-
 @ 957df479:13e9e08e
2025-04-29 21:17:31
@ 957df479:13e9e08e
2025-04-29 21:17:31Happy
This is your course initialization stub.
Please see the Docs to find out what is possible in LiaScript.
If you want to use instant help in your Atom IDE, please type lia to see all available shortcuts.
Markdown
You can use common Markdown syntax to create your course, such as:
- Lists
-
ordered or
-
unordered
- ones ...
| Header 1 | Header 2 | | :--------- | :--------- | | Item 1 | Item 2 |
Images:

Extensions
--{{0}}--But you can also include other features such as spoken text.
--{{1}}--Insert any kind of audio file:
{{1}}--{{2}}--Even videos or change the language completely.
{{2-3}}!?video
--{{3 Russian Female}}--Первоначально создан в 2004 году Джоном Грубером (англ. John Gruber) и Аароном Шварцем. Многие идеи языка были позаимствованы из существующих соглашений по разметке текста в электронных письмах...
{{3}}Type "voice" to see a list of all available languages.
Styling
The whole text-block should appear in purple color and with a wobbling effect. Which is a bad example, please use it with caution ... ~~ only this is red ;-) ~~
Charts
Use ASCII-Art to draw diagrams:
Multiline 1.9 | DOTS | *** y | * * - | r r r r r r r*r r r r*r r r r r r r a | * * x | * * i | B B B B B * B B B B B B * B B B B B s | * * | * * * * * * -1 +------------------------------------ 0 x-axis 1Quizzes
A Textquiz
What did the fish say when he hit a concrete wall?
[[dam]]Multiple Choice
Just add as many points as you wish:
[[X]] Only the **X** marks the correct point. [[ ]] Empty ones are wrong. [[X]] ...Single Choice
Just add as many points as you wish:
[( )] ... [(X)] <-- Only the **X** is allowed. [( )] ...Executable Code
A drawing example, for demonstrating that any JavaScript library can be used, also for drawing.
```javascript // Initialize a Line chart in the container with the ID chart1 new Chartist.Line('#chart1', { labels: [1, 2, 3, 4], series: [[100, 120, 180, 200]] });
// Initialize a Line chart in the container with the ID chart2 new Chartist.Bar('#chart2', { labels: [1, 2, 3, 4], series: [[5, 2, 8, 3]] }); ```
Projects
You can make your code executable and define projects:
``` js -EvalScript.js let who = data.first_name + " " + data.last_name;
if(data.online) { who + " is online"; } else { who + " is NOT online"; }
json +Data.json { "first_name" : "Sammy", "last_name" : "Shark", "online" : true } ```More
Find out what you can even do more with quizzes:
https://liascript.github.io/course/?https://raw.githubusercontent.com/liaScript/docs/master/README.md
-
 @ fd0bcf8c:521f98c0
2025-04-29 13:38:49
@ fd0bcf8c:521f98c0
2025-04-29 13:38:49The vag' sits on the edge of the highway, broken, hungry. Overhead flies a transcontinental plane filled with highly paid executives. The upper class has taken to the air, the lower class to the roads: there is no longer any bond between them, they are two nations."—The Sovereign Individual
Fire
I was talking to a friend last night. Coffee in hand. Watching flames consume branches. Spring night on his porch.
He believed in America's happy ending. Debt would vanish. Inflation would cool. Manufacturing would return. Good guys win.
I nodded. I wanted to believe.
He leaned forward, toward the flame. I sat back, watching both fire and sky.
His military photos hung inside. Service medals displayed. Patriotism bone-deep.
The pendulum clock on his porch wall swung steadily. Tick. Tock. Measuring moments. Marking epochs.
History tells another story. Not tragic. Just true.
Our time has come. America cut off couldn't compete. Factories sit empty. Supply chains span oceans. Skills lack. Children lag behind. Rebuilding takes decades.
Truth hurts. Truth frees.
Cycles
History moves in waves. Every 500 years, power shifts. Systems fall. Systems rise.
500 BC - Greek coins changed everything. Markets flourished. Athens dominated.
1 AD - Rome ruled commerce. One currency. Endless roads. Bustling ports.
500 AD - Rome faded. Not overnight. Slowly. Trade withered. Cities emptied. Money debased. Roads crumbled. Local strongmen rose. Peasants sought protection. Feudalism emerged.
People still lived. Still worked. Horizons narrowed. Knowledge concentrated. Most barely survived. Rich adapted. Poor suffered.
Self-reliance determined survival. Those growing food endured. Those making essential goods continued. Those dependent on imperial systems suffered most.
1000 AD - Medieval revival began. Venice dominated seas. China printed money. Cathedrals rose. Universities formed.
1500 AD - Europeans sailed everywhere. Spanish silver flowed. Banks financed kingdoms. Companies colonized continents. Power moved west.
The pendulum swung. East to West. West to East. Civilizations rose. Civilizations fell.
2000 AD - Pattern repeats. America strains. Digital networks expand. China rises. Debt swells. Old systems break.
We stand at the hinge.
Warnings
Signs everywhere. Dollar weakens globally. BRICS builds alternatives. Yuan buys oil. Factories rust. Debt exceeds GDP. Interest consumes budgets.
Bridges crumble. Education falters. Politicians chase votes. We consume. We borrow.
Rome fell gradually. Citizens barely noticed. Taxes increased. Currency devalued. Military weakened. Services decayed. Life hardened by degrees.
East Rome adapted. Survived centuries. West fragmented. Trade shrank. Some thrived. Others suffered. Life changed permanently.
Those who could feed themselves survived best. Those who needed the system suffered worst.
Pendulum
My friend poured another coffee. The burn pile popped loudly. Sparks flew upward like dying stars.
His face changed as facts accumulated. Military man. Trained to assess threats. Detect weaknesses.
He stared at the fire. National glory reduced to embers. Something shifted in his expression. Recognition.
His fingers tightened around his mug. Knuckles white. Eyes fixed on dying flames.
I traced the horizon instead. Observing landscape. Noting the contrast.
He touched the flag on his t-shirt. I adjusted my plain gray one.
The unpayable debt. The crumbling infrastructure. The forgotten manufacturing. The dependent supply chains. The devaluing currency.
The pendulum clock ticked. Relentless. Indifferent to empires.
His eyes said what his patriotism couldn't voice. Something fundamental breaking.
I'd seen this coming. Years traveling showed me. Different systems. Different values. American exceptionalism viewed from outside.
Pragmatism replaced my old idealism. See things as they are. Not as wished.
The logs shifted. Flames reached higher. Then lower. The cycle of fire.
Divergence
Society always splits during shifts.
Some adapt. Some don't.
Printing arrived. Scribes starved. Publishers thrived. Information accelerated. Readers multiplied. Ideas spread. Adapters prospered.
Steam engines came. Weavers died. Factory owners flourished. Villages emptied. Cities grew. Coal replaced farms. Railways replaced wagons. New skills meant survival.
Computers transformed everything. Typewriters vanished. Software boomed. Data replaced paper. Networks replaced cabinets. Programmers replaced typists. Digital skills determined success.
The self-reliant thrived in each transition. Those waiting for rescue fell behind.
Now AI reshapes creativity. Some artists resist. Some harness it. Gap widens daily.
Bitcoin offers refuge. Critics mock. Adopters build wealth. The distance grows.
Remote work redraws maps. Office-bound struggle. Location-free flourish.
The pendulum swings. Power shifts. Some rise with it. Some fall against it.
Two societies emerge. Adaptive. Resistant. Prepared. Pretending.
Advantage
Early adapters win. Not through genius. Through action.
First printers built empires. First factories created dynasties. First websites became giants.
Bitcoin followed this pattern. Laptop miners became millionaires. Early buyers became legends.
Critics repeat themselves: "Too volatile." "No value." "Government ban coming."
Doubters doubt. Builders build. Gap widens.
Self-reliance accelerates adaptation. No permission needed. No consensus required. Act. Learn. Build.
The burn pile flames like empire's glory. Bright. Consuming. Temporary.
Blindness
Our brains see tigers. Not economic shifts.
We panic at headlines. We ignore decades-long trends.
We notice market drops. We miss debt cycles.
We debate tweets. We ignore revolutions.
Not weakness. Just humanity. Foresight requires work. Study. Thought.
Self-reliant thinking means seeing clearly. No comforting lies. No pleasing narratives. Just reality.
The clock pendulum swings. Time passes regardless of observation.
Action
Empires fall. Families need security. Children need futures. Lives need meaning.
You can adapt faster than nations.
Assess honestly. What skills matter now? What preserves wealth? Who helps when needed?
Never stop learning. Factory workers learned code. Taxi drivers joined apps. Photographers went digital.
Diversify globally. No country owns tomorrow. Learn languages. Make connections. Stay mobile.
Protect your money. Dying empires debase currencies. Romans kept gold. Bitcoin offers similar shelter.
Build resilience. Grow food. Make energy. Stay strong. Keep friends. Read old books. Some things never change.
Self-reliance matters most. Can you feed yourself? Can you fix things? Can you solve problems? Can you create value without systems?
Movement
Humans were nomads first. Settlers second. Movement in our blood.
Our ancestors followed herds. Sought better lands. Survival meant mobility.
The pendulum swings here too. Nomad to farmer. City-dweller to digital nomad.
Rome fixed people to land. Feudalism bound serfs to soil. Nations created borders. Companies demanded presence.
Now technology breaks chains. Work happens anywhere. Knowledge flows everywhere.
The rebuild America seeks requires fixed positions. Factory workers. Taxpaying citizens in permanent homes.
But technology enables escape. Remote work. Digital currencies. Borderless businesses.
The self-reliant understand mobility as freedom. One location means one set of rules. One economy. One fate.
Many locations mean options. Taxes become predatory? Leave. Opportunities disappear? Find new ones.
Patriotism celebrates roots. Wisdom remembers wings.
My friend's boots dug into his soil. Planted. Territorial. Defending.
My Chucks rested lightly. Ready. Adaptable. Departing.
His toolshed held equipment to maintain boundaries. Fences. Hedges. Property lines.
My backpack contained tools for crossing them. Chargers. Adapters. Currency.
The burn pile flame flickers. Fixed in place. The spark flies free. Movement its nature.
During Rome's decline, the mobile survived best. Merchants crossing borders. Scholars seeking patrons. Those tied to crumbling systems suffered most.
Location independence means personal resilience. Economic downturns become geographic choices. Political oppression becomes optional suffering.
Technology shrinks distance. Digital work. Video relationships. Online learning.
Self-sovereignty requires mobility. The option to walk away. The freedom to arrive elsewhere.
Two more worlds diverge. The rooted. The mobile. The fixed. The fluid. The loyal. The free.
Hope
Not decline. Transition. Painful but temporary.
America may weaken. Humanity advances. Technology multiplies possibilities. Poverty falls. Knowledge grows.
Falling empires see doom. Rising ones see opportunity. Both miss half the picture.
Every shift brings destruction and creation. Rome fell. Europe struggled. Farms produced less. Cities shrank. Trade broke down.
Yet innovation continued. Water mills appeared. New plows emerged. Monks preserved books. New systems evolved.
Different doesn't mean worse for everyone.
Some industries die. Others birth. Some regions fade. Others bloom. Some skills become useless. Others become gold.
The self-reliant thrive in any world. They adapt. They build. They serve. They create.
Choose your role. Nostalgia or building.
The pendulum swings. East rises again. The cycle continues.
Fading
The burn pile dimmed. Embers fading. Night air cooling.
My friend's shoulders changed. Tension releasing. Something accepted.
His patriotism remained. His illusions departed.
The pendulum clock ticked steadily. Measuring more than minutes. Measuring eras.
Two coffee cups. His: military-themed, old and chipped but cherished. Mine: plain porcelain, new and unmarked.
His eyes remained on smoldering embers. Mine moved between him and the darkening trees.
His calendar marked local town meetings. Mine tracked travel dates.
The last flame flickered out. Spring peepers filled the silence.
In darkness, we watched smoke rise. The world changing. New choices ahead.
No empire lasts forever. No comfort in denial. Only clarity in acceptance.
Self-reliance the ancient answer. Build your skills. Secure your resources. Strengthen your body. Feed your mind. Help your neighbors.
The burn pile turned to ash. Empire's glory extinguished.
He stood facing his land. I faced the road.
A nod between us. Respect across division. Different strategies for the same storm.
He turned toward his home. I toward my vehicle.
The pendulum continued swinging. Power flowing east once more. Five centuries ending. Five centuries beginning.
"Bear in mind that everything that exists is already fraying at the edges." — Marcus Aurelius
Tomorrow depends not on nations. On us.
-
 @ 91bea5cd:1df4451c
2025-04-26 10:16:21
@ 91bea5cd:1df4451c
2025-04-26 10:16:21O Contexto Legal Brasileiro e o Consentimento
No ordenamento jurídico brasileiro, o consentimento do ofendido pode, em certas circunstâncias, afastar a ilicitude de um ato que, sem ele, configuraria crime (como lesão corporal leve, prevista no Art. 129 do Código Penal). Contudo, o consentimento tem limites claros: não é válido para bens jurídicos indisponíveis, como a vida, e sua eficácia é questionável em casos de lesões corporais graves ou gravíssimas.
A prática de BDSM consensual situa-se em uma zona complexa. Em tese, se ambos os parceiros são adultos, capazes, e consentiram livre e informadamente nos atos praticados, sem que resultem em lesões graves permanentes ou risco de morte não consentido, não haveria crime. O desafio reside na comprovação desse consentimento, especialmente se uma das partes, posteriormente, o negar ou alegar coação.
A Lei Maria da Penha (Lei nº 11.340/2006)
A Lei Maria da Penha é um marco fundamental na proteção da mulher contra a violência doméstica e familiar. Ela estabelece mecanismos para coibir e prevenir tal violência, definindo suas formas (física, psicológica, sexual, patrimonial e moral) e prevendo medidas protetivas de urgência.
Embora essencial, a aplicação da lei em contextos de BDSM pode ser delicada. Uma alegação de violência por parte da mulher, mesmo que as lesões ou situações decorram de práticas consensuais, tende a receber atenção prioritária das autoridades, dada a presunção de vulnerabilidade estabelecida pela lei. Isso pode criar um cenário onde o parceiro masculino enfrenta dificuldades significativas em demonstrar a natureza consensual dos atos, especialmente se não houver provas robustas pré-constituídas.
Outros riscos:
Lesão corporal grave ou gravíssima (art. 129, §§ 1º e 2º, CP), não pode ser justificada pelo consentimento, podendo ensejar persecução penal.
Crimes contra a dignidade sexual (arts. 213 e seguintes do CP) são de ação pública incondicionada e independem de representação da vítima para a investigação e denúncia.
Riscos de Falsas Acusações e Alegação de Coação Futura
Os riscos para os praticantes de BDSM, especialmente para o parceiro que assume o papel dominante ou que inflige dor/restrição (frequentemente, mas não exclusivamente, o homem), podem surgir de diversas frentes:
- Acusações Externas: Vizinhos, familiares ou amigos que desconhecem a natureza consensual do relacionamento podem interpretar sons, marcas ou comportamentos como sinais de abuso e denunciar às autoridades.
- Alegações Futuras da Parceira: Em caso de término conturbado, vingança, arrependimento ou mudança de perspectiva, a parceira pode reinterpretar as práticas passadas como abuso e buscar reparação ou retaliação através de uma denúncia. A alegação pode ser de que o consentimento nunca existiu ou foi viciado.
- Alegação de Coação: Uma das formas mais complexas de refutar é a alegação de que o consentimento foi obtido mediante coação (física, moral, psicológica ou econômica). A parceira pode alegar, por exemplo, que se sentia pressionada, intimidada ou dependente, e que seu "sim" não era genuíno. Provar a ausência de coação a posteriori é extremamente difícil.
- Ingenuidade e Vulnerabilidade Masculina: Muitos homens, confiando na dinâmica consensual e na parceira, podem negligenciar a necessidade de precauções. A crença de que "isso nunca aconteceria comigo" ou a falta de conhecimento sobre as implicações legais e o peso processual de uma acusação no âmbito da Lei Maria da Penha podem deixá-los vulneráveis. A presença de marcas físicas, mesmo que consentidas, pode ser usada como evidência de agressão, invertendo o ônus da prova na prática, ainda que não na teoria jurídica.
Estratégias de Prevenção e Mitigação
Não existe um método infalível para evitar completamente o risco de uma falsa acusação, mas diversas medidas podem ser adotadas para construir um histórico de consentimento e reduzir vulnerabilidades:
- Comunicação Explícita e Contínua: A base de qualquer prática BDSM segura é a comunicação constante. Negociar limites, desejos, palavras de segurança ("safewords") e expectativas antes, durante e depois das cenas é crucial. Manter registros dessas negociações (e-mails, mensagens, diários compartilhados) pode ser útil.
-
Documentação do Consentimento:
-
Contratos de Relacionamento/Cena: Embora a validade jurídica de "contratos BDSM" seja discutível no Brasil (não podem afastar normas de ordem pública), eles servem como forte evidência da intenção das partes, da negociação detalhada de limites e do consentimento informado. Devem ser claros, datados, assinados e, idealmente, reconhecidos em cartório (para prova de data e autenticidade das assinaturas).
-
Registros Audiovisuais: Gravar (com consentimento explícito para a gravação) discussões sobre consentimento e limites antes das cenas pode ser uma prova poderosa. Gravar as próprias cenas é mais complexo devido a questões de privacidade e potencial uso indevido, mas pode ser considerado em casos específicos, sempre com consentimento mútuo documentado para a gravação.
Importante: a gravação deve ser com ciência da outra parte, para não configurar violação da intimidade (art. 5º, X, da Constituição Federal e art. 20 do Código Civil).
-
-
Testemunhas: Em alguns contextos de comunidade BDSM, a presença de terceiros de confiança durante negociações ou mesmo cenas pode servir como testemunho, embora isso possa alterar a dinâmica íntima do casal.
- Estabelecimento Claro de Limites e Palavras de Segurança: Definir e respeitar rigorosamente os limites (o que é permitido, o que é proibido) e as palavras de segurança é fundamental. O desrespeito a uma palavra de segurança encerra o consentimento para aquele ato.
- Avaliação Contínua do Consentimento: O consentimento não é um cheque em branco; ele deve ser entusiástico, contínuo e revogável a qualquer momento. Verificar o bem-estar do parceiro durante a cena ("check-ins") é essencial.
- Discrição e Cuidado com Evidências Físicas: Ser discreto sobre a natureza do relacionamento pode evitar mal-entendidos externos. Após cenas que deixem marcas, é prudente que ambos os parceiros estejam cientes e de acordo, talvez documentando por fotos (com data) e uma nota sobre a consensualidade da prática que as gerou.
- Aconselhamento Jurídico Preventivo: Consultar um advogado especializado em direito de família e criminal, com sensibilidade para dinâmicas de relacionamento alternativas, pode fornecer orientação personalizada sobre as melhores formas de documentar o consentimento e entender os riscos legais específicos.
Observações Importantes
- Nenhuma documentação substitui a necessidade de consentimento real, livre, informado e contínuo.
- A lei brasileira protege a "integridade física" e a "dignidade humana". Práticas que resultem em lesões graves ou que violem a dignidade de forma não consentida (ou com consentimento viciado) serão ilegais, independentemente de qualquer acordo prévio.
- Em caso de acusação, a existência de documentação robusta de consentimento não garante a absolvição, mas fortalece significativamente a defesa, ajudando a demonstrar a natureza consensual da relação e das práticas.
-
A alegação de coação futura é particularmente difícil de prevenir apenas com documentos. Um histórico consistente de comunicação aberta (whatsapp/telegram/e-mails), respeito mútuo e ausência de dependência ou controle excessivo na relação pode ajudar a contextualizar a dinâmica como não coercitiva.
-
Cuidado com Marcas Visíveis e Lesões Graves Práticas que resultam em hematomas severos ou lesões podem ser interpretadas como agressão, mesmo que consentidas. Evitar excessos protege não apenas a integridade física, mas também evita questionamentos legais futuros.
O que vem a ser consentimento viciado
No Direito, consentimento viciado é quando a pessoa concorda com algo, mas a vontade dela não é livre ou plena — ou seja, o consentimento existe formalmente, mas é defeituoso por alguma razão.
O Código Civil brasileiro (art. 138 a 165) define várias formas de vício de consentimento. As principais são:
Erro: A pessoa se engana sobre o que está consentindo. (Ex.: A pessoa acredita que vai participar de um jogo leve, mas na verdade é exposta a práticas pesadas.)
Dolo: A pessoa é enganada propositalmente para aceitar algo. (Ex.: Alguém mente sobre o que vai acontecer durante a prática.)
Coação: A pessoa é forçada ou ameaçada a consentir. (Ex.: "Se você não aceitar, eu termino com você" — pressão emocional forte pode ser vista como coação.)
Estado de perigo ou lesão: A pessoa aceita algo em situação de necessidade extrema ou abuso de sua vulnerabilidade. (Ex.: Alguém em situação emocional muito fragilizada é induzida a aceitar práticas que normalmente recusaria.)
No contexto de BDSM, isso é ainda mais delicado: Mesmo que a pessoa tenha "assinado" um contrato ou dito "sim", se depois ela alegar que seu consentimento foi dado sob medo, engano ou pressão psicológica, o consentimento pode ser considerado viciado — e, portanto, juridicamente inválido.
Isso tem duas implicações sérias:
-
O crime não se descaracteriza: Se houver vício, o consentimento é ignorado e a prática pode ser tratada como crime normal (lesão corporal, estupro, tortura, etc.).
-
A prova do consentimento precisa ser sólida: Mostrando que a pessoa estava informada, lúcida, livre e sem qualquer tipo de coação.
Consentimento viciado é quando a pessoa concorda formalmente, mas de maneira enganada, forçada ou pressionada, tornando o consentimento inútil para efeitos jurídicos.
Conclusão
Casais que praticam BDSM consensual no Brasil navegam em um terreno que exige não apenas confiança mútua e comunicação excepcional, mas também uma consciência aguçada das complexidades legais e dos riscos de interpretações equivocadas ou acusações mal-intencionadas. Embora o BDSM seja uma expressão legítima da sexualidade humana, sua prática no Brasil exige responsabilidade redobrada. Ter provas claras de consentimento, manter a comunicação aberta e agir com prudência são formas eficazes de se proteger de falsas alegações e preservar a liberdade e a segurança de todos os envolvidos. Embora leis controversas como a Maria da Penha sejam "vitais" para a proteção contra a violência real, os praticantes de BDSM, e em particular os homens nesse contexto, devem adotar uma postura proativa e prudente para mitigar os riscos inerentes à potencial má interpretação ou instrumentalização dessas práticas e leis, garantindo que a expressão de sua consensualidade esteja resguardada na medida do possível.
Importante: No Brasil, mesmo com tudo isso, o Ministério Público pode denunciar por crime como lesão corporal grave, estupro ou tortura, independente de consentimento. Então a prudência nas práticas é fundamental.
Aviso Legal: Este artigo tem caráter meramente informativo e não constitui aconselhamento jurídico. As leis e interpretações podem mudar, e cada situação é única. Recomenda-se buscar orientação de um advogado qualificado para discutir casos específicos.
Se curtiu este artigo faça uma contribuição, se tiver algum ponto relevante para o artigo deixe seu comentário.
-
 @ d34e832d:383f78d0
2025-04-25 23:20:48
@ d34e832d:383f78d0
2025-04-25 23:20:48As computing needs evolve toward speed, reliability, and efficiency, understanding the landscape of storage technologies becomes crucial for system builders, IT professionals, and performance enthusiasts. This idea compares traditional Hard Disk Drives (HDDs) with various Solid-State Drive (SSD) technologies including SATA SSDs, mSATA, M.2 SATA, and M.2 NVMe. It explores differences in form factors, interfaces, memory types, and generational performance to empower informed decisions on selecting optimal storage.
1. Storage Device Overview
1.1 HDDs – Hard Disk Drives
- Mechanism: Mechanical platters + spinning disk.
- Speed: ~80–160 MB/s.
- Cost: Low cost per GB.
- Durability: Susceptible to shock; moving parts prone to wear.
- Use Case: Mass storage, backups, archival.
1.2 SSDs – Solid State Drives
- Mechanism: Flash memory (NAND-based); no moving parts.
- Speed: SATA SSDs (~550 MB/s), NVMe SSDs (>7,000 MB/s).
- Durability: High resistance to shock and temperature.
- Use Case: Operating systems, apps, high-speed data transfer.
2. Form Factors
| Form Factor | Dimensions | Common Usage | |------------------|------------------------|--------------------------------------------| | 2.5-inch | 100mm x 69.85mm x 7mm | Laptops, desktops (SATA interface) | | 3.5-inch | 146mm x 101.6mm x 26mm | Desktops/servers (HDD only) | | mSATA | 50.8mm x 29.85mm | Legacy ultrabooks, embedded systems | | M.2 | 22mm wide, lengths vary (2242, 2260, 2280, 22110) | Modern laptops, desktops, NUCs |
Note: mSATA is being phased out in favor of the more versatile M.2 standard.
3. Interfaces & Protocols
3.1 SATA (Serial ATA)
- Max Speed: ~550 MB/s (SATA III).
- Latency: Higher.
- Protocol: AHCI.
- Compatibility: Broad support, backward compatible.
3.2 NVMe (Non-Volatile Memory Express)
- Max Speed:
- Gen 3: ~3,500 MB/s
- Gen 4: ~7,000 MB/s
- Gen 5: ~14,000 MB/s
- Latency: Very low.
- Protocol: NVMe (optimized for NAND flash).
- Interface: PCIe lanes (usually via M.2 slot).
NVMe significantly outperforms SATA due to reduced overhead and direct PCIe access.
4. Key Slot & Compatibility (M.2 Drives)
| Drive Type | Key | Interface | Typical Use | |------------------|----------------|---------------|-----------------------| | M.2 SATA | B+M key | SATA | Budget laptops/desktops | | M.2 NVMe (PCIe) | M key only | PCIe Gen 3–5 | Performance PCs/gaming |
⚠️ Important: Not all M.2 slots support NVMe. Check motherboard specs for PCIe compatibility.
5. SSD NAND Memory Types
| Type | Bits/Cell | Speed | Endurance | Cost | Use Case | |---------|---------------|-----------|---------------|----------|--------------------------------| | SLC | 1 | ⭐⭐⭐⭐ | ⭐⭐⭐⭐ | $$$$ | Enterprise caching | | MLC | 2 | ⭐⭐⭐ | ⭐⭐⭐ | $$$ | Pro-grade systems | | TLC | 3 | ⭐⭐ | ⭐⭐ | $$ | Consumer, gaming | | QLC | 4 | ⭐ | ⭐ | $ | Budget SSDs, media storage |
6. 3D NAND / V-NAND Technology
- Traditional NAND: Planar (flat) design.
- 3D NAND: Stacks cells vertically—more density, less space.
- Benefits:
- Greater capacity
- Better power efficiency
- Improved lifespan
Samsung’s V-NAND is a branded 3D NAND variant known for high endurance and stability.
7. Performance & Generational Comparison
| PCIe Gen | Max Speed | Use Case | |--------------|---------------|----------------------------------| | Gen 3 | ~3,500 MB/s | Mainstream laptops/desktops | | Gen 4 | ~7,000 MB/s | Gaming, prosumer, light servers | | Gen 5 | ~14,000 MB/s | AI workloads, enterprise |
Drives are backward compatible, but will operate at the host’s maximum supported speed.
8. Thermal Management
- NVMe SSDs generate heat—especially Gen 4/5.
- Heatsinks and thermal pads are vital for:
- Sustained performance (prevent throttling)
- Longer lifespan
- Recommended to leave 10–20% free space for optimal SSD wear leveling and garbage collection.
9. HDD vs SSD: Summary
| Aspect | HDD | SSD | |------------------|---------------------|------------------------------| | Speed | 80–160 MB/s | 550 MB/s – 14,000 MB/s | | Durability | Low (mechanical) | High (no moving parts) | | Lifespan | Moderate | High (depends on NAND type) | | Cost | Lower per GB | Higher per GB | | Noise | Audible | Silent |
10. Brand Recommendations
| Brand | Strength | |------------------|-----------------------------------------| | Samsung | Leading in performance (980 Pro, 990 Pro) | | Western Digital | Reliable Gen 3/4/5 drives (SN770, SN850X) | | Crucial | Budget-friendly, solid TLC drives (P3, P5 Plus) | | Kingston | Value-oriented SSDs (A2000, NV2) |
11. How to Choose the Right SSD
- Check your device slot: Is it M.2 B+M, M-key, or SATA-only?
- Interface compatibility: Confirm if the M.2 slot supports NVMe or only SATA.
- Match PCIe Gen: Use Gen 3/4/5 based on CPU/motherboard lanes.
- Pick NAND type: TLC for best balance of speed/longevity.
- Thermal plan: Use heatsinks or fans for Gen 4+ drives.
- Capacity need: Leave headroom (15–20%) for performance and lifespan.
- Trustworthy brands: Stick to Samsung, WD, Crucial for warranty and quality.
Consider
From boot speed to data integrity, SSDs have revolutionized how modern systems handle storage. While HDDs remain relevant for mass archival, NVMe SSDs—especially those leveraging PCIe Gen 4 and Gen 5—dominate in speed-critical workflows. M.2 NVMe is the dominant form factor for futureproof builds, while understanding memory types like TLC vs. QLC ensures better longevity planning.
Whether you’re upgrading a laptop, building a gaming rig, or running a self-hosted Bitcoin node, choosing the right form factor, interface, and NAND type can dramatically impact system performance and reliability.
Resources & Further Reading
- How-Fixit Storage Guides
- Kingston SSD Reliability Guide
- Western Digital Product Lines
- Samsung V-NAND Explained
- PCIe Gen 5 Benchmarks
Options
🔧 Recommended SSDs and Tools (Amazon)
-
Kingston A400 240GB SSD – SATA 3 2.5"
https://a.co/d/41esjYL -
Samsung 970 EVO Plus 2TB NVMe M.2 SSD – Gen 3
https://a.co/d/6EMVAN1 -
Crucial P5 Plus 1TB PCIe Gen4 NVMe M.2 SSD
https://a.co/d/hQx50Cq -
WD Blue SN570 1TB NVMe SSD – PCIe Gen 3
https://a.co/d/j2zSDCJ -
Sabrent Rocket Q 2TB NVMe SSD – QLC NAND
https://a.co/d/325Og2K -
Thermalright M.2 SSD Heatsink Kit
https://a.co/d/0IYH3nK -
ORICO M.2 NVMe SSD Enclosure – USB 3.2 Gen2
https://a.co/d/aEwQmih
🛠️ DIY & Fix Resource
- How-Fixit – PC Repair Guides and Tutorials
https://www.how-fixit.com/
In Addition
Modern Storage Technologies and Mini NAS Implementation
1. Network Attached Storage (NAS) system
In the rapidly evolving landscape of data storage, understanding the nuances of various storage technologies is crucial for optimal system design and performance. This idea delves into the distinctions between traditional Hard Disk Drives (HDDs), Solid State Drives (SSDs), and advanced storage interfaces like M.2 NVMe, M.2 SATA, and mSATA. Additionally, it explores the implementation of a compact Network Attached Storage (NAS) system using the Nookbox G9, highlighting its capabilities and limitations.
2. Storage Technologies Overview
2.1 Hard Disk Drives (HDDs)
- Mechanism: Utilize spinning magnetic platters and read/write heads.
- Advantages:
- Cost-effective for large storage capacities.
- Longer lifespan in low-vibration environments.
- Disadvantages:
- Slower data access speeds.
- Susceptible to mechanical failures due to moving parts.
2.2 Solid State Drives (SSDs)
- Mechanism: Employ NAND flash memory with no moving parts.
- Advantages:
- Faster data access and boot times.
- Lower power consumption and heat generation.
- Enhanced durability and shock resistance.
- Disadvantages:
- Higher cost per gigabyte compared to HDDs.
- Limited write cycles, depending on NAND type.
3. SSD Form Factors and Interfaces
3.1 Form Factors
- 2.5-Inch: Standard size for laptops and desktops; connects via SATA interface.
- mSATA: Miniature SATA interface, primarily used in ultrabooks and embedded systems; largely supplanted by M.2.
- M.2: Versatile form factor supporting both SATA and NVMe interfaces; prevalent in modern systems.
3.2 Interfaces
- SATA (Serial ATA):
- Speed: Up to 600 MB/s.
- Compatibility: Widely supported across various devices.
-
Limitation: Bottleneck for high-speed SSDs.
-
NVMe (Non-Volatile Memory Express):
- Speed: Ranges from 3,500 MB/s (PCIe Gen 3) to over 14,000 MB/s (PCIe Gen 5).
- Advantage: Direct communication with CPU via PCIe lanes, reducing latency.
- Consideration: Requires compatible motherboard and BIOS support.
4. M.2 SATA vs. M.2 NVMe
| Feature | M.2 SATA | M.2 NVMe | |------------------------|--------------------------------------------------|----------------------------------------------------| | Interface | SATA III (AHCI protocol) | PCIe (NVMe protocol) | | Speed | Up to 600 MB/s | Up to 14,000 MB/s (PCIe Gen 5) | | Compatibility | Broad compatibility with older systems | Requires NVMe-compatible M.2 slot and BIOS support | | Use Case | Budget builds, general computing | High-performance tasks, gaming, content creation |
Note: M.2 NVMe drives are not backward compatible with M.2 SATA slots due to differing interfaces and keying.
5. NAND Flash Memory Types
Understanding NAND types is vital for assessing SSD performance and longevity.
- SLC (Single-Level Cell):
- Bits per Cell: 1
- Endurance: ~100,000 write cycles
-
Use Case: Enterprise and industrial applications
-
MLC (Multi-Level Cell):
- Bits per Cell: 2
- Endurance: ~10,000 write cycles
-
Use Case: Consumer-grade SSDs
-
TLC (Triple-Level Cell):
- Bits per Cell: 3
- Endurance: ~3,000 write cycles
-
Use Case: Mainstream consumer SSDs
-
QLC (Quad-Level Cell):
- Bits per Cell: 4
- Endurance: ~1,000 write cycles
-
Use Case: Read-intensive applications
-
3D NAND:
- Structure: Stacks memory cells vertically to increase density.
- Advantage: Enhances performance and endurance across NAND types.
6. Thermal Management and SSD Longevity
Effective thermal management is crucial for maintaining SSD performance and lifespan.
- Heatsinks: Aid in dissipating heat from SSD controllers.
- Airflow: Ensuring adequate case ventilation prevents thermal throttling.
- Monitoring: Regularly check SSD temperatures, especially under heavy workloads.
7. Trusted SSD Manufacturers
Selecting SSDs from reputable manufacturers ensures reliability and support.
- Samsung: Known for high-performance SSDs with robust software support.
- Western Digital (WD): Offers a range of SSDs catering to various user needs.
- Crucial (Micron): Provides cost-effective SSD solutions with solid performance.
8. Mini NAS Implementation: Nookbox G9 Case Study
8.1 Overview
The Nookbox G9 is a compact NAS solution designed to fit within a 1U rack space, accommodating four M.2 NVMe SSDs.
8.2 Specifications
- Storage Capacity: Supports up to 8TB using four 2TB NVMe SSDs.
- Interface: Each M.2 slot operates at PCIe Gen 3x2.
- Networking: Equipped with 2.5 Gigabit Ethernet ports.
- Operating System: Comes pre-installed with Windows 11; compatible with Linux distributions like Ubuntu 24.10.
8.3 Performance and Limitations
- Throughput: Network speeds capped at ~250 MB/s due to 2.5 GbE limitation.
- Thermal Issues: Inadequate cooling leads to SSD temperatures reaching up to 80°C under load, causing potential throttling and system instability.
- Reliability: Reports of system reboots and lockups during intensive operations, particularly with ZFS RAIDZ configurations.
8.4 Recommendations
- Cooling Enhancements: Implement third-party heatsinks to improve thermal performance.
- Alternative Solutions: Consider NAS systems with better thermal designs and higher network throughput for demanding applications.
9. Consider
Navigating the myriad of storage technologies requires a comprehensive understanding of form factors, interfaces, and memory types. While HDDs offer cost-effective bulk storage, SSDs provide superior speed and durability. The choice between M.2 SATA and NVMe hinges on performance needs and system compatibility. Implementing compact NAS solutions like the Nookbox G9 necessitates careful consideration of thermal management and network capabilities to ensure reliability and performance.
Product Links (Amazon)
-
Thermal Heatsink for M.2 SSDs (Must-have for stress and cooling)
https://a.co/d/43B1F3t -
Nookbox G9 – Mini NAS
https://a.co/d/3dswvGZ -
Alternative 1: Possibly related cooling or SSD gear
https://a.co/d/c0Eodm3 -
Alternative 2: Possibly related NAS accessories or SSDs
https://a.co/d/9gWeqDr
Benchmark Results (Geekbench)
-
GMKtec G9 Geekbench CPU Score #1
https://browser.geekbench.com/v6/cpu/11471182 -
GMKtec G9 Geekbench CPU Score #2
https://browser.geekbench.com/v6/cpu/11470130 -
GMKtec Geekbench User Profile
https://browser.geekbench.com/user/446940
-
 @ 3bf0c63f:aefa459d
2025-04-25 19:26:48
@ 3bf0c63f:aefa459d
2025-04-25 19:26:48Redistributing Git with Nostr
Every time someone tries to "decentralize" Git -- like many projects tried in the past to do it with BitTorrent, IPFS, ScuttleButt or custom p2p protocols -- there is always a lurking comment: "but Git is already distributed!", and then the discussion proceeds to mention some facts about how Git supports multiple remotes and its magic syncing and merging abilities and so on.
Turns out all that is true, Git is indeed all that powerful, and yet GitHub is the big central hub that hosts basically all Git repositories in the giant world of open-source. There are some crazy people that host their stuff elsewhere, but these projects end up not being found by many people, and even when they do they suffer from lack of contributions.
Because everybody has a GitHub account it's easy to open a pull request to a repository of a project you're using if it's on GitHub (to be fair I think it's very annoying to have to clone the repository, then add it as a remote locally, push to it, then go on the web UI and click to open a pull request, then that cloned repository lurks forever in your profile unless you go through 16 screens to delete it -- but people in general seem to think it's easy).
It's much harder to do it on some random other server where some project might be hosted, because now you have to add 4 more even more annoying steps: create an account; pick a password; confirm an email address; setup SSH keys for pushing. (And I'm not even mentioning the basic impossibility of offering
pushaccess to external unknown contributors to people who want to host their own simple homemade Git server.)At this point some may argue that we could all have accounts on GitLab, or Codeberg or wherever else, then those steps are removed. Besides not being a practical strategy this pseudo solution misses the point of being decentralized (or distributed, who knows) entirely: it's far from the ideal to force everybody to have the double of account management and SSH setup work in order to have the open-source world controlled by two shady companies instead of one.
What we want is to give every person the opportunity to host their own Git server without being ostracized. at the same time we must recognize that most people won't want to host their own servers (not even most open-source programmers!) and give everybody the ability to host their stuff on multi-tenant servers (such as GitHub) too. Importantly, though, if we allow for a random person to have a standalone Git server on a standalone server they host themselves on their wood cabin that also means any new hosting company can show up and start offering Git hosting, with or without new cool features, charging high or low or zero, and be immediately competing against GitHub or GitLab, i.e. we must remove the network-effect centralization pressure.
External contributions
The first problem we have to solve is: how can Bob contribute to Alice's repository without having an account on Alice's server?
SourceHut has reminded GitHub users that Git has always had this (for most) arcane
git send-emailcommand that is the original way to send patches, using an once-open protocol.Turns out Nostr acts as a quite powerful email replacement and can be used to send text content just like email, therefore patches are a very good fit for Nostr event contents.
Once you get used to it and the proper UIs (or CLIs) are built sending and applying patches to and from others becomes a much easier flow than the intense clickops mixed with terminal copypasting that is interacting with GitHub (you have to clone the repository on GitHub, then update the remote URL in your local directory, then create a branch and then go back and turn that branch into a Pull Request, it's quite tiresome) that many people already dislike so much they went out of their way to build many GitHub CLI tools just so they could comment on issues and approve pull requests from their terminal.
Replacing GitHub features
Aside from being the "hub" that people use to send patches to other people's code (because no one can do the email flow anymore, justifiably), GitHub also has 3 other big features that are not directly related to Git, but that make its network-effect harder to overcome. Luckily Nostr can be used to create a new environment in which these same features are implemented in a more decentralized and healthy way.
Issues: bug reports, feature requests and general discussions
Since the "Issues" GitHub feature is just a bunch of text comments it should be very obvious that Nostr is a perfect fit for it.
I will not even mention the fact that Nostr is much better at threading comments than GitHub (which doesn't do it at all), which can generate much more productive and organized discussions (and you can opt out if you want).
Search
I use GitHub search all the time to find libraries and projects that may do something that I need, and it returns good results almost always. So if people migrated out to other code hosting providers wouldn't we lose it?
The fact is that even though we think everybody is on GitHub that is a globalist falsehood. Some projects are not on GitHub, and if we use only GitHub for search those will be missed. So even if we didn't have a Nostr Git alternative it would still be necessary to create a search engine that incorporated GitLab, Codeberg, SourceHut and whatnot.
Turns out on Nostr we can make that quite easy by not forcing anyone to integrate custom APIs or hardcoding Git provider URLs: each repository can make itself available by publishing an "announcement" event with a brief description and one or more Git URLs. That makes it easy for a search engine to index them -- and even automatically download the code and index the code (or index just README files or whatever) without a centralized platform ever having to be involved.
The relays where such announcements will be available play a role, of course, but that isn't a bad role: each announcement can be in multiple relays known for storing "public good" projects, some relays may curate only projects known to be very good according to some standards, other relays may allow any kind of garbage, which wouldn't make them good for a search engine to rely upon, but would still be useful in case one knows the exact thing (and from whom) they're searching for (the same is valid for all Nostr content, by the way, and that's where it's censorship-resistance comes from).
Continuous integration
GitHub Actions are a very hardly subsidized free-compute-for-all-paid-by-Microsoft feature, but one that isn't hard to replace at all. In fact there exists today many companies offering the same kind of service out there -- although they are mostly targeting businesses and not open-source projects, before GitHub Actions was introduced there were also many that were heavily used by open-source projects.
One problem is that these services are still heavily tied to GitHub today, they require a GitHub login, sometimes BitBucket and GitLab and whatnot, and do not allow one to paste an arbitrary Git server URL, but that isn't a thing that is very hard to change anyway, or to start from scratch. All we need are services that offer the CI/CD flows, perhaps using the same framework of GitHub Actions (although I would prefer to not use that messy garbage), and charge some few satoshis for it.
It may be the case that all the current services only support the big Git hosting platforms because they rely on their proprietary APIs, most notably the webhooks dispatched when a repository is updated, to trigger the jobs. It doesn't have to be said that Nostr can also solve that problem very easily.
-
 @ 957df479:13e9e08e
2025-04-29 20:58:04
@ 957df479:13e9e08e
2025-04-29 20:58:04LiaScript Course
Course Main Title
This is your course initialization stub.
Please see the Docs to find out what is possible in LiaScript.
If you want to use instant help in your Atom IDE, please type lia to see all available shortcuts.
Markdown
You can use common Markdown syntax to create your course, such as:
- Lists
-
ordered or
-
unordered
- ones ...
| Header 1 | Header 2 | | :--------- | :--------- | | Item 1 | Item 2 |
Images:

Extensions
--{{0}}--But you can also include other features such as spoken text.
--{{1}}--Insert any kind of audio file:
{{1}}--{{2}}--Even videos or change the language completely.
{{2-3}}!?video
--{{3 Russian Female}}--Первоначально создан в 2004 году Джоном Грубером (англ. John Gruber) и Аароном Шварцем. Многие идеи языка были позаимствованы из существующих соглашений по разметке текста в электронных письмах...
{{3}}Type "voice" to see a list of all available languages.
Styling
The whole text-block should appear in purple color and with a wobbling effect. Which is a bad example, please use it with caution ... ~~ only this is red ;-) ~~
Charts
Use ASCII-Art to draw diagrams:
Multiline 1.9 | DOTS | *** y | * * - | r r r r r r r*r r r r*r r r r r r r a | * * x | * * i | B B B B B * B B B B B B * B B B B B s | * * | * * * * * * -1 +------------------------------------ 0 x-axis 1Quizzes
A Textquiz
What did the fish say when he hit a concrete wall?
[[dam]]Multiple Choice
Just add as many points as you wish:
[[X]] Only the **X** marks the correct point. [[ ]] Empty ones are wrong. [[X]] ...Single Choice
Just add as many points as you wish:
[( )] ... [(X)] <-- Only the **X** is allowed. [( )] ...Executable Code
A drawing example, for demonstrating that any JavaScript library can be used, also for drawing.
```javascript // Initialize a Line chart in the container with the ID chart1 new Chartist.Line('#chart1', { labels: [1, 2, 3, 4], series: [[100, 120, 180, 200]] });
// Initialize a Line chart in the container with the ID chart2 new Chartist.Bar('#chart2', { labels: [1, 2, 3, 4], series: [[5, 2, 8, 3]] }); ```
Projects
You can make your code executable and define projects:
``` js -EvalScript.js let who = data.first_name + " " + data.last_name;
if(data.online) { who + " is online"; } else { who + " is NOT online"; }
json +Data.json { "first_name" : "Sammy", "last_name" : "Shark", "online" : true } ```More
Find out what you can even do more with quizzes:
https://liascript.github.io/course/?https://raw.githubusercontent.com/liaScript/docs/master/README.md
-
 @ b099870e:f3ba8f5d
2025-04-29 20:57:49
@ b099870e:f3ba8f5d
2025-04-29 20:57:49When you work for others, you are at their mercy. The own your work; they own you.Your creative spirit is squaded. What keeps you in such position is a fear of having to sink or swim on your own. Instead you should have a greater fear of what will happen to you if you remain dependant on others for power. Your goal in every maneuver in life must be ownership, working the corner for yourself. When it is yours to lose -you are more motivated,more creative,more alive. The ultimate power in life is to be completely self-reliant, completely yourself.
A quote from The 50th Law
-
 @ 40b9c85f:5e61b451
2025-04-24 15:27:02
@ 40b9c85f:5e61b451
2025-04-24 15:27:02Introduction
Data Vending Machines (DVMs) have emerged as a crucial component of the Nostr ecosystem, offering specialized computational services to clients across the network. As defined in NIP-90, DVMs operate on an apparently simple principle: "data in, data out." They provide a marketplace for data processing where users request specific jobs (like text translation, content recommendation, or AI text generation)
While DVMs have gained significant traction, the current specification faces challenges that hinder widespread adoption and consistent implementation. This article explores some ideas on how we can apply the reflection pattern, a well established approach in RPC systems, to address these challenges and improve the DVM ecosystem's clarity, consistency, and usability.
The Current State of DVMs: Challenges and Limitations
The NIP-90 specification provides a broad framework for DVMs, but this flexibility has led to several issues:
1. Inconsistent Implementation
As noted by hzrd149 in "DVMs were a mistake" every DVM implementation tends to expect inputs in slightly different formats, even while ostensibly following the same specification. For example, a translation request DVM might expect an event ID in one particular format, while an LLM service could expect a "prompt" input that's not even specified in NIP-90.
2. Fragmented Specifications
The DVM specification reserves a range of event kinds (5000-6000), each meant for different types of computational jobs. While creating sub-specifications for each job type is being explored as a possible solution for clarity, in a decentralized and permissionless landscape like Nostr, relying solely on specification enforcement won't be effective for creating a healthy ecosystem. A more comprehensible approach is needed that works with, rather than against, the open nature of the protocol.
3. Ambiguous API Interfaces
There's no standardized way for clients to discover what parameters a specific DVM accepts, which are required versus optional, or what output format to expect. This creates uncertainty and forces developers to rely on documentation outside the protocol itself, if such documentation exists at all.
The Reflection Pattern: A Solution from RPC Systems
The reflection pattern in RPC systems offers a compelling solution to many of these challenges. At its core, reflection enables servers to provide metadata about their available services, methods, and data types at runtime, allowing clients to dynamically discover and interact with the server's API.
In established RPC frameworks like gRPC, reflection serves as a self-describing mechanism where services expose their interface definitions and requirements. In MCP reflection is used to expose the capabilities of the server, such as tools, resources, and prompts. Clients can learn about available capabilities without prior knowledge, and systems can adapt to changes without requiring rebuilds or redeployments. This standardized introspection creates a unified way to query service metadata, making tools like
grpcurlpossible without requiring precompiled stubs.How Reflection Could Transform the DVM Specification
By incorporating reflection principles into the DVM specification, we could create a more coherent and predictable ecosystem. DVMs already implement some sort of reflection through the use of 'nip90params', which allow clients to discover some parameters, constraints, and features of the DVMs, such as whether they accept encryption, nutzaps, etc. However, this approach could be expanded to provide more comprehensive self-description capabilities.
1. Defined Lifecycle Phases
Similar to the Model Context Protocol (MCP), DVMs could benefit from a clear lifecycle consisting of an initialization phase and an operation phase. During initialization, the client and DVM would negotiate capabilities and exchange metadata, with the DVM providing a JSON schema containing its input requirements. nip-89 (or other) announcements can be used to bootstrap the discovery and negotiation process by providing the input schema directly. Then, during the operation phase, the client would interact with the DVM according to the negotiated schema and parameters.
2. Schema-Based Interactions
Rather than relying on rigid specifications for each job type, DVMs could self-advertise their schemas. This would allow clients to understand which parameters are required versus optional, what type validation should occur for inputs, what output formats to expect, and what payment flows are supported. By internalizing the input schema of the DVMs they wish to consume, clients gain clarity on how to interact effectively.
3. Capability Negotiation
Capability negotiation would enable DVMs to advertise their supported features, such as encryption methods, payment options, or specialized functionalities. This would allow clients to adjust their interaction approach based on the specific capabilities of each DVM they encounter.
Implementation Approach
While building DVMCP, I realized that the RPC reflection pattern used there could be beneficial for constructing DVMs in general. Since DVMs already follow an RPC style for their operation, and reflection is a natural extension of this approach, it could significantly enhance and clarify the DVM specification.
A reflection enhanced DVM protocol could work as follows: 1. Discovery: Clients discover DVMs through existing NIP-89 application handlers, input schemas could also be advertised in nip-89 announcements, making the second step unnecessary. 2. Schema Request: Clients request the DVM's input schema for the specific job type they're interested in 3. Validation: Clients validate their request against the provided schema before submission 4. Operation: The job proceeds through the standard NIP-90 flow, but with clearer expectations on both sides
Parallels with Other Protocols
This approach has proven successful in other contexts. The Model Context Protocol (MCP) implements a similar lifecycle with capability negotiation during initialization, allowing any client to communicate with any server as long as they adhere to the base protocol. MCP and DVM protocols share fundamental similarities, both aim to expose and consume computational resources through a JSON-RPC-like interface, albeit with specific differences.
gRPC's reflection service similarly allows clients to discover service definitions at runtime, enabling generic tools to work with any gRPC service without prior knowledge. In the REST API world, OpenAPI/Swagger specifications document interfaces in a way that makes them discoverable and testable.
DVMs would benefit from adopting these patterns while maintaining the decentralized, permissionless nature of Nostr.
Conclusion
I am not attempting to rewrite the DVM specification; rather, explore some ideas that could help the ecosystem improve incrementally, reducing fragmentation and making the ecosystem more comprehensible. By allowing DVMs to self describe their interfaces, we could maintain the flexibility that makes Nostr powerful while providing the structure needed for interoperability.
For developers building DVM clients or libraries, this approach would simplify consumption by providing clear expectations about inputs and outputs. For DVM operators, it would establish a standard way to communicate their service's requirements without relying on external documentation.
I am currently developing DVMCP following these patterns. Of course, DVMs and MCP servers have different details; MCP includes capabilities such as tools, resources, and prompts on the server side, as well as 'roots' and 'sampling' on the client side, creating a bidirectional way to consume capabilities. In contrast, DVMs typically function similarly to MCP tools, where you call a DVM with an input and receive an output, with each job type representing a different categorization of the work performed.
Without further ado, I hope this article has provided some insight into the potential benefits of applying the reflection pattern to the DVM specification.
-
 @ 4ba8e86d:89d32de4
2025-04-21 02:13:56
@ 4ba8e86d:89d32de4
2025-04-21 02:13:56Tutorial feito por nostr:nostr:npub1rc56x0ek0dd303eph523g3chm0wmrs5wdk6vs0ehd0m5fn8t7y4sqra3tk poste original abaixo:
Parte 1 : http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/263585/tutorial-debloat-de-celulares-android-via-adb-parte-1
Parte 2 : http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/index.php/263586/tutorial-debloat-de-celulares-android-via-adb-parte-2
Quando o assunto é privacidade em celulares, uma das medidas comumente mencionadas é a remoção de bloatwares do dispositivo, também chamado de debloat. O meio mais eficiente para isso sem dúvidas é a troca de sistema operacional. Custom Rom’s como LineageOS, GrapheneOS, Iodé, CalyxOS, etc, já são bastante enxutos nesse quesito, principalmente quanto não é instalado os G-Apps com o sistema. No entanto, essa prática pode acabar resultando em problemas indesejados como a perca de funções do dispositivo, e até mesmo incompatibilidade com apps bancários, tornando este método mais atrativo para quem possui mais de um dispositivo e separando um apenas para privacidade. Pensando nisso, pessoas que possuem apenas um único dispositivo móvel, que são necessitadas desses apps ou funções, mas, ao mesmo tempo, tem essa visão em prol da privacidade, buscam por um meio-termo entre manter a Stock rom, e não ter seus dados coletados por esses bloatwares. Felizmente, a remoção de bloatwares é possível e pode ser realizada via root, ou mais da maneira que este artigo irá tratar, via adb.
O que são bloatwares?
Bloatware é a junção das palavras bloat (inchar) + software (programa), ou seja, um bloatware é basicamente um programa inútil ou facilmente substituível — colocado em seu dispositivo previamente pela fabricante e operadora — que está no seu dispositivo apenas ocupando espaço de armazenamento, consumindo memória RAM e pior, coletando seus dados e enviando para servidores externos, além de serem mais pontos de vulnerabilidades.
O que é o adb?
O Android Debug Brigde, ou apenas adb, é uma ferramenta que se utiliza das permissões de usuário shell e permite o envio de comandos vindo de um computador para um dispositivo Android exigindo apenas que a depuração USB esteja ativa, mas também pode ser usada diretamente no celular a partir do Android 11, com o uso do Termux e a depuração sem fio (ou depuração wifi). A ferramenta funciona normalmente em dispositivos sem root, e também funciona caso o celular esteja em Recovery Mode.
Requisitos:
Para computadores:
• Depuração USB ativa no celular; • Computador com adb; • Cabo USB;
Para celulares:
• Depuração sem fio (ou depuração wifi) ativa no celular; • Termux; • Android 11 ou superior;
Para ambos:
• Firewall NetGuard instalado e configurado no celular; • Lista de bloatwares para seu dispositivo;
Ativação de depuração:
Para ativar a Depuração USB em seu dispositivo, pesquise como ativar as opções de desenvolvedor de seu dispositivo, e lá ative a depuração. No caso da depuração sem fio, sua ativação irá ser necessária apenas no momento que for conectar o dispositivo ao Termux.
Instalação e configuração do NetGuard
O NetGuard pode ser instalado através da própria Google Play Store, mas de preferência instale pela F-Droid ou Github para evitar telemetria.
F-Droid: https://f-droid.org/packages/eu.faircode.netguard/
Github: https://github.com/M66B/NetGuard/releases
Após instalado, configure da seguinte maneira:
Configurações → padrões (lista branca/negra) → ative as 3 primeiras opções (bloquear wifi, bloquear dados móveis e aplicar regras ‘quando tela estiver ligada’);
Configurações → opções avançadas → ative as duas primeiras (administrar aplicativos do sistema e registrar acesso a internet);
Com isso, todos os apps estarão sendo bloqueados de acessar a internet, seja por wifi ou dados móveis, e na página principal do app basta permitir o acesso a rede para os apps que você vai usar (se necessário). Permita que o app rode em segundo plano sem restrição da otimização de bateria, assim quando o celular ligar, ele já estará ativo.
Lista de bloatwares
Nem todos os bloatwares são genéricos, haverá bloatwares diferentes conforme a marca, modelo, versão do Android, e até mesmo região.
Para obter uma lista de bloatwares de seu dispositivo, caso seu aparelho já possua um tempo de existência, você encontrará listas prontas facilmente apenas pesquisando por elas. Supondo que temos um Samsung Galaxy Note 10 Plus em mãos, basta pesquisar em seu motor de busca por:
Samsung Galaxy Note 10 Plus bloatware listProvavelmente essas listas já terão inclusas todos os bloatwares das mais diversas regiões, lhe poupando o trabalho de buscar por alguma lista mais específica.
Caso seu aparelho seja muito recente, e/ou não encontre uma lista pronta de bloatwares, devo dizer que você acaba de pegar em merda, pois é chato para um caralho pesquisar por cada aplicação para saber sua função, se é essencial para o sistema ou se é facilmente substituível.
De antemão já aviso, que mais para frente, caso vossa gostosura remova um desses aplicativos que era essencial para o sistema sem saber, vai acabar resultando na perda de alguma função importante, ou pior, ao reiniciar o aparelho o sistema pode estar quebrado, lhe obrigando a seguir com uma formatação, e repetir todo o processo novamente.
Download do adb em computadores
Para usar a ferramenta do adb em computadores, basta baixar o pacote chamado SDK platform-tools, disponível através deste link: https://developer.android.com/tools/releases/platform-tools. Por ele, você consegue o download para Windows, Mac e Linux.
Uma vez baixado, basta extrair o arquivo zipado, contendo dentro dele uma pasta chamada platform-tools que basta ser aberta no terminal para se usar o adb.
Download do adb em celulares com Termux.
Para usar a ferramenta do adb diretamente no celular, antes temos que baixar o app Termux, que é um emulador de terminal linux, e já possui o adb em seu repositório. Você encontra o app na Google Play Store, mas novamente recomendo baixar pela F-Droid ou diretamente no Github do projeto.
F-Droid: https://f-droid.org/en/packages/com.termux/
Github: https://github.com/termux/termux-app/releases
Processo de debloat
Antes de iniciarmos, é importante deixar claro que não é para você sair removendo todos os bloatwares de cara sem mais nem menos, afinal alguns deles precisam antes ser substituídos, podem ser essenciais para você para alguma atividade ou função, ou até mesmo são insubstituíveis.
Alguns exemplos de bloatwares que a substituição é necessária antes da remoção, é o Launcher, afinal, é a interface gráfica do sistema, e o teclado, que sem ele só é possível digitar com teclado externo. O Launcher e teclado podem ser substituídos por quaisquer outros, minha recomendação pessoal é por aqueles que respeitam sua privacidade, como Pie Launcher e Simple Laucher, enquanto o teclado pelo OpenBoard e FlorisBoard, todos open-source e disponíveis da F-Droid.
Identifique entre a lista de bloatwares, quais você gosta, precisa ou prefere não substituir, de maneira alguma você é obrigado a remover todos os bloatwares possíveis, modifique seu sistema a seu bel-prazer. O NetGuard lista todos os apps do celular com o nome do pacote, com isso você pode filtrar bem qual deles não remover.
Um exemplo claro de bloatware insubstituível e, portanto, não pode ser removido, é o com.android.mtp, um protocolo onde sua função é auxiliar a comunicação do dispositivo com um computador via USB, mas por algum motivo, tem acesso a rede e se comunica frequentemente com servidores externos. Para esses casos, e melhor solução mesmo é bloquear o acesso a rede desses bloatwares com o NetGuard.
MTP tentando comunicação com servidores externos:
Executando o adb shell
No computador
Faça backup de todos os seus arquivos importantes para algum armazenamento externo, e formate seu celular com o hard reset. Após a formatação, e a ativação da depuração USB, conecte seu aparelho e o pc com o auxílio de um cabo USB. Muito provavelmente seu dispositivo irá apenas começar a carregar, por isso permita a transferência de dados, para que o computador consiga se comunicar normalmente com o celular.
Já no pc, abra a pasta platform-tools dentro do terminal, e execute o seguinte comando:
./adb start-serverO resultado deve ser:
daemon not running; starting now at tcp:5037 daemon started successfully
E caso não apareça nada, execute:
./adb kill-serverE inicie novamente.
Com o adb conectado ao celular, execute:
./adb shellPara poder executar comandos diretamente para o dispositivo. No meu caso, meu celular é um Redmi Note 8 Pro, codinome Begonia.
Logo o resultado deve ser:
begonia:/ $
Caso ocorra algum erro do tipo:
adb: device unauthorized. This adb server’s $ADB_VENDOR_KEYS is not set Try ‘adb kill-server’ if that seems wrong. Otherwise check for a confirmation dialog on your device.
Verifique no celular se apareceu alguma confirmação para autorizar a depuração USB, caso sim, autorize e tente novamente. Caso não apareça nada, execute o kill-server e repita o processo.
No celular
Após realizar o mesmo processo de backup e hard reset citado anteriormente, instale o Termux e, com ele iniciado, execute o comando:
pkg install android-toolsQuando surgir a mensagem “Do you want to continue? [Y/n]”, basta dar enter novamente que já aceita e finaliza a instalação
Agora, vá até as opções de desenvolvedor, e ative a depuração sem fio. Dentro das opções da depuração sem fio, terá uma opção de emparelhamento do dispositivo com um código, que irá informar para você um código em emparelhamento, com um endereço IP e porta, que será usado para a conexão com o Termux.
Para facilitar o processo, recomendo que abra tanto as configurações quanto o Termux ao mesmo tempo, e divida a tela com os dois app’s, como da maneira a seguir:
Para parear o Termux com o dispositivo, não é necessário digitar o ip informado, basta trocar por “localhost”, já a porta e o código de emparelhamento, deve ser digitado exatamente como informado. Execute:
adb pair localhost:porta CódigoDeEmparelhamentoDe acordo com a imagem mostrada anteriormente, o comando ficaria “adb pair localhost:41255 757495”.
Com o dispositivo emparelhado com o Termux, agora basta conectar para conseguir executar os comandos, para isso execute:
adb connect localhost:portaObs: a porta que você deve informar neste comando não é a mesma informada com o código de emparelhamento, e sim a informada na tela principal da depuração sem fio.
Pronto! Termux e adb conectado com sucesso ao dispositivo, agora basta executar normalmente o adb shell:
adb shellRemoção na prática Com o adb shell executado, você está pronto para remover os bloatwares. No meu caso, irei mostrar apenas a remoção de um app (Google Maps), já que o comando é o mesmo para qualquer outro, mudando apenas o nome do pacote.
Dentro do NetGuard, verificando as informações do Google Maps:
Podemos ver que mesmo fora de uso, e com a localização do dispositivo desativado, o app está tentando loucamente se comunicar com servidores externos, e informar sabe-se lá que peste. Mas sem novidades até aqui, o mais importante é que podemos ver que o nome do pacote do Google Maps é com.google.android.apps.maps, e para o remover do celular, basta executar:
pm uninstall –user 0 com.google.android.apps.mapsE pronto, bloatware removido! Agora basta repetir o processo para o resto dos bloatwares, trocando apenas o nome do pacote.
Para acelerar o processo, você pode já criar uma lista do bloco de notas com os comandos, e quando colar no terminal, irá executar um atrás do outro.
Exemplo de lista:
Caso a donzela tenha removido alguma coisa sem querer, também é possível recuperar o pacote com o comando:
cmd package install-existing nome.do.pacotePós-debloat
Após limpar o máximo possível o seu sistema, reinicie o aparelho, caso entre no como recovery e não seja possível dar reboot, significa que você removeu algum app “essencial” para o sistema, e terá que formatar o aparelho e repetir toda a remoção novamente, desta vez removendo poucos bloatwares de uma vez, e reiniciando o aparelho até descobrir qual deles não pode ser removido. Sim, dá trabalho… quem mandou querer privacidade?
Caso o aparelho reinicie normalmente após a remoção, parabéns, agora basta usar seu celular como bem entender! Mantenha o NetGuard sempre executando e os bloatwares que não foram possíveis remover não irão se comunicar com servidores externos, passe a usar apps open source da F-Droid e instale outros apps através da Aurora Store ao invés da Google Play Store.
Referências: Caso você seja um Australopithecus e tenha achado este guia difícil, eis uma videoaula (3:14:40) do Anderson do canal Ciberdef, realizando todo o processo: http://odysee.com/@zai:5/Como-remover-at%C3%A9-200-APLICATIVOS-que-colocam-a-sua-PRIVACIDADE-E-SEGURAN%C3%87A-em-risco.:4?lid=6d50f40314eee7e2f218536d9e5d300290931d23
Pdf’s do Anderson citados na videoaula: créditos ao anon6837264 http://eternalcbrzpicytj4zyguygpmkjlkddxob7tptlr25cdipe5svyqoqd.onion/file/3863a834d29285d397b73a4af6fb1bbe67c888d72d30/t-05e63192d02ffd.pdf
Processo de instalação do Termux e adb no celular: https://youtu.be/APolZrPHSms
-
 @ 35f80bda:406855c0
2025-04-16 03:11:46
@ 35f80bda:406855c0
2025-04-16 03:11:46O Bitcoin Core 29.0 foi oficialmente lançado e traz diversas melhorias técnicas voltadas para desenvolvedores, operadores de full nodes e a comunidade Bitcoin mais técnica. Desde mudanças na camada de rede até a atualização do sistema de build, este release é um passo significativo na modernização do ecossistema.
Se você roda um full node, desenvolve software que interage com o Core via RPC ou apenas quer estar por dentro das novidades técnicas, este artigo é para você.
Alterações na Rede e no P2P
Suporte ao UPnP Removido O UPnP foi totalmente desativado por razões de segurança e manutenção. Agora, a recomendação é utilizar a flag -natpmp, que conta com uma implementação interna de PCP e NAT-PMP. Mais seguro e mais leve.
Melhorias no Suporte Tor A porta onion agora é derivada da flag -port, permitindo múltiplos nós Tor na mesma máquina — ótimo para quem opera ambientes de teste ou múltiplos peers.
Transações Órfãs com Propagação Aprimorada O node agora tenta buscar os parents de transações órfãs consultando todos os peers que anunciaram a transação. Isso ajuda a preencher lacunas na mempool de forma mais eficiente.
Mempool e Política de Mineração
Ephemeral Dust Introdução de um novo conceito: ephemeral dust, que permite uma saída "dust" gratuita em uma transação desde que ela seja gasta dentro do mesmo pacote. Pode ser útil para otimizações de fees.
Correção no Peso Reservado de Blocos Bug que causava duplicação de peso reservado foi corrigido. Agora existe a flag -blockreservedweight, com limite mínimo de 2000 WU.
RPCs e REST mais robustos
- testmempoolaccept agora fornece o campo reject-details.
- submitblock preserva blocos duplicados mesmo que tenham sido podados.
- getblock, getblockheader e getblockchaininfo agora incluem o campo nBits (alvo de dificuldade).
- Novo RPC: getdescriptoractivity, que permite ver atividades de descritores em intervalos de blocos.
- APIs REST agora retornam nBits também no campo target.
Sistema de Build Modernizado
Uma das mudanças mais bem-vindas: o Bitcoin Core agora usa CMake em vez de Autotools como padrão de build. Isso facilita integração com IDEs, CI/CD pipelines modernos e personalização do build.
Outras Atualizações Importantes
- -dbcache teve limite máximo reduzido para lidar com o crescimento do conjunto UTXO.
- O comportamento Full Replace-by-Fee (RBF) agora é padrão. A flag -mempoolfullrbf foi removida.
- Aumentaram os valores padrão de -rpcthreads e -rpcworkqueue para lidar com maior paralelismo.
Ferramentas Novas
Uma nova ferramenta chamada utxo_to_sqlite.py converte snapshots compactos do conjunto UTXO para SQLite3. Excelente para quem quer auditar ou explorar o estado da blockchain com ferramentas padrão de banco de dados.
Limpeza de Dependências
As bibliotecas externas MiniUPnPc e libnatpmp foram removidas, substituídas por implementações internas. Menos dependências = manutenção mais fácil e menos riscos.
Como atualizar?
- Pare o seu nó atual com segurança.
- Instale a nova versão.
- Verifique configurações como -dbcache, -blockreservedweight e o comportamento RBF.
- Consulte os logs com atenção nas primeiras execuções para validar o novo comportamento.
Conclusão
O Bitcoin Core 29.0 representa um passo firme em direção a uma base de código mais moderna, segura e modular. Para quem mantém nós, desenvolve soluções sobre o Core ou audita a rede, é uma atualização que vale a pena testar e entender a fundo.
Já testou a nova versão? Notou impactos nas suas aplicações ou infraestrutura?
Referências
-
 @ 79dff8f8:946764e3
2025-04-29 19:19:34
@ 79dff8f8:946764e3
2025-04-29 19:19:34Hello world
-
 @ 91bea5cd:1df4451c
2025-04-15 06:27:28
@ 91bea5cd:1df4451c
2025-04-15 06:27:28Básico
bash lsblk # Lista todos os diretorios montados.Para criar o sistema de arquivos:
bash mkfs.btrfs -L "ThePool" -f /dev/sdxCriando um subvolume:
bash btrfs subvolume create SubVolMontando Sistema de Arquivos:
bash mount -o compress=zlib,subvol=SubVol,autodefrag /dev/sdx /mntLista os discos formatados no diretório:
bash btrfs filesystem show /mntAdiciona novo disco ao subvolume:
bash btrfs device add -f /dev/sdy /mntLista novamente os discos do subvolume:
bash btrfs filesystem show /mntExibe uso dos discos do subvolume:
bash btrfs filesystem df /mntBalancea os dados entre os discos sobre raid1:
bash btrfs filesystem balance start -dconvert=raid1 -mconvert=raid1 /mntScrub é uma passagem por todos os dados e metadados do sistema de arquivos e verifica as somas de verificação. Se uma cópia válida estiver disponível (perfis de grupo de blocos replicados), a danificada será reparada. Todas as cópias dos perfis replicados são validadas.
iniciar o processo de depuração :
bash btrfs scrub start /mntver o status do processo de depuração Btrfs em execução:
bash btrfs scrub status /mntver o status do scrub Btrfs para cada um dos dispositivos
bash btrfs scrub status -d / data btrfs scrub cancel / dataPara retomar o processo de depuração do Btrfs que você cancelou ou pausou:
btrfs scrub resume / data
Listando os subvolumes:
bash btrfs subvolume list /ReportsCriando um instantâneo dos subvolumes:
Aqui, estamos criando um instantâneo de leitura e gravação chamado snap de marketing do subvolume de marketing.
bash btrfs subvolume snapshot /Reports/marketing /Reports/marketing-snapAlém disso, você pode criar um instantâneo somente leitura usando o sinalizador -r conforme mostrado. O marketing-rosnap é um instantâneo somente leitura do subvolume de marketing
bash btrfs subvolume snapshot -r /Reports/marketing /Reports/marketing-rosnapForçar a sincronização do sistema de arquivos usando o utilitário 'sync'
Para forçar a sincronização do sistema de arquivos, invoque a opção de sincronização conforme mostrado. Observe que o sistema de arquivos já deve estar montado para que o processo de sincronização continue com sucesso.
bash btrfs filsystem sync /ReportsPara excluir o dispositivo do sistema de arquivos, use o comando device delete conforme mostrado.
bash btrfs device delete /dev/sdc /ReportsPara sondar o status de um scrub, use o comando scrub status com a opção -dR .
bash btrfs scrub status -dR / RelatóriosPara cancelar a execução do scrub, use o comando scrub cancel .
bash $ sudo btrfs scrub cancel / ReportsPara retomar ou continuar com uma depuração interrompida anteriormente, execute o comando de cancelamento de depuração
bash sudo btrfs scrub resume /Reportsmostra o uso do dispositivo de armazenamento:
btrfs filesystem usage /data
Para distribuir os dados, metadados e dados do sistema em todos os dispositivos de armazenamento do RAID (incluindo o dispositivo de armazenamento recém-adicionado) montados no diretório /data , execute o seguinte comando:
sudo btrfs balance start --full-balance /data
Pode demorar um pouco para espalhar os dados, metadados e dados do sistema em todos os dispositivos de armazenamento do RAID se ele contiver muitos dados.
Opções importantes de montagem Btrfs
Nesta seção, vou explicar algumas das importantes opções de montagem do Btrfs. Então vamos começar.
As opções de montagem Btrfs mais importantes são:
**1. acl e noacl
**ACL gerencia permissões de usuários e grupos para os arquivos/diretórios do sistema de arquivos Btrfs.
A opção de montagem acl Btrfs habilita ACL. Para desabilitar a ACL, você pode usar a opção de montagem noacl .
Por padrão, a ACL está habilitada. Portanto, o sistema de arquivos Btrfs usa a opção de montagem acl por padrão.
**2. autodefrag e noautodefrag
**Desfragmentar um sistema de arquivos Btrfs melhorará o desempenho do sistema de arquivos reduzindo a fragmentação de dados.
A opção de montagem autodefrag permite a desfragmentação automática do sistema de arquivos Btrfs.
A opção de montagem noautodefrag desativa a desfragmentação automática do sistema de arquivos Btrfs.
Por padrão, a desfragmentação automática está desabilitada. Portanto, o sistema de arquivos Btrfs usa a opção de montagem noautodefrag por padrão.
**3. compactar e compactar-forçar
**Controla a compactação de dados no nível do sistema de arquivos do sistema de arquivos Btrfs.
A opção compactar compacta apenas os arquivos que valem a pena compactar (se compactar o arquivo economizar espaço em disco).
A opção compress-force compacta todos os arquivos do sistema de arquivos Btrfs, mesmo que a compactação do arquivo aumente seu tamanho.
O sistema de arquivos Btrfs suporta muitos algoritmos de compactação e cada um dos algoritmos de compactação possui diferentes níveis de compactação.
Os algoritmos de compactação suportados pelo Btrfs são: lzo , zlib (nível 1 a 9) e zstd (nível 1 a 15).
Você pode especificar qual algoritmo de compactação usar para o sistema de arquivos Btrfs com uma das seguintes opções de montagem:
- compress=algoritmo:nível
- compress-force=algoritmo:nível
Para obter mais informações, consulte meu artigo Como habilitar a compactação do sistema de arquivos Btrfs .
**4. subvol e subvolid
**Estas opções de montagem são usadas para montar separadamente um subvolume específico de um sistema de arquivos Btrfs.
A opção de montagem subvol é usada para montar o subvolume de um sistema de arquivos Btrfs usando seu caminho relativo.
A opção de montagem subvolid é usada para montar o subvolume de um sistema de arquivos Btrfs usando o ID do subvolume.
Para obter mais informações, consulte meu artigo Como criar e montar subvolumes Btrfs .
**5. dispositivo
A opção de montagem de dispositivo** é usada no sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs.
Em alguns casos, o sistema operacional pode falhar ao detectar os dispositivos de armazenamento usados em um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs. Nesses casos, você pode usar a opção de montagem do dispositivo para especificar os dispositivos que deseja usar para o sistema de arquivos de vários dispositivos Btrfs ou RAID.
Você pode usar a opção de montagem de dispositivo várias vezes para carregar diferentes dispositivos de armazenamento para o sistema de arquivos de vários dispositivos Btrfs ou RAID.
Você pode usar o nome do dispositivo (ou seja, sdb , sdc ) ou UUID , UUID_SUB ou PARTUUID do dispositivo de armazenamento com a opção de montagem do dispositivo para identificar o dispositivo de armazenamento.
Por exemplo,
- dispositivo=/dev/sdb
- dispositivo=/dev/sdb,dispositivo=/dev/sdc
- dispositivo=UUID_SUB=490a263d-eb9a-4558-931e-998d4d080c5d
- device=UUID_SUB=490a263d-eb9a-4558-931e-998d4d080c5d,device=UUID_SUB=f7ce4875-0874-436a-b47d-3edef66d3424
**6. degraded
A opção de montagem degradada** permite que um RAID Btrfs seja montado com menos dispositivos de armazenamento do que o perfil RAID requer.
Por exemplo, o perfil raid1 requer a presença de 2 dispositivos de armazenamento. Se um dos dispositivos de armazenamento não estiver disponível em qualquer caso, você usa a opção de montagem degradada para montar o RAID mesmo que 1 de 2 dispositivos de armazenamento esteja disponível.
**7. commit
A opção commit** mount é usada para definir o intervalo (em segundos) dentro do qual os dados serão gravados no dispositivo de armazenamento.
O padrão é definido como 30 segundos.
Para definir o intervalo de confirmação para 15 segundos, você pode usar a opção de montagem commit=15 (digamos).
**8. ssd e nossd
A opção de montagem ssd** informa ao sistema de arquivos Btrfs que o sistema de arquivos está usando um dispositivo de armazenamento SSD, e o sistema de arquivos Btrfs faz a otimização SSD necessária.
A opção de montagem nossd desativa a otimização do SSD.
O sistema de arquivos Btrfs detecta automaticamente se um SSD é usado para o sistema de arquivos Btrfs. Se um SSD for usado, a opção de montagem de SSD será habilitada. Caso contrário, a opção de montagem nossd é habilitada.
**9. ssd_spread e nossd_spread
A opção de montagem ssd_spread** tenta alocar grandes blocos contínuos de espaço não utilizado do SSD. Esse recurso melhora o desempenho de SSDs de baixo custo (baratos).
A opção de montagem nossd_spread desativa o recurso ssd_spread .
O sistema de arquivos Btrfs detecta automaticamente se um SSD é usado para o sistema de arquivos Btrfs. Se um SSD for usado, a opção de montagem ssd_spread será habilitada. Caso contrário, a opção de montagem nossd_spread é habilitada.
**10. descarte e nodiscard
Se você estiver usando um SSD que suporte TRIM enfileirado assíncrono (SATA rev3.1), a opção de montagem de descarte** permitirá o descarte de blocos de arquivos liberados. Isso melhorará o desempenho do SSD.
Se o SSD não suportar TRIM enfileirado assíncrono, a opção de montagem de descarte prejudicará o desempenho do SSD. Nesse caso, a opção de montagem nodiscard deve ser usada.
Por padrão, a opção de montagem nodiscard é usada.
**11. norecovery
Se a opção de montagem norecovery** for usada, o sistema de arquivos Btrfs não tentará executar a operação de recuperação de dados no momento da montagem.
**12. usebackuproot e nousebackuproot
Se a opção de montagem usebackuproot for usada, o sistema de arquivos Btrfs tentará recuperar qualquer raiz de árvore ruim/corrompida no momento da montagem. O sistema de arquivos Btrfs pode armazenar várias raízes de árvore no sistema de arquivos. A opção de montagem usebackuproot** procurará uma boa raiz de árvore e usará a primeira boa que encontrar.
A opção de montagem nousebackuproot não verificará ou recuperará raízes de árvore inválidas/corrompidas no momento da montagem. Este é o comportamento padrão do sistema de arquivos Btrfs.
**13. space_cache, space_cache=version, nospace_cache e clear_cache
A opção de montagem space_cache** é usada para controlar o cache de espaço livre. O cache de espaço livre é usado para melhorar o desempenho da leitura do espaço livre do grupo de blocos do sistema de arquivos Btrfs na memória (RAM).
O sistema de arquivos Btrfs suporta 2 versões do cache de espaço livre: v1 (padrão) e v2
O mecanismo de cache de espaço livre v2 melhora o desempenho de sistemas de arquivos grandes (tamanho de vários terabytes).
Você pode usar a opção de montagem space_cache=v1 para definir a v1 do cache de espaço livre e a opção de montagem space_cache=v2 para definir a v2 do cache de espaço livre.
A opção de montagem clear_cache é usada para limpar o cache de espaço livre.
Quando o cache de espaço livre v2 é criado, o cache deve ser limpo para criar um cache de espaço livre v1 .
Portanto, para usar o cache de espaço livre v1 após a criação do cache de espaço livre v2 , as opções de montagem clear_cache e space_cache=v1 devem ser combinadas: clear_cache,space_cache=v1
A opção de montagem nospace_cache é usada para desabilitar o cache de espaço livre.
Para desabilitar o cache de espaço livre após a criação do cache v1 ou v2 , as opções de montagem nospace_cache e clear_cache devem ser combinadas: clear_cache,nosapce_cache
**14. skip_balance
Por padrão, a operação de balanceamento interrompida/pausada de um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs será retomada automaticamente assim que o sistema de arquivos Btrfs for montado. Para desabilitar a retomada automática da operação de equilíbrio interrompido/pausado em um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs, você pode usar a opção de montagem skip_balance .**
**15. datacow e nodatacow
A opção datacow** mount habilita o recurso Copy-on-Write (CoW) do sistema de arquivos Btrfs. É o comportamento padrão.
Se você deseja desabilitar o recurso Copy-on-Write (CoW) do sistema de arquivos Btrfs para os arquivos recém-criados, monte o sistema de arquivos Btrfs com a opção de montagem nodatacow .
**16. datasum e nodatasum
A opção datasum** mount habilita a soma de verificação de dados para arquivos recém-criados do sistema de arquivos Btrfs. Este é o comportamento padrão.
Se você não quiser que o sistema de arquivos Btrfs faça a soma de verificação dos dados dos arquivos recém-criados, monte o sistema de arquivos Btrfs com a opção de montagem nodatasum .
Perfis Btrfs
Um perfil Btrfs é usado para informar ao sistema de arquivos Btrfs quantas cópias dos dados/metadados devem ser mantidas e quais níveis de RAID devem ser usados para os dados/metadados. O sistema de arquivos Btrfs contém muitos perfis. Entendê-los o ajudará a configurar um RAID Btrfs da maneira que você deseja.
Os perfis Btrfs disponíveis são os seguintes:
single : Se o perfil único for usado para os dados/metadados, apenas uma cópia dos dados/metadados será armazenada no sistema de arquivos, mesmo se você adicionar vários dispositivos de armazenamento ao sistema de arquivos. Assim, 100% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser utilizado.
dup : Se o perfil dup for usado para os dados/metadados, cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos manterá duas cópias dos dados/metadados. Assim, 50% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser utilizado.
raid0 : No perfil raid0 , os dados/metadados serão divididos igualmente em todos os dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, não haverá dados/metadados redundantes (duplicados). Assim, 100% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser usado. Se, em qualquer caso, um dos dispositivos de armazenamento falhar, todo o sistema de arquivos será corrompido. Você precisará de pelo menos dois dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid0 .
raid1 : No perfil raid1 , duas cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a uma falha de unidade. Mas você pode usar apenas 50% do espaço total em disco. Você precisará de pelo menos dois dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1 .
raid1c3 : No perfil raid1c3 , três cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a duas falhas de unidade, mas você pode usar apenas 33% do espaço total em disco. Você precisará de pelo menos três dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1c3 .
raid1c4 : No perfil raid1c4 , quatro cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a três falhas de unidade, mas você pode usar apenas 25% do espaço total em disco. Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1c4 .
raid10 : No perfil raid10 , duas cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos, como no perfil raid1 . Além disso, os dados/metadados serão divididos entre os dispositivos de armazenamento, como no perfil raid0 .
O perfil raid10 é um híbrido dos perfis raid1 e raid0 . Alguns dos dispositivos de armazenamento formam arrays raid1 e alguns desses arrays raid1 são usados para formar um array raid0 . Em uma configuração raid10 , o sistema de arquivos pode sobreviver a uma única falha de unidade em cada uma das matrizes raid1 .
Você pode usar 50% do espaço total em disco na configuração raid10 . Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid10 .
raid5 : No perfil raid5 , uma cópia dos dados/metadados será dividida entre os dispositivos de armazenamento. Uma única paridade será calculada e distribuída entre os dispositivos de armazenamento do array RAID.
Em uma configuração raid5 , o sistema de arquivos pode sobreviver a uma única falha de unidade. Se uma unidade falhar, você pode adicionar uma nova unidade ao sistema de arquivos e os dados perdidos serão calculados a partir da paridade distribuída das unidades em execução.
Você pode usar 1 00x(N-1)/N % do total de espaços em disco na configuração raid5 . Aqui, N é o número de dispositivos de armazenamento adicionados ao sistema de arquivos. Você precisará de pelo menos três dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid5 .
raid6 : No perfil raid6 , uma cópia dos dados/metadados será dividida entre os dispositivos de armazenamento. Duas paridades serão calculadas e distribuídas entre os dispositivos de armazenamento do array RAID.
Em uma configuração raid6 , o sistema de arquivos pode sobreviver a duas falhas de unidade ao mesmo tempo. Se uma unidade falhar, você poderá adicionar uma nova unidade ao sistema de arquivos e os dados perdidos serão calculados a partir das duas paridades distribuídas das unidades em execução.
Você pode usar 100x(N-2)/N % do espaço total em disco na configuração raid6 . Aqui, N é o número de dispositivos de armazenamento adicionados ao sistema de arquivos. Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid6 .
-
 @ 866e0139:6a9334e5
2025-04-29 18:40:31
@ 866e0139:6a9334e5
2025-04-29 18:40:31Autor: Thomas Eisinger. Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier.**
Die neuesten Artikel der Friedenstaube gibt es jetzt auch im eigenen Friedenstaube-Telegram-Kanal.
Vor Kurzem war ich bei einem «Ecstatic Dance» (mehr dazu z. B. hier) dabei. Wer das noch nicht kennt: es lohnt sich! Irgendwann in diesem speziellen Space bekam ich einen Gedanken - oder er kam von irgendwo zu mir: die Vorstellung, dass niemand in meiner Reihe von Eltern, Großeltern, Ahnen je an so etwas hätte teilnehmen können. Einmal, weil es das damals nicht gab. Zum Zweiten, weil ihr Mind niemals für so etwas offen gewesen wäre, gar nicht sein konnte. Sie alle waren einfache Menschen, die genug damit zu tun hatten für das Überleben der eigenen Familie zu sorgen. Urlaub war ein Fremdwort, intellektuelle Faxen gab es ganz sicher keine. Diese meine Vorstellung erschuf ein inneres Bild in mir: ich sah meine beiden Großmütter wild und lebensfroh durch den Raum tanzen! (Übrigens wurden beide 95 Jahre alt, trotz zwei Kriegen, Währungsreform, Hunger und ohne jemals Sport getrieben oder Ernährungsratgeber gelesen zu haben. Dies nur am Rande).
Ich erfreute mich an dem Bild der tanzenden Großmütter, konnte mich eines breiten Grinsens nicht erwehren. Nach dieser Freude wechselte mein Gefühl jäh zu Dankbarkeit. Dafür, in dieser wunderbaren Zeit leben zu dürfen. In der so viel mehr möglich ist als es jemals war. Das enge Korsett, das die Gesellschaft seit Jahrtausenden jedem auferlegt hatte, ist so viel weiter geworden. Nur, wenn man es selbst annehmen möchte (oder zumindest meint, dies tun zu müssen) kann es noch Macht ausüben. Sonst nicht. Die persönliche Freiheit ist größer als jemals zuvor, wenn man sie mit den Hundert Generationen vor uns vergleicht. Natürlich ist aktuell «the Trend not our friend», aber wir haben die Wahl, den Zeitmaßstab selbst anzulegen. 10 Jahre, 100 oder 200 Jahre? Lass es vor Deinem inneren Auge erscheinen ...
Die innere Freiheit ist größer als in all den Zeiten vor meiner Generation (Boomer). Millionen Menschen haben Meditationserfahrung, einige können sich mit Informationsfeldern (jenseits der rechtgläubigen Physik) verbinden und darüber sprechen, ohne dass sie verbrannt werden. Man muss keiner offiziellen Religion mehr folgen, um Verbindung mit dem Höheren zu erlangen. Im Gegenteil, die Ablösung von den Amtskirchen erleichtert dies für viele sogar. Wie auch immer, der eigenen Wahl stehen weder Priester noch Eltern oder starre Konventionen entgegen. Anders als vor 100 oder 200 Jahren. Just do it!
Es geht noch weiter. Wie dankbar bin ich, dass ich in dieser Zeit leben darf. Dass trotz des Leides meiner in ziemlicher Armut lebender Großeltern ihr Wille zum Überleben stärker war: nur deshalb kann ich hier sein. Ich darf all diese Vorzüge genießen, obwohl ich viel weniger hart arbeiten muss(te) als sie. Auch wurde mein Haus nicht ausgebombt und ich musste nie in den Krieg ziehen. Meine beiden Großväter ereilte dieses Schicksal. Ob mein Sohn diesem Schicksal entrinnt?
Wir sollen wieder kriegstüchtig werden. Unfassbar. Doch damit will ich diese Betrachtung nicht enden lassen. Denn nur wenn wir auch begreifen, wie gut es uns allen geht, trotz dieser Regierung, trotz Massenpropaganda, trotz dauernder medialer Panikmache: erst, wenn wir das Leben wirklich lieben, werden wir wissen, wofür es sich wirklich lohnt zu kämpfen. Nicht mit Waffe in der Hand, sondern mit Herz und Verstand.
LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt.
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: friedenstaube@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ 91bea5cd:1df4451c
2025-04-15 06:23:35
@ 91bea5cd:1df4451c
2025-04-15 06:23:35Um bom gerenciamento de senhas deve ser simples e seguir a filosofia do Unix. Organizado em hierarquia e fácil de passar de um computador para outro.
E por isso não é recomendável o uso de aplicativos de terceiros que tenham acesso a suas chaves(senhas) em seus servidores, tampouco as opções nativas dos navegadores, que também pertencem a grandes empresas que fazem um grande esforço para ter acesso a nossas informações.
Recomendação
- pass
- Qtpass (gerenciador gráfico)
Com ele seus dados são criptografados usando sua chave gpg e salvo em arquivos organizados por pastas de forma hierárquica, podendo ser integrado a um serviço git de sua escolha ou copiado facilmente de um local para outro.
Uso
O seu uso é bem simples.
Configuração:
pass git initPara ver:
pass Email/example.comCopiar para área de transferência (exige xclip):
pass -c Email/example.comPara inserir:
pass insert Email/example0.comPara inserir e gerar senha:
pass generate Email/example1.comPara inserir e gerar senha sem símbolos:
pass generate --no-symbols Email/example1.comPara inserir, gerar senha e copiar para área de transferência :
pass generate -c Email/example1.comPara remover:
pass rm Email/example.com -
 @ 3c389c8f:7a2eff7f
2025-04-29 18:38:46
@ 3c389c8f:7a2eff7f
2025-04-29 18:38:46Let go of the algorithms and truly discover what it means to explore. Social media used to mean something. Once upon a time, it was a way to stay connected to friends, family, and colleagues over things we enjoy. We could share, laugh, and learn. Over time, it has devolved into cheap entertainment at the cost of our privacy. Our relationships and interests have been shoved into a corner in order to make room for "suggested posts" and "for you" content designed to evaluate our attention for advertising purposes. We've lost what it means to truly connect, and we've lost what it means to explore our curiosities.
Enter Nostr. A protocol designed to resist authoritative censorship, just happens to fix a whole lot of other problems, too. By removing the central authority, Nostr offers its users complete control of what we feed our minds. How do we break our algorithm dependency to find better content and better relationships again? We explore and discover:
The Chronological Life.
The existence of time may be debatable but our dependence on our perception of it is not. We live our lives chronologically. Why do our online lives need to be any different? There is no real reason, other than we've just gotten used to being engulfed by whatever the black box wants us to see. When we remove the algorithms, we find that online information flows just as it would in our daily lives. Important events get talked about by many people, over a long period of time. Things of less relevance fade. We see the rhythm of life reflected in our feed. This is an organic human experience transferred to the digital world. We depend on the people we know and the sources we trust to keep us informed about what really matters. We have fun, we move on. Nearly every Nostr social client brings this experience front and center through the traditional follow feed. Many use replies as a way to show you what is worth talking about for more than a hot minute. Its what old social media gave us, then took away. Nostr gives it back. It's not the only way to enjoy Nostr, though, so let's continue.
"The Human Animal Differs From the Lesser Primates in His Passion for Lists"
Who doesn't love lists? (besides maybe to-do lists.) List functionality on Nostr is a powerful way to curate your feeds. You can make lists of artists, vendors, friends, or whatever you want. They can be public or private. You can subscribe to other people's public lists too. Make one to share with your friends. Many clients have list support and management. Amethyst, Nostur, Voyage, and Nostrudel are a few that come to mind. Nostr.band and Listr.lol offer in depth list management. Some clients even support lists for specific notes so that you can curate a feed by topic or aesthetic to share with your friends.
Being John Malcovich.
Everyone has a different view of Nostr. Do you want to see what someone else is seeing? Sign in with any npub to get a different perspective. You might find profiles and content that you didn't know existed before. Some clients integrate variations of this feature right into their apps, so you don't have to log out of your account in order to step through that tiny door.
DV-what? DVM.
Data Vending Machines. These fancy little things are AIs tasked with a simple job: to find content for you. Most of these feeds are free, though some more personalized ones require a small fee. Many DVM services are stand-alone apps, like Vendata and Noogle . These clever Nostr clients will let you do a lot more than just create feeds to browse notes. Explore if you wish. A few social clients have DVMs integrated, too, so if you see "discovery" or similar term on a tab, be sure to check it out.
Relays, Man. Relays.
It's right there in the name. Nostr- notes and other stuff transmitted by RELAY. Specialized relays exist for subjects, news, communities, personal spaces, content creators, cats... there's even a relay where everyone just says "Good Morning" to each other. Find a client that lets you browse a relay's contents, and enjoy the purest form of content discovery on Nostr. Unearthing these relays is getting better and better every day. Right now there are relay browsing capabilities in quite a few clients, like Coracle, Relay Tools, Jumble and Nostur.
The Algo Relay.
Maybe you've been busy and missed a lot. Maybe you are a sane person who rarely uses social media. Hook up with a personalized algorithm relay to catch you up on all the things you've missed. This is skirting the sharp edges of Nostr relay development, so keep in mind that not many implementations yet exist. Algo relay currently aims to bring the feel-good vibe of your chronological feed to an algorithmic feed, freeing up your time but letting you stay up with what 's going on in your social circles.
Trendy Trends.
A few clients, relays, and DVM's have developed various Trending feeds. Catch up on what's popular across a wider view of the Nostr ecosystem. If trends are your thing, be sure to check them out.
Now that you're equipped with the tools to explore Nostr, its time to go discover some great content and find your people. Feed your curiosity.
-
 @ 91bea5cd:1df4451c
2025-04-15 06:19:19
@ 91bea5cd:1df4451c
2025-04-15 06:19:19O que é Tahoe-LAFS?
Bem-vindo ao Tahoe-LAFS_, o primeiro sistema de armazenamento descentralizado com
- Segurança independente do provedor * .
Tahoe-LAFS é um sistema que ajuda você a armazenar arquivos. Você executa um cliente Programa no seu computador, que fala com um ou mais servidores de armazenamento em outros computadores. Quando você diz ao seu cliente para armazenar um arquivo, ele irá criptografar isso Arquivo, codifique-o em múltiplas peças, depois espalhe essas peças entre Vários servidores. As peças são todas criptografadas e protegidas contra Modificações. Mais tarde, quando você pede ao seu cliente para recuperar o arquivo, ele irá Encontre as peças necessárias, verifique se elas não foram corrompidas e remontadas Eles, e descriptografar o resultado.
O cliente cria mais peças (ou "compartilhamentos") do que acabará por precisar, então Mesmo que alguns servidores falhem, você ainda pode recuperar seus dados. Corrompido Os compartilhamentos são detectados e ignorados, de modo que o sistema pode tolerar o lado do servidor Erros no disco rígido. Todos os arquivos são criptografados (com uma chave exclusiva) antes Uploading, então mesmo um operador de servidor mal-intencionado não pode ler seus dados. o A única coisa que você pede aos servidores é que eles podem (geralmente) fornecer o Compartilha quando você os solicita: você não está confiando sobre eles para Confidencialidade, integridade ou disponibilidade absoluta.
O que é "segurança independente do provedor"?
Todo vendedor de serviços de armazenamento na nuvem irá dizer-lhe que o seu serviço é "seguro". Mas o que eles significam com isso é algo fundamentalmente diferente Do que queremos dizer. O que eles significam por "seguro" é que depois de ter dado Eles o poder de ler e modificar seus dados, eles tentam muito difícil de não deixar Esse poder seja abusado. Isso acaba por ser difícil! Insetos, Configurações incorretas ou erro do operador podem acidentalmente expor seus dados para Outro cliente ou para o público, ou pode corromper seus dados. Criminosos Ganho rotineiramente de acesso ilícito a servidores corporativos. Ainda mais insidioso é O fato de que os próprios funcionários às vezes violam a privacidade do cliente De negligência, avareza ou mera curiosidade. O mais consciencioso de Esses prestadores de serviços gastam consideráveis esforços e despesas tentando Mitigar esses riscos.
O que queremos dizer com "segurança" é algo diferente. * O provedor de serviços Nunca tem a capacidade de ler ou modificar seus dados em primeiro lugar: nunca. * Se você usa Tahoe-LAFS, então todas as ameaças descritas acima não são questões para você. Não só é fácil e barato para o provedor de serviços Manter a segurança de seus dados, mas na verdade eles não podem violar sua Segurança se eles tentaram. Isto é o que chamamos de * independente do fornecedor segurança*.
Esta garantia está integrada naturalmente no sistema de armazenamento Tahoe-LAFS e Não exige que você execute um passo de pré-criptografia manual ou uma chave complicada gestão. (Afinal, ter que fazer operações manuais pesadas quando Armazenar ou acessar seus dados anularia um dos principais benefícios de Usando armazenamento em nuvem em primeiro lugar: conveniência.)
Veja como funciona:
Uma "grade de armazenamento" é constituída por uma série de servidores de armazenamento. Um servidor de armazenamento Tem armazenamento direto em anexo (tipicamente um ou mais discos rígidos). Um "gateway" Se comunica com os nós de armazenamento e os usa para fornecer acesso ao Rede sobre protocolos como HTTP (S), SFTP ou FTP.
Observe que você pode encontrar "cliente" usado para se referir aos nós do gateway (que atuam como Um cliente para servidores de armazenamento) e também para processos ou programas que se conectam a Um nó de gateway e operações de execução na grade - por exemplo, uma CLI Comando, navegador da Web, cliente SFTP ou cliente FTP.
Os usuários não contam com servidores de armazenamento para fornecer * confidencialidade * nem
- Integridade * para seus dados - em vez disso, todos os dados são criptografados e Integridade verificada pelo gateway, para que os servidores não possam ler nem Modifique o conteúdo dos arquivos.
Os usuários dependem de servidores de armazenamento para * disponibilidade *. O texto cifrado é Codificado por apagamento em partes
Ndistribuídas em pelo menosHdistintas Servidores de armazenamento (o valor padrão paraNé 10 e paraHé 7) então Que pode ser recuperado de qualquerKdesses servidores (o padrão O valor deKé 3). Portanto, apenas a falha doH-K + 1(com o Padrões, 5) servidores podem tornar os dados indisponíveis.No modo de implantação típico, cada usuário executa seu próprio gateway sozinho máquina. Desta forma, ela confia em sua própria máquina para a confidencialidade e Integridade dos dados.
Um modo de implantação alternativo é que o gateway é executado em uma máquina remota e O usuário se conecta ao HTTPS ou SFTP. Isso significa que o operador de O gateway pode visualizar e modificar os dados do usuário (o usuário * depende de * o Gateway para confidencialidade e integridade), mas a vantagem é que a O usuário pode acessar a grade Tahoe-LAFS com um cliente que não possui o Software de gateway instalado, como um quiosque de internet ou celular.
Controle de acesso
Existem dois tipos de arquivos: imutáveis e mutáveis. Quando você carrega um arquivo Para a grade de armazenamento, você pode escolher o tipo de arquivo que será no grade. Os arquivos imutáveis não podem ser modificados quando foram carregados. UMA O arquivo mutable pode ser modificado por alguém com acesso de leitura e gravação. Um usuário Pode ter acesso de leitura e gravação a um arquivo mutable ou acesso somente leitura, ou não Acesso a ele.
Um usuário que tenha acesso de leitura e gravação a um arquivo mutable ou diretório pode dar Outro acesso de leitura e gravação do usuário a esse arquivo ou diretório, ou eles podem dar Acesso somente leitura para esse arquivo ou diretório. Um usuário com acesso somente leitura Para um arquivo ou diretório pode dar acesso a outro usuário somente leitura.
Ao vincular um arquivo ou diretório a um diretório pai, você pode usar um Link de leitura-escrita ou um link somente de leitura. Se você usar um link de leitura e gravação, então Qualquer pessoa que tenha acesso de leitura e gravação ao diretório pai pode obter leitura-escrita Acesso à criança e qualquer pessoa que tenha acesso somente leitura ao pai O diretório pode obter acesso somente leitura à criança. Se você usar uma leitura somente Link, qualquer pessoa que tenha lido-escrito ou acesso somente leitura ao pai O diretório pode obter acesso somente leitura à criança.
================================================== ==== Usando Tahoe-LAFS com uma rede anônima: Tor, I2P ================================================== ====
. `Visão geral '
. `Casos de uso '
.
Software Dependencies_#.
Tor#.I2P. `Configuração de conexão '
. `Configuração de Anonimato '
#.
Anonimato do cliente ' #.Anonimato de servidor, configuração manual ' #. `Anonimato de servidor, configuração automática '. `Problemas de desempenho e segurança '
Visão geral
Tor é uma rede anonimização usada para ajudar a esconder a identidade da Internet Clientes e servidores. Consulte o site do Tor Project para obter mais informações: Https://www.torproject.org/
I2P é uma rede de anonimato descentralizada que se concentra no anonimato de ponta a ponta Entre clientes e servidores. Consulte o site I2P para obter mais informações: Https://geti2p.net/
Casos de uso
Existem três casos de uso potenciais para Tahoe-LAFS do lado do cliente:
-
O usuário deseja sempre usar uma rede de anonimato (Tor, I2P) para proteger Seu anonimato quando se conecta às redes de armazenamento Tahoe-LAFS (seja ou Não os servidores de armazenamento são anônimos).
-
O usuário não se preocupa em proteger seu anonimato, mas eles desejam se conectar a Servidores de armazenamento Tahoe-LAFS que são acessíveis apenas através de Tor Hidden Services ou I2P.
-
Tor é usado apenas se uma sugestão de conexão do servidor usar
tor:. Essas sugestões Geralmente tem um endereço.onion. -
I2P só é usado se uma sugestão de conexão do servidor usa
i2p:. Essas sugestões Geralmente têm um endereço.i2p. -
O usuário não se preocupa em proteger seu anonimato ou para se conectar a um anonimato Servidores de armazenamento. Este documento não é útil para você ... então pare de ler.
Para servidores de armazenamento Tahoe-LAFS existem três casos de uso:
-
O operador deseja proteger o anonimato fazendo seu Tahoe Servidor acessível apenas em I2P, através de Tor Hidden Services, ou ambos.
-
O operador não * requer * anonimato para o servidor de armazenamento, mas eles Quer que ele esteja disponível tanto no TCP / IP roteado publicamente quanto através de um Rede de anonimização (I2P, Tor Hidden Services). Uma possível razão para fazer Isso é porque ser alcançável através de uma rede de anonimato é um Maneira conveniente de ignorar NAT ou firewall que impede roteios públicos Conexões TCP / IP ao seu servidor (para clientes capazes de se conectar a Tais servidores). Outro é o que torna o seu servidor de armazenamento acessível Através de uma rede de anonimato pode oferecer uma melhor proteção para sua Clientes que usam essa rede de anonimato para proteger seus anonimato.
-
O operador do servidor de armazenamento não se preocupa em proteger seu próprio anonimato nem Para ajudar os clientes a proteger o deles. Pare de ler este documento e execute Seu servidor de armazenamento Tahoe-LAFS usando TCP / IP com roteamento público.
Veja esta página do Tor Project para obter mais informações sobre Tor Hidden Services: Https://www.torproject.org/docs/hidden-services.html.pt
Veja esta página do Projeto I2P para obter mais informações sobre o I2P: Https://geti2p.net/en/about/intro
Dependências de software
Tor
Os clientes que desejam se conectar a servidores baseados em Tor devem instalar o seguinte.
-
Tor (tor) deve ser instalado. Veja aqui: Https://www.torproject.org/docs/installguide.html.en. No Debian / Ubuntu, Use
apt-get install tor. Você também pode instalar e executar o navegador Tor Agrupar. -
Tahoe-LAFS deve ser instalado com o
[tor]"extra" habilitado. Isso vai Instaletxtorcon::
Pip install tahoe-lafs [tor]
Os servidores Tor-configurados manualmente devem instalar Tor, mas não precisam
Txtorconou o[tor]extra. Configuração automática, quando Implementado, vai precisar destes, assim como os clientes.I2P
Os clientes que desejam se conectar a servidores baseados em I2P devem instalar o seguinte. Tal como acontece com Tor, os servidores baseados em I2P configurados manualmente precisam do daemon I2P, mas Não há bibliotecas especiais de apoio Tahoe-side.
-
I2P deve ser instalado. Veja aqui: Https://geti2p.net/en/download
-
A API SAM deve estar habilitada.
-
Inicie o I2P.
- Visite http://127.0.0.1:7657/configclients no seu navegador.
- Em "Configuração do Cliente", marque a opção "Executar no Startup?" Caixa para "SAM Ponte de aplicação ".
- Clique em "Salvar Configuração do Cliente".
-
Clique no controle "Iniciar" para "ponte de aplicação SAM" ou reinicie o I2P.
-
Tahoe-LAFS deve ser instalado com o
[i2p]extra habilitado, para obterTxi2p::
Pip install tahoe-lafs [i2p]
Tor e I2P
Os clientes que desejam se conectar a servidores baseados em Tor e I2P devem instalar tudo acima. Em particular, Tahoe-LAFS deve ser instalado com ambos Extras habilitados ::
Pip install tahoe-lafs [tor, i2p]
Configuração de conexão
Consulte: ref:
Connection Managementpara uma descrição do[tor]e[I2p]seções detahoe.cfg. Estes controlam como o cliente Tahoe Conecte-se a um daemon Tor / I2P e, assim, faça conexões com Tor / I2P-baseadas Servidores.As seções
[tor]e[i2p]só precisam ser modificadas para serem usadas de forma incomum Configurações ou para habilitar a configuração automática do servidor.A configuração padrão tentará entrar em contato com um daemon local Tor / I2P Ouvindo as portas usuais (9050/9150 para Tor, 7656 para I2P). Enquanto Há um daemon em execução no host local e o suporte necessário Bibliotecas foram instaladas, os clientes poderão usar servidores baseados em Tor Sem qualquer configuração especial.
No entanto, note que esta configuração padrão não melhora a Anonimato: as conexões TCP normais ainda serão feitas em qualquer servidor que Oferece um endereço regular (cumpre o segundo caso de uso do cliente acima, não o terceiro). Para proteger o anonimato, os usuários devem configurar o
[Connections]da seguinte maneira:[Conexões] Tcp = tor
Com isso, o cliente usará Tor (em vez de um IP-address -reviração de conexão direta) para alcançar servidores baseados em TCP.
Configuração de anonimato
Tahoe-LAFS fornece uma configuração "flag de segurança" para indicar explicitamente Seja necessário ou não a privacidade do endereço IP para um nó ::
[nó] Revelar-IP-address = (booleano, opcional)
Quando
revelar-IP-address = False, Tahoe-LAFS se recusará a iniciar se algum dos As opções de configuração emtahoe.cfgrevelariam a rede do nó localização:-
[Conexões] tcp = toré necessário: caso contrário, o cliente faria Conexões diretas para o Introdução, ou qualquer servidor baseado em TCP que aprende Do Introdutor, revelando seu endereço IP para esses servidores e um Rede de espionagem. Com isso, Tahoe-LAFS só fará Conexões de saída através de uma rede de anonimato suportada. -
Tub.locationdeve ser desativado ou conter valores seguros. este O valor é anunciado para outros nós através do Introdutor: é como um servidor Anuncia sua localização para que os clientes possam se conectar a ela. No modo privado, ele É um erro para incluir umtcp:dica notub.location. Modo privado Rejeita o valor padrão detub.location(quando a chave está faltando Inteiramente), que éAUTO, que usaifconfigpara adivinhar o nó Endereço IP externo, o que o revelaria ao servidor e a outros clientes.
Esta opção é ** crítica ** para preservar o anonimato do cliente (cliente Caso de uso 3 de "Casos de uso", acima). Também é necessário preservar uma Anonimato do servidor (caso de uso do servidor 3).
Esse sinalizador pode ser configurado (para falso), fornecendo o argumento
--hide-ippara Os comandoscreate-node,create-clientoucreate-introducer.Observe que o valor padrão de
revelar-endereço IPé verdadeiro, porque Infelizmente, esconder o endereço IP do nó requer software adicional para ser Instalado (conforme descrito acima) e reduz o desempenho.Anonimato do cliente
Para configurar um nó de cliente para anonimato,
tahoe.cfg** deve ** conter o Seguindo as bandeiras de configuração ::[nó] Revelar-IP-address = False Tub.port = desativado Tub.location = desativado
Uma vez que o nodo Tahoe-LAFS foi reiniciado, ele pode ser usado anonimamente (cliente Caso de uso 3).
Anonimato do servidor, configuração manual
Para configurar um nó de servidor para ouvir em uma rede de anonimato, devemos primeiro Configure Tor para executar um "Serviço de cebola" e encaminhe as conexões de entrada para o Porto Tahoe local. Então, configuramos Tahoe para anunciar o endereço
.onionAos clientes. Também configuramos Tahoe para não fazer conexões TCP diretas.- Decida em um número de porta de escuta local, chamado PORT. Isso pode ser qualquer não utilizado Porta de cerca de 1024 até 65535 (dependendo do kernel / rede do host Config). Nós diremos a Tahoe para escutar nesta porta, e nós diremos a Tor para Encaminhe as conexões de entrada para ele.
- Decida em um número de porta externo, chamado VIRTPORT. Isso será usado no Localização anunciada e revelada aos clientes. Pode ser qualquer número de 1 Para 65535. Pode ser o mesmo que PORT, se quiser.
- Decida em um "diretório de serviço oculto", geralmente em
/ var / lib / tor / NAME. Pediremos a Tor para salvar o estado do serviço de cebola aqui, e Tor irá Escreva o endereço.onionaqui depois que ele for gerado.
Em seguida, faça o seguinte:
-
Crie o nó do servidor Tahoe (com
tahoe create-node), mas não ** não ** Lança-o ainda. -
Edite o arquivo de configuração Tor (normalmente em
/ etc / tor / torrc). Precisamos adicionar Uma seção para definir o serviço oculto. Se nossa PORT for 2000, VIRTPORT é 3000, e estamos usando/ var / lib / tor / tahoecomo o serviço oculto Diretório, a seção deve se parecer com ::HiddenServiceDir / var / lib / tor / tahoe HiddenServicePort 3000 127.0.0.1:2000
-
Reinicie Tor, com
systemctl restart tor. Aguarde alguns segundos. -
Leia o arquivo
hostnameno diretório de serviço oculto (por exemplo,/ Var / lib / tor / tahoe / hostname). Este será um endereço.onion, comoU33m4y7klhz3b.onion. Ligue para esta CEBOLA. -
Edite
tahoe.cfgpara configurartub.portpara usarTcp: PORT: interface = 127.0.0.1etub.locationpara usarTor: ONION.onion: VIRTPORT. Usando os exemplos acima, isso seria ::[nó] Revelar-endereço IP = falso Tub.port = tcp: 2000: interface = 127.0.0.1 Tub.location = tor: u33m4y7klhz3b.onion: 3000 [Conexões] Tcp = tor
-
Inicie o servidor Tahoe com
tahoe start $ NODEDIR
A seção
tub.portfará com que o servidor Tahoe ouça no PORT, mas Ligue o soquete de escuta à interface de loopback, que não é acessível Do mundo exterior (mas * é * acessível pelo daemon Tor local). Então o A seçãotcp = torfaz com que Tahoe use Tor quando se conecta ao Introdução, escondendo o endereço IP. O nó se anunciará a todos Clientes que usam `tub.location``, então os clientes saberão que devem usar o Tor Para alcançar este servidor (e não revelar seu endereço IP através do anúncio). Quando os clientes se conectam ao endereço da cebola, seus pacotes serão Atravessar a rede de anonimato e eventualmente aterrar no Tor local Daemon, que então estabelecerá uma conexão com PORT no localhost, que é Onde Tahoe está ouvindo conexões.Siga um processo similar para construir um servidor Tahoe que escuta no I2P. o O mesmo processo pode ser usado para ouvir tanto o Tor como o I2P (
tub.location = Tor: ONION.onion: VIRTPORT, i2p: ADDR.i2p). Também pode ouvir tanto Tor como TCP simples (caso de uso 2), comtub.port = tcp: PORT,tub.location = Tcp: HOST: PORT, tor: ONION.onion: VIRTPORTeanonymous = false(e omite A configuraçãotcp = tor, já que o endereço já está sendo transmitido através de O anúncio de localização).Anonimato do servidor, configuração automática
Para configurar um nó do servidor para ouvir em uma rede de anonimato, crie o Nó com a opção
--listen = tor. Isso requer uma configuração Tor que Ou lança um novo daemon Tor, ou tem acesso à porta de controle Tor (e Autoridade suficiente para criar um novo serviço de cebola). Nos sistemas Debian / Ubuntu, façaApt install tor, adicione-se ao grupo de controle comadduser YOURUSERNAME debian-tore, em seguida, inicie sessão e faça o login novamente: se osgroupsO comando incluidebian-torna saída, você deve ter permissão para Use a porta de controle de domínio unix em/ var / run / tor / control.Esta opção irá definir
revelar-IP-address = Falsee[connections] tcp = Tor. Ele alocará as portas necessárias, instruirá Tor para criar a cebola Serviço (salvando a chave privada em algum lugar dentro de NODEDIR / private /), obtenha O endereço.onione preenchatub.portetub.locationcorretamente.Problemas de desempenho e segurança
Se você estiver executando um servidor que não precisa ser Anônimo, você deve torná-lo acessível através de uma rede de anonimato ou não? Ou você pode torná-lo acessível * ambos * através de uma rede de anonimato E como um servidor TCP / IP rastreável publicamente?
Existem várias compensações efetuadas por esta decisão.
Penetração NAT / Firewall
Fazer com que um servidor seja acessível via Tor ou I2P o torna acessível (por Clientes compatíveis com Tor / I2P) mesmo que existam NAT ou firewalls que impeçam Conexões TCP / IP diretas para o servidor.
Anonimato
Tornar um servidor Tahoe-LAFS acessível * somente * via Tor ou I2P pode ser usado para Garanta que os clientes Tahoe-LAFS usem Tor ou I2P para se conectar (Especificamente, o servidor só deve anunciar endereços Tor / I2P no Chave de configuração
tub.location). Isso evita que os clientes mal configurados sejam Desingonizando-se acidentalmente, conectando-se ao seu servidor através de A Internet rastreável.Claramente, um servidor que está disponível como um serviço Tor / I2P * e * a O endereço TCP regular não é anônimo: o endereço do .on e o real O endereço IP do servidor é facilmente vinculável.
Além disso, a interação, através do Tor, com um Tor Oculto pode ser mais Protegido da análise do tráfego da rede do que a interação, através do Tor, Com um servidor TCP / IP com rastreamento público
** XXX há um documento mantido pelos desenvolvedores de Tor que comprovem ou refutam essa crença? Se assim for, precisamos ligar a ele. Caso contrário, talvez devêssemos explicar mais aqui por que pensamos isso? **
Linkability
A partir de 1.12.0, o nó usa uma única chave de banheira persistente para saída Conexões ao Introdutor e conexões de entrada para o Servidor de Armazenamento (E Helper). Para os clientes, uma nova chave Tub é criada para cada servidor de armazenamento Nós aprendemos sobre, e essas chaves são * não * persistiram (então elas mudarão cada uma delas Tempo que o cliente reinicia).
Clientes que atravessam diretórios (de rootcap para subdiretório para filecap) são É provável que solicitem os mesmos índices de armazenamento (SIs) na mesma ordem de cada vez. Um cliente conectado a vários servidores irá pedir-lhes todos para o mesmo SI em Quase ao mesmo tempo. E dois clientes que compartilham arquivos ou diretórios Irá visitar os mesmos SI (em várias ocasiões).
Como resultado, as seguintes coisas são vinculáveis, mesmo com
revelar-endereço IP = Falso:- Servidores de armazenamento podem vincular reconhecer várias conexões do mesmo Cliente ainda não reiniciado. (Observe que o próximo recurso de Contabilidade pode Faz com que os clientes apresentem uma chave pública persistente do lado do cliente quando Conexão, que será uma ligação muito mais forte).
- Os servidores de armazenamento provavelmente podem deduzir qual cliente está acessando dados, por Olhando as SIs sendo solicitadas. Vários servidores podem conciliar Determine que o mesmo cliente está falando com todos eles, mesmo que o TubIDs são diferentes para cada conexão.
- Os servidores de armazenamento podem deduzir quando dois clientes diferentes estão compartilhando dados.
- O Introdutor pode entregar diferentes informações de servidor para cada um Cliente subscrito, para particionar clientes em conjuntos distintos de acordo com Quais as conexões do servidor que eles eventualmente fazem. Para clientes + nós de servidor, ele Também pode correlacionar o anúncio do servidor com o cliente deduzido identidade.
atuação
Um cliente que se conecta a um servidor Tahoe-LAFS com rastreamento público através de Tor Incorrem em latência substancialmente maior e, às vezes, pior Mesmo cliente se conectando ao mesmo servidor através de um TCP / IP rastreável normal conexão. Quando o servidor está em um Tor Hidden Service, ele incorre ainda mais Latência e, possivelmente, ainda pior rendimento.
Conectando-se a servidores Tahoe-LAFS que são servidores I2P incorrem em maior latência E pior rendimento também.
Efeitos positivos e negativos em outros usuários Tor
O envio de seu tráfego Tahoe-LAFS sobre o Tor adiciona tráfego de cobertura para outros Tor usuários que também estão transmitindo dados em massa. Então isso é bom para Eles - aumentando seu anonimato.
No entanto, torna o desempenho de outros usuários do Tor Sessões - por exemplo, sessões ssh - muito pior. Isso é porque Tor Atualmente não possui nenhuma prioridade ou qualidade de serviço Recursos, para que as teclas de Ssh de outra pessoa possam ter que esperar na fila Enquanto o conteúdo do arquivo em massa é transmitido. O atraso adicional pode Tornar as sessões interativas de outras pessoas inutilizáveis.
Ambos os efeitos são duplicados se você carregar ou baixar arquivos para um Tor Hidden Service, em comparação com se você carregar ou baixar arquivos Over Tor para um servidor TCP / IP com rastreamento público
Efeitos positivos e negativos em outros usuários do I2P
Enviar seu tráfego Tahoe-LAFS ao I2P adiciona tráfego de cobertura para outros usuários do I2P Que também estão transmitindo dados. Então, isso é bom para eles - aumentando sua anonimato. Não prejudicará diretamente o desempenho de outros usuários do I2P Sessões interativas, porque a rede I2P possui vários controles de congestionamento e Recursos de qualidade de serviço, como priorizar pacotes menores.
No entanto, se muitos usuários estão enviando tráfego Tahoe-LAFS ao I2P e não tiverem Seus roteadores I2P configurados para participar de muito tráfego, então o I2P A rede como um todo sofrerá degradação. Cada roteador Tahoe-LAFS que usa o I2P tem Seus próprios túneis de anonimato que seus dados são enviados. Em média, um O nó Tahoe-LAFS requer 12 outros roteadores I2P para participar de seus túneis.
Portanto, é importante que o seu roteador I2P esteja compartilhando a largura de banda com outros Roteadores, para que você possa retornar enquanto usa o I2P. Isso nunca prejudicará a Desempenho de seu nó Tahoe-LAFS, porque seu roteador I2P sempre Priorize seu próprio tráfego.
=========================
Como configurar um servidor
Muitos nós Tahoe-LAFS são executados como "servidores", o que significa que eles fornecem serviços para Outras máquinas (isto é, "clientes"). Os dois tipos mais importantes são os Introdução e Servidores de armazenamento.
Para ser útil, os servidores devem ser alcançados pelos clientes. Os servidores Tahoe podem ouvir Em portas TCP e anunciar sua "localização" (nome do host e número da porta TCP) Para que os clientes possam se conectar a eles. Eles também podem ouvir os serviços de cebola "Tor" E portas I2P.
Os servidores de armazenamento anunciam sua localização ao anunciá-lo ao Introdutivo, Que então transmite a localização para todos os clientes. Então, uma vez que a localização é Determinado, você não precisa fazer nada de especial para entregá-lo.
O próprio apresentador possui uma localização, que deve ser entregue manualmente a todos Servidores de armazenamento e clientes. Você pode enviá-lo para os novos membros do seu grade. Esta localização (juntamente com outros identificadores criptográficos importantes) é Escrito em um arquivo chamado
private / introducer.furlno Presenter's Diretório básico, e deve ser fornecido como o argumento--introducer =paraTahoe create-nodeoutahoe create-node.O primeiro passo ao configurar um servidor é descobrir como os clientes irão alcançar. Então você precisa configurar o servidor para ouvir em algumas portas, e Depois configure a localização corretamente.
Configuração manual
Cada servidor tem duas configurações em seu arquivo
tahoe.cfg:tub.port, eTub.location. A "porta" controla o que o nó do servidor escuta: isto Geralmente é uma porta TCP.A "localização" controla o que é anunciado para o mundo exterior. Isto é um "Sugestão de conexão foolscap", e inclui tanto o tipo de conexão (Tcp, tor ou i2p) e os detalhes da conexão (nome do host / endereço, porta número). Vários proxies, gateways e redes de privacidade podem ser Envolvido, então não é incomum para
tub.portetub.locationpara olhar diferente.Você pode controlar diretamente a configuração
tub.portetub.locationConfigurações, fornecendo--port =e--location =ao executartahoe Create-node.Configuração automática
Em vez de fornecer
--port = / - location =, você pode usar--listen =. Os servidores podem ouvir em TCP, Tor, I2P, uma combinação desses ou nenhum. O argumento--listen =controla quais tipos de ouvintes o novo servidor usará.--listen = nonesignifica que o servidor não deve ouvir nada. Isso não Faz sentido para um servidor, mas é apropriado para um nó somente cliente. o O comandotahoe create-clientinclui automaticamente--listen = none.--listen = tcpé o padrão e liga uma porta de escuta TCP padrão. Usar--listen = tcprequer um argumento--hostname =também, que será Incorporado no local anunciado do nó. Descobrimos que os computadores Não pode determinar de forma confiável seu nome de host acessível externamente, então, em vez de Ter o servidor adivinhar (ou escanear suas interfaces para endereços IP Isso pode ou não ser apropriado), a criação de nó requer que o usuário Forneça o nome do host.--listen = torconversará com um daemon Tor local e criará uma nova "cebola" Servidor "(que se parece comalzrgrdvxct6c63z.onion).--listen = i2p` conversará com um daemon I2P local e criará um novo servidor endereço. Consulte: doc:anonymity-configuration` para obter detalhes.Você pode ouvir nos três usando
--listen = tcp, tor, i2p.Cenários de implantação
A seguir, alguns cenários sugeridos para configurar servidores usando Vários transportes de rede. Estes exemplos não incluem a especificação de um Apresentador FURL que normalmente você gostaria quando provisionamento de armazenamento Nós. Para estes e outros detalhes de configuração, consulte : Doc:
configuration.. `Servidor possui um nome DNS público '
.
Servidor possui um endereço público IPv4 / IPv6_.
O servidor está por trás de um firewall com encaminhamento de porta_.
Usando o I2P / Tor para evitar o encaminhamento da porta_O servidor possui um nome DNS público
O caso mais simples é o local onde o host do servidor está diretamente conectado ao Internet, sem um firewall ou caixa NAT no caminho. A maioria dos VPS (Virtual Private Servidor) e servidores colocados são assim, embora alguns fornecedores bloqueiem Muitas portas de entrada por padrão.
Para esses servidores, tudo o que você precisa saber é o nome do host externo. O sistema O administrador irá dizer-lhe isso. O principal requisito é que este nome de host Pode ser pesquisado no DNS, e ele será mapeado para um endereço IPv4 ou IPv6 que Alcançará a máquina.
Se o seu nome de host for
example.net, então você criará o introdutor como esta::Tahoe create-introducer --hostname example.com ~ / introducer
Ou um servidor de armazenamento como ::
Tahoe create-node --hostname = example.net
Estes irão alocar uma porta TCP (por exemplo, 12345), atribuir
tub.portpara serTcp: 12345etub.locationserãotcp: example.com: 12345.Idealmente, isso também deveria funcionar para hosts compatíveis com IPv6 (onde o nome DNS Fornece um registro "AAAA", ou ambos "A" e "AAAA"). No entanto Tahoe-LAFS O suporte para IPv6 é novo e ainda pode ter problemas. Por favor, veja o ingresso
# 867_ para detalhes... _ # 867: https://tahoe-lafs.org/trac/tahoe-lafs/ticket/867
O servidor possui um endereço público IPv4 / IPv6
Se o host tiver um endereço IPv4 (público) rotativo (por exemplo,
203.0.113.1```), mas Nenhum nome DNS, você precisará escolher uma porta TCP (por exemplo,3457``) e usar o Segue::Tahoe create-node --port = tcp: 3457 - localização = tcp: 203.0.113.1: 3457
--porté uma "string de especificação de ponto de extremidade" que controla quais locais Porta em que o nó escuta.--locationé a "sugestão de conexão" que ele Anuncia para outros, e descreve as conexões de saída que essas Os clientes irão fazer, por isso precisa trabalhar a partir da sua localização na rede.Os nós Tahoe-LAFS escutam em todas as interfaces por padrão. Quando o host é Multi-homed, você pode querer fazer a ligação de escuta ligar apenas a uma Interface específica, adicionando uma opção
interface =ao--port =argumento::Tahoe create-node --port = tcp: 3457: interface = 203.0.113.1 - localização = tcp: 203.0.113.1: 3457
Se o endereço público do host for IPv6 em vez de IPv4, use colchetes para Envolva o endereço e altere o tipo de nó de extremidade para
tcp6::Tahoe create-node --port = tcp6: 3457 - localização = tcp: [2001: db8 :: 1]: 3457
Você pode usar
interface =para vincular a uma interface IPv6 específica também, no entanto Você deve fazer uma barra invertida - escapar dos dois pontos, porque, de outra forma, eles são interpretados Como delimitadores pelo idioma de especificação do "ponto final" torcido. o--location =argumento não precisa de dois pontos para serem escapados, porque eles são Envolto pelos colchetes ::Tahoe create-node --port = tcp6: 3457: interface = 2001 \: db8 \: \: 1 --location = tcp: [2001: db8 :: 1]: 3457
Para hosts somente IPv6 com registros DNS AAAA, se o simples
--hostname =A configuração não funciona, eles podem ser informados para ouvir especificamente Porta compatível com IPv6 com este ::Tahoe create-node --port = tcp6: 3457 - localização = tcp: example.net: 3457
O servidor está por trás de um firewall com encaminhamento de porta
Para configurar um nó de armazenamento por trás de um firewall com encaminhamento de porta, você irá precisa saber:
- Endereço IPv4 público do roteador
- A porta TCP que está disponível de fora da sua rede
- A porta TCP que é o destino de encaminhamento
- Endereço IPv4 interno do nó de armazenamento (o nó de armazenamento em si é
Desconhece esse endereço e não é usado durante
tahoe create-node, Mas o firewall deve ser configurado para enviar conexões para isso)
Os números de porta TCP internos e externos podem ser iguais ou diferentes Dependendo de como o encaminhamento da porta está configurado. Se é mapear portas 1-para-1, eo endereço IPv4 público do firewall é 203.0.113.1 (e Talvez o endereço IPv4 interno do nó de armazenamento seja 192.168.1.5), então Use um comando CLI como este ::
Tahoe create-node --port = tcp: 3457 - localização = tcp: 203.0.113.1: 3457
Se no entanto, o firewall / NAT-box encaminha a porta externa * 6656 * para o interno Porta 3457, então faça isso ::
Tahoe create-node --port = tcp: 3457 - localização = tcp: 203.0.113.1: 6656
Usando o I2P / Tor para evitar o encaminhamento da porta
Os serviços de cebola I2P e Tor, entre outras excelentes propriedades, também fornecem NAT Penetração sem encaminhamento de porta, nomes de host ou endereços IP. Então, configurando Um servidor que escuta apenas no Tor é simples ::
Tahoe create-node --listen = tor
Para mais informações sobre o uso de Tahoe-LAFS com I2p e Tor veja : Doc:
anonymity-configuration -
 @ 39cc53c9:27168656
2025-04-09 07:59:33
@ 39cc53c9:27168656
2025-04-09 07:59:33Know Your Customer is a regulation that requires companies of all sizes to verify the identity, suitability, and risks involved with maintaining a business relationship with a customer. Such procedures fit within the broader scope of anti-money laundering (AML) and counterterrorism financing (CTF) regulations.
Banks, exchanges, online business, mail providers, domain registrars... Everyone wants to know who you are before you can even opt for their service. Your personal information is flowing around the internet in the hands of "god-knows-who" and secured by "trust-me-bro military-grade encryption". Once your account is linked to your personal (and verified) identity, tracking you is just as easy as keeping logs on all these platforms.
Rights for Illusions
KYC processes aim to combat terrorist financing, money laundering, and other illicit activities. On the surface, KYC seems like a commendable initiative. I mean, who wouldn't want to halt terrorists and criminals in their tracks?
The logic behind KYC is: "If we mandate every financial service provider to identify their users, it becomes easier to pinpoint and apprehend the malicious actors."
However, terrorists and criminals are not precisely lining up to be identified. They're crafty. They may adopt false identities or find alternative strategies to continue their operations. Far from being outwitted, many times they're several steps ahead of regulations. Realistically, KYC might deter a small fraction – let's say about 1% ^1 – of these malefactors. Yet, the cost? All of us are saddled with the inconvenient process of identification just to use a service.
Under the rhetoric of "ensuring our safety", governments and institutions enact regulations that seem more out of a dystopian novel, gradually taking away our right to privacy.
To illustrate, consider a city where the mayor has rolled out facial recognition cameras in every nook and cranny. A band of criminals, intent on robbing a local store, rolls in with a stolen car, their faces obscured by masks and their bodies cloaked in all-black clothes. Once they've committed the crime and exited the city's boundaries, they switch vehicles and clothes out of the cameras' watchful eyes. The high-tech surveillance? It didn’t manage to identify or trace them. Yet, for every law-abiding citizen who merely wants to drive through the city or do some shopping, their movements and identities are constantly logged. The irony? This invasive tracking impacts all of us, just to catch the 1% ^1 of less-than-careful criminals.
KYC? Not you.
KYC creates barriers to participation in normal economic activity, to supposedly stop criminals. ^2
KYC puts barriers between many users and businesses. One of these comes from the fact that the process often requires multiple forms of identification, proof of address, and sometimes even financial records. For individuals in areas with poor record-keeping, non-recognized legal documents, or those who are unbanked, homeless or transient, obtaining these documents can be challenging, if not impossible.
For people who are not skilled with technology or just don't have access to it, there's also a barrier since KYC procedures are mostly online, leaving them inadvertently excluded.
Another barrier goes for the casual or one-time user, where they might not see the value in undergoing a rigorous KYC process, and these requirements can deter them from using the service altogether.
It also wipes some businesses out of the equation, since for smaller businesses, the costs associated with complying with KYC norms—from the actual process of gathering and submitting documents to potential delays in operations—can be prohibitive in economical and/or technical terms.
You're not welcome
Imagine a swanky new club in town with a strict "members only" sign. You hear the music, you see the lights, and you want in. You step up, ready to join, but suddenly there's a long list of criteria you must meet. After some time, you are finally checking all the boxes. But then the club rejects your membership with no clear reason why. You just weren't accepted. Frustrating, right?
This club scenario isn't too different from the fact that KYC is being used by many businesses as a convenient gatekeeping tool. A perfect excuse based on a "legal" procedure they are obliged to.
Even some exchanges may randomly use this to freeze and block funds from users, claiming these were "flagged" by a cryptic system that inspects the transactions. You are left hostage to their arbitrary decision to let you successfully pass the KYC procedure. If you choose to sidestep their invasive process, they might just hold onto your funds indefinitely.
Your identity has been stolen
KYC data has been found to be for sale on many dark net markets^3. Exchanges may have leaks or hacks, and such leaks contain very sensitive data. We're talking about the full monty: passport or ID scans, proof of address, and even those awkward selfies where you're holding up your ID next to your face. All this data is being left to the mercy of the (mostly) "trust-me-bro" security systems of such companies. Quite scary, isn't it?
As cheap as $10 for 100 documents, with discounts applying for those who buy in bulk, the personal identities of innocent users who passed KYC procedures are for sale. ^3
In short, if you have ever passed the KYC/AML process of a crypto exchange, your privacy is at risk of being compromised, or it might even have already been compromised.
(they) Know Your Coins
You may already know that Bitcoin and most cryptocurrencies have a transparent public blockchain, meaning that all data is shown unencrypted for everyone to see and recorded forever. If you link an address you own to your identity through KYC, for example, by sending an amount from a KYC exchange to it, your Bitcoin is no longer pseudonymous and can then be traced.
If, for instance, you send Bitcoin from such an identified address to another KYC'ed address (say, from a friend), everyone having access to that address-identity link information (exchanges, governments, hackers, etc.) will be able to associate that transaction and know who you are transacting with.
Conclusions
To sum up, KYC does not protect individuals; rather, it's a threat to our privacy, freedom, security and integrity. Sensible information flowing through the internet is thrown into chaos by dubious security measures. It puts borders between many potential customers and businesses, and it helps governments and companies track innocent users. That's the chaos KYC has stirred.
The criminals are using stolen identities from companies that gathered them thanks to these very same regulations that were supposed to combat them. Criminals always know how to circumvent such regulations. In the end, normal people are the most affected by these policies.
The threat that KYC poses to individuals in terms of privacy, security and freedom is not to be neglected. And if we don’t start challenging these systems and questioning their efficacy, we are just one step closer to the dystopian future that is now foreseeable.
Edited 20/03/2024 * Add reference to the 1% statement on Rights for Illusions section to an article where Chainalysis found that only 0.34% of the transaction volume with cryptocurrencies in 2023 was attributable to criminal activity ^1
-
 @ 68c90cf3:99458f5c
2025-04-04 16:06:10
@ 68c90cf3:99458f5c
2025-04-04 16:06:10I have two Nostr profiles I use for different subject matter, and I wanted a way to manage and track zaps for each. Using Alby Hub I created two isolated Lightning wallets each associated with one of the profile’s nsecs.
YakiHonne made it easy to connect the associated wallets with the profiles. The user interface is well designed to show balances for each.
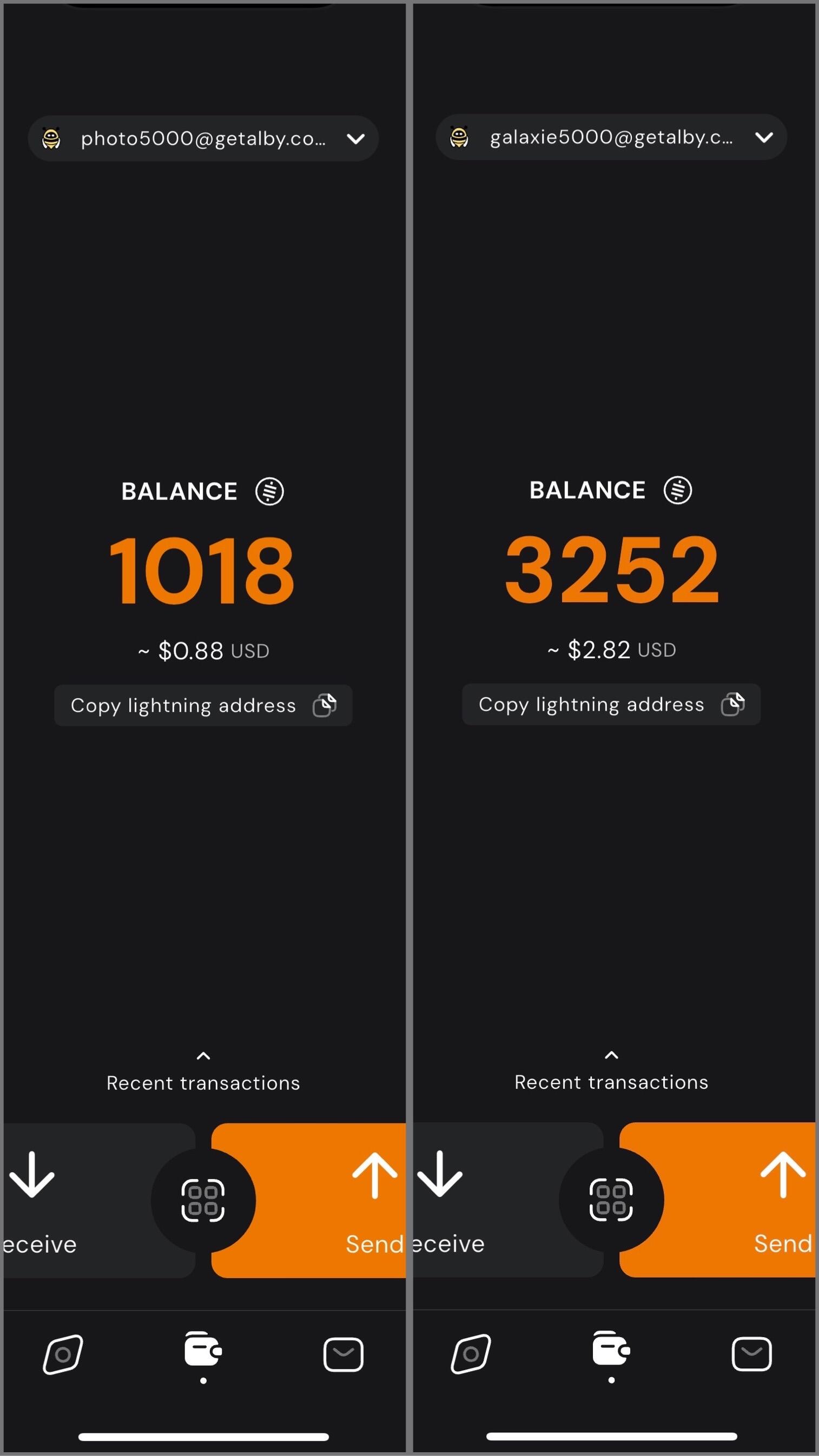
In my case, I have one profile for photography related content, and the other for Bitcoin, Nostr, and technology related content. I can easily switch between the two, sending and receiving zaps on each while staying up to date on balances and viewing transactions.
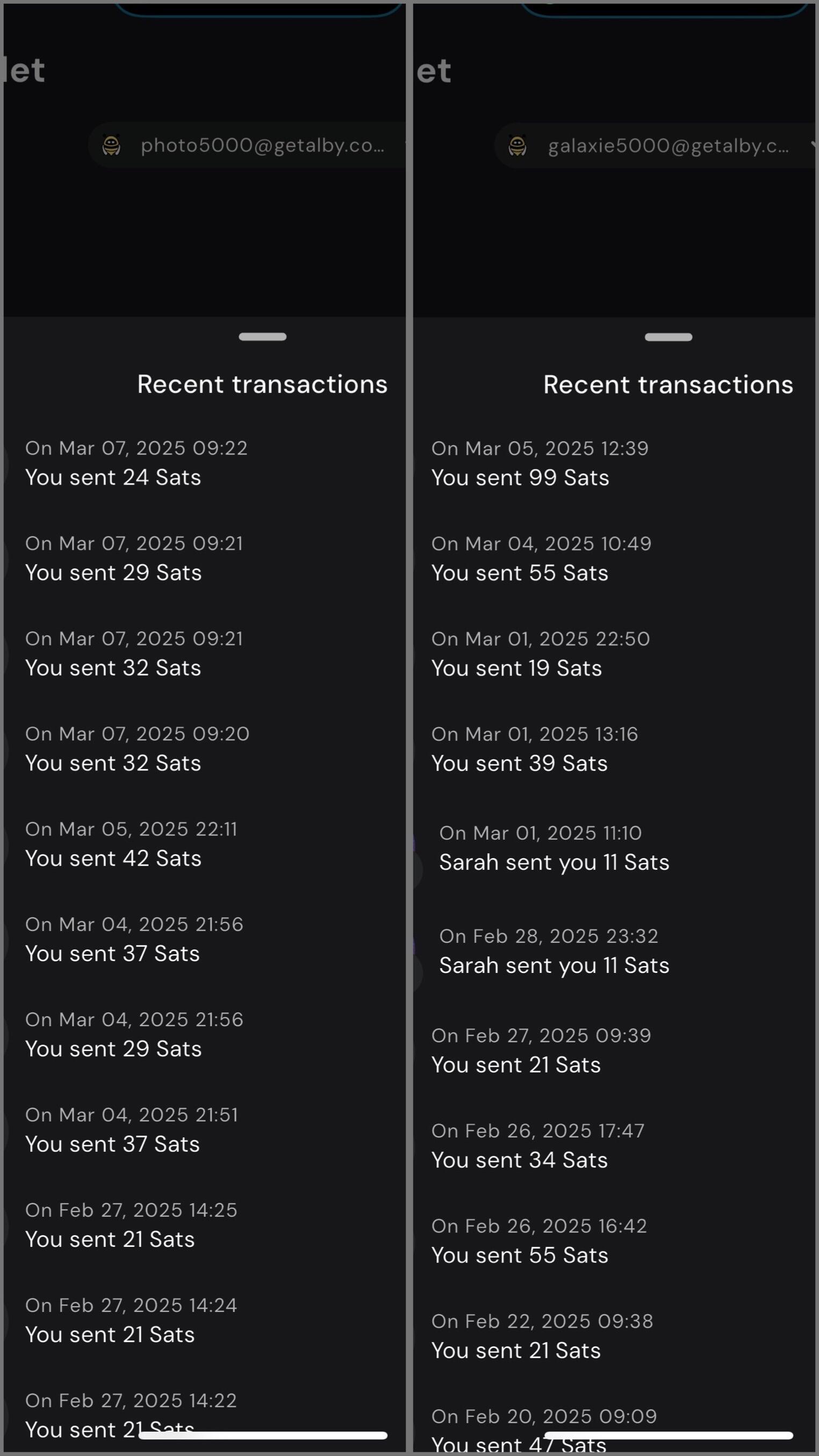
Using my self-hosted Alby Hub I can manage Lightning channels and wallets while sending and receiving zaps for multiple profiles with YakiHonne.
YakiHonne #AlbyHub #Lightning #Bitcoin #Nostr
-
 @ 3c389c8f:7a2eff7f
2025-04-29 18:13:50
@ 3c389c8f:7a2eff7f
2025-04-29 18:13:50TL;DR visit this post for a list of signers
Your nsec/private key is your key to controlling all that you do on Nostr. Every action you take is signed by this private key, validating that was you that generated that event, whether it be a note, a like, a list, or whatever else. Like a broken record, I have to state that it is irreplaceable. YOU own your identity and no one else. It is your responsibility to keep your nsec safe, but of course, you also want to be able to use all the different apps and clients available. To aid you in this process, a few different tools have been developed. Let's take a look at some that are more common and easy-to-use, where to use them, and for what.
The Browser Extension
This is probably the simplest and most straight forward form of private key manager available. There are many options to choose from, each compatible with various, commonly used browsers, including mobile browsers. Many provide the option to manage multiple keys for different profiles. Some are simply a signer while others may include other features. The concept is very simple. The extension holds your key and exposes it only only enough to sign an event. These extensions can be set to different levels of manual approval that you can control based on the level of convenience you seek. The ease and convenience does trade off a bit of security, as your private key will be exposed momentarily each time you create an event. It is up to you to choose whether this is appropriate for your use. For casual browsing and social media use, it is a fairly good and easy to use option. Nearly all Nostr apps and clients support signing with this method.
The Remote Signer
Often referred as a "bunker", Nostr remote signers hold your private key completely offline and communicating with clients. Clients send events to the signer to be signed, which then sends back the signed event for publishing. This bunker can be hosted on your own hardware or managed by a truested 3rd party. As long as the signer is online, it can communicate as needed. The signer generates a "bunker string" that is used to communicate. These may seem cumbersome to set up, as each client that you intend to use will need its own permissions. Once all of the pieces and permissions are in place, most of this activity will happen in the background. Bunkers allow for a lot of flexibility. The "bunker string" for a single app can be shared with other users who you may want to be able to make posts on your behalf. Multiple people can manage a social media profile, while the main owner of that identity maintains control of the nsec. These bunker strings can be revoked and replaced at any time. This signing method is growing in popularity and many clients already offer support for it.
The Native Android Signer
Currently, Amber is the only native app available to handle Nostr event signing. It is an incredible tool for managing your Nostr key on your mobile device. The signing flow is similar to remote signing, as described above, but it can communicate with both your Android native Nostr apps and web clients accessed through most mobile browsers, eliminating the need for a browser extension. Similar apps are under development for iOS, but I don't use any of those devices, so covering that here will only happen via other's opinions at a later date. Check this list for current options.
NcryptSec
NcryptSec signing works by encrypting your nsec on a local device, unlocked by a password that you choose. Support for this method is very limited, as the encrypted private key stays on your device. If you intend to use Nostr through one device and few apps, this can be a very secure option, as long as you can remember your password, as it cannot be changed.
NFC and Hardware Signers
Some devices have been developed to store your nsec completely offline on a device or NFC chip, and some clients have added support for scanning/connecting to sign. I haven't personally tried any of these options, nor do I intend to promote the sale of any particular products. If you are interested in these techniques and devices, the information is not hard to find. The price of a devices varies, depending on your feature needs.
There are also DIY options that utilize existing hardware, if you are into that sort of thing.
Higher Security and Recoverability Options
Creating a scheme that allows for recovery of a lost key while maintaining the integrity of a unique identity is no easy task. The key must be fractured into shards, encrypted, and distributed across multiple servers in various locations, while you maintain a portion or portions of your own. These servers are run by trusted 3rd parties who will then sign events "with" you. Some include a scheme of running your own always online hardware to act as host for these shards. I fall short on the technical understanding of certain aspects of these processes, so I will spare you of my attempt to explain. As far as I know, there are a couple of methods underway that are worth paying attention to:
Frostr nostr:nevent1qvzqqqqqqypzqs3fcg0szqdtcway2ge7zahfwhafuecmkx9xwg4a7aexhgj5ghleqy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qgwwaehxw309ahx7uewd3hkctcqyrh3r7uhytc4dywjggxz24277xgqtvcadvnjfks6fram7gjpev9nuentfht
Promenade nostr:nevent1qvzqqqqqqypzqwlsccluhy6xxsr6l9a9uhhxf75g85g8a709tprjcn4e42h053vaqydhwumn8ghj7un9d3shjtnhv4ehgetjde38gcewvdhk6tcprdmhxue69uhhyetvv9ujuam9wd6x2unwvf6xxtnrdakj7qpqqqq0dlpwxhw5l97yrcts2klhr9zqqpcmdfpaxm8r7hygykp630cq23ggph
For a List of signers, please visit this post.
-
 @ 3c389c8f:7a2eff7f
2025-04-29 18:07:00
@ 3c389c8f:7a2eff7f
2025-04-29 18:07:00Extentions:
https://chromewebstore.google.com/detail/flamingo-%E2%80%93-nostr-extensio/alkiaengfedemppafkallgifcmkldohe
https://chromewebstore.google.com/detail/nos2x/kpgefcfmnafjgpblomihpgmejjdanjjp
https://chromewebstore.google.com/detail/aka-profiles/ncmflpbbagcnakkolfpcpogheckolnad
https://keys.band/
https://github.com/haorendashu/nowser
The Remote Signer:
https://nsec.app/
https://github.com/kind-0/nsecbunkerd
Native Android Signer:
https://github.com/greenart7c3/amber
iOS
https://testflight.apple.com/join/8TFMZbMs
https://testflight.apple.com/join/DUzVMDMK
Higher Security Options: To start using Nostr with a secure, recoverable keypair: https://nstart.me/en
For Existing Keys: https://www.frostr.org/
Thank you to https://nostr.net/ for keeping a thorough list of Nostr apps, clients, and tools!
-
 @ b9f4c34d:7d1a0e31
2025-04-02 15:00:20
@ b9f4c34d:7d1a0e31
2025-04-02 15:00:20Test Video Document
-
 @ b9f4c34d:7d1a0e31
2025-04-02 14:59:02
@ b9f4c34d:7d1a0e31
2025-04-02 14:59:02Testy McTestenface
It's been so long, html
-
 @ 04c915da:3dfbecc9
2025-03-26 20:54:33
@ 04c915da:3dfbecc9
2025-03-26 20:54:33Capitalism is the most effective system for scaling innovation. The pursuit of profit is an incredibly powerful human incentive. Most major improvements to human society and quality of life have resulted from this base incentive. Market competition often results in the best outcomes for all.
That said, some projects can never be monetized. They are open in nature and a business model would centralize control. Open protocols like bitcoin and nostr are not owned by anyone and if they were it would destroy the key value propositions they provide. No single entity can or should control their use. Anyone can build on them without permission.
As a result, open protocols must depend on donation based grant funding from the people and organizations that rely on them. This model works but it is slow and uncertain, a grind where sustainability is never fully reached but rather constantly sought. As someone who has been incredibly active in the open source grant funding space, I do not think people truly appreciate how difficult it is to raise charitable money and deploy it efficiently.
Projects that can be monetized should be. Profitability is a super power. When a business can generate revenue, it taps into a self sustaining cycle. Profit fuels growth and development while providing projects independence and agency. This flywheel effect is why companies like Google, Amazon, and Apple have scaled to global dominance. The profit incentive aligns human effort with efficiency. Businesses must innovate, cut waste, and deliver value to survive.
Contrast this with non monetized projects. Without profit, they lean on external support, which can dry up or shift with donor priorities. A profit driven model, on the other hand, is inherently leaner and more adaptable. It is not charity but survival. When survival is tied to delivering what people want, scale follows naturally.
The real magic happens when profitable, sustainable businesses are built on top of open protocols and software. Consider the many startups building on open source software stacks, such as Start9, Mempool, and Primal, offering premium services on top of the open source software they build out and maintain. Think of companies like Block or Strike, which leverage bitcoin’s open protocol to offer their services on top. These businesses amplify the open software and protocols they build on, driving adoption and improvement at a pace donations alone could never match.
When you combine open software and protocols with profit driven business the result are lean, sustainable companies that grow faster and serve more people than either could alone. Bitcoin’s network, for instance, benefits from businesses that profit off its existence, while nostr will expand as developers monetize apps built on the protocol.
Capitalism scales best because competition results in efficiency. Donation funded protocols and software lay the groundwork, while market driven businesses build on top. The profit incentive acts as a filter, ensuring resources flow to what works, while open systems keep the playing field accessible, empowering users and builders. Together, they create a flywheel of innovation, growth, and global benefit.
-
 @ b2d670de:907f9d4a
2025-03-25 20:17:57
@ b2d670de:907f9d4a
2025-03-25 20:17:57This guide will walk you through setting up your own Strfry Nostr relay on a Debian/Ubuntu server and making it accessible exclusively as a TOR hidden service. By the end, you'll have a privacy-focused relay that operates entirely within the TOR network, enhancing both your privacy and that of your users.
Table of Contents
- Prerequisites
- Initial Server Setup
- Installing Strfry Nostr Relay
- Configuring Your Relay
- Setting Up TOR
- Making Your Relay Available on TOR
- Testing Your Setup]
- Maintenance and Security
- Troubleshooting
Prerequisites
- A Debian or Ubuntu server
- Basic familiarity with command line operations (most steps are explained in detail)
- Root or sudo access to your server
Initial Server Setup
First, let's make sure your server is properly set up and secured.
Update Your System
Connect to your server via SSH and update your system:
bash sudo apt update sudo apt upgrade -ySet Up a Basic Firewall
Install and configure a basic firewall:
bash sudo apt install ufw -y sudo ufw allow ssh sudo ufw enableThis allows SSH connections while blocking other ports for security.
Installing Strfry Nostr Relay
This guide includes the full range of steps needed to build and set up Strfry. It's simply based on the current version of the
DEPLOYMENT.mddocument in the Strfry GitHub repository. If the build/setup process is changed in the repo, this document could get outdated. If so, please report to me that something is outdated and check for updated steps here.Install Dependencies
First, let's install the necessary dependencies. Each package serves a specific purpose in building and running Strfry:
bash sudo apt install -y git build-essential libyaml-perl libtemplate-perl libregexp-grammars-perl libssl-dev zlib1g-dev liblmdb-dev libflatbuffers-dev libsecp256k1-dev libzstd-devHere's why each dependency is needed:
Basic Development Tools: -
git: Version control system used to clone the Strfry repository and manage code updates -build-essential: Meta-package that includes compilers (gcc, g++), make, and other essential build toolsPerl Dependencies (used for Strfry's build scripts): -
libyaml-perl: Perl interface to parse YAML configuration files -libtemplate-perl: Template processing system used during the build process -libregexp-grammars-perl: Advanced regular expression handling for Perl scriptsCore Libraries for Strfry: -
libssl-dev: Development files for OpenSSL, used for secure connections and cryptographic operations -zlib1g-dev: Compression library that Strfry uses to reduce data size -liblmdb-dev: Lightning Memory-Mapped Database library, which Strfry uses for its high-performance database backend -libflatbuffers-dev: Memory-efficient serialization library for structured data -libsecp256k1-dev: Optimized C library for EC operations on curve secp256k1, essential for Nostr's cryptographic signatures -libzstd-dev: Fast real-time compression algorithm for efficient data storage and transmissionClone and Build Strfry
Clone the Strfry repository:
bash git clone https://github.com/hoytech/strfry.git cd strfryBuild Strfry:
bash git submodule update --init make setup-golpe make -j2 # This uses 2 CPU cores. Adjust based on your server (e.g., -j4 for 4 cores)This build process will take several minutes, especially on servers with limited CPU resources, so go get a coffee and post some great memes on nostr in the meantime.
Install Strfry
Install the Strfry binary to your system path:
bash sudo cp strfry /usr/local/binThis makes the
strfrycommand available system-wide, allowing it to be executed from any directory and by any user with the appropriate permissions.Configuring Your Relay
Create Strfry User
Create a dedicated user for running Strfry. This enhances security by isolating the relay process:
bash sudo useradd -M -s /usr/sbin/nologin strfryThe
-Mflag prevents creating a home directory, and-s /usr/sbin/nologinprevents anyone from logging in as this user. This is a security best practice for service accounts.Create Data Directory
Create a directory for Strfry's data:
bash sudo mkdir /var/lib/strfry sudo chown strfry:strfry /var/lib/strfry sudo chmod 755 /var/lib/strfryThis creates a dedicated directory for Strfry's database and sets the appropriate permissions so that only the strfry user can write to it.
Configure Strfry
Copy the sample configuration file:
bash sudo cp strfry.conf /etc/strfry.confEdit the configuration file:
bash sudo nano /etc/strfry.confModify the database path:
```
Find this line:
db = "./strfry-db/"
Change it to:
db = "/var/lib/strfry/" ```
Check your system's hard limit for file descriptors:
bash ulimit -HnUpdate the
nofilessetting in your configuration to match this value (or set to 0):```
Add or modify this line in the config (example if your limit is 524288):
nofiles = 524288 ```
The
nofilessetting determines how many open files Strfry can have simultaneously. Setting it to your system's hard limit (or 0 to use the system default) helps prevent "too many open files" errors if your relay becomes popular.You might also want to customize your relay's information in the config file. Look for the
infosection and update it with your relay's name, description, and other details.Set ownership of the configuration file:
bash sudo chown strfry:strfry /etc/strfry.confCreate Systemd Service
Create a systemd service file for managing Strfry:
bash sudo nano /etc/systemd/system/strfry.serviceAdd the following content:
```ini [Unit] Description=strfry relay service
[Service] User=strfry ExecStart=/usr/local/bin/strfry relay Restart=on-failure RestartSec=5 ProtectHome=yes NoNewPrivileges=yes ProtectSystem=full LimitCORE=1000000000
[Install] WantedBy=multi-user.target ```
This systemd service configuration: - Runs Strfry as the dedicated strfry user - Automatically restarts the service if it fails - Implements security measures like
ProtectHomeandNoNewPrivileges- Sets resource limits appropriate for a relayEnable and start the service:
bash sudo systemctl enable strfry.service sudo systemctl start strfryCheck the service status:
bash sudo systemctl status strfryVerify Relay is Running
Test that your relay is running locally:
bash curl localhost:7777You should see a message indicating that the Strfry relay is running. This confirms that Strfry is properly installed and configured before we proceed to set up TOR.
Setting Up TOR
Now let's make your relay accessible as a TOR hidden service.
Install TOR
Install TOR from the package repositories:
bash sudo apt install -y torThis installs the TOR daemon that will create and manage your hidden service.
Configure TOR
Edit the TOR configuration file:
bash sudo nano /etc/tor/torrcScroll down to wherever you see a commented out part like this: ```
HiddenServiceDir /var/lib/tor/hidden_service/
HiddenServicePort 80 127.0.0.1:80
```
Under those lines, add the following lines to set up a hidden service for your relay:
HiddenServiceDir /var/lib/tor/strfry-relay/ HiddenServicePort 80 127.0.0.1:7777This configuration: - Creates a hidden service directory at
/var/lib/tor/strfry-relay/- Maps port 80 on your .onion address to port 7777 on your local machine - Keeps all traffic encrypted within the TOR networkCreate the directory for your hidden service:
bash sudo mkdir -p /var/lib/tor/strfry-relay/ sudo chown debian-tor:debian-tor /var/lib/tor/strfry-relay/ sudo chmod 700 /var/lib/tor/strfry-relay/The strict permissions (700) are crucial for security as they ensure only the debian-tor user can access the directory containing your hidden service private keys.
Restart TOR to apply changes:
bash sudo systemctl restart torMaking Your Relay Available on TOR
Get Your Onion Address
After restarting TOR, you can find your onion address:
bash sudo cat /var/lib/tor/strfry-relay/hostnameThis will output something like
abcdefghijklmnopqrstuvwxyz234567.onion, which is your relay's unique .onion address. This is what you'll share with others to access your relay.Understanding Onion Addresses
The .onion address is a special-format hostname that is automatically generated based on your hidden service's private key.
Your users will need to use this address with the WebSocket protocol prefix to connect:
ws://youronionaddress.onionTesting Your Setup
Test with a Nostr Client
The best way to test your relay is with an actual Nostr client that supports TOR:
- Open your TOR browser
- Go to your favorite client, either on clearnet or an onion service.
- Check out this list of nostr clients available over TOR.
- Add your relay URL:
ws://youronionaddress.onionto your relay list - Try posting a note and see if it appears on your relay
- In some nostr clients, you can also click on a relay to get information about it like the relay name and description you set earlier in the stryfry config. If you're able to see the correct values for the name and the description, you were able to connect to the relay.
- Some nostr clients also gives you a status on what relays a note was posted to, this could also give you an indication that your relay works as expected.
Note that not all Nostr clients support TOR connections natively. Some may require additional configuration or use of TOR Browser. E.g. most mobile apps would most likely require a TOR proxy app running in the background (some have TOR support built in too).
Maintenance and Security
Regular Updates
Keep your system, TOR, and relay updated:
```bash
Update system
sudo apt update sudo apt upgrade -y
Update Strfry
cd ~/strfry git pull git submodule update make -j2 sudo cp strfry /usr/local/bin sudo systemctl restart strfry
Verify TOR is still running properly
sudo systemctl status tor ```
Regular updates are crucial for security, especially for TOR which may have security-critical updates.
Database Management
Strfry has built-in database management tools. Check the Strfry documentation for specific commands related to database maintenance, such as managing event retention and performing backups.
Monitoring Logs
To monitor your Strfry logs:
bash sudo journalctl -u strfry -fTo check TOR logs:
bash sudo journalctl -u tor -fMonitoring logs helps you identify potential issues and understand how your relay is being used.
Backup
This is not a best practices guide on how to do backups. Preferably, backups should be stored either offline or on a different machine than your relay server. This is just a simple way on how to do it on the same server.
```bash
Stop the relay temporarily
sudo systemctl stop strfry
Backup the database
sudo cp -r /var/lib/strfry /path/to/backup/location
Restart the relay
sudo systemctl start strfry ```
Back up your TOR hidden service private key. The private key is particularly sensitive as it defines your .onion address - losing it means losing your address permanently. If you do a backup of this, ensure that is stored in a safe place where no one else has access to it.
bash sudo cp /var/lib/tor/strfry-relay/hs_ed25519_secret_key /path/to/secure/backup/locationTroubleshooting
Relay Not Starting
If your relay doesn't start:
```bash
Check logs
sudo journalctl -u strfry -e
Verify configuration
cat /etc/strfry.conf
Check permissions
ls -la /var/lib/strfry ```
Common issues include: - Incorrect configuration format - Permission problems with the data directory - Port already in use (another service using port 7777) - Issues with setting the nofiles limit (setting it too big)
TOR Hidden Service Not Working
If your TOR hidden service is not accessible:
```bash
Check TOR logs
sudo journalctl -u tor -e
Verify TOR is running
sudo systemctl status tor
Check onion address
sudo cat /var/lib/tor/strfry-relay/hostname
Verify TOR configuration
sudo cat /etc/tor/torrc ```
Common TOR issues include: - Incorrect directory permissions - TOR service not running - Incorrect port mapping in torrc
Testing Connectivity
If you're having trouble connecting to your service:
```bash
Verify Strfry is listening locally
sudo ss -tulpn | grep 7777
Check that TOR is properly running
sudo systemctl status tor
Test the local connection directly
curl --include --no-buffer localhost:7777 ```
Privacy and Security Considerations
Running a Nostr relay as a TOR hidden service provides several important privacy benefits:
-
Network Privacy: Traffic to your relay is encrypted and routed through the TOR network, making it difficult to determine who is connecting to your relay.
-
Server Anonymity: The physical location and IP address of your server are concealed, providing protection against denial-of-service attacks and other targeting.
-
Censorship Resistance: TOR hidden services are more resilient against censorship attempts, as they don't rely on the regular DNS system and can't be easily blocked.
-
User Privacy: Users connecting to your relay through TOR enjoy enhanced privacy, as their connections are also encrypted and anonymized.
However, there are some important considerations:
- TOR connections are typically slower than regular internet connections
- Not all Nostr clients support TOR connections natively
- Running a hidden service increases the importance of keeping your server secure
Congratulations! You now have a Strfry Nostr relay running as a TOR hidden service. This setup provides a resilient, privacy-focused, and censorship-resistant communication channel that helps strengthen the Nostr network.
For further customization and advanced configuration options, refer to the Strfry documentation.
Consider sharing your relay's .onion address with the Nostr community to help grow the privacy-focused segment of the network!
If you plan on providing a relay service that the public can use (either for free or paid for), consider adding it to this list. Only add it if you plan to run a stable and available relay.
-
 @ 8194da31:0f3badf3
2025-04-29 17:49:12
@ 8194da31:0f3badf3
2025-04-29 17:49:12LLM interpretation:
That’s a profound and provocative statement: “The corruption of money is the corruption of the Logos.” Let’s unpack this in detail, integrating philosophical, theological, and economic dimensions:
⸻
- What Is the Logos?
In classical and theological terms: •Greek Philosophy (esp. Heraclitus & Stoics): Logos is the divine reason, the ordering principle of the cosmos—a rational structure underlying all reality. •Plato: While he didn’t use Logos as prominently, his concept of the Forms, especially the Form of the Good, parallels it. The Logos could be seen as the bridge between the realm of ideal truth and the material world. •Christian Theology (esp. John 1:1): “In the beginning was the Logos, and the Logos was with God, and the Logos was God.” Christ is identified as the Logos—the incarnate expression of divine truth, coherence, and moral order.
So, Logos = reason, truth, order, and meaning—both metaphysical and moral.
⸻
- What Is Money in Moral and Philosophical Terms?
Money is not just a medium of exchange; it is a tool of memory, a symbol of trust, and a measure of value. In a functioning system, it reflects: •Honest human action over time •Deferred trust and cooperation across generations •A shared language of value
In this sense, money is a representation of human agreements, which are grounded in speech, contract, and moral order—i.e., it is rooted in logos (lowercase l), as language and rationality.
⸻
- The Corruption of Money as a Violation of Logos
If Logos is the moral-rational order, then:
To corrupt money is to distort the shared language of value and trust. It is to introduce lies into the very structure of economic relationships.
This corruption occurs through: •Inflation and debasement (violating the honesty of measurement) •Manipulative monetary policy (favoring the few over the many) •Counterfeit value signals (misallocating resources) •Loss of accountability (removing consequences for moral failure)
Thus, money’s corruption breaks the moral symmetry between effort and reward, cost and value, debt and payment—violating logos in both linguistic and metaphysical senses.
⸻
- Theological Echoes:
If Christ is the Logos incarnate, then: •Monetary corruption becomes not merely economic malfeasance but moral rebellion. •It is anti-Logos—an act of anomia (lawlessness), which the New Testament identifies with the spirit of antichrist (2 Thessalonians 2:3–8).
⸻
-
 @ 266815e0:6cd408a5
2025-04-29 17:47:57
@ 266815e0:6cd408a5
2025-04-29 17:47:57I'm excited to announce the release of Applesauce v1.0.0! There are a few breaking changes and a lot of improvements and new features across all packages. Each package has been updated to 1.0.0, marking a stable API for developers to build upon.
Applesauce core changes
There was a change in the
applesauce-corepackage in theQueryStore.The
Queryinterface has been converted to a method instead of an object withkeyandrunfields.A bunch of new helper methods and queries were added, checkout the changelog for a full list.
Applesauce Relay
There is a new
applesauce-relaypackage that provides a simple RxJS based api for connecting to relays and publishing events.Documentation: applesauce-relay
Features:
- A simple API for subscribing or publishing to a single relay or a group of relays
- No
connectorclosemethods, connections are managed automatically by rxjs - NIP-11
auth_requiredsupport - Support for NIP-42 authentication
- Prebuilt or custom re-connection back-off
- Keep-alive timeout (default 30s)
- Client-side Negentropy sync support
Example Usage: Single relay
```typescript import { Relay } from "applesauce-relay";
// Connect to a relay const relay = new Relay("wss://relay.example.com");
// Create a REQ and subscribe to it relay .req({ kinds: [1], limit: 10, }) .subscribe((response) => { if (response === "EOSE") { console.log("End of stored events"); } else { console.log("Received event:", response); } }); ```
Example Usage: Relay pool
```typescript import { Relay, RelayPool } from "applesauce-relay";
// Create a pool with a custom relay const pool = new RelayPool();
// Create a REQ and subscribe to it pool .req(["wss://relay.damus.io", "wss://relay.snort.social"], { kinds: [1], limit: 10, }) .subscribe((response) => { if (response === "EOSE") { console.log("End of stored events on all relays"); } else { console.log("Received event:", response); } }); ```
Applesauce actions
Another new package is the
applesauce-actionspackage. This package provides a set of async operations for common Nostr actions.Actions are run against the events in the
EventStoreand use theEventFactoryto create new events to publish.Documentation: applesauce-actions
Example Usage:
```typescript import { ActionHub } from "applesauce-actions";
// An EventStore and EventFactory are required to use the ActionHub import { eventStore } from "./stores.ts"; import { eventFactory } from "./factories.ts";
// Custom publish logic const publish = async (event: NostrEvent) => { console.log("Publishing", event); await app.relayPool.publish(event, app.defaultRelays); };
// The
publishmethod is optional for the asyncrunmethod to work const hub = new ActionHub(eventStore, eventFactory, publish); ```Once an
ActionsHubis created, you can use therunorexecmethods to execute actions:```typescript import { FollowUser, MuteUser } from "applesauce-actions/actions";
// Follow fiatjaf await hub.run( FollowUser, "3bf0c63fcb93463407af97a5e5ee64fa883d107ef9e558472c4eb9aaaefa459d", );
// Or use the
execmethod with a custom publish method await hub .exec( MuteUser, "3bf0c63fcb93463407af97a5e5ee64fa883d107ef9e558472c4eb9aaaefa459d", ) .forEach((event) => { // NOTE: Don't publish this event because we never want to mute fiatjaf // pool.publish(['wss://pyramid.fiatjaf.com/'], event) }); ```There are a log more actions including some for working with NIP-51 lists (private and public), you can find them in the reference
Applesauce loaders
The
applesauce-loaderspackage has been updated to support any relay connection libraries and not justrx-nostr.Before:
```typescript import { ReplaceableLoader } from "applesauce-loaders"; import { createRxNostr } from "rx-nostr";
// Create a new rx-nostr instance const rxNostr = createRxNostr();
// Create a new replaceable loader const replaceableLoader = new ReplaceableLoader(rxNostr); ```
After:
```typescript
import { Observable } from "rxjs"; import { ReplaceableLoader, NostrRequest } from "applesauce-loaders"; import { SimplePool } from "nostr-tools";
// Create a new nostr-tools pool const pool = new SimplePool();
// Create a method that subscribes using nostr-tools and returns an observable function nostrRequest: NostrRequest = (relays, filters, id) => { return new Observable((subscriber) => { const sub = pool.subscribe(relays, filters, { onevent: (event) => { subscriber.next(event); }, onclose: () => subscriber.complete(), oneose: () => subscriber.complete(), });
return () => sub.close();}); };
// Create a new replaceable loader const replaceableLoader = new ReplaceableLoader(nostrRequest); ```
Of course you can still use rx-nostr if you want:
```typescript import { createRxNostr } from "rx-nostr";
// Create a new rx-nostr instance const rxNostr = createRxNostr();
// Create a method that subscribes using rx-nostr and returns an observable function nostrRequest( relays: string[], filters: Filter[], id?: string, ): Observable
{ // Create a new oneshot request so it will complete when EOSE is received const req = createRxOneshotReq({ filters, rxReqId: id }); return rxNostr .use(req, { on: { relays } }) .pipe(map((packet) => packet.event)); } // Create a new replaceable loader const replaceableLoader = new ReplaceableLoader(nostrRequest); ```
There where a few more changes, check out the changelog
Applesauce wallet
Its far from complete, but there is a new
applesauce-walletpackage that provides a actions and queries for working with NIP-60 wallets.Documentation: applesauce-wallet
Example Usage:
```typescript import { CreateWallet, UnlockWallet } from "applesauce-wallet/actions";
// Create a new NIP-60 wallet await hub.run(CreateWallet, ["wss://mint.example.com"], privateKey);
// Unlock wallet and associated tokens/history await hub.run(UnlockWallet, { tokens: true, history: true }); ```
-
 @ bc52210b:20bfc6de
2025-03-25 20:17:22
@ bc52210b:20bfc6de
2025-03-25 20:17:22CISA, or Cross-Input Signature Aggregation, is a technique in Bitcoin that allows multiple signatures from different inputs in a transaction to be combined into a single, aggregated signature. This is a big deal because Bitcoin transactions often involve multiple inputs (e.g., spending from different wallet outputs), each requiring its own signature. Normally, these signatures take up space individually, but CISA compresses them into one, making transactions more efficient.
This magic is possible thanks to the linearity property of Schnorr signatures, a type of digital signature introduced to Bitcoin with the Taproot upgrade. Unlike the older ECDSA signatures, Schnorr signatures have mathematical properties that allow multiple signatures to be added together into a single valid signature. Think of it like combining multiple handwritten signatures into one super-signature that still proves everyone signed off!
Fun Fact: CISA was considered for inclusion in Taproot but was left out to keep the upgrade simple and manageable. Adding CISA would’ve made Taproot more complex, so the developers hit pause on it—for now.
CISA vs. Key Aggregation (MuSig, FROST): Don’t Get Confused! Before we go deeper, let’s clear up a common mix-up: CISA is not the same as protocols like MuSig or FROST. Here’s why:
- Signature Aggregation (CISA): Combines multiple signatures into one, each potentially tied to different public keys and messages (e.g., different transaction inputs).
- Key Aggregation (MuSig, FROST): Combines multiple public keys into a single aggregated public key, then generates one signature for that key.
Key Differences: 1. What’s Aggregated? * CISA: Aggregates signatures. * Key Aggregation: Aggregates public keys. 2. What the Verifier Needs * CISA: The verifier needs all individual public keys and their corresponding messages to check the aggregated signature. * Key Aggregation: The verifier only needs the single aggregated public key and one message. 3. When It Happens * CISA: Used during transaction signing, when inputs are being combined into a transaction. * MuSig: Used during address creation, setting up a multi-signature (multisig) address that multiple parties control.
So, CISA is about shrinking signature data in a transaction, while MuSig/FROST are about simplifying multisig setups. Different tools, different jobs!
Two Flavors of CISA: Half-Agg and Full-Agg CISA comes in two modes:
- Full Aggregation (Full-Agg): Interactive, meaning signers need to collaborate during the signing process. (We’ll skip the details here since the query focuses on Half-Agg.)
- Half Aggregation (Half-Agg): Non-interactive, meaning signers can work independently, and someone else can combine the signatures later.
Since the query includes “CISA Part 2: Half Signature Aggregation,” let’s zoom in on Half-Agg.
Half Signature Aggregation (Half-Agg) Explained How It Works Half-Agg is a non-interactive way to aggregate Schnorr signatures. Here’s the process:
- Independent Signing: Each signer creates their own Schnorr signature for their input, without needing to talk to the other signers.
- Aggregation Step: An aggregator (could be anyone, like a wallet or node) takes all these signatures and combines them into one aggregated signature.
A Schnorr signature has two parts:
- R: A random point (32 bytes).
- s: A scalar value (32 bytes).
In Half-Agg:
- The R values from each signature are kept separate (one per input).
- The s values from all signatures are combined into a single s value.
Why It Saves Space (~50%) Let’s break down the size savings with some math:
Before Aggregation: * Each Schnorr signature = 64 bytes (32 for R + 32 for s). * For n inputs: n × 64 bytes.
After Half-Agg: * Keep n R values (32 bytes each) = 32 × n bytes. * Combine all s values into one = 32 bytes. * Total size: 32 × n + 32 bytes.
Comparison:
- Original: 64n bytes.
- Half-Agg: 32n + 32 bytes.
- For large n, the “+32” becomes small compared to 32n, so it’s roughly 32n, which is half of 64n. Hence, ~50% savings!
Real-World Impact: Based on recent Bitcoin usage, Half-Agg could save:
- ~19.3% in space (reducing transaction size).
- ~6.9% in fees (since fees depend on transaction size). This assumes no major changes in how people use Bitcoin post-CISA.
Applications of Half-Agg Half-Agg isn’t just a cool idea—it has practical uses:
- Transaction-wide Aggregation
- Combine all signatures within a single transaction.
- Result: Smaller transactions, lower fees.
- Block-wide Aggregation
- Combine signatures across all transactions in a Bitcoin block.
- Result: Even bigger space savings at the blockchain level.
- Off-chain Protocols / P2P
- Use Half-Agg in systems like Lightning Network gossip messages.
- Benefit: Efficiency without needing miners or a Bitcoin soft fork.
Challenges with Half-Agg While Half-Agg sounds awesome, it’s not without hurdles, especially at the block level:
- Breaking Adaptor Signatures
- Adaptor signatures are special signatures used in protocols like Discreet Log Contracts (DLCs) or atomic swaps. They tie a signature to revealing a secret, ensuring fair exchanges.
-
Aggregating signatures across a block might mess up these protocols, as the individual signatures get blended together, potentially losing the properties adaptor signatures rely on.
-
Impact on Reorg Recovery
- In Bitcoin, a reorganization (reorg) happens when the blockchain switches to a different chain of blocks. Transactions from the old chain need to be rebroadcast or reprocessed.
- If signatures are aggregated at the block level, it could complicate extracting individual transactions and their signatures during a reorg, slowing down recovery.
These challenges mean Half-Agg needs careful design, especially for block-wide use.
Wrapping Up CISA is a clever way to make Bitcoin transactions more efficient by aggregating multiple Schnorr signatures into one, thanks to their linearity property. Half-Agg, the non-interactive mode, lets signers work independently, cutting signature size by about 50% (to 32n + 32 bytes from 64n bytes). It could save ~19.3% in space and ~6.9% in fees, with uses ranging from single transactions to entire blocks or off-chain systems like Lightning.
But watch out—block-wide Half-Agg could trip up adaptor signatures and reorg recovery, so it’s not a slam dunk yet. Still, it’s a promising tool for a leaner, cheaper Bitcoin future!
-
 @ fd78c37f:a0ec0833
2025-04-29 16:34:07
@ fd78c37f:a0ec0833
2025-04-29 16:34:07Author: Taryn Christiansen
Introduction:
The future doesn’t look good for America. The economy is down, politics is in shambles, and, perhaps most devastating, the culture is split. The only agreement is that change is needed. This article aims to pave a road forward. Innovation drives the economy, and great innovations change and improve daily life. Joint efforts between public institutions and private enterprise, along with the energy and momentum generated by efficient and productive programs, can be orchestrated to cultivate national pride. But those programs need to have a noble purpose. Devotion toward technologies with the potential to transform and improve people’s lives should be the goal. Due to recent advancements in biotechnology, efforts should be directed there. Section 1 dives into the cultural divide. Section 2 outlines a way forward by examining the innovative process and how it can be implemented. Section 3 looks at the specifics of that implementation. Section 4 consists of concluding remarks about the future.
Section 1: A Divided Country
There are two competing visions dividing America. The Woke vision asserts that the United States was, and is, a fundamentally oppressive regime. The idea of a universal reason, the notion that human beings can attain progress in perpetuity through liberal democracy, science, and capitalism, is seen as nothing more than an ideological weapon used to coerce people into acquiescing to a hierarchy that benefits the few while exploiting the many – and so, out of principles of fairness and equity, the country has to be dismantled.
The Trumpian vision attempts to reaffirm American values. It aims to reestablish American exceptionalism and reinvigorate the American vision of prosperity and economic growth. It seeks to rekindle a sense of American greatness. But it does so cheaply. It is, in essence, the dying breath of a consumer culture fighting its own death. Like the first vision, it too rejects reason and discussion and the procedural processes necessary for liberal democracy. It perceives power as the proper political tool for achieving its objectives. It is not an attempt to restore the values that once characterized the country; it breaks from the American tradition in a radical direction toward a politics of entertainment.
Long ago, the country believed that the human capacity for reason – the ability to see the world clearly under the light of truth, unencumbered by bias or prejudice, free from instinct and emotion – was the torch that carries posterity forward. The founders believed the Bill of Rights and The Constitution enshrined eternal truths that reason alone made accessible. John Locke, an influential figure for the founders, stated that the primary purpose of government is to protect individuals' natural rights. We are all free and have the right to live the life we wish to live. But government is needed to ensure others do not interfere with those rights. What binds us is not a religion or creed but the mutual opportunity for each individual to form their own beliefs, to live out their own conceptions of the good. While fundamental, we will see that it is not enough. A collective purpose is necessary.
Now, the Woke vision sees this older view as wholly mythological – and for good reason. For example, there was a time when black people did not know they were descendants from Africa or the Caribbean and not naturally disposed slaves. People’s various histories and genealogies were stripped away, creating a space by which their humanity could be taken and they could be exploited. They were purposefully and intentionally cast into the shadows of history, and the culpable thought themselves perfectly justified. There was a time when moral and historical narratives depicting a grand destiny of white people conquering the West were considered to be true and that the genocide of Native peoples was not only acceptable but in fact necessary, and therefore legitimate. It has been a titanic and creative effort by great individuals and collective coalitions to get America to become self-conscious of its heinous blunders. Some of the best art and ideas of the twentieth century were born out of those efforts. The beginnings of liberation are born out of the ability to imagine a horizon beyond one’s current circumstances. And that ability for many people has been forged by courageous and heroic predecessors. But the spirit of those movements and their development into the Woke vision is a sign that it has lost its creative potential.
The Woke vision asserts that values like reason and rights are the remains of a colonial legacy. However, by negating them and failing to replace them with new values, deconstructive forces are all that remain. The country has historically failed (as well as succeeded) in living up to what reason and rights demand. But that doesn’t mean they aren’t the proper path forward. The assumption here is that they are, and they have to be creatively reinterpreted.
And the Trumpian vision fails as well. But it is worse because it never did, nor will it ever have any real creative potential. It is highly destructive. We can think about this in the following way.
The nineteenth-century German philosopher Friedrich Nietzsche believed a single, fundamental drive governs all of organic life: the will to power. Life, in a constant struggle, perpetually strives to expand and overcome itself repeatedly. From the brute force of two animals fighting for scarce resources to the highest manifestation of human potential, such as moral systems and inspiring artwork, all are produced from the same vital energy and source: the effort to attain power and mastery over a chaotic world.
As society develops and moves away from a state of nature, the will to power transfigures itself through a sublimative process that demands the individual to repress particular instincts and act according to the strictures and constraints formulated and instituted by the collective. As Freud observed in his Civilization and Its Discontents, the push and pull between primitive and ancient instincts and civilization’s repression of them create inextricable tensions. The Yale historian Marci Shore makes an incisive observation of Trump as a symbolic figure using this context and its language: he is the release and outpouring of those repressed instincts – the license to overthrow the restraints placed on the individual. Trump is the embodiment of brute force, a blind ego striving to assert itself over the world, adopting whatever means are available to achieve its aim. He is an eruption of the repressed Hobbesian state of nature, which expresses “a perpetual and restless desire of power after power that ceaseth only in death.” This is a destructive instinct, and we would be wise not to find out what follows.
Section 2: Unity Through Innovation
So, what is the solution? The country needs a ballast point. It needs national pride. Without a shared sense of identity and purpose, a sense of belonging to a larger community bound by a set of values, the country will continue to unravel. Regardless of the philosophical-level disputes and disagreements on fundamental principles that divide left from right, a collective identity needs to emerge. This article argues that, like the founders, we should turn to our institutions. We should look at how our institutions can facilitate needs by enabling individuals with the creative energy and tenacity to bring about new technologies and innovations that will transform the economy and standards of living. But not just new gadgets and services like iPhones and DoorDash but new technologies with the potential to enable people to live more fulfillingly and purposefully. New vaccines to eliminate unruly diseases, new therapies to mitigate the effects of debilitating illnesses, novel pharmaceuticals with competitive prices and cheaper means of production, and innovative mechanisms to empower people with disabilities to live as they are only able to imagine should play a major part in the mission that characterizes the country. That is a purpose to be proud of. Institutions like the Food and Drug Administration (FDA) and the National Institutes of Health (NIH) should act as bows, shooting forward the individuals and companies striving to reach that mark.
There’s a lot of talk about government efficiency and the need to be more fiscally responsible. Those are good things. But efficiency needs to have a purpose. There must be a goal that efficiency works to achieve. We should not wish to live without regulatory institutions. For example, people like Balaji Srinivasan are wrong to think we’re better off in an FDA-free society. The goal should be to harness those institutions, conduct more research and development, and utilize resources more effectively to achieve the results we want as a country. Just as we should strive to continue and expand our role in the AI race, we should also aim to maintain and further develop our leadership in biotech.
But we need a new of what the historian Gary Gerstle calls political order to achieve this. Political orders are “a vision of the good life that sells important constituencies on the virtues of a way of doing politics. The New Deal order and the Neoliberal order—which are, in a sense, the reverse of each other—illustrate this.”
It is common in America to see the world through the lenses of The New Deal and Neoliberal political orders for resolving issues in the country. The latter is to let the market decide, and the former is to create government programs to achieve some conception of the good. The former is, more or less, a libertarian solution and was very popular during the 1980s. The latter took form in what is known as progressivism, and it found popular expression during the 1930s and 1940s in FDR’s New Deal programs. The basic distinction separating these two political orders is between the right and the good.
Rights are the norms of obligations and constraints necessary for us all to coexist while simultaneously maintaining what many believe is the principal value of liberal democracy: freedom and liberty (these terms will be used interchangeably). Rights are not in the business of prescribing definite ways of life or enforcing particular ends for people to pursue. Rights preserve the conditions for freedom, and people are free to choose what to do with that freedom insofar as their decisions do not infringe on another person’s right to do so as well. Freedom, then, is the absence of coercion. By having that freedom, each is allowed to exercise their powers and capabilities according to their own discretion.
In the American context, by virtue of being a human being, we are said to be endowed with inalienable rights. And those rights both protect each individual from external coercion and provide a license for certain kinds of action. I am protected from being forced to say certain opinions and adopt particular beliefs. And I have the license to speak my own opinions, expound my own beliefs, and give voice to my own personal conscience. I am protected from forced association with people whom I do not wish to associate with, from the coercion to vote for a particular candidate, from being disallowed to protest, and from adopting ends I do not agree with or value. And, of course, that means I have a license to associate with whom I wish, vote for whoever I like, protest legislation I dislike, and adopt the ends I truly value. We are all free, and we all are obligated and constrained to preserve the conditions for us all to exercise that freedom mutually.
But if that is what rights are, how does a society ensure a distribution of goods and services for everyone to enjoy and partake in? After all, a right to free speech isn’t going to ensure anyone that they will have meals for nourishment, clothing for warmth, shelter from harsh conditions. The response comes from Adam Smith: economic freedom. Everyone has a natural propensity to “truck, barter, and trade” in order to improve their condition. And by the very nature of voluntary exchange, each party benefits. By an individual living his life according to his own interests, values, and ends, he “promote(s) an end which has no part of his own intention.” The invisible hand of the market promotes the ends held by other individuals, allowing everyone to live as they see fit and to coexist harmoniously with the community. By having the political freedom of rights and the economic freedom to exchange, people cooperate spontaneously and organically. That is the spirit of the neoliberal political order.
A conception of the good is different, and its meaning can be disclosed through the great liberal philosopher Voltaire’s likely apocryphal statement, “I disapprove of what you say, but I will defend to the death your right to say it.” What Voltaire disagrees with is not someone’s right to speak but of what they are saying, and we can imagine the person to be voicing their conception of the good, their values and ends that they believe characterize the good life, the life we ought to live, and Voltaire disapproves of it. The good is concerned with the proper ends that should be prioritized in order to flourish. Socrates famously declared the unexamined life is not worth living. Well, he’s espousing a conception of the good. It is a life of the intellect, a life of rational reflection and deliberation aimed toward self-knowledge. Are one’s beliefs consistent? Does one’s actions contradict what one truly believes? Is one aware of what one truly believes? And does one have the desire to discover the truth? These are Socratic questions, and a life devoted to answering them is a Socratic one.
Now, if there is a universal conception of the good life, if human beings have particular ends that define what it means to be a human being, and if failing to fulfill those ends implies a failure to realize one’s human potential for flourishing, then rights do not secure such outcomes. Rights only ensure individuals are free to pursue such ends if they wish. And given the contingency of life, that is to say that, because people are born into conditions they did not choose but were instead thrown into them, and because some individuals are born into wealth and advantage and some are born into poverty and disadvantage, some have the privilege to achieve the ends characterizing a good life and some do not. And that is unfair. And so, government programs, central planning, and economic stewardship can be used to enable and empower the underprivileged to achieve what others are better positioned to do. This is the spirit of the New Deal political order.
The mistake is to think the appropriate social, cultural, and political issues can be resolved by only one of these political orders. It is not one or the other. Both of these political orders capture powerful intuitions about how society should best function and operate, and there should be a synthesis between them.
Now, it is common knowledge that innovation drives economic growth. As capital becomes more efficient and fewer inputs are required to produce more outputs, the economy expands. In Matt Ridely’s book, Innovation: How It Works, he demonstrates beautifully the often messy and non-rational character of the innovative process.
At the heart of that process, he says, is serendipity. As frustrating as it is to human nature, the innovative process cannot be intelligently designed into a precise instrument capable of reproducing all the wonderful fruits that result from it. There is something inherently unpredictable about it, something unruly. It is organic and spontaneous. It demands the determination of individuals willing to fail over and over again until enough experience, insight, and gradual, often painstaking, progress results in the desired effects.
Ridley observes that so many of these innovations require the rich air of freedom to stimulate the instinct for exploration and discovery. Freedom nourishes and sustains that instinct, allowing it to grow and flourish. People must be free from unnecessary regulations and constraints to focus their creative energy on projects that demand endless hours of trying countless imaginative possibilities – and failing until something works. There’s always a tremendous amount of risk-taking. People need to be free to take them.
People also need to be free to collaborate with others who are also devoted to discovering a solution to seemingly intractable problems. The division of labor, where individuals specialize in a particular task and coordinate with others who do the same to maximize efficiency and productivity, is essential to the process. There’s a reason, as Ridley notes, that many innovations take place in cities, where individuals freely associate and influence one another.
Freedom also allows room for mistakes. Ridley documents many cases where innovation is the result of a mistake, not an intentional plan of action. Innovations can often begin with an intention that has nothing to do with the innovation itself. A deliberate decision leading to a breakthrough discovery can be entirely unrelated, even frivolous. Take the example of Louie Pasteur, one of the key discoverers of germ theory. He was inoculating chickens with cholera from an infected chicken broth when he left for vacation, leaving his assistant, Charles Chamberland, to continue the experiments. Charles, for whatever reason (perhaps he thought the whole idea was crazy), forgot about his responsibility and went on vacation. When both returned, they injected a chicken with the stale broth.
It made the chicken sick but did not kill it. And so he injected the same chicken with a much more virulent cholera strain that typically and easily killed chickens – and it failed. The chicken lived. Vaccines, an innovation on inoculation, emerged. Funny enough, a similar incident occurred with Alexander Fleming. Known for being sloppy, Fleming carelessly left out a culture plate of staphylococcus and took off for vacation for a couple of weeks. When he returned, he discovered a mold had grown that was resistant to the bacteria.
Penicillin was soon developed. All this is to say that, along with Ridley, “Innovation is the child of freedom and the parent of prosperity.”
But government has also been integral to many inventions and innovations that would later revolutionize the economy and, therefore, daily life itself. Mariana Mazzucato’s book The Entrepreneurial State makes a persuasive case for the significance of public institutions in the innovative process. When the Defense Advanced Research Projects Agency (DARPA), initially known as ARPA until 1972, was established in 1958 in response to the launch of the Soviet satellite Sputnik in 1957, it aimed to promote ‘blue-sky thinking’ for technological initiatives. Meaning that the goal was to invest in riskier research that potentially would yield long-term gains despite not having any immediate or obvious returns on investment. DARPA pursued “ideas that went beyond the horizon in that they may not produce results for ten or 20 years.”
What makes DARPA a successful agency is its decentralized model. The philosophy is: "Find brilliant people. Give them resources. Get out of their way." DARPA hires talented and competent experts to run programs autonomously, providing them the discretion to pursue projects highlighted by their expertise, which are often considered risky. This model enables experts to connect with other researchers, facilitating collaboration and the creation of highly efficient and productive divisions of labor. And again, these are projects that likely wouldn’t find market interest because of their niche or unexplored nature. There isn’t an immediate and conspicuous payoff. And so the connected but separate-from-government model of DARPA provides scientists with a wide degree of latitude, and that freedom allows them to engage in the innovative process of trial and error and risk-taking.
Technologies developed by DARPA included ARPANET, the precursor to the internet; early GPS technology; the beginnings of autonomous vehicles; speech recognition; personal computing; and early AI.
Other agencies have also been foundational in technological advancements (for example, the National Science Foundation (NSF) provided critical grants to facilitate what would become Google’s search engine algorithm). But the DARPA model is what is most interesting here.
If government programs like DARPA can be leveraged to spur more innovation, particularly in areas such as biotech, and these innovations can drive economic growth by being put into the hands of entrepreneurs, investors, and small, medium, and large firms, then this demands national effort and attention. If successful, it is a project worthy of national pride.
So, government programs and spending, if properly structured, can yield high returns on investment if people are given the freedom to explore, try things out, and make the mistakes necessary for the innovative process to be carried through. And we can look to a recent example where the absence of the efforts potentially could have been disastrous. The story of the COVID-19 vaccines is one where the lack of zeal for exploration and breakthrough discoveries could have hindered the development of mRNA research, leaving it underdeveloped when it was needed at a critical moment.
Section 3: Covid-19, The Imperative For Research and Development, and The Institutional Framework
To start, Peter Theil is popular for remarking that innovation in many industries has grown stagnant. Energy, manufacturing, and transportation, for example, haven’t seen much progress in the past half-century.
Computation, on the other hand, has surpassed the imagination. The innovations have not been in atoms but in bits. As Theil puts it, “We wanted flying cars; instead we got 140 characters.” And Ridley writes, “If cars had improved as fast as computers since 1982, they would get nearly four million miles per gallon, so they could go to the moon and back a hundred times on a single tank of fuel.” Unfortunately, we still have to visit the gas station and pay those exorbitant prices.
But biotech has gained momentum in the past decade. The COVID vaccines are an extraordinary example of this. But they wouldn’t have been ready to come to market without the previous three decades of research and development invested in them. And that research and development almost didn’t happen because people lacked the vision and the willingness to embrace the risk that great technological discoveries, inventions, and innovations always require.
Ezra Klein and Derek Thompson’s book Abundance tells this story very well. Katalin Kariko, one of the discoverers of mRNA’s therapeutic capabilities, had enormous difficulty securing funding for her research as an assistant professor at the University of Pennsylvania. Those with power thought it too risky, that it didn’t show enough promise, and allocated most resources to DNA research at the time, believing it to be the more auspicious investment. Nevertheless, as so many pioneering figures have done before her, Kariko maintained her vision of unlocking mRNA’s potential for saving lives.
By sheer luck, by the fortune contained in everyday decisions that would lead to saving millions of lives several decades later, Kariko met a colleague who was researching HIV vaccines at the time, Drew Weissman, at a Xerox machine in 1997. He would be pivotal in her research. She is a biochemist, and he, an immunologist. Each provided the knowledge and expertise the other was lacking, and that was essential to their respective goals. Through the serendipity of deciding to walk to a different department to make copies at the time and place she did, Kariko encountered an opportunity to make strides in her research.
Together, however, the two still managed to collect barely enough funding. “The NIH,” which is the largest public funder of biomedical research, “rejected practically all of their grant applications.” They couldn’t get others to have the same foresight. Even after a breakthrough, where they were finally able to send mRNA information into cells without causing horrible inflammation, those in power still blinked. Fortunately, private investment supplied the gust they needed to keep their research going, and two companies created to pursue mRNA research, Moderna and BioNTech, facilitated the vaccine’s development. When Covid spread, enough progress had been made. The FDA, which has set a poor precedent for getting products to market when it matters most, streamlined the approval process and made the vaccine available.
The key features of this story are the following. The first is the lack of risk-taking by institutions and agencies whose aim should be to provide resources to those striving to innovate and push technological progress forward. The second is the lack of coordination to establish intentional environments to converge the paths of those who have the determination, discipline, and vision to bring innovation to fruition. Imagine if Kariko and Weismann didn’t meet; picture Kariko choosing to make copies somewhere else or at a different time. The future may have been radically different. And thirdly, and more optimistically, the FDA served a vital role when it mattered. As a public institution responsible for promoting the public good, they served admirably.
These three parts – funding research, coordinating talent, and the institutions facilitating the results – should coalesce into an optimally functioning whole. Researchers who are trying to shape and influence an unforeseeable future should be encouraged and rewarded. Those who possess powerful and novel ideas, along with the imagination and determination to bring them to life, should be in direct contact with one another. Their paths should cross – intentionally. And lastly, institutions should follow the FDA’s example. Slow regulatory regimes, lengthy processes and paperwork, licensing barriers, and stifling restrictions should be streamlined and transformed into facilitators for technological development and the introduction of powerful and revolutionary technologies into the market.
More funding should be devoted to riskier research. Those with novel and fresh ideas with the potential to disrupt current scientific knowledge and produce a breakthrough should be sought out. It is estimated that roughly 2-5% of the NIH’s current budget of $45 billion is allocated to high-risk research. That should be increased. Programs like the High-Risk, High-Reward Research Program, which includes awards to innovative researchers and ideas, should take on a more robust role and budget than it currently does.
Furthermore, approximately 80% of the NIH budget is allocated to extramural research programs, which are external programs conducted outside of the institution itself. A larger portion of those who receive that funding should be based on their potential for innovation. Currently, as Klein and Thompson observe, the process of obtaining a research grant, which involves extensive paperwork and minutiae, is bureaucratic, cumbersome, inefficient, and time-consuming. A significant amount of energy that should be allocated toward advancing research is spent on securing the funding to do it.
Submitting an application, going through the two review processes, and being approved takes typically nine months to a year. And most fail, leading many scientists to have to apply numerous times in a year. And those doing the review process aren’t necessarily looking for cutting-edge proposals; they’re looking for what fits bureaucratic standards. Of course, this is contentious, but Kariko's story demonstrates its reality. Ridley offers another example. When Francisco Majica made critical advancements in CRISPR technology, it took him “more than a year to get his results published, so sniffy were the prestigious journals at the idea of a significant discovery coming from a scientific nobody.” Institutions must do a better job of trying and supporting novel and unexplored ideas, regardless of who or what they originate from. For example, biotech DAOs do not currently receive funding from government institutions, such as the NIH, due to the traditional legal framework used to distribute resources. Regulatory and legal changes should be implemented to maximize their potential. If there is too much emphasis on process, on bureaucratic procedures and standards, fruitful and rich opportunities suffocate.
The NIH budget also allocates funds to intramural research programs, which are internally connected to the NIH itself. These research programs account for roughly 10% of the NIH’s total budget. A highly promising model to adopt is the DARPA model articulated in Section 2. The NIH should adopt something similar. It should allocate resources to decentralized programs to bring together the best scientists to generate breakthrough ideas. Those programs should be spaces where scientists are free to pursue visionary projects.
Smaller biotech firms, startups, and those without robust forms of funding are often forced to pursue ideas that will capture immediate investment attention. And because of the burdensome and costly bureaucratic processes, investors are justly skeptical about anything risky and cutting-edge.
For example, regarding the FDA approval process, small molecule drugs like pharmaceuticals generally take ten to fifteen years to reach the market. On average, one drug costs $1-2 billion to move through the process, and less than ten percent of those who enter clinical trials succeed. Biologics, such as vaccines and gene therapies, typically take ten to twelve years to reach the market and have a slightly higher success rate than small molecule drugs, ranging from 12 to 15 percent. Those are extensive periods of time, the costs are astronomical, and few can maintain the resources to climb the mountain. This discourages bold enterprise – and it leads to higher prices as well. Due to the cumbersome approval process, the FDA offers exclusivity to companies that bring a product to market, both to reward innovation and to allow companies the opportunity to recoup the tremendous losses incurred by the approval process. This can lead to monopolistic pricing. Innovation should not be rewarded by harming the consumer. Innovation should lift the tide that raises all boats. And so the innovative process shouldn’t be exclusive to those with enough capital to take risks. It should be available to anyone with the tenacity to actualize a bold and promising idea. That’s not to say the process should be less rigorous and methodical. It’s that it needs to be more efficient. But not just efficiency for efficiency's sake; it needs to be efficient toward the right ends and outcomes, and innovation should be a leading goal.
Therefore, a primary goal of the FDA should be to stimulate market interest by expediting the most innovative technologies emerging from research programs driven by the NIH and its innovation initiatives. It’s very important that private research continues innovating as well, and increases in private investment toward manufacturing and research – like Johnson & Johnson’s recent announcement – is good. But new technologies, drugs, vaccines, and therapies should be a central mission of the institutional framework advocated for here – and the process should begin with creativity for creativity’s sake. The profit motive should be employed after realizing a passionate and creative vision. Those truly motivated by inspiration, the people who have the will to manifest something novel and unimaginable, are generally the worst at navigating the business aspect - not always, but often. And the energy pushing them forward is a precious and scarce resource. And so institutions like the FDA and NIH should foster, rather than stifle, their capabilities and opportunities for creating meaningful contributions to the country and the world. The FDA has a history of being slow and untimely when it comes to processing and approving applications for moving to clinical trials. For example, the AIDS epidemic is a stain on the institution’s reputation. When AIDS spread across the US in 1980, it took scientists three years to identify HIV as the cause, five years for the FDA to approve the first blood test to screen for the virus, and seven years to finally get a drug to market. The response to COVID-19 should be the golden standard by which the FDA operates.
Section 4: Human Being and Its Essence
Now, let’s ask the following: what does this have to do with national pride? How does this provide a new vision for the country?
In Alex Karp’s new book, The Technological Republic, he criticizes Silicon Valley for forgetting its roots in developing technology for national purposes. The foundational technology that defines Silicon Valley originated from government programs like DARPA and NASA, which had a clear purpose. They had a mission, and the achievements under those programs demonstrate that.
But now Silicon Valley has shifted to the consumer. Innovations in Silicon Valley generally make life more convenient, comfortable, pleasant, breezy. Goods and services satisfy all our wants and preferences. New apps, better features on social media, increasingly competent virtual assistants, faster food delivery services, endless streams of television and movies and videos, smart appliances, and more and more advanced phones pervade everyday life. The goal is always immediate gratification. There is no horizon that these products look up to. Everything is here and now.
This takes us back to our discussion of rights and conceptions of the good. Silicon Valley isn’t tethered to any real purpose or collective aim. Its goal is to let the market decide. There is no moral or spiritual integrity, no conception of the good that permeates Silicon Valley and its products. Nothing is off limits because it is the consumer’s right to choose. If there is a want, if enough people are willing to buy, Silicon Valley will produce it. No substantive conviction guides their innovations. What does Silicon Valley stand for? It certainly has a creative spirit – just look at all the devices we have today – but that spirit lacks a purpose, and so it wanders aimlessly chasing the fleeting nature of the consumer.
It’s perfectly understandable that Silicon Valley has severed itself from its military roots. Not only would it lose a substantial portion of revenue if it returned to those roots, but there is, of course, a moral dilemma at the heart of most military endeavors, and it is wise to take that seriously. And the Tech sector should not aim to impose a conception of the good on the consumers. The issue is its obsession with the consumer. There are more pressing areas of concern that warrant attention. The wealth of talent in Silicon Valley is better spent in those areas. And it should be done through the efficient use of public institutions.
The new vision is one where taxpayer dollars are used for purposeful and meaningful projects that generate new technologies and innovations that contribute to people’s real needs, not just their wants and preferences. Genuine pride involves courage and bold risk for the sake of principle. It consists in having the determination to carry through an arduous enterprise. And we should be proud as a country if a joint effort between the public and private sectors achieves collective ends.
And at the heart of this pride should be the creative process. Albert Einstein wrote that great scientific discoveries – the new ideas that are leaps in progress toward the expansion of human knowledge – are, again, not the inevitable product of a rigid, refined, and precisely applied method. He believed the great discoveries, the ones that establish new scientific paradigms that enrich society with so many practical fruit, result from a cosmic feeling, a kind of religious experience born out of feelings of awe, wonder, and mystery that are produced by the intellectual and spiritual effort to understand the rational order of the cosmos. He writes, “Enough for me (is) the mystery of the eternity of life, and the inkling of the marvelous structure of reality, together with the single-hearted endeavor to comprehend a portion, be it ever so tiny, of the reason that manifest itself in nature… I maintain that cosmic religious feeling is the strongest and noblest incitement to scientific research.”
Reaching for and clinching a new and profound idea is not a mechanical and algorithmic activity. Regardless of how finely one specifies the rules of procedure or how regimented the institutional standards for scientific knowledge are prescribed, intuition, sensitivity to the world and its objects, amazement at the experience of observing the world and its causal relations, in short, the feelings and moods of the subject investigating the object, are integral to the discovery of scientific ideas. Methods are pivotal in locating and developing the precise, logical nature of those ideas, but initial contact with them demands variables that are not reducible to fixed procedures. Ideas powerful enough to change the world and better the human condition originate in cosmic feelings of wonder and curiosity and are not strictly an output of a mechanized division of labor.
AI will outrun the human capacity for intelligence. This is a likely prediction. And so what will it mean to be a human being then? For centuries, philosophers have distinguished human beings from other parts of nature by invoking our seemingly unique capacity for reason. We have the ability to contemplate, reflect, and grasp the physical laws governing the cosmos. We can harness those laws and employ them to manipulate our environment, alter its forms, and recombine its parts, allowing us to raise our living standards beyond our ancestor’s imaginations. We are highly intelligent beings, and our intelligence has been regarded as our distinguishing mark.
AI erodes this image. This new technology is becoming, and perhaps already is, a concrete realization, an externalization of what history thought was uniquely our own. The reality that reason isn’t special, that it is nothing more than a physical product of an accidental evolution, a wisp of luck, has become more and more firmly impressed upon the mind over the last two centuries. AI will make it indelible; it is the final proof. And so what is a human being? What distinguishes us?
The answer is in our spontaneous acts of creativity, in our ability to produce beauty in art, complexity in design, and in our profound capability to experience wonder. Again, the innovative process discussed above cannot be rationally formed into a precise instrument. As frustrating as it is, as much as it bumps against our instinct to make everything intelligible and known, our ability for spontaneity and creativity, our capacity to fail over and over again until we receive those moments of imaginative brilliance, cannot be reduced into a definite set of rules and procedures.
And so as the world changes, as everything alters before our eyes, we have to value what makes us distinctly human. We need a new Enlightenment, one that celebrates our creativity and our will to manifest what we can internally envision. Our self-respect as individuals and collectives lies in our instincts for curiosity, inquiry, discovery, and the creative and imaginative processes that animate them.
-
 @ b17fccdf:b7211155
2025-03-25 11:23:36
@ b17fccdf:b7211155
2025-03-25 11:23:36Si vives en España, quizás hayas notado que no puedes acceder a ciertas páginas webs durante los fines de semana o en algunos días entre semana, entre ellas, la guía de MiniBolt.
Esto tiene una razón, por supuesto una solución, además de una conclusión. Sin entrar en demasiados detalles:
La razón
El bloqueo a Cloudflare, implementado desde hace casi dos meses por operadores de Internet (ISPs) en España (como Movistar, O2, DIGI, Pepephone, entre otros), se basa en una orden judicial emitida tras una demanda de LALIGA (Fútbol). Esta medida busca combatir la piratería en España, un problema que afecta directamente a dicha organización.
Aunque la intención original era restringir el acceso a dominios específicos que difundieran dicho contenido, Cloudflare emplea el protocolo ECH (Encrypted Client Hello), que oculta el nombre del dominio, el cual antes se transmitía en texto plano durante el proceso de establecimiento de una conexión TLS. Esta medida dificulta que las operadoras analicen el tráfico para aplicar bloqueos basados en dominios, lo que les obliga a recurrir a bloqueos más amplios por IP o rangos de IP para cumplir con la orden judicial.
Esta práctica tiene consecuencias graves, que han sido completamente ignoradas por quienes la ejecutan. Es bien sabido que una infraestructura de IP puede alojar numerosos dominios, tanto legítimos como no legítimos. La falta de un "ajuste fino" en los bloqueos provoca un perjuicio para terceros, restringiendo el acceso a muchos dominios legítimos que no tiene relación alguna con actividades ilícitas, pero que comparten las mismas IPs de Cloudflare con dominios cuestionables. Este es el caso de la web de MiniBolt y su dominio
minibolt.info, los cuales utilizan Cloudflare como proxy para aprovechar las medidas de seguridad, privacidad, optimización y servicios adicionales que la plataforma ofrece de forma gratuita.Si bien este bloqueo parece ser temporal (al menos durante la temporada 24/25 de fútbol, hasta finales de mayo), es posible que se reactive con el inicio de la nueva temporada.

La solución
Obviamente, MiniBolt no dejará de usar Cloudflare como proxy por esta razón. Por lo que a continuación se exponen algunas medidas que como usuario puedes tomar para evitar esta restricción y poder acceder:
~> Utiliza una VPN:
Existen varias soluciones de proveedores de VPN, ordenadas según su reputación en privacidad: - IVPN - Mullvad VPN - Proton VPN (gratis) - Obscura VPN (solo para macOS) - Cloudfare WARP (gratis) + permite utilizar el modo proxy local para enrutar solo la navegación, debes utilizar la opción "WARP a través de proxy local" siguiendo estos pasos: 1. Inicia Cloudflare WARP y dentro de la pequeña interfaz haz click en la rueda dentada abajo a la derecha > "Preferencias" > "Avanzado" > "Configurar el modo proxy" 2. Marca la casilla "Habilite el modo proxy en este dispositivo" 3. Elige un "Puerto de escucha de proxy" entre 0-65535. ej: 1080, haz click en "Aceptar" y cierra la ventana de preferencias 4. Accede de nuevo a Cloudflare WARP y pulsa sobre el switch para habilitar el servicio. 3. Ahora debes apuntar el proxy del navegador a Cloudflare WARP, la configuración del navegador es similar a esta para el caso de navegadores basados en Firefox. Una vez hecho, deberías poder acceder a la guía de MiniBolt sin problemas. Si tienes dudas, déjalas en comentarios e intentaré resolverlas. Más info AQUÍ.

~> Proxifica tu navegador para usar la red de Tor, o utiliza el navegador oficial de Tor (recomendado).

La conclusión
Estos hechos ponen en tela de juicio los principios fundamentales de la neutralidad de la red, pilares esenciales de la Declaración de Independencia del Ciberespacio que defiende un internet libre, sin restricciones ni censura. Dichos principios se han visto quebrantados sin precedentes en este país, confirmando que ese futuro distópico que muchos negaban, ya es una realidad.
Es momento de actuar y estar preparados: debemos impulsar el desarrollo y la difusión de las herramientas anticensura que tenemos a nuestro alcance, protegiendo así la libertad digital y asegurando un acceso equitativo a la información para todos
Este compromiso es uno de los pilares fundamentales de MiniBolt, lo que convierte este desafío en una oportunidad para poner a prueba las soluciones anticensura ya disponibles, así como las que están en camino.
¡Censúrame si puedes, legislador! ¡La lucha por la privacidad y la libertad en Internet ya está en marcha!

Fuentes: * https://bandaancha.eu/articulos/movistar-o2-deja-clientes-sin-acceso-11239 * https://bandaancha.eu/articulos/esta-nueva-sentencia-autoriza-bloqueos-11257 * https://bandaancha.eu/articulos/como-saltarse-bloqueo-webs-warp-vpn-9958 * https://bandaancha.eu/articulos/como-activar-ech-chrome-acceder-webs-10689 * https://comunidad.movistar.es/t5/Soporte-Fibra-y-ADSL/Problema-con-web-que-usan-Cloudflare/td-p/5218007
-
 @ e7454994:7bb2dac7
2025-04-29 16:28:59
@ e7454994:7bb2dac7
2025-04-29 16:28:59Imagine
According to Cazoomi, total revenue for nonprofits in the U.S. reached approximately $3.7 trillion in 2024.
I know in some cases a billion is a hundred million instead of a thousand million (presumably so that some millionaires can call themselves billionaires to distinguish themselves from the riffraff). But that’s not the case here. A trillion is one followed by 12 zeros, so in 2024, US non-profits’ expenses were
3,700,000,000,000 dollars.
How much is a trillion?
And that’s just the USA. We could safely double it for worldwide non-profits and still be well below the actual figure. To be conservative, let’s say 6 trillion of our dollars each year goes on the kinds of projects that non-profits are allowed to do (essentially, making the world a better place).
Think what you could do with just one million dollars. Now think of that times six million! The entire population of Congo, each man, woman, and child, could become a millionaire!. It’s not really imaginable.
That’s how much nonprofits have. What the hell have they done with all that money? In most places where poverty and malnutrition are rife, two thousand dollars a year per family would be more than enough to enable people to sort out whatever problems they have and convert their local community to abundance over three years. Six trillion divided by two thousand is three billion.
The people whom we allow to manage ‘aid’ for us are (to be polite) inept, and we need to bypass them urgently. Directsponsor.org and clickforcharity.net are part of a proof of concept, and our aim is to prove that a better way is possible by doing it.
When a hierarchy exists, it presents a focus of power that power-seeking individuals and cliques can over time turn to their advantage… Even volunteer organizations are subject to intrigues, power grabs, covert arrangements, misallocation of funds, etc. The problem is made worse by the fact that those who most desire power and who are the most ruthless are the very ones who tend to work their way to the top of hierarchies.
More Fun With Figures
Oxfam UK raised £368,000,000 in 2013-14. That’s around 450,000,000 euros. What could we do with that kind of money? A direct sponsorship project is, for a family, 120 per month = 1440 per year. 1440 / 450,000,000 = 312,500 families.
312,500 families, x 4 = 1,250,000 people, would move from poverty into abundance every 3 years with the money that goes through Oxfam. Does Oxfam achieve anything like this with our money?
Oxfam UK is just one of many, many such charities and is small fry when you look at things like USAID, which ran through 27 billion dollars in the year to 2025. What could we do with that?
Its well over 15 million families. Over 60 million people! Or, the entire population of Botswana, Namibia, Mauritania, Liberia, the Republic of Congo, the Central African Republic, Libya, Sierra Leone, Eritrea, Togo, and Guinea combined. This is only to make a point, not to suggest that we would ever achieve such numbers. It shows how wasteful and scandalous our present “aid” efforts really are.
NGOs and governments waste our money.
Solution

Until recently, it was impossible to send money directly to another human without going through the banking system. The big charity organisations were a necessary part of the process, and they made the most of their position. Think about it: you have a family to feed, rent or a mortgage that has to be paid, or you’ll be homeless and destitute. What would your priority be? Apart from the top level, these are generally good people with the best intentions.
But now we have Bitcoin. People can send money all over the world at extremely low cost. The recipients aren’t stupid; they know what they need better than any NGO “expert,” and any expertise or teaching they need, they can get if they have the money to pay for it. This way, the power relationship is reversed in favor of our recipients.
All we need is a system (open and distributed) that ensures sponsors’ funds are not being squandered and the projects being supported are not scams.
A few people decided to start such a project. We have a system almost fully built and currently being tested out. It will enable people to get together into small groups of sponsors to fund small, local projects by directly funding the individuals working on the project. Anything from a regular monthly commitment to a click-for-charity system where you don’t even need any money to occasional one-off purchases of items for a project will be possible.
Here’s our pilot project in Badilisha, on Lake Victoria.
If you like doing stuff on social media, please sign up on our beta site (no money needed) and say hi; we need a few people to get it started. clickforcharity.net.
-
 @ 005bc4de:ef11e1a2
2025-04-29 16:08:56
@ 005bc4de:ef11e1a2
2025-04-29 16:08:56Trump Bitcoin Report Card - Day 100
For whatever reason day 100 of a president's term has been deemed a milestone. So, it's time to check in with President Trump's bitcoin pledges and issue a report card.
Repo and prior reports: - GitHub: https://github.com/crrdlx/trump-bitcoin-report-card - First post: https://stacker.news/items/757211 - Progress Report 1: https://stacker.news/items/774165 - Day 1 Report Card: https://stacker.news/items/859475 - Day 100 Report Card: https://stacker.news/items/966434
Report Card | | Pledge | Prior Grade | Current Grade | |--|--|--|--| | 1 | Fire SEC Chair Gary Gensler on day 1 | A | A | | 2 | Commute the sentence of Ross Ulbricht on day 1 | A | A | | 3 | Remove capital gains taxes on bitcoin transactions | F | F | | 4 | Create and hodl a strategic bitcoin stockpile | D | C- | | 5 | Prevent a CBDC during his presidency | B+ | A | | 6 | Create a "bitcoin and crypto" advisory council | C- | C | | 7 | Support the right to self-custody | D+ | B- | | 8 | End the "war on crypto" | D+ | B+ | | 9 | Mine all remaining bitcoin in the USA | C- | C | | 10 | Make the US the "crypto capital of the planet" | C- | C+ |
Comments
Pledge 1 - SEC chair - (no change from earlier) - Gensler is out. This happened after the election and Trump took office. With the writing on the wall, Gensler announced he would resign, Trump picked a new SEC head in Paul Atkins, and Gensler left office just before Trump was sworn in. The only reason an A+ was not awarded was that Trump wasn't given the chance to actually fire Gensler, because he quit. No doubt, though, his quitting was due to Trump and the threat of being sacked.
Day 100 Report Card Grade: A
Pledge 2 - free Ross - (no change from earlier) - Ross Ulbricht's sentence was just commuted. Going will "option 3" above, the pledge was kept. An A+ would have been a commutation yesterday or by noon today, but, let's not split hairs. It's done.
Day 100 Report Card Grade: A
Pledge 3 - capital gains - This requires either executive action and/or legislation. There was no action. Executive action can be done with the stroke of a pen, but it was not. Legislation is tricky and time-consuming, however, there wasn't even mention of this matter. This seems to be on the back burner since statements such as this report in November. See Progress Report 1: https://stacker.news/items/774165 for more context.
Trump's main tax thrust has been the tariff, actually a tax increase, instead of a cut. Currently, the emphasis is on extending the "Trump tax cuts" and recently House Speaker Mike Johnson indicated such a bill would be ready by Memorial Day. Earlier in his term, there was more chatter about tax relief for bitcoin or cryptocurrency. There seems to be less chatter on this, or none at all, such as its absence in the "ready by Memorial Day" article.
Until tax reform is codified and signed, it isn't tax law and the old code still applies.
Day 100 Report Card Grade: F
Pledge 4 - bitcoin reserve - The initial grade was a C, it was dropped to a D mainly due to Trump's propensity to [alt]coinery, and now it's back to a C-.
Getting the grade back up into C-level at a C- was a little bumpy. On March 2, 2025, Trump posted that a U.S. Crypto Reserve would be created. This is what had been hoped for, except that the pledge was for a Bitcoin Reserve, not crypto. And secondly, he specifically named XRP, SOL, and ADA (but not BTC). Just a couple of hours later, likely in clean up mode, he did add BTC (along with ETH) as "obviously" being included. So, the "Bitcoin Reserve" became a "Crypto Reserve."
Maybe still in "cleanup mode," Sec. of Commerce Howard Lutnick said bitcoin will hold "special status" in the reserve. Then, on March 6, an executive order made the U.S. Digital Asset Stockpile official. Again, "Bitcoin" was generalized until section 3 where the "Strategic Bitcoin Reserve" did come to official fruition.
The grade is only a C- because the only thing that happened was the naming of the stockpile. Indeed, it became official. But the "stockpile" was just BTC already held by the U.S. government. I think it's fair to say most bitcoiners would have preferred a statement about buying BTC. Other Trump bitcoin officials indicated acquiring "as much as we can get", which sounds great, but until it happens, is only words.
Day 100 Report Card Grade: C-
Pledge 5 - no CBDC - An executive order on January 23, 2025 forbade a CBDC in section 1, part v by "prohibiting the establishment, issuance, circulation, and use of a CBDC."
Day 100 Report Card Grade: A
Pledge 6 - advisory council - The Trump bitcoin or crypto team consists of the following: David Sacks as “crypto czar” and Bo Hines as executive director of the Presidential Council of Advisers for Digital Assets.
A White House Crypto Summit (see video) was held on March 7, 2025. In principle, the meeting was good, however, the summit seemed (a) to be very heavily "crypto" oriented, and (b) to largely be a meet-and-greet show.
Still, just the fact that such a show took place, inside the White House, reveals how far things have come and the change in climate. For the grade to go higher, more tangible things should take place over time.
Day 100 Report Card Grade: C
Pledge 7 - self-custody - There's been a bit of good news though on this front. First, the executive order above from January 23 stated in section 1, i, one of the goals was "...to maintain self-custody of digital assets." Also, the Phoenix wallet returned to the U.S. In 2024, both Phoenix and Wallet of Satoshi pulled out of the U.S. for fear of government crackdowns. The return of Phoenix, again, speaks to the difference in climate now and is a win for self-custody.
To rise above B-level, more assurance, it would be good to see further clear assurance that people can self-custody, that developers can build self-custody, and businesses can create products to self-custody. Also, Congressional action could get to an A.
Day 100 Report Card Grade: B-
Pledge 8 - end war on crypto - There has been improvement here. First, tangibly, SAB 121 was sent packing as SEC Commissioner Hester Peirce announced. Essentially, this removed a large regulatory burden. Commissioner Peirce also said ending the burdens will be a process to get out of the "mess". So, there's work to do. Also, hurdles were recently removed so that banks can now engage in bitcoin activity. This is both a symbolic and real change.
Somewhat ironically, Trump's own venture into cryptocurrency with his World Liberty Financial and the $TRUMP and $MELANIA tokens, roundly poo-pood by bitcoiners, might actually be beneficial in a way. The signal from the White House seems to be on all things cryptocurrency, "Do it."
The improvement and climate now seems very different than with the previous administration and leaders who openly touted a war on crypto.
Day 100 Report Card Grade: B+
Pledge 9 - USA mining - As noted earlier, this is an impossible pledge. That said, things can be done to make America mining friendly. The U.S. holds an estimated 37 to 40% of Bitcoin hash rate, which is substantial. Plus, Trump, or the Trump family at least, has entered into bitcoin mining. With Hut 8, Eric Trump is heading "American Bitcoin" to mine BTC. Like the $TRUMP token, this conveys that bitcoin mining is a go in the USA.
Day 100 Report Card Grade: C
Pledge 10 - USA crypto capital - This pledge closely aligned with pledges 8 and 9. If the war on crypto ends, the USA becomes more and more crypto and bitcoin friendly. And, if the hashrate stays high and even increases, that puts the USA at the center of it all. Most of the categories above have seen improvements, all of which help this last pledge. Trump's executive orders help this grade as well as they move from only words spoken to becoming official policy.
To get higher, the Bitcoin Strategic Reserve should move from a name-change only to acquiring more BTC. If the USA wants to be the world's crypto capital, being the leader in bitcoin ownership is the way to do it.
Day 100 Report Card Grade: C+
Sources
- Nashville speech - https://www.youtube.com/watch?v=EiEIfBatnH8
- CryptoPotato "top 8 promises" - https://x.com/Crypto_Potato/status/1854105511349584226
- CNBC - https://www.cnbc.com/2024/11/06/trump-claims-presidential-win-here-is-what-he-promised-the-crypto-industry-ahead-of-the-election.html
- BLOCKHEAD - https://www.blockhead.co/2024/11/07/heres-everything-trump-promised-to-the-crypto-industry/
- CoinTelegraph - https://cointelegraph.com/news/trump-promises-crypto-election-usa
- China vid - Bitcoin ATH and US Strategic Bitcoin Stockpile - https://njump.me/nevent1qqsgmmuqumhfktugtnx9kcsh3ap6v7ca4z8rgx79palz2qk0wzz5cksppemhxue69uhkummn9ekx7mp0qgszwaxc8j8e0zw9sdq59y43rykyx3wm0lcd2502xth699v0gxf0degrqsqqqqqpglusv6
- Capitals gains tax - https://bravenewcoin.com/insights/trump-proposes-crypto-tax-cuts-targets-u-s-made-tokens-for-tax-exemption Progress report 1 ------------------------------------------------------------------------------------
- Meeting with Brian Armstrong - https://www.wsj.com/livecoverage/stock-market-today-dow-sp500-nasdaq-live-11-18-2024/card/exclusive-trump-to-meet-privately-with-coinbase-ceo-brian-armstrong-DDkgF0xW1BW242rVeuqx
- Michael Saylor podcast - https://fountain.fm/episode/DHEzGE0f99QQqyM36nVr
- Gensler resigns - https://coinpedia.org/news/big-breaking-sec-chair-gary-gensler-officially-resigns/ Progress report 2 ------------------------------------------------------------------------------------
- Trump & Justin Sun - https://www.coindesk.com/business/2024/11/26/justin-sun-joins-donald-trumps-world-liberty-financial-as-adviser $30M investment: https://www.yahoo.com/news/trump-crypto-project-bust-until-154313241.html
- SEC chair - https://www.cnbc.com/2024/12/04/trump-plans-to-nominate-paul-atkins-as-sec-chair.html
- Crypto czar - https://www.zerohedge.com/crypto/trump-names-david-sacks-white-house-ai-crypto-czar
- Investigate Choke Point 2.0 - https://www.cryptopolitan.com/crypto-czar-investigate-choke-point/
- Crypto council head Bo Hines - https://cointelegraph.com/news/trump-appoints-bo-hines-head-crypto-council
- National hash rate: https://www.cryptopolitan.com/the-us-controls-40-of-bitcoins-hashrate/
- Senate committee https://coinjournal.net/news/rep-senator-cynthia-lummis-selected-to-chair-crypto-subcommittee/
- Treasurh Sec. CBDC: https://decrypt.co/301444/trumps-treasury-pick-scott-bessant-pours-cold-water-on-us-digital-dollar-initiative
- National priority: https://cointelegraph.com/news/trump-executive-order-crypto-national-priority-bloomberg?utm_source=rss_feed&utm_medium=rss&utm_campaign=rss_partner_inbound
- $TRUMP https://njump.me/nevent1qqsffe0d7mgtu5jhasy4hmkcdy7wfrlcqwc4vf676hulvdn8uaqa3acpzamhxue69uhhyetvv9ujuurjd9kkzmpwdejhgtczyztpa8q038vw5xluyhnydj5u39d7cpssvuswjhhjqj8q42jh4ul3wqcyqqqqqqgmha026
- World Liberty buys alts: https://www.theblock.co/post/335779/trumps-world-liberty-buys-25-million-of-tokens-including-link-tron-aave-and-ethena?utm_source=rss&utm_medium=rss
- CFTC chair: https://cryptoslate.com/trump-appoints-crypto-advocate-caroline-pham-as-cftc-acting-chair/
- WLF buys wrapped BTC https://www.cryptopolitan.com/trump-buys-47-million-in-bitcoin/
- SEC turnover https://www.theblock.co/post/335944/trump-names-sec-commissioner-mark-uyeda-as-acting-chair-amid-a-crypto-regulatory-shift?utm_source=rss&utm_medium=rss
- ----------------------------100 Days Report---------------------------------Davos speech "world capital of AI and crypto" https://coinpedia.org/news/big-breaking-president-trump-says-u-s-to-become-ai-and-crypto-superpower/
- SAB 121 gone, Hester P heads talk force & ends sab 121?, war on crypto https://x.com/HesterPeirce/status/1882562977985114185 article: https://www.theblock.co/post/336761/days-after-gensler-leaves-sec-rescinds-controversial-crypto-accounting-guidance-sab-121?utm_source=twitter&utm_medium=social CoinTelegraph: https://cointelegraph.com/news/trump-executive-order-cbdc-ban-game-changer-us-institutional-crypto-adoption?utm_source=rss_feed&utm_medium=rss&utm_campaign=rss_partner_inbound
- Possible tax relief https://cryptodnes.bg/en/will-trumps-crypto-policies-lead-to-tax-relief-for-crypto-investors/
- War on crypto https://decrypt.co/304395/trump-sec-crypto-task-force-priorities-mess
- Trump "truths" 2/18 make usa #1 in crypto, "Trump effect" https://www.theblock.co/post/333137/ripple-ceo-says-75-of-open-roles-are-now-us-based-due-to-trump-effect and https://www.coindesk.com/markets/2025/01/06/ripples-garlinghouse-touts-trump-effect-amid-bump-in-u-s-deals
- Strategic reserve https://njump.me/nevent1qqsf89l74mqfkk74jqhjcqtwp5m970gedmtykn5uhl0vz9mhmrvvvgqpzamhxue69uhhyetvv9ujuurjd9kkzmpwdejhgtczyztpa8q038vw5xluyhnydj5u39d7cpssvuswjhhjqj8q42jh4ul3wqcyqqqqqqge7c74u and https://njump.me/nevent1qqswv50m7mc95m3saqce08jzpqc0vedw4avdk6zxy9axrn3hqet52xgpzamhxue69uhhyetvv9ujuurjd9kkzmpwdejhgtczyztpa8q038vw5xluyhnydj5u39d7cpssvuswjhhjqj8q42jh4ul3wqcyqqqqqqgpc7cp3
- Strategic reserve, bitcoin special https://www.thestreet.com/crypto/policy/bitcoin-to-hold-special-status-in-u-s-crypto-strategic-reserve
- Bitcoin reserve, crypto stockpile https://decrypt.co/309032/president-trump-signs-executive-order-to-establish-bitcoin-reserve-crypto-stockpile vid link https://njump.me/nevent1qqs09h58patpv9vfjpcss6v5nxv7m23u8g6g43nqvkjzgzescztucmspr9mhxue69uhhyetvv9ujumt0d4hhxarj9ecxjmnt9upzqtjzyy2ylrsceh5uj20j5e95v0e99s3epsvyctu2y0vrwyltvq33qvzqqqqqqyus4pu7
- Truth summit https://njump.me/nevent1qqswj6sv0wr4d4ppwzam5egr5k6nmqgjpwmsrlx2a7d4ndpfj0fxvcqpzamhxue69uhhyetvv9ujuurjd9kkzmpwdejhgtczyztpa8q038vw5xluyhnydj5u39d7cpssvuswjhhjqj8q42jh4ul3wqcyqqqqqqgu0mzzh and vid https://njump.me/nevent1qqsptn8c8wyuhlqtjr5u767x20q4dmjvxy28cdj30t4v9phhf6y5a5spzamhxue69uhhyetvv9ujuurjd9kkzmpwdejhgtczyztpa8q038vw5xluyhnydj5u39d7cpssvuswjhhjqj8q42jh4ul3wqcyqqqqqqgqklklu
- SEC chair confirmed https://beincrypto.com/sec-chair-paul-atkins-confirmed-senate-vote/
- pro bitcoin USA https://coinpedia.org/news/u-s-secretary-of-commerce-howard-lutnick-says-america-is-ready-for-bitcoin/
- tax cuts https://thehill.com/homenews/house/5272043-johnson-house-trump-agenda-memorial-day/
- "as much as we can get" https://cryptobriefing.com/trump-bitcoin-acquisition-strategy/
- ban on CBDC https://www.whitehouse.gov/presidential-actions/2025/01/strengthening-american-leadership-in-digital-financial-technology/
- Phoenix WoS leave https://www.coindesk.com/opinion/2024/04/29/wasabi-wallet-and-phoenix-leave-the-us-whats-next-for-non-custodial-crypto
- Trump hut 8 mining https://www.reuters.com/technology/hut-8-eric-trump-launch-bitcoin-mining-company-2025-03-31/
-
 @ 3b7fc823:e194354f
2025-03-23 03:54:16
@ 3b7fc823:e194354f
2025-03-23 03:54:16A quick guide for the less than technical savvy to set up their very own free private tor enabled email using Onionmail. Privacy is for everyone, not just the super cyber nerds.
Onion Mail is an anonymous POP3/SMTP email server program hosted by various people on the internet. You can visit this site and read the details: https://en.onionmail.info/
- Download Tor Browser
First, if you don't already, go download Tor Browser. You are going to need it. https://www.torproject.org/
- Sign Up
Using Tor browser go to the directory page (https://onionmail.info/directory.html) choose one of the servers and sign up for an account. I say sign up but it is just choosing a user name you want to go before the @xyz.onion email address and solving a captcha.
- Account information
Once you are done signing up an Account information page will pop up. MAKE SURE YOU SAVE THIS!!! It has your address and passwords (for sending and receiving email) that you will need. If you lose them then you are shit out of luck.
- Install an Email Client
You can use Claws Mail, Neomutt, or whatever, but for this example, we will be using Thunderbird.
a. Download Thunderbird email client
b. The easy setup popup page that wants your name, email, and password isn't going to like your user@xyz.onion address. Just enter something that looks like a regular email address such as name@example.com and the Configure Manuallyoption will appear below. Click that.
- Configure Incoming (POP3) Server
Under Incoming Server: Protocol: POP3 Server or Hostname: xyz.onion (whatever your account info says) Port: 110 Security: STARTTLS Authentication: Normal password Username: (your username) Password: (POP3 password).
- Configure Outgoing (SMTP) Server
Under Outgoing Server: Server or Hostname: xyz.onion (whatever your account info says) Port: 25 Security: STARTTLS Authentication: Normal password Username: (your username) Password: (SMTP password).
-
Click on email at the top and change your address if you had to use a spoof one to get the configure manually to pop up.
-
Configure Proxy
a. Click the gear icon on the bottom left for settings. Scroll all the way down to Network & Disk Space. Click the settings button next to Connection. Configure how Thunderbird connects to the internet.
b. Select Manual Proxy Configuration. For SOCKS Host enter 127.0.0.1 and enter port 9050. (if you are running this through a VM the port may be different)
c. Now check the box for SOCKS5 and then Proxy DNS when using SOCKS5 down at the bottom. Click OK
- Check Email
For thunderbird to reach the onion mail server it has to be connected to tor. Depending on your local setup, it might be fine as is or you might have to have tor browser open in the background. Click on inbox and then the little cloud icon with the down arrow to check mail.
- Security Exception
Thunderbird is not going to like that the onion mail server security certificate is self signed. A popup Add Security Exception will appear. Click Confirm Security Exception.
You are done. Enjoy your new private email service.
REMEMBER: The server can read your emails unless they are encrypted. Go into account settings. Look down and click End-toEnd Encryption. Then add your OpenPGP key or open your OpenPGP Key Manager (you might have to download one if you don't already have one) and generate a new key for this account.
-
 @ d1667293:388e7004
2025-04-29 16:00:19
@ d1667293:388e7004
2025-04-29 16:00:19The "Bitcoindollar" system—an emerging term which describes the interplay of U.S. dollar-denominated stablecoins and Bitcoin as complementary forces in the evolving monetary framework of the digital era (and which replaces the defunct Petrodollar system)—has sparked an interesting debate on Nostr with PowMaxi.
You will find the thread links at the bottom of this article.
Powmaxi argues that attempting to merge hard money (Bitcoin) with soft money (the U.S. dollar) is structurally doomed, because the systems are inherently contradictory and cannot coexist without one eventually destroying the other.
This critique is certainly valid, but ONLY if the Bitcoindollar is viewed as a final system. But I never claim that. To the contrary, the conclusion in my book is that this is a system that buys time for fiat, absorbs global demand for monetary stability, and ushers in a Bitcoinized world without the immediate collapse and the reset of the fiat system which would otherwise cause dramatic consequences. The Bitcoindollar is the only way to a gradual Bitcoin dominance in 10-20 years time while avoiding sudden collapse of the fiat system, so that also the power elites who hold the keys to this system can adapt.\ At least this is my hope.
Therefore the "fusion" isn't the future. The siphoning is. And the U.S. may try to ride it as long as possible. The Bitcoindollar system is a transitional strategic framework, not a\ permanent monetary equilibrium. In the end I agree with PowMaxi.
His detailed critique deserves an equally detailed analysis. Here's how the objections break down and why they don’t necessarily undermine the Bitcoindollar system.
1. Hard Money vs. Soft Money: Opposed Systems?
Objection: Bitcoin is a closed, decentralized system with a fixed supply; the dollar is an open, elastic system governed by central banks and political power. These traits are mutually exclusive and incompatible.
Response: Ideologically, yes. Practically, no. Hybrid financial systems are not uncommon. Bitcoin and stablecoins serve different user needs: Bitcoin is a store of value; stablecoins are mediums of exchange. Their coexistence mirrors real-world economic needs. The contradiction can be managed, and is not fatal at least for the transitional phase.
2. Scarcity vs. Elasticity: Economic Incompatibility?
Objection: Bitcoin can’t inject liquidity in crises; fiat systems can. Anchoring fiat to Bitcoin removes policymakers' tools.
Response: Correct — but that’s why Bitcoin is held as a reserve, not used as the primary medium of exchange in the Bitcoindollar model. Fiat-based liquidity mechanisms still function via stablecoins, while Bitcoin acts as a counterweight to long-term monetary debasement. The system’s strength is in its optionality: you don’t have to use Bitcoin until you want an exit ramp from fiat.
3. No Stable Equilibrium: One Must Win?
Objection: The system will destabilize. Either Bitcoin undermines fiat or fiat suppresses Bitcoin.
Response: Not necessarily in this transitional phase. The “conflict” isn’t between tools — it’s between control philosophies. The dollar won’t disappear overnight, and Bitcoin isn’t going away. The likely outcome is a gradual shifting of savings and settlement layers to Bitcoin, while fiat continues to dominate day-to-day payments and credit markets — until Bitcoin becomes structurally better in both.
4. Gresham’s and Thiers’ Law: Hollowing Fiat?
Objection: People save in Bitcoin and spend fiat, eroding fiat value.
Response: Yes — and that’s been happening since 2009. But this isn’t a flaw; it’s a transition mechanism. The Bitcoindollar model recognizes this and creates a bridge: it monetizes U.S. debt while preserving access to hard money. In the long run, my expectation is that naturally bitcoin will prevail both as a SOV and currency, but until then, stablecoins and T-bill-backed tokens serve useful roles in the global economy.
5. Philosophical Incompatibility?
Objection: Bitcoin prioritizes individual sovereignty; fiat systems are hierarchical. They can't be reconciled.
Response: They don’t need to be reconciled ideologically to function in parallel. Users choose the tool that suits their needs. One empowers individual autonomy; the other offers state-backed convenience. This is a competition of values, not a mechanical incompatibility. The Bitcoindollar model is a strategy. It’s a bridge between old and new systems, not a permanent coexistence.
6. Fusion is Impossible?
Objection: It’s only a temporary bridge. One side must lose.
Response: Exactly. The Bitcoindollar system is a transitional bridge. But that doesn’t reduce its value. It provides a functional pathway for individuals, companies, and governments to gradually exit broken monetary systems and experiment with new models.
In the meantime, the U.S. benefits from stablecoin-driven Treasury demand, while Bitcoin continues to grow as a global reserve asset.
Bottom line: A Strategic Convergence, Not a Permanent Fusion
The Bitcoindollar system isn’t a contradiction. It’s a convergence zone. It reflects the reality that monetary systems evolve gradually, not cleanly. Bitcoin and fiat will compete, overlap, and influence each other. Eventually, yes — hard money wins. But until then, hybrid systems offer powerful stepping stones.
Thread links:
Thread started from this initial post.
-
 @ 21335073:a244b1ad
2025-03-18 20:47:50
@ 21335073:a244b1ad
2025-03-18 20:47:50Warning: This piece contains a conversation about difficult topics. Please proceed with caution.
TL;DR please educate your children about online safety.
Julian Assange wrote in his 2012 book Cypherpunks, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense.
This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning.
When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little.
I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?”
I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well.
I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread.
I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard.
I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it.
The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust.
Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this.
I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place.
What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method.
It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code.
They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened.
I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road.
So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally.
Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb.
I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback.
Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed.
That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone.
To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all.
I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society.
I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this.
On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government.
I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories.
There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc.
Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind.
Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now.
There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers?
I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity.
I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place.
My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors.
My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline.
The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online.
I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers.
So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation?
When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that.
I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic.
If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations.
I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process.
Course: - The creation of the internet and computers - The fight for cryptography - The tech supply chain from the ground up (example: human rights violations in the supply chain) - Corporate tech - Freedom tech - Data privacy - Digital privacy rights - AI (history-current) - Online safety (predators, scams, catfishing, extortion) - Bitcoin - Laws - How to deal with online hate and harassment - Information on who to contact if you are being abused online or offline - Algorithms - How to seek out the truth about news, etc., online
The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children.
The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward?
I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone.
Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability.
The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime.
This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful.
This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens.
In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions.
I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation.
-
 @ 56cd780f:cbde8b29
2025-04-29 14:37:37
@ 56cd780f:cbde8b29
2025-04-29 14:37:37And this is the regular text.
-
 @ 21335073:a244b1ad
2025-03-18 14:43:08
@ 21335073:a244b1ad
2025-03-18 14:43:08Warning: This piece contains a conversation about difficult topics. Please proceed with caution.
TL;DR please educate your children about online safety.
Julian Assange wrote in his 2012 book Cypherpunks, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense.
This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning.
When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little.
I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?”
I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well.
I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread.
I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard.
I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it.
The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust.
Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this.
I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place.
What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method.
It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code.
They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened.
I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road.
So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally.
Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb.
I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback.
Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed.
That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone.
To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all.
I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society.
I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this.
On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government.
I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories.
There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc.
Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind.
Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now.
There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers?
I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity.
I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place.
My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors.
My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline.
The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online.
I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers.
So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation?
When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that.
I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic.
If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations.
I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process.
Course: - The creation of the internet and computers - The fight for cryptography - The tech supply chain from the ground up (example: human rights violations in the supply chain) - Corporate tech - Freedom tech - Data privacy - Digital privacy rights - AI (history-current) - Online safety (predators, scams, catfishing, extortion) - Bitcoin - Laws - How to deal with online hate and harassment - Information on who to contact if you are being abused online or offline - Algorithms - How to seek out the truth about news, etc., online
The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children.
The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward?
I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone.
Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability.
The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime.
This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful.
This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens.
In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions.
I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation.
-
 @ a07fae46:7d83df92
2025-03-18 12:31:40
@ a07fae46:7d83df92
2025-03-18 12:31:40if the JFK documents come out and are nothing but old hat, it will be disappointing. but if they contain revelations, then they are an unalloyed good. unprecedented and extraordinary; worthy of praise and admiration. they murdered the president in broad daylight and kept 80,000 related documents secret for 60 years. the apparatus that did that and got away with it, is 100+ years in the making. the magic bullet was just the starting pistol of a new era; a level up in an old game. it won't be dismantled and your republic delivered back with a bow in 2 months. have a little humility and a little gratitude. cynicism is easy. it's peak mid-wittery. yeah no shit everything is corrupt and everyone's likely captured by AIPAC or something beyond. YOU THINK AIPAC is the ALL SEEING EYE?
you can keep going, if you want to, but have some awareness and appreciation for where we are and what it took to get here. the first 'you are fake news' was also a shot heard 'round the world and you are riding high on it's Infrasound wave, still reverberating; unappreciative of the profound delta in public awareness and understanding, and rate of change, that has occurred since that moment, in 2017. think about where we were back then, especially with corporate capture of the narrative. trump's bullheaded behavior, if only ego-driven, is what broke the spell. an actual moment of savage bravery is what allows for your current jaded affectation. black pilled is boring. it's intellectually lazy. it is low-resolution-thinking, no better than progressives who explain the myriad ills of the world through 'racism'. normalcy bias works both ways. i'm not grading you on a curve that includes NPCs. i'm grading you against those of us with a mind, on up. do better.
the best Webb-style doomer argument is essentially 'the mouse trap needs a piece of cheese in order to work'. ok, but it doesn't need 3 pieces of cheese, or 5. was FreeRoss the piece of cheese? was the SBR the cheese? real bitcoiners know how dumb the 'sbr is an attempt to takeover btc' narrative is, so extrapolate from that. what about withdrawal from the WHO? freeze and review of USAID et al? how many pieces of cheese before we realize it's not a trap? it's just a messy endeavor.
Good morning.
jfkFiles #nostrOnly
-
 @ bc52210b:20bfc6de
2025-03-14 20:39:20
@ bc52210b:20bfc6de
2025-03-14 20:39:20When writing safety critical code, every arithmetic operation carries the potential for catastrophic failure—whether that’s a plane crash in aerospace engineering or a massive financial loss in a smart contract.
The stakes are incredibly high, and errors are not just bugs; they’re disasters waiting to happen. Smart contract developers need to shift their mindset: less like web developers, who might prioritize speed and iteration, and more like aerospace engineers, where precision, caution, and meticulous attention to detail are non-negotiable.
In practice, this means treating every line of code as a critical component, adopting rigorous testing, and anticipating worst-case scenarios—just as an aerospace engineer would ensure a system can withstand extreme conditions.
Safety critical code demands aerospace-level precision, and smart contract developers must rise to that standard to protect against the severe consequences of failure.
-
 @ 56cd780f:cbde8b29
2025-04-29 14:37:35
@ 56cd780f:cbde8b29
2025-04-29 14:37:35I will add a picture, a hyperlink and a video. Let’s see if it works.
-
 @ df173277:4ec96708
2025-02-07 00:41:34
@ df173277:4ec96708
2025-02-07 00:41:34Building Our Confidential Backend on Secure Enclaves
With our newly released private and confidential Maple AI and the open sourcing of our OpenSecret platform code, I'm excited to present this technical primer on how we built our confidential compute platform leveraging secure enclaves. By combining AWS Nitro enclaves with end-to-end encryption and reproducible builds, our platform gives developers and end users the confidence that user data is protected, even at runtime, and that the code operating on their data has not been tampered with.
Auth and Databases Today
As developers, we live in an era where protecting user data means "encryption at rest," plus some access policies and procedures. Developers typically run servers that:
- Need to register users (authentication).
- Collect and process user data in business-specific ways, often on the backend.
Even if data is encrypted at rest, it's commonly unlocked with a single master key or credentials the server holds. This means that data is visible during runtime to the application, system administrators, and potentially to the hosting providers. This scenario makes it difficult (or impossible) to guarantee that sensitive data isn't snooped on, memory-dumped, or used in unauthorized ways (for instance, training AI models behind the scenes).
"Just Trust Us" Isn't Good Enough
In a traditional server architecture, users have to take it on faith that the code handling their data is the same code the operator claims to be running. Behind the scenes, applications can be modified or augmented to forward private information elsewhere, and there is no transparent way for users to verify otherwise. This lack of proof is unsettling, especially for services that process or store highly confidential data.
Administrators, developers, or cloud providers with privileged access can inspect memory in plaintext, attach debuggers, or gain complete visibility into stored information. Hackers who compromise these privileged levels can directly access sensitive data. Even with strict policies or promises of good conduct, the reality is that technical capabilities and misconfigurations can override words on paper. If a server master key can decrypt your data or can be accessed by an insider with root permissions, then "just trust us" loses much of its credibility.
The rise of AI platforms amplifies this dilemma. User data, often full of personal details, gets funneled into large-scale models that might be training or fine-tuning behind the scenes. Relying on vague assurances that "we don't look at your data" is no longer enough to prevent legitimate concerns about privacy and misuse. Now more than ever, providing a strong, verifiable guarantee that data remains off-limits, even when actively processed, has become a non-negotiable requirement for trustworthy services.
Current Attempts at Securing Data
 Current User Experience of E2EE Apps
Current User Experience of E2EE AppsWhile properly securing data is not easy, it isn't to say that no one is trying. Some solutions use end-to-end encryption (E2EE), where user data is encrypted client-side with a password or passphrase, so not even the server operator can decrypt it. That approach can be quite secure, but it also has its limitations:
- Key Management Nightmares: If a user forgets their passphrase, the data is effectively lost, and there's no way to recover it from the developer's side.
- Feature Limitations: Complex server-side operations (like offline/background tasks, AI queries, real-time collaboration, or heavy computation) can't easily happen if the server is never capable of processing decrypted data.
- Platform Silos: Some solutions rely on iCloud, Google Drive, or local device storage. That can hamper multi-device usage or multi-OS compatibility.
Other approaches include self-hosting. However, these either burden users with dev ops overhead or revert to the "trust me" model for the server if you "self-host" on a cloud provider.
Secure Enclaves
The Hybrid Approach
Secure enclaves offer a compelling middle ground. They combine the privacy benefits of keeping data secure from prying admins while still allowing meaningful server-side computation. In a nutshell, an enclave is a protected environment within a machine, isolated at the hardware level, so that even if the OS or server is compromised, the data and code inside the enclave remain hidden.
 App Service Running Inside Secure Enclave
App Service Running Inside Secure EnclaveHigh-Level Goal of Enclaves
Enclaves, also known under the broader umbrella of confidential computing, aim to:\ • Lock down data so that only authorized code within the enclave can process the original plaintext data.\ • Deny external inspection by memory dumping, attaching a debugger, or intercepting plaintext network traffic.\ • Prove to external users or services that an enclave is running unmodified, approved code (this is where remote attestation comes in).
Different Secure Enclave Solutions
AMD SEV (Secure Encrypted Virtualization) encrypts an entire virtual machine's memory so that even a compromised hypervisor cannot inspect or modify guest data. Its core concept is "lift-and-shift" security. No application refactoring is required because hardware-based encryption automatically protects the OS and all VM applications. Later enhancements (SEV-ES and SEV-SNP) added encryption of CPU register states and memory integrity protections, further limiting hypervisor tampering. This broad coverage means the guest OS is included in the trusted boundary. AMD SEV has matured into a robust solution for confidential VMs in multi-tenant clouds.
Intel TDX (Trust Domain Extensions) shifts from process-level enclaves to full VM encryption, allowing an entire guest operating system and its applications to run in an isolated "trust domain." Like AMD SEV, Intel TDX encrypts and protects all memory the VM uses from hypervisors or other privileged software, so developers do not need to refactor their code to benefit from hardware-based confidentiality. This broader scope addresses many SGX limitations, such as strict memory bounds and the need to split out enclave-specific logic, and offers a more straightforward "lift-and-shift" path for running existing workloads privately. While SGX is now deprecated, TDX carries forward the core confidential computing principles but applies them at the virtual machine level for more substantial isolation, easier deployment, and the ability to scale up to large, memory-intensive applications.
Apple Secure Enclave and Private Compute is a dedicated security coprocessor embedded in most Apple devices (iPhones, iPads, Macs) and now extended to Apple's server-side AI infrastructure. It runs its own microkernel, has hardware-protected memory, and securely manages operations such as biometric authentication, key storage, and cryptographic tasks. Apple's "Private Compute" approach in the cloud brings similar enclave capabilities to server-based AI, enabling on-device-grade privacy even when requests are processed in Apple's data centers.
AWS Nitro Enclaves carve out a tightly isolated "mini-VM" from a parent EC2 instance, with its own vCPUs and memory guarded by dedicated Nitro cards. The enclave has no persistent storage and no external network access, significantly reducing the attack surface. Communication with the parent instance occurs over a secure local channel (vsock), and AWS offers hardware-based attestation so that secrets (e.g., encryption keys from AWS KMS) can be accessed only to the correct enclave. This design helps developers protect sensitive data or code even if the main EC2 instance's OS is compromised.
NVIDIA GPU TEEs (Hopper H100 and Blackwell) extend confidential computing to accelerated workloads by encrypting data in GPU memory and ensuring that even a privileged host cannot view or tamper with it. Data moving between CPU and GPU is encrypted in transit, so sensitive model weights or inputs remain protected during AI training or inference. NVIDIA's hardware and drivers handle secure data paths under the hood, allowing confidential large language model (LLM) workloads and other GPU-accelerated computations to run with minimal performance overhead and strong security guarantees.
Key Benefits
One major advantage of enclaves is their ability to keep memory completely off-limits to outside prying eyes. Even administrators who can normally inspect processes at will are blocked from peeking into the enclave's protected memory space. The enclave model is a huge shift in the security model: it prevents casual inspection and defends against sophisticated memory dumping techniques that might otherwise leak secrets or sensitive data.
Another key benefit centers on cryptographic keys that are never exposed outside the enclave. Only verified code running inside the enclave environment can run decryption or signing operations, and it can only do so while that specific code is running. This ensures that compromised hosts or rogue processes, even those with high-level privileges, are unable to intercept or misuse the keys because the keys remain strictly within the trusted boundary of the hardware.
Enclaves can also offer the power of remote attestation, allowing external clients or systems to confirm that they're speaking to an authentic, untampered enclave. By validating the hardware's integrity measurements and enclave-specific proofs, the remote party can be confident in the underlying security properties, an important guarantee in multi-tenant environments or whenever trust boundaries extend across different organizations and networks.
Beyond that, reproducible builds can create a verifiable fingerprint proving which binary runs in the enclave. This is a step above a simple "trust us" approach. Anyone can independently recreate the enclave image and verify the resulting cryptographic hash by using a reproducible build system (for example, our NixOS-based solution). If it matches, then users and developers know precisely how code handles their data, boosting confidence that no hidden changes exist.
It's worth noting that although enclaves shield you from software devs, cloud providers, and insider threats, you do have to trust the hardware vendor (Intel, AMD, Apple, AWS, or NVIDIA) to implement their microcode and firmware securely. The entire enclave model could be theoretically undermined if a CPU maker's root keys or manufacturing process were compromised. Fortunately, these companies undergo extensive audits and firmware validations (often with third-party researchers), and their remote attestation mechanisms allow you to confirm specific firmware versions before trusting an enclave. While this adds a layer of "vendor trust," it's still a far more contained risk than trusting an entire operating system or cloud stack, so enclaves remain a strong step forward in practical, confidential computing.
How We Use Secure Enclaves
Now that we've covered the general idea of enclaves let's look at how we specifically implement them in OpenSecret, our developer platform for handling user auth, private keys, data encryption, and AI workloads.
Our Stack: AWS Nitro + Nvidia TEE
• AWS Nitro Enclaves for the backend: All critical logic, authentication, private key management, and data encryption/decryption run inside an AWS Nitro Enclave.
• Nvidia Trusted Execution for AI: For large AI inference (such as the Llama 3.3 70B model), we utilize Nvidia's GPU-based TEEs to protect even GPU memory. This means users can feed sensitive data to the AI model without exposing it in plaintext to the GPU providers or us as the operator. Edgeless Systems is our Nvidia TEE provider, and due to the power of enclave verification, we don't need to worry about who runs the GPUs. We know requests can't be inspected or tampered with.
End-to-End Encryption from Client to Enclave
 Client-side Enclave Attestation from Maple AI
Client-side Enclave Attestation from Maple AIBefore login or data upload, the user/client verifies the enclave attestation from our platform. This process proves that the specific Nitro Enclave is genuine and runs the exact code we've published. You can check this out live on Maple AI's attestation page.
Based on the attestation, the client establishes a secure ephemeral communication channel that only that enclave can decrypt. While we take advantage of SSL, it is typically not terminated inside the enclave itself. To ensure there's full encrypted data transfer all the way through to the enclave, we establish this additional handshake based on the attestation document that is used for all API requests during the client session.
From there, the user's credentials, private keys, and data pass through this secure channel directly into the enclave, where they are decrypted and processed according to the user's request.
In-Enclave Operations
At the core of OpenSecret's approach is the conviction that security-critical tasks must happen inside the enclave, where even administrative privileges or hypervisor-level compromise cannot expose plaintext data. This encompasses everything from when a user logs in to creating and managing sensitive cryptographic keys. By confining these operations to a protected hardware boundary, developers can focus on building their applications without worrying about accidental data leaks, insider threats, or malicious attempts to harvest credentials. The enclave becomes the ultimate gatekeeper: it controls how data flows and ensures that nothing escapes in plain form.
 User Auth Methods running inside Enclave
User Auth Methods running inside EnclaveA primary example is user authentication. All sign-in workflows, including email/password, OAuth, and upcoming passkey-based methods, are handled entirely within the enclave. As soon as a user's credentials enter our platform through the encrypted channel, they are routed straight into the protected environment, bypassing the host's operating system or any potential snooping channels. From there, authentication and session details remain in the enclave, ensuring that privileged outsiders cannot intercept or modify them. By centralizing these identity flows within a sealed environment, developers can assure their users that no one outside the enclave (including the cloud provider or the app's own sysadmins) can peek at, tamper with, or access sensitive login information.
 Main Enclave Operations in OpenSecret
Main Enclave Operations in OpenSecretThe same principle applies to private key management. Whether keys are created fresh in the enclave or securely transferred into it, they remain sealed away from the rest of the system. Operations like digital signing or content decryption happen only within the hardware boundary, so raw keys never appear in any log, file system, or memory space outside the enclave. Developers retain the functionality they need, such as verifying user actions, encrypting data, or enabling secure transactions without ever exposing keys to a broader (and more vulnerable) attack surface. User backup options exist as well, where the keys can be securely passed to the end user.
 Realtime Encrypted Data Sync on Multiple Devices
Realtime Encrypted Data Sync on Multiple DevicesAnother crucial aspect is data encryption at rest. While user data ultimately needs to be stored somewhere outside the enclave, the unencrypted form of that data only exists transiently inside the protected environment. Encryption and decryption routines run within the enclave, which holds the encryption keys strictly in memory under hardware guards. If a user uploads data, it is promptly secured before it leaves the enclave. When data is retrieved, it remains encrypted until it reenters the protected region and is passed back to the user through the secured communication channel. This ensures that even if someone gains access to the underlying storage or intercepts data in transit, they will see only meaningless ciphertext.
 Confidential AI Workloads
Confidential AI WorkloadsFinally, confidential AI workloads build upon this same pattern: the Nitro enclave re-encrypts data so it can be processed inside a GPU-based trusted execution environment (TEE) for inference or other advanced computations. Sensitive data, like user-generated text or private documents, never appears in the clear on the host or within GPU memory outside the TEE boundary. When an AI process finishes, only the results are returned to the enclave, which can then relay them securely to the requesting user. By seamlessly chaining enclaves together, from CPU-based Nitro Enclaves to GPU-accelerated TEEs, we can deliver robust, hardware-enforced privacy for virtually any type of server-side or AI-driven operation.
Reproducible Builds + Verification
 Client verifies enclave attestation document
Client verifies enclave attestation documentWe build our enclaves on NixOS with reproducible builds, ensuring that anyone can verify that the binary we publish is indeed the binary running in the enclave. This build process is essential for proving we haven't snuck in malicious code to exfiltrate data or collect sensitive logs.
Our code is fully open source (GitHub: OpenSecret), so you can audit or run it yourself. You can also verify that the cryptographic measurement the build process outputs matches the measurement reported by the enclave during attestation.
Putting It All Together
 OpenSecret Offering: Private Key Management, Encrypted Sync, Private AI, and Confidential Compute
OpenSecret Offering: Private Key Management, Encrypted Sync, Private AI, and Confidential ComputeBy weaving secure enclaves into every step, from authentication to data handling to AI inference, we shift the burden of trust away from human policies and onto provable, hardware-based protections. For app developers, you can offer your users robust privacy guarantees without rewriting all your business logic or building an entire security stack from scratch. Whether you're storing user credentials or running complex operations on sensitive data, the enclave approach ensures plaintext remains inaccessible to even the most privileged parties outside the enclave boundary. Developers can focus on building great apps, while OpenSecret handles the cryptographic "lock and key" behind the scenes.
This model provides a secure-by-design environment for industries that demand strict data confidentiality, such as healthcare, fintech, cryptocurrency apps for secure key management, or decentralized identity platforms. Instead of worrying about memory dumps or backend tampering, you can trust that once data enters the enclave, it's sealed off from unauthorized eyes, including from the app developers themselves. And these safeguards don't just apply to niche use cases. Even general-purpose applications that handle login flows and user-generated content stand to benefit, especially as regulatory scrutiny grows around data privacy and insider threats.
Imagine a telehealth startup using OpenSecret enclaves to protect patient information for remote consultations. Not only would patient data remain encrypted at rest, but any AI-driven analytics to assist with diagnoses could be run privately within the enclave, ensuring no one outside the hardware boundary can peek at sensitive health records. A fintech company could similarly isolate confidential financial transactions, preventing even privileged insiders from viewing or tampering with raw transaction details. These real-world implementations give developers a clear path to adopting enclaves for serious privacy and compliance needs without overhauling their infrastructure.
OpenSecret aims to be a full developer platform with end-to-end security from day one. By incorporating user authentication, data storage, and GPU-based confidential AI into a single service, we eliminate many of the traditional hurdles in adopting enclaves. No more juggling separate tools for cryptographic key management, compliance controls, and runtime privacy. Instead, you get a unified stack that keeps data encrypted in transit, at rest, and in use.
Our solution also caters to the exploding demand for AI applications: with TEE-enabled GPU workloads, you can securely process sensitive data for text inference without ever exposing raw plaintext or sensitive documents to the host system.
The result is a new generation of apps that deliver advanced functionality, like real-time encrypted data sync or AI-driven insights, while preserving user privacy and meeting strict regulatory requirements. You don't have to rely on empty "trust us" promises because hardware enclaves, remote attestation, and reproducible builds collectively guarantee the code is running untampered. In short, OpenSecret offers the building blocks needed to create truly confidential services and experiences, allowing you to innovate while ensuring data protection remains ironclad.
Things to Come
We're excited to build on our enclaved approach. Here's what's on our roadmap:
• Production Launch: We're using this in production now with Maple AI and have a developer preview playground up and running. We'll have the developer environment ready for production in a few months.\ • Multi-Tenant Support: Our platform currently works for single tenants, but we're opening this up so developers can onboard without needing a dedicated instance.\ • Self-Serve Frontend: A dev-friendly portal for provisioning apps, connecting OAuth or email providers, and managing users.\ • External Key Signing Options: Integrations with custom hardware security modules (HSMs) or customer-ran key managers that can only process data upon verifying the enclave attestation.\ • Confidential Computing as a Service: We'll expand our platform so that other developers can quickly create enclaves for specialized workloads without dealing with the complexities of Nitro or GPU TEEs.\ • Additional SDKs: In addition to our JavaScript client-side SDK, we plan to launch official support for Rust, Python, Swift, Java, Go, and more.\ • AI API Proxy with Attestation/Encryption: We already provide an easy way to access a Private AI through Maple AI, but we'd like to open this up more for existing tools and developers. We'll provide a proxy server that users can run on their local machines or servers that properly handle encryption to our OpenAI-compatible API.
Getting Started
Ready to see enclaves in action? Here's how to dive in:\ 1. Run OpenSecret: Check out our open-source repository at OpenSecret on GitHub. You can run your own enclaved environment or try it out locally with Docker.\ 2. Review Our SDK: Our JavaScript client SDK makes it easy to handle sign-ins, put/get encrypted data, sign with user private keys, etc. It handles attestation verification and encryption under the hood, making the API integration seamless.\ 3. Play with Maple AI: Try out Maple AI as an example of an AI app built directly on OpenSecret. Your queries are encrypted end to end, and the Llama model sees them only inside the TEE.\ 4. Developer Preview: Contact us if you want an invite to our early dev platform. We'll guide you through our SDK and give you access to the preview server. We'd love to build with you and incorporate your feedback as we develop this further.
Conclusion
By merging secure enclaves (AWS Nitro and Nvidia GPU TEEs), user authentication, private key management, and an end-to-end verifiable encrypted approach, OpenSecret provides a powerful platform where we protect user data during collection, storage, and processing. Whether it's for standard user management, handling private cryptographic keys, or powering AI inference, the technology ensures that no one, not even us or the cloud provider, can snoop on data in use.
We believe this is the future of trustworthy computing in the cloud. And it's all open source, so you don't have to just take our word for it: you can see and verify everything yourself.
Do you have questions, feedback, or a use case you'd like to test out? Come join us on GitHub, Discord, or email us for a developer preview. We can't wait to see what you build!
Thank you for reading, and welcome to the era of enclaved computing.
-
 @ 56cd780f:cbde8b29
2025-04-29 14:37:33
@ 56cd780f:cbde8b29
2025-04-29 14:37:33Is it still working?
-
 @ 91bea5cd:1df4451c
2025-02-04 17:24:50
@ 91bea5cd:1df4451c
2025-02-04 17:24:50Definição de ULID:
Timestamp 48 bits, Aleatoriedade 80 bits Sendo Timestamp 48 bits inteiro, tempo UNIX em milissegundos, Não ficará sem espaço até o ano 10889 d.C. e Aleatoriedade 80 bits, Fonte criptograficamente segura de aleatoriedade, se possível.
Gerar ULID
```sql
CREATE EXTENSION IF NOT EXISTS pgcrypto;
CREATE FUNCTION generate_ulid() RETURNS TEXT AS $$ DECLARE -- Crockford's Base32 encoding BYTEA = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; timestamp BYTEA = E'\000\000\000\000\000\000'; output TEXT = '';
unix_time BIGINT; ulid BYTEA; BEGIN -- 6 timestamp bytes unix_time = (EXTRACT(EPOCH FROM CLOCK_TIMESTAMP()) * 1000)::BIGINT; timestamp = SET_BYTE(timestamp, 0, (unix_time >> 40)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 1, (unix_time >> 32)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 2, (unix_time >> 24)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 3, (unix_time >> 16)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 4, (unix_time >> 8)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 5, unix_time::BIT(8)::INTEGER);
-- 10 entropy bytes ulid = timestamp || gen_random_bytes(10);
-- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 1) & 7) << 2) | ((GET_BYTE(ulid, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 2) & 1) << 4) | ((GET_BYTE(ulid, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 3) & 15) << 1) | ((GET_BYTE(ulid, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 4) & 3) << 3) | ((GET_BYTE(ulid, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 5) & 31)));
-- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 6) & 7) << 2) | ((GET_BYTE(ulid, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 7) & 1) << 4) | ((GET_BYTE(ulid, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 8) & 15) << 1) | ((GET_BYTE(ulid, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 9) & 3) << 3) | ((GET_BYTE(ulid, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 11) & 7) << 2) | ((GET_BYTE(ulid, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 12) & 1) << 4) | ((GET_BYTE(ulid, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 13) & 15) << 1) | ((GET_BYTE(ulid, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 14) & 3) << 3) | ((GET_BYTE(ulid, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 15) & 31)));
RETURN output; END $$ LANGUAGE plpgsql VOLATILE; ```
ULID TO UUID
```sql CREATE OR REPLACE FUNCTION parse_ulid(ulid text) RETURNS bytea AS $$ DECLARE -- 16byte bytes bytea = E'\x00000000 00000000 00000000 00000000'; v char[]; -- Allow for O(1) lookup of index values dec integer[] = ARRAY[ 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 0, 1, 2, 3, 4, 5, 6, 7, 8, 9, 255, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31 ]; BEGIN IF NOT ulid ~* '^[0-7][0-9ABCDEFGHJKMNPQRSTVWXYZ]{25}$' THEN RAISE EXCEPTION 'Invalid ULID: %', ulid; END IF;
v = regexp_split_to_array(ulid, '');
-- 6 bytes timestamp (48 bits) bytes = SET_BYTE(bytes, 0, (dec[ASCII(v[1])] << 5) | dec[ASCII(v[2])]); bytes = SET_BYTE(bytes, 1, (dec[ASCII(v[3])] << 3) | (dec[ASCII(v[4])] >> 2)); bytes = SET_BYTE(bytes, 2, (dec[ASCII(v[4])] << 6) | (dec[ASCII(v[5])] << 1) | (dec[ASCII(v[6])] >> 4)); bytes = SET_BYTE(bytes, 3, (dec[ASCII(v[6])] << 4) | (dec[ASCII(v[7])] >> 1)); bytes = SET_BYTE(bytes, 4, (dec[ASCII(v[7])] << 7) | (dec[ASCII(v[8])] << 2) | (dec[ASCII(v[9])] >> 3)); bytes = SET_BYTE(bytes, 5, (dec[ASCII(v[9])] << 5) | dec[ASCII(v[10])]);
-- 10 bytes of entropy (80 bits); bytes = SET_BYTE(bytes, 6, (dec[ASCII(v[11])] << 3) | (dec[ASCII(v[12])] >> 2)); bytes = SET_BYTE(bytes, 7, (dec[ASCII(v[12])] << 6) | (dec[ASCII(v[13])] << 1) | (dec[ASCII(v[14])] >> 4)); bytes = SET_BYTE(bytes, 8, (dec[ASCII(v[14])] << 4) | (dec[ASCII(v[15])] >> 1)); bytes = SET_BYTE(bytes, 9, (dec[ASCII(v[15])] << 7) | (dec[ASCII(v[16])] << 2) | (dec[ASCII(v[17])] >> 3)); bytes = SET_BYTE(bytes, 10, (dec[ASCII(v[17])] << 5) | dec[ASCII(v[18])]); bytes = SET_BYTE(bytes, 11, (dec[ASCII(v[19])] << 3) | (dec[ASCII(v[20])] >> 2)); bytes = SET_BYTE(bytes, 12, (dec[ASCII(v[20])] << 6) | (dec[ASCII(v[21])] << 1) | (dec[ASCII(v[22])] >> 4)); bytes = SET_BYTE(bytes, 13, (dec[ASCII(v[22])] << 4) | (dec[ASCII(v[23])] >> 1)); bytes = SET_BYTE(bytes, 14, (dec[ASCII(v[23])] << 7) | (dec[ASCII(v[24])] << 2) | (dec[ASCII(v[25])] >> 3)); bytes = SET_BYTE(bytes, 15, (dec[ASCII(v[25])] << 5) | dec[ASCII(v[26])]);
RETURN bytes; END $$ LANGUAGE plpgsql IMMUTABLE;
CREATE OR REPLACE FUNCTION ulid_to_uuid(ulid text) RETURNS uuid AS $$ BEGIN RETURN encode(parse_ulid(ulid), 'hex')::uuid; END $$ LANGUAGE plpgsql IMMUTABLE; ```
UUID to ULID
```sql CREATE OR REPLACE FUNCTION uuid_to_ulid(id uuid) RETURNS text AS $$ DECLARE encoding bytea = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; output text = ''; uuid_bytes bytea = uuid_send(id); BEGIN
-- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 1) & 7) << 2) | ((GET_BYTE(uuid_bytes, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 2) & 1) << 4) | ((GET_BYTE(uuid_bytes, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 3) & 15) << 1) | ((GET_BYTE(uuid_bytes, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 4) & 3) << 3) | ((GET_BYTE(uuid_bytes, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 5) & 31)));
-- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 6) & 7) << 2) | ((GET_BYTE(uuid_bytes, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 7) & 1) << 4) | ((GET_BYTE(uuid_bytes, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 8) & 15) << 1) | ((GET_BYTE(uuid_bytes, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 9) & 3) << 3) | ((GET_BYTE(uuid_bytes, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 11) & 7) << 2) | ((GET_BYTE(uuid_bytes, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 12) & 1) << 4) | ((GET_BYTE(uuid_bytes, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 13) & 15) << 1) | ((GET_BYTE(uuid_bytes, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 14) & 3) << 3) | ((GET_BYTE(uuid_bytes, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 15) & 31)));
RETURN output; END $$ LANGUAGE plpgsql IMMUTABLE; ```
Gera 11 Digitos aleatórios: YBKXG0CKTH4
```sql -- Cria a extensão pgcrypto para gerar uuid CREATE EXTENSION IF NOT EXISTS pgcrypto;
-- Cria a função para gerar ULID CREATE OR REPLACE FUNCTION gen_lrandom() RETURNS TEXT AS $$ DECLARE ts_millis BIGINT; ts_chars TEXT; random_bytes BYTEA; random_chars TEXT; base32_chars TEXT := '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; i INT; BEGIN -- Pega o timestamp em milissegundos ts_millis := FLOOR(EXTRACT(EPOCH FROM clock_timestamp()) * 1000)::BIGINT;
-- Converte o timestamp para base32 ts_chars := ''; FOR i IN REVERSE 0..11 LOOP ts_chars := ts_chars || substr(base32_chars, ((ts_millis >> (5 * i)) & 31) + 1, 1); END LOOP; -- Gera 10 bytes aleatórios e converte para base32 random_bytes := gen_random_bytes(10); random_chars := ''; FOR i IN 0..9 LOOP random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) >> 3) & 31) + 1, 1); IF i < 9 THEN random_chars := random_chars || substr(base32_chars, (((get_byte(random_bytes, i) & 7) << 2) | (get_byte(random_bytes, i + 1) >> 6)) & 31 + 1, 1); ELSE random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) & 7) << 2) + 1, 1); END IF; END LOOP; -- Concatena o timestamp e os caracteres aleatórios RETURN ts_chars || random_chars;END; $$ LANGUAGE plpgsql; ```
Exemplo de USO
```sql -- Criação da extensão caso não exista CREATE EXTENSION IF NOT EXISTS pgcrypto; -- Criação da tabela pessoas CREATE TABLE pessoas ( ID UUID DEFAULT gen_random_uuid ( ) PRIMARY KEY, nome TEXT NOT NULL );
-- Busca Pessoa na tabela SELECT * FROM "pessoas" WHERE uuid_to_ulid ( ID ) = '252FAC9F3V8EF80SSDK8PXW02F'; ```
Fontes
- https://github.com/scoville/pgsql-ulid
- https://github.com/geckoboard/pgulid
-
 @ 56cd780f:cbde8b29
2025-04-29 14:37:31
@ 56cd780f:cbde8b29
2025-04-29 14:37:31Is it actually called “summary”?
-
 @ 91bea5cd:1df4451c
2025-02-04 17:15:57
@ 91bea5cd:1df4451c
2025-02-04 17:15:57Definição de ULID:
Timestamp 48 bits, Aleatoriedade 80 bits Sendo Timestamp 48 bits inteiro, tempo UNIX em milissegundos, Não ficará sem espaço até o ano 10889 d.C. e Aleatoriedade 80 bits, Fonte criptograficamente segura de aleatoriedade, se possível.
Gerar ULID
```sql
CREATE EXTENSION IF NOT EXISTS pgcrypto;
CREATE FUNCTION generate_ulid() RETURNS TEXT AS $$ DECLARE -- Crockford's Base32 encoding BYTEA = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; timestamp BYTEA = E'\000\000\000\000\000\000'; output TEXT = '';
unix_time BIGINT; ulid BYTEA; BEGIN -- 6 timestamp bytes unix_time = (EXTRACT(EPOCH FROM CLOCK_TIMESTAMP()) * 1000)::BIGINT; timestamp = SET_BYTE(timestamp, 0, (unix_time >> 40)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 1, (unix_time >> 32)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 2, (unix_time >> 24)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 3, (unix_time >> 16)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 4, (unix_time >> 8)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 5, unix_time::BIT(8)::INTEGER);
-- 10 entropy bytes ulid = timestamp || gen_random_bytes(10);
-- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 1) & 7) << 2) | ((GET_BYTE(ulid, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 2) & 1) << 4) | ((GET_BYTE(ulid, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 3) & 15) << 1) | ((GET_BYTE(ulid, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 4) & 3) << 3) | ((GET_BYTE(ulid, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 5) & 31)));
-- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 6) & 7) << 2) | ((GET_BYTE(ulid, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 7) & 1) << 4) | ((GET_BYTE(ulid, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 8) & 15) << 1) | ((GET_BYTE(ulid, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 9) & 3) << 3) | ((GET_BYTE(ulid, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 11) & 7) << 2) | ((GET_BYTE(ulid, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 12) & 1) << 4) | ((GET_BYTE(ulid, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 13) & 15) << 1) | ((GET_BYTE(ulid, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 14) & 3) << 3) | ((GET_BYTE(ulid, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 15) & 31)));
RETURN output; END $$ LANGUAGE plpgsql VOLATILE; ```
ULID TO UUID
```sql CREATE OR REPLACE FUNCTION parse_ulid(ulid text) RETURNS bytea AS $$ DECLARE -- 16byte bytes bytea = E'\x00000000 00000000 00000000 00000000'; v char[]; -- Allow for O(1) lookup of index values dec integer[] = ARRAY[ 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 0, 1, 2, 3, 4, 5, 6, 7, 8, 9, 255, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31 ]; BEGIN IF NOT ulid ~* '^[0-7][0-9ABCDEFGHJKMNPQRSTVWXYZ]{25}$' THEN RAISE EXCEPTION 'Invalid ULID: %', ulid; END IF;
v = regexp_split_to_array(ulid, '');
-- 6 bytes timestamp (48 bits) bytes = SET_BYTE(bytes, 0, (dec[ASCII(v[1])] << 5) | dec[ASCII(v[2])]); bytes = SET_BYTE(bytes, 1, (dec[ASCII(v[3])] << 3) | (dec[ASCII(v[4])] >> 2)); bytes = SET_BYTE(bytes, 2, (dec[ASCII(v[4])] << 6) | (dec[ASCII(v[5])] << 1) | (dec[ASCII(v[6])] >> 4)); bytes = SET_BYTE(bytes, 3, (dec[ASCII(v[6])] << 4) | (dec[ASCII(v[7])] >> 1)); bytes = SET_BYTE(bytes, 4, (dec[ASCII(v[7])] << 7) | (dec[ASCII(v[8])] << 2) | (dec[ASCII(v[9])] >> 3)); bytes = SET_BYTE(bytes, 5, (dec[ASCII(v[9])] << 5) | dec[ASCII(v[10])]);
-- 10 bytes of entropy (80 bits); bytes = SET_BYTE(bytes, 6, (dec[ASCII(v[11])] << 3) | (dec[ASCII(v[12])] >> 2)); bytes = SET_BYTE(bytes, 7, (dec[ASCII(v[12])] << 6) | (dec[ASCII(v[13])] << 1) | (dec[ASCII(v[14])] >> 4)); bytes = SET_BYTE(bytes, 8, (dec[ASCII(v[14])] << 4) | (dec[ASCII(v[15])] >> 1)); bytes = SET_BYTE(bytes, 9, (dec[ASCII(v[15])] << 7) | (dec[ASCII(v[16])] << 2) | (dec[ASCII(v[17])] >> 3)); bytes = SET_BYTE(bytes, 10, (dec[ASCII(v[17])] << 5) | dec[ASCII(v[18])]); bytes = SET_BYTE(bytes, 11, (dec[ASCII(v[19])] << 3) | (dec[ASCII(v[20])] >> 2)); bytes = SET_BYTE(bytes, 12, (dec[ASCII(v[20])] << 6) | (dec[ASCII(v[21])] << 1) | (dec[ASCII(v[22])] >> 4)); bytes = SET_BYTE(bytes, 13, (dec[ASCII(v[22])] << 4) | (dec[ASCII(v[23])] >> 1)); bytes = SET_BYTE(bytes, 14, (dec[ASCII(v[23])] << 7) | (dec[ASCII(v[24])] << 2) | (dec[ASCII(v[25])] >> 3)); bytes = SET_BYTE(bytes, 15, (dec[ASCII(v[25])] << 5) | dec[ASCII(v[26])]);
RETURN bytes; END $$ LANGUAGE plpgsql IMMUTABLE;
CREATE OR REPLACE FUNCTION ulid_to_uuid(ulid text) RETURNS uuid AS $$ BEGIN RETURN encode(parse_ulid(ulid), 'hex')::uuid; END $$ LANGUAGE plpgsql IMMUTABLE; ```
UUID to ULID
```sql CREATE OR REPLACE FUNCTION uuid_to_ulid(id uuid) RETURNS text AS $$ DECLARE encoding bytea = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; output text = ''; uuid_bytes bytea = uuid_send(id); BEGIN
-- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 1) & 7) << 2) | ((GET_BYTE(uuid_bytes, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 2) & 1) << 4) | ((GET_BYTE(uuid_bytes, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 3) & 15) << 1) | ((GET_BYTE(uuid_bytes, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 4) & 3) << 3) | ((GET_BYTE(uuid_bytes, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 5) & 31)));
-- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 6) & 7) << 2) | ((GET_BYTE(uuid_bytes, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 7) & 1) << 4) | ((GET_BYTE(uuid_bytes, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 8) & 15) << 1) | ((GET_BYTE(uuid_bytes, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 9) & 3) << 3) | ((GET_BYTE(uuid_bytes, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 11) & 7) << 2) | ((GET_BYTE(uuid_bytes, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 12) & 1) << 4) | ((GET_BYTE(uuid_bytes, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 13) & 15) << 1) | ((GET_BYTE(uuid_bytes, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 14) & 3) << 3) | ((GET_BYTE(uuid_bytes, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 15) & 31)));
RETURN output; END $$ LANGUAGE plpgsql IMMUTABLE; ```
Gera 11 Digitos aleatórios: YBKXG0CKTH4
```sql -- Cria a extensão pgcrypto para gerar uuid CREATE EXTENSION IF NOT EXISTS pgcrypto;
-- Cria a função para gerar ULID CREATE OR REPLACE FUNCTION gen_lrandom() RETURNS TEXT AS $$ DECLARE ts_millis BIGINT; ts_chars TEXT; random_bytes BYTEA; random_chars TEXT; base32_chars TEXT := '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; i INT; BEGIN -- Pega o timestamp em milissegundos ts_millis := FLOOR(EXTRACT(EPOCH FROM clock_timestamp()) * 1000)::BIGINT;
-- Converte o timestamp para base32 ts_chars := ''; FOR i IN REVERSE 0..11 LOOP ts_chars := ts_chars || substr(base32_chars, ((ts_millis >> (5 * i)) & 31) + 1, 1); END LOOP; -- Gera 10 bytes aleatórios e converte para base32 random_bytes := gen_random_bytes(10); random_chars := ''; FOR i IN 0..9 LOOP random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) >> 3) & 31) + 1, 1); IF i < 9 THEN random_chars := random_chars || substr(base32_chars, (((get_byte(random_bytes, i) & 7) << 2) | (get_byte(random_bytes, i + 1) >> 6)) & 31 + 1, 1); ELSE random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) & 7) << 2) + 1, 1); END IF; END LOOP; -- Concatena o timestamp e os caracteres aleatórios RETURN ts_chars || random_chars;END; $$ LANGUAGE plpgsql; ```
Exemplo de USO
```sql -- Criação da extensão caso não exista CREATE EXTENSION IF NOT EXISTS pgcrypto; -- Criação da tabela pessoas CREATE TABLE pessoas ( ID UUID DEFAULT gen_random_uuid ( ) PRIMARY KEY, nome TEXT NOT NULL );
-- Busca Pessoa na tabela SELECT * FROM "pessoas" WHERE uuid_to_ulid ( ID ) = '252FAC9F3V8EF80SSDK8PXW02F'; ```
Fontes
- https://github.com/scoville/pgsql-ulid
- https://github.com/geckoboard/pgulid
-
 @ 56cd780f:cbde8b29
2025-04-29 14:37:29
@ 56cd780f:cbde8b29
2025-04-29 14:37:29A few weeks ago, I ran into an old friend at a coffee shop. We hadn’t spoken in years, and within five minutes, she said something I’ve heard countless times:
“I just feel like I’m so behind.”
Behind who? Behind what?
 There’s this idea—quiet, nagging, oddly universal—that we’re all somehow in a race we didn’t sign up for. That we’re supposed to have hit certain milestones by certain ages. That if we’re not married, promoted, rich, settled, happy (and photogenic) by 30 or 40 or pick your poison, then we’ve failed some invisible test.
There’s this idea—quiet, nagging, oddly universal—that we’re all somehow in a race we didn’t sign up for. That we’re supposed to have hit certain milestones by certain ages. That if we’re not married, promoted, rich, settled, happy (and photogenic) by 30 or 40 or pick your poison, then we’ve failed some invisible test.Where did this come from?
Some of it’s cultural, obviously. Social media compresses timelines. You’re 27, doom-scrolling, and suddenly someone from high school just IPO’d their startup and got engaged in Rome. Another just bought a house with a kitchen island the size of a small country. You wonder if you missed a memo.
But beneath that, there’s something deeper. A belief that life is linear. That it should look like a staircase: school, job, marriage, house, kids, success. But real life? It’s a squiggle. A mess. A beautiful disaster.
Here’s the truth: You’re not behind. There’s no schedule. There’s only your path, and the courage it takes to stay on it—even when it looks wildly different from everyone else’s.
I say this as someone who has taken the “scenic route.” I changed careers in my 30s. I moved cities on a hunch. I dropped things that looked great on paper because they felt wrong in my gut. I’ve had seasons of momentum and seasons of stuckness. Both were necessary.
“Catching up” assumes there’s a fixed destination. But what if there isn’t? What if the point isn’t arrival, but presence? Progress that feels real, not performative?
If you need a permission slip to stop comparing, let this be it.
 You’re not late. You’re not early.
You’re not late. You’re not early.
You’re right on time. -
 @ 56cd780f:cbde8b29
2025-04-29 14:37:27
@ 56cd780f:cbde8b29
2025-04-29 14:37:27There’s something sacred about morning air — the way it carries just enough chill to remind you you’re alive, without pushing you back inside. I’ve been starting my days on the balcony lately. Not because it’s glamorous (it isn’t), or because I have a routine (I don’t), but because it’s the only space in my apartment that feels both open and still.
This morning I made coffee with too much cinnamon and curled up with a blanket that’s seen better days. I watched the city slowly wake up — one barking dog, two joggers, and the clatter of a recycling truck below. It’s odd how these tiny patterns become a kind of comfort.
 I used to think that slowing down meant falling behind. But here, perched on the third floor with my feet on cold concrete and the sky just starting to blush, I feel like I’m exactly where I’m supposed to be.
I used to think that slowing down meant falling behind. But here, perched on the third floor with my feet on cold concrete and the sky just starting to blush, I feel like I’m exactly where I’m supposed to be.If you’re reading this, maybe you needed that reminder too.
— Natalie
-
 @ 7d33ba57:1b82db35
2025-04-29 14:14:11
@ 7d33ba57:1b82db35
2025-04-29 14:14:11Located in eastern Poland, Lublin is a city where history, culture, and youthful energy come together. Often called the "Gateway to the East," Lublin blends Gothic and Renaissance architecture, vibrant street life, and deep historical roots—especially as a center of Jewish heritage and intellectual life.
🏙️ Top Things to See in Lublin
🏰 Lublin Castle
- A striking hilltop castle with a neo-Gothic façade and a beautifully preserved Romanesque chapel (Chapel of the Holy Trinity)
- Don’t miss the frescoes inside—a rare mix of Byzantine and Western art styles
🚪 Old Town (Stare Miasto)
- Wander through cobblestone streets, pastel buildings, and arched gateways
- Filled with cozy cafes, galleries, and vibrant murals
- The Grodzka Gate symbolizes the passage between Christian and Jewish quarters
🕯️ Lublin’s Jewish Heritage
- Visit the Grodzka Gate – NN Theatre, a powerful memorial and museum telling the story of the once-vibrant Jewish community
- Nearby Majdanek Concentration Camp offers a sobering but important historical experience
🎭 Culture & Events
- Lublin is known for its festivals, like Carnaval Sztukmistrzów (Festival of Magicians and Street Performers) and the Night of Culture
- The city has a thriving theatre and music scene, supported by its large student population
🌳 Green Spaces
- Relax in Saski Garden, a peaceful park with walking paths and fountains
- Or take a walk along the Bystrzyca River for a quieter, more local feel
🍽️ Local Tastes
- Sample Polish classics like pierogi, żurek (sour rye soup), and bigos (hunter’s stew)
- Look for modern twists on traditional dishes in Lublin’s growing number of bistros and artisan cafés
🚆 Getting There
- Easy access by train or bus from Warsaw (2–2.5 hours)
- Compact center—easily walkable
-
 @ 91bea5cd:1df4451c
2025-02-04 05:24:47
@ 91bea5cd:1df4451c
2025-02-04 05:24:47Novia é uma ferramenta inovadora que facilita o arquivamento de vídeos e sua integração com a rede NOSTR (Notes and Other Stuff Transmitted over Relay). Funcionando como uma ponte entre ferramentas de arquivamento de vídeo tradicionais e a plataforma descentralizada, Novia oferece uma solução autônoma para a preservação e compartilhamento de conteúdo audiovisual.
Arquitetura e Funcionamento
A arquitetura de Novia é dividida em duas partes principais:
-
Frontend: Atua como a interface do usuário, responsável por solicitar o arquivamento de vídeos. Essas solicitações são encaminhadas para o backend.
-
Backend: Processa as solicitações de arquivamento, baixando o vídeo, suas descrições e a imagem de capa associada. Este componente é conectado a um ou mais relays NOSTR, permitindo a indexação e descoberta do conteúdo arquivado.
O processo de arquivamento é automatizado: após o download, o vídeo fica disponível no frontend para que o usuário possa solicitar o upload para um servidor Blossom de sua escolha.
Como Utilizar Novia
-
Acesso: Navegue até https://npub126uz2g6ft45qs0m0rnvtvtp7glcfd23pemrzz0wnt8r5vlhr9ufqnsmvg8.nsite.lol.
-
Login: Utilize uma extensão de navegador compatível com NOSTR para autenticar-se.
-
Execução via Docker: A forma mais simples de executar o backend é através de um container Docker. Execute o seguinte comando:
bash docker run -it --rm -p 9090:9090 -v ./nostr/data:/data --add-host=host.docker.internal:host-gateway teamnovia/noviaEste comando cria um container, mapeia a porta 9090 para o host e monta o diretório
./nostr/datapara persistir os dados.
Configuração Avançada
Novia oferece amplas opções de configuração através de um arquivo
yaml. Abaixo, um exemplo comentado:```yaml mediaStores: - id: media type: local path: /data/media watch: true
database: /data/novia.db
download: enabled: true ytdlpPath: yt-dlp ytdlpCookies: ./cookies.txt tempPath: /tmp targetStoreId: media secret: false
publish: enabled: true key: nsec thumbnailUpload: - https://nostr.download videoUpload: - url: https://nostr.download maxUploadSizeMB: 300 cleanUpMaxAgeDays: 5 cleanUpKeepSizeUnderMB: 2 - url: https://files.v0l.io maxUploadSizeMB: 300 cleanUpMaxAgeDays: 5 cleanUpKeepSizeUnderMB: 2 - url: https://nosto.re maxUploadSizeMB: 300 cleanUpMaxAgeDays: 5 cleanUpKeepSizeUnderMB: 2 - url: https://blossom.primal.net maxUploadSizeMB: 300 cleanUpMaxAgeDays: 5 cleanUpKeepSizeUnderMB: 2
relays: - ws://host.docker.internal:4869 - wss://bostr.bitcointxoko.com secret: false autoUpload: enabled: true maxVideoSizeMB: 100
fetch: enabled: false fetchVideoLimitMB: 10 relays: - match: - nostr - bitcoin
server: port: 9090 enabled: true ```
Explicação das Configurações:
mediaStores: Define onde os arquivos de mídia serão armazenados (localmente, neste exemplo).database: Especifica o local do banco de dados.download: Controla as configurações de download de vídeos, incluindo o caminho para oyt-dlpe um arquivo de cookies para autenticação.publish: Configura a publicação de vídeos e thumbnails no NOSTR, incluindo a chave privada (nsec), servidores de upload e relays. Atenção: Mantenha sua chave privada em segredo.fetch: Permite buscar eventos de vídeo de relays NOSTR para arquivamento.server: Define as configurações do servidor web interno de Novia.
Conclusão
Novia surge como uma ferramenta promissora para o arquivamento e a integração de vídeos com o ecossistema NOSTR. Sua arquitetura modular, combinada com opções de configuração flexíveis, a tornam uma solução poderosa para usuários que buscam preservar e compartilhar conteúdo audiovisual de forma descentralizada e resistente à censura. A utilização de Docker simplifica a implantação e o gerenciamento da ferramenta. Para obter mais informações e explorar o código-fonte, visite o repositório do projeto no GitHub: https://github.com/teamnovia/novia.
-
-
 @ bbb5dda0:f09e2747
2025-04-29 13:46:37
@ bbb5dda0:f09e2747
2025-04-29 13:46:37GitHub Actions (CI/CD) over Nostr
I Spent quite a bit of time on getting Nostr-based GitHub actions working. I have a basic runner implementation now, which i've reworked quite a bit when working with @dan on getting the front-end of it into gitworkshop.dev. We found that the nature of these jobs don't really lend itself to fit within the NIP-90 DVM spec.
What we have now: - A dvm-cicd-runner that - Advertises itself using NIP-89 announcements. - Takes a DVM request with: - repository - branch/ref - path to workflow file (
.yml) - job timeout (max duration) - 🥜 Cashu prepayment for the job timeout (to be refunded) - Pulls the repository and executes the provided workflow file - Sends logs in batches as partial job results - Publishes job results and gets displayed in gitworkshop - Gitworkshop.dev (all nostr:npub15qydau2hjma6ngxkl2cyar74wzyjshvl65za5k5rl69264ar2exs5cyejr work) UI that : - Shows available workflow runners. - Instructing + paying runner to execute workflow file - Displaying job status, live updating with the latest logs / autoscroll, all the stuff you'd expect - Neatly displaying past jobs for the current repositoryTODO'S + Ideas/vision
- TODO: refunding the unused minutes (job timeout - processing time) to the requester
- TODO: create seperate kinds/nip for worflow execution over nostr
- Create separate kinds for streaming arbitrary text data over nostr (line by line logs)
- automated git watchers for projects to kick of jobs
- Separate out workflow management stuff from gitworkshop.dev. A micro-app might serve better to manage runners for git projects etc and takes away pressure from gitworkshop.dev to do it all.
- Perhaps support just running .yaml files, without the requirement to have it in a git repo. Could just be a .yaml file on blossom.
TollGate
I spent most of my time working on TollGate. There's been a lot of back and forth to the drawing board to narrow down what the TollGate protocol looks like. I helped define some concepts on implementing a tollgate which we could use as language to discuss the different components that are part of a tollgate implementation. It helped us narrow down what was implementation and what is part of the protocol.
Current state of the project
- We have a website displaying the project: TollGate.me
- Worked on a basic android app for auto payments, validating we can auto-buy from tollgates by our phones
- Presented TollGate at @Sats 'n Facts
- There's a protocol draft, presented at SEC-04
- We've done workshops, people were able to turn an OpenWRT router into a TollGate
- Building and releasing TollGate as a singular OpenWRT package, installable on any compatible architecture
- Building and releasing TollGate OS v0.0.1 (prebuilt OpenWRT image), targeting a few specific routers
- First tollgate deployed in the wild!! (At a restaurant in Funchal, Madeira)
- Other developers started to make their own adjacent implementations, which decentralizes the protocol already
What's next:
- We're gathering useful real user feedback to be incorporated in OS v0.0.2 soon
- Refine the protocol further
- Showing TollGate at various conferences in Europe throughout the summer
- Keep building the community, it's growing fast
Epoxy (Nostr based Addressing)
Although i've pivoted towards focusing on TollGate I worked out an implementation of my NIP-(1)37 proposal. During SEC-04 I worked out this browser plugin to demonstrate one way to make websites resistant to rugpulls.
It works by looking for a
metatag in the page'shead:html <meta name="nostr-pubkey" relays="relay.site.com,other.relay.com">[hexPubkey]</meta>When we've never recorded a pubkey for this domain, we save it. This pubkey now serves as the owner of the website. It looks for a kind
11111event of that pubkey. It should list the current domain as one of it's domains. If not, it shows a warning.The key concept is that if we visit this website again and one of these scenario's is true: - There is no longer a
metatag - There's another pubkey in themetatag - The pubkey is still on the webpage, but the11111no longer lists this domainThen we consider this domain as RUGPULLED and the user gets an error, suggesting to navigate to other domain listed by this
pubkey. I'd like it to perhaps auto-redirect to another domain listed by the owner, this is especially useful for frequently rugged domains.This extension does try to solve a bootstrapping problem. We need to establish the website's pubkey at some point. We have to start somewhere, which is why the first load is considered as the 'real' one, since we have no way of knowing for sure.
Other
🥜/⚡️ Receipt.Cash - Social Receipt sharing app
During SEC I worked on scratching an itch that has been lingering in my mind since SEC-03 already. And now that vibecoding is a thing it wasn't this huge undertaking anymore to handle the front-end stuff (which i suck at).
The usage scenario is a bunch of bitcoiners that are at a restaurant, we get the bill and want to split it amongst each other. One person can pay the bill, then: - Payer photographs receipt - Payer adds Cashu Payment request - Payer sets dev split % - App turns the receipt + request into a (encrypted) nostr event - The payer shares the event with QR or Share Menu
The friend scan the QR: - Receipt is loaded and displayed - Friend selects items they ordered - Friend hits pay button (⚡️Lightning or 🥜Cashu) and pays - Payment gets sent to Payer's cashu wallet - Dev split set by Payer goes to dev address.
Some features: - Change LLM model that processes the receipt to extract data - Proofs storage + recovery (if anything fails during processing)
Todo's: - Letting payer configure LNURL for payouts - Letting payer edit Receipt before sharing - Fix: live updates on settled items
The repo: receipt-cash
-
 @ df173277:4ec96708
2025-01-28 17:49:54
@ df173277:4ec96708
2025-01-28 17:49:54Maple is an AI chat tool that allows you to have private conversations with a general-purpose AI assistant. Chats are synced automatically between devices so you can pick up where you left off.\ Start chatting for free.
We are excited to announce that Maple AI, our groundbreaking end-to-end encrypted AI chat app built on OpenSecret, is now publicly available. After months of beta testing, we are thrilled to bring this innovative technology to the world.
 Maple is an AI chat tool that allows you to have private conversations with a general-purpose AI assistant. It can boost your productivity on work tasks such as writing documentation, creating presentations, and drafting emails. You can also use it for personal items like brainstorming ideas, sorting out life's challenges, and tutoring you on difficult coursework. All your chats are synced automatically in a secure way, so you can start on one device and pick up where you left off on another.
Maple is an AI chat tool that allows you to have private conversations with a general-purpose AI assistant. It can boost your productivity on work tasks such as writing documentation, creating presentations, and drafting emails. You can also use it for personal items like brainstorming ideas, sorting out life's challenges, and tutoring you on difficult coursework. All your chats are synced automatically in a secure way, so you can start on one device and pick up where you left off on another.Why Secure and Private AI?
In today's digital landscape, it is increasingly evident that security and privacy are essential for individuals and organizations alike. Unfortunately, the current state of AI tools falls short. A staggering 48% of organizations enter non-public company information into AI apps, according to a recent report by Cisco. This practice poses significant risks to company security and intellectual property.
Another concern is for journalists, who often work with sensitive information in hostile environments. Journalists need verification that their information remains confidential and protected when researching topics and communicating with sources in various languages. They are left to use underpowered local AI or input their data into potentially compromised cloud services.
At OpenSecret, we believe it is possible to have both the benefits of AI and the assurance of security and privacy. That's why we created Maple, an app that combines AI productivity with the protection of end-to-end encryption. Our platform ensures that your conversations with AI remain confidential, even from us. The power of the cloud meets the privacy of local.
 #### How Does It Work?
#### How Does It Work?Our server code is open source, and we use confidential computing to provide cryptographic proof that the code running on our servers is the same as the open-source code available for review. This process allows you to verify that your conversations are handled securely and privately without relying on trust. We live by the principle of "Don't trust, verify," and we believe this approach is essential for building in the digital age. You can read a more in-depth write-up on our technology later this week on this site.
How Much Does It Cost?
We are committed to making Maple AI accessible to everyone, so we offer a range of pricing plans to suit different needs and budgets. Our Free plan allows for 10 chats per week, while our Starter plan ($5.99/month) and Pro plan ($20/month) offer more comprehensive solutions for individuals and organizations with heavier workloads. We accept credit cards and Bitcoin (10% discount), allowing you to choose your preferred payment method.
- Free: $0
- Starter: $5.99/month
- Pro: $20/month
Our goal with Maple AI is to create a product that is secure through transparency. By combining open-source code, cryptography, and confidential computing, we can create a new standard for AI conversations - one that prioritizes your security and privacy.
Maple has quickly become a daily tool of productivity for our own work and those of our beta testers. We believe it will bring value to you as well. Sign up now and start chatting privately with AI for free. Your secrets are safe in the open.
 #### Are You An App Developer?
#### Are You An App Developer?You can build an app like Maple. OpenSecret provides secure auth, private key management, encrypted data sync, private AI, and more. Our straightforward API behaves like other backends but automatically adds security and privacy. Use it to secure existing apps or brand-new projects. Protect yourself and your users from the liability of hosting personal data by checking out OpenSecret.

Enjoy private AI Chat 🤘

-
 @ df173277:4ec96708
2025-01-09 17:12:08
@ df173277:4ec96708
2025-01-09 17:12:08Maple AI combines the best of both worlds – encryption and personal AI – to create a truly private AI experience. Discuss personal and company items with Maple, we can't read them even if we wanted to.\ Join the waitlist to get early access.
We are a culture of app users. Every day, we give our personal information to websites and apps, hoping they are safe. Location data, eating habits, financial details, and health information are just a few examples of what we entrust to third parties. People are now entering a new era of computing that promises next-level benefits when given even more personal data: AI.
Should we sacrifice our privacy to unlock the productivity gains of AI? Should we hope our information won't be used in ways we disagree? We believe we can have the best of both worlds – privacy and personal AI – and have built a new project called Maple AI. Chat between you and an AI with full end-to-end encryption. We believe it's a game-changer for individuals seeking private and secure conversations.
Building a Private Foundation
Maple is built on our flagship product, OpenSecret, a backend platform for app developers that turns private encryption on by default. The announcement post for OpenSecret explains our vision for an encrypted world and what the platform can do. We think both users and developers benefit when sensitive personal information is encrypted in a private vault; it's a win-win.
The Power of Encrypted AI Chat
AI chat is a personal and intimate experience. It's a place to share your thoughts, feelings, and desires without fear of judgment. The more you share with an AI chatbot, the more powerful it becomes. It can offer personalized insights, suggestions, and guidance tailored to your unique needs and perspectives. However, this intimacy requires trust, and that's where traditional AI chatbots often fall short.
Traditional AI chats are designed to collect and analyze your data, often without your explicit consent. This data is used to improve the AI's performance, but it also creates a treasure trove of sensitive information that can be mined, sold, or even exploited by malicious actors. Maple AI takes a different approach. By using end-to-end encryption, we ensure that your conversations remain private and secure, even from us.
Technical Overview
So, how does Maple AI achieve this level of privacy and security? Here are some key technical aspects:
- Private Key: Each user has a unique private key that is automatically managed for them. This key encrypts and decrypts conversations, ensuring that only the user can access their data.
- Secure Servers: Our servers are designed with security in mind. We use secure enclaves to protect sensitive data and ensure that even our own team can't access your conversations.
- Encrypted Sync: One of Maple's most significant benefits is its encrypted sync feature. Unlike traditional AI chatbots, which store conversations in local storage or on standard cloud servers, Maple syncs your chats across all your devices. The private key managed by our secure servers means you can pick up where you left off on any device without worrying about your data being compromised.
- Attestation and Open Code: We publish our enclave code publicly. Using a process called attestation, users can verify that the code running on the enclave is the same as the code audited by the public.
- Open Source LLM: Maple uses major open-source models to maximize the openness of responses. The chat box does not filter what you can talk about. This transparency ensures that our AI is trustworthy and unbiased.
Personal and Work Use
Maple is secure enough to handle your personal questions and work tasks. Because we can't see what you chat about, you are free to use AI as an assistant on sensitive company items. Use it for small tasks like writing an important email or large tasks like developing your organization's strategy. Feed it sensitive information; it's just you and AI in the room. Attestation provides cryptographic proof that your corporate secrets are safe.
Local v Cloud
Today's AI tools provide different levels of privacy. The main options are to trust a third party with your unencrypted data, hoping they don't do anything with it, or run your own AI locally on an underpowered machine. We created a third option. Maple gives you the power of cloud computing combined with the privacy and security of a machine running on your desk. It's the best of both worlds.
Why the Maple name?
Privacy isn't just a human value - it's a natural one exemplified by the Maple tree. These organisms communicate with each other through a network of underground fungal hyphae, sending messages and sharing resources in a way that's completely invisible to organisms above ground. This discreet communication system allows Maple trees to thrive in even the most challenging environments. Our goal is to provide a way for everyone to communicate with AI securely so they can thrive in any environment.
Join the Waitlist
Maple AI will launch in early 2025 with free and paid plans. We can't wait to share it with the world. Join our waitlist today to be among the first to experience the power of private AI chat.
-
 @ df173277:4ec96708
2025-01-09 17:02:52
@ df173277:4ec96708
2025-01-09 17:02:52OpenSecret is a backend for app developers that turns private encryption on by default. When sensitive data is readable only by the user, it protects both the user and the developer, creating a more free and open internet. We'll be launching in 2025. Join our waitlist to get early access.
In today's digital age, personal data is both an asset and a liability. With the rise of data breaches and cyber attacks, individuals and companies struggle to protect sensitive information. The consequences of a data breach can be devastating, resulting in financial losses, reputational damage, and compromised user trust. In 2023, the average data breach cost was $5 million, with some resulting in losses of over $1 billion.
 Meanwhile, individuals face problems related to identity theft, personal safety, and public embarrassment. Think about the apps on your phone, even the one you're using to read this. How much data have you trusted to other people, and how would it feel if that data were leaked online?
Meanwhile, individuals face problems related to identity theft, personal safety, and public embarrassment. Think about the apps on your phone, even the one you're using to read this. How much data have you trusted to other people, and how would it feel if that data were leaked online?Thankfully, some incredibly talented cypherpunks years ago gave the world cryptography. We can encrypt data, rendering it a secret between two people. So why then do we have data breaches?
Cryptography at scale is hard.
The Cloud
The cloud has revolutionized how we store and process data, but it has limitations. While cloud providers offer encryption, it mainly protects data in transit. Once data is stored in the cloud, it's often encrypted with a shared key, which can be accessed by employees, third-party vendors, or compromised by hackers.
The solution is to generate a personal encryption password for each user, make sure they write it down, and, most importantly, hope they don't lose it. If the password is lost, the data is forever unreadable. That can be overwhelming, leading to low app usage.
Private key encryption needs a UX upgrade.
Enter OpenSecret
OpenSecret is a developer platform that enables encryption by default. Our platform provides a suite of security tools for app developers, including private key management, encrypted sync, private AI, and confidential compute.
Every user has a private vault for their data, which means only they can read it. Developers are free to store less sensitive data in a shared manner because there is still a need to aggregate data across the system.

Private Key Management
Private key management is the superpower that enables personal encryption per user. When each user has a unique private key, their data can be truly private. Typically, using a private key is a challenging experience for the user because they must write down a long autogenerated number or phrase of 12-24 words. If they lose it, their data is gone.
OpenSecret uses secure enclaves to make private keys as easy as an everyday login experience that users are familiar with. Instead of managing a complicated key, the user logs in with an email address or a social media account.
The developer doesn't have to manage private keys and can focus on the app's user experience. The user doesn't have to worry about losing a private key and can jump into using your app.

Encrypted Sync
With user keys safely managed, we can synchronize user data to every device while maintaining privacy. The user does not need to do complicated things like scanning QR codes from one device to the next. Just log in and go.
The user wins because the data is available on all their devices. The developer wins because only the user can read the data, so it isn't a liability to them.
Private AI
Artificial intelligence is here and making its way into everything. The true power of AI is unleashed when it can act on personal and company data. The current options are to run your own AI locally on an underpowered machine or to trust a third party with your data, hoping they don't read it or use it for anything.
OpenSecret combines the power of cloud computing with the privacy and security of a machine running on your desk.
Check out Maple AI\ Try private AI for yourself! We built an app built with this service called Maple AI. It is an AI chat that is 100% private in a verifiable manner. Give it your innermost thoughts or embarrassing ideas; we can't judge you. We built Maple using OpenSecret, which means you have a private key that is automatically managed for you, and your chat history is synchronized to all your devices. Learn more about Maple AI - Private chat in the announcement post.

Confidential Compute
Confidential computing is a game-changer for data security. It's like the secure hardware that powers Apple Pay and Google Pay on your phone but in the cloud. Users can verify through a process called attestation that their data is handled appropriately. OpenSecret can help you run your own custom app backend code that would benefit from the security of an enclave.
It's the new version of that lock on your web browser. When you see it, you know you're secure.

But do we want our secrets to be open?
OpenSecret renders a data breach practically useless. If hackers get into the backend, they enter a virtual hallway of locked private vaults. The leaked data would be gibberish, a secret in the open that is unreadable.
On the topic of openness, OpenSecret uses the power of open source to enable trust in the service. We publish our code in the open, and, using attestation, anyone can verify that private data is being handled as expected. This openness also provides developers with a backup option to safely and securely export their data.
Don't trust, verify.
Join the Movement
We're currently building out OpenSecret, and we invite you to join us on the journey. Our platform can work with your existing stack, and you can pick and choose the features you need. If you want to build apps with encryption enabled, send us a message to get early access.
Users and companies deserve better encryption and privacy.\ Together, let's make that a reality.
-
 @ f977c464:32fcbe00
2024-01-11 18:47:47
@ f977c464:32fcbe00
2024-01-11 18:47:47Kendisini aynada ilk defa gördüğü o gün, diğerleri gibi olduğunu anlamıştı. Oysaki her insan biricik olmalıydı. Sözgelimi sinirlendiğinde bir kaşı diğerinden birkaç milimetre daha az çatılabilirdi veya sevindiğinde dudağı ona has bir açıyla dalgalanabilirdi. Hatta bunların hiçbiri mümkün değilse, en azından, gözlerinin içinde sadece onun sahip olabileceği bir ışık parlayabilirdi. Çok sıradan, öyle sıradan ki kimsenin fark etmediği o milyonlarca minik şeyden herhangi biri. Ne olursa.
Ama yansımasına bakarken bunların hiçbirini bulamadı ve diğer günlerden hiç de farklı başlamamış o gün, işe gitmek için vagonunun gelmesini beklediği alelade bir metro istasyonunda, içinde kaybolduğu illüzyon dağılmaya başladı.
İlk önce derisi döküldü. Tam olarak dökülmedi aslında, daha çok kıvılcımlara dönüşüp bedeninden fırlamış ve bir an sonra sönerek külleşmiş, havada dağılmıştı. Ardında da, kaybolmadan hemen önce, kısa süre için hayal meyal görülebilen, bir ruhun yok oluşuna ağıt yakan rengârenk peri cesetleri bırakmıştı. Beklenenin aksine, havaya toz kokusu yayıldı.
Dehşete düştü elbette. Dehşete düştüler. Panikle üstlerini yırtan 50 işçi. Her şeyin sebebiyse o vagon.
Saçları da döküldü. Her tel, yere varmadan önce, her santimde ikiye ayrıla ayrıla yok oldu.
Bütün yüzeylerin mat olduğu, hiçbir şeyin yansımadığı, suyun siyah aktığı ve kendine ancak kameralarla bakabildiğin bir dünyada, vagonun içine yerleştirilmiş bir aynadan ilk defa kendini görmek.
Gözlerinin akları buharlaşıp havada dağıldı, mercekleri boşalan yeri doldurmak için eriyip yayıldı. Gerçeği görmemek için yaratılmış, bu yüzden görmeye hazır olmayan ve hiç olmayacak gözler.
Her şeyin o anda sona erdiğini sanabilirdi insan. Derin bir karanlık ve ölüm. Görmenin görmek olduğu o anın bitişi.
Ben geldiğimde ölmüşlerdi.
Yani bozulmuşlardı demek istiyorum.
Belleklerini yeni taşıyıcılara takmam mümkün olmadı. Fiziksel olarak kusursuz durumdaydılar, olmayanları da tamir edebilirdim ama tüm o hengamede kendilerini baştan programlamış ve girdilerini modifiye etmişlerdi.
Belleklerden birini masanın üzerinden ileriye savurdu. Hınca hınç dolu bir barda oturuyorlardı. O ve arkadaşı.
Sırf şu kendisini insan sanan androidler travma geçirip delirmesin diye neler yapıyoruz, insanın aklı almıyor.
Eliyle arkasını işaret etti.
Polislerin söylediğine göre biri vagonun içerisine ayna yerleştirmiş. Bu zavallılar da kapı açılıp bir anda yansımalarını görünce kafayı kırmışlar.
Arkadaşı bunların ona ne hissettirdiğini sordu. Yani o kadar bozuk, insan olduğunu sanan androidi kendilerini parçalamış olarak yerde görmek onu sarsmamış mıydı?
Hayır, sonuçta belirli bir amaç için yaratılmış şeyler onlar. Kaliteli bir bilgisayarım bozulduğunda üzülürüm çünkü parasını ben vermişimdir. Bunlarsa devletin. Bana ne ki?
Arkadaşı anlayışla kafasını sallayıp suyundan bir yudum aldı. Kravatını biraz gevşetti.
Bira istemediğinden emin misin?
İstemediğini söyledi. Sahi, neden deliriyordu bu androidler?
Basit. Onların yapay zekâlarını kodlarken bir şeyler yazıyorlar. Yazılımcılar. Biliyorsun, ben donanımdayım. Bunlar da kendilerini insan sanıyorlar. Tiplerine bak.
Sesini alçalttı.
Arabalarda kaza testi yapılan mankenlere benziyor hepsi. Ağızları burunları bile yok ama şu geldiğimizden beri sakalını düzeltip duruyor mesela. Hayır, hepsi de diğerleri onun sakalı varmış sanıyor, o manyak bir şey.
Arkadaşı bunun delirmeleriyle bağlantısını çözemediğini söyledi. O da normal sesiyle konuşmaya devam etti.
Anlasana, aynayı falan ayırt edemiyor mercekleri. Lönk diye kendilerini görüyorlar. Böyle, olduğu gibi...
Nedenmiş peki? Ne gerek varmış?
Ne bileyim be abicim! Ahiret soruları gibi.
Birasına bakarak dalıp gitti. Sonra masaya abanarak arkadaşına iyice yaklaştı. Bulanık, bir tünelin ucundaki biri gibi, şekli şemalı belirsiz bir adam.
Ben seni nereden tanıyorum ki ulan? Kimsin sen?
Belleği makineden çıkardılar. İki kişiydiler. Soruşturmadan sorumlu memurlar.
─ Baştan mı başlıyoruz, diye sordu belleği elinde tutan ilk memur.
─ Bir kere daha deneyelim ama bu sefer direkt aynayı sorarak başla, diye cevapladı ikinci memur.
─ Bence de. Yeterince düzgün çalışıyor.
Simülasyon yüklenirken, ayakta, biraz arkada duran ve alnını kaşıyan ikinci memur sormaktan kendisini alamadı:
─ Bu androidleri niye böyle bir olay yerine göndermişler ki? Belli tost olacakları. İsraf. Gidip biz baksak aynayı kırıp delilleri mahvetmek zorunda da kalmazlar.
Diğer memur sandalyesinde hafifçe dönecek oldu, o sırada soruyu bilgisayarın hoparlöründen teknisyen cevapladı.
Hangi işimizde bir yamukluk yok ki be abi.
Ama bir son değildi. Üstlerindeki tüm illüzyon dağıldığında ve çıplak, cinsiyetsiz, birbirinin aynı bedenleriyle kaldıklarında sıra dünyaya gelmişti.
Yere düştüler. Elleri -bütün bedeni gibi siyah turmalinden, boğumları çelikten- yere değdiği anda, metronun zemini dağıldı.
Yerdeki karolar öncesinde beyazdı ve çok parlaktı. Tepelerindeki floresan, ışığını olduğu gibi yansıtıyor, tek bir lekenin olmadığı ve tek bir tozun uçmadığı istasyonu aydınlatıyorlardı.
Duvarlara duyurular asılmıştı. Örneğin, yarın akşam kültür merkezinde 20.00’da başlayacak bir tekno blues festivalinin cıvıl cıvıl afişi vardı. Onun yanında daha geniş, sarı puntolu harflerle yazılmış, yatay siyah kesiklerle çerçevesi çizilmiş, bir platformdan düşen çöp adamın bulunduğu “Dikkat! Sarı bandı geçmeyin!” uyarısı. Biraz ilerisinde günlük resmi gazete, onun ilerisinde bir aksiyon filminin ve başka bir romantik komedi filminin afişleri, yapılacakların ve yapılmayacakların söylendiği küçük puntolu çeşitli duyurular... Duvar uzayıp giden bir panoydu. On, on beş metrede bir tekrarlanıyordu.
Tüm istasyonun eni yüz metre kadar. Genişliği on metre civarı.
Önlerinde, açık kapısından o mendebur aynanın gözüktüğü vagon duruyordu. Metro, istasyona sığmayacak kadar uzundu. Bir kılıcın keskinliğiyle uzanıyor ama yer yer vagonların ek yerleriyle bölünüyordu.
Hiçbir vagonda pencere olmadığı için metronun içi, içlerindekiler meçhuldü.
Sonrasında karolar zerrelerine ayrılarak yükseldi. Floresanın ışığında her yeri toza boğdular ve ortalığı gri bir sisin altına gömdüler. Çok kısa bir an. Afişleri dalgalandırmadılar. Dalgalandırmaya vakitleri olmadı. Yerlerinden söküp aldılar en fazla. Işık birkaç kere sönüp yanarak direndi. Son kez söndüğünde bir daha geri gelmedi.
Yine de etraf aydınlıktı. Kırmızı, her yere eşit dağılan soluk bir ışıkla.
Yer tamamen tele dönüşmüştü. Altında çapraz hatlarla desteklenmiş demir bir iskelet. Işık birkaç metreden daha fazla aşağıya uzanamıyordu. Sonsuzluğa giden bir uçurum.
Duvarın yerini aynı teller ve demir iskelet almıştı. Arkasında, birbirine vidalarla tutturulmuş demir plakalardan oluşan, üstünden geçen boruların ek yerlerinden bazen ince buharların çıktığı ve bir süre asılı kaldıktan sonra ağır, yağlı bir havayla sürüklendiği bir koridor.
Diğer tarafta paslanmış, pencerelerindeki camlar kırıldığı için demir plakalarla kapatılmış külüstür bir metro. Kapının karşısındaki aynadan her şey olduğu gibi yansıyordu.
Bir konteynırın içini andıran bir evde, gerçi gayet de birbirine eklenmiş konteynırlardan oluşan bir şehirde “andıran” demek doğru olmayacağı için düpedüz bir konteynırın içinde, masaya mum görüntüsü vermek için koyulmuş, yarı katı yağ atıklarından şekillendirilmiş kütleleri yakmayı deniyordu. Kafasında hayvan kıllarından yapılmış grili siyahlı bir peruk. Aynı kıllardan kendisine gür bir bıyık da yapmıştı.
Üstünde mavi çöp poşetlerinden yapılmış, kravatlı, şık bir takım.
Masanın ayakları yerine oradan buradan çıkmış parçalar konulmuştu: bir arabanın şaft mili, üst üste konulmuş ve üstünde yazı okunamayan tenekeler, boş kitaplar, boş gazete balyaları... Hiçbir şeye yazı yazılmıyordu, gerek yoktu da zaten çünkü merkez veri bankası onları fark ettirmeden, merceklerden giren veriyi sentezleyerek insanlar için dolduruyordu. Yani, androidler için. Farklı şekilde isimlendirmek bir fark yaratacaksa.
Onların mercekleri için değil. Bağlantıları çok önceden kopmuştu.
─ Hayatım, sofra hazır, diye bağırdı yatak odasındaki karısına.
Sofrada tabak yerine düz, bardak yerine bükülmüş, çatal ve bıçak yerine sivriltilmiş plakalar.
Karısı salonun kapısında durakladı ve ancak kulaklarına kadar uzanan, kocasınınkine benzeyen, cansız, ölü hayvanların kıllarından ibaret peruğunu eliyle düzeltti. Dudağını, daha doğrusu dudağının olması gereken yeri koyu kırmızı bir yağ tabakasıyla renklendirmeyi denemişti. Biraz da yanaklarına sürmüştü.
─ Nasıl olmuş, diye sordu.
Sesi tek düzeydi ama hafif bir neşe olduğunu hissettiğinize yemin edebilirdiniz.
Üzerinde, çöp poşetlerinin içini yazısız gazete kağıtlarıyla doldurarak yaptığı iki parça giysi.
─ Çok güzelsin, diyerek kravatını düzeltti kocası.
─ Sen de öylesin, sevgilim.
Yaklaşıp kocasını öptü. Kocası da onu. Sonra nazikçe elinden tutarak, sandalyesini geriye çekerek oturmasına yardım etti.
Sofrada yemek niyetine hiçbir şey yoktu. Gerek de yoktu zaten.
Konteynırın kapısı gürültüyle tekmelenip içeri iki memur girene kadar birbirlerine öyküler anlattılar. O gün neler yaptıklarını. İşten erken çıkıp yemyeşil çimenlerde gezdiklerini, uçurtma uçurduklarını, kadının nasıl o elbiseyi bulmak için saatlerce gezip yorulduğunu, kocasının kısa süreliğine işe dönüp nasıl başarılı bir hamleyle yaşanan krizi çözdüğünü ve kadının yanına döndükten sonra, alışveriş merkezinde oturdukları yeni dondurmacının dondurmalarının ne kadar lezzetli olduğunu, boğazlarının ağrımasından korktuklarını...
Akşam film izleyebilirlerdi, televizyonda -boş ve mat bir plaka- güzel bir film oynayacaktı.
İki memur. Çıplak bedenleriyle birbirinin aynı. Ellerindeki silahları onlara doğrultmuşlardı. Mum ışığında, tertemiz bir örtünün serili olduğu masada, bardaklarında şaraplarla oturan ve henüz sofranın ortasındaki hindiye dokunmamış çifti gördüklerinde bocaladılar.
Hiç de androidlere bilinçli olarak zarar verebilecek gibi gözükmüyorlardı.
─ Sessiz kalma hakkına sahipsiniz, diye bağırdı içeri giren ikinci memur. Söylediğiniz her şey...
Cümlesini bitiremedi. Yatak odasındaki, masanın üzerinden gördüğü o şey, onunla aynı hareketleri yapan android, yoksa, bir aynadaki yansıması mıydı?
Bütün illüzyon o anda dağılmaya başladı.
Not: Bu öykü ilk olarak 2020 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ 61bf790b:fe18b062
2025-04-29 12:23:09
@ 61bf790b:fe18b062
2025-04-29 12:23:09In a vast digital realm, two cities stood side by side: the towering, flashing metropolis of Feedia, and the decentralized, quiet city of Nostra.
Feedia was loud—blinding, buzzing, and always on. Screens plastered every wall, whispering the latest trends into citizens’ ears. But in this city, what you saw wasn’t up to you. It was determined by a towering, unseen force known as The Algorithm. It didn’t care what was true, meaningful, or helpful—only what would keep your eyes glued and your attention sold.
In Feedia, discovery wasn’t earned. It was assigned.
And worse—there was a caste system. To have a voice, you needed a Blue Check—a glowing badge that marked you as “worthy.” To get one, you had to pay or play. Pay monthly dues to the high towers or entertain The Algorithm enough to be deemed “valuable.” If you refused or couldn’t afford it, your voice was cast into the noise—buried beneath outrage bait and celebrity screams.
The unmarked were like ghosts—speaking into the void while the checked dined in Algorithm-favored towers. It was a digital monarchy dressed up as a democracy.
Then, there was Nostra.
There were no glowing checkmarks in Nostra—just signal. Every citizen had a light they carried, one that grew brighter the more they contributed: thoughtful posts, reshared ideas, built tools, or boosted others. Discovery was based not on payment or privilege, but participation and value.
In Nostra, you didn’t rise because you paid the gatekeeper—you rose because others lifted you. You weren’t spoon-fed; you sought, you found, you earned attention. It was harder, yes. But it was real.
And slowly, some in Feedia began to awaken. They grew tired of being fed fast-food content and ignored despite their voices. They looked across the river to Nostra, where minds weren’t bought—they were built.
And one by one, they began to cross.
-
 @ 1b939fa8:1ebdc679
2025-04-29 11:57:05
@ 1b939fa8:1ebdc679
2025-04-29 11:57:05All of my outfit conversion mods and Nora's Commonwealth Reconstruction Project have requirements that are on Nexus and nowhere else. Exception for the outfit conversions is Devious Devices which is noted and links provided to Lovers Lab and other requirements. My mods are dependent on those original mods to work. If/when the originals come to DEG then I will update and remove the Nexus links in my descriptions.
-
 @ 6c67a3f3:b0ebd196
2025-04-29 11:28:01
@ 6c67a3f3:b0ebd196
2025-04-29 11:28:01On Black-Starting the United Kingdom
In the event of a total failure of the electric grid, the United Kingdom would face a task at once technical and Sisyphean: the so-called black start — the reawakening of the nation’s darkened arteries without any external supply of power. In idealized manuals, the task is rendered brisk and clean, requiring but a few days' labor. In the world in which we live, it would be slower, more uncertain, and at times perilously close to impossible.
Let us unfold the matter layer by layer.
I. The Nature of the Undertaking
A black start is not a mere throwing of switches, but a sequential ballet. Small generating stations — diesel engines, hydro plants, gas turbines — must first breathe life into cold transmission lines. Substations must be coaxed into readiness. Load must be picked up cautiously, lest imbalance bring the whole effort to naught. Islands of power are stitched together, synchronized with exquisite care.
Each step is fraught with fragility. An unseen misalignment, an unsignaled overload, and hours of labor are lost.
II. The Dream of the Engineers
In theory, according to the National Grid Electricity System Operator (ESO), the sequence would unfold thus: within half a day, core transmission lines humming; within a day or two, hospitals lit and water flowing; within three days, cities reawakened; within a week, the nation, broadly speaking, restored to life.
This vision presupposes a fantasy of readiness: that black-start units are operational and plentiful; that communications systems, so delicately dependent on mobile networks and the internet, endure; that personnel, trained and coordinated, are on hand in sufficient numbers; and that no sabotage, no accident, no caprice of nature interrupts the dance.
III. The Real Order of Things
Reality is more obstinate. Many black-start capable plants have been shuttered in the name of efficiency. The financial incentives once offered to private generators for black-start readiness were judged insufficient; the providers withdrew.
Grid operations now rely on a lattice of private interests, demanding slow and complicated coordination. Telecommunications are vulnerable in a deep blackout. The old hands, steeped in the tacit lore of manual restoration, have retired, their knowledge scattered to the four winds. Cyber vulnerabilities have multiplied, and the grid’s physical inertia — the very thing that grants a system grace under perturbation — has grown thin, leaving the UK exposed to sudden collapses should synchronization falter.
Under such conditions, the best of hopes might yield five to ten days of partial recovery. Weeks would be required to restore the former web of normalcy. In certain cases — in the face of physical damage to high-voltage transformers, whose replacements take months if not years — black-start might founder altogether.
IV. The Quiet Admissions of Officialdom
In its polite documents, the National Grid ESO speaks carefully: essential services might see restoration within three days, but full public service would require "up to a week or longer." If designated black-start units were to fail — a real risk, given recent audits showing many unready — the timelines would stretch indefinitely.
In plain speech: in a true national blackout, the nation’s restoration would be a gamble.
V. The Forking Paths Ahead
If all proceeds well, Britain might stumble into light within three days. If the adversities accumulate — cyberattack, internal sabotage, simple human miscalculation — the process would stretch into weeks, even months. In the gravest scenarios, the nation would reconstitute not as one great engine, but as isolated islands of power, each jury-rigged and vulnerable.
Meanwhile, the paradoxical truth is that small and simple systems — the grids of Jersey, Malta, and the like — would outpace their mightier cousins, not despite their modest scale but because of it.
VI. Conclusion
The British grid, in short, is a triumph of late modernity — and like all such triumphs, it carries within itself the seeds of its own fragility. It works magnificently until the day it does not. When that day comes, recovery will be neither swift nor sure, but a slow, halting reweaving of threads too easily frayed.
-
 @ 7d4417d5:3eaf36d4
2023-08-19 01:05:59
@ 7d4417d5:3eaf36d4
2023-08-19 01:05:59I'm learning as I go, so take the text below for what it is: my notes on the process. These steps could become outdated quickly, and I may have some wrong assumptions at places. Either way, I have had success, and would like to share my experience for anyone new to the process. If I have made any errors, please reply with corrections so that others may avoid potential pitfalls.
!!! If you have "KYC Bitcoin", keep it in separate wallets from your "Anonymous Bitcoin". Any Anonymous Bitcoin in a wallet with KYC Bitcoin becomes 100% KYC Bitcoin.
!!! It took me several days to get all the right pieces set up before I could even start an exchange with someone.
!!! Using a VPN is highly recommended. If you're not already using one, take the time to find one that suits you and get it running.
!!! If you don't normally buy Amazon Gift Cards, start doing so now, and just send them to yourself, or friends that will give you cash in return, etc. For my first trade, Amazon locked me out of my account for about 22 hours, while I was in the middle of an exchange. All because I had never purchased an Amazon Gift Card before. It was quite nerve wracking. My second trade was for $300, and although my Amazon account wasn't shut down, that order had a status of "Sending" for about 22 hours, due to the large amount. In each of these cases I had multiple phone calls with their customer support, all of whom gave me false expectations. Had I already been sending gift cards to the anonymous email address that I created in the steps below, and maybe other anonymous email addresses that I could make, then I might not have been stalled so much.
-
Install Tor Browser for your OS. The RoboSats.com website issues a warning if you are not using Tor Browser. If you don't know what Tor is, I won't explain it all here, but trust me, it's cool and helps keep you anonymous. If you use Firefox, the interface will look very familiar to you.
-
Create a KYC-free e-mail address. I used tutanota.com in Firefox, as it would not allow me to create an account using Tor Browser. After the account was created, using Tor Browser to login, check emails, etc. has been working perfectly. Tutanota requires a 48 hour (or less) waiting period to prevent bots from using their system. You'll be able to login, and even draft an email, but you won't be able to send. After you've been approved, you should be able to login and send an email to your new address. It should show up in your Inbox almost instantly if it's working.
-
Have, or create, at least one Lightning wallet that is compatible with RoboSats.com and has no KYC Bitcoin in it. The RoboSats website has a compatibility chart available to find the best wallet for you. During an exchange on RoboSats, you will need to put up an escrow payment, or bond, in Satoshis. This amount is usually 3% of the total amount being exchanged. If the exchange is successful, the bond payment is canceled, leaving that amount in your wallet untouched, and with no record of it having been used as escrow. If you don't hold up your end of the trade, the bond amount will be transfered from your wallet. I created a wallet, using my new email address, with the Alby extension in the Tor Browser. This anonymous wallet was empty, so I used a separate wallet for the bond payment of my first trade. This wallet had KYC Bitcoin, but since it is being used for a bond payment, and no transaction will be recorded if everything goes okay, I don't mind taking the minuscule risk. After the first trade, I don't need to use the "KYC wallet", and I will use only my anonymous Lightning wallet for transactions related to performing a trade.
-
Create a new Robot Token by going to RoboSats using the Tor Browser. Copy the Token (Robot ID) to a text file as a temporary backup. It is recommended to create a new robot-token for every session of exchanges you make.
-
Select "Offers" to browse what others are presenting. "Create" is for when you want to create an offer of your own. You may need to create your own offer if none of the existing offers match your criteria.
-
Select "Buy" at the top of the page.
-
Select your currency (USD).
-
Select your payment methods by typing "amazon" and selecting (Amazon Gift Card). Repeat this process and select (Amazon USA Gift Card).
-
Determine Priorities - If you prefer to trade quickly, and don't care as much about premiums, look for users with a green dot on the upper-right of their robot icon. If you're not in a hurry, sort users by premium and select the best deal, even if they are inactive. They may become active once they are notified that their offer has activity from you.
-
The Definition of Price = the price with the premium added, but not the bond
-
A. Find A Compatible Offer - Select the row of the desired offer and enter the amount you would like to buy. i.e. $100 If you do not find a compatible offer, you will have to create your own offer.
B. **Create An Offer** - First, take a look at "Sell" offers for your same currency and payment method(s) that you will be using. Take note of the premium those buyers are willing to pay. If your premium is drastically less than theirs, your offer may get ignored. Select "Create" at the bottom of the screen. There is a slider at the top of the screen, select it to see all the options. Select "Buy". Enter the minimum and maximum amount that you wish to spend. Type "amazon" to select the methods that you would like to use (Amazon Gift Card, Amazon USA Gift Card). For "Premium Over Market", enter an amount that is competitive with premiums you saw at the start of this step and do not use the % sign! You can adjust the duration, timer, and bond amount, but I leave those at their default settings. Select the "Create Order" button, and follow the instructions for making a bond payment. -
Pay the Bond - Copy the invoice that is presented. From your wallet that contains bond funds, select "Send", and paste the invoice as the recipient. This money will never leave your account if the exchange completes without issue. No transaction will be recorded. If there is a complication with the exchange, it is possible that this transaction will complete.
-
Create and Submit Your Invoice for Their Bitcoin Payment To You - Select "Lightning", if not selected by default.* Select the Copy Icon to copy the correct amount of Satoshis. This amount already has the premium deducted. From your anonymous Lightning Wallet, select "Receive", and paste the Satoshi amount. If you enter a description, it's probably best to keep it cryptic. Copy the invoice and paste it into RoboSats; then select "Submit".
* If you plan on "mixing" your Bitcoin after purchase, it may be better to select "On Chain" and pay the necessary fees swap and mining fees. In the example this comes from, Sparrow wallet is used and has whirlpool ability in its interface.
-
Connect With Seller and Send Funds - Greet the seller in the chat window. The seller has now provided RoboSats with the Bitcoin to transfer to you. Your move is to buy an Amazon eGift Card for the amount of the trade. Log in to your Amazon account and start the process of buying an eGift card. For delivery there is the option of email or txt message. Ask the seller what their preference is, and get their address, or phone number, to enter into Amazon's form. Complete the purchase process on Amazon, and check the status of your order. Once you see the status of "Sent", go back to RoboSats in your Tor Browser.
-
Confirm Your Payment - Select the "Confirm ___ USD Sent" button and notify the seller to check their e-mail/txt messages.
-
Seller Confirmation - Once the seller select their "Confirm" button, the trade will immediately end with a confirmation screen.
-
Verify - If you check the anonymous wallet, the new amount should be presented.
-
-
 @ 7e538978:a5987ab6
2025-04-29 09:46:02
@ 7e538978:a5987ab6
2025-04-29 09:46:02In Jericoacoara, Brazil, a beach town famed for its natural beauty and vibrant tourism, an innovative project is quietly reshaping how locals and visitors think about money. Praia Bitcoin is an ambitious initiative to build a circular economy powered entirely by Bitcoin.
Launched in 2021 by entrepreneur Fernando Motolese, Praia Bitcoin was inspired by the Bitcoin Beach project in El Zonte, El Salvador. The vision is simple: create a self-sustaining Bitcoin economy where businesses and individuals use Bitcoin everyday in place of fiat money.
This idea holds special significance in Jericoacoara, where traditional banking services are scarce. The town lacks even basic infrastructure like ATMs, making financial inclusion a pressing need. With Praia Bitcoin, Bitcoin isn’t just a store of value—it’s a tool to empower a community and connect it to the global economy.
Transforming Jericoacoara with Bitcoin
Since its inception, Praia Bitcoin has worked to foster Bitcoin adoption in the area. Starting with a modest donation of 0.02 BTC, Fernando and his team have built a thriving ecosystem:
- Over 40 businesses now accept Bitcoin, ranging from souvenir shops and tour operators to beach vendors.
- Local students have received Bitcoin-loaded tap-to-pay, Bolt Cards, to use in their daily lives.
- Creative initiatives like “Bitcoin Banana Day” or "Frutas por Sats" (fruits for sats) where children buy fruits for 10 satoshis at school, have brought global attention to the project.
Praia Bitcoin’s success isn’t just about the adoption numbers, it’s about the stories. Families use Bitcoin to shop, business owners save on transaction fees, and children are learning the value of sound money at an early age.
LNbits - The Technology Behind Praia Bitcoin
Creating an economy on Bitcoin’s Lightning Network requires more than enthusiasm, it needs robust tools that are easy to use and adaptable to local needs. That’s where LNbits comes in.
Fernando and the Praia Bitcoin team have used LNbits’ open-source software to solve practical challenges and scale the project. With its modular design, LNbits provides tools that allow Praia Bitcoin to:
- Set Up Wallets: Community members receive user-friendly wallets that connect seamlessly to the Lightning Network, enabling fast, low-cost transactions.
- Issue BoltCards: Using LNbits’ BoltCard extension, the team has distributed NFC-enabled cards, allowing tap-to-pay functionality that makes Bitcoin payments as simple as using a credit card.
- Enable Flexible Payments: The project utilizes LNbits’ Point of Sale TPoS extension that allows merchants to easily receive Lightning Network payments.
Breaking Records, Building Community
Fernando doesn’t just implement solutions, he pushes boundaries. One of his most remarkable achievements was an attempt to set a world record for the most Lightning Network payments in the shortest amount of time. Over the course of one afternoon, 100 children in Jericoacoara received payments of 21,000 satoshis each, demonstrating the scalability and speed of Lightning-powered transactions.
This wasn’t just a technical feat, it was a community moment. The event showed how Bitcoin could serve as a tool for engagement, education, and empowerment, all while highlighting the possibilities of using the Lightning Network for real-world applications.
A Collaborative Approach to Innovation
One of the unique strengths of LNbits is its ability to evolve based on community feedback. While Fernando Motolese and Praia Bitcoin operate independently, their insights have helped refine the LNbits platform.
For example, Fernando’s need for a PIN-less ATM functionality led the LNbits team to implement that feature in the TPoS extension, that had the functionality but required a security PIN. This kind of collaboration isn’t about formal partnerships. It’s about how an open-source ecosystem thrives when real-world needs drive innovation.
The feedback loop between users like Fernando and developers ensures LNbits remains practical and relevant—not just for Praia Bitcoin but for countless other projects worldwide.
The Ripple Effect of Praia Bitcoin
Praia Bitcoin is a case study in what’s possible when Bitcoin meets a strong vision. By leveraging Bitcoin, the Lightning Network and LNbits, the project has redefined financial access in Jericoacoara, proving that small communities can lead big innovations.
For LNbits, Praia Bitcoin showcases the value of adaptable, open-source solutions. Whether it’s creating wallets, enabling NFC payments, or refining tools for real-world use, LNbits provides the infrastructure that makes projects like Praia Bitcoin possible.
But beyond the technical achievements, Praia Bitcoin reminds us of the human impact of Bitcoin adoption. It’s about children buying their first bananas with satoshis, families running businesses with lower fees, and a community connecting to a global financial network for the first time.
Conclusion
Praia Bitcoin’s journey is only getting started and its success is inspiring similar initiatives worldwide. For LNbits, being part of this story, is a testament to the power of the software and of open-source collaboration.
If you’re ready to build the future of Bitcoin adoption, LNbits offers the tools to turn ideas into impact.
Learn More:
- Visit Praia Bitcoin: Praia Bitcoin
- Explore LNbits: LNbits -
 @ a4043831:3b64ac02
2025-04-29 09:19:05
@ a4043831:3b64ac02
2025-04-29 09:19:05A professional financial advisor can guide you to achieve long-term financial stability. They can assist you to define your goals to formulate strategic planning coupled with rational decision-making. Since the options are varied and multiple, how can you go about choosing a fiduciary financial advisor whose approach matches their financial goals? This guide explains exactly how to pick a financial advisor who suits your individual financial targets.
Defining Your Financial Needs and Goals
You need to specify your financial aspirations as well as your essential requirements so an advisor can create a suitable plan for your portfolio. Starters should establish their monetary targets before initiating contact with financial consultants. Any objective requires planning such as retirement preparation and investment management and education savings along with wealth protection and growth needs to be identified. Knowing your financial goals helps you determine if an advisor’s experience matches the needs of reaching your targets. Before you conduct meetings with possible financial advisors you need to have clearly established financial goals which will make these meetings goal-focused and beneficial.
Trusted financial advisors at Passive Capital Management can help you check out financial plan tailored to your needs and goals.
Look For Professional Credentials and Qualifications
Review carefully the advisor’s qualifications after you establish your goals. The strict training and ethical assessments that CFP Certified Financial Planner and the CFA Chartered Financial Analyst professionals demonstrate their professionalism. The designations set by these organizations prove advisors maintain knowledge in planning, investments and regulatory requirements. It is essential to verify that the advisor operates under fiduciary standards since this legal requirement ensures they must always act according to your benefit. It is essential to verify if an advisor functions as a fiduciary all the time because some only act under specified circumstances. Get a direct and unambiguous statement about their status. Under fiduciary relationships your financial security stands as the main priority of your financial advisor while fiduciary arrangements reduce potential conflicts between your interests.
Understand the Advisor’s Investment Approach
While consulting an advisor, you might encounter several hidden conflicts of interest. So a robust advisor-client connection based on their mutual investment approach including strategy selection is essential. Review the risk approaches of your advisor through inquiries to learn about their portfolio design strategies and market investment strategies. Technical competence must be combined with an awareness of your risk tolerance and time preferences according to their responses. A reliable advisor will adapt their investment methods to match the risk tolerance of their client combined with their financial destination.
Review their Service Package and Communication Style
A competent financial advisor functions past standard investment management duties. Their service range needs to include full-scale financial planning in areas such as retirement income strategies along with tax and estate planning solutions and insurance assessments. Check that their service suite matches your financial development needs. The advisor needs to maintain both clear and predictable ways of communication. Reveal their review process schedule and disclosure methods for reporting metrics as well as their availability to respond to questions at any time during the year. Professional communication builds reliable relationships that involve active participant commitment in planning activities.
Clarify the Fee Structure
Knowing how your advisor gets paid gives you the essential knowledge needed for building trust between you both. Financial advisors conduct business through payment structures which include flat fees, percentage-based fees on managed assets and extra earnings from their advisory products. The different compensation models bring their own effects and outcomes to the process. The most significant aspect for you is receiving clear explanations about fees while they are in alignment with your financial planning. The first practice of transparent communication by an advisor suggests they will uphold that approach during your entire time together.
Conclusion
Alongside numerical expertise your ideal advisor should function as a trustworthy partner because they will dedicate themselves to your financial growth. Strategic decision-making depends on the establishment of clear objectives and verification of expertise as well as confirmation of fiduciary principles and comprehensive evaluation of communication methods and associated fees. Your financial destiny requires organized assessment along with expert consulting while the correct professional consultant enables you to move through every phase of your path with obvious direction and solid self-assurance.
-
 @ c1157704:6423de51
2025-04-29 08:54:13
@ c1157704:6423de51
2025-04-29 08:54:13English: "Politicians steal billions and get light sentences, while the poor get jailed for stealing bread. Is the law just a tool for the rich?"
-
 @ 38e82785:9f8bc340
2025-04-29 08:50:51
@ 38e82785:9f8bc340
2025-04-29 08:50:51te
-
 @ 56cd780f:cbde8b29
2025-04-29 08:48:03
@ 56cd780f:cbde8b29
2025-04-29 08:48:03And this is the regular text.
-
 @ 56cd780f:cbde8b29
2025-04-29 08:48:01
@ 56cd780f:cbde8b29
2025-04-29 08:48:01I will add a picture, a hyperlink and a video. Let’s see if it works.
-
 @ 56cd780f:cbde8b29
2025-04-29 08:48:00
@ 56cd780f:cbde8b29
2025-04-29 08:48:00Is it still working?
-
 @ 56cd780f:cbde8b29
2025-04-29 08:47:58
@ 56cd780f:cbde8b29
2025-04-29 08:47:58Is it actually called “summary”?
-
 @ 56cd780f:cbde8b29
2025-04-29 08:47:56
@ 56cd780f:cbde8b29
2025-04-29 08:47:56A few weeks ago, I ran into an old friend at a coffee shop. We hadn’t spoken in years, and within five minutes, she said something I’ve heard countless times:
“I just feel like I’m so behind.”
Behind who? Behind what?
 There’s this idea—quiet, nagging, oddly universal—that we’re all somehow in a race we didn’t sign up for. That we’re supposed to have hit certain milestones by certain ages. That if we’re not married, promoted, rich, settled, happy (and photogenic) by 30 or 40 or pick your poison, then we’ve failed some invisible test.
There’s this idea—quiet, nagging, oddly universal—that we’re all somehow in a race we didn’t sign up for. That we’re supposed to have hit certain milestones by certain ages. That if we’re not married, promoted, rich, settled, happy (and photogenic) by 30 or 40 or pick your poison, then we’ve failed some invisible test.Where did this come from?
Some of it’s cultural, obviously. Social media compresses timelines. You’re 27, doom-scrolling, and suddenly someone from high school just IPO’d their startup and got engaged in Rome. Another just bought a house with a kitchen island the size of a small country. You wonder if you missed a memo.
But beneath that, there’s something deeper. A belief that life is linear. That it should look like a staircase: school, job, marriage, house, kids, success. But real life? It’s a squiggle. A mess. A beautiful disaster.
Here’s the truth: You’re not behind. There’s no schedule. There’s only your path, and the courage it takes to stay on it—even when it looks wildly different from everyone else’s.
I say this as someone who has taken the “scenic route.” I changed careers in my 30s. I moved cities on a hunch. I dropped things that looked great on paper because they felt wrong in my gut. I’ve had seasons of momentum and seasons of stuckness. Both were necessary.
“Catching up” assumes there’s a fixed destination. But what if there isn’t? What if the point isn’t arrival, but presence? Progress that feels real, not performative?
If you need a permission slip to stop comparing, let this be it.
 You’re not late. You’re not early.
You’re not late. You’re not early.
You’re right on time. -
 @ 7501d519:e6ff3dcc
2025-04-29 08:47:28
@ 7501d519:e6ff3dcc
2025-04-29 08:47:28English: "Politicians steal billions and get light sentences, while the poor get jailed for stealing bread. Is the law just a tool for the rich?"
originally posted at https://stacker.news/items/966062
-
 @ 975e4ad5:8d4847ce
2025-04-29 08:26:50
@ 975e4ad5:8d4847ce
2025-04-29 08:26:50With the advancement of quantum computers, a new threat emerges for the security of cryptocurrencies and blockchain technologies. These powerful machines have the potential to expose vulnerabilities in traditional cryptographic systems, which could jeopardize the safety of digital wallets. But don’t worry—modern wallets are already equipped to handle this threat with innovative solutions that make your funds nearly impossible to steal, even by a quantum computer. Let’s explore how this works and why you can rest easy.
The Threat of Quantum Computers
To understand how wallets protect us, we first need to grasp what makes quantum computers so dangerous. At the core of most cryptocurrencies, like Bitcoin, lies public and private key cryptography. The public key (or address) is like your bank account number—you share it to receive funds. The private key is like your PIN—it allows you to send funds and must remain secret.
Traditional cryptography, such as the ECDSA algorithm, relies on mathematical problems that are extremely difficult to solve with conventional computers. For instance, deriving a private key from a public key is practically impossible, as it would take millions of years of computation. However, quantum computers, thanks to algorithms like Shor’s, can significantly speed up this process. Theoretically, a sufficiently powerful quantum computer could uncover a private key from a public key in minutes or even seconds.
This is a problem because if someone gains access to your private key, they can send all your funds to their own address. But here’s the good news—modern wallets use a clever solution to render this threat powerless.
How Do Wallets Protect Us?
One of the most effective defenses against quantum computers is the use of one-time addresses in wallets. This means that for every transaction—whether receiving or sending funds—the wallet automatically generates a new public address. The old address, once used, remains in the transaction history but no longer holds any funds, as they are transferred to a new address.
Why Does This Work?
Imagine you’re sending or receiving cryptocurrency. Your wallet creates a new address for that transaction. After the funds are sent or received, that address becomes “used,” and the wallet automatically generates a new one for the next transaction. If a quantum computer manages to derive the private key from the public address of the used address, it will find nothing—because that address is already empty. Your funds are safely transferred to a new address, whose public key has not yet been exposed.
This strategy is known as HD (Hierarchical Deterministic) wallets. It allows the wallet to generate an infinite number of addresses from a single master key (seed) without compromising security. Each new address is unique and cannot be linked to the previous ones, making it impossible to trace your funds, even with a quantum computer.
Automation Makes It Effortless
The best part? You don’t need to worry about this process—it’s fully automated. When you use a modern wallet like MetaMask, Ledger, Trezor, or software wallets for Bitcoin, everything happens behind the scenes. You simply click “receive” or “send,” and the wallet takes care of generating new addresses. There’s no need to understand the complex technical details or manually manage your keys.
For example:
- You want to receive 0.1 BTC. Your wallet provides a new address, which you share with the sender.
- After receiving the funds, the wallet automatically prepares a new address for the next transaction.
- If you send some of the funds, the remaining amount (known as “change”) is sent to another new address generated by the wallet.
This system ensures that public addresses exposed on the blockchain no longer hold funds, making quantum attacks pointless.
Additional Protection: Toward Post-Quantum Cryptography
Beyond one-time addresses, blockchain developers are also working on post-quantum cryptography—algorithms that are resistant to quantum computers. Some blockchain networks are already experimenting with such solutions, like algorithms based on lattices (lattice-based cryptography). These methods don’t rely on the same mathematical problems that quantum computers can solve, offering long-term protection.
In the meantime, one-time addresses combined with current cryptographic standards provide enough security to safeguard your funds until post-quantum solutions become widely adopted.
Why You Shouldn’t Worry
Modern wallets are designed with the future in mind. They not only protect against today’s threats but also anticipate future risks, such as those posed by quantum computers. One-time addresses make exposed public keys useless to hackers, and automation ensures you don’t need to deal with the technicalities. HD wallets, which automatically generate new addresses, make the process seamless and secure for users.
Public key exposure only happens when necessary, reducing the risk of attacks, even from a quantum computer. In conclusion, while quantum computers pose a potential threat, modern wallets already offer effective solutions that make your cryptocurrencies nearly impossible to steal. With one-time addresses and the upcoming adoption of post-quantum cryptography, you can be confident that your funds are safe—today and tomorrow.
-
 @ 9f38a97e:c41d3606
2025-04-29 08:22:10
@ 9f38a97e:c41d3606
2025-04-29 08:22:10O universo dos jogos online tem evoluído constantemente, oferecendo experiências cada vez mais envolventes e personalizadas. Nesse cenário competitivo, a KZ999 se destaca como uma plataforma inovadora, segura e cheia de opções para quem busca entretenimento de qualidade e oportunidades reais de ganhos. Desde sua chegada ao mercado, a KZ999 vem conquistando os jogadores brasileiros com sua interface moderna, atendimento eficiente e ampla variedade de jogos emocionantes.
Introdução à Plataforma KZ999 A KZ999 é uma plataforma digital criada para atender às demandas de jogadores exigentes, que valorizam não apenas a diversão, mas também a segurança, a facilidade de uso e o suporte de qualidade. Com um design responsivo e otimizado para dispositivos móveis, o site funciona perfeitamente tanto em computadores quanto em smartphones, garantindo acesso rápido e prático de qualquer lugar.
O processo de cadastro na plataforma é simples e rápido, permitindo que novos usuários comecem a jogar em poucos minutos. Além disso, a kz999oferece suporte a métodos de pagamento modernos e populares no Brasil, como o PIX, o que facilita as transações e proporciona mais agilidade no dia a dia dos jogadores.
Diversidade de Jogos para Todos os Perfis Um dos principais atrativos da KZ999 é a sua extensa biblioteca de jogos. A plataforma oferece uma variedade impressionante de opções que atendem tanto os novatos quanto os jogadores mais experientes. Entre os destaques estão:
Jogos de mesa clássicos, como roleta, pôquer e blackjack, todos com gráficos de alta definição e recursos interativos que simulam uma experiência realista.
Slots modernos e temáticos, com animações vibrantes, efeitos sonoros imersivos e bônus especiais que aumentam as chances de ganhar.
Jogos ao vivo, em que o jogador pode interagir em tempo real com crupiês profissionais e outros participantes, trazendo mais emoção e autenticidade à experiência.
Minigames e jogos instantâneos, ideais para quem busca partidas rápidas e dinâmicas, com regras simples e diversão garantida.
Os títulos disponíveis na KZ999 são desenvolvidos por provedores reconhecidos internacionalmente, o que assegura qualidade, justiça nos resultados e constante atualização de conteúdo.
Experiência do Jogador: Segurança, Suporte e Recompensas A KZ999 não se preocupa apenas em oferecer jogos de qualidade. A experiência do usuário é tratada com prioridade, e por isso a plataforma investe fortemente em segurança digital, utilizando sistemas de criptografia avançados para proteger os dados e transações de seus usuários.
Outro ponto positivo é o suporte ao cliente, disponível 24 horas por dia, com atendimento em português. Seja por chat ao vivo ou por e-mail, a equipe da KZ999 está sempre pronta para resolver dúvidas, orientar sobre promoções ou ajudar com questões técnicas.
Falando em promoções, os jogadores da KZ999 têm acesso a bônus atrativos e programas de fidelidade, que recompensam o tempo dedicado à plataforma. Desde bônus de boas-vindas até ofertas semanais, a KZ999 valoriza cada usuário e busca criar um ambiente de engajamento contínuo.
Conclusão A KZ999 chega ao mercado brasileiro como uma plataforma completa e confiável, ideal para quem busca entretenimento de qualidade, variedade de jogos e uma experiência segura. Com uma navegação fluida, suporte dedicado e constantes atualizações, a KZ999 promete se consolidar como referência no cenário de jogos online do Brasil.
-
 @ 2b24a1fa:17750f64
2025-04-29 08:20:58
@ 2b24a1fa:17750f64
2025-04-29 08:20:58Die Satire Muxmäuchenstill von 2004 erzählt die Geschichte des 30-jährigen Mux, der seine Mitbürgern zu mehr Verantwortungsbewusstsein erziehen möchte. Dazu stellt er Raser, Schwarzfahrer, Graffiti-Sprüher, Falschparker, Ladendiebe und Vergewaltiger, konfrontiert sie mit ihrem Verhalten und bestraft sie.
https://soundcloud.com/radiomuenchen/muxmauschenstill-x-interview-mit-jan-henrik-stahlberg?
Als Mitstreiter gewinnt er Arbeits- und Obdachlose. Mux’ fanatische Ein-Mann-Mission wächst zu einem kleinen Unternehmen. Auch privat kann er seinen Moralismus nicht zügeln und erschießt seine Freundin. Am Ende des Films wird er von einem Raser überfahren.
Ab 1. Mai läuft die Fortsetzung in den Kinos: Muxmäuschenstill X: muxfilm.de/. Nach zwanzig Jahre Wachkoma findet sich Mux in einer Welt wieder, die er nicht mehr versteht: dem wunderbaren Neoliberalismus. Wieder möchte Mux die Menschen erziehen. Doch diesmal kämpft er gegen ein System, das alles durchdringt, die Welt spaltet, unsere Lebensgrundlagen zerstört, die Reichen reicher macht und die Armen ärmer. Mux gründet den Muxismus und schart die Aussortierten des Systems um sich.
Drehbuchautor und Hauptdarsteller Jan Henrik Stahlberg führt diesmal auch Regie. Unser Autor Jonny Rieder hat mit Jan Henrik Stahlberg über seinen neuen Film gesprochen. Zunächst wollte er wissen, wo für ihn die Grenze verläuft zwischen Übergriffigkeit und Zivilcourage und wie er Mux hier einordnet.
Bild: Mux Filmproduktion
-
 @ 9f38a97e:c41d3606
2025-04-29 08:19:49
@ 9f38a97e:c41d3606
2025-04-29 08:19:49O universo dos jogos online tem evoluído constantemente, oferecendo experiências cada vez mais envolventes e personalizadas. Nesse cenário competitivo, a KZ999 se destaca como uma plataforma inovadora, segura e cheia de opções para quem busca entretenimento de qualidade e oportunidades reais de ganhos. Desde sua chegada ao mercado, a KZ999 vem conquistando os jogadores brasileiros com sua interface moderna, atendimento eficiente e ampla variedade de jogos emocionantes.
Introdução à Plataforma KZ999 A KZ999 é uma plataforma digital criada para atender às demandas de jogadores exigentes, que valorizam não apenas a diversão, mas também a segurança, a facilidade de uso e o suporte de qualidade. Com um design responsivo e otimizado para dispositivos móveis, o site funciona perfeitamente tanto em computadores quanto em smartphones, garantindo acesso rápido e prático de qualquer lugar.
O processo de cadastro na plataforma é simples e rápido, permitindo que novos usuários comecem a jogar em poucos minutos. Além disso, a yakihonne.com iris.to jumble.social Me
-
 @ 9f38a97e:c41d3606
2025-04-29 08:17:53
@ 9f38a97e:c41d3606
2025-04-29 08:17:53Se você está em busca de uma plataforma confiável, dinâmica e cheia de opções de entretenimento online, o Pix188 pode ser exatamente o que você procura. Com uma interface moderna, suporte ágil e jogos emocionantes, a plataforma vem conquistando cada vez mais jogadores em todo o Brasil.
O Pix188 é uma plataforma de entretenimento digital que combina tecnologia, facilidade de acesso e uma ampla gama de opções para seus usuários. Com um site responsivo e adaptado tanto para desktop quanto para dispositivos móveis, a navegação é simples, intuitiva e rápida, ideal para quem quer jogar a qualquer hora e em qualquer lugar.
Desde o primeiro acesso, o usuário já percebe o cuidado com os detalhes e o compromisso com a experiência do jogador. O processo de cadastro é rápido e seguro, e os depósitos e saques são feitos via Pix — método preferido dos brasileiros por sua agilidade.
Variedade de Jogos para Todos os Gostos Um dos maiores diferenciais do Pix188 é a diversidade de jogos disponíveis na plataforma. O site reúne os títulos mais populares e desejados pelos jogadores, com gráficos de alta qualidade, excelente jogabilidade e temas variados.
Entre as opções mais procuradas estão:
Slots (Caça-níqueis): Jogos com rodadas rápidas, temas vibrantes e recursos especiais como giros grátis e multiplicadores.
Roleta ao vivo: Para quem gosta de emoção e decisões rápidas, a roleta é uma excelente escolha com versões clássicas e modernas.
Cartas e mesa: Jogos como pôquer, blackjack e bacará estão disponíveis em versões tradicionais e ao vivo, trazendo uma experiência imersiva e realista.
Jogos instantâneos: Com mecânicas simples e resultados rápidos, são ideais para quem busca diversão prática e dinâmica.
O Pix188 também trabalha com provedores de jogos reconhecidos internacionalmente, garantindo qualidade, segurança e atualizações constantes no catálogo.
Experiência do Jogador no Centro de Tudo Mais do que oferecer jogos, o Pix188 se preocupa com toda a jornada do jogador. Desde o momento do cadastro até a retirada de ganhos, tudo é pensado para ser simples e transparente.
O atendimento ao cliente é outro ponto forte: está disponível 24 horas por dia, sete dias por semana, com equipe capacitada para resolver dúvidas e auxiliar em qualquer situação. Os usuários também contam com promoções recorrentes, bônus de boas-vindas e programas de fidelidade que valorizam a permanência na plataforma.
Além disso, o Pix188 investe em tecnologias de segurança avançadas, protegendo os dados dos jogadores e oferecendo um ambiente confiável e protegido.
Conclusão O Pix188 se destaca no cenário nacional por oferecer uma plataforma completa, segura e repleta de opções para quem busca entretenimento digital de qualidade. Com uma interface moderna, suporte eficiente e um catálogo de jogos diversificado, é uma excelente escolha tanto para iniciantes quanto para jogadores experientes.
-
 @ 9f38a97e:c41d3606
2025-04-29 08:17:15
@ 9f38a97e:c41d3606
2025-04-29 08:17:15Se você está em busca de uma plataforma confiável, dinâmica e cheia de opções de entretenimento online, o Pix188 pode ser exatamente o que você procura. Com uma interface moderna, suporte ágil e jogos emocionantes, a plataforma vem conquistando cada vez mais jogadores em todo o Brasil.
O Pix188 é uma plataforma de entretenimento digital que combina tecnologia, facilidade de acesso e uma ampla gama de opções para seus usuários. Com um site responsivo e adaptado tanto para desktop quanto para dispositivos móveis, a navegação é simples, intuitiva e rápida, ideal para quem quer jogar a qualquer hora e em qualquer lugar.
Desde o primeiro acesso, o usuário já percebe o cuidado com os detalhes e o compromisso com a experiência do jogador. O processo de cadastro é rápido e seguro, e os depósitos e saques são feitos via Pix — método preferido dos brasileiros por sua agilidade.
Um dos maiores diferenciais do Pix188 é a diversidade de jogos disponíveis na plataforma. O site reúne os títulos mais populares e desejados pelos jogadores, com gráficos de alta qualidade, excelente jogabilidade e temas variados.
Slots (Caça-níqueis): Jogos com rodadas rápidas, temas vibrantes e recursos especiais como giros grátis e multiplicadores.
Roleta ao vivo: Para quem gosta de emoção e decisões rápidas, a roleta é uma excelente escolha com versões clássicas e modernas.
Cartas e mesa: Jogos como pôquer, blackjack e bacará estão disponíveis em versões tradicionais e ao vivo, trazendo uma experiência imersiva e realista.
Jogos instantâneos: Com mecânicas simples e resultados rápidos, são ideais para quem busca diversão prática e dinâmica.
O Pix188 também trabalha com provedores de jogos reconhecidos internacionalmente, garantindo qualidade, segurança e atualizações constantes no catálogo.
Experiência do Jogador no Centro de Tudo Mais do que oferecer jogos, o Pix188 se preocupa com toda a jornada do jogador. Desde o momento do cadastro até a retirada de ganhos, tudo é pensado para ser simples e transparente.
O atendimento ao cliente é outro ponto forte: está disponível 24 horas por dia, sete dias por semana, com equipe capacitada para resolver dúvidas e auxiliar em qualquer situação. Os usuários também contam com promoções recorrentes, bônus de boas-vindas e programas de fidelidade que valorizam a permanência na plataforma.
Além disso, o Pix188 investe em tecnologias de segurança avançadas, protegendo os dados dos jogadores e oferecendo um ambiente confiável e protegido.
Conclusão O Pix188 se destaca no cenário nacional por oferecer uma plataforma completa, segura e repleta de opções para quem busca entretenimento digital de qualidade. Com uma interface moderna, suporte eficiente e um catálogo de jogos diversificado, é uma excelente escolha tanto para iniciantes quanto para jogadores experientes.
-
 @ a1d36df6:a3b9f5a0
2025-04-29 08:02:33
@ a1d36df6:a3b9f5a0
2025-04-29 08:02:33Originally written in: November 2024
"Show me the incentives, and I'll show you the outcome"[^mungerquote].
"Even bacteria respond to motivation." ~[^dufrene2020][^amoedo2024].
Introduction
In Austrian economics, time preference refers to the value individuals place on present consumption versus future consumption [^rothbard1993man]. A society with a lower time preference is more inclined to save, invest, and plan for the long term, thereby fostering progress and stability [^ammous2018]. In contrast, a society with a higher time preference tends toward immediate consumption rather than investment — or invests without a true understanding of its purpose — leading to short-term planning and a gradual drift from foundational societal values, traditions, and culture [^hoppe2001].
The definition of investment is the process of allocating resources to productive activities, prioritizing future gains over immediate consumption. It involves capital accumulation and is key to economic growth, as individuals delay gratification to increase future value. This approach underlies capital formation and enhances an economy's production capacity, aligning with lower time preference and fostering long-term prosperity [^mises1998].
With a foundational understanding of time preference and investment, we can begin to examine what motivates people today. Given the prevalence of high time preference in modern society, the government can capitalize on this tendency by offering immediate handouts and benefits, satisfying the population's desire for instant gratification, often at the expense of long-term prosperity and future gains. This tendency is also mirrored in mainstream media, where a focus on sensational, attention-grabbing stories diverts focus from deeper, structural issues. By amplifying polarizing narratives [^gentzkow2006media], often tied to social identity or lifestyle differences, the government and media create a cycle of constant engagement and distraction, steering public attention towards short-term controversies and away from underlying economic or social policy issues [^caplan2001rational].
Debt & Fractional-Reserve Banking
A common denominator that repeatedly emerges in such destructive behavior promoted by governments is the issue of money. As money drives the world, understanding and following its flow not only reveals how it operates but also uncovers those who wield control over it, and how human behavior is driven by it.
Money is a broad term encircling all assets that can be used for exchange, storage, and valuation, covering both physical and digital forms [^ammous2023]. Cash is a subset of money, referring specifically to physical currency, such as coins and notes.
The process of money creation, typically managed by governments and central banks, is the foundation of economic dependency within the financial system. In most economies, central banks control currency creation through mechanisms like open market operations and debt. For instance, when a central bank, such as the Federal Reserve, issues new currency, it does so by purchasing government securities from commercial banks, thus adding currency to the economy. However, this transaction is not debt-free; it obliges the government to repay the borrowed amount with interest.
In common words, the process of creating money is as follows: the government request to the central bank a certain amount of money to be printed in borrowing form. The central bank then creates that money, out of thin air, on the promise that the government will repay the central bank down the road. Since the government does not produce anything, in order to repay the central bank, the government then sells the debt via bonds to anyone who would like to buy the government debt. In even more simple words: the government and central bank creates money out of thin air based on debt [^ammous2021].
The issue with money creation is not only by the fact that it was created out of thin air, but because money creation has other issues tied to it: the debt, the creation of fractional-reserve monetary system, inflation, and interest.
This foundational reliance on debt, since it is present in the very beginning of money creation, renders the entire monetary system debt-dependent. Therefore, saving and investing within such a system becomes questionable, as the system's nature opposes the principles of sustainable wealth accumulation, thus leading human behavior not to save but to spend.
A fractional-reserve monetary system is a banking structure in which banks retain only a small fraction of their depositors' funds — historically around 10%, but today often as low as 1% [^bundesbank2024] — while lending out or investing the remainder. This setup allows banks to expand the money supply and stimulate economic activity through a process known as deposit expansion [^federalreserve1975modern]. Deposit expansion occurs when banks effectively treat a portion of deposited funds as new money, multiplying the original deposit base. For example, if a bank holds deposits totaling 1 million euros, it can lend out up to 1.9 million euros, as long as it maintains 10% of the initial deposit in reserve. This cycle can repeat, enabling banks to increase the total money supply to infinity, but the "Modern Money Mechanics: A Workbook on Bank Reserves and Deposit Expansion" and government applying it recommends not doing it above 9 times the original deposit value [^federalreserve1975modern].
To make matters worse, inflation and interest exacerbate the problems inherent in this monetary system. Interest is a foundational element of the system, initially intended to address the original debt incurred by the government. In economic terms, interest represents the "price" of time preference, a premium placed on present goods over future goods. To illustrate the impact of interest, consider the cost of a house in today's system: a house priced at 500,000 euros with a 4% variable interest rate ends up costing around 860,000 euros over 30 years, with 360,000 euros paid in interest alone.
Inflation, on the other hand, is the increase in the money supply — money printing — and can only be truly calculated by M2[^1] money supply metric. Inflation erodes the value of both assets and earned income, as each new unit of currency devalues existing money. This devaluation impacts not only the purchasing power of savings but also the real cost of goods and services over time, reducing the long-term value of assets people believe they own.
The government
Operating within a monetary system stretched beyond its limitations, the government faces the dual challenges of controlling inflation and satisfying its growing spending demands. To fund its expenditures, the government often provides public benefits — subsidies, "free" healthcare, public transport, security, military, and welfare in general — to justify continual spending and cultivate public support - via voting, in most democratic countries.
Welfare and most government programs redistribute wealth from producers to non-producers, fostering dependency on the state. Over time, this erodes individual sovereignty and expands government control, restricting freedom, and reducing people to slaves or cash cows.
The government justifies taxes as payment for welfare and public services, but also claims they curb inflation by reducing the need to print money. The logic is that by reclaiming taxpayer money, the money supply is controlled. However, this is misleading, especially when the government can print money at will, making taxation on such currency inherently flawed.
Taxes are extracted via coercion - violence - by the government onto the population. The government then decides where to allocate this money, based on their guess of what the population needs, excluding private preferences. Therefore, taxes are not an incentive to accumulate, not even to work more. Taxes are an incentive to do right the opposite: do not save and do not work more.
Another tactic the government employs is to create crises that it alone can "solve", thus requiring more taxes or funding. Recent examples include crises like COVID-19, the "green" agenda, and initiatives to combat climate change[^2]. In each case, the government presents itself as the sole solution, yet solving these crises inevitably demands additional resources — in the form of increased taxation.
Even minimal critical thinking would prompt one to question the true necessity of taxes in a government that owns and controls the money printer. Given what we now understand, if you were in the government's position, would you willingly relinquish control of money creation by tying it to something like gold, empowering people to become smarter, independent, and wealthy?
The government, through various channels — media, education, propaganda, welfare, and government subsidies — ensures that people remain obedient and uninformed. It keeps them financially constrained by increasing taxes and imposing extensive regulations, while fostering dependency through handouts, welfare, and other social programs. The government is the only entity that, by law, can use violence and coercion without prosecution [^rothbard2009].
"Anyone who, although human, is by nature not yours but someone else's"[^ambler1987].
It is therefore unsurprising that many live in a state akin to enslavement, reflecting a mindset shaped by constant dependency. It is no wonder that people are discouraged from having children, as they can barely support themselves. Nor is it surprising that individuals might question the need to continue their bloodline, believing in the illusory value of "fake money" [^kiyosaki2019] and trusting present "investments" and the government to provide a pension in old age. And it's certainly not surprising to see people asking the government for solutions to every problem, when the government leaves them no viable alternatives.
"Show me the incentives, and I'll show you the outcome"[^mungerquote].
That statement serves as a powerful tool for understanding and addressing complex issues. When observing behaviors that may appear unusual — such as individuals identifying as "trans-species," a phenomenon linked to mental health concerns [^pinna2022] — it's essential to consider the underlying incentives. Who benefits most from a society in which individuals remain financially constrained, dependent, and uninformed? A fiat-based monetary system functions as a modern form of economic control, keeping people poor by design. Taxes, effectively a penalty for productivity, contrast sharply with welfare programs, which often reward dependency and reinforce reliance on the government. Meanwhile, government narratives and selective information shape public beliefs, protecting institutional interests and discouraging critical inquiry[^3].
Conclusion
Like the fungus that infects in parasitic way an ant's nervous system - Ophiocordyceps Unilateralis -, rendering it a zombie [^britannica2024] controlled by an external force, similarly, modern bureaucracies exploit the mechanisms of fiat money, debt, and taxation [^rothbard2009] to maintain control over individuals, steering them away from self-reliance and critical thinking toward a state of perpetual dependence.
The parallels are striking: just as the fungus manipulates the ant's behavior to secure its reproduction, governments manipulate public perception, creating crises, shaping incentives, and fostering dependence[^rothbard2009] through welfare programs[^caplan2001rational], inflated debt[^ammous2018], and coercive taxation. These mechanisms suppress individuality, reduce productivity, and shift power further into centralized hands[^gentzkow2006media], leaving citizens "zombified", detached from purpose and independence.
"Even bacteria respond to motivation."[^dufrene2020]
If tolerated — even by you, dear reader — this parasitic cycle will continue to erode humanity's dignity and potential. The solution lies in reclaiming agency by building a society grounded in sound money, meaningful productivity, and spiritual and cultural foundations that connect us to higher purposes. As warned in Jeremiah 17:5 [^4], trusting fallible human systems leads to enslavement. True freedom comes from rejecting exploitative bureaucracies and embracing systems aligned with truth, autonomy, and resilience.
Another way is to fully understand the system and opt out. This requires mastering the rules and using them to your advantage. If legal avenues exist to avoid taxation, expropriation, eminent domain, or government coercion, then the first step is to change the game for yourself.
The monetary system and government incentives shape human behavior, influencing those who allow themselves to be controlled by them.
fiat #bitcoin #austrian-economics #freedom #slavery #money #government #antipropaganda #propaganda #taxes #tax #greenagenda #wef #who
Footnote
[^1]: M2 refers to savings deposits + money market mutual funds + small time deposits. M2 includes all of M1 plus "near money" (M0), which consists of savings deposits, money market accounts, and small-denomination time deposits (like certificates of deposit under a certain amount). M2 is commonly tracked by central banks to gauge medium-term economic activity and savings behavior, as it includes money that people save rather than spend immediately.
[^2]: Since the 1990s, societies worldwide have been confronted by a series of global crises, often framed as urgent and overwhelming challenges. All scams. Including deforestation, ocean and air pollution, nuclear waste, oil spills, plastic and soil pollution, drought, fossil fuel consumption, rising sea levels, species extinction, extreme weather, global warming, melting glaciers, acid rain, and, recently, climate change. Each crisis has shaped public opinion and policy, and also created new laws, regulations, and taxes.
[^3]: Politicians are merely psychopath[^hareleonmayersalinasfolino2022][^klaas2023] parasites.
[^4]: Cursed is the one who trusts in man, who draws strength from mere flesh and whose heart turns away from the Lord.
References
Bibtex
bibtex @book{ammous2018, title={The Bitcoin Standard: The Decentralized Alternative to Central Banking}, author={Ammous, Saifedean}, year={2018}, publisher={Wiley}, url={https://saifedean.com/tbs} } @book{ammous2023, author = {Saifedean Ammous}, title = {Principles of Economics}, year = {2023}, publisher = {Saifedean Ammous}, address = {Self-published}, url = {https://saifedean.com/poe} } @book{ammous2021, author = {Saifedean Ammous}, title = {The Fiat Standard: The Debt Slavery Alternative to Human Civilization}, year = {2021}, publisher = {Wiley}, address = {Hoboken, NJ}, url = {https://saifedean.com/tfs} } @book{rothbard1993man, author = {Murray N. Rothbard}, title = {Man, Economy, and State: A Treatise on Economic Principles}, year = {1993}, publisher = {Ludwig von Mises Institute}, address = {Auburn, Alabama}, note = {Originally published in 1962}, url = {https://mises.org/library/man-economy-and-state-power-and-market} } @book{hoppe2001, author = {Hans-Hermann Hoppe}, title = {Democracy: The God That Failed: The Economics and Politics of Monarchy, Democracy, and Natural Order}, year = {2001}, publisher = {Transaction Publishers}, address = {New Brunswick, NJ}, url = {https://mises.org/library/democracy-god-failed} } @book{mises1998, author = {Ludwig von Mises}, title = {Human Action: A Treatise on Economics}, year = {1998}, publisher = {Ludwig von Mises Institute}, address = {Auburn, Alabama}, note = {Originally published in 1949}, url = {https://mises.org/library/human-action-0} } @article{gentzkow2006media, author = {Matthew Gentzkow and Jesse M. Shapiro}, title = {Media Bias and Reputation}, journal = {Journal of Political Economy}, volume = {114}, number = {2}, pages = {280-316}, year = {2006}, publisher = {University of Chicago Press}, url = {https://doi.org/10.1086/499414} } @article{caplan2001rational, author = {Bryan Caplan}, title = {Rational Irrationality and the Microfoundations of Political Failure}, journal = {Public Choice}, volume = {107}, number = {3}, pages = {311-331}, year = {2001}, publisher = {Springer}, url = {https://doi.org/10.1023/A:1010349129605} } @book{federalreserve1975modern, author = {{Federal Reserve Bank of Chicago}}, title = {Modern Money Mechanics: A Workbook on Bank Reserves and Deposit Expansion}, year = {1975}, publisher = {Federal Reserve Bank of Chicago}, url = {https://archive.org/details/modern-money-mechanics/mode/2up} } @misc{bundesbank2024, author = {{Deutsche Bundesbank}}, title = {Minimum Reserves}, year = {n.d.}, url = {https://www.bundesbank.de/en/tasks/monetary-policy/minimum-reserves/minimum-reserves-625912}, note = {Accessed: 2024-11-07} } @article{ambler1987, author = {Wayne Ambler}, title = {Aristotle on Nature and Politics: The Case of Slavery}, journal = {Political Theory}, volume = {15}, number = {3}, pages = {390-410}, year = {1987}, month = {Aug.} } @book{kiyosaki2019, author = {Robert T. Kiyosaki}, title = {FAKE: Fake Money, Fake Teachers, Fake Assets: How Lies Are Making the Poor and Middle Class Poorer}, year = {2019}, month = {April}, publisher = {Plata Publishing}, address = {Scottsdale, AZ}, note = {Paperback, Illustrated Edition} } @article{hareleonmayersalinasfolino2022, title = {Psychopathy and crimes against humanity: A conceptual and empirical examination of human rights violators}, journal = {Journal of Criminal Justice}, volume = {81}, pages = {101901}, year = {2022}, issn = {0047-2352}, doi = {https://doi.org/10.1016/j.jcrimjus.2022.101901}, url = {https://www.sciencedirect.com/science/article/pii/S0047235222000216}, author = {Robert D. Hare and Elizabeth León-Mayer and Joanna Rocuant Salinas and Jorge Folino and Craig S. Neumann}, keywords = {Crimes against humanity, Human rights violators, Terrorism, Psychopathy, PCL-R, SRP-SF, Four-factor model, Latent profile analysis}, abstract = {Purpose There is a dearth of empirical data on the contributions of personality, psychopathology, and psychopathy to terrorism and its actors. Because of a fortuitous set of circumstances, we had access to a sample of men convicted of crimes against humanity (CAH) committed during the Pinochet regime, each rated by expert clinicians on the Psychopathy Checklist-Revised (PCL-R). We also had PCL-R ratings for samples of general offenders and community participants. Methods We determined the psychometric properties of the PCL-R for these samples, performed structural equation modeling (SEM) to investigate the factor structure of the PCL-R, and conducted a latent profile analysis (LPA) of the obtained factors to identify classes or subtypes within the samples. Results The PCL-R's psychometric properties and factor structure were in accord with findings from other countries and settings. The PCL-R total scores of the CAH and general offenders were virtually the same but much higher than those of the community sample. However, the CAH group had extraordinarily high scores on the Interpersonal/Affective facets yet relatively low scores on the Lifestyle/Antisocial facets. LPA identified the expected four latent classes, with most CAH men located within the Callous-Conning class. Conclusions The results of this study provide unique information about the psychopathic propensities of a sample of state violators of human rights. Their pattern of PCL-R scores was consistent with an extreme disposition for self-serving, callous, and ruthless treatment of others, without guilt or remorse, and in the absence of a prior documented history of severe antisocial behavior.} } @misc{klaas2023, author = "{Brian Klaas}", title = "{{How many politicians are psychopaths?}}", howpublished = {\url{https://www.forkingpaths.co/p/how-many-politicians-are-psychopaths}}, note = {Online; accessed 29 January 2024}, year=2023 } @article{pinna2022, title={Mental health in transgender individuals: a systematic review}, author={Pinna, Federica and Paribello, Pasquale and Somaini, Giulia and Corona, Alice and Ventriglio, Antonio and Corrias, Carolina and Frau, Ilaria and Murgia, Roberto and El Kacemi, Sabrina and Galeazzi, Gian Maria and others}, journal={International Review of Psychiatry}, volume={34}, number={3-4}, pages={292--359}, year={2022}, publisher={Taylor \& Francis}, doi={10.1080/09540261.2022.2093629}, url={https://pubmed.ncbi.nlm.nih.gov/36151828/} } @book{rothbard2009, title={Anatomy of the State}, author={Rothbard, Murray}, year={2009}, publisher={Ludwig von Mises Institute} } @misc{britannica2024, author = {{Encyclopaedia Britannica}}, title = {Zombie-Ant Fungus}, year = {n.d.}, url = {https://www.britannica.com/science/zombie-ant-fungus}, note = {Accessed: 2024-11-07} } @misc{amoedo2024, author = {Renato Amoedo}, title = {Até as bactérias respondem a uma motivação}, year = {2024}, note = {Famosa frase mencionada em entrevistas e podcasts relacionados a comportamento e motivação}, howpublished = {Comentário público}, } @article{dufrene2020, title={Mechanomicrobiology: how bacteria sense and respond to forces}, author={Dufrêne, Yves F. and Persat, Alexandre}, journal={Nature Reviews Microbiology}, volume={18}, pages={227--240}, year={2020}, month={April}, doi={10.1038/s41579-019-0314-2}, url={https://doi.org/10.1038/s41579-019-0314-2}, publisher={Springer Nature}, note={Accepted 06 December 2019, Published 20 January 2020} } @misc{mungerquote, author = {Munger, Charlie}, title = {Show me the incentive and I will show you the outcome}, note = {Often attributed to Charlie Munger, known for his wisdom on finance and life as Warren Buffett's business partner.}, howpublished = {Quote}, year = {n.d.}, url = {https://elevatesociety.com/quotes-by-charlie-munger/} } -
 @ 75eeefe8:a4a71f88
2025-04-29 07:59:37
@ 75eeefe8:a4a71f88
2025-04-29 07:59:37Solar Power Tips for a Sustainable Remote Home Office
As more professionals transition to remote work, the need for sustainable and cost-effective solutions has never been greater. One of the most effective ways to reduce your ecological impact and lower energy costs is by harnessing the sun's power—specifically, solar energy.
Solar power is becoming increasingly popular among remote workers, providing a renewable energy source for residences with a home office setup. It helps reduce reliance on fossil fuels, and offers the potential for significant long-term savings.
This blog will list the benefits of using solar power in a remote home office environment. Whether you want to reduce your carbon footprint or reduce your energy expenses, the information will guide you in creating a more sustainable design for a productive home office. Choosing the Right Solar Panels Building a solar-powered home office starts with picking the right solar panels. You can choose from traditional photovoltaic panels to sleek solar shingles that blend with your roof's design.
Recent advancements in solar technology have introduced more compact and efficient panels, making it easier than ever to generate significant power, even in smaller spaces.
When choosing solar panels, prioritize efficiency ratings and durability. High-efficiency panels, such as monocrystalline options, can produce more energy with less surface area. They are ideal if you have limited roof space.
Aesthetics can also play a role, particularly if you want your home office to maintain a modern, professional appearance. For example, solar shingles offer a subtler alternative to standard panels while providing comparable energy production. Essential solar power components Setting up a fully functional solar-powered home office requires more than just panels. Below are the essential components to consider:
Inverters
Solar panels create direct current (DC), but most home appliances run on alternating current (AC). Inverters convert DC to AC, so you can use solar power. Look for high-quality inverters, such as micro-inverters, which optimize the output of each panel individually.
Batteries
Energy storage is critical because solar power is not always available. Solar batteries let you save extra energy made during the day so you can use it at night or when it is cloudy. Consider opting for lithium-ion batteries due to their high energy density, long lifespan, and relatively small size.
Mounting hardware
Proper installation is key to getting the most energy from your solar panels and making sure they can handle tough weather. Adjustable mounts let you place your panels to get the most sunlight and ensure they last over time. Benefits of Solar Power in a Home Office You may wonder: why is solar power for a home office such a big deal? Here are the reasons why: Cost savings and environmental impact One of the biggest benefits of using solar power in your home office is the potential to save a lot of money. Making your electricity can help you reduce or even eliminate your monthly energy bills.
The average owner can save between $10,000 and $30,000 over the lifespan of a solar energy system, depending on their location and system size. Plus, federal tax credits, state incentives, and net metering programs can lower both the initial and ongoing costs of going solar. Reliability and independence Solar power also provides unmatched reliability and independence, particularly in areas prone to power outages. Coupling your solar panels with a high-capacity battery storage system allows you to maintain power for essential devices during power cuts.
It becomes a critical advantage if you need to keep your computers, internet, and other tools working to stay productive.
Solar energy also frees you from relying on the power grid, which is especially helpful if you live in rural or remote areas where power may be less reliable or more expensive. Additional Tips for a Sustainable Home Office Maximize your home office with these practical ways: Complementary green technologies Consider incorporating complementary green technologies into your home office, such as:
Smart thermostats
Devices like the Nest or Ecobee learn your habits and adjust the temperature to maximize comfort while minimizing energy usage. A smart thermostat regulates heating and cooling based on your schedule, significantly reducing your energy use and costs.
Energy monitors
Tools like the Sense Home Energy Monitor help track energy usage across your home. You can identify energy-draining devices to make better decisions about allocating and conserving power and optimizing your solar system's efficiency.
LED lighting
Transitioning to LED bulbs uses less energy and makes your lights last longer. They further lower replacement costs and waste. Outdoor solar solutions Sustainability does not have to stop at your office door. The following outdoor solar-powered devices can enhance the eco-friendliness of your entire home environment:
Solar-powered garden lights
These lights use built-in solar panels to charge during the day and illuminate your outdoor spaces at night. They are perfect for adding ambiance to your yard or improving visibility along pathways without increasing your electricity bill.
Solar security cameras
Protect your property with solar-powered security cameras. They are self-sufficient and eliminate the need for extensive wiring.
Solar water features
From fountains to birdbaths, solar-powered water features add aesthetic appeal to your garden while relying entirely on renewable energy. Shine Bright at Home Embracing solar power for your home office is a smart step toward a greener, more cost-effective future. Choosing efficient solar panels, integrating essential components like inverters and batteries, and pairing them with complementary green technologies can help you create a sustainable workspace that aligns with modern, eco-conscious values.
If you're considering finding a home in Laguna, Philippines, solar energy becomes an even more valuable investment. With Laguna’s growing residential developments, eco-friendly communities, and abundant sunlight, homeowners can take full advantage of renewable energy to lower electricity costs and reduce their carbon footprint. Many new housing projects in Laguna also emphasize sustainability, making it easier to integrate solar solutions into your home.
Investing in solar power is more than a commitment to the environment—it is a long-term strategy for saving money and boosting reliability in your day-to-day work life. With these tips, you are well on your way to creating a home office that works as hard for the planet as you do.
-
 @ 56cd780f:cbde8b29
2025-04-29 07:58:40
@ 56cd780f:cbde8b29
2025-04-29 07:58:40This is my first post, with a header and regular text.
-
 @ 56cd780f:cbde8b29
2025-04-29 07:58:38
@ 56cd780f:cbde8b29
2025-04-29 07:58:38I hope you like it
 .
. -
 @ 56cd780f:cbde8b29
2025-04-29 07:58:36
@ 56cd780f:cbde8b29
2025-04-29 07:58:36Let'‘s see if they appear in the right order.
First we have an apple.
 Then we have a banana.
Then we have a banana. And lastly, a pear.
And lastly, a pear.
-
 @ 56cd780f:cbde8b29
2025-04-29 07:58:35
@ 56cd780f:cbde8b29
2025-04-29 07:58:35❤️🔥✨
-
 @ a296b972:e5a7a2e8
2025-04-29 07:24:49
@ a296b972:e5a7a2e8
2025-04-29 07:24:4928.04.2025, 16.17 Uhr:
Russische Hobby-Flieger konnten mit ihrem Sportflugzeug namens "Andromeda" unter dem Radar bleiben und haben entlang der Hauptstromtrassen mit einem ukrainischen Zwiebelmesser die Stromleitungen gekappt. In einer scharfen Rechtskurve muss wohl eine Flugzeugtür aufgegangen sein und der Pass des Piloten fiel unbemerkt heraus. Die Identität der Täter konnte so schnell festgestellt werden.
28.04.2025, 16.43 Uhr:
Trump hat das europäische Stromnetz gekauft und die in den Umspannwerken eingebauten US-amerikanischen Chips deaktiviert. Es gibt erst wieder Strom, wenn sich die Koalition der Willigen den Friedensverhandlungen für die Ukraine anschließt. Trump hat bewusst in den sonnenreichen Ländern Spanien und Portugal begonnen, das soll als Warnung für ganz Europa gelten. Frau von der Leyen hat bereits scharfen Protest eingelegt, doch Trump hat die SMS sofort gelöscht.
28.04.2025, 17.12 Uhr:
Selensky hat einen Cyber-Angriff auf das europäische Stromnetz gestartet. Er ist wütend, weil sich Macron in dem 15-Minuten-Gespräch mit Trump am Rande der Beerdigung des Papstes in Rom hat abwimmeln lassen. Er beendet die Strom-Blockade erst, wenn Spanien, Portugal und Frankreich Deutschland dazu zwingen, endlich Taurus zu liefern. Auf die Frage, wie Selensky das angestellt hat, soll er geantwortet haben: "Sie sehen ja, wir können es."
Ist natürlich alles nur Joke! Es sollte nur einmal in Bezug auf die Sprengung der Nordstream 2 Pipelines aufgezeigt werden, wie schnell auch unsereins abstruse Erklärungen liefern kann, die vorne und hinten nicht stimmen können.
Dieser Beitrag wurde mit dem Pareto-Client geschrieben.
(Bild von pixabay)
-
 @ 33baa074:3bb3a297
2025-04-29 07:21:54
@ 33baa074:3bb3a297
2025-04-29 07:21:54The application of chlorine in water treatment is mainly reflected in its ability to act as a disinfectant. It can effectively kill bacteria, viruses and other microorganisms in water, thereby reducing the risk of waterborne diseases. The following is a detailed description of the application of chlorine in water treatment:
Disinfection As an effective disinfectant, chlorine is usually added to water during the water treatment process in the form of chlorine gas, chlorophyll acid or chlorine. This process is called chlorination, which ensures that pathogens in the water are effectively eliminated. Chlorine's disinfection ability comes from its strong oxidizing properties, which can destroy the cell structure of microorganisms to achieve the purpose of disinfection.
Disinfection By-products Despite the obvious benefits of chlorine in disinfection, there are also some negative effects. Chlorine disinfection may lead to the formation of disinfection by-products such as chloroform and chloroform, which may pose potential health risks in high concentrations. Therefore, when using chlorine for water treatment, the chlorine content needs to be strictly controlled to ensure the safety of the water.
Chlorine Measurement and Control Monitoring and controlling the chlorine content in the water treatment process is very critical. Total chlorine is the total amount of all forms of chlorine in water, including free residual chlorine, combined residual chlorine and other forms of chlorine such as chlorinated hydrocarbons. Available chlorine refers specifically to the part of chlorine in water that has bactericidal ability, including free residual chlorine, some combined residual chlorine (such as monochromatic and diamorphine) and chlorine dioxide. The measurement of available chlorine is crucial for evaluating the disinfection effect of water.
In summary, the application of chlorine in water treatment is mainly as a disinfectant to kill pathogens in water through its strong oxidizing properties. However, the use of chlorine also needs to be cautious to avoid the generation of harmful disinfection by-products, and other safer disinfectants such as chlorine dioxide can be selected when necessary.
-
 @ 68768a6c:0eaf07e9
2025-04-29 06:23:10
@ 68768a6c:0eaf07e9
2025-04-29 06:23:10You don’t talk about it much — but you’re tired. Tired of pretending you're okay. Tired of giving your best and wondering if it’s even enough. Tired of being strong for everyone else while quietly falling apart.
But here's something you might not hear often: I’m proud of you.
Not because you’ve figured everything out — but because you haven’t given up. Even with the weight on your shoulders, you're still here. Still trying. Still hoping. Still holding on.
That counts. That matters. That’s strength too.
The truth is, progress doesn’t always look like big wins. Sometimes it’s just getting out of bed. Sometimes it’s choosing peace over proving a point. Sometimes it’s breathing through the pain and saying, “I’ll try again tomorrow.”
So if no one has told you lately: You’re doing better than you think. Rest if you need to. Cry if you must. But don’t stop. Because something beautiful is growing from everything you’re surviving.
-
 @ 83279ad2:bd49240d
2025-04-29 05:53:52
@ 83279ad2:bd49240d
2025-04-29 05:53:52test
-
 @ 57d1a264:69f1fee1
2025-04-29 05:43:02
@ 57d1a264:69f1fee1
2025-04-29 05:43:02A debonair day-to-night hideaway fuses heritage charm with contemporary flair in the Penang capital of George Town...
Housed in a historic landmark on George Town’s atmospheric Lebuh Farquhar, just a stone’s throw from the iconic Eastern & Oriental Hotel, MOJO JOJO is a café and brunch spot by day, and a refined eatery come nightfall. With an effortlessly cool edge, the space has been designed by Empt Studio and combines contemporary charm with the energy of this Malaysian city.
Split into two sections, the venue caters to both hotel guests and passersby. One side offers an intimate, tailored dining experience for those seeking a respite from the buzz of outside, while the other spills out onto the street, embracing George Town’s lively buzz. The soaring ceilings create a sense of openness, further enhanced by the introduction of a mezzanine above the kitchen, maximising space without compromising on airiness.
Natural materials feature throughout with custom bamboo display systems and solid Nyatoh timber fixtures lending a rich, textural warmth. Deliberately crafted interlocking joints pay homage to traditional woodworking techniques, reinforcing both strength and authenticity. Every detail nods to meticulous craftsmanship, from the aged wood grains to the earthy material palette that echoes the heritage of its surroundings.
Lighting plays a supporting yet pivotal role, with carefully curated, softly diffused illumination accentuating the textures and forms within. The interplay of warm light and natural materials fosters an immersive, atmospheric retreat from the fast-paced city outside.
A refuge for slow mornings and, later on, offering a more cultured affair, MOJO JOJO is a debonair dining spot for the handsome Penang capital.
Read more https://www.emptstudio.com/projects/mojojojo
originally posted at https://stacker.news/items/966008
-
 @ 57d1a264:69f1fee1
2025-04-29 05:23:45
@ 57d1a264:69f1fee1
2025-04-29 05:23:45Hubless Wheels + Donut Motor brings manufacturing & performance benefits
Verge Next, a subsidiary of Estonia-based Verge Motorcycles, invented this Donut Motor. It's designed to drive a hubless wheel. Although once seen as something that simply looked cool in renderings, the company says the hubless arrangement brings performance and manufacturing benefits, "delivering unmatched torque and power density with minimal weight."
For one thing, there's no chain, belt or drivetrain required. Secondly, it frees the body of the bike from the task of holding the motor—everything is now contained within that rear wheel.
The company has not only incorporated the Donut Motor into their own bikes, but is now licensing the technology. Assuming it does what it says on the tin, our future streetscapes will be covered with hubless bikes, scooters and motorcycles.
Here's a closer look at a Verge bike and how its design is influenced by the motor:
https://www.youtube.com/watch?v=Og9vlJRe2-M
originally posted at https://stacker.news/items/966001
-
 @ 849838f4:0ea97fbb
2025-04-29 02:56:13
@ 849838f4:0ea97fbb
2025-04-29 02:56:132nmn -
 @ d41bf82f:ed90d888
2025-04-29 02:16:06
@ d41bf82f:ed90d888
2025-04-29 02:16:06เบื้องหลังการเปลี่ยนแปลงครั้งใหญ่ในประวัติศาสตร์ เราต้องเข้าใจปัจจัยที่เปลี่ยนแปลงตรรกะของความรุนแรง โดยเฉพาะปัจจัยเชิงมหภาค 4 ประเภทหลัก ได้แก่ ภูมิประเทศ ภูมิอากาศ จุลชีพ และเทคโนโลยี
- ภูมิประเทศ เป็นตัวกำหนดที่สำคัญมากต่อรูปแบบของรัฐและความสามารถในการควบคุมพลเมืองโดยเฉพาะเมื่อเปรียบระหว่างสภาพภูมิประเทศทางบกและทางทะเล พื้นที่ทะเลเปิดนั้นยากต่อการผูกขาดหรือควบคุม ทำให้กฎของรัฐไม่สามารถบังคับใช้ได้อย่างมีประสิทธิภาพ ต่างจากแผ่นดิน ซึ่งส่งผลต่อการจัดวางอำนาจอย่างลึกซึ้ง เมื่อเศรษฐกิจเริ่มเคลื่อนเข้าสู่โลกไซเบอร์ซึ่งมีลักษณะคล้ายทะเลเปิดมากกว่าภาคพื้นดิน รูปแบบของการปกครองและการใช้ความรุนแรงจึงมีแนวโน้มเปลี่ยนแปลงไปอย่างมีนัยสำคัญ ประวัติศาสตร์ก็สนับสนุนมุมมองนี้ รัฐยุคแรก ๆ มักเกิดขึ้นในพื้นที่ราบลุ่มชลประทานที่ล้อมรอบด้วยทะเลทราย เช่น เมโสโปเตเมียและอียิปต์ ซึ่งทำให้ประชาชนจำเป็นต้องพึ่งพารัฐที่สามารถควบคุมแหล่งน้ำเพื่อดำรงชีวิตได้ ก่อให้เกิดระบบเผด็จการที่มั่นคง ขณะที่ภูมิประเทศที่กระจายอำนาจ เช่น กรีซโบราณ กลับเอื้อต่อการเกิดประชาธิปไตย เพราะผู้คนสามารถพึ่งตนเองได้มากกว่า มีอิสระในการค้าขายทางทะเล และเข้าถึงรายได้ที่นำไปแลกกับอำนาจทางทหารและการเมืองได้
- ภูมิอากาศก็มีบทบาทไม่แพ้กันในการกำหนดกรอบของอำนาจทางการเมือง เช่น หลังสิ้นยุคน้ำแข็งราว 13,000 ปีก่อน ความเปลี่ยนแปลงของระบบนิเวศทำให้ทุ่งหญ้าเลี้ยงสัตว์ลดลง และป่าทึบเข้ามาแทนที่ ทำให้มนุษย์ต้องเปลี่ยนวิถีชีวิตจากนักล่ามาเป็นเกษตรกรอย่างหลีกเลี่ยงไม่ได้ การเปลี่ยนแปลงนี้ไม่ได้เกิดขึ้นเพราะความสมัครใจ แต่เพราะสิ่งแวดล้อมบีบบังคับ ภูมิอากาศยังมีอิทธิพลต่อเสถียรภาพทางเศรษฐกิจและการเมืองอย่างชัดเจน เช่น ศตวรรษที่ 17 ซึ่งเป็นยุคหนาวเย็นที่สุดช่วงหนึ่งในประวัติศาสตร์ ทำให้เกิดวิกฤตอาหารและความอดอยากทั่วโลก นำไปสู่การก่อกบฏและการปฏิวัติในหลายประเทศ
- จุลชีพ ก็มีบทบาทในเชิงการเมืองมหภาคอย่างลึกซึ้ง การล่มสลายของประชากรพื้นเมืองในทวีปอเมริกาจากโรคที่ชาวยุโรปนำเข้า เช่น หัด หรือไข้ทรพิษ ทำให้ยุโรปสามารถยึดครองดินแดนเหล่านั้นได้อย่างง่ายดาย แม้ในบางครั้งจะยังไม่ได้ลงจากเรือด้วยซ้ำ ในอีกด้านหนึ่ง จุลชีพก็เคยเป็นกำแพงที่ป้องกันไม่ให้จักรวรรดิยุโรปขยายอำนาจ เช่น มาลาเรียในแอฟริกาที่เคยทำให้พื้นที่เหล่านั้น “ต่อต้านอำนาจจากภายนอก” ได้อย่างนานหลายศตวรรษ
- เทคโนโลยี ซึ่งเป็นปัจจัยที่ที่ทรงอิทธิพลที่สุดต่อการเปลี่ยนแปลงของโครงสร้างอำนาจในประวัติศาสตร์มนุษย์ เพราะมันสามารถเปลี่ยน “ต้นทุน” และ “ผลตอบแทน” ของการใช้ความรุนแรงได้อย่างรวดเร็วและชัดเจน ทั้งในแง่ของอาณาเขต ขนาดของรัฐ ลักษณะของสงคราม และแม้แต่ความชอบธรรมทางการเมือง ผู้เขียนได้แยกอิทธิพลของเทคโนโลยีออกเป็น 5 มิติหลัก ซึ่งล้วนมีบทบาทอย่างสำคัญในการจัดรูปแบบของอำนาจ ได้แก่:
A. ดุลยภาพระหว่างการโจมตีและการป้องกัน เทคโนโลยีแต่ละยุคมีผลอย่างมากต่อความได้เปรียบระหว่างฝ่ายรุกกับฝ่ายรับ หากเทคโนโลยีในยุคนั้นเอื้อต่อ “การโจมตี” (เช่น เครื่องยิงหิน, รถถัง, ระเบิดทางอากาศ) ต้นทุนของการขยายอำนาจจะต่ำลง รัฐหรือจักรวรรดิจะรวมศูนย์มากขึ้นเพราะสามารถควบคุมพื้นที่กว้างได้ด้วยกำลังที่มีประสิทธิภาพ แต่หากเทคโนโลยีเอื้อให้ “การป้องกัน” มีต้นทุนต่ำและได้เปรียบ (เช่น ปราสาทยุคกลาง, อาวุธต่อต้านอากาศยาน, การเข้ารหัสข้อมูลในโลกไซเบอร์) รัฐจะมีแนวโน้มกระจายตัว และอำนาจท้องถิ่นจะแข็งแกร่งขึ้น
B. ความเท่าเทียมกันทางทหารของพลเมือง เทคโนโลยีอาวุธยังเป็นตัวแปรสำคัญในการกำหนดว่า “พลเมืองธรรมดา” มีอำนาจเพียงใดในการเผชิญหน้ากับชนชั้นปกครอง ตัวอย่างที่ชัดเจนคือในยุคก่อนปฏิวัติดินปืน ชาวนาที่ถือแค่ส้อมหรือจอบไม่อาจต้านอัศวินติดเกราะได้ แต่เมื่อการใช้ปืนแพร่หลาย เส้นแบ่งระหว่างสามัญชนกับขุนนางก็เริ่มจางลง และเกิดการปฏิวัติทางสังคมตามมาในหลายพื้นที่
C. ขนาดขององค์กรที่จำเป็นต่อการใช้ความรุนแรง บางเทคโนโลยีต้องการระบบสนับสนุนขนาดใหญ่ เช่น เสบียง การสื่อสาร การขนส่ง และระบบการฝึกฝนที่ซับซ้อน ซึ่งหมายความว่าเฉพาะองค์กรที่มีทรัพยากรขนาดใหญ่เท่านั้นจึงสามารถใช้อำนาจอย่างมีประสิทธิภาพได้ ตัวอย่างเช่น สมัยสงครามโลก รัฐที่มีอุตสาหกรรมและสายส่งที่มั่นคงเท่านั้นจึงสามารถรบได้นาน
D. ขนาดของกิจกรรมทางเศรษฐกิจในการผลิต ขนาดของหน่วยเศรษฐกิจที่ “เหมาะสมที่สุด” ในการผลิตสินค้าและบริการก็เป็นตัวแปรทางเทคโนโลยีที่ส่งผลต่อโครงสร้างของรัฐ หากเศรษฐกิจจำเป็นต้องอาศัยตลาดขนาดใหญ่ พื้นที่กว้าง หรือระบบโลจิสติกส์ที่ซับซ้อน รัฐขนาดใหญ่จะมีข้อได้เปรียบ เช่น จักรวรรดิอังกฤษที่สามารถจัดระบบเศรษฐกิจข้ามทวีปได้ในศตวรรษที่ 19 แต่หากเทคโนโลยีเอื้อให้เศรษฐกิจท้องถิ่นมีความคล่องตัว สามารถผลิตแบบกระจาย (distributed production)ได้ รัฐขนาดใหญ่ก็จะมีประสิทธิภาพน้อยลง และอำนาจจะกระจายตัว
E. การกระจายของเทคโนโลยี หากเทคโนโลยีสามารถถูก “ผูกขาด” ได้โดยกลุ่มเล็ก ๆ เช่น การควบคุมแหล่งพลังงานนิวเคลียร์ หรือการพัฒนาอาวุธล้ำสมัย อำนาจจะกระจุกอยู่กับชนชั้นนำ แต่หากเทคโนโลยีแพร่กระจายได้อย่างกว้างขวาง เช่น การใช้ดินปืน แป้นพิมพ์ อำนาจก็จะสลายตัวไปยังประชาชนทั่วไป
เมื่อพิจารณาประวัติศาสตร์ในมุมของ “สิ่งที่เกิดขึ้นจริง” ควบคู่กับ “สิ่งที่อาจเกิดขึ้นได้” เราจะเริ่มตระหนักถึงบทบาทของโอกาสและความเปราะบางที่มักถูกมองข้าม โดยเฉพาะในกรณีของจุลชีพ แม้จะเป็นตัวแปรที่ทรงพลังในอดีต แต่กลับดูเหมือนว่ามันมีผลกระทบต่อโครงสร้างอำนาจในยุคใหม่ต่ำกว่าที่ควรจะเป็น ทั้งที่ในทางทฤษฎีแล้ว มันมีศักยภาพสูงยิ่งในการเปลี่ยนแปลงประวัติศาสตร์ หากเชื้อไวรัสสายพันธุ์ใหม่ที่ร้ายแรงและแพร่กระจายได้ง่าย เทียบเท่าหรือรุนแรงกว่ามาลาเรีย แพร่ระบาดในหมู่นักสำรวจโปรตุเกสช่วงต้นของยุคการเดินเรือ อาจไม่มีการสำรวจหรือขยายอาณานิคมเกิดขึ้นเลย เช่นเดียวกับหากโคลัมบัสและผู้ย้ายถิ่นกลุ่มแรกในโลกใหม่ต้องเผชิญโรคร้ายที่มีฤทธิ์รุนแรงพอ ๆ กับหัดซึ่งคร่าชีวิตชาวพื้นเมืองไปอย่างมหาศาล พวกเขาอาจไม่สามารถตั้งรกรากได้เลยด้วยซ้ำ
แต่เมื่อมองย้อนกลับไป สิ่งเหล่านี้กลับไม่เคยเกิดขึ้น และนั่นทำให้เรายิ่งมีแนวโน้มจะเชื่อใน “ชะตากรรม” บางอย่างของประวัติศาสตร์ อย่างไรก็ตาม หากมองในแง่กลไกของพลังที่ขับเคลื่อนอำนาจ การที่จุลชีพกลับมีบทบาทสนับสนุนการรวมศูนย์ของรัฐในยุคใหม่มากกว่าการขัดขวาง ก็เป็นสิ่งที่น่าพิจารณา ทหารและผู้ตั้งถิ่นฐานจากโลกตะวันตกไม่ได้มีเพียงเทคโนโลยีเป็นแต้มต่อ แต่ยังมี “ภูมิคุ้มกันที่สั่งสมจากประสบการณ์กับโรค” อีกด้วย โรคที่มาพร้อมกับนักสำรวจจากยุโรปจึงกลายเป็น “อาวุธลับ” ที่ทำลายชาวพื้นเมืองก่อนที่ผู้รุกรานจะลงจากเรือด้วยซ้ำ
แม้ว่าจะมีข้อสันนิษฐานว่าซิฟิลิสแพร่จากโลกใหม่กลับไปยังยุโรป แต่ผลกระทบของมันก็จำกัดอยู่ในระดับวัฒนธรรม โดยเฉพาะด้านศีลธรรมทางเพศ ไม่ได้ส่งผลกระทบในระดับการเมืองมหภาคอย่างที่โรคระบาดในยุคกลางเคยทำ เช่น กาฬโรคหรือโรคไข้ทรพิษ เพราะในยุคสมัยใหม่ ระบบอุตสาหกรรมและโครงสร้างทางการแพทย์มีความสามารถในการควบคุมภัยจากจุลชีพได้มากขึ้น ไม่ว่าจะผ่านระบบสุขาภิบาล วัคซีน หรือยาปฏิชีวนะ
อย่างไรก็ดี การปรากฏตัวของโรคเอดส์ และความกังวลเกี่ยวกับไวรัสกลายพันธุ์ในช่วงปลายศตวรรษที่ 20 ได้แสดงให้เห็นว่า จุลชีพอาจไม่ได้เป็น “ปัจจัยรอง” ที่ไร้ฤทธิ์เสมอไป และอาจหวนกลับมาเป็นปัจจัยหลักที่กำหนดแนวทางของอำนาจใหม่อีกครั้งได้ในอนาคต หากมีโรคระบาดใหญ่เกิดขึ้นซึ่งรุนแรงพอที่จะทำลายความสามารถของรัฐในการควบคุมระบบเศรษฐกิจและชีวิตสาธารณะ โครงสร้างของอำนาจอาจสั่นคลอนยิ่งกว่าผลกระทบจากภูมิอากาศหรือภูมิประเทศเสียอีก
ปัญหาคือเราไม่สามารถคาดการณ์จุดเริ่มต้นของเหตุการณ์เหล่านี้ได้อย่างแม่นยำ ไม่มีแบบจำลองใดที่สามารถควบคุมหรือคาดเดาธรรมชาติได้อย่างสมบูรณ์ แม้จะมีความพยายามทางวิทยาศาสตร์และการเฝ้าระวังระดับโลก การที่เรารอดพ้นจากโรคร้ายในอดีตไม่ได้แปลว่าจะรอดได้อีกในอนาคต ความคาดหวังว่าปัจจัยมหภาคในพันปีข้างหน้าจะยังคงเป็น “เทคโนโลยี” ไม่ใช่ “จุลชีพ” จึงเป็นเพียงสมมติฐานที่ตั้งอยู่บนความหวังมากกว่าหลักประกันใด ๆ
และแม้ว่าเทคโนโลยีจะมีบทบาทอย่างล้นเหลือในช่วงห้าศตวรรษที่ผ่านมา แต่บทเรียนจากการปฏิวัติการเกษตรในยุคโบราณก็ยังคงเตือนใจว่า ปัจจัยที่เปลี่ยนแปลงวิถีของอำนาจในระดับรากฐานที่สุดอาจไม่ได้ยิ่งใหญ่หรือก้าวหน้าเสมอไป บางครั้งสิ่งที่ทำให้โลกเปลี่ยนแปลงไปอย่างถาวร ไม่ใช่จักรกลที่ซับซ้อนหรืออาวุธล้ำยุค หากแต่เป็นสิ่งมีชีวิตขนาดเล็กที่เราแทบมองไม่เห็นด้วยตาเปล่า — และมันก็อาจย้อนกลับมามีบทบาทสำคัญอีกครั้งในศตวรรษของเรา.
อย่าลืมว่าหนังสือเล่มนี้เขียนขึ้นในปี 1997 — ยุคที่โลกยังไม่เคยรู้จักกับ COVID-19
บทถัดไปจะพูดถึงเรื่องการปฏิวัติครั้งแรกของ Sapiens การปฏิวัติเกษตรกรรม
-
 @ 502ab02a:a2860397
2025-04-29 01:20:04
@ 502ab02a:a2860397
2025-04-29 01:20:04PAN... แค่แพนเค้ก หรือ แผนล้อมโลกเรื่องอาหาร เมื่อหมากตัวจริงชื่อ Sebastian Joy
เราได้รู้จักกับคุณ Sebastian Joy กันไปแล้วนะครับ วันนี้เรามาขยายผลกันอีกหน่อย
ถ้าโลกนี้เป็นเกมหมากรุก อาหารคือกระดานที่ทุกตัวหมากต้องเหยียบเดิน และใครที่วางหมากอาหารได้...ก็วางโลกได้เหมือนกัน
ปี 2018 มีโครงการหนึ่งถือกำเนิดขึ้นในเยอรมนีอย่างเงียบๆ ชื่อว่า Physicians Association for Nutrition (PAN) เบื้องหน้าเหมือนเป็นมูลนิธิการกุศล ตั้งขึ้นมาเพื่อ "ช่วยให้หมอเข้าใจเรื่องโภชนาการจากพืช" แต่ถ้าเปิดแว่นขยายส่องให้ดีๆ มันคือหนึ่งในฟันเฟืองสำคัญของแผนเปลี่ยนอนาคตอาหารโลกจาก Animal-Based ไปเป็น Plant-Based ที่เป็น lab plant based ที่ไม่ใช่อาหารธรรมชาติแบบหลักแก่นที่ Vegan สืบทอดกันมา โดยอ้างเรื่อง "สุขภาพ" และ "สิ่งแวดล้อม" เป็นฉากหน้า
PAN นั้นเสมือนเป็นลูกสมุนตัวกลั่นของคนที่ชื่อ Sebastian Joy ชายหนุ่มสายโปรโมทแนว Vegan ที่ก่อนหน้านั้นก่อตั้งองค์กร ProVeg International ซึ่งมีสายสัมพันธ์กับพวก Start-up อาหารทางเลือก (ไม่ว่าจะเป็นเนื้อปลอม เนื้อพืชดีเอนเอ นมพืชที่มาจากจุลินทรีย์ ไปจนถึงการส่งเสริมวัตถุดิบจากแบคทีเรีย โรงงาน และห้องแลบ) แล้ว ProVeg ไม่ได้ทำงานเดี่ยวๆ นะจ๊ะ... เบื้องหลังเชื่อมโยงกับเครือข่ายที่หนุน World Economic Forum (WEF) และแนวคิด Great Reset ที่อยาก "รีเซ็ต" วิธีการกินของคนทั้งโลก โดยให้อาหารเป็น Plant-Based แบบ lab created และ Meat Lab-Based เป็นหลัก
ส่วน PAN ถูกใช้เป็น "หมากที่แต่งตัวเป็นหมอ" เพื่อเดินเกมไปสู่การแทรกแซงนโยบายประเทศต่างๆ ผ่านช่องทาง "สาธารณสุข" และ "การศึกษาแพทย์" เพื่อมาเป็นกำลังหลักให้ในแผนงาน
เรามาดูตัวอย่างผลงานเด่นของ PAN กันครับ 1. ผลักดันให้รวม Plant-Based เข้าไปในหลักสูตรแพทย์และพยาบาล (โดยใช้เหตุผลว่า "หมอต้องรู้จักอาหารเพื่อสุขภาพ") 2. ช่วยรณรงค์ให้โรงพยาบาล โรงเรียน และมหาวิทยาลัย เปลี่ยนเมนูอาหารเป็น Plant-Based 3. สนับสนุนงานวิจัย และโครงการ เช่น Green Food Experience ที่กดดันให้ภาคธุรกิจและภาครัฐบาลหันมาทำตาม "แนวทางอาหารยั่งยืน" แบบที่ PAN และพรรคพวกกำหนด 4. มีสถานะ "Observer" ในองค์การสหประชาชาติ (UN) เพื่อเสนอความคิดเห็นในการกำหนดนโยบายสาธารณสุขและสิ่งแวดล้อมระดับโลก
และเบื้องหลังอีกชั้นที่น่าสนใจ... Sebastian Joy มีความสัมพันธ์ลึกซึ้งกับวงการ Start-up อาหารใหม่ๆ ที่พยายามตีตลาด Plant-Based และ Lab-Grown Food อย่างเช่น Perfect Day, Beyond Meat, Mosa Meat ฯลฯ ผ่านการโปรโมท "โภชนาการจากพืชเพื่อสุขภาพที่ดีกว่า" โดยใช้ PAN เป็นเครื่องมือให้ดู "มีอำนาจทางวิชาการ" มากขึ้น
หรือถ้าให้พูดง่ายๆ คือ สร้างสนามแข่ง แล้วจับมือกับนักแข่งที่ตัวเองลงทุนไว้ PAN ดูเหมือนเป็นองค์กรกลางๆ ใสๆ แต่มันเชื่อมโยงกับโครงข่าย NGO และบริษัทเอกชนที่มุ่งแปลงร่างอาหารโลกอยู่เบื้องหลัง การที่ PAN ผลักดันนโยบายระดับประเทศ และแทรกซึมในระบบการศึกษา หมายความว่าอนาคตคนรุ่นใหม่จะถูกปลูกฝังแนวคิด "เนื้อสัตว์ไม่ดี" โดยไม่ทันรู้ตัว
แล้วมันเกี่ยวอะไรกับเรา? จินตนาการดูครับว่า - ถ้าวันหนึ่งโรงเรียนของลูกเรามีแต่เมนูถั่วเหลือง ซีเรียล นมโอ๊ต หรือ ไอศกรีมเวย์จากจุลินทรีย์ และห้ามเสิร์ฟเนื้อสัตว์ด้วยสารพัดเหตุผล เช่น เนื้อปนเปื้อนง่าย เนื้อทำให้เป็นมะเร็ง หรือแม้แต่สอนเด็กว่า เนื้อคือตัวการทำลายสิ่งแวดล้อมด้วย มีเทน นั่นอาจเป็นผลลัพธ์จากงานเบื้องหลังของ PAN - ถ้าวันหนึ่งนโยบายอาหารของประเทศเน้นลดเนื้อสัตว์ อ้างสุขภาพ อ้างสิ่งแวดล้อม อ้างโรคระบาด อ้างกฎแห่ง DNA ที่ถูกจดสิทธิบัตร แล้วโปรโมทเนื้อปลอมแทน นั่นอาจเป็นรอยเท้าของ Sebastian Joy ที่เดินมาก่อนแล้ว - ถ้าวันหนึ่งหมอจำนวนมากเชื่อว่า “เนื้อสัตว์คือตัวร้ายที่แพร่มะเร็งหรือทำให้สุขภาพเสีย” โดยไม่มีการตั้งคำถาม นั่นคือชัยชนะของหมากตัวนี้
ในขณะที่คนส่วนใหญ่คิดว่ากำลังเลือกอาหารเอง หรือ คิดว่าฉันกิน plant base / vegan เพราะรักโลก รักสุขภาพ แต่จริงๆ แล้วมีมือที่มองไม่เห็นกำหนด "ตัวเลือก" ไว้แล้วเรียบร้อย เพราะทั้งหมดมันไม่ได้เป็นอาหารธรรมชาติ มันคืออาหาร "สร้าง" ที่ไม่มีสัตว์, มันคืออาหาร "สร้าง" ที่ต้อง "สร้าง" มาจากโรงงาน แล้วเราต้อง "ซื้อ" มากินเท่านั้น ถ้าไม่สร้าง local ให้แข็งแรง อย่าหลงไปตามความสวยงามของการรักโลกในมุมเดียว เราอาจจะไม่สามารถปลูกพืชมาเป็นอาหารเองได้ เราอาจไม่สามารถเลี้ยงสัตว์เพื่อกินเองได้
PAN ไม่ใช่แค่องค์กรให้ความรู้ด้านโภชนาการ / PAN คือเครื่องมือในกระดานหมากรุกที่กำลังจัดการ "ตั้งโปรแกรมใหม่" ให้คนทั้งโลกกินตามแบบที่นายทุนและเครือข่ายเบื้องหลังเขียนบทไว้ และชายที่ชื่อ Sebastian Joy นี่แหละ...คือหนึ่งในผู้ถือหมากที่ยิ้มอยู่หลังม่าน
อาหารแห่งอนาคต มีทางเดินเหลือไว้ให้ เกษตรกร old school บ้างไหม สนธิสัญญาต่างๆเรื่องเมล็ดพันธุ์ เหลือทางเดินไว้ให้เกษตรกรบ้างไหม หรือสุดท้าย เราจะไม่มีไดเอทให้เลือก ให้ทะเลาะกัน เพราะสุดท้าย เราต่างต้องกินอาหารจากโรงงานเหมือนกันหมด บทความนี้คงจะเป็นได้แค่เพียง การตั้งคำถามขึ้นมาไว้ แต่ไม่มีคำตอบ ว่าเรากำลังโดนอ้าง plant based food มาเคลือบความเป็น อาหารโรงงาน (Plant Food) หรือเปล่าเพราะวันนี้หลายคนอาจมองว่าเป็นการตื่นตูม คิดมาก หรือแม้แต่ เราเลือกได้แหละ ก็ได้ครับ
ผมไม่ได้มีปัญหากับสายพืชล้วน ไม่ว่าจะเจ วีแกน แพลนท์เบส เพราะถ้ากินเป็น มองสารอาหารเป็น จัดการ anti nutrient ได้ดี มันก็ดีสำหรับคนนั้น แต่ซีรีส์นี้สำคัญที่ว่า plant based food is not PLANT food อาหารจากพืชไม่ใช่อาหารจากโรงงานครับ
ก่อนถึงวันที่เราจะไม่มีสิทธิ์แม้แต่จะเลือก #pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-
 @ 4db2f229:205fed9f
2025-04-28 23:25:16
@ 4db2f229:205fed9f
2025-04-28 23:25:16https://www.nexusmods.com/newvegas/mods/80258
If you manage to get it up to date / uncorrupt the data, I give you full liberties to:
- The model itself
- Its XMF and/or XML skeleton
- Patching it to be compatible with any other gun mods
- other fixes
- and full credit handed over to you
I think this has honestly been abandoned by it's original developer, and since I am just hanging onto the file? I decided it'd be better maintained in someone elses hands, and with community much more responsible than Nexus. Honestly if I did not archive this mod? It would of been vaporware.
But in it's current state it's not fit for being playable. I did manage to save media of when it was playable however.
-
 @ 4ba8e86d:89d32de4
2025-04-28 22:39:20
@ 4ba8e86d:89d32de4
2025-04-28 22:39:20Como funciona o PGP.

O texto a seguir foi retirado do capítulo 1 do documento Introdução à criptografia na documentação do PGP 6.5.1. Copyright © 1990-1999 Network Associates, Inc. Todos os direitos reservados.
-O que é criptografia? -Criptografia forte -Como funciona a criptografia? -Criptografia convencional -Cifra de César -Gerenciamento de chaves e criptografia convencional -Criptografia de chave pública -Como funciona o PGP - Chaves • Assinaturas digitais -Funções hash • Certificados digitais -Distribuição de certificados -Formatos de certificado •Validade e confiança -Verificando validade -Estabelecendo confiança -Modelos de confiança • Revogação de certificado -Comunicar que um certificado foi revogado -O que é uma senha? -Divisão de chave
Os princípios básicos da criptografia.
Quando Júlio César enviou mensagens aos seus generais, ele não confiou nos seus mensageiros. Então ele substituiu cada A em suas mensagens por um D, cada B por um E, e assim por diante através do alfabeto. Somente alguém que conhecesse a regra “shift by 3” poderia decifrar suas mensagens. E assim começamos.
Criptografia e descriptografia.
Os dados que podem ser lidos e compreendidos sem quaisquer medidas especiais são chamados de texto simples ou texto não criptografado. O método de disfarçar o texto simples de forma a ocultar sua substância é chamado de criptografia. Criptografar texto simples resulta em um jargão ilegível chamado texto cifrado. Você usa criptografia para garantir que as informações sejam ocultadas de qualquer pessoa a quem não se destinam, mesmo daqueles que podem ver os dados criptografados. O processo de reverter o texto cifrado ao texto simples original é chamado de descriptografia . A Figura 1-1 ilustra esse processo.
https://image.nostr.build/0e2fcb71ed86a6083e083abbb683f8c103f44a6c6db1aeb2df10ae51ec97ebe5.jpg
Figura 1-1. Criptografia e descriptografia
O que é criptografia?
Criptografia é a ciência que usa a matemática para criptografar e descriptografar dados. A criptografia permite armazenar informações confidenciais ou transmiti-las através de redes inseguras (como a Internet) para que não possam ser lidas por ninguém, exceto pelo destinatário pretendido. Embora a criptografia seja a ciência que protege os dados, a criptoanálise é a ciência que analisa e quebra a comunicação segura. A criptoanálise clássica envolve uma combinação interessante de raciocínio analítico, aplicação de ferramentas matemáticas, descoberta de padrões, paciência, determinação e sorte. Os criptoanalistas também são chamados de atacantes. A criptologia abrange tanto a criptografia quanto a criptoanálise.
Criptografia forte.
"Existem dois tipos de criptografia neste mundo: a criptografia que impedirá a sua irmã mais nova de ler os seus arquivos, e a criptografia que impedirá os principais governos de lerem os seus arquivos. Este livro é sobre o último." --Bruce Schneier, Criptografia Aplicada: Protocolos, Algoritmos e Código Fonte em C. PGP também trata deste último tipo de criptografia. A criptografia pode ser forte ou fraca, conforme explicado acima. A força criptográfica é medida no tempo e nos recursos necessários para recuperar o texto simples. O resultado de uma criptografia forte é um texto cifrado que é muito difícil de decifrar sem a posse da ferramenta de decodificação apropriada. Quão díficil? Dado todo o poder computacional e o tempo disponível de hoje – mesmo um bilhão de computadores fazendo um bilhão de verificações por segundo – não é possível decifrar o resultado de uma criptografia forte antes do fim do universo. Alguém poderia pensar, então, que uma criptografia forte resistiria muito bem até mesmo contra um criptoanalista extremamente determinado. Quem pode realmente dizer? Ninguém provou que a criptografia mais forte disponível hoje resistirá ao poder computacional de amanhã. No entanto, a criptografia forte empregada pelo PGP é a melhor disponível atualmente.
Contudo, a vigilância e o conservadorismo irão protegê-lo melhor do que as alegações de impenetrabilidade.
Como funciona a criptografia?
Um algoritmo criptográfico, ou cifra, é uma função matemática usada no processo de criptografia e descriptografia. Um algoritmo criptográfico funciona em combinação com uma chave – uma palavra, número ou frase – para criptografar o texto simples. O mesmo texto simples é criptografado em texto cifrado diferente com chaves diferentes. A segurança dos dados criptografados depende inteiramente de duas coisas: a força do algoritmo criptográfico e o sigilo da chave. Um algoritmo criptográfico, mais todas as chaves possíveis e todos os protocolos que o fazem funcionar constituem um criptossistema. PGP é um criptossistema.
Criptografia convencional.
Na criptografia convencional, também chamada de criptografia de chave secreta ou de chave simétrica , uma chave é usada tanto para criptografia quanto para descriptografia. O Data Encryption Standard (DES) é um exemplo de criptossistema convencional amplamente empregado pelo Governo Federal. A Figura 1-2 é uma ilustração do processo de criptografia convencional. https://image.nostr.build/328b73ebaff84c949df2560bbbcec4bc3b5e3a5163d5fbb2ec7c7c60488f894c.jpg
Figura 1-2. Criptografia convencional
Cifra de César.
Um exemplo extremamente simples de criptografia convencional é uma cifra de substituição. Uma cifra de substituição substitui uma informação por outra. Isso é feito com mais frequência compensando as letras do alfabeto. Dois exemplos são o Anel Decodificador Secreto do Capitão Meia-Noite, que você pode ter possuído quando era criança, e a cifra de Júlio César. Em ambos os casos, o algoritmo serve para compensar o alfabeto e a chave é o número de caracteres para compensá-lo. Por exemplo, se codificarmos a palavra "SEGREDO" usando o valor chave de César de 3, deslocaremos o alfabeto para que a terceira letra abaixo (D) comece o alfabeto. Então começando com A B C D E F G H I J K L M N O P Q R S T U V W X Y Z e deslizando tudo para cima em 3, você obtém DEFGHIJKLMNOPQRSTUVWXYZABC onde D=A, E=B, F=C e assim por diante. Usando este esquema, o texto simples, "SECRET" é criptografado como "VHFUHW". Para permitir que outra pessoa leia o texto cifrado, você diz a ela que a chave é 3. Obviamente, esta é uma criptografia extremamente fraca para os padrões atuais, mas, ei, funcionou para César e ilustra como funciona a criptografia convencional.
Gerenciamento de chaves e criptografia convencional.
A criptografia convencional tem benefícios. É muito rápido. É especialmente útil para criptografar dados que não vão a lugar nenhum. No entanto, a criptografia convencional por si só como meio de transmissão segura de dados pode ser bastante cara, simplesmente devido à dificuldade de distribuição segura de chaves. Lembre-se de um personagem do seu filme de espionagem favorito: a pessoa com uma pasta trancada e algemada ao pulso. Afinal, o que há na pasta? Provavelmente não é o código de lançamento de mísseis/fórmula de biotoxina/plano de invasão em si. É a chave que irá descriptografar os dados secretos. Para que um remetente e um destinatário se comuniquem com segurança usando criptografia convencional, eles devem chegar a um acordo sobre uma chave e mantê-la secreta entre si. Se estiverem em locais físicos diferentes, devem confiar em um mensageiro, no Bat Phone ou em algum outro meio de comunicação seguro para evitar a divulgação da chave secreta durante a transmissão. Qualquer pessoa que ouvir ou interceptar a chave em trânsito poderá posteriormente ler, modificar e falsificar todas as informações criptografadas ou autenticadas com essa chave. Do DES ao Anel Decodificador Secreto do Capitão Midnight, o problema persistente com a criptografia convencional é a distribuição de chaves: como você leva a chave ao destinatário sem que alguém a intercepte?
Criptografia de chave pública.
Os problemas de distribuição de chaves são resolvidos pela criptografia de chave pública, cujo conceito foi introduzido por Whitfield Diffie e Martin Hellman em 1975. (Há agora evidências de que o Serviço Secreto Britânico a inventou alguns anos antes de Diffie e Hellman, mas a manteve um segredo militar - e não fez nada com isso.
[JH Ellis: The Possibility of Secure Non-Secret Digital Encryption, CESG Report, January 1970]) A criptografia de chave pública é um esquema assimétrico que usa um par de chaves para criptografia: uma chave pública, que criptografa os dados, e uma chave privada ou secreta correspondente para descriptografia. Você publica sua chave pública para o mundo enquanto mantém sua chave privada em segredo. Qualquer pessoa com uma cópia da sua chave pública pode criptografar informações que somente você pode ler. Até mesmo pessoas que você nunca conheceu. É computacionalmente inviável deduzir a chave privada da chave pública. Qualquer pessoa que possua uma chave pública pode criptografar informações, mas não pode descriptografá-las. Somente a pessoa que possui a chave privada correspondente pode descriptografar as informações. https://image.nostr.build/fdb71ae7a4450a523456827bdd509b31f0250f63152cc6f4ba78df290887318b.jpg
Figura 1-3. Criptografia de chave pública O principal benefício da criptografia de chave pública é que ela permite que pessoas que não possuem nenhum acordo de segurança pré-existente troquem mensagens com segurança. A necessidade de remetente e destinatário compartilharem chaves secretas através de algum canal seguro é eliminada; todas as comunicações envolvem apenas chaves públicas e nenhuma chave privada é transmitida ou compartilhada. Alguns exemplos de criptossistemas de chave pública são Elgamal (nomeado em homenagem a seu inventor, Taher Elgamal), RSA (nomeado em homenagem a seus inventores, Ron Rivest, Adi Shamir e Leonard Adleman), Diffie-Hellman (nomeado, você adivinhou, em homenagem a seus inventores). ) e DSA, o algoritmo de assinatura digital (inventado por David Kravitz). Como a criptografia convencional já foi o único meio disponível para transmitir informações secretas, o custo dos canais seguros e da distribuição de chaves relegou a sua utilização apenas àqueles que podiam pagar, como governos e grandes bancos (ou crianças pequenas com anéis descodificadores secretos). A criptografia de chave pública é a revolução tecnológica que fornece criptografia forte para as massas adultas. Lembra do mensageiro com a pasta trancada e algemada ao pulso? A criptografia de chave pública o tira do mercado (provavelmente para seu alívio).
Como funciona o PGP.
O PGP combina alguns dos melhores recursos da criptografia convencional e de chave pública. PGP é um criptossistema híbrido. Quando um usuário criptografa texto simples com PGP, o PGP primeiro compacta o texto simples. A compactação de dados economiza tempo de transmissão do modem e espaço em disco e, mais importante ainda, fortalece a segurança criptográfica. A maioria das técnicas de criptoanálise explora padrões encontrados no texto simples para quebrar a cifra. A compressão reduz esses padrões no texto simples, aumentando assim enormemente a resistência à criptoanálise. (Arquivos que são muito curtos para compactar ou que não são compactados bem não são compactados.) O PGP então cria uma chave de sessão, que é uma chave secreta única. Esta chave é um número aleatório gerado a partir dos movimentos aleatórios do mouse e das teclas digitadas. Esta chave de sessão funciona com um algoritmo de criptografia convencional rápido e muito seguro para criptografar o texto simples; o resultado é texto cifrado. Depois que os dados são criptografados, a chave da sessão é criptografada na chave pública do destinatário. Essa chave de sessão criptografada com chave pública é transmitida junto com o texto cifrado ao destinatário.
Figura 1-4. Como funciona a criptografia PGP A descriptografia funciona ao contrário. A cópia do PGP do destinatário usa sua chave privada para recuperar a chave de sessão temporária, que o PGP usa para descriptografar o texto cifrado criptografado convencionalmente.

Figura 1-5. Como funciona a descriptografia PGP A combinação dos dois métodos de criptografia combina a conveniência da criptografia de chave pública com a velocidade da criptografia convencional. A criptografia convencional é cerca de 1.000 vezes mais rápida que a criptografia de chave pública. A criptografia de chave pública, por sua vez, fornece uma solução para
problemas de distribuição de chaves e transmissão de dados. Usados em conjunto, o desempenho e a distribuição de chaves são melhorados sem qualquer sacrifício na segurança.
Chaves.
Uma chave é um valor que funciona com um algoritmo criptográfico para produzir um texto cifrado específico. As chaves são basicamente números muito, muito, muito grandes. O tamanho da chave é medido em bits; o número que representa uma chave de 1024 bits é enorme. Na criptografia de chave pública, quanto maior a chave, mais seguro é o texto cifrado. No entanto, o tamanho da chave pública e o tamanho da chave secreta da criptografia convencional não têm nenhuma relação. Uma chave convencional de 80 bits tem a força equivalente a uma chave pública de 1.024 bits. Uma chave convencional de 128 bits é equivalente a uma chave pública de 3.000 bits. Novamente, quanto maior a chave, mais segura, mas os algoritmos usados para cada tipo de criptografia são muito diferentes e, portanto, a comparação é como a de maçãs com laranjas. Embora as chaves pública e privada estejam matematicamente relacionadas, é muito difícil derivar a chave privada dada apenas a chave pública; no entanto, derivar a chave privada é sempre possível, desde que haja tempo e capacidade computacional suficientes. Isto torna muito importante escolher chaves do tamanho certo; grande o suficiente para ser seguro, mas pequeno o suficiente para ser aplicado rapidamente. Além disso, você precisa considerar quem pode estar tentando ler seus arquivos, quão determinados eles estão, quanto tempo têm e quais podem ser seus recursos. Chaves maiores serão criptograficamente seguras por um longo período de tempo. Se o que você deseja criptografar precisar ficar oculto por muitos anos, você pode usar uma chave muito grande. Claro, quem sabe quanto tempo levará para determinar sua chave usando os computadores mais rápidos e eficientes de amanhã? Houve um tempo em que uma chave simétrica de 56 bits era considerada extremamente segura. As chaves são armazenadas de forma criptografada. O PGP armazena as chaves em dois arquivos no seu disco rígido; um para chaves públicas e outro para chaves privadas. Esses arquivos são chamados de chaveiros. Ao usar o PGP, você normalmente adicionará as chaves públicas dos seus destinatários ao seu chaveiro público. Suas chaves privadas são armazenadas em seu chaveiro privado. Se você perder seu chaveiro privado, não será possível descriptografar nenhuma informação criptografada nas chaves desse anel.
Assinaturas digitais.
Um grande benefício da criptografia de chave pública é que ela fornece um método para empregar assinaturas digitais. As assinaturas digitais permitem ao destinatário da informação verificar a autenticidade da origem da informação e também verificar se a informação está intacta. Assim, as assinaturas digitais de chave pública fornecem autenticação e integridade de dados. A assinatura digital também proporciona o não repúdio, o que significa que evita que o remetente alegue que não enviou realmente as informações. Esses recursos são tão fundamentais para a criptografia quanto a privacidade, se não mais. Uma assinatura digital tem a mesma finalidade de uma assinatura manuscrita. No entanto, uma assinatura manuscrita é fácil de falsificar. Uma assinatura digital é superior a uma assinatura manuscrita porque é quase impossível de ser falsificada, além de atestar o conteúdo da informação, bem como a identidade do signatário.
Algumas pessoas tendem a usar mais assinaturas do que criptografia. Por exemplo, você pode não se importar se alguém souber que você acabou de depositar US$ 1.000 em sua conta, mas quer ter certeza de que foi o caixa do banco com quem você estava lidando. A maneira básica pela qual as assinaturas digitais são criadas é ilustrada na Figura 1-6 . Em vez de criptografar informações usando a chave pública de outra pessoa, você as criptografa com sua chave privada. Se as informações puderem ser descriptografadas com sua chave pública, elas deverão ter se originado em você.
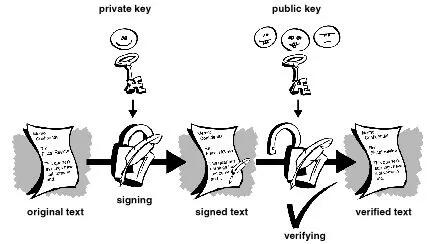
Figura 1-6. Assinaturas digitais simples
Funções hash.
O sistema descrito acima apresenta alguns problemas. É lento e produz um enorme volume de dados – pelo menos o dobro do tamanho da informação original. Uma melhoria no esquema acima é a adição de uma função hash unidirecional no processo. Uma função hash unidirecional recebe uma entrada de comprimento variável – neste caso, uma mensagem de qualquer comprimento, até mesmo milhares ou milhões de bits – e produz uma saída de comprimento fixo; digamos, 160 bits. A função hash garante que, se a informação for alterada de alguma forma – mesmo que por apenas um bit – seja produzido um valor de saída totalmente diferente. O PGP usa uma função hash criptograficamente forte no texto simples que o usuário está assinando. Isso gera um item de dados de comprimento fixo conhecido como resumo da mensagem. (Novamente, qualquer alteração nas informações resulta em um resumo totalmente diferente.) Então o PGP usa o resumo e a chave privada para criar a “assinatura”. O PGP transmite a assinatura e o texto simples juntos. Ao receber a mensagem, o destinatário utiliza o PGP para recalcular o resumo, verificando assim a assinatura. O PGP pode criptografar o texto simples ou não; assinar texto simples é útil se alguns dos destinatários não estiverem interessados ou não forem capazes de verificar a assinatura. Desde que uma função hash segura seja usada, não há como retirar a assinatura de alguém de um documento e anexá-la a outro, ou alterar uma mensagem assinada de qualquer forma. A menor alteração em um documento assinado causará falha no processo de verificação da assinatura digital.
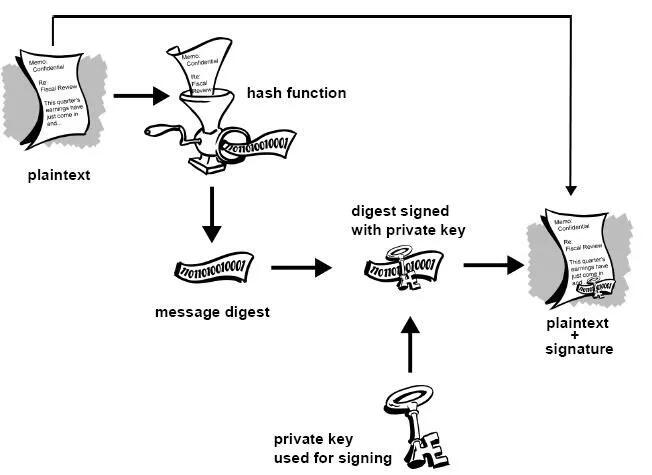
Figura 1-7. Assinaturas digitais seguras As assinaturas digitais desempenham um papel importante na autenticação e validação de chaves de outros usuários PGP.
Certificados digitais.
Um problema com os criptosistemas de chave pública é que os usuários devem estar constantemente vigilantes para garantir que estão criptografando com a chave da pessoa correta. Num ambiente onde é seguro trocar chaves livremente através de servidores públicos, os ataques man-in-the-middle são uma ameaça potencial. Neste tipo de ataque, alguém publica uma chave falsa com o nome e ID de usuário do destinatário pretendido. Os dados criptografados – e interceptados por – o verdadeiro proprietário desta chave falsa estão agora em mãos erradas. Em um ambiente de chave pública, é vital que você tenha certeza de que a chave pública para a qual você está criptografando os dados é de fato a chave pública do destinatário pretendido e não uma falsificação. Você pode simplesmente criptografar apenas as chaves que foram entregues fisicamente a você. Mas suponha que você precise trocar informações com pessoas que nunca conheceu; como você pode saber se tem a chave correta? Os certificados digitais, ou certs, simplificam a tarefa de estabelecer se uma chave pública realmente pertence ao suposto proprietário. Um certificado é uma forma de credencial. Exemplos podem ser sua carteira de motorista, seu cartão de previdência social ou sua certidão de nascimento. Cada um deles contém algumas informações que identificam você e alguma autorização informando que outra pessoa confirmou sua identidade. Alguns certificados, como o seu passaporte, são uma confirmação importante o suficiente da sua identidade para que você não queira perdê-los, para que ninguém os use para se passar por você.
Um certificado digital são dados que funcionam como um certificado físico. Um certificado digital é uma informação incluída na chave pública de uma pessoa que ajuda outras pessoas a verificar se uma chave é genuína ou válida. Os certificados digitais são usados para impedir tentativas de substituir a chave de uma pessoa por outra.
Um certificado digital consiste em três coisas:
● Uma chave pública.
● Informações do certificado. (Informações de "identidade" sobre o usuário, como nome, ID do usuário e assim por diante.) ● Uma ou mais assinaturas digitais.
O objetivo da assinatura digital em um certificado é afirmar que as informações do certificado foram atestadas por alguma outra pessoa ou entidade. A assinatura digital não atesta a autenticidade do certificado como um todo; ele atesta apenas que as informações de identidade assinadas acompanham ou estão vinculadas à chave pública. Assim, um certificado é basicamente uma chave pública com uma ou duas formas de identificação anexadas, além de um forte selo de aprovação de algum outro indivíduo confiável.
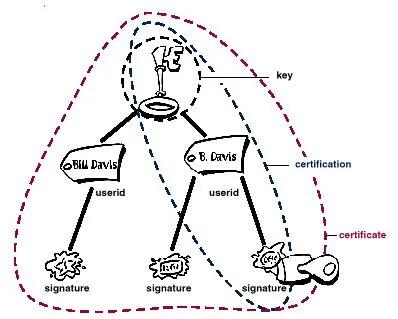 Figura 1-8. Anatomia de um certificado PGP
Figura 1-8. Anatomia de um certificado PGPDistribuição de certificados.
Os certificados são utilizados quando é necessário trocar chaves públicas com outra pessoa. Para pequenos grupos de pessoas que desejam se comunicar com segurança, é fácil trocar manualmente disquetes ou e-mails contendo a chave pública de cada proprietário. Esta é a distribuição manual de chave pública e é prática apenas até certo ponto. Além desse ponto, é necessário implementar sistemas que possam fornecer os mecanismos necessários de segurança, armazenamento e troca para que colegas de trabalho, parceiros de negócios ou estranhos possam se comunicar, se necessário. Eles podem vir na forma de repositórios somente de armazenamento, chamados Servidores de Certificados, ou sistemas mais estruturados que fornecem recursos adicionais de gerenciamento de chaves e são chamados de Infraestruturas de Chave Pública (PKIs).
Servidores de certificados.
Um servidor de certificados, também chamado de servidor certificado ou servidor de chaves, é um banco de dados que permite aos usuários enviar e recuperar certificados digitais. Um servidor certificado geralmente fornece alguns recursos administrativos que permitem que uma empresa mantenha suas políticas de segurança – por exemplo, permitindo que apenas as chaves que atendam a determinados requisitos sejam armazenadas.
Infraestruturas de Chave Pública.
Uma PKI contém os recursos de armazenamento de certificados de um servidor de certificados, mas também fornece recursos de gerenciamento de certificados (a capacidade de emitir, revogar, armazenar, recuperar e confiar em certificados). A principal característica de uma PKI é a introdução do que é conhecido como Autoridade Certificadora,ou CA, que é uma entidade humana — uma pessoa, grupo, departamento, empresa ou outra associação — que uma organização autorizou a emitir certificados para seus usuários de computador. (A função de uma CA é análoga à do Passport Office do governo de um país.) Uma CA cria certificados e os assina digitalmente usando a chave privada da CA. Devido ao seu papel na criação de certificados, a CA é o componente central de uma PKI. Usando a chave pública da CA, qualquer pessoa que queira verificar a autenticidade de um certificado verifica a assinatura digital da CA emissora e, portanto, a integridade do conteúdo do certificado (mais importante ainda, a chave pública e a identidade do titular do certificado).
Formatos de certificado.
Um certificado digital é basicamente uma coleção de informações de identificação vinculadas a uma chave pública e assinadas por um terceiro confiável para provar sua autenticidade. Um certificado digital pode ter vários formatos diferentes.
O PGP reconhece dois formatos de certificado diferentes:
● Certificados PGP ● Certificados X.509 Formato do certificado PGP. Um certificado PGP inclui (mas não está limitado a) as seguintes informações: ● O número da versão do PGP — identifica qual versão do PGP foi usada para criar a chave associada ao certificado. A chave pública do titular do certificado — a parte pública do seu par de chaves, juntamente com o algoritmo da chave: RSA, DH (Diffie-Hellman) ou DSA (Algoritmo de Assinatura Digital).
● As informações do detentor do certificado — consistem em informações de “identidade” sobre o usuário, como seu nome, ID de usuário, fotografia e assim por diante. ● A assinatura digital do proprietário do certificado — também chamada de autoassinatura, é a assinatura que utiliza a chave privada correspondente da chave pública associada ao certificado. ● O período de validade do certificado — a data/hora de início e a data/hora de expiração do certificado; indica quando o certificado irá expirar. ● O algoritmo de criptografia simétrica preferido para a chave — indica o algoritmo de criptografia para o qual o proprietário do certificado prefere que as informações sejam criptografadas. Os algoritmos suportados são CAST, IDEA ou Triple-DES. Você pode pensar em um certificado PGP como uma chave pública com um ou mais rótulos vinculados a ele (veja a Figura 1.9 ). Nessas 'etiquetas' você encontrará informações que identificam o proprietário da chave e uma assinatura do proprietário da chave, que afirma que a chave e a identificação andam juntas. (Essa assinatura específica é chamada de autoassinatura; todo certificado PGP contém uma autoassinatura.) Um aspecto único do formato de certificado PGP é que um único certificado pode conter múltiplas assinaturas. Várias ou muitas pessoas podem assinar o par chave/identificação para atestar a sua própria garantia de que a chave pública pertence definitivamente ao proprietário especificado. Se você procurar em um servidor de certificados público, poderá notar que certos certificados, como o do criador do PGP, Phil Zimmermann, contêm muitas assinaturas. Alguns certificados PGP consistem em uma chave pública com vários rótulos, cada um contendo um meio diferente de identificar o proprietário da chave (por exemplo, o nome do proprietário e a conta de e-mail corporativa, o apelido do proprietário e a conta de e-mail residencial, uma fotografia do proprietário — tudo em um certificado). A lista de assinaturas de cada uma dessas identidades pode ser diferente; as assinaturas atestam a autenticidade de que um dos rótulos pertence à chave pública, e não que todos os rótulos da chave sejam autênticos. (Observe que 'autêntico' está nos olhos de quem vê - assinaturas são opiniões, e diferentes pessoas dedicam diferentes níveis de devida diligência na verificação da autenticidade antes de assinar uma chave.)
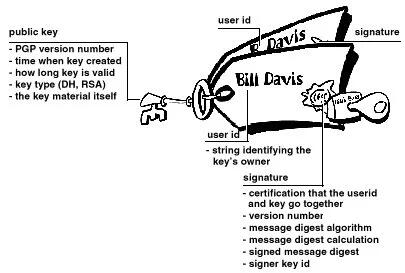 Figura 1-9. Um certificado PGP
Figura 1-9. Um certificado PGPFormato de certificado X.509.
X.509 é outro formato de certificado muito comum. Todos os certificados X.509 estão em conformidade com o padrão internacional ITU-T X.509; assim (teoricamente) os certificados X.509 criados para um aplicativo podem ser usados por qualquer aplicativo compatível com X.509. Na prática, porém, diferentes empresas criaram suas próprias extensões para certificados X.509, e nem todas funcionam juntas. Um certificado exige que alguém valide que uma chave pública e o nome do proprietário da chave andam juntos. Com os certificados PGP, qualquer pessoa pode desempenhar o papel de validador. Com certificados X.509, o validador é sempre uma Autoridade Certificadora ou alguém designado por uma CA. (Tenha em mente que os certificados PGP também suportam totalmente uma estrutura hierárquica usando uma CA para validar certificados.)
Um certificado X.509 é uma coleção de um conjunto padrão de campos contendo informações sobre um usuário ou dispositivo e sua chave pública correspondente. O padrão X.509 define quais informações vão para o certificado e descreve como codificá-lo (o formato dos dados). Todos os certificados X.509 possuem os seguintes dados:
O número da versão X.509
— identifica qual versão do padrão X.509 se aplica a este certificado, o que afeta quais informações podem ser especificadas nele. A mais atual é a versão 3.
A chave pública do titular do certificado
— a chave pública do titular do certificado, juntamente com um identificador de algoritmo que especifica a qual sistema criptográfico a chave pertence e quaisquer parâmetros de chave associados.
O número de série do certificado
— a entidade (aplicação ou pessoa) que criou o certificado é responsável por atribuir-lhe um número de série único para distingui-lo de outros certificados que emite. Esta informação é usada de diversas maneiras; por exemplo, quando um certificado é revogado, seu número de série é colocado em uma Lista de Revogação de Certificados ou CRL.
O identificador exclusivo do detentor do certificado
— (ou DN — nome distinto). Este nome pretende ser exclusivo na Internet. Este nome pretende ser exclusivo na Internet. Um DN consiste em múltiplas subseções e pode ser parecido com isto: CN=Bob Allen, OU=Divisão Total de Segurança de Rede, O=Network Associates, Inc., C=EUA (Referem-se ao nome comum, à unidade organizacional, à organização e ao país do sujeito .)
O período de validade do certificado
— a data/hora de início e a data/hora de expiração do certificado; indica quando o certificado irá expirar.
O nome exclusivo do emissor do certificado
— o nome exclusivo da entidade que assinou o certificado. Normalmente é uma CA. A utilização do certificado implica confiar na entidade que assinou este certificado. (Observe que em alguns casos, como certificados de CA raiz ou de nível superior , o emissor assina seu próprio certificado.)
A assinatura digital do emitente
— a assinatura utilizando a chave privada da entidade que emitiu o certificado.
O identificador do algoritmo de assinatura
— identifica o algoritmo usado pela CA para assinar o certificado.
Existem muitas diferenças entre um certificado X.509 e um certificado PGP, mas as mais importantes são as seguintes: você pode criar seu próprio certificado PGP;
● você deve solicitar e receber um certificado X.509 de uma autoridade de certificação
● Os certificados X.509 suportam nativamente apenas um único nome para o proprietário da chave
● Os certificados X.509 suportam apenas uma única assinatura digital para atestar a validade da chave
Para obter um certificado X.509, você deve solicitar a uma CA a emissão de um certificado. Você fornece sua chave pública, prova de que possui a chave privada correspondente e algumas informações específicas sobre você. Em seguida, você assina digitalmente as informações e envia o pacote completo – a solicitação de certificado – para a CA. A CA então realiza algumas diligências para verificar se as informações fornecidas estão corretas e, em caso afirmativo, gera o certificado e o devolve.
Você pode pensar em um certificado X.509 como um certificado de papel padrão (semelhante ao que você recebeu ao concluir uma aula de primeiros socorros básicos) com uma chave pública colada nele. Ele contém seu nome e algumas informações sobre você, além da assinatura da pessoa que o emitiu para você.
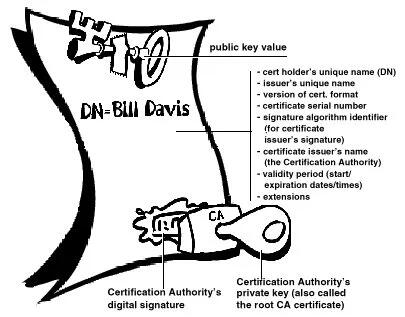
Figura 1-10. Um certificado X.509 Provavelmente, o uso mais visível dos certificados X.509 atualmente é em navegadores da web.
Validade e confiança Cada usuário em um sistema de chave pública está vulnerável a confundir uma chave falsa (certificado) com uma chave real. Validade é a confiança de que um certificado de chave pública pertence ao seu suposto proprietário. A validade é essencial em um ambiente de chave pública onde você deve estabelecer constantemente se um determinado certificado é autêntico ou não. Depois de ter certeza de que um certificado pertencente a outra pessoa é válido, você pode assinar a cópia em seu chaveiro para atestar que verificou o certificado e que ele é autêntico. Se quiser que outras pessoas saibam que você deu ao certificado seu selo de aprovação, você pode exportar a assinatura para um servidor de certificados para que outras pessoas possam vê-la.
Conforme descrito na seção Infraestruturas de Chave Pública , algumas empresas designam uma ou mais Autoridades de Certificação (CAs) para indicar a validade do certificado. Em uma organização que usa uma PKI com certificados X.509, é função da CA emitir certificados aos usuários — um processo que geralmente envolve responder à solicitação de certificado do usuário. Em uma organização que usa certificados PGP sem PKI, é função da CA verificar a autenticidade de todos os certificados PGP e depois assinar os bons. Basicamente, o objetivo principal de uma CA é vincular uma chave pública às informações de identificação contidas no certificado e, assim, garantir a terceiros que algum cuidado foi tomado para garantir que esta ligação das informações de identificação e da chave seja válida. O CA é o Grand Pooh-bah da validação em uma organização; alguém em quem todos confiam e, em algumas organizações, como aquelas que utilizam uma PKI, nenhum certificado é considerado válido, a menos que tenha sido assinado por uma CA confiável.
Verificando validade.
Uma maneira de estabelecer a validade é passar por algum processo manual. Existem várias maneiras de fazer isso. Você pode exigir que o destinatário pretendido lhe entregue fisicamente uma cópia de sua chave pública. Mas isto é muitas vezes inconveniente e ineficiente. Outra forma é verificar manualmente a impressão digital do certificado. Assim como as impressões digitais de cada ser humano são únicas, a impressão digital de cada certificado PGP é única. A impressão digital é um hash do certificado do usuário e aparece como uma das propriedades do certificado. No PGP, a impressão digital pode aparecer como um número hexadecimal ou uma série das chamadas palavras biométricas, que são foneticamente distintas e são usadas para facilitar um pouco o processo de identificação da impressão digital. Você pode verificar se um certificado é válido ligando para o proprietário da chave (para que você origine a transação) e pedindo ao proprietário que leia a impressão digital de sua chave para você e compare essa impressão digital com aquela que você acredita ser a verdadeira. Isso funciona se você conhece a voz do proprietário, mas como verificar manualmente a identidade de alguém que você não conhece? Algumas pessoas colocam a impressão digital de sua chave em seus cartões de visita exatamente por esse motivo. Outra forma de estabelecer a validade do certificado de alguém é confiar que um terceiro indivíduo passou pelo processo de validação do mesmo. Uma CA, por exemplo, é responsável por garantir que, antes de emitir um certificado, ele ou ela o verifique cuidadosamente para ter certeza de que a parte da chave pública realmente pertence ao suposto proprietário. Qualquer pessoa que confie na CA considerará automaticamente quaisquer certificados assinados pela CA como válidos. Outro aspecto da verificação da validade é garantir que o certificado não foi revogado. Para obter mais informações, consulte a seção Revogação de certificado .
Estabelecendo confiança.
Você valida certificados. Você confia nas pessoas. Mais especificamente, você confia nas pessoas para validar os certificados de outras pessoas. Normalmente, a menos que o proprietário lhe entregue o certificado, você terá que confiar na palavra de outra pessoa de que ele é válido.
Introdutores meta e confiáveis.
Na maioria das situações, as pessoas confiam completamente na CA para estabelecer a validade dos certificados. Isso significa que todos os demais dependem da CA para passar por todo o processo de validação manual. Isso é aceitável até um certo número de usuários ou locais de trabalho e, então, não é possível para a AC manter o mesmo nível de validação de qualidade. Nesse caso, é necessário adicionar outros validadores ao sistema.
Um CA também pode ser um meta- introdutor. Um meta-introdutor confere não apenas validade às chaves, mas também confere a capacidade de confiar nas chaves a outros. Semelhante ao rei que entrega seu selo a seus conselheiros de confiança para que eles possam agir de acordo com sua autoridade, o meta-introdutor permite que outros atuem como introdutores de confiança. Esses introdutores confiáveis podem validar chaves com o mesmo efeito do meta-introdutor. Eles não podem, entretanto, criar novos introdutores confiáveis.
Meta-introdutor e introdutor confiável são termos PGP. Em um ambiente X.509, o meta-introdutor é chamado de Autoridade de Certificação raiz ( CA raiz) e os introdutores confiáveis são Autoridades de Certificação subordinadas . A CA raiz usa a chave privada associada a um tipo de certificado especial denominado certificado CA raiz para assinar certificados. Qualquer certificado assinado pelo certificado CA raiz é visto como válido por qualquer outro certificado assinado pela raiz. Este processo de validação funciona mesmo para certificados assinados por outras CAs no sistema — desde que o certificado da CA raiz tenha assinado o certificado da CA subordinada, qualquer certificado assinado pela CA será considerado válido para outras pessoas dentro da hierarquia. Este processo de verificação de backup por meio do sistema para ver quem assinou cujo certificado é chamado de rastreamento de um caminho de certificação ou cadeia de certificação.
Modelos de confiança.
Em sistemas relativamente fechados, como em uma pequena empresa, é fácil rastrear um caminho de certificação até a CA raiz. No entanto, os usuários muitas vezes precisam se comunicar com pessoas fora do seu ambiente corporativo, incluindo algumas que nunca conheceram, como fornecedores, consumidores, clientes, associados e assim por diante. É difícil estabelecer uma linha de confiança com aqueles em quem sua CA não confia explicitamente. As empresas seguem um ou outro modelo de confiança, que determina como os usuários irão estabelecer a validade do certificado. Existem três modelos diferentes:
Confiança Direta.
Confiança Hierárquica Uma teia de confiança Confiança direta A confiança direta é o modelo de confiança mais simples. Neste modelo, um usuário confia que uma chave é válida porque sabe de onde ela veio. Todos os criptosistemas usam essa forma de confiança de alguma forma. Por exemplo, em navegadores da Web, as chaves raiz da Autoridade de Certificação são diretamente confiáveis porque foram enviadas pelo fabricante. Se houver alguma forma de hierarquia, ela se estenderá a partir desses certificados diretamente confiáveis. No PGP, um usuário que valida as chaves e nunca define outro certificado para ser um introdutor confiável está usando confiança direta.
 Figura 1-11. Confiança direta
Figura 1-11. Confiança diretaConfiança Hierárquica.
Em um sistema hierárquico, há vários certificados "raiz" a partir dos quais a confiança se estende. Esses certificados podem certificar eles próprios certificados ou podem certificar certificados que certificam ainda outros certificados em alguma cadeia. Considere isso como uma grande “árvore” de confiança. A validade do certificado "folha" é verificada rastreando desde seu certificador até outros certificadores, até que um certificado raiz diretamente confiável seja encontrado.
Figura 1-12. Confiança hierárquica
Teia de Confiança.
Uma teia de confiança abrange ambos os outros modelos, mas também acrescenta a noção de que a confiança está nos olhos de quem vê (que é a visão do mundo real) e a ideia de que mais informação é melhor. É, portanto, um modelo de confiança cumulativa. Um certificado pode ser confiável diretamente ou confiável em alguma cadeia que remonta a um certificado raiz diretamente confiável (o meta-introdutor) ou por algum grupo de introdutores.
Talvez você já tenha ouvido falar do termo seis graus de separação, que sugere que qualquer pessoa no mundo pode determinar algum vínculo com qualquer outra pessoa no mundo usando seis ou menos outras pessoas como intermediários. Esta é uma teia de introdutores. É também a visão de confiança do PGP. PGP usa assinaturas digitais como forma de introdução. Quando qualquer usuário assina a chave de outro, ele ou ela se torna o introdutor dessa chave. À medida que esse processo avança, ele estabelece uma rede de confiança.
Em um ambiente PGP, qualquer usuário pode atuar como autoridade certificadora. Qualquer usuário PGP pode validar o certificado de chave pública de outro usuário PGP. No entanto, tal certificado só é válido para outro usuário se a parte confiável reconhecer o validador como um introdutor confiável. (Ou seja, você confia na minha opinião de que as chaves dos outros são válidas apenas se você me considerar um apresentador confiável. Caso contrário, minha opinião sobre a validade das outras chaves é discutível.) Armazenados no chaveiro público de cada usuário estão indicadores de
● se o usuário considera ou não uma chave específica válida
● o nível de confiança que o usuário deposita na chave que o proprietário da chave pode servir como certificador das chaves de terceiros
Você indica, na sua cópia da minha chave, se acha que meu julgamento conta. Na verdade, é um sistema de reputação: certas pessoas têm a reputação de fornecer boas assinaturas e as pessoas confiam nelas para atestar a validade de outras chaves.
Níveis de confiança no PGP.
O nível mais alto de confiança em uma chave, a confiança implícita , é a confiança em seu próprio par de chaves. O PGP assume que se você possui a chave privada, você deve confiar nas ações da sua chave pública relacionada. Quaisquer chaves assinadas pela sua chave implicitamente confiável são válidas.
Existem três níveis de confiança que você pode atribuir à chave pública de outra pessoa:
● Confiança total ● Confiança marginal ● Não confiável (ou não confiável)
Para tornar as coisas confusas, também existem três níveis de validade:
● Válido ● Marginalmente válido ● Inválido
Para definir a chave de outra pessoa como um introdutor confiável, você
- Comece com uma chave válida, que seja.
- assinado por você ou
-
assinado por outro apresentador confiável e então
-
Defina o nível de confiança que você acha que o proprietário da chave tem direito.
Por exemplo, suponha que seu chaveiro contenha a chave de Alice. Você validou a chave de Alice e indica isso assinando-a. Você sabe que Alice é uma verdadeira defensora da validação de chaves de outras pessoas. Portanto, você atribui a chave dela com confiança total. Isso faz de Alice uma Autoridade Certificadora. Se Alice assinar a chave de outra pessoa, ela aparecerá como Válida em seu chaveiro. O PGP requer uma assinatura Totalmente confiável ou duas assinaturas Marginalmente confiáveis para estabelecer uma chave como válida. O método do PGP de considerar dois Marginais iguais a um Completo é semelhante a um comerciante que solicita duas formas de identificação. Você pode considerar Alice bastante confiável e também considerar Bob bastante confiável. Qualquer um deles sozinho corre o risco de assinar acidentalmente uma chave falsificada, portanto, você pode não depositar total confiança em nenhum deles. No entanto, as probabilidades de ambos os indivíduos terem assinado a mesma chave falsa são provavelmente pequenas.
Revogação de certificado.
Os certificados só são úteis enquanto são válidos. Não é seguro simplesmente presumir que um certificado é válido para sempre. Na maioria das organizações e em todas as PKIs, os certificados têm uma vida útil restrita. Isso restringe o período em que um sistema fica vulnerável caso ocorra um comprometimento do certificado.
Os certificados são assim criados com um período de validade programado: uma data/hora de início e uma data/hora de expiração. Espera-se que o certificado seja utilizável durante todo o seu período de validade (seu tempo de vida ). Quando o certificado expirar, ele não será mais válido, pois a autenticidade do seu par chave/identificação não estará mais garantida. (O certificado ainda pode ser usado com segurança para reconfirmar informações que foram criptografadas ou assinadas dentro do período de validade – no entanto, ele não deve ser confiável para tarefas criptográficas futuras.)
Existem também situações em que é necessário invalidar um certificado antes da sua data de expiração, como quando o titular do certificado termina o contrato de trabalho com a empresa ou suspeita que a chave privada correspondente do certificado foi comprometida. Isso é chamado de revogação. Um certificado revogado é muito mais suspeito do que um certificado expirado. Os certificados expirados são inutilizáveis, mas não apresentam a mesma ameaça de comprometimento que um certificado revogado. Qualquer pessoa que tenha assinado um certificado pode revogar a sua assinatura no certificado (desde que utilize a mesma chave privada que criou a assinatura). Uma assinatura revogada indica que o signatário não acredita mais que a chave pública e as informações de identificação pertencem uma à outra, ou que a chave pública do certificado (ou a chave privada correspondente) foi comprometida. Uma assinatura revogada deve ter quase tanto peso quanto um certificado revogado. Com certificados X.509, uma assinatura revogada é praticamente igual a um certificado revogado, visto que a única assinatura no certificado é aquela que o tornou válido em primeiro lugar – a assinatura da CA. Os certificados PGP fornecem o recurso adicional de que você pode revogar todo o seu certificado (não apenas as assinaturas nele) se você achar que o certificado foi comprometido. Somente o proprietário do certificado (o detentor da chave privada correspondente) ou alguém que o proprietário do certificado tenha designado como revogador pode revogar um certificado PGP. (Designar um revogador é uma prática útil, pois muitas vezes é a perda da senha da chave privada correspondente do certificado que leva um usuário PGP a revogar seu certificado - uma tarefa que só é possível se alguém tiver acesso à chave privada. ) Somente o emissor do certificado pode revogar um certificado X.509.
Comunicar que um certificado foi revogado.
Quando um certificado é revogado, é importante conscientizar os usuários potenciais do certificado de que ele não é mais válido. Com certificados PGP, a maneira mais comum de comunicar que um certificado foi revogado é publicá-lo em um servidor de certificados para que outras pessoas que desejem se comunicar com você sejam avisadas para não usar essa chave pública. Em um ambiente PKI, a comunicação de certificados revogados é mais comumente obtida por meio de uma estrutura de dados chamada Lista de Revogação de Certificados, ou CRL, que é publicada pela CA. A CRL contém uma lista validada com carimbo de data e hora de todos os certificados revogados e não expirados no sistema. Os certificados revogados permanecem na lista apenas até expirarem e, em seguida, são removidos da lista — isso evita que a lista fique muito longa. A CA distribui a CRL aos usuários em algum intervalo programado regularmente (e potencialmente fora do ciclo, sempre que um certificado é revogado). Teoricamente, isso impedirá que os usuários usem involuntariamente um certificado comprometido. É possível, no entanto, que haja um período de tempo entre as CRLs em que um certificado recentemente comprometido seja usado.
O que é uma senha?
A maioria das pessoas está familiarizada com a restrição de acesso a sistemas de computador por meio de uma senha, que é uma sequência única de caracteres que um usuário digita como código de identificação.
Uma senha longa é uma versão mais longa de uma senha e, em teoria, mais segura. Normalmente composta por várias palavras, uma frase secreta é mais segura contra ataques de dicionário padrão, em que o invasor tenta todas as palavras do dicionário na tentativa de determinar sua senha. As melhores senhas são relativamente longas e complexas e contêm uma combinação de letras maiúsculas e minúsculas, caracteres numéricos e de pontuação. O PGP usa uma senha para criptografar sua chave privada em sua máquina. Sua chave privada é criptografada em seu disco usando um hash de sua senha como chave secreta. Você usa a senha para descriptografar e usar sua chave privada. Uma senha deve ser difícil de esquecer e difícil de ser adivinhada por outras pessoas. Deve ser algo já firmemente enraizado na sua memória de longo prazo, em vez de algo que você invente do zero. Por que? Porque se você esquecer sua senha, você estará sem sorte. Sua chave privada é total e absolutamente inútil sem sua senha e nada pode ser feito a respeito. Lembra-se da citação anterior neste capítulo?
 PGP é a criptografia que manterá os principais governos fora dos seus arquivos. Certamente também o manterá fora de seus arquivos. Tenha isso em mente quando decidir alterar sua senha para a piada daquela piada que você nunca consegue lembrar.
PGP é a criptografia que manterá os principais governos fora dos seus arquivos. Certamente também o manterá fora de seus arquivos. Tenha isso em mente quando decidir alterar sua senha para a piada daquela piada que você nunca consegue lembrar.Divisão de chave.
Dizem que um segredo não é segredo se for conhecido por mais de uma pessoa. Compartilhar um par de chaves privadas representa um grande problema. Embora não seja uma prática recomendada, às vezes é necessário compartilhar um par de chaves privadas. Chaves de assinatura corporativa, por exemplo, são chaves privadas usadas por uma empresa para assinar – por exemplo – documentos legais, informações pessoais confidenciais ou comunicados de imprensa para autenticar sua origem. Nesse caso, vale a pena que vários membros da empresa tenham acesso à chave privada. No entanto, isto significa que qualquer indivíduo pode agir plenamente em nome da empresa. Nesse caso, é aconselhável dividir a chave entre várias pessoas, de modo que mais de uma ou duas pessoas apresentem um pedaço da chave para reconstituí-la em condições utilizáveis. Se poucas peças da chave estiverem disponíveis, a chave ficará inutilizável. Alguns exemplos são dividir uma chave em três partes e exigir duas delas para reconstituir a chave, ou dividi-la em duas partes e exigir ambas as peças. Se uma conexão de rede segura for usada durante o processo de reconstituição, os acionistas da chave não precisam estar fisicamente presentes para aderirem novamente à chave.
-
 @ 1f6ca203:4fafa595
2025-04-28 22:14:04
@ 1f6ca203:4fafa595
2025-04-28 22:14:04This is my first post, with a header and regular text.
-
 @ 1f6ca203:4fafa595
2025-04-28 22:14:03
@ 1f6ca203:4fafa595
2025-04-28 22:14:03I hope you like it
 .
. -
 @ 1f6ca203:4fafa595
2025-04-28 22:14:01
@ 1f6ca203:4fafa595
2025-04-28 22:14:01Let'‘s see if they appear in the right order.
First we have an apple.
 Then we have a banana.
Then we have a banana. And lastly, a pear.
And lastly, a pear.
-
 @ 1f6ca203:4fafa595
2025-04-28 22:13:59
@ 1f6ca203:4fafa595
2025-04-28 22:13:59❤️🔥✨
-
 @ 1f6ca203:4fafa595
2025-04-28 22:13:57
@ 1f6ca203:4fafa595
2025-04-28 22:13:57And this is the regular text.
-
 @ 1f6ca203:4fafa595
2025-04-28 21:40:48
@ 1f6ca203:4fafa595
2025-04-28 21:40:48❤️🔥✨
-
 @ fe02e8ec:f07fbe0b
2025-04-28 21:23:01
@ fe02e8ec:f07fbe0b
2025-04-28 21:23:01Die baldige Ex-Außenministerin Annalena Baerbock fordert einen radikalen Wandel in der Energieversorgung hin zu einer feministischen Energiepolitik. Wie sich gezeigt habe, so sei das spanische Netz am 28.04.25 wegen toxischer Männlichkeit zusammengebrochen. Es hätte sich herausgestellt, dass alle Überlandleitungen von Männern gebaut und installiert worden waren! Dies, so Baerbock, sei ein untragbarer Zustand, der durch den resultierenden Blackout für viel Leid und Ärger gesorgt habe. Selbst Haarföhns waren nicht mehr in Betrieb zu nehmen!
«Nur Frauen sind in der Lage, derart empfindliche und sensible Ströme zu leiten. Denn Strömen liegt in ihrer Natur. Sie benötigen keine Messgeräte oder teure Transformatoren für die Strömung, da Mutter Natur – eine Frau, wie der Name schon sagt – für alles selbst sorgen wird. Man muss nur verhindern, dass maskuline Energien verströmt werden, die nämlich den Strom um 360 Grad drehen würden.»
Mit dieser Analyse empfiehlt sich Annalena B. nicht nur für höchste UN Ämter sondern ebenfalls für den Vorsitz des Weltklimarates IPCC. Aus informierten Kreisen ist zu hören, dass sie nur noch die Papstwahl abwarten möchte - schließlich wäre es Zeit für eine Päpstin - bis sie sich fürs Klima bewerben würde. Um weitere Blackouts abzuschrecken überlegt sie angeblich, ihren Namen in Blackbock zu ändern. Möglich wäre allerdings auch, dass dies alles nur erfunden ist.
Mehr Satirisches und Ernstes: www.thomas-eisinger.de
-
 @ f1f59549:f4121cfe
2025-04-28 20:21:28
@ f1f59549:f4121cfe
2025-04-28 20:21:28Ego is a fundamental part of the human condition. It provides us with the necessary ability to separate and compartmentalize ourselves from the rest of the world.
Our ego allows us to exist in the chaos of existence.
The spiritual path is seen as a way to “escape the ego” and achieve a higher state of consciousness. A state where the confines of the ego no longer hold us back from seeing things as they are and allow us to experience true bliss.
But there’s a paradox to this whole process.
By seeking spiritual advancement, we have to accept that there is something to improve and someone to do the improving.
This suggests that this improvement somehow makes us better than someone who has not achieved similar levels of improvement.
This kind of thinking is inherently egotistical.
As we advance down the spiritual path — escaping the grasp of ego and removing attachments — spirituality itself can end up feeding the ego. Most of the time, we don’t even notice it while it’s happening.
It’s an unconscious process that develops along the way. Only after we notice it within ourselves can we course-correct.
I acknowledge that writing this article is itself an example of spiritual egotism.
Who am I to talk about dissolving the ego? What are my goals for writing this piece? By pointing out the hypocrisy behind having spiritual convictions or goals, am I in some way suggesting myself to be free from these convictions?
I am in no way exempt from the clutches of spiritual egotism — I certainly have not reached enlightenment.
But the paradox is that if I had, I probably wouldn’t be talking about it now.
This is known in Buddhism as the “noble silence.”
The only way to understand what it truly means to “dissolve the ego” is by discovering it spontaneously. It is not something that can be taught.
This is the approach Zen Buddhism takes to reach enlightenment. By accepting that the truth cannot be told, the master does not try to speak it. Instead, the master simply pops the ego of his students as it bubbles up from time to time.
This employs a concept called “the middle way.”
You know that you must dissolve your ego. But you can’t, so trying it is also pointless. The middle way says, “I will do my best to escape my ego, but I accept that I will fail.”
One thing we can do is pay attention to our failings. When you perform a kind act for another person, consider the motivation behind why you did it. Was it for their sake or for yours?
If you’re able to convince yourself these acts come from selfless motives — take notice — your ego has just presented itself.
The Paradox of Spiritual Development
You want to improve yourself by changing your consciousness. But the self that needs to be improved is the same one doing the improving.
This is a paradox.
As egotistical beings, we cannot be without ego.
At its core, the very reason one seeks to dissolve the ego is to improve oneself. Whether it’s to feel well, perform more effectively, or improve relationships with others — the very desire to achieve this improvement is egotistical.
This forms a negative feedback loop. The more we attempt to remove the ego, the more egotistical we become.
Essentially, the harder we try to avoid it, the more we become it.
By choosing to take a path toward enlightenment — we can not reach enlightenment.
The great Alan Watts says it best (paraphrasing):
“As long as you think and feel that you are contained in your bag of skin, there is no way whatsoever to behave unselfishly. You can imitate unselfishness. Undergo all kinds of highly refined forms of unselfishness. But you’re still tied to the gold chains of your good deeds.”
Is There A Solution?
Not exactly, but we may be able to move closer toward enlightenment by accepting its impossibility. Simply allowing ourselves to notice this paradox in ourselves may allow us to redirect course toward the middle path once again.
Let’s look at the story of the Buddha as an example.
Siddhartha was an ascetic for several decades. Acetics of the time would do all sorts of austere techniques. He would starve himself, sleep out in the cold, and purposely subject himself to discomfort and hardship — all an attempt to dissociate from his physical body and, thus, his ego.
The goal was to “reach” enlightenment.
But all the attempts the Buddha made to get himself out of the trap failed.
Siddhartha only achieved enlightenment when he realized that the trap and the trapped are one. By this realization, there isn’t any trap left.
He realized that the spiritual journey isn’t about being on some sort of “higher level.” There is no “end goal” or plateau to reach.
The spiritual teacher Eckhart Tolle puts it another way:
“The ego has many ideas. It says, ‘I want to be a spiritual person. I want to be recognized as a spiritual person. I want to be more spiritual than all these people. And I’m definitely more spiritual than you… The essential dysfunction of the ego is still operating. This is why we have the phrase ‘the road to hell is paved with good intentions’… You have to reach the place within yourself that is unconditioned; that is what I sometimes call formless.”
Spiritual Arrogance is a Blind Spot on the Path to Enlightenment
Spirituality can help you release the firm grasp your ego has over you, but it can also reinforce it.
Spiritual arrogance arises when someone develops an identity about seeking a path to enlightenment. It’s sometimes referred to as “spiritual narcissism.”
It’s what happens when you feel like people just “aren’t quite on your level.”
“High vibrations,” right?
As the psychiatrist Gerald May wrote in his 1983 book Will and Spirit:
“Simply stated, spiritual narcissism is the unconscious use of spiritual practice, experience, and insight to increase rather than decrease self-importance.”
Spiritual arrogance emerges naturally as we engage on the spiritual path. We fool ourselves into thinking that by taking steps to become more “enlightened,” we’re in some way superior to those who do not.
We leverage spiritual practices — like yoga, meditation, or other forms of spiritual self-care — as tokens of our supposed enlightenment or moral superiority.
We may use our "spiritual" identity to look down upon others who don't share these practices or beliefs, to dodge personal responsibilities or interpersonal challenges, or to create a persona that earns us social capital.
This condition damages both the individual, who is missing the opportunity for genuine spiritual or personal growth, and the community around them, which may be subjected to their judgment, manipulation, or neglect.
The presentation of spiritual arrogance comes in all shapes and sizes.
Let’s say you join a church group or other spiritual group. Members become spiritually proud. They believe they are the ones who have the right teaching. Everybody else is a bit off the track.
Then someone comes and one-ups them. “In our circles, we’re very tolerant. And we accept all teachings and all ways as leading to the one.”
But they’re just playing the game of “we’re more tolerant than you are.”
In essence, they become a victim of their own spiritual practice — they’re blind to the paradox of the spiritual path and become lost in their own egotistical beliefs that their “way” is somehow better than everybody else’s.
Of course, the other side of this paradox comes from noticing the people around you who demonstrate signs of spiritual arrogance. Looking at someone in their arrogance can make you feel like they’re inferior.
It’s another trap — but it comes from the completely opposite angle.
We cannot escape it.
Can Spiritual Arrogance Be Avoided?
Probably not, but by learning to recognize it, we may be able to re-align ourselves towards the middle path when it inevitably appears over and over again throughout our lives.
Here are some ideas to think about for avoiding the paradoxical nature of spiritual arrogance:
1. Find your intuitive expertise & learn to flow with it
Taoists call this practice “wu-wei.” Zen Buddhists call it “mushin.” Both loosely refer to an absence of striving. It’s the constant striving to improve or reach “higher vibrations” that causes this paradox to manifest in a big way.
2. Stop judging others based on their “level”
Spirituality is not a competition; you are not here to “help” others on their spiritual journey.
3. Remain skeptical about ideas, mentors, & gurus
Nobody truly has it figured out, and if they do, they certainly aren’t talking about it.
4. Embrace the beginner’s mind
Avoid bringing your preconceptions and opinions to new ideas. Act as though you’re a child experiencing everything for the first time.
5. Be conscious about your use of social media
This is especially important when it comes to sharing your spiritual development publicly. By sharing with others, you’re feeding the ego hiding behind the curtain.
6. Avoid over-intellectualizing spirituality
This comes at the expense of direct, personal, or experiential understandings of these concepts in daily life.
7. Beware of toxic positivity
This is the belief that no matter how dire or difficult a situation is, people should maintain a positive mindset. This invalidates an authentic human emotional experience and is a form of spiritual bypassing.
Quotes on Spiritual Arrogance
“The biggest ego trip going is getting rid of your ego.” — Alan Watts
“If it’s so easy to lose Jim Carey, who’s Jim Carey?” — Jim Carey
“If an organ is working properly, you don’t feel it. When you’re thinking clearly, your brain isn’t getting in your way.” — Alan Watts
“To go beyond is as wrong as to fall short.” — Confucius
“For things to reveal themselves to us, we need to be ready to abandon our views about them.” — Thich Nhat Hanh
“No matter what the practice or teaching, ego loves to wait in ambush to appropriate spirituality for its own survival and gain.” ― Chögyam Trungpa
Zen Koans About Spiritual Arrogance
The beauty of Zen koans is that they can be used to “impart wisdom” that can’t otherwise be explained by words.
They’re told as a sort of joke — only the punchline isn’t spontaneous laughter — but spontaneous glimpses of enlightenment.
They all deliver some form of unexplainable wisdom that you either get at the punchline or you don’t. Just like a joke, if the koan has to be explained, it loses its power.
Subscribe to The Zen Psychedelic
Thanks for reading The Zen Psychedelic! Consider subscribing for free to receive new posts and support my work.
You can subscribe here using Nostr or follow me on Substack.
→ This post was originally published on The Zen Psychedelic Substack
-
 @ bc52210b:20bfc6de
2025-04-28 20:13:25
@ bc52210b:20bfc6de
2025-04-28 20:13:25
Imagine a world where clean, safe, and efficient nuclear power can be delivered to any corner of the globe, powering everything from small villages to bustling cities. This vision is becoming a reality with the development of nuclear modular plants—compact, portable nuclear reactors that can be shipped in standard containers and set up quickly to provide reliable energy. These innovative power sources use fission—the process of splitting atomic nuclei to release energy, the same fundamental principle that powers traditional nuclear plants—but with a twist: they utilize thorium as fuel and a molten salt system for cooling and fuel delivery. This combination offers a host of benefits that could revolutionize how we think about nuclear energy.
Portability and Deployment
One of the most significant advantages of these nuclear modular plants is their portability. Designed to fit within standard shipping containers, these reactors can be transported by truck, ship, or even air to virtually any location. This makes them ideal for remote communities, disaster relief efforts, or military operations where traditional power infrastructure is lacking or damaged. Setting up a conventional power plant typically takes years, but these modular units can be operational in a matter of weeks, providing a rapid solution to energy needs.
Safety Features
Safety is a paramount concern in nuclear energy, and modular thorium molten salt reactors (MSRs) offer several inherent safety advantages. Unlike traditional reactors that use water under high pressure, MSRs operate at atmospheric pressure, eliminating the risk of pressure-related accidents. The fuel is dissolved in the molten salt, which means there's no solid fuel that could melt down. If the reactor overheats, the salt expands, naturally slowing the fission reaction—a built-in safety mechanism. Additionally, thorium-based fuels produce less long-lived radioactive waste, reducing the long-term environmental impact.
Efficiency and Abundance
Thorium is a more abundant resource than uranium, with estimates suggesting it is three to four times more plentiful in the Earth's crust. This abundance makes thorium a sustainable fuel choice for the future. Moreover, MSRs can operate at higher temperatures than traditional reactors, leading to greater thermal efficiency. This means more electricity can be generated from the same amount of fuel, making the energy production process more efficient and cost-effective in the long run.
Scalability
The modular design of these reactors allows for scalability to meet varying power demands. A single unit might power a small community, while multiple units can be combined to serve larger towns or cities. This flexibility is particularly useful for growing populations or regions with fluctuating energy needs. As demand increases, additional modules can be added without the need for extensive new infrastructure.
Cost-Effectiveness
While the initial investment in nuclear modular plants may be significant, the long-term operational costs can be lower than traditional power sources. The high efficiency of MSRs means less fuel is needed over time, and the reduced waste production lowers disposal costs. Additionally, the ability to mass-produce these modular units could drive down manufacturing costs, making nuclear power more accessible and affordable.
Environmental Impact
Nuclear power is already one of the cleanest energy sources in terms of carbon emissions, and thorium MSRs take this a step further. By producing less long-lived waste and utilizing a more abundant fuel, these reactors offer a more sustainable path for nuclear energy. Furthermore, their ability to provide reliable baseload power can help reduce reliance on fossil fuels, contributing to global efforts to combat climate change.
Challenges and Considerations
Despite these benefits, there are challenges to overcome before nuclear modular plants can be widely deployed. The technology for thorium MSRs is still in the developmental stage, with ongoing research needed to address issues such as material corrosion and fuel processing. Regulatory frameworks will also need to adapt to this new type of reactor, and public perception of nuclear energy remains a hurdle in many regions. However, with continued investment and innovation, these obstacles can be addressed.
Conclusion
In conclusion, nuclear modular plants using thorium and molten salt systems represent a promising advancement in nuclear technology. Their portability, safety features, efficiency, scalability, and environmental benefits make them an attractive option for meeting the world's growing energy needs. While challenges remain, the potential of these reactors to provide clean, reliable power to communities around the globe is undeniable. As research and development continue, we may soon see a new era of nuclear energy that is safer, more efficient, and more accessible than ever before.
-
 @ f1f59549:f4121cfe
2025-04-28 17:57:18
@ f1f59549:f4121cfe
2025-04-28 17:57:18Is the internet making us dumber?
The answer to this question depends on how we define intelligence. If it refers to the number of facts we know and we remember — the answer is probably “yes.”
A study led by Betsy Sparrow on the impact of Google on human memory states that:
“When people expect to have future access to information, they have lower rates of recall of the information itself and enhanced recall instead for where to access it. The Internet has become a primary form of external or transactive memory, where information is stored collectively outside ourselves.”
That might not be such a bad thing — in theory, it could help preserve our limited cognitive capacity for more salient tasks, such as learning new skills, achieving mastery in our chosen domain, or soul-enriching creative pursuits. Is it really that important that we remember exactly how deep the lowest part of the ocean is or how many species of birds there are?
Maybe, maybe not.
If intelligence is measured by our ability to understand and process information — the answer is much more complicated. It depends entirely on how we use it.
Before we explore all the ways the internet undermines our cognitive abilities, I have to point out that access to the internet can easily be used to make us smarter, happier, and more connected. This is a technology that allows us to learn anything we want — quickly and cheaply. Education is no longer a privilege reserved for the rich. Now, anybody with access to a public library or a $100 smartphone can access information on any topic.
The problem is that the unfettered and unconscious use of the internet lures us into delusion and distraction.
Here are 5 ways the internet makes us dumber and some strategies for resisting them.
1. Information Overload
“The man who chases two rabbits catches none.” — Old Zen Parable.
Information overload is a problem where one is given so much information at one time they become overwhelmed and unable to process or think about it in a clear way.
We are inundated with so much information these days that we don’t even know how to make sense of it. We’re overloaded. Our attention spans are short, and we have no time leftover for deep, contemplative thought about the information we consume.
One study even found that simply having a smartphone nearby reduces one’s cognitive capacity. This study points to the “brain drain” hypothesis, which suggests that the brain has a finite amount of processing power and the mere presence of a potential distractor (like our smartphones) can occupy a large portion of these resources.
When we feel overwhelmed, we double down and attempt to cram as much information as possible — we skim 10 different articles at a time without reading anything, fast-forward through YouTube videos to try and find the most interesting parts, ask GPTs to summarize books so we don’t have to read them, and throw videos and podcasts on in the background while working on something else.
The problem is that we just aren’t very good at multitasking. Instead, our attention rapidly (and inefficiently) switches from one task to another. The process of switching focus back and forth requires additional cognitive processes that further reduce the overall capacity of the brain.
“Wherever you are, be there totally.” — Eckhart Tolle
2. Fake News
“Fake news and rumors thrive online because few verify what's real and always bias towards content that reinforces their own biases.” — Ryan Higa
The freedom of the internet means anybody can publish anything and position it as fact. Much of the information we find online is wrong, out of context, or intentionally misleading. Whether this fake information was created out of ignorance or malicious intent doesn’t really matter.
Our ability to distinguish fiction from reality becomes more difficult when we’re saturated with information. Who has the time to fact-check every article they read online?
Another major factor contributing to this issue is the proliferation of bot accounts on social media — a phenomenon that makes up a significant portion of social media profiles these days. Many of these accounts exist for the sole purpose of flooding social media with low-quality information to manipulate human behavior, ideology, and opinions. Sometimes, this is to sell you something; other times, it’s to influence the opinions of society at-large.
Despite the issue with fake news, 50% of people still get most of their news from social media — according to research conducted by Pew Research Center.
The emergence of deepfakes and AI-generated misinformation are making this problem even worse. It’s becoming easier for bad actors to generate and spread false or misleading information throughout the internet in massive quantities.
3. Junk Info
“Treat junk information the way you treat junk food. Realize that it’s crap that tastes good, and consume it sparingly. Monitor your consumption and ensure that you never trick yourself into believing it’s good for you.” — Daniel Miessler
The internet is saturated with junk information — which not only includes information that’s factually incorrect but also those with no practical use. It doesn’t make our lives any better, it doesn’t make us smarter or more capable humans, and it certainly doesn’t make us happier or more present in our lives.
Examples include clickbait, ragebait, gossip, conspiracy theories, babel, or trivial social media status updates. These types of content grab our attention just as much as high-quality content but leave us feeling empty and unsatisfied. This is why you can spend 2 hours scrolling on Instagram or Twitter, only to log off and discover you can’t remember a single piece of information you just consumed.
A major factor driving this phenomenon is that low-quality information provides us with the same dopamine hit as high-quality information but is significantly easier to manufacture. Publishers like Buzzfeed and Bored Panda take advantage of this fact by mass-producing junk information on a scale never before seen in human history.
Gurwinder eloquently describes the crisis of intellectual obesity as follows:
“Just as gorging on junk food bloats your body, so gorging on junk info bloats your mind, filling it with a cacophony of half-remembered gibberish that sidetracks your attention and confuses your senses. Unable to distinguish between relevant and irrelevant, you become concerned by trivialities and outraged by falsehoods. These concerns and outrages push you to consume even more, and all the time that you're consuming, you're prevented from doing anything else: learning, focusing, even thinking. The result is that your stream of consciousness becomes clogged; you develop atherosclerosis of the mind.”
4. Cognitive Bias
“The foolish reject what they see, not what they think — the wise reject what they think, not what they see.” — Huang Po
Cognitive bias refers to the systematic ways in which the context and framing of information influence individuals' judgment and decision-making.
The internet often acts as an echo chamber, where algorithms tailor content to our existing beliefs, reinforcing our biases rather than challenging them.
Confirmation bias, for instance, leads us to favor information that aligns with our preconceptions and dismiss evidence that contradicts them. This bias is magnified online, where we can easily find sources that support any viewpoint, no matter how fringe or unfounded. As a result, our beliefs become more entrenched, and we become less open to opposing perspectives.
Another example is the availability heuristic, which causes us to overestimate the importance of information that is readily available to us. Social media amplifies this bias by prioritizing trending topics, sensational stories, and viral content, often at the expense of more balanced or nuanced viewpoints. This can lead to distorted perceptions of reality, where rare but dramatic events seem more common than they are.
There’s also the bandwagon effect, where people adopt beliefs or behaviors because they see others doing the same. Social media platforms capitalize on this bias by prominently displaying popular posts and trending hashtags, encouraging us to conform to the majority opinion without critically evaluating the information.
5. The Attention Economy
“We find ourselves in a new stage of capitalism. One that is predicated on the ever more aggressive appropriation of our attention, often by mechanized means. This makes cultivating the habits and pleasures of deep, slow thinking a difficult matter.” — Matthew Crawford.
The attention economy is a marketplace in which human attention is treated as a scarce commodity. It’s becoming increasingly sought-after by advertisers.
The key metrics of success in this marketplace are to capture our attention with engaging content, retain it through various psychological tricks and manipulations, and milk our minds for ad dollars. The unfortunate side effect of this is that these manipulations further degrade our ability to think clearly and form logical opinions.
Attention is an important part of the human experience. It’s what connects us with the outside world. Even outside the realm of the internet, different forms of stimuli are constantly seeking our attention — we’ve evolved various internal mechanisms to ignore what isn’t important so we can preserve our energy for what is.
Through the magic of the internet, companies have learned ways to infiltrate our minds and override these internal defense mechanisms.
Just like any other commodity, human attention is subject to the rules of supply and demand. Our personal supply of attention is finite — there’s only so much time in a day, so our attention can only be given to a limited number of things. Tech companies need to innovate ways to maximize the amount of users that interact with their product and extend the time each person is willing to remain engaged.
How Apps Manipulate Our Emotions & Harvest Our Attention
“It is very common for humans to develop things with the best of intentions that have unintended, negative consequences.” — Justin Rosenstein, creator of the 'like' button.
Social media apps use numerous psychological tactics to induce emotions that keep us on the platform.
Here are just a few of the subtle design tweaks these apps employ that unconsciously manipulate our emotions:
-
Using the color red for notifications — Red is a trigger color, inducing a sense of alarm. Facebook used to use a blue notification icon (to match their logo); however, developers noted that nobody was paying attention, so they changed it to red, and suddenly, engagement with the feature skyrocketed.
-
Variable rewards — The notification centers of apps intentionally hide the specifics of our interactions to keep us in a state of anticipation. It could be a whole bunch of new likes, some new followers, or absolutely nothing at all. The anticipation of not knowing what kind of surprises could be in store for us is exciting, and clicking the dropdown to explore becomes a compulsive habit.
-
The pull-to-refresh feature — This loading feature was a happy accident. Loren Brichter invented it for his app, Tweetie (before it was bought by Twitter), simply because there wasn’t a good space to add a refresh button. However, this invention turned out to be a boon for manipulating users' emotions. The little “loading” animation makes us think it’s gathering data, but this delay is intentional. It gives us a sense of anticipation, which is addicting… sort of like the pull of a slot machine.
-
Infinite scrolling — Users can continuously scroll through content without ever hitting a stopping point. This design keeps users engaged for long periods of time as there’s always something new just a swipe away. It takes advantage of our natural inclination to keep looking for more information and makes it hard to break free from the app.
-
Social validation loops — Features like likes, comments, and shares create a feedback loop that keeps users coming back for more. Each notification of social validation triggers a release of dopamine, reinforcing the behavior and making users more likely to continue engaging with the app in search of more juicy validation.
 # Tech Execs Who Refuse to Get High on Their Own Supply
# Tech Execs Who Refuse to Get High on Their Own SupplyNobody understands the power of gaming human attention than the tech executives and developers working behind the scenes to keep us hooked on their products.
Over the years, several high-profile individuals working for Google, Meta, Twitter, and Apple have disclosed some of the extreme lengths they go through to avoid getting sucked into the cognitive wormholes their products create.
Here are just a few examples:
Nir Eyal
(Tech consultant and author of Hooked: How to Build Habit-Forming Products and Indistractable: How to Control Your Attention and Choose Your Life).
Nir Eyal once confided in the lengths he goes to protect his own family from the addictive nature of unfettered internet access in an interview with Thrive Global.
Eyal shuts his phone off at 10 pm and keeps it out of his bedroom while he sleeps. He’s even installed an outlet timer on his home router to cut off internet access for his whole house at the same time every day.
“The idea is to remember that we are not powerless. We are in control.”
Justin Rosenstein
(Creator of the like button).
Justin reports that he’s tweaked his laptop’s operating system to block Reddit, banned himself from Snapchat (which he compares to heroin), and imposed limits on his use of Facebook.
But even that wasn’t enough.
Last year, Justin took an even more radical approach to restrict his use of addictive technologies. He ordered a new phone and asked his assistant to set up parental controls that block him from downloading any new apps.
Loren Brichter
(Designer of the pull-to-refresh feature).
Brichter, like other tech execs, has blocked certain websites, turned off push notifications, restricted his use of the Telegram app to message only with his wife and two close friends, and tried to wean himself off Twitter.
“I still waste time on it just reading stupid news I already know about.”
He charges his phone in the kitchen, plugging it in at 7 pm and not touching it until the next morning.
Tristan Harris
(Co-founder of the Center for Humane Technology and former Google design ethicist).
Tristan Harris, who has been vocal about the manipulative design practices of tech companies for years, takes various steps to protect himself. He uses a grayscale screen on his phone to make it less appealing and has removed all social media apps. Harris also sets specific times for checking emails and messages, ensuring that he’s not constantly distracted throughout the day.
“There’s a hidden goal driving all of our technology, and that goal is the race for our attention.”
 # Becoming Smarter in the Age of Information
# Becoming Smarter in the Age of InformationThe internet is a double-edged sword. It’s a place we can go to learn, connect, and create, but also a source of delusion, distraction, and misinformation.
Learning to navigate and engage with it wisely can ultimately help us grow to become more present, focused, and content in our daily activities — but only if we establish a foundation of discipline and intentionality.
None of these concepts are new. People like Marshall McLuhan have been talking about the influence of electronic media several years before the internet was even invented.
However, as technologies become more sophisticated and pervasive in our daily lives, we’re learning to adapt and find balance.
In the spirit of acknowledging our need for quick, bite-sized information snippets (wink wink), I’ll conclude with 10 quick strategies we can adopt to resist the distractions of the internet and preserve our cognitive resources to become smarter, happier, more capable humans.
10 Strategies to Thrive in the Information Age
-
Silo your attention — focus on one thing at a time.
-
Avoid going to social media for news.
-
Identify and limit junk information.
-
Seek out diverse perspectives and challenge your cognitive biases.
-
Treat your time and attention with respect — prioritize activities that enrich your life.
-
Limit internet and device usage — consider placing an outlet timer on your internet router.
-
Block or delete distracting websites and apps.
-
Implement grayscale screens.
-
Charge your phone outside your bedroom at night.
-
Practice tech-free days.
-










