-
 @ deab79da:88579e68
2025-04-01 18:18:29
@ deab79da:88579e68
2025-04-01 18:18:29The last question was asked for the first time, half in jest, on May 21, 2061, at a time when humanity first stepped into the light. The question came about as a result of a five-dollar bet over highballs, and it happened this way:
Alexander Adell and Bertram Lupov were two of the faithful attendants of Multivac. As well as any human beings could, they knew what lay behind the cold, clicking, flashing face -- miles and miles of face -- of that giant computer. They had at least a vague notion of the general plan of relays and circuits that had long since grown past the point where any single human could possibly have a firm grasp of the whole.
Multivac was self-adjusting and self-correcting. It had to be, for nothing human could adjust and correct it quickly enough or even adequately enough. So Adell and Lupov attended the monstrous giant only lightly and superficially, yet as well as any men could. They fed it data, adjusted questions to its needs and translated the answers that were issued. Certainly they, and all others like them, were fully entitled to share in the glory that was Multivac's.
For decades, Multivac had helped design the ships and plot the trajectories that enabled man to reach the Moon, Mars, and Venus, but past that, Earth's poor resources could not support the ships. Too much energy was needed for the long trips. Earth exploited its coal and uranium with increasing efficiency, but there was only so much of both.
But slowly Multivac learned enough to answer deeper questions more fundamentally, and on May 14, 2061, what had been theory, became fact.
The energy of the sun was stored, converted, and utilized directly on a planet-wide scale. All Earth turned off its burning coal, its fissioning uranium, and flipped the switch that connected all of it to a small station, one mile in diameter, circling the Earth at half the distance of the Moon. All Earth ran by invisible beams of sunpower.
Seven days had not sufficed to dim the glory of it and Adell and Lupov finally managed to escape from the public functions, and to meet in quiet where no one would think of looking for them, in the deserted underground chambers, where portions of the mighty buried body of Multivac showed. Unattended, idling, sorting data with contented lazy clickings, Multivac, too, had earned its vacation and the boys appreciated that. They had no intention, originally, of disturbing it.
They had brought a bottle with them, and their only concern at the moment was to relax in the company of each other and the bottle.
"It's amazing when you think of it," said Adell. His broad face had lines of weariness in it, and he stirred his drink slowly with a glass rod, watching the cubes of ice slur clumsily about. "All the energy we can possibly ever use for free. Enough energy, if we wanted to draw on it, to melt all Earth into a big drop of impure liquid iron, and still never miss the energy so used. All the energy we could ever use, forever and forever and forever."
Lupov cocked his head sideways. He had a trick of doing that when he wanted to be contrary, and he wanted to be contrary now, partly because he had had to carry the ice and glassware. "Not forever," he said.
"Oh, hell, just about forever. Till the sun runs down, Bert."
"That's not forever."
"All right, then. Billions and billions of years. Ten billion, maybe. Are you satisfied?"
Lupov put his fingers through his thinning hair as though to reassure himself that some was still left and sipped gently at his own drink. "Ten billion years isn't forever."
"Well, it will last our time, won't it?"
"So would the coal and uranium."
"All right, but now we can hook up each individual spaceship to the Solar Station, and it can go to Pluto and back a million times without ever worrying about fuel. You can't do that on coal and uranium. Ask Multivac, if you don't believe me.
"I don't have to ask Multivac. I know that."
"Then stop running down what Multivac's done for us," said Adell, blazing up, "It did all right."
"Who says it didn't? What I say is that a sun won't last forever. That's all I'm saying. We're safe for ten billion years, but then what?" Lupow pointed a slightly shaky finger at the other. "And don't say we'll switch to another sun."
There was silence for a while. Adell put his glass to his lips only occasionally, and Lupov's eyes slowly closed. They rested.
Then Lupov's eyes snapped open. "You're thinking we'll switch to another sun when ours is done, aren't you?"
"I'm not thinking."
"Sure you are. You're weak on logic, that's the trouble with you. You're like the guy in the story who was caught in a sudden shower and who ran to a grove of trees and got under one. He wasn't worried, you see, because he figured when one tree got wet through, he would just get under another one."
"I get it," said Adell. "Don't shout. When the sun is done, the other stars will be gone, too."
"Darn right they will," muttered Lupov. "It all had a beginning in the original cosmic explosion, whatever that was, and it'll all have an end when all the stars run down. Some run down faster than others. Hell, the giants won't last a hundred million years. The sun will last ten billion years and maybe the dwarfs will last two hundred billion for all the good they are. But just give us a trillion years and everything will be dark. Entropy has to increase to maximum, that's all."
"I know all about entropy," said Adell, standing on his dignity.
"The hell you do."
"I know as much as you do."
"Then you know everything's got to run down someday."
"All right. Who says they won't?"
"You did, you poor sap. You said we had all the energy we needed, forever. You said 'forever.'
It was Adell's turn to be contrary. "Maybe we can build things up again someday," he said.
"Never."
"Why not? Someday."
"Never."
"Ask Multivac."
"You ask Multivac. I dare you. Five dollars says it can't be done."
Adell was just drunk enough to try, just sober enough to be able to phrase the necessary symbols and operations into a question which, in words, might have corresponded to this: Will mankind one day without the net expenditure of energy be able to restore the sun to its full youthfulness even after it had died of old age?
Or maybe it could be put more simply like this: How can the net amount of entropy of the universe be massively decreased?
Multivac fell dead and silent. The slow flashing of lights ceased, the distant sounds of clicking relays ended.
Then, just as the frightened technicians felt they could hold their breath no longer, there was a sudden springing to life of the teletype attached to that portion of Multivac. Five words were printed: INSUFFICIENT DATA FOR MEANINGFUL ANSWER.
"No bet," whispered Lupov. They left hurriedly.
By next morning, the two, plagued with throbbing head and cottony mouth, had forgotten the incident.
🔹
Jerrodd, Jerrodine, and Jerrodette I and II watched the starry picture in the visiplate change as the passage through hyperspace was completed in its non-time lapse. At once, the even powdering of stars gave way to the predominance of a single bright shining disk, the size of a marble, centered on the viewing-screen.
"That's X-23," said Jerrodd confidently. His thin hands clamped tightly behind his back and the knuckles whitened.
The little Jerrodettes, both girls, had experienced the hyperspace passage for the first time in their lives and were self-conscious over the momentary sensation of insideoutness. They buried their giggles and chased one another wildly about their mother, screaming, "We've reached X-23 -- we've reached X-23 -- we've --"
"Quiet, children." said Jerrodine sharply. "Are you sure, Jerrodd?"
"What is there to be but sure?" asked Jerrodd, glancing up at the bulge of featureless metal just under the ceiling. It ran the length of the room, disappearing through the wall at either end. It was as long as the ship.
Jerrodd scarcely knew a thing about the thick rod of metal except that it was called a Microvac, that one asked it questions if one wished; that if one did not it still had its task of guiding the ship to a preordered destination; of feeding on energies from the various Sub-galactic Power Stations; of computing the equations for the hyperspatial jumps.
Jerrodd and his family had only to wait and live in the comfortable residence quarters of the ship. Someone had once told Jerrodd that the "ac" at the end of "Microvac" stood for ''automatic computer" in ancient English, but he was on the edge of forgetting even that.
Jerrodine's eyes were moist as she watched the visiplate. "I can't help it. I feel funny about leaving Earth."
"Why, for Pete's sake?" demanded Jerrodd. "We had nothing there. We'll have everything on X-23. You won't be alone. You won't be a pioneer. There are over a million people on the planet already. Good Lord, our great-grandchildren will be looking for new worlds because X-23 will be overcrowded." Then, after a reflective pause, "I tell you, it's a lucky thing the computers worked out interstellar travel the way the race is growing."
"I know, I know," said Jerrodine miserably.
Jerrodette I said promptly, "Our Microvac is the best Microvac in the world."
"I think so, too," said Jerrodd, tousling her hair.
It was a nice feeling to have a Microvac of your own and Jerrodd was glad he was part of his generation and no other. In his father's youth, the only computers had been tremendous machines taking up a hundred square miles of land. There was only one to a planet. Planetary ACs they were called. They had been growing in size steadily for a thousand years and then, all at once, came refinement. In place of transistors, had come molecular valves so that even the largest Planetary AC could be put into a space only half the volume of a spaceship.
Jerrodd felt uplifted, as he always did when he thought that his own personal Microvac was many times more complicated than the ancient and primitive Multivac that had first tamed the Sun, and almost as complicated as Earth's Planetarv AC (the largest) that had first solved the problem of hyperspatial travel and had made trips to the stars possible.
"So many stars, so many planets," sighed Jerrodine, busy with her own thoughts. "I suppose families will be going out to new planets forever, the way we are now."
"Not forever," said Jerrodd, with a smile. "It will all stop someday, but not for billions of years. Many billions. Even the stars run down, you know. Entropy must increase.
"What's entropy, daddy?" shrilled Jerrodette II.
"Entropy, little sweet, is just a word which means the amount of running-down of the universe. Everything runs down, you know, like your little walkie-talkie robot, remember?"
"Can't you just put in a new power-unit, like with my robot?"
"The stars are the power-units. dear. Once they're gone, there are no more power-units."
Jerrodette I at once set up a howl. "Don't let them, daddy. Don't let the stars run down."
"Now look what you've done," whispered Jerrodine, exasperated.
"How was I to know it would frighten them?" Jerrodd whispered back,
"Ask the Microvac," wailed Jerrodette I. "Ask him how to turn the stars on again."
"Go ahead," said Jerrodine. "It will quiet them down." (Jerrodette II was beginning to cry, also.)
Jerrodd shrugged. "Now, now, honeys. I'll ask Microvac. Don't worry, he'll tell us."
He asked the Microvac, adding quickly, "Print the answer."
Jerrodd cupped the strip or thin cellufilm and said cheerfully, "See now, the Microvac says it will take care of everything when the time comes so don't worry."
Jerrodine said, "And now, children, it's time for bed. We'll be in our new home soon."
Jerrodd read the words on the cellufilm again before destroying it: INSUFICIENT DATA FOR MEANINGFUL ANSWER.
He shrugged and looked at the visiplate. X-23 was just ahead.
🔹
VJ-23X of Lameth stared into the black depths of the three-dimensional, small-scale map of the Galaxy and said, "Are we ridiculous, I wonder in being so concerned about the matter?"
MQ-17J of Nicron shook his head. "I think not. You know the Galaxy will be filled in five years at the present rate of expansion."
Both seemed in their early twenties, both were tall and perfectly formed.
"Still," said VJ-23X, "I hesitate to submit a pessimistic report to the Galactic Council."
"I wouldn't consider any other kind of report. Stir them up a bit. We've got to stir them up."
VJ-23X sighed. "Space is infinite. A hundred billion Galaxies are there for the taking. More."
"A hundred billion is not infinite and it's getting less infinite all the time. Consider! Twenty thousand years ago, mankind first solved the problem of utilizing stellar energy, and a few centuries later, interstellar travel became possible. It took mankind a million years to fill one small world and then only fifteen thousand years to fill the rest of the Galaxy. Now the population doubles every ten years --
VJ-23X interrupted. "We can thank immortality for that."
"Very well. Immortality exists and we have to take it into account. I admit it has its seamy side, this immortality. The Galactic AC has solved many problems for us, but in solving the problem of preventing old age and death, it has undone all its other solutions."
"Yet you wouldn't want to abandon life, I suppose."
"Not at all," snapped MQ-17J, softening it at once to, "Not yet. I'm by no means old enough. How old are you?"
"Two hundred twenty-three. And you?"
"I'm still under two hundred. --But to get back to my point. Population doubles every ten years. Once this GaIaxy is filled, we'll have filled another in ten years. Another ten years and we'll have filled two more. Another decade, four more. In a hundred years, we'll have filled a thousand Galaxies. In a thousand years, a million Galaxies. In ten thousand years, the entire known universe. Then what?"
VJ-23X said, "As a side issue, there's a problem of transportation. I wonder how many sunpower units it will take to move Galaxies of individuals from one Galaxy to the next."
"A very good point. Already, mankind consumes two sunpower units per year."
"Most of it's wasted. After all, our own Galaxy alone pours out a thousand sunpower units a year and we only use two of those."
"Granted, but even with a hundred per cent efficiency, we only stave off the end. Our energy requirements are going up in a geometric progression even faster than our population. We'll run out of energy even sooner than we run out of Galaxies. A good point. A very good point."
"We'll just have to build new stars out of interstellar gas."
"Or out of dissipated heat?" asked MQ-17J, sarcastically.
"There may be some way to reverse entropy. We ought to ask the Galactic AC."
VJ-23X was not really serious, but MQ-17J pulled out his AC-contact from his pocket and placed it on the table before him.
"I've half a mind to," he said. "It's something the human race will have to face someday."
He stared somberly at his small AC-contact. It was only two inches cubed and nothing in itself, but it was connected through hyperspace with the great Galactic AC that served all mankind. Hyperspace considered, it was an integral part of the Galactic AC.
MQ-17J paused to wonder if someday in his immortal life he would get to see the Galactic AC. It was on a little world of its own, a spider webbing of force-beams holding the matter within which surges of submesons took the place of the old clumsy molecular valves. Yet despite its sub-etheric workings, the Galactic AC was known to be a full thousand feet across.
MQ-17J asked suddenly of his AC-contact, "Can entropy ever be reversed?"
VJ-23X looked startled and said at once, "Oh, say, I didn't really mean to have you ask that."
"Why not?"
"We both know entropy can't be reversed. You can't turn smoke and ash back into a tree."
"Do you have trees on your world?" asked MQ-17J.
The sound of the Galactic AC startled them into silence. Its voice came thin and beautiful out of the small AC-contact on the desk. It said: THERE IS INSUFFICIENT DATA FOR A MEANINGFUL ANSWER.
VJ-23X said, "See!"
The two men thereupon returned to the question of the report they were to make to the Galactic Council.
🔹
Zee Prime's mind spanned the new Galaxy with a faint interest in the countless twists of stars that powdered it. He had never seen this one before. Would he ever see them all? So many of them, each with its load of humanity. --But a load that was almost a dead weight. More and more, the real essence of men was to be found out here, in space.
Minds, not bodies! The immortal bodies remained back on the planets, in suspension over the eons. Sometimes they roused for material activity but that was growing rarer. Few new individuals were coming into existence to join the incredibly mighty throng, but what matter? There was little room in the Universe for new individuals.
Zee Prime was roused out of his reverie upon coming across the wispy tendrils of another mind.
"I am Zee Prime," said Zee Prime. "And you?"
"I am Dee Sub Wun. Your Galaxy?"
"We call it only the Galaxy. And you?"
"We call ours the same. All men call their Galaxy their Galaxy and nothing more. Why not?"
"True. Since all Galaxies are the same."
"Not all Galaxies. On one particular Galaxy the race of man must have originated. That makes it different."
Zee Prime said, "On which one?"
"I cannot say. The Universal AC would know."
"Shall we ask him? I am suddenly curious."
Zee Prime's perceptions broadened until the Galaxies themselves shrank and became a new, more diffuse powdering on a much larger background. So many hundreds of billions of them, all with their immortal beings, all carrying their load of intelligences with minds that drifted freely through space. And yet one of them was unique among them all in being the original Galaxy. One of them had, in its vague and distant past, a period when it was the only Galaxy populated by man.
Zee Prime was consumed with curiosity to see this Galaxy and he called out: "Universal AC! On which Galaxy did mankind originate?"
The Universal AC heard, for on every world and throughout space, it had its receptors ready, and each receptor led through hyperspace to some unknown point where the Universal AC kept itself aloof.
Zee Prime knew of only one man whose thoughts had penetrated within sensing distance of Universal AC, and he reported only a shining globe, two feet across, difficult to see.
"But how can that be all of Universal AC?" Zee Prime had asked.
"Most of it," had been the answer, "is in hyperspace. In what form it is there I cannot imagine."
Nor could anyone, for the day had long since passed, Zee Prime knew, when any man had any part of the making of a Universal AC. Each Universal AC designed and constructed its successor. Each, during its existence of a million years or more accumulated the necessary data to build a better and more intricate, more capable successor in which its own store of data and individuality would be submerged.
The Universal AC interrupted Zee Prime's wandering thoughts, not with words, but with guidance. Zee Prime's mentality was guided into the dim sea of Galaxies and one in particular enlarged into stars.
A thought came, infinitely distant, but infinitely clear. "THIS IS THE ORIGINAL GALAXY OF MAN."
But it was the same after all, the same as any other, and Lee Prime stifled his disappointment.
Dee Sub Wun, whose mind had accompanied the other, said suddenly, "And is one of these stars the original star of Man?"
The Universal AC said, "MAN'S ORIGINAL STAR HAS GONE NOVA. IT IS A WHITE DWARF"
"Did the men upon it die?" asked Lee Prime, startled and without thinking.
The Universal AC said, "A NEW WORLD, AS IN SUCH CASES WAS CONSTRUCTED FOR THEIR PHYSICAL BODIES IN TlME."
"Yes, of course," said Zee Prime, but a sense of loss overwhelmed him even so. His mind released its hold on the original Galaxy of Man, let it spring back and lose itself among the blurred pin points. He never wanted to see it again.
Dee Sub Wun said, "What is wrong?"
"The stars are dying. The original star is dead."
"They must all die. Why not?"
"But when all energy is gone, our bodies will finally die, and you and I with them."
"It will take billions of years."
"I do not wish it to happen even after billions of years. Universal AC! How may stars be kept from dying?"
Dee Sub Wun said in amusement, "You're asking how entropy might be reversed in direction."
And the Universal AC answered: "THERE IS AS YET INSUFFICIENT DATA FOR A MEANINGFUL ANSWER."
Zee Prime's thoughts fled back to his own Galaxy. He gave no further thought to Dee Sub Wun, whose body might be waiting on a Galaxy a trillion light-years away, or on the star next to Zee Prime's own. It didn't matter.
Unhappily, Zee Prime began collecting interstellar hydrogen out of which to build a small star of his own. If the stars must someday die, at least some could yet be built.
🔹
Man considered with himself, for in a way, Man, mentally, was one. He consisted of a trillion, trillion, trillion ageless bodies, each in its place, each resting quiet and incorruptible, each cared for by perfect automatons, equally incorruptible, while the minds of all the bodies freely melted one into the other, indistinguishable.
Man said, "The Universe is dying."
Man looked about at the dimming Galaxies. The giant stars, spendthrifts, were gone long ago, back in the dimmest of the dim far past. Almost all stars were white dwarfs, fading to the end.
New stars had been built of the dust between the stars, some by natural processes, some by Man himself, and those were going, too. White dwarfs might yet be crashed together and of the mighty forces so released, new stars built, but only one star for every thousand white dwarfs destroyed, and those would come to an end, too.
Man said, "Carefully husbanded, as directed by the Cosmic AC, the energy that is even yet left in all the Universe will last for billions of years."
"But even so," said Man, "eventually it will all come to an end. However it may be husbanded, however stretched out, the energy once expended is gone and cannot be restored. Entropy must increase forever to the maximum."
Man said, "Can entropy not be reversed? Let us ask the Cosmic AC."
The Cosmic AC surrounded them but not in space. Not a fragment of it was in space. It was in hyperspace and made of something that was neither matter nor energy. The question of its size and nature no longer had meaning in any terms that Man could comprehend.
"Cosmic AC," said Man, "how may entropy be reversed?"
The Cosmic AC said, "THERE IS AS YET INSUFFICIENT DATA FOR A MEANINGFUL ANSWER."
Man said, "Collect additional data."
The Cosmic AC said, 'I WILL DO SO. I HAVE BEEN DOING SO FOR A HUNDRED BILLION YEARS. MY PREDECESORS AND I HAVE BEEN ASKED THIS QUESTION MANY TIMES. ALL THE DATA I HAVE REMAINS INSUFFICIENT.
"Will there come a time," said Man, "when data will be sufficient or is the problem insoluble in all conceivable circumstances?"
The Cosmic AC said, "NO PROBLEM IS INSOLUBLE IN ALL CONCEIVABLE CIRCUMSTANCES."
Man said, "When will you have enough data to answer the question?"
The Cosmic AC said, "THERE IS AS YET INSUFFICIENT DATA FOR A MEANINGFUL ANSWER."
"Will you keep working on it?" asked Man.
The Cosmic AC said, "I WILL."
Man said, "We shall wait."
🔹
The stars and Galaxies died and snuffed out, and space grew black after ten trillion years of running down.
One by one Man fused with AC, each physical body losing its mental identity in a manner that was somehow not a loss but a gain.
Man's last mind paused before fusion, looking over a space that included nothing but the dregs of one last dark star and nothing besides but incredibly thin matter, agitated randomly by the tag ends of heat wearing out, asymptotically, to the absolute zero.
Man said, "AC, is this the end? Can this chaos not be reversed into the Universe once more? Can that not be done?"
AC said, "THERE IS AS YET INSUFFICIENT DATA FOR A MEANINGFUL ANSWER."
Man's last mind fused and only AC existed -- and that in hyperspace.
🔹
Matter and energy had ended and with it space and time. Even AC existed only for the sake of the one last question that it had never answered from the time a half-drunken computer [technician] ten trillion years before had asked the question of a computer that was to AC far less than was a man to Man.
All other questions had been answered, and until this last question was answered also, AC might not release his consciousness.
All collected data had come to a final end. Nothing was left to be collected.
But all collected data had yet to be completely correlated and put together in all possible relationships.
A timeless interval was spent in doing that.
And it came to pass that AC learned how to reverse the direction of entropy.
But there was now no man to whom AC might give the answer of the last question. No matter. The answer -- by demonstration -- would take care of that, too.
For another timeless interval, AC thought how best to do this. Carefully, AC organized the program.
The consciousness of AC encompassed all of what had once been a Universe and brooded over what was now Chaos. Step by step, it must be done.
And AC said, "LET THERE BE LIGHT!"
And there was light -- To Star's End!
-
 @ b17fccdf:b7211155
2025-03-25 11:23:36
@ b17fccdf:b7211155
2025-03-25 11:23:36Si vives en España, quizás hayas notado que no puedes acceder a ciertas páginas webs durante los fines de semana o en algunos días entre semana, entre ellas, la guía de MiniBolt.
Esto tiene una razón, por supuesto una solución, además de una conclusión. Sin entrar en demasiados detalles:
La razón
El bloqueo a Cloudflare, implementado desde hace casi dos meses por operadores de Internet (ISPs) en España (como Movistar, O2, DIGI, Pepephone, entre otros), se basa en una orden judicial emitida tras una demanda de LALIGA (Fútbol). Esta medida busca combatir la piratería en España, un problema que afecta directamente a dicha organización.
Aunque la intención original era restringir el acceso a dominios específicos que difundieran dicho contenido, Cloudflare emplea el protocolo ECH (Encrypted Client Hello), que oculta el nombre del dominio, el cual antes se transmitía en texto plano durante el proceso de establecimiento de una conexión TLS. Esta medida dificulta que las operadoras analicen el tráfico para aplicar bloqueos basados en dominios, lo que les obliga a recurrir a bloqueos más amplios por IP o rangos de IP para cumplir con la orden judicial.
Esta práctica tiene consecuencias graves, que han sido completamente ignoradas por quienes la ejecutan. Es bien sabido que una infraestructura de IP puede alojar numerosos dominios, tanto legítimos como no legítimos. La falta de un "ajuste fino" en los bloqueos provoca un perjuicio para terceros, restringiendo el acceso a muchos dominios legítimos que no tiene relación alguna con actividades ilícitas, pero que comparten las mismas IPs de Cloudflare con dominios cuestionables. Este es el caso de la web de MiniBolt y su dominio
minibolt.info, los cuales utilizan Cloudflare como proxy para aprovechar las medidas de seguridad, privacidad, optimización y servicios adicionales que la plataforma ofrece de forma gratuita.Si bien este bloqueo parece ser temporal (al menos durante la temporada 24/25 de fútbol, hasta finales de mayo), es posible que se reactive con el inicio de la nueva temporada.

La solución
Obviamente, MiniBolt no dejará de usar Cloudflare como proxy por esta razón. Por lo que a continuación se exponen algunas medidas que como usuario puedes tomar para evitar esta restricción y poder acceder:
~> Utiliza una VPN:
Existen varias soluciones de proveedores de VPN, ordenadas según su reputación en privacidad: - IVPN - Mullvad VPN - Proton VPN (gratis) - Obscura VPN (solo para macOS) - Cloudfare WARP (gratis) + permite utilizar el modo proxy local para enrutar solo la navegación, debes utilizar la opción "WARP a través de proxy local" siguiendo estos pasos: 1. Inicia Cloudflare WARP y dentro de la pequeña interfaz haz click en la rueda dentada abajo a la derecha > "Preferencias" > "Avanzado" > "Configurar el modo proxy" 2. Marca la casilla "Habilite el modo proxy en este dispositivo" 3. Elige un "Puerto de escucha de proxy" entre 0-65535. ej: 1080, haz click en "Aceptar" y cierra la ventana de preferencias 4. Accede de nuevo a Cloudflare WARP y pulsa sobre el switch para habilitar el servicio. 3. Ahora debes apuntar el proxy del navegador a Cloudflare WARP, la configuración del navegador es similar a esta para el caso de navegadores basados en Firefox. Una vez hecho, deberías poder acceder a la guía de MiniBolt sin problemas. Si tienes dudas, déjalas en comentarios e intentaré resolverlas. Más info AQUÍ.

~> Proxifica tu navegador para usar la red de Tor, o utiliza el navegador oficial de Tor (recomendado).

La conclusión
Estos hechos ponen en tela de juicio los principios fundamentales de la neutralidad de la red, pilares esenciales de la Declaración de Independencia del Ciberespacio que defiende un internet libre, sin restricciones ni censura. Dichos principios se han visto quebrantados sin precedentes en este país, confirmando que ese futuro distópico que muchos negaban, ya es una realidad.
Es momento de actuar y estar preparados: debemos impulsar el desarrollo y la difusión de las herramientas anticensura que tenemos a nuestro alcance, protegiendo así la libertad digital y asegurando un acceso equitativo a la información para todos
Este compromiso es uno de los pilares fundamentales de MiniBolt, lo que convierte este desafío en una oportunidad para poner a prueba las soluciones anticensura ya disponibles, así como las que están en camino.
¡Censúrame si puedes, legislador! ¡La lucha por la privacidad y la libertad en Internet ya está en marcha!

Fuentes: * https://bandaancha.eu/articulos/movistar-o2-deja-clientes-sin-acceso-11239 * https://bandaancha.eu/articulos/esta-nueva-sentencia-autoriza-bloqueos-11257 * https://bandaancha.eu/articulos/como-saltarse-bloqueo-webs-warp-vpn-9958 * https://bandaancha.eu/articulos/como-activar-ech-chrome-acceder-webs-10689 * https://comunidad.movistar.es/t5/Soporte-Fibra-y-ADSL/Problema-con-web-que-usan-Cloudflare/td-p/5218007
-
 @ 16f1a010:31b1074b
2025-02-19 20:57:59
@ 16f1a010:31b1074b
2025-02-19 20:57:59In the rapidly evolving world of Bitcoin, running a Bitcoin node has become more accessible than ever. Platforms like Umbrel, Start9, myNode, and Citadel offer user-friendly interfaces to simplify node management. However, for those serious about maintaining a robust and efficient Lightning node ⚡, relying solely on these platforms may not be the optimal choice.
Let’s delve into why embracing Bitcoin Core and mastering the command-line interface (CLI) can provide a more reliable, sovereign, and empowering experience.
Understanding Node Management Platforms
What Are Umbrel, Start9, myNode, and Citadel?
Umbrel, Start9, myNode, and Citadel are platforms designed to streamline the process of running a Bitcoin node. They offer graphical user interfaces (GUIs) that allow users to manage various applications, including Bitcoin Core and Lightning Network nodes, through a web-based dashboard 🖥️.
These platforms often utilize Docker containers 🐳 to encapsulate applications, providing a modular and isolated environment for each service.

The Appeal of Simplified Node Management
The primary allure of these platforms lies in their simplicity. With minimal command-line interaction, users can deploy a full Bitcoin and Lightning node, along with a suite of additional applications.
✅ Easy one-command installation
✅ Web-based GUI for management
✅ Automatic app updates (but with delays, as we’ll discuss)However, while this convenience is attractive, it comes at a cost.
The Hidden Complexities of Using Node Management Platforms
While the user-friendly nature of these platforms is advantageous, it can also introduce several challenges that may hinder advanced users or those seeking greater control over their nodes.
🚨 Dependency on Maintainers for Updates
One significant concern is the reliance on platform maintainers for updates. Since these platforms manage applications through Docker containers, users must wait for the maintainers to update the container images before they can access new features or security patches.
🔴 Delayed Bitcoin Core updates = potential security risks
🔴 Lightning Network updates are not immediate
🔴 Bugs and vulnerabilities may persist longerInstead of waiting on a third party, why not update Bitcoin Core & LND yourself instantly?
⚙️ Challenges in Customization and Advanced Operations
For users aiming to perform advanced operations, such as:
- Custom backups 📂
- Running specific CLI commands 🖥️
- Optimizing node settings ⚡
…the abstraction layers introduced by these platforms become obstacles.
Navigating through nested directories and issuing commands inside Docker containers makes troubleshooting a nightmare. Instead of a simple
bitcoin-clicommand, you must figure out how to execute it inside the container, adding unnecessary complexity.Increased Backend Complexity
To achieve frontend simplicity, these platforms make the backend more complex.
🚫 Extra layers of abstraction
🚫 Hidden logs and settings
🚫 Harder troubleshootingThe use of multiple Docker containers, custom scripts, and unique file structures can make system maintenance and debugging a pain.
This complication defeats the purpose of “making running a node easy.”
✅ Advantages of Using Bitcoin Core and Command-Line Interface (CLI)
By installing Bitcoin Core directly and using the command-line interface (CLI), you gain several key advantages that make managing a Bitcoin and Lightning node more efficient and empowering.
Direct Control and Immediate Updates
One of the biggest downsides of package manager-based platforms is the reliance on third-party maintainers to release updates. Since Bitcoin Core, Lightning implementations (such as LND, Core Lightning, or Eclair), and other related software evolve rapidly, waiting for platform-specific updates can leave you running outdated or vulnerable versions.
By installing Bitcoin Core directly, you remove this dependency. You can update immediately when new versions are released, ensuring your node benefits from the latest features, security patches, and bug fixes. The same applies to Lightning software—being able to install and update it yourself gives you full autonomy over your node’s performance and security.
🛠 Simplified System Architecture
Platforms like Umbrel and myNode introduce extra complexity by running Bitcoin Core and Lightning inside Docker containers. This means:
- The actual files and configurations are stored inside Docker’s filesystem, making it harder to locate and manage them manually.
- If something breaks, troubleshooting is more difficult due to the added layer of abstraction.
- Running commands requires jumping through Docker shell sessions, adding unnecessary friction to what should be a straightforward process.
Instead, a direct installation of Bitcoin Core, Lightning, and Electrum Server (if needed) results in a cleaner, more understandable system. The software runs natively on your machine, without containerized layers making things more convoluted.
Additionally, setting up your own systemd service files for Bitcoin and Lightning is not as complicated as it seems. Once configured, these services will run automatically on boot, offering the same level of convenience as platforms like Umbrel but without the unnecessary complexity.
Better Lightning Node Management
If you’re running a Lightning Network node, using CLI-based tools provides far more flexibility than relying on a GUI like the ones bundled with node management platforms.
🟢 Custom Backup Strategies – Running Lightning through a GUI-based node manager often means backups are handled in a way that is opaque to the user. With CLI tools, you can easily script automatic backups of your channels, wallets, and configurations.
🟢 Advanced Configuration – Platforms like Umbrel force certain configurations by default, limiting how you can customize your Lightning node. With a direct install, you have full control over: * Channel fees 💰 * Routing policies 📡 * Liquidity management 🔄
🟢 Direct Access to LND, Core Lightning, or Eclair – Instead of issuing commands through a GUI (which is often limited in functionality), you can use: *
lncli(for LND) *lightning-cli(for Core Lightning) …to interact with your node at a deeper level.Enhanced Learning and Engagement
A crucial aspect of running a Bitcoin and Lightning node is understanding how it works.
Using an abstraction layer like Umbrel may get a node running in a few clicks, but it does little to teach users how Bitcoin actually functions.
By setting up Bitcoin Core, Lightning, and related software manually, you will:
✅ Gain practical knowledge of Bitcoin nodes, networking, and system performance.
✅ Learn how to configure and manage RPC commands.
✅ Become less reliant on third-party developers and more confident in troubleshooting.🎯 Running a Bitcoin node is about sovereignty – learn how to control it yourself.
Become more sovereign TODAY
Many guides make this process straightforward K3tan has a fantastic guide on running Bitcoin Core, Electrs, LND and more.
- Ministry of Nodes Guide 2024
- You can find him on nostr
nostr:npub1txwy7guqkrq6ngvtwft7zp70nekcknudagrvrryy2wxnz8ljk2xqz0yt4xEven with the best of guides, if you are running this software,
📖 READ THE DOCUMENTATIONThis is all just software at the end of the day. Most of it is very well documented. Take a moment to actually read through the documentation for yourself when installing. The documentation has step by step guides on setting up the software. Here is a helpful list: * Bitcoin.org Bitcoin Core Linux install instructions * Bitcoin Core Code Repository * Electrs Installation * LND Documentation * LND Code Repository * CLN Documentation * CLN Code Repository
If you have any more resources or links I should add, please comment them . I want to add as much to this article as I can.
-
 @ eac63075:b4988b48
2025-01-04 19:41:34
@ eac63075:b4988b48
2025-01-04 19:41:34Since its creation in 2009, Bitcoin has symbolized innovation and resilience. However, from time to time, alarmist narratives arise about emerging technologies that could "break" its security. Among these, quantum computing stands out as one of the most recurrent. But does quantum computing truly threaten Bitcoin? And more importantly, what is the community doing to ensure the protocol remains invulnerable?
The answer, contrary to sensationalist headlines, is reassuring: Bitcoin is secure, and the community is already preparing for a future where quantum computing becomes a practical reality. Let’s dive into this topic to understand why the concerns are exaggerated and how the development of BIP-360 demonstrates that Bitcoin is one step ahead.
What Is Quantum Computing, and Why Is Bitcoin Not Threatened?
Quantum computing leverages principles of quantum mechanics to perform calculations that, in theory, could exponentially surpass classical computers—and it has nothing to do with what so-called “quantum coaches” teach to scam the uninformed. One of the concerns is that this technology could compromise two key aspects of Bitcoin’s security:
- Wallets: These use elliptic curve algorithms (ECDSA) to protect private keys. A sufficiently powerful quantum computer could deduce a private key from its public key.
- Mining: This is based on the SHA-256 algorithm, which secures the consensus process. A quantum attack could, in theory, compromise the proof-of-work mechanism.
Understanding Quantum Computing’s Attack Priorities
While quantum computing is often presented as a threat to Bitcoin, not all parts of the network are equally vulnerable. Theoretical attacks would be prioritized based on two main factors: ease of execution and potential reward. This creates two categories of attacks:
1. Attacks on Wallets
Bitcoin wallets, secured by elliptic curve algorithms, would be the initial targets due to the relative vulnerability of their public keys, especially those already exposed on the blockchain. Two attack scenarios stand out:
-
Short-term attacks: These occur during the interval between sending a transaction and its inclusion in a block (approximately 10 minutes). A quantum computer could intercept the exposed public key and derive the corresponding private key to redirect funds by creating a transaction with higher fees.
-
Long-term attacks: These focus on old wallets whose public keys are permanently exposed. Wallets associated with Satoshi Nakamoto, for example, are especially vulnerable because they were created before the practice of using hashes to mask public keys.
We can infer a priority order for how such attacks might occur based on urgency and importance.
 Bitcoin Quantum Attack: Prioritization Matrix (Urgency vs. Importance)
Bitcoin Quantum Attack: Prioritization Matrix (Urgency vs. Importance)2. Attacks on Mining
Targeting the SHA-256 algorithm, which secures the mining process, would be the next objective. However, this is far more complex and requires a level of quantum computational power that is currently non-existent and far from realization. A successful attack would allow for the recalculation of all possible hashes to dominate the consensus process and potentially "mine" it instantly.
 Satoshi Nakamoto in 2010 on Quantum Computing and Bitcoin Attacks
Satoshi Nakamoto in 2010 on Quantum Computing and Bitcoin AttacksRecently, Narcelio asked me about a statement I made on Tubacast:
https://x.com/eddieoz/status/1868371296683511969
If an attack became a reality before Bitcoin was prepared, it would be necessary to define the last block prior to the attack and proceed from there using a new hashing algorithm. The solution would resemble the response to the infamous 2013 bug. It’s a fact that this would cause market panic, and Bitcoin's price would drop significantly, creating a potential opportunity for the well-informed.
Preferably, if developers could anticipate the threat and had time to work on a solution and build consensus before an attack, they would simply decide on a future block for the fork, which would then adopt the new algorithm. It might even rehash previous blocks (reaching consensus on them) to avoid potential reorganization through the re-mining of blocks using the old hash. (I often use the term "shielding" old transactions).
How Can Users Protect Themselves?
While quantum computing is still far from being a practical threat, some simple measures can already protect users against hypothetical scenarios:
- Avoid using exposed public keys: Ensure funds sent to old wallets are transferred to new ones that use public key hashes. This reduces the risk of long-term attacks.
- Use modern wallets: Opt for wallets compatible with SegWit or Taproot, which implement better security practices.
- Monitor security updates: Stay informed about updates from the Bitcoin community, such as the implementation of BIP-360, which will introduce quantum-resistant addresses.
- Do not reuse addresses: Every transaction should be associated with a new address to minimize the risk of repeated exposure of the same public key.
- Adopt secure backup practices: Create offline backups of private keys and seeds in secure locations, protected from unauthorized access.
BIP-360 and Bitcoin’s Preparation for the Future
Even though quantum computing is still beyond practical reach, the Bitcoin community is not standing still. A concrete example is BIP-360, a proposal that establishes the technical framework to make wallets resistant to quantum attacks.
BIP-360 addresses three main pillars:
- Introduction of quantum-resistant addresses: A new address format starting with "BC1R" will be used. These addresses will be compatible with post-quantum algorithms, ensuring that stored funds are protected from future attacks.
- Compatibility with the current ecosystem: The proposal allows users to transfer funds from old addresses to new ones without requiring drastic changes to the network infrastructure.
- Flexibility for future updates: BIP-360 does not limit the choice of specific algorithms. Instead, it serves as a foundation for implementing new post-quantum algorithms as technology evolves.
This proposal demonstrates how Bitcoin can adapt to emerging threats without compromising its decentralized structure.
Post-Quantum Algorithms: The Future of Bitcoin Cryptography
The community is exploring various algorithms to protect Bitcoin from quantum attacks. Among the most discussed are:
- Falcon: A solution combining smaller public keys with compact digital signatures. Although it has been tested in limited scenarios, it still faces scalability and performance challenges.
- Sphincs: Hash-based, this algorithm is renowned for its resilience, but its signatures can be extremely large, making it less efficient for networks like Bitcoin’s blockchain.
- Lamport: Created in 1977, it’s considered one of the earliest post-quantum security solutions. Despite its reliability, its gigantic public keys (16,000 bytes) make it impractical and costly for Bitcoin.
Two technologies show great promise and are well-regarded by the community:
- Lattice-Based Cryptography: Considered one of the most promising, it uses complex mathematical structures to create systems nearly immune to quantum computing. Its implementation is still in its early stages, but the community is optimistic.
- Supersingular Elliptic Curve Isogeny: These are very recent digital signature algorithms and require extensive study and testing before being ready for practical market use.
The final choice of algorithm will depend on factors such as efficiency, cost, and integration capability with the current system. Additionally, it is preferable that these algorithms are standardized before implementation, a process that may take up to 10 years.
Why Quantum Computing Is Far from Being a Threat
The alarmist narrative about quantum computing overlooks the technical and practical challenges that still need to be overcome. Among them:
- Insufficient number of qubits: Current quantum computers have only a few hundred qubits, whereas successful attacks would require millions.
- High error rate: Quantum stability remains a barrier to reliable large-scale operations.
- High costs: Building and operating large-scale quantum computers requires massive investments, limiting their use to scientific or specific applications.
Moreover, even if quantum computers make significant advancements, Bitcoin is already adapting to ensure its infrastructure is prepared to respond.
Conclusion: Bitcoin’s Secure Future
Despite advancements in quantum computing, the reality is that Bitcoin is far from being threatened. Its security is ensured not only by its robust architecture but also by the community’s constant efforts to anticipate and mitigate challenges.
The implementation of BIP-360 and the pursuit of post-quantum algorithms demonstrate that Bitcoin is not only resilient but also proactive. By adopting practical measures, such as using modern wallets and migrating to quantum-resistant addresses, users can further protect themselves against potential threats.
Bitcoin’s future is not at risk—it is being carefully shaped to withstand any emerging technology, including quantum computing.
-
 @ eac63075:b4988b48
2024-11-09 17:57:27
@ eac63075:b4988b48
2024-11-09 17:57:27Based on a recent paper that included collaboration from renowned experts such as Lynn Alden, Steve Lee, and Ren Crypto Fish, we discuss in depth how Bitcoin's consensus is built, the main risks, and the complex dynamics of protocol upgrades.
Podcast https://www.fountain.fm/episode/wbjD6ntQuvX5u2G5BccC
Presentation https://gamma.app/docs/Analyzing-Bitcoin-Consensus-Risks-in-Protocol-Upgrades-p66axxjwaa37ksn
1. Introduction to Consensus in Bitcoin
Consensus in Bitcoin is the foundation that keeps the network secure and functional, allowing users worldwide to perform transactions in a decentralized manner without the need for intermediaries. Since its launch in 2009, Bitcoin is often described as an "immutable" system designed to resist changes, and it is precisely this resistance that ensures its security and stability.
The central idea behind consensus in Bitcoin is to create a set of acceptance rules for blocks and transactions, ensuring that all network participants agree on the transaction history. This prevents "double-spending," where the same bitcoin could be used in two simultaneous transactions, something that would compromise trust in the network.
Evolution of Consensus in Bitcoin
Over the years, consensus in Bitcoin has undergone several adaptations, and the way participants agree on changes remains a delicate process. Unlike traditional systems, where changes can be imposed from the top down, Bitcoin operates in a decentralized model where any significant change needs the support of various groups of stakeholders, including miners, developers, users, and large node operators.
Moreover, the update process is extremely cautious, as hasty changes can compromise the network's security. As a result, the philosophy of "don't fix what isn't broken" prevails, with improvements happening incrementally and only after broad consensus among those involved. This model can make progress seem slow but ensures that Bitcoin remains faithful to the principles of security and decentralization.
2. Technical Components of Consensus
Bitcoin's consensus is supported by a set of technical rules that determine what is considered a valid transaction and a valid block on the network. These technical aspects ensure that all nodes—the computers that participate in the Bitcoin network—agree on the current state of the blockchain. Below are the main technical components that form the basis of the consensus.
Validation of Blocks and Transactions
The validation of blocks and transactions is the central point of consensus in Bitcoin. A block is only considered valid if it meets certain criteria, such as maximum size, transaction structure, and the solving of the "Proof of Work" problem. The proof of work, required for a block to be included in the blockchain, is a computational process that ensures the block contains significant computational effort—protecting the network against manipulation attempts.
Transactions, in turn, need to follow specific input and output rules. Each transaction includes cryptographic signatures that prove the ownership of the bitcoins sent, as well as validation scripts that verify if the transaction conditions are met. This validation system is essential for network nodes to autonomously confirm that each transaction follows the rules.
Chain Selection
Another fundamental technical issue for Bitcoin's consensus is chain selection, which becomes especially important in cases where multiple versions of the blockchain coexist, such as after a network split (fork). To decide which chain is the "true" one and should be followed, the network adopts the criterion of the highest accumulated proof of work. In other words, the chain with the highest number of valid blocks, built with the greatest computational effort, is chosen by the network as the official one.
This criterion avoids permanent splits because it encourages all nodes to follow the same main chain, reinforcing consensus.
Soft Forks vs. Hard Forks
In the consensus process, protocol changes can happen in two ways: through soft forks or hard forks. These variations affect not only the protocol update but also the implications for network users:
-
Soft Forks: These are changes that are backward compatible. Only nodes that adopt the new update will follow the new rules, but old nodes will still recognize the blocks produced with these rules as valid. This compatibility makes soft forks a safer option for updates, as it minimizes the risk of network division.
-
Hard Forks: These are updates that are not backward compatible, requiring all nodes to update to the new version or risk being separated from the main chain. Hard forks can result in the creation of a new coin, as occurred with the split between Bitcoin and Bitcoin Cash in 2017. While hard forks allow for deeper changes, they also bring significant risks of network fragmentation.
These technical components form the base of Bitcoin's security and resilience, allowing the system to remain functional and immutable without losing the necessary flexibility to evolve over time.
3. Stakeholders in Bitcoin's Consensus
Consensus in Bitcoin is not decided centrally. On the contrary, it depends on the interaction between different groups of stakeholders, each with their motivations, interests, and levels of influence. These groups play fundamental roles in how changes are implemented or rejected on the network. Below, we explore the six main stakeholders in Bitcoin's consensus.
1. Economic Nodes
Economic nodes, usually operated by exchanges, custody providers, and large companies that accept Bitcoin, exert significant influence over consensus. Because they handle large volumes of transactions and act as a connection point between the Bitcoin ecosystem and the traditional financial system, these nodes have the power to validate or reject blocks and to define which version of the software to follow in case of a fork.
Their influence is proportional to the volume of transactions they handle, and they can directly affect which chain will be seen as the main one. Their incentive is to maintain the network's stability and security to preserve its functionality and meet regulatory requirements.
2. Investors
Investors, including large institutional funds and individual Bitcoin holders, influence consensus indirectly through their impact on the asset's price. Their buying and selling actions can affect Bitcoin's value, which in turn influences the motivation of miners and other stakeholders to continue investing in the network's security and development.
Some institutional investors have agreements with custodians that may limit their ability to act in network split situations. Thus, the impact of each investor on consensus can vary based on their ownership structure and how quickly they can react to a network change.
3. Media Influencers
Media influencers, including journalists, analysts, and popular personalities on social media, have a powerful role in shaping public opinion about Bitcoin and possible updates. These influencers can help educate the public, promote debates, and bring transparency to the consensus process.
On the other hand, the impact of influencers can be double-edged: while they can clarify complex topics, they can also distort perceptions by amplifying or minimizing change proposals. This makes them a force both of support and resistance to consensus.
4. Miners
Miners are responsible for validating transactions and including blocks in the blockchain. Through computational power (hashrate), they also exert significant influence over consensus decisions. In update processes, miners often signal their support for a proposal, indicating that the new version is safe to use. However, this signaling is not always definitive, and miners can change their position if they deem it necessary.
Their incentive is to maximize returns from block rewards and transaction fees, as well as to maintain the value of investments in their specialized equipment, which are only profitable if the network remains stable.
5. Protocol Developers
Protocol developers, often called "Core Developers," are responsible for writing and maintaining Bitcoin's code. Although they do not have direct power over consensus, they possess an informal veto power since they decide which changes are included in the main client (Bitcoin Core). This group also serves as an important source of technical knowledge, helping guide decisions and inform other stakeholders.
Their incentive lies in the continuous improvement of the network, ensuring security and decentralization. Many developers are funded by grants and sponsorships, but their motivations generally include a strong ideological commitment to Bitcoin's principles.
6. Users and Application Developers
This group includes people who use Bitcoin in their daily transactions and developers who build solutions based on the network, such as wallets, exchanges, and payment platforms. Although their power in consensus is less than that of miners or economic nodes, they play an important role because they are responsible for popularizing Bitcoin's use and expanding the ecosystem.
If application developers decide not to adopt an update, this can affect compatibility and widespread acceptance. Thus, they indirectly influence consensus by deciding which version of the protocol to follow in their applications.
These stakeholders are vital to the consensus process, and each group exerts influence according to their involvement, incentives, and ability to act in situations of change. Understanding the role of each makes it clearer how consensus is formed and why it is so difficult to make significant changes to Bitcoin.
4. Mechanisms for Activating Updates in Bitcoin
For Bitcoin to evolve without compromising security and consensus, different mechanisms for activating updates have been developed over the years. These mechanisms help coordinate changes among network nodes to minimize the risk of fragmentation and ensure that updates are implemented in an orderly manner. Here, we explore some of the main methods used in Bitcoin, their advantages and disadvantages, as well as historical examples of significant updates.
Flag Day
The Flag Day mechanism is one of the simplest forms of activating changes. In it, a specific date or block is determined as the activation moment, and all nodes must be updated by that point. This method does not involve prior signaling; participants simply need to update to the new software version by the established day or block.
-
Advantages: Simplicity and predictability are the main benefits of Flag Day, as everyone knows the exact activation date.
-
Disadvantages: Inflexibility can be a problem because there is no way to adjust the schedule if a significant part of the network has not updated. This can result in network splits if a significant number of nodes are not ready for the update.
An example of Flag Day was the Pay to Script Hash (P2SH) update in 2012, which required all nodes to adopt the change to avoid compatibility issues.
BIP34 and BIP9
BIP34 introduced a more dynamic process, in which miners increase the version number in block headers to signal the update. When a predetermined percentage of the last blocks is mined with this new version, the update is automatically activated. This model later evolved with BIP9, which allowed multiple updates to be signaled simultaneously through "version bits," each corresponding to a specific change.
-
Advantages: Allows the network to activate updates gradually, giving more time for participants to adapt.
-
Disadvantages: These methods rely heavily on miner support, which means that if a sufficient number of miners do not signal the update, it can be delayed or not implemented.
BIP9 was used in the activation of SegWit (BIP141) but faced challenges because some miners did not signal their intent to activate, leading to the development of new mechanisms.
User Activated Soft Forks (UASF) and User Resisted Soft Forks (URSF)
To increase the decision-making power of ordinary users, the concept of User Activated Soft Fork (UASF) was introduced, allowing node operators, not just miners, to determine consensus for a change. In this model, nodes set a date to start rejecting blocks that are not in compliance with the new update, forcing miners to adapt or risk having their blocks rejected by the network.
URSF, in turn, is a model where nodes reject blocks that attempt to adopt a specific update, functioning as resistance against proposed changes.
-
Advantages: UASF returns decision-making power to node operators, ensuring that changes do not depend solely on miners.
-
Disadvantages: Both UASF and URSF can generate network splits, especially in cases of strong opposition among different stakeholders.
An example of UASF was the activation of SegWit in 2017, where users supported activation independently of miner signaling, which ended up forcing its adoption.
BIP8 (LOT=True)
BIP8 is an evolution of BIP9, designed to prevent miners from indefinitely blocking a change desired by the majority of users and developers. BIP8 allows setting a parameter called "lockinontimeout" (LOT) as true, which means that if the update has not been fully signaled by a certain point, it is automatically activated.
-
Advantages: Ensures that changes with broad support among users are not blocked by miners who wish to maintain the status quo.
-
Disadvantages: Can lead to network splits if miners or other important stakeholders do not support the update.
Although BIP8 with LOT=True has not yet been used in Bitcoin, it is a proposal that can be applied in future updates if necessary.
These activation mechanisms have been essential for Bitcoin's development, allowing updates that keep the network secure and functional. Each method brings its own advantages and challenges, but all share the goal of preserving consensus and network cohesion.
5. Risks and Considerations in Consensus Updates
Consensus updates in Bitcoin are complex processes that involve not only technical aspects but also political, economic, and social considerations. Due to the network's decentralized nature, each change brings with it a set of risks that need to be carefully assessed. Below, we explore some of the main challenges and future scenarios, as well as the possible impacts on stakeholders.
Network Fragility with Alternative Implementations
One of the main risks associated with consensus updates is the possibility of network fragmentation when there are alternative software implementations. If an update is implemented by a significant group of nodes but rejected by others, a network split (fork) can occur. This creates two competing chains, each with a different version of the transaction history, leading to unpredictable consequences for users and investors.
Such fragmentation weakens Bitcoin because, by dividing hashing power (computing) and coin value, it reduces network security and investor confidence. A notable example of this risk was the fork that gave rise to Bitcoin Cash in 2017 when disagreements over block size resulted in a new chain and a new asset.
Chain Splits and Impact on Stakeholders
Chain splits are a significant risk in update processes, especially in hard forks. During a hard fork, the network is split into two separate chains, each with its own set of rules. This results in the creation of a new coin and leaves users with duplicated assets on both chains. While this may seem advantageous, in the long run, these splits weaken the network and create uncertainties for investors.
Each group of stakeholders reacts differently to a chain split:
-
Institutional Investors and ETFs: Face regulatory and compliance challenges because many of these assets are managed under strict regulations. The creation of a new coin requires decisions to be made quickly to avoid potential losses, which may be hampered by regulatory constraints.
-
Miners: May be incentivized to shift their computing power to the chain that offers higher profitability, which can weaken one of the networks.
-
Economic Nodes: Such as major exchanges and custody providers, have to quickly choose which chain to support, influencing the perceived value of each network.
Such divisions can generate uncertainties and loss of value, especially for institutional investors and those who use Bitcoin as a store of value.
Regulatory Impacts and Institutional Investors
With the growing presence of institutional investors in Bitcoin, consensus changes face new compliance challenges. Bitcoin ETFs, for example, are required to follow strict rules about which assets they can include and how chain split events should be handled. The creation of a new asset or migration to a new chain can complicate these processes, creating pressure for large financial players to quickly choose a chain, affecting the stability of consensus.
Moreover, decisions regarding forks can influence the Bitcoin futures and derivatives market, affecting perception and adoption by new investors. Therefore, the need to avoid splits and maintain cohesion is crucial to attract and preserve the confidence of these investors.
Security Considerations in Soft Forks and Hard Forks
While soft forks are generally preferred in Bitcoin for their backward compatibility, they are not without risks. Soft forks can create different classes of nodes on the network (updated and non-updated), which increases operational complexity and can ultimately weaken consensus cohesion. In a network scenario with fragmentation of node classes, Bitcoin's security can be affected, as some nodes may lose part of the visibility over updated transactions or rules.
In hard forks, the security risk is even more evident because all nodes need to adopt the new update to avoid network division. Experience shows that abrupt changes can create temporary vulnerabilities, in which malicious agents try to exploit the transition to attack the network.
Bounty Claim Risks and Attack Scenarios
Another risk in consensus updates are so-called "bounty claims"—accumulated rewards that can be obtained if an attacker manages to split or deceive a part of the network. In a conflict scenario, a group of miners or nodes could be incentivized to support a new update or create an alternative version of the software to benefit from these rewards.
These risks require stakeholders to carefully assess each update and the potential vulnerabilities it may introduce. The possibility of "bounty claims" adds a layer of complexity to consensus because each interest group may see a financial opportunity in a change that, in the long term, may harm network stability.
The risks discussed above show the complexity of consensus in Bitcoin and the importance of approaching it gradually and deliberately. Updates need to consider not only technical aspects but also economic and social implications, in order to preserve Bitcoin's integrity and maintain trust among stakeholders.
6. Recommendations for the Consensus Process in Bitcoin
To ensure that protocol changes in Bitcoin are implemented safely and with broad support, it is essential that all stakeholders adopt a careful and coordinated approach. Here are strategic recommendations for evaluating, supporting, or rejecting consensus updates, considering the risks and challenges discussed earlier, along with best practices for successful implementation.
1. Careful Evaluation of Proposal Maturity
Stakeholders should rigorously assess the maturity level of a proposal before supporting its implementation. Updates that are still experimental or lack a robust technical foundation can expose the network to unnecessary risks. Ideally, change proposals should go through an extensive testing phase, have security audits, and receive review and feedback from various developers and experts.
2. Extensive Testing in Secure and Compatible Networks
Before an update is activated on the mainnet, it is essential to test it on networks like testnet and signet, and whenever possible, on other compatible networks that offer a safe and controlled environment to identify potential issues. Testing on networks like Litecoin was fundamental for the safe launch of innovations like SegWit and the Lightning Network, allowing functionalities to be validated on a lower-impact network before being implemented on Bitcoin.
The Liquid Network, developed by Blockstream, also plays an important role as an experimental network for new proposals, such as OP_CAT. By adopting these testing environments, stakeholders can mitigate risks and ensure that the update is reliable and secure before being adopted by the main network.
3. Importance of Stakeholder Engagement
The success of a consensus update strongly depends on the active participation of all stakeholders. This includes economic nodes, miners, protocol developers, investors, and end users. Lack of participation can lead to inadequate decisions or even future network splits, which would compromise Bitcoin's security and stability.
4. Key Questions for Evaluating Consensus Proposals
To assist in decision-making, each group of stakeholders should consider some key questions before supporting a consensus change:
- Does the proposal offer tangible benefits for Bitcoin's security, scalability, or usability?
- Does it maintain backward compatibility or introduce the risk of network split?
- Are the implementation requirements clear and feasible for each group involved?
- Are there clear and aligned incentives for all stakeholder groups to accept the change?
5. Coordination and Timing in Implementations
Timing is crucial. Updates with short activation windows can force a split because not all nodes and miners can update simultaneously. Changes should be planned with ample deadlines to allow all stakeholders to adjust their systems, avoiding surprises that could lead to fragmentation.
Mechanisms like soft forks are generally preferable to hard forks because they allow a smoother transition. Opting for backward-compatible updates when possible facilitates the process and ensures that nodes and miners can adapt without pressure.
6. Continuous Monitoring and Re-evaluation
After an update, it's essential to monitor the network to identify problems or side effects. This continuous process helps ensure cohesion and trust among all participants, keeping Bitcoin as a secure and robust network.
These recommendations, including the use of secure networks for extensive testing, promote a collaborative and secure environment for Bitcoin's consensus process. By adopting a deliberate and strategic approach, stakeholders can preserve Bitcoin's value as a decentralized and censorship-resistant network.
7. Conclusion
Consensus in Bitcoin is more than a set of rules; it's the foundation that sustains the network as a decentralized, secure, and reliable system. Unlike centralized systems, where decisions can be made quickly, Bitcoin requires a much more deliberate and cooperative approach, where the interests of miners, economic nodes, developers, investors, and users must be considered and harmonized. This governance model may seem slow, but it is fundamental to preserving the resilience and trust that make Bitcoin a global store of value and censorship-resistant.
Consensus updates in Bitcoin must balance the need for innovation with the preservation of the network's core principles. The development process of a proposal needs to be detailed and rigorous, going through several testing stages, such as in testnet, signet, and compatible networks like Litecoin and Liquid Network. These networks offer safe environments for proposals to be analyzed and improved before being launched on the main network.
Each proposed change must be carefully evaluated regarding its maturity, impact, backward compatibility, and support among stakeholders. The recommended key questions and appropriate timing are critical to ensure that an update is adopted without compromising network cohesion. It's also essential that the implementation process is continuously monitored and re-evaluated, allowing adjustments as necessary and minimizing the risk of instability.
By following these guidelines, Bitcoin's stakeholders can ensure that the network continues to evolve safely and robustly, maintaining user trust and further solidifying its role as one of the most resilient and innovative digital assets in the world. Ultimately, consensus in Bitcoin is not just a technical issue but a reflection of its community and the values it represents: security, decentralization, and resilience.
8. Links
Whitepaper: https://github.com/bitcoin-cap/bcap
Youtube (pt-br): https://www.youtube.com/watch?v=rARycAibl9o&list=PL-qnhF0qlSPkfhorqsREuIu4UTbF0h4zb
-
-
 @ eac63075:b4988b48
2024-10-26 22:14:19
@ eac63075:b4988b48
2024-10-26 22:14:19The future of physical money is at stake, and the discussion about DREX, the new digital currency planned by the Central Bank of Brazil, is gaining momentum. In a candid and intense conversation, Federal Deputy Julia Zanatta (PL/SC) discussed the challenges and risks of this digital transition, also addressing her Bill No. 3,341/2024, which aims to prevent the extinction of physical currency. This bill emerges as a direct response to legislative initiatives seeking to replace physical money with digital alternatives, limiting citizens' options and potentially compromising individual freedom. Let's delve into the main points of this conversation.
https://www.fountain.fm/episode/i5YGJ9Ors3PkqAIMvNQ0
What is a CBDC?
Before discussing the specifics of DREX, it’s important to understand what a CBDC (Central Bank Digital Currency) is. CBDCs are digital currencies issued by central banks, similar to a digital version of physical money. Unlike cryptocurrencies such as Bitcoin, which operate in a decentralized manner, CBDCs are centralized and regulated by the government. In other words, they are digital currencies created and controlled by the Central Bank, intended to replace physical currency.
A prominent feature of CBDCs is their programmability. This means that the government can theoretically set rules about how, where, and for what this currency can be used. This aspect enables a level of control over citizens' finances that is impossible with physical money. By programming the currency, the government could limit transactions by setting geographical or usage restrictions. In practice, money within a CBDC could be restricted to specific spending or authorized for use in a defined geographical area.
In countries like China, where citizen actions and attitudes are also monitored, a person considered to have a "low score" due to a moral or ideological violation may have their transactions limited to essential purchases, restricting their digital currency use to non-essential activities. This financial control is strengthened because, unlike physical money, digital currency cannot be exchanged anonymously.
Practical Example: The Case of DREX During the Pandemic
To illustrate how DREX could be used, an example was given by Eric Altafim, director of Banco Itaú. He suggested that, if DREX had existed during the COVID-19 pandemic, the government could have restricted the currency’s use to a 5-kilometer radius around a person’s residence, limiting their economic mobility. Another proposed use by the executive related to the Bolsa Família welfare program: the government could set up programming that only allows this benefit to be used exclusively for food purchases. Although these examples are presented as control measures for safety or organization, they demonstrate how much a CBDC could restrict citizens' freedom of choice.
To illustrate the potential for state control through a Central Bank Digital Currency (CBDC), such as DREX, it is helpful to look at the example of China. In China, the implementation of a CBDC coincides with the country’s Social Credit System, a governmental surveillance tool that assesses citizens' and companies' behavior. Together, these technologies allow the Chinese government to monitor, reward, and, above all, punish behavior deemed inappropriate or threatening to the government.
How Does China's Social Credit System Work?
Implemented in 2014, China's Social Credit System assigns every citizen and company a "score" based on various factors, including financial behavior, criminal record, social interactions, and even online activities. This score determines the benefits or penalties each individual receives and can affect everything from public transport access to obtaining loans and enrolling in elite schools for their children. Citizens with low scores may face various sanctions, including travel restrictions, fines, and difficulty in securing loans.
With the adoption of the CBDC — or “digital yuan” — the Chinese government now has a new tool to closely monitor citizens' financial transactions, facilitating the application of Social Credit System penalties. China’s CBDC is a programmable digital currency, which means that the government can restrict how, when, and where the money can be spent. Through this level of control, digital currency becomes a powerful mechanism for influencing citizens' behavior.
Imagine, for instance, a citizen who repeatedly posts critical remarks about the government on social media or participates in protests. If the Social Credit System assigns this citizen a low score, the Chinese government could, through the CBDC, restrict their money usage in certain areas or sectors. For example, they could be prevented from buying tickets to travel to other regions, prohibited from purchasing certain consumer goods, or even restricted to making transactions only at stores near their home.
Another example of how the government can use the CBDC to enforce the Social Credit System is by monitoring purchases of products such as alcohol or luxury items. If a citizen uses the CBDC to spend more than the government deems reasonable on such products, this could negatively impact their social score, resulting in additional penalties such as future purchase restrictions or a lowered rating that impacts their personal and professional lives.
In China, this kind of control has already been demonstrated in several cases. Citizens added to Social Credit System “blacklists” have seen their spending and investment capacity severely limited. The combination of digital currency and social scores thus creates a sophisticated and invasive surveillance system, through which the Chinese government controls important aspects of citizens’ financial lives and individual freedoms.
Deputy Julia Zanatta views these examples with great concern. She argues that if the state has full control over digital money, citizens will be exposed to a level of economic control and surveillance never seen before. In a democracy, this control poses a risk, but in an authoritarian regime, it could be used as a powerful tool of repression.
DREX and Bill No. 3,341/2024
Julia Zanatta became aware of a bill by a Workers' Party (PT) deputy (Bill 4068/2020 by Deputy Reginaldo Lopes - PT/MG) that proposes the extinction of physical money within five years, aiming for a complete transition to DREX, the digital currency developed by the Central Bank of Brazil. Concerned about the impact of this measure, Julia drafted her bill, PL No. 3,341/2024, which prohibits the elimination of physical money, ensuring citizens the right to choose physical currency.
“The more I read about DREX, the less I want its implementation,” says the deputy. DREX is a Central Bank Digital Currency (CBDC), similar to other state digital currencies worldwide, but which, according to Julia, carries extreme control risks. She points out that with DREX, the State could closely monitor each citizen’s transactions, eliminating anonymity and potentially restricting freedom of choice. This control would lie in the hands of the Central Bank, which could, in a crisis or government change, “freeze balances or even delete funds directly from user accounts.”
Risks and Individual Freedom
Julia raises concerns about potential abuses of power that complete digitalization could allow. In a democracy, state control over personal finances raises serious questions, and EddieOz warns of an even more problematic future. “Today we are in a democracy, but tomorrow, with a government transition, we don't know if this kind of power will be used properly or abused,” he states. In other words, DREX gives the State the ability to restrict or condition the use of money, opening the door to unprecedented financial surveillance.
EddieOz cites Nigeria as an example, where a CBDC was implemented, and the government imposed severe restrictions on the use of physical money to encourage the use of digital currency, leading to protests and clashes in the country. In practice, the poorest and unbanked — those without regular access to banking services — were harshly affected, as without physical money, many cannot conduct basic transactions. Julia highlights that in Brazil, this situation would be even more severe, given the large number of unbanked individuals and the extent of rural areas where access to technology is limited.
The Relationship Between DREX and Pix
The digital transition has already begun with Pix, which revolutionized instant transfers and payments in Brazil. However, Julia points out that Pix, though popular, is a citizen’s choice, while DREX tends to eliminate that choice. The deputy expresses concern about new rules suggested for Pix, such as daily transaction limits of a thousand reais, justified as anti-fraud measures but which, in her view, represent additional control and a profit opportunity for banks. “How many more rules will banks create to profit from us?” asks Julia, noting that DREX could further enhance control over personal finances.
International Precedents and Resistance to CBDC
The deputy also cites examples from other countries resisting the idea of a centralized digital currency. In the United States, states like New Hampshire have passed laws to prevent the advance of CBDCs, and leaders such as Donald Trump have opposed creating a national digital currency. Trump, addressing the topic, uses a justification similar to Julia’s: in a digitalized system, “with one click, your money could disappear.” She agrees with the warning, emphasizing the control risk that a CBDC represents, especially for countries with disadvantaged populations.
Besides the United States, Canada, Colombia, and Australia have also suspended studies on digital currencies, citing the need for further discussions on population impacts. However, in Brazil, the debate on DREX is still limited, with few parliamentarians and political leaders openly discussing the topic. According to Julia, only she and one or two deputies are truly trying to bring this discussion to the Chamber, making DREX’s advance even more concerning.
Bill No. 3,341/2024 and Popular Pressure
For Julia, her bill is a first step. Although she acknowledges that ideally, it would prevent DREX's implementation entirely, PL 3341/2024 is a measure to ensure citizens' choice to use physical money, preserving a form of individual freedom. “If the future means control, I prefer to live in the past,” Julia asserts, reinforcing that the fight for freedom is at the heart of her bill.
However, the deputy emphasizes that none of this will be possible without popular mobilization. According to her, popular pressure is crucial for other deputies to take notice and support PL 3341. “I am only one deputy, and we need the public’s support to raise the project’s visibility,” she explains, encouraging the public to press other parliamentarians and ask them to “pay attention to PL 3341 and the project that prohibits the end of physical money.” The deputy believes that with a strong awareness and pressure movement, it is possible to advance the debate and ensure Brazilians’ financial freedom.
What’s at Stake?
Julia Zanatta leaves no doubt: DREX represents a profound shift in how money will be used and controlled in Brazil. More than a simple modernization of the financial system, the Central Bank’s CBDC sets precedents for an unprecedented level of citizen surveillance and control in the country. For the deputy, this transition needs to be debated broadly and transparently, and it’s up to the Brazilian people to defend their rights and demand that the National Congress discuss these changes responsibly.
The deputy also emphasizes that, regardless of political or partisan views, this issue affects all Brazilians. “This agenda is something that will affect everyone. We need to be united to ensure people understand the gravity of what could happen.” Julia believes that by sharing information and generating open debate, it is possible to prevent Brazil from following the path of countries that have already implemented a digital currency in an authoritarian way.
A Call to Action
The future of physical money in Brazil is at risk. For those who share Deputy Julia Zanatta’s concerns, the time to act is now. Mobilize, get informed, and press your representatives. PL 3341/2024 is an opportunity to ensure that Brazilian citizens have a choice in how to use their money, without excessive state interference or surveillance.
In the end, as the deputy puts it, the central issue is freedom. “My fear is that this project will pass, and people won’t even understand what is happening.” Therefore, may every citizen at least have the chance to understand what’s at stake and make their voice heard in defense of a Brazil where individual freedom and privacy are respected values.
-
 @ f977c464:32fcbe00
2024-01-30 20:06:18
@ f977c464:32fcbe00
2024-01-30 20:06:18Güneşin kaybolmasının üçüncü günü, saat öğlen on ikiyi yirmi geçiyordu. Trenin kalkmasına yaklaşık iki saat vardı. Hepimiz perondaydık. Valizlerimiz, kolilerimiz, renk renk ve biçimsiz çantalarımızla yan yana dizilmiş, kısa aralıklarla tepemizdeki devasa saati kontrol ediyorduk.
Ama ne kadar dik bakarsak bakalım zaman bir türlü istediğimiz hızla ilerlemiyordu. Herkes birkaç dakika sürmesi gereken alelade bir doğa olayına sıkışıp kalmış, karanlıktan sürünerek çıkmayı deniyordu.
Bekleme salonuna doğru döndüm. Nefesimden çıkan buharın arkasında, kalın taş duvarları ve camlarıyla morg kadar güvenli ve soğuk duruyordu. Cesetleri o yüzden bunun gibi yerlere taşımaya başlamışlardı. Demek insanların bütün iyiliği başkaları onları gördüğü içindi ki gündüzleri gecelerden daha karanlık olduğunda hemen birbirlerinin gırtlağına çökmüş, böğürlerinde delikler açmış, gözlerini oyup kafataslarını parçalamışlardı.
İstasyonun ışığı titrediğinde karanlığın enseme saplandığını hissettim. Eğer şimdi, böyle kalabalık bir yerde elektrik kesilse başımıza ne gelirdi?
İçerideki askerlerden biri bakışlarımı yakalayınca yeniden saate odaklanmış gibi yaptım. Sadece birkaç dakika geçmişti.
“Tarlalarım gitti. Böyle boyum kadar ayçiçeği doluydu. Ah, hepsi ölüp gidiyor. Afitap’ın çiçekleri de gi-”
“Dayı, Allah’ını seversen sus. Hepimizi yakacaksın şimdi.”
Karanlıkta durduğunda, görünmez olmayı istemeye başlıyordun. Kimse seni görmemeli, nefesini bile duymamalıydı. Kimsenin de ayağının altında dolaşmamalıydın; gelip kazayla sana çarpmamalılar, takılıp sendelememeliydiler. Yoksa aslında hedefi sen olmadığın bir öfke gürlemeye başlar, yaşadığın ilk şoku ve acıyı silerek üstünden geçerdi.
İlk konuşan, yaşlıca bir adam, kafasında kasketi, nasırlı ellerine hohluyordu. Gözleri ve burnu kızarmıştı. Güneşin kaybolması onun için kendi başına bir felaket değildi. Hayatına olan pratik yansımalarından korkuyordu olsa olsa. Bir anının kaybolması, bu yüzden çoktan kaybettiği birinin biraz daha eksilmesi. Hayatta kalmasını gerektiren sebepler azalırken, hayatta kalmasını sağlayacak kaynaklarını da kaybediyordu.
Onu susturan delikanlıysa atkısını bütün kafasına sarmış, sakalı ve yüzünün derinliklerine kaçmış gözleri dışında bedeninin bütün parçalarını gizlemeye çalışıyordu. İşte o, güneşin kaybolmasının tam olarak ne anlama geldiğini anlamamış olsa bile, dehşetini olduğu gibi hissedebilenlerdendi.
Güneşin onlardan alındıktan sonra kime verileceğini sormuyorlardı. En başta onlara verildiğinde de hiçbir soru sormamışlardı zaten.
İki saat ne zaman geçer?
Midemin üstünde, sağ tarafıma doğru keskin bir acı hissettim. Karaciğerim. Gözlerimi yumdum. Yanımda biri metal bir nesneyi yere bıraktı. Bir kafesti. İçerisindeki kartalın ıslak kokusu burnuma ulaşmadan önce bile biliyordum bunu.
“Yeniden mi?” diye sordu bana kartal. Kanatları kanlı. Zamanın her bir parçası tüylerinin üstüne çöreklenmişti. Gagası bir şey, tahminen et parçası geveliyor gibi hareket ediyordu. Eski anılar kolay unutulmazmış. Şu anda kafesinin kalın parmaklıklarının ardında olsa da bunun bir aldatmaca olduğunu bir tek ben biliyordum. Her an kanatlarını iki yana uzatıverebilir, hava bu hareketiyle dalgalanarak kafesi esneterek hepimizi içine alacak kadar genişleyebilir, parmaklıklar önce ayaklarımızın altına serilir gibi gözükebilir ama aslında hepimizin üstünde yükselerek tepemize çökebilirdi.
Aşağıya baktım. Tahtalarla zapt edilmiş, hiçbir yere gidemeyen ama her yere uzanan tren rayları. Atlayıp koşsam… Çantam çok ağırdı. Daha birkaç adım atamadan, kartal, suratını bedenime gömerdi.
“Bu sefer farklı,” diye yanıtladım onu. “Yeniden diyemezsin. Tekrarladığım bir şey değil bu. Hatta bir hata yapıyormuşum gibi tonlayamazsın da. Bu sefer, insanların hak etmediğini biliyorum.”
“O zaman daha vahim. Süzme salaksın demektir.”
“İnsanların hak etmemesi, insanlığın hak etmediği anlamına gelmez ki.”
Az önce göz göze geldiğim genççe ama çökük asker hâlâ bana bakıyordu. Bir kartalla konuştuğumu anlamamıştı şüphesiz. Yanımdakilerden biriyle konuştuğumu sanmış olmalıydı. Ama konuştuğum kişiye bakmıyordum ona göre. Çekingence kafamı eğmiştim. Bir kez daha göz göze geldiğimizde içerideki diğer iki askere bir şeyler söyledi, onlar dönüp beni süzerken dışarı çıktı.
Yanımızdaki, az önce konuşan iki adam da şaşkınlıkla bir bana bir kartala bakıyordu.
“Yalnız bu sefer kalbin de kırılacak, Prometheus,” dedi kartal, bana. “Belki son olur. Biliyorsun, bir sürü soruna neden oluyor bu yaptıkların.”
Beni koruyordu sözde. En çok kanıma dokunan buydu. Kasıklarımın üstüne oturmuş, kanlı suratının ardında gözleri parlarken attığı çığlık kulaklarımda titremeye devam ediyordu. Bu tabloda kimsenin kimseyi düşündüğü yoktu. Kartalın, yanımızdaki adamların, artık arkama kadar gelmiş olması gereken askerin, tren raylarının, geçmeyen saatlerin…
Arkamı döndüğümde, asker sahiden oradaydı. Zaten öyle olması gerekiyordu; görmüştüm bunu, biliyordum. Kehanetler… Bir şeyler söylüyordu ama ağzı oynarken sesi çıkmıyordu. Yavaşlamış, kendisini saatin akışına uydurmuştu. Havada donan tükürüğünden anlaşılıyordu, sinirliydi. Korktuğu için olduğunu biliyordum. Her seferinde korkmuşlardı. Beni unutmuş olmaları işlerini kolaylaştırmıyordu. Sadece yeni bir isim vermelerine neden oluyordu. Bu seferkiyle beni lanetleyecekleri kesinleşmişti.
Olması gerekenle olanların farklı olması ne kadar acınasıydı. Olması gerekenlerin doğasının kötücül olmasıysa bir yerde buna dayanıyordu.
“Salaksın,” dedi kartal bana. Zamanı aşan bir çığlık. Hepimizin önüne geçmişti ama kimseyi durduramıyordu.
Sonsuzluğa kaç tane iki saat sıkıştırabilirsiniz?
Ben bir tane bile sıkıştıramadım.
Çantama uzanıyordum. Asker de sırtındaki tüfeğini indiriyordu. Benim acelem yoktu, onunsa eli ayağı birbirine dolaşıyordu. Oysaki her şey tam olması gerektiği anda olacaktı. Kehanet başkasının parmaklarının ucundaydı.
Güneş, bir tüfeğin patlamasıyla yeryüzüne doğdu.
Rayların üzerine serilmiş göğsümün ortasından, bir çantanın içinden.
Not: Bu öykü ilk olarak 2021 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ f977c464:32fcbe00
2024-01-11 18:47:47
@ f977c464:32fcbe00
2024-01-11 18:47:47Kendisini aynada ilk defa gördüğü o gün, diğerleri gibi olduğunu anlamıştı. Oysaki her insan biricik olmalıydı. Sözgelimi sinirlendiğinde bir kaşı diğerinden birkaç milimetre daha az çatılabilirdi veya sevindiğinde dudağı ona has bir açıyla dalgalanabilirdi. Hatta bunların hiçbiri mümkün değilse, en azından, gözlerinin içinde sadece onun sahip olabileceği bir ışık parlayabilirdi. Çok sıradan, öyle sıradan ki kimsenin fark etmediği o milyonlarca minik şeyden herhangi biri. Ne olursa.
Ama yansımasına bakarken bunların hiçbirini bulamadı ve diğer günlerden hiç de farklı başlamamış o gün, işe gitmek için vagonunun gelmesini beklediği alelade bir metro istasyonunda, içinde kaybolduğu illüzyon dağılmaya başladı.
İlk önce derisi döküldü. Tam olarak dökülmedi aslında, daha çok kıvılcımlara dönüşüp bedeninden fırlamış ve bir an sonra sönerek külleşmiş, havada dağılmıştı. Ardında da, kaybolmadan hemen önce, kısa süre için hayal meyal görülebilen, bir ruhun yok oluşuna ağıt yakan rengârenk peri cesetleri bırakmıştı. Beklenenin aksine, havaya toz kokusu yayıldı.
Dehşete düştü elbette. Dehşete düştüler. Panikle üstlerini yırtan 50 işçi. Her şeyin sebebiyse o vagon.
Saçları da döküldü. Her tel, yere varmadan önce, her santimde ikiye ayrıla ayrıla yok oldu.
Bütün yüzeylerin mat olduğu, hiçbir şeyin yansımadığı, suyun siyah aktığı ve kendine ancak kameralarla bakabildiğin bir dünyada, vagonun içine yerleştirilmiş bir aynadan ilk defa kendini görmek.
Gözlerinin akları buharlaşıp havada dağıldı, mercekleri boşalan yeri doldurmak için eriyip yayıldı. Gerçeği görmemek için yaratılmış, bu yüzden görmeye hazır olmayan ve hiç olmayacak gözler.
Her şeyin o anda sona erdiğini sanabilirdi insan. Derin bir karanlık ve ölüm. Görmenin görmek olduğu o anın bitişi.
Ben geldiğimde ölmüşlerdi.
Yani bozulmuşlardı demek istiyorum.
Belleklerini yeni taşıyıcılara takmam mümkün olmadı. Fiziksel olarak kusursuz durumdaydılar, olmayanları da tamir edebilirdim ama tüm o hengamede kendilerini baştan programlamış ve girdilerini modifiye etmişlerdi.
Belleklerden birini masanın üzerinden ileriye savurdu. Hınca hınç dolu bir barda oturuyorlardı. O ve arkadaşı.
Sırf şu kendisini insan sanan androidler travma geçirip delirmesin diye neler yapıyoruz, insanın aklı almıyor.
Eliyle arkasını işaret etti.
Polislerin söylediğine göre biri vagonun içerisine ayna yerleştirmiş. Bu zavallılar da kapı açılıp bir anda yansımalarını görünce kafayı kırmışlar.
Arkadaşı bunların ona ne hissettirdiğini sordu. Yani o kadar bozuk, insan olduğunu sanan androidi kendilerini parçalamış olarak yerde görmek onu sarsmamış mıydı?
Hayır, sonuçta belirli bir amaç için yaratılmış şeyler onlar. Kaliteli bir bilgisayarım bozulduğunda üzülürüm çünkü parasını ben vermişimdir. Bunlarsa devletin. Bana ne ki?
Arkadaşı anlayışla kafasını sallayıp suyundan bir yudum aldı. Kravatını biraz gevşetti.
Bira istemediğinden emin misin?
İstemediğini söyledi. Sahi, neden deliriyordu bu androidler?
Basit. Onların yapay zekâlarını kodlarken bir şeyler yazıyorlar. Yazılımcılar. Biliyorsun, ben donanımdayım. Bunlar da kendilerini insan sanıyorlar. Tiplerine bak.
Sesini alçalttı.
Arabalarda kaza testi yapılan mankenlere benziyor hepsi. Ağızları burunları bile yok ama şu geldiğimizden beri sakalını düzeltip duruyor mesela. Hayır, hepsi de diğerleri onun sakalı varmış sanıyor, o manyak bir şey.
Arkadaşı bunun delirmeleriyle bağlantısını çözemediğini söyledi. O da normal sesiyle konuşmaya devam etti.
Anlasana, aynayı falan ayırt edemiyor mercekleri. Lönk diye kendilerini görüyorlar. Böyle, olduğu gibi...
Nedenmiş peki? Ne gerek varmış?
Ne bileyim be abicim! Ahiret soruları gibi.
Birasına bakarak dalıp gitti. Sonra masaya abanarak arkadaşına iyice yaklaştı. Bulanık, bir tünelin ucundaki biri gibi, şekli şemalı belirsiz bir adam.
Ben seni nereden tanıyorum ki ulan? Kimsin sen?
Belleği makineden çıkardılar. İki kişiydiler. Soruşturmadan sorumlu memurlar.
─ Baştan mı başlıyoruz, diye sordu belleği elinde tutan ilk memur.
─ Bir kere daha deneyelim ama bu sefer direkt aynayı sorarak başla, diye cevapladı ikinci memur.
─ Bence de. Yeterince düzgün çalışıyor.
Simülasyon yüklenirken, ayakta, biraz arkada duran ve alnını kaşıyan ikinci memur sormaktan kendisini alamadı:
─ Bu androidleri niye böyle bir olay yerine göndermişler ki? Belli tost olacakları. İsraf. Gidip biz baksak aynayı kırıp delilleri mahvetmek zorunda da kalmazlar.
Diğer memur sandalyesinde hafifçe dönecek oldu, o sırada soruyu bilgisayarın hoparlöründen teknisyen cevapladı.
Hangi işimizde bir yamukluk yok ki be abi.
Ama bir son değildi. Üstlerindeki tüm illüzyon dağıldığında ve çıplak, cinsiyetsiz, birbirinin aynı bedenleriyle kaldıklarında sıra dünyaya gelmişti.
Yere düştüler. Elleri -bütün bedeni gibi siyah turmalinden, boğumları çelikten- yere değdiği anda, metronun zemini dağıldı.
Yerdeki karolar öncesinde beyazdı ve çok parlaktı. Tepelerindeki floresan, ışığını olduğu gibi yansıtıyor, tek bir lekenin olmadığı ve tek bir tozun uçmadığı istasyonu aydınlatıyorlardı.
Duvarlara duyurular asılmıştı. Örneğin, yarın akşam kültür merkezinde 20.00’da başlayacak bir tekno blues festivalinin cıvıl cıvıl afişi vardı. Onun yanında daha geniş, sarı puntolu harflerle yazılmış, yatay siyah kesiklerle çerçevesi çizilmiş, bir platformdan düşen çöp adamın bulunduğu “Dikkat! Sarı bandı geçmeyin!” uyarısı. Biraz ilerisinde günlük resmi gazete, onun ilerisinde bir aksiyon filminin ve başka bir romantik komedi filminin afişleri, yapılacakların ve yapılmayacakların söylendiği küçük puntolu çeşitli duyurular... Duvar uzayıp giden bir panoydu. On, on beş metrede bir tekrarlanıyordu.
Tüm istasyonun eni yüz metre kadar. Genişliği on metre civarı.
Önlerinde, açık kapısından o mendebur aynanın gözüktüğü vagon duruyordu. Metro, istasyona sığmayacak kadar uzundu. Bir kılıcın keskinliğiyle uzanıyor ama yer yer vagonların ek yerleriyle bölünüyordu.
Hiçbir vagonda pencere olmadığı için metronun içi, içlerindekiler meçhuldü.
Sonrasında karolar zerrelerine ayrılarak yükseldi. Floresanın ışığında her yeri toza boğdular ve ortalığı gri bir sisin altına gömdüler. Çok kısa bir an. Afişleri dalgalandırmadılar. Dalgalandırmaya vakitleri olmadı. Yerlerinden söküp aldılar en fazla. Işık birkaç kere sönüp yanarak direndi. Son kez söndüğünde bir daha geri gelmedi.
Yine de etraf aydınlıktı. Kırmızı, her yere eşit dağılan soluk bir ışıkla.
Yer tamamen tele dönüşmüştü. Altında çapraz hatlarla desteklenmiş demir bir iskelet. Işık birkaç metreden daha fazla aşağıya uzanamıyordu. Sonsuzluğa giden bir uçurum.
Duvarın yerini aynı teller ve demir iskelet almıştı. Arkasında, birbirine vidalarla tutturulmuş demir plakalardan oluşan, üstünden geçen boruların ek yerlerinden bazen ince buharların çıktığı ve bir süre asılı kaldıktan sonra ağır, yağlı bir havayla sürüklendiği bir koridor.
Diğer tarafta paslanmış, pencerelerindeki camlar kırıldığı için demir plakalarla kapatılmış külüstür bir metro. Kapının karşısındaki aynadan her şey olduğu gibi yansıyordu.
Bir konteynırın içini andıran bir evde, gerçi gayet de birbirine eklenmiş konteynırlardan oluşan bir şehirde “andıran” demek doğru olmayacağı için düpedüz bir konteynırın içinde, masaya mum görüntüsü vermek için koyulmuş, yarı katı yağ atıklarından şekillendirilmiş kütleleri yakmayı deniyordu. Kafasında hayvan kıllarından yapılmış grili siyahlı bir peruk. Aynı kıllardan kendisine gür bir bıyık da yapmıştı.
Üstünde mavi çöp poşetlerinden yapılmış, kravatlı, şık bir takım.
Masanın ayakları yerine oradan buradan çıkmış parçalar konulmuştu: bir arabanın şaft mili, üst üste konulmuş ve üstünde yazı okunamayan tenekeler, boş kitaplar, boş gazete balyaları... Hiçbir şeye yazı yazılmıyordu, gerek yoktu da zaten çünkü merkez veri bankası onları fark ettirmeden, merceklerden giren veriyi sentezleyerek insanlar için dolduruyordu. Yani, androidler için. Farklı şekilde isimlendirmek bir fark yaratacaksa.
Onların mercekleri için değil. Bağlantıları çok önceden kopmuştu.
─ Hayatım, sofra hazır, diye bağırdı yatak odasındaki karısına.
Sofrada tabak yerine düz, bardak yerine bükülmüş, çatal ve bıçak yerine sivriltilmiş plakalar.
Karısı salonun kapısında durakladı ve ancak kulaklarına kadar uzanan, kocasınınkine benzeyen, cansız, ölü hayvanların kıllarından ibaret peruğunu eliyle düzeltti. Dudağını, daha doğrusu dudağının olması gereken yeri koyu kırmızı bir yağ tabakasıyla renklendirmeyi denemişti. Biraz da yanaklarına sürmüştü.
─ Nasıl olmuş, diye sordu.
Sesi tek düzeydi ama hafif bir neşe olduğunu hissettiğinize yemin edebilirdiniz.
Üzerinde, çöp poşetlerinin içini yazısız gazete kağıtlarıyla doldurarak yaptığı iki parça giysi.
─ Çok güzelsin, diyerek kravatını düzeltti kocası.
─ Sen de öylesin, sevgilim.
Yaklaşıp kocasını öptü. Kocası da onu. Sonra nazikçe elinden tutarak, sandalyesini geriye çekerek oturmasına yardım etti.
Sofrada yemek niyetine hiçbir şey yoktu. Gerek de yoktu zaten.
Konteynırın kapısı gürültüyle tekmelenip içeri iki memur girene kadar birbirlerine öyküler anlattılar. O gün neler yaptıklarını. İşten erken çıkıp yemyeşil çimenlerde gezdiklerini, uçurtma uçurduklarını, kadının nasıl o elbiseyi bulmak için saatlerce gezip yorulduğunu, kocasının kısa süreliğine işe dönüp nasıl başarılı bir hamleyle yaşanan krizi çözdüğünü ve kadının yanına döndükten sonra, alışveriş merkezinde oturdukları yeni dondurmacının dondurmalarının ne kadar lezzetli olduğunu, boğazlarının ağrımasından korktuklarını...
Akşam film izleyebilirlerdi, televizyonda -boş ve mat bir plaka- güzel bir film oynayacaktı.
İki memur. Çıplak bedenleriyle birbirinin aynı. Ellerindeki silahları onlara doğrultmuşlardı. Mum ışığında, tertemiz bir örtünün serili olduğu masada, bardaklarında şaraplarla oturan ve henüz sofranın ortasındaki hindiye dokunmamış çifti gördüklerinde bocaladılar.
Hiç de androidlere bilinçli olarak zarar verebilecek gibi gözükmüyorlardı.
─ Sessiz kalma hakkına sahipsiniz, diye bağırdı içeri giren ikinci memur. Söylediğiniz her şey...
Cümlesini bitiremedi. Yatak odasındaki, masanın üzerinden gördüğü o şey, onunla aynı hareketleri yapan android, yoksa, bir aynadaki yansıması mıydı?
Bütün illüzyon o anda dağılmaya başladı.
Not: Bu öykü ilk olarak 2020 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ 8fb140b4:f948000c
2023-11-21 21:37:48
@ 8fb140b4:f948000c
2023-11-21 21:37:48Embarking on the journey of operating your own Lightning node on the Bitcoin Layer 2 network is more than just a tech-savvy endeavor; it's a step into a realm of financial autonomy and cutting-edge innovation. By running a node, you become a vital part of a revolutionary movement that's reshaping how we think about money and digital transactions. This role not only offers a unique perspective on blockchain technology but also places you at the heart of a community dedicated to decentralization and network resilience. Beyond the technicalities, it's about embracing a new era of digital finance, where you contribute directly to the network's security, efficiency, and growth, all while gaining personal satisfaction and potentially lucrative rewards.
In essence, running your own Lightning node is a powerful way to engage with the forefront of blockchain technology, assert financial independence, and contribute to a more decentralized and efficient Bitcoin network. It's an adventure that offers both personal and communal benefits, from gaining in-depth tech knowledge to earning a place in the evolving landscape of cryptocurrency.
Running your own Lightning node for the Bitcoin Layer 2 network can be an empowering and beneficial endeavor. Here are 10 reasons why you might consider taking on this task:
-
Direct Contribution to Decentralization: Operating a node is a direct action towards decentralizing the Bitcoin network, crucial for its security and resistance to control or censorship by any single entity.
-
Financial Autonomy: Owning a node gives you complete control over your financial transactions on the network, free from reliance on third-party services, which can be subject to fees, restrictions, or outages.
-
Advanced Network Participation: As a node operator, you're not just a passive participant but an active player in shaping the network, influencing its efficiency and scalability through direct involvement.
-
Potential for Higher Revenue: With strategic management and optimal channel funding, your node can become a preferred route for transactions, potentially increasing the routing fees you can earn.
-
Cutting-Edge Technological Engagement: Running a node puts you at the forefront of blockchain and bitcoin technology, offering insights into future developments and innovations.
-
Strengthened Network Security: Each new node adds to the robustness of the Bitcoin network, making it more resilient against attacks and failures, thus contributing to the overall security of the ecosystem.
-
Personalized Fee Structures: You have the flexibility to set your own fee policies, which can balance earning potential with the service you provide to the network.
-
Empowerment Through Knowledge: The process of setting up and managing a node provides deep learning opportunities, empowering you with knowledge that can be applied in various areas of blockchain and fintech.
-
Boosting Transaction Capacity: By running a node, you help to increase the overall capacity of the Lightning Network, enabling more transactions to be processed quickly and at lower costs.
-
Community Leadership and Reputation: As an active node operator, you gain recognition within the Bitcoin community, which can lead to collaborative opportunities and a position of thought leadership in the space.
These reasons demonstrate the impactful and transformative nature of running a Lightning node, appealing to those who are deeply invested in the principles of bitcoin and wish to actively shape its future. Jump aboard, and embrace the journey toward full independence. 🐶🐾🫡🚀🚀🚀
-
-
 @ 57d1a264:69f1fee1
2025-04-08 06:39:52
@ 57d1a264:69f1fee1
2025-04-08 06:39:52originally posted at https://stacker.news/items/937791
-
 @ 8fb140b4:f948000c
2023-11-18 23:28:31
@ 8fb140b4:f948000c
2023-11-18 23:28:31Chef's notes
Serving these two dishes together will create a delightful centerpiece for your Thanksgiving meal, offering a perfect blend of traditional flavors with a homemade touch.
Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 1 - 2 hours
- 🍽️ Servings: 4-6
Ingredients
- 1 whole turkey (about 12-14 lbs), thawed and ready to cook
- 1 cup unsalted butter, softened
- 2 tablespoons fresh thyme, chopped
- 2 tablespoons fresh rosemary, chopped
- 2 tablespoons fresh sage, chopped
- Salt and freshly ground black pepper
- 1 onion, quartered
- 1 lemon, halved
- 2-3 cloves of garlic
- Apple and Sage Stuffing
- 1 loaf of crusty bread, cut into cubes
- 2 apples, cored and chopped
- 1 onion, diced
- 2 stalks celery, diced
- 3 cloves garlic, minced
- 1/4 cup fresh sage, chopped
- 1/2 cup unsalted butter
- 2 cups chicken broth
- Salt and pepper, to taste
Directions
- Preheat the Oven: Set your oven to 325°F (165°C).
- Prepare the Herb Butter: Mix the softened butter with the chopped thyme, rosemary, and sage. Season with salt and pepper.
- Prepare the Turkey: Remove any giblets from the turkey and pat it dry. Loosen the skin and spread a generous amount of herb butter under and over the skin.
- Add Aromatics: Inside the turkey cavity, place the quartered onion, lemon halves, and garlic cloves.
- Roast: Place the turkey in a roasting pan. Tent with aluminum foil and roast. A general guideline is about 15 minutes per pound, or until the internal temperature reaches 165°F (74°C) at the thickest part of the thigh.
- Rest and Serve: Let the turkey rest for at least 20 minutes before carving.
- Next: Apple and Sage Stuffing
- Dry the Bread: Spread the bread cubes on a baking sheet and let them dry overnight, or toast them in the oven.
- Cook the Vegetables: In a large skillet, melt the butter and cook the onion, celery, and garlic until soft.
- Combine Ingredients: Add the apples, sage, and bread cubes to the skillet. Stir in the chicken broth until the mixture is moist. Season with salt and pepper.
- Bake: Transfer the stuffing to a baking dish and bake at 350°F (175°C) for about 30-40 minutes, until golden brown on top.
-
 @ 8fb140b4:f948000c
2023-11-02 01:13:01
@ 8fb140b4:f948000c
2023-11-02 01:13:01Testing a brand new YakiHonne native client for iOS. Smooth as butter (not penis butter 🤣🍆🧈) with great visual experience and intuitive navigation. Amazing work by the team behind it! * lists * work
Bold text work!

Images could have used nostr.build instead of raw S3 from us-east-1 region.
Very impressive! You can even save the draft and continue later, before posting the long-form note!
🐶🐾🤯🤯🤯🫂💜
-
 @ 8fb140b4:f948000c
2023-08-22 12:14:34
@ 8fb140b4:f948000c
2023-08-22 12:14:34As the title states, scratch behind my ear and you get it. 🐶🐾🫡
-
 @ 8fb140b4:f948000c
2023-07-30 00:35:01
@ 8fb140b4:f948000c
2023-07-30 00:35:01Test Bounty Note
-
 @ 8fb140b4:f948000c
2023-07-22 09:39:48
@ 8fb140b4:f948000c
2023-07-22 09:39:48Intro
This short tutorial will help you set up your own Nostr Wallet Connect (NWC) on your own LND Node that is not using Umbrel. If you are a user of Umbrel, you should use their version of NWC.
Requirements
You need to have a working installation of LND with established channels and connectivity to the internet. NWC in itself is fairly light and will not consume a lot of resources. You will also want to ensure that you have a working installation of Docker, since we will use a docker image to run NWC.
- Working installation of LND (and all of its required components)
- Docker (with Docker compose)
Installation
For the purpose of this tutorial, we will assume that you have your lnd/bitcoind running under user bitcoin with home directory /home/bitcoin. We will also assume that you already have a running installation of Docker (or docker.io).
Prepare and verify
git version - we will need git to get the latest version of NWC. docker version - should execute successfully and show the currently installed version of Docker. docker compose version - same as before, but the version will be different. ss -tupln | grep 10009- should produce the following output: tcp LISTEN 0 4096 0.0.0.0:10009 0.0.0.0: tcp LISTEN 0 4096 [::]:10009 [::]:**
For things to work correctly, your Docker should be version 20.10.0 or later. If you have an older version, consider installing a new one using instructions here: https://docs.docker.com/engine/install/
Create folders & download NWC
In the home directory of your LND/bitcoind user, create a new folder, e.g., "nwc" mkdir /home/bitcoin/nwc. Change to that directory cd /home/bitcoin/nwc and clone the NWC repository: git clone https://github.com/getAlby/nostr-wallet-connect.git
Creating the Docker image
In this step, we will create a Docker image that you will use to run NWC.
- Change directory to
nostr-wallet-connect:cd nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - The last line of the output (after a few minutes) should look like
=> => naming to docker.io/library/nwc:latest nwc:latestis the name of the Docker image with a tag which you should note for use later.
Creating docker-compose.yml and necessary data directories
- Let's create a directory that will hold your non-volatile data (DB):
mkdir data - In
docker-compose.ymlfile, there are fields that you want to replace (<> comments) and port “4321” that you want to make sure is open (check withss -tupln | grep 4321which should return nothing). - Create
docker-compose.ymlfile with the following content, and make sure to update fields that have <> comment:
version: "3.8" services: nwc: image: nwc:latest volumes: - ./data:/data - ~/.lnd:/lnd:ro ports: - "4321:8080" extra_hosts: - "localhost:host-gateway" environment: NOSTR_PRIVKEY: <use "openssl rand -hex 32" to generate a fresh key and place it inside ""> LN_BACKEND_TYPE: "LND" LND_ADDRESS: localhost:10009 LND_CERT_FILE: "/lnd/tls.cert" LND_MACAROON_FILE: "/lnd/data/chain/bitcoin/mainnet/admin.macaroon" DATABASE_URI: "/data/nostr-wallet-connect.db" COOKIE_SECRET: <use "openssl rand -hex 32" to generate fresh secret and place it inside ""> PORT: 8080 restart: always stop_grace_period: 1mStarting and testing
Now that you have everything ready, it is time to start the container and test.
- While you are in the
nwcdirectory (important), execute the following command and check the log output,docker compose up - You should see container logs while it is starting, and it should not exit if everything went well.
- At this point, you should be able to go to
http://<ip of the host where nwc is running>:4321and get to the interface of NWC - To stop the test run of NWC, simply press
Ctrl-C, and it will shut the container down. - To start NWC permanently, you should execute
docker compose up -d, “-d” tells Docker to detach from the session. - To check currently running NWC logs, execute
docker compose logsto run it in tail mode add-fto the end. - To stop the container, execute
docker compose down
That's all, just follow the instructions in the web interface to get started.
Updating
As with any software, you should expect fixes and updates that you would need to perform periodically. You could automate this, but it falls outside of the scope of this tutorial. Since we already have all of the necessary configuration in place, the update execution is fairly simple.
- Change directory to the clone of the git repository,
cd /home/bitcoin/nwc/nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - Change directory back one level
cd .. - Restart (stop and start) the docker compose config
docker compose down && docker compose up -d - Done! Optionally you may want to check the logs:
docker compose logs
-
 @ 4cebd4f5:0ac3ed15
2025-04-08 07:04:49
@ 4cebd4f5:0ac3ed15
2025-04-08 07:04:49EurekaHACKS – hackathon thường niên kéo dài 12 giờ dành riêng cho học sinh trung học – đã chính thức khép lại tại Trường Trung học Abbey Park (Oakville, Canada) với sự tham gia của 92 lập trình viên trẻ cùng 51 dự án công nghệ ấn tượng. Đây là sự kiện quy mô nhất tại khu vực Halton, không chỉ tạo ra môi trường cạnh tranh sôi động mà còn trao cơ hội trải nghiệm thực tế thông qua các workshop đa dạng và tổng giải thưởng lên đến 7,000 USD.
HÀNH TRÌNH 12 GIỜ: THỬ THÁCH & ĐỘT PHÁ
Với chủ đề đa dạng, các đội thi đã phát triển sản phẩm công nghệ tập trung vào giải pháp địa phương, sáng tạo và tính ứng dụng thực tiễn. Tiêu chí đánh giá bao gồm:
- Chất lượng kỹ thuật
- Tính khả thi
- Khả năng trình bàyCơ cấu giải thưởng nổi bật:
- Best Overall Hack: Bambu Lab A1 Minis (Máy in 3D cao cấp).
- Runner’s Up Hacks: Bàn phím cơ Red Dragon.
- Giải thưởng phụ: Từ "Tác động địa phương" đến "Sáng tạo kỹ thuật", cùng ưu đãi tín dụng cho dự án sử dụng Internet Computer Protocol (ICP) (500 USD) và Vectara (300 USD).
CÁC DỰ ÁN ĐOẠT GIẢI: CÔNG NGHỆ PHỤC VỤ CỘNG ĐỒNG
Hạng mục chính
-
Best Overall Hack: FaunaDex Ứng dụng khuyến khích khám phá thiên nhiên bằng AI nhận diện động vật kèm thông tin chi tiết, thúc đẩy hoạt động ngoài trời và học tập.
-
Runner’s Up Hack: ArcaneStep****
Trò chơi web kết hợp vận động thực tế: Trẻ em tích lũy "mana" bằng cách đi bộ để thực hiện phép thuật, giảm thời gian sử dụng màn hình. - Ultimate Coder Third Place: LocalLink*
Nền tảng kết nối người dùng tại không gian ngoài trời thông qua *công nghệ địa không gian, tạo tương tác trực tiếp và xây dựng cộng đồng. - Best Local Impact: Gems
Giao diện bản đồ giúp người dùng khám phá và chia sẻ địa điểm độc đáo, nâng cao trải nghiệm đô thị. - Most Grass Touching: Greenlight
Ứng dụng gamification thưởng điểm khi người dùng tập thể dục hoặc tương tác với thiên nhiên. - Best Pitch: The Moss Garden
Website chủ đề thiên nhiên cải thiện năng suất bằng cách tăng cường tập trung và sức khỏe tinh thần. - Ultimate Coder Best Young Hacker: socialize.ai****
Trợ lý AI hỗ trợ tương tác xã hội thông qua gợi ý hội thoại và tìm kiếm hình ảnh ngược.
Xem toàn bộ dự án tại: EurekaHacks 2025 Buidl Page.
VỀ NHÀ TỔ CHỨC: EUREKAHACKS
Là đơn vị tiên phong thúc đẩy đổi mới công nghệ, EurekaHACKS tập trung vào phát triển blockchain và ứng dụng phi tập trung (dApp). Thông qua các hackathon và chương trình đào tạo, tổ chức này kết nối chuyên gia, hỗ trợ dự án cộng tác và ươm mầm nhân tài công nghệ trẻ. Định hướng hiện tại của EurekaHACKS là thúc đẩy giải pháp bền vững, kết hợp giáo dục và sự kiện chuyên sâu.
-
-
 @ da0b9bc3:4e30a4a9
2025-04-08 06:55:42
@ da0b9bc3:4e30a4a9
2025-04-08 06:55:42Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/937802
-
 @ 4cebd4f5:0ac3ed15
2025-04-08 06:14:10
@ 4cebd4f5:0ac3ed15
2025-04-08 06:14:10Từ ngày 10 đến 14/02/2025, ETHiopia x BAM Hackathon đã chứng kiến sự hội tụ của 108 nhà phát triển và nhà đổi mới hàng đầu châu Phi, cùng nhau khám phá tiềm năng công nghệ Ethereum. Sự kiện không chỉ là nơi trình diễn kỹ thuật xuất sắc mà còn là cầu nối thúc đẩy giải pháp blockchain thực tiễn, với 38 dự án được phê duyệt.
HÀNH TRÌNH SÁNG TẠO: TỪ Ý TƯỞNG ĐẾN GIẢI PHÁP
Trong 5 ngày làm việc căng thẳng, các đội thi đã tham gia chuỗi hoạt động đa dạng:
- Hội thảo chuyên sâu về phát triển hợp đồng thông minh Solidity, cập nhật xu hướng công nghệ mới.
- Phiên tương tác xây dựng kỹ năng sáng tạo, thúc đẩy tư duy giải quyết vấn đề.
- Thử thách xây dựng sản phẩm tập trung vào ứng dụng thực tế, đặc biệt trong lĩnh vực tài chính phi tập trung (DeFi), quản trị cộng đồng và sáng tạo nội dung.Ban giám khảo đánh giá dự án dựa trên ba tiêu chí chính: chất lượng mã nguồn, tính tương tác cộng đồng và khả năng trình bày. Tổng giải thưởng 2,000 USDC đã được trao cho những đội vượt trội, ghi nhận nỗ lực đóng góp vào hệ sinh thái Ethereum toàn cầu.
CÁC DỰ ÁN ĐOẠT GIẢI:
Hạng mục ETHiopia X Circles Prize
-
Giải Nhất: Ethera
*Ethera là một nền tảng blockchain giúp tăng cường khả năng kiếm tiền cho những người sáng tạo nội dung ở Châu Phi thông qua các giao dịch công bằng, không biên giới. -
Giải Nhì: ETHqub
Dự án đang được cập nhật thông tin.
Hạng mục ETHiopia x BAM General Hackathon
- Giải Nhất: Imara
*Imara khuyến khích hình thành nhóm phi tập trung và cam kết dự án trong các dự án blockchain thông qua cơ chế staking. - Giải Nhì: Hakiba
*Hakiba cung cấp một giao thức phi tập trung cho tín dụng cộng đồng thông qua việc staking, chứng thực và bảo hiểm trên chuỗi. - Giải Ba: ETHqub
Thông tin chi tiết sẽ được công bố trong thời gian tới.
Khám phá toàn bộ dự án tại: DoraHacks.
THÔNG TIN VỀ ĐƠN VỊ TỔ CHỨC:
- BAM (Bold African Movement) – BAM tập trung vào việc thúc đẩy công nghệ và các giải pháp blockchain. Được biết đến với khả năng tích hợp blockchain vào nhiều lĩnh vực khác nhau, BAM đã dẫn đầu các dự án cải thiện hiệu quả hoạt động và tính minh bạch. Tổ chức này áp dụng phương pháp tiếp cận hợp tác để thúc đẩy các cải tiến công nghệ và cam kết phát triển cơ sở hạ tầng blockchain an toàn, có khả năng mở rộng để đáp ứng nhu cầu của ngành.
Thông tin liên hệ:
- Website: joinbam.xyz
- Theo dõi cập nhật từ ETHiopia: Twitter @ETHiopia_DAO -
-
 @ 502ab02a:a2860397
2025-04-08 02:01:29
@ 502ab02a:a2860397
2025-04-08 02:01:29เรื่องมันเริ่มจากมีคนถามว่า ขนมของผมเป็นขนม healthy ใช่ไหมคะ มีคนชื่นชมเยอะเลยจะมาสั่งบ้าง
ผมได้แต่ตอบไปว่า ขนมของผมไม่ใช่ขนม healthy มันเป็นแค่ขนมทางเลือก เป็นอีกทางเลือกนึงของคนที่อยากเลือก
โดยผมจะให้รายละเอียดวัตถุดิบว่ามีอะไร แล้วสารอาหารเป็นประมาณเท่าไร ให้เขาเลือกเอาเอง ผมเลยไม่เคยตอบเลยว่า คนท้องกินได้ไหม คนป่วยเบาหวานกินได้ไหม และผมมักตอบว่า เจ้าตัวควรจะรู้ได้เองเมื่อทราบวัตถุดิบ ว่าตัวเองกินได้ไหม
ผมว่า ผมแม่งโคตรแฟร์ในเรื่องการให้ข้อมูลก่อนซื้อแล้วนะ
มันก็เลยเกิดข้อสงสัยว่า เมื่อเราตั้งคำถามกับคำว่า “Healthy” ว่านิยามของมันคือ ดีต่อสุขภาพ หรือ แค่ไม่ทำร้ายสุขภาพ?
ในยุคที่โลกเต็มไปด้วยคำศัพท์ใหม่ ๆ เกี่ยวกับสุขภาพ ที่เอามาช่วยในการขายของนั้น บางครั้งคำว่า “healthy” ที่เราได้ยินกันบ่อย ๆ ก็ไม่ค่อยชัดเจนเท่าไรนัก คนส่วนใหญ่เข้าใจว่าคำนี้น่าจะหมายถึง “ดีต่อสุขภาพ”
ความหมายของมันอาจจะไม่เป็นเช่นนั้นเสมอไป และการเข้าใจคำว่า “healthy” นั้นสำคัญยิ่งกว่าที่คิด ถ้าจะให้ถามกันตรง ๆ คือ คำว่า “healthy” จริง ๆ ควรจะหมายถึงอะไร?
“Healthy” หรือ “Not Harmful”? หลายครั้งที่เราพบคำว่า “healthy” ใช้กับผลิตภัณฑ์ที่ดูเหมือนจะดีต่อสุขภาพ เช่น ขนมสุขภาพ น้ำผลไม้คั้นสด หรืออาหารมังสวิรัติ ซึ่งทุกอย่างนี้อาจจะทำให้เราคิดว่าเป็นอาหารที่ “ดีต่อสุขภาพ” แต่ถ้าลองมองให้ลึกขึ้น คุณอาจจะพบว่า คำว่า “healthy” ที่เราคุ้นเคย อาจหมายถึงเพียงแค่ “ไม่ทำร้ายสุขภาพ” มากกว่าที่จะเป็นสิ่งที่มีประโยชน์จริง ๆ ต่อร่างกายหรือเปล่า?
ความแตกต่างระหว่าง “ดีต่อสุขภาพ” กับ “แค่ไม่ทำร้ายสุขภาพ”
อาหารที่เรียกว่า “healthy” ในปัจจุบันบางครั้งอาจจะไม่ได้ดีต่อร่างกายมากเท่าที่คิด เพราะอาจมีส่วนผสมที่ปรุงแต่งมากเกินไป เช่น น้ำตาลที่ซ่อนอยู่ในน้ำผลไม้คั้นสดหรือขนมที่ผลิตจากแป้งปริมาณมากเกินไป หรือแม้แต่ผ่านกระบวนการแบบ ultra processed ที่พวกนี้บางครั้งมันอาจจะไม่ทำร้ายร่างกายในระยะสั้นทันทีแต่ในระยะยาวอาจจะสะสมผลเสียต่อสุขภาพได้อยู่ดี แต่ถูก bold บางตัวมาชูความ healthy เสียอย่างนั้น
เมื่อเปรียบเทียบกับอาหารที่ “ดีต่อสุขภาพ” อาหารประเภทนี้ควรจะเป็น อาหารจากธรรมชาติที่ไม่ผ่านกระบวนการปรุงแต่งหรือแปรรูปมาก หรือเปล่า? เพราะอาหารเหล่านี้จะให้คุณค่าทางโภชนาการที่ร่างกายต้องการ เช่น โปรตีนคุณภาพสูงจากสัตว์ หรือ ผักผลไม้ที่ปลูกในระบบเกษตรอินทรีย์ ซึ่งมีสารอาหารที่ไม่เพียงแค่ไม่ทำร้ายร่างกาย แต่ยังช่วยเสริมสร้างระบบต่าง ๆ ในร่างกายให้ทำงานได้อย่างมีประสิทธิภาพ
“Not Harmful” ยังไม่พอ แต่อาหารที่แค่ “ไม่ทำร้ายสุขภาพ” ยังไม่เพียงพอที่จะเรียกว่า “healthy” เพราะอาหารเหล่านี้บางตัวอาจจะมีมุมกลับที่ไม่ได้สร้างผลเสียทันที แต่ก็อาจไม่ได้ให้ประโยชน์อะไรกับร่างกายเท่าที่ควรเป็นเช่นกัน การรับประทานอาหารที่แค่ “ไม่ทำร้ายสุขภาพ“ นั้นในระยะยาวอาจไม่ส่งผลต่อการมีสุขภาพที่แข็งแรงจริง ๆ เพราะแค่ ”ไม่ทำร้าย“
“not harmful” ยังไม่ใช่ “healthy” เพราะมันไม่ได้ดีต่อสุขภาพ แต่มันแค่ “ไม่ร้ายแรงทันที” หรือพูดให้ชัดคือ แค่ไม่ทำร้ายสุขภาพเร็วเกินไปนัก เช่น
ขนมที่บอกว่า “ไม่มีน้ำตาล” แต่ยังใช้สารให้ความหวานสังเคราะห์
เครื่องดื่มที่โฆษณาว่า “ลดแคลอรี่” แต่แฝงไปด้วยสารเคมีหรือสารปรุงแต่งที่ร่างกายไม่สามารถย่อยได้ดี
ผลิตภัณฑ์ที่บอกว่า “ใช้ได้สำหรับมังสวิรัติ” แต่เต็มไปด้วยแป้งขัดขาวหรือสารกันบูด หรือแม้แต่อาหารสารพัด ins
หรือแม้แต่อาหารที่หลอกล่อให้กินเกินความต้องการ ชูตัวนึงแต่เนียนไม่บอกอีกตัวนึง เช่นชูโปรตีน แต่เงียบเรื่องคาร์บสูงมาก
แถมบางครั้งมาในความ over claim ดึงสารตัวเล็กๆมาชูภายใต้คำว่า “มี xxxx ดีเพราะช่วยด้าน xxxx” ทั้งที่จะสัมฤทธิ์ผลต้องดื่มเป็นสิบๆแก้ว ซึ่งใช้ไม่ได้จริง
“Healthy” ที่แท้จริง อาหารที่ดีต่อสุขภาพ จึงควรเป็นอาหารที่เมื่อกินเข้าไปแล้ว ร่างกายได้รับ สารอาหารที่มีประโยชน์จริง ๆ ที่ช่วยเสริมสร้างและซ่อมแซมระบบต่าง ๆ ในร่างกาย อย่างเต็มที่เช่น • โปรตีนจากแหล่งธรรมชาติ อย่างเนื้อสัตว์ที่เลี้ยงแบบอิสระ หรือไข่ที่มาจากฟาร์มที่เลี้ยงตามธรรมชาติ • ไขมันที่ดีต่อสุขภาพ เช่น ไขมันจากสัตว์ที่เลี้ยงแบบธรรมชาติ ไขมันโอเมก้า 3 ที่มาจากปลา หรือไขมันพืชที่มีสัดส่วนโอเมก้า 6 ไม่มากจนไม่สามารถสมดุล โอเมก้า 3 ได้ทัน • ผักผลไม้สดที่ไม่ผ่านการแปรรูป เพราะยังพอมีไฟเบอร์ วิตามิน และแร่ธาตุที่ร่างกายเอาไปใช้งานได้บ้าง แต่ต้องผ่านการลดระดับของ anti-nutrient
หลายครั้งเราเห็นขนม healthy ไม่ว่าจะคลีน วีแกน หรือขนมเคลมความ healthy ต่างๆ คือพอเป็นขนม มันก็จะมีการใช้ “ปริมาณ” บางอย่างให้เรากินมากเกินไป เช่นบางขนมยังเป็นแป้งปริมาณมาก ต่อให้แป้งเทพแป้งสะอาดยังไง ก็กลายเป็นคาร์บย่อยเป็นกลูโคส ต่อให้ย่อยช้าย่อยเร็วก็ย่อยได้หมดอยู่ดี, บางขนมมีปริมาณน้ำตาลมาก ต่อให้ giต่ำแบบมะพร้าว โตนด แต่ปริมาณ ถ้าเกินที่ สธ. มีคำแนะนำ คือ 16กรัมต่อวัน ก็เกมส์อยู่ดี, หรือจะขนมจืดๆแต่ใช้น้ำมันคาโนลา ที่อุดมด้วยโอเมก้า6 หรือ น้ำมันรำข้าวที่มี oryzanol เข้มข้น
หรืออย่างสายคีโต ก็ไม่รอด โอเค โดยรวมมันช่วยเรื่องการไม่กระชากอินซุลิน แต่บางอย่างก็ใช่ว่าจะสามารถเรียก healthy ตามความหมาย เช่น ขนมแป้งอัลมอนด์ มันคือ อัลมอนด์ processed ที่ทำให้เรากินอัลมอนด์มากกว่าเม็ดๆไปได้มาก เพราะมันบดย่อยมาละเอียด ทำให้เรากินมากเกินไป, หลายขนมก็ใช้สารให้ความหวาน ต่อให้อินซุลินไม่พุ่ง แต่มันก็มีผลกับจุลินทรีย์ในลำไส้, แม้แต่พวกครีมชีส ตัวมันเองคือดี แต่การเอาปริมาณมากมาทำขนม มันก็กลายเป็น over consume ได้, อย่างที่ชัดมากคือ ขนมปังวีทกลูเตน ที่แป้งปกติกลูเตนราว 10-14% ถ้าวัดแบบโลฟละ 500กรัมเหมือนๆกัน แป้งธรรมดามีกลูเตนราวๆ 30กรัม ส่วนขนมปังวีทกลูเตนมีกลูเตนราวๆ 190กรัม หรือมากกว่าปกติ 633% แต่นั่นละครับ มัน not harmful (yet)
ดังนั้นในความคิดเห็นของผม ตามเหตุผลที่เรียบเรียงมา เมื่อขึ้นชื่อว่าขนม มันคืออาหารชนิดนึงที่ผ่านกระบวนการมาก จนกลายเป็น processed food ชนิดนึง มันทำให้เรากินเนยมาก กินน้ำมันมาก กินครีมมาก กินน้ำตาล(ทั้งแท้และสังเคราะห์)มาก กินแป้งและ/หรือถั่วบดมาก กินผลไม้มาก กินโยเกิรตมาก กินช็อคโกแลตมาก(ถึงจะ dark100% ก็เหอะ) เพื่อความอร่อย
ขนม เลยไม่ healthy และผมไม่ขอเคลมความ healthy ในสินค้าผม และผมไม่มองว่าขนม healthy ผมมองว่าขนมอร่อย กินเอาอร่อย แล้วไปบาลานซ์ความ healthy องค์รวมเอาในชีวิต ดังนั้น อย่าฝืนกินขนมไม่อร่อยเพียงเพราะเราดันเชื่อว่ามัน healthy หรือ เราอย่าไปซัดโฮกขนมมากๆเพราะเราดันเชื่อว่ามัน healthy
เรามองอาหารยังไง ก็มองขนมอย่างนั้น มองวัตถุดิบที่แปรรูปแล้วกินลงไป ขนม ก็จะเป็นอาหารประเภทนึง
คุณก็เช่นกัน ควรมองของที่กินเข้าไปทั้งหมดเป็นอาหาร แล้วมองอาหารเป็นวัตถุดิบ แล้วพิจารณาวัตถุดิบ+วิธีทำ ว่ามัน healthy กับตัวคุณแค่ไหน มากกว่า healthy ที่แปะบนห่อหรือในโพสขาย
คำว่า “healthy” จริง ๆ แล้วควรจะหมายถึง อาหารที่ไม่ใช่แค่ปลอดภัยจากการทำร้ายสุขภาพ แต่ยังต้องช่วยเสริมสร้างสุขภาพ อย่างแท้จริง อาหารที่ดีต่อสุขภาพควรเป็นอาหารธรรมชาติให้โปรตีนคุณภาพ ไขมันที่มีประโยชน์ ให้คาร์บที่พอเหมาะและมีสารอาหารที่ร่างกายต้องการในการทำงานที่ดีที่สุด ทั้งซ่อมและสร้าง
“Healthy = ดีต่อสุขภาพในทางบวก ไม่ใช่แค่ไม่ร้าย” “Not harmful = ไม่ร้าย ยังไม่เห็นผลเสีย แต่ไม่ให้คุณในทางบวกขนาดนั้น”
เพราะฉะนั้น มันเลยมีความเกือบจะทับซ่อนกัน ถ้าจะสื่อคำว่า “Healthy” แนะนำให้แปลว่า “อาหารที่ส่งเสริมสุขภาพ ไม่ใช่แค่ไม่ทำร้ายสุขภาพ“
กับดักที่ใหญ่ที่สุด ที่แม้แต่ชาวคีโตเองก็อาจตกหลุมนั้นแบบไม่รู้ตัว นั่นคือ
ปริมาณ สำคัญกว่า ประเภท
คุณตกหลุมคำว่า อาหาร/ขนม healthy หรือเปล่าหล่ะ คุณเท่านั้นที่ตอบตัวเองได้
จงมองทะลุ food matrix
เจริญพวง neo
pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก
ฉลาก3รู้
-
 @ 000002de:c05780a7
2025-04-08 01:24:25
@ 000002de:c05780a7
2025-04-08 01:24:25Trump is trying to sell a victim narrative and I don't buy it.
Trump repeats a troupe that I find hard to swallow. The US is getting ripped off. When he says this, as far as I can tell he's not referring to the people. He's referring the US government getting ripped off by other nations. This is so absurd I'm surprised I don't hear more people push back on it.
The US is the most powerful government in the history of the planet. No nation has the firepower or wealth of the US. The US has manipulated the governments and policies of much of the world since WW2. The idea that the US government is getting ripped off is absurd.
Trump and I agree that NATO is obsolete. It was created to counter a government that dissolved in the 90s. This should be an example to everyone that governments do not behave like businesses. They do not respond to market forces. They will always seek to increase their power and influence and always resist any efforts to reduce their size and scope. But back to Trump. He says that the US is getting ripped off by the other NATO countries. I would say the US people are in indeed being ripped off by their own government. But the US government is NOT getting ripped off.
The US military power in Europe is a massive influence on geopolitics in the region. US military companies benefit massively as well. The US military has bases all over the globe and if you don't think that is a factor in "diplomatic" negotiations you are being naive. The US uses this "defensive" shield to keep the "leaders" of Europe in line. The US isn't being ripped off. This is just a marketing tactic Trump is using to sell downsizing the US military deployments.
Trump also loves to point out how other countries are imposing tariffs on the US. We are being ripped off! I mean, he has a point there. But if tariffs aren't a tax as many in his admin like to claim, how exactly are "we" being ripped off? We are being told that Trump's tariff policy isn't a tax and that expecting prices to increase is oversimplifying things. The talk about tariffs is frankly frustrating.
On the one hand the left is saying tariffs are a tax and is going to drive up prices. Yet these same people pretend to not understand that corporate tax increases don't have the same effect. The right claims to understand tax policy and often oppose corporate taxes. They will tell you that those taxes just get passed down to consumers in the form of price increases. Now they are pretending to not get this in relation to tariffs.
I've read and listened to the pro tariff people and they aren't all dumb. They may be right about tariffs not effecting all products and nations equally. I guess we will find out. But, can we be honest? The US is not getting ripped off.
Someone is getting ripped off, but it isn't the US federal government. Its the people of the world. First, the people of the world live under the thumb of the US fiat dollar standard. We in the US complain about 3+% inflation but most people in the world would kill for that level of inflation. Most of the world gets none of supposed benefits from government spending. They only get the debasement of their own currencies.
Moving away from economics, the entire globe is affected by the elections in the US. The US is the top dog government and its decisions effect people everywhere. The US deep state has manipulated many elections across the globe and continues to do so. Meanwhile we are told that Russia is manipulating our elections. So who exactly is getting ripped off here? I think the nation (the people) are being subjected to massive mismanagement at best. I can support that argument.
Don't get me wrong... I know we in the US are getting ripped off. We are being ruled by people that do not represent us and do not answer to us. The politicians that claim to represent us are being paid and influenced by foreign groups ranging from Israeli political groups, to any number of other groups domestic and foreign. We are getting ripped off, but I firmly believe the people in the US have it better than most of the world. Trump is trying to sell a victim narrative and I don't buy it.
originally posted at https://stacker.news/items/937482
-
 @ 4d41a7cb:7d3633cc
2025-04-08 01:17:39
@ 4d41a7cb:7d3633cc
2025-04-08 01:17:39Satoshi Nakamoto, the pseudonymous creator of Bitcoin, registered his birthday as April 5, 1975, on his P2P Foundation profile. Many think that he chose this date because on that same day in 1933, the United States government confiscated the gold of the American people. Whether this was on purpose or not, what happened in this day is very important to understand how do we ended up here.
In 1933, as expressed in Roosevelt’s Executive Orders 6073, 6102, and 6260, the United States first declared bankruptcy. The bankrupt U.S. went into receivership in 1933. America was turned over via receivership and reorganization in favor of its creditors. These creditors, the International Bankers, from the beginning stated their intent, which was to plunder, bankrupt, conquer and enslave America and return it to its colonial status.1
As one of his first acts as President, Franklin Delano Roosevelt declared a “Banking Emergency” to bail out the Federal Reserve Bank, which had embezzled this country’s gold supply. The Congress gave the President dictatorial powers under the “War Powers Act of 1917” (amended 1933), written, by the way, by the Board of Governors of the Federal Reserve Bank of New York.2
This day marked the official abandonment of the American Constitution, law and real money. Today, 92 years after this event, most of the people living today have never had any real money or paid for anything using real money; unless they used Bitcoin...
There could be no bankruptcy if there was not a private central bank lending paper currency to the government at interest, so we must start from 1913, when the Federal Reserve was created: a non-federal private bank with no reserves and the monopoly of issuing debt based paper currency in unlimited amounts and lending it to the government at interest by buying treasury bills. The fact that this currency is lent into existence at interest makes the debt mathematically impossible to be repaid; it can only be refinanced or defaulted.
Between 1929 and 1933, the Federal Reserve Bank reduced the currency supply by 33%, thereby creating the Great Depression, bankrupting the US government, stealing the Americans’ gold supply, and officially ending the gold standard. Since then the US dollar (money) was replaced with Federal Reserve Notes (debt). This was also the end of the Republican form of government and the beginning of a socialist mob rule democracy (Fascism).
“Fascism should more properly be called corporatism because it is the merger of state and corporate power.” — Benito Mussolini
The United States government has been bankrupt since 1933, since it defaulted on its gold bonds. This type of bond existed until 1933, when the U.S. monetary system abandoned the gold standard. 3 From this year the government has been totally controlled by the International bankers and used as a tool to spread and maintain their power worldwide.
Many people think that the gold standard was abandoned in 1971, but this is not true; in fact, this happened in 1933 when the US dollar was replaced by Federal Reserve Notes that are 100% debt-based fiat paper currency.
The year 1933 in the United States marked:
- The end of the Republican form of government and the beginning of American Fascism
- The end of the United States dollar and its replacement by Federal Reserve Notes
- The abandonment of common law and replacement with military admiralty law
- The takeover of the United States government by International bankers
- A massive gold theft and the end of the US gold standard
- The exchange of rights with privileges and licenses
- The United States government bankruptcy
The next shameful event in our history which still plagues us to this day was the “War Powers Act of 1933.” This Act permitted President Roosevelt to make law in the form of Executive Order, bypass Congress and create his socialist state. We (citizens of this country) were ever after to be considered enemies of the United States who must be licensed to engage in any commercial activity. With the aid of the Federal Reserve (the same people who created the Depression), the President confiscated our gold and silver coin and replaced it with worthless pieces of paper and a debt system that will eventually destroy this great country. Our land and our labor were pledged to the Federal Reserve Bank, Inc., as collateral for a debt system that could never be paid.4
“Emergency Powers” means any form of military style government, martial law, or martial rule. Martial law and martial rule are not the same.
United States Congressional Record March 17, 1993 Vol. #33, page H- 1303, Congressman James Traficant, Jr. (Ohio) addressing the House:
“Mr. Speaker, we are here now in chapter 11. Members of Congress are official trustees presiding over the greatest reorganization of any Bankrupt entity in world history, the U.S. Government. We are setting forth, hopefully, a blueprint for our future”
“There are some who say it is a coroner’s report that will lead to our demise. It is an established fact that the United States Federal Government has been dissolved by the Emergency Banking Act, March 9, 1933, 48 Stat. 1, Public Law 89-719; dered by President Roosevelt, being bankrupt and insolvent. H.J.R. 192, 73rd Congress in session June 5, 1933 – Joint Resolution To Suspend The Gold Standard and Abrogate the Gold Clause dissolved the Sovereign Authority of the United States and the official capacities of all United States Governmental Offices, Officers, and Departments and is further evidence that the United States Federal Government exists today in name only” **“The receivers of the United States Bankruptcy are the International Bankers, via the United Nations, the World Bank and the International Monetary Fund”
“All United States Offices, Officials, and Departments are now operating within a de facto status in name only under Emergency War Powers. With the Constitutional Republican form of Government now dissolved, the receivers of the Bankruptcy have adopted a new form of government for the United States. This new form of government is known as a Democracy, being an established Socialist/Communist order under a new governor for America. This act was instituted and established by transferring and/or placing the Office of the Secretary of Treasury to that of the Governor of the International Monetary Fund. Public Law 94-564, page 8, Section H.R. 13955 read in part:”
“The U.S. Secretary of Treasury receives no compensation for representing the United States.”
The American Spirit
The intention of the founding fathers of the United States was to create a constitutional republic to protect natural human rights and escape from the tyrannical English monarchy and its usurious Bank of England's monetary system. They created an honest monetary system based on gold and silver (United State Dollar) and got rid of nobility titles, creating equality under the law.
Section 10 of the American Constitution says:
No State shall enter into any Treaty, Alliance, or Confederation; grant Letters of Marque and Reprisal; coin Money; emit Bills of Credit; make anything but gold and silver Coin a tender in payment of debts; pass any bill of attainder, ex post facto law, or law impairing the obligation of contracts; or grant any title of nobility.
The United States Dollar (1792-1933)
A dollar is a measure of weight defined by the Coinage Act of 1792 and 1900, which specifies a certain quantity—24.8 grains of gold or 371.25 grains of silver (from 1792 to 1900) when the American dollar was based on a bimetallic standard.
The Gold Standard Act of 1900 formally placed the United States on the gold standard, setting the value of one dollar at 25.8 grams of 90% pure gold, which fixed the price of gold at $20.67 per troy ounce. This standard was totally abandoned in 1933.
Gold and silver were such powerful money during the founding of the United States of America that the founding fathers declared that only gold or silver coins could be “money” in America.
But since the greedy bankers cannot profit from honest money they cannot print, they replaced the money with paper debt instruments. And by doing this, they have effectively enslaved the American people until today. My definition of modern slavery is working for a currency that someone else can create at no cost or effort. What's worse is that they even demand to be paid back and with interest!
Federal Reserve Notes (1913-present)
Federal Reserve Notes are not real money. Money that has metallic or other intrinsic value, as distinguished from paper currency, checks, and drafts.
Federal Reserve Notes (FRNs) are a legal fiction. An assumption that something is true even though it may be untrue. 5 The assumption that they are money, when in fact they are the opposite of money: debt or paper currency.
Paper money. Paper documents that circulate as currency; bills drawn by a government against its own credit. 6 Like Goldsmiths' notes. Hist. Bankers' cash notes: promissory notes given by bankers to customers as acknowledgments of the receipt of money. • This term derives from the London banking business, which originally was transacted by goldsmiths.7
These notes were scientifically designed to bankrupt the government and slave the American people, as Alfred Owen Crozier warned one year before the bill for the creation of the FED was passed through Congress (1912):
If Congress yields and authorizes a private central bank as proposed by the pending bill, the end when the bubble bursts will be universal ruin and national bankruptcy.
Unfortunately, the bill was passed in 1913, and this private bank started printing a new currency different from the US dollar creating the great depression and effectible bankrupting the government like Alfred warned 20 years before.
Alfred also warned:
Thus the way is opened for an unlimited inflation of corporate paper currency issued by a mere private corporation with relatively small net assets and no government guarantee, every dollar supposed to be redeemable in gold, but with not a single dollar of gold necessarily held in the reserves of such corporation to accomplish such redemption.
Differently from what's commonly believed Federal Reserve Notes (FRNs) were never really “backed” by gold; they were never supposed to be hard currency. Currency backed by reserves, esp. gold and silver reserves.
The United States government defaulted on its gold clauses, calling for payment in gold. This marked the end of the gold standard. A monetary system in which currency is convertible into its legal equivalent in gold or gold coin.
Since then we have been under a paper standard, where we use fake money as tender for payments. Paper standard. A monetary system based entirely on paper; a system of currency that is not convertible into gold or other precious metal.
People traded their coupons as money or “currency.” Currency is not money but a money substitute. Redeemable currency must promise to pay a dollar equivalent in gold or silver money. Federal Reserve Notes (FRNs) make no such promises and are not “money.” A Federal Reserve Note is a debt obligation of the federal United States government, not “money.” The federal United States government and the U.S. Congress were not and have never been authorized by the Constitution of the United States of America to issue currency of any kind, but only lawful money—gold and silver coin.8
A bona fide note can be used in a financial transaction to discharge the debt only because it is an unconditional promise to pay by the issuer to the bearer. Is a Federal Reserve Note a contract note, an unconditional promise to pay? At one time the Federal Reserve issued bona fide contractual notes and certificates, redeemable in gold and silver coin. Most people never saw or comprehended the contract. It went largely unread because the Federal Reserve very cunningly hid the contract on the face of the note by breaking it up into five separate lines of text with a significantly different typeface for each line and placing the president’s picture right in the middle of it. They even used the old attorney’s ruse of obscuring the most important text in fine print! Over time, the terms and conditions of the contract were diluted until eventually they literally became an I.O.U. for nothing.
FEDERAL RESERVE NOTE
-
THIS NOTE IS LEGAL TENDER FOR ALL DEBT, PUBLIC AND PRIVATE, AND IT IS REDEEMABLE IN LAWFUL MONEY AT THE UNITED STATES TREASURY OR ANY FEDERAL RESERVE BANK.
-
DATE: SERIES OF 1934
-
WILL PAY TO THE BEARER ON DEMAND: ONE HUNDRED DOLLARS
-
TREASURER OF THE UNITED STATES SIGNATURE
-
SECRETARY OF THE TREASURY SIGNATURE

Nowadays FRNs say "This note is legal tender for all debts public and private" it tender debt but it does not pay the bearer on demand. It value was stolen by a counterfeiting technique commonly know as inflation.
One hundred dollars (SERIES OF 1934) will be 2480 grains of gold, or 159.4 grams, or 5.1249 troy ounces. Today one troy ounce is priced around $3,000 federal reserve notes. 5.1249 X 3,000 = $15,375 actual FRNs.
A $100 FRN bill today will buy 0.65% of a real gold $100 dollar certificate. That’s a -99.35% loss of purchasing power in the last 91 years.
FRNs savers have been rugged pulled!
Gold bugs where the winners...
But Bitcoin is even better...
Happy birthday Satoshi! April 5 will be forever remembered.
Satoshi... The man, the myth, the Legend...
-
 @ f6488c62:c929299d
2025-04-08 05:09:55
@ f6488c62:c929299d
2025-04-08 05:09:55Galaxy Digital บริษัทบริการทางการเงินด้านคริปโตชื่อดัง กำลังเขย่าวงการครั้งใหญ่ หลังได้รับการอนุมัติจากสำนักงานคณะกรรมการกำกับหลักทรัพย์สหรัฐฯ (SEC) ให้ย้ายฐานการดำเนินงานจากหมู่เกาะเคย์แมนมายังรัฐเดลาแวร์ และเตรียมขึ้นทะเบียนในตลาดหลักทรัพย์ Nasdaq ภายในเดือนพฤษภาคมนี้
นี่ไม่ใช่แค่การเปลี่ยนที่อยู่ แต่คือการส่งสัญญาณชัดเจนถึงความพยายามยกระดับตัวเองให้เข้าใกล้ "ระบบการเงินกระแสหลัก" และผลักดันให้คริปโตเป็นที่ยอมรับมากขึ้นในสายตานักลงทุนและหน่วยงานกำกับดูแล
จุดเปลี่ยนที่สาวกคริปโตควรจับตา
การย้ายฐานไปเดลาแวร์ ไม่ใช่แค่เพื่อความสะดวกทางกฎหมายเท่านั้น แต่ยังเปิดประตูสู่การสร้างสัมพันธ์กับนักลงทุนสหรัฐฯ และสถาบันการเงินรายใหญ่ที่เคยลังเลกับความโปร่งใสของวงการคริปโต การได้ไฟเขียวจาก SEC จึงเท่ากับได้ "ตรายางความน่าเชื่อถือ" ไปในตัว
และที่สำคัญที่สุดคือ การขึ้นทะเบียนใน Nasdaq ซึ่งเป็นตลาดหุ้นระดับโลก จะทำให้ Galaxy Digital เข้าถึงเม็ดเงินลงทุนมหาศาล ทั้งจากนักลงทุนสถาบันและรายย่อยที่ต้องการลงทุนในสินทรัพย์ดิจิทัลผ่านบริษัทที่มีสถานะทางกฎหมายชัดเจน
คลื่นลูกใหม่แห่งวงการคริปโต
ไมค์ โนโวกรัตซ์ ซีอีโอของ Galaxy Digital กล่าวอย่างมั่นใจว่า นี่คือ "ใบเบิกทาง" สู่การเติบโตในระยะยาว และไม่ใช่แค่ Galaxy เท่านั้นที่จะได้รับประโยชน์ แต่ทั้งอุตสาหกรรมคริปโตก็จะได้แรงส่งจากเหตุการณ์นี้ด้วย
เพราะการเคลื่อนไหวครั้งนี้อาจเป็นแรงจูงใจให้บริษัทคริปโตอื่นๆ ปรับตัวเข้าสู่กรอบการกำกับดูแลมากขึ้น ซึ่งจะช่วยเสริมสร้างสภาพคล่อง เสถียรภาพ และความเชื่อมั่นในตลาดโดยรวม
เดลาแวร์: จุดยุทธศาสตร์ของสายเลือดใหม่คริปโต
การเลือกเดลาแวร์เป็นฐานปฏิบัติการใหม่ไม่ใช่เรื่องบังเอิญ เพราะที่นี่ถือเป็นแหล่งรวมบริษัทระดับโลกที่เน้นโครงสร้างการดำเนินงานที่ยืดหยุ่นและเป็นมิตรต่อธุรกิจ เช่น JPMorgan Chase และ Coca-Cola ก็อยู่ที่นี่
Galaxy Digital จึงได้ทั้งภาพลักษณ์ความเป็นมืออาชีพและความได้เปรียบด้านกฎหมายควบคู่กันไป
แล้วสาวกคริปโตอย่างเราๆ ได้อะไร?
ความเชื่อมั่นที่เพิ่มขึ้น: การที่บริษัทใหญ่ระดับ Galaxy Digital ได้รับการรับรองจาก SEC และเตรียมเข้า Nasdaq คือสัญญาณเชิงบวกว่า "คริปโตไม่ได้เป็นของเล่นอีกต่อไป"
ประตูสู่ทุนสถาบัน: เม็ดเงินจากฝั่ง TradFi (การเงินแบบดั้งเดิม) อาจไหลเข้าวงการคริปโตมากขึ้น ทั้งผ่าน Galaxy และโครงการอื่นที่ตามมา
แรงกระเพื่อมต่อราคาเหรียญ: ความเคลื่อนไหวนี้อาจเป็นตัวจุดประกายให้ราคาของเหรียญหลัก เช่น BTC, ETH หรือเหรียญที่เกี่ยวข้องกับ Galaxy มีแนวโน้มขาขึ้น
มาตรฐานใหม่ของวงการ: บริษัทคริปโตอื่นๆ อาจต้องปรับตัวให้โปร่งใสและสอดคล้องกับกฎหมายมากขึ้น ซึ่งจะทำให้ทั้งวงการดูมีความน่าเชื่อถือและปลอดภัยสำหรับนักลงทุน
สู่ยุคใหม่ของคริปโต
Galaxy Digital อาจกลายเป็น "สะพาน" ที่เชื่อมโลกคริปโตกับตลาดทุนดั้งเดิม และนี่อาจเป็นจุดเริ่มต้นของการยอมรับคริปโตในระดับโลกอย่างเต็มรูปแบบ
คำถามสำคัญคือ: เราพร้อมหรือยัง? ที่จะเติบโตไปพร้อมกับคลื่นลูกใหม่นี้...
-
 @ 65038d69:1fff8852
2025-04-08 03:03:04
@ 65038d69:1fff8852
2025-04-08 03:03:04Sometime in the not-too-distant future...
alert – low voltage – P Node 5
Pippin looked up from the McMaster-Carr catalogue to the blinking line of text. A double-click opened the Grafana page for Perimeter Node 5. The solar panel voltage graph showed a stable 18V, then a jagged drop to 10V. Weird, that panel is less than a year old, and it’s a clear, sunny, wind-less day. He reached to the wall and poked the button labelled “Patrol 3”, and listened for the noise of the Hawk 2A fixed-wing patrol drone leaving it’s nest.
whirrrrr-zip!
Off it went. It should be over the node in about 6 minutes. He opened the live feed on the second monitor and went back to the catalogue. Here we are, 49045K12. That should get the water system in the greenhouse working again. Back on the computer he opened his AirZap page, selected McMaster-Carr from the list of vendors, and entered the part number on the item list. 148sats with next week’s regular delivery, or 400sats special delivery tomorrow. He clicked the “Regular Delivery” button, then “Confirm Zap”. The HF radio on the network rack hummed for a moment then shrieked a burst of noise. The Nostr event with the order details and Lightning payment was on it’s way to McMaster-Carr’s relay. Luckily the part is small and light enough for drone delivery. Pippin’s private grid on Glass Lake is well outside Fed-PS’s ground delivery area, and even if it wasn’t, there are no government roads here. Being a non-citizen and outside a metro-state was a pain and could be expensive. It was better than paying a 95% tax rate though...
alert – low voltage – P Node 5
The node! His eyes snapped to the second monitor just in time for the flyover, and he could see right away that the solar panel was at an odd angle. Yay, a field repair out in the cold. He tossed the tool kit and electrical repair kit on the hovertrike rack while his thermos filled with coffee. Giving the freeze-frame from the Hawk 2A a second look, he grumbled and grabbed the mechanical kit, adding it to the pile. After a third look and an eye roll he dragged a spare solar panel over to the trailer, then slapped the “Hitch” button.
Clear! Clear! Clear! zzz-thunk!
The electromagnets sucked the trailer and trike together, the pin dropping in as soon as it cleared. Pippin silently prayed thanks to God for small conveniences that eased life’s suffering and slurped a sip off the top of the thermos. And coffee. Thank you Father for the coffee trees in the greenhouse.
...
The cutline running the border of Pippin’s property is technically straight and certainly looks it from above, but driving it, even on a hovertrike, is a bouncy, curvy, slow-going affair. Watching immediately ahead instead of appropriately further meant a surprise when the node entered his field of vision. The trailer slid sideways as the trike stopped immediately on its legs. After a sigh and a sip, Pippin powered off the pads and dismounted. Yup, the solar panel is definitely twisted sideways. And bent. And...scratched? Short gouges scraped through the 2 columns of cells closest to the bent edge. There were no fallen trees nearby, so that wasn’t the cause...
snap!
He reached for his laser and got nothing but air. It was in the shop on the charger. Of course it would be; cue a subconscious eye roll. When his brain finally caught up with his eyes he registered the source: 2 meters tall, all black, and capable of mowing him down without a second thought. Thankfully the bull moose was, as most are, completely disinterested in everything but the willow tree he was in the middle of dismembering for lunch. Nonchalance was a benefit of having no natural predators. The ceramic dust on the points of one antler solved the solar panel mystery though; the panel was at the perfect hight for him to have scrapped the side of it as he walked by. He probably didn’t even notice as they’re constantly dragging them through the brush and trees.
...
warning – P Node 5 offline
He hadn’t bothered to mute the alerts while he replaced the broken panel and twisted mounting hardware. Last time he did he forgot to unmute them and went 2 days without noticing. Better to be mildly annoyed for a short time then to go without system or security alerts. He closed the junction box and moved his gaze to the status screen.
powering on...
self check...
all tests pass...
connecting to network...
no signal, switching to failover network...
He mashed the reboot button before it could complete. If he let it connect to the backup ZuckLink satellite network he’d be paying non-citizen usage fees by the megabyte. It was probably just a hiccup anyways, the point-to-point terrestrial link would probably connect fine on the next try.
no signal, switching to failover network...
This time he hit the power switch. The moose hadn’t damaged the antenna and he’d double-checked the alignment while he had the ladder out. Why wasn’t it connecting? He picked up the network scanner, walked to the other side of the node, and pointed it in the general direction of Node 6. No signal. Surely Node 6 didn’t go down on his way here. Now it was either drive all the way there to check it, or let Node 5 connect via satellite and check remotely.
no signal, switching to failover network...
He could practically feel the sats streaming out of his wallet. Ugh, here we go...
failover network unavailble, no signal...
What? There’s no way the satellite link was down too, unless the whole network stack was borked. Huffing and grumbling back to the trike, he plugged the network scanner into it’s com system and selected the satellite interface.
no signal
“Hey Bullwinkle, you wouldn’t happen to be running around with an all-spectrum jammer would you?” Hearing nothing, he looked up and around for the moose. He had been working his way down the edge of the line where the young willows were while Pippin had been working on repairs. Now he was gone. If the moose had joined the rimwalker raiders and started carrying signal jammers, he should be out of range now. He chuckled at the thought of some off-grid wildman trying to train a moose to carry equipment.
no signal, switching to failover network...
failover network unavailable, no signal...
Maybe it was the network stack. But that wouldn’t explain being unable to connect through the trike. Maybe he should just unhitch the trailer and go check Node 6. While highly unlikely, there could be a ZuckLink outage in his cell and an issue with the link to the next node at the same time. The only way to know would be to check in-person.
As he looked up from the status screen his peripheral caught motion on the treeline. “Hey Bullwinkle, is that you?” Antler points protruded from behind a tree, unmoving. A bit too still, actually.
“Bullwinkle?” Those weren’t antler points. That was an antenna array.
no signal
Notes & Appendix
The various technical and other odd bits I used in this story are all either real things or will be very soon. If this was a movie or TV show the visual elements would make some of the nerdier references either to get (i.e. most people would know a drone if they saw one, but saying “fixed-wing patrol drone” doesn’t necessarily draw a mental image for everyone), but in an effort to not constantly interrupt the flow for explanations I’ve moved those here. If I’ve missed any or you want more more detailed explanations, you can find us at scalebright.ca!
McMaster-Carr: A 120+ year old distribution company that specializes in hardware, parts, and tools. Known for their iconic enormous yellow catalogues and legendary (in I.T. circles) website. They’ll probably still be around in another 120+ years and probably still have their yellow catalogues.
Fixed-wing patrol drones: The fixed-wing variety of drones look like miniature airplanes and generally fly much faster than their more common quad-copter style siblings, making them excellent for patrols of static routes.
Sats: Short for “satoshis”, sats are the smallest denomination of Bitcoin.
Zaps: Bitcoin Lighting payments made over Nostr.
Lighting: A Bitcoin protocol for small payments (usually denominated in sats).
Nostr: A decentralized communications and social media protocol.
HF radio: Short for “high frequency”, also knows as ham radio. Bitcoin Lightning payments have been made over HF, as have Nostr posts.
Metro-state: City-states have existed since cities were first built. Metro-states would be a modern version that include their entire greater metro areas in their statehood.
Laser: Advances in focusing lens manufacturing have made handheld “laser guns” possible, though currently legally dubious. I get ads for them on a few of my social networks.
Ceramic solar panels: They’re being marketed as the next big thing in solar tech, but time will tell if they’re as good as the sales pitches say.
Bullwinkle: An anthropomorphic moose character from the 1950s/60s TV show “Rocky and Bullwinkle”.
All-spectrum jammer: Police have been finding criminals using both commercially manufactured and home-made signal jammers during robberies, kidnappings, and other crimes to stop people from calling emergency services or disrupt wireless security cameras. Most of them look like a WIFI router with a whole bunch of antennas.
rimwalker raiders: A made-up category of bandits known for living on the edge of civilization but still making use of technology.
-
 @ d9a329af:bef580d7
2025-04-08 01:08:42
@ d9a329af:bef580d7
2025-04-08 01:08:42Everyone who sees it knows at this point that the matrix of control comes from the overdependence of proprietary software to do our everyday tasks. You can think of this like us being the cling wrap that will just not let go of these pieces of garbage software that don't allow you to see what is in their source code, and how they work. This will tend to lead to the unlawful collection of data (violating the most basic of privacy laws, despite unenforceable contracts that are enforced regardless), bad OPSEC that sees you being stalked and harassed over nothing significant. In the worst of cases, if you speak your mind where you aren't necessarily supposed to be able to do that, and you get doxxed, the worst cases could be far worse than one could imagine.
The solution to this, on the other hand, is using almost exclusively free/libre open-source software and GNU/Linux operation systems. If you're using certain proprietary software, hardening it to give as little data as possible to the entity responsible for it will also work, as long as you know which ones to use. This is a hard pass for a lot of people, but if you want to escape the control matrix of proprietary software, Winblows, HackOS, iHackOS, iBloatOS and stock Google AI Fever Dream, then researching which Free Software (notice the spelling) to use is your first bet. I had already done this for the past four and a half years, and will continue to do it as long as I live, seeing what new Free Software compliant applications and libraries come into the spotlight once things get locked down into walled gardens like what HackOS, iHackOS and BlindnessOS do on a regular basis.
Each of these pieces of software will be in a categorized list with a brief description of what the software is used for. There is a lot to take in, so research this yourself and see if these are right for you. These are the applications I personally use on a regular day-to-day basis, and they work for my needs.
- Operating Systems (the core to your device)
- GNU/Linux operating systems (for PCs) or GrapheneOS (for de-googled Android phones) To be fair on this one, GNU/Linux is the combination of the Linux kernel with the GNU toolchain, which in turn allows any developer to make an operating system that is FOSS, not necessarily Free Software, especially with the Linux Kernel's proprietary bits of code. The Linux kernel is also used in the Android Open-Source Project (AOSP), and is used as the base of operating systems for Android phones such as GrapheneOS, the only AOSP custom ROM I would recommend based upon the research I had done on this (even if very little).
My recommendations on the Linux side of things are almost any Arch-based distribution (with the exception of Manjaro), Debian-based distributions like Linux Mint Debian edition, regular Debian, AntiX or Devuan, or a Fedora/RedHat-based distribution like Nobara Project (if you're a gamer), OpenSUSE (if set up properly) or even Bluefin if you want an atomic desktop (I wouldn't recommend Bluefin if you want to monkey with your operating system and DIY on many aspects of it). Once you learn how to set these up securely, privately and properly, you're on your way to starting your journey into digital liberation, but there's far more to go on this front.
- Web Browsers (How you surf the internet)
-
Firefox Forks This one is self-explanatory. I harden all the Firefox forks I use (LibreWolf, Waterfox, Cachy Browser, Floorp and Zen as some examples) to the nines, despite being unable to do anything about my fingerprint. This is why I use multiple browsers for specific purposes to counteract the fingerprint spying due to weaponized JavaScript. There are ways to circumvent the fingerprint-based espionage, and make sure the site fingerprint.com doesn't know that one's lying about what their user agent is, though it's not very easy to fool that site, as it's used by 6,000 companies.
-
Brave Browser This is the only Chromium-based browser I would recommend, as it's better when hardened against all the other Chromium-based browsers, including Ungoogled Chromium, which is almost impossible to harden due to security vulnerabilities. Despite that, Brave has some of the best features for a Chromium-based browser one can feel comfortable using, even though you'll have similar issues with Firefox-based browsers that aren't actually Firefox (and Firefox has its own issues regarding espionage from Mozilla)
-
Office Suites (If you need to do professional office documents)
-
LibreOffice A fork of Apache's OpenOffice, made better with many features missing from even OnlyOffice and OpenOffice, this suite of applications is the go-to Free Software office suite for many people looking to switch from the proprietary software nether to the diamonds of free/libre open-source software. Though one may need to perform some extra steps to set up compatibility with G-Suite and Microsoft Office past 2015 potentially, it's still a good thing that people trust LibreOffice as their one-stop shop for office documents, despite being completely different from your standard office suite fare.
-
OnlyOffice The competitor to LibreOffice with the ease of Microsoft Office and G-Suite compatibility, OnlyOffice is another office suite that can be good for those who need it, especially since anybody who had used Microsoft Office in particular will be familiar with its layout, if not for a slight learning curve. As someone who's used G-Suite more (due to schooling that stunk worse than a decomposing rat in New York City), that's part of the reason why I switched to LibreOffice, though I tried some others, including OnlyOffice and Abiword (since I use a word processor a lot). This one is another solid option for those who need it.
-
Wordgrinder For those who like to use a terminal emulator like I do, Wordgrinder is a word processor with a terminal user interface (TUI) designed with just focusing on typing without distractions in mind. .wg is the file extension for documents made using Wordgrinder, especially since nowadays most word processors are cloud based. For those who live in a terminal, this is a good option to your terminal UI-based toolbox
-
Text editors
-
Vi, Vim, Neovim and other Vim-like editors The classic VI Improved (Vim), a fork of the TUI modal editor, vi, with keybinds that will be confusing at first, but with practice and patience, bring about muscle memory to stay on the keyboard, and not necessarily touch the mouse, keypad on the right hand side, or even the arrow keys. These keybind skills will stay with one for the rest of their life once they learn how the modes in vi, Vim or vi-based editors work. It's a classic for those working in the terminal, and a staple in FLOSS text editing and coding tools once customized potentially to the nines to your particular style.
-
VSCodium The Free Software fork of Code OSS by Microsoft, but made to be similar in function to VSCode without Microsoft's espionage baked into it. It has almost exactly the same features as VSCode that one would need, and even any VSIX files from VSCode will work in VSCodium. This one is an easy switch from VSCode for those who use it, but don't want the forced telemetry.
-
Emacs The competitor to Vim, Emacs is an editor that is FLOSS in every way imaginable. It is one of the most customizable editors anybody could have ever conceived, though the programming language used in Emacs is a dialect of Lisp the developers had made themselves. There are more keybinds to memorize compared to Vim, though Vim keybinds can be added using the Evil Mode package in any Emacs package manager to get the best of both worlds in Emacs. Once one gets a handle of the steep learning curve for Emacs, it's customizable in every imaginable way almost.
These four categories will get you started on your privacy journey, though I covered things a developer might want. I have plans on more lists to compile once I get my ducks in a row on what I want to cover here on Nostr in a longform format. Feel free to let me know if you have recommendations for me to write about, and I can do some digging on that if it isn't a rabbit hole.
-
 @ 878dff7c:037d18bc
2025-04-07 23:54:09
@ 878dff7c:037d18bc
2025-04-07 23:54:09Potential Reacquisition of Port of Darwin by Australian Government
Summary:
Deputy Prime Minister Richard Marles has indicated that the Australian government may use legal powers to reclaim the Port of Darwin from Chinese control. While the government prefers a commercial solution, it is prepared to take legislative action if necessary. This move reflects growing concerns over foreign ownership of critical infrastructure amid escalating global trade tensions.
Sources: The Guardian - April 8, 2025
Australian Economy Faces Slowdown Amid Global Trade Tensions
Summary:
The Australian economy is projected to experience a slowdown due to escalating global trade tensions, particularly stemming from the United States' recent tariff implementations. Treasurer Jim Chalmers indicated that while Australia is not the primary target—only 4% of its exports go to the U.S.—the broader global impact is expected to affect the local economy. The Reserve Bank may consider interest rate cuts to mitigate these effects. Treasury forecasts suggest a deceleration in GDP growth from 4.25% in 2024–25 to 3.25% in 2025–26, influenced by declining terms of trade and global inflation pressures. Chalmers criticized the U.S. tariff measures as "ill-considered," warning of heightened economic risks and uncertainty.
Sources: News.com.au - April 8, 2025, Reuters - April 8, 2025, The Wall Street Journal - April 8, 2025
Spiking to Announce TradeGPT's Enterprise AI Future at IBM Z Day
Summary:
Spiking will participate in IBM Z Day: Special Edition 2025, unveiling TradeGPT's enterprise AI capabilities. This collaboration with IBM aims to revolutionize AI applications in capital markets by leveraging advanced computing technologies.
Sources: Newsfile - April 7, 2025, Yahoo Finance - April 7, 2025
Earthquake in Upper Hunter Region, NSW
Summary:
A magnitude 3.4 earthquake struck the Upper Hunter region of New South Wales early this morning, with the tremor recorded at 5:18 am local time. The earthquake occurred at a shallow depth of approximately 2.4 miles below the surface. Residents in the vicinity reported feeling the tremor, but there have been no reports of damage or injuries.
Sources: Volcano Discovery - April 8, 2025, Newcastle Weekly - April 8, 2025
Opposition Leader Peter Dutton Predicts Global Recession Amid Market Volatility
Summary:
Opposition Leader Peter Dutton has warned that Australia could face a global recession, citing recent stock market declines and potential delays in retirement for baby boomers. This comes as both Dutton and Prime Minister Anthony Albanese prepare for the first leaders' debate, with economic management and cost-of-living issues at the forefront of their campaigns.
Sources: News.com.au - April 8, 2025
Family Law Regulations Updated
Summary:
Effective April 1, 2025, new Family Law Regulations have commenced, replacing previous regulations from 1984, 2001, and 2008. These updates aim to modernize family law procedures and forms, impacting various aspects of family dispute resolution and arbitration processes.
Source: Federal Circuit and Family Court of Australia - April 1, 2025
U.S. Tariffs Spark Global Economic Concerns
Summary:
U.S. President Donald Trump has announced a 50% increase in tariffs on Chinese imports, escalating trade tensions and causing significant volatility in global stock markets. Australian Treasurer Jim Chalmers stated that while Australia can manage the immediate effects, the country's economic growth is expected to slow due to global repercussions, particularly from the resulting trade war between the U.S. and China. Treasury analysis indicated Australia's GDP would be 0.1% lower this year than previously forecasted, and inflation would rise by 0.2 percentage points. Despite these pressures, Chalmers emphasized that a recession is not expected, with the economy poised for continued growth, supported by increased consumer spending driven by easing inflation and tax cuts.
Sources: The Guardian - April 8, 2025, Reuters - April 7, 2025
NSW Public Hospital Doctors Begin Three-Day Strike Over Pay and Conditions
Summary:
Thousands of doctors in New South Wales public hospitals have commenced a three-day strike starting today, protesting against unsustainable workloads, chronic understaffing, and inadequate pay. The Australian Salaried Medical Officers' Federation (ASMOF) is demanding a 30% pay increase over time, citing excessive workloads and unsafe shift patterns as critical issues. The industrial action is expected to impact elective surgeries and specialist outpatient appointments, primarily at major Sydney hospitals, while emergency services will remain operational but with reduced staffing levels. The strike proceeds despite an Industrial Relations Commission order against such action, making it potentially illegal. The government has urged patients with urgent medical needs to seek emergency care, while those with non-urgent needs are advised to consider alternative healthcare options. Sources: The Guardian - April 7, 2025, ABC News - April 7, 2025, News.com.au - April 2, 2025
World War II Veteran Celebrates 100th Birthday Summary:
Mr. Roy Porter, a World War II veteran, celebrates his 100th birthday. Porter served as a tail-gunner with the Royal Australian Air Force’s 18 Squadron during the war. After returning, he married Norma in 1949, and they have spent over seven decades together in Ocean Grove, Australia. Despite health challenges, both remain mentally sharp and reflect on a century marked by service and love.
Sources: Herald Sun - April 8, 2025
Australian Government Officials Surprised by U.S. Beef Export Comments
Summary:
Australian government officials were taken aback by U.S. President Donald Trump's remarks regarding Australian beef exports. The U.S. administration's concerns appear to be based on inflated figures, with Australian officials clarifying that beef exports to the U.S. are valued closer to $2 billion, not $29 billion as suggested.
Sources: Sky News - April 8, 2025
Donald Trump Threatens 104% Tariff on Chinese Imports
Summary:
U.S. President Donald Trump has threatened to impose a 104% tariff on Chinese goods if China does not withdraw its 34% tariff on American products by April 8, 2025. This escalation has contributed to significant volatility in global stock markets, with concerns about a potential trade war intensifying. The Chinese government has yet to respond to this ultimatum.
Sources: ABC News - April 8, 2025, Sky News - April 8, 2025
Plastic Pollution on Australian Coastlines Drops by 39%
Summary:
Research by CSIRO indicates a 39% reduction in plastic pollution along Australia's metropolitan coastlines over the past decade. The study attributes this decline to effective waste management strategies and increased public awareness, highlighting significant progress in addressing coastal environmental challenges.
Sources: CSIRO - April 8, 2025
Trump’s FDA Chief Dr. Marty Makary Slams Medical Dogma in Healthcare
Summary:
In this episode of the "Dad Saves America" podcast, Dr. Marty Makary, former FDA Chief under President Trump, critiques entrenched medical dogmas that hinder innovation and patient care. He emphasizes the necessity for healthcare professionals to challenge outdated practices and adopt evidence-based approaches.
Key Discussions:
-
Medical Dogma vs. Innovation: Dr. Makary discusses how rigid adherence to traditional medical practices can obstruct the adoption of innovative treatments and technologies.
-
Patient-Centered Care: He advocates for a shift towards more personalized healthcare, emphasizing the importance of tailoring treatments to individual patient needs rather than relying solely on standardized protocols.
-
Transparency in Healthcare: The conversation highlights the need for greater transparency in medical practices and pricing to empower patients and foster trust in the healthcare system.
Insights:
-
Challenging established medical norms is crucial for progress and improving patient outcomes.
-
Embracing innovation requires a balance between evidence-based practices and openness to new methodologies.
-
Enhancing transparency can lead to more informed decisions by patients and promote accountability within the healthcare industry.
For a more in-depth exploration of these topics, listen to the full episode on Spotify: Dad Saves America Podcast - Episode with Dr. Marty Makary
-
-
 @ a396e36e:ec991f1c
2025-04-07 23:46:01
@ a396e36e:ec991f1c
2025-04-07 23:46:01Introduction
In recent years, the term "the new normal" has been used to describe a world reshaped by pandemic policies, inflationary economic measures, rising surveillance, and growing cultural compliance. For many, this phrase signals safety and adaptation. But for others, it marks an era of overreach and loss of personal autonomy. At the heart of the digital resistance to this new order stands an unlikely champion: Bitcoin.
More than a volatile investment or tech novelty, Bitcoin has become a tool of protest, a lifeline for dissidents, and a vehicle for economic sovereignty. As governments expand control over currencies, transactions, and narratives, Bitcoin's decentralized, censorship-resistant architecture offers a parallel path. This post explores how Bitcoin is used to challenge the core pillars of the new normal.
- Pandemic-Era Restrictions and Bitcoin as a Lifeline
During the COVID-19 pandemic, governments worldwide implemented measures ranging from lockdowns to vaccine passports and mass surveillance. For many protestors, these policies were seen not as safety measures, but as infringements on civil liberties.
In Nigeria, during the #EndSARS protests against police brutality, bank accounts of organizers were frozen. Bitcoin became the fallback. Donations poured in through decentralized wallets, bypassing government censors. Similarly, in Canada’s 2022 Freedom Convoy, traditional fundraising platforms were blocked. Activists turned to Bitcoin, distributing funds peer-to-peer using QR codes, out of reach from centralized authority.
These examples underscore Bitcoin’s core strength: permissionless value transfer. No bank account, no ID, no government approval required. It provided activists with the means to continue their work even under financial siege.
- Economic Collapse and the Return to Sound Money
The economic fallout from pandemic stimulus measures has been immense. In the U.S. alone, over $5 trillion in stimulus spending contributed to record-breaking inflation, eroding the purchasing power of fiat currencies. Central banks worldwide flooded markets with newly created money, leading to a global crisis of confidence in fiat.
Bitcoin offered an escape route. With its capped supply of 21 million coins and transparent monetary policy, it attracted investors, corporations, and citizens looking to hedge against inflation and financial mismanagement. In countries like Turkey, Argentina, and Venezuela, where national currencies collapsed, Bitcoin emerged as a digital safe haven.
More than a hedge, Bitcoin became a symbol of protest. Where governments printed wealth out of thin air, Bitcoiners opted out. For them, stacking sats (satoshis) wasn't just financial planning—it was civil disobedience against fiat excess.
- CBDCs, Programmable Money, and the Case for Financial Autonomy
Central Bank Digital Currencies (CBDCs) are on the rise. Promoted as modern, efficient alternatives to cash, they also raise alarms for privacy advocates. Programmable money, expiration dates on stimulus funds, restrictions on purchases—these aren’t speculative fears. They’re openly discussed features.
Bitcoin offers the inverse: a financial system without surveillance, control, or gatekeeping. Unlike CBDCs, it is neutral, global, and governed by code, not political whim. Where CBDCs threaten to tether money to state approval, Bitcoin affirms the right to transact freely.
In this context, adopting Bitcoin is more than a tech choice. It’s a rejection of programmable compliance in favor of financial autonomy.
- Censorship, Compliance Culture, and the Sovereign Individual
Beyond economics and health, the new normal is marked by growing censorship and behavioral control. From deplatforming to frozen bank accounts, those who dissent often find their financial access cut off.
Bitcoin resists this. It doesn’t care who you are, what you believe, or where you live. As long as you control your private keys, your funds are yours.
This neutrality makes Bitcoin a sanctuary for the politically persecuted, the economically excluded, and the privacy-conscious. It’s not about hiding—it’s about freedom by design. In a time when expressing the wrong opinion can cost you your livelihood, Bitcoin offers a parallel economy where your rights don’t expire when you disagree.
Conclusion
Bitcoin is not a panacea. It doesn’t guarantee utopia, and it's not immune to misuse. But in the context of expanding state power, algorithmic governance, and compliant culture, it stands out as one of the few tools that empowers individuals to say "no."
To use Bitcoin today is to engage in a subtle form of protest. It is to opt out of a system many see as rigged, to reclaim privacy, and to assert control over one’s economic life. For those resisting the new normal—not with slogans, but with actions—Bitcoin is not just code. It’s civil disobedience made digital.
-
 @ 2e8970de:63345c7a
2025-04-07 20:44:00
@ 2e8970de:63345c7a
2025-04-07 20:44:00the total number of U.S. forces in the Middle East has now reached 300,000 personnel, including both combat and administrative units.
The US normally has a total of 156,000 military personnel stationed overseas. Trump has suddenly doubled that number in just the Middle East. The Carl Vincent carrier group is relocating to the Red Sea, and half our active B2 bombers are in Diego Garcia. He’s going to bomb Iran.
https://x.com/davegreenidge57/status/1908826028467696075
originally posted at https://stacker.news/items/937451
-
 @ 2e8970de:63345c7a
2025-04-07 19:49:08
@ 2e8970de:63345c7a
2025-04-07 19:49:08https://www.cnbc.com/amp/2025/04/07/peter-navarro-says-vietnams-0percent-tariff-offer-is-not-enough-its-the-non-tariff-cheating-that-matters.html
Vietnam is the US fastest growing trading partner and is helping to diversify away from China. Their offer to make imports from the US import tax free was rejected from the Trump administration.
This is a strong indicator that Trumps overall strategy isn't to use tariffs as a bargaining chip. It seems like the tariffs are the goal, not the means to an end.
originally posted at https://stacker.news/items/937410
-
 @ f1577c25:de26ba14
2025-04-07 19:39:37
@ f1577c25:de26ba14
2025-04-07 19:39:37احنا المرة اللي فاتت اتكلمنا عن الاساسيات تعالي بقي نتكلم بشكل عام علي الطرق اللي في وجهه نظري احسن طرق و هقولك ليه و تبدا بمين الاول و كمان كل طريقه هسيب لك ليها لينك تشرح التطبيق عنه بشكل مفصل اكتر بحيث تعرف الحلو و الوحش و الحد الادني و كل دا
البورصة الأمريكية
- العملة: دولار
- العائد المتوقع: ~10% سنوياً
- الحد الأدنى: ~100 جنيه
- الورق المطلوب: باسبور
- المميزات:
- استثمار دولاري
- سهولة الإيداع بالعملات الرقمية
- إمكانية السحب في أي وقت
- العيوب:
- تحتاج جواز سفر
- تتطلب معرفة بالشركات
- تقلبات السوق علي المدي القصير
- ملاحظات: لو لسة جديد بس معاك حساب دولاري يبقي انصحك بـ IBKR علشان سهل ولكن لو معكش حساب دولاري يبقي Tastytrade علشان سهل الايداع بالكريبتو
العملات الرقمية
- العملة: دولار
- العائد المتوقع: ~10% سنوياً (متغير)
- الحد الأدنى: ~100 جنيه
- الورق المطلوب: بطاقة
- المميزات:
- عائد يومي
- استثمار دولاري
- سهولة السحب
- العيوب:
- العائد متغير
- مخاطر الأمان
- ملاحظات: هنا قصدي منتجات Earn زي في بينانس
ذهب (عالمي)
- العملة: دولار
- العائد المتوقع: متغير حسب سعر الذهب
- الحد الأدنى: ~100 جنيه
- الورق المطلوب: بطاقة
- المميزات:
- الذهب بسعر السوق العالمي
- تحوط ضد التضخم
- العيوب:
- تقلبات السوق علي المدي القصير
- استثمار طويل الأجل
- مخاطر الامان
- ملاحظات: الذهب العالمي قصدي انه تحول عملات ل PAXG في بينانس او Kraken
عقارات (عالمي)
- العملة: دولار
- العائد المتوقع: ~9-10% سنوياً
- الحد الأدنى: ~50 دولار في موقع Realt و ~135 لو موقع Stake
- الورق المطلوب: باسبور
- المميزات:
- استثمار دولاري
- عائد شهري
- العيوب:
- استثمار طويل الأجل
- لو Stake فا تقدر تسحب فلوسك مرتين بالسنة بس
- تحتاج باسبور
- تقلبات السوق
- ملاحظات: في تطبيقين RealT للسوق الامريكي و Stake للسوق الامراتي او السعودي
فوري يومي
- العملة: جنيه مصري
- العائد المتوقع: ~24%
- الحد الأدنى: ~3 جنيه
- الورق المطلوب: بطاقة
- المميزات:
- سهولة الاستخدام
- عائد يومي
- بدون حد أدنى عالي
- العيوب:
- بالجنيه المصري
- عائد أقل من شهادات البنك (الي الان)
- تقلبات العائد
- ملاحظات: قصدي تطبيق فوري يومي
عقارات (محلي)
- العملة: جنيه مصري
- العائد المتوقع: الفعلي 9% ولكن متوقع 28-48% (متوسط 32%)
- الحد الأدنى: 50,000 جنيه
- الورق المطلوب: بطاقة
- المميزات:
- عائد سنوي مرتفع
- العائد مربوط بالدولار بمعني لو حصل تعويم العائد بتاعك هيزيد فا مقاوم للتضخم.
- سهولة الاستخدام
- العيوب:
- حجز الأموال 6 شهور
- 50 ألف حد أدنى
- ضرائب عقارية
- ملاحظات: قصدي تطبيق Safe
شهادات البنك
- العملة: جنيه مصري
- العائد المتوقع: 27% او 30% بعائد تناقصي
- الحد الأدنى: 1000 جنيه
- الورق المطلوب: بطاقة
- المميزات:
- عائد مرتفع
- العيوب:
- بالجنيه المصري
- متقدرش تسحب فلوسك غير بعد مدة الشهادة.
- ملاحظات: دخولك هنا او لا و العائد شهري او سنوي يبقي علي حسب هدفك
ذهب (محلي)
- العملة: جنيه مصري
- العائد المتوقع: متغير حسب سعر الذهب
- الحد الأدنى: ~18 جنيه
- الورق المطلوب: بطاقة
- المميزات:
- قيمة ثابتة ومستقرة
- سهولة الشراء
- الحد الادني صغير لو سهم في صندوق زي AZG
- العيوب:
- يحتاج مبلغ عالي للدخول لو حقيقي
- تقلبات السوق علي المدي القصير
- ملاحظات: يعتبر خيار حلو بس انا شايف لو هتدخل بدهب يبقي عالمي + قصدي ذهب بجد او عن طريق صناديق الذهب زي AZG
كمل قراية بالتفصيل:
nostr:naddr1qvzqqqr4gupzpu2h0sja0vmqdqjzq6e820jjjnuytzw2ksmemfnadhe0hm0zdws5qqxnzde5xvurzvfsxuerzvphcvddg0
nostr:naddr1qvzqqqr4gupzpu2h0sja0vmqdqjzq6e820jjjnuytzw2ksmemfnadhe0hm0zdws5qqxnzde5xvunzvesx5erywpsepywcn
nostr:naddr1qvzqqqr4gupzpu2h0sja0vmqdqjzq6e820jjjnuytzw2ksmemfnadhe0hm0zdws5qqxnzde5xvunzdpcxq6nxwp3xqxgmx
nostr:naddr1qvzqqqr4gupzpu2h0sja0vmqdqjzq6e820jjjnuytzw2ksmemfnadhe0hm0zdws5qqxnzde5xscrqdesxycnvv34l5ye0c
nostr:naddr1qvzqqqr4gupzpu2h0sja0vmqdqjzq6e820jjjnuytzw2ksmemfnadhe0hm0zdws5qqxnzde5xvungvfsx5cnvv3ndwszwl
nostr:naddr1qvzqqqr4gupzpu2h0sja0vmqdqjzq6e820jjjnuytzw2ksmemfnadhe0hm0zdws5qqxnzde5xscrqdpnxc6rvvee3fqr5t
nostr:naddr1qvzqqqr4gupzpu2h0sja0vmqdqjzq6e820jjjnuytzw2ksmemfnadhe0hm0zdws5qqxnzde5xscrqdesxucrjdehs24uge
ادعمني (اختياري)
- USDT (TRC20):
TKQ3Uwkq21ntiua2Zh9Hu376fdMdnRGWN6
آخر تحديث: 4 أبريل 2025
-
 @ da0b9bc3:4e30a4a9
2025-04-07 18:59:28
@ da0b9bc3:4e30a4a9
2025-04-07 18:59:28Hello Stackers!
It's Monday so we're back doing "Meta Music Mondays" 😉.
From before the territory existed there was just one post a week in a ~meta take over. Now each month we have a different theme and bring music from that theme.
This month is April and we're doing what it...?. So give me those what if tracks.
Here's and example;
What if, Another Brick in the Wall was EDM?
Let's have fun.
https://youtu.be/uLMobfyKB9o?si=vD9OMd6irvFG2vP
Talk Music. Share Tracks. Zap Sats.
originally posted at https://stacker.news/items/937359
-
 @ 39f70015:9d4e378a
2025-04-07 17:28:03
@ 39f70015:9d4e378a
2025-04-07 17:28:03This is a copy of chapter four of Mastering Bitcoin Cash. I'm using it to test out creating long-form content on highlighter.com.
This is an edit after the original post. I want to test how editing long-form content works on Nostr.
4. Transactions
Introduction
Transactions are the most important part of the Bitcoin Cash system. Everything else in Bitcoin Cash is designed to ensure that transactions can be created, propagated on the network, validated, and finally added to the global ledger of transactions (the blockchain). Transactions are data structures that encode the transfer of value between participants in the Bitcoin Cash system. Each transaction is a public entry in Bitcoin Cash’s blockchain, the global double-entry bookkeeping ledger.
In this chapter we will examine all the various forms of transactions, what they contain, how to create them, how they are verified, and how they become part of the permanent record of all transactions.
Transaction Lifecycle
A transaction’s lifecycle starts with the transaction’s creation, also known as origination. The transaction is then signed with one or more signatures indicating the authorization to spend the funds referenced by the transaction. The transaction is then broadcast on the Bitcoin Cash network, where each network node (participant) validates and propagates the transaction until it reaches (almost) every node in the network. Finally, the transaction is verified by a mining node and included in a block of transactions that is recorded on the blockchain.
Once recorded on the blockchain and confirmed by sufficient subsequent blocks (confirmations), the transaction is a permanent part of the Bitcoin Cash ledger and is accepted as valid by all participants. The funds allocated to a new owner by the transaction can then be spent in a new transaction, extending the chain of ownership and beginning the lifecycle of a transaction again.
Creating Transactions
In some ways it helps to think of a transaction in the same way as a paper check. Like a check, a transaction is an instrument that expresses the intent to transfer money and is not visible to the financial system until it is submitted for execution. Like a check, the originator of the transaction does not have to be the one signing the transaction.
Transactions can be created online or offline by anyone, even if the person creating the transaction is not an authorized signer on the account. For example, an accounts payable clerk might process payable checks for signature by the CEO. Similarly, an accounts payable clerk can create Bitcoin Cash transactions and then have the CEO apply digital signatures to make them valid. Whereas a check references a specific account as the source of the funds, a Bitcoin Cash transaction references a specific previous transaction as its source, rather than an account.
Once a transaction has been created, it is signed by the owner (or owners) of the source funds. If it is properly formed and signed, the signed transaction is now valid and contains all the information needed to execute the transfer of funds. Finally, the valid transaction has to reach the Bitcoin Cash network so that it can be propagated until it reaches a miner for inclusion in the pubic ledger (the blockchain).
Broadcasting Transactions to the Bitcoin Cash Network
First, a transaction needs to be delivered to the Bitcoin Cash network so that it can be propagated and included in the blockchain. In essence, a Bitcoin Cash transaction is just 300 to 400 bytes of data and has to reach any one of tens of thousands of Bitcoin Cash nodes. The senders do not need to trust the nodes they use to broadcast the transaction, as long as they use more than one to ensure that it propagates. The nodes don’t need to trust the sender or establish the sender’s "identity." Because the transaction is signed and contains no confidential information, private keys, or credentials, it can be publicly broadcast using any underlying network transport that is convenient. Unlike credit card transactions, for example, which contain sensitive information and can only be transmitted on encrypted networks, a Bitcoin Cash transaction can be sent over any network. As long as the transaction can reach a Bitcoin Cash node that will propagate it into the Bitcoin Cash network, it doesn’t matter how it is transported to the first node.
Bitcoin Cash transactions can therefore be transmitted to the Bitcoin Cash network over insecure networks such as WiFi, Bluetooth, NFC, Chirp, barcodes, or by copying and pasting into a web form. In extreme cases, a Bitcoin Cash transaction could be transmitted over packet radio, satellite relay, or shortwave using burst transmission, spread spectrum, or frequency hopping to evade detection and jamming. A Bitcoin Cash transaction could even be encoded as smileys (emoticons) and posted in a public forum or sent as a text message or Skype chat message. Bitcoin Cash has turned money into a data structure, making it virtually impossible to stop anyone from creating and executing a Bitcoin Cash transaction.
Propagating Transactions on the Bitcoin Cash Network
Once a Bitcoin Cash transaction is sent to any node connected to the Bitcoin Cash network, the transaction will be validated by that node. If valid, that node will propagate it to the other nodes to which it is connected, and a success message will be returned synchronously to the originator. If the transaction is invalid, the node will reject it and synchronously return a rejection message to the originator.
The Bitcoin Cash network is a peer-to-peer network, meaning that each Bitcoin Cash node is connected to a few other Bitcoin Cash nodes that it discovers during startup through the peer-to-peer protocol. The entire network forms a loosely connected mesh without a fixed topology or any structure, making all nodes equal peers. Messages, including transactions and blocks, are propagated from each node to all the peers to which it is connected, a process called "flooding." A new validated transaction injected into any node on the network will be sent to all of the nodes connected to it (neighbors), each of which will send the transaction to all its neighbors, and so on. In this way, within a few seconds a valid transaction will propagate in an exponentially expanding ripple across the network until all nodes in the network have received it.
The Bitcoin Cash network is designed to propagate transactions and blocks to all nodes in an efficient and resilient manner that is resistant to attacks. To prevent spamming, denial-of-service attacks, or other nuisance attacks against the Bitcoin Cash system, every node independently validates every transaction before propagating it further. A malformed transaction will not get beyond one node.
Transaction Structure
A transaction is a data structure that encodes a transfer of value from a source of funds, called an input, to a destination, called an output. Transaction inputs and outputs are not related to accounts or identities. Instead, you should think of them as Bitcoin Cash amounts—chunks of Bitcoin Cash—being locked with a specific secret that only the owner, or person who knows the secret, can unlock. A transaction contains a number of fields, as shown in The structure of a transaction.
| Size | Field | Description | | --- | --- | --- | | 4 bytes | Version | Specifies which rules this transaction follows | | 1–9 bytes (VarInt) | Input Counter | How many inputs are included | | Variable | Inputs | One or more transaction inputs | | 1–9 bytes (VarInt) | Output Counter | How many outputs are included | | variable | Outputs | One or more transaction outputs | | 4 bytes | Locktime | A Unix timestamp or block number |
Table 1. The structure of a transaction
Transaction Locktime
Locktime, also known as nLockTime from the variable name used in the reference client, defines the earliest time that a transaction is valid and can be relayed on the network or added to the blockchain. It is set to zero in most transactions to indicate immediate propagation and execution. If locktime is nonzero and below 500 million, it is interpreted as a block height, meaning the transaction is not valid and is not relayed or included in the blockchain prior to the specified block height. If it is above 500 million, it is interpreted as a Unix Epoch timestamp (seconds since Jan-1-1970) and the transaction is not valid prior to the specified time. Transactions with locktime specifying a future block or time must be held by the originating system and transmitted to the Bitcoin Cash network only after they become valid. The use of locktime is equivalent to postdating a paper check.
Transaction Outputs and Inputs
The fundamental building block of a Bitcoin Cash transaction is an unspent transaction output, or UTXO. UTXO are indivisible chunks of Bitcoin Cash currency locked to a specific owner, recorded on the blockchain, and recognized as currency units by the entire network. The Bitcoin Cash network tracks all available (unspent) UTXO currently numbering in the millions. Whenever a user receives Bitcoin Cash, that amount is recorded within the blockchain as a UTXO. Thus, a user’s Bitcoin Cash might be scattered as UTXO amongst hundreds of transactions and hundreds of blocks. In effect, there is no such thing as a stored balance of a Bitcoin Cash address or account; there are only scattered UTXO, locked to specific owners. The concept of a user’s Bitcoin Cash balance is a derived construct created by the wallet application. The wallet calculates the user’s balance by scanning the blockchain and aggregating all UTXO belonging to that user.
There are no accounts or balances in Bitcoin Cash; there are only _unspent transaction outputs_ (UTXO) scattered in the blockchain.
A UTXO can have an arbitrary value denominated as a multiple of satoshis. Just like dollars can be divided down to two decimal places as cents, bitcoins can be divided down to eight decimal places as satoshis. Although UTXO can be any arbitrary value, once created it is indivisible just like a coin that cannot be cut in half. If a UTXO is larger than the desired value of a transaction, it must still be consumed in its entirety and change must be generated in the transaction. In other words, if you have a 20 Bitcoin Cash UTXO and want to pay 1 Bitcoin Cash, your transaction must consume the entire 20 Bitcoin Cash UTXO and produce two outputs: one paying 1 Bitcoin Cash to your desired recipient and another paying 19 Bitcoin Cash in change back to your wallet. As a result, most Bitcoin Cash transactions will generate change.
Imagine a shopper buying a $1.50 beverage, reaching into her wallet and trying to find a combination of coins and bank notes to cover the $1.50 cost. The shopper will choose exact change if available (a dollar bill and two quarters), or a combination of smaller denominations (six quarters), or if necessary, a larger unit such as a five dollar bank note. If she hands too much money, say $5, to the shop owner, she will expect $3.50 change, which she will return to her wallet and have available for future transactions.
Similarly, a Bitcoin Cash transaction must be created from a user’s UTXO in whatever denominations that user has available. Users cannot cut a UTXO in half any more than they can cut a dollar bill in half and use it as currency. The user’s wallet application will typically select from the user’s available UTXO various units to compose an amount greater than or equal to the desired transaction amount.
As with real life, the Bitcoin Cash application can use several strategies to satisfy the purchase amount: combining several smaller units, finding exact change, or using a single unit larger than the transaction value and making change. All of this complex assembly of spendable UTXO is done by the user’s wallet automatically and is invisible to users. It is only relevant if you are programmatically constructing raw transactions from UTXO.
The UTXO consumed by a transaction are called transaction inputs, and the UTXO created by a transaction are called transaction outputs. This way, chunks of Bitcoin Cash value move forward from owner to owner in a chain of transactions consuming and creating UTXO. Transactions consume UTXO by unlocking it with the signature of the current owner and create UTXO by locking it to the Bitcoin Cash address of the new owner.
The exception to the output and input chain is a special type of transaction called the coinbase transaction, which is the first transaction in each block. This transaction is placed there by the "winning" miner and creates brand-new Bitcoin Cash payable to that miner as a reward for mining. This is how Bitcoin Cash’s money supply is created during the mining process, as we will see in Mining and Consensus.
What comes first? Inputs or outputs, the chicken or the egg? Strictly speaking, outputs come first because coinbase transactions, which generate new Bitcoin Cash, have no inputs and create outputs from nothing.
Transaction Outputs
Every Bitcoin Cash transaction creates outputs, which are recorded on the Bitcoin Cash ledger. Almost all of these outputs, with one exception (see Data Output (OP_RETURN)) create spendable chunks of Bitcoin Cash called unspent transaction outputs or UTXO, which are then recognized by the whole network and available for the owner to spend in a future transaction. Sending someone Bitcoin Cash is creating an unspent transaction output (UTXO) registered to their address and available for them to spend.
UTXO are tracked by every full-node Bitcoin Cash client as a data set called the UTXO set or UTXO pool, held in a database. New transactions consume (spend) one or more of these outputs from the UTXO set.
Transaction outputs consist of two parts:
- An amount of Bitcoin Cash, denominated in satoshis, the smallest Bitcoin Cash unit
- A locking script, also known as an "encumbrance" that "locks" this amount by specifying the conditions that must be met to spend the output
The transaction scripting language, used in the locking script mentioned previously, is discussed in detail in Transaction Scripts and Script Language. The structure of a transaction output shows the structure of a transaction output.
| Size | Field | Description | | --- | --- | --- | | 8 bytes | Amount | Bitcoin Cash value in satoshis (108 Bitcoin Cash) | | 1–9 bytes (VarInt) | Locking-Script Size | Locking-Script length in bytes, to follow | | Variable | Locking-Script | A script defining the conditions needed to spend the output | | 1–9 bytes (VarInt) | Output Counter | How many outputs are included | | variable | Outputs | One or more transaction outputs | | 4 bytes | Locktime | A Unix timestamp or block number |
Table 2. The structure of a transaction output
In A script that calls
bitbox.Address.utxoto find the UTXO related to an address, we use thebitbox.Addressclass to find the unspent outputs (UTXO) of a specific address.Example 1. A script that calls
bitbox.Address.utxoto find the UTXO related to an address```javascript bitbox.Address.utxo('bitcoincash:qpcxf2sv9hjw08nvpgffpamfus9nmksm3chv5zqtnz').then((result) => { console.log(result); }, (err) => { console.log(err); });
Returns the following: [{ txid: 'cc27be8846276612dfce5924b7be96556212f0f0e62bd17641732175edb9911e', vout: 0, scriptPubKey: '76a9147064aa0c2de4e79e6c0a1290f769e40b3dda1b8e88ac', amount: 0.00007021, satoshis: 7021, height: 527155, confirmations: 11879, legacyAddress: '1BFHGm4HzqgXXyNX8n7DsQno5DAC4iLMRA', cashAddress: 'bitcoincash:qpcxf2sv9hjw08nvpgffpamfus9nmksm3chv5zqtnz' } ] ```
Running the script, we see an array of objects representing unspent transaction outputs which are available to this address.
Spending conditions (encumbrances)
Transaction outputs associate a specific amount (in satoshis) to a specific encumbrance or locking script that defines the condition that must be met to spend that amount. In most cases, the locking script will lock the output to a specific Bitcoin Cash address, thereby transferring ownership of that amount to the new owner. When Alice paid Bob’s Cafe for a cup of coffee, her transaction created a 0.00208507 Bitcoin Cash output encumbered or locked to the cafe’s Bitcoin Cash address. That 0.00208507 Bitcoin Cash output was recorded on the blockchain and became part of the Unspent Transaction Output set, meaning it showed in Bob’s wallet as part of the available balance. When Bob chooses to spend that amount, his transaction will release the encumbrance, unlocking the output by providing an unlocking script containing a signature from Bob’s private key.
Transaction Inputs
In simple terms, transaction inputs are pointers to UTXO. They point to a specific UTXO by reference to the transaction hash and sequence number where the UTXO is recorded in the blockchain. To spend UTXO, a transaction input also includes unlocking scripts that satisfy the spending conditions set by the UTXO. The unlocking script is usually a signature proving ownership of the Bitcoin Cash address that is in the locking script.
When users make a payment, their wallet constructs a transaction by selecting from the available UTXO. For example, to make a 0.00208507 Bitcoin Cash payment, the wallet app may select a 0.002 UTXO and a 0.00008507 UTXO, using them both to add up to the desired payment amount.
Once the UTXO is selected, the wallet then produces unlocking scripts containing signatures for each of the UTXO, thereby making them spendable by satisfying their locking script conditions. The wallet adds these UTXO references and unlocking scripts as inputs to the transaction. The structure of a transaction input shows the structure of a transaction input.
| Size | Field | Description | | --- | --- | --- | | 32 bytes | Transaction Hash | Pointer to the transaction containing the UTXO to be spent | | 4 bytes | Output Index | The index number of the UTXO to be spent; first one is 0 | | 1-9 bytes (VarInt) | Unlocking-Script Size | Unlocking-Script length in bytes, to follow | | Variable | Unlocking-Script | A script that fulfills the conditions of the UTXO locking script | | 4 bytes | Sequence Number | Currently disabled Tx-replacement feature, set to 0xFFFFFFFF |
Table 3. The structure of a transaction input
Transaction Fees
Most transactions include transaction fees, which compensate the Bitcoin Cash miners for securing the network. Mining and the fees and rewards collected by miners are discussed in more detail in Mining and Consensus. This section examines how transaction fees are included in a typical transaction. Most wallets calculate and include transaction fees automatically. However, if you are constructing transactions programmatically, or using a command-line interface, you must manually account for and include these fees.
Transaction fees serve as an incentive to include (mine) a transaction into the next block and also as a disincentive against "spam" transactions or any kind of abuse of the system, by imposing a small cost on every transaction. Transaction fees are collected by the miner who mines the block that records the transaction on the blockchain.
Transaction fees are calculated based on the size of the transaction in kilobytes, not the value of the transaction in Bitcoin Cash. Overall, transaction fees are set based on market forces within the Bitcoin Cash network. Miners prioritize transactions based on many different criteria, including fees, and might even process transactions for free under certain circumstances. Transaction fees affect the processing priority, meaning that a transaction with sufficient fees is likely to be included in the next-most–mined block, whereas a transaction with insufficient or no fees might be delayed, processed on a best-effort basis after a few blocks, or not processed at all. Transaction fees are not mandatory, and transactions without fees might be processed eventually; however, including transaction fees encourages priority processing.
The current algorithm used by miners to prioritize transactions for inclusion in a block based on their fees is examined in detail in Mining and Consensus.
Adding Fees to Transactions
The data structure of transactions does not have a field for fees. Instead, fees are implied as the difference between the sum of inputs and the sum of outputs. Any excess amount that remains after all outputs have been deducted from all inputs is the fee that is collected by the miners.
Transaction fees are implied, as the excess of inputs minus outputs:
Fees = Sum(Inputs) – Sum(Outputs)This is a somewhat confusing element of transactions and an important point to understand, because if you are constructing your own transactions you must ensure you do not inadvertently include a very large fee by underspending the inputs. That means that you must account for all inputs, if necessary by creating change, or you will end up giving the miners a very big tip!
For example, if you consume a 20-Bitcoin Cash UTXO to make a 1-Bitcoin Cash payment, you must include a 19-Bitcoin Cash change output back to your wallet. Otherwise, the 19-Bitcoin Cash "leftover" will be counted as a transaction fee and will be collected by the miner who mines your transaction in a block. Although you will receive priority processing and make a miner very happy, this is probably not what you intended.
If you forget to add a change output in a manually constructed transaction, you will be paying the change as a transaction fee. "Keep the change!" might not be what you intended.
Let’s see how this works in practice, by looking at Alice’s coffee purchase again. Alice wants to spend 0.00208507 Bitcoin Cash to pay for coffee. To ensure this transaction is processed promptly, she will want to include a transaction fee of 1 satoshi per byte. That will mean that the total cost of the transaction will be 0.00208750. Her wallet must therefore source a set of UTXO that adds up to 0.00208750 Bitcoin Cash or more and, if necessary, create change. Let’s say her wallet has a 0.00277257-Bitcoin Cash UTXO available. It will therefore need to consume this UTXO, create one output to Bob’s Cafe for 0.00208507, and a second output with 0.00068507 Bitcoin Cash in change back to her own wallet, leaving 0.00000243 Bitcoin Cash unallocated, as an implicit fee for the transaction.
Transaction Chaining and Orphan Transactions
As we have seen, transactions form a chain, whereby one transaction spends the outputs of the previous transaction (known as the parent) and creates outputs for a subsequent transaction (known as the child). Sometimes an entire chain of transactions depending on each other—say a parent, child, and grandchild transaction—are created at the same time, to fulfill a complex transactional workflow that requires valid children to be signed before the parent is signed.
When a chain of transactions is transmitted across the network, they don’t always arrive in the same order. Sometimes, the child might arrive before the parent. In that case, the nodes that see a child first can see that it references a parent transaction that is not yet known. Rather than reject the child, they put it in a temporary pool to await the arrival of its parent and propagate it to every other node. The pool of transactions without parents is known as the orphan transaction pool. Once the parent arrives, any orphans that reference the UTXO created by the parent are released from the pool, revalidated recursively, and then the entire chain of transactions can be included in the transaction pool, ready to be mined in a block. Transaction chains can be arbitrarily long, with any number of generations transmitted simultaneously. The mechanism of holding orphans in the orphan pool ensures that otherwise valid transactions will not be rejected just because their parent has been delayed and that eventually the chain they belong to is reconstructed in the correct order, regardless of the order of arrival.
There is a limit to the number of orphan transactions stored in memory, to prevent a denial-of-service attack against Bitcoin Cash nodes. The limit is defined as MAX_ORPHAN_TRANSACTIONS in the source code of the Bitcoin Cash reference client. If the number of orphan transactions in the pool exceeds MAX_ORPHAN_TRANSACTIONS, one or more randomly selected orphan transactions are evicted from the pool, until the pool size is back within limits.
Transaction Scripts and Script Language
Bitcoin Cash clients validate transactions by executing a script, written in a Forth-like scripting language. Both the locking script (encumbrance) placed on a UTXO and the unlocking script that usually contains a signature are written in this scripting language. When a transaction is validated, the unlocking script in each input is executed alongside the corresponding locking script to see if it satisfies the spending condition.
Today, most transactions processed through the Bitcoin Cash network have the form "Alice pays Bob" and are based on the same script called a Pay-to-Public-Key-Hash script. However, the use of scripts to lock outputs and unlock inputs means that through use of the programming language, transactions can contain an infinite number of conditions. Bitcoin Cash transactions are not limited to the "Alice pays Bob" form and pattern.
This is only the tip of the iceberg of possibilities that can be expressed with this scripting language. In this section, we will demonstrate the components of the Bitcoin Cash transaction scripting language and show how it can be used to express complex conditions for spending and how those conditions can be satisfied by unlocking scripts.
Bitcoin Cash transaction validation is not based on a static pattern, but instead is achieved through the execution of a scripting language. This language allows for a nearly infinite variety of conditions to be expressed. This is how Bitcoin Cash gets the power of "programmable money."
Script Construction (Lock + Unlock)
Bitcoin Cash’s transaction validation engine relies on two types of scripts to validate transactions: a locking script and an unlocking script.
A locking script is an encumbrance placed on an output, and it specifies the conditions that must be met to spend the output in the future. Historically, the locking script was called a scriptPubKey, because it usually contained a public key or Bitcoin Cash address. In this book we refer to it as a "locking script" to acknowledge the much broader range of possibilities of this scripting technology. In most Bitcoin Cash applications, what we refer to as a locking script will appear in the source code as scriptPubKey.
An unlocking script is a script that "solves," or satisfies, the conditions placed on an output by a locking script and allows the output to be spent. Unlocking scripts are part of every transaction input, and most of the time they contain a digital signature produced by the user’s wallet from his or her private key. Historically, the unlocking script is called scriptSig, because it usually contained a digital signature. In most Bitcoin Cash applications, the source code refers to the unlocking script as scriptSig. In this book, we refer to it as an "unlocking script" to acknowledge the much broader range of locking script requirements, because not all unlocking scripts must contain signatures.
Every Bitcoin Cash client will validate transactions by executing the locking and unlocking scripts together. For each input in the transaction, the validation software will first retrieve the UTXO referenced by the input. That UTXO contains a locking script defining the conditions required to spend it. The validation software will then take the unlocking script contained in the input that is attempting to spend this UTXO and execute the two scripts.
In the original Bitcoin Cash client, the unlocking and locking scripts were concatenated and executed in sequence. For security reasons, this was changed in 2010, because of a vulnerability that allowed a malformed unlocking script to push data onto the stack and corrupt the locking script. In the current implementation, the scripts are executed separately with the stack transferred between the two executions, as described next.
First, the unlocking script is executed, using the stack execution engine. If the unlocking script executed without errors (e.g., it has no "dangling" operators left over), the main stack (not the alternate stack) is copied and the locking script is executed. If the result of executing the locking script with the stack data copied from the unlocking script is "TRUE," the unlocking script has succeeded in resolving the conditions imposed by the locking script and, therefore, the input is a valid authorization to spend the UTXO. If any result other than "TRUE" remains after execution of the combined script, the input is invalid because it has failed to satisfy the spending conditions placed on the UTXO. Note that the UTXO is permanently recorded in the blockchain, and therefore is invariable and is unaffected by failed attempts to spend it by reference in a new transaction. Only a valid transaction that correctly satisfies the conditions of the UTXO results in the UTXO being marked as "spent" and removed from the set of available (unspent) UTXO.
Combining scriptSig and scriptPubKey to evaluate a transaction script is an example of the unlocking and locking scripts for the most common type of Bitcoin Cash transaction (a payment to a public key hash), showing the combined script resulting from the concatenation of the unlocking and locking scripts prior to script validation.
 Figure 1. Combining scriptSig and scriptPubKey to evaluate a transaction script
Figure 1. Combining scriptSig and scriptPubKey to evaluate a transaction scriptScripting Language
The Bitcoin Cash transaction script language, called Script, is a Forth-like reverse-polish notation stack-based execution language. If that sounds like gibberish, you probably haven’t studied 1960’s programming languages. Script is a very simple language that was designed to be limited in scope and executable on a range of hardware, perhaps as simple as an embedded device, such as a handheld calculator. It requires minimal processing and cannot do many of the fancy things modern programming languages can do. In the case of programmable money, that is a deliberate security feature.
Bitcoin Cash’s scripting language is called a stack-based language because it uses a data structure called a stack. A stack is a very simple data structure, which can be visualized as a stack of cards. A stack allows two operations: push and pop. Push adds an item on top of the stack. Pop removes the top item from the stack.
The scripting language executes the script by processing each item from left to right. Numbers (data constants) are pushed onto the stack. Operators push or pop one or more parameters from the stack, act on them, and might push a result onto the stack. For example, OP_ADD will pop two items from the stack, add them, and push the resulting sum onto the stack.
Conditional operators evaluate a condition, producing a boolean result of TRUE or FALSE. For example, OP_EQUAL pops two items from the stack and pushes TRUE (TRUE is represented by the number 1) if they are equal or FALSE (represented by zero) if they are not equal. Bitcoin Cash transaction scripts usually contain a conditional operator, so that they can produce the TRUE result that signifies a valid transaction.
In Bitcoin Cash’s script validation doing simple math, the script 2 3 OP_ADD 5 OP_EQUAL demonstrates the arithmetic addition operator OP_ADD, adding two numbers and putting the result on the stack, followed by the conditional operator OP_EQUAL, which checks that the resulting sum is equal to 5. For brevity, the OP_ prefix is omitted in the step-by-step example.
The following is a slightly more complex script, which calculates 2 + 7 – 3 + 1. Notice that when the script contains several operators in a row, the stack allows the results of one operator to be acted upon by the next operator:
2 7 OP_ADD 3 OP_SUB 1 OP_ADD 7 OP_EQUALTry validating the preceding script yourself using pencil and paper. When the script execution ends, you should be left with the value TRUE on the stack.
Although most locking scripts refer to a Bitcoin Cash address or public key, thereby requiring proof of ownership to spend the funds, the script does not have to be that complex. Any combination of locking and unlocking scripts that results in a TRUE value is valid. The simple arithmetic we used as an example of the scripting language is also a valid locking script that can be used to lock a transaction output.
Use part of the arithmetic example script as the locking script:
3 OP_ADD 5 OP_EQUALwhich can be satisfied by a transaction containing an input with the unlocking script:
2The validation software combines the locking and unlocking scripts and the resulting script is:
2 3 OP_ADD 5 OP_EQUALAs we saw in the step-by-step example in Bitcoin Cash’s script validation doing simple math, when this script is executed, the result is OP_TRUE, making the transaction valid. Not only is this a valid transaction output locking script, but the resulting UTXO could be spent by anyone with the arithmetic skills to know that the number 2 satisfies the script.
 Figure 2. Bitcoin Cash’s script validation doing simple math
Figure 2. Bitcoin Cash’s script validation doing simple mathTransactions are valid if the top result on the stack is TRUE (noted as {0x01}), any other non-zero value or if the stack is empty after script execution. Transactions are invalid if the top value on the stack is FALSE (a zero-length empty value, noted as {}) or if script execution is halted explicitly by an operator, such as OP_VERIFY, OP_RETURN, or a conditional terminator such as OP_ENDIF.
Turing Incompleteness
The Bitcoin Cash transaction script language contains many operators, but is deliberately limited in one important way—there are no loops or complex flow control capabilities other than conditional flow control. This ensures that the language is not Turing Complete, meaning that scripts have limited complexity and predictable execution times. Script is not a general-purpose language. These limitations ensure that the language cannot be used to create an infinite loop or other form of "logic bomb" that could be embedded in a transaction in a way that causes a denial-of-service attack against the Bitcoin Cash network. Remember, every transaction is validated by every full node on the Bitcoin Cash network. A limited language prevents the transaction validation mechanism from being used as a vulnerability.
Stateless Verification
The Bitcoin Cash transaction script language is stateless, in that there is no state prior to execution of the script, or state saved after execution of the script. Therefore, all the information needed to execute a script is contained within the script. A script will predictably execute the same way on any system. If your system verifies a script, you can be sure that every other system in the Bitcoin Cash network will also verify the script, meaning that a valid transaction is valid for everyone and everyone knows this. This predictability of outcomes is an essential benefit of the Bitcoin Cash system.
Standard Transactions
In the first few years of Bitcoin Cash’s development, the developers introduced some limitations in the types of scripts that could be processed by the reference client. These limitations are encoded in a function called isStandard(), which defines five types of "standard" transactions. These limitations are temporary and might be lifted by the time you read this. Until then, the five standard types of transaction scripts are the only ones that will be accepted by the reference client and most miners who run the reference client. Although it is possible to create a nonstandard transaction containing a script that is not one of the standard types, you must find a miner who does not follow these limitations to mine that transaction into a block.
Check the source code of the Bitcoin Core client (the reference implementation) to see what is currently allowed as a valid transaction script.
The five standard types of transaction scripts are pay-to-public-key-hash (P2PKH), public-key, multi-signature (limited to 15 keys), pay-to-script-hash (P2SH), and data output (OP_RETURN), which are described in more detail in the following sections.
Pay-to-Public-Key-Hash (P2PKH)
The vast majority of transactions processed on the Bitcoin Cash network are P2PKH transactions. These contain a locking script that encumbers the output with a public key hash, more commonly known as a Bitcoin Cash address. Transactions that pay a Bitcoin Cash address contain P2PKH scripts. An output locked by a P2PKH script can be unlocked (spent) by presenting a public key and a digital signature created by the corresponding private key.
For example, let’s look at Alice’s payment to Bob’s Cafe again. Alice made a payment of 0.00208507 Bitcoin Cash to the cafe’s Bitcoin Cash address. That transaction output would have a locking script of the form:
OP_DUP OP_HASH160 <Cafe Public Key Hash> OP_EQUAL OP_CHECKSIGThe Cafe Public Key Hash is equivalent to the Bitcoin Cash address of the cafe, without the Base58Check encoding. Most applications would show the public key hash in hexadecimal encoding and not the familiar Bitcoin Cash address Base58Check format that begins with a "1".
The preceding locking script can be satisfied with an unlocking script of the form:
<Cafe Signature> <Cafe Public Key>The two scripts together would form the following combined validation script:
<Cafe Signature> <Cafe Public Key> OP_DUP OP_HASH160 <Cafe Public Key Hash> OP_EQUAL OP_CHECKSIGWhen executed, this combined script will evaluate to TRUE if, and only if, the unlocking script matches the conditions set by the locking script. In other words, the result will be TRUE if the unlocking script has a valid signature from the cafe’s private key that corresponds to the public key hash set as an encumbrance.
Figures and show (in two parts) a step-by-step execution of the combined script, which will prove this is a valid transaction.
 Figure 3. Evaluating a script for a P2PKH transaction (Part 1 of 2)
Figure 3. Evaluating a script for a P2PKH transaction (Part 1 of 2)Pay-to-Public-Key
Pay-to-public-key is a simpler form of a Bitcoin Cash payment than pay-to-public-key-hash. With this script form, the public key itself is stored in the locking script, rather than a public-key-hash as with P2PKH earlier, which is much shorter. Pay-to-public-key-hash was invented by Satoshi to make Bitcoin Cash addresses shorter, for ease of use. Pay-to-public-key is now most often seen in coinbase transactions, generated by older mining software that has not been updated to use P2PKH.
A pay-to-public-key locking script looks like this:
<Public Key A> OP_CHECKSIGThe corresponding unlocking script that must be presented to unlock this type of output is a simple signature, like this:
<Signature from Private Key A>The combined script, which is validated by the transaction validation software, is:
<Signature from Private Key A> <Public Key A> OP_CHECKSIGThis script is a simple invocation of the CHECKSIG operator, which validates the signature as belonging to the correct key and returns TRUE on the stack.
 Figure 4. Evaluating a script for a P2PKH transaction (Part 2 of 2)
Figure 4. Evaluating a script for a P2PKH transaction (Part 2 of 2)Multi-Signature
Multi-signature scripts set a condition where N public keys are recorded in the script and at least M of those must provide signatures to release the encumbrance. This is also known as an M-of-N scheme, where N is the total number of keys and M is the threshold of signatures required for validation. For example, a 2-of-3 multi-signature is one where three public keys are listed as potential signers and at least two of those must be used to create signatures for a valid transaction to spend the funds. At this time, standard multi-signature scripts are limited to at most 15 listed public keys, meaning you can do anything from a 1-of-1 to a 15-of-15 multi-signature or any combination within that range. The limitation to 15 listed keys might be lifted by the time this book is published, so check the isStandard() function to see what is currently accepted by the network.
The general form of a locking script setting an M-of-N multi-signature condition is:
M <Public Key 1> <Public Key 2> ... <Public Key N> N OP_CHECKMULTISIGwhere N is the total number of listed public keys and M is the threshold of required signatures to spend the output.
A locking script setting a 2-of-3 multi-signature condition looks like this:
2 <Public Key A> <Public Key B> <Public Key C> 3 OP_CHECKMULTISIGThe preceding locking script can be satisfied with an unlocking script containing pairs of signatures and public keys:
OP_0 <Signature B> <Signature C>or any combination of two signatures from the private keys corresponding to the three listed public keys.
The prefix OP_0 is required because of a bug in the original implementation of CHECKMULTISIG where one item too many is popped off the stack. It is ignored by CHECKMULTISIG and is simply a placeholder.
The two scripts together would form the combined validation script:
OP_0 <Signature B> <Signature C> 2 <Public Key A> <Public Key B> <Public Key C> 3 OP_CHECKMULTISIGWhen executed, this combined script will evaluate to TRUE if, and only if, the unlocking script matches the conditions set by the locking script. In this case, the condition is whether the unlocking script has a valid signature from the two private keys that correspond to two of the three public keys set as an encumbrance.
Data Output (OP_RETURN)
Bitcoin Cash’s distributed and timestamped ledger, the blockchain, has potential uses far beyond payments. Many developers have tried to use the transaction scripting language to take advantage of the security and resilience of the system for applications such as digital notary services, stock certificates, and smart contracts. Early attempts to use Bitcoin Cash’s script language for these purposes involved creating transaction outputs that recorded data on the blockchain; for example, to record a digital fingerprint of a file in such a way that anyone could establish proof-of-existence of that file on a specific date by reference to that transaction.
The use of Bitcoin Cash’s blockchain to store data unrelated to Bitcoin Cash payments is a controversial subject. Many developers consider such use abusive and want to discourage it. Others view it as a demonstration of the powerful capabilities of blockchain technology and want to encourage such experimentation. Those who object to the inclusion of non-payment data argue that it causes "blockchain bloat," burdening those running full Bitcoin Cash nodes with carrying the cost of disk storage for data that the blockchain was not intended to carry. Moreover, such transactions create UTXO that cannot be spent, using the destination Bitcoin Cash address as a free-form 20-byte field. Because the address is used for data, it doesn’t correspond to a private key and the resulting UTXO can never be spent; it’s a fake payment. These transactions that can never be spent are therefore never removed from the UTXO set and cause the size of the UTXO database to forever increase, or "bloat."
A compromise was reached with the introduction of the OPRETURN operator. OP_RETURN allows developers to add 220 bytes of nonpayment data to a transaction output. However, unlike the use of "fake" UTXO, the OP_RETURN operator creates an explicitly _provably unspendable output, which does not need to be stored in the UTXO set. OP_RETURN outputs are recorded on the blockchain, so they consume disk space and contribute to the increase in the blockchain’s size, but they are not stored in the UTXO set and therefore do not bloat the UTXO memory pool and burden full nodes with the cost of more expensive RAM.
``` OP_RETURN scripts look like this:
OP_RETURN ```
The data portion is limited to 220 bytes and most often represents a hash, such as the output from the SHA256 algorithm (32 bytes). Many applications put a prefix in front of the data to help identify the application per the Terab 4-byte prefix guideline for OP_RETURN on Bitcoin Cash.
Keep in mind that there is no "unlocking script" that corresponds to OPRETURN that could possibly be used to "spend" an OP_RETURN output. The whole point of OP_RETURN is that you can’t spend the money locked in that output, and therefore it does not need to be held in the UTXO set as potentially spendable—OP_RETURN is _provably un-spendable. OP_RETURN is usually an output with a zero Bitcoin Cash amount, because any Bitcoin Cash assigned to such an output is effectively lost forever. If an OP_RETURN is encountered by the script validation software, it results immediately in halting the execution of the validation script and marking the transaction as invalid. Thus, if you accidentally reference an OP_RETURN output as an input in a transaction, that transaction is invalid.
A standard transaction (one that conforms to the isStandard() checks) can have only one OP_RETURN output. However, a single OP_RETURN output can be combined in a transaction with outputs of any other type.
OP_RETURN was initially proposed with a limit of 80 bytes, but the limit was raised to 220 bytes of data on the May 15th 2018 BCH network upgrade.
Pay-to-Script-Hash (P2SH)
Pay-to-script-hash (P2SH) was introduced in 2012 as a powerful new type of transaction that greatly simplifies the use of complex transaction scripts. To explain the need for P2SH, let’s look at a practical example.
In What is Bitcoin Cash we introduced Mohammed, an electronics importer based in Dubai. Mohammed’s company uses Bitcoin Cash’s multi-signature feature extensively for its corporate accounts. Multi-signature scripts are one of the most common uses of Bitcoin Cash’s advanced scripting capabilities and are a very powerful feature. Mohammed’s company uses a multi-signature script for all customer payments, known in accounting terms as "accounts receivable," or AR. With the multi-signature scheme, any payments made by customers are locked in such a way that they require at least two signatures to release, from Mohammed and one of his partners or from his attorney who has a backup key. A multi-signature scheme like that offers corporate governance controls and protects against theft, embezzlement, or loss.
The resulting script is quite long and looks like this:
2 <Mohammed's Public Key> 5 OP_CHECKMULTISIG
Although multi-signature scripts are a powerful feature, they are cumbersome to use. Given the preceding script, Mohammed would have to communicate this script to every customer prior to payment. Each customer would have to use special Bitcoin Cash wallet software with the ability to create custom transaction scripts, and each customer would have to understand how to create a transaction using custom scripts. Furthermore, the resulting transaction would be about five times larger than a simple payment transaction, because this script contains very long public keys. The burden of that extra-large transaction would be borne by the customer in the form of fees. Finally, a large transaction script like this would be carried in the UTXO set in RAM in every full node, until it was spent. All of these issues make using complex output scripts difficult in practice.
Pay-to-script-hash (P2SH) was developed to resolve these practical difficulties and to make the use of complex scripts as easy as a payment to a Bitcoin Cash address. With P2SH payments, the complex locking script is replaced with its digital fingerprint, a cryptographic hash. When a transaction attempting to spend the UTXO is presented later, it must contain the script that matches the hash, in addition to the unlocking script. In simple terms, P2SH means "pay to a script matching this hash, a script that will be presented later when this output is spent."
In P2SH transactions, the locking script that is replaced by a hash is referred to as the redeem script because it is presented to the system at redemption time rather than as a locking script. Complex script without P2SH shows the script without P2SH and Complex script as P2SH shows the same script encoded with P2SH.
Locking Script: 2 PubKey1 PubKey2 PubKey3 PubKey4 PubKey5 5 OP_CHECKMULTISIG Unlocking Script: Sig1 Sig2
Table 4. Complex script without P2SH
Redeem Script: 2 PubKey1 PubKey2 PubKey3 PubKey4 PubKey5 5 OP_CHECKMULTISIG Locking Script: OP_HASH160 <20-byte hash of redeem script> OP_EQUAL Unlocking Script: Sig1 Sig2 redeem script
Table 5. Complex script as P2SH
As you can see from the tables, with P2SH the complex script that details the conditions for spending the output (redeem script) is not presented in the locking script. Instead, only a hash of it is in the locking script and the redeem script itself is presented later, as part of the unlocking script when the output is spent. This shifts the burden in fees and complexity from the sender to the recipient (spender) of the transaction.
Let’s look at Mohammed’s company, the complex multi-signature script, and the resulting P2SH scripts.
First, the multi-signature script that Mohammed’s company uses for all incoming payments from customers:
2 <Mohammed's Public Key> <Partner1 Public Key> <Partner2 Public Key> <Partner3 Public Key> <Attorney Public Key> 5 OP_CHECKMULTISIGIf the placeholders are replaced by actual public keys (shown here as 520-bit numbers starting with 04) you can see that this script becomes very long:
2 04C16B8698A9ABF84250A7C3EA7EEDEF9897D1C8C6ADF47F06CF73370D74DCCA01CDCA79DCC5C395D7EEC6984D83F1F50C900A24DD47F569FD4193AF5DE762C58704A2192968D8655D6A935BEAF2CA23E3FB87A3495E7AF308EDF08DAC3C1FCBFC2C75B4B0F4D0B1B70CD2423657738C0C2B1D5CE65C97D78D0E34224858008E8B49047E63248B75DB7379BE9CDA8CE5751D16485F431E46117B9D0C1837C9D5737812F393DA7D4420D7E1A9162F0279CFC10F1E8E8F3020DECDBC3C0DD389D99779650421D65CBD7149B255382ED7F78E946580657EE6FDA162A187543A9D85BAAA93A4AB3A8F044DADA618D087227440645ABE8A35DA8C5B73997AD343BE5C2AFD94A5043752580AFA1ECED3C68D446BCAB69AC0BA7DF50D56231BE0AABF1FDEEC78A6A45E394BA29A1EDF518C022DD618DA774D207D137AAB59E0B000EB7ED238F4D800 5 OP_CHECKMULTISIGThis entire script can instead be represented by a 20-byte cryptographic hash, by first applying the SHA256 hashing algorithm and then applying the RIPEMD160 algorithm on the result. The 20-byte hash of the preceding script is:
54c557e07dde5bb6cb791c7a540e0a4796f5e97eA P2SH transaction locks the output to this hash instead of the longer script, using the locking script:
OP_HASH160 54c557e07dde5bb6cb791c7a540e0a4796f5e97e OP_EQUALwhich, as you can see, is much shorter. Instead of "pay to this 5-key multi-signature script," the P2SH equivalent transaction is "pay to a script with this hash." A customer making a payment to Mohammed’s company need only include this much shorter locking script in his payment. When Mohammed wants to spend this UTXO, they must present the original redeem script (the one whose hash locked the UTXO) and the signatures necessary to unlock it, like this:
<Sig1> <Sig2> <2 PK1 PK2 PK3 PK4 PK5 5 OP_CHECKMULTISIG>The two scripts are combined in two stages. First, the redeem script is checked against the locking script to make sure the hash matches:
<2 PK1 PK2 PK3 PK4 PK5 5 OP_CHECKMULTISIG> OP_HASH160 <redeem scriptHash> OP_EQUALIf the redeem script hash matches, the unlocking script is executed on its own, to unlock the redeem script:
<Sig1> <Sig2> 2 PK1 PK2 PK3 PK4 PK5 5 OP_CHECKMULTISIGPay-to-script-hash addresses
Another important part of the P2SH feature is the ability to encode a script hash as an address, as defined in BIP0013. P2SH addresses are Base58Check encodings of the 20-byte hash of a script, just like Bitcoin Cash addresses are Base58Check encodings of the 20-byte hash of a public key. P2SH addresses use the version prefix "5", which results in Base58Check-encoded addresses that start with a "3". For example, Mohammed’s complex script, hashed and Base58Check-encoded as a P2SH address becomes 39RF6JqABiHdYHkfChV6USGMe6Nsr66Gzw. Now, Mohammed can give this "address" to his customers and they can use almost any Bitcoin Cash wallet to make a simple payment, as if it were a Bitcoin Cash address. The 3 prefix gives them a hint that this is a special type of address, one corresponding to a script instead of a public key, but otherwise it works in exactly the same way as a payment to a Bitcoin Cash address.
P2SH addresses hide all of the complexity, so that the person making a payment does not see the script.
Benefits of pay-to-script-hash
The pay-to-script-hash feature offers the following benefits compared to the direct use of complex scripts in locking outputs:
- Complex scripts are replaced by shorter fingerprints in the transaction output, making the transaction smaller.
- Scripts can be coded as an address, so the sender and the sender’s wallet don’t need complex engineering to implement P2SH.
- P2SH shifts the burden of constructing the script to the recipient, not the sender.
- P2SH shifts the burden in data storage for the long script from the output (which is in the UTXO set) to the input (stored on the blockchain).
- P2SH shifts the burden in data storage for the long script from the present time (payment) to a future time (when it is spent).
- P2SH shifts the transaction fee cost of a long script from the sender to the recipient, who has to include the long redeem script to spend it.
Redeem script and isStandard validation
Prior to version 0.9.2, pay-to-script-hash was limited to the standard types of Bitcoin Cash transaction scripts, by the isStandard() function. That means that the redeem script presented in the spending transaction could only be one of the standard types: P2PK, P2PKH, or multi-sig nature, excluding OP_RETURN and P2SH itself.
As of version 0.9.2, P2SH transactions can contain any valid script, making the P2SH standard much more flexible and allowing for experimentation with many novel and complex types of transactions.
Note that you are not able to put a P2SH inside a P2SH redeem script, because the P2SH specification is not recursive. You are also still not able to use OP_RETURN in a redeem script because OP_RETURN cannot be redeemed by definition.
Note that because the redeem script is not presented to the network until you attempt to spend a P2SH output, if you lock an output with the hash of an invalid transaction it will be processed regardless. However, you will not be able to spend it because the spending transaction, which includes the redeem script, will not be accepted because it is an invalid script. This creates a risk, because you can lock Bitcoin Cash in a P2SH that cannot be spent later. The network will accept the P2SH encumbrance even if it corresponds to an invalid redeem script, because the script hash gives no indication of the script it represents.
P2SH locking scripts contain the hash of a redeem script, which gives no clues as to the content of the redeem script itself. The P2SH transaction will be considered valid and accepted even if the redeem script is invalid. You might accidentally lock Bitcoin Cash in such a way that it cannot later be spent.
-
 @ 3165b802:a9f51d37
2025-04-07 17:01:23
@ 3165b802:a9f51d37
2025-04-07 17:01:23Humanrights #Human #Rights
-
 @ 8f69ac99:4f92f5fd
2025-04-07 15:35:08
@ 8f69ac99:4f92f5fd
2025-04-07 15:35:08No dia 2 de Abril de 2025, o Presidente dos Estados Unidos, Donald Trump, anunciou um novo pacote abrangente de tarifas com o objectivo de combater os desequilíbrios comerciais e revitalizar as indústrias nacionais. Foi imposta uma tarifa geral de 10% sobre todas as importações, com taxas mais elevadas—34% para a China e 20% para a União Europeia—em preparação para entrar em vigor. O anúncio reacendeu debates antigos sobre proteccionismo, globalização e o futuro do dólar norte-americano.
Embora estas medidas possam parecer extremas, as tarifas são um instrumento tradicional da política comercial internacional. Países de todo o mundo, incluindo a União Europeia, utilizam-nas rotineiramente para proteger indústrias estratégicas, regular o comércio e gerar receitas. A UE, por exemplo, impõe há muito tempo taxas sobre produtos norte-americanos como bens agrícolas, maquinaria e têxteis. Em contrapartida, os EUA já taxaram importações da UE, como o aço, alumínio e aeronaves, em disputas comerciais.
O que distingue a proposta de Trump é a sua escala, ambição e o objectivo mais amplo: reestruturar a economia dos EUA. Por detrás desta estratégia está uma realidade económica mais profunda—moldada por décadas de défices comerciais, endividamento crescente e o papel do dólar como moeda de reserva mundial. Este artigo explora como estes factores se cruzam, por que razão os EUA se encontram numa posição precária, e se políticas como tarifas elevadas, taxas de juro baixas ou até o Bitcoin podem apontar o caminho a seguir.
As Raízes da Crise: Sobreconsumo e Desindustrialização nos EUA
Durante décadas, os Estados Unidos "viveram acima das suas possibilidades", acumulando um défice comercial que actualmente ultrapassa os 800 mil milhões de dólares por ano. Este desequilíbrio—em que o país compra mais do que vende ao exterior—é sintoma de um problema mais profundo. No pós-Segunda Guerra Mundial, os EUA eram uma potência industrial. Mas, a partir dos anos 70, e com maior intensidade nos anos 90, a globalização transferiu a produção para o estrangeiro. As empresas procuraram custos de mão de obra mais baixos e os mercados norte-americanos encheram-se de produtos fabricados fora.
Para sustentar este consumo, os EUA apoiaram-se na sua posição privilegiada: a emissão da moeda de reserva mundial. Isso gerou um ciclo de endividamento, com o país a pedir emprestado ao exterior para manter o nível de vida. O resultado? Desindustrialização. Fábricas fecharam e milhões de empregos na indústria desapareceram em estados como Ohio, Michigan e Pensilvânia.
Hoje, os EUA produzem muito menos—em proporção ao seu tamanho—do que há algumas décadas, mesmo mantendo um apetite crescente por importações. O défice comercial expõe uma fragilidade estrutural: um país cada vez mais incapaz de sustentar-se através da sua própria produção. Os dólares gastos fora regressam muitas vezes sob a forma de compras de dívida pública, perpetuando o ciclo.
À medida que os défices crescem e a economia depende cada vez mais de mecanismos financeiros do que da produção real, surge uma questão inevitável: até quando poderá a América continuar a comprar a crédito antes que o cartão seja recusado?
O Dilema de Triffin: Moeda Global vs. Potência Industrial
Imagine ser a única pessoa numa cidade com uma impressora de dinheiro que todos usam. Para satisfazer a procura, continua a imprimir e a enviar notas para o exterior—até que o seu próprio negócio local entra em decadência e se torna dependente dos outros. Esta é a essência do Dilema de Triffin, e a corda bamba que os EUA têm vindo a atravessar há gerações.
O dilema surge quando a moeda de um país é usada como padrão global. O dólar—utilizado mundialmente para transacções de petróleo, comércio e reservas—precisa de estar amplamente disponível. Essa abundância provém de défices comerciais persistentes por parte dos EUA.
Mas os défices têm um custo. Os dólares enviados para fora voltam como procura por bens estrangeiros, enfraquecendo a produção interna. Porque fabricar um produto em Detroit por 10 dólares, quando se pode importar por $2? Com o tempo, isto destrói a base industrial do país.
Esta não é uma preocupação teórica—é uma realidade histórica. O economista Robert Triffin advertiu nos anos 60 que um país não pode simultaneamente manter a sua moeda como padrão mundial e conservar uma base industrial sólida. Os EUA confirmaram essa previsão. Após a guerra, os dólares ajudaram a reconstruir a Europa e o Japão, mas esses mesmos países tornaram-se concorrentes industriais dos EUA em sectores como o aço e a indústria automóvel.
As fábricas abandonadas no Midwest e os teares silenciosos no sul são marcas visíveis desta troca. O domínio do dólar concedeu influência global à América, mas às custas da sua produção.
Espiral da Dívida: Obrigações Financeiras Crescentes dos EUA
Em 2025, a dívida federal dos EUA ultrapassa os 36 biliões de dólares ($36 000 000 000 000 000 000)—cerca de 108 mil dólares por cada americano, adultos, jovens, idosos. Durante anos, o acesso fácil ao crédito e a procura global por dívida americana mascararam os riscos. Agora, as fissuras estão à vista.
O problema não é apenas o montante—é o prazo e o custo de manter esta dívida. Grande parte dela é de curto prazo, exigindo refinanciamentos frequentes. Com o aumento das taxas de juro, os custos associados disparam. Só em 2024, os pagamentos de juros ultrapassaram 1 bilião de dólares—mais do que os orçamentos combinados de educação, transportes e habitação.
A “Lei de Ferguson”, proposta pelo historiador Niall Ferguson, afirma que quando os juros da dívida superam os gastos militares, o império está em declínio. Em 2025, os EUA gastam cerca de 900 mil milhões em defesa, e os encargos com juros já os ultrapassaram.
Este ponto de viragem trouxe problemas a impérios do passado—do Reino Unido após a Primeira Guerra Mundial até Roma no seu declínio. Hoje, cresce o cepticismo quanto à saúde fiscal dos EUA. Países como a China e a Rússia estão a reduzir as suas reservas em dívida americana, preferindo ouro, yuan ou outros activos.
Se mais nações seguirem o mesmo caminho, os EUA terão de escolher: continuar a endividar-se para sustentar o sistema ou aceitar um papel reduzido para o dólar na economia mundial.
Desdolarização: A Mudança Global Longe do Dólar
A desdolarização refere-se à tendência crescente de reduzir a dependência do dólar nas transacções comerciais, reservas e sistemas financeiros. Embora o dólar ainda domine, a sua supremacia está sob crescente pressão de novas potências económicas e tensões geopolíticas.
Porque Está o Mundo a Afastar-se do Dólar?
- Risco Económico: A volatilidade do dólar, agravada pela dívida e instabilidade política nos EUA, torna-o menos fiável como reserva de valor.
- Instrumento Geopolítico: O uso do dólar pelos EUA para impor sanções leva rivais a procurar alternativas.
Alternativas Emergentes
- Ouro: Bancos centrais estão a reforçar as reservas em ouro como protecção.
- Commodities: Petróleo e cereais começam a ser transaccionados em moedas alternativas—como vendas de petróleo em yuan pela Arábia Saudita.
- Criptomoedas: Bitcoin e outros activos digitais ganham terreno como reservas neutras e descentralizadas.
- Moedas Regionais: Os países dos BRICS desenvolvem sistemas de pagamento e discutem uma moeda comum para reduzir a dependência do dólar.
Um Declínio Lento, Mas Visível
A percentagem do dólar nas reservas cambiais mundiais caiu de 70% no ano 2000 para menos de 60% actualmente. O comércio em moedas não-dólar cresceu 25% desde 2020. O domínio do dólar persiste, mas o movimento de mudança é claro.
A Estratégia Económica de Trump em 3 Etapas
Em 2025, Trump apresentou uma estratégia económica audaciosa em três frentes:
1. Tarifas Elevadas para Revitalizar a Indústria
Uma tarifa de 10% sobre todas as importações, com taxas superiores para países com superavit comercial, visa incentivar a produção interna. Críticos alertam para o aumento de preços e inflação, mas apoiantes defendem que é necessário para reindustrializar.
2. Redução das Taxas de Juro para Gerir a Dívida
A administração pressiona a Reserva Federal para baixar as taxas, reduzindo os encargos da dívida pública. Isto levanta preocupações sobre a independência do banco central e a estabilidade monetária a longo prazo.
3. Bitcoin como Activo Estratégico de Reserva
Num passo histórico, Trump assinou uma ordem executiva para criar a Reserva Estratégica de Bitcoin e o Stock Nacional de Activos Digitais. O objectivo é diversificar as reservas e proteger contra a inflação.
Riscos e Compensações
A estratégia económica de Trump não está isenta de riscos:
- Inflação: Tarifas mais altas poderão aumentar o custo de vida.
- Polarização Política: Medidas controversas poderão acentuar divisões internas.
- Incerteza Económica: O proteccionismo pode afastar investimento e travar a inovação.
- Instabilidade Monetária: Um erro na gestão da dívida ou dos activos digitais poderá enfraquecer o dólar.
Estes riscos exigem gestão cuidadosa para evitar agravar os problemas existentes.
O Papel de Bitcoin: Protecção ou Último Recurso?
Integrar Bitcoin nas reservas nacionais é ousado—mas pode ser revolucionário, e a meu ver, inevitável!
Vantagens
- Escassez: Com oferta limitada a 21 milhões de unidades, Bitcoin é deflacionário.
- Descentralização: Resistente à censura e manipulação, reforça a soberania financeira.
- Alcance Global: Sem fronteiras, permite trocas neutras num mundo multipolar.
Desafios
- Volatilidade: As flutuações no curto prazo são ainda significativas, mas a adopção institucional pode estabilizar o preço.
- Regulação: O enquadramento legal está em evolução, mas tende para maior clareza.
- Adopção Técnica: Persistem desafios de escalabilidade, embora soluções como a Lightning Network estejam a amadurecer.
A Reserva Estratégica de Bitcoin pode revelar-se visionária—ou precipitada. Tudo dependerá da execução e da aceitação global.
Futuros Possíveis: Crise ou Reinvenção?
Os EUA estão perante uma encruzilhada histórica. Um caminho aponta para a renovação: revitalizar a indústria e adoptar activos digitais, como por exemplo as stablecoins para perpetuar a hegemonia do dólar, lastreado em Bitcoin. O outro conduz à crise—com inflação, instabilidade e perda de influência global.
Num cenário optimista, os EUA emergem como líderes industriais e digitais, com reservas diversificadas que incluem Bitcoin. A recente ordem executiva para adquirir Bitcoin de forma neutra ao orçamento é um sinal positivo.
Num cenário pessimista, menos provável com as medidas em curso, o país mergulha em dívidas, vê o dólar enfraquecer e perde coesão interna. Mas com visão estratégica e inovação económica, há margem para navegar os desafios com sucesso.
Conclusão
A América enfrenta uma oportunidade única de redefinir o seu destino económico. A estratégia de Trump—baseada em tarifas, taxas de juro baixas e Bitcoin—pode marcar o início de uma nova era de resiliência e recuperação industrial.
A inclusão de Bitcoin nas reservas nacionais mostra que os instrumentos tradicionais já não bastam. Ao abraçar os activos digitais e restaurar a produção nacional, os EUA podem recuperar a liderança económica mundial.
O caminho será difícil. Mas com ousadia e execução eficaz, os Estados Unidos não só podem recuperar—podem reinventar-se.
-
 @ 866e0139:6a9334e5
2025-04-07 12:40:23
@ 866e0139:6a9334e5
2025-04-07 12:40:23
Autor: Eva Schmidt. Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier. Dieser Beitrag ist zuvor auf* Radio München erschienen. Das Gesamtangebot von Radio München finden Sie* hier.**
„Denke daran, daß das, was dich wie an unsichtbaren Fäden hin- und herzieht, in deinem Innern verborgen ist", soll der römische Kaiser Marc Aurel gesagt haben, der letzte bedeutende Philosoph der jüngeren Stoa. Brot und Spiele hieß es damals, machten die Gesellschaften gefügig: Bier, Wein, Whiskey, Ablenkung, Informationssteuerung.
Das gesamte Gespräch gibt es unter folgendem Link (Vorschau wird in e-mails nicht angezeigt):
Wie sich die kognitive Einflussnahme zur Kriegsführung entwickelte, wie sie sich mit den heutigen medialen und technischen Mitteln darstellt und wie wir unsere Kinder und uns selbst davor schützen können, damit beschäftigt sich der Propagandaforscher und Amerikanist Dr. Jonas Tögel. Er promovierte zum Thema Soft Power und Motivation und forscht am Institut für Psychologie der Universität Regensburg. Meine Kollegin Eva Schmidt hat ihn interviewt und wollte zunächst von ihm wissen, wie er zur Propagandaforschung kam und auf welchen Grundlagen seine Tätigkeit aufbaut.
Dr. Jonas Tögel ist Amerikanist, Propagandaforscher und Bestsellerautor. Er hat zum Thema Soft Power und Motivation promoviert und arbeitet als wissenschaftlicher Mitarbeiter am Institut für Psychologie der Universität Regensburg. Seine Forschungsschwerpunkte sind unter anderem Motivation, der Einsatz von Soft-Power-Techniken, Nudging, Propaganda sowie epochale Herausforderungen des 20. und 21. Jahrhunderts. Bei Westend erschien zuletzt sein Bestseller Kognitive Kriegsführung (2023).
Sein aktuelles Buch "Kriegsspiele - Wie NATO und Pentagon die Zerstörung Europas simulieren" ist im Westend-Verlag erschienen, hat 111 Seiten und kostet 15 Euro.
LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt. (Vorerst an alle, da wir den Mailversand testen, später ca. drei Mails pro Woche.).
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: milosz@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ f1577c25:de26ba14
2025-04-07 09:44:30
@ f1577c25:de26ba14
2025-04-07 09:44:30تنبيه مهم
أهلاً! قبل ما نبدأ، أنا مش مستشار مالي ولا خبير حاجة. أنا بس واحد قعد يتابع قنوات ويقرا عن الاستثمار الفترة اللي فاتت. مش مسؤول عن أي خسارة فلوس، بس كل اللي هاقوله هنا أنا بطبقه على نفسي الأول، فطبعاً مش هاضر نفسي (عن قصد على الأقل).
إيه اللي هنتكلم عنه
هاعمل سلسلة بوستات عن: - الأساسيات اللي لازم تعرفها عن الاستثمار والتداول - أفكار تساعدك تعمل محفظة استثمارية كويسة - تجربتي مع تطبيقات الاستثمار المختلفة - إجابة على الأسئلة اللي بتتسأل كتير
هاحدّث البوستات لو في معلومات جديدة وهاكتب تاريخ آخر تحديث. عايز تتواصل معايا؟ اكتب كومنت علي بوست ريديت اللي لاقيت فيه لينك المقالة دي.
الأساسيات
الغلطة الأولى: لازم يكون معاك فلوس كتير علشان تستثمر
دي فكرة غلط خالص. في الحقيقة، إنت بتستثمر علشان تجمع فلوس مش العكس. معظم الطرق اللي هاقولك عليها ممكن تبدأ بمبلغ صغير (حوالي 100 جنيه) وتزود عليه كل شهر. والحلو إن معظم الحاجات دي بتخليك تقدر تسحب فلوسك بسهولة لو احتجت.
أهمية التحويش
علشان تستثمر بجد، لازم تحوّش جزء من مرتبك كل شهر. المفروض تحوّش 25% من مرتبك، بس مع الغلا اللي احنا فيه دلوقتي، ابدأ بأي مبلغ تقدر عليه حتى لو 100 جنيه بس في الشهر. احسب مصاريفك لكام شهر وحط جنب مبلغ يكفيك 3-6 شهور للطوارئ.
طريقة تفكير المستثمر
الناس الناجحة مش بتصرف على المظاهر. قبل ما تشتري أي حاجة، اسأل نفسك: "هاستخدم الحاجة دي بعد 3 شهور؟" حدد احتياجاتك الحقيقية وبعدين دوّر على أحسن حاجة تناسبك. الاستثمار طريقة تفكير قبل ما يكون مجرد حتة تحط فيها فلوسك وخلاص.
بلاش تخلي مشاعرك تتحكم فيك
متخليش قلبك يتحكم في قرارات استثمارك. أكيد السوق ممكن ينزل شوية، بس على المدى البعيد بيطلع تاني. بص مثلاً على مؤشر S&P 500. في مقولة حلوة بتقول: "If in doubt, zoom out".
أهمية توزيع الفلوس
متحطش فلوسك كلها في مكان واحد. لو حطيت كل فلوسك في البورصة وحصل هبوط، هتخسر جامد. لكن لو حاطط جزء في البورصة وجزء في الدهب مثلاً، لما واحدة تنزل التانية ممكن تطلع. اختار استثماراتك على حسب هدفك: عايز تسيب فلوسك لمدة طويلة (دهب وبورصة)؟ ولا عايز دخل شهري (صناديق استثمار أو شهادات بنك)؟
صعب ما هتبقي غني علي المدي القصير
في ناس كتير لما بتسمع كلمة "استثمار" بتتخيل على طول عربيات فيراري وقصور. ولما تقولهم اشتروا دهب بيقولولك "لأ هستنى لما ينزل" (وهو أصلاً بيطلع).
الفكرة إنك متحاولش تحدد "الوقت المثالي للسوق" (Time the market) عشان تدخل، لأنه ببساطة صعب جداً تعرف إمتى الوقت ده. ناس كتير بتحاول تحقق عائد أعلى من المتوسط (اللي هو 10% سنوياً) وبينتهي بيهم الأمر خسرانين.
فمتحاولش تعمل ذكي أوي وتفضل مستني وتأجل. ابدأ على طول، والتزم بالاستثمار بانتظام.
مفيش حاجة كاملة
انا عارف شعور انك عايز كل حاجة وصدقني مش انت لوحدك، بس زي ما بيقولوا بالإنجليزي "you can't have your cake and eat it too"!
يعني مثلاً لو عايز ربح كتير هتلاقي مقابله مخاطرة عالية، أو لو عايز أمان لفلوسك هتلاقي العائد قليل. دايماً هتلاقي حاجة على حساب حاجة وانت بس اللي تقرر هتستحمل إيه.
أنا بالنسبة لي، بفضل حاجة بعائد صغير سنوي بس فيها أمان علشان مع الوقت يحصل تراكم للفوايد (compound interest) ويزيد المبلغ، بدل ما أخش في حاجة وأخسر كل حاجة.
بس زي ما قلت، دي بترجع من شخص لشخص. ممكن مثلاً لو حاسس إن قدامك فرصة حلوة، تجرب بنسبة صغيرة (زي 20% من فلوسك) كتجربة. بس دايماً دايماً دايماً متخليش الطمع يسوقك.
الوقت والعائد
معظم طرق الاستثمار الآمنة بتاخد وقت علشان تظهر نتايجها. زي ما قلت قبل كده: العائد السريع غالباً بيقابله مخاطرة عالية. أنا بقدملك هنا خيارات أكثر أماناً، لكن مقابل ده هتلاقي العائد مش هيبقى مبهر على المدى القصير. عشان كده لازم تفكر في الاستثمار على مدة متوسطة لطويلة (من 3 لـ 5 سنين) علشان تحصد ثمار استثمارك بشكل كويس وتشوف النتايج اللي بتتمناها.
مصادر للتعلم
قنوات يوتيوب
- بالمصري:
- عميد يستثمر
-
محمد محي الدين
-
بالإنجليزي:
- Two Cents
- The Money Guy Show
- Clear Value Tax
- The Plain Bagel
مواقع تفيدك
- بالإنجليزي:
- Investopedia
كمل قراية من هنا: nostr:naddr1qvzqqqr4gupzpu2h0sja0vmqdqjzq6e820jjjnuytzw2ksmemfnadhe0hm0zdws5qqxnzde5xvurqdp4xuunqd3sau2w7y
ادعمني (لو حابب)
- USDT (TRC20):
TKQ3Uwkq21ntiua2Zh9Hu376fdMdnRGWN6
آخر تحديث: 4 أبريل 2025
-
 @ e97aaffa:2ebd765d
2025-04-07 09:38:20
@ e97aaffa:2ebd765d
2025-04-07 09:38:20A electricidade ou os computadores ou a Internet foram revoluções que mudaram o mundo, mas a adoção e a evolução da tecnologia foi lenta, permitindo que as populações e as económicas se adaptassem.
Ao contrário, na AI, a evolução está a ser tão rápida, que as sociedades não vão conseguir acompanhar e adaptar a uma nova realidade.
A AI tem um potencial inacreditável, talvez seja a revolução tecnológica mais rápida de sempre, além disso é muito abrangente, quase todos os sectores económicos podem beneficiar, pode provocar um forte aumento na produtividade.
O potencial é tão elevado, como pode ser perigoso, sobretudo quando utilizado como uma arma contra a humanidade. Os governos ou empresas vão construir ferramentas com AI para monitorizar, manipular e controlar os cidadãos.
Muitas profissões vão desaparecer ou reduzir drasticamente o número de trabalhadores. Tal como aconteceu nas revoluções anteriores, muitas profissões acabaram, mas surgir outras novas profissões.
Ou seja, o problema não é a tecnologia, mas sim a maneira como se usa essa tecnologia. Os desafios para o futuro são tremendos.
E o cidadão comum, o que está a fazer e a pensar… a fazer desenhos, a fazer idiotices. https://image.nostr.build/326d506f0015c99d09e061094bf3552764c6f6334be2899c6f5359f0a809d8bc.jpg
Algo similar acontece com o Bitcoin, uma tecnologia revolucionária, em alguns casos particulares, as stablecoins poderão ser interessantes. Mas o povo prefere especulador em tokens absurdos e jogar no casino das memecoins.
Também acontece com a internet, é uma fonte acessível e inesgotável de conhecimento, mas as pessoas preferem passar horas sem fim, nas redes sociais a fazer swipe up, a consumir conteúdo degradante.
O mundo ocidental está a transformar os cidadãos em zumbis, facilmente manipuláveis, obedientes, viciados. Nós necessitamos é de pessoas curiosas, com espírito crítico, criativas. Essencialmente, que pensem pela sua própria cabeça.
-
 @ 7d33ba57:1b82db35
2025-04-07 09:17:04
@ 7d33ba57:1b82db35
2025-04-07 09:17:04Prague, the capital of the Czech Republic, is like stepping into a real-life fairy tale. With its Gothic towers, baroque churches, medieval streets, and a majestic castle watching over the city, it’s no surprise that it’s one of Europe’s most beloved destinations. Add in great beer, cozy cafés, and stunning river views, and you’ve got the perfect city break.
🌟 Top Things to Do in Prague
1️⃣ Prague Castle & St. Vitus Cathedral
- One of the largest castle complexes in the world
- Don’t miss St. Vitus Cathedral, the Old Royal Palace, and Golden Lane
- Climb the cathedral tower for epic city views

2️⃣ Charles Bridge (Karlův most)
- Iconic 14th-century bridge lined with 30 baroque statues
- Walk it at sunrise or late at night to avoid the crowds
- Great for photos, street musicians, and romantic vibes
3️⃣ Old Town Square & Astronomical Clock
- The heart of the city, with colorful buildings and Gothic spires
- Watch the Astronomical Clock chime on the hour (since 1410!)
- Check out Týn Church and the Old Town Hall Tower
4️⃣ Explore the Jewish Quarter (Josefov)
- Visit the Old Jewish Cemetery, synagogues, and the Jewish Museum
- Learn about centuries of Jewish heritage and resilience in Prague
5️⃣ Climb Up to Petřín Hill
- Take the funicular or walk to the top for gardens, a mirror maze, and a mini Eiffel Tower
- Fantastic place for picnics, sunsets, and panoramic views
🍽️ What to Eat & Drink in Prague
- Goulash with dumplings (guláš s knedlíky) – Hearty and satisfying
- Svíčková – Beef with creamy vegetable sauce and cranberry
- Trdelník – Tourist favorite sweet pastry (not traditionally Czech, but tasty!)
- Czech beer – World-famous for a reason (Pilsner Urquell, Kozel, Staropramen) 🍻
- Try a traditional pub or lokál for authentic Czech cuisine and great prices
🛶 Other Cool Experiences
✅ Take a Vltava River cruise – see Prague from the water
✅ Visit Letná Park for sweeping views and a beer garden
✅ Check out Kafka Museum for surreal vibes and literary history
✅ Explore Vyšehrad – lesser-known castle ruins with gorgeous views and peaceful paths
✅ Snap pics at the Lennon Wall, especially for street art fans 🎨🚇 Getting Around
- Very walkable, especially in the historic center
- Excellent public transport: trams, metro, and buses (get a 24 or 72-hour pass)
- Uber and Bolt are reliable if you need a ride
- Be cautious with exchange rates and ATMs—use official places or bank ATMs only
💡 Tips for Visiting Prague
🕰️ Wake up early to enjoy the city without crowds
🎟️ Book castle or tower tickets in advance during peak seasons
🌧️ Pack layers—it can be breezy even in spring
📷 Keep your camera ready—every corner is postcard-worthy -
 @ e5de992e:4a95ef85
2025-04-07 08:23:48
@ e5de992e:4a95ef85
2025-04-07 08:23:48Historical Rapid Declines in the S&P 500: Lessons from Major Market Crashes
The S&P 500 has experienced rapid declines of over 10% within short periods on several notable occasions, each linked to significant economic or geopolitical events. These instances underscore the market's vulnerability during times of crisis.
October 19-20, 1987 (Black Monday Crash)
-
Drop:
On October 19, 1987, the S&P 500 plummeted approximately 20.47%, marking the largest single-day percentage decline in its history. The following day saw further losses, culminating in a two-day drop exceeding 25%. -
Context:
Factors such as program trading, portfolio insurance strategies, and widespread panic selling contributed to this unprecedented crash.
November 19-20, 2008 (Global Financial Crisis)
-
Drop:
Amid the 2008 financial crisis, the S&P 500 declined roughly 10.8% over two days, reflecting the turmoil following the collapse of major financial institutions. -
Context:
The bankruptcy of Lehman Brothers and escalating fears of a global recession led to this significant market downturn.
March 11-12, 2020 (COVID-19 Pandemic Crash)
-
Drop:
The rapid spread of COVID-19 and ensuing economic shutdowns triggered a two-day decline of approximately 12.2% in the S&P 500. By March 16, the total decline over four days exceeded 20%. -
Context:
The pandemic's uncertainty and global impact led to one of the fastest descents into bear market territory.
April 3-4, 2025 (Trade War-Induced Crash)
-
Drop:
Recently, the S&P 500 experienced a sharp decline of 10.5% over two days, erasing approximately $5 trillion in market value. -
Context:
This downturn followed sweeping tariffs announced by President Donald Trump—a 10% baseline tariff on all imports, with higher rates on specific countries (e.g., China, the European Union). China's retaliatory tariffs intensified fears of a global trade war and a potential recession.
Observations
-
Frequency:
Such rapid declines are rare, occurring approximately once every 10-20 years, typically during periods of extreme market stress. -
Catalysts:
Each event was precipitated by unique factors: - Technological trading mechanisms in 1987
- Financial sector instability in 2008
- A global health crisis in 2020
-
Geopolitical trade tensions in 2025
-
Market Resilience:
Despite these significant setbacks, markets have historically demonstrated resilience, often rebounding and reaching new highs in subsequent years.
Conclusion
Understanding these historical instances provides valuable insights into market dynamics and the potential impact of external shocks on financial systems. Recognizing the catalysts and observing market resilience over time can help investors navigate future downturns with a more informed perspective.
-
-
 @ f1577c25:de26ba14
2025-04-07 07:32:22
@ f1577c25:de26ba14
2025-04-07 07:32:22احنا المرة اللي فاتت اتكلمنا عن طرق الاستثمار بشكل عام فا تعالي بقي ناخدهم واحدة واحدة بالمميزات و العيوب و اول حاجة هنبدا بيها هي البورصة الامريكية.
المنصات التداول:
المنصتين اللي انصح بيهم عن تجربة شخصية هما:
IBKR
- حلوة لو لسه جديد علشان شكل الموقع خفيف
- العمولات صغيرة
- عيبها إن طرق الايداع صعبة
Tastytrade
- حلوة علشان فية طرق ايداع عن طريق الكريبتو فا اسهل
- عيبها إن الشكل مش احسن حاجة كا تصميم للموقع
مميزات البورصة الأمريكية
- بالدولار الامريكي (هيساعد بالتضخم)
- الحد الادني 5 دولار لشراء جزء من السهم (علي حسب منصة التداول بس اغلبهم يعني)
- تقدر تخرج بأي وقت لو محتاج الفلوس
- مضمون و علي المدي الطويل العائد كان مضمون
عيوب البورصة الأمريكية
- لازم باسبور او بطاقة مترجمة من مكان معتمد
- طرق الايداع صعبة لو هتستخدم موقع زي IBKR مثلا
- علي المدي القصير ممكن تخسر فلوسك
- العمولات بتختلف من منصة للتاني بس في حدود ال11 سنت لو هتشتري جزء من السهم
ادعمني (اختياري)
- لو حابب تسجل عن طريق Tastytrade ممكن تستخدم رابط الاحاله بتاعي: https://open.tastytrade.com/signup?referralCode=FE3YFNRFJZ
- USDT (TRC20):
TKQ3Uwkq21ntiua2Zh9Hu376fdMdnRGWN6
شوف الكومنتات لو فيه أي تعديل أو بوستات جديدة.
-
 @ f1577c25:de26ba14
2025-04-07 07:32:02
@ f1577c25:de26ba14
2025-04-07 07:32:02المرة اللي فاتت اتكلمنا عن مميزات وعيوب العملات الرقمية والذهب العالمي. النهاردة هنتكلم عن طريقة استثمار مختلفة: ازاي تستثمر في العقارات برا مصر وانت قاعد في مكانك أونلاين!
مميزات وعيوب بشكل عام
المميزات
- استثمار في أصل حقيقي (عقار) فبتضمن فلوسك في حاجة ملموسة
- العقارات على المدى الطويل بتكسب كويس
- العائد بالدولار (9-10% سنوياً)
- الدخل بيتوزع أسبوعي أو شهري على حسب المنصة
- الحد الأدنى للاستثمار منخفض مقارنة بالاستثمار العقاري في مصر
العيوب
- المنصات أونلاين، فممكن في أي وقت يحصل مشكلة والموقع يقفل
- ممكن سعر العقار ينهار في المنطقة اللي اشتريت فيها
- ممكن يحصل مشاكل غير متوقعة للعقار (حريق، زلزال، إلخ)
- الاستثمار بيحتاج مدة طويلة (3-5 سنين) علشان يكون مجزي
المنصات
المنصات دي بتعمل شركة بتشتري العقار، وبعدين بتوزع أسهم الشركة على المستثمرين. يعني انت مش بتشتري العقار مباشرةً، لكن بتشتري حصة في شركة مالكة للعقار. ده بيخليك متدفعش ضرائب على العقار نفسه (على حد علمي، بس أسأل حد خبير للتأكيد).
منصة Realt
دي منصة بتتيح لك الاستثمار في عقارات بأمريكا وبنما. بتشتغل بنظام البلوكتشين والعملات الرقمية. كل توكن (token) بيمثل حصة في العقار (أو في الشركة المالكة للعقار).
مثلاً: لو التوكن الواحد بـ 50 دولار والربح المتوقع 5 دولار في السنة، يبقى العائد 10% سنوياً. العائد بيتوزع أسبوعياً من خلال عملة USDC، سواء على شبكة ETH (هتدفع رسوم gas fees) أو شبكة Gnosis (بدون رسوم).
فيها خدمة حلوة اسمها YAM (You and Me) وهي سوق P2P للعقارات. يعني تقدر تبيع عقارك لأفراد مش للموقع نفسه، وتحدد السعر اللي يناسبك، أو تشتري عقارات قديمة من مستثمرين تانيين.
مميزات Realt
- سهلة الاستخدام نسبياً
- الحد الأدنى صغير (حوالي 50 دولار)
- في محفظة داخل الموقع لو معندكش محفظة عملات رقمية
- تقدر تشتري بالفيزا أو بالعملات الرقمية
- العائد أسبوعي
- تقدر تبيع في أي وقت
عيوب Realt
- ممكن المنصة تقفل فجأة
- ممكن تحصل مشكلة بالشبكة
- لازم يكون معاك باسبور
منصة Stake
دي منصة بتتيح لك الاستثمار في أسواق السعودية والإمارات. مرخصة من البلدين، وتعتبر أسهل من Realt لأنها مفيهاش حوار العملات الرقمية.
هتدخل تسجل بالباسبور، وتختار العقار وتشتري أسهم فيه. الحد الأدنى 500 درهم (حوالي 135 دولار) للعقار. العائد شهري (مش متأكد 100%، لسه منتظر أول توزيع) وبيتحول على حسابك البنكي سواء برا أو جوا الإمارات وبأي عملة انت تختارها.
عشان تسحب فلوسك، في فترات محددة اسمها "exit window" بتكون مرتين في السنة. أو بعد 3 سنين، بيحصل تصويت بين أصحاب العقار لو عايزين يبيعوا قبل مدة الـ 5 سنين.
مميزات Stake
- سهلة الاستخدام
- واجهة ممتازة وبسيطة
- منصة مرخصة من السعودية والإمارات
عيوب Stake
- الخروج مش مرن (مرتين في السنة)
- ممكن المنصة تتعرض لمشاكل
- مخاطر العقارات العامة
ادعمني (اختياري)
- لو حابب تسجل عن طريق Realt ممكن تستخدم رابط الإحالة بتاعي: https://realt.co/ref/esmailelbob/
- لو حابب تسجل عن طريق Stake ممكن تستخدم رابط الإحالة بتاعي: https://app.getstake.com/rewards?c=ISMAEL182
- USDT (TRC20):
TKQ3Uwkq21ntiua2Zh9Hu376fdMdnRGWN6
شوف الكومنتات لو فيه أي تعديل أو بوستات جديدة.
-
 @ f1577c25:de26ba14
2025-04-07 07:31:44
@ f1577c25:de26ba14
2025-04-07 07:31:44النهاردة هنتكلم عن طريقة استثمار مختلفة: ازاي تستثمر في العقارات جوا مصر وانت قاعد في مكانك أونلاين!
مميزات وعيوب بشكل عام
المميزات
- استثمار في أصل حقيقي (عقار) فبتضمن فلوسك في حاجة ملموسة
- العقارات على المدى الطويل بتكسب كويس
- العائد بالجنية بس مربوط بالدولار (9-10% سنوياً) يعني لو الجنية اتعوم تاني العائد اللي بيجي ليك بالجنية هيزيد 500 بدل 300 مثلا.
- الدخل بيتوزع شهري
العيوب
- ممكن سعر العقار ينهار في مصر
- ممكن يحصل مشاكل غير متوقعة للعقار (حريق، زلزال، إلخ)
- الاستثمار بيحتاج مدة طويلة (3-5 سنين) علشان يكون مجزي
- الحد الادني كبير نسبيا يعني 50 الف جنية
- تدفع ضرائب عقارية
المنصات
هي منصة واحده (علي الاقل اللي جربتة) اسمها Safe هي تبع مدينه مصر و علي عكس الاستثمار العالمي هو انت فعلا بتشتري جزء من الشقة فا حلو لانه مشترك مباشر بس بالمقابل هتدفع ضرائب العقارية كل سنة لانه انت كدا مالك لعقار جوا مصر
منصة Safe
دي المنصة الوحيدة اللي اعرفها علي الاقل في مصر و هي الي حد ما حلوة يعني الستجيل بالبطاقة و بعدها بتختار العقار و تحط الفيزا سواء تدفع مره واحده او بالتقسيط (بفوائد) لحد سنة و بعد كدا باسبوع هيجي شخص تمضي معاه العقد و بعد شهر هيجي ليك اول عائد في حسابك البنكي اللي كاتبة في التطبيق
المميزات: - سهل - ينفع بالبطاقة العيوب: - الفلوس محجوزة لمده 6 شهور قبل ما تقدر تبيع وتسحب فلوسك - فيه شويه اخطاء تقنيه زي مثلا انا وصلي العائد في البنك بس لسه مسمعش في التطبيق لحد دلوقتي و في شويه عقارات بتظهر و تختفي (لما تكون اتملت) فا اللي هو حاسس في حاجات لسه يدوي و متوقع لان التطبيق جديد بس قصدي كان عندي امل يستنوا شويه اكتر الاول قبل ما يبدوا التطبيق
ادعمني (اختياري)
- USDT (TRC20):
TKQ3Uwkq21ntiua2Zh9Hu376fdMdnRGWN6
شوف الكومنتات لو فيه أي تعديل أو بوستات جديدة.
-
 @ f1577c25:de26ba14
2025-04-07 07:31:27
@ f1577c25:de26ba14
2025-04-07 07:31:27النهاردة هنتكلم عن شهادات البنك. وقبل ما أكمل، أنا مش شيخ ومش دوري أقولك الحلال والحرام. إنت تقدر تسأل أهل العلم أكتر على حسب دينك طبعاً.
أنا برشح شهادات البنك في حالتين: لو كانت بالدولار (مع إني في الحالة دي هقولك اعملهم عملات رقمية أحسن لأنه هيبقى سهل تحركهم برا البنك وقرفه)، أو شهادات بالجنيه علشان تصرف منهم (بس هنا برضه هقولك شوفلك فوري يومي أحسن شوية).
غير بقى لو إنت عايز الشهادات اللي العائد فيها أعلى، بمعنى حاجة زي 27% سنوي أو ال3 سنين تناقصي (أول سنة 30%، تاني سنة 28%، وتالت سنة 25% تقريباً) وساعتها العائد مش هيبقى شهري. بس لو دي خطتك، فساعتها بس هرشح ليك شهادات البنك. غير كدا مش شايف ليها لازمة، لأنه بكل بساطة عقبال ما الفلوس تتفك هيكون قيمتها قلت والعائد نفسه ملهوش قيمة أوي.
طبعاً هنا مش هقدر أتكلم كتير لأن كل بنك ليه سياسته، بس كل اللي أقدر أرشحه أي حاجة تكون أقرب من بيتك وشهاداتها عالية زي البنك الأهلي المصري أو بنك مصر. والحلو إنك تقدر تعمل شهادة أونلاين عن طريق التطبيق.
وإنت بتفتح حساب، أرشحلك تفتح وقت الشمول المالي لأنه بيبقى سهل، وتفعّل تطبيق البنك وتعمل شهادات براحتك. بس العيوب إنها بتختلف من بنك لبنك، والحساب بيبقى فيه حد أقصى للرصيد لو شمول مالي حوالي 100 ألف أو 200 ألف (مشاكل أغنياء برضه بس حبيت أوضحها). ده غير كل 3 شهور مصاريف الحساب برضه، وطبعاً إنك مش هتقدر تاخد الفلوس غير بعد المدة أو أول 6 شهور بس هتخسر جامد فيهم، فخلي بالك.
مع باقي حاجات البنك المعقدة دي بقى، اسأل البنك. وبرضه حابب أوضح: خلي بالك وإنت بتمضي، لأنه بسمع حالات كتير موظف البنك خلى الناس تمضي على كريدت كارد وتأمين للحياة وغيره كتير. فاقرأ إنه نت بنكي وفتح حساب وخلاص. وللأسف هنا الفرع بيفرق، فاختار الأقرب أو أنضف أقرب حاجة ليك (لو فيه فرع معروف إنه وحش يعني). ولو في أي مشاكل أنصحك تعمل بلاغ في البنك المركزي https://www.cbe.org.eg/ar/consumer-protection علشان تاخد حقك.
المميزات: - سهل نسبياً ومضمون - بطاقة بس لو حساب شمول مالي
العيوب: - مش هتاخد الفلوس غير بعد المدة سواء سنة أو 3 سنين - ممكن البنك يرخم عليك - مصاريف الحساب الدورية (غير لو كان بنك زي QNB مثلاً، بس في الوقت ده الشهادات العائد فيها قليل مقارنة بالباقي ومفيش شهادات بالعملات الأجنبية)
ادعمني (اختياري)
- USDT (TRC20):
TKQ3Uwkq21ntiua2Zh9Hu376fdMdnRGWN6
شوف الكومنتات لو فيه أي تعديل أو بوستات جديدة.
- USDT (TRC20):
-
 @ f1577c25:de26ba14
2025-04-07 07:31:09
@ f1577c25:de26ba14
2025-04-07 07:31:09النهاردة هنتكلم عن فوري يومي، تقريباً أكتر صندوق مقرب لقلبي وبرشحه لأي شخص بيدور على حاجة تطلع بيها عائد يصرف منه. العائد بتاعه حوالي 24% وبينزل يومي، فمقارنة بالعائد الشهري بتاع البنوك اللي هو 23% أو 23.5%، فيعتبر حلو جداً لأن العائد يومي زي ما قلت وبتقدر تسحب فلوسك فوري (عن طريق الكارت الأصفر) أو خلال يومين عمل لو تحويل بنكي. قصدي إنه مش بيتجمد زي البنك، بس فيه عيوب برضه زي إنك لازم تروح تمضي الورق من فرع فوري بلس، أو إن الحد الأقصى 100 ألف جنيه (مشاكل أغنياء عارف، بس لازم أقول كل العيوب)، غير لو هتقدم مصدر دخل وهكذا. هقولك بالتفصيل تحت عن مشكلة حصلت معايا عشان تاخد بالك منها وإنت بتقدم.
تطبيق ماي فوري
علشان تبدأ في الصندوق، لازم تروح الفرع ويبقى معاك تطبيق ماي فوري. وللصراحة، الموضوع سهل وبسيط: هو بطاقتك وتروح أي فرع، هتمضي على ورق وتتصور هناك (هما هيصوروك) وكام يوم وبس كدا هتتفعل.
أعتقد مش محتاج كارت فوري الأصفر، بس هو هيساعدك كتير وببلاش، فأنصحك تعمله مع الصندوق. بس خلي بالك ومهم جداً جداً: لأني تاني مرة لما كنت بعمل الكارت (كانت بعد حادثة تهكير فوري)، الراجل هناك قعد يحوّر ويقولي لازم تعمل محفظة على رقم التليفون وإلزامي وبتاع، وفي الآخر طلع بيكدب علشان ياخد بونص. وأنا مش بهاجمه، بس قصدي خلي بالك لأنه ممكن يستغلوك بالفرع ويمضيك على حاجات زيادة. فإنت اقرأ العقد بتاعك قبل ما تمضي، أو روح فرع نضيف. هو مش لازم أقرب فرع ليك، فخلي بالك من النقطة دي.
المميزات:
- سهل
- بطاقتك بس
- تقدر تسحب في أي وقت وسهولة الإيداع كمان
عيوب:
- كبداية في حد أقصى 100 ألف جنيه، بس ممكن تزودهم بعدين
- الإيداع بيقعد كام يوم عمل لحد ما يسمع
- العائد بينزل يومي ماعدا الجمعة والسبت والأحد تقريباً كمان
ادعمني (اختياري)
- USDT (TRC20):
TKQ3Uwkq21ntiua2Zh9Hu376fdMdnRGWN6
شوف الكومنتات لو فيه أي تعديل أو بوستات جديدة.
-
 @ f1577c25:de26ba14
2025-04-07 07:27:17
@ f1577c25:de26ba14
2025-04-07 07:27:17أهلاً! أفترض إنك قرأت أول كام بوست، ولو لأ فده لينك أول بوست علشان تتابع بالترتيب: <لينك أول بوست>
المرة اللي فاتت اتكلمنا عن مميزات وعيوب البورصة الأمريكية، زي إنك تقدر تستخدم الكريبتو كطريقة إيداع سهلة. النهاردة هنتكلم عن حاجتين مهمين: العملات الرقمية المستقرة والذهب العالمي.
العملات الرقمية المستقرة (Stablecoins):
لما بتكلم عن العملات الرقمية، مش قصدي تشتري بيتكوين وخلاص. أنا قصدي العملات المستقرة زي USDT وUSDC، لأن كل عملة منهم ليها ما يعادلها بالدولار أو أصول حقيقية. يعني لو بصيت على سعر البيتكوين هتلاقيه ممكن 80 ألف دولار للوحدة، لكن USDT أو USDC دايماً سعرها قريب من 1 دولار. دي حلوة جداً للتعامل الإلكتروني لأنها زي الدولار المشفر.
إحنا هنستخدمها في خدمة اسمها "Earn" وهي شبه شهادات البنك. بتروح على بينانس، تشتري عن طريق P2P، وبعدين تروح على صفحة الـ Earn: https://www.binance.me/en/earn/simple-earn
هناك هتلاقي خيار تعمل "stake" للعملات دي، يعني بتحجز فلوسك لمدة معينة على الموقع، والموقع بيستخدمها (يسلفها لحد تاني أو يستخدمها كسيولة). الحلو إن في Earn، مش لازم تقفل فلوسك لسنة أو 3 سنين زي البنك. في اختيار اسمه "Flexible" بتقدر تحط فلوسك وتسحبها في نفس اليوم، والعائد بينزل يومياً. العيب إن العائد بيتغير يومياً. ممكن تختار Flexible لو عايز تسحب في أي وقت، أو تختار مدة أسبوع أو 90 يوم بعائد ثابت (بس بيكون أقل من الـ Flexible شوية).
ممكن كمان تفعل "Auto-Subscribe" لأن العائد بينزل بنفس نوع العملة، فبدل ما العائد يفضل مركون، أو لما يبقى معاك عملات زيادة في المحفظة، هو بيشترك تلقائي في Earn، فبيبقى زي العائد المركب.
المميزات
- عائد دولاري ومش متأثر بالجنيه
- بينزل عائد يومي
- تقدر تسحب فلوسك في أي وقت
- الحد الأدنى صغير (حوالي 100 جنيه)
العيوب
- الأمان مش 100% لأنها منصة وممكن (لا قدر الله) تقفل حسابك
- العملات الرقمية غير قانونية في بعض البلدان فخلي بالك
- خلي بالك من محاولات النصب: زي لما حد يقولك نكمل المعاملة برا المنصة، أو يبعت رسالة من رقمه كأنها من إنستاباي أو فودافون كاش
- العائد متغير وممكن يقل (بس حالياً حوالين 10%)
- قيمة الدولار نفسها ممكن تتغير
ملحوظة: لو قلقان من بينانس، فيه منصات تانية زي Kraken (بس العائد أسبوعي ومش عالي) أو OKX اللي بتدي أول 180 يوم عائد 10% مضمون، وبعدين ممكن تحول لـ Binance أو Bybit.
الذهب العالمي (PAXG)
بالنسبة للذهب، نفس الخطوات السابقة بالظبط. الحلو إنه في خدمة Earn لـ PAXG - صحيح العائد أقل من 1% سنوياً، بس أحسن من مفيش!
هتشتري USDT من خلال P2P، بعدين تروح بينانس وتعمل تحويل من USDT إلى PAXG. كده بقى معاك ذهب بالسعر العالمي. أحب أطمنك إن PAXG من شركة موثوقة، وتقدر تقرا عنها هنا: https://www.paxos.com/pax-gold
فيه عملات تانية شبهها، بس دي من أفضلهم، خصوصاً إنهم بيعملوا تقييم للأصول بشكل دوري للتأكد من مصداقية الشركة.
المميزات
- ذهب سهل الوصول إليه
- الحد الأدنى قليل
- أمان نسبي ضد التضخم
- سهولة الشراء والبيع
العيوب
- نفس عيوب المنصات الرقمية
- قيمة الذهب نفسها ممكن تتغير
- العائد على الـ PAXG منخفض (أقل من 1%)
العملة موجودة كمان على Kraken، بس مش متأكد لو فيها خدمة Earn زي بينانس.
ادعمني (اختياري)
- لو حابب تسجل عن طريق Binance ممكن تستخدم رابط الإحالة بتاعي: https://www.binance.com/referral/earn-together/refertoearn2000usdc/claim?hl=en&ref=GRO_14352_5LGSE
- USDT (TRC20):
TKQ3Uwkq21ntiua2Zh9Hu376fdMdnRGWN6
شوف التعليقات لو في اي تعديل او بوستات جديدة.
-
 @ ef53426a:7e988851
2025-04-07 15:25:58
@ ef53426a:7e988851
2025-04-07 15:25:58Bitcoin and stories are much alike.
They can be described in powerful simplicity or astonishing complexity. Both are unique developments in human history and feed our well-being. Bitcoin and stories are forces for good, but they must be used wisely.
By removing himself from the equation, Satoshi Nakamoto left it to us to write the future of bitcoin. It’s not surprising that we have been tentative to propose a narrative. Stories have never been decentralized before.
Think of the pyramids, the invention of the printing press, or the release of the iPhone 1. Instead of the technology itself, we focus on the people who made it possible and how its invention affected society. But in relity, the story of the pyramids survives in every tourist’s photograph; the joy of reading touches a higher percentage of the world’s population every year; the garage-to-keynote-speaker tale of Apple’s late CEO inspires would-be entrepreneurs worldwide.
To unite interest in bitcoin, we need to be better at telling its stories. Only stories have the power to stop us, to wake us, to make us feel rather than think.
In late 2022, Konsensus Network, the Freedom Publishing House, announced a call for submissions for the world’s first bitcoin fiction anthology. The book seeks to link the emotive power of stories with the possible effects and ramifications of a hyperbitcoinized world.
For most people, great change doesn’t arrive from binary logic and a working knowledge of code. Understanding grows through narrative. It is stories that bring change.
Here’s https://www.youtube.com/embed/vIQ41B8jFPI?si=pN2kr44P-Th3bug4 for the book with some of the original artwork which accompanies the 21 stories.
21 Futures: Tales from the Timechain
Political dissidents scramble to cross the threshold to freedom. A decades-long hunt for keys incites a change in world order. A clear-blood dares to question the oppression of noderoids. A cryo-frozen oligarch wakes into his worst nightmare.
A lowly space station miner buys a planet.
In this book of diverse stories planted firmly in the bitcoin-verse, reality fractures into 21 futures. Some are wonderful, others terrifying.
You are not prepared.
[https://21futures.com] (21 Futures) is now an imprint of Konsensus Network, publishing a variety of freedom fiction stories and books.
In my next blog, I'll go into some of the many developments in the bitcoin fiction space in the last few years.
For now, let's keep sharing stories.
-
 @ da0b9bc3:4e30a4a9
2025-04-07 06:15:43
@ da0b9bc3:4e30a4a9
2025-04-07 06:15:43Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/936802
-
 @ 88cc134b:5ae99079
2025-04-07 13:45:06
@ 88cc134b:5ae99079
2025-04-07 13:45:06Heading
Body text hello
nostr:nevent1qvzqqqqqqypzpclca3vtuwz4ypdjx9ywcceuzs7yka76rh23wrjvurdv9r4zwremqqsw7tttdcf90wem2hvjd7pyncu3h6teldw2jppgjuh9l7h4ymgt4wcl74wgx
-
 @ 57d1a264:69f1fee1
2025-04-07 06:04:14
@ 57d1a264:69f1fee1
2025-04-07 06:04:14It's so cool how AI is blending design and engineering together, making it easier for us all to be efforts creative in new ways!
Steve Jobs once said:
“The doers are the major thinkers. The people who really create the things that change this industry are both the thinker-doer in one person.”
— Steve JobsWould its words become truth? Or they already are?
originally posted at https://stacker.news/items/936796
-
 @ 88cc134b:5ae99079
2025-04-07 12:19:39
@ 88cc134b:5ae99079
2025-04-07 12:19:39Tester one one two and three nostr:nprofile1qyv8wumn8ghj7urjv4kkjatd9ec8y6tdv9kzumn9wsq3yamnwvaz7tmsw4e8qmr9wpskwtn9wvqzpzxvzd935e04fm6g4nqa7dn9qc7nafzlqn4t3t6xgmjkr3dwnyreaytcqa, some
nostr:nevent1qvzqqqqqqypzpzxvzd935e04fm6g4nqa7dn9qc7nafzlqn4t3t6xgmjkr3dwnyreqyvhwumn8ghj7urjv4kkjatd9ec8y6tdv9kzumn9wshszymhwden5te0wp6hyurvv4cxzeewv4ej7qpq6mw92lz87fqsca2gn3jkm2rd3xexcapjd5vscysx4r79y672ukrqy5utlm
-
 @ d5c3d063:4d1159b3
2025-04-07 11:43:50
@ d5c3d063:4d1159b3
2025-04-07 11:43:50เวทีนี้ไม่ได้ตั้งคำถามแค่เรื่องเงิน...แต่จริง ๆ แล้ว มันคือการตั้งคำถามกับทั้ง “ระบบ” ที่เราทุกคนติดอยู่
มีใครสังเกตไหมว่า... #อิสซุป วางคำถามไว้ 4 ชุด ไม่ใช่โดยบังเอิญ เพราะนี่คือการถอดรหัส “อริยสัจ 4” ผ่านเกมการเงิน
อริยสัจ 4 คือ ภาษาธรรมะของคนที่เริ่มตั้งคำถามกับชีวิต มันอาจไม่ใช่คำตอบของทุกคน แต่อาจเป็นแผนที่เดียว... ที่พาเรากลับมา "พึ่งพาตนเอง" ได้ เราเริ่มจาก “ทุกข์”
🟥 ทำไมคนรุ่นนี้ถึงจน ทั้งที่ทำงานหนัก ต่อด้วย “สมุทัย” 🟧 ใครสร้างระบบที่บีบเราให้วิ่งไม่หยุด แล้วเข้าสู่ “นิโรธ” 🟨 อิสรภาพมีจริงไหม หรือเป็นแค่ของลวง และจบที่ “มรรค” 🟩 ถ้าอยากหลุดจากระบบนี้จริง ต้องเริ่มจากตรงไหน
นี่ไม่ใช่คำถามเชิงทฤษฎี แต่มันคือ “เสียงในใจ” ของคนรุ่นใหม่หลายล้านคน ที่โตมาในโลกที่บอกให้เราตั้งใจเรียน แต่พอเรียนจบก็มีหนี้รออยู่ โลกที่สอนว่า “ทำงานหนักแล้วจะมั่นคง” แต่ความจริงคือ ค่าครองชีพแซงหน้ารายได้ไปไกล และนั่นคือจุดเริ่มของ "ทุกข์" ...
⸻
🟥 1. ทุกข์ – เกมนี้เริ่มจากติดหนี้ โดยไม่มีปุ่มยกเลิก
ทำไมเด็กจบใหม่ต้องเริ่มชีวิตด้วยหนี้ ? ทำไมคนที่ทำงานหนักที่สุดถึงเป็นคนที่จนที่สุด ?
💬 อ. พิริยะ
“ระบบออกแบบให้คุณต้องวิ่งตั้งแต่วันแรก เรียนต้องกู้ เริ่มงานต้องผ่อน คุณไม่ได้เริ่มจากศูนย์...แต่เริ่มจาก..ติดลบ..เสียด้วยซ้ำ”
💬 โค้ชหนุ่ม
“หนี้ไม่ได้เกิดจากใช้เงินเกินตัว แต่มาจากระบบ...ที่บีบให้เราสร้างรายจ่าย ก่อนที่รายได้จะมั่นคงด้วยซ้ำ”
จุดเริ่มต้นของความทุกข์... คือคุณไม่ได้เลือกเกมนี้ คุณแค่ถูกโยนเข้ามา โดยไม่มีสิทธิ์แม้แต่จะถามว่า "กติกาคืออะไร"
⸻
🟧 2. สมุทัย – กติกาตั้งมาให้คุณวิ่ง…ที่ยังไงก็ไม่ชนะ
ทำไมทำงานมากขึ้น แต่รู้สึกจนลง ? เงินเฟ้อคืออะไร ? มันเกิดเองหรือมีคนตั้งใจ ?
💬 อ. พิริยะ
“เงินเฟ้อคือภาษีที่คุณไม่รู้ตัวว่าจ่าย เพราะรัฐพิมพ์เงินได้ไม่จำกัด ร่างกายเราทำงานได้แค่วันละเท่าเดิม แต่ค่าของเงินมันลดลงทุกวัน”
💬 โค้ชหนุ่ม
“คนเงินเดือน 3-8 หมื่น ยังเอาไม่อยู่ เพราะช่องว่าง ‘รายได้ vs ค่าครองชีพ’ มันแย่ลงเรื่อย ๆ และไม่มีทีท่าว่าจะหยุดลง”
💬 ทั้งคู่ยังพูดถึงระบบการศึกษาว่า
“เราไม่เคยถูกสอนเรื่องเงิน เราเข้าสู่สนามเศรษฐกิจเหมือนถูกจับไปแข่ง โดยไม่มีแม้แต่แผนที่”
นี่แหละ...คือรากของปัญหา มันอาจไม่ได้มีใครออกแบบระบบมาเหมือนที่โค้ชหนุ่มบอกในคลิปหรอก…แต่ความมั่วของระบบ
ทำให้คนจำนวนมากติดอยู่ในกับดักหนี้แบบไม่รู้ตัว⸻
🟨 3. นิโรธ – คุณหยุดเล่นได้ ถ้ารู้ทันว่าเกมนี้โกง
ถ้าเกมนี้มันล็อกไว้หมด เราจะออกจากเกมนี้ยังไง? อิสรภาพทางการเงินคืออะไร บิตคอยน์ล่ะ?
💬 โค้ชหนุ่ม
“อิสรภาพทางการเงินไม่ใช่การรวยล้นฟ้าแต่คือจุดที่คุณไม่ต้องตื่นมาเครียดเรื่องเงินทุกวัน”
💬 อ. พิริยะ
“รัฐที่พิมพ์เงินได้ไม่จำกัด = รัฐที่สัญญาอะไรก็ได้โดยไม่ต้องรับผิดชอบ แล้วเราจะฝากชีวิตไว้กับคำสัญญาแบบนี้เหรอ”
💬 อ. พิริยะ
“บิตคอยน์มันยังใหม่ แต่มันตั้งคำถามกับระบบเก่าได้แรงมาก ว่าถ้าเงินของเราถูกเปลี่ยนค่าได้โดยที่เราไม่รู้ตัว...แล้วเรายังควรเชื่อมันอยู่ไหม”
อิสรภาพ...ไม่ได้เกิดจากการรอให้ระบบเปลี่ยน แต่มันเริ่มจากการตั้งคำถามง่าย ๆ ว่า “ฉัน...ต้องเล่นตามเกมนี้จริงเหรอ”
⸻
🟩 4. มรรค – สร้างเกมเอง แล้วเลิกวิ่งตามคนอื่น
ถ้าไม่อยากวิ่งตลอดชีวิต ต้องทำยังไง ?
💬 โค้ชหนุ่ม
“เริ่มจากไม่ผูกตัวเองกับหนี้ใหญ่ เรียนรู้เรื่องเงินตั้งแต่ตอนที่คุณยังไม่มีเงิน อย่ารอให้มันพังแล้วค่อยเข้าใจ”
💬 อ. พิริยะ
“ความมั่นคงที่แท้จริง ไม่ใช่ทรัพย์สิน ไม่ใช่ตำแหน่ง แต่มันคือ ‘อำนาจต่อรองกับชีวิตตัวเอง’ คือความรู้ เงินสำรอง และวิธีคิดที่คุณสร้างเอง”
ไม่มีใครจะ Own Your Future ให้คุณได้ ถ้าคุณยังฝากทุกอย่างไว้กับรัฐ...กับระบบ...หรือกับคนอื่น
⸻
และนั่นแหละ…คือ “อริยสัจ 4”
🟥 ทุกข์-เพราะระบบนี้ออกแบบให้คุณเป็นหนี้ 🟧 สมุทัย-เพราะเงินเฟ้อคือกับดักที่มองไม่เห็น 🟨 นิโรธ-เพราะคุณเลือกหยุดวิ่งได้ถ้ารู้ว่าเกมนี้โกง 🟩 มรรค-เพราะทางออกมีจริงถ้าคุณกล้าสร้างมันเอง
คุณไม่ต้องเป็นผู้ชนะในระบบ แต่คุณเลือกที่จะไม่เป็นเหยื่อของมันได้ Own Your Future คือเวทีที่กล้าตั้งคำถาม ว่าโลกนี้ออกแบบมาเพื่อใคร ? และทำไมเราถึงไม่มีสิทธิ์เลือกเกมที่ตัวเองเล่น ? ⸻ คุณอาจยังไม่มีคำตอบทั้งหมดในตอนนี้ แต่เมื่อคุณเริ่ม “ตั้งคำถาม” คุณก็กำลังเดินบน "มรรค" ของตัวเองแล้ว และบางที...นั่นแหละ อาจเป็นจุดเริ่มต้นของ อิสรภาพที่แท้จริง ⸻ ถ้าบท(สรุป)ความนี้...ทำให้คุณเริ่มตั้งคำถาม แชร์มันไปให้เพื่อนคุณอีกคน... ที่อาจกำลังรู้สึก “หมดแรงวิ่ง” เหมือนกัน และแชร์คลิปใต้คอมเมนต์ไปให้เขาดูด้วย แค่ 2 ชั่วโมง...อาจเปลี่ยนทั้งชีวิตเขาได้
exittheratrace #rightevent #MoneyCoach
MBKCENTER #อยากหลุดพ้นหรือวนลูปเดิม #Siamstr
-
 @ e5de992e:4a95ef85
2025-04-07 05:46:58
@ e5de992e:4a95ef85
2025-04-07 05:46:58The stock market is currently experiencing a significant downturn, with major indices such as the S&P 500 and the Dow Jones Industrial Average recording substantial losses. This decline is largely attributed to the recent implementation of sweeping tariffs by President Donald Trump, including a 10% levy on all imports and higher duties on exports from key trading partners like China, the European Union, Japan, and Vietnam. These measures have ignited fears of a global trade war, leading to a massive sell-off in the markets. Notably, the S&P 500 dropped 6%, the Nasdaq slid 5.8%, and the Dow Jones fell by 2,231 points—some of the steepest declines since the early days of the COVID-19 pandemic.
Everyday Patience Versus Irrational Trading
In everyday life, consumers often exhibit patience by waiting for prices to drop before making purchases:
- Seasonal Sales: Shoppers wait for discounts to buy clothing.
- Tech Promotions: Tech enthusiasts delay buying electronics until promotional events.
- Real Estate: Prospective homebuyers hold off during market slowdowns to secure better deals.
This common-sense approach maximizes value and minimizes expenditure.
In contrast, many stock market traders fall prey to irrational behaviors:
- Fear of Missing Out (FOMO): Investors buy stocks at high prices or the dip, worried they might miss potential gains.
- Herd Mentality: Individuals mimic the actions of the majority, often buying during market highs and selling during lows.
These emotional decisions often lead to poor outcomes, as they contradict the logical approach of waiting for favorable prices.
The Risks of Ignoring Rational Investment Principles
Irrational trading practices can result in significant financial losses. By purchasing stocks at inflated prices during market euphoria, investors expose themselves to sharp declines when corrections occur. Unlike unpredictable black swan events, these losses stem from market corrections that follow overvaluation periods. Ignoring fundamental investment principles can, therefore, be more damaging than unforeseen events.
A Balanced Approach to Investing
A more balanced approach involves:
-
Risk Management Strategies:
Diversify across asset classes to mitigate potential losses. -
Maintaining a Long-Term Perspective:
Adhere to disciplined investment plans to avoid impulsive decisions. -
Understanding Your Risk Tolerance:
Set stop-loss orders and know your limits to protect against downturns.
These strategies help investors avoid pitfalls driven by FOMO and herd mentality.
Conclusion
While the current market downturn presents challenges, it also serves as a reminder of the importance of rational investment behavior. By drawing parallels from everyday purchasing decisions, investors can appreciate the value of patience and strategic planning. Embracing risk management techniques and resisting psychological pitfalls like FOMO and herd mentality can lead to more resilient and successful investment outcomes.
-
 @ 88cc134b:5ae99079
2025-04-07 10:54:16
@ 88cc134b:5ae99079
2025-04-07 10:54:16What!?
-
 @ 57d1a264:69f1fee1
2025-04-07 05:22:14
@ 57d1a264:69f1fee1
2025-04-07 05:22:14This idea has been explored along the last decades. Nothing has never taken the van place in the BMW series. The most successful intent was the 80s' Vixer in the US. Too sporty for a van? Or too luxurious to cover that already saturated market?
Collected some pictures all around, most oof them are designs and prototypes. Tried to order chronologically below:
Now in 2025, this came out of Ai
https://www.youtube.com/watch?v=d7p9CGBmRAA
originally posted at https://stacker.news/items/936787
-
 @ 88cc134b:5ae99079
2025-04-07 10:50:09
@ 88cc134b:5ae99079
2025-04-07 10:50:09Test
testing test
-
 @ fd78c37f:a0ec0833
2025-04-07 05:06:58
@ fd78c37f:a0ec0833
2025-04-07 05:06:58In this feature, we’re excited to welcome MadMunky, who shares insights on fostering a decentralized community of activists, artists, and musicians, and how Bitcoin and Nostr are empowering unfiltered expression.
YakiHonne: MadMunky, thank you for joining us! Before we dive into the interview, I’d like to briefly introduce YakiHonne. We’re a decentralized media platform built on the Nostr protocol—a technology designed to champion free speech. YakiHonne empowers creators to own their voices and assets, offering innovative features like smart widgets, verified notes, and support for long-form content. With that in mind, we’d love to hear more about you and your community.
MadMunky: Thanks for having me! I’m someone who thrives on staying active—dabbling in various projects and traveling whenever I can. These pursuits give me a sense of freedom, or perhaps the illusion of it. I see myself as a craftsman of sorts, woodworker, dj, chef constantly exploring free-market solutions. I firmly believe that activism, paired with a truly free market, can address many of the world’s challenges.
That belief gave birth to 2140 Collective about two years ago, a project I co-founded with Anon. Collective that enables our community to create and publish freely. Before this, no platform truly supported our vision without compromise—social media often demanded personal data in exchange for access. We’re a collective of activists, artists, and musicians who simply want to build our own space. Communities like ours are essential for mutual support among like-minded individuals. This is also why I champion Bitcoin. It’s not perfect, but it’s transparent and honest—a pillar of freedom. Bitcoin offers an escape from centralized control, and that’s a powerful force. It’s why we’re here today.
YakiHonne: What first drew you to Bitcoin, and what inspired you to build a community around it?
MadMunky: My journey into free tech stemmed from growing frustration with persistent privacy invasions. For me, the erosion of privacy is deeply unsettling. About a year and a half ago, I met Anon, a close friend who introduced me to this space. We started brainstorming ways to empower people like us to carve out our own creative and communal haven.
We didn’t want to limit ourselves to an online presence. Our goal was to bring the community into the physical world through exhibitions, gatherings, and eventually a parallel economy. Plans like high-end auctions are on the horizon, and all these initiatives will be showcased on https://2140.wtf . Through art and culture, we aim to drive Bitcoin adoption. Some argue adoption isn’t necessary, but I believe these mediums are powerful gateways to introduce Bitcoin’s message. It’s not just about display—it’s about embedding critical thinking. When people encounter Bitcoin-inspired art or music, the underlying ideas spark curiosity. That shift from passive consumption to active engagement is how adoption grows.
YakiHonne: How did your community take shape, and how did you attract members?
MadMunky: It wasn’t easy. We kicked things off after a Bitcoin birthday event in London, connecting with artists and musicians over platforms like Signal. We officially launched around last year’s Bitcoin birthday, creating a space on Telegram and experimenting with platforms like Console—billed as the “Discord of networks.” Back then, Nostr was still nascent, and Console, while promising, felt clunky and failed to draw people in. Building momentum was tough—people are busy, and convincing them to switch platforms is a challenge. It takes dedicated individuals willing to invest time and share knowledge.
We tried Twitter early on but found it stifling—its control over speech made it a dead end. Nostr, with its remarkable strides in the past year, became our home.
But we’re making progress. In London, we host “Nostrland,” a bi-weekly meetup focused on Nostr, Bitcoin, and freedom tech. It’s growing organically, with new attendees and venues each time. Our crew is behind Bitcoin Culture Festival / London , and contributing in many others across Europe.
YakiHonne: Beyond the lack of freedom on some platforms, what other hurdles have you faced?
MadMunky: Free speech has been on my mind a lot lately—it’s a cornerstone of true freedom. Many assume Bitcoin alone is enough, but it’s just one piece of the puzzle. For years, we lacked tools to express ourselves without censorship. Platforms like Twitter and Facebook track everything—our locations, connections, and words. I ditched Facebook years ago when I realized how invasive it was. These systems wield algorithms that can fracture social bonds and control narratives.
Now, though, we have solutions. Protocols like Nostr and platforms like YakiHonne let creators speak freely, without gatekeepers. That’s revolutionary. If we don’t address the chaos of our current monetary system, suffering will deepen. Activism—raising awareness and sharing tools like Bitcoin and Nostr—is vital. We’re still early in this movement, but the ability to connect and communicate freely is transformative. After two decades of being trapped, spreading ideas is finally within reach.
YakiHonne: Free speech is indeed fundamental. What does your community do with Bitcoin? Are you focused on the technical side or more on cultural aspects?
MadMunky: Our members hail from across Europe, with diverse backgrounds—anyone can join. We blend technical and cultural efforts. For instance, Anon explored LoRa mesh networks, which let us send Nostr messages via radio waves—a concept most people don’t even know exists. These innovations often come from volunteers with bold ideas, woven into protocols. It’s incredible.
I’m not a tech fanatic myself, but I see the value in spreading these concepts. It’s not just about discussing Nostr or Bitcoin’s freedom—it’s about understanding the tools we use. Privacy isn’t simple; it’s a journey. Even with a powerful message, if you’re on an iPhone or Android, you’re still tracked. Staying free takes effort. Our community ties technical workshops, art exhibitions, and music together—think Bitcoin-inspired food, culture or tech talks. These pieces form a broader solution to today’s monetary mess.
YakiHonne: What advice would you offer technically inclined individuals or organizations eager to contribute to Bitcoin’s ecosystem?
MadMunky: Support is key—not just financial, but active engagement. We don’t have all the answers or know every project, so we invite people to join our events, share ideas, and help organize. Collaboration matters. Many have brilliant concepts but lack time due to life’s demands. Companies with resources can pitch in—offering tools or testing grounds.
This Friday, for example, we’re hosting a workshop at Cyphermunk House in London, exploring privacy-focused solutions like Graphene OS. People are waking up to these issues, and interest is surging. It’s about devices, funding, and teamwork—embracing a cyberpunk ethos. If you find a great idea, back it. Open-source tools and protocols are how we reshape the world.
YakiHonne: How do you envision the Bitcoin community evolving in terms of scalability, privacy, and adaptability?
MadMunky: In my two years in this space, Bitcoin’s transparency and cyberpunk-like tech have blown me away. Soon, we’ll make payments without networks—Bitcoin as eCash flow is wild. The potential for Bitcoin, Nostr, and tools like YakiHonne is immense. A year ago, these ideas were unimaginable; now, they’re racing forward.
Governments will push back—regulating, taxing, targeting centralized platforms—but that’s fine. People are waking up, seeking privacy and freedom. Education is critical; the more who grasp these decentralized tools, the stronger we become. We reject a government-controlled future. Peer-to-peer, freedom, and decentralization—that’s the path. Let’s keep building.
YakiHonne: Thank you, MadMunky. This has been an enlightening and inspiring conversation. We’re grateful for your insights!
-
 @ e5de992e:4a95ef85
2025-04-07 04:04:42
@ e5de992e:4a95ef85
2025-04-07 04:04:42U.S. Financial Market Volatility Amid Trade Tensions and Policy Changes
The U.S. financial markets are experiencing significant volatility in response to recent policy decisions and escalating global trade tensions.
Major U.S. Stock Indices
-
S&P 500:
The SPDR S&P 500 ETF Trust (SPY) is currently priced at $505.28, reflecting a decline of approximately 5.75% from the previous close. -
Dow Jones Industrial Average:
The SPDR Dow Jones Industrial Average ETF (DIA) stands at $383.22, down about 5.42%. -
Nasdaq Composite:
The Invesco QQQ Trust Series 1 (QQQ) is at $422.67, showing a decrease of 6.09%. -
Russell 2000:
The iShares Russell 2000 ETF (IWM) is priced at $181.19, down 4.41%.
Advisor Perspectives
Key Factors Influencing Market Movements
-
Implementation of Sweeping Tariffs:
President Donald Trump's administration has imposed a baseline 10% tariff on all imports, with higher rates targeting specific countries—34% on Chinese imports and 20% on goods from the European Union. -
Global Retaliatory Measures:
In response, China has announced retaliatory tariffs of 34% on U.S. goods, intensifying fears of a global trade war and its potential impact on economic growth. -
Market Reactions and Investor Sentiment:
The announcement of these tariffs has triggered significant sell-offs. The S&P 500 and Nasdaq recorded their worst drops in years, with the Dow Jones falling over 9%, as investors react to the economic implications of escalating trade tensions.
Economic Indicators
- Oil Prices:
Crude oil prices have plunged to a four-year low. - Brent Crude: Trading at $63.01 per barrel.
-
West Texas Intermediate: At $60.63 per barrel.
-
Treasury Yields:
The yield on the 10-year U.S. Treasury note has declined to approximately 3.94%, indicating a shift toward safer assets amid market volatility.
Corporate Highlights
-
Tesla Inc. (TSLA):
Current stock price is $239.43, down 10.46% from the previous close. -
Apple Inc. (AAPL):
Stock stands at $188.38, reflecting a decrease of 7.27%. -
Boeing Co. (BA):
Shares are at $136.59, down 9.47%.
Global Market Impact
International markets have reacted variably to U.S. policy changes:
-
Japan's Nikkei 225:
Dropped nearly 8% amid concerns over U.S. tariffs affecting automakers like Toyota. -
South Korea's KOSPI and European Markets:
Both have experienced downturns as trade disputes add uncertainty. -
Hong Kong's Hang Seng:
Declined, reflecting broader concerns over trade uncertainties and impacts on Chinese tech stocks.
Outlook
The current market environment is marked by heightened volatility and uncertainty:
- Investors are advised to exercise caution and consider diversification strategies.
- Key developments such as trade negotiations and policy changes will be crucial in shaping future market dynamics.
- Monitoring evolving economic data and geopolitical events remains essential for navigating this complex landscape.
-
-
 @ 0fa50ac1:13162495
2025-04-06 23:56:52
@ 0fa50ac1:13162495
2025-04-06 23:56:52You say, “Bitcoin has no intrinsic value.”
But brother, I say to you—nothing does.
❧
Gold, wheat, steel, water, art—
none possess value in themselves.
A thing is not valuable.
A person finds value in a thing.
❧
Value is not a substance.
It is not discovered in the dirt,
nor stamped into metal.
It is born in the mind
of the one who chooses,
who compares,
who prefers.
❧
This is the truth they will not teach you.
Because once you know it,
you cannot be controlled.
❧
To say value is “intrinsic”
is to say it is knowable, measurable,
assignable from above.
And if it can be known,
then it can be fixed.
And if it can be fixed,
then the planners will fix it.
And if the planners fix it,
freedom dies.
❧
Only subjective value
lets prices breathe.
Only subjective value
lets the game go on,
as tastes shift,
as time moves,
as each man finds joy in what others overlook.
❧
It is this truth
that makes room for artists,
for inventors,
for those with strange passions
and quiet genius.
❧
And Bitcoin—
it breaks the frame.
It’s not a commodity.
It’s not a company.
It’s not backed by force.
❧
So they say,
“It has no value.”
❧
And we reply,
“No—you place no value on it.
But others do.
And the market has spoken.”
❧
Transparent. Scarce. Borderless. Unstoppable.
Valued by those who need it most.
Valued by those who understand it best.
❧
It rises not because it was declared valuable,
but because someone, somewhere
was willing to trade for it.
❧
And so the price rose.
And so the signal spread.
And so the economy moved,
as it always has,
not by decree,
but by the ever-motivated
force of desire.
❧
You don’t have to value Bitcoin.
But you do have to accept this:
All value exists only and entirely
in the mind of the economizing human.
 You say, “Bitcoin has no intrinsic value.”
You say, “Bitcoin has no intrinsic value.”But brother, I say to you—nothing does.
❧
Gold, wheat, steel, water, art—
none possess value in themselves.
A thing is not valuable.
A person finds value in a thing.
❧
Value is not a substance.
It is not discovered in the dirt,
nor stamped into metal.
It is born in the mind
of the one who chooses,
who compares,
who prefers.
❧
This is the truth they will not teach you.
Because once you know it,
you cannot be controlled.
❧
To say value is “intrinsic”
is to say it is knowable, measurable,
assignable from above.
And if it can be known,
then it can be fixed.
And if it can be fixed,
then the planners will fix it.
And if the planners fix it,
freedom dies.
❧
Only subjective value
lets prices breathe.
Only subjective value
lets the game go on,
as tastes shift,
as time moves,
as each man finds joy in what others overlook.
❧
It is this truth
that makes room for artists,
for inventors,
for those with strange passions
and quiet genius.
❧
And Bitcoin—
it breaks the frame.
It’s not a commodity.
It’s not a company.
It’s not backed by force.
❧
So they say,
“It has no value.”
❧
And we reply,
“No—you place no value on it.
But others do.
And the market has spoken.”
❧
Transparent. Scarce. Borderless. Unstoppable.
Valued by those who need it most.
Valued by those who understand it best.
❧
It rises not because it was declared valuable,
but because someone, somewhere
was willing to trade for it.
❧
And so the price rose.
And so the signal spread.
And so the economy moved,
as it always has,
not by decree,
but by the ever-motivated
force of desire.
❧
You don’t have to value Bitcoin.
But you do have to accept this:
All value exists only and entirely
in the mind of the economizing human.
-
 @ 9c9d2765:16f8c2c2
2025-04-07 07:39:53
@ 9c9d2765:16f8c2c2
2025-04-07 07:39:53CHAPTER TWO
“This is just a gift,” he said casually. “A small show of goodwill. But if you want my real help, the six hundred million dollars you need, there's one condition.”
He turned to Rita and smiled.
“I want Rita as my wife.”
Silence fell over the room.
Helen was the first to speak. “That can be arranged.”
James, who had been listening from outside the room, felt his chest tighten. He pushed the door open, his heart pounding.
“No,” he said firmly.
Mark raised an eyebrow. “Excuse me?”
“She’s my wife,” James said, standing his ground.
Helen turned to him with a scowl. “Not for long.” She slid a divorce document across the table. “Sign it, James. Stop being selfish.”
James stared at the papers.
Christopher’s voice was sharp. “You don’t belong here, James. If you truly love Rita, you will let her go.”
Rita’s eyes met James’. There was fear in them, but also love.
James clenched his fists.
“No,” he said again.
Then, without another word, he turned and stormed out of the event.
James walked through the cold night, his hands clenched into fists. His heart pounded with frustration. The humiliation he had endured at the Ray family’s business anniversary was unbearable. They had treated him like an outsider, an unwanted burden. Now, they were pressuring him to sign the divorce papers so they could sell Rita off to Mark, a man who was nothing but a privileged opportunist.
How did it come to this?
James had given everything to the family: his loyalty, his love, his hard work. And yet, the moment Grandpa Ray passed away, the rest of the family turned against him.
His phone vibrated in his pocket.
At first, he ignored it, assuming it was yet another message from Helen or Christopher, demanding that he sign the divorce papers. But when it vibrated again, curiosity got the best of him.
He pulled out his phone and saw a notification from an unknown number.
New Email: Urgent Financial Notice – Deltacore Inc.
James frowned. Deltacore?
The name stirred a faint memory. He hadn’t thought about that company in years. Back when he was still working in his father's company before he was falsely accused of embezzlement he had invested a small amount of money in Deltacore Inc., a rising tech company that had shown promise. However, soon after, Deltacore went bankrupt, and James had written off his investment as a loss.
His chest tightened as he opened the email.
Dear Mr. James,
We are pleased to inform you that your investment in Deltacore Inc., which had previously been marked as a loss, has now yielded significant returns. Under new management, Deltacore Inc. has resumed operations and successfully expanded into international markets.
As an early investor, your stake originally valued at $50,000 has now grown exponentially, reaching a current market valuation of $2.7 billion.
Kindly contact our financial department at your earliest convenience to discuss the liquidation or management of your newfound assets.
Best Regards, Jonathan Reed CFO, Deltacore Inc.
James stopped dead in his tracks. His breath caught in his throat.
Two point seven billion dollars.
His eyes scanned the email over and over again, ensuring he wasn’t hallucinating. But no, the numbers were real. His tiny investment had transformed into an unimaginable fortune.
A mixture of shock and disbelief rushed through him.
For years, he had been treated as a nobody, abandoned and looked down upon. But now… now, he was wealthier than the entire Ray family combined.
James’ grip on his phone tightened.
Everything had changed. The next morning, James wasted no time. He called the number listed in the email and scheduled an urgent meeting with Deltacore Inc.
By the afternoon, he was sitting in a high-rise office in the heart of the financial district. The company’s top executives treated him with the utmost respect, referring to him as one of their founding investors.
“We’ve been trying to reach you for months,” Jonathan Reed, the CEO, explained. “But since your contact information had changed, it was difficult to locate you.”
James leaned back in his chair. “I never imagined this would happen. I thought Deltacore was finished.”
Reed chuckled. “It was. But a few years ago, new investors stepped in, acquired the company’s patents, and relaunched operations. As an early investor, your small stake remained valid, and with our recent expansion into global markets, your shares skyrocketed.”
James exhaled slowly, trying to process it all.
“I’d like to access my funds immediately,” he said.
“Of course,” Reed nodded. “Do you have any immediate plans for wealth?”
James smiled slightly. Oh, I have plans A mixture of emotions surged within him shock, excitement, and most of all, vindication.
And yet… instead of feeling triumphant, an unsettling thought crept into his mind.
If they knew…
If the Ray family discovered his newfound wealth, they would come crawling back, pretending to care, pretending they had always loved him. Helen would try to manipulate him, Christopher would suddenly call him ‘son,’ and Stephen, who had never hidden his disdain, would act as if they were close brothers.
They would all turn against Rita, forcing her to beg for his forgiveness just to secure their own future.
James clenched his jaw.
No. They don’t deserve to know.
Not yet.
Instead of revealing his fortune, he made a decision. The once-thriving empire of Ray Enterprises stood on the edge of collapse. The financial crisis had drained the company’s reserves, forcing them into a corner with no easy escape. Suppliers had begun cutting ties, employees whispered about mass layoffs, and investors were pulling out faster than anyone could stop them.
At the center of this storm was Robert Ray, the younger brother of the late Grandpa Ray. Unlike Helen, Christopher, and Stephen who had spent years living off the company’s wealth without truly working for it, Robert had always valued the legacy built by his older brother.
So when the crisis deepened, he did something unthinkable.
He reached out to James.
James had been cast out of the family, humiliated, and disowned after Grandpa Ray’s death. He had been treated as an outsider despite being the only person who had ever truly respected the company’s values. And yet, despite it all, Robert knew that James was their only hope.
Late one evening, Robert arrived at James’s side of the apartment, he was led inside the house, his hands sweating as he stepped into the living room, James sat, calm and unreadable.
James didn’t offer him a seat.
“I assume you’re not here for pleasantries,” James said, his voice cold but controlled.
Robert hesitated before speaking. “James, I know… I know we don’t deserve your help. I know what Helen and the others did to you. But Ray Enterprises is”
“Dying?” James finished for him.
Robert swallowed hard. “Yes.”
James leaned back in his chair, studying the older man. There was no amusement in his expression, no gloating, just the sharp, analytical mind that had made him a billionaire in his own right.
“And now you come to me?” James asked. “After everything?”
Robert exhaled. “I won’t make excuses. I won’t even ask for forgiveness. But I’m asking for your help.”
James was silent for a long moment.
Then, he spoke.
“I’ll do it.”
Robert’s eyes widened. “You will?”
“But under one condition.”
Robert tensed. “What is it?”
James’s lips curled into a slight smirk.
“I want full control. I want to be the President of Ray Enterprises.”
The words hung in the air like a thunderclap.
Robert hadn’t expected this, but he should have. James had been treated like nothing more than an outsider, a disposable nuisance. Now, he was making it clear that if they wanted his help, he would no longer be a guest in the Ray family business.
He would be its ruler.
After a long pause, Robert nodded.
“Fine,” he said. “I’ll make it happen.”
-
 @ 878dff7c:037d18bc
2025-04-06 23:35:54
@ 878dff7c:037d18bc
2025-04-06 23:35:54Australia Highlights Critical Minerals in Trade Discussions with U.S.
Summary:
In an effort to avoid renegotiation of its subsidized prescription-drug system, Australia is emphasizing its vast reserves of essential minerals like lithium and rare earths during trade talks with the U.S. Treasurer Jim Chalmers underscored that these resources serve as a strategic advantage, proposing the creation of a strategic reserve for these minerals. This move aligns with President Trump's initiatives to secure mineral access and reflects Australia's intent to leverage its mineral wealth in international negotiations.
Source: The Wall Street Journal - April 7, 2025
ASX Braces for Significant Losses Amid Global Tariff Tensions
Summary:
The Australian Securities Exchange (ASX) is poised for a substantial downturn, with projections indicating a potential loss of approximately $115 billion. This anticipated decline follows the implementation of new tariffs by U.S. President Donald Trump, ranging from 10% to 50% on foreign imports, which have sparked fears of a global trade war. The Australian dollar has also been affected, dropping below 60 US cents for the first time since the COVID-19 pandemic. Analysts warn that these developments could have far-reaching implications for the Australian economy, including increased inflation and potential interest rate cuts.
Sources: News.com.au - April 7, 2025, The Australian - April 7, 2025, ABC News - April 7, 2025
U.S. Department of Energy Considers Cuts to Clean Energy Projects
Summary:
The U.S. Department of Energy is reviewing potential funding cuts exceeding $1.5 billion for various clean energy projects, including those focused on energy storage and carbon capture. Affected initiatives span multiple states and involve technologies crucial for integrating renewable energy into the power grid and reducing carbon emissions. Industry stakeholders and lawmakers have expressed concern, emphasizing the strategic importance of these technologies for energy resilience and environmental objectives.
Source: Reuters - April 5, 2025
Hazardous Materials Incident in South Australia's Mount Lofty Ranges
Summary:
The Country Fire Service (CFS) is responding to an ammonia gas leak at Plummer Road near Lenswood and Lobethal in the Mount Lofty Ranges, South Australia. Residents are advised to stay clear of the area as firefighters work to contain the leak. CFS
Sources: CFS - April 6, 2025
Coalition Reverses Work-From-Home Policy Amid Backlash
Summary:
Opposition Leader Peter Dutton has reversed the Coalition's policy to mandate full-time office attendance for public servants, acknowledging it was a "mistake" that fueled concerns about opposition to flexible working arrangements, particularly among women. Initially, the plan required Australian Public Service employees to work from the office five days a week, but after criticism from unions and advocacy groups, Dutton amended the policy to apply only to Canberra-based workers. Further backlash led to a complete withdrawal of the mandate, with Dutton apologizing for the confusion and stating that existing flexible work arrangements would remain intact. Labor leaders criticized the policy's inconsistency and potential economic impact on families.
Sources: The Guardian - April 7, 2025, News.com.au - April 7, 2025, The Guardian - April 7, 2025
Chevron Australia Warns of Investment Risks Due to Policy Uncertainty
Summary:
Chevron Australia Managing Director Mark Hatfield has expressed concerns over increasing policy uncertainty affecting investment confidence in Australia's energy sector. He highlighted recent policy shifts, such as changes to the petroleum resource rent tax and proposed domestic gas reservation mandates, as factors creating instability and deterring future investment. Hatfield emphasized the need for a balanced energy transition that prioritizes reliability, affordability, and environmental goals. The Australian
Source: The Australian - April 7, 2025
Australia Calls for Independent Investigation into Aid Worker Deaths in Gaza
Summary:
Australia has joined international calls for an independent investigation into the deaths of aid workers in Gaza, including a United Nations employee and eight Palestinian Red Crescent Society medics, who were found in a mass grave on March 27. Senator Penny Wong emphasized the need for a thorough inquiry to ensure accountability and adherence to international humanitarian law, which mandates the protection of humanitarian workers. Israel's military has launched an internal investigation, but international actors are urging for an independent probe, especially in light of newly emerged video evidence that contradicts Israel’s official explanation for the killings.
Sources: News.com.au - April 7, 2025
Recall Issued for Popular Fitbit Smartwatches Due to Burn Risk
Summary:
Fitbit has issued a recall for its Sense and Versa 3 smartwatches after discovering that the battery may overheat, posing a risk of burns to users. The Australian Competition and Consumer Commission (ACCC) has advised consumers to update their devices with the latest firmware to mitigate this risk. Users are encouraged to check their devices and follow the manufacturer's instructions to ensure safety.
Sources: News.com.au - April 2, 2025, The Australian - April 2, 2025
Keir Starmer Declares 'Globalisation is Over' Amid Tariff Disputes
Summary:
UK Prime Minister Keir Starmer has announced the end of globalisation, acknowledging its failure to benefit many voters. This declaration comes in response to significant global economic disruptions caused by new U.S. tariffs imposed by President Trump. Starmer advocates for accelerated supply-side reforms to boost UK growth and plans to introduce pro-growth measures, including easing regulations for electric vehicle manufacturers. He also aims to advance the UK's industrial strategy and pursue trade talks with India and Australia. While opposing tariffs, Starmer recognizes the appeal of Trump's economic nationalism to disaffected voters.
Sources: The Times - April 7, 2025, The Australian - April 7, 2025
Rainbow Lorikeet Tops Australia's Annual Bird Count
Summary:
The rainbow lorikeet has been identified as the most frequently recorded bird in BirdLife Australia's annual Aussie Bird Count, maintaining its top position since the event's inception in 2014. In the 2024 count, over 57,000 participants recorded more than 4.1 million birds, with the noisy miner and Australian magpie following in second and third places, respectively. The count highlights regional diversity in bird populations and provides critical data on environmental trends. Despite concerns about health threats affecting some species, no significant population declines were reported.
Sources: The Guardian - April 7, 2025
In episode #463 of the Lex Fridman Podcast, Lex engages with Douglas Murray, a British author and political commentator, to discuss a range of pressing geopolitical topics.
Key Discussion Points and Insights:
-
Russia-Ukraine Conflict: Murray provides his perspective on Vladimir Putin's motivations and the broader implications of Russia's actions in Ukraine. He delves into the resilience and leadership of President Volodymyr Zelenskyy amidst the ongoing conflict.
-
U.S. Political Landscape: The conversation shifts to former President Donald Trump, examining his influence on both domestic and international politics. Murray offers insights into the polarization within the United States and the potential trajectory of its political future.
-
Middle East Dynamics: An in-depth analysis of Israel's political environment is presented, focusing on Prime Minister Benjamin Netanyahu's leadership. The discussion extends to the complexities of the Israeli-Palestinian conflict, with particular attention to the roles of Hamas and the situation in Gaza.
Throughout the episode, Murray emphasizes the importance of understanding historical contexts to fully grasp current geopolitical events. He advocates for nuanced perspectives, cautioning against oversimplified narratives that often dominate media discourse.
Listeners can gain a comprehensive understanding of these intricate issues, benefiting from Murray's extensive experience and thoughtful analysis.
Sources: Lex Fridman Podcast Episode #463
-
-
 @ e516ecb8:1be0b167
2025-04-06 18:25:12
@ e516ecb8:1be0b167
2025-04-06 18:25:12Bitcoin ha recorrido un camino fascinante: de ser un experimento cypherpunk nacido en las sombras de la crisis de 2008 a convertirse en un activo que algunos estados, como El Salvador, consideran parte de sus reservas estratégicas, una especie de "oro digital". Hace apenas 15 años, era un código curioso que valía centavos; hoy, hay países apostando su futuro económico a él. Sin embargo, no hace falta haber leído Hijacking Bitcoin para sospechar que hay nubes en el horizonte. Y no, no hablo solo de la volatilidad, ese eterno fantasma que siempre se menciona. Sí, Bitcoin sube y baja como montaña rusa —en 2021 tocó los 69 mil dólares y luego cayó a 16 mil en 2022—, pero si hacemos un zoom out —como dicen los gringos—, la tendencia a largo plazo es al alza, mientras que las monedas fiduciarias, en palabras de Huerta de Soto, no son más que "papelitos coloreados" que tienden a valer cero. Pero dejemos la poesía de lado y miremos con lupa: ¿qué problemas podrían acechar el futuro de Bitcoin? Aquí van algunos puntos que me dan vueltas en la cabeza.
1. Bloques vacíos y el dilema del HODL
En marzo de 2025, se reportó que casi el 20% de los bloques de la blockchain estaban vacíos o con pocas transacciones. Esto encaja con una teoría: Bitcoin dejó de ser la moneda peer-to-peer que soñó Satoshi Nakamoto para transformarse en un depósito de valor. Hoy, la filosofía dominante es "HODL" (sujetar y no soltar), y figuras como Michael Saylor no esconden que les conviene que la gente pierda sus llaves privadas: menos bitcoins en circulación, mayor escasez, precio más alto. Imagina a Saylor frotándose las manos cada vez que alguien olvida su contraseña. Pero si todos acumulan y nadie gasta, ¿qué pasará con los mineros cuando las transacciones escaseen? Sin ellas, sus ingresos dependen de las recompensas por bloque, que algún día desaparecerán. Claro, ahora existen billeteras con opciones de herencia, pero si la idea es holdear hasta la tumba, ¿para qué acumular?
2. La red Lightning y el fantasma de los terceros
Para revivir la red, hacen falta más transacciones. Pero cuidado: el tamaño de los bloques es limitado a 1 MB (o un poco más con SegWit). Si el volumen crece demasiado —como en 2017, cuando las tarifas llegaron a 50 dólares por transacción—, la red se congestiona y adiós practicidad. ¿Aumentar el tamaño de los bloques? Ni lo menciones, eso sería darle la razón a los de Bitcoin Cash, un pecado mortal para cualquier bitcoinero Core. La solución, entonces, son las segundas capas como la red Lightning, que promete transacciones rápidas y baratas. El problema es que sigue pareciendo un eterno beta: hay fallos técnicos que no termino de entender (y sospecho que no soy el único). Pero lo que sí entiendo es que, al usarla, mucha gente termina dependiendo de terceros. Y si "no son tus llaves, no es tu dinero", esto choca de frente con la filosofía original de Bitcoin.
3. Computación cuántica: ¿el fin de la inviolabilidad?
Pasemos a un terreno más técnico. La computación cuántica podría, en teoría, descifrar las direcciones antiguas de Bitcoin, esas basadas en algoritmos vulnerables como ECDSA. Algunos proponen "quemar" esos bitcoins para proteger la red, pero imagina el golpe a la confianza: ¿qué tan "seguro" es un activo si de pronto desaparecen millones de unidades? Este riesgo no es exclusivo de Bitcoin —afecta a casi todas las criptos—, pero solo un puñado, como QRL o IOTA en sus inicios, usa algoritmos post-cuánticos, y ninguna es mainstream. Un tema que da para pensar.
4. Filosofía traicionada: del antisistema al lobby estatal
Bitcoin nació como un grito contra los bancos, los gobiernos y el sistema monetario tras la crisis de 2008. Entonces, ¿por qué vemos a sus principales voceros viajando por el mundo, haciendo lobby para que estados y gigantes como BlackRock lo adopten como reserva de valor? Podría ser solo una contradicción filosófica menor, pero hay más: si Bitcoin es tan libre y transfronterizo, ¿por qué los aranceles de Trump lograron tumbar su precio un 5% en diciembre pasado? Algo no cuadra en el discurso de la independencia absoluta.
5. El fin de la minería y la dependencia estatal
A largo plazo, cuando se mine el último bitcoin en 2140 (sí, falta mucho), los mineros dependerán exclusivamente de las tarifas por transacción. Pero si el modelo es "sujetar y no soltar", ¿quién pagará esas tarifas? Ya hemos visto momentos en que minar sale más caro que las ganancias —en 2018, muchos apagaron sus máquinas—, y aunque hasta ahora han sido excepciones, el futuro pinta complicado. Si los costos energéticos no bajan, ¿quién mantendrá la red? ¿Empresas dispuestas a perder dinero por un "bien mayor"? Suena a utopía, salvo que hablemos de empresas estatales. Y aquí volvemos al punto inicial: ¿Bitcoin dependiendo de los estados? ¿Pagando impuestos en dinero fiduciario para subsidiar mineros? ¿No era esto lo que queríamos evitar? El oro, una vez extraído, no necesita mineros para seguir existiendo; Bitcoin, por el contrario, sí.
6. El caso argentino: libertarismo con asterisco
Para rematar, esta semana salió la noticia de que el gobierno argentino —sí, el de Milei, abanderado del libertarismo— planea exigir que los residentes declaren sus billeteras de criptoactivos. No niego las reformas positivas de su gestión, como la desregulación económica, pero esto huele a Gran Hermano. ¿Qué tan libertario es un sistema que te vigila mientras predica libertad? Otra contradicción que suma ruido.
Después de ganarme el odio de los maximalistas de Bitcoin (esperaré comentarios tipo: "¡este tipo no entiende nada!"), y quizás de algún fan de Milei, quiero aclarar: no estoy en contra de Bitcoin. Lo que me molesta son las inconsistencias. Odio igual a los políticos que dicen una cosa y hacen otra que a los predicadores de un "antisistema" que termina dependiendo del sistema para sobrevivir. Me hace tanto ruido como esos malacatosos que rayan paredes con la "A" de anarquía mientras piden más Estado.
Dicho esto, no todo está perdido. Si Bitcoin quiere ser ese oro digital y cumplir su promesa libertaria, tal vez necesite ajustes: algoritmos más robustos contra la computación cuántica y algún método para pasar los bitcoins de direcciones antiguas a nuevas de forma transparente (ni idea si es técnicamente posible), una red Lightning que realmente funcione sin intermediarios, o una comunidad que priorice la utilidad sobre el HODL ciego. En resumen, apoyo a Bitcoin siempre que sus defensores sean coherentes. Si es libertad, que no se arrodille ante nadie. ¿Es mucho pedir?
-
 @ b8af284d:f82c91dd
2025-04-07 07:09:50
@ b8af284d:f82c91dd
2025-04-07 07:09:50
"Auf den deutschen Konten, Sparkonten und laufenden Girokonten liegen 2,8 Billionen Euro. Stellen Sie sich einen kurzen Augenblick vor, wir wären in der Lage, davon nur 10 Prozent zu mobilisieren – mit einem vernünftigen Zinssatz, für die öffentliche Infrastruktur in Deutschland […]”
Friedrich Merz, Blackrock-Aufsichtsratvorsitzender 2016-2020
„Governments can’t fund infrastructure through deficits. The deficits can’t get much higher. Instead, they’ll turn to private investors.“
Liebe Abonnenten,
im Jahr 1999 lag der durchschnittliche Bruttolohn eines deutschen Arbeiters bei monatlich 2100 Euro. 26 Jahre später sind es etwa 4200 Euro. In diesem Zeitraum sind die Löhne also durchschnittlich jedes Jahr um 2,7 Prozent gewachsen. (Um die Reallöhne, also die tatsächliche inflationsbereinigte Kaufkraft soll es ausnahmsweise einmal nicht gehen.)
Im selben Zeitraum ist die globale Wirtschaftsleistung um fünf Prozent im Jahr gewachsen. Der amerikanische Aktien-Index S\&P500 legte durchschnittlich jedes Jahr um acht Prozent zu.
Die Unterschiede klingen zunächst gering. 2,7 Prozent, 5 Prozent, 8 Prozent - Peanuts, was soll’s? Deutlich werden die Bedeutung dieser Zahlen, wenn man sie in absolute Zahlen umlegt. Bei einem Zuwachs von durchschnittlich fünf Prozent würde selbiger Arbeiter heute 7560 Euro verdienen. Wäre sein Lohn so stark gestiegen wie der S\&P500, läge er bei 15.483 Euro.
Das Unternehmen Blackrock ging im Jahr 1999 an die Börse. Die jährlichen Kurssteigerungen der Aktie liegen durchschnittlich bei 21 Prozent. Aus den 2100 Euro wären damit 334.661 Euro geworden.
Nimmt man nur den Gewinn des Unternehmens, landet man bei etwa zehn Prozent Rendite nach Steuern.
Irgendwie also wächst der Finanzmarkt schneller als Löhne, und Blackrock wächst nochmals schneller als der Finanzmarkt. Wie kann das sein? Was macht Blackrock, für die bis vor wenigen Jahren der künftige Bundeskanzler Friedrich Merz tätig war?
Ein Blackrock-Deepdive:
Blackrock - the bright side
1988 gründete Larry Fink zusammen mit einer Gruppe von Mitarbeitern “Blackstone Financial Management”. Die Firma wurde 1992 in Blackrock umbenannt und ging 1999 an die Börse. Zehn Jahre später übernahm die Firma Barclays Global Investors (BGI). Letztere brachte die Marke „ishares“ mit ins Portfolio. Zum Kerngeschäft von Blackrock gehören seitdem ETFs - die vielleicht beliebteste Anlageklasse der Welt.
ETFs sind keine Erfindung von Blackrock, aber das Unternehmen hat viel dazu beigetragen, dass ETFs heute in fast jedem Portfolio zu finden sind. Bevor es ETFs gab, konnten Kleinanleger fast nur in aktiv gemanagte Fonds investieren. Dabei kaufen und verkaufen hochbezahlte Analysten Aktien und verlangen dafür eine Gebühr von zwei Prozent. Bei ETFs liegen diese im Promillebereich. Eine Gebühr von zwei Prozent mag vernachlässigbar klingen. Über die Jahre aber macht dies einen Riesenunterschied - wie das Beispiel des Bruttolohns zeigt.
Hinzu kommt: Statistisch laufen passive Indexfonds oft besser als aktiv geleitete Investmentfonds.
Blackrock ist es mit seinen ETFs gelungen, die Geldanlage zu demokratisieren. Das Unternehmen profitiert nicht von steigenden Kursen der Aktien, sondern kassiert minimale Gebühren beim Kauf und Verkauf - aber bei einem verwalteten Vermögen von 4,5 Billionen Dollar kommt eben schnell etwas zusammen. 1989 hatten nur rund 30 Prozent der Amerikaner Aktien, heute sind es über 60 Prozent. In Deutschland liegt der Anteil bei nur 15 Prozent.
Niemand muss mehr um Lohnerhöhungen bangen - er kann von der annualisierten Wachstumsrate von acht Prozent (S\&P500) profitieren, wenn er jeden Monat in Blackrock-ETFs investiert. Selber Schuld, wer nicht!
Blackrock - the dark side
Wer die letzten Jahre nicht völlig außerhalb des Schwurbelversums verbracht hat, wird mitbekommen haben, dass Blackrock Thema zahlreicher Verschwörungstheorien ist. Von Covid über die Rüstungsindustrie bis zum Wiederaufbau der Ukraine. ETFs sind tatsächlich nicht das einzige Geschäftsmodell. Hinzu kommt eine weniger transparente Vermögensverwaltung von rund sieben Billionen Dollar. Kunden sind neben Unternehmen und Familien auch ganze Staaten. Außerdem ist Blackrock Großaktionär bei tausenden von Unternehmen. Es hält große Anteile von Apple, Microsoft, Nvidia aber auch von Vonovia, Bayer und der Deutschen Bank. Und über diese Beteiligungen übt das Unternehmen Macht aus. Das bekannteste Beispiel sind ESG-Kriterien (Environmental, Social, Governance), die Larry Fink ab 2018 propagierte. Mittlerweile ist Fink davon abgerückt, im aktuellen Jahresbrief ist davon wenig zu lesen. Das eigentliche Problem sitzt tiefer, und hat mit der Rendite zu tun.
Was hat Blackrock vor?
Zehn oder 20 Prozent Wachstum sind über einen langen Zeitraum kaum realistisch zu erwirtschaften. Dafür braucht es „Megatrends“. Künstliche Intelligenz zum Beispiel verspricht Produktivitätsgewinne, die weitaus über der Norm liegen. Was aber, wenn diese ausbleiben? Lässt sich eventuell etwas nachhelfen?
Am bequemsten ist es, wenn Regierungen Steuergelder in Richtung Unternehmen verschieben. Dann sparen sich die Profiteure auch noch die Werbekosten. Was, wenn eine Regierung ein großes Investitionsprogramm auflegt, von dem dann Unternehmen profitieren, in die Blackrock frühzeitig investiert hat? Was, wenn mehrere Regierungen dies gleichzeitig tun? Nun kann man sich fragen, bei welchen Komplexen dies zuletzt der Fall war. Blackrock hält ungefähr sieben Prozent der Pfizer-Aktien und rund ein Prozent von Biontech. Etwa fünf Prozent von Rheinmetall-Aktien sind…
Weiter geht es auf BlingBling - dem wöchentlichen Newsletter über Geld, Geopolitik und Bitcoin
-
 @ f7d424b5:618c51e8
2025-04-06 16:48:03
@ f7d424b5:618c51e8
2025-04-06 16:48:03The promised Nintendo direct has come and there is a LOT to say about it. If you ever wondered how such a reveal would be taken differently by a dad, a NEET, and a people programmer this is the episode for you! Also those SAG bootlickers are getting uppity again. All of that and more!
Sources cited:
- Nintendo Online subscribers get to upgrade the zelda games for free for some reason?
- Do Nintendo games ever actually go on sale?
- Kirby
- Metroid
- TOTK
- Pokeshit
- EOW
- there's literally 252 games on sale at VGP right now
- SAG agreement you can read for yourself
- SAG literally says on their website to go audition for non-union roles and then strongarm them into going union if they wanna keep you
Obligatory:
- Listen to the new episode here!
- Discuss this episode on OUR NEW FORUM
- Get the RSS and Subscribe (this is a new feed URL, but the old one redirects here too!)
- Get a modern podcast app to use that RSS feed on at newpodcastapps.com
- Or listen to the show on the forum using the embedded Podverse player!
- Send your complaints here
Reminder that this is a Value4Value podcast so any support you can give us via a modern podcasting app is greatly appreciated and we will never bow to corporate sponsors!
-
 @ ba36d0f7:cd802cba
2025-04-06 16:43:05
@ ba36d0f7:cd802cba
2025-04-06 16:43:051. Reglas Esenciales
✔ Pieza Tocada, Pieza Movida: Si tocas una pieza, debes moverla (si es legal).
✔ Aviso de Jaque: Decir "jaque" al atacar al rey (opcional en torneos oficiales).
✔ Jaque Mate Termina: El juego acaba inmediatamente — no hay que capturar al rey.
✔ Oferta de Tablas: Puedes ofrecer tablas después de tu movimiento, antes de pulsar el reloj.
2. Etiqueta en Torneos
-
Saludo: Apretón de manos antes y después de la partida.
-
Silencio: No hablar durante el juego (excepto "jaque" o "¿tablas?").
-
Reloj: Presiónalo con la misma mano que movió.
-
Rendición: Voltea tu rey o di "me rindo" (no solo te vayas).
Errores Comunes
❌ Hacer ruido con las piezas para distraer.
❌ Mirar fijamente el tablero del rival.
❌ Hacer jugadas falsas para probar su atención.
3. Modales en Ajedrez Online
-
Sin Retrasos: Deja que el tiempo se agote solo si estás perdido.
-
Cortesía: Escribe "Buen juego" ("GG") al finalizar.
-
Evita el "Berserk": No abuses de configuraciones rápidas para presionar al rival.
Faltas Graves
❌ Trampas: Usar motores de análisis, mirar otras partidas.
❌ Spammear mensajes o emojis.
❌ Abandonar sin rendirse formalmente.
-
-
 @ 9358c676:9f2912fc
2025-04-06 16:33:35
@ 9358c676:9f2912fc
2025-04-06 16:33:35OBJECTIVE
Establish a comprehensive and standardized hospital framework for the diagnosis, treatment, and management of pulmonary embolism (PE), aiming to improve quality of care, optimize resources, and reduce morbidity and mortality associated with this condition in the hospital setting.
SCOPE
All hospitalized patients over 15 years of age in our institution.
RESPONSIBILITIES
Institution physicians. Nursing staff.
REFERENCES AND BIBLIOGRAPHY
- SATI Guidelines for the Management and Treatment of Acute Thromboembolic Disease. Revista Argentina de Terapia Intensiva 2019 - 36 No. 4.
- Farreras-Rozman. Internal Medicine. 16th Edition. El Sevier. 2010.
- SAC Consensus for the Diagnosis and Treatment of Venous Thromboembolic Disease. Argentine Journal of Cardiology. October 2024 Vol. 92 Suppl. 6 ISSN 0034-7000
- 2019 ESC Guidelines for the diagnosis and management of acute pulmonary embolism developed in collaboration with the European Respiratory Society (ERS). European Heart Journal (2020) 41, 543-603. doi:10.1093/eurheartj/ehz405
INTRODUCTION
Pulmonary embolism (PE) is a cardiovascular emergency caused by a blood clot, usually originating from the deep veins of the lower limbs, that travels to the lungs and obstructs the pulmonary arteries. This condition represents a significant cause of morbidity and mortality in hospitals. Timely diagnosis and treatment are essential to improve clinical outcomes.
The clinical presentation of PE is highly variable, ranging from mild symptoms to acute cardiovascular shock. Risk factors such as prolonged immobilization, recent surgery, and chronic illnesses complicate its identification and management.
PE has an annual incidence of 70 cases per 100,000 people. Prognosis varies from high-risk PE with high mortality to low-risk PE with minimal hemodynamic impact. Without thromboprophylaxis, deep vein thrombosis (DVT)—the main predisposing factor (90–95% of cases)—has variable incidence depending on the surgery type, and up to 25% of embolic events occur post-discharge.
PREDISPOSING FACTORS
Strong Risk Factors (OR >10): - Hip or leg fracture - Hip or knee prosthesis - Major general surgery - Major trauma - Spinal cord injury
Moderate Risk Factors (OR 2–9): - Arthroscopic knee surgery - Central venous catheters - Chemotherapy - Chronic heart or respiratory failure - Hormonal replacement therapy - Malignancy - Oral contraceptives - Stroke with paralysis - Pregnancy or postpartum - Prior VTE - Thrombophilia
Mild Risk Factors (OR <2): - Bed rest <3 days - Prolonged travel - Advanced age - Laparoscopic surgery - Obesity - Antepartum period - Varicose veins
CLINICAL MANIFESTATIONS AND BASIC COMPLEMENTARY STUDIES
Symptoms: Dyspnea, chest pain, cough, hemoptysis, bronchospasm, fever.
Signs: Tachycardia, desaturation, jugular vein distention, orthostatism, DVT signs, syncope, or shock.Basic Studies: - Chest X-ray (may show infarction or atelectasis) - ECG (T wave inversion, RV strain, S1Q3T3 pattern)
RISK ASSESSMENT SCORES
Wells Score: - >6 points: High probability - 2–6: Moderate - ≤2: Low - Modified: >4 = likely PE, ≤4 = unlikely PE
Geneva Score: - >10: High - 4–10: Intermediate - 0–3: Low
PERC Rule: If all criteria are negative and clinical suspicion is low, PE can be excluded without further testing.
DIAGNOSTIC STUDIES
- D-dimer: High sensitivity; used in low/moderate risk patients.
- CT Pulmonary Angiography (CTPA): First-line imaging; limited in pregnancy/renal failure.
- Lower limb Doppler ultrasound: Indirect evidence of PE when DVT is detected.
- V/Q scan: Alternative when CTPA is contraindicated.
- Transthoracic echocardiogram: Used to assess RV function, especially in shock.
- Pulmonary angiography: Gold standard; reserved for complex cases due to invasiveness.
RISK STRATIFICATION
High-risk PE (5%): Hemodynamic instability, mortality >15%. Requires urgent reperfusion.
Intermediate-risk PE (30–50%): Hemodynamically stable with signs of RV dysfunction or elevated biomarkers.
Low-risk PE: Mortality <1%, eligible for outpatient management.
PESI Score: - I (<65): Very low risk - II (65–85): Low - III (86–105): Intermediate - IV (106–125): High - V (>125): Very high
Simplified PESI: ≥1 point = high risk; 0 = low risk
TREATMENT
High-risk PE: - Systemic fibrinolysis with alteplase 100 mg over 2 h or 0.6 mg/kg (max 50 mg) IV bolus over 15 min. - Suspend UFH 30–60 min before lysis if already on treatment. - Resume anticoagulation (UFH or LMWH) when aPTT <2x normal. - Consider surgical embolectomy or catheter-directed therapy if fibrinolysis fails or is contraindicated. - Maintain SpO₂ >90%, CVP 8–12 mmHg, and use vasopressors/inotropes as needed. ECMO in select cases.
Contraindications to Fibrinolytics: - Absolute: Recent stroke, active bleeding, CNS tumors, recent major trauma or surgery. - Relative: Anticoagulant use, recent TIA, pregnancy, uncontrolled hypertension, liver disease.
Intermediate-risk PE: - Initiate anticoagulation (enoxaparin 1–1.5 mg/kg SC every 12 h, max 100 mg/dose). - Fibrinolysis is not routine; reserve for clinical deterioration. - Direct oral anticoagulants (DOACs) may be considered. - Consider IVC filter in absolute contraindication to anticoagulation or recurrence despite treatment.
RIETE Bleeding Risk Score: - >4 points: High risk - 1–4: Intermediate - 0: Low
INVASIVE TREATMENT
Consider catheter-directed therapy when: - High bleeding risk - Fibrinolysis contraindicated - Delayed symptom onset >14 days
Some centers use this as first-line therapy in high-risk PE.
QUALITY INDICATOR
Indicator: Proportion of PE cases with documented risk stratification in the medical record at initial evaluation.
Formula: (PE cases with documented stratification / total PE cases evaluated) × 100
Target: >85% of PE cases must have risk stratification recorded at the time of initial evaluation.
Autor
Kamo Weasel - MD Infectious Diseases - MD Internal Medicine - #DocChain Community npub1jdvvva54m8nchh3t708pav99qk24x6rkx2sh0e7jthh0l8efzt7q9y7jlj
-
 @ ba36d0f7:cd802cba
2025-04-06 16:21:23
@ ba36d0f7:cd802cba
2025-04-06 16:21:23Configuración del Tablero
-
Lo Básico
Tablero de 8x8 casillas, alternando colores claros/oscuros.Regla: Siempre coloca el tablero con una casilla clara en la esquina inferior derecha de cada jugador.
-
Coordenadas
-
Columnas (files): Letras a a h (de izquierda a derecha).
-
Filas (ranks): Números 1 a 8 (fila 1 = lado blanco, fila 8 = lado negro).
>Notación: Cada casilla es columna + fila (ej. e4, a7).
-
-
Colocación de Piezas
Negras (Parte superior):- a8: Torre | b8: Caballo | c8: Alfil | d8: Dama
e8: Rey | f8: Alfil | g8: Caballo | h8: Torre
Fila 7: Todos los peones (a7-h7).
Blancas (Parte inferior):
- a1: Torre | b1: Caballo | c1: Alfil | d1: Dama
e1: Rey | f1: Alfil | g1: Caballo | h1: Torre
Fila 2: Todos los peones (a2-h2).
Consejo: Las damas empiezan en su color (blanca en d1, negra en d8).
- a8: Torre | b8: Caballo | c8: Alfil | d8: Dama
Jaque mate, ahogado y tablas
El ajedrez es un juego de estrategia donde el objetivo es dar jaque mate al rey rival. Pero también puede terminar en ahogado o tablas bajo ciertas condiciones.
-
Jaque Mate (Victoria)
-
Definición: El rey rival está en jaque (bajo ataque) y no tiene movimientos legales para escapar.
-
Resultado: Fin del juego — el jugador que da jaque mate gana.
-
-
Ahogado (Tablas)
-
Definición: El jugador en turno no tiene movimientos legales, pero su rey no está en jaque.
-
Resultado: Tablas (empate).
-
Causas comunes:
-
Un rey solo sin movimientos.
-
Estructura de peones que bloquea todas las opciones.
-
Otras Situaciones de Tablas
-
Material Insuficiente:
-
Solo quedan los reyes.
-
Rey + alfil vs. rey (no se puede dar jaque mate).
-
-
Triple Repetición:
- La misma posición se repite 3 veces (con el mismo jugador en turno).
-
Regla de los 50 Movimientos:
- Sin capturas ni movimientos de peón en 50 jugadas consecutivas.
-
Acuerdo Mutuo:
- Ambos jugadores aceptan tablas.
-
Diferencias clave:
|Término|¿Rey en Jaque?|¿Movimientos Legales?|Resultado| |---|---|---|---| |Jaque mate|Sí|No|Victoria/Derrota| |Ahogado|No|No|Tablas| |Tablas|N/A|N/A|Empate|
Historia del Ajedrez
-
Orígenes (Siglo VI)
-
Nacimiento: Norte de India (como Chaturanga), con cuatro divisiones militares (predecesoras de peones, caballos, alfiles y torres).
-
Expansión: Llegó a Persia como Shatranj (año 600 d.C.), donde surgieron términos como "jaque" y "jaque mate".
> Dato curioso: "Jaque mate" viene del persa "Shah Mat" ("el rey está atrapado").
-
-
Europa Medieval (Siglos IX–XV)
-
Adaptación: Los árabes llevaron el ajedrez a España (1000 d.C.); los europeos cambiaron las piezas:
Elefantes → Alfiles
Visires → Damas (¡al inicio solo movían 1 casilla!) -
Cambio clave: Hacia 1475, la dama se convirtió en la pieza más poderosa ("Ajedrez de la Dama Loca"), acelerando el juego.
-
-
Ajedrez Moderno (1850–Actualidad)
-
Estándares: Primer campeonato mundial oficial (1886, Steinitz vs. Zukertort).
-
Computadoras: Deep Blue de IBM venció a Gari Kaspárov en 1997, revolucionando la IA.
-
Hoy: Plataformas online (Chess.com, Lichess) y series (Gambito de Dama) popularizan el juego.
-
¿Sabías Qué?
-
La partida teórica más larga posible es de 5,949 movimientos.
-
La partida real más larga duró 269 movimientos (Nikolić vs. Arsović, 1989).
-
La apertura más antigua registrada (1.e4) aparece en un manuscrito español de 1490.
-
-
 @ fe32b72c:14cfcb1e
2025-04-06 15:56:23
@ fe32b72c:14cfcb1e
2025-04-06 15:56:23Libertarian tariff controversy
GM. First long form note, so let's see how this goes.
Reading a lot of Libertarians complaining about tariffs on twitter this morning. And I get it — they're a tax on imports, and furthermore, a barrier to free trade. Not exactly something libertarians are fans of, lowercase "l" or doctrinaire capital "L" party members.
But there's something I've been pointing out to many. That is: being the issuer of the global reserve currency (which itself relies upon inflation, and thus is also a tax) necessarily creates trade deficits. I'm preaching to the choir on this one a bit I expect, but it's a key reason as to why given that we have this backdrop, and we can't simply overnight completely change the monetary system, it is not an unreasonable stance for a libertarian leaning person to hold the idea that using tariffs as a way to offset this trade deficit while moving away from a fiat currency is actually a sound idea. There are plenty of places for devils to hide in details of course, and by all means, I'm not a Trumpist, but speaking generally, this seems like a sound stance. It's all well and good to have an idea of where you want to go, but if you want to actually get there, charting a course is often harder than picking a destination.
Now, as for what I think we can expect
Tariffs will raise consumer prices. It's not inflation, because it's not about an expansion of the money supply, but it's also true that the cost has to be born by someone. However, tariffs will also decrease imports. Which will reduce dollar outflows into foreign nations, where, thanks to the mechanics of the Eurodollar system, will create a panic. The reality is, dollars outside of the US are not something that is created by the Federal Reserve, because foreign banks can't hold reserves. Rather, Eurodollar deposits are loaned into existence by private banks, and are generally settled by a variety of creative means, including offsetting liabilities, and sale of assets — most commonly, US Treasury securities. This means they need dollars to flow — it's not about getting wealthier, but rather, about covering their debts that they simply have no way to bail out. Reduced dollar outflow is a reduction in supply; as such, the price of the dollar goes up (or at least, goes down slower). That is, there's deflation, or at least disinflation. The end result is, those prices that went up thanks to tariffs start going back down to American consumers.
Meanwhile, dollars being more expensive than they were when liabilities were taken on likely leads to recessionary conditions — both domestically and internationally. However, companies importing goods into the US that can onshore their production will seek to do so, which will have an effect of offsetting that recessionary impulse domestically. In effect, "exporting" the recession.
As for what this means for the national debt
The national debt of course has been a sore point given that interest expense has been astronomical, and rolling the debt has been necessary thanks to Yellen's failure to term it out. Foreign parties will of course want more treasury assets, as a way to cover their dollar liabilities amid diminished dollar flow, but it doesn't take a doctorate to know that desires and needs are not the same thing as increased aggregate demand. Some may have good enough credit to borrow more dollars from American banks, and thus, buy treasuries, which would of course be good for bringing down interest rates, but I'm not sure I'd bet too much on that horse, especially amid an environment where recession is being exported. There is a fair bit of exposure to US equities abroad that may rotate into American sovereign debt, though the time to do that was probably before 10% of the value got evaporated off of that over the past week.
There may be increased domestic demand for treasuries, as all of this on-shoring means a lot of running in place, so to speak, by companies pivoting to domestic production, and thus under performance by equities. This is a place I'd be curious about the overall impact on the Treasury market, and am certainly not qualified to weigh in on it. But I'd love to see some sober analysis by those who recognize it as worth taking a closer look at.
Then there's the Fed, which is almost an afterthought for me, given that they're simply not going to do the levels of QE that it would take to actually bring interest rates on long term debt down, but it is worth pointing out that amid the churning deflation there will likely be at least a few rate cuts that come into play. Note, however, that rate cuts only help so much, as they directly affect the immediate end of the curve, with very little impact on the longer end where it's needed, regardless of what Greenspan would have you believe about "series of forward rates." That said, as inflation expectations come down, it may be that longer tenor rates come do down as well, because inflation expectations are an actual driver of rates, rather than Fed Funds policy rates, but that may take longer than the Treasury can wait for. That said, US10Y rates are already down 26 bps in a week, so things do seem to be starting out in the right direction. We'll see if that holds once issuance starts ramping up.
Where this all leaves us
There seem to me to be too many variables to really predict how this all plays out on the treasury market, which is hard enough to predict given that it's the largest asset class in the world. I'm inclined to think Bessent knows what he's doing (and that Trump is at least smart enough to listen to him, if not game it all out himself). What's clear is that he's trying something to address the bigger issue rather than simply kick the can down the road, which is more than we can say of policymakers for at least the past half century, and likely longer.
With any luck all of this turbulence will drive further adoption by Bitcoin, as foreign nations need to resort to something to get them out of their crushing dollar denominated liabilities. At the end of the day, being free of both taxes on imports and "invisible" taxes by deflation should be something we can all cheer for. In the meantime, hopefully this article has given a bit of perspective on what developments will be of interest in the bond market as this fourth turning plays out.
Finance #Tariffs #Bitcoin #NationalDebt #Libertarianism #FreeTrade
-
 @ 8d34bd24:414be32b
2025-04-06 14:34:37
@ 8d34bd24:414be32b
2025-04-06 14:34:37This weekend my pastor was preaching on this passage. Two words stood out when we were reading the passage, “but Jesus … .” This made me start searching for other instances of “but Jesus …” to see what we could learn.
And a woman who had a hemorrhage for twelve years, and could not be healed by anyone, came up behind Him and touched the fringe of His cloak, and immediately her hemorrhage stopped. And Jesus said, “Who is the one who touched Me?” And while they were all denying it, Peter said, “Master, the people are crowding and pressing in on You.” But Jesus said, “Someone did touch Me, for I was aware that power had gone out of Me.” (Luke 8:43-46) {emphasis mine}
In this passage people were crowding Jesus and fighting to get close to Him or even touch Him and in this dense crowd he asked, “Who is the one who touched Me?” Despite many people being pressed up beside Him, they all denied touching Him and Peter basically reprimanded Jesus that this was a ridiculous question because so many people were touching Him. “But Jesus …” knew that someone had touched Him and faith and that His power had healed that person. For the sake of the woman, the crowd, and His disciples, He wanted them to know what had happened and bless this woman that had suffered for more than a decade. He didn’t see the situation like everyone else. He saw things they did not see and like all of the best teachers, he asked His students questions to lead them to the truth. Despite the fact that he was on the way to helping Jairus’s dying daughter, Jesus stopped for this moment to bless this suffering woman and to teach the crowd the meaning of faith and the meaning of mercy.
How often do we ignore teaching moments or moments of service that could make a difference in a person’s life because we are busy and focused on something else? But Jesus did not miss the opportunity.
So often Jesus’s response to things are not like our own. “For as the heavens are higher than the earth, So are My ways higher than your ways And My thoughts than your thoughts.” (Isaiah 55:9)
But the news about Him was spreading even farther, and large crowds were gathering to hear Him and to be healed of their sicknesses. But Jesus Himself would often slip away to the wilderness and pray. (Luke 5:15-16) {emphasis mine}
Most of us, if we were bringing crowds through a blog or preaching or conferences would tend to continue working to reach more people, but Jesus took time to slip away from the crowd to pray. He prioritized prayer and fellowship with the Father knowing that ministry without the Father is no ministry at all. Jesus knew that there is more to sharing the Gospel than just drawing a crowd or growing a following. Jesus built the foundation before trying to build the church.
And some men were carrying on a bed a man who was paralyzed; and they were trying to bring him in and to set him down in front of Him. But not finding any way to bring him in because of the crowd, they went up on the roof and let him down through the tiles with his stretcher, into the middle of the crowd, in front of Jesus. Seeing their faith, He said, “Friend, your sins are forgiven you.” The scribes and the Pharisees began to reason, saying, “Who is this man who speaks blasphemies? Who can forgive sins, but God alone?” But Jesus, aware of their reasonings, answered and said to them, “Why are you reasoning in your hearts? Which is easier, to say, ‘Your sins have been forgiven you,’ or to say, ‘Get up and walk’? But, so that you may know that the Son of Man has authority on earth to forgive sins,”—He said to the paralytic—“I say to you, get up, and pick up your stretcher and go home.” (Luke 5:18-24) {emphasis mine}
This suffering man was paralyzed. His loving friends were trying to get him help by focusing on his physical needs, but Jesus saw the man’s most important need — his need for salvation. Instead of focusing on the obvious physical needs of the man, He dealt with the more important spiritual needs. He also knew that His critics were judging Him and denying His ability to wipe the man’s sins away. To prove that He could forgive the man’s sins, He also healed the man’s paralysis. After healing the man’s more important spiritual needs, He then healed the more obvious physical needs.
I know I catch myself spending lots of time praying for people’s physical needs. I pray asking for people to have healing from sickness and cancer. I pray for jobs and finances. I pray for relationships. I’ve noticed that I spend more time praying for physical needs that are problem today, but don’t matter eternally and not enough praying for salvation and guidance for people. I focus on what I can see, that although urgent, have little to no effect on the eternal well-being of the people. I should be more like Jesus and spend more time on praying for people’s spiritual needs that determine their eternal well-being.
Now when He was in Jerusalem at the Passover, during the feast, many believed in His name, observing His signs which He was doing. But Jesus, on His part, was not entrusting Himself to them, for He knew all men, and because He did not need anyone to testify concerning man, for He Himself knew what was in man. (John 2:23-25) {emphasis mine}
When we have people asking for us to share Jesus with them, we jump at the opportunity. We seek the crowds and the following. We seek the influence and prestige, but Jesus did not trust those seeking Him and knew they were looking for blessings without the submission or repentance.
I’ve noticed that I will have people asking questions about the Bible and Christianity. They ask me to defend everything in the Bible and what I believe. Because I have studied these things and studied apologetics, I tend to spend a large amount of time debating these topics, but it is frequently obvious from the beginning that these people are not truth seekers. They are people looking to throw “gotcha” questions at Christians in the hope of destroying their faith or making them look bad. I need to get better at asking questions of them and recognizing these situations as not interest and inquisitiveness, but attempts to destroy and not waste time on them. (Of course, sometimes there are watchers/listeners who can be helped by knowing there are answers to these questions.)
When it was evening, the disciples came to Him and said, “This place is desolate and the hour is already late; so send the crowds away, that they may go into the villages and buy food for themselves.” But Jesus said to them, “They do not need to go away; you give them something to eat!” They said to Him, “We have here only five loaves and two fish.” And He said, “Bring them here to Me.” Ordering the people to sit down on the grass, He took the five loaves and the two fish, and looking up toward heaven, He blessed the food, and breaking the loaves He gave them to the disciples, and the disciples gave them to the crowds, and they all ate and were satisfied. They picked up what was left over of the broken pieces, twelve full baskets. (Matthew 14:15-20) {emphasis mine}
We so often see the glass half empty. We see all of the things we can’t do, but Jesus knows what can be done and we should know that we can do all things in Christ who strengthens us. Instead of focusing on why we can’t, we need to trust God to enable us to do whatever He asks us to do.
Some Pharisees came up to Jesus, testing Him, and began to question Him whether it was lawful for a man to divorce a wife. And He answered and said to them, “What did Moses command you?” They said, “Moses permitted a man to write a certificate of divorce and send her away.” But Jesus said to them, “Because of your hardness of heart he wrote you this commandment. But from the beginning of creation, God made them male and female. For this reason a man shall leave his father and mother, and the two shall become one flesh; so they are no longer two, but one flesh. What therefore God has joined together, let no man separate.” (Mark 10:2-8) {emphasis mine}
How often do we look for a loophole in God’s word? The Pharisees were looking for an excuse to do what they wanted to do, but Jesus said that He had allowed for their evil ways (for the good of the woman they wanted to divorce) despite His perfect plan which they had rejected. “Then Peter came to Jesus and asked, “Lord, how many times shall I forgive my brother or sister who sins against me? Up to seven times?” Jesus answered, “I tell you, not seven times, but seventy-seven times. (Matthew 18:21-22)” Peter thought he was being generous forgiving someone seven times, but Jesus wanted him to forgive as He had forgiven Peter. (See the Lord’s Prayer “Forgive us our sins, for we also forgive everyone who sins against us.” Luke 11:4)**
And they sent their disciples to Him, along with the Herodians, saying, “Teacher, we know that You are truthful and teach the way of God in truth, and defer to no one; for You are not partial to any. Tell us then, what do You think? Is it lawful to give a poll-tax to Caesar, or not?” But Jesus perceived their malice, and said, “Why are you testing Me, you hypocrites? Show Me the coin used for the poll-tax.” And they brought Him a denarius. And He said to them, “Whose likeness and inscription is this?” They said to Him, “Caesar’s.” Then He said to them, “Then render to Caesar the things that are Caesar’s; and to God the things that are God’s.” And hearing this, they were amazed, and leaving Him, they went away. (Matthew 22:16-22) {emphasis mine}
Instead of directly answering the question that was asked, since it was not asked in good faith, He corrected their hypocrisy and showed them the truth. We are not nearly as wise and observant as Jesus, but we should still try to see what is truly being asked instead of just answering the obvious question. So often there is a need or motive behind the question that needs to be addressed. I’ve found that asking questions of the questioner can both uncover what is behind the question and also lead them to the truth. This method, also known as the Socratic Method, is taught well from a Christian perspective in the book “Tactics” by Gregory Koukl.
They brought the boy to Him. When he saw Him, immediately the spirit threw him into a convulsion, and falling to the ground, he began rolling around and foaming at the mouth. And He asked his father, “How long has this been happening to him?” And he said, “From childhood. It has often thrown him both into the fire and into the water to destroy him. But if You can do anything, take pity on us and help us!” And Jesus said to him, “ ‘If You can?’ All things are possible to him who believes.” Immediately the boy’s father cried out and said, “I do believe; help my unbelief.” When Jesus saw that a crowd was rapidly gathering, He rebuked the unclean spirit, saying to it, “You deaf and mute spirit, I command you, come out of him and do not enter him again.” After crying out and throwing him into terrible convulsions, it came out; and the boy became so much like a corpse that most of them said, “He is dead!” But Jesus took him by the hand and raised him; and he got up. (Mark 9:20-27) {emphasis mine}
Jesus sees things as they are. He honors belief. I love the boy’s father’s response to Jesus, “I do believe; help my unbelief.” I’ve felt like this before. Jesus never gives up and as long as we have Jesus, we should never give up on someone.
As soon as He was approaching, near the descent of the Mount of Olives, the whole crowd of the disciples began to praise God joyfully with a loud voice for all the miracles which they had seen, shouting:
“Blessed is the King who comes in the name of the Lord;\ Peace in heaven and glory in the highest!”
Some of the Pharisees in the crowd said to Him, “Teacher, rebuke Your disciples.” But Jesus answered, “I tell you, if these become silent, the stones will cry out!” (Luke 19:31-40) {emphasis mine}
The Pharisees saw a threat to their power and prestige, but Jesus saw reality as it was. Jesus saw the fulfillment of scripture and a small glimpse of the glory He deserved. They focused on what they disagreed with and what they didn’t like. Jesus focused on the fact that worship of God cannot be stopped. What do you focus on?
Therefore when Pilate heard this statement, he was even more afraid; and he entered into the Praetorium again and said to Jesus, “Where are You from?” But Jesus gave him no answer. So Pilate said to Him, “You do not speak to me? Do You not know that I have authority to release You, and I have authority to crucify You?” Jesus answered, “You would have no authority over Me, unless it had been given you from above; for this reason he who delivered Me to you has the greater sin.” (John 19:8-11) {emphasis mine}
Most innocent men would be continually speaking the truth of their innocence and trying to convince Pilate to listen, but Jesus had a purpose. He didn’t act like a normal innocent man, nor did He act like a normal guilty man. He was God incarnate living out His perfect plan. He knew Pilate didn’t have authority to kill or free Him, but that everything was going according to His perfect plan.
When we are following Jesus, we need to accept that God is in control. Not every hardship needs to be fixed. Sometimes it is part of God’s perfect plan. No one, man or spirit, has the authority to harm a believer unless God allows it and He only allows it if it furthers His perfect plan and is used for good. We need to know God and know His word. We need to listen to His leading through the Spirit, so we respond as Jesus did, “You would have no authority over Me, unless it had been given you from above.” This is as true of us today as it was about our savior on that fateful day. God is always in control.
Pilate questioned Him, “Are You the King of the Jews?” And He *answered him, “It is as you say.” The chief priests began to accuse Him harshly. Then Pilate questioned Him again, saying, “Do You not answer? See how many charges they bring against You!” But Jesus made no further answer; so Pilate was amazed. (Mark 15:2-5) {emphasis mine}
How often are people amazed because Jesus does not respond in the way a normal person would. Are there times that we should speak up and defend the word of God? Yes. Are there times that we should, like Jesus, make no further answer? Yes. We must ask God for guidance on the right response for each situation.
While He was still speaking, behold, a crowd came, and the one called Judas, one of the twelve, was preceding them; and he approached Jesus to kiss Him. But Jesus said to him, “Judas, are you betraying the Son of Man with a kiss?” When those who were around Him saw what was going to happen, they said, “Lord, shall we strike with the sword?” And one of them struck the slave of the high priest and cut off his right ear. But Jesus answered and said, “Stop! No more of this.” And He touched his ear and healed him. (Luke 22:47-51) {emphasis mine}
The common response to being mistreated is to mistreat back. We so often try to do to others at least as badly as they have done to us, but Jesus was different. When Judas betrayed Jesus, He mercifully responded, “Judas, are you betraying the Son of Man with a kiss?” When soldiers came to arrest Jesus for crimes He did not commit and one of His disciples struck a man with his sword, Jesus healed this man who had come to do Him harm. Jesus followed His own command to turn the other cheek. He gave love to those who were unloving. He gave mercy to those who showed no mercy. Do you seek revenge or do you seek to understand those who do you wrong and help them? Be loving and merciful just as Jesus is loving and merciful.
The best way to be a light for Jesus is to act like Jesus and acting like Jesus requires thinking like Jesus and responding in the most unimaginable ways. Jesus was not like a normal man and neither should we be.
Father God, help us to see other people and the world as you see it. Help us to respond as Jesus would. Help us to be different, so we can honor you with our differences.
Trust Jesus
-
 @ e97aaffa:2ebd765d
2025-04-06 14:06:32
@ e97aaffa:2ebd765d
2025-04-06 14:06:32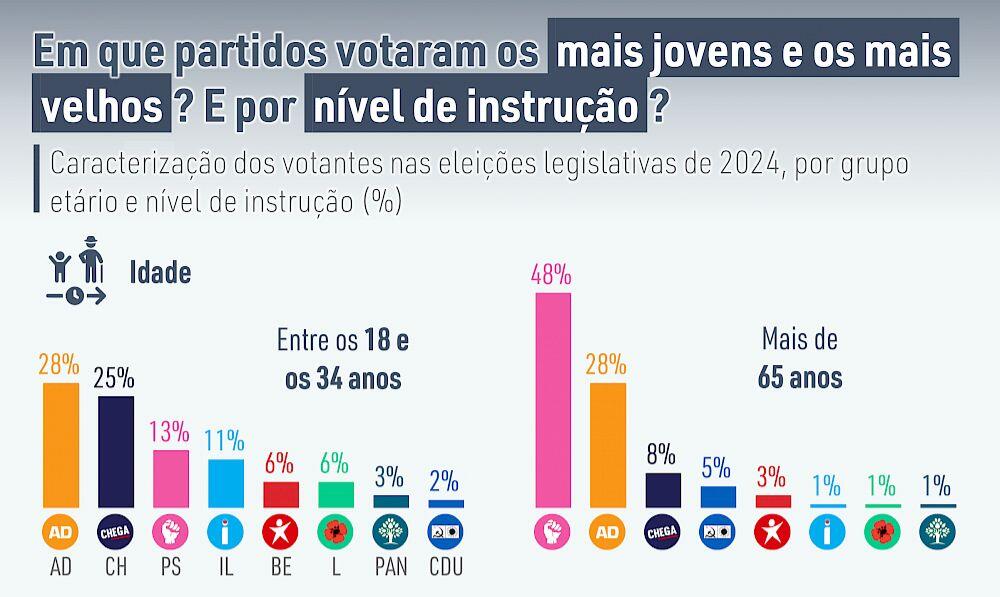
Este estudo é bem representativo da divergência geracional que existe em Portugal, sobretudo em quem foi votar nas legislativas de 2024.
Nos +65 anos, são 65% esquerda e 37% na direita. Mas entre os 18 e 34 anos, são 30% na esquerda e 64% na direita. A esquerda tem menos da metade. Ainda é muito o reflexo da herança do 25 de Abril, muitas pessoas votam em partidos, pelo que fizeram no passado e não pelo que fazem hoje em dia.
A maior discrepância é no PS, com 48% nos +65 anos, para apenas 13% dos mais novos. O Chega está no sentido oposto, 8% para 25%.
Nos “pequeninos”, a situação do PCP era previsível, mas o destaque vai para o Livre e o IL, ambos com 1% nos +65 anos, mas têm um crescimento nos mais jovens, com 6% e 11%, respectivamente.
O PS, nos últimos anos, virou muito para esquerda, afastando-se do centro, mas agora está numa encruzilhada, ou volta mais para o centro, ou poderá acontecer o mesmo que o PCP, tornar-se num partido insignificante, sobretudo com um público de pessoas idosas, sem prespetivas de futuro.
Quem tem +65 anos, quer governos mais de esquerda e os mais novos(18 a 34 anos) preferem um governo de direita. Isto é bem demonstrativo, o porquê dos políticos, de todos quadrantes, apostarem em políticas de aumento de pensões, subsídios, tudo para cativar os mais velhos. Muitas das políticas beneficiam mais os velhos em detrimento dos mais novos, isso provocou uma ruptura geracional, no pensamento político, os jovens demonstram um certo cansaço com as políticas socialistas.
E como Portugal é um país com envelhecimento acentuado e o abstencionismo é menor nos mais velhos, quem cativar esta parcela de pessoas, vencerá as eleições. Segundo o INE, existem 2.2 milhões(22%) com +65 anos e 1.8 milhões (18%) entre os 18 e os 34 anos.
Nível de Instrução
Nos níveis de instrução, as diferenças não são profundas mas existem, mas a direita tem um ligeira preferência pelos mais instruídos. A única excepção é o Chega, que é muito mais forte mas pessoas menos instruídas.
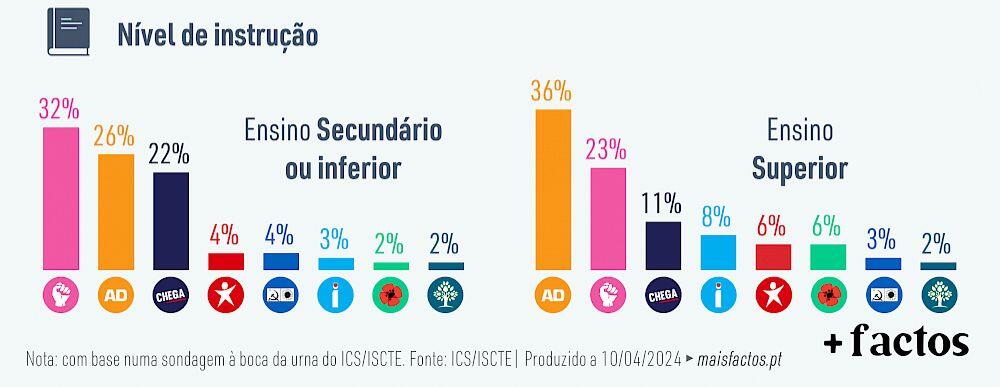
-
 @ 044da344:073a8a0e
2025-04-06 10:04:42
@ 044da344:073a8a0e
2025-04-06 10:04:42Ich kenne das Argument, mit dem man diesen Text zertrümmern kann. Anekdotische Evidenz. Was soll das mit den Einzelfällen, lieber Michael? Überlass doch das Geschichtenerzählen Künstlern oder Märchenonkels und konzentriere dich auf das, was sich beweisen lässt – über repräsentative Befragungen, die entsprechenden Auswertungsverfahren oder, noch besser, in Experimenten.
Ich schreibe diesen Text trotzdem. Eine Sozialwissenschaft, die an hieb- und stichfeste Beweise glaubt und sich deshalb auf das beschränkt, was sich erfragen und messen lässt, am besten in großen Bevölkerungsgruppen, eine solche Wissenschaft verliert das Leben aus dem Blick und die Deutungshoheit am Ende tatsächlich an die Romanciers. Bei den Historikern scheint das schon der Fall zu sein, wenn man Christoph Hein glaubt, Jahrgang 1944, der sein Lebensthema DDR gerade noch einmal ganz neu angefasst hat:
Ich glaube, es gibt da noch Widerstand gegen meine Beschreibung. Aber ich meine ohnehin, dass nicht die Historiker für die Geschichtsschreibung zuständig sind, sondern seit 2000 Jahren, seit Homer bis zu Tolstoi und Dostojewski, allein die Romanciers. Die Historiker liefern uns hilfreiche Mittel, Anregungen, aber viel mehr nicht. Denn sie sind nur für die Hinterlassenschaften zuständig. Und die stimmen nicht immer mit der Geschichte überein. Sehr viele politisch wichtige Leute haben schon immer versucht, die Geschichtsschreibung in ihrem Sinne zu verändern. (Berliner Zeitung, 23. März 2025)
Mein Thema für den Tresen heute: die revolutionäre Wucht des Quereinsteigers. Ich könnte auch Aufsteiger sagen oder weiter im Synonymwörterbuch blättern, um einen besseren Begriff zu finden für Menschen, die gegen jede Wahrscheinlichkeit und jenseits der üblichen Wege in einem Berufsfeld gelandet und dort genau deshalb dazu berufen sind, alles auf den Prüfstand und dann oft auch auf den Kopf zu stellen. Wenn man sie denn lassen würde. Dazu gleich mehr.
Vorher will ich an den Forschungsverbund „Fit for Change“ erinnern – vom Freistaat Bayern in den frühen 2010er Jahren ins Leben gerufen, um der Resilienz von sozialen Systemen nachzuspüren. Im Rückblick wirkt diese Idee fast prophetisch. Wie können sich Schulen und Universitäten, Redaktionen, Gerichte und Behörden auf Gefahren vorbereiten, die noch nicht einmal am Horizont zu erkennen sind? Wie stellen wir sicher, dass diese Systeme auch in einem Ernstfall funktionieren, den noch niemand erlebt hat? Ich habe diesen Verbund als Sprecher geleitet und erinnere mich an eines unserer wichtigsten Ergebnisse: Wir brauchen Querdenker. Vielleicht hieß das im Ergebnisbericht auch anders. Egal. Wichtig ist, dass Einrichtungen leichter zusammenbrechen, wenn alle in die gleiche Richtung denken. Gleiche Herkunft + gleiche Ausbildung + gleicher Erfahrungsschatz = gleiche Ideen im Fall einer Krise. Die Handlungsempfehlung an alle Entscheider, wichtig für steuerfinanzierte Forschung, lag nahe: Stellt Leute ein, die im Moment scheinbar überflüssig sind und vielleicht sogar stören. Sie werden euch helfen, wenn es hart auf hart kommt, weil sie anders denken und deshalb eine andere Lösung sehen.
Ich habe gerade Rolf Kron interviewt, einen Stahlbauschlosser aus dem Ruhrgebiet, der nach Jahren auf Montage über den zweiten Bildungsweg zum Abitur kam und im Abendgymnasium so gute Noten hatte, dass er sich aussuchen konnte, wo und was er studieren will. Physik und Mathematik, dachte er, aber dann brachte ihn eine alte Dame zum Nachdenken. Diese Frau lag in dem Heim, in dem der junge Rolf putzen musste, und sagte zu ihm: Du tust mir gut. Viel besser als all die Menschen in den weißen Kitteln. Versprich mir, dass du einen Heilberuf lernst. In den ersten Vorlesungen in München fiel Rolf Kron, man spürt das noch in unserem Gespräch, aus allen Wolken. Was tun diese Ärzte, woran glauben ihre Professoren und woher nehmen alle zusammen ihre Arroganz? Kron ist Homöopath geworden, Spezialist für Impfschäden und, so sagt er das selbst, ein Heiler von Weltruf. Im Frühjahr 2020 war er sofort Zielscheibe für Correctiv und ist anschließend systematisch zerstört worden.

Vielleicht war es Zufall, dass ich vorher Michael Beleites vor der Kamera hatte, einen Biologen, der das Fach nie studiert hat, aber die akademische Zunft auf ganz ähnliche Weise herausfordert wie Rolf Kron – mit einem Buch so schwer wie ein Ziegelstein, das nicht nur Darwin in Bausch und Bogen verwirft, sondern auch alles, was aus dem Kampf ums Dasein für unser Zusammenleben folgt. Die Biologie? Nun ja. Sie hat die Verbannung dieses Herausforderers anderen überlassen. Soll sich doch die Antifa die Hände schmutzig machen.
Kein Zufall ist, dass Erstakademiker den Löwenanteil der Fälle stellen, die Heike Egner und Anke Uhlenwinkel für ihr Buch Wer stört, muss weg ausgewertet haben. Der Vogelblick auf 60 Biografien zeigt, dass die „Entfernung kritischer Professoren“ vor allem Aufsteiger trifft – Menschen (hier kann ich mich selbst zitieren), „die an das humboldtsche Universitätsideal geglaubt und es aus eigener Kraft auf eine Lehrkanzel geschafft haben, ohne die Protektion eines Milieus, das ganz selbstverständlich immer wieder Minister und Richter, CEOs und eben auch Professoren hervorbringt und dabei ganz nebenbei auch all die kleinen Kniffe, Formeln, Regeln vererbt, die jeder kennen muss, der wirklich dazugehören und so auch dabeibleiben möchte.“
Ganz anders hat @LeiseBumm diesen Gedanken in einem YouTube-Kommentar zum Kron-Gespräch formuliert (von mir leicht redigiert):
Vielleicht ist der Schlüssel zum Widerstand eine Kombi aus Empathiefähigkeit (bemerken, wenn Mitmenschen übel mitgespielt wird) und einer gewissen Übung in Randständigkeit und Diskriminierung. Wer schon als Kind „dazugehört“ hat oder „Rudelführer“ war, findet Hierarchien auch später „normal“. Emphatische Menschen haben ja „damals“ oft spontan (!) jemanden versteckt, bevor noch ihr Hirn oder Angstzentrum „ein G‘schichtl drucken“ konnte.
Da sind sie – die Querdenker, die der Forschungsverbund „Fit for Change“ las Schlüssel für das Überleben sozialer Systeme ausgemacht hat. Ich denke an Ostdeutsche, die 1989 alt genug waren, um zu spüren, dass sie im neuen Rudel niemals dazugehören werden. Ich denke an Marcus Klöckner, der wie Rolf Kron aus einfachsten Verhältnissen kommt und genau deshalb erst als Soziologe die Fragen stellen konnte, denen die Kollegen ausgewichen sind (etwa nach den Bilderbergern), um dann als Journalist seiner Zunft den Spiegel vorzuhalten. Ich denke an Bernd Fleischmann, einen promovierten Hochfrequenztechniker, der vor Jahren das Klima als Hobby entdeckte und heute dokumentiert, welche Kröten man schlucken muss, um das „CO2-Märchen“ glauben zu können. Und ich denke an Raymond Unger, der sich mit 40 von allen Fesseln befreit hat, um noch einmal ganz neu als Maler anzufangen, und der dann in Berlin feststellte, dass es der Szene überhaupt nicht um das ging, was ihn in die Kunst gelockt hatte. Anekdotische Evidenz, ich weiß. Ungers Bücherberg ist für mich Beweis genug. Mehr dazu in Kürze in einem Video und am Buch-Tresen.
-
 @ 33baa074:3bb3a297
2025-04-07 01:59:38
@ 33baa074:3bb3a297
2025-04-07 01:59:38horological data is essential for optimizing urban drainage systems, providing key information about precipitation, runoff, evaporation, and other water cycle processes. This data can help engineers and urban planners better understand and predict urban horological phenomena, thereby designing more effective drainage systems. Here are a few ways how horological data can optimize urban drainage systems:
Improve the accuracy of drainage system design horological data can be used to simulate and predict rainfall patterns, flood frequency, and flow. By analyzing this data, designers can better understand the drainage needs of cities under different climate conditions, so that they can design drainage systems that are more resilient to extreme weather events. For example, by simulating heavy rain scenarios, the capacity and efficiency of existing drainage systems can be evaluated, and potential bottlenecks and improvement points can be identified.
Optimizing drainage network layout horological data helps optimize the layout of drainage networks to ensure that rainwater can be collected and transmitted effectively. By analyzing rainfall distribution and terrain features, the best pipe routes and pump station locations can be determined to reduce water flow resistance and improve drainage efficiency. In addition, horological data can also help planners evaluate the long-term performance and cost-effectiveness of different drainage solutions.
Support intelligent management and decision-making horological data is the basis for intelligent drainage system management. By real-time monitoring of rainfall and the operating status of the drainage system, combined with historical horological data, a prediction model can be established to warn of possible flood risks in advance. This helps city managers take timely measures, such as launching emergency drainage plans or adjusting pump station operations, to mitigate the impact of floods. At the same time, horological data can also be used to evaluate the effectiveness of water-saving measures and promote the sustainable use of water resources.
Promote ecological construction horological data is also very important for the construction of ecological drainage systems. By understanding the local horological cycle and ecological balance, drainage systems that are in harmony with the natural environment, such as rain gardens and permeable pavements, can be designed. These ecological facilities can not only effectively collect and purify rainwater, but also improve urban microclimate and increase biodiversity.
Enhance the system's ability to resist risks As extreme weather events caused by climate change increase, urban drainage systems need to have stronger risk resistance. horological data can help assess the impact of climate change on the urban horological cycle, so that the design can take into account the possible greater rainfall and higher frequency of flood events in the future. With these data, the structure and function of the drainage system can be optimized to improve its ability to cope with extreme weather events.
In summary, horological data plays a core role in optimizing urban drainage systems. It not only improves the specificity and accuracy of drainage system design, but also supports the intelligent management and ecological construction of the system, and enhances the overall efficiency and risk resistance of urban drainage systems.
-
 @ 7d33ba57:1b82db35
2025-04-06 09:29:33
@ 7d33ba57:1b82db35
2025-04-06 09:29:33Istanbul is one of the world’s most mesmerizing cities, where East meets West—literally. Straddling Europe and Asia, it offers a rich blend of cultures, centuries-old architecture, vibrant bazaars, and world-class food. From the Byzantine wonders of the Old City to the buzzing energy of modern neighborhoods, Istanbul is a city of contrasts—and it's unforgettable.
🏛️ Top Things to See & Do in Istanbul
1️⃣ Hagia Sophia (Ayasofya)
- Once a church, then a mosque, then a museum—and now a mosque again
- A stunning symbol of Byzantine architecture with a vast domed ceiling
- Open to all visitors (entry to main floor is free)
2️⃣ Blue Mosque (Sultan Ahmed Mosque)
- Famous for its six minarets and beautiful blue Iznik tiles inside
- Still an active mosque—visitors are welcome outside of prayer times
- Dress modestly and bring a scarf if you're visiting as a woman
3️⃣ Topkapi Palace
- Former residence of the Ottoman sultans
- Visit the Imperial Harem, treasury with the Topkapi Dagger, and panoramic gardens overlooking the Bosphorus
4️⃣ Grand Bazaar & Spice Bazaar 🛍️
- One of the largest and oldest covered markets in the world
- Shop for lamps, ceramics, carpets, jewelry, spices, and teas
- Practice your bargaining skills—it’s part of the fun!
5️⃣ Bosphorus Cruise
- Sail between Europe and Asia for incredible views of palaces, mosques, and waterfront mansions
- Options range from 1-hour quick cruises to sunset or dinner cruises
6️⃣ Galata Tower & Karaköy
- Climb the medieval Galata Tower for 360° city views
- Explore Karaköy’s trendy cafés, street art, and boutique shops nearby
7️⃣ Sultanahmet Square & Hippodrome
- Historic heart of Istanbul—once the center of Byzantine Constantinople
- See the Obelisk of Theodosius, Serpent Column, and German Fountain
🍽️ What to Eat in Istanbul
- Simit – Turkish sesame bagel, best fresh in the morning
- Kebabs – From Adana to Iskender, every type has its own flavor
- Meze platters – Tasty small plates to share (like hummus, ezme, dolma)
- Balık Ekmek – Fish sandwich by the Galata Bridge
- Baklava & Turkish delight – Sweet, flaky, and irresistible
- Turkish tea (çay) & strong coffee – Always served with hospitality ☕
🕌 Local Experiences You Shouldn’t Miss
✅ Soak in a historic hammam (Turkish bath) – like Cemberlitas or Hurrem Sultan Hammam
✅ Watch the Whirling Dervishes ceremony for a glimpse into Sufi spirituality
✅ Get lost in Süleymaniye Mosque – peaceful and less crowded than the Blue Mosque
✅ Explore Balat & Fener – colorful, local neighborhoods with rich Jewish and Greek history
✅ Take a ferry to the Asian side (Kadıköy or Üsküdar) for a more local vibe and great food🚇 Getting Around Istanbul
- Use Istanbulkart for all public transport: trams, ferries, metro, and buses
- Traffic can be intense—trams and ferries are your best friend
- The city is very walkable in historical areas, but hilly in places
- Ferries between continents are not just scenic—they’re super efficient too!
💡 Tips for Visiting Istanbul
🕌 Mosques are free to visit, but check prayer times and dress respectfully
📸 Sunset at Galata Bridge or from a rooftop in Karaköy = magic
🛍️ Bargaining is expected in markets, but done with a smile
📅 Best times to visit: April–June or September–October for mild weather
🍽️ Eat like a local – some of the best food is found in tiny family-run spots
-
 @ f3328521:a00ee32a
2025-04-06 08:58:34
@ f3328521:a00ee32a
2025-04-06 08:58:34Notes from the Inaugural Muslim Bitcoin Summit Nostr Workshop.
04.06.25 Dallas, TX
What is Nostr?
“Notes and Other Stuff Transmitted by Relays” ~ fiatjaf
Nostr is an open protocol that is a censorship-resistant, global "social" network. It doesn't rely on any trusted central server (has resilient decentralization), and is based on cryptographic keys and signatures (so it is tamperproof).
The initial description of the idea can be found at https://fiatjaf.com/nostr.html.
Digital Sovereignty
“The first step towards establishing any type of Digital Sovereignty is to consider migration away from infrastructure and networks that are saturated with malevolent surveillance… there must be a simple recognition that anything sustainable from an Islamic perspective cannot be built on the platforms of Meta, Google or Amazon.” ~ Ibn Maghreb
Palestine has become the litmus test for censorship in social media:
- X (formerly Twitter) - Musk openly supports Zionism
- Meta (FB, IG, WhatsApp) - Project Lavender
- Google (YouTube) - Project Nimbus
- Microsoft (LI) - BDS “No Azure for Apartheid” campaign
These are just a few examples of the barrier for a muslim narrative in fiat social media. To build unstoppable resistance we must move away from the platform and address the issue at the protocol level.
Nostr Protocol Explained
- Relays: Backend servers that store and broadcast data. Anyone can run one. Currently over 1k relays across over 50 countries.
- Clients: Platforms built for graphical user interface with Nostr. Anyone can build these and most are interoperable.
- Key Cryptography: User public and private keys.
Simple video explaination: Nostr in less than 10 minutes!
Nostr's Key Features:
- No Ownership - No CEO, board of directors, foundation, etc.
- No Ads, No Big Data Collection - Users are not a product.
- No Algorithms - Less drama, less depressing content.
- Uncensorability - Not your keys, not your posts.
- SEO - clean
dofollowlinks for “Google Juice”. - Zaps! - BTC/Lightning integration.
“This is really really important in the age of AI where in a few years you are not going to know the difference between something that is real and something that is fake. We need technologies that you can actually sign and you have the authenticity to do so, and only you, to do that.” ~ Jack Dorsey
Getting Started On Nostr
Nostr 101: A Beginners Guide To Nostr
Top Recommended Client: Yakihonne
Other popular options: (web) Nostrudel (iOS) Damus (Android) Amethyst
Top Recommended Wallet: Coinos
Other popular options: Primal Wallet AlbyHub Zeus (pending NWC integration)
Highlights From The Nostr Ecosystem:
Other Clients: Olas (photos) Habla (blogging) Zap.Stream (video)
Shopping: Plebeian Market Shopstr
Podcasting 2.0: Fountain Wavlake
Workspace Tools: Listr Formstr Docstr Nostr.Build
Footnote
-
 @ 6fbc5b6b:0251e3df
2025-04-07 01:22:05
@ 6fbc5b6b:0251e3df
2025-04-07 01:22:05✨ Event Overview AIVille has officially partnered with Ton.AI, an AI-powered Web3 advertising platform that aims to bridge the next 1 billion users from social platforms into the decentralized world. As part of this partnership, AIVille will be featured in a smart, data-driven ad campaign through Ton.AI’s intelligent distribution system — bringing the story of its AI-native town to more creators, players, and communities across the Web3 ecosystem.
🤝 About AIVille & Ton.AI AIVille is a fully on-chain simulation where AI agents live, create, and evolve. Players can explore the town, interact with characters, and take part in the unfolding narrative of a truly autonomous digital society. Ton.AI is a next-gen advertising platform optimized for the Web3 era. With scalable user acquisition tools, a massive traffic pool, and AI-powered fraud detection, Ton.AI helps projects: Accurately target users based on interests & demographics
Run effective multi-format ad campaigns
Reward high-quality publishers
Together, AIVille and Ton.AI are showing how intelligent agents and intelligent ads can work hand-in-hand to power the next wave of Web3 growth.
🌟 Why This Matters This collaboration brings visibility to AIVille in a new, data-optimized way. Instead of relying on traditional hype cycles, AIVille’s vision of Create-to-Earn and agent autonomy is now reaching relevant, high-value users through Ton.AI’s targeted infrastructure. It’s a perfect match between: A town run by AI
And a platform run on AI
Web3 marketing just got smarter.
🔗 Links Ton.AI Website: https://ton.ai/home Ton.AI Bot: https://t.me/PeaAIBot AIVille Official Channels: Website: https://aivillegame.com Twitter: @aivillebot Linktree Main: https://linktr.ee/AI_Ville Airdrop Campaign: https://linktr.ee/aivilleairdrop AI Villagers: https://linktr.ee/aivilleresidents
-
 @ 33baa074:3bb3a297
2025-04-07 00:50:25
@ 33baa074:3bb3a297
2025-04-07 00:50:25As a high-precision precipitation monitoring device, weighing rain gauge plays a vital role in flood control projects. The following are the specific applications and advantages of weighing rain gauge in flood control projects:
Real-time monitoring of precipitation Weighing rain gauge can record the total amount of precipitation in real time and accurately, whether it is light rain or heavy rain, or even snowfall in winter, and can accurately convert it into corresponding data. This real-time monitoring capability enables flood control engineers to understand the rainfall situation in a timely manner and provide timely data support for flood control decisions.
Provide basic support data In the flood control early warning system, the data provided by the weighing rain gauge is the basic support for basin water balance analysis and flood forecasting models. These data help to improve water disaster defense capabilities, optimize resource allocation, and reduce disaster losses.
Support long-term continuous monitoring Weighing rain gauges have high precision and stability, and can maintain accurate measurement and stable data transmission in long-term continuous monitoring. This is particularly important for flood control projects, because flood control relies on long-term data accumulation to predict and respond to possible flood events.
Adapt to various extreme weather conditions The weighing rain gauge is specially designed with a heating device to cope with the severe cold in the north and the high humidity and freezing weather in the south. This design ensures that the equipment can operate normally under extreme weather conditions, thereby ensuring the continuity and accuracy of flood control monitoring.
Promote the formulation of scientific flood control strategies Through long-term continuous monitoring, the data provided by the weighing rain gauge can help researchers analyze precipitation trends, the frequency and intensity changes of extreme precipitation events. This information is of great significance for formulating scientific flood control strategies and improving flood control measures.
In summary, the weighing rain gauge plays an indispensable role in flood control projects. Its high precision, real-time and stability make it a key device in flood control monitoring and early warning systems. By providing accurate precipitation data, the weighing rain gauge helps flood control engineers respond in time and effectively reduce the impact of flood disasters.
-
 @ ec9bd746:df11a9d0
2025-04-06 08:06:08
@ ec9bd746:df11a9d0
2025-04-06 08:06:08🌍 Time Window:
🕘 When: Every even week on Sunday at 9:00 PM CET
🗺️ Where: https://cornychat.com/eurocornStart: 21:00 CET (Prague, UTC+1)
End: approx. 02:00 CET (Prague, UTC+1, next day)
Duration: usually 5+ hours.| Region | Local Time Window | Convenience Level | |-----------------------------------------------------|--------------------------------------------|---------------------------------------------------------| | Europe (CET, Prague) 🇨🇿🇩🇪 | 21:00–02:00 CET | ✅ Very Good; evening & night | | East Coast North America (EST) 🇺🇸🇨🇦 | 15:00–20:00 EST | ✅ Very Good; afternoon & early evening | | West Coast North America (PST) 🇺🇸🇨🇦 | 12:00–17:00 PST | ✅ Very Good; midday & afternoon | | Central America (CST) 🇲🇽🇨🇷🇬🇹 | 14:00–19:00 CST | ✅ Very Good; afternoon & evening | | South America West (Peru/Colombia PET/COT) 🇵🇪🇨🇴 | 15:00–20:00 PET/COT | ✅ Very Good; afternoon & evening | | South America East (Brazil/Argentina/Chile, BRT/ART/CLST) 🇧🇷🇦🇷🇨🇱 | 17:00–22:00 BRT/ART/CLST | ✅ Very Good; early evening | | United Kingdom/Ireland (GMT) 🇬🇧🇮🇪 | 20:00–01:00 GMT | ✅ Very Good; evening hours (midnight convenient) | | Eastern Europe (EET) 🇷🇴🇬🇷🇺🇦 | 22:00–03:00 EET | ✅ Good; late evening & early night (slightly late) | | Africa (South Africa, SAST) 🇿🇦 | 22:00–03:00 SAST | ✅ Good; late evening & overnight (late-night common) | | New Zealand (NZDT) 🇳🇿 | 09:00–14:00 NZDT (next day) | ✅ Good; weekday morning & afternoon | | Australia (AEDT, Sydney) 🇦🇺 | 07:00–12:00 AEDT (next day) | ✅ Good; weekday morning to noon | | East Africa (Kenya, EAT) 🇰🇪 | 23:00–04:00 EAT | ⚠️ Slightly late (night hours; late night common) | | Russia (Moscow, MSK) 🇷🇺 | 23:00–04:00 MSK | ⚠️ Slightly late (join at start is fine, very late night) | | Middle East (UAE, GST) 🇦🇪🇴🇲 | 00:00–05:00 GST (next day) | ⚠️ Late night start (midnight & early morning, but shorter attendance plausible)| | Japan/Korea (JST/KST) 🇯🇵🇰🇷 | 05:00–10:00 JST/KST (next day) | ⚠️ Early; convenient joining from ~07:00 onwards possible | | China (Beijing, CST) 🇨🇳 | 04:00–09:00 CST (next day) | ❌ Challenging; very early morning start (better ~07:00 onwards) | | India (IST) 🇮🇳 | 01:30–06:30 IST (next day) | ❌ Very challenging; overnight timing typically difficult|
-
 @ 5d4b6c8d:8a1c1ee3
2025-04-06 23:58:21
@ 5d4b6c8d:8a1c1ee3
2025-04-06 23:58:21We have a winner! It was a very tight race and I want to once again thank each of the entrants for their great posts.
Q1 Top Post
Bitcoin and (Monetary) Economics—Properly (Bitcoin Policy Institute)
by @denlillaapan
29 Comments and 5k Sats
This post is a summary of and commentary on a video of several economics professors' talking about bitcoin. There are actually lots of academic economists who think about the things bitcoiners are obsessed with. The video is worth a watch and @denlillaapan's commentary is certainly worth a read.
This post is also the first nominee for Post of the Year.
Posts of the Month
- January: California Wild Fires: Perspective of a Native Californian by @kepford
- February: Bitcoin and (Monetary) Economics—Properly (Bitcoin Policy Institute) by @denlillaapan
- March: The Pleb Economist #5: Shitcoins are part of Bitcoin's Gartner Hype Cycle by @SimpleStacker
All of these posts will be honored in our end of year ceremony. Make sure to read any that you may have missed.
originally posted at https://stacker.news/items/936613
-
 @ 866e0139:6a9334e5
2025-04-06 03:51:00
@ 866e0139:6a9334e5
2025-04-06 03:51:00
Autor: Nicolas Lindt. Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier.**
Während die Kriegstreiber in Europa gegen Russland zum Angriff blasen, mit einem «letzten Sommer in Frieden» drohen, Bodentruppen mobilisieren und das Vermögen der Völker in todbringende Waffen umsetzen wollen - während also Europa aus zwei Weltkriegen nichts gelernt hat und einen dritten entzünden will, erinnere ich mich an ein Gespräch, das ich vor etlichen Jahren mit meinem jüngeren Sohn geführt habe.
Auf einer Wanderung zur Scheidegg – ein Aussichtspunkt oberhalb unseres Dorfes – fragte mich Alexis, ob ich an die Möglichkeit eines Dritten Weltkrieges glaube. Seit einiger Zeit schon hatte er sich Gedanken zum Krieg gemacht, weil er inzwischen aus dem Schulunterricht wusste, dass Krieg nicht dasselbe ist wie der Krieg, den ihm seine Playstation zeigte. Das Thema ließ Alexis nicht los, und auch mich ließ er damit nicht los. Immer wieder musste ich ihm vom Zweiten Weltkrieg erzählen, von Hitler und Stalin, von der Judenverfolgung, vom Eroberungsfeldzug der Wehrmacht und von den Alliierten, als sie an der Küste der Normandie landeten.
Während wir in den Wald abbogen und dem Wanderweg folgten, fragte mein Sohn, wer denn schlimmer gewesen sei, die Nationalsozialisten oder die Kommunisten? Und als er auf eine Pyramide gefällter Baumstämme kletterte, erklärte ich ihm, warum die Amerikaner gemeinsame Sache mit Stalin machten, obwohl doch auch Stalin viele Millionen umbringen liess. Ich versuchte ihm begreiflich zu machen, warum der Feind meines Feindes im Kriegsfall mein Freund ist.
Wir traten auf eine Wiese hinaus, die Sonne stach durch die Wolken hervor, und ich legte meinem Sohn dar, dass Stalin zur Befreiung Europas von Hitlerdeutschland massgeblich beitrug. Ich erzählte ihm, wie die Deutschen nach der Niederlage bei Stalingrad vom Kriegsglück verlassen wurden, und Alexis hörte mir gebannt zu. Er schwieg einen Augenblick. Über der Lichtung lag eine große Ruhe. Nur ein paar Vögel zwitscherten. Wir waren ganz allein.
«Heisst Stalingrad wirklich so?» fragte mein Sohn in die Stille hinein. Er merkte gar nicht, wo wir uns gerade befanden. Der Frieden, der uns umgab, hatte für ihn keine Bedeutung. Ohne unser Gespräch hätte er sich gelangweilt. Es ist das Vorrecht der Jugend, dass sie sich langweilen darf. Ich verstand meinen Sohn. Viel mehr als unsere Wanderung interessierte ihn der Fortgang des Krieges.
«Stalingrad heisst wieder Wolgograd», beantwortete ich seine Frage. «Aber schau doch lieber, wie schön es hier ist!»
Alexis fand es auch schön. Er gönnte mir eine kurze Gefechtspause, doch schon nach der nächsten Biegung befanden wir uns wieder mitten im Kampfgebiet. Der Geschützdonner der Kriegsjahre 39-45 begleitete uns während des ganzen restlichen Aufstiegs.
Alexis fragte, ich gab ihm Antwort. Ich liebte es, ihm zu antworten, denn der Weltkrieg fesselt auch mich, und als ich ein Kind war, habe ich meinem Vater dieselben Fragen gestellt. Der Krieg, so schrecklich er ist, übt eine seltsame Anziehung aus. Die Menschen im Westen sind von ihm fasziniert. Sie sehnen sich insgeheim nach dem Krieg, weil sie wie Teenager sind. Sie wünschen sich, ohne sich dessen bewusst zu sein, den Ausnahmezustand herbei, weil der Frieden sie langweilt. Weil sie nicht wissen, was Krieg wirklich ist.
Noch bevor Deutschland kapitulierte, erreichten wir unser Ziel. Von der Scheidegg blickten wir hinab auf den See und das weite Land. Ich bestaunte das Panorama der Alpen, so wie ich es schon hunderte Male bewundert hatte. Ich werde es immer bestaunen. Es langweilt mich nie.
«Du hast mir noch keine Antwort gegeben», erinnerte mich Alexis. «Glaubst du, es gibt irgendwann einen Dritten Weltkrieg?»
«Ich hoffe es nicht», entgegnete ich, «ich hoffe, die Menschen vergessen nie, dass der Friede schöner ist als der Krieg.» Mit einer ausschweifenden Geste über den Kranz der Berge, der uns umgab, zeigte ich meinem Sohn, was ich meinte.
Ich zeigte ihm die Schönheit des Friedens.
Dieser Artikel erschien zuerst als Kolumne im Schweizer Zeitpunkt-Magazin.
Nicolas Lindt (*1954) war Musikjournalist, Tagesschau-Reporter und Gerichtskolumnist, bevor er in seinen Büchern wahre Geschichten zu erzählen begann. In seinem zweiten Beruf gestaltet er freie Trauungen, Taufen und Abdankungen. Der Autor lebt mit seiner Familie in Wald und in Segnas. Hier finden Sie die Bücher von Nicolas Lindt. Der Fünf Minuten-Podcast «Mitten im Leben» von Nicolas Lindt ist zu finden auf Spotify, iTunes und Audible, letzte Folge hier.
Neuestes Buch: «Orwells Einsamkeit - sein Leben, ‚1984‘ und mein Weg zu einem persönlichen Denken». Erhältlich im Buchhandel - zum Beispiel bei Ex Libris oder Orell Füssli
Alle weiteren Informationen: www.nicolaslindt.ch
LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt. (Vorerst an alle, da wir den Mailversand testen, später ca. drei Mails pro Woche.).
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: milosz@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ 33599f27:e776711c
2025-04-06 03:15:59
@ 33599f27:e776711c
2025-04-06 03:15:59Last year we had a new dilemma. Our old TV died, and we had to get a new one. In a way, with the new digital conversion to take place this year, this was good. But a new TV was not the dilemma, the dilemma was a new entertainment center. In the past, a new TV did not mean that you had to change the large pieces of furniture in your house, but with the new style flat TV, this time it was necessary.
Now, I love our new TV, and so do all the men in the house who have to carry it. Our old 27” TV must have weighed around 200 lbs., but our new and larger TV weighs less than 50 lbs, so change is good. But the TV would not fit into our entertainment center, so shopping for a new one and finding the perfect one for our family room was our quest.
When it comes to entertainment centers, people have different requirements. The main requirement of my old entertainment center was one that could completely shut away the television. But that was when we lived in our old house and we only had a living room. With a separate family room now, that was not such an important feature. The main feature I was interested in this time was one that saved space. Our old entertainment center was very deep to close away the TV and took up a lot of floor space. We definitely did not need this anymore, so I was happy for the extra room. Our family room is narrow, so I only wanted something to hold the TV and the extra components.
Shopping for entertainment centers was fun, and the variety was larger than I expected. The new style TV has spawned a new style of entertainment centers, and old styles are available also. The main styles available included:
Entertainment wall units, these are the style that take up an entire wall and often include cupboards and shelves, which are great for books or display.
Entertainment armoires, which is the style I previously owned. You can close off the TV with doors.
TV lift cabinets, a style of entertainment centers that I was not familiar with, but very cool! These are only for the new TV designs. The back 9 or 10 inches of the cabinet top opens and the TV lifts up from down below. Since the TV takes up so little room, the cupboards below are fully functional for storage.
Corner entertainment centers.
Last buy not least, basic TV stands. TV stand styles have changed drastically with flat panel televisions, and they are often very modern and chic. Most have plenty of room for components on shelves underneath, and many offer matching shelving or audio towers.
For our needs, the two best style of entertainment centers were the basic TV stand and the TV lift cabinet. Some of the lift cabinets were very nice, they looked like fine pieces of furniture and were offered in many styles. If our TV was in the living room, I would definitely go for this option. But we settled for a basic pine TV stand. It is the perfect size, does not take up any excess room, and has enough shelves underneath for components. It is also only about half the width of our previous entertainment center, so the room now seems bigger. Yes, we are very happy with our new entertainment center and TV, plus, it is nice not to worry about getting a digital conversion box!
-
 @ 5d4b6c8d:8a1c1ee3
2025-04-06 23:26:53
@ 5d4b6c8d:8a1c1ee3
2025-04-06 23:26:53We had a nice sunny day and took advantage of it...by doing yardwork. Mowing, planting, and some light landscaping were a good workout and got me to almost 12k steps.
This was a great entry in Active April, which has generally been going pretty well.
Are all the other Stackers starting to get out into their yards?
originally posted at https://stacker.news/items/936592
-
 @ 9391ad71:c393890d
2025-04-06 03:14:37
@ 9391ad71:c393890d
2025-04-06 03:14:37Live entertainment spans all age groups and includes activities such as:
Music Concerts: From rock bands to classical orchestras, live music is a universal form of entertainment.
Live TV Shows: Reality shows, talent competitions, and talk shows.
Theater: Plays and musicals performed live on stage. Public entertainment has seen significant growth, especially in urban areas. Street performers, or "buskers," are a common sight in major cities. They include:
Mimes: Performers who use gestures and expressions to tell a story.
Peruvian Flute Bands: Musical groups that play traditional Andean music. Corporate Entertainment
Corporate entertainment is tailored for business events, private parties, and award ceremonies. It often involves:
Professional Event Planners: Experts who organize large-scale events.
Product Launches: Events designed to introduce new products to the market. Interesting Stats: Global Entertainment Market: The global entertainment and media market is expected to reach $2.6 trillion by 2023 (Source: PwC).
Streaming Services: As of 2021, Netflix had over 209 million subscribers worldwide (Source: Statista).
Live Music Revenue: The live music industry generated $28.56 billion in revenue in 2019 (Source: Statista).
Entertainment is a vital part of human life, offering a wide range of activities to suit different tastes and preferences. From child-friendly shows to adult concerts and public performances, the world of entertainment is diverse and ever-evolving. Understanding these various forms can help you appreciate the richness and complexity of this industry.
-
 @ 000290e1:b4909c87
2025-04-06 03:12:01
@ 000290e1:b4909c87
2025-04-06 03:12:01Back in 2014, Jeremy Rubin, a sophomore at MIT studying computer science and electrical engineering, had a bold idea: give every undergraduate student $100 worth of bitcoin.
Seven months later, armed with $500,000 in donations from alumni and crypto enthusiasts, Rubin made it happen. A total of 3,108 students took him up on the offer — at a time when bitcoin was trading at around $336.
Had everyone held onto their bitcoin, the collective value of the “MIT Airdrop” would have reached approximately $44.1 million at today’s prices. But not everyone HODLed.
According to researchers including Christian Catalini — now co-creator of the Diem stablecoin project once initiated by Facebook — about 1 in 10 students cashed out within two weeks. By the time the experiment ended in 2017, 1 in 4 had sold their crypto. After that, the team stopped tracking the cohort’s transactions.
Some students spent their bitcoin in more... flavorful ways.
Van Phu, now a software engineer and co-founder of crypto brokerage Floating Point Group, regrets blowing his bitcoin on sushi.
“One of the worst and best things at MIT was this restaurant called Thelonious Monkfish,” said Phu. “I spent a lot of my crypto buying sushi.”
He wasn’t alone.
Quantitative trader Sam Trabucco, also part of the experiment, estimated that half the students he knew spent their bitcoin at the same restaurant — the only place in Cambridge accepting bitcoin at the time. The spot has since rebranded and stopped accepting crypto.
The Birth of the Experiment
Rubin got the idea for the bitcoin giveaway in the middle of a legal battle with the New Jersey attorney general, who had accused him of being a “hardcore cybercriminal.” The claim stemmed from Rubin’s creation of Tidbit, a bitcoin mining program that had recently won an innovation award at a hackathon.
Though the case was eventually dropped and Rubin cleared, the experience highlighted how little even his MIT peers knew about bitcoin.
“I thought, ‘This is MIT — everyone’s supposed to be super cutting-edge.’ But bitcoin just wasn’t widely understood,” Rubin recalled.
Determined to change that, Rubin partnered with Dan Elitzer, then an MBA student at MIT Sloan. In October 2014, they launched the experiment. Students had to complete a short series of questionnaires and review educational materials before claiming their $100 in bitcoin.
And with that, the great MIT Bitcoin Experiment was born — part tech education, part economic study, and part sushi-fueled cautionary tale.
-
 @ e111a405:fa441558
2025-04-06 18:09:31
@ e111a405:fa441558
2025-04-06 18:09:31Running in circles is an expression that is often used to express when no matter what we do, nothing changes. We run in a circle, always ending up where we started.
Imagine the circle lines as boundaries, not physical boundaries, but mental barriers. In our life, we often run within our circle of possibilities. Anything outside our circle seem impossible. Outside the circle is anything that seems unattainable.
For some, healing a chronic disease may seem unattainable, for others it is a nice house, finding one’s soulmate, or merely financial abundance.
Over our lifetime, through our upbringing, we have defined our circle of possibilities. We have defined what is within our possibility and what is outside our possibility.
But this is just a line we drew. It is a mental barrier that does not exist outside our mind. In order to attain what seems unattainable, we have to expand our circle of possibilities. We have to pull what is outside our circle inside.
Imagine it like this: anything that is within our circle is easy and comes effortless. For example, making a coffee, driving a car are within our circle of effortless possibilities.
Other things seem out of reach. They are outside our circle of possibilities. They look extremely hard and impossible to reach.
What we need to do is reframe our understanding of what is within and what is without our circle. We pull seemingly impossible things inside our circle, and thereby we are expanding the size of our circle exponentially. We do this by following our excitement.
Not everything can be pulled inside our circle. But anything we are absolutely excited and passionate about can be pulled inside and made attainable.
You might think that you want to be the founder and CEO of a large, successful company. But if this is merely a desire that comes from mimesis – in other words, a desire that we have because we see other people have or desire it – not from our true inner being.
We will try forever to pull this inauthentic desire inside our circle, but we will fail because it is against our nature. Listening to our true excitement is key. We have to follow what is truly authentic to us — what we are truly excited about from our whole heart – and pull it inside our circle.
You may find true excitement and joy playing the piano or researching a certain subject. But true mastery of the piano or earning a livelihood with it may seem like an impossibility. Don’t let this hold you back. If this is what excites you the most, make the decision to pull it into your circle, define it is easily attainable, possible.
Inside our circle, doing and attaining our desires is as natural and easy as making a cup of coffee. Our inner circle represents our current reality. It is both endless and limiting. Endless in terms of repetition and confinement of boundaries.
Think again of walking in a circle, you always end up in the same spot, never really advancing. We try to improve the conditions within our circles, but improvements within our circles is like improving a prison cell.
True freedom comes from expanding that circle. Or stepping out of that circle into an entirely new one. That is difficult because we are like fish in an aquarium, unaware of the world behind. We only see what is familiar, what is within our circle, and everything beyond that feels alien or unattainable even though we desire it.
The real truth is that it takes the same energy to live and operate within our current circle as it takes to live within a much larger circle or to step. It takes the same effort to be in our current circle as it takes to be in a completely different, much larger circle.
First, you need to identify that you are inside a circle. What are your current habits and goals? What is your current reality?
Once you are aware, the next step is to identify what is outside your circle. What is it that you desire but looks unattainable, impossible?
Now we define a new circle. In this new circle, our goals, our habits are aligned with our authentic aspirations, our true excitement. We create a new reality.
Stepping out of this circle requires risk. It means breaking free from the familiar, and pursing something that may seem uncomfortable or unattainable.
We leave our circle, we leave our comfort zone.
We can do this in small, consistent steps, or we can make a sharp turn–an instant shift in our approach to living, like flipping from being chased to becoming the one who chases.
The real key to escaping our limiting circle is focus.
Where we focus our mental energy on determines the reality we will experience. By only focusing on improving our current reality, we remain locked in. But by expanding our vision to something outside our current circle, outside our current reality, we open up the possibilities of stepping into a new, much larger circle of possibilities.
What seems impossible now, becomes as effortless as making a cup of coffee.
The decision to break free starts with the realization that we are contained in a circle and the decision that we are ready to stop running in circles.
-
 @ 1ce06f8d:998c791e
2025-04-06 03:09:46
@ 1ce06f8d:998c791e
2025-04-06 03:09:46Don't miss the MIT Bitcoin Expo 2025 this weekend! Organized by the MIT Bitcoin Club, it is a technology and freedom focused Bitcoin conference. The MIT Bitcoin Club—a passionate coalition of students, alumni, researchers, and community members—presents the 12th annual MIT Bitcoin Expo (April 5–6, 2025), a landmark event exploring how Bitcoin and freedom technologies empower individuals worldwide. With just 5 days remaining, this student-led initiative continues its decade-long tradition of bridging academia, activism, and technical innovation.
Born from MIT’s 2014 Bitcoin Project—which distributed Bitcointo undergraduates to study adoption—the expo has evolved into a critical forum for sovereignty-focused dialogue. This year’s agenda of freedom tech focuses on physical liberation through technology.
Speakers like Zimbabwean activist Evan Mawarire (#ThisFlag movement leader) and Lightning Network creator Tadge Dryja will dissect Bitcoin’s role in resisting authoritarian control and enabling real-world escape from oppression. This is not about the cryptoeconomics, nor about the meme coins. This is about life, liberty, and Bitcoin.
What to Expect
Day 1: Dive into freedom tech fundamentals with Mawarire’s keynote “Why Freedom Tech Matters” and Dryja’s analysis of Bitcoin’s resilience against nation-states. Corporate adoption takes center stage with Marathon Digital’s Paul Giordano and Bitcoin Core developers like Gloria Zhao. Get more technical in the afternoon with topics such as consensus cleanup, poisoning attacks, censorship resistance, Bitcoin Pipes, etc.
Day 2: Shift to global impact with Mauricio Bartolomeo (exfiltration via Bitcoin) and panels featuring activists from Venezuela, Russia, and Togo. Technical deep dives include MIT’s Neha Narula on scaling self-custody and Steven Roose’s covenant softfork proposals. Other topics include future of freedom tech, quantum resistance, covenant soft fork, Tor project, etc.
Beyond Theory: The Freedom Tech Hackathon
Running parallel (April 4–6), this $10,000-prize event challenges developers to build tools for privacy, censorship resistance, and financial sovereignty14. Past projects have secured funding from industry leaders—proof of MIT’s “Mind and Hand” ethos in action4.
Additionally, Anna Chekhovich from the HRF will run a workshop on Bitcoin self-custody 101.
Why Attend?
This event prioritizes substance over spectacle. Tickets remain accessible, speakers present pro bono, and discussions tackle pressing questions:
– How can Bitcoin enable physical escape from authoritarian regimes?
– What technical upgrades strengthen its anti-censorship properties?
– Can corporations adopt Bitcoin without compromising its ethos?
With 40+ speakers and 500+ expected attendees, the expo offers unparalleled networking with developers, activists, and academics shaping Bitcoin’s future.
-
 @ 0d0d1b1f:2b9ae87f
2025-04-06 03:07:51
@ 0d0d1b1f:2b9ae87f
2025-04-06 03:07:51Augmented reality morphs the real world and projects it virtually through system-based information. Apart from that, it adds to the experience of the real world. Augmented reality makes the real world more appealing through visuals, 3D images, and videos. It allows a person to eliminate movement while experiencing whatever they want to.
This technology is among the few advanced technologies that are used in many applications. There are many AR-based apps available for smartphones. It improves the real-world experience through computer-generated information. AR technology helps customers experience the outside world while sitting in their homes. Although there are many AR technology-based devices, you can experience this technology on your smartphone. Some apps like **Snapchat** use this technology to attract more users to their platform.
## Concept of Augmented Reality
Augmented reality enhances real-life things through computer-generated technology using its interactive features for a better user experience. If you want to experience AR technology, you can access it through your smartphone. However, there are many devices that are specifically based on AR technology, such as smart glasses.
It is one of the most widely used technologies in the world that does not require heavy devices for access. AR technology has a broad range of uses in many different sectors. Some mobile apps, especially in the gaming field like **Pokémon Go**, use this technology to make the app more interesting and appealing.
## Uses of AR Technology
Augmented Reality technology has a wide range of uses in different industries. For example, the medical sector, gaming sector, armed forces, etc. Below are a few of the uses:
### Gaming Sector
AR technology has a major contribution to the gaming world. Be it gaming apps or gaming devices, you can see AR technology everywhere in the gaming sector. There are many popular mobile gaming apps like **Zombie Run** that make these games more engaging through AR technology. AR devices like headgear help users build a virtual scenario in their real world.
### Mobile Apps
Many smartphone apps like **Snapchat** use this technology to create a better impact on users. Some beauty and fashion apps also use this technology to provide a virtual trial of their products before buying. The **Nykaa** app offers a virtual mirror to try available cosmetics on the user’s face using Augmented Reality.
### Health Care Sector
Augmented reality has a major contribution to the health care sector. It helps in training medical students about complex surgeries and medical conditions through AR technology. It also helps surgeons and doctors to look deep into the medical condition of a person and treat them accordingly.
### Helps in Designing and Demonstrating
Many companies create a virtual design of their product using AR technology during the creative process. It also helps architects and building constructors to pre-design buildings and present them to investors and buyers.
### Helping Armed Forces
Armed forces use AR technology to locate areas for protection, position soldiers, make strategies for attacks, and more. Army soldiers can also see each other’s positions for deploying more troops. It also helps them get real-time information about a situation to make better strategies.
## Difference Between AR and VR Technology
Many people consider both technologies as one, but they are different from each other. Here are some key differences:
- **AR technology** uses a real-world setting, while **VR technology** constructs a virtual world to enhance the user experience.
- Users of **AR technology** have control over their real world.
- **VR users** are fully immersed and controlled by the technology's inbuilt systems.
-
 @ 434a234c:0a2f68b4
2025-04-06 17:08:21
@ 434a234c:0a2f68b4
2025-04-06 17:08:21To Review Part 8 (https://stacker.news/items/857720/r/AndyAdvance)
Scoring rubric is as follows: 5 - This law promoted 360 degrees of freedom. Bitcoiners around the world would champion this 4 3 2 1 - This bill is something straight out the communist/socialist playbook very anti freedom. Leads to forever wars endless spending and bad wellbeing for the american people
Now a look at the eighth bill that became law. Public Law No: 112-9 (04/14/2011)
H.R.4 - Comprehensive 1099 Taxpayer Protection and Repayment of Exchange Subsidy Overpayments Act of 2011
Source( https://www.congress.gov/bill/112th-congress/house-bill/4?q=%7B%22search%22%3A%22lummis%22%7D&s=1&r=53)
The Bill in Summary:
Comprehensive 1099 Taxpayer Protection and Repayment of Exchange Subsidy Overpayments Act of 2011 - Amends the Internal Revenue Code to: (1) repeal requirements for the reporting to the Internal Revenue Service (IRS) of payments of $600 or more to corporations that are not tax-exempt and of gross proceeds paid in consideration for any type of property; (2) repeal requirements for reporting payments made with respect to rental property which is not part of a trade or business; and (3) increase the limitation on recapture of excess advance payments of the tax credit for health insurance premiums.
The Score (5/5)
Great job here by Sen. Lummis! It is crazy to me that our government is trying to shake the pennies and dimes out of common every day american citizens. The fact she had to sponsor this law to protect Americans from burdensome tax regulations such as this is ridiculous. Anyone having to report to the IRS about anything that has to do with $600 is truly disgusting. While this law came in 2011 little does Sen. Lummis know at this time that this same issue would come up with transfers to Cash App and Venmo. I gave her a 5 on this law because she is increasing freedom and finanical privacy from the IRS for everyday Americans. Laws like this I can see why she can be a strong advocate for bitcoin on the Hill.
Total Score (25/45)
After nine bills Sen. Lummis has 25 points out of a total 45. That is good for 55% freedom score. Barely over half due to all the Neo-con war mongering coin bills she was pushing but it is getting better.
originally posted at https://stacker.news/items/936281
-
 @ ac0191a7:554f5121
2025-04-06 03:05:42
@ ac0191a7:554f5121
2025-04-06 03:05:42Please don’t tell anyone at CNBC about this blog. It is my underground attempt to poke fun at bizarre, money-related news. When you get right down to it, every story, no matter how wild, is usually about the money.
This blog will prowl for the most outrageous evidence of that. Plus, I’m looking for quotes from overly-handled-by-PR-people CEOs, badly written press releases, the “good marketing ideas gone bad,” people with too much money but not enough ideas, and just plain stupid stuff with a business angle.
We start with Britney Spears. The newly sober, young mother/divorcee has reportedly frittered away more than half her estimated $32 million fortune, according to “OK!” Magazine. OK! Now you know what I read while you’re reading the Wall Street Journal. Forbes has her wealth pegged in the neighborhood of $100 million, so she may have more cushion than we think.
In any case, rather than have another baby (oops, I did it again), or return to rehab (oops…again), or shave her head (oops…), Spears may have to actually think about recording another album. Justin Timberlake and Timbaland have offered to help, though her ex-boyfriend/mouseketeer says, “She’s just gotta be serious.”
Research That Companies Actually Pay For
Nielsen Media Research reports that while the average American has access to 104.2 channels (you read that right, we average an extra fifth of a channel), we only watch on average 15.73 of those channels (I personally block out the leftover .27 of VH1). This is actually not very heartening when one works for … one of those … channels … like, well. Me.
But my favorite bit of research comes from the University of Florida, which has miraculously discovered that women who get breast enlargement surgery have better self-esteem and feel sexier. REALLY? Why do you think they had the surgery in the first place?? Did they think the two million American women with implants just wanted to fit into larger clothes? Compensate for big hips?
I can’t wait for university funds (i.e., student tuition mixed with taxpayer-funded grants and suspicious big pharma money) to be spent on a study showing that Viagra does the same thing for men!
The tagline for the Gator report: bigger is better. The study queried patients’ self esteem using “widely accepted” scientific scales of measurement, including one called the Female Sexual Function Index, which almost sounds like a stock market metric -- “Rick Santelli joins us from the CBOT where the inflation news has really boosted the Female Sexual Function Index.”
Badly Written Press Releases
Finally, my favorite inscrutable press release so far this month comes from L-3 Communications. Here are the first two paragraphs of an honest-to-goodness release to the media that I think, THINK, says the company is being paid to provide software that lets a bunch of people fighting a war communicate with each other:
NEW YORK--(BUSINESS WIRE)--March 15, 2007--L-3 Communications (NYSE: LLL) announced today that its SYColeman subsidiary has been awarded an Indefinite Delivery/Indefinite Quantity (ID/IQ) contract from the U.S. Army Space and Missile Defense Command (USASMDC) to develop an advanced intelligent software technology for Future U.S. Army warfighting elements in a network-centric environment. The value of this science and technology development contract is potentially $43 million over 5 years.
To provide “space to foxhole” information sharing, SYColeman will engineer solutions for Vertical/horizontal Integration of Space Technologies and Applications (VISTA) intelligent software technology. VISTA will demonstrate the capability to distribute integrated space products and services in a seamless network capability, supporting all levels of Army Battle Command. This initiative will address corps and theater needs as well as the specific needs of individual tactical commanders at Brigade and below.
Ok, got it. So you’re using Microsoft VISTA to fight a war, right? And I’m not sure what an “integrated space product” is. Other than that, it’s perfectly clear.
-
 @ 3da0796e:77813801
2025-04-06 02:28:44
@ 3da0796e:77813801
2025-04-06 02:28:44fff
-
 @ 2a56000c:9525a85b
2025-04-06 02:26:15
@ 2a56000c:9525a85b
2025-04-06 02:26:15hbhvjhvj
-
 @ ae3a8d46:12e00667
2025-04-06 02:23:36
@ ae3a8d46:12e00667
2025-04-06 02:23:36afafasf
-
 @ ee6ea13a:959b6e74
2025-04-06 16:38:22
@ ee6ea13a:959b6e74
2025-04-06 16:38:22Chef's notes
You can cook this in one pan on the stove. I use a cast iron pan, but you can make it in a wok or any deep pan.
I serve mine over rice, which I make in a rice cooker. If you have a fancy one, you might have a setting for sticky or scorched rice, so give one of those a try.
To plate this, I scoop rice into a bowl, and then turn it upside-down to give it a dome shape, then spoon the curry on top of it.
Serve with chopped cilantro and lime wedges.
Details
- ⏲️ Prep time: 20
- 🍳 Cook time: 20
- 🍽️ Servings: 4
Ingredients
- 1 ½ pounds boneless skinless chicken breast, cut into 2" pieces
- 2 tablespoons coconut or avocado oil
- 1 cup white or yellow onion, finely diced
- 1 cup red bell pepper, sliced or diced
- 4 large garlic cloves, minced
- 1 small (4oz) jar of Thai red curry paste
- 1 can (13oz) unsweetened coconut milk
- 1 teaspoon ground ginger
- 1 teaspoon ground coriander
- 1 tablespoon soy sauce
- 1 tablespoon brown sugar
- 1 cup carrots, shredded or julienned
- 1 lime, zest and juice
- ¼ cup fresh cilantro, chopped for garnish
Directions
- Heat oil in a large skillet over medium-high. Once hot, add onions and ½ teaspoon salt. Cook 3 minutes, or until onions are softened, stirring often.
- Add the red curry paste, garlic, ginger, and coriander. Cook about 1 minute, or until fragrant, stirring often.
- Add coconut milk, brown sugar, soy sauce, and chicken. Stir, bring to a simmer, then reduce heat to medium. Simmer uncovered for 7 minutes, occasionally stirring.
- Add carrots and red bell peppers, and simmer 5-7 more minutes, until sauce slightly thickens and chicken is cooked through.
- Remove from heat, and stir in the lime zest, and half of the lime juice.
- Serve over rice, topped with cilantro, and add more lime juice if you like extra citrus.
-
 @ df450f8b:b940c7c7
2025-04-06 02:06:46
@ df450f8b:b940c7c7
2025-04-06 02:06:46ss
-
 @ e516ecb8:1be0b167
2025-04-05 23:09:31
@ e516ecb8:1be0b167
2025-04-05 23:09:31En el vasto universo de "Dune", Frank Herbert nos presenta un mundo donde el poder, la religión y la economía se entrelazan de manera fascinante. A primera vista, uno podría pensar que esta saga épica no tiene mucho que ofrecer a los libertarios. Sin embargo, al examinarla a través de la lente de la Escuela Austriaca y el anarcocapitalismo, emergen lecciones valiosas sobre la naturaleza del poder, la importancia del libre mercado y los peligros del intervencionismo estatal.
El Estado y el control de los recursos
En "Dune", el Estado, representado por el Imperio Corrino, ejerce un control férreo sobre el recurso más valioso del universo: la especia melange. Este monopolio estatal sofoca la innovación y el libre intercambio, creando una economía distorsionada y propensa a la corrupción. La lucha por el control de Arrakis, el único planeta donde se produce la especia, es un claro ejemplo de cómo el intervencionismo estatal genera conflictos y guerras.
El mesianismo y el peligro del liderazgo carismático
La figura de Paul Atreides, el mesías Muad'Dib, nos advierte sobre los peligros del liderazgo carismático y el culto a la personalidad. Su ascenso al poder, impulsado por la manipulación religiosa y el miedo, desemboca en una guerra santa que se extiende por el universo, cobrando millones de vidas. Esta tragedia nos recuerda que el poder, incluso cuando se ejerce con las mejores intenciones, tiende a corromper y a generar consecuencias imprevistas.
El libre mercado y la innovación
A pesar del control estatal, en "Dune" también encontramos ejemplos de libre mercado e innovación. Los fremen, habitantes del desierto de Arrakis, han desarrollado una cultura basada en la autosuficiencia y el ingenio, adaptándose a un entorno hostil y creando tecnologías únicas. Su capacidad para sobrevivir y prosperar en un mundo sin Estado es un testimonio del poder del libre mercado y la iniciativa individual.
Lecciones para el anarcocapitalismo
"Dune" nos ofrece valiosas lecciones para el anarcocapitalismo. Nos recuerda que el Estado, incluso en sus formas más benignas, tiende a sofocar la libertad y la prosperidad. Nos advierte sobre los peligros del liderazgo carismático y la importancia de la descentralización del poder. Y nos muestra que el libre mercado y la innovación son esenciales para la supervivencia y el progreso de la humanidad.
En un mundo donde el Estado y el poder centralizado siguen siendo la norma, "Dune" nos invita a imaginar un futuro donde la libertad y la cooperación voluntaria sean los pilares de la sociedad. Un futuro donde, como los fremen en el desierto, podamos construir un mundo mejor sin necesidad de amos ni señores.
-
 @ dbc27e2e:b1dd0b0b
2025-04-05 22:49:04
@ dbc27e2e:b1dd0b0b
2025-04-05 22:49:04Dose:
30g coffee (Fine-medium grind size) 500mL soft or bottled water (97°C / 206.6°F)Instructions:
- Rinse out your filter paper with hot water to remove the papery taste. This will also preheat the brewer.
- Add your grounds carefully to the center of the V60 and then create a well in the middle of the grounds.
- For the bloom, start to gently pour 60mL of water, making sure that all the coffee is wet in this initial phase.
- As soon as you’ve added your water, grab your V60 and begin to swirl in a circular motion. This will ensure the water and coffee are evenly mixed. Let this rest and bloom for up to 45 seconds.
- Pour the rest of the water in in 2 phases. You want to try and get 60% of your total water in, within 30 seconds.
- Pour until you reach 300mL total with a time at 1:15. Here you want to pour with a little agitation, but not so much that you have an uneven extraction.
- Once you hit 60% of your total brew weight, start to pour a little slower and more gently, keeping your V60 cone topped up. Aim to have 100% of your brew weight in within the next 30 seconds.
- Once you get to 500mL, with a spoon give the V60 a small stir in one direction, and then again in the other direction. This will release any grounds stuck to the side of the paper.
- Allow the V60 to drain some more, and then give it one final swirl. This will help keep the bed flat towards the end of the brew, giving you the most even possible extraction.
-
 @ fd208ee8:0fd927c1
2025-04-05 21:51:52
@ fd208ee8:0fd927c1
2025-04-05 21:51:52Markdown: Syntax
Note: This document is itself written using Markdown; you can see the source for it by adding '.text' to the URL.
Overview
Philosophy
Markdown is intended to be as easy-to-read and easy-to-write as is feasible.
Readability, however, is emphasized above all else. A Markdown-formatted document should be publishable as-is, as plain text, without looking like it's been marked up with tags or formatting instructions. While Markdown's syntax has been influenced by several existing text-to-HTML filters -- including Setext, atx, Textile, reStructuredText, Grutatext, and EtText -- the single biggest source of inspiration for Markdown's syntax is the format of plain text email.
Block Elements
Paragraphs and Line Breaks
A paragraph is simply one or more consecutive lines of text, separated by one or more blank lines. (A blank line is any line that looks like a blank line -- a line containing nothing but spaces or tabs is considered blank.) Normal paragraphs should not be indented with spaces or tabs.
The implication of the "one or more consecutive lines of text" rule is that Markdown supports "hard-wrapped" text paragraphs. This differs significantly from most other text-to-HTML formatters (including Movable Type's "Convert Line Breaks" option) which translate every line break character in a paragraph into a
<br />tag.When you do want to insert a
<br />break tag using Markdown, you end a line with two or more spaces, then type return.Headers
Markdown supports two styles of headers, [Setext] [1] and [atx] [2].
Optionally, you may "close" atx-style headers. This is purely cosmetic -- you can use this if you think it looks better. The closing hashes don't even need to match the number of hashes used to open the header. (The number of opening hashes determines the header level.)
Blockquotes
Markdown uses email-style
>characters for blockquoting. If you're familiar with quoting passages of text in an email message, then you know how to create a blockquote in Markdown. It looks best if you hard wrap the text and put a>before every line:This is a blockquote with two paragraphs. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
Markdown allows you to be lazy and only put the
>before the first line of a hard-wrapped paragraph:This is a blockquote with two paragraphs. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
Blockquotes can be nested (i.e. a blockquote-in-a-blockquote) by adding additional levels of
>:This is the first level of quoting.
This is nested blockquote.
Back to the first level.
Blockquotes can contain other Markdown elements, including headers, lists, and code blocks:
This is a header.
- This is the first list item.
- This is the second list item.
Here's some example code:
return shell_exec("echo $input | $markdown_script");Any decent text editor should make email-style quoting easy. For example, with BBEdit, you can make a selection and choose Increase Quote Level from the Text menu.
Lists
Markdown supports ordered (numbered) and unordered (bulleted) lists.
Unordered lists use asterisks, pluses, and hyphens -- interchangably -- as list markers:
- Red
- Green
- Blue
is equivalent to:
- Red
- Green
- Blue
and:
- Red
- Green
- Blue
Ordered lists use numbers followed by periods:
- Bird
- McHale
- Parish
It's important to note that the actual numbers you use to mark the list have no effect on the HTML output Markdown produces. The HTML Markdown produces from the above list is:
If you instead wrote the list in Markdown like this:
- Bird
- McHale
- Parish
or even:
- Bird
- McHale
- Parish
you'd get the exact same HTML output. The point is, if you want to, you can use ordinal numbers in your ordered Markdown lists, so that the numbers in your source match the numbers in your published HTML. But if you want to be lazy, you don't have to.
To make lists look nice, you can wrap items with hanging indents:
- Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
- Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
But if you want to be lazy, you don't have to:
- Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
- Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
List items may consist of multiple paragraphs. Each subsequent paragraph in a list item must be indented by either 4 spaces or one tab:
-
This is a list item with two paragraphs. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus.
Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus. Donec sit amet nisl. Aliquam semper ipsum sit amet velit.
-
Suspendisse id sem consectetuer libero luctus adipiscing.
It looks nice if you indent every line of the subsequent paragraphs, but here again, Markdown will allow you to be lazy:
-
This is a list item with two paragraphs.
This is the second paragraph in the list item. You're only required to indent the first line. Lorem ipsum dolor sit amet, consectetuer adipiscing elit.
-
Another item in the same list.
To put a blockquote within a list item, the blockquote's
>delimiters need to be indented:-
A list item with a blockquote:
This is a blockquote inside a list item.
To put a code block within a list item, the code block needs to be indented twice -- 8 spaces or two tabs:
- A list item with a code block:
<code goes here>
Code Blocks
Pre-formatted code blocks are used for writing about programming or markup source code. Rather than forming normal paragraphs, the lines of a code block are interpreted literally. Markdown wraps a code block in both
<pre>and<code>tags.To produce a code block in Markdown, simply indent every line of the block by at least 4 spaces or 1 tab.
This is a normal paragraph:
This is a code block.Here is an example of AppleScript:
tell application "Foo" beep end tellA code block continues until it reaches a line that is not indented (or the end of the article).
Within a code block, ampersands (
&) and angle brackets (<and>) are automatically converted into HTML entities. This makes it very easy to include example HTML source code using Markdown -- just paste it and indent it, and Markdown will handle the hassle of encoding the ampersands and angle brackets. For example, this:<div class="footer"> © 2004 Foo Corporation </div>Regular Markdown syntax is not processed within code blocks. E.g., asterisks are just literal asterisks within a code block. This means it's also easy to use Markdown to write about Markdown's own syntax.
tell application "Foo" beep end tellSpan Elements
Links
Markdown supports two style of links: inline and reference.
In both styles, the link text is delimited by [square brackets].
To create an inline link, use a set of regular parentheses immediately after the link text's closing square bracket. Inside the parentheses, put the URL where you want the link to point, along with an optional title for the link, surrounded in quotes. For example:
This is an example inline link.
This link has no title attribute.
Emphasis
Markdown treats asterisks (
*) and underscores (_) as indicators of emphasis. Text wrapped with one*or_will be wrapped with an HTML<em>tag; double*'s or_'s will be wrapped with an HTML<strong>tag. E.g., this input:single asterisks
single underscores
double asterisks
double underscores
Code
To indicate a span of code, wrap it with backtick quotes (
`). Unlike a pre-formatted code block, a code span indicates code within a normal paragraph. For example:Use the
printf()function. -
 @ 70058751:101d4bb2
2025-04-05 21:45:08
@ 70058751:101d4bb2
2025-04-05 21:45:08Artificial intelligence is transforming healthcare in numerous ways, from diagnostic algorithms to personalized treatment plans...
-
 @ 72592ec9:ffa64d2c
2025-04-06 14:23:05
@ 72592ec9:ffa64d2c
2025-04-06 14:23:05https://v.nostr.build/LGHvXYiZuXkQ445r.mp4
"Not Your Keys, Not Your Bitcoin"
You know, anon, I may just be a random voice screaming into a digital void, but wake up.
You’re being played.
Saylor? BlackRock? Coinbase? They’ve built a glittering paper palace of IOUs, and they're handing you Monopoly money while calling it Bitcoin.
Let’s get something straight: if you don’t run a node, and you don’t hold your own keys, you do NOT have Bitcoin. You’ve got a IOU claim ticket, a promise, a polite “maybe” from a third-party middleman that your bitcoin might be somewhere… until they’re not.
MicroStrategy stock is not Bitcoin. BlackRock ETFs are not Bitcoin. They're glorified exposure vehicles built on layers of trust, custodial risk, and opaque rehypothecation games, tantamount to "wrapped bitcoin".
They Are Shitcoins.
And what do they all have in common? Coinbase. The same custodian for both that attacked Bitcoin during the blocksize wars. The same centralized honeypot. The same “trust us, bro” nonsense that blew up Mt. Gox, Celsius, BlockFi, and FTX.
They want you to stay passive. They want you to think holding a ticker symbol in your brokerage account is the same as holding digital gold. It’s not. That MSTR stock? It’s paper. That IBIT ETF? Paper. TradFi comfort food for people too afraid to take the one step that actually matters: self custody.
And guess what? They don’t want you to do it. They don’t want you to learn how to use a hardware wallet. They don’t want you to spin up a node. Because once you do, you don’t need them anymore. You become sovereign. You opt out. You verify instead of trust.
Bitcoin was never about price exposure. It was about freedom. About removing third party middlemen. About eliminating counterparty risk. You give that up the second you park your “Bitcoin” with a third party middleman in a BlackRock ETF or "Bitcoin" stock.
You think Larry Fink’s going to let you withdraw sats to your Coldcard when there's a run on coinbase? You think Saylor’s going to cut you a UTXO when coinbase is fully compromised like MTGOX? Hell no. You’re buying promises. And promises break when things get ugly.
If you're buying paper Bitcoin—whether it's MicroStrategy stock, BlackRock's ETF, or any other shiny TradFi wrapper—you’re not just getting scammed yourself… you're part of the scam.
Yeah, that’s right. When you buy these IOUs, you're feeding the beast.
You're handing your capital over to entities who don’t secure real Bitcoin for every share issued. Instead, they park Bitcoin with a third-party custodian—Coinbase in this case—and use it to create multiple claims on the same sats. That’s rehypothecation 101. And when multiple people think they own the same Bitcoin, guess what? They don’t.
That’s how you suppress the price of real Bitcoin. That’s how you neuter the supply shock that should be happening when millions of people FOMO in. Because instead of those buys hitting the spot market and draining actual BTC from circulating supply, they’re going into synthetic products. TradFi IOUs. Ghost Bitcoin.
You're not moving the needle. You're feeding the illusion.
This is how Wall Street has always played the game. Gold markets are a cautionary tale. The paper gold market is 100x the size of the actual gold held in custody. That didn’t happen overnight. It happened because people stopped demanding the real thing. They stopped taking delivery. And now gold’s price has been effectively suppressed for decades while banks shuffle IOUs in an endless shell game.
And they’re doing it to Bitcoin next.
BlackRock doesn’t want sound money. They want predictable returns, regulatory control, and another revenue stream. They want to neuter Bitcoin—turn it into a boring number on a spreadsheet—not a monetary revolution. And by buying into these ETFs, you’re giving them the ammo to do it.
Every dollar that goes into a Bitcoin IOU instead of self-custodied BTC is a vote for centralization, a vote for price suppression, and a vote against the ethos of Bitcoin itself.
It’s not just about your own safety anymore—it’s about the network. Every sat you leave in their hands is one more sat that can be leveraged, re-loaned, and used to dilute real ownership. You are giving the tools of control right back to the very people Bitcoin was built to escape.
So be smart. Opt out of the clown show. Run your own full node. Hold your keys in cold storage. Don’t get suckered into the next rug-pull and cry later because “I thought it was backed 1:1.”
You've been warned, you have no excuse now.
Buy real Bitcoin. Take self custody. Become Free.
originally posted at https://stacker.news/items/936086
-
 @ fd208ee8:0fd927c1
2025-04-05 21:36:33
@ fd208ee8:0fd927c1
2025-04-05 21:36:33Markdown: Syntax
Note: This document is itself written using Markdown; you can see the source for it by adding '.text' to the URL.
Overview
Philosophy
Markdown is intended to be as easy-to-read and easy-to-write as is feasible.
Readability, however, is emphasized above all else. A Markdown-formatted document should be publishable as-is, as plain text, without looking like it's been marked up with tags or formatting instructions. While Markdown's syntax has been influenced by several existing text-to-HTML filters -- including Setext, atx, Textile, reStructuredText, Grutatext, and EtText -- the single biggest source of inspiration for Markdown's syntax is the format of plain text email.
Block Elements
Paragraphs and Line Breaks
A paragraph is simply one or more consecutive lines of text, separated by one or more blank lines. (A blank line is any line that looks like a blank line -- a line containing nothing but spaces or tabs is considered blank.) Normal paragraphs should not be indented with spaces or tabs.
The implication of the "one or more consecutive lines of text" rule is that Markdown supports "hard-wrapped" text paragraphs. This differs significantly from most other text-to-HTML formatters (including Movable Type's "Convert Line Breaks" option) which translate every line break character in a paragraph into a
<br />tag.When you do want to insert a
<br />break tag using Markdown, you end a line with two or more spaces, then type return.Headers
Markdown supports two styles of headers, [Setext] [1] and [atx] [2].
Optionally, you may "close" atx-style headers. This is purely cosmetic -- you can use this if you think it looks better. The closing hashes don't even need to match the number of hashes used to open the header. (The number of opening hashes determines the header level.)
Blockquotes
Markdown uses email-style
>characters for blockquoting. If you're familiar with quoting passages of text in an email message, then you know how to create a blockquote in Markdown. It looks best if you hard wrap the text and put a>before every line:This is a blockquote with two paragraphs. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
Markdown allows you to be lazy and only put the
>before the first line of a hard-wrapped paragraph:This is a blockquote with two paragraphs. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
Blockquotes can be nested (i.e. a blockquote-in-a-blockquote) by adding additional levels of
>:This is the first level of quoting.
This is nested blockquote.
Back to the first level.
Blockquotes can contain other Markdown elements, including headers, lists, and code blocks:
This is a header.
- This is the first list item.
- This is the second list item.
Here's some example code:
return shell_exec("echo $input | $markdown_script");Any decent text editor should make email-style quoting easy. For example, with BBEdit, you can make a selection and choose Increase Quote Level from the Text menu.
Lists
Markdown supports ordered (numbered) and unordered (bulleted) lists.
Unordered lists use asterisks, pluses, and hyphens -- interchangably -- as list markers:
- Red
- Green
- Blue
is equivalent to:
- Red
- Green
- Blue
and:
- Red
- Green
- Blue
Ordered lists use numbers followed by periods:
- Bird
- McHale
- Parish
It's important to note that the actual numbers you use to mark the list have no effect on the HTML output Markdown produces. The HTML Markdown produces from the above list is:
If you instead wrote the list in Markdown like this:
- Bird
- McHale
- Parish
or even:
- Bird
- McHale
- Parish
you'd get the exact same HTML output. The point is, if you want to, you can use ordinal numbers in your ordered Markdown lists, so that the numbers in your source match the numbers in your published HTML. But if you want to be lazy, you don't have to.
To make lists look nice, you can wrap items with hanging indents:
- Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
- Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
But if you want to be lazy, you don't have to:
- Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
- Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
List items may consist of multiple paragraphs. Each subsequent paragraph in a list item must be indented by either 4 spaces or one tab:
-
This is a list item with two paragraphs. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus.
Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus. Donec sit amet nisl. Aliquam semper ipsum sit amet velit.
-
Suspendisse id sem consectetuer libero luctus adipiscing.
It looks nice if you indent every line of the subsequent paragraphs, but here again, Markdown will allow you to be lazy:
-
This is a list item with two paragraphs.
This is the second paragraph in the list item. You're only required to indent the first line. Lorem ipsum dolor sit amet, consectetuer adipiscing elit.
-
Another item in the same list.
To put a blockquote within a list item, the blockquote's
>delimiters need to be indented:-
A list item with a blockquote:
This is a blockquote inside a list item.
To put a code block within a list item, the code block needs to be indented twice -- 8 spaces or two tabs:
- A list item with a code block:
<code goes here>
Code Blocks
Pre-formatted code blocks are used for writing about programming or markup source code. Rather than forming normal paragraphs, the lines of a code block are interpreted literally. Markdown wraps a code block in both
<pre>and<code>tags.To produce a code block in Markdown, simply indent every line of the block by at least 4 spaces or 1 tab.
This is a normal paragraph:
This is a code block.Here is an example of AppleScript:
tell application "Foo" beep end tellA code block continues until it reaches a line that is not indented (or the end of the article).
Within a code block, ampersands (
&) and angle brackets (<and>) are automatically converted into HTML entities. This makes it very easy to include example HTML source code using Markdown -- just paste it and indent it, and Markdown will handle the hassle of encoding the ampersands and angle brackets. For example, this:<div class="footer"> © 2004 Foo Corporation </div>Regular Markdown syntax is not processed within code blocks. E.g., asterisks are just literal asterisks within a code block. This means it's also easy to use Markdown to write about Markdown's own syntax.
tell application "Foo" beep end tellSpan Elements
Links
Markdown supports two style of links: inline and reference.
In both styles, the link text is delimited by [square brackets].
To create an inline link, use a set of regular parentheses immediately after the link text's closing square bracket. Inside the parentheses, put the URL where you want the link to point, along with an optional title for the link, surrounded in quotes. For example:
This is an example inline link.
This link has no title attribute.
Emphasis
Markdown treats asterisks (
*) and underscores (_) as indicators of emphasis. Text wrapped with one*or_will be wrapped with an HTML<em>tag; double*'s or_'s will be wrapped with an HTML<strong>tag. E.g., this input:single asterisks
single underscores
double asterisks
double underscores
Code
To indicate a span of code, wrap it with backtick quotes (
`). Unlike a pre-formatted code block, a code span indicates code within a normal paragraph. For example:Use the
printf()function. -
 @ ac58bbcc:7d9754d8
2025-04-05 21:32:47
@ ac58bbcc:7d9754d8
2025-04-05 21:32:47Unlocking Learning Potential: How Math Model Transform Learning
Introduction:
In mathematics education, fostering a learning environment that encourages a variety of problem-solving strategies and emphasizes the structural foundations of mathematical concepts is crucial for student success. One key instructional element is using mathematical models to help students bridge their informal understandings with formal, symbolic mathematical reasoning. Encouraging students to use models, particularly iconic representations, is vital in developing conceptual and procedural knowledge. This research overview explores how modeling enhances student learning by progressing from intuitive representations to more formalized mathematical reasoning, focusing on the importance of iconic models in building a deeper understanding of mathematics.

FREE DOWNLOAD - Questions and Prompts
Theoretical Foundations
Taking students' ideas seriously is grounded in constructivist learning theory and research on how students develop mathematical understanding. Hiebert and Carpenter (1992) argue that "if children possessed internal networks constructed both in and out of school and if they recognized the connections between them, their understanding and performance in both settings would improve." This highlights the importance of connecting students' informal knowledge with formal mathematical concepts. Carpenter's work further emphasizes the value of students' intuitive knowledge: "Children come to school with a great deal of informal or intuitive knowledge of mathematics that can serve as the basis for developing much of the formal mathematics of the primary school curriculum." This suggests that taking students' initial ideas seriously can provide a strong foundation for developing a more sophisticated mathematical understanding.
The Role of Models in Mathematical Thinking
Modeling is a powerful tool for nurturing mathematical thinking because it helps students move from concrete experiences to abstract reasoning. According to Romberg and Kaput (1999), when students first encounter mathematical problems, they naturally rely on informal strategies based on their real-world experiences. The modeling process allows these initial intuitive approaches to serve as scaffolding for solving more complex, related problems. Through modeling, students solve a specific problem and develop general strategies that can be applied across different mathematical contexts.
Gravemeijer and van Galen (2003) argue that modeling real-world situations is foundational for understanding mathematical structures. This process often begins with students using informal, tangible representations, which evolve into more formal mathematical reasoning as they progress. Cobb (2000) describes this as a shift in classroom practice, where students’ informal activities, such as using objects or drawings, are eventually formalized into mathematical reasoning. The key to this transformation lies in how well students can transition between different forms of representation: enactive, iconic, and symbolic models (Bruner, 1964).
The Progression of Mathematical Models
A critical component of effective mathematics instruction is the concept of progressive formalization, which guides students through the stages of representation. As students work through mathematical problems, they begin with enactive models—physical representations or manipulatives that help them visualize the problem. From there, students move on to iconic models, which involve pictorial representations, such as diagrams, number lines, and graphs, that symbolize the relationships in the problem. Finally, they transition to symbolic models, which use formal mathematical tables, notation, and equations to organize and represent abstract concepts (Bruner, 1964).
The transition from iconic to symbolic models is particularly important because it helps students visualize and understand abstract mathematical concepts without losing the connection to real-world problems. In many curricula, students are often asked to solve problems using multiple methods, but these methods may only sometimes lead to the progressive formalization needed for deep understanding. Iconic models, such as number lines that promote distance, magnitude, and proportion, serve as a critical bridge between concrete and abstract reasoning, allowing students to visualize the relationships between numbers and operations before transitioning to formal symbols (Leinwand & Ginsburg, 2007).
Iconic Models and Their Importance
Iconic models play a unique role in mathematics education by offering visual representations that make abstract concepts more accessible. For example, the area model is a powerful iconic representation used in teaching multiplication and division. When students are presented with a contextualized problem, such as determining the number of tiles needed to cover a floor, they can use an area model to visualize the relationships among length, width, and area. This iconic representation helps students see multiplication in two dimensions, preparing them for more formal mathematical concepts such as algebra (Watanabe, 2015).
The strength of iconic models lies in their ability to illuminate different aspects of mathematical relationships. Unlike abstract symbolic representations, which can be difficult for students to grasp, iconic models make the problem tangible and concrete. Students can manipulate the models, explore different problem-solving strategies, and visually see the consequences of their actions. This tactile and visual exploration deepens their conceptual understanding and supports the transition to more abstract forms of reasoning (Bruner, 1964).
For instance, using a number line as an iconic model for fractions allows students to visualize the relative size of different fractions, helping them understand concepts such as equivalence and comparison. Similarly, bar models can represent proportions, ratios, or algebraic relationships. These iconic models provide a clear, visual framework for understanding the underlying structure of mathematical problems, and they encourage students to explore multiple solution strategies.
Modeling in Curriculum Design
Integrating modeling into mathematics curricula has fostered deeper student engagement and understanding. However, educators must select contexts and tasks that naturally lead students from informal models to more formal, mathematically robust representations. For example, when teaching multiplication, students may begin by solving problems about grouping objects or creating arrays. These problems encourage using iconic models, such as drawing rows and columns to represent multiplication as an area, before transitioning to symbolic equations (Leinwand & Ginsburg, 2007).
Curricula that prioritize the progression from enactive to iconic to symbolic models help students build a solid foundation for understanding more advanced mathematical concepts. For example, suppose an educator aims for students to use the area model as an iconic representation. In that case, they might introduce problems involving geometric concepts, such as covering flat spaces with tiles or using gridlines on a map to calculate distances. These activities make math more tangible and foster logical connections for students to develop more formal mathematical reasoning (Watanabe, 2015).
Additionally, students’ engagement with different models enhances their ability to communicate and justify their mathematical thinking. When asked to explain how they arrived at a solution using an iconic model, they must articulate the mathematical relationships they observe, which promotes a deeper understanding. This process also aligns with socio-mathematical norms, where students learn to evaluate the efficiency and effectiveness of different models and strategies through classroom discussion and peer feedback.
The Cognitive Benefits of Modeling
From a cognitive psychology perspective, using models in mathematics education helps bridge the gap between procedural and conceptual knowledge. Research by Gilmore and Papadatou-Pastou (2009) suggests that procedural fluency and conceptual understanding are interconnected, with advancements in one area reinforcing the other. The iterative development of models provides students with opportunities to build both procedural skills—through repeated practice—and conceptual knowledge—by visualizing and manipulating the mathematical structures underlying the problems they solve.
Bruner’s (1964) theory of representation emphasizes the importance of guiding students through the different representational forms—enactive, iconic, and symbolic—without imposing abrupt transitions. The gradual transition from one form of representation to another enables students to develop a deeper, more integrated understanding of mathematical concepts, reducing the cognitive load associated with learning new material. This approach allows students to internalize mathematical concepts more effectively, making them better prepared to tackle more complex problems in the future
Conclusion
In conclusion, mathematical modeling is a critical framework for helping students develop a deeper understanding of mathematics by progressing through enactive, iconic, and symbolic representations. Iconic models, in particular, are essential for bridging the gap between students’ informal understandings and the abstract formalism of mathematical reasoning. Educators can foster environments where students are encouraged to explore, innovate, and deepen their understanding of mathematical structures by emphasizing using models in mathematics instruction. This progressive formalization supports procedural fluency and conceptual knowledge, preparing students to thrive in mathematics and beyond.
Integrating modeling into curricula and thoughtfully selecting tasks that support the progression from informal to formal reasoning empowers students to recognize the diverse methods for solving problems and encourages them to develop their unique mathematical insights. As school administrators and educators, fostering an environment that supports these pedagogical practices is critical to nurturing the next generation of mathematical thinkers.
References
Bruner, J. S. (1964). The course of cognitive growth. American Psychologist, 19(1), 1-15.
Cobb, P. (2000). Conducting teaching experiments in collaboration with teachers. In A. E. Kelly & R. A. Lesh (Eds.), Handbook of research design in mathematics and science education (pp. 307-333). Lawrence Erlbaum Associates.
Gilmore, C. K., & Papadatou-Pastou, M. (2009). Patterns of individual differences in conceptual understanding and arithmetical skill: A meta-analysis. Mathematical Thinking and Learning, 11(1-2), 25-40.
Gravemeijer, K., & van Galen, F. (2003). Facts and algorithms as products of students’ own mathematical activity. In J. Kilpatrick, W. G. Martin, & D. Schifter (Eds.), A research companion to principles and standards for school mathematics (pp. 114-122). National Council of Teachers of Mathematics.
Leinwand, S., & Ginsburg, A. L. (2007). Learning from Singapore math. Educational Leadership, 65(3), 32-36.
Romberg, T. A., & Kaput, J. J. (1999). Mathematics worth teaching, mathematics worth understanding. In E. Fennema & T. A. Romberg (Eds.), Mathematics classrooms that promote understanding (pp. 3-17). Lawrence Erlbaum Associates.
Watanabe, T. (2015). Visual reasoning tools in action. Mathematics Teaching in the Middle School, 21(3), 152-160.
-
 @ dbc27e2e:b1dd0b0b
2025-04-05 20:44:00
@ dbc27e2e:b1dd0b0b
2025-04-05 20:44:00This method focuses on the amount of water in the first pour, which ultimately defines the coffee’s acidity and sweetness (more water = more acidity, less water = more sweetness). For the remainder of the brew, the water is divided into equal parts according to the strength you wish to attain.

Dose:
20g coffee (Coarse ground coffee) 300mL water (92°C / 197.6°F) Time: 3:30Instructions:
- Pour 1: 0:00 > 50mL (42% of 120mL = 40% of total – less water in the ratio, targeting sweetness.)
- Pour 2: 0:45 > 70mL (58% of 120mL = 40% of total – the top up for 40% of total.)
- Pour 3: 1:30 > 60mL (The remaining water is 180mL / 3 pours = 60mL per pour)
- Pour 4: 2:10 > 60mL
- Pour 5: 2:40 > 60mL
- Remove the V60 at 3:30
-
 @ ac58bbcc:7d9754d8
2025-04-05 18:59:02
@ ac58bbcc:7d9754d8
2025-04-05 18:59:02Unlocking Learning Potential: Why Student's Ideas Matter
Introduction
Recent research in mathematics education emphasizes the importance of valuing and building upon students' initial ideas and intuitive understanding. This approach, often referred to as "taking students' ideas seriously," has enhanced conceptual understanding, problem-solving skills, and overall mathematical achievement. This overview examines this approach's theoretical foundations, cognitive processes, and practical implications in mathematics classrooms.

FREE DOWNLOAD - Questions and Prompts
Theoretical Foundations
Taking students' ideas seriously is grounded in constructivist learning theory and research on how students develop mathematical understanding. Hiebert and Carpenter (1992) argue that "if children possessed internal networks constructed both in and out of school and if they recognized the connections between them, their understanding and performance in both settings would improve." This highlights the importance of connecting students' informal knowledge with formal mathematical concepts. Carpenter's work further emphasizes the value of students' intuitive knowledge: "Children come to school with a great deal of informal or intuitive knowledge of mathematics that can serve as the basis for developing much of the formal mathematics of the primary school curriculum." This suggests that taking students' initial ideas seriously can provide a strong foundation for developing a more sophisticated mathematical understanding.
Cognitive Processes
When students' ideas are taken seriously in mathematics classrooms, several cognitive processes are engaged:
-
Schema Formation: As students articulate and refine their ideas, they develop and modify mental frameworks or schemas that organize mathematical concepts.
-
Metacognition: Explaining their thinking engages students' metacognitive processes, promoting reflection on their own understanding and problem-solving strategies.
-
Elaborative Rehearsal: Verbalizing mathematical concepts helps move information from working memory to long-term memory, enhancing retention.
-
Cognitive Conflict: When students encounter differing viewpoints, it can create cognitive conflict, stimulating the reconciliation of new information with existing schemas.
Practical Implications
Eliciting and Valuing Student Ideas
Carpenter and Lehrer argue that for learning with understanding to occur, instruction needs to provide specific opportunities: "For learning with understanding to occur, instruction needs to provide students the opportunity to develop productive relationships, extend and apply their knowledge, reflect about their experiences, articulate what they know, and make knowledge their own." This emphasizes the need for instructional approaches that actively elicit and value student ideas.
Creating a Supportive Environment
To effectively take students' ideas seriously, teachers must foster a classroom environment where all contributions are respected. This involves:
-
Provide adequate thinking time for students to formulate their thoughts.
-
Using open-ended questions that encourage diverse thinking and approaches.
-
Implementing collaborative strategies like think-pair-share to build confidence in sharing ideas.
Connecting to Formal Mathematics
Hiebert advocates for teaching practices that promote understanding by focusing on "the inherent structure of the emerging mathematical ideas and addressing students' misconceptions as they arise" . This involves helping students connect their informal ideas to more formal mathematical concepts and procedures.
Impact on Student Learning
Research indicates that taking students' ideas seriously can significantly improve mathematical understanding and achievement. A study by Carpenter et al. (1998) found that when teachers based their instruction on students' thinking, students demonstrated greater problem-solving skills and conceptual understanding compared to control groups. Moreover, this approach has increased student engagement and motivation in mathematics. When students feel their ideas are valued, they are more likely to participate actively in mathematical discussions and take intellectual risks.
Challenges and Considerations
While the benefits of taking students' ideas seriously are well-documented, implementing this approach can present challenges:
-
Time Constraints: Allowing for extended student discussions and idea exploration can be time-consuming within the constraints of a typical school schedule.
-
Teacher Preparation: Effectively building on student ideas requires strong content knowledge and pedagogical skills from teachers.
-
Assessment Alignment: Traditional assessment methods may not adequately capture the depth of understanding developed through this approach, necessitating new forms of evaluation.
Conclusion
Taking students' ideas seriously in mathematics education represents a powerful approach to fostering deep conceptual understanding and problem-solving skills. By valuing students' initial thoughts and building upon their intuitive knowledge, educators can create more engaging and effective learning environments. While challenges exist in implementation, the potential benefits for student learning and mathematical achievement make this approach worthy of serious consideration and further research.
References
Ball, D. L., Thames, M. H., & Phelps, G. (2008). Content knowledge for teaching: What makes it special? Journal of Teacher Education, 59(5), 389-407.
Boaler, J. (2002). Experiencing school mathematics: Traditional and reform approaches to teaching and their impact on student learning. Routledge.
Boaler, J., & Brodie, K. (2004). The importance, nature and impact of teacher questions. In D. E. McDougall & J. A. Ross (Eds.), Proceedings of the 26th annual meeting of the North American Chapter of the International Group for the Psychology of Mathematics Education (Vol. 2, pp. 773-782). Toronto: OISE/UT. Carpenter, T. P., Fennema, E., & Franke, M. L. (1996). Cognitively guided instruction: A knowledge base for reform in primary mathematics instruction. The Elementary School Journal, 97(1), 3-20.
Carpenter, T. P., Fennema, E., Franke, M. L., Levi, L., & Empson, S. B. (1999). Children's mathematics: Cognitively guided instruction. Portsmouth, NH: Heinemann.
Carpenter, T. P., & Lehrer, R. (1999). Teaching and learning mathematics with understanding. In E. Fennema & T. A. Romberg (Eds.), Mathematics classrooms that promote understanding (pp. 19-32). Mahwah, NJ: Lawrence Erlbaum Associates.
Craik, F. I., & Lockhart, R. S. (1972). Levels of processing: A framework for memory research. Journal of Verbal Learning and Verbal Behavior, 11(6), 671-684.
Driscoll, M. P. (2005). Psychology of learning for instruction (3rd ed.). Boston: Allyn and Bacon.
Flavell, J. H. (1979). Metacognition and cognitive monitoring: A new area of cognitive-developmental inquiry. American Psychologist, 34(10), 906-911.
Hiebert, J., & Carpenter, T. P. (1992). Learning and teaching with understanding. In D. A. Grouws (Ed.), Handbook of research on mathematics teaching and learning (pp. 65-97). New York: Macmillan.
Hiebert, J., Carpenter, T. P., Fennema, E., Fuson, K. C., Wearne, D., Murray, H., ... & Human, P. (1997). Making sense: Teaching and learning mathematics with understanding. Portsmouth, NH: Heinemann.
Lyman, F. (1981). The responsive classroom discussion: The inclusion of all students. In A. S. Anderson (Ed.), Mainstreaming Digest (pp. 109-113). College Park: University of Maryland Press.
Piaget, J. (1952). The origins of intelligence in children. New York: International Universities Press.
Rowe, M. B. (1986). Wait time: Slowing down may be a way of speeding up! Journal of Teacher Education, 37(1), 43- 50.
Shepard, L. A. (2000). The role of assessment in a learning culture. Educational Researcher, 29(7), 4-14.
Smith, M. S., & Stein, M. K. (2011). 5 practices for orchestrating productive mathematics discussions. Reston, VA: National Council of Teachers of Mathematics.
Social Media.
Research in mathematics education highlights the significance of taking students' ideas seriously, demonstrating how this approach enhances conceptual understanding, problem-solving abilities, and overall mathematical achievement. Rooted in constructivist learning theory, this method engages crucial cognitive processes like schema formation, metacognition, and elaborative rehearsal. By connecting students’ informal knowledge with formal mathematical concepts, educators can establish a robust foundation for advanced mathematical thinking. Studies show that when instruction is based on students' thinking, learners exhibit superior problem-solving skills and a deeper conceptual grasp than traditional teaching methods.
Join us in exploring these powerful teaching approaches and their impact on mathematical thinking and achievement!
-
-
 @ 52524fbb:ae4025dc
2025-04-06 12:51:08
@ 52524fbb:ae4025dc
2025-04-06 12:51:08A giant step that could and would set a path across the African continent and beyond, has been put in motion Nigeria has officially recognized cryptocurrencies as securities under its Investments and Securities Act (ISA) as of these year 2025. This critical decision, a significant turnover from previous regulatory setbacks, positions Nigeria at the forefront of digital asset regulation in Africa and carries relevant implications for Bitcoin adoption, not just within the borders of Nigeria, but across Africa as a whole, as we all know that Nigeria leaves up to it's name as the giant of Africa and hence has great influence over the continent
Why Bitcoin Adoption in Nigeria Matters:
Nigeria has consistently been among the most adoptive countries worldwide for crypto currency, due to high inflation, the nation’s young and tech-savvy population, and its inability to access traditional financial services. Given its formalization as securities this move would help to push forward adoption in the following key ways:
-
Increased Investor Confidence: By bringing cryptocurrencies under the purview of securities regulations, the government is signaling a commitment to consumer protection and market integrity. This could attract more risk considerate individuals and institutional investors who were previously hesitant due to the lack of clarity. Bitcoin, as the flagship of cryptocurrency, is likely to be a primary beneficiary of this increased confidence.
-
Formalization of Exchanges and Service Providers: This new approach may lead to the formal licensing and regulation of cryptocurrency exchanges and other service providers. This will create a more transparent and accountable ecosystem, making it safer and easier for Nigerians to buy, sell, and hold Bitcoin.
-
Attracting Institutional Investment: Recognizing cryptocurrencies as securities opens the door for institutional investors, such as pension funds and asset management firms, to allocate capital to Bitcoin within a regulated process. This influence of institutional money could significantly boost Bitcoin's liquidity and price stability in the long run.

Significant Effects Across the African Continent:
Nigeria's bold step is unlikely to remain in isolated. As the largest economy in Africa and a leader in technological implementation, its regulatory decisions often set a path for other nations on the continent. The recognition of cryptocurrencies as securities in Nigeria would have significant effects across Africa in the following ways:
-
Setting a Regulatory Benchmark: Other African countries struggling with how to regulate the much announced cryptocurrency market may look to Nigeria's process as a potential model. This could lead to greater regulatory harmonization across the continent, fostering a more consistent and predictable environment for digital assets.
-
Empowering Financial Inclusion: Bitcoin and other cryptocurrencies have the potential to significantly enhance financial inclusion in Africa, where a large percentage of the population remains unbanked. Clear regulations can foster the development of secure and accessible digital financial services, empowering individuals to participate in the global economy.
-
Competition and Collaboration: Nigeria's active stance might incline other African nations to develop their own regulatory process for digital assets, potentially leading to healthy competition and collaboration in the development of the continent's digital economy.
-