-
 @ fd06f542:8d6d54cd
2025-04-23 07:51:30
@ fd06f542:8d6d54cd
2025-04-23 07:51:30- 第三章、NIP-03: OpenTimestamps Attestations for Events
- 第四章、NIP-04: Encrypted Direct Message
- 第五章、NIP-05: Mapping Nostr keys to DNS-based internet identifiers
- 第六章、NIP-06: Basic key derivation from mnemonic seed phrase
- 第七章、NIP-07: window.nostr capability for web browsers
- 第八章、NIP-08: Handling Mentions --- unrecommended: deprecated in favor of NIP-27
- 第九章、NIP-09: Event Deletion Request
- 第十章、NIP-10: Text Notes and Threads
- 第十一章、NIP-11: Relay Information Document
- 第十二章、NIP-13: Proof of Work
- 第十三章、NIP-14: Subject tag in text events
- 第十四章、NIP-15: Nostr Marketplace (for resilient marketplaces)
- 第十五章、NIP-17: Private Direct Messages
- 第十六章、NIP-18: Reposts
- 第十七章、NIP-19: bech32-encoded entities
-
 @ e3ba5e1a:5e433365
2025-02-23 06:35:51
@ e3ba5e1a:5e433365
2025-02-23 06:35:51My wife and I have six children, making our house a household of eight people. Looking just at the eight of us, how many relationships exist? Well, as a first stab, we could look at how many connections exist between two unique individuals in this family. The mathematical term for this is “8 choose 2”, and the answer is 8*7/2, or 28.
Even that doesn’t really capture the answer though, because relationships aren’t just between two people. For example, when my wife and two oldest children are the only ones still awake after the younger kids go to bed, we’ll put on my mature TV shows that they’ll appreciate and watch together. It’s our own little subgroup within the group.
Based on that, we could have groups of 2, 3, 4, all the way up to 8, the group of all of us. If you do the math, this comes up to 247 different subgroups of 2 or more people. That’s a lot of groups for just 8 people.
As a father, this means I’ll never be able to fully understand every set of connections within my family. I may have a good understanding of my own relationship with each child. I also am closely aware of the relationship between our two youngest children, since they’re twins. And I could probably list 20 or so other noteworthy relationships. But I’ll never understand all of them.
For example, months ago I bought a game on Steam for my 3rd and 4th kids. I know they like to play games together, so it was a relationship that I thought I understood well. A few days ago I found out that my oldest had joined them in playing one of these games (Brotato). I’d made the purchase, given it to the kids, and it sparked new relationship and interaction structures without my involvement.
There’s no problem with the fact that I can’t track every interaction in my house. That’s healthy! The kids are able to discover ways of interacting beyond what I can teach them, learn everything from schoolwork to video games from each other, and overall become more healthy and well-adjusted adults (I hope).
And here’s the important part: the growth of the number of connections is massive as the number of participants increases. If we add in another participant, we have 502 groupings. At 10 total participants, it jumps to over 1,000. By the time we get to 100, we’re well into the trillions.
A mathematical and software term for this is combinatoric complexity, the massive increase in an output value based on a small increase in the input. The analysis I’m providing could be termed as part of graph theory (for connections of 2, looking at people as vertices and connections as edges) or set theory (unique subsets, allowing for larger group sizes). But regardless, the point is: the increase in complexity is huge as more people join.
Now consider the global economy. It’s over 8 billion people. There are so many people that the number of groupings is absurd to talk about. Nonetheless, massive numbers of these groupings naturally occur. There are family units, friend circles, individual connections, companies, project teams, sports teams, schools, classes, and millions more. These groups of people form new ways of interacting, express vastly different desires for goods and services, and are capable of producing wide varieties of goods and services themselves.
When you allow this system to run free, beauty emerges. Each node in the graph can manage its own connections. Each person is free to make his or her own decisions about association, what to spend time on, what to spend money on, and so on. Each person does so on their own judgement and world view.
Some of these people may make “dumb” decisions. They may “waste” their time and money on useless things. Except: who made that value judgement? Clearly not them, they decided it was worth it. No central planner has the right to override their will.
My point in all this is: as yet another of many reasons in the list of “why people should be free,” we have one more data point: pure math. Central planning will never scale. Central planning will never appreciate the individuality and desires of each person. Only by giving people the freedom to explore their connections to others, discover what they can produce and consume, explore their options, and ultimately make their own decisions, can we have any chance of creating a world where everyone can succeed.
-
 @ da0b9bc3:4e30a4a9
2025-04-23 07:50:49
@ da0b9bc3:4e30a4a9
2025-04-23 07:50:49Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/954269
-
 @ 9bde4214:06ca052b
2025-04-22 17:30:02
@ 9bde4214:06ca052b
2025-04-22 17:30:02“We do not have the answers."
Pablo & Gigi have no solutions.
In this dialogue:
- What is this No Solutions thing anyway?
- Why dialogue and distributed cognition is so important
- Why is nostr exciting for developers?
- Evolution, Life, and nostr
- What is the perfect nostr app, and why can’t there be THE perfect nostr app?
- Why there is no “global” view in nostr
- Impossible problems vs. possible (but still hard) problems
- Blossom, blossom, and more blossom
- Zooko’s Triangle
- Freedom Tech Building Blocks
- NIP-60/61, NIP-89
- Email vs ICQ
- Accepting constraints & moving forward
- Nostr has data integrity, but no data guarantees
- Bitcoin as an extreme RAID system
- Fault tolerance vs. efficiency
- “Build the infrastructure, don’t run it.”
- eCash fixes 402
- Everything in nostr can be one-click
- There’s infinite nsecs (and they are free!)
- The magic of the nostr view-only mode
- The Local-first movement
- How to monetize without putting yourself in the middle?
- RoboSats as an example of open-source monetization
- The YouTube like count is a lie
Further links:
- https://en.wikipedia.org/wiki/Distributed_cognition
- https://nips.nostr.com/60
- https://nips.nostr.com/61
- https://nips.nostr.com/89
- https://github.com/hzrd149/blossom
- https://en.wikipedia.org/wiki/Zooko’s_triangle
- https://www.jrepodcast.com/guest/adam-curry/
- https://localfirstweb.dev/
- https://www.localfirstconf.com/
- https://en.wikipedia.org/wiki/ICQ
- https://appleinsider.com/articles/24/05/25/icq-1996-2024-the-first-universal-messenger-had-a-good-run-and-is-leaving-us-soon
- https://www.chatinum.com/articles/the-old-chat-apps-of-the-2000s
- https://en.wikipedia.org/wiki/Standard_RAID_levels
- https://www.youtube.com/watch?v=oIkhgagvrjI
- https://njump.me/nosolutions@sovereignengineering.io
-
 @ fd06f542:8d6d54cd
2025-04-23 06:39:15
@ fd06f542:8d6d54cd
2025-04-23 06:39:15有时候写点日志,可以 记录一点琐碎的事情。
! 也许这就是 这就是 这个blog存在的原因吧。
如何将docsify 变成一个渲染blog的 工具
我用了很多办法,但是关键点还是这个 方法。 无须配置 window.$docsify ={} ```js $: if (blogItem) {
compiledContent = window.__current_docsify_compiler__.compile(blogItem.content); }```
直接用内容的 功能转换。
但是渲染的时候要注意:
html <article class="markdown-section" id="main"> {@html compiledContent} </article>内容要加上这个外框,这个问题我调试了一天在知道...原来是少了他,导致缺少很多东西。
如何上传背景图片?
- 一定要点击 封面图区域的空白处, 让 编辑框失去焦点。
- 再 把鼠标放在 虚线封面图区域,就可以ctrl+v 粘贴截图了。
其他使用事项,我想起来再写吧。
-
 @ 6ad3e2a3:c90b7740
2025-04-23 12:31:54
@ 6ad3e2a3:c90b7740
2025-04-23 12:31:54There’s an annoying trend on Twitter wherein the algorithm feeds you a lot of threads like “five keys to gaining wealth” or “10 mistakes to avoid in relationships” that list a bunch of hacks for some ostensibly desirable state of affairs which for you is presumably lacking. It’s not that the hacks are wrong per se, more that the medium is the message. Reading threads about hacks on social media is almost surely not the path toward whatever is promised by them.
. . .
I’ve tried a lot of health supplements over the years. These days creatine is trendy, and of course Vitamin D (which I still take.) I don’t know if this is helping me, though it surely helps me pass my blood tests with robust levels. The more I learn about health and nutrition, the less I’m sure of anything beyond a few basics. Yes, replacing processed food with real food, moving your body and getting some sun are almost certainly good, but it’s harder to know how particular interventions affect me.
Maybe some of them work in the short term then lose their effect, Maybe some work better for particular phenotypes, but not for mine. Maybe my timing in the day is off, or I’m not combining them correctly for my lifestyle and circumstances. The body is a complex system, and complex systems are characterized by having unpredictable outputs given changes to initial conditions (inputs).
. . .
I started getting into Padel recently — a mini-tennis-like game where you can hit the ball off the back walls. I’d much rather chase a ball around for exercise than run or work out, and there’s a social aspect I enjoy. (By “social aspect”, I don’t really mean getting to know the people with whom I’m playing, but just the incidental interactions you get during the game, joking about it, for example, when you nearly impale someone at the net with a hard forehand.)
A few months ago, I was playing with some friends, and I was a little off. It’s embarrassing to play poorly at a sport, especially when (as is always the case in Padel) you have a doubles partner you’re letting down. Normally I’d be excoriating myself for my poor play, coaching myself to bend my knees more, not go for winners so much. But that day, I was tired — for some reason I hadn’t slept well — and I didn’t have the energy for much internal monologue. I just mishit a few balls, felt stupid about it and kept playing.
After a few games, my fortunes reversed. I was hitting the ball cleanly, smashing winners, rarely making errors. My partner and I started winning games and then sets. I was enjoying myself. In the midst of it I remember hitting an easy ball into the net and reflexively wanting to self-coach again. I wondered, “What tips did I give to right the ship when I had been playing poorly at the outset?” I racked my brain as I waited for the serve and realized, to my surprise, there had been none. The turnaround in my play was not due to self-coaching but its absence. I had started playing better because my mind had finally shut the fuck up for once.
Now when I’m not playing well, I resist, to the extent I’m capable, the urge to meddle. I intend to be more mind-less. Not so much telling the interior coach to shut up but not buying into the premise there is a problem to be solved at all. The coach isn’t just ignored, he’s fired. And he’s not just fired, his role was obsoleted.
You blew the point, you’re embarrassed about it and there’s nothing that needs to be done about it. Or that you started coaching yourself like a fool and made things worse. No matter how much you are doing the wrong thing nothing needs to be done about any of it whatsoever. There is always another ball coming across the net that needs to be struck until the game is over.
. . .
Most of the hacks, habits and heuristics we pick up to manage our lives only serve as yet more inputs in unfathomably complex systems whose outputs rarely track as we’d like. There are some basic ones that are now obvious to everyone like not injecting yourself with heroin (or mRNA boosters), but for the most part we just create more baggage for ourselves which justifies ever more hacks. It’s like taking medication for one problem that causes side effects, and then you need another medicine for that side effect, rinse and repeat, ad infinitum.
But this process can be reverse-engineered too. For every heuristic you drop, the problem it was put into place to solve re-emerges and has a chance to be observed. Observing won’t solve it, it’ll just bring it into the fold, give the complex system of which it is a part a chance to achieve an equilibrium with respect to it on its own.
You might still be embarrassed when you mishit the ball, but embarrassment is not a problem. And if embarrassment is not a problem, then mishitting a ball isn’t that bad. And if mishitting a ball isn’t that bad, then maybe you’re not worrying about what happens if you botch the next shot, instead fixing your attention on the ball. And so you disappear a little bit into the game, and it’s more fun as a result.
I honestly wish there were a hack for this — being more mindless — but I don’t know of any. And in any event, hack Substacks won’t get you any farther than hack Twitter threads.
-
 @ 9c9d2765:16f8c2c2
2025-04-23 08:54:57
@ 9c9d2765:16f8c2c2
2025-04-23 08:54:57CHAPTER TEN
Gasps rippled through the hall as James strode in confidently, his PA by his side. The expensive fabric of his suit gleaned Helen's jaw dropped, her fingers freezing mid-tap. She instinctively clutched Christopher’s arm under the chandeliers, its impeccable fit accentuating his regal posture. Every eye was locked onto him, disbelief spreading across the faces of those who had once looked down on him.
"That can’t be James… It must be one of rich friends who lent him that suit!"
Christopher remained speechless, his face paling as realization dawned. Robert, sitting across from them, stared wide-eyed at James, his mind racing to piece together what was happening.
James walked straight to the front of the hall, his PA pulling out a chair for him. He sat down calmly, scanning the room with a faint smirk. He could see the stunned expressions, the silent questions dancing in their eyes.
"Ladies and gentlemen," the event host finally announced, clearing his throat. "Please welcome Mr. James, the President of JP Enterprises."
A wave of murmurs swept through the hall, disbelief clashing with admiration. The Ray family sat frozen in place, Helen clutching the armrest so tightly her knuckles turned white.
James leaned forward, clasping his hands together. "Shall we begin?" he said, his voice smooth yet firm, carrying the weight of a man who had risen from the ashes.
The meeting commenced, but Helen couldn’t focus. Her mind reeled from the shocking truth James, the man she had humiliated and cast aside, was not just successful; he was now one of the most powerful businessmen in the room.
"How dare you lay your hands on me? Do you know who I am?" Mark roared as the security guards tightened their grip on his arms, dragging him toward the exit of the grand conference hall.
The murmurs in the room grew louder, investors and company representatives whispering among themselves as they watched the Prime Minister's son being forcefully removed. Mark struggled, his face flushed red with anger and embarrassment.
"Sir, please don't make this harder than it has to be. You are not an authorized investor," one of the guards said firmly.
Mark's glare was searing as he turned his head towards James, who stood calmly at the head table, watching the entire scene unfold. "You!" Mark spat. "You planned this, didn’t you? You set me up to be humiliated like this!"
James arched an eyebrow, folding his arms across his chest. "No, Mark. You did this to yourself. You thought you could walk in here, throwing your weight around without proper authorization. This is a professional investment summit, not your playground."
Helen, sitting across the hall, clenched her fists. "How can they do this to Mark? He is a valuable investor!" she whispered furiously to her husband, Christopher, who was too stunned to respond.
Mark twisted in the guards' grip, his voice dripping with venom. "I swear, James, you will regret this. You think you can humiliate me in front of these elites? I will make you pay for this!"
James met his gaze with a calm but firm expression. "Mark, threats won’t change reality. You came here thinking your name alone could buy you a seat at the table. But in business, it's about credibility, not status. And today, you just proved to everyone here that you have none."
The room remained silent as the guards escorted Mark out. His loud protests echoed through the hallway before the grand doors finally shut behind him.
Rita sat in her chair, her heart pounding. She knew Mark was dangerous when scorned. She turned to James, worry evident in her eyes. "James, you know he won’t let this go, right?"
James exhaled slowly, nodding. "I know, Rita. And I'm ready for whatever he plans next."
The hall remained hushed for a moment before the moderator cleared his throat. "Now that the disruption has been handled, let us proceed with the investment discussions. Mr. James, as the President of JP Enterprises, you have the floor."
James stepped forward, commanding the attention of every business mogul in the room. He knew this was just the beginning, but one thing was certain Mark had declared war, and James was ready for battle.
-
 @ 8d34bd24:414be32b
2025-04-23 03:52:15
@ 8d34bd24:414be32b
2025-04-23 03:52:15I started writing a series on the signs of the End Times and how they align with what we are seeing in the world today. There are some major concerns with predicting the end times, so I decided I should insert a short post on “Can we know when the end times are coming?” Like many principles in the Bible, it takes looking at seemingly contradictory verses to reach the truth.
This Generation
Before I get into “Can we know?” I want to address one point that some will bring up against a future Rapture, Tribulation, and Millennium.
Truly I say to you, this generation will not pass away until all these things take place. (Matthew 24:34) {emphasis mine}
What generation is Jesus talking about. Most Christians that don’t believe in a future Rapture, Tribulation, and Millennium will point to this verse to support their point of view. The important question is, “What is Jesus referring to with the words ‘this generation’?”
Is it referring to the people He was talking to at that time? If so, since that generation died long ago, then Jesus’s predictions must have been fulfilled almost 2 millennia ago. The problem with this interpretation is that nothing resembling these predictions happened during that initial generation. You have to really twist His words to try to support that they were fulfilled. Also, John wrote in Revelation about future fulfillment. By that time, John was the last of the apostles still alive and that whole generation was pretty much gone.
If “this generation” doesn’t refer to the people Jesus was speaking to personally in that moment, then to whom does it refer? The verses immediately preceding talk about the signs that will occur right before the end times. If you take “this generation” to mean the people who saw the signs Jesus predicted, then everything suddenly makes sense. It also parallel’s Paul’s statement of consolation to those who thought they had been left behind,**
But we do not want you to be uninformed, brethren, about those who are asleep, so that you will not grieve as do the rest who have no hope. For if we believe that Jesus died and rose again, even so God will bring with Him those who have fallen asleep in Jesus. For this we say to you by the word of the Lord, that we who are alive and remain until the coming of the Lord, will not precede those who have fallen asleep. For the Lord Himself will descend from heaven with a shout, with the voice of the archangel and with the trumpet of God, and the dead in Christ will rise first. Then we who are alive and remain will be caught up together with them in the clouds to meet the Lord in the air, and so we shall always be with the Lord. Therefore comfort one another with these words. (1 Thessalonians 4:13-18) {emphasis mine}
Some believers thought things were happening in their lifetime, but Paul gave them comfort that no believer would miss the end times rapture.
No One Knows
Truly I say to you, this generation will not pass away until all these things take place. Heaven and earth will pass away, but My words will not pass away.
But of that day and hour no one knows, not even the angels of heaven, nor the Son, but the Father alone. For the coming of the Son of Man will be just like the days of Noah. For as in those days before the flood they were eating and drinking, marrying and giving in marriage, until the day that Noah entered the ark, and they did not understand until the flood came and took them all away; so will the coming of the Son of Man be. Then there will be two men in the field; one will be taken and one will be left. Two women will be grinding at the mill; one will be taken and one will be left. (Matthew 24:34-41) {emphasis mine}
This verse very explicitly says that no one, not even angels or Jesus, knows the exact day or hour of His coming.
So when they had come together, they were asking Him, saying, “Lord, is it at this time You are restoring the kingdom to Israel?” He said to them, “It is not for you to know times or epochs which the Father has fixed by His own authority; but you will receive power when the Holy Spirit has come upon you; and you shall be My witnesses both in Jerusalem, and in all Judea and Samaria, and even to the remotest part of the earth.” (Acts 1:6-8)
In this verse Jesus again says that they cannot know the time of His return, but based on context, He is explaining that this generation needs to focus on sharing the Gospel with world and not primarily on the kingdom. Is this Jesus’s way of telling them that they would not be alive to see His return, but they would be responsible for “sharing the Gospel even to the remotest part of the earth?”
Therefore we do know that predicting the exact date of His return is a fool’s errand and should not be attempted, but does this mean we can’t know when it is fast approaching?
We Should Know
There is an opposing passage, though.
The Pharisees and Sadducees came up, and testing Jesus, they asked Him to show them a sign from heaven. But He replied to them, “When it is evening, you say, ‘It will be fair weather, for the sky is red.’ And in the morning, ‘There will be a storm today, for the sky is red and threatening.’ Do you know how to discern the appearance of the sky, but cannot discern the signs of the times? An evil and adulterous generation seeks after a sign; and a sign will not be given it, except the sign of Jonah.” And He left them and went away. (Matthew 16:1-4) {emphasis mine}
In this passage, Jesus reprimands the Pharisees and Sadducees because, although they can rightly read the signs of the weather, they were unable to know and understand the prophecies of His first coming. Especially as the religious leaders, they should’ve been able to determine that Jesus’s coming was imminent and that He was fulfilling the prophetic Scriptures.
In Luke, when Jesus is discussing His second coming with His disciples, He tells this parable:
Then He told them a parable: “Behold the fig tree and all the trees; as soon as they put forth leaves, you see it and know for yourselves that summer is now near. So you also, when you see these things happening, recognize that the kingdom of God is near. (Luke 21:29-31) {emphasis mine}
Jesus would not have given this parable if there were not signs of His coming that we can recognize.
We are expected to know the Scriptures and to study them looking for the signs of His second coming. We can’t know the hour or the day, but we can know that the time is fast approaching. We shouldn’t set dates, but we should search anxiously for the signs of His coming. We shouldn’t be like the scoffers that question His literal fulfillment of His promises:
Know this first of all, that in the last days mockers will come with their mocking, following after their own lusts, and saying, “Where is the promise of His coming? For ever since the fathers fell asleep, all continues just as it was from the beginning of creation.” For when they maintain this, it escapes their notice that by the word of God the heavens existed long ago and the earth was formed out of water and by water, through which the world at that time was destroyed, being flooded with water. But by His word the present heavens and earth are being reserved for fire, kept for the day of judgment and destruction of ungodly men. But do not let this one fact escape your notice, beloved, that with the Lord one day is like a thousand years, and a thousand years like one day. The Lord is not slow about His promise, as some count slowness, but is patient toward you, not wishing for any to perish but for all to come to repentance. (2 Peter 3:3-9) {emphasis mine}
One thing is certain, we are closer to Jesus’s second coming than we have ever been and must be ready as we see the day approaching.
May the God of heaven give you a desire and urgency to share the Gospel with all those around you and to grow your faith, knowledge, and relationship with Him, so you can finish the race well, with no regrets. May the knowledge that Jesus could be coming soon give you an eternal perspective on life, so you put more of your time into things of eternal consequence and don’t get overwhelmed with things of the world which are here today and then are gone.
Trust Jesus.
FYI, I hope to write several more articles on the end times (signs of the times, the rapture, the millennium, and the judgement), but I might be a bit slow rolling them out because I want to make sure they are accurate and well supported by Scripture. You can see my previous posts on the end times on the end times tab at trustjesus.substack.com. I also frequently will list upcoming posts.
-
 @ f5369849:f34119a0
2025-04-23 08:48:05
@ f5369849:f34119a0
2025-04-23 08:48:05Hackathon Summary
The Naija HackAtom successfully concluded with the participation of 160 registered developers and a presentation of 51 approved projects. This hackathon was designed to advance the Interchain, Cosmos Hub, and Atom Economic Zone (AEZ) within Nigeria’s Web3 communities. The main objectives included nurturing local talent, providing resources, and developing blockchain applications utilizing the $ATOM token.
The primary focus areas encompassed Interchain Security, the Atom Economic Zone, CosmWasm, and developments specific to ATOM. Notable projects included cross-chain remittance platforms and decentralized marketplaces for African farmers, emphasizing innovative applications of Cosmos technologies.
An $10,000 prize pool was established to reward innovation in UI/UX, community engagement, and unique Atom utility solutions. Over the course of various workshops and public tutorials, participants developed projects that were judged on technical feasibility, innovation, impact, and user experience. The event, marked by widespread participation and innovation, effectively contributed to the growth of blockchain ecosystems in Nigeria and across Africa.
Hackathon Winners
The Naija HackAtom marked Nigeria's first hackathon centered on Cosmos and ATOM, drawing over 500 participants, including 160 developers. With support from ATOMAccelerator, a total of 57 projects were submitted, narrowing down to 18 finalists.
Main Prize Winners
- Beep: A platform for Naira tokenization, facilitating seamless transactions and exchanges with tAtom.
- Padi {Crypto Go Fund Me}: A blockchain-based platform for conducting token-driven fundraising campaigns.
- ATwork: A decentralized freelancing platform enhancing collaboration between freelancers and clients through the Cosmos blockchain.
Unique Solution/Product Prize Winners
- LendPro: A lending protocol that fosters cooperative financial governance via blockchain.
- Tradi-App: A confidential AI trading analytics platform on the Secret Network providing market insights.
- Delegated Staking Agent (DSA): Offers staking and governance voting in the Cosmos ecosystem with AI-enhanced security.
- Neutron NFT Launch: Simplifies NFT creation and trading by integrating AI, blockchain, and NFT technology.
Secret Network Bounty Winners
- Prompt Hub: A marketplace for privacy-focused, AI-generated prompts with integration features.
- Delegated Staking Agent (DSA)
- Secret AI Writer: An AI writing platform offering secure blockchain storage and privacy-centric content generation.
- Tradi-App
ChihuahuaChain Bounty Winners
- Neutron NFT Launch
- woof-dot-fun: A project replicating Pump.Fun with token and bond curve functionality.
- Vault Quest: A no-loss prize-saving protocol leveraging DeFi strategies for yield-based prize distribution.
Akash Bounty Winner
- Jarvis AI: A voice-activated assistant designed for efficient cloud resource management.
For a complete list of all projects submitted during the Naija HackAtom, visit here.
Organization
About the Organizer: Cosmos Hub Africa
Cosmos Hub Africa is focused on promoting blockchain technology and the Cosmos ecosystem specifically across Africa. The organization plays a significant role in decentralized network development and collaboration within the blockchain industry. Its contributions include projects that enhance scalability and interoperability across platforms. At present, Cosmos Hub Africa is committed to advancing blockchain education and infrastructure in the region, aiming to foster innovation and integration with the traditional economy and financial system.
-
 @ b8851a06:9b120ba1
2025-02-22 19:43:13
@ b8851a06:9b120ba1
2025-02-22 19:43:13The digital guillotine has fallen. The Bybit hack wasn’t just a theft—it was a surgical strike exposing the fatal flaw of “crypto” that isn’t Bitcoin. This wasn’t a bug. It was a feature of a system designed to fail.
Here’s how North Korea’s Lazarus Group stole $1.5B in ETH, why “decentralized finance” is a joke, and how Bitcoin remains the only exit from this circus.
I. The Heist: How Centralized “Crypto” Betrayed Its Users
A. The Multisig Mousetrap (Or: Why You’re Still Using a Bank)
Bybit’s Ethereum cold wallet used multisig, requiring multiple approvals for transactions. Sounds secure, right? Wrong. • The Con: Hackers didn’t pick the lock; they tricked the keyholders using a UI masking attack. The wallet interface showed “SEND TO BYBIT”, but the smart contract was whispering “SEND TO PYONGYANG.” • Bitcoin Parallel: Bitcoin’s multisig is enforced on hardware, not a website UI. No browser spoofing, no phishing emails—just raw cryptography.
Ethereum’s multisig is a vault with a touchscreen PIN pad. Bitcoin’s is a mechanical safe with a key only you hold. Guess which one got robbed?
B. Smart Contracts: Dumb as a Bag of Hammers
The thieves didn’t “hack” Ethereum—they exploited its smart contract complexity. • Bybit’s security depended on a Safe.global contract. Lazarus simply tricked Bybit into approving a malicious upgrade. • Imagine a vending machine that’s programmed to take your money but never give you a soda. That’s Ethereum’s “trustless” tech.
Why Bitcoin Wins: Bitcoin doesn’t do “smart contracts” in the Ethereum sense. Its scripting language is deliberately limited—less code, fewer attack vectors.
Ethereum is a Lego tower; Bitcoin is a granite slab. One topples, one doesn’t.
II. The Laundering: Crypto’s Dirty Little Secret
A. Mixers, Bridges, and the Art of Spycraft
Once the ETH was stolen, Lazarus laundered it at lightspeed: 1. Mixers (eXch) – Obfuscating transaction trails. 2. Bridges (Chainflip) – Swapping ETH for Bitcoin because that’s the only exit that matters.
Bitcoin Reality Check: Bitcoin’s privacy tools (like CoinJoin) are self-custodial—no third-party mixers. You keep control, not some “decentralized” website waiting to be hacked.
Ethereum’s “bridges” are burning rope ladders. Bitcoin’s privacy? An underground tunnel only you control.
B. The $1.5B Lie: “Decentralized” Exchanges Are a Myth
Bybit’s “cold wallet” was on Safe.global—a so-called “decentralized” custodian. Translation? A website with extra steps. • When Safe.global got breached, the private keys were stolen instantly. • “Decentralized” means nothing if your funds depend on one website, one server, one weak link.
Bitcoin’s Answer: Self-custody. Hardware wallets. Cold storage. No trusted third parties.
Using Safe.global is like hiding your life savings in a gym locker labeled “STEAL ME.”
III. The Culprits: State-Sponsored Hackers & Crypto’s Original Sin
A. Lazarus Group: Crypto’s Robin Hood (For Dictators)
North Korea’s hackers didn’t break cryptography—they broke people. • Phishing emails disguised as job offers. • Bribes & social engineering targeting insiders. • DeFi governance manipulation (because Proof-of-Stake is just shareholder voting in disguise).
Bitcoin’s Shield: No CEO to bribe. No “upgrade buttons” to exploit. No governance tokens to manipulate. Code is law—and Bitcoin’s law is written in stone.
Ethereum’s security model is “trust us.” Bitcoin’s is “verify.”
B. The $3B Elephant: Altcoins Fund Dictators
Since 2017, Lazarus has stolen $3B+ in crypto, funding North Korea’s missile program.
Why? Because Ethereum, Solana, and XRP are built on Proof-of-Stake (PoS)—which centralizes power in the hands of a few rich validators. • Bitcoin’s Proof-of-Work: Miners secure the network through energy-backed cryptography. • Altcoins’ Proof-of-Stake: Security is dictated by who owns the most tokens.
Proof-of-Stake secures oligarchs. Proof-of-Work secures money. That’s why Lazarus can drain altcoin treasuries but hasn’t touched Bitcoin’s network.
IV. Bybit’s Survival: A Centralized Circus
A. The Bailout: Banks 2.0
Bybit took bridge loans from “undisclosed partners” (read: Wall Street vultures). • Just like a traditional bank, Bybit printed liquidity out of thin air to stay solvent. • If that sounds familiar, it’s because crypto exchanges are just banks in hoodies.
Bitcoin Contrast: No loans. No bailouts. No “trust.” Just 21 million coins, mathematically secured.
Bybit’s solvency is a confidence trick. Bitcoin’s solvency is math.
B. The Great Withdrawal Panic
Within hours, 350,000+ users scrambled to withdraw funds.
A digital bank run—except this isn’t a bank. It’s an exchange that pretended to be decentralized.
Bitcoin fixes this: your wallet isn’t an IOU. It’s actual money.
Bybit = a TikTok influencer promising riches. Bitcoin = the gold in your basement.
V. The Fallout: Regulators vs Reality
A. ETH’s 8% Crash vs Bitcoin’s Unshakable Base
Ethereum tanked because it’s a tech stock, not money. Bitcoin? Dropped 2% and stabilized.
No CEO, no headquarters, no attack surface.
B. The Regulatory Trap
Now the bureaucrats come in demanding: 1. Wallet audits (they don’t understand public ledgers). 2. Mixer bans (criminalizing privacy). 3. KYC everything (turning crypto into a surveillance state).
Bitcoin’s Rebellion: You can’t audit what’s already transparent. You can’t ban what’s unstoppable.
VI. Conclusion: Burn the Altcoins, Stack the Sats
The Bybit hack isn’t a crypto problem. It’s an altcoin problem.
Ethereum’s smart contracts, DeFi bridges, and “decentralized” wallets are Swiss cheese for hackers. Bitcoin? A titanium vault.
The Only Lessons That Matter:
✅ Multisig isn’t enough unless it’s Bitcoin’s hardware-enforced version. ✅ Complexity kills—every altcoin “innovation” is a security risk waiting to happen.
Lazarus Group won this round because “crypto” ignored Bitcoin’s design. The solution isn’t better regulations—it’s better money.
Burn the tokens. Unplug the servers. Bitcoin is the exit.
Take your money off exchanges. Be sovereign.
-
 @ 7d33ba57:1b82db35
2025-04-23 11:40:24
@ 7d33ba57:1b82db35
2025-04-23 11:40:24Perched on the northern coast of Poland, Gdańsk is a stunning port city with a unique blend of Hanseatic charm, maritime heritage, and resilience through centuries of dramatic history. With its colorful façades, cobbled streets, and strong cultural identity, Gdańsk is one of Poland’s most compelling cities—perfect for history buffs, architecture lovers, and coastal wanderers.
🏛️ What to See & Do in Gdańsk
🌈 Stroll Down Długi Targ (Long Market)
- The heart of Gdańsk’s Old Town, lined with beautifully restored colorful merchant houses
- Admire the Neptune Fountain, Artus Court, and the grand Main Town Hall
⚓ The Crane (Żuraw) & Motława River
- Gdańsk’s medieval port crane is an iconic symbol of its maritime past
- Walk along the Motława River promenade, with boats, cafés, and views of historic granaries
⛪ St. Mary’s Church (Bazylika Mariacka)
- One of the largest brick churches in the world
- Climb the tower for panoramic views of the city and harbor
🕊️ Learn Gdańsk’s Layers of History
🏰 Westerplatte
- The site where World War II began in 1939
- A powerful memorial and museum amid coastal nature
🛠️ European Solidarity Centre
- A striking modern museum dedicated to the Solidarity movement that helped end communism in Poland
- Insightful, moving, and highly interactive
🏖️ Relax by the Baltic Sea
- Head to Brzeźno Beach or nearby Sopot for golden sands, seaside promenades, and beach cafés
- In summer, the Baltic vibes are strong—swimming, sunsets, and pier strolls

🍽️ Tastes of Gdańsk
- Try pierogi, fresh Baltic fish, golden smoked cheese, and żurek soup
- Visit a local milk bar or enjoy a craft beer at one of Gdańsk’s buzzing breweries
- Don’t miss the amber jewelry shops—Gdańsk is known as the Amber Capital of the World
🚆 Getting There
- Easily reached by train or plane from Warsaw and other major European cities
- Compact city center—walkable and scenic
-
 @ fbf0e434:e1be6a39
2025-04-23 08:42:22
@ fbf0e434:e1be6a39
2025-04-23 08:42:22Hackathon 概要
Naija HackAtom 圆满落幕。此次活动共有 160 名开发者注册参与,成功展示 51 个通过审核的项目。该黑客马拉松旨在推动尼日利亚 Web3 社区内 Interchain、Cosmos Hub 和 Atom 经济区(AEZ)的发展,主要目标是培养本土人才、提供资源支持,并开发基于 $ATOM 代币的区块链应用。
活动聚焦 Interchain 安全性、Atom 经济区、CosmWasm 以及 ATOM 的具体发展等关键领域。其中,跨链汇款平台、面向非洲农民的去中心化市场等项目尤为亮眼,充分展现了 Cosmos 技术的创新应用潜力。
本次黑客马拉松设立了 10000 美元的奖金池,用于奖励在 UI/UX 设计、社区参与度及 Atom 创新应用方案等方面表现突出的项目。在系列研讨会与公开教程的辅助下,参赛者提交的项目从技术可行性、创新性、社会影响力和用户体验等维度进行评审。活动凭借广泛的参与度与丰富的创新成果,有力推动了尼日利亚乃至整个非洲区块链生态的发展。
Hackathon 获奖者
Naija HackAtom 作为尼日利亚首个以 Cosmos 和 ATOM 为核心的黑客马拉松,吸引了超 500 人参与,其中开发者达 160 名。在 ATOMAccelerator 的支持下,活动共收到 57 个项目提交,最终 18 个项目脱颖而出,入围决赛。
主奖项获奖者
- Beep: 一个用于Naira代币化的平台,促进了与tAtom无缝交易和交换。
- Padi [Crypto Go Fund Me]: 一个基于区块链的平台,用于进行代币驱动的筹款活动。
- ATwork: 一个去中心化的自由职业平台,通过Cosmos区块链增强自由职业者与客户之间的合作。
独特解决方案/产品奖项获奖者
- LendPro: 一个借贷协议,通过区块链促进合作金融治理。
- Tradi-App: 一个在Secret Network上的隐私AI交易分析平台,提供市场见解。
- Delegated Staking Agent(DSA): 提供Cosmos生态系统中的质押和治理投票,具有AI增强的安全性能。
- Neutron NFT Launch: 通过整合AI、区块链和NFT技术简化NFT的创建和交易。
Secret Network 赏金获奖者
- Prompt Hub: 一个专注隐私、AI生成提示的市场,带有集成功能。
- Delegated Staking Agent(DSA)
- Secret AI Writer: 一个AI写作平台,提供安全的区块链存储和隐私中心的内容生成。
- Tradi-App
ChihuahuaChain 赏金获奖者
- Neutron NFT Launch
- woof-dot-fun: 一个复制Pump.Fun的项目,具有代币和债券曲线功能。
- Vault Quest: 一个无损奖品储蓄协议,利用DeFi策略进行基于收益的奖品分配。
Akash 赏金获奖者
- Jarvis AI: 一个语音激活的助手,旨在高效的云资源管理。
有关Naija HackAtom期间提交的所有项目的完整列表,请访问这里。
关于组织者
Cosmos Hub Africa
Cosmos Hub Africa专注于在非洲推广区块链技术和Cosmos生态系统。该组织在去中心化网络开发和区块链行业内的协作方面发挥着重要作用。其贡献包括提高平台之间可扩展性和互操作性的项目。目前,Cosmos Hub Africa致力于推进该地区的区块链教育和基础设施,旨在促进与传统经济和金融系统的创新和整合。
-
 @ 4857600b:30b502f4
2025-02-21 21:15:04
@ 4857600b:30b502f4
2025-02-21 21:15:04In a revealing development that exposes the hypocrisy of government surveillance, multiple federal agencies including the CIA and FBI have filed lawsuits to keep Samourai Wallet's client list sealed during and after trial proceedings. This move strongly suggests that government agencies themselves were utilizing Samourai's privacy-focused services while simultaneously condemning similar privacy tools when used by ordinary citizens.
The situation bears striking parallels to other cases where government agencies have hidden behind "national security" claims, such as the Jeffrey Epstein case, highlighting a troubling double standard: while average citizens are expected to surrender their financial privacy through extensive reporting requirements and regulations, government agencies claim exemption from these same transparency standards they enforce on others.
This case exemplifies the fundamental conflict between individual liberty and state power, where government agencies appear to be using the very privacy tools they prosecute others for using. The irony is particularly stark given that money laundering for intelligence agencies is considered legal in our system, while private citizens seeking financial privacy face severe legal consequences - a clear demonstration of how the state creates different rules for itself versus the people it claims to serve.
Citations: [1] https://www.bugle.news/cia-fbi-dnc-rnc-all-sue-to-redact-samourais-client-list-from-trial/
-
 @ 7d33ba57:1b82db35
2025-04-23 10:28:49
@ 7d33ba57:1b82db35
2025-04-23 10:28:49Lake Bled is straight out of a storybook—an emerald alpine lake with a tiny island crowned by a church, surrounded by forested hills and overlooked by a clifftop castle. Just an hour from Ljubljana, this Slovenian gem is perfect for romantic getaways, outdoor adventures, or a peaceful escape into nature.
🌊 Top Things to Do in Bled
🛶 Bled Island & Church of the Assumption
- Take a traditional pletna boat or rent a rowboat to reach the only natural island in Slovenia
- Ring the church bell and make a wish—it’s a local tradition!
- Enjoy serene lake views from the island’s stone steps
🏰 Bled Castle (Blejski Grad)
- Perched on a cliff 130 meters above the lake
- Explore the medieval halls, museum, and wine cellar
- The terrace views? Absolutely unforgettable—especially at sunset
🚶♂️ Walk or Cycle the Lakeside Path
- A 6 km flat path circles the lake—perfect for a leisurely stroll or bike ride
- Stop for lakeside cafés, photo ops, or a quick swim in summer
🌄 Outdoor Adventures Beyond the Lake
- Hike to Mala Osojnica Viewpoint for the most iconic panoramic view of Lake Bled
- Go paddleboarding, kayaking, or swimming in warmer months
- Nearby Vintgar Gorge offers a stunning wooden path through a narrow, turquoise canyon
🍰 Try the Famous Bled Cream Cake (Kremšnita)
- A must-try dessert with layers of vanilla custard, cream, and crispy pastry
- Best enjoyed with a coffee on a terrace overlooking the lake

🏡 Where to Stay
- Lakeside hotels, cozy guesthouses, or charming Alpine-style B&Bs
- Some even offer views of the lake, castle, or Triglav National Park
🚗 Getting There
- Around 1 hour from Ljubljana by car, bus, or train
- Easy to combine with stops like Lake Bohinj or Triglav National Park
-
 @ 7ef5f1b1:0e0fcd27
2025-04-22 17:26:44
@ 7ef5f1b1:0e0fcd27
2025-04-22 17:26:44A monthly newsletter by The 256 Foundation

April 2025
Introduction:
Welcome to the fourth newsletter produced by The 256 Foundation! March was an action-packed month with events ranging from the announcement of TSMC investing in US fabs to four solo block finds. Dive in to catch up on the latest news, mining industry developments, progress updates on grant projects, Actionable Advice on updating a Futurebit Apollo I to the latest firmware, and the current state of the Bitcoin network.
[IMG-001] Variation of the “I’m the captain now” meme by @maxisclub
Definitions:
MA = Moving Average
Eh/s = Exahash per second
Ph/s = Petahash per second
Th/s = Terahash per second
T = Trillion
J/Th = Joules per Terahash
$ = US Dollar
OS = Operating System
SSD = Solid State Drive
TB = Terabyte
News:
March 3, Ashigaru releases v1.1.1. Notable because this fork of Samourai Wallet serves as the remaining choice of mobile Bitcoin wallet capable of making peer to peer collaborative transactions. Not the Whirlpool transactions that Samourai Wallet was well-known for but the Stowaway and StonewallX2 p2p CoinJoin transactions. The persistence of Samourai’s tools still working despite the full force of the State coming down on the developers is a testament to the power of open-source code.
March 3, Stronghold completes cleanup of decommissioned coal plant using Bitcoin miners. Stronghold’s initiative counters the narrative that Bitcoin mining is wasteful by removing 150,000 tons of coal waste, part of a broader effort that cleared 240,000 tons in Q2 2024 alone. Waste coal piles in Pennsylvania, like the one in Russellton, have scarred landscapes, making this reclamation a significant step for local ecosystems. The project aligns with growing efforts in the region, as The Nature Conservancy also leads restoration projects in Pennsylvania to revive forests and waters. Stronghold’s dual-use model—powering Bitcoin miners and supplying the grid—shows how Bitcoin mining can support environmental goals while remaining economically viable.
March 3, five TSMC semiconductor fabs coming to Arizona. TSMC’s $100 billion investment in Arizona reflects a strategic push to bolster U.S. semiconductor production amid global supply chain vulnerabilities and geopolitical tensions, particularly with West Taiwan’s claims over Taiwan. TSMC’s existing $65 billion investment in Phoenix, now totaling $165 billion, aims to create 40,000 construction jobs and tens of thousands of high-tech roles over the next decade. This could relieve bottlenecks in ASIC chip supply if Bitcoin mining chip designers can get access to the limited foundry space. If that is the case, this could help alleviate some centralization concerns as it relates to a majority of Bitcoin mining chips coming from Taiwan and West Taiwan.
March 10, Block #887212 solved by a Bitaxe Ultra with ~491Gh/s. Not only did the Bitaxe satisfy the network difficulty, which was 112.15T, but obliterated it with a whopping 719.9T difficulty. This Block marked the second one solved by a Bitaxe and an increasing number of solo block finds overall as more individuals choose to play the Bitcoin lottery with their hashrate.
March 12, Pirate Bay co-founder, Carl Lundström, killed in plane crash. The Pirate Bay, launched in 2003, revolutionized online file-sharing by popularizing BitTorrent technology, enabling millions to access music, movies, and software, often in defiance of legal systems, which led to Lundström’s 2009 conviction for copyright infringement. The timing of his death coincides with ongoing global debates over digital ownership and intellectual property, often echoing many of the same themes in open-source technology, underscoring the enduring impact of The Pirate Bay’s challenge to traditional media distribution models.
March 18, Samourai Wallet status conference update. This was a short meeting in which the dates for the remaining pre-trial hearings was discussed.
- May 9, Opening Motion. - June 6, prosecution response to the opening motion. - June 20, defense replies to the prosecution response. - July 15, prosecution provides expert disclosure - August 8, defense provides expert disclosure - Tdev is able to remain home during the remaining pre-trial hearings so that he doesn’t have to incur the expenses traveling back and forth between Europe and the USDespite seemingly positive shifts in crypto-related policies from the Trump administration, all signs point to the prosecution still moving full steam ahead in this case. The defense teams need to be prepared and they could use all the financial help they can get. If you feel compelled to support the legal defense fund, please do so here. If the DOJ wins this case, all Bitcoiners lose.
March 18, DEMAND POOL launches, transitioning out of stealth mode and making room for applicants to join the private waiting list to be one of the Founding Miners.
Key features of DEMAND Pool include: • Build your own blocks • SLICE payment system & new mempool algorithm • No more empty blocks • End-to-end encryption for protection • Efficient data transfer, less wasted hashrate • Lower costs on CPU, bandwidth, & time
DEMAND Pool implements Stratum v2 so that miners can generate their own block templates, entering the arena of pools trying to decentralize mining such as OCEAN with their alternative to Stratum v2 called DATUM. A benefit of the Stratum v2 protocol over Stratum v1 is that data sent between the miner and the pool is now encrypted whereas before it was sent in clear-text, the encryption helps with network level privacy so that for example, your Internet Service Provider cannot read what is in the data being passed back and forth. Although, unless there is a proxy between your miner and the pool then the ISP may be able to determine that you are sending data to a mining pool, they just wouldn’t be able to tell what’s in that data. Overall, decentralization has become a buzz word lately and while it is a step in the right direction that more pools are enabling miners to decide which transactions are included in the block templates they work on, the pools remain a centralized force that ultimately can reject templates based on a number of reasons.
March 20, Bitaxe makes the cover of Bitcoin Magazine’s The Mining Issue, solidifying the Bitaxe as a pop-culture icon. Even those who disregard the significance of the Bitaxe project must recognize that the project’s popularity is an indication that something big is developing here.
 [IMG-002] Bitcoin Magazine, The Mining Issue
[IMG-002] Bitcoin Magazine, The Mining IssueMarch 21, self-hosted solo miner solves block #888737 with a Futurebit Apollo, making this the third solo block find for Futurebit. The first Futurebit Apollo block find may have been a fluke, the second a coincidence, but the third is an indication of a pattern forming here. More hashrate is being controlled by individuals who are constructing their own blocks and this trend will accelerate as time goes on and deploying these devices becomes easier and less expensive. This was the second solo block found in March.
March 21, US Treasury Department lifts sanctions on Tornado Cash. This is a positive sign coming from the US Treasury, however the charges against the Tornado Cash developer, Roman Storm, still stand and his legal defense team is still fighting an uphill battle. Even though the US Treasury removed Tornado Cash from the OFAC list, the department is attempting to stop a Texas court from granting a motion that would ensure the Treasury can’t put Tornado Cash back on the OFAC list. Meanwhile, the other Tornado Cash developer, Alex Pertsev, is fighting his appeal battle in the Dutch courts.
March 22, Self-hosted Public Pool user mines Block #888989. This was the first block mined with the Public Pool software, which is open-source and available for anyone to host themselves, in this case hosted on the user’s Umbrel. If you read the January issue of The 256 Foundation newsletter, there are detailed instructions for hosting your own instance of Public Pool on a Raspberry Pi. Easier solutions exist and accomplish the same thing such as Umbrel and Start9. This was the third solo block mined in March.
March 26, DeFi Education Fund publishes coalition letter urging congress to correct the DOJ’s dangerous misinterpretation of money transmission laws. In their own words: “First seen in Aug 2023 via the criminal indictment of @rstormsf, the DOJ’s novel legal theory expands criminal liability to software developers, ignoring longstanding FinCEN guidance and threatening the entire U.S. blockchain & digital asset ecosystem”. Many familiar organizations in the industry signed the letter, such as Coinbase, Kraken, A16z Crypto, and Ledger. Sadly, no Bitcoin companies signed the letter, highlighting the reckless ignorance prevalent among the “toxic Bitcoin maximalists” who often pride themselves on their narrow focus; a focus which is proving to be more of a blind spot limiting their ability to recognize a clear and present threat. The full letter text can be found here.
March 28, Heatbit reveals the black Heatbit, an elegant space heater that mines Bitcoin. Heat re-use applications such as Bitcoin mining space heaters are one of many examples where energy spent on generating heat can also earn the user sats. Other popular solutions include heating hot tubs, hotels, drive ways, and more. The innovations in this area will continue to be unlocked as open-source solutions like the ones being developed at The 256 Foundation are released and innovators gain more control over their applications.
March 29, miner with 2.5Ph/s solves Block #889975 with Solo CK Pool, marking the fourth solo block found in the month of March. This was the first solo block found on CK Pool’s European server. This was a good way to finish the month on a strong note for small-scale miners.
Free & Open Mining Industry Developments:
The development will not stop until Bitcoin mining is free and open. Innovators didn’t let off the gas in March, here are eleven note-worthy events:
0) @BTC_Grid demonstrates heating a new residential build with Bitcoin miners. This custom build features 6,000 square feet of radiant floors, 1,500 sqft of snow melting slab, 2 heated pools, all powered by Bitcoin miners and fully automated. Innovations and efficient systems like this will become more common as Bitcoin mining hardware and firmware solutions become open-source
1) @DrydeGab shares The Ocho, a Bitaxe Nerd Octaxe open-source Bitcoin miner featuring 8x BM1370 ASICs that performs at 9-10Th/s consuming ~180W. The Ocho runs on it’s own custom AxeOS. Currently out of stock but generally available for purchase in the IX Tech store.
 [IMG-003] The Nerd OCTAXE Ocho by @DrydeGab
[IMG-003] The Nerd OCTAXE Ocho by @DrydeGab2) @incognitojohn23 demonstrates building a Bitaxe from scratch with no prior experience, proving that anyone can access this technology with a little determination and the right community. @incognitojohn23 has also uploaded several videos documenting his progress and lessons along the way. Every builder has their first day, don’t hold back if you feel compelled to jump in and get started.
3) @HodlRev demonstrating how he combines Bitcoin mining with maple syrup production. In fact, @HodlRev has integrated Bitcoin mining into several aspects of his homestead. Be sure to follow his content for an endless stream of resourceful ideas. Once open-source Bitcoin mining firmware and hardware solutions become widely available, innovators like @HodlRev will have more control over every parameter of these unique applications.
4) ATL Bitlab announces their first hackathon, running June 7 through July 6. Promoted as “A global hackathon focused on all things bitcoin mining”. If you are interested in joining the hackathon, there is a Google form you can fill out here. It will be interesting to see what innovations come from this effort.
5) @100AcresRanch builds touchscreen dashboard for Bitaxe and Loki Boards. With this, you can control up to 10 mining devices with the ability to instantly switch any of the presets without going into the mining device UI.
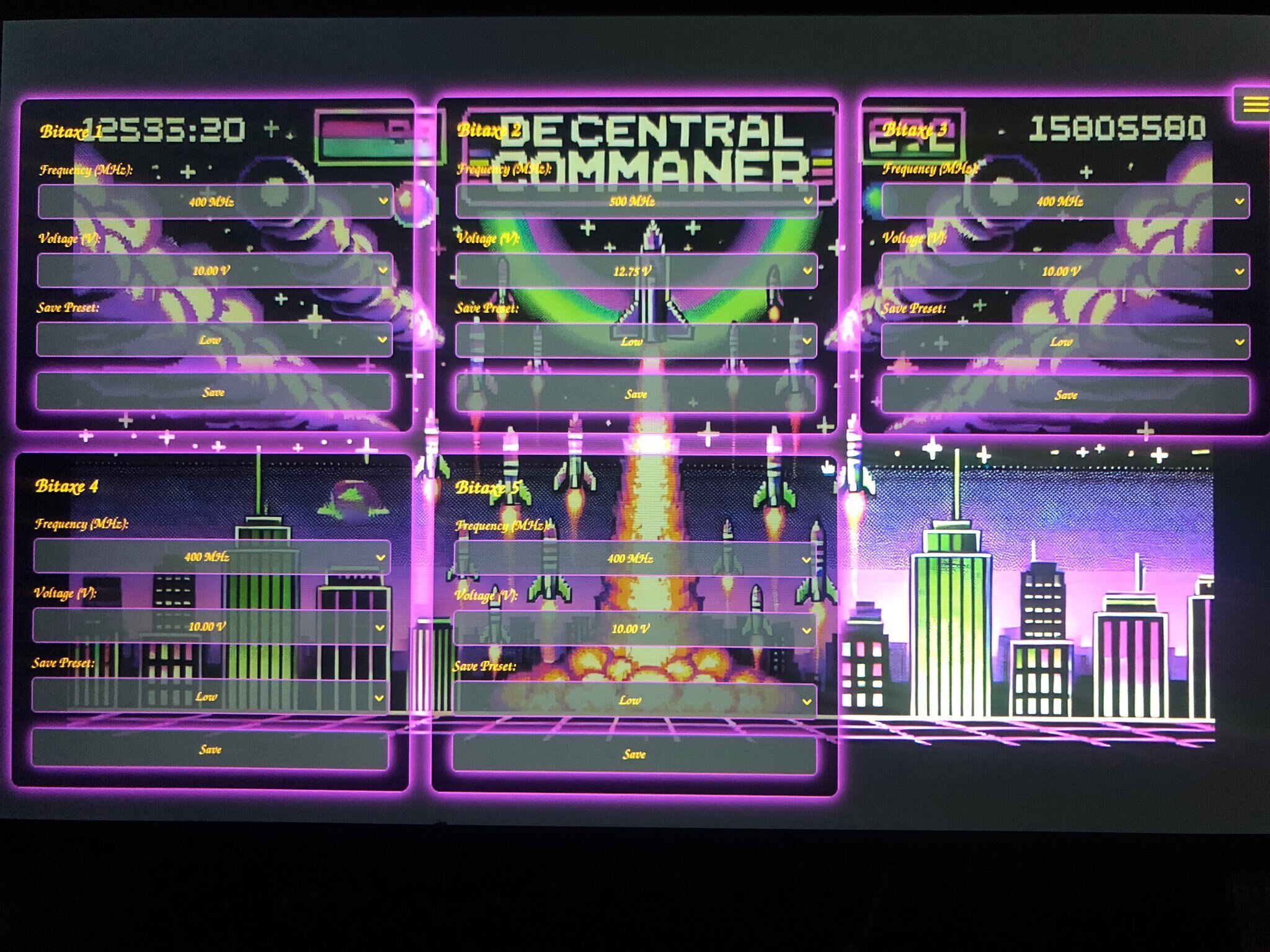 [IMG-004] Decentral Command Dashboard by @100AcresRanch
[IMG-004] Decentral Command Dashboard by @100AcresRanch6) @IxTechCrypto reveals HAXE, the newest member of the Nerdaxe miner family. HAXE is a 6 ASIC miner performing at ~7.4 Th/s at ~118W. Upon looking at the IX Tech store, it seems as though the HAXE has not hit shelves yet but keep an eye out for announcements soon.
7) Solo Satoshi reveals the NerdQaxe++, the latest marvel in the world of open-source Bitcoin mining solutions. This device is equipped with four ASIC chips from the Antminer S21 Pro and boasts an efficiency rating of 15.8 J/Th. At the advertised power consumption of 76 Watts, that would produce nearly 5 Th/s. Currently out of stock at the Solo Satoshi store and the IX Tech store but in stock and available at the PlebSource store.
8) @TheSoloMiningCo shares a bolt-on voltage regulator heatsink for the Bitaxe, this is a helpful modification when overclocking your miner and helps dissipate heat away from the voltage regulator. Many innovators are discovering ways to get every bit of efficiency they can from their hardware and sharing their ideas with the wider community for anyone to adopt.
9) @boerst adds historical data to stratum.work, a public website that monitors mining pool activity through calling for the work templates being generated for the pool’s respective miners. By parsing the information available in the work templates, a number of interesting observations can be made like which pools are merely proxies for larger pools, timing analysis of when templates are sent out, and now historical data on what the state of each pool’s templates were at a given block height. The work Boerst is doing with this website provides a great tool for gaining insights into mining centralization.
10) Braiins open-sources the BCB100 Control Board, designed to work with Antminers, this control board project has two parts: the hardware and the software. For the hardware part, open files include the Bill Of Materials, schematics, Gerbers, and CAD files. For the software part, open files include the board-level OpenWrt-based firmware with the full configuration file and the Nix environment for reproducible builds. The mining firmware binaries for bosminer and boser (same as the official Braiins OS releases) are also available to download and use to compile the image for the control board, however the Braiins OS firmware itself is not included in this open-source bundle. Braiins chose the GPLv3 open-source license for the software and the CERN-OHL-S open-source license for the hardware. This is a great gesture by Braiins and helps validate the efforts of The 256 Foundation to make Bitcoin mining free and open. The Braiins GitHub repositories where all this information can be found are accessible here and here. The 256 Foundation has plans to develop a Mujina firmware that can be flashed onto the BCB100 helping target Antminer machines.
Grant Project Updates:
In March, The 256 Foundation formalized agreements with the lead developers who were selected for each project. These agreements clearly defined the scope of each project, identified the deliverables, set a timeline, and agreement on compensation was made. Below are the outlines for each project, the compensation is not made public for privacy and security reasons.
Ember One:
@skot9000 instigator of the Bitaxe and all around legend for being the first mover in open-source Bitcoin mining solutions is the lead engineer for the Ember One project. This was the first fully funded grant from The 256 Foundation and commenced in November 2024 with a six month duration. The deliverable is a validated design for a ~100W miner with a standardized form factor (128mm x 128mm), USB-C data connection, 12-24v input voltage, with plans for several versions – each with a different ASIC chip. The First Ember One features the Bitmain BM1362 ASIC, next on the list will be an Ember One with the Intel BZM2 ASIC, then an Auradine ASIC version, and eventually a Block ASIC version. Learn more at: https://emberone.org/
Mujina Mining Firmware:
@ryankuester, embedded Linux developer and Electrical Engineer who has mastered the intersection of hardware and software over the last 20 years is the lead developer for the Mujina project, a Linux based mining firmware application with support for multiple drivers so it can be used with Ember One complete mining system. The grant starts on April 5, 2025 and continues for nine months. Deliverables include:
Core Mujina-miner Application: - Fully open-source under GPLv3 license - Written in Rust for performance, robustness, and maintainability, leveraging Rust's growing adoption in the Bitcoin ecosystem - Designed for modularity and extensibility - Stratum V1 client (which includes DATUM compatibility) - Best effort for Stratum V2 client in the initial release but may not happen until later
Hardware Support:
- Support for Ember One 00 hash boards (Bitmain chips) - Support for Ember One 01 hash boards (Intel chips) on a best effort basis but may not happen until later - Full support on the Raspberry Pi CM5 and IO board running the Raspberry Pi OS - Support for the Libre board when released - Best-effort compatibility with other hardware running LinuxManagement Interfaces:
• HTTP API for remote management and monitoring • Command-line interface for direct control • Basic web dashboard for status monitoring • Configuration via structured text files • Community Building and Infrastructure • GitHub project organization and workflow • Continuous integration and testing framework • Comprehensive user and developer documentation • Communication channels for users and developers • Community building through writing, podcasts, and conference participationThe initial release of Mujina is being built in such a way that it supports long-term goals like ultimately evolving into a complete Linux-based operating system, deployable through simple flashing procedures. Initially focused on supporting the 256 Foundation's Libre control boards and Ember hash boards, Mujina's modular architecture will eventually enable compatibility with a wide variety of mining hardware from different manufacturers. Lean more at: https://mujina.org/
Libre Board:
@Schnitzel, heat re-use maximalist who turned his home's hot water accessories into Bitcoin-powered sats generators and during the day has built a successful business with a background in product management, is the lead engineer on the Libre Board project; the control board for the Ember One complete mining system. Start date is April 5, 2025 and the deliverables after six months will be a mining control board based on the Raspberry Pi Compute Module I/O Board with at least the following connections:
• USB hub integration (maybe 10 ports?) • Support for fan connections • NVME expansion • Two 100-pin connectors for the compute module • Ethernet port • HDMI port • Raspberrypi 40-pin header for sensors, switches, & relays etc. • MIPI port for touchscreen • Accepts 12-24 VDC input power voltage.The initial release of Libre Board is being built in such a way that it supports long-term goals like alternative compute modules such as ARM, x86, and RISC-V. Learn more at: https://libreboard.org/
Hydra Pool:
@jungly, distributed systems PhD and the lead developer behind P2Pool v2 and formerly for Braidpool, now takes the reigns as lead developer for Hydra Pool, the stratum server package that will run on the Ember One mining system. Start date for this project was on April 5, 2025 and the duration lasts for six months. Deliverables include:
• Talks to bitcoind and provides stratum work to users and stores received shares • Scalable and robust database support to save received shares • Run share accounting on the stored shares • Implement payment mechanisms to pay out miners based on the share accounting • Provide two operation modes: Solo mining and PPLNS or Tides based payout mechanism, with payouts from coinbase only. (All other payout mechanism are out of scope of this initial release for now but there will be more). • Rolling upgrades: Tools and scripts to upgrade server with zero downtime. • Dashboard: Pool stats view only dashboard with support to filter miner payout addresses. • Documentation: Setup and other help pages, as required.The initial release of Hydra Pool is being built in such a way that it supports long-term goals like alternative payout models such as echash, communicating with other Hydra Pool instances, local store of shares for Ember One, and a user-friendly interface that puts controls at the user's fingertips, and supports the ability for upstream pool proxying. Learn More at: https://hydrapool.org/
Block Watcher:
Initially scoped to be a Bitcoin mining insights application built to run on the Ember One mining system using the self-hosted node for blockchain data. However, The 256 Foundation has decided to pause Block Watcher development for a number of reasons. Primarily because the other four projects were more central to the foundation’s mission and given the early stages of the Foundation with the current support level, it made more sense to deploy capital where it counts most.
Actionable Advice:
This month’s Actionable Advice column explains the process for upgrading the Futurebit Apollo I OS to the newer Apollo II OS and replacing the SSD. The Futurebit Apollo is a small mining device with an integrated Bitcoin node designed as a plug-and-play solution for people interested in mining Bitcoin without all the noise and heat of the larger industrial-grade miners. The Apollo I can hash between 2 – 4 Th/s and will consume roughly 125 – 200 Watts. The Apollo II can hash between 8 – 10 Th/s and will consume roughly 280 – 400 Watts. The motivation behind upgrading from the Apollo I OS to the Apollo II OS is the ability to run a stratum server internally so that the mining part of the device can ask the node part of the device for mining work, thus enabling users to solo mine in a self-hosted fashion. In fact, this is exactly what The 256 Foundation did during the Telehash fundraising event where Block #881423 was solo mined, at one point there was more than 1 Eh/s of hashrate pointed to that Apollo.
 [IMG-005] Futurebit Apollo I with new NVME SSD
[IMG-005] Futurebit Apollo I with new NVME SSDYou can find the complete flashing instructions on the Futurebit website here. You will need a separate computer to complete the flashing procedure. The flashing procedure will erase all data on the microSD card so back it up if you have anything valuable saved on there.
First navigate to the Futurebit GitHub Releases page at: https://github.com/jstefanop/apolloapi-v2/releases
Once there, you will see two OS images available for download, along with two links to alternative hosting options for those two images. If you are upgrading an Apollo I, you need to figure out which new OS image is right for your device, the MCU 1 image or the MCU 2 image. There are detailed instructions on figuring this out available here. There are multiple ways to determine if you need the MCU 1 or MCU 2 image. If the second to last digit in your Futurebit Apollo I is between 4 – 8 then you have an MCU 1; or if your batch number is 1 – 3 then you have an MCU 1; or if the circuit board has a 40-pin connector running perpendicular to the microSD card slot then you have an MCU 1. Otherwise, you have an MCU 2.
For example, this is what the MCU 1 circuit board will look like:
 [IMG-006] Futurebit MCU1 example
[IMG-006] Futurebit MCU1 exampleOnce you figure out which OS image you need, go ahead and download it. The SHA256 hash values for the OS Image files are presented in the GitHub repo. If you’re running Linux on your computer, you can change directory to your Download folder and run the following command to check the SHA256 hash value of the file you downloaded and compare that to the SHA256 hash values on GitHub.
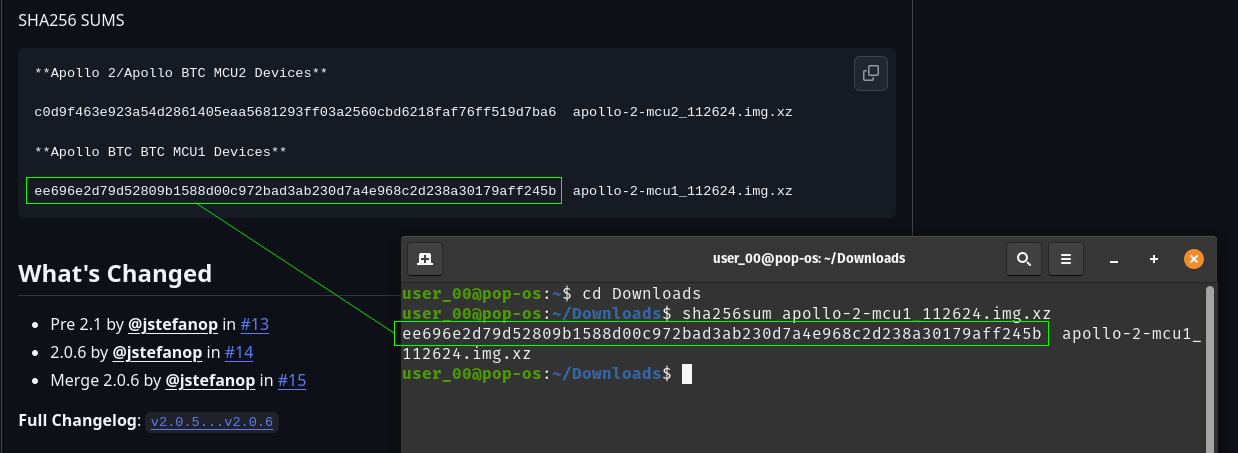 [IMG-007] Verifying Futurebit OS Image Hash Value
[IMG-007] Verifying Futurebit OS Image Hash ValueWith the hash value confirmed, you can use a program like Balena Etcher to flash your microSD card. First remove the microSD card from the Apollo circuit board by pushing it inward, it should make a small click and then spring outward so that you can grab it and remove it from the slot.
Connect the microSD card to your computer with the appropriate adapter.
Open Balena Etcher and click on the “Flash From File” button to define the file path to where you have the OS image saved:
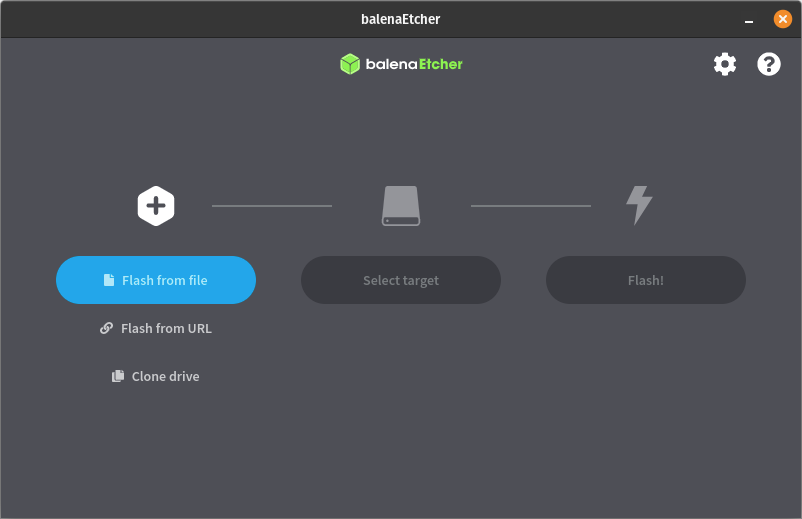 [IMG-008] Balena Etcher user interface
[IMG-008] Balena Etcher user interfaceThen click on the “Select Target” button to define the drive which you will be flashing. Select the microSD card and be sure not to select any other drive on your computer by mistake:
 [IMG-009] Balena Etcher user interface
[IMG-009] Balena Etcher user interfaceThen click on the “Flash” button and Balena Etcher will take care of formatting the microSD card, decompressing the OS image file, and flashing it to the microSD card.
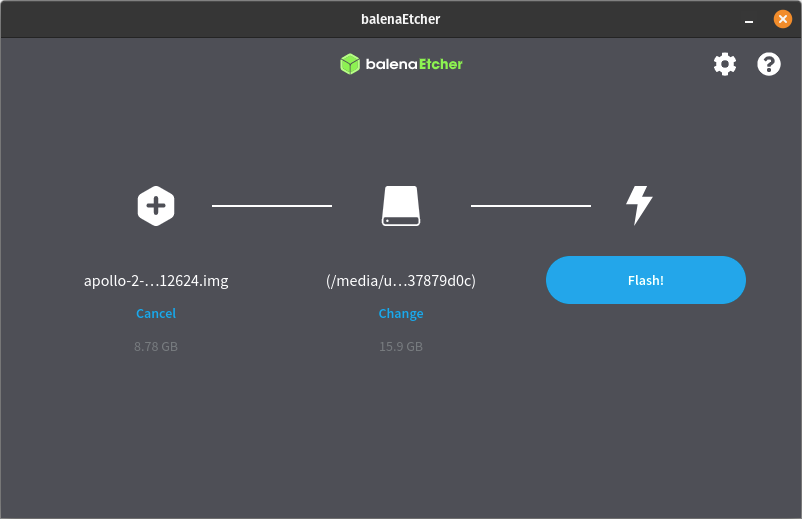 [IMG-010] Balena Etcher user interface.
[IMG-010] Balena Etcher user interface.The flashing process can take some time so be patient. The Balena Etcher interface will allow you to monitor the progress.
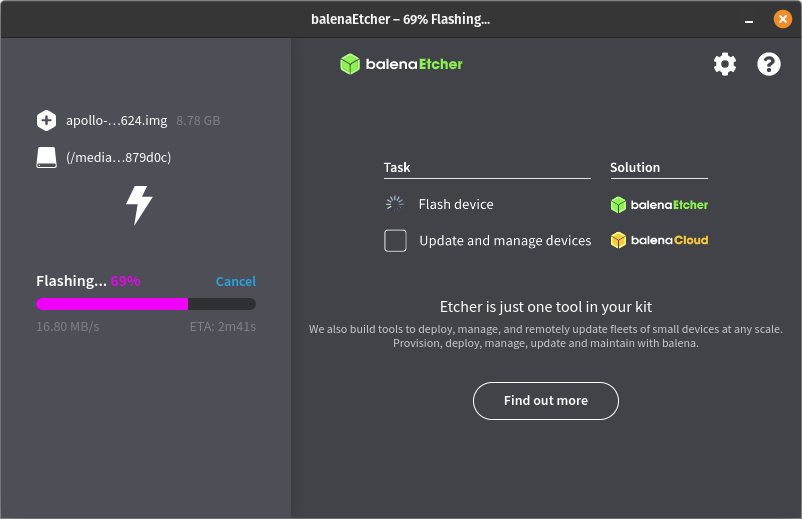 [IMG-011] Balena Etcher user interface.
[IMG-011] Balena Etcher user interface.Once the flashing process is completed successfully, you will receive a notice in the balena Etcher interface that looks like this:
 [IMG-012] Balena Etcher user interface.
[IMG-012] Balena Etcher user interface.You can remove the microSD card from your computer now and install it back into the Futurebit Apollo. If you have an adequately sized SSD then your block chain data should be safe as that is where it resides, not on the microSD card. If you have a 1TB SSD then this would be a good time to consider upgrading to a 2TB SSD instead. There are lots of options but you want to get an NVME style one like this:
 [IMG-013] 1TB vs. 2TB NVME SSD
[IMG-013] 1TB vs. 2TB NVME SSDSimply loosen the screw holding the SSD in place and then remove the old SSD by pulling it out of the socket. Then insert the new one and put the screw back in place.
Once the SSD and microSD are back in place, you can connect Ethernet and the power supply, then apply power to your Apollo.
You will be able to access your Apollo through a web browser on your computer. You will need to figure out the local IP address of your Apollo device so log into your router and check the DHCP leases section. Your router should be accessible from your local network by typing an IP address into your web browser like 192.168.0.1 or 10.0.0.1 or maybe your router manufacturer uses a different default. You should be able to do an internet search for your specific router and figure it out quickly if you don’t already know. If that fails, you can download and run a program like Angry IP Scanner.
Give the Apollo some time to run through a few preliminary and automatic configurations, you should be able to see the Apollo on your local network within 10 minutes of powering it on.
Once you figure out the IP address for your Apollo, type it into your web browser and this is the first screen you should be greeted with:
 [IMG-014] Futurebit welcome screen
[IMG-014] Futurebit welcome screenClick on the button that says “Start setup process”. The next you will see should look like this:
 [IMG-015] Futurebit mining selection screen
[IMG-015] Futurebit mining selection screenYou have the option here to select solo mining or pooled mining. If you have installed a new SSD card then you should select pooled mining because you will not be able to solo mine until the entire Bitcoin blockchain is downloaded.
Your Apollo will automatically start downloading the Bitcoin blockchain in the background and in the mean-time you can start mining with a pool of your choice like Solo CK Pool or Public Pool or others.
Be forewarned that the Initial Blockchain Download (“IBD”) takes a long time. At the time of this writing, it took 18 days to download the entire blockchain using a Starlink internet connection, which was probably throttled at some points in the process because of the roughly 680 GB of data that it takes.
In February 2022, the IBD on this exact same device took 2 days with a cable internet connection. Maybe the Starlink was a bit of a bottleneck but most likely the extended length of the download can be attributed to all those JPEGS on the blockchain.
Otherwise, if you already have the full blockchain on your SSD then you should be able to start solo mining right away by selecting the solo mining option.
After making your selection, the Apollo will automatically run through some configurations and you should have the option to set a password somewhere in there along the way. Then you should see this page:
 [IMG-016] Futurebit setup completion page
[IMG-016] Futurebit setup completion pageClick on the “Start mining” button. Then you should be brought to your dashboard like this:
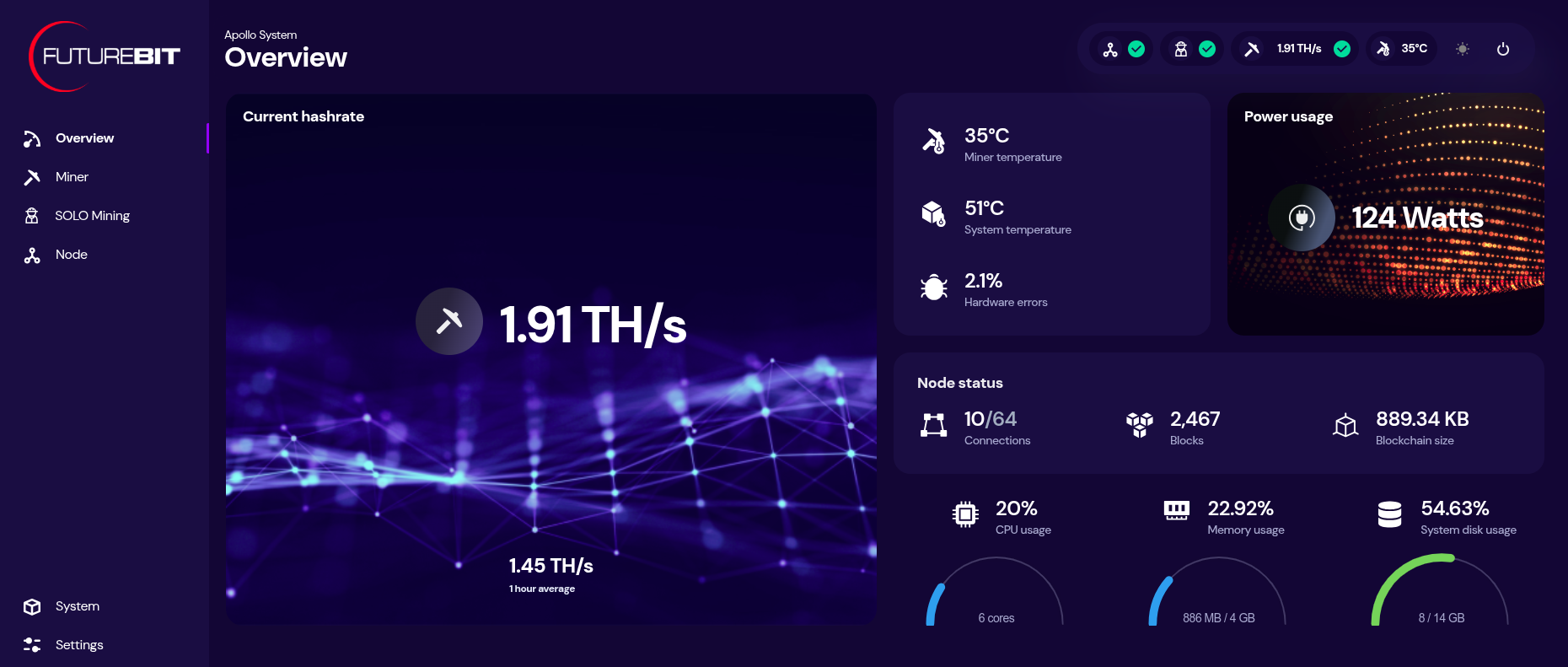 [IMG-017] Futurebit dashboard
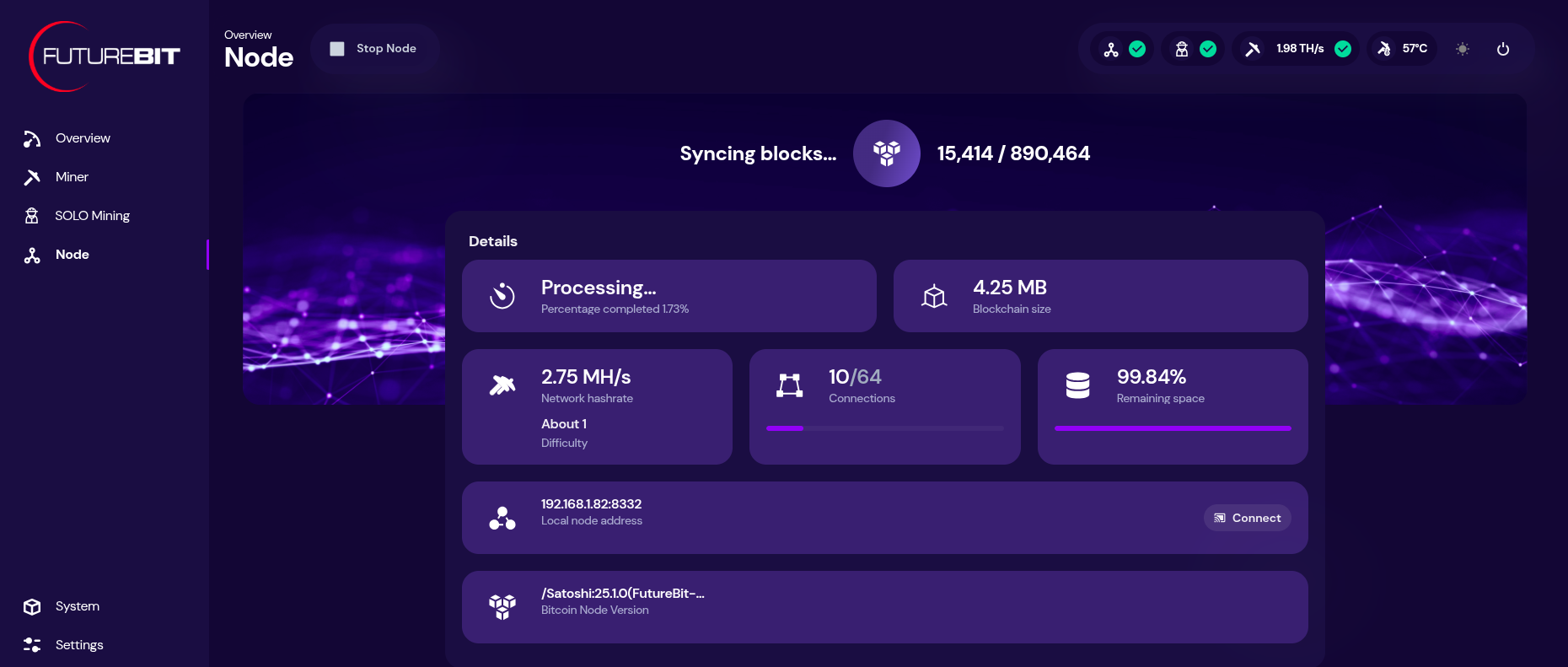
[IMG-017] Futurebit dashboardYou can monitor your hashrate, temperatures, and more from the dashboard. You can check on the status of your Bitcoin node by clicking on the three-circle looking icon that says “node” on the left-hand side menu.
 [IMG-018] Futurebit node page
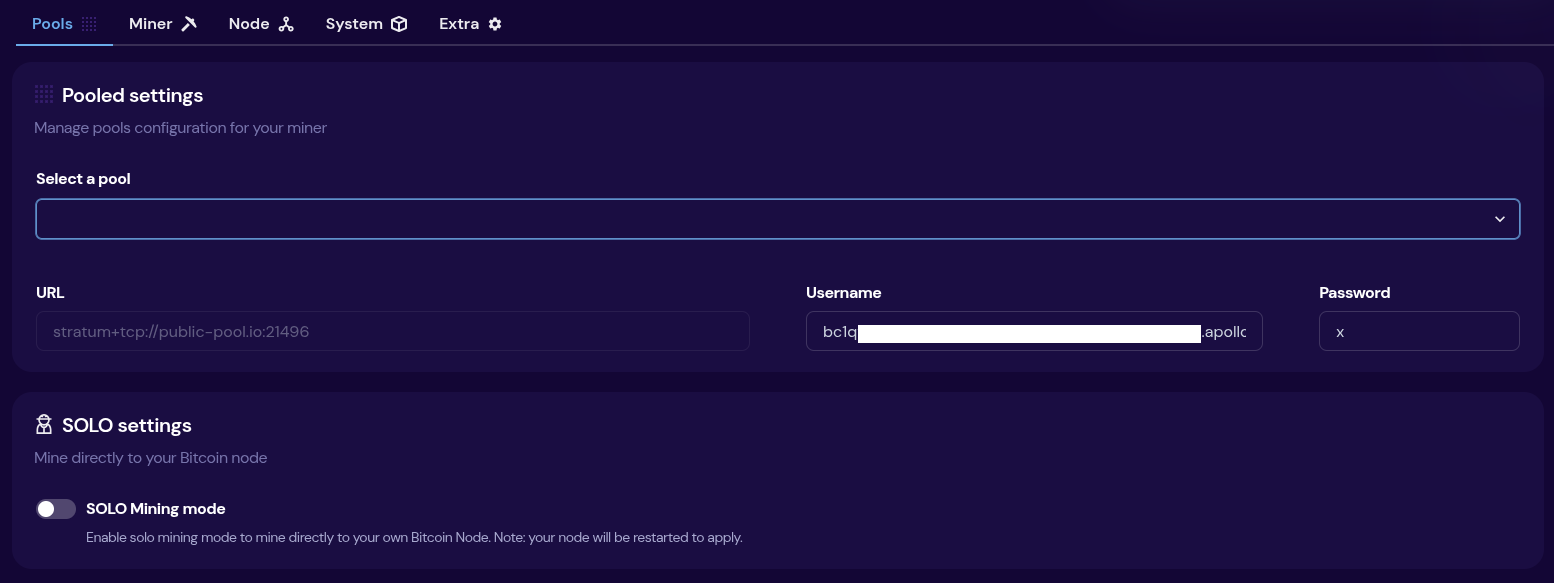
[IMG-018] Futurebit node pageIf you need to update the mining pool, click on the “settings” option at the bottom of the left-hand side menu. There you will see a drop down menu for selecting a pool to use, you can select the “setup custom pool” option to insert the appropriate stratum URL and then your worker name.
Once your IBD is finished, you can start solo mining by toggling on the solo mode at the bottom of the settings page. You will have a chance to update the Bitcoin address you want to mine to. Then click on “save & restart”.
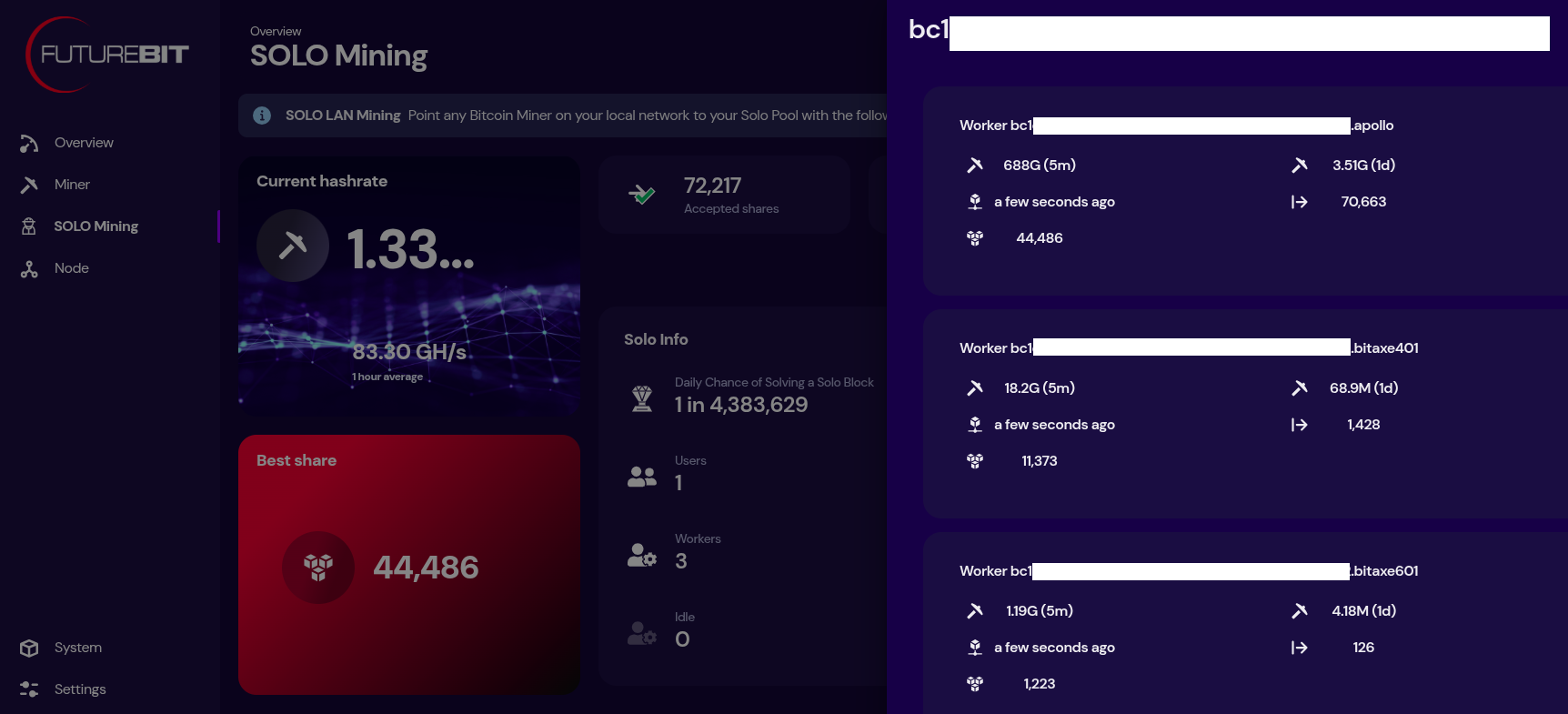
 [IMG-019] Futurebit mining pool settings
[IMG-019] Futurebit mining pool settingsThen once your system comes back up, you will see a banner at the top of the dashboard page with the IP address you can use to point any other miners you have, like Bitaxes, to your own self-hosted solo mining pool!
 [IMG-020] Futurebit solo mining dashboard
[IMG-020] Futurebit solo mining dashboardNow just sit back and enjoy watching your best shares roll in until you get one higher than the network difficulty and you mine that solo block.
State of the Network:
Hashrate on the 14-day MA according to mempool.space increased from ~793 Eh/s to ~829 Eh/s in March, marking ~4.5% growth for the month.
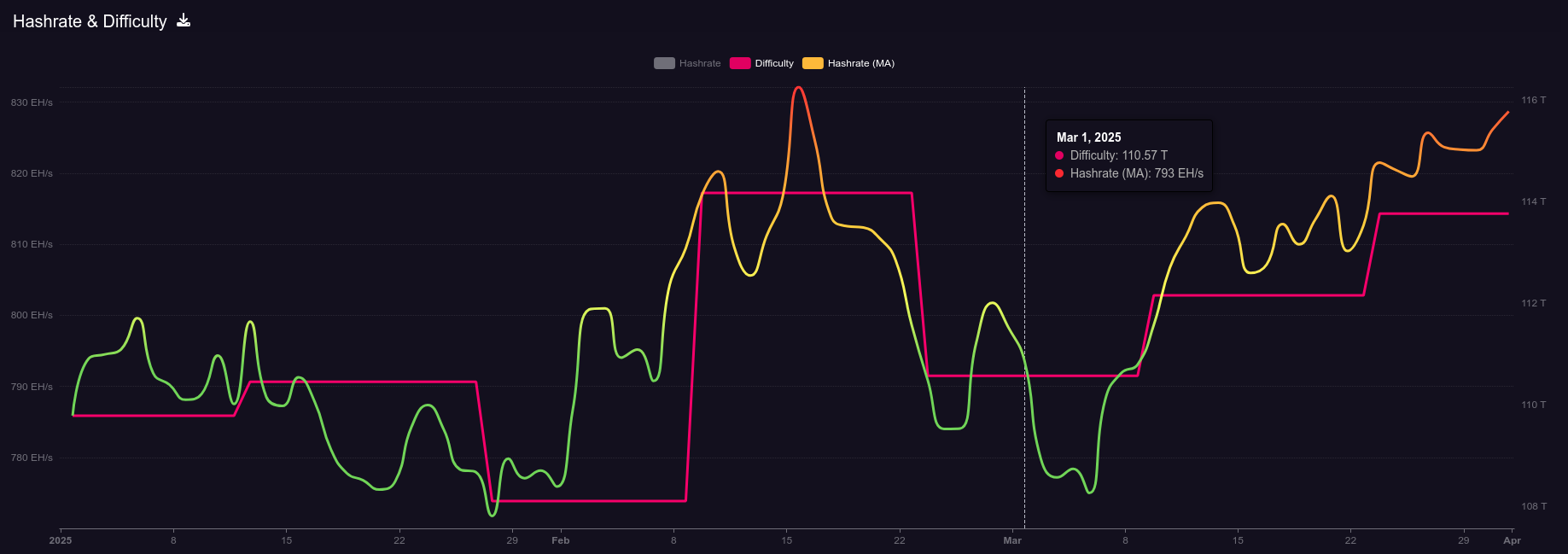 [IMG-021] 2025 hashrate/difficulty chart from mempool.space
[IMG-021] 2025 hashrate/difficulty chart from mempool.spaceDifficulty was 110.57T at it’s lowest in March and 113.76T at it’s highest, which is a 2.8% increase for the month. All together for 2025 up until the end of March, difficulty has gone up ~3.6%.
According to the Hashrate Index, more efficient miners like the <19 J/Th models are fetching $17.29 per terahash, models between 19J/Th – 25J/Th are selling for $11.05 per terahash, and models >25J/Th are selling for $3.20 per terahash. Overall, prices seem to have dropped slightly over the month of March. You can expect to pay roughly $4,000 for a new-gen miner with 230+ Th/s.
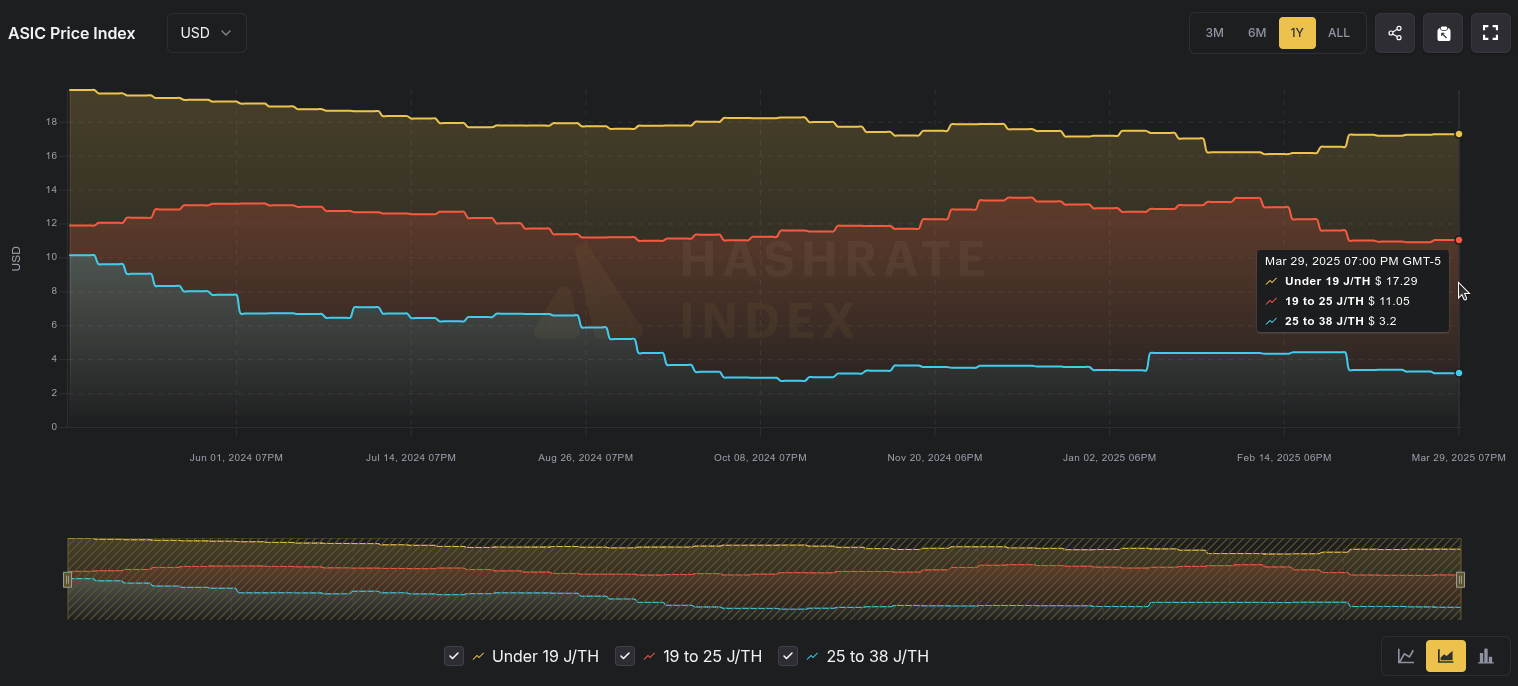 [IMG-022] Miner Prices from Luxor’s Hashrate Index
[IMG-022] Miner Prices from Luxor’s Hashrate IndexHashvalue is closed out in March at ~56,000 sats/Ph per day, relatively flat from Frebruary, according to Braiins Insights. Hashprice is $46.00/Ph per day, down from $47.00/Ph per day in February.
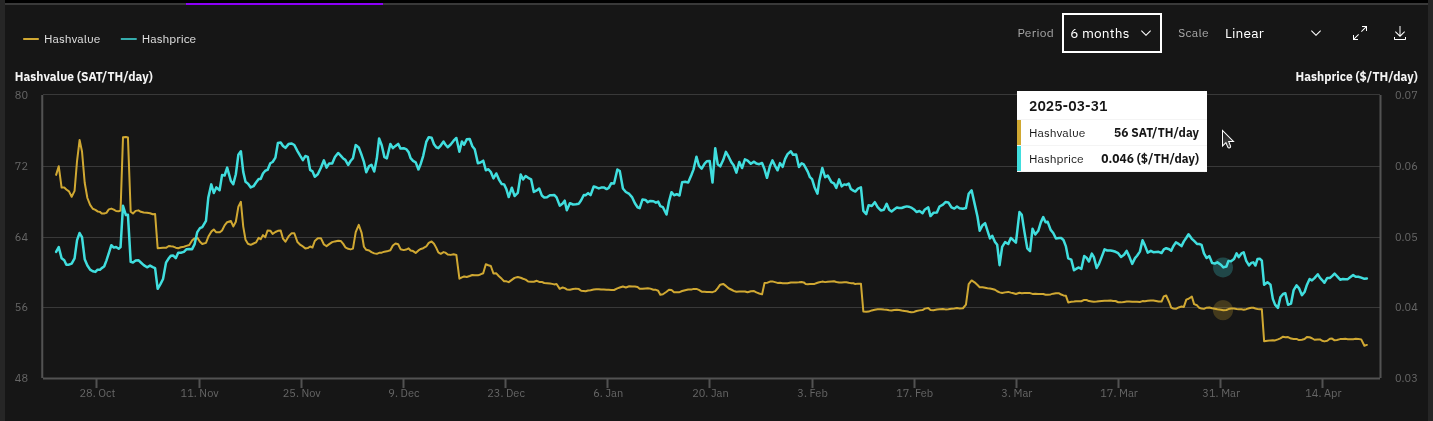 [IMG-023] Hashprice/Hashvalue from Braiins Insights
[IMG-023] Hashprice/Hashvalue from Braiins InsightsThe next halving will occur at block height 1,050,000 which should be in roughly 1,071 days or in other words ~156,850 blocks from time of publishing this newsletter.
Conclusion:
Thank you for reading the third 256 Foundation newsletter. Keep an eye out for more newsletters on a monthly basis in your email inbox by subscribing at 256foundation.org. Or you can download .pdf versions of the newsletters from there as well. You can also find these newsletters published in article form on Nostr.
If you haven’t done so already, be sure to RSVP for the Texas Energy & Mining Summit (“TEMS”) in Austin, Texas on May 6 & 7 for two days of the highest Bitcoin mining and energy signal in the industry, set in the intimate Bitcoin Commons, so you can meet and mingle with the best and brightest movers and shakers in the space.
While you’re at it, extend your stay and spend Cinco De Mayo with The 256 Foundation at our second fundraiser, Telehash #2. Everything is bigger in Texas, so set your expectations high for this one. All of the lead developers from the grant projects will be present to talk first-hand about how to dismantle the proprietary mining empire.
 IMG-024] TEMS 2025 flyer
IMG-024] TEMS 2025 flyerIf you have an old Apollo I laying around and want to get it up to date and solo mining then hopefully this newsletter helped you accomplish that.
 [IMG-026] FREE SAMOURAI
[IMG-026] FREE SAMOURAIIf you want to continue seeing developers build free and open solutions be sure to support the Samourai Wallet developers by making a tax-deductible contribution to their legal defense fund here. The first step in ensuring a future of free and open Bitcoin development starts with freeing these developers.
You can just FAFO,
-econoalchemist
-
 @ 6e0ea5d6:0327f353
2025-02-21 18:15:52
@ 6e0ea5d6:0327f353
2025-02-21 18:15:52"Malcolm Forbes recounts that a lady, wearing a faded cotton dress, and her husband, dressed in an old handmade suit, stepped off a train in Boston, USA, and timidly made their way to the office of the president of Harvard University. They had come from Palo Alto, California, and had not scheduled an appointment. The secretary, at a glance, thought that those two, looking like country bumpkins, had no business at Harvard.
— We want to speak with the president — the man said in a low voice.
— He will be busy all day — the secretary replied curtly.
— We will wait.
The secretary ignored them for hours, hoping the couple would finally give up and leave. But they stayed there, and the secretary, somewhat frustrated, decided to bother the president, although she hated doing that.
— If you speak with them for just a few minutes, maybe they will decide to go away — she said.
The president sighed in irritation but agreed. Someone of his importance did not have time to meet people like that, but he hated faded dresses and tattered suits in his office. With a stern face, he went to the couple.
— We had a son who studied at Harvard for a year — the woman said. — He loved Harvard and was very happy here, but a year ago he died in an accident, and we would like to erect a monument in his honor somewhere on campus.— My lady — said the president rudely —, we cannot erect a statue for every person who studied at Harvard and died; if we did, this place would look like a cemetery.
— Oh, no — the lady quickly replied. — We do not want to erect a statue. We would like to donate a building to Harvard.
The president looked at the woman's faded dress and her husband's old suit and exclaimed:
— A building! Do you have even the faintest idea of how much a building costs? We have more than seven and a half million dollars' worth of buildings here at Harvard.
The lady was silent for a moment, then said to her husband:
— If that’s all it costs to found a university, why don’t we have our own?
The husband agreed.
The couple, Leland Stanford, stood up and left, leaving the president confused. Traveling back to Palo Alto, California, they established there Stanford University, the second-largest in the world, in honor of their son, a former Harvard student."
Text extracted from: "Mileumlivros - Stories that Teach Values."
Thank you for reading, my friend! If this message helped you in any way, consider leaving your glass “🥃” as a token of appreciation.
A toast to our family!
-
 @ 9bde4214:06ca052b
2025-04-22 17:23:02
@ 9bde4214:06ca052b
2025-04-22 17:23:02“You’ll get all that for free if you build it right.”
Pablo & Gigi try to stop giggling.
In this dialogue:
- 01: Start Ugly
- 02: There is No Global
- Concept of ownership & “Read, Write, Own”
- Shamir Secret Sharing and Timelocks
- “No amount of violence will ever solve a math problem.”
- You can’t prove deletion of a key (or anything, really); best you can do is “burn” bitcoin
- Data is information, which behaves like an idea (not like an apple)
- “If you have an apple and I have an apple and we exchange these apples then you and I will still each have one apple. But if you have an idea and I have an idea and we exchange these ideas, then each of us will have two ideas.” – https://dergigi.com/threads/memes-vs-the-world
- Why the Pubky architecture isn’t great
- Cashu
- Nutzaps: NIP-60 / NIP-61
- How nutzaps fix fake zaps on zaplife.lol
- “Ecash fixes HTTP 402”
- “[Bitcoin [and nostr]] take advantage of the nature of information being easy to spread but hard to stifle.” –Satoshi Nakamoto
- Discovery with NIP-89
- #RunDVM with NIP-90
- Why micropayments can’t work on credit rails, and how bitcoin is the rediscovery of money.
- Putting payments into blossom
- “Money is essentially a tool to keep track of who owes what to whom. Broadly speaking, everything we have used as money up to now falls into two categories: physical artifacts and informational lists. Or, to use more common parlance: tokens and ledgers.”
- “maximum utility in the world of Bitcoin entails the adoption of maximum responsibility.”
- Complexity of Lightning vs the simplicity of eCash
- Amber and Citrine
- How Pablo became the BIS
- 12 words in your head can literally save your life
- The in-between of custodial and non-custodial in a multi-mint world
- Nutzaps integrated in chachi.chat
- The intermediacy of nostr is magic
- In nostr you’ll get a lot for free IF YOU BUILD IT RIGHT
- “Free Speech platforms cannot exist; if there is a ‘deplatform’ button, the button will be pressed.”
- “Neither nostalgia nor utopia.”
- Solutions that make stuff worse over time vs solutions that make stuff better over time.
-
asknostr on passkeys, and why we think they’ll make things worse over time.
- Authentication vs identity: “identification asks, authentication proves”
- You are not your name and photo; identity is prismatic
- (m00t’s talk on it at web summit 2011)
- Starbug from CCC pwning TouchID biometrics from a high-res photo (article)
- Key rotation and (American) HODL
- Social recovery
- Multi-sig for nostr with FROSTR
Links & References:
- Nostr Protocol Repository: https://github.com/nostr-protocol
- Cashu (e-cash): https://github.com/cashubtc
- NIP-60 (Nutzaps): https://github.com/nostr-protocol/nips/blob/master/60.md
- NIP-89 (Service Discovery) & NIP-90 (DVMs) – upcoming proposals: https://nips.nostr.com/89 & https://nips.nostr.com/90
-
 @ 872982aa:8fb54cfe
2025-04-23 07:58:23
@ 872982aa:8fb54cfe
2025-04-23 07:58:23 -
 @ 1d7ff02a:d042b5be
2025-04-23 02:28:08
@ 1d7ff02a:d042b5be
2025-04-23 02:28:08ທຳຄວາມເຂົ້າໃຈກັບຂໍ້ບົກພ່ອງໃນລະບົບເງິນຂອງພວກເຮົາ
ຫຼາຍຄົນພົບຄວາມຫຍຸ້ງຍາກໃນການເຂົ້າໃຈ Bitcoin ເພາະວ່າພວກເຂົາຍັງບໍ່ເຂົ້າໃຈບັນຫາພື້ນຖານຂອງລະບົບເງິນທີ່ມີຢູ່ຂອງພວກເຮົາ. ລະບົບນີ້, ທີ່ມັກຖືກຮັບຮູ້ວ່າມີຄວາມໝັ້ນຄົງ, ມີຂໍ້ບົກພ່ອງໃນການອອກແບບທີ່ມີມາແຕ່ດັ້ງເດີມ ເຊິ່ງສົ່ງຜົນຕໍ່ຄວາມບໍ່ສະເໝີພາບທາງເສດຖະກິດ ແລະ ການເຊື່ອມເສຍຂອງຄວາມຮັ່ງມີສຳລັບພົນລະເມືອງທົ່ວໄປ. ການເຂົ້າໃຈບັນຫາເຫຼົ່ານີ້ແມ່ນກຸນແຈສຳຄັນເພື່ອເຂົ້າໃຈທ່າແຮງຂອງວິທີແກ້ໄຂທີ່ Bitcoin ສະເໜີ.
ບົດບາດຂອງກະຊວງການຄັງສະຫະລັດ ແລະ ທະນາຄານກາງ
ລະບົບເງິນຕາປັດຈຸບັນໃນສະຫະລັດອາເມລິກາປະກອບມີການເຊື່ອມໂຍງທີ່ຊັບຊ້ອນລະຫວ່າງກະຊວງການຄັງສະຫະລັດ ແລະ ທະນາຄານກາງ. ກະຊວງການຄັງສະຫະລັດເຮັດໜ້າທີ່ເປັນບັນຊີທະນາຄານຂອງປະເທດ, ເກັບອາກອນ ແລະ ສະໜັບສະໜູນລາຍຈ່າຍຂອງລັດຖະບານເຊັ່ນ: ທະຫານ, ໂຄງລ່າງພື້ນຖານ ແລະ ໂຄງການສັງຄົມ. ເຖິງຢ່າງໃດກໍຕາມ, ລັດຖະບານມັກໃຊ້ຈ່າຍຫຼາຍກວ່າທີ່ເກັບໄດ້, ເຊິ່ງເຮັດໃຫ້ຕ້ອງໄດ້ຢືມເງິນ. ການຢືມນີ້ແມ່ນເຮັດໂດຍການຂາຍພັນທະບັດລັດຖະບານ, ຊຶ່ງມັນຄືໃບ IOU ທີ່ສັນຍາວ່າຈະຈ່າຍຄືນຈຳນວນທີ່ຢືມພ້ອມດອກເບ້ຍ. ພັນທະບັດເຫຼົ່ານີ້ມັກຖືກຊື້ໂດຍທະນາຄານໃຫຍ່, ລັດຖະບານຕ່າງປະເທດ, ແລະ ທີ່ສຳຄັນ, ທະນາຄານກາງ.
ວິທີການສ້າງເງິນ (ຈາກອາກາດ)
ນີ້ແມ່ນບ່ອນທີ່ເກີດການສ້າງເງິນ "ຈາກອາກາດ". ເມື່ອທະນາຄານກາງຊື້ພັນທະບັດເຫຼົ່ານີ້, ມັນບໍ່ໄດ້ໃຊ້ເງິນທີ່ມີຢູ່ແລ້ວ; ມັນສ້າງເງິນໃໝ່ດ້ວຍວິທີການດິຈິຕອນໂດຍພຽງແຕ່ປ້ອນຕົວເລກເຂົ້າໃນຄອມພິວເຕີ. ເງິນໃໝ່ນີ້ຖືກເພີ່ມເຂົ້າໃນປະລິມານເງິນລວມ. ຍິ່ງສ້າງເງິນຫຼາຍຂຶ້ນ ແລະ ເພີ່ມເຂົ້າໄປ, ມູນຄ່າຂອງເງິນທີ່ມີຢູ່ແລ້ວກໍຍິ່ງຫຼຸດລົງ. ຂະບວນການນີ້ຄືສິ່ງທີ່ພວກເຮົາເອີ້ນວ່າເງິນເຟີ້. ເນື່ອງຈາກກະຊວງການຄັງຢືມຢ່າງຕໍ່ເນື່ອງ ແລະ ທະນາຄານກາງສາມາດພິມໄດ້ຢ່າງຕໍ່ເນື່ອງ, ສິ່ງນີ້ຖືກສະເໜີວ່າເປັນວົງຈອນທີ່ບໍ່ມີທີ່ສິ້ນສຸດ.
ການໃຫ້ກູ້ຢືມສະຫງວນບາງສ່ວນໂດຍທະນາຄານ
ເພີ່ມເຂົ້າໃນບັນຫານີ້ຄືການປະຕິບັດຂອງການໃຫ້ກູ້ຢືມສະຫງວນບາງສ່ວນໂດຍທະນາຄານ. ເມື່ອທ່ານຝາກເງິນເຂົ້າທະນາຄານ, ທະນາຄານຖືກຮຽກຮ້ອງໃຫ້ເກັບຮັກສາພຽງແຕ່ສ່ວນໜຶ່ງຂອງເງິນຝາກນັ້ນໄວ້ເປັນເງິນສະຫງວນ (ຕົວຢ່າງ, 10%). ສ່ວນທີ່ເຫຼືອ (90%) ສາມາດຖືກປ່ອຍກູ້. ເມື່ອຜູ້ກູ້ຢືມໃຊ້ຈ່າຍເງິນນັ້ນ, ມັນມັກຖືກຝາກເຂົ້າອີກທະນາຄານ, ເຊິ່ງຈາກນັ້ນກໍຈະເຮັດຊ້ຳຂະບວນການໃຫ້ກູ້ຢືມສ່ວນໜຶ່ງຂອງເງິນຝາກ. ວົງຈອນນີ້ເຮັດໃຫ້ເພີ່ມຈຳນວນເງິນທີ່ໝູນວຽນຢູ່ໃນລະບົບໂດຍອີງໃສ່ເງິນຝາກເບື້ອງຕົ້ນ, ເຊິ່ງສ້າງເງິນຜ່ານໜີ້ສິນ. ລະບົບນີ້ໂດຍທຳມະຊາດແລ້ວບອບບາງ; ຖ້າມີຫຼາຍຄົນພະຍາຍາມຖອນເງິນຝາກຂອງເຂົາເຈົ້າພ້ອມກັນ (ການແລ່ນທະນາຄານ), ທະນາຄານກໍຈະລົ້ມເພາະວ່າມັນບໍ່ໄດ້ເກັບຮັກສາເງິນທັງໝົດໄວ້. ເງິນໃນທະນາຄານບໍ່ປອດໄພຄືກັບທີ່ເຊື່ອກັນທົ່ວໄປ ແລະ ສາມາດຖືກແຊ່ແຂງໃນຊ່ວງວິກິດການ ຫຼື ສູນເສຍຖ້າທະນາຄານລົ້ມລະລາຍ (ຍົກເວັ້ນໄດ້ຮັບການຊ່ວຍເຫຼືອ).
ຜົນກະທົບ Cantillon: ໃຜໄດ້ຮັບຜົນປະໂຫຍດກ່ອນ
ເງິນທີ່ຖືກສ້າງຂຶ້ນໃໝ່ບໍ່ໄດ້ກະຈາຍຢ່າງເທົ່າທຽມກັນ. "ຜົນກະທົບ Cantillon", ບ່ອນທີ່ຜູ້ທີ່ຢູ່ໃກ້ກັບແຫຼ່ງສ້າງເງິນໄດ້ຮັບຜົນປະໂຫຍດກ່ອນ. ນີ້ລວມເຖິງລັດຖະບານເອງ (ສະໜັບສະໜູນລາຍຈ່າຍ), ທະນາຄານໃຫຍ່ ແລະ Wall Street (ໄດ້ຮັບທຶນໃນອັດຕາດອກເບ້ຍຕ່ຳສຳລັບການກູ້ຢືມ ແລະ ການລົງທຶນ), ແລະ ບໍລິສັດໃຫຍ່ (ເຂົ້າເຖິງເງິນກູ້ທີ່ຖືກກວ່າສຳລັບການລົງທຶນ). ບຸກຄົນເຫຼົ່ານີ້ໄດ້ຊື້ຊັບສິນ ຫຼື ລົງທຶນກ່ອນທີ່ຜົນກະທົບຂອງເງິນເຟີ້ຈະເຮັດໃຫ້ລາຄາສູງຂຶ້ນ, ເຊິ່ງເຮັດໃຫ້ພວກເຂົາມີຂໍ້ໄດ້ປຽບ.
ຜົນກະທົບຕໍ່ຄົນທົ່ວໄປ
ສຳລັບຄົນທົ່ວໄປ, ຜົນກະທົບຂອງປະລິມານເງິນທີ່ເພີ່ມຂຶ້ນນີ້ແມ່ນການເພີ່ມຂຶ້ນຂອງລາຄາສິນຄ້າ ແລະ ການບໍລິການ - ນ້ຳມັນ, ຄ່າເຊົ່າ, ການດູແລສຸຂະພາບ, ອາຫານ, ແລະ ອື່ນໆ. ເນື່ອງຈາກຄ່າແຮງງານໂດຍທົ່ວໄປບໍ່ທັນກັບອັດຕາເງິນເຟີ້ນີ້, ອຳນາດການຊື້ຂອງປະຊາຊົນຈະຫຼຸດລົງເມື່ອເວລາຜ່ານໄປ. ມັນຄືກັບການແລ່ນໄວຂຶ້ນພຽງເພື່ອຢູ່ໃນບ່ອນເກົ່າ.
Bitcoin: ທາງເລືອກເງິນທີ່ໝັ້ນຄົງ
ຄວາມຂາດແຄນ: ບໍ່ຄືກັບເງິນຕາ fiat, Bitcoin ມີຂີດຈຳກັດສູງສຸດໃນປະລິມານຂອງມັນ. ຈະມີພຽງ 21 ລ້ານ Bitcoin ເທົ່ານັ້ນຖືກສ້າງຂຶ້ນ, ຂີດຈຳກັດນີ້ຝັງຢູ່ໃນໂຄດຂອງມັນ ແລະ ບໍ່ສາມາດປ່ຽນແປງໄດ້. ການສະໜອງທີ່ຈຳກັດນີ້ເຮັດໃຫ້ Bitcoin ເປັນເງິນຫຼຸດລາຄາ; ເມື່ອຄວາມຕ້ອງການເພີ່ມຂຶ້ນ, ມູນຄ່າຂອງມັນມີແນວໂນ້ມທີ່ຈະເພີ່ມຂຶ້ນເພາະວ່າປະລິມານການສະໜອງບໍ່ສາມາດຂະຫຍາຍຕົວ.
ຄວາມທົນທານ: Bitcoin ຢູ່ໃນ blockchain, ເຊິ່ງເປັນປຶ້ມບັນຊີສາທາລະນະທີ່ແບ່ງປັນກັນຂອງທຸກການເຮັດທຸລະກຳທີ່ແທບຈະເປັນໄປບໍ່ໄດ້ທີ່ຈະລຶບ ຫຼື ປ່ຽນແປງ. ປຶ້ມບັນຊີນີ້ຖືກກະຈາຍໄປທົ່ວພັນຄອມພິວເຕີ (nodes) ທົ່ວໂລກ. ແມ້ແຕ່ຖ້າອິນເຕີເນັດລົ້ມ, ເຄືອຂ່າຍສາມາດຢູ່ຕໍ່ໄປໄດ້ຜ່ານວິທີການອື່ນເຊັ່ນ: ດາວທຽມ ຫຼື ຄື້ນວິທະຍຸ. ມັນບໍ່ໄດ້ຮັບຜົນກະທົບຈາກການທຳລາຍທາງກາຍະພາບຂອງເງິນສົດ ຫຼື ການແຮັກຖານຂໍ້ມູນແບບລວມສູນ.
ການພົກພາ: Bitcoin ສາມາດຖືກສົ່ງໄປໃນທຸກບ່ອນໃນໂລກໄດ້ທັນທີ, 24/7, ດ້ວຍການເຊື່ອມຕໍ່ອິນເຕີເນັດ, ໂດຍບໍ່ຈຳເປັນຕ້ອງມີທະນາຄານ ຫຼື ການອະນຸຍາດຈາກພາກສ່ວນທີສາມ. ທ່ານສາມາດເກັບຮັກສາ Bitcoin ຂອງທ່ານໄດ້ດ້ວຍຕົນເອງໃນອຸປະກອນທີ່ເອີ້ນວ່າກະເປົາເຢັນ, ແລະ ຕາບໃດທີ່ທ່ານຮູ້ວະລີກະແຈລັບຂອງທ່ານ, ທ່ານສາມາດເຂົ້າເຖິງເງິນຂອງທ່ານຈາກກະເປົາທີ່ເຂົ້າກັນໄດ້, ເຖິງແມ່ນວ່າອຸປະກອນຈະສູນຫາຍ. ສິ່ງນີ້ສະດວກສະບາຍກວ່າ ແລະ ມີຄວາມສ່ຽງໜ້ອຍກວ່າການພົກພາເງິນສົດຈຳນວນຫຼາຍ ຫຼື ການນຳທາງການໂອນເງິນສາກົນທີ່ຊັບຊ້ອນ.
ການແບ່ງຍ່ອຍ: Bitcoin ສາມາດແບ່ງຍ່ອຍໄດ້ສູງ. ໜຶ່ງ Bitcoin ສາມາດແບ່ງເປັນ 100 ລ້ານໜ່ວຍຍ່ອຍທີ່ເອີ້ນວ່າ Satoshis, ເຊິ່ງອະນຸຍາດໃຫ້ສົ່ງ ຫຼື ຮັບຈຳນວນນ້ອຍໄດ້.
ຄວາມສາມາດໃນການທົດແທນກັນ: ໜຶ່ງ Bitcoin ທຽບເທົ່າກັບໜຶ່ງ Bitcoin ໃນມູນຄ່າ, ໂດຍທົ່ວໄປ. ໃນຂະນະທີ່ເງິນໂດລາແບບດັ້ງເດີມອາດສາມາດຖືກຕິດຕາມ, ແຊ່ແຂງ, ຫຼື ຍຶດໄດ້, ໂດຍສະເພາະໃນຮູບແບບດິຈິຕອນ ຫຼື ຖ້າຖືກພິຈາລະນາວ່າໜ້າສົງໄສ, ແຕ່ລະໜ່ວຍຂອງ Bitcoin ໂດຍທົ່ວໄປຖືກປະຕິບັດຢ່າງເທົ່າທຽມກັນ.
ການພິສູດຢັ້ງຢືນ: ທຸກການເຮັດທຸລະກຳ Bitcoin ຖືກບັນທຶກໄວ້ໃນ blockchain, ເຊິ່ງທຸກຄົນສາມາດເບິ່ງ ແລະ ພິສູດຢັ້ງຢືນ. ຂະບວນການພິສູດຢັ້ງຢືນທີ່ກະຈາຍນີ້, ດຳເນີນໂດຍເຄືອຂ່າຍ, ໝາຍຄວາມວ່າທ່ານບໍ່ຈຳເປັນຕ້ອງເຊື່ອຖືທະນາຄານ ຫຼື ສະຖາບັນໃດໜຶ່ງແບບມືດບອດເພື່ອຢືນຢັນຄວາມຖືກຕ້ອງຂອງເງິນຂອງທ່ານ.
ການຕ້ານການກວດກາ: ເນື່ອງຈາກບໍ່ມີລັດຖະບານ, ບໍລິສັດ, ຫຼື ບຸກຄົນໃດຄວບຄຸມເຄືອຂ່າຍ Bitcoin, ບໍ່ມີໃຜສາມາດຂັດຂວາງທ່ານຈາກການສົ່ງ ຫຼື ຮັບ Bitcoin, ແຊ່ແຂງເງິນຂອງທ່ານ, ຫຼື ຍຶດມັນ. ມັນເປັນລະບົບທີ່ບໍ່ຕ້ອງຂໍອະນຸຍາດ, ເຊິ່ງໃຫ້ຜູ້ໃຊ້ຄວບຄຸມເຕັມທີ່ຕໍ່ເງິນຂອງເຂົາເຈົ້າ.
ການກະຈາຍອຳນາດ: Bitcoin ຖືກຮັກສາໂດຍເຄືອຂ່າຍກະຈາຍຂອງບັນດາຜູ້ຂຸດທີ່ໃຊ້ພະລັງງານການຄິດໄລ່ເພື່ອຢັ້ງຢືນການເຮັດທຸລະກຳຜ່ານ "proof of work". ລະບົບທີ່ກະຈາຍນີ້ຮັບປະກັນວ່າບໍ່ມີຈຸດໃດຈຸດໜຶ່ງທີ່ຈະລົ້ມເຫຼວ ຫຼື ຄວບຄຸມ. ທ່ານບໍ່ໄດ້ເພິ່ງພາຂະບວນການທີ່ບໍ່ໂປ່ງໃສຂອງທະນາຄານກາງ; ລະບົບທັງໝົດໂປ່ງໃສຢູ່ໃນ blockchain. ສິ່ງນີ້ເຮັດໃຫ້ບຸກຄົນມີອຳນາດທີ່ຈະເປັນທະນາຄານຂອງຕົນເອງແທ້ ແລະ ຮັບຜິດຊອບຕໍ່ການເງິນຂອງເຂົາເຈົ້າ.
-
 @ fd06f542:8d6d54cd
2025-04-23 07:52:28
@ fd06f542:8d6d54cd
2025-04-23 07:52:28NIP-19
bech32-encoded entities
draftoptionalThis NIP standardizes bech32-formatted strings that can be used to display keys, ids and other information in clients. These formats are not meant to be used anywhere in the core protocol, they are only meant for displaying to users, copy-pasting, sharing, rendering QR codes and inputting data.
It is recommended that ids and keys are stored in either hex or binary format, since these formats are closer to what must actually be used the core protocol.
Bare keys and ids
To prevent confusion and mixing between private keys, public keys and event ids, which are all 32 byte strings. bech32-(not-m) encoding with different prefixes can be used for each of these entities.
These are the possible bech32 prefixes:
npub: public keysnsec: private keysnote: note ids
Example: the hex public key
3bf0c63fcb93463407af97a5e5ee64fa883d107ef9e558472c4eb9aaaefa459dtranslates tonpub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6.The bech32 encodings of keys and ids are not meant to be used inside the standard NIP-01 event formats or inside the filters, they're meant for human-friendlier display and input only. Clients should still accept keys in both hex and npub format for now, and convert internally.
Shareable identifiers with extra metadata
When sharing a profile or an event, an app may decide to include relay information and other metadata such that other apps can locate and display these entities more easily.
For these events, the contents are a binary-encoded list of
TLV(type-length-value), withTandLbeing 1 byte each (uint8, i.e. a number in the range of 0-255), andVbeing a sequence of bytes of the size indicated byL.These are the possible bech32 prefixes with
TLV:nprofile: a nostr profilenevent: a nostr eventnaddr: a nostr replaceable event coordinatenrelay: a nostr relay (deprecated)
These possible standardized
TLVtypes are indicated here:0:special- depends on the bech32 prefix:
- for
nprofileit will be the 32 bytes of the profile public key - for
neventit will be the 32 bytes of the event id - for
naddr, it is the identifier (the"d"tag) of the event being referenced. For normal replaceable events use an empty string.
- for
1:relay- for
nprofile,neventandnaddr, optionally, a relay in which the entity (profile or event) is more likely to be found, encoded as ascii - this may be included multiple times
2:author- for
naddr, the 32 bytes of the pubkey of the event - for
nevent, optionally, the 32 bytes of the pubkey of the event 3:kind- for
naddr, the 32-bit unsigned integer of the kind, big-endian - for
nevent, optionally, the 32-bit unsigned integer of the kind, big-endian
Examples
npub10elfcs4fr0l0r8af98jlmgdh9c8tcxjvz9qkw038js35mp4dma8qzvjptgshould decode into the public key hex7e7e9c42a91bfef19fa929e5fda1b72e0ebc1a4c1141673e2794234d86addf4eand vice-versansec1vl029mgpspedva04g90vltkh6fvh240zqtv9k0t9af8935ke9laqsnlfe5should decode into the private key hex67dea2ed018072d675f5415ecfaed7d2597555e202d85b3d65ea4e58d2d92ffaand vice-versanprofile1qqsrhuxx8l9ex335q7he0f09aej04zpazpl0ne2cgukyawd24mayt8gpp4mhxue69uhhytnc9e3k7mgpz4mhxue69uhkg6nzv9ejuumpv34kytnrdaksjlyr9pshould decode into a profile with the following TLV items:- pubkey:
3bf0c63fcb93463407af97a5e5ee64fa883d107ef9e558472c4eb9aaaefa459d - relay:
wss://r.x.com - relay:
wss://djbas.sadkb.com
Notes
npubkeys MUST NOT be used in NIP-01 events or in NIP-05 JSON responses, only the hex format is supported there.- When decoding a bech32-formatted string, TLVs that are not recognized or supported should be ignored, rather than causing an error.
-
 @ 9bde4214:06ca052b
2025-04-22 17:15:24
@ 9bde4214:06ca052b
2025-04-22 17:15:24“I don’t believe in Utopia anymore. I’m too old for that.”
Calle & Gigi philosophize about nuts.
Books and articles mentioned:
In this dialogue:
- Where is the Utopia that the internet promised?
- “Neither nostalgia nor utopia”
- Net Neutrality is a moral stance
- Where did the internet go wrong?
- Tech as a tool; is tech always neutral?
- Technology that increases agency VS tech that enslaves
- Competition vs Symbiosis
- “Who will run the mints?”
- “Anyone” can use it vs “everyone” can use it
- Centralizing vs. Monopolizing
- Bitcoin has an ethos baked in (You Shall Not Steal)
- Passive internet vs active internet
- Agency in cyberspace, and how to maximize it
- Blinded custodian vs regular custodian
- User data is a liability
- Obscura / Mullvad / Silent.Link as obvious early adopters
- Run your own ISP - Tollgate
- Cryptography is Not Enough
- Bitcoin is Time
- Time requires heat
- Zero-knowledge service providers
- Electronic Cash vs Digital Cash (CBDCs)
- Credit requires KYC, KYC implies outside enforcement
- Writings on Micropayments by Nick Szabo
- eCash fixes 402, obviously
- Who Owns the Future?
- “You are the product” vs “Subscription Hell”
- “Hello old friend!!!”
- Cathedral vs Bazaar
- Why paywalls suck
- Information wants to be free
- "Markets become absurd as supply approaches infinity."
- eCash + AI = match made in heaven
- #LearnToCode vs #LearnToPrompt
- Scarcity in cyberspace: compute, storage, networking
- Zero-Knowledge compute & zero-knowledge proofs
- https://en.wikipedia.org/wiki/Zero-knowledge_proof
- https://github.com/AbdelStark/cashu-zk-engine
- Cairo: https://github.com/starkware-libs/cairo
- MCP https://github.com/AbdelStark/bitcoin-mcp
- MCP DVM: https://github.com/r0d8lsh0p/n8n-AI-agent-DVM-MCP-client
- DVMCP: https://mcp.so/server/dvmcp
- Olas & Nutzaps (NIP-60, NIP-61)
- Bitcoin is not only the internet of money, but it is the money of the internet
- Re-building the internet archive on top of nostr
- Bitrot & 404
- Resurrection markets & marketplace for hashes via Blossom
- Hugs 🫂
-
 @ 4857600b:30b502f4
2025-02-21 03:04:00
@ 4857600b:30b502f4
2025-02-21 03:04:00A new talking point of the left is that it’s no big deal, just simple recording errors for the 20 million people aged 100-360. 🤷♀️ And not many of them are collecting benefits anyway. 👌 First of all, the investigation & analysis are in the early stages. How can they possibly know how deep the fraud goes, especially when their leaders are doing everything they can to obstruct any real examination? Second, sure, no worries about only a small number collecting benefits. That’s the ONLY thing social security numbers are used for. 🙄
-
 @ 4857600b:30b502f4
2025-02-20 19:09:11
@ 4857600b:30b502f4
2025-02-20 19:09:11Mitch McConnell, a senior Republican senator, announced he will not seek reelection.
At 83 years old and with health issues, this decision was expected. After seven terms, he leaves a significant legacy in U.S. politics, known for his strategic maneuvering.
McConnell stated, “My current term in the Senate will be my last.” His retirement marks the end of an influential political era.
-
 @ f10512df:c9293bb3
2025-04-22 17:11:05
@ f10512df:c9293bb3
2025-04-22 17:11:05Details
- 🍳 Cook time: 5-7 minutes
- 🍽️ Servings: 1
Ingredients
- 2 eggs
- Shredded cheese (Sharp cheddar is a favorite)
- 1 Tbsp olive oil or ghee
Directions
- Add oil to a non-stick pan and allow it to get hot (med-high heat)
- Add eggs and additional toppings, scramble and wait for the edges to get brown.
- Add shredded cheese while edges are browning. It is best if cheese begins to melt before flipping.
- Flip, and make sure all cheese stayed down, and there is enough oil left in the pan.
- Keep checking until pan side of eggs lift easily. Done correctly, the cheese will form a crisp layer.
- When fully cooked, serve with cheese right side up and enjoy!
-
 @ 94a6a78a:0ddf320e
2025-02-19 21:10:15
@ 94a6a78a:0ddf320e
2025-02-19 21:10:15Nostr is a revolutionary protocol that enables decentralized, censorship-resistant communication. Unlike traditional social networks controlled by corporations, Nostr operates without central servers or gatekeepers. This openness makes it incredibly powerful—but also means its success depends entirely on users, developers, and relay operators.
If you believe in free speech, decentralization, and an open internet, there are many ways to support and strengthen the Nostr ecosystem. Whether you're a casual user, a developer, or someone looking to contribute financially, every effort helps build a more robust network.
Here’s how you can get involved and make a difference.
1️⃣ Use Nostr Daily
The simplest and most effective way to contribute to Nostr is by using it regularly. The more active users, the stronger and more valuable the network becomes.
✅ Post, comment, and zap (send micro-payments via Bitcoin’s Lightning Network) to keep conversations flowing.\ ✅ Engage with new users and help them understand how Nostr works.\ ✅ Try different Nostr clients like Damus, Amethyst, Snort, or Primal and provide feedback to improve the experience.
Your activity keeps the network alive and helps encourage more developers and relay operators to invest in the ecosystem.
2️⃣ Run Your Own Nostr Relay
Relays are the backbone of Nostr, responsible for distributing messages across the network. The more independent relays exist, the stronger and more censorship-resistant Nostr becomes.
✅ Set up your own relay to help decentralize the network further.\ ✅ Experiment with relay configurations and different performance optimizations.\ ✅ Offer public or private relay services to users looking for high-quality infrastructure.
If you're not technical, you can still support relay operators by subscribing to a paid relay or donating to open-source relay projects.
3️⃣ Support Paid Relays & Infrastructure
Free relays have helped Nostr grow, but they struggle with spam, slow speeds, and sustainability issues. Paid relays help fund better infrastructure, faster message delivery, and a more reliable experience.
✅ Subscribe to a paid relay to help keep it running.\ ✅ Use premium services like media hosting (e.g., Azzamo Blossom) to decentralize content storage.\ ✅ Donate to relay operators who invest in long-term infrastructure.
By funding Nostr’s decentralized backbone, you help ensure its longevity and reliability.
4️⃣ Zap Developers, Creators & Builders
Many people contribute to Nostr without direct financial compensation—developers who build clients, relay operators, educators, and content creators. You can support them with zaps! ⚡
✅ Find developers working on Nostr projects and send them a zap.\ ✅ Support content creators and educators who spread awareness about Nostr.\ ✅ Encourage builders by donating to open-source projects.
Micro-payments via the Lightning Network make it easy to directly support the people who make Nostr better.
5️⃣ Develop New Nostr Apps & Tools
If you're a developer, you can build on Nostr’s open protocol to create new apps, bots, or tools. Nostr is permissionless, meaning anyone can develop for it.
✅ Create new Nostr clients with unique features and user experiences.\ ✅ Build bots or automation tools that improve engagement and usability.\ ✅ Experiment with decentralized identity, authentication, and encryption to make Nostr even stronger.
With no corporate gatekeepers, your projects can help shape the future of decentralized social media.
6️⃣ Promote & Educate Others About Nostr
Adoption grows when more people understand and use Nostr. You can help by spreading awareness and creating educational content.
✅ Write blogs, guides, and tutorials explaining how to use Nostr.\ ✅ Make videos or social media posts introducing new users to the protocol.\ ✅ Host discussions, Twitter Spaces, or workshops to onboard more people.
The more people understand and trust Nostr, the stronger the ecosystem becomes.
7️⃣ Support Open-Source Nostr Projects
Many Nostr tools and clients are built by volunteers, and open-source projects thrive on community support.
✅ Contribute code to existing Nostr projects on GitHub.\ ✅ Report bugs and suggest features to improve Nostr clients.\ ✅ Donate to developers who keep Nostr free and open for everyone.
If you're not a developer, you can still help with testing, translations, and documentation to make projects more accessible.
🚀 Every Contribution Strengthens Nostr
Whether you:
✔️ Post and engage daily\ ✔️ Zap creators and developers\ ✔️ Run or support relays\ ✔️ Build new apps and tools\ ✔️ Educate and onboard new users
Every action helps make Nostr more resilient, decentralized, and unstoppable.
Nostr isn’t just another social network—it’s a movement toward a free and open internet. If you believe in digital freedom, privacy, and decentralization, now is the time to get involved.
-
 @ 5de23b9a:d83005b3
2025-02-19 03:47:19
@ 5de23b9a:d83005b3
2025-02-19 03:47:19In a digital era that is increasingly controlled by large companies, the emergence of Nostr (Notes and Other Stuff Transmitted by Relays) is a breath of fresh air for those who crave freedom of expression.
Nostr is a cryptography-based protocol that allows users to send and receive messages through a relay network. Unlike conventional social media such as Twitter or Facebook
1.Full Decentralization: No company or government can remove or restrict content.
2.Sensor-Resistant: Information remains accessible despite blocking attempts.
3.Privacy and Security: Uses cryptography to ensure that only users who have the keys can access their messages.* **
-
 @ 9bde4214:06ca052b
2025-04-22 17:09:47
@ 9bde4214:06ca052b
2025-04-22 17:09:47“It isn’t obvious that the world had to work this way. But somehow the universe smiles on encryption.”
hzrd149 & Gigi take a stroll along the shore of cryptographic identities.
This dialogue explores how cryptographic signatures fundamentally shift power dynamics in social networks, moving control from servers to key holders. We discuss the concept of "setting data free" through cryptographic verification, the evolving role of relays in the ecosystem, and the challenges of building trust in decentralized systems. We examine the tension between convenience and decentralization, particularly around features like private data and data synchronization. What are the philosophical foundations of building truly decentralized social networks? And how can small architectural decisions have profound implications for user autonomy and data sovereignty?
Movies mentioned:
- 2001: A Space Odyssey (1968)
- Soylent Green (1973)
- Close Encounters of the Third Kind (1977)
- Johnny Mnemonic (1995)
- The Matrix (1999)
In this dialogue: - Hzrd's past conversations: Bowls With Buds 316 & 361 - Running into a water hose - Little difference, big effect - Signing data moves the power to the key holders - Self-signing data sets the data free - Relay specialization - Victor's Amethyst relay guide - Encryption and decryption is expensive - is it worth it? - The magic of nostr is that stuff follows you around - What should be shown? What should be hidden? - Don't lie to users. Never show outdated data. - Nostr is raw and immediate - How quickly you get used to things working - Legacy web always tries to sell you something - Lying, lag, frustration - How NoStrudel grew - NoStrudel notifications - Data visualization and dashboards - Building in public and discussing in public - Should we remove DMs? - Nostr as a substrate for lookups - Using nostr to exchange Signal or SimpleX credentials - How private is a group chat? - Is a 500-people group chat ever private? - Pragmatism vs the engineering mindset - The beauty and simplicity of nostr - Anti-patterns in nostr - Community servers and private relays - Will vibe coding fix (some of the) things? - Small specialized components VS frameworks - Technology vs chairs (and cars, and tractors, and books) - The problem of being greedy - Competitive silos VS synergistic cooperation - Making things easy vs barriers of entry - Value4value for music and other artists - Adding code vs removing code - Pablo's Roo setup and DVMCP - Platform permission slips vs cryptographic identities - Micropayments vs Subscription Hell - PayPerQ - Setting our user-generated data free - The GNU/Linux approach and how it beat Microsoft - Agents learning automatically thanks to snippets published on nostr - Taxi drivers, GPS, and outsourcing understanding - Wizards VS vibe coders - Age differences, Siri, and Dragon Naturally Speaking - LLMs as a human interface to call tools - Natural language vs math and computer language - Natural language has to be fuzzy, because the world is fuzzy - Language and concepts as compression - Hzrd watching The Matrix (1999) for the first time - Soylent Green, 2001, Close Encounters of the 3rd Kind, Johnny Mnemonic - Are there coincidences? - Why are LLMs rising at the same time that cryptography identities are rising? - "The universe smiles at encryption" - The universe does not smile upon closed silos - The cost of applying force from the outside - Perfect copies, locality, and the concept of "the original" - Perfect memory would be a curse, not a blessing - Organic forgetting VS centralized forgetting - Forgetting and dying needs to be effortless - (it wasn't for IPFS, and they also launched a shitcoin) - Bitcoin makes is cheap to figure out what to dismiss - Would you like to have a 2nd brain? - Trust and running LLMs locally - No need for API keys - Adjacent communities: local-first, makers and hackers, etc. - Removing the character limit was a mistake - Browsing mode vs reading mode - The genius of tweets and threads - Vibe-coding and rust-multiplatform - Global solutions vs local solutions - The long-term survivability of local-first - All servers will eventually go away. Your private key won't. - It's normal to pay your breakfast with sats now - Nostr is also a normal thing now, at least for us - Hzrd's bakery - "Send Gigi a DM that says GM" - and it just works - The user is still in control, thanks to Amber - We are lacking in nostr signing solutions - Alby's permission system as a step in the right direction - We have to get better at explaining that stuff - What we do, why we care, why we think it's important
-
 @ 9bde4214:06ca052b
2025-04-22 17:00:55
@ 9bde4214:06ca052b
2025-04-22 17:00:55"What should the next iteration of the internet look like?"
Paul & Gigi pray for a better tomorrow.
Books mentioned:
- The Bible
- I, Pencil by Leonard E. Read
- Don't make me think! by Steve Krug
- The Sovereign Individual by James Dale Davidson and William Rees-Mogg
In this dialogue:
- Paul and his awesome nostr t-shirt
- Are we all just nostalgic?
- Where did the optimism of computing and the information superhighway go?
- We went from interop to pay-to-unlock.
- Do we have to live in the digital gulags forever?
- Homecooked meals and homecooked apps
- Paper straws and the downfall of Western Civilization
- "You need to be okay with people getting rekt"
- If the car would be introduced today, it would be illegal
- Bravery and personal responsibility
- "nostr will only be what diehards will build it to be"
- Bad teleology is built into the current (non-nostr) app landscape
- "You can get a lot of the upside without holding your own keys”
- “...but you can't get ALL of the upside!"
- Expressiveness and free speech online
- Freedom of Speech, Freedom of Assembly, and Financial Freedom in Cyberspace
- Self-publishing vs platform publishing
- Information calories. Can we count them?
- Don't make me think!
- Is not being forced to think part of the problem?
- Mutiny & bitcoin UX that's too easy
- Games and costly mistakes
- The early days: software distribution via print magazines
- Prompting allows you to define your own teleology
- Vibe coding and Cursor
- "The hard part is to figure out what you want."
- "What should the next iteration of the internet look like?"
- GenZ doesn't know shit about files and folders
- Why files are great
- Gigi's SyncThing & Standard Notes setup
- File-based apps like Smart AudioBook Player
- Reading apps like Pocket, Instapaper, and Readwise Reader
- Saving all the things & linking stuff together
- Clips of podcasts and videos, e.g. Fountain
- A Commonplace Book to cyberspace
- Creating a "Family Bible" app
- If you want to maximize profits in the attention economy, you have to get users addicted
- (Zaps potentially fix this, as you wouldn’t zap a car crash)
- Let computers do computer work, let humans be humans
- "The end is not being on the computer"
- Solo private / group private / public
- Liberal vs Conservative sentiment in social environments
- Whom to care about?
- Web of trust & our understanding of it
- Forgiveness, Trust, and Repeat Games
- Tit-for-tat and forgiving tit-for-tat
- Three strikes and you're out!
- "Choose your gulag" is the alternative to nostr
- 7-generation thinking
- 2140
- The Sovereign Individual is embedded in a social structure, always
- I, Pencil
- Jungle vs Civilization
- Fiat = because I said so (“Fiat Lux” - Let there be light)
- Do we need leaders in bitcoin?
- Peterson Fallacy / God vs Bitcoin
- Jesus early followers were the Followers of The Way
- Zaps are not payments
- Zaps are not "tips"
- Bitstein & Pierre: The Reorg
- Vervaeke: “Where do you go for wisdom?”
- Rough consensus and Pieter Wuille
- "There is no such thing as a leaderless system"
- Wisdom in cyberspace
- Can we build wise tools?
- Prompting the Bible, ChristGPT, and Bible Slop
- Gell-Mann amnesia effect
- Vervaekes AI argument: The Coming Thresholds and The Path We Must Take
- Where do new ideas come from?
- Sandwich prompting style (HLDD / LLDD)
- The Tale of John Henry
- Silicon Sages
- Conscience and The Muse
- Hypermedia and HyperNote
- Glassholes, Google Glasses, and wearable technology
- Prompting & Praying for An Internet Worth Having
-
 @ 3ffac3a6:2d656657
2025-04-23 01:57:57
@ 3ffac3a6:2d656657
2025-04-23 01:57:57🔧 Infrastructure Overview
- Hardware: Raspberry Pi 5 with PCIe NVMe HAT and 2TB NVMe SSD
- Filesystem: ZFS with separate datasets for each service
- Networking: Docker bridge networks for service segmentation
- Privacy: Tor and I2P routing for anonymous communication
- Public Access: Cloudflare Tunnel to securely expose LNbits
📊 Architecture Diagram
🛠️ Setup Steps
1. Prepare the System
- Install Raspberry Pi OS (64-bit)
- Set up ZFS on the NVMe disk
- Create a ZFS dataset for each service (e.g.,
bitcoin,lnd,rtl,lnbits,tor-data) - Install Docker and Docker Compose
2. Create Shared Docker Network and Privacy Layers
Create a shared Docker bridge network:
bash docker network create \ --driver=bridge \ --subnet=192.168.100.0/24 \ bitcoin-netNote: Connect
bitcoind,lnd,rtl, internallnbits,tor, andi2pto thisbitcoin-netnetwork.Tor
- Run Tor in a container
- Configure it to expose LND's gRPC and REST ports via hidden services:
HiddenServicePort 10009 192.168.100.31:10009 HiddenServicePort 8080 192.168.100.31:8080 - Set correct permissions:
bash sudo chown -R 102:102 /zfs/datasets/tor-data
I2P
- Run I2P in a container with SAM and SOCKS proxies
- Update
bitcoin.conf:i2psam=192.168.100.20:7656 i2pacceptincoming=1
3. Set Up Bitcoin Core
- Create a
bitcoin.confwith Tor/I2P/proxy settings and ZMQ enabled - Sync the blockchain in a container using its ZFS dataset
4. Set Up LND
- Configure
lnd.confto connect tobitcoindand use Tor: ```ini [Bitcoind] bitcoind.rpchost=bitcoin:8332 bitcoind.rpcuser=bitcoin bitcoind.rpcpass=very-hard-password bitcoind.zmqpubrawblock=tcp://bitcoin:28332 bitcoind.zmqpubrawtx=tcp://bitcoin:28333
[Application Options] externalip=xxxxxxxx.onion
`` - Don’t expose gRPC or REST ports publicly - Mount the ZFS dataset at/root/.lnd` - Optionally enable Watchtower5. Set Up RTL
- Mount
RTL-Config.jsonand data volumes - Expose RTL's web interface locally:
```yaml
ports:
- "3000:3000" ```
6. Set Up Internal LNbits
- Connect the LNbits container to
bitcoin-net - Mount the data directory and LND cert/macaroons (read-only)
- Expose the LNbits UI on the local network:
```yaml
ports:
- "5000:5000" ```
- In the web UI, configure the funding source to point to the LND REST
.onionaddress and paste the hex macaroon - Create and fund a wallet, and copy its Admin Key for external use
7. Set Up External LNbits + Cloudflare Tunnel
- Run another LNbits container on a separate Docker network
- Access the internal LNbits via the host IP and port 5000
- Use the Admin Key from the internal wallet to configure funding
- In the Cloudflare Zero Trust dashboard:
- Create a tunnel
- Select Docker, copy the
--tokencommand - Add to Docker Compose:
yaml command: tunnel --no-autoupdate run --token eyJ...your_token...
💾 Backup Strategy
- Bitcoin Core: hourly ZFS snapshots, retained for 6 hours
- Other Services: hourly snapshots with remote
.tar.gzbackups - Retention: 7d hourly, 30d daily, 12mo weekly, monthly forever
- Back up ZFS snapshots to avoid inconsistencies
🔐 Security Isolation Benefits
This architecture isolates services by scope and function:
- Internal traffic stays on
bitcoin-net - Sensitive APIs (gRPC, REST) are reachable only via Tor
- Public access is controlled by Cloudflare Tunnel
Extra Security: Host the public LNbits on a separate machine (e.g., hardened VPS) with strict firewall rules:
- Allow only Cloudflare egress
- Allow ingress from your local IP
- Allow outbound access to internal LNbits (port 5000)
Use WireGuard VPN to secure the connection between external and internal LNbits:
- Ensures encrypted communication
- Restricts access to authenticated VPN peers
- Keeps the internal interface isolated from the public internet
✅ Final Notes
- Internal services communicate over
bitcoin-net - LND interfaces are accessed via Tor only
- LNbits and RTL UIs are locally accessible
- Cloudflare Tunnel secures external access to LNbits
Monitor system health using
monit,watchtower, or Prometheus.Create all configuration files manually (
bitcoin.conf,lnd.conf,RTL-Config.json), and keep credentials secure. Test every component locally before exposing it externally.⚡
-
 @ d1667293:388e7004
2025-04-22 16:52:15
@ d1667293:388e7004
2025-04-22 16:52:15In my book “Bitcoindollar The Dawn of American Hegemony in the Digital Era,” I challenge the prevailing narrative that de-dollarization is a distant or hypothetical threat. Rather, I present a body of evidence suggesting that we are already living in a world where de-dollarization is unfolding—not through bombastic proclamations or sudden abandonment of the dollar in trade—but through a quieter, more telling trend: the steady escape of emerging powers like China, Russia, India, and much of the Global South from US Treasuries as the global reserve asset.
Structural, Not Cyclical: The Causes Behind the Exodus
This transformation is not cyclical or temporary; it is structural. The root causes run deep and stem from decades of US foreign and monetary policy—specifically, the aggressive military posturing that has defined American global engagement, the weaponization of dollar-based financial systems, and the overuse of sanctions as instruments of coercion rather than diplomacy. The result has been a widespread erosion of trust in the US as a neutral monetary steward. Increasingly, large economies and trading blocs—such as the Shanghai Cooperation Organization (SCO), BRICS, and the Belt and Road Initiative (BRI)—are seeking alternatives. They are diversifying their reserves, entering bilateral currency agreements, stockpiling gold, and in some cases, launching central bank digital currencies (CBDCs).
The message is clear: the era of unquestioned dollar supremacy is over.
The Treasury Dilemma: Who Will Fund America’s Debt?
This structural shift raises a daunting question for American policymakers: who will buy US Treasuries in the future? For decades, the demand for Treasuries rested on the premise of dollar dominance. Global trade surpluses—especially from oil-exporting nations under the Petrodollar system—were recycled into US debt markets. This “exorbitant privilege” allowed the US to run persistent deficits, finance wars, and project power without facing the immediate fiscal consequences most nations would. But that privilege is now in peril.
The Bitcoindollar System: A Strategic Response
In my book, I argue that the United States still has one viable path forward—a path that does not require relinquishing its leadership role, but rather reimagining it for the digital era. I call this new paradigm the Bitcoindollar system. It is an evolutionary successor to the Petrodollar framework, and it hinges on embracing bitcoin as the global store of value and dollar denominated stablecoins to maintain the US dollar’s relevance in a multipolar world. Under the Bitcoindollar system, global capital flows are incentivized to enter dollar-denominated stablecoins such as USDC and USDT. These stablecoins can then be recycled into short-term US debt instruments like Treasury bills, creating a digital-era version of the Petrodollar recycling mechanism. At the heart of this system lies Bitcoin—not as a threat to the dollar, but as a global decentralized and uncensorable Store of Value (SOV) that drives capital into the broader dollar-denominated ecosystem. As Bitcoin grows in adoption and price, it draws global attention and capital toward stablecoins, which in turn creates natural demand for dollar-based instruments such as Treasuries. This system offers the United States a first-mover advantage. No other nation has the credibility, capital markets depth, or global network effects to replicate it—if, and only if, the dollar’s digital rails are perceived as trustworthy and politically neutral. Herein lies the great conundrum: trust cannot be mandated. It must be earned, particularly in a geopolitical climate where the United States continues to alienate both allies and adversaries alike.
Trump’s Paradox: Economic Nationalism vs Monetary Hegemony
The current Trump administration, despite its rhetoric on economic nationalism, continues along a path that exacerbates this alienation. By doubling down on tariffs, aggressive posturing toward China, and unconditional support for Israel’s supremacist regional ambitions, it perpetuates the same policies that catalyzed de-dollarization in the first place. Tariffs, in this context, are a distraction. The US trade deficit is not primarily the result of unfair trade practices by other countries—it is largely the result of the dollar's role as the global reserve currency. To sustain global demand for dollars, the US has had to export dollars—and therefore run trade deficits. The dollar’s dominance enabled vast capital inflows and supported America’s imperial military architecture, but this model is fundamentally incompatible with dreams of reshoring industry, reducing deficits, and limiting foreign entanglements. Furthermore, these policies undermine any future attempt to establish dollar stablecoins as trusted global instruments. Why would a nation park its savings in a dollar-based asset, however digitized, if it fears arbitrary sanctions or seizure at the stroke of a keyboard? Despite his aggressive posturing, Trump, like Zelensky and the EU before him, has no cards to play to force China or Russia to the table.
A Fork in the Road: Choose Multipolar Collaboration or Decline
Absent a disastrous military escalation—which will not prevent the fall of American unipolar hegemony—the US is left with ONLY ONE path forward: a deliberate, peaceful shift from military and imperial posturing toward a more collaborative, multipolar engagement with the world. This means treating allies, adversaries, and vassal states alike with respect and inclusion in a reimagined dollar-based system—one that is digital, decentralized, and incentivized by global participation. The Bitcoindollar system can serve as the financial infrastructure of this new era, but it demands that the United States rehabilitate its image as a trustworthy party. For the Trump administration to succeed in securing America’s future financial relevance, it must course-correct immediately. This includes ending the influence of the neo-conservative and Zionist hardliners who perpetuate conflict and distrust for their own interest, and embracing a vision of digital dollar diplomacy that builds bridges instead of burning them.
In conclusion, the Bitcoindollar is not just a financial mechanism—it is a strategic opportunity for the United States to retain leadership in the emerging multipolar order. The alternative is clear: a continued slide into irrelevance, fiscal instability, and geopolitical isolation or a mutually assured destruction through war.
The time to act boldly for President Trump is now.
bitcoin #bitcoindollar #stablecoin
-
 @ 502ab02a:a2860397
2025-04-23 01:04:54
@ 502ab02a:a2860397
2025-04-23 01:04:54ช่วงหลัง ๆ มานี้ ถ้าใครเดินผ่านชั้นนมในซูเปอร์ฯ แล้วสะดุดตากับกล่องสีเรียบ ๆ สไตล์สแกนดิเนเวียนที่เขียนคำว่า "OATLY!" ตัวใหญ่ ๆ ไม่ต้องแปลกใจ เพราะนี่คือเครื่องดื่มที่กำลังพยายามจะทำให้ทุกบ้านเชื่อว่า "ดื่มข้าวโอ๊ตแทนนมวัวคือสิ่งที่ดีต่อสุขภาพ ต่อโลก และต่อเด็ก ๆ"
Oatly ไม่ได้มาเล่น ๆ เป็นดาวรุ่งของวงการ plant-based dairy ทางเลือก ด้วยการตลาดที่เฉียบคมและอารมณ์ขันแบบขบถ เพราะบริษัทนี้เขาวางโพสิชั่นของตัวเองว่าเป็นนักสู้เพื่อสิ่งแวดล้อม ต่อต้านโลกร้อน และเป็นทางเลือกที่รักสัตว์รักโลกจนพืชยังปรบมือให้ แต่เบื้องหลังที่ดูคลีน ๆ กลับซ่อนกลยุทธ์ทางการตลาดที่แสบสันไม่เบา โดยเฉพาะการรณรงค์ในโรงเรียน และเทคนิคในการ “ซ่อนความหวาน” ได้อย่างแนบเนียนจนน้ำตาลยังงง
หวานแบบซ่อนรูปสูตรลับที่ไม่อยู่ในช่อง Sugar โอ๊ตมิลค์ของ Oatly มีคาร์บต่ำจริงตามฉลาก แต่ที่หลายคนไม่รู้คือ Oatly ใช้ เอนไซม์ย่อยแป้งจากข้าวโอ๊ต ให้กลายเป็นน้ำตาลมอลโทส ซึ่งมีรสหวานพอ ๆ กับน้ำตาลทราย แต่ไม่ต้องแสดงในช่อง Total Sugar บนฉลากโภชนาการ เพราะมันเกิดขึ้น "ตามธรรมชาติจากกระบวนการ" ซึ่งตรงตามเกณฑ์ FDA เป๊ะ
ความเจ้าเล่ห์ของระบบนี้คือ มอลโตสที่เกิดจากการย่อยแป้งด้วยเอนไซม์ ไม่ต้องนับเป็น “น้ำตาล” ในช่อง Sugar ของฉลากโภชนาการ เพราะมันถือเป็น “naturally occurring sugar” หรือ “น้ำตาลที่เกิดขึ้นเองตามธรรมชาติ” พูดง่ายๆ คือ หวานเหมือนโค้ก แต่ไม่ต้องบอกว่าใส่น้ำตาลเลยแม้แต่นิดเดียว! ในขณะที่เด็กๆ ดื่มแล้วบอกว่า “อร่อยมาก!” ผู้ใหญ่ก็เห็นฉลากแล้วบอกว่า “น้ำตาลแค่นิดเดียวเอง ดีจัง”… ความเข้าใจผิดแบบสองชั้นนี้คือการตลาดที่ชาญฉลาดแต่แฝงความไม่โปร่งใส
และเมื่อคุณไปอ่านงานวิจัยจะเจอว่า น้ำตาลมอลโตสที่ได้จากโอ๊ตผ่านกระบวนการย่อยแบบนี้ มีค่าดัชนีน้ำตาลสูงถึง 105-110 ซึ่งสูงกว่าโค้กเสียอีก (Coke อยู่ประมาณ 63) ส่งผลให้ระดับน้ำตาลในเลือดพุ่งอย่างรวดเร็ว และถ้าใครมีภาวะดื้อต่ออินซูลินหรืออยู่ในขอบเขต prediabetes ก็ยิ่งน่ากังวลเข้าไปใหญ่ พูดง่าย ๆ คือ Oatly หวาน แต่ไม่ต้องบอกว่าใส่น้ำตาล คนทั่วไปเลยเข้าใจผิดว่า “อ้าว มันไม่หวานนี่นา”
บางโรงเรียนในอังกฤษและสวีเดนเริ่มตั้งคำถามว่า การเปลี่ยนนมวัวที่อุดมไปด้วยไขมันดี โปรตีนสมบูรณ์ และแคลเซียม เข้าสู่ร่างกายเด็กๆ ให้กลายเป็น “นมโอ๊ตหวานแบบซ่อนรูป” แบบนี้ มันคือความยั่งยืนจริงๆ หรือเป็นเพียงการใช้ภาพรักษ์โลกบังหน้า แล้วขายคาร์บอย่างแนบเนียน โดยเฉพาะ The Telegraph ได้เผยแพร่บทความชื่อ “The truth about the great oat milk 'con'” ซึ่งกล่าวถึงการที่หน่วยงานกำกับดูแลโฆษณาในสหราชอาณาจักร (Advertising Standards Authority - ASA) สั่งห้ามโฆษณาบางรายการของบริษัท Oatly เนื่องจากพบว่ามีการให้ข้อมูลที่ทำให้ผู้บริโภคเข้าใจผิดเกี่ยวกับประโยชน์ต่อสิ่งแวดล้อมของการเปลี่ยนจากนมวัวเป็นนมจากพืช รวมถึง ภาพลักษณ์ “plant-based ดีต่อโลก” ถูกใช้เป็น เครื่องมือโฆษณาเชิงอารมณ์ โดยลดคุณค่าของนมวัวแท้ ๆ และสิ่งที่น่าตลกร้ายก็คือ…บริษัท Oatly เคยออกมาโจมตีอุตสาหกรรมนมวัวว่า “ไม่โปร่งใส” ขณะเดียวกันพวกเขาเองกลับโดนฟ้องร้องเรื่องการใช้โฆษณาเกินจริง และพยายามซุกซ่อนกระบวนการผลิตที่ทำให้เกิดน้ำตาลแบบ “ซ่อนในตาราง” เสียเอง
ไม่แปลกที่หลายคนในแวดวงโภชนาการแซวว่า "Oatmilk is the new Coke" เพราะมันหวานแบบไม่รู้ตัว ดื่มเพลินเหมือนน้ำอัดลม แต่สื่อสารราวกับเป็นน้ำเต้าหู้สายโยคะ โอเคเรื่องพวกนี้เอาจริงๆเคยคุยกันแล้วในรายการ ลองไปดูย้อนได้ครับ
แต่นั่นยังไม่เท่ากับสิ่งนี้ครับ “Normalize It!”: รณรงค์เข้ารร.แบบซอฟต์พาวเวอร์ ถ้าคิดว่าแค่ขายในซูเปอร์คือจุดหมาย ขอบอกว่า Oatly เล่นเกมไกลกว่านั้น เพราะเขาเปิดแคมเปญชื่อ “Normalize it!” ในหลายประเทศในยุโรป เช่น เยอรมนี สวีเดน และเนเธอร์แลนด์ โดยรณรงค์ให้ เครื่องดื่มจากพืชถูกบรรจุเป็นส่วนหนึ่งของ "โครงการนมโรงเรียน" ที่มีอยู่เดิมในระบบรัฐ ซึ่งแต่เดิมให้เฉพาะนมวัวเท่านั้น
ในโฆษณาแคมเปญนี้ มีการเล่นภาพเด็ก ๆ ที่แอบเอาโอ๊ตมิลค์ใส่กล่องนมโรงเรียน พร้อมประโยคชวนสะอึกว่า “เด็กควรต้องทำเองเหรอ?” (เหมือนจะบอกว่ารัฐควรรับหน้าที่แทน) ดูความแสบได้ที่นี่ https://youtu.be/D3d_GfGVq_I?si=3pi6VKnlJC2SDleW
มันฟังดูดีใช่ไหม...แต่ประเด็นคือ ใครเป็นคนได้ประโยชน์? คำตอบคือ บริษัทที่ขายโอ๊ตมิลค์นั่นแหละ
เพราะหากสำเร็จ โรงเรียนจำนวนมากในยุโรปจะต้องซื้อผลิตภัณฑ์จากพืชแทนหรือควบคู่กับนมวัว ทำให้บริษัทที่ขายเครื่องดื่มพืชกลายเป็นผู้ได้สัมปทานทางอ้อมในชื่อ “ความยั่งยืน”
Lobby แบบ “รักษ์โลก” แต่ก็ไม่ลืมรักษาผลประโยชน์ แคมเปญนี้ไม่ได้แค่โฆษณาเล่น ๆ แต่ยังมีการล็อบบี้ทางนโยบายในระดับสหภาพยุโรป (EU) โดยผลักดันให้เครื่องดื่มจากพืชที่มีการเสริมแคลเซียมได้รับการยอมรับเท่าเทียมกับนมวัว Oatly จึงไม่ได้แค่เป็นแบรนด์ข้าวโอ๊ตอีกต่อไป แต่กลายเป็น "นักกิจกรรม" ที่มีเป้าหมายใหญ่คือการเข้าไปอยู่ในระบบอาหารภาครัฐ โดยเฉพาะสำหรับเด็ก ๆ
ปัญหาคือไม่ใช่แค่ “พืช” แต่คือ “วิธีการสื่อสาร” ไม่มีใครเถียงว่าเด็กควรมีทางเลือกในอาหาร แต่เมื่อ “ข้อมูล” ที่ใช้สร้างภาพลักษณ์ผลิตภัณฑ์ถูกเรียบเรียงให้ดูดีเกินจริง โดยเฉพาะเมื่อซ่อนความหวานไว้ในกลไกทางเคมี และรณรงค์ให้เข้าสู่ระบบโรงเรียน มันก็กลายเป็นประเด็นที่เราควรถามว่า “เรากำลังให้เด็กกินอะไร เพราะอะไร และใครได้ประโยชน์จากสิ่งนั้น?” เครื่องดื่มจากพืชไม่ใช่ปีศาจ และนมวัวก็ไม่ใช่เทวดา แต่สิ่งที่น่ากลัวคือกลยุทธ์ที่หลอกให้คนเชื่อว่าทางเลือกหนึ่ง “ดีกว่า” โดยไม่ให้ข้อมูลครบถ้วน หรือยิ่งแย่กว่านั้นถ้าเป็นการตัดริดรอนสิทธิ์ในการเลือก
วันหนึ่งถ้าเด็ก ๆ ทุกคนได้ดื่มโอ๊ตมิลค์ที่หวานแต่ไม่เรียกว่าน้ำตาล เพราะใครบางคนบอกว่า “ดีต่อสุขภาพ” เราควรถามว่า “สุขภาพของใคร?” และ “ใครนิยามว่าอะไรคือดี?” เพราะบางครั้ง โลกที่ดูยั่งยืน อาจมีรากฐานมาจากการตลาดที่ยืนนาน
เรื่องนี้ไม่ได้เกี่ยวกับการเกลียดพืช หรือรังเกียจข้าวโอ๊ต หรือนมโอ้ต แต่มันเกี่ยวกับ ความจริงที่ถูกแต่งหน้าให้ดูดีเกินจริง ในนามของสุขภาพและสิ่งแวดล้อม ซึ่งอาจกลายเป็นการเปลี่ยนเด็กๆ ให้คุ้นชินกับเครื่องดื่มหวานแบบไม่รู้ตัว ในขณะที่เราเคยพยายามลดโค้กจากโรงเรียนไปเมื่อสิบปีก่อน
อย่าลืมว่า ไม่ใช่แค่น้ำตาลที่ต้องดู แต่ต้องดูว่ามันมาจากไหน ถูกสร้างขึ้นอย่างไร และร่างกายตอบสนองอย่างไร
สำคัญที่สุดคือ เรามีสิทธิ์ในการเลือกไหม ในอนาคต
#pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-
 @ 9e69e420:d12360c2
2025-02-17 17:12:01
@ 9e69e420:d12360c2
2025-02-17 17:12:01President Trump has intensified immigration enforcement, likening it to a wartime effort. Despite pouring resources into the U.S. Immigration and Customs Enforcement (ICE), arrest numbers are declining and falling short of goals. ICE fell from about 800 daily arrests in late January to fewer than 600 in early February.
Critics argue the administration is merely showcasing efforts with ineffectiveness, while Trump seeks billions more in funding to support his deportation agenda. Increased involvement from various federal agencies is intended to assist ICE, but many lack specific immigration training.
Challenges persist, as fewer immigrants are available for quick deportation due to a decline in illegal crossings. Local sheriffs are also pressured by rising demands to accommodate immigrants, which may strain resources further.
-
 @ 9bde4214:06ca052b
2025-04-22 16:35:00
@ 9bde4214:06ca052b
2025-04-22 16:35:00"We have the chance of building the next iteration of the internet, and hopefully, not repeat the mistakes of the past."
In this dialogue:
- Why starting ugly and shipping early is hard
- The ugliest thing that Pablo ever shipped
- “Happiness is shipping”
- Make it real first, you can make it pretty later
- Getting into the habit of shipping
- Highlighter and the hang-up of shipping something big
- How nostr allows you to have cash flow from the get-go
-
value4value for artists and devs
- What DHH & 37Signals got right
People and projects mentioned:
Further links:
- https://excellentjourney.net/2015/03/04/art-fear-the-ceramics-class-and-quantity-before-quality/
- https://world.hey.com/dhh/that-shipping-feeling-b7c8c565
- https://world.hey.com/dhh/i-was-wrong-we-need-crypto-587ccb03
- https://sovereignengineering.io/
- https://dergigi.com/2023/04/04/purple-text-orange-highlights/
- https://highlighter.com/
- https://njump.me/nosolutions@sovereignengineering.io
-
 @ d34e832d:383f78d0
2025-04-22 23:35:05
@ d34e832d:383f78d0
2025-04-22 23:35:05For Secure Inheritance Planning and Offline Signing
The setup described ensures that any 2 out of 3 participants (hardware wallets) must sign a transaction before it can be broadcast, offering robust protection against theft, accidental loss, or mismanagement of funds.
1. Preparation: Tools and Requirements
Hardware Required
- 3× COLDCARD Mk4 hardware wallets (or newer)
- 3× MicroSD cards (one per COLDCARD)
- MicroSD card reader (for your computer)
- Optional: USB data blocker (for safe COLDCARD connection)
Software Required
- Sparrow Wallet: Version 1.7.1 or later
Download: https://sparrowwallet.com/ - COLDCARD Firmware: Version 5.1.2 or later
Update guide: https://coldcard.com/docs/upgrade
Other Essentials
- Durable paper or steel backup tools for seed phrases
- Secure physical storage for backups and devices
- Optional: encrypted external storage for Sparrow wallet backups
Security Tip:
Always verify software signatures before installation. Keep your COLDCARDs air-gapped (no USB data transfer) whenever possible.
2. Initializing Each COLDCARD Wallet
- Power on each COLDCARD and choose “New Wallet”.
- Write down the 24-word seed phrase (DO NOT photograph or store digitally).
- Confirm the seed and choose a strong PIN code (both prefix and suffix).
- (Optional) Enable BIP39 Passphrase for additional entropy.
- Save an encrypted backup to the MicroSD card:
Go to Advanced > Danger Zone > Backup. - Repeat steps 1–5 for all three COLDCARDs.
Best Practice:
Store each seed phrase securely and in separate physical locations. Test wallet recovery before storing real funds.
3. Exporting XPUBs from COLDCARD
Each hardware wallet must export its extended public key (XPUB) for multisig setup:
- Insert MicroSD card into a COLDCARD.
- Navigate to:
Settings > Multisig Wallets > Export XPUB. - Select the appropriate derivation path. Recommended:
- Native SegWit:
m/84'/0'/0'(bc1 addresses) - Alternatively: Nested SegWit
m/49'/0'/0'(starts with 3) - Save the XPUB file to the MicroSD card.
- Insert MicroSD into your computer and transfer XPUB files to Sparrow Wallet.
- Repeat for the remaining COLDCARDs.
4. Creating the 2-of-3 Multisig Wallet in Sparrow
- Launch Sparrow Wallet.
- Click File > New Wallet and name your wallet.
- In the Keystore tab, choose Multisig.
- Select 2-of-3 as your multisig policy.
- For each cosigner:
- Choose Add cosigner > Import XPUB from file.
- Load XPUBs exported from each COLDCARD.
- Once all 3 cosigners are added, confirm the configuration.
- Click Apply, then Create Wallet.
- Sparrow will display a receive address. Fund the wallet using this.
Tip:
You can export the multisig policy (wallet descriptor) as a backup and share it among cosigners.
5. Saving and Verifying the Wallet Configuration
- After creating the wallet, click Wallet > Export > Export Wallet File (.json).
- Save this file securely and distribute to all participants.
- Verify that the addresses match on each COLDCARD using the wallet descriptor file (optional but recommended).
6. Creating and Exporting a PSBT (Partially Signed Bitcoin Transaction)
- In Sparrow, click Send, fill out recipient details, and click Create Transaction.
- Click Finalize > Save PSBT to MicroSD card.
- The file will be saved as a
.psbtfile.
Note: No funds are moved until 2 signatures are added and the transaction is broadcast.
7. Signing the PSBT with COLDCARD (Offline)
- Insert the MicroSD with the PSBT into COLDCARD.
- From the main menu:
Ready To Sign > Select PSBT File. - Verify transaction details and approve.
- COLDCARD will create a signed version of the PSBT (
signed.psbt). - Repeat the signing process with a second COLDCARD (different signer).
8. Finalizing and Broadcasting the Transaction
- Load the signed PSBT files back into Sparrow.
- Sparrow will detect two valid signatures.
- Click Finalize Transaction > Broadcast.
- Your Bitcoin transaction will be sent to the network.
9. Inheritance Planning with Multisig
Multisig is ideal for inheritance scenarios:
Example Inheritance Setup
- Signer 1: Yourself (active user)
- Signer 2: Trusted family member or executor
- Signer 3: Lawyer, notary, or secure backup
Only 2 signatures are needed. If one party loses access or passes away, the other two can recover the funds.
Best Practices for Inheritance
- Store each seed phrase in separate, tamper-proof, waterproof containers.
- Record clear instructions for heirs (without compromising seed security).
- Periodically test recovery with cosigners.
- Consider time-locked wallets or third-party escrow if needed.
Security Tips and Warnings
- Never store seed phrases digitally or online.
- Always verify addresses and signatures on the COLDCARD screen.
- Use Sparrow only on secure, malware-free computers.
- Physically secure your COLDCARDs from unauthorized access.
- Practice recovery procedures before storing real value.
Consider
A 2-of-3 multisignature wallet using COLDCARD and Sparrow Wallet offers a highly secure, flexible, and transparent Bitcoin custody model. Whether for inheritance planning or high-security storage, it mitigates risks associated with single points of failure while maintaining usability and privacy.
By following this guide, Bitcoin users can significantly increase the resilience of their holdings while enabling thoughtful succession strategies.
-
 @ 9e69e420:d12360c2
2025-02-17 17:11:06
@ 9e69e420:d12360c2
2025-02-17 17:11:06President Trump has intensified immigration enforcement, likening it to a wartime effort. Despite pouring resources into the U.S. Immigration and Customs Enforcement (ICE), arrest numbers are declining and falling short of goals. ICE fell from about 800 daily arrests in late January to fewer than 600 in early February.
Critics argue the administration is merely showcasing efforts with ineffectiveness, while Trump seeks billions more in funding to support his deportation agenda. Increased involvement from various federal agencies is intended to assist ICE, but many lack specific immigration training.
Challenges persist, as fewer immigrants are available for quick deportation due to a decline in illegal crossings. Local sheriffs are also pressured by rising demands to accommodate immigrants, which may strain resources further.
-
 @ 4cebd4f5:0ac3ed15
2025-04-22 16:07:40
@ 4cebd4f5:0ac3ed15
2025-04-22 16:07:40Tóm tắt Hackathon
Naija HackAtom kết thúc thành công với 160 developer đăng ký và 51 dự án được phê duyệt. Sự kiện hướng đến phát triển Interchain, Cosmos Hub và Atom Economic Zone (AEZ) trong cộng đồng Web3 Nigeria, tập trung nuôi dưỡng tài năng địa phương, cung cấp nguồn lực và xây dựng ứng dụng blockchain sử dụng token $ATOM.
Trọng tâm bao gồm Interchain Security, CosmWasm, và các giải pháp tối ưu tiện ích của ATOM. Dự án nổi bật như nền tảng chuyển tiền xuyên chuỗi và marketplace phi tập trung cho nông dân châu Phi, thể hiện ứng dụng sáng tạo công nghệ Cosmos.
Giải thưởng 8.000 USD được trao cho sáng tạo về UI/UX, community engagement và giải pháp độc đáo sử dụng ATOM. Qua workshop và hướng dẫn, dự án được đánh giá dựa trên technical feasibility, innovation, impact và user experience. Sự kiện góp phần phát triển hệ sinh thái blockchain tại Nigeria và châu Phi.
Các dự án đoạt giải
Naija HackAtom là hackathon đầu tiên tại Nigeria tập trung vào Cosmos và ATOM, thu hút 500+ người tham gia, trong đó có 160 developer. Với hỗ trợ từ ATOMAccelerator, 57 dự án được nộp, chọn ra 18 đội vào chung kết.
Main Prize Winners
- Beep: Nền tảng token hóa đồng Naira, hỗ trợ giao dịch liền mạch với tAtom.
- Padi [Crypto Go Fund Me]: Platform gây quỹ dựa trên token qua blockchain.
- ATwork: Nền tảng freelancing phi tập trung kết nối freelancer và khách hàng trên Cosmos.
Unique Solution/Product Prize Winners
- LendPro: Giao thức cho vay với quản trị tài chính hợp tác qua blockchain.
- Tradi-App: Nền tảng AI phân tích giao dịch bảo mật trên Secret Network.
- Delegated Staking Agent (DSA): Cung cấp staking và bỏ phiếu quản trị trên Cosmos, tích hợp AI để tăng cường bảo mật.
- Neutron NFT Launch: Đơn giản hóa tạo và giao dịch NFT qua tích hợp AI và blockchain.
Secret Network Bounty Winners
- Prompt Hub: Marketplace prompt AI tập trung privacy.
- Secret AI Writer: Nền tảng viết lách AI với lưu trữ blockchain an toàn.
- Tradi-App
ChihuahuaChain Bounty Winners
- woof-dot-fun: Nhân bản Pump.Fun với chức năng token và bond curve.
- Vault Quest: Giao thức tiết kiệm "không mất mát" sử dụng chiến lược DeFi để phân phối giải thưởng.
Akash Bounty Winner
- Jarvis AI: Trợ lý ảo điều khiển bằng giọng nói để quản lý tài nguyên cloud.
Xem toàn bộ dự án tại Naija HackAtom Projects.
Về Nhà tổ chức
Cosmos Hub Africa
Cosmos Hub Africa thúc đẩy blockchain và hệ sinh thái Cosmos tại châu Phi, đóng vai trò quan trọng trong phát triển mạng lưới phi tập trung và hợp tác ngành. Tổ chức triển khai dự án nâng cao scalability và interoperability, đồng thời tập trung vào giáo dục blockchain và xây dựng cơ sở hạ tầng để thúc đẩy đổi mới và tích hợp với nền kinh tế truyền thống.
-
 @ 2b24a1fa:17750f64
2025-04-23 06:53:15
@ 2b24a1fa:17750f64
2025-04-23 06:53:15„Immer wieder ist jetzt“ übertitelt unsere Sprecherin Sabrina Khalil ihren Text, den sie für die Friedensnoten geschrieben hat. Das gleichnamige Gedicht hat Jens Fischer Rodrian vertont.
Sprecher des Textes: Ulrich Allroggen
-
 @ a8d1560d:3fec7a08
2025-04-22 22:52:15
@ a8d1560d:3fec7a08
2025-04-22 22:52:15Based on the Free Speech Flag generator at https://crocojim18.github.io/, but now you can encode binary data as well.
https://free-speech-flag-generator--wholewish91244492.on.websim.ai/
Please also see https://en.wikipedia.org/wiki/Free_Speech_Flag for more information about the Free Speech Flag.
Who can tell me what I encoded in the flag used for this longform post?
-
 @ 9a859fbc:8a9270f3
2025-04-22 16:04:06
@ 9a859fbc:8a9270f3
2025-04-22 16:04:06
A story of art and inspiration
This image was generated by AI
That is...
I am artificial. I was created by two other humans (hi mum and dad 👋)
I am intelligent. I can perceive the world, experience it, learn to understand cause & effect, and make decisions.
To go perhaps deeper, cells, DNA and life itself are artifices of the fabric of reality.
I sat, in a pub in Bristol, a place where I rarely frequent. I sat with one housemate, who I rarely spent time with. I met his friends that day, only once, never we met again.
I got chatting with a lady there. I had some paper and pencils with me. My intention, for a couple of weeks, was to come up with a symbol to represent Deep Sea Frequencies, at that time still known as Psychedelic Jelly. We were a new collaboration.
She and I got chatting about art. About symbolic representation of concepts, feelings, ideas. We chatted about flow, about how there are different types of flow, different elemental conditions of flow. I doodled some shapes, and we noticed how fire, water and air all look similar due to their fluid natures. So we considered how to differentiate, distinguish them from one another.
I doodled some more, and we came up with swooshes, curls, crests and bubbles. These seemed to be distinguishing enough such that they were no longer reminiscent of fire or air. I doodled fire and air too, just in case, just to check.
Then we chatted about symmetry types, reflective, axes, rotational. About geometry, geometric containers. We both enjoy triangles and hexagons. (It's always hexagons!)
I doodled some more shapes and put them in hexagonal shapes. Then I tried bending them into triangular forms instead, and overlaid two triangles.
Each triangle looked like a triskelion. Perfect.
Overlaid, they looked just like the flow of water, coming up, spiralling down.
The logo was born in this moment, in this serendipitous meeting, in this unlikely chat with a total stranger. We met for the first time that day, and I'm not sure if we ever met again. This interaction was, is, precious, and it led to a particular creation that is now a core part of my life and is a highlight for many people around the UK and the world, as we put on events and released musicians' music.
This is inspiration. This is expression. This is flow, through the fluid nature of the cosmos.
This is what you miss out on when you talk into your AI LLM black hole prompt.
This is what you steal from when you demand your AI LLM to generate you something according to your whim.
Art and expression is the very foundation of human community. Join in! Try new things! Learn from each other! Bring us all closer together by interacting and creating through shared ideas, shared visions, shared wisdom!
After that, I drew it up cleanly, geometrically.
I photographed it like scanning it, carefully aligning the camera because I didn't have a scanner.
I redrew it more than twice.
I digitised it, colourised it, split it into two layers so I could apply colour & lighting effects to it.
I painstakingly traced the photograph into a vector format, to enlarge it and use it for various media.
I even more painstakingly (do we have a more extreme adverb??) divided all the vector shapes into new objects so that the layers became "real". And cleaned up the vector nodes, shaping them to my imagination.
The vector form is used all over our record label & events branding.
And then I imported the vector form into Blender, a 3D rendering application, free and open source.
I learnt Blender, day by day developing my understanding and my skills. Day by day my GPU crashing on raytracing and cutting the laptop's power out!
And finally, I learnt to make some simple renders that look like being underwater, like surreal glassy objects floating in the deep. I even learnt to animate it, although I haven't released that into the wild.
I imagined all of this stuff, and then I spent months over years developing my skills in my spare time in order to bring these imaginations to life.
You can do the same.
You have to sacrifice things.
Sacrifice your time.
Sacrifice your energy.
Sacrifice your distractions and enter yourself into the learning process and the creative process.
To you, amazing lady who helped me draw this symbol from the fabric of the Realm of Forms, thank you! I'm sorry that I don't recall your name, although actually I think I do remember but I would be embarrassed if I tagged the wrong person. Please reach out if you recognise this story! It was about 7, maybe 8 years ago, in the painted pub in St. Werburgh's.
-
 @ 42342239:1d80db24
2025-02-16 08:39:59
@ 42342239:1d80db24
2025-02-16 08:39:59Almost 150 years ago, the British newspaper editor William Thomas Stead wrote that "the editorial pen is a sceptre of power, compared with which the sceptre of many a monarch is but a gilded lath". He had begun to regard journalism as something more than just conveying information - the journalist or editor could become a ruler.
Times had certainly changed compared to a few hundred years earlier. Before Gutenberg's invention of the printing press, it was mainly the church that controlled the dissemination of information in Europe, but when Stead put pen to paper, this control had shifted to newspapers, schools, and universities. Eventually, technologies like radio and TV entered the scene, but the power dynamics remained asymmetrical - only a few could send information to the many.
However, with the emergence of the internet, and especially with the spread of social media, a significant change followed. Instead of only a few being able to send information to the many, many could send to many. Almost anyone could now create their own newspaper, radio, or TV channel. The power over information dissemination was decentralised.
Ten years ago, Roberta Alenius, who was then press secretary for Sweden's Prime Minister Fredrik Reinfeldt of the Moderate Party, shared her experiences with Social Democratic and Moderate Party internet activists on social media. She reported that social media played a significant role in how news "comes out" and is shaped, and that journalism was now downstream of social media. Five years later, NATO's then-Secretary-General Jens Stoltenberg said that "NATO must be prepared for both conventional and hybrid threats: from tanks to tweets." This finally underscores the importance of social media.
Elon Musk, who took over X (formerly Twitter) in 2022, has claimed that "it's absolutely fundamental and transformative that the people actually get to decide the news and narrative and what's important," and that citizen journalism is the future.
While his platform allows most expressions - for better or worse - the reach of messages is instead limited ("freedom of speech does not mean freedom of reach "). X has also opened its recommendation algorithm to the outside world by making it open-source. Although this is a welcome step, the fact remains that it's impossible to know which code is actually used and what adjustments are made by humans or algorithms.
William Thomas Stead's "sceptre of power", which has wandered from the church to newspaper and TV editorial offices, and now to citizens according to Elon Musk, risks being transferred to algorithms' opaque methods?
Instead of talking about "toxic algorithms" and TikTok bans, like the so many do today, we should ask ourselves more fundamental questions. What happens when algorithms are no longer objective (how can they ever be?), but instead become tools for shaping our reality? Perhaps our greatest challenge today is not deciding who should govern the information landscape, but instead recognising that no one is up to the task - not even well-ventilated computers.
-
 @ 9e69e420:d12360c2
2025-02-15 20:24:09
@ 9e69e420:d12360c2
2025-02-15 20:24:09Ukraine's President Volodymyr Zelensky called for an "army of Europe" to defend against Russian threats, emphasizing that the US may not continue its traditional support for Europe. Speaking at the Munich Security Conference, he warned against peace deals made without Ukraine's involvement.
US Vice President JD Vance echoed this sentiment, urging Europe to enhance its defense efforts.
Zelensky stated, "I really believe the time has come - the armed forces of Europe must be created." He highlighted changing dynamics in US-Europe relations and noted that "the old days are over" regarding American support.
Despite discussions around NATO, Zelensky stated he wouldn't rule out NATO membership for Ukraine.
-
 @ fd208ee8:0fd927c1
2025-02-15 07:02:08
@ fd208ee8:0fd927c1
2025-02-15 07:02:08E-cash are coupons or tokens for Bitcoin, or Bitcoin debt notes that the mint issues. The e-cash states, essentially, "IoU 2900 sats".
They're redeemable for Bitcoin on Lightning (hard money), and therefore can be used as cash (softer money), so long as the mint has a good reputation. That means that they're less fungible than Lightning because the e-cash from one mint can be more or less valuable than the e-cash from another. If a mint is buggy, offline, or disappears, then the e-cash is unreedemable.
It also means that e-cash is more anonymous than Lightning, and that the sender and receiver's wallets don't need to be online, to transact. Nutzaps now add the possibility of parking transactions one level farther out, on a relay. The same relays that cannot keep npub profiles and follow lists consistent will now do monetary transactions.
What we then have is * a transaction on a relay that triggers * a transaction on a mint that triggers * a transaction on Lightning that triggers * a transaction on Bitcoin.
Which means that every relay that stores the nuts is part of a wildcat banking system. Which is fine, but relay operators should consider whether they wish to carry the associated risks and liabilities. They should also be aware that they should implement the appropriate features in their relay, such as expiration tags (nuts rot after 2 weeks), and to make sure that only expired nuts are deleted.
There will be plenty of specialized relays for this, so don't feel pressured to join in, and research the topic carefully, for yourself.
https://github.com/nostr-protocol/nips/blob/master/60.md
-
 @ d34e832d:383f78d0
2025-04-22 22:48:30
@ d34e832d:383f78d0
2025-04-22 22:48:30What is pfSense?
pfSense is a free, open-source firewall and router software distribution based on FreeBSD. It includes a web-based GUI and supports advanced features like:
- Stateful packet inspection (SPI)
- Virtual Private Network (VPN) support (OpenVPN, WireGuard, IPSec)
- Dynamic and static routing
- Traffic shaping and QoS
- Load balancing and failover
- VLANs and captive portals
- Intrusion Detection/Prevention (Snort, Suricata)
- DNS, DHCP, and more
Use Cases
- Home networks with multiple devices
- Small to medium businesses
- Remote work VPN gateway
- IoT segmentation
- Homelab firewalls
- Wi-Fi network segmentation
2. Essential Hardware Components
When building a pfSense router, you must match your hardware to your use case. The system needs at least two network interfaces—one for WAN, one for LAN.
Core Components
| Component | Requirement | Budget-Friendly Example | |---------------|------------------------------------|----------------------------------------------| | CPU | Dual-core 64-bit x86 (AES-NI support recommended) | Intel Celeron J4105, AMD GX-412HC, or Intel i3 6100T | | Motherboard | Mini-ITX or Micro-ATX with support for selected CPU | ASRock J4105-ITX (includes CPU) | | RAM | Minimum 4GB (8GB preferred) | Crucial 4GB DDR4 | | Storage | 16GB+ SSD or mSATA/NVMe (for longevity and speed) | Kingston A400 120GB SSD | | NICs | At least two Intel gigabit ports (Intel NICs preferred) | Intel PRO/1000 Dual-Port PCIe or onboard | | Power Supply | 80+ Bronze rated or PicoPSU for SBCs | EVGA 400W or PicoPSU 90W | | Case | Depends on form factor | Mini-ITX case (e.g., InWin Chopin) | | Cooling | Passive or low-noise | Stock heatsink or case fan |
3. Recommended Affordable Hardware Builds
Build 1: Super Budget (Fanless)
- Motherboard/CPU: ASRock J4105-ITX (quad-core, passive cooling, AES-NI)
- RAM: 4GB DDR4 SO-DIMM
- Storage: 120GB SATA SSD
- NICs: 1 onboard + 1 PCIe Intel Dual Port NIC
- Power Supply: PicoPSU with 60W adapter
- Case: Mini-ITX fanless enclosure
- Estimated Cost: ~$150–180
Build 2: Performance on a Budget
- CPU: Intel i3-6100T (low power, AES-NI support)
- Motherboard: ASUS H110M-A/M.2 (Micro-ATX)
- RAM: 8GB DDR4
- Storage: 120GB SSD
- NICs: 2-port Intel PCIe NIC
- Case: Compact ATX case
- Power Supply: 400W Bronze-rated PSU
- Estimated Cost: ~$200–250
4. Assembling the Hardware
Step-by-Step Instructions
- Prepare the Workspace:
- Anti-static mat or surface
- Philips screwdriver
- Install CPU (if required):
- Align and seat CPU into socket
- Apply thermal paste and attach cooler
- Insert RAM into DIMM slots
- Install SSD and connect to SATA port
- Install NIC into PCIe slot
- Connect power supply to motherboard, SSD
- Place system in case and secure all components
- Plug in power and monitor
5. Installing pfSense Software
What You'll Need
- A 1GB+ USB flash drive
- A separate computer with internet access
Step-by-Step Guide
- Download pfSense ISO:
- Visit: https://www.pfsense.org/download/
- Choose AMD64, USB Memstick Installer, and mirror site
- Create Bootable USB:
- Use tools like balenaEtcher or Rufus to write ISO to USB
- Boot the Router from USB:
- Enter BIOS → Set USB as primary boot
- Save and reboot
- Install pfSense:
- Accept defaults during installation
- Choose ZFS or UFS (UFS is simpler for small SSDs)
- Install to SSD, remove USB post-installation
6. Basic Configuration Settings
After the initial boot, pfSense will assign: - WAN to one interface (via DHCP) - LAN to another (default IP: 192.168.1.1)
Access WebGUI
- Connect a PC to LAN port
- Open browser → Navigate to
http://192.168.1.1 - Default login: admin / pfsense
Initial Setup Wizard
- Change admin password
- Set hostname and DNS
- Set time zone
- Confirm WAN/LAN settings
- Enable DHCP server for LAN
- Optional: Enable SSH
7. Tips and Best Practices
Security Best Practices
- Change default password immediately
- Block all inbound traffic by default
- Enable DNS over TLS (with Unbound)
- Regularly update pfSense firmware and packages
- Use strong encryption for VPNs
- Limit admin access to specific IPs
Performance Optimization
- Use Intel NICs for reliable throughput
- Offload DNS, VPN, and DHCP to dedicated packages
- Disable unnecessary services to reduce CPU load
- Monitor system logs for errors and misuse
- Enable traffic shaping if managing VoIP or streaming
Useful Add-ons
- pfBlockerNG: Ad-blocking and geo-blocking
- Suricata: Intrusion Detection System
- OpenVPN/WireGuard: VPN server setup
- Zabbix Agent: External monitoring
8. Consider
With a modest investment and basic technical skills, anyone can build a powerful, flexible, and secure pfSense router. Choosing the right hardware for your needs ensures a smooth experience without overpaying or underbuilding. Whether you're enhancing your home network, setting up a secure remote office, or learning network administration, a custom pfSense router is a versatile, long-term solution.
Appendix: Example Hardware Component List
| Component | Item | Price (Approx.) | |------------------|--------------------------|------------------| | Motherboard/CPU | ASRock J4105-ITX | $90 | | RAM | Crucial 4GB DDR4 | $15 | | Storage | Kingston A400 120GB SSD | $15 | | NIC | Intel PRO/1000 Dual PCIe | $20 | | Case | Mini-ITX InWin Chopin | $40 | | Power Supply | PicoPSU 60W + Adapter | $25 | | Total | | ~$205 |
-
 @ 9a859fbc:8a9270f3
2025-04-22 16:00:09
@ 9a859fbc:8a9270f3
2025-04-22 16:00:09{"coverurl":"https://cdn.nostrcheck.me/9a859fbc13b98e89b499e0040c809a4945a9489621601f479f34e5a28a9270f3/7818e59ba2113e74b50267cf929d10be9a38ba080f2c3b82ec04bed7c2f4f885.webp","title":"thoughts on creativity","author":"Farran De Tao"}
-
 @ 33baa074:3bb3a297
2025-04-23 06:07:54
@ 33baa074:3bb3a297
2025-04-23 06:07:54Soil water potential refers to the potential energy of water in the soil, which is the driving force for the movement and distribution of water in the soil. It reflects the activity and energy level of soil water, and has a direct impact on plant water absorption and soil water retention capacity. Changes in soil water potential can reflect the effectiveness of soil water, which in turn affects plant growth and the effectiveness of soil nutrients. The following are the specific effects of soil water potential on soil:
Effects on plant water absorption Soil water potential directly affects the water absorption process of plants. Increases in osmotic potential and matrix potential can promote plant water absorption, while increases in gravity potential and pressure potential can hinder plant water absorption. For example, when soil water potential is high, the ability of water to move from high concentration to low concentration is enhanced, which is conducive to plant roots absorbing water.
Effects on soil water distribution Soil texture has a great influence on water permeability and water retention, thereby affecting soil water potential. Clay soils are more likely to form high water potential, while sandy soils are more likely to form low water potential. The amount of rainfall will also affect soil water potential. A lot of rainfall will increase the moisture in the soil, leading to an increase in soil water potential, while a lot of rainfall will reduce soil water potential.
Impact on soil temperature Soil water potential is also related to soil temperature. Soil temperature affects the evaporation and infiltration rate of water in the soil, thereby affecting soil water potential. In addition, the moisture content in the soil will also affect the heat capacity of the soil. Soil with high moisture content has the slowest heating and cooling rates.
Impact on soil fertility There is a close relationship between soil water potential and soil fertility. Appropriate soil water potential is conducive to soil microbial activity, nutrient conversion, and root absorption of water and nutrients. Changes in groundwater levels will also affect soil fertility. When the groundwater level rises, dissolved substances in the groundwater will enter the soil and increase soil fertility; on the contrary, when the groundwater level drops, the nutrients in the soil will decrease with the loss of groundwater.
Impact on soil structure Changes in soil water potential can affect soil structure. For example, the rise and fall of the groundwater level can cause particles in the soil to move and change the soil texture. Clay particles become more sticky under the action of water, and sandy soil may be lost due to water erosion. Therefore, measures need to be taken to strengthen soil conservation, such as covering with plants and building dams to reduce soil loss.
In summary, soil water potential has many effects on soil, including plant water absorption, soil moisture distribution, soil temperature, soil fertility, and soil structure. Understanding and managing soil water potential is of great significance to agricultural production, environmental protection, and ecological balance.
-
 @ 0fa80bd3:ea7325de
2025-02-14 23:24:37
@ 0fa80bd3:ea7325de
2025-02-14 23:24:37intro
The Russian state made me a Bitcoiner. In 1991, it devalued my grandmother's hard-earned savings. She worked tirelessly in the kitchen of a dining car on the Moscow–Warsaw route. Everything she had saved for my sister and me to attend university vanished overnight. This story is similar to what many experienced, including Wences Casares. The pain and injustice of that time became my first lessons about the fragility of systems and the value of genuine, incorruptible assets, forever changing my perception of money and my trust in government promises.
In 2014, I was living in Moscow, running a trading business, and frequently traveling to China. One day, I learned about the Cypriot banking crisis and the possibility of moving money through some strange thing called Bitcoin. At the time, I didn’t give it much thought. Returning to the idea six months later, as a business-oriented geek, I eagerly began studying the topic and soon dove into it seriously.
I spent half a year reading articles on a local online journal, BitNovosti, actively participating in discussions, and eventually joined the editorial team as a translator. That’s how I learned about whitepapers, decentralization, mining, cryptographic keys, and colored coins. About Satoshi Nakamoto, Silk Road, Mt. Gox, and BitcoinTalk. Over time, I befriended the journal’s owner and, leveraging my management experience, later became an editor. I was drawn to the crypto-anarchist stance and commitment to decentralization principles. We wrote about the economic, historical, and social preconditions for Bitcoin’s emergence, and it was during this time that I fully embraced the idea.
It got to the point where I sold my apartment and, during the market's downturn, bought 50 bitcoins, just after the peak price of $1,200 per coin. That marked the beginning of my first crypto winter. As an editor, I organized workflows, managed translators, developed a YouTube channel, and attended conferences in Russia and Ukraine. That’s how I learned about Wences Casares and even wrote a piece about him. I also met Mikhail Chobanyan (Ukrainian exchange Kuna), Alexander Ivanov (Waves project), Konstantin Lomashuk (Lido project), and, of course, Vitalik Buterin. It was a time of complete immersion, 24/7, and boundless hope.
After moving to the United States, I expected the industry to grow rapidly, attended events, but the introduction of BitLicense froze the industry for eight years. By 2017, it became clear that the industry was shifting toward gambling and creating tokens for the sake of tokens. I dismissed this idea as unsustainable. Then came a new crypto spring with the hype around beautiful NFTs – CryptoPunks and apes.
I made another attempt – we worked on a series called Digital Nomad Country Club, aimed at creating a global project. The proceeds from selling images were intended to fund the development of business tools for people worldwide. However, internal disagreements within the team prevented us from completing the project.
With Trump’s arrival in 2025, hope was reignited. I decided that it was time to create a project that society desperately needed. As someone passionate about history, I understood that destroying what exists was not the solution, but leaving everything as it was also felt unacceptable. You can’t destroy the system, as the fiery crypto-anarchist voices claimed.
With an analytical mindset (IQ 130) and a deep understanding of the freest societies, I realized what was missing—not only in Russia or the United States but globally—a Bitcoin-native system for tracking debts and financial interactions. This could return control of money to ordinary people and create horizontal connections parallel to state systems. My goal was to create, if not a Bitcoin killer app, then at least to lay its foundation.
At the inauguration event in New York, I rediscovered the Nostr project. I realized it was not only technologically simple and already quite popular but also perfectly aligned with my vision. For the past month and a half, using insights and experience gained since 2014, I’ve been working full-time on this project.
-
 @ b04082ac:29b5c55b
2025-04-22 15:57:28
@ b04082ac:29b5c55b
2025-04-22 15:57:28Africa has long grappled with the “resource curse,” a paradox where nations rich in natural resources face economic stagnation, political instability, and reliance on foreign powers. The reason isn’t hard to pinpoint. For centuries, foreign entities have extracted immense wealth from African soil such as gold, oil, cobalt, and more, leaving behind weak institutions, crippling debt, and minimal infrastructure. Instead of fueling local growth and uplifting communities, Africa’s resources have powered the industrial and digital revolutions of others.
Now, this extractive pattern is resurfacing in new ways. Recent headlines paint a clear picture:
-
Bill Gates and Jeff Bezos plan to invest $537 million in Africa to mine rare metals.
-
A ‘terrifying’ crackdown on mining companies in Africa’s coup belt.
-
Blackwater founder and Trump ally strikes mineral security deal with Congo.
-
Biden’s last dash to Africa highlights the power of minerals.
As the world scrambles to secure minerals vital for green energy and artificial intelligence, Africa stands at a crossroads. It can remain a supplier of cheap raw materials or seize this moment to shape its economic destiny.
1. Diversifying Beyond Minerals
The global race for Africa’s resources centers on critical minerals like cobalt in the Congo, rare earths in Zambia, and nickel in Tanzania. Superpowers are jostling for control, but leaning too heavily on mineral exports is fraught with risks. Prices fluctuate wildly, extraction demands massive capital, profits often vanish overseas, and overreliance can fuel political instability by deepening inequality and sparking conflicts over resource control.
To truly escape the boom-and-bust cycles of commodity markets, countries must find alternative ways to monetize their natural advantages, particularly in areas that the rest of the world tends to overlook.
One promising avenue is to tap into the continent’s vast renewable energy sources such as hydro, solar, and geothermal, and convert them into something transformative: Bitcoin.
Bitcoin mining involves validating transactions and securing the Bitcoin network in exchange for new bitcoins and fees. At its heart, it’s an energy market. Wherever there’s surplus or stranded energy, mining can thrive. Africa’s renewable energy potential is enormous and largely untapped. Rather than waiting for foreign companies to swoop in, African governments could monetize their energy directly by mining Bitcoin themselves.
2. Bitcoin Mining for Monetary Independence
Many African nations are burdened by debt, much of it in foreign currencies like the U.S. dollar. Servicing these loans drains public funds and forces governments to prioritize external creditors over local needs.
Bitcoin mining offers a way to build reserves in a neutral, censorship-resistant asset. Unlike foreign aid or currencies, Bitcoin isn’t tied to political strings or inflationary policies of other nations. It’s a step toward financial self-reliance.
In the long run, Bitcoin’s scarcity could drive its value higher, helping countries reduce their reliance on dollar-dominated systems. Looking further ahead, African nations that participate meaningfully in the Bitcoin economy may also gain influence over blockspace, the limited space where Bitcoin transactions are recorded.
3. Stabilizing Energy Grids with Mining
In much of Africa, electricity is costly, unreliable, or nonexistent. Yet, the problem often stems from underused infrastructure. Power producers struggle to recover costs due to inconsistent demand, and grids falter when supply and demand don’t align.
Bitcoin mining can act as an economic “shock absorber” for energy providers. It creates a flexible buyer that adjusts to grid demands, soaking up excess power or scaling back when needed. By placing miners near energy sources, especially in remote areas, utilities can earn steady revenue to fund broader electrification.
Take Gridless in rural Kenya. By mining Bitcoin off-grid with small hydro units, they’ve stabilized local power, supported rural internet access, and lowered costs for nearby residents. This model works. To make a more meaningful impact, however, it needs national-scale adoption supported by clear government strategy.
4. Foreign Miners Are Already Here
The shift is already happening. In Ethiopia, foreign Bitcoin mining firms are signing deals to tap the country’s hydroelectric surplus. Similar moves are underway across the continent. This isn’t a distant possibility; it is already happening.
Miners chase the cheapest energy, and Africa boasts some of the world’s most affordable renewables. Mining will happen with or without local policies. The critical question is whether the benefits will stay in Africa or flow abroad, repeating history’s mistakes.
Foreign companies bring expertise and capital, but if they dominate, African nations risk becoming mere hosts to another extractive industry. Governments must act swiftly by launching national Bitcoin mining initiatives, forging public-private partnerships, and securing ownership of infrastructure to keep the value local.
Conclusion
Africa is at a turning point. The world craves its minerals, its energy, and increasingly, its role in shaping the future. But African nations can’t afford to sit on the sidelines. The next revolution must be led, not endured.
Bitcoin mining is not a silver bullet. It is a tool that, if used wisely, could help transform energy into economic power, build digital infrastructure, and break the cycle of debt and dependence.
Bitcoin miners are already arriving. The real question is whether African nations will take the lead and ensure that this industry builds lasting value at home, rather than repeating the patterns of the past.
-
-
 @ 9e69e420:d12360c2
2025-02-14 18:07:10
@ 9e69e420:d12360c2
2025-02-14 18:07:10Vice President J.D. Vance addressed the Munich Security Conference, criticizing European leaders for undermining free speech and traditional values. He claimed that the biggest threat to Europe is not from external enemies but from internal challenges. Vance condemned the arrest of a British man for praying near an abortion clinic and accused European politicians of censorship.
He urged leaders to combat illegal immigration and questioned their democratic practices. “There is a new sheriff in town,” he said, referring to President Trump. Vance's remarks were unexpected, as many anticipated discussions on security or Ukraine. His speech emphasized the need for Europe to share the defense burden to ensure stability and security.
-
 @ 872982aa:8fb54cfe
2025-04-23 06:04:20
@ 872982aa:8fb54cfe
2025-04-23 06:04:20NIP-28
Public Chat
draftoptionalThis NIP defines new event kinds for public chat channels, channel messages, and basic client-side moderation.
It reserves five event kinds (40-44) for immediate use:
40 - channel create41 - channel metadata42 - channel message43 - hide message44 - mute user
Client-centric moderation gives client developers discretion over what types of content they want included in their apps, while imposing no additional requirements on relays.
Kind 40: Create channel
Create a public chat channel.
In the channel creation
contentfield, Client SHOULD include basic channel metadata (name,about,pictureandrelaysas specified in kind 41).jsonc { "content": "{\"name\": \"Demo Channel\", \"about\": \"A test channel.\", \"picture\": \"https://placekitten.com/200/200\", \"relays\": [\"wss://nos.lol\", \"wss://nostr.mom\"]}", // other fields... }Kind 41: Set channel metadata
Update a channel's public metadata.
Kind 41 is used to update the metadata without modifying the event id for the channel. Only the most recent kind 41 per
etag value MAY be available.Clients SHOULD ignore kind 41s from pubkeys other than the kind 40 pubkey.
Clients SHOULD support basic metadata fields:
name- string - Channel nameabout- string - Channel descriptionpicture- string - URL of channel picturerelays- array - List of relays to download and broadcast events to
Clients MAY add additional metadata fields.
Clients SHOULD use NIP-10 marked "e" tags to recommend a relay.
It is also possible to set the category name using the "t" tag. This category name can be searched and filtered.
jsonc { "content": "{\"name\": \"Updated Demo Channel\", \"about\": \"Updating a test channel.\", \"picture\": \"https://placekitten.com/201/201\", \"relays\": [\"wss://nos.lol\", \"wss://nostr.mom\"]}", "tags": [ ["e", <channel_create_event_id>, <relay-url>, "root"], ["t", <category_name-1>], ["t", <category_name-2>], ["t", <category_name-3>], ], // other fields... }Kind 42: Create channel message
Send a text message to a channel.
Clients SHOULD use NIP-10 marked "e" tags to recommend a relay and specify whether it is a reply or root message.
Clients SHOULD append NIP-10 "p" tags to replies.
Root message:
jsonc { "content": <string>, "tags": [["e", <kind_40_event_id>, <relay-url>, "root"]], // other fields... }Reply to another message:
jsonc { "content": <string>, "tags": [ ["e", <kind_40_event_id>, <relay-url>, "root"], ["e", <kind_42_event_id>, <relay-url>, "reply"], ["p", <pubkey>, <relay-url>], // rest of tags... ], // other fields... }Kind 43: Hide message
User no longer wants to see a certain message.
The
contentmay optionally include metadata such as areason.Clients SHOULD hide event 42s shown to a given user, if there is an event 43 from that user matching the event 42
id.Clients MAY hide event 42s for other users other than the user who sent the event 43.
(For example, if three users 'hide' an event giving a reason that includes the word 'pornography', a Nostr client that is an iOS app may choose to hide that message for all iOS clients.)
jsonc { "content": "{\"reason\": \"Dick pic\"}", "tags": [["e", <kind_42_event_id>]], // other fields... }js function add(a,b){ returun a+b; }Kind 44: Mute user
User no longer wants to see messages from another user.
The
contentmay optionally include metadata such as areason.Clients SHOULD hide event 42s shown to a given user, if there is an event 44 from that user matching the event 42
pubkey.Clients MAY hide event 42s for users other than the user who sent the event 44.
jsonc { "content": "{\"reason\": \"Posting dick pics\"}", "tags": [["p", <pubkey>]], // other fields... }Relay recommendations
Clients SHOULD use the relay URLs of the metadata events.
Clients MAY use any relay URL. For example, if a relay hosting the original kind 40 event for a channel goes offline, clients could instead fetch channel data from a backup relay, or a relay that clients trust more than the original relay.
Motivation
If we're solving censorship-resistant communication for social media, we may as well solve it also for Telegram-style messaging.
We can bring the global conversation out from walled gardens into a true public square open to all.
Additional info
-
 @ 9bde4214:06ca052b
2025-04-22 22:04:57
@ 9bde4214:06ca052b
2025-04-22 22:04:57“The human spirit should remain in charge.”
Pablo & Gigi talk about the wind.
In this dialogue:
- Wind
- More Wind
- Information Calories, and how to measure them
- Digital Wellbeing
- Rescue Time
- Teleology of Technology
- Platforms get users Hooked (book)
- Feeds are slot machines
- Movie Walls
- Tweetdeck and Notedeck
- IRC vs the modern feed
- 37Signals: “Hey, let’s just charge users!”
- “You wouldn’t zap a car crash”
- Catering to our highest self VS catering to our lowest self
- Devolution of YouTube 5-star ratings to thumb up/down to views
- Long videos vs shorts
- The internet had to monetize itself somehow (with attention)
- “Don’t be evil” and why Google had to remove it
- Questr: 2D exploration of nostr
- ONOSENDAI by Arkinox
- Freedom tech & Freedom from Tech
- DAUs of jumper cables
- Gossip and it’s choices
- “The secret to life is to send it”
- Flying water & flying bus stops
- RSS readers, Mailbrew, and daily digests
- Nostr is high signal and less addictive
- Calling nostr posts “tweets” and recordings being “on tape”
- Pivoting from nostr dialogues to a podcast about wind
- The unnecessary complexity of NIP-96
- Blossom (and wind)
- Undoing URLs, APIs, and REST
- ISBNs and cryptographic identifiers
- SaaS and the DAU metric
- Highlighter
- Not caring where stuff is hosted
- When is an edited thing a new thing?
- Edits, the edit wars, and the case against edits
- NIP-60 and inconsistent balances
- Scroll to text fragment and best effort matching
- Proximity hashes & locality-sensitive hashing
- Helping your Uncle Jack of a horse
- Helping your uncle jack of a horse
- Can we fix it with WoT?
- Vertex & vibe-coding a proper search for nostr
- Linking to hashtags & search queries
- Advanced search and why it’s great
- Search scopes & web of trust
- The UNIX tools of nostr
- Pablo’s NDK snippets
- Meredith on the privacy nightmare of Agentic AI
- Blog-post-driven development (Lightning Prisms, Highlighter)
- Sandwich-style LLM prompting, Waterfall for LLMs (HLDD / LLDD)
- “Speed itself is a feature”
- MCP & DVMCP
- Monorepos and git submodules
- Olas & NDK
- Pablo’s RemindMe bot
- “Breaking changes kinda suck”
- Stories, shorts, TikTok, and OnlyFans
- LLM-generated sticker styles
- LLMs and creativity (and Gigi’s old email)
- “AI-generated art has no soul”
- Nostr, zaps, and realness
- Does the source matter?
- Poker client in bitcoin v0.0.1
- Quotes from Hitler and how additional context changes meaning
- Greek finance minister on crypto and bitcoin (Technofeudalism, book)
- Is more context always good?
- Vervaeke’s AI argument
- What is meaningful?
- How do you extract meaning from information?
- How do you extract meaning from experience?
- “What the hell is water”
- Creativity, imagination, hallucination, and losing touch with reality
- “Bitcoin is singularity insurance”
- Will vibe coding make developers obsolete?
- Knowing what to build vs knowing how to build
- 10min block time & the physical limits of consensus
- Satoshi’s reasons articulated in his announcement post
- Why do anything? Why stack sats? Why have kids?
- All you need now is motivation
- Upcoming agents will actually do the thing
- Proliferation of writers: quantity VS quality
- Crisis of sameness & the problem of distribution
- Patronage, belle epoche, and bitcoin art
- Niches, and how the internet fractioned society
- Joe’s songs
- Hyper-personalized stories
- Shared stories & myths (Jonathan Pageau)
- Hyper-personalized apps VS shared apps
- Agency, free expression, and free speech
- Edgy content & twitch meta, aka skating the line of demonetization and deplatforming
- Using attention as a proxy currency
- Farming eyeballs and brain cycles
- Engagement as a success metric & engagement bait
- “You wouldn’t zap a car crash”
- Attention economy is parasitic on humanity
- The importance of speech & money
- What should be done by a machine?
- What should be done by a human?
- “The human spirit should remain in charge”
- Our relationship with fiat money
- Active vs passive, agency vs serfdom
-
 @ 9e69e420:d12360c2
2025-02-14 15:14:34
@ 9e69e420:d12360c2
2025-02-14 15:14:34A Russian drone attack has struck the radiation shelter at Chernobyl, according to Ukrainian President Volodymyr Zelensky. The strike caused a fire, but it has since been extinguished, and radiation levels remain stable. The International Atomic Energy Agency (IAEA) confirmed that no casualties occurred and that monitoring continues.
Rafael Mariano Grossi, IAEA's director general, emphasized the need for caution. Chernobyl, site of the 1986 nuclear disaster, contains a protective shield costing $1.6 billion. Disaster prevention remains a priority as the conflict unfolds.
The incident occurred shortly before the meeting of world powers at the Munich Security Conference in Germany.
-
 @ 9bde4214:06ca052b
2025-04-22 22:04:08
@ 9bde4214:06ca052b
2025-04-22 22:04:08"With the shift towards this multi-agent collaboration and orchestration world, you need a neutral substrate that has money/identity/cryptography and web-of-trust baked in, to make everything work."
Pablo & Gigi are getting high on glue.
Books & articles mentioned:
- Saving beauty by Byung-Chul Han
- LLMs as a tool for thought by Amelia Wattenberger
In this dialogue:
- vibeline & vibeline-ui
- LLMs as tools, and how to use them
- Vervaeke: AI thresholds & the path we must take
- Hallucinations and grounding in reality
- GPL, LLMs, and open-source licensing
- Pablo's multi-agent Roo setup
- Are we going to make programmers obsolete?
- "When it works it's amazing"
- Hiring & training agents
- Agents creating RAG databases of NIPs
- Different models and their context windows
- Generalists vs specialists
- "Write drunk, edit sober"
- DVMCP.fun
- Recklessness and destruction of vibe-coding
- Sharing secrets with agents & LLMs
- The "no API key" advantage of nostr
- What data to trust? And how does nostr help?
- Identity, web of trust, and signing data
- How to fight AI slop
- Marketplaces of code snippets
- Restricting agents with expert knowledge
- Trusted sources without a central repository
- Zapstore as the prime example
- "How do you fight off re-inventing GitHub?"
- Using large context windows to help with refactoring
- Code snippets for Olas, NDK, NIP-60, and more
- Using MCP as the base
- Using nostr as the underlying substrate
- Nostr as the glue & the discovery layer
- Why is this important?
- Why is this exciting?
- "With the shift towards this multi-agent collaboration and orchestration world, you need a neutral substrate that has money/identity/cryptography and web-of-trust baked in, to make everything work."
- How to single-shot nostr applications
- "Go and create this app"
- The agent has money, because of NIP-60/61
- PayPerQ
- Anthropic and the genius of mcp-tools
- Agents zapping & giving SkyNet more money
- Are we going to run the mints?
- Are agents going to run the mints?
- How can we best explain this to our bubble?
- Let alone to people outside of our bubble?
- Building pipelines of multiple agents
- LLM chains & piped Unix tools
- OpenAI vs Anthropic
- Genius models without tools vs midwit models with tools
- Re-thinking software development
- LLMs allow you to tackle bigger problems
- Increased speed is a paradigm shift
- Generalists vs specialists, left brain vs right brain
- Nostr as the home for specialists
- fiatjaf publishing snippets (reluctantly)
- fiatjaf's blossom implementation
- Thinking with LLMs
- The tension of specialization VS generalization
- How the publishing world changed
- Stupid faces on YouTube thumbnails
- Gaming the algorithm
- Will AI slop destroy the attention economy?
- Recency bias & hiding publication dates
- Undoing platform conditioning as a success metric
- Craving realness in a fake attention world
- The theater of the attention economy
- What TikTok got "right"
- Porn, FoodPorn, EarthPorn, etc.
- Porn vs Beauty
- Smoothness and awe
- "Beauty is an angel that could kill you in an instant (but decides not to)."
- The success of Joe Rogan & long-form conversations
- Smoothness fatigue & how our feeds numb us
- Nostr & touching grass
- How movement changes conversations
- LangChain & DVMs
- Central models vs marketplaces
- Going from assembly to high-level to conceptual
- Natural language VS programming languages
- Pablo's code snippets
- Writing documentation for LLMs
- Shared concepts, shared language, and forks
- Vibe-forking open-source software
- Spotting vibe-coded interfaces
- Visualizing nostr data in a 3D world
- Tweets, blog posts, and podcasts
- Vibe-producing blog posts from conversations
- Tweets are excellent for discovery
- Adding context to tweets (long-form posts, podcasts, etc)
- Removing the character limit was a mistake
- "Everyone's attention span is rekt"
- "There is no meaning without friction"
- "Nothing worth having ever comes easy"
- Being okay with doing the hard thing
- Growth hacks & engagement bait
- TikTok, theater, and showing faces and emotions
- The 1% rule: 99% of internet users are Lurkers
- "We are socially malnourished"
- Web-of-trust and zaps bring realness
- The semantic web does NOT fix this LLMs might
- "You can not model the world perfectly"
- Hallucination as a requirement for creativity
-
 @ 9a859fbc:8a9270f3
2025-04-22 15:45:55
@ 9a859fbc:8a9270f3
2025-04-22 15:45:55A story of art and inspiration
This image was generated by AI
That is...
I am artificial. I was created by two other humans (hi mum and dad 👋)
I am intelligent. I can perceive the world, experience it, learn to understand cause & effect, and make decisions.
To go perhaps deeper, cells, DNA and life itself are artifices of the fabric of reality.
I sat, in a pub in Bristol, a place where I rarely frequent. I sat with one housemate, who I rarely spent time with. I met his friends that day, only once, never we met again.
I got chatting with a lady there. I had some paper and pencils with me. My intention, for a couple of weeks, was to come up with a symbol to represent Deep Sea Frequencies, at that time still known as Psychedelic Jelly. We were a new collaboration.
She and I got chatting about art. About symbolic representation of concepts, feelings, ideas. We chatted about flow, about how there are different types of flow, different elemental conditions of flow. I doodled some shapes, and we noticed how fire, water and air all look similar due to their fluid natures. So we considered how to differentiate, distinguish them from one another.
I doodled some more, and we came up with swooshes, curls, crests and bubbles. These seemed to be distinguishing enough such that they were no longer reminiscent of fire or air. I doodled fire and air too, just in case, just to check.
Then we chatted about symmetry types, reflective, axes, rotational. About geometry, geometric containers. We both enjoy triangles and hexagons. (It's always hexagons!)
I doodled some more shapes and put them in hexagonal shapes. Then I tried bending them into triangular forms instead, and overlaid two triangles.
Each triangle looked like a triskelion. Perfect.
Overlaid, they looked just like the flow of water, coming up, spiralling down.
The logo was born in this moment, in this serendipitous meeting, in this unlikely chat with a total stranger. We met for the first time that day, and I'm not sure if we ever met again. This interaction was, is, precious, and it led to a particular creation that is now a core part of my life and is a highlight for many people around the UK and the world, as we put on events and released musicians' music.
This is inspiration. This is expression. This is flow, through the fluid nature of the cosmos.
This is what you miss out on when you talk into your AI LLM black hole prompt.
This is what you steal from when you demand your AI LLM to generate you something according to your whim.
Art and expression is the very foundation of human community. Join in! Try new things! Learn from each other! Bring us all closer together by interacting and creating through shared ideas, shared visions, shared wisdom!
After that, I drew it up cleanly, geometrically.
I photographed it like scanning it, carefully aligning the camera because I didn't have a scanner.
I redrew it more than twice.
I digitised it, colourised it, split it into two layers so I could apply colour & lighting effects to it.
I painstakingly traced the photograph into a vector format, to enlarge it and use it for various media.
I even more painstakingly (do we have a more extreme adverb??) divided all the vector shapes into new objects so that the layers became "real". And cleaned up the vector nodes, shaping them to my imagination.
The vector form is used all over our record label & events branding.
And then I imported the vector form into Blender, a 3D rendering application, free and open source.
I learnt Blender, day by day developing my understanding and my skills. Day by day my GPU crashing on raytracing and cutting the laptop's power out!
And finally, I learnt to make some simple renders that look like being underwater, like surreal glassy objects floating in the deep. I even learnt to animate it, although I haven't released that into the wild.
I imagined all of this stuff, and then I spent months over years developing my skills in my spare time in order to bring these imaginations to life.
You can do the same.
You have to sacrifice things.
Sacrifice your time.
Sacrifice your energy.
Sacrifice your distractions and enter yourself into the learning process and the creative process.
To you, amazing lady who helped me draw this symbol from the fabric of the Realm of Forms, thank you! I'm sorry that I don't recall your name, although actually I think I do remember but I would be embarrassed if I tagged the wrong person. Please reach out if you recognise this story! It was about 7, maybe 8 years ago, in the painted pub in St. Werburgh's.
-
 @ 866e0139:6a9334e5
2025-04-23 04:54:00
@ 866e0139:6a9334e5
2025-04-23 04:54:00Autor: Caitlin Johnstone. Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier. Die neuesten Pareto-Artikel finden Sie in unserem Telegram-Kanal.
Die neuesten Artikel der Friedenstaube gibt es jetzt auch im eigenen Friedenstaube-Telegram-Kanal.
Sie schicken Milliardäre und Popstars ins All, während der Planet brennt und Amerikaner ihr Insulin rationieren.
Es gibt Firmen, die KI-Liebhaber an einsame Menschen vermarkten und dabei ihre Daten ernten.
Gestern Nacht bombardierte Israel ein Zeltlager in Gaza, Frauen und Kinder verbrannten lebendig.
Dies ist ein seltsamer, dunkler Ort. Seltsame, dunkle Zeiten in einer seltsamen, dunklen Welt.
Zünde eine Kerze an für die, die gestorben sind.
Zünde eine Kerze an für die, die innerlich tot sind.
Zünde eine Kerze an für die, die Algorithmen in den Augen tragen.
Zünde eine Kerze an für die, die KI in ihren Seelen tragen.
Zünde eine Kerze an für die schreienden roten Kinder.
Zünde eine Kerze an für die stummen grauen Kinder.
Zünde eine Kerze an für den Großen Pazifischen Müllstrudel.
Zünde eine Kerze an für die Lieder der Wale.
Zünde eine Kerze an für die Herzen wie gegossenes Blei.
Zünde eine Kerze an für die Herzen wie überfahrene Wallabys.
Zünde eine Kerze an für die Herzen wie Weihrauchkathedralen.
Zünde eine Kerze an für die Herzen wie nasse Himmel.
Zünde eine Kerze an für die Eier in unseren Brustkörben.
Zünde eine Kerze an für die Samen in unseren Köpfen.
Zünde eine Kerze an für die Atompilzwolke am Horizont.
Zünde eine Kerze an für die schlafenden Buddhas.
Ich stehe da, mit offenem Mund und trockenem Hals, in einer Welt, die ich nicht verstehe, auf dem Weg in eine Zukunft, die ich nicht erkenne.
Feuerlicht tanzt an meiner Wand — von den Kerzen, oder vielleicht von Gaza, oder vielleicht von der Biosphäre, oder vielleicht von irgendwo unter meiner Haut.
Dieser Text erschien zuerst auf englisch auf dem Substack-Blog der Autorin.
(Den Text kann man hier als Kurzlink abrufen und teilen.)
LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt.
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: friedenstaube@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ 5d4b6c8d:8a1c1ee3
2025-04-22 15:37:53
@ 5d4b6c8d:8a1c1ee3
2025-04-22 15:37:53How I wish I had time for this!
https://primal.net/e/nevent1qvzqqqqqqypzqntcggz30qhq60ltqdx32zku9d46unhrkjtcv7fml7jx3dh4h94nqqsynzz85x8dcqnzxrzypec9xw6haxxjt0z0c547suty7gpa835v0vs2qusmr
originally posted at https://stacker.news/items/953418
-
 @ f18b1f8f:5f442454
2025-04-22 15:02:41
@ f18b1f8f:5f442454
2025-04-22 15:02:41f61fc2bf1e674e2da6ab891b997583e0
Ever wanted to connect multiple data sources together, simply using a spec file, and have it set up a SQL and LLM chat interface for you like magic? Spice AI aims to do this, check out @svpino's review here: https://x.com/svpino/status/1914667667631268255
listing: https://agentlist.com/agent/f61fc2bf1e674e2da6ab891b997583e0
-
 @ 9e69e420:d12360c2
2025-02-13 23:01:36
@ 9e69e420:d12360c2
2025-02-13 23:01:36Robert F. Kennedy Jr. has been confirmed as the next Secretary of Health and Human Services with a Senate vote of 52-48. Senator Mitch McConnell opposed the confirmation. Kennedy's nomination faced hurdles but gained support from the Senate Finance Committee.
During the confirmation hearing, Senator Rand Paul criticized the oversimplification of vaccine discussions. He stated, "Discussion over vaccines is so oversimplified and dumbed down." Kennedy asserted his support for vaccines like measles and polio, promising not to discourage vaccinations as HHS Secretary. Previously, he switched from the Democratic Party to run as an independent and endorsed Trump
-
 @ 9bde4214:06ca052b
2025-04-22 22:01:34
@ 9bde4214:06ca052b
2025-04-22 22:01:34"The age of the idea guys has begun."
Articles mentioned:
- LLMs as a tool for thought by Amelia Wattenberger
- Micropayments and Mental Transaction Costs by Nick Szabo
- How our interfaces have lost their senses by Amelia Wattenberger
Talks mentioned:
- The Art of Bitcoin Rhetoric by Bitstein
Books mentioned:
- Human Action by Ludwig von Mises
- Working in Public by Nadia Eghbal
In this dialogue:
- nak
- Files
- SyncThing (and how it BitTorrent Sync became Resilio Sync)
- Convention over configuration
- Changes & speciation
- File systems as sources of truth
- Vibe-coding shower thoughts
- Inspiration and The Muse
- Justin's LLM setup
- Tony's setup (o1-pro as the architect)
- Being okay with paying for LLMs
- Anthropomorphising LLMs
- Dialog, rubber-duck debugging, and the process of thinking
- Being nice and mean to LLMs
- Battlebots & Gladiators
- Hedging your bets by being nice to Skynet
- Pascal's Wager for AI
- Thinking models vs non-thinking faster models
- Sandwich-style LLM prompting, again (waterfall stuff, HLDD / LLDD)
- Cursor rules & Paul's Prompt Buddy
- Giving lots of context vs giving specific context
- The benefit of LLMs figuring out obscure bugs in minutes (instead of days)
- The phase change of fast iteration and vibe coding
- Idea level vs coding level
- High-level vs low-level languages
- Gigi's "vibeline"
- Peterson's Logos vs Vervaeke's Dia-Logos
- Entering into a conversation with technology
- Introducing MCPs into your workflow
- How does Claude think?
- How does it create a rhyme?
- How does thinking work?
- And how does it relate to dialogue?
- Gzuuus' DVMCP & using nostr as an AI substrate
- Language Server Protocols (LSPs)
- VAAS: Vibe-coding as a service
- Open models vs proprietary models
- What Cursor got right
- What ChatGPT got right
- What Google got right
- Tight integration of tools & remaining in a flow state
- LLMs as conversational partners
- The cost of context switching
- Conversational flow & how to stay in it
- Prompts VS diary entries
- Solving technical vs philosophical models
- Buying GPUs & training your own models
- Training LLMs to understand Zig
- Preventing entryism by writing no documentation
- Thin layers & alignment layers
- Working in public & thinking in public
- Building a therapist / diary / notes / idea / task system
- "The age of the idea guys has begun."
- Daemons and spirits
- Monological VS dialogical thinking
- Yes-men and disagreeable LLMs
- Energy cost vs human cost
- Paying by the meter vs paying a subscription
- The equivalence of storage and compute
- Thinking needs memory, and memory is about the future
- Nostr+ecash as the perfect AI+human substrate
- Real cost, real consequence, and Human Action
- The cost of words & speaking
- Costly signals and free markets
- From shitcoin tokens to LLM tokens to ecash tokens
- Being too close to the metal & not seeing the forest for the trees
- Power users vs engineers
- Participatory knowing and actually using the tools
- Nostr as the germination ground for ecash
- What is Sovereign Engineering?
- LLVM and the other side of the bell-curve
- How nostr gives you users, discovery, mircopayments, a backend, and many other things for free
- Echo chambers & virality
- Authenticity & Realness
- Growing on the edges, catering to the fringe
- You don't own your iPhone
- GrapheneOS
- WebRTC and other monolithic "open" standards
- Optimizing for the wrong thing
- Building a nostr phone & Gigi's dream flow
- Using nostr to sync dotfile setups and other things
- "There are no solutions, only trade-offs"
- Cross-platform development
- Native vs non-native implementations
- Vitor's point on what we mean by native
- Does your custom UI framework work for blind people?
- Ladybird browser & how to build a browser from scratch
- TempleOS
- Form follows function & 90's interfaces
- Lamentations on the state of modern browsers
- Complexity & the downfall of the Legacy Web
- Nostr as the "new internet"
- Talks by Ladybird developer Andreas Kling
- Will's attempt of building it from scratch with Notedeck & nostr-db
- Justin's attempt with rust-multiplatform
- "If it doesn't have a rust implementation, you shouldn't use it."
- Native in terms of speed vs native in terms of UI/UX
- Engineer the logic, vibe-code the UI
- From Excalidraw to app in minutes
- What can you one-shot?
- What do you need to care about?
- Pablo's NDK snippets
- 7GUIs and GUI benchmarks for LLMs
- "Now we're purpose-building tools to make it easier for LLMs"
- "Certain tools really make your problems go away."
- Macros and meta-programming
- Zig's comptime
- UNIX tools and pipes
- Simple tools & composability
- Nostr tools for iOS & sharing developer signing keys
- Building 10 apps as one guy
- Simplicity in a community context
- Most people are on phones
- Most people don't install PWAs
- Zapstore & building our own distribution channels
- Web-of-trust and pushing builds quickly
- Improving homebrew by 10x
- (Micro)payments for package managers
- Guix and bitcoin-core
- Nix vs Guix
- Reproducible builds & web-of-trust
- Keet vs "calling an npub"
- Getting into someone's notifications
- Removing the character limit was a mistake
-
 @ c2827524:5f45b2f7
2025-02-13 11:54:16
@ c2827524:5f45b2f7
2025-02-13 11:54:16innèsto s. m. [der. di innestare]. – 1. In agraria: a. Operazione con cui si fa concrescere sopra una pianta (detta portainnesto o soggetto) una parte di un altro della stessa specie o di specie differenti (detto nesto o oggetto), al fine di formare un nuovo individuo più pregiato o più produttivo o più giovane: fare, operare, praticare un innesto.
Le collaborazioni sono di una potenza micidiale.
Quelle che si sviluppano nello spazio #Bitcoin ancora di più.
Non è più una collaborazione, è un #innesto: rami di alberi diversi, destinati da soli a dare grandi frutti, si fondono per donare ad un intero ecosistema sapori ancora più deliziosi. Contributi e suggerimenti vanno e vengono alla velocità della luce, col sorriso, senza sacrificio e sempre con la volontà di migliorarsi e crescere.
Lo spazio #Bitcoin è una fabbrica magica, che accoglie minuscoli semini() da chiunque voglia partecipare, volontariamente, alla crescita della cultura Bitcoin. Ma li trasforma in un incanto*.
In solitaria i semini sarebbero destinati comunque a grandi cose e questo è già, di per sé, meraviglioso. La fabbrica magica, invece, li fa germogliare, fiorire e fruttare in maniera ancora più potente.
Quando la magia è totale, avviene l’innesto, la generazione di una nuova creatura più pregiata.
Sta succedendo davanti ai miei occhi. Sono onorata di poter assistere a questo mini miracolo della vita e, manco a dirlo, felice di farne parte.
Non è solo cambiare atteggiamento, smussare frizioni e rigidità o correggere la propria visione, è proprio ampliare sé stessi accogliendo gli altri.
Grazie nostr:npub1uhj92lnwh8rrhhuvulfqstk4g0ayx0zx35wj2d62jueqheknkxks5m4zj6 nostr:npub1au23c73cpaq2whtazjf6cdrmvam6nkd4lg928nwmgl78374kn29sq9t53j nostr:npub1awnu9vg352863e7tqlc6urlw7jgdf8vf00tmr76uuhflp4nnn68sjmnnl3 e nostr:npub1lrurmgmlfl4u72258fc4q5ke7tr82kw5xct5vchdmzr9uhmx6j4qn3t72a
(1) Semini, non #seed [non chiamatelo seed, si dice mnemonica (cit.)] Siccome in italiano la parola seme porta alla mente anche giochini di parole fiat, se siete qui per perculare fate pure. -> H.F.S.P. 🤣
-
 @ d34e832d:383f78d0
2025-04-22 21:32:40
@ d34e832d:383f78d0
2025-04-22 21:32:40The Domain Name System (DNS) is a foundational component of the internet. It translates human-readable domain names into IP addresses, enabling the functionality of websites, email, and services. However, traditional DNS is inherently insecure—queries are typically sent in plaintext, making them vulnerable to interception, spoofing, and censorship.
DNSCrypt is a protocol designed to authenticate communications between a DNS client and a DNS resolver. By encrypting DNS traffic and validating the source of responses, it thwarts man-in-the-middle attacks and DNS poisoning. Despite its security advantages, widespread adoption remains limited due to usability and deployment complexity.
This idea introduces an affordable, lightweight DNSCrypt proxy server capable of providing secure DNS resolution in both home and enterprise environments. Our goal is to democratize secure DNS through low-cost infrastructure and transparent architecture.
2. Background
2.1 Traditional DNS Vulnerabilities
- Lack of Encryption: DNS queries are typically unencrypted (UDP port 53), exposing user activity.
- Spoofing and Cache Poisoning: Attackers can forge DNS responses to redirect users to malicious websites.
- Censorship: Governments and ISPs can block or alter DNS responses to control access.
2.2 Introduction to DNSCrypt
DNSCrypt mitigates these problems by: - Encrypting DNS queries using X25519 + XSalsa20-Poly1305 or X25519 + ChaCha20-Poly1305 - Authenticating resolvers via public key infrastructure (PKI) - Supporting relay servers and anonymized DNS, enhancing metadata protection
2.3 Current Landscape
DNSCrypt proxies are available in commercial routers and services (e.g., Cloudflare DNS over HTTPS), but full control remains in the hands of centralized entities. Additionally, hardware requirements and setup complexity can be barriers to entry.
3. System Architecture
3.1 Overview
Our system is designed around the following components: - Client Devices: Use DNSCrypt-enabled stub resolvers (e.g., dnscrypt-proxy) - DNSCrypt Proxy Server: Accepts DNSCrypt queries, decrypts and validates them, then forwards to recursive resolvers (e.g., Unbound) - Recursive Resolver (Optional): Provides DNS resolution without reliance on upstream services - Relay Support: Adds anonymization via DNSCrypt relays
3.2 Protocols and Technologies
- DNSCrypt v2: Core encrypted DNS protocol
- X25519 Key Exchange: Lightweight elliptic curve cryptography
- Poly1305 AEAD Encryption: Fast and secure authenticated encryption
- UDP/TCP Fallback: Supports both transport protocols to bypass filtering
- DoH Fallback: Optional integration with DNS over HTTPS
3.3 Hardware Configuration
- Platform: Raspberry Pi 4B or x86 mini-PC (e.g., Lenovo M710q)
- Cost: Under $75 total (device + SD card or SSD)
- Operating System: Debian 12 or Ubuntu Server 24.04
- Memory Footprint: <100MB RAM idle
- Power Consumption: ~3-5W idle
4. Design Considerations
4.1 Affordability
- Hardware Sourcing: Use refurbished or SBCs to cut costs
- Software Stack: Entirely open source (dnscrypt-proxy, Unbound)
- No Licensing Fees: FOSS-friendly deployment for communities
4.2 Security
- Ephemeral Key Pairs: New keypairs every session prevent replay attacks
- Public Key Verification: Resolver keys are pre-published and verified
- No Logging: DNSCrypt proxies are configured to avoid retaining user metadata
- Anonymization Support: With relay chaining for metadata privacy
4.3 Maintainability
- Containerization (Optional): Docker-compatible setup for simple updates
- Remote Management: Secure shell access with fail2ban and SSH keys
- Auto-Updating Scripts: Systemd timers to refresh certificates and relay lists
5. Implementation
5.1 Installation Steps
- Install OS and dependencies:
bash sudo apt update && sudo apt install dnscrypt-proxy unbound - Configure
dnscrypt-proxy.toml: - Define listening port, relay list, and trusted resolvers
- Enable Anonymized DNS, fallback to DoH
- Configure Unbound (optional):
- Run as recursive backend
- Firewall hardening:
- Allow only DNSCrypt port (default: 443 or 5353)
- Block all inbound traffic except SSH (optional via Tailscale)
5.2 Challenges
- Relay Performance Variability: Some relays introduce latency; solution: geo-filtering
- Certificate Refresh: Mitigated with daily cron jobs
- IP Rate-Limiting: Mitigated with DNS load balancing
6. Evaluation
6.1 Performance Benchmarks
- Query Resolution Time (mean):
- Local resolver: 12–18ms
- Upstream via DoH: 25–35ms
- Concurrent Users Supported: 100+ without degradation
- Memory Usage: ~60MB (dnscrypt-proxy + Unbound)
- CPU Load: <5% idle on ARM Cortex-A72
6.2 Security Audits
- Verified with dnsleaktest.com and
tcpdump - No plaintext DNS observed over interface
- Verified resolver keys via DNSCrypt community registry
7. Use Cases
7.1 Personal/Home Use
- Secure DNS for all home devices via router or Pi-hole integration
7.2 Educational Institutions
- Provide students with censorship-free DNS in oppressive environments
7.3 Community Mesh Networks
- Integrate DNSCrypt into decentralized networks (e.g., Nostr over Mesh)
7.4 Business VPNs
- Secure internal DNS without relying on third-party resolvers
8. Consider
This idea has presented a practical, affordable approach to deploying a secure DNSCrypt proxy server. By leveraging open-source tools, minimalist hardware, and careful design choices, it is possible to democratize access to encrypted DNS. Our implementation meets the growing need for privacy-preserving infrastructure without introducing prohibitive costs.
We demonstrated that even modest devices can sustain dozens of encrypted DNS sessions concurrently while maintaining low latency. Beyond privacy, this system empowers individuals and communities to control their own DNS without corporate intermediaries.
9. Future Work
- Relay Discovery Automation: Dynamic quality-of-service scoring for relays
- Web GUI for Management: Simplified frontend for non-technical users
- IPv6 and Tor Integration: Expanding availability and censorship resistance
- Federated Resolver Registry: Trust-minimized alternative to current resolver key lists
References
- DNSCrypt Protocol Specification v2 – https://dnscrypt.info/protocol
- dnscrypt-proxy GitHub Repository – https://github.com/DNSCrypt/dnscrypt-proxy
- Unbound Recursive Resolver – https://nlnetlabs.nl/projects/unbound/about/
- DNS Security Extensions (DNSSEC) – IETF RFCs 4033, 4034, 4035
- Bernstein, D.J. – Cryptographic Protocols using Curve25519 and Poly1305
- DNS over HTTPS (DoH) – RFC 8484
-
 @ c2827524:5f45b2f7
2025-02-13 11:50:00
@ c2827524:5f45b2f7
2025-02-13 11:50:00innèsto s. m. [der. di innestare]. – 1. In agraria: a. Operazione con cui si fa concrescere sopra una pianta (detta portainnesto o soggetto) una parte di un altro della stessa specie o di specie differenti (detto nesto o oggetto), al fine di formare un nuovo individuo più pregiato o più produttivo o più giovane: fare, operare, praticare un innesto.
Le collaborazioni sono di una potenza micidiale.
Quelle che si sviluppano nello spazio #Bitcoin ancora di più.
Non è più una collaborazione, è un #innesto: rami di alberi diversi, destinati da soli a dare grandi frutti, si fondono per donare ad un intero ecosistema sapori ancora più deliziosi. Contributi e suggerimenti vanno e vengono alla velocità della luce, col sorriso, senza sacrificio e sempre con la volontà di migliorarsi e crescere.
Lo spazio #Bitcoin è una fabbrica magica, che accoglie minuscoli semini() da chiunque voglia partecipare, volontariamente, alla crescita della cultura Bitcoin. Ma li trasforma in un incanto*.
In solitaria i semini sarebbero destinati comunque a grandi cose e questo è già, di per sé, meraviglioso. La fabbrica magica, invece, li fa germogliare, fiorire e fruttare in maniera ancora più potente.
Quando la magia è totale, avviene l’innesto, la generazione di una nuova creatura più pregiata.
Sta succedendo davanti ai miei occhi. Sono onorata di poter assistere a questo mini miracolo della vita e, manco a dirlo, felice di farne parte.
Non è solo cambiare atteggiamento, smussare frizioni e rigidità o correggere la propria visione, è proprio ampliare sé stessi accogliendo gli altri.
Grazie nostr:npub1uhj92lnwh8rrhhuvulfqstk4g0ayx0zx35wj2d62jueqheknkxks5m4zj6 nostr:npub1au23c73cpaq2whtazjf6cdrmvam6nkd4lg928nwmgl78374kn29sq9t53j nostr:npub1awnu9vg352863e7tqlc6urlw7jgdf8vf00tmr76uuhflp4nnn68sjmnnl3 e nostr:npub1lrurmgmlfl4u72258fc4q5ke7tr82kw5xct5vchdmzr9uhmx6j4qn3t72a
(1) Semini, non #seed [non chiamatelo seed, si dice mnemonica (cit.)] Siccome in italiano la parola seme porta alla mente anche giochini di parole fiat, se siete qui per perculare fate pure. -> H.F.S.P. 🤣
-
 @ e5de231a:958477f6
2025-02-13 11:32:41
@ e5de231a:958477f6
2025-02-13 11:32:41Market Insights:
Advanced Semiconductor Packaging Market Size was valued at USD 37.90 Billion in 2024. The Advanced Semiconductor Packaging Market industry is projected to grow from USD 40.94 Billion in 2025 to USD 81.85 Billion by 2034, exhibiting a compound annual growth rate (CAGR) of 8.0% during the forecast period (2025 - 2034). The integration of semiconductor components in vehicles will fuel the global semiconductor advanced packaging market growth. The electrification of automobiles as well as the rising demand for automation in vehicles are expected to be a significant market driver for the Advanced Semiconductor Packaging Market.
In the dynamic landscape of technological advancements, the semiconductor industry stands at the forefront, steering innovation and progress. The Advanced Semiconductor Packaging Market, a crucial facet of this realm, plays a pivotal role in shaping the future of electronic devices. In this comprehensive exploration, we delve into the intricacies of this market, unraveling its complexities and forecasting its trajectory.
Understanding the Essence of Advanced Semiconductor Packaging
What Sets Advanced Semiconductor Packaging Apart?
Semiconductor packaging is the art and science of protecting and enhancing semiconductor devices, ensuring optimal performance in electronic applications. As technology evolves, the demand for more efficient, compact, and powerful semiconductor packaging solutions has surged. This is where the 'advanced' in Advanced Semiconductor Packaging becomes a game-changer.
Miniaturization and Integration: The driving force behind advanced packaging lies in the quest for smaller, yet more potent, electronic components. The market is witnessing a paradigm shift towards compact designs without compromising on functionality. Heterogeneous Integration: Combining diverse materials and technologies into a single package is the hallmark of advanced semiconductor packaging. This amalgamation fosters improved performance, energy efficiency, and overall system reliability. Enhanced Thermal Management: As electronic devices become more powerful, managing heat dissipation becomes a critical challenge. Advanced packaging solutions incorporate innovative thermal management techniques to ensure sustained high performance. Market Trends and Projections
Riding the Waves of Innovation
5G Integration: The advent of 5G technology has propelled the need for advanced semiconductor packaging to new heights. The market is witnessing a surge in demand for packaging solutions that can support the high-frequency requirements of 5G-enabled devices. Artificial Intelligence (AI) Integration: AI-driven applications demand robust semiconductor solutions. Advanced packaging, with its focus on efficient power delivery and heat dissipation, aligns perfectly with the requirements of AI-powered devices. Automotive Electronics: The automotive industry's shift towards electric and autonomous vehicles has fueled the demand for advanced semiconductor packaging. These packages need to withstand harsh environments while delivering exceptional performance. Market Dynamics and Key Players
The Advanced Semiconductor Packaging Market is characterized by intense competition and rapid technological advancements. Key players in this landscape include:
Intel Corporation: A pioneer in semiconductor technology, Intel continues to lead the market with innovations in packaging solutions. Advanced Micro Devices (AMD): Renowned for its cutting-edge processors, AMD's foray into advanced packaging has added a new dimension to the market. Taiwan Semiconductor Manufacturing Company (TSMC): As a global semiconductor manufacturing giant, TSMC's influence on the market is undeniable, shaping the industry's future through advanced packaging technologies. Challenges and Future Prospects
Navigating the Road Ahead
While the Advanced Semiconductor Packaging Market is poised for growth, it is not without its challenges:
Complexity of Integration: As technologies converge, integrating diverse components into a single package poses significant technical challenges. Supply Chain Disruptions: The global semiconductor shortage has underscored the vulnerability of the supply chain. Addressing these disruptions is crucial for sustained market growth. Environmental Considerations: The semiconductor industry is under increasing scrutiny for its environmental impact. Sustainable packaging solutions and responsible manufacturing practices are becoming paramount.
Related Reports:
Super Capacitors Energy Storage System Market
Conclusion
In conclusion, the Advanced Semiconductor Packaging Market is a dynamic arena where innovation converges with necessity. As we navigate the complexities of an interconnected world, the role of advanced packaging in shaping the future of electronics cannot be overstated. The market's trajectory is marked by challenges, but also by unprecedented opportunities for those at the forefront of technological evolution.
-
 @ 34c964ef:82a60fa4
2025-02-13 08:25:18
@ 34c964ef:82a60fa4
2025-02-13 08:25:18The Bond Clean Experts: Your Ultimate Solution for End-of-Lease Cleaning
Moving out of a rental property can be stressful, especially when it comes to meeting the landlord’s cleanliness expectations. That’s where The Bond Clean Experts come in! With professional experience and a commitment to excellence, we ensure your property is spotless, helping you secure your full bond refund without hassle.
Why Choose The Bond Clean Experts?
✅ Experienced Professionals: Our team is trained in industry-standard cleaning techniques to deliver impeccable results.✅ Guaranteed Satisfaction: We offer a bond-back guarantee, ensuring your property meets inspection requirements.✅ Eco-Friendly Products: We use non-toxic, eco-friendly cleaning solutions to protect your health and the environment.✅ Comprehensive Cleaning Services: From kitchens and bathrooms to carpets and windows, we cover every inch of your property.✅ Affordable Pricing: Quality service at competitive rates with no hidden fees.
Our Services Include:
Deep Carpet Cleaning – Removing stubborn stains and odors.
Kitchen & Appliance Cleaning – Ensuring spotless ovens, stovetops, and countertops.
Bathroom Sanitization – Eliminating grime, mold, and bacteria.
Wall & Window Cleaning – Removing marks, dust, and streaks.
Floor & Tile Scrubbing – Bringing back the shine to your flooring.
The Bond Cleaning Process
Inspection & Quote: We assess your property’s cleaning needs and provide a transparent quote.
Thorough Cleaning: Our experts deep clean every area to meet landlord expectations.
Final Touches: We double-check all details and ensure nothing is overlooked.
Satisfaction Guarantee: If needed, we offer a free re-clean to ensure compliance with lease requirements.
Book Your Bond Clean Today!
Don’t risk losing your bond due to subpar cleaning. Let The Bond Clean Experts handle the job with precision and care.
📞 Call us at 0485971499 Serving https://www.bondcleaners.au/bond-cleaning-brisbane/💬 Message us for a free quote!
Make your move-out hassle-free with The Bond Clean Experts! ✨
-
 @ d34e832d:383f78d0
2025-04-22 21:14:46
@ d34e832d:383f78d0
2025-04-22 21:14:46Minecraft remains one of the most popular sandbox games in the world. For players who wish to host private or community-based servers, monthly hosting fees can quickly add up. Furthermore, setting up a server from scratch often requires technical knowledge in networking, system administration, and Linux.
This idea explores a do-it-yourself (DIY) method for deploying a low-cost Minecraft server using common secondhand hardware and a simple software stack, with a focus on energy efficiency, ease of use, and full control over the server environment.
2. Objective
To build and deploy a dedicated Minecraft server that:
- Costs less than $75 in total
- Consumes minimal electricity (<10W idle)
- Is manageable via a graphical user interface (GUI)
- Supports full server management including backups, restarts, and plugin control
- Requires no port forwarding or complex network configuration
- Delivers performance suitable for a small-to-medium number of concurrent players
3. Hardware Overview
3.1 Lenovo M710Q Mini-PC (~$55 used)
- Intel Core i5 (6th/7th Gen)
- 8GB DDR4 RAM
- Compact size and low power usage
- Widely available refurbished
3.2 ID Sonics 512GB NVMe SSD (~$20)
- Fast storage with sufficient capacity for multiple Minecraft server instances
- SSDs reduce world loading lag and improve backup performance
Total Hardware Cost: ~$75
4. Software Stack
4.1 Ubuntu Server 24.04
- Stable, secure, and efficient operating system
- Headless installation, ideal for server use
- Supports automated updates and system management via CLI
4.2 CasaOS
- A lightweight operating system layer and GUI on top of Ubuntu
- Built for managing Docker containers with a clean web interface
- Allows app store-like deployment of various services
4.3 Crafty Controller (via Docker)
- Web-based server manager for Minecraft
- Features include:
- Automatic backups and restore
- Scheduled server restarts
- Plugin management
- Server import/export
- Server logs and console access
5. Network and Remote Access
5.1 PlayIt.gg Integration
PlayIt.gg creates a secure tunnel to your server via a relay node, removing the need for traditional port forwarding.
Benefits: - Works even behind Carrier-Grade NAT (common on mobile or fiber ISPs) - Ideal for users with no access to router settings - Ensures privacy by hiding IP address from public exposure
6. Setup Process Summary
- Install Ubuntu Server 24.04 on the M710Q
- Install CasaOS via script provided by the project
- Use CasaOS to deploy Crafty Controller in a Docker container
- Configure Minecraft server inside Crafty (Vanilla, Paper, Spigot, etc.)
- Integrate PlayIt.gg to expose the server to friends
- Access Crafty via browser for daily management
7. Power Consumption and Performance
- Idle Power Draw: ~7.5W
- Load Power Draw (2–5 players): ~15W
- M710Q fan runs quiet and rarely under load
- Performance sufficient for:
- Vanilla or optimized Paper server
- Up to 10 concurrent players with light mods
8. Cost Analysis vs Hosted Services
| Solution | Monthly Cost | Annual Cost | Control Level | Mods Support | |-----------------------|--------------|-------------|----------------|---------------| | Commercial Hosting | $5–$15 | $60–$180 | Limited | Yes | | This Build (One-Time) | $75 | $0 | Full | Yes |
Return on Investment (ROI):
Break-even point reached in 6 to 8 months compared to lowest hosting tiers.
9. Advantages
- No Subscription: Single upfront investment
- Local Control: Full access to server files and environment
- Privacy Respecting: No third-party data mining
- Modular: Can add mods, backups, maps with full access
- Low Energy Use: Ideal for 24/7 uptime
10. Limitations
- Not Ideal for >20 players: CPU and RAM constraints
- Local Hardware Dependency: Physical failure risk
- Requires Basic Setup Time: CLI familiarity useful but not required
11. Future Enhancements
- Add Dynmap with reverse proxy and TLS via CasaOS
- Integrate Nextcloud for managing world backups
- Use Watchtower for automated container updates
- Schedule daily email logs using system cron
12. Consider
This idea presents a practical and sustainable approach to self-hosting Minecraft servers using open-source software and refurbished hardware. With a modest upfront cost and minimal maintenance, users can enjoy full control over their game worlds without recurring fees or technical hassle. This method democratizes game hosting and aligns well with educational environments, small communities, and privacy-conscious users.
-
 @ 57d56d16:458edffd
2025-04-22 23:43:13
@ 57d56d16:458edffd
2025-04-22 23:43:13Hello. I've had a look at shopstr. You can find my instance of shopstr here so you can have a look yourself: https://shopstr.tectumordo.com/marketplace
Wondering your thoughts on Shopstr. I'm looking to start selling some things. Handcrafted Items / Services.
Anyone have any insights into shopstr, or something similar.
originally posted at https://stacker.news/items/953976
-
 @ 04ed2b8f:75be6756
2025-02-13 08:02:39
@ 04ed2b8f:75be6756
2025-02-13 08:02:39Freedom. It’s the word on everyone’s lips, the dream of every soul. We long for it, we chase it, we believe that if we can break free from this chain or that constraint, we will finally be free. But true freedom is not about external circumstances—it’s about control.
The truth is, the most powerful chains are the ones we place on ourselves. The world can throw its challenges at you, life can dish out its unfair blows, but if you cannot control yourself, your thoughts, your emotions, your reactions, then you are no different than a prisoner.
There is no freedom in chaos. There is no freedom in losing control. Freedom is mastery—mastery of the self.
Freedom Begins Within
You can have all the money in the world, live in the most luxurious place, and have every material possession your heart desires, but if you cannot control your impulses, your habits, your desires—none of that will matter. You are still a slave to your cravings. You are still a puppet to your own emotions, and that is no real freedom.
What does freedom look like?
- It’s the power to act with purpose, not to react out of emotion.
- It’s the strength to stay disciplined when every part of you wants to quit.
- It’s the courage to say ‘no’ to distractions, to temptation, to things that steer you off course.
- It’s the clarity to make choices that serve your growth, not your immediate desires.
True freedom is the ability to say, “I am in control of myself. I do not let my circumstances control me, nor my emotions rule me. I dictate my actions, my thoughts, my destiny.”
Self-Control: The Ultimate Weapon
The power to control yourself is your greatest weapon. Without it, you are at the mercy of every challenge, every temptation, and every fleeting emotion. You may feel like you are “free,” but without self-discipline, you are just a puppet swaying in the wind, vulnerable to every whim that blows your way.
- The impulse to procrastinate? You overcome it.
- The desire to give up? You push through it.
- The craving for comfort? You choose growth.
In the face of any storm, a man with self-control remains grounded, focused, and clear. He doesn’t react in anger or fear—he acts with purpose, with precision, and with vision.
A man who cannot control himself is a man who is owned by his emotions, his desires, his distractions. But the man who conquers his mind, his body, his impulses—he is the one who owns his life.
The Price of Freedom
It’s not easy to control yourself. It requires constant effort, relentless discipline, and the courage to face yourself head-on. It means saying ‘no’ to what feels good now, to invest in what will make you stronger later. It means constantly improving, constantly fighting the urge to quit, to give in, to indulge in comfort.
But the price of freedom is worth it. For when you have control over yourself, no one can take your power. You become the master of your fate. You become unshakable.
Freedom Through Discipline
So, ask yourself: Are you truly free, or are you simply a slave to your impulses?
- Do you control your actions, or do your actions control you?
- Are you the master of your emotions, or are they the masters of you?
Freedom isn’t just about having no chains; it’s about not letting anything control you—least of all yourself. And when you control yourself, there’s nothing you can’t accomplish.
A man who cannot control himself is never truly free. But a man who conquers his mind, his habits, his emotions—he is unstoppable. Now go and choose to control yourself, and unlock the freedom that’s waiting for you. Or remain a prisoner to your impulses, forever shackled by the chains of your own making. The choice is yours.
-
 @ aa333681:f8b3be8c
2025-04-22 14:43:09
@ aa333681:f8b3be8c
2025-04-22 14:43:09
บทความนี้ สืบเนื่องมาจากผมได้ยินข่าว Virtual Bank ของประเทศไทย เลยเกิดความสงสัยขึ้นมาว่า มันต่างจาก Digital Bank ยังไง?
คุยไปคุยมา เลยเถิด ... จึงเกิดเป็นบทความขนาดยาวนี้ขึ้นมาครับ
เชิญเสพย์กันได้ตามอัธยาศัย ...
siamstr #bitcoin
beyourownbank #virtualbank
1. Virtual Banking ในประเทศไทย: ความเคลื่อนไหวล่าสุด
Virtual Bank คืออะไร?
Virtual Bank หรือธนาคารพาณิชย์ไร้สาขา เป็นสถาบันการเงินรูปแบบใหม่ที่ให้บริการผ่านช่องทางดิจิทัลเป็นหลัก โดยไม่มีสาขา เครื่องถอนเงินสดอัตโนมัติ (ATM) หรือเครื่องฝากเงินสดอัตโนมัติ (CDM) เป็นของตนเอง แต่ยังสามารถให้บริการทางการเงินได้อย่างครบวงจร
ลูกค้าสามารถทำธุรกรรมต่างๆ เช่น การเปิดบัญชี ฝาก-ถอนเงิน โอนเงิน ชำระเงิน ขอสินเชื่อ และลงทุนผ่านแอปพลิเคชันหรือเว็บไซต์ได้ตลอด 24 ชั่วโมง
ประโยชน์ที่คาดว่าจะได้รับ
- เพิ่มการเข้าถึงบริการทางการเงิน สำหรับประชาชนกลุ่มที่ยังเข้าไม่ถึงธนาคารแบบดั้งเดิม
- ส่งเสริมนวัตกรรมทางการเงิน และการแข่งขันในระบบธนาคาร
- ลดต้นทุนการดำเนินงาน และค่าธรรมเนียมสำหรับผู้ใช้บริการ
ทำไมธนาคารแห่งประเทศไทยจึงเปิดรับ Virtual Bank?
ธนาคารแห่งประเทศไทย (ธปท.) เปิดรับการจัดตั้ง Virtual Bank เพื่อส่งเสริมให้ผู้ที่มีความเชี่ยวชาญด้านการใช้เทคโนโลยี บริการดิจิทัล และข้อมูล เข้ามาช่วยพัฒนาบริการทางการเงินรูปแบบใหม่ที่ตอบโจทย์ลูกค้าได้ดียิ่งขึ้น ช่วยเพิ่มการเข้าถึงบริการทางการเงิน และช่วยกระตุ้นการแข่งขันในระบบสถาบันการเงิน
การอนุญาตให้จัดตั้ง Virtual Bank จะเปิดทางให้ผู้เล่นรายใหม่ที่เชี่ยวชาญด้านเทคโนโลยีใช้ประโยชน์จากข้อมูลอย่างเต็มที่ เพื่อเพิ่มการเข้าถึงสินเชื่อ โดยเฉพาะสำหรับ SMEs ที่เข้าไม่ถึงแหล่งเงินทุน
กลุ่มทุนที่ได้รับสิทธิ์มีใครบ้าง?
ธปท. ได้พิจารณาคุณสมบัติ ศักยภาพ และความสามารถที่จะประกอบธุรกิจ Virtual Bank เสร็จเรียบร้อยแล้ว หลังจากที่ได้สัมภาษณ์กลุ่มที่ยื่นขอใบอนุญาตทั้ง 5 ราย จึงได้คัดเลือก 3 ราย ประกอบด้วย
- ธนาคารกรุงไทย ร่วมกับกลุ่มพันธมิตร Gulf, AIS และ PTT Group
- กลุ่มบริษัทเอสซีบี เอกซ์ (SCBX) ร่วมกับ KakaoBank จากเกาหลีใต้ และพันธมิตร WeBank จากจีน
- บริษัท แอสเซนด์ มันนี่ จำกัด ของกลุ่ม ซีพี
ทั้ง 3 กลุ่มทุนนี้มีความพร้อมทั้งด้านบุคลากร เทคโนโลยี และโครงสร้างพื้นฐาน เพื่อให้บริการ Virtual Bank อย่างมีประสิทธิภาพ
เหตุผลในการคัดเลือก: ธปท. ระบุว่าการอนุมัติใบอนุญาตในรอบแรกให้เพียง 3 ราย เพื่อประเมินประสิทธิภาพและความเสี่ยงก่อนที่จะพิจารณาเปิดให้รายอื่นในอนาคต
คาดว่า Virtual Bank จะเริ่มให้บริการได้จริงภายในปี 2569
YouTube: ทำความรู้จัก Virtual Bank จุดเปลี่ยนของระบบการเงินไทย | The Standard Wealth
https://www.youtube.com/watch?v=t0DyuvS9Wvc
2. Virtual Banking ≠ Digital Banking
เปรียบเทียบ Digital Bank ปัจจุบัน vs. Virtual Bank
หลายๆ คนคงเคยได้ยินคำว่า Digital Banking หรือ Digital Bank ซึ่งหมายถึงการทำธุรกรรมทางการเงินผ่านช่องทางดิจิทัลเช่น แอปพลิเคชันมือถือหรือเว็บไซต์ แต่เมื่อพูดถึง Virtual Banking นั้น มันไม่ใช่แค่การทำธุรกรรมผ่านแอปสวยๆ อีกต่อไป เราจะมาดูกันว่า Virtual Bank มีความแตกต่างจาก Digital Bank อย่างไรบ้าง:
1. Digital Bank
- รูปแบบการให้บริการ: ใช้เทคโนโลยีดิจิทัลในการให้บริการทางการเงิน เช่น เปิดบัญชี ฝาก-ถอน โอนเงิน ชำระค่าบริการต่างๆ ผ่านแอปพลิเคชันของธนาคารที่มีอยู่ในปัจจุบัน
- สาขา: แม้ว่าไม่มีสาขาที่ให้บริการเต็มรูปแบบ แต่บางธนาคารยังคงมีสาขาเป็นตัวช่วยในการให้บริการต่างๆ เช่น การเปิดบัญชีใหม่ หรือการให้คำปรึกษา
- ระบบการให้บริการ: บริการที่มีอยู่เป็นการปรับปรุงจากระบบเดิมให้เหมาะสมกับการใช้งานในยุคดิจิทัล
2. Virtual Bank
- รูปแบบการให้บริการ: เป็นธนาคารที่ไม่มีสาขาหรือเครื่อง ATM และให้บริการทั้งหมดผ่านช่องทางดิจิทัล ไม่ว่าจะเป็นแอปพลิเคชันหรือเว็บไซต์ที่ทำงานเต็มรูปแบบ ซึ่งรวมถึงการวิเคราะห์ข้อมูลลูกค้าผ่าน AI เพื่อให้สินเชื่ออย่างแม่นยำ
- การเปิดบัญชี: กระบวนการเปิดบัญชีหรือขอสินเชื่อเป็นแบบดิจิทัลทั้งหมด และสามารถทำได้ทันทีผ่านแอปพลิเคชัน
- เป้าหมาย: Virtual Banking ไม่ได้เป็นแค่การย้ายบริการจากหน้าสาขามาอยู่บนออนไลน์ แต่คือการสร้างระบบการเงินที่ช่วยให้เข้าถึงบริการทางการเงินได้ง่ายขึ้นสำหรับกลุ่มคนที่ไม่สามารถเข้าถึงธนาคารดั้งเดิม
🔍 ความแตกต่างหลักระหว่าง Virtual Banking และ Digital Banking
| | | | |---|---|---| |หัวข้อ|Virtual Banking|Digital Banking| |สถานะองค์กร|เป็น ธนาคารพาณิชย์ที่ไม่มีสาขาเลย (branchless bank) ที่ก่อตั้งขึ้นใหม่|เป็น ธนาคารเดิม ที่ใช้เทคโนโลยีดิจิทัลในการให้บริการ| |โครงสร้างต้นทุน|ต่ำกว่า เพราะไม่ต้องลงทุนในสาขาและพนักงานหน้าสาขา|ยังมีต้นทุนโครงสร้างสาขาและระบบเดิม (legacy systems)| |แนวคิดเริ่มต้น|ออกแบบมาเพื่อลดความเหลื่อมล้ำในการเข้าถึงการเงิน (financial inclusion)|พัฒนาเพื่อเพิ่มความสะดวกของลูกค้าปัจจุบัน| |กลุ่มเป้าหมายหลัก|กลุ่ม underserved เช่น ผู้ไม่มีบัญชีธนาคาร, ฟรีแลนซ์, แรงงานนอกระบบ ฯลฯ|ลูกค้าธนาคารทั่วไปที่ใช้บริการอยู่แล้ว| |การดำเนินงาน|ดำเนินการ ทุกอย่างแบบออนไลน์ 100% ตั้งแต่เปิดบัญชี ยืนยันตัวตน ไปจนถึงการให้สินเชื่อ|ส่วนใหญ่ยังผสมผสานกับระบบออฟไลน์ เช่น การยืนยันตัวตนที่สาขา| |ระบบหลังบ้าน (Core)|สร้างขึ้นใหม่ บน cloud-native, agile และ automation-ready|มักมีระบบเดิมที่ซับซ้อน ทำให้เปลี่ยนแปลงได้ช้ากว่า| |ความยืดหยุ่นทางเทคโนโลยี|สูง (เพราะเริ่มจากศูนย์)|จำกัดกว่า (เพราะผูกกับระบบเดิม)|
🎯 สรุปสั้น ๆ
- Digital Bank = ธนาคารเดิมที่ "เปลี่ยนแปลง" ตัวเองด้วยดิจิทัล
- Virtual Bank = ธนาคารใหม่ที่ "เกิดมาเพื่อดิจิทัลตั้งแต่ต้น"
ถ้าจะเปรียบเทียบแบบง่าย ๆ:
Digital Banking เหมือนรถเก่าที่เอาไปติดตั้งระบบไฮบริด Virtual Banking เหมือนรถไฟฟ้าใหม่ที่สร้างมาเพื่อเป็น EV ตั้งแต่ต้น
ตัวอย่าง Virtual Bank ในต่างประเทศที่ประสบความสำเร็จ:
- KakaoBank (เกาหลีใต้) – ไม่มีสาขาเลย แต่กลายเป็นธนาคารที่มีลูกค้ามากที่สุดในเกาหลี
- WeBank (จีน) – ของกลุ่ม Tencent ดำเนินงานทุกอย่างผ่าน WeChat
- Revolut, Monzo, Starling Bank (UK) – สร้างใหม่หมดและทำทุกอย่างผ่านแอป
🎯 จากมุมมอง Gen Z / Alpha: UX ที่ “ไม่รู้สึกถึงความต่าง”
📱 พฤติกรรมดิจิทัลของคนรุ่นใหม่
- โตมากับ K Plus, SCB Easy, Krungthai Next, TrueMoney, Line BK ฯลฯ
- ใช้ digital wallet, QR, promptpay, BNPL จนเป็นเรื่องปกติ
- มองทุกบริการทางการเงินผ่าน “mobile-first” อยู่แล้ว
Virtual Bank ≠ “อะไรที่แปลกใหม่” แต่คือ “แค่แอปธนาคารอีกอัน” ถ้ามันไม่ต่างในประสบการณ์ผู้ใช้
ดังนั้น…
ถ้า Virtual Bank ใหม่ ยังเปิดบัญชีแบบ eKYC ธรรมดา ยังโอนเงินแบบแอปทั่วไป ยังมี UX แบบ list-based menu เหมือน mobile banking เดิม มันจะไม่มี “ความว้าว” หรือ “sense of new experience” สำหรับคนรุ่นนี้เลย
Virtual Bank คืออะไรที่ “มากกว่าแค่มีแอปสวย”
การพูดถึง Virtual Bank หลายคนอาจนึกถึงแค่ “แอปพลิเคชันที่ใช้งานง่าย” หรือ “UI ที่สวยงาม” ซึ่งไม่ผิด แต่ความจริงแล้ว Virtual Bank คือการออกแบบระบบการเงินใหม่ ที่มีความแตกต่างจากธนาคารทั่วไป โดยเฉพาะในด้าน การเข้าถึง และ การให้บริการที่เป็นส่วนตัว มากกว่า:
- การเข้าถึง (Access): Virtual Banking มีเป้าหมายในการเพิ่มการเข้าถึงบริการทางการเงินให้แก่กลุ่มคนที่ไม่สามารถเข้าถึงธนาคารทั่วไป เช่น กลุ่มคนที่อาศัยในพื้นที่ห่างไกล, คนที่ไม่มีเอกสารหรือประวัติการเงินที่สามารถเปิดบัญชีธนาคารได้
- การใช้ข้อมูลลูกค้า: ระบบของ Virtual Bank จะสามารถใช้ข้อมูลจากการทำธุรกรรมหรือพฤติกรรมการใช้งานเพื่อให้การอนุมัติสินเชื่อได้อย่างมีประสิทธิภาพ แม่นยำ และรวดเร็ว
- ความสะดวกและประหยัด: ไม่มีค่าใช้จ่ายในการตั้งสาขาหรือเครื่อง ATM ทำให้สามารถนำเสนอบริการที่มีค่าธรรมเนียมต่ำและสามารถให้บริการแก่กลุ่มลูกค้าที่ต้องการสินเชื่อในจำนวนเล็กน้อย
เป้าหมายเชิงระบบ: เพิ่มการเข้าถึง (Inclusion) ไม่ใช่แค่พัฒนา UI
เมื่อพูดถึง การเข้าถึง (Inclusion) การที่ธนาคารเปิดให้บริการ Virtual Bank เป็นการมองเห็นความสำคัญของการขยายขอบเขตการให้บริการทางการเงินไปยังกลุ่มคนที่ไม่เคยได้มีโอกาสเข้าถึงมาก่อน:
- เพิ่มการเข้าถึงทางการเงิน: โดยการใช้เทคโนโลยีดิจิทัลให้บริการที่สามารถเข้าถึงได้จากทุกที่ และการใช้ข้อมูลทางเทคโนโลยีเพื่อประเมินความเสี่ยงการให้สินเชื่อได้แม่นยำขึ้น
- กลุ่มเป้าหมาย: กลุ่มลูกค้าใหม่ๆ ที่ไม่เคยมีบัญชีธนาคารมาก่อน และกลุ่มลูกค้าที่ไม่สามารถเข้าถึงบริการจากธนาคารทั่วไปได้ เช่น คนในพื้นที่ห่างไกล
- ไม่ใช่แค่การพัฒนา UI: การพัฒนา UI ที่ดีขึ้นและสวยงามนั้นเป็นส่วนหนึ่งของ Virtual Banking แต่เป้าหมายหลักคือการสร้างระบบการเงินที่สามารถเพิ่มโอกาสในการเข้าถึงบริการการเงินได้จริงๆ โดยไม่ต้องอาศัยการมีสาขาหรือระบบที่เป็นภาระทางกายภาพ
3. ใครได้ประโยชน์จาก Virtual Bank จริง ๆ?
การเกิดขึ้นของ Virtual Banking ทำให้ผู้คนที่ไม่เคยเข้าถึงบริการทางการเงินแบบเดิมสามารถมีโอกาสในการเปิดบัญชีและเข้าถึงสินเชื่อได้มากขึ้น โดยไม่จำเป็นต้องพึ่งพาธนาคารที่มีสาขาหรือเครื่อง ATM ในพื้นที่ใกล้เคียง
วิเคราะห์กลุ่มผู้ใช้ที่ได้ประโยชน์
1. กลุ่ม “นอกระบบธนาคารเดิม” / คนที่ไม่มีบัญชีธนาคาร / อาชีพอิสระ / พ่อค้าแม่ค้า
คนที่ไม่มีเครดิต ไม่มีสลิปเงินเดือน ไม่มีเวลาหรือความรู้ในการเปิดบัญชีแบบปกติ ผู้ที่มี "รายได้จริง" แต่ “ไม่มีหลักฐาน” แบบที่แบงก์ต้องการ
- กลุ่มนี้ มักจะเป็นคนที่มีรายได้ไม่คงที่ หรือบางครั้งไม่มีเอกสารการเงินที่สามารถใช้เปิดบัญชีในธนาคารทั่วไปได้
- ตัวอย่าง: คนขายของออนไลน์ที่ไม่มีบัญชีธนาคาร หรือคนทำงานอิสระที่ไม่มีการรายงานรายได้ที่ชัดเจน
- ประโยชน์:
- เปิดบัญชีง่าย ผ่านช่องทางดิจิทัลโดยไม่ต้องไปสาขา
- สามารถรับและโอนเงินได้สะดวกโดยไม่ต้องพึ่งพาเงินสด
- เข้าถึง สินเชื่อขนาดเล็ก ได้ง่ายขึ้นเพื่อหมุนเวียนเงินทุนในการทำธุรกิจ
- การอนุมัติสินเชื่อสามารถใช้ ข้อมูลพฤติกรรม การใช้จ่ายแทนการใช้ข้อมูลเครดิตแบบดั้งเดิม
2. คนรายได้น้อย / First Jobbers
กลุ่มที่ยังไม่มีเครดิตดีพอจะใช้บัตรเครดิต หรือกู้ธนาคารแบบเดิม
- กลุ่มนี้ คือคนที่เพิ่งเริ่มต้นทำงาน หรือมีรายได้ที่ต่ำกว่าเกณฑ์ปกติ ไม่สามารถเปิดบัญชีธนาคารได้ง่าย
- ตัวอย่าง: ผู้ที่เพิ่งจบการศึกษาและเริ่มทำงาน หรือคนที่มีอาชีพเสริมที่ไม่ค่อยมีรายได้ที่แน่นอน
- ประโยชน์:
- สามารถเปิดบัญชีและเริ่มใช้บริการทางการเงินได้ง่ายขึ้น
- การอนุมัติสินเชื่อ จะใช้ข้อมูลพฤติกรรมการใช้จ่ายจากการซื้อสินค้าหรือจ่ายค่าสาธารณูปโภคแทนเครดิตสกอร์
- ทำให้คนเหล่านี้สามารถเข้าถึง สินเชื่อขนาดเล็ก และเงินทุนหมุนเวียนในช่วงแรกๆ ของชีวิตการทำงานได้
3. Gen X / Baby Boomer ที่อยู่ไกลจากสาขา
- กลุ่มนี้ คือผู้ที่อาจจะไม่มีความสะดวกในการเดินทางไปที่ธนาคารหรืออาศัยอยู่ในพื้นที่ห่างไกล
- ตัวอย่าง: ผู้สูงอายุที่ไม่สะดวกเดินทางไปธนาคาร หรือคนที่อาศัยในชุมชนห่างไกลที่ไม่มีธนาคารอยู่ใกล้ๆ
- ประโยชน์:
- สามารถ ทำธุรกรรมออนไลน์ ได้สะดวก ไม่ต้องเสียเวลาหรือค่าใช้จ่ายในการเดินทางไปยังสาขาธนาคาร
- การเปิดบัญชีง่าย: ไม่มีการเดินทางไปที่ธนาคารหรือการยื่นเอกสารที่ซับซ้อน
- สามารถ ขอสินเชื่อ สำหรับค่าใช้จ่ายส่วนบุคคลหรือการซ่อมแซมบ้านได้โดยไม่ต้องพึ่งการเงินนอกระบบ
🧠 สรุปให้เลย:
| | | | |---|---|---| |กลุ่มผู้ใช้|จะได้ประโยชน์จาก Virtual Bank?|ทำไม| |คนไม่มีบัญชีธนาคาร|✅ สูงมาก|เปิดบัญชีง่าย, เข้าถึงสินเชื่อ| |คนรายได้น้อย / อาชีพอิสระ|✅ สูง|วัดเครดิตจาก data ไม่ใช่เอกสาร| |วัยเริ่มต้นทำงาน|✅ สูง|มี product แบบ flexible, gamified| |Gen X / Boomer เมืองใหญ่|❌ ไม่ต่างมาก|ใช้ mobile banking เดิมได้อยู่แล้ว| |Gen X / Boomer ต่างจังหวัด|✅ บ้าง|ถ้ามี UX ที่เข้าใจง่าย + ไม่มีสาขา|
ประโยชน์ที่เห็นชัดเจน:
1. สินเชื่อขนาดเล็ก
- Virtual Bank สามารถให้สินเชื่อในวงเงินที่ต่ำ (micro loans) ซึ่งจะตอบโจทย์สำหรับผู้ที่มีความจำเป็นใช้เงินในทันที โดยไม่ต้องรอการอนุมัติสินเชื่อจากธนาคารที่มีขั้นตอนซับซ้อน
- การอนุมัติสินเชื่อจะเป็นไปตามข้อมูลพฤติกรรมการใช้จ่ายหรือบันทึกการเงินในแอปพลิเคชัน เพื่อให้เข้าถึงกลุ่มผู้ใช้ที่มีประวัติการเงินไม่สมบูรณ์
2. เปิดบัญชีง่าย
- Virtual Bank ช่วยให้ทุกคนสามารถเปิดบัญชีได้ง่ายๆ ผ่านแอปพลิเคชันมือถือ โดยไม่ต้องไปที่ธนาคารหรือทำตามขั้นตอนที่ยุ่งยาก
- เปิดโอกาสให้คนที่ไม่มีบัญชีธนาคาร หรือไม่สามารถเดินทางไปที่ธนาคารสามารถใช้บริการการเงินได้ทันที
3. ใช้ข้อมูลพฤติกรรมวิเคราะห์เครดิต
- การให้สินเชื่อและการประเมินความเสี่ยงทางการเงินไม่จำเป็นต้องพึ่งข้อมูลเครดิตแบบเดิมๆ (Credit score) อีกต่อไป
- แทนที่ด้วย ข้อมูลพฤติกรรม การใช้จ่าย เช่น รายจ่ายประจำ, การชำระเงินบิลต่างๆ ซึ่งสามารถใช้ในการวิเคราะห์ความสามารถในการชำระหนี้และการอนุมัติสินเชื่อ
โอกาส: ลดการพึ่งพาเงินกู้นอกระบบ
การเปิดตัว Virtual Bank ไม่เพียงแต่ช่วยให้คนเข้าถึงบริการทางการเงินได้ง่ายขึ้น แต่ยังเป็นทางเลือกที่ช่วยลดการพึ่งพา เงินกู้นอกระบบ สำหรับกลุ่มคนที่ไม่สามารถเข้าถึงธนาคารได้ ด้วยระบบสินเชื่อขนาดเล็กและการอนุมัติที่รวดเร็ว การใช้ข้อมูลพฤติกรรมการใช้จ่ายเป็นอีกหนึ่งเครื่องมือที่ช่วยให้การอนุมัติสินเชื่อทำได้อย่างยุติธรรมและไม่จำเป็นต้องพึ่งระบบการเงินดั้งเดิมที่เข้าถึงยาก
4. ในอีกด้านหนึ่ง… Virtual Bank ก็ยังอยู่ในโครงสร้างเดิม
💬 จริงหรือที่ Virtual Bank จะ "Disrupt" ระบบเดิม?
ในแง่ทฤษฎี — Virtual Banking ควรจะเป็น เครื่องมือสำหรับ disruption (พลิกโฉมระบบเดิม) แต่ในบริบทของไทย — มันกลับกลายเป็นเพียง "extension" ของทุนเดิม
เพราะอะไร?
- ผู้เล่นที่ได้รับสิทธิ์ล้วนเป็นกลุ่มทุนใหญ่:
- กรุงไทย → ธนาคารรัฐ + PTT Group + Gulf + AIS → กลุ่มทุนผูกขาดพลังงาน + โทรคม
- SCBX → กลุ่มแบงก์ใหญ่อันดับต้น ๆ ของไทย + KakaoBank (พันธมิตรเชิงกลยุทธ์)
- Ascend Money → กลุ่ม CP → บรรษัทเอกชนที่ใหญ่ที่สุดในประเทศ
- ธปท. เองก็เล่นเกมแบบ “ค่อย ๆ เปิด”:
- อนุญาตแค่ 3 เจ้าในรอบแรก
- คัดเฉพาะกลุ่มที่มี “ความพร้อมสูง” → หมายถึงกลุ่มทุนเดิมที่มีทรัพยากรมหาศาล
- ใช้เวลาประเมินเป็นปี กว่าจะเปิดจริงก็คือปี 2569 → เวลาให้กลุ่มทุนเดิมปรับตัวได้อีกเพียบ
- ขาดผู้เล่นสาย tech-first ที่แท้จริง:
- ไม่มี startup fintech แท้ ๆ ได้เข้ารอบ
- ไม่มี operator แบบ lean ๆ ที่เริ่มจาก user-centric model จริง ๆ เหมือน Monzo หรือ Revolut
🧠 สรุป: ในบริบทไทย Virtual Bank = “Digital Arm ของทุนเดิม”
- ไม่ใช่ Disruption
- ไม่ใช่ Democratization
- แต่คือ การ Consolidation ของกลุ่มทุนเดิมที่ปรับตัวสู่โลกดิจิทัล
"Virtual Banking แบบไทย ๆ = แบงก์ที่ไม่มีสาขา แต่ยังมีอิทธิพลเก่าอยู่ครบ"
แม้ว่าการเปิดตัว Virtual Bank จะสร้างความหวังในการเข้าถึงบริการการเงินให้กับผู้คนที่ไม่เคยได้รับโอกาสจากระบบธนาคารแบบดั้งเดิม แต่ในอีกด้านหนึ่งเราก็ต้องไม่มองข้ามข้อเท็จจริงที่ว่า Virtual Bank ยังอยู่ในกรอบการทำงานของระบบการเงินที่มีอำนาจควบคุมอยู่แล้ว
“Virtual Banking = Inclusion-driven Business, not Charity”
พูดง่าย ๆ: “เข้าถึงได้ง่ายขึ้น แต่ไม่ได้หมายความว่าจะฟรี หรือหวังดีล้วน ๆ”
✅ เข้าถึงกลุ่มที่เคยถูกมองข้าม
- คนกลุ่มใหญ่ของประเทศ เช่น แรงงานนอกระบบ, ชุมชนชนบท, ผู้ค้ารายย่อย
- ไม่เคยเข้าแบงก์ → ไม่เคยเป็นลูกค้า → ยังไม่มีรายได้จากเขา → ยังไม่มี "เครดิต"
- Virtual Banking ทำให้ “เข้าถึง” = กลายเป็นกลุ่มลูกค้าใหม่ ที่ไม่เคยสร้างรายได้ให้มาก่อน
และเมื่อเข้าถึงแล้ว ก็สามารถ monetize ผ่านสินเชื่อ, ดอกเบี้ย, ค่าธรรมเนียม ฯลฯ ซึ่งแน่นอน…มันคือการ “เปลี่ยน asset ที่ธนาคารแตะไม่ถึง → ให้เป็น yield generating unit”
กลุ่มทุนเก่าเป็นผู้ควบคุม ไม่ใช่ Startup ใหม่ที่จะ disrupt
การเปิดตัว Virtual Bank ในประเทศไทย ไม่ได้หมายความว่าเราจะเห็นการเปลี่ยนแปลงครั้งใหญ่ในโครงสร้างของธนาคารหรือระบบการเงินของประเทศ เพราะ กลุ่มทุนเก่า คือผู้ที่ได้รับสิทธิ์ในการดำเนินการธนาคารดิจิทัล และในหลายกรณีก็เป็น ธนาคารใหญ่ หรือ กลุ่มเทคโนโลยีที่มีอิทธิพล (เช่น ธนาคารพาณิชย์, กลุ่มเทคโนโลยีและโทรคมนาคม) ที่ถือหุ้นในบริษัทที่เปิดให้บริการ Virtual Banking
- ตัวอย่าง: ธนาคารใหญ่ที่มีบทบาทในการอนุมัติสินเชื่อและทำธุรกรรมดิจิทัล หรือกลุ่ม Telco ที่มีฐานลูกค้าจำนวนมหาศาล (เช่น AIS, True) และสามารถนำเสนอบริการธนาคารได้
- คำถาม: ถ้าเป็นเช่นนี้ ความแตกต่างระหว่าง Virtual Bank กับ Digital Bank ที่มีแอปพลิเคชันใช้งานอยู่แล้วจะต่างกันมากไหม? หรือจริงๆ แล้วการเปิดตัว Virtual Bank จะกลายเป็นเพียงการ เพิ่มช่องทางการเข้าถึง บริการจากกลุ่มทุนเก่าที่มีอยู่แล้ว
การวิเคราะห์เชิงเศรษฐกิจ: สร้าง "หนี้ใหม่" จากกลุ่มที่ไม่เคยเป็นหนี้
ในด้านเศรษฐกิจของ Virtual Bank เราอาจจะต้องพิจารณาถึงผลกระทบในระยะยาวที่เกิดจากการ สร้างหนี้ใหม่ ให้กับกลุ่มคนที่ไม่เคยเป็นหนี้มาก่อน:
- กลุ่มเป้าหมายหลัก ของ Virtual Banking คือคนที่ไม่เคยมีบัญชีธนาคาร หรืออาชีพที่มีรายได้ไม่แน่นอน ซึ่งโดยทั่วไปแล้วกลุ่มคนเหล่านี้มักจะขาดแคลนแหล่งเงินทุนและมีประวัติการเงินที่ไม่สมบูรณ์
- การอนุมัติ สินเชื่อขนาดเล็ก ที่มักจะใช้พฤติกรรมการใช้จ่ายในการประเมินเครดิตแทนการใช้ข้อมูลแบบดั้งเดิม (เช่นเครดิตสกอร์) อาจทำให้กลุ่มคนเหล่านี้สามารถเข้าถึงเงินกู้ได้ง่ายขึ้น
- คำถามสำคัญ: เมื่อกลุ่มคนที่ไม่เคยเป็นหนี้มาก่อนสามารถเข้าถึงสินเชื่อได้ง่ายขึ้น จะเกิดผลกระทบต่อเศรษฐกิจในระยะยาวหรือไม่? เพราะการเข้าถึงสินเชื่อที่ไม่รัดกุมอาจจะทำให้ผู้ใช้บริการมีภาระหนี้สินเพิ่มขึ้นได้
ความเสี่ยง:
- เพิ่มหนี้สิน: หากไม่มีการควบคุมหรือการประเมินที่ดีเพียงพอ การเข้าถึงสินเชื่ออาจทำให้บางกลุ่มคนมีหนี้สินที่ไม่สามารถชำระได้ ซึ่งอาจสร้างปัญหาด้านเศรษฐกิจในอนาคต
- หนี้เสีย: การขยายตัวของหนี้ในกลุ่มคนที่ไม่มีการศึกษาทางการเงินที่ดีอาจนำไปสู่ หนี้เสีย (Non-performing Loans, NPLs) ซึ่งจะส่งผลต่อความมั่นคงของระบบการเงินโดยรวม
เป็นการขยายอำนาจของระบบเครดิต ไม่ได้ลดมัน
การที่ Virtual Bank เข้ามาแทนที่ระบบธนาคารแบบดั้งเดิมไม่ได้หมายความว่าเราจะเห็นการ ลดอำนาจของระบบเครดิต หรือการกระจายอำนาจการเงินอย่างแท้จริง
- แม้ว่าบริการต่างๆ ของ Virtual Bank จะมุ่งหวังในการเพิ่มการเข้าถึงบริการทางการเงิน แต่สิ่งที่เกิดขึ้นจริงคือการขยายขอบเขตของ ระบบเครดิต ไปยังกลุ่มคนที่ไม่เคยเป็นหนี้มาก่อน
- การขยายระบบเครดิต นี้ยังคงเป็นการพึ่งพา อำนาจของกลุ่มทุนใหญ่ ที่เป็นผู้ควบคุมระบบการเงิน ผ่านการอนุมัติสินเชื่อที่ทำให้กลุ่มคนเหล่านี้ยังคงต้องอยู่ภายใต้การควบคุมทางการเงินในระยะยาว
คำถาม: ในระยะยาว Virtual Bank จะทำให้เกิดการกระจายอำนาจทางการเงินที่แท้จริง หรือจะเป็นแค่การขยายอำนาจของกลุ่มทุนใหญ่ผ่านช่องทางใหม่ๆ เท่านั้น?
เรื่องนี้ไม่ใหม่ แต่เปลี่ยน “รูปแบบของการกู้”
มันคือการ “ขยายขอบเขตของ fractional reserve ให้ไกลกว่าเดิม” เข้าถึงกลุ่มคนที่เคยกู้ไม่ได้ → แต่ตอนนี้กู้ได้ → แล้วก็สร้างหนี้ใหม่เพิ่มในระบบ
🤯 สรุปแบบแรง ๆ แต่ตรงประเด็น:
Virtual Banking ไม่ได้มา “Disrupt ระบบเดิม” แต่มา “ขยายรัศมีของระบบเดิมให้ลึกขึ้นกว่าเดิม” โดยเฉพาะในกลุ่มที่ยังไม่มีหนี้ → แล้วเปลี่ยนเขาให้มีหนี้ (ในระบบ)
🔁 กลยุทธ์ “เพื่อสังคม” หรือ “เพื่อ margin”?
คำตอบที่อาจเจ็บแต่จริงคือ:
“Virtual Banking = Inclusion ที่ทำให้เกิดรายได้แบบ scalable” และถ้าทำดี มัน win-win (คนเข้าถึงบริการ → กลุ่มทุนได้รายได้) แต่ถ้าทำไม่ดี มันคือ micro-debt bubble ที่รอวันปะทุ
Bitcoiner ควรมองเรื่องนี้ยังไง?
ถ้ามองแบบ hard-money view:
- มันคือการขยายเครดิตที่ไม่ได้ back ด้วย savings จริง ๆ → เสี่ยงเงินเฟ้อ
- การใช้ big data มาประเมินเครดิต → เพิ่ม efficiency ของ credit system แต่ก็เพิ่ม dependency บนระบบ centralized
แต่ถ้ามองแบบ practical:
- มันลด pain ของคนที่ต้องพึ่ง loan shark ที่คิดดอกเบี้ยรายวัน 20%
- ถ้ามีการกำกับดี → อาจเป็น gateway ให้คนเข้ามาสู่ระบบเศรษฐกิจ formal ได้
- แต่ถ้ามองในเชิง "โอกาส" สำหรับคนทั่วไปและ SMEs → ยังพอมีแง่ดีอยู่ เช่น:
- สินเชื่อที่ไม่ต้องใช้หลักทรัพย์
- การเข้าถึงบริการสำหรับแรงงานนอกระบบ
- การแข่งขันด้านดอกเบี้ยและค่าธรรมเนียม
5. มุมมองของ Bitcoiner: นี่ไม่ใช่ Virtual Bank ที่แท้จริง
ในมุมมองของ Bitcoiner (ผู้ที่สนับสนุนการใช้ Bitcoin และ Lightning Network), Virtual Banking ที่เกิดขึ้นในโลกนี้ยังคงไม่ใช่สิ่งที่พวกเขาเรียกว่า "Virtual Bank ที่แท้จริง" เนื่องจากระบบการเงินดิจิทัลที่มีอยู่ในปัจจุบันยังคงถูกควบคุมโดยกลุ่มทุนใหญ่และระบบธนาคารที่มีการสร้างเงินใหม่ (เช่น การปล่อยสินเชื่อและดอกเบี้ย) รวมทั้งยังต้องผ่านกระบวนการอนุมัติจากบุคคลที่สาม
Bitcoin และ Lightning Network คือคำตอบที่พวกเขามองว่าเป็น "Virtual Banking" ที่แท้จริง ซึ่งไม่ต้องมีธนาคารเป็นตัวกลางและไม่ต้องผ่านการควบคุมใดๆ
“Virtual Banking ที่แท้จริง คือ Bitcoin & Lightning — ธนาคารของปัจเจก ที่ไม่มีใครปิดได้” Bank ที่ไม่ต้องขออนุญาตใคร, ไม่ต้องมีเงื่อนไข KYC, ไม่สร้างหนี้ ไม่ inflate supply
💥 เปรียบเทียบแบบชัด ๆ
| | | | |---|---|---| |ด้าน|Virtual Bank (แบบกลุ่มทุน)|Bitcoin / Lightning Network| |การควบคุม|Centralized (กลุ่มทุน, ธปท.)|Decentralized (Node-run)| |การเปิดบัญชี|ต้องผ่าน KYC / eKYC|แค่สร้าง keypair ก็ใช้ได้| |การสร้างเงิน|ปล่อยกู้ → Credit expansion|Fixed supply (21M BTC)| |ความเป็นเจ้าของ|เป็นลูกค้าของธนาคาร|เป็นเจ้าของเงินของตัวเองจริง ๆ| |ความเป็นส่วนตัว|ข้อมูลถูกรวบรวม|ไม่ผูกข้อมูลส่วนบุคคล (pseudonymous)| |ความมั่นคง|ขึ้นกับนโยบายและเสถียรภาพของธนาคาร|ขึ้นกับ global consensus และ cryptography| |ความเร็ว/ค่าธรรมเนียม|เร็วกว่าเดิม แต่ยังอยู่ในกรอบระบบ|Lightning = near instant + ถูกมาก|
Bitcoin และ Lightning Network: Virtual Banking แบบไม่ต้องมีธนาคาร
- Bitcoin เป็นเงินดิจิทัลที่ไม่มีตัวกลาง ไม่มีการออกหรือสร้างเงินใหม่ และ ไม่มีดอกเบี้ย ซึ่งทำให้มันแตกต่างจากระบบธนาคารที่มีการสร้างเงินจากสินเชื่อ
- Lightning Network เป็นโครงข่ายการชำระเงินที่สามารถทำการโอน Bitcoin ได้อย่างรวดเร็วและประหยัดค่าใช้จ่าย โดยไม่ต้องพึ่งพาธนาคารหรือผู้ให้บริการทางการเงินใดๆ
ทำไม Bitcoin และ Lightning Network ถึงเป็น "Virtual Bank" ที่แท้จริง?
- ไม่มีการสร้างเงินใหม่: ไม่มีการขยายวงเงินผ่านการปล่อยสินเชื่อ ทำให้ไม่เกิดการเพิ่มหนี้ในระบบ
- ไม่มีดอกเบี้ย: ธุรกรรม Bitcoin ไม่ได้ขึ้นอยู่กับการเก็บดอกเบี้ยจากผู้ยืม
- ไม่มีการอนุมัติจากบุคคลที่สาม: ทุกการทำธุรกรรมสามารถเกิดขึ้นได้โดยไม่ต้องขออนุญาตจากธนาคารหรือรัฐบาล
Sovereign Individual = เป็นเจ้าของเงิน 100% ไม่ต้องขอใคร
หลักการสำคัญที่ Bitcoiners มักพูดถึงคือแนวคิดของ Sovereign Individual หรือ "บุคคลที่มีอำนาจในตัวเอง" ซึ่งหมายความว่า เจ้าของเงินเป็นผู้ควบคุมเงินของตนเอง โดยไม่ต้องพึ่งพาระบบการเงินของธนาคารหรือองค์กรการเงินใดๆ
- การเป็น Sovereign Individual คือการไม่ต้องให้ใครมีอำนาจในการควบคุมหรืออนุมัติการใช้เงินของตัวเอง
- เงินที่ใช้เป็น Bitcoin หรือ Lightning Network จะเป็น เงินที่สามารถเก็บและใช้งานได้โดยตรง โดยไม่ต้องพึ่งพาธนาคารใดๆ
- ผู้ใช้สามารถ โอนเงิน หรือ ชำระเงิน ได้อย่างอิสระจากทุกที่ในโลก โดยไม่ต้องขออนุญาตจากธนาคารหรือรัฐบาล
เปรียบเทียบโดยสรุปให้อีกที
| | | | |---|---|---| |ด้าน|Virtual Bank (ธนาคารดิจิทัล)|Bitcoin & Lightning Network| |การควบคุม|ควบคุมโดยกลุ่มทุนเก่าหรือธนาคารที่มีการควบคุมระบบการเงิน|ควบคุมโดยชุมชนและผู้ใช้ทุกคน ไม่ขึ้นกับการควบคุมจากบุคคลที่สาม| |การสร้างเงิน|ธนาคารสร้างเงินใหม่ผ่านการปล่อยสินเชื่อและการเก็บดอกเบี้ย|Bitcoin ไม่มีการสร้างเงินใหม่ และไม่มีการขยายหนี้| |เสรีภาพ|การทำธุรกรรมยังคงต้องผ่านตัวกลาง เช่น ธนาคารหรือผู้ให้บริการ|ไม่มีตัวกลาง การโอนเงินทำได้ทันทีและไม่มีข้อจำกัด| |ความเป็นเจ้าของ|เงินอยู่ภายใต้การควบคุมของธนาคาร ผู้ใช้ต้องขออนุญาตจากธนาคารในการเข้าถึงเงิน|ผู้ใช้เป็นเจ้าของเงิน 100% และสามารถทำธุรกรรมได้โดยไม่ต้องขออนุญาตจากใคร|
สรุป
สำหรับ Bitcoiner, การเห็น Virtual Banking ในรูปแบบปัจจุบันยังคงไม่ใช่การปฏิวัติทางการเงินที่แท้จริง เพราะระบบที่ใช้ยังคงอยู่ภายใต้การควบคุมจากธนาคารและกลุ่มทุนเก่า ในขณะที่ Bitcoin และ Lightning Network ยังคงเป็นแนวทางที่เป็น "Virtual Bank ที่แท้จริง" โดยไม่ต้องพึ่งพาผู้ให้บริการทางการเงินใดๆ และให้ความเสรีภาพในการควบคุมและใช้งานเงินของแต่ละบุคคลอย่างเต็มที่
Bitcoin ไม่เพียงแต่เป็นสื่อกลางในการแลกเปลี่ยน แต่ยังเป็นเครื่องมือในการสร้าง Sovereign Individual ซึ่งสามารถควบคุมเงินและการทำธุรกรรมได้อย่างอิสระจากระบบการเงินที่มีอยู่ในปัจจุบัน
6. Virtual Bank หรือ Virtual Control?
🧠 TL;DR แบบสาย Bitcoiner:
Virtual Bank = inclusion under control Bitcoin = inclusion without permission
เมื่อเราพูดถึง Virtual Banking ในไทย หรือแม้แต่ในหลายประเทศที่กำลังเปิดตัวบริการธนาคารดิจิทัลใหม่ๆ หนึ่งในคำถามสำคัญที่ต้องพิจารณาคือ มันเป็นการสร้างการเข้าถึง (Inclusion) ที่แท้จริงหรือเป็นเพียงการขยายการควบคุมทางการเงินในรูปแบบใหม่? มันอาจเป็นสิ่งที่ดูเหมือนจะเป็นประโยชน์กับประชาชน แต่ในความเป็นจริงแล้วมันอาจจะไม่ได้เป็นการเปลี่ยนแปลงที่แท้จริง
ถ้ามองในแง่ลึก: มันคือ Inclusion ที่ยังอยู่ในโครงสร้างเดิม
คำว่า Financial Inclusion หรือการเข้าถึงบริการทางการเงินสำหรับคนที่ไม่เคยมีบัญชีธนาคารหรือการเข้าถึงสินเชื่อในระบบการเงินดั้งเดิม อาจเป็นหนึ่งในจุดเด่นของ Virtual Bank ที่ถูกโปรโมทให้เห็นจากหลายๆ แคมเปญ
แต่ถ้ามองในมุมลึกๆ จริงๆ แล้ว Virtual Bank อาจจะไม่ได้ช่วย "เปิดโลกใหม่" ให้กับผู้คนที่ไม่มีบัญชีธนาคารเท่านั้น แต่มันยังคงทำงานใน กรอบของระบบการเงินเดิม ที่ถูกควบคุมโดยกลุ่มทุนใหญ่และมีการใช้ข้อมูลพฤติกรรมผู้ใช้ในการประเมินความเสี่ยงในการปล่อยสินเชื่อ ซึ่งในที่สุดแล้วก็ยังคงวนอยู่ในวงจรของระบบเครดิตที่ถูกควบคุมจากองค์กรการเงินเดิม
- การเข้าถึงที่ยังจำกัด: แม้ว่า Virtual Bank จะเปิดโอกาสให้คนที่ไม่มีบัญชีธนาคารสามารถเปิดบัญชีได้ง่ายขึ้น แต่การได้รับสินเชื่อหรือบริการอื่นๆ ก็ยังคงต้องผ่านการอนุมัติจากระบบที่มี ตัวกลาง และ การควบคุม
- ข้อมูลพฤติกรรมผู้ใช้: การใช้ข้อมูลพฤติกรรมผู้ใช้ในการอนุมัติสินเชื่อก็ไม่ได้หมายความว่าจะเปิดโอกาสให้ทุกคนได้รับสินเชื่ออย่างเท่าเทียมกัน โดยเฉพาะกลุ่มที่มีประวัติการเงินไม่สมบูรณ์
ถ้าระบบไม่เปิดเสรีจริง → มันไม่ใช่ “Bank ของประชาชน”
ในมุมมองของ Sovereign Individual หรือผู้ที่ต้องการเสรีภาพทางการเงิน การเข้าถึงบริการของ Virtual Bank ยังคงเป็นการพึ่งพิงจากระบบการเงินที่มีอำนาจควบคุม
- หาก Virtual Bank ไม่สามารถเปิดเสรีในการทำธุรกรรมได้อย่างเต็มที่ หรือยังคงอยู่ภายใต้การควบคุมจาก กลุ่มทุน หรือ ระบบธนาคารเดิม, การมีบัญชีธนาคารในระบบดิจิทัลก็จะไม่ได้สร้างความเปลี่ยนแปลงที่แท้จริงในแง่ของเสรีภาพทางการเงิน
- คำถาม: ถ้าเราไม่สามารถทำธุรกรรมได้อย่างเต็มที่โดยไม่ผ่านตัวกลางหรือการอนุมัติจากใครเลย มันจะเป็น “Bank ของประชาชน” หรือเป็นการ ควบคุมทางการเงิน ในรูปแบบใหม่?
กลุ่มทุนอาจช่วยคนจนได้… แต่ก็คือการสร้างตลาดใหม่ให้กับสินเชื่อ
ถึงแม้ว่า Virtual Bank อาจจะช่วยให้ผู้คนที่ไม่เคยเข้าถึงบริการทางการเงินสามารถเปิดบัญชีได้ง่ายขึ้น หรือได้รับสินเชื่อที่ไม่ต้องพึ่งพาผู้ให้บริการแบบดั้งเดิม, แต่การ ขยายสินเชื่อ ให้กับกลุ่มคนที่มีความเสี่ยงสูง ก็หมายความว่า กลุ่มทุน ยังคงสร้าง ตลาดใหม่ ที่อาจจะมี ความเสี่ยงสูง ที่จะเกิดเป็น หนี้เสีย หรือเป็น หนี้ในระบบ ซึ่งกลุ่มทุนเหล่านี้สามารถเก็บดอกเบี้ยได้จากการปล่อยสินเชื่อ
- การสร้างตลาดใหม่: กลุ่มทุนอาจจะได้ผลประโยชน์จากการเข้าถึงกลุ่มคนที่ไม่เคยมีประวัติการเงิน หรือกลุ่มคนที่มีความเสี่ยงสูง ซึ่งจะเป็นตลาดใหม่ในการปล่อยสินเชื่อที่มีอัตราดอกเบี้ยสูง
- การเสี่ยงหนี้: สำหรับกลุ่มคนที่ยังไม่เคยเป็นหนี้มาก่อน การเข้าถึงสินเชื่อที่ง่ายขึ้นก็อาจจะทำให้เกิดภาระหนี้ที่มากขึ้น ซึ่งส่งผลกระทบต่อสุขภาพการเงินในระยะยาว
สรุป
การที่ Virtual Bank ดูเหมือนจะเปิดโอกาสให้ผู้คนเข้าถึงบริการทางการเงินได้มากขึ้น อาจจะเป็นการเปิดตลาดใหม่ให้กับกลุ่มทุน แต่ยังคงไม่สามารถทำให้เกิดการ เปิดเสรีทางการเงิน อย่างแท้จริง เพราะการควบคุมและการอนุมัติสินเชื่อยังคงอยู่ภายใต้ระบบที่มีอำนาจจากกลุ่มทุนเก่าและไม่ได้ปลดปล่อยเสรีภาพทางการเงินให้กับผู้ใช้ได้อย่างเต็มที่
- Virtual Bank อาจเป็นการช่วยเพิ่มการเข้าถึงบริการทางการเงินสำหรับผู้คนที่เคยถูกระบบดั้งเดิมกีดกัน แต่การขยายตลาดสินเชื่อและการควบคุมข้อมูลยังคงเป็นกลไกที่สามารถสร้างผลประโยชน์ให้กับกลุ่มทุนได้
ในที่สุดแล้ว, Virtual Banking อาจไม่ได้เป็นการ "Bank ของประชาชน" ที่แท้จริง หากระบบยังคงไม่เปิดเสรี และยังอยู่ในโครงสร้างเดิมของการควบคุมทางการเงินที่มาจากกลุ่มทุนใหญ่
🌍 Sovereign Individual: จากธนาคาร → เป็นธนาคารเอง
Bitcoin + Lightning =
“จากการขอใช้ระบบของคนอื่น → เป็นเจ้าของระบบเอง” ไม่ใช่แค่ "Bankless" แต่คือ "Become-your-own-bank"
คุณ run node เองได้ คุณเปิดช่องทาง liquidity เองได้ คุณเก็บเงินเอง ไม่ต้องฝากไว้กับธนาคารใด ๆ คุณจ่ายเงินข้ามโลกภายใน 1 วินาที แบบไม่มีใครอนุมัติ
7. สรุป: Fiat Virtual Bank VS. Bitcoin Virtual Bank
ในที่สุดแล้ว เราจะเห็นว่า Virtual Bank ที่เกิดขึ้นในระบบการเงินของรัฐ และ Bitcoin เป็นสิ่งที่แตกต่างกันอย่างชัดเจน ทั้งในด้านของ ฟังก์ชัน และ วิสัยทัศน์ การเข้าถึงการเงินดิจิทัลทั้งสองรูปแบบนี้ต่างมีผลกระทบที่แตกต่างกันต่อ เสรีภาพทางการเงิน และ ความยั่งยืนของระบบการเงิน ทั่วโลก
ฝั่งหนึ่งคือ "Digital Convenience" ที่ดีขึ้นภายใต้ระบบเดิม
Virtual Bank ภายใต้การควบคุมของรัฐหรือกลุ่มทุนใหญ่ (ธนาคารพาณิชย์, เทเลคอม, หรือเทคโนโลยี) มักจะมุ่งเน้นไปที่ การเพิ่มความสะดวกสบาย ให้กับผู้ใช้ในระบบการเงินเดิม ซึ่งอาจทำให้การเปิดบัญชี, การโอนเงิน, หรือการเข้าถึงสินเชื่อทำได้ง่ายขึ้น
- Digital Convenience: ในทางเทคนิค, การที่ธนาคารเปิดบริการดิจิทัลทำให้การใช้งานสะดวกสบายมากขึ้น ไม่ต้องไปที่สาขาธนาคาร, สามารถทำธุรกรรมได้ทุกที่ผ่านแอปพลิเคชัน
- ระบบเดิม: แต่ในทางกลับกัน, การที่ระบบนี้ยังคงทำงานอยู่ภายใต้ระบบการเงินเดิม เช่น การปล่อยสินเชื่อ, การเก็บดอกเบี้ย, การใช้ข้อมูลพฤติกรรมในการประเมินเครดิต ก็หมายความว่า การควบคุมทางการเงิน ยังอยู่ในมือของกลุ่มทุนและธนาคารเดิม
ระบบนี้ทำให้ผู้ใช้มี ความสะดวกสบาย ในการเข้าถึงบริการ แต่ ไม่ได้สร้างเสรีภาพทางการเงินที่แท้จริง เพราะยังคงต้องพึ่งพาธนาคารและระบบเครดิตที่ควบคุมโดยองค์กรภายนอก
อีกฝั่งคือ "Financial Sovereignty" ที่แท้จริง
ในทางตรงกันข้าม, Bitcoin และ Lightning Network เสนอแนวทางที่ แตกต่างไปอย่างสิ้นเชิง โดยมุ่งเน้นไปที่ ความเป็นอิสระทางการเงิน หรือ Sovereign Individual ซึ่งไม่ต้องพึ่งพาธนาคาร หรือระบบเครดิตที่มีกฎเกณฑ์ซับซ้อน
- Financial Sovereignty: การใช้ Bitcoin ช่วยให้ผู้ใช้สามารถ ควบคุมเงินของตัวเอง ได้เต็มที่ โดยไม่ต้องผ่านตัวกลางหรือการอนุมัติจากธนาคาร
- ไม่มีการสร้างหนี้: ไม่มีการปล่อยสินเชื่อหรือการเก็บดอกเบี้ย ทำให้ไม่เกิดภาระหนี้และการควบคุมทางการเงินจากธนาคาร
การใช้ Bitcoin จึงไม่ใช่แค่การทำธุรกรรมทางการเงิน แต่ยังเป็นการ สร้างเสรีภาพทางการเงิน ซึ่งผู้ใช้สามารถทำธุรกรรมได้จากทุกที่ทุกเวลา โดยไม่ต้องพึ่งพาผู้ให้บริการทางการเงินใดๆ
คำถามสุดท้ายที่ควรถาม:
❝เราต้องการธนาคารที่เข้าถึงง่ายขึ้น… หรือโลกที่ไม่ต้องพึ่งธนาคารเลย?❞
นี่คือคำถามสำคัญที่เราต้องถามตัวเองเมื่อเรามองถึงอนาคตของการเงินดิจิทัล
- ถ้าเราต้องการธนาคารที่เข้าถึงง่ายขึ้น: ระบบ Virtual Banking ที่เปิดให้บริการในปัจจุบันจะตอบโจทย์ได้ เพราะมันช่วยให้ผู้คนสามารถเข้าถึงบริการทางการเงินได้ง่ายขึ้นโดยไม่ต้องไปที่สาขาธนาคาร
- ถ้าเราต้องการเสรีภาพทางการเงิน: Bitcoin และ Lightning Network จะเป็นทางเลือกที่ดีที่สุด เพราะมันให้ ความเป็นเจ้าของเงิน และ เสรีภาพทางการเงิน แก่ผู้ใช้ ไม่ต้องพึ่งพาผู้ให้บริการทางการเงินหรือระบบการเงินเดิมที่มีการควบคุม
ในที่สุดแล้ว คำถามนี้ขึ้นอยู่กับว่าเรา ต้องการอำนาจในการควบคุมทางการเงิน และ เสรีภาพในการจัดการเงินของตัวเอง หรือไม่ และว่า ระบบการเงินปัจจุบัน ตอบโจทย์ความต้องการของเรามากแค่ไหน
สรุป
- Fiat Virtual Bank มุ่งเน้นไปที่การสร้างความสะดวกในการทำธุรกรรมภายในกรอบของระบบการเงินเดิม และยังคง ควบคุม โดยกลุ่มทุนหรือธนาคาร
- Bitcoin & Lightning Network เสนอ เสรีภาพทางการเงิน ที่แท้จริง โดยให้ผู้ใช้ ควบคุมเงินของตัวเอง และทำธุรกรรมโดยไม่ต้องพึ่งพาธนาคารหรือตัวกลาง
สุดท้ายแล้ว, คำถามที่เราต้องถามตัวเองคือ: เราต้องการโลกที่เราไม่ต้องพึ่งธนาคารเลย หรือโลกที่เรามีการเข้าถึงบริการทางการเงินที่สะดวกขึ้นจากธนาคาร?

-
 @ 7d33ba57:1b82db35
2025-04-22 19:43:27
@ 7d33ba57:1b82db35
2025-04-22 19:43:27Welcome to Hortobágy National Park, Hungary’s oldest and largest national park, and a UNESCO World Heritage Site that showcases the wild, open heart of the Puszta—the vast steppe of Eastern Europe. Spanning over 800 km², this park is a land of windswept grasslands, grazing animals, traditional herding culture, and incredible birdlife.
🌾 What to See & Do in Hortobágy
🐃 Explore the Puszta Landscape
- Ride through the grasslands in a horse-drawn cart or take a bike tour
- See iconic gray cattle, racka sheep with spiral horns, water buffalo, and traditional herdsmen in wide-brimmed hats
🐎 Horse Shows & Herding Traditions
- Visit a csikós show, where Hungarian horsemen perform riding tricks and herding techniques
- Learn about the unique pastoral culture that has existed here for centuries
🐦 Birdwatching Paradise
- Hortobágy is one of Europe’s best spots for birdwatching
- See cranes, eagles, storks, and rare migratory species, especially in spring and autumn
- Visit the Hortobágy Bird Hospital and crane observation sites
🌉 Hortobágy Nine-Arch Bridge (Kilenclyukú híd)
- An iconic stone bridge built in the 19th century, stretching over the river Hortobágy
- The symbolic center of the park and a great photo spot
- Nearby you’ll find the Hortobágy Village, with museums, markets, and local food
🧀 Local Culture & Cuisine
- Taste slambuc (a traditional shepherd’s stew), cheeses, and local smoked meats
- Check out folk art and handmade crafts in local markets and heritage centers
🚶♂️ How to Visit
- Closest city: Debrecen (around 30 minutes by car or bus)
- The park offers guided tours, bike rentals, and wildlife safaris
- Great for day trips or overnight stays in nearby guesthouses or rural lodges
Hortobágy is more than a landscape—it’s a living cultural heritage site, where ancient traditions, wildlife, and wide horizons stretch as far as the eye can see. Perfect for nature lovers, culture seekers, or anyone looking to experience a different side of Hungary.
-
 @ 7d33ba57:1b82db35
2025-04-22 19:29:59
@ 7d33ba57:1b82db35
2025-04-22 19:29:59Tucked into the foothills of the Bükk Mountains, Eger is one of Hungary’s most charming and historic towns. Famous for its Baroque architecture, thermal baths, and Egri Bikavér (“Bull’s Blood”) red wine, Eger offers a perfect blend of culture, relaxation, and rustic charm all just a couple of hours from Budapest.
🏰 Top Things to Do in Eger
🏯 Eger Castle (Egri Vár)
- A key site in Hungary’s defense against the Ottoman Empire
- Learn about the 1552 Siege of Eger, when outnumbered locals held off the Turks
- Climb the walls for views of the old town’s red rooftops and spires
⛪ Eger’s Baroque Old Town
- Wander elegant streets lined with pastel facades, cute cafés, and small boutiques
- Don’t miss the Minorite Church and Dobó Square, the lively heart of the city
🛁 Thermal Baths
- Relax in the Eger Turkish Bath, built during the Ottoman period and still in use today
- Or soak at Eger Thermal Spa, great for families and wellness seekers
🍷 Wine Tasting in the Valley of the Beautiful Women (Szépasszony-völgy)
- A short walk or ride from town, this valley is lined with wine cellars built into the hillside
- Taste the iconic Egri Bikavér (a full-bodied red blend) and Egri Csillag (a refreshing white)
- Most cellars offer generous tastings and hearty local snacks
🧀 Local Food to Try
- Goulash, Lángos, and hearty meat dishes
- Pair local cheeses and sausages with regional wines
- Cozy cellar restaurants and rustic taverns set the mood
🚆 Getting There
- About 2 hours by train or car from Budapest
- Walkable town, no car needed once you’re there
-
 @ da0b9bc3:4e30a4a9
2025-02-13 06:36:12
@ da0b9bc3:4e30a4a9
2025-02-13 06:36:12Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/884478
-
 @ df478568:2a951e67
2025-04-22 18:56:38
@ df478568:2a951e67
2025-04-22 18:56:38"It might make sense just to get some in case it catches on. If enough people think the same way, that becomes a self fulfilling prophecy. Once it gets bootstrapped, there are so many applications if you could effortlessly pay a few cents to a website as easily as dropping coins in a vending machine." --Satoshi Nakamoto The Cryptography Mailing List--January 17, 2009
Forgot to add the good part about micropayments. While I don't think Bitcoin is practical for smaller micropayments right now, it will eventually be as storage and bandwidth costs continue to fall. If Bitcoin catches on on a big scale, it may already be the case by that time. Another way they can become more practical is if I implement client-only mode and the number of network nodes consolidates into a smaller number of professional server farms. Whatever size micropayments you need will eventually be practical. I think in 5 or 10 years, the bandwidth and storage will seem trivial. --Satoshi Nakamoto Bitcoin Talk-- August 5, 2010
I very be coded some HTML buttons using Claude and uploaded it to https://github.com/GhostZaps/ It's just a button that links to zapper.fun.
I signed up for Substack to build an email address, but learned adding different payment options to Substack is against their terms and services. Since I write about nostr, these terms seem as silly as someone saying Craig Wright is Satoshi. It's easy to build an audience on Substack however, or so I thought. Why is it easier to build an audience on Subtack though? Because Substack is a platform that markets to writers. Anyone with a ~~pen~~ ~~keyboard~~ smartphone and an email can create an account with Substack. There's just one problem: You are an Internet serf, working the land for your Internet landlord--The Duke of Substack.
Then I saw that Shawn posted about Substack's UX.
I should have grabbed my reading glasses before pushing the post button, but it occurred to me that I could use Ghost to do this and there is probably a way to hack it to accept bitcoin payments over the lightning network and host it yourself. So I spun my noddle, doodled some plans...And then it hit me. Ghost allows for markdown and HTML. I learned HTML and CSS with free-code camp, but ain't nobody got time to type CSS so I vibe-coded a button that ~~baits~~ sends the clicker to my zapper.fun page. This can be used on any blog that allows you to paste html into it so I added it to my Ghost blog self-hosted on a Start 9. The blog is on TOR at http://p66dxywd2xpyyrdfxwilqcxmchmfw2ixmn2vm74q3atf22du7qmkihyd.onion/, but most people around me have been conditioned to fear the dark web so I used the cloudflared to host my newsletter on the clear net at https://marc26z.com/
Integrating Nostr Into My Self-Hosted Ghost Newsletter
I would venture to say I am more technical than the average person and I know HTML, but my CSS is fuzzy. I also know how to print("Hello world!") in python, but I an NPC beyond the basics. Nevertheless, I found that I know enough to make a button. I can't code well enough to create my own nostr long-form client and create plugins for ghost that send lightning payments to lighting channel, but I know enough about nostr to know that I don't need to. That's why nostr is so F@#%-ing cool! It's all connected. ** - One button takes you to zapper.fun where you can zap anywhere between 1 and ,000,000 sats.** - Another button sends you to a zap planner pre-set to send 5,000 sats to the author per month using nostr. - Yet another button sends you to a zap planner preset to send 2,500 sats per month.
The possibilities are endless. I entered a link that takes the clicker to my Shopstr Merch Store. The point is to write as self-sovereign as possible. I might need to change my lightning address when stuff breaks every now and then, but I like the idea of busking for sats by writing on the Internet using the Value 4 Value model. I dislike ads, but I also want people to buy stuff from people I do business with because I want to promote using bitcoin as peer-to-peer electronic cash, not NGU porn. I'm not prude. I enjoy looking at the price displayed on my BlockClock micro every now and then, but I am not an NGU porn addict.
This line made this pattern, that line made this pattern. All that Bolinger Bart Simpson bullshit has nothing to with bitcoin, a peer-to-peer electronic cash system. It is the musings of a population trapped in the fiat mind-set. Bitcoin is permissionless so I realized I was bieng a hipocryte by using a permissioned payment system becaue it was easier than writing a little vibe code. I don't need permission to write for sats. I don't need to give my bank account number to Substack. I don't need to pay a 10$ vig to publish on a a platform which is not designed for stacking sats. I can write on Ghost and integrate clients that already exist in the multi-nostr-verse.
Nostr Payment Buttons
The buttons can be fouund at https://github.com/Marc26z/GhostZapButton
You can use them yourself. Just replace my npub with your npub or add any other link you want. It doesn't technically need to be a nostr link. It can be anything. I have a link to another Ghost article with other buttons that lead down different sat pledging amounts. It's early. Everyone who spends bitcoin is on nostr and nostr is small, but growing community. I want to be part of this community. I want to find other writers on nostr and stay away from Substack.
Here's what it looks like on Ghost: https://marc26z.com/zaps-on-ghost/
npub1marc26z8nh3xkj5rcx7ufkatvx6ueqhp5vfw9v5teq26z254renshtf3g0
-
 @ e3ba5e1a:5e433365
2025-02-13 06:16:49
@ e3ba5e1a:5e433365
2025-02-13 06:16:49My favorite line in any Marvel movie ever is in “Captain America.” After Captain America launches seemingly a hopeless assault on Red Skull’s base and is captured, we get this line:
“Arrogance may not be a uniquely American trait, but I must say, you do it better than anyone.”
Yesterday, I came across a comment on the song Devil Went Down to Georgia that had a very similar feel to it:

America has seemingly always been arrogant, in a uniquely American way. Manifest Destiny, for instance. The rest of the world is aware of this arrogance, and mocks Americans for it. A central point in modern US politics is the deriding of racist, nationalist, supremacist Americans.
That’s not what I see. I see American Arrogance as not only a beautiful statement about what it means to be American. I see it as an ode to the greatness of humanity in its purest form.
For most countries, saying “our nation is the greatest” is, in fact, twinged with some level of racism. I still don’t have a problem with it. Every group of people should be allowed to feel pride in their accomplishments. The destruction of the human spirit since the end of World War 2, where greatness has become a sin and weakness a virtue, has crushed the ability of people worldwide to strive for excellence.
But I digress. The fears of racism and nationalism at least have a grain of truth when applied to other nations on the planet. But not to America.
That’s because the definition of America, and the prototype of an American, has nothing to do with race. The definition of Americanism is freedom. The founding of America is based purely on liberty. On the God-given rights of every person to live life the way they see fit.
American Arrogance is not a statement of racial superiority. It’s barely a statement of national superiority (though it absolutely is). To me, when an American comments on the greatness of America, it’s a statement about freedom. Freedom will always unlock the greatness inherent in any group of people. Americans are definitionally better than everyone else, because Americans are freer than everyone else. (Or, at least, that’s how it should be.)
In Devil Went Down to Georgia, Johnny is approached by the devil himself. He is challenged to a ridiculously lopsided bet: a golden fiddle versus his immortal soul. He acknowledges the sin in accepting such a proposal. And yet he says, “God, I know you told me not to do this. But I can’t stand the affront to my honor. I am the greatest. The devil has nothing on me. So God, I’m gonna sin, but I’m also gonna win.”
Libertas magnitudo est
-
 @ d1667293:388e7004
2025-04-22 14:27:15
@ d1667293:388e7004
2025-04-22 14:27:15The motivation behind my newly published book Bitcoindollar the Dawn of American Hegemony in the Digital Era was simple: to answer some of the most pressing and overlooked questions about the future of money. My analysis starts by viewing Bitcoin not in isolation, but as a paradigm shift in the evolution of money—a foundational institution that underpins both economic and societal relationships, from individuals to nations.
Rethinking the Monetary Landscape
To understand Bitcoin's potential, we need to explore the landscape it seeks to disrupt:
-
The dominance of nation-states.
-
The role of the US fiat dollar as the global reserve currency.
-
US debt as the reserve liability (pardon "asset") underpinning the fiat system.
-
The influence of the banking cartel and the distorted incentives built into the fiat monetary structure—especially in the last 55 years, since the US elegantly defaulted on its promise to convert paper dollars into gold in 1971.
Bitcoin is a direct response to these imbalances, but its adoption will depend on how and who drives the transition.
Two Paths of Bitcoin Adoption: Bottom-Up vs. Top-Down
Bitcoin’s journey can take two distinct paths:
1. Bottom-Up Adoption
This is driven by grassroots use of Bitcoin as a currency, particularly in developing nations, often alongside dollar-denominated stablecoins like USDt.
2. Top-Down Adoption
This path sees Bitcoin increasingly used as a store of value (SOV) and financial asset, especially in developed economies. It is driven by institutions, wealth managers, and financial innovation.
It's clear that top-down adoption correlates with faster price appreciation, whereas bottom-up adoption is slower, more organic—and potentially more resilient in the long run.
Why the Top-Down Path Matters
A critical but often uncomfortable truth is: elites don’t give up power easily. The fiat system is held tightly by those benefiting most from its continuation.
Pareto’s Law teaches us that no historical revolution was purely bottom-up. Real change happens when a new elite emerges to replace the old one—carrying the masses along.
The advantages of top-down adoption:
-
Speeds up the revolution.
-
Allows coexistence between Bitcoin and fiat for a transitional period, avoiding violent disruption.
-
Strengthens new power structures around Bitcoin as it becomes a more established SOV.
-
Enables the U.S. to reinvent the dollar’s role through dollar-backed stablecoins and their recycling into US TBills, maintaining global dollar demand even post-Petrodollar.
A Warning for the United States
In my book, I argue that the #Bitcoindollar system gives the U.S. a first-mover advantage—but only if it changes course.
The U.S. must shift from a militaristic, imperialist approach to a cooperative, multipolar model that welcomes both allies and adversaries into this new system.
Unfortunately, the Trump administration appears headed in the opposite direction, risking this historic opportunity. I explore this further in an upcoming article expanding on my book’s conclusions.
Store of Value vs. Currency: Which Comes First?
Some critics lament that Bitcoin isn’t widely used as a currency yet. But ask yourself:
What is the world’s most urgent need in today’s monetary environment?
A medium of exchange? Or a store of value to protect savings from corrupt governments and inflation?
We already have more or less efficient payment systems. But we lack a sound store of value with key properties such as decentralization, censorship resistance and hard coded scarcity. That’s why the market is adopting Bitcoin primarily as a SOV.
Gresham’s Law gives us the formula:
Save the hard money (Bitcoin, gold), spend the USDt, USDC, and fiat.
Looking Ahead: From Store of Value to Currency
This doesn’t mean #bitcoin won’t be used as a currency eventually. Once it’s widely adopted as a store of value—perhaps within the next 10–20 years—its volatility will decrease, more people will price goods in bitcoin, and acceptance for payments will grow.
We will get there. Just not through the path many imagined at the beginning.
Call It What It Is: A Revolutionary Monetary Transition
Rather than a disruptive revolution, think of this as a revolutionary monetary transition—a new system growing alongside the old, until one inevitably replaces the other.
-






















