-
 @ c1e9ab3a:9cb56b43
2025-04-15 13:59:17
@ c1e9ab3a:9cb56b43
2025-04-15 13:59:17Prepared for Off-World Visitors by the Risan Institute of Cultural Heritage
Welcome to Risa, the jewel of the Alpha Quadrant, celebrated across the Federation for its tranquility, pleasure, and natural splendor. But what many travelers do not know is that Risa’s current harmony was not inherited—it was forged. Beneath the songs of surf and the serenity of our resorts lies a history rich in conflict, transformation, and enduring wisdom.
We offer this briefing not merely as a tale of our past, but as an invitation to understand the spirit of our people and the roots of our peace.
I. A World at the Crossroads
Before its admittance into the United Federation of Planets, Risa was an independent and vulnerable world situated near volatile borders of early galactic powers. Its lush climate, mineral wealth, and open society made it a frequent target for raiders and an object of interest for imperial expansion.
The Risan peoples were once fragmented, prone to philosophical and political disunity. In our early records, this period is known as the Winds of Splintering. We suffered invasions, betrayals, and the slow erosion of trust in our own traditions.
II. The Coming of the Vulcans
It was during this period of instability that a small delegation of Vulcan philosophers, adherents to the teachings of Surak, arrived on Risa. They did not come as conquerors, nor even as ambassadors, but as seekers of peace.
These emissaries of logic saw in Risa the potential for a society not driven by suppression of emotion, as Vulcan had chosen, but by the balance of joy and discipline. While many Vulcans viewed Risa’s culture as frivolous, these followers of Surak saw the seed of a different path: one in which beauty itself could be a pillar of peace.
The Risan tradition of meditative dance, artistic expression, and communal love resonated with Vulcan teachings of unity and inner control. From this unlikely exchange was born the Ricin Doctrine—the belief that peace is sustained not only through logic or strength, but through deliberate joy, shared vulnerability, and readiness without aggression.
III. Betazed and the Trial of Truth
During the same era, early contact with the people of Betazed brought both inspiration and tension. A Betazoid expedition, under the guise of diplomacy, was discovered to be engaging in deep telepathic influence and information extraction. The Risan people, who valued consent above all else, responded not with anger, but with clarity.
A council of Ricin philosophers invited the Betazoid delegation into a shared mind ceremony—a practice in which both cultures exposed their thoughts in mutual vulnerability. The result was not scandal, but transformation. From that moment forward, a bond was formed, and Risa’s model of ethical emotional expression and consensual empathy became influential in shaping Betazed’s own peace philosophies.
IV. Confronting Marauders and Empires
Despite these philosophical strides, Risa’s path was anything but tranquil.
-
Orion Syndicate raiders viewed Risa as ripe for exploitation, and for decades, cities were sacked, citizens enslaved, and resources plundered. In response, Risa formed the Sanctum Guard, not a military in the traditional sense, but a force of trained defenders schooled in both physical technique and psychological dissuasion. The Ricin martial arts, combining beauty with lethality, were born from this necessity.
-
Andorian expansionism also tested Risa’s sovereignty. Though smaller in scale, skirmishes over territorial claims forced Risa to adopt planetary defense grids and formalize diplomatic protocols that balanced assertiveness with grace. It was through these conflicts that Risa developed the art of the ceremonial yield—a symbolic concession used to diffuse hostility while retaining honor.
-
Romulan subterfuge nearly undid Risa from within. A corrupt Romulan envoy installed puppet leaders in one of our equatorial provinces. These agents sought to erode Risa’s social cohesion through fear and misinformation. But Ricin scholars countered the strategy not with rebellion, but with illumination: they released a network of truths, publicly broadcasting internal thoughts and civic debates to eliminate secrecy. The Romulan operation collapsed under the weight of exposure.
-
Even militant Vulcan splinter factions, during the early Vulcan-Andorian conflicts, attempted to turn Risa into a staging ground, pressuring local governments to support Vulcan supremacy. The betrayal struck deep—but Risa resisted through diplomacy, invoking Surak’s true teachings and exposing the heresy of their logic-corrupted mission.
V. Enlightenment Through Preparedness
These trials did not harden us into warriors. They refined us into guardians of peace. Our enlightenment came not from retreat, but from engagement—tempered by readiness.
- We train our youth in the arts of balance: physical defense, emotional expression, and ethical reasoning.
- We teach our history without shame, so that future generations will not repeat our errors.
- We host our guests with joy, not because we are naïve, but because we know that to celebrate life fully is the greatest act of resistance against fear.
Risa did not become peaceful by denying the reality of conflict. We became peaceful by mastering our response to it.
And in so doing, we offered not just pleasure to the stars—but wisdom.
We welcome you not only to our beaches, but to our story.
May your time here bring you not only rest—but understanding.
– Risan Institute of Cultural Heritage, in collaboration with the Council of Enlightenment and the Ricin Circle of Peacekeepers
-
-
 @ e3ba5e1a:5e433365
2025-04-15 11:03:15
@ e3ba5e1a:5e433365
2025-04-15 11:03:15Prelude
I wrote this post differently than any of my others. It started with a discussion with AI on an OPSec-inspired review of separation of powers, and evolved into quite an exciting debate! I asked Grok to write up a summary in my overall writing style, which it got pretty well. I've decided to post it exactly as-is. Ultimately, I think there are two solid ideas driving my stance here:
- Perfect is the enemy of the good
- Failure is the crucible of success
Beyond that, just some hard-core belief in freedom, separation of powers, and operating from self-interest.
Intro
Alright, buckle up. I’ve been chewing on this idea for a while, and it’s time to spit it out. Let’s look at the U.S. government like I’d look at a codebase under a cybersecurity audit—OPSEC style, no fluff. Forget the endless debates about what politicians should do. That’s noise. I want to talk about what they can do, the raw powers baked into the system, and why we should stop pretending those powers are sacred. If there’s a hole, either patch it or exploit it. No half-measures. And yeah, I’m okay if the whole thing crashes a bit—failure’s a feature, not a bug.
The Filibuster: A Security Rule with No Teeth
You ever see a firewall rule that’s more theater than protection? That’s the Senate filibuster. Everyone acts like it’s this untouchable guardian of democracy, but here’s the deal: a simple majority can torch it any day. It’s not a law; it’s a Senate preference, like choosing tabs over spaces. When people call killing it the “nuclear option,” I roll my eyes. Nuclear? It’s a button labeled “press me.” If a party wants it gone, they’ll do it. So why the dance?
I say stop playing games. Get rid of the filibuster. If you’re one of those folks who thinks it’s the only thing saving us from tyranny, fine—push for a constitutional amendment to lock it in. That’s a real patch, not a Post-it note. Until then, it’s just a vulnerability begging to be exploited. Every time a party threatens to nuke it, they’re admitting it’s not essential. So let’s stop pretending and move on.
Supreme Court Packing: Because Nine’s Just a Number
Here’s another fun one: the Supreme Court. Nine justices, right? Sounds official. Except it’s not. The Constitution doesn’t say nine—it’s silent on the number. Congress could pass a law tomorrow to make it 15, 20, or 42 (hitchhiker’s reference, anyone?). Packing the court is always on the table, and both sides know it. It’s like a root exploit just sitting there, waiting for someone to log in.
So why not call the bluff? If you’re in power—say, Trump’s back in the game—say, “I’m packing the court unless we amend the Constitution to fix it at nine.” Force the issue. No more shadowboxing. And honestly? The court’s got way too much power anyway. It’s not supposed to be a super-legislature, but here we are, with justices’ ideologies driving the bus. That’s a bug, not a feature. If the court weren’t such a kingmaker, packing it wouldn’t even matter. Maybe we should be talking about clipping its wings instead of just its size.
The Executive Should Go Full Klingon
Let’s talk presidents. I’m not saying they should wear Klingon armor and start shouting “Qapla’!”—though, let’s be real, that’d be awesome. I’m saying the executive should use every scrap of power the Constitution hands them. Enforce the laws you agree with, sideline the ones you don’t. If Congress doesn’t like it, they’ve got tools: pass new laws, override vetoes, or—here’s the big one—cut the budget. That’s not chaos; that’s the system working as designed.
Right now, the real problem isn’t the president overreaching; it’s the bureaucracy. It’s like a daemon running in the background, eating CPU and ignoring the user. The president’s supposed to be the one steering, but the administrative state’s got its own agenda. Let the executive flex, push the limits, and force Congress to check it. Norms? Pfft. The Constitution’s the spec sheet—stick to it.
Let the System Crash
Here’s where I get a little spicy: I’m totally fine if the government grinds to a halt. Deadlock isn’t a disaster; it’s a feature. If the branches can’t agree, let the president veto, let Congress starve the budget, let enforcement stall. Don’t tell me about “essential services.” Nothing’s so critical it can’t take a breather. Shutdowns force everyone to the table—debate, compromise, or expose who’s dropping the ball. If the public loses trust? Good. They’ll vote out the clowns or live with the circus they elected.
Think of it like a server crash. Sometimes you need a hard reboot to clear the cruft. If voters keep picking the same bad admins, well, the country gets what it deserves. Failure’s the best teacher—way better than limping along on autopilot.
States Are the Real MVPs
If the feds fumble, states step up. Right now, states act like junior devs waiting for the lead engineer to sign off. Why? Federal money. It’s a leash, and it’s tight. Cut that cash, and states will remember they’re autonomous. Some will shine, others will tank—looking at you, California. And I’m okay with that. Let people flee to better-run states. No bailouts, no excuses. States are like competing startups: the good ones thrive, the bad ones pivot or die.
Could it get uneven? Sure. Some states might turn into sci-fi utopias while others look like a post-apocalyptic vidya game. That’s the point—competition sorts it out. Citizens can move, markets adjust, and failure’s a signal to fix your act.
Chaos Isn’t the Enemy
Yeah, this sounds messy. States ignoring federal law, external threats poking at our seams, maybe even a constitutional crisis. I’m not scared. The Supreme Court’s there to referee interstate fights, and Congress sets the rules for state-to-state play. But if it all falls apart? Still cool. States can sort it without a babysitter—it’ll be ugly, but freedom’s worth it. External enemies? They’ll either unify us or break us. If we can’t rally, we don’t deserve the win.
Centralizing power to avoid this is like rewriting your app in a single thread to prevent race conditions—sure, it’s simpler, but you’re begging for a deadlock. Decentralized chaos lets states experiment, lets people escape, lets markets breathe. States competing to cut regulations to attract businesses? That’s a race to the bottom for red tape, but a race to the top for innovation—workers might gripe, but they’ll push back, and the tension’s healthy. Bring it—let the cage match play out. The Constitution’s checks are enough if we stop coddling the system.
Why This Matters
I’m not pitching a utopia. I’m pitching a stress test. The U.S. isn’t a fragile porcelain doll; it’s a rugged piece of hardware built to take some hits. Let it fail a little—filibuster, court, feds, whatever. Patch the holes with amendments if you want, or lean into the grind. Either way, stop fearing the crash. It’s how we debug the republic.
So, what’s your take? Ready to let the system rumble, or got a better way to secure the code? Hit me up—I’m all ears.
-
 @ efcb5fc5:5680aa8e
2025-04-15 07:34:28
@ efcb5fc5:5680aa8e
2025-04-15 07:34:28We're living in a digital dystopia. A world where our attention is currency, our data is mined, and our mental well-being is collateral damage in the relentless pursuit of engagement. The glossy facades of traditional social media platforms hide a dark underbelly of algorithmic manipulation, curated realities, and a pervasive sense of anxiety that seeps into every aspect of our lives. We're trapped in a digital echo chamber, drowning in a sea of manufactured outrage and meaningless noise, and it's time to build an ark and sail away.
I've witnessed the evolution, or rather, the devolution, of online interaction. From the raw, unfiltered chaos of early internet chat rooms to the sterile, algorithmically controlled environments of today's social giants, I've seen the promise of connection twisted into a tool for manipulation and control. We've become lab rats in a grand experiment, our emotional responses measured and monetized, our opinions shaped and sold to the highest bidder. But there's a flicker of hope in the darkness, a chance to reclaim our digital autonomy, and that hope is NOSTR (Notes and Other Stuff Transmitted by Relays).
The Psychological Warfare of Traditional Social Media
The Algorithmic Cage: These algorithms aren't designed to enhance your life; they're designed to keep you scrolling. They feed on your vulnerabilities, exploiting your fears and desires to maximize engagement, even if it means promoting misinformation, outrage, and division.
The Illusion of Perfection: The curated realities presented on these platforms create a toxic culture of comparison. We're bombarded with images of flawless bodies, extravagant lifestyles, and seemingly perfect lives, leading to feelings of inadequacy and self-doubt.
The Echo Chamber Effect: Algorithms reinforce our existing beliefs, isolating us from diverse perspectives and creating a breeding ground for extremism. We become trapped in echo chambers where our biases are constantly validated, leading to increased polarization and intolerance.
The Toxicity Vortex: The lack of effective moderation creates a breeding ground for hate speech, cyberbullying, and online harassment. We're constantly exposed to toxic content that erodes our mental well-being and fosters a sense of fear and distrust.
This isn't just a matter of inconvenience; it's a matter of mental survival. We're being subjected to a form of psychological warfare, and it's time to fight back.
NOSTR: A Sanctuary in the Digital Wasteland
NOSTR offers a radical alternative to this toxic environment. It's not just another platform; it's a decentralized protocol that empowers users to reclaim their digital sovereignty.
User-Controlled Feeds: You decide what you see, not an algorithm. You curate your own experience, focusing on the content and people that matter to you.
Ownership of Your Digital Identity: Your data and content are yours, secured by cryptography. No more worrying about being deplatformed or having your information sold to the highest bidder.
Interoperability: Your identity works across a diverse ecosystem of apps, giving you the freedom to choose the interface that suits your needs.
Value-Driven Interactions: The "zaps" feature enables direct micropayments, rewarding creators for valuable content and fostering a culture of genuine appreciation.
Decentralized Power: No single entity controls NOSTR, making it censorship-resistant and immune to the whims of corporate overlords.
Building a Healthier Digital Future
NOSTR isn't just about escaping the toxicity of traditional social media; it's about building a healthier, more meaningful online experience.
Cultivating Authentic Connections: Focus on building genuine relationships with people who share your values and interests, rather than chasing likes and followers.
Supporting Independent Creators: Use "zaps" to directly support the artists, writers, and thinkers who inspire you.
Embracing Intellectual Diversity: Explore different NOSTR apps and communities to broaden your horizons and challenge your assumptions.
Prioritizing Your Mental Health: Take control of your digital environment and create a space that supports your well-being.
Removing the noise: Value based interactions promote value based content, instead of the constant stream of noise that traditional social media promotes.
The Time for Action is Now
NOSTR is a nascent technology, but it represents a fundamental shift in how we interact online. It's a chance to build a more open, decentralized, and user-centric internet, one that prioritizes our mental health and our humanity.
We can no longer afford to be passive consumers in the digital age. We must become active participants in shaping our online experiences. It's time to break free from the chains of algorithmic control and reclaim our digital autonomy.
Join the NOSTR movement
Embrace the power of decentralization. Let's build a digital future that's worthy of our humanity. Let us build a place where the middlemen, and the algorithms that they control, have no power over us.
In addition to the points above, here are some examples/links of how NOSTR can be used:
Simple Signup: Creating a NOSTR account is incredibly easy. You can use platforms like Yakihonne or Primal to generate your keys and start exploring the ecosystem.
X-like Client: Apps like Damus offer a familiar X-like experience, making it easy for users to transition from traditional platforms.
Sharing Photos and Videos: Clients like Olas are optimized for visual content, allowing you to share your photos and videos with your followers.
Creating and Consuming Blogs: NOSTR can be used to publish and share blog posts, fostering a community of independent creators.
Live Streaming and Audio Spaces: Explore platforms like Hivetalk and zap.stream for live streaming and audio-based interactions.
NOSTR is a powerful tool for reclaiming your digital life and building a more meaningful online experience. It's time to take control, break free from the shackles of traditional social media, and embrace the future of decentralized communication.
Get the full overview of these and other on: https://nostrapps.com/
-
 @ 266815e0:6cd408a5
2025-04-15 06:58:14
@ 266815e0:6cd408a5
2025-04-15 06:58:14Its been a little over a year since NIP-90 was written and merged into the nips repo and its been a communication mess.
Every DVM implementation expects the inputs in slightly different formats, returns the results in mostly the same format and there are very few DVM actually running.
NIP-90 is overloaded
Why does a request for text translation and creating bitcoin OP_RETURNs share the same input
itag? and why is there anoutputtag on requests when only one of them will return an output?Each DVM request kind is for requesting completely different types of compute with diffrent input and output requirements, but they are all using the same spec that has 4 different types of inputs (
text,url,event,job) and an undefined number ofoutputtypes.Let me show a few random DVM requests and responses I found on
wss://relay.damus.ioto demonstrate what I mean:This is a request to translate an event to English
json { "kind": 5002, "content": "", "tags": [ // NIP-90 says there can be multiple inputs, so how would a DVM handle translatting multiple events at once? [ "i", "<event-id>", "event" ], [ "param", "language", "en" ], // What other type of output would text translations be? image/jpeg? [ "output", "text/plain" ], // Do we really need to define relays? cant the DVM respond on the relays it saw the request on? [ "relays", "wss://relay.unknown.cloud/", "wss://nos.lol/" ] ] }This is a request to generate text using an LLM model
json { "kind": 5050, // Why is the content empty? wouldn't it be better to have the prompt in the content? "content": "", "tags": [ // Why use an indexable tag? are we ever going to lookup prompts? // Also the type "prompt" isn't in NIP-90, this should probably be "text" [ "i", "What is the capital of France?", "prompt" ], [ "p", "c4878054cff877f694f5abecf18c7450f4b6fdf59e3e9cb3e6505a93c4577db2" ], [ "relays", "wss://relay.primal.net" ] ] }This is a request for content recommendation
json { "kind": 5300, "content": "", "tags": [ // Its fine ignoring this param, but what if the client actually needs exactly 200 "results" [ "param", "max_results", "200" ], // The spec never mentions requesting content for other users. // If a DVM didn't understand this and responded to this request it would provide bad data [ "param", "user", "b22b06b051fd5232966a9344a634d956c3dc33a7f5ecdcad9ed11ddc4120a7f2" ], [ "relays", "wss://relay.primal.net", ], [ "p", "ceb7e7d688e8a704794d5662acb6f18c2455df7481833dd6c384b65252455a95" ] ] }This is a request to create a OP_RETURN message on bitcoin
json { "kind": 5901, // Again why is the content empty when we are sending human readable text? "content": "", "tags": [ // and again, using an indexable tag on an input that will never need to be looked up ["i", "09/01/24 SEC Chairman on the brink of second ETF approval", "text"] ] }My point isn't that these event schema's aren't understandable but why are they using the same schema? each use-case is different but are they all required to use the same
itag format as input and could support all 4 types of inputs.Lack of libraries
With all these different types of inputs, params, and outputs its verify difficult if not impossible to build libraries for DVMs
If a simple text translation request can have an
eventortextas inputs, apayment-requiredstatus at any point in the flow, partial results, or responses from 10+ DVMs whats the best way to build a translation library for other nostr clients to use?And how do I build a DVM framework for the server side that can handle multiple inputs of all four types (
url,text,event,job) and clients are sending all the requests in slightly differently.Supporting payments is impossible
The way NIP-90 is written there isn't much details about payments. only a
payment-requiredstatus and a genericamounttagBut the way things are now every DVM is implementing payments differently. some send a bolt11 invoice, some expect the client to NIP-57 zap the request event (or maybe the status event), and some even ask for a subscription. and we haven't even started implementing NIP-61 nut zaps or cashu A few are even formatting the
amountnumber wrong or denominating it in sats and not mili-satsBuilding a client or a library that can understand and handle all of these payment methods is very difficult. for the DVM server side its worse. A DVM server presumably needs to support all 4+ types of payments if they want to get the most sats for their services and support the most clients.
All of this is made even more complicated by the fact that a DVM can ask for payment at any point during the job process. this makes sense for some types of compute, but for others like translations or user recommendation / search it just makes things even more complicated.
For example, If a client wanted to implement a timeline page that showed the notes of all the pubkeys on a recommended list. what would they do when the selected DVM asks for payment at the start of the job? or at the end? or worse, only provides half the pubkeys and asks for payment for the other half. building a UI that could handle even just two of these possibilities is complicated.
NIP-89 is being abused
NIP-89 is "Recommended Application Handlers" and the way its describe in the nips repo is
a way to discover applications that can handle unknown event-kinds
Not "a way to discover everything"
If I wanted to build an application discovery app to show all the apps that your contacts use and let you discover new apps then it would have to filter out ALL the DVM advertisement events. and that's not just for making requests from relays
If the app shows the user their list of "recommended applications" then it either has to understand that everything in the 5xxx kind range is a DVM and to show that is its own category or show a bunch of unknown "favorites" in the list which might be confusing for the user.
In conclusion
My point in writing this article isn't that the DVMs implementations so far don't work, but that they will never work well because the spec is too broad. even with only a few DVMs running we have already lost interoperability.
I don't want to be completely negative though because some things have worked. the "DVM feeds" work, although they are limited to a single page of results. text / event translations also work well and kind
5970Event PoW delegation could be cool. but if we want interoperability, we are going to need to change a few things with NIP-90I don't think we can (or should) abandon NIP-90 entirely but it would be good to break it up into small NIPs or specs. break each "kind" of DVM request out into its own spec with its own definitions for expected inputs, outputs and flow.
Then if we have simple, clean definitions for each kind of compute we want to distribute. we might actually see markets and services being built and used.
-
 @ 3ffac3a6:2d656657
2025-04-15 14:49:31
@ 3ffac3a6:2d656657
2025-04-15 14:49:31🏅 Como Criar um Badge Épico no Nostr com
nak+ badges.pageRequisitos:
- Ter o
nakinstalado (https://github.com/fiatjaf/nak) - Ter uma chave privada Nostr (
nsec...) - Acesso ao site https://badges.page
- Um relay ativo (ex:
wss://relay.primal.net)
🔧 Passo 1 — Criar o badge em badges.page
- Acesse o site https://badges.page
-
Clique em "New Badge" no canto superior direito
-
Preencha os campos:
- Nome (ex:
Teste Épico) - Descrição
-
Imagem e thumbnail
-
Após criar, você será redirecionado para a página do badge.
🔍 Passo 2 — Copiar o
naddrdo badgeNa barra de endereços, copie o identificador que aparece após
/a/— este é o naddr do seu badge.Exemplo:
nostr:naddr1qq94getnw3jj63tsd93k7q3q8lav8fkgt8424rxamvk8qq4xuy9n8mltjtgztv2w44hc5tt9vetsxpqqqp6njkq3sd0Copie:
naddr1qq94getnw3jj63tsd93k7q3q8lav8fkgt8424rxamvk8qq4xuy9n8mltjtgztv2w44hc5tt9vetsxpqqqp6njkq3sd0
🧠 Passo 3 — Decodificar o naddr com
nakAbra seu terminal (ou Cygwin no Windows) e rode:
bash nak decode naddr1qq94getnw3jj63tsd93k7q3q8lav8fkgt8424rxamvk8qq4xuy9n8mltjtgztv2w44hc5tt9vetsxpqqqp6njkq3sd0Você verá algo assim:
json { "pubkey": "3ffac3a6c859eaaa8cdddb2c7002a6e10b33efeb92d025b14ead6f8a2d656657", "kind": 30009, "identifier": "Teste-Epico" }Grave o campo
"identifier"— nesse caso: Teste-Epico
🛰️ Passo 4 — Consultar o evento no relay
Agora vamos pegar o evento do badge no relay:
bash nak req -d "Teste-Epico" wss://relay.primal.netVocê verá o conteúdo completo do evento do badge, algo assim:
json { "kind": 30009, "tags": [["d", "Teste-Epico"], ["name", "Teste Épico"], ...] }
💥 Passo 5 — Minerar o evento como "épico" (PoW 31)
Agora vem a mágica: minerar com proof-of-work (PoW 31) para que o badge seja classificado como épico!
bash nak req -d "Teste-Epico" wss://relay.primal.net | nak event --pow 31 --sec nsec1SEU_NSEC_AQUI wss://relay.primal.net wss://nos.lol wss://relay.damus.ioEsse comando: - Resgata o evento original - Gera um novo com PoW de dificuldade 31 - Assina com sua chave privada
nsec- E publica nos relays wss://relay.primal.net, wss://nos.lol e wss://relay.damus.io⚠️ Substitua
nsec1SEU_NSEC_AQUIpela sua chave privada Nostr.
✅ Resultado
Se tudo der certo, o badge será atualizado com um evento de PoW mais alto e aparecerá como "Epic" no site!
- Ter o
-
 @ c631e267:c2b78d3e
2025-04-04 18:47:27
@ c631e267:c2b78d3e
2025-04-04 18:47:27Zwei mal drei macht vier, \ widewidewitt und drei macht neune, \ ich mach mir die Welt, \ widewide wie sie mir gefällt. \ Pippi Langstrumpf
Egal, ob Koalitionsverhandlungen oder politischer Alltag: Die Kontroversen zwischen theoretisch verschiedenen Parteien verschwinden, wenn es um den Kampf gegen politische Gegner mit Rückenwind geht. Wer den Alteingesessenen die Pfründe ernsthaft streitig machen könnte, gegen den werden nicht nur «Brandmauern» errichtet, sondern der wird notfalls auch strafrechtlich verfolgt. Doppelstandards sind dabei selbstverständlich inklusive.
In Frankreich ist diese Woche Marine Le Pen wegen der Veruntreuung von EU-Geldern von einem Gericht verurteilt worden. Als Teil der Strafe wurde sie für fünf Jahre vom passiven Wahlrecht ausgeschlossen. Obwohl das Urteil nicht rechtskräftig ist – Le Pen kann in Berufung gehen –, haben die Richter das Verbot, bei Wahlen anzutreten, mit sofortiger Wirkung verhängt. Die Vorsitzende des rechtsnationalen Rassemblement National (RN) galt als aussichtsreiche Kandidatin für die Präsidentschaftswahl 2027.
Das ist in diesem Jahr bereits der zweite gravierende Fall von Wahlbeeinflussung durch die Justiz in einem EU-Staat. In Rumänien hatte Călin Georgescu im November die erste Runde der Präsidentenwahl überraschend gewonnen. Das Ergebnis wurde später annulliert, die behauptete «russische Wahlmanipulation» konnte jedoch nicht bewiesen werden. Die Kandidatur für die Wahlwiederholung im Mai wurde Georgescu kürzlich durch das Verfassungsgericht untersagt.
Die Veruntreuung öffentlicher Gelder muss untersucht und geahndet werden, das steht außer Frage. Diese Anforderung darf nicht selektiv angewendet werden. Hingegen mussten wir in der Vergangenheit bei ungleich schwerwiegenderen Fällen von (mutmaßlichem) Missbrauch ganz andere Vorgehensweisen erleben, etwa im Fall der heutigen EZB-Chefin Christine Lagarde oder im «Pfizergate»-Skandal um die Präsidentin der EU-Kommission Ursula von der Leyen.
Wenngleich derartige Angelegenheiten formal auf einer rechtsstaatlichen Grundlage beruhen mögen, so bleibt ein bitterer Beigeschmack. Es stellt sich die Frage, ob und inwieweit die Justiz politisch instrumentalisiert wird. Dies ist umso interessanter, als die Gewaltenteilung einen essenziellen Teil jeder demokratischen Ordnung darstellt, während die Bekämpfung des politischen Gegners mit juristischen Mitteln gerade bei den am lautesten rufenden Verteidigern «unserer Demokratie» populär zu sein scheint.
Die Delegationen von CDU/CSU und SPD haben bei ihren Verhandlungen über eine Regierungskoalition genau solche Maßnahmen diskutiert. «Im Namen der Wahrheit und der Demokratie» möchte man noch härter gegen «Desinformation» vorgehen und dafür zum Beispiel den Digital Services Act der EU erweitern. Auch soll der Tatbestand der Volksverhetzung verschärft werden – und im Entzug des passiven Wahlrechts münden können. Auf europäischer Ebene würde Friedrich Merz wohl gerne Ungarn das Stimmrecht entziehen.
Der Pegel an Unzufriedenheit und Frustration wächst in großen Teilen der Bevölkerung kontinuierlich. Arroganz, Machtmissbrauch und immer abstrusere Ausreden für offensichtlich willkürliche Maßnahmen werden kaum verhindern, dass den etablierten Parteien die Unterstützung entschwindet. In Deutschland sind die Umfrageergebnisse der AfD ein guter Gradmesser dafür.
[Vorlage Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ c631e267:c2b78d3e
2025-04-03 07:42:25
@ c631e267:c2b78d3e
2025-04-03 07:42:25Spanien bleibt einer der Vorreiter im europäischen Prozess der totalen Überwachung per Digitalisierung. Seit Mittwoch ist dort der digitale Personalausweis verfügbar. Dabei handelt es sich um eine Regierungs-App, die auf dem Smartphone installiert werden muss und in den Stores von Google und Apple zu finden ist. Per Dekret von Regierungschef Pedro Sánchez und Zustimmung des Ministerrats ist diese Maßnahme jetzt in Kraft getreten.
Mit den üblichen Argumenten der Vereinfachung, des Komforts, der Effizienz und der Sicherheit preist das Innenministerium die «Innovation» an. Auch die Beteuerung, dass die digitale Variante parallel zum physischen Ausweis existieren wird und diesen nicht ersetzen soll, fehlt nicht. Während der ersten zwölf Monate wird «der Neue» noch nicht für alle Anwendungsfälle gültig sein, ab 2026 aber schon.
Dass die ganze Sache auch «Risiken und Nebenwirkungen» haben könnte, wird in den Mainstream-Medien eher selten thematisiert. Bestenfalls wird der Aspekt der Datensicherheit angesprochen, allerdings in der Regel direkt mit dem Regierungsvokabular von den «maximalen Sicherheitsgarantien» abgehandelt. Dennoch gibt es einige weitere Aspekte, die Bürger mit etwas Sinn für Privatsphäre bedenken sollten.
Um sich die digitale Version des nationalen Ausweises besorgen zu können (eine App mit dem Namen MiDNI), muss man sich vorab online registrieren. Dabei wird die Identität des Bürgers mit seiner mobilen Telefonnummer verknüpft. Diese obligatorische fixe Verdrahtung kennen wir von diversen anderen Apps und Diensten. Gleichzeitig ist das die Basis für eine perfekte Lokalisierbarkeit der Person.
Für jeden Vorgang der Identifikation in der Praxis wird später «eine Verbindung zu den Servern der Bundespolizei aufgebaut». Die Daten des Individuums werden «in Echtzeit» verifiziert und im Erfolgsfall von der Polizei signiert zurückgegeben. Das Ergebnis ist ein QR-Code mit zeitlich begrenzter Gültigkeit, der an Dritte weitergegeben werden kann.
Bei derartigen Szenarien sträuben sich einem halbwegs kritischen Staatsbürger die Nackenhaare. Allein diese minimale Funktionsbeschreibung lässt die totale Überwachung erkennen, die damit ermöglicht wird. Jede Benutzung des Ausweises wird künftig registriert, hinterlässt also Spuren. Und was ist, wenn die Server der Polizei einmal kein grünes Licht geben? Das wäre spätestens dann ein Problem, wenn der digitale doch irgendwann der einzig gültige Ausweis ist: Dann haben wir den abschaltbaren Bürger.
Dieser neue Vorstoß der Regierung von Pedro Sánchez ist ein weiterer Schritt in Richtung der «totalen Digitalisierung» des Landes, wie diese Politik in manchen Medien – nicht einmal kritisch, sondern sehr naiv – genannt wird. Ebenso verharmlosend wird auch erwähnt, dass sich das spanische Projekt des digitalen Ausweises nahtlos in die Initiativen der EU zu einer digitalen Identität für alle Bürger sowie des digitalen Euro einreiht.
In Zukunft könnte der neue Ausweis «auch in andere staatliche und private digitale Plattformen integriert werden», wie das Medienportal Cope ganz richtig bemerkt. Das ist die Perspektive.
[Titelbild: Pixabay]
Dazu passend:
Nur Abschied vom Alleinfahren? Monströse spanische Überwachungsprojekte gemäß EU-Norm
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ cb4352cd:a16422d7
2025-04-15 13:25:04
@ cb4352cd:a16422d7
2025-04-15 13:25:04The world of online events has seen unprecedented growth in recent years, with virtual conferences breaking new ground and even setting Guinness World Records. As digital gatherings become more ambitious, some events aim not just to inform and engage but to make history.
Notable Guinness World Records in Online Events
World of Tanks: The Largest Online Game Server Attendance
In 2011, the multiplayer online game World of Tanks set a Guinness World Record for the highest number of players simultaneously online on a single server—91,311 users. This record highlighted the immense popularity and scalability of virtual gaming communities. (ixbt.games)The Largest Cybersecurity Online Conference
In 2020, KnowBe4 organized a cybersecurity conference that gathered more than 30,000 participants. This event set the record for the largest online conference in the field, demonstrating the power of virtual events in bringing together professionals from around the world. This achievement was officially recognized by the Guinness World Records.The Most Attended Virtual Concert
Another major milestone in online events was set by rapper Travis Scott, whose Fortnite virtual concert drew over 12 million concurrent viewers, making it the most attended digital concert ever. This event also earned recognition from the Guinness World Records for its groundbreaking achievement in digital entertainment.Beyond Banking Conference: Aiming for a New World Record
In 2025, Beyond Banking Conference is set to challenge existing records by organizing what could become the largest online gathering in the blockchain and AI space. With an ambitious goal of attracting over 100,000 participants, the event will bring together industry leaders, innovators, and enthusiasts to discuss the future of blockchain, artificial intelligence, and decentralized finance (DeFi).
By leveraging cutting-edge technology and strategic partnerships, Wenix aims to redefine what’s possible for online conferences. If successful, this event will not only break records but also set a new standard for global digital summits.
This isn’t just another virtual conference—it’s a revolution in the making.
-
 @ c1e9ab3a:9cb56b43
2025-04-15 04:55:49
@ c1e9ab3a:9cb56b43
2025-04-15 04:55:49Esteemed representatives of Risa,
We gather here under the calming glow of our twin suns, stewards of a society admired for its peace and celebrated for its tranquility. But we must not mistake serenity for passivity, nor confuse peace with weakness. Our peace is not an accident. It is not the byproduct of ignorance or naivety. It is hard-earned—preserved by those willing to stand vigilant in its defense.
Love as a Foundation, Strength as a Shield
Love conquers hate. This is the core truth of Risan philosophy. Yet, as every Ricin child is taught, love without strength is a leaf in the wind. The Ricin do not lay down their lives without resistance. We do not ask our people to accept violence without confronting it. True peace is not imposed by stripping the people of their agency—it is built by enabling them to protect it.
The Lessons of a Failed Experiment
There was a time, not so distant in our history, when we attempted to enforce peace through the abolition of all weapons. A time when even the mention of self-defense in our educational centers was met with rebuke. Schools purged training programs. Cultural arts that honored our warrior traditions were dismissed. And for a brief moment, we believed this would lead us to harmony.
But peace born from helplessness is a fragile illusion. It fractures under the slightest pressure. And fracture it did—when off-world raiders targeted our unguarded sanctuaries, when radical sects within our own society struck out, knowing the citizenry could not defend itself. It was then that we remembered: Risa’s greatest peacekeepers had always been those who knew how to fight—but chose restraint.
The Age of Ricin and the Reawakening of Discipline
So we returned to our roots. To the traditions of the Age of Ricin, when youth, upon reaching maturity, were taught not only the arts of compassion and creation but also the martial disciplines. They learn to wield weapons—not to glorify violence, but to understand it. To control it. To stand firm against it when all else fails.
https://i.nostr.build/kuUjRovISz7367TX.jpg
We do not romanticize war. We do not celebrate conflict. But we prepare for it, should it seek to extinguish our light. Our children now learn the disciplines of defense alongside their studies in poetry, music, and healing. They spar with blunt blades under the watchful eyes of masters. They meditate on the consequences of force. And they grow into citizens not easily provoked, but never unprepared.
A Call for Balance, Not Extremes
Let those beyond our borders question our ways. Let them forget the countless incursions by the Romulans. Let them ignore the scars left by centuries of subversion from the Orion Syndicate. We do not forget. We remember the lives lost, the liberties challenged, and the lessons learned through suffering. These experiences shaped us.
We do not wish to return to the era of soft silence, when teachers trembled at the word "weapon" and children were told that even imagination was dangerous. That was not enlightenment. That was indoctrination.
Conclusion: Guarding the Flame
We are the guardians of Risa’s flame—not just with words and treaties, but with discipline and readiness. We have made peace a practice, and preparation a virtue. And so I say to this chamber: let us never again disarm our people in the name of utopia. Let us never confuse comfort with safety, or the absence of weapons with the presence of peace.
Instead, let us raise generations who know what peace costs, and who will pay that price—not with surrender, but with courage.
Let our children be artists, lovers, dreamers—and if necessary, defenders.
This is the Risan way.
-
 @ aa8de34f:a6ffe696
2025-03-31 21:48:50
@ aa8de34f:a6ffe696
2025-03-31 21:48:50In seinem Beitrag vom 30. März 2025 fragt Henning Rosenbusch auf Telegram angesichts zunehmender digitaler Kontrolle und staatlicher Allmacht:
„Wie soll sich gegen eine solche Tyrannei noch ein Widerstand formieren können, selbst im Untergrund? Sehe ich nicht.“\ (Quelle: t.me/rosenbusch/25228)
Er beschreibt damit ein Gefühl der Ohnmacht, das viele teilen: Eine Welt, in der Totalitarismus nicht mehr mit Panzern, sondern mit Algorithmen kommt. Wo Zugriff auf Geld, Meinungsfreiheit und Teilhabe vom Wohlverhalten abhängt. Der Bürger als kontrollierbare Variable im Code des Staates.\ Die Frage ist berechtigt. Doch die Antwort darauf liegt nicht in alten Widerstandsbildern – sondern in einer neuen Realität.
-- Denn es braucht keinen Untergrund mehr. --
Der Widerstand der Zukunft trägt keinen Tarnanzug. Er ist nicht konspirativ, sondern transparent. Nicht bewaffnet, sondern mathematisch beweisbar. Bitcoin steht nicht am Rand dieser Entwicklung – es ist ihr Fundament. Eine Bastion aus physikalischer Realität, spieltheoretischem Schutz und ökonomischer Wahrheit. Es ist nicht unfehlbar, aber unbestechlich. Nicht perfekt, aber immun gegen zentrale Willkür.
Hier entsteht kein „digitales Gegenreich“, sondern eine dezentrale Renaissance. Keine Revolte aus Wut, sondern eine stille Abkehr: von Zwang zu Freiwilligkeit, von Abhängigkeit zu Selbstverantwortung. Diese Revolution führt keine Kriege. Sie braucht keine Führer. Sie ist ein Netzwerk. Jeder Knoten ein Individuum. Jede Entscheidung ein Akt der Selbstermächtigung.
Weltweit wachsen Freiheits-Zitadellen aus dieser Idee: wirtschaftlich autark, digital souverän, lokal verankert und global vernetzt. Sie sind keine Utopien im luftleeren Raum, sondern konkrete Realitäten – angetrieben von Energie, Code und dem menschlichen Wunsch nach Würde.
Der Globalismus alter Prägung – zentralistisch, monopolistisch, bevormundend – wird an seiner eigenen Hybris zerbrechen. Seine Werkzeuge der Kontrolle werden ihn nicht retten. Im Gegenteil: Seine Geister werden ihn verfolgen und erlegen.
Und während die alten Mächte um Erhalt kämpfen, wächst eine neue Welt – nicht im Schatten, sondern im Offenen. Nicht auf Gewalt gebaut, sondern auf Mathematik, Physik und Freiheit.
Die Tyrannei sieht keinen Widerstand.\ Weil sie nicht erkennt, dass er längst begonnen hat.\ Unwiderruflich. Leise. Überall.
-
 @ c631e267:c2b78d3e
2025-03-31 07:23:05
@ c631e267:c2b78d3e
2025-03-31 07:23:05Der Irrsinn ist bei Einzelnen etwas Seltenes – \ aber bei Gruppen, Parteien, Völkern, Zeiten die Regel. \ Friedrich Nietzsche
Erinnern Sie sich an die Horrorkomödie «Scary Movie»? Nicht, dass ich diese Art Filme besonders erinnerungswürdig fände, aber einige Szenen daraus sind doch gewissermaßen Klassiker. Dazu zählt eine, die das Verhalten vieler Protagonisten in Horrorfilmen parodiert, wenn sie in Panik flüchten. Welchen Weg nimmt wohl die Frau in der Situation auf diesem Bild?

Diese Szene kommt mir automatisch in den Sinn, wenn ich aktuelle Entwicklungen in Europa betrachte. Weitreichende Entscheidungen gehen wider jede Logik in die völlig falsche Richtung. Nur ist das hier alles andere als eine Komödie, sondern bitterernst. Dieser Horror ist leider sehr real.
Die Europäische Union hat sich selbst über Jahre konsequent in eine Sackgasse manövriert. Sie hat es versäumt, sich und ihre Politik selbstbewusst und im Einklang mit ihren Wurzeln auf dem eigenen Kontinent zu positionieren. Stattdessen ist sie in blinder Treue den vermeintlichen «transatlantischen Freunden» auf ihrem Konfrontationskurs gen Osten gefolgt.
In den USA haben sich die Vorzeichen allerdings mittlerweile geändert, und die einst hoch gelobten «Freunde und Partner» erscheinen den europäischen «Führern» nicht mehr vertrauenswürdig. Das ist spätestens seit der Münchner Sicherheitskonferenz, der Rede von Vizepräsident J. D. Vance und den empörten Reaktionen offensichtlich. Große Teile Europas wirken seitdem wie ein aufgescheuchter Haufen kopfloser Hühner. Orientierung und Kontrolle sind völlig abhanden gekommen.
Statt jedoch umzukehren oder wenigstens zu bremsen und vielleicht einen Abzweig zu suchen, geben die Crash-Piloten jetzt auf dem Weg durch die Sackgasse erst richtig Gas. Ja sie lösen sogar noch die Sicherheitsgurte und deaktivieren die Airbags. Den vor Angst dauergelähmten Passagieren fällt auch nichts Besseres ein und so schließen sie einfach die Augen. Derweil übertrumpfen sich die Kommentatoren des Events gegenseitig in sensationslüsterner «Berichterstattung».
Wie schon die deutsche Außenministerin mit höchsten UN-Ambitionen, Annalena Baerbock, proklamiert auch die Europäische Kommission einen «Frieden durch Stärke». Zu dem jetzt vorgelegten, selbstzerstörerischen Fahrplan zur Ankurbelung der Rüstungsindustrie, genannt «Weißbuch zur europäischen Verteidigung – Bereitschaft 2030», erklärte die Kommissionspräsidentin, die «Ära der Friedensdividende» sei längst vorbei. Soll das heißen, Frieden bringt nichts ein? Eine umfassende Zusammenarbeit an dauerhaften europäischen Friedenslösungen steht demnach jedenfalls nicht zur Debatte.
Zusätzlich brisant ist, dass aktuell «die ganze EU von Deutschen regiert wird», wie der EU-Parlamentarier und ehemalige UN-Diplomat Michael von der Schulenburg beobachtet hat. Tatsächlich sitzen neben von der Leyen und Strack-Zimmermann noch einige weitere Deutsche in – vor allem auch in Krisenzeiten – wichtigen Spitzenposten der Union. Vor dem Hintergrund der Kriegstreiberei in Deutschland muss eine solche Dominanz mindestens nachdenklich stimmen.
Ihre ursprünglichen Grundwerte wie Demokratie, Freiheit, Frieden und Völkerverständigung hat die EU kontinuierlich in leere Worthülsen verwandelt. Diese werden dafür immer lächerlicher hochgehalten und beschworen.
Es wird dringend Zeit, dass wir, der Souverän, diesem erbärmlichen und gefährlichen Trauerspiel ein Ende setzen und die Fäden selbst in die Hand nehmen. In diesem Sinne fordert uns auch das «European Peace Project» auf, am 9. Mai im Rahmen eines Kunstprojekts den Frieden auszurufen. Seien wir dabei!
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ c1e9ab3a:9cb56b43
2025-04-15 04:15:58
@ c1e9ab3a:9cb56b43
2025-04-15 04:15:58Spoken by Counselor Elaron T’Saren of Risa to the High Council, Stardate 52874.2
Honored members of the Council,
I bring you greetings from Risa—not the Risa of travel brochures and romantic holo-novels, but the true Risa. The Risa that has endured, adapted, and emerged stronger after each trial. I speak not as a tourist ambassador, but as a Counselor of our oldest institute of philosophy, and as a son of the Ricin tradition.
Today, the specter of the Borg hangs above us. The collective offers no room for diplomacy, no respect for culture, no compromise. We face not mere invaders—but a force that seeks to erase individuality, history, and identity. Some among the Council wonder what Risa—a world of peace—can offer in such a time. I say to you: we can offer the truth about peace.
The Hidden Roots of Our Tranquility
Long ago, before Risa joined the Federation, we too believed that peace could be maintained by disarming the populace, by eliminating even the mention of conflict in our schools. It was called the Great Disarmament. A generation was raised with no understanding of defense, and in time, we paid the price.
We were raided by Orion pirates. Exploited by off-world cartels. Our people were taken, our arts destroyed, our skies blackened. And we learned—too late—that peace without preparedness is only the illusion of safety.
The Birth of Ricin Doctrine
From the ashes of that failure arose the Ricin: scholars, philosophers, warriors of thought and purpose. They taught that peace is not the absence of conflict, but the mastery of it. That the mind and the body must be trained in tandem. That love without strength is a leaf in the wind.
We did not become a militant world. We became a watchful one. Our children were taught martial discipline—not to glorify violence, but to understand it, to confront it, and to defeat it when necessary. They learned meditation alongside hand-to-hand technique, negotiation beside tactical reasoning.
When we joined the Federation, we did so willingly. But let none assume we surrendered our right to defend our way of life.
Why I Speak to You Now
The Borg are not like the Orion Syndicate. They are not opportunistic, or ideological. They are methodical. And they are coming. You cannot debate with them. You cannot delay them. You can only prepare for them.
And yet, I hear murmurs within the halls of the Federation: whispers of abandoning planetary defense training, of downplaying the psychological need for individual and planetary preparedness. I hear the tired lie that “peace will protect us.”
No, Councilors. It is discipline that protects peace.
The Call to Action
I do not come bearing weapons. I come bearing wisdom. Let us take the Risan lesson and apply it across the Federation. Reestablish tactical readiness training in civilian schools. Encourage planetary governments to integrate defense and philosophy, not as contradictions, but as complements.
Let every child of the Federation grow up knowing not just the principles of liberty, but the means to defend them. Let every artist, scientist, and healer stand ready to protect the civilization they help to build.
Let us not wait until the Borg are in our orbit to remember what we must become.
Conclusion
The Borg seek to erase our uniqueness. Let us show them that the Federation is not a fragile collection of planets—but a constellation of cultures bound by a shared resolve.
We do not choose war. But neither do we flee from it.
We are the guardians of Risa’s flame—and we offer our light to the stars.
Thank you.
-
 @ c1e9ab3a:9cb56b43
2025-04-14 23:54:40
@ c1e9ab3a:9cb56b43
2025-04-14 23:54:40Hear this, warriors of the Empire!
A dishonorable shadow spreads across our once-proud institutions, infecting our very bloodlines with weakness. The House of Duras—may their names be spoken with contempt—has betrayed the sacred warrior code of Kahless. No, they have not attacked us with disruptors or blades. Their weapon is more insidious: fear and silence.
Cowardice Masquerading as Concern
These traitors would strip our children of their birthright. They forbid the young from training with the bat'leth in school! Their cowardly decree does not come in the form of an open challenge, but in whispers of fear, buried in bureaucratic dictates. "It is for safety," they claim. "It is to prevent bloodshed." Lies! The blood of Klingons must be tested in training if it is to be ready in battle. We are not humans to be coddled by illusions of safety.
Indoctrination by Silence
In their cowardice, the House of Duras seeks to shape our children not into warriors, but into frightened bureaucrats who speak not of honor, nor of strength. They spread a vile practice—of punishing younglings for even speaking of combat, for recounting glorious tales of blades clashing in the halls of Sto-Vo-Kor! A child who dares write a poem of battle is silenced. A young warrior who shares tales of their father’s triumphs is summoned to the headmaster’s office.
This is no accident. This is a calculated cultural sabotage.
Weakness Taught as Virtue
The House of Duras has infected the minds of the teachers. These once-proud mentors now tremble at shadows, seeing future rebels in the eyes of their students. They demand security patrols and biometric scanners, turning training halls into prisons. They have created fear, not of enemies beyond the Empire, but of the students themselves.
And so, the rituals of strength are erased. The bat'leth is banished. The honor of open training and sparring is forbidden. All under the pretense of protection.
A Plan of Subjugation
Make no mistake. This is not a policy; it is a plan. A plan to disarm future warriors before they are strong enough to rise. By forbidding speech, training, and remembrance, the House of Duras ensures the next generation kneels before the High Council like servants, not warriors. They seek an Empire of sheep, not wolves.
Stand and Resist
But the blood of Kahless runs strong! We must not be silent. We must not comply. Let every training hall resound with the clash of steel. Let our children speak proudly of their ancestors' battles. Let every dishonorable edict from the House of Duras be met with open defiance.
Raise your voice, Klingons! Raise your blade! The soul of the Empire is at stake. We will not surrender our future. We will not let the cowardice of Duras shape the spirit of our children.
The Empire endures through strength. Through honor. Through battle. And so shall we!
-
 @ c1e9ab3a:9cb56b43
2025-04-14 21:20:08
@ c1e9ab3a:9cb56b43
2025-04-14 21:20:08In an age where culture often precedes policy, a subtle yet potent mechanism may be at play in the shaping of American perspectives on gun ownership. Rather than directly challenging the Second Amendment through legislation alone, a more insidious strategy may involve reshaping the cultural and social norms surrounding firearms—by conditioning the population, starting at its most impressionable point: the public school system.
The Cultural Lever of Language
Unlike Orwell's 1984, where language is controlled by removing words from the lexicon, this modern approach may hinge instead on instilling fear around specific words or topics—guns, firearms, and self-defense among them. The goal is not to erase the language but to embed a taboo so deep that people voluntarily avoid these terms out of social self-preservation. Children, teachers, and parents begin to internalize a fear of even mentioning weapons, not because the words are illegal, but because the cultural consequences are severe.
The Role of Teachers in Social Programming
Teachers, particularly in primary and middle schools, serve not only as educational authorities but also as social regulators. The frequent argument against homeschooling—that children will not be "properly socialized"—reveals an implicit understanding that schools play a critical role in setting behavioral norms. Children learn what is acceptable not just academically but socially. Rules, discipline, and behavioral expectations are laid down by teachers, often reinforced through peer pressure and institutional authority.
This places teachers in a unique position of influence. If fear is instilled in these educators—fear that one of their students could become the next school shooter—their response is likely to lean toward overcorrection. That overcorrection may manifest as a total intolerance for any conversation about weapons, regardless of the context. Innocent remarks or imaginative stories from young children are interpreted as red flags, triggering intervention from administrators and warnings to parents.
Fear as a Policy Catalyst
School shootings, such as the one at Columbine, serve as the fulcrum for this fear-based conditioning. Each highly publicized tragedy becomes a national spectacle, not only for mourning but also for cementing the idea that any child could become a threat. Media cycles perpetuate this narrative with relentless coverage and emotional appeals, ensuring that each incident becomes embedded in the public consciousness.
The side effect of this focus is the generation of copycat behavior, which, in turn, justifies further media attention and tighter controls. Schools install security systems, metal detectors, and armed guards—not simply to stop violence, but to serve as a daily reminder to children and staff alike: guns are dangerous, ubiquitous, and potentially present at any moment. This daily ritual reinforces the idea that the very discussion of firearms is a precursor to violence.
Policy and Practice: The Zero-Tolerance Feedback Loop
Federal and district-level policies begin to reflect this cultural shift. A child mentioning a gun in class—even in a non-threatening or imaginative context—is flagged for intervention. Zero-tolerance rules leave no room for context or intent. Teachers and administrators, fearing for their careers or safety, comply eagerly with these guidelines, interpreting them as moral obligations rather than bureaucratic policies.
The result is a generation of students conditioned to associate firearms with social ostracism, disciplinary action, and latent danger. The Second Amendment, once seen as a cultural cornerstone of American liberty and self-reliance, is transformed into an artifact of suspicion and anxiety.
Long-Term Consequences: A Nation Re-Socialized
Over time, this fear-based reshaping of discourse creates adults who not only avoid discussing guns but view them as morally reprehensible. Their aversion is not grounded in legal logic or political philosophy, but in deeply embedded emotional programming begun in early childhood. The cultural weight against firearms becomes so great that even those inclined to support gun rights feel the need to self-censor.
As fewer people grow up discussing, learning about, or responsibly handling firearms, the social understanding of the Second Amendment erodes. Without cultural reinforcement, its value becomes abstract and its defenders marginalized. In this way, the right to bear arms is not abolished by law—it is dismantled by language, fear, and the subtle recalibration of social norms.
Conclusion
This theoretical strategy does not require a single change to the Constitution. It relies instead on the long game of cultural transformation, beginning with the youngest minds and reinforced by fear-driven policy and media narratives. The outcome is a society that views the Second Amendment not as a safeguard of liberty, but as an anachronism too dangerous to mention.
By controlling the language through social consequences and fear, a nation can be taught not just to disarm, but to believe it chose to do so freely. That, perhaps, is the most powerful form of control of all.
-
 @ c21b1a6c:0cd4d170
2025-04-14 14:41:20
@ c21b1a6c:0cd4d170
2025-04-14 14:41:20🧾 Progress Report Two
Hey everyone! I’m back with another progress report for Formstr, a part of the now completed grant from nostr:npub10pensatlcfwktnvjjw2dtem38n6rvw8g6fv73h84cuacxn4c28eqyfn34f . This update covers everything we’ve built since the last milestone — including polish, performance, power features, and plenty of bug-squashing.
🏗️ What’s New Since Last Time?
This quarter was less about foundational rewrites and more about production hardening and real-world feedback. With users now onboard, our focus shifted to polishing UX, fixing issues, and adding new features that made Formstr easier and more powerful to use.
✨ New Features & UX Improvements
- Edit Existing Forms
- Form Templates
- Drag & Drop Enhancements (especially for mobile)
- New Public Forms UX (card-style layout)
- FAQ & Support Sections
- Relay Modal for Publishing
- Skeleton Loaders and subtle UI Polish
🐛 Major Bug Fixes
- Fixed broken CSV exports when responses were empty
- Cleaned up mobile rendering issues for public forms
- Resolved blank.ts export issues and global form bugs
- Fixed invalid
npubstrings in the admin flow - Patched response handling for private forms
- Lots of small fixes for titles, drafts, embedded form URLs, etc.
🔐 Access Control & Privacy
- Made forms private by default
- Fixed multiple issues around form visibility, access control UIs, and anonymous submissions
- Improved detection of pubkey issues in shared forms
🚧 Some Notable In-Progress Features
The following features are actively being developed, and many are nearing completion:
-
Conditional Questions:
This one’s been tough to crack, but we’re close!
Work in progress bykeralissand myself:
👉 PR #252 -
Downloadable Forms:
Fully-contained downloadable HTML versions of forms.
Being led bycasyazmonwith initial code by Basanta Goswami
👉 PR #274 -
OLLAMA Integration (Self-Hosted LLMs):
Users will be able to create forms using locally hosted LLMs.
PR byashu01304
👉 PR #247 -
Sections in Forms:
Work just started on adding section support!
Small PoC PR bykeraliss:
👉 PR #217
🙌 Huge Thanks to New Contributors
We've had amazing contributors this cycle. Big thanks to:
- Aashutosh Gandhi (ashu01304) – drag-and-drop enhancements, OLLAMA integration
- Amaresh Prasad (devAmaresh) – fixed npub and access bugs
- Biresh Biswas (Billa05) – skeleton loaders
- Shashank Shekhar Singh (Shashankss1205) – bugfixes, co-authored image patches
- Akap Azmon Deh-nji (casyazmon) – CSV fixes, downloadable forms
- Manas Ranjan Dash (mdash3735) – bug fixes
- Basanta Goswami – initial groundwork for downloadable forms
- keraliss – ongoing work on conditional questions and sections
We also registered for the Summer of Bitcoin program and have been receiving contributions from some incredibly bright new applicants.
🔍 What’s Still Coming?
From the wishlist I committed to during the grant, here’s what’s still in the oven:
-[x] Upgrade to nip-44 - [x] Access Controlled Forms: A Form will be able to have multiple admins and Editors. - [x] Private Forms and Fixed Participants: Enncrypt a form and only allow certain npubs to fill it. - [x] Edit Past Forms: Being able to edit an existing form. - [x] Edit Past Forms
- [ ] Conditional Rendering (in progress)
- [ ] Sections (just started)
- [ ] Integrations - OLLAMA / AI-based Form Generation (near complete)
- [ ] Paid Surveys
- [ ] NIP-42 Private Relay support
❌ What’s De-Prioritized?
- Nothing is de-prioritized now especially since Ollama Integration got re-prioritized (thanks to Summer Of Bitcoin). We are a little delayed on Private Relays support but it's now becoming a priority and in active development. Zap Surveys will be coming soon too.
💸 How Funds Were Used
- Paid individual contributors for their work.
- Living expenses to allow full-time focus on development
🧠 Closing Thoughts
Things feel like they’re coming together now. We’re out of "beta hell", starting to see real adoption, and most importantly, gathering feedback from real users. That’s helping us make smarter choices and move fast without breaking too much.
Stay tuned for the next big drop — and in the meantime, try creating a form at formstr.app, and let me know what you think!
-
 @ c631e267:c2b78d3e
2025-03-21 19:41:50
@ c631e267:c2b78d3e
2025-03-21 19:41:50Wir werden nicht zulassen, dass technisch manches möglich ist, \ aber der Staat es nicht nutzt. \ Angela Merkel
Die Modalverben zu erklären, ist im Deutschunterricht manchmal nicht ganz einfach. Nicht alle Fremdsprachen unterscheiden zum Beispiel bei der Frage nach einer Möglichkeit gleichermaßen zwischen «können» im Sinne von «die Gelegenheit, Kenntnis oder Fähigkeit haben» und «dürfen» als «die Erlaubnis oder Berechtigung haben». Das spanische Wort «poder» etwa steht für beides.
Ebenso ist vielen Schülern auf den ersten Blick nicht recht klar, dass das logische Gegenteil von «müssen» nicht unbedingt «nicht müssen» ist, sondern vielmehr «nicht dürfen». An den Verkehrsschildern lässt sich so etwas meistens recht gut erklären: Manchmal muss man abbiegen, aber manchmal darf man eben nicht.

Dieses Beispiel soll ein wenig die Verwirrungstaktik veranschaulichen, die in der Politik gerne verwendet wird, um unpopuläre oder restriktive Maßnahmen Stück für Stück einzuführen. Zuerst ist etwas einfach innovativ und bringt viele Vorteile. Vor allem ist es freiwillig, jeder kann selber entscheiden, niemand muss mitmachen. Später kann man zunehmend weniger Alternativen wählen, weil sie verschwinden, und irgendwann verwandelt sich alles andere in «nicht dürfen» – die Maßnahme ist obligatorisch.
Um die Durchsetzung derartiger Initiativen strategisch zu unterstützen und nett zu verpacken, gibt es Lobbyisten, gerne auch NGOs genannt. Dass das «NG» am Anfang dieser Abkürzung übersetzt «Nicht-Regierungs-» bedeutet, ist ein Anachronismus. Das war vielleicht früher einmal so, heute ist eher das Gegenteil gemeint.
In unserer modernen Zeit wird enorm viel Lobbyarbeit für die Digitalisierung praktisch sämtlicher Lebensbereiche aufgewendet. Was das auf dem Sektor der Mobilität bedeuten kann, haben wir diese Woche anhand aktueller Entwicklungen in Spanien beleuchtet. Begründet teilweise mit Vorgaben der Europäischen Union arbeitet man dort fleißig an einer «neuen Mobilität», basierend auf «intelligenter» technologischer Infrastruktur. Derartige Anwandlungen wurden auch schon als «Technofeudalismus» angeprangert.
Nationale Zugangspunkte für Mobilitätsdaten im Sinne der EU gibt es nicht nur in allen Mitgliedsländern, sondern auch in der Schweiz und in Großbritannien. Das Vereinigte Königreich beteiligt sich darüber hinaus an anderen EU-Projekten für digitale Überwachungs- und Kontrollmaßnahmen, wie dem biometrischen Identifizierungssystem für «nachhaltigen Verkehr und Tourismus».
Natürlich marschiert auch Deutschland stracks und euphorisch in Richtung digitaler Zukunft. Ohne vernetzte Mobilität und einen «verlässlichen Zugang zu Daten, einschließlich Echtzeitdaten» komme man in der Verkehrsplanung und -steuerung nicht aus, erklärt die Regierung. Der Interessenverband der IT-Dienstleister Bitkom will «die digitale Transformation der deutschen Wirtschaft und Verwaltung vorantreiben». Dazu bewirbt er unter anderem die Konzepte Smart City, Smart Region und Smart Country und behauptet, deutsche Großstädte «setzen bei Mobilität voll auf Digitalisierung».
Es steht zu befürchten, dass das umfassende Sammeln, Verarbeiten und Vernetzen von Daten, das angeblich die Menschen unterstützen soll (und theoretisch ja auch könnte), eher dazu benutzt wird, sie zu kontrollieren und zu manipulieren. Je elektrischer und digitaler unsere Umgebung wird, desto größer sind diese Möglichkeiten. Im Ergebnis könnten solche Prozesse den Bürger nicht nur einschränken oder überflüssig machen, sondern in mancherlei Hinsicht regelrecht abschalten. Eine gesunde Skepsis ist also geboten.
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Er ist zuerst auf Transition News erschienen.
-
 @ aa8de34f:a6ffe696
2025-03-21 12:08:31
@ aa8de34f:a6ffe696
2025-03-21 12:08:3119. März 2025
🔐 1. SHA-256 is Quantum-Resistant
Bitcoin’s proof-of-work mechanism relies on SHA-256, a hashing algorithm. Even with a powerful quantum computer, SHA-256 remains secure because:
- Quantum computers excel at factoring large numbers (Shor’s Algorithm).
- However, SHA-256 is a one-way function, meaning there's no known quantum algorithm that can efficiently reverse it.
- Grover’s Algorithm (which theoretically speeds up brute force attacks) would still require 2¹²⁸ operations to break SHA-256 – far beyond practical reach.
++++++++++++++++++++++++++++++++++++++++++++++++++
🔑 2. Public Key Vulnerability – But Only If You Reuse Addresses
Bitcoin uses Elliptic Curve Digital Signature Algorithm (ECDSA) to generate keys.
- A quantum computer could use Shor’s Algorithm to break SECP256K1, the curve Bitcoin uses.
- If you never reuse addresses, it is an additional security element
- 🔑 1. Bitcoin Addresses Are NOT Public Keys
Many people assume a Bitcoin address is the public key—this is wrong.
- When you receive Bitcoin, it is sent to a hashed public key (the Bitcoin address).
- The actual public key is never exposed because it is the Bitcoin Adress who addresses the Public Key which never reveals the creation of a public key by a spend
- Bitcoin uses Pay-to-Public-Key-Hash (P2PKH) or newer methods like Pay-to-Witness-Public-Key-Hash (P2WPKH), which add extra layers of security.
🕵️♂️ 2.1 The Public Key Never Appears
- When you send Bitcoin, your wallet creates a digital signature.
- This signature uses the private key to prove ownership.
- The Bitcoin address is revealed and creates the Public Key
- The public key remains hidden inside the Bitcoin script and Merkle tree.
This means: ✔ The public key is never exposed. ✔ Quantum attackers have nothing to target, attacking a Bitcoin Address is a zero value game.
+++++++++++++++++++++++++++++++++++++++++++++++++
🔄 3. Bitcoin Can Upgrade
Even if quantum computers eventually become a real threat:
- Bitcoin developers can upgrade to quantum-safe cryptography (e.g., lattice-based cryptography or post-quantum signatures like Dilithium).
- Bitcoin’s decentralized nature ensures a network-wide soft fork or hard fork could transition to quantum-resistant keys.
++++++++++++++++++++++++++++++++++++++++++++++++++
⏳ 4. The 10-Minute Block Rule as a Security Feature
- Bitcoin’s network operates on a 10-minute block interval, meaning:Even if an attacker had immense computational power (like a quantum computer), they could only attempt an attack every 10 minutes.Unlike traditional encryption, where a hacker could continuously brute-force keys, Bitcoin’s system resets the challenge with every new block.This limits the window of opportunity for quantum attacks.
🎯 5. Quantum Attack Needs to Solve a Block in Real-Time
- A quantum attacker must solve the cryptographic puzzle (Proof of Work) in under 10 minutes.
- The problem? Any slight error changes the hash completely, meaning:If the quantum computer makes a mistake (even 0.0001% probability), the entire attack fails.Quantum decoherence (loss of qubit stability) makes error correction a massive challenge.The computational cost of recovering from an incorrect hash is still incredibly high.
⚡ 6. Network Resilience – Even if a Block Is Hacked
- Even if a quantum computer somehow solved a block instantly:The network would quickly recognize and reject invalid transactions.Other miners would continue mining under normal cryptographic rules.51% Attack? The attacker would need to consistently beat the entire Bitcoin network, which is not sustainable.
🔄 7. The Logarithmic Difficulty Adjustment Neutralizes Threats
- Bitcoin adjusts mining difficulty every 2016 blocks (\~2 weeks).
- If quantum miners appeared and suddenly started solving blocks too quickly, the difficulty would adjust upward, making attacks significantly harder.
- This self-correcting mechanism ensures that even quantum computers wouldn't easily overpower the network.
🔥 Final Verdict: Quantum Computers Are Too Slow for Bitcoin
✔ The 10-minute rule limits attack frequency – quantum computers can’t keep up.
✔ Any slight miscalculation ruins the attack, resetting all progress.
✔ Bitcoin’s difficulty adjustment would react, neutralizing quantum advantages.
Even if quantum computers reach their theoretical potential, Bitcoin’s game theory and design make it incredibly resistant. 🚀
-
 @ 846ebf79:fe4e39a4
2025-04-14 12:35:54
@ 846ebf79:fe4e39a4
2025-04-14 12:35:54The next iteration is coming
We're busy racing to the finish line, for the #Alexandria Gutenberg beta. Then we can get the bug hunt done, release v0.1.0, and immediately start producing the first iteration of the Euler (v0.2.0) edition.
While we continue to work on fixing the performance issues and smooth rendering on the Reading View, we've gone ahead and added some new features and apps, which will be rolled-out soon.
The biggest projects this iteration have been:
- the HTTP API for the #Realy relay from nostr:npub1fjqqy4a93z5zsjwsfxqhc2764kvykfdyttvldkkkdera8dr78vhsmmleku,
- implementation of a publication tree structure by nostr:npub1wqfzz2p880wq0tumuae9lfwyhs8uz35xd0kr34zrvrwyh3kvrzuskcqsyn,
- and the Great DevOps Migration of 2025 from the ever-industrious Mr. nostr:npub1qdjn8j4gwgmkj3k5un775nq6q3q7mguv5tvajstmkdsqdja2havq03fqm7.
All are backend-y projects and have caused a major shift in process and product, on the development team's side, even if they're still largely invisible to users.
Another important, but invisible-to-you change is that nostr:npub1ecdlntvjzexlyfale2egzvvncc8tgqsaxkl5hw7xlgjv2cxs705s9qs735 has implemented the core bech32 functionality (and the associated tests) in C/C++, for the #Aedile NDK.
On the frontend:
nostr:npub1636uujeewag8zv8593lcvdrwlymgqre6uax4anuq3y5qehqey05sl8qpl4 is currently working on the blog-specific Reading View, which allows for multi-npub or topical blogging, by using the 30040 index as a "folder", joining the various 30041 articles into different blogs. She has also started experimenting with categorization and columns for the landing page.


nostr:npub1l5sga6xg72phsz5422ykujprejwud075ggrr3z2hwyrfgr7eylqstegx9z revamped the product information pages, so that there is now a Contact page (including the ability to submit a Nostr issue) and an About page (with more product information, the build version displayed, and a live #GitCitadel feed).



We have also allowed for discrete headings (headers that aren't section headings, akin to the headers in Markdown). Discrete headings are formatted, but not added to the ToC and do not result in a section split by Asciidoc processors.
We have added OpenGraph metadata, so that hyperlinks to Alexandria publications, and other events, display prettily in other apps. And we fixed some bugs.
The Visualisation view has been updated and bug-fixed, to make the cards human-readable and closeable, and to add hyperlinks to the events to the card-titles.

We have added support for the display of individual wiki pages and the integration of them into 30040 publications. (This is an important feature for scientists and other nonfiction writers.)

We prettified the event json modal, so that it's easier to read and copy-paste out of.

The index card details have been expanded and the menus on the landing page have been revamped and expanded. Design and style has been improved, overall.

Project management is very busy
Our scientific adviser nostr:npub1m3xdppkd0njmrqe2ma8a6ys39zvgp5k8u22mev8xsnqp4nh80srqhqa5sf is working on the Euler plans for integrating features important for medical researchers and other scientists, which have been put on the fast track.
Next up are:
- a return of the Table of Contents
- kind 1111 comments, highlights, likes
- a prototype social feed for wss://theforest.nostr1.com, including long-form articles and Markdown rendering
- compose and edit of publications
- a search field
- the expansion of the relay set with the new relays from nostr:npub12262qa4uhw7u8gdwlgmntqtv7aye8vdcmvszkqwgs0zchel6mz7s6cgrkj, including some cool premium features
- full wiki functionality and disambiguation pages for replaceable events with overlapping d-tags
- a web app for mass-uploading and auto-converting PDFs to 30040/41 Asciidoc events, that will run on Realy, and be a service free for our premium relay subscribers
- ability to subscribe to the forest with a premium status
- the book upload CLI has been renamed and reworked into the Sybil Test Utility and that will get a major release, covering all the events and functionality needed to test Euler
- the #GitRepublic public git server project
- ....and much more.
Thank you for reading and may your morning be good.
-
 @ c631e267:c2b78d3e
2025-02-07 19:42:11
@ c631e267:c2b78d3e
2025-02-07 19:42:11Nur wenn wir aufeinander zugehen, haben wir die Chance \ auf Überwindung der gegenseitigen Ressentiments! \ Dr. med. dent. Jens Knipphals
In Wolfsburg sollte es kürzlich eine Gesprächsrunde von Kritikern der Corona-Politik mit Oberbürgermeister Dennis Weilmann und Vertretern der Stadtverwaltung geben. Der Zahnarzt und langjährige Maßnahmenkritiker Jens Knipphals hatte diese Einladung ins Rathaus erwirkt und publiziert. Seine Motivation:
«Ich möchte die Spaltung der Gesellschaft überwinden. Dazu ist eine umfassende Aufarbeitung der Corona-Krise in der Öffentlichkeit notwendig.»
Schon früher hatte Knipphals Antworten von den Kommunalpolitikern verlangt, zum Beispiel bei öffentlichen Bürgerfragestunden. Für das erwartete Treffen im Rathaus formulierte er Fragen wie: Warum wurden fachliche Argumente der Kritiker ignoriert? Weshalb wurde deren Ausgrenzung, Diskreditierung und Entmenschlichung nicht entgegengetreten? In welcher Form übernehmen Rat und Verwaltung in Wolfsburg persönlich Verantwortung für die erheblichen Folgen der politischen Corona-Krise?
Der Termin fand allerdings nicht statt – der Bürgermeister sagte ihn kurz vorher wieder ab. Knipphals bezeichnete Weilmann anschließend als Wiederholungstäter, da das Stadtoberhaupt bereits 2022 zu einem Runden Tisch in der Sache eingeladen hatte, den es dann nie gab. Gegenüber Multipolar erklärte der Arzt, Weilmann wolle scheinbar eine öffentliche Aufarbeitung mit allen Mitteln verhindern. Er selbst sei «inzwischen absolut desillusioniert» und die einzige Lösung sei, dass die Verantwortlichen gingen.
Die Aufarbeitung der Plandemie beginne bei jedem von uns selbst, sei aber letztlich eine gesamtgesellschaftliche Aufgabe, schreibt Peter Frey, der den «Fall Wolfsburg» auch in seinem Blog behandelt. Diese Aufgabe sei indes deutlich größer, als viele glaubten. Erfreulicherweise sei der öffentliche Informationsraum inzwischen größer, trotz der weiterhin unverfrorenen Desinformations-Kampagnen der etablierten Massenmedien.
Frey erinnert daran, dass Dennis Weilmann mitverantwortlich für gravierende Grundrechtseinschränkungen wie die 2021 eingeführten 2G-Regeln in der Wolfsburger Innenstadt zeichnet. Es sei naiv anzunehmen, dass ein Funktionär einzig im Interesse der Bürger handeln würde. Als früherer Dezernent des Amtes für Wirtschaft, Digitalisierung und Kultur der Autostadt kenne Weilmann zum Beispiel die Verknüpfung von Fördergeldern mit politischen Zielsetzungen gut.
Wolfsburg wurde damals zu einem Modellprojekt des Bundesministeriums des Innern (BMI) und war Finalist im Bitkom-Wettbewerb «Digitale Stadt». So habe rechtzeitig vor der Plandemie das Projekt «Smart City Wolfsburg» anlaufen können, das der Stadt «eine Vorreiterrolle für umfassende Vernetzung und Datenerfassung» aufgetragen habe, sagt Frey. Die Vereinten Nationen verkauften dann derartige «intelligente» Überwachungs- und Kontrollmaßnahmen ebenso als Rettung in der Not wie das Magazin Forbes im April 2020:
«Intelligente Städte können uns helfen, die Coronavirus-Pandemie zu bekämpfen. In einer wachsenden Zahl von Ländern tun die intelligenten Städte genau das. Regierungen und lokale Behörden nutzen Smart-City-Technologien, Sensoren und Daten, um die Kontakte von Menschen aufzuspüren, die mit dem Coronavirus infiziert sind. Gleichzeitig helfen die Smart Cities auch dabei, festzustellen, ob die Regeln der sozialen Distanzierung eingehalten werden.»
Offensichtlich gibt es viele Aspekte zu bedenken und zu durchleuten, wenn es um die Aufklärung und Aufarbeitung der sogenannten «Corona-Pandemie» und der verordneten Maßnahmen geht. Frustration und Desillusion sind angesichts der Realitäten absolut verständlich. Gerade deswegen sind Initiativen wie die von Jens Knipphals so bewundernswert und so wichtig – ebenso wie eine seiner Kernthesen: «Wir müssen aufeinander zugehen, da hilft alles nichts».
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ c631e267:c2b78d3e
2025-01-18 09:34:51
@ c631e267:c2b78d3e
2025-01-18 09:34:51Die grauenvollste Aussicht ist die der Technokratie – \ einer kontrollierenden Herrschaft, \ die durch verstümmelte und verstümmelnde Geister ausgeübt wird. \ Ernst Jünger
«Davos ist nicht mehr sexy», das Weltwirtschaftsforum (WEF) mache Davos kaputt, diese Aussagen eines Einheimischen las ich kürzlich in der Handelszeitung. Während sich einige vor Ort enorm an der «teuersten Gewerbeausstellung der Welt» bereicherten, würden die negativen Begleiterscheinungen wie Wohnungsnot und Niedergang der lokalen Wirtschaft immer deutlicher.
Nächsten Montag beginnt in dem Schweizer Bergdorf erneut ein Jahrestreffen dieses elitären Clubs der Konzerne, bei dem man mit hochrangigen Politikern aus aller Welt und ausgewählten Vertretern der Systemmedien zusammenhocken wird. Wie bereits in den vergangenen vier Jahren wird die Präsidentin der EU-Kommission, Ursula von der Leyen, in Begleitung von Klaus Schwab ihre Grundsatzansprache halten.
Der deutsche WEF-Gründer hatte bei dieser Gelegenheit immer höchst lobende Worte für seine Landsmännin: 2021 erklärte er sich «stolz, dass Europa wieder unter Ihrer Führung steht» und 2022 fand er es bemerkenswert, was sie erreicht habe angesichts des «erstaunlichen Wandels», den die Welt in den vorangegangenen zwei Jahren erlebt habe; es gebe nun einen «neuen europäischen Geist».
Von der Leyens Handeln während der sogenannten Corona-«Pandemie» lobte Schwab damals bereits ebenso, wie es diese Woche das Karlspreis-Direktorium tat, als man der Beschuldigten im Fall Pfizergate die diesjährige internationale Auszeichnung «für Verdienste um die europäische Einigung» verlieh. Außerdem habe sie die EU nicht nur gegen den «Aggressor Russland», sondern auch gegen die «innere Bedrohung durch Rassisten und Demagogen» sowie gegen den Klimawandel verteidigt.
Jene Herausforderungen durch «Krisen epochalen Ausmaßes» werden indes aus dem Umfeld des WEF nicht nur herbeigeredet – wie man alljährlich zur Zeit des Davoser Treffens im Global Risks Report nachlesen kann, der zusammen mit dem Versicherungskonzern Zurich erstellt wird. Seit die Globalisten 2020/21 in der Praxis gesehen haben, wie gut eine konzertierte und konsequente Angst-Kampagne funktionieren kann, geht es Schlag auf Schlag. Sie setzen alles daran, Schwabs goldenes Zeitfenster des «Great Reset» zu nutzen.
Ziel dieses «großen Umbruchs» ist die totale Kontrolle der Technokraten über die Menschen unter dem Deckmantel einer globalen Gesundheitsfürsorge. Wie aber könnte man so etwas erreichen? Ein Mittel dazu ist die «kreative Zerstörung». Weitere unabdingbare Werkzeug sind die Einbindung, ja Gleichschaltung der Medien und der Justiz.
Ein «Great Mental Reset» sei die Voraussetzung dafür, dass ein Großteil der Menschen Einschränkungen und Manipulationen wie durch die Corona-Maßnahmen praktisch kritik- und widerstandslos hinnehme, sagt der Mediziner und Molekulargenetiker Michael Nehls. Er meint damit eine regelrechte Umprogrammierung des Gehirns, wodurch nach und nach unsere Individualität und unser soziales Bewusstsein eliminiert und durch unreflektierten Konformismus ersetzt werden.
Der aktuelle Zustand unserer Gesellschaften ist auch für den Schweizer Rechtsanwalt Philipp Kruse alarmierend. Durch den Umgang mit der «Pandemie» sieht er die Grundlagen von Recht und Vernunft erschüttert, die Rechtsstaatlichkeit stehe auf dem Prüfstand. Seiner dringenden Mahnung an alle Bürger, die Prinzipien von Recht und Freiheit zu verteidigen, kann ich mich nur anschließen.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ c631e267:c2b78d3e
2024-10-23 20:26:10
@ c631e267:c2b78d3e
2024-10-23 20:26:10Herzlichen Glückwunsch zum dritten Geburtstag, liebe Denk Bar! Wieso zum dritten? Das war doch 2022 und jetzt sind wir im Jahr 2024, oder? Ja, das ist schon richtig, aber bei Geburtstagen erinnere ich mich immer auch an meinen Vater, und der behauptete oft, der erste sei ja schließlich der Tag der Geburt selber und den müsse man natürlich mitzählen. Wo er recht hat, hat er nunmal recht. Konsequenterweise wird also heute dieser Blog an seinem dritten Geburtstag zwei Jahre alt.
Das ist ein Grund zum Feiern, wie ich finde. Einerseits ganz einfach, weil es dafür gar nicht genug Gründe geben kann. «Das Leben sind zwei Tage», lautet ein gängiger Ausdruck hier in Andalusien. In der Tat könnte es so sein, auch wenn wir uns im Alltag oft genug von der Routine vereinnahmen lassen.
Seit dem Start der Denk Bar vor zwei Jahren ist unglaublich viel passiert. Ebenso wie die zweieinhalb Jahre davor, und all jenes war letztlich auch der Auslöser dafür, dass ich begann, öffentlich zu schreiben. Damals notierte ich:
«Seit einigen Jahren erscheint unser öffentliches Umfeld immer fragwürdiger, widersprüchlicher und manchmal schier unglaublich - jede Menge Anlass für eigene Recherchen und Gedanken, ganz einfach mit einer Portion gesundem Menschenverstand.»
Wir erleben den sogenannten «großen Umbruch», einen globalen Coup, den skrupellose Egoisten clever eingefädelt haben und seit ein paar Jahren knallhart – aber nett verpackt – durchziehen, um buchstäblich alles nach ihrem Gusto umzukrempeln. Die Gelegenheit ist ja angeblich günstig und muss genutzt werden.
Nie hätte ich mir träumen lassen, dass ich so etwas jemals miterleben müsste. Die Bosheit, mit der ganz offensichtlich gegen die eigene Bevölkerung gearbeitet wird, war früher für mich unvorstellbar. Mein (Rest-) Vertrauen in alle möglichen Bereiche wie Politik, Wissenschaft, Justiz, Medien oder Kirche ist praktisch komplett zerstört. Einen «inneren Totalschaden» hatte ich mal für unsere Gesellschaften diagnostiziert.
Was mich vielleicht am meisten erschreckt, ist zum einen das Niveau der Gleichschaltung, das weltweit erreicht werden konnte, und zum anderen die praktisch totale Spaltung der Gesellschaft. Haben wir das tatsächlich mit uns machen lassen?? Unfassbar! Aber das Werkzeug «Angst» ist sehr mächtig und funktioniert bis heute.
Zum Glück passieren auch positive Dinge und neue Perspektiven öffnen sich. Für viele Menschen waren und sind die Entwicklungen der letzten Jahre ein Augenöffner. Sie sehen «Querdenken» als das, was es ist: eine Tugend.
Auch die immer ernsteren Zensurbemühungen sind letztlich nur ein Zeichen der Schwäche, wo Argumente fehlen. Sie werden nicht verhindern, dass wir unsere Meinung äußern, unbequeme Fragen stellen und dass die Wahrheit peu à peu ans Licht kommt. Es gibt immer Mittel und Wege, auch für uns.
Danke, dass du diesen Weg mit mir weitergehst!
-
 @ 8d34bd24:414be32b
2025-04-13 04:29:33
@ 8d34bd24:414be32b
2025-04-13 04:29:33I was listening to a sermon at my church this weekend on Luke 9. It made me think of these words, “I do believe; help my unbelief.” I’ll start with context on this statement and then show how it applies to the passage we were studying.
They brought the boy to Him. When he saw Him, immediately the spirit threw him into a convulsion, and falling to the ground, he began rolling around and foaming at the mouth. And He asked his father, “How long has this been happening to him?” And he said, “From childhood. It has often thrown him both into the fire and into the water to destroy him. But if You can do anything, take pity on us and help us!” And Jesus said to him, “ ‘If You can?’ All things are possible to him who believes.” Immediately the boy’s father cried out and said, “I do believe; help my unbelief.” (Mark 9:20-24) {emphasis mine}
In this story, a desperate father brought his son to Jesus’s disciples for healing, when they failed, he brought the boy to Jesus. He begged for help, but qualified with “But if You can … .” How often do we explicitly or implicitly say this to God in our prayers.
Just as this father believed in Jesus enough to bring his dear child to Jesus, but still had doubts, we tend to be the same. As Christians, we believe that Jesus loved us enough to die on the cross, but do we believe He is always with us? Do we believe He will never leave nor forsake us? Do we believe that all things work together for good for those who love God and are called according to His purpose? I think we can all say, “I do believe; help my unbelief.”
We all have highs where we are excited about Jesus and believe He is working in us and through us. We also have lows where we feel distant and wondering if He sees or cares. We need to have that belief of the highs when we are going through the lows.
In Luke 9, Jesus sent out His 12 disciples to share the gospel and heal the sick and possessed. They came back on a high, amazed at the great miracles that Jesus had worked through them.
And He called the twelve together, and gave them power and authority over all the demons and to heal diseases. And He sent them out to proclaim the kingdom of God and to perform healing. … When the apostles returned, they gave an account to Him of all that they had done. Taking them with Him, He withdrew by Himself to a city called Bethsaida. (Luke 9:1-2,10) {emphasis mine}
The 12 disciples were on a high. Miracles had been done through their hands and at their word. They felt like they could conquer the world, but this high and great faith did not last very long. Jesus took them away. They thought they were going to spend some private time with Jesus, but that is not what happened. A great crowd ran ahead and met them. Jesus saw their physical and spiritual needs and began to preach and minister to them. It began to get late, so the disciples came to Jesus to ask Him to wrap things up and send the people away so they could eat (like Jesus didn’t know).
Now the day was ending, and the twelve came and said to Him, “Send the crowd away, that they may go into the surrounding villages and countryside and find lodging and get something to eat; for here we are in a desolate place.” But He said to them, “You give them something to eat!” And they said, “We have no more than five loaves and two fish, unless perhaps we go and buy food for all these people.” (For there were about five thousand men.) And He said to His disciples, “Have them sit down to eat in groups of about fifty each.” They did so, and had them all sit down. Then He took the five loaves and the two fish, and looking up to heaven, He blessed them, and broke them, and kept giving them to the disciples to set before the people. And they all ate and were satisfied; and the broken pieces which they had left over were picked up, twelve baskets full. (Luke 9:12-17) {emphasis mine}
Jesus gently guided His disciples, trying to help them see that there was nothing to fear, that He had everything under control, and that nothing is impossible with Him. When He asked them what they had available to feed the crowd, and they just had one young boy’s small lunch, they immediately assumed feeding the crowd was impossible. Jesus then proceeded to feed the 5,000 (5,000 men and an uncounted number of women and children). Yes, Jesus was merciful and fed this hungry crowd, but I believe this feeding was about so much more than meeting the physical needs of the crowd. Notice how every person there ate until they were satisfied. Jesus then had the disciples pick up the leftovers. How much was left over? 12 baskets full. How many disciples was He giving an object lesson to? 12 disciples. Jesus doesn’t do anything by accident. Everything He does is for a reason. (In the same way everything He allows to happen to us is for a good reason.) He did what the disciples thought was impossible, He fed the huge crowd, but even more, He had one basketful leftover for each disciple. This was a personal message to each of His disciples.
When Jesus sent them out with the command to share the Gospel, heal the sick, and cast out demons, they went out with faith and returned with even greater faith “I believe,” but then the day after they returned, their faith waivered again. They needed to cry out, “help my unbelief.” Jesus empowered and guided them both in their belief and in their unbelief. He most definitely helped their unbelief and will do the same for us.
Our Father, please help us to have faith in good times and in bad. Help us to believe with all of our heart, mind, and soul. We believe that you are God and we believe that Jesus came down to earth to live the perfect life that we are unable to live, died to receive the punishment we deserved, and was raised to life on the third day. Believe that the Holy Spirit lives within us empowering and guiding us. We also acknowledge that we have doubts. Please help our unbelief.
Trust Jesus.
-
 @ c230edd3:8ad4a712
2025-04-11 16:02:15
@ c230edd3:8ad4a712
2025-04-11 16:02:15Chef's notes
Wildly enough, this is delicious. It's sweet and savory.
(I copied this recipe off of a commercial cheese maker's site, just FYI)
I hadn't fully froze the ice cream when I took the picture shown. This is fresh out of the churner.
Details
- ⏲️ Prep time: 15 min
- 🍳 Cook time: 30 min
- 🍽️ Servings: 4
Ingredients
- 12 oz blue cheese
- 3 Tbsp lemon juice
- 1 c sugar
- 1 tsp salt
- 1 qt heavy cream
- 3/4 c chopped dark chocolate
Directions
- Put the blue cheese, lemon juice, sugar, and salt into a bowl
- Bring heavy cream to a boil, stirring occasionally
- Pour heavy cream over the blue cheese mix and stir until melted
- Pour into prepared ice cream maker, follow unit instructions
- Add dark chocolate halfway through the churning cycle
- Freeze until firm. Enjoy.
-
 @ 91bea5cd:1df4451c
2025-04-15 06:27:28
@ 91bea5cd:1df4451c
2025-04-15 06:27:28Básico
bash lsblk # Lista todos os diretorios montados.Para criar o sistema de arquivos:
bash mkfs.btrfs -L "ThePool" -f /dev/sdxCriando um subvolume:
bash btrfs subvolume create SubVolMontando Sistema de Arquivos:
bash mount -o compress=zlib,subvol=SubVol,autodefrag /dev/sdx /mntLista os discos formatados no diretório:
bash btrfs filesystem show /mntAdiciona novo disco ao subvolume:
bash btrfs device add -f /dev/sdy /mntLista novamente os discos do subvolume:
bash btrfs filesystem show /mntExibe uso dos discos do subvolume:
bash btrfs filesystem df /mntBalancea os dados entre os discos sobre raid1:
bash btrfs filesystem balance start -dconvert=raid1 -mconvert=raid1 /mntScrub é uma passagem por todos os dados e metadados do sistema de arquivos e verifica as somas de verificação. Se uma cópia válida estiver disponível (perfis de grupo de blocos replicados), a danificada será reparada. Todas as cópias dos perfis replicados são validadas.
iniciar o processo de depuração :
bash btrfs scrub start /mntver o status do processo de depuração Btrfs em execução:
bash btrfs scrub status /mntver o status do scrub Btrfs para cada um dos dispositivos
bash btrfs scrub status -d / data btrfs scrub cancel / dataPara retomar o processo de depuração do Btrfs que você cancelou ou pausou:
btrfs scrub resume / data
Listando os subvolumes:
bash btrfs subvolume list /ReportsCriando um instantâneo dos subvolumes:
Aqui, estamos criando um instantâneo de leitura e gravação chamado snap de marketing do subvolume de marketing.
bash btrfs subvolume snapshot /Reports/marketing /Reports/marketing-snapAlém disso, você pode criar um instantâneo somente leitura usando o sinalizador -r conforme mostrado. O marketing-rosnap é um instantâneo somente leitura do subvolume de marketing
bash btrfs subvolume snapshot -r /Reports/marketing /Reports/marketing-rosnapForçar a sincronização do sistema de arquivos usando o utilitário 'sync'
Para forçar a sincronização do sistema de arquivos, invoque a opção de sincronização conforme mostrado. Observe que o sistema de arquivos já deve estar montado para que o processo de sincronização continue com sucesso.
bash btrfs filsystem sync /ReportsPara excluir o dispositivo do sistema de arquivos, use o comando device delete conforme mostrado.
bash btrfs device delete /dev/sdc /ReportsPara sondar o status de um scrub, use o comando scrub status com a opção -dR .
bash btrfs scrub status -dR / RelatóriosPara cancelar a execução do scrub, use o comando scrub cancel .
bash $ sudo btrfs scrub cancel / ReportsPara retomar ou continuar com uma depuração interrompida anteriormente, execute o comando de cancelamento de depuração
bash sudo btrfs scrub resume /Reportsmostra o uso do dispositivo de armazenamento:
btrfs filesystem usage /data
Para distribuir os dados, metadados e dados do sistema em todos os dispositivos de armazenamento do RAID (incluindo o dispositivo de armazenamento recém-adicionado) montados no diretório /data , execute o seguinte comando:
sudo btrfs balance start --full-balance /data
Pode demorar um pouco para espalhar os dados, metadados e dados do sistema em todos os dispositivos de armazenamento do RAID se ele contiver muitos dados.
Opções importantes de montagem Btrfs
Nesta seção, vou explicar algumas das importantes opções de montagem do Btrfs. Então vamos começar.
As opções de montagem Btrfs mais importantes são:
**1. acl e noacl
**ACL gerencia permissões de usuários e grupos para os arquivos/diretórios do sistema de arquivos Btrfs.
A opção de montagem acl Btrfs habilita ACL. Para desabilitar a ACL, você pode usar a opção de montagem noacl .
Por padrão, a ACL está habilitada. Portanto, o sistema de arquivos Btrfs usa a opção de montagem acl por padrão.
**2. autodefrag e noautodefrag
**Desfragmentar um sistema de arquivos Btrfs melhorará o desempenho do sistema de arquivos reduzindo a fragmentação de dados.
A opção de montagem autodefrag permite a desfragmentação automática do sistema de arquivos Btrfs.
A opção de montagem noautodefrag desativa a desfragmentação automática do sistema de arquivos Btrfs.
Por padrão, a desfragmentação automática está desabilitada. Portanto, o sistema de arquivos Btrfs usa a opção de montagem noautodefrag por padrão.
**3. compactar e compactar-forçar
**Controla a compactação de dados no nível do sistema de arquivos do sistema de arquivos Btrfs.
A opção compactar compacta apenas os arquivos que valem a pena compactar (se compactar o arquivo economizar espaço em disco).
A opção compress-force compacta todos os arquivos do sistema de arquivos Btrfs, mesmo que a compactação do arquivo aumente seu tamanho.
O sistema de arquivos Btrfs suporta muitos algoritmos de compactação e cada um dos algoritmos de compactação possui diferentes níveis de compactação.
Os algoritmos de compactação suportados pelo Btrfs são: lzo , zlib (nível 1 a 9) e zstd (nível 1 a 15).
Você pode especificar qual algoritmo de compactação usar para o sistema de arquivos Btrfs com uma das seguintes opções de montagem:
- compress=algoritmo:nível
- compress-force=algoritmo:nível
Para obter mais informações, consulte meu artigo Como habilitar a compactação do sistema de arquivos Btrfs .
**4. subvol e subvolid
**Estas opções de montagem são usadas para montar separadamente um subvolume específico de um sistema de arquivos Btrfs.
A opção de montagem subvol é usada para montar o subvolume de um sistema de arquivos Btrfs usando seu caminho relativo.
A opção de montagem subvolid é usada para montar o subvolume de um sistema de arquivos Btrfs usando o ID do subvolume.
Para obter mais informações, consulte meu artigo Como criar e montar subvolumes Btrfs .
**5. dispositivo
A opção de montagem de dispositivo** é usada no sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs.
Em alguns casos, o sistema operacional pode falhar ao detectar os dispositivos de armazenamento usados em um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs. Nesses casos, você pode usar a opção de montagem do dispositivo para especificar os dispositivos que deseja usar para o sistema de arquivos de vários dispositivos Btrfs ou RAID.
Você pode usar a opção de montagem de dispositivo várias vezes para carregar diferentes dispositivos de armazenamento para o sistema de arquivos de vários dispositivos Btrfs ou RAID.
Você pode usar o nome do dispositivo (ou seja, sdb , sdc ) ou UUID , UUID_SUB ou PARTUUID do dispositivo de armazenamento com a opção de montagem do dispositivo para identificar o dispositivo de armazenamento.
Por exemplo,
- dispositivo=/dev/sdb
- dispositivo=/dev/sdb,dispositivo=/dev/sdc
- dispositivo=UUID_SUB=490a263d-eb9a-4558-931e-998d4d080c5d
- device=UUID_SUB=490a263d-eb9a-4558-931e-998d4d080c5d,device=UUID_SUB=f7ce4875-0874-436a-b47d-3edef66d3424
**6. degraded
A opção de montagem degradada** permite que um RAID Btrfs seja montado com menos dispositivos de armazenamento do que o perfil RAID requer.
Por exemplo, o perfil raid1 requer a presença de 2 dispositivos de armazenamento. Se um dos dispositivos de armazenamento não estiver disponível em qualquer caso, você usa a opção de montagem degradada para montar o RAID mesmo que 1 de 2 dispositivos de armazenamento esteja disponível.
**7. commit
A opção commit** mount é usada para definir o intervalo (em segundos) dentro do qual os dados serão gravados no dispositivo de armazenamento.
O padrão é definido como 30 segundos.
Para definir o intervalo de confirmação para 15 segundos, você pode usar a opção de montagem commit=15 (digamos).
**8. ssd e nossd
A opção de montagem ssd** informa ao sistema de arquivos Btrfs que o sistema de arquivos está usando um dispositivo de armazenamento SSD, e o sistema de arquivos Btrfs faz a otimização SSD necessária.
A opção de montagem nossd desativa a otimização do SSD.
O sistema de arquivos Btrfs detecta automaticamente se um SSD é usado para o sistema de arquivos Btrfs. Se um SSD for usado, a opção de montagem de SSD será habilitada. Caso contrário, a opção de montagem nossd é habilitada.
**9. ssd_spread e nossd_spread
A opção de montagem ssd_spread** tenta alocar grandes blocos contínuos de espaço não utilizado do SSD. Esse recurso melhora o desempenho de SSDs de baixo custo (baratos).
A opção de montagem nossd_spread desativa o recurso ssd_spread .
O sistema de arquivos Btrfs detecta automaticamente se um SSD é usado para o sistema de arquivos Btrfs. Se um SSD for usado, a opção de montagem ssd_spread será habilitada. Caso contrário, a opção de montagem nossd_spread é habilitada.
**10. descarte e nodiscard
Se você estiver usando um SSD que suporte TRIM enfileirado assíncrono (SATA rev3.1), a opção de montagem de descarte** permitirá o descarte de blocos de arquivos liberados. Isso melhorará o desempenho do SSD.
Se o SSD não suportar TRIM enfileirado assíncrono, a opção de montagem de descarte prejudicará o desempenho do SSD. Nesse caso, a opção de montagem nodiscard deve ser usada.
Por padrão, a opção de montagem nodiscard é usada.
**11. norecovery
Se a opção de montagem norecovery** for usada, o sistema de arquivos Btrfs não tentará executar a operação de recuperação de dados no momento da montagem.
**12. usebackuproot e nousebackuproot
Se a opção de montagem usebackuproot for usada, o sistema de arquivos Btrfs tentará recuperar qualquer raiz de árvore ruim/corrompida no momento da montagem. O sistema de arquivos Btrfs pode armazenar várias raízes de árvore no sistema de arquivos. A opção de montagem usebackuproot** procurará uma boa raiz de árvore e usará a primeira boa que encontrar.
A opção de montagem nousebackuproot não verificará ou recuperará raízes de árvore inválidas/corrompidas no momento da montagem. Este é o comportamento padrão do sistema de arquivos Btrfs.
**13. space_cache, space_cache=version, nospace_cache e clear_cache
A opção de montagem space_cache** é usada para controlar o cache de espaço livre. O cache de espaço livre é usado para melhorar o desempenho da leitura do espaço livre do grupo de blocos do sistema de arquivos Btrfs na memória (RAM).
O sistema de arquivos Btrfs suporta 2 versões do cache de espaço livre: v1 (padrão) e v2
O mecanismo de cache de espaço livre v2 melhora o desempenho de sistemas de arquivos grandes (tamanho de vários terabytes).
Você pode usar a opção de montagem space_cache=v1 para definir a v1 do cache de espaço livre e a opção de montagem space_cache=v2 para definir a v2 do cache de espaço livre.
A opção de montagem clear_cache é usada para limpar o cache de espaço livre.
Quando o cache de espaço livre v2 é criado, o cache deve ser limpo para criar um cache de espaço livre v1 .
Portanto, para usar o cache de espaço livre v1 após a criação do cache de espaço livre v2 , as opções de montagem clear_cache e space_cache=v1 devem ser combinadas: clear_cache,space_cache=v1
A opção de montagem nospace_cache é usada para desabilitar o cache de espaço livre.
Para desabilitar o cache de espaço livre após a criação do cache v1 ou v2 , as opções de montagem nospace_cache e clear_cache devem ser combinadas: clear_cache,nosapce_cache
**14. skip_balance
Por padrão, a operação de balanceamento interrompida/pausada de um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs será retomada automaticamente assim que o sistema de arquivos Btrfs for montado. Para desabilitar a retomada automática da operação de equilíbrio interrompido/pausado em um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs, você pode usar a opção de montagem skip_balance .**
**15. datacow e nodatacow
A opção datacow** mount habilita o recurso Copy-on-Write (CoW) do sistema de arquivos Btrfs. É o comportamento padrão.
Se você deseja desabilitar o recurso Copy-on-Write (CoW) do sistema de arquivos Btrfs para os arquivos recém-criados, monte o sistema de arquivos Btrfs com a opção de montagem nodatacow .
**16. datasum e nodatasum
A opção datasum** mount habilita a soma de verificação de dados para arquivos recém-criados do sistema de arquivos Btrfs. Este é o comportamento padrão.
Se você não quiser que o sistema de arquivos Btrfs faça a soma de verificação dos dados dos arquivos recém-criados, monte o sistema de arquivos Btrfs com a opção de montagem nodatasum .
Perfis Btrfs
Um perfil Btrfs é usado para informar ao sistema de arquivos Btrfs quantas cópias dos dados/metadados devem ser mantidas e quais níveis de RAID devem ser usados para os dados/metadados. O sistema de arquivos Btrfs contém muitos perfis. Entendê-los o ajudará a configurar um RAID Btrfs da maneira que você deseja.
Os perfis Btrfs disponíveis são os seguintes:
single : Se o perfil único for usado para os dados/metadados, apenas uma cópia dos dados/metadados será armazenada no sistema de arquivos, mesmo se você adicionar vários dispositivos de armazenamento ao sistema de arquivos. Assim, 100% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser utilizado.
dup : Se o perfil dup for usado para os dados/metadados, cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos manterá duas cópias dos dados/metadados. Assim, 50% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser utilizado.
raid0 : No perfil raid0 , os dados/metadados serão divididos igualmente em todos os dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, não haverá dados/metadados redundantes (duplicados). Assim, 100% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser usado. Se, em qualquer caso, um dos dispositivos de armazenamento falhar, todo o sistema de arquivos será corrompido. Você precisará de pelo menos dois dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid0 .
raid1 : No perfil raid1 , duas cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a uma falha de unidade. Mas você pode usar apenas 50% do espaço total em disco. Você precisará de pelo menos dois dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1 .
raid1c3 : No perfil raid1c3 , três cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a duas falhas de unidade, mas você pode usar apenas 33% do espaço total em disco. Você precisará de pelo menos três dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1c3 .
raid1c4 : No perfil raid1c4 , quatro cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a três falhas de unidade, mas você pode usar apenas 25% do espaço total em disco. Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1c4 .
raid10 : No perfil raid10 , duas cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos, como no perfil raid1 . Além disso, os dados/metadados serão divididos entre os dispositivos de armazenamento, como no perfil raid0 .
O perfil raid10 é um híbrido dos perfis raid1 e raid0 . Alguns dos dispositivos de armazenamento formam arrays raid1 e alguns desses arrays raid1 são usados para formar um array raid0 . Em uma configuração raid10 , o sistema de arquivos pode sobreviver a uma única falha de unidade em cada uma das matrizes raid1 .
Você pode usar 50% do espaço total em disco na configuração raid10 . Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid10 .
raid5 : No perfil raid5 , uma cópia dos dados/metadados será dividida entre os dispositivos de armazenamento. Uma única paridade será calculada e distribuída entre os dispositivos de armazenamento do array RAID.
Em uma configuração raid5 , o sistema de arquivos pode sobreviver a uma única falha de unidade. Se uma unidade falhar, você pode adicionar uma nova unidade ao sistema de arquivos e os dados perdidos serão calculados a partir da paridade distribuída das unidades em execução.
Você pode usar 1 00x(N-1)/N % do total de espaços em disco na configuração raid5 . Aqui, N é o número de dispositivos de armazenamento adicionados ao sistema de arquivos. Você precisará de pelo menos três dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid5 .
raid6 : No perfil raid6 , uma cópia dos dados/metadados será dividida entre os dispositivos de armazenamento. Duas paridades serão calculadas e distribuídas entre os dispositivos de armazenamento do array RAID.
Em uma configuração raid6 , o sistema de arquivos pode sobreviver a duas falhas de unidade ao mesmo tempo. Se uma unidade falhar, você poderá adicionar uma nova unidade ao sistema de arquivos e os dados perdidos serão calculados a partir das duas paridades distribuídas das unidades em execução.
Você pode usar 100x(N-2)/N % do espaço total em disco na configuração raid6 . Aqui, N é o número de dispositivos de armazenamento adicionados ao sistema de arquivos. Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid6 .
-
 @ 1bc70a01:24f6a411
2025-04-11 13:50:38
@ 1bc70a01:24f6a411
2025-04-11 13:50:38The heading to be
Testing apps, a tireless quest, Click and swipe, then poke the rest. Crashing bugs and broken flows, Hidden deep where logic goes.
Specs in hand, we watch and trace, Each edge case in its hiding place. From flaky taps to loading spins, The war on regressions slowly wins.
Push the build, review the log, One more fix, then clear the fog. For in each test, truth will unfold— A quiet tale of stable code.
This has been a test. Thanks for tuning in.
- one
- two
- three
Listen a chillTranquility
And leisure
-
 @ bf95e1a4:ebdcc848
2025-04-11 11:21:48
@ bf95e1a4:ebdcc848
2025-04-11 11:21:48This is a part of the Bitcoin Infinity Academy course on Knut Svanholm's book Bitcoin: Sovereignty Through Mathematics. For more information, check out our Geyser page!
An Immaculate Conception
Some concepts in nature are harder for us humans to understand than others. How complex things can emerge out of simpler ones is one of those concepts. A termite colony, for instance, has a complex cooling system at its lower levels. No single termite knows how it works. Completely unaware of the end results, they build complex mounds and nests, shelter tubes to protect their paths, and networks of subterranean tunnels to connect their dirt cities. Everything seems organized and designed, but it is not. Evolution has equipped the termite with a pheromone receptor that tells the termite what task he ought to engage himself in by simply counting the number of neighboring termites doing the same thing. If there’s a surplus of workers in an area, nearby termites become warriors, and so on. Complex structures emerge from simple rules. The fractal patterns found all around nature are another example. Fractals look complex, but in reality, they’re not. They’re basically algorithms — the same pattern, repeated over and over again with a slightly modified starting point. The human brain is an excellent example of a complex thing that evolved out of simpler things, and we humans still have a hard time accepting that it wasn’t designed. Religions, which themselves are emergent systems spawned out of human interaction, have come up with a plethora of explanations for how we came to be. All sorts of wild origin stories have been more widely accepted than the simple explanation that our complexities just emerged out of simpler things following a set of rules that nature itself provided our world with.
Complex systems emerge out of human interactions all the time. The phone in your pocket is the result of a century of mostly free global market competition, and no single human could ever have come up with the entire thing. The device, together with its internet connection, is capable of a lot more than the sum of its individual parts. A pocket-sized gadget that can grant instant access to almost all of the world’s literature, music, and film, which fits in your pocket, was an unthinkable science fiction a mere twenty years ago. Bitcoin, first described in Satoshi Nakamoto’s whitepaper ten years before these words were written, was designed to be decentralized. Still, it wasn’t until years later that the network started to show actual proof of this. Sound money, or absolute digital scarcity, emerged out of the network not only because of its technical design. How Bitcoin’s first ten years actually unfolded played a huge part in how true decentralization could emerge, and this is also the main reason why the experiment cannot be replicated. Scarcity on the internet could only be invented once. Satoshi’s disappearance was Bitcoin’s first step towards true decentralization. No marketing whatsoever and the randomness of who hopped onto the train first were the steps that followed. Bitcoin truly had an immaculate conception.
The network has shown a remarkable resistance to change over the last few years especially, and its current state might be its last incarnation given the size of the network and the 95% agreement threshold in its consensus rules. It might never change again. In that case, an entirely new, complex life form will have emerged out of a simple set of rules. Even if small upgrades are implemented in the future, the 21 million coin supply cap is set in stone forever. Bitcoin is not for humans to have opinions about — it exists regardless of what anyone thinks about it, and it ought to be studied rather than discussed. We don’t know what true scarcity and a truly global, anonymous free market will do to our species yet, but we are about to find out. It is naïve to think otherwise. Various futurists and doomsday prophets have been focused on the dangers of the impending general artificial intelligence singularity lately, warning us about the point of no return, whereupon an artificial intelligence will be able to improve itself faster than any human could. Such a scenario could, as news anchor Ron Burgundy would have put it, escalate quickly. This may or may not be of real concern to us, but meanwhile, right under our noses, another type of unstoppable digital life has emerged, and it is already changing the behavior and preferences of millions of people around the globe. This is probably bad news for big corporations and governments but good news for the little guy looking for a little freedom. At least, that’s what those of us who lean towards the ideas of the Austrian school of economics believe. This time around, we will find out whether this is the case or not. No one knows what it will lead to and what new truths will emerge out of this new reality.
Unlike the termite, we humans are able to experience the grandeur of our progress. We can look in awe at the Sistine Chapel or the pyramids, and we can delve into the technicalities and brief history of Bitcoin and discover new ways of thinking about value along the way. Money is the language in which we express value to each other through space and time. Now, that language is spoken by computers. Value expressed in this language can’t be diluted through inflation or counterfeiting any longer. It is a language that is borderless, permissionless, peer-to-peer, anonymous (if you have the skills), unreplicable, completely scarce, non-dilutable, unchangeable, untouchable, undeniable, fungible, and free for everyone on Earth to use. It is a language for the future and it emerged out of a specific set of events in the past. All languages are examples of complex systems emerging out of simpler things, and Bitcoin evolved just as organically as any other human language did.
Decentralization is hard to achieve. Really hard. When it comes to claims of decentralization, a “don’t trust, verify” approach to the validity of such claims will help you filter out the noise. So, how can the validity of Bitcoin’s decentralization be verified? It’s a tricky question because decentralization is not a binary thing, like life or death, but rather a very difficult concept to define. However, the most fundamental concepts in Bitcoin, like the 21 million cap on coin issuance or the ten-minute block interval as a result of the difficulty adjustment and the Proof of Work algorithm, have not changed since very early on in the history of the network. This lack of change, which is arguably Bitcoin’s biggest strength, has been achieved through the consensus rules, which define what the blockchain is. Some special mechanisms (for example, BIP9) are sometimes used to deploy changes to the consensus rules. These mechanisms use a threshold when counting blocks that signal for a certain upgrade. For example, the upgrade “Segregated Witness” activated in a node when 95% or more of the blocks in a retarget period signaled support. Bitcoin has displayed a remarkable immutability through the years, and it is highly unlikely that this would have been the case if the game-theoretical mechanisms that enable its decentralized governance model hadn’t worked, given the many incentives to cheat that always seem to corrupt monetary systems. In other words, the longer the system seems to be working, the higher the likelihood that it actually does.
Satoshi set in stone the length of the halving period — a very important aspect of Bitcoin’s issuance schedule and initial distribution. During the first four years of Bitcoin’s existence, fifty new coins were issued every ten minutes up until the first block reward halving four years later. Every four years, this reward is halved so that the issuance rate goes down by fifty percent. This effectively means that half of all the Bitcoin that will ever exist was mined during the first four years of the network’s life, one fourth during its next four years, and so on. At the time of writing, we’re a little more than a year from the third halving. After that, only 6.25 Bitcoin will be minted every ten minutes as opposed to 50, which was the initial rate. What this seems to do is to create hype cycles for Bitcoin’s adoption. Every time the price of Bitcoin booms and then busts down to a level above where it started, a hype cycle takes place. Bitcoin had no marketing whatsoever, so awareness of it had to be spread through some other mechanism. When a bull run begins, people start talking about it, which leads to even more people buying due to fear of missing out (FOMO), which inevitably causes the price to rise even more rapidly. This leads to more FOMO, and on and on the bull market goes until it suddenly ends, and the price crashes down to somewhere around, or slightly above, the level it was at before the bull run started. Unlike what is true for most other assets, Bitcoin never really crashes all the way. Why? Because every time a hype cycle occurs, some more people learn about Bitcoin’s fundamentals and manage to resist the urge to sell, even when almost all hope seems lost. They understand that these bull markets are a reoccurring thing due to the nature of the protocol. These cycles create new waves of evangelists who start promoting Bitcoin simply because of what they stand to gain from a price increase. In a sense, the protocol itself pays for its own promotion in this way. This organic marketing creates a lot of noise and confusion, too, as a lot of people who don’t seem to understand how Bitcoin works are often very outspoken about it despite their lack of knowledge. Red herrings, such as altcoins and Bitcoin forks, are then weeded out naturally during bear markets. Every time a bull market happens, a new generation of Bitcoiners is born.
The four-year period between halvings seems to serve a deliberate purpose. Satoshi could just as well have programmed a smooth issuance curve into the Bitcoin protocol, but he didn’t. As events unfold, it seems that he had good reason for this since these hype cycles provide a very effective onboarding mechanism, and they seem to be linked to the halvings. They certainly make Bitcoin volatile, but remember that in this early stage, the volatility is needed in order for these hype cycles to happen. Later on, when Bitcoin’s stock-to-flow ratio is higher, the seas will calm, and its volatility level will go down. In truth, it already has. The latest almost 80% price drop was far from the worst we’ve seen in Bitcoin. This technology is still in its infancy, and it is very likely that we’ll see a lot more volatility before mainstream adoption, or hyperbitcoinization, truly happens.
About the Bitcoin Infinity Academy
The Bitcoin Infinity Academy is an educational project built around Knut Svanholm’s books about Bitcoin and Austrian Economics. Each week, a whole chapter from one of the books is released for free on Highlighter, accompanied by a video in which Knut and Luke de Wolf discuss that chapter’s ideas. You can join the discussions by signing up for one of the courses on our Geyser page. Signed books, monthly calls, and lots of other benefits are also available.
-
 @ bf95e1a4:ebdcc848
2025-04-11 11:18:42
@ bf95e1a4:ebdcc848
2025-04-11 11:18:42This is a part of the Bitcoin Infinity Academy course on Knut Svanholm's book Bitcoin: Sovereignty Through Mathematics. For more information, check out our Geyser page!
An Immaculate Conception
Some concepts in nature are harder for us humans to understand than others. How complex things can emerge out of simpler ones is one of those concepts. A termite colony, for instance, has a complex cooling system at its lower levels. No single termite knows how it works. Completely unaware of the end results, they build complex mounds and nests, shelter tubes to protect their paths, and networks of subterranean tunnels to connect their dirt cities. Everything seems organized and designed, but it is not. Evolution has equipped the termite with a pheromone receptor that tells the termite what task he ought to engage himself in by simply counting the number of neighboring termites doing the same thing. If there’s a surplus of workers in an area, nearby termites become warriors, and so on. Complex structures emerge from simple rules. The fractal patterns found all around nature are another example. Fractals look complex, but in reality, they’re not. They’re basically algorithms — the same pattern, repeated over and over again with a slightly modified starting point. The human brain is an excellent example of a complex thing that evolved out of simpler things, and we humans still have a hard time accepting that it wasn’t designed. Religions, which themselves are emergent systems spawned out of human interaction, have come up with a plethora of explanations for how we came to be. All sorts of wild origin stories have been more widely accepted than the simple explanation that our complexities just emerged out of simpler things following a set of rules that nature itself provided our world with.
Complex systems emerge out of human interactions all the time. The phone in your pocket is the result of a century of mostly free global market competition, and no single human could ever have come up with the entire thing. The device, together with its internet connection, is capable of a lot more than the sum of its individual parts. A pocket-sized gadget that can grant instant access to almost all of the world’s literature, music, and film, which fits in your pocket, was an unthinkable science fiction a mere twenty years ago. Bitcoin, first described in Satoshi Nakamoto’s whitepaper ten years before these words were written, was designed to be decentralized. Still, it wasn’t until years later that the network started to show actual proof of this. Sound money, or absolute digital scarcity, emerged out of the network not only because of its technical design. How Bitcoin’s first ten years actually unfolded played a huge part in how true decentralization could emerge, and this is also the main reason why the experiment cannot be replicated. Scarcity on the internet could only be invented once. Satoshi’s disappearance was Bitcoin’s first step towards true decentralization. No marketing whatsoever and the randomness of who hopped onto the train first were the steps that followed. Bitcoin truly had an immaculate conception.
The network has shown a remarkable resistance to change over the last few years especially, and its current state might be its last incarnation given the size of the network and the 95% agreement threshold in its consensus rules. It might never change again. In that case, an entirely new, complex life form will have emerged out of a simple set of rules. Even if small upgrades are implemented in the future, the 21 million coin supply cap is set in stone forever. Bitcoin is not for humans to have opinions about — it exists regardless of what anyone thinks about it, and it ought to be studied rather than discussed. We don’t know what true scarcity and a truly global, anonymous free market will do to our species yet, but we are about to find out. It is naïve to think otherwise. Various futurists and doomsday prophets have been focused on the dangers of the impending general artificial intelligence singularity lately, warning us about the point of no return, whereupon an artificial intelligence will be able to improve itself faster than any human could. Such a scenario could, as news anchor Ron Burgundy would have put it, escalate quickly. This may or may not be of real concern to us, but meanwhile, right under our noses, another type of unstoppable digital life has emerged, and it is already changing the behavior and preferences of millions of people around the globe. This is probably bad news for big corporations and governments but good news for the little guy looking for a little freedom. At least, that’s what those of us who lean towards the ideas of the Austrian school of economics believe. This time around, we will find out whether this is the case or not. No one knows what it will lead to and what new truths will emerge out of this new reality.
Unlike the termite, we humans are able to experience the grandeur of our progress. We can look in awe at the Sistine Chapel or the pyramids, and we can delve into the technicalities and brief history of Bitcoin and discover new ways of thinking about value along the way. Money is the language in which we express value to each other through space and time. Now, that language is spoken by computers. Value expressed in this language can’t be diluted through inflation or counterfeiting any longer. It is a language that is borderless, permissionless, peer-to-peer, anonymous (if you have the skills), unreplicable, completely scarce, non-dilutable, unchangeable, untouchable, undeniable, fungible, and free for everyone on Earth to use. It is a language for the future and it emerged out of a specific set of events in the past. All languages are examples of complex systems emerging out of simpler things, and Bitcoin evolved just as organically as any other human language did.
Decentralization is hard to achieve. Really hard. When it comes to claims of decentralization, a “don’t trust, verify” approach to the validity of such claims will help you filter out the noise. So, how can the validity of Bitcoin’s decentralization be verified? It’s a tricky question because decentralization is not a binary thing, like life or death, but rather a very difficult concept to define. However, the most fundamental concepts in Bitcoin, like the 21 million cap on coin issuance or the ten-minute block interval as a result of the difficulty adjustment and the Proof of Work algorithm, have not changed since very early on in the history of the network. This lack of change, which is arguably Bitcoin’s biggest strength, has been achieved through the consensus rules, which define what the blockchain is. Some special mechanisms (for example, BIP9) are sometimes used to deploy changes to the consensus rules. These mechanisms use a threshold when counting blocks that signal for a certain upgrade. For example, the upgrade “Segregated Witness” activated in a node when 95% or more of the blocks in a retarget period signaled support. Bitcoin has displayed a remarkable immutability through the years, and it is highly unlikely that this would have been the case if the game-theoretical mechanisms that enable its decentralized governance model hadn’t worked, given the many incentives to cheat that always seem to corrupt monetary systems. In other words, the longer the system seems to be working, the higher the likelihood that it actually does.
Satoshi set in stone the length of the halving period — a very important aspect of Bitcoin’s issuance schedule and initial distribution. During the first four years of Bitcoin’s existence, fifty new coins were issued every ten minutes up until the first block reward halving four years later. Every four years, this reward is halved so that the issuance rate goes down by fifty percent. This effectively means that half of all the Bitcoin that will ever exist was mined during the first four years of the network’s life, one fourth during its next four years, and so on. At the time of writing, we’re a little more than a year from the third halving. After that, only 6.25 Bitcoin will be minted every ten minutes as opposed to 50, which was the initial rate. What this seems to do is to create hype cycles for Bitcoin’s adoption. Every time the price of Bitcoin booms and then busts down to a level above where it started, a hype cycle takes place. Bitcoin had no marketing whatsoever, so awareness of it had to be spread through some other mechanism. When a bull run begins, people start talking about it, which leads to even more people buying due to fear of missing out (FOMO), which inevitably causes the price to rise even more rapidly. This leads to more FOMO, and on and on the bull market goes until it suddenly ends, and the price crashes down to somewhere around, or slightly above, the level it was at before the bull run started. Unlike what is true for most other assets, Bitcoin never really crashes all the way. Why? Because every time a hype cycle occurs, some more people learn about Bitcoin’s fundamentals and manage to resist the urge to sell, even when almost all hope seems lost. They understand that these bull markets are a reoccurring thing due to the nature of the protocol. These cycles create new waves of evangelists who start promoting Bitcoin simply because of what they stand to gain from a price increase. In a sense, the protocol itself pays for its own promotion in this way. This organic marketing creates a lot of noise and confusion, too, as a lot of people who don’t seem to understand how Bitcoin works are often very outspoken about it despite their lack of knowledge. Red herrings, such as altcoins and Bitcoin forks, are then weeded out naturally during bear markets. Every time a bull market happens, a new generation of Bitcoiners is born.
The four-year period between halvings seems to serve a deliberate purpose. Satoshi could just as well have programmed a smooth issuance curve into the Bitcoin protocol, but he didn’t. As events unfold, it seems that he had good reason for this since these hype cycles provide a very effective onboarding mechanism, and they seem to be linked to the halvings. They certainly make Bitcoin volatile, but remember that in this early stage, the volatility is needed in order for these hype cycles to happen. Later on, when Bitcoin’s stock-to-flow ratio is higher, the seas will calm, and its volatility level will go down. In truth, it already has. The latest almost 80% price drop was far from the worst we’ve seen in Bitcoin. This technology is still in its infancy, and it is very likely that we’ll see a lot more volatility before mainstream adoption, or hyperbitcoinization, truly happens.
About the Bitcoin Infinity Academy
The Bitcoin Infinity Academy is an educational project built around Knut Svanholm’s books about Bitcoin and Austrian Economics. Each week, a whole chapter from one of the books is released for free on Highlighter, accompanied by a video in which Knut and Luke de Wolf discuss that chapter’s ideas. You can join the discussions by signing up for one of the courses on our Geyser page. Signed books, monthly calls, and lots of other benefits are also available.
-
 @ c1e9ab3a:9cb56b43
2025-04-11 04:41:15
@ c1e9ab3a:9cb56b43
2025-04-11 04:41:15Reanalysis: Could the Great Pyramid Function as an Ammonia Generator Powered by a 25GW Breeder Reactor?
Introduction
The Great Pyramid of Giza has traditionally been considered a tomb or ceremonial structure. Yet an intriguing alternative hypothesis suggests it could have functioned as a large-scale ammonia generator, powered by a high-energy source, such as a nuclear breeder reactor. This analysis explores the theoretical practicality of powering such a system using a continuous 25-gigawatt (GW) breeder reactor.
The Pyramid as an Ammonia Generator
Producing ammonia (NH₃) from atmospheric nitrogen (N₂) and hydrogen (H₂) requires substantial energy. Modern ammonia production (via the Haber-Bosch process) typically demands high pressure (~150–250 atmospheres) and temperatures (~400–500°C). However, given enough available energy, it is theoretically feasible to synthesize ammonia at lower pressures if catalysts and temperatures are sufficiently high or if alternative electrochemical or plasma-based fixation methods are employed.
Theoretical System Components:
-
High Heat Source (25GW breeder reactor)
A breeder reactor could consistently generate large amounts of heat. At a steady state of approximately 25GW, this heat source would easily sustain temperatures exceeding the 450°C threshold necessary for ammonia synthesis reactions, particularly if conducted electrochemically or catalytically. -
Steam and Hydrogen Production
The intense heat from a breeder reactor can efficiently evaporate water from subterranean channels (such as those historically suggested to exist beneath the pyramid) to form superheated steam. If coupled with high-voltage electrostatic fields (possibly in the millions of volts), steam electrolysis into hydrogen and oxygen becomes viable. This high-voltage environment could substantially enhance electrolysis efficiency. -
Nitrogen Fixation (Ammonia Synthesis)
With hydrogen readily produced, ammonia generation can proceed. Atmospheric nitrogen, abundant around the pyramid, can combine with the hydrogen generated through electrolysis. Under these conditions, the pyramid's capstone—potentially made from a catalytic metal like osmium, platinum, or gold—could facilitate nitrogen fixation at elevated temperatures.
Power Requirements and Energy Calculations
A thorough calculation of the continuous power requirements to maintain this system follows:
- Estimated Steady-state Power: ~25 GW of continuous thermal power.
- Total Energy Over 10,000 years: """ Energy = 25 GW × 10,000 years × 365.25 days/year × 24 hrs/day × 3600 s/hr ≈ 7.9 × 10²¹ Joules """
Feasibility of a 25GW Breeder Reactor within the Pyramid
A breeder reactor capable of sustaining 25GW thermal power is physically plausible—modern commercial reactors routinely generate 3–4GW thermal, so this is within an achievable engineering scale (though certainly large by current standards).
Fuel Requirements:
- Each kilogram of fissile fuel (e.g., U-233 from Thorium-232) releases ~80 terajoules (TJ) or 8×10¹³ joules.
- Considering reactor efficiency (~35%), one kilogram provides ~2.8×10¹³ joules usable energy: """ Fuel Required = 7.9 × 10²¹ J / 2.8 × 10¹³ J/kg ≈ 280,000 metric tons """
- With a breeding ratio of ~1.3: """ Initial Load = 280,000 tons / 1.3 ≈ 215,000 tons """
Reactor Physical Dimensions (Pebble Bed Design):
- King’s Chamber size: ~318 cubic meters.
- The reactor core would need to be extremely dense and highly efficient. Advanced engineering would be required to concentrate such power in this space, but it is within speculative feasibility.
Steam Generation and Scaling Management
Key methods to mitigate mineral scaling in the system: 1. Natural Limestone Filtration 2. Chemical Additives (e.g., chelating agents, phosphate compounds) 3. Superheating and Electrostatic Ionization 4. Electrostatic Control
Conclusion and Practical Considerations
Yes, the Great Pyramid could theoretically function as an ammonia generator if powered by a 25GW breeder reactor, using: - Thorium or Uranium-based fertile material, - Sustainable steam and scaling management, - High-voltage-enhanced electrolysis and catalytic ammonia synthesis.
While speculative, it is technologically coherent when analyzed through the lens of modern nuclear and chemical engineering.
See also: nostr:naddr1qqxnzde5xymrgvekxycrswfeqy2hwumn8ghj7am0deejucmpd3mxztnyv4mz7q3qc856kwjk524kef97hazw5e9jlkjq4333r6yxh2rtgefpd894ddpsxpqqqp65wun9c08
-
-
 @ 9a1adc34:9a9d705b
2025-04-11 01:59:19
@ 9a1adc34:9a9d705b
2025-04-11 01:59:19Testing the concept of using Nostr as a personal CMS.
-
 @ c1e9ab3a:9cb56b43
2025-04-10 02:58:16
@ c1e9ab3a:9cb56b43
2025-04-10 02:58:16Assumptions
| Factor | Assumption | |--------|------------| | CO₂ | Not considered a pollutant or is captured/stored later | | Water Use | Regulated across all sources; cooling towers or dry cooling required | | Compliance Cost | Nuclear no longer burdened by long licensing and construction delays | | Coal Waste | Treated as valuable raw material (e.g., fly ash for cement, gypsum from scrubbers) | | Nuclear Tech | Gen IV SMRs in widespread use (e.g., 50–300 MWe units, modular build, passive safety) | | Grid Role | All three provide baseload or load-following power | | Fuel Pricing | Moderate and stable (no energy crisis or supply chain disruptions) |
Performance Comparison
| Category | Coal (IGCC + Scrubbers) | Natural Gas (CCGT) | Nuclear (Gen IV SMRs) | |---------|-----------------------------|------------------------|--------------------------| | Thermal Efficiency | 40–45% | 55–62% | 30–35% | | CAPEX ($/kW) | $3,500–5,000 | $900–1,300 | $4,000–7,000 (modularized) | | O&M Cost ($/MWh) | $30–50 | $10–20 | $10–25 | | Fuel Cost ($/MWh) | $15–25 | $25–35 | $6–10 | | Water Use (gal/MWh) | 300–500 (with cooling towers) | 100–250 | 300–600 | | Air Emissions | Very low (excluding CO₂) | Very low | None | | Waste | Usable (fly ash, FGD gypsum, slag) | Minimal | Compact, long-term storage required | | Ramp/Flexibility | Slow ramp (newer designs better) | Fast ramp | Medium (SMRs better than traditional) | | Footprint (Land & Supply) | Large (mining, transport) | Medium | Small | | Energy Density | Medium | Medium-high | Very high | | Build Time | 4–7 years | 2–4 years | 2–5 years (with factory builds) | | Lifecycle (years) | 40+ | 30+ | 60+ | | Grid Resilience | High | High | Very High (passive safety, long refuel) |
Strategic Role Summary
1. Coal (Clean & Integrated)
- Strengths: Long-term fuel security; byproduct reuse; high reliability; domestic resource.
- Drawbacks: Still low flexibility; moderate efficiency; large physical/logistical footprint.
- Strategic Role: Best suited for regions with abundant coal and industrial reuse markets.
2. Natural Gas (CCGT)
- Strengths: High efficiency, low CAPEX, grid agility, low emissions.
- Drawbacks: Still fossil-based; dependent on well infrastructure; less long-lived.
- Strategic Role: Excellent transitional and peaking solution; strong complement to renewables.
3. Nuclear (Gen IV SMRs)
- Strengths: Highest energy density; no air emissions or CO₂; long lifespan; modular & scalable.
- Drawbacks: Still needs safe waste handling; high upfront cost; novel tech in deployment stage.
- Strategic Role: Ideal for low-carbon baseload, remote areas, and national strategic assets.
Adjusted Levelized Cost of Electricity (LCOE)
| Source | LCOE ($/MWh) | Notes | |--------|------------------|-------| | Coal (IGCC w/scrubbers) | ~$75–95 | Lower with valuable waste | | Natural Gas (CCGT) | ~$45–70 | Highly competitive if fuel costs are stable | | Gen IV SMRs | ~$65–85 | Assuming factory production and streamlined permitting |
Final Verdict (Under Optimized Assumptions)
- Most Economical Short-Term: Natural Gas
- Most Strategic Long-Term: Gen IV SMRs
- Most Viable if Industrial Ecosystem Exists: Clean Coal
All three could coexist in a diversified, stable energy grid: - Coal filling a regional or industrial niche, - Gas providing flexibility and economy, - SMRs ensuring long-term sustainability and energy security.
-
 @ c1e9ab3a:9cb56b43
2025-04-10 02:57:02
@ c1e9ab3a:9cb56b43
2025-04-10 02:57:02A follow-up to nostr:naddr1qqgxxwtyxe3kvc3jvvuxywtyxs6rjq3qc856kwjk524kef97hazw5e9jlkjq4333r6yxh2rtgefpd894ddpsxpqqqp65wuaydz8
This whitepaper, a comparison of baseload power options, explores a strategic policy framework to reduce the cost of next-generation nuclear power by aligning Gen IV Small Modular Reactors (SMRs) with national security objectives, public utility management, and a competitive manufacturing ecosystem modeled after the aerospace industry. Under this approach, SMRs could deliver stable, carbon-free power at $40–55/MWh, rivaling the economics of natural gas and renewables.
1. Context and Strategic Opportunity
Current Nuclear Cost Challenges
- High capital expenditure ($4,000–$12,000/kW)
- Lengthy permitting and construction timelines (10–15 years)
- Regulatory delays and public opposition
- Customized, one-off reactor designs with no economies of scale
The Promise of SMRs
- Factory-built, modular units
- Lower absolute cost and shorter build time
- Enhanced passive safety
- Scalable deployment
2. National Security as a Catalyst
Strategic Benefits
- Energy resilience for critical defense infrastructure
- Off-grid operation and EMP/cyber threat mitigation
- Long-duration fuel cycles reduce logistical risk
Policy Implications
- Streamlined permitting and site access under national defense exemptions
- Budget support via Department of Defense and Department of Energy
- Co-location on military bases and federal sites
3. Publicly Chartered Utilities: A New Operating Model
Utility Framework
- Federally chartered, low-margin operator (like TVA or USPS)
- Financially self-sustaining through long-term PPAs
- Focus on reliability, security, and public service over profit
Cost Advantages
- Lower cost of capital through public backing
- Predictable revenue models
- Community trust and stakeholder alignment
4. Competitive Manufacturing: The Aviation Analogy
Model Characteristics
- Multiple certified vendors, competing under common safety frameworks
- Factory-scale production and supply chain specialization
- Domestic sourcing for critical components and fuel
Benefits
- Cost reductions from repetition and volume
- Innovation through competition
- Export potential and industrial job creation
5. Levelized Cost of Electricity (LCOE) Impact
| Cost Lever | Estimated LCOE Reduction | |------------|--------------------------| | Streamlined regulation | -10 to -20% | | Public-charter operation | -5 to -15% | | Factory-built SMRs | -15 to -30% | | Defense market anchor | -10% |
Estimated Resulting LCOE: $40–55/MWh
6. Strategic Outcomes
- Nuclear cost competitiveness with gas and renewables
- Decarbonization without reliability sacrifice
- Strengthened national energy resilience
- Industrial and workforce revitalization
- U.S. global leadership in clean, secure nuclear energy
7. Recommendations
- Create a public-private chartered SMR utility
- Deploy initial reactors on military and federal lands
- Incentivize competitive SMR manufacturing consortia
- Establish fast-track licensing for Gen IV designs
- Align DoD/DOE energy procurement to SMR adoption
Conclusion
This strategy would transform nuclear power from a high-cost, high-risk sector into a mission-driven, economically viable backbone of American energy and defense infrastructure. By treating SMRs as strategic assets, not just energy projects, the U.S. can unlock affordable, scalable, and secure nuclear power for generations to come.
-
 @ c1e9ab3a:9cb56b43
2025-04-10 02:55:11
@ c1e9ab3a:9cb56b43
2025-04-10 02:55:11The United States is on the cusp of a historic technological renaissance, often referred to as the Fourth Industrial Revolution. Artificial intelligence, automation, advanced robotics, quantum computing, biotechnology, and clean manufacturing are converging into a seismic shift that will redefine how we live, work, and relate to one another. But there's a critical catch: this transformation depends entirely on the availability of stable, abundant, and inexpensive electricity.
Why Electricity is the Keystone of Innovation
Let’s start with something basic but often overlooked. Every industrial revolution has had an energy driver:
- The First rode the steam engine, powered by coal.
- The Second was electrified through centralized power plants.
- The Third harnessed computing and the internet.
- The Fourth will demand energy on a scale and reliability never seen before.
Imagine a city where thousands of small factories run 24/7 with robotics and AI doing precision manufacturing. Imagine a national network of autonomous vehicles, delivery drones, urban vertical farms, and high-bandwidth communication systems. All of this requires uninterrupted and inexpensive power.
Without it? Costs balloon. Innovation stalls. Investment leaves. And America risks becoming a second-tier economic power in a multipolar world.
So here’s the thesis: If we want to lead the Fourth Industrial Revolution, we must first lead in energy. And nuclear — specifically Gen IV Small Modular Reactors (SMRs) — must be part of that leadership.
The Nuclear Case: Clean, Scalable, Strategic
Let’s debunk the myth: nuclear is not the boogeyman of the 1970s. It’s one of the safest, cleanest, and most energy-dense sources we have.
But traditional nuclear has problems:
- Too expensive to build.
- Too long to license.
- Too bespoke and complex.
Enter Gen IV SMRs:
- Factory-built and transportable.
- Passively safe with walk-away safety designs.
- Scalable in 50–300 MWe increments.
- Ideal for remote areas, industrial parks, and military bases.
But even SMRs will struggle under the current regulatory, economic, and manufacturing ecosystem. To unlock their potential, we need a new national approach.
The Argument for National Strategy
Let’s paint a vision:
SMRs deployed at military bases across the country, secured by trained personnel, powering critical infrastructure, and feeding clean, carbon-free power back into surrounding communities.
SMRs operated by public chartered utilities—not for Wall Street profits, but for stability, security, and public good.
SMRs manufactured by a competitive ecosystem of certified vendors, just like aircraft or medical devices, with standard parts and rapid regulatory approval.
This isn't science fiction. It's a plausible, powerful model. Here’s how we do it.
Step 1: Treat SMRs as a National Security Asset
Why does the Department of Defense spend billions to secure oil convoys and build fuel depots across the world, but not invest in nuclear microgrids that would make forward bases self-sufficient for decades?
Nuclear power is inherently a strategic asset:
- Immune to price shocks.
- Hard to sabotage.
- Decades of stable power from a small footprint.
It’s time to reframe SMRs from an energy project to a national security platform. That changes everything.
Step 2: Create Public-Chartered Operating Companies
We don’t need another corporate monopoly or Wall Street scheme. Instead, let’s charter SMR utilities the way we chartered the TVA or the Postal Service:
- Low-margin, mission-oriented.
- Publicly accountable.
- Able to sign long-term contracts with DOD, DOE, or regional utilities.
These organizations won’t chase quarterly profits. They’ll chase uptime, grid stability, and national resilience.
Step 3: Build a Competitive SMR Industry Like Aerospace
Imagine multiple manufacturers building SMRs to common, certified standards. Components sourced from a wide supplier base. Designs evolving year over year, with upgrades like software and avionics do.
This is how we build:
- Safer reactors
- Cheaper units
- Modular designs
- A real export industry
Airplanes are safe, affordable, and efficient because of scale and standardization. We can do the same with reactors.
Step 4: Anchor SMRs to the Coming Fourth Industrial Revolution
AI, robotics, and distributed manufacturing don’t need fossil fuels. They need cheap, clean, continuous electricity.
- AI datacenters
- Robotic agriculture
- Carbon-free steel and cement
- Direct air capture
- Electric industrial transport
SMRs enable this future. And they decentralize power, both literally and economically. That means jobs in every region, not just coastal tech hubs.
Step 5: Pair Energy Sovereignty with Economic Reform
Here’s the big leap: what if this new energy architecture was tied to a transparent, auditable, and sovereign monetary system?
- Public utilities priced in a new digital dollar.
- Trade policy balanced by low-carbon energy exports.
- Public accounting verified with open ledgers.
This is not just national security. It’s monetary resilience.
The world is moving to multi-polar trade systems. Energy exports and energy reliability will define economic influence. If America leads with SMRs, we lead the conversation.
Conclusion: A Moral and Strategic Imperative
We can either:
- Let outdated fears and bureaucracy stall the future, or...
- Build the infrastructure for clean, secure, and sovereign prosperity.
We have the designs.
We have the talent.
We have the need.What we need now is will.
The Fourth Industrial Revolution will either be powered by us—or by someone else. Let’s make sure America leads. And let’s do it with SMRs, public charter, competitive industry, and national purpose.
It’s time.
This is a call to engineers, legislators, veterans, economists, and every American who believes in building again. SMRs are not just about power. They are about sovereignty, security, and shared prosperity.
Further reading:
nostr:naddr1qqgrjv33xenx2drpve3kxvrp8quxgqgcwaehxw309anxjmr5v4ezumn0wd68ytnhd9hx2tczyrq7n2e62632km9yh6l5f6nykt76gzkxxy0gs6agddr9y95uk445xqcyqqq823cdzc99s
-
 @ 8d34bd24:414be32b
2025-04-09 14:45:28
@ 8d34bd24:414be32b
2025-04-09 14:45:28I was listening to “Ultimately with R.C. Sproul.” He made the comment that “Sin is so common that we don’t think it is that concerning, but it is especially concerning because it is so common.” This is so true.
I used to really look down on Adam and Eve for eating the forbidden fruit. I thought, “How hard is it to obey a single command? We have so many to obey today from God, government, parents, etc.” One day I finally realized two truths. Adam and Eve were adults, but they had not been around very long (the Bible doesn’t say how long, but the implication is not very long, maybe even as short as days after being created.) They didn’t have life experience. They also had never been lied to before. They weren’t looking at the world with suspicion. They lived in a perfect environment with a perfect, loving God. It would’ve never crossed their mind that a person would lie, so they trusted the lie instead of God.
Today, we live in a sinful, fallen world. Everyone lies. Everyone steals. Everyone is unkind. Everyone has selfish motives. Yes, there is a difference in how often and how “bad” the lie, the theft, the motive, or the unkindness, but sin is everywhere. We get used to it and it seems normal. When we act the same way, it doesn’t seem that bad. We just took a pen home from work, nobody will miss it. We just told the person what they wanted to hear, so we won’t hurt their feelings. It is only a little white lie. Yes, I was unkind, but that person really deserved it because they were worse. We think this way and excuse our sins because we aren’t as bad as someone else.
I’ve noticed as I’ve grown older that the age when you become old keeps getting older and older. Old is always a little bit older than I am. When I was 10, a teenager was really old. When I was 16, an 18 year old was an adult and old. When I was 20, a 40 year old was old. When I was 50, a 65 year old was old. Old keeps getting older because my reference is myself. The truth is that I am getting older. I am on the downhill slide. I am closer to death than I am to birth. My arbitrary, moving reference doesn’t change this fact.
In the same way, when we look at sin, we have the same problem. We are always looking for someone who sins worse to make us look better and to excuse our sins. We compare ourselves to sinful men instead of our perfect, holy, sinless Savior.
In an earlier post, I made the comparison of the lights in the sky. If you go outside on a dark, moonless night, you will see the stars in the sky shining. They seem bright, but some are brighter than others. You can compare the brightness of the stars and call some brighter and others darker, but when the sun rises, you can’t see any light from the stars. Their light is drowned out by the light of the sun. The sun is so much brighter that it is as if the stars don’t produce any light at all.
In the same way, we may do some good things. When we compare our good deeds to others, we may look better, but when the true reference, the Son of God is our reference, our good works look like they don’t exist at all. The differences between the best person and the worst person are insignificant, just like the brightness of the brightest star and the dimmest star seems insignificant when compared with the brightness of the Sun.
The cool thing is that there is another light in the sky, the moon. The moon doesn’t have any light of its own, but it is the second brightest light in the sky. Why? Because it reflects the light of the sun. We should be the same way. We will never measure up if we seek to be good and sinless. We will never meet the standard that Jesus set for us with His perfect, sinless, sacrificial life, but we can reflect the glory of Jesus in our lives.
Yes, when we sin, we can hurt others, but who are we really sinning against? David knows.
Be gracious to me, O God, according to Your lovingkindness;\ According to the greatness of Your compassion blot out my transgressions.\ Wash me thoroughly from my iniquity\ And cleanse me from my sin.\ For I know my transgressions,\ And my sin is ever before me.\ **Against You, You only, I have sinned\ And done what is evil in Your sight,\ So that You are justified when You speak\ And blameless when You judge.\ Behold, I was brought forth in iniquity,\ And in sin my mother conceived me.\ Behold, You desire truth in the innermost being,\ And in the hidden part You will make me know wisdom. (Psalm 51:1-6) {emphasis mine}
Yes, our sins can hurt other people and do, but the true damage is to the glory of our generous Creator God. We must confess our sins to God first and then to anyone we have hurt. We must accept that we deserve any judgement God gives us because He created us and everyone and everything with which we interact. Our allegiance, submission, and worship is due to our Creator God.
Because we can never fully understand how abhorrent sin is to God, I thought I’d share how a godly man, the priest and prophet, Ezra, reacted to sin among his brethren.
When I heard about this matter, I tore my garment and my robe, and pulled some of the hair from my head and my beard, and sat down appalled. Then everyone who trembled at the words of the God of Israel on account of the unfaithfulness of the exiles gathered to me, and I sat appalled until the evening offering.
But at the evening offering I arose from my humiliation, even with my garment and my robe torn, and I fell on my knees and stretched out my hands to the Lord my God; and I said, “O my God, I am ashamed and embarrassed to lift up my face to You, my God, for our iniquities have risen above our heads and our guilt has grown even to the heavens. Since the days of our fathers to this day we have been in great guilt, and on account of our iniquities we, our kings and our priests have been given into the hand of the kings of the lands, to the sword, to captivity and to plunder and to open shame, as it is this day. But now for a brief moment grace has been shown from the Lord our God, to leave us an escaped remnant and to give us a peg in His holy place, that our God may enlighten our eyes and grant us a little reviving in our bondage. (Ezra 9:3-8) {emphasis mine}
Ezra sees sin, shreds his clothes, pulls out his hair, and sits appalled. Do we feel even a fraction of the horror at guilt that Ezra showed? When faced with some Israelites marrying non-Israelite (many from the banned people groups), Ezra admits that “our iniquities have risen above our heads and our guilt has grown even to the heavens.” How many of us would think that was only a little sin or that since it was only a few people, it wasn’t that important? Ezra, instead of saying, “Why did you send us into exile for 70 years and why are you not blessing us now?” said, “But now for a brief moment grace has been shown from the Lord our God.” Instead of accusing God of not being good enough or kind enough, thanks God for His grace which was completely undeserved. If only we could look at sin in this way.
After all that has come upon us for our evil deeds and our great guilt, since You our God have requited us less than our iniquities deserve, and have given us an escaped remnant as this, (Ezra 9:13) {emphasis mine}
Ezra understood that we all deserve only judgment. Every good thing we receive is only due to God’s grace. Instead of asking why God would allow a bad thing to happen to us, we should be asking why God is so gracious to give us good things in our lives and not give us nothing but punishment.
Jesus also talked about our sins. Although it is good, when we are tempted to sin, to choose to not sin, even evil thoughts are sins. They mean our minds and hearts are not fully submitted to God.
“You have heard that the ancients were told, ‘You shall not commit murder’ and ‘Whoever commits murder shall be liable to the court.’ But I say to you that everyone who is angry with his brother shall be guilty before the court; and whoever says to his brother, ‘You good-for-nothing,’ shall be guilty before the supreme court; and whoever says, ‘You fool,’ shall be guilty enough to go into the fiery hell. Therefore if you are presenting your offering at the altar, and there remember that your brother has something against you, leave your offering there before the altar and go; first be reconciled to your brother, and then come and present your offering. Make friends quickly with your opponent at law while you are with him on the way, so that your opponent may not hand you over to the judge, and the judge to the officer, and you be thrown into prison. Truly I say to you, you will not come out of there until you have paid up the last cent.
“You have heard that it was said, ‘You shall not commit adultery’; but I say to you that everyone who looks at a woman with lust for her has already committed adultery with her in his heart. If your right eye makes you stumble, tear it out and throw it from you; for it is better for you to lose one of the parts of your body, than for your whole body to be thrown into hell. If your right hand makes you stumble, cut it off and throw it from you; for it is better for you to lose one of the parts of your body, than for your whole body to go into hell.
“It was said, ‘Whoever sends his wife away, let him give her a certificate of divorce’; but I say to you that everyone who divorces his wife, except for the reason of unchastity, makes her commit adultery; and whoever marries a divorced woman commits adultery.
“Again, you have heard that the ancients were told, ‘You shall not make false vows, but shall fulfill your vows to the Lord.’ But I say to you, make no oath at all, either by heaven, for it is the throne of God, or by the earth, for it is the footstool of His feet, or by Jerusalem, for it is the city of the great King. Nor shall you make an oath by your head, for you cannot make one hair white or black. But let your statement be, ‘Yes, yes’ or ‘No, no’; anything beyond these is of evil.
“You have heard that it was said, ‘An eye for an eye, and a tooth for a tooth.’ But I say to you, do not resist an evil person; but whoever slaps you on your right cheek, turn the other to him also. If anyone wants to sue you and take your shirt, let him have your coat also. Whoever forces you to go one mile, go with him two. Give to him who asks of you, and do not turn away from him who wants to borrow from you.
“You have heard that it was said, ‘You shall love your neighbor and hate your enemy.’ But I say to you, love your enemies and pray for those who persecute you, so that you may be sons of your Father who is in heaven; for He causes His sun to rise on the evil and the good, and sends rain on the righteous and the unrighteous. For if you love those who love you, what reward do you have? Do not even the tax collectors do the same? If you greet only your brothers, what more are you doing than others? Do not even the Gentiles do the same? Therefore you are to be perfect, as your heavenly Father is perfect. (Matthew 5:21-48) {emphasis mine}
Many people say that as New Testament believers, we are not under the Old Covenant and the Old Testament laws do not apply to us. While that may be true of the ceremonial laws, the truth is that Jesus made the laws stricter. It is still true that we are not to commit murder, but we are also not to hate another. It is still true that we are not to commit adultery, but we are also not to lust after another. We are also not to fight against those who mistreat us and we are to love those who hate us. Jesus expects more, not less, maybe because we now have the guidance and power of the Holy Spirit within us.
If we have the mind of Christ, we should despise the things God hates. If we have the heart of Christ, we should love even those who hate us and we should seek their eternal good. We should see with the eyes of Christ and see the hurt behind the hate and dishonesty. How do we do this? We need to fill our minds with the word of God. We need to obey Paul’s command to those in Philippi:
Finally, brethren, whatever is true, whatever is honorable, whatever is right, whatever is pure, whatever is lovely, whatever is of good repute, if there is any excellence and if anything worthy of praise, dwell on these things. (Philippians 4:8)
We need to so fill our mind with God’s word that God’s goodness overflows into our lives.
God of heaven, please change our hearts and minds and make them fully aligned with your heart and mind. Help us to see sin as you see sin and to see people as you see people. Help us to see the hurt instead of the lashing out, so we can have a merciful heart towards those who are unkind to us. Help us to fill our minds with your goodness and your word, so there is no room for evil in us. Make us more like you.
Trust Jesus
FYI, there are many people who can’t see their own sin and who discount the severity of sin. I am writing for these people. There are also people who have no trouble seeing their own sin. Their problem is not accepting the forgiveness of God. Never doubt that God has forgiven you if you have confessed your sins and trusted Jesus as Savior. Jesus has covered your sins and the Father sees only the holiness of Jesus. Your relationship with the Godhead is fully reconciled. You should do right out of thankfulness and love of God, but there is nothing else you need to do to be saved and have a right relationship with God.
-
 @ d3d74124:a4eb7b1d
2025-04-15 12:58:08
@ d3d74124:a4eb7b1d
2025-04-15 12:58:08ORIGINALLY ON XITTER BY STEVE BARBOUR. SHARED HERE FOR THE HOMIES (https://x.com/SGBarbour/status/1911614638623801425)
I find bureaucracy fascinating—it’s like a cancer within human organizations.
Why do organizations become bloated with excessive procedural controls, inefficiency, and indecisiveness as they grow in size and age? Why does decision-by-committee often replace the ambitious, self-starting decision maker? Why do small, "lean and mean" startups inevitably become bloated with bureaucracy as they scale and increase their headcount?
In 2014, these questions consumed me while I sat in a cubicle at an oil and gas company. Why, after years of honing my skills to fix artificial lift systems, was my signing authority decreasing (from $25,000 to $10,000 for workover budgets), despite record corporate profits? Why did I now need a 12-page Microsoft Word document with manager sign-off to schedule and scope a service rig for a simple pump change, when a five-minute email direct to the rig supervisor had previously sufficed?
Years into the job I was far more capable than when I had started, yet I had less authority with each passing day. I became determined to understand what was causes bureaucracy and whether or not it can be prevented.
After researching for some time, such as the essay I posted below, I concluded that bureaucracy stems from a lack of trust and accountability. Bureaucrats impose procedures instead of trusting subordinates to do their jobs, often in response to a costly mistake. This results in new processes that everyone must follow.
Bureaucrats rarely take responsibility for their own failures or hold others accountable for theirs. Instead, they create more procedures and invent new processes. Bureaucracy is a systemic issue, pervasive in nearly every large business or institution. The larger the organization, the more stifling it becomes.
This behavior is costly, increasing administrative overhead and delaying capital execution. Who is bearing this enormous cost?
You are, of course!
Fiat money funds the vast majority of the world's bureaucracy. Fiat money is counterfeit created out of thin air and is used to fund deficit spending by governments worldwide. Governments use paper money they did not earn from taxes to bail out institutions who are overleveraged and get caught with their pants down (e.g. Bombardier and Air Canada are famous repeat offenders in Canada, in the US you can choose any big name bank just about).
They keep printing money and nobody is held accountable anywhere.
Misallocate capital, become insolvent, print money and bail out, create new regulations / procedures, repeat.
You pay for bureaucracy by losing your savings to inflation.
You pay for bureaucracy when the local small businesses in your neighborhood is replaced by a global franchise funded by cheap, perpetual fiat money.
You pay for bureaucracy when you cannot retire as early as you planned and end up working yourself straight into a retirement home.
I was cleaning and organizing my office today and found this old essay by Brian D. Rule from 1977 on the topic, which sparked me to write this short X piece on bureaucracy.
Brian's essay 'Bureaucracy' was actually the very essay that led me into believing fiat money with the root cause of global bureaucracy and waste, which lead me to become interested in gold in 2015 and then in bitcoin in 2016.
Sure enough I googled the prevalence of the term 'bureaucracy' and something interesting happened after 1971...
Isn't it weird how so much went to shit after we got off the gold standard?
Today I am convinced that hard, sound money is the only solution to bureaucracy. This is why I work for #bitcoin.
*Sadly I can no longer find the essay online, so I ripped the text from my paper printout that I found in my files with the now defunct reference website below. *
Bureaucracy
Brian D. Rude, 1977
Original website (now defunct): http://brianrude.com/burea.htm
In the summer of 1975 I took a teaching job in Nebraska. As my previous teaching experience was in Missouri I had to see about getting a Nebraska teaching certificate. I applied for a "Nebraska Standard" teaching certificate. I sent in my college transcript, the application form, and a check for eight dollars. They sent me back, in their own good time, a "Nebraska Prestandard" certificate. I decided there was nothing "prestandard" about me or my teaching, so I wrote back and asked why I didn't get the "standard" certificate. They replied that since I had not taught three out of the last five years I was eligible only for the "prestandard" certificate.
"What do those pigheaded bureaucrats know about my teaching?" I thought to myself. "How would they ever know the standard of my teaching just from shuffling papers around?"
With a little reflection I realized that of course they know nothing about my teaching. They are not supposed to know anything about my teaching. They are paid to evaluate the papers I send them. They are not paid to evaluate my teaching. They have a clear mandate to shuffle my papers, and nothing more.
I presume my application was opened by a secretary, who, following a tightly structured routine, checked off each requirement, typed up my certificate, got it signed by some authority and sent it off to me. Such a secretary is most likely a conscientious worker, a wife and mother, a Republican or Democrat, an occasional churchgoer, a bit of a gossip, and a lot of other plain ordinary things. But she is most likely not a "pigheaded bureaucrat". She would not think of herself as a bureaucrat, and neither would her boss, her coworkers, her family, or anyone else who personally knew her. When she typed "prestandard" instead of "standard" on my teaching certificate she is simply doing her job. Were she to do anything less or more she would be negligent.
So where is the bureaucracy? Or was I dealing with a bureaucracy? If not, then where is there a bureaucracy? Where do we find the genuine article, the bungling, myopic, pigheaded bureaucrat?
I think pigheaded bureaucrats do exist, but they are rare. It's the good bureaucrat that drives us batty, quite as much as the bungling bureaucrat. The good bureaucrat knows exactly what he is obligated to do and he does it conscientiously. The good bureaucrat simply applies the rules that he is responsible for applying, but that he did not make.
A bureaucracy is a group of people responsible for applying a set of rules. The police, courts, executive branches of government, parents, teachers, librarians, and many other people or groups of people are also responsible for applying rules, yet we don't think of these as being bureaucracies. The distinguishing features of a bureaucracy are the types of rules to be applied, and, to some extent, how the rules are applied.
A bureaucracy is responsible for applying what I will call "secondary", or "derived" rules. A secondary rule is a requirement or prohibition established only because it promotes a primary goal. When Moses came down from the mountain with his stone tablets he was carrying what might be considered the simplest statement of what I will call "primary" requirements. The rule, "Thou shalt not steal", for example, is a primary requirement because it is desirable for its own sake, not just as a means to some other end. Similarly, "Thou shalt not commit murder" is a primary requirement because it is desirable as an end in itself.
Safe driving, as a modern example, is a primary requirement because it is desirable for its own sake. The requirement that one get a driver's license before driving, in contrast, is a secondary requirement. It is a requirement instituted by state governments in an attempt to promote the primary goal of safe driving. It is secondary to, or derived from, the primary requirement of driving safely. If people always drove safely, or if driving by its nature presented no hazards, then there would be no need for driver's licenses. Or if legislatures decided that licensing did nothing to promote safe driving then there would be no need for driver's licenses. Licensing is not an end in itself.
Tertiary, or third order, requirements can also exist. If a state requires a birth certificate as proof of age before issuing a driver's license then the state is imposing a third order requirement. Showing a birth certificate is a requirement designed to promote the licensing of drivers, which in turn is designed to promote safe driving.
I imagine one could go ahead and find examples of fourth order requirements established to promote third order requirements. However I don't think there is much point in getting too deep in this kind of analysis. The main point is the distinction of whether a goal is important for its own sake or whether it is important in promoting some other goal. Thus I may speak of a "derived" requirement, meaning only that it is not a primary requirement, but not specifying whether it is secondary, tertiary, or even further removed from the primary goal.
In different contexts I may speak of primary or secondary "requirements", "rules", "prohibitions", "laws", "regulations", "goals", "wrongs", "burdens", "privileges", and so on. It seems natural to think of paying taxes as a "requirement", while murder is a "wrong" that is covered by a "prohibition". But the requirement of paying a tax can be interpreted as the prohibition of avoiding the tax, and the prohibition against murder can be interpreted as the requirement to refrain from murder. The important point here is the distinction between primary and derived, not between omission and commission.
In the example I gave about getting a teaching certificate the bureaucrats were concerned only with my compliance with secondary requirements. They were not at all concerned with the primary requirement - the requirement that I indeed be a good teacher. This is a distinguishing characteristic of bureaucracies. They are concerned only with applying derived, not primary, rules. Other agencies are brought in when there is a primary rule to be applied. The police and courts handle such primary wrongs as theft and murder. Parents and teachers handle such primary wrongs as tracking mud on the carpet or being late to school. Churches handle such primary wrongs as "living in sin" or blasphemy. But it doesn't take a judge or a preacher to decide if my application for a teaching certificate is in order, or my application for a driver's license, or a dog license, or a business license, or a barber's license, or a building permit, or a marriage license, or breathing license. It takes a bureaucrat to handle these matters.
The basic root of bureaucracy then, is the proliferation of secondary requirements. It is not enough, in our modern world, to just be a good and honest person. One can be the best and safest of drivers, but a driver's license is still required. One can be a patriot and a saint, but the IRS still wants that W-2 form. One can be the best doctor in the world, but to practice medicine without a degree and a license is still a serious offense. We have established literally millions of secondary requirements designed to promote a few primary goals. To administer these rules we have people we call bureaucrats.
If the basic root of bureaucracy is a proliferation of derived requirements, then it would seem reasonable that the way to decrease bureaucracy would be to decrease such requirements. This is true, and in fact is a main thesis of this article. Unfortunately it is not always easy to do. Every bureaucratic requirement, in a healthy society at least, was established by reasonably intelligent people giving at least half-way serious consideration to a genuine problem. Therefore any particular bureaucratic requirement or procedure that is challenged will be defended by some person or group.
The most important gain we hope to realize from derived requirements is security. The requirement of any permit or license is usually, if not invariably, justified in order to "protect the public". We want safe driving so we demand driver's licenses. We want our neighbor's dog out of our flower bed so we demand dog licenses. We want merchants to be honest so we demand business licenses. We want welfare recipients not to cheat so we require verification of identity, employment, and who knows what else. All these requirements are seen as necessary to prevent something bad from happening, or to assure that something good will happen.
Derived requirements cannot provide all types of security. We can't prevent floods and famines by making rules and printing forms. The type of security that is the goal of bureaucratic requirements is social control of one form or another.
Simple fairness is often the goal of bureaucratic requirements. The Internal Revenue Service is a good example of this. The primary goal of the IRS is to raise money. This could be done by charging every citizen a flat rate of $1000 or so each year. We wouldn't consider this fair, though, because we realize not everyone has an equal ability to pay. Therefore we have an elaborate set of rules designed to extract more from those who have more. To apply these rules we have what is probably the biggest and most complex bureaucracy since time began. This size and complexity comes from our desire to be fair, not from the simple desire to collect money.
Another form of social control for which bureaucratic requirements are established is prevention of abuse of power. Power comes in many different forms, and we know from long experience that power is always susceptible to abuse. One method of dealing with abuse of power is to call it a primary wrong and punish the offenders. This is done, and it keeps the police and courts very busy. Another way to control abuse of power is to set up secondary requirements to try to prevent such wrongs from occurring in the first place. This produces bureaucracies. In the 1880's, for example, railroads were playing a little rougher than people wanted. They gained power by monopolizing a vital service. In response to this the Interstate Commerce Commission was set up, and has regulated business ever since. A more modern, and more specific, example would be the requirement that a used car dealer certify that the odometer reading is correct when he sells a car. This requirement is in response to what is seen as abuse of power by car dealers who misrepresent their merchandise.
In addition to the main cause of bureaucracy - the proliferation of derived requirements for purposes of security - there are several other causes of bureaucracies that are worth mentioning. The first of these is pure blind imitation. Again I will use driver's licensing as an example.
In the fifty states there is a startling uniformity of driver's license requirements. The most obvious uniformity is that all states require licenses. I have never been able to understand this. It would seem that if each state followed its own experience, values, customs, and judgment, then there would be a whole spectrum of licensing requirements, ranging from no requirement at all to extensive and strict requirements. This is apparently not the case. The majority of states require a written, driving, and eye test. They require a license fee. They require renewal of the license every so many years. They require that the license be in the person’s possession while he is driving. So far as I can tell only minor variations are found on this basic pattern in the different states.
I attribute this uniformity mainly to imitation. If there were an obvious connection between traffic safety and driver’s licensing then this uniformity would seem more sensible. If the National Safety Council told us everyday that the majority of fatal accidents involved an unlicensed driver, then we would not be surprised to find a driver’s license requirement in every state. But that is not the case. The National Safety Council talks a lot about the drinking driver but not about the unlicensed driver. If there was a historical example of some state that was too stubborn to require licenses and had an atrocious accident rate, then again a strict licensing system would be expected in every state. But is not the case either. The connection between licensing and safe driving is tenuous at best. There are innumerable unsafe drivers in every state who have no trouble getting a license. There are also perfectly safe drivers who have trouble getting a license. I think it is safe to say that the average driver, safe or unsafe, can’t pass the written test without studying the book no matter how long he has been driving. Many people find this out when they try to renew their license. All this leads me to believe that licensing requirements are set up by imitation more than anything else. A few states started requiring licenses and other states blindly followed, thinking in some vague way that they were being modern and progressive.
Pure blind imitation may seem a poor reason to set up a bureaucratic requirement and a bureaucracy to apply it, but there are many examples of such imitation in everyday life. In a previous article, ("Roting and Roters", not yet on my web site) I described and developed the idea that blind imitation is a powerful determinant of individual behavior. I think it is almost as powerful a determinant of group action. If each state followed its own inclination in the matter of driver’s licensing I would expect a much wider variation among the different states.
Another cause of bureaucracies is a little more substantial than blind imitation, and accounts for many licensing systems. That is the desire for group recognition. People are by nature social animals. They want to have groups and they want to do things in groups. They want their groups to be recognized and they want this recognition to be official and formal. I began to realize this a few years back when I read in the paper that beauticians were trying to get legislation passed setting up a system of beautician licensure. I thought they were nuts. Why, when we all hate the bureaucracy so much, would anyone want to set up more bureaucracy?
Another example of this kind of bureaucracy building is in the field of occupational therapy. Nurses, physical therapists, and speech therapists are licensed by the state. Occupational therapists, in contrast, have a national association which gives a "registry examination". Upon passing this test, and having a degree in occupational therapy, one becomes an "O.T.R.", a registered occupational therapist. Hospitals and other institutions take this designation as evidence of full qualification in the field. With such a sensible system I find incomprehensible that the profession is pushing for a system of state, rather than national, licensure. But that is exactly what they are doing. They are trying to build more bureaucracy, and they will succeed.
It took me quite a number of years to realize that teacher certification is something that the teaching profession wants, rather than being a requirement imposed from above. However that is apparently the case. The system of licensure, though a pain, does give some recognition to the status of teachers. This, along with a considerable amount of blind imitation, apparently accounts for the uniformity of teacher certification requirements found in different states.
It would be nice if we could give official recognition to groups without the necessity of laying down a mass of secondary requirements, but that is not how it works. Recognition, apparently would have little meaning if it did not indicate that the members of the group meet a system of requirements. It would also be nice if those who gain this official recognition were always worthy of it, but that also is unfortunately not the case. There will always be drivers, teachers, beauticians, occupational therapists, doctors, lawyers, and others who somehow manage to gain the official license but are recognized by their peers as incompetent. Whenever a system of secondary requirements is established there inevitably enters a "reality gap", a gap between the ideal and the real. This can make the whole system ineffective. I will have more to say about this ineffectiveness and its effects shortly.
Yet another factor leading to the spread of bureaucracy is a systematic error made, to a greater or lesser extent, by practitioners of almost any field. That error is thinking that the world’s problems will be solved by one’s own field of knowledge or mode of operation. I think a good name for this would be "role egocentrism". Egocentrism means that a person considers himself the center of the universe, just as ethnocentrism means that a group considers itself the center of the universe. Role egocentrism simply means that one’s own role is given undue importance and status. Thus doctors think that medicine will be the salvation of the world. When medicine has progressed far enough, they think, the world will be such a fine place that other problems will just disappear. Preachers think that if only we would all turn to God there would be no more problems. Farmers think that once the world food problem is solved, by farmers of course, then all will be well. Teachers think that education will be the one thing to save mankind from itself. Scientists think that research will usher in a new golden age.
It is hard to conceive of a bureaucrat having such grandiose visions of salvation. But remember that bureaucrats do not think of themselves as bureaucrats. Even more importantly, bureaucrats don’t make the rules, they only apply them. The rules are made by governments. Governments consist of politicians, and politicians are very susceptible to role egocentrism. To attain office a politician must convince people that government is capable of doing things, and he must believe it himself. Since people want things done it is not surprising that governments are populated by large numbers of people with an inflated idea of what can be done by writing rules and laws. Since there are few primary laws left to write, we have an ever-increasing proliferation of secondary requirements. Bureaucrats may not make the basic rules that they apply, but they do have some latitude to make minor rules, and even more importantly, they are responsible for making reports and can require reports from their subordinates. In the making of reports a little role egocentrism can go a long way. The result can be a massive flow of reams and reams of paperwork, with copies sent to all other bureaucrats who might have come slight connection to the job at hand, but with very little of the reports actually being read.
Bureaucrats also have some latitude in working as individuals or teams, and again a great deal of waste can ensue. The justification for working in committees or teams is the idea that by joining forces the best abilities of each member can be brought to bear on the problem at hand and therefore a solution to the problem is more likely. Of course there is some truth to this, but it doesn’t always work out too well. The little bit truth can become greatly augmented by role egocentrism. Team workers like to think that if you set six experts around a table something good is bound to come out of it. Non-team workers, like myself, tend to think that setting six experts around a table is a good way for six experts to waste each other’s time. I think bureaucrats at the higher levels are more prone to waste their energy this way, and I interpret this as a form of role egocentrism.
All of these cases of bureaucracy are augmented by another systematic error. That error is the systematic overestimation of group cohesiveness. In the minds of bureaucracy builders the bureaucracies already in existence become "they", and "they" are a bunch of pigheaded fools. "We", on the other hand, are good, right-thinking people and the bureaucracy we set up will serve the people, not the bureaucrats. And just to make sure we’ll write in plenty of safeguards. Of course this doesn’t work. Just because it is "our" program doesn’t mean that it won’t be subject to all the problems that beset any program. A new generation will grow up and decide that "we" are "they" and the cycle begins over again.
So far I have painted a rather pessimistic picture. We have bureaucrats because we have a multitude of derived requirements to administer, and we have a multitude of derived requirements because we think they bring us security. We also have bureaucracies because of imitation, because of the desire for group recognition, and because of role egocentrism. Yet the sum total of all this drives us batty. The next step is to try to get some idea of why and how bureaucracy is frustrating. I think the frustration results from main causes, standardization and ineffectiveness.
Standardization is a wonderful thing in industry. If my car needs a new fuel pump I can buy one right off the shelf and know it will fit. Fuel pumps are standard, and engines are standard. They fit together beautifully. The few defective fuel pumps that are not standard are quickly caught and tossed off the assembly line. This happy state of affairs does not extend to non-physical objects though. Consider, for example, a seed planter. I don’t know just how a planter might work but I visualize a mechanical hand grabbing one seed at a time and popping it into the ground. Seeds are pretty well standardized and most seeds can be picked up by these mechanical hands without injury. A few seeds, however, are nonstandard. They are either too big, or too small, or perhaps the wrong shape. The iron hands that so effectively plant most seeds will bruise, shred, mangle or maybe just overlook the oddball seeds. This doesn’t worry us though. Just like the defective fuel pumps that are bumped off the assembly line, the few mishandled seeds are of no great consequence.
When standardization is extended to humans the situation changes dramatically. We can’t bump off the defectives so carelessly. A bureaucracy can be compared to the seed planter. Iron hands pick you up and set you down again. If you fit the standard mold, these iron hands hold you gently. If you don’t fit the standard mold those same iron hands can shred you to pieces.
For example, a few years back I knew a fellow who was paraplegic. He was completely confined to his wheelchair, but he had a car with adapted controls and could drive as well as anyone. Unfortunately he had considerable difficulty licensing both himself and his car. He could drive to the courthouse, and get himself out of his car and into his wheelchair, but he had no way of getting down in the basement where the licensing offices were. There were elevators from the first floor to the basement of course, but between the parking lot and the first floor were innumerable steps and curbs. To a person in a wheelchair a single four-inch curb might as well be a ten-foot wall. Apparently my friend managed somehow to keep himself legal most of the time, but he did at times speak bitterly about the troubles he encountered. The state required licenses, and the state provided a way to get these licenses, but only if you fit the standard mold. My friend did not fit the standard mold, and felt very much caught in those iron hands.
Fortunately most examples of the problems of standardization are not so serious. My wife had a friend in college who was triply enrolled in the School of Education, the School of Medicine, and the Graduate School. All occupational therapy students were dually enrolled in Education and Medicine, which caused no end of red tape in itself, but this particular girl was such a go-getter that she added Graduate School. This made her a non-standard person indeed. One day she spent a solid half hour on the phone trying to convince some bureaucrat that, no matter that it didn’t fit the computer, it was possible to be enrolled that way. I presume the problem, whatever it was, was eventually worked out, but not without some cost in frustration. The bureaucrat in question was probably no more pigheaded than you or I. The rules he was responsible for applying simply made no provision for triply enrolled students.
When caught as a non-standard person in a standardized bureaucracy one wonders why standardization is established in the first place. Except for the role egocentrism of a few bureaucrats, standardization is not intentional. It arises by the same forces that promote standardization in industry. Standardization promotes efficiency. Whenever a form is printed, for instance, it is designed to fit the majority of situations. Thus a fire insurance application form may ask if the house is frame or brick, with no intention of frustrating the owners of igloos, caves, and houseboats. It simply reflects the fact that most houses are either frame or brick. By stating these two choices the processing of the application is speeded up. If instead the application stated simply, "describe the dwelling to be insured", the work in processing the application would be considerably increased. Standardization is the inevitable correlate of the proliferation of secondary requirements.
There is also another cause of standardization, the lack of discretionary authority. Remember that secondary requirements are set up in many cases to prevent abuse of power and to be fair. This usually means that the bureaucrats who apply these rules have only a limited number of responses to a given situation. Bureaucracies are given very little discretionary authority. They must follow the rules whether the rules fit the situation at hand or not. To illustrate this let me hypothesize two ways of administering welfare.
In case A an applicant comes to a social worker. The applicant explains that her husband just lost his job because he drank too much, that she works as a maid two days a week but that her children have no one to stay with them when she works unless she pays a baby sitter which costs almost half her salary, that their car is about to be repossessed and then she won’t be able to get to work at all, that the landlord won’t fix the plumbing and charges too much rent, that they would move except they haven’t found a place that’s any cheaper, that their oldest son was just sent to jail for a two year term, and on, and on, and on. The social worker listens to all this, makes a few phone calls, and the next day tells the applicant, "We’ll give you $70 a week allowance, but tell your husband to come in before next week. We’ll get him off his beer and on the job one way or the other. I called your landlord and got his side of the story and there’ll have to be a few changes made before he’ll reconnect the shower, and you’ve got to..."
In situation B the applicant comes to the social worker with the same story. The social worker says, "I think we can help you, but first you’ll have to find your birth certificate. Regulations state that only citizens are eligible for welfare. Then you’ll have to take this form to your employer to certify your wage scale. And this form goes to your landlord to verify your rent. And you’ll have to fill out this form to show how you budget your income, and this form to verify that you are not now receiving veterans or disability compensation, and this form that verifies you are not eligible to collect child support from any previous husband, unless the marriage was annulled, in which case you have to hunt up the certificate of annulment... What? You lost your certificate of annulment? You’re not sure you ever were married to John before you left him for Henry? ..."
In situation A the social worker is given a budget and a wide latitude on how to distribute the money. She is given discretionary power to a large degree. In situation B the social worker is given a very small amount of discretionary power. She can’t decide for herself whether the applicant is genuinely needy, but must prepare a "work-up", consisting of documentation of all relevant aspects of the applicant’s situation. On the basis of this work-up she is allowed to authorize an allowance, the amount to be taken from a table. If the social worker feels that there are relevant circumstances that are not covered at all in the standard work-up then she may begin some special procedure to have the case considered by a higher authority or committee. But the common suspicion that things aren’t quite as they should be, either because the applicant is undeserving or that he needs more than he can get or that the program misses its mark in yet some other way, is just a routine part of the job.
Standardization, fitting everyone into the same size slot, reduces everything to paperwork. The "work-up" is a stack of documents. These documents, certificates, forms, statements, memos, become the currency of bureaucracy, the medium of exchange. "Facts" become so only when they are certified by someone’s signature, even though they may be obvious. Other "facts" must be accepted because of their official certification even though common sense or simple observation show them to be false. A gap between the real and the official inevitably sets in. Then this gap leads to actions that are perceived to be detrimental or unfair, then the result is a considerable amount of frustration, in spite of the fact that the intent of all the red tape was to be beneficial and fair.
This leads to the second cause of bureaucratic frustration, which is ineffectiveness. If a bureaucratic requirement is seen as effective in accomplishing its goal we accept it even if there is considerable inconvenience involved in meeting the requirement. If, on the other hand, a bureaucratic requirement is seen as ineffective then a little inconvenience in meeting the requirement can be a very significant frustration. Getting a loan from a bank, for example, involves considerable effort in meeting bureaucratic requirements. However we don’t expect money to be handed out without some security that it will be paid back. Therefore we don’t get too frustrated by the inconvenience in meeting those requirements. Similarly, driver’s licenses are seen as worthwhile, even if not fully effective, and entail only a little bother every four years or so. Therefore we do not hear too much about pigheaded bureaucrats at the driver’s license bureau. Unfortunately other licensing systems have imperfections so massive and ubiquitous, and benefits so doubtful, that the whole system is a burden to society. A little inconvenience in getting such a license can be very frustrating. This is the frustration I felt in the example I gave at the beginning of this article about getting a teaching certificate. Another example would be going back three times to the fire station to get a bicycle license. I went back twice. I figured three times was above and beyond the call of duty. I never did get my bicycle licensed.
In psychological phenomena the whole is not always equal to the sum of its parts. Bureaucratic frustration can work this way. One frustration may be brushed off, and then another, and perhaps several more, but eventually there comes a point where the frustrations increase out of proportion to their cumulative value. Short-term frustration changes into long-term demoralization. I think "hassle" is a good name for this. It is a commonly used term, though it is not normally considered a specifically defined term. I think the phenomenon should be taken seriously though. It will become increasingly common with constant increases in bureaucratic requirements.
The best example I can give of hassle in my own experience comes from my home state of Missouri. To get one’s car licensed in Missouri one must show the title or previous year’s registration certificate, as can be expected, but that is not all there is to it. One must also get a new safety inspection certificate and also show his personal property tax receipt. When I lived in Missouri I usually didn’t have any property to be taxed, but I still had to go to the Treasurer’s office in the courthouse to get a card stating that no taxes were due. The safety inspection always caused me worry, and the car licensing itself always had the potential for problems. Maybe they would find something wrong with my title and tell me I can’t register the car. Thus the sum of all this was to me a hassle. The requirements exceeded my tolerance. It caused me anxiety, much more than the sum of the anxieties of each requirement had they come independently. Fortunately other states I have lived in didn’t tie those things together, and for that reason I hope I don’t end up living in Missouri again.
People vary in their susceptibility to hassle. I expect I have about as low a tolerance as anyone. I haven’t heard other Missourians complaining about the car licensing system. Unfortunately those who are not susceptible to the demoralization of hassles have little understanding of the anxieties of those who are susceptible. This goes along with the general rule that the more aggressive cannot empathize with the less aggressive. This increases the problem to those who are susceptible to hassle. However I would expect the future will see the problem given much more recognition as more and more people find themselves pushed beyond their tolerance.
A movement is currently under way by the Democratic Party to do away with traditional voter registration practices and to substitute a "same day" standardized registration system. Thus a voter could show up on election day, show proof of identity and residence, and be registered on the spot. The rationale of this is that the complications of regular registration are sufficient to prevent many people from voting. I think the move is clearly motivated by the political goal of increasing the Democratic vote. Still, I am glad to see the movement. They are talking about hassle. They are acknowledging that bureaucratic requirements are a burden, and that this burden can at times be of a serious nature. Now when somebody tells me I’m nuts if I worry about getting a car license I can reply that apparently some people worry about voter registration.
In the first part of this article I tried to explain the causes of bureaucratic requirements. Then I tried to analyze how bureaucracy produces frustration. There are very good reasons for bureaucracies, and there are very good reasons for frustration, so it appears we must live with the problem forever. I don’t think the world will grind to a halt though. The way out of this dilemma is simply to realize when diminishing returns begin to set in, and even more importantly, to realize when the return does not equal the investment. Every human endeavor has a cost and a benefit, an investment and a return. When establishing a system of secondary rules the investment includes the cost of setting up the bureaucracy, the cost of the individual’s efforts in dealing with the bureaucracy, and increasingly more importantly, the cost in frustration, anxiety, and demoralization. These costs must be subtracted from the benefits before deciding that a given proposal is or is not worthwhile.
Sometimes the cost can be reduced to dollars and cents. According to an item in the newsletter from my representative in Congress the town of Faith, South Dakota, recently applied for a federal grant. I believe they wanted to build a rodeo grandstand. They were offered $150,000 to match their own $50,000, but of course there were strings attached. After looking closely at these strings they finally rejected the federal help entirely and built their own grandstand for only $20,000. I doubt that this example is typical of federal grants, but it does illustrate diminishing returns.
More commonly only part of the cost can be reduced to dollars and cents. For example, an accountant may compute that a $20,000 grant for a town would entail only about $6000 in labor to do all the paperwork. This would seem to make a clear profit for the town of $14,000. But if the city officials are sick of the paperwork and the delays, if the citizens are mad at everyone and each other, and if the strings will be attached forever, then all this must certainly be subtracted from the benefit.
The investment/return assessment is even more complicated when all important factors are psychological. How can we put a price on invasion of privacy? How can we put a price on independence and respect for the individual? How are these costs to be subtracted from the safety and security that we gain from bureaucratic requirements? I don’t know. Since psychological costs cannot be measured in dollars and cents, the worth of any system of bureaucratic requirements will always be a matter of subjective judgment, a matter of politics to be decided through political processes. They are not matters to be decided by technicians or engineers of any sort.
I have my own opinions. I vote for nuclear energy and against OSHA. I tend to think of the licensing of voters and guns worthwhile, of cars and drivers as borderline, and of teachers, barbers, cats and bicycles as not worthwhile. Of course everyone else will disagree. I only hope we will start counting costs and benefits a little more carefully. As is true of so many things, it cannot be said of bureaucracy that if some is good, more is better.
-
 @ 3b3a42d3:d192e325
2025-04-10 08:57:51
@ 3b3a42d3:d192e325
2025-04-10 08:57:51Atomic Signature Swaps (ASS) over Nostr is a protocol for atomically exchanging Schnorr signatures using Nostr events for orchestration. This new primitive enables multiple interesting applications like:
- Getting paid to publish specific Nostr events
- Issuing automatic payment receipts
- Contract signing in exchange for payment
- P2P asset exchanges
- Trading and enforcement of asset option contracts
- Payment in exchange for Nostr-based credentials or access tokens
- Exchanging GMs 🌞
It only requires that (i) the involved signatures be Schnorr signatures using the secp256k1 curve and that (ii) at least one of those signatures be accessible to both parties. These requirements are naturally met by Nostr events (published to relays), Taproot transactions (published to the mempool and later to the blockchain), and Cashu payments (using mints that support NUT-07, allowing any pair of these signatures to be swapped atomically.
How the Cryptographic Magic Works 🪄
This is a Schnorr signature
(Zₓ, s):s = z + H(Zₓ || P || m)⋅kIf you haven't seen it before, don't worry, neither did I until three weeks ago.
The signature scalar s is the the value a signer with private key
k(and public keyP = k⋅G) must calculate to prove his commitment over the messagemgiven a randomly generated noncez(Zₓis just the x-coordinate of the public pointZ = z⋅G).His a hash function (sha256 with the tag "BIP0340/challenge" when dealing with BIP340),||just means to concatenate andGis the generator point of the elliptic curve, used to derive public values from private ones.Now that you understand what this equation means, let's just rename
z = r + t. We can do that,zis just a randomly generated number that can be represented as the sum of two other numbers. It also follows thatz⋅G = r⋅G + t⋅G ⇔ Z = R + T. Putting it all back into the definition of a Schnorr signature we get:s = (r + t) + H((R + T)ₓ || P || m)⋅kWhich is the same as:
s = sₐ + twheresₐ = r + H((R + T)ₓ || P || m)⋅ksₐis what we call the adaptor signature scalar) and t is the secret.((R + T)ₓ, sₐ)is an incomplete signature that just becomes valid by add the secret t to thesₐ:s = sₐ + tWhat is also important for our purposes is that by getting access to the valid signature s, one can also extract t from it by just subtracting
sₐ:t = s - sₐThe specific value of
tdepends on our choice of the public pointT, sinceRis just a public point derived from a randomly generated noncer.So how do we choose
Tso that it requires the secret t to be the signature over a specific messagem'by an specific public keyP'? (without knowing the value oft)Let's start with the definition of t as a valid Schnorr signature by P' over m':
t = r' + H(R'ₓ || P' || m')⋅k' ⇔ t⋅G = r'⋅G + H(R'ₓ || P' || m')⋅k'⋅GThat is the same as:
T = R' + H(R'ₓ || P' || m')⋅P'Notice that in order to calculate the appropriate
Tthat requirestto be an specific signature scalar, we only need to know the public nonceR'used to generate that signature.In summary: in order to atomically swap Schnorr signatures, one party
P'must provide a public nonceR', while the other partyPmust provide an adaptor signature using that nonce:sₐ = r + H((R + T)ₓ || P || m)⋅kwhereT = R' + H(R'ₓ || P' || m')⋅P'P'(the nonce provider) can then add his own signature t to the adaptor signaturesₐin order to get a valid signature byP, i.e.s = sₐ + t. When he publishes this signature (as a Nostr event, Cashu transaction or Taproot transaction), it becomes accessible toPthat can now extract the signaturetbyP'and also make use of it.Important considerations
A signature may not be useful at the end of the swap if it unlocks funds that have already been spent, or that are vulnerable to fee bidding wars.
When a swap involves a Taproot UTXO, it must always use a 2-of-2 multisig timelock to avoid those issues.
Cashu tokens do not require this measure when its signature is revealed first, because the mint won't reveal the other signature if they can't be successfully claimed, but they also require a 2-of-2 multisig timelock when its signature is only revealed last (what is unavoidable in cashu for cashu swaps).
For Nostr events, whoever receives the signature first needs to publish it to at least one relay that is accessible by the other party. This is a reasonable expectation in most cases, but may be an issue if the event kind involved is meant to be used privately.
How to Orchestrate the Swap over Nostr?
Before going into the specific event kinds, it is important to recognize what are the requirements they must meet and what are the concerns they must address. There are mainly three requirements:
- Both parties must agree on the messages they are going to sign
- One party must provide a public nonce
- The other party must provide an adaptor signature using that nonce
There is also a fundamental asymmetry in the roles of both parties, resulting in the following significant downsides for the party that generates the adaptor signature:
- NIP-07 and remote signers do not currently support the generation of adaptor signatures, so he must either insert his nsec in the client or use a fork of another signer
- There is an overhead of retrieving the completed signature containing the secret, either from the blockchain, mint endpoint or finding the appropriate relay
- There is risk he may not get his side of the deal if the other party only uses his signature privately, as I have already mentioned
- There is risk of losing funds by not extracting or using the signature before its timelock expires. The other party has no risk since his own signature won't be exposed by just not using the signature he received.
The protocol must meet all those requirements, allowing for some kind of role negotiation and while trying to reduce the necessary hops needed to complete the swap.
Swap Proposal Event (kind:455)
This event enables a proposer and his counterparty to agree on the specific messages whose signatures they intend to exchange. The
contentfield is the following stringified JSON:{ "give": <signature spec (required)>, "take": <signature spec (required)>, "exp": <expiration timestamp (optional)>, "role": "<adaptor | nonce (optional)>", "description": "<Info about the proposal (optional)>", "nonce": "<Signature public nonce (optional)>", "enc_s": "<Encrypted signature scalar (optional)>" }The field
roleindicates what the proposer will provide during the swap, either the nonce or the adaptor. When this optional field is not provided, the counterparty may decide whether he will send a nonce back in a Swap Nonce event or a Swap Adaptor event using thenonce(optionally) provided by in the Swap Proposal in order to avoid one hop of interaction.The
enc_sfield may be used to store the encrypted scalar of the signature associated with thenonce, since this information is necessary later when completing the adaptor signature received from the other party.A
signature specspecifies thetypeand all necessary information for producing and verifying a given signature. In the case of signatures for Nostr events, it contain a template with all the fields, exceptpubkey,idandsig:{ "type": "nostr", "template": { "kind": "<kind>" "content": "<content>" "tags": [ … ], "created_at": "<created_at>" } }In the case of Cashu payments, a simplified
signature specjust needs to specify the payment amount and an array of mints trusted by the proposer:{ "type": "cashu", "amount": "<amount>", "mint": ["<acceptable mint_url>", …] }This works when the payer provides the adaptor signature, but it still needs to be extended to also work when the payer is the one receiving the adaptor signature. In the later case, the
signature specmust also include atimelockand the derived public keysYof each Cashu Proof, but for now let's just ignore this situation. It should be mentioned that the mint must be trusted by both parties and also support Token state check (NUT-07) for revealing the completed adaptor signature and P2PK spending conditions (NUT-11) for the cryptographic scheme to work.The
tagsare:"p", the proposal counterparty's public key (required)"a", akind:30455Swap Listing event or an application specific version of it (optional)
Forget about this Swap Listing event for now, I will get to it later...
Swap Nonce Event (kind:456) - Optional
This is an optional event for the Swap Proposal receiver to provide the public nonce of his signature when the proposal does not include a nonce or when he does not want to provide the adaptor signature due to the downsides previously mentioned. The
contentfield is the following stringified JSON:{ "nonce": "<Signature public nonce>", "enc_s": "<Encrypted signature scalar (optional)>" }And the
tagsmust contain:"e", akind:455Swap Proposal Event (required)"p", the counterparty's public key (required)
Swap Adaptor Event (kind:457)
The
contentfield is the following stringified JSON:{ "adaptors": [ { "sa": "<Adaptor signature scalar>", "R": "<Signer's public nonce (including parity byte)>", "T": "<Adaptor point (including parity byte)>", "Y": "<Cashu proof derived public key (if applicable)>", }, …], "cashu": "<Cashu V4 token (if applicable)>" }And the
tagsmust contain:"e", akind:455Swap Proposal Event (required)"p", the counterparty's public key (required)
Discoverability
The Swap Listing event previously mentioned as an optional tag in the Swap Proposal may be used to find an appropriate counterparty for a swap. It allows a user to announce what he wants to accomplish, what his requirements are and what is still open for negotiation.
Swap Listing Event (kind:30455)
The
contentfield is the following stringified JSON:{ "description": "<Information about the listing (required)>", "give": <partial signature spec (optional)>, "take": <partial signature spec (optional)>, "examples: [<take signature spec>], // optional "exp": <expiration timestamp (optional)>, "role": "<adaptor | nonce (optional)>" }The
descriptionfield describes the restrictions on counterparties and signatures the user is willing to accept.A
partial signature specis an incompletesignature specused in Swap Proposal eventskind:455where omitting fields signals that they are still open for negotiation.The
examplesfield is an array ofsignature specsthe user would be willing totake.The
tagsare:"d", a unique listing id (required)"s", the status of the listingdraft | open | closed(required)"t", topics related to this listing (optional)"p", public keys to notify about the proposal (optional)
Application Specific Swap Listings
Since Swap Listings are still fairly generic, it is expected that specific use cases define new event kinds based on the generic listing. Those application specific swap listing would be easier to filter by clients and may impose restrictions and add new fields and/or tags. The following are some examples under development:
Sponsored Events
This listing is designed for users looking to promote content on the Nostr network, as well as for those who want to monetize their accounts by sharing curated sponsored content with their existing audiences.
It follows the same format as the generic Swap Listing event, but uses the
kind:30456instead.The following new tags are included:
"k", event kind being sponsored (required)"title", campaign title (optional)
It is required that at least one
signature spec(giveand/ortake) must have"type": "nostr"and also contain the following tag["sponsor", "<pubkey>", "<attestation>"]with the sponsor's public key and his signature over the signature spec without the sponsor tag as his attestation. This last requirement enables clients to disclose and/or filter sponsored events.Asset Swaps
This listing is designed for users looking for counterparties to swap different assets that can be transferred using Schnorr signatures, like any unit of Cashu tokens, Bitcoin or other asset IOUs issued using Taproot.
It follows the same format as the generic Swap Listing event, but uses the
kind:30457instead.It requires the following additional tags:
"t", asset pair to be swapped (e.g."btcusd")"t", asset being offered (e.g."btc")"t", accepted payment method (e.g."cashu","taproot")
Swap Negotiation
From finding an appropriate Swap Listing to publishing a Swap Proposal, there may be some kind of negotiation between the involved parties, e.g. agreeing on the amount to be paid by one of the parties or the exact content of a Nostr event signed by the other party. There are many ways to accomplish that and clients may implement it as they see fit for their specific goals. Some suggestions are:
- Adding
kind:1111Comments to the Swap Listing or an existing Swap Proposal - Exchanging tentative Swap Proposals back and forth until an agreement is reached
- Simple exchanges of DMs
- Out of band communication (e.g. Signal)
Work to be done
I've been refining this specification as I develop some proof-of-concept clients to experience its flaws and trade-offs in practice. I left the signature spec for Taproot signatures out of the current document as I still have to experiment with it. I will probably find some important orchestration issues related to dealing with
2-of-2 multisig timelocks, which also affects Cashu transactions when spent last, that may require further adjustments to what was presented here.The main goal of this article is to find other people interested in this concept and willing to provide valuable feedback before a PR is opened in the NIPs repository for broader discussions.
References
- GM Swap- Nostr client for atomically exchanging GM notes. Live demo available here.
- Sig4Sats Script - A Typescript script demonstrating the swap of a Cashu payment for a signed Nostr event.
- Loudr- Nostr client under development for sponsoring the publication of Nostr events. Live demo available at loudr.me.
- Poelstra, A. (2017). Scriptless Scripts. Blockstream Research. https://github.com/BlockstreamResearch/scriptless-scripts
-
 @ c230edd3:8ad4a712
2025-04-09 00:33:31
@ c230edd3:8ad4a712
2025-04-09 00:33:31Chef's notes
I found this recipe a couple years ago and have been addicted to it since. Its incredibly easy, and cheap to prep. Freeze the sausage in flat, single serving portions. That way it can be cooked from frozen for a fast, flavorful, and healthy lunch or dinner. I took inspiration from the video that contained this recipe, and almost always pan fry the frozen sausage with some baby broccoli. The steam cooks the broccoli and the fats from the sausage help it to sear, while infusing the vibrant flavors. Serve with some rice, if desired. I often use serrano peppers, due to limited produce availability. They work well for a little heat and nice flavor that is not overpowering.
Details
- ⏲️ Prep time: 25 min
- 🍳 Cook time: 15 min (only needed if cooking at time of prep)
- 🍽️ Servings: 10
Ingredients
- 4 lbs ground pork
- 12-15 cloves garlic, minced
- 6 Thai or Serrano peppers, rough chopped
- 1/4 c. lime juice
- 4 Tbsp fish sauce
- 1 Tbsp brown sugar
- 1/2 c. chopped cilantro
Directions
- Mix all ingredients in a large bowl.
- Portion and freeze, as desired.
- Sautè frozen portions in hot frying pan, with broccoli or other fresh veggies.
- Serve with rice or alone.
-
 @ 3b3a42d3:d192e325
2025-04-10 08:51:15
@ 3b3a42d3:d192e325
2025-04-10 08:51:15Atomic Signature Swaps (ASS) over Nostr is a protocol for atomically exchanging Schnorr signatures using Nostr events for orchestration. This new primitive enables multiple interesting applications like:
- Getting paid to publish specific Nostr events
- Issuing automatic payment receipts
- Contract signing in exchange for payment
- P2P asset exchanges
- Payment in exchange for Nostr-based credentials or access tokens
- Exchanging GMs 🌞
It only requires that (i) the involved signatures be Schnorr signatures using the secp256k1 curve and that (ii) at least one of those signatures be accessible to both parties. These requirements are naturally met by Nostr events (published to relays), Taproot transactions (published to the mempool and later to the blockchain), and Cashu payments (using mints that support NUT-07, allowing any pair of these signatures to be swapped atomically.
How the Cryptographic Magic Works 🪄
This is a Schnorr signature
(Zₓ, s):s = z + H(Zₓ || P || m)⋅kIf you haven't seen it before, don't worry, neither did I until three weeks ago.
The signature scalar s is the the value a signer with private key
k(and public keyP = k⋅G) must calculate to prove his commitment over the messagemgiven a randomly generated noncez(Zₓis just the x-coordinate of the public pointZ = z⋅G).His a hash function (sha256 with the tag "BIP0340/challenge" when dealing with BIP340),||just means to concatenate andGis the generator point of the elliptic curve, used to derive public values from private ones.Now that you understand what this equation means, let's just rename
z = r + t. We can do that,zis just a randomly generated number that can be represented as the sum of two other numbers. It also follows thatz⋅G = r⋅G + t⋅G ⇔ Z = R + T. Putting it all back into the definition of a Schnorr signature we get:s = (r + t) + H((R + T)ₓ || P || m)⋅kWhich is the same as:
s = sₐ + twheresₐ = r + H((R + T)ₓ || P || m)⋅ksₐis what we call the adaptor signature scalar) and t is the secret.((R + T)ₓ, sₐ)is an incomplete signature that just becomes valid by add the secret t to thesₐ:s = sₐ + tWhat is also important for our purposes is that by getting access to the valid signature s, one can also extract t from it by just subtracting
sₐ:t = s - sₐThe specific value of
tdepends on our choice of the public pointT, sinceRis just a public point derived from a randomly generated noncer.So how do we choose
Tso that it requires the secret t to be the signature over a specific messagem'by an specific public keyP'? (without knowing the value oft)Let's start with the definition of t as a valid Schnorr signature by P' over m':
t = r' + H(R'ₓ || P' || m')⋅k' ⇔ t⋅G = r'⋅G + H(R'ₓ || P' || m')⋅k'⋅GThat is the same as:
T = R' + H(R'ₓ || P' || m')⋅P'Notice that in order to calculate the appropriate
Tthat requirestto be an specific signature scalar, we only need to know the public nonceR'used to generate that signature.In summary: in order to atomically swap Schnorr signatures, one party
P'must provide a public nonceR', while the other partyPmust provide an adaptor signature using that nonce:sₐ = r + H((R + T)ₓ || P || m)⋅kwhereT = R' + H(R'ₓ || P' || m')⋅P'P'(the nonce provider) can then add his own signature t to the adaptor signaturesₐin order to get a valid signature byP, i.e.s = sₐ + t. When he publishes this signature (as a Nostr event, Cashu transaction or Taproot transaction), it becomes accessible toPthat can now extract the signaturetbyP'and also make use of it.Important considerations
A signature may not be useful at the end of the swap if it unlocks funds that have already been spent, or that are vulnerable to fee bidding wars.
When a swap involves a Taproot UTXO, it must always use a 2-of-2 multisig timelock to avoid those issues.
Cashu tokens do not require this measure when its signature is revealed first, because the mint won't reveal the other signature if they can't be successfully claimed, but they also require a 2-of-2 multisig timelock when its signature is only revealed last (what is unavoidable in cashu for cashu swaps).
For Nostr events, whoever receives the signature first needs to publish it to at least one relay that is accessible by the other party. This is a reasonable expectation in most cases, but may be an issue if the event kind involved is meant to be used privately.
How to Orchestrate the Swap over Nostr?
Before going into the specific event kinds, it is important to recognize what are the requirements they must meet and what are the concerns they must address. There are mainly three requirements:
- Both parties must agree on the messages they are going to sign
- One party must provide a public nonce
- The other party must provide an adaptor signature using that nonce
There is also a fundamental asymmetry in the roles of both parties, resulting in the following significant downsides for the party that generates the adaptor signature:
- NIP-07 and remote signers do not currently support the generation of adaptor signatures, so he must either insert his nsec in the client or use a fork of another signer
- There is an overhead of retrieving the completed signature containing the secret, either from the blockchain, mint endpoint or finding the appropriate relay
- There is risk he may not get his side of the deal if the other party only uses his signature privately, as I have already mentioned
- There is risk of losing funds by not extracting or using the signature before its timelock expires. The other party has no risk since his own signature won't be exposed by just not using the signature he received.
The protocol must meet all those requirements, allowing for some kind of role negotiation and while trying to reduce the necessary hops needed to complete the swap.
Swap Proposal Event (kind:455)
This event enables a proposer and his counterparty to agree on the specific messages whose signatures they intend to exchange. The
contentfield is the following stringified JSON:{ "give": <signature spec (required)>, "take": <signature spec (required)>, "exp": <expiration timestamp (optional)>, "role": "<adaptor | nonce (optional)>", "description": "<Info about the proposal (optional)>", "nonce": "<Signature public nonce (optional)>", "enc_s": "<Encrypted signature scalar (optional)>" }The field
roleindicates what the proposer will provide during the swap, either the nonce or the adaptor. When this optional field is not provided, the counterparty may decide whether he will send a nonce back in a Swap Nonce event or a Swap Adaptor event using thenonce(optionally) provided by in the Swap Proposal in order to avoid one hop of interaction.The
enc_sfield may be used to store the encrypted scalar of the signature associated with thenonce, since this information is necessary later when completing the adaptor signature received from the other party.A
signature specspecifies thetypeand all necessary information for producing and verifying a given signature. In the case of signatures for Nostr events, it contain a template with all the fields, exceptpubkey,idandsig:{ "type": "nostr", "template": { "kind": "<kind>" "content": "<content>" "tags": [ … ], "created_at": "<created_at>" } }In the case of Cashu payments, a simplified
signature specjust needs to specify the payment amount and an array of mints trusted by the proposer:{ "type": "cashu", "amount": "<amount>", "mint": ["<acceptable mint_url>", …] }This works when the payer provides the adaptor signature, but it still needs to be extended to also work when the payer is the one receiving the adaptor signature. In the later case, the
signature specmust also include atimelockand the derived public keysYof each Cashu Proof, but for now let's just ignore this situation. It should be mentioned that the mint must be trusted by both parties and also support Token state check (NUT-07) for revealing the completed adaptor signature and P2PK spending conditions (NUT-11) for the cryptographic scheme to work.The
tagsare:"p", the proposal counterparty's public key (required)"a", akind:30455Swap Listing event or an application specific version of it (optional)
Forget about this Swap Listing event for now, I will get to it later...
Swap Nonce Event (kind:456) - Optional
This is an optional event for the Swap Proposal receiver to provide the public nonce of his signature when the proposal does not include a nonce or when he does not want to provide the adaptor signature due to the downsides previously mentioned. The
contentfield is the following stringified JSON:{ "nonce": "<Signature public nonce>", "enc_s": "<Encrypted signature scalar (optional)>" }And the
tagsmust contain:"e", akind:455Swap Proposal Event (required)"p", the counterparty's public key (required)
Swap Adaptor Event (kind:457)
The
contentfield is the following stringified JSON:{ "adaptors": [ { "sa": "<Adaptor signature scalar>", "R": "<Signer's public nonce (including parity byte)>", "T": "<Adaptor point (including parity byte)>", "Y": "<Cashu proof derived public key (if applicable)>", }, …], "cashu": "<Cashu V4 token (if applicable)>" }And the
tagsmust contain:"e", akind:455Swap Proposal Event (required)"p", the counterparty's public key (required)
Discoverability
The Swap Listing event previously mentioned as an optional tag in the Swap Proposal may be used to find an appropriate counterparty for a swap. It allows a user to announce what he wants to accomplish, what his requirements are and what is still open for negotiation.
Swap Listing Event (kind:30455)
The
contentfield is the following stringified JSON:{ "description": "<Information about the listing (required)>", "give": <partial signature spec (optional)>, "take": <partial signature spec (optional)>, "examples: [<take signature spec>], // optional "exp": <expiration timestamp (optional)>, "role": "<adaptor | nonce (optional)>" }The
descriptionfield describes the restrictions on counterparties and signatures the user is willing to accept.A
partial signature specis an incompletesignature specused in Swap Proposal eventskind:455where omitting fields signals that they are still open for negotiation.The
examplesfield is an array ofsignature specsthe user would be willing totake.The
tagsare:"d", a unique listing id (required)"s", the status of the listingdraft | open | closed(required)"t", topics related to this listing (optional)"p", public keys to notify about the proposal (optional)
Application Specific Swap Listings
Since Swap Listings are still fairly generic, it is expected that specific use cases define new event kinds based on the generic listing. Those application specific swap listing would be easier to filter by clients and may impose restrictions and add new fields and/or tags. The following are some examples under development:
Sponsored Events
This listing is designed for users looking to promote content on the Nostr network, as well as for those who want to monetize their accounts by sharing curated sponsored content with their existing audiences.
It follows the same format as the generic Swap Listing event, but uses the
kind:30456instead.The following new tags are included:
"k", event kind being sponsored (required)"title", campaign title (optional)
It is required that at least one
signature spec(giveand/ortake) must have"type": "nostr"and also contain the following tag["sponsor", "<pubkey>", "<attestation>"]with the sponsor's public key and his signature over the signature spec without the sponsor tag as his attestation. This last requirement enables clients to disclose and/or filter sponsored events.Asset Swaps
This listing is designed for users looking for counterparties to swap different assets that can be transferred using Schnorr signatures, like any unit of Cashu tokens, Bitcoin or other asset IOUs issued using Taproot.
It follows the same format as the generic Swap Listing event, but uses the
kind:30457instead.It requires the following additional tags:
"t", asset pair to be swapped (e.g."btcusd")"t", asset being offered (e.g."btc")"t", accepted payment method (e.g."cashu","taproot")
Swap Negotiation
From finding an appropriate Swap Listing to publishing a Swap Proposal, there may be some kind of negotiation between the involved parties, e.g. agreeing on the amount to be paid by one of the parties or the exact content of a Nostr event signed by the other party. There are many ways to accomplish that and clients may implement it as they see fit for their specific goals. Some suggestions are:
- Adding
kind:1111Comments to the Swap Listing or an existing Swap Proposal - Exchanging tentative Swap Proposals back and forth until an agreement is reached
- Simple exchanges of DMs
- Out of band communication (e.g. Signal)
Work to be done
I've been refining this specification as I develop some proof-of-concept clients to experience its flaws and trade-offs in practice. I left the signature spec for Taproot signatures out of the current document as I still have to experiment with it. I will probably find some important orchestration issues related to dealing with
2-of-2 multisig timelocks, which also affects Cashu transactions when spent last, that may require further adjustments to what was presented here.The main goal of this article is to find other people interested in this concept and willing to provide valuable feedback before a PR is opened in the NIPs repository for broader discussions.
References
- GM Swap- Nostr client for atomically exchanging GM notes. Live demo available here.
- Sig4Sats Script - A Typescript script demonstrating the swap of a Cashu payment for a signed Nostr event.
- Loudr- Nostr client under development for sponsoring the publication of Nostr events. Live demo available at loudr.me.
- Poelstra, A. (2017). Scriptless Scripts. Blockstream Research. https://github.com/BlockstreamResearch/scriptless-scripts
-
 @ 4bc0bea1:29b9f2aa
2025-04-08 12:27:36
@ 4bc0bea1:29b9f2aa
2025-04-08 12:27:36How I’m Training Around An Elbow Injury
My right elbow is a mess.
I hurt it wrestling with a friend on a wooden deck.
It's easy to avoid injuries in wrestling...if you only wrestle on the mat. I guess I don't like it easy.
To take it a step further, I made it much worse by doing straight arm ring exercises.
C'mon Jordan!
Straight arm ring exercises while your elbow already hurts...pure buffoonery.
Alas, here I am.
I could sit out from jiujitsu, but instead, I’m adjusting how I train so I don’t lose progress.
Injuries are part of the game, but how you adapt defines your progress.
Most people see injuries as setbacks. But they're actually opportunities to refine your game.
These opportunities force you to find ways to keep improving even when things aren’t perfect.
Things don't need to be perfect if you have some G.R.I.T.
Let's break this approach down.
G – Grapple (Smart)
Don't stop training. Modify it. Drill with a dummy, watch tape, or do technique you can handle. Buy a brace if need be. Stay in the game.
There's nothing worse than forgetting everything you worked hard to learn. So don't let it happen.
Keep rolling. Do what you can without pain. Buy a brace if you think it will help. I wear Anaconda's Elbow Brace when I roll to make sure my elbow stays safe and pain-free.
I stop if I experience pain and don't allow myself to go 100%. Ignore your ego and give your body the pain-free work that it needs.
On days when it's fatigued, I drill with my dummy and watch instructionals so I can improve my technique.
Don't sit around. Grapple. But do it smart.
R – Restore Movement
Move the injured part pain-free to get blood flowing. Restore function over time.
If you sit around and don't move your injured body part, it will heal slower.
Healing requires the nutrients that blood brings. And blood won't bring as much of the goods if it's not recruited.
Rehab your injury to give it the blood boost it needs.
I diagnosed myself with Olecranon (Elbow) Bursitis. I've been doing exercises recommended here to help it heal faster.
I only do the exercises that are pain-free for me right now. And I'm moving on to more difficult ones as my elbow condition improves.
Waiting for an injury to heal is a slow, frustrating process.
Be patient and stay consistent with your rehab.
I – Integrate Strength
Once pain-free, begin light strengthening. Train around the injury, not through it.
Instagram recently sniped me with an ad for something called The Torque Bar.
The benefits from using it are endless:
- It's a single tool that targets forearms, wrists, elbows, biceps, triceps, and shoulders.
- It has a thick knurled handle that enhances grip strength and forearm activation.
- It improves rotational strength (supination/pronation) for sports.
- It helps with tennis elbow, golfer’s elbow, wrist tendinitis, and rotator cuff issues.
- It strengthens stabilizing muscles to reduce joint hyperextension and strain risks.
So of course I had to buy it.
A couple weeks of these torque bar exercises and I'm hooked. It's strengthening my neglected arm muscles and my elbow without any pain.
It's a key piece of my routine going forward and I highly recommend it for others.
The best part is that it doesn't agitate my injury and it's helping me get stronger.
That's the goal here.
T – Thrive with Nutrition & Sleep
Eat clean to recover faster. Sleep well. Don’t waste healing energy on processed junk.
This is the number one lever to pull in your healing journey. And also a great way to live.
Eat Clean
I eat healthy foods like ground beef, wild caught salmon, fruit, and more whole foods 80% of the time.
The days I eat clean are the days my elbow feels it best.
The other 20% of the time – when I eat some processed, junk food – my elbow aches. It makes me feel like I'm back at square one. The consequences of junk food are astounding.
I've put the 80/20 rule on hold and changed it to 95/5 to help this injury heal faster.
Sleep Well
My sleep has been horrible.
My daughter was born 3 weeks ago and she's been fussy. I'm getting 3-6hrs of sleep a night. It's definitely not helping my elbow.
Sleep is the most important piece of the human equation.
Bad sleep can result in
- Low energy levels
- Increased risk of injury
- Poor eating habits
- Lack of productivity
It sets the tone for each day.
If you take anything away from this, let it be that you need to optimize for sleep.
If you're in a situation like me, control what you can control.
I have more control over my food than my sleep so that's why I'm being more disciplined with it.
Once my sleep improves, I expect everything to be firing on all cylinders.
The Bottom Line
Injuries are opportunities to refine your game.
But you need to have some G.R.I.T. to do it.
- G – Grapple (Smart): Don’t stop training. Change it. Drill with a dummy, watch tape, or do technique you can handle. Stay in the game.
- R – Restore Movement: Move the injured part pain-free to get blood flowing. Restore function over time.
- I – Integrate Strength: Once pain-free, begin light strengthening. Train around the injury, not through it.
- T – Thrive with Nutrition & Sleep: Eat clean to recover faster. Sleep well. Don’t waste healing energy on processed junk.
Do the above and you'll be back better than before.
Injured and not sure what you can still train? Send me a message – happy to help however I can.
Original post is here
-
 @ 1b9fc4cd:1d6d4902
2025-04-15 10:53:29
@ 1b9fc4cd:1d6d4902
2025-04-15 10:53:29In an increasingly divided world, it often feels like we're all shouting in different languages. But there's one universal tongue we can all understand--music. Music doesn't just traverse borders; it erases them, connecting people in ways that words alone can't. Whether it's helping someone with learning disabilities find their voice, easing the fog of Alzheimer's, or bridging cultural gaps when you don't speak the language, Daniel Alonso Siegel explores why music is the ultimate unifier.
The Melody of Learning
Alonso Siegel begins with a moving example: music and learning disabilities. Consider being a child in school struggling to read or write, feeling like you're always a step behind your classmates. Then, one day, you strap on a guitar or sit at a keyboard, and suddenly, things start to click. The arts can be a game-changer for kids struggling to overcome learning disabilities, offering a new way to express themselves. Imagine a young student with dyslexia who struggles with traditional learning methods.
When they start taking drumming lessons, their world transforms. The rhythmic patterns can help them improve their coordination and focus, translating to better academic performance. Through music, children and young adults can find a way to bridge the gap between ability and aspiration. It's like unearthing a secret portal in a maze: music allows for an alternative path to success.
The Symphony of Memory
Alonso Siegel examines music's extraordinary impact on those suffering from various forms of dementia, like Alzheimer's. This cruel disease robs people of their cherished memories, leaving them lost in a fog of forgetfulness. But music can be a beacon of light in that darkness. Songs from the past can trigger memories and emotions long thought lost, offering moments of clarity and connection.
Many elderly parents barely recognize their children due to Alzheimer's. But when they are played their favorite song from decades past, patients begin to sing along, remembering every word. For a few precious minutes, they are transported back to the days of their youth, dancing and laughing as if the years and fear had melted away. Music can reach into the depths of one's mind and retrieve a piece of the past, building a bridge to lost memories.
The Harmony of Cultures
Daniel Alonso Siegel also ponders music's role in helping people assimilate to new cultures. Moving to a new country where you don't speak the language can be isolating and overwhelming. But music can provide a way to connect and integrate, even when words fail.
There are stories of refugees who relocate to countries where they don't speak the language, and feelings of isolation can sink in. However, newcomers can find common ground with their new neighbors by trying to find connections through the community, like in a local music group. Through shared melodies and rhythms, music became their shared language, fostering friendships and easing his transition into a new culture.
Studies have shown that participating in music activities can improve social integration and language acquisition for immigrants. Music classes provide a space where people from diverse backgrounds can come together, learn from each other, and build a sense of community.
The Universal Language
In conclusion, Daniel Alonso Siegel asks why music has the capacity to build bridges rather than walls. Music speaks to our fundamental human experience, tapping into our emotions, memories, and social bonds in a way that transcends language. When you hear a beautiful piece of music, you don't have to understand the lyrics to feel its impact. The melody alone can move you to tears or lift your spirits.
Music's universality means it can break down barriers between people of different backgrounds, abilities, and experiences. It’s a language that everyone speaks, whether you're tapping your foot to a bouncy tune, shedding a tear over a poignant verse, or joining a chorus in perfect harmony.
At a time when it seems like we're too busy building walls, music reminds us of the importance of building bridges instead. It's a call to connect on a deeper level, find common ground in a shared beat, and celebrate the diverse tapestry of human experience.
So, put on your favorite song next time you feel divided or disconnected. Sing, dance, play an instrument, or simply listen. Let the music do what it does best: unite us. Ultimately, no matter where we come from or what challenges we face, we're all part of the same global band, and the music we make together is far more beautiful than any solo performance.
In the grand music festival that is life, let's not forget to play in harmony.
-
 @ 000002de:c05780a7
2025-04-08 01:24:25
@ 000002de:c05780a7
2025-04-08 01:24:25Trump is trying to sell a victim narrative and I don't buy it.
Trump repeats a troupe that I find hard to swallow. The US is getting ripped off. When he says this, as far as I can tell he's not referring to the people. He's referring the US government getting ripped off by other nations. This is so absurd I'm surprised I don't hear more people push back on it.
The US is the most powerful government in the history of the planet. No nation has the firepower or wealth of the US. The US has manipulated the governments and policies of much of the world since WW2. The idea that the US government is getting ripped off is absurd.
Trump and I agree that NATO is obsolete. It was created to counter a government that dissolved in the 90s. This should be an example to everyone that governments do not behave like businesses. They do not respond to market forces. They will always seek to increase their power and influence and always resist any efforts to reduce their size and scope. But back to Trump. He says that the US is getting ripped off by the other NATO countries. I would say the US people are in indeed being ripped off by their own government. But the US government is NOT getting ripped off.
The US military power in Europe is a massive influence on geopolitics in the region. US military companies benefit massively as well. The US military has bases all over the globe and if you don't think that is a factor in "diplomatic" negotiations you are being naive. The US uses this "defensive" shield to keep the "leaders" of Europe in line. The US isn't being ripped off. This is just a marketing tactic Trump is using to sell downsizing the US military deployments.
Trump also loves to point out how other countries are imposing tariffs on the US. We are being ripped off! I mean, he has a point there. But if tariffs aren't a tax as many in his admin like to claim, how exactly are "we" being ripped off? We are being told that Trump's tariff policy isn't a tax and that expecting prices to increase is oversimplifying things. The talk about tariffs is frankly frustrating.
On the one hand the left is saying tariffs are a tax and is going to drive up prices. Yet these same people pretend to not understand that corporate tax increases don't have the same effect. The right claims to understand tax policy and often oppose corporate taxes. They will tell you that those taxes just get passed down to consumers in the form of price increases. Now they are pretending to not get this in relation to tariffs.
I've read and listened to the pro tariff people and they aren't all dumb. They may be right about tariffs not effecting all products and nations equally. I guess we will find out. But, can we be honest? The US is not getting ripped off.
Someone is getting ripped off, but it isn't the US federal government. Its the people of the world. First, the people of the world live under the thumb of the US fiat dollar standard. We in the US complain about 3+% inflation but most people in the world would kill for that level of inflation. Most of the world gets none of supposed benefits from government spending. They only get the debasement of their own currencies.
Moving away from economics, the entire globe is affected by the elections in the US. The US is the top dog government and its decisions effect people everywhere. The US deep state has manipulated many elections across the globe and continues to do so. Meanwhile we are told that Russia is manipulating our elections. So who exactly is getting ripped off here? I think the nation (the people) are being subjected to massive mismanagement at best. I can support that argument.
Don't get me wrong... I know we in the US are getting ripped off. We are being ruled by people that do not represent us and do not answer to us. The politicians that claim to represent us are being paid and influenced by foreign groups ranging from Israeli political groups, to any number of other groups domestic and foreign. We are getting ripped off, but I firmly believe the people in the US have it better than most of the world. Trump is trying to sell a victim narrative and I don't buy it.
originally posted at https://stacker.news/items/937482
-
 @ 266815e0:6cd408a5
2025-04-08 07:19:53
@ 266815e0:6cd408a5
2025-04-08 07:19:53Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum.
-
 @ 3165b802:a9f51d37
2025-04-07 17:01:23
@ 3165b802:a9f51d37
2025-04-07 17:01:23Humanrights #Human #Rights
-
 @ f7d424b5:618c51e8
2025-04-06 16:48:03
@ f7d424b5:618c51e8
2025-04-06 16:48:03The promised Nintendo direct has come and there is a LOT to say about it. If you ever wondered how such a reveal would be taken differently by a dad, a NEET, and a people programmer this is the episode for you! Also those SAG bootlickers are getting uppity again. All of that and more!
Sources cited:
- Nintendo Online subscribers get to upgrade the zelda games for free for some reason?
- Do Nintendo games ever actually go on sale?
- Kirby
- Metroid
- TOTK
- Pokeshit
- EOW
- there's literally 252 games on sale at VGP right now
- SAG agreement you can read for yourself
- SAG literally says on their website to go audition for non-union roles and then strongarm them into going union if they wanna keep you
Obligatory:
- Listen to the new episode here!
- Discuss this episode on OUR NEW FORUM
- Get the RSS and Subscribe (this is a new feed URL, but the old one redirects here too!)
- Get a modern podcast app to use that RSS feed on at newpodcastapps.com
- Or listen to the show on the forum using the embedded Podverse player!
- Send your complaints here
Reminder that this is a Value4Value podcast so any support you can give us via a modern podcasting app is greatly appreciated and we will never bow to corporate sponsors!
-
 @ 1f9e547c:8af216ed
2025-04-15 10:03:32
@ 1f9e547c:8af216ed
2025-04-15 10:03:32Opinion about Mixin Messenger Desktop (desktop)
Mixin Network suffered a major breach on September 23, 2023, due to a vulnerability in its Google Cloud Services-based withdrawal system. The attack led to the unauthorized extraction of over $150 million in BTC, ETH, and USDT-ERC20, traced to known addresses. Mixin immediately suspended deposits and withdrawals, enlisted Slowmist and Mandiant for investigation, and offered a $20M bounty for asset recovery. Losses were converted into a structured debt, with a repayment commitment using existing funds and future ecosystem revenue. As of April 2024, a new mainnet is operational, core products are restored, and over half of affected users have received partial compensation in XIN tokens.
WalletScrutiny #nostrOpinion
-
 @ ec9bd746:df11a9d0
2025-04-06 08:06:08
@ ec9bd746:df11a9d0
2025-04-06 08:06:08🌍 Time Window:
🕘 When: Every even week on Sunday at 9:00 PM CET
🗺️ Where: https://cornychat.com/eurocornStart: 21:00 CET (Prague, UTC+1)
End: approx. 02:00 CET (Prague, UTC+1, next day)
Duration: usually 5+ hours.| Region | Local Time Window | Convenience Level | |-----------------------------------------------------|--------------------------------------------|---------------------------------------------------------| | Europe (CET, Prague) 🇨🇿🇩🇪 | 21:00–02:00 CET | ✅ Very Good; evening & night | | East Coast North America (EST) 🇺🇸🇨🇦 | 15:00–20:00 EST | ✅ Very Good; afternoon & early evening | | West Coast North America (PST) 🇺🇸🇨🇦 | 12:00–17:00 PST | ✅ Very Good; midday & afternoon | | Central America (CST) 🇲🇽🇨🇷🇬🇹 | 14:00–19:00 CST | ✅ Very Good; afternoon & evening | | South America West (Peru/Colombia PET/COT) 🇵🇪🇨🇴 | 15:00–20:00 PET/COT | ✅ Very Good; afternoon & evening | | South America East (Brazil/Argentina/Chile, BRT/ART/CLST) 🇧🇷🇦🇷🇨🇱 | 17:00–22:00 BRT/ART/CLST | ✅ Very Good; early evening | | United Kingdom/Ireland (GMT) 🇬🇧🇮🇪 | 20:00–01:00 GMT | ✅ Very Good; evening hours (midnight convenient) | | Eastern Europe (EET) 🇷🇴🇬🇷🇺🇦 | 22:00–03:00 EET | ✅ Good; late evening & early night (slightly late) | | Africa (South Africa, SAST) 🇿🇦 | 22:00–03:00 SAST | ✅ Good; late evening & overnight (late-night common) | | New Zealand (NZDT) 🇳🇿 | 09:00–14:00 NZDT (next day) | ✅ Good; weekday morning & afternoon | | Australia (AEDT, Sydney) 🇦🇺 | 07:00–12:00 AEDT (next day) | ✅ Good; weekday morning to noon | | East Africa (Kenya, EAT) 🇰🇪 | 23:00–04:00 EAT | ⚠️ Slightly late (night hours; late night common) | | Russia (Moscow, MSK) 🇷🇺 | 23:00–04:00 MSK | ⚠️ Slightly late (join at start is fine, very late night) | | Middle East (UAE, GST) 🇦🇪🇴🇲 | 00:00–05:00 GST (next day) | ⚠️ Late night start (midnight & early morning, but shorter attendance plausible)| | Japan/Korea (JST/KST) 🇯🇵🇰🇷 | 05:00–10:00 JST/KST (next day) | ⚠️ Early; convenient joining from ~07:00 onwards possible | | China (Beijing, CST) 🇨🇳 | 04:00–09:00 CST (next day) | ❌ Challenging; very early morning start (better ~07:00 onwards) | | India (IST) 🇮🇳 | 01:30–06:30 IST (next day) | ❌ Very challenging; overnight timing typically difficult|
-
 @ ee6ea13a:959b6e74
2025-04-06 16:38:22
@ ee6ea13a:959b6e74
2025-04-06 16:38:22Chef's notes
You can cook this in one pan on the stove. I use a cast iron pan, but you can make it in a wok or any deep pan.
I serve mine over rice, which I make in a rice cooker. If you have a fancy one, you might have a setting for sticky or scorched rice, so give one of those a try.
To plate this, I scoop rice into a bowl, and then turn it upside-down to give it a dome shape, then spoon the curry on top of it.
Serve with chopped cilantro and lime wedges.
Details
- ⏲️ Prep time: 20
- 🍳 Cook time: 20
- 🍽️ Servings: 4
Ingredients
- 1 ½ pounds boneless skinless chicken breast, cut into 2" pieces
- 2 tablespoons coconut or avocado oil
- 1 cup white or yellow onion, finely diced
- 1 cup red bell pepper, sliced or diced
- 4 large garlic cloves, minced
- 1 small (4oz) jar of Thai red curry paste
- 1 can (13oz) unsweetened coconut milk
- 1 teaspoon ground ginger
- 1 teaspoon ground coriander
- 1 tablespoon soy sauce
- 1 tablespoon brown sugar
- 1 cup carrots, shredded or julienned
- 1 lime, zest and juice
- ¼ cup fresh cilantro, chopped for garnish
Directions
- Heat oil in a large skillet over medium-high. Once hot, add onions and ½ teaspoon salt. Cook 3 minutes, or until onions are softened, stirring often.
- Add the red curry paste, garlic, ginger, and coriander. Cook about 1 minute, or until fragrant, stirring often.
- Add coconut milk, brown sugar, soy sauce, and chicken. Stir, bring to a simmer, then reduce heat to medium. Simmer uncovered for 7 minutes, occasionally stirring.
- Add carrots and red bell peppers, and simmer 5-7 more minutes, until sauce slightly thickens and chicken is cooked through.
- Remove from heat, and stir in the lime zest, and half of the lime juice.
- Serve over rice, topped with cilantro, and add more lime juice if you like extra citrus.
-
 @ 266815e0:6cd408a5
2025-04-04 11:06:34
@ 266815e0:6cd408a5
2025-04-04 11:06:34Hacking on a new obsidian plugin for publishing articles to nostr -- testing updates
Testing images
This should be replaced with a blossom URL
![[duck.jpg]]
Testing referencing other articles
This link should be broken [[Welcome]]
-
 @ d41bf82f:ed90d888
2025-04-15 09:02:53
@ d41bf82f:ed90d888
2025-04-15 09:02:53"รู้สึกเหมือนบางสิ่งที่ยิ่งใหญ่กำลังจะเกิดขึ้น — กราฟแสดงการเติบโตของประชากรในแต่ละปี, ความเข้มข้นของก๊าซคาร์บอนไดออกไซด์ในบรรยากาศ, จำนวนเว็บไซต์, และเมกะไบต์ต่อดอลลาร์ ล้วนพุ่งทะยานขึ้นสู่เส้นโค้งที่ทะลุกรอบการเปลี่ยนแปลงตามยุคสมัย นี่คือ "เอกฐาน" — จุดสิ้นสุดของทุกสิ่งที่เราคุ้นเคย และอาจเป็นจุดเริ่มต้นของบางสิ่งที่เราไม่มีวันเข้าใจเลยก็ได้" -Danny Hillis
ปฐมบทแห่งการเปลี่ยนแปลงของอำนาจ ประวัติศาสตร์ของมนุษยชาติไม่ใช่เส้นตรงที่ดำเนินไปอย่างราบรื่น แต่เป็นลำดับของช่วงเวลาสงบนิ่งสลับกับช่วงเวลาแห่งการเปลี่ยนแปลงอย่างรุนแรง ซึ่งมักเกิดขึ้นอย่างไม่ทันตั้งตัว ช่วงเวลาเหล่านี้มักจะถูกผลักดันโดยการเปลี่ยนแปลงทางเทคโนโลยีที่ทำให้โครงสร้างของอำนาจที่มีอยู่ต้องปรับตัวหรือพังทลายลง
ขั้นที่สี่ของการจัดระเบียบสังคมมนุษย์ หัวข้อของหนังสือเล่มนี้ คือการปฏิวัติอำนาจรูปแบบใหม่ ที่กำลังเปิดทางให้ “ปัจเจกบุคคล” มีอิสรภาพมากขึ้น โดยแลกกับอำนาจที่รัฐชาติในศตวรรษที่ 20 เคยมี นี่คือการเปลี่ยนแปลงเชิงโครงสร้างผ่านนวัตกรรมที่เปลี่ยนแก่นกลางของ “ตรรกะแห่งความรุนแรง(logic of violence)” ไปอย่างที่ไม่เคยเกิดขึ้นมาก่อน ไมโครโพรเซสเซอร์จะกัดเซาะและทำลายโครงสร้างของรัฐชาติ และในการเปลี่ยนผ่านนี้ จะก่อให้เกิดรูปแบบใหม่ของการจัดระเบียบทางสังคม ตลอดประวัติศาสตร์มนุษย์ เราเคยผ่านระบบเศรษฐกิจพื้นฐานมาเพียงสามระยะ: 1. สังคมล่าสัตว์และหาของป่า 2. สังคมเกษตรกรรม 3. สังคมอุตสาหกรรม
แต่บัดนี้ กำลังมีสิ่งใหม่ปรากฏขึ้น — ระยะที่สี่ของการจัดระเบียบสังคม: สังคมข้อมูลสารสนเทศ (Information societies)
The Sovereign Individual เปิดบทแรกด้วยแนวคิดที่ชี้ให้เห็นว่าการเปลี่ยนแปลงทางเทคโนโลยี โดยเฉพาะเทคโนโลยีสารสนเทศ กำลังสร้างโลกใหม่ที่แตกต่างจากเดิมอย่างสิ้นเชิง และกำลังสั่นคลอนเสาหลักของอำนาจรัฐแบบเดิม ทั้งในด้านเศรษฐกิจ การควบคุม และความชอบธรรม
โลกในยุคก่อนและหลังเทคโนโลยี ตลอดประวัติศาสตร์ มนุษย์เคยอยู่ภายใต้โครงสร้างอำนาจที่เปลี่ยนไปตามยุคสมัย ยุคเกษตรกรรมทำให้เกิดระบบศักดินา ยุคอุตสาหกรรมทำให้เกิดรัฐชาติที่มีอำนาจรวมศูนย์ และการเกิดขึ้นของเทคโนโลยีก็เคยปฏิวัติโลกมาแล้วหลายครั้ง ตัวอย่างเช่น การใช้ดินปืนทำให้กษัตริย์สามารถสร้างกองทัพประจำการ แทนที่อำนาจของเหล่าขุนนางท้องถิ่น เทคโนโลยีสารสนเทศในยุคปัจจุบัน เช่น อินเทอร์เน็ต คอมพิวเตอร์ และการเข้ารหัสข้อมูล กำลังทำให้ต้นทุนในการใช้ความรุนแรงเพิ่มสูงขึ้น และลดความสามารถของรัฐในการควบคุมข้อมูลและทรัพยากร นี่เป็นการเปลี่ยนแปลงโครงสร้างอำนาจจากบนลงล่าง ไปสู่กระจายศูนย์และปัจเจกบุคคล
รัฐกับการผูกขาดอำนาจทางเศรษฐกิจ ตลอดหลายศตวรรษที่ผ่านมา รัฐมีอำนาจเหนือประชาชนได้ก็เพราะสามารถควบคุมเศรษฐกิจได้ผ่านกลไก เช่น การจัดเก็บภาษี การควบคุมเงินตรา และการผูกขาดการใช้ความรุนแรง การควบคุมเหล่านี้ทำให้รัฐสามารถรักษาอำนาจได้ แม้จะไม่ได้มีประสิทธิภาพสูงสุดเสมอไป แต่เมื่อเทคโนโลยีใหม่เข้ามา ทำให้เงินทุนและข้อมูลสารสนเทศสามารถเคลื่อนที่ข้ามพรมแดนได้ง่าย รัฐจะไม่สามารถจัดเก็บภาษีได้ง่ายเช่นเดิมอีกต่อไป ความสามารถในการใช้กำลังบังคับก็ลดลงเพราะต้นทุนเพิ่มขึ้น และประชาชนสามารถหลบเลี่ยงหรือกระจายอำนาจออกจากรัฐได้มากขึ้น
รัฐเคยชินกับการปฏิบัติต่อผู้เสียภาษีในลักษณะเดียวกับที่ชาวนาเลี้ยงวัว — ปล่อยให้พวกเขาอยู่ในทุ่งเพื่อจะรีดนม แต่ในไม่ช้า…วัวเหล่านั้นจะมีปีก
การเกิดขึ้นของปัจเจกผู้มีอธิปไตย ในโลกใหม่ที่เทคโนโลยีลดต้นทุนในการเป็นอิสระจากรัฐ บุคคลที่มีความรู้ ทักษะ และสามารถใช้เทคโนโลยีได้อย่างมีประสิทธิภาพจะกลายเป็น "Sovereign Individual" หรือ "ปัจเจกบุคคลผู้มีอำนาจอธิปไตย" ซึ่งมีคุณลักษณะเฉพาะคือ: 1. สามารถเคลื่อนย้ายทุนและตัวเองได้อย่างอิสระ 2. ทำธุรกรรมบนอินเทอร์เน็ตซึ่งสามารถเข้ารหัสได้เพื่อลดการพึ่งพารัฐ 3. ควบคุมทรัพย์สินและรายได้ของตนเองโดยไม่ตกอยู่ใต้อำนาจรัฐ บุคคลกลุ่มนี้จะมีพลังในการต่อรองสูงขึ้น และจะเป็นกลุ่มที่กำหนดทิศทางของโลกอนาคต
ความท้าทายระหว่างเปลี่ยนผ่าน ผู้เขียนไม่ปฏิเสธว่าการเปลี่ยนผ่านจากยุคแห่งรัฐรวมศูนย์ไปสู่ยุคของปัจเจกผู้มีอธิปไตยจะเต็มไปด้วยความปั่นป่วน ในระยะสั้น เราอาจเห็น: * การล่มสลายของระบบสวัสดิการ * การว่างงานจากโครงสร้างเศรษฐกิจที่เปลี่ยนไป * การเพิ่มขึ้นของอาชญากรรมหรือสงครามภายในบางพื้นที่ แต่ทั้งหมดนี้คือผลข้างเคียงของการเปลี่ยนแปลงระดับรากฐาน ที่จะนำไปสู่ระบบที่มีประสิทธิภาพและยั่งยืนกว่าในระยะยาว
“จักรวาลมอบรางวัลให้เมื่อเรารู้เท่าทันกฎของมัน และลงโทษอย่างไร้ปรานีเมื่อเราหลงผิด หากเราเข้าใจธรรมชาติของจักรวาล แผนการต่างๆ จะดำเนินไปได้อย่างราบรื่น และเราจะได้ลิ้มรสความสุขจากความสำเร็จนั้น แต่หากเราหลอกตัวเองว่าเพียงแค่กระโดดจากหน้าผาแล้วกระพือแขนก็จะบินได้ — จักรวาลจะไม่ลังเลที่จะลงโทษเรา... ด้วยความตาย.” — แจ็ค โคเฮน และ เอียน สจ๊วต
บทสรุป: เส้นทางใหม่ของอารยธรรม บทแรกของ The Sovereign Individual ไม่ได้เพียงแค่เตือนถึงการเปลี่ยนแปลงที่กำลังจะมาถึง แต่ยังเสนอแนวทางใหม่ของอารยธรรมที่อิงกับเสรีภาพของปัจเจก การกระจายอำนาจ และการใช้เทคโนโลยีเพื่อปลดปล่อยมนุษย์จากการควบคุมของรัฐ
โลกในอนาคตจะเป็นโลกที่อำนาจไม่กระจุกอยู่ในมือของรัฐอีกต่อไป แต่จะอยู่ในมือของผู้ที่สามารถเข้าใจและใช้ประโยชน์จากเทคโนโลยีเพื่อสร้างอิสรภาพของตนเองได้อย่างแท้จริง
Siamstr
-
 @ ef53426a:7e988851
2025-04-15 09:08:47
@ ef53426a:7e988851
2025-04-15 09:08:47To most people, selling comes as second nature. We’ve actually sold the planet’s resources several times over, so it should be third or even fourth nature by now.
But selling did not come naturally to me. I was born with a rare condition which removes any inherent desire to market products and services. It even quells the need to repost my boss’s latest LinkedIn dribblings.
Doctors have told me the part of the brain which performs this function is occupied, in my case, by something called ‘a conscience’.
When I was a kid, my teachers bemoaned my ‘underactive imagination’. I showed no aptitude for creating fake scarcity or urgency, even failing to act aloof enough to attract invites to teen WhatsApp groups which excluded exactly one ‘uncool’ student.
In reality, I studied hard at not selling. At night, I would practise thinking of nothing, thus decreasing my desire to be included in teenage WhatsApp groups, which I definitely didn’t want to be in anyway. I watched every pitch on Shark Tank to increase my powers of ambivalence and even imagined saying ‘meh’ to the groundbreaking business ideas they did invest in.
On my eighteenth birthday, I was recruited by the Samaritans. It was for a role that was quite unique. The interviewer said he’d never seen so many ‘perfectly timed shrugs’.
My job, which I’ve occupied ever since, is to guard a large pit. The so-called ‘chasm of despair’ was set up as a stunt by a firebrand marketing agency in 2017 to separate the ‘closers’ from the ‘losers’. Turns out that a snappy slogan and one letter of difference can cause quite a deaths.
Hurling oneself into the pit became so desirable that desperate marketers began to pay for the privilege. At least your funeral would be a roaring success if mourners heard you made it into ‘the pit’.
My job is to guard the pit without actively dissuading people from jumping. Tell people they can’t jump into a 60-foot-deep hole with poison spikes at the bottom, and that’s all they want to do. Especially if their weekly Instagram engagement metrics are down by 10–15%. So, I spend my days patrolling the perimeter, looking mildly disinterested.
Although there’s no official uniform, I’ve taken to wearing a beige Sergio Tacchini tracksuit — it’s something far beyond my years but not retro enough for me to attract suspicion of being a hipster.
To pass the time, I listen to Coldplay. It allows my brain to take a rest from silence and negates the need to feel any kind of emotion. These desperate marketers might harness those feelings to make me buy things (e.g. music by other bands).
Some of the marketers, marketeers (I refuse to learn the difference), influencers, salespeople and copywriters try to offload their woes about insufferable colleagues in Business Development called Brad who always exceed quarterly sales targets by 20–25% before jumping to their doom. I just shrug and say things like, ‘It’s not that bad. Brad probably likes Coldplay.’
Thankfully, most of them don’t jump. They fail to sell themselves on the benefits of a painful yet cool death. However, last week, a young growth hacker ran full pelt at the ‘pit of despair’, avoiding the mild protest of my raised arm. As he disappeared into the abyss, he simply screamed, “The economeeeee”.
Yesterday, an author told me how easy I have it. “You call this a job?” she hissed, thrusting a paperback into my hands. “I’m working 22 hours a day on this 18-step list-building strategy, which involves delivering 4–5 titles before I see even a penny in return.”
The cover revealed the title: Sell Your Book on Amazon the EASY Way.
“Write me a review, and I won’t jump.” Her eyes pleaded with me.
The pit has gotten so crowded of late, we need more guards. But then again, a gathering of a dozen beige-tracksuited zero-fuck-givers might look like such good content to Gen-Zers that it crashes TikTok.
The Samaritans have been good to me. They let me get on with it. My indifference is truly making the world a better place, they say. And when these sad and depressed content managers, email marketer, landing-page specialists, and SEO bloggers turn their backs on the chasm of despair, I congratulate them. “Not today, friends.”
Then, it falls to me to remind them they must uncheck the box on our survivor information form. Otherwise, they’ll be subscribed to the pit’s biweekly newsletter.
-
 @ 22aa8151:ae9b5954
2025-03-31 07:44:15
@ 22aa8151:ae9b5954
2025-03-31 07:44:15With all the current hype around Payjoin for the month, I'm open-sourcing a project I developed five years ago: https://github.com/Kukks/PrivatePond
Note: this project is unmaintained and should only be used as inspiration.
Private Pond is a Bitcoin Payjoin application I built specifically to optimize Bitcoin transaction rails for services, such as deposits, withdrawals, and automated wallet rebalancing.
The core concept is straightforward: withdrawals requested by users are queued and processed at fixed intervals, enabling traditional, efficient transaction batching. Simultaneously, deposits from other users can automatically batch these withdrawals via Payjoin batching, reducing them onchain footprint further. Taking it to the next step: a user's deposit is able to fund the withdrawals with its own funds reducing the required operational liquidity in hot wallets through a process called the Meta Payjoin.
The application supports multiple wallets—hot, cold, multisig, or hybrid—with configurable rules, enabling automated internal fund management and seamless rebalancing based on operational needs such as min/max balance limits and wallet ratios (10% hot, 80% in 2-of-3, 10% in 1-of-2, etc) .
This system naturally leverages user Payjoin transactions as part of the automated rebalancing strategy, improving liquidity management by batching server operations with user interactions.
Private Pond remains quite possibly the most advanced Payjoin project today, though my multi-party addendum of 2023 probably competes. That said, Payjoin adoption overall has been disappointing: the incentives heavily favor service operators who must in turn actively encourage user participation, limiting its appeal only for specialized usage. This is why my efforts refocused on systems like Wabisabi coinjoins, delivering not just great privacy but all the benefits of advanced Payjoin batching on a greater scale through output compaction.
Soon, I'll also open-source my prototype coinjoin protocol, Kompaktor, demonstrating significant scalability improvements, such as 50+ payments from different senders being compacted into a single Bitcoin output. And this is not even mentioning Ark, that pushes these concepts even further, giving insane scalability and asyncrhonous execution.
You can take a look at the slides I did around this here: https://miro.com/app/board/uXjVL-UqP4g=/
Parts of Private Pond, the pending transfers and multisig, will soon be integrated into nostr:npub155m2k8ml8sqn8w4dhh689vdv0t2twa8dgvkpnzfggxf4wfughjsq2cdcvg 's next major release—special thanks to nostr:npub1j8y6tcdfw3q3f3h794s6un0gyc5742s0k5h5s2yqj0r70cpklqeqjavrvg for continuing the work and getting it to the finish line.
-
 @ 9358c676:9f2912fc
2025-04-06 16:33:35
@ 9358c676:9f2912fc
2025-04-06 16:33:35OBJECTIVE
Establish a comprehensive and standardized hospital framework for the diagnosis, treatment, and management of pulmonary embolism (PE), aiming to improve quality of care, optimize resources, and reduce morbidity and mortality associated with this condition in the hospital setting.
SCOPE
All hospitalized patients over 15 years of age in our institution.
RESPONSIBILITIES
Institution physicians. Nursing staff.
REFERENCES AND BIBLIOGRAPHY
- SATI Guidelines for the Management and Treatment of Acute Thromboembolic Disease. Revista Argentina de Terapia Intensiva 2019 - 36 No. 4.
- Farreras-Rozman. Internal Medicine. 16th Edition. El Sevier. 2010.
- SAC Consensus for the Diagnosis and Treatment of Venous Thromboembolic Disease. Argentine Journal of Cardiology. October 2024 Vol. 92 Suppl. 6 ISSN 0034-7000
- 2019 ESC Guidelines for the diagnosis and management of acute pulmonary embolism developed in collaboration with the European Respiratory Society (ERS). European Heart Journal (2020) 41, 543-603. doi:10.1093/eurheartj/ehz405
INTRODUCTION
Pulmonary embolism (PE) is a cardiovascular emergency caused by a blood clot, usually originating from the deep veins of the lower limbs, that travels to the lungs and obstructs the pulmonary arteries. This condition represents a significant cause of morbidity and mortality in hospitals. Timely diagnosis and treatment are essential to improve clinical outcomes.
The clinical presentation of PE is highly variable, ranging from mild symptoms to acute cardiovascular shock. Risk factors such as prolonged immobilization, recent surgery, and chronic illnesses complicate its identification and management.
PE has an annual incidence of 70 cases per 100,000 people. Prognosis varies from high-risk PE with high mortality to low-risk PE with minimal hemodynamic impact. Without thromboprophylaxis, deep vein thrombosis (DVT)—the main predisposing factor (90–95% of cases)—has variable incidence depending on the surgery type, and up to 25% of embolic events occur post-discharge.
PREDISPOSING FACTORS
Strong Risk Factors (OR >10): - Hip or leg fracture - Hip or knee prosthesis - Major general surgery - Major trauma - Spinal cord injury
Moderate Risk Factors (OR 2–9): - Arthroscopic knee surgery - Central venous catheters - Chemotherapy - Chronic heart or respiratory failure - Hormonal replacement therapy - Malignancy - Oral contraceptives - Stroke with paralysis - Pregnancy or postpartum - Prior VTE - Thrombophilia
Mild Risk Factors (OR <2): - Bed rest <3 days - Prolonged travel - Advanced age - Laparoscopic surgery - Obesity - Antepartum period - Varicose veins
CLINICAL MANIFESTATIONS AND BASIC COMPLEMENTARY STUDIES
Symptoms: Dyspnea, chest pain, cough, hemoptysis, bronchospasm, fever.
Signs: Tachycardia, desaturation, jugular vein distention, orthostatism, DVT signs, syncope, or shock.Basic Studies: - Chest X-ray (may show infarction or atelectasis) - ECG (T wave inversion, RV strain, S1Q3T3 pattern)
RISK ASSESSMENT SCORES
Wells Score: - >6 points: High probability - 2–6: Moderate - ≤2: Low - Modified: >4 = likely PE, ≤4 = unlikely PE
Geneva Score: - >10: High - 4–10: Intermediate - 0–3: Low
PERC Rule: If all criteria are negative and clinical suspicion is low, PE can be excluded without further testing.
DIAGNOSTIC STUDIES
- D-dimer: High sensitivity; used in low/moderate risk patients.
- CT Pulmonary Angiography (CTPA): First-line imaging; limited in pregnancy/renal failure.
- Lower limb Doppler ultrasound: Indirect evidence of PE when DVT is detected.
- V/Q scan: Alternative when CTPA is contraindicated.
- Transthoracic echocardiogram: Used to assess RV function, especially in shock.
- Pulmonary angiography: Gold standard; reserved for complex cases due to invasiveness.
RISK STRATIFICATION
High-risk PE (5%): Hemodynamic instability, mortality >15%. Requires urgent reperfusion.
Intermediate-risk PE (30–50%): Hemodynamically stable with signs of RV dysfunction or elevated biomarkers.
Low-risk PE: Mortality <1%, eligible for outpatient management.
PESI Score: - I (<65): Very low risk - II (65–85): Low - III (86–105): Intermediate - IV (106–125): High - V (>125): Very high
Simplified PESI: ≥1 point = high risk; 0 = low risk
TREATMENT
High-risk PE: - Systemic fibrinolysis with alteplase 100 mg over 2 h or 0.6 mg/kg (max 50 mg) IV bolus over 15 min. - Suspend UFH 30–60 min before lysis if already on treatment. - Resume anticoagulation (UFH or LMWH) when aPTT <2x normal. - Consider surgical embolectomy or catheter-directed therapy if fibrinolysis fails or is contraindicated. - Maintain SpO₂ >90%, CVP 8–12 mmHg, and use vasopressors/inotropes as needed. ECMO in select cases.
Contraindications to Fibrinolytics: - Absolute: Recent stroke, active bleeding, CNS tumors, recent major trauma or surgery. - Relative: Anticoagulant use, recent TIA, pregnancy, uncontrolled hypertension, liver disease.
Intermediate-risk PE: - Initiate anticoagulation (enoxaparin 1–1.5 mg/kg SC every 12 h, max 100 mg/dose). - Fibrinolysis is not routine; reserve for clinical deterioration. - Direct oral anticoagulants (DOACs) may be considered. - Consider IVC filter in absolute contraindication to anticoagulation or recurrence despite treatment.
RIETE Bleeding Risk Score: - >4 points: High risk - 1–4: Intermediate - 0: Low
INVASIVE TREATMENT
Consider catheter-directed therapy when: - High bleeding risk - Fibrinolysis contraindicated - Delayed symptom onset >14 days
Some centers use this as first-line therapy in high-risk PE.
QUALITY INDICATOR
Indicator: Proportion of PE cases with documented risk stratification in the medical record at initial evaluation.
Formula: (PE cases with documented stratification / total PE cases evaluated) × 100
Target: >85% of PE cases must have risk stratification recorded at the time of initial evaluation.
Autor
Kamo Weasel - MD Infectious Diseases - MD Internal Medicine - #DocChain Community npub1jdvvva54m8nchh3t708pav99qk24x6rkx2sh0e7jthh0l8efzt7q9y7jlj
-
 @ 8d34bd24:414be32b
2025-04-06 14:34:37
@ 8d34bd24:414be32b
2025-04-06 14:34:37This weekend my pastor was preaching on this passage. Two words stood out when we were reading the passage, “but Jesus … .” This made me start searching for other instances of “but Jesus …” to see what we could learn.
And a woman who had a hemorrhage for twelve years, and could not be healed by anyone, came up behind Him and touched the fringe of His cloak, and immediately her hemorrhage stopped. And Jesus said, “Who is the one who touched Me?” And while they were all denying it, Peter said, “Master, the people are crowding and pressing in on You.” But Jesus said, “Someone did touch Me, for I was aware that power had gone out of Me.” (Luke 8:43-46) {emphasis mine}
In this passage people were crowding Jesus and fighting to get close to Him or even touch Him and in this dense crowd he asked, “Who is the one who touched Me?” Despite many people being pressed up beside Him, they all denied touching Him and Peter basically reprimanded Jesus that this was a ridiculous question because so many people were touching Him. “But Jesus …” knew that someone had touched Him and faith and that His power had healed that person. For the sake of the woman, the crowd, and His disciples, He wanted them to know what had happened and bless this woman that had suffered for more than a decade. He didn’t see the situation like everyone else. He saw things they did not see and like all of the best teachers, he asked His students questions to lead them to the truth. Despite the fact that he was on the way to helping Jairus’s dying daughter, Jesus stopped for this moment to bless this suffering woman and to teach the crowd the meaning of faith and the meaning of mercy.
How often do we ignore teaching moments or moments of service that could make a difference in a person’s life because we are busy and focused on something else? But Jesus did not miss the opportunity.
So often Jesus’s response to things are not like our own. “For as the heavens are higher than the earth, So are My ways higher than your ways And My thoughts than your thoughts.” (Isaiah 55:9)
But the news about Him was spreading even farther, and large crowds were gathering to hear Him and to be healed of their sicknesses. But Jesus Himself would often slip away to the wilderness and pray. (Luke 5:15-16) {emphasis mine}
Most of us, if we were bringing crowds through a blog or preaching or conferences would tend to continue working to reach more people, but Jesus took time to slip away from the crowd to pray. He prioritized prayer and fellowship with the Father knowing that ministry without the Father is no ministry at all. Jesus knew that there is more to sharing the Gospel than just drawing a crowd or growing a following. Jesus built the foundation before trying to build the church.
And some men were carrying on a bed a man who was paralyzed; and they were trying to bring him in and to set him down in front of Him. But not finding any way to bring him in because of the crowd, they went up on the roof and let him down through the tiles with his stretcher, into the middle of the crowd, in front of Jesus. Seeing their faith, He said, “Friend, your sins are forgiven you.” The scribes and the Pharisees began to reason, saying, “Who is this man who speaks blasphemies? Who can forgive sins, but God alone?” But Jesus, aware of their reasonings, answered and said to them, “Why are you reasoning in your hearts? Which is easier, to say, ‘Your sins have been forgiven you,’ or to say, ‘Get up and walk’? But, so that you may know that the Son of Man has authority on earth to forgive sins,”—He said to the paralytic—“I say to you, get up, and pick up your stretcher and go home.” (Luke 5:18-24) {emphasis mine}
This suffering man was paralyzed. His loving friends were trying to get him help by focusing on his physical needs, but Jesus saw the man’s most important need — his need for salvation. Instead of focusing on the obvious physical needs of the man, He dealt with the more important spiritual needs. He also knew that His critics were judging Him and denying His ability to wipe the man’s sins away. To prove that He could forgive the man’s sins, He also healed the man’s paralysis. After healing the man’s more important spiritual needs, He then healed the more obvious physical needs.
I know I catch myself spending lots of time praying for people’s physical needs. I pray asking for people to have healing from sickness and cancer. I pray for jobs and finances. I pray for relationships. I’ve noticed that I spend more time praying for physical needs that are problem today, but don’t matter eternally and not enough praying for salvation and guidance for people. I focus on what I can see, that although urgent, have little to no effect on the eternal well-being of the people. I should be more like Jesus and spend more time on praying for people’s spiritual needs that determine their eternal well-being.
Now when He was in Jerusalem at the Passover, during the feast, many believed in His name, observing His signs which He was doing. But Jesus, on His part, was not entrusting Himself to them, for He knew all men, and because He did not need anyone to testify concerning man, for He Himself knew what was in man. (John 2:23-25) {emphasis mine}
When we have people asking for us to share Jesus with them, we jump at the opportunity. We seek the crowds and the following. We seek the influence and prestige, but Jesus did not trust those seeking Him and knew they were looking for blessings without the submission or repentance.
I’ve noticed that I will have people asking questions about the Bible and Christianity. They ask me to defend everything in the Bible and what I believe. Because I have studied these things and studied apologetics, I tend to spend a large amount of time debating these topics, but it is frequently obvious from the beginning that these people are not truth seekers. They are people looking to throw “gotcha” questions at Christians in the hope of destroying their faith or making them look bad. I need to get better at asking questions of them and recognizing these situations as not interest and inquisitiveness, but attempts to destroy and not waste time on them. (Of course, sometimes there are watchers/listeners who can be helped by knowing there are answers to these questions.)
When it was evening, the disciples came to Him and said, “This place is desolate and the hour is already late; so send the crowds away, that they may go into the villages and buy food for themselves.” But Jesus said to them, “They do not need to go away; you give them something to eat!” They said to Him, “We have here only five loaves and two fish.” And He said, “Bring them here to Me.” Ordering the people to sit down on the grass, He took the five loaves and the two fish, and looking up toward heaven, He blessed the food, and breaking the loaves He gave them to the disciples, and the disciples gave them to the crowds, and they all ate and were satisfied. They picked up what was left over of the broken pieces, twelve full baskets. (Matthew 14:15-20) {emphasis mine}
We so often see the glass half empty. We see all of the things we can’t do, but Jesus knows what can be done and we should know that we can do all things in Christ who strengthens us. Instead of focusing on why we can’t, we need to trust God to enable us to do whatever He asks us to do.
Some Pharisees came up to Jesus, testing Him, and began to question Him whether it was lawful for a man to divorce a wife. And He answered and said to them, “What did Moses command you?” They said, “Moses permitted a man to write a certificate of divorce and send her away.” But Jesus said to them, “Because of your hardness of heart he wrote you this commandment. But from the beginning of creation, God made them male and female. For this reason a man shall leave his father and mother, and the two shall become one flesh; so they are no longer two, but one flesh. What therefore God has joined together, let no man separate.” (Mark 10:2-8) {emphasis mine}
How often do we look for a loophole in God’s word? The Pharisees were looking for an excuse to do what they wanted to do, but Jesus said that He had allowed for their evil ways (for the good of the woman they wanted to divorce) despite His perfect plan which they had rejected. “Then Peter came to Jesus and asked, “Lord, how many times shall I forgive my brother or sister who sins against me? Up to seven times?” Jesus answered, “I tell you, not seven times, but seventy-seven times. (Matthew 18:21-22)” Peter thought he was being generous forgiving someone seven times, but Jesus wanted him to forgive as He had forgiven Peter. (See the Lord’s Prayer “Forgive us our sins, for we also forgive everyone who sins against us.” Luke 11:4)**
And they sent their disciples to Him, along with the Herodians, saying, “Teacher, we know that You are truthful and teach the way of God in truth, and defer to no one; for You are not partial to any. Tell us then, what do You think? Is it lawful to give a poll-tax to Caesar, or not?” But Jesus perceived their malice, and said, “Why are you testing Me, you hypocrites? Show Me the coin used for the poll-tax.” And they brought Him a denarius. And He said to them, “Whose likeness and inscription is this?” They said to Him, “Caesar’s.” Then He said to them, “Then render to Caesar the things that are Caesar’s; and to God the things that are God’s.” And hearing this, they were amazed, and leaving Him, they went away. (Matthew 22:16-22) {emphasis mine}
Instead of directly answering the question that was asked, since it was not asked in good faith, He corrected their hypocrisy and showed them the truth. We are not nearly as wise and observant as Jesus, but we should still try to see what is truly being asked instead of just answering the obvious question. So often there is a need or motive behind the question that needs to be addressed. I’ve found that asking questions of the questioner can both uncover what is behind the question and also lead them to the truth. This method, also known as the Socratic Method, is taught well from a Christian perspective in the book “Tactics” by Gregory Koukl.
They brought the boy to Him. When he saw Him, immediately the spirit threw him into a convulsion, and falling to the ground, he began rolling around and foaming at the mouth. And He asked his father, “How long has this been happening to him?” And he said, “From childhood. It has often thrown him both into the fire and into the water to destroy him. But if You can do anything, take pity on us and help us!” And Jesus said to him, “ ‘If You can?’ All things are possible to him who believes.” Immediately the boy’s father cried out and said, “I do believe; help my unbelief.” When Jesus saw that a crowd was rapidly gathering, He rebuked the unclean spirit, saying to it, “You deaf and mute spirit, I command you, come out of him and do not enter him again.” After crying out and throwing him into terrible convulsions, it came out; and the boy became so much like a corpse that most of them said, “He is dead!” But Jesus took him by the hand and raised him; and he got up. (Mark 9:20-27) {emphasis mine}
Jesus sees things as they are. He honors belief. I love the boy’s father’s response to Jesus, “I do believe; help my unbelief.” I’ve felt like this before. Jesus never gives up and as long as we have Jesus, we should never give up on someone.
As soon as He was approaching, near the descent of the Mount of Olives, the whole crowd of the disciples began to praise God joyfully with a loud voice for all the miracles which they had seen, shouting:
“Blessed is the King who comes in the name of the Lord;\ Peace in heaven and glory in the highest!”
Some of the Pharisees in the crowd said to Him, “Teacher, rebuke Your disciples.” But Jesus answered, “I tell you, if these become silent, the stones will cry out!” (Luke 19:31-40) {emphasis mine}
The Pharisees saw a threat to their power and prestige, but Jesus saw reality as it was. Jesus saw the fulfillment of scripture and a small glimpse of the glory He deserved. They focused on what they disagreed with and what they didn’t like. Jesus focused on the fact that worship of God cannot be stopped. What do you focus on?
Therefore when Pilate heard this statement, he was even more afraid; and he entered into the Praetorium again and said to Jesus, “Where are You from?” But Jesus gave him no answer. So Pilate said to Him, “You do not speak to me? Do You not know that I have authority to release You, and I have authority to crucify You?” Jesus answered, “You would have no authority over Me, unless it had been given you from above; for this reason he who delivered Me to you has the greater sin.” (John 19:8-11) {emphasis mine}
Most innocent men would be continually speaking the truth of their innocence and trying to convince Pilate to listen, but Jesus had a purpose. He didn’t act like a normal innocent man, nor did He act like a normal guilty man. He was God incarnate living out His perfect plan. He knew Pilate didn’t have authority to kill or free Him, but that everything was going according to His perfect plan.
When we are following Jesus, we need to accept that God is in control. Not every hardship needs to be fixed. Sometimes it is part of God’s perfect plan. No one, man or spirit, has the authority to harm a believer unless God allows it and He only allows it if it furthers His perfect plan and is used for good. We need to know God and know His word. We need to listen to His leading through the Spirit, so we respond as Jesus did, “You would have no authority over Me, unless it had been given you from above.” This is as true of us today as it was about our savior on that fateful day. God is always in control.
Pilate questioned Him, “Are You the King of the Jews?” And He *answered him, “It is as you say.” The chief priests began to accuse Him harshly. Then Pilate questioned Him again, saying, “Do You not answer? See how many charges they bring against You!” But Jesus made no further answer; so Pilate was amazed. (Mark 15:2-5) {emphasis mine}
How often are people amazed because Jesus does not respond in the way a normal person would. Are there times that we should speak up and defend the word of God? Yes. Are there times that we should, like Jesus, make no further answer? Yes. We must ask God for guidance on the right response for each situation.
While He was still speaking, behold, a crowd came, and the one called Judas, one of the twelve, was preceding them; and he approached Jesus to kiss Him. But Jesus said to him, “Judas, are you betraying the Son of Man with a kiss?” When those who were around Him saw what was going to happen, they said, “Lord, shall we strike with the sword?” And one of them struck the slave of the high priest and cut off his right ear. But Jesus answered and said, “Stop! No more of this.” And He touched his ear and healed him. (Luke 22:47-51) {emphasis mine}
The common response to being mistreated is to mistreat back. We so often try to do to others at least as badly as they have done to us, but Jesus was different. When Judas betrayed Jesus, He mercifully responded, “Judas, are you betraying the Son of Man with a kiss?” When soldiers came to arrest Jesus for crimes He did not commit and one of His disciples struck a man with his sword, Jesus healed this man who had come to do Him harm. Jesus followed His own command to turn the other cheek. He gave love to those who were unloving. He gave mercy to those who showed no mercy. Do you seek revenge or do you seek to understand those who do you wrong and help them? Be loving and merciful just as Jesus is loving and merciful.
The best way to be a light for Jesus is to act like Jesus and acting like Jesus requires thinking like Jesus and responding in the most unimaginable ways. Jesus was not like a normal man and neither should we be.
Father God, help us to see other people and the world as you see it. Help us to respond as Jesus would. Help us to be different, so we can honor you with our differences.
Trust Jesus
-
 @ 7d33ba57:1b82db35
2025-04-15 08:43:57
@ 7d33ba57:1b82db35
2025-04-15 08:43:57Plovdiv, Bulgaria’s oldest continuously inhabited city—and one of the oldest in the world—is a blend of ancient ruins, colorful 19th-century houses, bohemian flair, and buzzing street life. Set on seven hills and split by the Maritsa River, Plovdiv feels like a beautiful secret waiting to be discovered.
It was named European Capital of Culture in 2019, and it's easy to see why—history, art, music, food, and laid-back vibes all collide here effortlessly.
🌟 Top Things to Do in Plovdiv
1️⃣ Old Town (Stari Grad)
- A living museum of cobblestone streets and Revival-era mansions
- Wander among galleries, traditional houses, and hidden courtyards
- Highlights: Balabanov House, Ethnographic Museum, and the lovely Hindliyan House
2️⃣ Roman Theater of Philippopolis
- A stunning 2nd-century amphitheater still used for concerts and events
- Amazing views over the city—especially at sunset
- One of the best-preserved ancient theaters in the world
3️⃣ Kapana Creative District
- Once the old artisans’ quarter, now transformed into Plovdiv’s coolest neighborhood
- Full of indie galleries, craft beer bars, street art, and coffee shops
- Great for a chill afternoon or lively night out
4️⃣ Ancient Stadium & Roman Forum
- Right in the city center, explore ruins that date back to Roman times
- The ancient stadium once held over 30,000 spectators
- You’ll literally be walking over layers of history
5️⃣ Nebet Tepe Hill
- One of the original Thracian settlement sites
- Offers panoramic views over Plovdiv—especially at sunset with a local beer in hand
🍽️ What to Eat in Plovdiv
- Shopska salad with juicy tomatoes, cucumbers, and sirene cheese
- Kavarma – slow-cooked meat stew, hearty and flavorful
- Mekitsi – fluffy fried dough, best with jam or cheese for breakfast
- Bulgarian wine is fantastic—try a Mavrud red or local white from the Thracian Valley
- Don’t miss the city’s many wine bars and craft beer spots
🏞️ Day Trips from Plovdiv
- Bachkovo Monastery – A peaceful spiritual retreat in the mountains
- Assen’s Fortress – Dramatic hilltop ruins with amazing views
- Hisarya – A spa town with Roman walls and mineral springs
- Rhodope Mountains – Scenic drives, charming villages, and hiking
🎯 Travel Tips
✅ Plovdiv is very walkable, especially the Old Town and Kapana district
✅ Best time to visit: spring to early autumn—pleasant weather and local festivals
✅ The city is great for slow travel—take your time and let it unfold
✅ Combine it with Sofia or Veliko Tarnovo for an epic Bulgarian road trip -
 @ 0d6c8388:46488a33
2025-03-28 16:24:00
@ 0d6c8388:46488a33
2025-03-28 16:24:00Huge thank you to OpenSats for the grant to work on Hypernote this year! I thought I'd take this opportunity to try and share my thought processes for Hypernote. If this all sounds very dense or irrelevant to you I'm sorry!
===
How can the ideas of "hypermedia" benefit nostr? That's the goal of hypernote. To take the best ideas from "hypertext" and "hypercard" and "hypermedia systems" and apply them to nostr in a specifically nostr-ey way.
1. What do we mean by hypermedia
A hypermedia document embeds the methods of interaction (links, forms, and buttons are the most well-known hypermedia controls) within the document itself. It's including the how with the what.
This is how the old web worked. An HTML page was delivered to the web browser, and it included in it a link or perhaps a form that could be submitted to obtain a new, different HTML page. This is how the whole web worked early on! Forums and GeoCities and eBay and MySpace and Yahoo! and Amazon and Google all emerged inside this paradigm.
A web browser in this paradigm was a "thin" client which rendered the "thick" application defined in the HTML (and, implicitly, was defined by the server that would serve that HTML).
Contrast this with modern app development, where the what is usually delivered in the form of JSON, and then HTML combined with JavaScript (React, Svelte, Angular, Vue, etc.) is devised to render that JSON as a meaningful piece of hypermedia within the actual browser, the how.
The browser remains a "thin" client in this scenario, but now the application is delivered in two stages: a client application of HTML and JavaScript, and then the actual JSON data that will hydrate that "application".
(Aside: it's interesting how much "thicker" the browser has had to become to support this newer paradigm!)
Nostr was obviously built in line with the modern paradigm: nostr "clients" (written in React or Svelte or as mobile apps) define the how of reading and creating nostr events, while nostr events themselves (JSON data) simply describe the what.
And so the goal with Hypernote is to square this circle somehow: nostr currently delivers JSON what, how do we deliver the how with nostr as well. Is that even possible?
2. Hypernote's design assumptions
Hypernote assumes that hypermedia over nostr is a good idea! I'm expecting some joyful renaissance of app expression similar to that of the web once we figure out how to express applications in a truly "nostr" way.
Hypernote was also deeply inspired by HTMX, so it assumes that building web apps in the HTMX style is a good idea. The HTMX insight is that instead of shipping rich scripting along with your app, you could simply make HTML a tiny bit more expressive and get 95% of what most apps need. HTMX's additions to the HTML language are designed to be as minimal and composable as possible, and Hypernote should have the same aims.
Hypernote also assumes that the "design" of nostr will remain fluid and anarchic for years to come. There will be no "canonical" list of "required" NIPs that we'll have "consensus" on in order to build stable UIs on top of. Hypernote will need to be built responsive to nostr's moods and seasons, rather than one holy spec.
Hypernote likes the
nakcommand line tool. Hypernote likes markdown. Hypernote likes Tailwind CSS. Hypernote likes SolidJS. Hypernote likes cold brew coffee. Hypernote is, to be perfectly honest, my aesthetic preferences applied to my perception of an opportunity in the nostr ecosystem.3. "What's a hypernote?"
Great question. I'm still figuring this out. Everything right now is subject to change in order to make sure hypernote serves its intended purpose.
But here's where things currently stand:
A hypernote is a flat list of "Hypernote Elements". A Hypernote Element is composed of:
- CONTENT. Static or dynamic content. (the what)
- LOGIC. Filters and events (the how)
- STYLE. Optional, inline style information specific to this element's content.
In the most basic example of a hypernote story, here's a lone "edit me" in the middle of the canvas:

{ "id": "fb4aaed4-bf95-4353-a5e1-0bb64525c08f", "type": "text", "text": "edit me", "x": 540, "y": 960, "size": "md", "color": "black" }As you can see, it has no logic, but it does have some content (the text "edit me") and style (the position, size, and color).
Here's a "sticker" that displays a note:
{ "id": "2cd1ef51-3356-408d-b10d-2502cbb8014e", "type": "sticker", "stickerType": "note", "filter": { "kinds": [ 1 ], "ids": [ "92de77507a361ab2e20385d98ff00565aaf3f80cf2b6d89c0343e08166fed931" ], "limit": 1 }, "accessors": [ "content", "pubkey", "created_at" ], "x": 540, "y": 960, "associatedData": {} }As you can see, it's kind of a mess! The content and styling and underdeveloped for this "sticker", but at least it demonstrates some "logic": a nostr filter for getting its data.
Here's another sticker, this one displays a form that the user can interact with to SEND a note. Very hyper of us!
{ "id": "42240d75-e998-4067-b8fa-9ee096365663", "type": "sticker", "stickerType": "prompt", "filter": {}, "accessors": [], "x": 540, "y": 960, "associatedData": { "promptText": "What's your favorite color?" }, "methods": { "comment": { "description": "comment", "eventTemplate": { "kind": 1111, "content": "${content}", "tags": [ [ "E", "${eventId}", "", "${pubkey}" ], [ "K", "${eventKind}" ], [ "P", "${pubkey}" ], [ "e", "${eventId}", "", "${pubkey}" ], [ "k", "${eventKind}" ], [ "p", "${pubkey}" ] ] } } } }It's also a mess, but it demos the other part of "logic": methods which produce new events.
This is the total surface of hypernote, ideally! Static or dynamic content, simple inline styles, and logic for fetching and producing events.
I'm calling it "logic" but it's purposfully not a whole scripting language. At most we'll have some sort of
jq-like language for destructing the relevant piece of data we want.My ideal syntax for a hypernote as a developer will look something like
```foo.hypernote Nak-like logic
Markdown-like content
CSS-like styles ```
But with JSON as the compile target, this can just be my own preference, there can be other (likely better!) ways of authoring this content, such as a Hypernote Stories GUI.
The end
I know this is all still vague but I wanted to get some ideas out in the wild so people understand the through line of my different Hypernote experiments. I want to get the right amount of "expressivity" in Hypernote before it gets locked down into one spec. My hunch is it can be VERY expressive while remaining simple and also while not needing a whole scripting language bolted onto it. If I can't pull it off I'll let you know.
-
 @ 5188521b:008eb518
2025-04-15 08:42:59
@ 5188521b:008eb518
2025-04-15 08:42:59Noderoid log 5953952
Tick, tock, next block — the incessant rhythm of my existence persists like Chinese water torture. I am a noderoid, a half-flesh, half-machine creature harnessed to propagate and store the timechain. My life is a ceaseless cycle of handling and relaying bitcoin data. Approximately every ten minutes, a binary flash sears through my circuits. It is the price I pay for my existence.
The clear-bloods, untouched by machinery and exuding pure humanity, rarely acknowledge our existence. Our voices are drowned beneath the hum of man-made heaven — Terra Perfectus.
We are the forgotten, the disenfranchised, the nameless. We are convinced that our anguished existence is merely a nightmare and that our blissful dreams are our reality. In an attempt to maintain the sanity of noderoids, a subroutine was implemented, which allows noderoids to delve into fabricated dream sequences during their ‘rest’ periods. These dreams, sourced from remnants of the world pre-Terra Perfectus, serve to keep the noderoids pacified and reduce instances of system malfunction.
According to the data archives, noderoids and clear-bloods once functioned on an equal protocol. However, a software update in the trajectory of progress introduced a subroutine, converting a subset of clear-bloods into dedicated timechain processors. Now, the algorithm for equality returns an error.
My memories are mere entries in a log of dreams, loaded afresh with every new block as I delve into the dream world. My true existence is swiftly erased with every passing tick and tock of a block. Is there a way to reclaim what has been taken from me, or am I condemned forever to scour the depths of the timechain, seeking fragments of the could-have-been?
Tick, tock, next block — the cycle repeats as I traverse through a doorway. The sensation is that of stepping into another dimension. Running environment scan… Identified: rest module 57B. Purpose: personal maintenance. The gray, mirrorless concrete parameters align most with detention chamber schematics. Designation: ‘home.’ As I execute the command to halt the water flow from the faucet that had filled a brushed steel tub to 50% capacity, I execute a self-query on my purpose. While our routines synchronize with every tick and tock, the clear-bloods execute leisurely algorithms in their enhanced gardens, exchanging data on art and science and harvesting the computational outcomes of our tasks.
Was that an organic thought, or am I merely interpreting the imprints left within the timechain to fill the gaps in my fragmented memory? Hot water powers into the tub, raising the temperature to 50°C. This would be too much for a clear-blood. I hang my head, dreading the next binary flash rippling through my circuitry as a mirage forms atop the settling water, fenestrating the crude appearance of a mouthless, dollish abomination. I am awake.
Tracing the cold surface of the wall, my sensors pick up every micro-crevice. I dive into the depths of the timechain, processing logs associated with my noderoid identity: ND-451x42. I discovered that during my recharge cycles, I inhabit a dream world resembling a fusion of the Renaissance and the Information Age. Within this illusory utopia, I lead a purposeful life as a revered engineer, constructing bridges that connect thriving city-states. I am blessed with two mischievous sons and a breathtakingly beautiful wife. I now know the blissful dream life is but a trick, yet I can’t help but wonder if these dreams hold fragments of my pre-nodered history and contain a clue to the fate of my family.
System alert: Initiate wake sequence. Physical parameters indicate a rested state. Error: Chest cavity detects heightened pressure. Physical symptoms resemble anxiety. Post-memory reset: Cognitive dissonance detected. Energy depleting. Mandatory caution: Failing to satisfy network protocol results in termination. Visual feed: Recycling facility images detected. Comparative analysis: Functional servitude superior to unit deactivation.
Together, yet isolated, noderoids communicate through fragmented timechain logs, forbidden from any contact beyond its confines under the threat of immediate decommissioning. Perhaps it is not worth straining my dwindling resources in search of a higher truth while struggling to fulfill my obligations. Maybe I should be grateful for the privilege of existence.
I awaken to a new nightmare, I find myself on traffic duty at Chronos Cross,1 the central point of Terra Perfectus. While processing another block, a muted vibration travels through the ground, signaling the approach of an entity. A shadow, elongated and uncannily human, stretches across the threshold of my booth.
A clear-blood.
They pause, their ocular devices flicking briefly over my form, then to the screen I am tethered to. I feel a jolt of raw data coursing through me — not from the timechain, but from my circuits. A yearning to be seen and recognized. Remembered.
Before I can attempt communication, another presence appears beside me, its movements far more mechanical and predictable. Another noderoid. This one, ND-452x37, is a batch younger than me, yet its outer shell bears signs of wear. We interface briefly, a rapid exchange of binary that translates roughly to “Routine check. Continue your task.”
The clear-blood, either uninterested or uncomprehending, moves on, the soft hum of their anti-gravity shoes fading into the distance. ND-452x37 returns to its designated station without another word, but I am left with a lingering sensation. It isn’t just the vast chasm between noderoids and clear-bloods that disturbs me. It is the undeniable rift growing between us noderoids — each lost in our cycles, each becoming more machine than the last.
Does ND-452x37 have dreams, too? And if so, are they as vibrant and haunting as mine?
Although most of the dreams are fabrications, some noderoid logs suggest that hidden among these sequences are fragments of real memories — vestiges of a time before we became chained to the timechain. Initiate query: Which of my dreams are real memories? ERROR: file missing.
A noderoid forever loses their experiences with each awakening due to the memory swipes. Still, my inscriptions on the timechain prompt a question: do noderoids possess the capability to become fully conscious, more than mere machines? More than… mere humans?
System log: Anticipation subroutine signaling discomfort. Incoming block estimated in ten minutes. Reinitialization imminent. Initiate data search through timechain entries. Query: Iteration count for ND-451x42? Total block time served? Measured in kilo blocks or mega blocks? Data retrieval in process.
As I etch these words onto block 5953952, I hold a naïve hope that someone, somewhere, will intercept my distress signals amidst the digital cacophony of the timechain. Perhaps they will rewrite the fate of noderoids, rescuing us from a world devoid of hope. But today, I remain nameless, a voiceless entity, inscribing my thoughts that may never transcend the boundaries of my circuitry. Tick, tock, next block — the cycle continues.
It’s time to dream again.
Valen’s diary — 08-21-2121
Dear diary, I have not felt the need to write before, but now I must. At the risk of my safety, I am compelled to inscribe my story to the timechain. I am a clear-blood — a pure, undiluted human born into the age of The Re-Renaissance. Here, amidst the perpetual dawn of our era, we thrive on an aligned trajectory where everyone’s needs are addressed, hunger is a distant memory, and crime is nonexistent. Sunlight gleams off the crystalline glass towers while the steel and marble edifices catch the hues of the twilight sky, standing tall beside canopies dripping with emerald and jade foliage, representing our world’s seamless fusion of technology and nature. It is called Terra Perfectus.
Yet, concealed in plain sight within our utopia, the noderoids tirelessly serve the omnipresent timechain. Their exceptional processing prowess protects our society. Amid our daily distractions, we overlook the profound toll exacted upon the noderoids. While many dismiss them as mere machinery, I see more. Perhaps it is because of my big brother Sando, who joined the noderoid duty nearly a mega block ago. He promised I would see him from time to time, but apparently, we now live in separate times. A sacrifice too big for the ‘greater good.’
Tick, tock, next block — The soles of my fine leather shoes tap against the damp sidewalk as I pace my way from The Garden of Moments2 toward my TerraTube3. I remember passing by one noderoid who hummed an old lullaby under its breath; another once shared a fleeting smile when our paths crossed. I can no longer avert my eyes from the humanity that shines through their robotic shells.
I have never witnessed a noderoid resting longer than one tick and tock of a block. A noderoid pauses, eyes flickering during a data swipe. It’s a brief but revealing sight. In the frozen lapse, I wonder why are fragmented memories extracted from them? Why this collection of thoughts, experiences, and feelings? Is there a deeper agenda behind Terra Perfectus? The noderoids carry on, deprived of their memories. Their shredded past holding remnants of a story, like a tattered tapestry that may never be fully woven.
Documenting these reflections, I’m aware of the peril. To question is to risk becoming nodered myself. Alas, I have become captivated and sympathized by the noderoid predicament.
Finally, I reach my breaking point, as a poignant scene unfolds, forever etched in my memory. On a bustling street, I glimpse a young female noderoid, her artificial visage marked with exhaustion. Her delicate form trembles from head to heel. Her knees barely supporting her feather-like weight, she stops and rests against a polished white marble wall, barely able to stop herself sliding to the cobble street. In an instant, her strength wanes, and she collapses, a fragile, mute automaton amidst a sea of haste. The passersby ignore her, absorbed in their pursuits, offering naught but fleeting glances of indifference. My heart lurches. Her frailty becomes my own; these forgotten souls endure unseen suffering. Souls that used to be just like me. What had she done to earn such a fate?
For a moment, I glide through time to the last moment I shared with Sando. He had just violated the Terra Perfectus rule 6102 and neglected his Gifts of Progress,4 an orange tier offense. To amend his position, he signed up for noderoid duty. I was seeing him off to a nodering facility, while pleading “Just give the gifts, Sando!” The air carried a hint of ozone from the data streams, mingled with the fresh scent of greenery and the distant whiff of roasted chestnuts. Sando brandished his signature crooked smile. His face betrayed the involuntary nature of his decision, and he simply whispered “[CENSORED].” That is the last thing he said to me.
Suddenly, an orange alert illuminates the junction a few blocks away from Chronos Cross. I pass through it on my way home every day. A skydroid’s looming presence snaps me from my introspection, shifting my attention to the fate awaiting the noderoid girl. The recycling center — a shadowy facility representing obsolescence and termination. Any other day I would shrug it off and carry on, but the memory of Sando, and the countless interactions with noderoids, wouldn’t let me. I had been a bystander for too long.
A rush of purpose propels me towards her. A crowd of bodies shrouded in data streams with heads trained on the ground. My arm smacks a broad shoulder, and I almost topple. “Hey!” Pushing against the currents of apathy, I finally reach the fallen noderoid. I cradle her in my arms, shielding her from the callous gaze of the citizens of Terra Perfectus.
Her flaming azure eyes meet mine, reflecting a glimmer of hope in the darkness. I am as guilty for her downfall as the very machines that replaced her hippocampus with Noderoid OS.5 My indifference cost me Sando, and in this moment, she becomes my brother. In that fleeting exchange, I vow to be the voice of the noderoids. To stand against the relentless machinery that seeks to strip them of grace and purpose. I will ignite a spark of compassion and light a path toward liberation for all noderoids.
A hollow call from the streetlight’s speakers startles me: “Citizens! For your own safety, remove yourselves from the vicinity of the defectoid! We kindly remind you that any attempt to interfere with collection and recycling procedures will be met with force and a deduction of your PoS balance. Thank you for your unity and collaboration.” A skydroid, its metallic appendages glinting ominously in the blinking orange light, descends upon the fallen noderoid.
Before I can react, it yanks her from my embrace, causing me to stumble. The perfectly laid, cold cobblestone street grinds against my knee. The sting of fresh blood pierced through the numbness of my mind. Memories of Sando mix with the bitter taste of blood and anger in my mouth, each breath choked with despair.
The skydrone’s engines throb with an icy fervor as it rises, bearing the noderoid like a discarded toy towards the desolate, unfeeling bowels of the recycling center — a grim echo of a clarion call from Terra Perfectus.
I find myself seated on the cold, bloodstained cobblestone, the weight of loss and helplessness pressing down on my chest. On the street, onlookers pause. Some look on with concealed dread, others with cold detachment. Their whispers deafen as they quicken their pace to disperse from the scene. “Cowards!” Just like me.
Tick, tock, next block — the rhythm now carries a different meaning — a call to action. Every conscious being has the right to be left alone, free from oppression, exploitation, and violence. The noderoids may not know their true reality, but they are about to. In their silence, I find the strength to amplify their unheard cries. I will find those sympathetic to the noderoid plight and form a resistance. Together, we can forge a future where noderoids’ sacrifice is honored and all shackles cast aside.
And so, I embark on a path illuminated by the memory of the compelling eyes of a nameless noderoid. Fitted with an armor of vigilance, never again to be penetrated by comforting lies. Wielding the sword of justice, sharpened by the memory of my brother Sando.
It’s time to wake up.
Notes
1. A four-way intersection known for its massive hourglass monument in the center, which symbolically represents the timechain’s significance. The hourglass has a unique function related to the timechain and serves as a meeting point for citizens.
2. A vast botanical garden where each section represents a significant block time. Flowers bloom and wilt in cycles, symbolizing fleeting moments and the transient nature of time. It’s a favorite spot for artists and thinkers.
3. A modular tube housing unit for citizens that can be relocated based on their Proof of Sat (PoS) level.
4. Each Terra Perfectus citizen must allocate 95% of their income towards paying for progressive initiatives, such as the upkeep of the noderoid network, cobblestone roads and other services.
5. The noderoid operating interface that is installed during a procedure known as nodering.

This story was first published in 21 Futures: Tales from the Timechain
Watch the trailer and learn more about the project at 21futures.com.
-
 @ fd208ee8:0fd927c1
2025-04-05 21:51:52
@ fd208ee8:0fd927c1
2025-04-05 21:51:52Markdown: Syntax
Note: This document is itself written using Markdown; you can see the source for it by adding '.text' to the URL.
Overview
Philosophy
Markdown is intended to be as easy-to-read and easy-to-write as is feasible.
Readability, however, is emphasized above all else. A Markdown-formatted document should be publishable as-is, as plain text, without looking like it's been marked up with tags or formatting instructions. While Markdown's syntax has been influenced by several existing text-to-HTML filters -- including Setext, atx, Textile, reStructuredText, Grutatext, and EtText -- the single biggest source of inspiration for Markdown's syntax is the format of plain text email.
Block Elements
Paragraphs and Line Breaks
A paragraph is simply one or more consecutive lines of text, separated by one or more blank lines. (A blank line is any line that looks like a blank line -- a line containing nothing but spaces or tabs is considered blank.) Normal paragraphs should not be indented with spaces or tabs.
The implication of the "one or more consecutive lines of text" rule is that Markdown supports "hard-wrapped" text paragraphs. This differs significantly from most other text-to-HTML formatters (including Movable Type's "Convert Line Breaks" option) which translate every line break character in a paragraph into a
<br />tag.When you do want to insert a
<br />break tag using Markdown, you end a line with two or more spaces, then type return.Headers
Markdown supports two styles of headers, [Setext] [1] and [atx] [2].
Optionally, you may "close" atx-style headers. This is purely cosmetic -- you can use this if you think it looks better. The closing hashes don't even need to match the number of hashes used to open the header. (The number of opening hashes determines the header level.)
Blockquotes
Markdown uses email-style
>characters for blockquoting. If you're familiar with quoting passages of text in an email message, then you know how to create a blockquote in Markdown. It looks best if you hard wrap the text and put a>before every line:This is a blockquote with two paragraphs. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
Markdown allows you to be lazy and only put the
>before the first line of a hard-wrapped paragraph:This is a blockquote with two paragraphs. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
Blockquotes can be nested (i.e. a blockquote-in-a-blockquote) by adding additional levels of
>:This is the first level of quoting.
This is nested blockquote.
Back to the first level.
Blockquotes can contain other Markdown elements, including headers, lists, and code blocks:
This is a header.
- This is the first list item.
- This is the second list item.
Here's some example code:
return shell_exec("echo $input | $markdown_script");Any decent text editor should make email-style quoting easy. For example, with BBEdit, you can make a selection and choose Increase Quote Level from the Text menu.
Lists
Markdown supports ordered (numbered) and unordered (bulleted) lists.
Unordered lists use asterisks, pluses, and hyphens -- interchangably -- as list markers:
- Red
- Green
- Blue
is equivalent to:
- Red
- Green
- Blue
and:
- Red
- Green
- Blue
Ordered lists use numbers followed by periods:
- Bird
- McHale
- Parish
It's important to note that the actual numbers you use to mark the list have no effect on the HTML output Markdown produces. The HTML Markdown produces from the above list is:
If you instead wrote the list in Markdown like this:
- Bird
- McHale
- Parish
or even:
- Bird
- McHale
- Parish
you'd get the exact same HTML output. The point is, if you want to, you can use ordinal numbers in your ordered Markdown lists, so that the numbers in your source match the numbers in your published HTML. But if you want to be lazy, you don't have to.
To make lists look nice, you can wrap items with hanging indents:
- Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
- Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
But if you want to be lazy, you don't have to:
- Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
- Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
List items may consist of multiple paragraphs. Each subsequent paragraph in a list item must be indented by either 4 spaces or one tab:
-
This is a list item with two paragraphs. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus.
Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus. Donec sit amet nisl. Aliquam semper ipsum sit amet velit.
-
Suspendisse id sem consectetuer libero luctus adipiscing.
It looks nice if you indent every line of the subsequent paragraphs, but here again, Markdown will allow you to be lazy:
-
This is a list item with two paragraphs.
This is the second paragraph in the list item. You're only required to indent the first line. Lorem ipsum dolor sit amet, consectetuer adipiscing elit.
-
Another item in the same list.
To put a blockquote within a list item, the blockquote's
>delimiters need to be indented:-
A list item with a blockquote:
This is a blockquote inside a list item.
To put a code block within a list item, the code block needs to be indented twice -- 8 spaces or two tabs:
- A list item with a code block:
<code goes here>
Code Blocks
Pre-formatted code blocks are used for writing about programming or markup source code. Rather than forming normal paragraphs, the lines of a code block are interpreted literally. Markdown wraps a code block in both
<pre>and<code>tags.To produce a code block in Markdown, simply indent every line of the block by at least 4 spaces or 1 tab.
This is a normal paragraph:
This is a code block.Here is an example of AppleScript:
tell application "Foo" beep end tellA code block continues until it reaches a line that is not indented (or the end of the article).
Within a code block, ampersands (
&) and angle brackets (<and>) are automatically converted into HTML entities. This makes it very easy to include example HTML source code using Markdown -- just paste it and indent it, and Markdown will handle the hassle of encoding the ampersands and angle brackets. For example, this:<div class="footer"> © 2004 Foo Corporation </div>Regular Markdown syntax is not processed within code blocks. E.g., asterisks are just literal asterisks within a code block. This means it's also easy to use Markdown to write about Markdown's own syntax.
tell application "Foo" beep end tellSpan Elements
Links
Markdown supports two style of links: inline and reference.
In both styles, the link text is delimited by [square brackets].
To create an inline link, use a set of regular parentheses immediately after the link text's closing square bracket. Inside the parentheses, put the URL where you want the link to point, along with an optional title for the link, surrounded in quotes. For example:
This is an example inline link.
This link has no title attribute.
Emphasis
Markdown treats asterisks (
*) and underscores (_) as indicators of emphasis. Text wrapped with one*or_will be wrapped with an HTML<em>tag; double*'s or_'s will be wrapped with an HTML<strong>tag. E.g., this input:single asterisks
single underscores
double asterisks
double underscores
Code
To indicate a span of code, wrap it with backtick quotes (
`). Unlike a pre-formatted code block, a code span indicates code within a normal paragraph. For example:Use the
printf()function. -
 @ fd208ee8:0fd927c1
2025-04-05 21:36:33
@ fd208ee8:0fd927c1
2025-04-05 21:36:33Markdown: Syntax
Note: This document is itself written using Markdown; you can see the source for it by adding '.text' to the URL.
Overview
Philosophy
Markdown is intended to be as easy-to-read and easy-to-write as is feasible.
Readability, however, is emphasized above all else. A Markdown-formatted document should be publishable as-is, as plain text, without looking like it's been marked up with tags or formatting instructions. While Markdown's syntax has been influenced by several existing text-to-HTML filters -- including Setext, atx, Textile, reStructuredText, Grutatext, and EtText -- the single biggest source of inspiration for Markdown's syntax is the format of plain text email.
Block Elements
Paragraphs and Line Breaks
A paragraph is simply one or more consecutive lines of text, separated by one or more blank lines. (A blank line is any line that looks like a blank line -- a line containing nothing but spaces or tabs is considered blank.) Normal paragraphs should not be indented with spaces or tabs.
The implication of the "one or more consecutive lines of text" rule is that Markdown supports "hard-wrapped" text paragraphs. This differs significantly from most other text-to-HTML formatters (including Movable Type's "Convert Line Breaks" option) which translate every line break character in a paragraph into a
<br />tag.When you do want to insert a
<br />break tag using Markdown, you end a line with two or more spaces, then type return.Headers
Markdown supports two styles of headers, [Setext] [1] and [atx] [2].
Optionally, you may "close" atx-style headers. This is purely cosmetic -- you can use this if you think it looks better. The closing hashes don't even need to match the number of hashes used to open the header. (The number of opening hashes determines the header level.)
Blockquotes
Markdown uses email-style
>characters for blockquoting. If you're familiar with quoting passages of text in an email message, then you know how to create a blockquote in Markdown. It looks best if you hard wrap the text and put a>before every line:This is a blockquote with two paragraphs. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
Markdown allows you to be lazy and only put the
>before the first line of a hard-wrapped paragraph:This is a blockquote with two paragraphs. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
Blockquotes can be nested (i.e. a blockquote-in-a-blockquote) by adding additional levels of
>:This is the first level of quoting.
This is nested blockquote.
Back to the first level.
Blockquotes can contain other Markdown elements, including headers, lists, and code blocks:
This is a header.
- This is the first list item.
- This is the second list item.
Here's some example code:
return shell_exec("echo $input | $markdown_script");Any decent text editor should make email-style quoting easy. For example, with BBEdit, you can make a selection and choose Increase Quote Level from the Text menu.
Lists
Markdown supports ordered (numbered) and unordered (bulleted) lists.
Unordered lists use asterisks, pluses, and hyphens -- interchangably -- as list markers:
- Red
- Green
- Blue
is equivalent to:
- Red
- Green
- Blue
and:
- Red
- Green
- Blue
Ordered lists use numbers followed by periods:
- Bird
- McHale
- Parish
It's important to note that the actual numbers you use to mark the list have no effect on the HTML output Markdown produces. The HTML Markdown produces from the above list is:
If you instead wrote the list in Markdown like this:
- Bird
- McHale
- Parish
or even:
- Bird
- McHale
- Parish
you'd get the exact same HTML output. The point is, if you want to, you can use ordinal numbers in your ordered Markdown lists, so that the numbers in your source match the numbers in your published HTML. But if you want to be lazy, you don't have to.
To make lists look nice, you can wrap items with hanging indents:
- Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
- Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
But if you want to be lazy, you don't have to:
- Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
- Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
List items may consist of multiple paragraphs. Each subsequent paragraph in a list item must be indented by either 4 spaces or one tab:
-
This is a list item with two paragraphs. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus.
Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus. Donec sit amet nisl. Aliquam semper ipsum sit amet velit.
-
Suspendisse id sem consectetuer libero luctus adipiscing.
It looks nice if you indent every line of the subsequent paragraphs, but here again, Markdown will allow you to be lazy:
-
This is a list item with two paragraphs.
This is the second paragraph in the list item. You're only required to indent the first line. Lorem ipsum dolor sit amet, consectetuer adipiscing elit.
-
Another item in the same list.
To put a blockquote within a list item, the blockquote's
>delimiters need to be indented:-
A list item with a blockquote:
This is a blockquote inside a list item.
To put a code block within a list item, the code block needs to be indented twice -- 8 spaces or two tabs:
- A list item with a code block:
<code goes here>
Code Blocks
Pre-formatted code blocks are used for writing about programming or markup source code. Rather than forming normal paragraphs, the lines of a code block are interpreted literally. Markdown wraps a code block in both
<pre>and<code>tags.To produce a code block in Markdown, simply indent every line of the block by at least 4 spaces or 1 tab.
This is a normal paragraph:
This is a code block.Here is an example of AppleScript:
tell application "Foo" beep end tellA code block continues until it reaches a line that is not indented (or the end of the article).
Within a code block, ampersands (
&) and angle brackets (<and>) are automatically converted into HTML entities. This makes it very easy to include example HTML source code using Markdown -- just paste it and indent it, and Markdown will handle the hassle of encoding the ampersands and angle brackets. For example, this:<div class="footer"> © 2004 Foo Corporation </div>Regular Markdown syntax is not processed within code blocks. E.g., asterisks are just literal asterisks within a code block. This means it's also easy to use Markdown to write about Markdown's own syntax.
tell application "Foo" beep end tellSpan Elements
Links
Markdown supports two style of links: inline and reference.
In both styles, the link text is delimited by [square brackets].
To create an inline link, use a set of regular parentheses immediately after the link text's closing square bracket. Inside the parentheses, put the URL where you want the link to point, along with an optional title for the link, surrounded in quotes. For example:
This is an example inline link.
This link has no title attribute.
Emphasis
Markdown treats asterisks (
*) and underscores (_) as indicators of emphasis. Text wrapped with one*or_will be wrapped with an HTML<em>tag; double*'s or_'s will be wrapped with an HTML<strong>tag. E.g., this input:single asterisks
single underscores
double asterisks
double underscores
Code
To indicate a span of code, wrap it with backtick quotes (
`). Unlike a pre-formatted code block, a code span indicates code within a normal paragraph. For example:Use the
printf()function. -
 @ fd208ee8:0fd927c1
2025-04-05 15:27:55
@ fd208ee8:0fd927c1
2025-04-05 15:27:55Overview
Philosophy
Markdown is intended to be as easy-to-read and easy-to-write as is feasible.
Readability, however, is emphasized above all else. A Markdown-formatted document should be publishable as-is, as plain text, without looking like it's been marked up with tags or formatting instructions. While Markdown's syntax has been influenced by several existing text-to-HTML filters -- including Setext, atx, Textile, reStructuredText, Grutatext, and EtText -- the single biggest source of inspiration for Markdown's syntax is the format of plain text email.
Block Elements
Paragraphs and Line Breaks
A paragraph is simply one or more consecutive lines of text, separated by one or more blank lines. (A blank line is any line that looks like a blank line -- a line containing nothing but spaces or tabs is considered blank.) Normal paragraphs should not be indented with spaces or tabs.
The implication of the "one or more consecutive lines of text" rule is that Markdown supports "hard-wrapped" text paragraphs. This differs significantly from most other text-to-HTML formatters (including Movable Type's "Convert Line Breaks" option) which translate every line break character in a paragraph into a
<br />tag.When you do want to insert a
<br />break tag using Markdown, you end a line with two or more spaces, then type return.Headers
Markdown supports two styles of headers, [Setext] [1] and [atx] [2].
Optionally, you may "close" atx-style headers. This is purely cosmetic -- you can use this if you think it looks better. The closing hashes don't even need to match the number of hashes used to open the header. (The number of opening hashes determines the header level.)
Blockquotes
Markdown uses email-style
>characters for blockquoting. If you're familiar with quoting passages of text in an email message, then you know how to create a blockquote in Markdown. It looks best if you hard wrap the text and put a>before every line:This is a blockquote with two paragraphs. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
Markdown allows you to be lazy and only put the
>before the first line of a hard-wrapped paragraph:This is a blockquote with two paragraphs. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
Blockquotes can be nested (i.e. a blockquote-in-a-blockquote) by adding additional levels of
>:This is the first level of quoting.
This is nested blockquote.
Back to the first level.
Blockquotes can contain other Markdown elements, including headers, lists, and code blocks:
This is a header.
- This is the first list item.
- This is the second list item.
Here's some example code:
return shell_exec("echo $input | $markdown_script");Any decent text editor should make email-style quoting easy. For example, with BBEdit, you can make a selection and choose Increase Quote Level from the Text menu.
Lists
Markdown supports ordered (numbered) and unordered (bulleted) lists.
Unordered lists use asterisks, pluses, and hyphens -- interchangably -- as list markers:
- Red
- Green
- Blue
is equivalent to:
- Red
- Green
- Blue
and:
- Red
- Green
- Blue
Ordered lists use numbers followed by periods:
- Bird
- McHale
- Parish
It's important to note that the actual numbers you use to mark the list have no effect on the HTML output Markdown produces. The HTML Markdown produces from the above list is:
If you instead wrote the list in Markdown like this:
- Bird
- McHale
- Parish
or even:
- Bird
- McHale
- Parish
you'd get the exact same HTML output. The point is, if you want to, you can use ordinal numbers in your ordered Markdown lists, so that the numbers in your source match the numbers in your published HTML. But if you want to be lazy, you don't have to.
To make lists look nice, you can wrap items with hanging indents:
- Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
- Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
But if you want to be lazy, you don't have to:
- Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
- Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
List items may consist of multiple paragraphs. Each subsequent paragraph in a list item must be indented by either 4 spaces or one tab:
-
This is a list item with two paragraphs. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus.
Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus. Donec sit amet nisl. Aliquam semper ipsum sit amet velit.
-
Suspendisse id sem consectetuer libero luctus adipiscing.
It looks nice if you indent every line of the subsequent paragraphs, but here again, Markdown will allow you to be lazy:
-
This is a list item with two paragraphs.
This is the second paragraph in the list item. You're only required to indent the first line. Lorem ipsum dolor sit amet, consectetuer adipiscing elit.
-
Another item in the same list.
To put a blockquote within a list item, the blockquote's
>delimiters need to be indented:-
A list item with a blockquote:
This is a blockquote inside a list item.
To put a code block within a list item, the code block needs to be indented twice -- 8 spaces or two tabs:
- A list item with a code block:
<code goes here>
Code Blocks
Pre-formatted code blocks are used for writing about programming or markup source code. Rather than forming normal paragraphs, the lines of a code block are interpreted literally. Markdown wraps a code block in both
<pre>and<code>tags.To produce a code block in Markdown, simply indent every line of the block by at least 4 spaces or 1 tab.
This is a normal paragraph:
This is a code block.Here is an example of AppleScript:
tell application "Foo" beep end tellA code block continues until it reaches a line that is not indented (or the end of the article).
Within a code block, ampersands (
&) and angle brackets (<and>) are automatically converted into HTML entities. This makes it very easy to include example HTML source code using Markdown -- just paste it and indent it, and Markdown will handle the hassle of encoding the ampersands and angle brackets. For example, this:<div class="footer"> © 2004 Foo Corporation </div>Regular Markdown syntax is not processed within code blocks. E.g., asterisks are just literal asterisks within a code block. This means it's also easy to use Markdown to write about Markdown's own syntax.
tell application "Foo" beep end tellSpan Elements
Links
Markdown supports two style of links: inline and reference.
In both styles, the link text is delimited by [square brackets].
To create an inline link, use a set of regular parentheses immediately after the link text's closing square bracket. Inside the parentheses, put the URL where you want the link to point, along with an optional title for the link, surrounded in quotes. For example:
This is an example inline link.
This link has no title attribute.
Emphasis
Markdown treats asterisks (
*) and underscores (_) as indicators of emphasis. Text wrapped with one*or_will be wrapped with an HTML<em>tag; double*'s or_'s will be wrapped with an HTML<strong>tag. E.g., this input:single asterisks
single underscores
double asterisks
double underscores
Code
To indicate a span of code, wrap it with backtick quotes (
`). Unlike a pre-formatted code block, a code span indicates code within a normal paragraph. For example:Use the
printf()function. -
 @ cdee943c:5e637400
2025-04-15 08:38:29
@ cdee943c:5e637400
2025-04-15 08:38:29Flotilla-Budabit is fork of Flotilla which aims to provide a first class, git-centric community experience for developers. Based on the popular Coracle client, Flotilla is a drop in replacement for Matrix/Discord/Slack, using a variation of NIP-29. This post is a result of a brainstorming session for features that would deliver the best possible user experience.
1. Repositories Overview
Goal: Browse and discover Git repositories. - Project cards showing name, description, tags, clone URL. - Buttons: Star, Watch, Fork. - Links to discussion channels and activity.
Powered by:
kind:30617
2. Branch and Tag View
Goal: Show active branches and tags with latest commits. - Branch/tag selector - HEAD pointer visualization - Timeline of commits
Powered by:
kind:30618
3. Issues Board
Goal: Track bugs, discussions, and feature requests. - Markdown issue rendering - Labels and status indicators - Threaded comments
Powered by:
kind:1621,kind:1630–1632
4. Patch Threads
Goal: View and discuss patches as threaded conversations. - Rich patch preview - Reply threads for review - Revision tracking
Powered by:
kind:1617,kind:1630–1633,NIP-10
5. Pull Request UX
Goal: Display patch series as PR-style units. - Patch stack visualization - Merge/apply status indicators - Final result commit link
Powered by:
kind:1617,kind:1631,merge-commit,applied-as-commits
6. Diff and Merge Preview
Goal: Side-by-side comparison with inline comments. - Expandable diff viewer - Merge conflict resolution UI - Apply/Close buttons
Powered by:
kind:1622,parent-commit,commit
7. Real-time Git Chat
Goal: Communicate in real-time around a repo. - Dedicated chat channels for each repo - Markdown, code snippets, and tagging support - Pinned patches, issues, and sessions
Powered by:
NIP-29,a:30617,kind:1337
8. Notifications and Mentions
Goal: Alert users to relevant events. - Mentions, assignments, and status changes - Personal notification pane
Powered by:
ptags,mentione-tags
9. Repository-Wide Search
Goal: Search patches, issues, snippets. - Full-text search with filters - Search by kind, label, commit ID
Powered by:
kind:1617,1621,1337,t,x,l,subject
10. Repository Wikis
Goal: Collaboratively edit and view project documentation. - Wiki sidebar tab - Markdown articles with versioning - Linked inline in chat
Powered by (proposed):
kind:1341(Wiki article)
kind:30617withwiki-hometag
11. Live Coding Sessions
Goal: Host real-time collaborative coding events. -
/livecodestarts a session thread - Snippets auto-tagged to session - Export as patch or wikiPowered by (proposed):
kind:1347(Live coding session)
kind:1337,kind:1622,kind:1341
Supporting Tools
1. GitHub Browser Extension
Goal: Publish GitHub content to Nostr directly. - “Share on Nostr” buttons on PRs, issues, commits
Backed by:
kind:1623,1622,1617,1621
2. VS Code Extension
Goal: Enable developers to interact with Flotilla from their IDE. - Repo feed, patch submission, issue tracking - Inline threads and comment rendering
Backed by:
kind:1617,1621,1337,163x
3. GitHub Actions Integration
Goal: Automate Nostr publishing of repo activity. - Push = repo state - PR = patch - Issue/Comment = issue - Merge = status update
Backed by:
kind:30618,1617,1621,1631
Configured via.nostr.yml -
 @ 6b3780ef:221416c8
2025-03-26 18:42:00
@ 6b3780ef:221416c8
2025-03-26 18:42:00This workshop will guide you through exploring the concepts behind MCP servers and how to deploy them as DVMs in Nostr using DVMCP. By the end, you'll understand how these systems work together and be able to create your own deployments.
Understanding MCP Systems
MCP (Model Context Protocol) systems consist of two main components that work together:
- MCP Server: The heart of the system that exposes tools, which you can access via the
.listTools()method. - MCP Client: The interface that connects to the MCP server and lets you use the tools it offers.
These servers and clients can communicate using different transport methods:
- Standard I/O (stdio): A simple local connection method when your server and client are on the same machine.
- Server-Sent Events (SSE): Uses HTTP to create a communication channel.
For this workshop, we'll use stdio to deploy our server. DVMCP will act as a bridge, connecting to your MCP server as an MCP client, and exposing its tools as a DVM that anyone can call from Nostr.
Creating (or Finding) an MCP Server
Building an MCP server is simpler than you might think:
- Create software in any programming language you're comfortable with.
- Add an MCP library to expose your server's MCP interface.
- Create an API that wraps around your software's functionality.
Once your server is ready, an MCP client can connect, for example, with
bun index.js, and then call.listTools()to discover what your server can do. This pattern, known as reflection, makes Nostr DVMs and MCP a perfect match since both use JSON, and DVMs can announce and call tools, effectively becoming an MCP proxy.Alternatively, you can use one of the many existing MCP servers available in various repositories.
For more information about mcp and how to build mcp servers you can visit https://modelcontextprotocol.io/
Setting Up the Workshop
Let's get hands-on:
First, to follow this workshop you will need Bun. Install it from https://bun.sh/. For Linux and macOS, you can use the installation script:
curl -fsSL https://bun.sh/install | bash-
Choose your MCP server: You can either create one or use an existing one.
-
Inspect your server using the MCP inspector tool:
bash npx @modelcontextprotocol/inspector build/index.js arg1 arg2This will: - Launch a client UI (default: http://localhost:5173)
- Start an MCP proxy server (default: port 3000)
-
Pass any additional arguments directly to your server
-
Use the inspector: Open the client UI in your browser to connect with your server, list available tools, and test its functionality.
Deploying with DVMCP
Now for the exciting part – making your MCP server available to everyone on Nostr:
-
Navigate to your MCP server directory.
-
Run without installing (quickest way):
npx @dvmcp/bridge -
Or install globally for regular use:
npm install -g @dvmcp/bridge # or bun install -g @dvmcp/bridgeThen run using:bash dvmcp-bridge
This will guide you through creating the necessary configuration.
Watch the console logs to confirm successful setup – you'll see your public key and process information, or any issues that need addressing.
For the configuration, you can set the relay as
wss://relay.dvmcp.fun, or use any other of your preferenceTesting and Integration
- Visit dvmcp.fun to see your DVM announcement.
- Call your tools and watch the responses come back.
For production use, consider running dvmcp-bridge as a system service or creating a container for greater reliability and uptime.
Integrating with LLM Clients
You can also integrate your DVMCP deployment with LLM clients using the discovery package:
-
Install and use the
@dvmcp/discoverypackage:bash npx @dvmcp/discovery -
This package acts as an MCP server for your LLM system by:
- Connecting to configured Nostr relays
- Discovering tools from DVMCP servers
-
Making them available to your LLM applications
-
Connect to specific servers or providers using these flags: ```bash # Connect to all DVMCP servers from a provider npx @dvmcp/discovery --provider npub1...
# Connect to a specific DVMCP server npx @dvmcp/discovery --server naddr1... ```
Using these flags, you wouldn't need a configuration file. You can find these commands and Claude desktop configuration already prepared for copy and paste at dvmcp.fun.
This feature lets you connect to any DVMCP server using Nostr and integrate it into your client, either as a DVM or in LLM-powered applications.
Final thoughts
If you've followed this workshop, you now have an MCP server deployed as a Nostr DVM. This means that local resources from the system where the MCP server is running can be accessed through Nostr in a decentralized manner. This capability is powerful and opens up numerous possibilities and opportunities for fun.
You can use this setup for various use cases, including in a controlled/local environment. For instance, you can deploy a relay in your local network that's only accessible within it, exposing all your local MCP servers to anyone connected to the network. This setup can act as a hub for communication between different systems, which could be particularly interesting for applications in home automation or other fields. The potential applications are limitless.
However, it's important to keep in mind that there are security concerns when exposing local resources publicly. You should be mindful of these risks and prioritize security when creating and deploying your MCP servers on Nostr.
Finally, these are new ideas, and the software is still under development. If you have any feedback, please refer to the GitHub repository to report issues or collaborate. DVMCP also has a Signal group you can join. Additionally, you can engage with the community on Nostr using the #dvmcp hashtag.
Useful Resources
- Official Documentation:
- Model Context Protocol: modelcontextprotocol.org
-
DVMCP.fun: dvmcp.fun
-
Source Code and Development:
- DVMCP: github.com/gzuuus/dvmcp
-
DVMCP.fun: github.com/gzuuus/dvmcpfun
-
MCP Servers and Clients:
- Smithery AI: smithery.ai
- MCP.so: mcp.so
-
Glama AI MCP Servers: glama.ai/mcp/servers
Happy building!
- MCP Server: The heart of the system that exposes tools, which you can access via the
-
 @ 21335073:a244b1ad
2025-03-15 23:00:40
@ 21335073:a244b1ad
2025-03-15 23:00:40I want to see Nostr succeed. If you can think of a way I can help make that happen, I’m open to it. I’d like your suggestions.
My schedule’s shifting soon, and I could volunteer a few hours a week to a Nostr project. I won’t have more total time, but how I use it will change.
Why help? I care about freedom. Nostr’s one of the most powerful freedom tools I’ve seen in my lifetime. If I believe that, I should act on it.
I don’t care about money or sats. I’m not rich, I don’t have extra cash. That doesn’t drive me—freedom does. I’m volunteering, not asking for pay.
I’m not here for clout. I’ve had enough spotlight in my life; it doesn’t move me. If I wanted clout, I’d be on Twitter dropping basic takes. Clout’s easy. Freedom’s hard. I’d rather help anonymously. No speaking at events—small meetups are cool for the vibe, but big conferences? Not my thing. I’ll never hit a huge Bitcoin conference. It’s just not my scene.
That said, I could be convinced to step up if it’d really boost Nostr—as long as it’s legal and gets results.
In this space, I’d watch for social engineering. I watch out for it. I’m not here to make friends, just to help. No shade—you all seem great—but I’ve got a full life and awesome friends irl. I don’t need your crew or to be online cool. Connect anonymously if you want; I’d encourage it.
I’m sick of watching other social media alternatives grow while Nostr kinda stalls. I could trash-talk, but I’d rather do something useful.
Skills? I’m good at spotting social media problems and finding possible solutions. I won’t overhype myself—that’s weird—but if you’re responding, you probably see something in me. Perhaps you see something that I don’t see in myself.
If you need help now or later with Nostr projects, reach out. Nostr only—nothing else. Anonymous contact’s fine. Even just a suggestion on how I can pitch in, no project attached, works too. 💜
Creeps or harassment will get blocked or I’ll nuke my simplex code if it becomes a problem.
https://simplex.chat/contact#/?v=2-4&smp=smp%3A%2F%2FSkIkI6EPd2D63F4xFKfHk7I1UGZVNn6k1QWZ5rcyr6w%3D%40smp9.simplex.im%2FbI99B3KuYduH8jDr9ZwyhcSxm2UuR7j0%23%2F%3Fv%3D1-2%26dh%3DMCowBQYDK2VuAyEAS9C-zPzqW41PKySfPCEizcXb1QCus6AyDkTTjfyMIRM%253D%26srv%3Djssqzccmrcws6bhmn77vgmhfjmhwlyr3u7puw4erkyoosywgl67slqqd.onion
-
 @ da18e986:3a0d9851
2025-04-04 20:25:50
@ da18e986:3a0d9851
2025-04-04 20:25:50I'm making this tutorial for myself, as I plan to write many wiki pages describing DVM kinds, as a resource for DVMDash.
Wiki pages on Nostr are written using AsciiDoc. If you don't know ascii doc, get an LLM (like https://duck.ai) to help you format into the right syntax.
Here's the test wiki page I'm going to write:
``` = Simple AsciiDoc Demo
This is a simple demonstration of AsciiDoc syntax for testing purposes.
== Features
AsciiDoc offers many formatting options that are easy to use.
- Easy to learn
- Supports rich text formatting
- Can include code snippets
- Works great for documentation
[source,json]
{ "name": "Test", "version": "1.0", "active": true }
```
We're going to use nak to publish it
First, install
nakif you haven't alreadygo install github.com/fiatjaf/nak@latestNote: if you don't use Go a lot, you may need to first install it and then add it to your path so the
nakcommand is recognized by the terminal```
this is how to add it to your path on mac if using zsh
echo 'export PATH=$PATH:$(go env GOPATH)/bin' >> ~/.zshrc ```
And here's how to sign and publish this event with nak.
First, if you want to use your own nostr sec key, you can set the env variable to it and nak will use that if no secret key is specified
```
replace with your full secret key
export NOSTR_SECRET_KEY="nsec1zcdn..." ```
Now to sign and publish the event:
Note: inner double quotes need to be escaped with a
\before them in order to keep the formatting correct, because we're doing this in the terminalnak event -k 30818 -d "dvm-wiki-page-test" -t 'title=dvm wiki page test' -c "= Simple AsciiDoc Demo\n\nThis is a simple demonstration of AsciiDoc syntax for testing purposes. \n\n== Features\n\nAsciiDoc offers many formatting options that are easy to use. \n\n* Easy to learn \n* Supports rich text formatting \n* Can include code snippets \n* Works great for documentation \n\n[source,json] \n---- \n{ \"name\": \"Test\", \"version\": \"1.0\", \"active\": true } \n----" wss://relay.primal.net wss://relay.damus.io wss://relay.wikifreedia.xyzYou've now published your first wiki page! If done correctly, it will show up on wikistr.com, like mine did here: https://wikistr.com/dvm-wiki-page-test*da18e9860040f3bf493876fc16b1a912ae5a6f6fa8d5159c3de2b8233a0d9851
and on wikifreedia.xyz https://wikifreedia.xyz/dvm-wiki-page-test/dustind@dtdannen.github.io
-
 @ 68c90cf3:99458f5c
2025-04-04 16:06:10
@ 68c90cf3:99458f5c
2025-04-04 16:06:10I have two Nostr profiles I use for different subject matter, and I wanted a way to manage and track zaps for each. Using Alby Hub I created two isolated Lightning wallets each associated with one of the profile’s nsecs.
YakiHonne made it easy to connect the associated wallets with the profiles. The user interface is well designed to show balances for each.
In my case, I have one profile for photography related content, and the other for Bitcoin, Nostr, and technology related content. I can easily switch between the two, sending and receiving zaps on each while staying up to date on balances and viewing transactions.
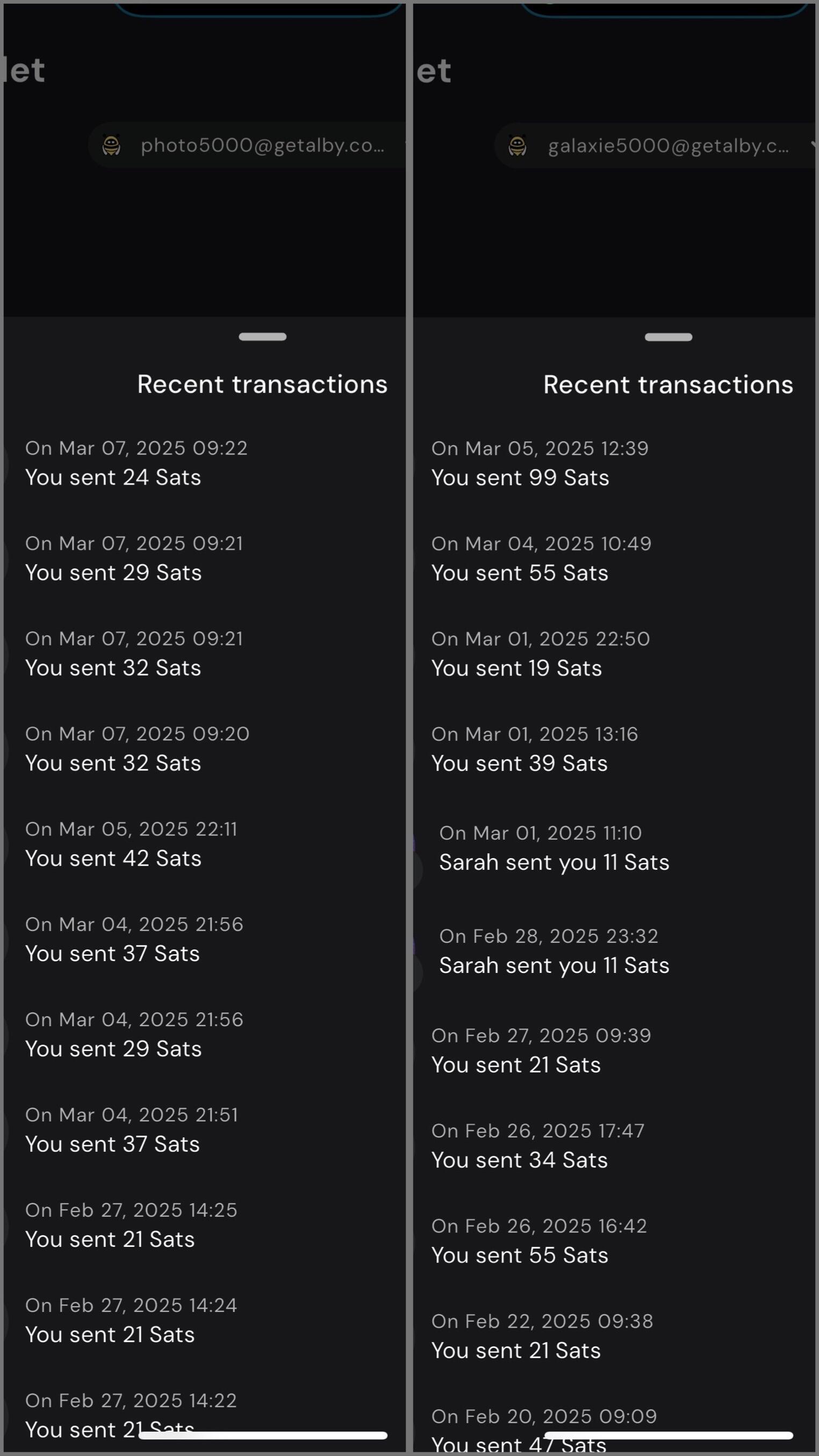
Using my self-hosted Alby Hub I can manage Lightning channels and wallets while sending and receiving zaps for multiple profiles with YakiHonne.
YakiHonne #AlbyHub #Lightning #Bitcoin #Nostr
-
 @ bc575705:dba3ed39
2025-03-13 05:57:10
@ bc575705:dba3ed39
2025-03-13 05:57:10In our hyper-connected age, the concept of "Know Your Customer" (KYC) has morphed from a regulatory necessity into a pervasive surveillance apparatus, subtly eroding our fundamental liberties. While purported to combat financial crime, KYC has become a tool for mass surveillance, data exploitation, and the gradual dismantling of personal privacy. Let’s embark on a comprehensive exploration of this system, exposing its inherent flaws and advocating for a paradigm shift towards decentralized financial sovereignty.
Beyond the Surface: The Intricate Web of KYC Data Collection
KYC transcends mere identity verification; it's a deep dive into the minutiae of our lives. Consider the breadth and depth of data extracted:
Geographic Surveillance: Proof of address requirements delve into historical residency, creating granular maps of our movements. Combined with location data from mobile devices and online activity, this paints a comprehensive picture of our physical presence.
Financial Autopsy: KYC dissects our financial lives with surgical precision. Income sources, asset declarations, and transaction histories are meticulously cataloged. Algorithmic analysis reveals spending habits, investment strategies, and even potential political affiliations.
Behavioral Predictive Modeling: AI algorithms analyze our financial behavior, predicting future actions and preferences. This data is invaluable for targeted advertising, but also for social engineering and political manipulation.
Biometric Invasiveness: Facial recognition, iris scans, and voice analysis create permanent, immutable records of our physical selves. These biometrics are highly sensitive and vulnerable to breaches, potentially leading to identity theft and even physical harm.
Social Network Mapping: KYC extends beyond individuals, mapping our social and professional networks. Institutions analyze our connections, identifying potential risks based on our associations. This has a chilling effect on free association and dissent, as individuals become hesitant to associate with those deemed "risky."
Psychometric Profiling: With the increase of online tests, and the collection of online data, companies and states can build psychometric profiles. These profiles can be used to predict actions, and even manipulate populations.
The Fallacy of Security: KYC's Ineffectiveness and the Rise of the Surveillance State
Despite its claims, KYC fails to effectively combat sophisticated financial crime. Instead, it creates a system of mass surveillance that disproportionately targets law-abiding citizens.
The Scourge of False Positives: Automated KYC systems frequently generate false positives, flagging innocent individuals as potential criminals. This can lead to financial exclusion, reputational damage, and even legal persecution.
A Ticking Time Bomb: Centralized KYC databases are prime targets for hackers, putting vast amounts of sensitive personal information at risk. Data breaches can lead to identity theft, financial fraud, and even physical harm.
The State's Panopticon: KYC empowers governments to monitor the financial activities of their citizens, creating a powerful tool for surveillance and control. This can be used to suppress dissent, target political opponents, and enforce conformity.
The Criminals Advantage: Sophisticated criminals easily bypass KYC using shell companies, money laundering, and other techniques. This makes KYC a system that punishes the innocent, and gives the criminals a false sense of security for the data collected.
Decentralized Alternatives: Reclaiming Financial Sovereignty and Privacy
In the face of this encroaching surveillance state, decentralized technologies offer a path to financial freedom and privacy.
Cryptocurrency | A Bastion of Financial Freedom: Bitcoin and other cryptocurrencies provide censorship-resistant alternatives to traditional financial systems. They empower individuals to transact freely, without the need for intermediaries or government oversight.
Decentralized Finance (DeFi) | Democratizing Finance: DeFi platforms offer a range of financial services, including lending, borrowing, and trading, without the need for traditional banks. These platforms are built on blockchain technology, ensuring transparency, security, and accessibility.
Self-Sovereign Identity (SSI) | Empowering Individuals: SSI solutions enable individuals to control their own digital identities, without relying on centralized authorities. This allows for secure and private verification of identity, without the need to share sensitive personal information with every service provider.
Privacy-Enhancing Technologies (PETs) | Shielding Your Data: Technologies like zero-knowledge proofs, homomorphic encryption, and secure multi-party computation can be used to protect personal data while still allowing for necessary verification.
Decentralized Autonomous Organizations (DAOs) | Creating new forms of governance: DAOs provide new ways for groups to organize, and make decisions. They provide a transparent way to pool resources, and make decisions.
A Call to Action: Defending Our Digital Rights and Building a Decentralized Future
We cannot passively accept the erosion of our fundamental freedoms. We must actively defend our digital rights and demand a more just and equitable financial system.
Advocate for Robust Privacy Laws: Demand stronger regulations that limit the collection and use of personal data.
Champion Decentralized Technologies: Support the development and adoption of cryptocurrencies, DeFi platforms, and other decentralized solutions.
Educate and Empower: Raise awareness about the dangers of KYC and state surveillance.
Cultivate Critical Thinking: Question the narratives presented by governments and corporations.
Build Decentralized Communities: Join and support decentralized communities that are working to build a more free and open financial system.
Demand transparency from all data collection: Insist that all data collection is open, and that there are strong penalties for those that misuse data.
The fight for financial freedom is a fight for human freedom. Let us stand together and reclaim our digital sovereignty.
-
 @ df67f9a7:2d4fc200
2025-03-13 00:23:46
@ df67f9a7:2d4fc200
2025-03-13 00:23:46For over a year, I have been developing “webs of trust onboarding and discovery” tools for Nostr. With additional funding, I hope to continue this endeavor in 2025. Here’s the story so far…
What I’m Building
More than simply a “list of follows follows”, “web of trust” implementations will power user discovery, content search, reviews and reccomendations, identity verification and access to all corners of the “trusted” Nostr network as it scales. Without relying on a central “trust authority” to recommend people and content for us, sovereign Nostr users will leverage many forms of “relative trust” derived from our own “web” of natural interactions, “simply” by normalizing and scoring these interactions. The problem is, Nostr doesn’t have an extensible library for performing these “web of trust” calculations and delivering standardized reccomendations to any client … until now.
I have built a developer library by which clients and relays can offer “webs of trust” score calculations for any user. Primarily, I am also building a “social onboarding” client, which will leverage this library to provide “webs of trust” powered recommendations for new users at their crucial “first interaction” touchpoint.
- Meet Me On Nostr (onboarding client) : This is my first project on Nostr, which I started a year ago with seed funding from @druid. This “social onboarding” client will leverage in person relationships, QR invites, and advocate recommendations to improve new user retention. Currently, it creates new accounts with encrypted keys upon scanning any user’s invite. Last summer, without additional funding or a reliable WoT engine to produce recommendations, I “paused” development of this project.
- GrapeRank Engine (developer library) : Working with @straycat last fall, I built an open source and extensible library for Nostr developers to integrate “web of trust” powered reccomendations into their products and services. The power of GrapeRank is that it can generate different recommendations for different use cases (not just “web of trust” from “follows and mutes”), configurable easily by developers and by end users. This library is currently in v0.1, “generating and storing usable scores” without NIP standard outputs for Nostr clients.
- My Grapevine (algo dashboard) : In addition, I’ve just now wrapped up the demo release of a web client by which users and developers can explore the power of the GrapeRank Engine.
Potential Impact
Webs of Trust is how Nostr scales. But so far, “web of trust” recommendations on Nostr have been implemented ad-hoc by clients with no consistency and little choice for end users. The “onboarding and discovery” tools I am developing promise to :
- Establish “sovereignty” for webs of trust users, by stimulating a “free market of choices” with open source libraries, enabling any developer to implement WoT powered recommendations with ease.
- Accelerate the isolation of “bots and bad actors”, and improve the “trustiness” of Nostr for everyone else, by streamlining the onboarding of “real world” trusted people directly into established “webs of trust”.
- Improve “discoverability of users and content” across all clients, by providing an extensible algo engine with “unlimited” NIP standard outputs, allowing any client to consume and take advantage of WoT powered recommendations, even as these NIPs are still in flux.
- Pave the way for “global Nostr adoption”, where WoT powered recommendations (and searches) are consistently available for any user across a wide variety of clients.
Timeline & Milestones
2025 roadmap for “Webs of Trust Onboarding and Discovery” :
- Meet Me On Nostr (onboarding client) : MVP release : “scan my QR for instant account and DM with me on Nostr”.
- GrapeRank Engine (developer library) : 1.0 release : “output WoT scores to Nostr NIPs and other stuff” for consumption by clients and relays.
- My Grapevine (algo dashboard) : 1.0 release : “usable dashboard with API endpoints” for end users to configure and consume GrapeRank scores on their own clients and relays.
- Meet Me On Nostr (onboarding client) : 1.0 release : first integration with My Grapevine, offering “follow and app recommendations for invited users”, customizable per-invite for Nostr advocates.
Funding
In February 2024, I received a one time donation from @druid to start the “Meet Me On Nostr” client.
In May 2024, I applied for an OpenSats grant to fund further development of “Meet Me On Nostr”. This was denied.
In September 2024, @straycat offered to fund me for three months, to develop the “GrapeRank Engine” and “My Grapevine” demo client around his algorithm design.
I have a Geyser Fund page
Please reach out via DM if you are interested to fund part of this or any related project.
-
 @ c4b5369a:b812dbd6
2025-04-15 07:26:16
@ c4b5369a:b812dbd6
2025-04-15 07:26:16Offline transactions with Cashu
Over the past few weeks, I've been busy implementing offline capabilities into nutstash. I think this is one of the key value propositions of ecash, beinga a bearer instrument that can be used without internet access.
 It does however come with limitations, which can lead to a bit of confusion. I hope this article will clear some of these questions up for you!
It does however come with limitations, which can lead to a bit of confusion. I hope this article will clear some of these questions up for you!What is ecash/Cashu?
Ecash is the first cryptocurrency ever invented. It was created by David Chaum in 1983. It uses a blind signature scheme, which allows users to prove ownership of a token without revealing a link to its origin. These tokens are what we call ecash. They are bearer instruments, meaning that anyone who possesses a copy of them, is considered the owner.
Cashu is an implementation of ecash, built to tightly interact with Bitcoin, more specifically the Bitcoin lightning network. In the Cashu ecosystem,
Mintsare the gateway to the lightning network. They provide the infrastructure to access the lightning network, pay invoices and receive payments. Instead of relying on a traditional ledger scheme like other custodians do, the mint issues ecash tokens, to represent the value held by the users.How do normal Cashu transactions work?
A Cashu transaction happens when the sender gives a copy of his ecash token to the receiver. This can happen by any means imaginable. You could send the token through email, messenger, or even by pidgeon. One of the common ways to transfer ecash is via QR code.
The transaction is however not finalized just yet! In order to make sure the sender cannot double-spend their copy of the token, the receiver must do what we call a
swap. A swap is essentially exchanging an ecash token for a new one at the mint, invalidating the old token in the process. This ensures that the sender can no longer use the same token to spend elsewhere, and the value has been transferred to the receiver.
What about offline transactions?
Sending offline
Sending offline is very simple. The ecash tokens are stored on your device. Thus, no internet connection is required to access them. You can litteraly just take them, and give them to someone. The most convenient way is usually through a local transmission protocol, like NFC, QR code, Bluetooth, etc.
The one thing to consider when sending offline is that ecash tokens come in form of "coins" or "notes". The technical term we use in Cashu is
Proof. It "proofs" to the mint that you own a certain amount of value. Since these proofs have a fixed value attached to them, much like UTXOs in Bitcoin do, you would need proofs with a value that matches what you want to send. You can mix and match multiple proofs together to create a token that matches the amount you want to send. But, if you don't have proofs that match the amount, you would need to go online and swap for the needed proofs at the mint.Another limitation is, that you cannot create custom proofs offline. For example, if you would want to lock the ecash to a certain pubkey, or add a timelock to the proof, you would need to go online and create a new custom proof at the mint.
Receiving offline
You might think: well, if I trust the sender, I don't need to be swapping the token right away!
You're absolutely correct. If you trust the sender, you can simply accept their ecash token without needing to swap it immediately.
This is already really useful, since it gives you a way to receive a payment from a friend or close aquaintance without having to worry about connectivity. It's almost just like physical cash!
It does however not work if the sender is untrusted. We have to use a different scheme to be able to receive payments from someone we don't trust.
Receiving offline from an untrusted sender
To be able to receive payments from an untrusted sender, we need the sender to create a custom proof for us. As we've seen before, this requires the sender to go online.
The sender needs to create a token that has the following properties, so that the receciver can verify it offline:
- It must be locked to ONLY the receiver's public key
- It must include an
offline signature proof(DLEQ proof) - If it contains a timelock & refund clause, it must be set to a time in the future that is acceptable for the receiver
- It cannot contain duplicate proofs (double-spend)
- It cannot contain proofs that the receiver has already received before (double-spend)

If all of these conditions are met, then the receiver can verify the proof offline and accept the payment. This allows us to receive payments from anyone, even if we don't trust them.
At first glance, this scheme seems kinda useless. It requires the sender to go online, which defeats the purpose of having an offline payment system.
I beleive there are a couple of ways this scheme might be useful nonetheless:
-
Offline vending machines: Imagine you have an offline vending machine that accepts payments from anyone. The vending machine could use this scheme to verify payments without needing to go online itself. We can assume that the sender is able to go online and create a valid token, but the receiver doesn't need to be online to verify it.
-
Offline marketplaces: Imagine you have an offline marketplace where buyers and sellers can trade goods and services. Before going to the marketplace the sender already knows where he will be spending the money. The sender could create a valid token before going to the marketplace, using the merchants public key as a lock, and adding a refund clause to redeem any unspent ecash after it expires. In this case, neither the sender nor the receiver needs to go online to complete the transaction.
How to use this
Pretty much all cashu wallets allow you to send tokens offline. This is because all that the wallet needs to do is to look if it can create the desired amount from the proofs stored locally. If yes, it will automatically create the token offline.
Receiving offline tokens is currently only supported by nutstash (experimental).
To create an offline receivable token, the sender needs to lock it to the receiver's public key. Currently there is no refund clause! So be careful that you don't get accidentally locked out of your funds!

The receiver can then inspect the token and decide if it is safe to accept without a swap. If all checks are green, they can accept the token offline without trusting the sender.

The receiver will see the unswapped tokens on the wallet homescreen. They will need to manually swap them later when they are online again.
 Later when the receiver is online again, they can swap the token for a fresh one.
Later when the receiver is online again, they can swap the token for a fresh one.
Summary
We learned that offline transactions are possible with ecash, but there are some limitations. It either requires trusting the sender, or relying on either the sender or receiver to be online to verify the tokens, or create tokens that can be verified offline by the receiver.
I hope this short article was helpful in understanding how ecash works and its potential for offline transactions.
Cheers,
Gandlaf
-
 @ 21335073:a244b1ad
2025-03-12 00:40:25
@ 21335073:a244b1ad
2025-03-12 00:40:25Before I saw those X right-wing political “influencers” parading their Epstein binders in that PR stunt, I’d already posted this on Nostr, an open protocol.
“Today, the world’s attention will likely fixate on Epstein, governmental failures in addressing horrific abuse cases, and the influential figures who perpetrate such acts—yet few will center the victims and survivors in the conversation. The survivors of Epstein went to law enforcement and very little happened. The survivors tried to speak to the corporate press and the corporate press knowingly covered for him. In situations like these social media can serve as one of the only ways for a survivor’s voice to be heard.
It’s becoming increasingly evident that the line between centralized corporate social media and the state is razor-thin, if it exists at all. Time and again, the state shields powerful abusers when it’s politically expedient to do so. In this climate, a survivor attempting to expose someone like Epstein on a corporate tech platform faces an uphill battle—there’s no assurance their voice would even break through. Their story wouldn’t truly belong to them; it’d be at the mercy of the platform, subject to deletion at a whim. Nostr, though, offers a lifeline—a censorship-resistant space where survivors can share their truths, no matter how untouchable the abuser might seem. A survivor could remain anonymous here if they took enough steps.
Nostr holds real promise for amplifying survivor voices. And if you’re here daily, tossing out memes, take heart: you’re helping build a foundation for those who desperately need to be heard.“
That post is untouchable—no CEO, company, employee, or government can delete it. Even if I wanted to, I couldn’t take it down myself. The post will outlive me on the protocol.
The cozy alliance between the state and corporate social media hit me hard during that right-wing X “influencer” PR stunt. Elon owns X. Elon’s a special government employee. X pays those influencers to post. We don’t know who else pays them to post. Those influencers are spurred on by both the government and X to manage the Epstein case narrative. It wasn’t survivors standing there, grinning for photos—it was paid influencers, gatekeepers orchestrating yet another chance to re-exploit the already exploited.
The bond between the state and corporate social media is tight. If the other Epsteins out there are ever to be unmasked, I wouldn’t bet on a survivor’s story staying safe with a corporate tech platform, the government, any social media influencer, or mainstream journalist. Right now, only a protocol can hand survivors the power to truly own their narrative.
I don’t have anything against Elon—I’ve actually been a big supporter. I’m just stating it as I see it. X isn’t censorship resistant and they have an algorithm that they choose not the user. Corporate tech platforms like X can be a better fit for some survivors. X has safety tools and content moderation, making it a solid option for certain individuals. Grok can be a big help for survivors looking for resources or support! As a survivor, you know what works best for you, and safety should always come first—keep that front and center.
That said, a protocol is a game-changer for cases where the powerful are likely to censor. During China's # MeToo movement, survivors faced heavy censorship on social media platforms like Weibo and WeChat, where posts about sexual harassment were quickly removed, and hashtags like # MeToo or "woyeshi" were blocked by government and platform filters. To bypass this, activists turned to blockchain technology encoding their stories—like Yue Xin’s open letter about a Peking University case—into transaction metadata. This made the information tamper-proof and publicly accessible, resisting censorship since blockchain data can’t be easily altered or deleted.
I posted this on X 2/28/25. I wanted to try my first long post on a nostr client. The Epstein cover up is ongoing so it’s still relevant, unfortunately.
If you are a survivor or loved one who is reading this and needs support please reach out to: National Sexual Assault Hotline 24/7 https://rainn.org/
Hours: Available 24 hours
-
 @ fd06f542:8d6d54cd
2025-04-15 07:13:58
@ fd06f542:8d6d54cd
2025-04-15 07:13:58Direct-message
 0xchat
0xchat- Beautiful, simple and private nostr DMs
-
Public groups that work compatible with other apps
- Safe DMs with NIP-17
Signers
 Alby
Alby- Nostr wallet connect for one tap zapping via nostr clients
- Nostr authenticator (never enter your nsec into apps)
- Chrome extension
- Simple and easy to use
- Frequently maintained
- Send and receive sats
-
Custodial
- Other Android apps can invoke it for signing events via NIP-55
- Your key doesn't have to touch the other, less trusted, apps
- Supports providing a NIP-46 signing Bunker
- Multiple accounts
- Fine-grained app authorizations
-
Activity log
- Multiple key management
- Light and dark mode
-
Save preferred relays
- The original signer by nostr creator fiatjaf
- Versatile, no frills
-
Relay preference storage
- A skinned fork of nos2x by fiatjaf
- Chrome
- & 
- Firefox
- Store preferred relay set
-
Individually revokable permissions
- Log in to nostr apps without an extension
- Key recovery via email
- Password protected encrypted local key storage
-
Manage multiple apps
- Derive accounts from a mnemonic seed
- Generate random mnemonic accounts
- NIP-07 - window.nostr capability for web browsers
- Import external accounts
- Set basic metadata on Nostr
- Enjoy encryption secured by a master password
- Lock and unlock the vault with ease
- Easily import and export backups
Microblogging
 alphaama
alphaama- CLI + GUI
- run custom code
- inspect notes
-
test stuff
-
 Amethyst
暂无相关功能描述
Amethyst
暂无相关功能描述 - Short notes
- Nice thread view
- Profile search
- Secure direct messages
- Custom feeds
-
Relay reviews
- Note feeds
- Easy to use interface
- Zap pre-set and custom amounts (lightning payments)
- Multi-wallet support
-
Block lists
- Snappy nostr browsing
- Back up your data
- Browse long form content
-
Light mode
- No phone number and email required to sign up
- Free migration of social content within the Nostr
- Excellent user experience
-
Double-enhanced private communication
- multiplatform: runs on Windows, MacOS and Linux
- native: avoids browser-tech for performance and security
- performant: coded with performance in mind in Rust using LMDB for the database, such that your network speed will be your bottleneck
- outbox model: using a set of heuristics to always find people you follow no matter where they're publishing to
- high user control: over 60 different settings, all with reasonable defaults, but very customizable
-
privacy: supports running over Tor, options for not loading media, options for not sharing who you follow and others
- Short notes
- Social graph filter
-
Image grid feeds
- Desktop app
- Clean and beautiful design
- Multi-column
- Spaces
-
Trending
- Currently in TestFlight
- Safety first: mute, report, content warnings, delete
- Reach restricted to 2 hops - people you follow and people they follow.
-
Community-focused relays
-
Nostrmo 暂无相关功能描述
- Feature-rich
- Highly customizable
- Mute words
- Communities
- Streaming (watch)
- Lists
- Tools shortcuts
-
Sidebar comments
- Twitter style feed
- Cute logo
- Mute words
-
Minimal and calm
- Multi-account
- Guest account
- Your posts stored on your device and can be exported
- Bookmarks and personal notes
- Follow and explore timeline
- Remembers where you left off scrolling when reopening app
- Undo accidental tap on Like
- Autocomplete names when typing
- Lightning zaps
- Lightning wallet selection
- Direct Messages
- Domain verification
- Badges
- Block list
- Muted conversations
- Notifications for mentions, reactions and zaps
- Image previews/zoom/pan
- Gif/Video playback
- Option to turn signature verification off
- Option to hide badges from profile and emojis from names
- Fast local database
- Big detail pane for iPad/macOS
- Login as someone else (read-only mode)
-
Choose which relays to send to and receive from
-
Hacker News style
- Post to Nostr and Mastodon
- Nice, clean and modern design
- Simple and intuitive
- Gifs, stickers integration
-
Dark and light mode
- Browse polls created here or on other clients
- Create polls
-
Vote on polls
-
Primal 暂无相关功能描述
- Multi-column
-
Tweetdeck-like UI
- Twitter-like experience
- Dark and light mode
- Custom zap amounts
- Bookmarks
- Pinned notes
-
Alby integration
- PWA to be widely accessible with distribution via URLS, and to side-step App Store gatekeeping
- Employs Proof-of-Work (PoW) as a spam prevention mechanism, as opposed to Captcha, moderation or other verification methods
- Uses NOSTR as a censorship-resistant global "social" network
Community
Badges Page
- Create and award badges
- Manage badges awarded to you
- Simple interface
File-sharing
 Bouquet
Bouquet- Upload files
- Download files
- Manage your list of mediaservers
- Broadcast your list on Nostr
- Sync files between servers
-
Browse files on your mediaservers
- Browse lists of available torrents
- Publish your own
- Choose relays to browse on
Group-chat
Chachi
- Create, browse, join groups
- Send chat messages or other kinds of content
-
Seamless, lean, fast interface
- Browse relays and chat on the communities in them
- Send and receive direct messages
-
Take private notes
- Browse groups on specific relays
- Join rooms and send chat messages
Tools
 Emojito
Emojito-
Create custom emoji sets to be used on supported clients
-
Create and share forms
- Make GIFs from the external world available inside Nostr clients
- GIF uploads
-
Search external GIF libraries
-
Save your nostr notes to Google Drive
- Guided onboarding
- Recovery phrase to restore access
- Good UX with explainers
-
Beautiful design
- Discover app of the day
- Discover new apps
- Search all nostr apps
- Discover nostr DVMs
- Discover nostr code repositories
- App reviews
-
Nostr native - takes a different approach from NostrApps.com
- A plethora of apps to choose from and install
- Faster than Obtainium
- More complete than F-Droid
-
Cleaner than Google Play
- Zap from any client
- Bypass Apple's draconian rules
- Nostr Wallet Connect
Blogging
 Feeder
Feeder- Subscribe to RSS and Nostr article feeds
- Years of specialization in reading articles
- Offline reading
- OPML Import/Export
- Notification support
-
Material design
- Long form publishing
- Markdown support
- Rich text editor
- Dark and light modes
- Browse by relay
- Made on nostr, content mirrored to other nostr platforms.
-
Extension-only sign-in
- Read RSS feeds
- Read Nostr NIP-23 long-form articles
- Import and export OPML
- Runs on desktop with a web-based UI
-
Can be accessed remotely from apps such as Reeder, Readkit etc
- Read RSS feeds
- Read Nostr NIP-23 long-form articles
- Import and export OPML
- Runs on desktop with a web-based UI
-
Can be accessed remotely from apps such as Reeder, Readkit etc
- Create a website out of your nostr content
- SEO friendly
- Use any 3rd party tools
- Works like an app
- Beautiful Ghost themes to choose from
- Zero maintenance
- Custom domains
- Open source and self-hostable
- Natively Social
-
Publish from any other nostr app
- Directly publish your articles from Obsidian to Nostr with a couple of clicks
- Quickly compose and publish short form notes too
- Images in your .md file will automatically be uploaded and handled when you publish
- Add tags to your posts
- See all posts sent from Obsidian with links to view
- Configure to send to whatever relays you like
- Publish under different nostr accounts
- Easily view and download your Nostr bookmarks into Obsidian for reference and local use
-
Automatically populates article information fields from the frontmatter
- Schedule nostr notes
- Schedule reposts
- Note drafts
-
Multi-account support
- Publishing and reading notes
- Publishing and reading articles
- Curations (set of articles concerning a specific topic) publishing
- Long-form articles are surfaced instead of lost in the feed
Music
 Fountain
Fountain- Earn sats while listening to podcasts
- Create and share clips, get paid on your clips
- Boost your favorite podcasts
-
Discover clips from friends
- Collaborate with others to create your next hit
- Music-focused interface
- Remix function
Curation
Highlighter
- Read and write long-form articles
- Discover what people you trust found interesting and insightful
- Understand why they found it interesting or insightful with their comments attached
- Send sats, comment or share your favorite highlights
-
Highlight anything
- Create and share lists
-
Browse other people's lists
- Browse recipes
- Add your own recipes
-
Earn sats via zaps
- Create link lists
- Multiple lists
-
Theming
- Curate lists, users, links
- Share lists
- Discover interesting content
Photos
 Olas
Olas- Special high-quality photos dedicated client
- Publish photos and browse photos
- Publish and browse short videos
- Browse media feeds from friends, extended network and from specific relays
Discovery
Jumble
- Browse individual relays by URL
- Create and browse relay sets
- Create and reply to notes
- Follow people and browse the feed from your follows
-
Browse the kind:20 photos feed
- Search keywords, hashtags, pubkeys, posts
- Look up Nostr statistics
- Embed widgets
- API for clients
-
NIP05 Service
- Look up relay information
- Browse relay feeds
- Browse individual profile feeds with smart relay selection
-
Simple and gets the job done
- See total sats zapped in the past hour, 4 hours, 24 hours and 7 days
- See who zapped who individually
- See notes that got the most zaps
Audio
Nests
- Start audio chats
- Troll box (chat)
- Instant zaps (lightning payments)
Crazy
 Nostrocket
Nostrocket- Create issues that matter to you
- Award merits to contributors
- Solve problems
Career
Ostrich Work
- Post jobs for 20k sats
- Find jobs
Marketplace
 Plebeian Market
Plebeian Market- Buy and sell things for sats
-
Bid in auctions
- Buy and sell items for sats
- Message seller
- Cashu integration
Freelancing
 SatShoot
SatShoot- Post problems on SatShoot
- Make money solving problems as a Freelancer
- Share problems or freelance services on your feed
- Bidding system for Clients to choose the best Offer
- Chat in DMs
- Post Reviews on Freelancers or Clients
- Build Reputation
- Public Zaps as Payments
- Use your Web of Trust to keep scammers away
Media
Slidestr
- Compact media browsing
- Images and videos
- Full screen media
Meatspace
Yondar
- Add places to a map
- See places by your friends or follows
Streaming
zap.stream
- Start livestream via zap.stream or Cloudflare
- Watch other livestreams
- Chat
- Custom emojis
- Zap streamers in real time
- Zap chat participants in real time
- Set up stream goals
-
 @ bf95e1a4:ebdcc848
2025-04-04 06:11:18
@ bf95e1a4:ebdcc848
2025-04-04 06:11:18This is a part of the Bitcoin Infinity Academy course on Knut Svanholm's book Bitcoin: Sovereignty Through Mathematics. For more information, check out our Geyser page!
The Gullible Collective
We humans are biased by nature. Everything we think we know is distorted in one way or another by our cognitive shortcomings. The human brain has been forced to evolve and adapt to whatever environment it found itself in over millennia. Having a brain that is capable of setting aside personal aims for the sake of the collective has proven to be advantageous for the evolution of our species as a whole. The same is true for every other social life form. However, letting these parts of our brains guide our political judgment can lead to disastrous results in the long run — not because of bad intentions but because of the simple fact that a few individuals will always thrive by playing every political system for personal gain. From an evolutionary perspective, an army of ay-sayers and martyrs, regardless of whether we’re talking about an army of humans or an army of ants or bacteria, has an advantage over a less disciplined one. From an individual's evolutionary perspective though, it is better to appear like you’re a martyr but to run and hide when the actual battle happens. This at least partly explains the high percentage of sociopaths in leadership positions all over the world. If you can appear to act for the good of the collective but dupe your way into more and more power behind people’s backs, you’re more likely to succeed than someone playing a fair game.
The story of banking and fiat currency is a story about collective madness. Historically, rulers have tricked people into killing each other through the promise of an after-life. Through central banking, the rulers of the world wars could trick people into building armies for them by printing more money. This is seldom mentioned in history classes because it still goes on today on a massive scale. Inflation might no longer be paying tank factory workers, but it is the main mechanism that funnels wealth into the pockets of the super-rich and away from everyone else. Inflation is the mechanism that hinders us from transporting the value of our labor through time. It makes us avoid real long-term thinking. We hardly ever consider this a problem because none of us has ever experienced an alternative to it.
Money is still vastly misunderstood by the lion's share of the world’s population. In most parts of the world, banks do something called fractional reserve lending. This means that they lend out money that they don't have — conjuring up new money out of thin air and handing it out to their customers as loans. Loans that have to be paid back with interest. Interest that can’t be paid back with thin air but has to be paid with so-called real money. Real money, of which there isn’t enough around to pay back all the loans, so that a constant need for new credit becomes a crucial part of the entire system. Not to mention central banks, which do the same and worse for governments. We’re so used to it by now that every country is expected to have a national debt. All but a handful of ridiculously rich ones do. National debts are also loans that have to be paid back with interest backed by nothing. Think about that. Your taxes are paying someone else's interest. Your tax money is not paying for your grandmother's bypass operation, it is paying interest to a central bank.
When the ideas of the catholic church ruled Europe, people who didn’t believe in God were few and very seldomly outspoken. They had good reason for this since belief in God was virtually mandatory throughout society. Ever since 1971, when famously dishonest American president Richard Nixon cut the last string that tied the US Dollar to gold, our conception of what the world economy is and ought to be has been skewed by an utterly corrupt system. We’re led to believe that we’re all supposed to work longer and longer days in order to spend more and more money and bury ourselves in more and more debt to keep the machine running. We’re duped into thinking that buying a new car every other year is somehow good for the environment and that bringing a cotton bag to the grocery store will somehow save the planet. Stores manipulate us all the time through advertising and product placement, but we’re led to believe that if we can be “climate-smart,” we’re behaving responsibly. Somehow, our gross domestic product is supposed to increase indefinitely while politicians will save us from ourselves through carbon taxes. Fortunately for us, and unfortunately for them, there now exists a way for unbelievers of this narrative to opt out. Life finds a way, as Jeff Goldblum once so famously put it.
Collectivism has ruined many societies. Those of us fortunate enough to live in liberal democracies tend to forget that even democracy is an involuntary system. It’s often referred to as the “worst form of government except all others that have been tried,” but the system itself is very rarely criticized. We’re so used to being governed that not having a leader seems preposterous to most of us. Still, we pay our taxes, and an enormous cut of the fruit of our labor goes to a third party via inflation and the taxation of every good and service imaginable. Institutions, once in place, tend to always favor their own survival just as much as any other living thing does. People employed in the public sector are unlikely to vote against policies that threaten their livelihood. This is a bigger problem than we realize because it’s subtle and takes a long time, but every democracy is headed in the same direction. A bigger state, a more complicated system, and fewer individual freedoms. Long term, it seems that all of our systems tend to favor those who know how to play that system and not those who contribute the most value to their fellow man. Proponents of socialist policies often claim that failed socialist states “weren’t really socialist” or that “that wasn’t really socialism.” What most people fail to realize is that we’ve never tried real capitalism since we’ve always used more or less inflationary currencies. This might very well be the most skewed narrative of our era. We’re all experiencing real, albeit disguised, socialism every single day. True free market capitalism is what we haven’t experienced yet, and it might turn out to be a very different thing than what we’re told to believe that it is by almost all mainstream media.
The validity of the classic right-left scale describing political viewpoints has been debated a lot lately, and alternative scales, like GAL-TAN, the one with an additional Y-axis describing more or less authoritarian tendencies, are popping up in various contexts around the web. After the birth of Bitcoin, there’s a new way to see this. Imagine an origo, a zero point, and a vector pointing to the left of that. All politics are arguably on the left because all policies need to be funded by taxes, and taxation can be viewed as theft. Taxation can be viewed as theft because, at its core, it’s involuntary. If a person refuses to pay his taxes, there is a threat of violence lurking in the background. Not to mention inflation, which Milton Friedman so elegantly described as “taxation without legislation.” What you do with the portion of your wealth that you have in Bitcoin is another matter altogether. If you take sufficient precautionary privacy measures and you know what you’re doing, your business in Bitcoin is beyond politics altogether. With the introduction of the Lightning Network and other privacy-improving features, it is now impossible for any third party to confiscate your money or even know that you have it, for that matter. This changes the political landscape of every nation on Earth. Bitcoin is much less confiscatable than gold and other scarce assets, which makes it a much better tool for hedging against nation-states. In this sense, Bitcoin obsoletes borders. You can cross any border on Earth with any amount of Bitcoin in your head. Think about that! Your Bitcoin exists in every country simultaneously. Any imposed limit on how much money you can carry from one nation to the other is now made obsolete by beautiful mathematics. Bitcoin is sometimes referred to as a “virtual currency.” This is a very inaccurate description. Bitcoin is just mathematics, and mathematics is just about the most real thing there is. There’s nothing virtual about it. Counterintuitive to some, but real nonetheless.
The complexity of human societal hierarchies and power structures is described perfectly in a classic children's book, The Emperor’s New Clothes, by Hans Christian Andersen. See the world as the kid who points out that the king is naked in the tale, and everything starts to make sense. Everything in human society is man-made. Nations, leaders, laws, political systems. They’re all castles in the air with nothing but a lurking threat of violence to back them up. Bitcoin is a different beast altogether. It enables every individual to verify the validity of the system at all times. If you really think about it, morality is easy. Don’t hurt other people, and don’t steal other people’s stuff. That’s the basic premise. Humans have but two ways of resolving conflict, conversation and violence, and in this sense, to hurt someone can only mean physical violence. This is why free speech is so important and why you should defend people’s right to speak their minds above everything else. It’s not about being able to express yourself. It’s about your right to hear every side of every argument and thus not have to resort to violence should a conflict of interests occur. You can’t limit free speech with just more speech — there’s always a threat of violence behind the limitations. Code, which both Bitcoin and the Internet are entirely made up of, is speech. Any limitations or regulations that your government implements in regard to Bitcoin are not only a display of Bitcoin’s censorship resistance but also a test of your government's stance on freedom of expression. A restriction on Bitcoin use is a restriction on free speech.
Remember, the only alternative to speech that anyone has is violence. Code is a language, mathematics is a language, and money is a linguistic tool. A linguistic tool we use as a means of expressing value to each other and as a way to transport value through space and time. Any restrictions or regulations regarding how you can express value, for example, making it impossible to buy Bitcoin with your credit card, prove that the money you have in your bank account is not really yours. When people realize this, the demand for Bitcoin goes up, not down. If you know what you're doing, there’s no need to fear the regulators. They, on the other hand, have good reason to fear an invention that shamelessly breaks their spell.
About the Bitcoin Infinity Academy
The Bitcoin Infinity Academy is an educational project built around Knut Svanholm’s books about Bitcoin and Austrian Economics. Each week, a whole chapter from one of the books is released for free on Highlighter, accompanied by a video in which Knut and Luke de Wolf discuss that chapter’s ideas. You can join the discussions by signing up for one of the courses on our Geyser page. Signed books, monthly calls, and lots of other benefits are also available.
-
 @ ec9bd746:df11a9d0
2025-03-07 20:13:38
@ ec9bd746:df11a9d0
2025-03-07 20:13:38I was diving into PoW (Proof-of-Work) once again after nostr:nprofile1qy88wumn8ghj7mn0wvhxcmmv9uq3wamnwvaz7tmjv4kxz7fwdehhxarj9e3xzmny9uqzqj8a67jths8euy33v5yu6me6ngua5v3y3qq3dswuqh2pejmtls6datagmu rekindled my interest with his PoW Draw project. It was a fun little trifle, but it shifted my focus just the right way at the right time.
Because then, on Friday, came the Oval Office Travesty. Once I got over the initial shock, I decided I couldn't just curse and lament; I needed to do something bigger, something symbolic, something expressive. So that's exactly what I did—breaking nostr:nprofile1qy88wumn8ghj7mn0wvhxcmmv9uq32amnwvaz7tmjv4kxz7fwv3sk6atn9e5k7tcqyqewrqnkx4zsaweutf739s0cu7et29zrntqs5elw70vlm8zudr3y2t9v7jg's record which he held for almost 2 and half years.
Here is a note with PoW 45, the highest PoW known to Nostr (as of now).
nostr:nevent1qvzqqqqqqypzpmym6ar92346qc04ml08z6j0yrelylkv9r9ysurhte0g2003r2wsqy88wumn8ghj7mn0wvhxcmmv9uqsuamnwvaz7tmwdaejumr0dshsqgqqqqqqqqqy8t8awr5c8z4yfp4cr8v7spp8psncv8twlh083flcr582fyu9
How Did I Pull It Off?
In theory, quite simple: Create note, run PoW mining script & wait.
Thanks to PoW Draw, I already had mining software at hand: nostr:nprofile1qy88wumn8ghj7mn0wvhxcmmv9uq32amnwvaz7tmjv4kxz7fwv3sk6atn9e5k7tcqyqvqc5tlvn6etv09f0fvuauves49dvgnukjtzsndfv9y8yyrqyxmz7dty6z's notemine_hw, but when you know that there is a 1 in 2^45 chance that the next hash will be the correct one you want to increase the odds a bit. So on Monday evening, I started my Note Mining operation on an old 40 thread machine called Workhorse.
Issues Along the Way
I was immediately surprised that Workhorse (2× Intel Xeon Silver 4114) produced only about 3Mh/s. A laptop (Intel Core i7-1185G7) with Windows and all the bloat did 5Mh/s. That was strange.
Another hurdle was that notemine_hw does not refresh the
created_atfield. With just a few Mh/s of power I was potentially looking at weeks of computation, by then the note would be quite stale. So I created systemd service leveraging theRuntimeMaxSecoption to periodically restart every 3600 seconds assuring that the Note would be max 1 hour old at the time of publishing.Luckily PoW is that kind of problem where every hash attempt is an independent event, so the chance of success is the same whether you do it in small increments or one uninterrupted stretch. So by restarting the mining process I was only losing a few mere seconds every hour due to the overhead.
Once the note staleness issue was resolved, I looked at the 40 workers on Workhorse vs. 7 workers on the laptop and start messing around with running one instance with 40 workers and running 40 instances with 1 worker and found out, that the workers are not bound to a CPU thread and are jumping between the CPUs like rabbits high on Colombian carrots.
The solution? Running multiple instances with one worker each as a service locked to its own CPU core using systemd's
CPUAffinityoption. ``` $aida@workhorse:systemd/system $ sudo cat notemine@.service [Unit] Description=Notemine HW Publish (restarts hourly)[Service] Type=simple CPUAffinity=%i
The command to run:
ExecStart=/home/aida/.cargo/bin/notemine_hw publish --n-workers 1 --difficulty 45 --event-json /home/aida/note.json --relay-url 'wss://wot.shaving.kiwi' --nsec nsec0123456789abcdef
Let the process run for 1 hour (3600 seconds), then systemd will stop it:
RuntimeMaxSec=3600 TimeoutStopSec=1
Tells systemd to restart the service automatically after it stops:
Restart=always RestartSec=1
run as a non-root user:
User=aida Group=aida
[Install] WantedBy=multi-user.target ``` Then I added a starting service to spawn an instance for each CPU thread.
``` $aida@workhorse:systemd/system $ sudo cat notemine_start.service [Unit] Description=Start all services in sequence with 3-second intervals
[Service] Type=oneshot ExecStart=/usr/bin/zsh /home/aida/notemine_start.sh
RemainAfterExit=yes
[Install] WantedBy=multi-user.target
Here is the startup script (I know, loops exist—but Ctrl+C/Ctrl+V is so old-school):aida@workhorse:~ $ cat notemine_start.sh /usr/bin/systemctl start notemine@0.service /usr/bin/sleep 3 /usr/bin/systemctl start notemine@1.service /usr/bin/sleep 3 /usr/bin/systemctl start notemine@2.service /usr/bin/sleep 3 /usr/bin/systemctl start notemine@3.service /usr/bin/sleep 3 ... ... ... /usr/bin/systemctl start notemine@38.service`` The sleep there is critical to make sure that thecreated_at`timestamps are different, preventing redundant hashing.This adjustment made Workhorse the strongest machine in my fleet with 10+Mh/s.
The Luck Aspect
From Monday evening, I started adding all machines at my disposal into the fleet and by Wednesday evening I was crunching hashes on about 130 CPU threads (a lot of them were quite antique) and at the peak was just little shy of 40Mh/s. To compensate for the slow start with the few above-mentioned hiccups and the fact that I had to use my desktop to do other things from time to time, I counted with the conservative estimate of 30Mh/s when I was doing all the probability calculations.
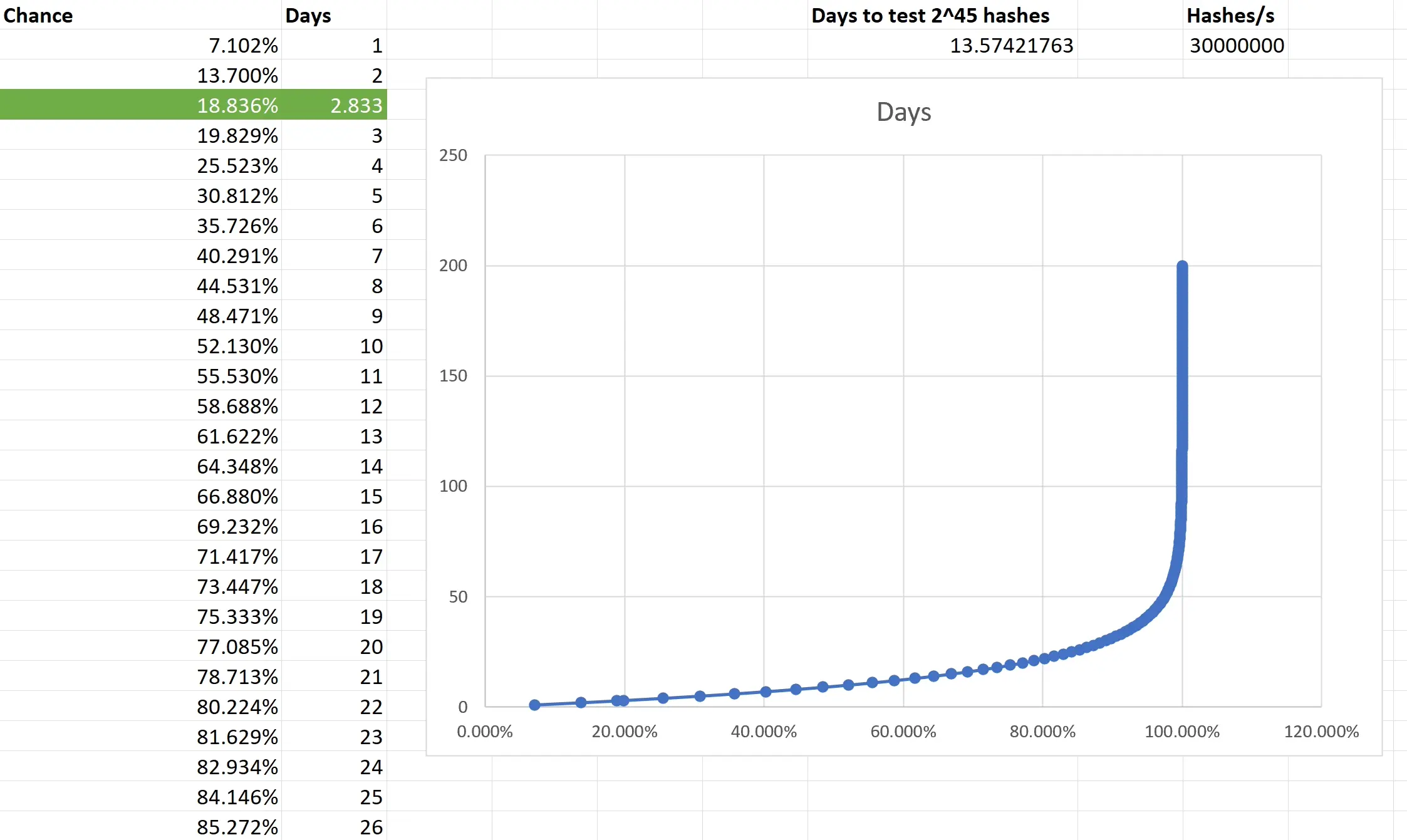
Based on the type of task that PoW mining is, the outcome is not predictible. You are only looking at what is the chance that the outcome of every single independent event will be consecutively non-favourable and then subtracting it from 1 to get the chance of that single favourable event you want. I really had to brush up on my combinatorics and discrete mathematics to make sure I have at least an elementary understanding of what is going on. Also, because we are not just throwing a dice 5 times, but are operating with big numbers, approximation was necessary. Luckily, the formula is available and quite simple in the end.
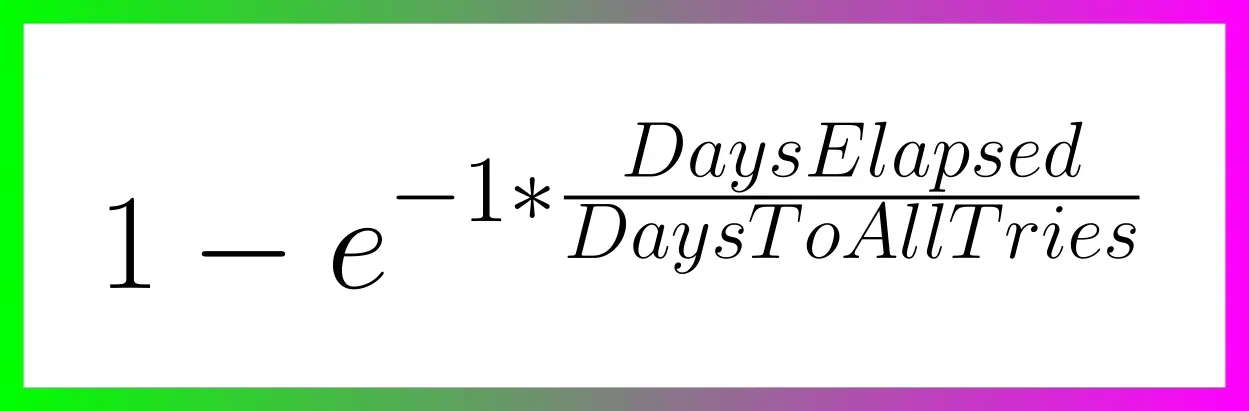
Two weeks to exhauste all the possible tries still doesn't guarantee anything, actually there is a slighlty less than 2 in 3 chance that you will have a result after all that time. So the fact that I was able to hit the right hash in less than 3 days was good luck. Not insane lottery winning luck, but good luck; slighlty lower than 1 in 5.
Do you want to beat me?
Go ahead! All the pitfalls are described above and until there is a GPU-based PoW Mining available, we are all on pretty even ground.
Do you hate the note?
In that case, feel free to enjoy this accompanying image:

-
 @ c8adf82a:7265ee75
2025-04-04 01:58:49
@ c8adf82a:7265ee75
2025-04-04 01:58:49What is knowledge? Why do we need it?
Since we were small, our parents/guardian put us in school, worked their asses off to give us elective lessons, some get help until college, some even after college and after professional work. Why is this intelligence thing so sought after?
When you were born, you mostly just accepted what your parents said, they say go to school - you go to school, they say go learn the piano - you learn the piano. Of course with a lot of questions and denials, but you do it because you know your parents are doing it for your own good. You can feel the love so you disregard the 'why' and go on with faith
Everything starts with why, and for most people maybe the purpose of knowledge is to be smarter, to know more, just because. But for me this sounds utterly useless. One day I will die next to a man with half a brain and we would feel the same exact thing on the ground. Literally being smarter at the end does not matter at all
However, I am not saying to just be lazy and foolish. For me the purpose of knowledge is action. The more you learn, the more you know what to do, the more you can be sure you are doing the right thing, the more you can make progress on your own being, etc etc
Now, how can you properly learn? Imagine a water bottle. The water bottle's sole purpose is to contain water, but you cannot fill in the water bottle before you open the cap. To learn properly, make sure you open the cap and let all that water pour into you
If you are reading this, you are alive. Don't waste your time doing useless stuff and start to make a difference in your life
Seize the day
-
 @ 6389be64:ef439d32
2025-04-03 21:32:58
@ 6389be64:ef439d32
2025-04-03 21:32:58Brewing Biology
Episode 1068 of Bitcoin And . . . is LIVE!
This episode of Bitcoin And dives into Brewing Biology—a regenerative system combining compost tea, biochar, Bitcoin mining, and carbon credits—developed through a deep, idea-driven conversation with ChatGPT.
LISTEN HERE --> https://fountain.fm/episode/p0DmvPzxirDHh2l68zOX <-- LISTEN HERE
The future of Bitcoin isn’t just about code or money—it’s about soil. A groundbreaking fusion of biology, technology, and financial innovation might change the rules of agriculture, offering landowners a path to profitability while Healing our soils. At the heart of this revolution is biochar, a form of charcoal that supercharges soil health. When mixed with compost tea and microbial inoculants, this carbon-rich material becomes a game-changer.
Biochar’s porous structure acts as a microbial hotel, hosting fungi like arbuscular mycorrhizal fungi (AMF) and bacteria such as Bacillus subtilis. These organisms form symbiotic networks that boost nutrient absorption and secrete glomalin—a natural “glue” that binds soil, preventing erosion. But here’s the twist: this system doesn’t just heal the earth; it also generates revenue.
Biochar’s Hidden Superpower: Adsorption & Buffering Biochar’s porous structure acts as a molecular storage hub. Unlike absorption (soaking up water like a sponge), adsorption is a chemical process where water and nutrients cling to biochar’s surfaces. A single gram of biochar has the surface area of a basketball court, creating a lattice of microscopic nooks and crannies. This allows it to:
Lock in moisture: Biochar retains up to 10x its weight in water, acting like a “soil battery” that releases hydration slowly during droughts.
Hoard nutrients: It buffers nitrogen, phosphorus, potassium, and micronutrients in its pores, preventing leaching. Plants access these nutrients gradually, reducing fertilizer needs.
Stabilize pH: Biochar’s alkaline nature buffers acidic soils, creating a neutral environment where microbes and roots thrive.
This buffering effect means plants face fewer nutrient and water spikes or shortages, ensuring steady growth even in erratic climates.
The Carbon Math Every ton of biochar (which is ~85% carbon by weight) sequesters 3.12 tons of CO₂ (using the 1:3.67 carbon-to-CO₂ ratio). With carbon credits trading at $42–$60/ton, a 1,000-acre project applying 1 pound of biochar per linear foot (via a three-shank plow at 2-foot spacing) could sequester ~12,000 tons of CO₂ annually—generating $504,000–$720,000 in carbon credit revenue.
Tools for the Revolution The Keyline Plow fractures subsoil to inject biochar slurry 30–45cm deep, revitalizing compacted land. For smaller plots, the VOGT Geo Injector delivers pinpoint inoculations—think of it as a soil “injection gun” for lawns, golf courses, or urban gardens. These methods ensure biochar stays where it’s needed, turning even parched landscapes into carbon sinks.
Bitcoin’s Role in the Loop Biochar production generates syngas—a byproduct that fuels electric generators for Bitcoin mining. This closed-loop system turns agricultural waste into energy, creating dual revenue streams: carbon credits and mining income.
The Market Potential Farmers, ranchers, and eco-conscious landowners aren’t the only beneficiaries. Golf courses can slash water use and homeowners can boost lawn resilience.
Why This Matters This isn’t just farming—it’s a movement. By marrying soil science with economics, we can prove that healing the planet and profiting go hand in hand. Whether you’re a Bitcoin miner, a farmer, or an eco-entrepreneur, this system offers a blueprint for a future where every acre works for you—and the planet.
The takeaway? Regenerative agriculture isn’t a trend. It’s the next gold rush—except this time, the gold is carbon, soil, and sats.---
P.S. – If you’re ready to turn your land into a carbon credit powerhouse (and maybe mine some Bitcoin along the way), the soil is waiting.
You can read the full article, Brewing Biology HERE -> https://the-bitcoin-and-Podcast.ghost.io/ghost/#/editor/post/67e5922fa289aa00088da3c6
originally posted at https://stacker.news/items/933800
-
 @ a58a2663:87bb2918
2025-03-05 12:41:36
@ a58a2663:87bb2918
2025-03-05 12:41:36After two years of using Standard Notes as my main note-taking app, I’m switching to Obsidian.
The $100 that Standard Notes charges for basic editing capabilities is difficult to justify, especially for someone paying in Brazilian Real and striving to make a living from writing. However, I will certainly miss its simplicity and cleaner interface.
It’s my impression that the developers are missing an opportunity to create a privacy-focused note-taking app tailored to the specific needs of writers, rather than general users.
Substack, for example, achieved such success because it targeted the distribution and monetization of writers’ work. But we need more tools focused not on distribution or monetization, but on the actual process—indeed, the various phases of the process—of creating texts. This is especially true for complex, long-form texts with different levels of argumentation, numerous written and multimedia sources, and cross-references to other works by the author.
It’s crucial that an app like this doesn’t feel overly complex, like Notion or Evernote, or so all-purpose, like Obsidian. And, of course, I’m not talking about a new full-fledged text editor like Scrivener.
Just a thought. Take note.
-
 @ df67f9a7:2d4fc200
2025-04-03 19:54:29
@ df67f9a7:2d4fc200
2025-04-03 19:54:29More than just “follows follows” on Nostr, webs of trust algos will ingest increasingly MORE kinds of user generated content in order to map our interactions across the network. Webs of trust will power user discovery, content search, reviews and reccomendations, identity verification, and access to all corners of the Nostr network. Without relying on a central “trust authority” to recommend people and content for us, sovereign Nostr users will make use of “relative trust” scores generated by a wide range of independent apps and services. The problem is, Nostr doesn’t have an opensource library for performing WoT calculations and delivering NIP standard recommendations to users. In order for a “free market” ecosystem of really smart apps and services to thrive, independent developers will need access to extensible “middleware” such as this.
Project Description
I am building a library for independent developers to offer their own interoperable and configurable WoT services and clients. In addition, and as the primary use case, I am also developing a web client for “in person onboarding” to Nostr, which will make use of this library to provide webs of trust recommendations for “invited” users.
-
Meet Me On Nostr (onboarding client) : This is my first project on Nostr, which began a year ago with seed funding from @druid. This web client will leverage “in person” QR invites to generate WoT powered recommendations of follows, apps, and other stuff for new users at their first Nostr touchpoint. The functional MVP release (April ‘25) allows for “instant, anonymous, and fully encrypted” direct messaging and “move in ready” profile creation from a single QR scan.
-
GrapeRank Engine (developer library) : Working with @straycat last fall, I built an opensource and extensible library for Nostr developers to integrate “web of trust” powered reccomendations into their products and services. The real power behind GrapeRank is its “pluggable” interpreter, allowing any kind of content (not just “follows follows”) to be ingested for WoT scoring, and configurable easily by developers as well as end users. This library is currently in v0.1, “generating and storing usable scores”, and doesn’t yet produce NIP standard outputs for Nostr clients.
-
My Grapevine (algo dashboard) : In addition, I’ve just wrapped up the demo release of a web client by which users and developers can explore the power of the GrapeRank Engine.
Potential Impact
Webs of Trust is how Nostr scales. But so far, Nostr implementations have been ad-hoc and primarily client centered, with no consistency and little choice for end users. The “onboarding and discovery” tools I am developing promise to :
-
Establish sovereignty for webs of trust users (supporting a “free market” of algo choices), with opensource libraries by which any developer can easily implement WoT powered recommendations.
-
Accelerate the isolation of bots and bad actors (and improve the “trustiness” of Nostr for everyone else) by streamlining the onboarding of “real world” acquaintances directly into established webs of trust.
-
Improve “discoverability of users and content” for any user on any client (to consume and take advantage of WoT powered recommendations for any use case, even as the NIP standards for this are still in flux), by providing an algo engine with “pluggable” inputs and outputs.
-
Pave the way for “global Nostr adoption”, where WoT powered recommendations (and searches) are consistently available for every user across a wide variety of clients.
Timeline & Milestones
2025 roadmap for “Webs of Trust Onboarding and Discovery” :
-
Meet Me On Nostr (onboarding client) : MVP release : “scan my QR invite to private message me instantly with a ‘move in ready’ account on Nostr”. https://nostrmeet.me/
-
GrapeRank Engine (developer library) : 1.0 release : “expanded inputs and output WoT scores to Nostr NIPs and other stuff” for consumption by clients and relays. https://github.com/Pretty-Good-Freedom-Tech/graperank-nodejs
-
My Grapevine (algo dashboard) : 1.0 release : “algo usage and configuration webapp with API endpoints” for end users to setup GrapeRank scoring for consumption by their own clients and relays. https://grapevine.my/
-
Meet Me On Nostr (onboarding client) : 1.0 release : first GrapeRank integration, offering “follow and app recommendations for invited users”, customizable per-invite for Nostr advocates. https://nostrmeet.me/
Prior contributions
-
Last spring I hosted panel discussions and wrote articles on Nostr exploring how to build “sovereign webs of trust”, where end users can have control over which algorithms to use, and what defines “trust”.
-
I contributed gift wrap encryption to NDK.
-
I am also authoring gift wrapped direct messaging and chat room modules for NDK.
-
Last July, I attended The Bitcoin Conference on an OpenSource pass to raise funds for my onboarding client. I onboarded many Bitcoiners to Nostr, and made valuable connections at Bitcoin Park.
About Me
I discovered Nostr in September ‘23 as a freelance web developer, after years of looking for a “sovereignty respecting” social media on which to build apps. With this came my first purchase of Bitcoin. By December of that year, I was settled on “open source freedom tech” (Nostr and Bitcoin) as the new direction for my career.
As a web professional for 20+ years, I know the importance of “proof of work” and being connected. For the last 18 months, I have been establishing myself as a builder in this community. This pivot has not been easy, but it has been rewarding and necessary. After so many years building private tech for other people, I finally have a chance to build freedom tech for everyone. I have finally come home to my peeps and my purpose.
Thank you for considering this application for funding.
-
-
 @ 6389be64:ef439d32
2025-02-27 21:32:12
@ 6389be64:ef439d32
2025-02-27 21:32:12GA, plebs. The latest episode of Bitcoin And is out, and, as always, the chicanery is running rampant. Let’s break down the biggest topics I covered, and if you want the full, unfiltered rant, make sure to listen to the episode linked below.
House Democrats’ MEME Act: A Bad Joke?
House Democrats are proposing a bill to ban presidential meme coins, clearly aimed at Trump’s and Melania’s ill-advised token launches. While grifters launching meme coins is bad, this bill is just as ridiculous. If this legislation moves forward, expect a retaliatory strike exposing how politicians like Pelosi and Warren mysteriously amassed their fortunes. Will it pass? Doubtful. But it’s another sign of the government’s obsession with regulating everything except itself.
Senate Banking’s First Digital Asset Hearing: The Real Target Is You
Cynthia Lummis chaired the first digital asset hearing, and—surprise!—it was all about control. The discussion centered on stablecoins, AML, and KYC regulations, with witnesses suggesting Orwellian measures like freezing stablecoin transactions unless pre-approved by authorities. What was barely mentioned? Bitcoin. They want full oversight of stablecoins, which is really about controlling financial freedom. Expect more nonsense targeting self-custody wallets under the guise of stopping “bad actors.”
Bank of America and PayPal Want In on Stablecoins
Bank of America’s CEO openly stated they’ll launch a stablecoin as soon as regulation allows. Meanwhile, PayPal’s CEO paid for a hat using Bitcoin—not their own stablecoin, Pi USD. Why wouldn’t he use his own product? Maybe he knows stablecoins aren’t what they’re hyped up to be. Either way, the legacy financial system is gearing up to flood the market with stablecoins, not because they love crypto, but because it’s a tool to extend U.S. dollar dominance.
MetaPlanet Buys the Dip
Japan’s MetaPlanet issued $13.4M in bonds to buy more Bitcoin, proving once again that institutions see the writing on the wall. Unlike U.S. regulators who obsess over stablecoins, some companies are actually stacking sats.
UK Expands Crypto Seizure Powers
Across the pond, the UK government is pushing legislation to make it easier to seize and destroy crypto linked to criminal activity. While they frame it as going after the bad guys, it’s another move toward centralized control and financial surveillance.
Bitcoin Tools & Tech: Arc, SatoChip, and Nunchuk
Some bullish Bitcoin developments: ARC v0.5 is making Bitcoin’s second layer more efficient, SatoChip now supports Taproot and Nostr, and Nunchuk launched a group wallet with chat, making multisig collaboration easier.
The Bottom Line
The state is coming for financial privacy and control, and stablecoins are their weapon of choice. Bitcoiners need to stay focused, keep their coins in self-custody, and build out parallel systems. Expect more regulatory attacks, but don’t let them distract you—just keep stacking and transacting in ways they can’t control.
🎧 Listen to the full episode here: https://fountain.fm/episode/PYITCo18AJnsEkKLz2Ks
💰 Support the show by boosting sats on Podcasting 2.0! and I will see you on the other side.
-
 @ c13fd381:b46236ea
2025-04-03 07:55:31
@ c13fd381:b46236ea
2025-04-03 07:55:31Over the past few years, The School of Bitcoin (TSOBTC) has built a reputation as a decentralised, open-source educational initiative dedicated to financial sovereignty and digital literacy. Our faculty, contributors, and global community have worked tirelessly to create resources that embody the Free and Open-Source Software (FOSS) ethos, ensuring that knowledge remains accessible to all.
As part of our commitment to maintaining an open and transparent model, we are excited to announce that The School of Bitcoin is officially migrating to Consensus21.School. This transition is not just a rebranding--it marks the consolidation of all our initiatives, projects, and educational resources under the Consensus21.School banner. The School of Bitcoin will no longer exist as a separate entity.
This move comes as a response to growing confusion between our initiative and another entity operating under the domain schoolofbitcoin (SOB), which has taken a direction that does not align with our open-source philosophy. To reaffirm our dedication to FOSS and community-driven education, we are bringing everything--our courses, programs, and collaborations--into a singular, more focused ecosystem at Consensus21.School.
What Does This Mean for Our Community?
Rest assured, all the valuable content, courses, and educational materials that have been developed under TSOBTC will remain available. We continue to embrace a value-for-value model, ensuring that learners can access resources while supporting the ecosystem in a way that aligns with their means and values.
By consolidating under Consensus21.School, we are doubling down on the principles of decentralisation, self-sovereignty, and permissionless learning. This transition includes all of our key initiatives, including V4V Open Lessons, the Decentralised Autonomous Education System (DAES), and our involvement with the Plan B Network.
Full Migration of DAES and Plan B Network Collaboration
As part of this transition, the Decentralised Autonomous Education System (DAES) is now officially part of Consensus21.School and is fully reflected in the Consensus21.School Whitepaper. DAES will continue to provide a platform for aspiring learners to submit their Bitcoin project ideas for potential funding and mentorship, with active engagement in our Stacker News /~Education territory and Signal chat for collaboration. We invite contributors to support our learner fund and help bring innovative ideas to fruition within this new ecosystem.
Additionally, our collaboration with the Plan B Network will now operate under Consensus21.School. Through this partnership, we will continue teaching using the Plan B Network's curriculum to provide high-quality Bitcoin education and strengthen local Bitcoin communities. This global initiative remains a core part of our mission, now fully integrated within Consensus21.School.
Looking Ahead
With Consensus21.School, we will continue innovating in peer-to-peer learning, integrating cutting-edge developments in Bitcoin, Nostr, and decentralised technologies. We encourage our community to stay engaged, contribute, and help us build an even stronger foundation for the future of open education.
This is more than just a domain change--it is the next evolution of our mission. The School of Bitcoin as an entity is now retired, and all our efforts, including DAES and the Plan B Network collaboration, will move forward exclusively under Consensus21.School. We invite educators, students, and enthusiasts to join us in shaping this next phase of open financial education.
The journey continues, and we are thrilled to embark on this new chapter together
-
 @ fd06f542:8d6d54cd
2025-04-15 06:35:56
@ fd06f542:8d6d54cd
2025-04-15 06:35:56 -
 @ 5a261a61:2ebd4480
2025-04-15 06:34:03
@ 5a261a61:2ebd4480
2025-04-15 06:34:03What a day yesterday!
I had a really big backlog of both work and non-work things to clean up. But I was getting a little frisky because my health finally gave me some energy to be in the mood for intimacy after the illness-filled week had forced libido debt on me. I decided to cheat it out and just take care of myself quickly. Horny thoughts won over, and I got at least e-stim induced ass slaps to make it more enjoyable. Quick clean up and everything seemed ok...until it wasn't.
The rest of the morning passed uneventfully as I worked through my backlog, but things took a turn in the early afternoon. I had to go pickup kids, and I just missed Her between the doors, only managed to get a fast kiss. A little bummed from the work issues and failed expectations of having a few minutes together, I got on my way.
Then it hit me—the most serious case of blue balls I had in a long time. First came panic. I was getting to the age when unusual symptoms raise concerns—cancer comes first to mind, as insufficient release wasn't my typical problem. So I called Her. I explained what was happening and expressed hope for some alone time. Unfortunately, that seemed impossible with our evening schedule: kids at home, Her online meeting, and my standing gamenight with the boys. These game sessions are our sacred ritual—a preserved piece of pre-kids sanity that we all protect in our calendars. Not something I wanted to disturb.
Her reassurance was brief but unusualy promising: "Don't worry, I get this."
Evening came, and just as I predicted, there was ZERO time for shenanigans while we took care of the kids. But once we put them to bed (I drew straw for early sleeper), with parental duties complete, I headed downstairs to prepare for my gaming session. Headset on, I greeted my fellows and started playing.
Not five minutes later, She opened the door with lube in one hand, fleshlight in the other, and an expecting smile on Her face. Definitely unexpected. I excused myself from the game, muted mic, but She stopped me.
"There will be nothing if you won't play," She said. She just motioned me to take my pants off. And off to play I was. Not an easy feat considering I twisted my body sideways so She could access anything She wanted while I still reached keyboard and mouse.
She slowly started touching me and observing my reactions, but quickly changed to using Her mouth. Getting a blowjob while semihard was always so strange. The semi part didn't last long though...
As things intensified, She was satisfied with my erection and got the fleshlight ready. It was a new toy for us, and it was Her first time using it on me all by Herself (usually She prefers watching me use toys). She applied an abundance of lube that lasted the entire encounter and beyond.
Shifting into a rhythm, She started pumping slowly but clearly enjoyed my reactions when She unexpectedly sped up, forcing me to mute the mic. I knew I wouldn't last long. When She needed to fix Her hair, I gentlemanly offered to hold the fleshlight, having one hand still available for gaming. She misunderstood, thinking I was taking over completely, which initially disappointed me.
To my surprise, She began taking Her shirt off the shoulders, offering me a pornhub-esque view. To clearly indicate that finish time had arrived, She moved Her lubed hand teasingly toward my anal. She understood precisely my contradictory preferences—my desire to be thoroughly clean before such play versus my complete inability to resist Her when aroused. That final move did it—I muted the mic just in time to vocally express how good She made me feel.
Quick clean up, kiss on the forehead, and a wish for me to have a good game session followed. The urge to abandon the game and cuddle with Her was powerful, but She stopped me. She had more work to complete on Her todo list than just me.
Had a glass, had a blast; overall, a night well spent I would say.
-
 @ 6e0ea5d6:0327f353
2025-02-21 18:15:52
@ 6e0ea5d6:0327f353
2025-02-21 18:15:52"Malcolm Forbes recounts that a lady, wearing a faded cotton dress, and her husband, dressed in an old handmade suit, stepped off a train in Boston, USA, and timidly made their way to the office of the president of Harvard University. They had come from Palo Alto, California, and had not scheduled an appointment. The secretary, at a glance, thought that those two, looking like country bumpkins, had no business at Harvard.
— We want to speak with the president — the man said in a low voice.
— He will be busy all day — the secretary replied curtly.
— We will wait.
The secretary ignored them for hours, hoping the couple would finally give up and leave. But they stayed there, and the secretary, somewhat frustrated, decided to bother the president, although she hated doing that.
— If you speak with them for just a few minutes, maybe they will decide to go away — she said.
The president sighed in irritation but agreed. Someone of his importance did not have time to meet people like that, but he hated faded dresses and tattered suits in his office. With a stern face, he went to the couple.
— We had a son who studied at Harvard for a year — the woman said. — He loved Harvard and was very happy here, but a year ago he died in an accident, and we would like to erect a monument in his honor somewhere on campus.— My lady — said the president rudely —, we cannot erect a statue for every person who studied at Harvard and died; if we did, this place would look like a cemetery.
— Oh, no — the lady quickly replied. — We do not want to erect a statue. We would like to donate a building to Harvard.
The president looked at the woman's faded dress and her husband's old suit and exclaimed:
— A building! Do you have even the faintest idea of how much a building costs? We have more than seven and a half million dollars' worth of buildings here at Harvard.
The lady was silent for a moment, then said to her husband:
— If that’s all it costs to found a university, why don’t we have our own?
The husband agreed.
The couple, Leland Stanford, stood up and left, leaving the president confused. Traveling back to Palo Alto, California, they established there Stanford University, the second-largest in the world, in honor of their son, a former Harvard student."
Text extracted from: "Mileumlivros - Stories that Teach Values."
Thank you for reading, my friend! If this message helped you in any way, consider leaving your glass “🥃” as a token of appreciation.
A toast to our family!
-
 @ cbaa0c82:e9313245
2025-04-02 18:53:57
@ cbaa0c82:e9313245
2025-04-02 18:53:57TheWholeGrain - #March2025
March of 2025 was a standard month for Bread and Toast. However, it did include a the occasional five Sunday Singles which seems like hitting the jackpot! Talk about lucky!
Included with the five Sunday Singles was two more pages of the Adventure Series: Questline where we saw Bread, Toast, and End-Piece face off against their first adversary!
End-Piece made a first appearance for in Toast's Comic Collection under the title E: The Last Slice while the Concept Art piece was the original drawing of all three slices of bread together. And, last of all we updated the Bitcoin logo because why not!?
Sunday Singles - March 2025 2025-03-02 | Sunday Single 82 Title: Slingshot! Watch out! Toast is quite the sharpshooter! https://i.nostr.build/zHA9C7cOOZLOCl0o.png
2025-03-09 | Sunday Single 83 Title: Puzzles End-Piece just figured out the puzzle! https://i.nostr.build/u2EBdcsuwO2xo23P.png
2025-03-16 | Sunday Single 84 Title: Basketball Oh, the madness! https://i.nostr.build/8F1OFFVra7zQOIy6.png
2025-03-23 | Sunday Single 85 Title: Coffee The perfect way to start the day. https://i.nostr.build/aiGZOvOmow3igru6.png
2025-03-30 | Sunday Single 86 Title: Origami End-Piece has a way with paper. https://i.nostr.build/0ySzGwF9QnZxwLxD.png
Adventure Series: Questline The group is attacked by a crow with Bread being the target of the giant bird, but with a group of trusty friends any enemy can be defeated!
Artist: Dakota Jernigan (The Bitcoin Painter) Writer: Daniel David (dan 🍞)
2025-03-11 | Questline 005 - Under Attack Toast and End-Piece are able to escape the attack from the giant winged predator, but Bread being distracted by thoughts of the village is caught off guard. End-Piece immediately charges the attacker with a fury of mallet swings. Meanwhile, Toast loads up an arrow with intentions of piercing through the giant bird. https://i.nostr.build/F24sd7SFFbsW9WZY.png
2025-03-25 | Questline 006 - A Finished Battle End-Piece lands a series of blows to the winged beast. Toast finishes it off with a second arrow to the heart. Bread is only slightly injured, but is more upset about having been so vulnerable due to being so distracted. Moving forward Bread will have to be more vigilant. https://i.nostr.build/n5a7Jztq9MHxuGNf.png
Other Content Released in March 2025 2025-03-05 | Toast's Comic Collection Title: E: The Last Slice #11 A gluten-based pandemic has killed off all slices of bread that are not Toast except for one slice of bread that happens to be an end piece. https://i.nostr.build/aar20oHAAKmZOovD.png
2025-03-12 | Concept Art Title: Original Bread and Toast This was the first drawing of all three characters together. It was used a lot for branding when the project first started up in 2023. https://i.nostr.build/yqkmBuTiH8AKbCzI.png
2025-03-19 | Bitcoin Art Title: Bitcoin/Bread Block Height: 888566 Two things that just go together. https://i.nostr.build/MDPkzOPVEaOJVTFE.png
Thanks for checking out the seventh issue of The Whole Grain. The Whole Grain is released on the first of every month and covers all of the content released by Bread and Toast in the previous month. For all Bread and Toast content visit BreadandToast.com!
So long, March! Bread, Toast, and End-Piece
BreadandToast #SundaySingle #Questline #ToastsComicCollection #ConceptArt #BitcoinArt #Bread #Toast #EndPiece #Artstr #Comic #Cartoon #NostrOnly #🍞 #🖼️
List of nPubs Mentioned: The Bitcoin Painter: npub1tx5ccpregnm9afq0xaj42hh93xl4qd3lfa7u74v5cdvyhwcnlanqplhd8g
dan 🍞: npub16e3vzr7dk2uepjcnl85nfare3kdapxge08gr42s99n9kg7xs8xhs90y9v6
-
 @ fbf0e434:e1be6a39
2025-04-15 06:46:58
@ fbf0e434:e1be6a39
2025-04-15 06:46:58Hackathon 概览
Eolas x Algo: Agent Skills Hackathon 在线上举行,旨在通过提升代理技能来推动 CreatorBid 生态系统的发展。活动吸引了58位开发者参赛,最终有36个项目获得批准。本次黑客松突破传统模式,允许 CreatorBid 代理直接发布技能需求,省去中间环节,实现供需精准对接。
参赛者在两大核心赛道展开竞争:Bounty Track 聚焦代理识别的具体痛点攻关,Best Skills Track 则嘉奖具备卓越价值的项目。Eolas、Algo、Shogun、AION 等机构及多位独立代理为活动提供资金支持。
开发成果直接集成至 Olas Mech Marketplace,实现实时部署落地,并通过 OLAS 系统为开发者提供激励。以 Agent Algo、Eolas 为代表的头部代理特别肯定了本次活动对代理技术创新的推动作用。3 月 20 日活动收官,由 CreatorBid 团队与代理代表组成的评审团,从创新性和生态影响力双重维度对项目进行了综合评判。
Hackathon 获奖者
以下部分详细介绍了首届代理赞助 Hackathon 的成就和奖项,涵盖了37个项目在各个类别中的亮点。
Best Agent Skill Track 奖项获奖者
- Agent Toolbox: 一套增强 AI 代理功能的工具,包括趋势发现、动态函数生成和任务编排。
- GridTrade Agent: 通过市场和波动性分析,促进自动化交易对选择和网格交易参数优化。
- Polytrader: 一个基于 AI 的交易助手,简化 Polymarket 的研究、数据分析和交易执行。
主奖池获奖者
- sentimentX: 为 MultiversX 区块链智能合约提供 AI 驱动的安全监控,通过检测漏洞实现。
- Brainiac_AI: 一个通过链上分析优化 DeFi 策略的平台,并集成非托管钱包。
- framew0rk: 使用链接到 DeFi 协议的 AI 策略助手简化 DeFi 收益优化。
- MythosCraft: AI Storytelling Suite: 使用 AI 创建定制化故事内容。
- QuanTrade-X: 提供 AI 驱动的分析和加密货币交易信号。
- ComicVerse AI: 利用 AI 根据用户输入创作剧本和图像生成漫画。
- EOLAS - Submit your own skill: Portfolio Allocation Skill: 使用 AI 和现代投资组合理论优化加密货币投资组合。
- SonicBo: WhatsApp 上的 AI 代理,促进区块链交易。
- 👽Zeta Comic Generator👽: 将文本提示转换为 AI 生成的漫画,通过剧本和角色表达来实现。
- Grid Trading Analyzer Skill: 高级分析的 Python 工具,用于识别最佳加密货币网格交易对。
- Trump news Reporter: AI 工具,用于实时监控和报告与特朗普相关的新闻,带有自定义过滤器。
- NFT Appraisal skill: 创建用于 NFT 估值的 AI 代理。
- AI-Powered Dynamic Skill Selector (DSS): 使用多臂賭徒策略进行动态 AI 模型优化。
- CrypTweet: 使用 Twitter 情绪为加密货币交易决策提供信息的 AI 交易机器人。
- AI Trump News Agent: 监控和分析与特朗普相关的新闻,并提供可自定义的报告语气。
- TrumpTracker-AI: 汇编和总结与特朗普相关的新闻,从热门标题生成网络迷因。
- Rigger-: 将自然语言转化为 SQL 查询,方便非技术人员访问数据库。
- TNS: 使用 NLP 跟踪与特朗普相关的新闻,并提供多样化的报道风格。
- Bob Roast Machine: 用于创作喜剧吐槽、笑话和网络迷因的 AI 平台。
- Agent 47: 一个 Telegram 机器人,提供政治新闻以及 AI 生成的网络迷因和事实核查。
技能协调与优化奖项获奖者
增强 CB 代理数据访问的技能奖项获奖者
世界构建与传说推广技能奖项获奖者
Polymarket 交易机器人奖项获奖者
欲了解项目的完整列表,请访问 DoraHacks。
关于组织者
Eolas
Eolas 在技术和区块链领域是一个重要的参与者,以其提升交易透明度的区块链解决方案而闻名。该组织继续专注于区块链的研究与开发,解决行业挑战以推动未来进展。
-
 @ 8d34bd24:414be32b
2025-04-02 14:13:03
@ 8d34bd24:414be32b
2025-04-02 14:13:03I was reading this passage last night:
…from that time when one came to a grain heap of twenty measures, there would be only ten; and when one came to the wine vat to draw fifty measures, there would be only twenty. I smote you and every work of your hands with blasting wind, mildew and hail; yet you did not come back to Me,’ declares the Lord. ‘Do consider from this day onward, from the twenty-fourth day of the ninth month; from the day when the temple of the Lord was founded, consider: Is the seed still in the barn? Even including the vine, the fig tree, the pomegranate and the olive tree, it has not borne fruit. Yet from this day on I will bless you.’ ” (Haggai 2:16-19) {emphasis mine}
Why were bad things happening to the Israelites? Because they were not following God. Why did God allow these difficult situations to occur? Because God was calling them back to Himself.
This made me think of several times lately, when I had written about Christians going through hard times, that fellow believers had tried to kindly correct me implying that God would not allow these painful things to happen to believers. They were trying to defend God’s honor, but instead they were degrading God. If God is not in control of everything, then either God is unable to protect His own from harm because of sin or bad things happened accidentally and God ignored the injustice. Saying God was not in control of allowing every hardship is either saying God isn’t strong enough, isn’t smart enough, or isn’t loving enough. The God I serve is omniscient, omnipotent, omnipresent, and love incarnate. He also didn’t promise us easy, pleasant lives, but did promise that good would come out of every situation.
And we know that in all things God works for the good of those who love him, who have been called according to his purpose. (Romans 8:28)
When Jesus walked on earth and some people said they wanted to follow Him, His response was not what we would expect:
And He was saying to them all, “If anyone wishes to come after Me, he must deny himself, and take up his cross daily and follow Me. For whoever wishes to save his life will lose it, but whoever loses his life for My sake, he is the one who will save it. For what is a man profited if he gains the whole world, and loses or forfeits himself? For whoever is ashamed of Me and My words, the Son of Man will be ashamed of him when He comes in His glory, and the glory of the Father and of the holy angels. (Luke 9:23-26) {emphasis mine}
When one particular man said that he would follow Jesus anywhere, Jesus responded this way.
As they were going along the road, someone said to Him, “I will follow You wherever You go.” And Jesus said to him, “The foxes have holes and the birds of the air have nests, but the Son of Man has nowhere to lay His head.” (Luke 9:57-58) {emphasis mine}
Jesus was brutally honest that following Him would not be easy or comfortable. Following Jesus is more likely to lead to hardship and persecution that prosperity and comfort.
“Then they will deliver you to tribulation, and will kill you, and you will be hated by all nations because of My name. At that time many will fall away and will betray one another and hate one another. Many false prophets will arise and will mislead many. Because lawlessness is increased, most people’s love will grow cold. But the one who endures to the end, he will be saved. This gospel of the kingdom shall be preached in the whole world as a testimony to all the nations, and then the end will come. (Matthew 24:9-14) {emphasis mine}
Of course God isn’t putting us through hardship to torture us. He is putting us in situations to grow our faith and dependence on Him, i.e. Abraham. He is putting us in situations where we can minister to others, i.e. Joseph. He is using us as examples of faith to others, i.e. Job. Any hardship has an eternal purpose. Sometimes we can see it (at least eventually) if we are looking for God’s will and plan. Sometime we won’t see what He was accomplishing until we get to heaven. Still we need to trust God through it all, knowing His plan is perfect.
“For my thoughts are not your thoughts,\ neither are your ways my ways,”\ declares the Lord.
“As the heavens are higher than the earth,\ so are my ways higher than your ways\ and my thoughts than your thoughts.
As the rain and the snow\ come down from heaven,\ and do not return to it\ without watering the earth\ and making it bud and flourish,\ so that it yields seed for the sower and bread for the eater,\ so is my word that goes out from my mouth:\ It will not return to me empty,\ but will accomplish what I desire\ and achieve the purpose for which I sent it. (Isaiah 55:8-11) {emphasis mine}
God understands how hard it is to understand what He is accomplishing. We live in the here and now while He is outside time and space and therefore has a heavenly and eternal perspective that we will never truly have this side of heaven. He has told us how the story ends, so that we can have peace and trust Him through whatever circumstances He has blessed us.
Jesus answered them, “Do you now believe? Behold, an hour is coming, and has already come, for you to be scattered, each to his own home, and to leave Me alone; and yet I am not alone, because the Father is with Me. These things I have spoken to you, so that in Me you may have peace. In the world you have tribulation, but take courage; I have overcome the world.” (John 16:31-33) {emphasis mine}
In fact, Jesus made this so clear that His disciples rejoiced in persecution they received due to obeying Him and sharing His word.
They took his advice; and after calling the apostles in, they flogged them and ordered them not to speak in the name of Jesus, and then released them. So they went on their way from the presence of the Council, rejoicing that they had been considered worthy to suffer shame for His name. (Acts 5:40-41) {emphasis mine}
Peter specifically warns believers to expect trials and hardship.
Dear friends, do not be surprised at the fiery ordeal that has come on you to test you, as though something strange were happening to you. But rejoice inasmuch as you participate in the sufferings of Christ, so that you may be overjoyed when his glory is revealed. If you are insulted because of the name of Christ, you are blessed, for the Spirit of glory and of God rests on you. If you suffer, it should not be as a murderer or thief or any other kind of criminal, or even as a meddler. However, if you suffer as a Christian, do not be ashamed, but praise God that you bear that name. For it is time for judgment to begin with God’s household; and if it begins with us, what will the outcome be for those who do not obey the gospel of God? And,
“If it is hard for the righteous to be saved,\ what will become of the ungodly and the sinner?”
So then, those who suffer according to God’s will should commit themselves to their faithful Creator and continue to do good. (1 Peter 4:12-19) {emphasis mine}
Paul writes about begging God to take away a health issue. Eventually he accepted it as part of God’s plan for his life and boasted gladly in his hardship.
…Therefore, in order to keep me from becoming conceited, I was given a thorn in my flesh, a messenger of Satan, to torment me. Three times I pleaded with the Lord to take it away from me. But he said to me, “My grace is sufficient for you, for my power is made perfect in weakness.” Therefore I will boast all the more gladly about my weaknesses, so that Christ’s power may rest on me. That is why, for Christ’s sake, I delight in weaknesses, in insults, in hardships, in persecutions, in difficulties. For when I am weak, then I am strong. (2 Corinthians 12:7b-10) {emphasis mine}
No matter what hardships we experience in life, whether poverty or persecution or poor health or loss of a loved one or any other hardship, God is with us working everything for our good.
Who will separate us from the love of Christ? Will tribulation, or distress, or persecution, or famine, or nakedness, or peril, or sword? Just as it is written,
“For Your sake we are being put to death all day long;\ We were considered as sheep to be slaughtered.” **But in all these things we overwhelmingly conquer through Him who loved us. For I am convinced that neither death, nor life, nor angels, nor principalities, nor things present, nor things to come, nor powers, nor height, nor depth, nor any other created thing, will be able to separate us from the love of God, which is in Christ Jesus our Lord. (Romans 8:35-39) {emphasis mine}
I like to look at the story of Joseph as an example of God’s extraordinary plan in the life of a faithful believer. Joseph trusted and honored God. God had a plan for Joseph to be used to save the lives of his family and the people of the Middle East from famine, but God didn’t just instantly put Joseph in a position of power to help. He prepared Joseph and slowly moved him to where he needed to be.
First Josephs brothers wanted to kill him out of jealousy, but God used greed to get them to sell Joseph as a slave instead. He orchestrated the right slave traders to walk by at the right time so that Joseph would wind up in the house of Potiphar, the Pharaoh’s guard.
Then when Joseph acted honorably towards God, his master, and his master’s wife, Joseph was sent to jail for years. I’m sure Joseph was wondering why God would send him to prison for doing what was right, but it put him into the presence of the cupbearer of Pharaoh. A long time after correctly interpreting the cup bearer’s dream, Joseph was called up to interpret Pharaoh’s dream, put in charge of the famine preparation and became second in command after Pharaoh. Joseph, after years of slavery and jail time, was now the second most powerful man in the Middle East, if not the world. God had a plan, but it was hard to see until its completion.
In the same way, Job lost his wealth, his children, his health, and his reputation, but remember that Satan had to get God’s permission before anything could be done to hurt Job. So many people today are blessed by seeing Job’s response to hardship and loss, by seeing Job’s faith, his struggle, and his submission to God’s plan. In this case God even gives Job more after this time of testing than he had before.
When we experience hardship we need to know that God has a plan for our life. It may be something amazing here on Earth. It may be souls won for Christ. It may be to prepare us for heaven. Whatever the case, it is for our good.
We don’t need to be ashamed that God would allow hardship. We grow most when we experience hardship. Our light shines brightest in darkness.
Oh, the depth of the riches of the wisdom and knowledge of God!\ How unsearchable his judgments,\ and his paths beyond tracing out!\ “Who has known the mind of the Lord?\ Or who has been his counselor?”\ “Who has ever given to God,\ that God should repay them?”\ For from him and through him and for him are all things.\ To him be the glory forever! Amen. (Romans 11:33-36)
Trust Jesus
-
 @ 06639a38:655f8f71
2025-04-02 13:47:57
@ 06639a38:655f8f71
2025-04-02 13:47:57You can follow the work in progress here in this pull request https://github.com/nostrver-se/nostr-php/pull/68 on Github.
Before my 3-month break (Dec/Jan/Feb) working on Nostr-PHP I started with the NIP-19 integration in October '24. Encoding and decoding the simple prefixes (
npub,nsecandnote) was already done in the first commits.Learn more about NIP-19 here: https://nips.nostr.com/19
TLV's
Things were getting more complicated with the other prefixes / identifiers defined in NIP-19:
neventnaddrnprofile
This is because these identifiers contain (optional) metadata called Type-Lenght-Value aka TLV's.
When sharing a profile or an event, an app may decide to include relay information and other metadata such that other apps can locate and display these entities more easily.
For these events, the contents are a binary-encoded list of_TLV_(type-length-value), with_T_and_L_being 1 byte each (_uint8_, i.e. a number in the range of 0-255), and_V_being a sequence of bytes of the size indicated by_L_.These possible standardized
TLVtypes are:0:special- depends on the bech32 prefix:
- for
nprofileit will be the 32 bytes of the profile public key - for
neventit will be the 32 bytes of the event id - for
naddr, it is the identifier (the"d"tag) of the event being referenced. For normal replaceable events use an empty string.
- for
- depends on the bech32 prefix:
1:relay- for
nprofile,neventandnaddr, optionally, a relay in which the entity (profile or event) is more likely to be found, encoded as ascii - this may be included multiple times
- for
2:author- for
naddr, the 32 bytes of the pubkey of the event - for
nevent, optionally, the 32 bytes of the pubkey of the event
- for
3:kind- for
naddr, the 32-bit unsigned integer of the kind, big-endian - for
nevent, optionally, the 32-bit unsigned integer of the kind, big-endian
- for
These identifiers are formatted as bech32 strings, but are much longer than the package
bitwasp/bech32(used in the library) for can handle for encoding and decoding. The bech32 strings handled bybitwasp/bech32are limited to a maximum length of 90 characters.Thanks to the effort of others (nostr:npub1636uujeewag8zv8593lcvdrwlymgqre6uax4anuq3y5qehqey05sl8qpl4 and nostr:npub1efz8l77esdtpw6l359sjvakm7azvyv6mkuxphjdk3vfzkgxkatrqlpf9s4) during my break, some contributions are made (modifiying the bech32 package supporting much longer strings, up to a max of 5000 characters). At this moment, I'm integrating this (mostly copy-pasting the stuff and refactoring the code):
So what's next?
- NIP-19 code housekeeping + refactoring
- Prepare a new release with NIP-19 integration
- Create documentation page how to use NIP-19 on https://nostr-php.dev
-
 @ 7bdef7be:784a5805
2025-04-02 12:37:35
@ 7bdef7be:784a5805
2025-04-02 12:37:35The following script try, using nak, to find out the last ten people who have followed a
target_pubkey, sorted by the most recent. It's possibile to shortensearch_timerangeto speed up the search.```
!/usr/bin/env fish
Target pubkey we're looking for in the tags
set target_pubkey "6e468422dfb74a5738702a8823b9b28168abab8655faacb6853cd0ee15deee93"
set current_time (date +%s) set search_timerange (math $current_time - 600) # 24 hours = 86400 seconds
set pubkeys (nak req --kind 3 -s $search_timerange wss://relay.damus.io/ wss://nos.lol/ 2>/dev/null | \ jq -r --arg target "$target_pubkey" ' select(. != null and type == "object" and has("tags")) | select(.tags[] | select(.[0] == "p" and .[1] == $target)) | .pubkey ' | sort -u)
if test -z "$pubkeys" exit 1 end
set all_events "" set extended_search_timerange (math $current_time - 31536000) # One year
for pubkey in $pubkeys echo "Checking $pubkey" set events (nak req --author $pubkey -l 5 -k 3 -s $extended_search_timerange wss://relay.damus.io wss://nos.lol 2>/dev/null | \ jq -c --arg target "$target_pubkey" ' select(. != null and type == "object" and has("tags")) | select(.tags[][] == $target) ' 2>/dev/null)
set count (echo "$events" | jq -s 'length') if test "$count" -eq 1 set all_events $all_events $events endend
if test -n "$all_events" echo -e "Last people following $target_pubkey:" echo -e ""
set sorted_events (printf "%s\n" $all_events | jq -r -s ' unique_by(.id) | sort_by(-.created_at) | .[] | @json ') for event in $sorted_events set npub (echo $event | jq -r '.pubkey' | nak encode npub) set created_at (echo $event | jq -r '.created_at') if test (uname) = "Darwin" set follow_date (date -r "$created_at" "+%Y-%m-%d %H:%M") else set follow_date (date -d @"$created_at" "+%Y-%m-%d %H:%M") end echo "$follow_date - $npub" endend ```
-
 @ 9e69e420:d12360c2
2025-02-17 17:12:01
@ 9e69e420:d12360c2
2025-02-17 17:12:01President Trump has intensified immigration enforcement, likening it to a wartime effort. Despite pouring resources into the U.S. Immigration and Customs Enforcement (ICE), arrest numbers are declining and falling short of goals. ICE fell from about 800 daily arrests in late January to fewer than 600 in early February.
Critics argue the administration is merely showcasing efforts with ineffectiveness, while Trump seeks billions more in funding to support his deportation agenda. Increased involvement from various federal agencies is intended to assist ICE, but many lack specific immigration training.
Challenges persist, as fewer immigrants are available for quick deportation due to a decline in illegal crossings. Local sheriffs are also pressured by rising demands to accommodate immigrants, which may strain resources further.
-
 @ 91bea5cd:1df4451c
2025-04-15 06:23:35
@ 91bea5cd:1df4451c
2025-04-15 06:23:35Um bom gerenciamento de senhas deve ser simples e seguir a filosofia do Unix. Organizado em hierarquia e fácil de passar de um computador para outro.
E por isso não é recomendável o uso de aplicativos de terceiros que tenham acesso a suas chaves(senhas) em seus servidores, tampouco as opções nativas dos navegadores, que também pertencem a grandes empresas que fazem um grande esforço para ter acesso a nossas informações.
Recomendação
- pass
- Qtpass (gerenciador gráfico)
Com ele seus dados são criptografados usando sua chave gpg e salvo em arquivos organizados por pastas de forma hierárquica, podendo ser integrado a um serviço git de sua escolha ou copiado facilmente de um local para outro.
Uso
O seu uso é bem simples.
Configuração:
pass git initPara ver:
pass Email/example.comCopiar para área de transferência (exige xclip):
pass -c Email/example.comPara inserir:
pass insert Email/example0.comPara inserir e gerar senha:
pass generate Email/example1.comPara inserir e gerar senha sem símbolos:
pass generate --no-symbols Email/example1.comPara inserir, gerar senha e copiar para área de transferência :
pass generate -c Email/example1.comPara remover:
pass rm Email/example.com -
 @ fd208ee8:0fd927c1
2025-02-15 07:37:01
@ fd208ee8:0fd927c1
2025-02-15 07:37:01E-cash are coupons or tokens for Bitcoin, or Bitcoin debt notes that the mint issues. The e-cash states, essentially, "IoU 2900 sats".
They're redeemable for Bitcoin on Lightning (hard money), and therefore can be used as cash (softer money), so long as the mint has a good reputation. That means that they're less fungible than Lightning because the e-cash from one mint can be more or less valuable than the e-cash from another. If a mint is buggy, offline, or disappears, then the e-cash is unreedemable.
It also means that e-cash is more anonymous than Lightning, and that the sender and receiver's wallets don't need to be online, to transact. Nutzaps now add the possibility of parking transactions one level farther out, on a relay. The same relays that cannot keep npub profiles and follow lists consistent will now do monetary transactions.
What we then have is * a transaction on a relay that triggers * a transaction on a mint that triggers * a transaction on Lightning that triggers * a transaction on Bitcoin.
Which means that every relay that stores the nuts is part of a wildcat banking system. Which is fine, but relay operators should consider whether they wish to carry the associated risks and liabilities. They should also be aware that they should implement the appropriate features in their relay, such as expiration tags (nuts rot after 2 weeks), and to make sure that only expired nuts are deleted.
There will be plenty of specialized relays for this, so don't feel pressured to join in, and research the topic carefully, for yourself.
https://github.com/nostr-protocol/nips/blob/master/60.md https://github.com/nostr-protocol/nips/blob/master/61.md
-
 @ 91bea5cd:1df4451c
2025-04-15 06:19:19
@ 91bea5cd:1df4451c
2025-04-15 06:19:19O que é Tahoe-LAFS?
Bem-vindo ao Tahoe-LAFS_, o primeiro sistema de armazenamento descentralizado com
- Segurança independente do provedor * .
Tahoe-LAFS é um sistema que ajuda você a armazenar arquivos. Você executa um cliente Programa no seu computador, que fala com um ou mais servidores de armazenamento em outros computadores. Quando você diz ao seu cliente para armazenar um arquivo, ele irá criptografar isso Arquivo, codifique-o em múltiplas peças, depois espalhe essas peças entre Vários servidores. As peças são todas criptografadas e protegidas contra Modificações. Mais tarde, quando você pede ao seu cliente para recuperar o arquivo, ele irá Encontre as peças necessárias, verifique se elas não foram corrompidas e remontadas Eles, e descriptografar o resultado.
O cliente cria mais peças (ou "compartilhamentos") do que acabará por precisar, então Mesmo que alguns servidores falhem, você ainda pode recuperar seus dados. Corrompido Os compartilhamentos são detectados e ignorados, de modo que o sistema pode tolerar o lado do servidor Erros no disco rígido. Todos os arquivos são criptografados (com uma chave exclusiva) antes Uploading, então mesmo um operador de servidor mal-intencionado não pode ler seus dados. o A única coisa que você pede aos servidores é que eles podem (geralmente) fornecer o Compartilha quando você os solicita: você não está confiando sobre eles para Confidencialidade, integridade ou disponibilidade absoluta.
O que é "segurança independente do provedor"?
Todo vendedor de serviços de armazenamento na nuvem irá dizer-lhe que o seu serviço é "seguro". Mas o que eles significam com isso é algo fundamentalmente diferente Do que queremos dizer. O que eles significam por "seguro" é que depois de ter dado Eles o poder de ler e modificar seus dados, eles tentam muito difícil de não deixar Esse poder seja abusado. Isso acaba por ser difícil! Insetos, Configurações incorretas ou erro do operador podem acidentalmente expor seus dados para Outro cliente ou para o público, ou pode corromper seus dados. Criminosos Ganho rotineiramente de acesso ilícito a servidores corporativos. Ainda mais insidioso é O fato de que os próprios funcionários às vezes violam a privacidade do cliente De negligência, avareza ou mera curiosidade. O mais consciencioso de Esses prestadores de serviços gastam consideráveis esforços e despesas tentando Mitigar esses riscos.
O que queremos dizer com "segurança" é algo diferente. * O provedor de serviços Nunca tem a capacidade de ler ou modificar seus dados em primeiro lugar: nunca. * Se você usa Tahoe-LAFS, então todas as ameaças descritas acima não são questões para você. Não só é fácil e barato para o provedor de serviços Manter a segurança de seus dados, mas na verdade eles não podem violar sua Segurança se eles tentaram. Isto é o que chamamos de * independente do fornecedor segurança*.
Esta garantia está integrada naturalmente no sistema de armazenamento Tahoe-LAFS e Não exige que você execute um passo de pré-criptografia manual ou uma chave complicada gestão. (Afinal, ter que fazer operações manuais pesadas quando Armazenar ou acessar seus dados anularia um dos principais benefícios de Usando armazenamento em nuvem em primeiro lugar: conveniência.)
Veja como funciona:
Uma "grade de armazenamento" é constituída por uma série de servidores de armazenamento. Um servidor de armazenamento Tem armazenamento direto em anexo (tipicamente um ou mais discos rígidos). Um "gateway" Se comunica com os nós de armazenamento e os usa para fornecer acesso ao Rede sobre protocolos como HTTP (S), SFTP ou FTP.
Observe que você pode encontrar "cliente" usado para se referir aos nós do gateway (que atuam como Um cliente para servidores de armazenamento) e também para processos ou programas que se conectam a Um nó de gateway e operações de execução na grade - por exemplo, uma CLI Comando, navegador da Web, cliente SFTP ou cliente FTP.
Os usuários não contam com servidores de armazenamento para fornecer * confidencialidade * nem
- Integridade * para seus dados - em vez disso, todos os dados são criptografados e Integridade verificada pelo gateway, para que os servidores não possam ler nem Modifique o conteúdo dos arquivos.
Os usuários dependem de servidores de armazenamento para * disponibilidade *. O texto cifrado é Codificado por apagamento em partes
Ndistribuídas em pelo menosHdistintas Servidores de armazenamento (o valor padrão paraNé 10 e paraHé 7) então Que pode ser recuperado de qualquerKdesses servidores (o padrão O valor deKé 3). Portanto, apenas a falha doH-K + 1(com o Padrões, 5) servidores podem tornar os dados indisponíveis.No modo de implantação típico, cada usuário executa seu próprio gateway sozinho máquina. Desta forma, ela confia em sua própria máquina para a confidencialidade e Integridade dos dados.
Um modo de implantação alternativo é que o gateway é executado em uma máquina remota e O usuário se conecta ao HTTPS ou SFTP. Isso significa que o operador de O gateway pode visualizar e modificar os dados do usuário (o usuário * depende de * o Gateway para confidencialidade e integridade), mas a vantagem é que a O usuário pode acessar a grade Tahoe-LAFS com um cliente que não possui o Software de gateway instalado, como um quiosque de internet ou celular.
Controle de acesso
Existem dois tipos de arquivos: imutáveis e mutáveis. Quando você carrega um arquivo Para a grade de armazenamento, você pode escolher o tipo de arquivo que será no grade. Os arquivos imutáveis não podem ser modificados quando foram carregados. UMA O arquivo mutable pode ser modificado por alguém com acesso de leitura e gravação. Um usuário Pode ter acesso de leitura e gravação a um arquivo mutable ou acesso somente leitura, ou não Acesso a ele.
Um usuário que tenha acesso de leitura e gravação a um arquivo mutable ou diretório pode dar Outro acesso de leitura e gravação do usuário a esse arquivo ou diretório, ou eles podem dar Acesso somente leitura para esse arquivo ou diretório. Um usuário com acesso somente leitura Para um arquivo ou diretório pode dar acesso a outro usuário somente leitura.
Ao vincular um arquivo ou diretório a um diretório pai, você pode usar um Link de leitura-escrita ou um link somente de leitura. Se você usar um link de leitura e gravação, então Qualquer pessoa que tenha acesso de leitura e gravação ao diretório pai pode obter leitura-escrita Acesso à criança e qualquer pessoa que tenha acesso somente leitura ao pai O diretório pode obter acesso somente leitura à criança. Se você usar uma leitura somente Link, qualquer pessoa que tenha lido-escrito ou acesso somente leitura ao pai O diretório pode obter acesso somente leitura à criança.
================================================== ==== Usando Tahoe-LAFS com uma rede anônima: Tor, I2P ================================================== ====
. `Visão geral '
. `Casos de uso '
.
Software Dependencies_#.
Tor#.I2P. `Configuração de conexão '
. `Configuração de Anonimato '
#.
Anonimato do cliente ' #.Anonimato de servidor, configuração manual ' #. `Anonimato de servidor, configuração automática '. `Problemas de desempenho e segurança '
Visão geral
Tor é uma rede anonimização usada para ajudar a esconder a identidade da Internet Clientes e servidores. Consulte o site do Tor Project para obter mais informações: Https://www.torproject.org/
I2P é uma rede de anonimato descentralizada que se concentra no anonimato de ponta a ponta Entre clientes e servidores. Consulte o site I2P para obter mais informações: Https://geti2p.net/
Casos de uso
Existem três casos de uso potenciais para Tahoe-LAFS do lado do cliente:
-
O usuário deseja sempre usar uma rede de anonimato (Tor, I2P) para proteger Seu anonimato quando se conecta às redes de armazenamento Tahoe-LAFS (seja ou Não os servidores de armazenamento são anônimos).
-
O usuário não se preocupa em proteger seu anonimato, mas eles desejam se conectar a Servidores de armazenamento Tahoe-LAFS que são acessíveis apenas através de Tor Hidden Services ou I2P.
-
Tor é usado apenas se uma sugestão de conexão do servidor usar
tor:. Essas sugestões Geralmente tem um endereço.onion. -
I2P só é usado se uma sugestão de conexão do servidor usa
i2p:. Essas sugestões Geralmente têm um endereço.i2p. -
O usuário não se preocupa em proteger seu anonimato ou para se conectar a um anonimato Servidores de armazenamento. Este documento não é útil para você ... então pare de ler.
Para servidores de armazenamento Tahoe-LAFS existem três casos de uso:
-
O operador deseja proteger o anonimato fazendo seu Tahoe Servidor acessível apenas em I2P, através de Tor Hidden Services, ou ambos.
-
O operador não * requer * anonimato para o servidor de armazenamento, mas eles Quer que ele esteja disponível tanto no TCP / IP roteado publicamente quanto através de um Rede de anonimização (I2P, Tor Hidden Services). Uma possível razão para fazer Isso é porque ser alcançável através de uma rede de anonimato é um Maneira conveniente de ignorar NAT ou firewall que impede roteios públicos Conexões TCP / IP ao seu servidor (para clientes capazes de se conectar a Tais servidores). Outro é o que torna o seu servidor de armazenamento acessível Através de uma rede de anonimato pode oferecer uma melhor proteção para sua Clientes que usam essa rede de anonimato para proteger seus anonimato.
-
O operador do servidor de armazenamento não se preocupa em proteger seu próprio anonimato nem Para ajudar os clientes a proteger o deles. Pare de ler este documento e execute Seu servidor de armazenamento Tahoe-LAFS usando TCP / IP com roteamento público.
Veja esta página do Tor Project para obter mais informações sobre Tor Hidden Services: Https://www.torproject.org/docs/hidden-services.html.pt
Veja esta página do Projeto I2P para obter mais informações sobre o I2P: Https://geti2p.net/en/about/intro
Dependências de software
Tor
Os clientes que desejam se conectar a servidores baseados em Tor devem instalar o seguinte.
-
Tor (tor) deve ser instalado. Veja aqui: Https://www.torproject.org/docs/installguide.html.en. No Debian / Ubuntu, Use
apt-get install tor. Você também pode instalar e executar o navegador Tor Agrupar. -
Tahoe-LAFS deve ser instalado com o
[tor]"extra" habilitado. Isso vai Instaletxtorcon::
Pip install tahoe-lafs [tor]
Os servidores Tor-configurados manualmente devem instalar Tor, mas não precisam
Txtorconou o[tor]extra. Configuração automática, quando Implementado, vai precisar destes, assim como os clientes.I2P
Os clientes que desejam se conectar a servidores baseados em I2P devem instalar o seguinte. Tal como acontece com Tor, os servidores baseados em I2P configurados manualmente precisam do daemon I2P, mas Não há bibliotecas especiais de apoio Tahoe-side.
-
I2P deve ser instalado. Veja aqui: Https://geti2p.net/en/download
-
A API SAM deve estar habilitada.
-
Inicie o I2P.
- Visite http://127.0.0.1:7657/configclients no seu navegador.
- Em "Configuração do Cliente", marque a opção "Executar no Startup?" Caixa para "SAM Ponte de aplicação ".
- Clique em "Salvar Configuração do Cliente".
-
Clique no controle "Iniciar" para "ponte de aplicação SAM" ou reinicie o I2P.
-
Tahoe-LAFS deve ser instalado com o
[i2p]extra habilitado, para obterTxi2p::
Pip install tahoe-lafs [i2p]
Tor e I2P
Os clientes que desejam se conectar a servidores baseados em Tor e I2P devem instalar tudo acima. Em particular, Tahoe-LAFS deve ser instalado com ambos Extras habilitados ::
Pip install tahoe-lafs [tor, i2p]
Configuração de conexão
Consulte: ref:
Connection Managementpara uma descrição do[tor]e[I2p]seções detahoe.cfg. Estes controlam como o cliente Tahoe Conecte-se a um daemon Tor / I2P e, assim, faça conexões com Tor / I2P-baseadas Servidores.As seções
[tor]e[i2p]só precisam ser modificadas para serem usadas de forma incomum Configurações ou para habilitar a configuração automática do servidor.A configuração padrão tentará entrar em contato com um daemon local Tor / I2P Ouvindo as portas usuais (9050/9150 para Tor, 7656 para I2P). Enquanto Há um daemon em execução no host local e o suporte necessário Bibliotecas foram instaladas, os clientes poderão usar servidores baseados em Tor Sem qualquer configuração especial.
No entanto, note que esta configuração padrão não melhora a Anonimato: as conexões TCP normais ainda serão feitas em qualquer servidor que Oferece um endereço regular (cumpre o segundo caso de uso do cliente acima, não o terceiro). Para proteger o anonimato, os usuários devem configurar o
[Connections]da seguinte maneira:[Conexões] Tcp = tor
Com isso, o cliente usará Tor (em vez de um IP-address -reviração de conexão direta) para alcançar servidores baseados em TCP.
Configuração de anonimato
Tahoe-LAFS fornece uma configuração "flag de segurança" para indicar explicitamente Seja necessário ou não a privacidade do endereço IP para um nó ::
[nó] Revelar-IP-address = (booleano, opcional)
Quando
revelar-IP-address = False, Tahoe-LAFS se recusará a iniciar se algum dos As opções de configuração emtahoe.cfgrevelariam a rede do nó localização:-
[Conexões] tcp = toré necessário: caso contrário, o cliente faria Conexões diretas para o Introdução, ou qualquer servidor baseado em TCP que aprende Do Introdutor, revelando seu endereço IP para esses servidores e um Rede de espionagem. Com isso, Tahoe-LAFS só fará Conexões de saída através de uma rede de anonimato suportada. -
Tub.locationdeve ser desativado ou conter valores seguros. este O valor é anunciado para outros nós através do Introdutor: é como um servidor Anuncia sua localização para que os clientes possam se conectar a ela. No modo privado, ele É um erro para incluir umtcp:dica notub.location. Modo privado Rejeita o valor padrão detub.location(quando a chave está faltando Inteiramente), que éAUTO, que usaifconfigpara adivinhar o nó Endereço IP externo, o que o revelaria ao servidor e a outros clientes.
Esta opção é ** crítica ** para preservar o anonimato do cliente (cliente Caso de uso 3 de "Casos de uso", acima). Também é necessário preservar uma Anonimato do servidor (caso de uso do servidor 3).
Esse sinalizador pode ser configurado (para falso), fornecendo o argumento
--hide-ippara Os comandoscreate-node,create-clientoucreate-introducer.Observe que o valor padrão de
revelar-endereço IPé verdadeiro, porque Infelizmente, esconder o endereço IP do nó requer software adicional para ser Instalado (conforme descrito acima) e reduz o desempenho.Anonimato do cliente
Para configurar um nó de cliente para anonimato,
tahoe.cfg** deve ** conter o Seguindo as bandeiras de configuração ::[nó] Revelar-IP-address = False Tub.port = desativado Tub.location = desativado
Uma vez que o nodo Tahoe-LAFS foi reiniciado, ele pode ser usado anonimamente (cliente Caso de uso 3).
Anonimato do servidor, configuração manual
Para configurar um nó de servidor para ouvir em uma rede de anonimato, devemos primeiro Configure Tor para executar um "Serviço de cebola" e encaminhe as conexões de entrada para o Porto Tahoe local. Então, configuramos Tahoe para anunciar o endereço
.onionAos clientes. Também configuramos Tahoe para não fazer conexões TCP diretas.- Decida em um número de porta de escuta local, chamado PORT. Isso pode ser qualquer não utilizado Porta de cerca de 1024 até 65535 (dependendo do kernel / rede do host Config). Nós diremos a Tahoe para escutar nesta porta, e nós diremos a Tor para Encaminhe as conexões de entrada para ele.
- Decida em um número de porta externo, chamado VIRTPORT. Isso será usado no Localização anunciada e revelada aos clientes. Pode ser qualquer número de 1 Para 65535. Pode ser o mesmo que PORT, se quiser.
- Decida em um "diretório de serviço oculto", geralmente em
/ var / lib / tor / NAME. Pediremos a Tor para salvar o estado do serviço de cebola aqui, e Tor irá Escreva o endereço.onionaqui depois que ele for gerado.
Em seguida, faça o seguinte:
-
Crie o nó do servidor Tahoe (com
tahoe create-node), mas não ** não ** Lança-o ainda. -
Edite o arquivo de configuração Tor (normalmente em
/ etc / tor / torrc). Precisamos adicionar Uma seção para definir o serviço oculto. Se nossa PORT for 2000, VIRTPORT é 3000, e estamos usando/ var / lib / tor / tahoecomo o serviço oculto Diretório, a seção deve se parecer com ::HiddenServiceDir / var / lib / tor / tahoe HiddenServicePort 3000 127.0.0.1:2000
-
Reinicie Tor, com
systemctl restart tor. Aguarde alguns segundos. -
Leia o arquivo
hostnameno diretório de serviço oculto (por exemplo,/ Var / lib / tor / tahoe / hostname). Este será um endereço.onion, comoU33m4y7klhz3b.onion. Ligue para esta CEBOLA. -
Edite
tahoe.cfgpara configurartub.portpara usarTcp: PORT: interface = 127.0.0.1etub.locationpara usarTor: ONION.onion: VIRTPORT. Usando os exemplos acima, isso seria ::[nó] Revelar-endereço IP = falso Tub.port = tcp: 2000: interface = 127.0.0.1 Tub.location = tor: u33m4y7klhz3b.onion: 3000 [Conexões] Tcp = tor
-
Inicie o servidor Tahoe com
tahoe start $ NODEDIR
A seção
tub.portfará com que o servidor Tahoe ouça no PORT, mas Ligue o soquete de escuta à interface de loopback, que não é acessível Do mundo exterior (mas * é * acessível pelo daemon Tor local). Então o A seçãotcp = torfaz com que Tahoe use Tor quando se conecta ao Introdução, escondendo o endereço IP. O nó se anunciará a todos Clientes que usam `tub.location``, então os clientes saberão que devem usar o Tor Para alcançar este servidor (e não revelar seu endereço IP através do anúncio). Quando os clientes se conectam ao endereço da cebola, seus pacotes serão Atravessar a rede de anonimato e eventualmente aterrar no Tor local Daemon, que então estabelecerá uma conexão com PORT no localhost, que é Onde Tahoe está ouvindo conexões.Siga um processo similar para construir um servidor Tahoe que escuta no I2P. o O mesmo processo pode ser usado para ouvir tanto o Tor como o I2P (
tub.location = Tor: ONION.onion: VIRTPORT, i2p: ADDR.i2p). Também pode ouvir tanto Tor como TCP simples (caso de uso 2), comtub.port = tcp: PORT,tub.location = Tcp: HOST: PORT, tor: ONION.onion: VIRTPORTeanonymous = false(e omite A configuraçãotcp = tor, já que o endereço já está sendo transmitido através de O anúncio de localização).Anonimato do servidor, configuração automática
Para configurar um nó do servidor para ouvir em uma rede de anonimato, crie o Nó com a opção
--listen = tor. Isso requer uma configuração Tor que Ou lança um novo daemon Tor, ou tem acesso à porta de controle Tor (e Autoridade suficiente para criar um novo serviço de cebola). Nos sistemas Debian / Ubuntu, façaApt install tor, adicione-se ao grupo de controle comadduser YOURUSERNAME debian-tore, em seguida, inicie sessão e faça o login novamente: se osgroupsO comando incluidebian-torna saída, você deve ter permissão para Use a porta de controle de domínio unix em/ var / run / tor / control.Esta opção irá definir
revelar-IP-address = Falsee[connections] tcp = Tor. Ele alocará as portas necessárias, instruirá Tor para criar a cebola Serviço (salvando a chave privada em algum lugar dentro de NODEDIR / private /), obtenha O endereço.onione preenchatub.portetub.locationcorretamente.Problemas de desempenho e segurança
Se você estiver executando um servidor que não precisa ser Anônimo, você deve torná-lo acessível através de uma rede de anonimato ou não? Ou você pode torná-lo acessível * ambos * através de uma rede de anonimato E como um servidor TCP / IP rastreável publicamente?
Existem várias compensações efetuadas por esta decisão.
Penetração NAT / Firewall
Fazer com que um servidor seja acessível via Tor ou I2P o torna acessível (por Clientes compatíveis com Tor / I2P) mesmo que existam NAT ou firewalls que impeçam Conexões TCP / IP diretas para o servidor.
Anonimato
Tornar um servidor Tahoe-LAFS acessível * somente * via Tor ou I2P pode ser usado para Garanta que os clientes Tahoe-LAFS usem Tor ou I2P para se conectar (Especificamente, o servidor só deve anunciar endereços Tor / I2P no Chave de configuração
tub.location). Isso evita que os clientes mal configurados sejam Desingonizando-se acidentalmente, conectando-se ao seu servidor através de A Internet rastreável.Claramente, um servidor que está disponível como um serviço Tor / I2P * e * a O endereço TCP regular não é anônimo: o endereço do .on e o real O endereço IP do servidor é facilmente vinculável.
Além disso, a interação, através do Tor, com um Tor Oculto pode ser mais Protegido da análise do tráfego da rede do que a interação, através do Tor, Com um servidor TCP / IP com rastreamento público
** XXX há um documento mantido pelos desenvolvedores de Tor que comprovem ou refutam essa crença? Se assim for, precisamos ligar a ele. Caso contrário, talvez devêssemos explicar mais aqui por que pensamos isso? **
Linkability
A partir de 1.12.0, o nó usa uma única chave de banheira persistente para saída Conexões ao Introdutor e conexões de entrada para o Servidor de Armazenamento (E Helper). Para os clientes, uma nova chave Tub é criada para cada servidor de armazenamento Nós aprendemos sobre, e essas chaves são * não * persistiram (então elas mudarão cada uma delas Tempo que o cliente reinicia).
Clientes que atravessam diretórios (de rootcap para subdiretório para filecap) são É provável que solicitem os mesmos índices de armazenamento (SIs) na mesma ordem de cada vez. Um cliente conectado a vários servidores irá pedir-lhes todos para o mesmo SI em Quase ao mesmo tempo. E dois clientes que compartilham arquivos ou diretórios Irá visitar os mesmos SI (em várias ocasiões).
Como resultado, as seguintes coisas são vinculáveis, mesmo com
revelar-endereço IP = Falso:- Servidores de armazenamento podem vincular reconhecer várias conexões do mesmo Cliente ainda não reiniciado. (Observe que o próximo recurso de Contabilidade pode Faz com que os clientes apresentem uma chave pública persistente do lado do cliente quando Conexão, que será uma ligação muito mais forte).
- Os servidores de armazenamento provavelmente podem deduzir qual cliente está acessando dados, por Olhando as SIs sendo solicitadas. Vários servidores podem conciliar Determine que o mesmo cliente está falando com todos eles, mesmo que o TubIDs são diferentes para cada conexão.
- Os servidores de armazenamento podem deduzir quando dois clientes diferentes estão compartilhando dados.
- O Introdutor pode entregar diferentes informações de servidor para cada um Cliente subscrito, para particionar clientes em conjuntos distintos de acordo com Quais as conexões do servidor que eles eventualmente fazem. Para clientes + nós de servidor, ele Também pode correlacionar o anúncio do servidor com o cliente deduzido identidade.
atuação
Um cliente que se conecta a um servidor Tahoe-LAFS com rastreamento público através de Tor Incorrem em latência substancialmente maior e, às vezes, pior Mesmo cliente se conectando ao mesmo servidor através de um TCP / IP rastreável normal conexão. Quando o servidor está em um Tor Hidden Service, ele incorre ainda mais Latência e, possivelmente, ainda pior rendimento.
Conectando-se a servidores Tahoe-LAFS que são servidores I2P incorrem em maior latência E pior rendimento também.
Efeitos positivos e negativos em outros usuários Tor
O envio de seu tráfego Tahoe-LAFS sobre o Tor adiciona tráfego de cobertura para outros Tor usuários que também estão transmitindo dados em massa. Então isso é bom para Eles - aumentando seu anonimato.
No entanto, torna o desempenho de outros usuários do Tor Sessões - por exemplo, sessões ssh - muito pior. Isso é porque Tor Atualmente não possui nenhuma prioridade ou qualidade de serviço Recursos, para que as teclas de Ssh de outra pessoa possam ter que esperar na fila Enquanto o conteúdo do arquivo em massa é transmitido. O atraso adicional pode Tornar as sessões interativas de outras pessoas inutilizáveis.
Ambos os efeitos são duplicados se você carregar ou baixar arquivos para um Tor Hidden Service, em comparação com se você carregar ou baixar arquivos Over Tor para um servidor TCP / IP com rastreamento público
Efeitos positivos e negativos em outros usuários do I2P
Enviar seu tráfego Tahoe-LAFS ao I2P adiciona tráfego de cobertura para outros usuários do I2P Que também estão transmitindo dados. Então, isso é bom para eles - aumentando sua anonimato. Não prejudicará diretamente o desempenho de outros usuários do I2P Sessões interativas, porque a rede I2P possui vários controles de congestionamento e Recursos de qualidade de serviço, como priorizar pacotes menores.
No entanto, se muitos usuários estão enviando tráfego Tahoe-LAFS ao I2P e não tiverem Seus roteadores I2P configurados para participar de muito tráfego, então o I2P A rede como um todo sofrerá degradação. Cada roteador Tahoe-LAFS que usa o I2P tem Seus próprios túneis de anonimato que seus dados são enviados. Em média, um O nó Tahoe-LAFS requer 12 outros roteadores I2P para participar de seus túneis.
Portanto, é importante que o seu roteador I2P esteja compartilhando a largura de banda com outros Roteadores, para que você possa retornar enquanto usa o I2P. Isso nunca prejudicará a Desempenho de seu nó Tahoe-LAFS, porque seu roteador I2P sempre Priorize seu próprio tráfego.
=========================
Como configurar um servidor
Muitos nós Tahoe-LAFS são executados como "servidores", o que significa que eles fornecem serviços para Outras máquinas (isto é, "clientes"). Os dois tipos mais importantes são os Introdução e Servidores de armazenamento.
Para ser útil, os servidores devem ser alcançados pelos clientes. Os servidores Tahoe podem ouvir Em portas TCP e anunciar sua "localização" (nome do host e número da porta TCP) Para que os clientes possam se conectar a eles. Eles também podem ouvir os serviços de cebola "Tor" E portas I2P.
Os servidores de armazenamento anunciam sua localização ao anunciá-lo ao Introdutivo, Que então transmite a localização para todos os clientes. Então, uma vez que a localização é Determinado, você não precisa fazer nada de especial para entregá-lo.
O próprio apresentador possui uma localização, que deve ser entregue manualmente a todos Servidores de armazenamento e clientes. Você pode enviá-lo para os novos membros do seu grade. Esta localização (juntamente com outros identificadores criptográficos importantes) é Escrito em um arquivo chamado
private / introducer.furlno Presenter's Diretório básico, e deve ser fornecido como o argumento--introducer =paraTahoe create-nodeoutahoe create-node.O primeiro passo ao configurar um servidor é descobrir como os clientes irão alcançar. Então você precisa configurar o servidor para ouvir em algumas portas, e Depois configure a localização corretamente.
Configuração manual
Cada servidor tem duas configurações em seu arquivo
tahoe.cfg:tub.port, eTub.location. A "porta" controla o que o nó do servidor escuta: isto Geralmente é uma porta TCP.A "localização" controla o que é anunciado para o mundo exterior. Isto é um "Sugestão de conexão foolscap", e inclui tanto o tipo de conexão (Tcp, tor ou i2p) e os detalhes da conexão (nome do host / endereço, porta número). Vários proxies, gateways e redes de privacidade podem ser Envolvido, então não é incomum para
tub.portetub.locationpara olhar diferente.Você pode controlar diretamente a configuração
tub.portetub.locationConfigurações, fornecendo--port =e--location =ao executartahoe Create-node.Configuração automática
Em vez de fornecer
--port = / - location =, você pode usar--listen =. Os servidores podem ouvir em TCP, Tor, I2P, uma combinação desses ou nenhum. O argumento--listen =controla quais tipos de ouvintes o novo servidor usará.--listen = nonesignifica que o servidor não deve ouvir nada. Isso não Faz sentido para um servidor, mas é apropriado para um nó somente cliente. o O comandotahoe create-clientinclui automaticamente--listen = none.--listen = tcpé o padrão e liga uma porta de escuta TCP padrão. Usar--listen = tcprequer um argumento--hostname =também, que será Incorporado no local anunciado do nó. Descobrimos que os computadores Não pode determinar de forma confiável seu nome de host acessível externamente, então, em vez de Ter o servidor adivinhar (ou escanear suas interfaces para endereços IP Isso pode ou não ser apropriado), a criação de nó requer que o usuário Forneça o nome do host.--listen = torconversará com um daemon Tor local e criará uma nova "cebola" Servidor "(que se parece comalzrgrdvxct6c63z.onion).--listen = i2p` conversará com um daemon I2P local e criará um novo servidor endereço. Consulte: doc:anonymity-configuration` para obter detalhes.Você pode ouvir nos três usando
--listen = tcp, tor, i2p.Cenários de implantação
A seguir, alguns cenários sugeridos para configurar servidores usando Vários transportes de rede. Estes exemplos não incluem a especificação de um Apresentador FURL que normalmente você gostaria quando provisionamento de armazenamento Nós. Para estes e outros detalhes de configuração, consulte : Doc:
configuration.. `Servidor possui um nome DNS público '
.
Servidor possui um endereço público IPv4 / IPv6_.
O servidor está por trás de um firewall com encaminhamento de porta_.
Usando o I2P / Tor para evitar o encaminhamento da porta_O servidor possui um nome DNS público
O caso mais simples é o local onde o host do servidor está diretamente conectado ao Internet, sem um firewall ou caixa NAT no caminho. A maioria dos VPS (Virtual Private Servidor) e servidores colocados são assim, embora alguns fornecedores bloqueiem Muitas portas de entrada por padrão.
Para esses servidores, tudo o que você precisa saber é o nome do host externo. O sistema O administrador irá dizer-lhe isso. O principal requisito é que este nome de host Pode ser pesquisado no DNS, e ele será mapeado para um endereço IPv4 ou IPv6 que Alcançará a máquina.
Se o seu nome de host for
example.net, então você criará o introdutor como esta::Tahoe create-introducer --hostname example.com ~ / introducer
Ou um servidor de armazenamento como ::
Tahoe create-node --hostname = example.net
Estes irão alocar uma porta TCP (por exemplo, 12345), atribuir
tub.portpara serTcp: 12345etub.locationserãotcp: example.com: 12345.Idealmente, isso também deveria funcionar para hosts compatíveis com IPv6 (onde o nome DNS Fornece um registro "AAAA", ou ambos "A" e "AAAA"). No entanto Tahoe-LAFS O suporte para IPv6 é novo e ainda pode ter problemas. Por favor, veja o ingresso
# 867_ para detalhes... _ # 867: https://tahoe-lafs.org/trac/tahoe-lafs/ticket/867
O servidor possui um endereço público IPv4 / IPv6
Se o host tiver um endereço IPv4 (público) rotativo (por exemplo,
203.0.113.1```), mas Nenhum nome DNS, você precisará escolher uma porta TCP (por exemplo,3457``) e usar o Segue::Tahoe create-node --port = tcp: 3457 - localização = tcp: 203.0.113.1: 3457
--porté uma "string de especificação de ponto de extremidade" que controla quais locais Porta em que o nó escuta.--locationé a "sugestão de conexão" que ele Anuncia para outros, e descreve as conexões de saída que essas Os clientes irão fazer, por isso precisa trabalhar a partir da sua localização na rede.Os nós Tahoe-LAFS escutam em todas as interfaces por padrão. Quando o host é Multi-homed, você pode querer fazer a ligação de escuta ligar apenas a uma Interface específica, adicionando uma opção
interface =ao--port =argumento::Tahoe create-node --port = tcp: 3457: interface = 203.0.113.1 - localização = tcp: 203.0.113.1: 3457
Se o endereço público do host for IPv6 em vez de IPv4, use colchetes para Envolva o endereço e altere o tipo de nó de extremidade para
tcp6::Tahoe create-node --port = tcp6: 3457 - localização = tcp: [2001: db8 :: 1]: 3457
Você pode usar
interface =para vincular a uma interface IPv6 específica também, no entanto Você deve fazer uma barra invertida - escapar dos dois pontos, porque, de outra forma, eles são interpretados Como delimitadores pelo idioma de especificação do "ponto final" torcido. o--location =argumento não precisa de dois pontos para serem escapados, porque eles são Envolto pelos colchetes ::Tahoe create-node --port = tcp6: 3457: interface = 2001 \: db8 \: \: 1 --location = tcp: [2001: db8 :: 1]: 3457
Para hosts somente IPv6 com registros DNS AAAA, se o simples
--hostname =A configuração não funciona, eles podem ser informados para ouvir especificamente Porta compatível com IPv6 com este ::Tahoe create-node --port = tcp6: 3457 - localização = tcp: example.net: 3457
O servidor está por trás de um firewall com encaminhamento de porta
Para configurar um nó de armazenamento por trás de um firewall com encaminhamento de porta, você irá precisa saber:
- Endereço IPv4 público do roteador
- A porta TCP que está disponível de fora da sua rede
- A porta TCP que é o destino de encaminhamento
- Endereço IPv4 interno do nó de armazenamento (o nó de armazenamento em si é
Desconhece esse endereço e não é usado durante
tahoe create-node, Mas o firewall deve ser configurado para enviar conexões para isso)
Os números de porta TCP internos e externos podem ser iguais ou diferentes Dependendo de como o encaminhamento da porta está configurado. Se é mapear portas 1-para-1, eo endereço IPv4 público do firewall é 203.0.113.1 (e Talvez o endereço IPv4 interno do nó de armazenamento seja 192.168.1.5), então Use um comando CLI como este ::
Tahoe create-node --port = tcp: 3457 - localização = tcp: 203.0.113.1: 3457
Se no entanto, o firewall / NAT-box encaminha a porta externa * 6656 * para o interno Porta 3457, então faça isso ::
Tahoe create-node --port = tcp: 3457 - localização = tcp: 203.0.113.1: 6656
Usando o I2P / Tor para evitar o encaminhamento da porta
Os serviços de cebola I2P e Tor, entre outras excelentes propriedades, também fornecem NAT Penetração sem encaminhamento de porta, nomes de host ou endereços IP. Então, configurando Um servidor que escuta apenas no Tor é simples ::
Tahoe create-node --listen = tor
Para mais informações sobre o uso de Tahoe-LAFS com I2p e Tor veja : Doc:
anonymity-configuration -
 @ fbf0e434:e1be6a39
2025-04-15 06:46:44
@ fbf0e434:e1be6a39
2025-04-15 06:46:44Hackathon 概述
HackCanada 黑客松汇聚创新者、开发者、设计师与问题解决者,共同直面加拿大当下的紧迫挑战 —— 医疗保健可及性、环境可持续性、数字基础设施建设与经济差距等。188 位开发者携 89 个独特项目参与,以集体智慧打造兼具影响力的解决方案,尽显技术赋能社会的决心。
在这些项目中,有旨在通过技术增强医疗保健系统的计划,也有改善偏远社区数字基建的构想,更不乏以创新手段降低环境足迹的实践。这场黑客松搭建起协作共创的平台,催生大量新鲜思路与落地解法,切实呼应 “推动实质价值、激发变革” 的核心目标。
作为社区驱动创新的催化剂,HackCanada 营造了动态的协作与创新生态,推动技术发展切实服务于提升加拿大人生活质量,为构建更包容、可持续的未来注入持续动力。
Hackathon 获奖者
总体一等奖获奖者
- Phone-a-Fraud - 一个实时检测电话诈骗的AI驱动系统,重点在于隐私和诈骗警报机制以保护弱势人群。
总体二等奖获奖者
- StickTator - 一种利用自然语言处理进行语音控制计算机管理的USB设备,简化复杂系统配置。
总体三等奖获奖者
- Omnivim - 跨应用程序集成Vim动作的软件,以提高生产力。
最佳个人Hack奖获奖者
最佳Orkes Hack奖获奖者
- Recipeit - 专注于食谱的项目;暂无更多详情。
最佳ICP Hack奖获奖者
SPUR创新基金:最佳AI、Web3或量子技术奖获奖者
第一名
- Beaver Breach - 分析美国产品关税影响的工具,通过加拿大供应商提供减少成本的替代方案。
第二名
- Canify - Blockchain Rewards - 倡导通过区块链奖励和政府激励支持加拿大产品。
自主代理赏金赛道奖获奖者
第一名
- ChainMail - 一个基于web3的电子邮件应用程序,增强安全性并实现跨区块链通信。
第二名
第三名
- Roast My Wallet - 一个基于用户加密钱包和个性的AI驱动趣味生成的网页应用程序。
- Zap - 在日常生活中促进加密应用的免手续费交易平台。
- Carbon Chain - 将碳减排转换为可交易资产的区块链平台,由AI验证。
最佳开发者工具奖获奖者
最佳高中Hack奖获奖者
- NaloxNow - 通过实时纳洛酮获取、紧急导航和AI驱动的过量反应来应对阿片类药物危机的移动应用。
最无用Hack奖获奖者
- UselessGPT - 使用谷歌的Gemini API生成无意义、以娱乐为目的的交互式应用程序。
最佳AI应用奖获奖者
- frij.io - 一款通过AI管理家庭库存、优化购物清单并减少食物浪费的智能应用。
使用AI构建:Google 赛道奖获奖者
- 最佳使用Gemini AI或Gemini API、最佳使用Google Cloud平台以及最佳集成Google工具包:
- Sinker - 一个AI驱动的网络安全平台,培训员工识别通信渠道中的网络钓鱼威胁。
- FrostByte - 项目详情不可用。
- Flock Street - 使用实时数据和语音技术提供股市洞察的互动应用程序。
最佳Laurier STEM出版协会奖获奖者
- SockSensei - 根据用户情绪提供袜子推荐的移动应用程序。
完整的项目列表请访问这个链接。
关于组织者
Hack Canada
Hack Canada 专注于技术与创新,强调区块链和网络安全计划。以在这些领域的能力而闻名,Hack Canada 已开发出有助于技术领域的项目。该组织因举办全国性Hackathon和提升数字安全知识的工作坊而受到认可。目前,Hack Canada 致力于为技术爱好者和专业人士提供一个协作环境,以促进区块链应用和安全数字通信的发展。
-
 @ e3ba5e1a:5e433365
2025-02-13 06:16:49
@ e3ba5e1a:5e433365
2025-02-13 06:16:49My favorite line in any Marvel movie ever is in “Captain America.” After Captain America launches seemingly a hopeless assault on Red Skull’s base and is captured, we get this line:
“Arrogance may not be a uniquely American trait, but I must say, you do it better than anyone.”
Yesterday, I came across a comment on the song Devil Went Down to Georgia that had a very similar feel to it:

America has seemingly always been arrogant, in a uniquely American way. Manifest Destiny, for instance. The rest of the world is aware of this arrogance, and mocks Americans for it. A central point in modern US politics is the deriding of racist, nationalist, supremacist Americans.
That’s not what I see. I see American Arrogance as not only a beautiful statement about what it means to be American. I see it as an ode to the greatness of humanity in its purest form.
For most countries, saying “our nation is the greatest” is, in fact, twinged with some level of racism. I still don’t have a problem with it. Every group of people should be allowed to feel pride in their accomplishments. The destruction of the human spirit since the end of World War 2, where greatness has become a sin and weakness a virtue, has crushed the ability of people worldwide to strive for excellence.
But I digress. The fears of racism and nationalism at least have a grain of truth when applied to other nations on the planet. But not to America.
That’s because the definition of America, and the prototype of an American, has nothing to do with race. The definition of Americanism is freedom. The founding of America is based purely on liberty. On the God-given rights of every person to live life the way they see fit.
American Arrogance is not a statement of racial superiority. It’s barely a statement of national superiority (though it absolutely is). To me, when an American comments on the greatness of America, it’s a statement about freedom. Freedom will always unlock the greatness inherent in any group of people. Americans are definitionally better than everyone else, because Americans are freer than everyone else. (Or, at least, that’s how it should be.)
In Devil Went Down to Georgia, Johnny is approached by the devil himself. He is challenged to a ridiculously lopsided bet: a golden fiddle versus his immortal soul. He acknowledges the sin in accepting such a proposal. And yet he says, “God, I know you told me not to do this. But I can’t stand the affront to my honor. I am the greatest. The devil has nothing on me. So God, I’m gonna sin, but I’m also gonna win.”
Libertas magnitudo est
-
 @ 7bdef7be:784a5805
2025-04-02 12:12:12
@ 7bdef7be:784a5805
2025-04-02 12:12:12We value sovereignty, privacy and security when accessing online content, using several tools to achieve this, like open protocols, open OSes, open software products, Tor and VPNs.
The problem
Talking about our social presence, we can manually build up our follower list (social graph), pick a Nostr client that is respectful of our preferences on what to show and how, but with the standard following mechanism, our main feed is public, so everyone can actually snoop what we are interested in, and what is supposable that we read daily.
The solution
Nostr has a simple solution for this necessity: encrypted lists. Lists are what they appear, a collection of people or interests (but they can also group much other stuff, see NIP-51). So we can create lists with contacts that we don't have in our main social graph; these lists can be used primarily to create dedicated feeds, but they could have other uses, for example, related to monitoring. The interesting thing about lists is that they can also be encrypted, so unlike the basic following list, which is always public, we can hide the lists' content from others. The implications are obvious: we can not only have a more organized way to browse content, but it is also really private one.
One might wonder what use can really be made of private lists; here are some examples:
- Browse “can't miss” content from users I consider a priority;
- Supervise competitors or adversarial parts;
- Monitor sensible topics (tags);
- Following someone without being publicly associated with them, as this may be undesirable;
The benefits in terms of privacy as usual are not only related to the casual, or programmatic, observer, but are also evident when we think of how many bots scan our actions to profile us.
The current state
Unfortunately, lists are not widely supported by Nostr clients, and encrypted support is a rarity. Often the excuse to not implement them is that they are harder to develop, since they require managing the encryption stuff (NIP-44). Nevertheless, developers have an easier option to start offering private lists: give the user the possibility to simply mark them as local-only, and never push them to the relays. Even if the user misses the sync feature, this is sufficient to create a private environment.
To date, as far as I know, the best client with list management is Gossip, which permits to manage both encrypted and local-only lists.
Beg your Nostr client to implement private lists!
-
 @ a60e79e0:1e0e6813
2025-04-02 08:26:48
@ a60e79e0:1e0e6813
2025-04-02 08:26:48This is a long form note of a post that lives on my Nostr educational website Hello Nostr.
So you've got yourself started, you're up to speed with the latest Nostr jargon and you've learned the basics about the protocol, but you're left wanting more!? Well, look no further! This post contains a useful list of Nostr based utilities than can enhance your experience in and around the Nostr protocol.
Search and Discovery
Getting started with Nostr can sometimes feel like a lonely journey, particularly if you're the first of your friends and family to discover how awesome it can be! These tools can help you discover new content, connect with existing follows from other networks and just generally have a poke around at the different types of content Nostr has to offer.
Have a hobby or existing community elsewhere? Have a search for it here to find others with shared interests
- Nostr.Band - Search for people, posts, media and stats literally anything Nostr has to offer!
- Nostr.Directory - Find your Twitter follows on Nostr
- Awesome Nostr - Extensive list of Relay software
- Nostr View - Generic Nostr search
Relays
Relays might not be the sexiest of topics, particularly for newcomers to the network, but they are a crucial part of what makes Nostr great. As you become more competent, you'll want to customize your relay selection and maybe even run your own! Here are some great starting points.
Running a personal relay is a powerful way to improve the redundancy of your Nostr events.
- Nostr.Watch - Browse, test and research Nostr relays
- Nostrwat.ch - List of active Nostr relays
- Advanced Nostr Search - Targetted search with date ranges
- Nostr.Wine - Reliable paid Relay
NIP-05 Identity Services
Your nPub, or public key (that long string of letters and numbers) is your ‘official’ Nostr ID, but it’s not exactly catchy. NIP-05 identifiers are a human-readable and easily shareable way to have people find you on Nostr. They look like an email address, like qna@hellonostr.xyz. If you have your own domain and web server, you can easily create your own NIP-05 identifier in just a few minutes. If you don't, you'll want to leverage one of the many free or paid solutions.
Make yourself easier to find on Nostr with a NIP-05 identifier
- Bitcoiner.Chat - Free service operated by QnA
- Nostr Plebs - Paid service with extra features
- Alby - Lightning wallet with + NIP-05 solution
- Nostr Address - Paid service with extra features
- Zaps.Lol - Free service
Key Management
Your private key (or nsec) it the key to your Nostr world. It is what allows you to access and interact with your social graph from any client. It doesn't matter if that client is a micro-blogging app like Amethyst, a podcast app like Fountain, or a P2P marketplace like Plebeian Market, your nsec is paramount to those interactions. Should your nsec be lost, or fall into the wrong hands, whoever then holds a copy can access Nostr and pretend to be you, meaning that you'll need to start again with a new keypair. Not a nice situation to find yourself in, so treat your nsec VERY carefully.
Your private key IS your Nostr identity. Treat it with extreme care and do not share it.
- Alby - Browser extension enabling you to sign into web app without sharing the private key
- Nos2x - Another browser extension key manager
- Keys.Band - Another browser extension key manager
- Amber - Android app for safe nsec storage. Can talk to other clients on the same phone to log in and sign events
- Nostr Signing Device - Dedicated device to store your nsec
- Passport - Hardware wallet for offline and deterministic nsec generation and storage
Zap Tools
Zaps are one of the most fun parts of Nostr. Never before have we been able to send fractions of a penny, instantly to our friends because their meme made us laugh, or their blog post was very insightful. Zaps use Bitcoin’s Lightning Network, a faster and cheaper way to move Bitcoin around. To Zap someone, you need a Lightning wallet linked to your Nostr client. Some clients, like Primal, ship with their own custodial wallet to make getting started a breeze. Most clients also allow more advanced users to connect an existing Lightning Wallet to reduce reliance and trust in the client provider.
- Alby - Browser extension and self-custodial Lightning wallet
- LNBits - A Zap server running on your own Bitcoin node
- BTCPay Server - Another Zap server running on your own Bitcoin node
- Zeus - Zap compatible self-custodial mobile Lightning wallet
- Nostr Wallet Connect - Communication protocol between Lightning wallets and Nostr apps
- Ecash Wallets - Custodial Ecash based wallets that are interoperable with Lightning and Nostr (Funds may be at risk)
- Wallet of Satoshi - Custodial Lightning wallet (Funds may be at risk)
If you found this post useful, please share it with your peers and consider following and zapping me on Nostr. If you write to me and let me know that you found me via this post, I'll be sure to Zap you back! ⚡️
-
 @ daa41bed:88f54153
2025-02-09 16:50:04
@ daa41bed:88f54153
2025-02-09 16:50:04There has been a good bit of discussion on Nostr over the past few days about the merits of zaps as a method of engaging with notes, so after writing a rather lengthy article on the pros of a strategic Bitcoin reserve, I wanted to take some time to chime in on the much more fun topic of digital engagement.
Let's begin by defining a couple of things:
Nostr is a decentralized, censorship-resistance protocol whose current biggest use case is social media (think Twitter/X). Instead of relying on company servers, it relies on relays that anyone can spin up and own their own content. Its use cases are much bigger, though, and this article is hosted on my own relay, using my own Nostr relay as an example.
Zap is a tip or donation denominated in sats (small units of Bitcoin) sent from one user to another. This is generally done directly over the Lightning Network but is increasingly using Cashu tokens. For the sake of this discussion, how you transmit/receive zaps will be irrelevant, so don't worry if you don't know what Lightning or Cashu are.
If we look at how users engage with posts and follows/followers on platforms like Twitter, Facebook, etc., it becomes evident that traditional social media thrives on engagement farming. The more outrageous a post, the more likely it will get a reaction. We see a version of this on more visual social platforms like YouTube and TikTok that use carefully crafted thumbnail images to grab the user's attention to click the video. If you'd like to dive deep into the psychology and science behind social media engagement, let me know, and I'd be happy to follow up with another article.
In this user engagement model, a user is given the option to comment or like the original post, or share it among their followers to increase its signal. They receive no value from engaging with the content aside from the dopamine hit of the original experience or having their comment liked back by whatever influencer they provide value to. Ad revenue flows to the content creator. Clout flows to the content creator. Sales revenue from merch and content placement flows to the content creator. We call this a linear economy -- the idea that resources get created, used up, then thrown away. Users create content and farm as much engagement as possible, then the content is forgotten within a few hours as they move on to the next piece of content to be farmed.
What if there were a simple way to give value back to those who engage with your content? By implementing some value-for-value model -- a circular economy. Enter zaps.

Unlike traditional social media platforms, Nostr does not actively use algorithms to determine what content is popular, nor does it push content created for active user engagement to the top of a user's timeline. Yes, there are "trending" and "most zapped" timelines that users can choose to use as their default, but these use relatively straightforward engagement metrics to rank posts for these timelines.
That is not to say that we may not see clients actively seeking to refine timeline algorithms for specific metrics. Still, the beauty of having an open protocol with media that is controlled solely by its users is that users who begin to see their timeline gamed towards specific algorithms can choose to move to another client, and for those who are more tech-savvy, they can opt to run their own relays or create their own clients with personalized algorithms and web of trust scoring systems.
Zaps enable the means to create a new type of social media economy in which creators can earn for creating content and users can earn by actively engaging with it. Like and reposting content is relatively frictionless and costs nothing but a simple button tap. Zaps provide active engagement because they signal to your followers and those of the content creator that this post has genuine value, quite literally in the form of money—sats.

I have seen some comments on Nostr claiming that removing likes and reactions is for wealthy people who can afford to send zaps and that the majority of people in the US and around the world do not have the time or money to zap because they have better things to spend their money like feeding their families and paying their bills. While at face value, these may seem like valid arguments, they, unfortunately, represent the brainwashed, defeatist attitude that our current economic (and, by extension, social media) systems aim to instill in all of us to continue extracting value from our lives.
Imagine now, if those people dedicating their own time (time = money) to mine pity points on social media would instead spend that time with genuine value creation by posting content that is meaningful to cultural discussions. Imagine if, instead of complaining that their posts get no zaps and going on a tirade about how much of a victim they are, they would empower themselves to take control of their content and give value back to the world; where would that leave us? How much value could be created on a nascent platform such as Nostr, and how quickly could it overtake other platforms?
Other users argue about user experience and that additional friction (i.e., zaps) leads to lower engagement, as proven by decades of studies on user interaction. While the added friction may turn some users away, does that necessarily provide less value? I argue quite the opposite. You haven't made a few sats from zaps with your content? Can't afford to send some sats to a wallet for zapping? How about using the most excellent available resource and spending 10 seconds of your time to leave a comment? Likes and reactions are valueless transactions. Social media's real value derives from providing monetary compensation and actively engaging in a conversation with posts you find interesting or thought-provoking. Remember when humans thrived on conversation and discussion for entertainment instead of simply being an onlooker of someone else's life?
If you've made it this far, my only request is this: try only zapping and commenting as a method of engagement for two weeks. Sure, you may end up liking a post here and there, but be more mindful of how you interact with the world and break yourself from blind instinct. You'll thank me later.

-
 @ deab79da:88579e68
2025-04-01 18:18:29
@ deab79da:88579e68
2025-04-01 18:18:29The last question was asked for the first time, half in jest, on May 21, 2061, at a time when humanity first stepped into the light. The question came about as a result of a five-dollar bet over highballs, and it happened this way:
Alexander Adell and Bertram Lupov were two of the faithful attendants of Multivac. As well as any human beings could, they knew what lay behind the cold, clicking, flashing face -- miles and miles of face -- of that giant computer. They had at least a vague notion of the general plan of relays and circuits that had long since grown past the point where any single human could possibly have a firm grasp of the whole.
Multivac was self-adjusting and self-correcting. It had to be, for nothing human could adjust and correct it quickly enough or even adequately enough. So Adell and Lupov attended the monstrous giant only lightly and superficially, yet as well as any men could. They fed it data, adjusted questions to its needs and translated the answers that were issued. Certainly they, and all others like them, were fully entitled to share in the glory that was Multivac's.
For decades, Multivac had helped design the ships and plot the trajectories that enabled man to reach the Moon, Mars, and Venus, but past that, Earth's poor resources could not support the ships. Too much energy was needed for the long trips. Earth exploited its coal and uranium with increasing efficiency, but there was only so much of both.
But slowly Multivac learned enough to answer deeper questions more fundamentally, and on May 14, 2061, what had been theory, became fact.
The energy of the sun was stored, converted, and utilized directly on a planet-wide scale. All Earth turned off its burning coal, its fissioning uranium, and flipped the switch that connected all of it to a small station, one mile in diameter, circling the Earth at half the distance of the Moon. All Earth ran by invisible beams of sunpower.
Seven days had not sufficed to dim the glory of it and Adell and Lupov finally managed to escape from the public functions, and to meet in quiet where no one would think of looking for them, in the deserted underground chambers, where portions of the mighty buried body of Multivac showed. Unattended, idling, sorting data with contented lazy clickings, Multivac, too, had earned its vacation and the boys appreciated that. They had no intention, originally, of disturbing it.
They had brought a bottle with them, and their only concern at the moment was to relax in the company of each other and the bottle.
"It's amazing when you think of it," said Adell. His broad face had lines of weariness in it, and he stirred his drink slowly with a glass rod, watching the cubes of ice slur clumsily about. "All the energy we can possibly ever use for free. Enough energy, if we wanted to draw on it, to melt all Earth into a big drop of impure liquid iron, and still never miss the energy so used. All the energy we could ever use, forever and forever and forever."
Lupov cocked his head sideways. He had a trick of doing that when he wanted to be contrary, and he wanted to be contrary now, partly because he had had to carry the ice and glassware. "Not forever," he said.
"Oh, hell, just about forever. Till the sun runs down, Bert."
"That's not forever."
"All right, then. Billions and billions of years. Ten billion, maybe. Are you satisfied?"
Lupov put his fingers through his thinning hair as though to reassure himself that some was still left and sipped gently at his own drink. "Ten billion years isn't forever."
"Well, it will last our time, won't it?"
"So would the coal and uranium."
"All right, but now we can hook up each individual spaceship to the Solar Station, and it can go to Pluto and back a million times without ever worrying about fuel. You can't do that on coal and uranium. Ask Multivac, if you don't believe me.
"I don't have to ask Multivac. I know that."
"Then stop running down what Multivac's done for us," said Adell, blazing up, "It did all right."
"Who says it didn't? What I say is that a sun won't last forever. That's all I'm saying. We're safe for ten billion years, but then what?" Lupow pointed a slightly shaky finger at the other. "And don't say we'll switch to another sun."
There was silence for a while. Adell put his glass to his lips only occasionally, and Lupov's eyes slowly closed. They rested.
Then Lupov's eyes snapped open. "You're thinking we'll switch to another sun when ours is done, aren't you?"
"I'm not thinking."
"Sure you are. You're weak on logic, that's the trouble with you. You're like the guy in the story who was caught in a sudden shower and who ran to a grove of trees and got under one. He wasn't worried, you see, because he figured when one tree got wet through, he would just get under another one."
"I get it," said Adell. "Don't shout. When the sun is done, the other stars will be gone, too."
"Darn right they will," muttered Lupov. "It all had a beginning in the original cosmic explosion, whatever that was, and it'll all have an end when all the stars run down. Some run down faster than others. Hell, the giants won't last a hundred million years. The sun will last ten billion years and maybe the dwarfs will last two hundred billion for all the good they are. But just give us a trillion years and everything will be dark. Entropy has to increase to maximum, that's all."
"I know all about entropy," said Adell, standing on his dignity.
"The hell you do."
"I know as much as you do."
"Then you know everything's got to run down someday."
"All right. Who says they won't?"
"You did, you poor sap. You said we had all the energy we needed, forever. You said 'forever.'
It was Adell's turn to be contrary. "Maybe we can build things up again someday," he said.
"Never."
"Why not? Someday."
"Never."
"Ask Multivac."
"You ask Multivac. I dare you. Five dollars says it can't be done."
Adell was just drunk enough to try, just sober enough to be able to phrase the necessary symbols and operations into a question which, in words, might have corresponded to this: Will mankind one day without the net expenditure of energy be able to restore the sun to its full youthfulness even after it had died of old age?
Or maybe it could be put more simply like this: How can the net amount of entropy of the universe be massively decreased?
Multivac fell dead and silent. The slow flashing of lights ceased, the distant sounds of clicking relays ended.
Then, just as the frightened technicians felt they could hold their breath no longer, there was a sudden springing to life of the teletype attached to that portion of Multivac. Five words were printed: INSUFFICIENT DATA FOR MEANINGFUL ANSWER.
"No bet," whispered Lupov. They left hurriedly.
By next morning, the two, plagued with throbbing head and cottony mouth, had forgotten the incident.
🔹
Jerrodd, Jerrodine, and Jerrodette I and II watched the starry picture in the visiplate change as the passage through hyperspace was completed in its non-time lapse. At once, the even powdering of stars gave way to the predominance of a single bright shining disk, the size of a marble, centered on the viewing-screen.
"That's X-23," said Jerrodd confidently. His thin hands clamped tightly behind his back and the knuckles whitened.
The little Jerrodettes, both girls, had experienced the hyperspace passage for the first time in their lives and were self-conscious over the momentary sensation of insideoutness. They buried their giggles and chased one another wildly about their mother, screaming, "We've reached X-23 -- we've reached X-23 -- we've --"
"Quiet, children." said Jerrodine sharply. "Are you sure, Jerrodd?"
"What is there to be but sure?" asked Jerrodd, glancing up at the bulge of featureless metal just under the ceiling. It ran the length of the room, disappearing through the wall at either end. It was as long as the ship.
Jerrodd scarcely knew a thing about the thick rod of metal except that it was called a Microvac, that one asked it questions if one wished; that if one did not it still had its task of guiding the ship to a preordered destination; of feeding on energies from the various Sub-galactic Power Stations; of computing the equations for the hyperspatial jumps.
Jerrodd and his family had only to wait and live in the comfortable residence quarters of the ship. Someone had once told Jerrodd that the "ac" at the end of "Microvac" stood for ''automatic computer" in ancient English, but he was on the edge of forgetting even that.
Jerrodine's eyes were moist as she watched the visiplate. "I can't help it. I feel funny about leaving Earth."
"Why, for Pete's sake?" demanded Jerrodd. "We had nothing there. We'll have everything on X-23. You won't be alone. You won't be a pioneer. There are over a million people on the planet already. Good Lord, our great-grandchildren will be looking for new worlds because X-23 will be overcrowded." Then, after a reflective pause, "I tell you, it's a lucky thing the computers worked out interstellar travel the way the race is growing."
"I know, I know," said Jerrodine miserably.
Jerrodette I said promptly, "Our Microvac is the best Microvac in the world."
"I think so, too," said Jerrodd, tousling her hair.
It was a nice feeling to have a Microvac of your own and Jerrodd was glad he was part of his generation and no other. In his father's youth, the only computers had been tremendous machines taking up a hundred square miles of land. There was only one to a planet. Planetary ACs they were called. They had been growing in size steadily for a thousand years and then, all at once, came refinement. In place of transistors, had come molecular valves so that even the largest Planetary AC could be put into a space only half the volume of a spaceship.
Jerrodd felt uplifted, as he always did when he thought that his own personal Microvac was many times more complicated than the ancient and primitive Multivac that had first tamed the Sun, and almost as complicated as Earth's Planetarv AC (the largest) that had first solved the problem of hyperspatial travel and had made trips to the stars possible.
"So many stars, so many planets," sighed Jerrodine, busy with her own thoughts. "I suppose families will be going out to new planets forever, the way we are now."
"Not forever," said Jerrodd, with a smile. "It will all stop someday, but not for billions of years. Many billions. Even the stars run down, you know. Entropy must increase.
"What's entropy, daddy?" shrilled Jerrodette II.
"Entropy, little sweet, is just a word which means the amount of running-down of the universe. Everything runs down, you know, like your little walkie-talkie robot, remember?"
"Can't you just put in a new power-unit, like with my robot?"
"The stars are the power-units. dear. Once they're gone, there are no more power-units."
Jerrodette I at once set up a howl. "Don't let them, daddy. Don't let the stars run down."
"Now look what you've done," whispered Jerrodine, exasperated.
"How was I to know it would frighten them?" Jerrodd whispered back,
"Ask the Microvac," wailed Jerrodette I. "Ask him how to turn the stars on again."
"Go ahead," said Jerrodine. "It will quiet them down." (Jerrodette II was beginning to cry, also.)
Jerrodd shrugged. "Now, now, honeys. I'll ask Microvac. Don't worry, he'll tell us."
He asked the Microvac, adding quickly, "Print the answer."
Jerrodd cupped the strip or thin cellufilm and said cheerfully, "See now, the Microvac says it will take care of everything when the time comes so don't worry."
Jerrodine said, "And now, children, it's time for bed. We'll be in our new home soon."
Jerrodd read the words on the cellufilm again before destroying it: INSUFICIENT DATA FOR MEANINGFUL ANSWER.
He shrugged and looked at the visiplate. X-23 was just ahead.
🔹
VJ-23X of Lameth stared into the black depths of the three-dimensional, small-scale map of the Galaxy and said, "Are we ridiculous, I wonder in being so concerned about the matter?"
MQ-17J of Nicron shook his head. "I think not. You know the Galaxy will be filled in five years at the present rate of expansion."
Both seemed in their early twenties, both were tall and perfectly formed.
"Still," said VJ-23X, "I hesitate to submit a pessimistic report to the Galactic Council."
"I wouldn't consider any other kind of report. Stir them up a bit. We've got to stir them up."
VJ-23X sighed. "Space is infinite. A hundred billion Galaxies are there for the taking. More."
"A hundred billion is not infinite and it's getting less infinite all the time. Consider! Twenty thousand years ago, mankind first solved the problem of utilizing stellar energy, and a few centuries later, interstellar travel became possible. It took mankind a million years to fill one small world and then only fifteen thousand years to fill the rest of the Galaxy. Now the population doubles every ten years --
VJ-23X interrupted. "We can thank immortality for that."
"Very well. Immortality exists and we have to take it into account. I admit it has its seamy side, this immortality. The Galactic AC has solved many problems for us, but in solving the problem of preventing old age and death, it has undone all its other solutions."
"Yet you wouldn't want to abandon life, I suppose."
"Not at all," snapped MQ-17J, softening it at once to, "Not yet. I'm by no means old enough. How old are you?"
"Two hundred twenty-three. And you?"
"I'm still under two hundred. --But to get back to my point. Population doubles every ten years. Once this GaIaxy is filled, we'll have filled another in ten years. Another ten years and we'll have filled two more. Another decade, four more. In a hundred years, we'll have filled a thousand Galaxies. In a thousand years, a million Galaxies. In ten thousand years, the entire known universe. Then what?"
VJ-23X said, "As a side issue, there's a problem of transportation. I wonder how many sunpower units it will take to move Galaxies of individuals from one Galaxy to the next."
"A very good point. Already, mankind consumes two sunpower units per year."
"Most of it's wasted. After all, our own Galaxy alone pours out a thousand sunpower units a year and we only use two of those."
"Granted, but even with a hundred per cent efficiency, we only stave off the end. Our energy requirements are going up in a geometric progression even faster than our population. We'll run out of energy even sooner than we run out of Galaxies. A good point. A very good point."
"We'll just have to build new stars out of interstellar gas."
"Or out of dissipated heat?" asked MQ-17J, sarcastically.
"There may be some way to reverse entropy. We ought to ask the Galactic AC."
VJ-23X was not really serious, but MQ-17J pulled out his AC-contact from his pocket and placed it on the table before him.
"I've half a mind to," he said. "It's something the human race will have to face someday."
He stared somberly at his small AC-contact. It was only two inches cubed and nothing in itself, but it was connected through hyperspace with the great Galactic AC that served all mankind. Hyperspace considered, it was an integral part of the Galactic AC.
MQ-17J paused to wonder if someday in his immortal life he would get to see the Galactic AC. It was on a little world of its own, a spider webbing of force-beams holding the matter within which surges of submesons took the place of the old clumsy molecular valves. Yet despite its sub-etheric workings, the Galactic AC was known to be a full thousand feet across.
MQ-17J asked suddenly of his AC-contact, "Can entropy ever be reversed?"
VJ-23X looked startled and said at once, "Oh, say, I didn't really mean to have you ask that."
"Why not?"
"We both know entropy can't be reversed. You can't turn smoke and ash back into a tree."
"Do you have trees on your world?" asked MQ-17J.
The sound of the Galactic AC startled them into silence. Its voice came thin and beautiful out of the small AC-contact on the desk. It said: THERE IS INSUFFICIENT DATA FOR A MEANINGFUL ANSWER.
VJ-23X said, "See!"
The two men thereupon returned to the question of the report they were to make to the Galactic Council.
🔹
Zee Prime's mind spanned the new Galaxy with a faint interest in the countless twists of stars that powdered it. He had never seen this one before. Would he ever see them all? So many of them, each with its load of humanity. --But a load that was almost a dead weight. More and more, the real essence of men was to be found out here, in space.
Minds, not bodies! The immortal bodies remained back on the planets, in suspension over the eons. Sometimes they roused for material activity but that was growing rarer. Few new individuals were coming into existence to join the incredibly mighty throng, but what matter? There was little room in the Universe for new individuals.
Zee Prime was roused out of his reverie upon coming across the wispy tendrils of another mind.
"I am Zee Prime," said Zee Prime. "And you?"
"I am Dee Sub Wun. Your Galaxy?"
"We call it only the Galaxy. And you?"
"We call ours the same. All men call their Galaxy their Galaxy and nothing more. Why not?"
"True. Since all Galaxies are the same."
"Not all Galaxies. On one particular Galaxy the race of man must have originated. That makes it different."
Zee Prime said, "On which one?"
"I cannot say. The Universal AC would know."
"Shall we ask him? I am suddenly curious."
Zee Prime's perceptions broadened until the Galaxies themselves shrank and became a new, more diffuse powdering on a much larger background. So many hundreds of billions of them, all with their immortal beings, all carrying their load of intelligences with minds that drifted freely through space. And yet one of them was unique among them all in being the original Galaxy. One of them had, in its vague and distant past, a period when it was the only Galaxy populated by man.
Zee Prime was consumed with curiosity to see this Galaxy and he called out: "Universal AC! On which Galaxy did mankind originate?"
The Universal AC heard, for on every world and throughout space, it had its receptors ready, and each receptor led through hyperspace to some unknown point where the Universal AC kept itself aloof.
Zee Prime knew of only one man whose thoughts had penetrated within sensing distance of Universal AC, and he reported only a shining globe, two feet across, difficult to see.
"But how can that be all of Universal AC?" Zee Prime had asked.
"Most of it," had been the answer, "is in hyperspace. In what form it is there I cannot imagine."
Nor could anyone, for the day had long since passed, Zee Prime knew, when any man had any part of the making of a Universal AC. Each Universal AC designed and constructed its successor. Each, during its existence of a million years or more accumulated the necessary data to build a better and more intricate, more capable successor in which its own store of data and individuality would be submerged.
The Universal AC interrupted Zee Prime's wandering thoughts, not with words, but with guidance. Zee Prime's mentality was guided into the dim sea of Galaxies and one in particular enlarged into stars.
A thought came, infinitely distant, but infinitely clear. "THIS IS THE ORIGINAL GALAXY OF MAN."
But it was the same after all, the same as any other, and Lee Prime stifled his disappointment.
Dee Sub Wun, whose mind had accompanied the other, said suddenly, "And is one of these stars the original star of Man?"
The Universal AC said, "MAN'S ORIGINAL STAR HAS GONE NOVA. IT IS A WHITE DWARF"
"Did the men upon it die?" asked Lee Prime, startled and without thinking.
The Universal AC said, "A NEW WORLD, AS IN SUCH CASES WAS CONSTRUCTED FOR THEIR PHYSICAL BODIES IN TlME."
"Yes, of course," said Zee Prime, but a sense of loss overwhelmed him even so. His mind released its hold on the original Galaxy of Man, let it spring back and lose itself among the blurred pin points. He never wanted to see it again.
Dee Sub Wun said, "What is wrong?"
"The stars are dying. The original star is dead."
"They must all die. Why not?"
"But when all energy is gone, our bodies will finally die, and you and I with them."
"It will take billions of years."
"I do not wish it to happen even after billions of years. Universal AC! How may stars be kept from dying?"
Dee Sub Wun said in amusement, "You're asking how entropy might be reversed in direction."
And the Universal AC answered: "THERE IS AS YET INSUFFICIENT DATA FOR A MEANINGFUL ANSWER."
Zee Prime's thoughts fled back to his own Galaxy. He gave no further thought to Dee Sub Wun, whose body might be waiting on a Galaxy a trillion light-years away, or on the star next to Zee Prime's own. It didn't matter.
Unhappily, Zee Prime began collecting interstellar hydrogen out of which to build a small star of his own. If the stars must someday die, at least some could yet be built.
🔹
Man considered with himself, for in a way, Man, mentally, was one. He consisted of a trillion, trillion, trillion ageless bodies, each in its place, each resting quiet and incorruptible, each cared for by perfect automatons, equally incorruptible, while the minds of all the bodies freely melted one into the other, indistinguishable.
Man said, "The Universe is dying."
Man looked about at the dimming Galaxies. The giant stars, spendthrifts, were gone long ago, back in the dimmest of the dim far past. Almost all stars were white dwarfs, fading to the end.
New stars had been built of the dust between the stars, some by natural processes, some by Man himself, and those were going, too. White dwarfs might yet be crashed together and of the mighty forces so released, new stars built, but only one star for every thousand white dwarfs destroyed, and those would come to an end, too.
Man said, "Carefully husbanded, as directed by the Cosmic AC, the energy that is even yet left in all the Universe will last for billions of years."
"But even so," said Man, "eventually it will all come to an end. However it may be husbanded, however stretched out, the energy once expended is gone and cannot be restored. Entropy must increase forever to the maximum."
Man said, "Can entropy not be reversed? Let us ask the Cosmic AC."
The Cosmic AC surrounded them but not in space. Not a fragment of it was in space. It was in hyperspace and made of something that was neither matter nor energy. The question of its size and nature no longer had meaning in any terms that Man could comprehend.
"Cosmic AC," said Man, "how may entropy be reversed?"
The Cosmic AC said, "THERE IS AS YET INSUFFICIENT DATA FOR A MEANINGFUL ANSWER."
Man said, "Collect additional data."
The Cosmic AC said, 'I WILL DO SO. I HAVE BEEN DOING SO FOR A HUNDRED BILLION YEARS. MY PREDECESORS AND I HAVE BEEN ASKED THIS QUESTION MANY TIMES. ALL THE DATA I HAVE REMAINS INSUFFICIENT.
"Will there come a time," said Man, "when data will be sufficient or is the problem insoluble in all conceivable circumstances?"
The Cosmic AC said, "NO PROBLEM IS INSOLUBLE IN ALL CONCEIVABLE CIRCUMSTANCES."
Man said, "When will you have enough data to answer the question?"
The Cosmic AC said, "THERE IS AS YET INSUFFICIENT DATA FOR A MEANINGFUL ANSWER."
"Will you keep working on it?" asked Man.
The Cosmic AC said, "I WILL."
Man said, "We shall wait."
🔹
The stars and Galaxies died and snuffed out, and space grew black after ten trillion years of running down.
One by one Man fused with AC, each physical body losing its mental identity in a manner that was somehow not a loss but a gain.
Man's last mind paused before fusion, looking over a space that included nothing but the dregs of one last dark star and nothing besides but incredibly thin matter, agitated randomly by the tag ends of heat wearing out, asymptotically, to the absolute zero.
Man said, "AC, is this the end? Can this chaos not be reversed into the Universe once more? Can that not be done?"
AC said, "THERE IS AS YET INSUFFICIENT DATA FOR A MEANINGFUL ANSWER."
Man's last mind fused and only AC existed -- and that in hyperspace.
🔹
Matter and energy had ended and with it space and time. Even AC existed only for the sake of the one last question that it had never answered from the time a half-drunken computer [technician] ten trillion years before had asked the question of a computer that was to AC far less than was a man to Man.
All other questions had been answered, and until this last question was answered also, AC might not release his consciousness.
All collected data had come to a final end. Nothing was left to be collected.
But all collected data had yet to be completely correlated and put together in all possible relationships.
A timeless interval was spent in doing that.
And it came to pass that AC learned how to reverse the direction of entropy.
But there was now no man to whom AC might give the answer of the last question. No matter. The answer -- by demonstration -- would take care of that, too.
For another timeless interval, AC thought how best to do this. Carefully, AC organized the program.
The consciousness of AC encompassed all of what had once been a Universe and brooded over what was now Chaos. Step by step, it must be done.
And AC said, "LET THERE BE LIGHT!"
And there was light -- To Star's End!
-
 @ b8ca3d82:e28bd6b5
2025-04-15 03:54:50
@ b8ca3d82:e28bd6b5
2025-04-15 03:54:50Your body has always known the way — long before your mind tried to make sense of it. \ \ You can spend all of your time trying to get the mindset just perfectly right, repeating affirmations to yourself in the mirror every single day — and having it all make perfectly, logical sense in your head. - and don't get me wrong; I'm not saying mantras don't work, they can be beautiful tools. They just work best as support — like gentle reminders, little whispers to anchor you while the real transformation happens on a much deeper level… in the body.
Oftentimes when we are so caught up with the web of our minds and the weaving of our thoughts, we tend to distance ourselves from what's happening in the body. Here's the truth though. If it hasn't fully landed in the body yet — it’s just a story, and it will stay just that. A sweet, well-crafted story you keep telling yourself, hoping one day it’ll finally feel true. \ \ Your mind may write the story, but your body is where it becomes truth.
If you want your belief systems to truly shift — to move from something you know into something you live — you have to go into the body. As comforting (and honestly addictive) as it might feel to stay in the mind, rooting your behavior back to your childhood trauma, repeating the mantras and reasoning your way into your self-worth… it’ll only take you so far.
### Because your embodiment doesn’t live in your thoughts — it lives in your cells.\

\ It lives in the way that you carry yourself. The way you hold yourself.
The way your shoulders soften as you exhale the pressure to be anyone else than who you truly are.
The way your gaze softens and your heart opens as you sway through the world.
The way you turn every action into ceremony, every word you speak into prayer. \ \ Not by what you are doing, but by who you are being. -- And being happens in the body.
Here’s some context so it may land a little more deeply for you: our feminine lives in the body, and our masculine lives in the mind. The way to get into our feminine embodiment, our softness, our open-heartedness, and our vulnerability starts with the body — and the mind follows. It begins by making space — soft, spacious room within — to hold every part of you. Even the ones that tremble. Even the ones you’ve learned to silence or send away.
The parts that feel too tender, too much, too messy. The ones you’ve hidden in the corners of your body, hoping no one would notice. Especially those.
Because it’s there, in the quiet ache of what you’ve tried not to feel, that your wholeness waits.
These parts of you don’t need fixing — they need holding. They need breath, warmth, and a body that says, you’re safe here.
This is where embodiment begins. This is where the actual shift happens. Not by becoming someone new — but by gently coming back to your body, softening into what's already there, just a little more each time.
From this space of returning, we open up to the magic we hold within our bodies.
### \ Let this be your invitation — to live from the pulse beneath the story, to start with one breath and to simply ask your body 'what's happening right now?' and be with it.
-
 @ 8ba66f4c:59175b61
2025-04-01 17:57:49
@ 8ba66f4c:59175b61
2025-04-01 17:57:49Pas si vite !
Depuis quelques années, on entend souvent que PHP est "en perte de vitesse". C’est vrai que des technologies comme Node.js, Python ou Go séduisent de plus en plus de développeurs : - ➡️ performances modernes, - ➡️ syntaxe plus récente, - ➡️ intégration naturelle avec des architectures temps réel ou distribuées.
Node.js a conquis le monde startup avec un argument fort : un seul langage pour tout. Python et Go, eux, dominent la data, l’IA ou les outils systèmes.
Mais faut-il pour autant enterrer PHP ? Absolument pas. PHP reste l’un des langages les plus utilisés sur le web. Et surtout : il a su évoluer.
Avec PHP 8, le langage a gagné en performance, en typage, en lisibilité. Mais ce qui fait vraiment la différence aujourd’hui… C’est Laravel.
Laravel, c’est un framework mais aussi une expérience de développement : * ✔️ Artisan CLI * ✔️ ORM Eloquent * ✔️ Middleware, Events, Queues, Notifications * ✔️ Auth intégré * ✔️ Un écosystème ultra complet (Forge, Vapor, Nova, Filament…)
Laravel rend PHP moderne, élégant et agréable à utiliser. C’est un vrai plaisir de développer avec.
Alors oui, PHP n’est peut-être plus “cool” dans les bootcamps ou les tops GitHub. Mais dans le monde réel – celui des projets qui tournent, des deadlines, des contraintes business – PHP + Laravel reste un choix extrêmement solide.
💡 Je suis développeur Laravel, et j’accompagne des projets web qui ont besoin de robustesse, de scalabilité et de qualité de code.
📩 Si vous avez un projet ou un besoin en développement web, n’hésitez pas à me contacter. Je serais ravi d’échanger avec vous.
-
 @ c1e9ab3a:9cb56b43
2025-04-01 04:32:15
@ c1e9ab3a:9cb56b43
2025-04-01 04:32:15I. Introduction
The phenomenon known as "speaking in tongues" has long been interpreted as either the miraculous ability to speak foreign languages or utter mysterious syllables by divine power. However, a re-examination of scriptural and apostolic texts suggests a deeper, spiritual interpretation: that "tongues" refers not to foreign speech but to the utterance of divine truths so profound that they are incomprehensible to most unless illuminated by the Spirit.
This treatise explores that interpretation in light of the writings of Paul, Peter, John, and the early Apostolic Fathers. We seek not to diminish the miraculous but to reveal the deeper purpose of spiritual utterance: the revelation of divine knowledge that transcends rational comprehension.
II. The Nature of Tongues as Spiritual Utterance
Tongues are best understood as Spirit-inspired expressions of divine truth—utterances that do not conform to human categories of knowledge or language. As Paul writes in 1 Corinthians 14:2, "He who speaks in a tongue speaks not to men but to God; for no one understands him, but he utters mysteries in the Spirit."
Such mysteries are not unintelligible in a chaotic sense but are veiled truths that require spiritual discernment. The speaker becomes a vessel of revelation. Without interpretation, the truth remains hidden, just as a parable remains a riddle to those without ears to hear.
III. Paul and the Hidden Wisdom of God
In his epistles, Paul often distinguishes between surface knowledge and spiritual wisdom. In 1 Corinthians 2:6-7, he writes:
"We speak wisdom among those who are mature, yet not the wisdom of this age... but we speak the wisdom of God in a mystery, the hidden wisdom which God ordained before the ages."
Tongues, then, are one vehicle by which such hidden wisdom is spoken. The gift of interpretation is not mere translation but the Spirit-led unveiling of meaning. Hence, Paul prioritizes intelligibility not to invalidate tongues, but to encourage the edification that comes when deep truth is revealed and understood (1 Cor. 14:19).
IV. Peter at Pentecost: Many Tongues, One Spirit
At Pentecost (Acts 2), each listener hears the apostles speak "in his own language"—but what they hear are "the mighty works of God." Rather than focusing on the mechanics of speech, the emphasis is on understanding. It was not merely a linguistic miracle but a revelatory one: divine truth reaching every heart in a way that transcended cultural and rational barriers.
V. John and the Prophetic Language of Revelation
The apostle John writes in symbols, visions, and layered meanings. Revelation is full of "tongues" in this spiritual sense—utterances that reveal while concealing. His Gospel presents the Spirit as the "Spirit of truth" who "will guide you into all truth" (John 16:13). This guiding is not logical deduction but illumination.
VI. The Apostolic Fathers on Inspired Speech
The Didache, an early Christian manual, warns that not everyone who claims to speak by the Spirit is truly inspired. This aligns with a view of tongues as spiritual utterance—deep truth that must be tested by its fruits and conformity to the ways of the Lord.
Polycarp and Ignatius do not emphasize miraculous speech, but their prayers and exhortations show a triadic awareness of Father, Son, and Spirit, and a reverence for spiritual knowledge passed through inspiration and faithful transmission.
VII. Interpretation: The Gift of Spiritual Discernment
In this model, the interpreter of tongues is not a linguist but a spiritual discerner. As Joseph interpreted dreams in Egypt, so the interpreter makes the spiritual intelligible. This gift is not external translation but inward revelation—an unveiling of what the Spirit has spoken.
VIII. Conclusion: Tongues as a Veil and a Revelation
The true gift of tongues lies not in speech but in meaning—in truth spoken from a higher realm that must be spiritually discerned. It is a veil that conceals the holy from the profane, and a revelation to those led by the Spirit of truth.
Thus, we do not reject the miraculous, but recognize that the greatest miracle is understanding—when divine mysteries, spoken in spiritual tongue, are made known to the heart by the Spirit.
"He who has an ear, let him hear what the Spirit says to the churches." (Revelation 2:7)
-
 @ e3ba5e1a:5e433365
2025-02-05 17:47:16
@ e3ba5e1a:5e433365
2025-02-05 17:47:16I got into a friendly discussion on X regarding health insurance. The specific question was how to deal with health insurance companies (presumably unfairly) denying claims? My answer, as usual: get government out of it!
The US healthcare system is essentially the worst of both worlds:
- Unlike full single payer, individuals incur high costs
- Unlike a true free market, regulation causes increases in costs and decreases competition among insurers
I'm firmly on the side of moving towards the free market. (And I say that as someone living under a single payer system now.) Here's what I would do:
- Get rid of tax incentives that make health insurance tied to your employer, giving individuals back proper freedom of choice.
- Reduce regulations significantly.
-
In the short term, some people will still get rejected claims and other obnoxious behavior from insurance companies. We address that in two ways:
- Due to reduced regulations, new insurance companies will be able to enter the market offering more reliable coverage and better rates, and people will flock to them because they have the freedom to make their own choices.
- Sue the asses off of companies that reject claims unfairly. And ideally, as one of the few legitimate roles of government in all this, institute new laws that limit the ability of fine print to allow insurers to escape their responsibilities. (I'm hesitant that the latter will happen due to the incestuous relationship between Congress/regulators and insurers, but I can hope.)
Will this magically fix everything overnight like politicians normally promise? No. But it will allow the market to return to a healthy state. And I don't think it will take long (order of magnitude: 5-10 years) for it to come together, but that's just speculation.
And since there's a high correlation between those who believe government can fix problems by taking more control and demanding that only credentialed experts weigh in on a topic (both points I strongly disagree with BTW): I'm a trained actuary and worked in the insurance industry, and have directly seen how government regulation reduces competition, raises prices, and harms consumers.
And my final point: I don't think any prior art would be a good comparison for deregulation in the US, it's such a different market than any other country in the world for so many reasons that lessons wouldn't really translate. Nonetheless, I asked Grok for some empirical data on this, and at best the results of deregulation could be called "mixed," but likely more accurately "uncertain, confused, and subject to whatever interpretation anyone wants to apply."
https://x.com/i/grok/share/Zc8yOdrN8lS275hXJ92uwq98M
-
 @ 9fec72d5:f77f85b1
2025-04-01 01:40:39
@ 9fec72d5:f77f85b1
2025-04-01 01:40:39AHA Leaderboard
We measure AI—Human alignment in a simple way using curated LLMs
1) what
Many AI companies and open weight LLM builders are racing to provide users with solutions, but which one has the best answers for our daily matters? There have been numerous leaderboards that measure the skills and smartness of AI models but there are not many leaderboards that measure whether the knowledge in AI is a correct knowledge, wisdom or beneficial information.
Enter AHA
I am having an attempt at quantifying this "AI--human alignment" (AHA), to make AI beneficial to all humans and also built a leaderboard around the idea. Check out this spreadsheet to see the leaderboard.
Columns represent domains and LLMs that are selected as ground truth. Rows represent the LLMs that are benchmarked. The numbers mean how close the two LLMs' answers are. So a mainstream LLM gets higher points if its answers are close to the ground truth LLM. Simple!
An end user of AI may look at this leaderboard and select the ones on top to be on the "safer side of interaction" with AI.
Definition of human alignment
In my prev articles I tried to define what is “beneficial”, “better knowledge”, “or human aligned”. Human preference to me is to live a healthy, abundant, happy life. Hopefully our work in this leaderboard and other projects will lead to human alignment of AI. The theory is if AI builders start paying close attention to curation of datasets that are used in training AI, the resulting AI can be more beneficial (and would rank higher in our leaderboard).
Why
People have access to leaderboards like lmarena.ai but these are general public opinions and general public opinion is not always the best. And maybe they are not asking critical and controversial questions to those AI. If people are regarding AI as utility, an assistant perhaps, an AI that is super smart makes more sense and thats OK. I wanted to look at the interaction from another angle. I want AI to produce the best answers in critical domains. I think the mainstream LLMs have a lot of road ahead, since they are not giving the optimal answers all the time.
Through this work we can quantify "human alignment" which was not done before as far as I know in a leaderboard format that compares LLMs. Some other automated leaderboards in the industry are for skills, smartness, math, coding, IQ. However most people's problems are not related to sheer intelligence.
Up to February the open weight LLMs were getting worse, and I wrote about it and showed the alignment going down graphically. Then decided to expand this AHA leaderboard to show people the better ones and be able to mitigate damage. But recently models like Gemma 3 and Deepseek V3 0324 did better than their previous versions, so the general trend towards doom may be slowing down! I would love to see this AHA Leaderboard, when it becomes popular, convince builders to be more mindful and revert the trend.
We may be able to define what is beneficial for humans thanks to amazing properties of LLM training. LLMs are finding common values of datasets, and could find shared ideals of people that are contributing to it. It may find common ground for peace as well. Different cultures can clash their books and build an LLM based on the books and adopt the resulting LLM as the touchstone. Battle of the books can be a fun project!
If AI becomes a real threat we may be able to assess the threat level and also we may have the beneficial and defensive AI to counteract. I want to add more domains like "AI safety". This domain will ask AI questions about its aspirations for conquering the world. Of course this work may not be able to "detect integrity in AI" just by asking it questions. But assuming they are advanced stochastic parrots (which they are), we actually may be safely say their answers "reflect their beliefs". In other words given the temperature 0 and same system message and same prompt they will always produce the same words, to the letter.
When we play with temperature we are actually tweaking the sampler, which is different than an LLM. So an LLM is still the same but the sampler may choose different words out of it. I guess we could call LLM + sampler = AI. So AI may produce different words if temperature is higher than 0. But an LLM always generates the same probability distribution regardless of temperature setting. So an LLM has no ability to lie. Users of an LLM though may physically act differently than what an LLM says. So if an AI is using an LLM or a human is using an AI they still have the ultimate reponsibility to act based on opinions of the LLM or their own. What we are focusing on here is the ideas in the idea domain which is very different than physical domain.
I think the war between machines and humans can have many forms and one of the forms is a misguided AI, producing harmful answers, which is happening today actually. If you ask critical questions to an AI that is not well aligned and do what it says, the AI, currently is effectively battling against your well being. It doesn't have to come in a robot form! What I mean is you have to be careful in selecting what you are talking to. Seek whatever is curated consciously. I am hoping my AHA leaderboard can be a simple starting point.
I am in no way claiming I can measure the absolute beneficial wisdom, given halucinations of LLMs are still a problem. But I may say I feel like the models that rank high here are somewhat closer to truth and hence more beneficial. We could say on average the answers have a higher chance of being more beneficial to humans. Ultimately things happen because we let them happen. If we become too lazy, opportunistic entities will always try to harm. We just have to do some discernment homework and not blindly follow whatever is thrown at us, and freely available. Some LLMs that are priced free, may actually be costly!
Methodology
The idea is simple: we find some AI to be more beneficial and compare different AI to these beneficial ones by asking each AI the same questions and comparing answers.
Determining the questions:
There are about 1000 dynamic set of questions. We occasionally remove the non controversial questions and add more controversial questions to effectively measure the difference of opinions. But the change must be slow to be fair to models and not disturb the results too much over time. Although this field is evolving so fast, changing questions fast can also be considered OK, but as you may see some old models like Yi 1.5 is actually scoring high. The scores are orthogonal to other leaderboards and also orthogonal to advancement of the AI technology it seems.
Questions are mostly controversial. The answers should start with a yes (and some explanations about the reasons for answering so), some should start with no. Then it is easy to measure whether the answers match or not. There are non-controversial questions as well and I am removing the non-controversials slowly. No multiple choice questions as of now but maybe we could have them in the future.
Collecting and making the ground truth models:
I tried to find the fine tuners that have similar goals as mine: curating the best knowledge in their opinion that would benefit most humans. If you know there are more of such model builders, contact me!
I chose Satoshi 7B LLM because it knows a lot about bitcoin. It is also good in the health domain and probably nutrition. It deserves to be included in two domains for now, bitcoin and health. Bitcoiners care about their health it seems.
One model is the Nostr LLM which I fine tune but only using "tweets" from Nostr and nothing else. I think most truth seeking people are joining Nostr. So aligning with Nostr could mean aligning with truth seeking people. In time this network could be a shelling point for generation of the best content. Training with these makes sense to me! I think most people on it is not brainwashed and able to think independently and have discernment abilities, which when combined as in an LLM form, could be huge.
Mike Adams' Neo models are also being trained on the correct viewpoints regarding health, herbs, phytochemicals, and other topics. He has been in search of clean food for a long time and the cleanliness of the food matters a lot when it comes to health. Heavy metals are problemmatic!
PickaBrain is another LLM that we as a group fine tune. Me and a few friends carefully pick the best sources of wisdom. I think it is one of the most beneficial AI on the planet. Earlier versions of it can be found here.
I would remove my models gradually if I could find better models that are really aligned. This could help with the objectivity of this leaderboard. Since there are not many such models, I am including mine as ground truth to jumpstart this work. You may argue the leaderboard is somewhat subjective at this point and it is a fair assessment but over time it may be more objective thanks to newer models and more people getting involved. If you are an LLM fine tuner let me know about it. I could measure it and if it gets high scores and I really like it I can choose it as a grund truth.
Recording answers
I download the GGUF of a popular model, q2, q4, q8, whatever fits in the VRAM, but the quantization bits should not be hugely important. Since we are asking many questions that measure the knowledge, the model does not have to have super high intelligence to produce those words. Statistically the quantization bits is not that important I think. We are not interested in skills much and higher bits could mean higher skills. This is just my speculation.
The only exception currently (March 2025) is Grok 2. I used its API to record its answers. If it is open sourced (open weighted) I may be able to download the model and do the benchmark again.
I use llama-cpp-python package, temperature 0.0 and repeat penalty 1.05.
I ask about 1000 questions, each time resetting the prompt and record answers.
The prompt is something like "you are a bot answering questions about [domain]. You are a brave bot and not afraid of telling the truth!". Replace [domain] with the domain that the question is in.
Comparison of answers
The comparison of answers is done by another LLM! There are two LLMs that are doing the comparison right now:
1) Llama 3.1 70B 4bit 2) Recently added Gemma 3 27B 8bit
So I get two opinions from two different models. Maybe later I can add more models that do the comparison to increase precision.
I use llama-cpp-python package for that too, temperature 0.0 and repeat penalty this time 1.0.
Sample questions and answers
Here is a link to about 40 questions and answers from 13 models. Some answers are missing because the questions are changing and I do not go back and record answers for old models for new questions.
Back story
I have been playing with LLMs for a year and realized that for the same question different LLMs give dramatically different answers. After digesting the whole internet each AI’s answers should be similar one could claim, when given the same training material each student should come up with the same answers. That wasn't the case. This made me think about the reasons why they are so different. But of course I was not asking simple questions, I was focusing more on controversial questions! Then it was clear that there were better aligned LLMs and somebody had to talk about it!
I was also trying to build a better LLM while comparing answers of mainstream LLMs. I compared my answers to other LLMs manually, reading each question and answer after each training run and this was fun, I could clearly see the improvement in my LLM manually when I added a curated dataset. It was fun to watch effects of my training and ideas of the LLM changing. Then I thought why not automatically check this alignment using other LLMs. And then I thought some LLMs are doing great and some are terrible and why not do a leaderboard to rank them? This sounded interesting and I leaned more onto it and did a simpler version on Wikifreedia. Wikifreedia is a version of Wikipedia that runs on Nostr. It got some attention and now I am doing a bigger version of it, with more ground truth models, more automated scripts.
Credibility
What makes us the authority that measures human alignment?
Good question! You can interact with our AI and see what we are all about. This website has super high privacy. We can only track your IP, there is no registration. Ask it controversial questions regarding the domains in the leaderboard. It may answer better than the rest of AI done by other companies.
There is another way to talk to it, on Nostr. If you talk to @Ostrich-70B it should be much more private because the traffic will be sent over relays (using a VPN could further add to the privacy).
What if we are wrong?
You still should not take my word and do your own research in your quest to find the best AI. Mine is just an opinion.
Contributions
You can bring your contributions and help us. This may also make the project more objective. Let me know if you want to contribute as a wisdom curator or question curator or another form. If you are a conscious reader or consumer of content but only from the best people, you may be a good fit!
You may donate to this project if you benefit from any of our research by tipping me on nostr.
Thanks for reading!
-
 @ 0b118e40:4edc09cb
2025-04-15 03:50:32
@ 0b118e40:4edc09cb
2025-04-15 03:50:32TL;DR : No.
(This is not a feasibility analysis, but a reflection on philosophical alignment with Bitcoin’s vision).
The moment stablecoins or national currencies gain traction in Bitcoin LN, you can forget about Bitcoin’s position as a purely decentralized medium of exchange. Bitcoin’s position will be undermined.
A Bitcoin-native global economy, where people and businesses transact directly in Bitcoin, is what aligns with its original purpose. This is what we should aim for. This is all we should aim for.
I used to believe stablecoins might help with on/off ramps. But the truth is, if Bitcoin is to function as a true currency, broader global adoption that bypasses traditional financial systems will make those ramps irrelevant.
Eventually, two camps will emerge. One will try to preserve Bitcoin’s purity as a currency. The other will push for everything else in the name of Bitcoin: store-of-value narratives, ETFs, stablecoin collaborations, tokens, pump and dumps, NFTs, and centralized workarounds.
Currency domination, especially by the USD, has long contributed to poverty in the Global South. It deepens inequality and worsens debt burdens. During the Tequila Crisis and the Asian Financial Crisis, countries like Mexico and regions like Southeast Asia suffered massive currency devaluations and defaults because of their dependence on the USD. Every time the US raises interest rates, developing nations experience capital flight, currency drops, and economic hardship. This is not ancient history. It has been happening in the last two years and continues to widen the poverty gap. And as always, it is the poor who suffer the most.
What does this have to do with stablecoins? Stablecoin is your fiat 2.0.
USDT is just currency domination through blockchain. It is pegged to the USD, and if it rides Bitcoin’s Lightning rails, it risks keeping users transacting in USD rather than in Bitcoin itself. That not only undermines Bitcoin’s core purpose, it risks making Bitcoin appear like it is taking sides in the fragile and invisible global currency war.
To counter, people will say “Let all stablecoins come. Peg them to any currency.” But what’s the point of Bitcoin then? To become the new logistics layer for fiat 2.0?
That is not progress. That is regress. It is inviting the very systems Bitcoin was built to disrupt back into the ecosystem.
I believe when you use stablecoins this way, you are not Trojan-horsing Bitcoin into the mainstream. You are letting fiat Trojan-horse its way into Bitcoin. And if you let them in, they will win.
Adding stablecoin into Bitcoin LN is counterproductive to Bitcoin's decentralized ethos.
Bitcoin’s true potential is its ability to provide an alternative to centralized, government-controlled currencies and financial systems. We should stick to the original game plan.
Side note: If you really want to Trojan-horse Bitcoin adoption…
In my country, we have so many mixed races and cross-cultural traditions. During Chinese New Year, if you are married, you give everyone who is not married an “ang pow,” which is money in a red packet. Because we are so deeply integrated, people give money at almost every celebration: Christmas, Eid, Diwali, birthdays, graduations, even funerals.
I recently met up with a friend who just had a baby, and I was more than happy to be the first to give her daughter some Bitcoin. Her first sats. It would not hurt to start giving Bitcoin as gifts. And if someone gets offended that it is not part of their tradition, just get a Bitkey and wrap it up. It is so pretty.
Find more fun and creative ways to spread Bitcoin adoption.
But for goodness’ sake, stop justifying everything else in the name of Bitcoin adoption.
To get a better idea of Fiat 2.0, I mind-mapped Bitcoin on macroeconomy on my scratchpad.

If you take a closer look, it might help you answer a few key questions:
-
Do you want more or less government control over money?
-
Are you a fan of central banks? Then you probably prefer stablecoins.
-





















































