a method of communication where data is sent from one source to multiple destinations simultaneously, but only to devices that wish to receive the data. Unlike broadcast, which sends data to all devices on a network, multicast targets specific receivers, reducing network traffic. This is commonly used for efficient data distribution in scenarios like streaming, conferencing, or large-scale data synchronization between devices.
> In a local first world where each device holds local copies of your nostr nodes, and each device transparently syncs with each other on the local network, each node becomes a backup. Your data becomes antifragile automatically. When a node goes down it can resync and recover from other nodes. Even if not all nodes have a complete collection, negentropy can pull down only what is needed from each device. All this can be done without internet.
>
> \-Will Casarin
In the context of Notedeck, multicast would allow multiple devices to sync their Nostr nodes with each other over a local network without needing an internet connection. Wild.
Notedeck aims to offer full customization too, including the ability to design and share custom skins, much like Winamp. Users will also be able to create personalized columns and, in the future, share their setups with others. This opens the door for power users to craft tailored Nostr experiences, leveraging their expertise in the protocol and applications. By sharing these configurations as "Starter Decks," they can simplify onboarding and showcase the best of Nostr’s ecosystem.
Nostr’s “Other Stuff” can often be difficult to discover, use, or understand. Many users doesn't understand or know how to use web browser extensions to login to applications. Let's not even get started with nsecbunkers. Notedeck will address this challenge by providing a native experience that brings these lesser-known applications, tools, and content into a user-friendly and accessible interface, making exploration seamless. However, that doesn't mean Notedeck should disregard power users that want to use nsecbunkers though - hint hint.
For anyone interested in watching Nostr be [developed live](https://github.com/damus-io/notedeck), right before your very eyes, Notedeck’s progress serves as a reminder of what’s possible when innovation meets dedication. The current alpha is already demonstrating its ability to handle complex use cases, and I’m excited to see how it continues to grow as it moves toward a full release later this year.
-

@ fd06f542:8d6d54cd
2025-03-30 02:10:24
NIP-03
======
OpenTimestamps Attestations for Events
--------------------------------------
`draft` `optional`
This NIP defines an event with `kind:1040` that can contain an [OpenTimestamps](https://opentimestamps.org/) proof for any other event:
```json
{
"kind": 1040
"tags": [
["e", <event-id>, <relay-url>],
["alt", "opentimestamps attestation"]
],
"content": <base64-encoded OTS file data>
}
```
- The OpenTimestamps proof MUST prove the referenced `e` event id as its digest.
- The `content` MUST be the full content of an `.ots` file containing at least one Bitcoin attestation. This file SHOULD contain a **single** Bitcoin attestation (as not more than one valid attestation is necessary and less bytes is better than more) and no reference to "pending" attestations since they are useless in this context.
### Example OpenTimestamps proof verification flow
Using [`nak`](https://github.com/fiatjaf/nak), [`jq`](https://jqlang.github.io/jq/) and [`ots`](https://github.com/fiatjaf/ots):
```bash
~> nak req -i e71c6ea722987debdb60f81f9ea4f604b5ac0664120dd64fb9d23abc4ec7c323 wss://nostr-pub.wellorder.net | jq -r .content | ots verify
> using an esplora server at https://blockstream.info/api
- sequence ending on block 810391 is valid
timestamp validated at block [810391]
```
-

@ 21335073:a244b1ad
2025-03-18 20:47:50
**Warning: This piece contains a conversation about difficult topics. Please proceed with caution.**
TL;DR please educate your children about online safety.
Julian Assange wrote in his 2012 book *Cypherpunks*, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense.
This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning.
When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little.
I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?”
I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well.
I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread.
I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard.
I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it.
The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust.
Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this.
I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place.
What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method.
It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code.
They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened.
I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road.
So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally.
Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb.
I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback.
Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed.
That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone.
To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all.
I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society.
I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this.
On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government.
I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories.
There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc.
Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind.
Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now.
There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers?
I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity.
I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place.
My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors.
My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline.
The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online.
I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers.
So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation?
When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that.
I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic.
If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations.
I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process.
**Course:**
- The creation of the internet and computers
- The fight for cryptography
- The tech supply chain from the ground up (example: human rights violations in the supply chain)
- Corporate tech
- Freedom tech
- Data privacy
- Digital privacy rights
- AI (history-current)
- Online safety (predators, scams, catfishing, extortion)
- Bitcoin
- Laws
- How to deal with online hate and harassment
- Information on who to contact if you are being abused online or offline
- Algorithms
- How to seek out the truth about news, etc., online
The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children.
The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward?
I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone.
Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability.
The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime.
This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful.
This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens.
In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions.
I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation.
-

@ f1989a96:bcaaf2c1
2025-04-03 14:30:08
Good morning, readers!
Georgian officials froze the bank accounts of five nonprofit organizations that provide financial and legal support to detained protesters. This follows rising public unrest as Georgia’s regime pushes new laws restricting free speech and assembly, introducing new fines and penalties, and expanding law enforcement powers. By eroding civil protections, the regime makes it more dangerous and costly for activists, dissenters, and everyday citizens to stand up against an increasingly repressive regime.\
\
Meanwhile, the Indian government introduced a new income tax bill that grants tax authorities sweeping surveillance power over anyone they “suspect” of tax evasion. If suspected, tax authorities are legally allowed to access Indians' email, social media, and bank accounts, raising obvious concerns over state overreach and invasions of individual financial privacy.\
\
In freedom tech news, HRF donated 1 billion satoshis to more than 20 projects worldwide, focusing on supporting human rights defenders and vulnerable communities under authoritarian regimes across Asia, Africa, and Latin America. These gifts advance censorship-resistant communications and transactions, bitcoin education, and privacy tools so that dissidents, nonprofits, and individuals may better protect their human rights and financial freedom. In this letter we also spotlight a new open-source mobile Bitcoin wallet called Cove. While still in beta, the wallet can be used with a hardware device or on its own as a hot wallet, offering a flexible self-custody setup for managing Bitcoin.
We end with a podcast in which HRF Chief Strategy Officer Alex Gladstein discusses the state of freedom tech and why Bitcoin stands as the most promising tool for financial liberation.
**Now, let’s get right to it!**
### [**SUBSCRIBE HERE**](https://mailchi.mp/hrf.org/financial-freedom-newsletter?mc_cid=bf652c0a5a)
## **GLOBAL NEWS**
#### **Georgia | Officials Freeze Accounts of Organizations Supporting Protesters**
Georgian officials have [frozen](https://www.amnesty.org/en/latest/news/2025/03/georgia-authorities-freeze-accounts-of-organizations-supporting-protesters-to-kill-the-peaceful-protests/) the bank accounts of five nonprofit organizations that provide financial and legal aid to dissenters. This comes in response to an uprising of protests over new controversial laws that restrict free expression and assembly, increase fines and detention periods, and expand law enforcement powers. Georgian officials justify the account freezes as part of an investigation into “sabotage,” yet they have provided no evidence. Amnesty International [warns](https://www.amnesty.org/en/latest/news/2025/03/georgia-authorities-freeze-accounts-of-organizations-supporting-protesters-to-kill-the-peaceful-protests/) this financial assault could “kill the entire protest movement.” Bitcoin provides a way to circumvent these struggles. Its uncensorable and permissionless nature has helped [sustain](https://www.journalofdemocracy.org/online-exclusive/how-to-dictator-proof-your-money/) pro-democracy movements across Belarus and Nigeria, proving it is capable of addressing the immense financial restrictions dictators impose.
#### **United Arab Emirates | Plans to Launch “Digital Durham” CBDC in 2025**
The United Arab Emirates (UAE) will [launch](https://www.businesstoday.in/technology/news/story/uae-to-launch-digital-dirham-by-year-end-to-modernise-payments-and-noost-financial-inclusion-470013-2025-03-31?utm_source=semafor#) its central bank digital currency (CBDC), the “[Digital Durham](https://cbdctracker.hrf.org/currency/united-arab-emirates),” by the end of 2025. [According](https://www.ledgerinsights.com/uae-to-launch-cbdc-in-q4-2025/) to the central bank, the CBDC will be available through licensed financial institutions and operate via a government-run digital wallet. Every transaction will be recorded on a permissioned blockchain run by the government. The central bank further [admitted](https://u.ae/en/about-the-uae/strategies-initiatives-and-awards/strategies-plans-and-visions/finance-and-economy/central-bank-digital-currency-strategy) the CBDC will replace cash and [assist](https://www.businesstoday.in/technology/news/story/uae-to-launch-digital-dirham-by-year-end-to-modernise-payments-and-noost-financial-inclusion-470013-2025-03-31?utm_source=semafor#) law enforcement “by leaving a digital trail for transactions involving illicit funds.” Officials [claim](https://www.businesstoday.in/technology/news/story/uae-to-launch-digital-dirham-by-year-end-to-modernise-payments-and-noost-financial-inclusion-470013-2025-03-31?utm_source=semafor#) this is to combat financial crime, but it also enables real-time surveillance and tracking of individual financial activity. In a country known for strict laws against dissent and extensive surveillance capabilities, it is not hard to see how a CBDC will erode the autonomy and rights of activists, dissenters, and others who oppose an increasingly authoritarian regime.
#### **India | Grants Tax Authorities Access to Citizens’ Online Data**
Starting in April 2026, the Indian government will [grant](https://economictimes.indiatimes.com/wealth/tax/your-email-and-social-media-account-can-be-accessed-by-income-tax-officer-starting-next-financial-year-in-these-cases/articleshow/118685184.cms) tax authorities legal access to the private online data of any citizen “suspected” of tax evasion. This will include legal access to personal emails, social media, and bank accounts. The new law expands on the Income Tax Act of 1961, which previously limited officials to searching physical premises for financial documents. Now, officials can bypass digital security measures and access private data without consent — all under a legal framework. This dissipation of financial privacy sets an intrusive precedent and opens the door to state-level corruption and surveillance in a country where the Modi regime has already made it clear they are happy to use financial repression to further cement their power.
#### **Myanmar | Bitcoin as a Tool Support Earthquake Disaster Relief**
Last week, a [7.7 magnitude earthquake](https://www.nytimes.com/2025/03/28/world/asia/earthquake-myanmar-thailand-death-toll.html) struck central Burma, with strong tremors reaching neighboring Thailand. The [official death toll ](https://www.reuters.com/business/environment/survivors-myanmar-quake-left-without-food-water-shelter-aid-groups-say-2025-04-01/)has surpassed 2700. And in Bangkok, a 33-story building under construction [collapsed](https://www.youtube.com/watch?v=ynrhyIh4ozo). Despite an already strenuous situation, Burma’s military junta continues its oppression. They are [blocking](https://www.nytimes.com/2025/03/31/world/asia/myanmar-earthquake-rescue.html) rescue teams from reaching the Sagaing region — the epicenter of the earthquake and the heart of Burma’s pro-democracy movement — and instead channeling aid to regime-controlled cities like Naypyidaw and Mandalay. The junta is also continuing to conduct air strikes on civilians and restricting equipment and fuel for aid groups, leaving a [million](https://data.unhcr.org/en/country/mmr) people in Sagaing to fend for themselves. In these repressive circumstances, Bitcoin can provide a censorship-resistant way to send funds directly to those affected.
#### **Angola | Regime Jacks Price of Diesel**
The Angolan regime [raised](https://www.rigzone.com/news/wire/angola_doubles_diesel_prices_after_imf_call_for_subsidy_cuts-25-mar-2025-180020-article/) diesel prices by 50% in the process of eliminating fuel subsidies. Diesel prices suddenly increased from 200 to 300 kwanza per liter, driving up transportation costs in a country where over half the population lives on [less](https://www.rigzone.com/news/wire/angola_doubles_diesel_prices_after_imf_call_for_subsidy_cuts-25-mar-2025-180020-article/) than $2 a day and inflation is over 42%. Previous fuel subsidy cuts in 2023 (where the price of diesel rose [80%](https://www.dw.com/en/angolan-police-crack-down-on-fuel-hike-protests/a-65978231)) sparked [protests](https://www.dw.com/en/angolan-police-crack-down-on-fuel-hike-protests/a-65978231) between taxi drivers, nonprofit workers, and law enforcement. This recent price increase now raises fears of renewed crackdowns. The Angolan regime also introduced new civil society laws that Guilherme Neves, chairman of the human rights organization Associacao Maos Livres, [describes](https://www.dw.com/en/angolan-police-crack-down-on-fuel-hike-protests/a-65978231) as a “license to erase non-governmental organizations that are not government-compliant.” Angolans find themselves in increasingly precarious financial positions as the government erodes the civil safeguards protecting nonprofits and dissenters.
#### **Nicaragua | Ortega’s Dismantling of Press Freedom**
Since coming to power in 2007, Ortega has [closed or seized](https://havanatimes.org/features/ortegas-war-on-journalism-in-nicaragua/) 61 media outlets, imprisoned countless journalists, and forced over 280 journalists into exile. His [assault on press freedom](https://havanatimes.org/features/ortegas-war-on-journalism-in-nicaragua/) has unfolded in two phases: initial raids on local radio stations and TV channels between 2007 and 2017, followed by full-scale censorship in 2018 on independent media outlets like [La Prensa](https://www.laprensani.com/) and [CONFIDENCIAL](https://confidencial.digital/). Ortega then intensified attacks from 2019 to 2021 by closing Nicaragua’s second-oldest newspaper and passing laws to [criminalize](https://havanatimes.org/features/ortegas-war-on-journalism-in-nicaragua/) free expression. This is a deliberate strategy to eliminate dissent and independent voices. What’s happening in Nicaragua highlights the importance of open and decentralized protocols like nostr, which allow journalists to publish freely without getting censored. While still early, it is becoming essential for sharing information absent the fear of being blocked or silenced by autocratic leaders.
## BITCOIN AND FREEDOM TECH NEWS
#### **HRF | Gifts 1 Billion Satoshis to 20+ Open Source Projects Worldwide**
HRF gifted 1 billion satoshis in its Q1 2025 round of [Bitcoin Development Fund](https://hrf.org/program/financial-freedom/bitcoin-development-fund/) (BDF) grants, supporting more than 20 open-source projects around the world. These projects advance Bitcoin education, open-source software, mining decentralization, and privacy tools for activists contending with authoritarian regimes across Asia, Latin America, and Africa. Supporting permissionless financial tools and censorship-resistant technologies empowers dissidents, journalists, and civil society to organize, transact, and communicate without state suppression and interference. Learn more about the grantees and their work [here](https://hrf.org/latest/hrf-bitcoin-development-fund-supports-20-projects-worldwide/).
#### **Cove | New Open-Source and Permissionless Bitcoin Wallet**
[Cove](https://github.com/bitcoinppl/cove) is a new open-source and permissionless mobile Bitcoin wallet that aims to put users in full control of their Bitcoin. Users can connect their own hardware wallet (to manage Bitcoin offline) or use Cove as a hot wallet (to manage Bitcoin online). It also allows users to create multiple wallets from the app itself. In the future, Cove plans to add Unspent Transaction Output (UTXO) selection and coin control, giving users more independence over their transactions and the tools to better protect their financial privacy. While still in beta and only suitable for test funds, this wallet holds promise as a privacy tool to equip dissidents with self-custodied Bitcoin. You can try it [here](https://github.com/bitcoinppl/cove).
#### **Second | New Ark Implementation Launches on Bitcoin Signet**
[Second](https://second.tech/), a company building on Ark, a protocol designed to help scale Bitcoin’s transaction throughput, [launched](https://blog.second.tech/try-ark-on-signet/?ref=nobsbitcoin.com) “Bark.” Bark is a test implementation of the Ark protocol deployed on Bitcoin’s [Signet](https://en.bitcoin.it/wiki/Signet) network (where developers test software). More broadly, the Ark protocol helps make Bitcoin transactions more private, faster, and cheaper, supporting the network in handling more transactions and users with the tradeoff of being less trusted than the mainchain, as funds stored in a noncustodial way on Ark can expire if not used. While it is still in early development, the test release of Bark marks a step toward deployment on the main Bitcoin network. Scaling solutions like Ark could be important for activists and individuals. They might ensure Bitcoin remains accessible to all, even as block space demand increases and network fees rise. Learn about it [here](https://blog.second.tech/try-ark-on-signet/?ref=nobsbitcoin.com).
#### **Braiins | Open Sources Bitcoin Control Board**
[Braiins](https://braiins.com/), a company building tools for Bitcoin mining, [open-sourced](https://x.com/BraiinsMining/status/1904601547855573458) its [BCB100](https://github.com/braiins/BCB100) Bitcoin Control Board, giving miners using their products greater insight and control over their Bitcoin mining hardware and firmware. Sharing the design files and firmware openly helps strengthen Bitcoin’s decentralization, making it more resilient against corporate or state interference. Specifically, open-sourcing mining hardware ensures individual miners can operate independently, reducing censorship risks across the entire network. In turn, this preserves financial freedom by keeping Bitcoin accessible and usable by dissidents, nonprofits, and individuals who need it most.
#### **African Bitcoiners | Publish Bitcoin Starter Guide**
[African Bitcoiners](https://x.com/afribitcoiners) just published “[Bitcoin: Africa’s Guide to Freedom Money](https://x.com/afribitcoiners/status/1904516726273851513),” a Bitcoin guide providing clear, practical insights into how Bitcoin can help people across the continent escape inflation, corrupt regimes, and failing financial systems. It covers essential topics to get started — from choosing a wallet to properly securing Bitcoin. In Africa, where some of the world’s longest-standing dictators restrict even basic financial activity, this guide is a powerful resource for human rights defenders, nonprofits, and everyday citizens. Read it[ here](https://bitcoiners.africa/bitcoin-africas-guide-to-freedom-money/).
#### **OpenSats | 10th Wave of Nostr Grants**
[OpenSats](https://opensats.org/), a nonprofit that supports open-source software development, [announced](https://opensats.org/blog/10th-wave-of-nostr-grants) its tenth wave of grants for projects in the nostr ecosystem. Nostr is a decentralized protocol that enables digital identity and communications outside the reach of authoritarian states. The grant round provides support to nostr Epoxy, which enhances access to nostr by circumventing censorship through a network of paid proxies. This ensures activists and dissidents can continue to communicate even in restrictive environments. Additionally, Zapstore received a grant for providing a permissionless app store built on nostr that enables developers to distribute software without corporate gatekeepers. This provides an open-source alternative to centralized app stores that often comply with government censorship and restrict dissidents’ access to freedom tools.
## RECOMMENDED CONTENT
#### **Freedom Tech with Alex Gladstein**
In this [episode](https://x.com/blockspacepod/status/1896229100702089589?s=46&t=yEPKerGEzeCp5j_mIaNJ8A) of The Gwart Show, Alex Gladstein, chief strategy officer at HRF, breaks down how and why Bitcoin serves as “money dictators can’t stop.” Drawing on more than 17 years of human rights work, he shares real-world examples of activists and citizens using Bitcoin to escape financial repression in authoritarian countries. Gladstein also explores privacy tools, cross-border payments, and why Bitcoin offers promising hope for financial freedom. Watch the full conversation [here](https://www.youtube.com/watch?v=5Ng961QZwI0).
#### **The State of Personal Online Security and Confidentiality with Meredith Whittaker**
In this [keynote](https://www.youtube.com/watch?v=AyH7zoP-JOg) for SXSW 2025, Signal CEO Meredith Whittaker shares her growing concerns around AI, personal data collection, and the erosion of privacy in today’s increasingly digital world. She emphasizes the need for more secure, uncensorable, and privacy-protecting technologies that shield users from surveillance and exploitation, especially in the context of authoritarian regimes. Watch the [full discussion](https://www.youtube.com/watch?v=AyH7zoP-JOg) for a pragmatic view into the future of digital privacy and security.
*If this article was forwarded to you and you enjoyed reading it, please consider subscribing to the Financial Freedom Report [here](https://mailchi.mp/hrf.org/financial-freedom-newsletter?mc_cid=bf652c0a5a).*
*Support the newsletter by donating bitcoin to HRF’s Financial Freedom program [via BTCPay](https://hrf.org/btc).*\
*Want to contribute to the newsletter? Submit tips, stories, news, and ideas by emailing us at ffreport @ [hrf.org](http://hrf.org/)*
*The Bitcoin Development Fund (BDF) is accepting grant proposals on an ongoing basis. The Bitcoin Development Fund is looking to support Bitcoin developers, community builders, and educators. Submit proposals [here](https://forms.monday.com/forms/57019f8829449d9e729d9e3545a237ea?r=use1)*.
[**Subscribe to newsletter**](http://financialfreedomreport.org/)
[**Apply for a grant**](https://forms.monday.com/forms/57019f8829449d9e729d9e3545a237ea?r=use1&mc_cid=39c1c9b7e8&mc_eid=778e9876e3)
[**Support our work**](https://hrf.org/btc?mc_cid=39c1c9b7e8&mc_eid=778e9876e3)
[**Visit our website**](https://hrf.org/programs/financial-freedom/)
-

@ 57d1a264:69f1fee1
2025-03-29 09:31:13
> "THE NATURE OF BITCOIN IS SUCH THAT ONCE VERSION 0.1 WAS RELEASED, THE CORE DESIGN WAS SET IN STONE FOR THE REST OF ITS LIFETIME."
<sub>- SATOSHI NAKAMOTO</sub>



"Reborn" is inspired by my Bitcoin journey and the many other people whose lives have been changed by Bitcoin. I’ve carved the hand in the “Gyan Mudra” or the “Mudra of Wisdom or Knowledge,” with an Opendime grasped between thumb and index finger alluding to the pursuit of Bitcoin knowledge. The hand emerges from rough, choppy water, and I've set the hand against an archway, through which, the copper leaf hints at the bright orange future made possible by Bitcoin.
Materials: Carrara Marble, Copper leaf, Opendime
Dimensions: 6" x 9" x 13"
Price: $30,000 or BTC equivalent
Enquire: https://www.vonbitcoin.com/available-works
X: https://x.com/BVBTC/status/1894463357316419960/photo/1
originally posted at https://stacker.news/items/928510
-

@ db11b320:05c5f7af
2025-03-29 19:04:19
magnet:?xt=urn:btih:9BAC9A3F98803AEA1EB28A0B60A562D7E3779710
-

@ a5142938:0ef19da3
2025-04-03 09:55:01
### Core Team
The Core Team drives the project and validates the content.
- [Jean-David Bar](https://njump.me/npub1qr4p7uamcpawv7cr8z9nlhmd60lylukf7lvmtlnpe7r4juwxudzq3hrnll)
To start, I'm managing the project solo. Contact me if you'd like to join!
### Content Enrichers
Our contributors make this site engaging and interesting.
-

@ 0d788b5e:c99ddea5
2025-03-29 02:40:37
- [首页](/readme.md)
- [第一章、 第一章标题](/chapter1.md)
- [第二章、 第二章标题](/chapter2.md)
-

@ 000002de:c05780a7
2025-04-01 18:04:17
Over and over again people fall for phishing scams. An email that looks like it is coming from a legit sender turns out to be a scam.
One way you can fight this attack is to only use an email client that displays the full email address. Not just part of it. Not just the from name. Do not assume that because an email has the name "Amazon" the from field that it is from Amazon.com. Look at the address.
Now, it is possible for someone to spoof an email address but most of the time the scams I see don't even do this. I suspect this is because of expansion of DMARC policies. Many people simply do not check the actual email address.
Other tips, don't click links in emails that you were not expecting to get like emails with log in links. Instead, visit the site and log in direction on the site. If you must click a link in an email look at the actual URL. Don't blindly click the link and for sure do not enter your credentials in a site without checking the domain. This is where password managers can help you out. Most filter passwords by URLs and will not suggest an account cred if you are on the wrong site.
I know many of you, maybe most of you know this stuff but I bet there are those that don't. Or, have become lazy.
originally posted at https://stacker.news/items/931364
-

@ 2183e947:f497b975
2025-03-29 02:41:34
Today I was invited to participate in the private beta of a new social media protocol called Pubky, designed by a bitcoin company called Synonym with the goal of being better than existing social media platforms. As a heavy nostr user, I thought I'd write up a comparison.
I can't tell you how to create your own accounts because it was made very clear that only *some* of the software is currently open source, and how this will all work is still a bit up in the air. The code that *is* open source can be found here: https://github.com/pubky -- and the most important repo there seems to be this one: https://github.com/pubky/pubky-core
You can also learn more about Pubky here: https://pubky.org/
That said, I used my invite code to create a pubky account and it seemed very similar to onboarding to nostr. I generated a private key, backed up 12 words, and the onboarding website gave me a public key.
Then I logged into a web-based client and it looked a lot like twitter. I saw a feed for posts by other users and saw options to reply to posts and give reactions, which, I saw, included hearts, thumbs up, and other emojis.
Then I investigated a bit deeper to see how much it was like nostr. I opened up my developer console and navigated to my networking tab, where, if this was nostr, I would expect to see queries to relays for posts. Here, though, I saw one query that seemed to be repeated on a loop, which went to a single server and provided it with my pubkey. That single query (well, a series of identical queries to the same server) seemed to return all posts that showed up on my feed. So I infer that the server "knows" what posts to show me (perhaps it has some sort of algorithm, though the marketing material says it does not use algorithms) and the query was on a loop so that if any new posts came in that the server thinks I might want to see, it can add them to my feed.
Then I checked what happens when I create a post. I did so and looked at what happened in my networking tab. If this was nostr, I would expect to see multiple copies of a signed messaged get sent to a bunch of relays. Here, though, I saw one message get sent to the same server that was populating my feed, and that message was not signed, it was a plaintext copy of my message.
I happened to be in a group chat with John Carvalho at the time, who is associated with pubky. I asked him what was going on, and he said that pubky is based around three types of servers: homeservers, DHT servers, and indexer servers. The homeserver is where you create posts and where you query for posts to show on your feed. DHT servers are used for censorship resistance: each user creates an entry on a DHT server saying what homeserver they use, and these entries are signed by their key.
As for indexers, I think those are supposed to speed up the use of the DHT servers. From what I could tell, indexers query DHT servers to find out what homeservers people use. When you query a homeserver for posts, it is supposed to reach out to indexer servers to find out the homeservers of people whose posts the homeserver decided to show you, and then query those homeservers for those posts. I believe they decided not to look up what homeservers people use directly on DHT servers directly because DHT servers are kind of slow, due to having to store and search through all sorts of non-social-media content, whereas indexers only store a simple db that maps each user's pubkey to their homeserver, so they are faster.
Based on all of this info, it seems like, to populate your feed, this is the series of steps:
- you tell your homeserver your pubkey
- it uses some sort of algorithm to decide whose posts to show you
- then looks up the homeservers used by those people on an indexer server
- then it fetches posts from their homeservers
- then your client displays them to you
To create a post, this is the series of steps:
- you tell your homeserver what you want to say to the world
- it stores that message in plaintext and merely asserts that it came from you (it's not signed)
- other people can find out what you said by querying for your posts on your homeserver
Since posts on homeservers are not signed, I asked John what prevents a homeserver from just making up stuff and claiming I said it. He said nothing stops them from doing that, and if you are using a homeserver that starts acting up in that manner, what you should do is start using a new homeserver and update your DHT record to point at your new homeserver instead of the old one. Then, indexers should update their db to show where your new homeserver is, and the homeservers of people who "follow" you should stop pulling content from your old homeserver and start pulling it from your new one. If their homeserver is misbehaving too, I'm not sure what would happen. Maybe it could refuse to show them the content you've posted on your new homeserver, keeping making up fake content on your behalf that you've never posted, and maybe the people you follow would never learn you're being impersonated or have moved to a new homeserver.
John also clarified that there is not currently any tooling for migrating user content from one homeserver to another. If pubky gets popular and a big homeserver starts misbehaving, users will probably need such a tool. But these are early days, so there aren't that many homeservers, and the ones that exist seem to be pretty trusted.
Anyway, those are my initial thoughts on Pubky. Learn more here: https://pubky.org/
-

@ ed84ce10:cccf4c2a
2025-03-18 14:19:19
## **The Evolution of Hackathons: From Offline to Online, Powering Frontier Innovation Worldwide**
Throughout the history of open-source platform technology, hackathons have been the launchpads for innovation—fueling breakthroughs, incubating the next generation of startups, and serving as the proving ground for builders. Over the past decade, [DoraHacks](https://dorahacks.io/) has led the charge, driving the hacker movement and open-source revolution. We didn’t just witness the evolution of hackathons—we architected it.
### **The Online Revolution of Hackathons**
Before 2020, hackathons were largely stuck in the physical world—you had to be in the room to participate. The idea of a fully online, global hackathon was a pipe dream. Then, [DoraHacks.io](http://dorahacks.io/) changed everything. Suddenly, a developer in Africa could win funding from a hackathon hosted by a Silicon Valley company. Geographic barriers collapsed. Today, over 95% of hackathons happen online.
### **The Infrastructure Revolution: Making Hackathons 10x More Effective**
[DoraHacks](https://dorahacks.io/) relentlessly iterated on the hackathon model. We built BUIDL pages for real-time project showcases, a world-class hackathon organizer dashboard, MACI-powered decentralized privacy governance, and Grant DAOs that provide ongoing funding. The result? [DoraHacks](https://dorahacks.io/) became the ultimate launchpad for hackers and early-stage builders.
### **The Ecosystem Revolution: Supercharging Open Innovation**
[DoraHacks](https://dorahacks.io/) became the backbone of Web3 innovation—from Ethereum, Solana, and BNB Chain to the next wave of blockchains like Aptos, Cosmos, Injective, TON, and Sonic. Since 2023, hackathons have expanded beyond crypto—quantum computing, commercial space tech, and AI-driven innovations are now being built on [DoraHacks](https://dorahacks.io/).
## **Rolling Hackathons and Uninterrupted BUIDLing - the New Standard for Ecosystem Growth**
**BUIDLs can be created spontaneously at any time.** Hosting Hackathons as short-term events held only once or twice a year is not conducive to attracting outstanding Hackers and high-quality projects to join the ecosystem and drive innovation in the long term. To remediate this, **Hackathons should be continuous and uninterrupted, serving as a long-term driving force within the developer ecosystem.**
Historically, the **high organizational costs** and **substantial resource investments** associated with frequent Hackathons meant that most emerging ecosystems couldn't afford to host them regularly. As a result, Hackathons became rare, annual spectacles, and for some projects, an unaffordable luxury. This model severely restricted developers' chances to participate and hindered the ecosystem's ability to innovate consistently. Let's imagine what would happen if an ecosystem held 12 or more Hackathons each year?
- **Developers have a clear loyalty incentive:** They would know that the ecosystem is committed to supporting and funding excellent developers and projects continuously, which would encourage them to make long-term investments and contribute regularly.
- **Missing out is no longer an issue:** Even if a developer couldn't attend a particular Hackathon, there would be another one soon, increasing accessibility.
- **Accelerated ecosystem innovation:** Frequent Hackathons would accelerate ecosystem innovation. Developers would be constantly pushed to explore new directions, significantly boosting the growth rate of the technological ecosystem.
Previously, **due to the limitations of costs and organizational difficulties, frequent Hackathons were almost unthinkable**. Only ecosystems with sufficient funds like Google and Amazon could afford rolling Hackathons. But now, **[DoraHacks](https://dorahacks.io/)' upcoming BUIDL AI platform tools** are set to change the game. These tools make it possible to organize 12 Hackathons in a year, and even go a step further by enabling the simultaneous hosting of multiple differently-themed Hackathons. This will help emerging ecosystems effectively incentivise developers, expand their technological influence, and increase the number of exceptional BUIDLs (projects) in their ecosystems.
**The majority of BUIDLs come about continuously and spontaneously and should be recognized and incentivized promptly, rather than having to wait for the single annual Hackathon.**
As the saying goes, **"He who wins over developers wins the world."** In the highly competitive Web3 space, Hackathons are an effective means of attracting developers, and **rolling Hackathons are the best way to achieve this**. For an ecosystem to stay competitive, it must ensure that developers always have opportunities to engage and create.
## **The AI Era of Hackathons: A 10x Opportunity, A 10x Challenge**
### **AI Turns Everyone Into a Hacker**
AI has obliterated repetitive work. Building is faster than ever. Anyone, from anywhere, can hack, ship, and scale with AI tools that accelerate ideation, development, and execution. The potential of hackathons in this AI-powered era is 10x bigger than ever before.
### **But Hackathon Infrastructure Is Stuck in the Past**
**Despite this massive opportunity, organizing hackathons remains painfully inefficient:**
- Most organizations don’t know how to run hackathons effectively.
- Even those who do lack time and resources to do it frequently.
- Ecosystem builders who have the resources can only host one hackathon per year.
**The result?**
- Hackathons are underutilized, slowing innovation.
- Ecosystem growth is bottlenecked by developer relations (DevRel) teams.
- Many ecosystems fail to maximize the potential of hackathons.
- Low-frequency hackathons waste hacker potential—builders sit idle when they could be shipping.
## **BUIDL AI: Unlocking the Infinite Potential of Hackathons**
We refuse to let inefficiency limit innovation. BUIDL AI is our answer.
[DoraHacks](https://dorahacks.io/) is launching BUIDL AI, the AI-powered Hackathon Co-Pilot that automates, scales, and supercharges hackathon organization.
### **BUIDL AI: The Game-Changing Features**
**1. Edit and Launch: One-Click Hackathon Deployment**
Organizers can now launch a hackathon in minutes by filling in basic details (prizes, themes, workshops, judges, etc.). No tedious manual setup.
**2. BUIDL Review: Submission Evaluation (10x Faster)**
Traditional hackathons get hundreds of submissions—judging takes hundreds of hours. BUIDL AI changes the game. It automatically scores projects based on completeness, originality, and theme relevance—filtering out low-quality submissions 10x faster than before.
**3. Automated Marketing: Instant Hackathon Reports**
After the hackathon ends, BUIDL AI auto-generates a full post-event report—highlighting winners, standout projects, and key takeaways—boosting visibility and impact.
**4. Seamless Interaction: Smarter Collaboration, No Bottlenecks**
BUIDL AI will interact with hackathon organizers to keep organizers in sync, alerting them about new submissions, pending approvals, and participant inquiries in real time. No more dropped balls.
**5. Multi-Hackathon Management: Scaling Innovation Without Limits**
Before BUIDL AI, running multiple hackathons at once was a logistical nightmare. Now, ecosystem builders can launch and manage multiple hackathons seamlessly, boosting innovation frequency exponentially
**The full BUIDL AI Beta version will release on April 15th, but multiple free BUIDL AI features have already been available on [DoraHacks.io](http://dorahacks.io/)!**
## **BUIDL AI: The Next Great Leap in Open Innovation**
Hackathons aren’t just competitions. They are the birthplace of the next trillion-dollar innovations.
With BUIDL AI, hackathons enter a new era—automated, intelligent, and infinitely scalable. This means more hackers, more builders, and more breakthrough projects than ever before.
At [DoraHacks](https://dorahacks.io/), we believe in an open, hacker-driven future. BUIDL AI is the rocket fuel for that future.
-

@ 1bda7e1f:bb97c4d9
2025-01-02 05:19:08
### Tldr
- Nostr is an open and interoperable protocol
- You can integrate it with workflow automation tools to augment your experience
- n8n is a great low/no-code workflow automation tool which you can host yourself
- Nostrobots allows you to integrate Nostr into n8n
- In this blog I create some workflow automations for Nostr
- A simple form to delegate posting notes
- Push notifications for mentions on multiple accounts
- Push notifications for your favourite accounts when they post a note
- All workflows are provided as open source with MIT license for you to use
### Inter-op All The Things
Nostr is a new open social protocol for the internet. This open nature exciting because of the opportunities for interoperability with other technologies. In [Using NFC Cards with Nostr]() I explored the `nostr:` URI to launch Nostr clients from a card tap.
The interoperability of Nostr doesn't stop there. The internet has many super-powers, and Nostr is open to all of them. Simply, there's no one to stop it. There is no one in charge, there are no permissioned APIs, and there are no risks of being de-platformed. If you can imagine technologies that would work well with Nostr, then any and all of them can ride on or alongside Nostr rails.
My mental model for why this is special is Google Wave ~2010. Google Wave was to be the next big platform. Lars was running it and had a big track record from Maps. I was excited for it. Then, Google pulled the plug. And, immediately all the time and capital invested in understanding and building on the platform was wasted.
This cannot happen to Nostr, as there is no one to pull the plug, and maybe even no plug to pull.
So long as users demand Nostr, Nostr will exist, and that is a pretty strong guarantee. It makes it worthwhile to invest in bringing Nostr into our other applications.
All we need are simple ways to plug things together.
### Nostr and Workflow Automation
Workflow automation is about helping people to streamline their work. As a user, the most common way I achieve this is by connecting disparate systems together. By setting up one system to trigger another or to move data between systems, I can solve for many different problems and become way more effective.
#### n8n for workflow automation
Many workflow automation tools exist. My favourite is [n8n](https://n8n.io/). n8n is a low/no-code workflow automation platform which allows you to build all kinds of workflows. You can use it for free, you can self-host it, it has a user-friendly UI and useful API. Vs Zapier it can be far more elaborate. Vs Make.com I find it to be more intuitive in how it abstracts away the right parts of the code, but still allows you to code when you need to.
Most importantly you can plug anything into n8n: You have built-in nodes for specific applications. HTTP nodes for any other API-based service. And community nodes built by individual community members for any other purpose you can imagine.
#### Eating my own dogfood
It's very clear to me that there is a big design space here just demanding to be explored. If you could integrate Nostr with anything, what would you do?
In my view the best way for anyone to start anything is by solving their own problem first (aka "scratching your own itch" and "eating your own dogfood"). As I get deeper into Nostr I find myself controlling multiple Npubs – to date I have a personal Npub, a brand Npub for a community I am helping, an AI assistant Npub, and various testing Npubs. I need ways to delegate access to those Npubs without handing over the keys, ways to know if they're mentioned, and ways to know if they're posting.
I can build workflows with n8n to solve these issues for myself to start with, and keep expanding from there as new needs come up.
### Running n8n with Nostrobots
I am mostly non-technical with a very helpful AI. To set up n8n to work with Nostr and operate these workflows should be possible for anyone with basic technology skills.
- I have a cheap VPS which currently runs my [HAVEN Nostr Relay](https://rodbishop.npub.pro/post/8ca68889/) and [Albyhub Lightning Node](https://rodbishop.npub.pro/post/setting-up-payments-on-nostr-7o6ls7/) in Docker containers,
- My objective was to set up n8n to run alongside these in a separate Docker container on the same server, install the required nodes, and then build and host my workflows.
#### Installing n8n
Self-hosting n8n could not be easier. I followed n8n's [Docker-Compose installation docs](https://docs.n8n.io/hosting/installation/server-setups/docker-compose/)–
- Install Docker and Docker-Compose if you haven't already,
- Create your ``docker-compose.yml`` and `.env` files from the docs,
- Create your data folder `sudo docker volume create n8n_data`,
- Start your container with `sudo docker compose up -d`,
- Your n8n instance should be online at port `5678`.
n8n is free to self-host but does require a license. Enter your credentials into n8n to get your free license key. You should now have access to the Workflow dashboard and can create and host any kind of workflows from there.
#### Installing Nostrobots
To integrate n8n nicely with Nostr, I used the [Nostrobots](https://github.com/ocknamo/n8n-nodes-nostrobots?tab=readme-ov-file) community node by [Ocknamo](nostr:npub1y6aja0kkc4fdvuxgqjcdv4fx0v7xv2epuqnddey2eyaxquznp9vq0tp75l).
In n8n parlance a "node" enables certain functionality as a step in a workflow e.g. a "set" node sets a variable, a "send email" node sends an email. n8n comes with all kinds of "official" nodes installed by default, and Nostr is not amongst them. However, n8n also comes with a framework for community members to create their own "community" nodes, which is where Nostrobots comes in.
You can only use a community node in a self-hosted n8n instance (which is what you have if you are running in Docker on your own server, but this limitation does prevent you from using n8n's own hosted alternative).
To install a community node, [see n8n community node docs](https://docs.n8n.io/integrations/community-nodes/installation/gui-install/). From your workflow dashboard–
- Click the "..." in the bottom left corner beside your username, and click "settings",
- Cilck "community nodes" left sidebar,
- Click "Install",
- Enter the "npm Package Name" which is `n8n-nodes-nostrobots`,
- Accept the risks and click "Install",
- Nostrobots is now added to your n8n instance.
#### Using Nostrobots
Nostrobots gives you nodes to help you build Nostr-integrated workflows–
- **Nostr Write** – for posting Notes to the Nostr network,
- **Nostr Read** – for reading Notes from the Nostr network, and
- **Nostr Utils** – for performing certain conversions you may need (e.g. from bech32 to hex).
Nostrobots has [good documentation](https://github.com/ocknamo/n8n-nodes-nostrobots?tab=readme-ov-file) on each node which focuses on simple use cases.
Each node has a "convenience mode" by default. For example, the "Read" Node by default will fetch Kind 1 notes by a simple filter, in Nostrobots parlance a "Strategy". For example, with Strategy set to "Mention" the node will accept a pubkey and fetch all Kind 1 notes that Mention the pubkey within a time period. This is very good for quick use.
What wasn't clear to me initially (until Ocknamo helped me out) is that advanced use cases are also possible.
Each node also has an advanced mode. For example, the "Read" Node can have "Strategy" set to "RawFilter(advanced)". Now the node will accept json (anything you like that complies with [NIP-01](https://github.com/nostr-protocol/nips/blob/master/01.md)). You can use this to query Notes (Kind 1) as above, and also Profiles (Kind 0), Follow Lists (Kind 3), Reactions (Kind 7), Zaps (Kind 9734/9735), and anything else you can think of.
#### Creating and adding workflows
With n8n and Nostrobots installed, you can now create or add any kind of Nostr Workflow Automation.
- Click "Add workflow" to go to the workflow builder screen,
- If you would like to build your own workflow, you can start with adding any node. Click "+" and see what is available. Type "Nostr" to explore the Nostrobots nodes you have added,
- If you would like to add workflows that someone else has built, click "..." in the top right. Then click "import from URL" and paste in the URL of any workflow you would like to use (including the ones I share later in this article).
### Nostr Workflow Automations
It's time to build some things!
#### A simple form to post a note to Nostr
I started very simply. I needed to delegate the ability to post to Npubs that I own in order that a (future) team can test things for me. I don't want to worry about managing or training those people on how to use keys, and I want to revoke access easily.
I needed a basic form with credentials that posted a Note.
For this I can use a very simple workflow–
- **A n8n Form node** – Creates a form for users to enter the note they wish to post. Allows for the form to be protected by a username and password. This node is the workflow "trigger" so that the workflow runs each time the form is submitted.
- **A Set node** – Allows me to set some variables, in this case I set the relays that I intend to use. I typically add a Set node immediately following the trigger node, and put all the variables I need in this. It helps to make the workflows easier to update and maintain.
- **A Nostr Write node** (from Nostrobots) – Writes a Kind-1 note to the Nostr network. It accepts Nostr credentials, the output of the Form node, and the relays from the Set node, and posts the Note to those relays.
Once the workflow is built, you can test it with the testing form URL, and set it to "Active" to use the production form URL. That's it. You can now give posting access to anyone for any Npub. To revoke access, simply change the credentials or set to workflow to "Inactive".
It may also be the world's simplest Nostr client.
You can find the [Nostr Form to Post a Note workflow here](https://github.com/r0d8lsh0p/nostr-n8n/blob/main/Nostr_Form_to_Post_a_Note.json).
#### Push notifications on mentions and new notes
One of the things Nostr is not very good at is push notifications. Furthermore I have some unique itches to scratch. I want–
- **To make sure I never miss a note addressed to any of my Npubs** – For this I want a push notification any time any Nostr user mentions any of my Npubs,
- **To make sure I always see all notes from key accounts** – For this I need a push notification any time any of my Npubs post any Notes to the network,
- **To get these notifications on all of my devices** – Not just my phone where my Nostr regular client lives, but also on each of my laptops to suit wherever I am working that day.
I needed to build a Nostr push notifications solution.
To build this workflow I had to string a few ideas together–
- **Triggering the node on a schedule** – Nostrobots does not include a trigger node. As every workflow starts with a trigger we needed a different method. I elected to run the workflow on a schedule of every 10-minutes. Frequent enough to see Notes while they are hot, but infrequent enough to not burden public relays or get rate-limited,
- **Storing a list of Npubs in a Nostr list** – I needed a way to store the list of Npubs that trigger my notifications. I initially used an array defined in the workflow, this worked fine. Then I decided to try Nostr lists ([NIP-51, kind 30000](https://github.com/nostr-protocol/nips/blob/master/51.md)). By defining my list of Npubs as a list published to Nostr I can control my list from within a Nostr client (e.g. [Listr.lol](https://listr.lol/npub1r0d8u8mnj6769500nypnm28a9hpk9qg8jr0ehe30tygr3wuhcnvs4rfsft) or [Nostrudel.ninja](https://nostrudel.ninja/#/lists)). Not only does this "just work", but because it's based on Nostr lists automagically Amethyst client allows me to browse that list as a Feed, and everyone I add gets notified in their Mentions,
- **Using specific relays** – I needed to query the right relays, including my own HAVEN relay inbox for notes addressed to me, and wss://purplepag.es for Nostr profile metadata,
- **Querying Nostr events** (with Nostrobots) – I needed to make use of many different Nostr queries and use quite a wide range of what Nostrobots can do–
- I read the EventID of my Kind 30000 list, to return the desired pubkeys,
- For notifications on mentions, I read all Kind 1 notes that mention that pubkey,
- For notifications on new notes, I read all Kind 1 notes published by that pubkey,
- Where there are notes, I read the Kind 0 profile metadata event of that pubkey to get the displayName of the relevant Npub,
- I transform the EventID into a Nevent to help clients find it.
- **Using the Nostr URI** – As I did with my NFC card article, I created a link with the `nostr:` URI prefix so that my phone's native client opens the link by default,
- **Push notifications solution** – I needed a push notifications solution. I found many with n8n integrations and chose to go with [Pushover](https://pushover.net/) which supports all my devices, has a free trial, and is unfairly cheap with a $5-per-device perpetual license.
Once the workflow was built, lists published, and Pushover installed on my phone, I was fully set up with push notifications on Nostr. I have used these workflows for several weeks now and made various tweaks as I went. They are feeling robust and I'd welcome you to give them a go.
You can find the [Nostr Push Notification If Mentioned here](https://github.com/r0d8lsh0p/nostr-n8n/blob/main/Nostr_Push_Notify_If_Mentioned.json) and [If Posts a Note here](https://github.com/r0d8lsh0p/nostr-n8n/blob/main/Nostr_Push_Notify_If_Post_a_Note.json).
In speaking with other Nostr users while I was building this, there are all kind of other needs for push notifications too – like on replies to a certain bookmarked note, or when a followed Npub starts streaming on zap.stream. These are all possible.
#### Use my workflows
I have open sourced all my workflows at my [Github](https://github.com/r0d8lsh0p/nostr-n8n) with MIT license and tried to write complete docs, so that you can import them into your n8n and configure them for your own use.
To import any of my workflows–
- Click on the workflow of your choice, e.g. "[Nostr_Push_Notify_If_Mentioned.json](https://github.com/r0d8lsh0p/nostr-n8n/blob/main/Nostr_Push_Notify_If_Mentioned.json "Nostr_Push_Notify_If_Mentioned.json")",
- Click on the "raw" button to view the raw JSON, ex any Github page layout,
- Copy that URL,
- Enter that URL in the "import from URL" dialog [mentioned above](#creating-and-adding-workflows).
To configure them–
- Prerequisites, credentials, and variables are all stated,
- In general any variables required are entered into a Set Node that follows the trigger node,
- Pushover has some extra setup but is very straightforward and documented in the workflow.
### What next?
Over my first four blogs I explored creating a good Nostr setup with [Vanity Npub](https://rodbishop.npub.pro/post/mining-your-vanity-pubkey-4iupbf/), [Lightning Payments](https://rodbishop.npub.pro/post/setting-up-payments-on-nostr-7o6ls7/), [Nostr Addresses at Your Domain](https://rodbishop.npub.pro/post/ee8a46bc/), and [Personal Nostr Relay](https://rodbishop.npub.pro/post/8ca68889/).
Then in my latest two blogs I explored different types of interoperability [with NFC cards](https://rodbishop.npub.pro/post/edde8387/) and now n8n Workflow Automation.
Thinking ahead n8n can power any kind of interoperability between Nostr and any other legacy technology solution. On my mind as I write this:
- Further enhancements to posting and delegating solutions and forms (enhanced UI or different note kinds),
- Automated or scheduled posting (such as auto-liking everything [Lyn Alden](nostr:npub1a2cww4kn9wqte4ry70vyfwqyqvpswksna27rtxd8vty6c74era8sdcw83a) posts),
- Further enhancements to push notifications, on new and different types of events (such as notifying me when I get a new follower, on replies to certain posts, or when a user starts streaming),
- All kinds of bridges, such as bridging notes to and from Telegram, Slack, or Campfire. Or bridging RSS or other event feeds to Nostr,
- All kinds of other automation (such as [BlackCoffee](nostr:npub1dqepr0g4t3ahvnjtnxazvws4rkqjpxl854n29wcew8wph0fmw90qlsmmgt) [controlling a coffee machine](https://primal.net/e/note16fzhh5yfc3u4kufx0mck63tsfperdrlpp96am2lmq066cnuqutds8retc3)),
- All kinds of AI Assistants and Agents,
In fact I have already released an open source workflow for an [AI Assistant](https://primal.net/p/npub1ahjpx53ewavp23g5zj9jgyfrpr8djmgjzg5mpe4xd0z69dqvq0kq2lf353), and will share more about that in my next blog.
Please be sure to let me know if you think there's another Nostr topic you'd like to see me tackle.
GM Nostr.
-

@ 0d788b5e:c99ddea5
2025-03-29 01:27:53
这是首页内容
-

@ 9e69e420:d12360c2
2025-02-17 17:12:01
President Trump has intensified immigration enforcement, likening it to a wartime effort. Despite pouring resources into the U.S. Immigration and Customs Enforcement (ICE), arrest numbers are declining and falling short of goals. ICE fell from about 800 daily arrests in late January to fewer than 600 in early February.
Critics argue the administration is merely showcasing efforts with ineffectiveness, while Trump seeks billions more in funding to support his deportation agenda. Increased involvement from various federal agencies is intended to assist ICE, but many lack specific immigration training.
Challenges persist, as fewer immigrants are available for quick deportation due to a decline in illegal crossings. Local sheriffs are also pressured by rising demands to accommodate immigrants, which may strain resources further.
-

@ 57d1a264:69f1fee1
2025-03-28 10:32:15
Bitcoin.design community is organizing another Designathon, from May 4-18. Let's get creative with bitcoin together. More to come very soon.

The first edition was a bursting success! the website still there https://events.bitcoin.design, and here their previous [announcement](https://bitcoindesign.substack.com/p/the-bitcoin-designathon-2022).
Look forward for this to happen!
Spread the voice:
N: [https://njump.me/nevent1qqsv9w8p93tadlnyx0rkhexj5l48l...](https://njump.me/nevent1qqsv9w8p93tadlnyx0rkhexj5l48lmw9jc7nhhauyq5w3cm4nfsm3mstqtk6m)
X: https://x.com/bitcoin_design/status/1905547407405768927
originally posted at https://stacker.news/items/927650
-

@ fd06f542:8d6d54cd
2025-03-28 02:27:52
NIP-02
======
Follow List
-----------
`final` `optional`
A special event with kind `3`, meaning "follow list" is defined as having a list of `p` tags, one for each of the followed/known profiles one is following.
Each tag entry should contain the key for the profile, a relay URL where events from that key can be found (can be set to an empty string if not needed), and a local name (or "petname") for that profile (can also be set to an empty string or not provided), i.e., `["p", <32-bytes hex key>, <main relay URL>, <petname>]`.
The `.content` is not used.
For example:
```jsonc
{
"kind": 3,
"tags": [
["p", "91cf9..4e5ca", "wss://alicerelay.com/", "alice"],
["p", "14aeb..8dad4", "wss://bobrelay.com/nostr", "bob"],
["p", "612ae..e610f", "ws://carolrelay.com/ws", "carol"]
],
"content": "",
// other fields...
}
```
Every new following list that gets published overwrites the past ones, so it should contain all entries. Relays and clients SHOULD delete past following lists as soon as they receive a new one.
Whenever new follows are added to an existing list, clients SHOULD append them to the end of the list, so they are stored in chronological order.
## Uses
### Follow list backup
If one believes a relay will store their events for sufficient time, they can use this kind-3 event to backup their following list and recover on a different device.
### Profile discovery and context augmentation
A client may rely on the kind-3 event to display a list of followed people by profiles one is browsing; make lists of suggestions on who to follow based on the follow lists of other people one might be following or browsing; or show the data in other contexts.
### Relay sharing
A client may publish a follow list with good relays for each of their follows so other clients may use these to update their internal relay lists if needed, increasing censorship-resistance.
### Petname scheme
The data from these follow lists can be used by clients to construct local ["petname"](http://www.skyhunter.com/marcs/petnames/IntroPetNames.html) tables derived from other people's follow lists. This alleviates the need for global human-readable names. For example:
A user has an internal follow list that says
```json
[
["p", "21df6d143fb96c2ec9d63726bf9edc71", "", "erin"]
]
```
And receives two follow lists, one from `21df6d143fb96c2ec9d63726bf9edc71` that says
```json
[
["p", "a8bb3d884d5d90b413d9891fe4c4e46d", "", "david"]
]
```
and another from `a8bb3d884d5d90b413d9891fe4c4e46d` that says
```json
[
["p", "f57f54057d2a7af0efecc8b0b66f5708", "", "frank"]
]
```
When the user sees `21df6d143fb96c2ec9d63726bf9edc71` the client can show _erin_ instead;
When the user sees `a8bb3d884d5d90b413d9891fe4c4e46d` the client can show _david.erin_ instead;
When the user sees `f57f54057d2a7af0efecc8b0b66f5708` the client can show _frank.david.erin_ instead.
-

@ fd06f542:8d6d54cd
2025-03-28 02:24:00
NIP-01
======
Basic protocol flow description
-------------------------------
`draft` `mandatory`
This NIP defines the basic protocol that should be implemented by everybody. New NIPs may add new optional (or mandatory) fields and messages and features to the structures and flows described here.
## Events and signatures
Each user has a keypair. Signatures, public key, and encodings are done according to the [Schnorr signatures standard for the curve `secp256k1`](https://bips.xyz/340).
The only object type that exists is the `event`, which has the following format on the wire:
```jsonc
{
"id": <32-bytes lowercase hex-encoded sha256 of the serialized event data>,
"pubkey": <32-bytes lowercase hex-encoded public key of the event creator>,
"created_at": <unix timestamp in seconds>,
"kind": <integer between 0 and 65535>,
"tags": [
[<arbitrary string>...],
// ...
],
"content": <arbitrary string>,
"sig": <64-bytes lowercase hex of the signature of the sha256 hash of the serialized event data, which is the same as the "id" field>
}
```
To obtain the `event.id`, we `sha256` the serialized event. The serialization is done over the UTF-8 JSON-serialized string (which is described below) of the following structure:
```
[
0,
<pubkey, as a lowercase hex string>,
<created_at, as a number>,
<kind, as a number>,
<tags, as an array of arrays of non-null strings>,
<content, as a string>
]
```
To prevent implementation differences from creating a different event ID for the same event, the following rules MUST be followed while serializing:
- UTF-8 should be used for encoding.
- Whitespace, line breaks or other unnecessary formatting should not be included in the output JSON.
- The following characters in the content field must be escaped as shown, and all other characters must be included verbatim:
- A line break (`0x0A`), use `\n`
- A double quote (`0x22`), use `\"`
- A backslash (`0x5C`), use `\\`
- A carriage return (`0x0D`), use `\r`
- A tab character (`0x09`), use `\t`
- A backspace, (`0x08`), use `\b`
- A form feed, (`0x0C`), use `\f`
### Tags
Each tag is an array of one or more strings, with some conventions around them. Take a look at the example below:
```jsonc
{
"tags": [
["e", "5c83da77af1dec6d7289834998ad7aafbd9e2191396d75ec3cc27f5a77226f36", "wss://nostr.example.com"],
["p", "f7234bd4c1394dda46d09f35bd384dd30cc552ad5541990f98844fb06676e9ca"],
["a", "30023:f7234bd4c1394dda46d09f35bd384dd30cc552ad5541990f98844fb06676e9ca:abcd", "wss://nostr.example.com"],
["alt", "reply"],
// ...
],
// ...
}
```
The first element of the tag array is referred to as the tag _name_ or _key_ and the second as the tag _value_. So we can safely say that the event above has an `e` tag set to `"5c83da77af1dec6d7289834998ad7aafbd9e2191396d75ec3cc27f5a77226f36"`, an `alt` tag set to `"reply"` and so on. All elements after the second do not have a conventional name.
This NIP defines 3 standard tags that can be used across all event kinds with the same meaning. They are as follows:
- The `e` tag, used to refer to an event: `["e", <32-bytes lowercase hex of the id of another event>, <recommended relay URL, optional>, <32-bytes lowercase hex of the author's pubkey, optional>]`
- The `p` tag, used to refer to another user: `["p", <32-bytes lowercase hex of a pubkey>, <recommended relay URL, optional>]`
- The `a` tag, used to refer to an addressable or replaceable event
- for an addressable event: `["a", "<kind integer>:<32-bytes lowercase hex of a pubkey>:<d tag value>", <recommended relay URL, optional>]`
- for a normal replaceable event: `["a", "<kind integer>:<32-bytes lowercase hex of a pubkey>:", <recommended relay URL, optional>]` (note: include the trailing colon)
As a convention, all single-letter (only english alphabet letters: a-z, A-Z) key tags are expected to be indexed by relays, such that it is possible, for example, to query or subscribe to events that reference the event `"5c83da77af1dec6d7289834998ad7aafbd9e2191396d75ec3cc27f5a77226f36"` by using the `{"#e": ["5c83da77af1dec6d7289834998ad7aafbd9e2191396d75ec3cc27f5a77226f36"]}` filter. Only the first value in any given tag is indexed.
### Kinds
Kinds specify how clients should interpret the meaning of each event and the other fields of each event (e.g. an `"r"` tag may have a meaning in an event of kind 1 and an entirely different meaning in an event of kind 10002). Each NIP may define the meaning of a set of kinds that weren't defined elsewhere. [NIP-10](10.md), for instance, especifies the `kind:1` text note for social media applications.
This NIP defines one basic kind:
- `0`: **user metadata**: the `content` is set to a stringified JSON object `{name: <nickname or full name>, about: <short bio>, picture: <url of the image>}` describing the user who created the event. [Extra metadata fields](24.md#kind-0) may be set. A relay may delete older events once it gets a new one for the same pubkey.
And also a convention for kind ranges that allow for easier experimentation and flexibility of relay implementation:
- for kind `n` such that `1000 <= n < 10000 || 4 <= n < 45 || n == 1 || n == 2`, events are **regular**, which means they're all expected to be stored by relays.
- for kind `n` such that `10000 <= n < 20000 || n == 0 || n == 3`, events are **replaceable**, which means that, for each combination of `pubkey` and `kind`, only the latest event MUST be stored by relays, older versions MAY be discarded.
- for kind `n` such that `20000 <= n < 30000`, events are **ephemeral**, which means they are not expected to be stored by relays.
- for kind `n` such that `30000 <= n < 40000`, events are **addressable** by their `kind`, `pubkey` and `d` tag value -- which means that, for each combination of `kind`, `pubkey` and the `d` tag value, only the latest event MUST be stored by relays, older versions MAY be discarded.
In case of replaceable events with the same timestamp, the event with the lowest id (first in lexical order) should be retained, and the other discarded.
When answering to `REQ` messages for replaceable events such as `{"kinds":[0],"authors":[<hex-key>]}`, even if the relay has more than one version stored, it SHOULD return just the latest one.
These are just conventions and relay implementations may differ.
## Communication between clients and relays
Relays expose a websocket endpoint to which clients can connect. Clients SHOULD open a single websocket connection to each relay and use it for all their subscriptions. Relays MAY limit number of connections from specific IP/client/etc.
### From client to relay: sending events and creating subscriptions
Clients can send 3 types of messages, which must be JSON arrays, according to the following patterns:
* `["EVENT", <event JSON as defined above>]`, used to publish events.
* `["REQ", <subscription_id>, <filters1>, <filters2>, ...]`, used to request events and subscribe to new updates.
* `["CLOSE", <subscription_id>]`, used to stop previous subscriptions.
`<subscription_id>` is an arbitrary, non-empty string of max length 64 chars. It represents a subscription per connection. Relays MUST manage `<subscription_id>`s independently for each WebSocket connection. `<subscription_id>`s are not guaranteed to be globally unique.
`<filtersX>` is a JSON object that determines what events will be sent in that subscription, it can have the following attributes:
```json
{
"ids": <a list of event ids>,
"authors": <a list of lowercase pubkeys, the pubkey of an event must be one of these>,
"kinds": <a list of a kind numbers>,
"#<single-letter (a-zA-Z)>": <a list of tag values, for #e — a list of event ids, for #p — a list of pubkeys, etc.>,
"since": <an integer unix timestamp in seconds. Events must have a created_at >= to this to pass>,
"until": <an integer unix timestamp in seconds. Events must have a created_at <= to this to pass>,
"limit": <maximum number of events relays SHOULD return in the initial query>
}
```
Upon receiving a `REQ` message, the relay SHOULD return events that match the filter. Any new events it receives SHOULD be sent to that same websocket until the connection is closed, a `CLOSE` event is received with the same `<subscription_id>`, or a new `REQ` is sent using the same `<subscription_id>` (in which case a new subscription is created, replacing the old one).
Filter attributes containing lists (`ids`, `authors`, `kinds` and tag filters like `#e`) are JSON arrays with one or more values. At least one of the arrays' values must match the relevant field in an event for the condition to be considered a match. For scalar event attributes such as `authors` and `kind`, the attribute from the event must be contained in the filter list. In the case of tag attributes such as `#e`, for which an event may have multiple values, the event and filter condition values must have at least one item in common.
The `ids`, `authors`, `#e` and `#p` filter lists MUST contain exact 64-character lowercase hex values.
The `since` and `until` properties can be used to specify the time range of events returned in the subscription. If a filter includes the `since` property, events with `created_at` greater than or equal to `since` are considered to match the filter. The `until` property is similar except that `created_at` must be less than or equal to `until`. In short, an event matches a filter if `since <= created_at <= until` holds.
All conditions of a filter that are specified must match for an event for it to pass the filter, i.e., multiple conditions are interpreted as `&&` conditions.
A `REQ` message may contain multiple filters. In this case, events that match any of the filters are to be returned, i.e., multiple filters are to be interpreted as `||` conditions.
The `limit` property of a filter is only valid for the initial query and MUST be ignored afterwards. When `limit: n` is present it is assumed that the events returned in the initial query will be the last `n` events ordered by the `created_at`. Newer events should appear first, and in the case of ties the event with the lowest id (first in lexical order) should be first. It is safe to return less events than `limit` specifies, but it is expected that relays do not return (much) more events than requested so clients don't get unnecessarily overwhelmed by data.
### From relay to client: sending events and notices
Relays can send 5 types of messages, which must also be JSON arrays, according to the following patterns:
* `["EVENT", <subscription_id>, <event JSON as defined above>]`, used to send events requested by clients.
* `["OK", <event_id>, <true|false>, <message>]`, used to indicate acceptance or denial of an `EVENT` message.
* `["EOSE", <subscription_id>]`, used to indicate the _end of stored events_ and the beginning of events newly received in real-time.
* `["CLOSED", <subscription_id>, <message>]`, used to indicate that a subscription was ended on the server side.
* `["NOTICE", <message>]`, used to send human-readable error messages or other things to clients.
This NIP defines no rules for how `NOTICE` messages should be sent or treated.
- `EVENT` messages MUST be sent only with a subscription ID related to a subscription previously initiated by the client (using the `REQ` message above).
- `OK` messages MUST be sent in response to `EVENT` messages received from clients, they must have the 3rd parameter set to `true` when an event has been accepted by the relay, `false` otherwise. The 4th parameter MUST always be present, but MAY be an empty string when the 3rd is `true`, otherwise it MUST be a string formed by a machine-readable single-word prefix followed by a `:` and then a human-readable message. Some examples:
* `["OK", "b1a649ebe8...", true, ""]`
* `["OK", "b1a649ebe8...", true, "pow: difficulty 25>=24"]`
* `["OK", "b1a649ebe8...", true, "duplicate: already have this event"]`
* `["OK", "b1a649ebe8...", false, "blocked: you are banned from posting here"]`
* `["OK", "b1a649ebe8...", false, "blocked: please register your pubkey at https://my-expensive-relay.example.com"]`
* `["OK", "b1a649ebe8...", false, "rate-limited: slow down there chief"]`
* `["OK", "b1a649ebe8...", false, "invalid: event creation date is too far off from the current time"]`
* `["OK", "b1a649ebe8...", false, "pow: difficulty 26 is less than 30"]`
* `["OK", "b1a649ebe8...", false, "restricted: not allowed to write."]`
* `["OK", "b1a649ebe8...", false, "error: could not connect to the database"]`
- `CLOSED` messages MUST be sent in response to a `REQ` when the relay refuses to fulfill it. It can also be sent when a relay decides to kill a subscription on its side before a client has disconnected or sent a `CLOSE`. This message uses the same pattern of `OK` messages with the machine-readable prefix and human-readable message. Some examples:
* `["CLOSED", "sub1", "unsupported: filter contains unknown elements"]`
* `["CLOSED", "sub1", "error: could not connect to the database"]`
* `["CLOSED", "sub1", "error: shutting down idle subscription"]`
- The standardized machine-readable prefixes for `OK` and `CLOSED` are: `duplicate`, `pow`, `blocked`, `rate-limited`, `invalid`, `restricted`, and `error` for when none of that fits.
-

@ 57d1a264:69f1fee1
2025-03-27 10:42:05
What we have been missing in [SN Press kit](https://stacker.news/items/872925/r/Design_r)? Most important, who the press kit is for? It's for us? It's for them? Them, who?
The first few editions of the press kit, I agree are mostly made by us, for us. A way to try to homogenize how we _speek_ out SN into the wild web. A way to have SN voice sync, loud and clear, to send out our message. In this case, I squeezed my mouse, creating a template for us [^1], stackers, to share when talking sales with possible businesses and merchants willing to invest some sats and engage with SN community. Here's the message and the sales pitch, v0.1:
## Reach Bitcoin’s Most Engaged Community – Zero Noise, Pure Signal.













- - -
Contributions to improve would be much appreciated. You can also help by simply commenting on each slide or leaving your feedback below, especially if you are a sale person or someone that has seen similar documents before.
This is the first interaction. Already noticed some issues, for example with the emojis and the fonts, especially when exporting, probably related to a penpot issue. The slides maybe render differently depending on the browser you're using.
- [▶️ Play](https://design.penpot.app/#/view?file-id=cec80257-5021-8137-8005-ef90a160b2c9&page-id=cec80257-5021-8137-8005-ef90a160b2ca§ion=interactions&index=0&interactions-mode=hide&zoom=fit) the file in your browser
- ⬇️ Save the [PDF file](https://mega.nz/file/TsBgkRoI#20HEb_zscozgJYlRGha0XiZvcXCJfLQONx2fc65WHKY)
@k00b it will be nice to have some real data, how we can get some basic audience insights? Even some inputs from Plausible, if still active, will be much useful.
[^1]: Territory founders. FYI: @Aardvark, @AGORA, @anna, @antic, @AtlantisPleb, @av, @Bell_curve, @benwehrman, @bitcoinplebdev, @Bitter, @BlokchainB, @ch0k1, @davidw, @ek, @elvismercury, @frostdragon, @grayruby, @HODLR, @inverselarp, @Jon_Hodl, @MaxAWebster, @mega_dreamer, @mrtali, @niftynei, @nout, @OneOneSeven, @PlebLab, @Public_N_M_E, @RDClark, @realBitcoinDog, @roytheholographicuniverse, @siggy47, @softsimon, @south_korea_ln, @theschoolofbitcoin, @TNStacker. @UCantDoThatDotNet, @Undisciplined
originally posted at https://stacker.news/items/926557
-

@ fd78c37f:a0ec0833
2025-03-18 10:44:40
In this edition, we’re thrilled to sit down with Tomek K from Bitcoin Alby, a passionate advocate for Bitcoin’s global adoption. Tomek K shares how Alby is driving innovation in the Bitcoin ecosystem and offers a glimpse into his vision for the cryptocurrency’s future. From his journey as a libertarian activist to co-founding the Bitcoin Film Festival, Tomek K’s story is one of curiosity, purpose, and a relentless pursuit of freedom through technology.
**YakiHonne**: Tomek K, it’s a pleasure to meet you! Today, we’re diving into your community topic—Alby Wallet. But before we begin, let me introduce our readers to Yakihonne. Yakihonne is a decentralized media client powered by the Nostr protocol, dedicated to promoting free speech through technology. It empowers creators to truly own their voices and assets, offering features like smart filtering, verified notes, and a focus on long-form content. So, Tomek, could you tell us about yourself and your work with Alby?
**Tomek K**: Of course! I’m Tomek K, originally from Poland, and right now, I’m speaking to you from Sri Lanka. I love traveling and observing how different countries adopt Bitcoin. For most of my career, I’ve been a free-market advocate, promoting economic freedom through various projects—essentially doing PR for capitalism. I’ve organized conferences, political demonstrations, economic seminars, summer festivals, and even opened a bar in Warsaw to spread these ideas in different ways.
During this advocacy work, I came across Bitcoin. At first, I didn’t pay much attention to it, but over time, I started feeling frustrated—our efforts raised awareness about freedom, but they didn’t bring measurable change. That led me to study Bitcoin more deeply, and I gradually shifted my focus to Bitcoin activism. Along the way, I collaborated with publishers to translate Bitcoin-related books into Polish and co-founded the Bitcoin Film Festival with friends from Meetup. Later, I joined Alby, marking my transition from free-market activism to Bitcoin promotion.
At the Bitcoin Film Festival, I handle operations and networking—organizing the event, managing logistics, and making things happen. Our team is small, but I enjoy the work. I’m passionate about Bitcoin because I came for the revolution, and I’m staying for the revolution.
That said, I don’t consider myself a Bitcoin absolutist. I see Bitcoin as a tool for freedom, not just a currency or a more efficient technology. If there were a better tool for advancing liberty and making societies freer, I’d probably focus on that. But for now, Bitcoin appears to be the most effective tool for freedom. Ultimately, I consider myself a “life maximalist”—because to live a good life, you need freedom, and to have freedom today, you need sound money. And right now, that money is Bitcoin.
**YakiHonne**: Was there a specific moment or event that sparked your interest in Bitcoin and motivated you to join the Alby community?
**Tomek K**: What attracted me to Bitcoin was its promise of global monetary independence and its ability to reduce the control of the Federal Reserve, central banks, and governments—the strongest and most covert control mechanisms in the world. Unfortunately, many people, even libertarians, often overlook this.
As for why I joined Alby, it’s because this startup is driven by values and mission rather than simply chasing profits, like selling tokens or games. This aligns well with my interest in the Lightning Network. As I explored Lightning more deeply, I came across Alby. I’ve always enjoyed testing new tools, trying them firsthand, and understanding the communities behind them—so naturally, I became part of it. Along the way, I also got to know some of the team members, which reinforced my involvement.
Additionally, Alby supported the Bitcoin Film Festival. While they weren’t the largest sponsor, their contribution was generous. The festival served as a great platform for them and other projects. I think it was good marketing because people like me—who have strong networking skills, arrange podcast interviews, and organize various activities—help build awareness and positive PR. That was part of my role.
If I had to pinpoint a single defining moment that led me here, I honestly couldn’t. Becoming a Bitcoiner doesn’t happen overnight. You can’t just read The Bitcoin Standard, declare that you understand Bitcoin, and instantly become a maximalist. Anyone who’s intellectually honest will admit that it takes multiple touchpoints—articles, films, career shifts, essays, hands-on experimentation, and actually using Bitcoin—to truly grasp its significance. I had many such moments along the way: reading The Bitcoin Standard, learning from friends who had a deeper understanding of Bitcoin, and working at Alby, which further expanded my knowledge of the Lightning Network’s capabilities and limitations. It wasn’t one turning point but a series of pivotal experiences that shaped my path.
**YakiHonne**: How did the Alby community start, and how did it attract its first members?
**Tomek K**: When I joined Alby, the community had already been established for some time. It originally emerged within the browser design community, where early users helped developers refine the product by providing feedback. That’s how the first members joined, and this process has been ongoing for four years now.
As for how Alby attracted members, it was through a mix of channels—social media (Twitter, Telegram, Discord), email engagement, and active participation in Bitcoin conferences. But the core strategy has always been openness, engaging with users, and listening to their feedback. Sometimes that means making a joke, sometimes defending against unfair criticism, and other times implementing requested features. We’ve always worked to maintain an active and friendly community atmosphere.
We also host bi-weekly community calls, which are a central part of our activities. Every two weeks, available team members meet with users for open Q&A sessions, issue discussions, and demonstrations of various projects integrating with Alby. I’ve participated in some of these calls, and they help maintain strong relationships with users, developers, and other projects—something crucial for the ecosystem. The Bitcoin technology landscape is somewhat fragmented, and grassroots coordination is necessary since there’s no single leader defining terminology or coding practices.
That’s also why Alby doesn’t exist in isolation. Almost everything we’ve built has been made possible by the creators of previous libraries, prior codebases, and collaborative efforts in writing specifications for protocols. Projects like Yakihonne and many others also recognize the importance of open-source collaboration. I think it’s essential to acknowledge the contributions of the open-source community. One thing I really appreciate is that Bitcoiners are driving open-source development in virtually every part of the world, all working toward a shared and meaningful goal.
**YakiHonne**:Were there any notable challenges in the early days that left a strong impression on you?
**Tomek K** :When I first joined Alby, I struggled with a bit of imposter syndrome for months. I was handling PR for the project, but I didn’t fully understand all the technical details—how certain protocols interact or what’s happening under the hood. It took time to get familiar with everything and really feel like I belonged.
Regulatory pressure has also been a huge challenge. In some cases, developers have been arrested, projects have had to leave certain countries, and users have been geoblocked based on their location. But challenges like these can also drive innovation. For example, Alby developed AlbyHub, an open-source self-custodial node, as a response to these kinds of issues.
There are always risks in this space—governments might suddenly demand a banking license or require compliance with new regulations. These are real obstacles, but we tackle them by embracing decentralization and open-source solutions. That’s how we ensure the project stays true to its mission and vision.

**YakiHonne**:If someone wanted to start a Bitcoin community today or grow an existing one, what advice would you give them?
**Tomek K**: The most important thing is to just get started. A community begins with action, and it takes more than one person. Even if it’s just you and a friend grabbing a beer, that’s already a start. Maybe after the first or second meetup, you post on Meetup.com, Twitter, or local forums:"Hey, we’re hosting a Bitcoin meetup in this city. We just want to connect with other Bitcoiners!" If you keep doing it consistently, the community will naturally grow. Over time, the bar where you meet might get interested in accepting Bitcoin, or you might meet some OGs in your area who decide to join—maybe they already run a business and want to support what you’re doing.
You don’t have to over-plan everything from the start. No need to think, “We need a podcast, 10 episodes, a logo…”—all that can come later. Just bootstrap it: organize a meetup, grab a beer, and get going. As you go, you’ll adapt, improve, and build recognition.Beyond that, it’s a great way to meet other Bitcoiners, develop leadership skills, and learn about community building. And at the very least, you’ll have fun doing it—which, honestly, is one of the main reasons I keep organizing meetups and other activities.
**YakiHonne**: Exactly, the key is to take action—just start and see where it leads. Does your community focus more on Bitcoin’s technical aspects, like coding and development, or do you emphasize non-technical areas such as education and outreach? Or do you try to balance both?
**Tomek K**: Our users come from all kinds of backgrounds. Some are very engaged and provide feedback regularly, while others prefer to stay in the background. Some attend our community calls, and within that group, some are developers actively building projects and collaborating with us. At the same time, there are developers we know are out there, but they never directly engage with us. That’s just how the Bitcoin community works—there’s no strict definition of being part of Alby. People engage in their own way. Some users are active on Discord, some aren’t, but we treat them all as part of the family, keeping them informed through newsletters, offering support, and making sure they stay updated with what’s happening at Alby.
As for whether we lean more toward technical development or non-technical outreach, there’s no clear-cut answer. Our community is diverse—we cater to a wide range of Lightning Network users. Some just use the browser extension, while others are deeply involved in our ecosystem. We also work with NGOs, educational initiatives, and community organizations. At the same time, we place a strong emphasis on developers and maintaining good relationships with them. Our repositories and developer portal offer useful libraries and examples, making it easier for both aspiring and experienced developers to integrate the Lightning Network into their projects. Developer relations are something we consider highly important.

**YakiHonne**: I understand that you're also the founder of another Bitcoin-related film project. Could you tell us a bit about it? What exactly inspired you to combine Bitcoin and filmmaking?
**Tomek K**: Yes, I founded Bitcoin Film Fest to help build what I call Bitcoin Cinema—an emerging industry that blends Bitcoin and filmmaking. I wanted to track everything happening at the intersection of these two worlds. Just like e-commerce, energy, and information technology, I believe the film industry will eventually be shaped by Bitcoin. And in fact, it’s already happening. There are Bitcoin-themed movies, and even major Hollywood productions have started including Bitcoin references. Bitcoin filmmakers, Bitcoin culture, and even a Bitcoin subculture already exist. We have our own heroes, stories, and values, and from this, films are being created. I love cinema, and I love Bitcoin—this was my way of bringing the two together.
The festival itself happened somewhat by accident—but maybe it was meant to be. It all started in Warsaw when I was organizing a Bitcoin meetup. I planned to screen a Bitcoin documentary, but due to technical issues, it didn’t happen. So, over a few beers, we came up with an idea: if we couldn’t show one film, why not go all in and create a full-scale Bitcoin film festival? We started researching and realized there were enough Bitcoin-related films out there to make it happen. So, we did.
The response from the community was overwhelmingly positive. It became clear that people wanted a space for Bitcoin cinema—a hub for information, networking, and collaboration. We started using the term “Binema” (Bitcoin Cinema) to describe this emerging genre. I find it fascinating to witness the growth of Bitcoin culture and storytelling. Before this, I had followed libertarian artistic movements closely, and now I see how important culture is for Bitcoin’s adoption—it’s not just about the technical and financial aspects.
Bitcoin adoption isn’t going to happen overnight, and it won’t happen without developers, educators, infrastructure builders, UX designers, and many others contributing to the ecosystem. Culture is one of the most powerful tools for shaping society, and I, like many others, am working to bring Bitcoin adoption closer through film. We’re witnessing the early days of Bitcoin cinema. I missed out on the birth of traditional cinema, but this time, I want to be part of it.
**YakiHonne**:In your region, does the government support or oppose Bitcoin? How has this stance impacted the development of the Bitcoin community so far?
**Tomek K** :Bitcoin doesn’t concern itself with nation-state borders, and frankly, we don’t either. The situation in Poland has little influence on what we do. The only connection is that I, along with two others, happen to be in Poland, but most of our team is globally distributed. On a broader scale, the U.S. tends to shape regulatory trends, and unfortunately, it often does so in a more restrictive way. However, Poland itself hasn’t had a significant impact on our work.
**YakiHonne**:Has your Bitcoin Film Fest community ever used film as a way to connect with members—perhaps by watching a Bitcoin-related movie or hosting a movie night to make things more fun and engaging? Have you done anything like that before?
**Tomek K**:Yes, absolutely! The film festival itself is a great example—we watch movies together and build a community around them. Aside from the festival we organized in Warsaw, we've also hosted film screenings at various Bitcoin events, like Sats and Facts in Thailand, BTC Prague, Plan B Lugano, Frimadera, Adopting Bitcoin, and several other conferences. We also organize online watch parties—actually, there's one happening next Sunday. The movie is available on Prime Video, but we'll sync up on Discord to watch it together, chat, and share our thoughts. We'll be announcing it on Twitter, so if you check Bitcoin Film Fest on Twitter, you'll find details on how to join.
Film has been a great way to connect with members and spark discussions. We've seen Bitcoin meetups worldwide organizing movie nights—our volunteer friends in Montenegro have hosted one, and our partners in Kenya and South Africa have done the same. Lately, movie nights have been happening more and more frequently, which is exciting.
It's still early—after all, Bitcoin is only 16 years old, so the selection of Bitcoin movies is still relatively small. Many of these films haven’t had large budgets or massive talent pools yet, but that’s changing. Right now, we’re primarily focused on showing films within the Bitcoin community rather than creating films aimed at the general public. That said, those kinds of projects are also emerging. I’m optimistic about the growth of Bitcoin cinema—better storytelling, AI-driven advancements, increasing interest from audiences, and even sponsors willing to invest in filmmakers. Big things are coming, and while we already have some great Bitcoin films, the best is yet to come. We’re still in the early days, and this is the time to contribute and help shape the future of Bitcoin cinema.
**YakiHonne**:We’ve come to the end of today’s interview, and I’ve truly enjoyed every moment of it. I’m very sure your idea will be incredibly engaging, inspiring more people and attracting a broad audience. Thank you so much for your time today—it was a great conversation.
-

@ 57d1a264:69f1fee1
2025-03-27 08:27:44
> The tech industry and its press have treated the rise of billion-scale social networks and ubiquitous smartphone apps as an unadulterated win for regular people, a triumph of usability and empowerment. They seldom talk about what we’ve lost along the way in this transition, and I find that younger folks may not even know how the web used to be.
`— Anil Dash, The Web We Lost, 13 Dec 2012`
https://www.youtube.com/watch?v=9KKMnoTTHJk&t=156s
So here’s a few glimpses of a web that’s mostly faded away: https://www.anildash.com/2012/12/13/the_web_we_lost/
The first step to disabusing them of this notion is for the people creating the next generation of social applications to learn a little bit of history, to know your shit, whether that’s about [Twitter’s business model](http://web.archive.org/web/20180120013123/http://anildash.com/2010/04/ten-years-of-twitter-ads.html) or [Google’s social features](http://web.archive.org/web/20170518203228/http://anildash.com/2012/04/why-you-cant-trust-tech-press-to-teach-you-about-the-tech-industry.html) or anything else. We have to know what’s been tried and failed, what good ideas were simply ahead of their time, and what opportunities have been lost in the current generation of dominant social networks.
originally posted at https://stacker.news/items/926499
-

@ fd06f542:8d6d54cd
2025-03-28 02:21:20
# NIPs
NIPs stand for **Nostr Implementation Possibilities**.
They exist to document what may be implemented by [Nostr](https://github.com/nostr-protocol/nostr)-compatible _relay_ and _client_ software.
---
- [List](#list)
- [Event Kinds](#event-kinds)
- [Message Types](#message-types)
- [Client to Relay](#client-to-relay)
- [Relay to Client](#relay-to-client)
- [Standardized Tags](#standardized-tags)
- [Criteria for acceptance of NIPs](#criteria-for-acceptance-of-nips)
- [Is this repository a centralizing factor?](#is-this-repository-a-centralizing-factor)
- [How this repository works](#how-this-repository-works)
- [Breaking Changes](#breaking-changes)
- [License](#license)
---
## List
- [NIP-01: Basic protocol flow description](01.md)
- [NIP-02: Follow List](02.md)
- [NIP-03: OpenTimestamps Attestations for Events](03.md)
- [NIP-04: Encrypted Direct Message](04.md) --- **unrecommended**: deprecated in favor of [NIP-17](17.md)
- [NIP-05: Mapping Nostr keys to DNS-based internet identifiers](05.md)
- [NIP-06: Basic key derivation from mnemonic seed phrase](06.md)
- [NIP-07: `window.nostr` capability for web browsers](07.md)
- [NIP-08: Handling Mentions](08.md) --- **unrecommended**: deprecated in favor of [NIP-27](27.md)
- [NIP-09: Event Deletion Request](09.md)
- [NIP-10: Text Notes and Threads](10.md)
- [NIP-11: Relay Information Document](11.md)
- [NIP-13: Proof of Work](13.md)
- [NIP-14: Subject tag in text events](14.md)
- [NIP-15: Nostr Marketplace (for resilient marketplaces)](15.md)
- [NIP-17: Private Direct Messages](17.md)
- [NIP-18: Reposts](18.md)
- [NIP-19: bech32-encoded entities](19.md)
- [NIP-21: `nostr:` URI scheme](21.md)
- [NIP-22: Comment](22.md)
- [NIP-23: Long-form Content](23.md)
- [NIP-24: Extra metadata fields and tags](24.md)
- [NIP-25: Reactions](25.md)
- [NIP-26: Delegated Event Signing](26.md)
- [NIP-27: Text Note References](27.md)
- [NIP-28: Public Chat](28.md)
- [NIP-29: Relay-based Groups](29.md)
- [NIP-30: Custom Emoji](30.md)
- [NIP-31: Dealing with Unknown Events](31.md)
- [NIP-32: Labeling](32.md)
- [NIP-34: `git` stuff](34.md)
- [NIP-35: Torrents](35.md)
- [NIP-36: Sensitive Content](36.md)
- [NIP-37: Draft Events](37.md)
- [NIP-38: User Statuses](38.md)
- [NIP-39: External Identities in Profiles](39.md)
- [NIP-40: Expiration Timestamp](40.md)
- [NIP-42: Authentication of clients to relays](42.md)
- [NIP-44: Encrypted Payloads (Versioned)](44.md)
- [NIP-45: Counting results](45.md)
- [NIP-46: Nostr Remote Signing](46.md)
- [NIP-47: Nostr Wallet Connect](47.md)
- [NIP-48: Proxy Tags](48.md)
- [NIP-49: Private Key Encryption](49.md)
- [NIP-50: Search Capability](50.md)
- [NIP-51: Lists](51.md)
- [NIP-52: Calendar Events](52.md)
- [NIP-53: Live Activities](53.md)
- [NIP-54: Wiki](54.md)
- [NIP-55: Android Signer Application](55.md)
- [NIP-56: Reporting](56.md)
- [NIP-57: Lightning Zaps](57.md)
- [NIP-58: Badges](58.md)
- [NIP-59: Gift Wrap](59.md)
- [NIP-60: Cashu Wallet](60.md)
- [NIP-61: Nutzaps](61.md)
- [NIP-62: Request to Vanish](62.md)
- [NIP-64: Chess (PGN)](64.md)
- [NIP-65: Relay List Metadata](65.md)
- [NIP-66: Relay Discovery and Liveness Monitoring](66.md)
- [NIP-68: Picture-first feeds](68.md)
- [NIP-69: Peer-to-peer Order events](69.md)
- [NIP-70: Protected Events](70.md)
- [NIP-71: Video Events](71.md)
- [NIP-72: Moderated Communities](72.md)
- [NIP-73: External Content IDs](73.md)
- [NIP-75: Zap Goals](75.md)
- [NIP-78: Application-specific data](78.md)
- [NIP-84: Highlights](84.md)
- [NIP-86: Relay Management API](86.md)
- [NIP-88: Polls](88.md)
- [NIP-89: Recommended Application Handlers](89.md)
- [NIP-90: Data Vending Machines](90.md)
- [NIP-92: Media Attachments](92.md)
- [NIP-94: File Metadata](94.md)
- [NIP-96: HTTP File Storage Integration](96.md)
- [NIP-98: HTTP Auth](98.md)
- [NIP-99: Classified Listings](99.md)
- [NIP-7D: Threads](7D.md)
- [NIP-C7: Chats](C7.md)
## Event Kinds
| kind | description | NIP |
| ------------- | ------------------------------- | -------------------------------------- |
| `0` | User Metadata | [01](01.md) |
| `1` | Short Text Note | [10](10.md) |
| `2` | Recommend Relay | 01 (deprecated) |
| `3` | Follows | [02](02.md) |
| `4` | Encrypted Direct Messages | [04](04.md) |
| `5` | Event Deletion Request | [09](09.md) |
| `6` | Repost | [18](18.md) |
| `7` | Reaction | [25](25.md) |
| `8` | Badge Award | [58](58.md) |
| `9` | Chat Message | [C7](C7.md) |
| `10` | Group Chat Threaded Reply | 29 (deprecated) |
| `11` | Thread | [7D](7D.md) |
| `12` | Group Thread Reply | 29 (deprecated) |
| `13` | Seal | [59](59.md) |
| `14` | Direct Message | [17](17.md) |
| `15` | File Message | [17](17.md) |
| `16` | Generic Repost | [18](18.md) |
| `17` | Reaction to a website | [25](25.md) |
| `20` | Picture | [68](68.md) |
| `21` | Video Event | [71](71.md) |
| `22` | Short-form Portrait Video Event | [71](71.md) |
| `30` | internal reference | [NKBIP-03] |
| `31` | external web reference | [NKBIP-03] |
| `32` | hardcopy reference | [NKBIP-03] |
| `33` | prompt reference | [NKBIP-03] |
| `40` | Channel Creation | [28](28.md) |
| `41` | Channel Metadata | [28](28.md) |
| `42` | Channel Message | [28](28.md) |
| `43` | Channel Hide Message | [28](28.md) |
| `44` | Channel Mute User | [28](28.md) |
| `62` | Request to Vanish | [62](62.md) |
| `64` | Chess (PGN) | [64](64.md) |
| `818` | Merge Requests | [54](54.md) |
| `1018` | Poll Response | [88](88.md) |
| `1021` | Bid | [15](15.md) |
| `1022` | Bid confirmation | [15](15.md) |
| `1040` | OpenTimestamps | [03](03.md) |
| `1059` | Gift Wrap | [59](59.md) |
| `1063` | File Metadata | [94](94.md) |
| `1068` | Poll | [88](88.md) |
| `1111` | Comment | [22](22.md) |
| `1311` | Live Chat Message | [53](53.md) |
| `1617` | Patches | [34](34.md) |
| `1621` | Issues | [34](34.md) |
| `1622` | Git Replies (deprecated) | [34](34.md) |
| `1630`-`1633` | Status | [34](34.md) |
| `1971` | Problem Tracker | [nostrocket][nostrocket] |
| `1984` | Reporting | [56](56.md) |
| `1985` | Label | [32](32.md) |
| `1986` | Relay reviews | |
| `1987` | AI Embeddings / Vector lists | [NKBIP-02] |
| `2003` | Torrent | [35](35.md) |
| `2004` | Torrent Comment | [35](35.md) |
| `2022` | Coinjoin Pool | [joinstr][joinstr] |
| `4550` | Community Post Approval | [72](72.md) |
| `5000`-`5999` | Job Request | [90](90.md) |
| `6000`-`6999` | Job Result | [90](90.md) |
| `7000` | Job Feedback | [90](90.md) |
| `7374` | Reserved Cashu Wallet Tokens | [60](60.md) |
| `7375` | Cashu Wallet Tokens | [60](60.md) |
| `7376` | Cashu Wallet History | [60](60.md) |
| `9000`-`9030` | Group Control Events | [29](29.md) |
| `9041` | Zap Goal | [75](75.md) |
| `9321` | Nutzap | [61](61.md) |
| `9467` | Tidal login | [Tidal-nostr] |
| `9734` | Zap Request | [57](57.md) |
| `9735` | Zap | [57](57.md) |
| `9802` | Highlights | [84](84.md) |
| `10000` | Mute list | [51](51.md) |
| `10001` | Pin list | [51](51.md) |
| `10002` | Relay List Metadata | [65](65.md), [51](51.md) |
| `10003` | Bookmark list | [51](51.md) |
| `10004` | Communities list | [51](51.md) |
| `10005` | Public chats list | [51](51.md) |
| `10006` | Blocked relays list | [51](51.md) |
| `10007` | Search relays list | [51](51.md) |
| `10009` | User groups | [51](51.md), [29](29.md) |
| `10013` | Private event relay list | [37](37.md) |
| `10015` | Interests list | [51](51.md) |
| `10019` | Nutzap Mint Recommendation | [61](61.md) |
| `10030` | User emoji list | [51](51.md) |
| `10050` | Relay list to receive DMs | [51](51.md), [17](17.md) |
| `10063` | User server list | [Blossom][blossom] |
| `10096` | File storage server list | [96](96.md) |
| `10166` | Relay Monitor Announcement | [66](66.md) |
| `13194` | Wallet Info | [47](47.md) |
| `17375` | Cashu Wallet Event | [60](60.md) |
| `21000` | Lightning Pub RPC | [Lightning.Pub][lnpub] |
| `22242` | Client Authentication | [42](42.md) |
| `23194` | Wallet Request | [47](47.md) |
| `23195` | Wallet Response | [47](47.md) |
| `24133` | Nostr Connect | [46](46.md) |
| `24242` | Blobs stored on mediaservers | [Blossom][blossom] |
| `27235` | HTTP Auth | [98](98.md) |
| `30000` | Follow sets | [51](51.md) |
| `30001` | Generic lists | 51 (deprecated) |
| `30002` | Relay sets | [51](51.md) |
| `30003` | Bookmark sets | [51](51.md) |
| `30004` | Curation sets | [51](51.md) |
| `30005` | Video sets | [51](51.md) |
| `30007` | Kind mute sets | [51](51.md) |
| `30008` | Profile Badges | [58](58.md) |
| `30009` | Badge Definition | [58](58.md) |
| `30015` | Interest sets | [51](51.md) |
| `30017` | Create or update a stall | [15](15.md) |
| `30018` | Create or update a product | [15](15.md) |
| `30019` | Marketplace UI/UX | [15](15.md) |
| `30020` | Product sold as an auction | [15](15.md) |
| `30023` | Long-form Content | [23](23.md) |
| `30024` | Draft Long-form Content | [23](23.md) |
| `30030` | Emoji sets | [51](51.md) |
| `30040` | Curated Publication Index | [NKBIP-01] |
| `30041` | Curated Publication Content | [NKBIP-01] |
| `30063` | Release artifact sets | [51](51.md) |
| `30078` | Application-specific Data | [78](78.md) |
| `30166` | Relay Discovery | [66](66.md) |
| `30267` | App curation sets | [51](51.md) |
| `30311` | Live Event | [53](53.md) |
| `30315` | User Statuses | [38](38.md) |
| `30388` | Slide Set | [Corny Chat][cornychat-slideset] |
| `30402` | Classified Listing | [99](99.md) |
| `30403` | Draft Classified Listing | [99](99.md) |
| `30617` | Repository announcements | [34](34.md) |
| `30618` | Repository state announcements | [34](34.md) |
| `30818` | Wiki article | [54](54.md) |
| `30819` | Redirects | [54](54.md) |
| `31234` | Draft Event | [37](37.md) |
| `31388` | Link Set | [Corny Chat][cornychat-linkset] |
| `31890` | Feed | [NUD: Custom Feeds][NUD: Custom Feeds] |
| `31922` | Date-Based Calendar Event | [52](52.md) |
| `31923` | Time-Based Calendar Event | [52](52.md) |
| `31924` | Calendar | [52](52.md) |
| `31925` | Calendar Event RSVP | [52](52.md) |
| `31989` | Handler recommendation | [89](89.md) |
| `31990` | Handler information | [89](89.md) | |
| `32267` | Software Application | | |
| `34550` | Community Definition | [72](72.md) |
| `38383` | Peer-to-peer Order events | [69](69.md) |
| `39000-9` | Group metadata events | [29](29.md) |
[NUD: Custom Feeds]: https://wikifreedia.xyz/cip-01/
[nostrocket]: https://github.com/nostrocket/NIPS/blob/main/Problems.md
[lnpub]: https://github.com/shocknet/Lightning.Pub/blob/master/proto/autogenerated/client.md
[cornychat-slideset]: https://cornychat.com/datatypes#kind30388slideset
[cornychat-linkset]: https://cornychat.com/datatypes#kind31388linkset
[joinstr]: https://gitlab.com/1440000bytes/joinstr/-/blob/main/NIP.md
[NKBIP-01]: https://wikistr.com/nkbip-01*fd208ee8c8f283780a9552896e4823cc9dc6bfd442063889577106940fd927c1
[NKBIP-02]: https://wikistr.com/nkbip-02*fd208ee8c8f283780a9552896e4823cc9dc6bfd442063889577106940fd927c1
[NKBIP-03]: https://wikistr.com/nkbip-03*fd208ee8c8f283780a9552896e4823cc9dc6bfd442063889577106940fd927c1
[blossom]: https://github.com/hzrd149/blossom
[Tidal-nostr]: https://wikistr.com/tidal-nostr
## Message types
### Client to Relay
| type | description | NIP |
| ------- | --------------------------------------------------- | ----------- |
| `EVENT` | used to publish events | [01](01.md) |
| `REQ` | used to request events and subscribe to new updates | [01](01.md) |
| `CLOSE` | used to stop previous subscriptions | [01](01.md) |
| `AUTH` | used to send authentication events | [42](42.md) |
| `COUNT` | used to request event counts | [45](45.md) |
### Relay to Client
| type | description | NIP |
| -------- | ------------------------------------------------------- | ----------- |
| `EOSE` | used to notify clients all stored events have been sent | [01](01.md) |
| `EVENT` | used to send events requested to clients | [01](01.md) |
| `NOTICE` | used to send human-readable messages to clients | [01](01.md) |
| `OK` | used to notify clients if an EVENT was successful | [01](01.md) |
| `CLOSED` | used to notify clients that a REQ was ended and why | [01](01.md) |
| `AUTH` | used to send authentication challenges | [42](42.md) |
| `COUNT` | used to send requested event counts to clients | [45](45.md) |
## Standardized Tags
| name | value | other parameters | NIP |
| ----------------- | ------------------------------------ | ------------------------------- | -------------------------------------------------- |
| `a` | coordinates to an event | relay URL | [01](01.md) |
| `A` | root address | relay URL | [22](22.md) |
| `d` | identifier | -- | [01](01.md) |
| `e` | event id (hex) | relay URL, marker, pubkey (hex) | [01](01.md), [10](10.md) |
| `E` | root event id | relay URL | [22](22.md) |
| `f` | currency code | -- | [69](69.md) |
| `g` | geohash | -- | [52](52.md) |
| `h` | group id | -- | [29](29.md) |
| `i` | external identity | proof, url hint | [35](35.md), [39](39.md), [73](73.md) |
| `I` | root external identity | -- | [22](22.md) |
| `k` | kind | -- | [18](18.md), [25](25.md), [72](72.md), [73](73.md) |
| `K` | root scope | -- | [22](22.md) |
| `l` | label, label namespace | -- | [32](32.md) |
| `L` | label namespace | -- | [32](32.md) |
| `m` | MIME type | -- | [94](94.md) |
| `p` | pubkey (hex) | relay URL, petname | [01](01.md), [02](02.md), [22](22.md) |
| `P` | pubkey (hex) | -- | [22](22.md), [57](57.md) |
| `q` | event id (hex) | relay URL, pubkey (hex) | [18](18.md) |
| `r` | a reference (URL, etc) | -- | [24](24.md), [25](25.md) |
| `r` | relay url | marker | [65](65.md) |
| `s` | status | -- | [69](69.md) |
| `t` | hashtag | -- | [24](24.md), [34](34.md), [35](35.md) |
| `u` | url | -- | [61](61.md), [98](98.md) |
| `x` | hash | -- | [35](35.md), [56](56.md) |
| `y` | platform | -- | [69](69.md) |
| `z` | order number | -- | [69](69.md) |
| `-` | -- | -- | [70](70.md) |
| `alt` | summary | -- | [31](31.md) |
| `amount` | millisatoshis, stringified | -- | [57](57.md) |
| `bolt11` | `bolt11` invoice | -- | [57](57.md) |
| `challenge` | challenge string | -- | [42](42.md) |
| `client` | name, address | relay URL | [89](89.md) |
| `clone` | git clone URL | -- | [34](34.md) |
| `content-warning` | reason | -- | [36](36.md) |
| `delegation` | pubkey, conditions, delegation token | -- | [26](26.md) |
| `description` | description | -- | [34](34.md), [57](57.md), [58](58.md) |
| `emoji` | shortcode, image URL | -- | [30](30.md) |
| `encrypted` | -- | -- | [90](90.md) |
| `expiration` | unix timestamp (string) | -- | [40](40.md) |
| `file` | full path (string) | -- | [35](35.md) |
| `goal` | event id (hex) | relay URL | [75](75.md) |
| `image` | image URL | dimensions in pixels | [23](23.md), [52](52.md), [58](58.md) |
| `imeta` | inline metadata | -- | [92](92.md) |
| `lnurl` | `bech32` encoded `lnurl` | -- | [57](57.md) |
| `location` | location string | -- | [52](52.md), [99](99.md) |
| `name` | name | -- | [34](34.md), [58](58.md), [72](72.md) |
| `nonce` | random | difficulty | [13](13.md) |
| `preimage` | hash of `bolt11` invoice | -- | [57](57.md) |
| `price` | price | currency, frequency | [99](99.md) |
| `proxy` | external ID | protocol | [48](48.md) |
| `published_at` | unix timestamp (string) | -- | [23](23.md) |
| `relay` | relay url | -- | [42](42.md), [17](17.md) |
| `relays` | relay list | -- | [57](57.md) |
| `server` | file storage server url | -- | [96](96.md) |
| `subject` | subject | -- | [14](14.md), [17](17.md), [34](34.md) |
| `summary` | summary | -- | [23](23.md), [52](52.md) |
| `thumb` | badge thumbnail | dimensions in pixels | [58](58.md) |
| `title` | article title | -- | [23](23.md) |
| `tracker` | torrent tracker URL | -- | [35](35.md) |
| `web` | webpage URL | -- | [34](34.md) |
| `zap` | pubkey (hex), relay URL | weight | [57](57.md) |
Please update these lists when proposing new NIPs.
## Criteria for acceptance of NIPs
1. They should be fully implemented in at least two clients and one relay -- when applicable.
2. They should make sense.
3. They should be optional and backwards-compatible: care must be taken such that clients and relays that choose to not implement them do not stop working when interacting with the ones that choose to.
4. There should be no more than one way of doing the same thing.
5. Other rules will be made up when necessary.
## Is this repository a centralizing factor?
To promote interoperability, we need standards that everybody can follow, and we need them to define a **single way of doing each thing** without ever hurting **backwards-compatibility**, and for that purpose there is no way around getting everybody to agree on the same thing and keep a centralized index of these standards. However the fact that such an index exists doesn't hurt the decentralization of Nostr. _At any point the central index can be challenged if it is failing to fulfill the needs of the protocol_ and it can migrate to other places and be maintained by other people.
It can even fork into multiple versions, and then some clients would go one way, others would go another way, and some clients would adhere to both competing standards. This would hurt the simplicity, openness and interoperability of Nostr a little, but everything would still work in the short term.
There is a list of notable Nostr software developers who have commit access to this repository, but that exists mostly for practical reasons, as by the nature of the thing we're dealing with the repository owner can revoke membership and rewrite history as they want -- and if these actions are unjustified or perceived as bad or evil the community must react.
## How this repository works
Standards may emerge in two ways: the first way is that someone starts doing something, then others copy it; the second way is that someone has an idea of a new standard that could benefit multiple clients and the protocol in general without breaking **backwards-compatibility** and the principle of having **a single way of doing things**, then they write that idea and submit it to this repository, other interested parties read it and give their feedback, then once most people reasonably agree we codify that in a NIP which client and relay developers that are interested in the feature can proceed to implement.
These two ways of standardizing things are supported by this repository. Although the second is preferred, an effort will be made to codify standards emerged outside this repository into NIPs that can be later referenced and easily understood and implemented by others -- but obviously as in any human system discretion may be applied when standards are considered harmful.
## Breaking Changes
[Breaking Changes](BREAKING.md)
## License
All NIPs are public domain.
## Contributors
<a align="center" href="https://github.com/nostr-protocol/nips/graphs/contributors">
<img src="https://contrib.rocks/image?repo=nostr-protocol/nips" />
</a>
-

@ 06bc9ab7:427c48f5
2025-03-17 15:46:23
#### [Bitcoin Safe]( https://bitcoin-safe.org) - A bitcoin savings wallet for the entire family
Designed for both beginners and power users, [Bitcoin Safe]( https://bitcoin-safe.org) combines security with an intuitive user experience. In this article, we dive deep into its features, unique benefits, and the powerful tools that make managing your Bitcoin wallet simple and secure.
##### Built for Learners
✔️ Step-by-step wallet setup [wizard]( https://bitcoin-safe.org/en/knowledge/setup-singlesig-wallet/) + PDF backup [sheets 📄]( https://bitcoin-safe.org/en/features/pdf-export/)
🧪 Test transactions to ensure all hardware signers are ready 🔑
🛡️ Secure: Hardware [signers]( https://bitcoin-safe.org/en/knowledge/supported-hardware-signers/) only – no hot wallet risks 🚫🔥
🌍 Multi-language support: 🇺🇸 🇨🇳 🇪🇸 🇯🇵 🇷🇺 🇵🇹 🇮🇳 🇮🇹 🇫🇷 🇩🇪 🇲🇲 🇰🇷
📁 Address [categories]( https://bitcoin-safe.org/en/features/category-drag-and-drop/) for easy organization
☁️ Label and category [synchronization]( https://bitcoin-safe.org/en/features/label-sync/), and cloud backup (optional)
💰 Automatic UTXO merging to save on fees
⚡ Fast syncing with Electrum servers, Compact Block Filters coming soon
##### Built for Power Users
🔐 Supports Coldcard, Bitbox02, Jade, Trezor, Passport, Keystone & [many more]( https://bitcoin-safe.org/en/knowledge/supported-hardware-signers/) 🏦
💬 Multi-party multisig chat & PSBT sharing (optional)
📊 Transaction flow [diagrams]( https://bitcoin-safe.org/en/features/money-flow-diagram/) to trace coin movements
🔍 Instant cross-wallet wallet [search]( https://bitcoin-safe.org/en/features/search/)
**⚙️** Set your own electrum server, mempool instance, and nostr relay
------
## Step-by-Step Wallet Setup
Whether you’re setting up a single-signature or multi-signature wallet, the setup wizard guides you every step of the way:

* **Single Sig Wizard:** Follow the intuitive wizard that walks you through each step. https://youtu.be/m0g6ytYTy0w
Clear instructions paired with hardware signer screen-shots, like the steps for a Coldcard
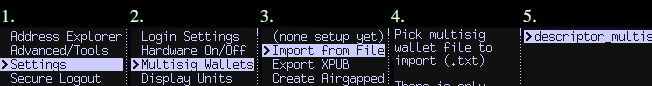
* **Multisig Wizard:** The wizard ensures you do all necessary steps for a Multisig wallet in the right order. Afterwards your Multisig is ready to use and all signers are tested. Check out https://bitcoin-safe.org/en/features/setup-multisignature-wallet/
* **PDF Backup:** The wizard will also generates 3 PDF backup sheets for a 2-of-3 multisig wallet, so ensure you always have your wallet descriptor together with the seed.
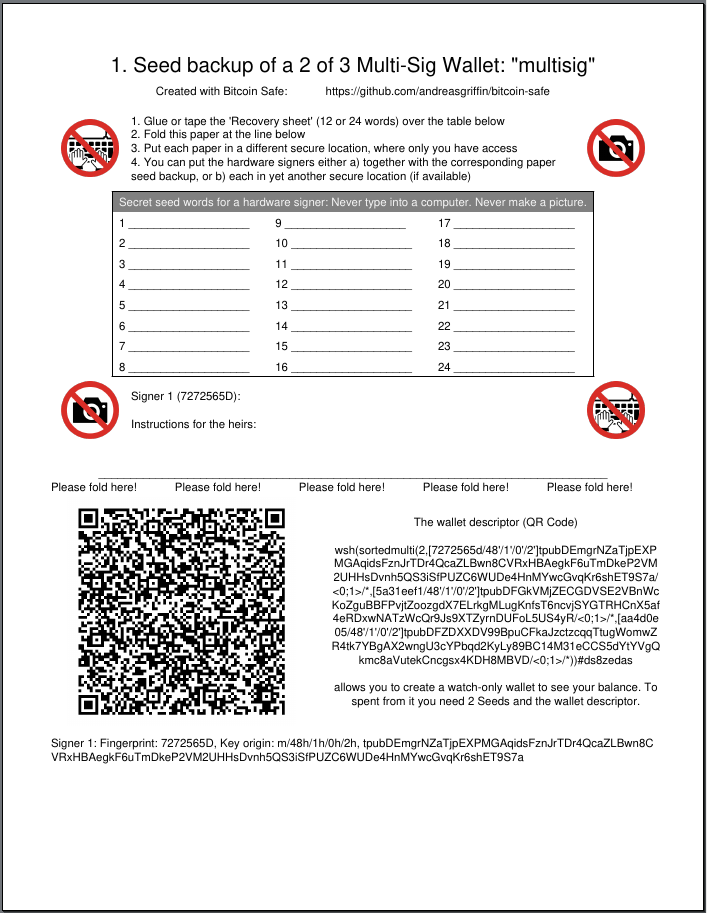
* **Hardware Signer Support:** [With full support]( https://bitcoin-safe.org/en/knowledge/supported-hardware-signers/) for major hardware signers your keys remain securely offline.
------
### Transaction Visualization
Visualize and navigate your transaction history:
- **Graphical Explorer:** An interactive transaction diagram lets you click on inputs and outputs to follow the money flow intuitively.
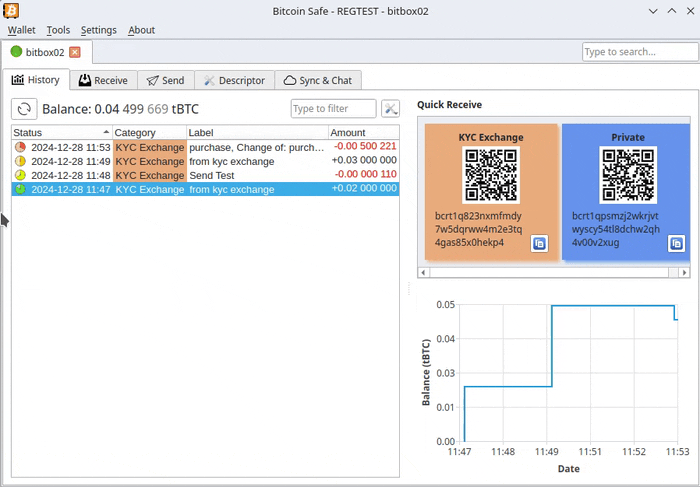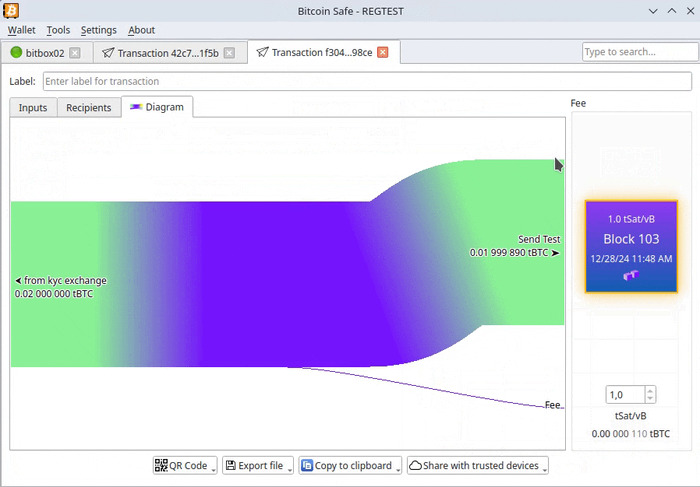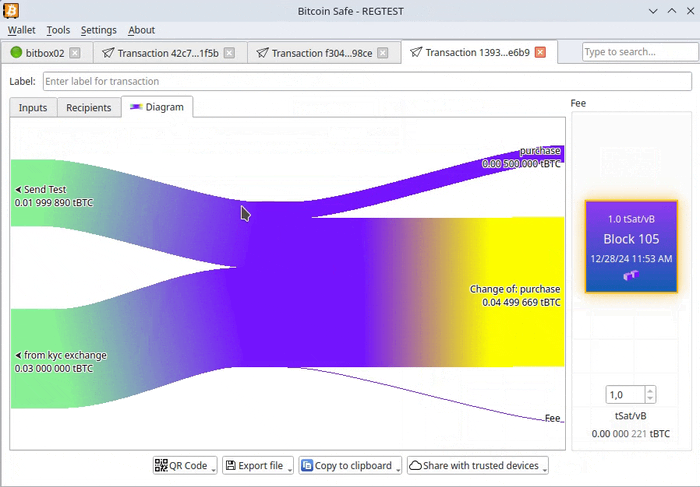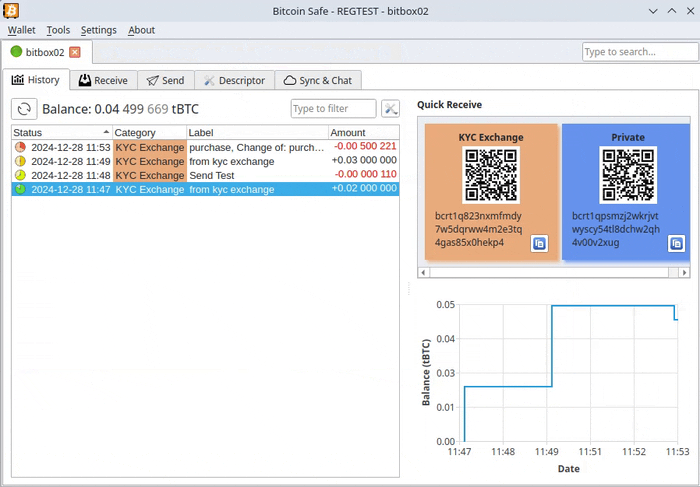
- **Coin Categories:** Organize your addresses into distinct coin categories (e.g., “KYC”, “Work”, “Friends”) so [Bitcoin Safe]( https://bitcoin-safe.org) automatically selects the correct inputs when creating PSBTs. 
It prevents you accidentally linking coin categories when creating a transaction, and warns you if mistakes happened in the past.
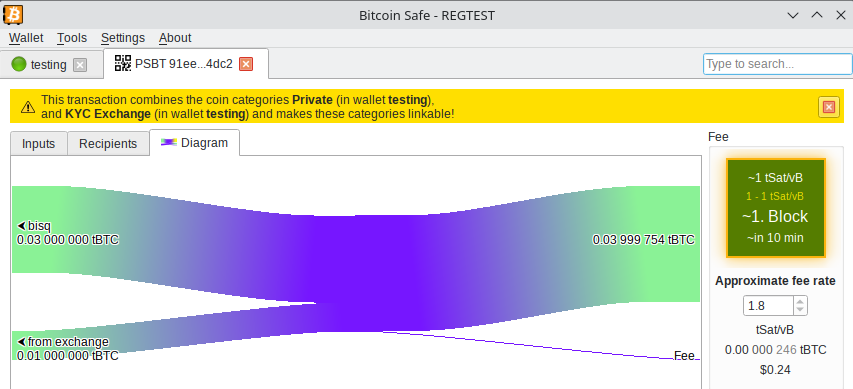
### Powerful Wallet Management Tools
- **Flexible Fee Selection:** Choose fees with one click using an intuitive mempool block preview.
- **UTXO Management:** Automatically (optional) merge UTXOs when fees are low.
- **CSV Table Export:** Right click, Drag&Drop, or CTRL+C for immediate CSV export for easy processing in Excel.
- **PDF Balance Statement:** Export the address balances for easy record keeping on paper.
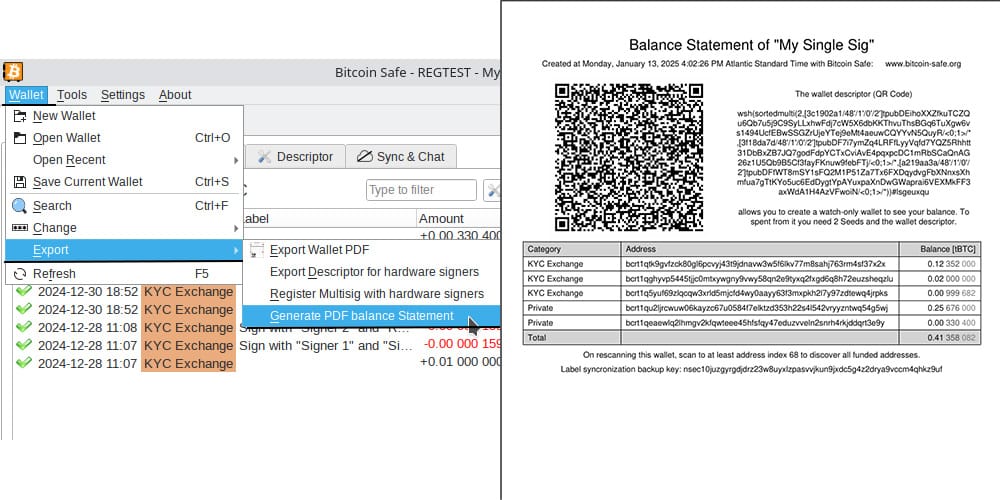
------
## Advanced Features for the Power-User
Sync & Chat is *off* by default (for the paranoid user), but can be enabled with just one click.
### Label Synchronization and Backup
- **Seamless Sync:** Using encrypted nostr messages, [Bitcoin Safe]( https://bitcoin-safe.org) synchronizes your coin categories and labels across multiple devices.
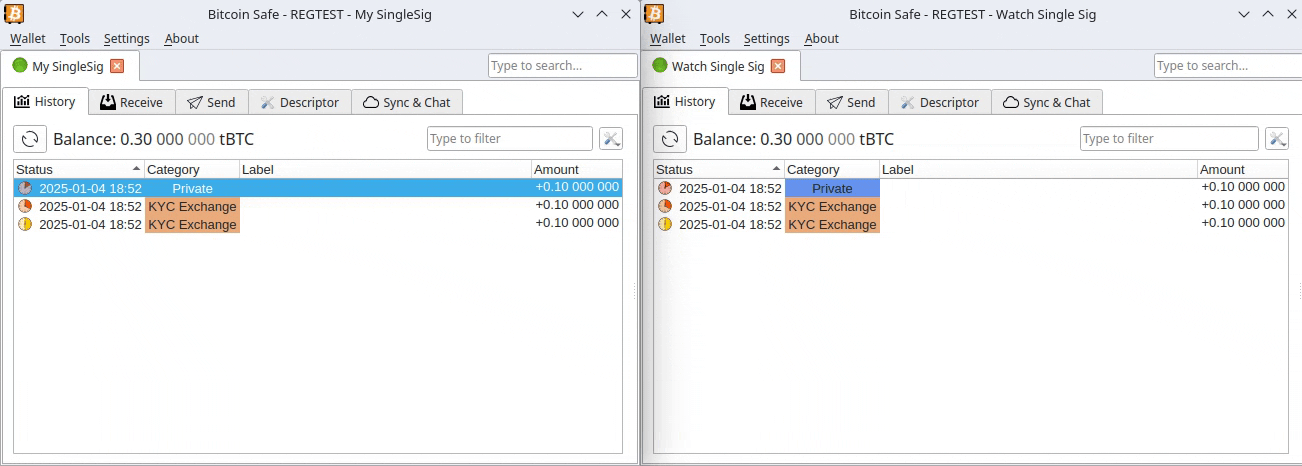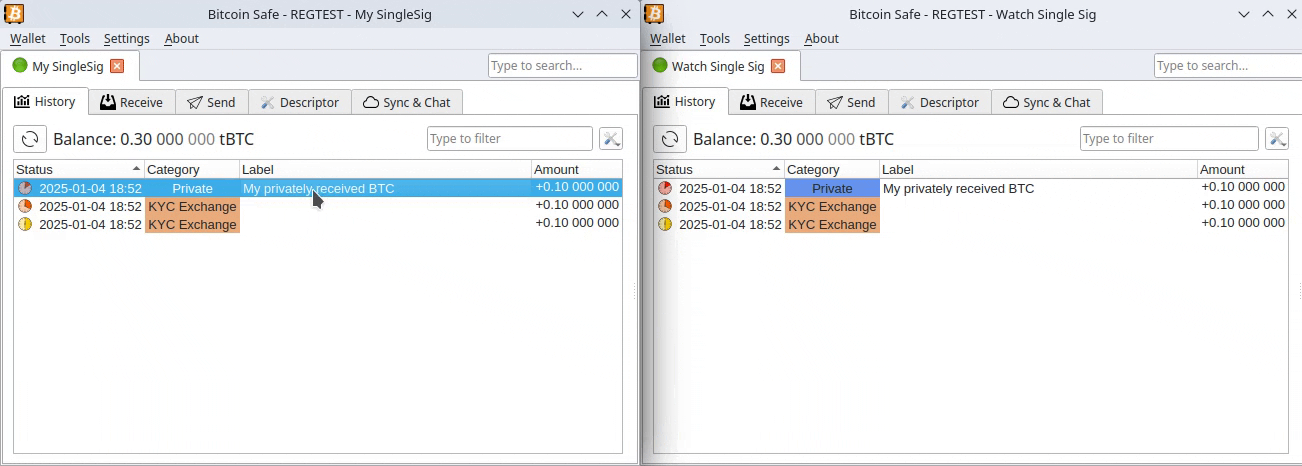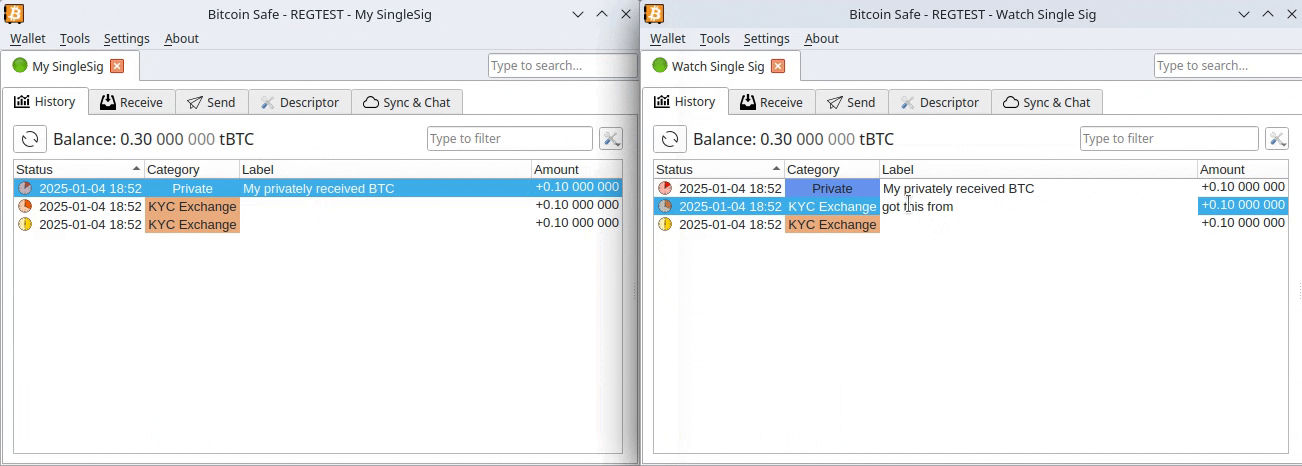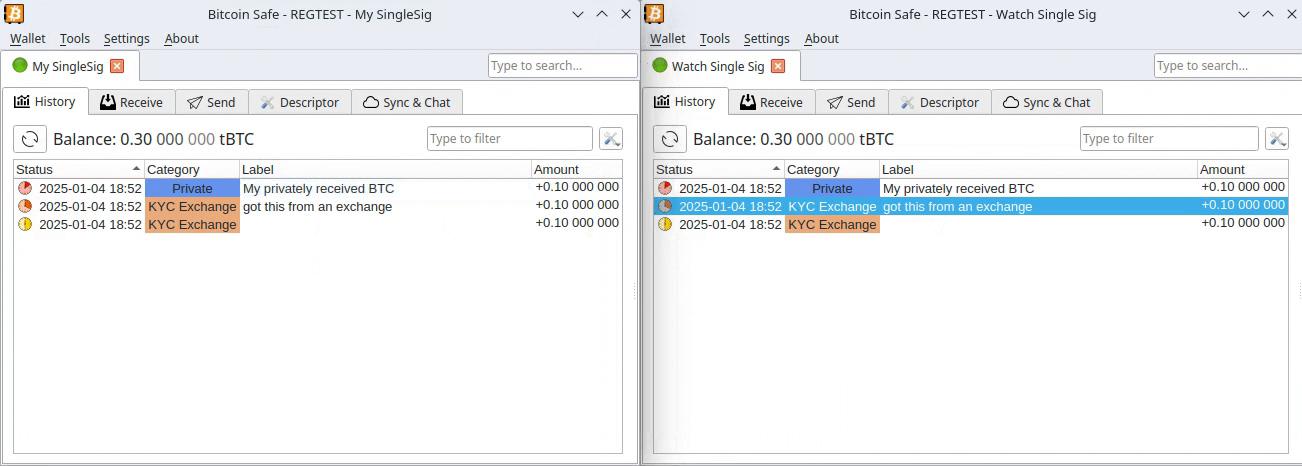
- **Easy Backup:** A short backup key is all you need to safeguard your coin categories and labels, ensuring your organization remains intact.
### Collaborative Multi-party Multisig
- **Group Chat Integration:** After creating your multisig wallet, [Bitcoin Safe]( https://bitcoin-safe.org) offers an encrypted nostr group chat for secure collaboration and **one-click PSBT sharing**.
- **User Authentication:** Each participant must authenticate every other user with a simple click, ensuring secure communication.
## Watch and Learn: Get Started with Bitcoin Safe
If you’re new to [Bitcoin Safe]( https://bitcoin-safe.org), a short video guide can make all the difference. Learn how to set up your [Bitcoin Safe]( https://bitcoin-safe.org) wallet in this detailed walk through:
https://youtu.be/m0g6ytYTy0w
Or see how to verify an address on your hardware singer:
https://youtu.be/h5FkOYj9OT8
Building up a knowledge base: https://bitcoin-safe.org/en/knowledge/
------
## Whats next?
- **Compact Block Filters!!!** They make electrum servers obsolete.
- **Why?** Compact Block Filters increase the network privacy dramatically, since you're not asking an electrum server to give you your transactions
- **Trade-off**: They are a little slower than electrum servers. For a savings wallet like [Bitcoin Safe]( https://bitcoin-safe.org) this should be OK.
- **How do they work?** Simply speaking: They ask normal bitcoin core nodes for a short summary of each block. And if the summary shows a transaction belonging to the wallet, the entire block is then downloaded from the bitcoin core node. The bitcoin core node does not learn however which of the many transactions in the block you were interested in. Read more [here]( https://ellemouton.com/posts/bip158/) and of course in the [bip]( https://bips.dev/158/).
- **When**: 2 weeks 😅. Lots of things need to be done until [Bitcoin Safe]( https://bitcoin-safe.org) can use the [bdk CBF/kyoto]( https://github.com/rustaceanrob/kyoto) client from [rustaceanrob]( https://github.com/rustaceanrob), so keep an eye out for updates and please give feedback when you use Bitcoin Safe.
Stay updated on [nostr]( https://primal.net/p/npub1q67f4d7qdja237us384ryeekxsz88lz5kaawrcynwe4hqsnufr6s27up0e) or on [GitHub]( https://github.com/andreasgriffin/bitcoin-safe).
## Thank you
A huge thanks goes to nostr:npub10pensatlcfwktnvjjw2dtem38n6rvw8g6fv73h84cuacxn4c28eqyfn34f for supporting this project with a [grant]( https://opensats.org/blog/tenth-wave-of-bitcoin-grants#bitcoin-safe) and nostr:npub1yrnuj56rnen08zp2h9h7p74ghgjx6ma39spmpj6w9hzxywutevsst7k5cx for the [Hackathon]( https://geyser.fund/grants/15) prize.
This wallet is only possible because it is building upon other peoples open source work. Most notably
* [bdk]( https://bitcoindevkit.org/) nostr:nprofile1qqsgkmgkmv63djkxmwvdlyaxx0xtsytvkyyg5fwzmp48pwd30f3jtxspzemhxue69uhhyetvv9ujuurjd9kkzmpwdejhgqg5waehxw309aex2mrp0yhxgctdw4eju6t0qyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqr8vuet
* and especially nostr:npub1thunderat5g552cuy7umk624ct5xe4tpgwr2jcjjq2gc0567wgrqnya79l , nostr:npub1reezn2ctrrg736uqj7mva9lsuwv0kr5asj4vvkwxnrwlhvxf98tsq99ty4 , and nostr:npub1ke470rdgnxg4gjs9cw3tv0dp690wl68f5xak5smflpsksedadd7qtf8jfm for dealing with my many feature requests and questions.
* [rustaceanrob]( https://github.com/rustaceanrob) building [kyoto]( https://github.com/rustaceanrob/kyoto) which implements CBF for BDK; a crucial library and will be able to replace electrum servers for many use cases
* [ndk]( https://github.com/rust-nostr/nostr) by nostr:nprofile1qqsx3kq3vkgczq9hmfplc28h687py42yvms3zkyxh8nmkvn0vhkyyuspz4mhxue69uhkummnw3ezummcw3ezuer9wchsz9thwden5te0wfjkccte9ejxzmt4wvhxjme0qy88wumn8ghj7mn0wvhxcmmv9u0uehfp
And of course, secure storage of bitcoin is only possible, because of the hardware signer manufacturers. Thanks to nostr:npub1az9xj85cmxv8e9j9y80lvqp97crsqdu2fpu3srwthd99qfu9qsgstam8y8 [Coldcard]( https://store.coinkite.com/promo/8BFF877000C34A86F410) , [Coldcard Q]( https://store.coinkite.com/promo/8BFF877000C34A86F410) , nostr:npub1tg779rlap8t4qm8lpgn89k7mr7pkxpaulupp0nq5faywr8h28llsj3cxmt [Bitbox02]( https://shiftcrypto.ch/bitbox02/?ref=MOB4dk7gpm) , nostr:npub1jg552aulj07skd6e7y2hu0vl5g8nl5jvfw8jhn6jpjk0vjd0waksvl6n8n [Blockstream Jade]( https://store.blockstream.com/?code=XEocg5boS77D) , [Trezor Safe]( https://trezor.io/trezor-safe-5-bitcoin-only), [Foundation Passport]( https://foundation.xyz/passport), [Keystone]( https://keyst.one), [Ledger]( https://shop.ledger.com/pages/ledger-nano-s-plus), [Specter Shield]( https://specter.solutions/hardware), and many more.
I also want to thank people who gave feedback and helped spread the knowledge of [Bitcoin Safe]( https://bitcoin-safe.org) (please forgive me if I forgot to mention you)
* nostr:npub1p5cmlt32vc3jefkl3ymdvm9zk892fsmkq79eq77uvkaqrnyktasqkpkgaw nostr:npub1s07s0h5mwcenfnyagme8shp9trnv964lulgvdmppgenuhtk9p4rsueuk63 nostr:npub18f3g76xc7xs430euwwl9gpn7ue7ux8vmtm9q8htn9s26d8c4neeqdraz3s nostr:npub1mtd7s63xd85ykv09p7y8wvg754jpsfpplxknh5xr0pu938zf86fqygqxas nostr:npub1kysd8m44dhv7ywa75u5z7w2w0gs4t6qzhgvjp555gfknasy3krlqfxde60 nostr:npub185pu2dsgg9d36uvvw7rwuy9aknn8hnknygr7x2yqa60ygvq6r8kqc836k8 nostr:npub1hkcgyqnsuaradq3g5hyvfdekwypc25494nmwggwpygxas7fcs4fst860fu nostr:npub1xsl0msy347vmj8gcpsjum6wwppc4ercvq4xfrhqmek2dqmqm0mtsyf35vx nostr:npub1hxjnw53mhghumt590kgd3fmqme8jzwwflyxesmm50nnapmqdzu7swqagw3
nostr:npub1ke470rdgnxg4gjs9cw3tv0dp690wl68f5xak5smflpsksedadd7qtf8jfm nostr:npub1sk26fxl4fy3vt8m5n0a6aturaql0w20nvh22q0cyaqm28tj7z8ss3lutc9 nostr:npub1r4llq2jcvq4g2tgha5amjz07zk7mrrcj89wllny9xwhhp5zzkklqk4jwja nostr:npub1p9v2zpwl28c0gu0vr2enp3lwdtv29scwpeqsnt0ngqf03vtlyxfqhkae5w nostr:npub1xkym0yaewlz0qfghtt7hjtnu28fxaa5rk3wtcek9d3x3ft2ns3lq775few nostr:npub1r8343wqpra05l3jnc4jud4xz7vlnyeslf7gfsty7ahpf92rhfmpsmqwym8 nostr:npub12zpfs3yq7we83yvypgsrw5f88y2fv780c2kfs89ge5qk6q3sfm7spks880 nostr:npub1yrnuj56rnen08zp2h9h7p74ghgjx6ma39spmpj6w9hzxywutevsst7k5cx https://x.com/91xTx93x2 https://x.com/afilini [rustaceanrob]( https://github.com/rustaceanrob)
-

@ b5d34eed:a7475cbf
2025-03-16 20:15:10
The internet has come a long way since its inception, but let’s be honest—it’s not exactly the utopia of freedom and openness we once imagined. Today, a handful of tech giants control most of our online interactions, from social media to payments. Enter the decentralized web, a movement that’s pushing back against this centralization. At the forefront of this revolution is Nostr, a simple yet powerful protocol that’s redefining how we think about social networking. And when you throw the Lightning Network into the mix, things get even more exciting. Let’s break it all down.
---
### **What’s Wrong with the Current Web?**
Before we dive into Nostr, let’s talk about why decentralization matters. The internet today is dominated by centralized platforms like Facebook, Twitter (now X), and Instagram. These platforms control what you see, how you interact, and even what you’re allowed to say. They harvest your data, sell it to advertisers, and can ban or silence you at their discretion. It’s a system that prioritizes profit over people.
Centralization also creates single points of failure. If a platform goes down, gets hacked, or decides to shut down, your data and connections disappear overnight. Remember when Twitter had outages, or when Facebook’s servers crashed? Millions of users were left stranded. This isn’t just inconvenient—it’s a fundamental flaw in how we’ve built the web.
---
### **Enter Nostr: A Breath of Fresh Air**
Nostr, which stands for *Notes and Other Stuff Transmitted by Relays*, is a decentralized protocol designed to fix these problems. Unlike traditional social media platforms, Nostr doesn’t rely on a central server. Instead, it uses a network of independent relays to transmit messages. Think of it as a decentralized Twitter, but without the corporate overlords.
Here’s why Nostr is a game-changer:
1. **No Central Authority**: Nostr doesn’t belong to any company or individual. It’s an open protocol, meaning anyone can build apps on top of it or run their own relay. This eliminates the risk of censorship or arbitrary bans.
2. **User Control**: With Nostr, you own your data. Your posts, messages, and connections are stored locally or on relays you choose. If one relay goes down, you can switch to another without losing anything.
3. **Interoperability**: Nostr is designed to work across different apps and platforms. This means you’re not locked into a single ecosystem. If you don’t like one Nostr client, you can switch to another without losing your followers or content.
4. **Simplicity**: Nostr’s protocol is intentionally simple. It doesn’t try to do everything at once, which makes it lightweight and easy to use. This simplicity also makes it more resilient and adaptable.
---
### **The Lightning Network: Powering Decentralized Payments**
Now, let’s talk about money. One of the coolest things about Nostr is its integration with the Lightning Network, a second-layer payment protocol built on top of Bitcoin. The Lightning Network enables fast, cheap, and scalable transactions, making it perfect for micropayments and tipping.
Here’s why this matters:
1. **Monetization Without Ads**: Traditional social media platforms rely on ads to make money. This creates a perverse incentive to keep you hooked and harvest your data. With Nostr and the Lightning Network, creators can monetize their content directly through tips or paid subscriptions. No ads, no middlemen—just a direct connection between creators and their audience.
2. **Global Payments**: The Lightning Network is borderless. Whether you’re tipping a blogger in Nigeria or buying a digital product from someone in Argentina, transactions are instant and cost just a fraction of a cent. This opens up new opportunities for global collaboration and commerce.
3. **Censorship-Resistant Money**: Just like Nostr resists censorship, the Lightning Network ensures that payments can’t be blocked or controlled by any central authority. This is especially important in regions where financial freedom is under threat.
---
### **Why Nostr and the Lightning Network Are a Perfect Match**
When you combine Nostr’s decentralized social networking with the Lightning Network’s payment capabilities, you get something truly special. Imagine a social media platform where you can tip your favorite creators, pay for premium content, or even buy goods and services—all without leaving the app. And because both Nostr and the Lightning Network are decentralized, you don’t have to worry about fees, censorship, or corporate interference.
For example, let’s say you’re a musician sharing your work on Nostr. Fans can tip you in Bitcoin via the Lightning Network, or you can sell exclusive content directly to your followers. The money goes straight to you, without a platform taking a cut. This creates a more equitable and sustainable model for creators.
---
### **The Bigger Picture: A Decentralized Future**
Nostr and the Lightning Network are just two pieces of a much larger puzzle. The decentralized web is about reclaiming control over our online lives—our data, our interactions, and our money. It’s about building a more open, resilient, and user-centric internet.
Of course, decentralization isn’t without its challenges. It can be harder to use than centralized alternatives, and it requires a shift in how we think about technology. But the benefits far outweigh the drawbacks. By embracing protocols like Nostr and the Lightning Network, we can create a web that’s truly by the people, for the people.
### Final Thoughts
The decentralized web isn’t just a tech trend—it’s a movement. Nostr and the Lightning Network are proof that we can build better, fairer systems when we prioritize freedom and innovation over profit and control. Whether you’re a creator, a developer, or just someone who’s tired of Big Tech’s grip on your online life, now’s the time to explore what the decentralized web has to offer.
-

@ 5d4b6c8d:8a1c1ee3
2025-04-01 13:41:45
I'm trying out a new month-long focus. For Active April, I'm going to be more proactive about doing stuff around the house that needs doing.
It's gonna get all Jordan Peterson cleaning your room up in here. Let's see how noticeable the consequences are.
- I predict a happier wife, for one.
- I'm also curious to see what kind of fitness impacts there are to increasing this kind of activity, compared to doing more exercise.
originally posted at https://stacker.news/items/931099
-

@ d5c3d063:4d1159b3
2025-04-03 04:09:56
### ทรัมป์ ขึ้นภาษีนำเข้า
สิ่งที่คุณเห็น…กับสิ่งที่คุณมองไม่เห็น
คุณ #เห็น แค่ฝั่งที่ดูดีในข่าวภาคค่ำ
แต่คุณ #ไม่เห็น
– คนทั้งประเทศ ต้องจ่ายของแพงขึ้น
– ธุรกิจเล็ก ๆ ที่พึ่งการนำเข้า…ถูกบีบให้ตาย
– ผู้บริโภคต้องเสียเงินมากขึ้น โดยไม่มีทางเลือก
รัฐอ้างว่า *"ปกป้องประเทศ"* แต่จริง ๆ แล้วเขาแค่
โยนภาระให้คนส่วนใหญ่ เพื่ออุ้มผลประโยชน์บางกลุ่ม
เหมือนที่ Bastiat เรียกว่า *“การปล้นที่ถูกกฎหมาย”*
Hazlitt ขยายต่อใน Economics in One Lesson ว่า
> เศรษฐศาสตร์ที่ดี ต้องมองให้พ้นจากผลเฉพาะหน้า
> และมองให้เห็นผลกระทบต่อทุกคน ไม่ใช่แค่บางกลุ่ม
เงินเฟ้อ คือการขโมยแบบเงียบ ๆ
ภาษีศุลกากร คือการปล้นอย่างเปิดเผย
วันนี้ #EIOL น่าจะถึงมือเพื่อนๆ หลายคนแล้ว เล่มนี้ไม่ต้องอ่านทีละบทก็ได้ ลองเปิดไปบทที่ 11 เลยแล้วจะเจอ**ค้อนปอน**สำหรับทุบมายาคดีทางเศรษฐกิจที่รัฐใช้กับเรามาทั้งชีวิต
อ่าน #เศรษฐศาสตร์เล่มเดียวจบ แล้วคุณอาจไม่มีวันมอง “นโยบายเพื่อประชาชน” ได้เหมือนเดิมอีก เพราะบางที...สิ่งที่คุณไม่เคยเห็น อาจเป็นสิ่งที่คุณควรรู้(เห็น)ให้เร็วที่สุด
#Siamstr
-

@ 57d1a264:69f1fee1
2025-03-27 08:11:33
Explore and reimagine programming interfaces beyond text (visual, tactile, spatial).
> _"The most dangerous thought you can have as a creative person is to think you know what you're doing."_
`— Richard Hamming` [^1]
https://www.youtube.com/watch?v=8pTEmbeENF4
For his recent DBX Conference talk, Victor took attendees back to the year 1973, donning the uniform of an IBM systems engineer of the times, delivering his presentation on an overhead projector. The '60s and early '70s were a fertile time for CS ideas, reminds Victor, but even more importantly, it was a time of unfettered thinking, unconstrained by programming dogma, authority, and tradition.

_'The most dangerous thought that you can have as a creative person is to think that you know what you're doing,'_ explains Victor. 'Because once you think you know what you're doing you stop looking around for other ways of doing things and you stop being able to see other ways of doing things. You become blind.' He concludes, 'I think you have to say: _"We don't know what programming is. We don't know what computing is. We don't even know what a computer is."_ And once you truly understand that, and once you truly believe that, then you're free, and you can think anything.'
More details at https://worrydream.com/dbx/
[^1]: Richard Hamming -- [The Art of Doing Science and Engineering, p5](http://worrydream.com/refs/Hamming_1997_-_The_Art_of_Doing_Science_and_Engineering.pdf) (pdf ebook)
originally posted at https://stacker.news/items/926493
-

@ fd06f542:8d6d54cd
2025-03-28 02:14:43
{"coverurl":"https://cdn.nostrcheck.me/fd06f542bc6c06a39881810de917e6c5d277dfb51689a568ad7b7a548d6d54cd/5ad7189d30c9b49aa61652d98ac7853217b7e445f863be09f9745c49df9f514c.webp","title":"Nostr protocol","author":"fiatjaf"}
-

@ e3ba5e1a:5e433365
2025-02-13 06:16:49
My favorite line in any Marvel movie ever is in “Captain America.” After Captain America launches seemingly a hopeless assault on Red Skull’s base and is captured, we get [this line](https://www.youtube.com/shorts/kqsomjpz7ok):
“Arrogance may not be a uniquely American trait, but I must say, you do it better than anyone.”
Yesterday, I came across a comment on the song [Devil Went Down to Georgia](https://youtu.be/ut8UqFlWdDc) that had a very similar feel to it:

America has seemingly always been arrogant, in a uniquely American way. Manifest Destiny, for instance. The rest of the world is aware of this arrogance, and mocks Americans for it. A central point in modern US politics is the deriding of racist, nationalist, supremacist Americans.
That’s not what I see. I see American Arrogance as not only a beautiful statement about what it means to be American. I see it as an ode to the greatness of humanity in its purest form.
For most countries, saying “our nation is the greatest” *is*, in fact, twinged with some level of racism. I still don’t have a problem with it. Every group of people *should* be allowed to feel pride in their accomplishments. The destruction of the human spirit since the end of World War 2, where greatness has become a sin and weakness a virtue, has crushed the ability of people worldwide to strive for excellence.
But I digress. The fears of racism and nationalism at least have a grain of truth when applied to other nations on the planet. But not to America.
That’s because the definition of America, and the prototype of an American, has nothing to do with race. The definition of Americanism is *freedom*. The founding of America is based purely on liberty. On the God-given rights of every person to live life the way they see fit.
American Arrogance is not a statement of racial superiority. It’s barely a statement of national superiority (though it absolutely is). To me, when an American comments on the greatness of America, it’s a statement about freedom. Freedom will always unlock the greatness inherent in any group of people. Americans are *definitionally* better than everyone else, because Americans are freer than everyone else. (Or, at least, that’s how it should be.)
In *Devil Went Down to Georgia*, Johnny is approached by the devil himself. He is challenged to a ridiculously lopsided bet: a golden fiddle versus his immortal soul. He acknowledges the sin in accepting such a proposal. And yet he says, “God, I know you told me not to do this. But I can’t stand the affront to my honor. I am the greatest. The devil has nothing on me. So God, I’m gonna sin, but I’m also gonna win.”
*Libertas magnitudo est*
-

@ 3c7dc2c5:805642a8
2025-04-02 21:15:55
## 🧠Quote(s) of the week:
CBDC the digital euro - a centralized solution in search of a problem. While the ECB may see it as a way to 'modernize' finance, true innovation comes from empowering individuals, not consolidating control. CBDCs are just surveillance tools disguised as innovation. Bitcoin is the only true digital money—decentralized, scarce, and free. Stack sats, not CBDCs.
## 🧡Bitcoin news🧡
2025
https://i.ibb.co/vx988kT1/Gn-Ix-Dp-YWs-AASkiw.jpg
On the 24th of March:
➡️The Pakistan central bank is exploring mining Bitcoin with excess electricity.
➡️'MicroStrategy just added another 7,000 Bitcoin to their treasury. They're now holding over 506,000 BTC ($44 billion).
Look at the corporate Bitcoin ownership breakdown:
- MicroStrategy: 506,000+ BTC
- Marathon: ~46,000 BTC (10x smaller)
- Riot: ~19,000 BTC (26x smaller)
That acquisition curve has gone parabolic since Q4 2024.
Strategy's buying pace now rivals what we're seeing from the Bitcoin ETFs, a single public company absorbing supply at an institutional scale.
Clear institutional conviction signal here.' -Ecoinometrics
➡️SQUARE CEO JACK DORSEY: "Bitcoin will make the current financial system feel as irrelevant as the fax machine."
On the 25th of March:
➡️'BITCOIN HASH-RIBBON FLASHES BUY SIGNAL
- This is one of the most reliable "buy" indicators.
- Significant price gains have followed 7 out of the last 7 times this indicator was triggered.' -Bitcoin Archive
(foto)
Bitcoin is always a buy. Just DCA.
➡️GameStop includes Bitcoin as a treasury reserve asset in its investment policy update. GameStop has $4.6 billion in cash to invest.
➡️Strategy’s sale of 8.5 million STRF shares closes today, unlocking $711 million in new capital to buy more Bitcoin.
➡️BBC News reports from a remote community of 15,000 people in the far north-western tip of Zambia relying on hydroelectric power, “The bitcoin mine now accounts for around 30% of the plant's revenue allowing them to keep the prices down for the local town” - Source: https://www.bbc.com/news/articles/cly4xe373p4o
Gridless is doing a splendid job in Africa and showing through proof-of-work that if you aren't mining Bitcoin, you are wasting energy. It's time for such communities to appear more around the world.
Daniel Batten: 'They couldn't resist zooming out and implying this is an outlier (it isn't, the majority of off-grid bitcoin mining operations are renewably powered). In doing so BBC made three factually incorrect statements at the end about Bitcoin mining straining grids (multiple peer-reviewed studies show the opposite is true), and "Greenidge gas power plant in New York which was renovated to mine bitcoin" (it didn't, it re-opened to supply power back to the grid), and stating that Bitcoin mining needs artificial govt incentives or rules to do the right thing (It doesn't, it's become 56.7% sustainably powered without any govt incentives)
But let's shine the light on the positive - it has far fewer factually incorrect statements than previous reporting, and it is a step in the right direction in its gradual journey towards objective Bitcoin reporting for a media company that has until now only published negative news stories on Bitcoin.'
➡️Femke Halsema, Mayor of Amsterdam, wants a national ban on Bitcoin payments: "It undermines our civilization".
I rather believe the opposite.
Under Femke Halsema - Amsterdam
- The number of civil servants increased by 50% (14K -> 20K)
- Debt increased by 150% (4 billion -> approx. 10 billion)
Despite high revenues, Amsterdam has to borrow nearly half a billion euros every year. Local taxes continue to rise, whether it's water authority taxes or property taxes (OZB). But, above all, you should be concerned about those 0.3% criminal Bitcoin / Crypto transactions (worldwide). The audacity.
Even if the Netherlands were to legally ban Bitcoin payments, users could easily continue trading through foreign exchanges or peer-to-peer platforms. A ban might actually push Bitcoin usage further underground, making oversight of suspicious transactions worse rather than better.
➡️Mt. Gox moves 11.501 Bitcoin ($1B) for creditor repayment.
➡️BlackRock launched a European Bitcoin ETP today - Bloomberg
➡️North Carolina introduces a bill to invest 5% of state funds into Bitcoin.
On the 26th of March:
➡️NYDIG just became a big Bitcoin miner.
Crusoe, the first to scale Bitcoin mining off flared gas (~200MW worth, across 425 data centers) has sold its entire Bitcoin mining business to NYDIG.
➡️Metaplanet has raised ~$55.2m (¥8.28b) of equity capital through three trading days this week while partially deleveraging with the redemption of $23.3m (¥3.5b) of 0% ordinary bonds.
➡️GameStop can service a loan of up to $100 BILLION for 4.6 years with its existing $4.6b cash balance at 1% interest.
That's twice the amount of Bitcoin Michael Saylor's Strategy currently holds.
➡️New feature by Protonmail enables their 100 million users to send Bitcoin using their email addresses.
➡️The Blockchain Group confirms the acquisition of 580 BTC for ~€47.3 million, the holding of a total of 620 BTC, and a BTC Yield of 709.8% YTD.
→ Confirmation of the acquisition of 580 BTC for ~€47.3 million at ~€81,550 per bitcoin
→ Total group holdings of 620 BTC for ~€50.5 million at ~€81,480 per bitcoin
→ Adoption of ‘BTC Yield’, ‘BTC Gain’, and ‘BTC € Gain’ as KPIs, following the steps of Strategy and Metaplanet
This is a major step in our Bitcoin Treasury Company strategy focused on increasing Bitcoin per share over time.
Source: https://t.co/QDj61ZDe6O
The Blockchain Group is Europe's First Bitcoin Treasury Company!
On the 27th of March:
➡️'Bitcoin's 4-year Compound Annual Growth Rate (CAGR) is at historic lows.' -Pierre Rochard
➡️Daniel Batten: Yet another paper on Bitcoin and energy
TL:DR: "The opportunities offered by bitcoin mining in reduction of the greenhouse gas emissions and renewable energy transition
are greater than generally assumed"
The journal has a (high) impact factor of 7.1."
Source: https://t.co/W3gytMgcpC
➡️A home miner with only 4 machines mined block 888737.
https://i.ibb.co/7xm91R4t/Gn-Ef-H9y-Ws-AA4jkn.jpg
Bitcoin proves anyone can participate and earn—true freedom!
➡️'Short-Term Holders have increased their Bitcoin holdings by 201,743 BTC to 5,750,076 BTC since January, remaining below previous cycle peaks.
200K BTC are currently held at an unrealized loss, representing about $17B.' -Bitcoin News
➡️Bitcoin mining hardware manufacturer Canaan signs a three-year colocation agreement with Mawson Infrastructure Group's Mawson Hosting LLC for facilities in Midland, Pennsylvania, and Edna, Texas. Most of the 4.7 EH/s hashrate is expected to be operational by Q2 2025.
On the 28th of March:
➡️If Saylor had bet on ETH instead of Bitcoin, Strategy would be down $9 billion, instead of up $9 billion like they are today.
ETHBTC made fresh lows 0.02210. Ether is down 74% against Bitcoin since switching from proof of work to proof of stake. Yikes!
➡️Representative introduces a strategic Bitcoin reserve bill in South Carolina.
➡️A Russian company built a Bitcoin mine in the Arctic.
Set in the frozen city of Norilsk, the facility taps into cheap excess energy from one of the world's most isolated industrial hubs.
➡️The price of bitcoin has nearly followed the same phases of volatility for 15 years, according to Fidelity.
https://i.ibb.co/LdQfrqG0/Gn-Ig-Skd-XMAAi-L3r.jpg
another great chart:
https://i.ibb.co/G4WmDjhd/Gn-JED1q-Xk-AAq-Kqk.jpg
On the 29th of March:
➡️Public miner MARA with a $2B common stock offering to buy more Bitcoin.
https://i.ibb.co/PZZxXJ37/Gn-Kj-Vqza-EAEUG-V.png
➡️California has officially included Bitcoin Rights protections in its newly proposed digital asset bill.
If passed, it will guarantee the right to self-custody for nearly 40M residents and prohibit discrimination against Bitcoin use.
➡️The number of addresses with more than one Bitcoin has fallen below 1 million, standing today at 995,207.
On the 31st of March:
➡️Larry Fink, Founder/CEO of BlackRock in his annual letter to shareholders:
“If the U.S. doesn't get its debt under control, if deficits keep ballooning, America risks losing that position to digital assets like Bitcoin."
https://www.blackrock.com/corporate/literature/presentation/larry-fink-annual-chairmans-letter.pdf
➡️Strategy has acquired 22,048 BTC for ~$1.92 billion at ~$86,969 per bitcoin and has achieved a BTC Yield of 11.0% YTD 2025. As of 3/30/2025, Strategy holds 528,185 $BTC acquired for ~$35.63 billion at ~$67,458 per bitcoin.
➡️ The Bitcoin Policy Institute releases a framework for the USA to buy $200 billion worth of #Bitcoin using Bit Bonds.
➡️Is Indonesia the next Bitcoin Country? Bitcoin Indonesia mapped out the entire Bitcoin ecosystem.
A new map shows Bitcoin adoption EXPLODING across the Southeast Asian island nation of Indonesia.
Check out all the communities, projects, and businesses embracing Bitcoin. The revolution is happening.
https://i.ibb.co/cXL8mC0x/Gnbdg-Lub-IAAdwcb.jpg
On the 1st of April:
➡️'Over 73,353 BTC were bought by corporations in Q1 2025.
Only 40,500 BTC new Bitcoin was mined, but still no supply shock, for now...
Which company do you want to see adopt BTC next?'
Here is the breakdown by Alec: https://x.com/Alec_Bitcoin/status/1907062290345783723
➡️After skeptics questioned Tether’s Bitcoin holdings, CEO Paolo Ardoino fired back, sharing the company’s BTC address with a confirmed balance of 92,646 BTC.
On the same day Tether bought 8,888 Bitcoin worth $735 million as per on-chain data. They now hold over 100,000 BTC.
➡️'GameStop just raised $1.48B. They are expected to use that and possibly more of the now $6B+ on their balance sheet to buy Bitcoin. A master class on how to pivot from meme stock to capitalize on volatility in the ultimate store of value.' -James Lavish
➡️Texas' state house Democrats have proposed a bill that would authorize up to $250 million in state investment in Bitcoin and up to $10 million for each municipality and county.
➡️Human Rights Foundation donates 10 Bitcoins worth $830,000 to over 20 projects worldwide.
Alex Gladstein: '1 billion sats gifted carefully to a variety of stellar organizations and individuals to support BTC privacy, decentralization, education, and p2p use, aimed at folks working under authoritarianism.'
## 💸Traditional Finance / Macro:
On the 29th of March
👉🏽'From Wednesday to Friday, the S&P 500 lost -$100 billion PER trading hour for a total of -$2 TRILLION.
Then, after the market closed on Friday, S&P 500 futures erased ANOTHER -$120 billion in minutes.' -TKL
## 🏦Banks:
👉🏽 no news
## 🌎Macro/Geopolitics:
On the 24th of March:
👉🏽Financelot: 'This is fascinating. The Dow Jones to Gold Ratio is about to cross a level only seen 4 times in history.
Every time it crossed this level it marked the beginning of an 18-month recession/depression.
1929, 1973, 2008 & 2025'
I don't think we won't see a depression. History rhymes but doesn't always mean it will repeat, although human behavior stays the same. For now, it means the market is overvalued, gold is undervalued, or both.
👉🏽US household wealth is falling:
US household equity wealth is set to drop a whopping -$3 trillion this quarter, the most since the 2022 bear market, according to BofA estimates.
By comparison, equity holdings rose +$9 trillion in 2024 to a record $56 trillion.
In other words, one-third of last year's gains have likely been wiped out due to the recent market pullback.
Furthermore, the top 10% of the wealthiest Americans own 87% of US stocks.
This, in turn, may negatively impact consumer spending as the top 10% reflect a record 50% of all consumer expenditures.
Consumer spending is set to slow in Q2 2025.' -TKL
👉🏽Demolition of the Boiler House at Moorburg Power Plant in Hamburg. Germany is preparing for combat by dynamiting its own modern energy infrastructure down. This was the most advanced coal plant. 6 years old and cost three billion euros. The Netherlands is following a similar policy—they poured concrete into their gas drilling pipes.
BowTiedMara on Twitter: "In 2022, a girl tied herself to the net at Roland Garros in protest, and she wore a T-shirt that said: "We have 1,028 days left."
Today, the 27th of March, marks those 1,028 days, and nothing happened.
Climate doomers are like Aztecs who think the sun stops unless they cut out some organs."
👉🏽Starting in April, the 66,000 employees of the European institutions will receive their seventh salary increase in just three years! Normally, this happens at most once per year. The President of the European Commission, Ursula von der Leyen, will see the largest increase, with her monthly salary rising to €34,800—an increase of €2,700—according to a report by the German newspaper Bild-Zeitung today.
For the Dutch readers: https://ejbron.wordpress.com/2025/03/24/eu-bureaucraten-en-politici-krijgen-de-7e-salarisverhoging-sinds-2022/
They are compensating for the inflation they impose on the EU. Lucky them Fair to say we need a DOGE in Europe.
On the 25th of March:
👉🏽Dutch minister announces a huge increase in excise duties of 25.8 cents on gasoline. On top of that, the price of gasoline will rise by an additional 7 cents due to the blending requirement and 11 cents due to the ETS-2 regulation. In a free market, prices would not be announced by politicians but would emerge through supply and demand. How I love the EU....although it is a bit more nuanced. The temporary discount is ending. Unless the parliament decides to extend it, the price of gasoline will rise. The Dutch government should simply spend less and abolish all taxes, excise duties, and levies on food, fuel, and energy. Never gonna happen though.
👉🏽"Shell will be thoroughly reviewing all its chemical divisions worldwide in the coming period. In Europe, this could lead to the partial or complete closure of various chemical branches." As mentioned multiple times last month, major industrial companies sounded the alarm. They warned that high energy costs in the Netherlands put their future at risk. Additionally, sustainability efforts and unclear government policies are challenging the sector. Frans Everts, President-Director of Shell Netherlands, warned that the entire industry could collapse.
The Green Deal is moving full speed ahead—soon everyone will be relying on food banks…
For the Dutch readers: https://nos.nl/artikel/2561036-shell-kijkt-naar-gedeeltelijke-sluiting-van-chemie-onderdelen
On the 26th of March:
👉🏽EU countries will start using a digital driver’s license from 2030. This is the result of negotiations between the European Parliament and EU member states. In the Netherlands, the digital license will be valid for ten years and will be accessible via an app. And we all know which app that will be! The EU Digital Wallet must be filled, after all.
Not just your driver’s license—everything will soon be linked to your digital identity. It’s all right there on the EU’s website, and it’s been planned for a long time. The COVID pass was already part of the rollout. The fact that they present these as separate steps just shows that they know people wouldn’t accept it if they were fully aware of what’s happening.
On the 27th of March:
👉🏽Gold surpasses $3,100 for the first time in history.
TKL: 'Gold prices have hit 50 all-time highs over the last 12 months, its best streak in 12 years.
This is also the 3rd-longest streak on record after a historic run during the late 1970s.
The 1970s came with a period of double-digit inflation, stagnant economic growth, and a high unemployment rate, also known as stagflation.
As a result, gold prices recorded 4 consecutive yearly gains.'
On the 31st of March for the first time, gold blasted through $100,000/kilogram.
This time, gold prices have rallied 39% over the last 12 months, are up 16% year-to-date, and are on track for the 3rd annual positive performance.'
👉🏽NATO Secretary General Rutte insists there will be no normalization of relations with Russia for decades to come.
On March 14, 2025, Bloomberg, Rutte says: "Once the war is over, relations with Russia will gradually be restored."
On March 26, 2025, Rutte said: "There will be no normalization of relations with Russia for decades, even after the war is over."
That is the Mark I know!
"Mark Rutte, the long-serving Dutch Prime Minister, earned the nickname “Pinokkio” (Dutch for Pinocchio) primarily because of perceived dishonesty or evasiveness in political debates and scandals. While some still view Rutte as a pragmatic and stable leader, the nickname “Pinokkio” reflects a broader public sentiment of distrust, especially among those who felt betrayed by his communication style or decisions.”
On the 28th of March:
👉🏽US consumers now expect 5.0%(!) inflation in the next twelve months. Inflation expectations have DOUBLED in just four months. That's huge! Long-term US inflation expectations have officially SURGED to 4.1%, the highest level since 1993.
Tariff front-running has led to a $300+ BILLION trade deficit in 2 months, and consumer sentiment has collapsed.
Atlanta Fed is now projecting that Q1 GDP will be -2.8%… a large contraction.
It’s negative even “gold adjusted”
4 weeks ago it was +2.3%
8 weeks ago it was +3.9%
Yikes!
👉🏽The State Department is officially shutting down USAID and has formally notified Congress of its closure.
The remaining 900 employees are set to be terminated.
👉🏽Argentina’s Economy Grows 6.5% in January. Argentina’s Poverty Rate Drops from 52.9% to 38.1% in 15 Months Under Javier Milei
👉🏽Fix the money, fix the world:
DOGE “There is actually really only ONE BANK ACCOUNT that's used to disperse ALL monies that go out of the federal government”
“It's a big one — A couple of weeks ago it had $800 billion in it, it's the treasury general account”
“We're serving 580+ agencies. And up until very recently, effectively they could say, make the payment and Treasury just sent it out as fast as possible. NO VERIFICATION”
“There's a $500 billion of fraud every year. There are hundreds of billion dollars of improper payments and we can't pass an audit. The consolidated financial report is produced by treasury and we cannot pass an audit”
Extremely fascinating interview by Bret Baier with the highly talented and competent DOGE team, which is rigorously streamlining the U.S. government bureaucracy. This work can only be done by competent (and motivated) outsiders with experience. Also urgently needed in the Netherlands, and in Europe.
On the 29th of March:
👉🏽'US debt has been "limited" by the $36.104 trillion debt ceiling since January but the liabilities don't stop rising. As of today, US debt is now ~$37 trillion.
Treasury has burned through $560BN of its cash balance in the past month. Just $280BN left.' -ZeroHedge
On the 1st of April:
In recent weeks, I have shared my opinion on the latest Dutch pension fund drama. This week:
https://i.ibb.co/96ZhS0W/Gn-XEVQRXw-AM6b0-A.jpg
APG and pension funds refused to invest in Dutch housing (for political reasons). This involved 25 billion euros.
Currently we almost have a political scandal over a medal, but the fact that our pension system is being put at risk...no biggie!?
For our own housing market? “Too political.”
For war and Brussels' military ambitions? €100,000,000,000—no problem.
They’re gambling with your pension while first-time buyers can’t afford a home and seniors struggle to make ends meet. Our money, their agenda.
Got Bitcoin?
I will end this Weekly Recap with a Stanley Druckenmiller quote:
"My favorite quote of all time is maybe Mark Twain: "Put all your eggs in one basket and watch the basket carefully."
"I tend to think that's what great investors do."
I know what I do and have. Bitcoin!
## 🎁If you have made it this far I would like to give you a little gift:
What Bitcoin Did:
Peter Dunworth is the Director of a multi-family office and is the co-founder of The Bitcoin Adviser. In this episode, they discuss why Bitcoin is the only asset that can recapitalize the financial system, why Peter believes Bitcoin could become a $100 trillion asset within a decade, why credit markets are ultimately a collateral problem, and why financializing Bitcoin might be necessary to save Main Street from being collateral damage. They also get into Australia's property obsession, GameStop’s pivot to Bitcoin, the difference between Bitcoin derivatives and the asset itself, and MicroStrategy.
https://www.youtube.com/watch?v=_bSprc0IAow
Credit: I have used multiple sources!
My savings account: Bitcoin The tool I recommend for setting up a Bitcoin savings plan: PocketBitcoin especially suited for beginners or people who want to invest in Bitcoin with an automated investment plan once a week or monthly.
`Use the code SE3997`
Get your Bitcoin out of exchanges. Save them on a hardware wallet, run your own node...be your own bank. Not your keys, not your coins. It's that simple. ⠀
⠀
⠀⠀ ⠀ ⠀⠀⠀
Do you think this post is helpful to you? If so, please share it and support my work with a zap.
▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃
⭐ Many thanks⭐
Felipe - Bitcoin Friday!
▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃
-

@ 6ad08392:ea301584
2025-03-14 19:03:20
In 2024, I was high as a kite on Nostr hopium and optimism. Early that year, my co-founder and I figured that we could use Nostr as a way to validate ambassadors on “Destination Bitcoin” - the germ of a travel app idea we had at the time that would turn into Satlantis. After some more digging and thinking, we realised that Nostr’s open social graph would be of major benefit, and in exploring that design space, the fuller idea of Satlantis formed: a new kind of social network for travel.
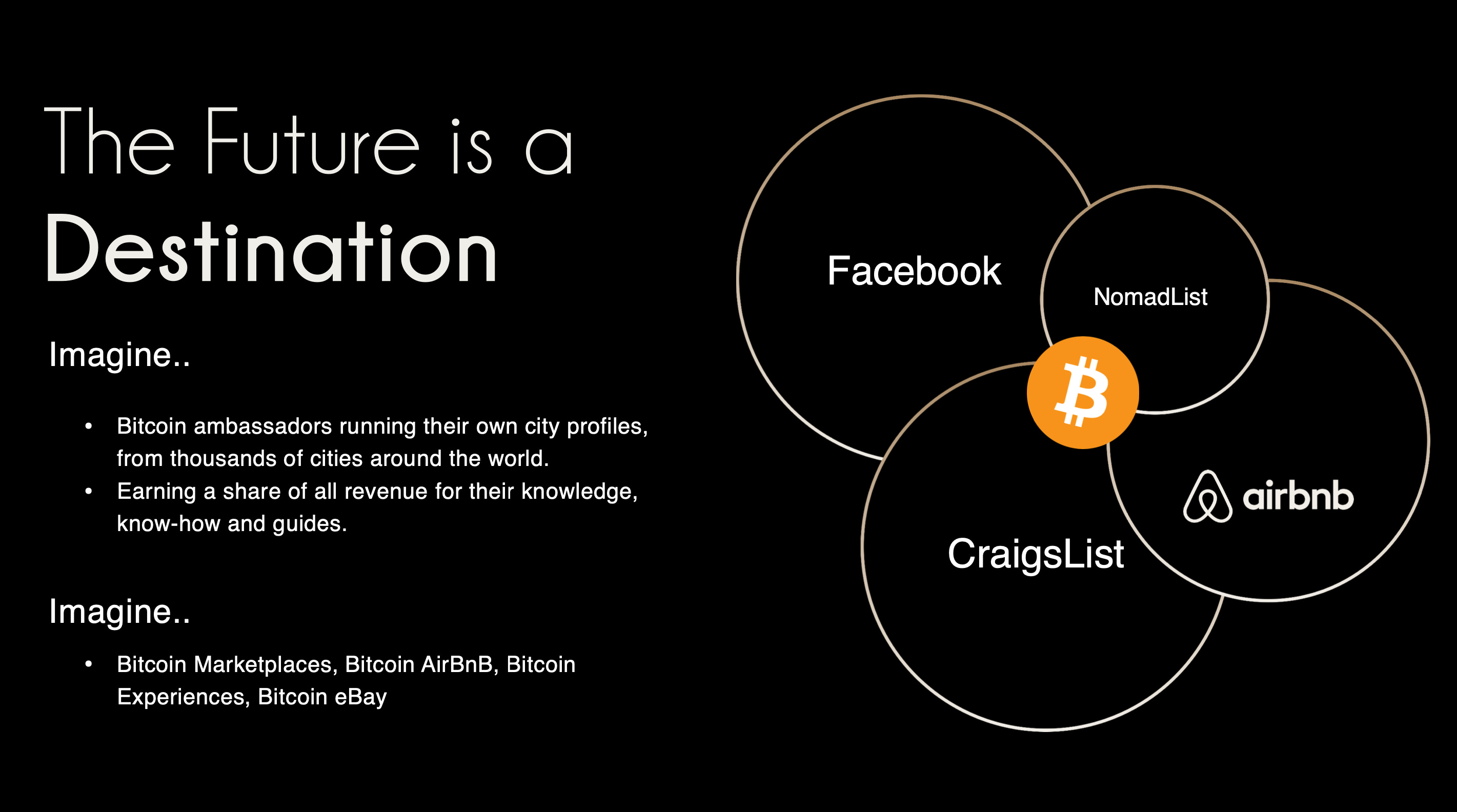###### ^^2 slides from the original idea here
I still remember the call I had with @pablof7z in January. I was in Dubai pitching the AI idea I was working on at the time, but all I could think and talk about was Satlantis and Nostr.
That conversation made me bullish AF. I came back from the trip convinced we’d struck gold. I pivoted the old company, re-organised the team and booked us for the Sovereign Engineering cohort in Madeira. We put together a whole product roadmap, go to market strategy and cap raise around the use of Nostr. We were going to be the ‘next big Nostr app’.
A couple of events followed in which I announced this all to the world: Bitcoin Atlantis in March and BTC Prague in June being the two main ones. The feedback was incredible. So we doubled down. After being the major financial backer for the Nostr Booth in Prague, I decided to help organise the Nostr Booth initiative and back it financially for a series of Latin American conferences in November. I was convinced this was the biggest thing since bitcoin, so much so that I spent over $50,000 in 2024 on Nostr marketing initiatives. I was certainly high on something.
# Sobering up
It’s March 2025 and I’ve sobered up. I now look at Nostr through a different lens. A more pragmatic one. I see Nostr as a tool, as an entrepreneur - who’s more interested in solving a problem, than fixating on the tool(s) being used - should.
A couple things changed for me. One was the sub-standard product we released in November. I was so focused on being a Nostr evangelist that I put our product second. Coupled with the extra technical debt we took on at Satlantis by making everything Nostr native, our product was crap. ***We traded usability & product stability for Nostr purism & evangelism.***
We built a whole suite of features using native event kinds (location kinds, calendar kinds, etc) that we thought other Nostr apps would also use and therefore be interoperable. Turns out no serious players were doing any of that, so we spent a bunch of time over-engineering for no benefit 😂
The other wake up call for me was the Twitter ban in Brazil. Being one of the largest markets for Twitter, I really thought it would have a material impact on global Nostr adoption. When basically nothing happened, I began to question things.
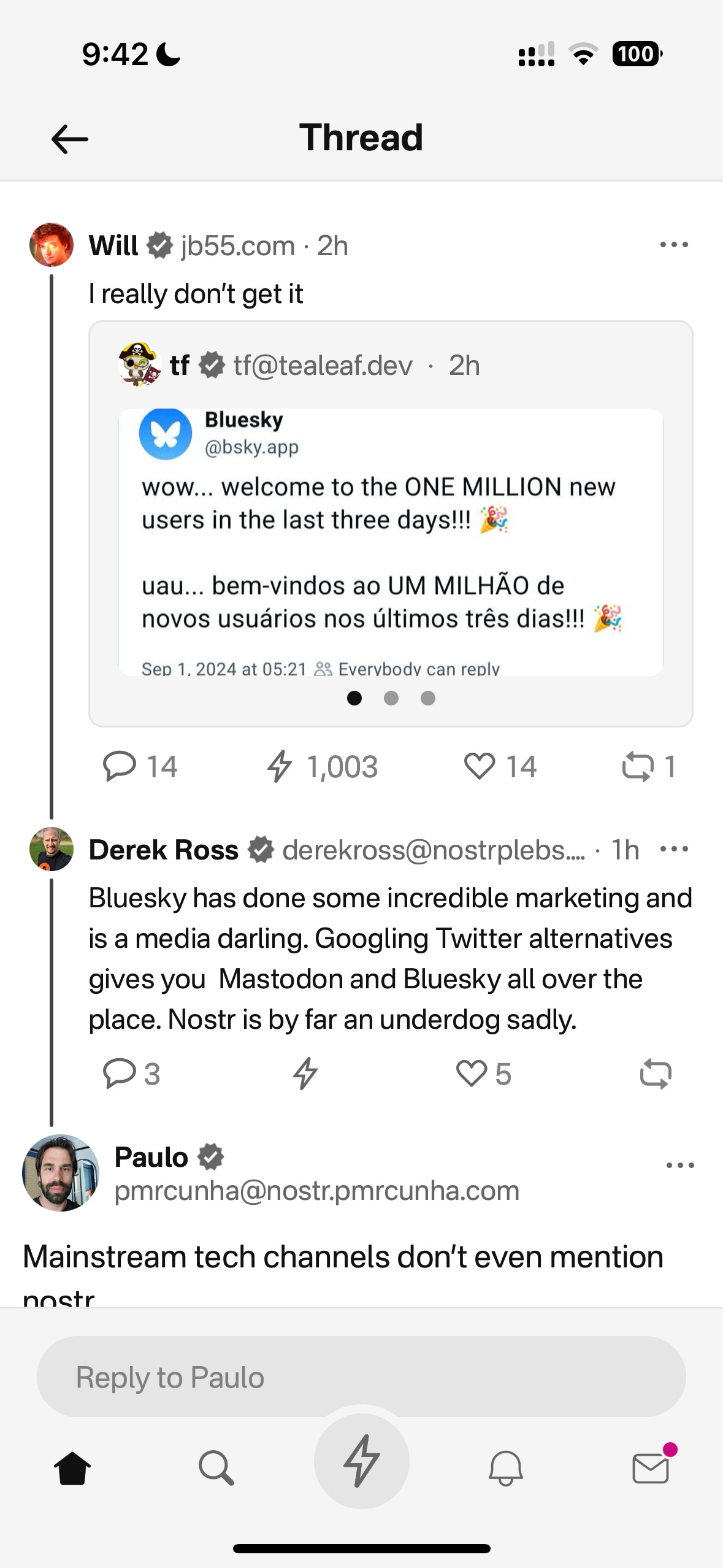
Combined, these experiences helped sober me up and I come down from my high. I was reading “the cold start problem” by Andrew Chen (ex-Uber) at the time and doing a deep dive on network effects. I came to the following realisation:
*Nostr’s network effect is going to take WAY longer than we all anticipated initially. This is going to be a long grind. And unlike bitcoin, winning is not inevitable. Bitcoin solves a much more important problem, and it’s the ONLY option. Nostr solves an important problem yes, but it’s far from the only approach. It’s just the implementation arguably in the lead right now.*
This sobering up led us to take a different approach with Nostr. We now view it as another tool in the tech-stack, no different to the use of React Native on mobile or AWS for infrastructure. Nostr is something to use if it makes the product better, or avoid if it makes the product and user experience worse. I will share more on this below, including our simple decision making framework. I’ll also present a few more potentially unpopular opinions about Nostr. Four in total actually:
1. Nostr is a tool, not a revolution
2. Nostr doesn’t solve the multiple social accounts problem
3. Nostr is not for censorship resistance
4. Grants come with a price
Let’s begin…
# Nostr is a tool, not a revolution
Nostr is full of Bitcoiners, and as much as we like to think we’re immune from shiny object syndrome, we are, somewhere deep down afflicted by it like other humans. That’s normal & fine. But…while Bitcoiners have successfully suppressed this desire when it comes to shitcoins, it lies dormant, yearning for the least shitcoin-like thing to emerge which we can throw our guiltless support behind.
That ***thing*** arrived and it’s called Nostr.
As a result, we’ve come to project the same kind of purity and maximalism onto it as we do with Bitcoin, because it shares some attributes and it’s clearly ***not*** a grift.
The trouble is, in doing so, we’ve put it in the same ***class*** as Bitcoin - which is an error.
Nostr is important and in its own small way, revolutionary, but it pales in comparison to Bitcoin’s importance. ***Think of it this way: If Bitcoin fails, civilisation is fucked. If Nostr fails, we’ll engineer another rich-identity protocol***. There is no need for the kind of immaculate conception and path dependence that was necessary for Bitcoin whose genesis and success has been a once in a civilisation event. Equivocating Nostr and Bitcoin to the degree that it has been, is a significant category error. Nostr may ‘win’ or it may just be an experiment on the path to something better. **And that’s ok !**
I don’t say this to piss anyone off, to piss on Nostr or to piss on myself. I say it because I’d prefer Nostr not remain a place where a few thousand people speak to each other about how cool Nostr is. That’s cute in the short term, but in the grand scheme of things, it’s a waste of a great tool that can make a significant corner of the Internet great again.
By removing the emotional charge and hopium from our relationship to Nostr, we can take a more sober, objective view of it (and hopefully use it more effectively).
Instead of making everything about Nostr (the tool), we can go back to doing what great product people and businesses do: make everything about the customer.
---
Nobody’s going around marketing their app as a “react native product” - and while I understand that’s a false equivalent in the sense that Nostr is a protocol, while react is a framework - the reality is that it DOES NOT MATTER.
**For 99.9999% of the world, what matters is the hole, not the drill.** Maybe 1000 people on Earth REALLY care that something is built on Nostr, but for everyone else, what matters is what the app or product does and the problem it solves. Realigning our focus in this way, and looking at not only Nostr, but also Bitcoin as a tool in the toolkit, has transformed the way we’re building.
This inspired an essay I wrote a couple weeks ago called “As Nostr as Possible”. It covers our updated approach to using and building WITH Nostr (not just ‘on’ it). You can find that here:
https://futuresocial.substack.com/p/as-nostr-as-possible-anap
If you’re too busy to read it, don’t fret. The entire theory can be summarised by the diagram below. This is how we now decide what to make Nostr-native, and what to just build on our own. And - as stated in the ANAP essay - that doesn’t mean we’ll never make certain features Nostr-native. If the argument is that Nostr is not going anywhere, then we can always come back to that feature and Nostr-fy it later when resources and protocol stability permit.
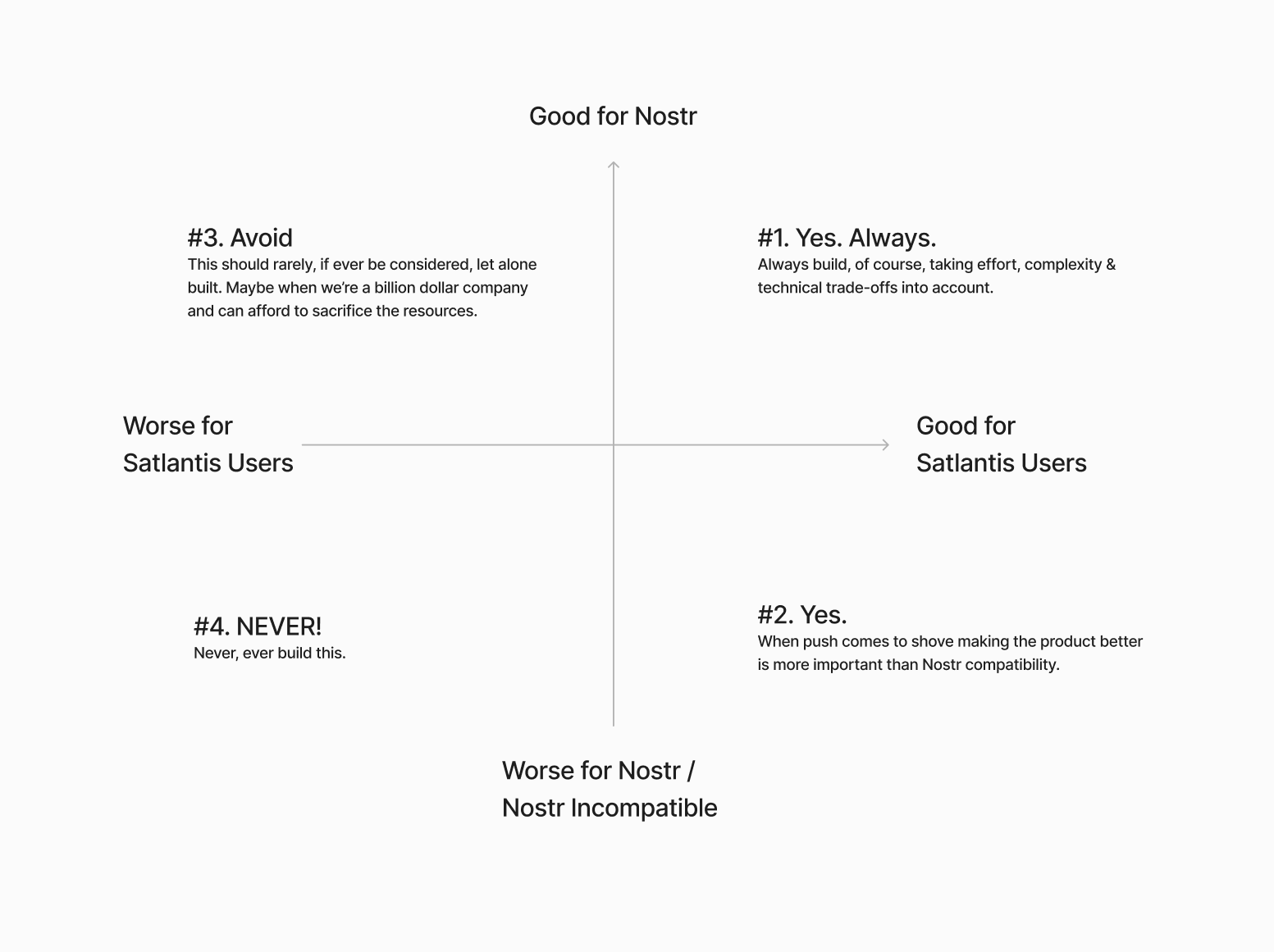
Next…
# The Nostr all in one approach is not all “positive”
Having one account accessible via many different apps might not be as positive as we initially thought.

If you have one unified presence online, across all of your socials, and you’re posting the same thing everywhere, then yes - being able to post content in one place and it being broadcast everywhere, is great. There’s a reason why people literally PAY for products like Hypefury, Buffer and Hootsuite (aside from scheduling).
BUT…..This is not always the case.
I’ve spoken to hundreds of creators and many have flagged this as a bug not a feature because they tend to have a different audience on different platforms and speak to them differently depending on the platform. We all know this. How you present yourself on LinkedIn is very different to how you do it on Instagram or X.
The story of Weishu (Tencent’s version of TikTok) comes to mind here. Tencent’s WeChat login worked against them because people didn’t want their social graph following them around. Users actually wanted freedom from their existing family & friends, so they chose Douyin (Chinese TikTok) instead.
Perhaps this is more relevant to something like WeChat because the social graph following you around is more personal, but we saw something similar with Instagram and Facebook. Despite over a decade of ownership, Facebook still keeps the social graphs separated.
All this to say that while having a different strategy & approach on different social apps is annoying, it allows users to tap into different markets because each silo has its own ‘flavour’. The people who just post the same thing everywhere are low-quality content creators anyway. The ones who actually care, are using each platform ***differently***.
*The ironic part here is that this is arguably more ‘decentralised’ than the protocol approach because these siloes form a ‘marketplace of communities’ which are all somewhat different.*
---
We need to find a smart way of doing this with Nostr. Some way of catering to the appropriate audience where it matters most. Perhaps this will be handled by clients, or by relays. One solution I’ve heard from people in the Nostr space is to just ‘spin up another nPub’ for your different audience. While I have no problem with people doing that - I have multiple nPubs myself - it’s clearly NOT a solution to the underlying problem here.
We’re experimenting with something. Whether it’s a good idea or not remains to be seen. Satlantis users will be able to curate their profiles and remove (hide / delete) content on our app. We’ll implement this in two stages:
**Stage 1: Simple**\
In the first iteration, we will not broadcast a delete request to relays. This means users can get a nicely curated profile page on Satlantis, but keep a record of their full profile elsewhere on other clients / relays.
**Stage 2: More complex**\
Later on, we’ll try to give people an option to “delete on Satlantis only” or “delete everywhere”. The difference here is more control for the user. Whether we get this far remains to be seen. We’ll need to experiment with the UX and see whether this is something people really want.
I’m sure neither of these solutions are ‘ideal’ - but they’re what we’re going to try until we have more time & resources to think this through more.
Next…
# Nostr is not for Censorship Resistance
I’m sorry to say, but this ship has sailed. At least for now. Maybe it’s a problem again in the future, but who knows when, and if it will ever be a big enough factor anyway.
The truth is, while WE all know that Nostr is superior because it’s a protocol, people do NOT care enough. They are more interested in what’s written ON the box, not what’s necessarily inside the box. 99% of people don’t know wtf a protocol is in the first place - let alone why it matters for censorship resistance to happen at that level, or more importantly, why they should trust ***Nostr*** to deliver on that promise.
Furthermore, the few people who did care about “free speech” are now placated enough with Rumble for Video, X for short form and Substack for long form. With Meta now paying lip-service to the movement, it’s game over for this narrative - at least for the foreseeable future.
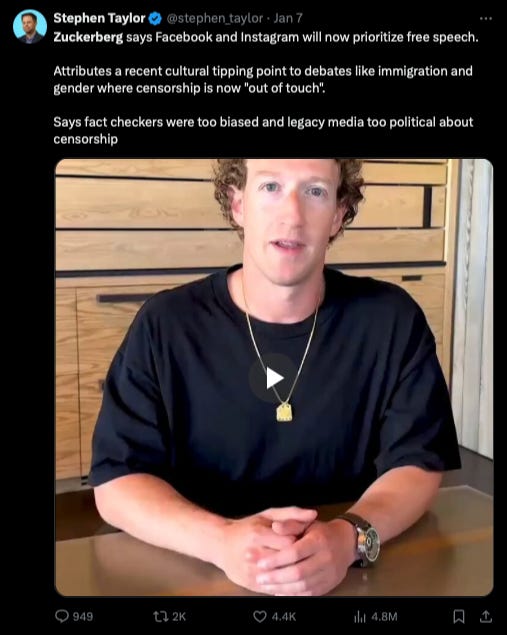The "space in people’s minds for censorship resistance has been filled. Both the ‘censorship resistance’ and ‘free speech’ ships have sailed (even though they were fake), and the people who cared enough all boarded.
For the normies who never cared, they still don’t care - or they found their way to the anti-platforms, like Threads, BlueSky or Pornhub.
The small minority of us still here on Nostr…are well…still here. Which is great, but if the goal is to grow the network effect here and bring in more people, then we need to find a new angle. Something more compelling than “your account won’t be deleted.”
I’m not 100% sure what that is. My instinct is that a “network of interoperable applications”, that don’t necessarily or explicitly brand themselves as Nostr, but have it under the hood is the right direction. I think the open social graph and using it in novel ways is compelling. Trouble is, this needs more really well-built and novel apps for non-sovereignty minded people (especially content creators) and people who don’t necessarily care about the reasons Nostr was first built. Also requires us to move beyond just building clones of what already exists.
We’ve been trying to do this Satlantis thing for almost a year now and it’s coming along - albeit WAY slower than I would’ve liked. We’re experimenting our way into a whole new category of product. Something different to what exists today. We’ve made a whole bunch of mistakes and at times I feel like a LARP considering the state of non-delivery.
BUT…what’s on the horizon is very special, and I think that all of the pain, effort and heartache along the way will be 100% worth it. We are going to deliver a killer product that people love, that solves a whole host of travel-related problems and has Nostr under the hood (where nobody, except those who care, will know).
# Grants come with a price
This one is less of an opinion and more of an observation. Not sure it really belongs in this essay, but I’ll make a small mention just as food for thought,
***Grants are a double-edged sword.***
I’m super grateful that OpenSats, et al, are supporting the protocol, and I don’t envy the job they have in trying to decipher what to support and what not to depending on what’s of benefit to the network versus what’s an end user product.
That being said, is the Nostr ecosystem too grant-dependent? This is not a criticism, but a question. Perhaps this is the right thing to do because of how young Nostr is. But I just can’t help but feel like there’s something a-miss.
Grants put the focus on Nostr, instead of the product or customer. Which is fine, if the work the grant covers is for Nostr protocol development or tooling. But when grants subsidise the development of end user products, it ties the builder / grant recipient to Nostr in a way that can misalign them to the customer’s needs. It’s a bit like getting a government grant to build something. **Who’s the real customer??**
Grants can therefore create an almost communist-like detachment from the market and false economic incentive. To reference the Nostr decision framework I showed you earlier, when you’ve been given a grant, you are focusing more on the X axis, not the Y. This is a trade-off, and all trade-offs have consequences.
Could grants be the reason Nostr is so full of hobbyists and experimental products, instead of serious products? Or is that just a function of how ambitious and early Nostr is?
I don’t know.
Nostr certainly needs better toolkits, SDKs, and infrastructure upon which app and product developers can build. I just hope the grant money finds its way there, and that it yields these tools. Otherwise app developers like us, won’t stick around and build on Nostr. We’ll swap it out with a better tool.
To be clear, this is not me pissing on Nostr or the Grantors. Jack, OpenSats and everyone who’s supported Nostr are incredible. I’m just asking the question.
Final thing I’ll leave this section with is a thought experiment: Would Nostr survive if OpenSats disappeared tomorrow?
Something to think about….
# Coda
If you read this far, thank you. There’s a bunch here to digest, and like I said earlier - this not about shitting on Nostr. It is just an enquiry mixed with a little classic Svetski-Sacred-Cow-Slaying.
I want to see Nostr succeed. Not only because I think it’s good for the world, but also because I think it is the best option. Which is why we’ve invested so much in it (something I’ll cover in an upcoming article: “Why we chose to build on Nostr”). I’m firmly of the belief that this is the right toolkit for an internet-native identity and open social graph. What I’m not so sure about is the echo chamber it’s become and the cult-like relationship people have with it.
I look forward to being witch-hunted and burnt at the stake by the Nostr purists for my heresy and blaspheming. I also look forward to some productive discussions as a result of reading this.
Thankyou for your attention.
Until next time.
-

@ 872982aa:8fb54cfe
2025-03-27 05:50:35
NIP-03
======
OpenTimestamps Attestations for Events
--------------------------------------
`draft` `optional`
This NIP defines an event with `kind:1040` that can contain an [OpenTimestamps](https://opentimestamps.org/) proof for any other event:
```json
{
"kind": 1040
"tags": [
["e", <event-id>, <relay-url>],
["alt", "opentimestamps attestation"]
],
"content": <base64-encoded OTS file data>
}
```
- The OpenTimestamps proof MUST prove the referenced `e` event id as its digest.
- The `content` MUST be the full content of an `.ots` file containing at least one Bitcoin attestation. This file SHOULD contain a **single** Bitcoin attestation (as not more than one valid attestation is necessary and less bytes is better than more) and no reference to "pending" attestations since they are useless in this context.
### Example OpenTimestamps proof verification flow
Using [`nak`](https://github.com/fiatjaf/nak), [`jq`](https://jqlang.github.io/jq/) and [`ots`](https://github.com/fiatjaf/ots):
```bash
~> nak req -i e71c6ea722987debdb60f81f9ea4f604b5ac0664120dd64fb9d23abc4ec7c323 wss://nostr-pub.wellorder.net | jq -r .content | ots verify
> using an esplora server at https://blockstream.info/api
- sequence ending on block 810391 is valid
timestamp validated at block [810391]
```
-

@ f9cf4e94:96abc355
2024-12-31 20:18:59
Scuttlebutt foi iniciado em maio de 2014 por Dominic Tarr ( [dominictarr]( https://github.com/dominictarr/scuttlebutt) ) como uma rede social alternativa off-line, primeiro para convidados, que permite aos usuários obter controle total de seus dados e privacidade. Secure Scuttlebutt ([ssb]( https://github.com/ssbc/ssb-db)) foi lançado pouco depois, o que coloca a privacidade em primeiro plano com mais recursos de criptografia.
Se você está se perguntando de onde diabos veio o nome Scuttlebutt:
> Este termo do século 19 para uma fofoca vem do Scuttlebutt náutico: “um barril de água mantido no convés, com um buraco para uma xícara”. A gíria náutica vai desde o hábito dos marinheiros de se reunir pelo boato até a fofoca, semelhante à fofoca do bebedouro.

Marinheiros se reunindo em torno da rixa. ( [fonte]( https://twitter.com/IntEtymology/status/998879578851508224) )
Dominic descobriu o termo boato em um [artigo de pesquisa]( https://www.cs.cornell.edu/home/rvr/papers/flowgossip.pdf) que leu.
Em sistemas distribuídos, [fofocar]( https://en.wikipedia.org/wiki/Gossip_protocol) é um processo de retransmissão de mensagens ponto a ponto; as mensagens são disseminadas de forma análoga ao “boca a boca”.
**Secure Scuttlebutt é um banco de dados de feeds imutáveis apenas para acréscimos, otimizado para replicação eficiente para protocolos ponto a ponto.** **Cada usuário tem um log imutável somente para acréscimos no qual eles podem gravar.** Eles gravam no log assinando mensagens com sua chave privada. Pense em um feed de usuário como seu próprio diário de bordo, como um diário [de bordo]( https://en.wikipedia.org/wiki/Logbook) (ou diário do capitão para os fãs de Star Trek), onde eles são os únicos autorizados a escrever nele, mas têm a capacidade de permitir que outros amigos ou colegas leiam ao seu diário de bordo, se assim o desejarem.
Cada mensagem possui um número de sequência e a mensagem também deve fazer referência à mensagem anterior por seu ID. O ID é um hash da mensagem e da assinatura. A estrutura de dados é semelhante à de uma lista vinculada. É essencialmente um log somente de acréscimo de JSON assinado. **Cada item adicionado a um log do usuário é chamado de mensagem.**
**Os logs do usuário são conhecidos como feed e um usuário pode seguir os feeds de outros usuários para receber suas atualizações.** Cada usuário é responsável por armazenar seu próprio feed. Quando Alice assina o feed de Bob, Bob baixa o log de feed de Alice. Bob pode verificar se o registro do feed realmente pertence a Alice verificando as assinaturas. Bob pode verificar as assinaturas usando a chave pública de Alice.

Estrutura de alto nível de um feed
**Pubs são servidores de retransmissão conhecidos como “super peers”. Pubs conectam usuários usuários e atualizações de fofocas a outros usuários conectados ao Pub. Um Pub é análogo a um pub da vida real, onde as pessoas vão para se encontrar e se socializar.** Para ingressar em um Pub, o usuário deve ser convidado primeiro. Um usuário pode solicitar um código de convite de um Pub; o Pub simplesmente gerará um novo código de convite, mas alguns Pubs podem exigir verificação adicional na forma de verificação de e-mail ou, com alguns Pubs, você deve pedir um código em um fórum público ou chat. Pubs também podem mapear aliases de usuário, como e-mails ou nome de usuário, para IDs de chave pública para facilitar os pares de referência.
Depois que o Pub enviar o código de convite ao usuário, o usuário resgatará o código, o que significa que o Pub seguirá o usuário, o que permite que o usuário veja as mensagens postadas por outros membros do Pub, bem como as mensagens de retransmissão do Pub pelo usuário a outros membros do Pub.
Além de retransmitir mensagens entre pares, os Pubs também podem armazenar as mensagens. Se Alice estiver offline e Bob transmitir atualizações de feed, Alice perderá a atualização. Se Alice ficar online, mas Bob estiver offline, não haverá como ela buscar o feed de Bob. Mas com um Pub, Alice pode buscar o feed no Pub mesmo se Bob estiver off-line porque o Pub está armazenando as mensagens. **Pubs são úteis porque assim que um colega fica online, ele pode sincronizar com o Pub para receber os feeds de seus amigos potencialmente offline.**
Um usuário pode, opcionalmente, executar seu próprio servidor Pub e abri-lo ao público ou permitir que apenas seus amigos participem, se assim o desejarem. Eles também podem ingressar em um Pub público. Aqui está uma lista de [Pubs públicos em que]( https://github.com/ssbc/ssb-server/wiki/Pub-Servers) todos podem participar **.** Explicaremos como ingressar em um posteriormente neste guia. **Uma coisa importante a observar é que o Secure Scuttlebutt em uma rede social somente para convidados significa que você deve ser “puxado” para entrar nos círculos sociais.** Se você responder às mensagens, os destinatários não serão notificados, a menos que estejam seguindo você de volta. O objetivo do SSB é criar “ilhas” isoladas de redes pares, ao contrário de uma rede pública onde qualquer pessoa pode enviar mensagens a qualquer pessoa.

Perspectivas dos participantes
## Scuttlebot
O software Pub é conhecido como servidor Scuttlebutt (servidor [ssb]( https://github.com/ssbc/ssb-server) ), mas também é conhecido como “Scuttlebot” e `sbot`na linha de comando. O servidor SSB adiciona comportamento de rede ao banco de dados Scuttlebutt (SSB). Estaremos usando o Scuttlebot ao longo deste tutorial.
**Os logs do usuário são conhecidos como feed e um usuário pode seguir os feeds de outros usuários para receber suas atualizações.** Cada usuário é responsável por armazenar seu próprio feed. Quando Alice assina o feed de Bob, Bob baixa o log de feed de Alice. Bob pode verificar se o registro do feed realmente pertence a Alice verificando as assinaturas. Bob pode verificar as assinaturas usando a chave pública de Alice.

Estrutura de alto nível de um feed
**Pubs são servidores de retransmissão conhecidos como “super peers”. Pubs conectam usuários usuários e atualizações de fofocas a outros usuários conectados ao Pub. Um Pub é análogo a um pub da vida real, onde as pessoas vão para se encontrar e se socializar.** Para ingressar em um Pub, o usuário deve ser convidado primeiro. Um usuário pode solicitar um código de convite de um Pub; o Pub simplesmente gerará um novo código de convite, mas alguns Pubs podem exigir verificação adicional na forma de verificação de e-mail ou, com alguns Pubs, você deve pedir um código em um fórum público ou chat. Pubs também podem mapear aliases de usuário, como e-mails ou nome de usuário, para IDs de chave pública para facilitar os pares de referência.
Depois que o Pub enviar o código de convite ao usuário, o usuário resgatará o código, o que significa que o Pub seguirá o usuário, o que permite que o usuário veja as mensagens postadas por outros membros do Pub, bem como as mensagens de retransmissão do Pub pelo usuário a outros membros do Pub.
Além de retransmitir mensagens entre pares, os Pubs também podem armazenar as mensagens. Se Alice estiver offline e Bob transmitir atualizações de feed, Alice perderá a atualização. Se Alice ficar online, mas Bob estiver offline, não haverá como ela buscar o feed de Bob. Mas com um Pub, Alice pode buscar o feed no Pub mesmo se Bob estiver off-line porque o Pub está armazenando as mensagens. **Pubs são úteis porque assim que um colega fica online, ele pode sincronizar com o Pub para receber os feeds de seus amigos potencialmente offline.**
Um usuário pode, opcionalmente, executar seu próprio servidor Pub e abri-lo ao público ou permitir que apenas seus amigos participem, se assim o desejarem. Eles também podem ingressar em um Pub público. Aqui está uma lista de [Pubs públicos em que]( https://github.com/ssbc/ssb-server/wiki/Pub-Servers) todos podem participar **.** Explicaremos como ingressar em um posteriormente neste guia. **Uma coisa importante a observar é que o Secure Scuttlebutt em uma rede social somente para convidados significa que você deve ser “puxado” para entrar nos círculos sociais.** Se você responder às mensagens, os destinatários não serão notificados, a menos que estejam seguindo você de volta. O objetivo do SSB é criar “ilhas” isoladas de redes pares, ao contrário de uma rede pública onde qualquer pessoa pode enviar mensagens a qualquer pessoa.


Perspectivas dos participantes
## Pubs - Hubs
### Pubs públicos
| Pub Name | Operator | Invite Code |
| ------------------------------------------------------------ | ------------------------------------------------------------ | ------------------------------------------------------------ |
| `scuttle.us` | [@Ryan]( https://keybase.io/ryan_singer) | `scuttle.us:8008:@WqcuCOIpLtXFRw/9vOAQJti8avTZ9vxT9rKrPo8qG6o=.ed25519~/ZUi9Chpl0g1kuWSrmehq2EwMQeV0Pd+8xw8XhWuhLE=` |
| [pub1.upsocial.com]( https://upsocial.com/) | [@freedomrules]( https://github.com/freedomrules) | `pub1.upsocial.com:8008:@gjlNF5Cyw3OKZxEoEpsVhT5Xv3HZutVfKBppmu42MkI=.ed25519~lMd6f4nnmBZEZSavAl4uahl+feajLUGqu8s2qdoTLi8=` |
| [Monero Pub]( https://xmr-pub.net/) | [@Denis]( https://github.com/Orville2112) | `xmr-pub.net:8008:@5hTpvduvbDyMLN2IdzDKa7nx7PSem9co3RsOmZoyyCM=.ed25519~vQU+r2HUd6JxPENSinUWdfqrJLlOqXiCbzHoML9iVN4=` |
| [FreeSocial]( https://freesocial.co/) | [@Jarland]( https://github.com/mxroute) | `pub.freesocial.co:8008:@ofYKOy2p9wsaxV73GqgOyh6C6nRGFM5FyciQyxwBd6A=.ed25519~ye9Z808S3KPQsV0MWr1HL0/Sh8boSEwW+ZK+8x85u9w=` |
| `ssb.vpn.net.br` | [@coffeverton]( https://about.me/coffeverton) | `ssb.vpn.net.br:8008:@ze8nZPcf4sbdULvknEFOCbVZtdp7VRsB95nhNw6/2YQ=.ed25519~D0blTolH3YoTwSAkY5xhNw8jAOjgoNXL/+8ZClzr0io=` |
| [gossip.noisebridge.info]( https://www.noisebridge.net/wiki/Pub) | [Noisebridge Hackerspace]( https://www.noisebridge.net/wiki/Unicorn) [@james.network]( https://james.network/) | `gossip.noisebridge.info:8008:@2NANnQVdsoqk0XPiJG2oMZqaEpTeoGrxOHJkLIqs7eY=.ed25519~JWTC6+rPYPW5b5zCion0gqjcJs35h6JKpUrQoAKWgJ4=` |
### Pubs privados
Você precisará entrar em contato com os proprietários desses bares para receber um convite.
| Pub Name | Operator | Contact |
| --------------------------------------------- | ------------------------------------------------------------ | ----------------------------------------------- |
| `many.butt.nz` | [@dinosaur]( https://dinosaur.is/) | [mikey@enspiral.com](mailto:mikey@enspiral.com) |
| `one.butt.nz` | [@dinosaur]( https://dinosaur.is/) | [mikey@enspiral.com](mailto:mikey@enspiral.com) |
| `ssb.mikey.nz` | [@dinosaur]( https://dinosaur.is/) | [mikey@enspiral.com](mailto:mikey@enspiral.com) |
| [ssb.celehner.com]( https://ssb.celehner.com/) | [@cel]( https://github.com/ssbc/ssb-server/wiki/@f/6sQ6d2CMxRUhLpspgGIulDxDCwYD7DzFzPNr7u5AU=.ed25519) | [cel@celehner.com](mailto:cel@celehner.com) |
### Pubs muito grandes
 *Aviso: embora tecnicamente funcione usar um convite para esses pubs, você provavelmente se divertirá se o fizer devido ao seu tamanho (muitas coisas para baixar, risco para bots / spammers / idiotas)* 
| Pub Name | Operator | Invite Code |
| --------------------------------------- | ----------------------------------------------- | ------------------------------------------------------------ |
| `scuttlebutt.de` | [SolSoCoG]( https://solsocog.de/impressum) | `scuttlebutt.de:8008:@yeh/GKxlfhlYXSdgU7CRLxm58GC42za3tDuC4NJld/k=.ed25519~iyaCpZ0co863K9aF+b7j8BnnHfwY65dGeX6Dh2nXs3c=` |
| `Lohn's Pub` | [@lohn]( https://github.com/lohn) | `p.lohn.in:8018:@LohnKVll9HdLI3AndEc4zwGtfdF/J7xC7PW9B/JpI4U=.ed25519~z3m4ttJdI4InHkCtchxTu26kKqOfKk4woBb1TtPeA/s=` |
| [Scuttle Space]( https://scuttle.space/) | [@guil-dot]( https://github.com/guil-dot) | Visit [scuttle.space]( https://scuttle.space/) |
| `SSB PeerNet US-East` | [timjrobinson]( https://github.com/timjrobinson) | `us-east.ssbpeer.net:8008:@sTO03jpVivj65BEAJMhlwtHXsWdLd9fLwyKAT1qAkc0=.ed25519~sXFc5taUA7dpGTJITZVDCRy2A9jmkVttsr107+ufInU=` |
| Hermies | s | net:hermies.club:8008~shs:uMYDVPuEKftL4SzpRGVyQxLdyPkOiX7njit7+qT/7IQ=:SSB+Room+PSK3TLYC2T86EHQCUHBUHASCASE18JBV24= |
## GUI - Interface Gráfica do Utilizador(Usuário)
### Patchwork - Uma GUI SSB (Descontinuado)
[**Patchwork**]( https://github.com/ssbc/patchwork) **é o aplicativo de mensagens e compartilhamento descentralizado construído em cima do SSB** . O protocolo scuttlebutt em si não mantém um conjunto de feeds nos quais um usuário está interessado, então um cliente é necessário para manter uma lista de feeds de pares em que seu respectivo usuário está interessado e seguindo.

Fonte: [scuttlebutt.nz]( https://www.scuttlebutt.nz/getting-started)
**Quando você instala e executa o Patchwork, você só pode ver e se comunicar com seus pares em sua rede local. Para acessar fora de sua LAN, você precisa se conectar a um Pub.** Um pub é apenas para convidados e eles retransmitem mensagens entre você e seus pares fora de sua LAN e entre outros Pubs.
Lembre-se de que você precisa seguir alguém para receber mensagens dessa pessoa. Isso reduz o envio de mensagens de spam para os usuários. Os usuários só veem as respostas das pessoas que seguem. Os dados são sincronizados no disco para funcionar offline, mas podem ser sincronizados diretamente com os pares na sua LAN por wi-fi ou bluetooth.
### Patchbay - Uma GUI Alternativa
Patchbay é um cliente de fofoca projetado para ser fácil de modificar e estender. Ele usa o mesmo banco de dados que [Patchwork]( https://github.com/ssbc/patchwork) e [Patchfoo]( https://github.com/ssbc/patchfoo) , então você pode facilmente dar uma volta com sua identidade existente.

### Planetary - GUI para IOS

[Planetary]( https://apps.apple.com/us/app/planetary-app/id1481617318) é um app com pubs pré-carregados para facilitar integração.
### Manyverse - GUI para Android

[Manyverse]( https://www.manyver.se/) é um aplicativo de rede social com recursos que você esperaria: posts, curtidas, perfis, mensagens privadas, etc. Mas não está sendo executado na nuvem de propriedade de uma empresa, em vez disso, as postagens de seus amigos e todos os seus dados sociais vivem inteiramente em seu telefone .
## Fontes
* https://scuttlebot.io/
* https://decentralized-id.com/decentralized-web/scuttlebot/#plugins
* https://medium.com/@miguelmota/getting-started-with-secure-scuttlebut-e6b7d4c5ecfd
* [**Secure Scuttlebutt**]( http://ssbc.github.io/secure-scuttlebutt/) **:** um protocolo de banco de dados global.
-

@ 0461fcbe:35a474dd
2025-03-13 23:10:12
## Background
I will start with a disclaimer: I'm all-in on Nostr. But before that, I spent 4 years building on ActivityPub. Then in Feb 2023 I built a bridge between ActivityPub and Nostr, and in Dec 2024 I built another bridge between Nostr and Bluesky. Most of all I am committed to open source and the decentralized vision. Having experience with all 3 major protocols, I still think Nostr is the best, but Bluesky outshines it in some major areas. The main reason for this blog is to explore the things Bluesky does better than us, and to point out why I still think Nostr is the best solution.
This is a technical blog. For a more high level overview of decentralized protocols, see: https://soapbox.pub/blog/comparing-protocols/
## Data Model
Nostr and Bluesky both allow users to store any type of data in a single, unified format. Nostr calls them *events*. Bluesky calls them *records*. They are mostly interchangeable ideas, but the way the data is stored and retrieved is very different.
It's worth noting that, like Nostr and ActivityPub, Bluesky is capable of doing anything under the sun. It's a misconception that it can't. You can build whatever Reddit, TikTok, or other stuff clone on Bluesky just fine. It's limited more by the huge knowledge gap you have to overcome than it is by anything about its data model.
### NSIDs vs Kinds
Nostr events use a "kind" number, eg `1`, to distinguish different type of events. Bluesky records use what they call an "NSID" (namespace identifier), eg `app.bsky.feed.post`, which is a reverse-DNS string notation.
Nostr's `"kind": 1` is equivalent to Bluesky's `"$type": app.bsky.feed.post`.
I think Bluesky's system is better, because it allows developers to feel like what they built is "real" without having to get it merged into the NIPs repo, which is basically like an IANA of Nostr kind numbers. I believe this causes significant problems on Nostr, and makes people feel like they are being held back by others. That being said, the counter-argument is that kind numbers encourage interoperability for the very same reasons. The barriers to adding new kinds pushes people to work with what's already there.
### Text Content Formatting
Kind 1 events ("plain text notes", ie "Tweets") on Nostr have developed in a haphazard way over time, by many people piling things onto it without taking a step back to assess a unified way to handle it. Some examples include:
- NIP-21 `nostr:` URIs
- `imeta` tags
- inline media embeds as URLs without `imeta` tags
- unspec'd Markdown rendering by some clients
- legacy specs such as positional mentions (eg, `#[0]`, mostly gone now)
What we have now is quite a mess, and it's something Bluesky beats us on badly.
Bluesky has a plaintext content field that can be displayed as-is. In addition, it has a "[facets](https://docs.bsky.app/docs/advanced-guides/post-richtext)" field, which is a structured JSON object, that adds rich-text information such as formatting (bold, italic, etc), links, mentions of users, and whatever else metadata about the text.
This is an extensible system that beats even options like Markdown, due to its ability to include native extension like mentions, and its ability to be parsed by any programming language or software environment.
Bluesky is the winner here.
### Syncronization
Nostr and Bluesky are both thought to be descended from Scuttlebutt, an older decentralized protocol.
On Scuttlebutt, a user's whole post history needed to be available for them to make a new post. Scuttlebutt uses a linked list, so each new event would need to reference the one before it. Only linear paths are allowed, so if a "fork" occurred (intentionally or not), only one version would be kept, and the other discarded. This lead to occasional publishing issues, but it allowed readers to assemble a complete view.
Nostr strayed from this draconian approach, removing it entirely and allowing user data to be fragmented. Meanwhile Bluesky, instead of removing it entirely, made it work more like git so that branches could be merged.
Both approaches have tradeoffs. Bluesky's approach has much higher complexity. Also, it's sometimes considered an advantage for events to be fragmented (eg Nostr allows sending DMs to specialized relays for enhanced privacy).
But Bluesky has a true account "sync" mechanism, and Nostr does not. Nostr can send filters to relays to gather events, but it cannot know when to stop looking. Proposals like Negentropy in Nostr do not solve author syncing, and only make typical relay filtering more efficient.
I think it's important to think about Nostr's "outbox" problem as a syncronization problem, and for Nostr to approach syncronization with the goal of syncronizing authors specifically.
I think Bluesky "wins" this one, if only because they have solved a problem that we haven't. Instead of copying their solution, I think Nostr should try to learn from this to recharacterize the "outbox" problem as an author syncing problem, and see if we can come up with a better solution that works for Nostr.
## Knowledge Gap
One of the biggest hurdles of Bluesky, and by extension one of the greates appeals of Nostr, is in how easy it is to learn and build on.
Nostr can be understood in a couple of hours. Mastering it is difficult, but limited only by your time and imagination. Hundreds of developers are building new projects on Nostr today. Based on my experience, it seems to me that the Nostr developer community is larger than that of both ActivityPub and Bluesky combined.
Bluesky on the other hand requires a Harvard degree in Blueskyology. I believe that ameteur coders feel a sense of superiority after spending six weeks learning how to commit a post. To learn Bluesky you will have to sift through thousands of technical documents about all kinds of abstractions, especially related to IPFS and IPLD. You will have to master unnecessary technologies like CBOR (which is basically just JSON except it's in binary and takes up the same amount of space). And you will be frequently pointed to academic topics such as "DAG" and "graph theory", all just to say "it's a fucking graph". I will never understand why people will take simple concepts such as a "tree", and then make it harder to understand on purpose by saying it's more than that.
While building on Bluesky, I began to question if the creators did this on purpose. I wondered if they tried to make it complex on purpose, as a sort of IQ test and protective measure to weed out the undeireables. In my view, a truly free and open network must be accessible to all, with the hope that even non-programmers could learn how it works.
Technical complexity is not just an issue of inclusion, but also security. ActivityPub software has been found to be littered with major security holes due to its inherently complex design, while Nostr's simple design makes its attack surface extremely minimal. Bluesky has already had a few mishaps, and it makes me wonder how Bluesky will fare in the long term.
## Decentralization
I will keep this short. Bluesky is designed to be decentralized, but isn't. It reminds me of the communist idea about the "withering away of the state". The idea is that you're supposed to first sieze power and become the new state, and then under your rule the state will slowly disappear because you are doing all the right communist things. I think this is basically how Bluesky sees itself (whether they agree with the analogy or not).
Nostr is decentralized, but it is a loaded gun. You're more likely to kill yourself with a gun than someone else. This is on purpose, because it wholly embraces the consequnces of being truly decentralized.
In my view Nostr gets it right. Social media has been done to death by now, so I do not think it's worth the compromise to prioritize UX over decentralization. If that's the case we have not fixed anything. It's best to start with the purist idea and work backwards to UX, rather than start with UX and work backwards to decentralization. Many people have already written extensively about the decentralization of Bluesky, so I'll leave it at that.
-

@ ef53426a:7e988851
2025-04-02 21:02:06
# Bartering and early money
\
Early societies bartered goods, but transactions were often complicated. The value of goods doesn’t always align.
Enter money. It’s used as an indirect exchange for any goods, so everyone wants it.
Early money wasn’t anything like what we use today. For example, the inhabitants of Yap Island (Micronesia) used large Rai stones for trade. New stones were dragged up a hill for everyone to see. The owner would then exchange part of the stone for goods and services.
As they were hard to quarry and move, Rai stones retained their value (salability). Then, an Irish-American captain started importing stones using modern technology. Soon enough, they became so common, they no longer worked as money.
---
# Gold — the basis for sound money
\
Smelting made it possible to create highly salable and transportable coins. Gold was best because it’s virtually impossible to destroy and can’t be synthesized using other materials. It has a fairly limited supply, which grows slowly and predictably (due to the difficulty of mining).
Technologies like the telegraph and trains made it easier for both people and goods to get from point A to point B. That, in turn, justified forms of payment like checks, paper receipts, and bills. But paper is not worth much unless it’s backed by something.
Governments worldwide issued paper money backed by precious metals, which they stored in vaults. By 1900, around 50 countries had adopted the Gold Standard. This was sound money.
---
# Currencies devalued
\
Roman emperor Julius Caesar issued the Aureus, an empire-standard coin containing 8 grams of gold. But as growth began to slow, rulers started ‘coin clipping’, reducing the quantity of precious metal in coins. This eventually triggered a series of economic crises that led to the downfall of the Roman Empire.
The gold standard had one major flaw: it had to be stored in bank vaults. This created a highly centralized system in which governments controlled the value of paper money. If they wanted to, they could always increase the supply of money without increasing the corresponding amount of gold.
In 1914, nearly every major European power decided to do this to fund their war operations. Rather than raising taxes, they simply printed new money with no extra gold. The standard had been abandoned.
---
# Government-backed money
\
Governments chose to introduce fiat money – currency backed by decree rather than gold. The adoption of the fiat system led to an age of unsound money shaped by ever-greater intervention in the economy as governments scrambled to stabilize their currencies.
By 1944, the end of the Second World War was in sight, and the victors began planning the postwar economic order. The world’s currencies would be tied to the US dollar at a fixed exchange rate. The dollar would in turn be tied to the value of gold, again at a fixed rate.
The United States bent the rules and inflated its own currency compared to gold. Other nations inflated their currencies compared to the dollar. On August 15, 1971, President Nixon announced that dollars would no longer be convertible to gold.
---
# Sound money = functioning economy
\
Sound money encourages people to save and invest, enabling sustainable, long-term growth. Why? Well, humans have a natural positive time preference: we prefer instant gratification over future gratification. Sound money prompts us to think more about the future.
The more capital accumulation there is, the greater the chance of stable, long-term economic growth. Unsound money distorts capital accumulation. When governments interfere with the money supply, they also interfere with prices. And prices give investors the information they need to make good decisions without having to learn every tiny detail about global events.
---
# Recessions and debt arise from unsound money
\
Government interference takes the form of central planning. No single person, agency, or department ever has access to all the information necessary to understand the vast and complex economy. Interventions distort markets, creating boom and bust cycles.
According to Keynes and his followers, the best way to respond to recessions is to increase spending. You could lower taxes, but people don’t usually spend their extra money. Raising taxes is unpopular, so governments invariably decide to increase the money supply. Saving becomes less attractive, creating a culture of unwise spending and growing debt.
We need to return to sound money and a new gold standard. Enter bitcoin.
---
# Bitcoin is scarce
\
Bitcoin has similar traits to gold. Its supply is literally fixed. Once there are 21 million bitcoins in circulation, no more will be issued.
The supply grows at a diminishing rate. Computers across the Bitcoin network pool their processing power to solve complex algorithmic problems. Once these puzzles have been cracked, the “miners” receive bitcoins as a reward.
Satoshi Nakamoto designed the system to avoid gold rushes. The algorithmic problems become more difficult to solve as the number of computers working on them rises, guaranteeing a steady and reliable supply. Also, the number of bitcoins issued is halved every four years, resulting in ever-smaller releases until 2140, after which no more coins will be released.
That makes bitcoin unique. It is the only good that is defined by absolute scarcity. No amount of time or resources can create more bitcoins than the programmed supply allows. The supply cannot be manipulated, making it a perfect store of value.
---
# Bitcoin is secure
\
The bitcoin ledger uses the public blockchain. When mining computers crack an algorithmic puzzle, they create a block. The blocks on the ledger contain details about every blockchain transaction ever completed. Every network user can view this information.
Ownership of bitcoins is only valid once it’s been registered on the blockchain. This is only possible if the majority of network users approve it, so there’s no need for a central authority to oversee transactions. While verifying new blocks requires virtually no energy, creating a fraudulent block would cost a significant amount of processing power.
Even if a user decided to expend vast amounts of energy and successfully hacked a majority of all network nodes to approve a fraudulent block, they’d gain very little. Trust in bitcoin would be lost, leading to a drop in demand and value.
---
# Challenges for adoption
\
Because bitcoin is new, demand has varied. The volatile price has, at times, undermined the currency’s status as an effective store of value.
Bitcoin’s transaction limit is currently set at 500,000 per day. That could be increased, but there will always be a daily cap. The more transactions that take place, the more nodes there’ll need to be. This increases transaction fees and the amount of processing power expended.
Bitcoin could be traded off the blockchain, meaning currencies will be backed by bitcoin. That would create a new standard, but it would also mean that new centralized institutions would need to manage this system.
---

This 5-minute summary did not use copyrighted material from the book. It aims simply to give readers a quick understanding of the book (which is well worth reading).
‘*The Bitcoin Standard: The Decentralized Alternative to Central Banking’* was written by economist Saifedean Ammous in 2018.
Buy the book and many more titles at [bitcoinbook.shop](bitcoinbook.shop)
-

@ 872982aa:8fb54cfe
2025-03-27 05:47:40
NIP-03
======
OpenTimestamps Attestations for Events
--------------------------------------
`draft` `optional`
This NIP defines an event with `kind:1040` that can contain an [OpenTimestamps](https://opentimestamps.org/) proof for any other event:
```json
{
"kind": 1040
"tags": [
["e", <event-id>, <relay-url>],
["alt", "opentimestamps attestation"]
],
"content": <base64-encoded OTS file data>
}
```
- The OpenTimestamps proof MUST prove the referenced `e` event id as its digest.
- The `content` MUST be the full content of an `.ots` file containing at least one Bitcoin attestation. This file SHOULD contain a **single** Bitcoin attestation (as not more than one valid attestation is necessary and less bytes is better than more) and no reference to "pending" attestations since they are useless in this context.
### Example OpenTimestamps proof verification flow
Using [`nak`](https://github.com/fiatjaf/nak), [`jq`](https://jqlang.github.io/jq/) and [`ots`](https://github.com/fiatjaf/ots):
```bash
~> nak req -i e71c6ea722987debdb60f81f9ea4f604b5ac0664120dd64fb9d23abc4ec7c323 wss://nostr-pub.wellorder.net | jq -r .content | ots verify
> using an esplora server at https://blockstream.info/api
- sequence ending on block 810391 is valid
timestamp validated at block [810391]
```
-

@ 91bea5cd:1df4451c
2025-02-04 17:24:50
### Definição de ULID:
Timestamp 48 bits, Aleatoriedade 80 bits
Sendo Timestamp 48 bits inteiro, tempo UNIX em milissegundos, Não ficará sem espaço até o ano 10889 d.C.
e Aleatoriedade 80 bits, Fonte criptograficamente segura de aleatoriedade, se possível.
#### Gerar ULID
```sql
CREATE EXTENSION IF NOT EXISTS pgcrypto;
CREATE FUNCTION generate_ulid()
RETURNS TEXT
AS $$
DECLARE
-- Crockford's Base32
encoding BYTEA = '0123456789ABCDEFGHJKMNPQRSTVWXYZ';
timestamp BYTEA = E'\\000\\000\\000\\000\\000\\000';
output TEXT = '';
unix_time BIGINT;
ulid BYTEA;
BEGIN
-- 6 timestamp bytes
unix_time = (EXTRACT(EPOCH FROM CLOCK_TIMESTAMP()) * 1000)::BIGINT;
timestamp = SET_BYTE(timestamp, 0, (unix_time >> 40)::BIT(8)::INTEGER);
timestamp = SET_BYTE(timestamp, 1, (unix_time >> 32)::BIT(8)::INTEGER);
timestamp = SET_BYTE(timestamp, 2, (unix_time >> 24)::BIT(8)::INTEGER);
timestamp = SET_BYTE(timestamp, 3, (unix_time >> 16)::BIT(8)::INTEGER);
timestamp = SET_BYTE(timestamp, 4, (unix_time >> 8)::BIT(8)::INTEGER);
timestamp = SET_BYTE(timestamp, 5, unix_time::BIT(8)::INTEGER);
-- 10 entropy bytes
ulid = timestamp || gen_random_bytes(10);
-- Encode the timestamp
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 224) >> 5));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 31)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 1) & 248) >> 3));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 1) & 7) << 2) | ((GET_BYTE(ulid, 2) & 192) >> 6)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 2) & 62) >> 1));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 2) & 1) << 4) | ((GET_BYTE(ulid, 3) & 240) >> 4)));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 3) & 15) << 1) | ((GET_BYTE(ulid, 4) & 128) >> 7)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 4) & 124) >> 2));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 4) & 3) << 3) | ((GET_BYTE(ulid, 5) & 224) >> 5)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 5) & 31)));
-- Encode the entropy
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 6) & 248) >> 3));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 6) & 7) << 2) | ((GET_BYTE(ulid, 7) & 192) >> 6)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 7) & 62) >> 1));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 7) & 1) << 4) | ((GET_BYTE(ulid, 8) & 240) >> 4)));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 8) & 15) << 1) | ((GET_BYTE(ulid, 9) & 128) >> 7)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 9) & 124) >> 2));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 9) & 3) << 3) | ((GET_BYTE(ulid, 10) & 224) >> 5)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 10) & 31)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 11) & 248) >> 3));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 11) & 7) << 2) | ((GET_BYTE(ulid, 12) & 192) >> 6)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 12) & 62) >> 1));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 12) & 1) << 4) | ((GET_BYTE(ulid, 13) & 240) >> 4)));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 13) & 15) << 1) | ((GET_BYTE(ulid, 14) & 128) >> 7)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 14) & 124) >> 2));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 14) & 3) << 3) | ((GET_BYTE(ulid, 15) & 224) >> 5)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 15) & 31)));
RETURN output;
END
$$
LANGUAGE plpgsql
VOLATILE;
```
#### ULID TO UUID
```sql
CREATE OR REPLACE FUNCTION parse_ulid(ulid text) RETURNS bytea AS $$
DECLARE
-- 16byte
bytes bytea = E'\\x00000000 00000000 00000000 00000000';
v char[];
-- Allow for O(1) lookup of index values
dec integer[] = ARRAY[
255, 255, 255, 255, 255, 255, 255, 255, 255, 255,
255, 255, 255, 255, 255, 255, 255, 255, 255, 255,
255, 255, 255, 255, 255, 255, 255, 255, 255, 255,
255, 255, 255, 255, 255, 255, 255, 255, 255, 255,
255, 255, 255, 255, 255, 255, 255, 0, 1, 2,
3, 4, 5, 6, 7, 8, 9, 255, 255, 255,
255, 255, 255, 255, 10, 11, 12, 13, 14, 15,
16, 17, 1, 18, 19, 1, 20, 21, 0, 22,
23, 24, 25, 26, 255, 27, 28, 29, 30, 31,
255, 255, 255, 255, 255, 255, 10, 11, 12, 13,
14, 15, 16, 17, 1, 18, 19, 1, 20, 21,
0, 22, 23, 24, 25, 26, 255, 27, 28, 29,
30, 31
];
BEGIN
IF NOT ulid ~* '^[0-7][0-9ABCDEFGHJKMNPQRSTVWXYZ]{25}$' THEN
RAISE EXCEPTION 'Invalid ULID: %', ulid;
END IF;
v = regexp_split_to_array(ulid, '');
-- 6 bytes timestamp (48 bits)
bytes = SET_BYTE(bytes, 0, (dec[ASCII(v[1])] << 5) | dec[ASCII(v[2])]);
bytes = SET_BYTE(bytes, 1, (dec[ASCII(v[3])] << 3) | (dec[ASCII(v[4])] >> 2));
bytes = SET_BYTE(bytes, 2, (dec[ASCII(v[4])] << 6) | (dec[ASCII(v[5])] << 1) | (dec[ASCII(v[6])] >> 4));
bytes = SET_BYTE(bytes, 3, (dec[ASCII(v[6])] << 4) | (dec[ASCII(v[7])] >> 1));
bytes = SET_BYTE(bytes, 4, (dec[ASCII(v[7])] << 7) | (dec[ASCII(v[8])] << 2) | (dec[ASCII(v[9])] >> 3));
bytes = SET_BYTE(bytes, 5, (dec[ASCII(v[9])] << 5) | dec[ASCII(v[10])]);
-- 10 bytes of entropy (80 bits);
bytes = SET_BYTE(bytes, 6, (dec[ASCII(v[11])] << 3) | (dec[ASCII(v[12])] >> 2));
bytes = SET_BYTE(bytes, 7, (dec[ASCII(v[12])] << 6) | (dec[ASCII(v[13])] << 1) | (dec[ASCII(v[14])] >> 4));
bytes = SET_BYTE(bytes, 8, (dec[ASCII(v[14])] << 4) | (dec[ASCII(v[15])] >> 1));
bytes = SET_BYTE(bytes, 9, (dec[ASCII(v[15])] << 7) | (dec[ASCII(v[16])] << 2) | (dec[ASCII(v[17])] >> 3));
bytes = SET_BYTE(bytes, 10, (dec[ASCII(v[17])] << 5) | dec[ASCII(v[18])]);
bytes = SET_BYTE(bytes, 11, (dec[ASCII(v[19])] << 3) | (dec[ASCII(v[20])] >> 2));
bytes = SET_BYTE(bytes, 12, (dec[ASCII(v[20])] << 6) | (dec[ASCII(v[21])] << 1) | (dec[ASCII(v[22])] >> 4));
bytes = SET_BYTE(bytes, 13, (dec[ASCII(v[22])] << 4) | (dec[ASCII(v[23])] >> 1));
bytes = SET_BYTE(bytes, 14, (dec[ASCII(v[23])] << 7) | (dec[ASCII(v[24])] << 2) | (dec[ASCII(v[25])] >> 3));
bytes = SET_BYTE(bytes, 15, (dec[ASCII(v[25])] << 5) | dec[ASCII(v[26])]);
RETURN bytes;
END
$$
LANGUAGE plpgsql
IMMUTABLE;
CREATE OR REPLACE FUNCTION ulid_to_uuid(ulid text) RETURNS uuid AS $$
BEGIN
RETURN encode(parse_ulid(ulid), 'hex')::uuid;
END
$$
LANGUAGE plpgsql
IMMUTABLE;
```
#### UUID to ULID
```sql
CREATE OR REPLACE FUNCTION uuid_to_ulid(id uuid) RETURNS text AS $$
DECLARE
encoding bytea = '0123456789ABCDEFGHJKMNPQRSTVWXYZ';
output text = '';
uuid_bytes bytea = uuid_send(id);
BEGIN
-- Encode the timestamp
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 224) >> 5));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 31)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 1) & 248) >> 3));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 1) & 7) << 2) | ((GET_BYTE(uuid_bytes, 2) & 192) >> 6)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 2) & 62) >> 1));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 2) & 1) << 4) | ((GET_BYTE(uuid_bytes, 3) & 240) >> 4)));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 3) & 15) << 1) | ((GET_BYTE(uuid_bytes, 4) & 128) >> 7)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 4) & 124) >> 2));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 4) & 3) << 3) | ((GET_BYTE(uuid_bytes, 5) & 224) >> 5)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 5) & 31)));
-- Encode the entropy
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 6) & 248) >> 3));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 6) & 7) << 2) | ((GET_BYTE(uuid_bytes, 7) & 192) >> 6)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 7) & 62) >> 1));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 7) & 1) << 4) | ((GET_BYTE(uuid_bytes, 8) & 240) >> 4)));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 8) & 15) << 1) | ((GET_BYTE(uuid_bytes, 9) & 128) >> 7)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 9) & 124) >> 2));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 9) & 3) << 3) | ((GET_BYTE(uuid_bytes, 10) & 224) >> 5)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 10) & 31)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 11) & 248) >> 3));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 11) & 7) << 2) | ((GET_BYTE(uuid_bytes, 12) & 192) >> 6)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 12) & 62) >> 1));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 12) & 1) << 4) | ((GET_BYTE(uuid_bytes, 13) & 240) >> 4)));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 13) & 15) << 1) | ((GET_BYTE(uuid_bytes, 14) & 128) >> 7)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 14) & 124) >> 2));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 14) & 3) << 3) | ((GET_BYTE(uuid_bytes, 15) & 224) >> 5)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 15) & 31)));
RETURN output;
END
$$
LANGUAGE plpgsql
IMMUTABLE;
```
#### Gera 11 Digitos aleatórios: YBKXG0CKTH4
```sql
-- Cria a extensão pgcrypto para gerar uuid
CREATE EXTENSION IF NOT EXISTS pgcrypto;
-- Cria a função para gerar ULID
CREATE OR REPLACE FUNCTION gen_lrandom()
RETURNS TEXT AS $$
DECLARE
ts_millis BIGINT;
ts_chars TEXT;
random_bytes BYTEA;
random_chars TEXT;
base32_chars TEXT := '0123456789ABCDEFGHJKMNPQRSTVWXYZ';
i INT;
BEGIN
-- Pega o timestamp em milissegundos
ts_millis := FLOOR(EXTRACT(EPOCH FROM clock_timestamp()) * 1000)::BIGINT;
-- Converte o timestamp para base32
ts_chars := '';
FOR i IN REVERSE 0..11 LOOP
ts_chars := ts_chars || substr(base32_chars, ((ts_millis >> (5 * i)) & 31) + 1, 1);
END LOOP;
-- Gera 10 bytes aleatórios e converte para base32
random_bytes := gen_random_bytes(10);
random_chars := '';
FOR i IN 0..9 LOOP
random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) >> 3) & 31) + 1, 1);
IF i < 9 THEN
random_chars := random_chars || substr(base32_chars, (((get_byte(random_bytes, i) & 7) << 2) | (get_byte(random_bytes, i + 1) >> 6)) & 31 + 1, 1);
ELSE
random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) & 7) << 2) + 1, 1);
END IF;
END LOOP;
-- Concatena o timestamp e os caracteres aleatórios
RETURN ts_chars || random_chars;
END;
$$ LANGUAGE plpgsql;
```
#### Exemplo de USO
```sql
-- Criação da extensão caso não exista
CREATE EXTENSION
IF
NOT EXISTS pgcrypto;
-- Criação da tabela pessoas
CREATE TABLE pessoas ( ID UUID DEFAULT gen_random_uuid ( ) PRIMARY KEY, nome TEXT NOT NULL );
-- Busca Pessoa na tabela
SELECT
*
FROM
"pessoas"
WHERE
uuid_to_ulid ( ID ) = '252FAC9F3V8EF80SSDK8PXW02F';
```
### Fontes
- https://github.com/scoville/pgsql-ulid
- https://github.com/geckoboard/pgulid
-

@ 872982aa:8fb54cfe
2025-03-27 05:47:06
- [首页](/readme.md)
- [第一章、 NIP-01: Basic protocol flow description](/01.md)
- [第二章、 NIP-02: Follow List](/02.md)
- [第三章、NIP-03: OpenTimestamps Attestations for Events](/03.md)
-

@ b4403b24:83542d4e
2025-03-31 14:31:53
🚀 Bitcoin Enthusiasts! Tomorrow the price of #BTCPrague2025 tickets goes up so take advantage of the 10% discount using code from the video - BTCBULGARIA.
✅ Network with leaders
✅ Learn blockchain strategies
✅ Gain crypto insights
Secure your spot NOW!
#Bitcoin #BTC #BTCPrague

originally posted at https://stacker.news/items/930210
-

@ e97aaffa:2ebd765d
2024-12-31 16:47:12
Último dia do ano, momento para tirar o pó da bola de cristal, para fazer reflexões, previsões e desejos para o próximo ano e seguintes.
Ano após ano, o Bitcoin evoluiu, foi ultrapassando etapas, tornou-se cada vez mais _mainstream_. Está cada vez mais difícil fazer previsões sobre o Bitcoin, já faltam poucas barreiras a serem ultrapassadas e as que faltam são altamente complexas ou tem um impacto profundo no sistema financeiro ou na sociedade. Estas alterações profundas tem que ser realizadas lentamente, porque uma alteração rápida poderia resultar em consequências terríveis, poderia provocar um retrocesso.
# Código do Bitcoin
No final de 2025, possivelmente vamos ter um _fork_, as discussões sobre os _covenants_ já estão avançadas, vão acelerar ainda mais. Já existe um consenso relativamente alto, a favor dos _covenants_, só falta decidir que modelo será escolhido. Penso que até ao final do ano será tudo decidido.
Depois dos _covenants,_ o próximo foco será para a criptografia post-quantum, que será o maior desafio que o Bitcoin enfrenta. Criar uma criptografia segura e que não coloque a descentralização em causa.
Espero muito de Ark, possivelmente a inovação do ano, gostaria de ver o Nostr a furar a bolha bitcoinheira e que o Cashu tivesse mais reconhecimento pelos _bitcoiners_.
Espero que surjam avanços significativos no BitVM2 e BitVMX.
Não sei o que esperar das layer 2 de Bitcoin, foram a maior desilusão de 2024. Surgiram com muita força, mas pouca coisa saiu do papel, foi uma mão cheia de nada. Uma parte dos projetos caiu na tentação da _shitcoinagem_, na criação de tokens, que tem um único objetivo, enriquecer os devs e os VCs.
Se querem ser levados a sério, têm que ser sérios.
> “À mulher de César não basta ser honesta, deve parecer honesta”
Se querem ter o apoio dos _bitcoiners_, sigam o _ethos_ do Bitcoin.
Neste ponto a atitude do pessoal da Ark é exemplar, em vez de andar a chorar no Twitter para mudar o código do Bitcoin, eles colocaram as mãos na massa e criaram o protocolo. É claro que agora está meio “coxo”, funciona com uma _multisig_ ou com os _covenants_ na Liquid. Mas eles estão a criar um produto, vão demonstrar ao mercado que o produto é bom e útil. Com a adoção, a comunidade vai perceber que o Ark necessita dos _covenants_ para melhorar a interoperabilidade e a soberania.
É este o pensamento certo, que deveria ser seguido pelos restantes e futuros projetos. É seguir aquele pensamento do J.F. Kennedy:
> “Não perguntem o que é que o vosso país pode fazer por vocês, perguntem o que é que vocês podem fazer pelo vosso país”
Ou seja, não fiquem à espera que o bitcoin mude, criem primeiro as inovações/tecnologia, ganhem adoção e depois demonstrem que a alteração do código camada base pode melhorar ainda mais o vosso projeto. A necessidade é que vai levar a atualização do código.
# Reservas Estratégicas de Bitcoin
## Bancos centrais
Com a eleição de Trump, emergiu a ideia de uma Reserva Estratégia de Bitcoin, tornou este conceito _mainstream_. Foi um _pivot_, a partir desse momento, foram enumerados os políticos de todo o mundo a falar sobre o assunto.
A Senadora Cynthia Lummis foi mais além e propôs um programa para adicionar 200 mil bitcoins à reserva ao ano, até 1 milhão de Bitcoin. Só que isto está a criar uma enorme expectativa na comunidade, só que pode resultar numa enorme desilusão. Porque no primeiro ano, o Trump em vez de comprar os 200 mil, pode apenas adicionar na reserva, os 198 mil que o Estado já tem em sua posse. Se isto acontecer, possivelmente vai resultar numa forte queda a curto prazo. Na minha opinião os bancos centrais deveriam seguir o exemplo de El Salvador, fazer um DCA diário.
Mais que comprar bitcoin, para mim, o mais importante é a criação da Reserva, é colocar o Bitcoin ao mesmo nível do ouro, o impacto para o resto do mundo será tremendo, a teoria dos jogos na sua plenitude. Muitos outros bancos centrais vão ter que comprar, para não ficarem atrás, além disso, vai transmitir uma mensagem à generalidade da população, que o Bitcoin é “afinal é algo seguro, com valor”.
Mas não foi Trump que iniciou esta teoria dos jogos, mas sim foi a primeira vítima dela. É o próprio Trump que o admite, que os EUA necessitam da reserva para não ficar atrás da China. Além disso, desde que os EUA utilizaram o dólar como uma arma, com sanção contra a Rússia, surgiram boatos de que a Rússia estaria a utilizar o Bitcoin para transações internacionais. Que foram confirmados recentemente, pelo próprio governo russo. Também há poucos dias, ainda antes deste reconhecimento público, Putin elogiou o Bitcoin, ao reconhecer que “Ninguém pode proibir o bitcoin”, defendendo como uma alternativa ao dólar. A narrativa está a mudar.
Já existem alguns países com Bitcoin, mas apenas dois o fizeram conscientemente (El Salvador e Butão), os restantes têm devido a apreensões. Hoje são poucos, mas 2025 será o início de uma corrida pelos bancos centrais. Esta corrida era algo previsível, o que eu não esperava é que acontecesse tão rápido.

## Empresas
A criação de reservas estratégicas não vai ficar apenas pelos bancos centrais, também vai acelerar fortemente nas empresas em 2025.

Mas as empresas não vão seguir a estratégia do Saylor, vão comprar bitcoin sem alavancagem, utilizando apenas os tesouros das empresas, como uma proteção contra a inflação. Eu não sou grande admirador do Saylor, prefiro muito mais, uma estratégia conservadora, sem qualquer alavancagem. Penso que as empresas vão seguir a sugestão da BlackRock, que aconselha um alocações de 1% a 3%.
Penso que 2025, ainda não será o ano da entrada das 6 magníficas (excepto Tesla), será sobretudo empresas de pequena e média dimensão. As magníficas ainda tem uma cota muito elevada de _shareholders_ com alguma idade, bastante conservadores, que têm dificuldade em compreender o Bitcoin, foi o que aconteceu recentemente com a Microsoft.
Também ainda não será em 2025, talvez 2026, a inclusão nativamente de wallet Bitcoin nos sistema da Apple Pay e da Google Pay. Seria um passo gigante para a adoção a nível mundial.
# ETFs
Os ETFs para mim são uma incógnita, tenho demasiadas dúvidas, como será 2025. Este ano os _inflows_ foram superiores a 500 mil bitcoins, o IBIT foi o lançamento de ETF mais bem sucedido da história. O sucesso dos ETFs, deve-se a 2 situações que nunca mais se vão repetir. O mercado esteve 10 anos à espera pela aprovação dos ETFs, a procura estava reprimida, isso foi bem notório nos primeiros meses, os _inflows_ foram brutais.
Também se beneficiou por ser um mercado novo, não existia _orderbook_ de vendas, não existia um mercado interno, praticamente era só _inflows_. Agora o mercado já estabilizou, a maioria das transações já são entre clientes dos próprios ETFs. Agora só uma pequena percentagem do volume das transações diárias vai resultar em _inflows_ ou _outflows_.
Estes dois fenómenos nunca mais se vão repetir, eu não acredito que o número de _inflows_ em BTC supere os número de 2024, em dólares vai superar, mas em btc não acredito que vá superar.
Mas em 2025 vão surgir uma infindável quantidade de novos produtos, derivativos, novos ETFs de cestos com outras criptos ou cestos com ativos tradicionais. O bitcoin será adicionado em produtos financeiros já existentes no mercado, as pessoas vão passar a deter bitcoin, sem o saberem.
Com o fim da operação ChokePoint 2.0, vai surgir uma nova onda de adoção e de produtos financeiros. Possivelmente vamos ver bancos tradicionais a disponibilizar produtos ou serviços de custódia aos seus clientes.
Eu adoraria ver o crescimento da adoção do bitcoin como moeda, só que a regulamentação não vai ajudar nesse processo.
# Preço
Eu acredito que o topo deste ciclo será alcançado no primeiro semestre, posteriormente haverá uma correção. Mas desta vez, eu acredito que a correção será muito menor que as anteriores, inferior a 50%, esta é a minha expectativa. Espero estar certo.
# Stablecoins de dólar
Agora saindo um pouco do universo do Bitcoin, acho importante destacar as _stablecoins_.
No último ciclo, eu tenho dividido o tempo, entre continuar a estudar o Bitcoin e estudar o sistema financeiro, as suas dinâmicas e o comportamento humano. Isto tem sido o meu foco de reflexão, imaginar a transformação que o mundo vai sofrer devido ao padrão Bitcoin. É uma ilusão acreditar que a transição de um padrão FIAT para um padrão Bitcoin vai ser rápida, vai existir um processo transitório que pode demorar décadas.
Com a re-entrada de Trump na Casa Branca, prometendo uma política altamente protecionista, vai provocar uma forte valorização do dólar, consequentemente as restantes moedas do mundo vão derreter. Provocando uma inflação generalizada, gerando uma corrida às _stablecoins_ de dólar nos países com moedas mais fracas. Trump vai ter uma política altamente expansionista, vai exportar dólares para todo o mundo, para financiar a sua própria dívida. A desigualdade entre os pobres e ricos irá crescer fortemente, aumentando a possibilidade de conflitos e revoltas.
> “Casa onde não há pão, todos ralham e ninguém tem razão”
Será mais lenha, para alimentar a fogueira, vai gravar os conflitos geopolíticos já existentes, ficando as sociedade ainda mais polarizadas.
Eu acredito que 2025, vai haver um forte crescimento na adoção das _stablecoins_ de dólares, esse forte crescimento vai agravar o problema sistémico que são as _stablecoins_. Vai ser o início do fim das _stablecoins_, pelo menos, como nós conhecemos hoje em dia.
## Problema sistémico
O sistema FIAT não nasceu de um dia para outro, foi algo que foi construído organicamente, ou seja, foi evoluindo ao longo dos anos, sempre que havia um problema/crise, eram criadas novas regras ou novas instituições para minimizar os problemas. Nestes quase 100 anos, desde os acordos de Bretton Woods, a evolução foram tantas, tornaram o sistema financeiro altamente complexo, burocrático e nada eficiente.
Na prática é um castelo de cartas construído sobre outro castelo de cartas e que por sua vez, foi construído sobre outro castelo de cartas.
As _stablecoins_ são um problema sistémico, devido às suas reservas em dólares e o sistema financeiro não está preparado para manter isso seguro. Com o crescimento das reservas ao longo dos anos, foi se agravando o problema.
No início a Tether colocava as reservas em bancos comerciais, mas com o crescimento dos dólares sob gestão, criou um problema nos bancos comerciais, devido à reserva fracionária. Essas enormes reservas da Tether estavam a colocar em risco a própria estabilidade dos bancos.
A Tether acabou por mudar de estratégia, optou por outros ativos, preferencialmente por títulos do tesouro/obrigações dos EUA. Só que a Tether continua a crescer e não dá sinais de abrandamento, pelo contrário.
Até o próprio mundo cripto, menosprezava a gravidade do problema da Tether/_stablecoins_ para o resto do sistema financeiro, porque o _marketcap_ do cripto ainda é muito pequeno. É verdade que ainda é pequeno, mas a Tether não o é, está no top 20 dos maiores detentores de títulos do tesouros dos EUA e está ao nível dos maiores bancos centrais do mundo. Devido ao seu tamanho, está a preocupar os responsáveis/autoridades/reguladores dos EUA, pode colocar em causa a estabilidade do sistema financeiro global, que está assente nessas obrigações.
Os títulos do tesouro dos EUA são o colateral mais utilizado no mundo, tanto por bancos centrais, como por empresas, é a charneira da estabilidade do sistema financeiro. Os títulos do tesouro são um assunto muito sensível. Na recente crise no Japão, do _carry trade_, o Banco Central do Japão tentou minimizar a desvalorização do iene através da venda de títulos dos EUA. Esta operação, obrigou a uma viagem de emergência, da Secretaria do Tesouro dos EUA, Janet Yellen ao Japão, onde disponibilizou liquidez para parar a venda de títulos por parte do Banco Central do Japão. Essa forte venda estava desestabilizando o mercado.
Os principais detentores de títulos do tesouros são institucionais, bancos centrais, bancos comerciais, fundo de investimento e gestoras, tudo administrado por gestores altamente qualificados, racionais e que conhecem a complexidade do mercado de obrigações.
O mundo cripto é seu oposto, é _naife_ com muita irracionalidade e uma forte pitada de loucura, na sua maioria nem faz a mínima ideia como funciona o sistema financeiro. Essa irracionalidade pode levar a uma “corrida bancária”, como aconteceu com o UST da Luna, que em poucas horas colapsou o projeto. Em termos de escala, a Luna ainda era muito pequena, por isso, o problema ficou circunscrito ao mundo cripto e a empresas ligadas diretamente ao cripto.
Só que a Tether é muito diferente, caso exista algum FUD, que obrigue a Tether a desfazer-se de vários biliões ou dezenas de biliões de dólares em títulos num curto espaço de tempo, poderia provocar consequências terríveis em todo o sistema financeiro. A Tether é grande demais, é já um problema sistémico, que vai agravar-se com o crescimento em 2025.
Não tenham dúvidas, se existir algum problema, o Tesouro dos EUA vai impedir a venda dos títulos que a Tether tem em sua posse, para salvar o sistema financeiro. O problema é, o que vai fazer a Tether, se ficar sem acesso às venda das reservas, como fará o _redeem_ dos dólares?
Como o crescimento do Tether é inevitável, o Tesouro e o FED estão com um grande problema em mãos, o que fazer com o Tether?
Mas o problema é que o atual sistema financeiro é como um curto cobertor: Quanto tapas a cabeça, destapas os pés; Ou quando tapas os pés, destapas a cabeça. Ou seja, para resolver o problema da guarda reservas da Tether, vai criar novos problemas, em outros locais do sistema financeiro e assim sucessivamente.
### Conta mestre
Uma possível solução seria dar uma conta mestre à Tether, dando o acesso direto a uma conta no FED, semelhante à que todos os bancos comerciais têm. Com isto, a Tether deixaria de necessitar os títulos do tesouro, depositando o dinheiro diretamente no banco central. Só que isto iria criar dois novos problemas, com o Custodia Bank e com o restante sistema bancário.
O Custodia Bank luta há vários anos contra o FED, nos tribunais pelo direito a ter licença bancária para um banco com _full-reserves_. O FED recusou sempre esse direito, com a justificativa que esse banco, colocaria em risco toda a estabilidade do sistema bancário existente, ou seja, todos os outros bancos poderiam colapsar. Perante a existência em simultâneo de bancos com reserva fracionária e com _full-reserves_, as pessoas e empresas iriam optar pelo mais seguro. Isso iria provocar uma corrida bancária, levando ao colapso de todos os bancos com reserva fracionária, porque no Custodia Bank, os fundos dos clientes estão 100% garantidos, para qualquer valor. Deixaria de ser necessário limites de fundos de Garantia de Depósitos.
Eu concordo com o FED nesse ponto, que os bancos com _full-reserves_ são uma ameaça a existência dos restantes bancos. O que eu discordo do FED, é a origem do problema, o problema não está nos bancos _full-reserves_, mas sim nos que têm reserva fracionária.
O FED ao conceder uma conta mestre ao Tether, abre um precedente, o Custodia Bank irá o aproveitar, reclamando pela igualdade de direitos nos tribunais e desta vez, possivelmente ganhará a sua licença.
Ainda há um segundo problema, com os restantes bancos comerciais. A Tether passaria a ter direitos similares aos bancos comerciais, mas os deveres seriam muito diferentes. Isto levaria os bancos comerciais aos tribunais para exigir igualdade de tratamento, é uma concorrência desleal. Isto é o bom dos tribunais dos EUA, são independentes e funcionam, mesmo contra o estado. Os bancos comerciais têm custos exorbitantes devido às políticas de _compliance_, como o KYC e AML. Como o governo não vai querer aliviar as regras, logo seria a Tether, a ser obrigada a fazer o _compliance_ dos seus clientes.
A obrigação do KYC para ter _stablecoins_ iriam provocar um terramoto no mundo cripto.
Assim, é pouco provável que seja a solução para a Tether.
### FED
Só resta uma hipótese, ser o próprio FED a controlar e a gerir diretamente as _stablecoins_ de dólar, nacionalizado ou absorvendo as existentes. Seria uma espécie de CBDC. Isto iria provocar um novo problema, um problema diplomático, porque as _stablecoins_ estão a colocar em causa a soberania monetária dos outros países. Atualmente as _stablecoins_ estão um pouco protegidas porque vivem num limbo jurídico, mas a partir do momento que estas são controladas pelo governo americano, tudo muda. Os países vão exigir às autoridades americanas medidas que limitem o uso nos seus respectivos países.
Não existe uma solução boa, o sistema FIAT é um castelo de cartas, qualquer carta que se mova, vai provocar um desmoronamento noutro local. As autoridades não poderão adiar mais o problema, terão que o resolver de vez, senão, qualquer dia será tarde demais. Se houver algum problema, vão colocar a responsabilidade no cripto e no Bitcoin. Mas a verdade, a culpa é inteiramente dos políticos, da sua incompetência em resolver os problemas a tempo.
Será algo para acompanhar futuramente, mas só para 2026, talvez…
É curioso, há uns anos pensava-se que o Bitcoin seria a maior ameaça ao sistema ao FIAT, mas afinal, a maior ameaça aos sistema FIAT é o próprio FIAT(_stablecoins_). A ironia do destino.
Isto é como uma corrida, o Bitcoin é aquele atleta que corre ao seu ritmo, umas vezes mais rápido, outras vezes mais lento, mas nunca pára. O FIAT é o atleta que dá tudo desde da partida, corre sempre em velocidade máxima. Só que a vida e o sistema financeiro não é uma prova de 100 metros, mas sim uma maratona.
# Europa
2025 será um ano desafiante para todos europeus, sobretudo devido à entrada em vigor da regulamentação (MiCA). Vão começar a sentir na pele a regulamentação, vão agravar-se os problemas com os _compliance_, problemas para comprovar a origem de fundos e outras burocracias. Vai ser lindo.
O _Travel Route_ passa a ser obrigatório, os europeus serão obrigados a fazer o KYC nas transações. A _Travel Route_ é uma suposta lei para criar mais transparência, mas prática, é uma lei de controle, de monitorização e para limitar as liberdades individuais dos cidadãos.
O MiCA também está a colocar problemas nas _stablecoins_ de Euro, a Tether para já preferiu ficar de fora da europa. O mais ridículo é que as novas regras obrigam os emissores a colocar 30% das reservas em bancos comerciais. Os burocratas europeus não compreendem que isto coloca em risco a estabilidade e a solvência dos próprios bancos, ficam propensos a corridas bancárias.
O MiCA vai obrigar a todas as exchanges a estar registadas em solo europeu, ficando vulnerável ao temperamento dos burocratas. Ainda não vai ser em 2025, mas a UE vai impor políticas de controle de capitais, é inevitável, as exchanges serão obrigadas a usar em exclusividade _stablecoins_ de euro, as restantes _stablecoins_ serão deslistadas.
Todas estas novas regras do MiCA, são extremamente restritas, não é para garantir mais segurança aos cidadãos europeus, mas sim para garantir mais controle sobre a população. A UE está cada vez mais perto da autocracia, do que da democracia. A minha única esperança no horizonte, é que o sucesso das políticas cripto nos EUA, vai obrigar a UE a recuar e a aligeirar as regras, a teoria dos jogos é implacável. Mas esse recuo, nunca acontecerá em 2025, vai ser um longo período conturbado.
# Recessão
Os mercados estão todos em máximos históricos, isto não é sustentável por muito tempo, suspeito que no final de 2025 vai acontecer alguma correção nos mercados. A queda só não será maior, porque os bancos centrais vão imprimir dinheiro, muito dinheiro, como se não houvesse amanhã. Vão voltar a resolver os problemas com a injeção de liquidez na economia, é empurrar os problemas com a barriga, em de os resolver. Outra vez o efeito Cantillon.
Será um ano muito desafiante a nível político, onde o papel dos políticos será fundamental. A crise política na França e na Alemanha, coloca a UE órfã, sem um comandante ao leme do navio. 2025 estará condicionado pelas eleições na Alemanha, sobretudo no resultado do AfD, que podem colocar em causa a propriedade UE e o euro.
Possivelmente, só o fim da guerra poderia minimizar a crise, algo que é muito pouco provável acontecer.
Em Portugal, a economia parece que está mais ou menos equilibrada, mas começam a aparecer alguns sinais preocupantes. Os jogos de sorte e azar estão em máximos históricos, batendo o recorde de 2014, época da grande crise, não é um bom sinal, possivelmente já existe algum desespero no ar.
A Alemanha é o motor da Europa, quanto espirra, Portugal constipa-se. Além do problema da Alemanha, a Espanha também está à beira de uma crise, são os países que mais influenciam a economia portuguesa.
Se existir uma recessão mundial, terá um forte impacto no turismo, que é hoje em dia o principal motor de Portugal.
# Brasil
Brasil é algo para acompanhar em 2025, sobretudo a nível macro e a nível político. Existe uma possibilidade de uma profunda crise no Brasil, sobretudo na sua moeda. O banco central já anda a queimar as reservas para minimizar a desvalorização do Real.

Sem mudanças profundas nas políticas fiscais, as reservas vão se esgotar. As políticas de controle de capitais são um cenário plausível, será interesse de acompanhar, como o governo irá proceder perante a existência do Bitcoin e _stablecoins_. No Brasil existe um forte adoção, será um bom _case study_, certamente irá repetir-se em outros países num futuro próximo.
Os próximos tempos não serão fáceis para os brasileiros, especialmente para os que não têm Bitcoin.
# Blockchain
Em 2025, possivelmente vamos ver os primeiros passos da BlackRock para criar a primeira bolsa de valores, exclusivamente em _blockchain_. Eu acredito que a BlackRock vai criar uma própria _blockchain_, toda controlada por si, onde estarão os RWAs, para fazer concorrência às tradicionais bolsas de valores. Será algo interessante de acompanhar.
-----------
Estas são as minhas previsões, eu escrevi isto muito em cima do joelho, certamente esqueci-me de algumas coisas, se for importante acrescentarei nos comentários. A maioria das previsões só acontecerá após 2025, mas fica aqui a minha opinião.
Isto é apenas a minha opinião, **Don’t Trust, Verify**!
-

@ 17538dc2:71ed77c4
2025-04-02 16:04:59
The MacOS security update summary is a reminder that laptops and desktops are incredibly compromised.
### macOS Sequoia 15.4
Released March 31, 2025
Accessibility
Available for: macOS Sequoia
Impact: An app may be able to access sensitive user data
Description: A logging issue was addressed with improved data redaction.
CVE-2025-24202: Zhongcheng Li from IES Red Team of ByteDance
AccountPolicy
Available for: macOS Sequoia
Impact: A malicious app may be able to gain root privileges
Description: This issue was addressed by removing the vulnerable code.
CVE-2025-24234: an anonymous researcher
AirDrop
Available for: macOS Sequoia
Impact: An app may be able to read arbitrary file metadata
Description: A permissions issue was addressed with additional restrictions.
CVE-2025-24097: Ron Masas of BREAKPOINT.SH
App Store
Available for: macOS Sequoia
Impact: A malicious app may be able to access private information
Description: This issue was addressed by removing the vulnerable code.
CVE-2025-24276: an anonymous researcher
AppleMobileFileIntegrity
Available for: macOS Sequoia
Impact: An app may be able to modify protected parts of the file system
Description: The issue was addressed with improved checks.
CVE-2025-24272: Mickey Jin (@patch1t)
AppleMobileFileIntegrity
Available for: macOS Sequoia
Impact: An app may be able to access protected user data
Description: A downgrade issue was addressed with additional code-signing restrictions.
CVE-2025-24239: Wojciech Regula of SecuRing (wojciechregula.blog)
AppleMobileFileIntegrity
Available for: macOS Sequoia
Impact: A malicious app may be able to read or write to protected files
Description: A permissions issue was addressed with additional restrictions.
CVE-2025-24233: Claudio Bozzato and Francesco Benvenuto of Cisco Talos.
AppleMobileFileIntegrity
Available for: macOS Sequoia
Impact: An app may be able to access user-sensitive data
Description: A privacy issue was addressed by removing the vulnerable code.
CVE-2025-30443: Bohdan Stasiuk (@bohdan_stasiuk)
Audio
Available for: macOS Sequoia
Impact: Processing a maliciously crafted font may result in the disclosure of process memory
Description: The issue was addressed with improved memory handling.
CVE-2025-24244: Hossein Lotfi (@hosselot) of Trend Micro Zero Day Initiative
Audio
Available for: macOS Sequoia
Impact: Processing a maliciously crafted file may lead to arbitrary code execution
Description: The issue was addressed with improved memory handling.
CVE-2025-24243: Hossein Lotfi (@hosselot) of Trend Micro Zero Day Initiative
Authentication Services
Available for: macOS Sequoia
Impact: Password autofill may fill in passwords after failing authentication
Description: This issue was addressed through improved state management.
CVE-2025-30430: Dominik Rath
Authentication Services
Available for: macOS Sequoia
Impact: A malicious website may be able to claim WebAuthn credentials from another website that shares a registrable suffix
Description: The issue was addressed with improved input validation.
CVE-2025-24180: Martin Kreichgauer of Google Chrome
Authentication Services
Available for: macOS Sequoia
Impact: A malicious app may be able to access a user's saved passwords
Description: This issue was addressed by adding a delay between verification code attempts.
CVE-2025-24245: Ian Mckay (@iann0036)
Automator
Available for: macOS Sequoia
Impact: An app may be able to access protected user data
Description: A permissions issue was addressed by removing vulnerable code and adding additional checks.
CVE-2025-30460: an anonymous researcher
BiometricKit
Available for: macOS Sequoia
Impact: An app may be able to cause unexpected system termination
Description: A buffer overflow was addressed with improved bounds checking.
CVE-2025-24237: Yutong Xiu
Calendar
Available for: macOS Sequoia
Impact: An app may be able to break out of its sandbox
Description: A path handling issue was addressed with improved validation.
CVE-2025-30429: Denis Tokarev (@illusionofcha0s)
Calendar
Available for: macOS Sequoia
Impact: An app may be able to break out of its sandbox
Description: This issue was addressed with improved checks.
CVE-2025-24212: Denis Tokarev (@illusionofcha0s)
CloudKit
Available for: macOS Sequoia
Impact: A malicious app may be able to access private information
Description: The issue was addressed with improved checks.
CVE-2025-24215: Kirin (@Pwnrin)
CoreAudio
Available for: macOS Sequoia
Impact: Parsing a file may lead to an unexpected app termination
Description: The issue was addressed with improved checks.
CVE-2025-24163: Google Threat Analysis Group
CoreAudio
Available for: macOS Sequoia
Impact: Playing a malicious audio file may lead to an unexpected app termination
Description: An out-of-bounds read issue was addressed with improved input validation.
CVE-2025-24230: Hossein Lotfi (@hosselot) of Trend Micro Zero Day Initiative
CoreMedia
Available for: macOS Sequoia
Impact: Processing a maliciously crafted video file may lead to unexpected app termination or corrupt process memory
Description: This issue was addressed with improved memory handling.
CVE-2025-24211: Hossein Lotfi (@hosselot) of Trend Micro Zero Day Initiative
CoreMedia
Available for: macOS Sequoia
Impact: An app may be able to access sensitive user data
Description: An access issue was addressed with additional sandbox restrictions.
CVE-2025-24236: Csaba Fitzl (@theevilbit) and Nolan Astrein of Kandji
CoreMedia
Available for: macOS Sequoia
Impact: Processing a maliciously crafted video file may lead to unexpected app termination or corrupt process memory
Description: The issue was addressed with improved memory handling.
CVE-2025-24190: Hossein Lotfi (@hosselot) of Trend Micro Zero Day Initiative
CoreMedia Playback
Available for: macOS Sequoia
Impact: A malicious app may be able to access private information
Description: A path handling issue was addressed with improved validation.
CVE-2025-30454: pattern-f (@pattern_F_)
CoreServices
Description: This issue was addressed through improved state management.
CVE-2025-31191: Jonathan Bar Or (@yo_yo_yo_jbo) of Microsoft, and an anonymous researcher
Available for: macOS Sequoia
Impact: An app may be able to access sensitive user data
CoreText
Available for: macOS Sequoia
Impact: Processing a maliciously crafted font may result in the disclosure of process memory
Description: An out-of-bounds read issue was addressed with improved input validation.
CVE-2025-24182: Hossein Lotfi (@hosselot) of Trend Micro Zero Day Initiative
Crash Reporter
Available for: macOS Sequoia
Impact: An app may be able to gain root privileges
Description: A parsing issue in the handling of directory paths was addressed with improved path validation.
CVE-2025-24277: Csaba Fitzl (@theevilbit) of Kandji and Gergely Kalman (@gergely_kalman), and an anonymous researcher
curl
Available for: macOS Sequoia
Impact: An input validation issue was addressed
Description: This is a vulnerability in open source code and Apple Software is among the affected projects. The CVE-ID was assigned by a third party. Learn more about the issue and CVE-ID at cve.org.
CVE-2024-9681
Disk Images
Available for: macOS Sequoia
Impact: An app may be able to break out of its sandbox
Description: A file access issue was addressed with improved input validation.
CVE-2025-24255: an anonymous researcher
DiskArbitration
Available for: macOS Sequoia
Impact: An app may be able to gain root privileges
Description: A parsing issue in the handling of directory paths was addressed with improved path validation.
CVE-2025-30456: Gergely Kalman (@gergely_kalman)
DiskArbitration
Available for: macOS Sequoia
Impact: An app may be able to gain root privileges
Description: A permissions issue was addressed with additional restrictions.
CVE-2025-24267: an anonymous researcher
Dock
Available for: macOS Sequoia
Impact: A malicious app may be able to access private information
Description: The issue was addressed with improved checks.
CVE-2025-30455: Mickey Jin (@patch1t), and an anonymous researcher
Dock
Available for: macOS Sequoia
Impact: An app may be able to modify protected parts of the file system
Description: This issue was addressed by removing the vulnerable code.
CVE-2025-31187: Rodolphe BRUNETTI (@eisw0lf) of Lupus Nova
dyld
Available for: macOS Sequoia
Impact: Apps that appear to use App Sandbox may be able to launch without restrictions
Description: A library injection issue was addressed with additional restrictions.
CVE-2025-30462: Pietro Francesco Tirenna, Davide Silvetti, Abdel Adim Oisfi of Shielder (shielder.com)
FaceTime
Available for: macOS Sequoia
Impact: An app may be able to access sensitive user data
Description: This issue was addressed with improved redaction of sensitive information.
CVE-2025-30451: Kirin (@Pwnrin) and luckyu (@uuulucky)
FeedbackLogger
Available for: macOS Sequoia
Impact: An app may be able to access sensitive user data
Description: This issue was addressed with improved data protection.
CVE-2025-24281: Rodolphe BRUNETTI (@eisw0lf)
Focus
Available for: macOS Sequoia
Impact: An attacker with physical access to a locked device may be able to view sensitive user information
Description: The issue was addressed with improved checks.
CVE-2025-30439: Andr.Ess
Focus
Available for: macOS Sequoia
Impact: An app may be able to access sensitive user data
Description: A logging issue was addressed with improved data redaction.
CVE-2025-24283: Kirin (@Pwnrin)
Foundation
Available for: macOS Sequoia
Impact: An app may be able to access protected user data
Description: An access issue was addressed with additional sandbox restrictions on the system pasteboards.
CVE-2025-30461: an anonymous researcher
Foundation
Available for: macOS Sequoia
Impact: An app may be able to access sensitive user data
Description: The issue was resolved by sanitizing logging
CVE-2025-30447: LFY@secsys from Fudan University
Foundation
Available for: macOS Sequoia
Impact: An app may be able to cause a denial-of-service
Description: An uncontrolled format string issue was addressed with improved input validation.
CVE-2025-24199: Manuel Fernandez (Stackhopper Security)
GPU Drivers
Available for: macOS Sequoia
Impact: An app may be able to cause unexpected system termination or corrupt kernel memory
Description: An out-of-bounds write issue was addressed with improved bounds checking.
CVE-2025-30464: ABC Research s.r.o.
CVE-2025-24273: Wang Yu of Cyberserval
GPU Drivers
Available for: macOS Sequoia
Impact: An app may be able to disclose kernel memory
Description: The issue was addressed with improved bounds checks.
CVE-2025-24256: Anonymous working with Trend Micro Zero Day Initiative, Murray Mike
Handoff
Available for: macOS Sequoia
Impact: An app may be able to access sensitive user data
Description: The issue was addressed with improved restriction of data container access.
CVE-2025-30463: mzzzz__
ImageIO
Available for: macOS Sequoia
Impact: Parsing an image may lead to disclosure of user information
Description: A logic error was addressed with improved error handling.
CVE-2025-24210: Anonymous working with Trend Micro Zero Day Initiative
Installer
Available for: macOS Sequoia
Impact: An app may be able to check the existence of an arbitrary path on the file system
Description: A permissions issue was addressed with additional sandbox restrictions.
CVE-2025-24249: YingQi Shi(@Mas0nShi) of DBAppSecurity's WeBin lab and Minghao Lin (@Y1nKoc)
Installer
Available for: macOS Sequoia
Impact: A sandboxed app may be able to access sensitive user data
Description: A logic issue was addressed with improved checks.
CVE-2025-24229: an anonymous researcher
IOGPUFamily
Available for: macOS Sequoia
Impact: An app may be able to cause unexpected system termination or write kernel memory
Description: An out-of-bounds write issue was addressed with improved input validation.
CVE-2025-24257: Wang Yu of Cyberserval
IOMobileFrameBuffer
Available for: macOS Sequoia
Impact: An app may be able to corrupt coprocessor memory
Description: The issue was addressed with improved bounds checks.
CVE-2025-30437: Ye Zhang (@VAR10CK) of Baidu Security
Kerberos Helper
Available for: macOS Sequoia
Impact: A remote attacker may be able to cause unexpected app termination or heap corruption
Description: A memory initialization issue was addressed with improved memory handling.
CVE-2025-24235: Dave G.
Kernel
Available for: macOS Sequoia
Impact: An app may be able to access protected user data
Description: The issue was addressed with improved checks.
CVE-2025-24204: Koh M. Nakagawa (@tsunek0h) of FFRI Security, Inc.
Kernel
Available for: macOS Sequoia
Impact: An app may be able to modify protected parts of the file system
Description: The issue was addressed with improved checks.
CVE-2025-24203: Ian Beer of Google Project Zero
Kernel
Available for: macOS Sequoia
Impact: An attacker with user privileges may be able to read kernel memory
Description: A type confusion issue was addressed with improved memory handling.
CVE-2025-24196: Joseph Ravichandran (@0xjprx) of MIT CSAIL
LaunchServices
Available for: macOS Sequoia
Impact: A malicious JAR file may bypass Gatekeeper checks
Description: This issue was addressed with improved handling of executable types.
CVE-2025-24148: Kenneth Chew
libarchive
Available for: macOS Sequoia
Impact: An input validation issue was addressed
Description: This is a vulnerability in open source code and Apple Software is among the affected projects. The CVE-ID was assigned by a third party. Learn more about the issue and CVE-ID at cve.org.
CVE-2024-48958
Libinfo
Available for: macOS Sequoia
Impact: A user may be able to elevate privileges
Description: An integer overflow was addressed with improved input validation.
CVE-2025-24195: Paweł Płatek (Trail of Bits)
libnetcore
Available for: macOS Sequoia
Impact: Processing maliciously crafted web content may result in the disclosure of process memory
Description: A logic issue was addressed with improved checks.
CVE-2025-24194: an anonymous researcher
libxml2
Available for: macOS Sequoia
Impact: Parsing a file may lead to an unexpected app termination
Description: This is a vulnerability in open source code and Apple Software is among the affected projects. The CVE-ID was assigned by a third party. Learn more about the issue and CVE-ID at cve.org.
CVE-2025-27113
CVE-2024-56171
libxpc
Available for: macOS Sequoia
Impact: An app may be able to break out of its sandbox
Description: This issue was addressed through improved state management.
CVE-2025-24178: an anonymous researcher
libxpc
Available for: macOS Sequoia
Impact: An app may be able to delete files for which it does not have permission
Description: This issue was addressed with improved handling of symlinks.
CVE-2025-31182: Alex Radocea and Dave G. of Supernetworks, 风沐云烟(@binary_fmyy) and Minghao Lin(@Y1nKoc)
libxpc
Available for: macOS Sequoia
Impact: An app may be able to gain elevated privileges
Description: A logic issue was addressed with improved checks.
CVE-2025-24238: an anonymous researcher
Mail
Available for: macOS Sequoia
Impact: "Block All Remote Content" may not apply for all mail previews
Description: A permissions issue was addressed with additional sandbox restrictions.
CVE-2025-24172: an anonymous researcher
manpages
Available for: macOS Sequoia
Impact: An app may be able to access sensitive user data
Description: This issue was addressed with improved validation of symlinks.
CVE-2025-30450: Pwn2car
Maps
Available for: macOS Sequoia
Impact: An app may be able to read sensitive location information
Description: A path handling issue was addressed with improved logic.
CVE-2025-30470: LFY@secsys from Fudan University
NetworkExtension
Available for: macOS Sequoia
Impact: An app may be able to enumerate a user's installed apps
Description: This issue was addressed with additional entitlement checks.
CVE-2025-30426: Jimmy
Notes
Available for: macOS Sequoia
Impact: A sandboxed app may be able to access sensitive user data in system logs
Description: A privacy issue was addressed with improved private data redaction for log entries.
CVE-2025-24262: LFY@secsys from Fudan University
NSDocument
Available for: macOS Sequoia
Impact: A malicious app may be able to access arbitrary files
Description: This issue was addressed through improved state management.
CVE-2025-24232: an anonymous researcher
OpenSSH
Available for: macOS Sequoia
Impact: An app may be able to access user-sensitive data
Description: An injection issue was addressed with improved validation.
CVE-2025-24246: Mickey Jin (@patch1t)
PackageKit
Available for: macOS Sequoia
Impact: An app may be able to modify protected parts of the file system
Description: The issue was addressed with improved checks.
CVE-2025-24261: Mickey Jin (@patch1t)
PackageKit
Available for: macOS Sequoia
Impact: An app may be able to modify protected parts of the file system
Description: A logic issue was addressed with improved checks.
CVE-2025-24164: Mickey Jin (@patch1t)
PackageKit
Available for: macOS Sequoia
Impact: A malicious app with root privileges may be able to modify the contents of system files
Description: A permissions issue was addressed with additional restrictions.
CVE-2025-30446: Pedro Tôrres (@t0rr3sp3dr0)
Parental Controls
Available for: macOS Sequoia
Impact: An app may be able to retrieve Safari bookmarks without an entitlement check
Description: This issue was addressed with additional entitlement checks.
CVE-2025-24259: Noah Gregory (wts.dev)
Photos Storage
Available for: macOS Sequoia
Impact: Deleting a conversation in Messages may expose user contact information in system logging
Description: A logging issue was addressed with improved data redaction.
CVE-2025-30424: an anonymous researcher
Power Services
Available for: macOS Sequoia
Impact: An app may be able to break out of its sandbox
Description: This issue was addressed with additional entitlement checks.
CVE-2025-24173: Mickey Jin (@patch1t)
Python
Available for: macOS Sequoia
Impact: A remote attacker may be able to bypass sender policy checks and deliver malicious content via email
Description: This is a vulnerability in open source code and Apple Software is among the affected projects. The CVE-ID was assigned by a third party. Learn more about the issue and CVE-ID at cve.org.
CVE-2023-27043
RPAC
Available for: macOS Sequoia
Impact: An app may be able to modify protected parts of the file system
Description: The issue was addressed with improved validation of environment variables.
CVE-2025-24191: Claudio Bozzato and Francesco Benvenuto of Cisco Talos
Safari
Available for: macOS Sequoia
Impact: Visiting a malicious website may lead to user interface spoofing
Description: The issue was addressed with improved UI.
CVE-2025-24113: @RenwaX23
Safari
Available for: macOS Sequoia
Impact: Visiting a malicious website may lead to address bar spoofing
Description: The issue was addressed with improved checks.
CVE-2025-30467: @RenwaX23
Safari
Available for: macOS Sequoia
Impact: A website may be able to access sensor information without user consent
Description: The issue was addressed with improved checks.
CVE-2025-31192: Jaydev Ahire
Safari
Available for: macOS Sequoia
Impact: A download's origin may be incorrectly associated
Description: This issue was addressed through improved state management.
CVE-2025-24167: Syarif Muhammad Sajjad
Sandbox
Available for: macOS Sequoia
Impact: An app may be able to access removable volumes without user consent
Description: A permissions issue was addressed with additional restrictions.
CVE-2025-24093: Yiğit Can YILMAZ (@yilmazcanyigit)
Sandbox
Available for: macOS Sequoia
Impact: An input validation issue was addressed
Description: The issue was addressed with improved checks.
CVE-2025-30452: an anonymous researcher
Sandbox
Available for: macOS Sequoia
Impact: An app may be able to access protected user data
Description: A permissions issue was addressed with additional restrictions.
CVE-2025-24181: Arsenii Kostromin (0x3c3e)
SceneKit
Available for: macOS Sequoia
Impact: An app may be able to read files outside of its sandbox
Description: A permissions issue was addressed with additional restrictions.
CVE-2025-30458: Mickey Jin (@patch1t)
Security
Available for: macOS Sequoia
Impact: A remote user may be able to cause a denial-of-service
Description: A validation issue was addressed with improved logic.
CVE-2025-30471: Bing Shi, Wenchao Li, Xiaolong Bai of Alibaba Group, Luyi Xing of Indiana University Bloomington
Security
Available for: macOS Sequoia
Impact: A malicious app acting as a HTTPS proxy could get access to sensitive user data
Description: This issue was addressed with improved access restrictions.
CVE-2025-24250: Wojciech Regula of SecuRing (wojciechregula.blog)
Share Sheet
Available for: macOS Sequoia
Impact: A malicious app may be able to dismiss the system notification on the Lock Screen that a recording was started
Description: This issue was addressed with improved access restrictions.
CVE-2025-30438: Halle Winkler, Politepix theoffcuts.org
Shortcuts
Available for: macOS Sequoia
Impact: A shortcut may be able to access files that are normally inaccessible to the Shortcuts app
Description: A permissions issue was addressed with improved validation.
CVE-2025-30465: an anonymous researcher
Shortcuts
Available for: macOS Sequoia
Impact: An app may be able to access user-sensitive data
Description: An access issue was addressed with additional sandbox restrictions.
CVE-2025-24280: Kirin (@Pwnrin)
Shortcuts
Available for: macOS Sequoia
Impact: A Shortcut may run with admin privileges without authentication
Description: An authentication issue was addressed with improved state management.
CVE-2025-31194: Dolf Hoegaerts
Shortcuts
Available for: macOS Sequoia
Impact: A shortcut may be able to access files that are normally inaccessible to the Shortcuts app
Description: This issue was addressed with improved access restrictions.
CVE-2025-30433: Andrew James Gonzalez
Siri
Available for: macOS Sequoia
Impact: An app may be able to access sensitive user data
Description: The issue was addressed with improved restriction of data container access.
CVE-2025-31183: Kirin (@Pwnrin), Bohdan Stasiuk (@bohdan_stasiuk)
Siri
Available for: macOS Sequoia
Impact: A sandboxed app may be able to access sensitive user data in system logs
Description: This issue was addressed with improved redaction of sensitive information.
CVE-2025-30435: K宝 (@Pwnrin) and luckyu (@uuulucky)
Siri
Available for: macOS Sequoia
Impact: An app may be able to access sensitive user data
Description: This issue was addressed with improved redaction of sensitive information.
CVE-2025-24217: Kirin (@Pwnrin)
Siri
Available for: macOS Sequoia
Impact: An app may be able to access sensitive user data
Description: A privacy issue was addressed by not logging contents of text fields.
CVE-2025-24214: Kirin (@Pwnrin)
Siri
Available for: macOS Sequoia
Impact: An app may be able to enumerate devices that have signed into the user's Apple Account
Description: A permissions issue was addressed with additional restrictions.
CVE-2025-24248: Minghao Lin (@Y1nKoc) and Tong Liu@Lyutoon_ and 风(binary_fmyy) and F00L
Siri
Available for: macOS Sequoia
Impact: An app may be able to access user-sensitive data
Description: An authorization issue was addressed with improved state management.
CVE-2025-24205: YingQi Shi(@Mas0nShi) of DBAppSecurity's WeBin lab and Minghao Lin (@Y1nKoc)
Siri
Available for: macOS Sequoia
Impact: An attacker with physical access may be able to use Siri to access sensitive user data
Description: This issue was addressed by restricting options offered on a locked device.
CVE-2025-24198: Richard Hyunho Im (@richeeta) with routezero.security
SMB
Available for: macOS Sequoia
Impact: An app may be able to cause unexpected system termination
Description: The issue was addressed with improved memory handling.
CVE-2025-24269: Alex Radocea of Supernetworks
SMB
Available for: macOS Sequoia
Impact: Mounting a maliciously crafted SMB network share may lead to system termination
Description: A race condition was addressed with improved locking.
CVE-2025-30444: Dave G.
SMB
Available for: macOS Sequoia
Impact: An app may be able to execute arbitrary code with kernel privileges
Description: A buffer overflow issue was addressed with improved memory handling.
CVE-2025-24228: Joseph Ravichandran (@0xjprx) of MIT CSAIL
smbx
Available for: macOS Sequoia
Impact: An attacker in a privileged position may be able to perform a denial-of-service
Description: The issue was addressed with improved memory handling.
CVE-2025-24260: zbleet of QI-ANXIN TianGong Team
Software Update
Available for: macOS Sequoia
Impact: An app may be able to modify protected parts of the file system
Description: A library injection issue was addressed with additional restrictions.
CVE-2025-24282: Claudio Bozzato and Francesco Benvenuto of Cisco Talos
Software Update
Available for: macOS Sequoia
Impact: A user may be able to elevate privileges
Description: This issue was addressed with improved validation of symlinks.
CVE-2025-24254: Arsenii Kostromin (0x3c3e)
Software Update
Available for: macOS Sequoia
Impact: An app may be able to modify protected parts of the file system
Description: The issue was addressed with improved checks.
CVE-2025-24231: Claudio Bozzato and Francesco Benvenuto of Cisco Talos
StickerKit
Available for: macOS Sequoia
Impact: An app may be able to observe unprotected user data
Description: A privacy issue was addressed by moving sensitive data to a protected location.
CVE-2025-24263: Cristian Dinca of "Tudor Vianu" National High School of Computer Science, Romania
Storage Management
Available for: macOS Sequoia
Impact: An app may be able to enable iCloud storage features without user consent
Description: A permissions issue was addressed with additional restrictions.
CVE-2025-24207: YingQi Shi (@Mas0nShi) of DBAppSecurity's WeBin lab, 风沐云烟 (binary_fmyy) and Minghao Lin (@Y1nKoc)
StorageKit
Available for: macOS Sequoia
Impact: An app may be able to gain root privileges
Description: A permissions issue was addressed with additional restrictions.
CVE-2025-30449: Arsenii Kostromin (0x3c3e), and an anonymous researcher
StorageKit
Available for: macOS Sequoia
Impact: An app may be able to access protected user data
Description: This issue was addressed with improved handling of symlinks.
CVE-2025-24253: Mickey Jin (@patch1t), Csaba Fitzl (@theevilbit) of Kandji
StorageKit
Available for: macOS Sequoia
Impact: An app may be able to access user-sensitive data
Description: A race condition was addressed with additional validation.
CVE-2025-24240: Mickey Jin (@patch1t)
StorageKit
Available for: macOS Sequoia
Impact: An app may be able to bypass Privacy preferences
Description: A race condition was addressed with additional validation.
CVE-2025-31188: Mickey Jin (@patch1t)
Summarization Services
Available for: macOS Sequoia
Impact: An app may be able to access information about a user's contacts
Description: A privacy issue was addressed with improved private data redaction for log entries.
CVE-2025-24218: Kirin and FlowerCode, Bohdan Stasiuk (@bohdan_stasiuk)
System Settings
Available for: macOS Sequoia
Impact: An app may be able to access protected user data
Description: This issue was addressed with improved validation of symlinks.
CVE-2025-24278: Zhongquan Li (@Guluisacat)
System Settings
Available for: macOS Sequoia
Impact: An app with root privileges may be able to access private information
Description: This issue was addressed with improved handling of symlinks.
CVE-2025-24242: Koh M. Nakagawa (@tsunek0h) of FFRI Security, Inc.
SystemMigration
Available for: macOS Sequoia
Impact: A malicious app may be able to create symlinks to protected regions of the disk
Description: This issue was addressed with improved validation of symlinks.
CVE-2025-30457: Mickey Jin (@patch1t)
Voice Control
Available for: macOS Sequoia
Impact: An app may be able to access contacts
Description: This issue was addressed with improved file handling.
CVE-2025-24279: Mickey Jin (@patch1t)
Web Extensions
Available for: macOS Sequoia
Impact: An app may gain unauthorized access to Local Network
Description: This issue was addressed with improved permissions checking.
CVE-2025-31184: Alexander Heinrich (@Sn0wfreeze), SEEMOO, TU Darmstadt & Mathy Vanhoef (@vanhoefm) and Jeroen Robben (@RobbenJeroen), DistriNet, KU Leuven
Web Extensions
Available for: macOS Sequoia
Impact: Visiting a website may leak sensitive data
Description: A script imports issue was addressed with improved isolation.
CVE-2025-24192: Vsevolod Kokorin (Slonser) of Solidlab
WebKit
Available for: macOS Sequoia
Impact: Processing maliciously crafted web content may lead to an unexpected Safari crash
Description: The issue was addressed with improved memory handling.
WebKit Bugzilla: 285892
CVE-2025-24264: Gary Kwong, and an anonymous researcher
WebKit Bugzilla: 284055
CVE-2025-24216: Paul Bakker of ParagonERP
WebKit
Available for: macOS Sequoia
Impact: A type confusion issue could lead to memory corruption
Description: This issue was addressed with improved handling of floats.
WebKit Bugzilla: 286694
CVE-2025-24213: Google V8 Security Team
WebKit
Available for: macOS Sequoia
Impact: Processing maliciously crafted web content may lead to an unexpected process crash
Description: A buffer overflow issue was addressed with improved memory handling.
WebKit Bugzilla: 286462
CVE-2025-24209: Francisco Alonso (@revskills), and an anonymous researcher
WebKit
Available for: macOS Sequoia
Impact: Processing maliciously crafted web content may lead to an unexpected Safari crash
Description: A use-after-free issue was addressed with improved memory management.
WebKit Bugzilla: 285643
CVE-2025-30427: rheza (@ginggilBesel)
WebKit
Available for: macOS Sequoia
Impact: A malicious website may be able to track users in Safari private browsing mode
Description: This issue was addressed through improved state management.
WebKit Bugzilla: 286580
CVE-2025-30425: an anonymous researcher
WindowServer
Available for: macOS Sequoia
Impact: An attacker may be able to cause unexpected app termination
Description: A type confusion issue was addressed with improved checks.
CVE-2025-24247: PixiePoint Security
WindowServer
Available for: macOS Sequoia
Impact: An app may be able to trick a user into copying sensitive data to the pasteboard
Description: A configuration issue was addressed with additional restrictions.
CVE-2025-24241: Andreas Hegenberg (folivora.AI GmbH)
Xsan
Available for: macOS Sequoia
Impact: An app may be able to cause unexpected system termination
Description: A buffer overflow was addressed with improved bounds checking.
CVE-2025-24266: an anonymous researcher
Xsan
Available for: macOS Sequoia
Impact: An app may be able to cause unexpected system termination
Description: An out-of-bounds read was addressed with improved bounds checking.
CVE-2025-24265: an anonymous researcher
Xsan
Available for: macOS Sequoia
Impact: An app may be able to cause unexpected system termination or corrupt kernel memory
Description: A buffer overflow issue was addressed with improved memory handling.
CVE-2025-24157: an anonymous researcher
-

@ 06639a38:655f8f71
2025-04-02 13:47:57
You can follow the work in progress here in this pull request [https://github.com/nostrver-se/nostr-php/pull/68](https://github.com/nostrver-se/nostr-php/pull/68) on Github.
Before my 3-month break (Dec/Jan/Feb) working on Nostr-PHP I started with the NIP-19 integration in October '24. Encoding and decoding the simple prefixes (`npub`, `nsec` and `note`) was already done in the first commits.
Learn more about NIP-19 here: [https://nips.nostr.com/19](https://nips.nostr.com/19)
### **TLV's**
Things were getting more complicated with the other prefixes / identifiers defined in NIP-19:
* `nevent`
* `naddr`
* `nprofile`
This is because these identifiers contain (optional) metadata called Type-Lenght-Value aka TLV's.
_When sharing a profile or an event, an app may decide to include relay information and other metadata such that other apps can locate and display these entities more easily._
_For these events, the contents are a binary-encoded list of_ `_TLV_` _(type-length-value), with_ `_T_` _and_ `_L_` _being 1 byte each (_`_uint8_`_, i.e. a number in the range of 0-255), and_ `_V_` _being a sequence of bytes of the size indicated by_ `_L_`_._
These possible standardized `TLV` types are:
* `0`_:_ `special`
* _depends on the bech32 prefix:_
* _for_ `nprofile` _it will be the 32 bytes of the profile public key_
* _for_ `nevent` _it will be the 32 bytes of the event id_
* _for_ `naddr`_, it is the identifier (the_ `"d"` _tag) of the event being referenced. For normal replaceable events use an empty string._
* `1`_:_ `relay`
* _for_ `nprofile`_,_ `nevent` _and_ `naddr`_, optionally, a relay in which the entity (profile or event) is more likely to be found, encoded as ascii_
* _this may be included multiple times_
* `2`_:_ `author`
* _for_ `naddr`_, the 32 bytes of the pubkey of the event_
* _for_ `nevent`_, optionally, the 32 bytes of the pubkey of the event_
* `3`_:_ `kind`
* _for_ `naddr`_, the 32-bit unsigned integer of the kind, big-endian_
* _for_ `nevent`_, optionally, the 32-bit unsigned integer of the kind, big-endian_
These identifiers are formatted as bech32 strings, but are much longer than the package `bitwasp/bech32` (used in the library) for can handle for encoding and decoding. The bech32 strings handled by `bitwasp/bech32` are limited to a maximum length of 90 characters.
Thanks to the effort of others (nostr:npub1636uujeewag8zv8593lcvdrwlymgqre6uax4anuq3y5qehqey05sl8qpl4 and nostr:npub1efz8l77esdtpw6l359sjvakm7azvyv6mkuxphjdk3vfzkgxkatrqlpf9s4) during my break, some contributions are made (modifiying the bech32 package supporting much longer strings, up to a max of 5000 characters). At this moment, I'm integrating this (mostly copy-pasting the stuff and refactoring the code):
* [https://github.com/nostrver-se/nostr-php/issues/74](https://github.com/nostrver-se/nostr-php/issues/74)
* [https://github.com/nostriphant/nip-19](https://github.com/nostriphant/nip-19)
### **So what's next?**
* NIP-19 code housekeeping + refactoring
* Prepare a new release with NIP-19 integration
* Create documentation page how to use NIP-19 on [https://nostr-php.dev](https://nostr-php.dev)
-

@ 9dd283b1:cf9b6beb
2025-03-31 13:21:08
Do you still feel anxiety when Bitcoin's price drops significantly, even though you're in fiat profit (100% +) ? Why or why not? And when did you truly stop feeling any emotional attachment to the price fluctuations?
originally posted at https://stacker.news/items/930139
-

@ 57d1a264:69f1fee1
2025-03-16 14:17:25
Recently we shared an update for a new Open Cash Foundation website https://stacker.news/items/811604/r/Design_r Today a new logo by Vladimir Krstić!




File available for review at https://www.figma.com/design/Yxb4JEsjHYSibY06T8piB7/OpenCash%3A-Logo?node-id=151-249&p=f&t=FYyeTBkJznCKdbd7-0
https://primal.net/e/nevent1qvzqqqqqqypzqhzsmgfjj3l68068t84e0rtcfkcjh2k3c0jmdft4gy9wke2x8x6tqyg8wumn8ghj7efwdehhxtnvdakz7qgkwaehxw309ajkgetw9ehx7um5wghxcctwvshszrnhwden5te0dehhxtnvdakz7qpqryz9rj0wgshykjuzqksxxs50l7jfnwyvtkfmdvmudrg92s3xuxys8fqzr7
originally posted at https://stacker.news/items/914665
 @ 04c915da:3dfbecc9
2025-03-26 20:54:33Capitalism is the most effective system for scaling innovation. The pursuit of profit is an incredibly powerful human incentive. Most major improvements to human society and quality of life have resulted from this base incentive. Market competition often results in the best outcomes for all. That said, some projects can never be monetized. They are open in nature and a business model would centralize control. Open protocols like bitcoin and nostr are not owned by anyone and if they were it would destroy the key value propositions they provide. No single entity can or should control their use. Anyone can build on them without permission. As a result, open protocols must depend on donation based grant funding from the people and organizations that rely on them. This model works but it is slow and uncertain, a grind where sustainability is never fully reached but rather constantly sought. As someone who has been incredibly active in the open source grant funding space, I do not think people truly appreciate how difficult it is to raise charitable money and deploy it efficiently. Projects that can be monetized should be. Profitability is a super power. When a business can generate revenue, it taps into a self sustaining cycle. Profit fuels growth and development while providing projects independence and agency. This flywheel effect is why companies like Google, Amazon, and Apple have scaled to global dominance. The profit incentive aligns human effort with efficiency. Businesses must innovate, cut waste, and deliver value to survive. Contrast this with non monetized projects. Without profit, they lean on external support, which can dry up or shift with donor priorities. A profit driven model, on the other hand, is inherently leaner and more adaptable. It is not charity but survival. When survival is tied to delivering what people want, scale follows naturally. The real magic happens when profitable, sustainable businesses are built on top of open protocols and software. Consider the many startups building on open source software stacks, such as Start9, Mempool, and Primal, offering premium services on top of the open source software they build out and maintain. Think of companies like Block or Strike, which leverage bitcoin’s open protocol to offer their services on top. These businesses amplify the open software and protocols they build on, driving adoption and improvement at a pace donations alone could never match. When you combine open software and protocols with profit driven business the result are lean, sustainable companies that grow faster and serve more people than either could alone. Bitcoin’s network, for instance, benefits from businesses that profit off its existence, while nostr will expand as developers monetize apps built on the protocol. Capitalism scales best because competition results in efficiency. Donation funded protocols and software lay the groundwork, while market driven businesses build on top. The profit incentive acts as a filter, ensuring resources flow to what works, while open systems keep the playing field accessible, empowering users and builders. Together, they create a flywheel of innovation, growth, and global benefit.
@ 04c915da:3dfbecc9
2025-03-26 20:54:33Capitalism is the most effective system for scaling innovation. The pursuit of profit is an incredibly powerful human incentive. Most major improvements to human society and quality of life have resulted from this base incentive. Market competition often results in the best outcomes for all. That said, some projects can never be monetized. They are open in nature and a business model would centralize control. Open protocols like bitcoin and nostr are not owned by anyone and if they were it would destroy the key value propositions they provide. No single entity can or should control their use. Anyone can build on them without permission. As a result, open protocols must depend on donation based grant funding from the people and organizations that rely on them. This model works but it is slow and uncertain, a grind where sustainability is never fully reached but rather constantly sought. As someone who has been incredibly active in the open source grant funding space, I do not think people truly appreciate how difficult it is to raise charitable money and deploy it efficiently. Projects that can be monetized should be. Profitability is a super power. When a business can generate revenue, it taps into a self sustaining cycle. Profit fuels growth and development while providing projects independence and agency. This flywheel effect is why companies like Google, Amazon, and Apple have scaled to global dominance. The profit incentive aligns human effort with efficiency. Businesses must innovate, cut waste, and deliver value to survive. Contrast this with non monetized projects. Without profit, they lean on external support, which can dry up or shift with donor priorities. A profit driven model, on the other hand, is inherently leaner and more adaptable. It is not charity but survival. When survival is tied to delivering what people want, scale follows naturally. The real magic happens when profitable, sustainable businesses are built on top of open protocols and software. Consider the many startups building on open source software stacks, such as Start9, Mempool, and Primal, offering premium services on top of the open source software they build out and maintain. Think of companies like Block or Strike, which leverage bitcoin’s open protocol to offer their services on top. These businesses amplify the open software and protocols they build on, driving adoption and improvement at a pace donations alone could never match. When you combine open software and protocols with profit driven business the result are lean, sustainable companies that grow faster and serve more people than either could alone. Bitcoin’s network, for instance, benefits from businesses that profit off its existence, while nostr will expand as developers monetize apps built on the protocol. Capitalism scales best because competition results in efficiency. Donation funded protocols and software lay the groundwork, while market driven businesses build on top. The profit incentive acts as a filter, ensuring resources flow to what works, while open systems keep the playing field accessible, empowering users and builders. Together, they create a flywheel of innovation, growth, and global benefit. @ 21335073:a244b1ad
2025-03-15 23:00:40I want to see Nostr succeed. If you can think of a way I can help make that happen, I’m open to it. I’d like your suggestions. My schedule’s shifting soon, and I could volunteer a few hours a week to a Nostr project. I won’t have more total time, but how I use it will change. Why help? I care about freedom. Nostr’s one of the most powerful freedom tools I’ve seen in my lifetime. If I believe that, I should act on it. I don’t care about money or sats. I’m not rich, I don’t have extra cash. That doesn’t drive me—freedom does. I’m volunteering, not asking for pay. I’m not here for clout. I’ve had enough spotlight in my life; it doesn’t move me. If I wanted clout, I’d be on Twitter dropping basic takes. Clout’s easy. Freedom’s hard. I’d rather help anonymously. No speaking at events—small meetups are cool for the vibe, but big conferences? Not my thing. I’ll never hit a huge Bitcoin conference. It’s just not my scene. That said, I could be convinced to step up if it’d really boost Nostr—as long as it’s legal and gets results. In this space, I’d watch for social engineering. I watch out for it. I’m not here to make friends, just to help. No shade—you all seem great—but I’ve got a full life and awesome friends irl. I don’t need your crew or to be online cool. Connect anonymously if you want; I’d encourage it. I’m sick of watching other social media alternatives grow while Nostr kinda stalls. I could trash-talk, but I’d rather do something useful. Skills? I’m good at spotting social media problems and finding possible solutions. I won’t overhype myself—that’s weird—but if you’re responding, you probably see something in me. Perhaps you see something that I don’t see in myself. If you need help now or later with Nostr projects, reach out. Nostr only—nothing else. Anonymous contact’s fine. Even just a suggestion on how I can pitch in, no project attached, works too. 💜 Creeps or harassment will get blocked or I’ll nuke my simplex code if it becomes a problem. https://simplex.chat/contact#/?v=2-4&smp=smp%3A%2F%2FSkIkI6EPd2D63F4xFKfHk7I1UGZVNn6k1QWZ5rcyr6w%3D%40smp9.simplex.im%2FbI99B3KuYduH8jDr9ZwyhcSxm2UuR7j0%23%2F%3Fv%3D1-2%26dh%3DMCowBQYDK2VuAyEAS9C-zPzqW41PKySfPCEizcXb1QCus6AyDkTTjfyMIRM%253D%26srv%3Djssqzccmrcws6bhmn77vgmhfjmhwlyr3u7puw4erkyoosywgl67slqqd.onion
@ 21335073:a244b1ad
2025-03-15 23:00:40I want to see Nostr succeed. If you can think of a way I can help make that happen, I’m open to it. I’d like your suggestions. My schedule’s shifting soon, and I could volunteer a few hours a week to a Nostr project. I won’t have more total time, but how I use it will change. Why help? I care about freedom. Nostr’s one of the most powerful freedom tools I’ve seen in my lifetime. If I believe that, I should act on it. I don’t care about money or sats. I’m not rich, I don’t have extra cash. That doesn’t drive me—freedom does. I’m volunteering, not asking for pay. I’m not here for clout. I’ve had enough spotlight in my life; it doesn’t move me. If I wanted clout, I’d be on Twitter dropping basic takes. Clout’s easy. Freedom’s hard. I’d rather help anonymously. No speaking at events—small meetups are cool for the vibe, but big conferences? Not my thing. I’ll never hit a huge Bitcoin conference. It’s just not my scene. That said, I could be convinced to step up if it’d really boost Nostr—as long as it’s legal and gets results. In this space, I’d watch for social engineering. I watch out for it. I’m not here to make friends, just to help. No shade—you all seem great—but I’ve got a full life and awesome friends irl. I don’t need your crew or to be online cool. Connect anonymously if you want; I’d encourage it. I’m sick of watching other social media alternatives grow while Nostr kinda stalls. I could trash-talk, but I’d rather do something useful. Skills? I’m good at spotting social media problems and finding possible solutions. I won’t overhype myself—that’s weird—but if you’re responding, you probably see something in me. Perhaps you see something that I don’t see in myself. If you need help now or later with Nostr projects, reach out. Nostr only—nothing else. Anonymous contact’s fine. Even just a suggestion on how I can pitch in, no project attached, works too. 💜 Creeps or harassment will get blocked or I’ll nuke my simplex code if it becomes a problem. https://simplex.chat/contact#/?v=2-4&smp=smp%3A%2F%2FSkIkI6EPd2D63F4xFKfHk7I1UGZVNn6k1QWZ5rcyr6w%3D%40smp9.simplex.im%2FbI99B3KuYduH8jDr9ZwyhcSxm2UuR7j0%23%2F%3Fv%3D1-2%26dh%3DMCowBQYDK2VuAyEAS9C-zPzqW41PKySfPCEizcXb1QCus6AyDkTTjfyMIRM%253D%26srv%3Djssqzccmrcws6bhmn77vgmhfjmhwlyr3u7puw4erkyoosywgl67slqqd.onion @ 04c915da:3dfbecc9
2025-03-10 23:31:30Bitcoin has always been rooted in freedom and resistance to authority. I get that many of you are conflicted about the US Government stacking but by design we cannot stop anyone from using bitcoin. Many have asked me for my thoughts on the matter, so let’s rip it. **Concern** One of the most glaring issues with the strategic bitcoin reserve is its foundation, built on stolen bitcoin. For those of us who value private property this is an obvious betrayal of our core principles. Rather than proof of work, the bitcoin that seeds this reserve has been taken by force. The US Government should return the bitcoin stolen from Bitfinex and the Silk Road. Usually stolen bitcoin for the reserve creates a perverse incentive. If governments see a bitcoin as a valuable asset, they will ramp up efforts to confiscate more bitcoin. The precedent is a major concern, and I stand strongly against it, but it should be also noted that governments were already seizing coin before the reserve so this is not really a change in policy. Ideally all seized bitcoin should be burned, by law. This would align incentives properly and make it less likely for the government to actively increase coin seizures. Due to the truly scarce properties of bitcoin, all burned bitcoin helps existing holders through increased purchasing power regardless. This change would be unlikely but those of us in policy circles should push for it regardless. It would be best case scenario for American bitcoiners and would create a strong foundation for the next century of American leadership. **Optimism** The entire point of bitcoin is that we can spend or save it without permission. That said, it is a massive benefit to not have one of the strongest governments in human history actively trying to ruin our lives. Since the beginning, bitcoiners have faced horrible regulatory trends. KYC, surveillance, and legal cases have made using bitcoin and building bitcoin businesses incredibly difficult. It is incredibly important to note that over the past year that trend has reversed for the first time in a decade. A strategic bitcoin reserve is a key driver of this shift. By holding bitcoin, the strongest government in the world has signaled that it is not just a fringe technology but rather truly valuable, legitimate, and worth stacking. This alignment of incentives changes everything. The US Government stacking proves bitcoin’s worth. The resulting purchasing power appreciation helps all of us who are holding coin and as bitcoin succeeds our government receives direct benefit. A beautiful positive feedback loop. **Realism** We are trending in the right direction. A strategic bitcoin reserve is a sign that the state sees bitcoin as an asset worth embracing rather than destroying. That said, there is a lot of work left to be done. We cannot be lulled into complacency, the time to push forward is now, and we cannot take our foot off the gas. We have a seat at the table for the first time ever. Let's make it worth it. We must protect the right to free usage of bitcoin and other digital technologies. Freedom in the digital age must be taken and defended, through both technical and political avenues. Multiple privacy focused developers are facing long jail sentences for building tools that protect our freedom. These cases are not just legal battles. They are attacks on the soul of bitcoin. We need to rally behind them, fight for their freedom, and ensure the ethos of bitcoin survives this new era of government interest. The strategic reserve is a step in the right direction, but it is up to us to hold the line and shape the future.
@ 04c915da:3dfbecc9
2025-03-10 23:31:30Bitcoin has always been rooted in freedom and resistance to authority. I get that many of you are conflicted about the US Government stacking but by design we cannot stop anyone from using bitcoin. Many have asked me for my thoughts on the matter, so let’s rip it. **Concern** One of the most glaring issues with the strategic bitcoin reserve is its foundation, built on stolen bitcoin. For those of us who value private property this is an obvious betrayal of our core principles. Rather than proof of work, the bitcoin that seeds this reserve has been taken by force. The US Government should return the bitcoin stolen from Bitfinex and the Silk Road. Usually stolen bitcoin for the reserve creates a perverse incentive. If governments see a bitcoin as a valuable asset, they will ramp up efforts to confiscate more bitcoin. The precedent is a major concern, and I stand strongly against it, but it should be also noted that governments were already seizing coin before the reserve so this is not really a change in policy. Ideally all seized bitcoin should be burned, by law. This would align incentives properly and make it less likely for the government to actively increase coin seizures. Due to the truly scarce properties of bitcoin, all burned bitcoin helps existing holders through increased purchasing power regardless. This change would be unlikely but those of us in policy circles should push for it regardless. It would be best case scenario for American bitcoiners and would create a strong foundation for the next century of American leadership. **Optimism** The entire point of bitcoin is that we can spend or save it without permission. That said, it is a massive benefit to not have one of the strongest governments in human history actively trying to ruin our lives. Since the beginning, bitcoiners have faced horrible regulatory trends. KYC, surveillance, and legal cases have made using bitcoin and building bitcoin businesses incredibly difficult. It is incredibly important to note that over the past year that trend has reversed for the first time in a decade. A strategic bitcoin reserve is a key driver of this shift. By holding bitcoin, the strongest government in the world has signaled that it is not just a fringe technology but rather truly valuable, legitimate, and worth stacking. This alignment of incentives changes everything. The US Government stacking proves bitcoin’s worth. The resulting purchasing power appreciation helps all of us who are holding coin and as bitcoin succeeds our government receives direct benefit. A beautiful positive feedback loop. **Realism** We are trending in the right direction. A strategic bitcoin reserve is a sign that the state sees bitcoin as an asset worth embracing rather than destroying. That said, there is a lot of work left to be done. We cannot be lulled into complacency, the time to push forward is now, and we cannot take our foot off the gas. We have a seat at the table for the first time ever. Let's make it worth it. We must protect the right to free usage of bitcoin and other digital technologies. Freedom in the digital age must be taken and defended, through both technical and political avenues. Multiple privacy focused developers are facing long jail sentences for building tools that protect our freedom. These cases are not just legal battles. They are attacks on the soul of bitcoin. We need to rally behind them, fight for their freedom, and ensure the ethos of bitcoin survives this new era of government interest. The strategic reserve is a step in the right direction, but it is up to us to hold the line and shape the future. @ 04c915da:3dfbecc9
2025-03-07 00:26:37There is something quietly rebellious about stacking sats. In a world obsessed with instant gratification, choosing to patiently accumulate Bitcoin, one sat at a time, feels like a middle finger to the hype machine. But to do it right, you have got to stay humble. Stack too hard with your head in the clouds, and you will trip over your own ego before the next halving even hits. **Small Wins** Stacking sats is not glamorous. Discipline. Stacking every day, week, or month, no matter the price, and letting time do the heavy lifting. Humility lives in that consistency. You are not trying to outsmart the market or prove you are the next "crypto" prophet. Just a regular person, betting on a system you believe in, one humble stack at a time. Folks get rekt chasing the highs. They ape into some shitcoin pump, shout about it online, then go silent when they inevitably get rekt. The ones who last? They stack. Just keep showing up. Consistency. Humility in action. Know the game is long, and you are not bigger than it. **Ego is Volatile** Bitcoin’s swings can mess with your head. One day you are up 20%, feeling like a genius and the next down 30%, questioning everything. Ego will have you panic selling at the bottom or over leveraging the top. Staying humble means patience, a true bitcoin zen. Do not try to "beat” Bitcoin. Ride it. Stack what you can afford, live your life, and let compounding work its magic. **Simplicity** There is a beauty in how stacking sats forces you to rethink value. A sat is worth less than a penny today, but every time you grab a few thousand, you plant a seed. It is not about flaunting wealth but rather building it, quietly, without fanfare. That mindset spills over. Cut out the noise: the overpriced coffee, fancy watches, the status games that drain your wallet. Humility is good for your soul and your stack. I have a buddy who has been stacking since 2015. Never talks about it unless you ask. Lives in a decent place, drives an old truck, and just keeps stacking. He is not chasing clout, he is chasing freedom. That is the vibe: less ego, more sats, all grounded in life. **The Big Picture** Stack those sats. Do it quietly, do it consistently, and do not let the green days puff you up or the red days break you down. Humility is the secret sauce, it keeps you grounded while the world spins wild. In a decade, when you look back and smile, it will not be because you shouted the loudest. It will be because you stayed the course, one sat at a time. \ \ Stay Humble and Stack Sats. 🫡
@ 04c915da:3dfbecc9
2025-03-07 00:26:37There is something quietly rebellious about stacking sats. In a world obsessed with instant gratification, choosing to patiently accumulate Bitcoin, one sat at a time, feels like a middle finger to the hype machine. But to do it right, you have got to stay humble. Stack too hard with your head in the clouds, and you will trip over your own ego before the next halving even hits. **Small Wins** Stacking sats is not glamorous. Discipline. Stacking every day, week, or month, no matter the price, and letting time do the heavy lifting. Humility lives in that consistency. You are not trying to outsmart the market or prove you are the next "crypto" prophet. Just a regular person, betting on a system you believe in, one humble stack at a time. Folks get rekt chasing the highs. They ape into some shitcoin pump, shout about it online, then go silent when they inevitably get rekt. The ones who last? They stack. Just keep showing up. Consistency. Humility in action. Know the game is long, and you are not bigger than it. **Ego is Volatile** Bitcoin’s swings can mess with your head. One day you are up 20%, feeling like a genius and the next down 30%, questioning everything. Ego will have you panic selling at the bottom or over leveraging the top. Staying humble means patience, a true bitcoin zen. Do not try to "beat” Bitcoin. Ride it. Stack what you can afford, live your life, and let compounding work its magic. **Simplicity** There is a beauty in how stacking sats forces you to rethink value. A sat is worth less than a penny today, but every time you grab a few thousand, you plant a seed. It is not about flaunting wealth but rather building it, quietly, without fanfare. That mindset spills over. Cut out the noise: the overpriced coffee, fancy watches, the status games that drain your wallet. Humility is good for your soul and your stack. I have a buddy who has been stacking since 2015. Never talks about it unless you ask. Lives in a decent place, drives an old truck, and just keeps stacking. He is not chasing clout, he is chasing freedom. That is the vibe: less ego, more sats, all grounded in life. **The Big Picture** Stack those sats. Do it quietly, do it consistently, and do not let the green days puff you up or the red days break you down. Humility is the secret sauce, it keeps you grounded while the world spins wild. In a decade, when you look back and smile, it will not be because you shouted the loudest. It will be because you stayed the course, one sat at a time. \ \ Stay Humble and Stack Sats. 🫡 @ 04c915da:3dfbecc9
2025-03-04 17:00:18This piece is the first in a series that will focus on things I think are a priority if your focus is similar to mine: building a strong family and safeguarding their future. --- Choosing the ideal place to raise a family is one of the most significant decisions you will ever make. For simplicity sake I will break down my thought process into key factors: strong property rights, the ability to grow your own food, access to fresh water, the freedom to own and train with guns, and a dependable community. **A Jurisdiction with Strong Property Rights** Strong property rights are essential and allow you to build on a solid foundation that is less likely to break underneath you. Regions with a history of limited government and clear legal protections for landowners are ideal. Personally I think the US is the single best option globally, but within the US there is a wide difference between which state you choose. Choose carefully and thoughtfully, think long term. Obviously if you are not American this is not a realistic option for you, there are other solid options available especially if your family has mobility. I understand many do not have this capability to easily move, consider that your first priority, making movement and jurisdiction choice possible in the first place. **Abundant Access to Fresh Water** Water is life. I cannot overstate the importance of living somewhere with reliable, clean, and abundant freshwater. Some regions face water scarcity or heavy regulations on usage, so prioritizing a place where water is plentiful and your rights to it are protected is critical. Ideally you should have well access so you are not tied to municipal water supplies. In times of crisis or chaos well water cannot be easily shutoff or disrupted. If you live in an area that is drought prone, you are one drought away from societal chaos. Not enough people appreciate this simple fact. **Grow Your Own Food** A location with fertile soil, a favorable climate, and enough space for a small homestead or at the very least a garden is key. In stable times, a small homestead provides good food and important education for your family. In times of chaos your family being able to grow and raise healthy food provides a level of self sufficiency that many others will lack. Look for areas with minimal restrictions, good weather, and a culture that supports local farming. **Guns** The ability to defend your family is fundamental. A location where you can legally and easily own guns is a must. Look for places with a strong gun culture and a political history of protecting those rights. Owning one or two guns is not enough and without proper training they will be a liability rather than a benefit. Get comfortable and proficient. Never stop improving your skills. If the time comes that you must use a gun to defend your family, the skills must be instinct. Practice. Practice. Practice. **A Strong Community You Can Depend On** No one thrives alone. A ride or die community that rallies together in tough times is invaluable. Seek out a place where people know their neighbors, share similar values, and are quick to lend a hand. Lead by example and become a good neighbor, people will naturally respond in kind. Small towns are ideal, if possible, but living outside of a major city can be a solid balance in terms of work opportunities and family security. --- Let me know if you found this helpful. My plan is to break down how I think about these five key subjects in future posts.
@ 04c915da:3dfbecc9
2025-03-04 17:00:18This piece is the first in a series that will focus on things I think are a priority if your focus is similar to mine: building a strong family and safeguarding their future. --- Choosing the ideal place to raise a family is one of the most significant decisions you will ever make. For simplicity sake I will break down my thought process into key factors: strong property rights, the ability to grow your own food, access to fresh water, the freedom to own and train with guns, and a dependable community. **A Jurisdiction with Strong Property Rights** Strong property rights are essential and allow you to build on a solid foundation that is less likely to break underneath you. Regions with a history of limited government and clear legal protections for landowners are ideal. Personally I think the US is the single best option globally, but within the US there is a wide difference between which state you choose. Choose carefully and thoughtfully, think long term. Obviously if you are not American this is not a realistic option for you, there are other solid options available especially if your family has mobility. I understand many do not have this capability to easily move, consider that your first priority, making movement and jurisdiction choice possible in the first place. **Abundant Access to Fresh Water** Water is life. I cannot overstate the importance of living somewhere with reliable, clean, and abundant freshwater. Some regions face water scarcity or heavy regulations on usage, so prioritizing a place where water is plentiful and your rights to it are protected is critical. Ideally you should have well access so you are not tied to municipal water supplies. In times of crisis or chaos well water cannot be easily shutoff or disrupted. If you live in an area that is drought prone, you are one drought away from societal chaos. Not enough people appreciate this simple fact. **Grow Your Own Food** A location with fertile soil, a favorable climate, and enough space for a small homestead or at the very least a garden is key. In stable times, a small homestead provides good food and important education for your family. In times of chaos your family being able to grow and raise healthy food provides a level of self sufficiency that many others will lack. Look for areas with minimal restrictions, good weather, and a culture that supports local farming. **Guns** The ability to defend your family is fundamental. A location where you can legally and easily own guns is a must. Look for places with a strong gun culture and a political history of protecting those rights. Owning one or two guns is not enough and without proper training they will be a liability rather than a benefit. Get comfortable and proficient. Never stop improving your skills. If the time comes that you must use a gun to defend your family, the skills must be instinct. Practice. Practice. Practice. **A Strong Community You Can Depend On** No one thrives alone. A ride or die community that rallies together in tough times is invaluable. Seek out a place where people know their neighbors, share similar values, and are quick to lend a hand. Lead by example and become a good neighbor, people will naturally respond in kind. Small towns are ideal, if possible, but living outside of a major city can be a solid balance in terms of work opportunities and family security. --- Let me know if you found this helpful. My plan is to break down how I think about these five key subjects in future posts. @ 04c915da:3dfbecc9
2025-02-25 03:55:08Here’s a revised timeline of macro-level events from *The Mandibles: A Family, 2029–2047* by Lionel Shriver, reimagined in a world where Bitcoin is adopted as a widely accepted form of money, altering the original narrative’s assumptions about currency collapse and economic control. In Shriver’s original story, the failure of Bitcoin is assumed amid the dominance of the bancor and the dollar’s collapse. Here, Bitcoin’s success reshapes the economic and societal trajectory, decentralizing power and challenging state-driven outcomes. ### Part One: 2029–2032 - **2029 (Early Year)**\ The United States faces economic strain as the dollar weakens against global shifts. However, Bitcoin, having gained traction emerges as a viable alternative. Unlike the original timeline, the bancor—a supranational currency backed by a coalition of nations—struggles to gain footing as Bitcoin’s decentralized adoption grows among individuals and businesses worldwide, undermining both the dollar and the bancor. - **2029 (Mid-Year: The Great Renunciation)**\ Treasury bonds lose value, and the government bans Bitcoin, labeling it a threat to sovereignty (mirroring the original bancor ban). However, a Bitcoin ban proves unenforceable—its decentralized nature thwarts confiscation efforts, unlike gold in the original story. Hyperinflation hits the dollar as the U.S. prints money, but Bitcoin’s fixed supply shields adopters from currency devaluation, creating a dual-economy split: dollar users suffer, while Bitcoin users thrive. - **2029 (Late Year)**\ Dollar-based inflation soars, emptying stores of goods priced in fiat currency. Meanwhile, Bitcoin transactions flourish in underground and online markets, stabilizing trade for those plugged into the bitcoin ecosystem. Traditional supply chains falter, but peer-to-peer Bitcoin networks enable local and international exchange, reducing scarcity for early adopters. The government’s gold confiscation fails to bolster the dollar, as Bitcoin’s rise renders gold less relevant. - **2030–2031**\ Crime spikes in dollar-dependent urban areas, but Bitcoin-friendly regions see less chaos, as digital wallets and smart contracts facilitate secure trade. The U.S. government doubles down on surveillance to crack down on bitcoin use. A cultural divide deepens: centralized authority weakens in Bitcoin-adopting communities, while dollar zones descend into lawlessness. - **2032**\ By this point, Bitcoin is de facto legal tender in parts of the U.S. and globally, especially in tech-savvy or libertarian-leaning regions. The federal government’s grip slips as tax collection in dollars plummets—Bitcoin’s traceability is low, and citizens evade fiat-based levies. Rural and urban Bitcoin hubs emerge, while the dollar economy remains fractured. ### Time Jump: 2032–2047 - Over 15 years, Bitcoin solidifies as a global reserve currency, eroding centralized control. The U.S. government adapts, grudgingly integrating bitcoin into policy, though regional autonomy grows as Bitcoin empowers local economies. ### Part Two: 2047 - **2047 (Early Year)**\ The U.S. is a hybrid state: Bitcoin is legal tender alongside a diminished dollar. Taxes are lower, collected in BTC, reducing federal overreach. Bitcoin’s adoption has decentralized power nationwide. The bancor has faded, unable to compete with Bitcoin’s grassroots momentum. - **2047 (Mid-Year)**\ Travel and trade flow freely in Bitcoin zones, with no restrictive checkpoints. The dollar economy lingers in poorer areas, marked by decay, but Bitcoin’s dominance lifts overall prosperity, as its deflationary nature incentivizes saving and investment over consumption. Global supply chains rebound, powered by bitcoin enabled efficiency. - **2047 (Late Year)**\ The U.S. is a patchwork of semi-autonomous zones, united by Bitcoin’s universal acceptance rather than federal control. Resource scarcity persists due to past disruptions, but economic stability is higher than in Shriver’s original dystopia—Bitcoin’s success prevents the authoritarian slide, fostering a freer, if imperfect, society. ### Key Differences - **Currency Dynamics**: Bitcoin’s triumph prevents the bancor’s dominance and mitigates hyperinflation’s worst effects, offering a lifeline outside state control. - **Government Power**: Centralized authority weakens as Bitcoin evades bans and taxation, shifting power to individuals and communities. - **Societal Outcome**: Instead of a surveillance state, 2047 sees a decentralized, bitcoin driven world—less oppressive, though still stratified between Bitcoin haves and have-nots. This reimagining assumes Bitcoin overcomes Shriver’s implied skepticism to become a robust, adopted currency by 2029, fundamentally altering the novel’s bleak trajectory.
@ 04c915da:3dfbecc9
2025-02-25 03:55:08Here’s a revised timeline of macro-level events from *The Mandibles: A Family, 2029–2047* by Lionel Shriver, reimagined in a world where Bitcoin is adopted as a widely accepted form of money, altering the original narrative’s assumptions about currency collapse and economic control. In Shriver’s original story, the failure of Bitcoin is assumed amid the dominance of the bancor and the dollar’s collapse. Here, Bitcoin’s success reshapes the economic and societal trajectory, decentralizing power and challenging state-driven outcomes. ### Part One: 2029–2032 - **2029 (Early Year)**\ The United States faces economic strain as the dollar weakens against global shifts. However, Bitcoin, having gained traction emerges as a viable alternative. Unlike the original timeline, the bancor—a supranational currency backed by a coalition of nations—struggles to gain footing as Bitcoin’s decentralized adoption grows among individuals and businesses worldwide, undermining both the dollar and the bancor. - **2029 (Mid-Year: The Great Renunciation)**\ Treasury bonds lose value, and the government bans Bitcoin, labeling it a threat to sovereignty (mirroring the original bancor ban). However, a Bitcoin ban proves unenforceable—its decentralized nature thwarts confiscation efforts, unlike gold in the original story. Hyperinflation hits the dollar as the U.S. prints money, but Bitcoin’s fixed supply shields adopters from currency devaluation, creating a dual-economy split: dollar users suffer, while Bitcoin users thrive. - **2029 (Late Year)**\ Dollar-based inflation soars, emptying stores of goods priced in fiat currency. Meanwhile, Bitcoin transactions flourish in underground and online markets, stabilizing trade for those plugged into the bitcoin ecosystem. Traditional supply chains falter, but peer-to-peer Bitcoin networks enable local and international exchange, reducing scarcity for early adopters. The government’s gold confiscation fails to bolster the dollar, as Bitcoin’s rise renders gold less relevant. - **2030–2031**\ Crime spikes in dollar-dependent urban areas, but Bitcoin-friendly regions see less chaos, as digital wallets and smart contracts facilitate secure trade. The U.S. government doubles down on surveillance to crack down on bitcoin use. A cultural divide deepens: centralized authority weakens in Bitcoin-adopting communities, while dollar zones descend into lawlessness. - **2032**\ By this point, Bitcoin is de facto legal tender in parts of the U.S. and globally, especially in tech-savvy or libertarian-leaning regions. The federal government’s grip slips as tax collection in dollars plummets—Bitcoin’s traceability is low, and citizens evade fiat-based levies. Rural and urban Bitcoin hubs emerge, while the dollar economy remains fractured. ### Time Jump: 2032–2047 - Over 15 years, Bitcoin solidifies as a global reserve currency, eroding centralized control. The U.S. government adapts, grudgingly integrating bitcoin into policy, though regional autonomy grows as Bitcoin empowers local economies. ### Part Two: 2047 - **2047 (Early Year)**\ The U.S. is a hybrid state: Bitcoin is legal tender alongside a diminished dollar. Taxes are lower, collected in BTC, reducing federal overreach. Bitcoin’s adoption has decentralized power nationwide. The bancor has faded, unable to compete with Bitcoin’s grassroots momentum. - **2047 (Mid-Year)**\ Travel and trade flow freely in Bitcoin zones, with no restrictive checkpoints. The dollar economy lingers in poorer areas, marked by decay, but Bitcoin’s dominance lifts overall prosperity, as its deflationary nature incentivizes saving and investment over consumption. Global supply chains rebound, powered by bitcoin enabled efficiency. - **2047 (Late Year)**\ The U.S. is a patchwork of semi-autonomous zones, united by Bitcoin’s universal acceptance rather than federal control. Resource scarcity persists due to past disruptions, but economic stability is higher than in Shriver’s original dystopia—Bitcoin’s success prevents the authoritarian slide, fostering a freer, if imperfect, society. ### Key Differences - **Currency Dynamics**: Bitcoin’s triumph prevents the bancor’s dominance and mitigates hyperinflation’s worst effects, offering a lifeline outside state control. - **Government Power**: Centralized authority weakens as Bitcoin evades bans and taxation, shifting power to individuals and communities. - **Societal Outcome**: Instead of a surveillance state, 2047 sees a decentralized, bitcoin driven world—less oppressive, though still stratified between Bitcoin haves and have-nots. This reimagining assumes Bitcoin overcomes Shriver’s implied skepticism to become a robust, adopted currency by 2029, fundamentally altering the novel’s bleak trajectory. @ 6e0ea5d6:0327f353
2025-02-21 18:15:52"Malcolm Forbes recounts that a lady, wearing a faded cotton dress, and her husband, dressed in an old handmade suit, stepped off a train in Boston, USA, and timidly made their way to the office of the president of Harvard University. They had come from Palo Alto, California, and had not scheduled an appointment. The secretary, at a glance, thought that those two, looking like country bumpkins, had no business at Harvard. — We want to speak with the president — the man said in a low voice. — He will be busy all day — the secretary replied curtly. — We will wait. The secretary ignored them for hours, hoping the couple would finally give up and leave. But they stayed there, and the secretary, somewhat frustrated, decided to bother the president, although she hated doing that. — If you speak with them for just a few minutes, maybe they will decide to go away — she said. The president sighed in irritation but agreed. Someone of his importance did not have time to meet people like that, but he hated faded dresses and tattered suits in his office. With a stern face, he went to the couple. — We had a son who studied at Harvard for a year — the woman said. — He loved Harvard and was very happy here, but a year ago he died in an accident, and we would like to erect a monument in his honor somewhere on campus. — My lady — said the president rudely —, we cannot erect a statue for every person who studied at Harvard and died; if we did, this place would look like a cemetery. — Oh, no — the lady quickly replied. — We do not want to erect a statue. We would like to donate a building to Harvard. The president looked at the woman's faded dress and her husband's old suit and exclaimed: — A building! Do you have even the faintest idea of how much a building costs? We have more than seven and a half million dollars' worth of buildings here at Harvard. The lady was silent for a moment, then said to her husband: — If that’s all it costs to found a university, why don’t we have our own? The husband agreed. The couple, Leland Stanford, stood up and left, leaving the president confused. Traveling back to Palo Alto, California, they established there Stanford University, the second-largest in the world, in honor of their son, a former Harvard student." Text extracted from: "Mileumlivros - Stories that Teach Values." Thank you for reading, my friend! If this message helped you in any way, consider leaving your glass “🥃” as a token of appreciation. A toast to our family!
@ 6e0ea5d6:0327f353
2025-02-21 18:15:52"Malcolm Forbes recounts that a lady, wearing a faded cotton dress, and her husband, dressed in an old handmade suit, stepped off a train in Boston, USA, and timidly made their way to the office of the president of Harvard University. They had come from Palo Alto, California, and had not scheduled an appointment. The secretary, at a glance, thought that those two, looking like country bumpkins, had no business at Harvard. — We want to speak with the president — the man said in a low voice. — He will be busy all day — the secretary replied curtly. — We will wait. The secretary ignored them for hours, hoping the couple would finally give up and leave. But they stayed there, and the secretary, somewhat frustrated, decided to bother the president, although she hated doing that. — If you speak with them for just a few minutes, maybe they will decide to go away — she said. The president sighed in irritation but agreed. Someone of his importance did not have time to meet people like that, but he hated faded dresses and tattered suits in his office. With a stern face, he went to the couple. — We had a son who studied at Harvard for a year — the woman said. — He loved Harvard and was very happy here, but a year ago he died in an accident, and we would like to erect a monument in his honor somewhere on campus. — My lady — said the president rudely —, we cannot erect a statue for every person who studied at Harvard and died; if we did, this place would look like a cemetery. — Oh, no — the lady quickly replied. — We do not want to erect a statue. We would like to donate a building to Harvard. The president looked at the woman's faded dress and her husband's old suit and exclaimed: — A building! Do you have even the faintest idea of how much a building costs? We have more than seven and a half million dollars' worth of buildings here at Harvard. The lady was silent for a moment, then said to her husband: — If that’s all it costs to found a university, why don’t we have our own? The husband agreed. The couple, Leland Stanford, stood up and left, leaving the president confused. Traveling back to Palo Alto, California, they established there Stanford University, the second-largest in the world, in honor of their son, a former Harvard student." Text extracted from: "Mileumlivros - Stories that Teach Values." Thank you for reading, my friend! If this message helped you in any way, consider leaving your glass “🥃” as a token of appreciation. A toast to our family! @ 0fa80bd3:ea7325de
2025-02-14 23:24:37#intro The Russian state made me a Bitcoiner. In 1991, it devalued my grandmother's hard-earned savings. She worked tirelessly in the kitchen of a dining car on the Moscow–Warsaw route. Everything she had saved for my sister and me to attend university vanished overnight. This story is similar to what many experienced, including Wences Casares. The pain and injustice of that time became my first lessons about the fragility of systems and the value of genuine, incorruptible assets, forever changing my perception of money and my trust in government promises. In 2014, I was living in Moscow, running a trading business, and frequently traveling to China. One day, I learned about the Cypriot banking crisis and the possibility of moving money through some strange thing called Bitcoin. At the time, I didn’t give it much thought. Returning to the idea six months later, as a business-oriented geek, I eagerly began studying the topic and soon dove into it seriously. I spent half a year reading articles on a local online journal, BitNovosti, actively participating in discussions, and eventually joined the editorial team as a translator. That’s how I learned about whitepapers, decentralization, mining, cryptographic keys, and colored coins. About Satoshi Nakamoto, Silk Road, Mt. Gox, and BitcoinTalk. Over time, I befriended the journal’s owner and, leveraging my management experience, later became an editor. I was drawn to the crypto-anarchist stance and commitment to decentralization principles. We wrote about the economic, historical, and social preconditions for Bitcoin’s emergence, and it was during this time that I fully embraced the idea. It got to the point where I sold my apartment and, during the market's downturn, bought 50 bitcoins, just after the peak price of $1,200 per coin. That marked the beginning of my first crypto winter. As an editor, I organized workflows, managed translators, developed a YouTube channel, and attended conferences in Russia and Ukraine. That’s how I learned about Wences Casares and even wrote a piece about him. I also met Mikhail Chobanyan (Ukrainian exchange Kuna), Alexander Ivanov (Waves project), Konstantin Lomashuk (Lido project), and, of course, Vitalik Buterin. It was a time of complete immersion, 24/7, and boundless hope. After moving to the United States, I expected the industry to grow rapidly, attended events, but the introduction of BitLicense froze the industry for eight years. By 2017, it became clear that the industry was shifting toward gambling and creating tokens for the sake of tokens. I dismissed this idea as unsustainable. Then came a new crypto spring with the hype around beautiful NFTs – CryptoPunks and apes. I made another attempt – we worked on a series called Digital Nomad Country Club, aimed at creating a global project. The proceeds from selling images were intended to fund the development of business tools for people worldwide. However, internal disagreements within the team prevented us from completing the project. With Trump’s arrival in 2025, hope was reignited. I decided that it was time to create a project that society desperately needed. As someone passionate about history, I understood that destroying what exists was not the solution, but leaving everything as it was also felt unacceptable. You can’t destroy the system, as the fiery crypto-anarchist voices claimed. With an analytical mindset (IQ 130) and a deep understanding of the freest societies, I realized what was missing—not only in Russia or the United States but globally—a Bitcoin-native system for tracking debts and financial interactions. This could return control of money to ordinary people and create horizontal connections parallel to state systems. My goal was to create, if not a Bitcoin killer app, then at least to lay its foundation. At the inauguration event in New York, I rediscovered the Nostr project. I realized it was not only technologically simple and already quite popular but also perfectly aligned with my vision. For the past month and a half, using insights and experience gained since 2014, I’ve been working full-time on this project.
@ 0fa80bd3:ea7325de
2025-02-14 23:24:37#intro The Russian state made me a Bitcoiner. In 1991, it devalued my grandmother's hard-earned savings. She worked tirelessly in the kitchen of a dining car on the Moscow–Warsaw route. Everything she had saved for my sister and me to attend university vanished overnight. This story is similar to what many experienced, including Wences Casares. The pain and injustice of that time became my first lessons about the fragility of systems and the value of genuine, incorruptible assets, forever changing my perception of money and my trust in government promises. In 2014, I was living in Moscow, running a trading business, and frequently traveling to China. One day, I learned about the Cypriot banking crisis and the possibility of moving money through some strange thing called Bitcoin. At the time, I didn’t give it much thought. Returning to the idea six months later, as a business-oriented geek, I eagerly began studying the topic and soon dove into it seriously. I spent half a year reading articles on a local online journal, BitNovosti, actively participating in discussions, and eventually joined the editorial team as a translator. That’s how I learned about whitepapers, decentralization, mining, cryptographic keys, and colored coins. About Satoshi Nakamoto, Silk Road, Mt. Gox, and BitcoinTalk. Over time, I befriended the journal’s owner and, leveraging my management experience, later became an editor. I was drawn to the crypto-anarchist stance and commitment to decentralization principles. We wrote about the economic, historical, and social preconditions for Bitcoin’s emergence, and it was during this time that I fully embraced the idea. It got to the point where I sold my apartment and, during the market's downturn, bought 50 bitcoins, just after the peak price of $1,200 per coin. That marked the beginning of my first crypto winter. As an editor, I organized workflows, managed translators, developed a YouTube channel, and attended conferences in Russia and Ukraine. That’s how I learned about Wences Casares and even wrote a piece about him. I also met Mikhail Chobanyan (Ukrainian exchange Kuna), Alexander Ivanov (Waves project), Konstantin Lomashuk (Lido project), and, of course, Vitalik Buterin. It was a time of complete immersion, 24/7, and boundless hope. After moving to the United States, I expected the industry to grow rapidly, attended events, but the introduction of BitLicense froze the industry for eight years. By 2017, it became clear that the industry was shifting toward gambling and creating tokens for the sake of tokens. I dismissed this idea as unsustainable. Then came a new crypto spring with the hype around beautiful NFTs – CryptoPunks and apes. I made another attempt – we worked on a series called Digital Nomad Country Club, aimed at creating a global project. The proceeds from selling images were intended to fund the development of business tools for people worldwide. However, internal disagreements within the team prevented us from completing the project. With Trump’s arrival in 2025, hope was reignited. I decided that it was time to create a project that society desperately needed. As someone passionate about history, I understood that destroying what exists was not the solution, but leaving everything as it was also felt unacceptable. You can’t destroy the system, as the fiery crypto-anarchist voices claimed. With an analytical mindset (IQ 130) and a deep understanding of the freest societies, I realized what was missing—not only in Russia or the United States but globally—a Bitcoin-native system for tracking debts and financial interactions. This could return control of money to ordinary people and create horizontal connections parallel to state systems. My goal was to create, if not a Bitcoin killer app, then at least to lay its foundation. At the inauguration event in New York, I rediscovered the Nostr project. I realized it was not only technologically simple and already quite popular but also perfectly aligned with my vision. For the past month and a half, using insights and experience gained since 2014, I’ve been working full-time on this project. @ daa41bed:88f54153
2025-02-09 16:50:04There has been a good bit of discussion on Nostr over the past few days about the merits of zaps as a method of engaging with notes, so after writing a rather lengthy [article on the pros of a strategic Bitcoin reserve](https://geek.npub.pro/post/dxqkgnjplttkvetprg8ox/), I wanted to take some time to chime in on the much more fun topic of digital engagement. Let's begin by defining a couple of things: **Nostr** is a decentralized, censorship-resistance protocol whose current biggest use case is social media (think Twitter/X). Instead of relying on company servers, it relies on relays that anyone can spin up and own their own content. Its use cases are much bigger, though, and this article is hosted on my own relay, using my own Nostr relay as an example. **Zap** is a tip or donation denominated in sats (small units of Bitcoin) sent from one user to another. This is generally done directly over the Lightning Network but is increasingly using Cashu tokens. For the sake of this discussion, how you transmit/receive zaps will be irrelevant, so don't worry if you don't know what [Lightning](https://lightning.network/) or [Cashu](https://cashu.space/) are. If we look at how users engage with posts and follows/followers on platforms like Twitter, Facebook, etc., it becomes evident that traditional social media thrives on engagement farming. The more outrageous a post, the more likely it will get a reaction. We see a version of this on more visual social platforms like YouTube and TikTok that use carefully crafted thumbnail images to grab the user's attention to click the video. If you'd like to dive deep into the psychology and science behind social media engagement, let me know, and I'd be happy to follow up with another article. In this user engagement model, a user is given the option to comment or like the original post, or share it among their followers to increase its signal. They receive no value from engaging with the content aside from the dopamine hit of the original experience or having their comment liked back by whatever influencer they provide value to. Ad revenue flows to the content creator. Clout flows to the content creator. Sales revenue from merch and content placement flows to the content creator. We call this a linear economy -- the idea that resources get created, used up, then thrown away. Users create content and farm as much engagement as possible, then the content is forgotten within a few hours as they move on to the next piece of content to be farmed. What if there were a simple way to give value back to those who engage with your content? By implementing some value-for-value model -- a circular economy. Enter zaps.  Unlike traditional social media platforms, Nostr does not actively use algorithms to determine what content is popular, nor does it push content created for active user engagement to the top of a user's timeline. Yes, there are "trending" and "most zapped" timelines that users can choose to use as their default, but these use relatively straightforward engagement metrics to rank posts for these timelines. That is not to say that we may not see clients actively seeking to refine timeline algorithms for specific metrics. Still, the beauty of having an open protocol with media that is controlled solely by its users is that users who begin to see their timeline gamed towards specific algorithms can choose to move to another client, and for those who are more tech-savvy, they can opt to run their own relays or create their own clients with personalized algorithms and web of trust scoring systems. Zaps enable the means to create a new type of social media economy in which creators can earn for creating content and users can earn by actively engaging with it. Like and reposting content is relatively frictionless and costs nothing but a simple button tap. Zaps provide active engagement because they signal to your followers and those of the content creator that this post has genuine value, quite literally in the form of money—sats.  I have seen some comments on Nostr claiming that removing likes and reactions is for wealthy people who can afford to send zaps and that the majority of people in the US and around the world do not have the time or money to zap because they have better things to spend their money like feeding their families and paying their bills. While at face value, these may seem like valid arguments, they, unfortunately, represent the brainwashed, defeatist attitude that our current economic (and, by extension, social media) systems aim to instill in all of us to continue extracting value from our lives. Imagine now, if those people dedicating their own time (time = money) to mine pity points on social media would instead spend that time with genuine value creation by posting content that is meaningful to cultural discussions. Imagine if, instead of complaining that their posts get no zaps and going on a tirade about how much of a victim they are, they would empower themselves to take control of their content and give value back to the world; where would that leave us? How much value could be created on a nascent platform such as Nostr, and how quickly could it overtake other platforms? Other users argue about user experience and that additional friction (i.e., zaps) leads to lower engagement, as proven by decades of studies on user interaction. While the added friction may turn some users away, does that necessarily provide less value? I argue quite the opposite. You haven't made a few sats from zaps with your content? Can't afford to send some sats to a wallet for zapping? How about using the most excellent available resource and spending 10 seconds of your time to leave a comment? Likes and reactions are valueless transactions. Social media's real value derives from providing monetary compensation and actively engaging in a conversation with posts you find interesting or thought-provoking. Remember when humans thrived on conversation and discussion for entertainment instead of simply being an onlooker of someone else's life? If you've made it this far, my only request is this: try only zapping and commenting as a method of engagement for two weeks. Sure, you may end up liking a post here and there, but be more mindful of how you interact with the world and break yourself from blind instinct. You'll thank me later. 
@ daa41bed:88f54153
2025-02-09 16:50:04There has been a good bit of discussion on Nostr over the past few days about the merits of zaps as a method of engaging with notes, so after writing a rather lengthy [article on the pros of a strategic Bitcoin reserve](https://geek.npub.pro/post/dxqkgnjplttkvetprg8ox/), I wanted to take some time to chime in on the much more fun topic of digital engagement. Let's begin by defining a couple of things: **Nostr** is a decentralized, censorship-resistance protocol whose current biggest use case is social media (think Twitter/X). Instead of relying on company servers, it relies on relays that anyone can spin up and own their own content. Its use cases are much bigger, though, and this article is hosted on my own relay, using my own Nostr relay as an example. **Zap** is a tip or donation denominated in sats (small units of Bitcoin) sent from one user to another. This is generally done directly over the Lightning Network but is increasingly using Cashu tokens. For the sake of this discussion, how you transmit/receive zaps will be irrelevant, so don't worry if you don't know what [Lightning](https://lightning.network/) or [Cashu](https://cashu.space/) are. If we look at how users engage with posts and follows/followers on platforms like Twitter, Facebook, etc., it becomes evident that traditional social media thrives on engagement farming. The more outrageous a post, the more likely it will get a reaction. We see a version of this on more visual social platforms like YouTube and TikTok that use carefully crafted thumbnail images to grab the user's attention to click the video. If you'd like to dive deep into the psychology and science behind social media engagement, let me know, and I'd be happy to follow up with another article. In this user engagement model, a user is given the option to comment or like the original post, or share it among their followers to increase its signal. They receive no value from engaging with the content aside from the dopamine hit of the original experience or having their comment liked back by whatever influencer they provide value to. Ad revenue flows to the content creator. Clout flows to the content creator. Sales revenue from merch and content placement flows to the content creator. We call this a linear economy -- the idea that resources get created, used up, then thrown away. Users create content and farm as much engagement as possible, then the content is forgotten within a few hours as they move on to the next piece of content to be farmed. What if there were a simple way to give value back to those who engage with your content? By implementing some value-for-value model -- a circular economy. Enter zaps.  Unlike traditional social media platforms, Nostr does not actively use algorithms to determine what content is popular, nor does it push content created for active user engagement to the top of a user's timeline. Yes, there are "trending" and "most zapped" timelines that users can choose to use as their default, but these use relatively straightforward engagement metrics to rank posts for these timelines. That is not to say that we may not see clients actively seeking to refine timeline algorithms for specific metrics. Still, the beauty of having an open protocol with media that is controlled solely by its users is that users who begin to see their timeline gamed towards specific algorithms can choose to move to another client, and for those who are more tech-savvy, they can opt to run their own relays or create their own clients with personalized algorithms and web of trust scoring systems. Zaps enable the means to create a new type of social media economy in which creators can earn for creating content and users can earn by actively engaging with it. Like and reposting content is relatively frictionless and costs nothing but a simple button tap. Zaps provide active engagement because they signal to your followers and those of the content creator that this post has genuine value, quite literally in the form of money—sats.  I have seen some comments on Nostr claiming that removing likes and reactions is for wealthy people who can afford to send zaps and that the majority of people in the US and around the world do not have the time or money to zap because they have better things to spend their money like feeding their families and paying their bills. While at face value, these may seem like valid arguments, they, unfortunately, represent the brainwashed, defeatist attitude that our current economic (and, by extension, social media) systems aim to instill in all of us to continue extracting value from our lives. Imagine now, if those people dedicating their own time (time = money) to mine pity points on social media would instead spend that time with genuine value creation by posting content that is meaningful to cultural discussions. Imagine if, instead of complaining that their posts get no zaps and going on a tirade about how much of a victim they are, they would empower themselves to take control of their content and give value back to the world; where would that leave us? How much value could be created on a nascent platform such as Nostr, and how quickly could it overtake other platforms? Other users argue about user experience and that additional friction (i.e., zaps) leads to lower engagement, as proven by decades of studies on user interaction. While the added friction may turn some users away, does that necessarily provide less value? I argue quite the opposite. You haven't made a few sats from zaps with your content? Can't afford to send some sats to a wallet for zapping? How about using the most excellent available resource and spending 10 seconds of your time to leave a comment? Likes and reactions are valueless transactions. Social media's real value derives from providing monetary compensation and actively engaging in a conversation with posts you find interesting or thought-provoking. Remember when humans thrived on conversation and discussion for entertainment instead of simply being an onlooker of someone else's life? If you've made it this far, my only request is this: try only zapping and commenting as a method of engagement for two weeks. Sure, you may end up liking a post here and there, but be more mindful of how you interact with the world and break yourself from blind instinct. You'll thank me later.  @ e3ba5e1a:5e433365
2025-02-05 17:47:16I got into a [friendly discussion](https://x.com/snoyberg/status/1887007888117252142) on X regarding health insurance. The specific question was how to deal with health insurance companies (presumably unfairly) denying claims? My answer, as usual: get government out of it! The US healthcare system is essentially the worst of both worlds: * Unlike full single payer, individuals incur high costs * Unlike a true free market, regulation causes increases in costs and decreases competition among insurers I'm firmly on the side of moving towards the free market. (And I say that as someone living under a single payer system now.) Here's what I would do: * Get rid of tax incentives that make health insurance tied to your employer, giving individuals back proper freedom of choice. * Reduce regulations significantly. * In the short term, some people will still get rejected claims and other obnoxious behavior from insurance companies. We address that in two ways: 1. Due to reduced regulations, new insurance companies will be able to enter the market offering more reliable coverage and better rates, and people will flock to them because they have the freedom to make their own choices. 2. Sue the asses off of companies that reject claims unfairly. And ideally, as one of the few legitimate roles of government in all this, institute new laws that limit the ability of fine print to allow insurers to escape their responsibilities. (I'm hesitant that the latter will happen due to the incestuous relationship between Congress/regulators and insurers, but I can hope.) Will this magically fix everything overnight like politicians normally promise? No. But it will allow the market to return to a healthy state. And I don't think it will take long (order of magnitude: 5-10 years) for it to come together, but that's just speculation. And since there's a high correlation between those who believe government can fix problems by taking more control and demanding that only credentialed experts weigh in on a topic (both points I strongly disagree with BTW): I'm a trained actuary and worked in the insurance industry, and have directly seen how government regulation reduces competition, raises prices, and harms consumers. And my final point: I don't think any prior art would be a good comparison for deregulation in the US, it's such a different market than any other country in the world for so many reasons that lessons wouldn't really translate. Nonetheless, I asked Grok for some empirical data on this, and at best the results of deregulation could be called "mixed," but likely more accurately "uncertain, confused, and subject to whatever interpretation anyone wants to apply." https://x.com/i/grok/share/Zc8yOdrN8lS275hXJ92uwq98M
@ e3ba5e1a:5e433365
2025-02-05 17:47:16I got into a [friendly discussion](https://x.com/snoyberg/status/1887007888117252142) on X regarding health insurance. The specific question was how to deal with health insurance companies (presumably unfairly) denying claims? My answer, as usual: get government out of it! The US healthcare system is essentially the worst of both worlds: * Unlike full single payer, individuals incur high costs * Unlike a true free market, regulation causes increases in costs and decreases competition among insurers I'm firmly on the side of moving towards the free market. (And I say that as someone living under a single payer system now.) Here's what I would do: * Get rid of tax incentives that make health insurance tied to your employer, giving individuals back proper freedom of choice. * Reduce regulations significantly. * In the short term, some people will still get rejected claims and other obnoxious behavior from insurance companies. We address that in two ways: 1. Due to reduced regulations, new insurance companies will be able to enter the market offering more reliable coverage and better rates, and people will flock to them because they have the freedom to make their own choices. 2. Sue the asses off of companies that reject claims unfairly. And ideally, as one of the few legitimate roles of government in all this, institute new laws that limit the ability of fine print to allow insurers to escape their responsibilities. (I'm hesitant that the latter will happen due to the incestuous relationship between Congress/regulators and insurers, but I can hope.) Will this magically fix everything overnight like politicians normally promise? No. But it will allow the market to return to a healthy state. And I don't think it will take long (order of magnitude: 5-10 years) for it to come together, but that's just speculation. And since there's a high correlation between those who believe government can fix problems by taking more control and demanding that only credentialed experts weigh in on a topic (both points I strongly disagree with BTW): I'm a trained actuary and worked in the insurance industry, and have directly seen how government regulation reduces competition, raises prices, and harms consumers. And my final point: I don't think any prior art would be a good comparison for deregulation in the US, it's such a different market than any other country in the world for so many reasons that lessons wouldn't really translate. Nonetheless, I asked Grok for some empirical data on this, and at best the results of deregulation could be called "mixed," but likely more accurately "uncertain, confused, and subject to whatever interpretation anyone wants to apply." https://x.com/i/grok/share/Zc8yOdrN8lS275hXJ92uwq98M @ 9e69e420:d12360c2
2025-02-01 11:16:04 Federal employees must remove pronouns from email signatures by the end of the day. This directive comes from internal memos tied to two executive orders signed by Donald Trump. The orders target diversity and equity programs within the government.  CDC, Department of Transportation, and Department of Energy employees were affected. Staff were instructed to make changes in line with revised policy prohibiting certain language. One CDC employee shared frustration, stating, “In my decade-plus years at CDC, I've never been told what I can and can't put in my email signature.” The directive is part of a broader effort to eliminate DEI initiatives from federal discourse.
@ 9e69e420:d12360c2
2025-02-01 11:16:04 Federal employees must remove pronouns from email signatures by the end of the day. This directive comes from internal memos tied to two executive orders signed by Donald Trump. The orders target diversity and equity programs within the government.  CDC, Department of Transportation, and Department of Energy employees were affected. Staff were instructed to make changes in line with revised policy prohibiting certain language. One CDC employee shared frustration, stating, “In my decade-plus years at CDC, I've never been told what I can and can't put in my email signature.” The directive is part of a broader effort to eliminate DEI initiatives from federal discourse. @ 6389be64:ef439d32
2025-04-03 21:32:58Brewing Biology Episode 1068 of Bitcoin And . . . is LIVE! This episode of Bitcoin And dives into Brewing Biology—a regenerative system combining compost tea, biochar, Bitcoin mining, and carbon credits—developed through a deep, idea-driven conversation with ChatGPT. LISTEN HERE --> https://fountain.fm/episode/p0DmvPzxirDHh2l68zOX <-- LISTEN HERE The future of Bitcoin isn’t just about code or money—it’s about soil. A groundbreaking fusion of biology, technology, and financial innovation might change the rules of agriculture, offering landowners a path to profitability while Healing our soils. At the heart of this revolution is biochar, a form of charcoal that supercharges soil health. When mixed with compost tea and microbial inoculants, this carbon-rich material becomes a game-changer. Biochar’s porous structure acts as a microbial hotel, hosting fungi like arbuscular mycorrhizal fungi (AMF) and bacteria such as Bacillus subtilis. These organisms form symbiotic networks that boost nutrient absorption and secrete glomalin—a natural “glue” that binds soil, preventing erosion. But here’s the twist: this system doesn’t just heal the earth; it also generates revenue. Biochar’s Hidden Superpower: Adsorption & Buffering Biochar’s porous structure acts as a molecular storage hub. Unlike absorption (soaking up water like a sponge), adsorption is a chemical process where water and nutrients cling to biochar’s surfaces. A single gram of biochar has the surface area of a basketball court, creating a lattice of microscopic nooks and crannies. This allows it to: Lock in moisture: Biochar retains up to 10x its weight in water, acting like a “soil battery” that releases hydration slowly during droughts. Hoard nutrients: It buffers nitrogen, phosphorus, potassium, and micronutrients in its pores, preventing leaching. Plants access these nutrients gradually, reducing fertilizer needs. Stabilize pH: Biochar’s alkaline nature buffers acidic soils, creating a neutral environment where microbes and roots thrive. This buffering effect means plants face fewer nutrient and water spikes or shortages, ensuring steady growth even in erratic climates. The Carbon Math Every ton of biochar (which is ~85% carbon by weight) sequesters 3.12 tons of CO₂ (using the 1:3.67 carbon-to-CO₂ ratio). With carbon credits trading at $42–$60/ton, a 1,000-acre project applying 1 pound of biochar per linear foot (via a three-shank plow at 2-foot spacing) could sequester ~12,000 tons of CO₂ annually—generating $504,000–$720,000 in carbon credit revenue. Tools for the Revolution The Keyline Plow fractures subsoil to inject biochar slurry 30–45cm deep, revitalizing compacted land. For smaller plots, the VOGT Geo Injector delivers pinpoint inoculations—think of it as a soil “injection gun” for lawns, golf courses, or urban gardens. These methods ensure biochar stays where it’s needed, turning even parched landscapes into carbon sinks. Bitcoin’s Role in the Loop Biochar production generates syngas—a byproduct that fuels electric generators for Bitcoin mining. This closed-loop system turns agricultural waste into energy, creating dual revenue streams: carbon credits and mining income. The Market Potential Farmers, ranchers, and eco-conscious landowners aren’t the only beneficiaries. Golf courses can slash water use and homeowners can boost lawn resilience. Why This Matters This isn’t just farming—it’s a movement. By marrying soil science with economics, we can prove that healing the planet and profiting go hand in hand. Whether you’re a Bitcoin miner, a farmer, or an eco-entrepreneur, this system offers a blueprint for a future where every acre works for you—and the planet. The takeaway? Regenerative agriculture isn’t a trend. It’s the next gold rush—except this time, the gold is carbon, soil, and sats.--- P.S. – If you’re ready to turn your land into a carbon credit powerhouse (and maybe mine some Bitcoin along the way), the soil is waiting. You can read the full article, Brewing Biology HERE -> https://the-bitcoin-and-Podcast.ghost.io/ghost/#/editor/post/67e5922fa289aa00088da3c6 originally posted at https://stacker.news/items/933800
@ 6389be64:ef439d32
2025-04-03 21:32:58Brewing Biology Episode 1068 of Bitcoin And . . . is LIVE! This episode of Bitcoin And dives into Brewing Biology—a regenerative system combining compost tea, biochar, Bitcoin mining, and carbon credits—developed through a deep, idea-driven conversation with ChatGPT. LISTEN HERE --> https://fountain.fm/episode/p0DmvPzxirDHh2l68zOX <-- LISTEN HERE The future of Bitcoin isn’t just about code or money—it’s about soil. A groundbreaking fusion of biology, technology, and financial innovation might change the rules of agriculture, offering landowners a path to profitability while Healing our soils. At the heart of this revolution is biochar, a form of charcoal that supercharges soil health. When mixed with compost tea and microbial inoculants, this carbon-rich material becomes a game-changer. Biochar’s porous structure acts as a microbial hotel, hosting fungi like arbuscular mycorrhizal fungi (AMF) and bacteria such as Bacillus subtilis. These organisms form symbiotic networks that boost nutrient absorption and secrete glomalin—a natural “glue” that binds soil, preventing erosion. But here’s the twist: this system doesn’t just heal the earth; it also generates revenue. Biochar’s Hidden Superpower: Adsorption & Buffering Biochar’s porous structure acts as a molecular storage hub. Unlike absorption (soaking up water like a sponge), adsorption is a chemical process where water and nutrients cling to biochar’s surfaces. A single gram of biochar has the surface area of a basketball court, creating a lattice of microscopic nooks and crannies. This allows it to: Lock in moisture: Biochar retains up to 10x its weight in water, acting like a “soil battery” that releases hydration slowly during droughts. Hoard nutrients: It buffers nitrogen, phosphorus, potassium, and micronutrients in its pores, preventing leaching. Plants access these nutrients gradually, reducing fertilizer needs. Stabilize pH: Biochar’s alkaline nature buffers acidic soils, creating a neutral environment where microbes and roots thrive. This buffering effect means plants face fewer nutrient and water spikes or shortages, ensuring steady growth even in erratic climates. The Carbon Math Every ton of biochar (which is ~85% carbon by weight) sequesters 3.12 tons of CO₂ (using the 1:3.67 carbon-to-CO₂ ratio). With carbon credits trading at $42–$60/ton, a 1,000-acre project applying 1 pound of biochar per linear foot (via a three-shank plow at 2-foot spacing) could sequester ~12,000 tons of CO₂ annually—generating $504,000–$720,000 in carbon credit revenue. Tools for the Revolution The Keyline Plow fractures subsoil to inject biochar slurry 30–45cm deep, revitalizing compacted land. For smaller plots, the VOGT Geo Injector delivers pinpoint inoculations—think of it as a soil “injection gun” for lawns, golf courses, or urban gardens. These methods ensure biochar stays where it’s needed, turning even parched landscapes into carbon sinks. Bitcoin’s Role in the Loop Biochar production generates syngas—a byproduct that fuels electric generators for Bitcoin mining. This closed-loop system turns agricultural waste into energy, creating dual revenue streams: carbon credits and mining income. The Market Potential Farmers, ranchers, and eco-conscious landowners aren’t the only beneficiaries. Golf courses can slash water use and homeowners can boost lawn resilience. Why This Matters This isn’t just farming—it’s a movement. By marrying soil science with economics, we can prove that healing the planet and profiting go hand in hand. Whether you’re a Bitcoin miner, a farmer, or an eco-entrepreneur, this system offers a blueprint for a future where every acre works for you—and the planet. The takeaway? Regenerative agriculture isn’t a trend. It’s the next gold rush—except this time, the gold is carbon, soil, and sats.--- P.S. – If you’re ready to turn your land into a carbon credit powerhouse (and maybe mine some Bitcoin along the way), the soil is waiting. You can read the full article, Brewing Biology HERE -> https://the-bitcoin-and-Podcast.ghost.io/ghost/#/editor/post/67e5922fa289aa00088da3c6 originally posted at https://stacker.news/items/933800 @ 000002de:c05780a7
2025-04-03 17:27:03### I score zero points. How about you? https://m.primal.net/QDDi.jpg I almost called this a boomer test but its more of a Gen X test. __Credit to Jack Spirko for sharing this on Twitter.__ originally posted at https://stacker.news/items/933537
@ 000002de:c05780a7
2025-04-03 17:27:03### I score zero points. How about you? https://m.primal.net/QDDi.jpg I almost called this a boomer test but its more of a Gen X test. __Credit to Jack Spirko for sharing this on Twitter.__ originally posted at https://stacker.news/items/933537 @ 0fa80bd3:ea7325de
2025-01-29 05:55:02The land that belongs to the indigenous peoples of Russia has been seized by a gang of killers who have unleashed a war of extermination. They wipe out anyone who refuses to conform to their rules. Those who disagree and stay behind are tortured and killed in prisons and labor camps. Those who flee lose their homeland, dissolve into foreign cultures, and fade away. And those who stand up to protect their people are attacked by the misled and deceived. The deceived die for the unchecked greed of a single dictator—thousands from both sides, people who just wanted to live, raise their kids, and build a future. Now, they are forced to make an impossible choice: abandon their homeland or die. Some perish on the battlefield, others lose themselves in exile, stripped of their identity, scattered in a world that isn’t theirs. There’s been endless debate about how to fix this, how to clear the field of the weeds that choke out every new sprout, every attempt at change. But the real problem? We can’t play by their rules. We can’t speak their language or use their weapons. We stand for humanity, and no matter how righteous our cause, we will not multiply suffering. Victory doesn’t come from matching the enemy—it comes from staying ahead, from using tools they haven’t mastered yet. That’s how wars are won. Our only resource is the **will of the people** to rewrite the order of things. Historian Timothy Snyder once said that a nation cannot exist without a city. A city is where the most active part of a nation thrives. But the cities are occupied. The streets are watched. Gatherings are impossible. They control the money. They control the mail. They control the media. And any dissent is crushed before it can take root. So I started asking myself: **How do we stop this fragmentation?** How do we create a space where people can **rebuild their connections** when they’re ready? How do we build a **self-sustaining network**, where everyone contributes and benefits proportionally, while keeping their freedom to leave intact? And more importantly—**how do we make it spread, even in occupied territory?** In 2009, something historic happened: **the internet got its own money.** Thanks to **Satoshi Nakamoto**, the world took a massive leap forward. Bitcoin and decentralized ledgers shattered the idea that money must be controlled by the state. Now, to move or store value, all you need is an address and a key. A tiny string of text, easy to carry, impossible to seize. That was the year money broke free. The state lost its grip. Its biggest weapon—physical currency—became irrelevant. Money became **purely digital.** The internet was already **a sanctuary for information**, a place where people could connect and organize. But with Bitcoin, it evolved. Now, **value itself** could flow freely, beyond the reach of authorities. Think about it: when seedlings are grown in controlled environments before being planted outside, they **get stronger, survive longer, and bear fruit faster.** That’s how we handle crops in harsh climates—nurture them until they’re ready for the wild. Now, picture the internet as that **controlled environment** for **ideas**. Bitcoin? It’s the **fertile soil** that lets them grow. A testing ground for new models of interaction, where concepts can take root before they move into the real world. If **nation-states are a battlefield, locked in a brutal war for territory, the internet is boundless.** It can absorb any number of ideas, any number of people, and it doesn’t **run out of space.** But for this ecosystem to thrive, people need safe ways to communicate, to share ideas, to build something real—**without surveillance, without censorship, without the constant fear of being erased.** This is where **Nostr** comes in. Nostr—"Notes and Other Stuff Transmitted by Relays"—is more than just a messaging protocol. **It’s a new kind of city.** One that **no dictator can seize**, no corporation can own, no government can shut down. It’s built on **decentralization, encryption, and individual control.** Messages don’t pass through central servers—they are relayed through independent nodes, and users choose which ones to trust. There’s no master switch to shut it all down. Every person owns their identity, their data, their connections. And no one—no state, no tech giant, no algorithm—can silence them. In a world where cities fall and governments fail, **Nostr is a city that cannot be occupied.** A place for ideas, for networks, for freedom. A city that grows stronger **the more people build within it**.
@ 0fa80bd3:ea7325de
2025-01-29 05:55:02The land that belongs to the indigenous peoples of Russia has been seized by a gang of killers who have unleashed a war of extermination. They wipe out anyone who refuses to conform to their rules. Those who disagree and stay behind are tortured and killed in prisons and labor camps. Those who flee lose their homeland, dissolve into foreign cultures, and fade away. And those who stand up to protect their people are attacked by the misled and deceived. The deceived die for the unchecked greed of a single dictator—thousands from both sides, people who just wanted to live, raise their kids, and build a future. Now, they are forced to make an impossible choice: abandon their homeland or die. Some perish on the battlefield, others lose themselves in exile, stripped of their identity, scattered in a world that isn’t theirs. There’s been endless debate about how to fix this, how to clear the field of the weeds that choke out every new sprout, every attempt at change. But the real problem? We can’t play by their rules. We can’t speak their language or use their weapons. We stand for humanity, and no matter how righteous our cause, we will not multiply suffering. Victory doesn’t come from matching the enemy—it comes from staying ahead, from using tools they haven’t mastered yet. That’s how wars are won. Our only resource is the **will of the people** to rewrite the order of things. Historian Timothy Snyder once said that a nation cannot exist without a city. A city is where the most active part of a nation thrives. But the cities are occupied. The streets are watched. Gatherings are impossible. They control the money. They control the mail. They control the media. And any dissent is crushed before it can take root. So I started asking myself: **How do we stop this fragmentation?** How do we create a space where people can **rebuild their connections** when they’re ready? How do we build a **self-sustaining network**, where everyone contributes and benefits proportionally, while keeping their freedom to leave intact? And more importantly—**how do we make it spread, even in occupied territory?** In 2009, something historic happened: **the internet got its own money.** Thanks to **Satoshi Nakamoto**, the world took a massive leap forward. Bitcoin and decentralized ledgers shattered the idea that money must be controlled by the state. Now, to move or store value, all you need is an address and a key. A tiny string of text, easy to carry, impossible to seize. That was the year money broke free. The state lost its grip. Its biggest weapon—physical currency—became irrelevant. Money became **purely digital.** The internet was already **a sanctuary for information**, a place where people could connect and organize. But with Bitcoin, it evolved. Now, **value itself** could flow freely, beyond the reach of authorities. Think about it: when seedlings are grown in controlled environments before being planted outside, they **get stronger, survive longer, and bear fruit faster.** That’s how we handle crops in harsh climates—nurture them until they’re ready for the wild. Now, picture the internet as that **controlled environment** for **ideas**. Bitcoin? It’s the **fertile soil** that lets them grow. A testing ground for new models of interaction, where concepts can take root before they move into the real world. If **nation-states are a battlefield, locked in a brutal war for territory, the internet is boundless.** It can absorb any number of ideas, any number of people, and it doesn’t **run out of space.** But for this ecosystem to thrive, people need safe ways to communicate, to share ideas, to build something real—**without surveillance, without censorship, without the constant fear of being erased.** This is where **Nostr** comes in. Nostr—"Notes and Other Stuff Transmitted by Relays"—is more than just a messaging protocol. **It’s a new kind of city.** One that **no dictator can seize**, no corporation can own, no government can shut down. It’s built on **decentralization, encryption, and individual control.** Messages don’t pass through central servers—they are relayed through independent nodes, and users choose which ones to trust. There’s no master switch to shut it all down. Every person owns their identity, their data, their connections. And no one—no state, no tech giant, no algorithm—can silence them. In a world where cities fall and governments fail, **Nostr is a city that cannot be occupied.** A place for ideas, for networks, for freedom. A city that grows stronger **the more people build within it**. @ 6be5cc06:5259daf0
2025-01-21 20:58:37A seguir, veja como instalar e configurar o **Privoxy** no **Pop!_OS**. --- ### **1. Instalar o Tor e o Privoxy** Abra o terminal e execute: ```bash sudo apt update sudo apt install tor privoxy ``` **Explicação:** - **Tor:** Roteia o tráfego pela rede Tor. - **Privoxy:** Proxy avançado que intermedia a conexão entre aplicativos e o Tor. --- ### **2. Configurar o Privoxy** Abra o arquivo de configuração do Privoxy: ```bash sudo nano /etc/privoxy/config ``` Navegue até a última linha (atalho: **`Ctrl`** + **`/`** depois **`Ctrl`** + **`V`** para navegar diretamente até a última linha) e insira: ```bash forward-socks5 / 127.0.0.1:9050 . ``` Isso faz com que o **Privoxy** envie todo o tráfego para o **Tor** através da porta **9050**. Salve (**`CTRL`** + **`O`** e **`Enter`**) e feche (**`CTRL`** + **`X`**) o arquivo. --- ### **3. Iniciar o Tor e o Privoxy** Agora, inicie e habilite os serviços: ```bash sudo systemctl start tor sudo systemctl start privoxy sudo systemctl enable tor sudo systemctl enable privoxy ``` **Explicação:** - **start:** Inicia os serviços. - **enable:** Faz com que iniciem automaticamente ao ligar o PC. --- ### **4. Configurar o Navegador Firefox** Para usar a rede **Tor** com o Firefox: 1. Abra o Firefox. 2. Acesse **Configurações** → **Configurar conexão**. 3. Selecione **Configuração manual de proxy**. 4. Configure assim: - **Proxy HTTP:** `127.0.0.1` - **Porta:** `8118` (porta padrão do **Privoxy**) - **Domínio SOCKS (v5):** `127.0.0.1` - **Porta:** `9050` 5. Marque a opção **"Usar este proxy também em HTTPS"**. 6. Clique em **OK**. --- ### **5. Verificar a Conexão com o Tor** Abra o navegador e acesse: ```text https://check.torproject.org/ ``` Se aparecer a mensagem **"Congratulations. This browser is configured to use Tor."**, a configuração está correta. --- ### **Dicas Extras** - **Privoxy** pode ser ajustado para bloquear anúncios e rastreadores. - Outros aplicativos também podem ser configurados para usar o **Privoxy**.
@ 6be5cc06:5259daf0
2025-01-21 20:58:37A seguir, veja como instalar e configurar o **Privoxy** no **Pop!_OS**. --- ### **1. Instalar o Tor e o Privoxy** Abra o terminal e execute: ```bash sudo apt update sudo apt install tor privoxy ``` **Explicação:** - **Tor:** Roteia o tráfego pela rede Tor. - **Privoxy:** Proxy avançado que intermedia a conexão entre aplicativos e o Tor. --- ### **2. Configurar o Privoxy** Abra o arquivo de configuração do Privoxy: ```bash sudo nano /etc/privoxy/config ``` Navegue até a última linha (atalho: **`Ctrl`** + **`/`** depois **`Ctrl`** + **`V`** para navegar diretamente até a última linha) e insira: ```bash forward-socks5 / 127.0.0.1:9050 . ``` Isso faz com que o **Privoxy** envie todo o tráfego para o **Tor** através da porta **9050**. Salve (**`CTRL`** + **`O`** e **`Enter`**) e feche (**`CTRL`** + **`X`**) o arquivo. --- ### **3. Iniciar o Tor e o Privoxy** Agora, inicie e habilite os serviços: ```bash sudo systemctl start tor sudo systemctl start privoxy sudo systemctl enable tor sudo systemctl enable privoxy ``` **Explicação:** - **start:** Inicia os serviços. - **enable:** Faz com que iniciem automaticamente ao ligar o PC. --- ### **4. Configurar o Navegador Firefox** Para usar a rede **Tor** com o Firefox: 1. Abra o Firefox. 2. Acesse **Configurações** → **Configurar conexão**. 3. Selecione **Configuração manual de proxy**. 4. Configure assim: - **Proxy HTTP:** `127.0.0.1` - **Porta:** `8118` (porta padrão do **Privoxy**) - **Domínio SOCKS (v5):** `127.0.0.1` - **Porta:** `9050` 5. Marque a opção **"Usar este proxy também em HTTPS"**. 6. Clique em **OK**. --- ### **5. Verificar a Conexão com o Tor** Abra o navegador e acesse: ```text https://check.torproject.org/ ``` Se aparecer a mensagem **"Congratulations. This browser is configured to use Tor."**, a configuração está correta. --- ### **Dicas Extras** - **Privoxy** pode ser ajustado para bloquear anúncios e rastreadores. - Outros aplicativos também podem ser configurados para usar o **Privoxy**. @ 9e69e420:d12360c2
2025-01-21 19:31:48Oregano oil is a potent natural compound that offers numerous scientifically-supported health benefits. ## Active Compounds The oil's therapeutic properties stem from its key bioactive components: - Carvacrol and thymol (primary active compounds) - Polyphenols and other antioxidant ## Antimicrobial Properties **Bacterial Protection** The oil demonstrates powerful antibacterial effects, even against antibiotic-resistant strains like MRSA and other harmful bacteria. Studies show it effectively inactivates various pathogenic bacteria without developing resistance. **Antifungal Effects** It effectively combats fungal infections, particularly Candida-related conditions like oral thrush, athlete's foot, and nail infections. ## Digestive Health Benefits Oregano oil supports digestive wellness by: - Promoting gastric juice secretion and enzyme production - Helping treat Small Intestinal Bacterial Overgrowth (SIBO) - Managing digestive discomfort, bloating, and IBS symptoms ## Anti-inflammatory and Antioxidant Effects The oil provides significant protective benefits through: - Powerful antioxidant activity that fights free radicals - Reduction of inflammatory markers in the body - Protection against oxidative stress-related conditions ## Respiratory Support It aids respiratory health by: - Loosening mucus and phlegm - Suppressing coughs and throat irritation - Supporting overall respiratory tract function ## Additional Benefits **Skin Health** - Improves conditions like psoriasis, acne, and eczema - Supports wound healing through antibacterial action - Provides anti-aging benefits through antioxidant properties **Cardiovascular Health** Studies show oregano oil may help: - Reduce LDL (bad) cholesterol levels - Support overall heart health **Pain Management** The oil demonstrates effectiveness in: - Reducing inflammation-related pain - Managing muscle discomfort - Providing topical pain relief ## Safety Note While oregano oil is generally safe, it's highly concentrated and should be properly diluted before use Consult a healthcare provider before starting supplementation, especially if taking other medications.
@ 9e69e420:d12360c2
2025-01-21 19:31:48Oregano oil is a potent natural compound that offers numerous scientifically-supported health benefits. ## Active Compounds The oil's therapeutic properties stem from its key bioactive components: - Carvacrol and thymol (primary active compounds) - Polyphenols and other antioxidant ## Antimicrobial Properties **Bacterial Protection** The oil demonstrates powerful antibacterial effects, even against antibiotic-resistant strains like MRSA and other harmful bacteria. Studies show it effectively inactivates various pathogenic bacteria without developing resistance. **Antifungal Effects** It effectively combats fungal infections, particularly Candida-related conditions like oral thrush, athlete's foot, and nail infections. ## Digestive Health Benefits Oregano oil supports digestive wellness by: - Promoting gastric juice secretion and enzyme production - Helping treat Small Intestinal Bacterial Overgrowth (SIBO) - Managing digestive discomfort, bloating, and IBS symptoms ## Anti-inflammatory and Antioxidant Effects The oil provides significant protective benefits through: - Powerful antioxidant activity that fights free radicals - Reduction of inflammatory markers in the body - Protection against oxidative stress-related conditions ## Respiratory Support It aids respiratory health by: - Loosening mucus and phlegm - Suppressing coughs and throat irritation - Supporting overall respiratory tract function ## Additional Benefits **Skin Health** - Improves conditions like psoriasis, acne, and eczema - Supports wound healing through antibacterial action - Provides anti-aging benefits through antioxidant properties **Cardiovascular Health** Studies show oregano oil may help: - Reduce LDL (bad) cholesterol levels - Support overall heart health **Pain Management** The oil demonstrates effectiveness in: - Reducing inflammation-related pain - Managing muscle discomfort - Providing topical pain relief ## Safety Note While oregano oil is generally safe, it's highly concentrated and should be properly diluted before use Consult a healthcare provider before starting supplementation, especially if taking other medications. @ 21335073:a244b1ad
2025-03-18 14:43:08**Warning: This piece contains a conversation about difficult topics. Please proceed with caution.** TL;DR please educate your children about online safety. Julian Assange wrote in his 2012 book *Cypherpunks*, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense. This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning. When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little. I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?” I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well. I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread. I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard. I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it. The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust. Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this. I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place. What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method. It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code. They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened. I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road. So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally. Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb. I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback. Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed. That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone. To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all. I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society. I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this. On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government. I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories. There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc. Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind. Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now. There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers? I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity. I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place. My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors. My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline. The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online. I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers. So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation? When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that. I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic. If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations. I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process. **Course:** - The creation of the internet and computers - The fight for cryptography - The tech supply chain from the ground up (example: human rights violations in the supply chain) - Corporate tech - Freedom tech - Data privacy - Digital privacy rights - AI (history-current) - Online safety (predators, scams, catfishing, extortion) - Bitcoin - Laws - How to deal with online hate and harassment - Information on who to contact if you are being abused online or offline - Algorithms - How to seek out the truth about news, etc., online The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children. The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward? I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone. Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability. The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime. This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful. This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens. In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions. I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation.
@ 21335073:a244b1ad
2025-03-18 14:43:08**Warning: This piece contains a conversation about difficult topics. Please proceed with caution.** TL;DR please educate your children about online safety. Julian Assange wrote in his 2012 book *Cypherpunks*, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense. This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning. When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little. I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?” I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well. I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread. I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard. I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it. The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust. Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this. I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place. What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method. It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code. They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened. I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road. So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally. Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb. I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback. Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed. That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone. To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all. I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society. I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this. On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government. I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories. There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc. Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind. Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now. There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers? I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity. I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place. My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors. My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline. The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online. I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers. So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation? When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that. I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic. If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations. I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process. **Course:** - The creation of the internet and computers - The fight for cryptography - The tech supply chain from the ground up (example: human rights violations in the supply chain) - Corporate tech - Freedom tech - Data privacy - Digital privacy rights - AI (history-current) - Online safety (predators, scams, catfishing, extortion) - Bitcoin - Laws - How to deal with online hate and harassment - Information on who to contact if you are being abused online or offline - Algorithms - How to seek out the truth about news, etc., online The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children. The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward? I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone. Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability. The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime. This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful. This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens. In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions. I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation. @ fd06f542:8d6d54cd
2025-04-02 08:04:17{"coverurl":"https://cdn.nostrcheck.me/fd06f542bc6c06a39881810de917e6c5d277dfb51689a568ad7b7a548d6d54cd/1dd58d181d40edb7df942b5b16be3f82e95348a471d5a3620a9585f0af784fee.webp","title":"nostr资源收集","author":"nostrbook"}
@ fd06f542:8d6d54cd
2025-04-02 08:04:17{"coverurl":"https://cdn.nostrcheck.me/fd06f542bc6c06a39881810de917e6c5d277dfb51689a568ad7b7a548d6d54cd/1dd58d181d40edb7df942b5b16be3f82e95348a471d5a3620a9585f0af784fee.webp","title":"nostr资源收集","author":"nostrbook"} @ fd06f542:8d6d54cd
2025-04-02 02:55:14- [首页](/readme.md) - [第一章、开发者指南](/01.md) - [第二章、使用教程](/02.md)
@ fd06f542:8d6d54cd
2025-04-02 02:55:14- [首页](/readme.md) - [第一章、开发者指南](/01.md) - [第二章、使用教程](/02.md) @ 6be5cc06:5259daf0
2025-01-21 01:51:46## Bitcoin: Um sistema de dinheiro eletrônico direto entre pessoas. Satoshi Nakamoto satoshin@gmx.com www.bitcoin.org --- ### Resumo O Bitcoin é uma forma de dinheiro digital que permite pagamentos diretos entre pessoas, sem a necessidade de um banco ou instituição financeira. Ele resolve um problema chamado **gasto duplo**, que ocorre quando alguém tenta gastar o mesmo dinheiro duas vezes. Para evitar isso, o Bitcoin usa uma rede descentralizada onde todos trabalham juntos para verificar e registrar as transações. As transações são registradas em um livro público chamado **blockchain**, protegido por uma técnica chamada **Prova de Trabalho**. Essa técnica cria uma cadeia de registros que não pode ser alterada sem refazer todo o trabalho já feito. Essa cadeia é mantida pelos computadores que participam da rede, e a mais longa é considerada a verdadeira. Enquanto a maior parte do poder computacional da rede for controlada por participantes honestos, o sistema continuará funcionando de forma segura. A rede é flexível, permitindo que qualquer pessoa entre ou saia a qualquer momento, sempre confiando na cadeia mais longa como prova do que aconteceu. --- ### 1. Introdução Hoje, quase todos os pagamentos feitos pela internet dependem de bancos ou empresas como processadores de pagamento (cartões de crédito, por exemplo) para funcionar. Embora esse sistema seja útil, ele tem problemas importantes porque é baseado em **confiança**. Primeiro, essas empresas podem reverter pagamentos, o que é útil em caso de erros, mas cria custos e incertezas. Isso faz com que pequenas transações, como pagar centavos por um serviço, se tornem inviáveis. Além disso, os comerciantes são obrigados a desconfiar dos clientes, pedindo informações extras e aceitando fraudes como algo inevitável. Esses problemas não existem no dinheiro físico, como o papel-moeda, onde o pagamento é final e direto entre as partes. No entanto, não temos como enviar dinheiro físico pela internet sem depender de um intermediário confiável. O que precisamos é de um **sistema de pagamento eletrônico baseado em provas matemáticas**, não em confiança. Esse sistema permitiria que qualquer pessoa enviasse dinheiro diretamente para outra, sem depender de bancos ou processadores de pagamento. Além disso, as transações seriam irreversíveis, protegendo vendedores contra fraudes, mas mantendo a possibilidade de soluções para disputas legítimas. Neste documento, apresentamos o **Bitcoin**, que resolve o problema do gasto duplo usando uma rede descentralizada. Essa rede cria um registro público e protegido por cálculos matemáticos, que garante a ordem das transações. Enquanto a maior parte da rede for controlada por pessoas honestas, o sistema será seguro contra ataques. --- ### 2. Transações Para entender como funciona o Bitcoin, é importante saber como as transações são realizadas. Imagine que você quer transferir uma "moeda digital" para outra pessoa. No sistema do Bitcoin, essa "moeda" é representada por uma sequência de registros que mostram quem é o atual dono. Para transferi-la, você adiciona um novo registro comprovando que agora ela pertence ao próximo dono. Esse registro é protegido por um tipo especial de assinatura digital. #### O que é uma assinatura digital? Uma assinatura digital é como uma senha secreta, mas muito mais segura. No Bitcoin, cada usuário tem duas chaves: uma "chave privada", que é secreta e serve para criar a assinatura, e uma "chave pública", que pode ser compartilhada com todos e é usada para verificar se a assinatura é válida. Quando você transfere uma moeda, usa sua chave privada para assinar a transação, provando que você é o dono. A próxima pessoa pode usar sua chave pública para confirmar isso. #### Como funciona na prática? Cada "moeda" no Bitcoin é, na verdade, uma cadeia de assinaturas digitais. Vamos imaginar o seguinte cenário: 1. A moeda está com o Dono 0 (você). Para transferi-la ao Dono 1, você assina digitalmente a transação com sua chave privada. Essa assinatura inclui o código da transação anterior (chamado de "hash") e a chave pública do Dono 1. 2. Quando o Dono 1 quiser transferir a moeda ao Dono 2, ele assinará a transação seguinte com sua própria chave privada, incluindo também o hash da transação anterior e a chave pública do Dono 2. 3. Esse processo continua, formando uma "cadeia" de transações. Qualquer pessoa pode verificar essa cadeia para confirmar quem é o atual dono da moeda. #### Resolvendo o problema do gasto duplo Um grande desafio com moedas digitais é o "gasto duplo", que é quando uma mesma moeda é usada em mais de uma transação. Para evitar isso, muitos sistemas antigos dependiam de uma entidade central confiável, como uma casa da moeda, que verificava todas as transações. No entanto, isso criava um ponto único de falha e centralizava o controle do dinheiro. O Bitcoin resolve esse problema de forma inovadora: ele usa uma rede descentralizada onde todos os participantes (os "nós") têm acesso a um registro completo de todas as transações. Cada nó verifica se as transações são válidas e se a moeda não foi gasta duas vezes. Quando a maioria dos nós concorda com a validade de uma transação, ela é registrada permanentemente na blockchain. #### Por que isso é importante? Essa solução elimina a necessidade de confiar em uma única entidade para gerenciar o dinheiro, permitindo que qualquer pessoa no mundo use o Bitcoin sem precisar de permissão de terceiros. Além disso, ela garante que o sistema seja seguro e resistente a fraudes. --- ### 3. Servidor Timestamp Para assegurar que as transações sejam realizadas de forma segura e transparente, o sistema Bitcoin utiliza algo chamado de "servidor de registro de tempo" (timestamp). Esse servidor funciona como um registro público que organiza as transações em uma ordem específica. Ele faz isso agrupando várias transações em blocos e criando um código único chamado "hash". Esse hash é como uma impressão digital que representa todo o conteúdo do bloco. O hash de cada bloco é amplamente divulgado, como se fosse publicado em um jornal ou em um fórum público. Esse processo garante que cada bloco de transações tenha um registro de quando foi criado e que ele existia naquele momento. Além disso, cada novo bloco criado contém o hash do bloco anterior, formando uma cadeia contínua de blocos conectados — conhecida como blockchain. Com isso, se alguém tentar alterar qualquer informação em um bloco anterior, o hash desse bloco mudará e não corresponderá ao hash armazenado no bloco seguinte. Essa característica torna a cadeia muito segura, pois qualquer tentativa de fraude seria imediatamente detectada. O sistema de timestamps é essencial para provar a ordem cronológica das transações e garantir que cada uma delas seja única e autêntica. Dessa forma, ele reforça a segurança e a confiança na rede Bitcoin. --- ### 4. Prova-de-Trabalho Para implementar o registro de tempo distribuído no sistema Bitcoin, utilizamos um mecanismo chamado prova-de-trabalho. Esse sistema é semelhante ao Hashcash, desenvolvido por Adam Back, e baseia-se na criação de um código único, o "hash", por meio de um processo computacionalmente exigente. A prova-de-trabalho envolve encontrar um valor especial que, quando processado junto com as informações do bloco, gere um hash que comece com uma quantidade específica de zeros. Esse valor especial é chamado de "nonce". Encontrar o nonce correto exige um esforço significativo do computador, porque envolve tentativas repetidas até que a condição seja satisfeita. Esse processo é importante porque torna extremamente difícil alterar qualquer informação registrada em um bloco. Se alguém tentar mudar algo em um bloco, seria necessário refazer o trabalho de computação não apenas para aquele bloco, mas também para todos os blocos que vêm depois dele. Isso garante a segurança e a imutabilidade da blockchain. A prova-de-trabalho também resolve o problema de decidir qual cadeia de blocos é a válida quando há múltiplas cadeias competindo. A decisão é feita pela cadeia mais longa, pois ela representa o maior esforço computacional já realizado. Isso impede que qualquer indivíduo ou grupo controle a rede, desde que a maioria do poder de processamento seja mantida por participantes honestos. Para garantir que o sistema permaneça eficiente e equilibrado, a dificuldade da prova-de-trabalho é ajustada automaticamente ao longo do tempo. Se novos blocos estiverem sendo gerados rapidamente, a dificuldade aumenta; se estiverem sendo gerados muito lentamente, a dificuldade diminui. Esse ajuste assegura que novos blocos sejam criados aproximadamente a cada 10 minutos, mantendo o sistema estável e funcional. --- ### 5. Rede A rede Bitcoin é o coração do sistema e funciona de maneira distribuída, conectando vários participantes (ou nós) para garantir o registro e a validação das transações. Os passos para operar essa rede são: 1. **Transmissão de Transações**: Quando alguém realiza uma nova transação, ela é enviada para todos os nós da rede. Isso é feito para garantir que todos estejam cientes da operação e possam validá-la. 2. **Coleta de Transações em Blocos**: Cada nó agrupa as novas transações recebidas em um "bloco". Este bloco será preparado para ser adicionado à cadeia de blocos (a blockchain). 3. **Prova-de-Trabalho**: Os nós competem para resolver a prova-de-trabalho do bloco, utilizando poder computacional para encontrar um hash válido. Esse processo é como resolver um quebra-cabeça matemático difícil. 4. **Envio do Bloco Resolvido**: Quando um nó encontra a solução para o bloco (a prova-de-trabalho), ele compartilha esse bloco com todos os outros nós na rede. 5. **Validação do Bloco**: Cada nó verifica o bloco recebido para garantir que todas as transações nele contidas sejam válidas e que nenhuma moeda tenha sido gasta duas vezes. Apenas blocos válidos são aceitos. 6. **Construção do Próximo Bloco**: Os nós que aceitaram o bloco começam a trabalhar na criação do próximo bloco, utilizando o hash do bloco aceito como base (hash anterior). Isso mantém a continuidade da cadeia. #### Resolução de Conflitos e Escolha da Cadeia Mais Longa Os nós sempre priorizam a cadeia mais longa, pois ela representa o maior esforço computacional já realizado, garantindo maior segurança. Se dois blocos diferentes forem compartilhados simultaneamente, os nós trabalharão no primeiro bloco recebido, mas guardarão o outro como uma alternativa. Caso o segundo bloco eventualmente forme uma cadeia mais longa (ou seja, tenha mais blocos subsequentes), os nós mudarão para essa nova cadeia. #### Tolerância a Falhas A rede é robusta e pode lidar com mensagens que não chegam a todos os nós. Uma transação não precisa alcançar todos os nós de imediato; basta que chegue a um número suficiente deles para ser incluída em um bloco. Da mesma forma, se um nó não receber um bloco em tempo hábil, ele pode solicitá-lo ao perceber que está faltando quando o próximo bloco é recebido. Esse mecanismo descentralizado permite que a rede Bitcoin funcione de maneira segura, confiável e resiliente, sem depender de uma autoridade central. --- ### 6. Incentivo O incentivo é um dos pilares fundamentais que sustenta o funcionamento da rede Bitcoin, garantindo que os participantes (nós) continuem operando de forma honesta e contribuindo com recursos computacionais. Ele é estruturado em duas partes principais: a recompensa por mineração e as taxas de transação. #### Recompensa por Mineração Por convenção, o primeiro registro em cada bloco é uma transação especial que cria novas moedas e as atribui ao criador do bloco. Essa recompensa incentiva os mineradores a dedicarem poder computacional para apoiar a rede. Como não há uma autoridade central para emitir moedas, essa é a maneira pela qual novas moedas entram em circulação. Esse processo pode ser comparado ao trabalho de garimpeiros, que utilizam recursos para colocar mais ouro em circulação. No caso do Bitcoin, o "recurso" consiste no tempo de CPU e na energia elétrica consumida para resolver a prova-de-trabalho. #### Taxas de Transação Além da recompensa por mineração, os mineradores também podem ser incentivados pelas taxas de transação. Se uma transação utiliza menos valor de saída do que o valor de entrada, a diferença é tratada como uma taxa, que é adicionada à recompensa do bloco contendo essa transação. Com o passar do tempo e à medida que o número de moedas em circulação atinge o limite predeterminado, essas taxas de transação se tornam a principal fonte de incentivo, substituindo gradualmente a emissão de novas moedas. Isso permite que o sistema opere sem inflação, uma vez que o número total de moedas permanece fixo. #### Incentivo à Honestidade O design do incentivo também busca garantir que os participantes da rede mantenham um comportamento honesto. Para um atacante que consiga reunir mais poder computacional do que o restante da rede, ele enfrentaria duas escolhas: 1. Usar esse poder para fraudar o sistema, como reverter transações e roubar pagamentos. 2. Seguir as regras do sistema, criando novos blocos e recebendo recompensas legítimas. A lógica econômica favorece a segunda opção, pois um comportamento desonesto prejudicaria a confiança no sistema, diminuindo o valor de todas as moedas, incluindo aquelas que o próprio atacante possui. Jogar dentro das regras não apenas maximiza o retorno financeiro, mas também preserva a validade e a integridade do sistema. Esse mecanismo garante que os incentivos econômicos estejam alinhados com o objetivo de manter a rede segura, descentralizada e funcional ao longo do tempo. --- ### 7. Recuperação do Espaço em Disco Depois que uma moeda passa a estar protegida por muitos blocos na cadeia, as informações sobre as transações antigas que a geraram podem ser descartadas para economizar espaço em disco. Para que isso seja possível sem comprometer a segurança, as transações são organizadas em uma estrutura chamada "árvore de Merkle". Essa árvore funciona como um resumo das transações: em vez de armazenar todas elas, guarda apenas um "hash raiz", que é como uma assinatura compacta que representa todo o grupo de transações. Os blocos antigos podem, então, ser simplificados, removendo as partes desnecessárias dessa árvore. Apenas a raiz do hash precisa ser mantida no cabeçalho do bloco, garantindo que a integridade dos dados seja preservada, mesmo que detalhes específicos sejam descartados. Para exemplificar: imagine que você tenha vários recibos de compra. Em vez de guardar todos os recibos, você cria um documento e lista apenas o valor total de cada um. Mesmo que os recibos originais sejam descartados, ainda é possível verificar a soma com base nos valores armazenados. Além disso, o espaço ocupado pelos blocos em si é muito pequeno. Cada bloco sem transações ocupa apenas cerca de 80 bytes. Isso significa que, mesmo com blocos sendo gerados a cada 10 minutos, o crescimento anual em espaço necessário é insignificante: apenas 4,2 MB por ano. Com a capacidade de armazenamento dos computadores crescendo a cada ano, esse espaço continuará sendo trivial, garantindo que a rede possa operar de forma eficiente sem problemas de armazenamento, mesmo a longo prazo. --- ### 8. Verificação de Pagamento Simplificada É possível confirmar pagamentos sem a necessidade de operar um nó completo da rede. Para isso, o usuário precisa apenas de uma cópia dos cabeçalhos dos blocos da cadeia mais longa (ou seja, a cadeia com maior esforço de trabalho acumulado). Ele pode verificar a validade de uma transação ao consultar os nós da rede até obter a confirmação de que tem a cadeia mais longa. Para isso, utiliza-se o ramo Merkle, que conecta a transação ao bloco em que ela foi registrada. Entretanto, o método simplificado possui limitações: ele não pode confirmar uma transação isoladamente, mas sim assegurar que ela ocupa um lugar específico na cadeia mais longa. Dessa forma, se um nó da rede aprova a transação, os blocos subsequentes reforçam essa aceitação. A verificação simplificada é confiável enquanto a maioria dos nós da rede for honesta. Contudo, ela se torna vulnerável caso a rede seja dominada por um invasor. Nesse cenário, um atacante poderia fabricar transações fraudulentas que enganariam o usuário temporariamente até que o invasor obtivesse controle completo da rede. Uma estratégia para mitigar esse risco é configurar alertas nos softwares de nós completos. Esses alertas identificam blocos inválidos, sugerindo ao usuário baixar o bloco completo para confirmar qualquer inconsistência. Para maior segurança, empresas que realizam pagamentos frequentes podem preferir operar seus próprios nós, reduzindo riscos e permitindo uma verificação mais direta e confiável. --- ### 9. Combinando e Dividindo Valor No sistema Bitcoin, cada unidade de valor é tratada como uma "moeda" individual, mas gerenciar cada centavo como uma transação separada seria impraticável. Para resolver isso, o Bitcoin permite que valores sejam combinados ou divididos em transações, facilitando pagamentos de qualquer valor. #### Entradas e Saídas Cada transação no Bitcoin é composta por: - **Entradas**: Representam os valores recebidos em transações anteriores. - **Saídas**: Correspondem aos valores enviados, divididos entre os destinatários e, eventualmente, o troco para o remetente. Normalmente, uma transação contém: - Uma única entrada com valor suficiente para cobrir o pagamento. - Ou várias entradas combinadas para atingir o valor necessário. O valor total das saídas nunca excede o das entradas, e a diferença (se houver) pode ser retornada ao remetente como **troco**. #### Exemplo Prático Imagine que você tem duas entradas: 1. 0,03 BTC 2. 0,07 BTC Se deseja enviar 0,08 BTC para alguém, a transação terá: - **Entrada**: As duas entradas combinadas (0,03 + 0,07 BTC = 0,10 BTC). - **Saídas**: Uma para o destinatário (0,08 BTC) e outra como troco para você (0,02 BTC). Essa flexibilidade permite que o sistema funcione sem precisar manipular cada unidade mínima individualmente. #### Difusão e Simplificação A difusão de transações, onde uma depende de várias anteriores e assim por diante, não representa um problema. Não é necessário armazenar ou verificar o histórico completo de uma transação para utilizá-la, já que o registro na blockchain garante sua integridade. --- ### 10. Privacidade O modelo bancário tradicional oferece um certo nível de privacidade, limitando o acesso às informações financeiras apenas às partes envolvidas e a um terceiro confiável (como bancos ou instituições financeiras). No entanto, o Bitcoin opera de forma diferente, pois todas as transações são publicamente registradas na blockchain. Apesar disso, a privacidade pode ser mantida utilizando **chaves públicas anônimas**, que desvinculam diretamente as transações das identidades das partes envolvidas. #### Fluxo de Informação - No **modelo tradicional**, as transações passam por um terceiro confiável que conhece tanto o remetente quanto o destinatário. - No **Bitcoin**, as transações são anunciadas publicamente, mas sem revelar diretamente as identidades das partes. Isso é comparável a dados divulgados por bolsas de valores, onde informações como o tempo e o tamanho das negociações (a "fita") são públicas, mas as identidades das partes não. #### Protegendo a Privacidade Para aumentar a privacidade no Bitcoin, são adotadas as seguintes práticas: 1. **Chaves Públicas Anônimas**: Cada transação utiliza um par de chaves diferentes, dificultando a associação com um proprietário único. 2. **Prevenção de Ligação**: Ao usar chaves novas para cada transação, reduz-se a possibilidade de links evidentes entre múltiplas transações realizadas pelo mesmo usuário. #### Riscos de Ligação Embora a privacidade seja fortalecida, alguns riscos permanecem: - Transações **multi-entrada** podem revelar que todas as entradas pertencem ao mesmo proprietário, caso sejam necessárias para somar o valor total. - O proprietário da chave pode ser identificado indiretamente por transações anteriores que estejam conectadas. --- ### 11. Cálculos Imagine que temos um sistema onde as pessoas (ou computadores) competem para adicionar informações novas (blocos) a um grande registro público (a cadeia de blocos ou blockchain). Este registro é como um livro contábil compartilhado, onde todos podem verificar o que está escrito. Agora, vamos pensar em um cenário: um atacante quer enganar o sistema. Ele quer mudar informações já registradas para beneficiar a si mesmo, por exemplo, desfazendo um pagamento que já fez. Para isso, ele precisa criar uma versão alternativa do livro contábil (a cadeia de blocos dele) e convencer todos os outros participantes de que essa versão é a verdadeira. Mas isso é extremamente difícil. #### Como o Ataque Funciona Quando um novo bloco é adicionado à cadeia, ele depende de cálculos complexos que levam tempo e esforço. Esses cálculos são como um grande quebra-cabeça que precisa ser resolvido. - Os “bons jogadores” (nós honestos) estão sempre trabalhando juntos para resolver esses quebra-cabeças e adicionar novos blocos à cadeia verdadeira. - O atacante, por outro lado, precisa resolver quebra-cabeças sozinho, tentando “alcançar” a cadeia honesta para que sua versão alternativa pareça válida. Se a cadeia honesta já está vários blocos à frente, o atacante começa em desvantagem, e o sistema está projetado para que a dificuldade de alcançá-los aumente rapidamente. #### A Corrida Entre Cadeias Você pode imaginar isso como uma corrida. A cada bloco novo que os jogadores honestos adicionam à cadeia verdadeira, eles se distanciam mais do atacante. Para vencer, o atacante teria que resolver os quebra-cabeças mais rápido que todos os outros jogadores honestos juntos. Suponha que: - A rede honesta tem **80% do poder computacional** (ou seja, resolve 8 de cada 10 quebra-cabeças). - O atacante tem **20% do poder computacional** (ou seja, resolve 2 de cada 10 quebra-cabeças). Cada vez que a rede honesta adiciona um bloco, o atacante tem que "correr atrás" e resolver mais quebra-cabeças para alcançar. #### Por Que o Ataque Fica Cada Vez Mais Improvável? Vamos usar uma fórmula simples para mostrar como as chances de sucesso do atacante diminuem conforme ele precisa "alcançar" mais blocos: P = (q/p)^z - **q** é o poder computacional do atacante (20%, ou 0,2). - **p** é o poder computacional da rede honesta (80%, ou 0,8). - **z** é a diferença de blocos entre a cadeia honesta e a cadeia do atacante. Se o atacante está 5 blocos atrás (z = 5): P = (0,2 / 0,8)^5 = (0,25)^5 = 0,00098, (ou, 0,098%) Isso significa que o atacante tem menos de 0,1% de chance de sucesso — ou seja, é muito improvável. Se ele estiver 10 blocos atrás (z = 10): P = (0,2 / 0,8)^10 = (0,25)^10 = 0,000000095, (ou, 0,0000095%). Neste caso, as chances de sucesso são praticamente **nulas**. #### Um Exemplo Simples Se você jogar uma moeda, a chance de cair “cara” é de 50%. Mas se precisar de 10 caras seguidas, sua chance já é bem menor. Se precisar de 20 caras seguidas, é quase impossível. No caso do Bitcoin, o atacante precisa de muito mais do que 20 caras seguidas. Ele precisa resolver quebra-cabeças extremamente difíceis e alcançar os jogadores honestos que estão sempre à frente. Isso faz com que o ataque seja inviável na prática. #### Por Que Tudo Isso é Seguro? - **A probabilidade de sucesso do atacante diminui exponencialmente.** Isso significa que, quanto mais tempo passa, menor é a chance de ele conseguir enganar o sistema. - **A cadeia verdadeira (honesta) está protegida pela força da rede.** Cada novo bloco que os jogadores honestos adicionam à cadeia torna mais difícil para o atacante alcançar. #### E Se o Atacante Tentar Continuar? O atacante poderia continuar tentando indefinidamente, mas ele estaria gastando muito tempo e energia sem conseguir nada. Enquanto isso, os jogadores honestos estão sempre adicionando novos blocos, tornando o trabalho do atacante ainda mais inútil. Assim, o sistema garante que a cadeia verdadeira seja extremamente segura e que ataques sejam, na prática, impossíveis de ter sucesso. --- ### 12. Conclusão Propusemos um sistema de transações eletrônicas que elimina a necessidade de confiança, baseando-se em assinaturas digitais e em uma rede peer-to-peer que utiliza prova de trabalho. Isso resolve o problema do gasto duplo, criando um histórico público de transações imutável, desde que a maioria do poder computacional permaneça sob controle dos participantes honestos. A rede funciona de forma simples e descentralizada, com nós independentes que não precisam de identificação ou coordenação direta. Eles entram e saem livremente, aceitando a cadeia de prova de trabalho como registro do que ocorreu durante sua ausência. As decisões são tomadas por meio do poder de CPU, validando blocos legítimos, estendendo a cadeia e rejeitando os inválidos. Com este mecanismo de consenso, todas as regras e incentivos necessários para o funcionamento seguro e eficiente do sistema são garantidos. --- Faça o download do whitepaper original em português: https://bitcoin.org/files/bitcoin-paper/bitcoin_pt_br.pdf
@ 6be5cc06:5259daf0
2025-01-21 01:51:46## Bitcoin: Um sistema de dinheiro eletrônico direto entre pessoas. Satoshi Nakamoto satoshin@gmx.com www.bitcoin.org --- ### Resumo O Bitcoin é uma forma de dinheiro digital que permite pagamentos diretos entre pessoas, sem a necessidade de um banco ou instituição financeira. Ele resolve um problema chamado **gasto duplo**, que ocorre quando alguém tenta gastar o mesmo dinheiro duas vezes. Para evitar isso, o Bitcoin usa uma rede descentralizada onde todos trabalham juntos para verificar e registrar as transações. As transações são registradas em um livro público chamado **blockchain**, protegido por uma técnica chamada **Prova de Trabalho**. Essa técnica cria uma cadeia de registros que não pode ser alterada sem refazer todo o trabalho já feito. Essa cadeia é mantida pelos computadores que participam da rede, e a mais longa é considerada a verdadeira. Enquanto a maior parte do poder computacional da rede for controlada por participantes honestos, o sistema continuará funcionando de forma segura. A rede é flexível, permitindo que qualquer pessoa entre ou saia a qualquer momento, sempre confiando na cadeia mais longa como prova do que aconteceu. --- ### 1. Introdução Hoje, quase todos os pagamentos feitos pela internet dependem de bancos ou empresas como processadores de pagamento (cartões de crédito, por exemplo) para funcionar. Embora esse sistema seja útil, ele tem problemas importantes porque é baseado em **confiança**. Primeiro, essas empresas podem reverter pagamentos, o que é útil em caso de erros, mas cria custos e incertezas. Isso faz com que pequenas transações, como pagar centavos por um serviço, se tornem inviáveis. Além disso, os comerciantes são obrigados a desconfiar dos clientes, pedindo informações extras e aceitando fraudes como algo inevitável. Esses problemas não existem no dinheiro físico, como o papel-moeda, onde o pagamento é final e direto entre as partes. No entanto, não temos como enviar dinheiro físico pela internet sem depender de um intermediário confiável. O que precisamos é de um **sistema de pagamento eletrônico baseado em provas matemáticas**, não em confiança. Esse sistema permitiria que qualquer pessoa enviasse dinheiro diretamente para outra, sem depender de bancos ou processadores de pagamento. Além disso, as transações seriam irreversíveis, protegendo vendedores contra fraudes, mas mantendo a possibilidade de soluções para disputas legítimas. Neste documento, apresentamos o **Bitcoin**, que resolve o problema do gasto duplo usando uma rede descentralizada. Essa rede cria um registro público e protegido por cálculos matemáticos, que garante a ordem das transações. Enquanto a maior parte da rede for controlada por pessoas honestas, o sistema será seguro contra ataques. --- ### 2. Transações Para entender como funciona o Bitcoin, é importante saber como as transações são realizadas. Imagine que você quer transferir uma "moeda digital" para outra pessoa. No sistema do Bitcoin, essa "moeda" é representada por uma sequência de registros que mostram quem é o atual dono. Para transferi-la, você adiciona um novo registro comprovando que agora ela pertence ao próximo dono. Esse registro é protegido por um tipo especial de assinatura digital. #### O que é uma assinatura digital? Uma assinatura digital é como uma senha secreta, mas muito mais segura. No Bitcoin, cada usuário tem duas chaves: uma "chave privada", que é secreta e serve para criar a assinatura, e uma "chave pública", que pode ser compartilhada com todos e é usada para verificar se a assinatura é válida. Quando você transfere uma moeda, usa sua chave privada para assinar a transação, provando que você é o dono. A próxima pessoa pode usar sua chave pública para confirmar isso. #### Como funciona na prática? Cada "moeda" no Bitcoin é, na verdade, uma cadeia de assinaturas digitais. Vamos imaginar o seguinte cenário: 1. A moeda está com o Dono 0 (você). Para transferi-la ao Dono 1, você assina digitalmente a transação com sua chave privada. Essa assinatura inclui o código da transação anterior (chamado de "hash") e a chave pública do Dono 1. 2. Quando o Dono 1 quiser transferir a moeda ao Dono 2, ele assinará a transação seguinte com sua própria chave privada, incluindo também o hash da transação anterior e a chave pública do Dono 2. 3. Esse processo continua, formando uma "cadeia" de transações. Qualquer pessoa pode verificar essa cadeia para confirmar quem é o atual dono da moeda. #### Resolvendo o problema do gasto duplo Um grande desafio com moedas digitais é o "gasto duplo", que é quando uma mesma moeda é usada em mais de uma transação. Para evitar isso, muitos sistemas antigos dependiam de uma entidade central confiável, como uma casa da moeda, que verificava todas as transações. No entanto, isso criava um ponto único de falha e centralizava o controle do dinheiro. O Bitcoin resolve esse problema de forma inovadora: ele usa uma rede descentralizada onde todos os participantes (os "nós") têm acesso a um registro completo de todas as transações. Cada nó verifica se as transações são válidas e se a moeda não foi gasta duas vezes. Quando a maioria dos nós concorda com a validade de uma transação, ela é registrada permanentemente na blockchain. #### Por que isso é importante? Essa solução elimina a necessidade de confiar em uma única entidade para gerenciar o dinheiro, permitindo que qualquer pessoa no mundo use o Bitcoin sem precisar de permissão de terceiros. Além disso, ela garante que o sistema seja seguro e resistente a fraudes. --- ### 3. Servidor Timestamp Para assegurar que as transações sejam realizadas de forma segura e transparente, o sistema Bitcoin utiliza algo chamado de "servidor de registro de tempo" (timestamp). Esse servidor funciona como um registro público que organiza as transações em uma ordem específica. Ele faz isso agrupando várias transações em blocos e criando um código único chamado "hash". Esse hash é como uma impressão digital que representa todo o conteúdo do bloco. O hash de cada bloco é amplamente divulgado, como se fosse publicado em um jornal ou em um fórum público. Esse processo garante que cada bloco de transações tenha um registro de quando foi criado e que ele existia naquele momento. Além disso, cada novo bloco criado contém o hash do bloco anterior, formando uma cadeia contínua de blocos conectados — conhecida como blockchain. Com isso, se alguém tentar alterar qualquer informação em um bloco anterior, o hash desse bloco mudará e não corresponderá ao hash armazenado no bloco seguinte. Essa característica torna a cadeia muito segura, pois qualquer tentativa de fraude seria imediatamente detectada. O sistema de timestamps é essencial para provar a ordem cronológica das transações e garantir que cada uma delas seja única e autêntica. Dessa forma, ele reforça a segurança e a confiança na rede Bitcoin. --- ### 4. Prova-de-Trabalho Para implementar o registro de tempo distribuído no sistema Bitcoin, utilizamos um mecanismo chamado prova-de-trabalho. Esse sistema é semelhante ao Hashcash, desenvolvido por Adam Back, e baseia-se na criação de um código único, o "hash", por meio de um processo computacionalmente exigente. A prova-de-trabalho envolve encontrar um valor especial que, quando processado junto com as informações do bloco, gere um hash que comece com uma quantidade específica de zeros. Esse valor especial é chamado de "nonce". Encontrar o nonce correto exige um esforço significativo do computador, porque envolve tentativas repetidas até que a condição seja satisfeita. Esse processo é importante porque torna extremamente difícil alterar qualquer informação registrada em um bloco. Se alguém tentar mudar algo em um bloco, seria necessário refazer o trabalho de computação não apenas para aquele bloco, mas também para todos os blocos que vêm depois dele. Isso garante a segurança e a imutabilidade da blockchain. A prova-de-trabalho também resolve o problema de decidir qual cadeia de blocos é a válida quando há múltiplas cadeias competindo. A decisão é feita pela cadeia mais longa, pois ela representa o maior esforço computacional já realizado. Isso impede que qualquer indivíduo ou grupo controle a rede, desde que a maioria do poder de processamento seja mantida por participantes honestos. Para garantir que o sistema permaneça eficiente e equilibrado, a dificuldade da prova-de-trabalho é ajustada automaticamente ao longo do tempo. Se novos blocos estiverem sendo gerados rapidamente, a dificuldade aumenta; se estiverem sendo gerados muito lentamente, a dificuldade diminui. Esse ajuste assegura que novos blocos sejam criados aproximadamente a cada 10 minutos, mantendo o sistema estável e funcional. --- ### 5. Rede A rede Bitcoin é o coração do sistema e funciona de maneira distribuída, conectando vários participantes (ou nós) para garantir o registro e a validação das transações. Os passos para operar essa rede são: 1. **Transmissão de Transações**: Quando alguém realiza uma nova transação, ela é enviada para todos os nós da rede. Isso é feito para garantir que todos estejam cientes da operação e possam validá-la. 2. **Coleta de Transações em Blocos**: Cada nó agrupa as novas transações recebidas em um "bloco". Este bloco será preparado para ser adicionado à cadeia de blocos (a blockchain). 3. **Prova-de-Trabalho**: Os nós competem para resolver a prova-de-trabalho do bloco, utilizando poder computacional para encontrar um hash válido. Esse processo é como resolver um quebra-cabeça matemático difícil. 4. **Envio do Bloco Resolvido**: Quando um nó encontra a solução para o bloco (a prova-de-trabalho), ele compartilha esse bloco com todos os outros nós na rede. 5. **Validação do Bloco**: Cada nó verifica o bloco recebido para garantir que todas as transações nele contidas sejam válidas e que nenhuma moeda tenha sido gasta duas vezes. Apenas blocos válidos são aceitos. 6. **Construção do Próximo Bloco**: Os nós que aceitaram o bloco começam a trabalhar na criação do próximo bloco, utilizando o hash do bloco aceito como base (hash anterior). Isso mantém a continuidade da cadeia. #### Resolução de Conflitos e Escolha da Cadeia Mais Longa Os nós sempre priorizam a cadeia mais longa, pois ela representa o maior esforço computacional já realizado, garantindo maior segurança. Se dois blocos diferentes forem compartilhados simultaneamente, os nós trabalharão no primeiro bloco recebido, mas guardarão o outro como uma alternativa. Caso o segundo bloco eventualmente forme uma cadeia mais longa (ou seja, tenha mais blocos subsequentes), os nós mudarão para essa nova cadeia. #### Tolerância a Falhas A rede é robusta e pode lidar com mensagens que não chegam a todos os nós. Uma transação não precisa alcançar todos os nós de imediato; basta que chegue a um número suficiente deles para ser incluída em um bloco. Da mesma forma, se um nó não receber um bloco em tempo hábil, ele pode solicitá-lo ao perceber que está faltando quando o próximo bloco é recebido. Esse mecanismo descentralizado permite que a rede Bitcoin funcione de maneira segura, confiável e resiliente, sem depender de uma autoridade central. --- ### 6. Incentivo O incentivo é um dos pilares fundamentais que sustenta o funcionamento da rede Bitcoin, garantindo que os participantes (nós) continuem operando de forma honesta e contribuindo com recursos computacionais. Ele é estruturado em duas partes principais: a recompensa por mineração e as taxas de transação. #### Recompensa por Mineração Por convenção, o primeiro registro em cada bloco é uma transação especial que cria novas moedas e as atribui ao criador do bloco. Essa recompensa incentiva os mineradores a dedicarem poder computacional para apoiar a rede. Como não há uma autoridade central para emitir moedas, essa é a maneira pela qual novas moedas entram em circulação. Esse processo pode ser comparado ao trabalho de garimpeiros, que utilizam recursos para colocar mais ouro em circulação. No caso do Bitcoin, o "recurso" consiste no tempo de CPU e na energia elétrica consumida para resolver a prova-de-trabalho. #### Taxas de Transação Além da recompensa por mineração, os mineradores também podem ser incentivados pelas taxas de transação. Se uma transação utiliza menos valor de saída do que o valor de entrada, a diferença é tratada como uma taxa, que é adicionada à recompensa do bloco contendo essa transação. Com o passar do tempo e à medida que o número de moedas em circulação atinge o limite predeterminado, essas taxas de transação se tornam a principal fonte de incentivo, substituindo gradualmente a emissão de novas moedas. Isso permite que o sistema opere sem inflação, uma vez que o número total de moedas permanece fixo. #### Incentivo à Honestidade O design do incentivo também busca garantir que os participantes da rede mantenham um comportamento honesto. Para um atacante que consiga reunir mais poder computacional do que o restante da rede, ele enfrentaria duas escolhas: 1. Usar esse poder para fraudar o sistema, como reverter transações e roubar pagamentos. 2. Seguir as regras do sistema, criando novos blocos e recebendo recompensas legítimas. A lógica econômica favorece a segunda opção, pois um comportamento desonesto prejudicaria a confiança no sistema, diminuindo o valor de todas as moedas, incluindo aquelas que o próprio atacante possui. Jogar dentro das regras não apenas maximiza o retorno financeiro, mas também preserva a validade e a integridade do sistema. Esse mecanismo garante que os incentivos econômicos estejam alinhados com o objetivo de manter a rede segura, descentralizada e funcional ao longo do tempo. --- ### 7. Recuperação do Espaço em Disco Depois que uma moeda passa a estar protegida por muitos blocos na cadeia, as informações sobre as transações antigas que a geraram podem ser descartadas para economizar espaço em disco. Para que isso seja possível sem comprometer a segurança, as transações são organizadas em uma estrutura chamada "árvore de Merkle". Essa árvore funciona como um resumo das transações: em vez de armazenar todas elas, guarda apenas um "hash raiz", que é como uma assinatura compacta que representa todo o grupo de transações. Os blocos antigos podem, então, ser simplificados, removendo as partes desnecessárias dessa árvore. Apenas a raiz do hash precisa ser mantida no cabeçalho do bloco, garantindo que a integridade dos dados seja preservada, mesmo que detalhes específicos sejam descartados. Para exemplificar: imagine que você tenha vários recibos de compra. Em vez de guardar todos os recibos, você cria um documento e lista apenas o valor total de cada um. Mesmo que os recibos originais sejam descartados, ainda é possível verificar a soma com base nos valores armazenados. Além disso, o espaço ocupado pelos blocos em si é muito pequeno. Cada bloco sem transações ocupa apenas cerca de 80 bytes. Isso significa que, mesmo com blocos sendo gerados a cada 10 minutos, o crescimento anual em espaço necessário é insignificante: apenas 4,2 MB por ano. Com a capacidade de armazenamento dos computadores crescendo a cada ano, esse espaço continuará sendo trivial, garantindo que a rede possa operar de forma eficiente sem problemas de armazenamento, mesmo a longo prazo. --- ### 8. Verificação de Pagamento Simplificada É possível confirmar pagamentos sem a necessidade de operar um nó completo da rede. Para isso, o usuário precisa apenas de uma cópia dos cabeçalhos dos blocos da cadeia mais longa (ou seja, a cadeia com maior esforço de trabalho acumulado). Ele pode verificar a validade de uma transação ao consultar os nós da rede até obter a confirmação de que tem a cadeia mais longa. Para isso, utiliza-se o ramo Merkle, que conecta a transação ao bloco em que ela foi registrada. Entretanto, o método simplificado possui limitações: ele não pode confirmar uma transação isoladamente, mas sim assegurar que ela ocupa um lugar específico na cadeia mais longa. Dessa forma, se um nó da rede aprova a transação, os blocos subsequentes reforçam essa aceitação. A verificação simplificada é confiável enquanto a maioria dos nós da rede for honesta. Contudo, ela se torna vulnerável caso a rede seja dominada por um invasor. Nesse cenário, um atacante poderia fabricar transações fraudulentas que enganariam o usuário temporariamente até que o invasor obtivesse controle completo da rede. Uma estratégia para mitigar esse risco é configurar alertas nos softwares de nós completos. Esses alertas identificam blocos inválidos, sugerindo ao usuário baixar o bloco completo para confirmar qualquer inconsistência. Para maior segurança, empresas que realizam pagamentos frequentes podem preferir operar seus próprios nós, reduzindo riscos e permitindo uma verificação mais direta e confiável. --- ### 9. Combinando e Dividindo Valor No sistema Bitcoin, cada unidade de valor é tratada como uma "moeda" individual, mas gerenciar cada centavo como uma transação separada seria impraticável. Para resolver isso, o Bitcoin permite que valores sejam combinados ou divididos em transações, facilitando pagamentos de qualquer valor. #### Entradas e Saídas Cada transação no Bitcoin é composta por: - **Entradas**: Representam os valores recebidos em transações anteriores. - **Saídas**: Correspondem aos valores enviados, divididos entre os destinatários e, eventualmente, o troco para o remetente. Normalmente, uma transação contém: - Uma única entrada com valor suficiente para cobrir o pagamento. - Ou várias entradas combinadas para atingir o valor necessário. O valor total das saídas nunca excede o das entradas, e a diferença (se houver) pode ser retornada ao remetente como **troco**. #### Exemplo Prático Imagine que você tem duas entradas: 1. 0,03 BTC 2. 0,07 BTC Se deseja enviar 0,08 BTC para alguém, a transação terá: - **Entrada**: As duas entradas combinadas (0,03 + 0,07 BTC = 0,10 BTC). - **Saídas**: Uma para o destinatário (0,08 BTC) e outra como troco para você (0,02 BTC). Essa flexibilidade permite que o sistema funcione sem precisar manipular cada unidade mínima individualmente. #### Difusão e Simplificação A difusão de transações, onde uma depende de várias anteriores e assim por diante, não representa um problema. Não é necessário armazenar ou verificar o histórico completo de uma transação para utilizá-la, já que o registro na blockchain garante sua integridade. --- ### 10. Privacidade O modelo bancário tradicional oferece um certo nível de privacidade, limitando o acesso às informações financeiras apenas às partes envolvidas e a um terceiro confiável (como bancos ou instituições financeiras). No entanto, o Bitcoin opera de forma diferente, pois todas as transações são publicamente registradas na blockchain. Apesar disso, a privacidade pode ser mantida utilizando **chaves públicas anônimas**, que desvinculam diretamente as transações das identidades das partes envolvidas. #### Fluxo de Informação - No **modelo tradicional**, as transações passam por um terceiro confiável que conhece tanto o remetente quanto o destinatário. - No **Bitcoin**, as transações são anunciadas publicamente, mas sem revelar diretamente as identidades das partes. Isso é comparável a dados divulgados por bolsas de valores, onde informações como o tempo e o tamanho das negociações (a "fita") são públicas, mas as identidades das partes não. #### Protegendo a Privacidade Para aumentar a privacidade no Bitcoin, são adotadas as seguintes práticas: 1. **Chaves Públicas Anônimas**: Cada transação utiliza um par de chaves diferentes, dificultando a associação com um proprietário único. 2. **Prevenção de Ligação**: Ao usar chaves novas para cada transação, reduz-se a possibilidade de links evidentes entre múltiplas transações realizadas pelo mesmo usuário. #### Riscos de Ligação Embora a privacidade seja fortalecida, alguns riscos permanecem: - Transações **multi-entrada** podem revelar que todas as entradas pertencem ao mesmo proprietário, caso sejam necessárias para somar o valor total. - O proprietário da chave pode ser identificado indiretamente por transações anteriores que estejam conectadas. --- ### 11. Cálculos Imagine que temos um sistema onde as pessoas (ou computadores) competem para adicionar informações novas (blocos) a um grande registro público (a cadeia de blocos ou blockchain). Este registro é como um livro contábil compartilhado, onde todos podem verificar o que está escrito. Agora, vamos pensar em um cenário: um atacante quer enganar o sistema. Ele quer mudar informações já registradas para beneficiar a si mesmo, por exemplo, desfazendo um pagamento que já fez. Para isso, ele precisa criar uma versão alternativa do livro contábil (a cadeia de blocos dele) e convencer todos os outros participantes de que essa versão é a verdadeira. Mas isso é extremamente difícil. #### Como o Ataque Funciona Quando um novo bloco é adicionado à cadeia, ele depende de cálculos complexos que levam tempo e esforço. Esses cálculos são como um grande quebra-cabeça que precisa ser resolvido. - Os “bons jogadores” (nós honestos) estão sempre trabalhando juntos para resolver esses quebra-cabeças e adicionar novos blocos à cadeia verdadeira. - O atacante, por outro lado, precisa resolver quebra-cabeças sozinho, tentando “alcançar” a cadeia honesta para que sua versão alternativa pareça válida. Se a cadeia honesta já está vários blocos à frente, o atacante começa em desvantagem, e o sistema está projetado para que a dificuldade de alcançá-los aumente rapidamente. #### A Corrida Entre Cadeias Você pode imaginar isso como uma corrida. A cada bloco novo que os jogadores honestos adicionam à cadeia verdadeira, eles se distanciam mais do atacante. Para vencer, o atacante teria que resolver os quebra-cabeças mais rápido que todos os outros jogadores honestos juntos. Suponha que: - A rede honesta tem **80% do poder computacional** (ou seja, resolve 8 de cada 10 quebra-cabeças). - O atacante tem **20% do poder computacional** (ou seja, resolve 2 de cada 10 quebra-cabeças). Cada vez que a rede honesta adiciona um bloco, o atacante tem que "correr atrás" e resolver mais quebra-cabeças para alcançar. #### Por Que o Ataque Fica Cada Vez Mais Improvável? Vamos usar uma fórmula simples para mostrar como as chances de sucesso do atacante diminuem conforme ele precisa "alcançar" mais blocos: P = (q/p)^z - **q** é o poder computacional do atacante (20%, ou 0,2). - **p** é o poder computacional da rede honesta (80%, ou 0,8). - **z** é a diferença de blocos entre a cadeia honesta e a cadeia do atacante. Se o atacante está 5 blocos atrás (z = 5): P = (0,2 / 0,8)^5 = (0,25)^5 = 0,00098, (ou, 0,098%) Isso significa que o atacante tem menos de 0,1% de chance de sucesso — ou seja, é muito improvável. Se ele estiver 10 blocos atrás (z = 10): P = (0,2 / 0,8)^10 = (0,25)^10 = 0,000000095, (ou, 0,0000095%). Neste caso, as chances de sucesso são praticamente **nulas**. #### Um Exemplo Simples Se você jogar uma moeda, a chance de cair “cara” é de 50%. Mas se precisar de 10 caras seguidas, sua chance já é bem menor. Se precisar de 20 caras seguidas, é quase impossível. No caso do Bitcoin, o atacante precisa de muito mais do que 20 caras seguidas. Ele precisa resolver quebra-cabeças extremamente difíceis e alcançar os jogadores honestos que estão sempre à frente. Isso faz com que o ataque seja inviável na prática. #### Por Que Tudo Isso é Seguro? - **A probabilidade de sucesso do atacante diminui exponencialmente.** Isso significa que, quanto mais tempo passa, menor é a chance de ele conseguir enganar o sistema. - **A cadeia verdadeira (honesta) está protegida pela força da rede.** Cada novo bloco que os jogadores honestos adicionam à cadeia torna mais difícil para o atacante alcançar. #### E Se o Atacante Tentar Continuar? O atacante poderia continuar tentando indefinidamente, mas ele estaria gastando muito tempo e energia sem conseguir nada. Enquanto isso, os jogadores honestos estão sempre adicionando novos blocos, tornando o trabalho do atacante ainda mais inútil. Assim, o sistema garante que a cadeia verdadeira seja extremamente segura e que ataques sejam, na prática, impossíveis de ter sucesso. --- ### 12. Conclusão Propusemos um sistema de transações eletrônicas que elimina a necessidade de confiança, baseando-se em assinaturas digitais e em uma rede peer-to-peer que utiliza prova de trabalho. Isso resolve o problema do gasto duplo, criando um histórico público de transações imutável, desde que a maioria do poder computacional permaneça sob controle dos participantes honestos. A rede funciona de forma simples e descentralizada, com nós independentes que não precisam de identificação ou coordenação direta. Eles entram e saem livremente, aceitando a cadeia de prova de trabalho como registro do que ocorreu durante sua ausência. As decisões são tomadas por meio do poder de CPU, validando blocos legítimos, estendendo a cadeia e rejeitando os inválidos. Com este mecanismo de consenso, todas as regras e incentivos necessários para o funcionamento seguro e eficiente do sistema são garantidos. --- Faça o download do whitepaper original em português: https://bitcoin.org/files/bitcoin-paper/bitcoin_pt_br.pdf @ f9cf4e94:96abc355
2025-01-18 06:09:50Para esse exemplo iremos usar: | Nome | Imagem | Descrição | | --------------- | ------------------------------------------------------------ | ------------------------------------------------------------ | | Raspberry PI B+ |  | **Cortex-A53 (ARMv8) 64-bit a 1.4GHz e 1 GB de SDRAM LPDDR2,** | | Pen drive |  | **16Gb** | Recomendo que use o **Ubuntu Server** para essa instalação. Você pode baixar o Ubuntu para Raspberry Pi [aqui]( https://ubuntu.com/download/raspberry-pi). O passo a passo para a instalação do Ubuntu no Raspberry Pi está disponível [aqui]( https://ubuntu.com/tutorials/how-to-install-ubuntu-on-your-raspberry-pi). **Não instale um desktop** (como xubuntu, lubuntu, xfce, etc.). --- ## Passo 1: Atualizar o Sistema 🖥️ Primeiro, atualize seu sistema e instale o Tor: ```bash apt update apt install tor ``` --- ## Passo 2: Criar o Arquivo de Serviço `nrs.service` 🔧 Crie o arquivo de serviço que vai gerenciar o servidor Nostr. Você pode fazer isso com o seguinte conteúdo: ```unit [Unit] Description=Nostr Relay Server Service After=network.target [Service] Type=simple WorkingDirectory=/opt/nrs ExecStart=/opt/nrs/nrs-arm64 Restart=on-failure [Install] WantedBy=multi-user.target ``` --- ## Passo 3: Baixar o Binário do Nostr 🚀 Baixe o binário mais recente do Nostr [aqui no GitHub]( https://github.com/gabrielmoura/SimpleNosrtRelay/releases). --- ## Passo 4: Criar as Pastas Necessárias 📂 Agora, crie as pastas para o aplicativo e o pendrive: ```bash mkdir -p /opt/nrs /mnt/edriver ``` --- ## Passo 5: Listar os Dispositivos Conectados 🔌 Para saber qual dispositivo você vai usar, liste todos os dispositivos conectados: ```bash lsblk ``` --- ## Passo 6: Formatando o Pendrive 💾 Escolha o pendrive correto (por exemplo, `/dev/sda`) e formate-o: ```bash mkfs.vfat /dev/sda ``` --- ## Passo 7: Montar o Pendrive 💻 Monte o pendrive na pasta `/mnt/edriver`: ```bash mount /dev/sda /mnt/edriver ``` --- ## Passo 8: Verificar UUID dos Dispositivos 📋 Para garantir que o sistema monte o pendrive automaticamente, liste os UUID dos dispositivos conectados: ```bash blkid ``` --- ## Passo 9: Alterar o `fstab` para Montar o Pendrive Automáticamente 📝 Abra o arquivo `/etc/fstab` e adicione uma linha para o pendrive, com o UUID que você obteve no passo anterior. A linha deve ficar assim: ```fstab UUID=9c9008f8-f852 /mnt/edriver vfat defaults 0 0 ``` --- ## Passo 10: Copiar o Binário para a Pasta Correta 📥 Agora, copie o binário baixado para a pasta `/opt/nrs`: ```bash cp nrs-arm64 /opt/nrs ``` --- ## Passo 11: Criar o Arquivo de Configuração 🛠️ Crie o arquivo de configuração com o seguinte conteúdo e salve-o em `/opt/nrs/config.yaml`: ```yaml app_env: production info: name: Nostr Relay Server description: Nostr Relay Server pub_key: "" contact: "" url: http://localhost:3334 icon: https://external-content.duckduckgo.com/iu/?u= https://public.bnbstatic.com/image/cms/crawler/COINCU_NEWS/image-495-1024x569.png base_path: /mnt/edriver negentropy: true ``` --- ## Passo 12: Copiar o Serviço para o Diretório de Systemd ⚙️ Agora, copie o arquivo `nrs.service` para o diretório `/etc/systemd/system/`: ```bash cp nrs.service /etc/systemd/system/ ``` Recarregue os serviços e inicie o serviço `nrs`: ```bash systemctl daemon-reload systemctl enable --now nrs.service ``` --- ## Passo 13: Configurar o Tor 🌐 Abra o arquivo de configuração do Tor `/var/lib/tor/torrc` e adicione a seguinte linha: ```torrc HiddenServiceDir /var/lib/tor/nostr_server/ HiddenServicePort 80 127.0.0.1:3334 ``` --- ## Passo 14: Habilitar e Iniciar o Tor 🧅 Agora, ative e inicie o serviço Tor: ```bash systemctl enable --now tor.service ``` O Tor irá gerar um endereço `.onion` para o seu servidor Nostr. Você pode encontrá-lo no arquivo `/var/lib/tor/nostr_server/hostname`. --- ## Observações ⚠️ - Com essa configuração, **os dados serão salvos no pendrive**, enquanto o binário ficará no cartão SD do Raspberry Pi. - O endereço `.onion` do seu servidor Nostr será algo como: `ws://y3t5t5wgwjif<exemplo>h42zy7ih6iwbyd.onion`. --- Agora, seu servidor Nostr deve estar configurado e funcionando com Tor! 🥳 Se este artigo e as informações aqui contidas forem úteis para você, convidamos a considerar uma doação ao autor como forma de reconhecimento e incentivo à produção de novos conteúdos.
@ f9cf4e94:96abc355
2025-01-18 06:09:50Para esse exemplo iremos usar: | Nome | Imagem | Descrição | | --------------- | ------------------------------------------------------------ | ------------------------------------------------------------ | | Raspberry PI B+ |  | **Cortex-A53 (ARMv8) 64-bit a 1.4GHz e 1 GB de SDRAM LPDDR2,** | | Pen drive |  | **16Gb** | Recomendo que use o **Ubuntu Server** para essa instalação. Você pode baixar o Ubuntu para Raspberry Pi [aqui]( https://ubuntu.com/download/raspberry-pi). O passo a passo para a instalação do Ubuntu no Raspberry Pi está disponível [aqui]( https://ubuntu.com/tutorials/how-to-install-ubuntu-on-your-raspberry-pi). **Não instale um desktop** (como xubuntu, lubuntu, xfce, etc.). --- ## Passo 1: Atualizar o Sistema 🖥️ Primeiro, atualize seu sistema e instale o Tor: ```bash apt update apt install tor ``` --- ## Passo 2: Criar o Arquivo de Serviço `nrs.service` 🔧 Crie o arquivo de serviço que vai gerenciar o servidor Nostr. Você pode fazer isso com o seguinte conteúdo: ```unit [Unit] Description=Nostr Relay Server Service After=network.target [Service] Type=simple WorkingDirectory=/opt/nrs ExecStart=/opt/nrs/nrs-arm64 Restart=on-failure [Install] WantedBy=multi-user.target ``` --- ## Passo 3: Baixar o Binário do Nostr 🚀 Baixe o binário mais recente do Nostr [aqui no GitHub]( https://github.com/gabrielmoura/SimpleNosrtRelay/releases). --- ## Passo 4: Criar as Pastas Necessárias 📂 Agora, crie as pastas para o aplicativo e o pendrive: ```bash mkdir -p /opt/nrs /mnt/edriver ``` --- ## Passo 5: Listar os Dispositivos Conectados 🔌 Para saber qual dispositivo você vai usar, liste todos os dispositivos conectados: ```bash lsblk ``` --- ## Passo 6: Formatando o Pendrive 💾 Escolha o pendrive correto (por exemplo, `/dev/sda`) e formate-o: ```bash mkfs.vfat /dev/sda ``` --- ## Passo 7: Montar o Pendrive 💻 Monte o pendrive na pasta `/mnt/edriver`: ```bash mount /dev/sda /mnt/edriver ``` --- ## Passo 8: Verificar UUID dos Dispositivos 📋 Para garantir que o sistema monte o pendrive automaticamente, liste os UUID dos dispositivos conectados: ```bash blkid ``` --- ## Passo 9: Alterar o `fstab` para Montar o Pendrive Automáticamente 📝 Abra o arquivo `/etc/fstab` e adicione uma linha para o pendrive, com o UUID que você obteve no passo anterior. A linha deve ficar assim: ```fstab UUID=9c9008f8-f852 /mnt/edriver vfat defaults 0 0 ``` --- ## Passo 10: Copiar o Binário para a Pasta Correta 📥 Agora, copie o binário baixado para a pasta `/opt/nrs`: ```bash cp nrs-arm64 /opt/nrs ``` --- ## Passo 11: Criar o Arquivo de Configuração 🛠️ Crie o arquivo de configuração com o seguinte conteúdo e salve-o em `/opt/nrs/config.yaml`: ```yaml app_env: production info: name: Nostr Relay Server description: Nostr Relay Server pub_key: "" contact: "" url: http://localhost:3334 icon: https://external-content.duckduckgo.com/iu/?u= https://public.bnbstatic.com/image/cms/crawler/COINCU_NEWS/image-495-1024x569.png base_path: /mnt/edriver negentropy: true ``` --- ## Passo 12: Copiar o Serviço para o Diretório de Systemd ⚙️ Agora, copie o arquivo `nrs.service` para o diretório `/etc/systemd/system/`: ```bash cp nrs.service /etc/systemd/system/ ``` Recarregue os serviços e inicie o serviço `nrs`: ```bash systemctl daemon-reload systemctl enable --now nrs.service ``` --- ## Passo 13: Configurar o Tor 🌐 Abra o arquivo de configuração do Tor `/var/lib/tor/torrc` e adicione a seguinte linha: ```torrc HiddenServiceDir /var/lib/tor/nostr_server/ HiddenServicePort 80 127.0.0.1:3334 ``` --- ## Passo 14: Habilitar e Iniciar o Tor 🧅 Agora, ative e inicie o serviço Tor: ```bash systemctl enable --now tor.service ``` O Tor irá gerar um endereço `.onion` para o seu servidor Nostr. Você pode encontrá-lo no arquivo `/var/lib/tor/nostr_server/hostname`. --- ## Observações ⚠️ - Com essa configuração, **os dados serão salvos no pendrive**, enquanto o binário ficará no cartão SD do Raspberry Pi. - O endereço `.onion` do seu servidor Nostr será algo como: `ws://y3t5t5wgwjif<exemplo>h42zy7ih6iwbyd.onion`. --- Agora, seu servidor Nostr deve estar configurado e funcionando com Tor! 🥳 Se este artigo e as informações aqui contidas forem úteis para você, convidamos a considerar uma doação ao autor como forma de reconhecimento e incentivo à produção de novos conteúdos. @ 6b3780ef:221416c8
2025-03-26 18:42:00This workshop will guide you through exploring the concepts behind MCP servers and how to deploy them as DVMs in Nostr using DVMCP. By the end, you'll understand how these systems work together and be able to create your own deployments. ## Understanding MCP Systems MCP (Model Context Protocol) systems consist of two main components that work together: 1. **MCP Server**: The heart of the system that exposes tools, which you can access via the `.listTools()` method. 2. **MCP Client**: The interface that connects to the MCP server and lets you use the tools it offers. These servers and clients can communicate using different transport methods: - **Standard I/O (stdio)**: A simple local connection method when your server and client are on the same machine. - **Server-Sent Events (SSE)**: Uses HTTP to create a communication channel. For this workshop, we'll use stdio to deploy our server. DVMCP will act as a bridge, connecting to your MCP server as an MCP client, and exposing its tools as a DVM that anyone can call from Nostr. ## Creating (or Finding) an MCP Server Building an MCP server is simpler than you might think: 1. Create software in any programming language you're comfortable with. 2. Add an MCP library to expose your server's MCP interface. 3. Create an API that wraps around your software's functionality. Once your server is ready, an MCP client can connect, for example, with `bun index.js`, and then call `.listTools()` to discover what your server can do. This pattern, known as reflection, makes Nostr DVMs and MCP a perfect match since both use JSON, and DVMs can announce and call tools, effectively becoming an MCP proxy. Alternatively, you can use one of the many existing MCP servers available in various repositories. For more information about mcp and how to build mcp servers you can visit https://modelcontextprotocol.io/ ## Setting Up the Workshop Let's get hands-on: First, to follow this workshop you will need Bun. Install it from https://bun.sh/. For Linux and macOS, you can use the installation script: ``` curl -fsSL https://bun.sh/install | bash ``` 1. **Choose your MCP server**: You can either create one or use an existing one. 2. **Inspect your server** using the MCP inspector tool: ```bash npx @modelcontextprotocol/inspector build/index.js arg1 arg2 ``` This will: - Launch a client UI (default: http://localhost:5173) - Start an MCP proxy server (default: port 3000) - Pass any additional arguments directly to your server 3. **Use the inspector**: Open the client UI in your browser to connect with your server, list available tools, and test its functionality. ## Deploying with DVMCP Now for the exciting part – making your MCP server available to everyone on Nostr: 1. Navigate to your MCP server directory. 2. Run without installing (quickest way): ``` npx @dvmcp/bridge ``` 3. Or install globally for regular use: ``` npm install -g @dvmcp/bridge # or bun install -g @dvmcp/bridge ``` Then run using: ```bash dvmcp-bridge ``` This will guide you through creating the necessary configuration. Watch the console logs to confirm successful setup – you'll see your public key and process information, or any issues that need addressing. For the configuration, you can set the relay as `wss://relay.dvmcp.fun` , or use any other of your preference ## Testing and Integration 1. **Visit [dvmcp.fun](https://dvmcp.fun)** to see your DVM announcement. 2. Call your tools and watch the responses come back. For production use, consider running dvmcp-bridge as a system service or creating a container for greater reliability and uptime. ## Integrating with LLM Clients You can also integrate your DVMCP deployment with LLM clients using the discovery package: 1. Install and use the `@dvmcp/discovery` package: ```bash npx @dvmcp/discovery ``` 2. This package acts as an MCP server for your LLM system by: - Connecting to configured Nostr relays - Discovering tools from DVMCP servers - Making them available to your LLM applications 3. Connect to specific servers or providers using these flags: ```bash # Connect to all DVMCP servers from a provider npx @dvmcp/discovery --provider npub1... # Connect to a specific DVMCP server npx @dvmcp/discovery --server naddr1... ``` Using these flags, you wouldn't need a configuration file. You can find these commands and Claude desktop configuration already prepared for copy and paste at [dvmcp.fun](https://dvmcp.fun). This feature lets you connect to any DVMCP server using Nostr and integrate it into your client, either as a DVM or in LLM-powered applications. ## Final thoughts If you've followed this workshop, you now have an MCP server deployed as a Nostr DVM. This means that local resources from the system where the MCP server is running can be accessed through Nostr in a decentralized manner. This capability is powerful and opens up numerous possibilities and opportunities for fun. You can use this setup for various use cases, including in a controlled/local environment. For instance, you can deploy a relay in your local network that's only accessible within it, exposing all your local MCP servers to anyone connected to the network. This setup can act as a hub for communication between different systems, which could be particularly interesting for applications in home automation or other fields. The potential applications are limitless. However, it's important to keep in mind that there are security concerns when exposing local resources publicly. You should be mindful of these risks and prioritize security when creating and deploying your MCP servers on Nostr. Finally, these are new ideas, and the software is still under development. If you have any feedback, please refer to the GitHub repository to report issues or collaborate. DVMCP also has a Signal group you can join. Additionally, you can engage with the community on Nostr using the #dvmcp hashtag. ## Useful Resources - **Official Documentation**: - Model Context Protocol: [modelcontextprotocol.org](https://modelcontextprotocol.org) - DVMCP.fun: [dvmcp.fun](https://dvmcp.fun) - **Source Code and Development**: - DVMCP: [github.com/gzuuus/dvmcp](https://github.com/gzuuus/dvmcp) - DVMCP.fun: [github.com/gzuuus/dvmcpfun](https://github.com/gzuuus/dvmcpfun) - **MCP Servers and Clients**: - Smithery AI: [smithery.ai](https://smithery.ai) - MCP.so: [mcp.so](https://mcp.so) - Glama AI MCP Servers: [glama.ai/mcp/servers](https://glama.ai/mcp/servers) - [Signal group](https://signal.group/#CjQKIOgvfFJf8ZFZ1SsMx7teFqNF73sZ9Elaj_v5i6RSjDHmEhA5v69L4_l2dhQfwAm2SFGD) Happy building!
@ 6b3780ef:221416c8
2025-03-26 18:42:00This workshop will guide you through exploring the concepts behind MCP servers and how to deploy them as DVMs in Nostr using DVMCP. By the end, you'll understand how these systems work together and be able to create your own deployments. ## Understanding MCP Systems MCP (Model Context Protocol) systems consist of two main components that work together: 1. **MCP Server**: The heart of the system that exposes tools, which you can access via the `.listTools()` method. 2. **MCP Client**: The interface that connects to the MCP server and lets you use the tools it offers. These servers and clients can communicate using different transport methods: - **Standard I/O (stdio)**: A simple local connection method when your server and client are on the same machine. - **Server-Sent Events (SSE)**: Uses HTTP to create a communication channel. For this workshop, we'll use stdio to deploy our server. DVMCP will act as a bridge, connecting to your MCP server as an MCP client, and exposing its tools as a DVM that anyone can call from Nostr. ## Creating (or Finding) an MCP Server Building an MCP server is simpler than you might think: 1. Create software in any programming language you're comfortable with. 2. Add an MCP library to expose your server's MCP interface. 3. Create an API that wraps around your software's functionality. Once your server is ready, an MCP client can connect, for example, with `bun index.js`, and then call `.listTools()` to discover what your server can do. This pattern, known as reflection, makes Nostr DVMs and MCP a perfect match since both use JSON, and DVMs can announce and call tools, effectively becoming an MCP proxy. Alternatively, you can use one of the many existing MCP servers available in various repositories. For more information about mcp and how to build mcp servers you can visit https://modelcontextprotocol.io/ ## Setting Up the Workshop Let's get hands-on: First, to follow this workshop you will need Bun. Install it from https://bun.sh/. For Linux and macOS, you can use the installation script: ``` curl -fsSL https://bun.sh/install | bash ``` 1. **Choose your MCP server**: You can either create one or use an existing one. 2. **Inspect your server** using the MCP inspector tool: ```bash npx @modelcontextprotocol/inspector build/index.js arg1 arg2 ``` This will: - Launch a client UI (default: http://localhost:5173) - Start an MCP proxy server (default: port 3000) - Pass any additional arguments directly to your server 3. **Use the inspector**: Open the client UI in your browser to connect with your server, list available tools, and test its functionality. ## Deploying with DVMCP Now for the exciting part – making your MCP server available to everyone on Nostr: 1. Navigate to your MCP server directory. 2. Run without installing (quickest way): ``` npx @dvmcp/bridge ``` 3. Or install globally for regular use: ``` npm install -g @dvmcp/bridge # or bun install -g @dvmcp/bridge ``` Then run using: ```bash dvmcp-bridge ``` This will guide you through creating the necessary configuration. Watch the console logs to confirm successful setup – you'll see your public key and process information, or any issues that need addressing. For the configuration, you can set the relay as `wss://relay.dvmcp.fun` , or use any other of your preference ## Testing and Integration 1. **Visit [dvmcp.fun](https://dvmcp.fun)** to see your DVM announcement. 2. Call your tools and watch the responses come back. For production use, consider running dvmcp-bridge as a system service or creating a container for greater reliability and uptime. ## Integrating with LLM Clients You can also integrate your DVMCP deployment with LLM clients using the discovery package: 1. Install and use the `@dvmcp/discovery` package: ```bash npx @dvmcp/discovery ``` 2. This package acts as an MCP server for your LLM system by: - Connecting to configured Nostr relays - Discovering tools from DVMCP servers - Making them available to your LLM applications 3. Connect to specific servers or providers using these flags: ```bash # Connect to all DVMCP servers from a provider npx @dvmcp/discovery --provider npub1... # Connect to a specific DVMCP server npx @dvmcp/discovery --server naddr1... ``` Using these flags, you wouldn't need a configuration file. You can find these commands and Claude desktop configuration already prepared for copy and paste at [dvmcp.fun](https://dvmcp.fun). This feature lets you connect to any DVMCP server using Nostr and integrate it into your client, either as a DVM or in LLM-powered applications. ## Final thoughts If you've followed this workshop, you now have an MCP server deployed as a Nostr DVM. This means that local resources from the system where the MCP server is running can be accessed through Nostr in a decentralized manner. This capability is powerful and opens up numerous possibilities and opportunities for fun. You can use this setup for various use cases, including in a controlled/local environment. For instance, you can deploy a relay in your local network that's only accessible within it, exposing all your local MCP servers to anyone connected to the network. This setup can act as a hub for communication between different systems, which could be particularly interesting for applications in home automation or other fields. The potential applications are limitless. However, it's important to keep in mind that there are security concerns when exposing local resources publicly. You should be mindful of these risks and prioritize security when creating and deploying your MCP servers on Nostr. Finally, these are new ideas, and the software is still under development. If you have any feedback, please refer to the GitHub repository to report issues or collaborate. DVMCP also has a Signal group you can join. Additionally, you can engage with the community on Nostr using the #dvmcp hashtag. ## Useful Resources - **Official Documentation**: - Model Context Protocol: [modelcontextprotocol.org](https://modelcontextprotocol.org) - DVMCP.fun: [dvmcp.fun](https://dvmcp.fun) - **Source Code and Development**: - DVMCP: [github.com/gzuuus/dvmcp](https://github.com/gzuuus/dvmcp) - DVMCP.fun: [github.com/gzuuus/dvmcpfun](https://github.com/gzuuus/dvmcpfun) - **MCP Servers and Clients**: - Smithery AI: [smithery.ai](https://smithery.ai) - MCP.so: [mcp.so](https://mcp.so) - Glama AI MCP Servers: [glama.ai/mcp/servers](https://glama.ai/mcp/servers) - [Signal group](https://signal.group/#CjQKIOgvfFJf8ZFZ1SsMx7teFqNF73sZ9Elaj_v5i6RSjDHmEhA5v69L4_l2dhQfwAm2SFGD) Happy building! @ c631e267:c2b78d3e
2025-04-03 07:42:25**Spanien bleibt einer der Vorreiter im europäischen Prozess der totalen Überwachung** per Digitalisierung. Seit Mittwoch ist dort der digitale Personalausweis verfügbar. Dabei handelt es sich um eine Regierungs-[App](https://play.google.com/store/apps/details?id=es.gob.interior.policia.midni), die auf dem Smartphone installiert werden muss und in den Stores von Google und Apple zu finden ist. Per Dekret von Regierungschef Pedro Sánchez und Zustimmung des Ministerrats ist diese Maßnahme jetzt [in Kraft](https://archive.is/89H4i) getreten. **Mit den üblichen Argumenten der Vereinfachung,** des Komforts, der Effizienz und der Sicherheit preist das Innenministerium die «Innovation» an. Auch die Beteuerung, dass die digitale Variante parallel zum physischen Ausweis existieren wird und diesen nicht ersetzen soll, fehlt nicht. Während der ersten zwölf Monate wird «der Neue» noch nicht für alle Anwendungsfälle gültig sein, ab 2026 aber schon. **Dass die ganze Sache auch «Risiken und Nebenwirkungen» haben könnte,** wird in den Mainstream-Medien eher selten thematisiert. Bestenfalls wird der Aspekt der Datensicherheit angesprochen, allerdings in der Regel direkt mit dem Regierungsvokabular von den «maximalen Sicherheitsgarantien» abgehandelt. Dennoch gibt es einige weitere Aspekte, die Bürger mit etwas Sinn für Privatsphäre bedenken sollten. **Um sich die digitale Version des nationalen Ausweises besorgen zu können** (eine App mit dem Namen MiDNI), muss man sich vorab online [registrieren](https://www.midni.gob.es). Dabei wird die Identität des Bürgers mit seiner mobilen Telefonnummer verknüpft. Diese obligatorische fixe Verdrahtung kennen wir von diversen anderen Apps und Diensten. Gleichzeitig ist das die Basis für eine perfekte Lokalisierbarkeit der Person. **Für jeden Vorgang der Identifikation in der Praxis wird später** «eine Verbindung zu den Servern der Bundespolizei aufgebaut». Die Daten des Individuums werden «in Echtzeit» verifiziert und im Erfolgsfall von der Polizei signiert zurückgegeben. Das Ergebnis ist ein QR-Code mit zeitlich begrenzter Gültigkeit, der an Dritte weitergegeben werden kann. **Bei derartigen Szenarien sträuben sich einem halbwegs kritischen Staatsbürger die Nackenhaare.** Allein diese minimale Funktionsbeschreibung lässt die totale Überwachung erkennen, die damit ermöglicht wird. Jede Benutzung des Ausweises wird künftig registriert, hinterlässt also Spuren. Und was ist, wenn die Server der Polizei einmal kein grünes Licht geben? Das wäre spätestens dann ein Problem, wenn der digitale doch irgendwann der einzig gültige Ausweis ist: Dann haben wir den abschaltbaren Bürger. **Dieser neue Vorstoß der Regierung von Pedro Sánchez ist ein weiterer Schritt** in Richtung der [«totalen Digitalisierung»](https://archive.is/Gwc4B) des Landes, wie diese Politik in manchen Medien – nicht einmal kritisch, sondern sehr naiv – genannt wird. Ebenso verharmlosend wird auch erwähnt, dass sich das spanische Projekt des digitalen Ausweises nahtlos in die Initiativen der EU zu einer digitalen Identität für alle Bürger sowie des digitalen Euro einreiht. **In Zukunft könnte der neue Ausweis** «auch in andere staatliche und private digitale Plattformen integriert werden», wie das Medienportal *Cope* ganz richtig bemerkt. Das ist die Perspektive. *\[Titelbild:* *[Pixabay](https://pixabay.com/de/photos/liebe-love-herz-rose-bindung-3141742/)]* *Dazu passend:* [Nur Abschied vom Alleinfahren? Monströse spanische Überwachungsprojekte gemäß EU-Norm](https://pareto.space/a/naddr1qqxnzde5xg6r2wphxscryvpjqgs2jhrzgwzvvzgz42kfmef2kr7w8x573k4r62c5ydjh8gyn6dz4ytqrqsqqqa28fq5d4m) *** Dieser Beitrag wurde mit dem [Pareto-Client](https://pareto.space/read) geschrieben und ist zuerst auf ***[Transition News](https://transition-news.org/spanien-erneut-europaisches-versuchslabor-der-digitale-ausweis-ist-da)*** erschienen.
@ c631e267:c2b78d3e
2025-04-03 07:42:25**Spanien bleibt einer der Vorreiter im europäischen Prozess der totalen Überwachung** per Digitalisierung. Seit Mittwoch ist dort der digitale Personalausweis verfügbar. Dabei handelt es sich um eine Regierungs-[App](https://play.google.com/store/apps/details?id=es.gob.interior.policia.midni), die auf dem Smartphone installiert werden muss und in den Stores von Google und Apple zu finden ist. Per Dekret von Regierungschef Pedro Sánchez und Zustimmung des Ministerrats ist diese Maßnahme jetzt [in Kraft](https://archive.is/89H4i) getreten. **Mit den üblichen Argumenten der Vereinfachung,** des Komforts, der Effizienz und der Sicherheit preist das Innenministerium die «Innovation» an. Auch die Beteuerung, dass die digitale Variante parallel zum physischen Ausweis existieren wird und diesen nicht ersetzen soll, fehlt nicht. Während der ersten zwölf Monate wird «der Neue» noch nicht für alle Anwendungsfälle gültig sein, ab 2026 aber schon. **Dass die ganze Sache auch «Risiken und Nebenwirkungen» haben könnte,** wird in den Mainstream-Medien eher selten thematisiert. Bestenfalls wird der Aspekt der Datensicherheit angesprochen, allerdings in der Regel direkt mit dem Regierungsvokabular von den «maximalen Sicherheitsgarantien» abgehandelt. Dennoch gibt es einige weitere Aspekte, die Bürger mit etwas Sinn für Privatsphäre bedenken sollten. **Um sich die digitale Version des nationalen Ausweises besorgen zu können** (eine App mit dem Namen MiDNI), muss man sich vorab online [registrieren](https://www.midni.gob.es). Dabei wird die Identität des Bürgers mit seiner mobilen Telefonnummer verknüpft. Diese obligatorische fixe Verdrahtung kennen wir von diversen anderen Apps und Diensten. Gleichzeitig ist das die Basis für eine perfekte Lokalisierbarkeit der Person. **Für jeden Vorgang der Identifikation in der Praxis wird später** «eine Verbindung zu den Servern der Bundespolizei aufgebaut». Die Daten des Individuums werden «in Echtzeit» verifiziert und im Erfolgsfall von der Polizei signiert zurückgegeben. Das Ergebnis ist ein QR-Code mit zeitlich begrenzter Gültigkeit, der an Dritte weitergegeben werden kann. **Bei derartigen Szenarien sträuben sich einem halbwegs kritischen Staatsbürger die Nackenhaare.** Allein diese minimale Funktionsbeschreibung lässt die totale Überwachung erkennen, die damit ermöglicht wird. Jede Benutzung des Ausweises wird künftig registriert, hinterlässt also Spuren. Und was ist, wenn die Server der Polizei einmal kein grünes Licht geben? Das wäre spätestens dann ein Problem, wenn der digitale doch irgendwann der einzig gültige Ausweis ist: Dann haben wir den abschaltbaren Bürger. **Dieser neue Vorstoß der Regierung von Pedro Sánchez ist ein weiterer Schritt** in Richtung der [«totalen Digitalisierung»](https://archive.is/Gwc4B) des Landes, wie diese Politik in manchen Medien – nicht einmal kritisch, sondern sehr naiv – genannt wird. Ebenso verharmlosend wird auch erwähnt, dass sich das spanische Projekt des digitalen Ausweises nahtlos in die Initiativen der EU zu einer digitalen Identität für alle Bürger sowie des digitalen Euro einreiht. **In Zukunft könnte der neue Ausweis** «auch in andere staatliche und private digitale Plattformen integriert werden», wie das Medienportal *Cope* ganz richtig bemerkt. Das ist die Perspektive. *\[Titelbild:* *[Pixabay](https://pixabay.com/de/photos/liebe-love-herz-rose-bindung-3141742/)]* *Dazu passend:* [Nur Abschied vom Alleinfahren? Monströse spanische Überwachungsprojekte gemäß EU-Norm](https://pareto.space/a/naddr1qqxnzde5xg6r2wphxscryvpjqgs2jhrzgwzvvzgz42kfmef2kr7w8x573k4r62c5ydjh8gyn6dz4ytqrqsqqqa28fq5d4m) *** Dieser Beitrag wurde mit dem [Pareto-Client](https://pareto.space/read) geschrieben und ist zuerst auf ***[Transition News](https://transition-news.org/spanien-erneut-europaisches-versuchslabor-der-digitale-ausweis-ist-da)*** erschienen. @ fd06f542:8d6d54cd
2025-04-02 01:35:00## nostrbook 技术框架 源代码在 github.com ``` git clone https://github.com/nostrbook/nostrbook cd nostrbook npm install npm run dev ``` * 网站主框架 vite + svelte * 网站浏览书框架 docsify ## 网站主框架 svelte 为主,daisyui (tailwindcss) css 。 页面的逻辑结构 都是 svelte搭建的, 采用了 layout 左侧菜单。 菜单代码 在 https://github.com/nostrbook/nostrbook/blob/main/src/lib/SideMenu.svelte 菜单里用了弹框登录,弹框的代码基本是问的 AI。 子页面和 路由器看sveltekit规则编写。 ### 书籍的数据 https://github.com/nostrbook/nostrbook/blob/main/src/lib/bookevent.ts 使用的nostr ndk 库来读写 relay。 书的 tag, 内容就是 标题,封面和作者。 ``` [ ['t',booktag], ['title',content['title']], ]; ``` ### 章节的数据 ``` [ ['t',chaptertag], ['title',title], ['d',filename + "-" + bookid], ['e',bookid], ]; ``` 这里面的 d,采用了 文件名 + bookid,所以每一本的章节名的文件名是唯一的。 ### 配置文件 src/lib/config.ts,主要配置 服务器的地址 * 图片文件 nip96 服务器 * relays 服务器 * book的tag ,测试和 release不一样。 如果自己部署独有的服务器也可以不一样。这样内容可以垂直。 ### 首页采用了缓冲机制 首页的内容来自 书籍的列表, 用booktag和30023来区分是不是书籍信息。 为了搜索引擎友好,让页面加载就有数据。 采用了 src/hooks.server.ts 预备加载数据,数据会被首页面 src/routes/+page.server.ts 传给 page.svelte去渲染。 这一切都是后台完成的。html页面加载的时候数据都已经渲染完成了。所以对搜索引擎非常友好。搞定了google,seo。 但是为了数据的完整性, 页面起来后会继续读取列表,这时候可能会显示最新的数据。
@ fd06f542:8d6d54cd
2025-04-02 01:35:00## nostrbook 技术框架 源代码在 github.com ``` git clone https://github.com/nostrbook/nostrbook cd nostrbook npm install npm run dev ``` * 网站主框架 vite + svelte * 网站浏览书框架 docsify ## 网站主框架 svelte 为主,daisyui (tailwindcss) css 。 页面的逻辑结构 都是 svelte搭建的, 采用了 layout 左侧菜单。 菜单代码 在 https://github.com/nostrbook/nostrbook/blob/main/src/lib/SideMenu.svelte 菜单里用了弹框登录,弹框的代码基本是问的 AI。 子页面和 路由器看sveltekit规则编写。 ### 书籍的数据 https://github.com/nostrbook/nostrbook/blob/main/src/lib/bookevent.ts 使用的nostr ndk 库来读写 relay。 书的 tag, 内容就是 标题,封面和作者。 ``` [ ['t',booktag], ['title',content['title']], ]; ``` ### 章节的数据 ``` [ ['t',chaptertag], ['title',title], ['d',filename + "-" + bookid], ['e',bookid], ]; ``` 这里面的 d,采用了 文件名 + bookid,所以每一本的章节名的文件名是唯一的。 ### 配置文件 src/lib/config.ts,主要配置 服务器的地址 * 图片文件 nip96 服务器 * relays 服务器 * book的tag ,测试和 release不一样。 如果自己部署独有的服务器也可以不一样。这样内容可以垂直。 ### 首页采用了缓冲机制 首页的内容来自 书籍的列表, 用booktag和30023来区分是不是书籍信息。 为了搜索引擎友好,让页面加载就有数据。 采用了 src/hooks.server.ts 预备加载数据,数据会被首页面 src/routes/+page.server.ts 传给 page.svelte去渲染。 这一切都是后台完成的。html页面加载的时候数据都已经渲染完成了。所以对搜索引擎非常友好。搞定了google,seo。 但是为了数据的完整性, 页面起来后会继续读取列表,这时候可能会显示最新的数据。 @ 8d34bd24:414be32b
2025-04-02 14:13:03I was reading this passage last night: > …from that time when one came to a grain heap of twenty measures, there would be only ten; and when one came to the wine vat to draw fifty measures, there would be only twenty. I smote you and every work of your hands with blasting wind, mildew and hail; **yet you did not come back to Me**,’ declares the Lord. ‘Do consider from this day onward, from the twenty-fourth day of the ninth month; from the day when the temple of the Lord was founded, consider: Is the seed still in the barn? Even including the vine, the fig tree, the pomegranate and the olive tree, it has not borne fruit. **Yet from this day on I will bless you**.’ ” (Haggai 2:16-19) {emphasis mine} Why were bad things happening to the Israelites? Because they were not following God. Why did God allow these difficult situations to occur? Because God was calling them back to Himself. This made me think of several times lately, when I had written about Christians going through hard times, that fellow believers had tried to kindly correct me implying that God would not allow these painful things to happen to believers. They were trying to defend God’s honor, but instead they were degrading God. If God is not in control of everything, then either God is unable to protect His own from harm because of sin or bad things happened accidentally and God ignored the injustice. Saying God was not in control of allowing every hardship is either saying God isn’t strong enough, isn’t smart enough, or isn’t loving enough. The God I serve is omniscient, omnipotent, omnipresent, and love incarnate. He also didn’t promise us easy, pleasant lives, but did promise that good would come out of every situation. > And we know that in all things God works for the good of those who love him, who have been called according to his purpose. (Romans 8:28) When Jesus walked on earth and some people said they wanted to follow Him, His response was not what we would expect: > And He was saying to them all, “**If anyone wishes to come after Me, he must deny himself, and take up his cross daily and follow Me**. For whoever wishes to save his life will lose it, but whoever loses his life for My sake, he is the one who will save it. For what is a man profited if he gains the whole world, and loses or forfeits himself? For whoever is ashamed of Me and My words, the Son of Man will be ashamed of him when He comes in His glory, and the glory of the Father and of the holy angels. (Luke 9:23-26) {emphasis mine} When one particular man said that he would follow Jesus anywhere, Jesus responded this way. > As they were going along the road, someone said to Him, “I will follow You wherever You go.” And Jesus said to him, “**The foxes have holes and the birds of the air have nests, but the Son of Man has nowhere to lay His head**.” (Luke 9:57-58) {emphasis mine} Jesus was brutally honest that following Him would not be easy or comfortable. Following Jesus is more likely to lead to hardship and persecution that prosperity and comfort. > “Then **they will deliver you to tribulation, and will kill you, and you will be hated by all nations because of My name**. At that time many will fall away and will betray one another and hate one another. Many false prophets will arise and will mislead many. Because lawlessness is increased, most people’s love will grow cold. But **the one who endures to the end, he will be saved**. This gospel of the kingdom shall be preached in the whole world as a testimony to all the nations, and then the end will come. (Matthew 24:9-14) {emphasis mine} Of course God isn’t putting us through hardship to torture us. He is putting us in situations to grow our faith and dependence on Him, i.e. Abraham. He is putting us in situations where we can minister to others, i.e. Joseph. He is using us as examples of faith to others, i.e. Job. Any hardship has an eternal purpose. Sometimes we can see it (at least eventually) if we are looking for God’s will and plan. Sometime we won’t see what He was accomplishing until we get to heaven. Still we need to trust God through it all, knowing His plan is perfect. > “**For my thoughts are not your thoughts,\ > neither are your ways my ways**,”\ > declares the Lord. > > “As the heavens are higher than the earth,\ > so are **my ways higher than your ways**\ > and my thoughts than your thoughts. > > As the rain and the snow\ > come down from heaven,\ > and do not return to it\ > without watering the earth\ > and making it bud and flourish,\ > so that it yields seed for the sower and bread for the eater,\ > so is **my word that goes out from my mouth:\ > It will not return to me empty,\ > but will accomplish what I desire\ > and achieve the purpose for which I sent it**. (Isaiah 55:8-11) {emphasis mine} God understands how hard it is to understand what He is accomplishing. We live in the here and now while He is outside time and space and therefore has a heavenly and eternal perspective that we will never truly have this side of heaven. He has told us how the story ends, so that we can have peace and trust Him through whatever circumstances He has blessed us. > Jesus answered them, “Do you now believe? Behold, an hour is coming, and has already come, for you to be scattered, each to his own home, and to leave Me alone; and yet I am not alone, because the Father is with Me. **These things I have spoken to you, so that in Me you may have peace. In the world you have tribulation, but take courage; I have overcome the world**.” (John 16:31-33) {emphasis mine} In fact, Jesus made this so clear that His disciples rejoiced in persecution they received due to obeying Him and sharing His word. > They took his advice; and after calling the apostles in, they flogged them and ordered them not to speak in the name of Jesus, and *then* released them. So they went on their way from the presence of the Council, **rejoicing that they had been considered worthy to suffer shame for *His* name**. (Acts 5:40-41) {emphasis mine} Peter specifically warns believers to expect trials and hardship. > Dear friends, **do not be surprised at the fiery ordeal that has come on you to test you, as though something strange were happening to you**. But rejoice inasmuch as you participate in the sufferings of Christ, so that you may be overjoyed when his glory is revealed. **If you are insulted because of the name of Christ, you are blessed**, for the Spirit of glory and of God rests on you. If you suffer, it should not be as a murderer or thief or any other kind of criminal, or even as a meddler. However, **if you suffer as a Christian, do not be ashamed, but praise God** that you bear that name. For it is time for judgment to begin with God’s household; and if it begins with us, what will the outcome be for those who do not obey the gospel of God? And, > > “If it is hard for the righteous to be saved,\ > what will become of the ungodly and the sinner?” > > So then, those who suffer according to God’s will should commit themselves to their faithful Creator and continue to do good. (1 Peter 4:12-19) {emphasis mine} Paul writes about begging God to take away a health issue. Eventually he accepted it as part of God’s plan for his life and boasted gladly in his hardship. > …Therefore, in order **to keep me from becoming conceited, I was given a thorn** in my flesh, a messenger of Satan, to torment me. Three times **I pleaded with the Lord to take it away from me. But he said to me, “My grace is sufficient for you**, for my power is made perfect in weakness.” Therefore **I will boast all the more gladly about my weaknesses, so that Christ’s power may rest on me**. That is why, for Christ’s sake, I delight in weaknesses, in insults, in hardships, in persecutions, in difficulties. For when I am weak, then I am strong. (2 Corinthians 12:7b-10) {emphasis mine} No matter what hardships we experience in life, whether poverty or persecution or poor health or loss of a loved one or any other hardship, God is with us working everything for our good. > Who will separate us from the love of Christ? Will tribulation, or distress, or persecution, or famine, or nakedness, or peril, or sword? Just as it is written, > > “For Your sake we are being put to death all day long;\ > We were considered as sheep to be slaughtered.” > ****But in all these things we overwhelmingly conquer through Him who loved us**. For I am convinced that neither death, nor life, nor angels, nor principalities, nor things present, nor things to come, nor powers, nor height, nor depth, nor any other created thing, will be able to separate us from the love of God, which is in Christ Jesus our Lord. (Romans 8:35-39) {emphasis mine} I like to look at the story of Joseph as an example of God’s extraordinary plan in the life of a faithful believer. Joseph trusted and honored God. God had a plan for Joseph to be used to save the lives of his family and the people of the Middle East from famine, but God didn’t just instantly put Joseph in a position of power to help. He prepared Joseph and slowly moved him to where he needed to be. First Josephs brothers wanted to kill him out of jealousy, but God used greed to get them to sell Joseph as a slave instead. He orchestrated the right slave traders to walk by at the right time so that Joseph would wind up in the house of Potiphar, the Pharaoh’s guard. Then when Joseph acted honorably towards God, his master, and his master’s wife, Joseph was sent to jail for years. I’m sure Joseph was wondering why God would send him to prison for doing what was right, but it put him into the presence of the cupbearer of Pharaoh. A long time after correctly interpreting the cup bearer’s dream, Joseph was called up to interpret Pharaoh’s dream, put in charge of the famine preparation and became second in command after Pharaoh. Joseph, after years of slavery and jail time, was now the second most powerful man in the Middle East, if not the world. God had a plan, but it was hard to see until its completion. In the same way, Job lost his wealth, his children, his health, and his reputation, but remember that Satan had to get God’s permission before anything could be done to hurt Job. So many people today are blessed by seeing Job’s response to hardship and loss, by seeing Job’s faith, his struggle, and his submission to God’s plan. In this case God even gives Job more after this time of testing than he had before. When we experience hardship we need to know that God has a plan for our life. It may be something amazing here on Earth. It may be souls won for Christ. It may be to prepare us for heaven. Whatever the case, it is for our good. We don’t need to be ashamed that God would allow hardship. We grow most when we experience hardship. Our light shines brightest in darkness. > Oh, the depth of the riches of the wisdom and knowledge of God!\ > How unsearchable his judgments,\ > and his paths beyond tracing out!\ > “Who has known the mind of the Lord?\ > Or who has been his counselor?”\ > “Who has ever given to God,\ > that God should repay them?”\ > For from him and through him and for him are all things.\ > To him be the glory forever! Amen. (Romans 11:33-36) Trust Jesus
@ 8d34bd24:414be32b
2025-04-02 14:13:03I was reading this passage last night: > …from that time when one came to a grain heap of twenty measures, there would be only ten; and when one came to the wine vat to draw fifty measures, there would be only twenty. I smote you and every work of your hands with blasting wind, mildew and hail; **yet you did not come back to Me**,’ declares the Lord. ‘Do consider from this day onward, from the twenty-fourth day of the ninth month; from the day when the temple of the Lord was founded, consider: Is the seed still in the barn? Even including the vine, the fig tree, the pomegranate and the olive tree, it has not borne fruit. **Yet from this day on I will bless you**.’ ” (Haggai 2:16-19) {emphasis mine} Why were bad things happening to the Israelites? Because they were not following God. Why did God allow these difficult situations to occur? Because God was calling them back to Himself. This made me think of several times lately, when I had written about Christians going through hard times, that fellow believers had tried to kindly correct me implying that God would not allow these painful things to happen to believers. They were trying to defend God’s honor, but instead they were degrading God. If God is not in control of everything, then either God is unable to protect His own from harm because of sin or bad things happened accidentally and God ignored the injustice. Saying God was not in control of allowing every hardship is either saying God isn’t strong enough, isn’t smart enough, or isn’t loving enough. The God I serve is omniscient, omnipotent, omnipresent, and love incarnate. He also didn’t promise us easy, pleasant lives, but did promise that good would come out of every situation. > And we know that in all things God works for the good of those who love him, who have been called according to his purpose. (Romans 8:28) When Jesus walked on earth and some people said they wanted to follow Him, His response was not what we would expect: > And He was saying to them all, “**If anyone wishes to come after Me, he must deny himself, and take up his cross daily and follow Me**. For whoever wishes to save his life will lose it, but whoever loses his life for My sake, he is the one who will save it. For what is a man profited if he gains the whole world, and loses or forfeits himself? For whoever is ashamed of Me and My words, the Son of Man will be ashamed of him when He comes in His glory, and the glory of the Father and of the holy angels. (Luke 9:23-26) {emphasis mine} When one particular man said that he would follow Jesus anywhere, Jesus responded this way. > As they were going along the road, someone said to Him, “I will follow You wherever You go.” And Jesus said to him, “**The foxes have holes and the birds of the air have nests, but the Son of Man has nowhere to lay His head**.” (Luke 9:57-58) {emphasis mine} Jesus was brutally honest that following Him would not be easy or comfortable. Following Jesus is more likely to lead to hardship and persecution that prosperity and comfort. > “Then **they will deliver you to tribulation, and will kill you, and you will be hated by all nations because of My name**. At that time many will fall away and will betray one another and hate one another. Many false prophets will arise and will mislead many. Because lawlessness is increased, most people’s love will grow cold. But **the one who endures to the end, he will be saved**. This gospel of the kingdom shall be preached in the whole world as a testimony to all the nations, and then the end will come. (Matthew 24:9-14) {emphasis mine} Of course God isn’t putting us through hardship to torture us. He is putting us in situations to grow our faith and dependence on Him, i.e. Abraham. He is putting us in situations where we can minister to others, i.e. Joseph. He is using us as examples of faith to others, i.e. Job. Any hardship has an eternal purpose. Sometimes we can see it (at least eventually) if we are looking for God’s will and plan. Sometime we won’t see what He was accomplishing until we get to heaven. Still we need to trust God through it all, knowing His plan is perfect. > “**For my thoughts are not your thoughts,\ > neither are your ways my ways**,”\ > declares the Lord. > > “As the heavens are higher than the earth,\ > so are **my ways higher than your ways**\ > and my thoughts than your thoughts. > > As the rain and the snow\ > come down from heaven,\ > and do not return to it\ > without watering the earth\ > and making it bud and flourish,\ > so that it yields seed for the sower and bread for the eater,\ > so is **my word that goes out from my mouth:\ > It will not return to me empty,\ > but will accomplish what I desire\ > and achieve the purpose for which I sent it**. (Isaiah 55:8-11) {emphasis mine} God understands how hard it is to understand what He is accomplishing. We live in the here and now while He is outside time and space and therefore has a heavenly and eternal perspective that we will never truly have this side of heaven. He has told us how the story ends, so that we can have peace and trust Him through whatever circumstances He has blessed us. > Jesus answered them, “Do you now believe? Behold, an hour is coming, and has already come, for you to be scattered, each to his own home, and to leave Me alone; and yet I am not alone, because the Father is with Me. **These things I have spoken to you, so that in Me you may have peace. In the world you have tribulation, but take courage; I have overcome the world**.” (John 16:31-33) {emphasis mine} In fact, Jesus made this so clear that His disciples rejoiced in persecution they received due to obeying Him and sharing His word. > They took his advice; and after calling the apostles in, they flogged them and ordered them not to speak in the name of Jesus, and *then* released them. So they went on their way from the presence of the Council, **rejoicing that they had been considered worthy to suffer shame for *His* name**. (Acts 5:40-41) {emphasis mine} Peter specifically warns believers to expect trials and hardship. > Dear friends, **do not be surprised at the fiery ordeal that has come on you to test you, as though something strange were happening to you**. But rejoice inasmuch as you participate in the sufferings of Christ, so that you may be overjoyed when his glory is revealed. **If you are insulted because of the name of Christ, you are blessed**, for the Spirit of glory and of God rests on you. If you suffer, it should not be as a murderer or thief or any other kind of criminal, or even as a meddler. However, **if you suffer as a Christian, do not be ashamed, but praise God** that you bear that name. For it is time for judgment to begin with God’s household; and if it begins with us, what will the outcome be for those who do not obey the gospel of God? And, > > “If it is hard for the righteous to be saved,\ > what will become of the ungodly and the sinner?” > > So then, those who suffer according to God’s will should commit themselves to their faithful Creator and continue to do good. (1 Peter 4:12-19) {emphasis mine} Paul writes about begging God to take away a health issue. Eventually he accepted it as part of God’s plan for his life and boasted gladly in his hardship. > …Therefore, in order **to keep me from becoming conceited, I was given a thorn** in my flesh, a messenger of Satan, to torment me. Three times **I pleaded with the Lord to take it away from me. But he said to me, “My grace is sufficient for you**, for my power is made perfect in weakness.” Therefore **I will boast all the more gladly about my weaknesses, so that Christ’s power may rest on me**. That is why, for Christ’s sake, I delight in weaknesses, in insults, in hardships, in persecutions, in difficulties. For when I am weak, then I am strong. (2 Corinthians 12:7b-10) {emphasis mine} No matter what hardships we experience in life, whether poverty or persecution or poor health or loss of a loved one or any other hardship, God is with us working everything for our good. > Who will separate us from the love of Christ? Will tribulation, or distress, or persecution, or famine, or nakedness, or peril, or sword? Just as it is written, > > “For Your sake we are being put to death all day long;\ > We were considered as sheep to be slaughtered.” > ****But in all these things we overwhelmingly conquer through Him who loved us**. For I am convinced that neither death, nor life, nor angels, nor principalities, nor things present, nor things to come, nor powers, nor height, nor depth, nor any other created thing, will be able to separate us from the love of God, which is in Christ Jesus our Lord. (Romans 8:35-39) {emphasis mine} I like to look at the story of Joseph as an example of God’s extraordinary plan in the life of a faithful believer. Joseph trusted and honored God. God had a plan for Joseph to be used to save the lives of his family and the people of the Middle East from famine, but God didn’t just instantly put Joseph in a position of power to help. He prepared Joseph and slowly moved him to where he needed to be. First Josephs brothers wanted to kill him out of jealousy, but God used greed to get them to sell Joseph as a slave instead. He orchestrated the right slave traders to walk by at the right time so that Joseph would wind up in the house of Potiphar, the Pharaoh’s guard. Then when Joseph acted honorably towards God, his master, and his master’s wife, Joseph was sent to jail for years. I’m sure Joseph was wondering why God would send him to prison for doing what was right, but it put him into the presence of the cupbearer of Pharaoh. A long time after correctly interpreting the cup bearer’s dream, Joseph was called up to interpret Pharaoh’s dream, put in charge of the famine preparation and became second in command after Pharaoh. Joseph, after years of slavery and jail time, was now the second most powerful man in the Middle East, if not the world. God had a plan, but it was hard to see until its completion. In the same way, Job lost his wealth, his children, his health, and his reputation, but remember that Satan had to get God’s permission before anything could be done to hurt Job. So many people today are blessed by seeing Job’s response to hardship and loss, by seeing Job’s faith, his struggle, and his submission to God’s plan. In this case God even gives Job more after this time of testing than he had before. When we experience hardship we need to know that God has a plan for our life. It may be something amazing here on Earth. It may be souls won for Christ. It may be to prepare us for heaven. Whatever the case, it is for our good. We don’t need to be ashamed that God would allow hardship. We grow most when we experience hardship. Our light shines brightest in darkness. > Oh, the depth of the riches of the wisdom and knowledge of God!\ > How unsearchable his judgments,\ > and his paths beyond tracing out!\ > “Who has known the mind of the Lord?\ > Or who has been his counselor?”\ > “Who has ever given to God,\ > that God should repay them?”\ > For from him and through him and for him are all things.\ > To him be the glory forever! Amen. (Romans 11:33-36) Trust Jesus @ 04c915da:3dfbecc9
2025-03-25 17:43:44One of the most common criticisms leveled against nostr is the perceived lack of assurance when it comes to data storage. Critics argue that without a centralized authority guaranteeing that all data is preserved, important information will be lost. They also claim that running a relay will become prohibitively expensive. While there is truth to these concerns, they miss the mark. The genius of nostr lies in its flexibility, resilience, and the way it harnesses human incentives to ensure data availability in practice. A nostr relay is simply a server that holds cryptographically verifiable signed data and makes it available to others. Relays are simple, flexible, open, and require no permission to run. Critics are right that operating a relay attempting to store all nostr data will be costly. What they miss is that most will not run all encompassing archive relays. Nostr does not rely on massive archive relays. Instead, anyone can run a relay and choose to store whatever subset of data they want. This keeps costs low and operations flexible, making relay operation accessible to all sorts of individuals and entities with varying use cases. Critics are correct that there is no ironclad guarantee that every piece of data will always be available. Unlike bitcoin where data permanence is baked into the system at a steep cost, nostr does not promise that every random note or meme will be preserved forever. That said, in practice, any data perceived as valuable by someone will likely be stored and distributed by multiple entities. If something matters to someone, they will keep a signed copy. Nostr is the Streisand Effect in protocol form. The Streisand effect is when an attempt to suppress information backfires, causing it to spread even further. With nostr, anyone can broadcast signed data, anyone can store it, and anyone can distribute it. Try to censor something important? Good luck. The moment it catches attention, it will be stored on relays across the globe, copied, and shared by those who find it worth keeping. Data deemed important will be replicated across servers by individuals acting in their own interest. Nostr’s distributed nature ensures that the system does not rely on a single point of failure or a corporate overlord. Instead, it leans on the collective will of its users. The result is a network where costs stay manageable, participation is open to all, and valuable verifiable data is stored and distributed forever.
@ 04c915da:3dfbecc9
2025-03-25 17:43:44One of the most common criticisms leveled against nostr is the perceived lack of assurance when it comes to data storage. Critics argue that without a centralized authority guaranteeing that all data is preserved, important information will be lost. They also claim that running a relay will become prohibitively expensive. While there is truth to these concerns, they miss the mark. The genius of nostr lies in its flexibility, resilience, and the way it harnesses human incentives to ensure data availability in practice. A nostr relay is simply a server that holds cryptographically verifiable signed data and makes it available to others. Relays are simple, flexible, open, and require no permission to run. Critics are right that operating a relay attempting to store all nostr data will be costly. What they miss is that most will not run all encompassing archive relays. Nostr does not rely on massive archive relays. Instead, anyone can run a relay and choose to store whatever subset of data they want. This keeps costs low and operations flexible, making relay operation accessible to all sorts of individuals and entities with varying use cases. Critics are correct that there is no ironclad guarantee that every piece of data will always be available. Unlike bitcoin where data permanence is baked into the system at a steep cost, nostr does not promise that every random note or meme will be preserved forever. That said, in practice, any data perceived as valuable by someone will likely be stored and distributed by multiple entities. If something matters to someone, they will keep a signed copy. Nostr is the Streisand Effect in protocol form. The Streisand effect is when an attempt to suppress information backfires, causing it to spread even further. With nostr, anyone can broadcast signed data, anyone can store it, and anyone can distribute it. Try to censor something important? Good luck. The moment it catches attention, it will be stored on relays across the globe, copied, and shared by those who find it worth keeping. Data deemed important will be replicated across servers by individuals acting in their own interest. Nostr’s distributed nature ensures that the system does not rely on a single point of failure or a corporate overlord. Instead, it leans on the collective will of its users. The result is a network where costs stay manageable, participation is open to all, and valuable verifiable data is stored and distributed forever. @ 6389be64:ef439d32
2025-01-16 15:44:06## Black Locust can grow up to 170 ft tall ## Grows 3-4 ft. per year ## Native to North America ## Cold hardy in zones 3 to 8  ## Firewood - BLT wood, on a pound for pound basis is roughly half that of Anthracite Coal - Since its growth is fast, firewood can be plentiful ## Timber  - Rot resistant due to a naturally produced robinin in the wood - 100 year life span in full soil contact! (better than cedar performance) - Fence posts - Outdoor furniture - Outdoor decking - Sustainable due to its fast growth and spread - Can be coppiced (cut to the ground) - Can be pollarded (cut above ground) - Its dense wood makes durable tool handles, boxes (tool), and furniture - The wood is tougher than hickory, which is tougher than hard maple, which is tougher than oak. - A very low rate of expansion and contraction - Hardwood flooring - The highest tensile beam strength of any American tree - The wood is beautiful ## Legume - Nitrogen fixer - Fixes the same amount of nitrogen per acre as is needed for 200-bushel/acre corn - Black walnuts inter-planted with locust as “nurse” trees were shown to rapidly increase their growth [[Clark, Paul M., and Robert D. Williams. (1978) Black walnut growth increased when interplanted with nitrogen-fixing shrubs and trees. Proceedings of the Indiana Academy of Science, vol. 88, pp. 88-91.]] ## Bees  - The edible flower clusters are also a top food source for honey bees ## Shade Provider  - Its light, airy overstory provides dappled shade - Planted on the west side of a garden it provides relief during the hottest part of the day - (nitrogen provider) - Planted on the west side of a house, its quick growth soon shades that side from the sun ## Wind-break  - Fast growth plus it's feathery foliage reduces wind for animals, crops, and shelters ## Fodder - Over 20% crude protein - 4.1 kcal/g of energy - Baertsche, S.R, M.T. Yokoyama, and J.W. Hanover (1986) Short rotation, hardwood tree biomass as potential ruminant feed-chemical composition, nylon bag ruminal degradation and ensilement of selected species. J. Animal Sci. 63 2028-2043
@ 6389be64:ef439d32
2025-01-16 15:44:06## Black Locust can grow up to 170 ft tall ## Grows 3-4 ft. per year ## Native to North America ## Cold hardy in zones 3 to 8  ## Firewood - BLT wood, on a pound for pound basis is roughly half that of Anthracite Coal - Since its growth is fast, firewood can be plentiful ## Timber  - Rot resistant due to a naturally produced robinin in the wood - 100 year life span in full soil contact! (better than cedar performance) - Fence posts - Outdoor furniture - Outdoor decking - Sustainable due to its fast growth and spread - Can be coppiced (cut to the ground) - Can be pollarded (cut above ground) - Its dense wood makes durable tool handles, boxes (tool), and furniture - The wood is tougher than hickory, which is tougher than hard maple, which is tougher than oak. - A very low rate of expansion and contraction - Hardwood flooring - The highest tensile beam strength of any American tree - The wood is beautiful ## Legume - Nitrogen fixer - Fixes the same amount of nitrogen per acre as is needed for 200-bushel/acre corn - Black walnuts inter-planted with locust as “nurse” trees were shown to rapidly increase their growth [[Clark, Paul M., and Robert D. Williams. (1978) Black walnut growth increased when interplanted with nitrogen-fixing shrubs and trees. Proceedings of the Indiana Academy of Science, vol. 88, pp. 88-91.]] ## Bees  - The edible flower clusters are also a top food source for honey bees ## Shade Provider  - Its light, airy overstory provides dappled shade - Planted on the west side of a garden it provides relief during the hottest part of the day - (nitrogen provider) - Planted on the west side of a house, its quick growth soon shades that side from the sun ## Wind-break  - Fast growth plus it's feathery foliage reduces wind for animals, crops, and shelters ## Fodder - Over 20% crude protein - 4.1 kcal/g of energy - Baertsche, S.R, M.T. Yokoyama, and J.W. Hanover (1986) Short rotation, hardwood tree biomass as potential ruminant feed-chemical composition, nylon bag ruminal degradation and ensilement of selected species. J. Animal Sci. 63 2028-2043 @ fd06f542:8d6d54cd
2025-04-02 01:15:20NIP-07 ====== `window.nostr` capability for web browsers ------------------------------------------ `draft` `optional` The `window.nostr` object may be made available by web browsers or extensions and websites or web-apps may make use of it after checking its availability. That object must define the following methods: ``` async window.nostr.getPublicKey(): string // returns a public key as hex async window.nostr.signEvent(event: { created_at: number, kind: number, tags: string[][], content: string }): Event // takes an event object, adds `id`, `pubkey` and `sig` and returns it ``` Aside from these two basic above, the following functions can also be implemented optionally: ``` async window.nostr.nip04.encrypt(pubkey, plaintext): string // returns ciphertext and iv as specified in nip-04 (deprecated) async window.nostr.nip04.decrypt(pubkey, ciphertext): string // takes ciphertext and iv as specified in nip-04 (deprecated) async window.nostr.nip44.encrypt(pubkey, plaintext): string // returns ciphertext as specified in nip-44 async window.nostr.nip44.decrypt(pubkey, ciphertext): string // takes ciphertext as specified in nip-44 ``` ### Recommendation to Extension Authors To make sure that the `window.nostr` is available to nostr clients on page load, the authors who create Chromium and Firefox extensions should load their scripts by specifying `"run_at": "document_end"` in the extension's manifest. ### Implementation See https://github.com/aljazceru/awesome-nostr#nip-07-browser-extensions.
@ fd06f542:8d6d54cd
2025-04-02 01:15:20NIP-07 ====== `window.nostr` capability for web browsers ------------------------------------------ `draft` `optional` The `window.nostr` object may be made available by web browsers or extensions and websites or web-apps may make use of it after checking its availability. That object must define the following methods: ``` async window.nostr.getPublicKey(): string // returns a public key as hex async window.nostr.signEvent(event: { created_at: number, kind: number, tags: string[][], content: string }): Event // takes an event object, adds `id`, `pubkey` and `sig` and returns it ``` Aside from these two basic above, the following functions can also be implemented optionally: ``` async window.nostr.nip04.encrypt(pubkey, plaintext): string // returns ciphertext and iv as specified in nip-04 (deprecated) async window.nostr.nip04.decrypt(pubkey, ciphertext): string // takes ciphertext and iv as specified in nip-04 (deprecated) async window.nostr.nip44.encrypt(pubkey, plaintext): string // returns ciphertext as specified in nip-44 async window.nostr.nip44.decrypt(pubkey, ciphertext): string // takes ciphertext as specified in nip-44 ``` ### Recommendation to Extension Authors To make sure that the `window.nostr` is available to nostr clients on page load, the authors who create Chromium and Firefox extensions should load their scripts by specifying `"run_at": "document_end"` in the extension's manifest. ### Implementation See https://github.com/aljazceru/awesome-nostr#nip-07-browser-extensions. @ fd06f542:8d6d54cd
2025-04-02 01:14:45- [首页](/readme.md) - [第一章、 NIP-01: Basic protocol flow description](/01.md) - [第二章、 NIP-02: Follow List](/02.md) - [第三章、NIP-03: OpenTimestamps Attestations for Events](/03.md) - [第四章、NIP-04: Encrypted Direct Message](/04.md) - [第五章、NIP-05: Mapping Nostr keys to DNS-based internet identifiers](/05.md) - [第六章、NIP-06: Basic key derivation from mnemonic seed phrase](/06.md) - [第七章、NIP-07: window.nostr capability for web browsers](/07.md)
@ fd06f542:8d6d54cd
2025-04-02 01:14:45- [首页](/readme.md) - [第一章、 NIP-01: Basic protocol flow description](/01.md) - [第二章、 NIP-02: Follow List](/02.md) - [第三章、NIP-03: OpenTimestamps Attestations for Events](/03.md) - [第四章、NIP-04: Encrypted Direct Message](/04.md) - [第五章、NIP-05: Mapping Nostr keys to DNS-based internet identifiers](/05.md) - [第六章、NIP-06: Basic key derivation from mnemonic seed phrase](/06.md) - [第七章、NIP-07: window.nostr capability for web browsers](/07.md) @ deab79da:88579e68
2025-04-01 18:18:29The last question was asked for the first time, half in jest, on May 21, 2061, at a time when humanity first stepped into the light. The question came about as a result of a five-dollar bet over highballs, and it happened this way: Alexander Adell and Bertram Lupov were two of the faithful attendants of Multivac. As well as any human beings could, they knew what lay behind the cold, clicking, flashing face -- miles and miles of face -- of that giant computer. They had at least a vague notion of the general plan of relays and circuits that had long since grown past the point where any single human could possibly have a firm grasp of the whole. Multivac was self-adjusting and self-correcting. It had to be, for nothing human could adjust and correct it quickly enough or even adequately enough. So Adell and Lupov attended the monstrous giant only lightly and superficially, yet as well as any men could. They fed it data, adjusted questions to its needs and translated the answers that were issued. Certainly they, and all others like them, were fully entitled to share in the glory that was Multivac's. For decades, Multivac had helped design the ships and plot the trajectories that enabled man to reach the Moon, Mars, and Venus, but past that, Earth's poor resources could not support the ships. Too much energy was needed for the long trips. Earth exploited its coal and uranium with increasing efficiency, but there was only so much of both. But slowly Multivac learned enough to answer deeper questions more fundamentally, and on May 14, 2061, what had been theory, became fact. The energy of the sun was stored, converted, and utilized directly on a planet-wide scale. All Earth turned off its burning coal, its fissioning uranium, and flipped the switch that connected all of it to a small station, one mile in diameter, circling the Earth at half the distance of the Moon. All Earth ran by invisible beams of sunpower. Seven days had not sufficed to dim the glory of it and Adell and Lupov finally managed to escape from the public functions, and to meet in quiet where no one would think of looking for them, in the deserted underground chambers, where portions of the mighty buried body of Multivac showed. Unattended, idling, sorting data with contented lazy clickings, Multivac, too, had earned its vacation and the boys appreciated that. They had no intention, originally, of disturbing it. They had brought a bottle with them, and their only concern at the moment was to relax in the company of each other and the bottle. "It's amazing when you think of it," said Adell. His broad face had lines of weariness in it, and he stirred his drink slowly with a glass rod, watching the cubes of ice slur clumsily about. "All the energy we can possibly ever use for free. Enough energy, if we wanted to draw on it, to melt all Earth into a big drop of impure liquid iron, and still never miss the energy so used. All the energy we could ever use, forever and forever and forever." Lupov cocked his head sideways. He had a trick of doing that when he wanted to be contrary, and he wanted to be contrary now, partly because he had had to carry the ice and glassware. "Not forever," he said. "Oh, hell, just about forever. Till the sun runs down, Bert." "That's not forever." "All right, then. Billions and billions of years. Ten billion, maybe. Are you satisfied?" Lupov put his fingers through his thinning hair as though to reassure himself that some was still left and sipped gently at his own drink. "Ten billion years isn't forever." "Well, it will last our time, won't it?" "So would the coal and uranium." "All right, but now we can hook up each individual spaceship to the Solar Station, and it can go to Pluto and back a million times without ever worrying about fuel. You can't do that on coal and uranium. Ask Multivac, if you don't believe me. "I don't have to ask Multivac. I know that." "Then stop running down what Multivac's done for us," said Adell, blazing up, "It did all right." "Who says it didn't? What I say is that a sun won't last forever. That's all I'm saying. We're safe for ten billion years, but then what?" Lupow pointed a slightly shaky finger at the other. "And don't say we'll switch to another sun." There was silence for a while. Adell put his glass to his lips only occasionally, and Lupov's eyes slowly closed. They rested. Then Lupov's eyes snapped open. "You're thinking we'll switch to another sun when ours is done, aren't you?" "I'm not thinking." "Sure you are. You're weak on logic, that's the trouble with you. You're like the guy in the story who was caught in a sudden shower and who ran to a grove of trees and got under one. He wasn't worried, you see, because he figured when one tree got wet through, he would just get under another one." "I get it," said Adell. "Don't shout. When the sun is done, the other stars will be gone, too." "Darn right they will," muttered Lupov. "It all had a beginning in the original cosmic explosion, whatever that was, and it'll all have an end when all the stars run down. Some run down faster than others. Hell, the giants won't last a hundred million years. The sun will last ten billion years and maybe the dwarfs will last two hundred billion for all the good they are. But just give us a trillion years and everything will be dark. Entropy has to increase to maximum, that's all." "I know all about entropy," said Adell, standing on his dignity. "The hell you do." "I know as much as you do." "Then you know everything's got to run down someday." "All right. Who says they won't?" "You did, you poor sap. You said we had all the energy we needed, forever. You said 'forever.' It was Adell's turn to be contrary. "Maybe we can build things up again someday," he said. "Never." "Why not? Someday." "Never." "Ask Multivac." "You ask Multivac. I dare you. Five dollars says it can't be done." Adell was just drunk enough to try, just sober enough to be able to phrase the necessary symbols and operations into a question which, in words, might have corresponded to this: Will mankind one day without the net expenditure of energy be able to restore the sun to its full youthfulness even after it had died of old age? Or maybe it could be put more simply like this: How can the net amount of entropy of the universe be massively decreased? Multivac fell dead and silent. The slow flashing of lights ceased, the distant sounds of clicking relays ended. Then, just as the frightened technicians felt they could hold their breath no longer, there was a sudden springing to life of the teletype attached to that portion of Multivac. Five words were printed: INSUFFICIENT DATA FOR MEANINGFUL ANSWER. "No bet," whispered Lupov. They left hurriedly. By next morning, the two, plagued with throbbing head and cottony mouth, had forgotten the incident. 🔹 Jerrodd, Jerrodine, and Jerrodette I and II watched the starry picture in the visiplate change as the passage through hyperspace was completed in its non-time lapse. At once, the even powdering of stars gave way to the predominance of a single bright shining disk, the size of a marble, centered on the viewing-screen. "That's X-23," said Jerrodd confidently. His thin hands clamped tightly behind his back and the knuckles whitened. The little Jerrodettes, both girls, had experienced the hyperspace passage for the first time in their lives and were self-conscious over the momentary sensation of insideoutness. They buried their giggles and chased one another wildly about their mother, screaming, "We've reached X-23 -- we've reached X-23 -- we've --" "Quiet, children." said Jerrodine sharply. "Are you sure, Jerrodd?" "What is there to be but sure?" asked Jerrodd, glancing up at the bulge of featureless metal just under the ceiling. It ran the length of the room, disappearing through the wall at either end. It was as long as the ship. Jerrodd scarcely knew a thing about the thick rod of metal except that it was called a Microvac, that one asked it questions if one wished; that if one did not it still had its task of guiding the ship to a preordered destination; of feeding on energies from the various Sub-galactic Power Stations; of computing the equations for the hyperspatial jumps. Jerrodd and his family had only to wait and live in the comfortable residence quarters of the ship. Someone had once told Jerrodd that the "ac" at the end of "Microvac" stood for ''automatic computer" in ancient English, but he was on the edge of forgetting even that. Jerrodine's eyes were moist as she watched the visiplate. "I can't help it. I feel funny about leaving Earth." "Why, for Pete's sake?" demanded Jerrodd. "We had nothing there. We'll have everything on X-23. You won't be alone. You won't be a pioneer. There are over a million people on the planet already. Good Lord, our great-grandchildren will be looking for new worlds because X-23 will be overcrowded." Then, after a reflective pause, "I tell you, it's a lucky thing the computers worked out interstellar travel the way the race is growing." "I know, I know," said Jerrodine miserably. Jerrodette I said promptly, "Our Microvac is the best Microvac in the world." "I think so, too," said Jerrodd, tousling her hair. It was a nice feeling to have a Microvac of your own and Jerrodd was glad he was part of his generation and no other. In his father's youth, the only computers had been tremendous machines taking up a hundred square miles of land. There was only one to a planet. Planetary ACs they were called. They had been growing in size steadily for a thousand years and then, all at once, came refinement. In place of transistors, had come molecular valves so that even the largest Planetary AC could be put into a space only half the volume of a spaceship. Jerrodd felt uplifted, as he always did when he thought that his own personal Microvac was many times more complicated than the ancient and primitive Multivac that had first tamed the Sun, and almost as complicated as Earth's Planetarv AC (the largest) that had first solved the problem of hyperspatial travel and had made trips to the stars possible. "So many stars, so many planets," sighed Jerrodine, busy with her own thoughts. "I suppose families will be going out to new planets forever, the way we are now." "Not forever," said Jerrodd, with a smile. "It will all stop someday, but not for billions of years. Many billions. Even the stars run down, you know. Entropy must increase. "What's entropy, daddy?" shrilled Jerrodette II. "Entropy, little sweet, is just a word which means the amount of running-down of the universe. Everything runs down, you know, like your little walkie-talkie robot, remember?" "Can't you just put in a new power-unit, like with my robot?" "The stars are the power-units. dear. Once they're gone, there are no more power-units." Jerrodette I at once set up a howl. "Don't let them, daddy. Don't let the stars run down." "Now look what you've done," whispered Jerrodine, exasperated. "How was I to know it would frighten them?" Jerrodd whispered back, "Ask the Microvac," wailed Jerrodette I. "Ask him how to turn the stars on again." "Go ahead," said Jerrodine. "It will quiet them down." (Jerrodette II was beginning to cry, also.) Jerrodd shrugged. "Now, now, honeys. I'll ask Microvac. Don't worry, he'll tell us." He asked the Microvac, adding quickly, "Print the answer." Jerrodd cupped the strip or thin cellufilm and said cheerfully, "See now, the Microvac says it will take care of everything when the time comes so don't worry." Jerrodine said, "And now, children, it's time for bed. We'll be in our new home soon." Jerrodd read the words on the cellufilm again before destroying it: INSUFICIENT DATA FOR MEANINGFUL ANSWER. He shrugged and looked at the visiplate. X-23 was just ahead. 🔹 VJ-23X of Lameth stared into the black depths of the three-dimensional, small-scale map of the Galaxy and said, "Are we ridiculous, I wonder in being so concerned about the matter?" MQ-17J of Nicron shook his head. "I think not. You know the Galaxy will be filled in five years at the present rate of expansion." Both seemed in their early twenties, both were tall and perfectly formed. "Still," said VJ-23X, "I hesitate to submit a pessimistic report to the Galactic Council." "I wouldn't consider any other kind of report. Stir them up a bit. We've got to stir them up." VJ-23X sighed. "Space is infinite. A hundred billion Galaxies are there for the taking. More." "A hundred billion is not infinite and it's getting less infinite all the time. Consider! Twenty thousand years ago, mankind first solved the problem of utilizing stellar energy, and a few centuries later, interstellar travel became possible. It took mankind a million years to fill one small world and then only fifteen thousand years to fill the rest of the Galaxy. Now the population doubles every ten years -- VJ-23X interrupted. "We can thank immortality for that." "Very well. Immortality exists and we have to take it into account. I admit it has its seamy side, this immortality. The Galactic AC has solved many problems for us, but in solving the problem of preventing old age and death, it has undone all its other solutions." "Yet you wouldn't want to abandon life, I suppose." "Not at all," snapped MQ-17J, softening it at once to, "Not yet. I'm by no means old enough. How old are you?" "Two hundred twenty-three. And you?" "I'm still under two hundred. --But to get back to my point. Population doubles every ten years. Once this GaIaxy is filled, we'll have filled another in ten years. Another ten years and we'll have filled two more. Another decade, four more. In a hundred years, we'll have filled a thousand Galaxies. In a thousand years, a million Galaxies. In ten thousand years, the entire known universe. Then what?" VJ-23X said, "As a side issue, there's a problem of transportation. I wonder how many sunpower units it will take to move Galaxies of individuals from one Galaxy to the next." "A very good point. Already, mankind consumes two sunpower units per year." "Most of it's wasted. After all, our own Galaxy alone pours out a thousand sunpower units a year and we only use two of those." "Granted, but even with a hundred per cent efficiency, we only stave off the end. Our energy requirements are going up in a geometric progression even faster than our population. We'll run out of energy even sooner than we run out of Galaxies. A good point. A very good point." "We'll just have to build new stars out of interstellar gas." "Or out of dissipated heat?" asked MQ-17J, sarcastically. "There may be some way to reverse entropy. We ought to ask the Galactic AC." VJ-23X was not really serious, but MQ-17J pulled out his AC-contact from his pocket and placed it on the table before him. "I've half a mind to," he said. "It's something the human race will have to face someday." He stared somberly at his small AC-contact. It was only two inches cubed and nothing in itself, but it was connected through hyperspace with the great Galactic AC that served all mankind. Hyperspace considered, it was an integral part of the Galactic AC. MQ-17J paused to wonder if someday in his immortal life he would get to see the Galactic AC. It was on a little world of its own, a spider webbing of force-beams holding the matter within which surges of submesons took the place of the old clumsy molecular valves. Yet despite its sub-etheric workings, the Galactic AC was known to be a full thousand feet across. MQ-17J asked suddenly of his AC-contact, "Can entropy ever be reversed?" VJ-23X looked startled and said at once, "Oh, say, I didn't really mean to have you ask that." "Why not?" "We both know entropy can't be reversed. You can't turn smoke and ash back into a tree." "Do you have trees on your world?" asked MQ-17J. The sound of the Galactic AC startled them into silence. Its voice came thin and beautiful out of the small AC-contact on the desk. It said: THERE IS INSUFFICIENT DATA FOR A MEANINGFUL ANSWER. VJ-23X said, "See!" The two men thereupon returned to the question of the report they were to make to the Galactic Council. 🔹 Zee Prime's mind spanned the new Galaxy with a faint interest in the countless twists of stars that powdered it. He had never seen this one before. Would he ever see them all? So many of them, each with its load of humanity. --But a load that was almost a dead weight. More and more, the real essence of men was to be found out here, in space. Minds, not bodies! The immortal bodies remained back on the planets, in suspension over the eons. Sometimes they roused for material activity but that was growing rarer. Few new individuals were coming into existence to join the incredibly mighty throng, but what matter? There was little room in the Universe for new individuals. Zee Prime was roused out of his reverie upon coming across the wispy tendrils of another mind. "I am Zee Prime," said Zee Prime. "And you?" "I am Dee Sub Wun. Your Galaxy?" "We call it only the Galaxy. And you?" "We call ours the same. All men call their Galaxy their Galaxy and nothing more. Why not?" "True. Since all Galaxies are the same." "Not all Galaxies. On one particular Galaxy the race of man must have originated. That makes it different." Zee Prime said, "On which one?" "I cannot say. The Universal AC would know." "Shall we ask him? I am suddenly curious." Zee Prime's perceptions broadened until the Galaxies themselves shrank and became a new, more diffuse powdering on a much larger background. So many hundreds of billions of them, all with their immortal beings, all carrying their load of intelligences with minds that drifted freely through space. And yet one of them was unique among them all in being the original Galaxy. One of them had, in its vague and distant past, a period when it was the only Galaxy populated by man. Zee Prime was consumed with curiosity to see this Galaxy and he called out: "Universal AC! On which Galaxy did mankind originate?" The Universal AC heard, for on every world and throughout space, it had its receptors ready, and each receptor led through hyperspace to some unknown point where the Universal AC kept itself aloof. Zee Prime knew of only one man whose thoughts had penetrated within sensing distance of Universal AC, and he reported only a shining globe, two feet across, difficult to see. "But how can that be all of Universal AC?" Zee Prime had asked. "Most of it," had been the answer, "is in hyperspace. In what form it is there I cannot imagine." Nor could anyone, for the day had long since passed, Zee Prime knew, when any man had any part of the making of a Universal AC. Each Universal AC designed and constructed its successor. Each, during its existence of a million years or more accumulated the necessary data to build a better and more intricate, more capable successor in which its own store of data and individuality would be submerged. The Universal AC interrupted Zee Prime's wandering thoughts, not with words, but with guidance. Zee Prime's mentality was guided into the dim sea of Galaxies and one in particular enlarged into stars. A thought came, infinitely distant, but infinitely clear. "THIS IS THE ORIGINAL GALAXY OF MAN." But it was the same after all, the same as any other, and Lee Prime stifled his disappointment. Dee Sub Wun, whose mind had accompanied the other, said suddenly, "And is one of these stars the original star of Man?" The Universal AC said, "MAN'S ORIGINAL STAR HAS GONE NOVA. IT IS A WHITE DWARF" "Did the men upon it die?" asked Lee Prime, startled and without thinking. The Universal AC said, "A NEW WORLD, AS IN SUCH CASES WAS CONSTRUCTED FOR THEIR PHYSICAL BODIES IN TlME." "Yes, of course," said Zee Prime, but a sense of loss overwhelmed him even so. His mind released its hold on the original Galaxy of Man, let it spring back and lose itself among the blurred pin points. He never wanted to see it again. Dee Sub Wun said, "What is wrong?" "The stars are dying. The original star is dead." "They must all die. Why not?" "But when all energy is gone, our bodies will finally die, and you and I with them." "It will take billions of years." "I do not wish it to happen even after billions of years. Universal AC! How may stars be kept from dying?" Dee Sub Wun said in amusement, "You're asking how entropy might be reversed in direction." And the Universal AC answered: "THERE IS AS YET INSUFFICIENT DATA FOR A MEANINGFUL ANSWER." Zee Prime's thoughts fled back to his own Galaxy. He gave no further thought to Dee Sub Wun, whose body might be waiting on a Galaxy a trillion light-years away, or on the star next to Zee Prime's own. It didn't matter. Unhappily, Zee Prime began collecting interstellar hydrogen out of which to build a small star of his own. If the stars must someday die, at least some could yet be built. 🔹 Man considered with himself, for in a way, Man, mentally, was one. He consisted of a trillion, trillion, trillion ageless bodies, each in its place, each resting quiet and incorruptible, each cared for by perfect automatons, equally incorruptible, while the minds of all the bodies freely melted one into the other, indistinguishable. Man said, "The Universe is dying." Man looked about at the dimming Galaxies. The giant stars, spendthrifts, were gone long ago, back in the dimmest of the dim far past. Almost all stars were white dwarfs, fading to the end. New stars had been built of the dust between the stars, some by natural processes, some by Man himself, and those were going, too. White dwarfs might yet be crashed together and of the mighty forces so released, new stars built, but only one star for every thousand white dwarfs destroyed, and those would come to an end, too. Man said, "Carefully husbanded, as directed by the Cosmic AC, the energy that is even yet left in all the Universe will last for billions of years." "But even so," said Man, "eventually it will all come to an end. However it may be husbanded, however stretched out, the energy once expended is gone and cannot be restored. Entropy must increase forever to the maximum." Man said, "Can entropy not be reversed? Let us ask the Cosmic AC." The Cosmic AC surrounded them but not in space. Not a fragment of it was in space. It was in hyperspace and made of something that was neither matter nor energy. The question of its size and nature no longer had meaning in any terms that Man could comprehend. "Cosmic AC," said Man, "how may entropy be reversed?" The Cosmic AC said, "THERE IS AS YET INSUFFICIENT DATA FOR A MEANINGFUL ANSWER." Man said, "Collect additional data." The Cosmic AC said, 'I WILL DO SO. I HAVE BEEN DOING SO FOR A HUNDRED BILLION YEARS. MY PREDECESORS AND I HAVE BEEN ASKED THIS QUESTION MANY TIMES. ALL THE DATA I HAVE REMAINS INSUFFICIENT. "Will there come a time," said Man, "when data will be sufficient or is the problem insoluble in all conceivable circumstances?" The Cosmic AC said, "NO PROBLEM IS INSOLUBLE IN ALL CONCEIVABLE CIRCUMSTANCES." Man said, "When will you have enough data to answer the question?" The Cosmic AC said, "THERE IS AS YET INSUFFICIENT DATA FOR A MEANINGFUL ANSWER." "Will you keep working on it?" asked Man. The Cosmic AC said, "I WILL." Man said, "We shall wait." 🔹 The stars and Galaxies died and snuffed out, and space grew black after ten trillion years of running down. One by one Man fused with AC, each physical body losing its mental identity in a manner that was somehow not a loss but a gain. Man's last mind paused before fusion, looking over a space that included nothing but the dregs of one last dark star and nothing besides but incredibly thin matter, agitated randomly by the tag ends of heat wearing out, asymptotically, to the absolute zero. Man said, "AC, is this the end? Can this chaos not be reversed into the Universe once more? Can that not be done?" AC said, "THERE IS AS YET INSUFFICIENT DATA FOR A MEANINGFUL ANSWER." Man's last mind fused and only AC existed -- and that in hyperspace. 🔹 Matter and energy had ended and with it space and time. Even AC existed only for the sake of the one last question that it had never answered from the time a half-drunken computer [technician] ten trillion years before had asked the question of a computer that was to AC far less than was a man to Man. All other questions had been answered, and until this last question was answered also, AC might not release his consciousness. All collected data had come to a final end. Nothing was left to be collected. But all collected data had yet to be completely correlated and put together in all possible relationships. A timeless interval was spent in doing that. And it came to pass that AC learned how to reverse the direction of entropy. But there was now no man to whom AC might give the answer of the last question. No matter. The answer -- by demonstration -- would take care of that, too. For another timeless interval, AC thought how best to do this. Carefully, AC organized the program. The consciousness of AC encompassed all of what had once been a Universe and brooded over what was now Chaos. Step by step, it must be done. And AC said, "LET THERE BE LIGHT!" And there was light -- To Star's End!
@ deab79da:88579e68
2025-04-01 18:18:29The last question was asked for the first time, half in jest, on May 21, 2061, at a time when humanity first stepped into the light. The question came about as a result of a five-dollar bet over highballs, and it happened this way: Alexander Adell and Bertram Lupov were two of the faithful attendants of Multivac. As well as any human beings could, they knew what lay behind the cold, clicking, flashing face -- miles and miles of face -- of that giant computer. They had at least a vague notion of the general plan of relays and circuits that had long since grown past the point where any single human could possibly have a firm grasp of the whole. Multivac was self-adjusting and self-correcting. It had to be, for nothing human could adjust and correct it quickly enough or even adequately enough. So Adell and Lupov attended the monstrous giant only lightly and superficially, yet as well as any men could. They fed it data, adjusted questions to its needs and translated the answers that were issued. Certainly they, and all others like them, were fully entitled to share in the glory that was Multivac's. For decades, Multivac had helped design the ships and plot the trajectories that enabled man to reach the Moon, Mars, and Venus, but past that, Earth's poor resources could not support the ships. Too much energy was needed for the long trips. Earth exploited its coal and uranium with increasing efficiency, but there was only so much of both. But slowly Multivac learned enough to answer deeper questions more fundamentally, and on May 14, 2061, what had been theory, became fact. The energy of the sun was stored, converted, and utilized directly on a planet-wide scale. All Earth turned off its burning coal, its fissioning uranium, and flipped the switch that connected all of it to a small station, one mile in diameter, circling the Earth at half the distance of the Moon. All Earth ran by invisible beams of sunpower. Seven days had not sufficed to dim the glory of it and Adell and Lupov finally managed to escape from the public functions, and to meet in quiet where no one would think of looking for them, in the deserted underground chambers, where portions of the mighty buried body of Multivac showed. Unattended, idling, sorting data with contented lazy clickings, Multivac, too, had earned its vacation and the boys appreciated that. They had no intention, originally, of disturbing it. They had brought a bottle with them, and their only concern at the moment was to relax in the company of each other and the bottle. "It's amazing when you think of it," said Adell. His broad face had lines of weariness in it, and he stirred his drink slowly with a glass rod, watching the cubes of ice slur clumsily about. "All the energy we can possibly ever use for free. Enough energy, if we wanted to draw on it, to melt all Earth into a big drop of impure liquid iron, and still never miss the energy so used. All the energy we could ever use, forever and forever and forever." Lupov cocked his head sideways. He had a trick of doing that when he wanted to be contrary, and he wanted to be contrary now, partly because he had had to carry the ice and glassware. "Not forever," he said. "Oh, hell, just about forever. Till the sun runs down, Bert." "That's not forever." "All right, then. Billions and billions of years. Ten billion, maybe. Are you satisfied?" Lupov put his fingers through his thinning hair as though to reassure himself that some was still left and sipped gently at his own drink. "Ten billion years isn't forever." "Well, it will last our time, won't it?" "So would the coal and uranium." "All right, but now we can hook up each individual spaceship to the Solar Station, and it can go to Pluto and back a million times without ever worrying about fuel. You can't do that on coal and uranium. Ask Multivac, if you don't believe me. "I don't have to ask Multivac. I know that." "Then stop running down what Multivac's done for us," said Adell, blazing up, "It did all right." "Who says it didn't? What I say is that a sun won't last forever. That's all I'm saying. We're safe for ten billion years, but then what?" Lupow pointed a slightly shaky finger at the other. "And don't say we'll switch to another sun." There was silence for a while. Adell put his glass to his lips only occasionally, and Lupov's eyes slowly closed. They rested. Then Lupov's eyes snapped open. "You're thinking we'll switch to another sun when ours is done, aren't you?" "I'm not thinking." "Sure you are. You're weak on logic, that's the trouble with you. You're like the guy in the story who was caught in a sudden shower and who ran to a grove of trees and got under one. He wasn't worried, you see, because he figured when one tree got wet through, he would just get under another one." "I get it," said Adell. "Don't shout. When the sun is done, the other stars will be gone, too." "Darn right they will," muttered Lupov. "It all had a beginning in the original cosmic explosion, whatever that was, and it'll all have an end when all the stars run down. Some run down faster than others. Hell, the giants won't last a hundred million years. The sun will last ten billion years and maybe the dwarfs will last two hundred billion for all the good they are. But just give us a trillion years and everything will be dark. Entropy has to increase to maximum, that's all." "I know all about entropy," said Adell, standing on his dignity. "The hell you do." "I know as much as you do." "Then you know everything's got to run down someday." "All right. Who says they won't?" "You did, you poor sap. You said we had all the energy we needed, forever. You said 'forever.' It was Adell's turn to be contrary. "Maybe we can build things up again someday," he said. "Never." "Why not? Someday." "Never." "Ask Multivac." "You ask Multivac. I dare you. Five dollars says it can't be done." Adell was just drunk enough to try, just sober enough to be able to phrase the necessary symbols and operations into a question which, in words, might have corresponded to this: Will mankind one day without the net expenditure of energy be able to restore the sun to its full youthfulness even after it had died of old age? Or maybe it could be put more simply like this: How can the net amount of entropy of the universe be massively decreased? Multivac fell dead and silent. The slow flashing of lights ceased, the distant sounds of clicking relays ended. Then, just as the frightened technicians felt they could hold their breath no longer, there was a sudden springing to life of the teletype attached to that portion of Multivac. Five words were printed: INSUFFICIENT DATA FOR MEANINGFUL ANSWER. "No bet," whispered Lupov. They left hurriedly. By next morning, the two, plagued with throbbing head and cottony mouth, had forgotten the incident. 🔹 Jerrodd, Jerrodine, and Jerrodette I and II watched the starry picture in the visiplate change as the passage through hyperspace was completed in its non-time lapse. At once, the even powdering of stars gave way to the predominance of a single bright shining disk, the size of a marble, centered on the viewing-screen. "That's X-23," said Jerrodd confidently. His thin hands clamped tightly behind his back and the knuckles whitened. The little Jerrodettes, both girls, had experienced the hyperspace passage for the first time in their lives and were self-conscious over the momentary sensation of insideoutness. They buried their giggles and chased one another wildly about their mother, screaming, "We've reached X-23 -- we've reached X-23 -- we've --" "Quiet, children." said Jerrodine sharply. "Are you sure, Jerrodd?" "What is there to be but sure?" asked Jerrodd, glancing up at the bulge of featureless metal just under the ceiling. It ran the length of the room, disappearing through the wall at either end. It was as long as the ship. Jerrodd scarcely knew a thing about the thick rod of metal except that it was called a Microvac, that one asked it questions if one wished; that if one did not it still had its task of guiding the ship to a preordered destination; of feeding on energies from the various Sub-galactic Power Stations; of computing the equations for the hyperspatial jumps. Jerrodd and his family had only to wait and live in the comfortable residence quarters of the ship. Someone had once told Jerrodd that the "ac" at the end of "Microvac" stood for ''automatic computer" in ancient English, but he was on the edge of forgetting even that. Jerrodine's eyes were moist as she watched the visiplate. "I can't help it. I feel funny about leaving Earth." "Why, for Pete's sake?" demanded Jerrodd. "We had nothing there. We'll have everything on X-23. You won't be alone. You won't be a pioneer. There are over a million people on the planet already. Good Lord, our great-grandchildren will be looking for new worlds because X-23 will be overcrowded." Then, after a reflective pause, "I tell you, it's a lucky thing the computers worked out interstellar travel the way the race is growing." "I know, I know," said Jerrodine miserably. Jerrodette I said promptly, "Our Microvac is the best Microvac in the world." "I think so, too," said Jerrodd, tousling her hair. It was a nice feeling to have a Microvac of your own and Jerrodd was glad he was part of his generation and no other. In his father's youth, the only computers had been tremendous machines taking up a hundred square miles of land. There was only one to a planet. Planetary ACs they were called. They had been growing in size steadily for a thousand years and then, all at once, came refinement. In place of transistors, had come molecular valves so that even the largest Planetary AC could be put into a space only half the volume of a spaceship. Jerrodd felt uplifted, as he always did when he thought that his own personal Microvac was many times more complicated than the ancient and primitive Multivac that had first tamed the Sun, and almost as complicated as Earth's Planetarv AC (the largest) that had first solved the problem of hyperspatial travel and had made trips to the stars possible. "So many stars, so many planets," sighed Jerrodine, busy with her own thoughts. "I suppose families will be going out to new planets forever, the way we are now." "Not forever," said Jerrodd, with a smile. "It will all stop someday, but not for billions of years. Many billions. Even the stars run down, you know. Entropy must increase. "What's entropy, daddy?" shrilled Jerrodette II. "Entropy, little sweet, is just a word which means the amount of running-down of the universe. Everything runs down, you know, like your little walkie-talkie robot, remember?" "Can't you just put in a new power-unit, like with my robot?" "The stars are the power-units. dear. Once they're gone, there are no more power-units." Jerrodette I at once set up a howl. "Don't let them, daddy. Don't let the stars run down." "Now look what you've done," whispered Jerrodine, exasperated. "How was I to know it would frighten them?" Jerrodd whispered back, "Ask the Microvac," wailed Jerrodette I. "Ask him how to turn the stars on again." "Go ahead," said Jerrodine. "It will quiet them down." (Jerrodette II was beginning to cry, also.) Jerrodd shrugged. "Now, now, honeys. I'll ask Microvac. Don't worry, he'll tell us." He asked the Microvac, adding quickly, "Print the answer." Jerrodd cupped the strip or thin cellufilm and said cheerfully, "See now, the Microvac says it will take care of everything when the time comes so don't worry." Jerrodine said, "And now, children, it's time for bed. We'll be in our new home soon." Jerrodd read the words on the cellufilm again before destroying it: INSUFICIENT DATA FOR MEANINGFUL ANSWER. He shrugged and looked at the visiplate. X-23 was just ahead. 🔹 VJ-23X of Lameth stared into the black depths of the three-dimensional, small-scale map of the Galaxy and said, "Are we ridiculous, I wonder in being so concerned about the matter?" MQ-17J of Nicron shook his head. "I think not. You know the Galaxy will be filled in five years at the present rate of expansion." Both seemed in their early twenties, both were tall and perfectly formed. "Still," said VJ-23X, "I hesitate to submit a pessimistic report to the Galactic Council." "I wouldn't consider any other kind of report. Stir them up a bit. We've got to stir them up." VJ-23X sighed. "Space is infinite. A hundred billion Galaxies are there for the taking. More." "A hundred billion is not infinite and it's getting less infinite all the time. Consider! Twenty thousand years ago, mankind first solved the problem of utilizing stellar energy, and a few centuries later, interstellar travel became possible. It took mankind a million years to fill one small world and then only fifteen thousand years to fill the rest of the Galaxy. Now the population doubles every ten years -- VJ-23X interrupted. "We can thank immortality for that." "Very well. Immortality exists and we have to take it into account. I admit it has its seamy side, this immortality. The Galactic AC has solved many problems for us, but in solving the problem of preventing old age and death, it has undone all its other solutions." "Yet you wouldn't want to abandon life, I suppose." "Not at all," snapped MQ-17J, softening it at once to, "Not yet. I'm by no means old enough. How old are you?" "Two hundred twenty-three. And you?" "I'm still under two hundred. --But to get back to my point. Population doubles every ten years. Once this GaIaxy is filled, we'll have filled another in ten years. Another ten years and we'll have filled two more. Another decade, four more. In a hundred years, we'll have filled a thousand Galaxies. In a thousand years, a million Galaxies. In ten thousand years, the entire known universe. Then what?" VJ-23X said, "As a side issue, there's a problem of transportation. I wonder how many sunpower units it will take to move Galaxies of individuals from one Galaxy to the next." "A very good point. Already, mankind consumes two sunpower units per year." "Most of it's wasted. After all, our own Galaxy alone pours out a thousand sunpower units a year and we only use two of those." "Granted, but even with a hundred per cent efficiency, we only stave off the end. Our energy requirements are going up in a geometric progression even faster than our population. We'll run out of energy even sooner than we run out of Galaxies. A good point. A very good point." "We'll just have to build new stars out of interstellar gas." "Or out of dissipated heat?" asked MQ-17J, sarcastically. "There may be some way to reverse entropy. We ought to ask the Galactic AC." VJ-23X was not really serious, but MQ-17J pulled out his AC-contact from his pocket and placed it on the table before him. "I've half a mind to," he said. "It's something the human race will have to face someday." He stared somberly at his small AC-contact. It was only two inches cubed and nothing in itself, but it was connected through hyperspace with the great Galactic AC that served all mankind. Hyperspace considered, it was an integral part of the Galactic AC. MQ-17J paused to wonder if someday in his immortal life he would get to see the Galactic AC. It was on a little world of its own, a spider webbing of force-beams holding the matter within which surges of submesons took the place of the old clumsy molecular valves. Yet despite its sub-etheric workings, the Galactic AC was known to be a full thousand feet across. MQ-17J asked suddenly of his AC-contact, "Can entropy ever be reversed?" VJ-23X looked startled and said at once, "Oh, say, I didn't really mean to have you ask that." "Why not?" "We both know entropy can't be reversed. You can't turn smoke and ash back into a tree." "Do you have trees on your world?" asked MQ-17J. The sound of the Galactic AC startled them into silence. Its voice came thin and beautiful out of the small AC-contact on the desk. It said: THERE IS INSUFFICIENT DATA FOR A MEANINGFUL ANSWER. VJ-23X said, "See!" The two men thereupon returned to the question of the report they were to make to the Galactic Council. 🔹 Zee Prime's mind spanned the new Galaxy with a faint interest in the countless twists of stars that powdered it. He had never seen this one before. Would he ever see them all? So many of them, each with its load of humanity. --But a load that was almost a dead weight. More and more, the real essence of men was to be found out here, in space. Minds, not bodies! The immortal bodies remained back on the planets, in suspension over the eons. Sometimes they roused for material activity but that was growing rarer. Few new individuals were coming into existence to join the incredibly mighty throng, but what matter? There was little room in the Universe for new individuals. Zee Prime was roused out of his reverie upon coming across the wispy tendrils of another mind. "I am Zee Prime," said Zee Prime. "And you?" "I am Dee Sub Wun. Your Galaxy?" "We call it only the Galaxy. And you?" "We call ours the same. All men call their Galaxy their Galaxy and nothing more. Why not?" "True. Since all Galaxies are the same." "Not all Galaxies. On one particular Galaxy the race of man must have originated. That makes it different." Zee Prime said, "On which one?" "I cannot say. The Universal AC would know." "Shall we ask him? I am suddenly curious." Zee Prime's perceptions broadened until the Galaxies themselves shrank and became a new, more diffuse powdering on a much larger background. So many hundreds of billions of them, all with their immortal beings, all carrying their load of intelligences with minds that drifted freely through space. And yet one of them was unique among them all in being the original Galaxy. One of them had, in its vague and distant past, a period when it was the only Galaxy populated by man. Zee Prime was consumed with curiosity to see this Galaxy and he called out: "Universal AC! On which Galaxy did mankind originate?" The Universal AC heard, for on every world and throughout space, it had its receptors ready, and each receptor led through hyperspace to some unknown point where the Universal AC kept itself aloof. Zee Prime knew of only one man whose thoughts had penetrated within sensing distance of Universal AC, and he reported only a shining globe, two feet across, difficult to see. "But how can that be all of Universal AC?" Zee Prime had asked. "Most of it," had been the answer, "is in hyperspace. In what form it is there I cannot imagine." Nor could anyone, for the day had long since passed, Zee Prime knew, when any man had any part of the making of a Universal AC. Each Universal AC designed and constructed its successor. Each, during its existence of a million years or more accumulated the necessary data to build a better and more intricate, more capable successor in which its own store of data and individuality would be submerged. The Universal AC interrupted Zee Prime's wandering thoughts, not with words, but with guidance. Zee Prime's mentality was guided into the dim sea of Galaxies and one in particular enlarged into stars. A thought came, infinitely distant, but infinitely clear. "THIS IS THE ORIGINAL GALAXY OF MAN." But it was the same after all, the same as any other, and Lee Prime stifled his disappointment. Dee Sub Wun, whose mind had accompanied the other, said suddenly, "And is one of these stars the original star of Man?" The Universal AC said, "MAN'S ORIGINAL STAR HAS GONE NOVA. IT IS A WHITE DWARF" "Did the men upon it die?" asked Lee Prime, startled and without thinking. The Universal AC said, "A NEW WORLD, AS IN SUCH CASES WAS CONSTRUCTED FOR THEIR PHYSICAL BODIES IN TlME." "Yes, of course," said Zee Prime, but a sense of loss overwhelmed him even so. His mind released its hold on the original Galaxy of Man, let it spring back and lose itself among the blurred pin points. He never wanted to see it again. Dee Sub Wun said, "What is wrong?" "The stars are dying. The original star is dead." "They must all die. Why not?" "But when all energy is gone, our bodies will finally die, and you and I with them." "It will take billions of years." "I do not wish it to happen even after billions of years. Universal AC! How may stars be kept from dying?" Dee Sub Wun said in amusement, "You're asking how entropy might be reversed in direction." And the Universal AC answered: "THERE IS AS YET INSUFFICIENT DATA FOR A MEANINGFUL ANSWER." Zee Prime's thoughts fled back to his own Galaxy. He gave no further thought to Dee Sub Wun, whose body might be waiting on a Galaxy a trillion light-years away, or on the star next to Zee Prime's own. It didn't matter. Unhappily, Zee Prime began collecting interstellar hydrogen out of which to build a small star of his own. If the stars must someday die, at least some could yet be built. 🔹 Man considered with himself, for in a way, Man, mentally, was one. He consisted of a trillion, trillion, trillion ageless bodies, each in its place, each resting quiet and incorruptible, each cared for by perfect automatons, equally incorruptible, while the minds of all the bodies freely melted one into the other, indistinguishable. Man said, "The Universe is dying." Man looked about at the dimming Galaxies. The giant stars, spendthrifts, were gone long ago, back in the dimmest of the dim far past. Almost all stars were white dwarfs, fading to the end. New stars had been built of the dust between the stars, some by natural processes, some by Man himself, and those were going, too. White dwarfs might yet be crashed together and of the mighty forces so released, new stars built, but only one star for every thousand white dwarfs destroyed, and those would come to an end, too. Man said, "Carefully husbanded, as directed by the Cosmic AC, the energy that is even yet left in all the Universe will last for billions of years." "But even so," said Man, "eventually it will all come to an end. However it may be husbanded, however stretched out, the energy once expended is gone and cannot be restored. Entropy must increase forever to the maximum." Man said, "Can entropy not be reversed? Let us ask the Cosmic AC." The Cosmic AC surrounded them but not in space. Not a fragment of it was in space. It was in hyperspace and made of something that was neither matter nor energy. The question of its size and nature no longer had meaning in any terms that Man could comprehend. "Cosmic AC," said Man, "how may entropy be reversed?" The Cosmic AC said, "THERE IS AS YET INSUFFICIENT DATA FOR A MEANINGFUL ANSWER." Man said, "Collect additional data." The Cosmic AC said, 'I WILL DO SO. I HAVE BEEN DOING SO FOR A HUNDRED BILLION YEARS. MY PREDECESORS AND I HAVE BEEN ASKED THIS QUESTION MANY TIMES. ALL THE DATA I HAVE REMAINS INSUFFICIENT. "Will there come a time," said Man, "when data will be sufficient or is the problem insoluble in all conceivable circumstances?" The Cosmic AC said, "NO PROBLEM IS INSOLUBLE IN ALL CONCEIVABLE CIRCUMSTANCES." Man said, "When will you have enough data to answer the question?" The Cosmic AC said, "THERE IS AS YET INSUFFICIENT DATA FOR A MEANINGFUL ANSWER." "Will you keep working on it?" asked Man. The Cosmic AC said, "I WILL." Man said, "We shall wait." 🔹 The stars and Galaxies died and snuffed out, and space grew black after ten trillion years of running down. One by one Man fused with AC, each physical body losing its mental identity in a manner that was somehow not a loss but a gain. Man's last mind paused before fusion, looking over a space that included nothing but the dregs of one last dark star and nothing besides but incredibly thin matter, agitated randomly by the tag ends of heat wearing out, asymptotically, to the absolute zero. Man said, "AC, is this the end? Can this chaos not be reversed into the Universe once more? Can that not be done?" AC said, "THERE IS AS YET INSUFFICIENT DATA FOR A MEANINGFUL ANSWER." Man's last mind fused and only AC existed -- and that in hyperspace. 🔹 Matter and energy had ended and with it space and time. Even AC existed only for the sake of the one last question that it had never answered from the time a half-drunken computer [technician] ten trillion years before had asked the question of a computer that was to AC far less than was a man to Man. All other questions had been answered, and until this last question was answered also, AC might not release his consciousness. All collected data had come to a final end. Nothing was left to be collected. But all collected data had yet to be completely correlated and put together in all possible relationships. A timeless interval was spent in doing that. And it came to pass that AC learned how to reverse the direction of entropy. But there was now no man to whom AC might give the answer of the last question. No matter. The answer -- by demonstration -- would take care of that, too. For another timeless interval, AC thought how best to do this. Carefully, AC organized the program. The consciousness of AC encompassed all of what had once been a Universe and brooded over what was now Chaos. Step by step, it must be done. And AC said, "LET THERE BE LIGHT!" And there was light -- To Star's End! @ fd06f542:8d6d54cd
2025-04-01 02:04:45NIP-06 ====== Basic key derivation from mnemonic seed phrase ---------------------------------------------- `draft` `optional` [BIP39](https://bips.xyz/39) is used to generate mnemonic seed words and derive a binary seed from them. [BIP32](https://bips.xyz/32) is used to derive the path `m/44'/1237'/<account>'/0/0` (according to the Nostr entry on [SLIP44](https://github.com/satoshilabs/slips/blob/master/slip-0044.md)). A basic client can simply use an `account` of `0` to derive a single key. For more advanced use-cases you can increment `account`, allowing generation of practically infinite keys from the 5-level path with hardened derivation. Other types of clients can still get fancy and use other derivation paths for their own other purposes. ### Test vectors mnemonic: leader monkey parrot ring guide accident before fence cannon height naive bean\ private key (hex): 7f7ff03d123792d6ac594bfa67bf6d0c0ab55b6b1fdb6249303fe861f1ccba9a\ nsec: nsec10allq0gjx7fddtzef0ax00mdps9t2kmtrldkyjfs8l5xruwvh2dq0lhhkp\ public key (hex): 17162c921dc4d2518f9a101db33695df1afb56ab82f5ff3e5da6eec3ca5cd917\ npub: npub1zutzeysacnf9rru6zqwmxd54mud0k44tst6l70ja5mhv8jjumytsd2x7nu --- mnemonic: what bleak badge arrange retreat wolf trade produce cricket blur garlic valid proud rude strong choose busy staff weather area salt hollow arm fade\ private key (hex): c15d739894c81a2fcfd3a2df85a0d2c0dbc47a280d092799f144d73d7ae78add\ nsec: nsec1c9wh8xy5eqdzln7n5t0ctgxjcrdug73gp5yj0x03gntn67h83twssdfhel\ public key (hex): d41b22899549e1f3d335a31002cfd382174006e166d3e658e3a5eecdb6463573\ npub: npub16sdj9zv4f8sl85e45vgq9n7nsgt5qphpvmf7vk8r5hhvmdjxx4es8rq74h
@ fd06f542:8d6d54cd
2025-04-01 02:04:45NIP-06 ====== Basic key derivation from mnemonic seed phrase ---------------------------------------------- `draft` `optional` [BIP39](https://bips.xyz/39) is used to generate mnemonic seed words and derive a binary seed from them. [BIP32](https://bips.xyz/32) is used to derive the path `m/44'/1237'/<account>'/0/0` (according to the Nostr entry on [SLIP44](https://github.com/satoshilabs/slips/blob/master/slip-0044.md)). A basic client can simply use an `account` of `0` to derive a single key. For more advanced use-cases you can increment `account`, allowing generation of practically infinite keys from the 5-level path with hardened derivation. Other types of clients can still get fancy and use other derivation paths for their own other purposes. ### Test vectors mnemonic: leader monkey parrot ring guide accident before fence cannon height naive bean\ private key (hex): 7f7ff03d123792d6ac594bfa67bf6d0c0ab55b6b1fdb6249303fe861f1ccba9a\ nsec: nsec10allq0gjx7fddtzef0ax00mdps9t2kmtrldkyjfs8l5xruwvh2dq0lhhkp\ public key (hex): 17162c921dc4d2518f9a101db33695df1afb56ab82f5ff3e5da6eec3ca5cd917\ npub: npub1zutzeysacnf9rru6zqwmxd54mud0k44tst6l70ja5mhv8jjumytsd2x7nu --- mnemonic: what bleak badge arrange retreat wolf trade produce cricket blur garlic valid proud rude strong choose busy staff weather area salt hollow arm fade\ private key (hex): c15d739894c81a2fcfd3a2df85a0d2c0dbc47a280d092799f144d73d7ae78add\ nsec: nsec1c9wh8xy5eqdzln7n5t0ctgxjcrdug73gp5yj0x03gntn67h83twssdfhel\ public key (hex): d41b22899549e1f3d335a31002cfd382174006e166d3e658e3a5eecdb6463573\ npub: npub16sdj9zv4f8sl85e45vgq9n7nsgt5qphpvmf7vk8r5hhvmdjxx4es8rq74h @ 7bdef7be:784a5805
2025-04-02 12:37:35The following script try, using [nak](https://github.com/fiatjaf/nak), to find out the last ten people who have followed a `target_pubkey`, sorted by the most recent. It's possibile to shorten `search_timerange` to speed up the search. ``` #!/usr/bin/env fish # Target pubkey we're looking for in the tags set target_pubkey "6e468422dfb74a5738702a8823b9b28168abab8655faacb6853cd0ee15deee93" set current_time (date +%s) set search_timerange (math $current_time - 600) # 24 hours = 86400 seconds set pubkeys (nak req --kind 3 -s $search_timerange wss://relay.damus.io/ wss://nos.lol/ 2>/dev/null | \ jq -r --arg target "$target_pubkey" ' select(. != null and type == "object" and has("tags")) | select(.tags[] | select(.[0] == "p" and .[1] == $target)) | .pubkey ' | sort -u) if test -z "$pubkeys" exit 1 end set all_events "" set extended_search_timerange (math $current_time - 31536000) # One year for pubkey in $pubkeys echo "Checking $pubkey" set events (nak req --author $pubkey -l 5 -k 3 -s $extended_search_timerange wss://relay.damus.io wss://nos.lol 2>/dev/null | \ jq -c --arg target "$target_pubkey" ' select(. != null and type == "object" and has("tags")) | select(.tags[][] == $target) ' 2>/dev/null) set count (echo "$events" | jq -s 'length') if test "$count" -eq 1 set all_events $all_events $events end end if test -n "$all_events" echo -e "Last people following $target_pubkey:" echo -e "" set sorted_events (printf "%s\n" $all_events | jq -r -s ' unique_by(.id) | sort_by(-.created_at) | .[] | @json ') for event in $sorted_events set npub (echo $event | jq -r '.pubkey' | nak encode npub) set created_at (echo $event | jq -r '.created_at') if test (uname) = "Darwin" set follow_date (date -r "$created_at" "+%Y-%m-%d %H:%M") else set follow_date (date -d @"$created_at" "+%Y-%m-%d %H:%M") end echo "$follow_date - $npub" end end ```
@ 7bdef7be:784a5805
2025-04-02 12:37:35The following script try, using [nak](https://github.com/fiatjaf/nak), to find out the last ten people who have followed a `target_pubkey`, sorted by the most recent. It's possibile to shorten `search_timerange` to speed up the search. ``` #!/usr/bin/env fish # Target pubkey we're looking for in the tags set target_pubkey "6e468422dfb74a5738702a8823b9b28168abab8655faacb6853cd0ee15deee93" set current_time (date +%s) set search_timerange (math $current_time - 600) # 24 hours = 86400 seconds set pubkeys (nak req --kind 3 -s $search_timerange wss://relay.damus.io/ wss://nos.lol/ 2>/dev/null | \ jq -r --arg target "$target_pubkey" ' select(. != null and type == "object" and has("tags")) | select(.tags[] | select(.[0] == "p" and .[1] == $target)) | .pubkey ' | sort -u) if test -z "$pubkeys" exit 1 end set all_events "" set extended_search_timerange (math $current_time - 31536000) # One year for pubkey in $pubkeys echo "Checking $pubkey" set events (nak req --author $pubkey -l 5 -k 3 -s $extended_search_timerange wss://relay.damus.io wss://nos.lol 2>/dev/null | \ jq -c --arg target "$target_pubkey" ' select(. != null and type == "object" and has("tags")) | select(.tags[][] == $target) ' 2>/dev/null) set count (echo "$events" | jq -s 'length') if test "$count" -eq 1 set all_events $all_events $events end end if test -n "$all_events" echo -e "Last people following $target_pubkey:" echo -e "" set sorted_events (printf "%s\n" $all_events | jq -r -s ' unique_by(.id) | sort_by(-.created_at) | .[] | @json ') for event in $sorted_events set npub (echo $event | jq -r '.pubkey' | nak encode npub) set created_at (echo $event | jq -r '.created_at') if test (uname) = "Darwin" set follow_date (date -r "$created_at" "+%Y-%m-%d %H:%M") else set follow_date (date -d @"$created_at" "+%Y-%m-%d %H:%M") end echo "$follow_date - $npub" end end ``` @ aa8de34f:a6ffe696
2025-03-31 21:48:50In seinem Beitrag vom 30. März 2025 fragt Henning Rosenbusch auf Telegram angesichts zunehmender digitaler Kontrolle und staatlicher Allmacht: > „Wie soll sich gegen eine solche Tyrannei noch ein Widerstand formieren können, selbst im Untergrund? Sehe ich nicht.“\ > ([Quelle: t.me/rosenbusch/25228](https://t.me/rosenbusch/25228)) Er beschreibt damit ein Gefühl der Ohnmacht, das viele teilen: Eine Welt, in der Totalitarismus nicht mehr mit Panzern, sondern mit Algorithmen kommt. Wo Zugriff auf Geld, Meinungsfreiheit und Teilhabe vom Wohlverhalten abhängt. Der Bürger als kontrollierbare Variable im Code des Staates.\ Die Frage ist berechtigt. Doch die Antwort darauf liegt nicht in alten Widerstandsbildern – sondern in einer neuen Realität. \-- Denn es braucht keinen Untergrund mehr. -- Der Widerstand der Zukunft trägt keinen Tarnanzug. Er ist nicht konspirativ, sondern transparent. Nicht bewaffnet, sondern mathematisch beweisbar. Bitcoin steht nicht am Rand dieser Entwicklung – es ist ihr Fundament. Eine Bastion aus physikalischer Realität, spieltheoretischem Schutz und ökonomischer Wahrheit. Es ist nicht unfehlbar, aber unbestechlich. Nicht perfekt, aber immun gegen zentrale Willkür. Hier entsteht kein „digitales Gegenreich“, sondern eine dezentrale Renaissance. Keine Revolte aus Wut, sondern eine stille Abkehr: von Zwang zu Freiwilligkeit, von Abhängigkeit zu Selbstverantwortung. Diese Revolution führt keine Kriege. Sie braucht keine Führer. Sie ist ein Netzwerk. Jeder Knoten ein Individuum. Jede Entscheidung ein Akt der Selbstermächtigung. Weltweit wachsen Freiheits-Zitadellen aus dieser Idee: wirtschaftlich autark, digital souverän, lokal verankert und global vernetzt. Sie sind keine Utopien im luftleeren Raum, sondern konkrete Realitäten – angetrieben von Energie, Code und dem menschlichen Wunsch nach Würde. Der Globalismus alter Prägung – zentralistisch, monopolistisch, bevormundend – wird an seiner eigenen Hybris zerbrechen. Seine Werkzeuge der Kontrolle werden ihn nicht retten. Im Gegenteil: Seine Geister werden ihn verfolgen und erlegen. Und während die alten Mächte um Erhalt kämpfen, wächst eine neue Welt – nicht im Schatten, sondern im Offenen. Nicht auf Gewalt gebaut, sondern auf Mathematik, Physik und Freiheit. Die Tyrannei sieht keinen Widerstand.\ Weil sie nicht erkennt, dass er längst begonnen hat.\ Unwiderruflich. Leise. Überall.
@ aa8de34f:a6ffe696
2025-03-31 21:48:50In seinem Beitrag vom 30. März 2025 fragt Henning Rosenbusch auf Telegram angesichts zunehmender digitaler Kontrolle und staatlicher Allmacht: > „Wie soll sich gegen eine solche Tyrannei noch ein Widerstand formieren können, selbst im Untergrund? Sehe ich nicht.“\ > ([Quelle: t.me/rosenbusch/25228](https://t.me/rosenbusch/25228)) Er beschreibt damit ein Gefühl der Ohnmacht, das viele teilen: Eine Welt, in der Totalitarismus nicht mehr mit Panzern, sondern mit Algorithmen kommt. Wo Zugriff auf Geld, Meinungsfreiheit und Teilhabe vom Wohlverhalten abhängt. Der Bürger als kontrollierbare Variable im Code des Staates.\ Die Frage ist berechtigt. Doch die Antwort darauf liegt nicht in alten Widerstandsbildern – sondern in einer neuen Realität. \-- Denn es braucht keinen Untergrund mehr. -- Der Widerstand der Zukunft trägt keinen Tarnanzug. Er ist nicht konspirativ, sondern transparent. Nicht bewaffnet, sondern mathematisch beweisbar. Bitcoin steht nicht am Rand dieser Entwicklung – es ist ihr Fundament. Eine Bastion aus physikalischer Realität, spieltheoretischem Schutz und ökonomischer Wahrheit. Es ist nicht unfehlbar, aber unbestechlich. Nicht perfekt, aber immun gegen zentrale Willkür. Hier entsteht kein „digitales Gegenreich“, sondern eine dezentrale Renaissance. Keine Revolte aus Wut, sondern eine stille Abkehr: von Zwang zu Freiwilligkeit, von Abhängigkeit zu Selbstverantwortung. Diese Revolution führt keine Kriege. Sie braucht keine Führer. Sie ist ein Netzwerk. Jeder Knoten ein Individuum. Jede Entscheidung ein Akt der Selbstermächtigung. Weltweit wachsen Freiheits-Zitadellen aus dieser Idee: wirtschaftlich autark, digital souverän, lokal verankert und global vernetzt. Sie sind keine Utopien im luftleeren Raum, sondern konkrete Realitäten – angetrieben von Energie, Code und dem menschlichen Wunsch nach Würde. Der Globalismus alter Prägung – zentralistisch, monopolistisch, bevormundend – wird an seiner eigenen Hybris zerbrechen. Seine Werkzeuge der Kontrolle werden ihn nicht retten. Im Gegenteil: Seine Geister werden ihn verfolgen und erlegen. Und während die alten Mächte um Erhalt kämpfen, wächst eine neue Welt – nicht im Schatten, sondern im Offenen. Nicht auf Gewalt gebaut, sondern auf Mathematik, Physik und Freiheit. Die Tyrannei sieht keinen Widerstand.\ Weil sie nicht erkennt, dass er längst begonnen hat.\ Unwiderruflich. Leise. Überall. @ 5d4b6c8d:8a1c1ee3
2025-04-02 13:15:30I've always loved Westbrook. He plays so hard and does things through sheer force of will that no one else has ever been able to do. He's also the last guy you want on the court at the end of close games. No one has ever so reliably made poor choices in late game, or even just end of clock, situations. Here are some highlights from the epic Nuggets vs T-Wolves game, which Russ completely blew at the end. https://youtu.be/rgtzQxRpH6c I've said before that I think Russ' career +/- would be 4 points higher if coaches had never let him play at the ends of quarters. Translation for non-analytics nerds: Russ has blown virtually every final possession throughout his entire career. It's unbelievable. Is there anyone I'm overlooking as a worse clutch performer? originally posted at https://stacker.news/items/932077
@ 5d4b6c8d:8a1c1ee3
2025-04-02 13:15:30I've always loved Westbrook. He plays so hard and does things through sheer force of will that no one else has ever been able to do. He's also the last guy you want on the court at the end of close games. No one has ever so reliably made poor choices in late game, or even just end of clock, situations. Here are some highlights from the epic Nuggets vs T-Wolves game, which Russ completely blew at the end. https://youtu.be/rgtzQxRpH6c I've said before that I think Russ' career +/- would be 4 points higher if coaches had never let him play at the ends of quarters. Translation for non-analytics nerds: Russ has blown virtually every final possession throughout his entire career. It's unbelievable. Is there anyone I'm overlooking as a worse clutch performer? originally posted at https://stacker.news/items/932077 @ fd06f542:8d6d54cd
2025-03-31 10:00:34NIP-05 ====== Mapping Nostr keys to DNS-based internet identifiers ---------------------------------------------------- `final` `optional` On events of kind `0` (`user metadata`) one can specify the key `"nip05"` with an [internet identifier](https://datatracker.ietf.org/doc/html/rfc5322#section-3.4.1) (an email-like address) as the value. Although there is a link to a very liberal "internet identifier" specification above, NIP-05 assumes the `<local-part>` part will be restricted to the characters `a-z0-9-_.`, case-insensitive. Upon seeing that, the client splits the identifier into `<local-part>` and `<domain>` and use these values to make a GET request to `https://<domain>/.well-known/nostr.json?name=<local-part>`. The result should be a JSON document object with a key `"names"` that should then be a mapping of names to hex formatted public keys. If the public key for the given `<name>` matches the `pubkey` from the `user metadata` event, the client then concludes that the given pubkey can indeed be referenced by its identifier. ### Example If a client sees an event like this: ```jsonc { "pubkey": "b0635d6a9851d3aed0cd6c495b282167acf761729078d975fc341b22650b07b9", "kind": 0, "content": "{\"name\": \"bob\", \"nip05\": \"bob@example.com\"}" // other fields... } ``` It will make a GET request to `https://example.com/.well-known/nostr.json?name=bob` and get back a response that will look like ```json { "names": { "bob": "b0635d6a9851d3aed0cd6c495b282167acf761729078d975fc341b22650b07b9" } } ``` or with the **recommended** `"relays"` attribute: ```json { "names": { "bob": "b0635d6a9851d3aed0cd6c495b282167acf761729078d975fc341b22650b07b9" }, "relays": { "b0635d6a9851d3aed0cd6c495b282167acf761729078d975fc341b22650b07b9": [ "wss://relay.example.com", "wss://relay2.example.com" ] } } ``` If the pubkey matches the one given in `"names"` (as in the example above) that means the association is right and the `"nip05"` identifier is valid and can be displayed. The recommended `"relays"` attribute may contain an object with public keys as properties and arrays of relay URLs as values. When present, that can be used to help clients learn in which relays the specific user may be found. Web servers which serve `/.well-known/nostr.json` files dynamically based on the query string SHOULD also serve the relays data for any name they serve in the same reply when that is available. ## Finding users from their NIP-05 identifier A client may implement support for finding users' public keys from _internet identifiers_, the flow is the same as above, but reversed: first the client fetches the _well-known_ URL and from there it gets the public key of the user, then it tries to fetch the kind `0` event for that user and check if it has a matching `"nip05"`. ## Notes ### Identification, not verification The NIP-05 is not intended to _verify_ a user, but only to _identify_ them, for the purpose of facilitating the exchange of a contact or their search. Exceptions are people who own (e.g., a company) or are connected (e.g., a project) to a well-known domain, who can exploit NIP-05 as an attestation of their relationship with it, and thus to the organization behind it, thereby gaining an element of trust. ### User discovery implementation suggestion A client can use this to allow users to search other profiles. If a client has a search box or something like that, a user may be able to type "bob@example.com" there and the client would recognize that and do the proper queries to obtain a pubkey and suggest that to the user. ### Clients must always follow public keys, not NIP-05 addresses For example, if after finding that `bob@bob.com` has the public key `abc...def`, the user clicks a button to follow that profile, the client must keep a primary reference to `abc...def`, not `bob@bob.com`. If, for any reason, the address `https://bob.com/.well-known/nostr.json?name=bob` starts returning the public key `1d2...e3f` at any time in the future, the client must not replace `abc...def` in his list of followed profiles for the user (but it should stop displaying "bob@bob.com" for that user, as that will have become an invalid `"nip05"` property). ### Public keys must be in hex format Keys must be returned in hex format. Keys in NIP-19 `npub` format are only meant to be used for display in client UIs, not in this NIP. ### Showing just the domain as an identifier Clients may treat the identifier `_@domain` as the "root" identifier, and choose to display it as just the `<domain>`. For example, if Bob owns `bob.com`, he may not want an identifier like `bob@bob.com` as that is redundant. Instead, Bob can use the identifier `_@bob.com` and expect Nostr clients to show and treat that as just `bob.com` for all purposes. ### Reasoning for the `/.well-known/nostr.json?name=<local-part>` format By adding the `<local-part>` as a query string instead of as part of the path, the protocol can support both dynamic servers that can generate JSON on-demand and static servers with a JSON file in it that may contain multiple names. ### Allowing access from JavaScript apps JavaScript Nostr apps may be restricted by browser [CORS][] policies that prevent them from accessing `/.well-known/nostr.json` on the user's domain. When CORS prevents JS from loading a resource, the JS program sees it as a network failure identical to the resource not existing, so it is not possible for a pure-JS app to tell the user for certain that the failure was caused by a CORS issue. JS Nostr apps that see network failures requesting `/.well-known/nostr.json` files may want to recommend to users that they check the CORS policy of their servers, e.g.: ```bash $ curl -sI https://example.com/.well-known/nostr.json?name=bob | grep -i ^Access-Control Access-Control-Allow-Origin: * ``` Users should ensure that their `/.well-known/nostr.json` is served with the HTTP header `Access-Control-Allow-Origin: *` to ensure it can be validated by pure JS apps running in modern browsers. [CORS]: https://developer.mozilla.org/en-US/docs/Web/HTTP/CORS ### Security Constraints The `/.well-known/nostr.json` endpoint MUST NOT return any HTTP redirects. Fetchers MUST ignore any HTTP redirects given by the `/.well-known/nostr.json` endpoint.
@ fd06f542:8d6d54cd
2025-03-31 10:00:34NIP-05 ====== Mapping Nostr keys to DNS-based internet identifiers ---------------------------------------------------- `final` `optional` On events of kind `0` (`user metadata`) one can specify the key `"nip05"` with an [internet identifier](https://datatracker.ietf.org/doc/html/rfc5322#section-3.4.1) (an email-like address) as the value. Although there is a link to a very liberal "internet identifier" specification above, NIP-05 assumes the `<local-part>` part will be restricted to the characters `a-z0-9-_.`, case-insensitive. Upon seeing that, the client splits the identifier into `<local-part>` and `<domain>` and use these values to make a GET request to `https://<domain>/.well-known/nostr.json?name=<local-part>`. The result should be a JSON document object with a key `"names"` that should then be a mapping of names to hex formatted public keys. If the public key for the given `<name>` matches the `pubkey` from the `user metadata` event, the client then concludes that the given pubkey can indeed be referenced by its identifier. ### Example If a client sees an event like this: ```jsonc { "pubkey": "b0635d6a9851d3aed0cd6c495b282167acf761729078d975fc341b22650b07b9", "kind": 0, "content": "{\"name\": \"bob\", \"nip05\": \"bob@example.com\"}" // other fields... } ``` It will make a GET request to `https://example.com/.well-known/nostr.json?name=bob` and get back a response that will look like ```json { "names": { "bob": "b0635d6a9851d3aed0cd6c495b282167acf761729078d975fc341b22650b07b9" } } ``` or with the **recommended** `"relays"` attribute: ```json { "names": { "bob": "b0635d6a9851d3aed0cd6c495b282167acf761729078d975fc341b22650b07b9" }, "relays": { "b0635d6a9851d3aed0cd6c495b282167acf761729078d975fc341b22650b07b9": [ "wss://relay.example.com", "wss://relay2.example.com" ] } } ``` If the pubkey matches the one given in `"names"` (as in the example above) that means the association is right and the `"nip05"` identifier is valid and can be displayed. The recommended `"relays"` attribute may contain an object with public keys as properties and arrays of relay URLs as values. When present, that can be used to help clients learn in which relays the specific user may be found. Web servers which serve `/.well-known/nostr.json` files dynamically based on the query string SHOULD also serve the relays data for any name they serve in the same reply when that is available. ## Finding users from their NIP-05 identifier A client may implement support for finding users' public keys from _internet identifiers_, the flow is the same as above, but reversed: first the client fetches the _well-known_ URL and from there it gets the public key of the user, then it tries to fetch the kind `0` event for that user and check if it has a matching `"nip05"`. ## Notes ### Identification, not verification The NIP-05 is not intended to _verify_ a user, but only to _identify_ them, for the purpose of facilitating the exchange of a contact or their search. Exceptions are people who own (e.g., a company) or are connected (e.g., a project) to a well-known domain, who can exploit NIP-05 as an attestation of their relationship with it, and thus to the organization behind it, thereby gaining an element of trust. ### User discovery implementation suggestion A client can use this to allow users to search other profiles. If a client has a search box or something like that, a user may be able to type "bob@example.com" there and the client would recognize that and do the proper queries to obtain a pubkey and suggest that to the user. ### Clients must always follow public keys, not NIP-05 addresses For example, if after finding that `bob@bob.com` has the public key `abc...def`, the user clicks a button to follow that profile, the client must keep a primary reference to `abc...def`, not `bob@bob.com`. If, for any reason, the address `https://bob.com/.well-known/nostr.json?name=bob` starts returning the public key `1d2...e3f` at any time in the future, the client must not replace `abc...def` in his list of followed profiles for the user (but it should stop displaying "bob@bob.com" for that user, as that will have become an invalid `"nip05"` property). ### Public keys must be in hex format Keys must be returned in hex format. Keys in NIP-19 `npub` format are only meant to be used for display in client UIs, not in this NIP. ### Showing just the domain as an identifier Clients may treat the identifier `_@domain` as the "root" identifier, and choose to display it as just the `<domain>`. For example, if Bob owns `bob.com`, he may not want an identifier like `bob@bob.com` as that is redundant. Instead, Bob can use the identifier `_@bob.com` and expect Nostr clients to show and treat that as just `bob.com` for all purposes. ### Reasoning for the `/.well-known/nostr.json?name=<local-part>` format By adding the `<local-part>` as a query string instead of as part of the path, the protocol can support both dynamic servers that can generate JSON on-demand and static servers with a JSON file in it that may contain multiple names. ### Allowing access from JavaScript apps JavaScript Nostr apps may be restricted by browser [CORS][] policies that prevent them from accessing `/.well-known/nostr.json` on the user's domain. When CORS prevents JS from loading a resource, the JS program sees it as a network failure identical to the resource not existing, so it is not possible for a pure-JS app to tell the user for certain that the failure was caused by a CORS issue. JS Nostr apps that see network failures requesting `/.well-known/nostr.json` files may want to recommend to users that they check the CORS policy of their servers, e.g.: ```bash $ curl -sI https://example.com/.well-known/nostr.json?name=bob | grep -i ^Access-Control Access-Control-Allow-Origin: * ``` Users should ensure that their `/.well-known/nostr.json` is served with the HTTP header `Access-Control-Allow-Origin: *` to ensure it can be validated by pure JS apps running in modern browsers. [CORS]: https://developer.mozilla.org/en-US/docs/Web/HTTP/CORS ### Security Constraints The `/.well-known/nostr.json` endpoint MUST NOT return any HTTP redirects. Fetchers MUST ignore any HTTP redirects given by the `/.well-known/nostr.json` endpoint. @ 04c915da:3dfbecc9
2025-03-13 19:39:28In much of the world, it is incredibly difficult to access U.S. dollars. Local currencies are often poorly managed and riddled with corruption. Billions of people demand a more reliable alternative. While the dollar has its own issues of corruption and mismanagement, it is widely regarded as superior to the fiat currencies it competes with globally. As a result, Tether has found massive success providing low cost, low friction access to dollars. Tether claims 400 million total users, is on track to add 200 million more this year, processes 8.1 million transactions daily, and facilitates $29 billion in daily transfers. Furthermore, their estimates suggest nearly 40% of users rely on it as a savings tool rather than just a transactional currency. Tether’s rise has made the company a financial juggernaut. Last year alone, Tether raked in over $13 billion in profit, with a lean team of less than 100 employees. Their business model is elegantly simple: hold U.S. Treasuries and collect the interest. With over $113 billion in Treasuries, Tether has turned a straightforward concept into a profit machine. Tether’s success has resulted in many competitors eager to claim a piece of the pie. This has triggered a massive venture capital grift cycle in USD tokens, with countless projects vying to dethrone Tether. Due to Tether’s entrenched network effect, these challengers face an uphill battle with little realistic chance of success. Most educated participants in the space likely recognize this reality but seem content to perpetuate the grift, hoping to cash out by dumping their equity positions on unsuspecting buyers before they realize the reality of the situation. Historically, Tether’s greatest vulnerability has been U.S. government intervention. For over a decade, the company operated offshore with few allies in the U.S. establishment, making it a major target for regulatory action. That dynamic has shifted recently and Tether has seized the opportunity. By actively courting U.S. government support, Tether has fortified their position. This strategic move will likely cement their status as the dominant USD token for years to come. While undeniably a great tool for the millions of users that rely on it, Tether is not without flaws. As a centralized, trusted third party, it holds the power to freeze or seize funds at its discretion. Corporate mismanagement or deliberate malpractice could also lead to massive losses at scale. In their goal of mitigating regulatory risk, Tether has deepened ties with law enforcement, mirroring some of the concerns of potential central bank digital currencies. In practice, Tether operates as a corporate CBDC alternative, collaborating with authorities to surveil and seize funds. The company proudly touts partnerships with leading surveillance firms and its own data reveals cooperation in over 1,000 law enforcement cases, with more than $2.5 billion in funds frozen. --- The global demand for Tether is undeniable and the company’s profitability reflects its unrivaled success. Tether is owned and operated by bitcoiners and will likely continue to push forward strategic goals that help the movement as a whole. Recent efforts to mitigate the threat of U.S. government enforcement will likely solidify their network effect and stifle meaningful adoption of rival USD tokens or CBDCs. Yet, for all their achievements, Tether is simply a worse form of money than bitcoin. Tether requires trust in a centralized entity, while bitcoin can be saved or spent without permission. Furthermore, Tether is tied to the value of the US Dollar which is designed to lose purchasing power over time, while bitcoin, as a truly scarce asset, is designed to increase in purchasing power with adoption. As people awaken to the risks of Tether’s control, and the benefits bitcoin provides, bitcoin adoption will likely surpass it.
@ 04c915da:3dfbecc9
2025-03-13 19:39:28In much of the world, it is incredibly difficult to access U.S. dollars. Local currencies are often poorly managed and riddled with corruption. Billions of people demand a more reliable alternative. While the dollar has its own issues of corruption and mismanagement, it is widely regarded as superior to the fiat currencies it competes with globally. As a result, Tether has found massive success providing low cost, low friction access to dollars. Tether claims 400 million total users, is on track to add 200 million more this year, processes 8.1 million transactions daily, and facilitates $29 billion in daily transfers. Furthermore, their estimates suggest nearly 40% of users rely on it as a savings tool rather than just a transactional currency. Tether’s rise has made the company a financial juggernaut. Last year alone, Tether raked in over $13 billion in profit, with a lean team of less than 100 employees. Their business model is elegantly simple: hold U.S. Treasuries and collect the interest. With over $113 billion in Treasuries, Tether has turned a straightforward concept into a profit machine. Tether’s success has resulted in many competitors eager to claim a piece of the pie. This has triggered a massive venture capital grift cycle in USD tokens, with countless projects vying to dethrone Tether. Due to Tether’s entrenched network effect, these challengers face an uphill battle with little realistic chance of success. Most educated participants in the space likely recognize this reality but seem content to perpetuate the grift, hoping to cash out by dumping their equity positions on unsuspecting buyers before they realize the reality of the situation. Historically, Tether’s greatest vulnerability has been U.S. government intervention. For over a decade, the company operated offshore with few allies in the U.S. establishment, making it a major target for regulatory action. That dynamic has shifted recently and Tether has seized the opportunity. By actively courting U.S. government support, Tether has fortified their position. This strategic move will likely cement their status as the dominant USD token for years to come. While undeniably a great tool for the millions of users that rely on it, Tether is not without flaws. As a centralized, trusted third party, it holds the power to freeze or seize funds at its discretion. Corporate mismanagement or deliberate malpractice could also lead to massive losses at scale. In their goal of mitigating regulatory risk, Tether has deepened ties with law enforcement, mirroring some of the concerns of potential central bank digital currencies. In practice, Tether operates as a corporate CBDC alternative, collaborating with authorities to surveil and seize funds. The company proudly touts partnerships with leading surveillance firms and its own data reveals cooperation in over 1,000 law enforcement cases, with more than $2.5 billion in funds frozen. --- The global demand for Tether is undeniable and the company’s profitability reflects its unrivaled success. Tether is owned and operated by bitcoiners and will likely continue to push forward strategic goals that help the movement as a whole. Recent efforts to mitigate the threat of U.S. government enforcement will likely solidify their network effect and stifle meaningful adoption of rival USD tokens or CBDCs. Yet, for all their achievements, Tether is simply a worse form of money than bitcoin. Tether requires trust in a centralized entity, while bitcoin can be saved or spent without permission. Furthermore, Tether is tied to the value of the US Dollar which is designed to lose purchasing power over time, while bitcoin, as a truly scarce asset, is designed to increase in purchasing power with adoption. As people awaken to the risks of Tether’s control, and the benefits bitcoin provides, bitcoin adoption will likely surpass it. @ c631e267:c2b78d3e
2025-03-31 07:23:05*Der Irrsinn ist bei Einzelnen etwas Seltenes –* *\ aber bei Gruppen, Parteien, Völkern, Zeiten die Regel.* *\ Friedrich Nietzsche*   **Erinnern Sie sich an die Horrorkomödie «Scary Movie»?** Nicht, dass ich diese Art Filme besonders erinnerungswürdig fände, aber einige Szenen daraus sind doch gewissermaßen Klassiker. Dazu zählt eine, die das Verhalten vieler Protagonisten in Horrorfilmen parodiert, wenn sie in Panik flüchten. Welchen Weg nimmt wohl die Frau in der Situation auf diesem Bild?  **Diese Szene kommt mir automatisch in den Sinn,** wenn ich aktuelle Entwicklungen in Europa betrachte. Weitreichende Entscheidungen gehen wider jede Logik in die völlig falsche Richtung. Nur ist das hier alles andere als eine Komödie, sondern bitterernst. Dieser Horror ist leider sehr real. **Die Europäische Union hat sich selbst über Jahre** konsequent in eine Sackgasse manövriert. Sie hat es versäumt, sich und ihre Politik selbstbewusst und im Einklang mit ihren Wurzeln auf dem eigenen Kontinent zu positionieren. Stattdessen ist sie in blinder Treue den vermeintlichen «transatlantischen Freunden» auf ihrem Konfrontationskurs gen Osten gefolgt. **In den USA haben sich die Vorzeichen allerdings mittlerweile geändert,** und die einst hoch gelobten «Freunde und Partner» erscheinen den europäischen «Führern» nicht mehr vertrauenswürdig. Das ist spätestens seit der Münchner Sicherheitskonferenz, der Rede von Vizepräsident J. D. Vance und den empörten Reaktionen offensichtlich. Große Teile Europas wirken seitdem wie ein aufgescheuchter Haufen kopfloser Hühner. Orientierung und Kontrolle sind völlig abhanden gekommen. **Statt jedoch umzukehren oder wenigstens zu bremsen** und vielleicht einen Abzweig zu suchen, geben die Crash-Piloten jetzt auf dem Weg durch die Sackgasse erst richtig Gas. Ja sie lösen sogar noch die Sicherheitsgurte und deaktivieren die Airbags. Den vor Angst dauergelähmten Passagieren fällt auch nichts Besseres ein und so schließen sie einfach die Augen. Derweil übertrumpfen sich die [Kommentatoren](https://transition-news.org/wird-ihr-stahlhelm-schon-gegossen) des Events gegenseitig in sensationslüsterner «Berichterstattung». **Wie schon die deutsche Außenministerin mit höchsten UN-Ambitionen,** Annalena Baerbock, proklamiert auch die Europäische Kommission einen «Frieden durch Stärke». Zu dem jetzt vorgelegten, [selbstzerstörerischen](https://transition-news.org/okonomen-eu-rustet-auf-und-schiesst-sich-selbst-ins-knie) Fahrplan zur Ankurbelung der Rüstungsindustrie, genannt «Weißbuch zur europäischen Verteidigung – Bereitschaft 2030», [erklärte](https://ec.europa.eu/commission/presscorner/detail/de/ip_25_793) die Kommissionspräsidentin, die «Ära der Friedensdividende» sei längst vorbei. Soll das heißen, Frieden bringt nichts ein? Eine umfassende Zusammenarbeit an dauerhaften europäischen Friedenslösungen steht demnach jedenfalls nicht zur Debatte. **Zusätzlich brisant ist, dass aktuell «die ganze EU** **[von Deutschen regiert](https://transition-news.org/die-ganze-eu-wird-von-deutschen-regiert)** **wird»,** wie der EU-Parlamentarier und ehemalige UN-Diplomat Michael von der Schulenburg beobachtet hat. Tatsächlich sitzen neben von der Leyen und Strack-Zimmermann noch einige weitere Deutsche in – vor allem auch in Krisenzeiten – wichtigen Spitzenposten der Union. Vor dem Hintergrund der Kriegstreiberei in Deutschland muss eine solche Dominanz mindestens nachdenklich stimmen. **Ihre ursprünglichen Grundwerte wie Demokratie, Freiheit, Frieden und Völkerverständigung** hat die EU kontinuierlich in leere Worthülsen verwandelt. Diese werden dafür immer lächerlicher hochgehalten und beschworen. **Es wird dringend Zeit, dass wir, der Souverän,** diesem erbärmlichen und gefährlichen Trauerspiel ein Ende setzen und die Fäden selbst in die Hand nehmen. In diesem Sinne fordert uns auch das «European Peace Project» auf, am 9. Mai im Rahmen eines Kunstprojekts [den Frieden auszurufen](https://transition-news.org/ein-zeichen-fur-die-friedliche-zukunft-europas-setzen). Seien wir dabei! *\[Titelbild:* *[Pixabay](https://pixabay.com/de/illustrations/vertical-abstract-concept-car-8992833/)]* *** Dieser Beitrag wurde mit dem [Pareto-Client](https://pareto.space/read) geschrieben und ist zuerst auf ***[Transition News](https://transition-news.org/mit-vollgas-in-die-sackgasse)*** erschienen.
@ c631e267:c2b78d3e
2025-03-31 07:23:05*Der Irrsinn ist bei Einzelnen etwas Seltenes –* *\ aber bei Gruppen, Parteien, Völkern, Zeiten die Regel.* *\ Friedrich Nietzsche*   **Erinnern Sie sich an die Horrorkomödie «Scary Movie»?** Nicht, dass ich diese Art Filme besonders erinnerungswürdig fände, aber einige Szenen daraus sind doch gewissermaßen Klassiker. Dazu zählt eine, die das Verhalten vieler Protagonisten in Horrorfilmen parodiert, wenn sie in Panik flüchten. Welchen Weg nimmt wohl die Frau in der Situation auf diesem Bild?  **Diese Szene kommt mir automatisch in den Sinn,** wenn ich aktuelle Entwicklungen in Europa betrachte. Weitreichende Entscheidungen gehen wider jede Logik in die völlig falsche Richtung. Nur ist das hier alles andere als eine Komödie, sondern bitterernst. Dieser Horror ist leider sehr real. **Die Europäische Union hat sich selbst über Jahre** konsequent in eine Sackgasse manövriert. Sie hat es versäumt, sich und ihre Politik selbstbewusst und im Einklang mit ihren Wurzeln auf dem eigenen Kontinent zu positionieren. Stattdessen ist sie in blinder Treue den vermeintlichen «transatlantischen Freunden» auf ihrem Konfrontationskurs gen Osten gefolgt. **In den USA haben sich die Vorzeichen allerdings mittlerweile geändert,** und die einst hoch gelobten «Freunde und Partner» erscheinen den europäischen «Führern» nicht mehr vertrauenswürdig. Das ist spätestens seit der Münchner Sicherheitskonferenz, der Rede von Vizepräsident J. D. Vance und den empörten Reaktionen offensichtlich. Große Teile Europas wirken seitdem wie ein aufgescheuchter Haufen kopfloser Hühner. Orientierung und Kontrolle sind völlig abhanden gekommen. **Statt jedoch umzukehren oder wenigstens zu bremsen** und vielleicht einen Abzweig zu suchen, geben die Crash-Piloten jetzt auf dem Weg durch die Sackgasse erst richtig Gas. Ja sie lösen sogar noch die Sicherheitsgurte und deaktivieren die Airbags. Den vor Angst dauergelähmten Passagieren fällt auch nichts Besseres ein und so schließen sie einfach die Augen. Derweil übertrumpfen sich die [Kommentatoren](https://transition-news.org/wird-ihr-stahlhelm-schon-gegossen) des Events gegenseitig in sensationslüsterner «Berichterstattung». **Wie schon die deutsche Außenministerin mit höchsten UN-Ambitionen,** Annalena Baerbock, proklamiert auch die Europäische Kommission einen «Frieden durch Stärke». Zu dem jetzt vorgelegten, [selbstzerstörerischen](https://transition-news.org/okonomen-eu-rustet-auf-und-schiesst-sich-selbst-ins-knie) Fahrplan zur Ankurbelung der Rüstungsindustrie, genannt «Weißbuch zur europäischen Verteidigung – Bereitschaft 2030», [erklärte](https://ec.europa.eu/commission/presscorner/detail/de/ip_25_793) die Kommissionspräsidentin, die «Ära der Friedensdividende» sei längst vorbei. Soll das heißen, Frieden bringt nichts ein? Eine umfassende Zusammenarbeit an dauerhaften europäischen Friedenslösungen steht demnach jedenfalls nicht zur Debatte. **Zusätzlich brisant ist, dass aktuell «die ganze EU** **[von Deutschen regiert](https://transition-news.org/die-ganze-eu-wird-von-deutschen-regiert)** **wird»,** wie der EU-Parlamentarier und ehemalige UN-Diplomat Michael von der Schulenburg beobachtet hat. Tatsächlich sitzen neben von der Leyen und Strack-Zimmermann noch einige weitere Deutsche in – vor allem auch in Krisenzeiten – wichtigen Spitzenposten der Union. Vor dem Hintergrund der Kriegstreiberei in Deutschland muss eine solche Dominanz mindestens nachdenklich stimmen. **Ihre ursprünglichen Grundwerte wie Demokratie, Freiheit, Frieden und Völkerverständigung** hat die EU kontinuierlich in leere Worthülsen verwandelt. Diese werden dafür immer lächerlicher hochgehalten und beschworen. **Es wird dringend Zeit, dass wir, der Souverän,** diesem erbärmlichen und gefährlichen Trauerspiel ein Ende setzen und die Fäden selbst in die Hand nehmen. In diesem Sinne fordert uns auch das «European Peace Project» auf, am 9. Mai im Rahmen eines Kunstprojekts [den Frieden auszurufen](https://transition-news.org/ein-zeichen-fur-die-friedliche-zukunft-europas-setzen). Seien wir dabei! *\[Titelbild:* *[Pixabay](https://pixabay.com/de/illustrations/vertical-abstract-concept-car-8992833/)]* *** Dieser Beitrag wurde mit dem [Pareto-Client](https://pareto.space/read) geschrieben und ist zuerst auf ***[Transition News](https://transition-news.org/mit-vollgas-in-die-sackgasse)*** erschienen. @ fd06f542:8d6d54cd
2025-03-31 02:07:43## 什么是nostrbook? ----- nostrbook 是基于nostr 社区技术存储在 nostr relay server上的长文(30023)文章。 查看浏览,采用的是 [docsify](https://docsify.js.org/#/) 技术。 整个网站技术不会占用部署服务器太多的存储空间,可以实现轻量级部署。 任何人可以部署服务器,或者本地部署 查看本站所有的书籍。 ## nostrbook 可以服务哪些人? ----- * 开发者,如果你想二次开发,看[第一章、开发者指南](/01.md) * 写书作者,看[第二章、使用教程](/02.md) * 读者 你就直接点开看。 ## nostrbook未来如何发展? ----- * 可能会增加 blog功能,有些时候你就想随心写点日志,那么用blog功能也可以。 * 点赞互动、留言功能。
@ fd06f542:8d6d54cd
2025-03-31 02:07:43## 什么是nostrbook? ----- nostrbook 是基于nostr 社区技术存储在 nostr relay server上的长文(30023)文章。 查看浏览,采用的是 [docsify](https://docsify.js.org/#/) 技术。 整个网站技术不会占用部署服务器太多的存储空间,可以实现轻量级部署。 任何人可以部署服务器,或者本地部署 查看本站所有的书籍。 ## nostrbook 可以服务哪些人? ----- * 开发者,如果你想二次开发,看[第一章、开发者指南](/01.md) * 写书作者,看[第二章、使用教程](/02.md) * 读者 你就直接点开看。 ## nostrbook未来如何发展? ----- * 可能会增加 blog功能,有些时候你就想随心写点日志,那么用blog功能也可以。 * 点赞互动、留言功能。 @ 07f367da:0e76880d
2025-04-03 17:59:21윤석열 탄핵 선고를 앞둔 4월 3일. 우리 노동조합은 서울 마포구 소재의 한 활동지원기관 앞에서 선전전을 진행했다. 노동조합은 한 활동지원사의 민원을 통해 해당 활동지원기관이 일요일에 일해도 평일 임금을 지급한다는 사실을 파악했다. 활동지원사의 민원에 관심을 가진 한 언론사의 기자는 활동지원기관과 구청, 서울시, 노조에 문의하며 팩트체크를 진행하고 있는데, 이 과정에서 노조는 해당 기관이 일요일에 일을 해도 평일 임금을 지급하고 있다는 사실을 명확히 확인했다. 자신이 받는 임금에 대한 사실관계를 노동자들은 잘 알지 못한다. 활동지원사는 기관에 자신의 임금에 대해 문의해도 속 시원한 답을 듣지 못한다. 활동지원사들이 하나같이 하는 이야기가 기관에 물어봐도 제대로 설명을 해주지 않는다는 하소연이다. 당사자 활동지원사는 노조에 민원을 제기하고, 또 기자가 취재한 내용들을 통해서야 자신의 임금이 자신도 모르게 어떻게 변화했는지를 알아가고 있다. 사업장의 임급지급 행위에 대한 가치판단이나 평가 이전에 노동자들은 그 사실 자체를 모를 가능성이 높다. 노조는 이 사실을 활동지원사들에게 알리려 선전전을 진행하기로 했다. 선전전 진행 중 정말 충격적인 경험을 했다. 노동조합의 선전활동은 정당한 노조활동이고 일상적인 활동이다. 여태 여러 사업장에서 선전활동을 했지만, 이런 경우는 정말 처음이었다. 사업장들은 신경 거슬러 하고 적대적인 대우를 하곤 했지만, 가장 강한 대처가 경찰에 신고하여 공권력의 개입을 요청하고, 경찰은 충돌을 방지하는 선에서 대처한다. 그런데 오늘은 장애인 기관장이 선전활동을 하지 말라고 계속 항의하며 방해하더니 소속 활동지원팀 인력은 노동조합이 활동지원사에게 선전물을 전달하려 하니 몸으로 막기까지 한다. 무엇을 그렇게 숨기고 싶을까? 노동조합의 활동을 몸으로 막으면서까지 싫어할 이유가 무엇일까? 노동조합의 활동이 그들에게 무엇으로 다가갔을까? 여러 질문이 든다. 충격적인 것은 이 기관의 대표가 우리노조가 예전에 청와대 앞에서 기자회견 할 때 연대 발언을 하러 왔던 활동가라는 점이다. 장애인 당사자이자 인권운동 활동가가 사용자로, 그리고 사회복지사 노동자들이 전담인력으로 고용되어 사측을 대신해 활동지원사 노동자들이 응당 자신에 대해 알아야 할 사항을 은폐한다. 사장이 되어 권력을 행사하면서도 장애인이라는 정체성으로 자신의 지위를 지우려 하고, 전담인력이라는 지위로 노동자들을 지휘하면서도 같은 노동자라며 위계를 삭제한다. 그리고 정작 현장에서 장애인에게 활동지원을 제공하는 활동지원사들은 대부분 고령의 여성들로 정보약자에 해당한다. 우리에게도 민주주의가 올까. 나는 저들이 활동으로 세상을 좋게 만드는 것을 상쇄할 정도로 더 세상을 나쁘게 만들고 있다고 생각한다. 타인에 의해 돈벌이 수단으로 이용당하는 사람은 자신 또한 타인을 돈벌이 수단으로 활용할 가능성이 높다. 그 타인에는 장애인도 포함된다. 나는 시설사회가 끝나도 장애인학대가 끝나리라는 믿음이 없다. 우리는 어차피 서로를 돈벌이 수단으로만 삼는 사회에서 살고 있기 때문이다.
@ 07f367da:0e76880d
2025-04-03 17:59:21윤석열 탄핵 선고를 앞둔 4월 3일. 우리 노동조합은 서울 마포구 소재의 한 활동지원기관 앞에서 선전전을 진행했다. 노동조합은 한 활동지원사의 민원을 통해 해당 활동지원기관이 일요일에 일해도 평일 임금을 지급한다는 사실을 파악했다. 활동지원사의 민원에 관심을 가진 한 언론사의 기자는 활동지원기관과 구청, 서울시, 노조에 문의하며 팩트체크를 진행하고 있는데, 이 과정에서 노조는 해당 기관이 일요일에 일을 해도 평일 임금을 지급하고 있다는 사실을 명확히 확인했다. 자신이 받는 임금에 대한 사실관계를 노동자들은 잘 알지 못한다. 활동지원사는 기관에 자신의 임금에 대해 문의해도 속 시원한 답을 듣지 못한다. 활동지원사들이 하나같이 하는 이야기가 기관에 물어봐도 제대로 설명을 해주지 않는다는 하소연이다. 당사자 활동지원사는 노조에 민원을 제기하고, 또 기자가 취재한 내용들을 통해서야 자신의 임금이 자신도 모르게 어떻게 변화했는지를 알아가고 있다. 사업장의 임급지급 행위에 대한 가치판단이나 평가 이전에 노동자들은 그 사실 자체를 모를 가능성이 높다. 노조는 이 사실을 활동지원사들에게 알리려 선전전을 진행하기로 했다. 선전전 진행 중 정말 충격적인 경험을 했다. 노동조합의 선전활동은 정당한 노조활동이고 일상적인 활동이다. 여태 여러 사업장에서 선전활동을 했지만, 이런 경우는 정말 처음이었다. 사업장들은 신경 거슬러 하고 적대적인 대우를 하곤 했지만, 가장 강한 대처가 경찰에 신고하여 공권력의 개입을 요청하고, 경찰은 충돌을 방지하는 선에서 대처한다. 그런데 오늘은 장애인 기관장이 선전활동을 하지 말라고 계속 항의하며 방해하더니 소속 활동지원팀 인력은 노동조합이 활동지원사에게 선전물을 전달하려 하니 몸으로 막기까지 한다. 무엇을 그렇게 숨기고 싶을까? 노동조합의 활동을 몸으로 막으면서까지 싫어할 이유가 무엇일까? 노동조합의 활동이 그들에게 무엇으로 다가갔을까? 여러 질문이 든다. 충격적인 것은 이 기관의 대표가 우리노조가 예전에 청와대 앞에서 기자회견 할 때 연대 발언을 하러 왔던 활동가라는 점이다. 장애인 당사자이자 인권운동 활동가가 사용자로, 그리고 사회복지사 노동자들이 전담인력으로 고용되어 사측을 대신해 활동지원사 노동자들이 응당 자신에 대해 알아야 할 사항을 은폐한다. 사장이 되어 권력을 행사하면서도 장애인이라는 정체성으로 자신의 지위를 지우려 하고, 전담인력이라는 지위로 노동자들을 지휘하면서도 같은 노동자라며 위계를 삭제한다. 그리고 정작 현장에서 장애인에게 활동지원을 제공하는 활동지원사들은 대부분 고령의 여성들로 정보약자에 해당한다. 우리에게도 민주주의가 올까. 나는 저들이 활동으로 세상을 좋게 만드는 것을 상쇄할 정도로 더 세상을 나쁘게 만들고 있다고 생각한다. 타인에 의해 돈벌이 수단으로 이용당하는 사람은 자신 또한 타인을 돈벌이 수단으로 활용할 가능성이 높다. 그 타인에는 장애인도 포함된다. 나는 시설사회가 끝나도 장애인학대가 끝나리라는 믿음이 없다. 우리는 어차피 서로를 돈벌이 수단으로만 삼는 사회에서 살고 있기 때문이다. @ 57d1a264:69f1fee1
2025-03-29 18:02:16> This UX research has been redacted by @iqra from the Bitcoin.Design [community](https://discord.gg/K7aQ5PErht), and shared for review and feedback! Don't be shy, share your thoughts.  - - - ## 1️⃣ Introduction #### Project Overview 📌 **Product:** BlueWallet (Bitcoin Wallet) 📌 **Goal:** Improve onboarding flow and enhance accessibility for a better user experience. 📌 **Role:** UX Designer 📌 **Tools Used:** Figma, Notion #### Why This Case Study? 🔹 BlueWallet is a self-custodial Bitcoin wallet, but **users struggle with onboarding due to unclear instructions**. 🔹 **Accessibility issues** (low contrast, small fonts) create **barriers for visually impaired users**. 🔹 Competitors like **Trust Wallet and MetaMask offer better-guided onboarding**. This case study presents **UX/UI improvements** to make BlueWallet **more intuitive and inclusive**. - - - ## 2️⃣ Problem Statement: Why BlueWalletʼs Onboarding Needs Improvement #### 🔹 **Current Challenges:** 1️⃣ **Onboarding Complexity** - BlueWallet lacks **step-by-step guidance**, leaving users confused about wallet creation and security.   2️⃣ **No Educational Introduction** - Users land directly on the wallet screen with **no explanation of private keys, recovery phrases, or transactions**. 3️⃣ **Transaction Flow Issues** - Similar-looking **"Send" and "Receive" buttons** cause confusion. 4️⃣ **Poor Accessibility** - Small fonts and low contrast make navigation difficult. #### 🔍 **Impact on Users:** **Higher drop-off rates** due to frustration during onboarding. **Security risks** as users skip key wallet setup steps. **Limited accessibility** for users with visual impairments. #### 📌 **Competitive Gap:** Unlike competitors (Trust Wallet, MetaMask), BlueWallet does not offer: ✅ A guided onboarding process ✅ Security education during setup ✅ Intuitive transaction flow      Somehow, this wallet has much better UI than the BlueWallet Bitcoin wallet. - - - ## 3️⃣ User Research & Competitive Analysis #### User Testing Findings 🔹 Conducted usability testing with **5 users** onboarding for the first time. 🔹 **Key Findings:** ✅ 3 out of 5 users **felt lost** due to missing explanations. ✅ 60% **had trouble distinguishing transaction buttons**. ✅ 80% **found the text difficult to read** due to low contrast. #### Competitive Analysis We compared BlueWallet with top crypto wallets: | Wallet | Onboarding UX | Security Guidance | Accessibility Features | |---|---|---|---| | BlueWallet | ❌ No guided onboarding | ❌ Minimal explanation | ❌ Low contrast, small fonts | | Trust Wallet | ✅ Step-by-step setup | ✅ Security best practices | ✅ High contrast UI | | MetaMask | ✅ Interactive tutorial | ✅ Private key education | ✅ Clear transaction buttons | 📌 **Key Insight:** BlueWallet lacks **guided setup and accessibility enhancements**, making it harder for beginners. ## 📌 User Persona To better understand the users facing onboarding challenges, I developed a **persona** based on research and usability testing. #### 🔹 Persona 1: Alex Carter (Bitcoin Beginner & Investor) 👤 **Profile:** - **Age:** 28 - **Occupation:** Freelance Digital Marketer - **Tech Knowledge:** Moderate - Familiar with online transactions, new to Bitcoin) - **Pain Points:** - Finds **Bitcoin wallets confusing**. - - Doesnʼt understand **seed phrases & security features**. - - **Worried about losing funds** due to a lack of clarity in transactions. 📌 **Needs:** ✅ A **simple, guided** wallet setup. ✅ **Clear explanations** of security terms (without jargon). ✅ Easy-to-locate **Send/Receive buttons**. 📌 **Persona Usage in Case Study:** - Helps define **who we are designing for**. - Guides **design decisions** by focusing on user needs. #### 🔹 Persona 2: Sarah Mitchell (Accessibility Advocate & Tech Enthusiast) 👤 **Profile:** - **Age:** 35 - **Occupation:** UX Researcher & Accessibility Consultant - **Tech Knowledge:** High (Uses Bitcoin but struggles with accessibility barriers) 📌 **Pain Points:** ❌ Struggles with small font sizes & low contrast. ❌ Finds the UI difficult to navigate with a screen reader. ❌ Confused by identical-looking transaction buttons. 📌 **Needs:** ✅ A **high-contrast UI** that meets **WCAG accessibility standards**. ✅ **Larger fonts & scalable UI elements** for better readability. ✅ **Keyboard & screen reader-friendly navigation** for seamless interaction. 📌 **Why This Persona Matters:** - Represents users with visual impairments who rely on accessible design. - Ensures the design accommodates inclusive UX principles. - - - ## 4️⃣ UX/UI Solutions & Design Improvements #### 📌 Before (Current Issues) ❌ Users land **directly on the wallet screen** with no instructions. ❌ **"Send" & "Receive" buttons look identical** , causing transaction confusion. ❌ **Small fonts & low contrast** reduce readability. #### ✅ After (Proposed Fixes) ✅ **Step-by-step onboarding** explaining wallet creation, security, and transactions. ✅ **Visually distinct transaction buttons** (color and icon changes). ✅ **WCAG-compliant text contrast & larger fonts** for better readability. #### 1️⃣ Redesigned Onboarding Flow ✅ Added a **progress indicator** so users see where they are in setup. ✅ Used **plain, non-technical language** to explain wallet creation & security. ✅ Introduced a **"Learn More" button** to educate users on security. #### 2️⃣ Accessibility Enhancements ✅ Increased **contrast ratio** for better text readability. ✅ Used **larger fonts & scalable UI elements**. ✅ Ensured **screen reader compatibility** (VoiceOver & TalkBack support). #### 3️⃣ Transaction Flow Optimization ✅ Redesigned **"Send" & "Receive" buttons** for clear distinction. ✅ Added **clearer icons & tooltips** for transaction steps. ## 5️⃣ Wireframes & Design Improvements: #### 🔹 Welcome Screen (First Screen When User Opens Wallet) **📌 Goal: Give a brief introduction & set user expectations** ✅ App logo + **short tagline** (e.g., "Secure, Simple, Self-Custody Bitcoin Wallet") ✅ **1-2 line explanation** of what BlueWallet is (e.g., "Your gateway to managing Bitcoin securely.") ✅ **"Get Started" button** → Le ads to **next step: Wallet Setup** ✅ **"Already have a wallet?"** → Import option 🔹 **Example UI Elements:** - BlueWallet Logo - **Title:** "Welcome to BlueWallet" - **Subtitle:** "Easily store, send, and receive Bitcoin." - CTA: "Get Started" (Primary) | "Import Wallet" (Secondary)  #### 🔹 Screen 2: Choose Wallet Type (New or Import) **📌 Goal: Let users decide how to proceed** ✅ **Two clear options:** - **Create a New Wallet** (For first-time users) - **Import Existing Wallet** (For users with a backup phrase) ✅ Brief explanation of each option 🔹 **Example UI Elements: - **Title:** "How do you want to start?" - **Buttons:** "Create New Wallet" | "Import Wallet"  #### 🔹 Screen 3: Security & Seed Phrase Setup (Critical Step) **📌 Goal: Educate users about wallet security & backups** ✅ Explain **why seed phrases are important** ✅ **Clear step-by-step instructions** on writing down & storing the phrase ✅ **Warning:** "If you lose your recovery phrase, you lose access to your wallet." ✅ **CTA:** "Generate Seed Phrase" → Next step 🔹 **Example UI Elements: - Title:** "Secure Your Wallet" - **Subtitle:** "Your seed phrase is the key to your Bitcoin. Keep it safe!" - **Button:** "Generate Seed Phrase"  ## 🔹 Screen 4: Seed Phrase Display & Confirmation **📌 Goal: Ensure users write down the phrase correctly** ✅ Display **12- or 24-word** seed phrase ✅ **“I have written it downˮ checkbox** before proceeding ✅ Next screen: **Verify seed phrase** (drag & drop, re-enter some words) 🔹 **Example UI Elements:** - **Title:** "Write Down Your Seed Phrase" - List of 12/24 Words (Hidden by Default) - **Checkbox:** "I have safely stored my phrase" - **Button:** "Continue"  ### 🔹 Screen 5: Wallet Ready! (Final Step) **📌 Goal: Confirm setup & guide users on next actions** ✅ **Success message** ("Your wallet is ready!") ✅ **Encourage first action:** - “Receive Bitcoinˮ → Show wallet address - “Send Bitcoinˮ → Walkthrough on making transactions ✅ Short explainer: Where to find the Send/Receive buttons 🔹 **Example UI Elements:** - **Title:** "You're All Set!" - **Subtitle:** "Start using BlueWallet now." - **Buttons:** "Receive Bitcoin" | "View Wallet"  - - - ## 5️⃣ Prototype & User Testing Results 🔹 **Created an interactive prototype in Figma** to test the new experience. 🔹 **User Testing Results:** ✅ **40% faster onboarding completion time.** ✅ **90% of users found transaction buttons clearer.** 🔹 **User Feedback:** ✅ “Now I understand the security steps clearly.ˮ ✅ “The buttons are easier to find and use.ˮ - - - ## 6️⃣ Why This Matters: Key Takeaways 📌 **Impact of These UX/UI Changes:** ✅ **Reduced user frustration** by providing a step-by-step onboarding guide. ✅ **Improved accessibility** , making the wallet usable for all. ✅ **More intuitive transactions** , reducing errors. - - - ## 7️⃣ Direct link to figma file and Prototype Figma file: [https://www.figma.com/design/EPb4gVgAMEgF5GBDdtt81Z/Blue-Wallet-UI- Improvements?node-id=0-1&t=Y2ni1SfvuQQnoB7s-1](https://www.figma.com/design/EPb4gVgAMEgF5GBDdtt81Z/Blue-Wallet-UI- Improvements?node-id=0-1&t=Y2ni1SfvuQQnoB7s-1) Prototype: [https://www.figma.com/proto/EPb4gVgAMEgF5GBDdtt81Z/Blue-Wallet-UI- Improvements?node-id=1-2&p=f&t=FndTJQNCE7nEIa84-1&scaling=scale- down&content-scaling=fixed&page-id=0%3A1&starting-point-node- id=1%3A2&show-proto-sidebar=1](https://www.figma.com/proto/EPb4gVgAMEgF5GBDdtt81Z/Blue-Wallet-UI- Improvements?node-id=1-2&p=f&t=FndTJQNCE7nEIa84-1&scaling=scale- down&content-scaling=fixed&page-id=0%3A1&starting-point-node- id=1%3A2&show-proto-sidebar=1) Original PDF available from [here](https://cdn.discordapp.com/attachments/903126164795699212/1355561527394173243/faf3ee46-b501-459c-ba0e-bf7e38843bc8_UX_Case_Study__1.pdf?ex=67e9608d&is=67e80f0d&hm=d0c386ce2cfd6e0ebe6bde0a904e884229f52bf547adf1f7bc884e17bb4aa59e&) originally posted at https://stacker.news/items/928822
@ 57d1a264:69f1fee1
2025-03-29 18:02:16> This UX research has been redacted by @iqra from the Bitcoin.Design [community](https://discord.gg/K7aQ5PErht), and shared for review and feedback! Don't be shy, share your thoughts.  - - - ## 1️⃣ Introduction #### Project Overview 📌 **Product:** BlueWallet (Bitcoin Wallet) 📌 **Goal:** Improve onboarding flow and enhance accessibility for a better user experience. 📌 **Role:** UX Designer 📌 **Tools Used:** Figma, Notion #### Why This Case Study? 🔹 BlueWallet is a self-custodial Bitcoin wallet, but **users struggle with onboarding due to unclear instructions**. 🔹 **Accessibility issues** (low contrast, small fonts) create **barriers for visually impaired users**. 🔹 Competitors like **Trust Wallet and MetaMask offer better-guided onboarding**. This case study presents **UX/UI improvements** to make BlueWallet **more intuitive and inclusive**. - - - ## 2️⃣ Problem Statement: Why BlueWalletʼs Onboarding Needs Improvement #### 🔹 **Current Challenges:** 1️⃣ **Onboarding Complexity** - BlueWallet lacks **step-by-step guidance**, leaving users confused about wallet creation and security.   2️⃣ **No Educational Introduction** - Users land directly on the wallet screen with **no explanation of private keys, recovery phrases, or transactions**. 3️⃣ **Transaction Flow Issues** - Similar-looking **"Send" and "Receive" buttons** cause confusion. 4️⃣ **Poor Accessibility** - Small fonts and low contrast make navigation difficult. #### 🔍 **Impact on Users:** **Higher drop-off rates** due to frustration during onboarding. **Security risks** as users skip key wallet setup steps. **Limited accessibility** for users with visual impairments. #### 📌 **Competitive Gap:** Unlike competitors (Trust Wallet, MetaMask), BlueWallet does not offer: ✅ A guided onboarding process ✅ Security education during setup ✅ Intuitive transaction flow      Somehow, this wallet has much better UI than the BlueWallet Bitcoin wallet. - - - ## 3️⃣ User Research & Competitive Analysis #### User Testing Findings 🔹 Conducted usability testing with **5 users** onboarding for the first time. 🔹 **Key Findings:** ✅ 3 out of 5 users **felt lost** due to missing explanations. ✅ 60% **had trouble distinguishing transaction buttons**. ✅ 80% **found the text difficult to read** due to low contrast. #### Competitive Analysis We compared BlueWallet with top crypto wallets: | Wallet | Onboarding UX | Security Guidance | Accessibility Features | |---|---|---|---| | BlueWallet | ❌ No guided onboarding | ❌ Minimal explanation | ❌ Low contrast, small fonts | | Trust Wallet | ✅ Step-by-step setup | ✅ Security best practices | ✅ High contrast UI | | MetaMask | ✅ Interactive tutorial | ✅ Private key education | ✅ Clear transaction buttons | 📌 **Key Insight:** BlueWallet lacks **guided setup and accessibility enhancements**, making it harder for beginners. ## 📌 User Persona To better understand the users facing onboarding challenges, I developed a **persona** based on research and usability testing. #### 🔹 Persona 1: Alex Carter (Bitcoin Beginner & Investor) 👤 **Profile:** - **Age:** 28 - **Occupation:** Freelance Digital Marketer - **Tech Knowledge:** Moderate - Familiar with online transactions, new to Bitcoin) - **Pain Points:** - Finds **Bitcoin wallets confusing**. - - Doesnʼt understand **seed phrases & security features**. - - **Worried about losing funds** due to a lack of clarity in transactions. 📌 **Needs:** ✅ A **simple, guided** wallet setup. ✅ **Clear explanations** of security terms (without jargon). ✅ Easy-to-locate **Send/Receive buttons**. 📌 **Persona Usage in Case Study:** - Helps define **who we are designing for**. - Guides **design decisions** by focusing on user needs. #### 🔹 Persona 2: Sarah Mitchell (Accessibility Advocate & Tech Enthusiast) 👤 **Profile:** - **Age:** 35 - **Occupation:** UX Researcher & Accessibility Consultant - **Tech Knowledge:** High (Uses Bitcoin but struggles with accessibility barriers) 📌 **Pain Points:** ❌ Struggles with small font sizes & low contrast. ❌ Finds the UI difficult to navigate with a screen reader. ❌ Confused by identical-looking transaction buttons. 📌 **Needs:** ✅ A **high-contrast UI** that meets **WCAG accessibility standards**. ✅ **Larger fonts & scalable UI elements** for better readability. ✅ **Keyboard & screen reader-friendly navigation** for seamless interaction. 📌 **Why This Persona Matters:** - Represents users with visual impairments who rely on accessible design. - Ensures the design accommodates inclusive UX principles. - - - ## 4️⃣ UX/UI Solutions & Design Improvements #### 📌 Before (Current Issues) ❌ Users land **directly on the wallet screen** with no instructions. ❌ **"Send" & "Receive" buttons look identical** , causing transaction confusion. ❌ **Small fonts & low contrast** reduce readability. #### ✅ After (Proposed Fixes) ✅ **Step-by-step onboarding** explaining wallet creation, security, and transactions. ✅ **Visually distinct transaction buttons** (color and icon changes). ✅ **WCAG-compliant text contrast & larger fonts** for better readability. #### 1️⃣ Redesigned Onboarding Flow ✅ Added a **progress indicator** so users see where they are in setup. ✅ Used **plain, non-technical language** to explain wallet creation & security. ✅ Introduced a **"Learn More" button** to educate users on security. #### 2️⃣ Accessibility Enhancements ✅ Increased **contrast ratio** for better text readability. ✅ Used **larger fonts & scalable UI elements**. ✅ Ensured **screen reader compatibility** (VoiceOver & TalkBack support). #### 3️⃣ Transaction Flow Optimization ✅ Redesigned **"Send" & "Receive" buttons** for clear distinction. ✅ Added **clearer icons & tooltips** for transaction steps. ## 5️⃣ Wireframes & Design Improvements: #### 🔹 Welcome Screen (First Screen When User Opens Wallet) **📌 Goal: Give a brief introduction & set user expectations** ✅ App logo + **short tagline** (e.g., "Secure, Simple, Self-Custody Bitcoin Wallet") ✅ **1-2 line explanation** of what BlueWallet is (e.g., "Your gateway to managing Bitcoin securely.") ✅ **"Get Started" button** → Le ads to **next step: Wallet Setup** ✅ **"Already have a wallet?"** → Import option 🔹 **Example UI Elements:** - BlueWallet Logo - **Title:** "Welcome to BlueWallet" - **Subtitle:** "Easily store, send, and receive Bitcoin." - CTA: "Get Started" (Primary) | "Import Wallet" (Secondary)  #### 🔹 Screen 2: Choose Wallet Type (New or Import) **📌 Goal: Let users decide how to proceed** ✅ **Two clear options:** - **Create a New Wallet** (For first-time users) - **Import Existing Wallet** (For users with a backup phrase) ✅ Brief explanation of each option 🔹 **Example UI Elements: - **Title:** "How do you want to start?" - **Buttons:** "Create New Wallet" | "Import Wallet"  #### 🔹 Screen 3: Security & Seed Phrase Setup (Critical Step) **📌 Goal: Educate users about wallet security & backups** ✅ Explain **why seed phrases are important** ✅ **Clear step-by-step instructions** on writing down & storing the phrase ✅ **Warning:** "If you lose your recovery phrase, you lose access to your wallet." ✅ **CTA:** "Generate Seed Phrase" → Next step 🔹 **Example UI Elements: - Title:** "Secure Your Wallet" - **Subtitle:** "Your seed phrase is the key to your Bitcoin. Keep it safe!" - **Button:** "Generate Seed Phrase"  ## 🔹 Screen 4: Seed Phrase Display & Confirmation **📌 Goal: Ensure users write down the phrase correctly** ✅ Display **12- or 24-word** seed phrase ✅ **“I have written it downˮ checkbox** before proceeding ✅ Next screen: **Verify seed phrase** (drag & drop, re-enter some words) 🔹 **Example UI Elements:** - **Title:** "Write Down Your Seed Phrase" - List of 12/24 Words (Hidden by Default) - **Checkbox:** "I have safely stored my phrase" - **Button:** "Continue"  ### 🔹 Screen 5: Wallet Ready! (Final Step) **📌 Goal: Confirm setup & guide users on next actions** ✅ **Success message** ("Your wallet is ready!") ✅ **Encourage first action:** - “Receive Bitcoinˮ → Show wallet address - “Send Bitcoinˮ → Walkthrough on making transactions ✅ Short explainer: Where to find the Send/Receive buttons 🔹 **Example UI Elements:** - **Title:** "You're All Set!" - **Subtitle:** "Start using BlueWallet now." - **Buttons:** "Receive Bitcoin" | "View Wallet"  - - - ## 5️⃣ Prototype & User Testing Results 🔹 **Created an interactive prototype in Figma** to test the new experience. 🔹 **User Testing Results:** ✅ **40% faster onboarding completion time.** ✅ **90% of users found transaction buttons clearer.** 🔹 **User Feedback:** ✅ “Now I understand the security steps clearly.ˮ ✅ “The buttons are easier to find and use.ˮ - - - ## 6️⃣ Why This Matters: Key Takeaways 📌 **Impact of These UX/UI Changes:** ✅ **Reduced user frustration** by providing a step-by-step onboarding guide. ✅ **Improved accessibility** , making the wallet usable for all. ✅ **More intuitive transactions** , reducing errors. - - - ## 7️⃣ Direct link to figma file and Prototype Figma file: [https://www.figma.com/design/EPb4gVgAMEgF5GBDdtt81Z/Blue-Wallet-UI- Improvements?node-id=0-1&t=Y2ni1SfvuQQnoB7s-1](https://www.figma.com/design/EPb4gVgAMEgF5GBDdtt81Z/Blue-Wallet-UI- Improvements?node-id=0-1&t=Y2ni1SfvuQQnoB7s-1) Prototype: [https://www.figma.com/proto/EPb4gVgAMEgF5GBDdtt81Z/Blue-Wallet-UI- Improvements?node-id=1-2&p=f&t=FndTJQNCE7nEIa84-1&scaling=scale- down&content-scaling=fixed&page-id=0%3A1&starting-point-node- id=1%3A2&show-proto-sidebar=1](https://www.figma.com/proto/EPb4gVgAMEgF5GBDdtt81Z/Blue-Wallet-UI- Improvements?node-id=1-2&p=f&t=FndTJQNCE7nEIa84-1&scaling=scale- down&content-scaling=fixed&page-id=0%3A1&starting-point-node- id=1%3A2&show-proto-sidebar=1) Original PDF available from [here](https://cdn.discordapp.com/attachments/903126164795699212/1355561527394173243/faf3ee46-b501-459c-ba0e-bf7e38843bc8_UX_Case_Study__1.pdf?ex=67e9608d&is=67e80f0d&hm=d0c386ce2cfd6e0ebe6bde0a904e884229f52bf547adf1f7bc884e17bb4aa59e&) originally posted at https://stacker.news/items/928822 @ 6389be64:ef439d32
2025-01-13 21:50:59Bitcoin is more than money, more than an asset, and more than a store of value. Bitcoin is a Prime Mover, an enabler and it ignites imaginations. It certainly fueled an idea in my mind. The idea integrates sensors, computational prowess, actuated machinery, power conversion, and electronic communications to form an autonomous, machined creature roaming forests and harvesting the most widespread and least energy-dense fuel source available. I call it the Forest Walker and it eats wood, and mines Bitcoin. I know what you're thinking. Why not just put Bitcoin mining rigs where they belong: in a hosted facility sporting electricity from energy-dense fuels like natural gas, climate-controlled with excellent data piping in and out? Why go to all the trouble building a robot that digests wood creating flammable gasses fueling an engine to run a generator powering Bitcoin miners? It's all about synergy. Bitcoin mining enables the realization of multiple, seemingly unrelated, yet useful activities. Activities considered un-profitable if not for Bitcoin as the Prime Mover. This is much more than simply mining the greatest asset ever conceived by humankind. It’s about the power of synergy, which Bitcoin plays only one of many roles. The synergy created by this system can stabilize forests' fire ecology while generating multiple income streams. That’s the realistic goal here and requires a brief history of American Forest management before continuing. # Smokey The Bear In 1944, the Smokey Bear Wildfire Prevention Campaign began in the United States. “Only YOU can prevent forest fires” remains the refrain of the Ad Council’s longest running campaign. The Ad Council is a U.S. non-profit set up by the American Association of Advertising Agencies and the Association of National Advertisers in 1942. It would seem that the U.S. Department of the Interior was concerned about pesky forest fires and wanted them to stop. So, alongside a national policy of extreme fire suppression they enlisted the entire U.S. population to get onboard via the Ad Council and it worked. Forest fires were almost obliterated and everyone was happy, right? Wrong. Smokey is a fantastically successful bear so forest fires became so few for so long that the fuel load - dead wood - in forests has become very heavy. So heavy that when a fire happens (and they always happen) it destroys everything in its path because the more fuel there is the hotter that fire becomes. Trees, bushes, shrubs, and all other plant life cannot escape destruction (not to mention homes and businesses). The soil microbiology doesn’t escape either as it is burned away even in deeper soils. To add insult to injury, hydrophobic waxy residues condense on the soil surface, forcing water to travel over the ground rather than through it eroding forest soils. Good job, Smokey. Well done, Sir! Most terrestrial ecologies are “fire ecologies”. Fire is a part of these systems’ fuel load and pest management. Before we pretended to “manage” millions of acres of forest, fires raged over the world, rarely damaging forests. The fuel load was always too light to generate fires hot enough to moonscape mountainsides. Fires simply burned off the minor amounts of fuel accumulated since the fire before. The lighter heat, smoke, and other combustion gasses suppressed pests, keeping them in check and the smoke condensed into a plant growth accelerant called wood vinegar, not a waxy cap on the soil. These fires also cleared out weak undergrowth, cycled minerals, and thinned the forest canopy, allowing sunlight to penetrate to the forest floor. Without a fire’s heat, many pine tree species can’t sow their seed. The heat is required to open the cones (the seed bearing structure) of Spruce, Cypress, Sequoia, Jack Pine, Lodgepole Pine and many more. Without fire forests can’t have babies. The idea was to protect the forests, and it isn't working. So, in a world of fire, what does an ally look like and what does it do? # Meet The Forest Walker For the Forest Walker to work as a mobile, autonomous unit, a solid platform that can carry several hundred pounds is required. It so happens this chassis already exists but shelved. Introducing the Legged Squad Support System (LS3). A joint project between Boston Dynamics, DARPA, and the United States Marine Corps, the quadrupedal robot is the size of a cow, can carry 400 pounds (180 kg) of equipment, negotiate challenging terrain, and operate for 24 hours before needing to refuel. Yes, it had an engine. Abandoned in 2015, the thing was too noisy for military deployment and maintenance "under fire" is never a high-quality idea. However, we can rebuild it to act as a platform for the Forest Walker; albeit with serious alterations. It would need to be bigger, probably. Carry more weight? Definitely. Maybe replace structural metal with carbon fiber and redesign much as 3D printable parts for more effective maintenance. The original system has a top operational speed of 8 miles per hour. For our purposes, it only needs to move about as fast as a grazing ruminant. Without the hammering vibrations of galloping into battle, shocks of exploding mortars, and drunken soldiers playing "Wrangler of Steel Machines", time between failures should be much longer and the overall energy consumption much lower. The LS3 is a solid platform to build upon. Now it just needs to be pulled out of the mothballs, and completely refitted with outboard equipment. # The Small Branch Chipper When I say “Forest fuel load” I mean the dead, carbon containing litter on the forest floor. Duff (leaves), fine-woody debris (small branches), and coarse woody debris (logs) are the fuel that feeds forest fires. Walk through any forest in the United States today and you will see quite a lot of these materials. Too much, as I have described. Some of these fuel loads can be 8 tons per acre in pine and hardwood forests and up to 16 tons per acre at active logging sites. That’s some big wood and the more that collects, the more combustible danger to the forest it represents. It also provides a technically unlimited fuel supply for the Forest Walker system. The problem is that this detritus has to be chewed into pieces that are easily ingestible by the system for the gasification process (we’ll get to that step in a minute). What we need is a wood chipper attached to the chassis (the LS3); its “mouth”. A small wood chipper handling material up to 2.5 - 3.0 inches (6.3 - 7.6 cm) in diameter would eliminate a substantial amount of fuel. There is no reason for Forest Walker to remove fallen trees. It wouldn’t have to in order to make a real difference. It need only identify appropriately sized branches and grab them. Once loaded into the chipper’s intake hopper for further processing, the beast can immediately look for more “food”. This is essentially kindling that would help ignite larger logs. If it’s all consumed by Forest Walker, then it’s not present to promote an aggravated conflagration. I have glossed over an obvious question: How does Forest Walker see and identify branches and such? LiDaR (Light Detection and Ranging) attached to Forest Walker images the local area and feed those data to onboard computers for processing. Maybe AI plays a role. Maybe simple machine learning can do the trick. One thing is for certain: being able to identify a stick and cause robotic appendages to pick it up is not impossible. Great! We now have a quadrupedal robot autonomously identifying and “eating” dead branches and other light, combustible materials. Whilst strolling through the forest, depleting future fires of combustibles, Forest Walker has already performed a major function of this system: making the forest safer. It's time to convert this low-density fuel into a high-density fuel Forest Walker can leverage. Enter the gasification process. # The Gassifier The gasifier is the heart of the entire system; it’s where low-density fuel becomes the high-density fuel that powers the entire system. Biochar and wood vinegar are process wastes and I’ll discuss why both are powerful soil amendments in a moment, but first, what’s gasification? Reacting shredded carbonaceous material at high temperatures in a low or no oxygen environment converts the biomass into biochar, wood vinegar, heat, and Synthesis Gas (Syngas). Syngas consists primarily of hydrogen, carbon monoxide, and methane. All of which are extremely useful fuels in a gaseous state. Part of this gas is used to heat the input biomass and keep the reaction temperature constant while the internal combustion engine that drives the generator to produce electrical power consumes the rest. Critically, this gasification process is “continuous feed”. Forest Walker must intake biomass from the chipper, process it to fuel, and dump the waste (CO2, heat, biochar, and wood vinegar) continuously. It cannot stop. Everything about this system depends upon this continual grazing, digestion, and excretion of wastes just as a ruminal does. And, like a ruminant, all waste products enhance the local environment. When I first heard of gasification, I didn’t believe that it was real. Running an electric generator from burning wood seemed more akin to “conspiracy fantasy” than science. Not only is gasification real, it’s ancient technology. A man named Dean Clayton first started experiments on gasification in 1699 and in 1901 gasification was used to power a vehicle. By the end of World War II, there were 500,000 Syngas powered vehicles in Germany alone because of fossil fuel rationing during the war. The global gasification market was $480 billion in 2022 and projected to be as much as $700 billion by 2030 (Vantage Market Research). Gasification technology is the best choice to power the Forest Walker because it’s self-contained and we want its waste products. # Biochar: The Waste Biochar (AKA agricultural charcoal) is fairly simple: it’s almost pure, solid carbon that resembles charcoal. Its porous nature packs large surface areas into small, 3 dimensional nuggets. Devoid of most other chemistry, like hydrocarbons (methane) and ash (minerals), biochar is extremely lightweight. Do not confuse it with the charcoal you buy for your grill. Biochar doesn’t make good grilling charcoal because it would burn too rapidly as it does not contain the multitude of flammable components that charcoal does. Biochar has several other good use cases. Water filtration, water retention, nutrient retention, providing habitat for microscopic soil organisms, and carbon sequestration are the main ones that we are concerned with here. Carbon has an amazing ability to adsorb (substances stick to and accumulate on the surface of an object) manifold chemistries. Water, nutrients, and pollutants tightly bind to carbon in this format. So, biochar makes a respectable filter and acts as a “battery” of water and nutrients in soils. Biochar adsorbs and holds on to seven times its weight in water. Soil containing biochar is more drought resilient than soil without it. Adsorbed nutrients, tightly sequestered alongside water, get released only as plants need them. Plants must excrete protons (H+) from their roots to disgorge water or positively charged nutrients from the biochar's surface; it's an active process. Biochar’s surface area (where adsorption happens) can be 500 square meters per gram or more. That is 10% larger than an official NBA basketball court for every gram of biochar. Biochar’s abundant surface area builds protective habitats for soil microbes like fungi and bacteria and many are critical for the health and productivity of the soil itself. The “carbon sequestration” component of biochar comes into play where “carbon credits” are concerned. There is a financial market for carbon. Not leveraging that market for revenue is foolish. I am climate agnostic. All I care about is that once solid carbon is inside the soil, it will stay there for thousands of years, imparting drought resiliency, fertility collection, nutrient buffering, and release for that time span. I simply want as much solid carbon in the soil because of the undeniably positive effects it has, regardless of any climactic considerations. # Wood Vinegar: More Waste Another by-product of the gasification process is wood vinegar (Pyroligneous acid). If you have ever seen Liquid Smoke in the grocery store, then you have seen wood vinegar. Principally composed of acetic acid, acetone, and methanol wood vinegar also contains ~200 other organic compounds. It would seem intuitive that condensed, liquefied wood smoke would at least be bad for the health of all living things if not downright carcinogenic. The counter intuition wins the day, however. Wood vinegar has been used by humans for a very long time to promote digestion, bowel, and liver health; combat diarrhea and vomiting; calm peptic ulcers and regulate cholesterol levels; and a host of other benefits. For centuries humans have annually burned off hundreds of thousands of square miles of pasture, grassland, forest, and every other conceivable terrestrial ecosystem. Why is this done? After every burn, one thing becomes obvious: the almost supernatural growth these ecosystems exhibit after the burn. How? Wood vinegar is a component of this growth. Even in open burns, smoke condenses and infiltrates the soil. That is when wood vinegar shows its quality. This stuff beefs up not only general plant growth but seed germination as well and possesses many other qualities that are beneficial to plants. It’s a pesticide, fungicide, promotes beneficial soil microorganisms, enhances nutrient uptake, and imparts disease resistance. I am barely touching a long list of attributes here, but you want wood vinegar in your soil (alongside biochar because it adsorbs wood vinegar as well). # The Internal Combustion Engine Conversion of grazed forage to chemical, then mechanical, and then electrical energy completes the cycle. The ICE (Internal Combustion Engine) converts the gaseous fuel output from the gasifier to mechanical energy, heat, water vapor, and CO2. It’s the mechanical energy of a rotating drive shaft that we want. That rotation drives the electric generator, which is the heartbeat we need to bring this monster to life. Luckily for us, combined internal combustion engine and generator packages are ubiquitous, delivering a defined energy output given a constant fuel input. It’s the simplest part of the system. The obvious question here is whether the amount of syngas provided by the gasification process will provide enough energy to generate enough electrons to run the entire system or not. While I have no doubt the energy produced will run Forest Walker's main systems the question is really about the electrons left over. Will it be enough to run the Bitcoin mining aspect of the system? Everything is a budget. # CO2 Production For Growth Plants are lollipops. No matter if it’s a tree or a bush or a shrubbery, the entire thing is mostly sugar in various formats but mostly long chain carbohydrates like lignin and cellulose. Plants need three things to make sugar: CO2, H2O and light. In a forest, where tree densities can be quite high, CO2 availability becomes a limiting growth factor. It’d be in the forest interests to have more available CO2 providing for various sugar formation providing the organism with food and structure. An odd thing about tree leaves, the openings that allow gasses like the ever searched for CO2 are on the bottom of the leaf (these are called stomata). Not many stomata are topside. This suggests that trees and bushes have evolved to find gasses like CO2 from below, not above and this further suggests CO2 might be in higher concentrations nearer the soil. The soil life (bacterial, fungi etc.) is constantly producing enormous amounts of CO2 and it would stay in the soil forever (eventually killing the very soil life that produces it) if not for tidal forces. Water is everywhere and whether in pools, lakes, oceans or distributed in “moist” soils water moves towards to the moon. The water in the soil and also in the water tables below the soil rise toward the surface every day. When the water rises, it expels the accumulated gasses in the soil into the atmosphere and it’s mostly CO2. It’s a good bet on how leaves developed high populations of stomata on the underside of leaves. As the water relaxes (the tide goes out) it sucks oxygenated air back into the soil to continue the functions of soil life respiration. The soil “breathes” albeit slowly. The gasses produced by the Forest Walker’s internal combustion engine consist primarily of CO2 and H2O. Combusting sugars produce the same gasses that are needed to construct the sugars because the universe is funny like that. The Forest Walker is constantly laying down these critical construction elements right where the trees need them: close to the ground to be gobbled up by the trees. # The Branch Drones During the last ice age, giant mammals populated North America - forests and otherwise. Mastodons, woolly mammoths, rhinos, short-faced bears, steppe bison, caribou, musk ox, giant beavers, camels, gigantic ground-dwelling sloths, glyptodons, and dire wolves were everywhere. Many were ten to fifteen feet tall. As they crashed through forests, they would effectively cleave off dead side-branches of trees, halting the spread of a ground-based fire migrating into the tree crown ("laddering") which is a death knell for a forest. These animals are all extinct now and forests no longer have any manner of pruning services. But, if we build drones fitted with cutting implements like saws and loppers, optical cameras and AI trained to discern dead branches from living ones, these drones could effectively take over pruning services by identifying, cutting, and dropping to the forest floor, dead branches. The dropped branches simply get collected by the Forest Walker as part of its continual mission. The drones dock on the back of the Forest Walker to recharge their batteries when low. The whole scene would look like a grazing cow with some flies bothering it. This activity breaks the link between a relatively cool ground based fire and the tree crowns and is a vital element in forest fire control. # The Bitcoin Miner Mining is one of four monetary incentive models, making this system a possibility for development. The other three are US Dept. of the Interior, township, county, and electrical utility company easement contracts for fuel load management, global carbon credits trading, and data set sales. All the above depends on obvious questions getting answered. I will list some obvious ones, but this is not an engineering document and is not the place for spreadsheets. How much Bitcoin one Forest Walker can mine depends on everything else. What amount of biomass can we process? Will that biomass flow enough Syngas to keep the lights on? Can the chassis support enough mining ASICs and supporting infrastructure? What does that weigh and will it affect field performance? How much power can the AC generator produce? Other questions that are more philosophical persist. Even if a single Forest Walker can only mine scant amounts of BTC per day, that pales to how much fuel material it can process into biochar. We are talking about millions upon millions of forested acres in need of fuel load management. What can a single Forest Walker do? I am not thinking in singular terms. The Forest Walker must operate as a fleet. What could 50 do? 500? What is it worth providing a service to the world by managing forest fuel loads? Providing proof of work to the global monetary system? Seeding soil with drought and nutrient resilience by the excretion, over time, of carbon by the ton? What did the last forest fire cost? # The Mesh Network What could be better than one bitcoin mining, carbon sequestering, forest fire squelching, soil amending behemoth? Thousands of them, but then they would need to be able to talk to each other to coordinate position, data handling, etc. Fitted with a mesh networking device, like goTenna or Meshtastic LoRa equipment enables each Forest Walker to communicate with each other. Now we have an interconnected fleet of Forest Walkers relaying data to each other and more importantly, aggregating all of that to the last link in the chain for uplink. Well, at least Bitcoin mining data. Since block data is lightweight, transmission of these data via mesh networking in fairly close quartered environs is more than doable. So, how does data transmit to the Bitcoin Network? How do the Forest Walkers get the previous block data necessary to execute on mining? # Back To The Chain Getting Bitcoin block data to and from the network is the last puzzle piece. The standing presumption here is that wherever a Forest Walker fleet is operating, it is NOT within cell tower range. We further presume that the nearest Walmart Wi-Fi is hours away. Enter the Blockstream Satellite or something like it. A separate, ground-based drone will have two jobs: To stay as close to the nearest Forest Walker as it can and to provide an antennae for either terrestrial or orbital data uplink. Bitcoin-centric data is transmitted to the "uplink drone" via the mesh networked transmitters and then sent on to the uplink and the whole flow goes in the opposite direction as well; many to one and one to many. We cannot transmit data to the Blockstream satellite, and it will be up to Blockstream and companies like it to provide uplink capabilities in the future and I don't doubt they will. Starlink you say? What’s stopping that company from filtering out block data? Nothing because it’s Starlink’s system and they could decide to censor these data. It seems we may have a problem sending and receiving Bitcoin data in back country environs. But, then again, the utility of this system in staunching the fuel load that creates forest fires is extremely useful around forested communities and many have fiber, Wi-Fi and cell towers. These communities could be a welcoming ground zero for first deployments of the Forest Walker system by the home and business owners seeking fire repression. In the best way, Bitcoin subsidizes the safety of the communities. # Sensor Packages ### LiDaR The benefit of having a Forest Walker fleet strolling through the forest is the never ending opportunity for data gathering. A plethora of deployable sensors gathering hyper-accurate data on everything from temperature to topography is yet another revenue generator. Data is valuable and the Forest Walker could generate data sales to various government entities and private concerns. LiDaR (Light Detection and Ranging) can map topography, perform biomass assessment, comparative soil erosion analysis, etc. It so happens that the Forest Walker’s ability to “see,” to navigate about its surroundings, is LiDaR driven and since it’s already being used, we can get double duty by harvesting that data for later use. By using a laser to send out light pulses and measuring the time it takes for the reflection of those pulses to return, very detailed data sets incrementally build up. Eventually, as enough data about a certain area becomes available, the data becomes useful and valuable. Forestry concerns, both private and public, often use LiDaR to build 3D models of tree stands to assess the amount of harvest-able lumber in entire sections of forest. Consulting companies offering these services charge anywhere from several hundred to several thousand dollars per square kilometer for such services. A Forest Walker generating such assessments on the fly while performing its other functions is a multi-disciplinary approach to revenue generation. ### pH, Soil Moisture, and Cation Exchange Sensing The Forest Walker is quadrupedal, so there are four contact points to the soil. Why not get a pH data point for every step it takes? We can also gather soil moisture data and cation exchange capacities at unheard of densities because of sampling occurring on the fly during commission of the system’s other duties. No one is going to build a machine to do pH testing of vast tracts of forest soils, but that doesn’t make the data collected from such an endeavor valueless. Since the Forest Walker serves many functions at once, a multitude of data products can add to the return on investment component. ### Weather Data Temperature, humidity, pressure, and even data like evapotranspiration gathered at high densities on broad acre scales have untold value and because the sensors are lightweight and don’t require large power budgets, they come along for the ride at little cost. But, just like the old mantra, “gas, grass, or ass, nobody rides for free”, these sensors provide potential revenue benefits just by them being present. I’ve touched on just a few data genres here. In fact, the question for universities, governmental bodies, and other institutions becomes, “How much will you pay us to attach your sensor payload to the Forest Walker?” # Noise Suppression Only you can prevent Metallica filling the surrounds with 120 dB of sound. Easy enough, just turn the car stereo off. But what of a fleet of 50 Forest Walkers operating in the backcountry or near a township? 500? 5000? Each one has a wood chipper, an internal combustion engine, hydraulic pumps, actuators, and more cooling fans than you can shake a stick at. It’s a walking, screaming fire-breathing dragon operating continuously, day and night, twenty-four hours a day, three hundred sixty-five days a year. The sound will negatively affect all living things and that impacts behaviors. Serious engineering consideration and prowess must deliver a silencing blow to the major issue of noise. It would be foolish to think that a fleet of Forest Walkers could be silent, but if not a major design consideration, then the entire idea is dead on arrival. Townships would not allow them to operate even if they solved the problem of widespread fuel load and neither would governmental entities, and rightly so. Nothing, not man nor beast, would want to be subjected to an eternal, infernal scream even if it were to end within days as the fleet moved further away after consuming what it could. Noise and heat are the only real pollutants of this system; taking noise seriously from the beginning is paramount. # Fire Safety A “fire-breathing dragon” is not the worst description of the Forest Walker. It eats wood, combusts it at very high temperatures and excretes carbon; and it does so in an extremely flammable environment. Bad mix for one Forest Walker, worse for many. One must take extreme pains to ensure that during normal operation, a Forest Walker could fall over, walk through tinder dry brush, or get pounded into the ground by a meteorite from Krypton and it wouldn’t destroy epic swaths of trees and baby deer. I envision an ultimate test of a prototype to include dowsing it in grain alcohol while it’s wrapped up in toilet paper like a pledge at a fraternity party. If it runs for 72 hours and doesn’t set everything on fire, then maybe outside entities won’t be fearful of something that walks around forests with a constant fire in its belly. # The Wrap How we think about what can be done with and adjacent to Bitcoin is at least as important as Bitcoin’s economic standing itself. For those who will tell me that this entire idea is without merit, I say, “OK, fine. You can come up with something, too.” What can we plug Bitcoin into that, like a battery, makes something that does not work, work? That’s the lesson I get from this entire exercise. No one was ever going to hire teams of humans to go out and "clean the forest". There's no money in that. The data collection and sales from such an endeavor might provide revenues over the break-even point but investment demands Alpha in this day and age. But, plug Bitcoin into an almost viable system and, voilà! We tip the scales to achieve lift-off. Let’s face it, we haven’t scratched the surface of Bitcoin’s forcing function on our minds. Not because it’s Bitcoin, but because of what that invention means. The question that pushes me to approach things this way is, “what can we create that one system’s waste is another system’s feedstock?” The Forest Walker system’s only real waste is the conversion of low entropy energy (wood and syngas) into high entropy energy (heat and noise). All other output is beneficial to humanity. Bitcoin, I believe, is the first product of a new mode of human imagination. An imagination newly forged over the past few millennia of being lied to, stolen from, distracted and otherwise mis-allocated to a black hole of the nonsensical. We are waking up. What I have presented is not science fiction. Everything I have described here is well within the realm of possibility. The question is one of viability, at least in terms of the detritus of the old world we find ourselves departing from. This system would take a non-trivial amount of time and resources to develop. I think the system would garner extensive long-term contracts from those who have the most to lose from wildfires, the most to gain from hyperaccurate data sets, and, of course, securing the most precious asset in the world. Many may not see it that way, for they seek Alpha and are therefore blind to other possibilities. Others will see only the possibilities; of thinking in a new way, of looking at things differently, and dreaming of what comes next.
@ 6389be64:ef439d32
2025-01-13 21:50:59Bitcoin is more than money, more than an asset, and more than a store of value. Bitcoin is a Prime Mover, an enabler and it ignites imaginations. It certainly fueled an idea in my mind. The idea integrates sensors, computational prowess, actuated machinery, power conversion, and electronic communications to form an autonomous, machined creature roaming forests and harvesting the most widespread and least energy-dense fuel source available. I call it the Forest Walker and it eats wood, and mines Bitcoin. I know what you're thinking. Why not just put Bitcoin mining rigs where they belong: in a hosted facility sporting electricity from energy-dense fuels like natural gas, climate-controlled with excellent data piping in and out? Why go to all the trouble building a robot that digests wood creating flammable gasses fueling an engine to run a generator powering Bitcoin miners? It's all about synergy. Bitcoin mining enables the realization of multiple, seemingly unrelated, yet useful activities. Activities considered un-profitable if not for Bitcoin as the Prime Mover. This is much more than simply mining the greatest asset ever conceived by humankind. It’s about the power of synergy, which Bitcoin plays only one of many roles. The synergy created by this system can stabilize forests' fire ecology while generating multiple income streams. That’s the realistic goal here and requires a brief history of American Forest management before continuing. # Smokey The Bear In 1944, the Smokey Bear Wildfire Prevention Campaign began in the United States. “Only YOU can prevent forest fires” remains the refrain of the Ad Council’s longest running campaign. The Ad Council is a U.S. non-profit set up by the American Association of Advertising Agencies and the Association of National Advertisers in 1942. It would seem that the U.S. Department of the Interior was concerned about pesky forest fires and wanted them to stop. So, alongside a national policy of extreme fire suppression they enlisted the entire U.S. population to get onboard via the Ad Council and it worked. Forest fires were almost obliterated and everyone was happy, right? Wrong. Smokey is a fantastically successful bear so forest fires became so few for so long that the fuel load - dead wood - in forests has become very heavy. So heavy that when a fire happens (and they always happen) it destroys everything in its path because the more fuel there is the hotter that fire becomes. Trees, bushes, shrubs, and all other plant life cannot escape destruction (not to mention homes and businesses). The soil microbiology doesn’t escape either as it is burned away even in deeper soils. To add insult to injury, hydrophobic waxy residues condense on the soil surface, forcing water to travel over the ground rather than through it eroding forest soils. Good job, Smokey. Well done, Sir! Most terrestrial ecologies are “fire ecologies”. Fire is a part of these systems’ fuel load and pest management. Before we pretended to “manage” millions of acres of forest, fires raged over the world, rarely damaging forests. The fuel load was always too light to generate fires hot enough to moonscape mountainsides. Fires simply burned off the minor amounts of fuel accumulated since the fire before. The lighter heat, smoke, and other combustion gasses suppressed pests, keeping them in check and the smoke condensed into a plant growth accelerant called wood vinegar, not a waxy cap on the soil. These fires also cleared out weak undergrowth, cycled minerals, and thinned the forest canopy, allowing sunlight to penetrate to the forest floor. Without a fire’s heat, many pine tree species can’t sow their seed. The heat is required to open the cones (the seed bearing structure) of Spruce, Cypress, Sequoia, Jack Pine, Lodgepole Pine and many more. Without fire forests can’t have babies. The idea was to protect the forests, and it isn't working. So, in a world of fire, what does an ally look like and what does it do? # Meet The Forest Walker For the Forest Walker to work as a mobile, autonomous unit, a solid platform that can carry several hundred pounds is required. It so happens this chassis already exists but shelved. Introducing the Legged Squad Support System (LS3). A joint project between Boston Dynamics, DARPA, and the United States Marine Corps, the quadrupedal robot is the size of a cow, can carry 400 pounds (180 kg) of equipment, negotiate challenging terrain, and operate for 24 hours before needing to refuel. Yes, it had an engine. Abandoned in 2015, the thing was too noisy for military deployment and maintenance "under fire" is never a high-quality idea. However, we can rebuild it to act as a platform for the Forest Walker; albeit with serious alterations. It would need to be bigger, probably. Carry more weight? Definitely. Maybe replace structural metal with carbon fiber and redesign much as 3D printable parts for more effective maintenance. The original system has a top operational speed of 8 miles per hour. For our purposes, it only needs to move about as fast as a grazing ruminant. Without the hammering vibrations of galloping into battle, shocks of exploding mortars, and drunken soldiers playing "Wrangler of Steel Machines", time between failures should be much longer and the overall energy consumption much lower. The LS3 is a solid platform to build upon. Now it just needs to be pulled out of the mothballs, and completely refitted with outboard equipment. # The Small Branch Chipper When I say “Forest fuel load” I mean the dead, carbon containing litter on the forest floor. Duff (leaves), fine-woody debris (small branches), and coarse woody debris (logs) are the fuel that feeds forest fires. Walk through any forest in the United States today and you will see quite a lot of these materials. Too much, as I have described. Some of these fuel loads can be 8 tons per acre in pine and hardwood forests and up to 16 tons per acre at active logging sites. That’s some big wood and the more that collects, the more combustible danger to the forest it represents. It also provides a technically unlimited fuel supply for the Forest Walker system. The problem is that this detritus has to be chewed into pieces that are easily ingestible by the system for the gasification process (we’ll get to that step in a minute). What we need is a wood chipper attached to the chassis (the LS3); its “mouth”. A small wood chipper handling material up to 2.5 - 3.0 inches (6.3 - 7.6 cm) in diameter would eliminate a substantial amount of fuel. There is no reason for Forest Walker to remove fallen trees. It wouldn’t have to in order to make a real difference. It need only identify appropriately sized branches and grab them. Once loaded into the chipper’s intake hopper for further processing, the beast can immediately look for more “food”. This is essentially kindling that would help ignite larger logs. If it’s all consumed by Forest Walker, then it’s not present to promote an aggravated conflagration. I have glossed over an obvious question: How does Forest Walker see and identify branches and such? LiDaR (Light Detection and Ranging) attached to Forest Walker images the local area and feed those data to onboard computers for processing. Maybe AI plays a role. Maybe simple machine learning can do the trick. One thing is for certain: being able to identify a stick and cause robotic appendages to pick it up is not impossible. Great! We now have a quadrupedal robot autonomously identifying and “eating” dead branches and other light, combustible materials. Whilst strolling through the forest, depleting future fires of combustibles, Forest Walker has already performed a major function of this system: making the forest safer. It's time to convert this low-density fuel into a high-density fuel Forest Walker can leverage. Enter the gasification process. # The Gassifier The gasifier is the heart of the entire system; it’s where low-density fuel becomes the high-density fuel that powers the entire system. Biochar and wood vinegar are process wastes and I’ll discuss why both are powerful soil amendments in a moment, but first, what’s gasification? Reacting shredded carbonaceous material at high temperatures in a low or no oxygen environment converts the biomass into biochar, wood vinegar, heat, and Synthesis Gas (Syngas). Syngas consists primarily of hydrogen, carbon monoxide, and methane. All of which are extremely useful fuels in a gaseous state. Part of this gas is used to heat the input biomass and keep the reaction temperature constant while the internal combustion engine that drives the generator to produce electrical power consumes the rest. Critically, this gasification process is “continuous feed”. Forest Walker must intake biomass from the chipper, process it to fuel, and dump the waste (CO2, heat, biochar, and wood vinegar) continuously. It cannot stop. Everything about this system depends upon this continual grazing, digestion, and excretion of wastes just as a ruminal does. And, like a ruminant, all waste products enhance the local environment. When I first heard of gasification, I didn’t believe that it was real. Running an electric generator from burning wood seemed more akin to “conspiracy fantasy” than science. Not only is gasification real, it’s ancient technology. A man named Dean Clayton first started experiments on gasification in 1699 and in 1901 gasification was used to power a vehicle. By the end of World War II, there were 500,000 Syngas powered vehicles in Germany alone because of fossil fuel rationing during the war. The global gasification market was $480 billion in 2022 and projected to be as much as $700 billion by 2030 (Vantage Market Research). Gasification technology is the best choice to power the Forest Walker because it’s self-contained and we want its waste products. # Biochar: The Waste Biochar (AKA agricultural charcoal) is fairly simple: it’s almost pure, solid carbon that resembles charcoal. Its porous nature packs large surface areas into small, 3 dimensional nuggets. Devoid of most other chemistry, like hydrocarbons (methane) and ash (minerals), biochar is extremely lightweight. Do not confuse it with the charcoal you buy for your grill. Biochar doesn’t make good grilling charcoal because it would burn too rapidly as it does not contain the multitude of flammable components that charcoal does. Biochar has several other good use cases. Water filtration, water retention, nutrient retention, providing habitat for microscopic soil organisms, and carbon sequestration are the main ones that we are concerned with here. Carbon has an amazing ability to adsorb (substances stick to and accumulate on the surface of an object) manifold chemistries. Water, nutrients, and pollutants tightly bind to carbon in this format. So, biochar makes a respectable filter and acts as a “battery” of water and nutrients in soils. Biochar adsorbs and holds on to seven times its weight in water. Soil containing biochar is more drought resilient than soil without it. Adsorbed nutrients, tightly sequestered alongside water, get released only as plants need them. Plants must excrete protons (H+) from their roots to disgorge water or positively charged nutrients from the biochar's surface; it's an active process. Biochar’s surface area (where adsorption happens) can be 500 square meters per gram or more. That is 10% larger than an official NBA basketball court for every gram of biochar. Biochar’s abundant surface area builds protective habitats for soil microbes like fungi and bacteria and many are critical for the health and productivity of the soil itself. The “carbon sequestration” component of biochar comes into play where “carbon credits” are concerned. There is a financial market for carbon. Not leveraging that market for revenue is foolish. I am climate agnostic. All I care about is that once solid carbon is inside the soil, it will stay there for thousands of years, imparting drought resiliency, fertility collection, nutrient buffering, and release for that time span. I simply want as much solid carbon in the soil because of the undeniably positive effects it has, regardless of any climactic considerations. # Wood Vinegar: More Waste Another by-product of the gasification process is wood vinegar (Pyroligneous acid). If you have ever seen Liquid Smoke in the grocery store, then you have seen wood vinegar. Principally composed of acetic acid, acetone, and methanol wood vinegar also contains ~200 other organic compounds. It would seem intuitive that condensed, liquefied wood smoke would at least be bad for the health of all living things if not downright carcinogenic. The counter intuition wins the day, however. Wood vinegar has been used by humans for a very long time to promote digestion, bowel, and liver health; combat diarrhea and vomiting; calm peptic ulcers and regulate cholesterol levels; and a host of other benefits. For centuries humans have annually burned off hundreds of thousands of square miles of pasture, grassland, forest, and every other conceivable terrestrial ecosystem. Why is this done? After every burn, one thing becomes obvious: the almost supernatural growth these ecosystems exhibit after the burn. How? Wood vinegar is a component of this growth. Even in open burns, smoke condenses and infiltrates the soil. That is when wood vinegar shows its quality. This stuff beefs up not only general plant growth but seed germination as well and possesses many other qualities that are beneficial to plants. It’s a pesticide, fungicide, promotes beneficial soil microorganisms, enhances nutrient uptake, and imparts disease resistance. I am barely touching a long list of attributes here, but you want wood vinegar in your soil (alongside biochar because it adsorbs wood vinegar as well). # The Internal Combustion Engine Conversion of grazed forage to chemical, then mechanical, and then electrical energy completes the cycle. The ICE (Internal Combustion Engine) converts the gaseous fuel output from the gasifier to mechanical energy, heat, water vapor, and CO2. It’s the mechanical energy of a rotating drive shaft that we want. That rotation drives the electric generator, which is the heartbeat we need to bring this monster to life. Luckily for us, combined internal combustion engine and generator packages are ubiquitous, delivering a defined energy output given a constant fuel input. It’s the simplest part of the system. The obvious question here is whether the amount of syngas provided by the gasification process will provide enough energy to generate enough electrons to run the entire system or not. While I have no doubt the energy produced will run Forest Walker's main systems the question is really about the electrons left over. Will it be enough to run the Bitcoin mining aspect of the system? Everything is a budget. # CO2 Production For Growth Plants are lollipops. No matter if it’s a tree or a bush or a shrubbery, the entire thing is mostly sugar in various formats but mostly long chain carbohydrates like lignin and cellulose. Plants need three things to make sugar: CO2, H2O and light. In a forest, where tree densities can be quite high, CO2 availability becomes a limiting growth factor. It’d be in the forest interests to have more available CO2 providing for various sugar formation providing the organism with food and structure. An odd thing about tree leaves, the openings that allow gasses like the ever searched for CO2 are on the bottom of the leaf (these are called stomata). Not many stomata are topside. This suggests that trees and bushes have evolved to find gasses like CO2 from below, not above and this further suggests CO2 might be in higher concentrations nearer the soil. The soil life (bacterial, fungi etc.) is constantly producing enormous amounts of CO2 and it would stay in the soil forever (eventually killing the very soil life that produces it) if not for tidal forces. Water is everywhere and whether in pools, lakes, oceans or distributed in “moist” soils water moves towards to the moon. The water in the soil and also in the water tables below the soil rise toward the surface every day. When the water rises, it expels the accumulated gasses in the soil into the atmosphere and it’s mostly CO2. It’s a good bet on how leaves developed high populations of stomata on the underside of leaves. As the water relaxes (the tide goes out) it sucks oxygenated air back into the soil to continue the functions of soil life respiration. The soil “breathes” albeit slowly. The gasses produced by the Forest Walker’s internal combustion engine consist primarily of CO2 and H2O. Combusting sugars produce the same gasses that are needed to construct the sugars because the universe is funny like that. The Forest Walker is constantly laying down these critical construction elements right where the trees need them: close to the ground to be gobbled up by the trees. # The Branch Drones During the last ice age, giant mammals populated North America - forests and otherwise. Mastodons, woolly mammoths, rhinos, short-faced bears, steppe bison, caribou, musk ox, giant beavers, camels, gigantic ground-dwelling sloths, glyptodons, and dire wolves were everywhere. Many were ten to fifteen feet tall. As they crashed through forests, they would effectively cleave off dead side-branches of trees, halting the spread of a ground-based fire migrating into the tree crown ("laddering") which is a death knell for a forest. These animals are all extinct now and forests no longer have any manner of pruning services. But, if we build drones fitted with cutting implements like saws and loppers, optical cameras and AI trained to discern dead branches from living ones, these drones could effectively take over pruning services by identifying, cutting, and dropping to the forest floor, dead branches. The dropped branches simply get collected by the Forest Walker as part of its continual mission. The drones dock on the back of the Forest Walker to recharge their batteries when low. The whole scene would look like a grazing cow with some flies bothering it. This activity breaks the link between a relatively cool ground based fire and the tree crowns and is a vital element in forest fire control. # The Bitcoin Miner Mining is one of four monetary incentive models, making this system a possibility for development. The other three are US Dept. of the Interior, township, county, and electrical utility company easement contracts for fuel load management, global carbon credits trading, and data set sales. All the above depends on obvious questions getting answered. I will list some obvious ones, but this is not an engineering document and is not the place for spreadsheets. How much Bitcoin one Forest Walker can mine depends on everything else. What amount of biomass can we process? Will that biomass flow enough Syngas to keep the lights on? Can the chassis support enough mining ASICs and supporting infrastructure? What does that weigh and will it affect field performance? How much power can the AC generator produce? Other questions that are more philosophical persist. Even if a single Forest Walker can only mine scant amounts of BTC per day, that pales to how much fuel material it can process into biochar. We are talking about millions upon millions of forested acres in need of fuel load management. What can a single Forest Walker do? I am not thinking in singular terms. The Forest Walker must operate as a fleet. What could 50 do? 500? What is it worth providing a service to the world by managing forest fuel loads? Providing proof of work to the global monetary system? Seeding soil with drought and nutrient resilience by the excretion, over time, of carbon by the ton? What did the last forest fire cost? # The Mesh Network What could be better than one bitcoin mining, carbon sequestering, forest fire squelching, soil amending behemoth? Thousands of them, but then they would need to be able to talk to each other to coordinate position, data handling, etc. Fitted with a mesh networking device, like goTenna or Meshtastic LoRa equipment enables each Forest Walker to communicate with each other. Now we have an interconnected fleet of Forest Walkers relaying data to each other and more importantly, aggregating all of that to the last link in the chain for uplink. Well, at least Bitcoin mining data. Since block data is lightweight, transmission of these data via mesh networking in fairly close quartered environs is more than doable. So, how does data transmit to the Bitcoin Network? How do the Forest Walkers get the previous block data necessary to execute on mining? # Back To The Chain Getting Bitcoin block data to and from the network is the last puzzle piece. The standing presumption here is that wherever a Forest Walker fleet is operating, it is NOT within cell tower range. We further presume that the nearest Walmart Wi-Fi is hours away. Enter the Blockstream Satellite or something like it. A separate, ground-based drone will have two jobs: To stay as close to the nearest Forest Walker as it can and to provide an antennae for either terrestrial or orbital data uplink. Bitcoin-centric data is transmitted to the "uplink drone" via the mesh networked transmitters and then sent on to the uplink and the whole flow goes in the opposite direction as well; many to one and one to many. We cannot transmit data to the Blockstream satellite, and it will be up to Blockstream and companies like it to provide uplink capabilities in the future and I don't doubt they will. Starlink you say? What’s stopping that company from filtering out block data? Nothing because it’s Starlink’s system and they could decide to censor these data. It seems we may have a problem sending and receiving Bitcoin data in back country environs. But, then again, the utility of this system in staunching the fuel load that creates forest fires is extremely useful around forested communities and many have fiber, Wi-Fi and cell towers. These communities could be a welcoming ground zero for first deployments of the Forest Walker system by the home and business owners seeking fire repression. In the best way, Bitcoin subsidizes the safety of the communities. # Sensor Packages ### LiDaR The benefit of having a Forest Walker fleet strolling through the forest is the never ending opportunity for data gathering. A plethora of deployable sensors gathering hyper-accurate data on everything from temperature to topography is yet another revenue generator. Data is valuable and the Forest Walker could generate data sales to various government entities and private concerns. LiDaR (Light Detection and Ranging) can map topography, perform biomass assessment, comparative soil erosion analysis, etc. It so happens that the Forest Walker’s ability to “see,” to navigate about its surroundings, is LiDaR driven and since it’s already being used, we can get double duty by harvesting that data for later use. By using a laser to send out light pulses and measuring the time it takes for the reflection of those pulses to return, very detailed data sets incrementally build up. Eventually, as enough data about a certain area becomes available, the data becomes useful and valuable. Forestry concerns, both private and public, often use LiDaR to build 3D models of tree stands to assess the amount of harvest-able lumber in entire sections of forest. Consulting companies offering these services charge anywhere from several hundred to several thousand dollars per square kilometer for such services. A Forest Walker generating such assessments on the fly while performing its other functions is a multi-disciplinary approach to revenue generation. ### pH, Soil Moisture, and Cation Exchange Sensing The Forest Walker is quadrupedal, so there are four contact points to the soil. Why not get a pH data point for every step it takes? We can also gather soil moisture data and cation exchange capacities at unheard of densities because of sampling occurring on the fly during commission of the system’s other duties. No one is going to build a machine to do pH testing of vast tracts of forest soils, but that doesn’t make the data collected from such an endeavor valueless. Since the Forest Walker serves many functions at once, a multitude of data products can add to the return on investment component. ### Weather Data Temperature, humidity, pressure, and even data like evapotranspiration gathered at high densities on broad acre scales have untold value and because the sensors are lightweight and don’t require large power budgets, they come along for the ride at little cost. But, just like the old mantra, “gas, grass, or ass, nobody rides for free”, these sensors provide potential revenue benefits just by them being present. I’ve touched on just a few data genres here. In fact, the question for universities, governmental bodies, and other institutions becomes, “How much will you pay us to attach your sensor payload to the Forest Walker?” # Noise Suppression Only you can prevent Metallica filling the surrounds with 120 dB of sound. Easy enough, just turn the car stereo off. But what of a fleet of 50 Forest Walkers operating in the backcountry or near a township? 500? 5000? Each one has a wood chipper, an internal combustion engine, hydraulic pumps, actuators, and more cooling fans than you can shake a stick at. It’s a walking, screaming fire-breathing dragon operating continuously, day and night, twenty-four hours a day, three hundred sixty-five days a year. The sound will negatively affect all living things and that impacts behaviors. Serious engineering consideration and prowess must deliver a silencing blow to the major issue of noise. It would be foolish to think that a fleet of Forest Walkers could be silent, but if not a major design consideration, then the entire idea is dead on arrival. Townships would not allow them to operate even if they solved the problem of widespread fuel load and neither would governmental entities, and rightly so. Nothing, not man nor beast, would want to be subjected to an eternal, infernal scream even if it were to end within days as the fleet moved further away after consuming what it could. Noise and heat are the only real pollutants of this system; taking noise seriously from the beginning is paramount. # Fire Safety A “fire-breathing dragon” is not the worst description of the Forest Walker. It eats wood, combusts it at very high temperatures and excretes carbon; and it does so in an extremely flammable environment. Bad mix for one Forest Walker, worse for many. One must take extreme pains to ensure that during normal operation, a Forest Walker could fall over, walk through tinder dry brush, or get pounded into the ground by a meteorite from Krypton and it wouldn’t destroy epic swaths of trees and baby deer. I envision an ultimate test of a prototype to include dowsing it in grain alcohol while it’s wrapped up in toilet paper like a pledge at a fraternity party. If it runs for 72 hours and doesn’t set everything on fire, then maybe outside entities won’t be fearful of something that walks around forests with a constant fire in its belly. # The Wrap How we think about what can be done with and adjacent to Bitcoin is at least as important as Bitcoin’s economic standing itself. For those who will tell me that this entire idea is without merit, I say, “OK, fine. You can come up with something, too.” What can we plug Bitcoin into that, like a battery, makes something that does not work, work? That’s the lesson I get from this entire exercise. No one was ever going to hire teams of humans to go out and "clean the forest". There's no money in that. The data collection and sales from such an endeavor might provide revenues over the break-even point but investment demands Alpha in this day and age. But, plug Bitcoin into an almost viable system and, voilà! We tip the scales to achieve lift-off. Let’s face it, we haven’t scratched the surface of Bitcoin’s forcing function on our minds. Not because it’s Bitcoin, but because of what that invention means. The question that pushes me to approach things this way is, “what can we create that one system’s waste is another system’s feedstock?” The Forest Walker system’s only real waste is the conversion of low entropy energy (wood and syngas) into high entropy energy (heat and noise). All other output is beneficial to humanity. Bitcoin, I believe, is the first product of a new mode of human imagination. An imagination newly forged over the past few millennia of being lied to, stolen from, distracted and otherwise mis-allocated to a black hole of the nonsensical. We are waking up. What I have presented is not science fiction. Everything I have described here is well within the realm of possibility. The question is one of viability, at least in terms of the detritus of the old world we find ourselves departing from. This system would take a non-trivial amount of time and resources to develop. I think the system would garner extensive long-term contracts from those who have the most to lose from wildfires, the most to gain from hyperaccurate data sets, and, of course, securing the most precious asset in the world. Many may not see it that way, for they seek Alpha and are therefore blind to other possibilities. Others will see only the possibilities; of thinking in a new way, of looking at things differently, and dreaming of what comes next. @ e4950c93:1b99eccd
2025-04-03 14:53:56**Heureu-x-se d’avoir trouvé une information utile sur ce site ?** Soutenez le projet en faisant un don pour le faire vivre et remercier les contribut-eur-rice-s. --- **En bitcoin** <img src="https://coinos.io/qr/bc1q79er6c5mvvktvmvcstsnelv4j6tv3wdhw2k7ej/raw" width="200" height="200"> bc1qkm8me8l9563wvsl9sklzt4hdcuny3tlejznj7d ⚡️` origin-nature@coinos.io` --- **En euros, dollars, ou toute autre monnaie prise en charge** *Promesses uniquement pour le moment :* <a href="https://liberapay.com/origin-nature/"> <img src="!(image)[https://liberapay.com/assets/liberapay/icon-v2_black-on-yellow.svg]?etag=._QLQJKsW7OwBQqn7ASPxRA~~" width="200" height="200"> </a> --- Contactez-nous si vous souhaitez faire un don avec toute autre cryptomonnaie. --- ### 💡 Un modèle de partage de la valeur La moitié des dons est redistribuée aux contribut-eur-rice-s qui créent la valeur du site, pour expérimenter un modèle de partage de revenus sur Internet — un modèle qui respecte vos données et ne cherche pas à capter votre attention. L’autre moitié permet de couvrir les frais de fonctionnement du site.
@ e4950c93:1b99eccd
2025-04-03 14:53:56**Heureu-x-se d’avoir trouvé une information utile sur ce site ?** Soutenez le projet en faisant un don pour le faire vivre et remercier les contribut-eur-rice-s. --- **En bitcoin** <img src="https://coinos.io/qr/bc1q79er6c5mvvktvmvcstsnelv4j6tv3wdhw2k7ej/raw" width="200" height="200"> bc1qkm8me8l9563wvsl9sklzt4hdcuny3tlejznj7d ⚡️` origin-nature@coinos.io` --- **En euros, dollars, ou toute autre monnaie prise en charge** *Promesses uniquement pour le moment :* <a href="https://liberapay.com/origin-nature/"> <img src="!(image)[https://liberapay.com/assets/liberapay/icon-v2_black-on-yellow.svg]?etag=._QLQJKsW7OwBQqn7ASPxRA~~" width="200" height="200"> </a> --- Contactez-nous si vous souhaitez faire un don avec toute autre cryptomonnaie. --- ### 💡 Un modèle de partage de la valeur La moitié des dons est redistribuée aux contribut-eur-rice-s qui créent la valeur du site, pour expérimenter un modèle de partage de revenus sur Internet — un modèle qui respecte vos données et ne cherche pas à capter votre attention. L’autre moitié permet de couvrir les frais de fonctionnement du site. @ fd78c37f:a0ec0833
2025-04-01 11:49:06In this edition, we invited Keypleb, the founder of Bitcoin Indonesia, to share how he built the Bitcoin community in Indonesia, overcoming challenges like member turnover and venue selection, while driving the adoption and growth of Bitcoin. **YakiHonne**: Welcome, Keypleb. Before we begin, let me briefly introduce YakiHonne. YakiHonne is a decentralized media client built on Nostr—a protocol designed to empower freedom of speech through technology. It enables creators to own their voices and assets while offering innovative tools like smart widgets, verified notes, and support for long-form content. We focus on free speech and free media by user privacy and data to be protected. So before starting the interview, I'd like to hear about yourself and your community. **Keypleb**:My name is Keypleb, though it’s a pseudonym—a name I use to respect privacy. I'm a co-founder of Bitcoin Indonesia, Bitcoin House Bali, and Code Orange, a new developer school we launched at a conference just a few days ago. We focus on driving adoption through meetups, hackathons, and technical workshops. I'll dive into more details later, but that's a brief overview. I'm based in Bali now, though I travel a lot and consider myself quite nomadic. Great to be here. **YakiHonne**: What sparked your interest in Bitcoin and what motivated you to create a community on Bitcoin? **Keypleb**:I first got interested in Bitcoin because it solved a specific problem. At the time, I didn’t know exactly what the solution was, but the problem was that I couldn’t afford a home. Back in 2019, I was living in London, and a two-bedroom apartment was £600,000, which was insanely expensive. First-time buyers like myself simply couldn’t afford it. Why was it so expensive? Why was buying a house so hard? During the COVID lockdown, I had more time on my hands and started listening to Michael Saylor on a Bitcoin podcast, where he talked about how the system is rigged, and that’s why people work hard but still can’t afford a house. That really resonated with me. So I started looking for a community, but unfortunately, there wasn’t one.. **Keypleb**:After moving to Bali, I attended a lot of crypto meetups, especially scammy altcoin ones, thinking, “There has to be a solution.” But none of them resonated with me. There was no sense of freedom, and no real discussion about inflation resistance. I remembered a podcast from Dea Reskita, an Indonesian host who’s pretty well-known online. I reached out to her and said, “ you’ve got to help me. I’m surrounded by all these shitcoiners, and I can’t take it anymore. I need a real community. Is anything happening?” She replied, “Yes, something is happening. We should restart these meetups next month.” And that’s how it all began. **Keypleb**:There’s also another story about how we started Bitcoin House and how Bitcoin in Asia came to be, but maybe I’ll save that for later. Anyway, the spark of interest came from Bitcoin solving a real problem, and my drive to keep going came from the lack of quality meetups. Now, we’ve hosted 31 meetups, launched Bitcoin House and Code Orange, and the movement is growing rapidly.  **YakiHonne**: That’s such an amazing story—going from being on the brink of homelessness to creating something so impactful, and keeping it running every day, bringing new people into the journey. It’s truly inspiring. I’m curious about how the community started. How did you manage to attract members and build a strong community? What challenges did you face along the way? **Keypleb**:It all started with our first meetup at the end of 2022, which was two and a half years ago now. At that time, we sent out an email to a group from a previous database, and the first meetup had around 20 people, which was a good start. However, problems quickly arose as people started dropping off, and the community lacked retention. In Bali, people come and go, usually staying for no more than two months, leading to a lack of long-term participation. This became one of our challenges: how to attract more people and, more importantly, get the same people to keep coming back. While I've been coming back for two and a half years, not everyone is able to return as often, and that has been a real challenge. **Keypleb**:Actually, I should also mention how I met my co-founders—Marius, Diana, and Dimas. We met at the 2023 Indonesia Bitcoin Conference. As time went on, we kept hosting meetups and had a lot of fun each time, though the locations kept changing. One of the initial challenges was that we didn't realize the importance of having a fixed meetup location. We changed venues several times before we realized that having a consistent location is crucial. If anyone wants to run a meetup, it's best to always choose a fixed location. We learned this through trial and error, but now it's no longer an issue. **Keypleb**:Since the conference, my co-founders and I have been working together, consistently putting in the effort. This is why our community has grown so large—so far, we are hosting 31 monthly meetups, 6 of which are in Bali. This means there is a bitcoin meetup almost every day on a regular basis. We've also established Bitcoin House Bali, a physical space, and the movement is growing rapidly. Without this movement, the region would face many challenges, including inflation and heavy censorship. It all started from just one meetup.  **YakiHonne**: It's amazing to see how you met your co-founders and how you’ve built something incredible that continues to grow today. What advice would you give to someone looking to start a successful Bitcoin community right now? **Keypleb**:First, one very important piece of advice is to ensure that every meetup is held at the same location regularly. We realized this challenge through trial and error. To help others who are interested, we’ve published our meetup guide on GitHub, where everyone can check it out. For example, meetups should be held regularly, ideally once a month, or even once a week. In Chiang Mai, the Bitcoin meetup starts every Thursday at 7 PM, and everyone knows the time and location, making it easy to join without having to look up the next meetup. **Keypleb**:Additionally, our meetup structure is very simple. First, we do a round of introductions where everyone shares their name, where they’re from, and what Bitcoin means to them. This usually takes about 15 minutes. Then, we discuss three main questions: First, why do we need Bitcoin? The discussion typically focuses on two main issues Bitcoin addresses: inflation and censorship;Secondly, how to buy Bitcoin? We usually ask who wants to buy some Bitcoin, and then we do a small purchase together and conduct a P2P trade to demonstrate how easy it is to buy Bitcoin. Lastly, how to store Bitcoin? We introduce self-custody and show how to use hardware wallets (like Trezor), explaining the concept of the 12 words and private keys. **Keypleb**:The whole meetup usually wraps up in about an hour, after which people can continue socializing at Bitcoin House or wherever the meetup is taking place. In short, keeping the meetup simple and efficient, and ensuring a fixed location for each event, are key factors in building a successful community. **YakiHonne**: What's the major approach? Is it more technical, or do you focus on non-technical aspects, or do you cover both? **Keypleb**:Our approach includes both technical and non-technical content. Initially, our meetups were completely non-technical, just casual gatherings for people to socialize. Over time, however, we've evolved to incorporate more technical content. **Keypleb**:Out of the 31 monthly regular meetups we host, most of them have been non-technical, simply regular gatherings held at the same time and place according to our meetup guide. For example, we host the “Bitcoin for Beginners” meetup, which is designed for newcomers and takes place every second Friday of the month at 5 PM at the Bitcoin House Bali. This is entirely non-technical. Additionally, every Wednesday at Bitcoin House, we host the “My First Bitcoin” course. While the course touches on some technical aspects, such as seed phrases and backups, it’s still beginner-friendly and not too technical. The course runs for 10 weeks, and we plan to offer it in the local language at Bali University to help the local community better understand Bitcoin. **Keypleb**:On the other hand, we also offer highly technical content. We launched a new program called “Code Orange,” which is specifically designed for developers and programmers. We use the “Decoding Bitcoin” website, created by Jamal, which is a learning platform for developers. Many developer schools, like Code Orange, use this resource. Additionally, we host “Code Orange” meetups where we dive into the technical aspects of Bitcoin, such as how mining works and how to prevent single points of failure. **Keypleb**:We also organize technical workshops, such as “How to Defend Against a Five-Dollar Wrench Attack,” which is closely related to security. Recently, there have been some kidnapping incidents in Bali, and many people are concerned about their Bitcoin being stolen. To address this, we plan to hold a workshop on how to protect Bitcoin against such attacks. Additionally, we host hackathons and other high-tech events, and we just completed a very successful beginner-level hackathon. **Keypleb**:In summary, our community caters to everyone, from beginners to technical experts. For beginners, we offer easy-to-understand, non-technical content, while for experienced Bitcoiners, we provide in-depth technical material.  **YakiHonne**: It's great to approach it in both ways, so everyone gets their own "piece of the cake."Now, I'd like to dive into the technical side. What advice would you give to technically inclined individuals or organizations looking to contribute to the Bitcoin ecosystem? How should they approach the technical aspects of Bitcoin if they want to get involved? **Keypleb**:I have some additional advice. First, technical individuals can sign up for the “Decoding Bitcoin” course that starts on 18th March 2025 or join our “Code Orange” program and participate in the end-of-year hackathon. If they are technically proficient, this will be a great opportunity. “Decoding Bitcoin” is great for beginners, but it’s also useful for technical individuals. If someone is very skilled, they can start contributing code right away. If they find the course too easy, they can skip it and dive directly into more advanced projects. Additionally, Bitshala and Chaincode Labs offer advanced courses, which more technically advanced individuals can choose to pursue.  **Keypleb**:Additionally, it's worth mentioning that the Bitcoin Dev Project has a great platform where technical individuals can find “Good First Issue” or open-source projects to start contributing code. You'll learn about the philosophy behind Bitcoin and why it's more meaningful than other “shitcoins.” Once you’ve taken enough “orange pills” (the philosophy and technology of Bitcoin), you can dive deeper into Bitcoin core development and potentially start coding in C++. If you're interested, you can join specific projects like Nostr, Fedimint or E-Cash. **YakiHonne**: I’d like to move on to the next question: How do you see Bitcoin communities evolving as technology progresses, particularly in areas like scalability, privacy, and adaptability to other systems? Keypleb:I believe the Bitcoin community will continue to evolve, and it has already made incredible progress. Two and a half years ago, we started alone in Bali, with just ourselves. We began in the official phase and have had numerous conversations throughout the year. For example, we are now starting a Bitcoin club at a university in Bali; we just need to find a passionate, driven “Bitcoin maximalist,” and the Bitcoin club will begin. Like what our friends did in Banyuwangi, Indonesia, these clubs could eventually evolve into Bitcoin houses. **Keypleb**:Regarding privacy and scalability, the community is making strides. We’re big fans of Fedi, which builds on top of the Fedimint protocol and uses e-cash to scale Bitcoin while improving privacy. Fedi low fees and high privacy potential give Bitcoin great opportunities in this area. **Keypleb**:As for Bitcoin's compatibility with fiat systems, although Bitcoin payments are illegal in some countries like Indonesia, smart developers across Southeast Asia are working on legal solutions. For example, there's a website called Pleb QR that works in Thailand, allowing you to pay in fiat via the Lightning Network. Koral is another app specifically for Indonesia. These kinds of testing products already exist and are physically possible, but we’re just waiting on regulations. My influential friends are actively lobbying the government for adoption. **Keypleb**:In summary, privacy, scalability, and compatibility with fiat systems are all works in progress, and they will continue to evolve positively. There will be more meetups, more wallet downloads, and more adoption—there’s no doubt about that. **YakiHonne**: You mentioned the concept of cross-country issues, so I have one last question: How is the government’s stance on Bitcoin? Is the political climate supportive or against Bitcoin? How do you see the government's approach to Bitcoin in your community or environment? **Keypleb**:This reminds me of a person, Jeff Booth, who once said, “We are them, the government is made up of us.” In Indonesia, many politicians actually support Bitcoin, and many of them mine Bitcoin themselves. When money is involved, the incentive is strong, and politicians naturally like to make more money. As a result, Indonesia has a large Bitcoin mining scene. However, overall, the Indonesian government is against Bitcoin, as seen in their ban on Bitcoin payments. The 2011 currency law states that any currency other than the Indonesian Rupiah (IDR) cannot be used, and violators can face up to one year in prison or a fine. This means you cannot pay with US dollars, lira, euros, pesos or pounds. **Keypleb**:This shows that the government’s legal system is somewhat fragile. It’s understandable that the government is concerned about disruptive technologies like Bitcoin, especially with such a fragile fiat system. Indonesia has also seen many arrests. In 2016, Bank Indonesia issued a letter announcing a crackdown on cryptocurrency payments. Those involved in paying in Bitcoin had their funds seized, and the police cooperated in shutting down businesses accepting Bitcoin payments in the cities. While this isn't very friendly, it does highlight the fragility of the existing system. We also believe that a new executive order may be introduced in the future, similar to when President Roosevelt in 1933 ordered Americans to hand over all their gold with his Executive Order 6102. If it happened before, it could happen again. **Keypleb**:Therefore, we predict that Bitcoin custody could become a legal issue, which is one of the reasons we blur the faces of participants at every meetup. We need to protect the community from any potential risks. But overall, we remain optimistic. Despite the government ban, the ideology of Bitcoin is unstoppable, and its spread cannot be stopped. So, we are very optimistic about the future. **YakiHonne**: I think almost every government around the world, even in Africa, faces similar issues with Bitcoin. Some governments might want Bitcoin but hesitate to openly accept it due to the fear of it undermining the traditional financial system, which, of course, could eventually happen. But hopefully, as the new generation comes into power, we'll see more Bitcoin-friendly governments. So, thank you so much for sharing your insights and advice. I really appreciate your time and the valuable input you've provided. **Keypleb**:I'm really glad this conversation enlightened me. I enjoyed it a lot, and it made me reflect on how much work we're doing and how valuable it is. There are a lot of problems out there, with censorship being the biggest one, followed by inflation, which is also a major issue depending on the region. But Bitcoin is open, the community is growing, and people are fighting against censorship and internet shutdowns in places like Indonesia and beyond. The movement is definitely growing. So, I'm very happy to be here and have this chat. Thanks again. Bitcoin Indonesia nostr: nostr:npub1y4qd2zhtn05gnsaaq5xfejzfk4a32638tx6gpp9g8k6e42g9d66qaxhcr3 Keypleb nostr: nostr:npub190trvg63e6tyqlwlj6lccqpftx76lckj25c006vwx3dzvdl88yxs2nyqdx
@ fd78c37f:a0ec0833
2025-04-01 11:49:06In this edition, we invited Keypleb, the founder of Bitcoin Indonesia, to share how he built the Bitcoin community in Indonesia, overcoming challenges like member turnover and venue selection, while driving the adoption and growth of Bitcoin. **YakiHonne**: Welcome, Keypleb. Before we begin, let me briefly introduce YakiHonne. YakiHonne is a decentralized media client built on Nostr—a protocol designed to empower freedom of speech through technology. It enables creators to own their voices and assets while offering innovative tools like smart widgets, verified notes, and support for long-form content. We focus on free speech and free media by user privacy and data to be protected. So before starting the interview, I'd like to hear about yourself and your community. **Keypleb**:My name is Keypleb, though it’s a pseudonym—a name I use to respect privacy. I'm a co-founder of Bitcoin Indonesia, Bitcoin House Bali, and Code Orange, a new developer school we launched at a conference just a few days ago. We focus on driving adoption through meetups, hackathons, and technical workshops. I'll dive into more details later, but that's a brief overview. I'm based in Bali now, though I travel a lot and consider myself quite nomadic. Great to be here. **YakiHonne**: What sparked your interest in Bitcoin and what motivated you to create a community on Bitcoin? **Keypleb**:I first got interested in Bitcoin because it solved a specific problem. At the time, I didn’t know exactly what the solution was, but the problem was that I couldn’t afford a home. Back in 2019, I was living in London, and a two-bedroom apartment was £600,000, which was insanely expensive. First-time buyers like myself simply couldn’t afford it. Why was it so expensive? Why was buying a house so hard? During the COVID lockdown, I had more time on my hands and started listening to Michael Saylor on a Bitcoin podcast, where he talked about how the system is rigged, and that’s why people work hard but still can’t afford a house. That really resonated with me. So I started looking for a community, but unfortunately, there wasn’t one.. **Keypleb**:After moving to Bali, I attended a lot of crypto meetups, especially scammy altcoin ones, thinking, “There has to be a solution.” But none of them resonated with me. There was no sense of freedom, and no real discussion about inflation resistance. I remembered a podcast from Dea Reskita, an Indonesian host who’s pretty well-known online. I reached out to her and said, “ you’ve got to help me. I’m surrounded by all these shitcoiners, and I can’t take it anymore. I need a real community. Is anything happening?” She replied, “Yes, something is happening. We should restart these meetups next month.” And that’s how it all began. **Keypleb**:There’s also another story about how we started Bitcoin House and how Bitcoin in Asia came to be, but maybe I’ll save that for later. Anyway, the spark of interest came from Bitcoin solving a real problem, and my drive to keep going came from the lack of quality meetups. Now, we’ve hosted 31 meetups, launched Bitcoin House and Code Orange, and the movement is growing rapidly.  **YakiHonne**: That’s such an amazing story—going from being on the brink of homelessness to creating something so impactful, and keeping it running every day, bringing new people into the journey. It’s truly inspiring. I’m curious about how the community started. How did you manage to attract members and build a strong community? What challenges did you face along the way? **Keypleb**:It all started with our first meetup at the end of 2022, which was two and a half years ago now. At that time, we sent out an email to a group from a previous database, and the first meetup had around 20 people, which was a good start. However, problems quickly arose as people started dropping off, and the community lacked retention. In Bali, people come and go, usually staying for no more than two months, leading to a lack of long-term participation. This became one of our challenges: how to attract more people and, more importantly, get the same people to keep coming back. While I've been coming back for two and a half years, not everyone is able to return as often, and that has been a real challenge. **Keypleb**:Actually, I should also mention how I met my co-founders—Marius, Diana, and Dimas. We met at the 2023 Indonesia Bitcoin Conference. As time went on, we kept hosting meetups and had a lot of fun each time, though the locations kept changing. One of the initial challenges was that we didn't realize the importance of having a fixed meetup location. We changed venues several times before we realized that having a consistent location is crucial. If anyone wants to run a meetup, it's best to always choose a fixed location. We learned this through trial and error, but now it's no longer an issue. **Keypleb**:Since the conference, my co-founders and I have been working together, consistently putting in the effort. This is why our community has grown so large—so far, we are hosting 31 monthly meetups, 6 of which are in Bali. This means there is a bitcoin meetup almost every day on a regular basis. We've also established Bitcoin House Bali, a physical space, and the movement is growing rapidly. Without this movement, the region would face many challenges, including inflation and heavy censorship. It all started from just one meetup.  **YakiHonne**: It's amazing to see how you met your co-founders and how you’ve built something incredible that continues to grow today. What advice would you give to someone looking to start a successful Bitcoin community right now? **Keypleb**:First, one very important piece of advice is to ensure that every meetup is held at the same location regularly. We realized this challenge through trial and error. To help others who are interested, we’ve published our meetup guide on GitHub, where everyone can check it out. For example, meetups should be held regularly, ideally once a month, or even once a week. In Chiang Mai, the Bitcoin meetup starts every Thursday at 7 PM, and everyone knows the time and location, making it easy to join without having to look up the next meetup. **Keypleb**:Additionally, our meetup structure is very simple. First, we do a round of introductions where everyone shares their name, where they’re from, and what Bitcoin means to them. This usually takes about 15 minutes. Then, we discuss three main questions: First, why do we need Bitcoin? The discussion typically focuses on two main issues Bitcoin addresses: inflation and censorship;Secondly, how to buy Bitcoin? We usually ask who wants to buy some Bitcoin, and then we do a small purchase together and conduct a P2P trade to demonstrate how easy it is to buy Bitcoin. Lastly, how to store Bitcoin? We introduce self-custody and show how to use hardware wallets (like Trezor), explaining the concept of the 12 words and private keys. **Keypleb**:The whole meetup usually wraps up in about an hour, after which people can continue socializing at Bitcoin House or wherever the meetup is taking place. In short, keeping the meetup simple and efficient, and ensuring a fixed location for each event, are key factors in building a successful community. **YakiHonne**: What's the major approach? Is it more technical, or do you focus on non-technical aspects, or do you cover both? **Keypleb**:Our approach includes both technical and non-technical content. Initially, our meetups were completely non-technical, just casual gatherings for people to socialize. Over time, however, we've evolved to incorporate more technical content. **Keypleb**:Out of the 31 monthly regular meetups we host, most of them have been non-technical, simply regular gatherings held at the same time and place according to our meetup guide. For example, we host the “Bitcoin for Beginners” meetup, which is designed for newcomers and takes place every second Friday of the month at 5 PM at the Bitcoin House Bali. This is entirely non-technical. Additionally, every Wednesday at Bitcoin House, we host the “My First Bitcoin” course. While the course touches on some technical aspects, such as seed phrases and backups, it’s still beginner-friendly and not too technical. The course runs for 10 weeks, and we plan to offer it in the local language at Bali University to help the local community better understand Bitcoin. **Keypleb**:On the other hand, we also offer highly technical content. We launched a new program called “Code Orange,” which is specifically designed for developers and programmers. We use the “Decoding Bitcoin” website, created by Jamal, which is a learning platform for developers. Many developer schools, like Code Orange, use this resource. Additionally, we host “Code Orange” meetups where we dive into the technical aspects of Bitcoin, such as how mining works and how to prevent single points of failure. **Keypleb**:We also organize technical workshops, such as “How to Defend Against a Five-Dollar Wrench Attack,” which is closely related to security. Recently, there have been some kidnapping incidents in Bali, and many people are concerned about their Bitcoin being stolen. To address this, we plan to hold a workshop on how to protect Bitcoin against such attacks. Additionally, we host hackathons and other high-tech events, and we just completed a very successful beginner-level hackathon. **Keypleb**:In summary, our community caters to everyone, from beginners to technical experts. For beginners, we offer easy-to-understand, non-technical content, while for experienced Bitcoiners, we provide in-depth technical material.  **YakiHonne**: It's great to approach it in both ways, so everyone gets their own "piece of the cake."Now, I'd like to dive into the technical side. What advice would you give to technically inclined individuals or organizations looking to contribute to the Bitcoin ecosystem? How should they approach the technical aspects of Bitcoin if they want to get involved? **Keypleb**:I have some additional advice. First, technical individuals can sign up for the “Decoding Bitcoin” course that starts on 18th March 2025 or join our “Code Orange” program and participate in the end-of-year hackathon. If they are technically proficient, this will be a great opportunity. “Decoding Bitcoin” is great for beginners, but it’s also useful for technical individuals. If someone is very skilled, they can start contributing code right away. If they find the course too easy, they can skip it and dive directly into more advanced projects. Additionally, Bitshala and Chaincode Labs offer advanced courses, which more technically advanced individuals can choose to pursue.  **Keypleb**:Additionally, it's worth mentioning that the Bitcoin Dev Project has a great platform where technical individuals can find “Good First Issue” or open-source projects to start contributing code. You'll learn about the philosophy behind Bitcoin and why it's more meaningful than other “shitcoins.” Once you’ve taken enough “orange pills” (the philosophy and technology of Bitcoin), you can dive deeper into Bitcoin core development and potentially start coding in C++. If you're interested, you can join specific projects like Nostr, Fedimint or E-Cash. **YakiHonne**: I’d like to move on to the next question: How do you see Bitcoin communities evolving as technology progresses, particularly in areas like scalability, privacy, and adaptability to other systems? Keypleb:I believe the Bitcoin community will continue to evolve, and it has already made incredible progress. Two and a half years ago, we started alone in Bali, with just ourselves. We began in the official phase and have had numerous conversations throughout the year. For example, we are now starting a Bitcoin club at a university in Bali; we just need to find a passionate, driven “Bitcoin maximalist,” and the Bitcoin club will begin. Like what our friends did in Banyuwangi, Indonesia, these clubs could eventually evolve into Bitcoin houses. **Keypleb**:Regarding privacy and scalability, the community is making strides. We’re big fans of Fedi, which builds on top of the Fedimint protocol and uses e-cash to scale Bitcoin while improving privacy. Fedi low fees and high privacy potential give Bitcoin great opportunities in this area. **Keypleb**:As for Bitcoin's compatibility with fiat systems, although Bitcoin payments are illegal in some countries like Indonesia, smart developers across Southeast Asia are working on legal solutions. For example, there's a website called Pleb QR that works in Thailand, allowing you to pay in fiat via the Lightning Network. Koral is another app specifically for Indonesia. These kinds of testing products already exist and are physically possible, but we’re just waiting on regulations. My influential friends are actively lobbying the government for adoption. **Keypleb**:In summary, privacy, scalability, and compatibility with fiat systems are all works in progress, and they will continue to evolve positively. There will be more meetups, more wallet downloads, and more adoption—there’s no doubt about that. **YakiHonne**: You mentioned the concept of cross-country issues, so I have one last question: How is the government’s stance on Bitcoin? Is the political climate supportive or against Bitcoin? How do you see the government's approach to Bitcoin in your community or environment? **Keypleb**:This reminds me of a person, Jeff Booth, who once said, “We are them, the government is made up of us.” In Indonesia, many politicians actually support Bitcoin, and many of them mine Bitcoin themselves. When money is involved, the incentive is strong, and politicians naturally like to make more money. As a result, Indonesia has a large Bitcoin mining scene. However, overall, the Indonesian government is against Bitcoin, as seen in their ban on Bitcoin payments. The 2011 currency law states that any currency other than the Indonesian Rupiah (IDR) cannot be used, and violators can face up to one year in prison or a fine. This means you cannot pay with US dollars, lira, euros, pesos or pounds. **Keypleb**:This shows that the government’s legal system is somewhat fragile. It’s understandable that the government is concerned about disruptive technologies like Bitcoin, especially with such a fragile fiat system. Indonesia has also seen many arrests. In 2016, Bank Indonesia issued a letter announcing a crackdown on cryptocurrency payments. Those involved in paying in Bitcoin had their funds seized, and the police cooperated in shutting down businesses accepting Bitcoin payments in the cities. While this isn't very friendly, it does highlight the fragility of the existing system. We also believe that a new executive order may be introduced in the future, similar to when President Roosevelt in 1933 ordered Americans to hand over all their gold with his Executive Order 6102. If it happened before, it could happen again. **Keypleb**:Therefore, we predict that Bitcoin custody could become a legal issue, which is one of the reasons we blur the faces of participants at every meetup. We need to protect the community from any potential risks. But overall, we remain optimistic. Despite the government ban, the ideology of Bitcoin is unstoppable, and its spread cannot be stopped. So, we are very optimistic about the future. **YakiHonne**: I think almost every government around the world, even in Africa, faces similar issues with Bitcoin. Some governments might want Bitcoin but hesitate to openly accept it due to the fear of it undermining the traditional financial system, which, of course, could eventually happen. But hopefully, as the new generation comes into power, we'll see more Bitcoin-friendly governments. So, thank you so much for sharing your insights and advice. I really appreciate your time and the valuable input you've provided. **Keypleb**:I'm really glad this conversation enlightened me. I enjoyed it a lot, and it made me reflect on how much work we're doing and how valuable it is. There are a lot of problems out there, with censorship being the biggest one, followed by inflation, which is also a major issue depending on the region. But Bitcoin is open, the community is growing, and people are fighting against censorship and internet shutdowns in places like Indonesia and beyond. The movement is definitely growing. So, I'm very happy to be here and have this chat. Thanks again. Bitcoin Indonesia nostr: nostr:npub1y4qd2zhtn05gnsaaq5xfejzfk4a32638tx6gpp9g8k6e42g9d66qaxhcr3 Keypleb nostr: nostr:npub190trvg63e6tyqlwlj6lccqpftx76lckj25c006vwx3dzvdl88yxs2nyqdx @ fd06f542:8d6d54cd
2025-03-31 01:55:18## 什么是nostrbook? ----- nostrbook 是基于nostr 社区技术存储在 nostr relay server上的长文(30023)文章。 查看浏览,采用的是 [docsify](https://docsify.js.org/#/) 技术。整个网站技术无须部署服务器占用太多的存储空间。 可以实现轻量级部署。
@ fd06f542:8d6d54cd
2025-03-31 01:55:18## 什么是nostrbook? ----- nostrbook 是基于nostr 社区技术存储在 nostr relay server上的长文(30023)文章。 查看浏览,采用的是 [docsify](https://docsify.js.org/#/) 技术。整个网站技术无须部署服务器占用太多的存储空间。 可以实现轻量级部署。 @ fd06f542:8d6d54cd
2025-03-31 01:45:36{"coverurl":"https://cdn.nostrcheck.me/fd06f542bc6c06a39881810de917e6c5d277dfb51689a568ad7b7a548d6d54cd/232dd9c092e023beecb5410052bd48add702765258dcc66f176a56f02b09cf6a.webp","title":"NostrBook站点日记","author":"nostrbook"}
@ fd06f542:8d6d54cd
2025-03-31 01:45:36{"coverurl":"https://cdn.nostrcheck.me/fd06f542bc6c06a39881810de917e6c5d277dfb51689a568ad7b7a548d6d54cd/232dd9c092e023beecb5410052bd48add702765258dcc66f176a56f02b09cf6a.webp","title":"NostrBook站点日记","author":"nostrbook"} @ fd06f542:8d6d54cd
2025-03-30 02:16:24> __Warning__ `unrecommended`: deprecated in favor of [NIP-17](17.md) NIP-04 ====== Encrypted Direct Message ------------------------ `final` `unrecommended` `optional` A special event with kind `4`, meaning "encrypted direct message". It is supposed to have the following attributes: **`content`** MUST be equal to the base64-encoded, aes-256-cbc encrypted string of anything a user wants to write, encrypted using a shared cipher generated by combining the recipient's public-key with the sender's private-key; this appended by the base64-encoded initialization vector as if it was a querystring parameter named "iv". The format is the following: `"content": "<encrypted_text>?iv=<initialization_vector>"`. **`tags`** MUST contain an entry identifying the receiver of the message (such that relays may naturally forward this event to them), in the form `["p", "<pubkey, as a hex string>"]`. **`tags`** MAY contain an entry identifying the previous message in a conversation or a message we are explicitly replying to (such that contextual, more organized conversations may happen), in the form `["e", "<event_id>"]`. **Note**: By default in the [libsecp256k1](https://github.com/bitcoin-core/secp256k1) ECDH implementation, the secret is the SHA256 hash of the shared point (both X and Y coordinates). In Nostr, only the X coordinate of the shared point is used as the secret and it is NOT hashed. If using libsecp256k1, a custom function that copies the X coordinate must be passed as the `hashfp` argument in `secp256k1_ecdh`. See [here](https://github.com/bitcoin-core/secp256k1/blob/master/src/modules/ecdh/main_impl.h#L29). Code sample for generating such an event in JavaScript: ```js import crypto from 'crypto' import * as secp from '@noble/secp256k1' let sharedPoint = secp.getSharedSecret(ourPrivateKey, '02' + theirPublicKey) let sharedX = sharedPoint.slice(1, 33) let iv = crypto.randomFillSync(new Uint8Array(16)) var cipher = crypto.createCipheriv( 'aes-256-cbc', Buffer.from(sharedX), iv ) let encryptedMessage = cipher.update(text, 'utf8', 'base64') encryptedMessage += cipher.final('base64') let ivBase64 = Buffer.from(iv.buffer).toString('base64') let event = { pubkey: ourPubKey, created_at: Math.floor(Date.now() / 1000), kind: 4, tags: [['p', theirPublicKey]], content: encryptedMessage + '?iv=' + ivBase64 } ``` ## Security Warning This standard does not go anywhere near what is considered the state-of-the-art in encrypted communication between peers, and it leaks metadata in the events, therefore it must not be used for anything you really need to keep secret, and only with relays that use `AUTH` to restrict who can fetch your `kind:4` events. ## Client Implementation Warning Clients *should not* search and replace public key or note references from the `.content`. If processed like a regular text note (where `@npub...` is replaced with `#[0]` with a `["p", "..."]` tag) the tags are leaked and the mentioned user will receive the message in their inbox.
@ fd06f542:8d6d54cd
2025-03-30 02:16:24> __Warning__ `unrecommended`: deprecated in favor of [NIP-17](17.md) NIP-04 ====== Encrypted Direct Message ------------------------ `final` `unrecommended` `optional` A special event with kind `4`, meaning "encrypted direct message". It is supposed to have the following attributes: **`content`** MUST be equal to the base64-encoded, aes-256-cbc encrypted string of anything a user wants to write, encrypted using a shared cipher generated by combining the recipient's public-key with the sender's private-key; this appended by the base64-encoded initialization vector as if it was a querystring parameter named "iv". The format is the following: `"content": "<encrypted_text>?iv=<initialization_vector>"`. **`tags`** MUST contain an entry identifying the receiver of the message (such that relays may naturally forward this event to them), in the form `["p", "<pubkey, as a hex string>"]`. **`tags`** MAY contain an entry identifying the previous message in a conversation or a message we are explicitly replying to (such that contextual, more organized conversations may happen), in the form `["e", "<event_id>"]`. **Note**: By default in the [libsecp256k1](https://github.com/bitcoin-core/secp256k1) ECDH implementation, the secret is the SHA256 hash of the shared point (both X and Y coordinates). In Nostr, only the X coordinate of the shared point is used as the secret and it is NOT hashed. If using libsecp256k1, a custom function that copies the X coordinate must be passed as the `hashfp` argument in `secp256k1_ecdh`. See [here](https://github.com/bitcoin-core/secp256k1/blob/master/src/modules/ecdh/main_impl.h#L29). Code sample for generating such an event in JavaScript: ```js import crypto from 'crypto' import * as secp from '@noble/secp256k1' let sharedPoint = secp.getSharedSecret(ourPrivateKey, '02' + theirPublicKey) let sharedX = sharedPoint.slice(1, 33) let iv = crypto.randomFillSync(new Uint8Array(16)) var cipher = crypto.createCipheriv( 'aes-256-cbc', Buffer.from(sharedX), iv ) let encryptedMessage = cipher.update(text, 'utf8', 'base64') encryptedMessage += cipher.final('base64') let ivBase64 = Buffer.from(iv.buffer).toString('base64') let event = { pubkey: ourPubKey, created_at: Math.floor(Date.now() / 1000), kind: 4, tags: [['p', theirPublicKey]], content: encryptedMessage + '?iv=' + ivBase64 } ``` ## Security Warning This standard does not go anywhere near what is considered the state-of-the-art in encrypted communication between peers, and it leaks metadata in the events, therefore it must not be used for anything you really need to keep secret, and only with relays that use `AUTH` to restrict who can fetch your `kind:4` events. ## Client Implementation Warning Clients *should not* search and replace public key or note references from the `.content`. If processed like a regular text note (where `@npub...` is replaced with `#[0]` with a `["p", "..."]` tag) the tags are leaked and the mentioned user will receive the message in their inbox. @ 57d1a264:69f1fee1
2025-03-29 17:15:17 - Once activated, "Accept From Any Mint” is the default setting. This is the easiest way to get started, let's the user start acceptance Cashu ecash just out of the box. - If someone does want to be selective, they can choose “Accept From Trusted Mints,” and that brings up a field where they can add specific mint URLs they trust. - “Find a Mint” section on the right with a button links directly to bitcoinmints.com, already filtered for Cashu mints, so users can easily browse options. - Mint info modal shows mint technical details stuff from the NUT06 spec. Since this is geared towards the more technical users I left the field names and NUT number as-is instead of trying to make it more semantic. originally posted at https://stacker.news/items/928800
@ 57d1a264:69f1fee1
2025-03-29 17:15:17 - Once activated, "Accept From Any Mint” is the default setting. This is the easiest way to get started, let's the user start acceptance Cashu ecash just out of the box. - If someone does want to be selective, they can choose “Accept From Trusted Mints,” and that brings up a field where they can add specific mint URLs they trust. - “Find a Mint” section on the right with a button links directly to bitcoinmints.com, already filtered for Cashu mints, so users can easily browse options. - Mint info modal shows mint technical details stuff from the NUT06 spec. Since this is geared towards the more technical users I left the field names and NUT number as-is instead of trying to make it more semantic. originally posted at https://stacker.news/items/928800 @ b2caa9b3:9eab0fb5
2025-04-01 20:29:01 For years, I’ve been shifting my life away from traditional systems and toward Bitcoin. I calculate my expenses in sats, buy airtime and online data with BTC, and continue exploring new ways to integrate Bitcoin into my daily life. While I’m not yet fully living on Bitcoin, I am getting closer with each step.  Since discovering Nostr, my perspective on decentralization has deepened. More than just a financial shift, it's a complete lifestyle transformation. Years ago, after facing injustice in my home country, I took the first step toward a new way of living. That decision led me to where I am today—a minimalist, a nomad, and a believer in financial freedom through Bitcoin.  I once served in the military, owned a house, and drove a nice car. My life looked very different back then. But over time, I realized that true freedom wasn’t in possessions—it was in mobility, independence, and the ability to control my own finances. Now, all I own fits into a backpack weighing less than 12 kg. My lifestyle is simple, yet rich in experiences. March 14 marks eight years since I embraced my nomadic lifestyle. What started as a leap into the unknown has become my way of life. Living with less has given me more—the freedom to move, to explore, and to be truly independent. The more I immerse myself in the Bitcoin ecosystem, the more I see its potential to reshape not only my life but the world around me.  The journey isn’t over. In fact, it’s just beginning. Let’s see where this path leads as I go further into the blockchain revolution!   
@ b2caa9b3:9eab0fb5
2025-04-01 20:29:01 For years, I’ve been shifting my life away from traditional systems and toward Bitcoin. I calculate my expenses in sats, buy airtime and online data with BTC, and continue exploring new ways to integrate Bitcoin into my daily life. While I’m not yet fully living on Bitcoin, I am getting closer with each step.  Since discovering Nostr, my perspective on decentralization has deepened. More than just a financial shift, it's a complete lifestyle transformation. Years ago, after facing injustice in my home country, I took the first step toward a new way of living. That decision led me to where I am today—a minimalist, a nomad, and a believer in financial freedom through Bitcoin.  I once served in the military, owned a house, and drove a nice car. My life looked very different back then. But over time, I realized that true freedom wasn’t in possessions—it was in mobility, independence, and the ability to control my own finances. Now, all I own fits into a backpack weighing less than 12 kg. My lifestyle is simple, yet rich in experiences. March 14 marks eight years since I embraced my nomadic lifestyle. What started as a leap into the unknown has become my way of life. Living with less has given me more—the freedom to move, to explore, and to be truly independent. The more I immerse myself in the Bitcoin ecosystem, the more I see its potential to reshape not only my life but the world around me.  The journey isn’t over. In fact, it’s just beginning. Let’s see where this path leads as I go further into the blockchain revolution!    @ 5ffb8e1b:255b6735
2025-03-29 13:57:02As a fellow Nostrich you might have noticed some of my #arlist posts. It is my effort to curate artists that are active on Nostr and make it easier for other users to find content that they are interested in. By now I have posted six or seven posts mentioning close to fifty artists, the problem so far is that it's only a list of handles and it is up to reader to click on each in order to find out what are the artist behind the names all about. Now I am going to start creating blog posts with a few artists mentioned in each, with short descriptions of their work and an image or to. I would love to have some more automated mode of curation but I still couldn't figure out what is a good way for it. I've looked at Listr, Primal custom feeds and Yakihonne curations but none seem to enable me to make a list of npubs that is then turned into a feed that I could publicly share for others to views. Any advice on how to achieve this is VERY welcome ! And now lets get to the first batch of artists I want to share with you. ### Eugene Gorbachenko ### nostr:npub1082uhnrnxu7v0gesfl78uzj3r89a8ds2gj3dvuvjnw5qlz4a7udqwrqdnd Artist from Ukrain creating amazing realistic watercolor paintings. He is very active on Nostr but is very unnoticed for some stange reason. Make sure to repost the painting that you liked the most to help other Nostr users to discover his great art. ![!(image)[https://m.primal.net/PxJc.png]]() ### Siritravelsketch ### nostr:npub14lqzjhfvdc9psgxzznq8xys8pfq8p4fqsvtr6llyzraq90u9m8fqevhssu a a lovely lady from Thailand making architecture from all around the world spring alive in her ink skethes. Dynamic lines gives it a dreamy magical feel, sometimes supported by soft watercolor strokes takes you to a ferytale layer of reality. ![!(image)[https://m.primal.net/PxJj.png]]() ### BureuGewas ### nostr:npub1k78qzy2s9ap4klshnu9tcmmcnr3msvvaeza94epsgptr7jce6p9sa2ggp4 a a master of the clasic oil painting. From traditional still life to modern day subjects his paintings makes you feel the textures and light of the scene more intense then reality itself. ![!(image)[https://m.primal.net/PxKS.png]]() You can see that I'm no art critic, but I am trying my best. If anyone else is interested to join me in this curration adventure feel free to reach out ! With love, Agi Choote
@ 5ffb8e1b:255b6735
2025-03-29 13:57:02As a fellow Nostrich you might have noticed some of my #arlist posts. It is my effort to curate artists that are active on Nostr and make it easier for other users to find content that they are interested in. By now I have posted six or seven posts mentioning close to fifty artists, the problem so far is that it's only a list of handles and it is up to reader to click on each in order to find out what are the artist behind the names all about. Now I am going to start creating blog posts with a few artists mentioned in each, with short descriptions of their work and an image or to. I would love to have some more automated mode of curation but I still couldn't figure out what is a good way for it. I've looked at Listr, Primal custom feeds and Yakihonne curations but none seem to enable me to make a list of npubs that is then turned into a feed that I could publicly share for others to views. Any advice on how to achieve this is VERY welcome ! And now lets get to the first batch of artists I want to share with you. ### Eugene Gorbachenko ### nostr:npub1082uhnrnxu7v0gesfl78uzj3r89a8ds2gj3dvuvjnw5qlz4a7udqwrqdnd Artist from Ukrain creating amazing realistic watercolor paintings. He is very active on Nostr but is very unnoticed for some stange reason. Make sure to repost the painting that you liked the most to help other Nostr users to discover his great art. ![!(image)[https://m.primal.net/PxJc.png]]() ### Siritravelsketch ### nostr:npub14lqzjhfvdc9psgxzznq8xys8pfq8p4fqsvtr6llyzraq90u9m8fqevhssu a a lovely lady from Thailand making architecture from all around the world spring alive in her ink skethes. Dynamic lines gives it a dreamy magical feel, sometimes supported by soft watercolor strokes takes you to a ferytale layer of reality. ![!(image)[https://m.primal.net/PxJj.png]]() ### BureuGewas ### nostr:npub1k78qzy2s9ap4klshnu9tcmmcnr3msvvaeza94epsgptr7jce6p9sa2ggp4 a a master of the clasic oil painting. From traditional still life to modern day subjects his paintings makes you feel the textures and light of the scene more intense then reality itself. ![!(image)[https://m.primal.net/PxKS.png]]() You can see that I'm no art critic, but I am trying my best. If anyone else is interested to join me in this curration adventure feel free to reach out ! With love, Agi Choote @ 220522c2:61e18cb4
2025-03-25 16:05:27`draft` `optional` ## Abstract This NIP defines a new event kind for sharing and storing code snippets. Unlike regular text notes (`kind:1`), code snippets have specialized metadata like language, extension, and other code-specific attributes that enhance discoverability, syntax highlighting, and improved user experience. ## Event Kind This NIP defines `kind:1337` as a code snippet event. The `.content` field contains the actual code snippet text. ## Optional Tags - `filename` - Filename of the code snippet - `l` - Programming language name (lowercase). Examples: "javascript", "python", "rust" - `extension` - File extension (without the dot). Examples: "js", "py", "rs" - `description` - Brief description of what the code does - `runtime` - Runtime or environment specification (e.g., "node v18.15.0", "python 3.11") - `license` - License under which the code is shared (e.g., "MIT", "GPL-3.0", "Apache-2.0") - `dep` - Dependency required for the code to run (can be repeated) - `repo` - Reference to a repository where this code originates ## Format ```json { "id": "<32-bytes lowercase hex-encoded SHA-256 of the the serialized event data>", "pubkey": "<32-bytes lowercase hex-encoded public key of the event creator>", "created_at": <Unix timestamp in seconds>, "kind": 1337, "content": "function helloWorld() {\n console.log('Hello, Nostr!');\n}\n\nhelloWorld();", "tags": [ ["l", "javascript"], ["extension", "js"], ["filename", "hello-world.js"], ["description", "A basic JavaScript function that prints 'Hello, Nostr!' to the console"], ["runtime", "node v18.15.0"], ["license", "MIT"], ["repo", "https://github.com/nostr-protocol/nostr"] ], "sig": "<64-bytes signature of the id>" } ``` ## Client Behavior Clients that support this NIP SHOULD: 1. Display code snippets with proper syntax highlighting based on the language. 2. Allow copying the full code snippet with a single action. 3. Render the code with appropriate formatting, preserving whitespace and indentation. 4. Display the language and extension prominently. 5. Provide "run" functionality for supported languages when possible. 6. Display the description (if available) as part of the snippet presentation. Clients MAY provide additional functionality such as: 1. Code editing capabilities 2. Forking/modifying snippets 3. Creating executable environments based on the runtime/dependencies 4. Downloading the snippet as a file using the provided extension 5. Sharing the snippet with attribution ## References - [PR](https://github.com/nostr-protocol/nips/pull/1852) - posted w/ [comet](https://comet.md) - [notebin](https://notebin.io) - [snipsnip](https://snipsnip.dev) #nip #grownostr
@ 220522c2:61e18cb4
2025-03-25 16:05:27`draft` `optional` ## Abstract This NIP defines a new event kind for sharing and storing code snippets. Unlike regular text notes (`kind:1`), code snippets have specialized metadata like language, extension, and other code-specific attributes that enhance discoverability, syntax highlighting, and improved user experience. ## Event Kind This NIP defines `kind:1337` as a code snippet event. The `.content` field contains the actual code snippet text. ## Optional Tags - `filename` - Filename of the code snippet - `l` - Programming language name (lowercase). Examples: "javascript", "python", "rust" - `extension` - File extension (without the dot). Examples: "js", "py", "rs" - `description` - Brief description of what the code does - `runtime` - Runtime or environment specification (e.g., "node v18.15.0", "python 3.11") - `license` - License under which the code is shared (e.g., "MIT", "GPL-3.0", "Apache-2.0") - `dep` - Dependency required for the code to run (can be repeated) - `repo` - Reference to a repository where this code originates ## Format ```json { "id": "<32-bytes lowercase hex-encoded SHA-256 of the the serialized event data>", "pubkey": "<32-bytes lowercase hex-encoded public key of the event creator>", "created_at": <Unix timestamp in seconds>, "kind": 1337, "content": "function helloWorld() {\n console.log('Hello, Nostr!');\n}\n\nhelloWorld();", "tags": [ ["l", "javascript"], ["extension", "js"], ["filename", "hello-world.js"], ["description", "A basic JavaScript function that prints 'Hello, Nostr!' to the console"], ["runtime", "node v18.15.0"], ["license", "MIT"], ["repo", "https://github.com/nostr-protocol/nostr"] ], "sig": "<64-bytes signature of the id>" } ``` ## Client Behavior Clients that support this NIP SHOULD: 1. Display code snippets with proper syntax highlighting based on the language. 2. Allow copying the full code snippet with a single action. 3. Render the code with appropriate formatting, preserving whitespace and indentation. 4. Display the language and extension prominently. 5. Provide "run" functionality for supported languages when possible. 6. Display the description (if available) as part of the snippet presentation. Clients MAY provide additional functionality such as: 1. Code editing capabilities 2. Forking/modifying snippets 3. Creating executable environments based on the runtime/dependencies 4. Downloading the snippet as a file using the provided extension 5. Sharing the snippet with attribution ## References - [PR](https://github.com/nostr-protocol/nips/pull/1852) - posted w/ [comet](https://comet.md) - [notebin](https://notebin.io) - [snipsnip](https://snipsnip.dev) #nip #grownostr @ 4c96d763:80c3ee30
2025-03-24 01:43:12# Changes ## Ahmed Bedair (2): - Fix build.rs to link Security framework only for Apple targets - switch from string matching to checking the CARGO_CFG_TARGET_VENDOR value instead ## Jack Chakany (1): - update thiserror from 2.0.3 to 2.0.7 ## Ken Sedgwick (5): - drive-by warning cleanup - added multiple event unit tests - add (passing) unit test for Mention::Profile relays - drive-by clippy fixes - add relays_iter to bech32_{nprofile,nevent,naddr} ## William Casarin (32): - async: adding efficient, poll-based stream support - Release v0.5.0 - add get_profilekey_by_pubkey - nostrdb: fix subscription memory leaks - test: "fix" flaky text - release v0.5.1 - expose {Mut,}FilterField - unsubscribe from SubscriptionStreams on Drop - debug log subcount - bump nostrdb to fix since in kind queries - expose process_client_event - stream: fix polling issues leading to missed events - tags: add porcelain api for getting ids and strings - nostrdb: update to silence annoying debug logs - build: minor makefile changes - update posix bindings - filter: add nip50 search field - windows: update bindings for search features - filter: add json display - Revert "filter: add json display" - filter: fix memory leak in clone - unix: fix bindgen for writer scratch changes - win: bindgen for windows - fix lint - feat: add relay index and ingestion metadata - Release v0.6.0 - misc stuff - fix potential relay index corruption - v0.6.1 - add author_kinds query plan execution - filter: expose initial buffer size option - attempt macos build fix ## Yuki Kishimoto (2): - Take an iterator of `&str` in `Filter::tags` - Remove `tracing-subscriber` dep ## kernelkind (1): - add search_profile pushed to [nostrdb-rs:refs/heads/master](http://git.jb55.com/nostrdb-rs/commit/0d28fab41e2b829c149086a2449dbda162318abb.html)
@ 4c96d763:80c3ee30
2025-03-24 01:43:12# Changes ## Ahmed Bedair (2): - Fix build.rs to link Security framework only for Apple targets - switch from string matching to checking the CARGO_CFG_TARGET_VENDOR value instead ## Jack Chakany (1): - update thiserror from 2.0.3 to 2.0.7 ## Ken Sedgwick (5): - drive-by warning cleanup - added multiple event unit tests - add (passing) unit test for Mention::Profile relays - drive-by clippy fixes - add relays_iter to bech32_{nprofile,nevent,naddr} ## William Casarin (32): - async: adding efficient, poll-based stream support - Release v0.5.0 - add get_profilekey_by_pubkey - nostrdb: fix subscription memory leaks - test: "fix" flaky text - release v0.5.1 - expose {Mut,}FilterField - unsubscribe from SubscriptionStreams on Drop - debug log subcount - bump nostrdb to fix since in kind queries - expose process_client_event - stream: fix polling issues leading to missed events - tags: add porcelain api for getting ids and strings - nostrdb: update to silence annoying debug logs - build: minor makefile changes - update posix bindings - filter: add nip50 search field - windows: update bindings for search features - filter: add json display - Revert "filter: add json display" - filter: fix memory leak in clone - unix: fix bindgen for writer scratch changes - win: bindgen for windows - fix lint - feat: add relay index and ingestion metadata - Release v0.6.0 - misc stuff - fix potential relay index corruption - v0.6.1 - add author_kinds query plan execution - filter: expose initial buffer size option - attempt macos build fix ## Yuki Kishimoto (2): - Take an iterator of `&str` in `Filter::tags` - Remove `tracing-subscriber` dep ## kernelkind (1): - add search_profile pushed to [nostrdb-rs:refs/heads/master](http://git.jb55.com/nostrdb-rs/commit/0d28fab41e2b829c149086a2449dbda162318abb.html) @ fd06f542:8d6d54cd
2025-03-30 02:11:00NIP-03 ====== OpenTimestamps Attestations for Events -------------------------------------- `draft` `optional` This NIP defines an event with `kind:1040` that can contain an [OpenTimestamps](https://opentimestamps.org/) proof for any other event: ```json { "kind": 1040 "tags": [ ["e", <event-id>, <relay-url>], ["alt", "opentimestamps attestation"] ], "content": <base64-encoded OTS file data> } ``` - The OpenTimestamps proof MUST prove the referenced `e` event id as its digest. - The `content` MUST be the full content of an `.ots` file containing at least one Bitcoin attestation. This file SHOULD contain a **single** Bitcoin attestation (as not more than one valid attestation is necessary and less bytes is better than more) and no reference to "pending" attestations since they are useless in this context. ### Example OpenTimestamps proof verification flow Using [`nak`](https://github.com/fiatjaf/nak), [`jq`](https://jqlang.github.io/jq/) and [`ots`](https://github.com/fiatjaf/ots): ```bash ~> nak req -i e71c6ea722987debdb60f81f9ea4f604b5ac0664120dd64fb9d23abc4ec7c323 wss://nostr-pub.wellorder.net | jq -r .content | ots verify > using an esplora server at https://blockstream.info/api - sequence ending on block 810391 is valid timestamp validated at block [810391] ```
@ fd06f542:8d6d54cd
2025-03-30 02:11:00NIP-03 ====== OpenTimestamps Attestations for Events -------------------------------------- `draft` `optional` This NIP defines an event with `kind:1040` that can contain an [OpenTimestamps](https://opentimestamps.org/) proof for any other event: ```json { "kind": 1040 "tags": [ ["e", <event-id>, <relay-url>], ["alt", "opentimestamps attestation"] ], "content": <base64-encoded OTS file data> } ``` - The OpenTimestamps proof MUST prove the referenced `e` event id as its digest. - The `content` MUST be the full content of an `.ots` file containing at least one Bitcoin attestation. This file SHOULD contain a **single** Bitcoin attestation (as not more than one valid attestation is necessary and less bytes is better than more) and no reference to "pending" attestations since they are useless in this context. ### Example OpenTimestamps proof verification flow Using [`nak`](https://github.com/fiatjaf/nak), [`jq`](https://jqlang.github.io/jq/) and [`ots`](https://github.com/fiatjaf/ots): ```bash ~> nak req -i e71c6ea722987debdb60f81f9ea4f604b5ac0664120dd64fb9d23abc4ec7c323 wss://nostr-pub.wellorder.net | jq -r .content | ots verify > using an esplora server at https://blockstream.info/api - sequence ending on block 810391 is valid timestamp validated at block [810391] ``` @ a60e79e0:1e0e6813
2025-03-23 16:10:10**This is a long form note test of a post that lives on my Nostr educational website [Hello Nostr](https://hellonostr.xyz) ** In early 2025, social media is the most common use case for Nostr (and probably the reason you're reading this). Nostr is SO much [more](https://hellonostr.xyz/tags/?tag=other) than just social media, but that's where the bulk of the activity is, and is what I'm focusing on in this post. Even though the protocol is still so young, that has not prevented an explosion of excellent [social media](https://hellonostr.xyz/tags/?tag=social) focused clients that predominantly coalesce around the Twitter (X) style feed, containing shorter form content, often with images, and the ability to comment, like and share. This first steps guide showcases one of the most polished and simplest examples of such a client, [Primal](https://primal.net). Primal is a cross platform app, that also works on your computer too. The steps that follow are demonstrated on iPhone, but should be identical for Android users. There may be some topics of concepts here that are new to you, to learn more about them, check out our [Nostr 101](https://hellonostr.xyz/101) to learn more about Nostr basics and why it matters. You can and should explore all of the other options available to you, that's the beauty of Nostr, you're free to choose how and where to interact with your social network. No lock in. No walled gardens. True freedom.  # Getting Started 1. Go to your app store and download Primal to your [Android](https://play.google.com/store/apps/details?id=net.primal.android) or [iPhone](https://apps.apple.com/us/app/primal/id1673134518) 2. Open Primal and choose Create Account. Choose your public display name and add a short bio about yourself.  3. Select your chosen interests from the list provided. This will bootstrap your feed and auto-follow a number of accounts so that your feed is not completely empty when starting out.  4. Review your account info and tap Create Account Now. Take note of the fact that 'Your Nostr Key is available in your Account Settings'. We'll revisit this shortly.  5. Next is an optional step of activating the wallet feature within Primal. Having a wallet within your social client enables you to send and receive value (known as 'Zaps') in the form of Bitcoin. On Facebook and Twitter you can like a post, but it means much more to send someone fractions of a penny (or more if you like) to show your appreciation for their insights. You'll need to provide some personal information to enable the wallet, including an email address. > Using the internal wallet and purchasing sats with your credit card will tie your Nostr identity to your real ID. Think **very** carefully before carrying out this step. <br/> Learn more in the detailed section at the end of this post.  6. That's it, you're now set up and ready to start sharing your thoughts, feelings and memes with the world via a decentralized and censorship resistant social network. To post your first note and say hello to the Nostr world, tap the + in the bottom right corner.  7. If you activated the wallet at step 5, you might want to deposit some Bitcoin in there to allow you to send some value to your friends. There are three main ways to do this: - Post some awesome content and have people send you value in the form of 'Zaps' - Send some Bitcoin from a wallet you already have - Purchase some directly within Primal The latter is made very simple thanks to the in-app purchase feature, which allows you to purchase a small amount with the card you likely already have connected to your Apple/Google account. All you need to do is tap 'Buy Sats Now'.  8. Next, let's look at the different feeds available on our home screen. Tap 'Latest' at the top of the screen and you can toggle between three different types of home feeds, great for discovering new people and content.  9. Let's assume you already have some friends on Nostr and want to find and follow them. Tap the search icon in the top right corner, the enter the name of the person you want to follow. Once on their profile, simply tap the 'Follow' button.  10. So you found a friend and want to start interacting with them so they know you made it over to Nostr. Simply find a note you like and choose from the different types of interactions available. From left to right they are: - **Comment** - **Zap** (send value from your wallet to theirs) - **Like** - **Repost** - **Bookmark**  When Zapping, a single tap will send a tiny amount of 42 sats. If you want to send more, or a custom amount, tap and hold the zap button to bring up a selector menu. All default zap amounts are configurable in the app settings page.  11. After you've started posting and interacting with others, you'll likely receive some notifications to tell you. Notifications can be filtered into interaction types.  12. Another great way to find more people to follow and interact with is to use the discover page. To open it, tap the compass in the bottom right corner of the screen. Here you'll be able to browse different types of pre-built feeds, trending profiles, notes with large zaps and extra topics.  # The Important Part You might have noticed that throughout that setup, you were not asked for a unique username, nor were you asked for a password. So how the hell is this secure? What happens if you log out? Is your account lost forever? This is where Nostr really starts to shine. Just like in Bitcoin or other cryptocurrencies, your Nostr account is protected by a 'Private Key'. Anyone with knowledge of the private key can access your account **in any Nostr client**. No private key, no access. So let's make sure you have a backup copy of it, so you can still recover access to your account in the event you lose your phone! Tap on your profile image in the top left of the screen. Then tap Settings > Keys. Here you'll see two keys, one public and one private. Your public key is how people find you on Nostr. It is often referred to by its more technical name 'nPub' which is the prefix if the key itself. Your public key is designed to be exactly that, public! Your private key is sometimes referred to by its technical name 'nSec' which is also the prefix of the key. Copy your private key and paste it somewhere safe and secure, in a location accessible independently from your phone, and only by you.  If you were to lose your phone, or accidentally delete the Primal app, now all you'd need to do is head back to step 1 above and choose Sign In. You'd then be asked to paste your private key, after which your profile and content would be magically restored. > Your private key can be imported into any other Nostr social client for the same result. # Things to Consider This post has one primary focus - To get you from zero to posting and zapping in the quickest time and with the least friction. To achieve this, there are some trade-offs made that you should be aware of. ### Custodial Wallet The built in wallet is a custodial one. This means that the funds within are ultimately controlled by the developers behind Primal. They may be good actors, but you should approach the amount of money you maintain inside this wallet accordingly. If your wallet balance ever gets to a balance that makes you uncomfortable, you should send a good chunk of it out to another Bitcoin wallet where you control the keys. I recommend [Phoenix](https://phoenix.acinq.co/) or [Zeus](https://zeusln.com/). > Those sats are never truly yours until you withdraw them to a self-custodial wallet ### Wallet Privacy If you choose to top up the wallet using the convenient in-app purchase method, you will tie that small amount of Bitcoin ownership to your Nostr account. If you Nostr account is literally your name, you might not have an issue with this, but often times people like to remain pseudonymous online. If you fall into that category, using your credit card to deposit Bitcoin into your Nostr account is not a good idea. Android users of Primal can use an advanced technology called Nostr Wallet Connect (NWC) to connect an external Lightning wallet to their Nostr account in Primal. We'll cover this in a subsequent post. > Your private key allows you to take your profile and social network to any other client --- If you found this post useful, please share it with your peers and consider following and zapping me on Nostr. If you write to me and let me know that you found me via this post, I'll be sure to Zap you back! ⚡️
@ a60e79e0:1e0e6813
2025-03-23 16:10:10**This is a long form note test of a post that lives on my Nostr educational website [Hello Nostr](https://hellonostr.xyz) ** In early 2025, social media is the most common use case for Nostr (and probably the reason you're reading this). Nostr is SO much [more](https://hellonostr.xyz/tags/?tag=other) than just social media, but that's where the bulk of the activity is, and is what I'm focusing on in this post. Even though the protocol is still so young, that has not prevented an explosion of excellent [social media](https://hellonostr.xyz/tags/?tag=social) focused clients that predominantly coalesce around the Twitter (X) style feed, containing shorter form content, often with images, and the ability to comment, like and share. This first steps guide showcases one of the most polished and simplest examples of such a client, [Primal](https://primal.net). Primal is a cross platform app, that also works on your computer too. The steps that follow are demonstrated on iPhone, but should be identical for Android users. There may be some topics of concepts here that are new to you, to learn more about them, check out our [Nostr 101](https://hellonostr.xyz/101) to learn more about Nostr basics and why it matters. You can and should explore all of the other options available to you, that's the beauty of Nostr, you're free to choose how and where to interact with your social network. No lock in. No walled gardens. True freedom.  # Getting Started 1. Go to your app store and download Primal to your [Android](https://play.google.com/store/apps/details?id=net.primal.android) or [iPhone](https://apps.apple.com/us/app/primal/id1673134518) 2. Open Primal and choose Create Account. Choose your public display name and add a short bio about yourself.  3. Select your chosen interests from the list provided. This will bootstrap your feed and auto-follow a number of accounts so that your feed is not completely empty when starting out.  4. Review your account info and tap Create Account Now. Take note of the fact that 'Your Nostr Key is available in your Account Settings'. We'll revisit this shortly.  5. Next is an optional step of activating the wallet feature within Primal. Having a wallet within your social client enables you to send and receive value (known as 'Zaps') in the form of Bitcoin. On Facebook and Twitter you can like a post, but it means much more to send someone fractions of a penny (or more if you like) to show your appreciation for their insights. You'll need to provide some personal information to enable the wallet, including an email address. > Using the internal wallet and purchasing sats with your credit card will tie your Nostr identity to your real ID. Think **very** carefully before carrying out this step. <br/> Learn more in the detailed section at the end of this post.  6. That's it, you're now set up and ready to start sharing your thoughts, feelings and memes with the world via a decentralized and censorship resistant social network. To post your first note and say hello to the Nostr world, tap the + in the bottom right corner.  7. If you activated the wallet at step 5, you might want to deposit some Bitcoin in there to allow you to send some value to your friends. There are three main ways to do this: - Post some awesome content and have people send you value in the form of 'Zaps' - Send some Bitcoin from a wallet you already have - Purchase some directly within Primal The latter is made very simple thanks to the in-app purchase feature, which allows you to purchase a small amount with the card you likely already have connected to your Apple/Google account. All you need to do is tap 'Buy Sats Now'.  8. Next, let's look at the different feeds available on our home screen. Tap 'Latest' at the top of the screen and you can toggle between three different types of home feeds, great for discovering new people and content.  9. Let's assume you already have some friends on Nostr and want to find and follow them. Tap the search icon in the top right corner, the enter the name of the person you want to follow. Once on their profile, simply tap the 'Follow' button.  10. So you found a friend and want to start interacting with them so they know you made it over to Nostr. Simply find a note you like and choose from the different types of interactions available. From left to right they are: - **Comment** - **Zap** (send value from your wallet to theirs) - **Like** - **Repost** - **Bookmark**  When Zapping, a single tap will send a tiny amount of 42 sats. If you want to send more, or a custom amount, tap and hold the zap button to bring up a selector menu. All default zap amounts are configurable in the app settings page.  11. After you've started posting and interacting with others, you'll likely receive some notifications to tell you. Notifications can be filtered into interaction types.  12. Another great way to find more people to follow and interact with is to use the discover page. To open it, tap the compass in the bottom right corner of the screen. Here you'll be able to browse different types of pre-built feeds, trending profiles, notes with large zaps and extra topics.  # The Important Part You might have noticed that throughout that setup, you were not asked for a unique username, nor were you asked for a password. So how the hell is this secure? What happens if you log out? Is your account lost forever? This is where Nostr really starts to shine. Just like in Bitcoin or other cryptocurrencies, your Nostr account is protected by a 'Private Key'. Anyone with knowledge of the private key can access your account **in any Nostr client**. No private key, no access. So let's make sure you have a backup copy of it, so you can still recover access to your account in the event you lose your phone! Tap on your profile image in the top left of the screen. Then tap Settings > Keys. Here you'll see two keys, one public and one private. Your public key is how people find you on Nostr. It is often referred to by its more technical name 'nPub' which is the prefix if the key itself. Your public key is designed to be exactly that, public! Your private key is sometimes referred to by its technical name 'nSec' which is also the prefix of the key. Copy your private key and paste it somewhere safe and secure, in a location accessible independently from your phone, and only by you.  If you were to lose your phone, or accidentally delete the Primal app, now all you'd need to do is head back to step 1 above and choose Sign In. You'd then be asked to paste your private key, after which your profile and content would be magically restored. > Your private key can be imported into any other Nostr social client for the same result. # Things to Consider This post has one primary focus - To get you from zero to posting and zapping in the quickest time and with the least friction. To achieve this, there are some trade-offs made that you should be aware of. ### Custodial Wallet The built in wallet is a custodial one. This means that the funds within are ultimately controlled by the developers behind Primal. They may be good actors, but you should approach the amount of money you maintain inside this wallet accordingly. If your wallet balance ever gets to a balance that makes you uncomfortable, you should send a good chunk of it out to another Bitcoin wallet where you control the keys. I recommend [Phoenix](https://phoenix.acinq.co/) or [Zeus](https://zeusln.com/). > Those sats are never truly yours until you withdraw them to a self-custodial wallet ### Wallet Privacy If you choose to top up the wallet using the convenient in-app purchase method, you will tie that small amount of Bitcoin ownership to your Nostr account. If you Nostr account is literally your name, you might not have an issue with this, but often times people like to remain pseudonymous online. If you fall into that category, using your credit card to deposit Bitcoin into your Nostr account is not a good idea. Android users of Primal can use an advanced technology called Nostr Wallet Connect (NWC) to connect an external Lightning wallet to their Nostr account in Primal. We'll cover this in a subsequent post. > Your private key allows you to take your profile and social network to any other client --- If you found this post useful, please share it with your peers and consider following and zapping me on Nostr. If you write to me and let me know that you found me via this post, I'll be sure to Zap you back! ⚡️ @ e3ba5e1a:5e433365
2025-01-13 16:47:27My blog posts and reading material have both been on a decidedly economics-heavy slant recently. The topic today, incentives, squarely falls into the category of economics. However, when I say economics, I’m not talking about “analyzing supply and demand curves.” I’m talking about the true basis of economics: understanding how human beings make decisions in a world of scarcity. A fair definition of incentive is “a reward or punishment that motivates behavior to achieve a desired outcome.” When most people think about economic incentives, they’re thinking of money. If I offer my son $5 if he washes the dishes, I’m incentivizing certain behavior. We can’t guarantee that he’ll do what I want him to do, but we can agree that the incentive structure itself will guide and ultimately determine what outcome will occur. The great thing about monetary incentives is how easy they are to talk about and compare. “Would I rather make $5 washing the dishes or $10 cleaning the gutters?” But much of the world is incentivized in non-monetary ways too. For example, using the “punishment” half of the definition above, I might threaten my son with losing Nintendo Switch access if he doesn’t wash the dishes. No money is involved, but I’m still incentivizing behavior. And there are plenty of incentives beyond our direct control\! My son is *also* incentivized to not wash dishes because it’s boring, or because he has some friends over that he wants to hang out with, or dozens of other things. Ultimately, the conflicting array of different incentive structures placed on him will ultimately determine what actions he chooses to take. ## Why incentives matter A phrase I see often in discussions—whether they are political, parenting, economic, or business—is “if they could **just** do…” Each time I see that phrase, I cringe a bit internally. Usually, the underlying assumption of the statement is “if people would behave contrary to their incentivized behavior then things would be better.” For example: * If my kids would just go to bed when I tell them, they wouldn’t be so cranky in the morning. * If people would just use the recycling bin, we wouldn’t have such a landfill problem. * If people would just stop being lazy, our team would deliver our project on time. In all these cases, the speakers are seemingly flummoxed as to why the people in question don’t behave more rationally. The problem is: each group is behaving perfectly rationally. * The kids have a high time preference, and care more about the joy of staying up now than the crankiness in the morning. Plus, they don’t really suffer the consequences of morning crankiness, their parents do. * No individual suffers much from their individual contribution to a landfill. If they stopped growing the size of the landfill, it would make an insignificant difference versus the amount of effort they need to engage in to properly recycle. * If a team doesn’t properly account for the productivity of individuals on a project, each individual receives less harm from their own inaction. Sure, the project may be delayed, company revenue may be down, and they may even risk losing their job when the company goes out of business. But their laziness individually won’t determine the entirety of that outcome. By contrast, they greatly benefit from being lazy by getting to relax at work, go on social media, read a book, or do whatever else they do when they’re supposed to be working.  My point here is that, as long as you ignore the reality of how incentives drive human behavior, you’ll fail at getting the outcomes you want. If everything I wrote up until now made perfect sense, you understand the premise of this blog post. The rest of it will focus on a bunch of real-world examples to hammer home the point, and demonstrate how versatile this mental model is. ## Running a company Let’s say I run my own company, with myself as the only employee. My personal revenue will be 100% determined by my own actions. If I decide to take Tuesday afternoon off and go fishing, I’ve chosen to lose that afternoon’s revenue. Implicitly, I’ve decided that the enjoyment I get from an afternoon of fishing is greater than the potential revenue. You may think I’m being lazy, but it’s my decision to make. In this situation, the incentive–money–is perfectly aligned with my actions. Compare this to a typical company/employee relationship. I might have a bank of Paid Time Off (PTO) days, in which case once again my incentives are relatively aligned. I know that I can take off 15 days throughout the year, and I’ve chosen to use half a day for the fishing trip. All is still good. What about unlimited time off? Suddenly incentives are starting to misalign. I don’t directly pay a price for not showing up to work on Tuesday. Or Wednesday as well, for that matter. I might ultimately be fired for not doing my job, but that will take longer to work its way through the system than simply not making any money for the day taken off. Compensation overall falls into this misaligned incentive structure. Let’s forget about taking time off. Instead, I work full time on a software project I’m assigned. But instead of using the normal toolchain we’re all used to at work, I play around with a new programming language. I get the fun and joy of playing with new technology, and potentially get to pad my resume a bit when I’m ready to look for a new job. But my current company gets slower results, less productivity, and is forced to subsidize my extracurricular learning. When a CEO has a bonus structure based on profitability, he’ll do everything he can to make the company profitable. This might include things that actually benefit the company, like improving product quality, reducing internal red tape, or finding cheaper vendors. But it might also include destructive practices, like slashing the R\&D budget to show massive profits this year, in exchange for a catastrophe next year when the next version of the product fails to ship.  Or my favorite example. My parents owned a business when I was growing up. They had a back office where they ran operations like accounting. All of the furniture was old couches from our house. After all, any money they spent on furniture came right out of their paychecks\! But in a large corporate environment, each department is generally given a budget for office furniture, a budget which doesn’t roll over year-to-year. The result? Executives make sure to spend the entire budget each year, often buying furniture far more expensive than they would choose if it was their own money. There are plenty of details you can quibble with above. It’s in a company’s best interest to give people downtime so that they can come back recharged. Having good ergonomic furniture can in fact increase productivity in excess of the money spent on it. But overall, the picture is pretty clear: in large corporate structures, you’re guaranteed to have mismatches between the company’s goals and the incentive structure placed on individuals. Using our model from above, we can lament how lazy, greedy, and unethical the employees are for doing what they’re incentivized to do instead of what’s right. But that’s simply ignoring the reality of human nature. # Moral hazard Moral hazard is a situation where one party is incentivized to take on more risk because another party will bear the consequences. Suppose I tell my son when he turns 21 (or whatever legal gambling age is) that I’ll cover all his losses for a day at the casino, but he gets to keep all the winnings. What do you think he’s going to do? The most logical course of action is to place the largest possible bets for as long as possible, asking me to cover each time he loses, and taking money off the table and into his bank account each time he wins.  But let’s look at a slightly more nuanced example. I go to a bathroom in the mall. As I’m leaving, I wash my hands. It will take me an extra 1 second to turn off the water when I’m done washing. That’s a trivial price to pay. If I *don’t* turn off the water, the mall will have to pay for many liters of wasted water, benefiting no one. But I won’t suffer any consequences at all. This is also a moral hazard, but most people will still turn off the water. Why? Usually due to some combination of other reasons such as: 1. We’re so habituated to turning off the water that we don’t even consider *not* turning it off. Put differently, the mental effort needed to not turn off the water is more expensive than the 1 second of time to turn it off. 2. Many of us have been brought up with a deep guilt about wasting resources like water. We have an internal incentive structure that makes the 1 second to turn off the water much less costly than the mental anguish of the waste we created. 3. We’re afraid we’ll be caught by someone else and face some kind of social repercussions. (Or maybe more than social. Are you sure there isn’t a law against leaving the water tap on?) Even with all that in place, you may notice that many public bathrooms use automatic water dispensers. Sure, there’s a sanitation reason for that, but it’s also to avoid this moral hazard. A common denominator in both of these is that the person taking the action that causes the liability (either the gambling or leaving the water on) is not the person who bears the responsibility for that liability (the father or the mall owner). Generally speaking, the closer together the person making the decision and the person incurring the liability are, the smaller the moral hazard. It’s easy to demonstrate that by extending the casino example a bit. I said it was the father who was covering the losses of the gambler. Many children (though not all) would want to avoid totally bankrupting their parents, or at least financially hurting them. Instead, imagine that someone from the IRS shows up at your door, hands you a credit card, and tells you you can use it at a casino all day, taking home all the chips you want. The money is coming from the government. How many people would put any restriction on how much they spend? And since we’re talking about the government already… ## Government moral hazards As I was preparing to write this blog post, the California wildfires hit. The discussions around those wildfires gave a *huge* number of examples of moral hazards. I decided to cherry-pick a few for this post. The first and most obvious one: California is asking for disaster relief funds from the federal government. That sounds wonderful. These fires were a natural disaster, so why shouldn’t the federal government pitch in and help take care of people? The problem is, once again, a moral hazard. In the case of the wildfires, California and Los Angeles both had ample actions they could have taken to mitigate the destruction of this fire: better forest management, larger fire department, keeping the water reservoirs filled, and probably much more that hasn’t come to light yet. If the federal government bails out California, it will be a clear message for the future: your mistakes will be fixed by others. You know what kind of behavior that incentivizes? More risky behavior\! Why spend state funds on forest management and extra firefighters—activities that don’t win politicians a lot of votes in general—when you could instead spend it on a football stadium, higher unemployment payments, or anything else, and then let the feds cover the cost of screw-ups. You may notice that this is virtually identical to the 2008 “too big to fail” bail-outs. Wall Street took insanely risky behavior, reaped huge profits for years, and when they eventually got caught with their pants down, the rest of us bailed them out. “Privatizing profits, socializing losses.”  And here’s the absolute best part of this: I can’t even truly blame either California *or* Wall Street. (I mean, I *do* blame them, I think their behavior is reprehensible, but you’ll see what I mean.) In a world where the rules of the game implicitly include the bail-out mentality, you would be harming your citizens/shareholders/investors if you didn’t engage in that risky behavior. Since everyone is on the hook for those socialized losses, your best bet is to maximize those privatized profits. There’s a lot more to government and moral hazard, but I think these two cases demonstrate the crux pretty solidly. But let’s leave moral hazard behind for a bit and get to general incentivization discussions. # Non-monetary competition At least 50% of the economics knowledge I have comes from the very first econ course I took in college. That professor was amazing, and had some very colorful stories. I can’t vouch for the veracity of the two I’m about to share, but they definitely drive the point home. In the 1970s, the US had an oil shortage. To “fix” this problem, they instituted price caps on gasoline, which of course resulted in insufficient gasoline. To “fix” this problem, they instituted policies where, depending on your license plate number, you could only fill up gas on certain days of the week. (Irrelevant detail for our point here, but this just resulted in people filling up their tanks more often, no reduction in gas usage.) Anyway, my professor’s wife had a friend. My professor described in *great* detail how attractive this woman was. I’ll skip those details here since this is a PG-rated blog. In any event, she never had any trouble filling up her gas tank any day of the week. She would drive up, be told she couldn’t fill up gas today, bat her eyes at the attendant, explain how helpless she was, and was always allowed to fill up gas. This is a demonstration of *non-monetary compensation*. Most of the time in a free market, capitalist economy, people are compensated through money. When price caps come into play, there’s a limit to how much monetary compensation someone can receive. And in that case, people find other ways of competing. Like this woman’s case: through using flirtatious behavior to compensate the gas station workers to let her cheat the rules. The other example was much more insidious. Santa Monica had a problem: it was predominantly wealthy and white. They wanted to fix this problem, and decided to put in place rent controls. After some time, they discovered that Santa Monica had become *wealthier and whiter*, the exact opposite of their desired outcome. Why would that happen? Someone investigated, and ended up interviewing a landlady that demonstrated the reason. She was an older white woman, and admittedly racist. Prior to the rent controls, she would list her apartments in the newspaper, and would be legally obligated to rent to anyone who could afford it. Once rent controls were in place, she took a different tact. She knew that she would only get a certain amount for the apartment, and that the demand for apartments was higher than the supply. That meant she could be picky. She ended up finding tenants through friends-of-friends. Since it wasn’t an official advertisement, she wasn’t legally required to rent it out if someone could afford to pay. Instead, she got to interview people individually and then make them an offer. Normally, that would have resulted in receiving a lower rental price, but not under rent controls. So who did she choose? A young, unmarried, wealthy, white woman. It made perfect sense. Women were less intimidating and more likely to maintain the apartment better. Wealthy people, she determined, would be better tenants. (I have no idea if this is true in practice or not, I’m not a landlord myself.) Unmarried, because no kids running around meant less damage to the property. And, of course, white. Because she was racist, and her incentive structure made her prefer whites. You can deride her for being racist, I won’t disagree with you. But it’s simply the reality. Under the non-rent-control scenario, her profit motive for money outweighed her racism motive. But under rent control, the monetary competition was removed, and she was free to play into her racist tendencies without facing any negative consequences. ## Bureaucracy These were the two examples I remember for that course. But non-monetary compensation pops up in many more places. One highly pertinent example is bureaucracies. Imagine you have a government office, or a large corporation’s acquisition department, or the team that apportions grants at a university. In all these cases, you have a group of people making decisions about handing out money that has no monetary impact on them. If they give to the best qualified recipients, they receive no raises. If they spend the money recklessly on frivolous projects, they face no consequences. Under such an incentivization scheme, there’s little to encourage the bureaucrats to make intelligent funding decisions. Instead, they’ll be incentivized to spend the money where they recognize non-monetary benefits. This is why it’s so common to hear about expensive meals, gift bags at conferences, and even more inappropriate ways of trying to curry favor with those that hold the purse strings. Compare that ever so briefly with the purchases made by a small mom-and-pop store like my parents owned. Could my dad take a bribe to buy from a vendor who’s ripping him off? Absolutely he could\! But he’d lose more on the deal than he’d make on the bribe, since he’s directly incentivized by the deal itself. It would make much more sense for him to go with the better vendor, save $5,000 on the deal, and then treat himself to a lavish $400 meal to celebrate. # Government incentivized behavior This post is getting longer in the tooth than I’d intended, so I’ll finish off with this section and make it a bit briefer. Beyond all the methods mentioned above, government has another mechanism for modifying behavior: through directly changing incentives via legislation, regulation, and monetary policy. Let’s see some examples: * Artificial modification of interest rates encourages people to take on more debt than they would in a free capital market, leading to [malinvestment](https://en.wikipedia.org/wiki/Malinvestment) and a consumer debt crisis, and causing the boom-bust cycle we all painfully experience. * Going along with that, giving tax breaks on interest payments further artificially incentivizes people to take on debt that they wouldn’t otherwise. * During COVID-19, at some points unemployment benefits were greater than minimum wage, incentivizing people to rather stay home and not work than get a job, leading to reduced overall productivity in the economy and more printed dollars for benefits. In other words, it was a perfect recipe for inflation. * The tax code gives deductions to “help” people. That might be true, but the real impact is incentivizing people to make decisions they wouldn’t have otherwise. For example, giving out tax deductions on children encourages having more kids. Tax deductions on childcare and preschools incentivizes dual-income households. Whether or not you like the outcomes, it’s clear that it’s government that’s encouraging these outcomes to happen. * Tax incentives cause people to engage in behavior they wouldn’t otherwise (daycare+working mother, for example). * Inflation means that the value of your money goes down over time, which encourages people to spend more today, when their money has a larger impact. (Milton Friedman described this as [high living](https://www.youtube.com/watch?v=ZwNDd2_beTU).) # Conclusion The idea here is simple, and fully encapsulated in the title: incentives determine outcomes. If you want to know how to get a certain outcome from others, incentivize them to want that to happen. If you want to understand why people act in seemingly irrational ways, check their incentives. If you’re confused why leaders (and especially politicians) seem to engage in destructive behavior, check their incentives. We can bemoan these realities all we want, but they *are* realities. While there are some people who have a solid internal moral and ethical code, and that internal code incentivizes them to behave against their externally-incentivized interests, those people are rare. And frankly, those people are self-defeating. People *should* take advantage of the incentives around them. Because if they don’t, someone else will. (If you want a literary example of that last comment, see the horse in Animal Farm.) How do we improve the world under these conditions? Make sure the incentives align well with the overall goals of society. To me, it’s a simple formula: * Focus on free trade, value for value, as the basis of a society. In that system, people are always incentivized to provide value to other people. * Reduce the size of bureaucracies and large groups of all kinds. The larger an organization becomes, the farther the consequences of decisions are from those who make them. * And since the nature of human beings will be to try and create areas where they can control the incentive systems to their own benefits, make that as difficult as possible. That comes in the form of strict limits on government power, for example. And even if you don’t want to buy in to this conclusion, I hope the rest of the content was educational, and maybe a bit entertaining\!
@ e3ba5e1a:5e433365
2025-01-13 16:47:27My blog posts and reading material have both been on a decidedly economics-heavy slant recently. The topic today, incentives, squarely falls into the category of economics. However, when I say economics, I’m not talking about “analyzing supply and demand curves.” I’m talking about the true basis of economics: understanding how human beings make decisions in a world of scarcity. A fair definition of incentive is “a reward or punishment that motivates behavior to achieve a desired outcome.” When most people think about economic incentives, they’re thinking of money. If I offer my son $5 if he washes the dishes, I’m incentivizing certain behavior. We can’t guarantee that he’ll do what I want him to do, but we can agree that the incentive structure itself will guide and ultimately determine what outcome will occur. The great thing about monetary incentives is how easy they are to talk about and compare. “Would I rather make $5 washing the dishes or $10 cleaning the gutters?” But much of the world is incentivized in non-monetary ways too. For example, using the “punishment” half of the definition above, I might threaten my son with losing Nintendo Switch access if he doesn’t wash the dishes. No money is involved, but I’m still incentivizing behavior. And there are plenty of incentives beyond our direct control\! My son is *also* incentivized to not wash dishes because it’s boring, or because he has some friends over that he wants to hang out with, or dozens of other things. Ultimately, the conflicting array of different incentive structures placed on him will ultimately determine what actions he chooses to take. ## Why incentives matter A phrase I see often in discussions—whether they are political, parenting, economic, or business—is “if they could **just** do…” Each time I see that phrase, I cringe a bit internally. Usually, the underlying assumption of the statement is “if people would behave contrary to their incentivized behavior then things would be better.” For example: * If my kids would just go to bed when I tell them, they wouldn’t be so cranky in the morning. * If people would just use the recycling bin, we wouldn’t have such a landfill problem. * If people would just stop being lazy, our team would deliver our project on time. In all these cases, the speakers are seemingly flummoxed as to why the people in question don’t behave more rationally. The problem is: each group is behaving perfectly rationally. * The kids have a high time preference, and care more about the joy of staying up now than the crankiness in the morning. Plus, they don’t really suffer the consequences of morning crankiness, their parents do. * No individual suffers much from their individual contribution to a landfill. If they stopped growing the size of the landfill, it would make an insignificant difference versus the amount of effort they need to engage in to properly recycle. * If a team doesn’t properly account for the productivity of individuals on a project, each individual receives less harm from their own inaction. Sure, the project may be delayed, company revenue may be down, and they may even risk losing their job when the company goes out of business. But their laziness individually won’t determine the entirety of that outcome. By contrast, they greatly benefit from being lazy by getting to relax at work, go on social media, read a book, or do whatever else they do when they’re supposed to be working.  My point here is that, as long as you ignore the reality of how incentives drive human behavior, you’ll fail at getting the outcomes you want. If everything I wrote up until now made perfect sense, you understand the premise of this blog post. The rest of it will focus on a bunch of real-world examples to hammer home the point, and demonstrate how versatile this mental model is. ## Running a company Let’s say I run my own company, with myself as the only employee. My personal revenue will be 100% determined by my own actions. If I decide to take Tuesday afternoon off and go fishing, I’ve chosen to lose that afternoon’s revenue. Implicitly, I’ve decided that the enjoyment I get from an afternoon of fishing is greater than the potential revenue. You may think I’m being lazy, but it’s my decision to make. In this situation, the incentive–money–is perfectly aligned with my actions. Compare this to a typical company/employee relationship. I might have a bank of Paid Time Off (PTO) days, in which case once again my incentives are relatively aligned. I know that I can take off 15 days throughout the year, and I’ve chosen to use half a day for the fishing trip. All is still good. What about unlimited time off? Suddenly incentives are starting to misalign. I don’t directly pay a price for not showing up to work on Tuesday. Or Wednesday as well, for that matter. I might ultimately be fired for not doing my job, but that will take longer to work its way through the system than simply not making any money for the day taken off. Compensation overall falls into this misaligned incentive structure. Let’s forget about taking time off. Instead, I work full time on a software project I’m assigned. But instead of using the normal toolchain we’re all used to at work, I play around with a new programming language. I get the fun and joy of playing with new technology, and potentially get to pad my resume a bit when I’m ready to look for a new job. But my current company gets slower results, less productivity, and is forced to subsidize my extracurricular learning. When a CEO has a bonus structure based on profitability, he’ll do everything he can to make the company profitable. This might include things that actually benefit the company, like improving product quality, reducing internal red tape, or finding cheaper vendors. But it might also include destructive practices, like slashing the R\&D budget to show massive profits this year, in exchange for a catastrophe next year when the next version of the product fails to ship.  Or my favorite example. My parents owned a business when I was growing up. They had a back office where they ran operations like accounting. All of the furniture was old couches from our house. After all, any money they spent on furniture came right out of their paychecks\! But in a large corporate environment, each department is generally given a budget for office furniture, a budget which doesn’t roll over year-to-year. The result? Executives make sure to spend the entire budget each year, often buying furniture far more expensive than they would choose if it was their own money. There are plenty of details you can quibble with above. It’s in a company’s best interest to give people downtime so that they can come back recharged. Having good ergonomic furniture can in fact increase productivity in excess of the money spent on it. But overall, the picture is pretty clear: in large corporate structures, you’re guaranteed to have mismatches between the company’s goals and the incentive structure placed on individuals. Using our model from above, we can lament how lazy, greedy, and unethical the employees are for doing what they’re incentivized to do instead of what’s right. But that’s simply ignoring the reality of human nature. # Moral hazard Moral hazard is a situation where one party is incentivized to take on more risk because another party will bear the consequences. Suppose I tell my son when he turns 21 (or whatever legal gambling age is) that I’ll cover all his losses for a day at the casino, but he gets to keep all the winnings. What do you think he’s going to do? The most logical course of action is to place the largest possible bets for as long as possible, asking me to cover each time he loses, and taking money off the table and into his bank account each time he wins.  But let’s look at a slightly more nuanced example. I go to a bathroom in the mall. As I’m leaving, I wash my hands. It will take me an extra 1 second to turn off the water when I’m done washing. That’s a trivial price to pay. If I *don’t* turn off the water, the mall will have to pay for many liters of wasted water, benefiting no one. But I won’t suffer any consequences at all. This is also a moral hazard, but most people will still turn off the water. Why? Usually due to some combination of other reasons such as: 1. We’re so habituated to turning off the water that we don’t even consider *not* turning it off. Put differently, the mental effort needed to not turn off the water is more expensive than the 1 second of time to turn it off. 2. Many of us have been brought up with a deep guilt about wasting resources like water. We have an internal incentive structure that makes the 1 second to turn off the water much less costly than the mental anguish of the waste we created. 3. We’re afraid we’ll be caught by someone else and face some kind of social repercussions. (Or maybe more than social. Are you sure there isn’t a law against leaving the water tap on?) Even with all that in place, you may notice that many public bathrooms use automatic water dispensers. Sure, there’s a sanitation reason for that, but it’s also to avoid this moral hazard. A common denominator in both of these is that the person taking the action that causes the liability (either the gambling or leaving the water on) is not the person who bears the responsibility for that liability (the father or the mall owner). Generally speaking, the closer together the person making the decision and the person incurring the liability are, the smaller the moral hazard. It’s easy to demonstrate that by extending the casino example a bit. I said it was the father who was covering the losses of the gambler. Many children (though not all) would want to avoid totally bankrupting their parents, or at least financially hurting them. Instead, imagine that someone from the IRS shows up at your door, hands you a credit card, and tells you you can use it at a casino all day, taking home all the chips you want. The money is coming from the government. How many people would put any restriction on how much they spend? And since we’re talking about the government already… ## Government moral hazards As I was preparing to write this blog post, the California wildfires hit. The discussions around those wildfires gave a *huge* number of examples of moral hazards. I decided to cherry-pick a few for this post. The first and most obvious one: California is asking for disaster relief funds from the federal government. That sounds wonderful. These fires were a natural disaster, so why shouldn’t the federal government pitch in and help take care of people? The problem is, once again, a moral hazard. In the case of the wildfires, California and Los Angeles both had ample actions they could have taken to mitigate the destruction of this fire: better forest management, larger fire department, keeping the water reservoirs filled, and probably much more that hasn’t come to light yet. If the federal government bails out California, it will be a clear message for the future: your mistakes will be fixed by others. You know what kind of behavior that incentivizes? More risky behavior\! Why spend state funds on forest management and extra firefighters—activities that don’t win politicians a lot of votes in general—when you could instead spend it on a football stadium, higher unemployment payments, or anything else, and then let the feds cover the cost of screw-ups. You may notice that this is virtually identical to the 2008 “too big to fail” bail-outs. Wall Street took insanely risky behavior, reaped huge profits for years, and when they eventually got caught with their pants down, the rest of us bailed them out. “Privatizing profits, socializing losses.”  And here’s the absolute best part of this: I can’t even truly blame either California *or* Wall Street. (I mean, I *do* blame them, I think their behavior is reprehensible, but you’ll see what I mean.) In a world where the rules of the game implicitly include the bail-out mentality, you would be harming your citizens/shareholders/investors if you didn’t engage in that risky behavior. Since everyone is on the hook for those socialized losses, your best bet is to maximize those privatized profits. There’s a lot more to government and moral hazard, but I think these two cases demonstrate the crux pretty solidly. But let’s leave moral hazard behind for a bit and get to general incentivization discussions. # Non-monetary competition At least 50% of the economics knowledge I have comes from the very first econ course I took in college. That professor was amazing, and had some very colorful stories. I can’t vouch for the veracity of the two I’m about to share, but they definitely drive the point home. In the 1970s, the US had an oil shortage. To “fix” this problem, they instituted price caps on gasoline, which of course resulted in insufficient gasoline. To “fix” this problem, they instituted policies where, depending on your license plate number, you could only fill up gas on certain days of the week. (Irrelevant detail for our point here, but this just resulted in people filling up their tanks more often, no reduction in gas usage.) Anyway, my professor’s wife had a friend. My professor described in *great* detail how attractive this woman was. I’ll skip those details here since this is a PG-rated blog. In any event, she never had any trouble filling up her gas tank any day of the week. She would drive up, be told she couldn’t fill up gas today, bat her eyes at the attendant, explain how helpless she was, and was always allowed to fill up gas. This is a demonstration of *non-monetary compensation*. Most of the time in a free market, capitalist economy, people are compensated through money. When price caps come into play, there’s a limit to how much monetary compensation someone can receive. And in that case, people find other ways of competing. Like this woman’s case: through using flirtatious behavior to compensate the gas station workers to let her cheat the rules. The other example was much more insidious. Santa Monica had a problem: it was predominantly wealthy and white. They wanted to fix this problem, and decided to put in place rent controls. After some time, they discovered that Santa Monica had become *wealthier and whiter*, the exact opposite of their desired outcome. Why would that happen? Someone investigated, and ended up interviewing a landlady that demonstrated the reason. She was an older white woman, and admittedly racist. Prior to the rent controls, she would list her apartments in the newspaper, and would be legally obligated to rent to anyone who could afford it. Once rent controls were in place, she took a different tact. She knew that she would only get a certain amount for the apartment, and that the demand for apartments was higher than the supply. That meant she could be picky. She ended up finding tenants through friends-of-friends. Since it wasn’t an official advertisement, she wasn’t legally required to rent it out if someone could afford to pay. Instead, she got to interview people individually and then make them an offer. Normally, that would have resulted in receiving a lower rental price, but not under rent controls. So who did she choose? A young, unmarried, wealthy, white woman. It made perfect sense. Women were less intimidating and more likely to maintain the apartment better. Wealthy people, she determined, would be better tenants. (I have no idea if this is true in practice or not, I’m not a landlord myself.) Unmarried, because no kids running around meant less damage to the property. And, of course, white. Because she was racist, and her incentive structure made her prefer whites. You can deride her for being racist, I won’t disagree with you. But it’s simply the reality. Under the non-rent-control scenario, her profit motive for money outweighed her racism motive. But under rent control, the monetary competition was removed, and she was free to play into her racist tendencies without facing any negative consequences. ## Bureaucracy These were the two examples I remember for that course. But non-monetary compensation pops up in many more places. One highly pertinent example is bureaucracies. Imagine you have a government office, or a large corporation’s acquisition department, or the team that apportions grants at a university. In all these cases, you have a group of people making decisions about handing out money that has no monetary impact on them. If they give to the best qualified recipients, they receive no raises. If they spend the money recklessly on frivolous projects, they face no consequences. Under such an incentivization scheme, there’s little to encourage the bureaucrats to make intelligent funding decisions. Instead, they’ll be incentivized to spend the money where they recognize non-monetary benefits. This is why it’s so common to hear about expensive meals, gift bags at conferences, and even more inappropriate ways of trying to curry favor with those that hold the purse strings. Compare that ever so briefly with the purchases made by a small mom-and-pop store like my parents owned. Could my dad take a bribe to buy from a vendor who’s ripping him off? Absolutely he could\! But he’d lose more on the deal than he’d make on the bribe, since he’s directly incentivized by the deal itself. It would make much more sense for him to go with the better vendor, save $5,000 on the deal, and then treat himself to a lavish $400 meal to celebrate. # Government incentivized behavior This post is getting longer in the tooth than I’d intended, so I’ll finish off with this section and make it a bit briefer. Beyond all the methods mentioned above, government has another mechanism for modifying behavior: through directly changing incentives via legislation, regulation, and monetary policy. Let’s see some examples: * Artificial modification of interest rates encourages people to take on more debt than they would in a free capital market, leading to [malinvestment](https://en.wikipedia.org/wiki/Malinvestment) and a consumer debt crisis, and causing the boom-bust cycle we all painfully experience. * Going along with that, giving tax breaks on interest payments further artificially incentivizes people to take on debt that they wouldn’t otherwise. * During COVID-19, at some points unemployment benefits were greater than minimum wage, incentivizing people to rather stay home and not work than get a job, leading to reduced overall productivity in the economy and more printed dollars for benefits. In other words, it was a perfect recipe for inflation. * The tax code gives deductions to “help” people. That might be true, but the real impact is incentivizing people to make decisions they wouldn’t have otherwise. For example, giving out tax deductions on children encourages having more kids. Tax deductions on childcare and preschools incentivizes dual-income households. Whether or not you like the outcomes, it’s clear that it’s government that’s encouraging these outcomes to happen. * Tax incentives cause people to engage in behavior they wouldn’t otherwise (daycare+working mother, for example). * Inflation means that the value of your money goes down over time, which encourages people to spend more today, when their money has a larger impact. (Milton Friedman described this as [high living](https://www.youtube.com/watch?v=ZwNDd2_beTU).) # Conclusion The idea here is simple, and fully encapsulated in the title: incentives determine outcomes. If you want to know how to get a certain outcome from others, incentivize them to want that to happen. If you want to understand why people act in seemingly irrational ways, check their incentives. If you’re confused why leaders (and especially politicians) seem to engage in destructive behavior, check their incentives. We can bemoan these realities all we want, but they *are* realities. While there are some people who have a solid internal moral and ethical code, and that internal code incentivizes them to behave against their externally-incentivized interests, those people are rare. And frankly, those people are self-defeating. People *should* take advantage of the incentives around them. Because if they don’t, someone else will. (If you want a literary example of that last comment, see the horse in Animal Farm.) How do we improve the world under these conditions? Make sure the incentives align well with the overall goals of society. To me, it’s a simple formula: * Focus on free trade, value for value, as the basis of a society. In that system, people are always incentivized to provide value to other people. * Reduce the size of bureaucracies and large groups of all kinds. The larger an organization becomes, the farther the consequences of decisions are from those who make them. * And since the nature of human beings will be to try and create areas where they can control the incentive systems to their own benefits, make that as difficult as possible. That comes in the form of strict limits on government power, for example. And even if you don’t want to buy in to this conclusion, I hope the rest of the content was educational, and maybe a bit entertaining\! @ 000002de:c05780a7
2025-04-01 20:17:26I know I'm not alone in this. I don't trust the government. Any government. Its the rational response when you discover just how often its agents lie, steal, and kill. Honestly, I do not understand why so many people do trust the government. The reality is that if your team is in power, you tend to trust it. If not, you still mostly trust it but less so. That's my feel for most people at least. Trump and Rubio are bragging about how many MS-13 gang members are being deported. Many are being shipped to prisons in El Salvador. Obviously I am not opposed to criminals being put in prisons. But, how do we know these guys are actually guilty of anything other than being in the US illegally. Actually we don't even know that. It wouldn't be so bad if these people were just being shipped back to their home countries. But, instead they are getting sent straight to prison. No trial. Just the government picking people up and shipping them to prison. Is this what you signed up for Trump supporters? Many Trump supporters opposed the GW Bush policies of throwing people in off-shore prisons. Some of them US citizens. With no trial. Now these people seem rather silent. Its troubling to me. Why? Well, because the government sucks. Even if they have good intentions they make mistakes. The Innocence Project is just one group that has shown how often our legal system falsely imprisons people. I would be shocked if there weren't any Innocent men being sent to suffer in El Salvador's prisons. You may say, well these are bad dudes and we need to clean up the mess Biden made. I have sympathy for that position. But do we really want to set this president? TDS is real but it is valid to have concerns about the actions of the Trump admin. This is not the American way. Not the way I was taught at least. This is just a strong man taking action and disregarding the values of this nation and the rights of human beings. Think about it. originally posted at https://stacker.news/items/931505
@ 000002de:c05780a7
2025-04-01 20:17:26I know I'm not alone in this. I don't trust the government. Any government. Its the rational response when you discover just how often its agents lie, steal, and kill. Honestly, I do not understand why so many people do trust the government. The reality is that if your team is in power, you tend to trust it. If not, you still mostly trust it but less so. That's my feel for most people at least. Trump and Rubio are bragging about how many MS-13 gang members are being deported. Many are being shipped to prisons in El Salvador. Obviously I am not opposed to criminals being put in prisons. But, how do we know these guys are actually guilty of anything other than being in the US illegally. Actually we don't even know that. It wouldn't be so bad if these people were just being shipped back to their home countries. But, instead they are getting sent straight to prison. No trial. Just the government picking people up and shipping them to prison. Is this what you signed up for Trump supporters? Many Trump supporters opposed the GW Bush policies of throwing people in off-shore prisons. Some of them US citizens. With no trial. Now these people seem rather silent. Its troubling to me. Why? Well, because the government sucks. Even if they have good intentions they make mistakes. The Innocence Project is just one group that has shown how often our legal system falsely imprisons people. I would be shocked if there weren't any Innocent men being sent to suffer in El Salvador's prisons. You may say, well these are bad dudes and we need to clean up the mess Biden made. I have sympathy for that position. But do we really want to set this president? TDS is real but it is valid to have concerns about the actions of the Trump admin. This is not the American way. Not the way I was taught at least. This is just a strong man taking action and disregarding the values of this nation and the rights of human beings. Think about it. originally posted at https://stacker.news/items/931505 @ 592295cf:413a0db9
2025-03-29 10:59:52The journey starts from the links in this article [nostr-quick-start-guide](https://spatianostra.com/nostr-quick-start-guide/) Starting from these links building a simple path should not cover everything, because impossible. Today I saw that Verbiricha in his workshop on his channel used nstart, but then I distracted And I didn't see how he did it. ----- Go to [nstart.me](https://nstart.me/) and read: Each user is identified by a cryptographic keypair Public key, Private key (is a lot of stuff) You can insert a nickname and go, the nickname is not unique there is a email backup things interesting, but a little boring, i try to generate an email doesn't even require a strong password ok. I received the email, great, it shows me the nsec encrypted in clear, Send a copy of the file with a password, which contains the password encrypted key I know and I know it's a tongue dump. ## Multi signer bunker That's stuff, let's see what he says. They live the private key and send it to servers and you can recompose it to login at a site of the protocol nostr. If one of these servers goes offline you have the private key that you downloaded first and then reactivate a bunker. All very complicated. But if one of the servers goes offline, how can I remake the split? Maybe he's still testing. Nobody tells you where these bunkers are. Okay I have a string that is my bunker (buker://), I downloaded it, easy no, now will tell me which client accepts the bunker.. . ## Follow someone before you start? Is a cluster of 5 people Snowden, Micheal Dilger, jb55, Fiatjaf, Dianele. I choice Snowden profile, or you can select multiple profiles, extra wild. ## Now select 5 clients ### *Coracle, Chachi, Olas, Nostur, Jumble* ### The first is *Coracle* Login, ok I try to post a note and signing your note the spin does not end. Maybe the bunker is diffective. ### Let's try *Chachi* Simpler than Coracle, it has a type login that says bunker. see if I can post It worked, cool, I managed to post in a group. ## Olas is an app but also a website, but on the website requires an extension, which I do not have with this account. > If I download an app how do I pass the bunker on the phone, is it still a password, a qrcode, a qrcode + password, something > like that, but many start from the phone so maybe it's easy for them. > I try to download it and see if it allows me to connect with a bunker. > Okay I used private-qrcode and it worked, I couldn't do it directly from Olas because it didn't have permissions and the qrcode was < encrypted, so I went to the same site and had the bunker copied and glued on Olas **Ok then I saw that there was the qrcode image of the bunker for apps** lol moment Ok, I liked it, I can say it's a victory. Looks like none of Snowden's followers are *Olas*'s lover, maybe the smart pack has to predict a photographer or something like that. Okay I managed to post on *Olas*, so it works, Expiration time is broken. ### As for *Nostur*, I don't have an ios device so I'm going to another one. ### Login with *Jumble*, it works is a web app I took almost an hour to do the whole route. But this was just one link there are two more # Extensions nostr NIP-07 ### The true path is [nip-07-browser-extensions | nostr.net](https://nostr.net/#nip-07-browser-extensions) There are 19 links, maybe there are too many? I mention the most famous, or active at the moment 1. **Aka-profiles**: [Aka-profiles](https://github.com/neilck/aka-extension) Alby I don't know if it's a route to recommend 2. **Blockcore** [Blockcore wallet](https://chromewebstore.google.com/detail/blockcore-wallet/peigonhbenoefaeplkpalmafieegnapj) 3. **Nos2x** [Nos2x](https://github.com/fiatjaf/nos2x?tab=readme-ov-file) 4. **Nos2xfox** (fork for firefox) [Nos2xfox](https://diegogurpegui.com/nos2x-fox/) Nostore is (archived, read-only) 5. **Nostrame** [Nostrame](https://github.com/Anderson-Juhasc/nostrame) 6. **Nowser** per IOS [Nowser](https://github.com/haorendashu/nowser) 7. **One key** (was tricky) [One key](https://chromewebstore.google.com/detail/onekey/jnmbobjmhlngoefaiojfljckilhhlhcj) Another half hour to search all sites # Nostrapps Here you can make paths ### Then nstart selects Coracle, Chachi, Olas,Nostur and Jumble Good apps might be Amethyst, 0xchat, Yakihonne, Primal, Damus for IOS maybe: Primal, Olas, Damus, Nostur, Nos-Social, Nostrmo On the site there are some categories, I select some with the respective apps Let's see the categories Go to [Nostrapps](https://nostrapps.com/) and read: ## Microbbloging: Primal ## Streaming: **Zap stream** ## Blogging: **Yakihonne** ## Group chat: **Chachi** ## Community: **Flotilla** ## Tools: **Form** * ## Discovery: **Zapstore** (even if it is not in this catrgory) ## Direct Message: **0xchat**
@ 592295cf:413a0db9
2025-03-29 10:59:52The journey starts from the links in this article [nostr-quick-start-guide](https://spatianostra.com/nostr-quick-start-guide/) Starting from these links building a simple path should not cover everything, because impossible. Today I saw that Verbiricha in his workshop on his channel used nstart, but then I distracted And I didn't see how he did it. ----- Go to [nstart.me](https://nstart.me/) and read: Each user is identified by a cryptographic keypair Public key, Private key (is a lot of stuff) You can insert a nickname and go, the nickname is not unique there is a email backup things interesting, but a little boring, i try to generate an email doesn't even require a strong password ok. I received the email, great, it shows me the nsec encrypted in clear, Send a copy of the file with a password, which contains the password encrypted key I know and I know it's a tongue dump. ## Multi signer bunker That's stuff, let's see what he says. They live the private key and send it to servers and you can recompose it to login at a site of the protocol nostr. If one of these servers goes offline you have the private key that you downloaded first and then reactivate a bunker. All very complicated. But if one of the servers goes offline, how can I remake the split? Maybe he's still testing. Nobody tells you where these bunkers are. Okay I have a string that is my bunker (buker://), I downloaded it, easy no, now will tell me which client accepts the bunker.. . ## Follow someone before you start? Is a cluster of 5 people Snowden, Micheal Dilger, jb55, Fiatjaf, Dianele. I choice Snowden profile, or you can select multiple profiles, extra wild. ## Now select 5 clients ### *Coracle, Chachi, Olas, Nostur, Jumble* ### The first is *Coracle* Login, ok I try to post a note and signing your note the spin does not end. Maybe the bunker is diffective. ### Let's try *Chachi* Simpler than Coracle, it has a type login that says bunker. see if I can post It worked, cool, I managed to post in a group. ## Olas is an app but also a website, but on the website requires an extension, which I do not have with this account. > If I download an app how do I pass the bunker on the phone, is it still a password, a qrcode, a qrcode + password, something > like that, but many start from the phone so maybe it's easy for them. > I try to download it and see if it allows me to connect with a bunker. > Okay I used private-qrcode and it worked, I couldn't do it directly from Olas because it didn't have permissions and the qrcode was < encrypted, so I went to the same site and had the bunker copied and glued on Olas **Ok then I saw that there was the qrcode image of the bunker for apps** lol moment Ok, I liked it, I can say it's a victory. Looks like none of Snowden's followers are *Olas*'s lover, maybe the smart pack has to predict a photographer or something like that. Okay I managed to post on *Olas*, so it works, Expiration time is broken. ### As for *Nostur*, I don't have an ios device so I'm going to another one. ### Login with *Jumble*, it works is a web app I took almost an hour to do the whole route. But this was just one link there are two more # Extensions nostr NIP-07 ### The true path is [nip-07-browser-extensions | nostr.net](https://nostr.net/#nip-07-browser-extensions) There are 19 links, maybe there are too many? I mention the most famous, or active at the moment 1. **Aka-profiles**: [Aka-profiles](https://github.com/neilck/aka-extension) Alby I don't know if it's a route to recommend 2. **Blockcore** [Blockcore wallet](https://chromewebstore.google.com/detail/blockcore-wallet/peigonhbenoefaeplkpalmafieegnapj) 3. **Nos2x** [Nos2x](https://github.com/fiatjaf/nos2x?tab=readme-ov-file) 4. **Nos2xfox** (fork for firefox) [Nos2xfox](https://diegogurpegui.com/nos2x-fox/) Nostore is (archived, read-only) 5. **Nostrame** [Nostrame](https://github.com/Anderson-Juhasc/nostrame) 6. **Nowser** per IOS [Nowser](https://github.com/haorendashu/nowser) 7. **One key** (was tricky) [One key](https://chromewebstore.google.com/detail/onekey/jnmbobjmhlngoefaiojfljckilhhlhcj) Another half hour to search all sites # Nostrapps Here you can make paths ### Then nstart selects Coracle, Chachi, Olas,Nostur and Jumble Good apps might be Amethyst, 0xchat, Yakihonne, Primal, Damus for IOS maybe: Primal, Olas, Damus, Nostur, Nos-Social, Nostrmo On the site there are some categories, I select some with the respective apps Let's see the categories Go to [Nostrapps](https://nostrapps.com/) and read: ## Microbbloging: Primal ## Streaming: **Zap stream** ## Blogging: **Yakihonne** ## Group chat: **Chachi** ## Community: **Flotilla** ## Tools: **Form** * ## Discovery: **Zapstore** (even if it is not in this catrgory) ## Direct Message: **0xchat** @ 21335073:a244b1ad
2025-03-20 13:16:22I’d never had the chance to watch Harry Potter on the big screen before. Experiencing the first movie in 3D was nothing short of spectacular. Right from the opening scene with Albus Dumbledore, I was floored—the makeup and costumes were so vivid, it felt like pure magic unfolding before my eyes. It’s clear that real masters of their craft worked behind the scenes, and their artistry shines through. The sets? Absolutely jaw-dropping! The level of detail in Diagon Alley was beyond impressive. Seeing legends like Alan Rickman as Snape and Maggie Smith as Minerva McGonagall on that massive 3D screen was an unforgettable thrill. The film is packed with phenomenal actors, and it was a joy to catch every tiny eye twitch and subtle nuance of their performances brought to life. It was a mind-blowing experience, and I’d wholeheartedly recommend it to anyone who gets the chance. Don’t forget to have a little whimsical fun sometimes my friends. 🪄
@ 21335073:a244b1ad
2025-03-20 13:16:22I’d never had the chance to watch Harry Potter on the big screen before. Experiencing the first movie in 3D was nothing short of spectacular. Right from the opening scene with Albus Dumbledore, I was floored—the makeup and costumes were so vivid, it felt like pure magic unfolding before my eyes. It’s clear that real masters of their craft worked behind the scenes, and their artistry shines through. The sets? Absolutely jaw-dropping! The level of detail in Diagon Alley was beyond impressive. Seeing legends like Alan Rickman as Snape and Maggie Smith as Minerva McGonagall on that massive 3D screen was an unforgettable thrill. The film is packed with phenomenal actors, and it was a joy to catch every tiny eye twitch and subtle nuance of their performances brought to life. It was a mind-blowing experience, and I’d wholeheartedly recommend it to anyone who gets the chance. Don’t forget to have a little whimsical fun sometimes my friends. 🪄 @ 3f770d65:7a745b24
2025-01-12 21:03:36I’ve been using Notedeck for several months, starting with its extremely early and experimental alpha versions, all the way to its current, more stable alpha releases. The journey has been fascinating, as I’ve had the privilege of watching it evolve from a concept into a functional and promising tool. In its earliest stages, Notedeck was raw—offering glimpses of its potential but still far from practical for daily use. Even then, the vision behind it was clear: a platform designed to redefine how we interact with Nostr by offering flexibility and power for all users. I'm very bullish on Notedeck. Why? Because Will Casarin is making it! Duh! 😂 Seriously though, if we’re reimagining the web and rebuilding portions of the Internet, it’s important to recognize [the potential of Notedeck](https://damus.io/notedeck/). If Nostr is reimagining the web, then Notedeck is reimagining the Nostr client. Notedeck isn’t just another Nostr app—it’s more a Nostr browser that functions more like an operating system with micro-apps. How cool is that? Much like how Google's Chrome evolved from being a web browser with a task manager into ChromeOS, a full blown operating system, Notedeck aims to transform how we interact with the Nostr. It goes beyond individual apps, offering a foundation for a fully integrated ecosystem built around Nostr. As a Nostr evangelist, I love to scream **INTEROPERABILITY** and tout every application's integrations. Well, Notedeck has the potential to be one of the best platforms to showcase these integrations in entirely new and exciting ways. Do you want an Olas feed of images? Add the media column. Do you want a feed of live video events? Add the zap.stream column. Do you want Nostr Nests or audio chats? Add that column to your Notedeck. Git? Email? Books? Chat and DMs? It's all possible. Not everyone wants a super app though, and that’s okay. As with most things in the Nostr ecosystem, flexibility is key. Notedeck gives users the freedom to choose how they engage with it—whether it’s simply following hashtags or managing straightforward feeds. You'll be able to tailor Notedeck to fit your needs, using it as extensively or minimally as you prefer. Notedeck is designed with a local-first approach, utilizing Nostr content stored directly on your device via the local nostrdb. This will enable a plethora of advanced tools such as search and filtering, the creation of custom feeds, and the ability to develop personalized algorithms across multiple Notedeck micro-applications—all with unparalleled flexibility. Notedeck also supports multicast. Let's geek out for a second. Multicast is a method of communication where data is sent from one source to multiple destinations simultaneously, but only to devices that wish to receive the data. Unlike broadcast, which sends data to all devices on a network, multicast targets specific receivers, reducing network traffic. This is commonly used for efficient data distribution in scenarios like streaming, conferencing, or large-scale data synchronization between devices. > In a local first world where each device holds local copies of your nostr nodes, and each device transparently syncs with each other on the local network, each node becomes a backup. Your data becomes antifragile automatically. When a node goes down it can resync and recover from other nodes. Even if not all nodes have a complete collection, negentropy can pull down only what is needed from each device. All this can be done without internet. > > \-Will Casarin In the context of Notedeck, multicast would allow multiple devices to sync their Nostr nodes with each other over a local network without needing an internet connection. Wild. Notedeck aims to offer full customization too, including the ability to design and share custom skins, much like Winamp. Users will also be able to create personalized columns and, in the future, share their setups with others. This opens the door for power users to craft tailored Nostr experiences, leveraging their expertise in the protocol and applications. By sharing these configurations as "Starter Decks," they can simplify onboarding and showcase the best of Nostr’s ecosystem. Nostr’s “Other Stuff” can often be difficult to discover, use, or understand. Many users doesn't understand or know how to use web browser extensions to login to applications. Let's not even get started with nsecbunkers. Notedeck will address this challenge by providing a native experience that brings these lesser-known applications, tools, and content into a user-friendly and accessible interface, making exploration seamless. However, that doesn't mean Notedeck should disregard power users that want to use nsecbunkers though - hint hint. For anyone interested in watching Nostr be [developed live](https://github.com/damus-io/notedeck), right before your very eyes, Notedeck’s progress serves as a reminder of what’s possible when innovation meets dedication. The current alpha is already demonstrating its ability to handle complex use cases, and I’m excited to see how it continues to grow as it moves toward a full release later this year.
@ 3f770d65:7a745b24
2025-01-12 21:03:36I’ve been using Notedeck for several months, starting with its extremely early and experimental alpha versions, all the way to its current, more stable alpha releases. The journey has been fascinating, as I’ve had the privilege of watching it evolve from a concept into a functional and promising tool. In its earliest stages, Notedeck was raw—offering glimpses of its potential but still far from practical for daily use. Even then, the vision behind it was clear: a platform designed to redefine how we interact with Nostr by offering flexibility and power for all users. I'm very bullish on Notedeck. Why? Because Will Casarin is making it! Duh! 😂 Seriously though, if we’re reimagining the web and rebuilding portions of the Internet, it’s important to recognize [the potential of Notedeck](https://damus.io/notedeck/). If Nostr is reimagining the web, then Notedeck is reimagining the Nostr client. Notedeck isn’t just another Nostr app—it’s more a Nostr browser that functions more like an operating system with micro-apps. How cool is that? Much like how Google's Chrome evolved from being a web browser with a task manager into ChromeOS, a full blown operating system, Notedeck aims to transform how we interact with the Nostr. It goes beyond individual apps, offering a foundation for a fully integrated ecosystem built around Nostr. As a Nostr evangelist, I love to scream **INTEROPERABILITY** and tout every application's integrations. Well, Notedeck has the potential to be one of the best platforms to showcase these integrations in entirely new and exciting ways. Do you want an Olas feed of images? Add the media column. Do you want a feed of live video events? Add the zap.stream column. Do you want Nostr Nests or audio chats? Add that column to your Notedeck. Git? Email? Books? Chat and DMs? It's all possible. Not everyone wants a super app though, and that’s okay. As with most things in the Nostr ecosystem, flexibility is key. Notedeck gives users the freedom to choose how they engage with it—whether it’s simply following hashtags or managing straightforward feeds. You'll be able to tailor Notedeck to fit your needs, using it as extensively or minimally as you prefer. Notedeck is designed with a local-first approach, utilizing Nostr content stored directly on your device via the local nostrdb. This will enable a plethora of advanced tools such as search and filtering, the creation of custom feeds, and the ability to develop personalized algorithms across multiple Notedeck micro-applications—all with unparalleled flexibility. Notedeck also supports multicast. Let's geek out for a second. Multicast is a method of communication where data is sent from one source to multiple destinations simultaneously, but only to devices that wish to receive the data. Unlike broadcast, which sends data to all devices on a network, multicast targets specific receivers, reducing network traffic. This is commonly used for efficient data distribution in scenarios like streaming, conferencing, or large-scale data synchronization between devices. > In a local first world where each device holds local copies of your nostr nodes, and each device transparently syncs with each other on the local network, each node becomes a backup. Your data becomes antifragile automatically. When a node goes down it can resync and recover from other nodes. Even if not all nodes have a complete collection, negentropy can pull down only what is needed from each device. All this can be done without internet. > > \-Will Casarin In the context of Notedeck, multicast would allow multiple devices to sync their Nostr nodes with each other over a local network without needing an internet connection. Wild. Notedeck aims to offer full customization too, including the ability to design and share custom skins, much like Winamp. Users will also be able to create personalized columns and, in the future, share their setups with others. This opens the door for power users to craft tailored Nostr experiences, leveraging their expertise in the protocol and applications. By sharing these configurations as "Starter Decks," they can simplify onboarding and showcase the best of Nostr’s ecosystem. Nostr’s “Other Stuff” can often be difficult to discover, use, or understand. Many users doesn't understand or know how to use web browser extensions to login to applications. Let's not even get started with nsecbunkers. Notedeck will address this challenge by providing a native experience that brings these lesser-known applications, tools, and content into a user-friendly and accessible interface, making exploration seamless. However, that doesn't mean Notedeck should disregard power users that want to use nsecbunkers though - hint hint. For anyone interested in watching Nostr be [developed live](https://github.com/damus-io/notedeck), right before your very eyes, Notedeck’s progress serves as a reminder of what’s possible when innovation meets dedication. The current alpha is already demonstrating its ability to handle complex use cases, and I’m excited to see how it continues to grow as it moves toward a full release later this year. @ fd06f542:8d6d54cd
2025-03-30 02:10:24NIP-03 ====== OpenTimestamps Attestations for Events -------------------------------------- `draft` `optional` This NIP defines an event with `kind:1040` that can contain an [OpenTimestamps](https://opentimestamps.org/) proof for any other event: ```json { "kind": 1040 "tags": [ ["e", <event-id>, <relay-url>], ["alt", "opentimestamps attestation"] ], "content": <base64-encoded OTS file data> } ``` - The OpenTimestamps proof MUST prove the referenced `e` event id as its digest. - The `content` MUST be the full content of an `.ots` file containing at least one Bitcoin attestation. This file SHOULD contain a **single** Bitcoin attestation (as not more than one valid attestation is necessary and less bytes is better than more) and no reference to "pending" attestations since they are useless in this context. ### Example OpenTimestamps proof verification flow Using [`nak`](https://github.com/fiatjaf/nak), [`jq`](https://jqlang.github.io/jq/) and [`ots`](https://github.com/fiatjaf/ots): ```bash ~> nak req -i e71c6ea722987debdb60f81f9ea4f604b5ac0664120dd64fb9d23abc4ec7c323 wss://nostr-pub.wellorder.net | jq -r .content | ots verify > using an esplora server at https://blockstream.info/api - sequence ending on block 810391 is valid timestamp validated at block [810391] ```
@ fd06f542:8d6d54cd
2025-03-30 02:10:24NIP-03 ====== OpenTimestamps Attestations for Events -------------------------------------- `draft` `optional` This NIP defines an event with `kind:1040` that can contain an [OpenTimestamps](https://opentimestamps.org/) proof for any other event: ```json { "kind": 1040 "tags": [ ["e", <event-id>, <relay-url>], ["alt", "opentimestamps attestation"] ], "content": <base64-encoded OTS file data> } ``` - The OpenTimestamps proof MUST prove the referenced `e` event id as its digest. - The `content` MUST be the full content of an `.ots` file containing at least one Bitcoin attestation. This file SHOULD contain a **single** Bitcoin attestation (as not more than one valid attestation is necessary and less bytes is better than more) and no reference to "pending" attestations since they are useless in this context. ### Example OpenTimestamps proof verification flow Using [`nak`](https://github.com/fiatjaf/nak), [`jq`](https://jqlang.github.io/jq/) and [`ots`](https://github.com/fiatjaf/ots): ```bash ~> nak req -i e71c6ea722987debdb60f81f9ea4f604b5ac0664120dd64fb9d23abc4ec7c323 wss://nostr-pub.wellorder.net | jq -r .content | ots verify > using an esplora server at https://blockstream.info/api - sequence ending on block 810391 is valid timestamp validated at block [810391] ``` @ 21335073:a244b1ad
2025-03-18 20:47:50**Warning: This piece contains a conversation about difficult topics. Please proceed with caution.** TL;DR please educate your children about online safety. Julian Assange wrote in his 2012 book *Cypherpunks*, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense. This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning. When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little. I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?” I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well. I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread. I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard. I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it. The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust. Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this. I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place. What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method. It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code. They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened. I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road. So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally. Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb. I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback. Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed. That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone. To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all. I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society. I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this. On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government. I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories. There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc. Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind. Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now. There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers? I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity. I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place. My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors. My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline. The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online. I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers. So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation? When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that. I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic. If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations. I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process. **Course:** - The creation of the internet and computers - The fight for cryptography - The tech supply chain from the ground up (example: human rights violations in the supply chain) - Corporate tech - Freedom tech - Data privacy - Digital privacy rights - AI (history-current) - Online safety (predators, scams, catfishing, extortion) - Bitcoin - Laws - How to deal with online hate and harassment - Information on who to contact if you are being abused online or offline - Algorithms - How to seek out the truth about news, etc., online The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children. The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward? I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone. Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability. The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime. This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful. This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens. In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions. I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation.
@ 21335073:a244b1ad
2025-03-18 20:47:50**Warning: This piece contains a conversation about difficult topics. Please proceed with caution.** TL;DR please educate your children about online safety. Julian Assange wrote in his 2012 book *Cypherpunks*, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense. This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning. When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little. I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?” I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well. I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread. I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard. I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it. The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust. Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this. I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place. What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method. It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code. They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened. I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road. So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally. Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb. I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback. Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed. That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone. To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all. I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society. I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this. On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government. I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories. There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc. Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind. Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now. There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers? I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity. I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place. My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors. My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline. The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online. I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers. So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation? When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that. I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic. If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations. I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process. **Course:** - The creation of the internet and computers - The fight for cryptography - The tech supply chain from the ground up (example: human rights violations in the supply chain) - Corporate tech - Freedom tech - Data privacy - Digital privacy rights - AI (history-current) - Online safety (predators, scams, catfishing, extortion) - Bitcoin - Laws - How to deal with online hate and harassment - Information on who to contact if you are being abused online or offline - Algorithms - How to seek out the truth about news, etc., online The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children. The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward? I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone. Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability. The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime. This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful. This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens. In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions. I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation. @ f1989a96:bcaaf2c1
2025-04-03 14:30:08Good morning, readers! Georgian officials froze the bank accounts of five nonprofit organizations that provide financial and legal support to detained protesters. This follows rising public unrest as Georgia’s regime pushes new laws restricting free speech and assembly, introducing new fines and penalties, and expanding law enforcement powers. By eroding civil protections, the regime makes it more dangerous and costly for activists, dissenters, and everyday citizens to stand up against an increasingly repressive regime.\ \ Meanwhile, the Indian government introduced a new income tax bill that grants tax authorities sweeping surveillance power over anyone they “suspect” of tax evasion. If suspected, tax authorities are legally allowed to access Indians' email, social media, and bank accounts, raising obvious concerns over state overreach and invasions of individual financial privacy.\ \ In freedom tech news, HRF donated 1 billion satoshis to more than 20 projects worldwide, focusing on supporting human rights defenders and vulnerable communities under authoritarian regimes across Asia, Africa, and Latin America. These gifts advance censorship-resistant communications and transactions, bitcoin education, and privacy tools so that dissidents, nonprofits, and individuals may better protect their human rights and financial freedom. In this letter we also spotlight a new open-source mobile Bitcoin wallet called Cove. While still in beta, the wallet can be used with a hardware device or on its own as a hot wallet, offering a flexible self-custody setup for managing Bitcoin. We end with a podcast in which HRF Chief Strategy Officer Alex Gladstein discusses the state of freedom tech and why Bitcoin stands as the most promising tool for financial liberation. **Now, let’s get right to it!** ### [**SUBSCRIBE HERE**](https://mailchi.mp/hrf.org/financial-freedom-newsletter?mc_cid=bf652c0a5a) ## **GLOBAL NEWS** #### **Georgia | Officials Freeze Accounts of Organizations Supporting Protesters** Georgian officials have [frozen](https://www.amnesty.org/en/latest/news/2025/03/georgia-authorities-freeze-accounts-of-organizations-supporting-protesters-to-kill-the-peaceful-protests/) the bank accounts of five nonprofit organizations that provide financial and legal aid to dissenters. This comes in response to an uprising of protests over new controversial laws that restrict free expression and assembly, increase fines and detention periods, and expand law enforcement powers. Georgian officials justify the account freezes as part of an investigation into “sabotage,” yet they have provided no evidence. Amnesty International [warns](https://www.amnesty.org/en/latest/news/2025/03/georgia-authorities-freeze-accounts-of-organizations-supporting-protesters-to-kill-the-peaceful-protests/) this financial assault could “kill the entire protest movement.” Bitcoin provides a way to circumvent these struggles. Its uncensorable and permissionless nature has helped [sustain](https://www.journalofdemocracy.org/online-exclusive/how-to-dictator-proof-your-money/) pro-democracy movements across Belarus and Nigeria, proving it is capable of addressing the immense financial restrictions dictators impose. #### **United Arab Emirates | Plans to Launch “Digital Durham” CBDC in 2025** The United Arab Emirates (UAE) will [launch](https://www.businesstoday.in/technology/news/story/uae-to-launch-digital-dirham-by-year-end-to-modernise-payments-and-noost-financial-inclusion-470013-2025-03-31?utm_source=semafor#) its central bank digital currency (CBDC), the “[Digital Durham](https://cbdctracker.hrf.org/currency/united-arab-emirates),” by the end of 2025. [According](https://www.ledgerinsights.com/uae-to-launch-cbdc-in-q4-2025/) to the central bank, the CBDC will be available through licensed financial institutions and operate via a government-run digital wallet. Every transaction will be recorded on a permissioned blockchain run by the government. The central bank further [admitted](https://u.ae/en/about-the-uae/strategies-initiatives-and-awards/strategies-plans-and-visions/finance-and-economy/central-bank-digital-currency-strategy) the CBDC will replace cash and [assist](https://www.businesstoday.in/technology/news/story/uae-to-launch-digital-dirham-by-year-end-to-modernise-payments-and-noost-financial-inclusion-470013-2025-03-31?utm_source=semafor#) law enforcement “by leaving a digital trail for transactions involving illicit funds.” Officials [claim](https://www.businesstoday.in/technology/news/story/uae-to-launch-digital-dirham-by-year-end-to-modernise-payments-and-noost-financial-inclusion-470013-2025-03-31?utm_source=semafor#) this is to combat financial crime, but it also enables real-time surveillance and tracking of individual financial activity. In a country known for strict laws against dissent and extensive surveillance capabilities, it is not hard to see how a CBDC will erode the autonomy and rights of activists, dissenters, and others who oppose an increasingly authoritarian regime. #### **India | Grants Tax Authorities Access to Citizens’ Online Data** Starting in April 2026, the Indian government will [grant](https://economictimes.indiatimes.com/wealth/tax/your-email-and-social-media-account-can-be-accessed-by-income-tax-officer-starting-next-financial-year-in-these-cases/articleshow/118685184.cms) tax authorities legal access to the private online data of any citizen “suspected” of tax evasion. This will include legal access to personal emails, social media, and bank accounts. The new law expands on the Income Tax Act of 1961, which previously limited officials to searching physical premises for financial documents. Now, officials can bypass digital security measures and access private data without consent — all under a legal framework. This dissipation of financial privacy sets an intrusive precedent and opens the door to state-level corruption and surveillance in a country where the Modi regime has already made it clear they are happy to use financial repression to further cement their power. #### **Myanmar | Bitcoin as a Tool Support Earthquake Disaster Relief** Last week, a [7.7 magnitude earthquake](https://www.nytimes.com/2025/03/28/world/asia/earthquake-myanmar-thailand-death-toll.html) struck central Burma, with strong tremors reaching neighboring Thailand. The [official death toll ](https://www.reuters.com/business/environment/survivors-myanmar-quake-left-without-food-water-shelter-aid-groups-say-2025-04-01/)has surpassed 2700. And in Bangkok, a 33-story building under construction [collapsed](https://www.youtube.com/watch?v=ynrhyIh4ozo). Despite an already strenuous situation, Burma’s military junta continues its oppression. They are [blocking](https://www.nytimes.com/2025/03/31/world/asia/myanmar-earthquake-rescue.html) rescue teams from reaching the Sagaing region — the epicenter of the earthquake and the heart of Burma’s pro-democracy movement — and instead channeling aid to regime-controlled cities like Naypyidaw and Mandalay. The junta is also continuing to conduct air strikes on civilians and restricting equipment and fuel for aid groups, leaving a [million](https://data.unhcr.org/en/country/mmr) people in Sagaing to fend for themselves. In these repressive circumstances, Bitcoin can provide a censorship-resistant way to send funds directly to those affected. #### **Angola | Regime Jacks Price of Diesel** The Angolan regime [raised](https://www.rigzone.com/news/wire/angola_doubles_diesel_prices_after_imf_call_for_subsidy_cuts-25-mar-2025-180020-article/) diesel prices by 50% in the process of eliminating fuel subsidies. Diesel prices suddenly increased from 200 to 300 kwanza per liter, driving up transportation costs in a country where over half the population lives on [less](https://www.rigzone.com/news/wire/angola_doubles_diesel_prices_after_imf_call_for_subsidy_cuts-25-mar-2025-180020-article/) than $2 a day and inflation is over 42%. Previous fuel subsidy cuts in 2023 (where the price of diesel rose [80%](https://www.dw.com/en/angolan-police-crack-down-on-fuel-hike-protests/a-65978231)) sparked [protests](https://www.dw.com/en/angolan-police-crack-down-on-fuel-hike-protests/a-65978231) between taxi drivers, nonprofit workers, and law enforcement. This recent price increase now raises fears of renewed crackdowns. The Angolan regime also introduced new civil society laws that Guilherme Neves, chairman of the human rights organization Associacao Maos Livres, [describes](https://www.dw.com/en/angolan-police-crack-down-on-fuel-hike-protests/a-65978231) as a “license to erase non-governmental organizations that are not government-compliant.” Angolans find themselves in increasingly precarious financial positions as the government erodes the civil safeguards protecting nonprofits and dissenters. #### **Nicaragua | Ortega’s Dismantling of Press Freedom** Since coming to power in 2007, Ortega has [closed or seized](https://havanatimes.org/features/ortegas-war-on-journalism-in-nicaragua/) 61 media outlets, imprisoned countless journalists, and forced over 280 journalists into exile. His [assault on press freedom](https://havanatimes.org/features/ortegas-war-on-journalism-in-nicaragua/) has unfolded in two phases: initial raids on local radio stations and TV channels between 2007 and 2017, followed by full-scale censorship in 2018 on independent media outlets like [La Prensa](https://www.laprensani.com/) and [CONFIDENCIAL](https://confidencial.digital/). Ortega then intensified attacks from 2019 to 2021 by closing Nicaragua’s second-oldest newspaper and passing laws to [criminalize](https://havanatimes.org/features/ortegas-war-on-journalism-in-nicaragua/) free expression. This is a deliberate strategy to eliminate dissent and independent voices. What’s happening in Nicaragua highlights the importance of open and decentralized protocols like nostr, which allow journalists to publish freely without getting censored. While still early, it is becoming essential for sharing information absent the fear of being blocked or silenced by autocratic leaders. ## BITCOIN AND FREEDOM TECH NEWS #### **HRF | Gifts 1 Billion Satoshis to 20+ Open Source Projects Worldwide** HRF gifted 1 billion satoshis in its Q1 2025 round of [Bitcoin Development Fund](https://hrf.org/program/financial-freedom/bitcoin-development-fund/) (BDF) grants, supporting more than 20 open-source projects around the world. These projects advance Bitcoin education, open-source software, mining decentralization, and privacy tools for activists contending with authoritarian regimes across Asia, Latin America, and Africa. Supporting permissionless financial tools and censorship-resistant technologies empowers dissidents, journalists, and civil society to organize, transact, and communicate without state suppression and interference. Learn more about the grantees and their work [here](https://hrf.org/latest/hrf-bitcoin-development-fund-supports-20-projects-worldwide/). #### **Cove | New Open-Source and Permissionless Bitcoin Wallet** [Cove](https://github.com/bitcoinppl/cove) is a new open-source and permissionless mobile Bitcoin wallet that aims to put users in full control of their Bitcoin. Users can connect their own hardware wallet (to manage Bitcoin offline) or use Cove as a hot wallet (to manage Bitcoin online). It also allows users to create multiple wallets from the app itself. In the future, Cove plans to add Unspent Transaction Output (UTXO) selection and coin control, giving users more independence over their transactions and the tools to better protect their financial privacy. While still in beta and only suitable for test funds, this wallet holds promise as a privacy tool to equip dissidents with self-custodied Bitcoin. You can try it [here](https://github.com/bitcoinppl/cove). #### **Second | New Ark Implementation Launches on Bitcoin Signet** [Second](https://second.tech/), a company building on Ark, a protocol designed to help scale Bitcoin’s transaction throughput, [launched](https://blog.second.tech/try-ark-on-signet/?ref=nobsbitcoin.com) “Bark.” Bark is a test implementation of the Ark protocol deployed on Bitcoin’s [Signet](https://en.bitcoin.it/wiki/Signet) network (where developers test software). More broadly, the Ark protocol helps make Bitcoin transactions more private, faster, and cheaper, supporting the network in handling more transactions and users with the tradeoff of being less trusted than the mainchain, as funds stored in a noncustodial way on Ark can expire if not used. While it is still in early development, the test release of Bark marks a step toward deployment on the main Bitcoin network. Scaling solutions like Ark could be important for activists and individuals. They might ensure Bitcoin remains accessible to all, even as block space demand increases and network fees rise. Learn about it [here](https://blog.second.tech/try-ark-on-signet/?ref=nobsbitcoin.com). #### **Braiins | Open Sources Bitcoin Control Board** [Braiins](https://braiins.com/), a company building tools for Bitcoin mining, [open-sourced](https://x.com/BraiinsMining/status/1904601547855573458) its [BCB100](https://github.com/braiins/BCB100) Bitcoin Control Board, giving miners using their products greater insight and control over their Bitcoin mining hardware and firmware. Sharing the design files and firmware openly helps strengthen Bitcoin’s decentralization, making it more resilient against corporate or state interference. Specifically, open-sourcing mining hardware ensures individual miners can operate independently, reducing censorship risks across the entire network. In turn, this preserves financial freedom by keeping Bitcoin accessible and usable by dissidents, nonprofits, and individuals who need it most. #### **African Bitcoiners | Publish Bitcoin Starter Guide** [African Bitcoiners](https://x.com/afribitcoiners) just published “[Bitcoin: Africa’s Guide to Freedom Money](https://x.com/afribitcoiners/status/1904516726273851513),” a Bitcoin guide providing clear, practical insights into how Bitcoin can help people across the continent escape inflation, corrupt regimes, and failing financial systems. It covers essential topics to get started — from choosing a wallet to properly securing Bitcoin. In Africa, where some of the world’s longest-standing dictators restrict even basic financial activity, this guide is a powerful resource for human rights defenders, nonprofits, and everyday citizens. Read it[ here](https://bitcoiners.africa/bitcoin-africas-guide-to-freedom-money/). #### **OpenSats | 10th Wave of Nostr Grants** [OpenSats](https://opensats.org/), a nonprofit that supports open-source software development, [announced](https://opensats.org/blog/10th-wave-of-nostr-grants) its tenth wave of grants for projects in the nostr ecosystem. Nostr is a decentralized protocol that enables digital identity and communications outside the reach of authoritarian states. The grant round provides support to nostr Epoxy, which enhances access to nostr by circumventing censorship through a network of paid proxies. This ensures activists and dissidents can continue to communicate even in restrictive environments. Additionally, Zapstore received a grant for providing a permissionless app store built on nostr that enables developers to distribute software without corporate gatekeepers. This provides an open-source alternative to centralized app stores that often comply with government censorship and restrict dissidents’ access to freedom tools. ## RECOMMENDED CONTENT #### **Freedom Tech with Alex Gladstein** In this [episode](https://x.com/blockspacepod/status/1896229100702089589?s=46&t=yEPKerGEzeCp5j_mIaNJ8A) of The Gwart Show, Alex Gladstein, chief strategy officer at HRF, breaks down how and why Bitcoin serves as “money dictators can’t stop.” Drawing on more than 17 years of human rights work, he shares real-world examples of activists and citizens using Bitcoin to escape financial repression in authoritarian countries. Gladstein also explores privacy tools, cross-border payments, and why Bitcoin offers promising hope for financial freedom. Watch the full conversation [here](https://www.youtube.com/watch?v=5Ng961QZwI0). #### **The State of Personal Online Security and Confidentiality with Meredith Whittaker** In this [keynote](https://www.youtube.com/watch?v=AyH7zoP-JOg) for SXSW 2025, Signal CEO Meredith Whittaker shares her growing concerns around AI, personal data collection, and the erosion of privacy in today’s increasingly digital world. She emphasizes the need for more secure, uncensorable, and privacy-protecting technologies that shield users from surveillance and exploitation, especially in the context of authoritarian regimes. Watch the [full discussion](https://www.youtube.com/watch?v=AyH7zoP-JOg) for a pragmatic view into the future of digital privacy and security. *If this article was forwarded to you and you enjoyed reading it, please consider subscribing to the Financial Freedom Report [here](https://mailchi.mp/hrf.org/financial-freedom-newsletter?mc_cid=bf652c0a5a).* *Support the newsletter by donating bitcoin to HRF’s Financial Freedom program [via BTCPay](https://hrf.org/btc).*\ *Want to contribute to the newsletter? Submit tips, stories, news, and ideas by emailing us at ffreport @ [hrf.org](http://hrf.org/)* *The Bitcoin Development Fund (BDF) is accepting grant proposals on an ongoing basis. The Bitcoin Development Fund is looking to support Bitcoin developers, community builders, and educators. Submit proposals [here](https://forms.monday.com/forms/57019f8829449d9e729d9e3545a237ea?r=use1)*. [**Subscribe to newsletter**](http://financialfreedomreport.org/) [**Apply for a grant**](https://forms.monday.com/forms/57019f8829449d9e729d9e3545a237ea?r=use1&mc_cid=39c1c9b7e8&mc_eid=778e9876e3) [**Support our work**](https://hrf.org/btc?mc_cid=39c1c9b7e8&mc_eid=778e9876e3) [**Visit our website**](https://hrf.org/programs/financial-freedom/)
@ f1989a96:bcaaf2c1
2025-04-03 14:30:08Good morning, readers! Georgian officials froze the bank accounts of five nonprofit organizations that provide financial and legal support to detained protesters. This follows rising public unrest as Georgia’s regime pushes new laws restricting free speech and assembly, introducing new fines and penalties, and expanding law enforcement powers. By eroding civil protections, the regime makes it more dangerous and costly for activists, dissenters, and everyday citizens to stand up against an increasingly repressive regime.\ \ Meanwhile, the Indian government introduced a new income tax bill that grants tax authorities sweeping surveillance power over anyone they “suspect” of tax evasion. If suspected, tax authorities are legally allowed to access Indians' email, social media, and bank accounts, raising obvious concerns over state overreach and invasions of individual financial privacy.\ \ In freedom tech news, HRF donated 1 billion satoshis to more than 20 projects worldwide, focusing on supporting human rights defenders and vulnerable communities under authoritarian regimes across Asia, Africa, and Latin America. These gifts advance censorship-resistant communications and transactions, bitcoin education, and privacy tools so that dissidents, nonprofits, and individuals may better protect their human rights and financial freedom. In this letter we also spotlight a new open-source mobile Bitcoin wallet called Cove. While still in beta, the wallet can be used with a hardware device or on its own as a hot wallet, offering a flexible self-custody setup for managing Bitcoin. We end with a podcast in which HRF Chief Strategy Officer Alex Gladstein discusses the state of freedom tech and why Bitcoin stands as the most promising tool for financial liberation. **Now, let’s get right to it!** ### [**SUBSCRIBE HERE**](https://mailchi.mp/hrf.org/financial-freedom-newsletter?mc_cid=bf652c0a5a) ## **GLOBAL NEWS** #### **Georgia | Officials Freeze Accounts of Organizations Supporting Protesters** Georgian officials have [frozen](https://www.amnesty.org/en/latest/news/2025/03/georgia-authorities-freeze-accounts-of-organizations-supporting-protesters-to-kill-the-peaceful-protests/) the bank accounts of five nonprofit organizations that provide financial and legal aid to dissenters. This comes in response to an uprising of protests over new controversial laws that restrict free expression and assembly, increase fines and detention periods, and expand law enforcement powers. Georgian officials justify the account freezes as part of an investigation into “sabotage,” yet they have provided no evidence. Amnesty International [warns](https://www.amnesty.org/en/latest/news/2025/03/georgia-authorities-freeze-accounts-of-organizations-supporting-protesters-to-kill-the-peaceful-protests/) this financial assault could “kill the entire protest movement.” Bitcoin provides a way to circumvent these struggles. Its uncensorable and permissionless nature has helped [sustain](https://www.journalofdemocracy.org/online-exclusive/how-to-dictator-proof-your-money/) pro-democracy movements across Belarus and Nigeria, proving it is capable of addressing the immense financial restrictions dictators impose. #### **United Arab Emirates | Plans to Launch “Digital Durham” CBDC in 2025** The United Arab Emirates (UAE) will [launch](https://www.businesstoday.in/technology/news/story/uae-to-launch-digital-dirham-by-year-end-to-modernise-payments-and-noost-financial-inclusion-470013-2025-03-31?utm_source=semafor#) its central bank digital currency (CBDC), the “[Digital Durham](https://cbdctracker.hrf.org/currency/united-arab-emirates),” by the end of 2025. [According](https://www.ledgerinsights.com/uae-to-launch-cbdc-in-q4-2025/) to the central bank, the CBDC will be available through licensed financial institutions and operate via a government-run digital wallet. Every transaction will be recorded on a permissioned blockchain run by the government. The central bank further [admitted](https://u.ae/en/about-the-uae/strategies-initiatives-and-awards/strategies-plans-and-visions/finance-and-economy/central-bank-digital-currency-strategy) the CBDC will replace cash and [assist](https://www.businesstoday.in/technology/news/story/uae-to-launch-digital-dirham-by-year-end-to-modernise-payments-and-noost-financial-inclusion-470013-2025-03-31?utm_source=semafor#) law enforcement “by leaving a digital trail for transactions involving illicit funds.” Officials [claim](https://www.businesstoday.in/technology/news/story/uae-to-launch-digital-dirham-by-year-end-to-modernise-payments-and-noost-financial-inclusion-470013-2025-03-31?utm_source=semafor#) this is to combat financial crime, but it also enables real-time surveillance and tracking of individual financial activity. In a country known for strict laws against dissent and extensive surveillance capabilities, it is not hard to see how a CBDC will erode the autonomy and rights of activists, dissenters, and others who oppose an increasingly authoritarian regime. #### **India | Grants Tax Authorities Access to Citizens’ Online Data** Starting in April 2026, the Indian government will [grant](https://economictimes.indiatimes.com/wealth/tax/your-email-and-social-media-account-can-be-accessed-by-income-tax-officer-starting-next-financial-year-in-these-cases/articleshow/118685184.cms) tax authorities legal access to the private online data of any citizen “suspected” of tax evasion. This will include legal access to personal emails, social media, and bank accounts. The new law expands on the Income Tax Act of 1961, which previously limited officials to searching physical premises for financial documents. Now, officials can bypass digital security measures and access private data without consent — all under a legal framework. This dissipation of financial privacy sets an intrusive precedent and opens the door to state-level corruption and surveillance in a country where the Modi regime has already made it clear they are happy to use financial repression to further cement their power. #### **Myanmar | Bitcoin as a Tool Support Earthquake Disaster Relief** Last week, a [7.7 magnitude earthquake](https://www.nytimes.com/2025/03/28/world/asia/earthquake-myanmar-thailand-death-toll.html) struck central Burma, with strong tremors reaching neighboring Thailand. The [official death toll ](https://www.reuters.com/business/environment/survivors-myanmar-quake-left-without-food-water-shelter-aid-groups-say-2025-04-01/)has surpassed 2700. And in Bangkok, a 33-story building under construction [collapsed](https://www.youtube.com/watch?v=ynrhyIh4ozo). Despite an already strenuous situation, Burma’s military junta continues its oppression. They are [blocking](https://www.nytimes.com/2025/03/31/world/asia/myanmar-earthquake-rescue.html) rescue teams from reaching the Sagaing region — the epicenter of the earthquake and the heart of Burma’s pro-democracy movement — and instead channeling aid to regime-controlled cities like Naypyidaw and Mandalay. The junta is also continuing to conduct air strikes on civilians and restricting equipment and fuel for aid groups, leaving a [million](https://data.unhcr.org/en/country/mmr) people in Sagaing to fend for themselves. In these repressive circumstances, Bitcoin can provide a censorship-resistant way to send funds directly to those affected. #### **Angola | Regime Jacks Price of Diesel** The Angolan regime [raised](https://www.rigzone.com/news/wire/angola_doubles_diesel_prices_after_imf_call_for_subsidy_cuts-25-mar-2025-180020-article/) diesel prices by 50% in the process of eliminating fuel subsidies. Diesel prices suddenly increased from 200 to 300 kwanza per liter, driving up transportation costs in a country where over half the population lives on [less](https://www.rigzone.com/news/wire/angola_doubles_diesel_prices_after_imf_call_for_subsidy_cuts-25-mar-2025-180020-article/) than $2 a day and inflation is over 42%. Previous fuel subsidy cuts in 2023 (where the price of diesel rose [80%](https://www.dw.com/en/angolan-police-crack-down-on-fuel-hike-protests/a-65978231)) sparked [protests](https://www.dw.com/en/angolan-police-crack-down-on-fuel-hike-protests/a-65978231) between taxi drivers, nonprofit workers, and law enforcement. This recent price increase now raises fears of renewed crackdowns. The Angolan regime also introduced new civil society laws that Guilherme Neves, chairman of the human rights organization Associacao Maos Livres, [describes](https://www.dw.com/en/angolan-police-crack-down-on-fuel-hike-protests/a-65978231) as a “license to erase non-governmental organizations that are not government-compliant.” Angolans find themselves in increasingly precarious financial positions as the government erodes the civil safeguards protecting nonprofits and dissenters. #### **Nicaragua | Ortega’s Dismantling of Press Freedom** Since coming to power in 2007, Ortega has [closed or seized](https://havanatimes.org/features/ortegas-war-on-journalism-in-nicaragua/) 61 media outlets, imprisoned countless journalists, and forced over 280 journalists into exile. His [assault on press freedom](https://havanatimes.org/features/ortegas-war-on-journalism-in-nicaragua/) has unfolded in two phases: initial raids on local radio stations and TV channels between 2007 and 2017, followed by full-scale censorship in 2018 on independent media outlets like [La Prensa](https://www.laprensani.com/) and [CONFIDENCIAL](https://confidencial.digital/). Ortega then intensified attacks from 2019 to 2021 by closing Nicaragua’s second-oldest newspaper and passing laws to [criminalize](https://havanatimes.org/features/ortegas-war-on-journalism-in-nicaragua/) free expression. This is a deliberate strategy to eliminate dissent and independent voices. What’s happening in Nicaragua highlights the importance of open and decentralized protocols like nostr, which allow journalists to publish freely without getting censored. While still early, it is becoming essential for sharing information absent the fear of being blocked or silenced by autocratic leaders. ## BITCOIN AND FREEDOM TECH NEWS #### **HRF | Gifts 1 Billion Satoshis to 20+ Open Source Projects Worldwide** HRF gifted 1 billion satoshis in its Q1 2025 round of [Bitcoin Development Fund](https://hrf.org/program/financial-freedom/bitcoin-development-fund/) (BDF) grants, supporting more than 20 open-source projects around the world. These projects advance Bitcoin education, open-source software, mining decentralization, and privacy tools for activists contending with authoritarian regimes across Asia, Latin America, and Africa. Supporting permissionless financial tools and censorship-resistant technologies empowers dissidents, journalists, and civil society to organize, transact, and communicate without state suppression and interference. Learn more about the grantees and their work [here](https://hrf.org/latest/hrf-bitcoin-development-fund-supports-20-projects-worldwide/). #### **Cove | New Open-Source and Permissionless Bitcoin Wallet** [Cove](https://github.com/bitcoinppl/cove) is a new open-source and permissionless mobile Bitcoin wallet that aims to put users in full control of their Bitcoin. Users can connect their own hardware wallet (to manage Bitcoin offline) or use Cove as a hot wallet (to manage Bitcoin online). It also allows users to create multiple wallets from the app itself. In the future, Cove plans to add Unspent Transaction Output (UTXO) selection and coin control, giving users more independence over their transactions and the tools to better protect their financial privacy. While still in beta and only suitable for test funds, this wallet holds promise as a privacy tool to equip dissidents with self-custodied Bitcoin. You can try it [here](https://github.com/bitcoinppl/cove). #### **Second | New Ark Implementation Launches on Bitcoin Signet** [Second](https://second.tech/), a company building on Ark, a protocol designed to help scale Bitcoin’s transaction throughput, [launched](https://blog.second.tech/try-ark-on-signet/?ref=nobsbitcoin.com) “Bark.” Bark is a test implementation of the Ark protocol deployed on Bitcoin’s [Signet](https://en.bitcoin.it/wiki/Signet) network (where developers test software). More broadly, the Ark protocol helps make Bitcoin transactions more private, faster, and cheaper, supporting the network in handling more transactions and users with the tradeoff of being less trusted than the mainchain, as funds stored in a noncustodial way on Ark can expire if not used. While it is still in early development, the test release of Bark marks a step toward deployment on the main Bitcoin network. Scaling solutions like Ark could be important for activists and individuals. They might ensure Bitcoin remains accessible to all, even as block space demand increases and network fees rise. Learn about it [here](https://blog.second.tech/try-ark-on-signet/?ref=nobsbitcoin.com). #### **Braiins | Open Sources Bitcoin Control Board** [Braiins](https://braiins.com/), a company building tools for Bitcoin mining, [open-sourced](https://x.com/BraiinsMining/status/1904601547855573458) its [BCB100](https://github.com/braiins/BCB100) Bitcoin Control Board, giving miners using their products greater insight and control over their Bitcoin mining hardware and firmware. Sharing the design files and firmware openly helps strengthen Bitcoin’s decentralization, making it more resilient against corporate or state interference. Specifically, open-sourcing mining hardware ensures individual miners can operate independently, reducing censorship risks across the entire network. In turn, this preserves financial freedom by keeping Bitcoin accessible and usable by dissidents, nonprofits, and individuals who need it most. #### **African Bitcoiners | Publish Bitcoin Starter Guide** [African Bitcoiners](https://x.com/afribitcoiners) just published “[Bitcoin: Africa’s Guide to Freedom Money](https://x.com/afribitcoiners/status/1904516726273851513),” a Bitcoin guide providing clear, practical insights into how Bitcoin can help people across the continent escape inflation, corrupt regimes, and failing financial systems. It covers essential topics to get started — from choosing a wallet to properly securing Bitcoin. In Africa, where some of the world’s longest-standing dictators restrict even basic financial activity, this guide is a powerful resource for human rights defenders, nonprofits, and everyday citizens. Read it[ here](https://bitcoiners.africa/bitcoin-africas-guide-to-freedom-money/). #### **OpenSats | 10th Wave of Nostr Grants** [OpenSats](https://opensats.org/), a nonprofit that supports open-source software development, [announced](https://opensats.org/blog/10th-wave-of-nostr-grants) its tenth wave of grants for projects in the nostr ecosystem. Nostr is a decentralized protocol that enables digital identity and communications outside the reach of authoritarian states. The grant round provides support to nostr Epoxy, which enhances access to nostr by circumventing censorship through a network of paid proxies. This ensures activists and dissidents can continue to communicate even in restrictive environments. Additionally, Zapstore received a grant for providing a permissionless app store built on nostr that enables developers to distribute software without corporate gatekeepers. This provides an open-source alternative to centralized app stores that often comply with government censorship and restrict dissidents’ access to freedom tools. ## RECOMMENDED CONTENT #### **Freedom Tech with Alex Gladstein** In this [episode](https://x.com/blockspacepod/status/1896229100702089589?s=46&t=yEPKerGEzeCp5j_mIaNJ8A) of The Gwart Show, Alex Gladstein, chief strategy officer at HRF, breaks down how and why Bitcoin serves as “money dictators can’t stop.” Drawing on more than 17 years of human rights work, he shares real-world examples of activists and citizens using Bitcoin to escape financial repression in authoritarian countries. Gladstein also explores privacy tools, cross-border payments, and why Bitcoin offers promising hope for financial freedom. Watch the full conversation [here](https://www.youtube.com/watch?v=5Ng961QZwI0). #### **The State of Personal Online Security and Confidentiality with Meredith Whittaker** In this [keynote](https://www.youtube.com/watch?v=AyH7zoP-JOg) for SXSW 2025, Signal CEO Meredith Whittaker shares her growing concerns around AI, personal data collection, and the erosion of privacy in today’s increasingly digital world. She emphasizes the need for more secure, uncensorable, and privacy-protecting technologies that shield users from surveillance and exploitation, especially in the context of authoritarian regimes. Watch the [full discussion](https://www.youtube.com/watch?v=AyH7zoP-JOg) for a pragmatic view into the future of digital privacy and security. *If this article was forwarded to you and you enjoyed reading it, please consider subscribing to the Financial Freedom Report [here](https://mailchi.mp/hrf.org/financial-freedom-newsletter?mc_cid=bf652c0a5a).* *Support the newsletter by donating bitcoin to HRF’s Financial Freedom program [via BTCPay](https://hrf.org/btc).*\ *Want to contribute to the newsletter? Submit tips, stories, news, and ideas by emailing us at ffreport @ [hrf.org](http://hrf.org/)* *The Bitcoin Development Fund (BDF) is accepting grant proposals on an ongoing basis. The Bitcoin Development Fund is looking to support Bitcoin developers, community builders, and educators. Submit proposals [here](https://forms.monday.com/forms/57019f8829449d9e729d9e3545a237ea?r=use1)*. [**Subscribe to newsletter**](http://financialfreedomreport.org/) [**Apply for a grant**](https://forms.monday.com/forms/57019f8829449d9e729d9e3545a237ea?r=use1&mc_cid=39c1c9b7e8&mc_eid=778e9876e3) [**Support our work**](https://hrf.org/btc?mc_cid=39c1c9b7e8&mc_eid=778e9876e3) [**Visit our website**](https://hrf.org/programs/financial-freedom/) @ 57d1a264:69f1fee1
2025-03-29 09:31:13> "THE NATURE OF BITCOIN IS SUCH THAT ONCE VERSION 0.1 WAS RELEASED, THE CORE DESIGN WAS SET IN STONE FOR THE REST OF ITS LIFETIME." <sub>- SATOSHI NAKAMOTO</sub>    "Reborn" is inspired by my Bitcoin journey and the many other people whose lives have been changed by Bitcoin. I’ve carved the hand in the “Gyan Mudra” or the “Mudra of Wisdom or Knowledge,” with an Opendime grasped between thumb and index finger alluding to the pursuit of Bitcoin knowledge. The hand emerges from rough, choppy water, and I've set the hand against an archway, through which, the copper leaf hints at the bright orange future made possible by Bitcoin. Materials: Carrara Marble, Copper leaf, Opendime Dimensions: 6" x 9" x 13" Price: $30,000 or BTC equivalent Enquire: https://www.vonbitcoin.com/available-works X: https://x.com/BVBTC/status/1894463357316419960/photo/1 originally posted at https://stacker.news/items/928510
@ 57d1a264:69f1fee1
2025-03-29 09:31:13> "THE NATURE OF BITCOIN IS SUCH THAT ONCE VERSION 0.1 WAS RELEASED, THE CORE DESIGN WAS SET IN STONE FOR THE REST OF ITS LIFETIME." <sub>- SATOSHI NAKAMOTO</sub>    "Reborn" is inspired by my Bitcoin journey and the many other people whose lives have been changed by Bitcoin. I’ve carved the hand in the “Gyan Mudra” or the “Mudra of Wisdom or Knowledge,” with an Opendime grasped between thumb and index finger alluding to the pursuit of Bitcoin knowledge. The hand emerges from rough, choppy water, and I've set the hand against an archway, through which, the copper leaf hints at the bright orange future made possible by Bitcoin. Materials: Carrara Marble, Copper leaf, Opendime Dimensions: 6" x 9" x 13" Price: $30,000 or BTC equivalent Enquire: https://www.vonbitcoin.com/available-works X: https://x.com/BVBTC/status/1894463357316419960/photo/1 originally posted at https://stacker.news/items/928510 @ db11b320:05c5f7af
2025-03-29 19:04:19magnet:?xt=urn:btih:9BAC9A3F98803AEA1EB28A0B60A562D7E3779710
@ db11b320:05c5f7af
2025-03-29 19:04:19magnet:?xt=urn:btih:9BAC9A3F98803AEA1EB28A0B60A562D7E3779710 @ a5142938:0ef19da3
2025-04-03 09:55:01### Core Team The Core Team drives the project and validates the content. - [Jean-David Bar](https://njump.me/npub1qr4p7uamcpawv7cr8z9nlhmd60lylukf7lvmtlnpe7r4juwxudzq3hrnll) To start, I'm managing the project solo. Contact me if you'd like to join! ### Content Enrichers Our contributors make this site engaging and interesting.
@ a5142938:0ef19da3
2025-04-03 09:55:01### Core Team The Core Team drives the project and validates the content. - [Jean-David Bar](https://njump.me/npub1qr4p7uamcpawv7cr8z9nlhmd60lylukf7lvmtlnpe7r4juwxudzq3hrnll) To start, I'm managing the project solo. Contact me if you'd like to join! ### Content Enrichers Our contributors make this site engaging and interesting. @ 0d788b5e:c99ddea5
2025-03-29 02:40:37- [首页](/readme.md) - [第一章、 第一章标题](/chapter1.md) - [第二章、 第二章标题](/chapter2.md)
@ 0d788b5e:c99ddea5
2025-03-29 02:40:37- [首页](/readme.md) - [第一章、 第一章标题](/chapter1.md) - [第二章、 第二章标题](/chapter2.md) @ 000002de:c05780a7
2025-04-01 18:04:17Over and over again people fall for phishing scams. An email that looks like it is coming from a legit sender turns out to be a scam. One way you can fight this attack is to only use an email client that displays the full email address. Not just part of it. Not just the from name. Do not assume that because an email has the name "Amazon" the from field that it is from Amazon.com. Look at the address. Now, it is possible for someone to spoof an email address but most of the time the scams I see don't even do this. I suspect this is because of expansion of DMARC policies. Many people simply do not check the actual email address. Other tips, don't click links in emails that you were not expecting to get like emails with log in links. Instead, visit the site and log in direction on the site. If you must click a link in an email look at the actual URL. Don't blindly click the link and for sure do not enter your credentials in a site without checking the domain. This is where password managers can help you out. Most filter passwords by URLs and will not suggest an account cred if you are on the wrong site. I know many of you, maybe most of you know this stuff but I bet there are those that don't. Or, have become lazy. originally posted at https://stacker.news/items/931364
@ 000002de:c05780a7
2025-04-01 18:04:17Over and over again people fall for phishing scams. An email that looks like it is coming from a legit sender turns out to be a scam. One way you can fight this attack is to only use an email client that displays the full email address. Not just part of it. Not just the from name. Do not assume that because an email has the name "Amazon" the from field that it is from Amazon.com. Look at the address. Now, it is possible for someone to spoof an email address but most of the time the scams I see don't even do this. I suspect this is because of expansion of DMARC policies. Many people simply do not check the actual email address. Other tips, don't click links in emails that you were not expecting to get like emails with log in links. Instead, visit the site and log in direction on the site. If you must click a link in an email look at the actual URL. Don't blindly click the link and for sure do not enter your credentials in a site without checking the domain. This is where password managers can help you out. Most filter passwords by URLs and will not suggest an account cred if you are on the wrong site. I know many of you, maybe most of you know this stuff but I bet there are those that don't. Or, have become lazy. originally posted at https://stacker.news/items/931364 @ 2183e947:f497b975
2025-03-29 02:41:34Today I was invited to participate in the private beta of a new social media protocol called Pubky, designed by a bitcoin company called Synonym with the goal of being better than existing social media platforms. As a heavy nostr user, I thought I'd write up a comparison. I can't tell you how to create your own accounts because it was made very clear that only *some* of the software is currently open source, and how this will all work is still a bit up in the air. The code that *is* open source can be found here: https://github.com/pubky -- and the most important repo there seems to be this one: https://github.com/pubky/pubky-core You can also learn more about Pubky here: https://pubky.org/ That said, I used my invite code to create a pubky account and it seemed very similar to onboarding to nostr. I generated a private key, backed up 12 words, and the onboarding website gave me a public key. Then I logged into a web-based client and it looked a lot like twitter. I saw a feed for posts by other users and saw options to reply to posts and give reactions, which, I saw, included hearts, thumbs up, and other emojis. Then I investigated a bit deeper to see how much it was like nostr. I opened up my developer console and navigated to my networking tab, where, if this was nostr, I would expect to see queries to relays for posts. Here, though, I saw one query that seemed to be repeated on a loop, which went to a single server and provided it with my pubkey. That single query (well, a series of identical queries to the same server) seemed to return all posts that showed up on my feed. So I infer that the server "knows" what posts to show me (perhaps it has some sort of algorithm, though the marketing material says it does not use algorithms) and the query was on a loop so that if any new posts came in that the server thinks I might want to see, it can add them to my feed. Then I checked what happens when I create a post. I did so and looked at what happened in my networking tab. If this was nostr, I would expect to see multiple copies of a signed messaged get sent to a bunch of relays. Here, though, I saw one message get sent to the same server that was populating my feed, and that message was not signed, it was a plaintext copy of my message. I happened to be in a group chat with John Carvalho at the time, who is associated with pubky. I asked him what was going on, and he said that pubky is based around three types of servers: homeservers, DHT servers, and indexer servers. The homeserver is where you create posts and where you query for posts to show on your feed. DHT servers are used for censorship resistance: each user creates an entry on a DHT server saying what homeserver they use, and these entries are signed by their key. As for indexers, I think those are supposed to speed up the use of the DHT servers. From what I could tell, indexers query DHT servers to find out what homeservers people use. When you query a homeserver for posts, it is supposed to reach out to indexer servers to find out the homeservers of people whose posts the homeserver decided to show you, and then query those homeservers for those posts. I believe they decided not to look up what homeservers people use directly on DHT servers directly because DHT servers are kind of slow, due to having to store and search through all sorts of non-social-media content, whereas indexers only store a simple db that maps each user's pubkey to their homeserver, so they are faster. Based on all of this info, it seems like, to populate your feed, this is the series of steps: - you tell your homeserver your pubkey - it uses some sort of algorithm to decide whose posts to show you - then looks up the homeservers used by those people on an indexer server - then it fetches posts from their homeservers - then your client displays them to you To create a post, this is the series of steps: - you tell your homeserver what you want to say to the world - it stores that message in plaintext and merely asserts that it came from you (it's not signed) - other people can find out what you said by querying for your posts on your homeserver Since posts on homeservers are not signed, I asked John what prevents a homeserver from just making up stuff and claiming I said it. He said nothing stops them from doing that, and if you are using a homeserver that starts acting up in that manner, what you should do is start using a new homeserver and update your DHT record to point at your new homeserver instead of the old one. Then, indexers should update their db to show where your new homeserver is, and the homeservers of people who "follow" you should stop pulling content from your old homeserver and start pulling it from your new one. If their homeserver is misbehaving too, I'm not sure what would happen. Maybe it could refuse to show them the content you've posted on your new homeserver, keeping making up fake content on your behalf that you've never posted, and maybe the people you follow would never learn you're being impersonated or have moved to a new homeserver. John also clarified that there is not currently any tooling for migrating user content from one homeserver to another. If pubky gets popular and a big homeserver starts misbehaving, users will probably need such a tool. But these are early days, so there aren't that many homeservers, and the ones that exist seem to be pretty trusted. Anyway, those are my initial thoughts on Pubky. Learn more here: https://pubky.org/
@ 2183e947:f497b975
2025-03-29 02:41:34Today I was invited to participate in the private beta of a new social media protocol called Pubky, designed by a bitcoin company called Synonym with the goal of being better than existing social media platforms. As a heavy nostr user, I thought I'd write up a comparison. I can't tell you how to create your own accounts because it was made very clear that only *some* of the software is currently open source, and how this will all work is still a bit up in the air. The code that *is* open source can be found here: https://github.com/pubky -- and the most important repo there seems to be this one: https://github.com/pubky/pubky-core You can also learn more about Pubky here: https://pubky.org/ That said, I used my invite code to create a pubky account and it seemed very similar to onboarding to nostr. I generated a private key, backed up 12 words, and the onboarding website gave me a public key. Then I logged into a web-based client and it looked a lot like twitter. I saw a feed for posts by other users and saw options to reply to posts and give reactions, which, I saw, included hearts, thumbs up, and other emojis. Then I investigated a bit deeper to see how much it was like nostr. I opened up my developer console and navigated to my networking tab, where, if this was nostr, I would expect to see queries to relays for posts. Here, though, I saw one query that seemed to be repeated on a loop, which went to a single server and provided it with my pubkey. That single query (well, a series of identical queries to the same server) seemed to return all posts that showed up on my feed. So I infer that the server "knows" what posts to show me (perhaps it has some sort of algorithm, though the marketing material says it does not use algorithms) and the query was on a loop so that if any new posts came in that the server thinks I might want to see, it can add them to my feed. Then I checked what happens when I create a post. I did so and looked at what happened in my networking tab. If this was nostr, I would expect to see multiple copies of a signed messaged get sent to a bunch of relays. Here, though, I saw one message get sent to the same server that was populating my feed, and that message was not signed, it was a plaintext copy of my message. I happened to be in a group chat with John Carvalho at the time, who is associated with pubky. I asked him what was going on, and he said that pubky is based around three types of servers: homeservers, DHT servers, and indexer servers. The homeserver is where you create posts and where you query for posts to show on your feed. DHT servers are used for censorship resistance: each user creates an entry on a DHT server saying what homeserver they use, and these entries are signed by their key. As for indexers, I think those are supposed to speed up the use of the DHT servers. From what I could tell, indexers query DHT servers to find out what homeservers people use. When you query a homeserver for posts, it is supposed to reach out to indexer servers to find out the homeservers of people whose posts the homeserver decided to show you, and then query those homeservers for those posts. I believe they decided not to look up what homeservers people use directly on DHT servers directly because DHT servers are kind of slow, due to having to store and search through all sorts of non-social-media content, whereas indexers only store a simple db that maps each user's pubkey to their homeserver, so they are faster. Based on all of this info, it seems like, to populate your feed, this is the series of steps: - you tell your homeserver your pubkey - it uses some sort of algorithm to decide whose posts to show you - then looks up the homeservers used by those people on an indexer server - then it fetches posts from their homeservers - then your client displays them to you To create a post, this is the series of steps: - you tell your homeserver what you want to say to the world - it stores that message in plaintext and merely asserts that it came from you (it's not signed) - other people can find out what you said by querying for your posts on your homeserver Since posts on homeservers are not signed, I asked John what prevents a homeserver from just making up stuff and claiming I said it. He said nothing stops them from doing that, and if you are using a homeserver that starts acting up in that manner, what you should do is start using a new homeserver and update your DHT record to point at your new homeserver instead of the old one. Then, indexers should update their db to show where your new homeserver is, and the homeservers of people who "follow" you should stop pulling content from your old homeserver and start pulling it from your new one. If their homeserver is misbehaving too, I'm not sure what would happen. Maybe it could refuse to show them the content you've posted on your new homeserver, keeping making up fake content on your behalf that you've never posted, and maybe the people you follow would never learn you're being impersonated or have moved to a new homeserver. John also clarified that there is not currently any tooling for migrating user content from one homeserver to another. If pubky gets popular and a big homeserver starts misbehaving, users will probably need such a tool. But these are early days, so there aren't that many homeservers, and the ones that exist seem to be pretty trusted. Anyway, those are my initial thoughts on Pubky. Learn more here: https://pubky.org/ @ ed84ce10:cccf4c2a
2025-03-18 14:19:19## **The Evolution of Hackathons: From Offline to Online, Powering Frontier Innovation Worldwide** Throughout the history of open-source platform technology, hackathons have been the launchpads for innovation—fueling breakthroughs, incubating the next generation of startups, and serving as the proving ground for builders. Over the past decade, [DoraHacks](https://dorahacks.io/) has led the charge, driving the hacker movement and open-source revolution. We didn’t just witness the evolution of hackathons—we architected it. ### **The Online Revolution of Hackathons** Before 2020, hackathons were largely stuck in the physical world—you had to be in the room to participate. The idea of a fully online, global hackathon was a pipe dream. Then, [DoraHacks.io](http://dorahacks.io/) changed everything. Suddenly, a developer in Africa could win funding from a hackathon hosted by a Silicon Valley company. Geographic barriers collapsed. Today, over 95% of hackathons happen online. ### **The Infrastructure Revolution: Making Hackathons 10x More Effective** [DoraHacks](https://dorahacks.io/) relentlessly iterated on the hackathon model. We built BUIDL pages for real-time project showcases, a world-class hackathon organizer dashboard, MACI-powered decentralized privacy governance, and Grant DAOs that provide ongoing funding. The result? [DoraHacks](https://dorahacks.io/) became the ultimate launchpad for hackers and early-stage builders. ### **The Ecosystem Revolution: Supercharging Open Innovation** [DoraHacks](https://dorahacks.io/) became the backbone of Web3 innovation—from Ethereum, Solana, and BNB Chain to the next wave of blockchains like Aptos, Cosmos, Injective, TON, and Sonic. Since 2023, hackathons have expanded beyond crypto—quantum computing, commercial space tech, and AI-driven innovations are now being built on [DoraHacks](https://dorahacks.io/). ## **Rolling Hackathons and Uninterrupted BUIDLing - the New Standard for Ecosystem Growth** **BUIDLs can be created spontaneously at any time.** Hosting Hackathons as short-term events held only once or twice a year is not conducive to attracting outstanding Hackers and high-quality projects to join the ecosystem and drive innovation in the long term. To remediate this, **Hackathons should be continuous and uninterrupted, serving as a long-term driving force within the developer ecosystem.** Historically, the **high organizational costs** and **substantial resource investments** associated with frequent Hackathons meant that most emerging ecosystems couldn't afford to host them regularly. As a result, Hackathons became rare, annual spectacles, and for some projects, an unaffordable luxury. This model severely restricted developers' chances to participate and hindered the ecosystem's ability to innovate consistently. Let's imagine what would happen if an ecosystem held 12 or more Hackathons each year? - **Developers have a clear loyalty incentive:** They would know that the ecosystem is committed to supporting and funding excellent developers and projects continuously, which would encourage them to make long-term investments and contribute regularly. - **Missing out is no longer an issue:** Even if a developer couldn't attend a particular Hackathon, there would be another one soon, increasing accessibility. - **Accelerated ecosystem innovation:** Frequent Hackathons would accelerate ecosystem innovation. Developers would be constantly pushed to explore new directions, significantly boosting the growth rate of the technological ecosystem. Previously, **due to the limitations of costs and organizational difficulties, frequent Hackathons were almost unthinkable**. Only ecosystems with sufficient funds like Google and Amazon could afford rolling Hackathons. But now, **[DoraHacks](https://dorahacks.io/)' upcoming BUIDL AI platform tools** are set to change the game. These tools make it possible to organize 12 Hackathons in a year, and even go a step further by enabling the simultaneous hosting of multiple differently-themed Hackathons. This will help emerging ecosystems effectively incentivise developers, expand their technological influence, and increase the number of exceptional BUIDLs (projects) in their ecosystems. **The majority of BUIDLs come about continuously and spontaneously and should be recognized and incentivized promptly, rather than having to wait for the single annual Hackathon.** As the saying goes, **"He who wins over developers wins the world."** In the highly competitive Web3 space, Hackathons are an effective means of attracting developers, and **rolling Hackathons are the best way to achieve this**. For an ecosystem to stay competitive, it must ensure that developers always have opportunities to engage and create. ## **The AI Era of Hackathons: A 10x Opportunity, A 10x Challenge** ### **AI Turns Everyone Into a Hacker** AI has obliterated repetitive work. Building is faster than ever. Anyone, from anywhere, can hack, ship, and scale with AI tools that accelerate ideation, development, and execution. The potential of hackathons in this AI-powered era is 10x bigger than ever before. ### **But Hackathon Infrastructure Is Stuck in the Past** **Despite this massive opportunity, organizing hackathons remains painfully inefficient:** - Most organizations don’t know how to run hackathons effectively. - Even those who do lack time and resources to do it frequently. - Ecosystem builders who have the resources can only host one hackathon per year. **The result?** - Hackathons are underutilized, slowing innovation. - Ecosystem growth is bottlenecked by developer relations (DevRel) teams. - Many ecosystems fail to maximize the potential of hackathons. - Low-frequency hackathons waste hacker potential—builders sit idle when they could be shipping. ## **BUIDL AI: Unlocking the Infinite Potential of Hackathons** We refuse to let inefficiency limit innovation. BUIDL AI is our answer. [DoraHacks](https://dorahacks.io/) is launching BUIDL AI, the AI-powered Hackathon Co-Pilot that automates, scales, and supercharges hackathon organization. ### **BUIDL AI: The Game-Changing Features** **1. Edit and Launch: One-Click Hackathon Deployment** Organizers can now launch a hackathon in minutes by filling in basic details (prizes, themes, workshops, judges, etc.). No tedious manual setup. **2. BUIDL Review: Submission Evaluation (10x Faster)** Traditional hackathons get hundreds of submissions—judging takes hundreds of hours. BUIDL AI changes the game. It automatically scores projects based on completeness, originality, and theme relevance—filtering out low-quality submissions 10x faster than before. **3. Automated Marketing: Instant Hackathon Reports** After the hackathon ends, BUIDL AI auto-generates a full post-event report—highlighting winners, standout projects, and key takeaways—boosting visibility and impact. **4. Seamless Interaction: Smarter Collaboration, No Bottlenecks** BUIDL AI will interact with hackathon organizers to keep organizers in sync, alerting them about new submissions, pending approvals, and participant inquiries in real time. No more dropped balls. **5. Multi-Hackathon Management: Scaling Innovation Without Limits** Before BUIDL AI, running multiple hackathons at once was a logistical nightmare. Now, ecosystem builders can launch and manage multiple hackathons seamlessly, boosting innovation frequency exponentially **The full BUIDL AI Beta version will release on April 15th, but multiple free BUIDL AI features have already been available on [DoraHacks.io](http://dorahacks.io/)!** ## **BUIDL AI: The Next Great Leap in Open Innovation** Hackathons aren’t just competitions. They are the birthplace of the next trillion-dollar innovations. With BUIDL AI, hackathons enter a new era—automated, intelligent, and infinitely scalable. This means more hackers, more builders, and more breakthrough projects than ever before. At [DoraHacks](https://dorahacks.io/), we believe in an open, hacker-driven future. BUIDL AI is the rocket fuel for that future.
@ ed84ce10:cccf4c2a
2025-03-18 14:19:19## **The Evolution of Hackathons: From Offline to Online, Powering Frontier Innovation Worldwide** Throughout the history of open-source platform technology, hackathons have been the launchpads for innovation—fueling breakthroughs, incubating the next generation of startups, and serving as the proving ground for builders. Over the past decade, [DoraHacks](https://dorahacks.io/) has led the charge, driving the hacker movement and open-source revolution. We didn’t just witness the evolution of hackathons—we architected it. ### **The Online Revolution of Hackathons** Before 2020, hackathons were largely stuck in the physical world—you had to be in the room to participate. The idea of a fully online, global hackathon was a pipe dream. Then, [DoraHacks.io](http://dorahacks.io/) changed everything. Suddenly, a developer in Africa could win funding from a hackathon hosted by a Silicon Valley company. Geographic barriers collapsed. Today, over 95% of hackathons happen online. ### **The Infrastructure Revolution: Making Hackathons 10x More Effective** [DoraHacks](https://dorahacks.io/) relentlessly iterated on the hackathon model. We built BUIDL pages for real-time project showcases, a world-class hackathon organizer dashboard, MACI-powered decentralized privacy governance, and Grant DAOs that provide ongoing funding. The result? [DoraHacks](https://dorahacks.io/) became the ultimate launchpad for hackers and early-stage builders. ### **The Ecosystem Revolution: Supercharging Open Innovation** [DoraHacks](https://dorahacks.io/) became the backbone of Web3 innovation—from Ethereum, Solana, and BNB Chain to the next wave of blockchains like Aptos, Cosmos, Injective, TON, and Sonic. Since 2023, hackathons have expanded beyond crypto—quantum computing, commercial space tech, and AI-driven innovations are now being built on [DoraHacks](https://dorahacks.io/). ## **Rolling Hackathons and Uninterrupted BUIDLing - the New Standard for Ecosystem Growth** **BUIDLs can be created spontaneously at any time.** Hosting Hackathons as short-term events held only once or twice a year is not conducive to attracting outstanding Hackers and high-quality projects to join the ecosystem and drive innovation in the long term. To remediate this, **Hackathons should be continuous and uninterrupted, serving as a long-term driving force within the developer ecosystem.** Historically, the **high organizational costs** and **substantial resource investments** associated with frequent Hackathons meant that most emerging ecosystems couldn't afford to host them regularly. As a result, Hackathons became rare, annual spectacles, and for some projects, an unaffordable luxury. This model severely restricted developers' chances to participate and hindered the ecosystem's ability to innovate consistently. Let's imagine what would happen if an ecosystem held 12 or more Hackathons each year? - **Developers have a clear loyalty incentive:** They would know that the ecosystem is committed to supporting and funding excellent developers and projects continuously, which would encourage them to make long-term investments and contribute regularly. - **Missing out is no longer an issue:** Even if a developer couldn't attend a particular Hackathon, there would be another one soon, increasing accessibility. - **Accelerated ecosystem innovation:** Frequent Hackathons would accelerate ecosystem innovation. Developers would be constantly pushed to explore new directions, significantly boosting the growth rate of the technological ecosystem. Previously, **due to the limitations of costs and organizational difficulties, frequent Hackathons were almost unthinkable**. Only ecosystems with sufficient funds like Google and Amazon could afford rolling Hackathons. But now, **[DoraHacks](https://dorahacks.io/)' upcoming BUIDL AI platform tools** are set to change the game. These tools make it possible to organize 12 Hackathons in a year, and even go a step further by enabling the simultaneous hosting of multiple differently-themed Hackathons. This will help emerging ecosystems effectively incentivise developers, expand their technological influence, and increase the number of exceptional BUIDLs (projects) in their ecosystems. **The majority of BUIDLs come about continuously and spontaneously and should be recognized and incentivized promptly, rather than having to wait for the single annual Hackathon.** As the saying goes, **"He who wins over developers wins the world."** In the highly competitive Web3 space, Hackathons are an effective means of attracting developers, and **rolling Hackathons are the best way to achieve this**. For an ecosystem to stay competitive, it must ensure that developers always have opportunities to engage and create. ## **The AI Era of Hackathons: A 10x Opportunity, A 10x Challenge** ### **AI Turns Everyone Into a Hacker** AI has obliterated repetitive work. Building is faster than ever. Anyone, from anywhere, can hack, ship, and scale with AI tools that accelerate ideation, development, and execution. The potential of hackathons in this AI-powered era is 10x bigger than ever before. ### **But Hackathon Infrastructure Is Stuck in the Past** **Despite this massive opportunity, organizing hackathons remains painfully inefficient:** - Most organizations don’t know how to run hackathons effectively. - Even those who do lack time and resources to do it frequently. - Ecosystem builders who have the resources can only host one hackathon per year. **The result?** - Hackathons are underutilized, slowing innovation. - Ecosystem growth is bottlenecked by developer relations (DevRel) teams. - Many ecosystems fail to maximize the potential of hackathons. - Low-frequency hackathons waste hacker potential—builders sit idle when they could be shipping. ## **BUIDL AI: Unlocking the Infinite Potential of Hackathons** We refuse to let inefficiency limit innovation. BUIDL AI is our answer. [DoraHacks](https://dorahacks.io/) is launching BUIDL AI, the AI-powered Hackathon Co-Pilot that automates, scales, and supercharges hackathon organization. ### **BUIDL AI: The Game-Changing Features** **1. Edit and Launch: One-Click Hackathon Deployment** Organizers can now launch a hackathon in minutes by filling in basic details (prizes, themes, workshops, judges, etc.). No tedious manual setup. **2. BUIDL Review: Submission Evaluation (10x Faster)** Traditional hackathons get hundreds of submissions—judging takes hundreds of hours. BUIDL AI changes the game. It automatically scores projects based on completeness, originality, and theme relevance—filtering out low-quality submissions 10x faster than before. **3. Automated Marketing: Instant Hackathon Reports** After the hackathon ends, BUIDL AI auto-generates a full post-event report—highlighting winners, standout projects, and key takeaways—boosting visibility and impact. **4. Seamless Interaction: Smarter Collaboration, No Bottlenecks** BUIDL AI will interact with hackathon organizers to keep organizers in sync, alerting them about new submissions, pending approvals, and participant inquiries in real time. No more dropped balls. **5. Multi-Hackathon Management: Scaling Innovation Without Limits** Before BUIDL AI, running multiple hackathons at once was a logistical nightmare. Now, ecosystem builders can launch and manage multiple hackathons seamlessly, boosting innovation frequency exponentially **The full BUIDL AI Beta version will release on April 15th, but multiple free BUIDL AI features have already been available on [DoraHacks.io](http://dorahacks.io/)!** ## **BUIDL AI: The Next Great Leap in Open Innovation** Hackathons aren’t just competitions. They are the birthplace of the next trillion-dollar innovations. With BUIDL AI, hackathons enter a new era—automated, intelligent, and infinitely scalable. This means more hackers, more builders, and more breakthrough projects than ever before. At [DoraHacks](https://dorahacks.io/), we believe in an open, hacker-driven future. BUIDL AI is the rocket fuel for that future. @ 1bda7e1f:bb97c4d9
2025-01-02 05:19:08### Tldr - Nostr is an open and interoperable protocol - You can integrate it with workflow automation tools to augment your experience - n8n is a great low/no-code workflow automation tool which you can host yourself - Nostrobots allows you to integrate Nostr into n8n - In this blog I create some workflow automations for Nostr - A simple form to delegate posting notes - Push notifications for mentions on multiple accounts - Push notifications for your favourite accounts when they post a note - All workflows are provided as open source with MIT license for you to use ### Inter-op All The Things Nostr is a new open social protocol for the internet. This open nature exciting because of the opportunities for interoperability with other technologies. In [Using NFC Cards with Nostr]() I explored the `nostr:` URI to launch Nostr clients from a card tap. The interoperability of Nostr doesn't stop there. The internet has many super-powers, and Nostr is open to all of them. Simply, there's no one to stop it. There is no one in charge, there are no permissioned APIs, and there are no risks of being de-platformed. If you can imagine technologies that would work well with Nostr, then any and all of them can ride on or alongside Nostr rails. My mental model for why this is special is Google Wave ~2010. Google Wave was to be the next big platform. Lars was running it and had a big track record from Maps. I was excited for it. Then, Google pulled the plug. And, immediately all the time and capital invested in understanding and building on the platform was wasted. This cannot happen to Nostr, as there is no one to pull the plug, and maybe even no plug to pull. So long as users demand Nostr, Nostr will exist, and that is a pretty strong guarantee. It makes it worthwhile to invest in bringing Nostr into our other applications. All we need are simple ways to plug things together. ### Nostr and Workflow Automation Workflow automation is about helping people to streamline their work. As a user, the most common way I achieve this is by connecting disparate systems together. By setting up one system to trigger another or to move data between systems, I can solve for many different problems and become way more effective. #### n8n for workflow automation Many workflow automation tools exist. My favourite is [n8n](https://n8n.io/). n8n is a low/no-code workflow automation platform which allows you to build all kinds of workflows. You can use it for free, you can self-host it, it has a user-friendly UI and useful API. Vs Zapier it can be far more elaborate. Vs Make.com I find it to be more intuitive in how it abstracts away the right parts of the code, but still allows you to code when you need to. Most importantly you can plug anything into n8n: You have built-in nodes for specific applications. HTTP nodes for any other API-based service. And community nodes built by individual community members for any other purpose you can imagine. #### Eating my own dogfood It's very clear to me that there is a big design space here just demanding to be explored. If you could integrate Nostr with anything, what would you do? In my view the best way for anyone to start anything is by solving their own problem first (aka "scratching your own itch" and "eating your own dogfood"). As I get deeper into Nostr I find myself controlling multiple Npubs – to date I have a personal Npub, a brand Npub for a community I am helping, an AI assistant Npub, and various testing Npubs. I need ways to delegate access to those Npubs without handing over the keys, ways to know if they're mentioned, and ways to know if they're posting. I can build workflows with n8n to solve these issues for myself to start with, and keep expanding from there as new needs come up. ### Running n8n with Nostrobots I am mostly non-technical with a very helpful AI. To set up n8n to work with Nostr and operate these workflows should be possible for anyone with basic technology skills. - I have a cheap VPS which currently runs my [HAVEN Nostr Relay](https://rodbishop.npub.pro/post/8ca68889/) and [Albyhub Lightning Node](https://rodbishop.npub.pro/post/setting-up-payments-on-nostr-7o6ls7/) in Docker containers, - My objective was to set up n8n to run alongside these in a separate Docker container on the same server, install the required nodes, and then build and host my workflows. #### Installing n8n Self-hosting n8n could not be easier. I followed n8n's [Docker-Compose installation docs](https://docs.n8n.io/hosting/installation/server-setups/docker-compose/)– - Install Docker and Docker-Compose if you haven't already, - Create your ``docker-compose.yml`` and `.env` files from the docs, - Create your data folder `sudo docker volume create n8n_data`, - Start your container with `sudo docker compose up -d`, - Your n8n instance should be online at port `5678`. n8n is free to self-host but does require a license. Enter your credentials into n8n to get your free license key. You should now have access to the Workflow dashboard and can create and host any kind of workflows from there. #### Installing Nostrobots To integrate n8n nicely with Nostr, I used the [Nostrobots](https://github.com/ocknamo/n8n-nodes-nostrobots?tab=readme-ov-file) community node by [Ocknamo](nostr:npub1y6aja0kkc4fdvuxgqjcdv4fx0v7xv2epuqnddey2eyaxquznp9vq0tp75l). In n8n parlance a "node" enables certain functionality as a step in a workflow e.g. a "set" node sets a variable, a "send email" node sends an email. n8n comes with all kinds of "official" nodes installed by default, and Nostr is not amongst them. However, n8n also comes with a framework for community members to create their own "community" nodes, which is where Nostrobots comes in. You can only use a community node in a self-hosted n8n instance (which is what you have if you are running in Docker on your own server, but this limitation does prevent you from using n8n's own hosted alternative). To install a community node, [see n8n community node docs](https://docs.n8n.io/integrations/community-nodes/installation/gui-install/). From your workflow dashboard– - Click the "..." in the bottom left corner beside your username, and click "settings", - Cilck "community nodes" left sidebar, - Click "Install", - Enter the "npm Package Name" which is `n8n-nodes-nostrobots`, - Accept the risks and click "Install", - Nostrobots is now added to your n8n instance. #### Using Nostrobots Nostrobots gives you nodes to help you build Nostr-integrated workflows– - **Nostr Write** – for posting Notes to the Nostr network, - **Nostr Read** – for reading Notes from the Nostr network, and - **Nostr Utils** – for performing certain conversions you may need (e.g. from bech32 to hex). Nostrobots has [good documentation](https://github.com/ocknamo/n8n-nodes-nostrobots?tab=readme-ov-file) on each node which focuses on simple use cases. Each node has a "convenience mode" by default. For example, the "Read" Node by default will fetch Kind 1 notes by a simple filter, in Nostrobots parlance a "Strategy". For example, with Strategy set to "Mention" the node will accept a pubkey and fetch all Kind 1 notes that Mention the pubkey within a time period. This is very good for quick use. What wasn't clear to me initially (until Ocknamo helped me out) is that advanced use cases are also possible. Each node also has an advanced mode. For example, the "Read" Node can have "Strategy" set to "RawFilter(advanced)". Now the node will accept json (anything you like that complies with [NIP-01](https://github.com/nostr-protocol/nips/blob/master/01.md)). You can use this to query Notes (Kind 1) as above, and also Profiles (Kind 0), Follow Lists (Kind 3), Reactions (Kind 7), Zaps (Kind 9734/9735), and anything else you can think of. #### Creating and adding workflows With n8n and Nostrobots installed, you can now create or add any kind of Nostr Workflow Automation. - Click "Add workflow" to go to the workflow builder screen, - If you would like to build your own workflow, you can start with adding any node. Click "+" and see what is available. Type "Nostr" to explore the Nostrobots nodes you have added, - If you would like to add workflows that someone else has built, click "..." in the top right. Then click "import from URL" and paste in the URL of any workflow you would like to use (including the ones I share later in this article). ### Nostr Workflow Automations It's time to build some things! #### A simple form to post a note to Nostr I started very simply. I needed to delegate the ability to post to Npubs that I own in order that a (future) team can test things for me. I don't want to worry about managing or training those people on how to use keys, and I want to revoke access easily. I needed a basic form with credentials that posted a Note. For this I can use a very simple workflow– - **A n8n Form node** – Creates a form for users to enter the note they wish to post. Allows for the form to be protected by a username and password. This node is the workflow "trigger" so that the workflow runs each time the form is submitted. - **A Set node** – Allows me to set some variables, in this case I set the relays that I intend to use. I typically add a Set node immediately following the trigger node, and put all the variables I need in this. It helps to make the workflows easier to update and maintain. - **A Nostr Write node** (from Nostrobots) – Writes a Kind-1 note to the Nostr network. It accepts Nostr credentials, the output of the Form node, and the relays from the Set node, and posts the Note to those relays. Once the workflow is built, you can test it with the testing form URL, and set it to "Active" to use the production form URL. That's it. You can now give posting access to anyone for any Npub. To revoke access, simply change the credentials or set to workflow to "Inactive". It may also be the world's simplest Nostr client. You can find the [Nostr Form to Post a Note workflow here](https://github.com/r0d8lsh0p/nostr-n8n/blob/main/Nostr_Form_to_Post_a_Note.json). #### Push notifications on mentions and new notes One of the things Nostr is not very good at is push notifications. Furthermore I have some unique itches to scratch. I want– - **To make sure I never miss a note addressed to any of my Npubs** – For this I want a push notification any time any Nostr user mentions any of my Npubs, - **To make sure I always see all notes from key accounts** – For this I need a push notification any time any of my Npubs post any Notes to the network, - **To get these notifications on all of my devices** – Not just my phone where my Nostr regular client lives, but also on each of my laptops to suit wherever I am working that day. I needed to build a Nostr push notifications solution. To build this workflow I had to string a few ideas together– - **Triggering the node on a schedule** – Nostrobots does not include a trigger node. As every workflow starts with a trigger we needed a different method. I elected to run the workflow on a schedule of every 10-minutes. Frequent enough to see Notes while they are hot, but infrequent enough to not burden public relays or get rate-limited, - **Storing a list of Npubs in a Nostr list** – I needed a way to store the list of Npubs that trigger my notifications. I initially used an array defined in the workflow, this worked fine. Then I decided to try Nostr lists ([NIP-51, kind 30000](https://github.com/nostr-protocol/nips/blob/master/51.md)). By defining my list of Npubs as a list published to Nostr I can control my list from within a Nostr client (e.g. [Listr.lol](https://listr.lol/npub1r0d8u8mnj6769500nypnm28a9hpk9qg8jr0ehe30tygr3wuhcnvs4rfsft) or [Nostrudel.ninja](https://nostrudel.ninja/#/lists)). Not only does this "just work", but because it's based on Nostr lists automagically Amethyst client allows me to browse that list as a Feed, and everyone I add gets notified in their Mentions, - **Using specific relays** – I needed to query the right relays, including my own HAVEN relay inbox for notes addressed to me, and wss://purplepag.es for Nostr profile metadata, - **Querying Nostr events** (with Nostrobots) – I needed to make use of many different Nostr queries and use quite a wide range of what Nostrobots can do– - I read the EventID of my Kind 30000 list, to return the desired pubkeys, - For notifications on mentions, I read all Kind 1 notes that mention that pubkey, - For notifications on new notes, I read all Kind 1 notes published by that pubkey, - Where there are notes, I read the Kind 0 profile metadata event of that pubkey to get the displayName of the relevant Npub, - I transform the EventID into a Nevent to help clients find it. - **Using the Nostr URI** – As I did with my NFC card article, I created a link with the `nostr:` URI prefix so that my phone's native client opens the link by default, - **Push notifications solution** – I needed a push notifications solution. I found many with n8n integrations and chose to go with [Pushover](https://pushover.net/) which supports all my devices, has a free trial, and is unfairly cheap with a $5-per-device perpetual license. Once the workflow was built, lists published, and Pushover installed on my phone, I was fully set up with push notifications on Nostr. I have used these workflows for several weeks now and made various tweaks as I went. They are feeling robust and I'd welcome you to give them a go. You can find the [Nostr Push Notification If Mentioned here](https://github.com/r0d8lsh0p/nostr-n8n/blob/main/Nostr_Push_Notify_If_Mentioned.json) and [If Posts a Note here](https://github.com/r0d8lsh0p/nostr-n8n/blob/main/Nostr_Push_Notify_If_Post_a_Note.json). In speaking with other Nostr users while I was building this, there are all kind of other needs for push notifications too – like on replies to a certain bookmarked note, or when a followed Npub starts streaming on zap.stream. These are all possible. #### Use my workflows I have open sourced all my workflows at my [Github](https://github.com/r0d8lsh0p/nostr-n8n) with MIT license and tried to write complete docs, so that you can import them into your n8n and configure them for your own use. To import any of my workflows– - Click on the workflow of your choice, e.g. "[Nostr_Push_Notify_If_Mentioned.json](https://github.com/r0d8lsh0p/nostr-n8n/blob/main/Nostr_Push_Notify_If_Mentioned.json "Nostr_Push_Notify_If_Mentioned.json")", - Click on the "raw" button to view the raw JSON, ex any Github page layout, - Copy that URL, - Enter that URL in the "import from URL" dialog [mentioned above](#creating-and-adding-workflows). To configure them– - Prerequisites, credentials, and variables are all stated, - In general any variables required are entered into a Set Node that follows the trigger node, - Pushover has some extra setup but is very straightforward and documented in the workflow. ### What next? Over my first four blogs I explored creating a good Nostr setup with [Vanity Npub](https://rodbishop.npub.pro/post/mining-your-vanity-pubkey-4iupbf/), [Lightning Payments](https://rodbishop.npub.pro/post/setting-up-payments-on-nostr-7o6ls7/), [Nostr Addresses at Your Domain](https://rodbishop.npub.pro/post/ee8a46bc/), and [Personal Nostr Relay](https://rodbishop.npub.pro/post/8ca68889/). Then in my latest two blogs I explored different types of interoperability [with NFC cards](https://rodbishop.npub.pro/post/edde8387/) and now n8n Workflow Automation. Thinking ahead n8n can power any kind of interoperability between Nostr and any other legacy technology solution. On my mind as I write this: - Further enhancements to posting and delegating solutions and forms (enhanced UI or different note kinds), - Automated or scheduled posting (such as auto-liking everything [Lyn Alden](nostr:npub1a2cww4kn9wqte4ry70vyfwqyqvpswksna27rtxd8vty6c74era8sdcw83a) posts), - Further enhancements to push notifications, on new and different types of events (such as notifying me when I get a new follower, on replies to certain posts, or when a user starts streaming), - All kinds of bridges, such as bridging notes to and from Telegram, Slack, or Campfire. Or bridging RSS or other event feeds to Nostr, - All kinds of other automation (such as [BlackCoffee](nostr:npub1dqepr0g4t3ahvnjtnxazvws4rkqjpxl854n29wcew8wph0fmw90qlsmmgt) [controlling a coffee machine](https://primal.net/e/note16fzhh5yfc3u4kufx0mck63tsfperdrlpp96am2lmq066cnuqutds8retc3)), - All kinds of AI Assistants and Agents, In fact I have already released an open source workflow for an [AI Assistant](https://primal.net/p/npub1ahjpx53ewavp23g5zj9jgyfrpr8djmgjzg5mpe4xd0z69dqvq0kq2lf353), and will share more about that in my next blog. Please be sure to let me know if you think there's another Nostr topic you'd like to see me tackle. GM Nostr.
@ 1bda7e1f:bb97c4d9
2025-01-02 05:19:08### Tldr - Nostr is an open and interoperable protocol - You can integrate it with workflow automation tools to augment your experience - n8n is a great low/no-code workflow automation tool which you can host yourself - Nostrobots allows you to integrate Nostr into n8n - In this blog I create some workflow automations for Nostr - A simple form to delegate posting notes - Push notifications for mentions on multiple accounts - Push notifications for your favourite accounts when they post a note - All workflows are provided as open source with MIT license for you to use ### Inter-op All The Things Nostr is a new open social protocol for the internet. This open nature exciting because of the opportunities for interoperability with other technologies. In [Using NFC Cards with Nostr]() I explored the `nostr:` URI to launch Nostr clients from a card tap. The interoperability of Nostr doesn't stop there. The internet has many super-powers, and Nostr is open to all of them. Simply, there's no one to stop it. There is no one in charge, there are no permissioned APIs, and there are no risks of being de-platformed. If you can imagine technologies that would work well with Nostr, then any and all of them can ride on or alongside Nostr rails. My mental model for why this is special is Google Wave ~2010. Google Wave was to be the next big platform. Lars was running it and had a big track record from Maps. I was excited for it. Then, Google pulled the plug. And, immediately all the time and capital invested in understanding and building on the platform was wasted. This cannot happen to Nostr, as there is no one to pull the plug, and maybe even no plug to pull. So long as users demand Nostr, Nostr will exist, and that is a pretty strong guarantee. It makes it worthwhile to invest in bringing Nostr into our other applications. All we need are simple ways to plug things together. ### Nostr and Workflow Automation Workflow automation is about helping people to streamline their work. As a user, the most common way I achieve this is by connecting disparate systems together. By setting up one system to trigger another or to move data between systems, I can solve for many different problems and become way more effective. #### n8n for workflow automation Many workflow automation tools exist. My favourite is [n8n](https://n8n.io/). n8n is a low/no-code workflow automation platform which allows you to build all kinds of workflows. You can use it for free, you can self-host it, it has a user-friendly UI and useful API. Vs Zapier it can be far more elaborate. Vs Make.com I find it to be more intuitive in how it abstracts away the right parts of the code, but still allows you to code when you need to. Most importantly you can plug anything into n8n: You have built-in nodes for specific applications. HTTP nodes for any other API-based service. And community nodes built by individual community members for any other purpose you can imagine. #### Eating my own dogfood It's very clear to me that there is a big design space here just demanding to be explored. If you could integrate Nostr with anything, what would you do? In my view the best way for anyone to start anything is by solving their own problem first (aka "scratching your own itch" and "eating your own dogfood"). As I get deeper into Nostr I find myself controlling multiple Npubs – to date I have a personal Npub, a brand Npub for a community I am helping, an AI assistant Npub, and various testing Npubs. I need ways to delegate access to those Npubs without handing over the keys, ways to know if they're mentioned, and ways to know if they're posting. I can build workflows with n8n to solve these issues for myself to start with, and keep expanding from there as new needs come up. ### Running n8n with Nostrobots I am mostly non-technical with a very helpful AI. To set up n8n to work with Nostr and operate these workflows should be possible for anyone with basic technology skills. - I have a cheap VPS which currently runs my [HAVEN Nostr Relay](https://rodbishop.npub.pro/post/8ca68889/) and [Albyhub Lightning Node](https://rodbishop.npub.pro/post/setting-up-payments-on-nostr-7o6ls7/) in Docker containers, - My objective was to set up n8n to run alongside these in a separate Docker container on the same server, install the required nodes, and then build and host my workflows. #### Installing n8n Self-hosting n8n could not be easier. I followed n8n's [Docker-Compose installation docs](https://docs.n8n.io/hosting/installation/server-setups/docker-compose/)– - Install Docker and Docker-Compose if you haven't already, - Create your ``docker-compose.yml`` and `.env` files from the docs, - Create your data folder `sudo docker volume create n8n_data`, - Start your container with `sudo docker compose up -d`, - Your n8n instance should be online at port `5678`. n8n is free to self-host but does require a license. Enter your credentials into n8n to get your free license key. You should now have access to the Workflow dashboard and can create and host any kind of workflows from there. #### Installing Nostrobots To integrate n8n nicely with Nostr, I used the [Nostrobots](https://github.com/ocknamo/n8n-nodes-nostrobots?tab=readme-ov-file) community node by [Ocknamo](nostr:npub1y6aja0kkc4fdvuxgqjcdv4fx0v7xv2epuqnddey2eyaxquznp9vq0tp75l). In n8n parlance a "node" enables certain functionality as a step in a workflow e.g. a "set" node sets a variable, a "send email" node sends an email. n8n comes with all kinds of "official" nodes installed by default, and Nostr is not amongst them. However, n8n also comes with a framework for community members to create their own "community" nodes, which is where Nostrobots comes in. You can only use a community node in a self-hosted n8n instance (which is what you have if you are running in Docker on your own server, but this limitation does prevent you from using n8n's own hosted alternative). To install a community node, [see n8n community node docs](https://docs.n8n.io/integrations/community-nodes/installation/gui-install/). From your workflow dashboard– - Click the "..." in the bottom left corner beside your username, and click "settings", - Cilck "community nodes" left sidebar, - Click "Install", - Enter the "npm Package Name" which is `n8n-nodes-nostrobots`, - Accept the risks and click "Install", - Nostrobots is now added to your n8n instance. #### Using Nostrobots Nostrobots gives you nodes to help you build Nostr-integrated workflows– - **Nostr Write** – for posting Notes to the Nostr network, - **Nostr Read** – for reading Notes from the Nostr network, and - **Nostr Utils** – for performing certain conversions you may need (e.g. from bech32 to hex). Nostrobots has [good documentation](https://github.com/ocknamo/n8n-nodes-nostrobots?tab=readme-ov-file) on each node which focuses on simple use cases. Each node has a "convenience mode" by default. For example, the "Read" Node by default will fetch Kind 1 notes by a simple filter, in Nostrobots parlance a "Strategy". For example, with Strategy set to "Mention" the node will accept a pubkey and fetch all Kind 1 notes that Mention the pubkey within a time period. This is very good for quick use. What wasn't clear to me initially (until Ocknamo helped me out) is that advanced use cases are also possible. Each node also has an advanced mode. For example, the "Read" Node can have "Strategy" set to "RawFilter(advanced)". Now the node will accept json (anything you like that complies with [NIP-01](https://github.com/nostr-protocol/nips/blob/master/01.md)). You can use this to query Notes (Kind 1) as above, and also Profiles (Kind 0), Follow Lists (Kind 3), Reactions (Kind 7), Zaps (Kind 9734/9735), and anything else you can think of. #### Creating and adding workflows With n8n and Nostrobots installed, you can now create or add any kind of Nostr Workflow Automation. - Click "Add workflow" to go to the workflow builder screen, - If you would like to build your own workflow, you can start with adding any node. Click "+" and see what is available. Type "Nostr" to explore the Nostrobots nodes you have added, - If you would like to add workflows that someone else has built, click "..." in the top right. Then click "import from URL" and paste in the URL of any workflow you would like to use (including the ones I share later in this article). ### Nostr Workflow Automations It's time to build some things! #### A simple form to post a note to Nostr I started very simply. I needed to delegate the ability to post to Npubs that I own in order that a (future) team can test things for me. I don't want to worry about managing or training those people on how to use keys, and I want to revoke access easily. I needed a basic form with credentials that posted a Note. For this I can use a very simple workflow– - **A n8n Form node** – Creates a form for users to enter the note they wish to post. Allows for the form to be protected by a username and password. This node is the workflow "trigger" so that the workflow runs each time the form is submitted. - **A Set node** – Allows me to set some variables, in this case I set the relays that I intend to use. I typically add a Set node immediately following the trigger node, and put all the variables I need in this. It helps to make the workflows easier to update and maintain. - **A Nostr Write node** (from Nostrobots) – Writes a Kind-1 note to the Nostr network. It accepts Nostr credentials, the output of the Form node, and the relays from the Set node, and posts the Note to those relays. Once the workflow is built, you can test it with the testing form URL, and set it to "Active" to use the production form URL. That's it. You can now give posting access to anyone for any Npub. To revoke access, simply change the credentials or set to workflow to "Inactive". It may also be the world's simplest Nostr client. You can find the [Nostr Form to Post a Note workflow here](https://github.com/r0d8lsh0p/nostr-n8n/blob/main/Nostr_Form_to_Post_a_Note.json). #### Push notifications on mentions and new notes One of the things Nostr is not very good at is push notifications. Furthermore I have some unique itches to scratch. I want– - **To make sure I never miss a note addressed to any of my Npubs** – For this I want a push notification any time any Nostr user mentions any of my Npubs, - **To make sure I always see all notes from key accounts** – For this I need a push notification any time any of my Npubs post any Notes to the network, - **To get these notifications on all of my devices** – Not just my phone where my Nostr regular client lives, but also on each of my laptops to suit wherever I am working that day. I needed to build a Nostr push notifications solution. To build this workflow I had to string a few ideas together– - **Triggering the node on a schedule** – Nostrobots does not include a trigger node. As every workflow starts with a trigger we needed a different method. I elected to run the workflow on a schedule of every 10-minutes. Frequent enough to see Notes while they are hot, but infrequent enough to not burden public relays or get rate-limited, - **Storing a list of Npubs in a Nostr list** – I needed a way to store the list of Npubs that trigger my notifications. I initially used an array defined in the workflow, this worked fine. Then I decided to try Nostr lists ([NIP-51, kind 30000](https://github.com/nostr-protocol/nips/blob/master/51.md)). By defining my list of Npubs as a list published to Nostr I can control my list from within a Nostr client (e.g. [Listr.lol](https://listr.lol/npub1r0d8u8mnj6769500nypnm28a9hpk9qg8jr0ehe30tygr3wuhcnvs4rfsft) or [Nostrudel.ninja](https://nostrudel.ninja/#/lists)). Not only does this "just work", but because it's based on Nostr lists automagically Amethyst client allows me to browse that list as a Feed, and everyone I add gets notified in their Mentions, - **Using specific relays** – I needed to query the right relays, including my own HAVEN relay inbox for notes addressed to me, and wss://purplepag.es for Nostr profile metadata, - **Querying Nostr events** (with Nostrobots) – I needed to make use of many different Nostr queries and use quite a wide range of what Nostrobots can do– - I read the EventID of my Kind 30000 list, to return the desired pubkeys, - For notifications on mentions, I read all Kind 1 notes that mention that pubkey, - For notifications on new notes, I read all Kind 1 notes published by that pubkey, - Where there are notes, I read the Kind 0 profile metadata event of that pubkey to get the displayName of the relevant Npub, - I transform the EventID into a Nevent to help clients find it. - **Using the Nostr URI** – As I did with my NFC card article, I created a link with the `nostr:` URI prefix so that my phone's native client opens the link by default, - **Push notifications solution** – I needed a push notifications solution. I found many with n8n integrations and chose to go with [Pushover](https://pushover.net/) which supports all my devices, has a free trial, and is unfairly cheap with a $5-per-device perpetual license. Once the workflow was built, lists published, and Pushover installed on my phone, I was fully set up with push notifications on Nostr. I have used these workflows for several weeks now and made various tweaks as I went. They are feeling robust and I'd welcome you to give them a go. You can find the [Nostr Push Notification If Mentioned here](https://github.com/r0d8lsh0p/nostr-n8n/blob/main/Nostr_Push_Notify_If_Mentioned.json) and [If Posts a Note here](https://github.com/r0d8lsh0p/nostr-n8n/blob/main/Nostr_Push_Notify_If_Post_a_Note.json). In speaking with other Nostr users while I was building this, there are all kind of other needs for push notifications too – like on replies to a certain bookmarked note, or when a followed Npub starts streaming on zap.stream. These are all possible. #### Use my workflows I have open sourced all my workflows at my [Github](https://github.com/r0d8lsh0p/nostr-n8n) with MIT license and tried to write complete docs, so that you can import them into your n8n and configure them for your own use. To import any of my workflows– - Click on the workflow of your choice, e.g. "[Nostr_Push_Notify_If_Mentioned.json](https://github.com/r0d8lsh0p/nostr-n8n/blob/main/Nostr_Push_Notify_If_Mentioned.json "Nostr_Push_Notify_If_Mentioned.json")", - Click on the "raw" button to view the raw JSON, ex any Github page layout, - Copy that URL, - Enter that URL in the "import from URL" dialog [mentioned above](#creating-and-adding-workflows). To configure them– - Prerequisites, credentials, and variables are all stated, - In general any variables required are entered into a Set Node that follows the trigger node, - Pushover has some extra setup but is very straightforward and documented in the workflow. ### What next? Over my first four blogs I explored creating a good Nostr setup with [Vanity Npub](https://rodbishop.npub.pro/post/mining-your-vanity-pubkey-4iupbf/), [Lightning Payments](https://rodbishop.npub.pro/post/setting-up-payments-on-nostr-7o6ls7/), [Nostr Addresses at Your Domain](https://rodbishop.npub.pro/post/ee8a46bc/), and [Personal Nostr Relay](https://rodbishop.npub.pro/post/8ca68889/). Then in my latest two blogs I explored different types of interoperability [with NFC cards](https://rodbishop.npub.pro/post/edde8387/) and now n8n Workflow Automation. Thinking ahead n8n can power any kind of interoperability between Nostr and any other legacy technology solution. On my mind as I write this: - Further enhancements to posting and delegating solutions and forms (enhanced UI or different note kinds), - Automated or scheduled posting (such as auto-liking everything [Lyn Alden](nostr:npub1a2cww4kn9wqte4ry70vyfwqyqvpswksna27rtxd8vty6c74era8sdcw83a) posts), - Further enhancements to push notifications, on new and different types of events (such as notifying me when I get a new follower, on replies to certain posts, or when a user starts streaming), - All kinds of bridges, such as bridging notes to and from Telegram, Slack, or Campfire. Or bridging RSS or other event feeds to Nostr, - All kinds of other automation (such as [BlackCoffee](nostr:npub1dqepr0g4t3ahvnjtnxazvws4rkqjpxl854n29wcew8wph0fmw90qlsmmgt) [controlling a coffee machine](https://primal.net/e/note16fzhh5yfc3u4kufx0mck63tsfperdrlpp96am2lmq066cnuqutds8retc3)), - All kinds of AI Assistants and Agents, In fact I have already released an open source workflow for an [AI Assistant](https://primal.net/p/npub1ahjpx53ewavp23g5zj9jgyfrpr8djmgjzg5mpe4xd0z69dqvq0kq2lf353), and will share more about that in my next blog. Please be sure to let me know if you think there's another Nostr topic you'd like to see me tackle. GM Nostr. @ 0d788b5e:c99ddea5
2025-03-29 01:27:53这是首页内容
@ 0d788b5e:c99ddea5
2025-03-29 01:27:53这是首页内容 @ 9e69e420:d12360c2
2025-02-17 17:12:01President Trump has intensified immigration enforcement, likening it to a wartime effort. Despite pouring resources into the U.S. Immigration and Customs Enforcement (ICE), arrest numbers are declining and falling short of goals. ICE fell from about 800 daily arrests in late January to fewer than 600 in early February. Critics argue the administration is merely showcasing efforts with ineffectiveness, while Trump seeks billions more in funding to support his deportation agenda. Increased involvement from various federal agencies is intended to assist ICE, but many lack specific immigration training. Challenges persist, as fewer immigrants are available for quick deportation due to a decline in illegal crossings. Local sheriffs are also pressured by rising demands to accommodate immigrants, which may strain resources further.
@ 9e69e420:d12360c2
2025-02-17 17:12:01President Trump has intensified immigration enforcement, likening it to a wartime effort. Despite pouring resources into the U.S. Immigration and Customs Enforcement (ICE), arrest numbers are declining and falling short of goals. ICE fell from about 800 daily arrests in late January to fewer than 600 in early February. Critics argue the administration is merely showcasing efforts with ineffectiveness, while Trump seeks billions more in funding to support his deportation agenda. Increased involvement from various federal agencies is intended to assist ICE, but many lack specific immigration training. Challenges persist, as fewer immigrants are available for quick deportation due to a decline in illegal crossings. Local sheriffs are also pressured by rising demands to accommodate immigrants, which may strain resources further. @ 57d1a264:69f1fee1
2025-03-28 10:32:15Bitcoin.design community is organizing another Designathon, from May 4-18. Let's get creative with bitcoin together. More to come very soon.  The first edition was a bursting success! the website still there https://events.bitcoin.design, and here their previous [announcement](https://bitcoindesign.substack.com/p/the-bitcoin-designathon-2022). Look forward for this to happen! Spread the voice: N: [https://njump.me/nevent1qqsv9w8p93tadlnyx0rkhexj5l48l...](https://njump.me/nevent1qqsv9w8p93tadlnyx0rkhexj5l48lmw9jc7nhhauyq5w3cm4nfsm3mstqtk6m) X: https://x.com/bitcoin_design/status/1905547407405768927 originally posted at https://stacker.news/items/927650
@ 57d1a264:69f1fee1
2025-03-28 10:32:15Bitcoin.design community is organizing another Designathon, from May 4-18. Let's get creative with bitcoin together. More to come very soon.  The first edition was a bursting success! the website still there https://events.bitcoin.design, and here their previous [announcement](https://bitcoindesign.substack.com/p/the-bitcoin-designathon-2022). Look forward for this to happen! Spread the voice: N: [https://njump.me/nevent1qqsv9w8p93tadlnyx0rkhexj5l48l...](https://njump.me/nevent1qqsv9w8p93tadlnyx0rkhexj5l48lmw9jc7nhhauyq5w3cm4nfsm3mstqtk6m) X: https://x.com/bitcoin_design/status/1905547407405768927 originally posted at https://stacker.news/items/927650 @ fd06f542:8d6d54cd
2025-03-28 02:27:52NIP-02 ====== Follow List ----------- `final` `optional` A special event with kind `3`, meaning "follow list" is defined as having a list of `p` tags, one for each of the followed/known profiles one is following. Each tag entry should contain the key for the profile, a relay URL where events from that key can be found (can be set to an empty string if not needed), and a local name (or "petname") for that profile (can also be set to an empty string or not provided), i.e., `["p", <32-bytes hex key>, <main relay URL>, <petname>]`. The `.content` is not used. For example: ```jsonc { "kind": 3, "tags": [ ["p", "91cf9..4e5ca", "wss://alicerelay.com/", "alice"], ["p", "14aeb..8dad4", "wss://bobrelay.com/nostr", "bob"], ["p", "612ae..e610f", "ws://carolrelay.com/ws", "carol"] ], "content": "", // other fields... } ``` Every new following list that gets published overwrites the past ones, so it should contain all entries. Relays and clients SHOULD delete past following lists as soon as they receive a new one. Whenever new follows are added to an existing list, clients SHOULD append them to the end of the list, so they are stored in chronological order. ## Uses ### Follow list backup If one believes a relay will store their events for sufficient time, they can use this kind-3 event to backup their following list and recover on a different device. ### Profile discovery and context augmentation A client may rely on the kind-3 event to display a list of followed people by profiles one is browsing; make lists of suggestions on who to follow based on the follow lists of other people one might be following or browsing; or show the data in other contexts. ### Relay sharing A client may publish a follow list with good relays for each of their follows so other clients may use these to update their internal relay lists if needed, increasing censorship-resistance. ### Petname scheme The data from these follow lists can be used by clients to construct local ["petname"](http://www.skyhunter.com/marcs/petnames/IntroPetNames.html) tables derived from other people's follow lists. This alleviates the need for global human-readable names. For example: A user has an internal follow list that says ```json [ ["p", "21df6d143fb96c2ec9d63726bf9edc71", "", "erin"] ] ``` And receives two follow lists, one from `21df6d143fb96c2ec9d63726bf9edc71` that says ```json [ ["p", "a8bb3d884d5d90b413d9891fe4c4e46d", "", "david"] ] ``` and another from `a8bb3d884d5d90b413d9891fe4c4e46d` that says ```json [ ["p", "f57f54057d2a7af0efecc8b0b66f5708", "", "frank"] ] ``` When the user sees `21df6d143fb96c2ec9d63726bf9edc71` the client can show _erin_ instead; When the user sees `a8bb3d884d5d90b413d9891fe4c4e46d` the client can show _david.erin_ instead; When the user sees `f57f54057d2a7af0efecc8b0b66f5708` the client can show _frank.david.erin_ instead.
@ fd06f542:8d6d54cd
2025-03-28 02:27:52NIP-02 ====== Follow List ----------- `final` `optional` A special event with kind `3`, meaning "follow list" is defined as having a list of `p` tags, one for each of the followed/known profiles one is following. Each tag entry should contain the key for the profile, a relay URL where events from that key can be found (can be set to an empty string if not needed), and a local name (or "petname") for that profile (can also be set to an empty string or not provided), i.e., `["p", <32-bytes hex key>, <main relay URL>, <petname>]`. The `.content` is not used. For example: ```jsonc { "kind": 3, "tags": [ ["p", "91cf9..4e5ca", "wss://alicerelay.com/", "alice"], ["p", "14aeb..8dad4", "wss://bobrelay.com/nostr", "bob"], ["p", "612ae..e610f", "ws://carolrelay.com/ws", "carol"] ], "content": "", // other fields... } ``` Every new following list that gets published overwrites the past ones, so it should contain all entries. Relays and clients SHOULD delete past following lists as soon as they receive a new one. Whenever new follows are added to an existing list, clients SHOULD append them to the end of the list, so they are stored in chronological order. ## Uses ### Follow list backup If one believes a relay will store their events for sufficient time, they can use this kind-3 event to backup their following list and recover on a different device. ### Profile discovery and context augmentation A client may rely on the kind-3 event to display a list of followed people by profiles one is browsing; make lists of suggestions on who to follow based on the follow lists of other people one might be following or browsing; or show the data in other contexts. ### Relay sharing A client may publish a follow list with good relays for each of their follows so other clients may use these to update their internal relay lists if needed, increasing censorship-resistance. ### Petname scheme The data from these follow lists can be used by clients to construct local ["petname"](http://www.skyhunter.com/marcs/petnames/IntroPetNames.html) tables derived from other people's follow lists. This alleviates the need for global human-readable names. For example: A user has an internal follow list that says ```json [ ["p", "21df6d143fb96c2ec9d63726bf9edc71", "", "erin"] ] ``` And receives two follow lists, one from `21df6d143fb96c2ec9d63726bf9edc71` that says ```json [ ["p", "a8bb3d884d5d90b413d9891fe4c4e46d", "", "david"] ] ``` and another from `a8bb3d884d5d90b413d9891fe4c4e46d` that says ```json [ ["p", "f57f54057d2a7af0efecc8b0b66f5708", "", "frank"] ] ``` When the user sees `21df6d143fb96c2ec9d63726bf9edc71` the client can show _erin_ instead; When the user sees `a8bb3d884d5d90b413d9891fe4c4e46d` the client can show _david.erin_ instead; When the user sees `f57f54057d2a7af0efecc8b0b66f5708` the client can show _frank.david.erin_ instead. @ fd06f542:8d6d54cd
2025-03-28 02:24:00NIP-01 ====== Basic protocol flow description ------------------------------- `draft` `mandatory` This NIP defines the basic protocol that should be implemented by everybody. New NIPs may add new optional (or mandatory) fields and messages and features to the structures and flows described here. ## Events and signatures Each user has a keypair. Signatures, public key, and encodings are done according to the [Schnorr signatures standard for the curve `secp256k1`](https://bips.xyz/340). The only object type that exists is the `event`, which has the following format on the wire: ```jsonc { "id": <32-bytes lowercase hex-encoded sha256 of the serialized event data>, "pubkey": <32-bytes lowercase hex-encoded public key of the event creator>, "created_at": <unix timestamp in seconds>, "kind": <integer between 0 and 65535>, "tags": [ [<arbitrary string>...], // ... ], "content": <arbitrary string>, "sig": <64-bytes lowercase hex of the signature of the sha256 hash of the serialized event data, which is the same as the "id" field> } ``` To obtain the `event.id`, we `sha256` the serialized event. The serialization is done over the UTF-8 JSON-serialized string (which is described below) of the following structure: ``` [ 0, <pubkey, as a lowercase hex string>, <created_at, as a number>, <kind, as a number>, <tags, as an array of arrays of non-null strings>, <content, as a string> ] ``` To prevent implementation differences from creating a different event ID for the same event, the following rules MUST be followed while serializing: - UTF-8 should be used for encoding. - Whitespace, line breaks or other unnecessary formatting should not be included in the output JSON. - The following characters in the content field must be escaped as shown, and all other characters must be included verbatim: - A line break (`0x0A`), use `\n` - A double quote (`0x22`), use `\"` - A backslash (`0x5C`), use `\\` - A carriage return (`0x0D`), use `\r` - A tab character (`0x09`), use `\t` - A backspace, (`0x08`), use `\b` - A form feed, (`0x0C`), use `\f` ### Tags Each tag is an array of one or more strings, with some conventions around them. Take a look at the example below: ```jsonc { "tags": [ ["e", "5c83da77af1dec6d7289834998ad7aafbd9e2191396d75ec3cc27f5a77226f36", "wss://nostr.example.com"], ["p", "f7234bd4c1394dda46d09f35bd384dd30cc552ad5541990f98844fb06676e9ca"], ["a", "30023:f7234bd4c1394dda46d09f35bd384dd30cc552ad5541990f98844fb06676e9ca:abcd", "wss://nostr.example.com"], ["alt", "reply"], // ... ], // ... } ``` The first element of the tag array is referred to as the tag _name_ or _key_ and the second as the tag _value_. So we can safely say that the event above has an `e` tag set to `"5c83da77af1dec6d7289834998ad7aafbd9e2191396d75ec3cc27f5a77226f36"`, an `alt` tag set to `"reply"` and so on. All elements after the second do not have a conventional name. This NIP defines 3 standard tags that can be used across all event kinds with the same meaning. They are as follows: - The `e` tag, used to refer to an event: `["e", <32-bytes lowercase hex of the id of another event>, <recommended relay URL, optional>, <32-bytes lowercase hex of the author's pubkey, optional>]` - The `p` tag, used to refer to another user: `["p", <32-bytes lowercase hex of a pubkey>, <recommended relay URL, optional>]` - The `a` tag, used to refer to an addressable or replaceable event - for an addressable event: `["a", "<kind integer>:<32-bytes lowercase hex of a pubkey>:<d tag value>", <recommended relay URL, optional>]` - for a normal replaceable event: `["a", "<kind integer>:<32-bytes lowercase hex of a pubkey>:", <recommended relay URL, optional>]` (note: include the trailing colon) As a convention, all single-letter (only english alphabet letters: a-z, A-Z) key tags are expected to be indexed by relays, such that it is possible, for example, to query or subscribe to events that reference the event `"5c83da77af1dec6d7289834998ad7aafbd9e2191396d75ec3cc27f5a77226f36"` by using the `{"#e": ["5c83da77af1dec6d7289834998ad7aafbd9e2191396d75ec3cc27f5a77226f36"]}` filter. Only the first value in any given tag is indexed. ### Kinds Kinds specify how clients should interpret the meaning of each event and the other fields of each event (e.g. an `"r"` tag may have a meaning in an event of kind 1 and an entirely different meaning in an event of kind 10002). Each NIP may define the meaning of a set of kinds that weren't defined elsewhere. [NIP-10](10.md), for instance, especifies the `kind:1` text note for social media applications. This NIP defines one basic kind: - `0`: **user metadata**: the `content` is set to a stringified JSON object `{name: <nickname or full name>, about: <short bio>, picture: <url of the image>}` describing the user who created the event. [Extra metadata fields](24.md#kind-0) may be set. A relay may delete older events once it gets a new one for the same pubkey. And also a convention for kind ranges that allow for easier experimentation and flexibility of relay implementation: - for kind `n` such that `1000 <= n < 10000 || 4 <= n < 45 || n == 1 || n == 2`, events are **regular**, which means they're all expected to be stored by relays. - for kind `n` such that `10000 <= n < 20000 || n == 0 || n == 3`, events are **replaceable**, which means that, for each combination of `pubkey` and `kind`, only the latest event MUST be stored by relays, older versions MAY be discarded. - for kind `n` such that `20000 <= n < 30000`, events are **ephemeral**, which means they are not expected to be stored by relays. - for kind `n` such that `30000 <= n < 40000`, events are **addressable** by their `kind`, `pubkey` and `d` tag value -- which means that, for each combination of `kind`, `pubkey` and the `d` tag value, only the latest event MUST be stored by relays, older versions MAY be discarded. In case of replaceable events with the same timestamp, the event with the lowest id (first in lexical order) should be retained, and the other discarded. When answering to `REQ` messages for replaceable events such as `{"kinds":[0],"authors":[<hex-key>]}`, even if the relay has more than one version stored, it SHOULD return just the latest one. These are just conventions and relay implementations may differ. ## Communication between clients and relays Relays expose a websocket endpoint to which clients can connect. Clients SHOULD open a single websocket connection to each relay and use it for all their subscriptions. Relays MAY limit number of connections from specific IP/client/etc. ### From client to relay: sending events and creating subscriptions Clients can send 3 types of messages, which must be JSON arrays, according to the following patterns: * `["EVENT", <event JSON as defined above>]`, used to publish events. * `["REQ", <subscription_id>, <filters1>, <filters2>, ...]`, used to request events and subscribe to new updates. * `["CLOSE", <subscription_id>]`, used to stop previous subscriptions. `<subscription_id>` is an arbitrary, non-empty string of max length 64 chars. It represents a subscription per connection. Relays MUST manage `<subscription_id>`s independently for each WebSocket connection. `<subscription_id>`s are not guaranteed to be globally unique. `<filtersX>` is a JSON object that determines what events will be sent in that subscription, it can have the following attributes: ```json { "ids": <a list of event ids>, "authors": <a list of lowercase pubkeys, the pubkey of an event must be one of these>, "kinds": <a list of a kind numbers>, "#<single-letter (a-zA-Z)>": <a list of tag values, for #e — a list of event ids, for #p — a list of pubkeys, etc.>, "since": <an integer unix timestamp in seconds. Events must have a created_at >= to this to pass>, "until": <an integer unix timestamp in seconds. Events must have a created_at <= to this to pass>, "limit": <maximum number of events relays SHOULD return in the initial query> } ``` Upon receiving a `REQ` message, the relay SHOULD return events that match the filter. Any new events it receives SHOULD be sent to that same websocket until the connection is closed, a `CLOSE` event is received with the same `<subscription_id>`, or a new `REQ` is sent using the same `<subscription_id>` (in which case a new subscription is created, replacing the old one). Filter attributes containing lists (`ids`, `authors`, `kinds` and tag filters like `#e`) are JSON arrays with one or more values. At least one of the arrays' values must match the relevant field in an event for the condition to be considered a match. For scalar event attributes such as `authors` and `kind`, the attribute from the event must be contained in the filter list. In the case of tag attributes such as `#e`, for which an event may have multiple values, the event and filter condition values must have at least one item in common. The `ids`, `authors`, `#e` and `#p` filter lists MUST contain exact 64-character lowercase hex values. The `since` and `until` properties can be used to specify the time range of events returned in the subscription. If a filter includes the `since` property, events with `created_at` greater than or equal to `since` are considered to match the filter. The `until` property is similar except that `created_at` must be less than or equal to `until`. In short, an event matches a filter if `since <= created_at <= until` holds. All conditions of a filter that are specified must match for an event for it to pass the filter, i.e., multiple conditions are interpreted as `&&` conditions. A `REQ` message may contain multiple filters. In this case, events that match any of the filters are to be returned, i.e., multiple filters are to be interpreted as `||` conditions. The `limit` property of a filter is only valid for the initial query and MUST be ignored afterwards. When `limit: n` is present it is assumed that the events returned in the initial query will be the last `n` events ordered by the `created_at`. Newer events should appear first, and in the case of ties the event with the lowest id (first in lexical order) should be first. It is safe to return less events than `limit` specifies, but it is expected that relays do not return (much) more events than requested so clients don't get unnecessarily overwhelmed by data. ### From relay to client: sending events and notices Relays can send 5 types of messages, which must also be JSON arrays, according to the following patterns: * `["EVENT", <subscription_id>, <event JSON as defined above>]`, used to send events requested by clients. * `["OK", <event_id>, <true|false>, <message>]`, used to indicate acceptance or denial of an `EVENT` message. * `["EOSE", <subscription_id>]`, used to indicate the _end of stored events_ and the beginning of events newly received in real-time. * `["CLOSED", <subscription_id>, <message>]`, used to indicate that a subscription was ended on the server side. * `["NOTICE", <message>]`, used to send human-readable error messages or other things to clients. This NIP defines no rules for how `NOTICE` messages should be sent or treated. - `EVENT` messages MUST be sent only with a subscription ID related to a subscription previously initiated by the client (using the `REQ` message above). - `OK` messages MUST be sent in response to `EVENT` messages received from clients, they must have the 3rd parameter set to `true` when an event has been accepted by the relay, `false` otherwise. The 4th parameter MUST always be present, but MAY be an empty string when the 3rd is `true`, otherwise it MUST be a string formed by a machine-readable single-word prefix followed by a `:` and then a human-readable message. Some examples: * `["OK", "b1a649ebe8...", true, ""]` * `["OK", "b1a649ebe8...", true, "pow: difficulty 25>=24"]` * `["OK", "b1a649ebe8...", true, "duplicate: already have this event"]` * `["OK", "b1a649ebe8...", false, "blocked: you are banned from posting here"]` * `["OK", "b1a649ebe8...", false, "blocked: please register your pubkey at https://my-expensive-relay.example.com"]` * `["OK", "b1a649ebe8...", false, "rate-limited: slow down there chief"]` * `["OK", "b1a649ebe8...", false, "invalid: event creation date is too far off from the current time"]` * `["OK", "b1a649ebe8...", false, "pow: difficulty 26 is less than 30"]` * `["OK", "b1a649ebe8...", false, "restricted: not allowed to write."]` * `["OK", "b1a649ebe8...", false, "error: could not connect to the database"]` - `CLOSED` messages MUST be sent in response to a `REQ` when the relay refuses to fulfill it. It can also be sent when a relay decides to kill a subscription on its side before a client has disconnected or sent a `CLOSE`. This message uses the same pattern of `OK` messages with the machine-readable prefix and human-readable message. Some examples: * `["CLOSED", "sub1", "unsupported: filter contains unknown elements"]` * `["CLOSED", "sub1", "error: could not connect to the database"]` * `["CLOSED", "sub1", "error: shutting down idle subscription"]` - The standardized machine-readable prefixes for `OK` and `CLOSED` are: `duplicate`, `pow`, `blocked`, `rate-limited`, `invalid`, `restricted`, and `error` for when none of that fits.
@ fd06f542:8d6d54cd
2025-03-28 02:24:00NIP-01 ====== Basic protocol flow description ------------------------------- `draft` `mandatory` This NIP defines the basic protocol that should be implemented by everybody. New NIPs may add new optional (or mandatory) fields and messages and features to the structures and flows described here. ## Events and signatures Each user has a keypair. Signatures, public key, and encodings are done according to the [Schnorr signatures standard for the curve `secp256k1`](https://bips.xyz/340). The only object type that exists is the `event`, which has the following format on the wire: ```jsonc { "id": <32-bytes lowercase hex-encoded sha256 of the serialized event data>, "pubkey": <32-bytes lowercase hex-encoded public key of the event creator>, "created_at": <unix timestamp in seconds>, "kind": <integer between 0 and 65535>, "tags": [ [<arbitrary string>...], // ... ], "content": <arbitrary string>, "sig": <64-bytes lowercase hex of the signature of the sha256 hash of the serialized event data, which is the same as the "id" field> } ``` To obtain the `event.id`, we `sha256` the serialized event. The serialization is done over the UTF-8 JSON-serialized string (which is described below) of the following structure: ``` [ 0, <pubkey, as a lowercase hex string>, <created_at, as a number>, <kind, as a number>, <tags, as an array of arrays of non-null strings>, <content, as a string> ] ``` To prevent implementation differences from creating a different event ID for the same event, the following rules MUST be followed while serializing: - UTF-8 should be used for encoding. - Whitespace, line breaks or other unnecessary formatting should not be included in the output JSON. - The following characters in the content field must be escaped as shown, and all other characters must be included verbatim: - A line break (`0x0A`), use `\n` - A double quote (`0x22`), use `\"` - A backslash (`0x5C`), use `\\` - A carriage return (`0x0D`), use `\r` - A tab character (`0x09`), use `\t` - A backspace, (`0x08`), use `\b` - A form feed, (`0x0C`), use `\f` ### Tags Each tag is an array of one or more strings, with some conventions around them. Take a look at the example below: ```jsonc { "tags": [ ["e", "5c83da77af1dec6d7289834998ad7aafbd9e2191396d75ec3cc27f5a77226f36", "wss://nostr.example.com"], ["p", "f7234bd4c1394dda46d09f35bd384dd30cc552ad5541990f98844fb06676e9ca"], ["a", "30023:f7234bd4c1394dda46d09f35bd384dd30cc552ad5541990f98844fb06676e9ca:abcd", "wss://nostr.example.com"], ["alt", "reply"], // ... ], // ... } ``` The first element of the tag array is referred to as the tag _name_ or _key_ and the second as the tag _value_. So we can safely say that the event above has an `e` tag set to `"5c83da77af1dec6d7289834998ad7aafbd9e2191396d75ec3cc27f5a77226f36"`, an `alt` tag set to `"reply"` and so on. All elements after the second do not have a conventional name. This NIP defines 3 standard tags that can be used across all event kinds with the same meaning. They are as follows: - The `e` tag, used to refer to an event: `["e", <32-bytes lowercase hex of the id of another event>, <recommended relay URL, optional>, <32-bytes lowercase hex of the author's pubkey, optional>]` - The `p` tag, used to refer to another user: `["p", <32-bytes lowercase hex of a pubkey>, <recommended relay URL, optional>]` - The `a` tag, used to refer to an addressable or replaceable event - for an addressable event: `["a", "<kind integer>:<32-bytes lowercase hex of a pubkey>:<d tag value>", <recommended relay URL, optional>]` - for a normal replaceable event: `["a", "<kind integer>:<32-bytes lowercase hex of a pubkey>:", <recommended relay URL, optional>]` (note: include the trailing colon) As a convention, all single-letter (only english alphabet letters: a-z, A-Z) key tags are expected to be indexed by relays, such that it is possible, for example, to query or subscribe to events that reference the event `"5c83da77af1dec6d7289834998ad7aafbd9e2191396d75ec3cc27f5a77226f36"` by using the `{"#e": ["5c83da77af1dec6d7289834998ad7aafbd9e2191396d75ec3cc27f5a77226f36"]}` filter. Only the first value in any given tag is indexed. ### Kinds Kinds specify how clients should interpret the meaning of each event and the other fields of each event (e.g. an `"r"` tag may have a meaning in an event of kind 1 and an entirely different meaning in an event of kind 10002). Each NIP may define the meaning of a set of kinds that weren't defined elsewhere. [NIP-10](10.md), for instance, especifies the `kind:1` text note for social media applications. This NIP defines one basic kind: - `0`: **user metadata**: the `content` is set to a stringified JSON object `{name: <nickname or full name>, about: <short bio>, picture: <url of the image>}` describing the user who created the event. [Extra metadata fields](24.md#kind-0) may be set. A relay may delete older events once it gets a new one for the same pubkey. And also a convention for kind ranges that allow for easier experimentation and flexibility of relay implementation: - for kind `n` such that `1000 <= n < 10000 || 4 <= n < 45 || n == 1 || n == 2`, events are **regular**, which means they're all expected to be stored by relays. - for kind `n` such that `10000 <= n < 20000 || n == 0 || n == 3`, events are **replaceable**, which means that, for each combination of `pubkey` and `kind`, only the latest event MUST be stored by relays, older versions MAY be discarded. - for kind `n` such that `20000 <= n < 30000`, events are **ephemeral**, which means they are not expected to be stored by relays. - for kind `n` such that `30000 <= n < 40000`, events are **addressable** by their `kind`, `pubkey` and `d` tag value -- which means that, for each combination of `kind`, `pubkey` and the `d` tag value, only the latest event MUST be stored by relays, older versions MAY be discarded. In case of replaceable events with the same timestamp, the event with the lowest id (first in lexical order) should be retained, and the other discarded. When answering to `REQ` messages for replaceable events such as `{"kinds":[0],"authors":[<hex-key>]}`, even if the relay has more than one version stored, it SHOULD return just the latest one. These are just conventions and relay implementations may differ. ## Communication between clients and relays Relays expose a websocket endpoint to which clients can connect. Clients SHOULD open a single websocket connection to each relay and use it for all their subscriptions. Relays MAY limit number of connections from specific IP/client/etc. ### From client to relay: sending events and creating subscriptions Clients can send 3 types of messages, which must be JSON arrays, according to the following patterns: * `["EVENT", <event JSON as defined above>]`, used to publish events. * `["REQ", <subscription_id>, <filters1>, <filters2>, ...]`, used to request events and subscribe to new updates. * `["CLOSE", <subscription_id>]`, used to stop previous subscriptions. `<subscription_id>` is an arbitrary, non-empty string of max length 64 chars. It represents a subscription per connection. Relays MUST manage `<subscription_id>`s independently for each WebSocket connection. `<subscription_id>`s are not guaranteed to be globally unique. `<filtersX>` is a JSON object that determines what events will be sent in that subscription, it can have the following attributes: ```json { "ids": <a list of event ids>, "authors": <a list of lowercase pubkeys, the pubkey of an event must be one of these>, "kinds": <a list of a kind numbers>, "#<single-letter (a-zA-Z)>": <a list of tag values, for #e — a list of event ids, for #p — a list of pubkeys, etc.>, "since": <an integer unix timestamp in seconds. Events must have a created_at >= to this to pass>, "until": <an integer unix timestamp in seconds. Events must have a created_at <= to this to pass>, "limit": <maximum number of events relays SHOULD return in the initial query> } ``` Upon receiving a `REQ` message, the relay SHOULD return events that match the filter. Any new events it receives SHOULD be sent to that same websocket until the connection is closed, a `CLOSE` event is received with the same `<subscription_id>`, or a new `REQ` is sent using the same `<subscription_id>` (in which case a new subscription is created, replacing the old one). Filter attributes containing lists (`ids`, `authors`, `kinds` and tag filters like `#e`) are JSON arrays with one or more values. At least one of the arrays' values must match the relevant field in an event for the condition to be considered a match. For scalar event attributes such as `authors` and `kind`, the attribute from the event must be contained in the filter list. In the case of tag attributes such as `#e`, for which an event may have multiple values, the event and filter condition values must have at least one item in common. The `ids`, `authors`, `#e` and `#p` filter lists MUST contain exact 64-character lowercase hex values. The `since` and `until` properties can be used to specify the time range of events returned in the subscription. If a filter includes the `since` property, events with `created_at` greater than or equal to `since` are considered to match the filter. The `until` property is similar except that `created_at` must be less than or equal to `until`. In short, an event matches a filter if `since <= created_at <= until` holds. All conditions of a filter that are specified must match for an event for it to pass the filter, i.e., multiple conditions are interpreted as `&&` conditions. A `REQ` message may contain multiple filters. In this case, events that match any of the filters are to be returned, i.e., multiple filters are to be interpreted as `||` conditions. The `limit` property of a filter is only valid for the initial query and MUST be ignored afterwards. When `limit: n` is present it is assumed that the events returned in the initial query will be the last `n` events ordered by the `created_at`. Newer events should appear first, and in the case of ties the event with the lowest id (first in lexical order) should be first. It is safe to return less events than `limit` specifies, but it is expected that relays do not return (much) more events than requested so clients don't get unnecessarily overwhelmed by data. ### From relay to client: sending events and notices Relays can send 5 types of messages, which must also be JSON arrays, according to the following patterns: * `["EVENT", <subscription_id>, <event JSON as defined above>]`, used to send events requested by clients. * `["OK", <event_id>, <true|false>, <message>]`, used to indicate acceptance or denial of an `EVENT` message. * `["EOSE", <subscription_id>]`, used to indicate the _end of stored events_ and the beginning of events newly received in real-time. * `["CLOSED", <subscription_id>, <message>]`, used to indicate that a subscription was ended on the server side. * `["NOTICE", <message>]`, used to send human-readable error messages or other things to clients. This NIP defines no rules for how `NOTICE` messages should be sent or treated. - `EVENT` messages MUST be sent only with a subscription ID related to a subscription previously initiated by the client (using the `REQ` message above). - `OK` messages MUST be sent in response to `EVENT` messages received from clients, they must have the 3rd parameter set to `true` when an event has been accepted by the relay, `false` otherwise. The 4th parameter MUST always be present, but MAY be an empty string when the 3rd is `true`, otherwise it MUST be a string formed by a machine-readable single-word prefix followed by a `:` and then a human-readable message. Some examples: * `["OK", "b1a649ebe8...", true, ""]` * `["OK", "b1a649ebe8...", true, "pow: difficulty 25>=24"]` * `["OK", "b1a649ebe8...", true, "duplicate: already have this event"]` * `["OK", "b1a649ebe8...", false, "blocked: you are banned from posting here"]` * `["OK", "b1a649ebe8...", false, "blocked: please register your pubkey at https://my-expensive-relay.example.com"]` * `["OK", "b1a649ebe8...", false, "rate-limited: slow down there chief"]` * `["OK", "b1a649ebe8...", false, "invalid: event creation date is too far off from the current time"]` * `["OK", "b1a649ebe8...", false, "pow: difficulty 26 is less than 30"]` * `["OK", "b1a649ebe8...", false, "restricted: not allowed to write."]` * `["OK", "b1a649ebe8...", false, "error: could not connect to the database"]` - `CLOSED` messages MUST be sent in response to a `REQ` when the relay refuses to fulfill it. It can also be sent when a relay decides to kill a subscription on its side before a client has disconnected or sent a `CLOSE`. This message uses the same pattern of `OK` messages with the machine-readable prefix and human-readable message. Some examples: * `["CLOSED", "sub1", "unsupported: filter contains unknown elements"]` * `["CLOSED", "sub1", "error: could not connect to the database"]` * `["CLOSED", "sub1", "error: shutting down idle subscription"]` - The standardized machine-readable prefixes for `OK` and `CLOSED` are: `duplicate`, `pow`, `blocked`, `rate-limited`, `invalid`, `restricted`, and `error` for when none of that fits. @ 57d1a264:69f1fee1
2025-03-27 10:42:05What we have been missing in [SN Press kit](https://stacker.news/items/872925/r/Design_r)? Most important, who the press kit is for? It's for us? It's for them? Them, who? The first few editions of the press kit, I agree are mostly made by us, for us. A way to try to homogenize how we _speek_ out SN into the wild web. A way to have SN voice sync, loud and clear, to send out our message. In this case, I squeezed my mouse, creating a template for us [^1], stackers, to share when talking sales with possible businesses and merchants willing to invest some sats and engage with SN community. Here's the message and the sales pitch, v0.1: ## Reach Bitcoin’s Most Engaged Community – Zero Noise, Pure Signal.              - - - Contributions to improve would be much appreciated. You can also help by simply commenting on each slide or leaving your feedback below, especially if you are a sale person or someone that has seen similar documents before. This is the first interaction. Already noticed some issues, for example with the emojis and the fonts, especially when exporting, probably related to a penpot issue. The slides maybe render differently depending on the browser you're using. - [▶️ Play](https://design.penpot.app/#/view?file-id=cec80257-5021-8137-8005-ef90a160b2c9&page-id=cec80257-5021-8137-8005-ef90a160b2ca§ion=interactions&index=0&interactions-mode=hide&zoom=fit) the file in your browser - ⬇️ Save the [PDF file](https://mega.nz/file/TsBgkRoI#20HEb_zscozgJYlRGha0XiZvcXCJfLQONx2fc65WHKY) @k00b it will be nice to have some real data, how we can get some basic audience insights? Even some inputs from Plausible, if still active, will be much useful. [^1]: Territory founders. FYI: @Aardvark, @AGORA, @anna, @antic, @AtlantisPleb, @av, @Bell_curve, @benwehrman, @bitcoinplebdev, @Bitter, @BlokchainB, @ch0k1, @davidw, @ek, @elvismercury, @frostdragon, @grayruby, @HODLR, @inverselarp, @Jon_Hodl, @MaxAWebster, @mega_dreamer, @mrtali, @niftynei, @nout, @OneOneSeven, @PlebLab, @Public_N_M_E, @RDClark, @realBitcoinDog, @roytheholographicuniverse, @siggy47, @softsimon, @south_korea_ln, @theschoolofbitcoin, @TNStacker. @UCantDoThatDotNet, @Undisciplined originally posted at https://stacker.news/items/926557
@ 57d1a264:69f1fee1
2025-03-27 10:42:05What we have been missing in [SN Press kit](https://stacker.news/items/872925/r/Design_r)? Most important, who the press kit is for? It's for us? It's for them? Them, who? The first few editions of the press kit, I agree are mostly made by us, for us. A way to try to homogenize how we _speek_ out SN into the wild web. A way to have SN voice sync, loud and clear, to send out our message. In this case, I squeezed my mouse, creating a template for us [^1], stackers, to share when talking sales with possible businesses and merchants willing to invest some sats and engage with SN community. Here's the message and the sales pitch, v0.1: ## Reach Bitcoin’s Most Engaged Community – Zero Noise, Pure Signal.              - - - Contributions to improve would be much appreciated. You can also help by simply commenting on each slide or leaving your feedback below, especially if you are a sale person or someone that has seen similar documents before. This is the first interaction. Already noticed some issues, for example with the emojis and the fonts, especially when exporting, probably related to a penpot issue. The slides maybe render differently depending on the browser you're using. - [▶️ Play](https://design.penpot.app/#/view?file-id=cec80257-5021-8137-8005-ef90a160b2c9&page-id=cec80257-5021-8137-8005-ef90a160b2ca§ion=interactions&index=0&interactions-mode=hide&zoom=fit) the file in your browser - ⬇️ Save the [PDF file](https://mega.nz/file/TsBgkRoI#20HEb_zscozgJYlRGha0XiZvcXCJfLQONx2fc65WHKY) @k00b it will be nice to have some real data, how we can get some basic audience insights? Even some inputs from Plausible, if still active, will be much useful. [^1]: Territory founders. FYI: @Aardvark, @AGORA, @anna, @antic, @AtlantisPleb, @av, @Bell_curve, @benwehrman, @bitcoinplebdev, @Bitter, @BlokchainB, @ch0k1, @davidw, @ek, @elvismercury, @frostdragon, @grayruby, @HODLR, @inverselarp, @Jon_Hodl, @MaxAWebster, @mega_dreamer, @mrtali, @niftynei, @nout, @OneOneSeven, @PlebLab, @Public_N_M_E, @RDClark, @realBitcoinDog, @roytheholographicuniverse, @siggy47, @softsimon, @south_korea_ln, @theschoolofbitcoin, @TNStacker. @UCantDoThatDotNet, @Undisciplined originally posted at https://stacker.news/items/926557 @ fd78c37f:a0ec0833
2025-03-18 10:44:40In this edition, we’re thrilled to sit down with Tomek K from Bitcoin Alby, a passionate advocate for Bitcoin’s global adoption. Tomek K shares how Alby is driving innovation in the Bitcoin ecosystem and offers a glimpse into his vision for the cryptocurrency’s future. From his journey as a libertarian activist to co-founding the Bitcoin Film Festival, Tomek K’s story is one of curiosity, purpose, and a relentless pursuit of freedom through technology. **YakiHonne**: Tomek K, it’s a pleasure to meet you! Today, we’re diving into your community topic—Alby Wallet. But before we begin, let me introduce our readers to Yakihonne. Yakihonne is a decentralized media client powered by the Nostr protocol, dedicated to promoting free speech through technology. It empowers creators to truly own their voices and assets, offering features like smart filtering, verified notes, and a focus on long-form content. So, Tomek, could you tell us about yourself and your work with Alby? **Tomek K**: Of course! I’m Tomek K, originally from Poland, and right now, I’m speaking to you from Sri Lanka. I love traveling and observing how different countries adopt Bitcoin. For most of my career, I’ve been a free-market advocate, promoting economic freedom through various projects—essentially doing PR for capitalism. I’ve organized conferences, political demonstrations, economic seminars, summer festivals, and even opened a bar in Warsaw to spread these ideas in different ways. During this advocacy work, I came across Bitcoin. At first, I didn’t pay much attention to it, but over time, I started feeling frustrated—our efforts raised awareness about freedom, but they didn’t bring measurable change. That led me to study Bitcoin more deeply, and I gradually shifted my focus to Bitcoin activism. Along the way, I collaborated with publishers to translate Bitcoin-related books into Polish and co-founded the Bitcoin Film Festival with friends from Meetup. Later, I joined Alby, marking my transition from free-market activism to Bitcoin promotion. At the Bitcoin Film Festival, I handle operations and networking—organizing the event, managing logistics, and making things happen. Our team is small, but I enjoy the work. I’m passionate about Bitcoin because I came for the revolution, and I’m staying for the revolution. That said, I don’t consider myself a Bitcoin absolutist. I see Bitcoin as a tool for freedom, not just a currency or a more efficient technology. If there were a better tool for advancing liberty and making societies freer, I’d probably focus on that. But for now, Bitcoin appears to be the most effective tool for freedom. Ultimately, I consider myself a “life maximalist”—because to live a good life, you need freedom, and to have freedom today, you need sound money. And right now, that money is Bitcoin. **YakiHonne**: Was there a specific moment or event that sparked your interest in Bitcoin and motivated you to join the Alby community? **Tomek K**: What attracted me to Bitcoin was its promise of global monetary independence and its ability to reduce the control of the Federal Reserve, central banks, and governments—the strongest and most covert control mechanisms in the world. Unfortunately, many people, even libertarians, often overlook this. As for why I joined Alby, it’s because this startup is driven by values and mission rather than simply chasing profits, like selling tokens or games. This aligns well with my interest in the Lightning Network. As I explored Lightning more deeply, I came across Alby. I’ve always enjoyed testing new tools, trying them firsthand, and understanding the communities behind them—so naturally, I became part of it. Along the way, I also got to know some of the team members, which reinforced my involvement. Additionally, Alby supported the Bitcoin Film Festival. While they weren’t the largest sponsor, their contribution was generous. The festival served as a great platform for them and other projects. I think it was good marketing because people like me—who have strong networking skills, arrange podcast interviews, and organize various activities—help build awareness and positive PR. That was part of my role. If I had to pinpoint a single defining moment that led me here, I honestly couldn’t. Becoming a Bitcoiner doesn’t happen overnight. You can’t just read The Bitcoin Standard, declare that you understand Bitcoin, and instantly become a maximalist. Anyone who’s intellectually honest will admit that it takes multiple touchpoints—articles, films, career shifts, essays, hands-on experimentation, and actually using Bitcoin—to truly grasp its significance. I had many such moments along the way: reading The Bitcoin Standard, learning from friends who had a deeper understanding of Bitcoin, and working at Alby, which further expanded my knowledge of the Lightning Network’s capabilities and limitations. It wasn’t one turning point but a series of pivotal experiences that shaped my path. **YakiHonne**: How did the Alby community start, and how did it attract its first members? **Tomek K**: When I joined Alby, the community had already been established for some time. It originally emerged within the browser design community, where early users helped developers refine the product by providing feedback. That’s how the first members joined, and this process has been ongoing for four years now. As for how Alby attracted members, it was through a mix of channels—social media (Twitter, Telegram, Discord), email engagement, and active participation in Bitcoin conferences. But the core strategy has always been openness, engaging with users, and listening to their feedback. Sometimes that means making a joke, sometimes defending against unfair criticism, and other times implementing requested features. We’ve always worked to maintain an active and friendly community atmosphere. We also host bi-weekly community calls, which are a central part of our activities. Every two weeks, available team members meet with users for open Q&A sessions, issue discussions, and demonstrations of various projects integrating with Alby. I’ve participated in some of these calls, and they help maintain strong relationships with users, developers, and other projects—something crucial for the ecosystem. The Bitcoin technology landscape is somewhat fragmented, and grassroots coordination is necessary since there’s no single leader defining terminology or coding practices. That’s also why Alby doesn’t exist in isolation. Almost everything we’ve built has been made possible by the creators of previous libraries, prior codebases, and collaborative efforts in writing specifications for protocols. Projects like Yakihonne and many others also recognize the importance of open-source collaboration. I think it’s essential to acknowledge the contributions of the open-source community. One thing I really appreciate is that Bitcoiners are driving open-source development in virtually every part of the world, all working toward a shared and meaningful goal. **YakiHonne**:Were there any notable challenges in the early days that left a strong impression on you? **Tomek K** :When I first joined Alby, I struggled with a bit of imposter syndrome for months. I was handling PR for the project, but I didn’t fully understand all the technical details—how certain protocols interact or what’s happening under the hood. It took time to get familiar with everything and really feel like I belonged. Regulatory pressure has also been a huge challenge. In some cases, developers have been arrested, projects have had to leave certain countries, and users have been geoblocked based on their location. But challenges like these can also drive innovation. For example, Alby developed AlbyHub, an open-source self-custodial node, as a response to these kinds of issues. There are always risks in this space—governments might suddenly demand a banking license or require compliance with new regulations. These are real obstacles, but we tackle them by embracing decentralization and open-source solutions. That’s how we ensure the project stays true to its mission and vision.  **YakiHonne**:If someone wanted to start a Bitcoin community today or grow an existing one, what advice would you give them? **Tomek K**: The most important thing is to just get started. A community begins with action, and it takes more than one person. Even if it’s just you and a friend grabbing a beer, that’s already a start. Maybe after the first or second meetup, you post on Meetup.com, Twitter, or local forums:"Hey, we’re hosting a Bitcoin meetup in this city. We just want to connect with other Bitcoiners!" If you keep doing it consistently, the community will naturally grow. Over time, the bar where you meet might get interested in accepting Bitcoin, or you might meet some OGs in your area who decide to join—maybe they already run a business and want to support what you’re doing. You don’t have to over-plan everything from the start. No need to think, “We need a podcast, 10 episodes, a logo…”—all that can come later. Just bootstrap it: organize a meetup, grab a beer, and get going. As you go, you’ll adapt, improve, and build recognition.Beyond that, it’s a great way to meet other Bitcoiners, develop leadership skills, and learn about community building. And at the very least, you’ll have fun doing it—which, honestly, is one of the main reasons I keep organizing meetups and other activities. **YakiHonne**: Exactly, the key is to take action—just start and see where it leads. Does your community focus more on Bitcoin’s technical aspects, like coding and development, or do you emphasize non-technical areas such as education and outreach? Or do you try to balance both? **Tomek K**: Our users come from all kinds of backgrounds. Some are very engaged and provide feedback regularly, while others prefer to stay in the background. Some attend our community calls, and within that group, some are developers actively building projects and collaborating with us. At the same time, there are developers we know are out there, but they never directly engage with us. That’s just how the Bitcoin community works—there’s no strict definition of being part of Alby. People engage in their own way. Some users are active on Discord, some aren’t, but we treat them all as part of the family, keeping them informed through newsletters, offering support, and making sure they stay updated with what’s happening at Alby. As for whether we lean more toward technical development or non-technical outreach, there’s no clear-cut answer. Our community is diverse—we cater to a wide range of Lightning Network users. Some just use the browser extension, while others are deeply involved in our ecosystem. We also work with NGOs, educational initiatives, and community organizations. At the same time, we place a strong emphasis on developers and maintaining good relationships with them. Our repositories and developer portal offer useful libraries and examples, making it easier for both aspiring and experienced developers to integrate the Lightning Network into their projects. Developer relations are something we consider highly important.  **YakiHonne**: I understand that you're also the founder of another Bitcoin-related film project. Could you tell us a bit about it? What exactly inspired you to combine Bitcoin and filmmaking? **Tomek K**: Yes, I founded Bitcoin Film Fest to help build what I call Bitcoin Cinema—an emerging industry that blends Bitcoin and filmmaking. I wanted to track everything happening at the intersection of these two worlds. Just like e-commerce, energy, and information technology, I believe the film industry will eventually be shaped by Bitcoin. And in fact, it’s already happening. There are Bitcoin-themed movies, and even major Hollywood productions have started including Bitcoin references. Bitcoin filmmakers, Bitcoin culture, and even a Bitcoin subculture already exist. We have our own heroes, stories, and values, and from this, films are being created. I love cinema, and I love Bitcoin—this was my way of bringing the two together. The festival itself happened somewhat by accident—but maybe it was meant to be. It all started in Warsaw when I was organizing a Bitcoin meetup. I planned to screen a Bitcoin documentary, but due to technical issues, it didn’t happen. So, over a few beers, we came up with an idea: if we couldn’t show one film, why not go all in and create a full-scale Bitcoin film festival? We started researching and realized there were enough Bitcoin-related films out there to make it happen. So, we did. The response from the community was overwhelmingly positive. It became clear that people wanted a space for Bitcoin cinema—a hub for information, networking, and collaboration. We started using the term “Binema” (Bitcoin Cinema) to describe this emerging genre. I find it fascinating to witness the growth of Bitcoin culture and storytelling. Before this, I had followed libertarian artistic movements closely, and now I see how important culture is for Bitcoin’s adoption—it’s not just about the technical and financial aspects. Bitcoin adoption isn’t going to happen overnight, and it won’t happen without developers, educators, infrastructure builders, UX designers, and many others contributing to the ecosystem. Culture is one of the most powerful tools for shaping society, and I, like many others, am working to bring Bitcoin adoption closer through film. We’re witnessing the early days of Bitcoin cinema. I missed out on the birth of traditional cinema, but this time, I want to be part of it. **YakiHonne**:In your region, does the government support or oppose Bitcoin? How has this stance impacted the development of the Bitcoin community so far? **Tomek K** :Bitcoin doesn’t concern itself with nation-state borders, and frankly, we don’t either. The situation in Poland has little influence on what we do. The only connection is that I, along with two others, happen to be in Poland, but most of our team is globally distributed. On a broader scale, the U.S. tends to shape regulatory trends, and unfortunately, it often does so in a more restrictive way. However, Poland itself hasn’t had a significant impact on our work. **YakiHonne**:Has your Bitcoin Film Fest community ever used film as a way to connect with members—perhaps by watching a Bitcoin-related movie or hosting a movie night to make things more fun and engaging? Have you done anything like that before? **Tomek K**:Yes, absolutely! The film festival itself is a great example—we watch movies together and build a community around them. Aside from the festival we organized in Warsaw, we've also hosted film screenings at various Bitcoin events, like Sats and Facts in Thailand, BTC Prague, Plan B Lugano, Frimadera, Adopting Bitcoin, and several other conferences. We also organize online watch parties—actually, there's one happening next Sunday. The movie is available on Prime Video, but we'll sync up on Discord to watch it together, chat, and share our thoughts. We'll be announcing it on Twitter, so if you check Bitcoin Film Fest on Twitter, you'll find details on how to join. Film has been a great way to connect with members and spark discussions. We've seen Bitcoin meetups worldwide organizing movie nights—our volunteer friends in Montenegro have hosted one, and our partners in Kenya and South Africa have done the same. Lately, movie nights have been happening more and more frequently, which is exciting. It's still early—after all, Bitcoin is only 16 years old, so the selection of Bitcoin movies is still relatively small. Many of these films haven’t had large budgets or massive talent pools yet, but that’s changing. Right now, we’re primarily focused on showing films within the Bitcoin community rather than creating films aimed at the general public. That said, those kinds of projects are also emerging. I’m optimistic about the growth of Bitcoin cinema—better storytelling, AI-driven advancements, increasing interest from audiences, and even sponsors willing to invest in filmmakers. Big things are coming, and while we already have some great Bitcoin films, the best is yet to come. We’re still in the early days, and this is the time to contribute and help shape the future of Bitcoin cinema. **YakiHonne**:We’ve come to the end of today’s interview, and I’ve truly enjoyed every moment of it. I’m very sure your idea will be incredibly engaging, inspiring more people and attracting a broad audience. Thank you so much for your time today—it was a great conversation.
@ fd78c37f:a0ec0833
2025-03-18 10:44:40In this edition, we’re thrilled to sit down with Tomek K from Bitcoin Alby, a passionate advocate for Bitcoin’s global adoption. Tomek K shares how Alby is driving innovation in the Bitcoin ecosystem and offers a glimpse into his vision for the cryptocurrency’s future. From his journey as a libertarian activist to co-founding the Bitcoin Film Festival, Tomek K’s story is one of curiosity, purpose, and a relentless pursuit of freedom through technology. **YakiHonne**: Tomek K, it’s a pleasure to meet you! Today, we’re diving into your community topic—Alby Wallet. But before we begin, let me introduce our readers to Yakihonne. Yakihonne is a decentralized media client powered by the Nostr protocol, dedicated to promoting free speech through technology. It empowers creators to truly own their voices and assets, offering features like smart filtering, verified notes, and a focus on long-form content. So, Tomek, could you tell us about yourself and your work with Alby? **Tomek K**: Of course! I’m Tomek K, originally from Poland, and right now, I’m speaking to you from Sri Lanka. I love traveling and observing how different countries adopt Bitcoin. For most of my career, I’ve been a free-market advocate, promoting economic freedom through various projects—essentially doing PR for capitalism. I’ve organized conferences, political demonstrations, economic seminars, summer festivals, and even opened a bar in Warsaw to spread these ideas in different ways. During this advocacy work, I came across Bitcoin. At first, I didn’t pay much attention to it, but over time, I started feeling frustrated—our efforts raised awareness about freedom, but they didn’t bring measurable change. That led me to study Bitcoin more deeply, and I gradually shifted my focus to Bitcoin activism. Along the way, I collaborated with publishers to translate Bitcoin-related books into Polish and co-founded the Bitcoin Film Festival with friends from Meetup. Later, I joined Alby, marking my transition from free-market activism to Bitcoin promotion. At the Bitcoin Film Festival, I handle operations and networking—organizing the event, managing logistics, and making things happen. Our team is small, but I enjoy the work. I’m passionate about Bitcoin because I came for the revolution, and I’m staying for the revolution. That said, I don’t consider myself a Bitcoin absolutist. I see Bitcoin as a tool for freedom, not just a currency or a more efficient technology. If there were a better tool for advancing liberty and making societies freer, I’d probably focus on that. But for now, Bitcoin appears to be the most effective tool for freedom. Ultimately, I consider myself a “life maximalist”—because to live a good life, you need freedom, and to have freedom today, you need sound money. And right now, that money is Bitcoin. **YakiHonne**: Was there a specific moment or event that sparked your interest in Bitcoin and motivated you to join the Alby community? **Tomek K**: What attracted me to Bitcoin was its promise of global monetary independence and its ability to reduce the control of the Federal Reserve, central banks, and governments—the strongest and most covert control mechanisms in the world. Unfortunately, many people, even libertarians, often overlook this. As for why I joined Alby, it’s because this startup is driven by values and mission rather than simply chasing profits, like selling tokens or games. This aligns well with my interest in the Lightning Network. As I explored Lightning more deeply, I came across Alby. I’ve always enjoyed testing new tools, trying them firsthand, and understanding the communities behind them—so naturally, I became part of it. Along the way, I also got to know some of the team members, which reinforced my involvement. Additionally, Alby supported the Bitcoin Film Festival. While they weren’t the largest sponsor, their contribution was generous. The festival served as a great platform for them and other projects. I think it was good marketing because people like me—who have strong networking skills, arrange podcast interviews, and organize various activities—help build awareness and positive PR. That was part of my role. If I had to pinpoint a single defining moment that led me here, I honestly couldn’t. Becoming a Bitcoiner doesn’t happen overnight. You can’t just read The Bitcoin Standard, declare that you understand Bitcoin, and instantly become a maximalist. Anyone who’s intellectually honest will admit that it takes multiple touchpoints—articles, films, career shifts, essays, hands-on experimentation, and actually using Bitcoin—to truly grasp its significance. I had many such moments along the way: reading The Bitcoin Standard, learning from friends who had a deeper understanding of Bitcoin, and working at Alby, which further expanded my knowledge of the Lightning Network’s capabilities and limitations. It wasn’t one turning point but a series of pivotal experiences that shaped my path. **YakiHonne**: How did the Alby community start, and how did it attract its first members? **Tomek K**: When I joined Alby, the community had already been established for some time. It originally emerged within the browser design community, where early users helped developers refine the product by providing feedback. That’s how the first members joined, and this process has been ongoing for four years now. As for how Alby attracted members, it was through a mix of channels—social media (Twitter, Telegram, Discord), email engagement, and active participation in Bitcoin conferences. But the core strategy has always been openness, engaging with users, and listening to their feedback. Sometimes that means making a joke, sometimes defending against unfair criticism, and other times implementing requested features. We’ve always worked to maintain an active and friendly community atmosphere. We also host bi-weekly community calls, which are a central part of our activities. Every two weeks, available team members meet with users for open Q&A sessions, issue discussions, and demonstrations of various projects integrating with Alby. I’ve participated in some of these calls, and they help maintain strong relationships with users, developers, and other projects—something crucial for the ecosystem. The Bitcoin technology landscape is somewhat fragmented, and grassroots coordination is necessary since there’s no single leader defining terminology or coding practices. That’s also why Alby doesn’t exist in isolation. Almost everything we’ve built has been made possible by the creators of previous libraries, prior codebases, and collaborative efforts in writing specifications for protocols. Projects like Yakihonne and many others also recognize the importance of open-source collaboration. I think it’s essential to acknowledge the contributions of the open-source community. One thing I really appreciate is that Bitcoiners are driving open-source development in virtually every part of the world, all working toward a shared and meaningful goal. **YakiHonne**:Were there any notable challenges in the early days that left a strong impression on you? **Tomek K** :When I first joined Alby, I struggled with a bit of imposter syndrome for months. I was handling PR for the project, but I didn’t fully understand all the technical details—how certain protocols interact or what’s happening under the hood. It took time to get familiar with everything and really feel like I belonged. Regulatory pressure has also been a huge challenge. In some cases, developers have been arrested, projects have had to leave certain countries, and users have been geoblocked based on their location. But challenges like these can also drive innovation. For example, Alby developed AlbyHub, an open-source self-custodial node, as a response to these kinds of issues. There are always risks in this space—governments might suddenly demand a banking license or require compliance with new regulations. These are real obstacles, but we tackle them by embracing decentralization and open-source solutions. That’s how we ensure the project stays true to its mission and vision.  **YakiHonne**:If someone wanted to start a Bitcoin community today or grow an existing one, what advice would you give them? **Tomek K**: The most important thing is to just get started. A community begins with action, and it takes more than one person. Even if it’s just you and a friend grabbing a beer, that’s already a start. Maybe after the first or second meetup, you post on Meetup.com, Twitter, or local forums:"Hey, we’re hosting a Bitcoin meetup in this city. We just want to connect with other Bitcoiners!" If you keep doing it consistently, the community will naturally grow. Over time, the bar where you meet might get interested in accepting Bitcoin, or you might meet some OGs in your area who decide to join—maybe they already run a business and want to support what you’re doing. You don’t have to over-plan everything from the start. No need to think, “We need a podcast, 10 episodes, a logo…”—all that can come later. Just bootstrap it: organize a meetup, grab a beer, and get going. As you go, you’ll adapt, improve, and build recognition.Beyond that, it’s a great way to meet other Bitcoiners, develop leadership skills, and learn about community building. And at the very least, you’ll have fun doing it—which, honestly, is one of the main reasons I keep organizing meetups and other activities. **YakiHonne**: Exactly, the key is to take action—just start and see where it leads. Does your community focus more on Bitcoin’s technical aspects, like coding and development, or do you emphasize non-technical areas such as education and outreach? Or do you try to balance both? **Tomek K**: Our users come from all kinds of backgrounds. Some are very engaged and provide feedback regularly, while others prefer to stay in the background. Some attend our community calls, and within that group, some are developers actively building projects and collaborating with us. At the same time, there are developers we know are out there, but they never directly engage with us. That’s just how the Bitcoin community works—there’s no strict definition of being part of Alby. People engage in their own way. Some users are active on Discord, some aren’t, but we treat them all as part of the family, keeping them informed through newsletters, offering support, and making sure they stay updated with what’s happening at Alby. As for whether we lean more toward technical development or non-technical outreach, there’s no clear-cut answer. Our community is diverse—we cater to a wide range of Lightning Network users. Some just use the browser extension, while others are deeply involved in our ecosystem. We also work with NGOs, educational initiatives, and community organizations. At the same time, we place a strong emphasis on developers and maintaining good relationships with them. Our repositories and developer portal offer useful libraries and examples, making it easier for both aspiring and experienced developers to integrate the Lightning Network into their projects. Developer relations are something we consider highly important.  **YakiHonne**: I understand that you're also the founder of another Bitcoin-related film project. Could you tell us a bit about it? What exactly inspired you to combine Bitcoin and filmmaking? **Tomek K**: Yes, I founded Bitcoin Film Fest to help build what I call Bitcoin Cinema—an emerging industry that blends Bitcoin and filmmaking. I wanted to track everything happening at the intersection of these two worlds. Just like e-commerce, energy, and information technology, I believe the film industry will eventually be shaped by Bitcoin. And in fact, it’s already happening. There are Bitcoin-themed movies, and even major Hollywood productions have started including Bitcoin references. Bitcoin filmmakers, Bitcoin culture, and even a Bitcoin subculture already exist. We have our own heroes, stories, and values, and from this, films are being created. I love cinema, and I love Bitcoin—this was my way of bringing the two together. The festival itself happened somewhat by accident—but maybe it was meant to be. It all started in Warsaw when I was organizing a Bitcoin meetup. I planned to screen a Bitcoin documentary, but due to technical issues, it didn’t happen. So, over a few beers, we came up with an idea: if we couldn’t show one film, why not go all in and create a full-scale Bitcoin film festival? We started researching and realized there were enough Bitcoin-related films out there to make it happen. So, we did. The response from the community was overwhelmingly positive. It became clear that people wanted a space for Bitcoin cinema—a hub for information, networking, and collaboration. We started using the term “Binema” (Bitcoin Cinema) to describe this emerging genre. I find it fascinating to witness the growth of Bitcoin culture and storytelling. Before this, I had followed libertarian artistic movements closely, and now I see how important culture is for Bitcoin’s adoption—it’s not just about the technical and financial aspects. Bitcoin adoption isn’t going to happen overnight, and it won’t happen without developers, educators, infrastructure builders, UX designers, and many others contributing to the ecosystem. Culture is one of the most powerful tools for shaping society, and I, like many others, am working to bring Bitcoin adoption closer through film. We’re witnessing the early days of Bitcoin cinema. I missed out on the birth of traditional cinema, but this time, I want to be part of it. **YakiHonne**:In your region, does the government support or oppose Bitcoin? How has this stance impacted the development of the Bitcoin community so far? **Tomek K** :Bitcoin doesn’t concern itself with nation-state borders, and frankly, we don’t either. The situation in Poland has little influence on what we do. The only connection is that I, along with two others, happen to be in Poland, but most of our team is globally distributed. On a broader scale, the U.S. tends to shape regulatory trends, and unfortunately, it often does so in a more restrictive way. However, Poland itself hasn’t had a significant impact on our work. **YakiHonne**:Has your Bitcoin Film Fest community ever used film as a way to connect with members—perhaps by watching a Bitcoin-related movie or hosting a movie night to make things more fun and engaging? Have you done anything like that before? **Tomek K**:Yes, absolutely! The film festival itself is a great example—we watch movies together and build a community around them. Aside from the festival we organized in Warsaw, we've also hosted film screenings at various Bitcoin events, like Sats and Facts in Thailand, BTC Prague, Plan B Lugano, Frimadera, Adopting Bitcoin, and several other conferences. We also organize online watch parties—actually, there's one happening next Sunday. The movie is available on Prime Video, but we'll sync up on Discord to watch it together, chat, and share our thoughts. We'll be announcing it on Twitter, so if you check Bitcoin Film Fest on Twitter, you'll find details on how to join. Film has been a great way to connect with members and spark discussions. We've seen Bitcoin meetups worldwide organizing movie nights—our volunteer friends in Montenegro have hosted one, and our partners in Kenya and South Africa have done the same. Lately, movie nights have been happening more and more frequently, which is exciting. It's still early—after all, Bitcoin is only 16 years old, so the selection of Bitcoin movies is still relatively small. Many of these films haven’t had large budgets or massive talent pools yet, but that’s changing. Right now, we’re primarily focused on showing films within the Bitcoin community rather than creating films aimed at the general public. That said, those kinds of projects are also emerging. I’m optimistic about the growth of Bitcoin cinema—better storytelling, AI-driven advancements, increasing interest from audiences, and even sponsors willing to invest in filmmakers. Big things are coming, and while we already have some great Bitcoin films, the best is yet to come. We’re still in the early days, and this is the time to contribute and help shape the future of Bitcoin cinema. **YakiHonne**:We’ve come to the end of today’s interview, and I’ve truly enjoyed every moment of it. I’m very sure your idea will be incredibly engaging, inspiring more people and attracting a broad audience. Thank you so much for your time today—it was a great conversation. @ 57d1a264:69f1fee1
2025-03-27 08:27:44> The tech industry and its press have treated the rise of billion-scale social networks and ubiquitous smartphone apps as an unadulterated win for regular people, a triumph of usability and empowerment. They seldom talk about what we’ve lost along the way in this transition, and I find that younger folks may not even know how the web used to be. `— Anil Dash, The Web We Lost, 13 Dec 2012` https://www.youtube.com/watch?v=9KKMnoTTHJk&t=156s So here’s a few glimpses of a web that’s mostly faded away: https://www.anildash.com/2012/12/13/the_web_we_lost/ The first step to disabusing them of this notion is for the people creating the next generation of social applications to learn a little bit of history, to know your shit, whether that’s about [Twitter’s business model](http://web.archive.org/web/20180120013123/http://anildash.com/2010/04/ten-years-of-twitter-ads.html) or [Google’s social features](http://web.archive.org/web/20170518203228/http://anildash.com/2012/04/why-you-cant-trust-tech-press-to-teach-you-about-the-tech-industry.html) or anything else. We have to know what’s been tried and failed, what good ideas were simply ahead of their time, and what opportunities have been lost in the current generation of dominant social networks. originally posted at https://stacker.news/items/926499
@ 57d1a264:69f1fee1
2025-03-27 08:27:44> The tech industry and its press have treated the rise of billion-scale social networks and ubiquitous smartphone apps as an unadulterated win for regular people, a triumph of usability and empowerment. They seldom talk about what we’ve lost along the way in this transition, and I find that younger folks may not even know how the web used to be. `— Anil Dash, The Web We Lost, 13 Dec 2012` https://www.youtube.com/watch?v=9KKMnoTTHJk&t=156s So here’s a few glimpses of a web that’s mostly faded away: https://www.anildash.com/2012/12/13/the_web_we_lost/ The first step to disabusing them of this notion is for the people creating the next generation of social applications to learn a little bit of history, to know your shit, whether that’s about [Twitter’s business model](http://web.archive.org/web/20180120013123/http://anildash.com/2010/04/ten-years-of-twitter-ads.html) or [Google’s social features](http://web.archive.org/web/20170518203228/http://anildash.com/2012/04/why-you-cant-trust-tech-press-to-teach-you-about-the-tech-industry.html) or anything else. We have to know what’s been tried and failed, what good ideas were simply ahead of their time, and what opportunities have been lost in the current generation of dominant social networks. originally posted at https://stacker.news/items/926499 @ fd06f542:8d6d54cd
2025-03-28 02:21:20# NIPs NIPs stand for **Nostr Implementation Possibilities**. They exist to document what may be implemented by [Nostr](https://github.com/nostr-protocol/nostr)-compatible _relay_ and _client_ software. --- - [List](#list) - [Event Kinds](#event-kinds) - [Message Types](#message-types) - [Client to Relay](#client-to-relay) - [Relay to Client](#relay-to-client) - [Standardized Tags](#standardized-tags) - [Criteria for acceptance of NIPs](#criteria-for-acceptance-of-nips) - [Is this repository a centralizing factor?](#is-this-repository-a-centralizing-factor) - [How this repository works](#how-this-repository-works) - [Breaking Changes](#breaking-changes) - [License](#license) --- ## List - [NIP-01: Basic protocol flow description](01.md) - [NIP-02: Follow List](02.md) - [NIP-03: OpenTimestamps Attestations for Events](03.md) - [NIP-04: Encrypted Direct Message](04.md) --- **unrecommended**: deprecated in favor of [NIP-17](17.md) - [NIP-05: Mapping Nostr keys to DNS-based internet identifiers](05.md) - [NIP-06: Basic key derivation from mnemonic seed phrase](06.md) - [NIP-07: `window.nostr` capability for web browsers](07.md) - [NIP-08: Handling Mentions](08.md) --- **unrecommended**: deprecated in favor of [NIP-27](27.md) - [NIP-09: Event Deletion Request](09.md) - [NIP-10: Text Notes and Threads](10.md) - [NIP-11: Relay Information Document](11.md) - [NIP-13: Proof of Work](13.md) - [NIP-14: Subject tag in text events](14.md) - [NIP-15: Nostr Marketplace (for resilient marketplaces)](15.md) - [NIP-17: Private Direct Messages](17.md) - [NIP-18: Reposts](18.md) - [NIP-19: bech32-encoded entities](19.md) - [NIP-21: `nostr:` URI scheme](21.md) - [NIP-22: Comment](22.md) - [NIP-23: Long-form Content](23.md) - [NIP-24: Extra metadata fields and tags](24.md) - [NIP-25: Reactions](25.md) - [NIP-26: Delegated Event Signing](26.md) - [NIP-27: Text Note References](27.md) - [NIP-28: Public Chat](28.md) - [NIP-29: Relay-based Groups](29.md) - [NIP-30: Custom Emoji](30.md) - [NIP-31: Dealing with Unknown Events](31.md) - [NIP-32: Labeling](32.md) - [NIP-34: `git` stuff](34.md) - [NIP-35: Torrents](35.md) - [NIP-36: Sensitive Content](36.md) - [NIP-37: Draft Events](37.md) - [NIP-38: User Statuses](38.md) - [NIP-39: External Identities in Profiles](39.md) - [NIP-40: Expiration Timestamp](40.md) - [NIP-42: Authentication of clients to relays](42.md) - [NIP-44: Encrypted Payloads (Versioned)](44.md) - [NIP-45: Counting results](45.md) - [NIP-46: Nostr Remote Signing](46.md) - [NIP-47: Nostr Wallet Connect](47.md) - [NIP-48: Proxy Tags](48.md) - [NIP-49: Private Key Encryption](49.md) - [NIP-50: Search Capability](50.md) - [NIP-51: Lists](51.md) - [NIP-52: Calendar Events](52.md) - [NIP-53: Live Activities](53.md) - [NIP-54: Wiki](54.md) - [NIP-55: Android Signer Application](55.md) - [NIP-56: Reporting](56.md) - [NIP-57: Lightning Zaps](57.md) - [NIP-58: Badges](58.md) - [NIP-59: Gift Wrap](59.md) - [NIP-60: Cashu Wallet](60.md) - [NIP-61: Nutzaps](61.md) - [NIP-62: Request to Vanish](62.md) - [NIP-64: Chess (PGN)](64.md) - [NIP-65: Relay List Metadata](65.md) - [NIP-66: Relay Discovery and Liveness Monitoring](66.md) - [NIP-68: Picture-first feeds](68.md) - [NIP-69: Peer-to-peer Order events](69.md) - [NIP-70: Protected Events](70.md) - [NIP-71: Video Events](71.md) - [NIP-72: Moderated Communities](72.md) - [NIP-73: External Content IDs](73.md) - [NIP-75: Zap Goals](75.md) - [NIP-78: Application-specific data](78.md) - [NIP-84: Highlights](84.md) - [NIP-86: Relay Management API](86.md) - [NIP-88: Polls](88.md) - [NIP-89: Recommended Application Handlers](89.md) - [NIP-90: Data Vending Machines](90.md) - [NIP-92: Media Attachments](92.md) - [NIP-94: File Metadata](94.md) - [NIP-96: HTTP File Storage Integration](96.md) - [NIP-98: HTTP Auth](98.md) - [NIP-99: Classified Listings](99.md) - [NIP-7D: Threads](7D.md) - [NIP-C7: Chats](C7.md) ## Event Kinds | kind | description | NIP | | ------------- | ------------------------------- | -------------------------------------- | | `0` | User Metadata | [01](01.md) | | `1` | Short Text Note | [10](10.md) | | `2` | Recommend Relay | 01 (deprecated) | | `3` | Follows | [02](02.md) | | `4` | Encrypted Direct Messages | [04](04.md) | | `5` | Event Deletion Request | [09](09.md) | | `6` | Repost | [18](18.md) | | `7` | Reaction | [25](25.md) | | `8` | Badge Award | [58](58.md) | | `9` | Chat Message | [C7](C7.md) | | `10` | Group Chat Threaded Reply | 29 (deprecated) | | `11` | Thread | [7D](7D.md) | | `12` | Group Thread Reply | 29 (deprecated) | | `13` | Seal | [59](59.md) | | `14` | Direct Message | [17](17.md) | | `15` | File Message | [17](17.md) | | `16` | Generic Repost | [18](18.md) | | `17` | Reaction to a website | [25](25.md) | | `20` | Picture | [68](68.md) | | `21` | Video Event | [71](71.md) | | `22` | Short-form Portrait Video Event | [71](71.md) | | `30` | internal reference | [NKBIP-03] | | `31` | external web reference | [NKBIP-03] | | `32` | hardcopy reference | [NKBIP-03] | | `33` | prompt reference | [NKBIP-03] | | `40` | Channel Creation | [28](28.md) | | `41` | Channel Metadata | [28](28.md) | | `42` | Channel Message | [28](28.md) | | `43` | Channel Hide Message | [28](28.md) | | `44` | Channel Mute User | [28](28.md) | | `62` | Request to Vanish | [62](62.md) | | `64` | Chess (PGN) | [64](64.md) | | `818` | Merge Requests | [54](54.md) | | `1018` | Poll Response | [88](88.md) | | `1021` | Bid | [15](15.md) | | `1022` | Bid confirmation | [15](15.md) | | `1040` | OpenTimestamps | [03](03.md) | | `1059` | Gift Wrap | [59](59.md) | | `1063` | File Metadata | [94](94.md) | | `1068` | Poll | [88](88.md) | | `1111` | Comment | [22](22.md) | | `1311` | Live Chat Message | [53](53.md) | | `1617` | Patches | [34](34.md) | | `1621` | Issues | [34](34.md) | | `1622` | Git Replies (deprecated) | [34](34.md) | | `1630`-`1633` | Status | [34](34.md) | | `1971` | Problem Tracker | [nostrocket][nostrocket] | | `1984` | Reporting | [56](56.md) | | `1985` | Label | [32](32.md) | | `1986` | Relay reviews | | | `1987` | AI Embeddings / Vector lists | [NKBIP-02] | | `2003` | Torrent | [35](35.md) | | `2004` | Torrent Comment | [35](35.md) | | `2022` | Coinjoin Pool | [joinstr][joinstr] | | `4550` | Community Post Approval | [72](72.md) | | `5000`-`5999` | Job Request | [90](90.md) | | `6000`-`6999` | Job Result | [90](90.md) | | `7000` | Job Feedback | [90](90.md) | | `7374` | Reserved Cashu Wallet Tokens | [60](60.md) | | `7375` | Cashu Wallet Tokens | [60](60.md) | | `7376` | Cashu Wallet History | [60](60.md) | | `9000`-`9030` | Group Control Events | [29](29.md) | | `9041` | Zap Goal | [75](75.md) | | `9321` | Nutzap | [61](61.md) | | `9467` | Tidal login | [Tidal-nostr] | | `9734` | Zap Request | [57](57.md) | | `9735` | Zap | [57](57.md) | | `9802` | Highlights | [84](84.md) | | `10000` | Mute list | [51](51.md) | | `10001` | Pin list | [51](51.md) | | `10002` | Relay List Metadata | [65](65.md), [51](51.md) | | `10003` | Bookmark list | [51](51.md) | | `10004` | Communities list | [51](51.md) | | `10005` | Public chats list | [51](51.md) | | `10006` | Blocked relays list | [51](51.md) | | `10007` | Search relays list | [51](51.md) | | `10009` | User groups | [51](51.md), [29](29.md) | | `10013` | Private event relay list | [37](37.md) | | `10015` | Interests list | [51](51.md) | | `10019` | Nutzap Mint Recommendation | [61](61.md) | | `10030` | User emoji list | [51](51.md) | | `10050` | Relay list to receive DMs | [51](51.md), [17](17.md) | | `10063` | User server list | [Blossom][blossom] | | `10096` | File storage server list | [96](96.md) | | `10166` | Relay Monitor Announcement | [66](66.md) | | `13194` | Wallet Info | [47](47.md) | | `17375` | Cashu Wallet Event | [60](60.md) | | `21000` | Lightning Pub RPC | [Lightning.Pub][lnpub] | | `22242` | Client Authentication | [42](42.md) | | `23194` | Wallet Request | [47](47.md) | | `23195` | Wallet Response | [47](47.md) | | `24133` | Nostr Connect | [46](46.md) | | `24242` | Blobs stored on mediaservers | [Blossom][blossom] | | `27235` | HTTP Auth | [98](98.md) | | `30000` | Follow sets | [51](51.md) | | `30001` | Generic lists | 51 (deprecated) | | `30002` | Relay sets | [51](51.md) | | `30003` | Bookmark sets | [51](51.md) | | `30004` | Curation sets | [51](51.md) | | `30005` | Video sets | [51](51.md) | | `30007` | Kind mute sets | [51](51.md) | | `30008` | Profile Badges | [58](58.md) | | `30009` | Badge Definition | [58](58.md) | | `30015` | Interest sets | [51](51.md) | | `30017` | Create or update a stall | [15](15.md) | | `30018` | Create or update a product | [15](15.md) | | `30019` | Marketplace UI/UX | [15](15.md) | | `30020` | Product sold as an auction | [15](15.md) | | `30023` | Long-form Content | [23](23.md) | | `30024` | Draft Long-form Content | [23](23.md) | | `30030` | Emoji sets | [51](51.md) | | `30040` | Curated Publication Index | [NKBIP-01] | | `30041` | Curated Publication Content | [NKBIP-01] | | `30063` | Release artifact sets | [51](51.md) | | `30078` | Application-specific Data | [78](78.md) | | `30166` | Relay Discovery | [66](66.md) | | `30267` | App curation sets | [51](51.md) | | `30311` | Live Event | [53](53.md) | | `30315` | User Statuses | [38](38.md) | | `30388` | Slide Set | [Corny Chat][cornychat-slideset] | | `30402` | Classified Listing | [99](99.md) | | `30403` | Draft Classified Listing | [99](99.md) | | `30617` | Repository announcements | [34](34.md) | | `30618` | Repository state announcements | [34](34.md) | | `30818` | Wiki article | [54](54.md) | | `30819` | Redirects | [54](54.md) | | `31234` | Draft Event | [37](37.md) | | `31388` | Link Set | [Corny Chat][cornychat-linkset] | | `31890` | Feed | [NUD: Custom Feeds][NUD: Custom Feeds] | | `31922` | Date-Based Calendar Event | [52](52.md) | | `31923` | Time-Based Calendar Event | [52](52.md) | | `31924` | Calendar | [52](52.md) | | `31925` | Calendar Event RSVP | [52](52.md) | | `31989` | Handler recommendation | [89](89.md) | | `31990` | Handler information | [89](89.md) | | | `32267` | Software Application | | | | `34550` | Community Definition | [72](72.md) | | `38383` | Peer-to-peer Order events | [69](69.md) | | `39000-9` | Group metadata events | [29](29.md) | [NUD: Custom Feeds]: https://wikifreedia.xyz/cip-01/ [nostrocket]: https://github.com/nostrocket/NIPS/blob/main/Problems.md [lnpub]: https://github.com/shocknet/Lightning.Pub/blob/master/proto/autogenerated/client.md [cornychat-slideset]: https://cornychat.com/datatypes#kind30388slideset [cornychat-linkset]: https://cornychat.com/datatypes#kind31388linkset [joinstr]: https://gitlab.com/1440000bytes/joinstr/-/blob/main/NIP.md [NKBIP-01]: https://wikistr.com/nkbip-01*fd208ee8c8f283780a9552896e4823cc9dc6bfd442063889577106940fd927c1 [NKBIP-02]: https://wikistr.com/nkbip-02*fd208ee8c8f283780a9552896e4823cc9dc6bfd442063889577106940fd927c1 [NKBIP-03]: https://wikistr.com/nkbip-03*fd208ee8c8f283780a9552896e4823cc9dc6bfd442063889577106940fd927c1 [blossom]: https://github.com/hzrd149/blossom [Tidal-nostr]: https://wikistr.com/tidal-nostr ## Message types ### Client to Relay | type | description | NIP | | ------- | --------------------------------------------------- | ----------- | | `EVENT` | used to publish events | [01](01.md) | | `REQ` | used to request events and subscribe to new updates | [01](01.md) | | `CLOSE` | used to stop previous subscriptions | [01](01.md) | | `AUTH` | used to send authentication events | [42](42.md) | | `COUNT` | used to request event counts | [45](45.md) | ### Relay to Client | type | description | NIP | | -------- | ------------------------------------------------------- | ----------- | | `EOSE` | used to notify clients all stored events have been sent | [01](01.md) | | `EVENT` | used to send events requested to clients | [01](01.md) | | `NOTICE` | used to send human-readable messages to clients | [01](01.md) | | `OK` | used to notify clients if an EVENT was successful | [01](01.md) | | `CLOSED` | used to notify clients that a REQ was ended and why | [01](01.md) | | `AUTH` | used to send authentication challenges | [42](42.md) | | `COUNT` | used to send requested event counts to clients | [45](45.md) | ## Standardized Tags | name | value | other parameters | NIP | | ----------------- | ------------------------------------ | ------------------------------- | -------------------------------------------------- | | `a` | coordinates to an event | relay URL | [01](01.md) | | `A` | root address | relay URL | [22](22.md) | | `d` | identifier | -- | [01](01.md) | | `e` | event id (hex) | relay URL, marker, pubkey (hex) | [01](01.md), [10](10.md) | | `E` | root event id | relay URL | [22](22.md) | | `f` | currency code | -- | [69](69.md) | | `g` | geohash | -- | [52](52.md) | | `h` | group id | -- | [29](29.md) | | `i` | external identity | proof, url hint | [35](35.md), [39](39.md), [73](73.md) | | `I` | root external identity | -- | [22](22.md) | | `k` | kind | -- | [18](18.md), [25](25.md), [72](72.md), [73](73.md) | | `K` | root scope | -- | [22](22.md) | | `l` | label, label namespace | -- | [32](32.md) | | `L` | label namespace | -- | [32](32.md) | | `m` | MIME type | -- | [94](94.md) | | `p` | pubkey (hex) | relay URL, petname | [01](01.md), [02](02.md), [22](22.md) | | `P` | pubkey (hex) | -- | [22](22.md), [57](57.md) | | `q` | event id (hex) | relay URL, pubkey (hex) | [18](18.md) | | `r` | a reference (URL, etc) | -- | [24](24.md), [25](25.md) | | `r` | relay url | marker | [65](65.md) | | `s` | status | -- | [69](69.md) | | `t` | hashtag | -- | [24](24.md), [34](34.md), [35](35.md) | | `u` | url | -- | [61](61.md), [98](98.md) | | `x` | hash | -- | [35](35.md), [56](56.md) | | `y` | platform | -- | [69](69.md) | | `z` | order number | -- | [69](69.md) | | `-` | -- | -- | [70](70.md) | | `alt` | summary | -- | [31](31.md) | | `amount` | millisatoshis, stringified | -- | [57](57.md) | | `bolt11` | `bolt11` invoice | -- | [57](57.md) | | `challenge` | challenge string | -- | [42](42.md) | | `client` | name, address | relay URL | [89](89.md) | | `clone` | git clone URL | -- | [34](34.md) | | `content-warning` | reason | -- | [36](36.md) | | `delegation` | pubkey, conditions, delegation token | -- | [26](26.md) | | `description` | description | -- | [34](34.md), [57](57.md), [58](58.md) | | `emoji` | shortcode, image URL | -- | [30](30.md) | | `encrypted` | -- | -- | [90](90.md) | | `expiration` | unix timestamp (string) | -- | [40](40.md) | | `file` | full path (string) | -- | [35](35.md) | | `goal` | event id (hex) | relay URL | [75](75.md) | | `image` | image URL | dimensions in pixels | [23](23.md), [52](52.md), [58](58.md) | | `imeta` | inline metadata | -- | [92](92.md) | | `lnurl` | `bech32` encoded `lnurl` | -- | [57](57.md) | | `location` | location string | -- | [52](52.md), [99](99.md) | | `name` | name | -- | [34](34.md), [58](58.md), [72](72.md) | | `nonce` | random | difficulty | [13](13.md) | | `preimage` | hash of `bolt11` invoice | -- | [57](57.md) | | `price` | price | currency, frequency | [99](99.md) | | `proxy` | external ID | protocol | [48](48.md) | | `published_at` | unix timestamp (string) | -- | [23](23.md) | | `relay` | relay url | -- | [42](42.md), [17](17.md) | | `relays` | relay list | -- | [57](57.md) | | `server` | file storage server url | -- | [96](96.md) | | `subject` | subject | -- | [14](14.md), [17](17.md), [34](34.md) | | `summary` | summary | -- | [23](23.md), [52](52.md) | | `thumb` | badge thumbnail | dimensions in pixels | [58](58.md) | | `title` | article title | -- | [23](23.md) | | `tracker` | torrent tracker URL | -- | [35](35.md) | | `web` | webpage URL | -- | [34](34.md) | | `zap` | pubkey (hex), relay URL | weight | [57](57.md) | Please update these lists when proposing new NIPs. ## Criteria for acceptance of NIPs 1. They should be fully implemented in at least two clients and one relay -- when applicable. 2. They should make sense. 3. They should be optional and backwards-compatible: care must be taken such that clients and relays that choose to not implement them do not stop working when interacting with the ones that choose to. 4. There should be no more than one way of doing the same thing. 5. Other rules will be made up when necessary. ## Is this repository a centralizing factor? To promote interoperability, we need standards that everybody can follow, and we need them to define a **single way of doing each thing** without ever hurting **backwards-compatibility**, and for that purpose there is no way around getting everybody to agree on the same thing and keep a centralized index of these standards. However the fact that such an index exists doesn't hurt the decentralization of Nostr. _At any point the central index can be challenged if it is failing to fulfill the needs of the protocol_ and it can migrate to other places and be maintained by other people. It can even fork into multiple versions, and then some clients would go one way, others would go another way, and some clients would adhere to both competing standards. This would hurt the simplicity, openness and interoperability of Nostr a little, but everything would still work in the short term. There is a list of notable Nostr software developers who have commit access to this repository, but that exists mostly for practical reasons, as by the nature of the thing we're dealing with the repository owner can revoke membership and rewrite history as they want -- and if these actions are unjustified or perceived as bad or evil the community must react. ## How this repository works Standards may emerge in two ways: the first way is that someone starts doing something, then others copy it; the second way is that someone has an idea of a new standard that could benefit multiple clients and the protocol in general without breaking **backwards-compatibility** and the principle of having **a single way of doing things**, then they write that idea and submit it to this repository, other interested parties read it and give their feedback, then once most people reasonably agree we codify that in a NIP which client and relay developers that are interested in the feature can proceed to implement. These two ways of standardizing things are supported by this repository. Although the second is preferred, an effort will be made to codify standards emerged outside this repository into NIPs that can be later referenced and easily understood and implemented by others -- but obviously as in any human system discretion may be applied when standards are considered harmful. ## Breaking Changes [Breaking Changes](BREAKING.md) ## License All NIPs are public domain. ## Contributors <a align="center" href="https://github.com/nostr-protocol/nips/graphs/contributors"> <img src="https://contrib.rocks/image?repo=nostr-protocol/nips" /> </a>
@ fd06f542:8d6d54cd
2025-03-28 02:21:20# NIPs NIPs stand for **Nostr Implementation Possibilities**. They exist to document what may be implemented by [Nostr](https://github.com/nostr-protocol/nostr)-compatible _relay_ and _client_ software. --- - [List](#list) - [Event Kinds](#event-kinds) - [Message Types](#message-types) - [Client to Relay](#client-to-relay) - [Relay to Client](#relay-to-client) - [Standardized Tags](#standardized-tags) - [Criteria for acceptance of NIPs](#criteria-for-acceptance-of-nips) - [Is this repository a centralizing factor?](#is-this-repository-a-centralizing-factor) - [How this repository works](#how-this-repository-works) - [Breaking Changes](#breaking-changes) - [License](#license) --- ## List - [NIP-01: Basic protocol flow description](01.md) - [NIP-02: Follow List](02.md) - [NIP-03: OpenTimestamps Attestations for Events](03.md) - [NIP-04: Encrypted Direct Message](04.md) --- **unrecommended**: deprecated in favor of [NIP-17](17.md) - [NIP-05: Mapping Nostr keys to DNS-based internet identifiers](05.md) - [NIP-06: Basic key derivation from mnemonic seed phrase](06.md) - [NIP-07: `window.nostr` capability for web browsers](07.md) - [NIP-08: Handling Mentions](08.md) --- **unrecommended**: deprecated in favor of [NIP-27](27.md) - [NIP-09: Event Deletion Request](09.md) - [NIP-10: Text Notes and Threads](10.md) - [NIP-11: Relay Information Document](11.md) - [NIP-13: Proof of Work](13.md) - [NIP-14: Subject tag in text events](14.md) - [NIP-15: Nostr Marketplace (for resilient marketplaces)](15.md) - [NIP-17: Private Direct Messages](17.md) - [NIP-18: Reposts](18.md) - [NIP-19: bech32-encoded entities](19.md) - [NIP-21: `nostr:` URI scheme](21.md) - [NIP-22: Comment](22.md) - [NIP-23: Long-form Content](23.md) - [NIP-24: Extra metadata fields and tags](24.md) - [NIP-25: Reactions](25.md) - [NIP-26: Delegated Event Signing](26.md) - [NIP-27: Text Note References](27.md) - [NIP-28: Public Chat](28.md) - [NIP-29: Relay-based Groups](29.md) - [NIP-30: Custom Emoji](30.md) - [NIP-31: Dealing with Unknown Events](31.md) - [NIP-32: Labeling](32.md) - [NIP-34: `git` stuff](34.md) - [NIP-35: Torrents](35.md) - [NIP-36: Sensitive Content](36.md) - [NIP-37: Draft Events](37.md) - [NIP-38: User Statuses](38.md) - [NIP-39: External Identities in Profiles](39.md) - [NIP-40: Expiration Timestamp](40.md) - [NIP-42: Authentication of clients to relays](42.md) - [NIP-44: Encrypted Payloads (Versioned)](44.md) - [NIP-45: Counting results](45.md) - [NIP-46: Nostr Remote Signing](46.md) - [NIP-47: Nostr Wallet Connect](47.md) - [NIP-48: Proxy Tags](48.md) - [NIP-49: Private Key Encryption](49.md) - [NIP-50: Search Capability](50.md) - [NIP-51: Lists](51.md) - [NIP-52: Calendar Events](52.md) - [NIP-53: Live Activities](53.md) - [NIP-54: Wiki](54.md) - [NIP-55: Android Signer Application](55.md) - [NIP-56: Reporting](56.md) - [NIP-57: Lightning Zaps](57.md) - [NIP-58: Badges](58.md) - [NIP-59: Gift Wrap](59.md) - [NIP-60: Cashu Wallet](60.md) - [NIP-61: Nutzaps](61.md) - [NIP-62: Request to Vanish](62.md) - [NIP-64: Chess (PGN)](64.md) - [NIP-65: Relay List Metadata](65.md) - [NIP-66: Relay Discovery and Liveness Monitoring](66.md) - [NIP-68: Picture-first feeds](68.md) - [NIP-69: Peer-to-peer Order events](69.md) - [NIP-70: Protected Events](70.md) - [NIP-71: Video Events](71.md) - [NIP-72: Moderated Communities](72.md) - [NIP-73: External Content IDs](73.md) - [NIP-75: Zap Goals](75.md) - [NIP-78: Application-specific data](78.md) - [NIP-84: Highlights](84.md) - [NIP-86: Relay Management API](86.md) - [NIP-88: Polls](88.md) - [NIP-89: Recommended Application Handlers](89.md) - [NIP-90: Data Vending Machines](90.md) - [NIP-92: Media Attachments](92.md) - [NIP-94: File Metadata](94.md) - [NIP-96: HTTP File Storage Integration](96.md) - [NIP-98: HTTP Auth](98.md) - [NIP-99: Classified Listings](99.md) - [NIP-7D: Threads](7D.md) - [NIP-C7: Chats](C7.md) ## Event Kinds | kind | description | NIP | | ------------- | ------------------------------- | -------------------------------------- | | `0` | User Metadata | [01](01.md) | | `1` | Short Text Note | [10](10.md) | | `2` | Recommend Relay | 01 (deprecated) | | `3` | Follows | [02](02.md) | | `4` | Encrypted Direct Messages | [04](04.md) | | `5` | Event Deletion Request | [09](09.md) | | `6` | Repost | [18](18.md) | | `7` | Reaction | [25](25.md) | | `8` | Badge Award | [58](58.md) | | `9` | Chat Message | [C7](C7.md) | | `10` | Group Chat Threaded Reply | 29 (deprecated) | | `11` | Thread | [7D](7D.md) | | `12` | Group Thread Reply | 29 (deprecated) | | `13` | Seal | [59](59.md) | | `14` | Direct Message | [17](17.md) | | `15` | File Message | [17](17.md) | | `16` | Generic Repost | [18](18.md) | | `17` | Reaction to a website | [25](25.md) | | `20` | Picture | [68](68.md) | | `21` | Video Event | [71](71.md) | | `22` | Short-form Portrait Video Event | [71](71.md) | | `30` | internal reference | [NKBIP-03] | | `31` | external web reference | [NKBIP-03] | | `32` | hardcopy reference | [NKBIP-03] | | `33` | prompt reference | [NKBIP-03] | | `40` | Channel Creation | [28](28.md) | | `41` | Channel Metadata | [28](28.md) | | `42` | Channel Message | [28](28.md) | | `43` | Channel Hide Message | [28](28.md) | | `44` | Channel Mute User | [28](28.md) | | `62` | Request to Vanish | [62](62.md) | | `64` | Chess (PGN) | [64](64.md) | | `818` | Merge Requests | [54](54.md) | | `1018` | Poll Response | [88](88.md) | | `1021` | Bid | [15](15.md) | | `1022` | Bid confirmation | [15](15.md) | | `1040` | OpenTimestamps | [03](03.md) | | `1059` | Gift Wrap | [59](59.md) | | `1063` | File Metadata | [94](94.md) | | `1068` | Poll | [88](88.md) | | `1111` | Comment | [22](22.md) | | `1311` | Live Chat Message | [53](53.md) | | `1617` | Patches | [34](34.md) | | `1621` | Issues | [34](34.md) | | `1622` | Git Replies (deprecated) | [34](34.md) | | `1630`-`1633` | Status | [34](34.md) | | `1971` | Problem Tracker | [nostrocket][nostrocket] | | `1984` | Reporting | [56](56.md) | | `1985` | Label | [32](32.md) | | `1986` | Relay reviews | | | `1987` | AI Embeddings / Vector lists | [NKBIP-02] | | `2003` | Torrent | [35](35.md) | | `2004` | Torrent Comment | [35](35.md) | | `2022` | Coinjoin Pool | [joinstr][joinstr] | | `4550` | Community Post Approval | [72](72.md) | | `5000`-`5999` | Job Request | [90](90.md) | | `6000`-`6999` | Job Result | [90](90.md) | | `7000` | Job Feedback | [90](90.md) | | `7374` | Reserved Cashu Wallet Tokens | [60](60.md) | | `7375` | Cashu Wallet Tokens | [60](60.md) | | `7376` | Cashu Wallet History | [60](60.md) | | `9000`-`9030` | Group Control Events | [29](29.md) | | `9041` | Zap Goal | [75](75.md) | | `9321` | Nutzap | [61](61.md) | | `9467` | Tidal login | [Tidal-nostr] | | `9734` | Zap Request | [57](57.md) | | `9735` | Zap | [57](57.md) | | `9802` | Highlights | [84](84.md) | | `10000` | Mute list | [51](51.md) | | `10001` | Pin list | [51](51.md) | | `10002` | Relay List Metadata | [65](65.md), [51](51.md) | | `10003` | Bookmark list | [51](51.md) | | `10004` | Communities list | [51](51.md) | | `10005` | Public chats list | [51](51.md) | | `10006` | Blocked relays list | [51](51.md) | | `10007` | Search relays list | [51](51.md) | | `10009` | User groups | [51](51.md), [29](29.md) | | `10013` | Private event relay list | [37](37.md) | | `10015` | Interests list | [51](51.md) | | `10019` | Nutzap Mint Recommendation | [61](61.md) | | `10030` | User emoji list | [51](51.md) | | `10050` | Relay list to receive DMs | [51](51.md), [17](17.md) | | `10063` | User server list | [Blossom][blossom] | | `10096` | File storage server list | [96](96.md) | | `10166` | Relay Monitor Announcement | [66](66.md) | | `13194` | Wallet Info | [47](47.md) | | `17375` | Cashu Wallet Event | [60](60.md) | | `21000` | Lightning Pub RPC | [Lightning.Pub][lnpub] | | `22242` | Client Authentication | [42](42.md) | | `23194` | Wallet Request | [47](47.md) | | `23195` | Wallet Response | [47](47.md) | | `24133` | Nostr Connect | [46](46.md) | | `24242` | Blobs stored on mediaservers | [Blossom][blossom] | | `27235` | HTTP Auth | [98](98.md) | | `30000` | Follow sets | [51](51.md) | | `30001` | Generic lists | 51 (deprecated) | | `30002` | Relay sets | [51](51.md) | | `30003` | Bookmark sets | [51](51.md) | | `30004` | Curation sets | [51](51.md) | | `30005` | Video sets | [51](51.md) | | `30007` | Kind mute sets | [51](51.md) | | `30008` | Profile Badges | [58](58.md) | | `30009` | Badge Definition | [58](58.md) | | `30015` | Interest sets | [51](51.md) | | `30017` | Create or update a stall | [15](15.md) | | `30018` | Create or update a product | [15](15.md) | | `30019` | Marketplace UI/UX | [15](15.md) | | `30020` | Product sold as an auction | [15](15.md) | | `30023` | Long-form Content | [23](23.md) | | `30024` | Draft Long-form Content | [23](23.md) | | `30030` | Emoji sets | [51](51.md) | | `30040` | Curated Publication Index | [NKBIP-01] | | `30041` | Curated Publication Content | [NKBIP-01] | | `30063` | Release artifact sets | [51](51.md) | | `30078` | Application-specific Data | [78](78.md) | | `30166` | Relay Discovery | [66](66.md) | | `30267` | App curation sets | [51](51.md) | | `30311` | Live Event | [53](53.md) | | `30315` | User Statuses | [38](38.md) | | `30388` | Slide Set | [Corny Chat][cornychat-slideset] | | `30402` | Classified Listing | [99](99.md) | | `30403` | Draft Classified Listing | [99](99.md) | | `30617` | Repository announcements | [34](34.md) | | `30618` | Repository state announcements | [34](34.md) | | `30818` | Wiki article | [54](54.md) | | `30819` | Redirects | [54](54.md) | | `31234` | Draft Event | [37](37.md) | | `31388` | Link Set | [Corny Chat][cornychat-linkset] | | `31890` | Feed | [NUD: Custom Feeds][NUD: Custom Feeds] | | `31922` | Date-Based Calendar Event | [52](52.md) | | `31923` | Time-Based Calendar Event | [52](52.md) | | `31924` | Calendar | [52](52.md) | | `31925` | Calendar Event RSVP | [52](52.md) | | `31989` | Handler recommendation | [89](89.md) | | `31990` | Handler information | [89](89.md) | | | `32267` | Software Application | | | | `34550` | Community Definition | [72](72.md) | | `38383` | Peer-to-peer Order events | [69](69.md) | | `39000-9` | Group metadata events | [29](29.md) | [NUD: Custom Feeds]: https://wikifreedia.xyz/cip-01/ [nostrocket]: https://github.com/nostrocket/NIPS/blob/main/Problems.md [lnpub]: https://github.com/shocknet/Lightning.Pub/blob/master/proto/autogenerated/client.md [cornychat-slideset]: https://cornychat.com/datatypes#kind30388slideset [cornychat-linkset]: https://cornychat.com/datatypes#kind31388linkset [joinstr]: https://gitlab.com/1440000bytes/joinstr/-/blob/main/NIP.md [NKBIP-01]: https://wikistr.com/nkbip-01*fd208ee8c8f283780a9552896e4823cc9dc6bfd442063889577106940fd927c1 [NKBIP-02]: https://wikistr.com/nkbip-02*fd208ee8c8f283780a9552896e4823cc9dc6bfd442063889577106940fd927c1 [NKBIP-03]: https://wikistr.com/nkbip-03*fd208ee8c8f283780a9552896e4823cc9dc6bfd442063889577106940fd927c1 [blossom]: https://github.com/hzrd149/blossom [Tidal-nostr]: https://wikistr.com/tidal-nostr ## Message types ### Client to Relay | type | description | NIP | | ------- | --------------------------------------------------- | ----------- | | `EVENT` | used to publish events | [01](01.md) | | `REQ` | used to request events and subscribe to new updates | [01](01.md) | | `CLOSE` | used to stop previous subscriptions | [01](01.md) | | `AUTH` | used to send authentication events | [42](42.md) | | `COUNT` | used to request event counts | [45](45.md) | ### Relay to Client | type | description | NIP | | -------- | ------------------------------------------------------- | ----------- | | `EOSE` | used to notify clients all stored events have been sent | [01](01.md) | | `EVENT` | used to send events requested to clients | [01](01.md) | | `NOTICE` | used to send human-readable messages to clients | [01](01.md) | | `OK` | used to notify clients if an EVENT was successful | [01](01.md) | | `CLOSED` | used to notify clients that a REQ was ended and why | [01](01.md) | | `AUTH` | used to send authentication challenges | [42](42.md) | | `COUNT` | used to send requested event counts to clients | [45](45.md) | ## Standardized Tags | name | value | other parameters | NIP | | ----------------- | ------------------------------------ | ------------------------------- | -------------------------------------------------- | | `a` | coordinates to an event | relay URL | [01](01.md) | | `A` | root address | relay URL | [22](22.md) | | `d` | identifier | -- | [01](01.md) | | `e` | event id (hex) | relay URL, marker, pubkey (hex) | [01](01.md), [10](10.md) | | `E` | root event id | relay URL | [22](22.md) | | `f` | currency code | -- | [69](69.md) | | `g` | geohash | -- | [52](52.md) | | `h` | group id | -- | [29](29.md) | | `i` | external identity | proof, url hint | [35](35.md), [39](39.md), [73](73.md) | | `I` | root external identity | -- | [22](22.md) | | `k` | kind | -- | [18](18.md), [25](25.md), [72](72.md), [73](73.md) | | `K` | root scope | -- | [22](22.md) | | `l` | label, label namespace | -- | [32](32.md) | | `L` | label namespace | -- | [32](32.md) | | `m` | MIME type | -- | [94](94.md) | | `p` | pubkey (hex) | relay URL, petname | [01](01.md), [02](02.md), [22](22.md) | | `P` | pubkey (hex) | -- | [22](22.md), [57](57.md) | | `q` | event id (hex) | relay URL, pubkey (hex) | [18](18.md) | | `r` | a reference (URL, etc) | -- | [24](24.md), [25](25.md) | | `r` | relay url | marker | [65](65.md) | | `s` | status | -- | [69](69.md) | | `t` | hashtag | -- | [24](24.md), [34](34.md), [35](35.md) | | `u` | url | -- | [61](61.md), [98](98.md) | | `x` | hash | -- | [35](35.md), [56](56.md) | | `y` | platform | -- | [69](69.md) | | `z` | order number | -- | [69](69.md) | | `-` | -- | -- | [70](70.md) | | `alt` | summary | -- | [31](31.md) | | `amount` | millisatoshis, stringified | -- | [57](57.md) | | `bolt11` | `bolt11` invoice | -- | [57](57.md) | | `challenge` | challenge string | -- | [42](42.md) | | `client` | name, address | relay URL | [89](89.md) | | `clone` | git clone URL | -- | [34](34.md) | | `content-warning` | reason | -- | [36](36.md) | | `delegation` | pubkey, conditions, delegation token | -- | [26](26.md) | | `description` | description | -- | [34](34.md), [57](57.md), [58](58.md) | | `emoji` | shortcode, image URL | -- | [30](30.md) | | `encrypted` | -- | -- | [90](90.md) | | `expiration` | unix timestamp (string) | -- | [40](40.md) | | `file` | full path (string) | -- | [35](35.md) | | `goal` | event id (hex) | relay URL | [75](75.md) | | `image` | image URL | dimensions in pixels | [23](23.md), [52](52.md), [58](58.md) | | `imeta` | inline metadata | -- | [92](92.md) | | `lnurl` | `bech32` encoded `lnurl` | -- | [57](57.md) | | `location` | location string | -- | [52](52.md), [99](99.md) | | `name` | name | -- | [34](34.md), [58](58.md), [72](72.md) | | `nonce` | random | difficulty | [13](13.md) | | `preimage` | hash of `bolt11` invoice | -- | [57](57.md) | | `price` | price | currency, frequency | [99](99.md) | | `proxy` | external ID | protocol | [48](48.md) | | `published_at` | unix timestamp (string) | -- | [23](23.md) | | `relay` | relay url | -- | [42](42.md), [17](17.md) | | `relays` | relay list | -- | [57](57.md) | | `server` | file storage server url | -- | [96](96.md) | | `subject` | subject | -- | [14](14.md), [17](17.md), [34](34.md) | | `summary` | summary | -- | [23](23.md), [52](52.md) | | `thumb` | badge thumbnail | dimensions in pixels | [58](58.md) | | `title` | article title | -- | [23](23.md) | | `tracker` | torrent tracker URL | -- | [35](35.md) | | `web` | webpage URL | -- | [34](34.md) | | `zap` | pubkey (hex), relay URL | weight | [57](57.md) | Please update these lists when proposing new NIPs. ## Criteria for acceptance of NIPs 1. They should be fully implemented in at least two clients and one relay -- when applicable. 2. They should make sense. 3. They should be optional and backwards-compatible: care must be taken such that clients and relays that choose to not implement them do not stop working when interacting with the ones that choose to. 4. There should be no more than one way of doing the same thing. 5. Other rules will be made up when necessary. ## Is this repository a centralizing factor? To promote interoperability, we need standards that everybody can follow, and we need them to define a **single way of doing each thing** without ever hurting **backwards-compatibility**, and for that purpose there is no way around getting everybody to agree on the same thing and keep a centralized index of these standards. However the fact that such an index exists doesn't hurt the decentralization of Nostr. _At any point the central index can be challenged if it is failing to fulfill the needs of the protocol_ and it can migrate to other places and be maintained by other people. It can even fork into multiple versions, and then some clients would go one way, others would go another way, and some clients would adhere to both competing standards. This would hurt the simplicity, openness and interoperability of Nostr a little, but everything would still work in the short term. There is a list of notable Nostr software developers who have commit access to this repository, but that exists mostly for practical reasons, as by the nature of the thing we're dealing with the repository owner can revoke membership and rewrite history as they want -- and if these actions are unjustified or perceived as bad or evil the community must react. ## How this repository works Standards may emerge in two ways: the first way is that someone starts doing something, then others copy it; the second way is that someone has an idea of a new standard that could benefit multiple clients and the protocol in general without breaking **backwards-compatibility** and the principle of having **a single way of doing things**, then they write that idea and submit it to this repository, other interested parties read it and give their feedback, then once most people reasonably agree we codify that in a NIP which client and relay developers that are interested in the feature can proceed to implement. These two ways of standardizing things are supported by this repository. Although the second is preferred, an effort will be made to codify standards emerged outside this repository into NIPs that can be later referenced and easily understood and implemented by others -- but obviously as in any human system discretion may be applied when standards are considered harmful. ## Breaking Changes [Breaking Changes](BREAKING.md) ## License All NIPs are public domain. ## Contributors <a align="center" href="https://github.com/nostr-protocol/nips/graphs/contributors"> <img src="https://contrib.rocks/image?repo=nostr-protocol/nips" /> </a> @ 06bc9ab7:427c48f5
2025-03-17 15:46:23#### [Bitcoin Safe]( https://bitcoin-safe.org) - A bitcoin savings wallet for the entire family Designed for both beginners and power users, [Bitcoin Safe]( https://bitcoin-safe.org) combines security with an intuitive user experience. In this article, we dive deep into its features, unique benefits, and the powerful tools that make managing your Bitcoin wallet simple and secure. ##### Built for Learners ✔️ Step-by-step wallet setup [wizard]( https://bitcoin-safe.org/en/knowledge/setup-singlesig-wallet/) + PDF backup [sheets 📄]( https://bitcoin-safe.org/en/features/pdf-export/) 🧪 Test transactions to ensure all hardware signers are ready 🔑 🛡️ Secure: Hardware [signers]( https://bitcoin-safe.org/en/knowledge/supported-hardware-signers/) only – no hot wallet risks 🚫🔥 🌍 Multi-language support: 🇺🇸 🇨🇳 🇪🇸 🇯🇵 🇷🇺 🇵🇹 🇮🇳 🇮🇹 🇫🇷 🇩🇪 🇲🇲 🇰🇷 📁 Address [categories]( https://bitcoin-safe.org/en/features/category-drag-and-drop/) for easy organization ☁️ Label and category [synchronization]( https://bitcoin-safe.org/en/features/label-sync/), and cloud backup (optional) 💰 Automatic UTXO merging to save on fees ⚡ Fast syncing with Electrum servers, Compact Block Filters coming soon ##### Built for Power Users 🔐 Supports Coldcard, Bitbox02, Jade, Trezor, Passport, Keystone & [many more]( https://bitcoin-safe.org/en/knowledge/supported-hardware-signers/) 🏦 💬 Multi-party multisig chat & PSBT sharing (optional) 📊 Transaction flow [diagrams]( https://bitcoin-safe.org/en/features/money-flow-diagram/) to trace coin movements 🔍 Instant cross-wallet wallet [search]( https://bitcoin-safe.org/en/features/search/) **⚙️** Set your own electrum server, mempool instance, and nostr relay ------ ## Step-by-Step Wallet Setup Whether you’re setting up a single-signature or multi-signature wallet, the setup wizard guides you every step of the way:  * **Single Sig Wizard:** Follow the intuitive wizard that walks you through each step. https://youtu.be/m0g6ytYTy0w Clear instructions paired with hardware signer screen-shots, like the steps for a Coldcard  * **Multisig Wizard:** The wizard ensures you do all necessary steps for a Multisig wallet in the right order. Afterwards your Multisig is ready to use and all signers are tested. Check out https://bitcoin-safe.org/en/features/setup-multisignature-wallet/ * **PDF Backup:** The wizard will also generates 3 PDF backup sheets for a 2-of-3 multisig wallet, so ensure you always have your wallet descriptor together with the seed.  * **Hardware Signer Support:** [With full support]( https://bitcoin-safe.org/en/knowledge/supported-hardware-signers/) for major hardware signers your keys remain securely offline. ------ ### Transaction Visualization Visualize and navigate your transaction history: - **Graphical Explorer:** An interactive transaction diagram lets you click on inputs and outputs to follow the money flow intuitively.  - **Coin Categories:** Organize your addresses into distinct coin categories (e.g., “KYC”, “Work”, “Friends”) so [Bitcoin Safe]( https://bitcoin-safe.org) automatically selects the correct inputs when creating PSBTs.  It prevents you accidentally linking coin categories when creating a transaction, and warns you if mistakes happened in the past.  ### Powerful Wallet Management Tools - **Flexible Fee Selection:** Choose fees with one click using an intuitive mempool block preview. - **UTXO Management:** Automatically (optional) merge UTXOs when fees are low. - **CSV Table Export:** Right click, Drag&Drop, or CTRL+C for immediate CSV export for easy processing in Excel. - **PDF Balance Statement:** Export the address balances for easy record keeping on paper.  ------ ## Advanced Features for the Power-User Sync & Chat is *off* by default (for the paranoid user), but can be enabled with just one click. ### Label Synchronization and Backup - **Seamless Sync:** Using encrypted nostr messages, [Bitcoin Safe]( https://bitcoin-safe.org) synchronizes your coin categories and labels across multiple devices.  - **Easy Backup:** A short backup key is all you need to safeguard your coin categories and labels, ensuring your organization remains intact. ### Collaborative Multi-party Multisig - **Group Chat Integration:** After creating your multisig wallet, [Bitcoin Safe]( https://bitcoin-safe.org) offers an encrypted nostr group chat for secure collaboration and **one-click PSBT sharing**.  - **User Authentication:** Each participant must authenticate every other user with a simple click, ensuring secure communication. ## Watch and Learn: Get Started with Bitcoin Safe If you’re new to [Bitcoin Safe]( https://bitcoin-safe.org), a short video guide can make all the difference. Learn how to set up your [Bitcoin Safe]( https://bitcoin-safe.org) wallet in this detailed walk through: https://youtu.be/m0g6ytYTy0w Or see how to verify an address on your hardware singer: https://youtu.be/h5FkOYj9OT8 Building up a knowledge base: https://bitcoin-safe.org/en/knowledge/ ------ ## Whats next? - **Compact Block Filters!!!** They make electrum servers obsolete. - **Why?** Compact Block Filters increase the network privacy dramatically, since you're not asking an electrum server to give you your transactions - **Trade-off**: They are a little slower than electrum servers. For a savings wallet like [Bitcoin Safe]( https://bitcoin-safe.org) this should be OK. - **How do they work?** Simply speaking: They ask normal bitcoin core nodes for a short summary of each block. And if the summary shows a transaction belonging to the wallet, the entire block is then downloaded from the bitcoin core node. The bitcoin core node does not learn however which of the many transactions in the block you were interested in. Read more [here]( https://ellemouton.com/posts/bip158/) and of course in the [bip]( https://bips.dev/158/). - **When**: 2 weeks 😅. Lots of things need to be done until [Bitcoin Safe]( https://bitcoin-safe.org) can use the [bdk CBF/kyoto]( https://github.com/rustaceanrob/kyoto) client from [rustaceanrob]( https://github.com/rustaceanrob), so keep an eye out for updates and please give feedback when you use Bitcoin Safe. Stay updated on [nostr]( https://primal.net/p/npub1q67f4d7qdja237us384ryeekxsz88lz5kaawrcynwe4hqsnufr6s27up0e) or on [GitHub]( https://github.com/andreasgriffin/bitcoin-safe). ## Thank you A huge thanks goes to nostr:npub10pensatlcfwktnvjjw2dtem38n6rvw8g6fv73h84cuacxn4c28eqyfn34f for supporting this project with a [grant]( https://opensats.org/blog/tenth-wave-of-bitcoin-grants#bitcoin-safe) and nostr:npub1yrnuj56rnen08zp2h9h7p74ghgjx6ma39spmpj6w9hzxywutevsst7k5cx for the [Hackathon]( https://geyser.fund/grants/15) prize. This wallet is only possible because it is building upon other peoples open source work. Most notably * [bdk]( https://bitcoindevkit.org/) nostr:nprofile1qqsgkmgkmv63djkxmwvdlyaxx0xtsytvkyyg5fwzmp48pwd30f3jtxspzemhxue69uhhyetvv9ujuurjd9kkzmpwdejhgqg5waehxw309aex2mrp0yhxgctdw4eju6t0qyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqr8vuet * and especially nostr:npub1thunderat5g552cuy7umk624ct5xe4tpgwr2jcjjq2gc0567wgrqnya79l , nostr:npub1reezn2ctrrg736uqj7mva9lsuwv0kr5asj4vvkwxnrwlhvxf98tsq99ty4 , and nostr:npub1ke470rdgnxg4gjs9cw3tv0dp690wl68f5xak5smflpsksedadd7qtf8jfm for dealing with my many feature requests and questions. * [rustaceanrob]( https://github.com/rustaceanrob) building [kyoto]( https://github.com/rustaceanrob/kyoto) which implements CBF for BDK; a crucial library and will be able to replace electrum servers for many use cases * [ndk]( https://github.com/rust-nostr/nostr) by nostr:nprofile1qqsx3kq3vkgczq9hmfplc28h687py42yvms3zkyxh8nmkvn0vhkyyuspz4mhxue69uhkummnw3ezummcw3ezuer9wchsz9thwden5te0wfjkccte9ejxzmt4wvhxjme0qy88wumn8ghj7mn0wvhxcmmv9u0uehfp And of course, secure storage of bitcoin is only possible, because of the hardware signer manufacturers. Thanks to nostr:npub1az9xj85cmxv8e9j9y80lvqp97crsqdu2fpu3srwthd99qfu9qsgstam8y8 [Coldcard]( https://store.coinkite.com/promo/8BFF877000C34A86F410) , [Coldcard Q]( https://store.coinkite.com/promo/8BFF877000C34A86F410) , nostr:npub1tg779rlap8t4qm8lpgn89k7mr7pkxpaulupp0nq5faywr8h28llsj3cxmt [Bitbox02]( https://shiftcrypto.ch/bitbox02/?ref=MOB4dk7gpm) , nostr:npub1jg552aulj07skd6e7y2hu0vl5g8nl5jvfw8jhn6jpjk0vjd0waksvl6n8n [Blockstream Jade]( https://store.blockstream.com/?code=XEocg5boS77D) , [Trezor Safe]( https://trezor.io/trezor-safe-5-bitcoin-only), [Foundation Passport]( https://foundation.xyz/passport), [Keystone]( https://keyst.one), [Ledger]( https://shop.ledger.com/pages/ledger-nano-s-plus), [Specter Shield]( https://specter.solutions/hardware), and many more. I also want to thank people who gave feedback and helped spread the knowledge of [Bitcoin Safe]( https://bitcoin-safe.org) (please forgive me if I forgot to mention you) * nostr:npub1p5cmlt32vc3jefkl3ymdvm9zk892fsmkq79eq77uvkaqrnyktasqkpkgaw nostr:npub1s07s0h5mwcenfnyagme8shp9trnv964lulgvdmppgenuhtk9p4rsueuk63 nostr:npub18f3g76xc7xs430euwwl9gpn7ue7ux8vmtm9q8htn9s26d8c4neeqdraz3s nostr:npub1mtd7s63xd85ykv09p7y8wvg754jpsfpplxknh5xr0pu938zf86fqygqxas nostr:npub1kysd8m44dhv7ywa75u5z7w2w0gs4t6qzhgvjp555gfknasy3krlqfxde60 nostr:npub185pu2dsgg9d36uvvw7rwuy9aknn8hnknygr7x2yqa60ygvq6r8kqc836k8 nostr:npub1hkcgyqnsuaradq3g5hyvfdekwypc25494nmwggwpygxas7fcs4fst860fu nostr:npub1xsl0msy347vmj8gcpsjum6wwppc4ercvq4xfrhqmek2dqmqm0mtsyf35vx nostr:npub1hxjnw53mhghumt590kgd3fmqme8jzwwflyxesmm50nnapmqdzu7swqagw3 nostr:npub1ke470rdgnxg4gjs9cw3tv0dp690wl68f5xak5smflpsksedadd7qtf8jfm nostr:npub1sk26fxl4fy3vt8m5n0a6aturaql0w20nvh22q0cyaqm28tj7z8ss3lutc9 nostr:npub1r4llq2jcvq4g2tgha5amjz07zk7mrrcj89wllny9xwhhp5zzkklqk4jwja nostr:npub1p9v2zpwl28c0gu0vr2enp3lwdtv29scwpeqsnt0ngqf03vtlyxfqhkae5w nostr:npub1xkym0yaewlz0qfghtt7hjtnu28fxaa5rk3wtcek9d3x3ft2ns3lq775few nostr:npub1r8343wqpra05l3jnc4jud4xz7vlnyeslf7gfsty7ahpf92rhfmpsmqwym8 nostr:npub12zpfs3yq7we83yvypgsrw5f88y2fv780c2kfs89ge5qk6q3sfm7spks880 nostr:npub1yrnuj56rnen08zp2h9h7p74ghgjx6ma39spmpj6w9hzxywutevsst7k5cx https://x.com/91xTx93x2 https://x.com/afilini [rustaceanrob]( https://github.com/rustaceanrob)
@ 06bc9ab7:427c48f5
2025-03-17 15:46:23#### [Bitcoin Safe]( https://bitcoin-safe.org) - A bitcoin savings wallet for the entire family Designed for both beginners and power users, [Bitcoin Safe]( https://bitcoin-safe.org) combines security with an intuitive user experience. In this article, we dive deep into its features, unique benefits, and the powerful tools that make managing your Bitcoin wallet simple and secure. ##### Built for Learners ✔️ Step-by-step wallet setup [wizard]( https://bitcoin-safe.org/en/knowledge/setup-singlesig-wallet/) + PDF backup [sheets 📄]( https://bitcoin-safe.org/en/features/pdf-export/) 🧪 Test transactions to ensure all hardware signers are ready 🔑 🛡️ Secure: Hardware [signers]( https://bitcoin-safe.org/en/knowledge/supported-hardware-signers/) only – no hot wallet risks 🚫🔥 🌍 Multi-language support: 🇺🇸 🇨🇳 🇪🇸 🇯🇵 🇷🇺 🇵🇹 🇮🇳 🇮🇹 🇫🇷 🇩🇪 🇲🇲 🇰🇷 📁 Address [categories]( https://bitcoin-safe.org/en/features/category-drag-and-drop/) for easy organization ☁️ Label and category [synchronization]( https://bitcoin-safe.org/en/features/label-sync/), and cloud backup (optional) 💰 Automatic UTXO merging to save on fees ⚡ Fast syncing with Electrum servers, Compact Block Filters coming soon ##### Built for Power Users 🔐 Supports Coldcard, Bitbox02, Jade, Trezor, Passport, Keystone & [many more]( https://bitcoin-safe.org/en/knowledge/supported-hardware-signers/) 🏦 💬 Multi-party multisig chat & PSBT sharing (optional) 📊 Transaction flow [diagrams]( https://bitcoin-safe.org/en/features/money-flow-diagram/) to trace coin movements 🔍 Instant cross-wallet wallet [search]( https://bitcoin-safe.org/en/features/search/) **⚙️** Set your own electrum server, mempool instance, and nostr relay ------ ## Step-by-Step Wallet Setup Whether you’re setting up a single-signature or multi-signature wallet, the setup wizard guides you every step of the way:  * **Single Sig Wizard:** Follow the intuitive wizard that walks you through each step. https://youtu.be/m0g6ytYTy0w Clear instructions paired with hardware signer screen-shots, like the steps for a Coldcard  * **Multisig Wizard:** The wizard ensures you do all necessary steps for a Multisig wallet in the right order. Afterwards your Multisig is ready to use and all signers are tested. Check out https://bitcoin-safe.org/en/features/setup-multisignature-wallet/ * **PDF Backup:** The wizard will also generates 3 PDF backup sheets for a 2-of-3 multisig wallet, so ensure you always have your wallet descriptor together with the seed.  * **Hardware Signer Support:** [With full support]( https://bitcoin-safe.org/en/knowledge/supported-hardware-signers/) for major hardware signers your keys remain securely offline. ------ ### Transaction Visualization Visualize and navigate your transaction history: - **Graphical Explorer:** An interactive transaction diagram lets you click on inputs and outputs to follow the money flow intuitively.  - **Coin Categories:** Organize your addresses into distinct coin categories (e.g., “KYC”, “Work”, “Friends”) so [Bitcoin Safe]( https://bitcoin-safe.org) automatically selects the correct inputs when creating PSBTs.  It prevents you accidentally linking coin categories when creating a transaction, and warns you if mistakes happened in the past.  ### Powerful Wallet Management Tools - **Flexible Fee Selection:** Choose fees with one click using an intuitive mempool block preview. - **UTXO Management:** Automatically (optional) merge UTXOs when fees are low. - **CSV Table Export:** Right click, Drag&Drop, or CTRL+C for immediate CSV export for easy processing in Excel. - **PDF Balance Statement:** Export the address balances for easy record keeping on paper.  ------ ## Advanced Features for the Power-User Sync & Chat is *off* by default (for the paranoid user), but can be enabled with just one click. ### Label Synchronization and Backup - **Seamless Sync:** Using encrypted nostr messages, [Bitcoin Safe]( https://bitcoin-safe.org) synchronizes your coin categories and labels across multiple devices.  - **Easy Backup:** A short backup key is all you need to safeguard your coin categories and labels, ensuring your organization remains intact. ### Collaborative Multi-party Multisig - **Group Chat Integration:** After creating your multisig wallet, [Bitcoin Safe]( https://bitcoin-safe.org) offers an encrypted nostr group chat for secure collaboration and **one-click PSBT sharing**.  - **User Authentication:** Each participant must authenticate every other user with a simple click, ensuring secure communication. ## Watch and Learn: Get Started with Bitcoin Safe If you’re new to [Bitcoin Safe]( https://bitcoin-safe.org), a short video guide can make all the difference. Learn how to set up your [Bitcoin Safe]( https://bitcoin-safe.org) wallet in this detailed walk through: https://youtu.be/m0g6ytYTy0w Or see how to verify an address on your hardware singer: https://youtu.be/h5FkOYj9OT8 Building up a knowledge base: https://bitcoin-safe.org/en/knowledge/ ------ ## Whats next? - **Compact Block Filters!!!** They make electrum servers obsolete. - **Why?** Compact Block Filters increase the network privacy dramatically, since you're not asking an electrum server to give you your transactions - **Trade-off**: They are a little slower than electrum servers. For a savings wallet like [Bitcoin Safe]( https://bitcoin-safe.org) this should be OK. - **How do they work?** Simply speaking: They ask normal bitcoin core nodes for a short summary of each block. And if the summary shows a transaction belonging to the wallet, the entire block is then downloaded from the bitcoin core node. The bitcoin core node does not learn however which of the many transactions in the block you were interested in. Read more [here]( https://ellemouton.com/posts/bip158/) and of course in the [bip]( https://bips.dev/158/). - **When**: 2 weeks 😅. Lots of things need to be done until [Bitcoin Safe]( https://bitcoin-safe.org) can use the [bdk CBF/kyoto]( https://github.com/rustaceanrob/kyoto) client from [rustaceanrob]( https://github.com/rustaceanrob), so keep an eye out for updates and please give feedback when you use Bitcoin Safe. Stay updated on [nostr]( https://primal.net/p/npub1q67f4d7qdja237us384ryeekxsz88lz5kaawrcynwe4hqsnufr6s27up0e) or on [GitHub]( https://github.com/andreasgriffin/bitcoin-safe). ## Thank you A huge thanks goes to nostr:npub10pensatlcfwktnvjjw2dtem38n6rvw8g6fv73h84cuacxn4c28eqyfn34f for supporting this project with a [grant]( https://opensats.org/blog/tenth-wave-of-bitcoin-grants#bitcoin-safe) and nostr:npub1yrnuj56rnen08zp2h9h7p74ghgjx6ma39spmpj6w9hzxywutevsst7k5cx for the [Hackathon]( https://geyser.fund/grants/15) prize. This wallet is only possible because it is building upon other peoples open source work. Most notably * [bdk]( https://bitcoindevkit.org/) nostr:nprofile1qqsgkmgkmv63djkxmwvdlyaxx0xtsytvkyyg5fwzmp48pwd30f3jtxspzemhxue69uhhyetvv9ujuurjd9kkzmpwdejhgqg5waehxw309aex2mrp0yhxgctdw4eju6t0qyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqr8vuet * and especially nostr:npub1thunderat5g552cuy7umk624ct5xe4tpgwr2jcjjq2gc0567wgrqnya79l , nostr:npub1reezn2ctrrg736uqj7mva9lsuwv0kr5asj4vvkwxnrwlhvxf98tsq99ty4 , and nostr:npub1ke470rdgnxg4gjs9cw3tv0dp690wl68f5xak5smflpsksedadd7qtf8jfm for dealing with my many feature requests and questions. * [rustaceanrob]( https://github.com/rustaceanrob) building [kyoto]( https://github.com/rustaceanrob/kyoto) which implements CBF for BDK; a crucial library and will be able to replace electrum servers for many use cases * [ndk]( https://github.com/rust-nostr/nostr) by nostr:nprofile1qqsx3kq3vkgczq9hmfplc28h687py42yvms3zkyxh8nmkvn0vhkyyuspz4mhxue69uhkummnw3ezummcw3ezuer9wchsz9thwden5te0wfjkccte9ejxzmt4wvhxjme0qy88wumn8ghj7mn0wvhxcmmv9u0uehfp And of course, secure storage of bitcoin is only possible, because of the hardware signer manufacturers. Thanks to nostr:npub1az9xj85cmxv8e9j9y80lvqp97crsqdu2fpu3srwthd99qfu9qsgstam8y8 [Coldcard]( https://store.coinkite.com/promo/8BFF877000C34A86F410) , [Coldcard Q]( https://store.coinkite.com/promo/8BFF877000C34A86F410) , nostr:npub1tg779rlap8t4qm8lpgn89k7mr7pkxpaulupp0nq5faywr8h28llsj3cxmt [Bitbox02]( https://shiftcrypto.ch/bitbox02/?ref=MOB4dk7gpm) , nostr:npub1jg552aulj07skd6e7y2hu0vl5g8nl5jvfw8jhn6jpjk0vjd0waksvl6n8n [Blockstream Jade]( https://store.blockstream.com/?code=XEocg5boS77D) , [Trezor Safe]( https://trezor.io/trezor-safe-5-bitcoin-only), [Foundation Passport]( https://foundation.xyz/passport), [Keystone]( https://keyst.one), [Ledger]( https://shop.ledger.com/pages/ledger-nano-s-plus), [Specter Shield]( https://specter.solutions/hardware), and many more. I also want to thank people who gave feedback and helped spread the knowledge of [Bitcoin Safe]( https://bitcoin-safe.org) (please forgive me if I forgot to mention you) * nostr:npub1p5cmlt32vc3jefkl3ymdvm9zk892fsmkq79eq77uvkaqrnyktasqkpkgaw nostr:npub1s07s0h5mwcenfnyagme8shp9trnv964lulgvdmppgenuhtk9p4rsueuk63 nostr:npub18f3g76xc7xs430euwwl9gpn7ue7ux8vmtm9q8htn9s26d8c4neeqdraz3s nostr:npub1mtd7s63xd85ykv09p7y8wvg754jpsfpplxknh5xr0pu938zf86fqygqxas nostr:npub1kysd8m44dhv7ywa75u5z7w2w0gs4t6qzhgvjp555gfknasy3krlqfxde60 nostr:npub185pu2dsgg9d36uvvw7rwuy9aknn8hnknygr7x2yqa60ygvq6r8kqc836k8 nostr:npub1hkcgyqnsuaradq3g5hyvfdekwypc25494nmwggwpygxas7fcs4fst860fu nostr:npub1xsl0msy347vmj8gcpsjum6wwppc4ercvq4xfrhqmek2dqmqm0mtsyf35vx nostr:npub1hxjnw53mhghumt590kgd3fmqme8jzwwflyxesmm50nnapmqdzu7swqagw3 nostr:npub1ke470rdgnxg4gjs9cw3tv0dp690wl68f5xak5smflpsksedadd7qtf8jfm nostr:npub1sk26fxl4fy3vt8m5n0a6aturaql0w20nvh22q0cyaqm28tj7z8ss3lutc9 nostr:npub1r4llq2jcvq4g2tgha5amjz07zk7mrrcj89wllny9xwhhp5zzkklqk4jwja nostr:npub1p9v2zpwl28c0gu0vr2enp3lwdtv29scwpeqsnt0ngqf03vtlyxfqhkae5w nostr:npub1xkym0yaewlz0qfghtt7hjtnu28fxaa5rk3wtcek9d3x3ft2ns3lq775few nostr:npub1r8343wqpra05l3jnc4jud4xz7vlnyeslf7gfsty7ahpf92rhfmpsmqwym8 nostr:npub12zpfs3yq7we83yvypgsrw5f88y2fv780c2kfs89ge5qk6q3sfm7spks880 nostr:npub1yrnuj56rnen08zp2h9h7p74ghgjx6ma39spmpj6w9hzxywutevsst7k5cx https://x.com/91xTx93x2 https://x.com/afilini [rustaceanrob]( https://github.com/rustaceanrob) @ b5d34eed:a7475cbf
2025-03-16 20:15:10The internet has come a long way since its inception, but let’s be honest—it’s not exactly the utopia of freedom and openness we once imagined. Today, a handful of tech giants control most of our online interactions, from social media to payments. Enter the decentralized web, a movement that’s pushing back against this centralization. At the forefront of this revolution is Nostr, a simple yet powerful protocol that’s redefining how we think about social networking. And when you throw the Lightning Network into the mix, things get even more exciting. Let’s break it all down. --- ### **What’s Wrong with the Current Web?** Before we dive into Nostr, let’s talk about why decentralization matters. The internet today is dominated by centralized platforms like Facebook, Twitter (now X), and Instagram. These platforms control what you see, how you interact, and even what you’re allowed to say. They harvest your data, sell it to advertisers, and can ban or silence you at their discretion. It’s a system that prioritizes profit over people. Centralization also creates single points of failure. If a platform goes down, gets hacked, or decides to shut down, your data and connections disappear overnight. Remember when Twitter had outages, or when Facebook’s servers crashed? Millions of users were left stranded. This isn’t just inconvenient—it’s a fundamental flaw in how we’ve built the web. --- ### **Enter Nostr: A Breath of Fresh Air** Nostr, which stands for *Notes and Other Stuff Transmitted by Relays*, is a decentralized protocol designed to fix these problems. Unlike traditional social media platforms, Nostr doesn’t rely on a central server. Instead, it uses a network of independent relays to transmit messages. Think of it as a decentralized Twitter, but without the corporate overlords. Here’s why Nostr is a game-changer: 1. **No Central Authority**: Nostr doesn’t belong to any company or individual. It’s an open protocol, meaning anyone can build apps on top of it or run their own relay. This eliminates the risk of censorship or arbitrary bans. 2. **User Control**: With Nostr, you own your data. Your posts, messages, and connections are stored locally or on relays you choose. If one relay goes down, you can switch to another without losing anything. 3. **Interoperability**: Nostr is designed to work across different apps and platforms. This means you’re not locked into a single ecosystem. If you don’t like one Nostr client, you can switch to another without losing your followers or content. 4. **Simplicity**: Nostr’s protocol is intentionally simple. It doesn’t try to do everything at once, which makes it lightweight and easy to use. This simplicity also makes it more resilient and adaptable. --- ### **The Lightning Network: Powering Decentralized Payments** Now, let’s talk about money. One of the coolest things about Nostr is its integration with the Lightning Network, a second-layer payment protocol built on top of Bitcoin. The Lightning Network enables fast, cheap, and scalable transactions, making it perfect for micropayments and tipping. Here’s why this matters: 1. **Monetization Without Ads**: Traditional social media platforms rely on ads to make money. This creates a perverse incentive to keep you hooked and harvest your data. With Nostr and the Lightning Network, creators can monetize their content directly through tips or paid subscriptions. No ads, no middlemen—just a direct connection between creators and their audience. 2. **Global Payments**: The Lightning Network is borderless. Whether you’re tipping a blogger in Nigeria or buying a digital product from someone in Argentina, transactions are instant and cost just a fraction of a cent. This opens up new opportunities for global collaboration and commerce. 3. **Censorship-Resistant Money**: Just like Nostr resists censorship, the Lightning Network ensures that payments can’t be blocked or controlled by any central authority. This is especially important in regions where financial freedom is under threat. --- ### **Why Nostr and the Lightning Network Are a Perfect Match** When you combine Nostr’s decentralized social networking with the Lightning Network’s payment capabilities, you get something truly special. Imagine a social media platform where you can tip your favorite creators, pay for premium content, or even buy goods and services—all without leaving the app. And because both Nostr and the Lightning Network are decentralized, you don’t have to worry about fees, censorship, or corporate interference. For example, let’s say you’re a musician sharing your work on Nostr. Fans can tip you in Bitcoin via the Lightning Network, or you can sell exclusive content directly to your followers. The money goes straight to you, without a platform taking a cut. This creates a more equitable and sustainable model for creators. --- ### **The Bigger Picture: A Decentralized Future** Nostr and the Lightning Network are just two pieces of a much larger puzzle. The decentralized web is about reclaiming control over our online lives—our data, our interactions, and our money. It’s about building a more open, resilient, and user-centric internet. Of course, decentralization isn’t without its challenges. It can be harder to use than centralized alternatives, and it requires a shift in how we think about technology. But the benefits far outweigh the drawbacks. By embracing protocols like Nostr and the Lightning Network, we can create a web that’s truly by the people, for the people. ### Final Thoughts The decentralized web isn’t just a tech trend—it’s a movement. Nostr and the Lightning Network are proof that we can build better, fairer systems when we prioritize freedom and innovation over profit and control. Whether you’re a creator, a developer, or just someone who’s tired of Big Tech’s grip on your online life, now’s the time to explore what the decentralized web has to offer.
@ b5d34eed:a7475cbf
2025-03-16 20:15:10The internet has come a long way since its inception, but let’s be honest—it’s not exactly the utopia of freedom and openness we once imagined. Today, a handful of tech giants control most of our online interactions, from social media to payments. Enter the decentralized web, a movement that’s pushing back against this centralization. At the forefront of this revolution is Nostr, a simple yet powerful protocol that’s redefining how we think about social networking. And when you throw the Lightning Network into the mix, things get even more exciting. Let’s break it all down. --- ### **What’s Wrong with the Current Web?** Before we dive into Nostr, let’s talk about why decentralization matters. The internet today is dominated by centralized platforms like Facebook, Twitter (now X), and Instagram. These platforms control what you see, how you interact, and even what you’re allowed to say. They harvest your data, sell it to advertisers, and can ban or silence you at their discretion. It’s a system that prioritizes profit over people. Centralization also creates single points of failure. If a platform goes down, gets hacked, or decides to shut down, your data and connections disappear overnight. Remember when Twitter had outages, or when Facebook’s servers crashed? Millions of users were left stranded. This isn’t just inconvenient—it’s a fundamental flaw in how we’ve built the web. --- ### **Enter Nostr: A Breath of Fresh Air** Nostr, which stands for *Notes and Other Stuff Transmitted by Relays*, is a decentralized protocol designed to fix these problems. Unlike traditional social media platforms, Nostr doesn’t rely on a central server. Instead, it uses a network of independent relays to transmit messages. Think of it as a decentralized Twitter, but without the corporate overlords. Here’s why Nostr is a game-changer: 1. **No Central Authority**: Nostr doesn’t belong to any company or individual. It’s an open protocol, meaning anyone can build apps on top of it or run their own relay. This eliminates the risk of censorship or arbitrary bans. 2. **User Control**: With Nostr, you own your data. Your posts, messages, and connections are stored locally or on relays you choose. If one relay goes down, you can switch to another without losing anything. 3. **Interoperability**: Nostr is designed to work across different apps and platforms. This means you’re not locked into a single ecosystem. If you don’t like one Nostr client, you can switch to another without losing your followers or content. 4. **Simplicity**: Nostr’s protocol is intentionally simple. It doesn’t try to do everything at once, which makes it lightweight and easy to use. This simplicity also makes it more resilient and adaptable. --- ### **The Lightning Network: Powering Decentralized Payments** Now, let’s talk about money. One of the coolest things about Nostr is its integration with the Lightning Network, a second-layer payment protocol built on top of Bitcoin. The Lightning Network enables fast, cheap, and scalable transactions, making it perfect for micropayments and tipping. Here’s why this matters: 1. **Monetization Without Ads**: Traditional social media platforms rely on ads to make money. This creates a perverse incentive to keep you hooked and harvest your data. With Nostr and the Lightning Network, creators can monetize their content directly through tips or paid subscriptions. No ads, no middlemen—just a direct connection between creators and their audience. 2. **Global Payments**: The Lightning Network is borderless. Whether you’re tipping a blogger in Nigeria or buying a digital product from someone in Argentina, transactions are instant and cost just a fraction of a cent. This opens up new opportunities for global collaboration and commerce. 3. **Censorship-Resistant Money**: Just like Nostr resists censorship, the Lightning Network ensures that payments can’t be blocked or controlled by any central authority. This is especially important in regions where financial freedom is under threat. --- ### **Why Nostr and the Lightning Network Are a Perfect Match** When you combine Nostr’s decentralized social networking with the Lightning Network’s payment capabilities, you get something truly special. Imagine a social media platform where you can tip your favorite creators, pay for premium content, or even buy goods and services—all without leaving the app. And because both Nostr and the Lightning Network are decentralized, you don’t have to worry about fees, censorship, or corporate interference. For example, let’s say you’re a musician sharing your work on Nostr. Fans can tip you in Bitcoin via the Lightning Network, or you can sell exclusive content directly to your followers. The money goes straight to you, without a platform taking a cut. This creates a more equitable and sustainable model for creators. --- ### **The Bigger Picture: A Decentralized Future** Nostr and the Lightning Network are just two pieces of a much larger puzzle. The decentralized web is about reclaiming control over our online lives—our data, our interactions, and our money. It’s about building a more open, resilient, and user-centric internet. Of course, decentralization isn’t without its challenges. It can be harder to use than centralized alternatives, and it requires a shift in how we think about technology. But the benefits far outweigh the drawbacks. By embracing protocols like Nostr and the Lightning Network, we can create a web that’s truly by the people, for the people. ### Final Thoughts The decentralized web isn’t just a tech trend—it’s a movement. Nostr and the Lightning Network are proof that we can build better, fairer systems when we prioritize freedom and innovation over profit and control. Whether you’re a creator, a developer, or just someone who’s tired of Big Tech’s grip on your online life, now’s the time to explore what the decentralized web has to offer. @ 5d4b6c8d:8a1c1ee3
2025-04-01 13:41:45I'm trying out a new month-long focus. For Active April, I'm going to be more proactive about doing stuff around the house that needs doing. It's gonna get all Jordan Peterson cleaning your room up in here. Let's see how noticeable the consequences are. - I predict a happier wife, for one. - I'm also curious to see what kind of fitness impacts there are to increasing this kind of activity, compared to doing more exercise. originally posted at https://stacker.news/items/931099
@ 5d4b6c8d:8a1c1ee3
2025-04-01 13:41:45I'm trying out a new month-long focus. For Active April, I'm going to be more proactive about doing stuff around the house that needs doing. It's gonna get all Jordan Peterson cleaning your room up in here. Let's see how noticeable the consequences are. - I predict a happier wife, for one. - I'm also curious to see what kind of fitness impacts there are to increasing this kind of activity, compared to doing more exercise. originally posted at https://stacker.news/items/931099 @ d5c3d063:4d1159b3
2025-04-03 04:09:56### ทรัมป์ ขึ้นภาษีนำเข้า สิ่งที่คุณเห็น…กับสิ่งที่คุณมองไม่เห็น คุณ #เห็น แค่ฝั่งที่ดูดีในข่าวภาคค่ำ แต่คุณ #ไม่เห็น – คนทั้งประเทศ ต้องจ่ายของแพงขึ้น – ธุรกิจเล็ก ๆ ที่พึ่งการนำเข้า…ถูกบีบให้ตาย – ผู้บริโภคต้องเสียเงินมากขึ้น โดยไม่มีทางเลือก รัฐอ้างว่า *"ปกป้องประเทศ"* แต่จริง ๆ แล้วเขาแค่ โยนภาระให้คนส่วนใหญ่ เพื่ออุ้มผลประโยชน์บางกลุ่ม เหมือนที่ Bastiat เรียกว่า *“การปล้นที่ถูกกฎหมาย”* Hazlitt ขยายต่อใน Economics in One Lesson ว่า > เศรษฐศาสตร์ที่ดี ต้องมองให้พ้นจากผลเฉพาะหน้า > และมองให้เห็นผลกระทบต่อทุกคน ไม่ใช่แค่บางกลุ่ม เงินเฟ้อ คือการขโมยแบบเงียบ ๆ ภาษีศุลกากร คือการปล้นอย่างเปิดเผย วันนี้ #EIOL น่าจะถึงมือเพื่อนๆ หลายคนแล้ว เล่มนี้ไม่ต้องอ่านทีละบทก็ได้ ลองเปิดไปบทที่ 11 เลยแล้วจะเจอ**ค้อนปอน**สำหรับทุบมายาคดีทางเศรษฐกิจที่รัฐใช้กับเรามาทั้งชีวิต อ่าน #เศรษฐศาสตร์เล่มเดียวจบ แล้วคุณอาจไม่มีวันมอง “นโยบายเพื่อประชาชน” ได้เหมือนเดิมอีก เพราะบางที...สิ่งที่คุณไม่เคยเห็น อาจเป็นสิ่งที่คุณควรรู้(เห็น)ให้เร็วที่สุด #Siamstr
@ d5c3d063:4d1159b3
2025-04-03 04:09:56### ทรัมป์ ขึ้นภาษีนำเข้า สิ่งที่คุณเห็น…กับสิ่งที่คุณมองไม่เห็น คุณ #เห็น แค่ฝั่งที่ดูดีในข่าวภาคค่ำ แต่คุณ #ไม่เห็น – คนทั้งประเทศ ต้องจ่ายของแพงขึ้น – ธุรกิจเล็ก ๆ ที่พึ่งการนำเข้า…ถูกบีบให้ตาย – ผู้บริโภคต้องเสียเงินมากขึ้น โดยไม่มีทางเลือก รัฐอ้างว่า *"ปกป้องประเทศ"* แต่จริง ๆ แล้วเขาแค่ โยนภาระให้คนส่วนใหญ่ เพื่ออุ้มผลประโยชน์บางกลุ่ม เหมือนที่ Bastiat เรียกว่า *“การปล้นที่ถูกกฎหมาย”* Hazlitt ขยายต่อใน Economics in One Lesson ว่า > เศรษฐศาสตร์ที่ดี ต้องมองให้พ้นจากผลเฉพาะหน้า > และมองให้เห็นผลกระทบต่อทุกคน ไม่ใช่แค่บางกลุ่ม เงินเฟ้อ คือการขโมยแบบเงียบ ๆ ภาษีศุลกากร คือการปล้นอย่างเปิดเผย วันนี้ #EIOL น่าจะถึงมือเพื่อนๆ หลายคนแล้ว เล่มนี้ไม่ต้องอ่านทีละบทก็ได้ ลองเปิดไปบทที่ 11 เลยแล้วจะเจอ**ค้อนปอน**สำหรับทุบมายาคดีทางเศรษฐกิจที่รัฐใช้กับเรามาทั้งชีวิต อ่าน #เศรษฐศาสตร์เล่มเดียวจบ แล้วคุณอาจไม่มีวันมอง “นโยบายเพื่อประชาชน” ได้เหมือนเดิมอีก เพราะบางที...สิ่งที่คุณไม่เคยเห็น อาจเป็นสิ่งที่คุณควรรู้(เห็น)ให้เร็วที่สุด #Siamstr @ 57d1a264:69f1fee1
2025-03-27 08:11:33Explore and reimagine programming interfaces beyond text (visual, tactile, spatial). > _"The most dangerous thought you can have as a creative person is to think you know what you're doing."_ `— Richard Hamming` [^1] https://www.youtube.com/watch?v=8pTEmbeENF4 For his recent DBX Conference talk, Victor took attendees back to the year 1973, donning the uniform of an IBM systems engineer of the times, delivering his presentation on an overhead projector. The '60s and early '70s were a fertile time for CS ideas, reminds Victor, but even more importantly, it was a time of unfettered thinking, unconstrained by programming dogma, authority, and tradition.  _'The most dangerous thought that you can have as a creative person is to think that you know what you're doing,'_ explains Victor. 'Because once you think you know what you're doing you stop looking around for other ways of doing things and you stop being able to see other ways of doing things. You become blind.' He concludes, 'I think you have to say: _"We don't know what programming is. We don't know what computing is. We don't even know what a computer is."_ And once you truly understand that, and once you truly believe that, then you're free, and you can think anything.' More details at https://worrydream.com/dbx/ [^1]: Richard Hamming -- [The Art of Doing Science and Engineering, p5](http://worrydream.com/refs/Hamming_1997_-_The_Art_of_Doing_Science_and_Engineering.pdf) (pdf ebook) originally posted at https://stacker.news/items/926493
@ 57d1a264:69f1fee1
2025-03-27 08:11:33Explore and reimagine programming interfaces beyond text (visual, tactile, spatial). > _"The most dangerous thought you can have as a creative person is to think you know what you're doing."_ `— Richard Hamming` [^1] https://www.youtube.com/watch?v=8pTEmbeENF4 For his recent DBX Conference talk, Victor took attendees back to the year 1973, donning the uniform of an IBM systems engineer of the times, delivering his presentation on an overhead projector. The '60s and early '70s were a fertile time for CS ideas, reminds Victor, but even more importantly, it was a time of unfettered thinking, unconstrained by programming dogma, authority, and tradition.  _'The most dangerous thought that you can have as a creative person is to think that you know what you're doing,'_ explains Victor. 'Because once you think you know what you're doing you stop looking around for other ways of doing things and you stop being able to see other ways of doing things. You become blind.' He concludes, 'I think you have to say: _"We don't know what programming is. We don't know what computing is. We don't even know what a computer is."_ And once you truly understand that, and once you truly believe that, then you're free, and you can think anything.' More details at https://worrydream.com/dbx/ [^1]: Richard Hamming -- [The Art of Doing Science and Engineering, p5](http://worrydream.com/refs/Hamming_1997_-_The_Art_of_Doing_Science_and_Engineering.pdf) (pdf ebook) originally posted at https://stacker.news/items/926493 @ fd06f542:8d6d54cd
2025-03-28 02:14:43{"coverurl":"https://cdn.nostrcheck.me/fd06f542bc6c06a39881810de917e6c5d277dfb51689a568ad7b7a548d6d54cd/5ad7189d30c9b49aa61652d98ac7853217b7e445f863be09f9745c49df9f514c.webp","title":"Nostr protocol","author":"fiatjaf"}
@ fd06f542:8d6d54cd
2025-03-28 02:14:43{"coverurl":"https://cdn.nostrcheck.me/fd06f542bc6c06a39881810de917e6c5d277dfb51689a568ad7b7a548d6d54cd/5ad7189d30c9b49aa61652d98ac7853217b7e445f863be09f9745c49df9f514c.webp","title":"Nostr protocol","author":"fiatjaf"} @ e3ba5e1a:5e433365
2025-02-13 06:16:49My favorite line in any Marvel movie ever is in “Captain America.” After Captain America launches seemingly a hopeless assault on Red Skull’s base and is captured, we get [this line](https://www.youtube.com/shorts/kqsomjpz7ok): “Arrogance may not be a uniquely American trait, but I must say, you do it better than anyone.” Yesterday, I came across a comment on the song [Devil Went Down to Georgia](https://youtu.be/ut8UqFlWdDc) that had a very similar feel to it:  America has seemingly always been arrogant, in a uniquely American way. Manifest Destiny, for instance. The rest of the world is aware of this arrogance, and mocks Americans for it. A central point in modern US politics is the deriding of racist, nationalist, supremacist Americans. That’s not what I see. I see American Arrogance as not only a beautiful statement about what it means to be American. I see it as an ode to the greatness of humanity in its purest form. For most countries, saying “our nation is the greatest” *is*, in fact, twinged with some level of racism. I still don’t have a problem with it. Every group of people *should* be allowed to feel pride in their accomplishments. The destruction of the human spirit since the end of World War 2, where greatness has become a sin and weakness a virtue, has crushed the ability of people worldwide to strive for excellence. But I digress. The fears of racism and nationalism at least have a grain of truth when applied to other nations on the planet. But not to America. That’s because the definition of America, and the prototype of an American, has nothing to do with race. The definition of Americanism is *freedom*. The founding of America is based purely on liberty. On the God-given rights of every person to live life the way they see fit. American Arrogance is not a statement of racial superiority. It’s barely a statement of national superiority (though it absolutely is). To me, when an American comments on the greatness of America, it’s a statement about freedom. Freedom will always unlock the greatness inherent in any group of people. Americans are *definitionally* better than everyone else, because Americans are freer than everyone else. (Or, at least, that’s how it should be.) In *Devil Went Down to Georgia*, Johnny is approached by the devil himself. He is challenged to a ridiculously lopsided bet: a golden fiddle versus his immortal soul. He acknowledges the sin in accepting such a proposal. And yet he says, “God, I know you told me not to do this. But I can’t stand the affront to my honor. I am the greatest. The devil has nothing on me. So God, I’m gonna sin, but I’m also gonna win.” *Libertas magnitudo est*
@ e3ba5e1a:5e433365
2025-02-13 06:16:49My favorite line in any Marvel movie ever is in “Captain America.” After Captain America launches seemingly a hopeless assault on Red Skull’s base and is captured, we get [this line](https://www.youtube.com/shorts/kqsomjpz7ok): “Arrogance may not be a uniquely American trait, but I must say, you do it better than anyone.” Yesterday, I came across a comment on the song [Devil Went Down to Georgia](https://youtu.be/ut8UqFlWdDc) that had a very similar feel to it:  America has seemingly always been arrogant, in a uniquely American way. Manifest Destiny, for instance. The rest of the world is aware of this arrogance, and mocks Americans for it. A central point in modern US politics is the deriding of racist, nationalist, supremacist Americans. That’s not what I see. I see American Arrogance as not only a beautiful statement about what it means to be American. I see it as an ode to the greatness of humanity in its purest form. For most countries, saying “our nation is the greatest” *is*, in fact, twinged with some level of racism. I still don’t have a problem with it. Every group of people *should* be allowed to feel pride in their accomplishments. The destruction of the human spirit since the end of World War 2, where greatness has become a sin and weakness a virtue, has crushed the ability of people worldwide to strive for excellence. But I digress. The fears of racism and nationalism at least have a grain of truth when applied to other nations on the planet. But not to America. That’s because the definition of America, and the prototype of an American, has nothing to do with race. The definition of Americanism is *freedom*. The founding of America is based purely on liberty. On the God-given rights of every person to live life the way they see fit. American Arrogance is not a statement of racial superiority. It’s barely a statement of national superiority (though it absolutely is). To me, when an American comments on the greatness of America, it’s a statement about freedom. Freedom will always unlock the greatness inherent in any group of people. Americans are *definitionally* better than everyone else, because Americans are freer than everyone else. (Or, at least, that’s how it should be.) In *Devil Went Down to Georgia*, Johnny is approached by the devil himself. He is challenged to a ridiculously lopsided bet: a golden fiddle versus his immortal soul. He acknowledges the sin in accepting such a proposal. And yet he says, “God, I know you told me not to do this. But I can’t stand the affront to my honor. I am the greatest. The devil has nothing on me. So God, I’m gonna sin, but I’m also gonna win.” *Libertas magnitudo est* @ 3c7dc2c5:805642a8
2025-04-02 21:15:55## 🧠Quote(s) of the week: CBDC the digital euro - a centralized solution in search of a problem. While the ECB may see it as a way to 'modernize' finance, true innovation comes from empowering individuals, not consolidating control. CBDCs are just surveillance tools disguised as innovation. Bitcoin is the only true digital money—decentralized, scarce, and free. Stack sats, not CBDCs. ## 🧡Bitcoin news🧡 2025 https://i.ibb.co/vx988kT1/Gn-Ix-Dp-YWs-AASkiw.jpg On the 24th of March: ➡️The Pakistan central bank is exploring mining Bitcoin with excess electricity. ➡️'MicroStrategy just added another 7,000 Bitcoin to their treasury. They're now holding over 506,000 BTC ($44 billion). Look at the corporate Bitcoin ownership breakdown: - MicroStrategy: 506,000+ BTC - Marathon: ~46,000 BTC (10x smaller) - Riot: ~19,000 BTC (26x smaller) That acquisition curve has gone parabolic since Q4 2024. Strategy's buying pace now rivals what we're seeing from the Bitcoin ETFs, a single public company absorbing supply at an institutional scale. Clear institutional conviction signal here.' -Ecoinometrics ➡️SQUARE CEO JACK DORSEY: "Bitcoin will make the current financial system feel as irrelevant as the fax machine." On the 25th of March: ➡️'BITCOIN HASH-RIBBON FLASHES BUY SIGNAL - This is one of the most reliable "buy" indicators. - Significant price gains have followed 7 out of the last 7 times this indicator was triggered.' -Bitcoin Archive (foto) Bitcoin is always a buy. Just DCA. ➡️GameStop includes Bitcoin as a treasury reserve asset in its investment policy update. GameStop has $4.6 billion in cash to invest. ➡️Strategy’s sale of 8.5 million STRF shares closes today, unlocking $711 million in new capital to buy more Bitcoin. ➡️BBC News reports from a remote community of 15,000 people in the far north-western tip of Zambia relying on hydroelectric power, “The bitcoin mine now accounts for around 30% of the plant's revenue allowing them to keep the prices down for the local town” - Source: https://www.bbc.com/news/articles/cly4xe373p4o Gridless is doing a splendid job in Africa and showing through proof-of-work that if you aren't mining Bitcoin, you are wasting energy. It's time for such communities to appear more around the world. Daniel Batten: 'They couldn't resist zooming out and implying this is an outlier (it isn't, the majority of off-grid bitcoin mining operations are renewably powered). In doing so BBC made three factually incorrect statements at the end about Bitcoin mining straining grids (multiple peer-reviewed studies show the opposite is true), and "Greenidge gas power plant in New York which was renovated to mine bitcoin" (it didn't, it re-opened to supply power back to the grid), and stating that Bitcoin mining needs artificial govt incentives or rules to do the right thing (It doesn't, it's become 56.7% sustainably powered without any govt incentives) But let's shine the light on the positive - it has far fewer factually incorrect statements than previous reporting, and it is a step in the right direction in its gradual journey towards objective Bitcoin reporting for a media company that has until now only published negative news stories on Bitcoin.' ➡️Femke Halsema, Mayor of Amsterdam, wants a national ban on Bitcoin payments: "It undermines our civilization". I rather believe the opposite. Under Femke Halsema - Amsterdam - The number of civil servants increased by 50% (14K -> 20K) - Debt increased by 150% (4 billion -> approx. 10 billion) Despite high revenues, Amsterdam has to borrow nearly half a billion euros every year. Local taxes continue to rise, whether it's water authority taxes or property taxes (OZB). But, above all, you should be concerned about those 0.3% criminal Bitcoin / Crypto transactions (worldwide). The audacity. Even if the Netherlands were to legally ban Bitcoin payments, users could easily continue trading through foreign exchanges or peer-to-peer platforms. A ban might actually push Bitcoin usage further underground, making oversight of suspicious transactions worse rather than better. ➡️Mt. Gox moves 11.501 Bitcoin ($1B) for creditor repayment. ➡️BlackRock launched a European Bitcoin ETP today - Bloomberg ➡️North Carolina introduces a bill to invest 5% of state funds into Bitcoin. On the 26th of March: ➡️NYDIG just became a big Bitcoin miner. Crusoe, the first to scale Bitcoin mining off flared gas (~200MW worth, across 425 data centers) has sold its entire Bitcoin mining business to NYDIG. ➡️Metaplanet has raised ~$55.2m (¥8.28b) of equity capital through three trading days this week while partially deleveraging with the redemption of $23.3m (¥3.5b) of 0% ordinary bonds. ➡️GameStop can service a loan of up to $100 BILLION for 4.6 years with its existing $4.6b cash balance at 1% interest. That's twice the amount of Bitcoin Michael Saylor's Strategy currently holds. ➡️New feature by Protonmail enables their 100 million users to send Bitcoin using their email addresses. ➡️The Blockchain Group confirms the acquisition of 580 BTC for ~€47.3 million, the holding of a total of 620 BTC, and a BTC Yield of 709.8% YTD. → Confirmation of the acquisition of 580 BTC for ~€47.3 million at ~€81,550 per bitcoin → Total group holdings of 620 BTC for ~€50.5 million at ~€81,480 per bitcoin → Adoption of ‘BTC Yield’, ‘BTC Gain’, and ‘BTC € Gain’ as KPIs, following the steps of Strategy and Metaplanet This is a major step in our Bitcoin Treasury Company strategy focused on increasing Bitcoin per share over time. Source: https://t.co/QDj61ZDe6O The Blockchain Group is Europe's First Bitcoin Treasury Company! On the 27th of March: ➡️'Bitcoin's 4-year Compound Annual Growth Rate (CAGR) is at historic lows.' -Pierre Rochard ➡️Daniel Batten: Yet another paper on Bitcoin and energy TL:DR: "The opportunities offered by bitcoin mining in reduction of the greenhouse gas emissions and renewable energy transition are greater than generally assumed" The journal has a (high) impact factor of 7.1." Source: https://t.co/W3gytMgcpC ➡️A home miner with only 4 machines mined block 888737. https://i.ibb.co/7xm91R4t/Gn-Ef-H9y-Ws-AA4jkn.jpg Bitcoin proves anyone can participate and earn—true freedom! ➡️'Short-Term Holders have increased their Bitcoin holdings by 201,743 BTC to 5,750,076 BTC since January, remaining below previous cycle peaks. 200K BTC are currently held at an unrealized loss, representing about $17B.' -Bitcoin News ➡️Bitcoin mining hardware manufacturer Canaan signs a three-year colocation agreement with Mawson Infrastructure Group's Mawson Hosting LLC for facilities in Midland, Pennsylvania, and Edna, Texas. Most of the 4.7 EH/s hashrate is expected to be operational by Q2 2025. On the 28th of March: ➡️If Saylor had bet on ETH instead of Bitcoin, Strategy would be down $9 billion, instead of up $9 billion like they are today. ETHBTC made fresh lows 0.02210. Ether is down 74% against Bitcoin since switching from proof of work to proof of stake. Yikes! ➡️Representative introduces a strategic Bitcoin reserve bill in South Carolina. ➡️A Russian company built a Bitcoin mine in the Arctic. Set in the frozen city of Norilsk, the facility taps into cheap excess energy from one of the world's most isolated industrial hubs. ➡️The price of bitcoin has nearly followed the same phases of volatility for 15 years, according to Fidelity. https://i.ibb.co/LdQfrqG0/Gn-Ig-Skd-XMAAi-L3r.jpg another great chart: https://i.ibb.co/G4WmDjhd/Gn-JED1q-Xk-AAq-Kqk.jpg On the 29th of March: ➡️Public miner MARA with a $2B common stock offering to buy more Bitcoin. https://i.ibb.co/PZZxXJ37/Gn-Kj-Vqza-EAEUG-V.png ➡️California has officially included Bitcoin Rights protections in its newly proposed digital asset bill. If passed, it will guarantee the right to self-custody for nearly 40M residents and prohibit discrimination against Bitcoin use. ➡️The number of addresses with more than one Bitcoin has fallen below 1 million, standing today at 995,207. On the 31st of March: ➡️Larry Fink, Founder/CEO of BlackRock in his annual letter to shareholders: “If the U.S. doesn't get its debt under control, if deficits keep ballooning, America risks losing that position to digital assets like Bitcoin." https://www.blackrock.com/corporate/literature/presentation/larry-fink-annual-chairmans-letter.pdf ➡️Strategy has acquired 22,048 BTC for ~$1.92 billion at ~$86,969 per bitcoin and has achieved a BTC Yield of 11.0% YTD 2025. As of 3/30/2025, Strategy holds 528,185 $BTC acquired for ~$35.63 billion at ~$67,458 per bitcoin. ➡️ The Bitcoin Policy Institute releases a framework for the USA to buy $200 billion worth of #Bitcoin using Bit Bonds. ➡️Is Indonesia the next Bitcoin Country? Bitcoin Indonesia mapped out the entire Bitcoin ecosystem. A new map shows Bitcoin adoption EXPLODING across the Southeast Asian island nation of Indonesia. Check out all the communities, projects, and businesses embracing Bitcoin. The revolution is happening. https://i.ibb.co/cXL8mC0x/Gnbdg-Lub-IAAdwcb.jpg On the 1st of April: ➡️'Over 73,353 BTC were bought by corporations in Q1 2025. Only 40,500 BTC new Bitcoin was mined, but still no supply shock, for now... Which company do you want to see adopt BTC next?' Here is the breakdown by Alec: https://x.com/Alec_Bitcoin/status/1907062290345783723 ➡️After skeptics questioned Tether’s Bitcoin holdings, CEO Paolo Ardoino fired back, sharing the company’s BTC address with a confirmed balance of 92,646 BTC. On the same day Tether bought 8,888 Bitcoin worth $735 million as per on-chain data. They now hold over 100,000 BTC. ➡️'GameStop just raised $1.48B. They are expected to use that and possibly more of the now $6B+ on their balance sheet to buy Bitcoin. A master class on how to pivot from meme stock to capitalize on volatility in the ultimate store of value.' -James Lavish ➡️Texas' state house Democrats have proposed a bill that would authorize up to $250 million in state investment in Bitcoin and up to $10 million for each municipality and county. ➡️Human Rights Foundation donates 10 Bitcoins worth $830,000 to over 20 projects worldwide. Alex Gladstein: '1 billion sats gifted carefully to a variety of stellar organizations and individuals to support BTC privacy, decentralization, education, and p2p use, aimed at folks working under authoritarianism.' ## 💸Traditional Finance / Macro: On the 29th of March 👉🏽'From Wednesday to Friday, the S&P 500 lost -$100 billion PER trading hour for a total of -$2 TRILLION. Then, after the market closed on Friday, S&P 500 futures erased ANOTHER -$120 billion in minutes.' -TKL ## 🏦Banks: 👉🏽 no news ## 🌎Macro/Geopolitics: On the 24th of March: 👉🏽Financelot: 'This is fascinating. The Dow Jones to Gold Ratio is about to cross a level only seen 4 times in history. Every time it crossed this level it marked the beginning of an 18-month recession/depression. 1929, 1973, 2008 & 2025' I don't think we won't see a depression. History rhymes but doesn't always mean it will repeat, although human behavior stays the same. For now, it means the market is overvalued, gold is undervalued, or both. 👉🏽US household wealth is falling: US household equity wealth is set to drop a whopping -$3 trillion this quarter, the most since the 2022 bear market, according to BofA estimates. By comparison, equity holdings rose +$9 trillion in 2024 to a record $56 trillion. In other words, one-third of last year's gains have likely been wiped out due to the recent market pullback. Furthermore, the top 10% of the wealthiest Americans own 87% of US stocks. This, in turn, may negatively impact consumer spending as the top 10% reflect a record 50% of all consumer expenditures. Consumer spending is set to slow in Q2 2025.' -TKL 👉🏽Demolition of the Boiler House at Moorburg Power Plant in Hamburg. Germany is preparing for combat by dynamiting its own modern energy infrastructure down. This was the most advanced coal plant. 6 years old and cost three billion euros. The Netherlands is following a similar policy—they poured concrete into their gas drilling pipes. BowTiedMara on Twitter: "In 2022, a girl tied herself to the net at Roland Garros in protest, and she wore a T-shirt that said: "We have 1,028 days left." Today, the 27th of March, marks those 1,028 days, and nothing happened. Climate doomers are like Aztecs who think the sun stops unless they cut out some organs." 👉🏽Starting in April, the 66,000 employees of the European institutions will receive their seventh salary increase in just three years! Normally, this happens at most once per year. The President of the European Commission, Ursula von der Leyen, will see the largest increase, with her monthly salary rising to €34,800—an increase of €2,700—according to a report by the German newspaper Bild-Zeitung today. For the Dutch readers: https://ejbron.wordpress.com/2025/03/24/eu-bureaucraten-en-politici-krijgen-de-7e-salarisverhoging-sinds-2022/ They are compensating for the inflation they impose on the EU. Lucky them Fair to say we need a DOGE in Europe. On the 25th of March: 👉🏽Dutch minister announces a huge increase in excise duties of 25.8 cents on gasoline. On top of that, the price of gasoline will rise by an additional 7 cents due to the blending requirement and 11 cents due to the ETS-2 regulation. In a free market, prices would not be announced by politicians but would emerge through supply and demand. How I love the EU....although it is a bit more nuanced. The temporary discount is ending. Unless the parliament decides to extend it, the price of gasoline will rise. The Dutch government should simply spend less and abolish all taxes, excise duties, and levies on food, fuel, and energy. Never gonna happen though. 👉🏽"Shell will be thoroughly reviewing all its chemical divisions worldwide in the coming period. In Europe, this could lead to the partial or complete closure of various chemical branches." As mentioned multiple times last month, major industrial companies sounded the alarm. They warned that high energy costs in the Netherlands put their future at risk. Additionally, sustainability efforts and unclear government policies are challenging the sector. Frans Everts, President-Director of Shell Netherlands, warned that the entire industry could collapse. The Green Deal is moving full speed ahead—soon everyone will be relying on food banks… For the Dutch readers: https://nos.nl/artikel/2561036-shell-kijkt-naar-gedeeltelijke-sluiting-van-chemie-onderdelen On the 26th of March: 👉🏽EU countries will start using a digital driver’s license from 2030. This is the result of negotiations between the European Parliament and EU member states. In the Netherlands, the digital license will be valid for ten years and will be accessible via an app. And we all know which app that will be! The EU Digital Wallet must be filled, after all. Not just your driver’s license—everything will soon be linked to your digital identity. It’s all right there on the EU’s website, and it’s been planned for a long time. The COVID pass was already part of the rollout. The fact that they present these as separate steps just shows that they know people wouldn’t accept it if they were fully aware of what’s happening. On the 27th of March: 👉🏽Gold surpasses $3,100 for the first time in history. TKL: 'Gold prices have hit 50 all-time highs over the last 12 months, its best streak in 12 years. This is also the 3rd-longest streak on record after a historic run during the late 1970s. The 1970s came with a period of double-digit inflation, stagnant economic growth, and a high unemployment rate, also known as stagflation. As a result, gold prices recorded 4 consecutive yearly gains.' On the 31st of March for the first time, gold blasted through $100,000/kilogram. This time, gold prices have rallied 39% over the last 12 months, are up 16% year-to-date, and are on track for the 3rd annual positive performance.' 👉🏽NATO Secretary General Rutte insists there will be no normalization of relations with Russia for decades to come. On March 14, 2025, Bloomberg, Rutte says: "Once the war is over, relations with Russia will gradually be restored." On March 26, 2025, Rutte said: "There will be no normalization of relations with Russia for decades, even after the war is over." That is the Mark I know! "Mark Rutte, the long-serving Dutch Prime Minister, earned the nickname “Pinokkio” (Dutch for Pinocchio) primarily because of perceived dishonesty or evasiveness in political debates and scandals. While some still view Rutte as a pragmatic and stable leader, the nickname “Pinokkio” reflects a broader public sentiment of distrust, especially among those who felt betrayed by his communication style or decisions.” On the 28th of March: 👉🏽US consumers now expect 5.0%(!) inflation in the next twelve months. Inflation expectations have DOUBLED in just four months. That's huge! Long-term US inflation expectations have officially SURGED to 4.1%, the highest level since 1993. Tariff front-running has led to a $300+ BILLION trade deficit in 2 months, and consumer sentiment has collapsed. Atlanta Fed is now projecting that Q1 GDP will be -2.8%… a large contraction. It’s negative even “gold adjusted” 4 weeks ago it was +2.3% 8 weeks ago it was +3.9% Yikes! 👉🏽The State Department is officially shutting down USAID and has formally notified Congress of its closure. The remaining 900 employees are set to be terminated. 👉🏽Argentina’s Economy Grows 6.5% in January. Argentina’s Poverty Rate Drops from 52.9% to 38.1% in 15 Months Under Javier Milei 👉🏽Fix the money, fix the world: DOGE “There is actually really only ONE BANK ACCOUNT that's used to disperse ALL monies that go out of the federal government” “It's a big one — A couple of weeks ago it had $800 billion in it, it's the treasury general account” “We're serving 580+ agencies. And up until very recently, effectively they could say, make the payment and Treasury just sent it out as fast as possible. NO VERIFICATION” “There's a $500 billion of fraud every year. There are hundreds of billion dollars of improper payments and we can't pass an audit. The consolidated financial report is produced by treasury and we cannot pass an audit” Extremely fascinating interview by Bret Baier with the highly talented and competent DOGE team, which is rigorously streamlining the U.S. government bureaucracy. This work can only be done by competent (and motivated) outsiders with experience. Also urgently needed in the Netherlands, and in Europe. On the 29th of March: 👉🏽'US debt has been "limited" by the $36.104 trillion debt ceiling since January but the liabilities don't stop rising. As of today, US debt is now ~$37 trillion. Treasury has burned through $560BN of its cash balance in the past month. Just $280BN left.' -ZeroHedge On the 1st of April: In recent weeks, I have shared my opinion on the latest Dutch pension fund drama. This week: https://i.ibb.co/96ZhS0W/Gn-XEVQRXw-AM6b0-A.jpg APG and pension funds refused to invest in Dutch housing (for political reasons). This involved 25 billion euros. Currently we almost have a political scandal over a medal, but the fact that our pension system is being put at risk...no biggie!? For our own housing market? “Too political.” For war and Brussels' military ambitions? €100,000,000,000—no problem. They’re gambling with your pension while first-time buyers can’t afford a home and seniors struggle to make ends meet. Our money, their agenda. Got Bitcoin? I will end this Weekly Recap with a Stanley Druckenmiller quote: "My favorite quote of all time is maybe Mark Twain: "Put all your eggs in one basket and watch the basket carefully." "I tend to think that's what great investors do." I know what I do and have. Bitcoin! ## 🎁If you have made it this far I would like to give you a little gift: What Bitcoin Did: Peter Dunworth is the Director of a multi-family office and is the co-founder of The Bitcoin Adviser. In this episode, they discuss why Bitcoin is the only asset that can recapitalize the financial system, why Peter believes Bitcoin could become a $100 trillion asset within a decade, why credit markets are ultimately a collateral problem, and why financializing Bitcoin might be necessary to save Main Street from being collateral damage. They also get into Australia's property obsession, GameStop’s pivot to Bitcoin, the difference between Bitcoin derivatives and the asset itself, and MicroStrategy. https://www.youtube.com/watch?v=_bSprc0IAow Credit: I have used multiple sources! My savings account: Bitcoin The tool I recommend for setting up a Bitcoin savings plan: PocketBitcoin especially suited for beginners or people who want to invest in Bitcoin with an automated investment plan once a week or monthly. `Use the code SE3997` Get your Bitcoin out of exchanges. Save them on a hardware wallet, run your own node...be your own bank. Not your keys, not your coins. It's that simple. ⠀ ⠀ ⠀⠀ ⠀ ⠀⠀⠀ Do you think this post is helpful to you? If so, please share it and support my work with a zap. ▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃ ⭐ Many thanks⭐ Felipe - Bitcoin Friday! ▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃
@ 3c7dc2c5:805642a8
2025-04-02 21:15:55## 🧠Quote(s) of the week: CBDC the digital euro - a centralized solution in search of a problem. While the ECB may see it as a way to 'modernize' finance, true innovation comes from empowering individuals, not consolidating control. CBDCs are just surveillance tools disguised as innovation. Bitcoin is the only true digital money—decentralized, scarce, and free. Stack sats, not CBDCs. ## 🧡Bitcoin news🧡 2025 https://i.ibb.co/vx988kT1/Gn-Ix-Dp-YWs-AASkiw.jpg On the 24th of March: ➡️The Pakistan central bank is exploring mining Bitcoin with excess electricity. ➡️'MicroStrategy just added another 7,000 Bitcoin to their treasury. They're now holding over 506,000 BTC ($44 billion). Look at the corporate Bitcoin ownership breakdown: - MicroStrategy: 506,000+ BTC - Marathon: ~46,000 BTC (10x smaller) - Riot: ~19,000 BTC (26x smaller) That acquisition curve has gone parabolic since Q4 2024. Strategy's buying pace now rivals what we're seeing from the Bitcoin ETFs, a single public company absorbing supply at an institutional scale. Clear institutional conviction signal here.' -Ecoinometrics ➡️SQUARE CEO JACK DORSEY: "Bitcoin will make the current financial system feel as irrelevant as the fax machine." On the 25th of March: ➡️'BITCOIN HASH-RIBBON FLASHES BUY SIGNAL - This is one of the most reliable "buy" indicators. - Significant price gains have followed 7 out of the last 7 times this indicator was triggered.' -Bitcoin Archive (foto) Bitcoin is always a buy. Just DCA. ➡️GameStop includes Bitcoin as a treasury reserve asset in its investment policy update. GameStop has $4.6 billion in cash to invest. ➡️Strategy’s sale of 8.5 million STRF shares closes today, unlocking $711 million in new capital to buy more Bitcoin. ➡️BBC News reports from a remote community of 15,000 people in the far north-western tip of Zambia relying on hydroelectric power, “The bitcoin mine now accounts for around 30% of the plant's revenue allowing them to keep the prices down for the local town” - Source: https://www.bbc.com/news/articles/cly4xe373p4o Gridless is doing a splendid job in Africa and showing through proof-of-work that if you aren't mining Bitcoin, you are wasting energy. It's time for such communities to appear more around the world. Daniel Batten: 'They couldn't resist zooming out and implying this is an outlier (it isn't, the majority of off-grid bitcoin mining operations are renewably powered). In doing so BBC made three factually incorrect statements at the end about Bitcoin mining straining grids (multiple peer-reviewed studies show the opposite is true), and "Greenidge gas power plant in New York which was renovated to mine bitcoin" (it didn't, it re-opened to supply power back to the grid), and stating that Bitcoin mining needs artificial govt incentives or rules to do the right thing (It doesn't, it's become 56.7% sustainably powered without any govt incentives) But let's shine the light on the positive - it has far fewer factually incorrect statements than previous reporting, and it is a step in the right direction in its gradual journey towards objective Bitcoin reporting for a media company that has until now only published negative news stories on Bitcoin.' ➡️Femke Halsema, Mayor of Amsterdam, wants a national ban on Bitcoin payments: "It undermines our civilization". I rather believe the opposite. Under Femke Halsema - Amsterdam - The number of civil servants increased by 50% (14K -> 20K) - Debt increased by 150% (4 billion -> approx. 10 billion) Despite high revenues, Amsterdam has to borrow nearly half a billion euros every year. Local taxes continue to rise, whether it's water authority taxes or property taxes (OZB). But, above all, you should be concerned about those 0.3% criminal Bitcoin / Crypto transactions (worldwide). The audacity. Even if the Netherlands were to legally ban Bitcoin payments, users could easily continue trading through foreign exchanges or peer-to-peer platforms. A ban might actually push Bitcoin usage further underground, making oversight of suspicious transactions worse rather than better. ➡️Mt. Gox moves 11.501 Bitcoin ($1B) for creditor repayment. ➡️BlackRock launched a European Bitcoin ETP today - Bloomberg ➡️North Carolina introduces a bill to invest 5% of state funds into Bitcoin. On the 26th of March: ➡️NYDIG just became a big Bitcoin miner. Crusoe, the first to scale Bitcoin mining off flared gas (~200MW worth, across 425 data centers) has sold its entire Bitcoin mining business to NYDIG. ➡️Metaplanet has raised ~$55.2m (¥8.28b) of equity capital through three trading days this week while partially deleveraging with the redemption of $23.3m (¥3.5b) of 0% ordinary bonds. ➡️GameStop can service a loan of up to $100 BILLION for 4.6 years with its existing $4.6b cash balance at 1% interest. That's twice the amount of Bitcoin Michael Saylor's Strategy currently holds. ➡️New feature by Protonmail enables their 100 million users to send Bitcoin using their email addresses. ➡️The Blockchain Group confirms the acquisition of 580 BTC for ~€47.3 million, the holding of a total of 620 BTC, and a BTC Yield of 709.8% YTD. → Confirmation of the acquisition of 580 BTC for ~€47.3 million at ~€81,550 per bitcoin → Total group holdings of 620 BTC for ~€50.5 million at ~€81,480 per bitcoin → Adoption of ‘BTC Yield’, ‘BTC Gain’, and ‘BTC € Gain’ as KPIs, following the steps of Strategy and Metaplanet This is a major step in our Bitcoin Treasury Company strategy focused on increasing Bitcoin per share over time. Source: https://t.co/QDj61ZDe6O The Blockchain Group is Europe's First Bitcoin Treasury Company! On the 27th of March: ➡️'Bitcoin's 4-year Compound Annual Growth Rate (CAGR) is at historic lows.' -Pierre Rochard ➡️Daniel Batten: Yet another paper on Bitcoin and energy TL:DR: "The opportunities offered by bitcoin mining in reduction of the greenhouse gas emissions and renewable energy transition are greater than generally assumed" The journal has a (high) impact factor of 7.1." Source: https://t.co/W3gytMgcpC ➡️A home miner with only 4 machines mined block 888737. https://i.ibb.co/7xm91R4t/Gn-Ef-H9y-Ws-AA4jkn.jpg Bitcoin proves anyone can participate and earn—true freedom! ➡️'Short-Term Holders have increased their Bitcoin holdings by 201,743 BTC to 5,750,076 BTC since January, remaining below previous cycle peaks. 200K BTC are currently held at an unrealized loss, representing about $17B.' -Bitcoin News ➡️Bitcoin mining hardware manufacturer Canaan signs a three-year colocation agreement with Mawson Infrastructure Group's Mawson Hosting LLC for facilities in Midland, Pennsylvania, and Edna, Texas. Most of the 4.7 EH/s hashrate is expected to be operational by Q2 2025. On the 28th of March: ➡️If Saylor had bet on ETH instead of Bitcoin, Strategy would be down $9 billion, instead of up $9 billion like they are today. ETHBTC made fresh lows 0.02210. Ether is down 74% against Bitcoin since switching from proof of work to proof of stake. Yikes! ➡️Representative introduces a strategic Bitcoin reserve bill in South Carolina. ➡️A Russian company built a Bitcoin mine in the Arctic. Set in the frozen city of Norilsk, the facility taps into cheap excess energy from one of the world's most isolated industrial hubs. ➡️The price of bitcoin has nearly followed the same phases of volatility for 15 years, according to Fidelity. https://i.ibb.co/LdQfrqG0/Gn-Ig-Skd-XMAAi-L3r.jpg another great chart: https://i.ibb.co/G4WmDjhd/Gn-JED1q-Xk-AAq-Kqk.jpg On the 29th of March: ➡️Public miner MARA with a $2B common stock offering to buy more Bitcoin. https://i.ibb.co/PZZxXJ37/Gn-Kj-Vqza-EAEUG-V.png ➡️California has officially included Bitcoin Rights protections in its newly proposed digital asset bill. If passed, it will guarantee the right to self-custody for nearly 40M residents and prohibit discrimination against Bitcoin use. ➡️The number of addresses with more than one Bitcoin has fallen below 1 million, standing today at 995,207. On the 31st of March: ➡️Larry Fink, Founder/CEO of BlackRock in his annual letter to shareholders: “If the U.S. doesn't get its debt under control, if deficits keep ballooning, America risks losing that position to digital assets like Bitcoin." https://www.blackrock.com/corporate/literature/presentation/larry-fink-annual-chairmans-letter.pdf ➡️Strategy has acquired 22,048 BTC for ~$1.92 billion at ~$86,969 per bitcoin and has achieved a BTC Yield of 11.0% YTD 2025. As of 3/30/2025, Strategy holds 528,185 $BTC acquired for ~$35.63 billion at ~$67,458 per bitcoin. ➡️ The Bitcoin Policy Institute releases a framework for the USA to buy $200 billion worth of #Bitcoin using Bit Bonds. ➡️Is Indonesia the next Bitcoin Country? Bitcoin Indonesia mapped out the entire Bitcoin ecosystem. A new map shows Bitcoin adoption EXPLODING across the Southeast Asian island nation of Indonesia. Check out all the communities, projects, and businesses embracing Bitcoin. The revolution is happening. https://i.ibb.co/cXL8mC0x/Gnbdg-Lub-IAAdwcb.jpg On the 1st of April: ➡️'Over 73,353 BTC were bought by corporations in Q1 2025. Only 40,500 BTC new Bitcoin was mined, but still no supply shock, for now... Which company do you want to see adopt BTC next?' Here is the breakdown by Alec: https://x.com/Alec_Bitcoin/status/1907062290345783723 ➡️After skeptics questioned Tether’s Bitcoin holdings, CEO Paolo Ardoino fired back, sharing the company’s BTC address with a confirmed balance of 92,646 BTC. On the same day Tether bought 8,888 Bitcoin worth $735 million as per on-chain data. They now hold over 100,000 BTC. ➡️'GameStop just raised $1.48B. They are expected to use that and possibly more of the now $6B+ on their balance sheet to buy Bitcoin. A master class on how to pivot from meme stock to capitalize on volatility in the ultimate store of value.' -James Lavish ➡️Texas' state house Democrats have proposed a bill that would authorize up to $250 million in state investment in Bitcoin and up to $10 million for each municipality and county. ➡️Human Rights Foundation donates 10 Bitcoins worth $830,000 to over 20 projects worldwide. Alex Gladstein: '1 billion sats gifted carefully to a variety of stellar organizations and individuals to support BTC privacy, decentralization, education, and p2p use, aimed at folks working under authoritarianism.' ## 💸Traditional Finance / Macro: On the 29th of March 👉🏽'From Wednesday to Friday, the S&P 500 lost -$100 billion PER trading hour for a total of -$2 TRILLION. Then, after the market closed on Friday, S&P 500 futures erased ANOTHER -$120 billion in minutes.' -TKL ## 🏦Banks: 👉🏽 no news ## 🌎Macro/Geopolitics: On the 24th of March: 👉🏽Financelot: 'This is fascinating. The Dow Jones to Gold Ratio is about to cross a level only seen 4 times in history. Every time it crossed this level it marked the beginning of an 18-month recession/depression. 1929, 1973, 2008 & 2025' I don't think we won't see a depression. History rhymes but doesn't always mean it will repeat, although human behavior stays the same. For now, it means the market is overvalued, gold is undervalued, or both. 👉🏽US household wealth is falling: US household equity wealth is set to drop a whopping -$3 trillion this quarter, the most since the 2022 bear market, according to BofA estimates. By comparison, equity holdings rose +$9 trillion in 2024 to a record $56 trillion. In other words, one-third of last year's gains have likely been wiped out due to the recent market pullback. Furthermore, the top 10% of the wealthiest Americans own 87% of US stocks. This, in turn, may negatively impact consumer spending as the top 10% reflect a record 50% of all consumer expenditures. Consumer spending is set to slow in Q2 2025.' -TKL 👉🏽Demolition of the Boiler House at Moorburg Power Plant in Hamburg. Germany is preparing for combat by dynamiting its own modern energy infrastructure down. This was the most advanced coal plant. 6 years old and cost three billion euros. The Netherlands is following a similar policy—they poured concrete into their gas drilling pipes. BowTiedMara on Twitter: "In 2022, a girl tied herself to the net at Roland Garros in protest, and she wore a T-shirt that said: "We have 1,028 days left." Today, the 27th of March, marks those 1,028 days, and nothing happened. Climate doomers are like Aztecs who think the sun stops unless they cut out some organs." 👉🏽Starting in April, the 66,000 employees of the European institutions will receive their seventh salary increase in just three years! Normally, this happens at most once per year. The President of the European Commission, Ursula von der Leyen, will see the largest increase, with her monthly salary rising to €34,800—an increase of €2,700—according to a report by the German newspaper Bild-Zeitung today. For the Dutch readers: https://ejbron.wordpress.com/2025/03/24/eu-bureaucraten-en-politici-krijgen-de-7e-salarisverhoging-sinds-2022/ They are compensating for the inflation they impose on the EU. Lucky them Fair to say we need a DOGE in Europe. On the 25th of March: 👉🏽Dutch minister announces a huge increase in excise duties of 25.8 cents on gasoline. On top of that, the price of gasoline will rise by an additional 7 cents due to the blending requirement and 11 cents due to the ETS-2 regulation. In a free market, prices would not be announced by politicians but would emerge through supply and demand. How I love the EU....although it is a bit more nuanced. The temporary discount is ending. Unless the parliament decides to extend it, the price of gasoline will rise. The Dutch government should simply spend less and abolish all taxes, excise duties, and levies on food, fuel, and energy. Never gonna happen though. 👉🏽"Shell will be thoroughly reviewing all its chemical divisions worldwide in the coming period. In Europe, this could lead to the partial or complete closure of various chemical branches." As mentioned multiple times last month, major industrial companies sounded the alarm. They warned that high energy costs in the Netherlands put their future at risk. Additionally, sustainability efforts and unclear government policies are challenging the sector. Frans Everts, President-Director of Shell Netherlands, warned that the entire industry could collapse. The Green Deal is moving full speed ahead—soon everyone will be relying on food banks… For the Dutch readers: https://nos.nl/artikel/2561036-shell-kijkt-naar-gedeeltelijke-sluiting-van-chemie-onderdelen On the 26th of March: 👉🏽EU countries will start using a digital driver’s license from 2030. This is the result of negotiations between the European Parliament and EU member states. In the Netherlands, the digital license will be valid for ten years and will be accessible via an app. And we all know which app that will be! The EU Digital Wallet must be filled, after all. Not just your driver’s license—everything will soon be linked to your digital identity. It’s all right there on the EU’s website, and it’s been planned for a long time. The COVID pass was already part of the rollout. The fact that they present these as separate steps just shows that they know people wouldn’t accept it if they were fully aware of what’s happening. On the 27th of March: 👉🏽Gold surpasses $3,100 for the first time in history. TKL: 'Gold prices have hit 50 all-time highs over the last 12 months, its best streak in 12 years. This is also the 3rd-longest streak on record after a historic run during the late 1970s. The 1970s came with a period of double-digit inflation, stagnant economic growth, and a high unemployment rate, also known as stagflation. As a result, gold prices recorded 4 consecutive yearly gains.' On the 31st of March for the first time, gold blasted through $100,000/kilogram. This time, gold prices have rallied 39% over the last 12 months, are up 16% year-to-date, and are on track for the 3rd annual positive performance.' 👉🏽NATO Secretary General Rutte insists there will be no normalization of relations with Russia for decades to come. On March 14, 2025, Bloomberg, Rutte says: "Once the war is over, relations with Russia will gradually be restored." On March 26, 2025, Rutte said: "There will be no normalization of relations with Russia for decades, even after the war is over." That is the Mark I know! "Mark Rutte, the long-serving Dutch Prime Minister, earned the nickname “Pinokkio” (Dutch for Pinocchio) primarily because of perceived dishonesty or evasiveness in political debates and scandals. While some still view Rutte as a pragmatic and stable leader, the nickname “Pinokkio” reflects a broader public sentiment of distrust, especially among those who felt betrayed by his communication style or decisions.” On the 28th of March: 👉🏽US consumers now expect 5.0%(!) inflation in the next twelve months. Inflation expectations have DOUBLED in just four months. That's huge! Long-term US inflation expectations have officially SURGED to 4.1%, the highest level since 1993. Tariff front-running has led to a $300+ BILLION trade deficit in 2 months, and consumer sentiment has collapsed. Atlanta Fed is now projecting that Q1 GDP will be -2.8%… a large contraction. It’s negative even “gold adjusted” 4 weeks ago it was +2.3% 8 weeks ago it was +3.9% Yikes! 👉🏽The State Department is officially shutting down USAID and has formally notified Congress of its closure. The remaining 900 employees are set to be terminated. 👉🏽Argentina’s Economy Grows 6.5% in January. Argentina’s Poverty Rate Drops from 52.9% to 38.1% in 15 Months Under Javier Milei 👉🏽Fix the money, fix the world: DOGE “There is actually really only ONE BANK ACCOUNT that's used to disperse ALL monies that go out of the federal government” “It's a big one — A couple of weeks ago it had $800 billion in it, it's the treasury general account” “We're serving 580+ agencies. And up until very recently, effectively they could say, make the payment and Treasury just sent it out as fast as possible. NO VERIFICATION” “There's a $500 billion of fraud every year. There are hundreds of billion dollars of improper payments and we can't pass an audit. The consolidated financial report is produced by treasury and we cannot pass an audit” Extremely fascinating interview by Bret Baier with the highly talented and competent DOGE team, which is rigorously streamlining the U.S. government bureaucracy. This work can only be done by competent (and motivated) outsiders with experience. Also urgently needed in the Netherlands, and in Europe. On the 29th of March: 👉🏽'US debt has been "limited" by the $36.104 trillion debt ceiling since January but the liabilities don't stop rising. As of today, US debt is now ~$37 trillion. Treasury has burned through $560BN of its cash balance in the past month. Just $280BN left.' -ZeroHedge On the 1st of April: In recent weeks, I have shared my opinion on the latest Dutch pension fund drama. This week: https://i.ibb.co/96ZhS0W/Gn-XEVQRXw-AM6b0-A.jpg APG and pension funds refused to invest in Dutch housing (for political reasons). This involved 25 billion euros. Currently we almost have a political scandal over a medal, but the fact that our pension system is being put at risk...no biggie!? For our own housing market? “Too political.” For war and Brussels' military ambitions? €100,000,000,000—no problem. They’re gambling with your pension while first-time buyers can’t afford a home and seniors struggle to make ends meet. Our money, their agenda. Got Bitcoin? I will end this Weekly Recap with a Stanley Druckenmiller quote: "My favorite quote of all time is maybe Mark Twain: "Put all your eggs in one basket and watch the basket carefully." "I tend to think that's what great investors do." I know what I do and have. Bitcoin! ## 🎁If you have made it this far I would like to give you a little gift: What Bitcoin Did: Peter Dunworth is the Director of a multi-family office and is the co-founder of The Bitcoin Adviser. In this episode, they discuss why Bitcoin is the only asset that can recapitalize the financial system, why Peter believes Bitcoin could become a $100 trillion asset within a decade, why credit markets are ultimately a collateral problem, and why financializing Bitcoin might be necessary to save Main Street from being collateral damage. They also get into Australia's property obsession, GameStop’s pivot to Bitcoin, the difference between Bitcoin derivatives and the asset itself, and MicroStrategy. https://www.youtube.com/watch?v=_bSprc0IAow Credit: I have used multiple sources! My savings account: Bitcoin The tool I recommend for setting up a Bitcoin savings plan: PocketBitcoin especially suited for beginners or people who want to invest in Bitcoin with an automated investment plan once a week or monthly. `Use the code SE3997` Get your Bitcoin out of exchanges. Save them on a hardware wallet, run your own node...be your own bank. Not your keys, not your coins. It's that simple. ⠀ ⠀ ⠀⠀ ⠀ ⠀⠀⠀ Do you think this post is helpful to you? If so, please share it and support my work with a zap. ▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃ ⭐ Many thanks⭐ Felipe - Bitcoin Friday! ▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃ @ 6ad08392:ea301584
2025-03-14 19:03:20In 2024, I was high as a kite on Nostr hopium and optimism. Early that year, my co-founder and I figured that we could use Nostr as a way to validate ambassadors on “Destination Bitcoin” - the germ of a travel app idea we had at the time that would turn into Satlantis. After some more digging and thinking, we realised that Nostr’s open social graph would be of major benefit, and in exploring that design space, the fuller idea of Satlantis formed: a new kind of social network for travel. ###### ^^2 slides from the original idea here I still remember the call I had with @pablof7z in January. I was in Dubai pitching the AI idea I was working on at the time, but all I could think and talk about was Satlantis and Nostr. That conversation made me bullish AF. I came back from the trip convinced we’d struck gold. I pivoted the old company, re-organised the team and booked us for the Sovereign Engineering cohort in Madeira. We put together a whole product roadmap, go to market strategy and cap raise around the use of Nostr. We were going to be the ‘next big Nostr app’. A couple of events followed in which I announced this all to the world: Bitcoin Atlantis in March and BTC Prague in June being the two main ones. The feedback was incredible. So we doubled down. After being the major financial backer for the Nostr Booth in Prague, I decided to help organise the Nostr Booth initiative and back it financially for a series of Latin American conferences in November. I was convinced this was the biggest thing since bitcoin, so much so that I spent over $50,000 in 2024 on Nostr marketing initiatives. I was certainly high on something. # Sobering up It’s March 2025 and I’ve sobered up. I now look at Nostr through a different lens. A more pragmatic one. I see Nostr as a tool, as an entrepreneur - who’s more interested in solving a problem, than fixating on the tool(s) being used - should. A couple things changed for me. One was the sub-standard product we released in November. I was so focused on being a Nostr evangelist that I put our product second. Coupled with the extra technical debt we took on at Satlantis by making everything Nostr native, our product was crap. ***We traded usability & product stability for Nostr purism & evangelism.*** We built a whole suite of features using native event kinds (location kinds, calendar kinds, etc) that we thought other Nostr apps would also use and therefore be interoperable. Turns out no serious players were doing any of that, so we spent a bunch of time over-engineering for no benefit 😂 The other wake up call for me was the Twitter ban in Brazil. Being one of the largest markets for Twitter, I really thought it would have a material impact on global Nostr adoption. When basically nothing happened, I began to question things.  Combined, these experiences helped sober me up and I come down from my high. I was reading “the cold start problem” by Andrew Chen (ex-Uber) at the time and doing a deep dive on network effects. I came to the following realisation: *Nostr’s network effect is going to take WAY longer than we all anticipated initially. This is going to be a long grind. And unlike bitcoin, winning is not inevitable. Bitcoin solves a much more important problem, and it’s the ONLY option. Nostr solves an important problem yes, but it’s far from the only approach. It’s just the implementation arguably in the lead right now.* This sobering up led us to take a different approach with Nostr. We now view it as another tool in the tech-stack, no different to the use of React Native on mobile or AWS for infrastructure. Nostr is something to use if it makes the product better, or avoid if it makes the product and user experience worse. I will share more on this below, including our simple decision making framework. I’ll also present a few more potentially unpopular opinions about Nostr. Four in total actually: 1. Nostr is a tool, not a revolution 2. Nostr doesn’t solve the multiple social accounts problem 3. Nostr is not for censorship resistance 4. Grants come with a price Let’s begin… # Nostr is a tool, not a revolution Nostr is full of Bitcoiners, and as much as we like to think we’re immune from shiny object syndrome, we are, somewhere deep down afflicted by it like other humans. That’s normal & fine. But…while Bitcoiners have successfully suppressed this desire when it comes to shitcoins, it lies dormant, yearning for the least shitcoin-like thing to emerge which we can throw our guiltless support behind. That ***thing*** arrived and it’s called Nostr. As a result, we’ve come to project the same kind of purity and maximalism onto it as we do with Bitcoin, because it shares some attributes and it’s clearly ***not*** a grift. The trouble is, in doing so, we’ve put it in the same ***class*** as Bitcoin - which is an error. Nostr is important and in its own small way, revolutionary, but it pales in comparison to Bitcoin’s importance. ***Think of it this way: If Bitcoin fails, civilisation is fucked. If Nostr fails, we’ll engineer another rich-identity protocol***. There is no need for the kind of immaculate conception and path dependence that was necessary for Bitcoin whose genesis and success has been a once in a civilisation event. Equivocating Nostr and Bitcoin to the degree that it has been, is a significant category error. Nostr may ‘win’ or it may just be an experiment on the path to something better. **And that’s ok !** I don’t say this to piss anyone off, to piss on Nostr or to piss on myself. I say it because I’d prefer Nostr not remain a place where a few thousand people speak to each other about how cool Nostr is. That’s cute in the short term, but in the grand scheme of things, it’s a waste of a great tool that can make a significant corner of the Internet great again. By removing the emotional charge and hopium from our relationship to Nostr, we can take a more sober, objective view of it (and hopefully use it more effectively). Instead of making everything about Nostr (the tool), we can go back to doing what great product people and businesses do: make everything about the customer. --- Nobody’s going around marketing their app as a “react native product” - and while I understand that’s a false equivalent in the sense that Nostr is a protocol, while react is a framework - the reality is that it DOES NOT MATTER. **For 99.9999% of the world, what matters is the hole, not the drill.** Maybe 1000 people on Earth REALLY care that something is built on Nostr, but for everyone else, what matters is what the app or product does and the problem it solves. Realigning our focus in this way, and looking at not only Nostr, but also Bitcoin as a tool in the toolkit, has transformed the way we’re building. This inspired an essay I wrote a couple weeks ago called “As Nostr as Possible”. It covers our updated approach to using and building WITH Nostr (not just ‘on’ it). You can find that here: https://futuresocial.substack.com/p/as-nostr-as-possible-anap If you’re too busy to read it, don’t fret. The entire theory can be summarised by the diagram below. This is how we now decide what to make Nostr-native, and what to just build on our own. And - as stated in the ANAP essay - that doesn’t mean we’ll never make certain features Nostr-native. If the argument is that Nostr is not going anywhere, then we can always come back to that feature and Nostr-fy it later when resources and protocol stability permit.  Next… # The Nostr all in one approach is not all “positive” Having one account accessible via many different apps might not be as positive as we initially thought.  If you have one unified presence online, across all of your socials, and you’re posting the same thing everywhere, then yes - being able to post content in one place and it being broadcast everywhere, is great. There’s a reason why people literally PAY for products like Hypefury, Buffer and Hootsuite (aside from scheduling). BUT…..This is not always the case. I’ve spoken to hundreds of creators and many have flagged this as a bug not a feature because they tend to have a different audience on different platforms and speak to them differently depending on the platform. We all know this. How you present yourself on LinkedIn is very different to how you do it on Instagram or X. The story of Weishu (Tencent’s version of TikTok) comes to mind here. Tencent’s WeChat login worked against them because people didn’t want their social graph following them around. Users actually wanted freedom from their existing family & friends, so they chose Douyin (Chinese TikTok) instead. Perhaps this is more relevant to something like WeChat because the social graph following you around is more personal, but we saw something similar with Instagram and Facebook. Despite over a decade of ownership, Facebook still keeps the social graphs separated. All this to say that while having a different strategy & approach on different social apps is annoying, it allows users to tap into different markets because each silo has its own ‘flavour’. The people who just post the same thing everywhere are low-quality content creators anyway. The ones who actually care, are using each platform ***differently***. *The ironic part here is that this is arguably more ‘decentralised’ than the protocol approach because these siloes form a ‘marketplace of communities’ which are all somewhat different.* --- We need to find a smart way of doing this with Nostr. Some way of catering to the appropriate audience where it matters most. Perhaps this will be handled by clients, or by relays. One solution I’ve heard from people in the Nostr space is to just ‘spin up another nPub’ for your different audience. While I have no problem with people doing that - I have multiple nPubs myself - it’s clearly NOT a solution to the underlying problem here. We’re experimenting with something. Whether it’s a good idea or not remains to be seen. Satlantis users will be able to curate their profiles and remove (hide / delete) content on our app. We’ll implement this in two stages: **Stage 1: Simple**\ In the first iteration, we will not broadcast a delete request to relays. This means users can get a nicely curated profile page on Satlantis, but keep a record of their full profile elsewhere on other clients / relays. **Stage 2: More complex**\ Later on, we’ll try to give people an option to “delete on Satlantis only” or “delete everywhere”. The difference here is more control for the user. Whether we get this far remains to be seen. We’ll need to experiment with the UX and see whether this is something people really want. I’m sure neither of these solutions are ‘ideal’ - but they’re what we’re going to try until we have more time & resources to think this through more. Next… # Nostr is not for Censorship Resistance I’m sorry to say, but this ship has sailed. At least for now. Maybe it’s a problem again in the future, but who knows when, and if it will ever be a big enough factor anyway. The truth is, while WE all know that Nostr is superior because it’s a protocol, people do NOT care enough. They are more interested in what’s written ON the box, not what’s necessarily inside the box. 99% of people don’t know wtf a protocol is in the first place - let alone why it matters for censorship resistance to happen at that level, or more importantly, why they should trust ***Nostr*** to deliver on that promise. Furthermore, the few people who did care about “free speech” are now placated enough with Rumble for Video, X for short form and Substack for long form. With Meta now paying lip-service to the movement, it’s game over for this narrative - at least for the foreseeable future. The "space in people’s minds for censorship resistance has been filled. Both the ‘censorship resistance’ and ‘free speech’ ships have sailed (even though they were fake), and the people who cared enough all boarded. For the normies who never cared, they still don’t care - or they found their way to the anti-platforms, like Threads, BlueSky or Pornhub. The small minority of us still here on Nostr…are well…still here. Which is great, but if the goal is to grow the network effect here and bring in more people, then we need to find a new angle. Something more compelling than “your account won’t be deleted.” I’m not 100% sure what that is. My instinct is that a “network of interoperable applications”, that don’t necessarily or explicitly brand themselves as Nostr, but have it under the hood is the right direction. I think the open social graph and using it in novel ways is compelling. Trouble is, this needs more really well-built and novel apps for non-sovereignty minded people (especially content creators) and people who don’t necessarily care about the reasons Nostr was first built. Also requires us to move beyond just building clones of what already exists. We’ve been trying to do this Satlantis thing for almost a year now and it’s coming along - albeit WAY slower than I would’ve liked. We’re experimenting our way into a whole new category of product. Something different to what exists today. We’ve made a whole bunch of mistakes and at times I feel like a LARP considering the state of non-delivery. BUT…what’s on the horizon is very special, and I think that all of the pain, effort and heartache along the way will be 100% worth it. We are going to deliver a killer product that people love, that solves a whole host of travel-related problems and has Nostr under the hood (where nobody, except those who care, will know).  # Grants come with a price This one is less of an opinion and more of an observation. Not sure it really belongs in this essay, but I’ll make a small mention just as food for thought, ***Grants are a double-edged sword.*** I’m super grateful that OpenSats, et al, are supporting the protocol, and I don’t envy the job they have in trying to decipher what to support and what not to depending on what’s of benefit to the network versus what’s an end user product. That being said, is the Nostr ecosystem too grant-dependent? This is not a criticism, but a question. Perhaps this is the right thing to do because of how young Nostr is. But I just can’t help but feel like there’s something a-miss. Grants put the focus on Nostr, instead of the product or customer. Which is fine, if the work the grant covers is for Nostr protocol development or tooling. But when grants subsidise the development of end user products, it ties the builder / grant recipient to Nostr in a way that can misalign them to the customer’s needs. It’s a bit like getting a government grant to build something. **Who’s the real customer??** Grants can therefore create an almost communist-like detachment from the market and false economic incentive. To reference the Nostr decision framework I showed you earlier, when you’ve been given a grant, you are focusing more on the X axis, not the Y. This is a trade-off, and all trade-offs have consequences. Could grants be the reason Nostr is so full of hobbyists and experimental products, instead of serious products? Or is that just a function of how ambitious and early Nostr is? I don’t know. Nostr certainly needs better toolkits, SDKs, and infrastructure upon which app and product developers can build. I just hope the grant money finds its way there, and that it yields these tools. Otherwise app developers like us, won’t stick around and build on Nostr. We’ll swap it out with a better tool. To be clear, this is not me pissing on Nostr or the Grantors. Jack, OpenSats and everyone who’s supported Nostr are incredible. I’m just asking the question. Final thing I’ll leave this section with is a thought experiment: Would Nostr survive if OpenSats disappeared tomorrow? Something to think about…. # Coda If you read this far, thank you. There’s a bunch here to digest, and like I said earlier - this not about shitting on Nostr. It is just an enquiry mixed with a little classic Svetski-Sacred-Cow-Slaying. I want to see Nostr succeed. Not only because I think it’s good for the world, but also because I think it is the best option. Which is why we’ve invested so much in it (something I’ll cover in an upcoming article: “Why we chose to build on Nostr”). I’m firmly of the belief that this is the right toolkit for an internet-native identity and open social graph. What I’m not so sure about is the echo chamber it’s become and the cult-like relationship people have with it. I look forward to being witch-hunted and burnt at the stake by the Nostr purists for my heresy and blaspheming. I also look forward to some productive discussions as a result of reading this. Thankyou for your attention. Until next time.
@ 6ad08392:ea301584
2025-03-14 19:03:20In 2024, I was high as a kite on Nostr hopium and optimism. Early that year, my co-founder and I figured that we could use Nostr as a way to validate ambassadors on “Destination Bitcoin” - the germ of a travel app idea we had at the time that would turn into Satlantis. After some more digging and thinking, we realised that Nostr’s open social graph would be of major benefit, and in exploring that design space, the fuller idea of Satlantis formed: a new kind of social network for travel. ###### ^^2 slides from the original idea here I still remember the call I had with @pablof7z in January. I was in Dubai pitching the AI idea I was working on at the time, but all I could think and talk about was Satlantis and Nostr. That conversation made me bullish AF. I came back from the trip convinced we’d struck gold. I pivoted the old company, re-organised the team and booked us for the Sovereign Engineering cohort in Madeira. We put together a whole product roadmap, go to market strategy and cap raise around the use of Nostr. We were going to be the ‘next big Nostr app’. A couple of events followed in which I announced this all to the world: Bitcoin Atlantis in March and BTC Prague in June being the two main ones. The feedback was incredible. So we doubled down. After being the major financial backer for the Nostr Booth in Prague, I decided to help organise the Nostr Booth initiative and back it financially for a series of Latin American conferences in November. I was convinced this was the biggest thing since bitcoin, so much so that I spent over $50,000 in 2024 on Nostr marketing initiatives. I was certainly high on something. # Sobering up It’s March 2025 and I’ve sobered up. I now look at Nostr through a different lens. A more pragmatic one. I see Nostr as a tool, as an entrepreneur - who’s more interested in solving a problem, than fixating on the tool(s) being used - should. A couple things changed for me. One was the sub-standard product we released in November. I was so focused on being a Nostr evangelist that I put our product second. Coupled with the extra technical debt we took on at Satlantis by making everything Nostr native, our product was crap. ***We traded usability & product stability for Nostr purism & evangelism.*** We built a whole suite of features using native event kinds (location kinds, calendar kinds, etc) that we thought other Nostr apps would also use and therefore be interoperable. Turns out no serious players were doing any of that, so we spent a bunch of time over-engineering for no benefit 😂 The other wake up call for me was the Twitter ban in Brazil. Being one of the largest markets for Twitter, I really thought it would have a material impact on global Nostr adoption. When basically nothing happened, I began to question things.  Combined, these experiences helped sober me up and I come down from my high. I was reading “the cold start problem” by Andrew Chen (ex-Uber) at the time and doing a deep dive on network effects. I came to the following realisation: *Nostr’s network effect is going to take WAY longer than we all anticipated initially. This is going to be a long grind. And unlike bitcoin, winning is not inevitable. Bitcoin solves a much more important problem, and it’s the ONLY option. Nostr solves an important problem yes, but it’s far from the only approach. It’s just the implementation arguably in the lead right now.* This sobering up led us to take a different approach with Nostr. We now view it as another tool in the tech-stack, no different to the use of React Native on mobile or AWS for infrastructure. Nostr is something to use if it makes the product better, or avoid if it makes the product and user experience worse. I will share more on this below, including our simple decision making framework. I’ll also present a few more potentially unpopular opinions about Nostr. Four in total actually: 1. Nostr is a tool, not a revolution 2. Nostr doesn’t solve the multiple social accounts problem 3. Nostr is not for censorship resistance 4. Grants come with a price Let’s begin… # Nostr is a tool, not a revolution Nostr is full of Bitcoiners, and as much as we like to think we’re immune from shiny object syndrome, we are, somewhere deep down afflicted by it like other humans. That’s normal & fine. But…while Bitcoiners have successfully suppressed this desire when it comes to shitcoins, it lies dormant, yearning for the least shitcoin-like thing to emerge which we can throw our guiltless support behind. That ***thing*** arrived and it’s called Nostr. As a result, we’ve come to project the same kind of purity and maximalism onto it as we do with Bitcoin, because it shares some attributes and it’s clearly ***not*** a grift. The trouble is, in doing so, we’ve put it in the same ***class*** as Bitcoin - which is an error. Nostr is important and in its own small way, revolutionary, but it pales in comparison to Bitcoin’s importance. ***Think of it this way: If Bitcoin fails, civilisation is fucked. If Nostr fails, we’ll engineer another rich-identity protocol***. There is no need for the kind of immaculate conception and path dependence that was necessary for Bitcoin whose genesis and success has been a once in a civilisation event. Equivocating Nostr and Bitcoin to the degree that it has been, is a significant category error. Nostr may ‘win’ or it may just be an experiment on the path to something better. **And that’s ok !** I don’t say this to piss anyone off, to piss on Nostr or to piss on myself. I say it because I’d prefer Nostr not remain a place where a few thousand people speak to each other about how cool Nostr is. That’s cute in the short term, but in the grand scheme of things, it’s a waste of a great tool that can make a significant corner of the Internet great again. By removing the emotional charge and hopium from our relationship to Nostr, we can take a more sober, objective view of it (and hopefully use it more effectively). Instead of making everything about Nostr (the tool), we can go back to doing what great product people and businesses do: make everything about the customer. --- Nobody’s going around marketing their app as a “react native product” - and while I understand that’s a false equivalent in the sense that Nostr is a protocol, while react is a framework - the reality is that it DOES NOT MATTER. **For 99.9999% of the world, what matters is the hole, not the drill.** Maybe 1000 people on Earth REALLY care that something is built on Nostr, but for everyone else, what matters is what the app or product does and the problem it solves. Realigning our focus in this way, and looking at not only Nostr, but also Bitcoin as a tool in the toolkit, has transformed the way we’re building. This inspired an essay I wrote a couple weeks ago called “As Nostr as Possible”. It covers our updated approach to using and building WITH Nostr (not just ‘on’ it). You can find that here: https://futuresocial.substack.com/p/as-nostr-as-possible-anap If you’re too busy to read it, don’t fret. The entire theory can be summarised by the diagram below. This is how we now decide what to make Nostr-native, and what to just build on our own. And - as stated in the ANAP essay - that doesn’t mean we’ll never make certain features Nostr-native. If the argument is that Nostr is not going anywhere, then we can always come back to that feature and Nostr-fy it later when resources and protocol stability permit.  Next… # The Nostr all in one approach is not all “positive” Having one account accessible via many different apps might not be as positive as we initially thought.  If you have one unified presence online, across all of your socials, and you’re posting the same thing everywhere, then yes - being able to post content in one place and it being broadcast everywhere, is great. There’s a reason why people literally PAY for products like Hypefury, Buffer and Hootsuite (aside from scheduling). BUT…..This is not always the case. I’ve spoken to hundreds of creators and many have flagged this as a bug not a feature because they tend to have a different audience on different platforms and speak to them differently depending on the platform. We all know this. How you present yourself on LinkedIn is very different to how you do it on Instagram or X. The story of Weishu (Tencent’s version of TikTok) comes to mind here. Tencent’s WeChat login worked against them because people didn’t want their social graph following them around. Users actually wanted freedom from their existing family & friends, so they chose Douyin (Chinese TikTok) instead. Perhaps this is more relevant to something like WeChat because the social graph following you around is more personal, but we saw something similar with Instagram and Facebook. Despite over a decade of ownership, Facebook still keeps the social graphs separated. All this to say that while having a different strategy & approach on different social apps is annoying, it allows users to tap into different markets because each silo has its own ‘flavour’. The people who just post the same thing everywhere are low-quality content creators anyway. The ones who actually care, are using each platform ***differently***. *The ironic part here is that this is arguably more ‘decentralised’ than the protocol approach because these siloes form a ‘marketplace of communities’ which are all somewhat different.* --- We need to find a smart way of doing this with Nostr. Some way of catering to the appropriate audience where it matters most. Perhaps this will be handled by clients, or by relays. One solution I’ve heard from people in the Nostr space is to just ‘spin up another nPub’ for your different audience. While I have no problem with people doing that - I have multiple nPubs myself - it’s clearly NOT a solution to the underlying problem here. We’re experimenting with something. Whether it’s a good idea or not remains to be seen. Satlantis users will be able to curate their profiles and remove (hide / delete) content on our app. We’ll implement this in two stages: **Stage 1: Simple**\ In the first iteration, we will not broadcast a delete request to relays. This means users can get a nicely curated profile page on Satlantis, but keep a record of their full profile elsewhere on other clients / relays. **Stage 2: More complex**\ Later on, we’ll try to give people an option to “delete on Satlantis only” or “delete everywhere”. The difference here is more control for the user. Whether we get this far remains to be seen. We’ll need to experiment with the UX and see whether this is something people really want. I’m sure neither of these solutions are ‘ideal’ - but they’re what we’re going to try until we have more time & resources to think this through more. Next… # Nostr is not for Censorship Resistance I’m sorry to say, but this ship has sailed. At least for now. Maybe it’s a problem again in the future, but who knows when, and if it will ever be a big enough factor anyway. The truth is, while WE all know that Nostr is superior because it’s a protocol, people do NOT care enough. They are more interested in what’s written ON the box, not what’s necessarily inside the box. 99% of people don’t know wtf a protocol is in the first place - let alone why it matters for censorship resistance to happen at that level, or more importantly, why they should trust ***Nostr*** to deliver on that promise. Furthermore, the few people who did care about “free speech” are now placated enough with Rumble for Video, X for short form and Substack for long form. With Meta now paying lip-service to the movement, it’s game over for this narrative - at least for the foreseeable future. The "space in people’s minds for censorship resistance has been filled. Both the ‘censorship resistance’ and ‘free speech’ ships have sailed (even though they were fake), and the people who cared enough all boarded. For the normies who never cared, they still don’t care - or they found their way to the anti-platforms, like Threads, BlueSky or Pornhub. The small minority of us still here on Nostr…are well…still here. Which is great, but if the goal is to grow the network effect here and bring in more people, then we need to find a new angle. Something more compelling than “your account won’t be deleted.” I’m not 100% sure what that is. My instinct is that a “network of interoperable applications”, that don’t necessarily or explicitly brand themselves as Nostr, but have it under the hood is the right direction. I think the open social graph and using it in novel ways is compelling. Trouble is, this needs more really well-built and novel apps for non-sovereignty minded people (especially content creators) and people who don’t necessarily care about the reasons Nostr was first built. Also requires us to move beyond just building clones of what already exists. We’ve been trying to do this Satlantis thing for almost a year now and it’s coming along - albeit WAY slower than I would’ve liked. We’re experimenting our way into a whole new category of product. Something different to what exists today. We’ve made a whole bunch of mistakes and at times I feel like a LARP considering the state of non-delivery. BUT…what’s on the horizon is very special, and I think that all of the pain, effort and heartache along the way will be 100% worth it. We are going to deliver a killer product that people love, that solves a whole host of travel-related problems and has Nostr under the hood (where nobody, except those who care, will know).  # Grants come with a price This one is less of an opinion and more of an observation. Not sure it really belongs in this essay, but I’ll make a small mention just as food for thought, ***Grants are a double-edged sword.*** I’m super grateful that OpenSats, et al, are supporting the protocol, and I don’t envy the job they have in trying to decipher what to support and what not to depending on what’s of benefit to the network versus what’s an end user product. That being said, is the Nostr ecosystem too grant-dependent? This is not a criticism, but a question. Perhaps this is the right thing to do because of how young Nostr is. But I just can’t help but feel like there’s something a-miss. Grants put the focus on Nostr, instead of the product or customer. Which is fine, if the work the grant covers is for Nostr protocol development or tooling. But when grants subsidise the development of end user products, it ties the builder / grant recipient to Nostr in a way that can misalign them to the customer’s needs. It’s a bit like getting a government grant to build something. **Who’s the real customer??** Grants can therefore create an almost communist-like detachment from the market and false economic incentive. To reference the Nostr decision framework I showed you earlier, when you’ve been given a grant, you are focusing more on the X axis, not the Y. This is a trade-off, and all trade-offs have consequences. Could grants be the reason Nostr is so full of hobbyists and experimental products, instead of serious products? Or is that just a function of how ambitious and early Nostr is? I don’t know. Nostr certainly needs better toolkits, SDKs, and infrastructure upon which app and product developers can build. I just hope the grant money finds its way there, and that it yields these tools. Otherwise app developers like us, won’t stick around and build on Nostr. We’ll swap it out with a better tool. To be clear, this is not me pissing on Nostr or the Grantors. Jack, OpenSats and everyone who’s supported Nostr are incredible. I’m just asking the question. Final thing I’ll leave this section with is a thought experiment: Would Nostr survive if OpenSats disappeared tomorrow? Something to think about…. # Coda If you read this far, thank you. There’s a bunch here to digest, and like I said earlier - this not about shitting on Nostr. It is just an enquiry mixed with a little classic Svetski-Sacred-Cow-Slaying. I want to see Nostr succeed. Not only because I think it’s good for the world, but also because I think it is the best option. Which is why we’ve invested so much in it (something I’ll cover in an upcoming article: “Why we chose to build on Nostr”). I’m firmly of the belief that this is the right toolkit for an internet-native identity and open social graph. What I’m not so sure about is the echo chamber it’s become and the cult-like relationship people have with it. I look forward to being witch-hunted and burnt at the stake by the Nostr purists for my heresy and blaspheming. I also look forward to some productive discussions as a result of reading this. Thankyou for your attention. Until next time. @ 872982aa:8fb54cfe
2025-03-27 05:50:35NIP-03 ====== OpenTimestamps Attestations for Events -------------------------------------- `draft` `optional` This NIP defines an event with `kind:1040` that can contain an [OpenTimestamps](https://opentimestamps.org/) proof for any other event: ```json { "kind": 1040 "tags": [ ["e", <event-id>, <relay-url>], ["alt", "opentimestamps attestation"] ], "content": <base64-encoded OTS file data> } ``` - The OpenTimestamps proof MUST prove the referenced `e` event id as its digest. - The `content` MUST be the full content of an `.ots` file containing at least one Bitcoin attestation. This file SHOULD contain a **single** Bitcoin attestation (as not more than one valid attestation is necessary and less bytes is better than more) and no reference to "pending" attestations since they are useless in this context. ### Example OpenTimestamps proof verification flow Using [`nak`](https://github.com/fiatjaf/nak), [`jq`](https://jqlang.github.io/jq/) and [`ots`](https://github.com/fiatjaf/ots): ```bash ~> nak req -i e71c6ea722987debdb60f81f9ea4f604b5ac0664120dd64fb9d23abc4ec7c323 wss://nostr-pub.wellorder.net | jq -r .content | ots verify > using an esplora server at https://blockstream.info/api - sequence ending on block 810391 is valid timestamp validated at block [810391] ```
@ 872982aa:8fb54cfe
2025-03-27 05:50:35NIP-03 ====== OpenTimestamps Attestations for Events -------------------------------------- `draft` `optional` This NIP defines an event with `kind:1040` that can contain an [OpenTimestamps](https://opentimestamps.org/) proof for any other event: ```json { "kind": 1040 "tags": [ ["e", <event-id>, <relay-url>], ["alt", "opentimestamps attestation"] ], "content": <base64-encoded OTS file data> } ``` - The OpenTimestamps proof MUST prove the referenced `e` event id as its digest. - The `content` MUST be the full content of an `.ots` file containing at least one Bitcoin attestation. This file SHOULD contain a **single** Bitcoin attestation (as not more than one valid attestation is necessary and less bytes is better than more) and no reference to "pending" attestations since they are useless in this context. ### Example OpenTimestamps proof verification flow Using [`nak`](https://github.com/fiatjaf/nak), [`jq`](https://jqlang.github.io/jq/) and [`ots`](https://github.com/fiatjaf/ots): ```bash ~> nak req -i e71c6ea722987debdb60f81f9ea4f604b5ac0664120dd64fb9d23abc4ec7c323 wss://nostr-pub.wellorder.net | jq -r .content | ots verify > using an esplora server at https://blockstream.info/api - sequence ending on block 810391 is valid timestamp validated at block [810391] ``` @ f9cf4e94:96abc355
2024-12-31 20:18:59Scuttlebutt foi iniciado em maio de 2014 por Dominic Tarr ( [dominictarr]( https://github.com/dominictarr/scuttlebutt) ) como uma rede social alternativa off-line, primeiro para convidados, que permite aos usuários obter controle total de seus dados e privacidade. Secure Scuttlebutt ([ssb]( https://github.com/ssbc/ssb-db)) foi lançado pouco depois, o que coloca a privacidade em primeiro plano com mais recursos de criptografia. Se você está se perguntando de onde diabos veio o nome Scuttlebutt: > Este termo do século 19 para uma fofoca vem do Scuttlebutt náutico: “um barril de água mantido no convés, com um buraco para uma xícara”. A gíria náutica vai desde o hábito dos marinheiros de se reunir pelo boato até a fofoca, semelhante à fofoca do bebedouro.  Marinheiros se reunindo em torno da rixa. ( [fonte]( https://twitter.com/IntEtymology/status/998879578851508224) ) Dominic descobriu o termo boato em um [artigo de pesquisa]( https://www.cs.cornell.edu/home/rvr/papers/flowgossip.pdf) que leu. Em sistemas distribuídos, [fofocar]( https://en.wikipedia.org/wiki/Gossip_protocol) é um processo de retransmissão de mensagens ponto a ponto; as mensagens são disseminadas de forma análoga ao “boca a boca”. **Secure Scuttlebutt é um banco de dados de feeds imutáveis apenas para acréscimos, otimizado para replicação eficiente para protocolos ponto a ponto.** **Cada usuário tem um log imutável somente para acréscimos no qual eles podem gravar.** Eles gravam no log assinando mensagens com sua chave privada. Pense em um feed de usuário como seu próprio diário de bordo, como um diário [de bordo]( https://en.wikipedia.org/wiki/Logbook) (ou diário do capitão para os fãs de Star Trek), onde eles são os únicos autorizados a escrever nele, mas têm a capacidade de permitir que outros amigos ou colegas leiam ao seu diário de bordo, se assim o desejarem. Cada mensagem possui um número de sequência e a mensagem também deve fazer referência à mensagem anterior por seu ID. O ID é um hash da mensagem e da assinatura. A estrutura de dados é semelhante à de uma lista vinculada. É essencialmente um log somente de acréscimo de JSON assinado. **Cada item adicionado a um log do usuário é chamado de mensagem.** **Os logs do usuário são conhecidos como feed e um usuário pode seguir os feeds de outros usuários para receber suas atualizações.** Cada usuário é responsável por armazenar seu próprio feed. Quando Alice assina o feed de Bob, Bob baixa o log de feed de Alice. Bob pode verificar se o registro do feed realmente pertence a Alice verificando as assinaturas. Bob pode verificar as assinaturas usando a chave pública de Alice.  Estrutura de alto nível de um feed **Pubs são servidores de retransmissão conhecidos como “super peers”. Pubs conectam usuários usuários e atualizações de fofocas a outros usuários conectados ao Pub. Um Pub é análogo a um pub da vida real, onde as pessoas vão para se encontrar e se socializar.** Para ingressar em um Pub, o usuário deve ser convidado primeiro. Um usuário pode solicitar um código de convite de um Pub; o Pub simplesmente gerará um novo código de convite, mas alguns Pubs podem exigir verificação adicional na forma de verificação de e-mail ou, com alguns Pubs, você deve pedir um código em um fórum público ou chat. Pubs também podem mapear aliases de usuário, como e-mails ou nome de usuário, para IDs de chave pública para facilitar os pares de referência. Depois que o Pub enviar o código de convite ao usuário, o usuário resgatará o código, o que significa que o Pub seguirá o usuário, o que permite que o usuário veja as mensagens postadas por outros membros do Pub, bem como as mensagens de retransmissão do Pub pelo usuário a outros membros do Pub. Além de retransmitir mensagens entre pares, os Pubs também podem armazenar as mensagens. Se Alice estiver offline e Bob transmitir atualizações de feed, Alice perderá a atualização. Se Alice ficar online, mas Bob estiver offline, não haverá como ela buscar o feed de Bob. Mas com um Pub, Alice pode buscar o feed no Pub mesmo se Bob estiver off-line porque o Pub está armazenando as mensagens. **Pubs são úteis porque assim que um colega fica online, ele pode sincronizar com o Pub para receber os feeds de seus amigos potencialmente offline.** Um usuário pode, opcionalmente, executar seu próprio servidor Pub e abri-lo ao público ou permitir que apenas seus amigos participem, se assim o desejarem. Eles também podem ingressar em um Pub público. Aqui está uma lista de [Pubs públicos em que]( https://github.com/ssbc/ssb-server/wiki/Pub-Servers) todos podem participar **.** Explicaremos como ingressar em um posteriormente neste guia. **Uma coisa importante a observar é que o Secure Scuttlebutt em uma rede social somente para convidados significa que você deve ser “puxado” para entrar nos círculos sociais.** Se você responder às mensagens, os destinatários não serão notificados, a menos que estejam seguindo você de volta. O objetivo do SSB é criar “ilhas” isoladas de redes pares, ao contrário de uma rede pública onde qualquer pessoa pode enviar mensagens a qualquer pessoa.  Perspectivas dos participantes ## Scuttlebot O software Pub é conhecido como servidor Scuttlebutt (servidor [ssb]( https://github.com/ssbc/ssb-server) ), mas também é conhecido como “Scuttlebot” e `sbot`na linha de comando. O servidor SSB adiciona comportamento de rede ao banco de dados Scuttlebutt (SSB). Estaremos usando o Scuttlebot ao longo deste tutorial. **Os logs do usuário são conhecidos como feed e um usuário pode seguir os feeds de outros usuários para receber suas atualizações.** Cada usuário é responsável por armazenar seu próprio feed. Quando Alice assina o feed de Bob, Bob baixa o log de feed de Alice. Bob pode verificar se o registro do feed realmente pertence a Alice verificando as assinaturas. Bob pode verificar as assinaturas usando a chave pública de Alice.  Estrutura de alto nível de um feed **Pubs são servidores de retransmissão conhecidos como “super peers”. Pubs conectam usuários usuários e atualizações de fofocas a outros usuários conectados ao Pub. Um Pub é análogo a um pub da vida real, onde as pessoas vão para se encontrar e se socializar.** Para ingressar em um Pub, o usuário deve ser convidado primeiro. Um usuário pode solicitar um código de convite de um Pub; o Pub simplesmente gerará um novo código de convite, mas alguns Pubs podem exigir verificação adicional na forma de verificação de e-mail ou, com alguns Pubs, você deve pedir um código em um fórum público ou chat. Pubs também podem mapear aliases de usuário, como e-mails ou nome de usuário, para IDs de chave pública para facilitar os pares de referência. Depois que o Pub enviar o código de convite ao usuário, o usuário resgatará o código, o que significa que o Pub seguirá o usuário, o que permite que o usuário veja as mensagens postadas por outros membros do Pub, bem como as mensagens de retransmissão do Pub pelo usuário a outros membros do Pub. Além de retransmitir mensagens entre pares, os Pubs também podem armazenar as mensagens. Se Alice estiver offline e Bob transmitir atualizações de feed, Alice perderá a atualização. Se Alice ficar online, mas Bob estiver offline, não haverá como ela buscar o feed de Bob. Mas com um Pub, Alice pode buscar o feed no Pub mesmo se Bob estiver off-line porque o Pub está armazenando as mensagens. **Pubs são úteis porque assim que um colega fica online, ele pode sincronizar com o Pub para receber os feeds de seus amigos potencialmente offline.** Um usuário pode, opcionalmente, executar seu próprio servidor Pub e abri-lo ao público ou permitir que apenas seus amigos participem, se assim o desejarem. Eles também podem ingressar em um Pub público. Aqui está uma lista de [Pubs públicos em que]( https://github.com/ssbc/ssb-server/wiki/Pub-Servers) todos podem participar **.** Explicaremos como ingressar em um posteriormente neste guia. **Uma coisa importante a observar é que o Secure Scuttlebutt em uma rede social somente para convidados significa que você deve ser “puxado” para entrar nos círculos sociais.** Se você responder às mensagens, os destinatários não serão notificados, a menos que estejam seguindo você de volta. O objetivo do SSB é criar “ilhas” isoladas de redes pares, ao contrário de uma rede pública onde qualquer pessoa pode enviar mensagens a qualquer pessoa.   Perspectivas dos participantes ## Pubs - Hubs ### Pubs públicos | Pub Name | Operator | Invite Code | | ------------------------------------------------------------ | ------------------------------------------------------------ | ------------------------------------------------------------ | | `scuttle.us` | [@Ryan]( https://keybase.io/ryan_singer) | `scuttle.us:8008:@WqcuCOIpLtXFRw/9vOAQJti8avTZ9vxT9rKrPo8qG6o=.ed25519~/ZUi9Chpl0g1kuWSrmehq2EwMQeV0Pd+8xw8XhWuhLE=` | | [pub1.upsocial.com]( https://upsocial.com/) | [@freedomrules]( https://github.com/freedomrules) | `pub1.upsocial.com:8008:@gjlNF5Cyw3OKZxEoEpsVhT5Xv3HZutVfKBppmu42MkI=.ed25519~lMd6f4nnmBZEZSavAl4uahl+feajLUGqu8s2qdoTLi8=` | | [Monero Pub]( https://xmr-pub.net/) | [@Denis]( https://github.com/Orville2112) | `xmr-pub.net:8008:@5hTpvduvbDyMLN2IdzDKa7nx7PSem9co3RsOmZoyyCM=.ed25519~vQU+r2HUd6JxPENSinUWdfqrJLlOqXiCbzHoML9iVN4=` | | [FreeSocial]( https://freesocial.co/) | [@Jarland]( https://github.com/mxroute) | `pub.freesocial.co:8008:@ofYKOy2p9wsaxV73GqgOyh6C6nRGFM5FyciQyxwBd6A=.ed25519~ye9Z808S3KPQsV0MWr1HL0/Sh8boSEwW+ZK+8x85u9w=` | | `ssb.vpn.net.br` | [@coffeverton]( https://about.me/coffeverton) | `ssb.vpn.net.br:8008:@ze8nZPcf4sbdULvknEFOCbVZtdp7VRsB95nhNw6/2YQ=.ed25519~D0blTolH3YoTwSAkY5xhNw8jAOjgoNXL/+8ZClzr0io=` | | [gossip.noisebridge.info]( https://www.noisebridge.net/wiki/Pub) | [Noisebridge Hackerspace]( https://www.noisebridge.net/wiki/Unicorn) [@james.network]( https://james.network/) | `gossip.noisebridge.info:8008:@2NANnQVdsoqk0XPiJG2oMZqaEpTeoGrxOHJkLIqs7eY=.ed25519~JWTC6+rPYPW5b5zCion0gqjcJs35h6JKpUrQoAKWgJ4=` | ### Pubs privados Você precisará entrar em contato com os proprietários desses bares para receber um convite. | Pub Name | Operator | Contact | | --------------------------------------------- | ------------------------------------------------------------ | ----------------------------------------------- | | `many.butt.nz` | [@dinosaur]( https://dinosaur.is/) | [mikey@enspiral.com](mailto:mikey@enspiral.com) | | `one.butt.nz` | [@dinosaur]( https://dinosaur.is/) | [mikey@enspiral.com](mailto:mikey@enspiral.com) | | `ssb.mikey.nz` | [@dinosaur]( https://dinosaur.is/) | [mikey@enspiral.com](mailto:mikey@enspiral.com) | | [ssb.celehner.com]( https://ssb.celehner.com/) | [@cel]( https://github.com/ssbc/ssb-server/wiki/@f/6sQ6d2CMxRUhLpspgGIulDxDCwYD7DzFzPNr7u5AU=.ed25519) | [cel@celehner.com](mailto:cel@celehner.com) | ### Pubs muito grandes  *Aviso: embora tecnicamente funcione usar um convite para esses pubs, você provavelmente se divertirá se o fizer devido ao seu tamanho (muitas coisas para baixar, risco para bots / spammers / idiotas)*  | Pub Name | Operator | Invite Code | | --------------------------------------- | ----------------------------------------------- | ------------------------------------------------------------ | | `scuttlebutt.de` | [SolSoCoG]( https://solsocog.de/impressum) | `scuttlebutt.de:8008:@yeh/GKxlfhlYXSdgU7CRLxm58GC42za3tDuC4NJld/k=.ed25519~iyaCpZ0co863K9aF+b7j8BnnHfwY65dGeX6Dh2nXs3c=` | | `Lohn's Pub` | [@lohn]( https://github.com/lohn) | `p.lohn.in:8018:@LohnKVll9HdLI3AndEc4zwGtfdF/J7xC7PW9B/JpI4U=.ed25519~z3m4ttJdI4InHkCtchxTu26kKqOfKk4woBb1TtPeA/s=` | | [Scuttle Space]( https://scuttle.space/) | [@guil-dot]( https://github.com/guil-dot) | Visit [scuttle.space]( https://scuttle.space/) | | `SSB PeerNet US-East` | [timjrobinson]( https://github.com/timjrobinson) | `us-east.ssbpeer.net:8008:@sTO03jpVivj65BEAJMhlwtHXsWdLd9fLwyKAT1qAkc0=.ed25519~sXFc5taUA7dpGTJITZVDCRy2A9jmkVttsr107+ufInU=` | | Hermies | s | net:hermies.club:8008~shs:uMYDVPuEKftL4SzpRGVyQxLdyPkOiX7njit7+qT/7IQ=:SSB+Room+PSK3TLYC2T86EHQCUHBUHASCASE18JBV24= | ## GUI - Interface Gráfica do Utilizador(Usuário) ### Patchwork - Uma GUI SSB (Descontinuado) [**Patchwork**]( https://github.com/ssbc/patchwork) **é o aplicativo de mensagens e compartilhamento descentralizado construído em cima do SSB** . O protocolo scuttlebutt em si não mantém um conjunto de feeds nos quais um usuário está interessado, então um cliente é necessário para manter uma lista de feeds de pares em que seu respectivo usuário está interessado e seguindo.  Fonte: [scuttlebutt.nz]( https://www.scuttlebutt.nz/getting-started) **Quando você instala e executa o Patchwork, você só pode ver e se comunicar com seus pares em sua rede local. Para acessar fora de sua LAN, você precisa se conectar a um Pub.** Um pub é apenas para convidados e eles retransmitem mensagens entre você e seus pares fora de sua LAN e entre outros Pubs. Lembre-se de que você precisa seguir alguém para receber mensagens dessa pessoa. Isso reduz o envio de mensagens de spam para os usuários. Os usuários só veem as respostas das pessoas que seguem. Os dados são sincronizados no disco para funcionar offline, mas podem ser sincronizados diretamente com os pares na sua LAN por wi-fi ou bluetooth. ### Patchbay - Uma GUI Alternativa Patchbay é um cliente de fofoca projetado para ser fácil de modificar e estender. Ele usa o mesmo banco de dados que [Patchwork]( https://github.com/ssbc/patchwork) e [Patchfoo]( https://github.com/ssbc/patchfoo) , então você pode facilmente dar uma volta com sua identidade existente.  ### Planetary - GUI para IOS  [Planetary]( https://apps.apple.com/us/app/planetary-app/id1481617318) é um app com pubs pré-carregados para facilitar integração. ### Manyverse - GUI para Android  [Manyverse]( https://www.manyver.se/) é um aplicativo de rede social com recursos que você esperaria: posts, curtidas, perfis, mensagens privadas, etc. Mas não está sendo executado na nuvem de propriedade de uma empresa, em vez disso, as postagens de seus amigos e todos os seus dados sociais vivem inteiramente em seu telefone . ## Fontes * https://scuttlebot.io/ * https://decentralized-id.com/decentralized-web/scuttlebot/#plugins * https://medium.com/@miguelmota/getting-started-with-secure-scuttlebut-e6b7d4c5ecfd * [**Secure Scuttlebutt**]( http://ssbc.github.io/secure-scuttlebutt/) **:** um protocolo de banco de dados global.
@ f9cf4e94:96abc355
2024-12-31 20:18:59Scuttlebutt foi iniciado em maio de 2014 por Dominic Tarr ( [dominictarr]( https://github.com/dominictarr/scuttlebutt) ) como uma rede social alternativa off-line, primeiro para convidados, que permite aos usuários obter controle total de seus dados e privacidade. Secure Scuttlebutt ([ssb]( https://github.com/ssbc/ssb-db)) foi lançado pouco depois, o que coloca a privacidade em primeiro plano com mais recursos de criptografia. Se você está se perguntando de onde diabos veio o nome Scuttlebutt: > Este termo do século 19 para uma fofoca vem do Scuttlebutt náutico: “um barril de água mantido no convés, com um buraco para uma xícara”. A gíria náutica vai desde o hábito dos marinheiros de se reunir pelo boato até a fofoca, semelhante à fofoca do bebedouro.  Marinheiros se reunindo em torno da rixa. ( [fonte]( https://twitter.com/IntEtymology/status/998879578851508224) ) Dominic descobriu o termo boato em um [artigo de pesquisa]( https://www.cs.cornell.edu/home/rvr/papers/flowgossip.pdf) que leu. Em sistemas distribuídos, [fofocar]( https://en.wikipedia.org/wiki/Gossip_protocol) é um processo de retransmissão de mensagens ponto a ponto; as mensagens são disseminadas de forma análoga ao “boca a boca”. **Secure Scuttlebutt é um banco de dados de feeds imutáveis apenas para acréscimos, otimizado para replicação eficiente para protocolos ponto a ponto.** **Cada usuário tem um log imutável somente para acréscimos no qual eles podem gravar.** Eles gravam no log assinando mensagens com sua chave privada. Pense em um feed de usuário como seu próprio diário de bordo, como um diário [de bordo]( https://en.wikipedia.org/wiki/Logbook) (ou diário do capitão para os fãs de Star Trek), onde eles são os únicos autorizados a escrever nele, mas têm a capacidade de permitir que outros amigos ou colegas leiam ao seu diário de bordo, se assim o desejarem. Cada mensagem possui um número de sequência e a mensagem também deve fazer referência à mensagem anterior por seu ID. O ID é um hash da mensagem e da assinatura. A estrutura de dados é semelhante à de uma lista vinculada. É essencialmente um log somente de acréscimo de JSON assinado. **Cada item adicionado a um log do usuário é chamado de mensagem.** **Os logs do usuário são conhecidos como feed e um usuário pode seguir os feeds de outros usuários para receber suas atualizações.** Cada usuário é responsável por armazenar seu próprio feed. Quando Alice assina o feed de Bob, Bob baixa o log de feed de Alice. Bob pode verificar se o registro do feed realmente pertence a Alice verificando as assinaturas. Bob pode verificar as assinaturas usando a chave pública de Alice.  Estrutura de alto nível de um feed **Pubs são servidores de retransmissão conhecidos como “super peers”. Pubs conectam usuários usuários e atualizações de fofocas a outros usuários conectados ao Pub. Um Pub é análogo a um pub da vida real, onde as pessoas vão para se encontrar e se socializar.** Para ingressar em um Pub, o usuário deve ser convidado primeiro. Um usuário pode solicitar um código de convite de um Pub; o Pub simplesmente gerará um novo código de convite, mas alguns Pubs podem exigir verificação adicional na forma de verificação de e-mail ou, com alguns Pubs, você deve pedir um código em um fórum público ou chat. Pubs também podem mapear aliases de usuário, como e-mails ou nome de usuário, para IDs de chave pública para facilitar os pares de referência. Depois que o Pub enviar o código de convite ao usuário, o usuário resgatará o código, o que significa que o Pub seguirá o usuário, o que permite que o usuário veja as mensagens postadas por outros membros do Pub, bem como as mensagens de retransmissão do Pub pelo usuário a outros membros do Pub. Além de retransmitir mensagens entre pares, os Pubs também podem armazenar as mensagens. Se Alice estiver offline e Bob transmitir atualizações de feed, Alice perderá a atualização. Se Alice ficar online, mas Bob estiver offline, não haverá como ela buscar o feed de Bob. Mas com um Pub, Alice pode buscar o feed no Pub mesmo se Bob estiver off-line porque o Pub está armazenando as mensagens. **Pubs são úteis porque assim que um colega fica online, ele pode sincronizar com o Pub para receber os feeds de seus amigos potencialmente offline.** Um usuário pode, opcionalmente, executar seu próprio servidor Pub e abri-lo ao público ou permitir que apenas seus amigos participem, se assim o desejarem. Eles também podem ingressar em um Pub público. Aqui está uma lista de [Pubs públicos em que]( https://github.com/ssbc/ssb-server/wiki/Pub-Servers) todos podem participar **.** Explicaremos como ingressar em um posteriormente neste guia. **Uma coisa importante a observar é que o Secure Scuttlebutt em uma rede social somente para convidados significa que você deve ser “puxado” para entrar nos círculos sociais.** Se você responder às mensagens, os destinatários não serão notificados, a menos que estejam seguindo você de volta. O objetivo do SSB é criar “ilhas” isoladas de redes pares, ao contrário de uma rede pública onde qualquer pessoa pode enviar mensagens a qualquer pessoa.  Perspectivas dos participantes ## Scuttlebot O software Pub é conhecido como servidor Scuttlebutt (servidor [ssb]( https://github.com/ssbc/ssb-server) ), mas também é conhecido como “Scuttlebot” e `sbot`na linha de comando. O servidor SSB adiciona comportamento de rede ao banco de dados Scuttlebutt (SSB). Estaremos usando o Scuttlebot ao longo deste tutorial. **Os logs do usuário são conhecidos como feed e um usuário pode seguir os feeds de outros usuários para receber suas atualizações.** Cada usuário é responsável por armazenar seu próprio feed. Quando Alice assina o feed de Bob, Bob baixa o log de feed de Alice. Bob pode verificar se o registro do feed realmente pertence a Alice verificando as assinaturas. Bob pode verificar as assinaturas usando a chave pública de Alice.  Estrutura de alto nível de um feed **Pubs são servidores de retransmissão conhecidos como “super peers”. Pubs conectam usuários usuários e atualizações de fofocas a outros usuários conectados ao Pub. Um Pub é análogo a um pub da vida real, onde as pessoas vão para se encontrar e se socializar.** Para ingressar em um Pub, o usuário deve ser convidado primeiro. Um usuário pode solicitar um código de convite de um Pub; o Pub simplesmente gerará um novo código de convite, mas alguns Pubs podem exigir verificação adicional na forma de verificação de e-mail ou, com alguns Pubs, você deve pedir um código em um fórum público ou chat. Pubs também podem mapear aliases de usuário, como e-mails ou nome de usuário, para IDs de chave pública para facilitar os pares de referência. Depois que o Pub enviar o código de convite ao usuário, o usuário resgatará o código, o que significa que o Pub seguirá o usuário, o que permite que o usuário veja as mensagens postadas por outros membros do Pub, bem como as mensagens de retransmissão do Pub pelo usuário a outros membros do Pub. Além de retransmitir mensagens entre pares, os Pubs também podem armazenar as mensagens. Se Alice estiver offline e Bob transmitir atualizações de feed, Alice perderá a atualização. Se Alice ficar online, mas Bob estiver offline, não haverá como ela buscar o feed de Bob. Mas com um Pub, Alice pode buscar o feed no Pub mesmo se Bob estiver off-line porque o Pub está armazenando as mensagens. **Pubs são úteis porque assim que um colega fica online, ele pode sincronizar com o Pub para receber os feeds de seus amigos potencialmente offline.** Um usuário pode, opcionalmente, executar seu próprio servidor Pub e abri-lo ao público ou permitir que apenas seus amigos participem, se assim o desejarem. Eles também podem ingressar em um Pub público. Aqui está uma lista de [Pubs públicos em que]( https://github.com/ssbc/ssb-server/wiki/Pub-Servers) todos podem participar **.** Explicaremos como ingressar em um posteriormente neste guia. **Uma coisa importante a observar é que o Secure Scuttlebutt em uma rede social somente para convidados significa que você deve ser “puxado” para entrar nos círculos sociais.** Se você responder às mensagens, os destinatários não serão notificados, a menos que estejam seguindo você de volta. O objetivo do SSB é criar “ilhas” isoladas de redes pares, ao contrário de uma rede pública onde qualquer pessoa pode enviar mensagens a qualquer pessoa.   Perspectivas dos participantes ## Pubs - Hubs ### Pubs públicos | Pub Name | Operator | Invite Code | | ------------------------------------------------------------ | ------------------------------------------------------------ | ------------------------------------------------------------ | | `scuttle.us` | [@Ryan]( https://keybase.io/ryan_singer) | `scuttle.us:8008:@WqcuCOIpLtXFRw/9vOAQJti8avTZ9vxT9rKrPo8qG6o=.ed25519~/ZUi9Chpl0g1kuWSrmehq2EwMQeV0Pd+8xw8XhWuhLE=` | | [pub1.upsocial.com]( https://upsocial.com/) | [@freedomrules]( https://github.com/freedomrules) | `pub1.upsocial.com:8008:@gjlNF5Cyw3OKZxEoEpsVhT5Xv3HZutVfKBppmu42MkI=.ed25519~lMd6f4nnmBZEZSavAl4uahl+feajLUGqu8s2qdoTLi8=` | | [Monero Pub]( https://xmr-pub.net/) | [@Denis]( https://github.com/Orville2112) | `xmr-pub.net:8008:@5hTpvduvbDyMLN2IdzDKa7nx7PSem9co3RsOmZoyyCM=.ed25519~vQU+r2HUd6JxPENSinUWdfqrJLlOqXiCbzHoML9iVN4=` | | [FreeSocial]( https://freesocial.co/) | [@Jarland]( https://github.com/mxroute) | `pub.freesocial.co:8008:@ofYKOy2p9wsaxV73GqgOyh6C6nRGFM5FyciQyxwBd6A=.ed25519~ye9Z808S3KPQsV0MWr1HL0/Sh8boSEwW+ZK+8x85u9w=` | | `ssb.vpn.net.br` | [@coffeverton]( https://about.me/coffeverton) | `ssb.vpn.net.br:8008:@ze8nZPcf4sbdULvknEFOCbVZtdp7VRsB95nhNw6/2YQ=.ed25519~D0blTolH3YoTwSAkY5xhNw8jAOjgoNXL/+8ZClzr0io=` | | [gossip.noisebridge.info]( https://www.noisebridge.net/wiki/Pub) | [Noisebridge Hackerspace]( https://www.noisebridge.net/wiki/Unicorn) [@james.network]( https://james.network/) | `gossip.noisebridge.info:8008:@2NANnQVdsoqk0XPiJG2oMZqaEpTeoGrxOHJkLIqs7eY=.ed25519~JWTC6+rPYPW5b5zCion0gqjcJs35h6JKpUrQoAKWgJ4=` | ### Pubs privados Você precisará entrar em contato com os proprietários desses bares para receber um convite. | Pub Name | Operator | Contact | | --------------------------------------------- | ------------------------------------------------------------ | ----------------------------------------------- | | `many.butt.nz` | [@dinosaur]( https://dinosaur.is/) | [mikey@enspiral.com](mailto:mikey@enspiral.com) | | `one.butt.nz` | [@dinosaur]( https://dinosaur.is/) | [mikey@enspiral.com](mailto:mikey@enspiral.com) | | `ssb.mikey.nz` | [@dinosaur]( https://dinosaur.is/) | [mikey@enspiral.com](mailto:mikey@enspiral.com) | | [ssb.celehner.com]( https://ssb.celehner.com/) | [@cel]( https://github.com/ssbc/ssb-server/wiki/@f/6sQ6d2CMxRUhLpspgGIulDxDCwYD7DzFzPNr7u5AU=.ed25519) | [cel@celehner.com](mailto:cel@celehner.com) | ### Pubs muito grandes  *Aviso: embora tecnicamente funcione usar um convite para esses pubs, você provavelmente se divertirá se o fizer devido ao seu tamanho (muitas coisas para baixar, risco para bots / spammers / idiotas)*  | Pub Name | Operator | Invite Code | | --------------------------------------- | ----------------------------------------------- | ------------------------------------------------------------ | | `scuttlebutt.de` | [SolSoCoG]( https://solsocog.de/impressum) | `scuttlebutt.de:8008:@yeh/GKxlfhlYXSdgU7CRLxm58GC42za3tDuC4NJld/k=.ed25519~iyaCpZ0co863K9aF+b7j8BnnHfwY65dGeX6Dh2nXs3c=` | | `Lohn's Pub` | [@lohn]( https://github.com/lohn) | `p.lohn.in:8018:@LohnKVll9HdLI3AndEc4zwGtfdF/J7xC7PW9B/JpI4U=.ed25519~z3m4ttJdI4InHkCtchxTu26kKqOfKk4woBb1TtPeA/s=` | | [Scuttle Space]( https://scuttle.space/) | [@guil-dot]( https://github.com/guil-dot) | Visit [scuttle.space]( https://scuttle.space/) | | `SSB PeerNet US-East` | [timjrobinson]( https://github.com/timjrobinson) | `us-east.ssbpeer.net:8008:@sTO03jpVivj65BEAJMhlwtHXsWdLd9fLwyKAT1qAkc0=.ed25519~sXFc5taUA7dpGTJITZVDCRy2A9jmkVttsr107+ufInU=` | | Hermies | s | net:hermies.club:8008~shs:uMYDVPuEKftL4SzpRGVyQxLdyPkOiX7njit7+qT/7IQ=:SSB+Room+PSK3TLYC2T86EHQCUHBUHASCASE18JBV24= | ## GUI - Interface Gráfica do Utilizador(Usuário) ### Patchwork - Uma GUI SSB (Descontinuado) [**Patchwork**]( https://github.com/ssbc/patchwork) **é o aplicativo de mensagens e compartilhamento descentralizado construído em cima do SSB** . O protocolo scuttlebutt em si não mantém um conjunto de feeds nos quais um usuário está interessado, então um cliente é necessário para manter uma lista de feeds de pares em que seu respectivo usuário está interessado e seguindo.  Fonte: [scuttlebutt.nz]( https://www.scuttlebutt.nz/getting-started) **Quando você instala e executa o Patchwork, você só pode ver e se comunicar com seus pares em sua rede local. Para acessar fora de sua LAN, você precisa se conectar a um Pub.** Um pub é apenas para convidados e eles retransmitem mensagens entre você e seus pares fora de sua LAN e entre outros Pubs. Lembre-se de que você precisa seguir alguém para receber mensagens dessa pessoa. Isso reduz o envio de mensagens de spam para os usuários. Os usuários só veem as respostas das pessoas que seguem. Os dados são sincronizados no disco para funcionar offline, mas podem ser sincronizados diretamente com os pares na sua LAN por wi-fi ou bluetooth. ### Patchbay - Uma GUI Alternativa Patchbay é um cliente de fofoca projetado para ser fácil de modificar e estender. Ele usa o mesmo banco de dados que [Patchwork]( https://github.com/ssbc/patchwork) e [Patchfoo]( https://github.com/ssbc/patchfoo) , então você pode facilmente dar uma volta com sua identidade existente.  ### Planetary - GUI para IOS  [Planetary]( https://apps.apple.com/us/app/planetary-app/id1481617318) é um app com pubs pré-carregados para facilitar integração. ### Manyverse - GUI para Android  [Manyverse]( https://www.manyver.se/) é um aplicativo de rede social com recursos que você esperaria: posts, curtidas, perfis, mensagens privadas, etc. Mas não está sendo executado na nuvem de propriedade de uma empresa, em vez disso, as postagens de seus amigos e todos os seus dados sociais vivem inteiramente em seu telefone . ## Fontes * https://scuttlebot.io/ * https://decentralized-id.com/decentralized-web/scuttlebot/#plugins * https://medium.com/@miguelmota/getting-started-with-secure-scuttlebut-e6b7d4c5ecfd * [**Secure Scuttlebutt**]( http://ssbc.github.io/secure-scuttlebutt/) **:** um protocolo de banco de dados global. @ 0461fcbe:35a474dd
2025-03-13 23:10:12## Background I will start with a disclaimer: I'm all-in on Nostr. But before that, I spent 4 years building on ActivityPub. Then in Feb 2023 I built a bridge between ActivityPub and Nostr, and in Dec 2024 I built another bridge between Nostr and Bluesky. Most of all I am committed to open source and the decentralized vision. Having experience with all 3 major protocols, I still think Nostr is the best, but Bluesky outshines it in some major areas. The main reason for this blog is to explore the things Bluesky does better than us, and to point out why I still think Nostr is the best solution. This is a technical blog. For a more high level overview of decentralized protocols, see: https://soapbox.pub/blog/comparing-protocols/ ## Data Model Nostr and Bluesky both allow users to store any type of data in a single, unified format. Nostr calls them *events*. Bluesky calls them *records*. They are mostly interchangeable ideas, but the way the data is stored and retrieved is very different. It's worth noting that, like Nostr and ActivityPub, Bluesky is capable of doing anything under the sun. It's a misconception that it can't. You can build whatever Reddit, TikTok, or other stuff clone on Bluesky just fine. It's limited more by the huge knowledge gap you have to overcome than it is by anything about its data model. ### NSIDs vs Kinds Nostr events use a "kind" number, eg `1`, to distinguish different type of events. Bluesky records use what they call an "NSID" (namespace identifier), eg `app.bsky.feed.post`, which is a reverse-DNS string notation. Nostr's `"kind": 1` is equivalent to Bluesky's `"$type": app.bsky.feed.post`. I think Bluesky's system is better, because it allows developers to feel like what they built is "real" without having to get it merged into the NIPs repo, which is basically like an IANA of Nostr kind numbers. I believe this causes significant problems on Nostr, and makes people feel like they are being held back by others. That being said, the counter-argument is that kind numbers encourage interoperability for the very same reasons. The barriers to adding new kinds pushes people to work with what's already there. ### Text Content Formatting Kind 1 events ("plain text notes", ie "Tweets") on Nostr have developed in a haphazard way over time, by many people piling things onto it without taking a step back to assess a unified way to handle it. Some examples include: - NIP-21 `nostr:` URIs - `imeta` tags - inline media embeds as URLs without `imeta` tags - unspec'd Markdown rendering by some clients - legacy specs such as positional mentions (eg, `#[0]`, mostly gone now) What we have now is quite a mess, and it's something Bluesky beats us on badly. Bluesky has a plaintext content field that can be displayed as-is. In addition, it has a "[facets](https://docs.bsky.app/docs/advanced-guides/post-richtext)" field, which is a structured JSON object, that adds rich-text information such as formatting (bold, italic, etc), links, mentions of users, and whatever else metadata about the text. This is an extensible system that beats even options like Markdown, due to its ability to include native extension like mentions, and its ability to be parsed by any programming language or software environment. Bluesky is the winner here. ### Syncronization Nostr and Bluesky are both thought to be descended from Scuttlebutt, an older decentralized protocol. On Scuttlebutt, a user's whole post history needed to be available for them to make a new post. Scuttlebutt uses a linked list, so each new event would need to reference the one before it. Only linear paths are allowed, so if a "fork" occurred (intentionally or not), only one version would be kept, and the other discarded. This lead to occasional publishing issues, but it allowed readers to assemble a complete view. Nostr strayed from this draconian approach, removing it entirely and allowing user data to be fragmented. Meanwhile Bluesky, instead of removing it entirely, made it work more like git so that branches could be merged. Both approaches have tradeoffs. Bluesky's approach has much higher complexity. Also, it's sometimes considered an advantage for events to be fragmented (eg Nostr allows sending DMs to specialized relays for enhanced privacy). But Bluesky has a true account "sync" mechanism, and Nostr does not. Nostr can send filters to relays to gather events, but it cannot know when to stop looking. Proposals like Negentropy in Nostr do not solve author syncing, and only make typical relay filtering more efficient. I think it's important to think about Nostr's "outbox" problem as a syncronization problem, and for Nostr to approach syncronization with the goal of syncronizing authors specifically. I think Bluesky "wins" this one, if only because they have solved a problem that we haven't. Instead of copying their solution, I think Nostr should try to learn from this to recharacterize the "outbox" problem as an author syncing problem, and see if we can come up with a better solution that works for Nostr. ## Knowledge Gap One of the biggest hurdles of Bluesky, and by extension one of the greates appeals of Nostr, is in how easy it is to learn and build on. Nostr can be understood in a couple of hours. Mastering it is difficult, but limited only by your time and imagination. Hundreds of developers are building new projects on Nostr today. Based on my experience, it seems to me that the Nostr developer community is larger than that of both ActivityPub and Bluesky combined. Bluesky on the other hand requires a Harvard degree in Blueskyology. I believe that ameteur coders feel a sense of superiority after spending six weeks learning how to commit a post. To learn Bluesky you will have to sift through thousands of technical documents about all kinds of abstractions, especially related to IPFS and IPLD. You will have to master unnecessary technologies like CBOR (which is basically just JSON except it's in binary and takes up the same amount of space). And you will be frequently pointed to academic topics such as "DAG" and "graph theory", all just to say "it's a fucking graph". I will never understand why people will take simple concepts such as a "tree", and then make it harder to understand on purpose by saying it's more than that. While building on Bluesky, I began to question if the creators did this on purpose. I wondered if they tried to make it complex on purpose, as a sort of IQ test and protective measure to weed out the undeireables. In my view, a truly free and open network must be accessible to all, with the hope that even non-programmers could learn how it works. Technical complexity is not just an issue of inclusion, but also security. ActivityPub software has been found to be littered with major security holes due to its inherently complex design, while Nostr's simple design makes its attack surface extremely minimal. Bluesky has already had a few mishaps, and it makes me wonder how Bluesky will fare in the long term. ## Decentralization I will keep this short. Bluesky is designed to be decentralized, but isn't. It reminds me of the communist idea about the "withering away of the state". The idea is that you're supposed to first sieze power and become the new state, and then under your rule the state will slowly disappear because you are doing all the right communist things. I think this is basically how Bluesky sees itself (whether they agree with the analogy or not). Nostr is decentralized, but it is a loaded gun. You're more likely to kill yourself with a gun than someone else. This is on purpose, because it wholly embraces the consequnces of being truly decentralized. In my view Nostr gets it right. Social media has been done to death by now, so I do not think it's worth the compromise to prioritize UX over decentralization. If that's the case we have not fixed anything. It's best to start with the purist idea and work backwards to UX, rather than start with UX and work backwards to decentralization. Many people have already written extensively about the decentralization of Bluesky, so I'll leave it at that.
@ 0461fcbe:35a474dd
2025-03-13 23:10:12## Background I will start with a disclaimer: I'm all-in on Nostr. But before that, I spent 4 years building on ActivityPub. Then in Feb 2023 I built a bridge between ActivityPub and Nostr, and in Dec 2024 I built another bridge between Nostr and Bluesky. Most of all I am committed to open source and the decentralized vision. Having experience with all 3 major protocols, I still think Nostr is the best, but Bluesky outshines it in some major areas. The main reason for this blog is to explore the things Bluesky does better than us, and to point out why I still think Nostr is the best solution. This is a technical blog. For a more high level overview of decentralized protocols, see: https://soapbox.pub/blog/comparing-protocols/ ## Data Model Nostr and Bluesky both allow users to store any type of data in a single, unified format. Nostr calls them *events*. Bluesky calls them *records*. They are mostly interchangeable ideas, but the way the data is stored and retrieved is very different. It's worth noting that, like Nostr and ActivityPub, Bluesky is capable of doing anything under the sun. It's a misconception that it can't. You can build whatever Reddit, TikTok, or other stuff clone on Bluesky just fine. It's limited more by the huge knowledge gap you have to overcome than it is by anything about its data model. ### NSIDs vs Kinds Nostr events use a "kind" number, eg `1`, to distinguish different type of events. Bluesky records use what they call an "NSID" (namespace identifier), eg `app.bsky.feed.post`, which is a reverse-DNS string notation. Nostr's `"kind": 1` is equivalent to Bluesky's `"$type": app.bsky.feed.post`. I think Bluesky's system is better, because it allows developers to feel like what they built is "real" without having to get it merged into the NIPs repo, which is basically like an IANA of Nostr kind numbers. I believe this causes significant problems on Nostr, and makes people feel like they are being held back by others. That being said, the counter-argument is that kind numbers encourage interoperability for the very same reasons. The barriers to adding new kinds pushes people to work with what's already there. ### Text Content Formatting Kind 1 events ("plain text notes", ie "Tweets") on Nostr have developed in a haphazard way over time, by many people piling things onto it without taking a step back to assess a unified way to handle it. Some examples include: - NIP-21 `nostr:` URIs - `imeta` tags - inline media embeds as URLs without `imeta` tags - unspec'd Markdown rendering by some clients - legacy specs such as positional mentions (eg, `#[0]`, mostly gone now) What we have now is quite a mess, and it's something Bluesky beats us on badly. Bluesky has a plaintext content field that can be displayed as-is. In addition, it has a "[facets](https://docs.bsky.app/docs/advanced-guides/post-richtext)" field, which is a structured JSON object, that adds rich-text information such as formatting (bold, italic, etc), links, mentions of users, and whatever else metadata about the text. This is an extensible system that beats even options like Markdown, due to its ability to include native extension like mentions, and its ability to be parsed by any programming language or software environment. Bluesky is the winner here. ### Syncronization Nostr and Bluesky are both thought to be descended from Scuttlebutt, an older decentralized protocol. On Scuttlebutt, a user's whole post history needed to be available for them to make a new post. Scuttlebutt uses a linked list, so each new event would need to reference the one before it. Only linear paths are allowed, so if a "fork" occurred (intentionally or not), only one version would be kept, and the other discarded. This lead to occasional publishing issues, but it allowed readers to assemble a complete view. Nostr strayed from this draconian approach, removing it entirely and allowing user data to be fragmented. Meanwhile Bluesky, instead of removing it entirely, made it work more like git so that branches could be merged. Both approaches have tradeoffs. Bluesky's approach has much higher complexity. Also, it's sometimes considered an advantage for events to be fragmented (eg Nostr allows sending DMs to specialized relays for enhanced privacy). But Bluesky has a true account "sync" mechanism, and Nostr does not. Nostr can send filters to relays to gather events, but it cannot know when to stop looking. Proposals like Negentropy in Nostr do not solve author syncing, and only make typical relay filtering more efficient. I think it's important to think about Nostr's "outbox" problem as a syncronization problem, and for Nostr to approach syncronization with the goal of syncronizing authors specifically. I think Bluesky "wins" this one, if only because they have solved a problem that we haven't. Instead of copying their solution, I think Nostr should try to learn from this to recharacterize the "outbox" problem as an author syncing problem, and see if we can come up with a better solution that works for Nostr. ## Knowledge Gap One of the biggest hurdles of Bluesky, and by extension one of the greates appeals of Nostr, is in how easy it is to learn and build on. Nostr can be understood in a couple of hours. Mastering it is difficult, but limited only by your time and imagination. Hundreds of developers are building new projects on Nostr today. Based on my experience, it seems to me that the Nostr developer community is larger than that of both ActivityPub and Bluesky combined. Bluesky on the other hand requires a Harvard degree in Blueskyology. I believe that ameteur coders feel a sense of superiority after spending six weeks learning how to commit a post. To learn Bluesky you will have to sift through thousands of technical documents about all kinds of abstractions, especially related to IPFS and IPLD. You will have to master unnecessary technologies like CBOR (which is basically just JSON except it's in binary and takes up the same amount of space). And you will be frequently pointed to academic topics such as "DAG" and "graph theory", all just to say "it's a fucking graph". I will never understand why people will take simple concepts such as a "tree", and then make it harder to understand on purpose by saying it's more than that. While building on Bluesky, I began to question if the creators did this on purpose. I wondered if they tried to make it complex on purpose, as a sort of IQ test and protective measure to weed out the undeireables. In my view, a truly free and open network must be accessible to all, with the hope that even non-programmers could learn how it works. Technical complexity is not just an issue of inclusion, but also security. ActivityPub software has been found to be littered with major security holes due to its inherently complex design, while Nostr's simple design makes its attack surface extremely minimal. Bluesky has already had a few mishaps, and it makes me wonder how Bluesky will fare in the long term. ## Decentralization I will keep this short. Bluesky is designed to be decentralized, but isn't. It reminds me of the communist idea about the "withering away of the state". The idea is that you're supposed to first sieze power and become the new state, and then under your rule the state will slowly disappear because you are doing all the right communist things. I think this is basically how Bluesky sees itself (whether they agree with the analogy or not). Nostr is decentralized, but it is a loaded gun. You're more likely to kill yourself with a gun than someone else. This is on purpose, because it wholly embraces the consequnces of being truly decentralized. In my view Nostr gets it right. Social media has been done to death by now, so I do not think it's worth the compromise to prioritize UX over decentralization. If that's the case we have not fixed anything. It's best to start with the purist idea and work backwards to UX, rather than start with UX and work backwards to decentralization. Many people have already written extensively about the decentralization of Bluesky, so I'll leave it at that. @ ef53426a:7e988851
2025-04-02 21:02:06# Bartering and early money \ Early societies bartered goods, but transactions were often complicated. The value of goods doesn’t always align. Enter money. It’s used as an indirect exchange for any goods, so everyone wants it. Early money wasn’t anything like what we use today. For example, the inhabitants of Yap Island (Micronesia) used large Rai stones for trade. New stones were dragged up a hill for everyone to see. The owner would then exchange part of the stone for goods and services. As they were hard to quarry and move, Rai stones retained their value (salability). Then, an Irish-American captain started importing stones using modern technology. Soon enough, they became so common, they no longer worked as money. --- # Gold — the basis for sound money \ Smelting made it possible to create highly salable and transportable coins. Gold was best because it’s virtually impossible to destroy and can’t be synthesized using other materials. It has a fairly limited supply, which grows slowly and predictably (due to the difficulty of mining). Technologies like the telegraph and trains made it easier for both people and goods to get from point A to point B. That, in turn, justified forms of payment like checks, paper receipts, and bills. But paper is not worth much unless it’s backed by something. Governments worldwide issued paper money backed by precious metals, which they stored in vaults. By 1900, around 50 countries had adopted the Gold Standard. This was sound money. --- # Currencies devalued \ Roman emperor Julius Caesar issued the Aureus, an empire-standard coin containing 8 grams of gold. But as growth began to slow, rulers started ‘coin clipping’, reducing the quantity of precious metal in coins. This eventually triggered a series of economic crises that led to the downfall of the Roman Empire. The gold standard had one major flaw: it had to be stored in bank vaults. This created a highly centralized system in which governments controlled the value of paper money. If they wanted to, they could always increase the supply of money without increasing the corresponding amount of gold. In 1914, nearly every major European power decided to do this to fund their war operations. Rather than raising taxes, they simply printed new money with no extra gold. The standard had been abandoned. --- # Government-backed money \ Governments chose to introduce fiat money – currency backed by decree rather than gold. The adoption of the fiat system led to an age of unsound money shaped by ever-greater intervention in the economy as governments scrambled to stabilize their currencies. By 1944, the end of the Second World War was in sight, and the victors began planning the postwar economic order. The world’s currencies would be tied to the US dollar at a fixed exchange rate. The dollar would in turn be tied to the value of gold, again at a fixed rate. The United States bent the rules and inflated its own currency compared to gold. Other nations inflated their currencies compared to the dollar. On August 15, 1971, President Nixon announced that dollars would no longer be convertible to gold. --- # Sound money = functioning economy \ Sound money encourages people to save and invest, enabling sustainable, long-term growth. Why? Well, humans have a natural positive time preference: we prefer instant gratification over future gratification. Sound money prompts us to think more about the future. The more capital accumulation there is, the greater the chance of stable, long-term economic growth. Unsound money distorts capital accumulation. When governments interfere with the money supply, they also interfere with prices. And prices give investors the information they need to make good decisions without having to learn every tiny detail about global events. --- # Recessions and debt arise from unsound money \ Government interference takes the form of central planning. No single person, agency, or department ever has access to all the information necessary to understand the vast and complex economy. Interventions distort markets, creating boom and bust cycles. According to Keynes and his followers, the best way to respond to recessions is to increase spending. You could lower taxes, but people don’t usually spend their extra money. Raising taxes is unpopular, so governments invariably decide to increase the money supply. Saving becomes less attractive, creating a culture of unwise spending and growing debt. We need to return to sound money and a new gold standard. Enter bitcoin. --- # Bitcoin is scarce \ Bitcoin has similar traits to gold. Its supply is literally fixed. Once there are 21 million bitcoins in circulation, no more will be issued. The supply grows at a diminishing rate. Computers across the Bitcoin network pool their processing power to solve complex algorithmic problems. Once these puzzles have been cracked, the “miners” receive bitcoins as a reward. Satoshi Nakamoto designed the system to avoid gold rushes. The algorithmic problems become more difficult to solve as the number of computers working on them rises, guaranteeing a steady and reliable supply. Also, the number of bitcoins issued is halved every four years, resulting in ever-smaller releases until 2140, after which no more coins will be released. That makes bitcoin unique. It is the only good that is defined by absolute scarcity. No amount of time or resources can create more bitcoins than the programmed supply allows. The supply cannot be manipulated, making it a perfect store of value. --- # Bitcoin is secure \ The bitcoin ledger uses the public blockchain. When mining computers crack an algorithmic puzzle, they create a block. The blocks on the ledger contain details about every blockchain transaction ever completed. Every network user can view this information. Ownership of bitcoins is only valid once it’s been registered on the blockchain. This is only possible if the majority of network users approve it, so there’s no need for a central authority to oversee transactions. While verifying new blocks requires virtually no energy, creating a fraudulent block would cost a significant amount of processing power. Even if a user decided to expend vast amounts of energy and successfully hacked a majority of all network nodes to approve a fraudulent block, they’d gain very little. Trust in bitcoin would be lost, leading to a drop in demand and value. --- # Challenges for adoption \ Because bitcoin is new, demand has varied. The volatile price has, at times, undermined the currency’s status as an effective store of value. Bitcoin’s transaction limit is currently set at 500,000 per day. That could be increased, but there will always be a daily cap. The more transactions that take place, the more nodes there’ll need to be. This increases transaction fees and the amount of processing power expended. Bitcoin could be traded off the blockchain, meaning currencies will be backed by bitcoin. That would create a new standard, but it would also mean that new centralized institutions would need to manage this system. ---  This 5-minute summary did not use copyrighted material from the book. It aims simply to give readers a quick understanding of the book (which is well worth reading). ‘*The Bitcoin Standard: The Decentralized Alternative to Central Banking’* was written by economist Saifedean Ammous in 2018. Buy the book and many more titles at [bitcoinbook.shop](bitcoinbook.shop)
@ ef53426a:7e988851
2025-04-02 21:02:06# Bartering and early money \ Early societies bartered goods, but transactions were often complicated. The value of goods doesn’t always align. Enter money. It’s used as an indirect exchange for any goods, so everyone wants it. Early money wasn’t anything like what we use today. For example, the inhabitants of Yap Island (Micronesia) used large Rai stones for trade. New stones were dragged up a hill for everyone to see. The owner would then exchange part of the stone for goods and services. As they were hard to quarry and move, Rai stones retained their value (salability). Then, an Irish-American captain started importing stones using modern technology. Soon enough, they became so common, they no longer worked as money. --- # Gold — the basis for sound money \ Smelting made it possible to create highly salable and transportable coins. Gold was best because it’s virtually impossible to destroy and can’t be synthesized using other materials. It has a fairly limited supply, which grows slowly and predictably (due to the difficulty of mining). Technologies like the telegraph and trains made it easier for both people and goods to get from point A to point B. That, in turn, justified forms of payment like checks, paper receipts, and bills. But paper is not worth much unless it’s backed by something. Governments worldwide issued paper money backed by precious metals, which they stored in vaults. By 1900, around 50 countries had adopted the Gold Standard. This was sound money. --- # Currencies devalued \ Roman emperor Julius Caesar issued the Aureus, an empire-standard coin containing 8 grams of gold. But as growth began to slow, rulers started ‘coin clipping’, reducing the quantity of precious metal in coins. This eventually triggered a series of economic crises that led to the downfall of the Roman Empire. The gold standard had one major flaw: it had to be stored in bank vaults. This created a highly centralized system in which governments controlled the value of paper money. If they wanted to, they could always increase the supply of money without increasing the corresponding amount of gold. In 1914, nearly every major European power decided to do this to fund their war operations. Rather than raising taxes, they simply printed new money with no extra gold. The standard had been abandoned. --- # Government-backed money \ Governments chose to introduce fiat money – currency backed by decree rather than gold. The adoption of the fiat system led to an age of unsound money shaped by ever-greater intervention in the economy as governments scrambled to stabilize their currencies. By 1944, the end of the Second World War was in sight, and the victors began planning the postwar economic order. The world’s currencies would be tied to the US dollar at a fixed exchange rate. The dollar would in turn be tied to the value of gold, again at a fixed rate. The United States bent the rules and inflated its own currency compared to gold. Other nations inflated their currencies compared to the dollar. On August 15, 1971, President Nixon announced that dollars would no longer be convertible to gold. --- # Sound money = functioning economy \ Sound money encourages people to save and invest, enabling sustainable, long-term growth. Why? Well, humans have a natural positive time preference: we prefer instant gratification over future gratification. Sound money prompts us to think more about the future. The more capital accumulation there is, the greater the chance of stable, long-term economic growth. Unsound money distorts capital accumulation. When governments interfere with the money supply, they also interfere with prices. And prices give investors the information they need to make good decisions without having to learn every tiny detail about global events. --- # Recessions and debt arise from unsound money \ Government interference takes the form of central planning. No single person, agency, or department ever has access to all the information necessary to understand the vast and complex economy. Interventions distort markets, creating boom and bust cycles. According to Keynes and his followers, the best way to respond to recessions is to increase spending. You could lower taxes, but people don’t usually spend their extra money. Raising taxes is unpopular, so governments invariably decide to increase the money supply. Saving becomes less attractive, creating a culture of unwise spending and growing debt. We need to return to sound money and a new gold standard. Enter bitcoin. --- # Bitcoin is scarce \ Bitcoin has similar traits to gold. Its supply is literally fixed. Once there are 21 million bitcoins in circulation, no more will be issued. The supply grows at a diminishing rate. Computers across the Bitcoin network pool their processing power to solve complex algorithmic problems. Once these puzzles have been cracked, the “miners” receive bitcoins as a reward. Satoshi Nakamoto designed the system to avoid gold rushes. The algorithmic problems become more difficult to solve as the number of computers working on them rises, guaranteeing a steady and reliable supply. Also, the number of bitcoins issued is halved every four years, resulting in ever-smaller releases until 2140, after which no more coins will be released. That makes bitcoin unique. It is the only good that is defined by absolute scarcity. No amount of time or resources can create more bitcoins than the programmed supply allows. The supply cannot be manipulated, making it a perfect store of value. --- # Bitcoin is secure \ The bitcoin ledger uses the public blockchain. When mining computers crack an algorithmic puzzle, they create a block. The blocks on the ledger contain details about every blockchain transaction ever completed. Every network user can view this information. Ownership of bitcoins is only valid once it’s been registered on the blockchain. This is only possible if the majority of network users approve it, so there’s no need for a central authority to oversee transactions. While verifying new blocks requires virtually no energy, creating a fraudulent block would cost a significant amount of processing power. Even if a user decided to expend vast amounts of energy and successfully hacked a majority of all network nodes to approve a fraudulent block, they’d gain very little. Trust in bitcoin would be lost, leading to a drop in demand and value. --- # Challenges for adoption \ Because bitcoin is new, demand has varied. The volatile price has, at times, undermined the currency’s status as an effective store of value. Bitcoin’s transaction limit is currently set at 500,000 per day. That could be increased, but there will always be a daily cap. The more transactions that take place, the more nodes there’ll need to be. This increases transaction fees and the amount of processing power expended. Bitcoin could be traded off the blockchain, meaning currencies will be backed by bitcoin. That would create a new standard, but it would also mean that new centralized institutions would need to manage this system. ---  This 5-minute summary did not use copyrighted material from the book. It aims simply to give readers a quick understanding of the book (which is well worth reading). ‘*The Bitcoin Standard: The Decentralized Alternative to Central Banking’* was written by economist Saifedean Ammous in 2018. Buy the book and many more titles at [bitcoinbook.shop](bitcoinbook.shop) @ 872982aa:8fb54cfe
2025-03-27 05:47:40NIP-03 ====== OpenTimestamps Attestations for Events -------------------------------------- `draft` `optional` This NIP defines an event with `kind:1040` that can contain an [OpenTimestamps](https://opentimestamps.org/) proof for any other event: ```json { "kind": 1040 "tags": [ ["e", <event-id>, <relay-url>], ["alt", "opentimestamps attestation"] ], "content": <base64-encoded OTS file data> } ``` - The OpenTimestamps proof MUST prove the referenced `e` event id as its digest. - The `content` MUST be the full content of an `.ots` file containing at least one Bitcoin attestation. This file SHOULD contain a **single** Bitcoin attestation (as not more than one valid attestation is necessary and less bytes is better than more) and no reference to "pending" attestations since they are useless in this context. ### Example OpenTimestamps proof verification flow Using [`nak`](https://github.com/fiatjaf/nak), [`jq`](https://jqlang.github.io/jq/) and [`ots`](https://github.com/fiatjaf/ots): ```bash ~> nak req -i e71c6ea722987debdb60f81f9ea4f604b5ac0664120dd64fb9d23abc4ec7c323 wss://nostr-pub.wellorder.net | jq -r .content | ots verify > using an esplora server at https://blockstream.info/api - sequence ending on block 810391 is valid timestamp validated at block [810391] ```
@ 872982aa:8fb54cfe
2025-03-27 05:47:40NIP-03 ====== OpenTimestamps Attestations for Events -------------------------------------- `draft` `optional` This NIP defines an event with `kind:1040` that can contain an [OpenTimestamps](https://opentimestamps.org/) proof for any other event: ```json { "kind": 1040 "tags": [ ["e", <event-id>, <relay-url>], ["alt", "opentimestamps attestation"] ], "content": <base64-encoded OTS file data> } ``` - The OpenTimestamps proof MUST prove the referenced `e` event id as its digest. - The `content` MUST be the full content of an `.ots` file containing at least one Bitcoin attestation. This file SHOULD contain a **single** Bitcoin attestation (as not more than one valid attestation is necessary and less bytes is better than more) and no reference to "pending" attestations since they are useless in this context. ### Example OpenTimestamps proof verification flow Using [`nak`](https://github.com/fiatjaf/nak), [`jq`](https://jqlang.github.io/jq/) and [`ots`](https://github.com/fiatjaf/ots): ```bash ~> nak req -i e71c6ea722987debdb60f81f9ea4f604b5ac0664120dd64fb9d23abc4ec7c323 wss://nostr-pub.wellorder.net | jq -r .content | ots verify > using an esplora server at https://blockstream.info/api - sequence ending on block 810391 is valid timestamp validated at block [810391] ``` @ 91bea5cd:1df4451c
2025-02-04 17:24:50### Definição de ULID: Timestamp 48 bits, Aleatoriedade 80 bits Sendo Timestamp 48 bits inteiro, tempo UNIX em milissegundos, Não ficará sem espaço até o ano 10889 d.C. e Aleatoriedade 80 bits, Fonte criptograficamente segura de aleatoriedade, se possível. #### Gerar ULID ```sql CREATE EXTENSION IF NOT EXISTS pgcrypto; CREATE FUNCTION generate_ulid() RETURNS TEXT AS $$ DECLARE -- Crockford's Base32 encoding BYTEA = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; timestamp BYTEA = E'\\000\\000\\000\\000\\000\\000'; output TEXT = ''; unix_time BIGINT; ulid BYTEA; BEGIN -- 6 timestamp bytes unix_time = (EXTRACT(EPOCH FROM CLOCK_TIMESTAMP()) * 1000)::BIGINT; timestamp = SET_BYTE(timestamp, 0, (unix_time >> 40)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 1, (unix_time >> 32)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 2, (unix_time >> 24)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 3, (unix_time >> 16)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 4, (unix_time >> 8)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 5, unix_time::BIT(8)::INTEGER); -- 10 entropy bytes ulid = timestamp || gen_random_bytes(10); -- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 1) & 7) << 2) | ((GET_BYTE(ulid, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 2) & 1) << 4) | ((GET_BYTE(ulid, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 3) & 15) << 1) | ((GET_BYTE(ulid, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 4) & 3) << 3) | ((GET_BYTE(ulid, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 5) & 31))); -- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 6) & 7) << 2) | ((GET_BYTE(ulid, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 7) & 1) << 4) | ((GET_BYTE(ulid, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 8) & 15) << 1) | ((GET_BYTE(ulid, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 9) & 3) << 3) | ((GET_BYTE(ulid, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 11) & 7) << 2) | ((GET_BYTE(ulid, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 12) & 1) << 4) | ((GET_BYTE(ulid, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 13) & 15) << 1) | ((GET_BYTE(ulid, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 14) & 3) << 3) | ((GET_BYTE(ulid, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 15) & 31))); RETURN output; END $$ LANGUAGE plpgsql VOLATILE; ``` #### ULID TO UUID ```sql CREATE OR REPLACE FUNCTION parse_ulid(ulid text) RETURNS bytea AS $$ DECLARE -- 16byte bytes bytea = E'\\x00000000 00000000 00000000 00000000'; v char[]; -- Allow for O(1) lookup of index values dec integer[] = ARRAY[ 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 0, 1, 2, 3, 4, 5, 6, 7, 8, 9, 255, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31 ]; BEGIN IF NOT ulid ~* '^[0-7][0-9ABCDEFGHJKMNPQRSTVWXYZ]{25}$' THEN RAISE EXCEPTION 'Invalid ULID: %', ulid; END IF; v = regexp_split_to_array(ulid, ''); -- 6 bytes timestamp (48 bits) bytes = SET_BYTE(bytes, 0, (dec[ASCII(v[1])] << 5) | dec[ASCII(v[2])]); bytes = SET_BYTE(bytes, 1, (dec[ASCII(v[3])] << 3) | (dec[ASCII(v[4])] >> 2)); bytes = SET_BYTE(bytes, 2, (dec[ASCII(v[4])] << 6) | (dec[ASCII(v[5])] << 1) | (dec[ASCII(v[6])] >> 4)); bytes = SET_BYTE(bytes, 3, (dec[ASCII(v[6])] << 4) | (dec[ASCII(v[7])] >> 1)); bytes = SET_BYTE(bytes, 4, (dec[ASCII(v[7])] << 7) | (dec[ASCII(v[8])] << 2) | (dec[ASCII(v[9])] >> 3)); bytes = SET_BYTE(bytes, 5, (dec[ASCII(v[9])] << 5) | dec[ASCII(v[10])]); -- 10 bytes of entropy (80 bits); bytes = SET_BYTE(bytes, 6, (dec[ASCII(v[11])] << 3) | (dec[ASCII(v[12])] >> 2)); bytes = SET_BYTE(bytes, 7, (dec[ASCII(v[12])] << 6) | (dec[ASCII(v[13])] << 1) | (dec[ASCII(v[14])] >> 4)); bytes = SET_BYTE(bytes, 8, (dec[ASCII(v[14])] << 4) | (dec[ASCII(v[15])] >> 1)); bytes = SET_BYTE(bytes, 9, (dec[ASCII(v[15])] << 7) | (dec[ASCII(v[16])] << 2) | (dec[ASCII(v[17])] >> 3)); bytes = SET_BYTE(bytes, 10, (dec[ASCII(v[17])] << 5) | dec[ASCII(v[18])]); bytes = SET_BYTE(bytes, 11, (dec[ASCII(v[19])] << 3) | (dec[ASCII(v[20])] >> 2)); bytes = SET_BYTE(bytes, 12, (dec[ASCII(v[20])] << 6) | (dec[ASCII(v[21])] << 1) | (dec[ASCII(v[22])] >> 4)); bytes = SET_BYTE(bytes, 13, (dec[ASCII(v[22])] << 4) | (dec[ASCII(v[23])] >> 1)); bytes = SET_BYTE(bytes, 14, (dec[ASCII(v[23])] << 7) | (dec[ASCII(v[24])] << 2) | (dec[ASCII(v[25])] >> 3)); bytes = SET_BYTE(bytes, 15, (dec[ASCII(v[25])] << 5) | dec[ASCII(v[26])]); RETURN bytes; END $$ LANGUAGE plpgsql IMMUTABLE; CREATE OR REPLACE FUNCTION ulid_to_uuid(ulid text) RETURNS uuid AS $$ BEGIN RETURN encode(parse_ulid(ulid), 'hex')::uuid; END $$ LANGUAGE plpgsql IMMUTABLE; ``` #### UUID to ULID ```sql CREATE OR REPLACE FUNCTION uuid_to_ulid(id uuid) RETURNS text AS $$ DECLARE encoding bytea = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; output text = ''; uuid_bytes bytea = uuid_send(id); BEGIN -- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 1) & 7) << 2) | ((GET_BYTE(uuid_bytes, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 2) & 1) << 4) | ((GET_BYTE(uuid_bytes, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 3) & 15) << 1) | ((GET_BYTE(uuid_bytes, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 4) & 3) << 3) | ((GET_BYTE(uuid_bytes, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 5) & 31))); -- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 6) & 7) << 2) | ((GET_BYTE(uuid_bytes, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 7) & 1) << 4) | ((GET_BYTE(uuid_bytes, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 8) & 15) << 1) | ((GET_BYTE(uuid_bytes, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 9) & 3) << 3) | ((GET_BYTE(uuid_bytes, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 11) & 7) << 2) | ((GET_BYTE(uuid_bytes, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 12) & 1) << 4) | ((GET_BYTE(uuid_bytes, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 13) & 15) << 1) | ((GET_BYTE(uuid_bytes, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 14) & 3) << 3) | ((GET_BYTE(uuid_bytes, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 15) & 31))); RETURN output; END $$ LANGUAGE plpgsql IMMUTABLE; ``` #### Gera 11 Digitos aleatórios: YBKXG0CKTH4 ```sql -- Cria a extensão pgcrypto para gerar uuid CREATE EXTENSION IF NOT EXISTS pgcrypto; -- Cria a função para gerar ULID CREATE OR REPLACE FUNCTION gen_lrandom() RETURNS TEXT AS $$ DECLARE ts_millis BIGINT; ts_chars TEXT; random_bytes BYTEA; random_chars TEXT; base32_chars TEXT := '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; i INT; BEGIN -- Pega o timestamp em milissegundos ts_millis := FLOOR(EXTRACT(EPOCH FROM clock_timestamp()) * 1000)::BIGINT; -- Converte o timestamp para base32 ts_chars := ''; FOR i IN REVERSE 0..11 LOOP ts_chars := ts_chars || substr(base32_chars, ((ts_millis >> (5 * i)) & 31) + 1, 1); END LOOP; -- Gera 10 bytes aleatórios e converte para base32 random_bytes := gen_random_bytes(10); random_chars := ''; FOR i IN 0..9 LOOP random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) >> 3) & 31) + 1, 1); IF i < 9 THEN random_chars := random_chars || substr(base32_chars, (((get_byte(random_bytes, i) & 7) << 2) | (get_byte(random_bytes, i + 1) >> 6)) & 31 + 1, 1); ELSE random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) & 7) << 2) + 1, 1); END IF; END LOOP; -- Concatena o timestamp e os caracteres aleatórios RETURN ts_chars || random_chars; END; $$ LANGUAGE plpgsql; ``` #### Exemplo de USO ```sql -- Criação da extensão caso não exista CREATE EXTENSION IF NOT EXISTS pgcrypto; -- Criação da tabela pessoas CREATE TABLE pessoas ( ID UUID DEFAULT gen_random_uuid ( ) PRIMARY KEY, nome TEXT NOT NULL ); -- Busca Pessoa na tabela SELECT * FROM "pessoas" WHERE uuid_to_ulid ( ID ) = '252FAC9F3V8EF80SSDK8PXW02F'; ``` ### Fontes - https://github.com/scoville/pgsql-ulid - https://github.com/geckoboard/pgulid
@ 91bea5cd:1df4451c
2025-02-04 17:24:50### Definição de ULID: Timestamp 48 bits, Aleatoriedade 80 bits Sendo Timestamp 48 bits inteiro, tempo UNIX em milissegundos, Não ficará sem espaço até o ano 10889 d.C. e Aleatoriedade 80 bits, Fonte criptograficamente segura de aleatoriedade, se possível. #### Gerar ULID ```sql CREATE EXTENSION IF NOT EXISTS pgcrypto; CREATE FUNCTION generate_ulid() RETURNS TEXT AS $$ DECLARE -- Crockford's Base32 encoding BYTEA = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; timestamp BYTEA = E'\\000\\000\\000\\000\\000\\000'; output TEXT = ''; unix_time BIGINT; ulid BYTEA; BEGIN -- 6 timestamp bytes unix_time = (EXTRACT(EPOCH FROM CLOCK_TIMESTAMP()) * 1000)::BIGINT; timestamp = SET_BYTE(timestamp, 0, (unix_time >> 40)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 1, (unix_time >> 32)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 2, (unix_time >> 24)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 3, (unix_time >> 16)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 4, (unix_time >> 8)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 5, unix_time::BIT(8)::INTEGER); -- 10 entropy bytes ulid = timestamp || gen_random_bytes(10); -- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 1) & 7) << 2) | ((GET_BYTE(ulid, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 2) & 1) << 4) | ((GET_BYTE(ulid, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 3) & 15) << 1) | ((GET_BYTE(ulid, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 4) & 3) << 3) | ((GET_BYTE(ulid, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 5) & 31))); -- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 6) & 7) << 2) | ((GET_BYTE(ulid, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 7) & 1) << 4) | ((GET_BYTE(ulid, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 8) & 15) << 1) | ((GET_BYTE(ulid, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 9) & 3) << 3) | ((GET_BYTE(ulid, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 11) & 7) << 2) | ((GET_BYTE(ulid, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 12) & 1) << 4) | ((GET_BYTE(ulid, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 13) & 15) << 1) | ((GET_BYTE(ulid, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 14) & 3) << 3) | ((GET_BYTE(ulid, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 15) & 31))); RETURN output; END $$ LANGUAGE plpgsql VOLATILE; ``` #### ULID TO UUID ```sql CREATE OR REPLACE FUNCTION parse_ulid(ulid text) RETURNS bytea AS $$ DECLARE -- 16byte bytes bytea = E'\\x00000000 00000000 00000000 00000000'; v char[]; -- Allow for O(1) lookup of index values dec integer[] = ARRAY[ 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 0, 1, 2, 3, 4, 5, 6, 7, 8, 9, 255, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31 ]; BEGIN IF NOT ulid ~* '^[0-7][0-9ABCDEFGHJKMNPQRSTVWXYZ]{25}$' THEN RAISE EXCEPTION 'Invalid ULID: %', ulid; END IF; v = regexp_split_to_array(ulid, ''); -- 6 bytes timestamp (48 bits) bytes = SET_BYTE(bytes, 0, (dec[ASCII(v[1])] << 5) | dec[ASCII(v[2])]); bytes = SET_BYTE(bytes, 1, (dec[ASCII(v[3])] << 3) | (dec[ASCII(v[4])] >> 2)); bytes = SET_BYTE(bytes, 2, (dec[ASCII(v[4])] << 6) | (dec[ASCII(v[5])] << 1) | (dec[ASCII(v[6])] >> 4)); bytes = SET_BYTE(bytes, 3, (dec[ASCII(v[6])] << 4) | (dec[ASCII(v[7])] >> 1)); bytes = SET_BYTE(bytes, 4, (dec[ASCII(v[7])] << 7) | (dec[ASCII(v[8])] << 2) | (dec[ASCII(v[9])] >> 3)); bytes = SET_BYTE(bytes, 5, (dec[ASCII(v[9])] << 5) | dec[ASCII(v[10])]); -- 10 bytes of entropy (80 bits); bytes = SET_BYTE(bytes, 6, (dec[ASCII(v[11])] << 3) | (dec[ASCII(v[12])] >> 2)); bytes = SET_BYTE(bytes, 7, (dec[ASCII(v[12])] << 6) | (dec[ASCII(v[13])] << 1) | (dec[ASCII(v[14])] >> 4)); bytes = SET_BYTE(bytes, 8, (dec[ASCII(v[14])] << 4) | (dec[ASCII(v[15])] >> 1)); bytes = SET_BYTE(bytes, 9, (dec[ASCII(v[15])] << 7) | (dec[ASCII(v[16])] << 2) | (dec[ASCII(v[17])] >> 3)); bytes = SET_BYTE(bytes, 10, (dec[ASCII(v[17])] << 5) | dec[ASCII(v[18])]); bytes = SET_BYTE(bytes, 11, (dec[ASCII(v[19])] << 3) | (dec[ASCII(v[20])] >> 2)); bytes = SET_BYTE(bytes, 12, (dec[ASCII(v[20])] << 6) | (dec[ASCII(v[21])] << 1) | (dec[ASCII(v[22])] >> 4)); bytes = SET_BYTE(bytes, 13, (dec[ASCII(v[22])] << 4) | (dec[ASCII(v[23])] >> 1)); bytes = SET_BYTE(bytes, 14, (dec[ASCII(v[23])] << 7) | (dec[ASCII(v[24])] << 2) | (dec[ASCII(v[25])] >> 3)); bytes = SET_BYTE(bytes, 15, (dec[ASCII(v[25])] << 5) | dec[ASCII(v[26])]); RETURN bytes; END $$ LANGUAGE plpgsql IMMUTABLE; CREATE OR REPLACE FUNCTION ulid_to_uuid(ulid text) RETURNS uuid AS $$ BEGIN RETURN encode(parse_ulid(ulid), 'hex')::uuid; END $$ LANGUAGE plpgsql IMMUTABLE; ``` #### UUID to ULID ```sql CREATE OR REPLACE FUNCTION uuid_to_ulid(id uuid) RETURNS text AS $$ DECLARE encoding bytea = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; output text = ''; uuid_bytes bytea = uuid_send(id); BEGIN -- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 1) & 7) << 2) | ((GET_BYTE(uuid_bytes, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 2) & 1) << 4) | ((GET_BYTE(uuid_bytes, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 3) & 15) << 1) | ((GET_BYTE(uuid_bytes, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 4) & 3) << 3) | ((GET_BYTE(uuid_bytes, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 5) & 31))); -- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 6) & 7) << 2) | ((GET_BYTE(uuid_bytes, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 7) & 1) << 4) | ((GET_BYTE(uuid_bytes, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 8) & 15) << 1) | ((GET_BYTE(uuid_bytes, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 9) & 3) << 3) | ((GET_BYTE(uuid_bytes, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 11) & 7) << 2) | ((GET_BYTE(uuid_bytes, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 12) & 1) << 4) | ((GET_BYTE(uuid_bytes, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 13) & 15) << 1) | ((GET_BYTE(uuid_bytes, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 14) & 3) << 3) | ((GET_BYTE(uuid_bytes, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 15) & 31))); RETURN output; END $$ LANGUAGE plpgsql IMMUTABLE; ``` #### Gera 11 Digitos aleatórios: YBKXG0CKTH4 ```sql -- Cria a extensão pgcrypto para gerar uuid CREATE EXTENSION IF NOT EXISTS pgcrypto; -- Cria a função para gerar ULID CREATE OR REPLACE FUNCTION gen_lrandom() RETURNS TEXT AS $$ DECLARE ts_millis BIGINT; ts_chars TEXT; random_bytes BYTEA; random_chars TEXT; base32_chars TEXT := '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; i INT; BEGIN -- Pega o timestamp em milissegundos ts_millis := FLOOR(EXTRACT(EPOCH FROM clock_timestamp()) * 1000)::BIGINT; -- Converte o timestamp para base32 ts_chars := ''; FOR i IN REVERSE 0..11 LOOP ts_chars := ts_chars || substr(base32_chars, ((ts_millis >> (5 * i)) & 31) + 1, 1); END LOOP; -- Gera 10 bytes aleatórios e converte para base32 random_bytes := gen_random_bytes(10); random_chars := ''; FOR i IN 0..9 LOOP random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) >> 3) & 31) + 1, 1); IF i < 9 THEN random_chars := random_chars || substr(base32_chars, (((get_byte(random_bytes, i) & 7) << 2) | (get_byte(random_bytes, i + 1) >> 6)) & 31 + 1, 1); ELSE random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) & 7) << 2) + 1, 1); END IF; END LOOP; -- Concatena o timestamp e os caracteres aleatórios RETURN ts_chars || random_chars; END; $$ LANGUAGE plpgsql; ``` #### Exemplo de USO ```sql -- Criação da extensão caso não exista CREATE EXTENSION IF NOT EXISTS pgcrypto; -- Criação da tabela pessoas CREATE TABLE pessoas ( ID UUID DEFAULT gen_random_uuid ( ) PRIMARY KEY, nome TEXT NOT NULL ); -- Busca Pessoa na tabela SELECT * FROM "pessoas" WHERE uuid_to_ulid ( ID ) = '252FAC9F3V8EF80SSDK8PXW02F'; ``` ### Fontes - https://github.com/scoville/pgsql-ulid - https://github.com/geckoboard/pgulid @ 872982aa:8fb54cfe
2025-03-27 05:47:06- [首页](/readme.md) - [第一章、 NIP-01: Basic protocol flow description](/01.md) - [第二章、 NIP-02: Follow List](/02.md) - [第三章、NIP-03: OpenTimestamps Attestations for Events](/03.md)
@ 872982aa:8fb54cfe
2025-03-27 05:47:06- [首页](/readme.md) - [第一章、 NIP-01: Basic protocol flow description](/01.md) - [第二章、 NIP-02: Follow List](/02.md) - [第三章、NIP-03: OpenTimestamps Attestations for Events](/03.md) @ b4403b24:83542d4e
2025-03-31 14:31:53🚀 Bitcoin Enthusiasts! Tomorrow the price of #BTCPrague2025 tickets goes up so take advantage of the 10% discount using code from the video - BTCBULGARIA. ✅ Network with leaders ✅ Learn blockchain strategies ✅ Gain crypto insights Secure your spot NOW! #Bitcoin #BTC #BTCPrague  originally posted at https://stacker.news/items/930210
@ b4403b24:83542d4e
2025-03-31 14:31:53🚀 Bitcoin Enthusiasts! Tomorrow the price of #BTCPrague2025 tickets goes up so take advantage of the 10% discount using code from the video - BTCBULGARIA. ✅ Network with leaders ✅ Learn blockchain strategies ✅ Gain crypto insights Secure your spot NOW! #Bitcoin #BTC #BTCPrague  originally posted at https://stacker.news/items/930210 @ e97aaffa:2ebd765d
2024-12-31 16:47:12Último dia do ano, momento para tirar o pó da bola de cristal, para fazer reflexões, previsões e desejos para o próximo ano e seguintes. Ano após ano, o Bitcoin evoluiu, foi ultrapassando etapas, tornou-se cada vez mais _mainstream_. Está cada vez mais difícil fazer previsões sobre o Bitcoin, já faltam poucas barreiras a serem ultrapassadas e as que faltam são altamente complexas ou tem um impacto profundo no sistema financeiro ou na sociedade. Estas alterações profundas tem que ser realizadas lentamente, porque uma alteração rápida poderia resultar em consequências terríveis, poderia provocar um retrocesso. # Código do Bitcoin No final de 2025, possivelmente vamos ter um _fork_, as discussões sobre os _covenants_ já estão avançadas, vão acelerar ainda mais. Já existe um consenso relativamente alto, a favor dos _covenants_, só falta decidir que modelo será escolhido. Penso que até ao final do ano será tudo decidido. Depois dos _covenants,_ o próximo foco será para a criptografia post-quantum, que será o maior desafio que o Bitcoin enfrenta. Criar uma criptografia segura e que não coloque a descentralização em causa. Espero muito de Ark, possivelmente a inovação do ano, gostaria de ver o Nostr a furar a bolha bitcoinheira e que o Cashu tivesse mais reconhecimento pelos _bitcoiners_. Espero que surjam avanços significativos no BitVM2 e BitVMX. Não sei o que esperar das layer 2 de Bitcoin, foram a maior desilusão de 2024. Surgiram com muita força, mas pouca coisa saiu do papel, foi uma mão cheia de nada. Uma parte dos projetos caiu na tentação da _shitcoinagem_, na criação de tokens, que tem um único objetivo, enriquecer os devs e os VCs. Se querem ser levados a sério, têm que ser sérios. > “À mulher de César não basta ser honesta, deve parecer honesta” Se querem ter o apoio dos _bitcoiners_, sigam o _ethos_ do Bitcoin. Neste ponto a atitude do pessoal da Ark é exemplar, em vez de andar a chorar no Twitter para mudar o código do Bitcoin, eles colocaram as mãos na massa e criaram o protocolo. É claro que agora está meio “coxo”, funciona com uma _multisig_ ou com os _covenants_ na Liquid. Mas eles estão a criar um produto, vão demonstrar ao mercado que o produto é bom e útil. Com a adoção, a comunidade vai perceber que o Ark necessita dos _covenants_ para melhorar a interoperabilidade e a soberania. É este o pensamento certo, que deveria ser seguido pelos restantes e futuros projetos. É seguir aquele pensamento do J.F. Kennedy: > “Não perguntem o que é que o vosso país pode fazer por vocês, perguntem o que é que vocês podem fazer pelo vosso país” Ou seja, não fiquem à espera que o bitcoin mude, criem primeiro as inovações/tecnologia, ganhem adoção e depois demonstrem que a alteração do código camada base pode melhorar ainda mais o vosso projeto. A necessidade é que vai levar a atualização do código. # Reservas Estratégicas de Bitcoin ## Bancos centrais Com a eleição de Trump, emergiu a ideia de uma Reserva Estratégia de Bitcoin, tornou este conceito _mainstream_. Foi um _pivot_, a partir desse momento, foram enumerados os políticos de todo o mundo a falar sobre o assunto. A Senadora Cynthia Lummis foi mais além e propôs um programa para adicionar 200 mil bitcoins à reserva ao ano, até 1 milhão de Bitcoin. Só que isto está a criar uma enorme expectativa na comunidade, só que pode resultar numa enorme desilusão. Porque no primeiro ano, o Trump em vez de comprar os 200 mil, pode apenas adicionar na reserva, os 198 mil que o Estado já tem em sua posse. Se isto acontecer, possivelmente vai resultar numa forte queda a curto prazo. Na minha opinião os bancos centrais deveriam seguir o exemplo de El Salvador, fazer um DCA diário. Mais que comprar bitcoin, para mim, o mais importante é a criação da Reserva, é colocar o Bitcoin ao mesmo nível do ouro, o impacto para o resto do mundo será tremendo, a teoria dos jogos na sua plenitude. Muitos outros bancos centrais vão ter que comprar, para não ficarem atrás, além disso, vai transmitir uma mensagem à generalidade da população, que o Bitcoin é “afinal é algo seguro, com valor”. Mas não foi Trump que iniciou esta teoria dos jogos, mas sim foi a primeira vítima dela. É o próprio Trump que o admite, que os EUA necessitam da reserva para não ficar atrás da China. Além disso, desde que os EUA utilizaram o dólar como uma arma, com sanção contra a Rússia, surgiram boatos de que a Rússia estaria a utilizar o Bitcoin para transações internacionais. Que foram confirmados recentemente, pelo próprio governo russo. Também há poucos dias, ainda antes deste reconhecimento público, Putin elogiou o Bitcoin, ao reconhecer que “Ninguém pode proibir o bitcoin”, defendendo como uma alternativa ao dólar. A narrativa está a mudar. Já existem alguns países com Bitcoin, mas apenas dois o fizeram conscientemente (El Salvador e Butão), os restantes têm devido a apreensões. Hoje são poucos, mas 2025 será o início de uma corrida pelos bancos centrais. Esta corrida era algo previsível, o que eu não esperava é que acontecesse tão rápido.  ## Empresas A criação de reservas estratégicas não vai ficar apenas pelos bancos centrais, também vai acelerar fortemente nas empresas em 2025.  Mas as empresas não vão seguir a estratégia do Saylor, vão comprar bitcoin sem alavancagem, utilizando apenas os tesouros das empresas, como uma proteção contra a inflação. Eu não sou grande admirador do Saylor, prefiro muito mais, uma estratégia conservadora, sem qualquer alavancagem. Penso que as empresas vão seguir a sugestão da BlackRock, que aconselha um alocações de 1% a 3%. Penso que 2025, ainda não será o ano da entrada das 6 magníficas (excepto Tesla), será sobretudo empresas de pequena e média dimensão. As magníficas ainda tem uma cota muito elevada de _shareholders_ com alguma idade, bastante conservadores, que têm dificuldade em compreender o Bitcoin, foi o que aconteceu recentemente com a Microsoft. Também ainda não será em 2025, talvez 2026, a inclusão nativamente de wallet Bitcoin nos sistema da Apple Pay e da Google Pay. Seria um passo gigante para a adoção a nível mundial. # ETFs Os ETFs para mim são uma incógnita, tenho demasiadas dúvidas, como será 2025. Este ano os _inflows_ foram superiores a 500 mil bitcoins, o IBIT foi o lançamento de ETF mais bem sucedido da história. O sucesso dos ETFs, deve-se a 2 situações que nunca mais se vão repetir. O mercado esteve 10 anos à espera pela aprovação dos ETFs, a procura estava reprimida, isso foi bem notório nos primeiros meses, os _inflows_ foram brutais. Também se beneficiou por ser um mercado novo, não existia _orderbook_ de vendas, não existia um mercado interno, praticamente era só _inflows_. Agora o mercado já estabilizou, a maioria das transações já são entre clientes dos próprios ETFs. Agora só uma pequena percentagem do volume das transações diárias vai resultar em _inflows_ ou _outflows_. Estes dois fenómenos nunca mais se vão repetir, eu não acredito que o número de _inflows_ em BTC supere os número de 2024, em dólares vai superar, mas em btc não acredito que vá superar. Mas em 2025 vão surgir uma infindável quantidade de novos produtos, derivativos, novos ETFs de cestos com outras criptos ou cestos com ativos tradicionais. O bitcoin será adicionado em produtos financeiros já existentes no mercado, as pessoas vão passar a deter bitcoin, sem o saberem. Com o fim da operação ChokePoint 2.0, vai surgir uma nova onda de adoção e de produtos financeiros. Possivelmente vamos ver bancos tradicionais a disponibilizar produtos ou serviços de custódia aos seus clientes. Eu adoraria ver o crescimento da adoção do bitcoin como moeda, só que a regulamentação não vai ajudar nesse processo. # Preço Eu acredito que o topo deste ciclo será alcançado no primeiro semestre, posteriormente haverá uma correção. Mas desta vez, eu acredito que a correção será muito menor que as anteriores, inferior a 50%, esta é a minha expectativa. Espero estar certo. # Stablecoins de dólar Agora saindo um pouco do universo do Bitcoin, acho importante destacar as _stablecoins_. No último ciclo, eu tenho dividido o tempo, entre continuar a estudar o Bitcoin e estudar o sistema financeiro, as suas dinâmicas e o comportamento humano. Isto tem sido o meu foco de reflexão, imaginar a transformação que o mundo vai sofrer devido ao padrão Bitcoin. É uma ilusão acreditar que a transição de um padrão FIAT para um padrão Bitcoin vai ser rápida, vai existir um processo transitório que pode demorar décadas. Com a re-entrada de Trump na Casa Branca, prometendo uma política altamente protecionista, vai provocar uma forte valorização do dólar, consequentemente as restantes moedas do mundo vão derreter. Provocando uma inflação generalizada, gerando uma corrida às _stablecoins_ de dólar nos países com moedas mais fracas. Trump vai ter uma política altamente expansionista, vai exportar dólares para todo o mundo, para financiar a sua própria dívida. A desigualdade entre os pobres e ricos irá crescer fortemente, aumentando a possibilidade de conflitos e revoltas. > “Casa onde não há pão, todos ralham e ninguém tem razão” Será mais lenha, para alimentar a fogueira, vai gravar os conflitos geopolíticos já existentes, ficando as sociedade ainda mais polarizadas. Eu acredito que 2025, vai haver um forte crescimento na adoção das _stablecoins_ de dólares, esse forte crescimento vai agravar o problema sistémico que são as _stablecoins_. Vai ser o início do fim das _stablecoins_, pelo menos, como nós conhecemos hoje em dia. ## Problema sistémico O sistema FIAT não nasceu de um dia para outro, foi algo que foi construído organicamente, ou seja, foi evoluindo ao longo dos anos, sempre que havia um problema/crise, eram criadas novas regras ou novas instituições para minimizar os problemas. Nestes quase 100 anos, desde os acordos de Bretton Woods, a evolução foram tantas, tornaram o sistema financeiro altamente complexo, burocrático e nada eficiente. Na prática é um castelo de cartas construído sobre outro castelo de cartas e que por sua vez, foi construído sobre outro castelo de cartas. As _stablecoins_ são um problema sistémico, devido às suas reservas em dólares e o sistema financeiro não está preparado para manter isso seguro. Com o crescimento das reservas ao longo dos anos, foi se agravando o problema. No início a Tether colocava as reservas em bancos comerciais, mas com o crescimento dos dólares sob gestão, criou um problema nos bancos comerciais, devido à reserva fracionária. Essas enormes reservas da Tether estavam a colocar em risco a própria estabilidade dos bancos. A Tether acabou por mudar de estratégia, optou por outros ativos, preferencialmente por títulos do tesouro/obrigações dos EUA. Só que a Tether continua a crescer e não dá sinais de abrandamento, pelo contrário. Até o próprio mundo cripto, menosprezava a gravidade do problema da Tether/_stablecoins_ para o resto do sistema financeiro, porque o _marketcap_ do cripto ainda é muito pequeno. É verdade que ainda é pequeno, mas a Tether não o é, está no top 20 dos maiores detentores de títulos do tesouros dos EUA e está ao nível dos maiores bancos centrais do mundo. Devido ao seu tamanho, está a preocupar os responsáveis/autoridades/reguladores dos EUA, pode colocar em causa a estabilidade do sistema financeiro global, que está assente nessas obrigações. Os títulos do tesouro dos EUA são o colateral mais utilizado no mundo, tanto por bancos centrais, como por empresas, é a charneira da estabilidade do sistema financeiro. Os títulos do tesouro são um assunto muito sensível. Na recente crise no Japão, do _carry trade_, o Banco Central do Japão tentou minimizar a desvalorização do iene através da venda de títulos dos EUA. Esta operação, obrigou a uma viagem de emergência, da Secretaria do Tesouro dos EUA, Janet Yellen ao Japão, onde disponibilizou liquidez para parar a venda de títulos por parte do Banco Central do Japão. Essa forte venda estava desestabilizando o mercado. Os principais detentores de títulos do tesouros são institucionais, bancos centrais, bancos comerciais, fundo de investimento e gestoras, tudo administrado por gestores altamente qualificados, racionais e que conhecem a complexidade do mercado de obrigações. O mundo cripto é seu oposto, é _naife_ com muita irracionalidade e uma forte pitada de loucura, na sua maioria nem faz a mínima ideia como funciona o sistema financeiro. Essa irracionalidade pode levar a uma “corrida bancária”, como aconteceu com o UST da Luna, que em poucas horas colapsou o projeto. Em termos de escala, a Luna ainda era muito pequena, por isso, o problema ficou circunscrito ao mundo cripto e a empresas ligadas diretamente ao cripto. Só que a Tether é muito diferente, caso exista algum FUD, que obrigue a Tether a desfazer-se de vários biliões ou dezenas de biliões de dólares em títulos num curto espaço de tempo, poderia provocar consequências terríveis em todo o sistema financeiro. A Tether é grande demais, é já um problema sistémico, que vai agravar-se com o crescimento em 2025. Não tenham dúvidas, se existir algum problema, o Tesouro dos EUA vai impedir a venda dos títulos que a Tether tem em sua posse, para salvar o sistema financeiro. O problema é, o que vai fazer a Tether, se ficar sem acesso às venda das reservas, como fará o _redeem_ dos dólares? Como o crescimento do Tether é inevitável, o Tesouro e o FED estão com um grande problema em mãos, o que fazer com o Tether? Mas o problema é que o atual sistema financeiro é como um curto cobertor: Quanto tapas a cabeça, destapas os pés; Ou quando tapas os pés, destapas a cabeça. Ou seja, para resolver o problema da guarda reservas da Tether, vai criar novos problemas, em outros locais do sistema financeiro e assim sucessivamente. ### Conta mestre Uma possível solução seria dar uma conta mestre à Tether, dando o acesso direto a uma conta no FED, semelhante à que todos os bancos comerciais têm. Com isto, a Tether deixaria de necessitar os títulos do tesouro, depositando o dinheiro diretamente no banco central. Só que isto iria criar dois novos problemas, com o Custodia Bank e com o restante sistema bancário. O Custodia Bank luta há vários anos contra o FED, nos tribunais pelo direito a ter licença bancária para um banco com _full-reserves_. O FED recusou sempre esse direito, com a justificativa que esse banco, colocaria em risco toda a estabilidade do sistema bancário existente, ou seja, todos os outros bancos poderiam colapsar. Perante a existência em simultâneo de bancos com reserva fracionária e com _full-reserves_, as pessoas e empresas iriam optar pelo mais seguro. Isso iria provocar uma corrida bancária, levando ao colapso de todos os bancos com reserva fracionária, porque no Custodia Bank, os fundos dos clientes estão 100% garantidos, para qualquer valor. Deixaria de ser necessário limites de fundos de Garantia de Depósitos. Eu concordo com o FED nesse ponto, que os bancos com _full-reserves_ são uma ameaça a existência dos restantes bancos. O que eu discordo do FED, é a origem do problema, o problema não está nos bancos _full-reserves_, mas sim nos que têm reserva fracionária. O FED ao conceder uma conta mestre ao Tether, abre um precedente, o Custodia Bank irá o aproveitar, reclamando pela igualdade de direitos nos tribunais e desta vez, possivelmente ganhará a sua licença. Ainda há um segundo problema, com os restantes bancos comerciais. A Tether passaria a ter direitos similares aos bancos comerciais, mas os deveres seriam muito diferentes. Isto levaria os bancos comerciais aos tribunais para exigir igualdade de tratamento, é uma concorrência desleal. Isto é o bom dos tribunais dos EUA, são independentes e funcionam, mesmo contra o estado. Os bancos comerciais têm custos exorbitantes devido às políticas de _compliance_, como o KYC e AML. Como o governo não vai querer aliviar as regras, logo seria a Tether, a ser obrigada a fazer o _compliance_ dos seus clientes. A obrigação do KYC para ter _stablecoins_ iriam provocar um terramoto no mundo cripto. Assim, é pouco provável que seja a solução para a Tether. ### FED Só resta uma hipótese, ser o próprio FED a controlar e a gerir diretamente as _stablecoins_ de dólar, nacionalizado ou absorvendo as existentes. Seria uma espécie de CBDC. Isto iria provocar um novo problema, um problema diplomático, porque as _stablecoins_ estão a colocar em causa a soberania monetária dos outros países. Atualmente as _stablecoins_ estão um pouco protegidas porque vivem num limbo jurídico, mas a partir do momento que estas são controladas pelo governo americano, tudo muda. Os países vão exigir às autoridades americanas medidas que limitem o uso nos seus respectivos países. Não existe uma solução boa, o sistema FIAT é um castelo de cartas, qualquer carta que se mova, vai provocar um desmoronamento noutro local. As autoridades não poderão adiar mais o problema, terão que o resolver de vez, senão, qualquer dia será tarde demais. Se houver algum problema, vão colocar a responsabilidade no cripto e no Bitcoin. Mas a verdade, a culpa é inteiramente dos políticos, da sua incompetência em resolver os problemas a tempo. Será algo para acompanhar futuramente, mas só para 2026, talvez… É curioso, há uns anos pensava-se que o Bitcoin seria a maior ameaça ao sistema ao FIAT, mas afinal, a maior ameaça aos sistema FIAT é o próprio FIAT(_stablecoins_). A ironia do destino. Isto é como uma corrida, o Bitcoin é aquele atleta que corre ao seu ritmo, umas vezes mais rápido, outras vezes mais lento, mas nunca pára. O FIAT é o atleta que dá tudo desde da partida, corre sempre em velocidade máxima. Só que a vida e o sistema financeiro não é uma prova de 100 metros, mas sim uma maratona. # Europa 2025 será um ano desafiante para todos europeus, sobretudo devido à entrada em vigor da regulamentação (MiCA). Vão começar a sentir na pele a regulamentação, vão agravar-se os problemas com os _compliance_, problemas para comprovar a origem de fundos e outras burocracias. Vai ser lindo. O _Travel Route_ passa a ser obrigatório, os europeus serão obrigados a fazer o KYC nas transações. A _Travel Route_ é uma suposta lei para criar mais transparência, mas prática, é uma lei de controle, de monitorização e para limitar as liberdades individuais dos cidadãos. O MiCA também está a colocar problemas nas _stablecoins_ de Euro, a Tether para já preferiu ficar de fora da europa. O mais ridículo é que as novas regras obrigam os emissores a colocar 30% das reservas em bancos comerciais. Os burocratas europeus não compreendem que isto coloca em risco a estabilidade e a solvência dos próprios bancos, ficam propensos a corridas bancárias. O MiCA vai obrigar a todas as exchanges a estar registadas em solo europeu, ficando vulnerável ao temperamento dos burocratas. Ainda não vai ser em 2025, mas a UE vai impor políticas de controle de capitais, é inevitável, as exchanges serão obrigadas a usar em exclusividade _stablecoins_ de euro, as restantes _stablecoins_ serão deslistadas. Todas estas novas regras do MiCA, são extremamente restritas, não é para garantir mais segurança aos cidadãos europeus, mas sim para garantir mais controle sobre a população. A UE está cada vez mais perto da autocracia, do que da democracia. A minha única esperança no horizonte, é que o sucesso das políticas cripto nos EUA, vai obrigar a UE a recuar e a aligeirar as regras, a teoria dos jogos é implacável. Mas esse recuo, nunca acontecerá em 2025, vai ser um longo período conturbado. # Recessão Os mercados estão todos em máximos históricos, isto não é sustentável por muito tempo, suspeito que no final de 2025 vai acontecer alguma correção nos mercados. A queda só não será maior, porque os bancos centrais vão imprimir dinheiro, muito dinheiro, como se não houvesse amanhã. Vão voltar a resolver os problemas com a injeção de liquidez na economia, é empurrar os problemas com a barriga, em de os resolver. Outra vez o efeito Cantillon. Será um ano muito desafiante a nível político, onde o papel dos políticos será fundamental. A crise política na França e na Alemanha, coloca a UE órfã, sem um comandante ao leme do navio. 2025 estará condicionado pelas eleições na Alemanha, sobretudo no resultado do AfD, que podem colocar em causa a propriedade UE e o euro. Possivelmente, só o fim da guerra poderia minimizar a crise, algo que é muito pouco provável acontecer. Em Portugal, a economia parece que está mais ou menos equilibrada, mas começam a aparecer alguns sinais preocupantes. Os jogos de sorte e azar estão em máximos históricos, batendo o recorde de 2014, época da grande crise, não é um bom sinal, possivelmente já existe algum desespero no ar. A Alemanha é o motor da Europa, quanto espirra, Portugal constipa-se. Além do problema da Alemanha, a Espanha também está à beira de uma crise, são os países que mais influenciam a economia portuguesa. Se existir uma recessão mundial, terá um forte impacto no turismo, que é hoje em dia o principal motor de Portugal. # Brasil Brasil é algo para acompanhar em 2025, sobretudo a nível macro e a nível político. Existe uma possibilidade de uma profunda crise no Brasil, sobretudo na sua moeda. O banco central já anda a queimar as reservas para minimizar a desvalorização do Real.  Sem mudanças profundas nas políticas fiscais, as reservas vão se esgotar. As políticas de controle de capitais são um cenário plausível, será interesse de acompanhar, como o governo irá proceder perante a existência do Bitcoin e _stablecoins_. No Brasil existe um forte adoção, será um bom _case study_, certamente irá repetir-se em outros países num futuro próximo. Os próximos tempos não serão fáceis para os brasileiros, especialmente para os que não têm Bitcoin. # Blockchain Em 2025, possivelmente vamos ver os primeiros passos da BlackRock para criar a primeira bolsa de valores, exclusivamente em _blockchain_. Eu acredito que a BlackRock vai criar uma própria _blockchain_, toda controlada por si, onde estarão os RWAs, para fazer concorrência às tradicionais bolsas de valores. Será algo interessante de acompanhar. ----------- Estas são as minhas previsões, eu escrevi isto muito em cima do joelho, certamente esqueci-me de algumas coisas, se for importante acrescentarei nos comentários. A maioria das previsões só acontecerá após 2025, mas fica aqui a minha opinião. Isto é apenas a minha opinião, **Don’t Trust, Verify**!
@ e97aaffa:2ebd765d
2024-12-31 16:47:12Último dia do ano, momento para tirar o pó da bola de cristal, para fazer reflexões, previsões e desejos para o próximo ano e seguintes. Ano após ano, o Bitcoin evoluiu, foi ultrapassando etapas, tornou-se cada vez mais _mainstream_. Está cada vez mais difícil fazer previsões sobre o Bitcoin, já faltam poucas barreiras a serem ultrapassadas e as que faltam são altamente complexas ou tem um impacto profundo no sistema financeiro ou na sociedade. Estas alterações profundas tem que ser realizadas lentamente, porque uma alteração rápida poderia resultar em consequências terríveis, poderia provocar um retrocesso. # Código do Bitcoin No final de 2025, possivelmente vamos ter um _fork_, as discussões sobre os _covenants_ já estão avançadas, vão acelerar ainda mais. Já existe um consenso relativamente alto, a favor dos _covenants_, só falta decidir que modelo será escolhido. Penso que até ao final do ano será tudo decidido. Depois dos _covenants,_ o próximo foco será para a criptografia post-quantum, que será o maior desafio que o Bitcoin enfrenta. Criar uma criptografia segura e que não coloque a descentralização em causa. Espero muito de Ark, possivelmente a inovação do ano, gostaria de ver o Nostr a furar a bolha bitcoinheira e que o Cashu tivesse mais reconhecimento pelos _bitcoiners_. Espero que surjam avanços significativos no BitVM2 e BitVMX. Não sei o que esperar das layer 2 de Bitcoin, foram a maior desilusão de 2024. Surgiram com muita força, mas pouca coisa saiu do papel, foi uma mão cheia de nada. Uma parte dos projetos caiu na tentação da _shitcoinagem_, na criação de tokens, que tem um único objetivo, enriquecer os devs e os VCs. Se querem ser levados a sério, têm que ser sérios. > “À mulher de César não basta ser honesta, deve parecer honesta” Se querem ter o apoio dos _bitcoiners_, sigam o _ethos_ do Bitcoin. Neste ponto a atitude do pessoal da Ark é exemplar, em vez de andar a chorar no Twitter para mudar o código do Bitcoin, eles colocaram as mãos na massa e criaram o protocolo. É claro que agora está meio “coxo”, funciona com uma _multisig_ ou com os _covenants_ na Liquid. Mas eles estão a criar um produto, vão demonstrar ao mercado que o produto é bom e útil. Com a adoção, a comunidade vai perceber que o Ark necessita dos _covenants_ para melhorar a interoperabilidade e a soberania. É este o pensamento certo, que deveria ser seguido pelos restantes e futuros projetos. É seguir aquele pensamento do J.F. Kennedy: > “Não perguntem o que é que o vosso país pode fazer por vocês, perguntem o que é que vocês podem fazer pelo vosso país” Ou seja, não fiquem à espera que o bitcoin mude, criem primeiro as inovações/tecnologia, ganhem adoção e depois demonstrem que a alteração do código camada base pode melhorar ainda mais o vosso projeto. A necessidade é que vai levar a atualização do código. # Reservas Estratégicas de Bitcoin ## Bancos centrais Com a eleição de Trump, emergiu a ideia de uma Reserva Estratégia de Bitcoin, tornou este conceito _mainstream_. Foi um _pivot_, a partir desse momento, foram enumerados os políticos de todo o mundo a falar sobre o assunto. A Senadora Cynthia Lummis foi mais além e propôs um programa para adicionar 200 mil bitcoins à reserva ao ano, até 1 milhão de Bitcoin. Só que isto está a criar uma enorme expectativa na comunidade, só que pode resultar numa enorme desilusão. Porque no primeiro ano, o Trump em vez de comprar os 200 mil, pode apenas adicionar na reserva, os 198 mil que o Estado já tem em sua posse. Se isto acontecer, possivelmente vai resultar numa forte queda a curto prazo. Na minha opinião os bancos centrais deveriam seguir o exemplo de El Salvador, fazer um DCA diário. Mais que comprar bitcoin, para mim, o mais importante é a criação da Reserva, é colocar o Bitcoin ao mesmo nível do ouro, o impacto para o resto do mundo será tremendo, a teoria dos jogos na sua plenitude. Muitos outros bancos centrais vão ter que comprar, para não ficarem atrás, além disso, vai transmitir uma mensagem à generalidade da população, que o Bitcoin é “afinal é algo seguro, com valor”. Mas não foi Trump que iniciou esta teoria dos jogos, mas sim foi a primeira vítima dela. É o próprio Trump que o admite, que os EUA necessitam da reserva para não ficar atrás da China. Além disso, desde que os EUA utilizaram o dólar como uma arma, com sanção contra a Rússia, surgiram boatos de que a Rússia estaria a utilizar o Bitcoin para transações internacionais. Que foram confirmados recentemente, pelo próprio governo russo. Também há poucos dias, ainda antes deste reconhecimento público, Putin elogiou o Bitcoin, ao reconhecer que “Ninguém pode proibir o bitcoin”, defendendo como uma alternativa ao dólar. A narrativa está a mudar. Já existem alguns países com Bitcoin, mas apenas dois o fizeram conscientemente (El Salvador e Butão), os restantes têm devido a apreensões. Hoje são poucos, mas 2025 será o início de uma corrida pelos bancos centrais. Esta corrida era algo previsível, o que eu não esperava é que acontecesse tão rápido.  ## Empresas A criação de reservas estratégicas não vai ficar apenas pelos bancos centrais, também vai acelerar fortemente nas empresas em 2025.  Mas as empresas não vão seguir a estratégia do Saylor, vão comprar bitcoin sem alavancagem, utilizando apenas os tesouros das empresas, como uma proteção contra a inflação. Eu não sou grande admirador do Saylor, prefiro muito mais, uma estratégia conservadora, sem qualquer alavancagem. Penso que as empresas vão seguir a sugestão da BlackRock, que aconselha um alocações de 1% a 3%. Penso que 2025, ainda não será o ano da entrada das 6 magníficas (excepto Tesla), será sobretudo empresas de pequena e média dimensão. As magníficas ainda tem uma cota muito elevada de _shareholders_ com alguma idade, bastante conservadores, que têm dificuldade em compreender o Bitcoin, foi o que aconteceu recentemente com a Microsoft. Também ainda não será em 2025, talvez 2026, a inclusão nativamente de wallet Bitcoin nos sistema da Apple Pay e da Google Pay. Seria um passo gigante para a adoção a nível mundial. # ETFs Os ETFs para mim são uma incógnita, tenho demasiadas dúvidas, como será 2025. Este ano os _inflows_ foram superiores a 500 mil bitcoins, o IBIT foi o lançamento de ETF mais bem sucedido da história. O sucesso dos ETFs, deve-se a 2 situações que nunca mais se vão repetir. O mercado esteve 10 anos à espera pela aprovação dos ETFs, a procura estava reprimida, isso foi bem notório nos primeiros meses, os _inflows_ foram brutais. Também se beneficiou por ser um mercado novo, não existia _orderbook_ de vendas, não existia um mercado interno, praticamente era só _inflows_. Agora o mercado já estabilizou, a maioria das transações já são entre clientes dos próprios ETFs. Agora só uma pequena percentagem do volume das transações diárias vai resultar em _inflows_ ou _outflows_. Estes dois fenómenos nunca mais se vão repetir, eu não acredito que o número de _inflows_ em BTC supere os número de 2024, em dólares vai superar, mas em btc não acredito que vá superar. Mas em 2025 vão surgir uma infindável quantidade de novos produtos, derivativos, novos ETFs de cestos com outras criptos ou cestos com ativos tradicionais. O bitcoin será adicionado em produtos financeiros já existentes no mercado, as pessoas vão passar a deter bitcoin, sem o saberem. Com o fim da operação ChokePoint 2.0, vai surgir uma nova onda de adoção e de produtos financeiros. Possivelmente vamos ver bancos tradicionais a disponibilizar produtos ou serviços de custódia aos seus clientes. Eu adoraria ver o crescimento da adoção do bitcoin como moeda, só que a regulamentação não vai ajudar nesse processo. # Preço Eu acredito que o topo deste ciclo será alcançado no primeiro semestre, posteriormente haverá uma correção. Mas desta vez, eu acredito que a correção será muito menor que as anteriores, inferior a 50%, esta é a minha expectativa. Espero estar certo. # Stablecoins de dólar Agora saindo um pouco do universo do Bitcoin, acho importante destacar as _stablecoins_. No último ciclo, eu tenho dividido o tempo, entre continuar a estudar o Bitcoin e estudar o sistema financeiro, as suas dinâmicas e o comportamento humano. Isto tem sido o meu foco de reflexão, imaginar a transformação que o mundo vai sofrer devido ao padrão Bitcoin. É uma ilusão acreditar que a transição de um padrão FIAT para um padrão Bitcoin vai ser rápida, vai existir um processo transitório que pode demorar décadas. Com a re-entrada de Trump na Casa Branca, prometendo uma política altamente protecionista, vai provocar uma forte valorização do dólar, consequentemente as restantes moedas do mundo vão derreter. Provocando uma inflação generalizada, gerando uma corrida às _stablecoins_ de dólar nos países com moedas mais fracas. Trump vai ter uma política altamente expansionista, vai exportar dólares para todo o mundo, para financiar a sua própria dívida. A desigualdade entre os pobres e ricos irá crescer fortemente, aumentando a possibilidade de conflitos e revoltas. > “Casa onde não há pão, todos ralham e ninguém tem razão” Será mais lenha, para alimentar a fogueira, vai gravar os conflitos geopolíticos já existentes, ficando as sociedade ainda mais polarizadas. Eu acredito que 2025, vai haver um forte crescimento na adoção das _stablecoins_ de dólares, esse forte crescimento vai agravar o problema sistémico que são as _stablecoins_. Vai ser o início do fim das _stablecoins_, pelo menos, como nós conhecemos hoje em dia. ## Problema sistémico O sistema FIAT não nasceu de um dia para outro, foi algo que foi construído organicamente, ou seja, foi evoluindo ao longo dos anos, sempre que havia um problema/crise, eram criadas novas regras ou novas instituições para minimizar os problemas. Nestes quase 100 anos, desde os acordos de Bretton Woods, a evolução foram tantas, tornaram o sistema financeiro altamente complexo, burocrático e nada eficiente. Na prática é um castelo de cartas construído sobre outro castelo de cartas e que por sua vez, foi construído sobre outro castelo de cartas. As _stablecoins_ são um problema sistémico, devido às suas reservas em dólares e o sistema financeiro não está preparado para manter isso seguro. Com o crescimento das reservas ao longo dos anos, foi se agravando o problema. No início a Tether colocava as reservas em bancos comerciais, mas com o crescimento dos dólares sob gestão, criou um problema nos bancos comerciais, devido à reserva fracionária. Essas enormes reservas da Tether estavam a colocar em risco a própria estabilidade dos bancos. A Tether acabou por mudar de estratégia, optou por outros ativos, preferencialmente por títulos do tesouro/obrigações dos EUA. Só que a Tether continua a crescer e não dá sinais de abrandamento, pelo contrário. Até o próprio mundo cripto, menosprezava a gravidade do problema da Tether/_stablecoins_ para o resto do sistema financeiro, porque o _marketcap_ do cripto ainda é muito pequeno. É verdade que ainda é pequeno, mas a Tether não o é, está no top 20 dos maiores detentores de títulos do tesouros dos EUA e está ao nível dos maiores bancos centrais do mundo. Devido ao seu tamanho, está a preocupar os responsáveis/autoridades/reguladores dos EUA, pode colocar em causa a estabilidade do sistema financeiro global, que está assente nessas obrigações. Os títulos do tesouro dos EUA são o colateral mais utilizado no mundo, tanto por bancos centrais, como por empresas, é a charneira da estabilidade do sistema financeiro. Os títulos do tesouro são um assunto muito sensível. Na recente crise no Japão, do _carry trade_, o Banco Central do Japão tentou minimizar a desvalorização do iene através da venda de títulos dos EUA. Esta operação, obrigou a uma viagem de emergência, da Secretaria do Tesouro dos EUA, Janet Yellen ao Japão, onde disponibilizou liquidez para parar a venda de títulos por parte do Banco Central do Japão. Essa forte venda estava desestabilizando o mercado. Os principais detentores de títulos do tesouros são institucionais, bancos centrais, bancos comerciais, fundo de investimento e gestoras, tudo administrado por gestores altamente qualificados, racionais e que conhecem a complexidade do mercado de obrigações. O mundo cripto é seu oposto, é _naife_ com muita irracionalidade e uma forte pitada de loucura, na sua maioria nem faz a mínima ideia como funciona o sistema financeiro. Essa irracionalidade pode levar a uma “corrida bancária”, como aconteceu com o UST da Luna, que em poucas horas colapsou o projeto. Em termos de escala, a Luna ainda era muito pequena, por isso, o problema ficou circunscrito ao mundo cripto e a empresas ligadas diretamente ao cripto. Só que a Tether é muito diferente, caso exista algum FUD, que obrigue a Tether a desfazer-se de vários biliões ou dezenas de biliões de dólares em títulos num curto espaço de tempo, poderia provocar consequências terríveis em todo o sistema financeiro. A Tether é grande demais, é já um problema sistémico, que vai agravar-se com o crescimento em 2025. Não tenham dúvidas, se existir algum problema, o Tesouro dos EUA vai impedir a venda dos títulos que a Tether tem em sua posse, para salvar o sistema financeiro. O problema é, o que vai fazer a Tether, se ficar sem acesso às venda das reservas, como fará o _redeem_ dos dólares? Como o crescimento do Tether é inevitável, o Tesouro e o FED estão com um grande problema em mãos, o que fazer com o Tether? Mas o problema é que o atual sistema financeiro é como um curto cobertor: Quanto tapas a cabeça, destapas os pés; Ou quando tapas os pés, destapas a cabeça. Ou seja, para resolver o problema da guarda reservas da Tether, vai criar novos problemas, em outros locais do sistema financeiro e assim sucessivamente. ### Conta mestre Uma possível solução seria dar uma conta mestre à Tether, dando o acesso direto a uma conta no FED, semelhante à que todos os bancos comerciais têm. Com isto, a Tether deixaria de necessitar os títulos do tesouro, depositando o dinheiro diretamente no banco central. Só que isto iria criar dois novos problemas, com o Custodia Bank e com o restante sistema bancário. O Custodia Bank luta há vários anos contra o FED, nos tribunais pelo direito a ter licença bancária para um banco com _full-reserves_. O FED recusou sempre esse direito, com a justificativa que esse banco, colocaria em risco toda a estabilidade do sistema bancário existente, ou seja, todos os outros bancos poderiam colapsar. Perante a existência em simultâneo de bancos com reserva fracionária e com _full-reserves_, as pessoas e empresas iriam optar pelo mais seguro. Isso iria provocar uma corrida bancária, levando ao colapso de todos os bancos com reserva fracionária, porque no Custodia Bank, os fundos dos clientes estão 100% garantidos, para qualquer valor. Deixaria de ser necessário limites de fundos de Garantia de Depósitos. Eu concordo com o FED nesse ponto, que os bancos com _full-reserves_ são uma ameaça a existência dos restantes bancos. O que eu discordo do FED, é a origem do problema, o problema não está nos bancos _full-reserves_, mas sim nos que têm reserva fracionária. O FED ao conceder uma conta mestre ao Tether, abre um precedente, o Custodia Bank irá o aproveitar, reclamando pela igualdade de direitos nos tribunais e desta vez, possivelmente ganhará a sua licença. Ainda há um segundo problema, com os restantes bancos comerciais. A Tether passaria a ter direitos similares aos bancos comerciais, mas os deveres seriam muito diferentes. Isto levaria os bancos comerciais aos tribunais para exigir igualdade de tratamento, é uma concorrência desleal. Isto é o bom dos tribunais dos EUA, são independentes e funcionam, mesmo contra o estado. Os bancos comerciais têm custos exorbitantes devido às políticas de _compliance_, como o KYC e AML. Como o governo não vai querer aliviar as regras, logo seria a Tether, a ser obrigada a fazer o _compliance_ dos seus clientes. A obrigação do KYC para ter _stablecoins_ iriam provocar um terramoto no mundo cripto. Assim, é pouco provável que seja a solução para a Tether. ### FED Só resta uma hipótese, ser o próprio FED a controlar e a gerir diretamente as _stablecoins_ de dólar, nacionalizado ou absorvendo as existentes. Seria uma espécie de CBDC. Isto iria provocar um novo problema, um problema diplomático, porque as _stablecoins_ estão a colocar em causa a soberania monetária dos outros países. Atualmente as _stablecoins_ estão um pouco protegidas porque vivem num limbo jurídico, mas a partir do momento que estas são controladas pelo governo americano, tudo muda. Os países vão exigir às autoridades americanas medidas que limitem o uso nos seus respectivos países. Não existe uma solução boa, o sistema FIAT é um castelo de cartas, qualquer carta que se mova, vai provocar um desmoronamento noutro local. As autoridades não poderão adiar mais o problema, terão que o resolver de vez, senão, qualquer dia será tarde demais. Se houver algum problema, vão colocar a responsabilidade no cripto e no Bitcoin. Mas a verdade, a culpa é inteiramente dos políticos, da sua incompetência em resolver os problemas a tempo. Será algo para acompanhar futuramente, mas só para 2026, talvez… É curioso, há uns anos pensava-se que o Bitcoin seria a maior ameaça ao sistema ao FIAT, mas afinal, a maior ameaça aos sistema FIAT é o próprio FIAT(_stablecoins_). A ironia do destino. Isto é como uma corrida, o Bitcoin é aquele atleta que corre ao seu ritmo, umas vezes mais rápido, outras vezes mais lento, mas nunca pára. O FIAT é o atleta que dá tudo desde da partida, corre sempre em velocidade máxima. Só que a vida e o sistema financeiro não é uma prova de 100 metros, mas sim uma maratona. # Europa 2025 será um ano desafiante para todos europeus, sobretudo devido à entrada em vigor da regulamentação (MiCA). Vão começar a sentir na pele a regulamentação, vão agravar-se os problemas com os _compliance_, problemas para comprovar a origem de fundos e outras burocracias. Vai ser lindo. O _Travel Route_ passa a ser obrigatório, os europeus serão obrigados a fazer o KYC nas transações. A _Travel Route_ é uma suposta lei para criar mais transparência, mas prática, é uma lei de controle, de monitorização e para limitar as liberdades individuais dos cidadãos. O MiCA também está a colocar problemas nas _stablecoins_ de Euro, a Tether para já preferiu ficar de fora da europa. O mais ridículo é que as novas regras obrigam os emissores a colocar 30% das reservas em bancos comerciais. Os burocratas europeus não compreendem que isto coloca em risco a estabilidade e a solvência dos próprios bancos, ficam propensos a corridas bancárias. O MiCA vai obrigar a todas as exchanges a estar registadas em solo europeu, ficando vulnerável ao temperamento dos burocratas. Ainda não vai ser em 2025, mas a UE vai impor políticas de controle de capitais, é inevitável, as exchanges serão obrigadas a usar em exclusividade _stablecoins_ de euro, as restantes _stablecoins_ serão deslistadas. Todas estas novas regras do MiCA, são extremamente restritas, não é para garantir mais segurança aos cidadãos europeus, mas sim para garantir mais controle sobre a população. A UE está cada vez mais perto da autocracia, do que da democracia. A minha única esperança no horizonte, é que o sucesso das políticas cripto nos EUA, vai obrigar a UE a recuar e a aligeirar as regras, a teoria dos jogos é implacável. Mas esse recuo, nunca acontecerá em 2025, vai ser um longo período conturbado. # Recessão Os mercados estão todos em máximos históricos, isto não é sustentável por muito tempo, suspeito que no final de 2025 vai acontecer alguma correção nos mercados. A queda só não será maior, porque os bancos centrais vão imprimir dinheiro, muito dinheiro, como se não houvesse amanhã. Vão voltar a resolver os problemas com a injeção de liquidez na economia, é empurrar os problemas com a barriga, em de os resolver. Outra vez o efeito Cantillon. Será um ano muito desafiante a nível político, onde o papel dos políticos será fundamental. A crise política na França e na Alemanha, coloca a UE órfã, sem um comandante ao leme do navio. 2025 estará condicionado pelas eleições na Alemanha, sobretudo no resultado do AfD, que podem colocar em causa a propriedade UE e o euro. Possivelmente, só o fim da guerra poderia minimizar a crise, algo que é muito pouco provável acontecer. Em Portugal, a economia parece que está mais ou menos equilibrada, mas começam a aparecer alguns sinais preocupantes. Os jogos de sorte e azar estão em máximos históricos, batendo o recorde de 2014, época da grande crise, não é um bom sinal, possivelmente já existe algum desespero no ar. A Alemanha é o motor da Europa, quanto espirra, Portugal constipa-se. Além do problema da Alemanha, a Espanha também está à beira de uma crise, são os países que mais influenciam a economia portuguesa. Se existir uma recessão mundial, terá um forte impacto no turismo, que é hoje em dia o principal motor de Portugal. # Brasil Brasil é algo para acompanhar em 2025, sobretudo a nível macro e a nível político. Existe uma possibilidade de uma profunda crise no Brasil, sobretudo na sua moeda. O banco central já anda a queimar as reservas para minimizar a desvalorização do Real.  Sem mudanças profundas nas políticas fiscais, as reservas vão se esgotar. As políticas de controle de capitais são um cenário plausível, será interesse de acompanhar, como o governo irá proceder perante a existência do Bitcoin e _stablecoins_. No Brasil existe um forte adoção, será um bom _case study_, certamente irá repetir-se em outros países num futuro próximo. Os próximos tempos não serão fáceis para os brasileiros, especialmente para os que não têm Bitcoin. # Blockchain Em 2025, possivelmente vamos ver os primeiros passos da BlackRock para criar a primeira bolsa de valores, exclusivamente em _blockchain_. Eu acredito que a BlackRock vai criar uma própria _blockchain_, toda controlada por si, onde estarão os RWAs, para fazer concorrência às tradicionais bolsas de valores. Será algo interessante de acompanhar. ----------- Estas são as minhas previsões, eu escrevi isto muito em cima do joelho, certamente esqueci-me de algumas coisas, se for importante acrescentarei nos comentários. A maioria das previsões só acontecerá após 2025, mas fica aqui a minha opinião. Isto é apenas a minha opinião, **Don’t Trust, Verify**! @ 17538dc2:71ed77c4
2025-04-02 16:04:59The MacOS security update summary is a reminder that laptops and desktops are incredibly compromised. ### macOS Sequoia 15.4 Released March 31, 2025 Accessibility Available for: macOS Sequoia Impact: An app may be able to access sensitive user data Description: A logging issue was addressed with improved data redaction. CVE-2025-24202: Zhongcheng Li from IES Red Team of ByteDance AccountPolicy Available for: macOS Sequoia Impact: A malicious app may be able to gain root privileges Description: This issue was addressed by removing the vulnerable code. CVE-2025-24234: an anonymous researcher AirDrop Available for: macOS Sequoia Impact: An app may be able to read arbitrary file metadata Description: A permissions issue was addressed with additional restrictions. CVE-2025-24097: Ron Masas of BREAKPOINT.SH App Store Available for: macOS Sequoia Impact: A malicious app may be able to access private information Description: This issue was addressed by removing the vulnerable code. CVE-2025-24276: an anonymous researcher AppleMobileFileIntegrity Available for: macOS Sequoia Impact: An app may be able to modify protected parts of the file system Description: The issue was addressed with improved checks. CVE-2025-24272: Mickey Jin (@patch1t) AppleMobileFileIntegrity Available for: macOS Sequoia Impact: An app may be able to access protected user data Description: A downgrade issue was addressed with additional code-signing restrictions. CVE-2025-24239: Wojciech Regula of SecuRing (wojciechregula.blog) AppleMobileFileIntegrity Available for: macOS Sequoia Impact: A malicious app may be able to read or write to protected files Description: A permissions issue was addressed with additional restrictions. CVE-2025-24233: Claudio Bozzato and Francesco Benvenuto of Cisco Talos. AppleMobileFileIntegrity Available for: macOS Sequoia Impact: An app may be able to access user-sensitive data Description: A privacy issue was addressed by removing the vulnerable code. CVE-2025-30443: Bohdan Stasiuk (@bohdan_stasiuk) Audio Available for: macOS Sequoia Impact: Processing a maliciously crafted font may result in the disclosure of process memory Description: The issue was addressed with improved memory handling. CVE-2025-24244: Hossein Lotfi (@hosselot) of Trend Micro Zero Day Initiative Audio Available for: macOS Sequoia Impact: Processing a maliciously crafted file may lead to arbitrary code execution Description: The issue was addressed with improved memory handling. CVE-2025-24243: Hossein Lotfi (@hosselot) of Trend Micro Zero Day Initiative Authentication Services Available for: macOS Sequoia Impact: Password autofill may fill in passwords after failing authentication Description: This issue was addressed through improved state management. CVE-2025-30430: Dominik Rath Authentication Services Available for: macOS Sequoia Impact: A malicious website may be able to claim WebAuthn credentials from another website that shares a registrable suffix Description: The issue was addressed with improved input validation. CVE-2025-24180: Martin Kreichgauer of Google Chrome Authentication Services Available for: macOS Sequoia Impact: A malicious app may be able to access a user's saved passwords Description: This issue was addressed by adding a delay between verification code attempts. CVE-2025-24245: Ian Mckay (@iann0036) Automator Available for: macOS Sequoia Impact: An app may be able to access protected user data Description: A permissions issue was addressed by removing vulnerable code and adding additional checks. CVE-2025-30460: an anonymous researcher BiometricKit Available for: macOS Sequoia Impact: An app may be able to cause unexpected system termination Description: A buffer overflow was addressed with improved bounds checking. CVE-2025-24237: Yutong Xiu Calendar Available for: macOS Sequoia Impact: An app may be able to break out of its sandbox Description: A path handling issue was addressed with improved validation. CVE-2025-30429: Denis Tokarev (@illusionofcha0s) Calendar Available for: macOS Sequoia Impact: An app may be able to break out of its sandbox Description: This issue was addressed with improved checks. CVE-2025-24212: Denis Tokarev (@illusionofcha0s) CloudKit Available for: macOS Sequoia Impact: A malicious app may be able to access private information Description: The issue was addressed with improved checks. CVE-2025-24215: Kirin (@Pwnrin) CoreAudio Available for: macOS Sequoia Impact: Parsing a file may lead to an unexpected app termination Description: The issue was addressed with improved checks. CVE-2025-24163: Google Threat Analysis Group CoreAudio Available for: macOS Sequoia Impact: Playing a malicious audio file may lead to an unexpected app termination Description: An out-of-bounds read issue was addressed with improved input validation. CVE-2025-24230: Hossein Lotfi (@hosselot) of Trend Micro Zero Day Initiative CoreMedia Available for: macOS Sequoia Impact: Processing a maliciously crafted video file may lead to unexpected app termination or corrupt process memory Description: This issue was addressed with improved memory handling. CVE-2025-24211: Hossein Lotfi (@hosselot) of Trend Micro Zero Day Initiative CoreMedia Available for: macOS Sequoia Impact: An app may be able to access sensitive user data Description: An access issue was addressed with additional sandbox restrictions. CVE-2025-24236: Csaba Fitzl (@theevilbit) and Nolan Astrein of Kandji CoreMedia Available for: macOS Sequoia Impact: Processing a maliciously crafted video file may lead to unexpected app termination or corrupt process memory Description: The issue was addressed with improved memory handling. CVE-2025-24190: Hossein Lotfi (@hosselot) of Trend Micro Zero Day Initiative CoreMedia Playback Available for: macOS Sequoia Impact: A malicious app may be able to access private information Description: A path handling issue was addressed with improved validation. CVE-2025-30454: pattern-f (@pattern_F_) CoreServices Description: This issue was addressed through improved state management. CVE-2025-31191: Jonathan Bar Or (@yo_yo_yo_jbo) of Microsoft, and an anonymous researcher Available for: macOS Sequoia Impact: An app may be able to access sensitive user data CoreText Available for: macOS Sequoia Impact: Processing a maliciously crafted font may result in the disclosure of process memory Description: An out-of-bounds read issue was addressed with improved input validation. CVE-2025-24182: Hossein Lotfi (@hosselot) of Trend Micro Zero Day Initiative Crash Reporter Available for: macOS Sequoia Impact: An app may be able to gain root privileges Description: A parsing issue in the handling of directory paths was addressed with improved path validation. CVE-2025-24277: Csaba Fitzl (@theevilbit) of Kandji and Gergely Kalman (@gergely_kalman), and an anonymous researcher curl Available for: macOS Sequoia Impact: An input validation issue was addressed Description: This is a vulnerability in open source code and Apple Software is among the affected projects. The CVE-ID was assigned by a third party. Learn more about the issue and CVE-ID at cve.org. CVE-2024-9681 Disk Images Available for: macOS Sequoia Impact: An app may be able to break out of its sandbox Description: A file access issue was addressed with improved input validation. CVE-2025-24255: an anonymous researcher DiskArbitration Available for: macOS Sequoia Impact: An app may be able to gain root privileges Description: A parsing issue in the handling of directory paths was addressed with improved path validation. CVE-2025-30456: Gergely Kalman (@gergely_kalman) DiskArbitration Available for: macOS Sequoia Impact: An app may be able to gain root privileges Description: A permissions issue was addressed with additional restrictions. CVE-2025-24267: an anonymous researcher Dock Available for: macOS Sequoia Impact: A malicious app may be able to access private information Description: The issue was addressed with improved checks. CVE-2025-30455: Mickey Jin (@patch1t), and an anonymous researcher Dock Available for: macOS Sequoia Impact: An app may be able to modify protected parts of the file system Description: This issue was addressed by removing the vulnerable code. CVE-2025-31187: Rodolphe BRUNETTI (@eisw0lf) of Lupus Nova dyld Available for: macOS Sequoia Impact: Apps that appear to use App Sandbox may be able to launch without restrictions Description: A library injection issue was addressed with additional restrictions. CVE-2025-30462: Pietro Francesco Tirenna, Davide Silvetti, Abdel Adim Oisfi of Shielder (shielder.com) FaceTime Available for: macOS Sequoia Impact: An app may be able to access sensitive user data Description: This issue was addressed with improved redaction of sensitive information. CVE-2025-30451: Kirin (@Pwnrin) and luckyu (@uuulucky) FeedbackLogger Available for: macOS Sequoia Impact: An app may be able to access sensitive user data Description: This issue was addressed with improved data protection. CVE-2025-24281: Rodolphe BRUNETTI (@eisw0lf) Focus Available for: macOS Sequoia Impact: An attacker with physical access to a locked device may be able to view sensitive user information Description: The issue was addressed with improved checks. CVE-2025-30439: Andr.Ess Focus Available for: macOS Sequoia Impact: An app may be able to access sensitive user data Description: A logging issue was addressed with improved data redaction. CVE-2025-24283: Kirin (@Pwnrin) Foundation Available for: macOS Sequoia Impact: An app may be able to access protected user data Description: An access issue was addressed with additional sandbox restrictions on the system pasteboards. CVE-2025-30461: an anonymous researcher Foundation Available for: macOS Sequoia Impact: An app may be able to access sensitive user data Description: The issue was resolved by sanitizing logging CVE-2025-30447: LFY@secsys from Fudan University Foundation Available for: macOS Sequoia Impact: An app may be able to cause a denial-of-service Description: An uncontrolled format string issue was addressed with improved input validation. CVE-2025-24199: Manuel Fernandez (Stackhopper Security) GPU Drivers Available for: macOS Sequoia Impact: An app may be able to cause unexpected system termination or corrupt kernel memory Description: An out-of-bounds write issue was addressed with improved bounds checking. CVE-2025-30464: ABC Research s.r.o. CVE-2025-24273: Wang Yu of Cyberserval GPU Drivers Available for: macOS Sequoia Impact: An app may be able to disclose kernel memory Description: The issue was addressed with improved bounds checks. CVE-2025-24256: Anonymous working with Trend Micro Zero Day Initiative, Murray Mike Handoff Available for: macOS Sequoia Impact: An app may be able to access sensitive user data Description: The issue was addressed with improved restriction of data container access. CVE-2025-30463: mzzzz__ ImageIO Available for: macOS Sequoia Impact: Parsing an image may lead to disclosure of user information Description: A logic error was addressed with improved error handling. CVE-2025-24210: Anonymous working with Trend Micro Zero Day Initiative Installer Available for: macOS Sequoia Impact: An app may be able to check the existence of an arbitrary path on the file system Description: A permissions issue was addressed with additional sandbox restrictions. CVE-2025-24249: YingQi Shi(@Mas0nShi) of DBAppSecurity's WeBin lab and Minghao Lin (@Y1nKoc) Installer Available for: macOS Sequoia Impact: A sandboxed app may be able to access sensitive user data Description: A logic issue was addressed with improved checks. CVE-2025-24229: an anonymous researcher IOGPUFamily Available for: macOS Sequoia Impact: An app may be able to cause unexpected system termination or write kernel memory Description: An out-of-bounds write issue was addressed with improved input validation. CVE-2025-24257: Wang Yu of Cyberserval IOMobileFrameBuffer Available for: macOS Sequoia Impact: An app may be able to corrupt coprocessor memory Description: The issue was addressed with improved bounds checks. CVE-2025-30437: Ye Zhang (@VAR10CK) of Baidu Security Kerberos Helper Available for: macOS Sequoia Impact: A remote attacker may be able to cause unexpected app termination or heap corruption Description: A memory initialization issue was addressed with improved memory handling. CVE-2025-24235: Dave G. Kernel Available for: macOS Sequoia Impact: An app may be able to access protected user data Description: The issue was addressed with improved checks. CVE-2025-24204: Koh M. Nakagawa (@tsunek0h) of FFRI Security, Inc. Kernel Available for: macOS Sequoia Impact: An app may be able to modify protected parts of the file system Description: The issue was addressed with improved checks. CVE-2025-24203: Ian Beer of Google Project Zero Kernel Available for: macOS Sequoia Impact: An attacker with user privileges may be able to read kernel memory Description: A type confusion issue was addressed with improved memory handling. CVE-2025-24196: Joseph Ravichandran (@0xjprx) of MIT CSAIL LaunchServices Available for: macOS Sequoia Impact: A malicious JAR file may bypass Gatekeeper checks Description: This issue was addressed with improved handling of executable types. CVE-2025-24148: Kenneth Chew libarchive Available for: macOS Sequoia Impact: An input validation issue was addressed Description: This is a vulnerability in open source code and Apple Software is among the affected projects. The CVE-ID was assigned by a third party. Learn more about the issue and CVE-ID at cve.org. CVE-2024-48958 Libinfo Available for: macOS Sequoia Impact: A user may be able to elevate privileges Description: An integer overflow was addressed with improved input validation. CVE-2025-24195: Paweł Płatek (Trail of Bits) libnetcore Available for: macOS Sequoia Impact: Processing maliciously crafted web content may result in the disclosure of process memory Description: A logic issue was addressed with improved checks. CVE-2025-24194: an anonymous researcher libxml2 Available for: macOS Sequoia Impact: Parsing a file may lead to an unexpected app termination Description: This is a vulnerability in open source code and Apple Software is among the affected projects. The CVE-ID was assigned by a third party. Learn more about the issue and CVE-ID at cve.org. CVE-2025-27113 CVE-2024-56171 libxpc Available for: macOS Sequoia Impact: An app may be able to break out of its sandbox Description: This issue was addressed through improved state management. CVE-2025-24178: an anonymous researcher libxpc Available for: macOS Sequoia Impact: An app may be able to delete files for which it does not have permission Description: This issue was addressed with improved handling of symlinks. CVE-2025-31182: Alex Radocea and Dave G. of Supernetworks, 风沐云烟(@binary_fmyy) and Minghao Lin(@Y1nKoc) libxpc Available for: macOS Sequoia Impact: An app may be able to gain elevated privileges Description: A logic issue was addressed with improved checks. CVE-2025-24238: an anonymous researcher Mail Available for: macOS Sequoia Impact: "Block All Remote Content" may not apply for all mail previews Description: A permissions issue was addressed with additional sandbox restrictions. CVE-2025-24172: an anonymous researcher manpages Available for: macOS Sequoia Impact: An app may be able to access sensitive user data Description: This issue was addressed with improved validation of symlinks. CVE-2025-30450: Pwn2car Maps Available for: macOS Sequoia Impact: An app may be able to read sensitive location information Description: A path handling issue was addressed with improved logic. CVE-2025-30470: LFY@secsys from Fudan University NetworkExtension Available for: macOS Sequoia Impact: An app may be able to enumerate a user's installed apps Description: This issue was addressed with additional entitlement checks. CVE-2025-30426: Jimmy Notes Available for: macOS Sequoia Impact: A sandboxed app may be able to access sensitive user data in system logs Description: A privacy issue was addressed with improved private data redaction for log entries. CVE-2025-24262: LFY@secsys from Fudan University NSDocument Available for: macOS Sequoia Impact: A malicious app may be able to access arbitrary files Description: This issue was addressed through improved state management. CVE-2025-24232: an anonymous researcher OpenSSH Available for: macOS Sequoia Impact: An app may be able to access user-sensitive data Description: An injection issue was addressed with improved validation. CVE-2025-24246: Mickey Jin (@patch1t) PackageKit Available for: macOS Sequoia Impact: An app may be able to modify protected parts of the file system Description: The issue was addressed with improved checks. CVE-2025-24261: Mickey Jin (@patch1t) PackageKit Available for: macOS Sequoia Impact: An app may be able to modify protected parts of the file system Description: A logic issue was addressed with improved checks. CVE-2025-24164: Mickey Jin (@patch1t) PackageKit Available for: macOS Sequoia Impact: A malicious app with root privileges may be able to modify the contents of system files Description: A permissions issue was addressed with additional restrictions. CVE-2025-30446: Pedro Tôrres (@t0rr3sp3dr0) Parental Controls Available for: macOS Sequoia Impact: An app may be able to retrieve Safari bookmarks without an entitlement check Description: This issue was addressed with additional entitlement checks. CVE-2025-24259: Noah Gregory (wts.dev) Photos Storage Available for: macOS Sequoia Impact: Deleting a conversation in Messages may expose user contact information in system logging Description: A logging issue was addressed with improved data redaction. CVE-2025-30424: an anonymous researcher Power Services Available for: macOS Sequoia Impact: An app may be able to break out of its sandbox Description: This issue was addressed with additional entitlement checks. CVE-2025-24173: Mickey Jin (@patch1t) Python Available for: macOS Sequoia Impact: A remote attacker may be able to bypass sender policy checks and deliver malicious content via email Description: This is a vulnerability in open source code and Apple Software is among the affected projects. The CVE-ID was assigned by a third party. Learn more about the issue and CVE-ID at cve.org. CVE-2023-27043 RPAC Available for: macOS Sequoia Impact: An app may be able to modify protected parts of the file system Description: The issue was addressed with improved validation of environment variables. CVE-2025-24191: Claudio Bozzato and Francesco Benvenuto of Cisco Talos Safari Available for: macOS Sequoia Impact: Visiting a malicious website may lead to user interface spoofing Description: The issue was addressed with improved UI. CVE-2025-24113: @RenwaX23 Safari Available for: macOS Sequoia Impact: Visiting a malicious website may lead to address bar spoofing Description: The issue was addressed with improved checks. CVE-2025-30467: @RenwaX23 Safari Available for: macOS Sequoia Impact: A website may be able to access sensor information without user consent Description: The issue was addressed with improved checks. CVE-2025-31192: Jaydev Ahire Safari Available for: macOS Sequoia Impact: A download's origin may be incorrectly associated Description: This issue was addressed through improved state management. CVE-2025-24167: Syarif Muhammad Sajjad Sandbox Available for: macOS Sequoia Impact: An app may be able to access removable volumes without user consent Description: A permissions issue was addressed with additional restrictions. CVE-2025-24093: Yiğit Can YILMAZ (@yilmazcanyigit) Sandbox Available for: macOS Sequoia Impact: An input validation issue was addressed Description: The issue was addressed with improved checks. CVE-2025-30452: an anonymous researcher Sandbox Available for: macOS Sequoia Impact: An app may be able to access protected user data Description: A permissions issue was addressed with additional restrictions. CVE-2025-24181: Arsenii Kostromin (0x3c3e) SceneKit Available for: macOS Sequoia Impact: An app may be able to read files outside of its sandbox Description: A permissions issue was addressed with additional restrictions. CVE-2025-30458: Mickey Jin (@patch1t) Security Available for: macOS Sequoia Impact: A remote user may be able to cause a denial-of-service Description: A validation issue was addressed with improved logic. CVE-2025-30471: Bing Shi, Wenchao Li, Xiaolong Bai of Alibaba Group, Luyi Xing of Indiana University Bloomington Security Available for: macOS Sequoia Impact: A malicious app acting as a HTTPS proxy could get access to sensitive user data Description: This issue was addressed with improved access restrictions. CVE-2025-24250: Wojciech Regula of SecuRing (wojciechregula.blog) Share Sheet Available for: macOS Sequoia Impact: A malicious app may be able to dismiss the system notification on the Lock Screen that a recording was started Description: This issue was addressed with improved access restrictions. CVE-2025-30438: Halle Winkler, Politepix theoffcuts.org Shortcuts Available for: macOS Sequoia Impact: A shortcut may be able to access files that are normally inaccessible to the Shortcuts app Description: A permissions issue was addressed with improved validation. CVE-2025-30465: an anonymous researcher Shortcuts Available for: macOS Sequoia Impact: An app may be able to access user-sensitive data Description: An access issue was addressed with additional sandbox restrictions. CVE-2025-24280: Kirin (@Pwnrin) Shortcuts Available for: macOS Sequoia Impact: A Shortcut may run with admin privileges without authentication Description: An authentication issue was addressed with improved state management. CVE-2025-31194: Dolf Hoegaerts Shortcuts Available for: macOS Sequoia Impact: A shortcut may be able to access files that are normally inaccessible to the Shortcuts app Description: This issue was addressed with improved access restrictions. CVE-2025-30433: Andrew James Gonzalez Siri Available for: macOS Sequoia Impact: An app may be able to access sensitive user data Description: The issue was addressed with improved restriction of data container access. CVE-2025-31183: Kirin (@Pwnrin), Bohdan Stasiuk (@bohdan_stasiuk) Siri Available for: macOS Sequoia Impact: A sandboxed app may be able to access sensitive user data in system logs Description: This issue was addressed with improved redaction of sensitive information. CVE-2025-30435: K宝 (@Pwnrin) and luckyu (@uuulucky) Siri Available for: macOS Sequoia Impact: An app may be able to access sensitive user data Description: This issue was addressed with improved redaction of sensitive information. CVE-2025-24217: Kirin (@Pwnrin) Siri Available for: macOS Sequoia Impact: An app may be able to access sensitive user data Description: A privacy issue was addressed by not logging contents of text fields. CVE-2025-24214: Kirin (@Pwnrin) Siri Available for: macOS Sequoia Impact: An app may be able to enumerate devices that have signed into the user's Apple Account Description: A permissions issue was addressed with additional restrictions. CVE-2025-24248: Minghao Lin (@Y1nKoc) and Tong Liu@Lyutoon_ and 风(binary_fmyy) and F00L Siri Available for: macOS Sequoia Impact: An app may be able to access user-sensitive data Description: An authorization issue was addressed with improved state management. CVE-2025-24205: YingQi Shi(@Mas0nShi) of DBAppSecurity's WeBin lab and Minghao Lin (@Y1nKoc) Siri Available for: macOS Sequoia Impact: An attacker with physical access may be able to use Siri to access sensitive user data Description: This issue was addressed by restricting options offered on a locked device. CVE-2025-24198: Richard Hyunho Im (@richeeta) with routezero.security SMB Available for: macOS Sequoia Impact: An app may be able to cause unexpected system termination Description: The issue was addressed with improved memory handling. CVE-2025-24269: Alex Radocea of Supernetworks SMB Available for: macOS Sequoia Impact: Mounting a maliciously crafted SMB network share may lead to system termination Description: A race condition was addressed with improved locking. CVE-2025-30444: Dave G. SMB Available for: macOS Sequoia Impact: An app may be able to execute arbitrary code with kernel privileges Description: A buffer overflow issue was addressed with improved memory handling. CVE-2025-24228: Joseph Ravichandran (@0xjprx) of MIT CSAIL smbx Available for: macOS Sequoia Impact: An attacker in a privileged position may be able to perform a denial-of-service Description: The issue was addressed with improved memory handling. CVE-2025-24260: zbleet of QI-ANXIN TianGong Team Software Update Available for: macOS Sequoia Impact: An app may be able to modify protected parts of the file system Description: A library injection issue was addressed with additional restrictions. CVE-2025-24282: Claudio Bozzato and Francesco Benvenuto of Cisco Talos Software Update Available for: macOS Sequoia Impact: A user may be able to elevate privileges Description: This issue was addressed with improved validation of symlinks. CVE-2025-24254: Arsenii Kostromin (0x3c3e) Software Update Available for: macOS Sequoia Impact: An app may be able to modify protected parts of the file system Description: The issue was addressed with improved checks. CVE-2025-24231: Claudio Bozzato and Francesco Benvenuto of Cisco Talos StickerKit Available for: macOS Sequoia Impact: An app may be able to observe unprotected user data Description: A privacy issue was addressed by moving sensitive data to a protected location. CVE-2025-24263: Cristian Dinca of "Tudor Vianu" National High School of Computer Science, Romania Storage Management Available for: macOS Sequoia Impact: An app may be able to enable iCloud storage features without user consent Description: A permissions issue was addressed with additional restrictions. CVE-2025-24207: YingQi Shi (@Mas0nShi) of DBAppSecurity's WeBin lab, 风沐云烟 (binary_fmyy) and Minghao Lin (@Y1nKoc) StorageKit Available for: macOS Sequoia Impact: An app may be able to gain root privileges Description: A permissions issue was addressed with additional restrictions. CVE-2025-30449: Arsenii Kostromin (0x3c3e), and an anonymous researcher StorageKit Available for: macOS Sequoia Impact: An app may be able to access protected user data Description: This issue was addressed with improved handling of symlinks. CVE-2025-24253: Mickey Jin (@patch1t), Csaba Fitzl (@theevilbit) of Kandji StorageKit Available for: macOS Sequoia Impact: An app may be able to access user-sensitive data Description: A race condition was addressed with additional validation. CVE-2025-24240: Mickey Jin (@patch1t) StorageKit Available for: macOS Sequoia Impact: An app may be able to bypass Privacy preferences Description: A race condition was addressed with additional validation. CVE-2025-31188: Mickey Jin (@patch1t) Summarization Services Available for: macOS Sequoia Impact: An app may be able to access information about a user's contacts Description: A privacy issue was addressed with improved private data redaction for log entries. CVE-2025-24218: Kirin and FlowerCode, Bohdan Stasiuk (@bohdan_stasiuk) System Settings Available for: macOS Sequoia Impact: An app may be able to access protected user data Description: This issue was addressed with improved validation of symlinks. CVE-2025-24278: Zhongquan Li (@Guluisacat) System Settings Available for: macOS Sequoia Impact: An app with root privileges may be able to access private information Description: This issue was addressed with improved handling of symlinks. CVE-2025-24242: Koh M. Nakagawa (@tsunek0h) of FFRI Security, Inc. SystemMigration Available for: macOS Sequoia Impact: A malicious app may be able to create symlinks to protected regions of the disk Description: This issue was addressed with improved validation of symlinks. CVE-2025-30457: Mickey Jin (@patch1t) Voice Control Available for: macOS Sequoia Impact: An app may be able to access contacts Description: This issue was addressed with improved file handling. CVE-2025-24279: Mickey Jin (@patch1t) Web Extensions Available for: macOS Sequoia Impact: An app may gain unauthorized access to Local Network Description: This issue was addressed with improved permissions checking. CVE-2025-31184: Alexander Heinrich (@Sn0wfreeze), SEEMOO, TU Darmstadt & Mathy Vanhoef (@vanhoefm) and Jeroen Robben (@RobbenJeroen), DistriNet, KU Leuven Web Extensions Available for: macOS Sequoia Impact: Visiting a website may leak sensitive data Description: A script imports issue was addressed with improved isolation. CVE-2025-24192: Vsevolod Kokorin (Slonser) of Solidlab WebKit Available for: macOS Sequoia Impact: Processing maliciously crafted web content may lead to an unexpected Safari crash Description: The issue was addressed with improved memory handling. WebKit Bugzilla: 285892 CVE-2025-24264: Gary Kwong, and an anonymous researcher WebKit Bugzilla: 284055 CVE-2025-24216: Paul Bakker of ParagonERP WebKit Available for: macOS Sequoia Impact: A type confusion issue could lead to memory corruption Description: This issue was addressed with improved handling of floats. WebKit Bugzilla: 286694 CVE-2025-24213: Google V8 Security Team WebKit Available for: macOS Sequoia Impact: Processing maliciously crafted web content may lead to an unexpected process crash Description: A buffer overflow issue was addressed with improved memory handling. WebKit Bugzilla: 286462 CVE-2025-24209: Francisco Alonso (@revskills), and an anonymous researcher WebKit Available for: macOS Sequoia Impact: Processing maliciously crafted web content may lead to an unexpected Safari crash Description: A use-after-free issue was addressed with improved memory management. WebKit Bugzilla: 285643 CVE-2025-30427: rheza (@ginggilBesel) WebKit Available for: macOS Sequoia Impact: A malicious website may be able to track users in Safari private browsing mode Description: This issue was addressed through improved state management. WebKit Bugzilla: 286580 CVE-2025-30425: an anonymous researcher WindowServer Available for: macOS Sequoia Impact: An attacker may be able to cause unexpected app termination Description: A type confusion issue was addressed with improved checks. CVE-2025-24247: PixiePoint Security WindowServer Available for: macOS Sequoia Impact: An app may be able to trick a user into copying sensitive data to the pasteboard Description: A configuration issue was addressed with additional restrictions. CVE-2025-24241: Andreas Hegenberg (folivora.AI GmbH) Xsan Available for: macOS Sequoia Impact: An app may be able to cause unexpected system termination Description: A buffer overflow was addressed with improved bounds checking. CVE-2025-24266: an anonymous researcher Xsan Available for: macOS Sequoia Impact: An app may be able to cause unexpected system termination Description: An out-of-bounds read was addressed with improved bounds checking. CVE-2025-24265: an anonymous researcher Xsan Available for: macOS Sequoia Impact: An app may be able to cause unexpected system termination or corrupt kernel memory Description: A buffer overflow issue was addressed with improved memory handling. CVE-2025-24157: an anonymous researcher
@ 17538dc2:71ed77c4
2025-04-02 16:04:59The MacOS security update summary is a reminder that laptops and desktops are incredibly compromised. ### macOS Sequoia 15.4 Released March 31, 2025 Accessibility Available for: macOS Sequoia Impact: An app may be able to access sensitive user data Description: A logging issue was addressed with improved data redaction. CVE-2025-24202: Zhongcheng Li from IES Red Team of ByteDance AccountPolicy Available for: macOS Sequoia Impact: A malicious app may be able to gain root privileges Description: This issue was addressed by removing the vulnerable code. CVE-2025-24234: an anonymous researcher AirDrop Available for: macOS Sequoia Impact: An app may be able to read arbitrary file metadata Description: A permissions issue was addressed with additional restrictions. CVE-2025-24097: Ron Masas of BREAKPOINT.SH App Store Available for: macOS Sequoia Impact: A malicious app may be able to access private information Description: This issue was addressed by removing the vulnerable code. CVE-2025-24276: an anonymous researcher AppleMobileFileIntegrity Available for: macOS Sequoia Impact: An app may be able to modify protected parts of the file system Description: The issue was addressed with improved checks. CVE-2025-24272: Mickey Jin (@patch1t) AppleMobileFileIntegrity Available for: macOS Sequoia Impact: An app may be able to access protected user data Description: A downgrade issue was addressed with additional code-signing restrictions. CVE-2025-24239: Wojciech Regula of SecuRing (wojciechregula.blog) AppleMobileFileIntegrity Available for: macOS Sequoia Impact: A malicious app may be able to read or write to protected files Description: A permissions issue was addressed with additional restrictions. CVE-2025-24233: Claudio Bozzato and Francesco Benvenuto of Cisco Talos. AppleMobileFileIntegrity Available for: macOS Sequoia Impact: An app may be able to access user-sensitive data Description: A privacy issue was addressed by removing the vulnerable code. CVE-2025-30443: Bohdan Stasiuk (@bohdan_stasiuk) Audio Available for: macOS Sequoia Impact: Processing a maliciously crafted font may result in the disclosure of process memory Description: The issue was addressed with improved memory handling. CVE-2025-24244: Hossein Lotfi (@hosselot) of Trend Micro Zero Day Initiative Audio Available for: macOS Sequoia Impact: Processing a maliciously crafted file may lead to arbitrary code execution Description: The issue was addressed with improved memory handling. CVE-2025-24243: Hossein Lotfi (@hosselot) of Trend Micro Zero Day Initiative Authentication Services Available for: macOS Sequoia Impact: Password autofill may fill in passwords after failing authentication Description: This issue was addressed through improved state management. CVE-2025-30430: Dominik Rath Authentication Services Available for: macOS Sequoia Impact: A malicious website may be able to claim WebAuthn credentials from another website that shares a registrable suffix Description: The issue was addressed with improved input validation. CVE-2025-24180: Martin Kreichgauer of Google Chrome Authentication Services Available for: macOS Sequoia Impact: A malicious app may be able to access a user's saved passwords Description: This issue was addressed by adding a delay between verification code attempts. CVE-2025-24245: Ian Mckay (@iann0036) Automator Available for: macOS Sequoia Impact: An app may be able to access protected user data Description: A permissions issue was addressed by removing vulnerable code and adding additional checks. CVE-2025-30460: an anonymous researcher BiometricKit Available for: macOS Sequoia Impact: An app may be able to cause unexpected system termination Description: A buffer overflow was addressed with improved bounds checking. CVE-2025-24237: Yutong Xiu Calendar Available for: macOS Sequoia Impact: An app may be able to break out of its sandbox Description: A path handling issue was addressed with improved validation. CVE-2025-30429: Denis Tokarev (@illusionofcha0s) Calendar Available for: macOS Sequoia Impact: An app may be able to break out of its sandbox Description: This issue was addressed with improved checks. CVE-2025-24212: Denis Tokarev (@illusionofcha0s) CloudKit Available for: macOS Sequoia Impact: A malicious app may be able to access private information Description: The issue was addressed with improved checks. CVE-2025-24215: Kirin (@Pwnrin) CoreAudio Available for: macOS Sequoia Impact: Parsing a file may lead to an unexpected app termination Description: The issue was addressed with improved checks. CVE-2025-24163: Google Threat Analysis Group CoreAudio Available for: macOS Sequoia Impact: Playing a malicious audio file may lead to an unexpected app termination Description: An out-of-bounds read issue was addressed with improved input validation. CVE-2025-24230: Hossein Lotfi (@hosselot) of Trend Micro Zero Day Initiative CoreMedia Available for: macOS Sequoia Impact: Processing a maliciously crafted video file may lead to unexpected app termination or corrupt process memory Description: This issue was addressed with improved memory handling. CVE-2025-24211: Hossein Lotfi (@hosselot) of Trend Micro Zero Day Initiative CoreMedia Available for: macOS Sequoia Impact: An app may be able to access sensitive user data Description: An access issue was addressed with additional sandbox restrictions. CVE-2025-24236: Csaba Fitzl (@theevilbit) and Nolan Astrein of Kandji CoreMedia Available for: macOS Sequoia Impact: Processing a maliciously crafted video file may lead to unexpected app termination or corrupt process memory Description: The issue was addressed with improved memory handling. CVE-2025-24190: Hossein Lotfi (@hosselot) of Trend Micro Zero Day Initiative CoreMedia Playback Available for: macOS Sequoia Impact: A malicious app may be able to access private information Description: A path handling issue was addressed with improved validation. CVE-2025-30454: pattern-f (@pattern_F_) CoreServices Description: This issue was addressed through improved state management. CVE-2025-31191: Jonathan Bar Or (@yo_yo_yo_jbo) of Microsoft, and an anonymous researcher Available for: macOS Sequoia Impact: An app may be able to access sensitive user data CoreText Available for: macOS Sequoia Impact: Processing a maliciously crafted font may result in the disclosure of process memory Description: An out-of-bounds read issue was addressed with improved input validation. CVE-2025-24182: Hossein Lotfi (@hosselot) of Trend Micro Zero Day Initiative Crash Reporter Available for: macOS Sequoia Impact: An app may be able to gain root privileges Description: A parsing issue in the handling of directory paths was addressed with improved path validation. CVE-2025-24277: Csaba Fitzl (@theevilbit) of Kandji and Gergely Kalman (@gergely_kalman), and an anonymous researcher curl Available for: macOS Sequoia Impact: An input validation issue was addressed Description: This is a vulnerability in open source code and Apple Software is among the affected projects. The CVE-ID was assigned by a third party. Learn more about the issue and CVE-ID at cve.org. CVE-2024-9681 Disk Images Available for: macOS Sequoia Impact: An app may be able to break out of its sandbox Description: A file access issue was addressed with improved input validation. CVE-2025-24255: an anonymous researcher DiskArbitration Available for: macOS Sequoia Impact: An app may be able to gain root privileges Description: A parsing issue in the handling of directory paths was addressed with improved path validation. CVE-2025-30456: Gergely Kalman (@gergely_kalman) DiskArbitration Available for: macOS Sequoia Impact: An app may be able to gain root privileges Description: A permissions issue was addressed with additional restrictions. CVE-2025-24267: an anonymous researcher Dock Available for: macOS Sequoia Impact: A malicious app may be able to access private information Description: The issue was addressed with improved checks. CVE-2025-30455: Mickey Jin (@patch1t), and an anonymous researcher Dock Available for: macOS Sequoia Impact: An app may be able to modify protected parts of the file system Description: This issue was addressed by removing the vulnerable code. CVE-2025-31187: Rodolphe BRUNETTI (@eisw0lf) of Lupus Nova dyld Available for: macOS Sequoia Impact: Apps that appear to use App Sandbox may be able to launch without restrictions Description: A library injection issue was addressed with additional restrictions. CVE-2025-30462: Pietro Francesco Tirenna, Davide Silvetti, Abdel Adim Oisfi of Shielder (shielder.com) FaceTime Available for: macOS Sequoia Impact: An app may be able to access sensitive user data Description: This issue was addressed with improved redaction of sensitive information. CVE-2025-30451: Kirin (@Pwnrin) and luckyu (@uuulucky) FeedbackLogger Available for: macOS Sequoia Impact: An app may be able to access sensitive user data Description: This issue was addressed with improved data protection. CVE-2025-24281: Rodolphe BRUNETTI (@eisw0lf) Focus Available for: macOS Sequoia Impact: An attacker with physical access to a locked device may be able to view sensitive user information Description: The issue was addressed with improved checks. CVE-2025-30439: Andr.Ess Focus Available for: macOS Sequoia Impact: An app may be able to access sensitive user data Description: A logging issue was addressed with improved data redaction. CVE-2025-24283: Kirin (@Pwnrin) Foundation Available for: macOS Sequoia Impact: An app may be able to access protected user data Description: An access issue was addressed with additional sandbox restrictions on the system pasteboards. CVE-2025-30461: an anonymous researcher Foundation Available for: macOS Sequoia Impact: An app may be able to access sensitive user data Description: The issue was resolved by sanitizing logging CVE-2025-30447: LFY@secsys from Fudan University Foundation Available for: macOS Sequoia Impact: An app may be able to cause a denial-of-service Description: An uncontrolled format string issue was addressed with improved input validation. CVE-2025-24199: Manuel Fernandez (Stackhopper Security) GPU Drivers Available for: macOS Sequoia Impact: An app may be able to cause unexpected system termination or corrupt kernel memory Description: An out-of-bounds write issue was addressed with improved bounds checking. CVE-2025-30464: ABC Research s.r.o. CVE-2025-24273: Wang Yu of Cyberserval GPU Drivers Available for: macOS Sequoia Impact: An app may be able to disclose kernel memory Description: The issue was addressed with improved bounds checks. CVE-2025-24256: Anonymous working with Trend Micro Zero Day Initiative, Murray Mike Handoff Available for: macOS Sequoia Impact: An app may be able to access sensitive user data Description: The issue was addressed with improved restriction of data container access. CVE-2025-30463: mzzzz__ ImageIO Available for: macOS Sequoia Impact: Parsing an image may lead to disclosure of user information Description: A logic error was addressed with improved error handling. CVE-2025-24210: Anonymous working with Trend Micro Zero Day Initiative Installer Available for: macOS Sequoia Impact: An app may be able to check the existence of an arbitrary path on the file system Description: A permissions issue was addressed with additional sandbox restrictions. CVE-2025-24249: YingQi Shi(@Mas0nShi) of DBAppSecurity's WeBin lab and Minghao Lin (@Y1nKoc) Installer Available for: macOS Sequoia Impact: A sandboxed app may be able to access sensitive user data Description: A logic issue was addressed with improved checks. CVE-2025-24229: an anonymous researcher IOGPUFamily Available for: macOS Sequoia Impact: An app may be able to cause unexpected system termination or write kernel memory Description: An out-of-bounds write issue was addressed with improved input validation. CVE-2025-24257: Wang Yu of Cyberserval IOMobileFrameBuffer Available for: macOS Sequoia Impact: An app may be able to corrupt coprocessor memory Description: The issue was addressed with improved bounds checks. CVE-2025-30437: Ye Zhang (@VAR10CK) of Baidu Security Kerberos Helper Available for: macOS Sequoia Impact: A remote attacker may be able to cause unexpected app termination or heap corruption Description: A memory initialization issue was addressed with improved memory handling. CVE-2025-24235: Dave G. Kernel Available for: macOS Sequoia Impact: An app may be able to access protected user data Description: The issue was addressed with improved checks. CVE-2025-24204: Koh M. Nakagawa (@tsunek0h) of FFRI Security, Inc. Kernel Available for: macOS Sequoia Impact: An app may be able to modify protected parts of the file system Description: The issue was addressed with improved checks. CVE-2025-24203: Ian Beer of Google Project Zero Kernel Available for: macOS Sequoia Impact: An attacker with user privileges may be able to read kernel memory Description: A type confusion issue was addressed with improved memory handling. CVE-2025-24196: Joseph Ravichandran (@0xjprx) of MIT CSAIL LaunchServices Available for: macOS Sequoia Impact: A malicious JAR file may bypass Gatekeeper checks Description: This issue was addressed with improved handling of executable types. CVE-2025-24148: Kenneth Chew libarchive Available for: macOS Sequoia Impact: An input validation issue was addressed Description: This is a vulnerability in open source code and Apple Software is among the affected projects. The CVE-ID was assigned by a third party. Learn more about the issue and CVE-ID at cve.org. CVE-2024-48958 Libinfo Available for: macOS Sequoia Impact: A user may be able to elevate privileges Description: An integer overflow was addressed with improved input validation. CVE-2025-24195: Paweł Płatek (Trail of Bits) libnetcore Available for: macOS Sequoia Impact: Processing maliciously crafted web content may result in the disclosure of process memory Description: A logic issue was addressed with improved checks. CVE-2025-24194: an anonymous researcher libxml2 Available for: macOS Sequoia Impact: Parsing a file may lead to an unexpected app termination Description: This is a vulnerability in open source code and Apple Software is among the affected projects. The CVE-ID was assigned by a third party. Learn more about the issue and CVE-ID at cve.org. CVE-2025-27113 CVE-2024-56171 libxpc Available for: macOS Sequoia Impact: An app may be able to break out of its sandbox Description: This issue was addressed through improved state management. CVE-2025-24178: an anonymous researcher libxpc Available for: macOS Sequoia Impact: An app may be able to delete files for which it does not have permission Description: This issue was addressed with improved handling of symlinks. CVE-2025-31182: Alex Radocea and Dave G. of Supernetworks, 风沐云烟(@binary_fmyy) and Minghao Lin(@Y1nKoc) libxpc Available for: macOS Sequoia Impact: An app may be able to gain elevated privileges Description: A logic issue was addressed with improved checks. CVE-2025-24238: an anonymous researcher Mail Available for: macOS Sequoia Impact: "Block All Remote Content" may not apply for all mail previews Description: A permissions issue was addressed with additional sandbox restrictions. CVE-2025-24172: an anonymous researcher manpages Available for: macOS Sequoia Impact: An app may be able to access sensitive user data Description: This issue was addressed with improved validation of symlinks. CVE-2025-30450: Pwn2car Maps Available for: macOS Sequoia Impact: An app may be able to read sensitive location information Description: A path handling issue was addressed with improved logic. CVE-2025-30470: LFY@secsys from Fudan University NetworkExtension Available for: macOS Sequoia Impact: An app may be able to enumerate a user's installed apps Description: This issue was addressed with additional entitlement checks. CVE-2025-30426: Jimmy Notes Available for: macOS Sequoia Impact: A sandboxed app may be able to access sensitive user data in system logs Description: A privacy issue was addressed with improved private data redaction for log entries. CVE-2025-24262: LFY@secsys from Fudan University NSDocument Available for: macOS Sequoia Impact: A malicious app may be able to access arbitrary files Description: This issue was addressed through improved state management. CVE-2025-24232: an anonymous researcher OpenSSH Available for: macOS Sequoia Impact: An app may be able to access user-sensitive data Description: An injection issue was addressed with improved validation. CVE-2025-24246: Mickey Jin (@patch1t) PackageKit Available for: macOS Sequoia Impact: An app may be able to modify protected parts of the file system Description: The issue was addressed with improved checks. CVE-2025-24261: Mickey Jin (@patch1t) PackageKit Available for: macOS Sequoia Impact: An app may be able to modify protected parts of the file system Description: A logic issue was addressed with improved checks. CVE-2025-24164: Mickey Jin (@patch1t) PackageKit Available for: macOS Sequoia Impact: A malicious app with root privileges may be able to modify the contents of system files Description: A permissions issue was addressed with additional restrictions. CVE-2025-30446: Pedro Tôrres (@t0rr3sp3dr0) Parental Controls Available for: macOS Sequoia Impact: An app may be able to retrieve Safari bookmarks without an entitlement check Description: This issue was addressed with additional entitlement checks. CVE-2025-24259: Noah Gregory (wts.dev) Photos Storage Available for: macOS Sequoia Impact: Deleting a conversation in Messages may expose user contact information in system logging Description: A logging issue was addressed with improved data redaction. CVE-2025-30424: an anonymous researcher Power Services Available for: macOS Sequoia Impact: An app may be able to break out of its sandbox Description: This issue was addressed with additional entitlement checks. CVE-2025-24173: Mickey Jin (@patch1t) Python Available for: macOS Sequoia Impact: A remote attacker may be able to bypass sender policy checks and deliver malicious content via email Description: This is a vulnerability in open source code and Apple Software is among the affected projects. The CVE-ID was assigned by a third party. Learn more about the issue and CVE-ID at cve.org. CVE-2023-27043 RPAC Available for: macOS Sequoia Impact: An app may be able to modify protected parts of the file system Description: The issue was addressed with improved validation of environment variables. CVE-2025-24191: Claudio Bozzato and Francesco Benvenuto of Cisco Talos Safari Available for: macOS Sequoia Impact: Visiting a malicious website may lead to user interface spoofing Description: The issue was addressed with improved UI. CVE-2025-24113: @RenwaX23 Safari Available for: macOS Sequoia Impact: Visiting a malicious website may lead to address bar spoofing Description: The issue was addressed with improved checks. CVE-2025-30467: @RenwaX23 Safari Available for: macOS Sequoia Impact: A website may be able to access sensor information without user consent Description: The issue was addressed with improved checks. CVE-2025-31192: Jaydev Ahire Safari Available for: macOS Sequoia Impact: A download's origin may be incorrectly associated Description: This issue was addressed through improved state management. CVE-2025-24167: Syarif Muhammad Sajjad Sandbox Available for: macOS Sequoia Impact: An app may be able to access removable volumes without user consent Description: A permissions issue was addressed with additional restrictions. CVE-2025-24093: Yiğit Can YILMAZ (@yilmazcanyigit) Sandbox Available for: macOS Sequoia Impact: An input validation issue was addressed Description: The issue was addressed with improved checks. CVE-2025-30452: an anonymous researcher Sandbox Available for: macOS Sequoia Impact: An app may be able to access protected user data Description: A permissions issue was addressed with additional restrictions. CVE-2025-24181: Arsenii Kostromin (0x3c3e) SceneKit Available for: macOS Sequoia Impact: An app may be able to read files outside of its sandbox Description: A permissions issue was addressed with additional restrictions. CVE-2025-30458: Mickey Jin (@patch1t) Security Available for: macOS Sequoia Impact: A remote user may be able to cause a denial-of-service Description: A validation issue was addressed with improved logic. CVE-2025-30471: Bing Shi, Wenchao Li, Xiaolong Bai of Alibaba Group, Luyi Xing of Indiana University Bloomington Security Available for: macOS Sequoia Impact: A malicious app acting as a HTTPS proxy could get access to sensitive user data Description: This issue was addressed with improved access restrictions. CVE-2025-24250: Wojciech Regula of SecuRing (wojciechregula.blog) Share Sheet Available for: macOS Sequoia Impact: A malicious app may be able to dismiss the system notification on the Lock Screen that a recording was started Description: This issue was addressed with improved access restrictions. CVE-2025-30438: Halle Winkler, Politepix theoffcuts.org Shortcuts Available for: macOS Sequoia Impact: A shortcut may be able to access files that are normally inaccessible to the Shortcuts app Description: A permissions issue was addressed with improved validation. CVE-2025-30465: an anonymous researcher Shortcuts Available for: macOS Sequoia Impact: An app may be able to access user-sensitive data Description: An access issue was addressed with additional sandbox restrictions. CVE-2025-24280: Kirin (@Pwnrin) Shortcuts Available for: macOS Sequoia Impact: A Shortcut may run with admin privileges without authentication Description: An authentication issue was addressed with improved state management. CVE-2025-31194: Dolf Hoegaerts Shortcuts Available for: macOS Sequoia Impact: A shortcut may be able to access files that are normally inaccessible to the Shortcuts app Description: This issue was addressed with improved access restrictions. CVE-2025-30433: Andrew James Gonzalez Siri Available for: macOS Sequoia Impact: An app may be able to access sensitive user data Description: The issue was addressed with improved restriction of data container access. CVE-2025-31183: Kirin (@Pwnrin), Bohdan Stasiuk (@bohdan_stasiuk) Siri Available for: macOS Sequoia Impact: A sandboxed app may be able to access sensitive user data in system logs Description: This issue was addressed with improved redaction of sensitive information. CVE-2025-30435: K宝 (@Pwnrin) and luckyu (@uuulucky) Siri Available for: macOS Sequoia Impact: An app may be able to access sensitive user data Description: This issue was addressed with improved redaction of sensitive information. CVE-2025-24217: Kirin (@Pwnrin) Siri Available for: macOS Sequoia Impact: An app may be able to access sensitive user data Description: A privacy issue was addressed by not logging contents of text fields. CVE-2025-24214: Kirin (@Pwnrin) Siri Available for: macOS Sequoia Impact: An app may be able to enumerate devices that have signed into the user's Apple Account Description: A permissions issue was addressed with additional restrictions. CVE-2025-24248: Minghao Lin (@Y1nKoc) and Tong Liu@Lyutoon_ and 风(binary_fmyy) and F00L Siri Available for: macOS Sequoia Impact: An app may be able to access user-sensitive data Description: An authorization issue was addressed with improved state management. CVE-2025-24205: YingQi Shi(@Mas0nShi) of DBAppSecurity's WeBin lab and Minghao Lin (@Y1nKoc) Siri Available for: macOS Sequoia Impact: An attacker with physical access may be able to use Siri to access sensitive user data Description: This issue was addressed by restricting options offered on a locked device. CVE-2025-24198: Richard Hyunho Im (@richeeta) with routezero.security SMB Available for: macOS Sequoia Impact: An app may be able to cause unexpected system termination Description: The issue was addressed with improved memory handling. CVE-2025-24269: Alex Radocea of Supernetworks SMB Available for: macOS Sequoia Impact: Mounting a maliciously crafted SMB network share may lead to system termination Description: A race condition was addressed with improved locking. CVE-2025-30444: Dave G. SMB Available for: macOS Sequoia Impact: An app may be able to execute arbitrary code with kernel privileges Description: A buffer overflow issue was addressed with improved memory handling. CVE-2025-24228: Joseph Ravichandran (@0xjprx) of MIT CSAIL smbx Available for: macOS Sequoia Impact: An attacker in a privileged position may be able to perform a denial-of-service Description: The issue was addressed with improved memory handling. CVE-2025-24260: zbleet of QI-ANXIN TianGong Team Software Update Available for: macOS Sequoia Impact: An app may be able to modify protected parts of the file system Description: A library injection issue was addressed with additional restrictions. CVE-2025-24282: Claudio Bozzato and Francesco Benvenuto of Cisco Talos Software Update Available for: macOS Sequoia Impact: A user may be able to elevate privileges Description: This issue was addressed with improved validation of symlinks. CVE-2025-24254: Arsenii Kostromin (0x3c3e) Software Update Available for: macOS Sequoia Impact: An app may be able to modify protected parts of the file system Description: The issue was addressed with improved checks. CVE-2025-24231: Claudio Bozzato and Francesco Benvenuto of Cisco Talos StickerKit Available for: macOS Sequoia Impact: An app may be able to observe unprotected user data Description: A privacy issue was addressed by moving sensitive data to a protected location. CVE-2025-24263: Cristian Dinca of "Tudor Vianu" National High School of Computer Science, Romania Storage Management Available for: macOS Sequoia Impact: An app may be able to enable iCloud storage features without user consent Description: A permissions issue was addressed with additional restrictions. CVE-2025-24207: YingQi Shi (@Mas0nShi) of DBAppSecurity's WeBin lab, 风沐云烟 (binary_fmyy) and Minghao Lin (@Y1nKoc) StorageKit Available for: macOS Sequoia Impact: An app may be able to gain root privileges Description: A permissions issue was addressed with additional restrictions. CVE-2025-30449: Arsenii Kostromin (0x3c3e), and an anonymous researcher StorageKit Available for: macOS Sequoia Impact: An app may be able to access protected user data Description: This issue was addressed with improved handling of symlinks. CVE-2025-24253: Mickey Jin (@patch1t), Csaba Fitzl (@theevilbit) of Kandji StorageKit Available for: macOS Sequoia Impact: An app may be able to access user-sensitive data Description: A race condition was addressed with additional validation. CVE-2025-24240: Mickey Jin (@patch1t) StorageKit Available for: macOS Sequoia Impact: An app may be able to bypass Privacy preferences Description: A race condition was addressed with additional validation. CVE-2025-31188: Mickey Jin (@patch1t) Summarization Services Available for: macOS Sequoia Impact: An app may be able to access information about a user's contacts Description: A privacy issue was addressed with improved private data redaction for log entries. CVE-2025-24218: Kirin and FlowerCode, Bohdan Stasiuk (@bohdan_stasiuk) System Settings Available for: macOS Sequoia Impact: An app may be able to access protected user data Description: This issue was addressed with improved validation of symlinks. CVE-2025-24278: Zhongquan Li (@Guluisacat) System Settings Available for: macOS Sequoia Impact: An app with root privileges may be able to access private information Description: This issue was addressed with improved handling of symlinks. CVE-2025-24242: Koh M. Nakagawa (@tsunek0h) of FFRI Security, Inc. SystemMigration Available for: macOS Sequoia Impact: A malicious app may be able to create symlinks to protected regions of the disk Description: This issue was addressed with improved validation of symlinks. CVE-2025-30457: Mickey Jin (@patch1t) Voice Control Available for: macOS Sequoia Impact: An app may be able to access contacts Description: This issue was addressed with improved file handling. CVE-2025-24279: Mickey Jin (@patch1t) Web Extensions Available for: macOS Sequoia Impact: An app may gain unauthorized access to Local Network Description: This issue was addressed with improved permissions checking. CVE-2025-31184: Alexander Heinrich (@Sn0wfreeze), SEEMOO, TU Darmstadt & Mathy Vanhoef (@vanhoefm) and Jeroen Robben (@RobbenJeroen), DistriNet, KU Leuven Web Extensions Available for: macOS Sequoia Impact: Visiting a website may leak sensitive data Description: A script imports issue was addressed with improved isolation. CVE-2025-24192: Vsevolod Kokorin (Slonser) of Solidlab WebKit Available for: macOS Sequoia Impact: Processing maliciously crafted web content may lead to an unexpected Safari crash Description: The issue was addressed with improved memory handling. WebKit Bugzilla: 285892 CVE-2025-24264: Gary Kwong, and an anonymous researcher WebKit Bugzilla: 284055 CVE-2025-24216: Paul Bakker of ParagonERP WebKit Available for: macOS Sequoia Impact: A type confusion issue could lead to memory corruption Description: This issue was addressed with improved handling of floats. WebKit Bugzilla: 286694 CVE-2025-24213: Google V8 Security Team WebKit Available for: macOS Sequoia Impact: Processing maliciously crafted web content may lead to an unexpected process crash Description: A buffer overflow issue was addressed with improved memory handling. WebKit Bugzilla: 286462 CVE-2025-24209: Francisco Alonso (@revskills), and an anonymous researcher WebKit Available for: macOS Sequoia Impact: Processing maliciously crafted web content may lead to an unexpected Safari crash Description: A use-after-free issue was addressed with improved memory management. WebKit Bugzilla: 285643 CVE-2025-30427: rheza (@ginggilBesel) WebKit Available for: macOS Sequoia Impact: A malicious website may be able to track users in Safari private browsing mode Description: This issue was addressed through improved state management. WebKit Bugzilla: 286580 CVE-2025-30425: an anonymous researcher WindowServer Available for: macOS Sequoia Impact: An attacker may be able to cause unexpected app termination Description: A type confusion issue was addressed with improved checks. CVE-2025-24247: PixiePoint Security WindowServer Available for: macOS Sequoia Impact: An app may be able to trick a user into copying sensitive data to the pasteboard Description: A configuration issue was addressed with additional restrictions. CVE-2025-24241: Andreas Hegenberg (folivora.AI GmbH) Xsan Available for: macOS Sequoia Impact: An app may be able to cause unexpected system termination Description: A buffer overflow was addressed with improved bounds checking. CVE-2025-24266: an anonymous researcher Xsan Available for: macOS Sequoia Impact: An app may be able to cause unexpected system termination Description: An out-of-bounds read was addressed with improved bounds checking. CVE-2025-24265: an anonymous researcher Xsan Available for: macOS Sequoia Impact: An app may be able to cause unexpected system termination or corrupt kernel memory Description: A buffer overflow issue was addressed with improved memory handling. CVE-2025-24157: an anonymous researcher @ 06639a38:655f8f71
2025-04-02 13:47:57You can follow the work in progress here in this pull request [https://github.com/nostrver-se/nostr-php/pull/68](https://github.com/nostrver-se/nostr-php/pull/68) on Github. Before my 3-month break (Dec/Jan/Feb) working on Nostr-PHP I started with the NIP-19 integration in October '24. Encoding and decoding the simple prefixes (`npub`, `nsec` and `note`) was already done in the first commits. Learn more about NIP-19 here: [https://nips.nostr.com/19](https://nips.nostr.com/19) ### **TLV's** Things were getting more complicated with the other prefixes / identifiers defined in NIP-19: * `nevent` * `naddr` * `nprofile` This is because these identifiers contain (optional) metadata called Type-Lenght-Value aka TLV's. _When sharing a profile or an event, an app may decide to include relay information and other metadata such that other apps can locate and display these entities more easily._ _For these events, the contents are a binary-encoded list of_ `_TLV_` _(type-length-value), with_ `_T_` _and_ `_L_` _being 1 byte each (_`_uint8_`_, i.e. a number in the range of 0-255), and_ `_V_` _being a sequence of bytes of the size indicated by_ `_L_`_._ These possible standardized `TLV` types are: * `0`_:_ `special` * _depends on the bech32 prefix:_ * _for_ `nprofile` _it will be the 32 bytes of the profile public key_ * _for_ `nevent` _it will be the 32 bytes of the event id_ * _for_ `naddr`_, it is the identifier (the_ `"d"` _tag) of the event being referenced. For normal replaceable events use an empty string._ * `1`_:_ `relay` * _for_ `nprofile`_,_ `nevent` _and_ `naddr`_, optionally, a relay in which the entity (profile or event) is more likely to be found, encoded as ascii_ * _this may be included multiple times_ * `2`_:_ `author` * _for_ `naddr`_, the 32 bytes of the pubkey of the event_ * _for_ `nevent`_, optionally, the 32 bytes of the pubkey of the event_ * `3`_:_ `kind` * _for_ `naddr`_, the 32-bit unsigned integer of the kind, big-endian_ * _for_ `nevent`_, optionally, the 32-bit unsigned integer of the kind, big-endian_ These identifiers are formatted as bech32 strings, but are much longer than the package `bitwasp/bech32` (used in the library) for can handle for encoding and decoding. The bech32 strings handled by `bitwasp/bech32` are limited to a maximum length of 90 characters. Thanks to the effort of others (nostr:npub1636uujeewag8zv8593lcvdrwlymgqre6uax4anuq3y5qehqey05sl8qpl4 and nostr:npub1efz8l77esdtpw6l359sjvakm7azvyv6mkuxphjdk3vfzkgxkatrqlpf9s4) during my break, some contributions are made (modifiying the bech32 package supporting much longer strings, up to a max of 5000 characters). At this moment, I'm integrating this (mostly copy-pasting the stuff and refactoring the code): * [https://github.com/nostrver-se/nostr-php/issues/74](https://github.com/nostrver-se/nostr-php/issues/74) * [https://github.com/nostriphant/nip-19](https://github.com/nostriphant/nip-19) ### **So what's next?** * NIP-19 code housekeeping + refactoring * Prepare a new release with NIP-19 integration * Create documentation page how to use NIP-19 on [https://nostr-php.dev](https://nostr-php.dev)
@ 06639a38:655f8f71
2025-04-02 13:47:57You can follow the work in progress here in this pull request [https://github.com/nostrver-se/nostr-php/pull/68](https://github.com/nostrver-se/nostr-php/pull/68) on Github. Before my 3-month break (Dec/Jan/Feb) working on Nostr-PHP I started with the NIP-19 integration in October '24. Encoding and decoding the simple prefixes (`npub`, `nsec` and `note`) was already done in the first commits. Learn more about NIP-19 here: [https://nips.nostr.com/19](https://nips.nostr.com/19) ### **TLV's** Things were getting more complicated with the other prefixes / identifiers defined in NIP-19: * `nevent` * `naddr` * `nprofile` This is because these identifiers contain (optional) metadata called Type-Lenght-Value aka TLV's. _When sharing a profile or an event, an app may decide to include relay information and other metadata such that other apps can locate and display these entities more easily._ _For these events, the contents are a binary-encoded list of_ `_TLV_` _(type-length-value), with_ `_T_` _and_ `_L_` _being 1 byte each (_`_uint8_`_, i.e. a number in the range of 0-255), and_ `_V_` _being a sequence of bytes of the size indicated by_ `_L_`_._ These possible standardized `TLV` types are: * `0`_:_ `special` * _depends on the bech32 prefix:_ * _for_ `nprofile` _it will be the 32 bytes of the profile public key_ * _for_ `nevent` _it will be the 32 bytes of the event id_ * _for_ `naddr`_, it is the identifier (the_ `"d"` _tag) of the event being referenced. For normal replaceable events use an empty string._ * `1`_:_ `relay` * _for_ `nprofile`_,_ `nevent` _and_ `naddr`_, optionally, a relay in which the entity (profile or event) is more likely to be found, encoded as ascii_ * _this may be included multiple times_ * `2`_:_ `author` * _for_ `naddr`_, the 32 bytes of the pubkey of the event_ * _for_ `nevent`_, optionally, the 32 bytes of the pubkey of the event_ * `3`_:_ `kind` * _for_ `naddr`_, the 32-bit unsigned integer of the kind, big-endian_ * _for_ `nevent`_, optionally, the 32-bit unsigned integer of the kind, big-endian_ These identifiers are formatted as bech32 strings, but are much longer than the package `bitwasp/bech32` (used in the library) for can handle for encoding and decoding. The bech32 strings handled by `bitwasp/bech32` are limited to a maximum length of 90 characters. Thanks to the effort of others (nostr:npub1636uujeewag8zv8593lcvdrwlymgqre6uax4anuq3y5qehqey05sl8qpl4 and nostr:npub1efz8l77esdtpw6l359sjvakm7azvyv6mkuxphjdk3vfzkgxkatrqlpf9s4) during my break, some contributions are made (modifiying the bech32 package supporting much longer strings, up to a max of 5000 characters). At this moment, I'm integrating this (mostly copy-pasting the stuff and refactoring the code): * [https://github.com/nostrver-se/nostr-php/issues/74](https://github.com/nostrver-se/nostr-php/issues/74) * [https://github.com/nostriphant/nip-19](https://github.com/nostriphant/nip-19) ### **So what's next?** * NIP-19 code housekeeping + refactoring * Prepare a new release with NIP-19 integration * Create documentation page how to use NIP-19 on [https://nostr-php.dev](https://nostr-php.dev) @ 9dd283b1:cf9b6beb
2025-03-31 13:21:08Do you still feel anxiety when Bitcoin's price drops significantly, even though you're in fiat profit (100% +) ? Why or why not? And when did you truly stop feeling any emotional attachment to the price fluctuations? originally posted at https://stacker.news/items/930139
@ 9dd283b1:cf9b6beb
2025-03-31 13:21:08Do you still feel anxiety when Bitcoin's price drops significantly, even though you're in fiat profit (100% +) ? Why or why not? And when did you truly stop feeling any emotional attachment to the price fluctuations? originally posted at https://stacker.news/items/930139 @ 57d1a264:69f1fee1
2025-03-16 14:17:25Recently we shared an update for a new Open Cash Foundation website https://stacker.news/items/811604/r/Design_r Today a new logo by Vladimir Krstić!     File available for review at https://www.figma.com/design/Yxb4JEsjHYSibY06T8piB7/OpenCash%3A-Logo?node-id=151-249&p=f&t=FYyeTBkJznCKdbd7-0 https://primal.net/e/nevent1qvzqqqqqqypzqhzsmgfjj3l68068t84e0rtcfkcjh2k3c0jmdft4gy9wke2x8x6tqyg8wumn8ghj7efwdehhxtnvdakz7qgkwaehxw309ajkgetw9ehx7um5wghxcctwvshszrnhwden5te0dehhxtnvdakz7qpqryz9rj0wgshykjuzqksxxs50l7jfnwyvtkfmdvmudrg92s3xuxys8fqzr7 originally posted at https://stacker.news/items/914665
@ 57d1a264:69f1fee1
2025-03-16 14:17:25Recently we shared an update for a new Open Cash Foundation website https://stacker.news/items/811604/r/Design_r Today a new logo by Vladimir Krstić!     File available for review at https://www.figma.com/design/Yxb4JEsjHYSibY06T8piB7/OpenCash%3A-Logo?node-id=151-249&p=f&t=FYyeTBkJznCKdbd7-0 https://primal.net/e/nevent1qvzqqqqqqypzqhzsmgfjj3l68068t84e0rtcfkcjh2k3c0jmdft4gy9wke2x8x6tqyg8wumn8ghj7efwdehhxtnvdakz7qgkwaehxw309ajkgetw9ehx7um5wghxcctwvshszrnhwden5te0dehhxtnvdakz7qpqryz9rj0wgshykjuzqksxxs50l7jfnwyvtkfmdvmudrg92s3xuxys8fqzr7 originally posted at https://stacker.news/items/914665