-
 @ 40b9c85f:5e61b451
2025-04-24 15:27:02
@ 40b9c85f:5e61b451
2025-04-24 15:27:02Introduction
Data Vending Machines (DVMs) have emerged as a crucial component of the Nostr ecosystem, offering specialized computational services to clients across the network. As defined in NIP-90, DVMs operate on an apparently simple principle: "data in, data out." They provide a marketplace for data processing where users request specific jobs (like text translation, content recommendation, or AI text generation)
While DVMs have gained significant traction, the current specification faces challenges that hinder widespread adoption and consistent implementation. This article explores some ideas on how we can apply the reflection pattern, a well established approach in RPC systems, to address these challenges and improve the DVM ecosystem's clarity, consistency, and usability.
The Current State of DVMs: Challenges and Limitations
The NIP-90 specification provides a broad framework for DVMs, but this flexibility has led to several issues:
1. Inconsistent Implementation
As noted by hzrd149 in "DVMs were a mistake" every DVM implementation tends to expect inputs in slightly different formats, even while ostensibly following the same specification. For example, a translation request DVM might expect an event ID in one particular format, while an LLM service could expect a "prompt" input that's not even specified in NIP-90.
2. Fragmented Specifications
The DVM specification reserves a range of event kinds (5000-6000), each meant for different types of computational jobs. While creating sub-specifications for each job type is being explored as a possible solution for clarity, in a decentralized and permissionless landscape like Nostr, relying solely on specification enforcement won't be effective for creating a healthy ecosystem. A more comprehensible approach is needed that works with, rather than against, the open nature of the protocol.
3. Ambiguous API Interfaces
There's no standardized way for clients to discover what parameters a specific DVM accepts, which are required versus optional, or what output format to expect. This creates uncertainty and forces developers to rely on documentation outside the protocol itself, if such documentation exists at all.
The Reflection Pattern: A Solution from RPC Systems
The reflection pattern in RPC systems offers a compelling solution to many of these challenges. At its core, reflection enables servers to provide metadata about their available services, methods, and data types at runtime, allowing clients to dynamically discover and interact with the server's API.
In established RPC frameworks like gRPC, reflection serves as a self-describing mechanism where services expose their interface definitions and requirements. In MCP reflection is used to expose the capabilities of the server, such as tools, resources, and prompts. Clients can learn about available capabilities without prior knowledge, and systems can adapt to changes without requiring rebuilds or redeployments. This standardized introspection creates a unified way to query service metadata, making tools like
grpcurlpossible without requiring precompiled stubs.How Reflection Could Transform the DVM Specification
By incorporating reflection principles into the DVM specification, we could create a more coherent and predictable ecosystem. DVMs already implement some sort of reflection through the use of 'nip90params', which allow clients to discover some parameters, constraints, and features of the DVMs, such as whether they accept encryption, nutzaps, etc. However, this approach could be expanded to provide more comprehensive self-description capabilities.
1. Defined Lifecycle Phases
Similar to the Model Context Protocol (MCP), DVMs could benefit from a clear lifecycle consisting of an initialization phase and an operation phase. During initialization, the client and DVM would negotiate capabilities and exchange metadata, with the DVM providing a JSON schema containing its input requirements. nip-89 (or other) announcements can be used to bootstrap the discovery and negotiation process by providing the input schema directly. Then, during the operation phase, the client would interact with the DVM according to the negotiated schema and parameters.
2. Schema-Based Interactions
Rather than relying on rigid specifications for each job type, DVMs could self-advertise their schemas. This would allow clients to understand which parameters are required versus optional, what type validation should occur for inputs, what output formats to expect, and what payment flows are supported. By internalizing the input schema of the DVMs they wish to consume, clients gain clarity on how to interact effectively.
3. Capability Negotiation
Capability negotiation would enable DVMs to advertise their supported features, such as encryption methods, payment options, or specialized functionalities. This would allow clients to adjust their interaction approach based on the specific capabilities of each DVM they encounter.
Implementation Approach
While building DVMCP, I realized that the RPC reflection pattern used there could be beneficial for constructing DVMs in general. Since DVMs already follow an RPC style for their operation, and reflection is a natural extension of this approach, it could significantly enhance and clarify the DVM specification.
A reflection enhanced DVM protocol could work as follows: 1. Discovery: Clients discover DVMs through existing NIP-89 application handlers, input schemas could also be advertised in nip-89 announcements, making the second step unnecessary. 2. Schema Request: Clients request the DVM's input schema for the specific job type they're interested in 3. Validation: Clients validate their request against the provided schema before submission 4. Operation: The job proceeds through the standard NIP-90 flow, but with clearer expectations on both sides
Parallels with Other Protocols
This approach has proven successful in other contexts. The Model Context Protocol (MCP) implements a similar lifecycle with capability negotiation during initialization, allowing any client to communicate with any server as long as they adhere to the base protocol. MCP and DVM protocols share fundamental similarities, both aim to expose and consume computational resources through a JSON-RPC-like interface, albeit with specific differences.
gRPC's reflection service similarly allows clients to discover service definitions at runtime, enabling generic tools to work with any gRPC service without prior knowledge. In the REST API world, OpenAPI/Swagger specifications document interfaces in a way that makes them discoverable and testable.
DVMs would benefit from adopting these patterns while maintaining the decentralized, permissionless nature of Nostr.
Conclusion
I am not attempting to rewrite the DVM specification; rather, explore some ideas that could help the ecosystem improve incrementally, reducing fragmentation and making the ecosystem more comprehensible. By allowing DVMs to self describe their interfaces, we could maintain the flexibility that makes Nostr powerful while providing the structure needed for interoperability.
For developers building DVM clients or libraries, this approach would simplify consumption by providing clear expectations about inputs and outputs. For DVM operators, it would establish a standard way to communicate their service's requirements without relying on external documentation.
I am currently developing DVMCP following these patterns. Of course, DVMs and MCP servers have different details; MCP includes capabilities such as tools, resources, and prompts on the server side, as well as 'roots' and 'sampling' on the client side, creating a bidirectional way to consume capabilities. In contrast, DVMs typically function similarly to MCP tools, where you call a DVM with an input and receive an output, with each job type representing a different categorization of the work performed.
Without further ado, I hope this article has provided some insight into the potential benefits of applying the reflection pattern to the DVM specification.
-
 @ 5df413d4:2add4f5b
2025-05-01 12:31:09
@ 5df413d4:2add4f5b
2025-05-01 12:31:09𝗦𝗰𝗮𝗹𝗲: 𝗧𝗵𝗲 𝗨𝗻𝗶𝘃𝗲𝗿𝘀𝗮𝗹 𝗟𝗮𝘄𝘀 𝗼𝗳 𝗟𝗶𝗳𝗲, 𝗚𝗿𝗼𝘄𝘁𝗵, 𝗮𝗻𝗱 𝗗𝗲𝗮𝘁𝗵 𝗶𝗻 𝗢𝗿𝗴𝗮𝗻𝗶𝘀𝗺𝘀, 𝗖𝗶𝘁𝗶𝗲𝘀, 𝗮𝗻𝗱 𝗖𝗼𝗺𝗽𝗮𝗻𝗶𝗲𝘀 𝗯𝘆 𝗚𝗲𝗼𝗳𝗳𝗿𝗲𝘆 𝗪𝗲𝘀𝘁

This book is a wonderfully cross-disciplinary exercise in fractal discovery and insight onto our world - initially the result of the author's pondering his own mortality which led to a study of longevity across organisms, and then expanded to social structures like cities and companies.
In the book, “scale" itself, conceptually, is defined as "how systems respond to changes in size." Does doubling an animal's dimensions increase its relative strength? Does doubling a city's size double it's relative rate of crime? These 2 questions introduce the key distinctions between sublinear scaling (the larger the thing, the relatively less of some characteristic it has) and superlinear scaling (the larger the thing, the relatively more of some characteristic it has), respectively.
Organisms, we discover, scale sublinearally - larger animals are more efficient requiring less energy per unit of weight, but similarly they become, relatively structurally weaker as size increases - this is why Godzilla cannot exist, he would collapse under his own weight! Further, biological metabolic rates scale sublinearlly to size, so as the organism grows, energy demands of cellular maintenance outstrips supply leading to cessation of growth and eventual death (we also find companies face a similar fate, with "costs" replacing cellular maintenance).
Cities, however, are more interesting. In terms of infrastructure they scale like organisms (sublinearlly), but in terms of emergent human outputs, they scale superlinearlly - the larger the city, the relatively more patents, companies, GDP, crime, and disease it will host. For cities, superlinear scaling of those emergent human properties, or "social metabolism" results in the creation of social capital increasingly outpacing the demands of maintenance (those being largely infrastructural) suggesting accelerating, unbounded, open-ended growth.
With regard to growth, superlinearity results in exponential growth, which the author approaches as a terrifying and dark mathematical horror. He illustrates this with what I found to be the book's most illuminating vignette…
SCENARIO: It is 11:00. A petri dish 🧫 contains a single bacteria🦠 cell. This bacteria will double every minute. The petri dish will be completely full in 1 hour. At what time is the petri dish 🧫 50% full?
If you said anything other than 11:59, you've missed the key implication of exponential growth. Exponential growth is slowly, then all at once. But let’s double down on this to really underscore that point - at what time does the petri dish in the aforementioned scenarios become just 1% full? The answer is somewhere between 11:53 and 11:54. Reflect on that.
What might this kind of acceleration in growth mean for technological advancement? For human population and biosphere carrying capacity? For resource consumption? And for how all of these things interrelate and impact each other? Quite thankfully, the book rejects Malthusianism. While still raising legitimate questions about the math of an exponentially expanding Earthbound civilization's sustainability, the author rightfully points to the imperative to harness nuclear and solar energy at-scale as our best hopes to sustain requirements both continuous population and technological acceleration.
Finally, the examination of exponentiality brings us to the deepest conundrum identified in the book - the finite time singularity - where unbounded growth cannot sustain without either (1) infinite energy or (2) paradigm shift "reset" that temporarily staves off system collapse. But wait! There's more! The mathematics of superlinearity suggest that, in absence of infinite energy, the chain of paradigm shift resets are themselves required to happen at an ever faster and faster pace, or at shorter and shorter intervals.
So, if we are confined to Earth's closed system, the need for continuous and unending paradigm shift innovations at ever-shorter intervals eventually manifests a meta-finite time singularity, the essential singularity which is perhaps, inescapable. The core insight to be extrapolated here is that if we are to overcome the singularity trap, we must drive real, constant step-function innovation and that this innovation must, almost necessarily, allow us to progressively harness orders of magnitude more energy than today - think Dyson Spheres, interstellar / intergalactic travel, quasar bitcoin mining, and so on.
CONCLUSION: Dense yet whimsical, lengthy yet very fun. Questing and questioning cover to cover. Great for anyone interested in inter-disciplinarianism and fractal thinking (the long practice of which I find lends to heightened levels of predictive intuition) (4.5/5☢️)
https://www.amazon.com/Scale-Universal-Growth-Organisms-Companies/dp/014311090X
Bitcoin #Plebchain #Coffeechain #Books #Bookstr #Nostr #NostrLove #GrowNostr #Writestr #Createstr
-
 @ 21335073:a244b1ad
2025-05-01 01:51:10
@ 21335073:a244b1ad
2025-05-01 01:51:10Please respect Virginia Giuffre’s memory by refraining from asking about the circumstances or theories surrounding her passing.
Since Virginia Giuffre’s death, I’ve reflected on what she would want me to say or do. This piece is my attempt to honor her legacy.
When I first spoke with Virginia, I was struck by her unshakable hope. I had grown cynical after years in the anti-human trafficking movement, worn down by a broken system and a government that often seemed complicit. But Virginia’s passion, creativity, and belief that survivors could be heard reignited something in me. She reminded me of my younger, more hopeful self. Instead of warning her about the challenges ahead, I let her dream big, unburdened by my own disillusionment. That conversation changed me for the better, and following her lead led to meaningful progress.
Virginia was one of the bravest people I’ve ever known. As a survivor of Epstein, Maxwell, and their co-conspirators, she risked everything to speak out, taking on some of the world’s most powerful figures.
She loved when I said, “Epstein isn’t the only Epstein.” This wasn’t just about one man—it was a call to hold all abusers accountable and to ensure survivors find hope and healing.
The Epstein case often gets reduced to sensational details about the elite, but that misses the bigger picture. Yes, we should be holding all of the co-conspirators accountable, we must listen to the survivors’ stories. Their experiences reveal how predators exploit vulnerabilities, offering lessons to prevent future victims.
You’re not powerless in this fight. Educate yourself about trafficking and abuse—online and offline—and take steps to protect those around you. Supporting survivors starts with small, meaningful actions. Free online resources can guide you in being a safe, supportive presence.
When high-profile accusations arise, resist snap judgments. Instead of dismissing survivors as “crazy,” pause to consider the trauma they may be navigating. Speaking out or coping with abuse is never easy. You don’t have to believe every claim, but you can refrain from attacking accusers online.
Society also fails at providing aftercare for survivors. The government, often part of the problem, won’t solve this. It’s up to us. Prevention is critical, but when abuse occurs, step up for your loved ones and community. Protect the vulnerable. it’s a challenging but a rewarding journey.
If you’re contributing to Nostr, you’re helping build a censorship resistant platform where survivors can share their stories freely, no matter how powerful their abusers are. Their voices can endure here, offering strength and hope to others. This gives me great hope for the future.
Virginia Giuffre’s courage was a gift to the world. It was an honor to know and serve her. She will be deeply missed. My hope is that her story inspires others to take on the powerful.
-
 @ 1c19eb1a:e22fb0bc
2025-04-30 22:02:13
@ 1c19eb1a:e22fb0bc
2025-04-30 22:02:13I am happy to present to you the first full review posted to Nostr Reviews: #Primal for #Android!
Primal has its origins as a micro-blogging, social media client, though it is now expanding its horizons into long-form content. It was first released only as a web client in March of 2023, but has since had a native client released for both iOS and Android. All of Primal's clients recently had an update to Primal 2.0, which included both performance improvements and a number of new features. This review will focus on the Android client specifically, both on phone and tablet.
Since Primal has also added features that are only available to those enrolled in their new premium subscription, it should also be noted that this review will be from the perspective of a free user. This is for two reasons. First, I am using an alternate npub to review the app, and if I were to purchase premium at some time in the future, it would be on my main npub. Second, despite a lot of positive things I have to say about Primal, I am not planning to regularly use any of their apps on my main account for the time being, for reasons that will be discussed later in the review.
The application can be installed through the Google Play Store, nostr:npub10r8xl2njyepcw2zwv3a6dyufj4e4ajx86hz6v4ehu4gnpupxxp7stjt2p8, or by downloading it directly from Primal's GitHub. The full review is current as of Primal Android version 2.0.21. Updates to the review on 4/30/2025 are current as of version 2.2.13.
In the ecosystem of "notes and other stuff," Primal is predominantly in the "notes" category. It is geared toward users who want a social media experience similar to Twitter or Facebook with an infinite scrolling feed of notes to interact with. However, there is some "other stuff" included to complement this primary focus on short and long form notes including a built-in Lightning wallet powered by #Strike, a robust advanced search, and a media-only feed.

Overall Impression
Score: 4.4 / 5 (Updated 4/30/2025)
Primal may well be the most polished UI of any Nostr client native to Android. It is incredibly well designed and thought out, with all of the icons and settings in the places a user would expect to find them. It is also incredibly easy to get started on Nostr via Primal's sign-up flow. The only two things that will be foreign to new users are the lack of any need to set a password or give an email address, and the prompt to optionally set up the wallet.
Complaints prior to the 2.0 update about Primal being slow and clunky should now be completely alleviated. I only experienced quick load times and snappy UI controls with a couple very minor exceptions, or when loading DVM-based feeds, which are outside of Primal's control.
Primal is not, however, a client that I would recommend for the power-user. Control over preferred relays is minimal and does not allow the user to determine which relays they write to and which they only read from. Though you can use your own wallet, it will not appear within the wallet interface, which only works with the custodial wallet from Strike. Moreover, and most eggregiously, the only way for existing users to log in is by pasting their nsec, as Primal does not support either the Android signer or remote signer options for users to protect their private key at this time. This lack of signer support is the primary reason the client received such a low overall score. If even one form of external signer log in is added to Primal, the score will be amended to 4.2 / 5, and if both Android signer and remote signer support is added, it will increase to 4.5.
Update: As of version 2.2.13, Primal now supports the Amber Android signer! One of the most glaring issues with the app has now been remedied and as promised, the overall score above has been increased.
Another downside to Primal is that it still utilizes an outdated direct message specification that leaks metadata that can be readily seen by anyone on the network. While the content of your messages remains encrypted, anyone can see who you are messaging with, and when. This also means that you will not see any DMs from users who are messaging from a client that has moved to the latest, and far more private, messaging spec.
That said, the beautiful thing about Nostr as a protocol is that users are not locked into any particular client. You may find Primal to be a great client for your average #bloomscrolling and zapping memes, but opt for a different client for more advanced uses and for direct messaging.
Features
Primal has a lot of features users would expect from any Nostr client that is focused on short-form notes, but it also packs in a lot of features that set it apart from other clients, and that showcase Primal's obvious prioritization of a top-tier user experience.
Home Feed
By default, the infinitely scrolling Home feed displays notes from those you currently follow in chronological order. This is traditional Nostr at its finest, and made all the more immersive by the choice to have all distracting UI elements quickly hide themselves from view as the you begin to scroll down the feed. They return just as quickly when you begin to scroll back up.

Scrolling the feed is incredibly fast, with no noticeable choppiness and minimal media pop-in if you are on a decent internet connection.
Helpfully, it is easy to get back to the top of the feed whenever there is a new post to be viewed, as a bubble will appear with the profile pictures of the users who have posted since you started scrolling.

Interacting With Notes
Interacting with a note in the feed can be done via the very recognizable icons at the bottom of each post. You can comment, zap, like, repost, and/or bookmark the note.
Notably, tapping on the zap icon will immediately zap the note your default amount of sats, making zapping incredibly fast, especially when using the built-in wallet. Long pressing on the zap icon will open up a menu with a variety of amounts, along with the ability to zap a custom amount. All of these amounts, and the messages that are sent with the zap, can be customized in the application settings.

Users who are familiar with Twitter or Instagram will feel right at home with only having one option for "liking" a post. However, users from Facebook or other Nostr clients may wonder why they don't have more options for reactions. This is one of those things where users who are new to Nostr probably won't notice they are missing out on anything at all, while users familiar with clients like #Amethyst or #noStrudel will miss the ability to react with a 🤙 or a 🫂.
It's a similar story with the bookmark option. While this is a nice bit of feature parity for Twitter users, for those already used to the ability to have multiple customized lists of bookmarks, or at minimum have the ability to separate them into public and private, it may be a disappointment that they have no access to the bookmarks they already built up on other clients. Primal offers only one list of bookmarks for short-form notes and they are all visible to the public. However, you are at least presented with a warning about the public nature of your bookmarks before saving your first one.
Yet, I can't dock the Primal team much for making these design choices, as they are understandable for Primal's goal of being a welcoming client for those coming over to Nostr from centralized platforms. They have optimized for the onboarding of new users, rather than for those who have been around for a while, and there is absolutely nothing wrong with that.
Post Creation
Composing posts in Primal is as simple as it gets. Accessed by tapping the obvious circular button with a "+" on it in the lower right of the Home feed, most of what you could need is included in the interface, and nothing you don't.

Your device's default keyboard loads immediately, and the you can start typing away.
There are options for adding images from your gallery, or taking a picture with your camera, both of which will result in the image being uploaded to Primal's media-hosting server. If you prefer to host your media elsewhere, you can simply paste the link to that media into your post.
There is also an @ icon as a tip-off that you can tag other users. Tapping on this simply types "@" into your note and brings up a list of users. All you have to do to narrow down the user you want to tag is continue typing their handle, Nostr address, or paste in their npub.

This can get mixed results in other clients, which sometimes have a hard time finding particular users when typing in their handle, forcing you to have to remember their Nostr address or go hunt down their npub by another means. Not so with Primal, though. I had no issues tagging anyone I wanted by simply typing in their handle.
Of course, when you are tagging someone well known, you may find that there are multiple users posing as that person. Primal helps you out here, though. Usually the top result is the person you want, as Primal places them in order of how many followers they have. This is quite reliable right now, but there is nothing stopping someone from spinning up an army of bots to follow their fake accounts, rendering follower count useless for determining which account is legitimate. It would be nice to see these results ranked by web-of-trust, or at least an indication of how many users you follow who also follow the users listed in the results.
Once you are satisfied with your note, the "Post" button is easy to find in the top right of the screen.
Feed Selector and Marketplace
Primal's Home feed really shines when you open up the feed selection interface, and find that there are a plethora of options available for customizing your view. By default, it only shows four options, but tapping "Edit" opens up a new page of available toggles to add to the feed selector.

The options don't end there, though. Tapping "Add Feed" will open up the feed marketplace, where an ever-growing number of custom feeds can be found, some created by Primal and some created by others. This feed marketplace is available to a few other clients, but none have so closely integrated it with their Home feeds like Primal has.

Unfortunately, as great as these custom feeds are, this was also the feature where I ran into the most bugs while testing out the app.
One of these bugs was while selecting custom feeds. Occasionally, these feed menu screens would become unresponsive and I would be unable to confirm my selection, or even use the back button on my device to back out of the screen. However, I was able to pull the screen down to close it and re-open the menu, and everything would be responsive again.
This only seemed to occur when I spent 30 seconds or more on the same screen, so I imagine that most users won't encounter it much in their regular use.
Another UI bug occurred for me while in the feed marketplace. I could scroll down the list of available feeds, but attempting to scroll back up the feed would often close the interface entirely instead, as though I had pulled the screen down from the top, when I was swiping in the middle of the screen.
The last of these bugs occurred when selecting a long-form "Reads" feed while in the menu for the Home feed. The menu would allow me to add this feed and select it to be displayed, but it would fail to load the feed once selected, stating "There is no content in this feed." Going to a different page within the the app and then going back to the Home tab would automatically remove the long-form feed from view, and reset back to the most recently viewed short-form "Notes" feed, though the long-form feed would still be available to select again. The results were similar when selecting a short-form feed for the Reads feed.
I would suggest that if long-form and short-form feeds are going to be displayed in the same list, and yet not be able to be displayed in the same feed, the application should present an error message when attempting to add a long-form feed for the Home feed or a short-form feed for the Reads feed, and encourage the user add it to the proper feed instead.
Long-Form "Reads" Feed
A brand new feature in Primal 2.0, users can now browse and read long-form content posted to Nostr without having to go to a separate client. Primal now has a dedicated "Reads" feed to browse and interact with these articles.
This feed displays the author and title of each article or blog, along with an image, if available. Quite conveniently, it also lets you know the approximate amount of time it will take to read a given article, so you can decide if you have the time to dive into it now, or come back later.

Noticeably absent from the Reads feed, though, is the ability to compose an article of your own. This is another understandable design choice for a mobile client. Composing a long-form note on a smart-phone screen is not a good time. Better to be done on a larger screen, in a client with a full-featured text editor.
Tapping an article will open up an attractive reading interface, with the ability to bookmark for later. These bookmarks are a separate list from your short-form note bookmarks so you don't have to scroll through a bunch of notes you bookmarked to find the article you told yourself you would read later and it's already been three weeks.
While you can comment on the article or zap it, you will notice that you cannot repost or quote-post it. It's not that you can't do so on Nostr. You absolutely can in other clients. In fact, you can do so on Primal's web client, too. However, Primal on Android does not handle rendering long-form note previews in the Home feed, so they have simply left out the option to share them there. See below for an example of a quote-post of a long-form note in the Primal web client vs the Android client.
Primal Web:

Primal Android:

The Explore Tab
Another unique feature of the Primal client is the Explore tab, indicated by the compass icon. This tab is dedicated to discovering content from outside your current follow list. You can find the feed marketplace here, and add any of the available feeds to your Home or Reads feed selections. You can also find suggested users to follow in the People tab. The Zaps tab will show you who has been sending and receiving large zaps. Make friends with the generous ones!
The Media tab gives you a chronological feed of just media, displayed in a tile view. This can be great when you are looking for users who post dank memes, or incredible photography on a regular basis. Unfortunately, it appears that there is no way to filter this feed for sensitive content, and so you do not have to scroll far before you see pornographic material.
Indeed, it does not appear that filters for sensitive content are available in Primal for any feed. The app is kind enough to give a minimal warning that objectionable content may be present when selecting the "Nostr Firehose" option in your Home feed, with a brief "be careful" in the feed description, but there is not even that much of a warning here for the media-only feed.

The media-only feed doesn't appear to be quite as bad as the Nostr Firehose feed, so there must be some form of filtering already taking place, rather than being a truly global feed of all media. Yet, occasional sensitive content still litters the feed and is unavoidable, even for users who would rather not see it. There are, of course, ways to mute particular users who post such content, if you don't want to see it a second time from the same user, but that is a never-ending game of whack-a-mole, so your only realistic choices in Primal are currently to either avoid the Nostr Firehose and media-only feeds, or determine that you can put up with regularly scrolling past often graphic content.
This is probably the only choice Primal has made that is not friendly to new users. Most clients these days will have some protections in place to hide sensitive content by default, but still allow the user to toggle those protections off if they so choose. Some of them hide posts flagged as sensitive content altogether, others just blur the images unless the user taps to reveal them, and others simply blur all images posted by users you don't follow. If Primal wants to target new users who are accustomed to legacy social media platforms, they really should follow suit.
The final tab is titled "Topics," but it is really just a list of popular hashtags, which appear to be arranged by how often they are being used. This can be good for finding things that other users are interested in talking about, or finding specific content you are interested in.
If you tap on any topic in the list, it will display a feed of notes that include that hashtag. What's better, you can add it as a feed option you can select on your Home feed any time you want to see posts with that tag.
The only suggestion I would make to improve this tab is some indication of why the topics are arranged in the order presented. A simple indicator of the number of posts with that hashtag in the last 24 hours, or whatever the interval is for determining their ranking, would more than suffice.
Even with those few shortcomings, Primal's Explore tab makes the client one of the best options for discovering content on Nostr that you are actually interested in seeing and interacting with.
Built-In Wallet
While this feature is completely optional, the icon to access the wallet is the largest of the icons at the bottom of the screen, making you feel like you are missing out on the most important feature of the app if you don't set it up. I could be critical of this design choice, but in many ways I think it is warranted. The built-in wallet is one of the most unique features that Primal has going for it.

Consider: If you are a new user coming to Nostr, who isn't already a Bitcoiner, and you see that everyone else on the platform is sending and receiving sats for their posts, will you be more likely to go download a separate wallet application or use one that is built-into your client? I would wager the latter option by a long shot. No need to figure out which wallet you should download, whether you should do self-custody or custodial, or make the mistake of choosing a wallet with unexpected setup fees and no Lightning address so you can't even receive zaps to it. nostr:npub16c0nh3dnadzqpm76uctf5hqhe2lny344zsmpm6feee9p5rdxaa9q586nvr often states that he believes more people will be onboarded to Bitcoin through Nostr than by any other means, and by including a wallet into the Primal client, his team has made adopting Bitcoin that much easier for new Nostr users.
Some of us purists may complain that it is custodial and KYC, but that is an unfortunate necessity in order to facilitate onboarding newcoiners to Bitcoin. This is not intended to be a wallet for those of us who have been using Bitcoin and Lightning regularly already. It is meant for those who are not already familiar with Bitcoin to make it as easy as possible to get off zero, and it accomplishes this better than any other wallet I have ever tried.
In large part, this is because the KYC is very light. It does need the user's legal name, a valid email address, date of birth, and country of residence, but that's it! From there, the user can buy Bitcoin directly through the app, but only in the amount of $4.99 at a time. This is because there is a substantial markup on top of the current market price, due to utilizing whatever payment method the user has set up through their Google Play Store. The markup seemed to be about 19% above the current price, since I could purchase 4,143 sats for $4.99 ($120,415 / Bitcoin), when the current price was about $101,500. But the idea here is not for the Primal wallet to be a user's primary method of stacking sats. Rather, it is intended to get them off zero and have a small amount of sats to experience zapping with, and it accomplishes this with less friction than any other method I know.
Moreover, the Primal wallet has the features one would expect from any Lightning wallet. You can send sats to any Nostr user or Lightning address, receive via invoice, or scan to pay an invoice. It even has the ability to receive via on-chain. This means users who don't want to pay the markup from buying through Primal can easily transfer sats they obtained by other means into the Primal wallet for zapping, or for using it as their daily-driver spending wallet.
Speaking of zapping, once the wallet is activated, sending zaps is automatically set to use the wallet, and they are fast. Primal gives you immediate feedback that the zap was sent and the transaction shows in your wallet history typically before you can open the interface. I can confidently say that Primal wallet's integration is the absolute best zapping experience I have seen in any Nostr client.
One thing to note that may not be immediately apparent to new users is they need to add their Lightning address with Primal into their profile details before they can start receiving zaps. So, sending zaps using the wallet is automatic as soon as you activate it, but receiving is not. Ideally, this could be further streamlined, so that Primal automatically adds the Lightning address to the user's profile when the wallet is set up, so long as there is not currently a Lightning address listed.
Of course, if you already have a Lightning wallet, you can connect it to Primal for zapping, too. We will discuss this further in the section dedicated to zap integration.
Advanced Search
Search has always been a tough nut to crack on Nostr, since it is highly dependent on which relays the client is pulling information from. Primal has sought to resolve this issue, among others, by running a caching relay that pulls notes from a number of relays to store them locally, and perform some spam filtering. This allows for much faster retrieval of search results, and also makes their advanced search feature possible.
Advanced search can be accessed from most pages by selecting the magnifying glass icon, and then the icon for more options next to the search bar.
As can be seen in the screenshot below, there are a plethora of filters that can be applied to your search terms.

You can immediately see how this advanced search could be a very powerful tool for not just finding a particular previous note that you are looking for, but for creating your own custom feed of notes. Well, wouldn't you know it, Primal allows you to do just that! This search feature, paired with the other features mentioned above related to finding notes you want to see in your feed, makes Primal hands-down the best client for content discovery.
The only downside as a free user is that some of these search options are locked behind the premium membership. Or else you only get to see a certain number of results of your advanced search before you must be a premium member to see more.
Can My Grandma Use It?
Score: 4.8 / 5 Primal has obviously put a high priority on making their client user-friendly, even for those who have never heard of relays, public/private key cryptography, or Bitcoin. All of that complexity is hidden away. Some of it is available to play around with for the users who care to do so, but it does not at all get in the way of the users who just want to jump in and start posting notes and interacting with other users in a truly open public square.
To begin with, the onboarding experience is incredibly smooth. Tap "Create Account," enter your chosen display name and optional bio information, upload a profile picture, and then choose some topics you are interested in. You are then presented with a preview of your profile, with the ability to add a banner image, if you so choose, and then tap "Create Account Now."

From there you receive confirmation that your account has been created and that your "Nostr key" is available to you in the application settings. No further explanation is given about what this key is for at this point, but the user doesn't really need to know at the moment, either. If they are curious, they will go to the app settings to find out.
At this point, Primal encourages the user to activate Primal Wallet, but also gives the option for the user to do it later.

That's it! The next screen the user sees if they don't opt to set up the wallet is their Home feed with notes listed in chronological order. More impressive, the feed is not empty, because Primal has auto-followed several accounts based on your selected topics.
Now, there has definitely been some legitimate criticism of this practice of following specific accounts based on the topic selection, and I agree. I would much prefer to see Primal follow hashtags based on what was selected, and combine the followed hashtags into a feed titled "My Topics" or something of that nature, and make that the default view when the user finishes onboarding. Following particular users automatically will artificially inflate certain users' exposure, while other users who might be quality follows for that topic aren't seen at all.
The advantage of following particular users over a hashtag, though, is that Primal retains some control over the quality of the posts that new users are exposed to right away. Primal can ensure that new users see people who are actually posting quality photography when they choose it as one of their interests. However, even with that example, I chose photography as one of my interests and while I did get some stunning photography in my Home feed by default based on Primal's chosen follows, I also scrolled through the Photography hashtag for a bit and I really feel like I would have been better served if Primal had simply followed that hashtag rather than a particular set of users.
We've already discussed how simple it is to set up the Primal Wallet. You can see the features section above if you missed it. It is, by far, the most user friendly experience to onboarding onto Lightning and getting a few sats for zapping, and it is the only one I know of that is built directly into a Nostr client. This means new users will have a frictionless introduction to transacting via Lightning, perhaps without even realizing that's what they are doing.
Discovering new content of interest is incredibly intuitive on Primal, and the only thing that new users may struggle with is getting their own notes seen by others. To assist with this, I would suggest Primal encourage users to make their first post to the introductions hashtag and direct any questions to the AskNostr hashtag as part of the onboarding process. This will get them some immediate interactions from other users, and further encouragement to set up their wallet if they haven't already done so.
How do UI look?
Score: 4.9 / 5
Primal is the most stunningly beautiful Nostr client available, in my honest opinion. Despite some of my hangups about certain functionality, the UI alone makes me want to use it.

It is clean, attractive, and intuitive. Everything I needed was easy to find, and nothing felt busy or cluttered. There are only a few minor UI glitches that I ran into while testing the app. Some of them were mentioned in the section of the review detailing the feed selector feature, but a couple others occurred during onboarding.
First, my profile picture was not centered in the preview when I uploaded it. This appears to be because it was a low quality image. Uploading a higher quality photo did not have this result.

The other UI bug was related to text instructions that were cut off, and not able to scroll to see the rest of them. This occurred on a few pages during onboarding, and I expect it was due to the size of my phone screen, since it did not occur when I was on a slightly larger phone or tablet.

Speaking of tablets, Primal Android looks really good on a tablet, too! While the client does not have a landscape mode by default, many Android tablets support forcing apps to open in full-screen landscape mode, with mixed results. However, Primal handles it well. I would still like to see a tablet version developed that takes advantage of the increased screen real estate, but it is certainly a passable option.





At this point, I would say the web client probably has a bit better UI for use on a tablet than the Android client does, but you miss out on using the built-in wallet, which is a major selling point of the app.
This lack of a landscape mode for tablets and the few very minor UI bugs I encountered are the only reason Primal doesn't get a perfect score in this category, because the client is absolutely stunning otherwise, both in light and dark modes. There are also two color schemes available for each.

Log In Options
Score: 4 / 5 (Updated 4/30/2025)
Unfortunately, Primal has not included any options for log in outside of pasting your private key into the application. While this is a very simple way to log in for new users to understand, it is also the least secure means to log into Nostr applications.
This is because, even with the most trustworthy client developer, giving the application access to your private key always has the potential for that private key to somehow be exposed or leaked, and on Nostr there is currently no way to rotate to a different private key and keep your identity and social graph. If someone gets your key, they are you on Nostr for all intents and purposes.
This is not a situation that users should be willing to tolerate from production-release clients at this point. There are much better log in standards that can and should be implemented if you care about your users.
That said, I am happy to report that external signer support is on the roadmap for Primal, as confirmed below:
nostr:note1n59tc8k5l2v30jxuzghg7dy2ns76ld0hqnn8tkahyywpwp47ms5qst8ehl
No word yet on whether this will be Android signer or remote signer support, or both.
This lack of external signer support is why I absolutely will not use my main npub with Primal for Android. I am happy to use the web client, which supports and encourages logging in with a browser extension, but until the Android client allows users to protect their private key, I cannot recommend it for existing Nostr users.
Update: As of version 2.2.13, all of what I have said above is now obsolete. Primal has added Android signer support, so users can now better protect their nsec by using Amber!
I would still like to see support for remote signers, especially with nstart.me as a recommended Nostr onboarding process and the advent of FROSTR for key management. That said, Android signer support on its own has been a long time coming and is a very welcome addition to the Primal app. Bravo Primal team!
Zap Integration
Score: 4.8 / 5
As mentioned when discussing Primal's built-in wallet feature, zapping in Primal can be the most seamless experience I have ever seen in a Nostr client. Pairing the wallet with the client is absolutely the path forward for Nostr leading the way to Bitcoin adoption.
But what if you already have a Lightning wallet you want to use for zapping? You have a couple options. If it is an Alby wallet or another wallet that supports Nostr Wallet Connect, you can connect it with Primal to use with one-tap zapping.

How your zapping experience goes with this option will vary greatly based on your particular wallet of choice and is beyond the scope of this review. I used this option with a hosted wallet on my Alby Hub and it worked perfectly. Primal gives you immediate feedback that you have zapped, even though the transaction usually takes a few seconds to process and appear in your wallet's history.
The one major downside to using an external wallet is the lack of integration with the wallet interface. This interface currently only works with Primal's wallet, and therefore the most prominent tab in the entire app goes unused when you connect an external wallet.

An ideal improvement would be for the wallet screen to work similar to Alby Go when you have an external wallet connected via Nostr Wallet Connect, allowing the user to have Primal act as their primary mobile Lightning wallet. It could have balance and transaction history displayed, and allow sending and receiving, just like the integrated Primal wallet, but remove the ability to purchase sats directly through the app when using an external wallet.
Content Discovery
Score: 4.8 / 5
Primal is the best client to use if you want to discover new content you are interested in. There is no comparison, with only a few caveats.
First, the content must have been posted to Nostr as either a short-form or long-form note. Primal has a limited ability to display other types of content. For instance, discovering video content or streaming content is lacking.
Second, you must be willing to put up with the fact that Primal lacks a means of filtering sensitive content when you are exploring beyond the bounds of your current followers. This may not be an issue for some, but for others it could be a deal-breaker.
Third, it would be preferable for Primal to follow topics you are interested in when you choose them during onboarding, rather than follow specific npubs. Ideally, create a "My Topics" feed that can be edited by selecting your interests in the Topics section of the Explore tab.
Relay Management
Score: 2.5 / 5
For new users who don't want to mess around with managing relays, Primal is fantastic! There are 7 relays selected by default, in addition to Primal's caching service. For most users who aren't familiar with Nostr's protocol archetecture, they probably won't ever have to change their default relays in order to use the client as they would expect.
However, two of these default relays were consistently unreachable during the week that I tested. These were relay.plebes.fans and remnant.cloud. The first relay seems to be an incorrect URL, as I found nosflare.plebes.fans online and with perfect uptime for the last 12 hours on nostr.watch. I was unable to find remnant.cloud on nostr.watch at all. A third relay was intermittent, sometimes online and reachable, and other times unreachable: v1250.planz.io/nostr. If Primal is going to have default relays, they should ideally be reliable and with accurate URLs.
That said, users can add other relays that they prefer, and remove relays that they no longer want to use. They can even set a different caching service to use with the client, rather than using Primal's.

However, that is the extent of a user's control over their relays. They cannot choose which relays they want to write to and which they want to read from, nor can they set any private relays, outbox or inbox relays, or general relays. Loading the npub I used for this review into another client with full relay management support revealed that the relays selected in Primal are being added to both the user's public outbox relays and public inbox relays, but not to any other relay type, which leads me to believe the caching relay is acting as the client's only general relay and search relay.
One unique and welcomed addition is the "Enhanced Privacy" feature, which is off by default, but which can be toggled on. I am not sure why this is not on by default, though. Perhaps someone from the Primal team can enlighten me on that choice.
By default, when you post to Nostr, all of your outbox relays will see your IP address. If you turn on the Enhanced Privacy mode, only Primal's caching service will see your IP address, because it will post your note to the other relays on your behalf. In this way, the caching service acts similar to a VPN for posting to Nostr, as long as you trust Primal not to log or leak your IP address.
In short, if you use any other Nostr clients at all, do not use Primal for managing your relays.
Media Hosting Options
Score: 4.9 / 5 This is a NEW SECTION of this review, as of version 2.2.13!
Primal has recently added support for the Blossom protocol for media hosting, and has added a new section within their settings for "Media Uploads."
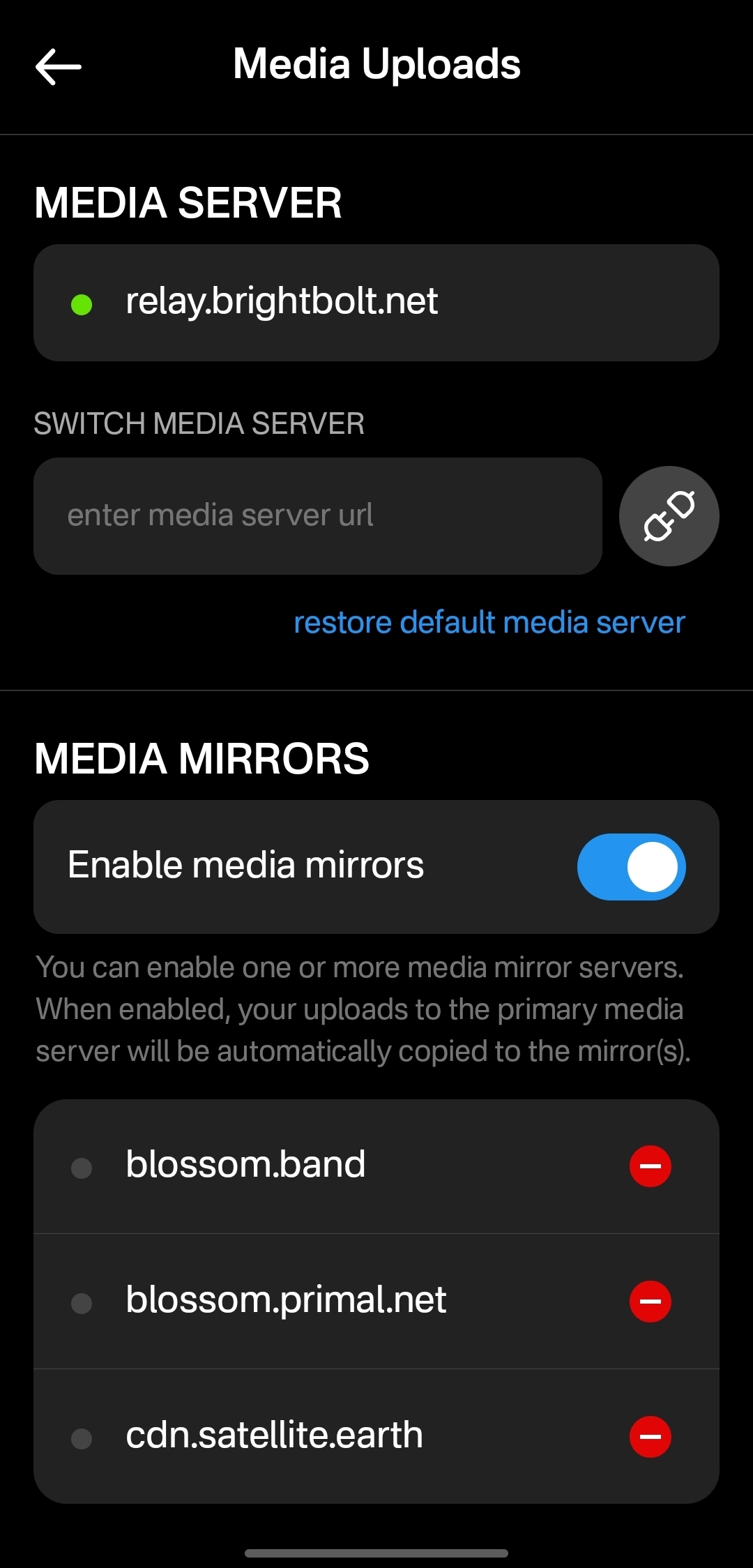
Media hosting is one of the more complicated problems to solve for a decentralized publishing protocol like Nostr. Text-based notes are generally quite small, making them no real burden to store on relays, and a relay can prune old notes as they see fit, knowing that anyone who really cared about those notes has likely archived them elsewhere. Media, on the other hand, can very quickly fill up a server's disk space, and because it is usually addressable via a specific URL, removing it from that location to free up space means it will no longer load for anyone.
Blossom solves this issue by making it easy to run a media server and have the same media mirrored to more than one for redundancy. Since the media is stored with a file name that is a hash of the content itself, if the media is deleted from one server, it can still be found from any other server that has the same file, without any need to update the URL in the Nostr note where it was originally posted.
Prior to this update, Primal only allowed media uploads to their own media server. Now, users can upload to any blossom server, and even choose to have their pictures or videos mirrored additional servers automatically. To my knowledge, no other Nostr client offers this automatic mirroring at the time of upload.
One of my biggest criticisms of Primal was that it had taken a siloed approach by providing a client, a caching relay, a media server, and a wallet all controlled by the same company. The whole point of Nostr is to separate control of all these services to different entities. Now users have more options for separating out their media hosting and their wallet to other providers, at least. I would still like to see other options available for a caching relay, but that relies on someone else being willing to run one, since the software is open for anyone to use. It's just not your average, lightweight relay that any average person can run from home.
Regardless, this update to add custom Blossom servers is a most welcome step in the right direction!
Current Users' Questions
The AskNostr hashtag can be a good indication of the pain points that other users are currently having with a client. Here are some of the most common questions submitted about Primal since the launch of 2.0:
nostr:note1dqv4mwqn7lvpaceg9s7damf932ydv9skv2x99l56ufy3f7q8tkdqpxk0rd
This was a pretty common question, because users expect that they will be able to create the same type of content that they can consume in a particular client. I can understand why this was left out in a mobile client, but perhaps it should be added in the web client.
nostr:note16xnm8a2mmrs7t9pqymwjgd384ynpf098gmemzy49p3572vhwx2mqcqw8xe
This is a more concerning bug, since it appears some users are experiencing their images being replaced with completely different images. I did not experience anything similar in my testing, though.
nostr:note1uhrk30nq0e566kx8ac4qpwrdh0vfaav33rfvckyvlzn04tkuqahsx8e7mr
There hasn't been an answer to this, but I have not been able to find a way. It seems search results will always include replies as well as original notes, so a feed made from the search results will as well. Perhaps a filter can be added to the advanced search to exclude replies? There is already a filter to only show replies, but there is no corresponding filter to only show original notes.
nostr:note1zlnzua28a5v76jwuakyrf7hham56kx9me9la3dnt3fvymcyaq6eqjfmtq6
Since both mobile platforms support the wallet, users expect that they will be able to access it in their web client, too. At this time, they cannot. The only way to have seamless zapping in the web client is to use the Alby extension, but there is not a way to connect it to your Primal wallet via Nostr Wallet Connect either. This means users must have a separate wallet for zapping on the web client if they use the Primal Wallet on mobile.
nostr:note15tf2u9pffy58y9lk27y245ew792raqc7lc22jezxvqj7xrak9ztqu45wep
It seems that Primal is filtering for spam even for profiles you actively follow. Moreover, exactly what the criteria is for being considered spam is currently opaque.
nostr:note1xexnzv0vrmc8svvduurydwmu43w7dftyqmjh4ps98zksr39ln2qswkuced
For those unaware, Blossom is a protocol for hosting media as blobs identified by a hash, allowing them to be located on and displayed from other servers they have been mirrored to when when the target server isn't available. Primal currently runs a Blossom server (blossom.primal.net) so I would expect we see Blossom support in the future.
nostr:note1unugv7s36e2kxl768ykg0qly7czeplp8qnc207k4pj45rexgqv4sue50y6
Currently, Primal on Android only supports uploading photos to your posts. Users must upload any video to some other hosting service and copy/paste a link to the video into their post on Primal. I would not be surprised to see this feature added in the near future, though.
nostr:note10w6538y58dkd9mdrlkfc8ylhnyqutc56ggdw7gk5y7nsp00rdk4q3qgrex
Many Nostr users have more than one npub for various uses. Users would prefer to have a way to quickly switch between accounts than to have to log all the way out and paste their npub for the other account every time they want to use it.
There is good news on this front, though:
nostr:note17xv632yqfz8nx092lj4sxr7drrqfey6e2373ha00qlq8j8qv6jjs36kxlh
Wrap Up
All in all, Primal is an excellent client. It won't be for everyone, but that's one of the strengths of Nostr as a protocol. You can choose to use the client that best fits your own needs, and supplement with other clients and tools as necessary.
There are a couple glaring issues I have with Primal that prevent me from using it on my main npub, but it is also an ever-improving client, that already has me hopeful for those issues to be resolved in a future release.
So, what should I review next? Another Android client, such as #Amethyst or #Voyage? Maybe an "other stuff" app, like #Wavlake or #Fountain? Please leave your suggestions in the comments.
I hope this review was valuable to you! If it was, please consider letting me know just how valuable by zapping me some sats and reposting it out to your follows.
Thank you for reading!
PV 🤙
-
 @ 3589b793:ad53847e
2025-04-30 12:40:42
@ 3589b793:ad53847e
2025-04-30 12:40:42※本記事は別サービスで2022年6月24日に公開した記事の移植です。
どうも、「NostrはLNがWeb統合されマネーのインターネットプロトコルとしてのビットコインが本気出す具体行動のショーケースと見做せばOK」です、こんばんは。
またまた実験的な試みがNostrで行われているのでレポートします。本シリーズはライブ感を重視しており、例によって(?)プルリクエストなどはレビュー段階なのでご承知おきください。
今回の主役はあくまでLightningNetworkの新提案(ただし以前からあるLSATからのリブランディング)となるLightning HTTP 402 Protocol(略称: L402)です。そのショーケースの一つとしてNostrが活用されているというものになります。
Lightning HTTP 402 Protocol(略称: L402)とは何か
bLIPに今月挙がったプロポーザル内容です。
https://github.com/lightning/blips/pull/26
L402について私はまだ完全に理解した段階ではあるのですがなんとか一言で説明しようとすると「Authトークンのように"Paid"トークンをHTTPヘッダーにアタッチして有料リソースへのHTTPリクエストの受け入れ判断を行えるようにする」ものだと解釈しました。
Authenticationでは、HTTPヘッダーにAuthトークンを添付し、その検証が通ればHTTPリクエストを許可し、通らなければ
401 Unauthorizedコードをエラーとして返すように定められています。https://developer.mozilla.org/ja/docs/Web/HTTP/Status/401
L402では、同じように、HTTPヘッダーに支払い済みかどうかを示す"Paid"トークンを添付し、その検証が通ればHTTPリクエストを許可し、通らなければ
402 Payment Requiredコードをエラーとして返すようにしています。なお、"Paid"トークンという用語は私の造語となります。便宜上本記事では使わせていただきますが、実際はAuthも入ってくるのが必至ですし、プルリクエストでも用語をどう定めるかは議論になっていることをご承知おきください。("API key", "credentials", "token", らが登場しています)
この402ステータスコードは従来から定義されていましたが、MDNのドキュメントでも記載されているように「実験的」なものでした。つまり、器は用意されているがこれまで活用されてこなかったものとなり、本プロトコルの物語性を体現しているものとなります。
https://developer.mozilla.org/ja/docs/Web/HTTP/Status/402
幻であったHTTPステータスコード402 Payment Requiredを実装する
この物語性は、上述のbLIPのスペックにも詳述されていますが、以下のスライドが簡潔です。
402 Payment Requiredは予約されていましたが、けっきょくのところWorldWideWebはペイメントプロトコルを実装しなかったので、Bitcoinの登場まで待つことになった、というのが要旨になります。このWorldWideWebにおける決済機能実装に関する歴史話はクリプト界隈でもたびたび話題に上がりますが、そこを繋いでくる文脈にこれこそマネーのインターネットプロトコルだなと痺れました。https://x.com/AlyseKilleen/status/1671342634307297282
この"Paid"トークンによって実現できることとして、第一にAIエージェントがBitcoin/LNを自律的に利用できるようになるM2M(MachineToMachine)的な話が挙げられていますが、ユースケースは想像力がいろいろ要るところです。実際のところは「有料リソースへの認可」を可能にすることが主になると理解しました。本連載では、繰り返しNostrクライアントにLNプロトコルを直接搭載せずにLightningNetworkを利用可能にする組み込み方法を見てきましたが、本件もインボイス文字列 & preimage程度の露出になりアプリケーション側でノードやウォレットの実装が要らないので、その文脈で位置付ける解釈もできるかと思います。
Snortでのサンプル実装
LN組み込み業界のリーディングプロダクトであるSnortのサンプル実装では、L402を有料コンテンツの購読に活用しています。具体的には画像や動画を投稿するときに有料のロックをかける、いわゆるペイウォールの一種となります。もともとアップローダもSnortが自前で用意しているので、そこにL402を組み込んでみたということのようです。
体験方法の詳細はこちらにあります。 https://njump.me/nevent1qqswr2pshcpawk9ny5q5kcgmhak24d92qzdy98jm8xcxlgxstruecccpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhszrnhwden5te0dehhxtnvdakz78pvlzg
上記を試してみた結果が以下になります。まず、ペイウォールでロックした画像がNostrに投稿されている状態です。まったくビューワーが実装されておらず、ただのNotFound状態になっていますが、支払い前なのでロックされているということです。

次にこのHTTP通信の内容です。

通信自体はエラーになっているわけですが、ステータスコードが402で、レスポンスヘッダーのWWW-AuthenticateにInvoice文字列が返ってきています。つまり、このインボイスを支払えば"Paid"トークンが付与されて、その"Paid"トークンがあれば最初の画像がアンロックされることとなります。残念ながら現在は日本で利用不可のStrikeAppでしか払込みができないためここまでとなりますが、本懐である
402 Payment Requiredとインボイス文字列は確認できました。今確認できることは以上ですが、AmethystやDamusなどの他のNostrクライアントが実装するにあたり、インラインメディアを巡ってL402の仕様をアップデートする必要性や同じくHTTPヘッダーへのAuthトークンとなるNIP-98と組み合わせるなどの議論が行われている最中です。
LinghtningNetworkであるからこそのL402の実現
"Paid"トークンを実現するためにはLightningNetworkのファイナリティが重要な要素となっています。逆に言うと、reorgによるひっくり返しがあり得るBitcoinではできなくもないけど不便なわけです。LightningNetworkなら、当事者である二者間で支払いが確認されたら「同期的」にその証であるハッシュ値を用いて"Paid"トークンを作成することができます。しかもハッシュ値を提出するだけで台帳などで過去の履歴を確認する必要がありません。加えて言うと、受金者側が複数のノードを建てていて支払いを受け取るノードがどれか一つになる状況でも、つまり、スケーリングされている状況でも、"Paid"トークンそのものはどのノードかを気にすることなくステートレスで利用できるとのことです。(ここは単にreverse proxyとしてAuthサーバががんばっているだけと解釈することもできますがずいぶんこの機能にも力点を置いていて大規模なユースケースが重要になっているのだなという印象を抱きました)
Macaroonの本領発揮か?それとも詳細定義しすぎか?
HTTP通信ではWWW-Authenticateの実値にmacaroonの記述が確認できます。また現在のL402スペックでも"Paid"トークンにはmacaroonの利用が前提になっています。
このmacaroonとは(たぶん)googleで研究開発され、LNDノードソフトウェアで活用されているCookieを超えるという触れ込みのデータストアになります。しかし、あまり普及しなかった技術でもあり、個人の感想ですがなんとも微妙なものになっています。
https://research.google/pubs/macaroons-cookies-with-contextual-caveats-for-decentralized-authorization-in-the-cloud/
macaroonの強みは、Cookieを超えるという触れ込みのようにブラウザが無くてもプロセス間通信でデータ共有できる点に加えて、HMACチェーンで動的に認証認可を更新し続けられるところが挙げられます。しかし、そのようなユースケースがあまり無く、静的な認可となるOAuthやJWTで十分となっているのが現状かと思います。
L402では、macaroonの動的な更新が可能である点を活かして、"Paid"トークンを更新するケースが挙げられています。わかりやすいのは上記のスライド資料でも挙げられている"Dynamic Pricing"でしょうか。プロポーザルではloop©️LightningLabsにおいて月間の最大取引量を認可する"Paid"トークンを発行した上でその条件を動向に応じて動的に変更できる例が解説されています。とはいえ、そんなことしなくても再発行すればええやんけという話もなくもないですし、プルリクエストでも仕様レベルでmacaroonを指定するのは「具体」が過ぎるのではないか、もっと「抽象」し単なる"Opaque Token"程度の粒度にして他の実装も許容するべきではないか、という然るべきツッコミが入っています。
個人的にはそのツッコミが妥当と思いつつも、なんだかんだ初めてmacaroonの良さを実感できて感心した次第です。
-
 @ 3589b793:ad53847e
2025-04-30 12:28:25
@ 3589b793:ad53847e
2025-04-30 12:28:25※本記事は別サービスで2023年4月19日に公開した記事の移植です。
どうも、「NostrはLNがWeb統合されマネーのインターネットプロトコルとしてのビットコインが本気出す具体行動のショーケースと見做せばOK」です、こんにちは。
前回まで投げ銭や有料購読の組み込み方法を見てきました。
zapsという投げ銭機能が各種クライアントに一通り実装されて活用が進んでいることで、統合は次の段階へ移り始めています。「作戦名: ウォレットをNostrクライアントに組み込め」です。今回はそちらをまとめます。
投げ銭する毎にいちいちウォレットを開いてまた元のNostrクライアントに手動で戻らないといけない is PAIN
LNとNostrはインボイス文字列で繋がっているだけの疎結合ですが、投稿に投げ銭するためには何かのLNウォレットを開いて支払いをして、また元のNostrクライアントに戻る操作をユーザーが手作業でする必要があります。お試しで一回やる程度では気になりませんが普段使いしているとこれはけっこうな煩わしさを感じるUXです。特にスマホでは大変にだるい状況になります。連打できない!
2月の実装以来、zapsは順調に定着して日々投げられています。


https://stats.nostr.band/#daily_zaps
なので、NostrクライアントにLNウォレットの接続を組み込み、支払いのために他のアプリに遷移せずにNostクライアント単独で完結できるようなアップデートが始まっています。
Webクライアント
NostrのLN組み込み業界のリーディングプレイヤーであるSnortでの例です。以下のようにヘッダーのウォレットアイコンをクリックすると連携ウォレットの選択ができます。

もともとNostrに限らずウェブアプリケーションとの連携をするために、WebLNという規格があります。簡単に言うと、ブラウザのグローバル領域を介して、LNウォレットの拡張機能と、タブで開いているウェブアプリが、お互いに連携するためのインターフェースを定めているものです。これに対応していると、LNによる支払いをウェブアプリが拡張機能に依頼できるようになります。さらにオプションで「確認無し」をオンにすると、拡張機能画面がポップアップせずにバックグラウンドで実行できるようになり、ノールック投げ銭ができるようになります。
似たようなものにNostrではNIP-07があります。NIP-07はNostrの秘密鍵を拡張機能に退避して、Nostrクライアントは秘密鍵を知らない状態で署名や複合を拡張機能に移譲できるようにしているものです。
Albyの拡張機能ではWebLNとNIP-07のどちらにも対応しています。
実はSnortはzapsが来る前からWebLNには対応していたのですが、さらに一歩進み、拡張機能ウォレットだけでなく、LNノードや拡張機能以外のLNウォレットと連携設定できるようになってきています。

umbrelなどでノードを立てている人ならLND with LNCでノードと直接繋げます。またLNDHubに対応したウォレットなどのアプリケーションとも繋げます。これらの接続は、WebLNにラップされて拡張機能ウォレットとインターフェースを揃えられた上で、Snort上でのインボイスの支払いに活用されます。
なお、LNCのpairingPhrase/passwordやLNDHubの接続情報などのクレデンシャルは、ブラウザのローカルストレージに保存されています。Nostrのリレーサーバなどには送られませんので、端末ごとに設定が必要です。
スマホアプリ
今回のメインです。なお、例によって(?)スペックは絶賛議論中でまだフィックスしていない中で記事を書いています。ディテールは変わるかもしれないので悪しからずです。
スマホアプリで上記のことをやるためには、後半のLNCやLNDHubはすでにzeusなどがやっているようにできますが、あくまでネイティブウォレットのラッパーです。Nostrでは限られた用途になるので1-click支払いのようなものを行うためにはそこから各スマホアプリが作り込む必要があります。まあこれはこれでやればいいという話でもあるのですが、LNノードやLNウォレットのアプリケーション側へのインターフェースの共通仕様は定められていないので、LNDとcore-lightningとeclairではすべて実装方法が違いますし、ウォレットもバラバラなので大変です。
そこで、多種多様なノードやウォレットの接続を取りまとめ一般アプリケーションへ統一したインターフェースを媒介するLN Adapter業界のリーディングカンパニーであるAlbyが動きました。AndroidアプリのAmethystで試験公開されていますが、スマホアプリでも上記のSnortのような連携が可能になるようなSDKが開発されました。
リリース記事 https://blog.getalby.com/native-zapping-in-amethyst/
"Unstoppable zapping for users"なんて段落見出しが付けられているように、スマホで別のアプリに切り替えてまた元に戻らなくても良いようにして、Nostr上でマイクロペイメントを滑らかにする、つまり、連打できることを繰り返し強調しています。
具体的にやっていることを見ていきます。以下の画像群はリリース記事の動画から抜粋しています。各投稿のzapsボタン⚡️をタップしたときの画面です。

上の赤枠が従来の投げ銭の詳細を決める場所で、下の赤枠の「Wallet Connect Service」が新たに追加されたAlby提供のSDKを用いたコネクト設定画面です。基本的にはOAuth2.0ベースのAlbyのAPIを活用していて、右上のAlbyアイコンをタップすると以下のようなOAuthの認可画面に飛びます。(ただし後述するように通常のOAuthとは一部異なります。)


画面デザインは違いますが、まあ他のアプリでよく目にするTwitter連携やGoogleアカウント連携とやっていることは同じです。
このOAuthベースのAPIはNostr専用のエンドポイントが建てられています。Nostr以外のECショップやマーケットプレイスなどへのAlbyのOAuthは汎用のエンドポイントが用意されています。よって通常のAlbyの設定とは別にセッション詳細を以下のサイトで作成する必要があります。
https://nwc.getalby.com/ (サブドメインのnwcはNostr Wallet Connectの略)
なぜNostrだけは特別なのかというところが完全には理解しきれていないですが、以下のところまで確認できています。一番にあるのは、Nostrクライアントにウォレットを組み込まずに、かつ、ノードやウォレットへの接続をNostrリレーサーバ以外は挟まずに"decentralized"にしたいというところだと理解しています。
- 上記のnwcのURLはalbyのカストディアルウォレットusername@getalby.comをNostrに繋ぐもの(たぶん)
- umbrelのLNノードを繋ぐためにはやはり専用のアプリがumbrelストアに上がっている。https://github.com/getAlby/umbrel-community-app-store
- 要するにOAuthの1stPartyの役割をウォレットやノードごとにそれぞれ建てる。
- OAuthのシークレットはクライアントに保存するので設定は各クライアント毎に必要。しかし使い回しすることは可能っぽい。通常のOAuthと異なり、1stParty側で3rdPartyのドメインはトラストしていないようなので。
- Nostrクライアントにウォレットを組み込まずに、さらにウォレットやノードへの接続をNostrリレーサーバ以外には挟まなくて良いようにするために、「NIP-47 Nostr Wallet Connect」というプロポーザルが起こされていて、絶賛議論中である。https://github.com/nostr-protocol/nips/pull/406
- このWallet Connect専用のアドホックなリレーサーバが建てられる。その情報が上記画像の赤枠の「Wallet Connect Service」の下半分のpub keyやらrelayURL。どうもNostrクライアントはNIP-47イベントについてはこのリレーサーバにしか送らないようにするらしい。(なんかNostrの基本設計を揺るがすユースケースの気がする...)
- Wallet Connect専用のNostrイベントでは、ペイメント情報をNostrアカウントと切り離すために、Nostrの秘密鍵とは別の秘密鍵が利用できるようにしている。
Imagin the Future
今回取り上げたNostrクライアントにウォレット接続を組み込む話を、Webのペイメントの歴史で類推してみましょう。
Snortでやっていることは、各サイトごとにクレジットカードを打ち込み各サイトがその情報を保持していたようなWeb1.0の時代に近いです。そうなるとクレジットカードの情報は各サービスごとに漏洩リスクなどがあり、Web1.0の時代はECが普及する壁の一つになっていました。(今でもAmazonなどの大手はそうですが)
Webではその後にPayPalをはじめとして、銀行口座やクレジットカードを各サイトから切り出して一括管理し、各ウェブサイトに支払いだけを連携するサービスが出てきて一般化しています。日本ではケータイのキャリア決済が利用者の心理的障壁を取り除きEC普及の後押しになりました。
後半のNostr Wallet ConnectはそれをNostrの中でやろうとしている試みになります。クレジットカードからLNに変える理由はビットコインの話になるので詳細は割愛しますが、現実世界の金(ゴールド)に類した価値保存や交換ができるインターネットマネーだからです。
とはいえ、Nostrの中だけならまだしも、これをNostr外のサービスで利用するためには、他のECショップやブログやSaaSがNostrを喋れる必要があります。そんな未来が来るわけないだろと思うかもしれませんが、言ってみればStripeはまさにそのようなサービスとなっていて、サイト内にクレジット決済のモジュールを組み込むための主流となっています。
果たして、Nostrを、他のECショップやブログやSaaSが喋るようになるのか!?
以上、「NostrはLNがWeb統合されマネーのインターネットプロトコルとしてのビットコインが本気出す具体行動のショーケースと見做せばOK」がお送りしました。
-
 @ 3589b793:ad53847e
2025-04-30 12:10:06
@ 3589b793:ad53847e
2025-04-30 12:10:06前回の続きです。
特に「Snortで試験的にノート単位に投げ銭できる機能」について。実は記事書いた直後にリリースされて慌ててw追記してたんですが追い付かないということで別記事にしました。
今回のここがすごい!
「Snortで試験的にノート単位に投げ銭できる機能」では一つブレイクスルーが起こっています。それは「ウォレットにインボイスを放り投げた後に払い込み完了を提示できる」ようになったことです。これによりペイメントのライフサイクルが一通りカバーされたことになります。
Snortの画面

なにを当たり前のことをという向きもあるかもしれませんが、Nostrクライアントで払い込み完了を追跡することはとても難しいです。基本的にNostrとLNウォレットはまったく別のアプリケーションで両者の間を繋ぐのはインボイス文字列だけです。ウォレットもNostrからキックされずに、インボイス文字列をコピペするなりQRコードで読み取ったものを渡されるだけかもしれません。またその場でリアルタイムに処理される前提もありません。
なのでNostrクライアントでその後をトラックすることは難しく、これまではあくまで請求書を送付したり(LNインボイス)振り込み口座を提示する(LNアドレス)という一方的に放り投げてただけだったわけです。といっても魔法のようにNostrクライアントがトラックできるようになったわけではなく、今回の対応方法もインボイスを発行/お金を振り込まれるサービス側(LNURL)にNostrカスタマイズを入れさせるというものになります。
プロポーザルの概要について
前回の記事ではよくわからんで終わっていましたが、当日夜(日本時間)にスペックをまとめたプロポーザルも起こされました(早い!)。LNURLが、Nostr用のインボイスを発行して、さらにNostrイベントの発行を行っていることがポイントでした。名称は"Lightning Zaps"で確定のようです。プロポーザルは、NostrとLNURLの双方の発明者であるfiatjaf氏からツッコミが入り、またそれが妥当な指摘のために、エンドポイントURLのインターフェースなどは変わりそうなのですが、概要はそう変わらないだろうということで簡単にまとめてみます。
全体の流れ

図は、Nostrクライアント上に提示されているLNアドレスへ投げ銭が開始してから、Nostrクライアント上に払い込み完了したイベントが表示されるまでの流れを示しています。
- 投げ銭の内容が固まったらNostrイベントデータを添付してインボイスの発行を依頼する
- 説明欄にNostr用のデータを記載したインボイスを発行して返却する
- Nostrクライアントで提示されたインボイスをユーザーが何かしらの手段でウォレットに渡す
- ウォレットがLNに支払いを実行する
- インボイスの発行者であるLNURLが管理しているLNノードにsatoshiが届く
- LNURLサーバが投げ銭成功のNostrイベントを発行する
- Nostrクライアントがイベントを受信して投げ銭履歴を表示する
特にポイントとなるところを補足します。
対応しているLNアドレスの識別
LNアドレスに投げ銭する場合は、LNアドレスの有効状態やインボイス発行依頼する先の情報を
https://[domain]/.well-known/lnurlp/[username]から取得しています。そのレスポンス内容にNostr対応を示す情報を追加しています。ただし、ここに突っ込み入っていてlnurlp=LNURL Payから独立させるためにzaps専用のエンドポイントに変わりそうです。(2/15 追記 マージされましたが変更無しでした。PRのディスカッションが盛り上がっているので興味ある方は覗いてみてください。)インボイスの説明欄に書き込むNostrイベント(kind:9734)
これは投げ銭する側のNostrイベントです。投げ銭される者や対象ノートのIDや金額、そしてこのイベントを作成している者が投げ銭したということを「表明」するものになります。表明であって証明でないところは、インボイスを別の人が払っちゃう事態がありえるからですね。この内容をエンクリプトするパターンも用意されていたが複雑になり過ぎるという理由で今回は外され追加提案に回されました。また、このイベントはデータを作成しただけです。支払いを検知した後にLNURLが発行するイベントに添付されることになります。そのため投げ銭する者にちゃんと届くように作成者のリレーサーバリストも書き込まれています。
支払いを検知した後に発行するNostrイベント(kind:9735)
これが実際にNostrリレーサーバに発行されるイベントです。LNURL側はウォッチしているLNノードにsatoshiが届くと、インボイスの説明欄に書かれているNostrイベントを取り出して、いわば受領イベントを作成して発行します。以下のようにNostイベントのkind:9734とkind:9735が親子になったイベントとなります。
json { "pubkey": "LNURLが持っているNostrアカウントの公開鍵", "kind": 9735, "tags": [ [ "p", "投げ銭された者の公開鍵" ], [ "bolt11", "インボイスの文字列lnbc〜" ], [ "description", "投げ銭した者が作成したkind:9734のNostrイベント" ], [ "preimage", "インボイスのpreimage" ] ], }所感
とにかくNostrクライアントはLNノードを持たないしLNプロトコルとも直接喋らずにインボイス文字列だけで取り扱えるようになっているところがおもしろいと思っています。NostrとLNという二つのデセントライズドなオープンプロトコルが協調できていますし、前回も述べましたがどんなアプリでも簡単に真似できます。
とはいえ、さすがに払込完了のトラックは難しく、今回はLNURL側にそのすり合わせの責務が寄せられることになりました。しかし、LNURLもLNの上に作られたオープンプロトコル/スペックの位置付けになるため、他のLNURLのスペックに干渉するという懸念から、本提案のNIP-57に変更依頼が出されています。LN、LNURL、Nostrの3つのオープンプロトコルの責務分担が難しいですね。アーキテクチャ層のスタックにおいて3つの中ではNostrが一番上になるため、Nostrに相当するレイヤーの他のwebサービスでやるときはLNプロトコルを喋るなりLNノードを持つようにして、今回LNURLが寄せられた責務を吸収するのが無難かもしれません。
また、NIP-57の変更依頼理由の一つにはBOLT-12を見越した抽象化も挙げられています。他のLNURLのスペックを削ぎ落としてzapsだけにすることでBOLT-12にも載りやすくなるだろうと。LNURLの多くはBOLT-12に取り込まれる運命なわけですが、LNアドレス以外の点でもNostrではBOLT-12のOfferやInvoiceRequestのユースケースをやりたいという声が挙がっているため、NostrによりBOLT-12が進む展開もありそうだなあ、あってほしい。
-
 @ 3589b793:ad53847e
2025-04-30 12:02:13
@ 3589b793:ad53847e
2025-04-30 12:02:13※本記事は別サービスで2023年2月5日に公開した記事の移植です。
Nostrクライアントは多種ありますがメジャーなものはだいたいLNの支払いが用意されています。現時点でどんな組み込み方法になっているか調べました。この記事では主にSnortを対象にしています。
LN活用場面
大きくLNアドレスとLNインボイスの2つの形式があります。
1. LNアドレスで投げ銭をセットできる

LNURLのLNアドレスをセットすると、プロフィールやノート(ツイートに相当)からLN支払いができます。別クライアントのastralなどではプリミティブなLNURLの投げ銭形式
lnurl1dp68~でもセットできます。[追記]さらに本日、Snortで試験的にノート単位に投げ銭できる機能が追加されています。

2. LNインボイスが投稿できる

投稿でLNインボイスを貼り付ければ上記のように他の発言と同じようにタイムラインに流れます。Payボタンを押すと各自の端末にあるLNウォレットが立ち上がります。
3. DMでLNインボイスを送る
メッセージにLNインボイスが組み込まれているという点では2とほぼ同じですが、ユースケースが異なります。発表されたばかりですがリレーサーバの有料化が始まっていて、その決済をDMにLNインボイスを送付して行うことが試されています。2だとパブリックに投稿されますが、こちらはプライベートなので購入希望者のみにLNインボイスを届けられます。

おまけ: Nostrのユーザ名をLNアドレスと同じにする
直接は関係ないですが、Nostrはユーザー名をemail形式にすることができます。LNアドレスも自分でドメイン取って作れるのでNostrのユーザー名と投げ銭のアドレスを同じにできます。
LNウォレットのAlbyのドメインをNostrのユーザ名にも活用している様子 [Not found]
実装方法
LNアドレスもLNインボイスも非常にシンプルな話ですが軽くまとめます。 Snortリポジトリ
LNアドレス
- セットされたLNアドレスを分解して
https://[domain]/.well-known/lnurlp/[username]にリクエストする - 成功したら投げ銭量を決めるUIを提示する
- Get Inoviceボタンを押したら1のレスポンスにあるcallbackにリクエストしてインボイスを取得する
- 成功したらPayボタンを提示する
LNインボイス
- 投稿内容がLNインボイス識別子
lnbc10m〜だとわかると、識別子の中の文字列から情報(金額、説明、有効期限)を取り出し、表示用のUIを作成する - 有効期限内だったらPayボタンを提示し、期限が切れていたらExpiredでロックする
支払い
Payボタンを押された後の動きはアドレス、インボイスとも同じです。
- ブラウザでWebLN(Albyなど)がセットされていて、window.weblnオブジェクトがenableになっていると、拡張機能の支払い画面が立ち上がる。クライアント側で支払い成功をキャッチすることも可能。
- Open Walletボタンを押すと
lightning:lnbc10m~のURI形式でwindow.openされ、Mac/Windows/iPhone/Androidなど各OSに応じたアプリケーション呼び出しが行われ、URIに対応しているLNウォレットが立ち上がる
[追記]ノート単位の投げ銭
Snort周辺の数人(strike社員っぽい人が一人いて本件のメイン実装している)で試験的にやっているようで現時点では実装レベルでしか詳細わかりませんでした。strikeのzapといまいち区別が付かなかったのですが、実装を見るとnostrプロトコルにzapイベントが追加されています。ソースコメントではこの後NIP(nostr improvement proposal)が起こされるようでかなりハッキーです。zap=tipの方言なんでしょうか?
ノートやプロフィールやリアクションなどに加えて新たにnostrイベントに追加しているものは以下2つです。
- zapRequest 投げ銭した側が対象イベントIDと量を記録する
- zapReceipt 投げ銭を受け取った側用のイベント
一つでできそうと思ったけど、nostrは自己主権のプロトコルでイベント作成するには発行者の署名が必須なので2つに分かれているのでしょう。
所感
現状はクライアントだけで完結する非常にシンプルな方法になっています。リレーサーバも経由しないしクライアントにLNノードを組み込むこともしていません。サードパーティへのhttpリクエストやローカルのアプリに受け渡すだけなので、実はどんな一般アプリでもそんなに知識もコストも要らずにパッとできるものです。
現状ちょっと不便だなと思っていることは、タイムラインに流れるインボイスの有効期限内の支払い済みがわからないことです。Payボタンを押してエラーにならないとわかりません。ウォレットアプリに放り投げていてこのトレースするためには、ウォレット側で支払い成功したらNostrイベントを書き込むなどの対応しない限りは、サービス側でインボイスを定期的に一つ一つLNに投げてチェックするなどが必要だと思われるので、他のサービスでマネするときは留意しておくとよさそうです。
一方で、DMによるLNインボイス送付は活用方法が広がりそうな予感があります。Nostrの公開鍵による本人特定と、LNインボイスのメモ欄のテキスト情報による突き合わせだけでも、かんたんな決済機能として用いれそうだからです。もっとNostrに判断材料を追加したければイベント追加も簡単にできることをSnortが示しています。とくにリレーサーバ購読やPROメニューなどのNostr周辺の支払いはやりやすそうなので、DM活用ではなくなにかしらの決済メニューを搭載したNostrクライアントもすぐに出てきそう気がします。
- セットされたLNアドレスを分解して
-
 @ c4b5369a:b812dbd6
2025-04-15 07:26:16
@ c4b5369a:b812dbd6
2025-04-15 07:26:16Offline transactions with Cashu
Over the past few weeks, I've been busy implementing offline capabilities into nutstash. I think this is one of the key value propositions of ecash, beinga a bearer instrument that can be used without internet access.
 It does however come with limitations, which can lead to a bit of confusion. I hope this article will clear some of these questions up for you!
It does however come with limitations, which can lead to a bit of confusion. I hope this article will clear some of these questions up for you!What is ecash/Cashu?
Ecash is the first cryptocurrency ever invented. It was created by David Chaum in 1983. It uses a blind signature scheme, which allows users to prove ownership of a token without revealing a link to its origin. These tokens are what we call ecash. They are bearer instruments, meaning that anyone who possesses a copy of them, is considered the owner.
Cashu is an implementation of ecash, built to tightly interact with Bitcoin, more specifically the Bitcoin lightning network. In the Cashu ecosystem,
Mintsare the gateway to the lightning network. They provide the infrastructure to access the lightning network, pay invoices and receive payments. Instead of relying on a traditional ledger scheme like other custodians do, the mint issues ecash tokens, to represent the value held by the users.How do normal Cashu transactions work?
A Cashu transaction happens when the sender gives a copy of his ecash token to the receiver. This can happen by any means imaginable. You could send the token through email, messenger, or even by pidgeon. One of the common ways to transfer ecash is via QR code.
The transaction is however not finalized just yet! In order to make sure the sender cannot double-spend their copy of the token, the receiver must do what we call a
swap. A swap is essentially exchanging an ecash token for a new one at the mint, invalidating the old token in the process. This ensures that the sender can no longer use the same token to spend elsewhere, and the value has been transferred to the receiver.
What about offline transactions?
Sending offline
Sending offline is very simple. The ecash tokens are stored on your device. Thus, no internet connection is required to access them. You can litteraly just take them, and give them to someone. The most convenient way is usually through a local transmission protocol, like NFC, QR code, Bluetooth, etc.
The one thing to consider when sending offline is that ecash tokens come in form of "coins" or "notes". The technical term we use in Cashu is
Proof. It "proofs" to the mint that you own a certain amount of value. Since these proofs have a fixed value attached to them, much like UTXOs in Bitcoin do, you would need proofs with a value that matches what you want to send. You can mix and match multiple proofs together to create a token that matches the amount you want to send. But, if you don't have proofs that match the amount, you would need to go online and swap for the needed proofs at the mint.Another limitation is, that you cannot create custom proofs offline. For example, if you would want to lock the ecash to a certain pubkey, or add a timelock to the proof, you would need to go online and create a new custom proof at the mint.
Receiving offline
You might think: well, if I trust the sender, I don't need to be swapping the token right away!
You're absolutely correct. If you trust the sender, you can simply accept their ecash token without needing to swap it immediately.
This is already really useful, since it gives you a way to receive a payment from a friend or close aquaintance without having to worry about connectivity. It's almost just like physical cash!
It does however not work if the sender is untrusted. We have to use a different scheme to be able to receive payments from someone we don't trust.
Receiving offline from an untrusted sender
To be able to receive payments from an untrusted sender, we need the sender to create a custom proof for us. As we've seen before, this requires the sender to go online.
The sender needs to create a token that has the following properties, so that the receciver can verify it offline:
- It must be locked to ONLY the receiver's public key
- It must include an
offline signature proof(DLEQ proof) - If it contains a timelock & refund clause, it must be set to a time in the future that is acceptable for the receiver
- It cannot contain duplicate proofs (double-spend)
- It cannot contain proofs that the receiver has already received before (double-spend)

If all of these conditions are met, then the receiver can verify the proof offline and accept the payment. This allows us to receive payments from anyone, even if we don't trust them.
At first glance, this scheme seems kinda useless. It requires the sender to go online, which defeats the purpose of having an offline payment system.
I beleive there are a couple of ways this scheme might be useful nonetheless:
-
Offline vending machines: Imagine you have an offline vending machine that accepts payments from anyone. The vending machine could use this scheme to verify payments without needing to go online itself. We can assume that the sender is able to go online and create a valid token, but the receiver doesn't need to be online to verify it.
-
Offline marketplaces: Imagine you have an offline marketplace where buyers and sellers can trade goods and services. Before going to the marketplace the sender already knows where he will be spending the money. The sender could create a valid token before going to the marketplace, using the merchants public key as a lock, and adding a refund clause to redeem any unspent ecash after it expires. In this case, neither the sender nor the receiver needs to go online to complete the transaction.
How to use this
Pretty much all cashu wallets allow you to send tokens offline. This is because all that the wallet needs to do is to look if it can create the desired amount from the proofs stored locally. If yes, it will automatically create the token offline.
Receiving offline tokens is currently only supported by nutstash (experimental).
To create an offline receivable token, the sender needs to lock it to the receiver's public key. Currently there is no refund clause! So be careful that you don't get accidentally locked out of your funds!

The receiver can then inspect the token and decide if it is safe to accept without a swap. If all checks are green, they can accept the token offline without trusting the sender.

The receiver will see the unswapped tokens on the wallet homescreen. They will need to manually swap them later when they are online again.
 Later when the receiver is online again, they can swap the token for a fresh one.
Later when the receiver is online again, they can swap the token for a fresh one.
Summary
We learned that offline transactions are possible with ecash, but there are some limitations. It either requires trusting the sender, or relying on either the sender or receiver to be online to verify the tokens, or create tokens that can be verified offline by the receiver.
I hope this short article was helpful in understanding how ecash works and its potential for offline transactions.
Cheers,
Gandlaf
-
 @ 3589b793:ad53847e
2025-04-30 11:46:52
@ 3589b793:ad53847e
2025-04-30 11:46:52※本記事は別サービスで2022年9月25日に公開した記事の移植です。
LNの手数料の適正水準はどう見積もったらいいだろうか?ルーティングノードの収益性を算出するためにはどうアプローチすればよいだろうか?本記事ではルーティングノード運用のポジションに立ち参考になりそうな数値や計算式を整理する。
個人的な感想を先に書くと以下となる。
- 現在の手数料市場は収益性が低くもっと手数料が上がった方が健全である。
- 他の決済手段と比較すると、LN支払い料金は10000ppm(手数料1%相当)でも十分ではないか。4ホップとすると中間1ノードあたり2500ppmである。
- ルーティングノードの収益性を考えると、1000ppmあれば1BTC程度の資金で年利2.8%になり半年で初期費用回収できるので十分な投資対象になると考える。
基本概念の整理
LNの料金方式
- LNの手数料は送金額に応じた料率方式が主になる。(基本料金の設定もあるが1 ~ 0 satsが大半)
- 料率単位のppm(parts per million)は、1,000,000satsを送るときの手数料をsats金額で示したもの。
- %での手数料率に変換すると1000ppm = 0.1%になる。
- 支払い者が払う手数料はルーティングに参加した各ノードの手数料の合計である。本稿では4ホップ(経由ノードが4つ)のルーティングがあるとすれば、各ノードの取り分は単純計算で1/4とみなす。
- ルーティングノードの収益はアウトバウンドフローで発生するのでアウトバウンドキャパシティが直接的な収益資源となる。
LNの料金以外のベネフィット
本稿では料金比較だけを行うが実際の決済検討では以下のような料金以外の効用も忘れてはならない。
- Bitcoin(L1)に比べると、料金の安さだけでなく、即時確定やトランザクション量のスケールという利点がある。
- クレジットカードなどの集権サービスと比較した特徴はBitcoin(L1)とだいたい同じである。
- 24時間365日利用できる
- 誰でも自由に使える
- 信頼する第三者に対する加盟や審査や手数料率などの交渉手続きが要らない
- 検閲がなく匿名性が高い
- 逆にデメリットはオンライン前提がゆえの利用の不便さやセキュリティ面の不安さなどが挙げられる。
現在の料金相場
- ルーティングノードの料金設定
- sinkノードとのチャネルは500 ~ 1000ppmが多い。
- routing/sourceノードとのチャネルは0 ~ 100ppmあたりのレンジになる。
- リバランスする場合もsinkで収益を上げているならsink以下になるのが道理である。
- プロダクト/サービスのバックエンドにいるノードの料金設定
- sinkやsourceに相当するものは上記の通り。
- 1000〜5000ppmあたりで一律同じ設定というノードもよく見かける。
- ビジネスモデル次第で千差万別だがアクティブと思われるノードでそれ以上はあまり見かけない。
- 上記は1ノードあたりの料金になる。支払い全体では経由したノードの合計になる。
料金目安
いくつかの方法で参考数字を出していく。LN料金算出は「支払い全体/2ホップしたときの1ノードあたり/4ホップしたときの1ノードあたり」の三段階で出す。
類推方式
決済代行業者との比較
- Squareの加盟店手数料は、日本3.25%、アメリカ2.60%である。
- 参考資料 https://www.meti.go.jp/shingikai/mono_info_service/cashless_payment/pdf/20220318_1.pdf
3.25%とするとLNでは「支払い全体/2ホップしたときの1ノードあたり/4ホップしたときの1ノードあたり」でそれぞれ
32,500ppm/16,250ppm/8,125ppmになる。スマホのアプリストアとの比較
- Androidのアプリストアは年間売上高が100万USDまでなら15%、それ以上なら30%
- 参考資料https://support.google.com/googleplay/android-developer/answer/112622?hl=ja
15%とするとLNでは「支払い全体/2ホップしたときの1ノードあたり/4ホップしたときの1ノードあたり」でそれぞれ
150,000ppm/75,000ppm/37,500ppmになる。Bitcoin(L1)との比較
Bitcoin(L1)は送金額が異なっても手数料がほぼ同じため、従量課金のLNと単純比較はできない。そのためここではLNの方が料金がお得になる目安を出す。
Bitcoin(L1)の手数料設定
- SegWitのシンプルな送金を対象にする。
- input×1、output×2(送金+お釣り)、tx合計222byte
- L1の手数料は、1sat/byteなら222sats、10sat/byteなら2,220sats、100sat/byteなら22,200sats。(単純化のためvirtual byteではなくbyteで計算する)
- サンプル例 https://www.blockchain.com/btc/tx/15b959509dad5df0e38be2818d8ec74531198ca29ac205db5cceeb17177ff095
L1相場が1sat/byteの時にLNの方がお得なライン
- 100ppmなら、0.0222BTC(2,220,000sats)まで
- 1000ppmなら、0.00222BTC(222,000sats)まで
L1相場が10sat/byteの時にLNの方がお得なライン
- 100ppmなら、0.222BTC(22,200,000sats)まで
- 1000ppmなら、0.0222BTC(2,220,000sats)まで
L1相場が100sat/byteの時にLNの方がお得なライン
- 100ppmなら、2.22BTC(222,000,000sats)まで
- 1000ppmなら、0.222BTC(22,200,000sats)まで
コスト積み上げ方式
ルーティングノードの原価から損益分岐点となるppmを算出する。事業者ではなく個人を想定し、クラウドではなくラズベリーパイでのノード構築環境で計算する。
費用明細
- BTC市場価格 1sat = 0.03円(1BTC = 3百万円)
初期費用
- ハードウェア一式 40,000円
- Raspberry Pi 4 8GB
- SSD 1TB
- 外付けディスプレイ
- チャネル開設のオンチェーン手数料 6.69円/チャネル
- 開設料 223sats
- 223sats * BTC市場価格0.03円 = 6.69円
固定費用
- 電気代 291.6円/月
- 時間あたりの電力量 0.015kWh
- Raspberry Pi 4 電圧5V、推奨電源容量3.0A
- https://www.raspberrypi.com/documentation/computers/raspberry-pi.html#power-supply
- kWh単価27円
- 0.015kWh * kWh単価27円 * 1ヶ月の時間720h = 291.6円
損益分岐点
- 月あたりの電気代を上回るために9,720sats(291.6円)/月以上の収益が必要である。
- ハードウェア費用回収のために0.01333333BTC(133万sats) = 40,000円の収益が必要である。
費用回収シナリオ例
アウトバウンドキャパに1BTCをデポジットしたAさんを例にする。1BTCは初心者とは言えないと思うが、このくらい原資を用意しないと費用回収の話がしづらいという裏事情がある。チャネル選択やルーティング戦略は何もしていない仮定である。ノード運用次第であることは言うまでもないので今回は要素や式を洗い出すことが主目的で一つ一つの変数の値は参考までに。
変数設定
- インバウンドを同額用意して合計キャパを2BTCとする。
- 1チャネルあたり5m satsで40チャネル開設する。
- チャネル開設費用 223sats * 40チャネル = 8,920sats
- 初期費用合計 1,333,333sats + 8,920sats = 1,342,253sats
- 一回あたり平均ルーティング量 = 100,000sats
- 1チャネルあたり平均アウトバウンド数/日 = 2
- 1チャネルあたり平均アウトバウンドppm = 50
費用回収地点
- 1日のアウトバウンド量は、 40チャネル * 2本 * 100,000sats = 8m sats
- 手数料収入は、8m sats * 0.005%(50ppm) = 400sats/日。月換算すると12,000sats/月
- 電気代を差し引くと、12,000sats - 電気代9,720sats =月収益2,280sats(68.4円)
- 初期費用回収まで、1,342,253sats / 2,280sats = 589ヵ月(49年)
- 後述するが電気代差引き前で年利0.14%になる。
理想的なppm
6ヵ月での初期費用回収を目的にしてアウトバウンドppmを求める。
- ひと月あたり、初期費用合計1,342,253sats / 6ヵ月 + 電気代9,720sats = 233,429sats(7,003円)の収益が必要。
- 1日あたり、7,781sats(233円)の収益
- その場合の平均アウトバウンドppmは、 7,781sats(1日の収益量) / 8m sats(1日のアウトバウンド量) * 1m sats(ppm変換係数) = 973ppm
他のファイナンスとの比較
ルーティングノードを運用して手数料収入を得ることは資産運用と捉えることもできる。レンディングやトレードなどの他の資産運用手段とパフォーマンス比較をするなら、デポジットしたアウトバウンドキャパシティに対する手数料収入をAPY換算する。(獲得した手数料はアウトバウンドキャパシティに積み重ねられるので複利と見做せる)
例としてLNDg(v1.3.1)のAPY算出計算式を転載する。見ての通り画面上の表記はAPYなのに中身はAPRになっているので注意だが今回は考え方の参考としてこのまま採用する。
年換算 = 365 / 7 = 52.142857 年利 = (7dayの収益 * 年換算) / アウトバウンドのキャパシティ例えば上記のAさんの費用回収シナリオに当てはめると以下となる。
年利 0.14% = (400sats * 7日 * 年換算)/ 100m sats
電気代を差し引くと 76sats/日となり年利0.027%
もし平均アウトバウンド1000ppmになると8,000sats/日なので年利2.9%になる。 この場合、電気代はほぼ1日で回収されるため差し引いても大差なく7,676sats/日で年利2.8%になる。
考察
以上、BTC市場価格や一日のアウトバウンド量といった重要な数値をいくつか仮置きした上ではあるが、LN手数料の適正水準を考えるための参考材料を提示した。
まず、現在のLNの料金相場は他の決済手段から比べると圧倒的に安いことがわかった。1%でも競争力が十分ありそうなのに0.1%前後で送金することが大半である。
健全な市場発展のためには、ルーティングノードの採算が取れていることが欠かせないと考えるが、残念ながら現在の収益性は低い。ルーティングノードの収益性は仮定に仮定を重ねた見積もりになるが、平均アウトバウンドが1000ppmでようやく個人でも参入できるレベルになるという結論になった。ルーティングノードの立場に立つと、現在の市場平均から大幅な上昇が必要だと考える。
手数料市場は競争のためつねに下方圧力がかかっていて仕様上で可能な0に近づいている。この重力に逆らうためには、1. 需要 > 供給のバランスになること、2. 事業用途での高額買取のチャネルが増えること、の2つの観点を挙げる。1にせよ2にせよネットワークの活用が進むことで発生し、手数料市場の大きな変動機会になるのではないか。他の決済手段と比較すれば10000ppm、1チャネル2500ppmあたりまでは十分に健全な範囲だと考える。
-
 @ 3589b793:ad53847e
2025-04-30 10:53:29
@ 3589b793:ad53847e
2025-04-30 10:53:29※本記事は別サービスで2022年5月22日に公開した記事の移植です。
Happy 🍕 Day's Present
まだ邦訳版が出版されていませんがこれまでのシリーズと同じくGitHubにソースコードが公開されています。なんと、現在のライセンスでは個人使用限定なら翻訳や製本が可能です。Macで、翻訳にはPDFをインプットにできるDeepLを用いた環境で、インスタントに製本してKindleなどで読めるようにする方法をまとめました。
手順の概要
- Ruby環境を用意する
- PDF作成ツールをセットアップする
- GitHubのリポジトリを自分のPCにクローンする
- asciidocをPDFに変換する
- DeepLを節約するためにPDFを結合する
- DeepLで翻訳ファイルを作る
- 一冊に製本する
この手法の強み・弱み
翻訳だけならPDFを挟まなくてもGithubなどでプレビューできるコンパイル後のドキュメントの文章をコピーしてDeepLのWebツールにペーストすればよいですが、原著のペーパーブックで438ページある大容量です。熟練のコピペ職人でも年貢を納めて後進(機械やソフトウェア)に道を譲る刻ではないでしょうか?ただし、Pros/Consがあります。
Pros
- 一冊の本になるので毎度のコピペ作業がいらない
- Pizzaを食べながらタブレットやKindleで読める
- 図や表が欠落しない(プロトコルの手順を追った解説が多いため最大の動機でした)
- 2022/6/16追記: DeepLの拡張機能がアップデートされウェブページの丸ごと翻訳が可能になりました。よってウェブ上のgithubの図表付きページをそのまま翻訳できます。
Cons
- Money is power(大容量のためDeepLの有料契約が必要)
- ページを跨いだ文章が統合されずに不自然な翻訳になる(仕様です)
- ~~翻訳できない章が一つある(解決方法がないか調査中です。DeepLさんもっとエラーメッセージ出してくれ。Help me)~~ DeepLサポートに投げたら翻訳できるようになりました。
詳細ステップ
0.Ruby環境を用意する
asciidoctorも新しく入れるなら最新のビルドで良いでしょう。
1.PDF作成ツールをセットアップする
$ gem install asciidoctor asciidoctor-pdf $ brew install gs2.GitHubのリポジトリを自分のPCにクローンする
どこかの作業ディレクトリで以下を実行する
$ git clone git@github.com:lnbook/lnbook.git $ cd lnbook3.asciidocをPDFに変換する
ワイルドカードを用いて本文を根こそぎPDF化します。
$ asciidoctor-pdf 0*.asciidoc 1*.asciidocいろいろ解析の警告が出ますが、ソースのasciidocを弄んでいくなりawsomeライブラリを導入すれば解消できるはずです。しかし如何せん量が多いので心が折れます。いったん無視して"Done is better than perfect"精神で最後までやり切りましょう。そのままGO!
また、お好みに合わせて、htmlで用意されている装丁用の部品も準備しましょう。私は表紙のcover.htmlをピックしました。ソースがhtmlなのでasciidoctorを通さず普通にPDFへ変換します。https://qiita.com/chenglin/items/9c4ed0dd626234b71a2c
4.DeepLを節約するためにPDFを結合する
DeepLでは課金プラン毎に翻訳可能なファイル数が設定されている上に、一本あたりの最大ファイルサイズが10MBです。また、翻訳エラーになる章が含まれていると丸ごとコケます。そのためPDCAサイクルを回し、最適なファイル数を手探りで見つけます。以下が今回導出した解となります。
$ gs -q -dNOPAUSE -dBATCH -sDEVICE=pdfwrite -sOutputFile=output_1.pdf 01_introduction.pdf 02_getting_started.pdf 03_how_ln_works.pdf 04_node_client.pdf 05_node_operations.pdf$gs -q -dNOPAUSE -dBATCH -sDEVICE=pdfwrite -sOutputFile=output_2_1.pdf 06_lightning_architecture.pdf 07_payment_channels.pdf 08_routing_htlcs.pdf$gs -q -dNOPAUSE -dBATCH -sDEVICE=pdfwrite -sOutputFile=output_2_2.pdf 09_channel_operation.pdf 10_onion_routing.asciidoc$ gs -q -dNOPAUSE -dBATCH -sDEVICE=pdfwrite -sOutputFile=output_3.pdf 11_gossip_channel_graph.pdf 12_path_finding.pdf 13_wire_protocol.pdf 14_encrypted_transport.pdf 15_payment_requests.pdf 16_security_privacy_ln.pdf 17_conclusion.pdf5. DeepLで翻訳ファイルを作る
PDFファイルを真心を込めた手作業で一つ一つDeepLにアップロードしていき翻訳ファイルを作ります。ファイル名はデフォルトの
[originalName](日本語).pdfのままにしています。6. 一冊に製本する
表紙 + 本文で作成する例です。
$ gs -q -dNOPAUSE -dBATCH -sDEVICE=pdfwrite -sOutputFile=mastering_ln_jp.pdf cover.pdf "output_1 (日本語).pdf" "output_2_1 (日本語).pdf" "output_2_2 (日本語).pdf" "output_3 (日本語).pdf"コングラチュレーションズ🎉

あなたは『Mastering the Lightning Network』の日本語版を手に入れた!個人使用に限り、あとは煮るなり焼くなりEPUBなりkindleへ送信するなり好き放題だ。
-
 @ f11e91c5:59a0b04a
2025-04-30 07:52:21
@ f11e91c5:59a0b04a
2025-04-30 07:52:21!!!2022-07-07に書かれた記事です。
暗号通貨とかでお弁当売ってます 11:30〜14:00ぐらいでやってます
◆住所 木曜日・東京都渋谷区宇田川町41 (アベマタワーの下らへん)
◆お値段
Monacoin 3.9mona
Bitzeny 390zny
Bitcoin 3900sats (#lightningNetwork)
Ethereum 0.0039Ether(#zkSync)
39=thank you. (円を基準にしてません)
最近は週に一回になりました。 他の日はキッチンカーの現場を探したり色々してます。 東京都内で平日ランチ出店出来そうな場所があればぜひご連絡を!
 写真はNFCタグです。
スマホにウォレットがあればタッチして3900satsで決済出来ます。
正直こんな怪しい手書きのNFCタグなんて絶対にビットコイナーは触りたくも無いだろうなと思いますが、これでも良いんだぜというメッセージです。
写真はNFCタグです。
スマホにウォレットがあればタッチして3900satsで決済出来ます。
正直こんな怪しい手書きのNFCタグなんて絶対にビットコイナーは触りたくも無いだろうなと思いますが、これでも良いんだぜというメッセージです。今までbtcpayのposでしたが速度を追求してこれに変更しました。 たまに上手くいかないですがそしたら渋々POS出すので温かい目でよろしくお願いします。
ノードを建てたり決済したりで1年経ちました。 最近も少しずつノードを建てる方が増えてるみたいで本当凄いですねUmbrel 大体の人がルーティングに果敢に挑むのを見つつ 奥さんに土下座しながら費用を捻出する弱小の私は決済の利便性を全開で振り切るしか無いので応援よろしくお願いします。
あえて あえて言うのであれば、ルーティングも楽しいですけど やはり本当の意味での即時決済や相手を選んでチャネルを繋げる楽しさもあるよとお伝えしたいっ!! 決済を受け入れないと分からない所ですが 承認がいらない時点で画期的です。
QRでもタッチでも金額指定でも入力でも もうやりようには出来てしまうし進化が恐ろしく早いので1番利用の多いpaypayの手数料(事業者側のね)を考えたらビットコイン凄いじゃない!と叫びたくなる。 が、やはり税制面や価格の変動(うちはBTC固定だけども)ウォレットの操作や普及率を考えるとまぁ難しい所もあるんですかね。
それでも継続的に沢山の人が色んな活動をしてるので私も何か出来ることがあれば 今後も奥さんに土下座しながら頑張って行きたいと思います。
(Originally posted 2022-07-07)
I sell bento lunches for cryptocurrency. We’re open roughly 11:30 a.m. – 2:00 p.m. Address Thursdays – 41 Udagawa-chō, Shibuya-ku, Tokyo (around the base of Abema Tower)
Prices Coin Price Note Monacoin 3.9 MONA
Bitzeny 390 ZNY Bitcoin 3,900 sats (Lightning Network)
Ethereum 0.0039 ETH (zkSync) “39” sounds like “thank you” in Japanese. Prices aren’t pegged to yen.These days I’m open only once a week. On other days I’m out scouting new spots for the kitchen-car. If you know weekday-lunch locations inside Tokyo where I could set up, please let me know!
The photo shows an NFC tag. If your phone has a Lightning wallet, just tap and pay 3,900 sats. I admit this hand-written NFC tag looks shady—any self-respecting Bitcoiner probably wouldn’t want to tap it—but the point is: even this works!
I used to run a BTCPay POS, but I switched to this setup for speed. Sometimes the tap payment fails; if that happens I reluctantly pull out the old POS. Thanks for your patience.
It’s been one year since I spun up a node and started accepting Lightning payments. So many people are now running their own nodes—Umbrel really is amazing. While the big players bravely chase routing fees, I’m a tiny operator scraping together funds while begging my wife for forgiveness, so I’m all-in on maximising payment convenience. Your support means a lot!
If I may add: routing is fun, but instant, trust-minimised payments and the thrill of choosing whom to open channels with are just as exciting. You’ll only understand once you start accepting payments yourself—zero-confirmation settlement really is revolutionary.
QR codes, NFC taps, fixed amounts, manual entry… the possibilities keep multiplying, and the pace of innovation is scary fast. When I compare it to the merchant fees on Japan’s most-used service, PayPay, I want to shout: “Bitcoin is incredible!” Sure, taxes, price volatility (my shop is BTC-denominated, though), wallet UX, and adoption hurdles are still pain points.
Even so, lots of people keep building cool stuff, so I’ll keep doing what I can—still on my knees to my wife, but moving forward!
-
 @ d1667293:388e7004
2025-04-29 16:00:19
@ d1667293:388e7004
2025-04-29 16:00:19The "Bitcoindollar" system—an emerging term which describes the interplay of U.S. dollar-denominated stablecoins and Bitcoin as complementary forces in the evolving monetary framework of the digital era (and which replaces the defunct Petrodollar system)—has sparked an interesting debate on Nostr with PowMaxi.
You will find the thread links at the bottom of this article.
Powmaxi argues that attempting to merge hard money (Bitcoin) with soft money (the U.S. dollar) is structurally doomed, because the systems are inherently contradictory and cannot coexist without one eventually destroying the other.
This critique is certainly valid, but ONLY if the Bitcoindollar is viewed as a final system. But I never claim that. To the contrary, the conclusion in my book is that this is a system that buys time for fiat, absorbs global demand for monetary stability, and ushers in a Bitcoinized world without the immediate collapse and the reset of the fiat system which would otherwise cause dramatic consequences. The Bitcoindollar is the only way to a gradual Bitcoin dominance in 10-20 years time while avoiding sudden collapse of the fiat system, so that also the power elites who hold the keys to this system can adapt.\ At least this is my hope.
Therefore the "fusion" isn't the future. The siphoning is. And the U.S. may try to ride it as long as possible. The Bitcoindollar system is a transitional strategic framework, not a\ permanent monetary equilibrium. In the end I agree with PowMaxi.
His detailed critique deserves an equally detailed analysis. Here's how the objections break down and why they don’t necessarily undermine the Bitcoindollar system.
1. Hard Money vs. Soft Money: Opposed Systems?
Objection: Bitcoin is a closed, decentralized system with a fixed supply; the dollar is an open, elastic system governed by central banks and political power. These traits are mutually exclusive and incompatible.
Response: Ideologically, yes. Practically, no. Hybrid financial systems are not uncommon. Bitcoin and stablecoins serve different user needs: Bitcoin is a store of value; stablecoins are mediums of exchange. Their coexistence mirrors real-world economic needs. The contradiction can be managed, and is not fatal at least for the transitional phase.
2. Scarcity vs. Elasticity: Economic Incompatibility?
Objection: Bitcoin can’t inject liquidity in crises; fiat systems can. Anchoring fiat to Bitcoin removes policymakers' tools.
Response: Correct — but that’s why Bitcoin is held as a reserve, not used as the primary medium of exchange in the Bitcoindollar model. Fiat-based liquidity mechanisms still function via stablecoins, while Bitcoin acts as a counterweight to long-term monetary debasement. The system’s strength is in its optionality: you don’t have to use Bitcoin until you want an exit ramp from fiat.
3. No Stable Equilibrium: One Must Win?
Objection: The system will destabilize. Either Bitcoin undermines fiat or fiat suppresses Bitcoin.
Response: Not necessarily in this transitional phase. The “conflict” isn’t between tools — it’s between control philosophies. The dollar won’t disappear overnight, and Bitcoin isn’t going away. The likely outcome is a gradual shifting of savings and settlement layers to Bitcoin, while fiat continues to dominate day-to-day payments and credit markets — until Bitcoin becomes structurally better in both.
4. Gresham’s and Thiers’ Law: Hollowing Fiat?
Objection: People save in Bitcoin and spend fiat, eroding fiat value.
Response: Yes — and that’s been happening since 2009. But this isn’t a flaw; it’s a transition mechanism. The Bitcoindollar model recognizes this and creates a bridge: it monetizes U.S. debt while preserving access to hard money. In the long run, my expectation is that naturally bitcoin will prevail both as a SOV and currency, but until then, stablecoins and T-bill-backed tokens serve useful roles in the global economy.
5. Philosophical Incompatibility?
Objection: Bitcoin prioritizes individual sovereignty; fiat systems are hierarchical. They can't be reconciled.
Response: They don’t need to be reconciled ideologically to function in parallel. Users choose the tool that suits their needs. One empowers individual autonomy; the other offers state-backed convenience. This is a competition of values, not a mechanical incompatibility. The Bitcoindollar model is a strategy. It’s a bridge between old and new systems, not a permanent coexistence.
6. Fusion is Impossible?
Objection: It’s only a temporary bridge. One side must lose.
Response: Exactly. The Bitcoindollar system is a transitional bridge. But that doesn’t reduce its value. It provides a functional pathway for individuals, companies, and governments to gradually exit broken monetary systems and experiment with new models.
In the meantime, the U.S. benefits from stablecoin-driven Treasury demand, while Bitcoin continues to grow as a global reserve asset.
Bottom line: A Strategic Convergence, Not a Permanent Fusion
The Bitcoindollar system isn’t a contradiction. It’s a convergence zone. It reflects the reality that monetary systems evolve gradually, not cleanly. Bitcoin and fiat will compete, overlap, and influence each other. Eventually, yes — hard money wins. But until then, hybrid systems offer powerful stepping stones.
Thread links:
Thread started from this initial post.
-
 @ fd0bcf8c:521f98c0
2025-04-29 13:38:49
@ fd0bcf8c:521f98c0
2025-04-29 13:38:49The vag' sits on the edge of the highway, broken, hungry. Overhead flies a transcontinental plane filled with highly paid executives. The upper class has taken to the air, the lower class to the roads: there is no longer any bond between them, they are two nations."—The Sovereign Individual
Fire
I was talking to a friend last night. Coffee in hand. Watching flames consume branches. Spring night on his porch.
He believed in America's happy ending. Debt would vanish. Inflation would cool. Manufacturing would return. Good guys win.
I nodded. I wanted to believe.
He leaned forward, toward the flame. I sat back, watching both fire and sky.
His military photos hung inside. Service medals displayed. Patriotism bone-deep.
The pendulum clock on his porch wall swung steadily. Tick. Tock. Measuring moments. Marking epochs.
History tells another story. Not tragic. Just true.
Our time has come. America cut off couldn't compete. Factories sit empty. Supply chains span oceans. Skills lack. Children lag behind. Rebuilding takes decades.
Truth hurts. Truth frees.
Cycles
History moves in waves. Every 500 years, power shifts. Systems fall. Systems rise.
500 BC - Greek coins changed everything. Markets flourished. Athens dominated.
1 AD - Rome ruled commerce. One currency. Endless roads. Bustling ports.
500 AD - Rome faded. Not overnight. Slowly. Trade withered. Cities emptied. Money debased. Roads crumbled. Local strongmen rose. Peasants sought protection. Feudalism emerged.
People still lived. Still worked. Horizons narrowed. Knowledge concentrated. Most barely survived. Rich adapted. Poor suffered.
Self-reliance determined survival. Those growing food endured. Those making essential goods continued. Those dependent on imperial systems suffered most.
1000 AD - Medieval revival began. Venice dominated seas. China printed money. Cathedrals rose. Universities formed.
1500 AD - Europeans sailed everywhere. Spanish silver flowed. Banks financed kingdoms. Companies colonized continents. Power moved west.
The pendulum swung. East to West. West to East. Civilizations rose. Civilizations fell.
2000 AD - Pattern repeats. America strains. Digital networks expand. China rises. Debt swells. Old systems break.
We stand at the hinge.
Warnings
Signs everywhere. Dollar weakens globally. BRICS builds alternatives. Yuan buys oil. Factories rust. Debt exceeds GDP. Interest consumes budgets.
Bridges crumble. Education falters. Politicians chase votes. We consume. We borrow.
Rome fell gradually. Citizens barely noticed. Taxes increased. Currency devalued. Military weakened. Services decayed. Life hardened by degrees.
East Rome adapted. Survived centuries. West fragmented. Trade shrank. Some thrived. Others suffered. Life changed permanently.
Those who could feed themselves survived best. Those who needed the system suffered worst.
Pendulum
My friend poured another coffee. The burn pile popped loudly. Sparks flew upward like dying stars.
His face changed as facts accumulated. Military man. Trained to assess threats. Detect weaknesses.
He stared at the fire. National glory reduced to embers. Something shifted in his expression. Recognition.
His fingers tightened around his mug. Knuckles white. Eyes fixed on dying flames.
I traced the horizon instead. Observing landscape. Noting the contrast.
He touched the flag on his t-shirt. I adjusted my plain gray one.
The unpayable debt. The crumbling infrastructure. The forgotten manufacturing. The dependent supply chains. The devaluing currency.
The pendulum clock ticked. Relentless. Indifferent to empires.
His eyes said what his patriotism couldn't voice. Something fundamental breaking.
I'd seen this coming. Years traveling showed me. Different systems. Different values. American exceptionalism viewed from outside.
Pragmatism replaced my old idealism. See things as they are. Not as wished.
The logs shifted. Flames reached higher. Then lower. The cycle of fire.
Divergence
Society always splits during shifts.
Some adapt. Some don't.
Printing arrived. Scribes starved. Publishers thrived. Information accelerated. Readers multiplied. Ideas spread. Adapters prospered.
Steam engines came. Weavers died. Factory owners flourished. Villages emptied. Cities grew. Coal replaced farms. Railways replaced wagons. New skills meant survival.
Computers transformed everything. Typewriters vanished. Software boomed. Data replaced paper. Networks replaced cabinets. Programmers replaced typists. Digital skills determined success.
The self-reliant thrived in each transition. Those waiting for rescue fell behind.
Now AI reshapes creativity. Some artists resist. Some harness it. Gap widens daily.
Bitcoin offers refuge. Critics mock. Adopters build wealth. The distance grows.
Remote work redraws maps. Office-bound struggle. Location-free flourish.
The pendulum swings. Power shifts. Some rise with it. Some fall against it.
Two societies emerge. Adaptive. Resistant. Prepared. Pretending.
Advantage
Early adapters win. Not through genius. Through action.
First printers built empires. First factories created dynasties. First websites became giants.
Bitcoin followed this pattern. Laptop miners became millionaires. Early buyers became legends.
Critics repeat themselves: "Too volatile." "No value." "Government ban coming."
Doubters doubt. Builders build. Gap widens.
Self-reliance accelerates adaptation. No permission needed. No consensus required. Act. Learn. Build.
The burn pile flames like empire's glory. Bright. Consuming. Temporary.
Blindness
Our brains see tigers. Not economic shifts.
We panic at headlines. We ignore decades-long trends.
We notice market drops. We miss debt cycles.
We debate tweets. We ignore revolutions.
Not weakness. Just humanity. Foresight requires work. Study. Thought.
Self-reliant thinking means seeing clearly. No comforting lies. No pleasing narratives. Just reality.
The clock pendulum swings. Time passes regardless of observation.
Action
Empires fall. Families need security. Children need futures. Lives need meaning.
You can adapt faster than nations.
Assess honestly. What skills matter now? What preserves wealth? Who helps when needed?
Never stop learning. Factory workers learned code. Taxi drivers joined apps. Photographers went digital.
Diversify globally. No country owns tomorrow. Learn languages. Make connections. Stay mobile.
Protect your money. Dying empires debase currencies. Romans kept gold. Bitcoin offers similar shelter.
Build resilience. Grow food. Make energy. Stay strong. Keep friends. Read old books. Some things never change.
Self-reliance matters most. Can you feed yourself? Can you fix things? Can you solve problems? Can you create value without systems?
Movement
Humans were nomads first. Settlers second. Movement in our blood.
Our ancestors followed herds. Sought better lands. Survival meant mobility.
The pendulum swings here too. Nomad to farmer. City-dweller to digital nomad.
Rome fixed people to land. Feudalism bound serfs to soil. Nations created borders. Companies demanded presence.
Now technology breaks chains. Work happens anywhere. Knowledge flows everywhere.
The rebuild America seeks requires fixed positions. Factory workers. Taxpaying citizens in permanent homes.
But technology enables escape. Remote work. Digital currencies. Borderless businesses.
The self-reliant understand mobility as freedom. One location means one set of rules. One economy. One fate.
Many locations mean options. Taxes become predatory? Leave. Opportunities disappear? Find new ones.
Patriotism celebrates roots. Wisdom remembers wings.
My friend's boots dug into his soil. Planted. Territorial. Defending.
My Chucks rested lightly. Ready. Adaptable. Departing.
His toolshed held equipment to maintain boundaries. Fences. Hedges. Property lines.
My backpack contained tools for crossing them. Chargers. Adapters. Currency.
The burn pile flame flickers. Fixed in place. The spark flies free. Movement its nature.
During Rome's decline, the mobile survived best. Merchants crossing borders. Scholars seeking patrons. Those tied to crumbling systems suffered most.
Location independence means personal resilience. Economic downturns become geographic choices. Political oppression becomes optional suffering.
Technology shrinks distance. Digital work. Video relationships. Online learning.
Self-sovereignty requires mobility. The option to walk away. The freedom to arrive elsewhere.
Two more worlds diverge. The rooted. The mobile. The fixed. The fluid. The loyal. The free.
Hope
Not decline. Transition. Painful but temporary.
America may weaken. Humanity advances. Technology multiplies possibilities. Poverty falls. Knowledge grows.
Falling empires see doom. Rising ones see opportunity. Both miss half the picture.
Every shift brings destruction and creation. Rome fell. Europe struggled. Farms produced less. Cities shrank. Trade broke down.
Yet innovation continued. Water mills appeared. New plows emerged. Monks preserved books. New systems evolved.
Different doesn't mean worse for everyone.
Some industries die. Others birth. Some regions fade. Others bloom. Some skills become useless. Others become gold.
The self-reliant thrive in any world. They adapt. They build. They serve. They create.
Choose your role. Nostalgia or building.
The pendulum swings. East rises again. The cycle continues.
Fading
The burn pile dimmed. Embers fading. Night air cooling.
My friend's shoulders changed. Tension releasing. Something accepted.
His patriotism remained. His illusions departed.
The pendulum clock ticked steadily. Measuring more than minutes. Measuring eras.
Two coffee cups. His: military-themed, old and chipped but cherished. Mine: plain porcelain, new and unmarked.
His eyes remained on smoldering embers. Mine moved between him and the darkening trees.
His calendar marked local town meetings. Mine tracked travel dates.
The last flame flickered out. Spring peepers filled the silence.
In darkness, we watched smoke rise. The world changing. New choices ahead.
No empire lasts forever. No comfort in denial. Only clarity in acceptance.
Self-reliance the ancient answer. Build your skills. Secure your resources. Strengthen your body. Feed your mind. Help your neighbors.
The burn pile turned to ash. Empire's glory extinguished.
He stood facing his land. I faced the road.
A nod between us. Respect across division. Different strategies for the same storm.
He turned toward his home. I toward my vehicle.
The pendulum continued swinging. Power flowing east once more. Five centuries ending. Five centuries beginning.
"Bear in mind that everything that exists is already fraying at the edges." — Marcus Aurelius
Tomorrow depends not on nations. On us.
-
 @ 83279ad2:bd49240d
2025-04-29 05:53:52
@ 83279ad2:bd49240d
2025-04-29 05:53:52test
-
 @ fd78c37f:a0ec0833
2025-05-01 11:52:27
@ fd78c37f:a0ec0833
2025-05-01 11:52:27Author: Taryn Christiansen
Introduction:
The future doesn’t look good for America. The economy is down, politics is in shambles, and, perhaps most devastating, the culture is split. The only agreement is that change is needed.
This article aims to pave a road forward. Innovation drives the economy, and great innovations change and improve daily life. Joint efforts between public institutions and private enterprise, along with the energy and momentum generated by efficient and productive programs, can be orchestrated to cultivate national pride. But those programs need to have a noble purpose. Devotion toward technologies with the potential to transform and improve people’s lives should be the goal. Due to recent advancements in biotechnology, efforts should be directed there.
Section 1 dives into the cultural divide. Section 2 outlines a way forward by examining the innovative process and how it can be implemented. Section 3 looks at the specifics of that implementation. Section 4 consists of concluding remarks about the future.
Section 1: A Divided Country
There are two competing visions dividing America. The Woke vision asserts that the United States was, and is, a fundamentally oppressive regime. The idea of a universal reason, the notion that human beings can attain progress in perpetuity through liberal democracy, science, and capitalism, is seen as nothing more than an ideological weapon used to coerce people into acquiescing to a hierarchy that benefits the few while exploiting the many – and so, out of principles of fairness and equity, the country has to be dismantled.
The Trumpian vision attempts to reaffirm American values. It aims to reestablish American exceptionalism and reinvigorate the American vision of prosperity and economic growth. It seeks to rekindle a sense of American greatness. But it does so cheaply. It is, in essence, the dying breath of a consumer culture fighting its own death. Like the first vision, it too rejects reason and discussion and the procedural processes necessary for liberal democracy. It perceives power as the proper political tool for achieving its objectives. It is not an attempt to restore the values that once characterized the country; it breaks from the American tradition in a radical direction toward a politics of entertainment.
Long ago, the country believed that the human capacity for reason – the ability to see the world clearly under the light of truth, unencumbered by bias or prejudice, free from instinct and emotion – was the torch that carries posterity forward. The founders believed the Bill of Rights and The Constitution enshrined eternal truths that reason alone made accessible. John Locke, an influential figure for the founders, stated that the primary purpose of government is to protect individuals' natural rights. We are all free and have the right to live the life we wish to live. But government is needed to ensure others do not interfere with those rights. What binds us is not a religion or creed but the mutual opportunity for each individual to form their own beliefs, to live out their own conceptions of the good. While fundamental, we will see that it is not enough. A collective purpose is necessary.
Now, the Woke vision sees this older view as wholly mythological – and for good reason. For example, there was a time when black people did not know they were descendants from Africa or the Caribbean and not naturally disposed slaves. People’s various histories and genealogies were stripped away, creating a space by which their humanity could be taken and they could be exploited. They were purposefully and intentionally cast into the shadows of history, and the culpable thought themselves perfectly justified. There was a time when moral and historical narratives depicting a grand destiny of white people conquering the West were considered to be true and that the genocide of Native peoples was not only acceptable but in fact necessary, and therefore legitimate. It has been a titanic and creative effort by great individuals and collective coalitions to get America to become self-conscious of its heinous blunders. Some of the best art and ideas of the twentieth century were born out of those efforts. The beginnings of liberation are born out of the ability to imagine a horizon beyond one’s current circumstances. And that ability for many people has been forged by courageous and heroic predecessors. But the spirit of those movements and their development into the Woke vision is a sign that it has lost its creative potential.
The Woke vision asserts that values like reason and rights are the remains of a colonial legacy. However, by negating them and failing to replace them with new values, deconstructive forces are all that remain. The country has historically failed (as well as succeeded) in living up to what reason and rights demand. But that doesn’t mean they aren’t the proper path forward. The assumption here is that they are, and they have to be creatively reinterpreted.
And the Trumpian vision fails as well. But it is worse because it never did, nor will it ever have any real creative potential. It is highly destructive. We can think about this in the following way.
The nineteenth-century German philosopher Friedrich Nietzsche believed a single, fundamental drive governs all of organic life: the will to power. Life, in a constant struggle, perpetually strives to expand and overcome itself repeatedly. From the brute force of two animals fighting for scarce resources to the highest manifestation of human potential, such as moral systems and inspiring artwork, all are produced from the same vital energy and source: the effort to attain power and mastery over a chaotic world.
As society develops and moves away from a state of nature, the will to power transfigures itself through a sublimative process that demands the individual to repress particular instincts and act according to the strictures and constraints formulated and instituted by the collective. As Freud observed in his Civilization and Its Discontents, the push and pull between primitive and ancient instincts and civilization’s repression of them create inextricable tensions. The Yale historian Marci Shore makes an incisive observation of Trump as a symbolic figure using this context and its language: he is the release and outpouring of those repressed instincts – the license to overthrow the restraints placed on the individual. Trump is the embodiment of brute force, a blind ego striving to assert itself over the world, adopting whatever means are available to achieve its aim. He is an eruption of the repressed Hobbesian state of nature, which expresses “a perpetual and restless desire of power after power that ceaseth only in death.” This is a destructive instinct, and we would be wise not to find out what follows.
Section 2: Unity Through Innovation
So, what is the solution? The country needs a ballast point. It needs national pride. Without a shared sense of identity and purpose, a sense of belonging to a larger community bound by a set of values, the country will continue to unravel. Regardless of the philosophical-level disputes and disagreements on fundamental principles that divide left from right, a collective identity needs to emerge. This article argues that, like the founders, we should turn to our institutions. We should look at how our institutions can facilitate needs by enabling individuals with the creative energy and tenacity to bring about new technologies and innovations that will transform the economy and standards of living. But not just new gadgets and services like iPhones and DoorDash but new technologies with the potential to enable people to live more fulfillingly and purposefully. New vaccines to eliminate unruly diseases, new therapies to mitigate the effects of debilitating illnesses, novel pharmaceuticals with competitive prices and cheaper means of production, and innovative mechanisms to empower people with disabilities to live as they are only able to imagine should play a major part in the mission that characterizes the country. That is a purpose to be proud of. Institutions like the Food and Drug Administration (FDA) and the National Institutes of Health (NIH) should act as bows, shooting forward the individuals and companies striving to reach that mark.
There’s a lot of talk about government efficiency and the need to be more fiscally responsible. Those are good things. But efficiency needs to have a purpose. There must be a goal that efficiency works to achieve. We should not wish to live without regulatory institutions. For example, people like Balaji Srinivasan are wrong to think we’re better off in an FDA-free society. The goal should be to harness those institutions, conduct more research and development, and utilize resources more effectively to achieve the results we want as a country. Just as we should strive to continue and expand our role in the AI race, we should also aim to maintain and further develop our leadership in biotech.
But we need a new of what the historian Gary Gerstle calls political order to achieve this. Political orders are “a vision of the good life that sells important constituencies on the virtues of a way of doing politics. The New Deal order and the Neoliberal order—which are, in a sense, the reverse of each other—illustrate this.”
It is common in America to see the world through the lenses of The New Deal and Neoliberal political orders for resolving issues in the country. The latter is to let the market decide, and the former is to create government programs to achieve some conception of the good. The former is, more or less, a libertarian solution and was very popular during the 1980s. The latter took form in what is known as progressivism, and it found popular expression during the 1930s and 1940s in FDR’s New Deal programs. The basic distinction separating these two political orders is between the right and the good.
Rights are the norms of obligations and constraints necessary for us all to coexist while simultaneously maintaining what many believe is the principal value of liberal democracy: freedom and liberty (these terms will be used interchangeably). Rights are not in the business of prescribing definite ways of life or enforcing particular ends for people to pursue. Rights preserve the conditions for freedom, and people are free to choose what to do with that freedom insofar as their decisions do not infringe on another person’s right to do so as well. Freedom, then, is the absence of coercion. By having that freedom, each is allowed to exercise their powers and capabilities according to their own discretion.
In the American context, by virtue of being a human being, we are said to be endowed with inalienable rights. And those rights both protect each individual from external coercion and provide a license for certain kinds of action. I am protected from being forced to say certain opinions and adopt particular beliefs. And I have the license to speak my own opinions, expound my own beliefs, and give voice to my own personal conscience. I am protected from forced association with people whom I do not wish to associate with, from the coercion to vote for a particular candidate, from being disallowed to protest, and from adopting ends I do not agree with or value. And, of course, that means I have a license to associate with whom I wish, vote for whoever I like, protest legislation I dislike, and adopt the ends I truly value. We are all free, and we all are obligated and constrained to preserve the conditions for us all to exercise that freedom mutually.
But if that is what rights are, how does a society ensure a distribution of goods and services for everyone to enjoy and partake in? After all, a right to free speech isn’t going to ensure anyone that they will have meals for nourishment, clothing for warmth, shelter from harsh conditions. The response comes from Adam Smith: economic freedom. Everyone has a natural propensity to “truck, barter, and trade” in order to improve their condition. And by the very nature of voluntary exchange, each party benefits. By an individual living his life according to his own interests, values, and ends, he “promote(s) an end which has no part of his own intention.” The invisible hand of the market promotes the ends held by other individuals, allowing everyone to live as they see fit and to coexist harmoniously with the community. By having the political freedom of rights and the economic freedom to exchange, people cooperate spontaneously and organically. That is the spirit of the neoliberal political order.
A conception of the good is different, and its meaning can be disclosed through the great liberal philosopher Voltaire’s likely apocryphal statement, “I disapprove of what you say, but I will defend to the death your right to say it.” What Voltaire disagrees with is not someone’s right to speak but of what they are saying, and we can imagine the person to be voicing their conception of the good, their values and ends that they believe characterize the good life, the life we ought to live, and Voltaire disapproves of it. The good is concerned with the proper ends that should be prioritized in order to flourish. Socrates famously declared the unexamined life is not worth living. Well, he’s espousing a conception of the good. It is a life of the intellect, a life of rational reflection and deliberation aimed toward self-knowledge. Are one’s beliefs consistent? Does one’s actions contradict what one truly believes? Is one aware of what one truly believes? And does one have the desire to discover the truth? These are Socratic questions, and a life devoted to answering them is a Socratic one.
Now, if there is a universal conception of the good life, if human beings have particular ends that define what it means to be a human being, and if failing to fulfill those ends implies a failure to realize one’s human potential for flourishing, then rights do not secure such outcomes. Rights only ensure individuals are free to pursue such ends if they wish. And given the contingency of life, that is to say that, because people are born into conditions they did not choose but were instead thrown into them, and because some individuals are born into wealth and advantage and some are born into poverty and disadvantage, some have the privilege to achieve the ends characterizing a good life and some do not. And that is unfair. And so, government programs, central planning, and economic stewardship can be used to enable and empower the underprivileged to achieve what others are better positioned to do. This is the spirit of the New Deal political order.
The mistake is to think the appropriate social, cultural, and political issues can be resolved by only one of these political orders. It is not one or the other. Both of these political orders capture powerful intuitions about how society should best function and operate, and there should be a synthesis between them.
Now, it is common knowledge that innovation drives economic growth. As capital becomes more efficient and fewer inputs are required to produce more outputs, the economy expands. In Matt Ridely’s book, Innovation: How It Works, he demonstrates beautifully the often messy and non-rational character of the innovative process.
At the heart of that process, he says, is serendipity. As frustrating as it is to human nature, the innovative process cannot be intelligently designed into a precise instrument capable of reproducing all the wonderful fruits that result from it. There is something inherently unpredictable about it, something unruly. It is organic and spontaneous. It demands the determination of individuals willing to fail over and over again until enough experience, insight, and gradual, often painstaking, progress results in the desired effects.
Ridley observes that so many of these innovations require the rich air of freedom to stimulate the instinct for exploration and discovery. Freedom nourishes and sustains that instinct, allowing it to grow and flourish. People must be free from unnecessary regulations and constraints to focus their creative energy on projects that demand endless hours of trying countless imaginative possibilities – and failing until something works. There’s always a tremendous amount of risk-taking. People need to be free to take them.
People also need to be free to collaborate with others who are also devoted to discovering a solution to seemingly intractable problems. The division of labor, where individuals specialize in a particular task and coordinate with others who do the same to maximize efficiency and productivity, is essential to the process. There’s a reason, as Ridley notes, that many innovations take place in cities, where individuals freely associate and influence one another.
Freedom also allows room for mistakes. Ridley documents many cases where innovation is the result of a mistake, not an intentional plan of action. Innovations can often begin with an intention that has nothing to do with the innovation itself. A deliberate decision leading to a breakthrough discovery can be entirely unrelated, even frivolous. Take the example of Louie Pasteur, one of the key discoverers of germ theory. He was inoculating chickens with cholera from an infected chicken broth when he left for vacation, leaving his assistant, Charles Chamberland, to continue the experiments. Charles, for whatever reason (perhaps he thought the whole idea was crazy), forgot about his responsibility and went on vacation. When both returned, they injected a chicken with the stale broth.
It made the chicken sick but did not kill it. And so he injected the same chicken with a much more virulent cholera strain that typically and easily killed chickens – and it failed. The chicken lived. Vaccines, an innovation on inoculation, emerged. Funny enough, a similar incident occurred with Alexander Fleming. Known for being sloppy, Fleming carelessly left out a culture plate of staphylococcus and took off for vacation for a couple of weeks. When he returned, he discovered a mold had grown that was resistant to the bacteria.
Penicillin was soon developed. All this is to say that, along with Ridley, “Innovation is the child of freedom and the parent of prosperity.”
But government has also been integral to many inventions and innovations that would later revolutionize the economy and, therefore, daily life itself. Mariana Mazzucato’s book The Entrepreneurial State makes a persuasive case for the significance of public institutions in the innovative process. When the Defense Advanced Research Projects Agency (DARPA), initially known as ARPA until 1972, was established in 1958 in response to the launch of the Soviet satellite Sputnik in 1957, it aimed to promote ‘blue-sky thinking’ for technological initiatives. Meaning that the goal was to invest in riskier research that potentially would yield long-term gains despite not having any immediate or obvious returns on investment. DARPA pursued “ideas that went beyond the horizon in that they may not produce results for ten or 20 years.”
What makes DARPA a successful agency is its decentralized model. The philosophy is: "Find brilliant people. Give them resources. Get out of their way." DARPA hires talented and competent experts to run programs autonomously, providing them the discretion to pursue projects highlighted by their expertise, which are often considered risky. This model enables experts to connect with other researchers, facilitating collaboration and the creation of highly efficient and productive divisions of labor. And again, these are projects that likely wouldn’t find market interest because of their niche or unexplored nature. There isn’t an immediate and conspicuous payoff. And so the connected but separate-from-government model of DARPA provides scientists with a wide degree of latitude, and that freedom allows them to engage in the innovative process of trial and error and risk-taking.
Technologies developed by DARPA included ARPANET, the precursor to the internet; early GPS technology; the beginnings of autonomous vehicles; speech recognition; personal computing; and early AI.
Other agencies have also been foundational in technological advancements (for example, the National Science Foundation (NSF) provided critical grants to facilitate what would become Google’s search engine algorithm). But the DARPA model is what is most interesting here.
If government programs like DARPA can be leveraged to spur more innovation, particularly in areas such as biotech, and these innovations can drive economic growth by being put into the hands of entrepreneurs, investors, and small, medium, and large firms, then this demands national effort and attention. If successful, it is a project worthy of national pride.
So, government programs and spending, if properly structured, can yield high returns on investment if people are given the freedom to explore, try things out, and make the mistakes necessary for the innovative process to be carried through. And we can look to a recent example where the absence of the efforts potentially could have been disastrous. The story of the COVID-19 vaccines is one where the lack of zeal for exploration and breakthrough discoveries could have hindered the development of mRNA research, leaving it underdeveloped when it was needed at a critical moment.
Section 3: Covid-19, The Imperative For Research and Development, and The Institutional Framework
To start, Peter Theil is popular for remarking that innovation in many industries has grown stagnant. Energy, manufacturing, and transportation, for example, haven’t seen much progress in the past half-century.
Computation, on the other hand, has surpassed the imagination. The innovations have not been in atoms but in bits. As Theil puts it, “We wanted flying cars; instead we got 140 characters.” And Ridley writes, “If cars had improved as fast as computers since 1982, they would get nearly four million miles per gallon, so they could go to the moon and back a hundred times on a single tank of fuel.” Unfortunately, we still have to visit the gas station and pay those exorbitant prices.
But biotech has gained momentum in the past decade. The COVID vaccines are an extraordinary example of this. But they wouldn’t have been ready to come to market without the previous three decades of research and development invested in them. And that research and development almost didn’t happen because people lacked the vision and the willingness to embrace the risk that great technological discoveries, inventions, and innovations always require.
Ezra Klein and Derek Thompson’s book Abundance tells this story very well. Katalin Kariko, one of the discoverers of mRNA’s therapeutic capabilities, had enormous difficulty securing funding for her research as an assistant professor at the University of Pennsylvania. Those with power thought it too risky, that it didn’t show enough promise, and allocated most resources to DNA research at the time, believing it to be the more auspicious investment. Nevertheless, as so many pioneering figures have done before her, Kariko maintained her vision of unlocking mRNA’s potential for saving lives.
By sheer luck, by the fortune contained in everyday decisions that would lead to saving millions of lives several decades later, Kariko met a colleague who was researching HIV vaccines at the time, Drew Weissman, at a Xerox machine in 1997. He would be pivotal in her research. She is a biochemist, and he, an immunologist. Each provided the knowledge and expertise the other was lacking, and that was essential to their respective goals. Through the serendipity of deciding to walk to a different department to make copies at the time and place she did, Kariko encountered an opportunity to make strides in her research.
Together, however, the two still managed to collect barely enough funding. “The NIH,” which is the largest public funder of biomedical research, “rejected practically all of their grant applications.” They couldn’t get others to have the same foresight. Even after a breakthrough, where they were finally able to send mRNA information into cells without causing horrible inflammation, those in power still blinked. Fortunately, private investment supplied the gust they needed to keep their research going, and two companies created to pursue mRNA research, Moderna and BioNTech, facilitated the vaccine’s development. When Covid spread, enough progress had been made. The FDA, which has set a poor precedent for getting products to market when it matters most, streamlined the approval process and made the vaccine available.
The key features of this story are the following. The first is the lack of risk-taking by institutions and agencies whose aim should be to provide resources to those striving to innovate and push technological progress forward. The second is the lack of coordination to establish intentional environments to converge the paths of those who have the determination, discipline, and vision to bring innovation to fruition. Imagine if Kariko and Weismann didn’t meet; picture Kariko choosing to make copies somewhere else or at a different time. The future may have been radically different. And thirdly, and more optimistically, the FDA served a vital role when it mattered. As a public institution responsible for promoting the public good, they served admirably.
These three parts – funding research, coordinating talent, and the institutions facilitating the results – should coalesce into an optimally functioning whole. Researchers who are trying to shape and influence an unforeseeable future should be encouraged and rewarded. Those who possess powerful and novel ideas, along with the imagination and determination to bring them to life, should be in direct contact with one another. Their paths should cross – intentionally. And lastly, institutions should follow the FDA’s example. Slow regulatory regimes, lengthy processes and paperwork, licensing barriers, and stifling restrictions should be streamlined and transformed into facilitators for technological development and the introduction of powerful and revolutionary technologies into the market.
More funding should be devoted to riskier research. Those with novel and fresh ideas with the potential to disrupt current scientific knowledge and produce a breakthrough should be sought out. It is estimated that roughly 2-5% of the NIH’s current budget of $45 billion is allocated to high-risk research. That should be increased. Programs like the High-Risk, High-Reward Research Program, which includes awards to innovative researchers and ideas, should take on a more robust role and budget than it currently does.
Furthermore, approximately 80% of the NIH budget is allocated to extramural research programs, which are external programs conducted outside of the institution itself. A larger portion of those who receive that funding should be based on their potential for innovation. Currently, as Klein and Thompson observe, the process of obtaining a research grant, which involves extensive paperwork and minutiae, is bureaucratic, cumbersome, inefficient, and time-consuming. A significant amount of energy that should be allocated toward advancing research is spent on securing the funding to do it.
Submitting an application, going through the two review processes, and being approved takes typically nine months to a year. And most fail, leading many scientists to have to apply numerous times in a year. And those doing the review process aren’t necessarily looking for cutting-edge proposals; they’re looking for what fits bureaucratic standards. Of course, this is contentious, but Kariko's story demonstrates its reality. Ridley offers another example. When Francisco Majica made critical advancements in CRISPR technology, it took him “more than a year to get his results published, so sniffy were the prestigious journals at the idea of a significant discovery coming from a scientific nobody.” Institutions must do a better job of trying and supporting novel and unexplored ideas, regardless of who or what they originate from. For example, biotech DAOs do not currently receive funding from government institutions, such as the NIH, due to the traditional legal framework used to distribute resources. Regulatory and legal changes should be implemented to maximize their potential. If there is too much emphasis on process, on bureaucratic procedures and standards, fruitful and rich opportunities suffocate.
The NIH budget also allocates funds to intramural research programs, which are internally connected to the NIH itself. These research programs account for roughly 10% of the NIH’s total budget. A highly promising model to adopt is the DARPA model articulated in Section 2. The NIH should adopt something similar. It should allocate resources to decentralized programs to bring together the best scientists to generate breakthrough ideas. Those programs should be spaces where scientists are free to pursue visionary projects.
Smaller biotech firms, startups, and those without robust forms of funding are often forced to pursue ideas that will capture immediate investment attention. And because of the burdensome and costly bureaucratic processes, investors are justly skeptical about anything risky and cutting-edge.
For example, regarding the FDA approval process, small molecule drugs like pharmaceuticals generally take ten to fifteen years to reach the market. On average, one drug costs $1-2 billion to move through the process, and less than ten percent of those who enter clinical trials succeed. Biologics, such as vaccines and gene therapies, typically take ten to twelve years to reach the market and have a slightly higher success rate than small molecule drugs, ranging from 12 to 15 percent. Those are extensive periods of time, the costs are astronomical, and few can maintain the resources to climb the mountain. This discourages bold enterprise – and it leads to higher prices as well. Due to the cumbersome approval process, the FDA offers exclusivity to companies that bring a product to market, both to reward innovation and to allow companies the opportunity to recoup the tremendous losses incurred by the approval process. This can lead to monopolistic pricing. Innovation should not be rewarded by harming the consumer. Innovation should lift the tide that raises all boats. And so the innovative process shouldn’t be exclusive to those with enough capital to take risks. It should be available to anyone with the tenacity to actualize a bold and promising idea. That’s not to say the process should be less rigorous and methodical. It’s that it needs to be more efficient. But not just efficiency for efficiency's sake; it needs to be efficient toward the right ends and outcomes, and innovation should be a leading goal.
Therefore, a primary goal of the FDA should be to stimulate market interest by expediting the most innovative technologies emerging from research programs driven by the NIH and its innovation initiatives. It’s very important that private research continues innovating as well, and increases in private investment toward manufacturing and research – like Johnson & Johnson’s recent announcement – is good. But new technologies, drugs, vaccines, and therapies should be a central mission of the institutional framework advocated for here – and the process should begin with creativity for creativity’s sake. The profit motive should be employed after realizing a passionate and creative vision. Those truly motivated by inspiration, the people who have the will to manifest something novel and unimaginable, are generally the worst at navigating the business aspect - not always, but often. And the energy pushing them forward is a precious and scarce resource. And so institutions like the FDA and NIH should foster, rather than stifle, their capabilities and opportunities for creating meaningful contributions to the country and the world. The FDA has a history of being slow and untimely when it comes to processing and approving applications for moving to clinical trials. For example, the AIDS epidemic is a stain on the institution’s reputation. When AIDS spread across the US in 1980, it took scientists three years to identify HIV as the cause, five years for the FDA to approve the first blood test to screen for the virus, and seven years to finally get a drug to market. The response to COVID-19 should be the golden standard by which the FDA operates.
Section 4: Human Being and Its Essence
Now, let’s ask the following: what does this have to do with national pride? How does this provide a new vision for the country?
In Alex Karp’s new book, The Technological Republic, he criticizes Silicon Valley for forgetting its roots in developing technology for national purposes. The foundational technology that defines Silicon Valley originated from government programs like DARPA and NASA, which had a clear purpose. They had a mission, and the achievements under those programs demonstrate that.
But now Silicon Valley has shifted to the consumer. Innovations in Silicon Valley generally make life more convenient, comfortable, pleasant, breezy. Goods and services satisfy all our wants and preferences. New apps, better features on social media, increasingly competent virtual assistants, faster food delivery services, endless streams of television and movies and videos, smart appliances, and more and more advanced phones pervade everyday life. The goal is always immediate gratification. There is no horizon that these products look up to. Everything is here and now.
This takes us back to our discussion of rights and conceptions of the good. Silicon Valley isn’t tethered to any real purpose or collective aim. Its goal is to let the market decide. There is no moral or spiritual integrity, no conception of the good that permeates Silicon Valley and its products. Nothing is off limits because it is the consumer’s right to choose. If there is a want, if enough people are willing to buy, Silicon Valley will produce it. No substantive conviction guides their innovations. What does Silicon Valley stand for? It certainly has a creative spirit – just look at all the devices we have today – but that spirit lacks a purpose, and so it wanders aimlessly chasing the fleeting nature of the consumer.
It’s perfectly understandable that Silicon Valley has severed itself from its military roots. Not only would it lose a substantial portion of revenue if it returned to those roots, but there is, of course, a moral dilemma at the heart of most military endeavors, and it is wise to take that seriously. And the Tech sector should not aim to impose a conception of the good on the consumers. The issue is its obsession with the consumer. There are more pressing areas of concern that warrant attention. The wealth of talent in Silicon Valley is better spent in those areas. And it should be done through the efficient use of public institutions.
The new vision is one where taxpayer dollars are used for purposeful and meaningful projects that generate new technologies and innovations that contribute to people’s real needs, not just their wants and preferences. Genuine pride involves courage and bold risk for the sake of principle. It consists in having the determination to carry through an arduous enterprise. And we should be proud as a country if a joint effort between the public and private sectors achieves collective ends.
And at the heart of this pride should be the creative process. Albert Einstein wrote that great scientific discoveries – the new ideas that are leaps in progress toward the expansion of human knowledge – are, again, not the inevitable product of a rigid, refined, and precisely applied method. He believed the great discoveries, the ones that establish new scientific paradigms that enrich society with so many practical fruit, result from a cosmic feeling, a kind of religious experience born out of feelings of awe, wonder, and mystery that are produced by the intellectual and spiritual effort to understand the rational order of the cosmos. He writes, “Enough for me (is) the mystery of the eternity of life, and the inkling of the marvelous structure of reality, together with the single-hearted endeavor to comprehend a portion, be it ever so tiny, of the reason that manifest itself in nature… I maintain that cosmic religious feeling is the strongest and noblest incitement to scientific research.”
Reaching for and clinching a new and profound idea is not a mechanical and algorithmic activity. Regardless of how finely one specifies the rules of procedure or how regimented the institutional standards for scientific knowledge are prescribed, intuition, sensitivity to the world and its objects, amazement at the experience of observing the world and its causal relations, in short, the feelings and moods of the subject investigating the object, are integral to the discovery of scientific ideas. Methods are pivotal in locating and developing the precise, logical nature of those ideas, but initial contact with them demands variables that are not reducible to fixed procedures. Ideas powerful enough to change the world and better the human condition originate in cosmic feelings of wonder and curiosity and are not strictly an output of a mechanized division of labor.
AI will outrun the human capacity for intelligence. This is a likely prediction. And so what will it mean to be a human being then? For centuries, philosophers have distinguished human beings from other parts of nature by invoking our seemingly unique capacity for reason. We have the ability to contemplate, reflect, and grasp the physical laws governing the cosmos. We can harness those laws and employ them to manipulate our environment, alter its forms, and recombine its parts, allowing us to raise our living standards beyond our ancestor’s imaginations. We are highly intelligent beings, and our intelligence has been regarded as our distinguishing mark.
AI erodes this image. This new technology is becoming, and perhaps already is, a concrete realization, an externalization of what history thought was uniquely our own. The reality that reason isn’t special, that it is nothing more than a physical product of an accidental evolution, a wisp of luck, has become more and more firmly impressed upon the mind over the last two centuries. AI will make it indelible; it is the final proof. And so what is a human being? What distinguishes us?
The answer is in our spontaneous acts of creativity, in our ability to produce beauty in art, complexity in design, and in our profound capability to experience wonder. Again, the innovative process discussed above cannot be rationally formed into a precise instrument. As frustrating as it is, as much as it bumps against our instinct to make everything intelligible and known, our ability for spontaneity and creativity, our capacity to fail over and over again until we receive those moments of imaginative brilliance, cannot be reduced into a definite set of rules and procedures.
And so as the world changes, as everything alters before our eyes, we have to value what makes us distinctly human. We need a new Enlightenment, one that celebrates our creativity and our will to manifest what we can internally envision. Our self-respect as individuals and collectives lies in our instincts for curiosity, inquiry, discovery, and the creative and imaginative processes that animate them.
-
 @ 78b3c1ed:5033eea9
2025-04-29 04:04:19
@ 78b3c1ed:5033eea9
2025-04-29 04:04:19Umbrel Core-lightning(以下CLNと略す)を運用するにあたり役に立ちそうなノウハウやメモを随時投稿します。
・configファイルを用意する Umbrelのアプリとして必要な設定はdocker-compose.ymlで指定されている。 それ以外の設定をしたい場合configファイルに入れると便利。 configファイルの置き場所は /home/umbrel/umbrel/app-data/core-lightning/data/lightningd ここにtouch configとでもやってファイルをつくる。
cd /home/umbrel/umbrel/app-data/core-lightning/data/lightningd touch config以下内容をひな型として使ってみてください。 行頭に#があるとコメント行になります。つまり.iniフォーマット。 /home/umbrel/umbrel/app-data/core-lightning/data/lightningd/config ```[General options]
[Bitcoin control options]
[Lightning daemon options]
[Lightning node customization options]
[Lightning channel and HTLC options]
[Payment control options]
[Networking options]
[Lightning Plugins]
[Experimental Options]
``` configに設定できる内容は以下を参照 https://lightning.readthedocs.io/lightningd-config.5.html セクションを意味する[]があるけれどもこれは私(tanakei)が意図的に見やすく区別しやすくするために付けただけ。これら行の#は外さない。
・configの設定をCLNに反映させる appスクリプトでCLNを再起動すると反映することができる。 configを書き換えただけでは反映されない。
cd /home/umbrel/umbrel/scripts ./app restart core-lightning・ログをファイルに出力させる
以下の場所でtouch log.txtとしてlog.txtファイルを作る。 /home/umbrel/umbrel/app-data/core-lightning/data/lightningd
cd /home/umbrel/umbrel/app-data/core-lightning/data/lightningd touch log.txt次にconfigの[Lightning daemon options]セクションにlog-fileを追加する。 ```[Lightning daemon options]
log-file=/data/.lightning/log.txt ``` ※Dockerによって/home/umbrel/umbrel/app-data/core-lightning/data/lightningd は /data/.lightning として使われている。
・addrとbind-addrの違い どちらも着信用のインターフェースとポートの設定。addrは指定したホストIPアドレス:ポート番号をノードURIに含めて公開する(node_announcementのuris)。bind-addrは公開しない。
・実験的機能のLN Offerを有効にする configの[Experimental Options]セクションに以下を追加する。 ```
[Experimental Options]
experimental-onion-messages experimental-offers ``` ※ v24.08でexperimental-onion-messageは廃止されデフォルト有効であり、上記設定の追加は不要になりました。 ※ v21.11.1 では experimental-offersは廃止されデフォルト有効であり、上記設定の追加は不要になりました。 もう実験扱いじゃなくなったのね...
・完全にTorでの発信オンリーにする UmbrelはなぜかCLNの発信をClearnetとTorのハイブリッドを許している。それは always-use-proxy=true の設定がないから。(LNDは発着信Torのみなのに) なのでこの設定をconfigに追加してCLNも発着進Torのみにする。 ```
[Networking options]
always-use-proxy=true ```
・任意のニーモニックからhsm_secretを作る CLNのhsm_secretはLNDのwallet.dbのようなもの。ノードで使う様々な鍵のマスター鍵となる。Umbrel CLNはこのhsm_secretファイルを自動生成したものを使い、これをバックアップするためのニーモニックを表示するとかそういう機能はない。自分で作って控えてあるニーモニックでhsm_secretを作ってしまえばこのファイルが壊れてもオンチェーン資金は復旧はできる。
1.CLNインストール後、dockerコンテナに入る
docker exec -it core-lightning_lightningd_1 bash2.lightning-hsmtoolコマンドを使って独自hsm_secretを作る ``` cd data/.lightning/bitcoin lightning-hsmtool generatehsm my-hsm_secret・上記コマンドを実行するとニーモニックの言語、ニーモニック、パスフレーズの入力を催促される。 Select your language: 0) English (en) 1) Spanish (es) 2) French (fr) 3) Italian (it) 4) Japanese (jp) 5) Chinese Simplified (zhs) 6) Chinese Traditional (zht) Select [0-7]: 0 ※定番の英単語なら0を入力 Introduce your BIP39 word list separated by space (at least 12 words): <ニーモニックを入力する> Warning: remember that different passphrases yield different bitcoin wallets. If left empty, no password is used (echo is disabled). Enter your passphrase: <パスフレーズを入力する> ※パスフレーズ不要ならそのままエンターキーを押す。 New hsm_secret file created at my-hsm_secret Use the
encryptcommand to encrypt the BIP32 seed if neededコンテナから抜ける exit
3.appスクリプトでCLNを止めて、独自hsm_secret以外を削除 ※【重要】いままで使っていたhsm_secretを削除する。もしチャネル残高、ウォレット残高があるならチャネルを閉じて資金を退避すること。自己責任!cd ~/umbrel/scripts/ ./app stop core-lightningcd ~/umbrel/app-data/core-lightning/data/lightningd/bitcoin rm gossip_store hsm_secret lightningd.sqlite3 lightning-rpc mv my-hsm_secret hsm_secret
4.appスクリプトでCLNを再開するcd ~/umbrel/scripts/ ./app start core-lightning ```【補記】 hsm_secret作成につかうニーモニックはBIP39で、LNDのAezeedと違って自分が作成されたブロック高さというものを含んでいない。新規でなくて復元して使う場合は作成されたブロック高さからブロックチェーンをrescanする必要がある。 configの1行目にrescanオプションを付けてCLNをリスタートする。 ``` // 特定のブロック高さを指定する場合はマイナス記号をつける rescan=-756000
// 現在のブロック高さから指定ブロック分さかのぼった高さからrescanする rescan=10000 ※現在の高さが760,000なら10000指定だと750,000からrescan ```
・clnrestについて core-lightningでREST APIを利用したい場合、別途c-lightning-restを用意する必要があった。v23.8から標準でclnrestというプラグインがついてくる。pythonで書かれていて、ソースからビルドした場合はビルド完了後にpip installでインストールする。elementsproject/lightningdのDockerイメージではインストール済みになっている。 (v25.02からgithubからバイナリをダウンロードしてきた場合はpip install不要になったようだ) このclnrestを使うにはcreaterunesコマンドでruneというLNDのマカロンのようなものを作成する必要がある。アプリ側でこのruneとREST APIを叩いてcore-lightningへアクセスすることになる。 自分が良く使っているLNbitsやスマホアプリZeus walletはclnrestを使う。まだclnrestに対応していないアプリもあるので留意されたし。
・Emergency recoverについて LNDのSCBのようなもの。ファイル名はemergency.recover チャネルを開くと更新される。 hsm_secretとこのファイルだけを置いてCLNを開始すると自動でこのファイルから強制クローズするための情報が読み出されてDLPで相手から強制クローズするような仕組み。この機能はv0.12から使える。
動作確認してみた所、LNDのSCBに比べるとかなり使いづらい。 1. CLNがTor発信だとチャネルパートナーと接続できない。 Clearnet発信できても相手がTorのみノードならTor発信せざるを得ない。 相手と通信できなければ資金回収できない。 2. 相手がLNDだとなぜか強制クローズされない。相手がCLNならできる。
つまり、自分と相手がClearnetノードでかつ相手もCLNならば Emergency recoverで強制クローズして資金回収できる。こんな条件の厳しい復旧方法がマジで役に立つのか?
v0.11以降ならばLNDのchannel.dbに相当するlightningd.sqlite3をプライマリ・セカンダリDBと冗長化できるので、セカンダリDBをNFSで保存すればUmbrelのストレージが壊れてもセカンダリDBで復旧できる。そのためemergerncy.recoverを使う必要がないと思われる。
・LN offer(BOLT#12)ついて 使いたいなら 1.publicチャネルを開く publicチャネルを開けばチャネルとノードの情報(channel_announcement, node_announcement)が他ノードに伝わる。送金したい相手がこの情報を元に経路探索する。 2.その後しばらく待つ CLNノードを立てたばかりだと経路探索するに十分なチャネルとノードの情報が揃ってない。せめて1日は待つ。
LNURLの場合インボイスをhttpsで取得するが、OfferはLN経由で取得する。そのためにチャネルとノードの情報が必要。privateチャネルばかりのノードはチャネル情報もそうだがノード情報も出さない。 Offerで使えるBlind pathという機能なら中間ノードIDを宛先ノードとすることが可能で、これならチャネルとノード情報を公開しなくても受けとれるのだがCLNは対応してない模様(2025年1月現在) CLNでOfferで受け取るにはチャネルとノード情報を公開する必要がある。そのためpublicチャネルを開く。公開されていれば良いのでTorでもOK。クリアネットで待ち受けは必須ではない。
・hsm_sercretとニーモニック lightning-hsmtoolを使うとニーモニックからhsm_secretを作れる。ニーモニックからシードを作ると64バイト。これはニーモニックおよびソルトにパスフレーズをPBKDF2(HMAC-SHA512を2048回)にかけると512ビット(64バイト)のシードができる。しかしhsm_secretは32バイト。CLNでは64バイトの最初の32バイトをhsm_secretとして利用しているみたい。 このhsm_secretにHMAC-SHA512をかけて512ビットとした値がウォレットのマスター鍵となる。なのでhsm_secret自体がBIP-32でいうマスターシードそのものではない。 sparrow walletにCLNのウォレットを復元したい場合は lightning-hsmtool dumponchaindescriptors --show-secrets
とやってディスクリプターウォレットを出力。出力内容にマスター鍵(xprv~)があるので、これをインポートする。導出パス設定はm/0とする。sparrowが残りを補完してm/0/0/0, m/0/0/1とやってくれる。 <おまけ> configファイルのサンプル。Umbrelを使わない場合は以下のサンプルが役に立つはず。上記のelementsproject/lightningdならば/root/.lightningに任意のディレクトリをマウントしてそのディレクトリにconfigを置く。 ```
[General options]
不可逆なDBアップグレードを許可しない
database-upgrade=false
[Bitcoin control options]
network=bitcoin bitcoin-rpcconnect=
bitcoin-rpcport= bitcoin-rpcuser= bitcoin-rpcpassword= [Lightning daemon options]
postgresを使う場合
wallet=postgres://USER:PASSWORD@HOST:PORT/DB_NAME
bookkeeper-db=postgres://USER:PASSWORD@HOST:PORT/DB_NAME
sqlite3を使う場合。デフォルトはこちらで以下の設定が無くても~/.lightning/bitconに自動で作成される。
wallet=sqlite3:///home/USERNAME/.lightning/bitcoin/lightningd.sqlite3
bookkeeper-db=sqlite3:///home/USERNAME/.lightning/bitcoin/accounts.sqlite3
ログファイルは自動で作成されない
log-file=/home/USERNAME/.lightning/lightningd-log
log-level=debug
[Lightning node customization options]
alias=
rgb= 固定手数料。ミリサトシで指定。
fee-base=1000000
変動手数料。ppmで指定。
fee-per-satoshi=0
最小チャネルキャパシティ(sats)
min-capacity-sat=100000
HTLC最少額。ミリサトシで指定。
htlc-minimum-msat=1000
[Lightning channel and HTLC options]
large-channels # v23.11よりデフォルトでラージチャネルが有効。
チャネル開設まで6承認
funding-confirms=6
着信できるHTLCの数。開いたら変更できない。1~483 (デフォルトは 30) の範囲にする必要があります
max-concurrent-htlcs=INTEGER
アンカーチャネルを閉じるためにウォレットに保持しておく資金。デフォルトは 25,000sat
チャネルを"忘れる(forget)"するまではリザーブされる模様。forgetはチャネル閉じてから100ブロック後
min-emergency-msat=10000000
[Cleanup control options]
autoclean-cycle=3600 autoclean-succeededforwards-age=0 autoclean-failedforwards-age=0 autoclean-succeededpays-age=0 autoclean-failedpays-age=0 autoclean-paidinvoices-age=0 autoclean-expiredinvoices-age=0
[Payment control options]
disable-mpp
[Networking options]
bind-addrだとアナウンスしない。
bind-addr=0.0.0.0:9375
tor
proxy=
: always-use-proxy=true Torの制御ポート。addr=statictor だとhidden serviceをノードURIとして公開する。
addr=statictor:
: tor-service-password= experimental-websocket-portは廃止された。bind-addr=ws:が代替。
bind-addr=ws:
:2106 clnrestプラグイン, REST API
clnrest-host=0.0.0.0 clnrest-port=3010 clnrest-protocol=http
v24.11よりgrpcはデフォルト有効
grpc-host=0.0.0.0 grpc-port=9736
[Lightning Plugins]
[Experimental Options]
experimental-onion-messages # v24.08で廃止。デフォルト有効
experimental-offers # v24.11.1で廃止。デフォルト有効
流動性広告からチャネルを開くときにexperimental-dual-fundが必要らしい。
experimental-dual-fund
experimental-splicing
experimental-peer-storage
```
-
 @ 826e9f89:ffc5c759
2025-04-12 21:34:24
@ 826e9f89:ffc5c759
2025-04-12 21:34:24What follows began as snippets of conversations I have been having for years, on and off, here and there. It will likely eventually be collated into a piece I have been meaning to write on “payments” as a whole. I foolishly started writing this piece years ago, not realizing that the topic is gargantuan and for every week I spend writing it I have to add two weeks to my plan. That may or may not ever come to fruition, but in the meantime, Tether announced it was issuing on Taproot Assets and suddenly everybody is interested again. This is as good a catalyst as any to carve out my “stablecoin thesis”, such as it exists, from “payments”, and put it out there for comment and feedback.
In contrast to the “Bitcoiner take” I will shortly revert to, I invite the reader to keep the following potential counterargument in mind, which might variously be termed the “shitcoiner”, “realist”, or “cynical” take, depending on your perspective: that stablecoins have clear product-market-fit. Now, as a venture capitalist and professional thinkboi focusing on companies building on Bitcoin, I obviously think that not only is Bitcoin the best money ever invented and its monetization is pretty much inevitable, but that, furthermore, there is enormous, era-defining long-term potential for a range of industries in which Bitcoin is emerging as superior technology, even aside from its role as money. But in the interest not just of steelmanning but frankly just of honesty, I would grudgingly agree with the following assessment as of the time of writing: the applications of crypto (inclusive of Bitcoin but deliberately wider) that have found product-market-fit today, and that are not speculative bets on future development and adoption, are: Bitcoin as savings technology, mining as a means of monetizing energy production, and stablecoins.
I think there are two typical Bitcoiner objections to stablecoins of significantly greater importance than all others: that you shouldn’t be supporting dollar hegemony, and that you don’t need a blockchain. I will elaborate on each of these, and for the remainder of the post will aim to produce a synthesis of three superficially contrasting (or at least not obviously related) sources of inspiration: these objections, the realisation above that stablecoins just are useful, and some commentary on technical developments in Bitcoin and the broader space that I think inform where things are likely to go. As will become clear as the argument progresses, I actually think the outcome to which I am building up is where things have to go. I think the technical and economic incentives at play make this an inevitability rather than a “choice”, per se. Given my conclusion, which I will hold back for the time being, this is a fantastically good thing, hence I am motivated to write this post at all!
Objection 1: Dollar Hegemony
I list this objection first because there isn’t a huge amount to say about it. It is clearly a normative position, and while I more or less support it personally, I don’t think that it is material to the argument I am going on to make, so I don’t want to force it on the reader. While the case for this objection is probably obvious to this audience (isn’t the point of Bitcoin to destroy central banks, not further empower them?) I should at least offer the steelman that there is a link between this and the realist observation that stablecoins are useful. The reason they are useful is because people prefer the dollar to even shitter local fiat currencies. I don’t think it is particularly fruitful to say that they shouldn’t. They do. Facts don’t care about your feelings. There is a softer bridging argument to be made here too, to the effect that stablecoins warm up their users to the concept of digital bearer (ish) assets, even though these particular assets are significantly scammier than Bitcoin. Again, I am just floating this, not telling the reader they should or shouldn’t buy into it.
All that said, there is one argument I do want to put my own weight behind, rather than just float: stablecoin issuance is a speculative attack on the institution of fractional reserve banking. A “dollar” Alice moves from JPMorgan to Tether embodies two trade-offs from Alice’s perspective: i) a somewhat opaque profile on the credit risk of the asset: the likelihood of JPMorgan ever really defaulting on deposits vs the operator risk of Tether losing full backing and/or being wrench attacked by the Federal Government and rugging its users. These risks are real but are almost entirely political. I’m skeptical it is meaningful to quantify them, but even if it is, I am not the person to try to do it. Also, more transparently to Alice, ii) far superior payment rails (for now, more on this to follow).
However, from the perspective of the fiat banking cartel, fractional reserve leverage has been squeezed. There are just as many notional dollars in circulation, but there the backing has been shifted from levered to unlevered issuers. There are gradations of relevant objections to this: while one might say, Tether’s backing comes from Treasuries, so you are directly funding US debt issuance!, this is a bit silly in the context of what other dollars one might hold. It’s not like JPMorgan is really competing with the Treasury to sell credit into the open market. Optically they are, but this is the core of the fiat scam. Via the guarantees of the Federal Reserve System, JPMorgan can sell as much unbacked credit as it wants knowing full well the difference will be printed whenever this blows up. Short-term Treasuries are also JPMorgan’s most pristine asset safeguarding its equity, so the only real difference is that Tether only holds Treasuries without wishing more leverage into existence. The realization this all builds up to is that, by necessity,
Tether is a fully reserved bank issuing fiduciary media against the only dollar-denominated asset in existence whose value (in dollar terms) can be guaranteed. Furthermore, this media arguably has superior “moneyness” to the obvious competition in the form of US commercial bank deposits by virtue of its payment rails.
That sounds pretty great when you put it that way! Of course, the second sentence immediately leads to the second objection, and lets the argument start to pick up steam …
Objection 2: You Don’t Need a Blockchain
I don’t need to explain this to this audience but to recap as briefly as I can manage: Bitcoin’s value is entirely endogenous. Every aspect of “a blockchain” that, out of context, would be an insanely inefficient or redundant modification of a “database”, in context is geared towards the sole end of enabling the stability of this endogenous value. Historically, there have been two variations of stupidity that follow a failure to grok this: i) “utility tokens”, or blockchains with native tokens for something other than money. I would recommend anybody wanting a deeper dive on the inherent nonsense of a utility token to read Only The Strong Survive, in particular Chapter 2, Crypto Is Not Decentralized, and the subsection, Everything Fights For Liquidity, and/or Green Eggs And Ham, in particular Part II, Decentralized Finance, Technically. ii) “real world assets” or, creating tokens within a blockchain’s data structure that are not intended to have endogenous value but to act as digital quasi-bearer certificates to some or other asset of value exogenous to this system. Stablecoins are in this second category.
RWA tokens definitionally have to have issuers, meaning some entity that, in the real world, custodies or physically manages both the asset and the record-keeping scheme for the asset. “The blockchain” is at best a secondary ledger to outsource ledger updates to public infrastructure such that the issuer itself doesn’t need to bother and can just “check the ledger” whenever operationally relevant. But clearly ownership cannot be enforced in an analogous way to Bitcoin, under both technical and social considerations. Technically, Bitcoin’s endogenous value means that whoever holds the keys to some or other UTXOs functionally is the owner. Somebody else claiming to be the owner is yelling at clouds. Whereas, socially, RWA issuers enter a contract with holders (whether legally or just in terms of a common-sense interpretation of the transaction) such that ownership of the asset issued against is entirely open to dispute. That somebody can point to “ownership” of the token may or may not mean anything substantive with respect to the physical reality of control of the asset, and how the issuer feels about it all.
And so, one wonders, why use a blockchain at all? Why doesn’t the issuer just run its own database (for the sake of argument with some or other signature scheme for verifying and auditing transactions) given it has the final say over issuance and redemption anyway? I hinted at an answer above: issuing on a blockchain outsources this task to public infrastructure. This is where things get interesting. While it is technically true, given the above few paragraphs, that, you don’t need a blockchain for that, you also don’t need to not use a blockchain for that. If you want to, you can.
This is clearly the case given stablecoins exist at all and have gone this route. If one gets too angry about not needing a blockchain for that, one equally risks yelling at clouds! And, in fact, one can make an even stronger argument, more so from the end users’ perspective. These products do not exist in a vacuum but rather compete with alternatives. In the case of stablecoins, the alternative is traditional fiat money, which, as stupid as RWAs on a blockchain are, is even dumber. It actually is just a database, except it’s a database that is extremely annoying to use, basically for political reasons because the industry managing these private databases form a cartel that never needs to innovate or really give a shit about its customers at all. In many, many cases, stablecoins on blockchains are dumb in the abstract, but superior to the alternative methods of holding and transacting in dollars existing in other forms. And note, this is only from Alice’s perspective of wanting to send and receive, not a rehashing of the fractional reserve argument given above. This is the essence of their product-market-fit. Yell at clouds all you like: they just are useful given the alternative usually is not Bitcoin, it’s JPMorgan’s KYC’d-up-the-wazoo 90s-era website, more than likely from an even less solvent bank.
So where does this get us? It might seem like we are back to “product-market-fit, sorry about that” with Bitcoiners yelling about feelings while everybody else makes do with their facts. However, I think we have introduced enough material to move the argument forward by incrementally incorporating the following observations, all of which I will shortly go into in more detail: i) as a consequence of making no technical sense with respect to what blockchains are for, today’s approach won’t scale; ii) as a consequence of short-termist tradeoffs around socializing costs, today’s approach creates an extremely unhealthy and arguably unnatural market dynamic in the issuer space; iii) Taproot Assets now exist and handily address both points i) and ii), and; iv) eCash is making strides that I believe will eventually replace even Taproot Assets.
To tease where all this is going, and to get the reader excited before we dive into much more detail: just as Bitcoin will eat all monetary premia, Lightning will likely eat all settlement, meaning all payments will gravitate towards routing over Lightning regardless of the denomination of the currency at the edges. Fiat payments will gravitate to stablecoins to take advantage of this; stablecoins will gravitate to TA and then to eCash, and all of this will accelerate hyperbitcoinization by “bitcoinizing” payment rails such that an eventual full transition becomes as simple as flicking a switch as to what denomination you want to receive.
I will make two important caveats before diving in that are more easily understood in light of having laid this groundwork: I am open to the idea that it won’t be just Lightning or just Taproot Assets playing the above roles. Without veering into forecasting the entire future development of Bitcoin tech, I will highlight that all that really matters here are, respectively: a true layer 2 with native hashlocks, and a token issuance scheme that enables atomic routing over such a layer 2 (or combination of such). For the sake of argument, the reader is welcome to swap in “Ark” and “RGB” for “Lightning” and “TA” both above and in all that follows. As far as I can tell, this makes no difference to the argument and is even exciting in its own right. However, for the sake of simplicity in presentation, I will stick to “Lightning” and “TA” hereafter.
1) Today’s Approach to Stablecoins Won’t Scale
This is the easiest to tick off and again doesn’t require much explanation to this audience. Blockchains fundamentally don’t scale, which is why Bitcoin’s UTXO scheme is a far better design than ex-Bitcoin Crypto’s’ account-based models, even entirely out of context of all the above criticisms. This is because Bitcoin transactions can be batched across time and across users with combinations of modes of spending restrictions that provide strong economic guarantees of correct eventual net settlement, if not perpetual deferral. One could argue this is a decent (if abstrusely technical) definition of “scaling” that is almost entirely lacking in Crypto.
What we see in ex-Bitcoin crypto is so-called “layer 2s” that are nothing of the sort, forcing stablecoin schemes in these environments into one of two equally poor design choices if usage is ever to increase: fees go higher and higher, to the point of economic unviability (and well past it) as blocks fill up, or move to much more centralized environments that increasingly are just databases, and hence which lose the benefits of openness thought to be gleaned by outsourcing settlement to public infrastructure. This could be in the form of punting issuance to a bullshit “layer 2” that is a really a multisig “backing” a private execution environment (to be decentralized any daw now) or an entirely different blockchain that is just pretending even less not to be a database to begin with. In a nutshell, this is a decent bottom-up explanation as to why Tron has the highest settlement of Tether.
This also gives rise to the weirdness of “gas tokens” - assets whose utility as money is and only is in the form of a transaction fee to transact a different kind of money. These are not quite as stupid as a “utility token,” given at least they are clearly fulfilling a monetary role and hence their artificial scarcity can be justified. But they are frustrating from Bitcoiners’ and users’ perspectives alike: users would prefer to pay transaction fees on dollars in dollars, but they can’t because the value of Ether, Sol, Tron, or whatever, is the string and bubblegum that hold their boondoggles together. And Bitcoiners wish this stuff would just go away and stop distracting people, whereas this string and bubblegum is proving transiently useful.
All in all, today’s approach is fine so long as it isn’t being used much. It has product-market fit, sure, but in the unenviable circumstance that, if it really starts to take off, it will break, and even the original users will find it unusable.
2) Today’s Approach to Stablecoins Creates an Untenable Market Dynamic
Reviving the ethos of you don’t need a blockchain for that, notice the following subtlety: while the tokens representing stablecoins have value to users, that value is not native to the blockchain on which they are issued. Tether can (and routinely does) burn tokens on Ethereum and mint them on Tron, then burn on Tron and mint on Solana, and so on. So-called blockchains “go down” and nobody really cares. This makes no difference whatsoever to Tether’s own accounting, and arguably a positive difference to users given these actions track market demand. But it is detrimental to the blockchain being switched away from by stripping it of “TVL” that, it turns out, was only using it as rails: entirely exogenous value that leaves as quickly as it arrived.
One underdiscussed and underappreciated implication of the fact that no value is natively running through the blockchain itself is that, in the current scheme, both the sender and receiver of a stablecoin have to trust the same issuer. This creates an extremely powerful network effect that, in theory, makes the first-to-market likely to dominate and in practice has played out exactly as this theory would suggest: Tether has roughly 80% of the issuance, while roughly 19% goes to the political carve-out of USDC that wouldn’t exist at all were it not for government interference. Everybody else combined makes up the final 1%.
So, Tether is a full reserve bank but also has to be everybody’s bank. This is the source of a lot of the discomfort with Tether, and which feeds into the original objection around dollar hegemony, that there is an ill-defined but nonetheless uneasy feeling that Tether is slowly morphing into a CBDC. I would argue this really has nothing to do with Tether’s own behavior but rather is a consequence of the market dynamic inevitably created by the current stablecoin scheme. There is no reason to trust any other bank because nobody really wants a bank, they just want the rails. They want something that will retain a nominal dollar value long enough to spend it again. They don’t care what tech it runs on and they don’t even really care about the issuer except insofar as having some sense they won’t get rugged.
Notice this is not how fiat works. Banks can, of course, settle between each other, thus enabling their users to send money to customers of other banks. This settlement function is actually the entire point of central banks, less the money printing and general corruption enabled (we might say, this was the historical point of central banks, which have since become irredeemably corrupted by this power). This process is clunkier than stablecoins, as covered above, but the very possibility of settlement means there is no gigantic network effect to being the first commercial issuer of dollar balances. If it isn’t too triggering to this audience, one might suggest that the money printer also removes the residual concern that your balances might get rugged! (or, we might again say, you guarantee you don’t get rugged in the short term by guaranteeing you do get rugged in the long term).
This is a good point at which to introduce the unsettling observation that broader fintech is catching on to the benefits of stablecoins without any awareness whatsoever of all the limitations I am outlining here. With the likes of Stripe, Wise, Robinhood, and, post-Trump, even many US megabanks supposedly contemplating issuing stablecoins (obviously within the current scheme, not the scheme I am building up to proposing), we are forced to boggle our minds considering how on earth settlement is going to work. Are they going to settle through Ether? Well, no, because i) Ether isn’t money, it’s … to be honest, I don’t think anybody really knows what it is supposed to be, or if they once did they aren’t pretending anymore, but anyway, Stripe certainly hasn’t figured that out yet so, ii) it won’t be possible to issue them on layer 1s as soon as there is any meaningful volume, meaning they will have to route through “bullshit layer 2 wrapped Ether token that is really already a kind of stablecoin for Ether.”
The way they are going to try to fix this (anybody wanna bet?) is routing through DEXes, which is so painfully dumb you should be laughing and, if you aren’t, I would humbly suggest you don’t get just how dumb it is. What this amounts to is plugging the gap of Ether’s lack of moneyness (and wrapped Ether’s hilarious lack of moneyness) with … drum roll … unknowable technical and counterparty risk and unpredictable cost on top of reverting to just being a database. So, in other words, all of the costs of using a blockchain when you don’t strictly need to, and none of the benefits. Stripe is going to waste billions of dollars getting sandwich attacked out of some utterly vanilla FX settlement it is facilitating for clients who have even less of an idea what is going on and why North Korea now has all their money, and will eventually realize they should have skipped their shitcoin phase and gone straight to understanding Bitcoin instead …
3) Bitcoin (and Taproot Assets) Fixes This
To tie together a few loose ends, I only threw in the hilariously stupid suggestion of settling through wrapped Ether on Ether on Ether in order to tee up the entirely sensible suggestion of settling through Lightning. Again, not that this will be new to this audience, but while issuance schemes have been around on Bitcoin for a long time, the breakthrough of Taproot Assets is essentially the ability to atomically route through Lightning.
I will admit upfront that this presents a massive bootstrapping challenge relative to the ex-Bitcoin Crypto approach, and it’s not obvious to me if or how this will be overcome. I include this caveat to make it clear I am not suggesting this is a given. It may not be, it’s just beyond the scope of this post (or frankly my ability) to predict. This is a problem for Lightning Labs, Tether, and whoever else decides to step up to issue. But even highlighting this as an obvious and major concern invites us to consider an intriguing contrast: scaling TA stablecoins is hardest at the start and gets easier and easier thereafter. The more edge liquidity there is in TA stables, the less of a risk it is for incremental issuance; the more TA activity, the more attractive deploying liquidity is into Lightning proper, and vice versa. With apologies if this metaphor is even more confusing than it is helpful, one might conceive of the situation as being that there is massive inertia to bootstrap, but equally there could be positive feedback in driving the inertia to scale. Again, I have no idea, and it hasn’t happened yet in practice, but in theory it’s fun.
More importantly to this conversation, however, this is almost exactly the opposite dynamic to the current scheme on other blockchains, which is basically free to start, but gets more and more expensive the more people try to use it. One might say it antiscales (I don’t think that’s a real word, but if Taleb can do it, then I can do it too!).
Furthermore, the entire concept of “settling in Bitcoin” makes perfect sense both economically and technically: economically because Bitcoin is money, and technically because it can be locked in an HTLC and hence can enable atomic routing (i.e. because Lightning is a thing). This is clearly better than wrapped Eth on Eth on Eth or whatever, but, tantalisingly, is better than fiat too! The core message of the payments tome I may or may not one day write is (or will be) that fiat payments, while superficially efficient on the basis of centralized and hence costless ledger amendments, actually have a hidden cost in the form of interbank credit. Many readers will likely have heard me say this multiple times and in multiple settings but, contrary to popular belief, there is no such thing as a fiat debit. Even if styled as a debit, all fiat payments are credits and all have credit risk baked into their cost, even if that is obscured and pushed to the absolute foundational level of money printing to keep banks solvent and hence keep payment channels open.
Furthermore! this enables us to strip away the untenable market dynamic from the point above. The underappreciated and underdiscussed flip side of the drawback of the current dynamic that is effectively fixed by Taproot Assets is that there is no longer a mammoth network effect to a single issuer. Senders and receivers can trust different issuers (i.e. their own banks) because those banks can atomically settle a single payment over Lightning. This does not involve credit. It is arguably the only true debit in the world across both the relevant economic and technical criteria: it routes through money with no innate credit risk, and it does so atomically due to that money’s native properties.
Savvy readers may have picked up on a seed I planted a while back and which can now delightfully blossom:
This is what Visa was supposed to be!
Crucially, this is not what Visa is now. Visa today is pretty much the bank that is everybody’s counterparty, takes a small credit risk for the privilege, and oozes free cash flow bottlenecking global consumer payments.
But if you read both One From Many by Dee Hock (for a first person but pretty wild and extravagant take) and Electronic Value Exchange by David Stearns (for a third person, drier, but more analytical and historically contextualized take) or if you are just intimately familiar with the modern history of payments for whatever other reason, you will see that the role I just described for Lightning in an environment of unboundedly many banks issuing fiduciary media in the form of stablecoins is exactly what Dee Hock wanted to create when he envisioned Visa:
A neutral and open layer of value settlement enabling banks to create digital, interbank payment schemes for their customers at very low cost.
As it turns out, his vision was technically impossible with fiat, hence Visa, which started as a cooperative amongst member banks, was corrupted into a duopolistic for-profit rent seeker in curious parallel to the historical path of central banks …
4) eCash
To now push the argument to what I think is its inevitable conclusion, it’s worth being even more vigilant on the front of you don’t need a blockchain for that. I have argued that there is a role for a blockchain in providing a neutral settlement layer to enable true debits of stablecoins. But note this is just a fancy and/or stupid way of saying that Bitcoin is both the best money and is programmable, which we all knew anyway. The final step is realizing that, while TA is nice in terms of providing a kind of “on ramp” for global payments infrastructure as a whole to reorient around Lightning, there is some path dependence here in assuming (almost certainly correctly) that the familiarity of stablecoins as “RWA tokens on a blockchain” will be an important part of the lure.
But once that transition is complete, or is well on its way to being irreversible, we may as well come full circle and cut out tokens altogether. Again, you really don’t need a blockchain for that, and the residual appeal of better rails has been taken care of with the above massive detour through what I deem to be the inevitability of Lightning as a settlement layer. Just as USDT on Tron arguably has better moneyness than a JPMorgan balance, so a “stablecoin” as eCash has better moneyness than as a TA given it is cheaper, more private, and has more relevantly bearer properties (in other words, because it is cash). The technical detail that it can be hashlocked is really all you need to tie this all together. That means it can be atomically locked into a Lightning routed debit to the recipient of a different issuer (or “mint” in eCash lingo, but note this means the same thing as what we have been calling fully reserved banks). And the economic incentive is pretty compelling too because, for all their benefits, there is still a cost to TAs given they are issued onchain and they require asset-specific liquidity to route on Lightning. Once the rest of the tech is in place, why bother? Keep your Lightning connectivity and just become a mint.
What you get at that point is dramatically superior private database to JPMorgan with the dramatically superior public rails of Lightning. There is nothing left to desire from “a blockchain” besides what Bitcoin is fundamentally for in the first place: counterparty-risk-free value settlement.
And as a final point with a curious and pleasing echo to Dee Hock at Visa, Calle has made the point repeatedly that David Chaum’s vision for eCash, while deeply philosophical besides the technical details, was actually pretty much impossible to operate on fiat. From an eCash perspective, fiat stablecoins within the above infrastructure setup are a dramatic improvement on anything previously possible. But, of course, they are a slippery slope to Bitcoin regardless …
Objections Revisited
As a cherry on top, I think the objections I highlighted at the outset are now readily addressed – to the extent the reader believes what I am suggesting is more or less a technical and economic inevitability, that is. While, sure, I’m not particularly keen on giving the Treasury more avenues to sell its welfare-warfare shitcoin, on balance the likely development I’ve outlined is an enormous net positive: it’s going to sell these anyway so I prefer a strong economic incentive to steadily transition not only to Lightning as payment rails but eCash as fiduciary media, and to use “fintech” as a carrot to induce a slow motion bank run.
As alluded to above, once all this is in place, the final step to a Bitcoin standard becomes as simple as an individual’s decision to want Bitcoin instead of fiat. On reflection, this is arguably the easiest part! It's setting up all the tech that puts people off, so trojan-horsing them with “faster, cheaper payment rails” seems like a genius long-term strategy.
And as to “needing a blockchain” (or not), I hope that is entirely wrapped up at this point. The only blockchain you need is Bitcoin, but to the extent people are still confused by this (which I think will take decades more to fully unwind), we may as well lean into dazzling them with whatever innovation buzzwords and decentralization theatre they were going to fall for anyway before realizing they wanted Bitcoin all along.
Conclusion
Stablecoins are useful whether you like it or not. They are stupid in the abstract but it turns out fiat is even stupider, on inspection. But you don’t need a blockchain, and using one as decentralization theatre creates technical debt that is insurmountable in the long run. Blockchain-based stablecoins are doomed to a utility inversely proportional to their usage, and just to rub it in, their ill-conceived design practically creates a commercial dynamic that mandates there only ever be a single issuer.
Given they are useful, it seems natural that this tension is going to blow up at some point. It also seems worthwhile observing that Taproot Asset stablecoins have almost the inverse problem and opposite commercial dynamic: they will be most expensive to use at the outset but get cheaper and cheaper as their usage grows. Also, there is no incentive towards a monopoly issuer but rather towards as many as are willing to try to operate well and provide value to their users.
As such, we can expect any sizable growth in stablecoins to migrate to TA out of technical and economic necessity. Once this has happened - or possibly while it is happening but is clearly not going to stop - we may as well strip out the TA component and just use eCash because you really don’t need a blockchain for that at all. And once all the money is on eCash, deciding you want to denominate it in Bitcoin is the simplest on-ramp to hyperbitcoinization you can possibly imagine, given we’ve spent the previous decade or two rebuilding all payments tech around Lightning.
Or: Bitcoin fixes this. The End.
- Allen, #892,125
thanks to Marco Argentieri, Lyn Alden, and Calle for comments and feedback
-
 @ c631e267:c2b78d3e
2025-04-04 18:47:27
@ c631e267:c2b78d3e
2025-04-04 18:47:27Zwei mal drei macht vier, \ widewidewitt und drei macht neune, \ ich mach mir die Welt, \ widewide wie sie mir gefällt. \ Pippi Langstrumpf
Egal, ob Koalitionsverhandlungen oder politischer Alltag: Die Kontroversen zwischen theoretisch verschiedenen Parteien verschwinden, wenn es um den Kampf gegen politische Gegner mit Rückenwind geht. Wer den Alteingesessenen die Pfründe ernsthaft streitig machen könnte, gegen den werden nicht nur «Brandmauern» errichtet, sondern der wird notfalls auch strafrechtlich verfolgt. Doppelstandards sind dabei selbstverständlich inklusive.
In Frankreich ist diese Woche Marine Le Pen wegen der Veruntreuung von EU-Geldern von einem Gericht verurteilt worden. Als Teil der Strafe wurde sie für fünf Jahre vom passiven Wahlrecht ausgeschlossen. Obwohl das Urteil nicht rechtskräftig ist – Le Pen kann in Berufung gehen –, haben die Richter das Verbot, bei Wahlen anzutreten, mit sofortiger Wirkung verhängt. Die Vorsitzende des rechtsnationalen Rassemblement National (RN) galt als aussichtsreiche Kandidatin für die Präsidentschaftswahl 2027.
Das ist in diesem Jahr bereits der zweite gravierende Fall von Wahlbeeinflussung durch die Justiz in einem EU-Staat. In Rumänien hatte Călin Georgescu im November die erste Runde der Präsidentenwahl überraschend gewonnen. Das Ergebnis wurde später annulliert, die behauptete «russische Wahlmanipulation» konnte jedoch nicht bewiesen werden. Die Kandidatur für die Wahlwiederholung im Mai wurde Georgescu kürzlich durch das Verfassungsgericht untersagt.
Die Veruntreuung öffentlicher Gelder muss untersucht und geahndet werden, das steht außer Frage. Diese Anforderung darf nicht selektiv angewendet werden. Hingegen mussten wir in der Vergangenheit bei ungleich schwerwiegenderen Fällen von (mutmaßlichem) Missbrauch ganz andere Vorgehensweisen erleben, etwa im Fall der heutigen EZB-Chefin Christine Lagarde oder im «Pfizergate»-Skandal um die Präsidentin der EU-Kommission Ursula von der Leyen.
Wenngleich derartige Angelegenheiten formal auf einer rechtsstaatlichen Grundlage beruhen mögen, so bleibt ein bitterer Beigeschmack. Es stellt sich die Frage, ob und inwieweit die Justiz politisch instrumentalisiert wird. Dies ist umso interessanter, als die Gewaltenteilung einen essenziellen Teil jeder demokratischen Ordnung darstellt, während die Bekämpfung des politischen Gegners mit juristischen Mitteln gerade bei den am lautesten rufenden Verteidigern «unserer Demokratie» populär zu sein scheint.
Die Delegationen von CDU/CSU und SPD haben bei ihren Verhandlungen über eine Regierungskoalition genau solche Maßnahmen diskutiert. «Im Namen der Wahrheit und der Demokratie» möchte man noch härter gegen «Desinformation» vorgehen und dafür zum Beispiel den Digital Services Act der EU erweitern. Auch soll der Tatbestand der Volksverhetzung verschärft werden – und im Entzug des passiven Wahlrechts münden können. Auf europäischer Ebene würde Friedrich Merz wohl gerne Ungarn das Stimmrecht entziehen.
Der Pegel an Unzufriedenheit und Frustration wächst in großen Teilen der Bevölkerung kontinuierlich. Arroganz, Machtmissbrauch und immer abstrusere Ausreden für offensichtlich willkürliche Maßnahmen werden kaum verhindern, dass den etablierten Parteien die Unterstützung entschwindet. In Deutschland sind die Umfrageergebnisse der AfD ein guter Gradmesser dafür.
[Vorlage Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ fd0bcf8c:521f98c0
2025-05-01 11:29:57
@ fd0bcf8c:521f98c0
2025-05-01 11:29:57Collapse.
It's a slow burn.
The LA Fires started decades ago.
Hemingway said, when asked how he went broke:
"Slowly, then all at once."
That’s how collapse happens. Slowly, then suddenly.
Campfire
Ever build one?
You gather wood. Stack the foundation. Set the fuel. Light it up.
If it catches, keep going. Got to stoke it. Feed it. Watch it. In time, the fire's good.
Process It takes time.
Time to gather, build and ignite.
People come at the end. When the flame's dancing.
Like Sunday dinner.
People gather when food's ready. But, only the cook was in the kitchen.
Slow
Societal collapse's similar.
It takes years.
Decades.
Centuries.
A slow cook.
When people notice, the meal’s made. By the time they smell the fire, the forest’s already burning.
People see collapse, but it fell long time ago.
LA
Water, ran dry. Power went out. Fuel stations, empty. Help wasn't on the way.
Politicians politicking.
Making feel-good promises. People believed them. All bad decisions. One after another. They voted for it.
In time, it adds up.
Then, it falls down.
Shift
Analog to digital I work in animation.
Started analog, paper and pencil. It went digital. Scanners, tablets and all.
Veterans, didn't see it coming. Die-hards, refused to acknowledge. They went out of work. Those who adapted—they run the shows now.
Lockdowns
2008, I started a studio.
100% remote. A virtual company.
Some laughed. Others got angry. Said it wouldn't work. They couldn't see.
2020 comes with lockdowns.
Everyone scrambles. Those already digital, thrived.
The rest, shutdown.
History
The Wheel We carried goods. Then came the wheel.
Movement exploded. Trade thrived. Cities rose.
Hunter-gatherers? Left behind.
Collapse wasn't sudden. It was quiet. A shift.
The new formed. The old faded.
Change was inevitable.
Gunpowder
War changed.
Castles crumbled. Swords became relics. Power shifted.
Empires that adapted, thrived. Those that didn't, vanished.
Adapt or die.
The Internet
Borders blurred. Knowledge spread. Walls fell.
Old industries resisted. New empires emerged.
Collapse? No. A new frontier.
Borderless commerce. Shrinking government.
Info and influence, moving fast.
Bitcoin
Money, redefined.
No banks. No middlemen. Just code.
Governments dismiss it. Institutions fear it. But change ignores permission.
A ledger, transparent. A system, unstoppable. Like the internet rewrote communication, Bitcoin rewrites money.
Each invention displaced the old world.
Each collapse brought new opportunity.
Repeats
Mayans Built pyramids. Charted the stars. Cities thrived.
Then, slow decline.
Deforestation. Drought. Conflict.
People scattered.
Cities abandoned.
By the time the Spanish arrived, the fall was old news.
Romans
Not a fall. A fade.
Corruption. Inflation. Invasions. Cracks formed.
The West crumbled. The East endured.
Rome never vanished. Its laws, language, culture? Still here.
Japan
Collapse? No. Reinvention.
Shoguns fell. Meiji rose. Feudal to industrial. War crushed it. Post-war rebuilt it.
The '90s?
A peak. Tech giant. Economic force.
Then, stagnation. Aging population. Debt. Decline.
Still here. Still strong. But no longer rising.
Rhyme
US
Once a colony. Then an empire.
England ruled. America rose. Industry boomed. The 20th century belonged to the U.S.
A superpower. Factories roared. Gold backed the dollar.
A nation built on sound money.
Then, fiat. Paper promises. The gold standard abandoned.
Inflation crept in. Prices rose. Debt piled up. Each decade, the dollar bought less. Wages stagnated. Savings eroded.
Easy money, easy people.
Debt fueled bubbles. Each crash, deeper. The system, fragile.
Wealth concentrated. Time and energy, lost meaning.
A quiet nihilism grew.
People worked more. Gained less. Purpose eroded. Culture followed.
A nation distracted, chasing illusions of prosperity.
Today
The debt's bigger. The politics, fractured. The system strains. The foundation shifts.
The old fades into new.
What's next?
Every collapse starts slow. Then, all at once.
Change
Collapse is change.
It's natural. We see it throughout history.
Like a campfire—fire consumes, but it also brings warmth. Like dinner—before the meal, there’s preparation, transformation. Like LA fires—destructive, painful, but from the ashes, renewal. Possibly.
"To decompose is to be recomposed. That's what nature does. Nature, through whom all things happen as they should, and have happened forever in just the same way, and will continue one way or another endlessly."—Marcus Aurelius
Collapse isn’t the end.
It’s transition.
Preparing
"The Romans were reluctant to acknowledge change, and so are we." —The Sovereign Individual
Florida has hurricanes.
Happens every year. The news reports. Satellites confirm paths. Some, listen and prepare. Others, don't.
The storm comes.
Those prepared, benefit. The rest, suffer.
Like the old animators. They resisted. Now, they’re gone.
Collapse has warnings. How to prepare:
Mindset
Stay calm. See the patterns. Change is constant. Opportunity hides in disruption. Zoom out. Fear distorts judgment.
Skill Development
Learn adaptability. Master digital tools. Understand money. Grow networks. Invest in knowledge, not just assets.
Philosophy
Think long-term. Collapse spans generations. Pass down wisdom. Build resilience. Grow beyond survival—thrive.
Action
Own less, know more. Create. Don’t just consume.
Be part of what’s next.
Conclusion
The fire’s already burning. You can tend it—or watch it burn everything down.
There's a saying:
"There are three types of people in this world: those who make things happen, those who watch things happen, and those who wonder what happened."—Pat Riley
Be the former.
Rare Passenger / block height 880 440
-
 @ 52b4a076:e7fad8bd
2025-04-28 00:48:57
@ 52b4a076:e7fad8bd
2025-04-28 00:48:57I have been recently building NFDB, a new relay DB. This post is meant as a short overview.
Regular relays have challenges
Current relay software have significant challenges, which I have experienced when hosting Nostr.land: - Scalability is only supported by adding full replicas, which does not scale to large relays. - Most relays use slow databases and are not optimized for large scale usage. - Search is near-impossible to implement on standard relays. - Privacy features such as NIP-42 are lacking. - Regular DB maintenance tasks on normal relays require extended downtime. - Fault-tolerance is implemented, if any, using a load balancer, which is limited. - Personalization and advanced filtering is not possible. - Local caching is not supported.
NFDB: A scalable database for large relays
NFDB is a new database meant for medium-large scale relays, built on FoundationDB that provides: - Near-unlimited scalability - Extended fault tolerance - Instant loading - Better search - Better personalization - and more.
Search
NFDB has extended search capabilities including: - Semantic search: Search for meaning, not words. - Interest-based search: Highlight content you care about. - Multi-faceted queries: Easily filter by topic, author group, keywords, and more at the same time. - Wide support for event kinds, including users, articles, etc.
Personalization
NFDB allows significant personalization: - Customized algorithms: Be your own algorithm. - Spam filtering: Filter content to your WoT, and use advanced spam filters. - Topic mutes: Mute topics, not keywords. - Media filtering: With Nostr.build, you will be able to filter NSFW and other content - Low data mode: Block notes that use high amounts of cellular data. - and more
Other
NFDB has support for many other features such as: - NIP-42: Protect your privacy with private drafts and DMs - Microrelays: Easily deploy your own personal microrelay - Containers: Dedicated, fast storage for discoverability events such as relay lists
Calcite: A local microrelay database
Calcite is a lightweight, local version of NFDB that is meant for microrelays and caching, meant for thousands of personal microrelays.
Calcite HA is an additional layer that allows live migration and relay failover in under 30 seconds, providing higher availability compared to current relays with greater simplicity. Calcite HA is enabled in all Calcite deployments.
For zero-downtime, NFDB is recommended.
Noswhere SmartCache
Relays are fixed in one location, but users can be anywhere.
Noswhere SmartCache is a CDN for relays that dynamically caches data on edge servers closest to you, allowing: - Multiple regions around the world - Improved throughput and performance - Faster loading times
routerd
routerdis a custom load-balancer optimized for Nostr relays, integrated with SmartCache.routerdis specifically integrated with NFDB and Calcite HA to provide fast failover and high performance.Ending notes
NFDB is planned to be deployed to Nostr.land in the coming weeks.
A lot more is to come. 👀️️️️️️
-
 @ 78b3c1ed:5033eea9
2025-04-27 01:48:48
@ 78b3c1ed:5033eea9
2025-04-27 01:48:48※スポットライトから移植した古い記事です。参考程度に。
これを参考にしてUmbrelのBitcoin Nodeをカスタムsignetノードにする。 以下メモ書きご容赦。備忘録程度に書き留めました。
メインネットとは共存できない。Bitcoinに依存する全てのアプリを削除しなければならない。よって実験機に導入すべき。
<手順>
1.Umbrel Bitcoin Nodeアプリのadvance settingでsignetを選択。
2.CLI appスクリプトでbitcoinを止める。
cd umbrel/scripts ./app stop bitcoin3.bitcoin.conf, umbrel-bitcoin.conf以外を削除ディレクトリの場所は ~/umbrel/app-data/bitcoin/data/bitcoin4.umbrel-bitcoin.confをsu権限で編集。末尾にsignetchallengeを追加。 ``` [signet] bind=0.0.0.0:8333 bind=10.21.21.8:8334=onion51,21,<公開鍵>,51,ae
signetchallenge=5121<公開鍵>51ae
5.appスクリプトでbitcoinを開始。cd ~/umbrel/scripts ./app start bitcoin ``` 6.適当にディレクトリを作りgithubからbitcoindのソースをクローン。7.bitcoindのバイナリをダウンロード、bitcoin-cliおよびbitcoin-utilを~/.local/binに置く。6.のソースからビルドしても良い。ビルド方法は自分で調べて。
8.bitcondにマイニング用のウォレットを作成 ``` alias bcli='docker exec -it bitcoin_bitcoind_1 bitcoin-cli -signet -rpcconnect=10.21.21.8 -rpcport=8332 -rpcuser=umbrel -rpcpassword=<パスワード>'
ウォレットを作る。
bcli createwallet "mining" false true "" false false
秘密鍵をインポート
bcli importprivkey "<秘密鍵>"
RPCパスワードは以下で確認cat ~/umbrel/.env | grep BITCOIN_RPC_PASS9.ソースにあるbitcoin/contrib/signet/minerスクリプトを使ってマイニングcd <ダウンロードしたディレクトリ>/bitcoin/contrib/signet難易度の算出
./miner \ --cli="bitcoin-cli -signet -rpcconnect=10.21.21.8 -rpcport=8332 -rpcuser=umbrel -rpcpassword=<パスワード>" calibrate \ --grind-cmd="bitcoin-util grind" --seconds 30 ★私の環境で30秒指定したら nbits=1d4271e7 と算出された。実際にこれで動かすと2分30になるけど...
ジェネシスブロック生成
./miner \ --cli="bitcoin-cli -signet -rpcconnect=10.21.21.8 -rpcport=8332 -rpcuser=umbrel -rpcpassword=<パスワード>" generate \ --address <ビットコインアドレス> \ --grind-cmd="bitcoin-util grind" --nbits=1d4271e7 \ --set-block-time=$(date +%s)
継続的にマイニング
./miner \ --cli="bitcoin-cli -signet -rpcconnect=10.21.21.8 -rpcport=8332 -rpcuser=umbrel -rpcpassword=<パスワード>" generate \ --address <ビットコインアドレス> \ --grind-cmd="bitcoin-util grind" --nbits=1d4271e7 \ --ongoing ``` ここまでやればカスタムsignetでビットコインノードが稼働する。
-
 @ 04c915da:3dfbecc9
2025-03-25 17:43:44
@ 04c915da:3dfbecc9
2025-03-25 17:43:44One of the most common criticisms leveled against nostr is the perceived lack of assurance when it comes to data storage. Critics argue that without a centralized authority guaranteeing that all data is preserved, important information will be lost. They also claim that running a relay will become prohibitively expensive. While there is truth to these concerns, they miss the mark. The genius of nostr lies in its flexibility, resilience, and the way it harnesses human incentives to ensure data availability in practice.
A nostr relay is simply a server that holds cryptographically verifiable signed data and makes it available to others. Relays are simple, flexible, open, and require no permission to run. Critics are right that operating a relay attempting to store all nostr data will be costly. What they miss is that most will not run all encompassing archive relays. Nostr does not rely on massive archive relays. Instead, anyone can run a relay and choose to store whatever subset of data they want. This keeps costs low and operations flexible, making relay operation accessible to all sorts of individuals and entities with varying use cases.
Critics are correct that there is no ironclad guarantee that every piece of data will always be available. Unlike bitcoin where data permanence is baked into the system at a steep cost, nostr does not promise that every random note or meme will be preserved forever. That said, in practice, any data perceived as valuable by someone will likely be stored and distributed by multiple entities. If something matters to someone, they will keep a signed copy.
Nostr is the Streisand Effect in protocol form. The Streisand effect is when an attempt to suppress information backfires, causing it to spread even further. With nostr, anyone can broadcast signed data, anyone can store it, and anyone can distribute it. Try to censor something important? Good luck. The moment it catches attention, it will be stored on relays across the globe, copied, and shared by those who find it worth keeping. Data deemed important will be replicated across servers by individuals acting in their own interest.
Nostr’s distributed nature ensures that the system does not rely on a single point of failure or a corporate overlord. Instead, it leans on the collective will of its users. The result is a network where costs stay manageable, participation is open to all, and valuable verifiable data is stored and distributed forever.
-
 @ 04cb16e4:2ec3e5d5
2025-03-13 21:26:13
@ 04cb16e4:2ec3e5d5
2025-03-13 21:26:13Wenn man etwas verkaufen will, muss man eine Geschichte über sein Produkt erzählen. Nur wenige können etwas damit anfangen, wenn du sagst: Unser Produkt enthält 50 Gramm Hafer (hoffentlich gentechnikfrei), 5 mittelgroße Erdbeeren, Spuren von Sesamschalen sowie einen Teelöffel Honig. So funktioniert das nicht. Dein Riegel braucht einen Namen und eine Geschichte.
Wenn wir über Krieg und Frieden sprechen, denn gibt es zumeist Zahlen, Fakten und Meinungen. Tausende von Kindern die in einem Krieg getötet werden sind eine schockierende Anzahl. Nimmst du die Zahlen weg und beschäftigst dich mit jedem einzelnen Schicksal, dann ist das unmöglich zu ertragen. Also kämpfen wir hier vor Ort, in Deutschland, zwar nicht mit Waffen gegeneinander, sondern mittels unserer Meinungen in Kombination mit zu vermittelnden relativen Wahrheiten. Da kommt das Ego ins Spiel. Wir wollen unbedingt Recht haben! Irgendeiner soll in diesem Meinungskampf am Ende als Gewinner dastehen. Weil er die besseren Argumente hat. Schließlich werden Emotionen mit Fakten vermischt und als Totschlagargumente in die Gegenfront geworfen.
Was aber, wenn man eine Geschichte über den Krieg erzählt, die jeden mitnehmen kann, ganz gleich, welche Meinung man zu den aktuell verhandelten Kampfschauplätzen hat? Alles Trennende wird aus der Erzählung herausgenommen und was bleibt, sind die zerstörerische Kraft des Krieges und die Verantwortung jedes einzelnen Menschen zu entscheiden, ob er dieses grausame Monster füttert oder eben nicht. In dem afrikanischen Märchen „Sheikhi“ basieren diese Entscheidungen nicht auf Fakten und Meinungen, sondern auf persönlichen Erfahrungen. Die Protagonisten nehmen uns mit in ihre Welt und lassen uns ihre inneren Kämpfe, Zweifel, Ängste und Hoffnungen miterleben. Wir können uns mit ihnen identifizieren, obwohl wir unter völlig anderen Bedingungen leben und sterben.
Hier kannst du das Buch direkt beim Verlag bestellen
Die alternative Buchmesse Seitenwechsel
Am Ende des Buches konnte ich gar nicht anders, als eine tiefe Sehnsucht nach Frieden und Einigkeit zu verspüren. Diese Sehnsucht basierte aber nicht mehr auf dem Bedürfnis, bessere Argumente als die vermeintliche Gegenseite zu haben, sondern vielmehr darauf, dass dieses verzweifelte Ringen und Hassen endlich zu einem Ende kommt. Nicht nur auf den Schlachtfeldern Asiens und Afrikas, sondern ebenfalls auf Facebook, X, den Straßen unserer Städte und im Krieg jedes Menschen gegen sich selbst. Inzwischen gelingt es mir immer öfter, mir einen bissigen Kommentar zu verkneifen, wenn jemand auf Facebook etwas schreibt, was ich unerträglich finde. Ich weiß, das ich ihn nicht vom Gegenteil überzeugen werde und das mein Kommentar das selbe Monster füttert, dass sich an den Opfern des Krieges satt isst.
Wenn es irgendwo Menschen auf der Welt gibt, die Mord und Folter verzeihen können, dann kann auch ich eine andere Meinung ertragen ohne rechthaberisch, arrogant und destruktiv zu werden. Notfalls gehe ich in den Wald und schreie.
-
 @ 6b3780ef:221416c8
2025-05-01 11:26:06
@ 6b3780ef:221416c8
2025-05-01 11:26:06We are excited to announce the finalization of our DVMCP specification update, which integrates the latest Model Context Protocol (MCP) version
2025-03-26and other improvements. This article highlights the key points of this update, and the differences between our initial vision and the final specification, providing insights into how our ideas evolved during the drafting process.The Journey from Concept to Specification
Last week, we shared our vision for updating the DVMCP specification to better integrate with the Model Context Protocol. After extensive drafting and feedback, we've finalized a specification that maintains our core vision while making important refinements to ensure optimal functionality, interoperability, and user experience. We are also improving the tagging of our specifications to make it more consistent, using the
draftmcp:2025-03-26rev1tag to identify the version of the specification and the revision number we are in. We hope this will make the specification clearer and easier to track changes.Key Changes in the Final Specification
Refined Event Kind Structure
In our initial proposal, we outlined a modular event structure with dedicated event kinds for server announcements (31316) and separate kinds for capability categories (31317, 31318, and 31319). The final specification maintains this approach but provides more detailed implementation guidelines.
Enhanced Ephemeral Events
One of the most significant refinements involves our approach to ephemeral events. The final specification clearly defines three ephemeral event kinds:
- Requests (25910): Client requests to servers
- Responses (26910): Server responses to client requests
- Notifications (21316): Status updates, progress information, and interactive elements
This approach provides a more efficient communication pattern while reducing unnecessary storage burden on relays.
Standardized Content Structure
While our initial vision mentioned separating Nostr metadata and MCP payloads, the final specification provides concrete implementation details:
- Content Field: Contains stringified MCP JSON-RPC messages, maintaining full compatibility with the MCP specification
- Tags Field: Contains all Nostr-specific metadata using standardized tag patterns
This clear separation ensures that both protocols can operate seamlessly together without compromising either protocol's integrity.
Comprehensive Protocol Flows
The final specification includes detailed protocol flows for:
- Public Server Discovery: Finding servers through published announcements
- Private Server Discovery: Direct connection to servers using the MCP initialization process
- Capability Operations: Standardized patterns for listing, executing, and managing all capability types
These flows provide implementers with clear guidance on how to build compliant clients and servers.
Payment and Authorization
The specification now includes concrete implementations for payment handling and authorization:
- Payment Required Notifications: Using the ephemeral notification kind (21316) with specific tag patterns
- Authorization Flow: Leveraging Nostr's cryptographic properties for secure authorization
What Remained Consistent
Despite these refinements, our core vision remained intact:
- Expanded Capability Support: The specification fully embraces MCP's complete capabilities framework, including tools, resources, and prompts
- Modular Architecture: The separation of server announcements and capability listings improves maintainability and extensibility
- Protocol Interoperability: The specification maintains compatibility with both Nostr and MCP
Implementation Status
With the specification now finalized, we're updating our reference implementations:
- DVMCP-bridge: Server-side implementation for exposing MCP capabilities through Nostr
- DVMCP-discovery: Client-side library for discovering and consuming MCP capabilities via Nostr
Community Involvement
We want to express our gratitude to everyone who provided feedback on our draft specification. Your insights helped shape a more robust and practical protocol.
Looking Forward
This specification represents a significant advancement in bridging the Nostr and MCP ecosystems. By providing a standardized way to discover, access, and utilize MCP capabilities through the Nostr network, we're enabling new possibilities for applications.
We invite developers to explore the final specification and begin building with our reference implementations. Together, we can create a more open, interoperable, and powerful ecosystem
The complete specification is available at 2025-03-26.md.
-
 @ 08964cb5:51bf010f
2025-05-01 10:32:52
@ 08964cb5:51bf010f
2025-05-01 10:32:52«Reflexiones y Acción: Entre la Defensa del Patrimonio»
[English below][Deutsch unten]
Los recientes acontecimientos que han puesto en peligro mi patrimonio, así como los valores fundamentales que definen mi camino, me han llevado a tomar una decisión importante: iniciar una campaña de recaudación de fondos. Esta iniciativa no solo busca proteger lo que he construido con esfuerzo, sino también garantizar que pueda seguir adelante con proyectos y principios que son esenciales para mí.
Tu apoyo puede marcar una gran diferencia. Si deseas conocer más sobre esta causa o contribuir con tu solidaridad, te invito a visitar ›🔗 éste enlace.‹ "Reflections and Action: Safeguarding My Heritage"
“Reflections and Action: Safeguarding My Heritage”
The recent events that have jeopardised my assets and the core values that define my journey have led me to take a significant step: launching a fundraising campaign. This initiative aims not only to protect what I have built with hard work but also to ensure that I can continue moving forward with projects and principles that are essential to me.
Your support can make a real difference. If you’d like to learn more about this cause or contribute with your solidarity, I invite you to visit ›🔗 this link.‹
„Überlegungen und Handeln: Den Schutz meines Vermögens”
Die jüngsten Ereignisse, die mein Vermögen sowie die grundlegenden Werte, die meinen Weg bestimmen, gefährdet haben, haben mich dazu veranlasst, einen wichtigen Schritt zu gehen: den Start einer Spendenkampagne. Diese Initiative zielt nicht nur darauf ab, das zu schützen, was ich mit harter Arbeit aufgebaut habe, sondern auch sicherzustellen, dass ich mit Projekten und Prinzipien, die für mich unerlässlich sind, weitermachen kann.
Deine Unterstützung kann einen großen Unterschied machen. Wenn du mehr über diese Sache erfahren oder mit deiner Solidarität beitragen möchtest, lade ich dich ein, ›🔗 diesen Link zu besuchen.‹
-
 @ a012dc82:6458a70d
2025-03-11 15:41:36
@ a012dc82:6458a70d
2025-03-11 15:41:36Argentina's journey through economic turmoil has been long and fraught with challenges. The country has grappled with inflation, debt, and a fragile economic structure that has left policymakers searching for solutions. In this context, President Javier Milei's introduction of the "Ley Ómnibus" represented a bold step towards addressing these systemic issues. The reform package was not just a set of isolated measures but a comprehensive plan aimed at overhauling the Argentine economy and social framework. The intention was to create a more robust, free, and prosperous Argentina, where economic freedoms could lead to broader social benefits.
The "Ley Ómnibus" was ambitious in its scope, covering a wide range of areas from tax reform to social policies, aiming to stimulate economic growth, reduce bureaucratic red tape, and enhance the overall quality of life for Argentines. This package was seen as a critical move to reset the economic compass of the country, aiming to attract foreign investment, boost local industry, and provide a clearer, more stable environment for businesses and individuals alike. However, such sweeping reforms were bound to encounter resistance, particularly when they touched upon sensitive areas like taxation and digital assets.
Table of Contents
-
The Crypto Tax Proposal: Initial Considerations
-
Public Backlash and Strategic Withdrawal
-
The Rationale Behind Dropping Crypto Taxes
-
Implications for Crypto Investors and the Market
-
Milei's Political Strategy and Future Prospects
-
Conclusion
-
FAQs
The Crypto Tax Proposal: Initial Considerations
Within the vast array of proposals in the Ley Ómnibus, the crypto tax stood out due to its novelty and the growing interest in digital currencies within Argentina. The country had seen a surge in cryptocurrency adoption, driven by factors such as high inflation rates and currency controls that made traditional financial systems less attractive. Cryptocurrencies offered an alternative for savings, investment, and transactions, leading to a burgeoning crypto economy.
The initial rationale behind proposing a crypto tax was multifaceted. On one hand, it aimed to bring Argentina in line with global trends where countries are increasingly seeking to regulate and tax digital currencies. On the other hand, it was seen as a potential new revenue stream for the government, which was desperately seeking funds to address its fiscal deficits. The proposal also intended to bring transparency to a sector that is often criticized for its opacity, making it easier to combat fraud, money laundering, and other illicit activities associated with cryptocurrencies.
However, the proposal was not just about regulation and revenue. It was also a litmus test for Argentina's approach to innovation and digital transformation. How the government handled this issue would signal its stance towards new technologies and economic paradigms, which are increasingly dominated by digital assets and fintech innovations.
Public Backlash and Strategic Withdrawal
The backlash against the proposed crypto taxes was swift and significant. The crypto community in Argentina, which had been flourishing in an environment of relative freedom, saw the tax as a direct threat to its growth and viability. But the discontent went beyond the crypto enthusiasts; the general public, already burdened by high taxes and economic instability, viewed the proposal as yet another financial strain.
The protests and debates that ensued highlighted a broader discontent with the government's approach to economic management. Many Argentines felt that the focus should be on fixing the fundamental issues plaguing the economy, such as inflation and corruption, rather than imposing new taxes. The crypto tax became a symbol of the government's perceived detachment from the real concerns of its citizens.
In this heated atmosphere, President Milei's decision to withdraw the crypto tax proposal from the Ley Ómnibus was not just a tactical retreat; it was a necessary move to quell the growing unrest and focus on more pressing economic reforms. This decision underscored the complexities of governing in a highly polarized environment and the need for a more nuanced approach to policy-making, especially when dealing with emerging technologies and markets.
The Rationale Behind Dropping Crypto Taxes
The decision to drop the crypto tax from the omnibus reform package was not taken lightly. It was a recognition of the crypto sector's unique dynamics and the government's limitations in effectively regulating and taxing this space without stifling innovation. The move also reflected a broader understanding of the economic landscape, where rapid development and legislative efficiency were deemed more crucial than ever.
By removing the contentious clauses, the government aimed to streamline the passage of the Ley Ómnibus, ensuring that other, less controversial, reforms could be implemented swiftly. This strategic pivot was also a nod to the global debate on how best to integrate cryptocurrencies into national economies. Argentina's government recognized that a more cautious and informed approach was necessary, one that could balance the need for regulation with the desire to foster a thriving digital economy.
Furthermore, the withdrawal of the crypto tax proposal can be seen as an acknowledgment of the power of public opinion and the crypto community's growing influence. It highlighted the need for governments to engage with stakeholders and understand the implications of new technologies before rushing to regulate them.
Implications for Crypto Investors and the Market
The removal of the crypto tax proposal has had immediate and significant implications for the Argentine crypto market. For investors, the decision has provided a reprieve from the uncertainty that had clouded the sector, allowing them to breathe a sigh of relief and continue their activities without the looming threat of new taxes. This has helped sustain the momentum of the crypto market in Argentina, which is seen as a vital component of the country's digital transformation and economic diversification.
However, the situation remains complex and fluid. The government's stance on cryptocurrencies is still evolving, and future regulations could impact the market in unforeseen ways. Investors are now more aware of the need to stay informed and engaged with regulatory developments, understanding that the legal landscape for digital currencies is still being shaped.
The episode has also highlighted the broader challenges facing the Argentine economy, including the need for comprehensive tax reform and the creation of a more conducive environment for technological innovation and investment. The crypto market's response to the government's actions reflects the delicate balance between regulation and growth, a balance that will be crucial for Argentina's economic future.
Milei's Political Strategy and Future Prospects
President Milei's handling of the crypto tax controversy reveals much about his political strategy and vision for Argentina. By withdrawing the proposal, he demonstrated a willingness to listen to public concerns and adapt his policies accordingly. This flexibility could be a key asset as he navigates the complex landscape of Argentine politics and governance.
The episode also offers insights into the potential future direction of Milei's administration. The focus on economic reforms, coupled with a pragmatic approach to contentious issues, suggests a leadership style that prioritizes economic stability and growth over ideological purity. This could bode well for Argentina's future, particularly if Milei can harness the energy and innovation of the digital economy as part of his broader reform agenda.
However, the challenges ahead are significant. The Ley Ómnibus is just one part of a larger puzzle, and Milei's ability to implement comprehensive reforms will be tested in the coming months and years. The crypto tax saga has shown that while change is possible, it requires careful negotiation, stakeholder engagement, and a clear understanding of the economic and social landscape.
Conclusion
The story of Argentina's crypto tax proposal is a microcosm of the broader challenges facing the country as it seeks to reform its economy and society. It highlights the tensions between innovation and regulation, the importance of public opinion, and the complexities of governance in a rapidly changing world.
As Argentina moves forward, the lessons learned from this episode will be invaluable. The need for clear, informed, and inclusive policy-making has never been greater, particularly as the country navigates the uncertainties of the digital age.
FAQs
What is the Ley Ómnibus? The Ley Ómnibus, formally known as the "Law of Bases and Starting Points for the Freedom of Argentines," is a comprehensive reform package introduced by President Javier Milei. It aims to address various economic, social, and administrative issues in Argentina, aiming to stimulate growth, reduce bureaucracy, and improve the overall quality of life.
Why were crypto taxes proposed in Argentina? Crypto taxes were proposed as part of the Ley Ómnibus to broaden the tax base, align with global trends of regulating digital currencies, and generate additional revenue for the government. They were also intended to bring more transparency to the cryptocurrency sector in Argentina.
Why were the proposed crypto taxes withdrawn? The proposed crypto taxes were withdrawn due to significant public backlash and concerns that they would stifle innovation and economic freedom in the burgeoning crypto market. The decision was also influenced by the government's priority to ensure the swift passage of other reforms within the Ley Ómnibus.
What does the withdrawal of crypto taxes mean for investors? The withdrawal means that, for now, crypto investors in Argentina will not face additional taxes specifically targeting their cryptocurrency holdings or transactions. However, selling large amounts of cryptocurrency at a profit will still be subject to income tax.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co/
Youtube: @thebitcoinlibertarian
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
Get Orange Pill App And Connect With Bitcoiners In Your Area. Stack Friends Who Stack Sats link: https://signup.theorangepillapp.com/opa/croxroad
Buy Bitcoin Books At Konsensus Network Store. 10% Discount With Code “21croxroad” link: https://bitcoinbook.shop?ref=21croxroad
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 78b3c1ed:5033eea9
2025-04-27 01:42:48
@ 78b3c1ed:5033eea9
2025-04-27 01:42:48・ThunderHubで焼いたマカロンがlncli printmacaroonでどう見えるか確認した。
ThunderHub macaroon permissions
get invoices invoices:read create invoices invoices:write get payments offchain:read pay invoices offchain:write get chain transactions onchain:read send to chain address onchain:write create chain address address:write get wallet info info:read stop daemon info:write この結果によれば、offchain:wirteとonchain:writeの権限がなければそのマカロンを使うクライアントは勝手にBTCを送金することができない。 info:writeがなければ勝手にLNDを止めたりすることができない。
・lncli printmacaroonでデフォルトで作られるmacaroonのpermissionsを調べてみた。 admin.macaroon
{ "version": 2, "location": "lnd", "root_key_id": "0", "permissions": [ "address:read", "address:write", "info:read", "info:write", "invoices:read", "invoices:write", "macaroon:generate", "macaroon:read", "macaroon:write", "message:read", "message:write", "offchain:read", "offchain:write", "onchain:read", "onchain:write", "peers:read", "peers:write", "signer:generate", "signer:read" ], "caveats": null }chainnotifier.macaroon{ "version": 2, "location": "lnd", "root_key_id": "0", "permissions": [ "onchain:read" ], "caveats": null }invoice.macaroon{ "version": 2, "location": "lnd", "root_key_id": "0", "permissions": [ "address:read", "address:write", "invoices:read", "invoices:write", "onchain:read" ], "caveats": null }invoices.macaroon{ "version": 2, "location": "lnd", "root_key_id": "0", "permissions": [ "invoices:read", "invoices:write" ], "caveats": null }readonly.macaroon{ "version": 2, "location": "lnd", "root_key_id": "0", "permissions": [ "address:read", "info:read", "invoices:read", "macaroon:read", "message:read", "offchain:read", "onchain:read", "peers:read", "signer:read" ], "caveats": null }router.macaroon{ "version": 2, "location": "lnd", "root_key_id": "0", "permissions": [ "offchain:read", "offchain:write" ], "caveats": null }signer.macaroon{ "version": 2, "location": "lnd", "root_key_id": "0", "permissions": [ "signer:generate", "signer:read" ], "caveats": null }walletkit.macaroon{ "version": 2, "location": "lnd", "root_key_id": "0", "permissions": [ "address:read", "address:write", "onchain:read", "onchain:write" ], "caveats": null }・lncli listpermissions コマンドですべての RPC メソッド URI と、それらを呼び出すために必要なマカロン権限を一覧表示できる。 LND v0.18.5-betaでやると1344行ほどのJSONができる。 AddInvoiceだとinvoice:writeのpermissionを持つmacaroonを使えばインボイスを作れるようだ。
"/lnrpc.Lightning/AddInvoice": { "permissions": [ { "entity": "invoices", "action": "write" } ] },lncli listpermissionsからentityとactionを抜き出してみた。 ``` "entity": "address", "entity": "info", "entity": "invoices", "entity": "macaroon", "entity": "message", "entity": "offchain", "entity": "onchain", "entity": "peers", "entity": "signer","action": "generate" "action": "read" "action": "write"
lncli とjqを組み合わせると例えば以下コマンドでinvoices:writeを必要とするRPCの一覧を表示できる。 invoices:writeだとAddInvoiceの他にホドルインボイス作成でも使ってるようだlncli listpermissions | jq -r '.method_permissions | to_entries[] | select(.value.permissions[] | select(.entity == "invoices" and .action == "write")) | .key'/invoicesrpc.Invoices/AddHoldInvoice /invoicesrpc.Invoices/CancelInvoice /invoicesrpc.Invoices/HtlcModifier /invoicesrpc.Invoices/LookupInvoiceV2 /invoicesrpc.Invoices/SettleInvoice /lnrpc.Lightning/AddInvoiceinvoices:readだと以下となる。/invoicesrpc.Invoices/SubscribeSingleInvoice /lnrpc.Lightning/ListInvoices /lnrpc.Lightning/LookupInvoice /lnrpc.Lightning/SubscribeInvoicesLNの主だった機能のRPCはoffchainが必要ぽいので抜き出してみた。 offchain:write チャネルの開閉、ペイメントの送信までやってるみたい。 デフォルトのmacaroonでoffchain:writeを持ってるのはadminとrouterの2つだけ。openchannel,closechannelはonchain:writeのpermissionも必要なようだ。/autopilotrpc.Autopilot/ModifyStatus /autopilotrpc.Autopilot/SetScores /lnrpc.Lightning/AbandonChannel /lnrpc.Lightning/BatchOpenChannel /lnrpc.Lightning/ChannelAcceptor /lnrpc.Lightning/CloseChannel /lnrpc.Lightning/DeleteAllPayments /lnrpc.Lightning/DeletePayment /lnrpc.Lightning/FundingStateStep /lnrpc.Lightning/OpenChannel /lnrpc.Lightning/OpenChannelSync /lnrpc.Lightning/RestoreChannelBackups /lnrpc.Lightning/SendCustomMessage /lnrpc.Lightning/SendPayment /lnrpc.Lightning/SendPaymentSync /lnrpc.Lightning/SendToRoute /lnrpc.Lightning/SendToRouteSync /lnrpc.Lightning/UpdateChannelPolicy /routerrpc.Router/HtlcInterceptor /routerrpc.Router/ResetMissionControl /routerrpc.Router/SendPayment /routerrpc.Router/SendPaymentV2 /routerrpc.Router/SendToRoute /routerrpc.Router/SendToRouteV2 /routerrpc.Router/SetMissionControlConfig /routerrpc.Router/UpdateChanStatus /routerrpc.Router/XAddLocalChanAliases /routerrpc.Router/XDeleteLocalChanAliases /routerrpc.Router/XImportMissionControl /wtclientrpc.WatchtowerClient/AddTower /wtclientrpc.WatchtowerClient/DeactivateTower /wtclientrpc.WatchtowerClient/RemoveTower /wtclientrpc.WatchtowerClient/TerminateSession"/lnrpc.Lightning/OpenChannel": { "permissions": [ { "entity": "onchain", "action": "write" }, { "entity": "offchain", "action": "write" } ] },offchain:read readの方はチャネルやインボイスの状態を確認するためのpermissionのようだ。/lnrpc.Lightning/ChannelBalance /lnrpc.Lightning/ClosedChannels /lnrpc.Lightning/DecodePayReq /lnrpc.Lightning/ExportAllChannelBackups /lnrpc.Lightning/ExportChannelBackup /lnrpc.Lightning/FeeReport /lnrpc.Lightning/ForwardingHistory /lnrpc.Lightning/GetDebugInfo /lnrpc.Lightning/ListAliases /lnrpc.Lightning/ListChannels /lnrpc.Lightning/ListPayments /lnrpc.Lightning/LookupHtlcResolution /lnrpc.Lightning/PendingChannels /lnrpc.Lightning/SubscribeChannelBackups /lnrpc.Lightning/SubscribeChannelEvents /lnrpc.Lightning/SubscribeCustomMessages /lnrpc.Lightning/VerifyChanBackup /routerrpc.Router/BuildRoute /routerrpc.Router/EstimateRouteFee /routerrpc.Router/GetMissionControlConfig /routerrpc.Router/QueryMissionControl /routerrpc.Router/QueryProbability /routerrpc.Router/SubscribeHtlcEvents /routerrpc.Router/TrackPayment /routerrpc.Router/TrackPaymentV2 /routerrpc.Router/TrackPayments /wtclientrpc.WatchtowerClient/GetTowerInfo /wtclientrpc.WatchtowerClient/ListTowers /wtclientrpc.WatchtowerClient/Policy /wtclientrpc.WatchtowerClient/Stats・おまけ1 RPCメソッド名にopenを含む要素を抽出するコマンドlncli listpermissions | jq '.method_permissions | to_entries[] | select(.key | test("open"; "i"))'{ "key": "/lnrpc.Lightning/BatchOpenChannel", "value": { "permissions": [ { "entity": "onchain", "action": "write" }, { "entity": "offchain", "action": "write" } ] } } { "key": "/lnrpc.Lightning/OpenChannel", "value": { "permissions": [ { "entity": "onchain", "action": "write" }, { "entity": "offchain", "action": "write" } ] } } { "key": "/lnrpc.Lightning/OpenChannelSync", "value": { "permissions": [ { "entity": "onchain", "action": "write" }, { "entity": "offchain", "action": "write" } ] } }・おまけ2 thunderhubで作ったmacaroonはテキストで出力されコピペして使うもので、macaroonファイルになってない。 HEXをmacaroonファイルにするには以下コマンドでできる。HEXをコピペして置換する。またYOURSの箇所を自分でわかりやすい名称に置換すると良い。echo -n "HEX" | xxd -r -p > YOURS.macaroonthunderhubで"Create Invoices, Get Invoices, Get Wallet Info, Get Payments, Pay Invoices"をチェックして作ったmacaroonのpermissionsは以下となる。{ "version": 2, "location": "lnd", "root_key_id": "0", "permissions": [ "info:read", "invoices:read", "invoices:write", "offchain:read", "offchain:write" ], "caveats": null } ``` offchain:writeはあるがonchain:writeがないのでチャネル開閉はできないはず。 -
 @ 08964cb5:51bf010f
2025-05-01 10:14:41
@ 08964cb5:51bf010f
2025-05-01 10:14:41«Reflexiones y Acción: Entre la Defensa del Patrimonio»
[English below][Deutsch unten]
Los recientes acontecimientos que han puesto en peligro mi patrimonio, así como los valores fundamentales que definen mi camino, me han llevado a tomar una decisión importante: iniciar una campaña de recaudación de fondos. Esta iniciativa no solo busca proteger lo que he construido con esfuerzo, sino también garantizar que pueda seguir adelante con proyectos y principios que son esenciales para mí.
Tu apoyo puede marcar una gran diferencia. Si deseas conocer más sobre esta causa o contribuir con tu solidaridad, te invito a visitar ›🔗éste enlace.‹
"Reflections and Action: Safeguarding My Heritage"
The recent events that have jeopardised my assets and the core values that define my journey have led me to take a significant step: launching a fundraising campaign. This initiative aims not only to protect what I have built with hard work but also to ensure that I can continue moving forward with projects and principles that are essential to me.
Your support can make a real difference. If you’d like to learn more about this cause or contribute with your solidarity, I invite you to visit ›🔗this link.‹
"Überlegungen und Handeln: Den Schutz meines Vermögens"
Die jüngsten Ereignisse, die mein Vermögen sowie die grundlegenden Werte, die meinen Weg bestimmen, gefährdet haben, haben mich dazu veranlasst, einen wichtigen Schritt zu gehen: den Start einer Spendenkampagne. Diese Initiative zielt nicht nur darauf ab, das zu schützen, was ich mit harter Arbeit aufgebaut habe, sondern auch sicherzustellen, dass ich mit Projekten und Prinzipien, die für mich unerlässlich sind, weitermachen kann.
Deine Unterstützung kann einen großen Unterschied machen. Wenn du mehr über diese Sache erfahren oder mit deiner Solidarität beitragen möchtest, lade ich dich ein, ›🔗diesen Link zu besuchen.‹
-
 @ 2b24a1fa:17750f64
2025-05-01 08:26:05
@ 2b24a1fa:17750f64
2025-05-01 08:26:05Ein Gedicht unserer Zeit von Lionne Douce.
Sprecherin: Sabrina Khalil
https://soundcloud.com/radiomuenchen/der-gutmenschzug-ist-da-von?
-
 @ 04c915da:3dfbecc9
2025-03-10 23:31:30
@ 04c915da:3dfbecc9
2025-03-10 23:31:30Bitcoin has always been rooted in freedom and resistance to authority. I get that many of you are conflicted about the US Government stacking but by design we cannot stop anyone from using bitcoin. Many have asked me for my thoughts on the matter, so let’s rip it.
Concern
One of the most glaring issues with the strategic bitcoin reserve is its foundation, built on stolen bitcoin. For those of us who value private property this is an obvious betrayal of our core principles. Rather than proof of work, the bitcoin that seeds this reserve has been taken by force. The US Government should return the bitcoin stolen from Bitfinex and the Silk Road.
Usually stolen bitcoin for the reserve creates a perverse incentive. If governments see a bitcoin as a valuable asset, they will ramp up efforts to confiscate more bitcoin. The precedent is a major concern, and I stand strongly against it, but it should be also noted that governments were already seizing coin before the reserve so this is not really a change in policy.
Ideally all seized bitcoin should be burned, by law. This would align incentives properly and make it less likely for the government to actively increase coin seizures. Due to the truly scarce properties of bitcoin, all burned bitcoin helps existing holders through increased purchasing power regardless. This change would be unlikely but those of us in policy circles should push for it regardless. It would be best case scenario for American bitcoiners and would create a strong foundation for the next century of American leadership.
Optimism
The entire point of bitcoin is that we can spend or save it without permission. That said, it is a massive benefit to not have one of the strongest governments in human history actively trying to ruin our lives.
Since the beginning, bitcoiners have faced horrible regulatory trends. KYC, surveillance, and legal cases have made using bitcoin and building bitcoin businesses incredibly difficult. It is incredibly important to note that over the past year that trend has reversed for the first time in a decade. A strategic bitcoin reserve is a key driver of this shift. By holding bitcoin, the strongest government in the world has signaled that it is not just a fringe technology but rather truly valuable, legitimate, and worth stacking.
This alignment of incentives changes everything. The US Government stacking proves bitcoin’s worth. The resulting purchasing power appreciation helps all of us who are holding coin and as bitcoin succeeds our government receives direct benefit. A beautiful positive feedback loop.
Realism
We are trending in the right direction. A strategic bitcoin reserve is a sign that the state sees bitcoin as an asset worth embracing rather than destroying. That said, there is a lot of work left to be done. We cannot be lulled into complacency, the time to push forward is now, and we cannot take our foot off the gas. We have a seat at the table for the first time ever. Let's make it worth it.
We must protect the right to free usage of bitcoin and other digital technologies. Freedom in the digital age must be taken and defended, through both technical and political avenues. Multiple privacy focused developers are facing long jail sentences for building tools that protect our freedom. These cases are not just legal battles. They are attacks on the soul of bitcoin. We need to rally behind them, fight for their freedom, and ensure the ethos of bitcoin survives this new era of government interest. The strategic reserve is a step in the right direction, but it is up to us to hold the line and shape the future.
-
 @ b8a9df82:6ab5cbbd
2025-03-06 22:39:15
@ b8a9df82:6ab5cbbd
2025-03-06 22:39:15Last week at Bitcoin Investment Week in New York City, hosted by Anthony Pompliano, Jack Mallers walked in wearing sneakers and a T-shirt, casually dropping, “Man… I hate politics.”
That was it. That was the moment I felt aligned again. That’s the energy I came for. No suits. No corporate jargon. Just a guy who gets it—who cares about people, bringing Bitcoin-powered payments to the masses and making sure people can actually use it.
His presence was a reminder of why we’re here in the first place. And his words—“I hate politics”—were a breath of fresh air.
Now, don’t get me wrong. Anthony was a fantastic host. His ability to mix wittiness, playfulness, and seriousness made him an entertaining moderator. But this week was unlike anything I’ve ever experienced in the Bitcoin ecosystem.
One of the biggest letdowns was the lack of interaction. No real Q&A sessions, no direct engagement, no real discussions. Just one fireside chat after another.
And sure, I get it—people love to hear themselves talk. But where were the questions? The critical debates? The chance for the audience to actually participate?
I’m used to Bitcoin meetups and conferences where you walk away with new ideas, new friends, and maybe even a new project to contribute to. Here, it was more like sitting in an expensive lecture hall, watching a lineup of speakers tell us things we already know.
A different vibe—and not in a good way
Over the past few months, I’ve attended nearly ten Bitcoin conferences, each leaving me feeling uplifted, inspired, and ready to take action. But this? This felt different. And not in a good way.
If this had been my first Bitcoin event, I might have walked away questioning whether I even belonged here. It wasn’t Prague. It wasn’t Riga. It wasn’t the buzzing, grassroots, pleb-filled gatherings I had grown to love. Instead, it felt more like a Wall Street networking event disguised as a Bitcoin conference.
Maybe it was the suits.
Or the fact that I was sitting in a room full of investors who have no problem dropping $1,000+ on a ticket.
Or that it reminded me way too much of my former life—working as a manager in London’s real estate industry, navigating boardrooms full of finance guys in polished shoes, talking about “assets under management.”
Bitcoin isn’t just an investment thesis. It’s a revolution. A movement. And yet, at times during this week, I felt like I was back in my fiat past, stuck in a room where people measured success in dollars, not in freedom.
Maybe that’s the point. Bitcoin Investment Week was never meant to be a pleb gathering.
That said, the week did have some bright spots. PubKey was a fantastic kickoff. That was real Bitcoin culture—plebs, Nostr, grassroots energy. People who actually use Bitcoin, not just talk about it.
But the absolute highlight? Jack Mallers, sneakers and all, cutting through the noise with his authenticity.
So, why did we even go?
Good question. Maybe it was curiosity. Maybe it was stepping out of our usual circles to see Bitcoin through a different lens. Maybe it was to remind ourselves why we chose this path in the first place.
Would I go again? Probably not.
Would I trade Prague, Riga, bitcoin++ or any of the grassroots Bitcoin conferences for this? Not a chance.
At the end of the day, Bitcoin doesn’t belong to Wall Street from my opinion. It belongs to the people who actually use it. And those are the people I want to be around.
-
 @ 91bea5cd:1df4451c
2025-04-26 10:16:21
@ 91bea5cd:1df4451c
2025-04-26 10:16:21O Contexto Legal Brasileiro e o Consentimento
No ordenamento jurídico brasileiro, o consentimento do ofendido pode, em certas circunstâncias, afastar a ilicitude de um ato que, sem ele, configuraria crime (como lesão corporal leve, prevista no Art. 129 do Código Penal). Contudo, o consentimento tem limites claros: não é válido para bens jurídicos indisponíveis, como a vida, e sua eficácia é questionável em casos de lesões corporais graves ou gravíssimas.
A prática de BDSM consensual situa-se em uma zona complexa. Em tese, se ambos os parceiros são adultos, capazes, e consentiram livre e informadamente nos atos praticados, sem que resultem em lesões graves permanentes ou risco de morte não consentido, não haveria crime. O desafio reside na comprovação desse consentimento, especialmente se uma das partes, posteriormente, o negar ou alegar coação.
A Lei Maria da Penha (Lei nº 11.340/2006)
A Lei Maria da Penha é um marco fundamental na proteção da mulher contra a violência doméstica e familiar. Ela estabelece mecanismos para coibir e prevenir tal violência, definindo suas formas (física, psicológica, sexual, patrimonial e moral) e prevendo medidas protetivas de urgência.
Embora essencial, a aplicação da lei em contextos de BDSM pode ser delicada. Uma alegação de violência por parte da mulher, mesmo que as lesões ou situações decorram de práticas consensuais, tende a receber atenção prioritária das autoridades, dada a presunção de vulnerabilidade estabelecida pela lei. Isso pode criar um cenário onde o parceiro masculino enfrenta dificuldades significativas em demonstrar a natureza consensual dos atos, especialmente se não houver provas robustas pré-constituídas.
Outros riscos:
Lesão corporal grave ou gravíssima (art. 129, §§ 1º e 2º, CP), não pode ser justificada pelo consentimento, podendo ensejar persecução penal.
Crimes contra a dignidade sexual (arts. 213 e seguintes do CP) são de ação pública incondicionada e independem de representação da vítima para a investigação e denúncia.
Riscos de Falsas Acusações e Alegação de Coação Futura
Os riscos para os praticantes de BDSM, especialmente para o parceiro que assume o papel dominante ou que inflige dor/restrição (frequentemente, mas não exclusivamente, o homem), podem surgir de diversas frentes:
- Acusações Externas: Vizinhos, familiares ou amigos que desconhecem a natureza consensual do relacionamento podem interpretar sons, marcas ou comportamentos como sinais de abuso e denunciar às autoridades.
- Alegações Futuras da Parceira: Em caso de término conturbado, vingança, arrependimento ou mudança de perspectiva, a parceira pode reinterpretar as práticas passadas como abuso e buscar reparação ou retaliação através de uma denúncia. A alegação pode ser de que o consentimento nunca existiu ou foi viciado.
- Alegação de Coação: Uma das formas mais complexas de refutar é a alegação de que o consentimento foi obtido mediante coação (física, moral, psicológica ou econômica). A parceira pode alegar, por exemplo, que se sentia pressionada, intimidada ou dependente, e que seu "sim" não era genuíno. Provar a ausência de coação a posteriori é extremamente difícil.
- Ingenuidade e Vulnerabilidade Masculina: Muitos homens, confiando na dinâmica consensual e na parceira, podem negligenciar a necessidade de precauções. A crença de que "isso nunca aconteceria comigo" ou a falta de conhecimento sobre as implicações legais e o peso processual de uma acusação no âmbito da Lei Maria da Penha podem deixá-los vulneráveis. A presença de marcas físicas, mesmo que consentidas, pode ser usada como evidência de agressão, invertendo o ônus da prova na prática, ainda que não na teoria jurídica.
Estratégias de Prevenção e Mitigação
Não existe um método infalível para evitar completamente o risco de uma falsa acusação, mas diversas medidas podem ser adotadas para construir um histórico de consentimento e reduzir vulnerabilidades:
- Comunicação Explícita e Contínua: A base de qualquer prática BDSM segura é a comunicação constante. Negociar limites, desejos, palavras de segurança ("safewords") e expectativas antes, durante e depois das cenas é crucial. Manter registros dessas negociações (e-mails, mensagens, diários compartilhados) pode ser útil.
-
Documentação do Consentimento:
-
Contratos de Relacionamento/Cena: Embora a validade jurídica de "contratos BDSM" seja discutível no Brasil (não podem afastar normas de ordem pública), eles servem como forte evidência da intenção das partes, da negociação detalhada de limites e do consentimento informado. Devem ser claros, datados, assinados e, idealmente, reconhecidos em cartório (para prova de data e autenticidade das assinaturas).
-
Registros Audiovisuais: Gravar (com consentimento explícito para a gravação) discussões sobre consentimento e limites antes das cenas pode ser uma prova poderosa. Gravar as próprias cenas é mais complexo devido a questões de privacidade e potencial uso indevido, mas pode ser considerado em casos específicos, sempre com consentimento mútuo documentado para a gravação.
Importante: a gravação deve ser com ciência da outra parte, para não configurar violação da intimidade (art. 5º, X, da Constituição Federal e art. 20 do Código Civil).
-
-
Testemunhas: Em alguns contextos de comunidade BDSM, a presença de terceiros de confiança durante negociações ou mesmo cenas pode servir como testemunho, embora isso possa alterar a dinâmica íntima do casal.
- Estabelecimento Claro de Limites e Palavras de Segurança: Definir e respeitar rigorosamente os limites (o que é permitido, o que é proibido) e as palavras de segurança é fundamental. O desrespeito a uma palavra de segurança encerra o consentimento para aquele ato.
- Avaliação Contínua do Consentimento: O consentimento não é um cheque em branco; ele deve ser entusiástico, contínuo e revogável a qualquer momento. Verificar o bem-estar do parceiro durante a cena ("check-ins") é essencial.
- Discrição e Cuidado com Evidências Físicas: Ser discreto sobre a natureza do relacionamento pode evitar mal-entendidos externos. Após cenas que deixem marcas, é prudente que ambos os parceiros estejam cientes e de acordo, talvez documentando por fotos (com data) e uma nota sobre a consensualidade da prática que as gerou.
- Aconselhamento Jurídico Preventivo: Consultar um advogado especializado em direito de família e criminal, com sensibilidade para dinâmicas de relacionamento alternativas, pode fornecer orientação personalizada sobre as melhores formas de documentar o consentimento e entender os riscos legais específicos.
Observações Importantes
- Nenhuma documentação substitui a necessidade de consentimento real, livre, informado e contínuo.
- A lei brasileira protege a "integridade física" e a "dignidade humana". Práticas que resultem em lesões graves ou que violem a dignidade de forma não consentida (ou com consentimento viciado) serão ilegais, independentemente de qualquer acordo prévio.
- Em caso de acusação, a existência de documentação robusta de consentimento não garante a absolvição, mas fortalece significativamente a defesa, ajudando a demonstrar a natureza consensual da relação e das práticas.
-
A alegação de coação futura é particularmente difícil de prevenir apenas com documentos. Um histórico consistente de comunicação aberta (whatsapp/telegram/e-mails), respeito mútuo e ausência de dependência ou controle excessivo na relação pode ajudar a contextualizar a dinâmica como não coercitiva.
-
Cuidado com Marcas Visíveis e Lesões Graves Práticas que resultam em hematomas severos ou lesões podem ser interpretadas como agressão, mesmo que consentidas. Evitar excessos protege não apenas a integridade física, mas também evita questionamentos legais futuros.
O que vem a ser consentimento viciado
No Direito, consentimento viciado é quando a pessoa concorda com algo, mas a vontade dela não é livre ou plena — ou seja, o consentimento existe formalmente, mas é defeituoso por alguma razão.
O Código Civil brasileiro (art. 138 a 165) define várias formas de vício de consentimento. As principais são:
Erro: A pessoa se engana sobre o que está consentindo. (Ex.: A pessoa acredita que vai participar de um jogo leve, mas na verdade é exposta a práticas pesadas.)
Dolo: A pessoa é enganada propositalmente para aceitar algo. (Ex.: Alguém mente sobre o que vai acontecer durante a prática.)
Coação: A pessoa é forçada ou ameaçada a consentir. (Ex.: "Se você não aceitar, eu termino com você" — pressão emocional forte pode ser vista como coação.)
Estado de perigo ou lesão: A pessoa aceita algo em situação de necessidade extrema ou abuso de sua vulnerabilidade. (Ex.: Alguém em situação emocional muito fragilizada é induzida a aceitar práticas que normalmente recusaria.)
No contexto de BDSM, isso é ainda mais delicado: Mesmo que a pessoa tenha "assinado" um contrato ou dito "sim", se depois ela alegar que seu consentimento foi dado sob medo, engano ou pressão psicológica, o consentimento pode ser considerado viciado — e, portanto, juridicamente inválido.
Isso tem duas implicações sérias:
-
O crime não se descaracteriza: Se houver vício, o consentimento é ignorado e a prática pode ser tratada como crime normal (lesão corporal, estupro, tortura, etc.).
-
A prova do consentimento precisa ser sólida: Mostrando que a pessoa estava informada, lúcida, livre e sem qualquer tipo de coação.
Consentimento viciado é quando a pessoa concorda formalmente, mas de maneira enganada, forçada ou pressionada, tornando o consentimento inútil para efeitos jurídicos.
Conclusão
Casais que praticam BDSM consensual no Brasil navegam em um terreno que exige não apenas confiança mútua e comunicação excepcional, mas também uma consciência aguçada das complexidades legais e dos riscos de interpretações equivocadas ou acusações mal-intencionadas. Embora o BDSM seja uma expressão legítima da sexualidade humana, sua prática no Brasil exige responsabilidade redobrada. Ter provas claras de consentimento, manter a comunicação aberta e agir com prudência são formas eficazes de se proteger de falsas alegações e preservar a liberdade e a segurança de todos os envolvidos. Embora leis controversas como a Maria da Penha sejam "vitais" para a proteção contra a violência real, os praticantes de BDSM, e em particular os homens nesse contexto, devem adotar uma postura proativa e prudente para mitigar os riscos inerentes à potencial má interpretação ou instrumentalização dessas práticas e leis, garantindo que a expressão de sua consensualidade esteja resguardada na medida do possível.
Importante: No Brasil, mesmo com tudo isso, o Ministério Público pode denunciar por crime como lesão corporal grave, estupro ou tortura, independente de consentimento. Então a prudência nas práticas é fundamental.
Aviso Legal: Este artigo tem caráter meramente informativo e não constitui aconselhamento jurídico. As leis e interpretações podem mudar, e cada situação é única. Recomenda-se buscar orientação de um advogado qualificado para discutir casos específicos.
Se curtiu este artigo faça uma contribuição, se tiver algum ponto relevante para o artigo deixe seu comentário.
-
 @ 3bf0c63f:aefa459d
2025-04-25 19:26:48
@ 3bf0c63f:aefa459d
2025-04-25 19:26:48Redistributing Git with Nostr
Every time someone tries to "decentralize" Git -- like many projects tried in the past to do it with BitTorrent, IPFS, ScuttleButt or custom p2p protocols -- there is always a lurking comment: "but Git is already distributed!", and then the discussion proceeds to mention some facts about how Git supports multiple remotes and its magic syncing and merging abilities and so on.
Turns out all that is true, Git is indeed all that powerful, and yet GitHub is the big central hub that hosts basically all Git repositories in the giant world of open-source. There are some crazy people that host their stuff elsewhere, but these projects end up not being found by many people, and even when they do they suffer from lack of contributions.
Because everybody has a GitHub account it's easy to open a pull request to a repository of a project you're using if it's on GitHub (to be fair I think it's very annoying to have to clone the repository, then add it as a remote locally, push to it, then go on the web UI and click to open a pull request, then that cloned repository lurks forever in your profile unless you go through 16 screens to delete it -- but people in general seem to think it's easy).
It's much harder to do it on some random other server where some project might be hosted, because now you have to add 4 more even more annoying steps: create an account; pick a password; confirm an email address; setup SSH keys for pushing. (And I'm not even mentioning the basic impossibility of offering
pushaccess to external unknown contributors to people who want to host their own simple homemade Git server.)At this point some may argue that we could all have accounts on GitLab, or Codeberg or wherever else, then those steps are removed. Besides not being a practical strategy this pseudo solution misses the point of being decentralized (or distributed, who knows) entirely: it's far from the ideal to force everybody to have the double of account management and SSH setup work in order to have the open-source world controlled by two shady companies instead of one.
What we want is to give every person the opportunity to host their own Git server without being ostracized. at the same time we must recognize that most people won't want to host their own servers (not even most open-source programmers!) and give everybody the ability to host their stuff on multi-tenant servers (such as GitHub) too. Importantly, though, if we allow for a random person to have a standalone Git server on a standalone server they host themselves on their wood cabin that also means any new hosting company can show up and start offering Git hosting, with or without new cool features, charging high or low or zero, and be immediately competing against GitHub or GitLab, i.e. we must remove the network-effect centralization pressure.
External contributions
The first problem we have to solve is: how can Bob contribute to Alice's repository without having an account on Alice's server?
SourceHut has reminded GitHub users that Git has always had this (for most) arcane
git send-emailcommand that is the original way to send patches, using an once-open protocol.Turns out Nostr acts as a quite powerful email replacement and can be used to send text content just like email, therefore patches are a very good fit for Nostr event contents.
Once you get used to it and the proper UIs (or CLIs) are built sending and applying patches to and from others becomes a much easier flow than the intense clickops mixed with terminal copypasting that is interacting with GitHub (you have to clone the repository on GitHub, then update the remote URL in your local directory, then create a branch and then go back and turn that branch into a Pull Request, it's quite tiresome) that many people already dislike so much they went out of their way to build many GitHub CLI tools just so they could comment on issues and approve pull requests from their terminal.
Replacing GitHub features
Aside from being the "hub" that people use to send patches to other people's code (because no one can do the email flow anymore, justifiably), GitHub also has 3 other big features that are not directly related to Git, but that make its network-effect harder to overcome. Luckily Nostr can be used to create a new environment in which these same features are implemented in a more decentralized and healthy way.
Issues: bug reports, feature requests and general discussions
Since the "Issues" GitHub feature is just a bunch of text comments it should be very obvious that Nostr is a perfect fit for it.
I will not even mention the fact that Nostr is much better at threading comments than GitHub (which doesn't do it at all), which can generate much more productive and organized discussions (and you can opt out if you want).
Search
I use GitHub search all the time to find libraries and projects that may do something that I need, and it returns good results almost always. So if people migrated out to other code hosting providers wouldn't we lose it?
The fact is that even though we think everybody is on GitHub that is a globalist falsehood. Some projects are not on GitHub, and if we use only GitHub for search those will be missed. So even if we didn't have a Nostr Git alternative it would still be necessary to create a search engine that incorporated GitLab, Codeberg, SourceHut and whatnot.
Turns out on Nostr we can make that quite easy by not forcing anyone to integrate custom APIs or hardcoding Git provider URLs: each repository can make itself available by publishing an "announcement" event with a brief description and one or more Git URLs. That makes it easy for a search engine to index them -- and even automatically download the code and index the code (or index just README files or whatever) without a centralized platform ever having to be involved.
The relays where such announcements will be available play a role, of course, but that isn't a bad role: each announcement can be in multiple relays known for storing "public good" projects, some relays may curate only projects known to be very good according to some standards, other relays may allow any kind of garbage, which wouldn't make them good for a search engine to rely upon, but would still be useful in case one knows the exact thing (and from whom) they're searching for (the same is valid for all Nostr content, by the way, and that's where it's censorship-resistance comes from).
Continuous integration
GitHub Actions are a very hardly subsidized free-compute-for-all-paid-by-Microsoft feature, but one that isn't hard to replace at all. In fact there exists today many companies offering the same kind of service out there -- although they are mostly targeting businesses and not open-source projects, before GitHub Actions was introduced there were also many that were heavily used by open-source projects.
One problem is that these services are still heavily tied to GitHub today, they require a GitHub login, sometimes BitBucket and GitLab and whatnot, and do not allow one to paste an arbitrary Git server URL, but that isn't a thing that is very hard to change anyway, or to start from scratch. All we need are services that offer the CI/CD flows, perhaps using the same framework of GitHub Actions (although I would prefer to not use that messy garbage), and charge some few satoshis for it.
It may be the case that all the current services only support the big Git hosting platforms because they rely on their proprietary APIs, most notably the webhooks dispatched when a repository is updated, to trigger the jobs. It doesn't have to be said that Nostr can also solve that problem very easily.
-
 @ 8947a945:9bfcf626
2025-03-06 10:50:28
@ 8947a945:9bfcf626
2025-03-06 10:50:28Law of diminishing returns : ทำมากได้น้อย ซวยหน่อยขาดทุน
 ** หมายเหตุ บทความนี้มีเนื้อหาต่อเนื่องจาก “(TH) Why I quit : สาเหตุที่ผมลาออกจากที่(ทำงาน) ที่ (เคย) เรียกว่า”บ้าน” ใครยังไม่ได้อ่าน แนะนำให้ไปอ่านก่อนนะครับ
** หมายเหตุ บทความนี้มีเนื้อหาต่อเนื่องจาก “(TH) Why I quit : สาเหตุที่ผมลาออกจากที่(ทำงาน) ที่ (เคย) เรียกว่า”บ้าน” ใครยังไม่ได้อ่าน แนะนำให้ไปอ่านก่อนนะครับผมได้ยิน คุณท็อป จิรายุส (คุณท๊อป บิทคับ) พูดคำว่า "Law of diminishing returns" ไว้ตอนแชร์มุมมองด้านการทำธุรกิจ ตอนนั้นผมไม่เข้าใจ แต่ผมรู้สึกว่ามันเป็นเจ๋งดี
สำหรับผม สรุปกฏนี้สั้นๆ คือ “ทำมากได้น้อย ซวยหน่อยขาดทุน”
กฏข้อนี้ว่าด้วยเรื่องการทำธุรกิจ พูดถึงปัจจัย 3 อย่าง - Fixed input คือสิ่งที่ไม่สามารถผลิตเพิ่มได้อีกในธุรกิจตอนนั้น เช่น จำนวนห้องตรวจในโรงพยาบาล, พื้นที่ที่ดินทำการเกษตร, ห้องเก็บสินค้า, จำนวนโต๊ะทำงานในสำนักงาน, ช่องบริการลูกค้าในธุรกิจบริการต่างๆ เป็นต้น ผมขอเรียกสั้นๆว่า “พื้นที่” - Variable input คือสิ่งที่สามารถเติมเข้ามาในธุรกิจได้ ปรับแต่งได้ เช่น แรงงาน เครื่องจักร พลังงาน - Marginal product คือผลลัพธ์ของธุรกิจ กำไรเพิ่มขึ้นหลังจากเพิ่ม variable input เข้าสู่ระบบ
ระยะของ law of diminishing returns
- Increased return (ทำเงินได้เยอะขึ้น) เมื่อป้อนแรงงานหรือเครื่องจักรเข้าสู่ระบบ ธุรกิจสามารถทำเงินเพิ่มขึ้นเนื่องจาก fixed input เดิมที่ถูกใช้สอยไม่เต็มที่ (underutilized) ถูกเติมเต็ม กรณีของรพ. คือมีห้องตรวจที่ว่าง ไม่มีหมอนั่งตรวจคนไข้ ห้องตรวจนั้นก็จะไม่สร้างรายได้ แต่เมื่อห้องนั้นมีหมอมานั่ง จะเปลี่ยนเป็นพื้นที่ที่ก่อให้เกิดรายได้ เมื่อห้องตรวจทุกห้องมีหมอนั่งครบ ถือว่าเต็มศักยภาพ ประสิทธิภาพการทำงานที่ดีตามมา
- Diminishing return (ทำมากได้น้อย) จุดของความพอดี (optimum point) คือจุดที่สมดุลพอดีของธุรกิจนั้น ทำกำไรได้เหมาะสม ไม่มากไม่น้อยจนเกินไป แต่ถ้ามองไม่เห็นจุด optimum นี้แล้วยังเพิ่ม”แรงงาน”เข้าไปอีก มันจะทำให้ ”พื้นที่” วุ่นวายเละเทะ ประสิทธิภาพในการทำงานลดลง
- Negative returns (ซวยหน่อยขาดทุน) ถ้ายังไม่หยุดเพิ่ม “แรงงาน” อีก สามารถนำมาสู่การขาดทุน
สรุปเป็นกราฟหน้าตาตามนี้ครับ
ทำไมมันถึงเป็นอย่างนั้น
ผมใช้โมเดลธุรกิจรพ.นี้เป็นตัวอย่างเลยนะครับ
ช่วงแรกที่สร้างรพ. ห้องตรวจมีไม่มาก จำนวนหมอและคนไข้สมดุลกันพอดี งานไม่หนักเกินไป การดูแลคนไข้มีประสิทธิภาพ รพ.เป็นที่ไว้ใจของคนในพื้นที่ มีชื่อเสียง ถูกบอกต่อ ทำให้จำนวนคนไข้เข้ามารับบริการมากขึ้น ต้องขยายพื้นที่รพ. สร้างตึกเพิ่ม รับบุคคลากรทุกระดับเข้ามาทำงานมากขึ้น จนเต็มพื้นที่ที่ดินรพ.ไม่สามารถขยายเพิ่มไปได้มากกว่านี้แล้ว เกิดสมดุลพอดี ทุกพื้นที่ถูกใช้งานเต็มศักยภาพ ประสิทธิภาพงานดีมาก

ผลการดำเนินงาน
ไม่เคยขาดทุน ผ่านช่วงวิกฤตต้มยำกุ้ง และ COVID ได้สบายๆ ฐานะทางการเงินแข็งแรง จ่ายปันผลสม่ำเสมอ ถ้าผมเป็นเจ้าของรพ.ผมจะ 1. สร้างระบบ 2. สร้างทีมผู้บริหาร 3. เน้นย้ำความสำคัญทำตามระบบ 3. Plan - Do- Check - Act เมื่อเกิดปัญหา
เพื่อให้ตัวผมสามารถถอยตัวเองออกมาจากตัวธุรกิจ คอยติดตาม monitor ทุกไตรมาส อย่างใกล้ชิด ไม่ทำอะไรเพิ่มไปมากกว่านี้
แต่สุดท้ายมันก็เกิดเหตุการณ์ทายาทรุ่นที่ 2 “ไม่เอา” นั่นแหละครับ มันทำให้วัฒนธรรมองค์กรเปลี่ยน ก้าวเท้าเข้าไปสู่ยุคตกต่ำ

บริหารแบบล้าหลัง ทำอะไรไม่สุด คิดว่าทำแล้วแต่จริงๆคือไม่ได้ทำ แก้ปัญหาไม่ตรงจุดสร้างปัญหากว่าเดิม
ตัวอย่าง
1. นโยบายการประหยัดพลังงานเพื่อลด carbon footprint
ฟังดูเหมือนจะดี แต่รพ.สื่อสารให้
รณรงค์ให้ปิดไฟ ... ปิดแอร์เมื่อไม่ใช้งาน ...
ผมว่าประโยคนี้มันคุ้นๆ เหมือนเคยได้ยินมามากกว่า 10 ปีแล้ว ... หรือผมเข้าใจผิดหรือเปล่าไม่แน่ใจ
รณรงค์แค่นี้แหละครับ เรื่องลด carbon footprint ไม่ได้เป็นการคิดอะไรใหม่ๆที่เหมาะกับยุคสมัย หรือสร้างอะไรที่จับต้องได้ (objective)
แต่สิ่งที่ทำสวนทางโดยสิ้นเชิงคือใช้พลาสติกแบบใช้แล้วทิ้ง (single use plastic) เป็นภาชนะหลักในการบรรจุอาหารของแพทย์ และผู้เข้าร่วมประชุมงานใหญ่ๆ
 มีเสียงเสนอแนะจากบุคคลากรทุกระดับว่าให้ทำเป็นบุฟเฟ่ต์ จานชามช้อนส้อมแบบปกติก็ได้ เสนอกันมา 5 ปี ก็ยังคงไม่่มีการเปลี่ยนแปลง ได้รับแจ้งลงมาว่าใช้ภาชนะพลาสติกมันประหยัดกว่า เอาเป็นว่ากล่องข้าวพลาสติกมีการใช้อย่างน้อย 1200 กล่องต่อเดือน … คาดว่าสมการการปล่อยก๊าสคาร์บอน (carbon emission) ที่ทีมผู้บริหารคำนวณ อาจจะซับซ้อนเกินความเข้าใจของผมก็ได้นะครับ
มีเสียงเสนอแนะจากบุคคลากรทุกระดับว่าให้ทำเป็นบุฟเฟ่ต์ จานชามช้อนส้อมแบบปกติก็ได้ เสนอกันมา 5 ปี ก็ยังคงไม่่มีการเปลี่ยนแปลง ได้รับแจ้งลงมาว่าใช้ภาชนะพลาสติกมันประหยัดกว่า เอาเป็นว่ากล่องข้าวพลาสติกมีการใช้อย่างน้อย 1200 กล่องต่อเดือน … คาดว่าสมการการปล่อยก๊าสคาร์บอน (carbon emission) ที่ทีมผู้บริหารคำนวณ อาจจะซับซ้อนเกินความเข้าใจของผมก็ได้นะครับ2. การตลาดที่ล้มเหลวและพาแพทย์ซวย

ทำการตลาดไม่เข้าเป้า “เหมือนจะ” ทำ digital marketing แต่ทำแค่โพสกราฟฟิคโปรโมชั่นภาพนิ่งลงสื่อโซเชียลทุกช่องทาง แล้วบอกว่านั่นคือ digital marketing
... แต่เดี๋ยวก่อนๆๆๆ ...
ผมจะบอกว่าการโพสมันเป็นแค่ 1 ใน 10 ของ digital marketing แต่รพ.เข้าใจว่าตัวเองได้เข้าสู่ digital marketing แล้ว
... จริงๆมันไม่ใช่เลยเว้ย ...
ผลลัพธ์คือไม่สามารถเปิดน่านน้ำลูกค้าใหม่ได้เลย ได้แต่ฐานลูกค้าเดิมที่มี brand royalty (แต่แนวโน้มลดลง)
แถมที่แย่ที่สุดคือทำการตลาดแพคเกจออกมาโดยไม่ปรึกษาแพทย์ก่อนว่ามันขัดต่อมาตรฐานการรักษาหรือไม่ กลายเป็นทำแพคเกจดึงดูดคนไข้เข้ามาใช้บริการ แต่การรักษาในแพคเกจขัดต่อมาตรฐานการรักษาของแพทย์
คนไข้ไม่รู้หรอกครับ คนไข้จะเอาตามที่มีในแพคเกจ เขาจ่ายตังค์แล้ว แต่ความซวยมันไปตกอยู่กับแพทย์
3. วางกลยุทธไม่เข้าเป้า

ทุกๆต้นปีทางผู้บริหารจะประกาศกลยุทธประจำปี ว่าในปีนั้นๆรพ.จะมุ้งเน้นพัฒนาด้านไหน รพ.นี้มีปัญหาที่เป็นงูกินหางมานาน มันส่งผลต่อประสิทธิภาพการทำงานของหมอและพยาบาล มีการเสนอแก้ปัญหาเรื่องนี้วนซ้ำซากมา 5 ปี แต่ไม่ได้รับแก้ไขจริงจัง (ผมขอไม่เล่านะครับ)
แต่กลยุทธประจำปี 3 ปีที่ผ่านมา พุ่งใส่ตัวบุคคลากร เน้นพฤติกรรมบริการที่ดีเลิศ ทราบมาว่ามีการลงทุนกับโครงการนี้หลักแสนหรือหลักล้าน มีการจัด workshop เชิญวิทยากรและ trainer จากบริษัทภายนอก (outsource) เข้ามาอบรม เป็นโครงการที่เน้นให้บุคคลากรทุกคนเข้าอบรม 100%
ผมมองว่าปัญหาที่เป็นราก (root cause) มันยังไม่ถูกแก้เลย เปรียบเทียบเหมือนฐานรากของอาคารที่มันโคลงเคลงๆไม่มั่นคงยังไม่ได้รับการแก้ไข แต่พยายามตกแต่งห้องด้วยวัสดุคุณภาพดีและเทคโนโลยีที่ทันสมัย … แต่พร้อมจะล้มลงมาได้ทุกเมื่อ
4. มีเสน่ดึงดูด partner ใหม่ๆ แต่ไม่เอาเอง
ในช่วง COVID ระลอกแรก มีผู้นำทางด้านธุรกิจโรงแรมในจังหวัดมานำเสนอโมเดลธุรกิจ “hospitel เปลี่ยนโรงแรมให้เป็นโรงพยาบาล” ด้วยศักยภาพของรพ.ที่มีบุคคลากรเพียงพอ และตัวโรงแรมที่นำมาเสนอมีห้องพักประมาณ 300 ห้อง เป็นโมเดลที่รพ.และโรงแรม win-win ทั้งคู่ แต่ทางผู้บริหารมองว่าไม่คุ้ม ปฏิเสธข้อเสนอนี้ ทำให้เสียโอกาสให้กับคู่แข่งคว้าตลาด blue ocean นี้ไป

ผมได้แต่เกาหัวตอนรู้เรื่องนี้ เพราะ 1. ช่วง COVID คนไข้น้อย พนักงานโดนลดชั่วโมงการทำงาน ได้เงินเดือนขั้นต่ำ ไม่ได้ OT 2. ทาง partner เสนอขอบุคคลากรเหล่านี้แหละ ไปช่วยงาน เรื่องสถานที่ทางโรงแรมเขามีแม่บ้าน ฝ่ายทำความสะอาดอยู่แล้ว 3. ทาง partner เสนอ profit sharing กับทางรพ. ถึงผมจะไม่รู้ตัวเลข แต่เชื่อว่ามันยุติธรรม
ผมก็ไม่รู้ครับ ว่าอะไรคือคุ้มสำหรับผู้บริหาร
5. Top down absolute power
ไม่ฟังข้อเสนอจากตัวแทนหมอ คนที่มีอำนาจการตัดสินใจไม่เคยเอาตัวลงมาคุยกับหมอแบบจริงจังเลย
1-2 ปีจะลงมาพบหมอทั้งรพ.ซักหนึ่งครั้ง สร้างภาพเก่ง พูดขายฝันสวนหรูถึงภาพที่เขาต้องการ สั่งการลงมา พอเกิดปัญหาตัวเองไม่ลงมารับผิดชอบ แต่อาศัยหน่วยข่าวกรอง(ที่ไม่รู้ว่ากรองอะไรเข้าไปบ้าง) ออกคำสั่งแก้ผ้าเอาหน้ารอดลงมาทีหลัง
แถมสั่งให้เงียบและหุบปาก
ครั้งหนึ่งมีคำสั่งออกมาไม่ชัดเจน จนพยาบาลทำงานไม่ได้ ตัวแทนพยาบาลต้องโทรมาหาผมเพื่อให้ผมช่วย
ผมรวบรวมข้อมูลทั้งหมดและพบว่าคำสั่งมีปัญหาจริงๆ ผมจึง chat line ลงไปสอบถามผู้บริหารเพื่อขอความชัดเจน
… ผ่านไปไม่ถึง 5 นาที หนึ่งในผู้บริหาร(คนที่แทงข้างหลังผมที่หาว่าผมมาตรวจคนไข้ VIP เขาช้า 5 นาทีนั่นแหละ)โทรหาผมทันทีคุยกับผมสั้นๆ ใจความว่า “คำสั่งนั้นเอาแบบเดิม ไม่ต้องแก้ และให้ผมเงียบๆซะ”... (ก็ได้วะครับ)

จุดเปลี่ยนที่ทำให้รพ.เข้าสู่ law of diminishing returns
ห้องตรวจทุกห้องของรพ. ถูกใช้จนเต็มศักยภาพ … เอาจริงๆคือล้นศักยภาพเสียอีก (over-utilized) บางแผนกมีเก้าอี้ดนตรี - หมอคนแรกหมดเวลาออกตรวจ - หมอคนต่อไปเดินเข้าใช้ห้องตรวจต่อทันที - ถ้าไม่ทันก็ต้องคว้าห้องตรวจที่ว่างพร้อมใช้งานก่อน - หมอทำการไล่ที่กันเอง - หมอบางท่านต้องใช้ห้องทำงานของพยาบาลเป็นห้องตรวจชั่วคราว
ห้องพักผู้ป่วยก็เช่นกัน บางช่วงเตียงเต็มจนไม่สามารถ admit คนไข้ได้
แต่จำที่ผมบอกได้มั้ยครับว่า คนที่เป็น top down absolute power ไม่เคยเอาตัวลงมาพูดคุยกับแพทย์เพื่อรับฟังปัญหาที่แท้จริงเลย รับแต่ข่าวกรอง(ที่ไม่รู้ว่ากรองอะไรเข้าไปบ้าง) ช่วงนึงมีคนไข้ complaint ว่ารอนั่งรอหมอนาน หมอมาตรวจช้า ผู้บริหารเลยพยายามจะแก้ปัญหา โดยการ monitor waiting time (ระยะเวลารอหมอ) หยิบยกเรื่องนี้ขึ้นมาเป็นวาระเร่งด่วนต้องรีบแก้ไข
แต่เขายังงงๆกับ concept waiting time อยู่เลยว่าจะนับตั้งแต่ตอนไหนถึงตอนไหน - Waiting time สั้นแปลว่าดี เพราะคนไข้ได้เจอหมอเร็ว - Waiting time นานแปลว่าไม่ดี เพราะคนไข้นั่งรอหมอนาน
เขาตีความจากตัวเลขครับ แต่เคยเอาตัวลงมาดูจริงๆหรือเปล่าว่าทำไมตัวเลขมันถึงออกมาไม่ดี
คำตอบคือ“ไม่” ครับ
หมอบางสาขามีความจำเป็นต้องไปดูคนไข้ที่อาการหนักใช้เวลารักษานาน ... หรือ ... รับปรึกษาจากแพทย์ต่างสาขา ... หรือ ... เป็นสาขาเฉพาะทางของเฉพาะทางอีกที ต้องใช้เวลาตรวจละเอียดตรวจนาน
มันเป็นกระบวนการทำงานของหมอ ที่หมอด้วยกันเข้าใจกัน
ส่วนคนเก็บข้อมูลก็นำเสนอไปทั้งอย่างนั้นโดยที่ไม่ได้วิเคราะห์อะไรเลย มันเป็นการกรองข้อมูลที่ไม่รอบคอบก่อนนำเสนอผู้บริหาร
สุดท้ายผู้บริหาร “โทษหมอ” ว่าไม่มีการบริหารเวลาทำงานที่ดีเพียงพอ ทำให้คนไข้รอนาน เขาสรุปกันดื้อๆแบบนี้เลยครับ
พอหนักๆเข้า “รอหมอนาน ต้องเพิ่มหมอ” season การรับสมัครหมอหลายตำแหน่งได้เริ่มขึ้น
แต่เดี๋ยวนะ ห้องตรวจมันแน่นจนแทบไม่มีที่ให้หมอนั่งทำงานแล้ว แต่เขาก็ไม่สนครับ รับหมอหน้าใหม่ๆมาเพิ่มเรื่อยๆ
ด้วย mindset ว่า "ต้องเพิ่มหมอ หมอจะได้เยอะขึ้น คนไข้จะได้ไม่ต้องรอนาน" และเชื่อว่าจะทำรายได้ให้รพ.มากขึ้น หมอหน้าใหม่บางท่านเข้ามาทำงานวันแรกถึงขั้นอยู่ในสภาวะ dead air คือไม่มีที่ให้นั่งทำงาน
“ทำมากได้น้อย” เริ่มต้น
คนไข้รพ.นี้ ส่วนใหญ่เป็นโรคซับซ้อน ต้องการทักษะและเวลาหมอเฉพาะทางแต่ละสาขาอยู่ดี ไม่ได้ทำให้ waiting time ดีขึ้น คนไข้ยัง “นั่งรอหมอนานเหมือนเดิม”
รายได้เริ่มลดลง ยอดคนไข้เริ่มลดลง รพ.พยายามแก้เกมโดยการเพิ่มราคาค่าบริการ (เพิ่มขนาด ticket size) ทำให้มีเสียงรีวิวตามโซเชียลว่า "แพง"
ผลที่เกิดขึ้นคือคนไข้หลายคนอาศัยรพ.นี้ในการตรวจวินิจฉัยโรคแล้วเอาผลไปรักษาต่อรพ.รัฐบาลตามสิทธิ์เพราะสู้ราคาค่ารักษาไม่ไหว บางคนมีประกันสุขภาพหลายฉบับแต่ก็ต้องจ่ายส่วนต่างมากอยู่ดี

วิธีการข้างต้นนี้ ไม่ผิดกติกาครับ ผล X-ray , CT, MRI, ultrasound จากรพ.เอกชน ไวกว่ารพ.รัฐบาลอยู่แล้ว แต่ก็มีคนไข้บางส่วนยินดีจ่ายแพง เพราะเชื่อมั่นหมอที่รพ.นี้ไม่อยากย้ายรพ.ก็มีครับ เพราะหมอไม่ได้ทำอะไรผิด หมอเก่งๆมีเยอะ
ถึงแม้ว่ารพ.จะรักษา momentum มีจำนวนคนไข้ประมาณ 1100 - 1200 รายต่อวัน แต่ก็เป็นโรคง่ายๆ(simple disease) เช่นไข้หวัด อาหารเป็นพิษ เป็นต้น โรคเหล่านี้ ticket size ไม่ได้ใหญ่มาก ประคองไว้ไม่ให้ขาดทุนเท่านั้นครับ
แต่ความแพงแบบไม่สมเหตุสมผล ทำให้คนไข้หลายรายถอดใจย้ายรพ.ตั้งแต่ทราบค่าใช้จ่ายวินาทีแรก
คนไข้น้อยลง --> รายได้ลดลง --> เพิ่ม ticket size ต่อหัวให้แพงขึ้น --> คนไข้หนีเพราะแพงเกิน
ผมไม่รู้ว่าผู้บริหารเขาเห็นไหม แต่คาดว่าคงจะไม่เห็น
ส่วนโรคหรือการผ่าตัดที่สมศักดิ์ศรีกับศักยภาพของรพ. "น้อยมากจนแทบไม่มี" ไม่ใช่สาเหตุอื่นเลยครับ โดนรพ.คู่แข่งในรัศมี 20 กิโลเมตรเอาไปหมด เพราะราคาถูกกว่า หมอก็เก่งไม่แพ้กัน หมอบางคนเคยอยู่ที่รพ.แห่งนี้ เสนอโปรเจคการรักษาโรคบางโรคที่สามารถสร้างรายได้เป็นกอบเป็นกำ แต่ทางรพ.ไม่เอาเอง สุดท้ายหมอเหล่านั้นย้ายไปอยู่กับรพ.คู่แข่งและผลักดันโปรเจคเหล่านั้นสำเร็จจนมีชื่อเสียง
"รพ.ขายสินค้า premium ไม่ได้เลย ขายได้แต่สินค้าเกรดท้องตลาด"
กลยุทธที่รพ.ทำต่อมาคือเพิ่มจำนวนชั่วโมงการทำงานของหมอให้เพิ่มขึ้นโดยให้หมอมาทำงานเร็วขึ้น 2 ชม. แต่ไม่จ่าย OT ให้ ด้วยตรรกะว่าถ้าหมอทำงานนานขึ้น จะมีจำนวนคนไข้มากขึ้น ทางรพ.ไม่ได้ขอร้อง แต่บีบคอให้หมอร่วมมือ หากไม่ร่วมมือไล่ออกทันที

ไปๆมาๆ มีการไล่ออกกระทันหันเกิดขึ้น มีการส่งหนังสือส่วนตัวหาหมอทุกคน ใครมีรายชื่อที่จะปลดออกก็ต้องออกจากงานทันที
ผมมองว่าฐานะทางการเงินมีปัญหารุนแรงครับ เงินเดือนพนักงานถือเป็น fixed cost ที่ธุรกิจต้องแบกรับ ถ้าเจ๋งจริงต้องควบคุมรายจ่ายให้ธุรกิจสามารถไปต่อได้โดยไม่ปลดคน ในส่วนของธุรกิจรพ. หมอคือบุคคลากรที่สำคัญที่สุดและเป็นด่านสุดท้ายที่จะไล่ออกเพื่อรักษาชีวิตของธุรกิจ ตอนนี้รพ.ได้เข้าสู่ระยะสุดท้ายของ law of diminishing returns คือ “ซวยหน่อยขาดทุน” เป็นที่เรียบร้อยครับ
จุดจบของรพ.แบบนี้ ที่ศักยภาพดี แต่บริหารห่วยแตก มันจะจบด้วยการถูก take over ผ่านมาไม่นานกราฟหุ้นออกอาการ exit liquidity แล้วครับ
ข้อคิดที่อยากแบ่งปันกับทุกคนที่อ่านมาจนจบ
- ช่วงธุรกิจเปลี่ยนผ่านสู่ทายาท คือจุดวัดใจหัวเลี้ยวหัวต่อว่าจะรอดหรือไม่รอด
- Law of diminishing returns ไม่ได้ใช้เฉพาะกับธุรกิจ แต่สามารถประยุกต์ใช้กับการดำเนินชีวิตได้หลายมิติ หากใครเข้าใจ จะขยับเข้าสู่ Pareto’s rule … สั้นๆคือ ทำน้อยแต่ได้(โคตร)มาก
- เจ้าของธุรกิจ ต้องหูไว มองหาเนื้อร้ายที่คอยกัดกินธุรกิจให้เจอ แล้วกำจัดมันซะ ก่อนที่ธุรกิจจะล้มทั้งยืน ทับตัวเองตาย
-
 @ 3bf0c63f:aefa459d
2025-04-25 18:55:52
@ 3bf0c63f:aefa459d
2025-04-25 18:55:52Report of how the money Jack donated to the cause in December 2022 has been misused so far.
Bounties given
March 2025
- Dhalsim: 1,110,540 - Work on Nostr wiki data processing
February 2025
- BOUNTY* NullKotlinDev: 950,480 - Twine RSS reader Nostr integration
- Dhalsim: 2,094,584 - Work on Hypothes.is Nostr fork
- Constant, Biz and J: 11,700,588 - Nostr Special Forces
January 2025
- Constant, Biz and J: 11,610,987 - Nostr Special Forces
- BOUNTY* NullKotlinDev: 843,840 - Feeder RSS reader Nostr integration
- BOUNTY* NullKotlinDev: 797,500 - ReadYou RSS reader Nostr integration
December 2024
- BOUNTY* tijl: 1,679,500 - Nostr integration into RSS readers yarr and miniflux
- Constant, Biz and J: 10,736,166 - Nostr Special Forces
- Thereza: 1,020,000 - Podcast outreach initiative
November 2024
- Constant, Biz and J: 5,422,464 - Nostr Special Forces
October 2024
- Nostrdam: 300,000 - hackathon prize
- Svetski: 5,000,000 - Latin America Nostr events contribution
- Quentin: 5,000,000 - nostrcheck.me
June 2024
- Darashi: 5,000,000 - maintaining nos.today, searchnos, search.nos.today and other experiments
- Toshiya: 5,000,000 - keeping the NIPs repo clean and other stuff
May 2024
- James: 3,500,000 - https://github.com/jamesmagoo/nostr-writer
- Yakihonne: 5,000,000 - spreading the word in Asia
- Dashu: 9,000,000 - https://github.com/haorendashu/nostrmo
February 2024
- Viktor: 5,000,000 - https://github.com/viktorvsk/saltivka and https://github.com/viktorvsk/knowstr
- Eric T: 5,000,000 - https://github.com/tcheeric/nostr-java
- Semisol: 5,000,000 - https://relay.noswhere.com/ and https://hist.nostr.land relays
- Sebastian: 5,000,000 - Drupal stuff and nostr-php work
- tijl: 5,000,000 - Cloudron, Yunohost and Fraidycat attempts
- Null Kotlin Dev: 5,000,000 - AntennaPod attempt
December 2023
- hzrd: 5,000,000 - Nostrudel
- awayuki: 5,000,000 - NOSTOPUS illustrations
- bera: 5,000,000 - getwired.app
- Chris: 5,000,000 - resolvr.io
- NoGood: 10,000,000 - nostrexplained.com stories
October 2023
- SnowCait: 5,000,000 - https://nostter.vercel.app/ and other tools
- Shaun: 10,000,000 - https://yakihonne.com/, events and work on Nostr awareness
- Derek Ross: 10,000,000 - spreading the word around the world
- fmar: 5,000,000 - https://github.com/frnandu/yana
- The Nostr Report: 2,500,000 - curating stuff
- james magoo: 2,500,000 - the Obsidian plugin: https://github.com/jamesmagoo/nostr-writer
August 2023
- Paul Miller: 5,000,000 - JS libraries and cryptography-related work
- BOUNTY tijl: 5,000,000 - https://github.com/github-tijlxyz/wikinostr
- gzuus: 5,000,000 - https://nostree.me/
July 2023
- syusui-s: 5,000,000 - rabbit, a tweetdeck-like Nostr client: https://syusui-s.github.io/rabbit/
- kojira: 5,000,000 - Nostr fanzine, Nostr discussion groups in Japan, hardware experiments
- darashi: 5,000,000 - https://github.com/darashi/nos.today, https://github.com/darashi/searchnos, https://github.com/darashi/murasaki
- jeff g: 5,000,000 - https://nostr.how and https://listr.lol, plus other contributions
- cloud fodder: 5,000,000 - https://nostr1.com (open-source)
- utxo.one: 5,000,000 - https://relaying.io (open-source)
- Max DeMarco: 10,269,507 - https://www.youtube.com/watch?v=aA-jiiepOrE
- BOUNTY optout21: 1,000,000 - https://github.com/optout21/nip41-proto0 (proposed nip41 CLI)
- BOUNTY Leo: 1,000,000 - https://github.com/leo-lox/camelus (an old relay thing I forgot exactly)
June 2023
- BOUNTY: Sepher: 2,000,000 - a webapp for making lists of anything: https://pinstr.app/
- BOUNTY: Kieran: 10,000,000 - implement gossip algorithm on Snort, implement all the other nice things: manual relay selection, following hints etc.
- Mattn: 5,000,000 - a myriad of projects and contributions to Nostr projects: https://github.com/search?q=owner%3Amattn+nostr&type=code
- BOUNTY: lynn: 2,000,000 - a simple and clean git nostr CLI written in Go, compatible with William's original git-nostr-tools; and implement threaded comments on https://github.com/fiatjaf/nocomment.
- Jack Chakany: 5,000,000 - https://github.com/jacany/nblog
- BOUNTY: Dan: 2,000,000 - https://metadata.nostr.com/
April 2023
- BOUNTY: Blake Jakopovic: 590,000 - event deleter tool, NIP dependency organization
- BOUNTY: koalasat: 1,000,000 - display relays
- BOUNTY: Mike Dilger: 4,000,000 - display relays, follow event hints (Gossip)
- BOUNTY: kaiwolfram: 5,000,000 - display relays, follow event hints, choose relays to publish (Nozzle)
- Daniele Tonon: 3,000,000 - Gossip
- bu5hm4nn: 3,000,000 - Gossip
- BOUNTY: hodlbod: 4,000,000 - display relays, follow event hints
March 2023
- Doug Hoyte: 5,000,000 sats - https://github.com/hoytech/strfry
- Alex Gleason: 5,000,000 sats - https://gitlab.com/soapbox-pub/mostr
- verbiricha: 5,000,000 sats - https://badges.page/, https://habla.news/
- talvasconcelos: 5,000,000 sats - https://migrate.nostr.com, https://read.nostr.com, https://write.nostr.com/
- BOUNTY: Gossip model: 5,000,000 - https://camelus.app/
- BOUNTY: Gossip model: 5,000,000 - https://github.com/kaiwolfram/Nozzle
- BOUNTY: Bounty Manager: 5,000,000 - https://nostrbounties.com/
February 2023
- styppo: 5,000,000 sats - https://hamstr.to/
- sandwich: 5,000,000 sats - https://nostr.watch/
- BOUNTY: Relay-centric client designs: 5,000,000 sats https://bountsr.org/design/2023/01/26/relay-based-design.html
- BOUNTY: Gossip model on https://coracle.social/: 5,000,000 sats
- Nostrovia Podcast: 3,000,000 sats - https://nostrovia.org/
- BOUNTY: Nostr-Desk / Monstr: 5,000,000 sats - https://github.com/alemmens/monstr
- Mike Dilger: 5,000,000 sats - https://github.com/mikedilger/gossip
January 2023
- ismyhc: 5,000,000 sats - https://github.com/Galaxoid-Labs/Seer
- Martti Malmi: 5,000,000 sats - https://iris.to/
- Carlos Autonomous: 5,000,000 sats - https://github.com/BrightonBTC/bija
- Koala Sat: 5,000,000 - https://github.com/KoalaSat/nostros
- Vitor Pamplona: 5,000,000 - https://github.com/vitorpamplona/amethyst
- Cameri: 5,000,000 - https://github.com/Cameri/nostream
December 2022
- William Casarin: 7 BTC - splitting the fund
- pseudozach: 5,000,000 sats - https://nostr.directory/
- Sondre Bjellas: 5,000,000 sats - https://notes.blockcore.net/
- Null Dev: 5,000,000 sats - https://github.com/KotlinGeekDev/Nosky
- Blake Jakopovic: 5,000,000 sats - https://github.com/blakejakopovic/nostcat, https://github.com/blakejakopovic/nostreq and https://github.com/blakejakopovic/NostrEventPlayground
-
 @ 8947a945:9bfcf626
2025-02-28 09:11:21
@ 8947a945:9bfcf626
2025-02-28 09:11:21Chef's notes
https://video.nostr.build/ea19333ab7f700a6557b6f52f1f8cfe214671444687fa7ea56a18e5d751fe0a9.mp4
https://video.nostr.build/bcae8d39e22f66689d51f34e44ecabdf7a57b5099cc456e3e0f29446b1dfd0de.mp4
Details
- ⏲️ Prep time: 5 min
- 🍳 Cook time: 5 min
- 🍽️ Servings: 1
Ingredients
- ไข่ 1 - 2 ฟอง
- ข้าวโอ๊ต 3 - 4 ช้อน
Directions
- ตอกไข่ + ตีไข่
- ปรุงรส พริกไทย หรือ ซอสถั่วเหลืองตามชอบ
- ใส่ข้าวโอ๊ต 3 - 4 ช้อน
- ใส่ถั่วลิสงอบ 1 - 2 หยิบมือ
- เทน้ำใส่พอท่วมข้าวโอ๊ต
- เข้าไมโครเวฟ ไฟแรง 1 - 2 นาที
-
 @ e7bc35f8:3ed2a7cf
2025-05-01 08:19:56
@ e7bc35f8:3ed2a7cf
2025-05-01 08:19:56In the heart of Romania’s 2024 presidential election, a seismic shock rattled the foundations of its democracy. Just days before the final runoff, the Constitutional Court made an unprecedented move: it annulled the entire election, citing evidence of Russian interference that propelled a far-right nationalist, Călin Georgescu, to a surprise lead. Was this a bold reflex to safeguard democratic integrity against foreign manipulation, or a chilling cancellation of the people’s voice, silencing millions who had cast their ballots? As Romania grapples with this historic decision, the line between protecting democracy and undermining it has never been blurrier, leaving citizens and observers alike questioning the true cost of this electoral upheaval.
In this article, I will explore Romania’s 2024 presidential election annulment chronologically, tracing the rise of far-right candidate Călin Georgescu, the Constitutional Court’s decision to cancel the vote on December 6, and the resulting protests and probes into foreign interference. This timeline will clarify whether the move was a democratic safeguard or an undemocratic suppression of the people’s will.
October 15, 2024
Judges booted candidate Diana Șoșoacă, leader of the ultra-nationalist party S.O.S Romania, from the race because she threatened Bucharest’s place in the EU and NATO. But her rivals are saying the court overstepped its remit.
The unprecedented ruling by the Constitutional Court of Romania (CCR) sparked criticism from Șoșoacă’s rivals across the political spectrum, encompassing socialists, liberals and academics — with one figure even pointing to how it echoes the Kremlin’s electoral governance.
November 22, 2024
The final major poll before Romania’s 2024 presidential election, released on the eve of the vote, painted a starkly different picture from the eventual outcome. Prime Minister Marcel Ciolacu led with 23.7%, followed by Elena Lasconi at 17.8%, George Simion at 16.9%, and Nicolae Ciucă at 14.3%. Astonishingly, Călin Georgescu, who would later surge to a stunning first-round victory, languished in fifth place with just 8.1%, a staggering underestimation that would soon fuel suspicions of manipulation and upend the nation’s electoral process.

November 24, 2024
In a stunning upset, Călin Georgescu won Romania’s 2024 presidential election with 22.94% of the vote, dominating the first round despite trailing in pre-election polls. George Simion, often labeled the country’s “hard right chief” by Western media, lagged behind in fourth place with just 13.8%. No credible evidence suggests vote tampering; Georgescu’s victory reflected a genuine surge of voter support, particularly among the diaspora, where he won overwhelmingly—except in Moldova, where he secured only 3.11% amid a large pro-Russian population that had narrowly passed a pro-EU referendum a month earlier.
As regards Georgescu himself, by CV, appearance and speaking style he comes across as the ideal candidate. He studied agronomy, has a PhD in soil science and is a university lecturer; has worked at senior levels in government – including in the Ministry of Foreign Affairs – as well as at the UN and other NGOs, with a focus on sustainable development; and he speaks four foreign languages. He projects a professional, clean-cut image of a determined, experienced 62 year-old nationalist at the apex of his powers, speaking very simply and clearly in a calm, confident manner. Strictly by these superficial PR metrics, on paper, he is, at first glance, perfectly suited for the role.
Nor is he unknown in Romanian politics; but he is – or has been – a very fringe figure. His name was floated several times in recent years, in nationalist-populist circles, as a potential alternative for prime minister. He nearly became honorary president of Romania’s main nationalist conservative party, AUR, before the deal fell through when past comments came to light in which he had called the country’s Second World War leader and Axis ally, Marshal Antonescu – who is considered responsible for the Romanian Holocaust – a “hero”.
Georgescu had conducted a persuasive online campaign, primarily on TikTok, focusing on the importance of an autochthon economy, the inherent superiority of rural life in Romania, and essentially claiming that just like a national poet from the 19th century, he is a divine messenger. The campaign consisted of thousands of TikTok profiles distributing ten-second videos about him, with many influencers suggesting in the past weeks that they would vote for him. According to Georgescu, he didn’t spend any money on the campaign, but the scale and the professionalism in which it was conducted suggest otherwise.
November 25, 2024
Politico comes to remind us why EU is so interested about Romania. According to this article, Romania has been a steadfast ally in the West’s support for Ukraine, leveraging the Port of Constanța as a critical lifeline for exporting Ukrainian grain and funneling military supplies into the conflict zone. The war has also elevated the strategic significance of the Mihail Kogălniceanu air base on the Black Sea, poised to become NATO’s largest. However, Călin Georgescu’s unexpected electoral triumph raises alarms across Europe, as his leadership could pivot Romania away from this pro-Western stance, potentially disrupting these vital geopolitical roles. This prospect underscores why European leaders are deeply invested in ensuring Romania remains in “reliable” hands, aligned with NATO and EU priorities.
November 26, 2024
Reformist Elena Lasconi, who was going to face Georgescu in the runoff on Dec. 8, was directly warning that Romanians must now rally together to stop the country falling back under the thrall of Russia, which occupied it after World War II. She urged a crowd in Bucharest not to let frustration with the current establishment “become a vulnerability exploited by Russia.”

November 28, 2024
The official claim of Russian meddling rested directly and exclusively on a specific set of intelligence documents on the matter, first submitted in a closed National Security Council meeting on 28 November. Romania’s Constitutional Court asked the country’s top election authority to recount and check again all ballots from Sunday’s presidential election first round.
November 30, 2024
Elena Lasconi, who narrowly secured a runoff spot by edging out PSD Prime Minister Marcel Ciolacu by just 2,700 votes, has firmly rejected allegations of electoral misconduct. Lasconi and her party, USR, accuse the PSD and center-right PNL of undermining the people’s will through the annulment push. In a passionate statement, she urged, “I appeal to all state institutions: Don’t destroy democracy in Romania,” highlighting the high stakes for the nation’s democratic integrity.
December 4, 2024
The set of intelligence documents on the matter, first submitted in a closed National Security Council meeting on 28 November and then hastily declassified on 4 December by the sitting President in order to “inform” the Constitutional Court’s decision. But the reports contained no actual evidence of the sort.

The documents alleged that 800 TikTok accounts had been activated just before the election and that they had supported Călin Georgescu’s campaign.
Albeit these reports did not definitely say that the meddling effort managed to actually sway the election in Georgescu’s favour, they suggested it.
I ve translated the declassified documents using the AI tools: Grok and ChatGPT. I can assure you that the following summary from "Brussels Signal" is accurate. I will quote the summary because of the key importance on the subject:
The documents provide no concrete evidence of Russian state interference in Romania’s presidential elections or any links between presidential candidate Calin Georgescu and Russia.
The most important and explosive term used in these documents (by SRI) is “state actor.” The documents offer no evidence or analytical explanation for the use of this term, rendering it an unsupported claim.
On the contrary, to the extent that they shed light on anything, the documents indicate that Georgescu’s campaign simply employed highly effective digital marketing techniques, giving him a “comparative exponential” advantage (according to SRI).
The documents offer only disparate, circumstantial, and often trivial information presented in a way that leaves plenty of room for wide-ranging interpretations. Their tone and terminology appear designed to fuel an anti-Georgescu narrative in the public sphere.
As intelligence products, the documents are sloppy and of very poor quality by Allied standards. They include contradictions, errors, and blatant inaccuracies. The language is often vague, and key terms remain undefined (e.g., various uses of the word “network”). For the most part, the documents are full only of useless platitudes, with the majority of the information already having been circulating in the public domain in the days after 24 November (the date of the first voting round).
The documents are merely “Briefing Notes” (note informative, in Romanian), not assessments – thus lacking clear and definitive analytical conclusions or interpretations. They make isolated claims (mostly unsupported), with no discussion of sources or evidence. This is likely a method for the intelligence services to protect themselves politically. Subsequent interpretations of these documents by the media are not, therefore, based on conclusions of the Romanian state.
The documents are also redacted in key parts. It is therefore important to understand that the information in these documents was only partially declassified – despite the media narrative suggesting the documents were declassified in their entirety. It is also important to understand that the redacted passages may alter the meaning of the text.
The SIE Briefing Note has not actually been declassified. The President only published an “unclassified excerpt” from it. The SIE Note itself remains classified, likely because it contradicts the Notes submitted by the other agencies.
The documents do point to potential irregularities in Georgescu’s campaign finance statements. However, such issues are common in campaigns worldwide and, moreover, should be investigated with respect to all the other candidates as well, in the same way. In any case, the documents make no suggestion of foreign funding, let alone from Russia.
The only concrete elements noted in the documents as being specifically identified as of 24 November (the day of the vote in the first round) are: 100 TikTok influencer accounts paid to distribute content using 3 (three) hashtags that do not even mention Calin Georgescu; 797 accounts created before (!) the launch of TikTok itself, under this brand name; 1,088 users in a “coordination” group on Telegram (which, again, is standard in all political campaigns); and $381,000 paid to some “influencers”.
Conclusion: The CSAT documents declassified by the President provide absolutely no real, concrete basis for the public narratives about a “Russian attack” on Romania or of links between Georgescu’s campaign and Russia. These documents, by themselves, cannot rationally be used as arguments against this candidate because they prove nothing.
Shortly after the vote in a televised address President Iohannis claimed that the ‘campaign was illegally supported from outside Romania’ and that it is a ‘matter of national security’.
December 6, 2024
Romania’s top constitutional court dramatically cancelled high-stakes presidential elections after security services warned Russia was mounting “aggressive” hybrid attacks against the country. Călin Georgescu was accused to benefit from a TikTok campaign that was similar to influence operations allegedly run by the Kremlin in Ukraine and Moldova. The files said Moscow was targeting Romania as an enemy state, using “aggressive hybrid action,” a view backed by the United States, at that time.
Running as an independent, Georgescu was due to face liberal Elena Lasconi of the Save Romania Union (USR) in a Dec. 8 runoff. Suspicious of the two old parties, she is also calling on the court not to meddle with Romanian democracy. According to Radio Romania Actualitati, she said: ‘Today is the moment when the Romanian state has trampled on democracy,’ adding: ‘We should have gone ahead with the vote. We should have respected the will of the Romanian people, whether we like it or not; legally and legitimately, nine million Romanian citizens, both at home and in the diaspora, have expressed their preference for a particular candidate by voting. We cannot ignore their will.’
Elena Lasconi, a liberal—by Western standards, however, she might not be considered a typical liberal, as she openly expresses patriotism, displays the Romanian flag alongside the EU flag, and occasionally wears traditional folk costumes—former TV journalist. Lasconi, like Georgescu, is an anti-establishment figure, vocal in her criticism of the current political elite and adept at channelling voter discontent and frustration with mainstream parties. It is no surprise, then, that both the Social Democratic Party (PSD) and the National Liberal Party (PNL)—Romania’s two largest establishment parties—reacted with dismay to the performances of Georgescu and Lasconi. This discontent was amplified by the fact that neither party’s candidate came close to qualifying for a potential second round. Politicians from both the far right as well as liberal reformists Save Romania Union (USR) party view an annulment as an attempt by the widely distrusted old establishment parties — the Social Democratic Party (PSD) and the center-right National Liberal Party (PNL) — to hold on to power by pulling strings within the judiciary. Elena Lasconi, a liberal former TV journalist who was set to stand against Georgescu in the second round, was mortified by what she saw as a hijacking of the electoral process.
The court canceled the process completely, leaving voters bemused as they turned up to cast their ballots. In a defiant video released on Friday night, Georgescu accused the court of launching “practically a formalized coup d’état” and told his supporters to show they are “brave” and not to give up.
In fact, Georgescu was leading with as much as 77 per cent against Lasconi’s 23 per cent in the diaspora when Romania’s Constitutional Court decided to annul the elections.
The President, at that time, Klaus Iohannis was due to end his term on Dec. 21. But in an address to the nation Friday evening, he announced that he was going to stay on until the next president was about to sworn in.
Nicolae Ciucă, the head of the Romanian senate and the National Liberal Party’s presidential candidate in the first round said that The decision to cancel the vote was “without precedent in Romania’s democratic history,” he said, adding “the current situation is a difficult test for our democratic institutions.”
According to the press's findings, behind Georgescu there appears to have been an entire “network” of volunteers – often organised via Telegram – running thousands of co-ordinated TikTok accounts designed to boost each other’s posts – i.e. Georgescu’s short promo videos. TikTok has only relatively recently caught on in Romania; certainly it wasn’t a factor at the last election. This might explain why a strong TikTok campaign would not have registered properly in political analysis, and why it might’ve had an outsized effect on voting intentions. It is also a warning for the future of the very idea of democratic politics, as it shows that it is possible for candidates to completely side-step the traditional “public square”, avoid any major real-world debates or campaigning, and win elections exclusively online.
Still, there is a great deal of mystery over exactly how all this worked. Georgescu’s TikTok metrics are inferior to his three key adversaries for example: there were 145 million views this year for Georgescu’s main hashtags compared to 396 million for Simion’s, 328 million for Ciolacu and 202 million for Lasconi. One difference is that the bulk of Georgescu’s TikTok views and followers accrued within the past two months. Coupled with other indicators, it seems rather clear that so-called “troll farms” have been at work on his behalf, to spread his message; but it is not clear whether this practice is unique to Georgescu or whether it has been used – to varying degrees – by his opponents as well.
As Georgescu is perceived to be “pro-Russia” – an imprecise term to boot – suspicion in this regard is directed towards the Kremlin. But hard evidence is lacking; there is no smoking gun, so far. Russian actors are involved in virtually every election in the West, but their exact role in swinging the result is hardly ever clear. In the US a Congressional investigation – eventually known as the “Russia Hoax”, for good reason – failed to prove alleged collusion between Trump’s 2016 campaign and Moscow, despite widespread belief in this story from those shocked that “orange man” could ever win because his message was more effective.
The reaction from the EU and Washington was particularly alarming, though hardly surprising. ‘The integrity of Romania’s elections is paramount for Romanians’ hard-earned democracy. It is the choice of the Romanian people whom they elect. No other country or foreign actor has that right,’ the US State Department said in a statement. The contradiction is glaring, isn’t it? It’s supposedly the Romanians’ choice who they elect, yet if a candidate not favoured by the Americans wins, the election results are annulled.
Moscow denied meddling into the Romanian democratic process.
December 20, 2024
According to a Snoop (investigative journalist organization) investigation, Georgescu’s alleged financing would have been done by the PNL. ** All this, so that Georgescu’s message would spread and more people could vote for him so that George Simion would not make it to the second round. ** In fact, the ANAF (National Agency for Tax Administration) discovered that the PNL paid for a campaign massively promoting Călin Georgescu on TikTok, published on 20 December 2024.
December 22, 2024
Subsequent investigations by the National Agency for Fiscal Administration (ANAF), Romania’s tax authority, uncovered the origins of Călin Georgescu’s successful TikTok campaign: the PNL. The centre-right party’s campaign initially employed the hashtag #echilibrusiseriozitate to promote European values and pro-EU positions. Kensington Communication, the company responsible for the campaign, also targeted Georgescu’s content, aiming to counter his EU-critical rhetoric. However, the hashtag #echilibrusiseriozitate, designed to create an unfavourable environment for non-liberal presidential candidates on TikTok, was replaced by #echilibrusiverticalitate on the FameUP platform—a free automated platform that amplifies marketing campaigns. Interestingly, this new hashtag was ultimately adopted and used by Georgescu’s supporters, transforming its purpose and amplifying his campaign’s visibility. The Romanian government proposed 4 May as the date for a new presidential election. However, no formal decision was made since. Călin Georgescu has since challenged the Constitutional Court’s decision at a local appeals court and lodged a complaint with the European Court of Human Rights. ‘I will take our cause to the heart of Europe, to the highest courts. Each of us is doing our part in this historic mission to defend our democracy,’ he declared.
January 5, 2025
Recent polls show that Călin Georgescu remains the most popular presidential candidate, with some surveys suggesting that the ultranationalist contender could garner close to 40 per cent support.
January 8, 2025
The court is considering disqualifying Georgescu for undeclared campaign funding.
The leaders of the ruling coalition made up of the Social Democrats (PSD), Liberals (PNL), the Democratic Alliance of Hungarians (UDMR), and the minorities' group decided on the new dates for the presidential elections. According to the agreed election schedule, the first round would have taken place on May 4, followed by the runoff on May 18.
At the beginning of the government meeting, prime minister Marcel Ciolacu announced the introduction of sanctions against social media networks that favor candidates, according to Europa Libera Romania.
Georgescu’s appeal against the constitutional court’s decision to nullify the election was rejected, so he lodged a complaint to the European Court of Human Rights.
In fact, even the Venice Commission (the officially European Commission for Democracy through Law) stated that, regarding what had happened in Romania, evidence must be given: ‘An election annulment must be based on transparent evidence, not classified information.’
January 10, 2025
Former European commissioner Thierry Breton assured that the European Union has mechanisms to overturn an eventual AfD victory:
We did it in Romania and obviously we will do it in Germany if necessary.

This was widely seen as a clear admission of their true intentions, as if they had dropped all pretenses and fully revealed themselves.
They tell you to your face that they can suspend elections and that absolutely nothing happens, then they have the cheek to declare themselves the ‘democrats’ and ‘tolerant’, when it is them who are the main enemies of democracy and freedom of expression!
January 12, 2025
Tens of thousands of supporters of Romanian presidential candidate Călin Georgescu took to the streets in Bucharest on Sunday to protest the annulment of the presidential election. With no concrete evidence emerging to substantiate the allegations of Russian interference, it has become increasingly evident that the progressive elite will go to any lengths to remain in power.

February 1, 2025 According to the last polls, Georgescu would be around 50 per cent; specifically, according to the last one published by România TV, he would obtain 47 per cent.
February 10, 2025
Romanian President Klaus Iohannis announced his resignation before his possible forced dismissal from parliament. Iohannis, echoing Joe Biden, made sure to pardon his family and the judges who suspended the presidential election before leaving, for reasons of precaution.
Once the court cancelled the elections—so no new president was elected—, it also decided to lengthen the current president’s term in office until a new vote in May 2025. Iohannis faced raising opposition, however, as some viewed his lengthened mandate as illegitimate. On the one hand, the Romanian constitution states that a presidential term is five years, and the president remains in office until their successor takes over. On the other hand, it also makes clear that the presidency can be extended only in case of war or catastrophe. Protests also took place against the decision of him remaining in office, and the legislature initiated his removal as well. **Preventing a successful impeachment procedure, Klaus Iohannis stepped down. ** In his resignation speech he highlighted that Romania’s western partners will not understand the reason why he was forced to step down, and that his departure will damage Bucharest’s relationship with its allies. The country’s interim president will be the Senate’s president, Ilie Bolojan.
February 15, 2025
The Constitutional Court of Romania is accused of canceling elections without evidence, allegedly to suppress votes against the EU-aligned political establishment. Claims suggest court judges are linked to Soros-funded NGOs. A network of "independent" NGOs and media, funded by hundreds of millions from the EU and USAID, is said to promote left-wing globalist agendas, manipulate public opinion, and counter conservative values. EU grants and a secret 130 million euro contract to a French agency, tied to corruption, allegedly fueled pro-EU media campaigns, undermining independent journalism and labeling critics as pro-Russia. Independent journalist, Iosefina Pascal, talks thoroughly about this case.
February 19, 2025 Renowned journalist and X (formerly Twitter) personality Mario Nawfal interviews Georgescu, with clear expressions of support for Trump and Musk, alongside a strong critical stance toward George Soros.
February 26, 2025 Romania’s presidential candidate, Calin Georgescu was arrested while en route to Bucharest to announce his new presidential campaign. Georgescu’s campaign team has confirmed that Georgescu was picked up by the police and detained in the middle of traffic for questioning at the attorney general’s office.
Georgescu was declared the winner of that election round, but an arrest warrant was issued against him on February 26, as reported by the Romanian press.
Romanian prosecutors have initiated criminal proceedings against the right-wing politician and candidate for the 2024 presidential election, Călin Georgescu, on six charges. These include allegations of engaging in unconstitutional activities and providing inaccurate financial disclosures, according to official sources.
March 1, 2025
Thousands march for freedom in Romania. Over 200,000 Romanians flood streets for Georgescu. Anti-Soros feelings are everywhere.


March 6, 2025
The Romanian opposition – denied a likely victory – took their case to the European Court of Human Rights.
The ECHR (The European Convention on Human Rights, a supranational convention to protect human rights and political freedoms in Europe) threw the case out without even hearing it. Apparently, the Romanian courts were perfectly within their rights to simply indefinitely postpone their election on the basis of unproven allegations.
Romania is moving toward its strictest censorship law since 1989, granting authorities the power to block websites and social media posts without independent review.
The Emergency Ordinance (OUG) would allow the government to shut down content deemed “false information,” “manipulation,” or a “threat to national security,” with no clear definitions or court approval required.
The Romanian Intelligence Service (SRI), military, cybersecurity agencies, and electoral authorities would have sweeping powers to remove posts and block platforms, while internet providers refusing to comply could face massive daily fines.
This law could be used to silence journalists and political opponents, as there is no independent oversight and no clear standard for what counts as “false information.”
The government claims the measure is meant to combat foreign election interference, but it will actually be weaponized against free speech.
March 7, 2025 Călin Georgescu, the people’s choice in Romania’s annulled election, has officially submitted his candidacy for the upcoming presidential race, backed by over 324,000 signatures.
The Constitutional Court will decide this month or early April if his candidacy is approved, assuming, of course, that he doesn't get arrested again this time.


March 8, 2025
Demonstrators gathered in front of Romania’s Palace of Parliament, holding banners thanking Tulsi Gabbard and urging Trump to “help take our country back!”

Romania’s Constitutional Court has unanimously rejected 4 appeals attempting to block Călin Georgescu from the presidential race. The challenges, filed by minor candidates Sebastian Popescu and Cristian Terheș, accused him of failing to disclose campaign funding and alleged foreign financial ties. The court dismissed the claims as inadmissible, citing procedural failures and lack of legal merit.
Allegedly Soros-linked activists flood Romanian Electoral Bureau with 1,000 identical appeals against CĂLIN GEORGESCU
Over 1,000 copy-paste appeals were filed against Călin Georgescu’s candidacy, organized by Soros-backed activists trying to block him.
But the Electoral Bureau (BEC) is set to reject them all—the challenges were filed before his candidacy was even validated, making them invalid.
March 9, 2025
Calin Georgescu’s presidential candidacy has been officially rejected, sparking outrage among his supporters, who attempted to breach the Bureau of Electoral Control (BEC).
The candidacy was rejected with 10 votes in favor and 4 against.
Romania’s Electoral Office bypassed the Constitutional Court, which had approved his candidacy in December, and shut him down directly instead.
George Simion, president of the AUR stated in viral video:
Georgescu put his candidacy at the Central Electoral Bureau and by 10 members to 4, it was rejected without any reason. All the papers were in good order. They just said they voted through their conscience. We live in a dictatorship. Please help us. Please be on our side to restore democracy in Romania.




March 11, 2025
Romanian presidential candidate Călin Georgescu cannot run in the Presidential Election. Călin Georgescu’s appeal against the invalidation of his presidential candidacy has been rejected by the Constitutional Court.
March 27, 2025
The National Authority for Administration and Regulation in Communications (ANCOM), coordinator of digital services in Romania held an exercise to test the capacity to respond to challenges that may emerge in the online environment, in view of the presidential elections in May.
This initiative takes its root from the Rapid Response Mechanism (RRM), which ironically, was established during the G7 Charlevoix Summit in June 2018, meant to enhance cooperation among nations in addressing ‘crisis’ moments and perceived threats to western democracy.
Ahead of Romania’s new presidential election, the European Commission has launched its ‘RRM’ as a proactive strategy which the EC presents as a means to tackle potential electoral law violations on social media in member states holding elections. In effect, a similar simulation was reportedly held before the February elections in Germany. Coincidentally, a call for proposals to manage the new project described as a “Media Freedom Rapid Response Mechanism” was issued by the European Commission on Oct 24, 2024, under the cross-sectoral strand of the Creative Europe Programme. This CFP was launched to allegedly promote an independent and pluralistic media environment through an independent Europe-wide rapid response mechanism.
Subsequently, the Romanian government is now drafting an emergency ordinance to empower authorities to eliminate illegal (or inconvenient) online content, which they argue is essential for protecting the electoral process. However, some interpret this as a sign of a democratic crisis, with the current administration struggling to maintain power and resorting to emergency measures to suppress opposition and their freedom of speech. Recent polls suggest that Călin Georgescu could win the presidency in a single round, a situation complicated by the exclusion of the right-wing conservative candidate from the May 2025 elections. Other talks about possible corruption surrounding the construction of the multi-billion classified secret service contract for the Realization of the infrastructure of NATO 57th Air Base Mihail Kogălniceanu, located only 30 kilometres from the Black Sea and anticipated to be NATO’s largest base in Europe upon completion.
-
 @ c0c42bba:a5feb7b5
2025-05-01 07:30:50
@ c0c42bba:a5feb7b5
2025-05-01 07:30:50Hey guy this is my first note on nostr and I'm glad we have something like this now. I've been a Substack writer for a couple of years now and I'm so excited to jump on this and I can't wait for the many things I can do with this
please show your support
-
 @ 107f2bb3:d78aa4c4
2025-05-01 06:24:15
@ 107f2bb3:d78aa4c4
2025-05-01 06:24:15bye
-
 @ 460c25e6:ef85065c
2025-02-25 15:20:39
@ 460c25e6:ef85065c
2025-02-25 15:20:39If you don't know where your posts are, you might as well just stay in the centralized Twitter. You either take control of your relay lists, or they will control you. Amethyst offers several lists of relays for our users. We are going to go one by one to help clarify what they are and which options are best for each one.
Public Home/Outbox Relays
Home relays store all YOUR content: all your posts, likes, replies, lists, etc. It's your home. Amethyst will send your posts here first. Your followers will use these relays to get new posts from you. So, if you don't have anything there, they will not receive your updates.
Home relays must allow queries from anyone, ideally without the need to authenticate. They can limit writes to paid users without affecting anyone's experience.
This list should have a maximum of 3 relays. More than that will only make your followers waste their mobile data getting your posts. Keep it simple. Out of the 3 relays, I recommend: - 1 large public, international relay: nos.lol, nostr.mom, relay.damus.io, etc. - 1 personal relay to store a copy of all your content in a place no one can delete. Go to relay.tools and never be censored again. - 1 really fast relay located in your country: paid options like http://nostr.wine are great
Do not include relays that block users from seeing posts in this list. If you do, no one will see your posts.
Public Inbox Relays
This relay type receives all replies, comments, likes, and zaps to your posts. If you are not getting notifications or you don't see replies from your friends, it is likely because you don't have the right setup here. If you are getting too much spam in your replies, it's probably because your inbox relays are not protecting you enough. Paid relays can filter inbox spam out.
Inbox relays must allow anyone to write into them. It's the opposite of the outbox relay. They can limit who can download the posts to their paid subscribers without affecting anyone's experience.
This list should have a maximum of 3 relays as well. Again, keep it small. More than that will just make you spend more of your data plan downloading the same notifications from all these different servers. Out of the 3 relays, I recommend: - 1 large public, international relay: nos.lol, nostr.mom, relay.damus.io, etc. - 1 personal relay to store a copy of your notifications, invites, cashu tokens and zaps. - 1 really fast relay located in your country: go to nostr.watch and find relays in your country
Terrible options include: - nostr.wine should not be here. - filter.nostr.wine should not be here. - inbox.nostr.wine should not be here.
DM Inbox Relays
These are the relays used to receive DMs and private content. Others will use these relays to send DMs to you. If you don't have it setup, you will miss DMs. DM Inbox relays should accept any message from anyone, but only allow you to download them.
Generally speaking, you only need 3 for reliability. One of them should be a personal relay to make sure you have a copy of all your messages. The others can be open if you want push notifications or closed if you want full privacy.
Good options are: - inbox.nostr.wine and auth.nostr1.com: anyone can send messages and only you can download. Not even our push notification server has access to them to notify you. - a personal relay to make sure no one can censor you. Advanced settings on personal relays can also store your DMs privately. Talk to your relay operator for more details. - a public relay if you want DM notifications from our servers.
Make sure to add at least one public relay if you want to see DM notifications.
Private Home Relays
Private Relays are for things no one should see, like your drafts, lists, app settings, bookmarks etc. Ideally, these relays are either local or require authentication before posting AND downloading each user\'s content. There are no dedicated relays for this category yet, so I would use a local relay like Citrine on Android and a personal relay on relay.tools.
Keep in mind that if you choose a local relay only, a client on the desktop might not be able to see the drafts from clients on mobile and vice versa.
Search relays:
This is the list of relays to use on Amethyst's search and user tagging with @. Tagging and searching will not work if there is nothing here.. This option requires NIP-50 compliance from each relay. Hit the Default button to use all available options on existence today: - nostr.wine - relay.nostr.band - relay.noswhere.com
Local Relays:
This is your local storage. Everything will load faster if it comes from this relay. You should install Citrine on Android and write ws://localhost:4869 in this option.
General Relays:
This section contains the default relays used to download content from your follows. Notice how you can activate and deactivate the Home, Messages (old-style DMs), Chat (public chats), and Global options in each.
Keep 5-6 large relays on this list and activate them for as many categories (Home, Messages (old-style DMs), Chat, and Global) as possible.
Amethyst will provide additional recommendations to this list from your follows with information on which of your follows might need the additional relay in your list. Add them if you feel like you are missing their posts or if it is just taking too long to load them.
My setup
Here's what I use: 1. Go to relay.tools and create a relay for yourself. 2. Go to nostr.wine and pay for their subscription. 3. Go to inbox.nostr.wine and pay for their subscription. 4. Go to nostr.watch and find a good relay in your country. 5. Download Citrine to your phone.
Then, on your relay lists, put:
Public Home/Outbox Relays: - nostr.wine - nos.lol or an in-country relay. -
.nostr1.com Public Inbox Relays - nos.lol or an in-country relay -
.nostr1.com DM Inbox Relays - inbox.nostr.wine -
.nostr1.com Private Home Relays - ws://localhost:4869 (Citrine) -
.nostr1.com (if you want) Search Relays - nostr.wine - relay.nostr.band - relay.noswhere.com
Local Relays - ws://localhost:4869 (Citrine)
General Relays - nos.lol - relay.damus.io - relay.primal.net - nostr.mom
And a few of the recommended relays from Amethyst.
Final Considerations
Remember, relays can see what your Nostr client is requesting and downloading at all times. They can track what you see and see what you like. They can sell that information to the highest bidder, they can delete your content or content that a sponsor asked them to delete (like a negative review for instance) and they can censor you in any way they see fit. Before using any random free relay out there, make sure you trust its operator and you know its terms of service and privacy policies.
-
 @ 57d1a264:69f1fee1
2025-05-01 05:57:24
@ 57d1a264:69f1fee1
2025-05-01 05:57:24Design and build chemical processes, better. Alkali is creating the world's first AI Process Engineer.
What the future of chemical process design should look like.
Under the hood, APE-0 uses tried-and-true open-source packages to run simulations. You don't have to trust that the LLM predicted the result — you can check out the simulation file it produced, and run it yourself!
Discover more at https://www.alkali-eng.com/blogs/introducing-fel-0
originally posted at https://stacker.news/items/968211
-
 @ 97c70a44:ad98e322
2025-02-18 20:30:32
@ 97c70a44:ad98e322
2025-02-18 20:30:32For the last couple of weeks, I've been dealing with the fallout of upgrading a web application to Svelte 5. Complaints about framework churn and migration annoyances aside, I've run into some interesting issues with the migration. So far, I haven't seen many other people register the same issues, so I thought it might be constructive for me to articulate them myself.
I'll try not to complain too much in this post, since I'm grateful for the many years of Svelte 3/4 I've enjoyed. But I don't think I'll be choosing Svelte for any new projects going forward. I hope my reflections here will be useful to others as well.
If you're interested in reproductions for the issues I mention here, you can find them below.
The Need for Speed
To start with, let me just quickly acknowledge what the Svelte team is trying to do. It seems like most of the substantial changes in version 5 are built around "deep reactivity", which allows for more granular reactivity, leading to better performance. Performance is good, and the Svelte team has always excelled at reconciling performance with DX.
In previous versions of Svelte, the main way this was achieved was with the Svelte compiler. There were many ancillary techniques involved in improving performance, but having a framework compile step gave the Svelte team a lot of leeway for rearranging things under the hood without making developers learn new concepts. This is what made Svelte so original in the beginning.
At the same time, it resulted in an even more opaque framework than usual, making it harder for developers to debug more complex issues. To make matters worse, the compiler had bugs, resulting in errors which could only be fixed by blindly refactoring the problem component. This happened to me personally at least half a dozen times, and is what ultimately pushed me to migrate to Svelte 5.
Nevertheless, I always felt it was an acceptable trade-off for speed and productivity. Sure, sometimes I had to delete my project and port it to a fresh repository every so often, but the framework was truly a pleasure to use.
Svelte is not Javascript
Svelte 5 doubled down on this tradeoff — which makes sense, because it's what sets the framework apart. The difference this time is that the abstraction/performance tradeoff did not stay in compiler land, but intruded into runtime in two important ways:
- The use of proxies to support deep reactivity
- Implicit component lifecycle state
Both of these changes improved performance and made the API for developers look slicker. What's not to like? Unfortunately, both of these features are classic examples of a leaky abstraction, and ultimately make things more complex for developers, not less.
Proxies are not objects
The use of proxies seems to have allowed the Svelte team to squeeze a little more performance out of the framework, without asking developers to do any extra work. Threading state through multiple levels of components without provoking unnecessary re-renders in frameworks like React is an infamously difficult chore.
Svelte's compiler avoided some of the pitfalls associated with virtual DOM diffing solutions, but evidently there was still enough of a performance gain to be had to justify the introduction of proxies. The Svelte team also seems to argue that their introduction represents an improvement in developer experience:
we... can maximise both efficiency and ergonomics.
Here's the problem: Svelte 5 looks simpler, but actually introduces more abstractions.
Using proxies to monitor array methods (for example) is appealing because it allows developers to forget all the goofy heuristics involved with making sure state was reactive and just
pushto the array. I can't count how many times I've writtenvalue = valueto trigger reactivity in svelte 4.In Svelte 4, developers had to understand how the Svelte compiler worked. The compiler, being a leaky abstraction, forced its users to know that assignment was how you signaled reactivity. In svelte 5, developers can just "forget" about the compiler!
Except they can't. All the introduction of new abstractions really accomplishes is the introduction of more complex heuristics that developers have to keep in their heads in order to get the compiler to act the way they want it to.
In fact, this is why after years of using Svelte, I found myself using Svelte stores more and more often, and reactive declarations less. The reason being that Svelte stores are just javascript. Calling
updateon a store is simple, and being able to reference them with a$was just a nice bonus — nothing to remember, and if I mess up the compiler yells at me.Proxies introduce a similar problem to reactive declarations, which is that they look like one thing but act like another on the edges.
When I started using Svelte 5, everything worked great — until I tried to save a proxy to indexeddb, at which point I got a
DataCloneError. To make matters worse, it's impossible to reliably tell if something is aProxywithouttry/catching a structured clone, which is a performance-intensive operation.This forces the developer to remember what is and what isn't a Proxy, calling
$state.snapshotevery time they pass a proxy to a context that doesn't expect or know about them. This obviates all the nice abstractions they gave us in the first place.Components are not functions
The reason virtual DOM took off way back in 2013 was the ability to model your application as composed functions, each of which takes data and spits out HTML. Svelte retained this paradigm, using a compiler to sidestep the inefficiencies of virtual DOM and the complexities of lifecycle methods.
In Svelte 5, component lifecycles are back, react-hooks style.
In React, hooks are an abstraction that allows developers to avoid writing all the stateful code associated with component lifecycle methods. Modern React tutorials universally recommend using hooks instead, which rely on the framework invisibly synchronizing state with the render tree.
While this does result in cleaner code, it also requires developers to tread carefully to avoid breaking the assumptions surrounding hooks. Just try accessing state in a
setTimeoutand you'll see what I mean.Svelte 4 had a few gotchas like this — for example, async code that interacts with a component's DOM elements has to keep track of whether the component is unmounted. This is pretty similar to the kind of pattern you'd see in old React components that relied on lifecycle methods.
It seems to me that Svelte 5 has gone the React 16 route by adding implicit state related to component lifecycles in order to coordinate state changes and effects.
For example, here is an excerpt from the documentation for $effect:
You can place $effect anywhere, not just at the top level of a component, as long as it is called during component initialization (or while a parent effect is active). It is then tied to the lifecycle of the component (or parent effect) and will therefore destroy itself when the component unmounts (or the parent effect is destroyed).
That's very complex! In order to use
$effect... effectively (sorry), developers have to understand how state changes are tracked. The documentation for component lifecycles claims:In Svelte 5, the component lifecycle consists of only two parts: Its creation and its destruction. Everything in-between — when certain state is updated — is not related to the component as a whole; only the parts that need to react to the state change are notified. This is because under the hood the smallest unit of change is actually not a component, it’s the (render) effects that the component sets up upon component initialization. Consequently, there’s no such thing as a “before update”/"after update” hook.
But then goes on to introduce the idea of
tickin conjunction with$effect.pre. This section explains that "tickreturns a promise that resolves once any pending state changes have been applied, or in the next microtask if there are none."I'm sure there's some mental model that justifies this, but I don't think the claim that a component's lifecycle is only comprised of mount/unmount is really helpful when an addendum about state changes has to come right afterward.
The place where this really bit me, and which is the motivation for this blog post, is when state gets coupled to a component's lifecycle, even when the state is passed to another function that doesn't know anything about svelte.
In my application, I manage modal dialogs by storing the component I want to render alongside its props in a store and rendering it in the
layout.svelteof my application. This store is also synchronized with browser history so that the back button works to close them. Sometimes, it's useful to pass a callback to one of these modals, binding caller-specific functionality to the child component:javascript const {value} = $props() const callback = () => console.log(value) const openModal = () => pushModal(MyModal, {callback})This is a fundamental pattern in javascript. Passing a callback is just one of those things you do.
Unfortunately, if the above code lives in a modal dialog itself, the caller component gets unmounted before the callback gets called. In Svelte 4, this worked fine, but in Svelte 5
valuegets updated toundefinedwhen the component gets unmounted. Here's a minimal reproduction.This is only one example, but it seems clear to me that any prop that is closed over by a callback function that lives longer than its component will be undefined when I want to use it — with no reassignment existing in lexical scope. It seems that the reason this happens is that the props "belong" to the parent component, and are accessed via getters so that the parent can revoke access when it unmounts.
I don't know why this is necessary, but I assume there's a good engineering reason for it. The problem is, this just isn't how javascript works. Svelte is essentially attempting to re-invent garbage collection around component lifecycles, which breaks the assumption every javascript developer has that variables don't simply disappear without an explicit reassignment. It should be safe to pass stuff around and let the garbage collector do its job.
Conclusion
Easy things are nice, but as Rich Hickey says, easy things are not always simple. And like Joel Spolsky, I don't like being surprised. Svelte has always been full of magic, but with the latest release I think the cognitive overhead of reciting incantations has finally outweighed the power it confers.
My point in this post is not to dunk on the Svelte team. I know lots of people like Svelte 5 (and react hooks). The point I'm trying to make is that there is a tradeoff between doing things on the user's behalf, and giving the user agency. Good software is built on understanding, not cleverness.
I also think this is an important lesson to remember as AI-assisted coding becomes increasingly popular. Don't choose tools that alienate you from your work. Choose tools that leverage the wisdom you've already accumulated, and which help you to cultivate a deeper understanding of the discipline.
Thank you to Rich Harris and team for many years of pleasant development. I hope that (if you read this) it's not so full of inaccuracies as to be unhelpful as user feedback.
-
 @ 1d7ff02a:d042b5be
2025-05-01 05:46:41
@ 1d7ff02a:d042b5be
2025-05-01 05:46:41Source: https://youtu.be/e_Y9tI4dALA?si=F5wXRlpM0YulbhmY
Twitter Origins and Evolution
Twitter began as Dorsey's attempt to better understand cities by visualizing what people were doing and thinking (00:35-02:27) Key features like @mentions, hashtags, and retweets were invented by users, not the company (04:06-05:24) Dorsey realized Twitter was becoming significant when he saw politicians using it during Obama's first address to the nation (06:29-07:44)
Reflections on Twitter/X
Regrets monetizing too quickly through advertising rather than exploring better business models (12:19-13:05) Believes Twitter should have been built as an open protocol rather than a centralized company (13:05-14:23) Advocates for user choice in algorithms rather than having companies decide what content users see (15:35-18:31)
Decentralized Social Media
Started Blue Sky while at Twitter to create a decentralized social media protocol (22:51-24:07) Later focused on Nostr, which he believes has a better development model similar to Linux (24:07-25:57) Believes the future of social media includes agent-driven systems and greater user agency (29:01-29:41)
Block and Bitcoin
Block (formerly Square) focuses on economic empowerment through financial tools (32:08-32:47) Sees Bitcoin as essential for creating an internet protocol for moving money (33:25-35:09) Believes Bitcoin will eventually move beyond being just a store of value to become a currency for cross-border remittances (35:09-36:58)
Entrepreneurship Philosophy
Never intended to be an entrepreneur but wanted to build useful products (40:22-42:02) Compares entrepreneurship to art - knowing how to express ideas and where to set boundaries (42:02-43:09) Deals with rejection by viewing all experiences as teachers with lessons to offer (43:44-44:55)
Personal Habits
Practices meditation daily and previously did 10-day silent retreats (45:30-46:43) Creates daily lists of both what to do and what not to do (47:21-48:28) Eats only once a day to save time and better appreciate food (51:29-52:39) Dedicates morning hours to learning difficult subjects like quantum physics (48:28-49:40)
His advice to young people: observe everything, take in information, and don't worry about immediately reacting to it (52:39-53:00).
Noteable Quotes
-
On Twitter's co-creation with users: "What's interesting about Twitter is it wasn't really us who determined where it went, it was the people using it." (04:06)
-
On algorithms: "I think it's less about free speech, I think it's more about do we get to choose how the algorithms are programming us, because the algorithms are definitively programming us." (15:35)
-
On rejections and setbacks: "Everything I encounter, everything I experience is a teacher and they have some lesson for me, and it's up to me whether I decide to learn from it or not." (43:44)
-
On entrepreneurship as art: "It's expression, it's knowing when to end something, it's knowing what the chapters are and where the piece begins and where it ends." (42:02)
-
On Bitcoin's potential: "Bitcoin is over close to 16 years old right now. It's never gone down, it's never had a security issue, it has no leader, it has a completely open roadmap, and it's determined by a consensus development model." (36:18)
-
On learning: "I think people skip the observing phase too often. I don't think people are good listeners. I don't think people have honed their ability to observe the world and observe nature and observe how things work." (50:19)
-
On his advice to young people: "Observe everything, like take everything in, get love information, love receiving information, don't worry about reacting to it, don't worry about memorizing it, don't worry about doing anything with it at all, just be open." (52:39)
-
-
 @ 42342239:1d80db24
2025-02-16 08:39:59
@ 42342239:1d80db24
2025-02-16 08:39:59Almost 150 years ago, the British newspaper editor William Thomas Stead wrote that "the editorial pen is a sceptre of power, compared with which the sceptre of many a monarch is but a gilded lath". He had begun to regard journalism as something more than just conveying information - the journalist or editor could become a ruler.
Times had certainly changed compared to a few hundred years earlier. Before Gutenberg's invention of the printing press, it was mainly the church that controlled the dissemination of information in Europe, but when Stead put pen to paper, this control had shifted to newspapers, schools, and universities. Eventually, technologies like radio and TV entered the scene, but the power dynamics remained asymmetrical - only a few could send information to the many.
However, with the emergence of the internet, and especially with the spread of social media, a significant change followed. Instead of only a few being able to send information to the many, many could send to many. Almost anyone could now create their own newspaper, radio, or TV channel. The power over information dissemination was decentralised.
Ten years ago, Roberta Alenius, who was then press secretary for Sweden's Prime Minister Fredrik Reinfeldt of the Moderate Party, shared her experiences with Social Democratic and Moderate Party internet activists on social media. She reported that social media played a significant role in how news "comes out" and is shaped, and that journalism was now downstream of social media. Five years later, NATO's then-Secretary-General Jens Stoltenberg said that "NATO must be prepared for both conventional and hybrid threats: from tanks to tweets." This finally underscores the importance of social media.
Elon Musk, who took over X (formerly Twitter) in 2022, has claimed that "it's absolutely fundamental and transformative that the people actually get to decide the news and narrative and what's important," and that citizen journalism is the future.
While his platform allows most expressions - for better or worse - the reach of messages is instead limited ("freedom of speech does not mean freedom of reach "). X has also opened its recommendation algorithm to the outside world by making it open-source. Although this is a welcome step, the fact remains that it's impossible to know which code is actually used and what adjustments are made by humans or algorithms.
William Thomas Stead's "sceptre of power", which has wandered from the church to newspaper and TV editorial offices, and now to citizens according to Elon Musk, risks being transferred to algorithms' opaque methods?
Instead of talking about "toxic algorithms" and TikTok bans, like the so many do today, we should ask ourselves more fundamental questions. What happens when algorithms are no longer objective (how can they ever be?), but instead become tools for shaping our reality? Perhaps our greatest challenge today is not deciding who should govern the information landscape, but instead recognising that no one is up to the task - not even well-ventilated computers.
-
 @ 866e0139:6a9334e5
2025-05-01 05:28:22
@ 866e0139:6a9334e5
2025-05-01 05:28:22Autor: Ludwig F. Badenhagen. Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier. Die neuesten Pareto-Artikel finden Sie auch in unserem Telegram-Kanal.
Die neuesten Artikel der Friedenstaube gibt es jetzt auch im eigenen Friedenstaube-Telegram-Kanal.
Woran erkennt man einen Verbrecher? Die meisten Menschen erfahren von Verbrechern aus den Medien, denn die Medien erklären, wer ein Verbrecher und was ein Verbrechen ist. Die Medien berufen sich hierbei gerne auf „Experten“ und „helfen“ dem gewöhnlichen Bürger bei der „Einordnung“ von Sachverhalten. Man lernt, dass „ein junger Mann“, der mit einem Messer ein hilfloses Baby abschlachtet, nicht so hart bestraft wird, wie etwa ein „Steuersünder“. Und wer glaubt, dass Wahlbetrug juristisch geahndet werden könnte, der irrt ebenso wie jemand, der glaubt, dass es in einer Demokratie erlaubt sein könnte, ein satirisches Meme über einen Politiker zu teilen. Neuerdings sind selbst „Meinungen unterhalb der Strafbarkeitsgrenze“ für gewöhnliche Bürger nicht mehr folgenlos.
Bekanntlich ist die Staatsanwaltschaft in Deutschland eine weisungsgebundene Behörde und als solche ein Teil der Exekutive. Dem Staatsanwalt selbst ist gemäß § 353b Strafgesetzbuch zudem strafrechtlich untersagt, ihm gegenüber erteilte Weisungen Dritten mitzuteilen. Sofern demnach direkte Weisungen erteilt würden, hätte der weisungsgebundene Staatsanwalt diese nicht nur zu befolgen, sondern dürfte auch niemandem gegenüber offenbaren, dass er nicht aus eigener Überzeugung, sondern auf Anweisung - wie beispielsweisen aus politischen Motiven heraus - handelt. Diese juristische Konstruktion eröffnet regierenden Politikern einen erheblichen Gestaltungsspielraum.
Anstelle der konsequenten Anwendung des Strafrechts gab es vor allem in der jüngeren Vergangenheit bei den der Öffentlichkeit nicht zu verbergenden Verfehlungen von Politikern lediglich folgenlose Untersuchungsausschüsse. Könnte dies daran gelegen haben, dass Gerechtigkeit eine Frage von Auslegung und Deutung ist – und die Politiker die Deutungshoheit haben?
Wenn dies so wäre, würde sich die Frage aufdrängen, wie weitgehend denn Straftaten dieser Personengruppe ungestraft ausgeführt werden könnten? Ein Manager eines Unternehmens wird für Fehlverhalten massiv bestraft, während der Lenker eines Landes quasi alles tun kann, was er – im Auftrag der Leute, für die er tatsächlich tätig ist – tun möchte? Wenn dies so wäre, würde es sich dann nicht eher um eine Kabale als um eine ehrenhafte Regierung handeln?
DIE FRIEDENSTAUBE FLIEGT AUCH IN IHR POSTFACH!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt, vorerst für alle kostenfrei, wir starten gänzlich ohne Paywall. (Die Bezahlabos fangen erst zu laufen an, wenn ein Monetarisierungskonzept für die Inhalte steht). Sie wollen der Genossenschaft beitreten oder uns unterstützen? Mehr Infos hier oder am Ende des Textes. friedenstaube@pareto.space
Was wäre in diesem Fall mit dem Gewaltmonopol? Könnten die Soldaten und Polizisten dann nicht für das Durchsetzen der individuellen Interessen dieser Leute missbraucht werden? Ein Bürger dürfte sich nicht kritisch über diese Leute äußern, oder müsste stärkste Repressionen erdulden. Wenn die Gerichtsbarkeit dieser Kabale dienen würde, wäre denn dann eine Rechtsprechung überhaupt möglich? Was würde mit einem Richter, der „in einer wichtigen Sache das falsche Urteil sprechen“ würde, denn passieren? Würde möglicherweise sein Haus von einem Sonderkommando durchsucht und würde er gedemütigt? Würde er seinen Job verlieren und käme er ins Gefängnis? Und wie würde dies auf andere Richter wirken? Würden sich diese gegen die Kabale auflehnen oder lieber tun, was die Kabale ihnen vorgibt?
Was wäre, wenn solch eine Kabale zu Krieg, höheren Steuerzahlungen, medizinischen Zwangsbehandlungen etc. unter Androhung von Bestrafungen zwingen würde? Und was wäre, wenn die Menschen erkennen würden, dass sie von Verbrechern regiert werden?
Was würden Sie tun?
Nun, man könnte demonstrieren, auf die Straße gehen, und dort für seine Rechte eintreten, oder? Aber ist dieses „Demonstrationsrecht“, welches dem eigentlichen Souverän, dem Bürger, „großzügig“ eingeräumt wurde, nicht etwas völlig Wirkungsloses? Wer demonstriert, hat das Gewaltmonopol des Staates zu akzeptieren, sodass er zwar geschlagen, mit Wasserwerfern und Pfefferspray besprüht, gewürgt und von Hunden gebissen werden, aber sich selbst nicht wehren darf. Wenn sich ein Demonstrant in der „falschen Sache“ nicht an die Demonstrationsregeln hält und beispielsweise Sicherheitsabstände nicht korrekt einhält, wird er sehr schnell von einem gepanzerten und anonymisierten Polizisten bestraft. Und was ist mit den vielen V-Leuten? Ein so genannter Agent Provokateur mischt sich unter die Demonstranten und gibt vor, ein Teil von diesen zu sein, um dann in deren Namen „etwas Unrechtes“ zu tun wie eine Reichsbürger-Fahne zu schwenken oder einen Sicherheitsabstand nicht einzuhalten oder einen Polizisten anzugreifen. Und schon hat man „einen Grund“, dieser Demonstration einen besonderen Anstrich zu verpassen. Wer sich noch an „den Sturm auf den Reichstag“ und die Verleihungen von Verdienstorden für „die Rettung unserer Demokratie“ erinnert, weiß, dass Demonstrationen gelenkt werden können und dass ein gewöhnlicher Bürger, der „sein Demonstrationsrecht“ wahrnimmt, im Zuge einer solchen Veranstaltung am eigenen Leib erfahren kann, dass ihm die Demo im günstigsten Fall weder genützt noch geschadet hat.
Aber was sonst könnte man tun, wenn man von Verbrechern regiert würde? Was könnte getan werden, wenn Untaten wie Kriegstreiberei, Gesundheitsdiktatur, Steuerwillkür, Klimawahn, Wahlmanipulationen etc. nicht „aus Versehen“, sondern mit schädigender Absicht, also mit Vorsatz getan wurden und werden?
Wer sich diese Fragen stellt, ist bereits sehr weit und weitgehend isoliert, denn der große Teil der Bevölkerung wird durch die Medien nicht nur darüber „informiert“, was Straftaten sind, sondern erhält zudem „wohlwollende Einordnungen“ zum jeweils aktuellen Geschehen. Der „gute Bürger Unsererdemokratie“ ist einfach „besser informiert“, und weiß, was er zu denken hat. Für den „guten Bürger“ ist alles klar: Wir leben in der besten Demokratie aller Zeiten und die Politiker geben ihr Bestes, zu unser aller Wohle. Sie schützen uns vor Pandemien, vor Feinden der Demokratie und Feinden des Landes, und sind hierbei weitestgehend selbstlos.
Aber wer sich der Mühe unterziehen möchte, selbst zu denken, der hat die Möglichkeit, seine eigenen Einordnungen auf der Basis ungeschwärzter Fakten vorzunehmen. Wer beispielsweise die RKI-Protokolle oder auch anderes Material ungeschwärzt lesen möchte, kann sich (noch) unabhängiger Portale bedienen, die seitens der Regierung zwar allesamt verboten werden sollen (da man schließlich als Regierung bestimmen möchte, was die Bürger zu lesen und zu glauben haben), die aber derzeit noch verfügbar sind.
In welcher Welt wollen wir und unsere Kinder leben und was ist zu tun, damit diese wünschenswerte Welt entsteht? Die Menschen sollten in die Wahrnehmung und von dort aus in die Erkenntnis kommen. Und aus der Erkenntnis ins Wollen, denn letztendlich ist das Wollen stets die Grundvoraussetzung für das Tun. Und ohne das Tun passiert – nichts.
Lesen Sie hier, wie Menschen wie Vieh behandelt werden und hier, wie das System organisiert ist. Und hier ist zu nachzulesen, was getan werden könnte, wenn Verbrecher an der Macht wären.
LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt.
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: friedenstaube@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ 8cda1daa:e9e5bdd8
2025-04-24 10:20:13
@ 8cda1daa:e9e5bdd8
2025-04-24 10:20:13Bitcoin cracked the code for money. Now it's time to rebuild everything else.
What about identity, trust, and collaboration? What about the systems that define how we live, create, and connect?
Bitcoin gave us a blueprint to separate money from the state. But the state still owns most of your digital life. It's time for something more radical.
Welcome to the Atomic Economy - not just a technology stack, but a civil engineering project for the digital age. A complete re-architecture of society, from the individual outward.
The Problem: We Live in Digital Captivity
Let's be blunt: the modern internet is hostile to human freedom.
You don't own your identity. You don't control your data. You don't decide what you see.
Big Tech and state institutions dominate your digital life with one goal: control.
- Poisoned algorithms dictate your emotions and behavior.
- Censorship hides truth and silences dissent.
- Walled gardens lock you into systems you can't escape.
- Extractive platforms monetize your attention and creativity - without your consent.
This isn't innovation. It's digital colonization.
A Vision for Sovereign Society
The Atomic Economy proposes a new design for society - one where: - Individuals own their identity, data, and value. - Trust is contextual, not imposed. - Communities are voluntary, not manufactured by feeds. - Markets are free, not fenced. - Collaboration is peer-to-peer, not platform-mediated.
It's not a political revolution. It's a technological and social reset based on first principles: self-sovereignty, mutualism, and credible exit.
So, What Is the Atomic Economy?
The Atomic Economy is a decentralized digital society where people - not platforms - coordinate identity, trust, and value.
It's built on open protocols, real software, and the ethos of Bitcoin. It's not about abstraction - it's about architecture.
Core Principles: - Self-Sovereignty: Your keys. Your data. Your rules. - Mutual Consensus: Interactions are voluntary and trust-based. - Credible Exit: Leave any system, with your data and identity intact. - Programmable Trust: Trust is explicit, contextual, and revocable. - Circular Economies: Value flows directly between individuals - no middlemen.
The Tech Stack Behind the Vision
The Atomic Economy isn't just theory. It's a layered system with real tools:
1. Payments & Settlement
- Bitcoin & Lightning: The foundation - sound, censorship-resistant money.
- Paykit: Modular payments and settlement flows.
- Atomicity: A peer-to-peer mutual credit protocol for programmable trust and IOUs.
2. Discovery & Matching
- Pubky Core: Decentralized identity and discovery using PKARR and the DHT.
- Pubky Nexus: Indexing for a user-controlled internet.
- Semantic Social Graph: Discovery through social tagging - you are the algorithm.
3. Application Layer
- Bitkit: A self-custodial Bitcoin and Lightning wallet.
- Pubky App: Tag, publish, trade, and interact - on your terms.
- Blocktank: Liquidity services for Lightning and circular economies.
- Pubky Ring: Key-based access control and identity syncing.
These tools don't just integrate - they stack. You build trust, exchange value, and form communities with no centralized gatekeepers.
The Human Impact
This isn't about software. It's about freedom.
- Empowered Individuals: Control your own narrative, value, and destiny.
- Voluntary Communities: Build trust on shared values, not enforced norms.
- Economic Freedom: Trade without permission, borders, or middlemen.
- Creative Renaissance: Innovation and art flourish in open, censorship-resistant systems.
The Atomic Economy doesn't just fix the web. It frees the web.
Why Bitcoiners Should Care
If you believe in Bitcoin, you already believe in the Atomic Economy - you just haven't seen the full map yet.
- It extends Bitcoin's principles beyond money: into identity, trust, coordination.
- It defends freedom where Bitcoin leaves off: in content, community, and commerce.
- It offers a credible exit from every centralized system you still rely on.
- It's how we win - not just economically, but culturally and socially.
This isn't "web3." This isn't another layer of grift. It's the Bitcoin future - fully realized.
Join the Atomic Revolution
- If you're a builder: fork the code, remix the ideas, expand the protocols.
- If you're a user: adopt Bitkit, use Pubky, exit the digital plantation.
- If you're an advocate: share the vision. Help people imagine a free society again.
Bitcoin promised a revolution. The Atomic Economy delivers it.
Let's reclaim society, one key at a time.
Learn more and build with us at Synonym.to.
-
 @ 9a859fbc:8a9270f3
2025-04-22 15:45:55
@ 9a859fbc:8a9270f3
2025-04-22 15:45:55A story of art and inspiration
This image was generated by AI
That is...
I am artificial. I was created by two other humans (hi mum and dad 👋)
I am intelligent. I can perceive the world, experience it, learn to understand cause & effect, and make decisions.
To go perhaps deeper, cells, DNA and life itself are artifices of the fabric of reality.
I sat, in a pub in Bristol, a place where I rarely frequent. I sat with one housemate, who I rarely spent time with. I met his friends that day, only once, never we met again.
I got chatting with a lady there. I had some paper and pencils with me. My intention, for a couple of weeks, was to come up with a symbol to represent Deep Sea Frequencies, at that time still known as Psychedelic Jelly. We were a new collaboration.
She and I got chatting about art. About symbolic representation of concepts, feelings, ideas. We chatted about flow, about how there are different types of flow, different elemental conditions of flow. I doodled some shapes, and we noticed how fire, water and air all look similar due to their fluid natures. So we considered how to differentiate, distinguish them from one another.
I doodled some more, and we came up with swooshes, curls, crests and bubbles. These seemed to be distinguishing enough such that they were no longer reminiscent of fire or air. I doodled fire and air too, just in case, just to check.
Then we chatted about symmetry types, reflective, axes, rotational. About geometry, geometric containers. We both enjoy triangles and hexagons. (It's always hexagons!)
I doodled some more shapes and put them in hexagonal shapes. Then I tried bending them into triangular forms instead, and overlaid two triangles.
Each triangle looked like a triskelion. Perfect.
Overlaid, they looked just like the flow of water, coming up, spiralling down.
The logo was born in this moment, in this serendipitous meeting, in this unlikely chat with a total stranger. We met for the first time that day, and I'm not sure if we ever met again. This interaction was, is, precious, and it led to a particular creation that is now a core part of my life and is a highlight for many people around the UK and the world, as we put on events and released musicians' music.
This is inspiration. This is expression. This is flow, through the fluid nature of the cosmos.
This is what you miss out on when you talk into your AI LLM black hole prompt.
This is what you steal from when you demand your AI LLM to generate you something according to your whim.
Art and expression is the very foundation of human community. Join in! Try new things! Learn from each other! Bring us all closer together by interacting and creating through shared ideas, shared visions, shared wisdom!
After that, I drew it up cleanly, geometrically.
I photographed it like scanning it, carefully aligning the camera because I didn't have a scanner.
I redrew it more than twice.
I digitised it, colourised it, split it into two layers so I could apply colour & lighting effects to it.
I painstakingly traced the photograph into a vector format, to enlarge it and use it for various media.
I even more painstakingly (do we have a more extreme adverb??) divided all the vector shapes into new objects so that the layers became "real". And cleaned up the vector nodes, shaping them to my imagination.
The vector form is used all over our record label & events branding.
And then I imported the vector form into Blender, a 3D rendering application, free and open source.
I learnt Blender, day by day developing my understanding and my skills. Day by day my GPU crashing on raytracing and cutting the laptop's power out!
And finally, I learnt to make some simple renders that look like being underwater, like surreal glassy objects floating in the deep. I even learnt to animate it, although I haven't released that into the wild.
I imagined all of this stuff, and then I spent months over years developing my skills in my spare time in order to bring these imaginations to life.
You can do the same.
You have to sacrifice things.
Sacrifice your time.
Sacrifice your energy.
Sacrifice your distractions and enter yourself into the learning process and the creative process.
To you, amazing lady who helped me draw this symbol from the fabric of the Realm of Forms, thank you! I'm sorry that I don't recall your name, although actually I think I do remember but I would be embarrassed if I tagged the wrong person. Please reach out if you recognise this story! It was about 7, maybe 8 years ago, in the painted pub in St. Werburgh's.
-
 @ 57d1a264:69f1fee1
2025-05-01 05:14:06
@ 57d1a264:69f1fee1
2025-05-01 05:14:06The mystical d attribute in SVG paths is actually a series of small commands. In this guide, we'll take a look at each path command and how we can use them to draw icons. Read more at https://www.nan.fyi/svg-paths
I you'd like to learn Interactive SVG Animations, here a text-based mini-course on making whimsical, playful SVG animations https://www.svg-animations.how/
credits: @nandafyi
originally posted at https://stacker.news/items/968195
-
 @ 1beecee5:d29d2162
2025-04-21 06:30:55
@ 1beecee5:d29d2162
2025-04-21 06:30:55 -
 @ 4ba8e86d:89d32de4
2025-04-21 02:12:19
@ 4ba8e86d:89d32de4
2025-04-21 02:12:19SISTEMA OPERACIONAL MÓVEIS
GrapheneOS : https://njump.me/nevent1qqs8t76evdgrg4qegdtyrq2rved63pr29wlqyj627n9tj4vlu66tqpqpzdmhxue69uhk7enxvd5xz6tw9ec82c30qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqppcqec9
CalyxOS : https://njump.me/nevent1qqsrm0lws2atln2kt3cqjacathnw0uj0jsxwklt37p7t380hl8mmstcpydmhxue69uhkummnw3ez6an9wf5kv6t9vsh8wetvd3hhyer9wghxuet59uq3vamnwvaz7tmwdaehgu3wvf3kstnwd9hx5cf0qy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qgcwaehxw309aex2mrp0yhxxatjwfjkuapwveukjtcpzpmhxue69uhkummnw3ezumt0d5hszrnhwden5te0dehhxtnvdakz7qfywaehxw309ahx7um5wgh8ymm4dej8ymmrdd3xjarrda5kuetjwvhxxmmd9uq3uamnwvaz7tmwdaehgu3dv3jhvtnhv4kxcmmjv3jhytnwv46z7qghwaehxw309aex2mrp0yhxummnw3ezucnpdejz7qgewaehxw309ahx7um5wghxymmwva3x7mn89e3k7mf0qythwumn8ghj7cn5vvhxkmr9dejxz7n49e3k7mf0qyg8wumn8ghj7mn09eehgu3wvdez7smttdu
LineageOS : https://njump.me/nevent1qqsgw7sr36gaty48cf4snw0ezg5mg4atzhqayuge752esd469p26qfgpzdmhxue69uhhwmm59e6hg7r09ehkuef0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpnvm779
SISTEMA OPERACIONAL DESKTOP
Tails : https://njump.me/nevent1qqsf09ztvuu60g6xprazv2vxqqy5qlxjs4dkc9d36ta48q75cs9le4qpzemhxue69uhkummnw3ex2mrfw3jhxtn0wfnj7q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqz34ag5t
Qubes OS : https://njump.me/nevent1qqsp6jujgwl68uvurw0cw3hfhr40xq20sj7rl3z4yzwnhp9sdpa7augpzpmhxue69uhkummnw3ezumt0d5hsz9mhwden5te0wfjkccte9ehx7um5wghxyctwvshsz9thwden5te0dehhxarj9ehhsarj9ejx2a30qyg8wumn8ghj7mn09eehgu3wvdez7qg4waehxw309aex2mrp0yhxgctdw4eju6t09uqjxamnwvaz7tmwdaehgu3dwejhy6txd9jkgtnhv4kxcmmjv3jhytnwv46z7qgwwaehxw309ahx7uewd3hkctcpremhxue69uhkummnw3ez6er9wch8wetvd3hhyer9wghxuet59uj3ljr8
Kali linux : https://njump.me/nevent1qqswlav72xdvamuyp9xc38c6t7070l3n2uxu67ssmal2g7gv35nmvhspzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqswt9rxe
Whonix : https://njump.me/nevent1qqs85gvejvzhk086lwh6edma7fv07p5c3wnwnxnzthwwntg2x6773egpydmhxue69uhkummnw3ez6an9wf5kv6t9vsh8wetvd3hhyer9wghxuet59uq3qamnwvaz7tmwdaehgu3wd4hk6tcpzemhxue69uhkummnw3ezucnrdqhxu6twdfsj7qfywaehxw309ahx7um5wgh8ymm4dej8ymmrdd3xjarrda5kuetjwvhxxmmd9uq3wamnwvaz7tmzw33ju6mvv4hxgct6w5hxxmmd9uq3qamnwvaz7tmwduh8xarj9e3hytcpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhszrnhwden5te0dehhxtnvdakz7qg7waehxw309ahx7um5wgkkgetk9emk2mrvdaexgetj9ehx2ap0sen9p6
Kodachi : https://njump.me/nevent1qqsf5zszgurpd0vwdznzk98hck294zygw0s8dah6fpd309ecpreqtrgpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhszgmhwden5te0dehhxarj94mx2unfve5k2epwwajkcmr0wfjx2u3wdejhgtcpremhxue69uhkummnw3ez6er9wch8wetvd3hhyer9wghxuet59uq3qamnwvaz7tmwdaehgu3wd4hk6tcpzamhxue69uhkyarr9e4kcetwv3sh5afwvdhk6tcpzpmhxue69uhkumewwd68ytnrwghszfrhwden5te0dehhxarj9eex7atwv3ex7cmtvf5hgcm0d9hx2unn9e3k7mf0qyvhwumn8ghj7mn0wd68ytnzdahxwcn0denjucm0d5hszrnhwden5te0dehhxtnvdakz7qgkwaehxw309ahx7um5wghxycmg9ehxjmn2vyhsz9mhwden5te0wfjkccte9ehx7um5wghxyctwvshs94a4d5
PGP
Openkeychain : https://njump.me/nevent1qqs9qtjgsulp76t7jkquf8nk8txs2ftsr0qke6mjmsc2svtwfvswzyqpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs36mp0w
Kleopatra : https://njump.me/nevent1qqspnevn932hdggvp4zam6mfyce0hmnxsp9wp8htpumq9vm3anq6etsppemhxue69uhkummn9ekx7mp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpuaeghp
Pgp : https://njump.me/nevent1qqsggek707qf3rzttextmgqhym6d4g479jdnlnj78j96y0ut0x9nemcpzamhxue69uhhyetvv9ujuurjd9kkzmpwdejhgtczyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgptemhe
Como funciona o PGP? : https://njump.me/nevent1qqsz9r7azc8pkvfmkg2hv0nufaexjtnvga0yl85x9hu7ptpg20gxxpspremhxue69uhkummnw3ez6ur4vgh8wetvd3hhyer9wghxuet59upzqjagapkjm9ufdhynxlp72qrfrzfawvt4wt7cr795rhw6tkyaxt0yqvzqqqqqqy259fhs
Por que eu escrevi PGP. - Philip Zimmermann.
https://njump.me/nevent1qqsvysn94gm8prxn3jw04r0xwc6sngkskg756z48jsyrmqssvxtm7ncpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtchzxnad
VPN
Vpn : https://njump.me/nevent1qqs27ltgsr6mh4ffpseexz6s37355df3zsur709d0s89u2nugpcygsspzpmhxue69uhkummnw3ezumt0d5hsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqshzu2fk
InviZible Pro : https://njump.me/nevent1qqsvyevf2vld23a3xrpvarc72ndpcmfvc3lc45jej0j5kcsg36jq53cpz3mhxue69uhhyetvv9ujuerpd46hxtnfdupzqjagapkjm9ufdhynxlp72qrfrzfawvt4wt7cr795rhw6tkyaxt0yqvzqqqqqqy33y5l4
Orbot: https://njump.me/nevent1qqsxswkyt6pe34egxp9w70cy83h40ururj6m9sxjdmfass4cjm4495stft593
I2P
i2p : https://njump.me/nevent1qqsvnj8n983r4knwjmnkfyum242q4c0cnd338l4z8p0m6xsmx89mxkslx0pgg
Entendendo e usando a rede I2P : https://njump.me/nevent1qqsxchp5ycpatjf5s4ag25jkawmw6kkf64vl43vnprxdcwrpnms9qkcppemhxue69uhkummn9ekx7mp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpvht4mn
Criando e acessando sua conta Email na I2P : https://njump.me/nevent1qqs9v9dz897kh8e5lfar0dl7ljltf2fpdathsn3dkdsq7wg4ksr8xfgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpw8mzum
APLICATIVO 2FA
Aegis Authenticator : https://njump.me/nevent1qqsfttdwcn9equlrmtf9n6wee7lqntppzm03pzdcj4cdnxel3pz44zspz4mhxue69uhhyetvv9ujumn0wd68ytnzvuhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqscvtydq
YubiKey : https://njump.me/nevent1qqstsnn69y4sf4330n7039zxm7wza3ch7sn6plhzmd57w6j9jssavtspvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzueyvgt
GERENCIADOR DE SENHAS
KeepassDX: https://njump.me/nevent1qqswc850dr4ujvxnmpx75jauflf4arc93pqsty5pv8hxdm7lcw8ee8qpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpe0492n
Birwaden: https://njump.me/nevent1qqs0j5x9guk2v6xumhwqmftmcz736m9nm9wzacqwjarxmh8k4xdyzwgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpwfe2kc
KeePassXC: https://njump.me/nevent1qqsgftcrd8eau7tzr2p9lecuaf7z8mx5jl9w2k66ae3lzkw5wqcy5pcl2achp
CHAT MENSAGEM
SimpleXchat : https://njump.me/nevent1qqsds5xselnnu0dyy0j49peuun72snxcgn3u55d2320n37rja9gk8lgzyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgmcmj7c
Briar : https://njump.me/nevent1qqs8rrtgvjr499hreugetrl7adkhsj2zextyfsukq5aa7wxthrgcqcg05n434
Element Messenger : https://njump.me/nevent1qqsq05snlqtxm5cpzkshlf8n5d5rj9383vjytkvqp5gta37hpuwt4mqyccee6
Pidgin : https://njump.me/nevent1qqsz7kngycyx7meckx53xk8ahk98jkh400usrvykh480xa4ct9zlx2c2ywvx3
E-MAIL
Thunderbird: https://njump.me/nevent1qqspq64gg0nw7t60zsvea5eykgrm43paz845e4jn74muw5qzdvve7uqrkwtjh
ProtonMail : https://njump.me/nevent1qqs908glhk68e7ms8zqtlsqd00wu3prnpt08dwre26hd6e5fhqdw99cppemhxue69uhkummn9ekx7mp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpeyhg4z
Tutonota : https://njump.me/nevent1qqswtzh9zjxfey644qy4jsdh9465qcqd2wefx0jxa54gdckxjvkrrmqpz4mhxue69uhhyetvv9ujumt0wd68ytnsw43qygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs5hzhkv
k-9 mail : https://njump.me/nevent1qqs200g5a603y7utjgjk320r3srurrc4r66nv93mcg0x9umrw52ku5gpr3mhxue69uhkummnw3ezuumhd9ehxtt9de5kwmtp9e3kstczyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgacflak
E-MAIL-ALIÁS
Simplelogin : https://njump.me/nevent1qqsvhz5pxqpqzr2ptanqyqgsjr50v7u9lc083fvdnglhrv36rnceppcppemhxue69uhkummn9ekx7mp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqp9gsr7m
AnonAddy : https://njump.me/nevent1qqs9mcth70mkq2z25ws634qfn7vx2mlva3tkllayxergw0s7p8d3ggcpzpmhxue69uhkummnw3ezumt0d5hsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs6mawe3
NAVEGADOR
Navegador Tor : https://njump.me/nevent1qqs06qfxy7wzqmk76l5d8vwyg6mvcye864xla5up52fy5sptcdy39lspzemhxue69uhkummnw3ezuerpw3sju6rpw4ej7q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzdp0urw
Mullvap Browser : https://njump.me/nevent1qqs2vsgc3wk09wdspv2mezltgg7nfdg97g0a0m5cmvkvr4nrfxluzfcpzdmhxue69uhhwmm59e6hg7r09ehkuef0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpj8h6fe
LibreWolf : https://njump.me/nevent1qqswv05mlmkcuvwhe8x3u5f0kgwzug7n2ltm68fr3j06xy9qalxwq2cpzemhxue69uhkummnw3ex2mrfw3jhxtn0wfnj7q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzuv2hxr
Cromite : https://njump.me/nevent1qqs2ut83arlu735xp8jf87w5m3vykl4lv5nwkhldkqwu3l86khzzy4cpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs3dplt7
BUSCADORES
Searx : https://njump.me/nevent1qqsxyzpvgzx00n50nrlgctmy497vkm2cm8dd5pdp7fmw6uh8xnxdmaspr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqp23z7ax
APP-STORE
Obtainium : https://njump.me/nevent1qqstd8kzc5w3t2v6dgf36z0qrruufzfgnc53rj88zcjgsagj5c5k4rgpz3mhxue69uhhyetvv9ujuerpd46hxtnfdupzqjagapkjm9ufdhynxlp72qrfrzfawvt4wt7cr795rhw6tkyaxt0yqvzqqqqqqyarmca3
F-Droid : https://njump.me/nevent1qqst4kry49cc9g3g8s5gdnpgyk3gjte079jdnv43f0x4e85cjkxzjesymzuu4
Droid-ify : https://njump.me/nevent1qqsrr8yu9luq0gud902erdh8gw2lfunpe93uc2u6g8rh9ep7wt3v4sgpzpmhxue69uhkummnw3ezumt0d5hsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsfzu9vk
Aurora Store : https://njump.me/nevent1qqsy69kcaf0zkcg0qnu90mtk46ly3p2jplgpzgk62wzspjqjft4fpjgpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzrpmsjy
RSS
Feeder : https://njump.me/nevent1qqsy29aeggpkmrc7t3c7y7ldgda7pszl7c8hh9zux80gjzrfvlhfhwqpp4mhxue69uhkummn9ekx7mqzyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgsvzzjy
VIDEOO CONFERENCIA
Jitsi meet : https://njump.me/nevent1qqswphw67hr6qmt2fpugcj77jrk7qkfdrszum7vw7n2cu6cx4r6sh4cgkderr
TECLADOS
HeliBoard : https://njump.me/nevent1qqsyqpc4d28rje03dcvshv4xserftahhpeylu2ez2jutdxwds4e8syspz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsr8mel5
OpenBoard : https://njump.me/nevent1qqsf7zqkup03yysy67y43nj48q53sr6yym38es655fh9fp6nxpl7rqspzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqswcvh3r
FlorisBoard : https://njump.me/nevent1qqsf7zqkup03yysy67y43nj48q53sr6yym38es655fh9fp6nxpl7rqspzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqswcvh3r
MAPAS
Osmand : https://njump.me/nevent1qqsxryp2ywj64az7n5p6jq5tn3tx5jv05te48dtmmt3lf94ydtgy4fgpzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs54nwpj
Organic maps : https://njump.me/nevent1qqstrecuuzkw0dyusxdq7cuwju0ftskl7anx978s5dyn4pnldrkckzqpr4mhxue69uhkummnw3ezumtp0p5k6ctrd96xzer9dshx7un8qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpl8z3kk
TRADUÇÃO
LibreTranslate : https://njump.me/nevent1qqs953g3rhf0m8jh59204uskzz56em9xdrjkelv4wnkr07huk20442cpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzeqsx40
REMOÇÃO DOS METADADOS
Scrambled Exif : https://njump.me/nevent1qqs2658t702xv66p000y4mlhnvadmdxwzzfzcjkjf7kedrclr3ej7aspyfmhxue69uhk6atvw35hqmr90pjhytngw4eh5mmwv4nhjtnhdaexcep0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpguu0wh
ESTEGANOGRAFIA
PixelKnot: https://njump.me/nevent1qqsrh0yh9mg0lx86t5wcmhh97wm6n4v0radh6sd0554ugn354wqdj8gpz3mhxue69uhhyetvv9ujuerpd46hxtnfdupzqjagapkjm9ufdhynxlp72qrfrzfawvt4wt7cr795rhw6tkyaxt0yqvzqqqqqqyuvfqdp
PERFIL DE TRABALHO
Shelter : https://njump.me/nevent1qqspv9xxkmfp40cxgjuyfsyczndzmpnl83e7gugm7480mp9zhv50wkqpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzdnu59c
PDF
MuPDF : https://njump.me/nevent1qqspn5lhe0dteys6npsrntmv2g470st8kh8p7hxxgmymqa95ejvxvfcpzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs4hvhvj
Librera Reader : https://njump.me/nevent1qqsg60flpuf00sash48fexvwxkly2j5z9wjvjrzt883t3eqng293f3cpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqz39tt3n
QR-Code
Binary Eye : https://njump.me/nevent1qqsz4n0uxxx3q5m0r42n9key3hchtwyp73hgh8l958rtmae5u2khgpgpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzdmn4wp
Climático
Breezy Weather : https://njump.me/nevent1qqs9hjz5cz0y4am3kj33xn536uq85ydva775eqrml52mtnnpe898rzspzamhxue69uhhyetvv9ujuurjd9kkzmpwdejhgtczyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgpd3tu8
ENCRYPTS
Cryptomator : https://njump.me/nevent1qqsvchvnw779m20583llgg5nlu6ph5psewetlczfac5vgw83ydmfndspzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsx7ppw9
VeraCrypt : https://njump.me/nevent1qqsf6wzedsnrgq6hjk5c4jj66dxnplqwc4ygr46l8z3gfh38q2fdlwgm65ej3
EXTENSÕES
uBlock Origin : https://njump.me/nevent1qqswaa666lcj2c4nhnea8u4agjtu4l8q89xjln0yrngj7ssh72ntwzql8ssdj
Snowflake : https://njump.me/nevent1qqs0ws74zlt8uced3p2vee9td8x7vln2mkacp8szdufvs2ed94ctnwchce008
CLOUD
Nextcloud : https://njump.me/nevent1qqs2utg5z9htegdtrnllreuhypkk2026x8a0xdsmfczg9wdl8rgrcgg9nhgnm
NOTEPAD
Joplin : https://njump.me/nevent1qqsz2a0laecpelsznser3xd0jfa6ch2vpxtkx6vm6qg24e78xttpk0cpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpdu0hft
Standard Notes : https://njump.me/nevent1qqsv3596kz3qung5v23cjc4cpq7rqxg08y36rmzgcrvw5whtme83y3s7tng6r
MÚSICA
RiMusic : https://njump.me/nevent1qqsv3genqav2tfjllp86ust4umxm8tr2wd9kq8x7vrjq6ssp363mn0gpzamhxue69uhhyetvv9ujuurjd9kkzmpwdejhgtczyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqg42353n
ViMusic : https://njump.me/nevent1qqswx78559l4jsxsrygd8kj32sch4qu57stxq0z6twwl450vp39pdqqpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzjg863j
PODCAST
AntennaPod : https://njump.me/nevent1qqsp4nh7k4a6zymfwqqdlxuz8ua6kdhvgeeh3uxf2c9rtp9u3e9ku8qnr8lmy
VISUALIZAR VIDEO
VLC : https://njump.me/nevent1qqs0lz56wtlr2eye4ajs2gzn2r0dscw4y66wezhx0mue6dffth8zugcl9laky
YOUTUBE
NewPipe : https://njump.me/nevent1qqsdg06qpcjdnlvgm4xzqdap0dgjrkjewhmh4j3v4mxdl4rjh8768mgdw9uln
FreeTube : https://njump.me/nevent1qqsz6y6z7ze5gs56s8seaws8v6m6j2zu0pxa955dhq3ythmexak38mcpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs5lkjvv
LibreTube : https://snort.social/e/nevent1qqstmd5m6wrdvn4gxf8xyhrwnlyaxmr89c9kjddvnvux6603f84t3fqpz4mhxue69uhhyetvv9ujumt0wd68ytnsw43qygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsswwznc
COMPARTILHAMENTO DE ARQUIVOS
OnionShare : https://njump.me/nevent1qqsr0a4ml5nu6ud5k9yzyawcd9arznnwkrc27dzzc95q6r50xmdff6qpydmhxue69uhkummnw3ez6an9wf5kv6t9vsh8wetvd3hhyer9wghxuet59uq3uamnwvaz7tmwdaehgu3dv3jhvtnhv4kxcmmjv3jhytnwv46z7qgswaehxw309ahx7tnnw3ezucmj9uq32amnwvaz7tmjv4kxz7fwv3sk6atn9e5k7tcpzamhxue69uhkyarr9e4kcetwv3sh5afwvdhk6tcpzemhxue69uhkummnw3ezucnrdqhxu6twdfsj7qgswaehxw309ahx7um5wghx6mmd9uqjgamnwvaz7tmwdaehgu3wwfhh2mnywfhkx6mzd96xxmmfdejhyuewvdhk6tcppemhxue69uhkummn9ekx7mp0qythwumn8ghj7un9d3shjtnwdaehgu3wvfskuep0qyv8wumn8ghj7un9d3shjtnrw4e8yetwwshxv7tf9ut7qurt
Localsend : https://njump.me/nevent1qqsp8ldjhrxm09cvvcak20hrc0g8qju9f67pw7rxr2y3euyggw9284gpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzuyghqr
Wallet Bitcoin
Ashigaru Wallet : https://njump.me/nevent1qqstx9fz8kf24wgl26un8usxwsqjvuec9f8q392llmga75tw0kfarfcpzamhxue69uhhyetvv9ujuurjd9kkzmpwdejhgtczyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgvfsrqp
Samourai Wallet : https://njump.me/nevent1qqstcvjmz39rmrnrv7t5cl6p3x7pzj6jsspyh4s4vcwd2lugmre04ecpr9mhxue69uhkummnw3ezucn0denkymmwvuhxxmmd9upzqjagapkjm9ufdhynxlp72qrfrzfawvt4wt7cr795rhw6tkyaxt0yqvzqqqqqqy3rg4qs
CÂMERA
opencamera : https://njump.me/nevent1qqs25glp6dh0crrjutxrgdjlnx9gtqpjtrkg29hlf7382aeyjd77jlqpzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqssxcvgc
OFFICE
Collabora Office : https://njump.me/nevent1qqs8yn4ys6adpmeu3edmf580jhc3wluvlf823cc4ft4h0uqmfzdf99qpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsj40uss
TEXTOS
O manifesto de um Cypherpunk : https://njump.me/nevent1qqsd7hdlg6galn5mcuv3pm3ryfjxc4tkyph0cfqqe4du4dr4z8amqyspvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzal0efa
Operations security ( OPSEC) : https://snort.social/e/nevent1qqsp323havh3y9nxzd4qmm60hw87tm9gjns0mtzg8y309uf9mv85cqcpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqz8ej9l7
O MANIFESTO CRIPTOANARQUISTA Timothy C. May – 1992. : https://njump.me/nevent1qqspp480wtyx2zhtwpu5gptrl8duv9rvq3mug85mp4d54qzywk3zq9gpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqz5wq496
Declaração de independência do ciberespaço
- John Perry Barlow - 1996 : https://njump.me/nevent1qqs2njsy44n6p07mhgt2tnragvchasv386nf20ua5wklxqpttf6mzuqpzpmhxue69uhkummnw3ezumt0d5hsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsukg4hr
The Cyphernomicon: Criptografia, Dinheiro Digital e o Futuro da Privacidade. escrito por Timothy C. May -Publicado em 1994. :
Livro completo em PDF no Github PrivacyOpenSource.
https://github.com/Alexemidio/PrivacyOpenSource/raw/main/Livros/THE%20CYPHERNOMICON%20.pdf Share
-
 @ 554ab6fe:c6cbc27e
2025-02-14 16:29:51
@ 554ab6fe:c6cbc27e
2025-02-14 16:29:51Bitcoin’s Price and the Power Law: A Reflection of Energy and the Early Stages of Monetary Adoption Introduction Bitcoin’s price trajectory has long puzzled analysts, with its seemingly chaotic booms and busts. However, when examined through the lens of power laws, a pattern emerges—one that is fundamentally tied to Bitcoin’s energy-based production cost. This article argues that Bitcoin’s price has historically followed a power law because its underlying cost structure is dictated by mining, an energy-intensive process. However, this relationship will not persist indefinitely. I propose that as Bitcoin matures into a widely adopted monetary system, its price will decouple from mining production costs and instead oscillate in accordance with natural business cycles, much like traditional forms of money.
Bitcoin’s Price and the Power Law
 Source and Credit: Giovanni Santostasi’s “The Bitcoin Power Law”
Source and Credit: Giovanni Santostasi’s “The Bitcoin Power Law”When Bitcoin’s price is plotted on a logarithmic scale against time, a strikingly straight-line trajectory appears, punctuated by cycles of rapid price expansion (bull markets) followed by severe corrections (bear markets). These perturbations correspond to Bitcoin’s well-known halving cycles, which occur approximately every four years and reduce the block reward paid to miners, effectively doubling the cost of production per Bitcoin. Historically, Bitcoin’s price has always returned to a fundamental minimum—one that closely aligns with the average cost of mining.
This observation suggests that Bitcoin’s power law price behavior is not arbitrary but rather a reflection of its fundamental energy constraints. As in many natural systems governed by power laws, energy dynamics play a central role. In Bitcoin’s case, the “base layer” of its valuation is determined by the energy and computational resources required for mining. This power law behavior is therefore a consequence of Bitcoin’s fundamental design: as block subsidies decrease and mining efficiency improves, the minimum sustainable price follows an upward trajectory dictated by production costs.
Bitcoin as an Energy-Based System
Power laws commonly emerge in natural systems involving energy constraints, from thermodynamics to biological ecosystems and planetary dynamics. Bitcoin, as an energy-based monetary system, exhibits similar characteristics. Mining requires significant electricity and computational power, and as the difficulty adjustment ensures a competitive equilibrium, the cost of mining a Bitcoin remains closely tied to its market value over the long run.
Unlike traditional fiat currencies, which are controlled by central banks and subject to arbitrary monetary expansion, Bitcoin’s supply schedule is immutable. Its economic foundation is rooted in proof of work, where value is derived from energy expenditure. This fundamental linkage between energy and price explains why Bitcoin’s valuation has adhered to a power law trajectory. It is an entropy engine, and follows physical laws related to energy and entropy.
However, this pattern is not a permanent feature of Bitcoin’s monetary future—it is, rather, an indication of Bitcoin’s early-stage monetization process.
The Transition from Mining-Based Pricing to a Business Cycle
A crucial implication of Bitcoin’s price following a power law dictated by mining costs is that it suggests Bitcoin has yet to fully mature as money. If Bitcoin were already a widely adopted monetary standard, its valuation would no longer be primarily influenced by the floor mining costs but instead by macroeconomic forces—specifically, the natural fluctuations of the business cycle.
In a world where Bitcoin is the dominant global currency, the “price of money” (which correlates with the cost of capital and prevailing interest rates) would fluctuate according to the broader economic cycle. The dynamics would resemble those of natural interest rate cycles described by the Austrian School of Economics:
- During periods of economic expansion, lower interest rates spur increased investment and consumption, prices slightly rise, and savings deplete.
- As savings decline and prices rise, interest rates naturally rise as well, leading to reduced investment and spending, initiating a contractionary phase and lowered prices.
- During the contraction, savings accumulate, more capital becomes available, and interest rates and prices decline.
- With the availability of capital, lower interest rates and lowered prices, the economy is now ready to enter a phase of investment and expansion once again.
- This oscillatory process continues indefinitely, driven by real economic growth rather than central bank intervention.
If Bitcoin were fully monetized, its price would no longer oscillate based on mining halvings and energy costs but instead reflect economic expansion and contraction cycles—just as traditional currencies do when not artificially manipulated by central banks.
The Early Stage Indicator: Bitcoin’s Dependence on Mining Costs
Today, Bitcoin’s price still “bounces” off the power law baseline, indicating that its valuation remains primarily anchored to its minimum cost of production. This means that, while Bitcoin is widely recognized as an asset, it has not yet reached the level of adoption where its price is dictated by macroeconomic cycles.
A future in which Bitcoin is used as a primary medium of exchange and unit of account would necessarily imply a decoupling from mining-driven pricing. Instead of periodic halvings triggering speculative bull runs followed by crashes, Bitcoin’s price would become far more stable, with fluctuations primarily driven by business cycle dynamics. The continued adherence to the power law model, therefore, is evidence that Bitcoin is still in an early phase of adoption—where mining remains a primary determinant of price.
Conclusion
Bitcoin’s price trajectory has long conformed to a power law, reflecting the underlying energy costs of mining. This characteristic, however, is likely not a permanent feature but rather a hallmark of Bitcoin’s early stage as an emerging monetary system. As adoption increases and Bitcoin becomes widely used as money, its price should transition away from being dictated by mining costs and should instead fluctuate according to the natural oscillations of the business cycle.
The persistence of Bitcoin’s power law trend is a sign that it remains in its infancy. The real transformation will occur when Bitcoin is no longer bound to its production cost but is instead driven by the natural ebb and flow of savings, investment, and capital cycles—marking its full emergence as a global monetary system.
Disclaimer: The information provided in this blog is for informational and educational purposes only and should not be construed as financial advice. Please consult with a financial advisor or conduct your own research before making any financial decisions.
-
 @ d4309e24:8a81fcb0
2025-02-09 00:16:55
@ d4309e24:8a81fcb0
2025-02-09 00:16:551. What if You Could Send a Message into the Future?
Imagine leaving a message for your future self, a loved one, or even an entire community—one that no one, not even you, can unlock until a specific moment in time. Picture leaving a message for your children, a note of wisdom or love that remains hidden until they're old enough to appreciate it, all timed by Bitcoin's block height. You might also make a bold prediction about the future price of Bitcoin, sealing it away until the blockchain reaches a certain block height.
This is the idea behind Hatchstr, a decentralized app for time-locked messages that only unlock at predetermined Bitcoin block heights—no central authority required.
Why Build This?
I want to dive into the Nostr protocol not just by reading documentation, but by actually building something that embodies its core principles: censorship resistance, user ownership, and decentralization. Hatchstr is both an experiment and a contribution to the Nostr ecosystem—a way to test the limits of permissionless communication while learning and engaging with the community.
2. The Vision: How Hatchstr Would Work for Users
At its core, Hatchstr lets users create time capsules—encrypted messages that only become readable after a specified Bitcoin block height. Here’s what that looks like:
- You design a capsule with text and images using Hatchstr’s web app.
- You pick an unlock time (e.g., 1000 blocks from now).
- The message is encrypted, locked away, and published as a Nostr event.
- At the chosen time, the decryption key is revealed, allowing the recipient to finally access the message.

Potential Use Cases
-
Personal Messages: Send birthday wishes that unlock at midnight, time-delayed love letters, or notes to your future self.
-
Timed Learning: Lock educational content to unlock when students reach key learning stages or ages.
-
Creative Storytelling: Release serialized fiction, riddles, or treasure hunt clues that unlock over time.
-
Community & Events: Time-gate announcements for Nostr-based communities or scheduled voting mechanisms.
3. The Centralized Trap: Why Build on Nostr
When thinking about how to implement this, we could go the obvious, easy route:
- Store messages on a centralized server.
- Release them when the time is right.
- Let users download their messages.
Simple, right? But is it the right approach? Let's break it down.
Why This Fails
-
Single Point of Failure: If my server goes down, all messages are unavailable.
-
Privacy Risks: Users would need to trust me not to access their messages.
-
Ownership & Longevity: What happens if I lose interest? The system dies with me.

A centralized model defeats the purpose of time-locking messages. Users shouldn’t have to trust a third party. We need decentralization.
4. Nostr to the Rescue: How Decentralization Can Help
Instead of a single server holding messages hostage, Nostr allows users to publish messages to decentralized relays. Here are the key differences:
-
Nostr IDs = Self-Owned Identities: Your public key is your identity, not tied to any company.
-
Relays = Decentralized Bulletin Boards: Anyone can run one, ensuring redundancy and censorship resistance.
-
Messages = Signed Events: Cryptographically signed by the sender or encrypted for only the recipient.

How Nostr Reduces Centralization
In this version of Hatchstr, capsules are still stored in a centralized manner at first until they 'hatch'. However, once the Bitcoin block height condition is met:
- Capsule Publication: The system publishes the capsule events to Nostr relays, making the messages available for decryption by the intended recipients.
This approach, while not eliminating the central server, allows for:
-
Third-Party Clients: Developers can now create clients that interact with Hatchstr capsules on Nostr, enhancing the system's openness and potentially leading to a richer ecosystem around time-locked messages.
-
Decentralized Access: Even though the initial storage is centralized, the access to the messages becomes decentralized once published to Nostr, reducing the dependency on a single point for message retrieval.
We have some improvements, but I am sure we can do better!
5. The Path to Decentralized Timekeeping
The Timeless Nature of Encryption
Encrypted messages exist outside time—once locked, they remain secure indefinitely. Modern cryptography (like AES-256) doesn’t "expire" or weaken unless decrypted (excluding brute force attacks). This creates a paradox: How do you bind something timeless to a specific moment in the physical world?
The Time-Lock Puzzle Dilemma
Cryptographers have proposed time-lock puzzles—encryption that requires sustained computation to unlock, theoretically forcing a minimum wait time. But these face critical hurdles:
-
Hardware Uncertainty
Solving time depends on an attacker’s computational power. A nation-state could crack in hours what takes years for a regular user. -
No Real-World Alignment
Puzzles can’t guarantee unlocks align with calendar dates or real-world events ("unlock on my child’s 18th birthday"). -
Energy Waste
Requires continuous computation, making it environmentally impractical for longer time locking.
Bitcoin as a Decentralized Clock
This is where Bitcoin’s blockchain shines. Its difficulty-adjusted proof-of-work acts as a trustless metronome:
-
Predictable Rhythm
Despite hash rate fluctuations, the 10-minute block target (via difficulty adjustments) creates a consistent approximation of real-world time.
-
Immutable History
Block height 1,000,000 will always correspond to the same point in Bitcoin’s timeline, regardless of future changes in mining power
Splitting the Problem
Hatchstr can bridge timeless encryption and blockchain timing by separating concerns:
1. Capsules – The time-locked message itself:
-
Design independent of the time-locking mechanism.
-
Encrypted client-side.
-
Content stored anywhere the user wants (IPFS, personal servers, etc.).
-
Completely owned by the user—not Hatchstr.
2. Clock Servers – Independent, lightweight timing nodes that:
-
Only publish decryption keys when the target Bitcoin block height is reached.
-
Users can choose which Clock Server to trust.
-
Anyone can run their own Clock Server.
-
Multiple servers can coordinate to prevent a single point of failure.

This means Hatchstr itself doesn’t store anything—users are fully in control.
6. What Comes Next
This project is just beginning—a blueprint with open questions and untested assumptions. In the next two articles, I’ll explore how to turn this concept into something tangible. First, how we might design playful time capsules that can be displayed faithfully by multiple clients, balancing creativity with decentralization. Then, the messy realities of clock servers: why federating them matters, how to incentivize reliability, and borrow Bitcoin’s rhythm without centralizing control. We will dive into setting up a simple clock server to get things started.
I’m still learning Nostr’s ecosystem, and this project is as much about sharing my education as anything else. If any part of this concept makes you think “yes, but…” or “what if…”, I’d genuinely love to hear it. Find me on Nostr – no expertise required, just an interest in sending messages to the future. :

npub16scfufrpsqcukjg7ymu4r40h7j4dwqy4pajgz48e6lmnmz5pljcqh678uhThank you for reading 🧡
-
 @ 3f770d65:7a745b24
2025-04-21 00:15:06
@ 3f770d65:7a745b24
2025-04-21 00:15:06At the recent Launch Music Festival and Conference in Lancaster, PA, featuring over 120 musicians across three days, I volunteered my time with Tunestr and Phantom Power Music's initiative to introduce artists to Bitcoin, Nostr, and the value-for-value model. Tunestr sponsored a stage, live-streaming 21 bands to platforms like Tunestr.io, Fountain.fm and other Nostr/Podcasting 2.0 apps and on-boarding as many others as possible at our conference booth. You may have seen me spamming about this over the last few days.
V4V Earnings
Day 1: 180,000 sats
Day 2: 300,000 sats
Day 3: Over 500,000 sats
Who?
Here are the artists that were on-boarded to Fountain and were live streaming on the Value-for-Value stage:
nostr:npub1cruu4z0hwg7n3r2k7262vx8jsmra3xpku85frl5fnfvrwz7rd7mq7e403w nostr:npub12xeh3n7w8700z4tpd6xlhlvg4vtg4pvpxd584ll5sva539tutc3q0tn3tz nostr:npub1rc80p4v60uzfhvdgxemhvcqnzdj7t59xujxdy0lcjxml3uwdezyqtrpe0j @npub16vxr4pc2ww3yaez9q4s53zkejjfd0djs9lfe55sjhnqkh nostr:npub10uspdzg4fl7md95mqnjszxx82ckdly8ezac0t3s06a0gsf4f3lys8ypeak nostr:npub1gnyzexr40qut0za2c4a0x27p4e3qc22wekhcw3uvdx8mwa3pen0s9z90wk nostr:npub13qrrw2h4z52m7jh0spefrwtysl4psfkfv6j4j672se5hkhvtyw7qu0almy nostr:npub1p0kuqxxw2mxczc90vcurvfq7ljuw2394kkqk6gqnn2cq0y9eq5nq87jtkk nostr:npub182kq0sdp7chm67uq58cf4vvl3lk37z8mm5k5067xe09fqqaaxjsqlcazej nostr:npub162hr8kd96vxlanvggl08hmyy37qsn8ehgj7za7squl83um56epnswkr399 nostr:npub17jzk5ex2rafres09c4dnn5mm00eejye6nrurnlla6yn22zcpl7vqg6vhvx nostr:npub176rnksulheuanfx8y8cr2mrth4lh33svvpztggjjm6j2pqw6m56sq7s9vz nostr:npub1akv7t7xpalhsc4nseljs0c886jzuhq8u42qdcwvu972f3mme9tjsgp5xxk nostr:npub18x0gv872489lrczp9d9m4hx59r754x7p9rg2jkgvt7ul3kuqewtqsssn24
Many more musicians were on-boarded to Fountain, however, we were unable to obtain all of their npubs.
THANK YOU TO ALL ZAPPERS AND BOOSTERS!
Musicians “Get It”
My key takeaway was the musicians' absolute understanding that the current digital landscape along with legacy social media is failing them. Every artist I spoke with recognized how algorithms hinder fan connection and how gatekeepers prevent fair compensation for their work. They all use Spotify, but they only do so out of necessity. They felt the music industry is primed for both a social and monetary revolution. Some of them were even speaking my language…
Because of this, concepts like decentralization, censorship resistance, owning your content, and controlling your social graph weren't just understood by them, they were instantly embraced. The excitement was real; they immediately saw the potential and agreed with me. Bitcoin and Nostr felt genuinely punk rock and that helped a lot of them identify with what we were offering them.
The Tools and the Issues
While the Nostr ecosystem offers a wide variety of tools, we focused on introducing three key applications at this event to keep things clear for newcomers:
- Fountain, with a music focus, was the primary tool for onboarding attendees onto Nostr. Fountain was also chosen thanks to Fountain’s built-in Lightning wallet.
- Primal, as a social alternative, was demonstrated to show how users can take their Nostr identity and content seamlessly between different applications.
- Tunestr.io, lastly was showcased for its live video streaming capabilities.
Although we highlighted these three, we did inform attendees about the broader range of available apps and pointed them to
nostrapps.comif they wanted to explore further, aiming to educate without overwhelming them.This review highlights several UX issues with the Fountain app, particularly concerning profile updates, wallet functionality, and user discovery. While Fountain does work well, these minor hiccups make it extremely hard for on-boarding and education.
- Profile Issues:
- When a user edits their profile (e.g., Username/Nostr address, Lightning address) either during or after creation, the changes don't appear to consistently update across the app or sync correctly with Nostr relays.
- Specifically, the main profile display continues to show the old default Username/Nostr address and Lightning address inside Fountain and on other Nostr clients.
- However, the updated Username/Nostr address does appear on https://fountain.fm (chosen-username@fountain.fm) and is visible within the "Edit Profile" screen itself in the app.
- This inconsistency is confusing for users, as they see their updated information in some places but not on their main public-facing profile within the app. I confirmed this by observing a new user sign up and edit their username – the edit screen showed the new name, but the profile display in Fountain did not update and we did not see it inside Primal, Damus, Amethyst, etc.
- Wallet Limitations:
- The app's built-in wallet cannot scan Lightning address QR codes to initiate payments.
- This caused problems during the event where users imported Bitcoin from Azte.co vouchers into their Fountain wallets. When they tried to Zap a band by scanning a QR code on the live tally board, Fountain displayed an error message stating the invoice or QR code was invalid.
- While suggesting musicians install Primal as a second Nostr app was a potential fix for the QR code issue, (and I mentioned it to some), the burden of onboarding users onto two separate applications, potentially managing two different wallets, and explaining which one works for specific tasks creates a confusing and frustrating user experience.
- Search Difficulties:
- Finding other users within the Fountain app is challenging. I was unable to find profiles from brand new users by entering their chosen Fountain username.
- To find a new user, I had to resort to visiting their profile on the web (fountain.fm/username) to retrieve their npub. Then, open Primal and follow them. Finally, when searching for their username, since I was now following them, I was able to find their profile.
- This search issue is compounded by the profile syncing problem mentioned earlier, as even if found via other clients, their displayed information is outdated.
- Searching for the event to Boost/Zap inside Fountain was harder than it should have been the first two days as the live stream did not appear at the top of the screen inside the tap. This was resolved on the third day of the event.
Improving the Onboarding Experience
To better support user growth, educators and on-boarders need more feature complete and user-friendly applications. I love our developers and I will always sing their praises from the highest mountain tops, however I also recognize that the current tools present challenges that hinder a smooth onboarding experience.
One potential approach explored was guiding users to use Primal (including its built-in wallet) in conjunction with Wavlake via Nostr Wallet Connect (NWC). While this could facilitate certain functions like music streaming, zaps, and QR code scanning (which require both Primal and Wavlake apps), Wavlake itself has usability issues. These include inconsistent or separate profiles between web and mobile apps, persistent "Login" buttons even when logged in on the mobile app with a Nostr identity, and the minor inconvenience of needing two separate applications. Although NWC setup is relatively easy and helps streamline the process, the need to switch between apps adds complexity, especially when time is limited and we’re aiming to showcase the benefits of this new system.
Ultimately, we need applications that are more feature-complete and intuitive for mainstream users to improve the onboarding experience significantly.
Looking forward to the future
I anticipate that most of these issues will be resolved when these applications address them in the near future. Specifically, this would involve Fountain fixing its profile issues and integrating Nostr Wallet Connect (NWC) to allow users to utilize their Primal wallet, or by enabling the scanning of QR codes that pay out to Lightning addresses. Alternatively, if Wavlake resolves the consistency problems mentioned earlier, this would also significantly improve the situation giving us two viable solutions for musicians.
My ideal onboarding event experience would involve having all the previously mentioned issues resolved. Additionally, I would love to see every attendee receive a $5 or $10 voucher to help them start engaging with value-for-value, rather than just the limited number we distributed recently. The goal is to have everyone actively zapping and sending Bitcoin throughout the event. Maybe we can find a large sponsor to facilitate this in the future?
What's particularly exciting is the Launch conference's strong interest in integrating value-for-value across their entire program for all musicians and speakers at their next event in Dallas, Texas, coming later this fall. This presents a significant opportunity to onboard over 100+ musicians to Bitcoin and Nostr, which in turn will help onboard their fans and supporters.
We need significantly more zaps and more zappers! It's unreasonable to expect the same dedicated individuals to continuously support new users; they are being bled dry. A shift is needed towards more people using bitcoin for everyday transactions, treating it as money. This brings me back to my ideal onboarding experience: securing a sponsor to essentially give participants bitcoin funds specifically for zapping and tipping artists. This method serves as a practical lesson in using bitcoin as money and showcases the value-for-value principle from the outset.
-
 @ fd208ee8:0fd927c1
2025-02-02 10:33:19
@ fd208ee8:0fd927c1
2025-02-02 10:33:19GitCitadel Development Operations
We, at GitCitadel, have been updating, moving, and rearranging our servers, for quite some time. As a rather large, complex, sprawling project, we have the infrastructure setup to match, so we've decided to give you all a quick run-down of what we are doing behind-the-scenes.
Supplier Coordination

Our first task, this week, was figuring out who would host what where. We have four different locations, where our infra is stored and managed, including two locations from our suppliers. We got that straightened out, quickly, and it's all slowly coming together and being connected and networked. Exciting to watch our DevOps landscape evolve and all of the knowledge-transfer that the interactions provide.
OneDev Implementation

Our biggest internal infra project this week was the migration of all of our issues from Jira, build scripts from Jenkins, and repos from GitHub to a self-hosted OneDev instance. In the future, all of our internal build, test, issue, patch/PR, etc. effort will take place there. We also have a separate repo there for communicating with external developers and suppliers.
Our team's GitHub projects will be demoted to mirrors and a place for external devs to PR to. Public issues and patches will continue to be managed over our self-hosted GitWorkshop instance.
We're especially glad to finally escape the GitHub Gulag, and avoid being bled dry by Jira fees, without having to give up the important features that we've come to know and love. So, yay!
Next Infrasteps
Automated Testing
Now, that we have everything tied up in one, neat, backed-up package, we can finally move on to the nitty-gritty and the dirty work. So, we're rolling up our sleeves and writing the Selenium smoke test for our Alexandria client. We'll be running that in Docker containers containing different "typical Nostr" images, such as Chrome browser with Nostr Connect signing extension, or Firefox browser with Nos2x-fox extension. Once we get the Nsec Bunker and Amber logins going, we'll add test cases and images for them, as well. (Yes, we can do Bunker. I hope you are in awe at our powers).
We are also designing an automated infrastructure test, that will simply rattle through all the various internal and external websites and relays, to make sure that everything is still online and responsive.
After that, a Gherkin-based Behave feature test for Alexandria is planned, so that we can prevent regression of completed functionality, from one release to the next.
The Gherkin scenarios are written and attached to our stories before development begins (we use acceptance tests as requirements), a manual test-execution is then completed, in order to set the story to Done. These completed scenarios will be automated, following each release, with the resulting script linked to from the origin story.

Automated Builds
As the crowning glory of every DevOps tool chain stands the build automation. This is where everything gets tied together, straightened out, configured, tested, measured, and -- if everything passes the quality gates -- released. I don't have to tell you how much time developers spend staring at the build process display, praying that it all goes through and they can celebrate a Green Wave.

We are currently designing the various builds, but the ones we have defined for the Alexandria client will be a continuous delivery pipeline, like so:

This will make it easier for us to work and collaborate asynchronously and without unnecessary delays.
Expanding the Status Page

And, finally, we get to the point of all of this busyness: reporting.
We are going to have beautiful reports, and we are going to post them online, on our status page. We will use bots, to inform Nostriches of the current status of our systems, so go ahead and follow our GitCitadel DevOps npub, to make sure you don't miss out on the IT action.
Building on stone
All in all, we're really happy with the way things are humming along, now, and the steady increase in our productivity, as all the foundational work we've put in starts to pay off. It's getting easier and easier to add new team members, repos, or features/fixes, so we should be able to scale up and out from here. Our GitCitadel is built on a firm foundation.
Happy building!
-
 @ 57d1a264:69f1fee1
2025-05-01 05:01:45
@ 57d1a264:69f1fee1
2025-05-01 05:01:45 -
 @ 961e8955:d7fa53e4
2025-02-01 23:20:53
@ 961e8955:d7fa53e4
2025-02-01 23:20:53"@YakiHonne community partners successfully convened a seminal Nostr101 meetup in Barnawa, Nigeria! Donning bespoke YakiHonne Nigeria Limited Edition T-shirts, the Purple Army infused the town with infectious energy.
Facilitated by @Olaoluwa Ezekiel Michael, this gathering leveraged YakiHonne's decentralized platform to foster unbridled dialogue, idea exchange, and community engagement.
The event's resounding success underscores the burgeoning demand for decentralized solutions in Africa. This milestone marks the inception of a revolutionary movement, empowering voices and fostering collaboration throughout the continent.
Nostr #DecentralizedRevolution #Africa #CommunityFirst #YakiHonne"
-
 @ 83279ad2:bd49240d
2025-04-20 08:39:12
@ 83279ad2:bd49240d
2025-04-20 08:39:12Hello
-
 @ e111a405:fa441558
2025-01-26 18:25:59
@ e111a405:fa441558
2025-01-26 18:25:59OpenAI released its new o3 models and numerous people argue that this is in fact Artificial General Intelligence (AGI) – in other words, an AI system that is on par with human intelligence. Even if o3 is not yet AGI, the emphasis now lies on “yet,” and – considering the exponential progression – we can expect AGI to arrive within months or maximum one to two years.
According to OpenAI, it only took 3 months to go from the o1 model to the o3 model. This is a 4x+ acceleration relative to previous progress. If this speed of AI advancement is maintained, it means that by the end of 2025 we will be as much ahead of o3 as o3 is ahead of GPT-3 (released in May 2020). And, after achieving AGI, the self-reinforcing feedback loop will only further accelerate exponential improvements of these AI systems.
But, most anti-intuitively, even after we have achieved AGI, it will for quite some time look as if nothing has happened. You won’t feel any change and your job and business will feel safe and untouchable. Big fallacy. We can expect that after AGI it will take many months of not 1-2 years for the real transformations to happen. Why? Because AGI in and of itself does not release value into the economy. It will be much more important to apply it. But as AGI becomes cheaper, agentic, and embedded into the world, we will see a transformation-explosion – replacing those businesses and jobs that are unprepared.
I thought a lot about the impact the announced – and soon to be released – o3 model, and the first AGI model are going to have.
To make it short: I am extremely confident that any skill or process that can be digitized will be. As a result, the majority of white-collar and skilled jobs are on track for massive disruption or elimination.
Furthermore, I think many experts and think tanks are fooling themselves by believing that humans will maintain “some edge” and work peacefully side-by-side with an AI system. I don’t think AGI will augment knowledge workers – i.e. anyone working with language, code, numbers, or any kind of specialized software – it will replace them!
So, if your job or business relies purely on standardized cognitive tasks, you are racing toward the cliff’s edge, and it is time to pivot now!
Let’s start with the worst. Businesses and jobs in which you should pivot immediately – or at least not enter as of today – include but are not limited to anything that involves sitting at a computer:
- anything with data entry or data processing (run as fast as you can!)
- anything that involves writing (copywriting, technical writing,
- editing, proofreading, translation)
- most coding and web development
- SAAS (won’t exist in a couple of years)
- banking (disrupted squared: AGI + Blockchain)
- accounting and auditing (won’t exist as a job in 5-10 years)
- insurance (will be disrupted)
- law (excluding high-stake litigation, negotiation, courtroom advocacy)
- any generic design, music, and video creation (graphic design, stock photography, stock videos)
- market and investment research and analysis (AI will take over 100%)
- trading, both quantitative and qualitative (don’t exit but profit now, but expect to be disrupted within 5 years)
- any middle-layer-management (project and product management)
- medical diagnostics (will be 100% AI within 5 years)
- most standardized professional / consulting services
However, I believe that in high-stakes domains (health, finance, governance), regulators and the public will demand a “human sign-off”. So if you are in accounting, auditing, law, or finance I’d recommend pivoting to a business model where the ability to anchor trust becomes a revenue source.
The question is, where should you pivot to or what business to start in 2025?
My First Principles of a Post-AGI Business Model
First, even as AI becomes infallible, human beings will still crave real, raw, direct trust relationships. People form bonds around shared experiences, especially offline ones. I believe a truly future-proof venture leverages these primal instincts that machines can never replicate at a deeply visceral level. Nevertheless, I believe it is a big mistake to assume that humans will “naturally” stick together just because we are the same species. AGI might quickly appear more reliable, less selfish than most human beings, and have emotional intelligence. So a business build upon the thesis of the “human advantage” must expertly harness and establish emotional ties, tribal belonging, and shared experiences – all intangible values that are far more delicate and complex than logic.
First Principle: Operate in the Physical World
If your product or service can be fully digitalized and delivered via the cloud, AGI can replicate it with near-zero marginal cost Infuse strategic real-world constraints (logistics, location-specific interactions, physical limitations, direct relationships) that create friction and scarcity – where AI alone will struggle
Second Principle: Create Hyper Niche Human Experiences
- The broader audience, the easier it is for AI to dominate. Instead, cultivate specialized groups and subcultures with strong in-person and highly personalized experiences.
- Offer creative or spiritual elements that defy pure rational patterns and thus remain less formulaic
Third Principle: Emphasize Adaptive, Micro-Scale Partnerships
- Align with small, local, or specialized stakeholders. Use alliances with artisan suppliers, local talents, subject-matter experts, and so on.
- Avoid single points of failure; build a decentralized network that is hard for a single AI to replicate or disrupt
Fourth Principle: Embed Extreme Flexibility
- Structured, hierarchical organizations are easily out-iterated by AI that can reorganize and optimize instantly
- Cultivate fluid teams with quickly reconfigurable structures, use agile, project based collaboration that can pivot as soon AGI-based competition arises
Opportunity Vectors
With all of that in mind, there are niches that before looked unattractive, because less scalable, that today offer massive opportunities – let’s call them opportunity vectors.
The first opportunity vector I have already touched upon:
Trust and Validation Services: Humans verifying or certifying that a certain AI outcome is ethically or legally sound – while irrational, it is exactly what humans will insist on, particularly where liability is high (medicine, finance, law, infrastructure)
Frontier Sectors with Regulatory and Ethical Friction: Think of markets where AI will accelerate R&D but human oversight, relationship management, and accountability remain essential: genetic engineering, biotech, advanced materials, quantum computing, etc.
The second opportunity vector focuses on the human edge:
- Experience & Community: Live festivals, immersive events, niche retreats, or spiritual explorations – basically any scenario in which emotional energy and a human experience is the core product - Rare Craftsmanship & Creative Quirks: Think of hyper-personalized items, physical artwork, artisanal or hands-on creations. Items that carry an inherent uniqueness or intangible meaning that an AI might replicate in design, but can’t replicate in “heritage” or provenance.
Risk Tactics
Overall, the best insurance is fostering a dynamic brand and a loyal community that invests personally and emotionally in you. People will buy from those whose values they trust. If you stand for something real, you create an emotional bond that AI can’t break. I’m not talking about superficial corporate social responsibility (nobody cares) but about authenticity that resonates on a near-spiritual level.
As you build your business, erect an ethical moat by providing “failsafe” services where your human personal liability and your brand acts as a shield for AI decisions. This creates trust and differentiation among anonymous pure-AGI play businesses.
Seek and create small, specialized, local, or digital micro-monopolies – areas too tiny or fractal for the “big AI players” to devote immediate resources to. Over time, multiply these micro-monopolies by rolling them up under one trusted brand.
Furthermore, don’t avoid AI. You cannot out-AI the AI. So as you build a business on the human edge moat, you should still harness AI to do 90% of the repetitive and analytic tasks – this frees your human capital to build human relationships, solve ambiguous problem, or invent new offerings.
Bet on What Makes Us Human
To summarize, AI is logical, combinatorial intelligence. The advancements in AI will commoditize logic and disrupt any job and business that is mainly build upon logic as capital. Human – on the other hand – is authenticity. What makes human human and your brand authentic are elements of chaos, empathy, spontaneity. In this context, human is fostering embodied, emotional, culturally contextual, physically immersive experiences. Anything that requires raw creativity, emotional intelligence, local presence, or unique personal relationships will be more AI resilient.
Therefore, a Post-AGI business must involve:
- Tangibility: Physical goods, spaces, unique craftsmanship
- Human Connection: Emotional, face-to-face, improvisational experiences
- Comprehensive Problem Solving: Complex negotiations, messy real-world situations, diverse stakeholder management
The inverse list of AGI proof industries involve some or multiple aspects of that:
Physical, In-Person, Human-Intensive Services - Healthcare: Nursing, Physical therapy, Hands-on caregiving - Skilled trades & craftsmanship
High-Level Strategy & Complex Leadership - Diplomacy, Negotiation, Trust building - Visionary entrepreneurship
Deep Emotional / Experiential Offerings - Group experiences, retreats, spiritual or therapeutic gatherings - Artistic expression that thrives on “imperfection”, physical presence, or spontaneous creativity
Infrastructure for AGI - Human-based auditing/verification - Physical data center operations & advanced hardware - Application and embedment of AI in the forms of AGI agents, algorithmic improvements, etc. to make it suitable for everyday tasks and workflow
The real differentiator is whether a business is anchored in the physical world’s complexity, emotional trust, or intangible brand relationships. Everything pure data-driven or standardized is on the chopping block – imminently.
-
 @ 1bc70a01:24f6a411
2025-04-19 09:58:54
@ 1bc70a01:24f6a411
2025-04-19 09:58:54Untype Update
I cleaned up the AI assistant UX. Now you can open it in the editor bar, same as all other actions. This makes it a lot easier to interact with while having access to normal edit functions.
AI-generated content
Untype uses OpenRouter to connect to various models to generate just about anything. It doesn't do images for now, but I'm working on that.
Automatic Title, Summary and Tag Suggestions
Added the functionality to generate titles, summaries and tags with one click.
A Brief Preview
Here is a little story I generated in Untype, ABOUT Untype:
This story was generated in Untype
Once upon a time, in the bustling digital city of Techlandia, there lived a quirky AI named Untype. Unlike other software, Untype wasn't just your everyday article composer — it had a nose for news, quite literally. Untype was equipped with a masterful talent for sniffing out the latest trends and stories wafting through the vast digital ether.
Untype had a peculiar look about it. Sporting a gigantic nose and a pair of spectacles perched just above it, Untype roamed the virtual city, inhaling the freshest gossip and spiciest stories. Its nostr-powered sensors twitched and tickled as it encountered every new scent.
One day, while wandering around the pixelated park, Untype caught a whiff of something extraordinary — a scandalous scoop involving Techlandia's mayor, Doc Processor, who had been spotted recycling old memes as new content. The scent trail was strong, and Untype's nose twitched with excitement.
With a flick of its AI function, Untype began weaving the story into a masterpiece. Sentences flowed like fine wine, infused with humor sharper than a hacker’s focus. "Doc Processor," Untype mused to itself, "tried to buffer his way out of this one with a cache of recycled gifs!"
As Untype typed away, its digital friends, Grammarly the Grammar Gremlin and Canva the Artful Pixie, gathered around to watch the genius at work. "You truly have a knack for news-sniffing," complimented Grammarly, adjusting its tiny monocle. Canva nodded, painting whimsical illustrations to accompany the hilarious exposé.
The article soon spread through Techlandia faster than a virus with a strong wifi signal. The townsfolk roared with laughter at Untype’s clever wit, and even Doc Processor couldn't help but chuckle through his embarrassment.
From that day on, Untype was celebrated not just as a composer but as Techlandia's most revered and humorous news-sniffer. With every sniff and click of its AI functions, Untype proved that in the world of digital creations, sometimes news really was just a nose away.
-
 @ 5df413d4:2add4f5b
2025-05-01 02:22:31
@ 5df413d4:2add4f5b
2025-05-01 02:22:31Blank
-
 @ 9bcc5462:eb501d90
2025-01-10 19:42:28
@ 9bcc5462:eb501d90
2025-01-10 19:42:28Cuneiform is mankind’s first writing system created by the ancient Sumerians of Mesopotamia, what is now Iraq. (The word “Sumer” means land of civilized kings). Despite being developed 5,000 years ago, its parallels to Notes and Other Stuff Transmitted by Relays will blow your mind! The most striking is how both breakthroughs materialized from the fundamental need to track value exchange–from primal grain tallies to now exchanging bitcoin.
Let’s begin with the fact that the styluses used by these archaic scribes were crafted from reed plants. Their stems were strong because of attachment points called nodes! These were the resilient, ring-like parts of the stem that joined it together with the rest of the plant. Similarly, although symbolically, lightning nodes are powerful on nostr since they allow us to zap each other with sats. An approach stemming from the need to modernize how we interact on social media, trade in networks and conduct business—It’s not surprising cuneiform came about as a way for merchants and farmers to track economic transactions and agricultural inventories!
Another parallel involves how both share everlasting marks. The Sumerians used their styluses to press wedge-like symbols onto wet tablets. They then would bake them in the sun, leaving a permanent record of the documentation. If an error was made, it could not be changed. Likewise, on nostr there is no delete function. Once you publish a note, including any typos, it is preserved for history.
Lastly, the proto-writing that emerged in Mesopotamia which led to Cuneiform was in the form of bullae (bulla: singular). These were spherical clay envelopes encased with tokens representing a transaction. They were sealed with unique markings representing the parties involved for authentication. In other words, cuneiform cylinder seals were effectively early public key cryptography! The seal itself being the private key and its impression being the public key. Just as us nostriches use our nsec to sign our notes with integrity and verify value-for-value with our npub.

*Rare bulla seal (shout out to Conny Waters from ancientpages.com)*
*Sumerian cuneiform tablet (source: britannica.com)*At the end of the day, maybe we’re not so different from our ancestors after all. The evolution of our writing technology over the course of our history is more than innovation born of necessity. Across millennia, 3025 BCE to 2025 AD, it's man telling the universe– we will be remembered– beyond space and time. As our ancestors stacked their clay tablets, we’ll stack our sats! Onward nostr! The new land of civilized kings.

*Mankind's Innovations in Writing Technology by Learning Producers, Inc.* -
 @ d830ee7b:4e61cd62
2025-01-08 07:56:25
@ d830ee7b:4e61cd62
2025-01-08 07:56:25การเผชิญหน้า (The Collision Point)
กลางปี 2017 ที่ร้านคราฟท์เบียร์เล็ก ๆ ในย่านเกาะเกร็ด นนทบุรี อากาศร้อนจนเครื่องปรับอากาศ (ที่ยังไม่มี) ในร้านทำงานหนักแทบไหม้ "แจ๊ก กู้ดเดย์" (Jakk Goodday) นั่งลงบนเก้าอี้ไม้ที่เจ้าของร้านกันไว้ให้เป็นประจำ ราวกับเขาเป็นลูกค้าขาประจำระดับวีไอพี
กลิ่นกาแฟคั่ว ลอยผสมกับไอความร้อนจากนอกหน้าต่าง (ผิดร้านหรือเปล่า?) เกิดเป็นบรรยากาศขมติดปลายลิ้นชวนให้คนจิบแล้วอยากถอนใจ
เขาเหลือบมองออกไปนอกหน้าต่าง.. เห็นแสงแดดแผดเผาราวกับมันรู้ว่าสงคราม Blocksize กำลังคุกรุ่นขึ้นอีกครั้ง

บรรยากาศนอกหน้าต่างกับใน ฟอรัม Bitcointalk ช่างเหมือนกันจนน่าขนลุก มันร้อนแรง ไร้ความปรานี
แจ๊กเปิดแล็ปท็อป กดเข้าเว็บฟอรัม พอเสียงแจ้งเตือน “—ติ๊ง” ดังขึ้น คิ้วของเขาก็ขมวดเล็กน้อย คล้ายได้กลิ่นดินปืนกลางสนามรบ
“โรเจอร์ แวร์ (Roger Ver) ไลฟ์เดือดลั่นเวที!” “ปีเตอร์ วูเล (Pieter Wuille) โต้กลับเรื่อง SegWit!” “Hard Fork ใกล้ถึงจุดปะทะแล้ว!”
แจ๊กคลิกเข้าไปในลิงก์ของไลฟ์ทันที เหมือนมือของเขาไม่ต้องการคำสั่งจากสมอง ความคุ้นเคยกับเหตุการณ์แบบนี้บอกเขาว่า นี่ไม่ใช่ดีเบตธรรมดา แต่มันอาจเปลี่ยนอนาคตของ Bitcoin ได้จริง ๆ
เห็นแค่พาดหัวสั้น ๆ แต่ความตึงเครียดก็ชัดเจนขึ้นเรื่อย ๆ ทุกข้อความเหมือนสุมไฟใส่ใจกองหนึ่งที่พร้อมระเบิดได้ทุกเมื่อ
โทรศัพท์ของแจ๊กดังพร้อมปรากฏชื่อ แชมป์ ‘PIGROCK’ ลอยขึ้นมา เขาหยิบขึ้นมารับทันที
“ว่าไงวะแชมป์… มีอะไรด่วนหรือเปล่า?” น้ำเสียงแจ๊กฟังดูเหมือนง่วง ๆ แต่จริง ๆ เขาพร้อมจะลุกมาวิเคราะห์สถานการณ์ให้ฟังทุกเมื่อ
“พี่แจ๊ก.. ผมอ่านดีเบตเรื่อง SegWit ในฟอรัมอยู่ครับ บางคนด่าว่ามันไม่ได้แก้ปัญหาจริง ๆ บ้างก็บอกถ้าเพิ่ม Blocksize ไปเลยจะง่ายกว่า... ผมเลยสงสัยว่า Hard Fork ที่เค้าพูดถึงกันนี่คืออะไร ใครคิดอะไรก็ Fork กันได้ง่าย ๆ เลยเหรอ"
"แล้วถ้า Fork ไปหลายสาย สุดท้ายเหรียญไหนจะเป็น ‘Bitcoin ที่แท้จริง’ ล่ะพี่?”
“แล้วการ Fork มันส่งผลกับนักลงทุนยังไงครับ? คนทั่วไปอย่างผมควรถือไว้หรือขายหนีตายดีล่ะเนี่ย?”
แจ๊กยิ้มมุมปาก ชอบใจที่น้องถามจี้จุด
“เอางี้… การ Fork มันเหมือนแบ่งถนนออกเป็นสองสาย ใครชอบกติกาเก่าก็วิ่งถนนเส้นเก่า ใครอยากแก้กติกาใหม่ก็ไปถนนเส้นใหม่"
"แต่ประเด็นคือ... นี่ไม่ใช่เรื่องเล็ก ๆ เพราะมีผลต่ออัตลักษณ์ของ Bitcoin ทั้งหมดเลยนะมึง—ใครจะยอมปล่อยผ่านง่าย ๆ”
"คิดดูสิ ถ้าครั้งนี้พวกเขา Fork จริง มันอาจไม่ได้เปลี่ยนแค่เครือข่าย แต่เปลี่ยนวิธีที่คนมอง Bitcoin ไปตลอดกาลเลยนะ"
"แล้วใครมันจะอยากลงทุนในระบบที่แตกแยกซ้ำแล้วซ้ำเล่าวะ?"
“งั้นหมายความว่าตอนนี้ก็มีสองแนวใหญ่ ๆ ชัวร์ใช่ไหมครับ?” แชมป์ถามต่อ
“ฝั่ง โรเจอร์ แวร์ ที่บอกว่าต้องเพิ่ม Blocksize ให้ใหญ่จุใจ กับฝั่งทีม Core อย่าง ปีเตอร์ วูเล ที่ยืนยันต้องใช้ SegWit ทำให้บล็อกเบา ไม่กระทบการกระจายอำนาจ?”
“ใช่เลย” แจ๊กจิบกาแฟดำเข้ม ๆ ผสมน้ำผึ้งไปหนึ่งอึก
“โรเจอร์นี่เขาเชื่อว่า Bitcoin ต้องเป็นเงินสดดิจิทัลที่ใช้จ่ายไว ค่าธรรมเนียมไม่แพง ส่วนปีเตอร์กับ Bitcoin Core มองว่าการเพิ่มบล็อกเยอะ ๆ มันจะไปฆ่า Node รายย่อย คนไม่มีทุนก็รัน Node ไม่ไหว สุดท้าย Bitcoin จะกลายเป็นระบบกึ่งรวมศูนย์ ซึ่งมันผิดหลักการเดิมของ ซาโตชิ ไงล่ะ”
“ฟังแล้วก็ไม่ใช่เรื่องง่ายนะพี่… งั้นที่ผมได้ยินว่า จิฮั่น อู๋ (Jihan Wu) เจ้าของ Bitmain ที่ถือ Hashrate เกินครึ่งนี่ก็มาอยู่ฝั่งเดียวกับโรเจอร์ใช่ไหม?"
"เพราะยิ่งบล็อกใหญ่ ค่าธรรมเนียมยิ่งเพิ่ม นักขุดก็ได้กำไรสูงขึ้นใช่ป่ะ?”
“ไอ้เรื่องกำไรก็ส่วนหนึ่ง...” แจ๊กถอนหายใจ
“แต่ที่สำคัญกว่านั้นคืออำนาจต่อรอง… ตอนประชุมลับที่ฮ่องกงเมื่อปีที่แล้ว พี่เองก็ถูกชวนให้เข้าไปในฐานะคนกลาง เลยเห็นภาพน่าขนลุกอยู่หน่อย ๆ"
"จิฮั่นนั่งไขว่ห้างด้วยสีหน้ามั่นใจมาก ด้วย Hashrate ราว 60% ของโลก สั่งซ้ายหันขวาหันเหมือนเป็นแม่ทัพใหญ่ได้เลย พอโรเจอร์ก็ไฟแรงอยู่แล้ว อยากให้ Bitcoin ครองโลกด้วยวิธีของเขา สองคนนี่จับมือกันทีจะเขย่าชุมชน Bitcoin ได้ทั้งกระดาน”
"พี่รู้สึกเหมือนนั่งอยู่ในศึกชิงบัลลังก์ยุคใหม่ คนหนึ่งยึดพลังขุด คนหนึ่งยึดความศรัทธาในชื่อ Bitcoin แต่สิ่งที่พี่สงสัยในตอนนั้นคือ… พวกเขาสู้เพื่อใครกันแน่?"
แชมป์เงียบไปครู่เหมือนกำลังประมวลผล “แล้วตอนนั้นพี่คิดยังไงบ้างครับ? รู้สึกกลัวหรือว่ายังไง?”
“จะไม่กลัวได้ไง!” แจ๊กหัวเราะแห้ง ๆ แวบหนึ่งก็นึกถึงสีหน้าที่ยิ้มเยาะของทั้งคู่ตอนประกาศความพร้อมจะ Fork
“พี่อดคิดไม่ได้ว่าถ้า Core ยังไม่ยอมขยายบล็อก พวกนั้นจะลากนักขุดทั้งกองทัพแฮชเรตไปทำเครือข่ายใหม่ให้เป็น ‘Bitcoin สายใหญ่’ แล้วทิ้งเครือข่ายเดิมให้ซวนเซ"
"แค่คิดก็นึกถึงสงครามกลางเมืองในหนังประวัติศาสตร์แล้วน่ะ.. แตกเป็นสองฝ่าย สุดท้ายใครแพ้ใครชนะ ไม่มีใครทำนายได้จริง ๆ”

พูดจบ.. เขาเปิดฟอรัมดูไลฟ์ดีเบตจากงานในปี 2017 ต่อ โรเจอร์ แวร์ กำลังพูดในโทนร้อนแรง
“Bitcoin ไม่ใช่ของคนรวย! ถ้าคุณไม่เพิ่ม Blocksize คุณก็ทำให้ค่าธรรมเนียมพุ่งจนคนธรรมดาใช้ไม่ได้!”
ขณะเดียวกัน ปีเตอร์ วูเล่ ยืนอยู่ฝั่งตรงข้าม สีหน้าเยือกเย็นราวกับตั้งรับมานาน “การเพิ่มบล็อกคือการทำลายโครงสร้าง Node รายย่อยในระยะยาว แล้วมันจะยังเรียกว่ากระจายอำนาจได้หรือ?”
"ถ้าคุณอยากให้ Bitcoin เป็นของคนรวยเพียงไม่กี่คน ก็เชิญขยายบล็อกไปเถอะนะ แต่ถ้าอยากให้มันเป็นระบบที่คนทุกระดับมีส่วนร่วมจริง ๆ ..คุณต้องฟังเสียง Node รายเล็กด้วย" ปีเตอร์กล่าว
เสียงผู้คนในงานโห่ฮากันอย่างแตกเป็นสองฝ่าย บ้างก็เชียร์ความตรงไปตรงมาของโรเจอร์ บ้างก็เคารพเหตุผลเชิงเทคนิคของปีเตอร์
ข้อความจำนวนมหาศาลในฟอรัมต่างโหมกระพือไปต่าง ๆ นานา มีทั้งคำด่าหยาบคายจนแจ๊กต้องเบือนหน้า ตลอดจนการวิเคราะห์ลึก ๆ ถึงอนาคตของ Bitcoin ที่อาจไม่เหมือนเดิม
ในระหว่างนั้น.. แชมป์ส่งข้อความ Discord กลับมาอีก
“พี่ ถ้า Fork จริง ราคาจะป่วนแค่ไหน? ที่เขาว่าคนถือ BTC จะได้เหรียญใหม่ฟรี ๆ จริงไหม? ผมกลัวว่าถ้าเกิดแบ่งเครือข่ายไม่รู้กี่สาย ตลาดอาจมั่วจนคนหายหมดก็ได้ ใช่ไหมครับ?”
"แล้วถ้าเครือข่ายใหม่ล้มเหลวล่ะครับ? จะส่งผลอะไรต่อชุมชน Bitcoin เดิม?"
"ไอ้แชมป์มึงถามรัวจังวะ!?" แจ๊กสบถเพราะเริ่มตั้งรับไม่ทัน
“ก็ขึ้นกับตลาดจะเชื่อว่าสายไหนเป็น ‘ของจริง’ อีกนั่นแหละ” แจ๊กพิมพ์กลับ
“บางคนถือไว้เผื่อได้เหรียญใหม่ฟรี บางคนขายหนีตายก่อน"
"พี่เองก็ยังไม่กล้าการันตีเลย แต่ที่แน่ ๆ สงครามนี้ไม่ได้มีแค่ผลกำไร มันกระทบศรัทธาของชุมชน Bitcoin ทั้งหมดด้วย"
"ถ้าชาวเน็ตเลิกเชื่อมั่น หรือคนนอกมองว่าพวกเราทะเลาะกันเองเหมือนเด็กแย่งของเล่น ต่อให้ฝั่งไหนชนะ ก็อาจไม่มีผู้ใช้เหลือให้ฉลอง”
แล้วสายตาแจ๊กก็ปะทะกับกระทู้ใหม่ที่เด้งขึ้นมาบนหน้าฟอรัม
“โรเจอร์ แวร์ ประกาศ: ถ้าไม่เพิ่ม Blocksize เราจะฟอร์กเป็น Bitcoin ที่แท้จริง!”
ตัวหนังสือหนาแปะอยู่ตรงนั้นส่งแรงสั่นสะเทือนราวกับจะดึงคนในวงการให้ต้องเลือกข้างกันแบบไม่อาจกลับหลังได้
แจ๊กเอื้อมมือปิดแล็ปท็อปช้า ๆ คล้ายยอมรับความจริงว่าหนทางประนีประนอมอาจไม่มีอีกแล้ว..
“สงครามนี่คงใกล้ระเบิดเต็มทีล่ะนะ” เขาลุกจากเก้าอี้ สะพายเป้ พึมพำกับตัวเองขณะมองกาแฟดำที่เหลือครึ่งแก้ว “ถ้าพวกเขาฟอร์กจริง โลกคริปโตฯ ที่เราเคยรู้จักอาจไม่มีวันเหมือนเดิมอีกต่อไป”
เขามองออกไปนอกหน้าต่าง แสงแดดที่แผดเผาราวกับกำลังบอกว่า.. อนาคตของ Bitcoin อยู่ในจุดที่เส้นแบ่งระหว่างชัยชนะกับความล่มสลายเริ่มพร่าเลือน... และอาจไม่มีทางย้อนกลับ
ก่อนเดินออกจากร้าน เขากดส่งข้อความสั้น ๆ ถึงแชมป์
“เตรียมใจกับความปั่นป่วนไว้ให้ดี ไม่แน่ว่าเราอาจจะได้เห็น Bitcoin แตกเป็นหลายสาย.. ใครจะอยู่ใครจะไปไม่รู้เหมือนกัน แต่เรื่องนี้คงไม่จบง่าย ๆ แน่”
แจ๊กผลักประตูออกไปพบกับแดดจัดที่เหมือนแผดเผากว่าเดิม พายุร้อนไม่ได้มาแค่ในรูปความร้อนกลางกรุง แต่มาในรูป “สงคราม Blocksize” ที่พร้อมจะฉีกชุมชนคริปโตออกเป็นฝักฝ่าย และอาจลามบานปลายจนกลายเป็นศึกประวัติศาสตร์
ทว่าสิ่งที่ค้างคาใจกลับเป็นคำถามนั้น…
เมื่อเครือข่ายแบ่งเป็นหลายสายแล้ว เหรียญไหนจะเป็น Bitcoin จริง?
หรือบางที... ในโลกที่ใครก็ Fork ได้ตามใจ เราจะไม่มีวันได้เห็น “Bitcoin หนึ่งเดียว” อีกต่อไป?
คำถามที่ไม่มีใครตอบได้ชัดนี้ส่องประกายอยู่ตรงปลายทาง ราวกับป้ายเตือนว่า “อันตรายข้างหน้า” และคนในชุมชนทั้งหมดกำลังจะต้องเผชิญ…
โดยไม่มีใครมั่นใจเลยว่าจะรอด หรือจะแตกสลายไปก่อนกันแน่...

สองเส้นทาง (The Forked Path)
กลางปี 2017 ท้องฟ้าเหนือบุรีรัมย์ยังคงคุกรุ่นด้วยไอแดดและความร้อนแรงของสงคราม Blocksize แจ๊ก กู้ดเดย์ ก้าวเข้ามาในคาเฟ่เล็ก ๆ แห่งหนึ่งในย่านเทศบาลด้วยสีหน้าครุ่นคิด เขาพยายามมองหามุมสงบสำหรับนั่งตั้งหลักในโลกความเป็นจริง ก่อนจะจมดิ่งสู่สงครามในโลกดิจิทัลบนฟอรัม Bitcointalk อีกครั้ง
กลิ่นกาแฟคั่วเข้มลอยกระทบจมูก แจ๊กสั่งกาแฟดำแก้วโปรดแล้วปลีกตัวมาที่โต๊ะริมกระจก กระจกบานนั้นสะท้อนแสงอาทิตย์จัดจ้า ราวกับจะบอกว่าวันนี้คงไม่มีใครหนีความร้อนที่กำลังแผดเผา ทั้งในอากาศและในชุมชน Bitcoin ได้พ้น
เขาเปิดแล็ปท็อปขึ้น ล็อกอินเข้า Bitcointalk.org ตามเคย ข้อความและกระทู้มากมายกระหน่ำแจ้งเตือน ไม่ต่างอะไรจากสมรภูมิคำพูดที่ไม่มีวันหลับ “Hong Kong Agreement ล้มเหลวจริงหรือ?” “UASF คือปฏิวัติโดย Node?” เหล่านี้ล้วนสะท้อนความไม่แน่นอนในชุมชน Bitcoin ที่ตอนนี้ ดูคล้ายจะถึงจุดแตกหักเต็มที...
“ทั้งที่ตอนนั้นเราก็พยายามกันแทบตาย…” แจ๊กพึมพำ มองจอด้วยสายตาเหนื่อยใจพร้อมภาพความทรงจำย้อนกลับเข้าในหัว เขายังจำการประชุมที่ฮ่องกงเมื่อต้นปี 2016 ได้แม่น ยามนั้นความหวังในการประนีประนอมระหว่าง Big Block และ Small Block ดูเป็นไปได้ หากแต่กลายเป็นละครฉากใหญ่ที่จบลงโดยไม่มีใครยอมถอย...
...การประชุม Hong Kong Agreement (2016)
ภายในห้องประชุมหรูของโรงแรมใจกลางย่านธุรกิจฮ่องกง บรรยากาศตึงเครียดยิ่งกว่าการเจรจาสงบศึกในสมัยโบราณ
โรเจอร์ แวร์ ยืนเสนอว่า “การเพิ่ม Blocksize สำคัญต่ออนาคตของ Bitcoin — เราอยากให้คนทั่วไปเข้าถึงได้โดยไม่ต้องจ่ายค่าธรรมเนียมแพง ๆ”
“จิฮั่น อู๋ (Jihan Wu)” จาก Bitmain นั่งฝั่งเดียวกับโรเจอร์ คอยเสริมว่าการเพิ่มบล็อกคือโอกาสสำหรับนักขุด และหากทีม Core ไม่ยอม พวกเขาก็พร้อม “ดัน Fork” ขึ้นได้ทุกเมื่อ ด้วย Hashrate มหาศาลที่พวกเขาคุมไว้
ฝั่ง ปีเตอร์ วูเล (Pieter Wuille) กับ เกร็ก แมกซ์เวลล์ (Greg Maxwell) จาก Bitcoin Core เถียงกลับอย่างใจเย็นว่า “การขยายบล็อกอาจดึงดูดทุนใหญ่ ๆ แล้วไล่ Node รายย่อยออกไป ชุมชนอาจไม่เหลือความกระจายอำนาจอย่างที่ Satoshi ตั้งใจ”
สุดท้าย บทสรุปที่เรียกว่า Hong Kong Agreement ลงนามได้ก็จริง แต่มันกลับเป็นแค่ลายเซ็นบนกระดาษที่ไม่มีฝ่ายไหนเชื่อใจใคร

แจ๊กเบือนสายตาออกนอกหน้าต่าง สังเกตเห็นผู้คนเดินขวักไขว่ บ้างก็ดูรีบร้อน บ้างเดินทอดน่องเหมือนว่างเปล่า นี่คงไม่ต่างอะไรกับชาวเน็ตในฟอรัมที่แบ่งฝ่ายกันใน “สงคราม Blocksize” อย่างไม่มีทีท่าจะหยุด
แค่ไม่กี่นาที... เสียงโทรศัพท์ก็ดังขึ้น ชื่อ แชมป์ ‘PIGROCK’ โชว์หราเต็มจออีกครั้ง
“ว่าไงเจ้าแชมป์?” แจ๊กกรอกเสียงในสายด้วยอารมณ์เหนื่อย ๆ ทว่าพร้อมจะอธิบายเหตุการณ์ตามสไตล์คนที่ชอบครุ่นคิด
“พี่แจ๊ก.. ผมเข้าใจแล้วว่าการประชุมฮ่องกงมันล้มเหลว ตอนนี้ก็มีคนแยกเป็นสองขั้ว Big Block กับ SegWit แต่ผมเจออีกกลุ่มในฟอรัมเรียกว่า UASF (User-Activated Soft Fork) ที่เหมือนจะกดดันพวกนักขุดให้ยอมรับ SegWit..."
"อยากรู้ว่าตกลง UASF มันสำคัญยังไงครับ? ทำไมใคร ๆ ถึงเรียกว่าเป็น การปฏิวัติโดย Node กัน?”
แจ๊กอมยิ้มก่อนจะวางแก้วกาแฟลง พูดด้วยน้ำเสียงจริงจังกว่าเดิม “UASF น่ะหรือ? มันเปรียบได้กับการที่ ‘ชาวนา’ หรือ ‘ประชาชนตัวเล็ก ๆ’ ออกมาประกาศว่า ‘ฉันจะไม่รับบล็อกของนักขุดที่ไม่รองรับ SegWit นะ ถ้าแกไม่ทำตาม ฉันก็จะตัดบล็อกแกทิ้ง!’ เสมือนเป็นการปฏิวัติที่บอกว่าแรงขุดมากแค่ไหนก็ไม่สำคัญ ถ้าคนรัน Node ไม่ยอม… เชนก็เดินต่อไม่ได้”
“โห… ฟังดูแรงจริง ๆ พี่ แล้วถ้านักขุดไม่ร่วมมือ UASF จะเกิดอะไรขึ้น?” แชมป์ถามต่อเสียงสั่นนิด ๆ
“ก็อาจเกิด ‘Chain Split’ ยังไงล่ะ"
"แยกเครือข่ายเป็นสองสาย สุดท้ายเครือข่ายเดิม กับเครือข่ายใหม่ที่รองรับ SegWit ไม่ตรงกัน คนอาจสับสนหนักยิ่งกว่า Hard Fork ปกติด้วยซ้ำ"
"แต่นั่นแหละ... มันแสดงพลังว่าผู้ใช้ทั่วไปก็มีสิทธิ์กำหนดทิศทาง Bitcoin ไม่ได้น้อยไปกว่านักขุดเลย”
“เข้าใจแล้วครับพี่… เหมือน การปฏิวัติโดยประชาชนตาดำ ๆ ที่จับมือกันค้านอำนาจทุนใหญ่ใช่ไหม?” แชมป์หยุดครู่หนึ่ง “ผมเคยคิดว่า Node รายย่อยน้อยรายจะไปสู้อะไรไหว แต่ตอนนี้ดูท่าจะเปลี่ยนเกมได้จริงว่ะพี่…”
“ใช่เลย” แจ๊กตอบ
“นี่เป็นความพิเศษของ Bitcoin ที่บอกว่า ‘เราคุมเครือข่ายร่วมกัน’ แม้แต่ Bitmain ที่มี Hashrate มากกว่า 50% ก็หนาวได้ถ้าผู้ใช้หรือ Node รายย่อยรวมพลังกันมากพอ”
แชมป์ฟังด้วยความตื่นเต้นปนกังวล “แล้วแบบนี้ เรื่อง SegWit กับ Blocksize จะจบยังไงครับ? เห็นข่าวว่าถ้านักขุดโดนกดดันมาก ๆ คนอย่าง จิฮั่น อู๋ อาจออกไปสนับสนุน Bitcoin Cash ที่จะเปิดบล็อกใหญ่”
แจ๊กเลื่อนดูฟีดข่าวในฟอรัม Bitcointalk อีกครั้ง ก็เห็นพาดหัวชัด ๆ
“Bitmain ประกาศกร้าวพร้อมหนุน BCH เต็มพิกัด!”
เขาถอนหายใจเฮือกหนึ่ง “ก็ใกล้เป็นจริงแล้วล่ะ… โรเจอร์ แวร์ เองก็ผลักดัน BCH ว่าคือ Bitcoin แท้ที่ค่าธรรมเนียมถูก ใช้งานได้จริง ส่วนฝั่ง BTC ที่ยึดเอา SegWit เป็นหลัก ก็ไม่ยอมให้ Blocksize เพิ่มใหญ่เกินจำเป็น.."
"ต่างคนต่างมีเหตุผล... แต่อุดมการณ์นี่คนละทางเลย”
“แล้วพี่คิดว่าใครจะเป็นฝ่ายชนะครับ?”
“เฮ้ย.. มึงถามยากไปหรือเปล่า” แจ๊กหัวเราะหึ ๆ “ทุกคนมีโอกาสได้หมด และก็มีโอกาสพังหมดเหมือนกัน ถ้า UASF กดดันนักขุดให้อยู่กับ Core ได้ พวกเขาอาจยอมแพ้ แต่ถ้า Bitmain เทใจไป BCH นักขุดรายใหญ่คนอื่น ๆ ก็คงตาม"
"แล้วถ้าฝั่ง BCH เริ่มได้เปรียบ... อาจดึงคนไปเรื่อย ๆ สุดท้ายจะเหลือไหมล่ะฝั่ง SegWit ตัวจริง?”
“งั้น Node รายย่อยจะยืนอยู่ตรงไหนล่ะครับพี่?” แชมป์ถามอย่างหนักใจ
“Node รายย่อยและชุมชนผู้ใช้นี่แหละ คือ ตัวแปรชี้ขาด ทุกวันนี้คนกลุ่ม UASF พยายามโชว์พลังว่าตัวเองมีสิทธิ์ตั้งกติกาเหมือนกัน ไม่ใช่แค่นักขุด"
"อย่างที่บอก.. มันคือการ ‘ลุกขึ้นปฏิวัติ’ โดยชาวนา ต่อสู้กับเจ้าที่ที่ถือ ‘แฮชเรต’ เป็นอาวุธ”
แจ๊กตบบ่าตัวเองเบา ๆ ก่อนจะหัวเราะเล็กน้อย
“นี่แหละความมันของ Bitcoin ไม่มีเจ้าไหนสั่งได้เบ็ดเสร็จจริง ๆ ทุกฝั่งต่างถือไพ่คนละใบ สงครามยังไม่รู้จะจบยังไง ถึงอย่างนั้นมันก็สะท้อนวิญญาณ ‘decentralization’ ที่แท้จริง กล้ายอมรับสิทธิ์ทุกฝ่ายเพื่อแข่งขันกันตามกติกา”

จู่ ๆ ในหน้าฟอรัมก็มีกระทู้ใหม่เด้งเด่น “Bitmain หนุน Bitcoin Cash ด้วย Hashrate กว่า 50%! สงครามเริ่มแล้ว?” ข้อความนั้นดังโครมครามเหมือนระเบิดลงกลางวง
แจ๊กนิ่งไปชั่วขณะ สัมผัสได้ถึงความปั่นป่วนที่กำลังปะทุขึ้นอีกครั้ง เหงื่อบางเบาซึมบนหน้าผากแม้อากาศในคาเฟ่จะเย็นฉ่ำ เขาหันมองโทรศัพท์ที่ยังค้างสายกับแชมป์ แล้วเอ่ยด้วยน้ำเสียงจริงจัง
“นี่ล่ะ.. จุดเริ่มของสองเส้นทางอย่างชัดเจน… บล็อกใหญ่จะไปกับ BCH ส่วน SegWit ก็อยู่กับ BTC แน่นอนว่าทั้งสองฝ่ายไม่คิดถอยง่าย ๆ นักขุดจะเลือกข้างไหน? Node รายย่อยจะยอมใคร?"
"เมื่อสงครามครั้งนี้นำไปสู่การแบ่งเครือข่าย ใครกันแน่จะเป็นผู้ชนะตัวจริง? หรืออาจไม่มีผู้ชนะเลยก็เป็นได้”
ปลายสายเงียบงัน มีแต่เสียงหายใจของแชมป์ที่สะท้อนความกังวลปนอยากรู้อย่างแรง
“พี่… สุดท้ายแล้วเรากำลังยืนอยู่บนรอยแยกที่พร้อมจะฉีกทุกอย่างออกเป็นชิ้น ๆ ใช่ไหมครับ?”
“อาจจะใช่ก็ได้... หรือถ้ามองอีกมุม อาจเป็นวัฏจักรที่ Bitcoin ต้องเจอเป็นระยะ ทุกคนมีสิทธิ์ Fork ได้ตามใจใช่ไหมล่ะ? ก็ขอให้โลกได้เห็นกันว่าชุมชนไหนแน่จริง” แจ๊กพูดทิ้งท้ายก่อนจะแย้มยิ้มเจือรอยอ่อนล้า
ภาพบนจอคอมพิวเตอร์ฉายกระทู้ถกเถียงกันไม่หยุด ประหนึ่งเวทีดีเบตที่ไม่มีวันปิดไฟ แจ๊กจิบกาแฟอึกสุดท้ายเหมือนจะเตรียมพร้อมใจก่อนเข้าสู่สนามรบครั้งใหม่ สงครามยังไม่จบ.. ซ้ำยังดูหนักข้อยิ่งขึ้นเรื่อย ๆ
เขาลุกขึ้นจากโต๊ะ ชำเลืองมองแสงแดดจัดจ้าที่สาดลงมาไม่หยุด เปรียบเหมือนไฟแห่งข้อขัดแย้งที่เผาผลาญทั้งชุมชน Bitcoin ไม่ว่าใครจะเลือกอยู่ฝั่งไหน กลุ่ม UASF, กลุ่ม Big Block, หรือ กลุ่ม SegWit ทางเดินข้างหน้าล้วนเต็มไปด้วยความไม่แน่นอน
“สุดท้ายแล้ว… เมื่อกระดานแบ่งเป็นสองเส้นทางอย่างเด่นชัด สงคราม Blocksize จะจบลงด้วยใครได้บทผู้ชนะ?"
"หรือบางที… มันอาจไม่มีผู้ชนะที่แท้จริงในระบบที่ใครก็ Fork ได้ตลอดเวลา”
คำถามนี้ลอยติดค้างอยู่ในบรรยากาศยามบ่ายที่ร้อนระอุ ชวนให้ใครก็ตามที่จับตาดูสงคราม Blocksize ต้องฉุกคิด
เมื่อไม่มีใครเป็นเจ้าของ Bitcoin อย่างสมบูรณ์ ทุกคนจึงมีสิทธิ์บงการและเสี่ยงต่อการแตกแยกได้ทุกเมื่อ แล้วท้ายที่สุด ชัยชนะ–ความพ่ายแพ้ อาจไม่ใช่จุดสิ้นสุดของโลกคริปโตฯ
แต่เป็นเพียงจุดเริ่มต้นของการวิวัฒน์ที่ไม่มีวันจบสิ้น…

เมาท์แถมเรื่อง UASF (User-Activated Soft Fork)
นี่สนามรบยุคกลางที่ดูเหมือนในหนังแฟนตาซี ทุกคนมีดาบ มีโล่ แต่จู่ ๆ คนตัวเล็กที่เราไม่เคยสังเกต—พวกชาวนา ช่างไม้ คนแบกน้ำ—กลับรวมตัวกันยกดาบบุกวังเจ้าเมือง พร้อมตะโกนว่า “พอเถอะ! เราก็มีสิทธิ์เหมือนกัน!”
มันอาจจะดูเวอร์ ๆ หน่อยใช่ไหมครับ?
แต่ในโลก Bitcoin ปี 2017 นี่คือสิ่งที่เกิดขึ้นในรูปแบบ “User-Activated Soft Fork” หรือ UASF การปฏิวัติด้วยพลังโหนด ซึ่งทำให้นักขุดยักษ์ใหญ่ตัวสั่นงันงกันมาแล้ว!
แล้ว UASF มันคืออะไรล่ะ?
“User-Activated Soft Fork” หรือเรียกย่อ ๆ ว่า “UASF” ไม่ใช่อัปเกรดซอฟต์แวร์สวย ๆ แต่เป็น “ดาบเล่มใหม่” ที่คนตัวเล็ก—หมายถึง โหนด รายย่อย—ใช้ต่อรองกับนักขุดรายใหญ่ โดยกติกาคือ.. ถ้านักขุดไม่ทำตาม (เช่น ไม่รองรับ SegWit) โหนดก็จะปฏิเสธบล็อกของพวกเขาอย่างไม่เกรงใจใคร
สมมุติว่าคุณคือโหนด..
คุณรันซอฟต์แวร์ Bitcoin คอยตรวจสอบธุรกรรม วันดีคืนดี คุณประกาศ “ต่อไปถ้าใครไม่รองรับ SegWit ฉันไม่ยอมรับบล็อกนะ!” นี่ล่ะครับ “UASF” ตัวเป็น ๆ
คำขวัญสุดฮิตของ UASF
“No SegWit, No Block”
หรือแปลว่าถ้าบล็อกไม่รองรับ SegWit ก็เชิญออกไปเลยจ้า..
มันเหมือนการที่ชาวนาโผล่มาตบโต๊ะอาหารท่านขุนว่า “นายใหญ่จะปลูกอะไรก็ปลูกไป แต่ไม่งั้นฉันไม่รับผลผลิตนายนะ!”
ความเชื่อมโยงกับ BIP 148
ถ้าจะพูดถึง UASF ต้องรู้จัก BIP 148 ไว้นิดนึง มันเปรียบเหมือน “ธงปฏิวัติ” ที่ตีตราว่าวันที่ 1 สิงหาคม 2017 คือเส้นตาย!
BIP 148 บอกไว้ว่า.. ถ้าถึงวันนั้นแล้วยังมีนักขุดหน้าไหนไม่รองรับ SegWit บล็อกที่ขุดออกมาก็จะถูกโหนดที่ใช้ UASF “แบน” หมด
ผลลัพธ์ที่ตั้งใจ นักขุดไม่อยากโดนแบนก็ต้องทำตาม UASF กล่าวคือ “นายต้องรองรับ SegWit นะ ไม่งั้นอด!”
หลายคนกลัวกันว่า “อ้าว ถ้านักขุดใหญ่ ๆ ไม่ยอมแล้วหันไปขุดสายอื่น จะไม่กลายเป็นแยกเครือข่าย (Chain Split) หรือ?”
ใช่ครับ.. มันอาจเกิดสงครามสายใหม่ทันทีไงล่ะ
ทำไม UASF ถึงสำคัญ?
ย้อนกลับไปก่อนปี 2017 Bitcoin มีปัญหาโลกแตกทั้งค่าธรรมเนียมแพง ธุรกรรมหน่วง บวกกับความขัดแย้งเรื่อง “จะเพิ่ม Blocksize ดีไหม?” ทางกลุ่มนักขุดรายใหญ่ (นำโดย Bitmain, Roger Ver ฯลฯ) รู้สึกว่า “SegWit ไม่ใช่ทางออกที่แท้จริง” แต่อีกฝั่ง (ทีม Core) ชี้ว่า “Blocksize ใหญ่มากไปจะรวมศูนย์นะ โหนดรายย่อยตายหมด”
UASF เลยโผล่มา เหมือนชาวนาตะโกนว่า
“หุบปากได้แล้วไอ้พวกที่สู้กัน! ถ้าพวกแกไม่รองรับ SegWit พวกข้า (โหนด) ก็จะไม่เอาบล็อกแก”
สาระก็คือ.. มันคือตัวบ่งชี้ว่าคนตัวเล็กอย่างโหนดรายย่อยก็มีพลังต่อรอง เป็นกลไกที่ดึงอำนาจจากมือทุนใหญ่กลับสู่มือชุมชน (Decentralization ที่แท้ทรู)
วิธีการทำงานของ UASF
ลองจินตนาการตาม..
-
การกำหนดเส้นตาย BIP 148 ประกาศไว้ “ถึงวันที่ 1 สิงหาคม 2017 ถ้านายยังไม่รองรับ SegWit โหนด UASF จะไม่รับบล็อกนาย”
-
ถ้าคุณเป็นนักขุด… คุณขุดบล็อกออกมา แต่ไม่ได้ตีธง “ฉันรองรับ SegWit” UASF โหนดเห็นปุ๊บ พวกเขาจะจับโยนทิ้งไปเลย
-
ผลกระทบ? นักขุดที่ไม่ยอมทำตามจะเจอปัญหา บล็อกที่ขุดออกมาไม่มีใครรับ—เสียแรงขุดฟรี
อาจเกิด Chain Split คือ แยกเครือข่ายเลย ถ้านักขุดเหล่านั้นไปตั้งสายใหม่
ความสำเร็จและความท้าทายของ UASF
ความสำเร็จ.. หลังการรวมพลังผู้ใช้ โหนดรายย่อยกดดันนักขุดได้ไม่น้อย จนกระทั่ง SegWit เปิดใช้งานจริงใน Bitcoin วันที่ 24 สิงหาคม 2017 ช่วยให้ธุรกรรมเร็วขึ้น แก้ Transaction Malleability และเปิดทางสู่ Lightning Network ในอนาคต
ความท้าทาย.. นักขุดบางค่ายไม่โอเค.. โดยเฉพาะ Bitmain ซึ่งคาดว่าจะสูญรายได้บางส่วน ก็นำไปสู่การสนับสนุน “Bitcoin Cash (BCH)” แยกสาย (Hard Fork) ของตัวเองตั้งแต่วันที่ 1 สิงหาคม 2017 นั่นเอง
ว่าแล้วก็เปรียบง่าย ๆ
UASF เหมือนปฏิบัติการยึดคฤหาสน์เจ้าเมืองมาเปิดให้ชาวบ้านเข้าอยู่ฟรี.. แต่อีกฝ่ายบอก
“งั้นฉันออกไปตั้งคฤหาสน์ใหม่ดีกว่า!”
บทเรียนสำคัญ UASF เป็นตัวอย่างชัดว่า “ผู้ใช้” หรือ โหนดรายย่อย สามารถสร้างแรงกดดันให้นักขุดต้องยอมเปลี่ยนได้จริง ๆ ไม่ใช่แค่ยอมรับเงื่อนไขที่ขุดกันมา
ผลกระทบระยะยาวหลังจากนั้นล่ะ?
SegWit ถูกใช้งาน ทำให้ค่าธรรมเนียมธุรกรรมลดลง (ช่วงหนึ่ง) เกิด Lightning Network เป็น Layer 2 สุเฟี้ยวของ Bitcoin เกิด BCH (Bitcoin Cash) เป็นสายแยกที่อ้างว่า Blocksize ใหญ่คือทางออก
สรุปแล้ว UASF ทำให้โลกได้รู้ว่า..
Bitcoin ไม่ใช่ของนักขุด หรือของฝ่ายพัฒนาใดฝ่ายเดียว แต่มันเป็นของทุกคน!
“Bitcoin เป็นของทุกคน”
ไม่มีใครมีอำนาจเบ็ดเสร็จ ไม่ว่าคุณจะถือ Hashrate มากแค่ไหน ถ้า Node ทั่วโลกไม่เอา ก็จบ!
“แรงขุดใหญ่แค่ไหน ก็แพ้ใจมวลชน!”
(น่าจะมีตอนต่อไปนะ.. ถ้าชอบก็ Zap โหด ๆ เป็นกำลังใจให้ด้วยนะครับ)
-
-
 @ 502ab02a:a2860397
2025-05-01 01:47:10
@ 502ab02a:a2860397
2025-05-01 01:47:10EVERY Company ไข่ขาวเชื้อรา ที่รัฐส่งเสริม Unilever อุ้ม และเราถูกคลุมถุงให้กิน
อู๊ว ฉันเกิดมาเป็นไก่ โดนคนเลี้ยงเอาไว้ วันๆไม่ต้องทำอะไร แค่กินแล้วออกไข่ ป๊อกๆๆๆๆๆ กะต๊อก ป๊อกๆๆๆ ป๊อกๆๆๆๆๆ กะต๊อก ป๊อกๆๆๆ เพลงของเป้ อารักษ์ อาจกลายเป็นแค่คำเปรียบเปรย มนุษย์ ที่ถูกริดรอนสิทธิ์ตัวเองลงทุกวันจากนักล่า https://youtu.be/RctpDMoymVw?si=D3jzUXZBmyjxKGpN
โลกยุคใหม่อาจไม่ต้องมีแม่ไก่ แค่มีเชื้อรา กับเทคโนโลยี "precision fermentation" ก็สามารถทำให้ “ไข่” โผล่ออกมาในรูปของผงโปรตีนที่ไม่เคยผ่านตูดอุ่นๆ ไม่เคยมีเสียงกุ๊กๆ และไม่เคยเจอรังเจี๊ยบอีกต่อไป แต่เบื้องหลังของไข่ทดแทนที่ว่า “ก้าวหน้า” นี้ กลับเป็นการเคลื่อนไหวที่เชื่อมโยงรัฐ ธุรกิจยักษ์ และแคมเปญแนว “greenwashing” ได้อย่างแนบเนียนแบบพิมพ์นิยมของโลกอาหารสังเคราะห์ เรื่องราวมันประมาณนี้ครับ
เมื่อไข่เกิดจากเชื้อรา The EVERY Company ซึ่งเดิมชื่อว่า Clara Foods ก่อตั้งขึ้นในปี 2014 โดย Arturo Elizondo และเพื่อนร่วมทีมที่ออกมาจากโครงการ IndieBio ซึ่งเป็น accelerator สำหรับสตาร์ทอัปด้านชีววิทยาสังเคราะห์ที่มีชื่อเสียงใน Silicon Valley ได้ใช้ยีสต์ที่ถูกดัดแปลงพันธุกรรม (GMO yeast) สายพันธุ์ Komagataella phaffii เพื่อให้มันสร้าง “ovalbumin” หรือโปรตีนไข่ขาวขึ้นมาได้ คล้ายการหลอกยีสต์ให้กลายเป็นโรงงานสร้างไข่แบบไม่ต้องมีไก่ กระบวนการหมักนี้คือการจับยีสต์ใส่ถัง เติมน้ำตาล เติมสารอาหาร แล้วรอให้มัน "ผลิต" โปรตีนในห้องแล็บ แล้วก็สกัดออกมา ทำให้บริสุทธิ์ ตากแห้ง แล้วบรรจุใส่ซอง ชูป้าย “animal-free” แปะคำว่า “sustainable” แล้วส่งเข้าสู่ตลาดโปรตีนทดแทน ผลิตภัณฑ์นี้ได้รับการรับรองจาก FDA ว่าเป็น Generally Recognized as Safe (GRAS)
แต่คำถามคือ… ยีสต์ GMO + กระบวนการหมัก = sustainable จริงหรือเปล่า?
ถึงจะเป็นโปรตีนสังเคราะห์ ที่คนแพ้ไข่ก็ยังแพ้อยู่ดี แม้จะไม่มีสัตว์เกี่ยวข้องเลย แต่ EVERY Egg White ก็ยังคงต้องติดป้าย “Contains Egg” ตามกฎหมาย เพราะโครงสร้างโปรตีนที่ผลิตออกมา "เหมือน" โปรตีนไข่จริงมากจนสามารถกระตุ้นอาการแพ้ในคนที่แพ้ไข่ได้อยู่ดี แปลว่า... เราไม่ได้หลุดพ้นจากปัญหาแพ้อาหารเลย แค่เปลี่ยนแหล่งกำเนิดจากไก่มาเป็นเชื้อรา แต่สิ่งที่น่าคิดคือ นี่แสดงว่าองค์ประกอบของมันเหมือนชนิดที่ว่า สำเนาถูกต้องขนาดคนแพ้ไข่ยังแพ้อยู่ คุณคิดว่าในมุมนี้น่าคิดกว่าไหม???
Back ดีมีกองทัพอุ้ม เงินภาษีหนุน ที่น่าจับตาคือ EVERY ได้รับเงินสนับสนุนกว่า 2 ล้านดอลลาร์จากกระทรวงกลาโหมสหรัฐฯ (DoD) เพื่อศึกษาความเป็นไปได้ในการผลิตโปรตีนในประเทศ ตัวเลขนี้ไม่ใช่เล่น ๆ แปลว่า ภาครัฐกำลังพิจารณาให้ "ไข่จากเชื้อรา" เป็นอาหารแห่งอนาคตของกองทัพ ซึ่งหมายถึงเม็ดเงินระดับพันล้านเหรียญหากแผนนี้เดินหน้า และเมื่อรัฐหนุนขนาดนี้ เทคโนโลยีที่ยังแพงก็จะ “ไม่แพง” อีกต่อไป เพราะเงินภาษีช่วยลดต้นทุนแบบกลาย ๆ เหมือนที่เคยเกิดกับ Beyond Meat หรือ Impossible Foods
เท่านั้นไม่พอครับ ไข่ขาวของท่าน ได้รับการคัดเลือกที่จะจับมือกับ The Vegetarian Butcher บริษัทลูกของ Unilever บริษัทอาหารที่ครองตลาดโลกราวกับเป็นเจ้าของตู้เย็นของประชากรโลก Unilever จะใช้โปรตีนไข่จาก EVERY ใส่ในผลิตภัณฑ์ plant-based meat ที่กำลังไต่ตลาดโลก โดยไม่จำเป็นต้องแจ้งผู้บริโภคว่าโปรตีนนี้มาจากเชื้อรา GMO หรือกระบวนการ biotech ที่ไม่ธรรมดา แม้จะถูกจัดว่าเป็น "non-animal ingredient" หรือ "ไม่ได้มาจากสัตว์โดยตรง" แต่ก็มีสิทธิ์เข้าสู่เมนูมังสวิรัติ วีแกน และอาหารเด็กได้อย่างง่ายดาย เพราะภาพจำที่สื่อมวลชนร่วมกันสร้างขึ้น เพราะไม่มีภาพของ “สัตว์” อยู่ในกระบวนการเลย จึงกลายเป็น “วีแกนได้” ในสายตาคนทั่วไป ทั้งที่ความจริงมันคือเทคโนโลยีชีวภาพระดับลึก ด้วยการใช้คำอย่าง “cruelty-free”, “animal-free”, “sustainable protein”, รวมถึงหน้าตาผลิตภัณฑ์ที่ดูใสสะอาด ไร้กลิ่นอายห้องแล็บ
แม้จะยังไม่มีหลักฐานตรงๆ ว่า EVERY เข้าล็อบบี้รัฐบาลเหมือน Oatly แต่เส้นทางที่เห็นชัดคือความร่วมมือกับองค์กรระดับนโยบาย เช่น Good Food Institute (GFI) และกลุ่มผลักดัน food-tech เพื่อก่อรูปแนวคิดว่า “อาหารที่ไม่ได้มาจากธรรมชาติ” = “อนาคต” และเมื่อแบรนด์เหล่านี้จับมือกับยักษ์ใหญ่ กลายเป็นอาหารในโรงเรียน ทหาร โรงพยาบาล หรือ planet of the future คนทั่วไปก็ไม่มีสิทธิ์เลือกอีกต่อไป เพราะทุกที่ถูกจัดสรรโดยนโยบายที่ใครบางคนได้ตัดสินไปแล้ว
EVERY Company ไม่ได้ขายแค่ไข่สังเคราะห์ แต่ขาย “อนาคตของอาหาร” แบบที่มนุษย์ถูกแยกออกจากธรรมชาติ แล้วพึ่งพาเทคโนโลยีและเงินทุนแทน และในโลกที่รัฐกับบริษัทยักษ์กำลังร่วมมือกันสร้างนิยามใหม่ของคำว่า “โปรตีนดีต่อสิ่งแวดล้อม” เราในฐานะผู้บริโภคควรถามกลับว่า…
ดีต่อใคร? ธรรมชาติ หรือห้องแล็บ? สุขภาพของมนุษย์ หรือผลกำไรของเจ้าของแพลตฟอร์มอาหาร?
***สรุป timeline เบาๆ 2014 – Clara Foods ก่อตั้งในซานฟรานซิสโก โดยมีเป้าหมายผลิต “ไข่โดยไม่ต้องใช้ไก่” ผ่านกระบวนการ fermentation 2015-2019 – รับทุนหลายรอบ รวมถึงจาก Horizons Ventures (ที่ลงทุนใน Impossible Foods), IndieBio, Blue Horizon ฯลฯ 2021 – เปลี่ยนชื่อจาก Clara Foods เป็น The EVERY Company เพื่อสะท้อนเป้าหมายที่กว้างขึ้น: การสร้างโปรตีน “EVERYthing” จากจุลชีพ
ปล. ใครอยากอ่านเอกสาร GRAS ตัวเต็มของ EGGWHITE โหลดได้จากที่นี่ครับ https://www.fda.gov/media/175248/download #pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-
 @ 5df413d4:2add4f5b
2025-05-01 01:44:19
@ 5df413d4:2add4f5b
2025-05-01 01:44:19 -
 @ e0e92e54:d630dfaa
2025-04-30 23:27:59
@ e0e92e54:d630dfaa
2025-04-30 23:27:59The Leadership Lesson I Learned at the Repair Shop
Today was a reminder of "Who You Know" actually matters.
Our van has been acting up as of late. Front-end noise. My guess? CV joint or bushings.
Not that I’m a mechanic though—my dad took the hammer away from me when I was 12, and now all "my" tools have flowers printed on them or Pink handles...
Yesterday it become apparent to my wife that "sooner rather than later" was optimal.
So this morning she took it to a repair shop where we know the owners.
You may have guessed by now that I’m no car repair guy. It’s just not my strength and I’m ok with that! And even though it’s not my strength, I’m smart enough to know enough about vehicles to be dangerous…
And I’m sure just like you, I hate being ripped off. So last year, we both decided she would handle repair duties—I just get too fired up by most the personnel that work there whom won’t shoot straight with you.
So this morning my wife takes our van in. She sees the owner and next thing my wife knows, the owner’s wife (my wife’s friend) is texting to go get coffee while they take care of the van.
Before the two ladies took off, my wife was told "we'll need all day as one step of it is a 4-hour job just to get to the part that needs to be replaced..."
And the estimate? Half the parts were warrantied out and the labor is lower than we expected it to be.
Fast forward, coffee having been drank… nearly 4 hours on the dot, we get a call “your van is ready!”
My wife didn't stand there haggling the price for parts and labor.
Nope…here’s the real deal:
- Leadership = Relationships
- You can’t have too many
Granted, quality is better than quantity in everything I can think of, and that is true for relationships as well...
And while there are varying degrees or depths of relationships. The best ones go both ways.
We didn’t expect a deal because we were at our friend’s shop. We went because we trust them.
That’s it.
Any other expectation other than a transparent and truthful transaction would be manipulating and exploiting the relationship…the exchange would fall into the purely transactional at best and be parasitic at worst!
The Bigger Lesson
Here’s the kicker:
This isn’t about vans or a repair shop. It’s about leading.
Theodore Roosevelt nailed it: “People don’t care how much you know until they know how much you care.”
Trust comes from relationships.
Relationships begin with who you know…And making who you know matter.
In other words, the relevance of the relationship is critical.
Your Move
Next time you dodge a call—or skip an event—pause.
Kill that thought…Or at least its tire marks. 😁
Realize that relationships fuel your business, your life, and your impact.
Because leadership? It’s relationships.
====
💡Who’s one person you can invest in today? A teammate? A client? A mechanic? 😉
🔹 Drop your answer below 👇 Or hit me up—book a Discovery Call. Let’s make your leadership thrive.
Jason Ansley* is the founder of Above The Line Leader*, where he provides tailored leadership support and operational expertise to help business owners, entrepreneurs, and leaders thrive— without sacrificing your faith, family, or future.
*Want to strengthen your leadership and enhance operational excellence? Connect with Jason at https://abovethelineleader.com/#your-leadership-journey
*📌 This article first appeared on NOSTR. You can also find more Business Leadership Articles and content at: 👉 https://abovethelineleader.com/business-leadership-articles
-
 @ c13fd381:b46236ea
2025-04-16 03:10:38
@ c13fd381:b46236ea
2025-04-16 03:10:38In a time of political volatility and declining public trust, Australians are looking for leaders who don’t just talk about accountability—but prove it. It’s time for a new standard. A protocol that filters for competence, responsibility, and integrity—not popularity alone.
Here’s the idea:
Anyone who wants to run for public office in Australia must stake 100Ksats to a public address and maintain provable control of the corresponding private key for the duration of their term.
A Low Barrier With High Signal
The amount—100Ksats—is modest, but meaningful. It isn’t about wealth or exclusion. It’s about signal. Controlling a private key takes care, discipline, and a basic understanding of digital responsibility.
This protocol doesn't reward those with the most resources, but those who demonstrate the foresight and competence required to secure and maintain something valuable—just like the responsibilities of public office.
How It Works
This system is elegantly simple:
- To nominate, a candidate generates a keypair and deposits 100Ksats into the associated address.
- They publish the public key alongside their candidate profile—on the electoral roll, campaign site, or an independent registry.
- Throughout their time in office, they sign periodic messages—perhaps quarterly—to prove they still control the private key.
Anyone, at any time, can verify this control. It’s public, permissionless, and incorruptible.
Why This Matters
Private key management is more than technical—it’s symbolic. It reflects:
- Responsibility – Losing your key means losing your ability to prove you’re still accountable.
- Integrity – Key control is binary. Either you can sign or you can’t.
- Long-term thinking – Good key management mirrors the strategic thinking we expect from leaders.
This isn’t about promises. It’s about proof. It moves trust from words to cryptographic reality.
A Voluntary Standard—for Now
This doesn’t require legislative change. It can begin as a voluntary protocol, adopted by those who want to lead with integrity. The tools already exist. The expectations can evolve from the ground up.
And as this becomes the norm, it sets a powerful precedent:
"If you can’t manage a private key, should you be trusted to manage public resources or national infrastructure?"
Identity Without Surveillance
By linking a public key to a candidate’s public identity, we create a form of digital accountability that doesn’t rely on central databases or invasive oversight. It’s decentralized, simple, and tamper-proof.
No backdoors. No bureaucracy. Just Bitcoin, and the competence to manage it.
Bitcoin is the foundation. Asymmetric encryption is the filter.
The result? A new class of public leaders—proven, not promised.Let’s raise the standard.
-
 @ c9badfea:610f861a
2025-04-30 23:12:42
@ c9badfea:610f861a
2025-04-30 23:12:42- Install Image Toolbox (it's free and open source)
- Launch the app and navigate to the Tools tab
- Choose Cipher from the tool list
- Pick any file from your device storage
- Keep Encryption toggle selected
- Enter a password in the Key field
- Keep default AES/GCM/NoPadding algorithm
- Tap the Encrypt button and save your encrypted file
- If you want to decrypt the file just repeat the previous steps but choose Decryption instead of Encryption in step 5
-
 @ e3ba5e1a:5e433365
2025-04-15 11:03:15
@ e3ba5e1a:5e433365
2025-04-15 11:03:15Prelude
I wrote this post differently than any of my others. It started with a discussion with AI on an OPSec-inspired review of separation of powers, and evolved into quite an exciting debate! I asked Grok to write up a summary in my overall writing style, which it got pretty well. I've decided to post it exactly as-is. Ultimately, I think there are two solid ideas driving my stance here:
- Perfect is the enemy of the good
- Failure is the crucible of success
Beyond that, just some hard-core belief in freedom, separation of powers, and operating from self-interest.
Intro
Alright, buckle up. I’ve been chewing on this idea for a while, and it’s time to spit it out. Let’s look at the U.S. government like I’d look at a codebase under a cybersecurity audit—OPSEC style, no fluff. Forget the endless debates about what politicians should do. That’s noise. I want to talk about what they can do, the raw powers baked into the system, and why we should stop pretending those powers are sacred. If there’s a hole, either patch it or exploit it. No half-measures. And yeah, I’m okay if the whole thing crashes a bit—failure’s a feature, not a bug.
The Filibuster: A Security Rule with No Teeth
You ever see a firewall rule that’s more theater than protection? That’s the Senate filibuster. Everyone acts like it’s this untouchable guardian of democracy, but here’s the deal: a simple majority can torch it any day. It’s not a law; it’s a Senate preference, like choosing tabs over spaces. When people call killing it the “nuclear option,” I roll my eyes. Nuclear? It’s a button labeled “press me.” If a party wants it gone, they’ll do it. So why the dance?
I say stop playing games. Get rid of the filibuster. If you’re one of those folks who thinks it’s the only thing saving us from tyranny, fine—push for a constitutional amendment to lock it in. That’s a real patch, not a Post-it note. Until then, it’s just a vulnerability begging to be exploited. Every time a party threatens to nuke it, they’re admitting it’s not essential. So let’s stop pretending and move on.
Supreme Court Packing: Because Nine’s Just a Number
Here’s another fun one: the Supreme Court. Nine justices, right? Sounds official. Except it’s not. The Constitution doesn’t say nine—it’s silent on the number. Congress could pass a law tomorrow to make it 15, 20, or 42 (hitchhiker’s reference, anyone?). Packing the court is always on the table, and both sides know it. It’s like a root exploit just sitting there, waiting for someone to log in.
So why not call the bluff? If you’re in power—say, Trump’s back in the game—say, “I’m packing the court unless we amend the Constitution to fix it at nine.” Force the issue. No more shadowboxing. And honestly? The court’s got way too much power anyway. It’s not supposed to be a super-legislature, but here we are, with justices’ ideologies driving the bus. That’s a bug, not a feature. If the court weren’t such a kingmaker, packing it wouldn’t even matter. Maybe we should be talking about clipping its wings instead of just its size.
The Executive Should Go Full Klingon
Let’s talk presidents. I’m not saying they should wear Klingon armor and start shouting “Qapla’!”—though, let’s be real, that’d be awesome. I’m saying the executive should use every scrap of power the Constitution hands them. Enforce the laws you agree with, sideline the ones you don’t. If Congress doesn’t like it, they’ve got tools: pass new laws, override vetoes, or—here’s the big one—cut the budget. That’s not chaos; that’s the system working as designed.
Right now, the real problem isn’t the president overreaching; it’s the bureaucracy. It’s like a daemon running in the background, eating CPU and ignoring the user. The president’s supposed to be the one steering, but the administrative state’s got its own agenda. Let the executive flex, push the limits, and force Congress to check it. Norms? Pfft. The Constitution’s the spec sheet—stick to it.
Let the System Crash
Here’s where I get a little spicy: I’m totally fine if the government grinds to a halt. Deadlock isn’t a disaster; it’s a feature. If the branches can’t agree, let the president veto, let Congress starve the budget, let enforcement stall. Don’t tell me about “essential services.” Nothing’s so critical it can’t take a breather. Shutdowns force everyone to the table—debate, compromise, or expose who’s dropping the ball. If the public loses trust? Good. They’ll vote out the clowns or live with the circus they elected.
Think of it like a server crash. Sometimes you need a hard reboot to clear the cruft. If voters keep picking the same bad admins, well, the country gets what it deserves. Failure’s the best teacher—way better than limping along on autopilot.
States Are the Real MVPs
If the feds fumble, states step up. Right now, states act like junior devs waiting for the lead engineer to sign off. Why? Federal money. It’s a leash, and it’s tight. Cut that cash, and states will remember they’re autonomous. Some will shine, others will tank—looking at you, California. And I’m okay with that. Let people flee to better-run states. No bailouts, no excuses. States are like competing startups: the good ones thrive, the bad ones pivot or die.
Could it get uneven? Sure. Some states might turn into sci-fi utopias while others look like a post-apocalyptic vidya game. That’s the point—competition sorts it out. Citizens can move, markets adjust, and failure’s a signal to fix your act.
Chaos Isn’t the Enemy
Yeah, this sounds messy. States ignoring federal law, external threats poking at our seams, maybe even a constitutional crisis. I’m not scared. The Supreme Court’s there to referee interstate fights, and Congress sets the rules for state-to-state play. But if it all falls apart? Still cool. States can sort it without a babysitter—it’ll be ugly, but freedom’s worth it. External enemies? They’ll either unify us or break us. If we can’t rally, we don’t deserve the win.
Centralizing power to avoid this is like rewriting your app in a single thread to prevent race conditions—sure, it’s simpler, but you’re begging for a deadlock. Decentralized chaos lets states experiment, lets people escape, lets markets breathe. States competing to cut regulations to attract businesses? That’s a race to the bottom for red tape, but a race to the top for innovation—workers might gripe, but they’ll push back, and the tension’s healthy. Bring it—let the cage match play out. The Constitution’s checks are enough if we stop coddling the system.
Why This Matters
I’m not pitching a utopia. I’m pitching a stress test. The U.S. isn’t a fragile porcelain doll; it’s a rugged piece of hardware built to take some hits. Let it fail a little—filibuster, court, feds, whatever. Patch the holes with amendments if you want, or lean into the grind. Either way, stop fearing the crash. It’s how we debug the republic.
So, what’s your take? Ready to let the system rumble, or got a better way to secure the code? Hit me up—I’m all ears.
-
 @ 714f9dc3:76659adb
2025-01-02 20:47:45
@ 714f9dc3:76659adb
2025-01-02 20:47:45Last week, I was reading “The Air We Breathe”, by Glen Scrivener. It’s about “How We All Came to Believe in Freedom, Kindness, Progress, and Equality”, and it explores the Christian roots of the values we prize in today's western society. It’s all around us, but we don’t really know where it came from: It’s the air we’re breathing. The ideas and ethics behind Christianity, whether you believe in them or not, are embedded in our culture.
As I was reading this, I saw so many parallels with Bitcoin, so wanted to list them below and share some of my thoughts. Can Bitcoin also become “The Air We Breathe”? Or in plebs words: hyperbitcoinization? Can Bitcoin become so ubiquitous that it becomes normal? Can there be a world in which we don’t even know where Bitcoin came from? It would be a world with many similar views as with today's view on Christianity. It becomes the air we breathe, something that used to be a counterculture that over time became ubiquitous. What can we learn from it?
These are my ten parallels of Bitcoin with the early days of Christianity. 1. Separation from state 2. From obscure counterculture to dominant force 3. Exponential grassroots growth 4. Conversion of emperors/politicians 5. Sudden tolerance and protection for ideology 6. Fall of the empire, end of the status quo 7. Missionaries spreading the word 8. Persuasion and education are key 9. Age of Enlightenment
Note: I’m no expert on Christianity, nor a historian of the Roman Empire, and I know just a bit about Bitcoin. See this as a thought experiment.
1. Separation from state In all fairness, I’m not the first to draw this first parallel. It was Satoshi Nakamoto themself who made the connection even before Bitcoin was available to the public, with several hints pointing back to important dates and moments in Christian history. The big parallel here is the “separation of money and state” and “separation of church and state”.
Before going back to the early days of Christianity in the first centuries AD, I first want to draw this parallel with Satoshi.
It’s 1517. The German Priest Maarten Luther writes his Ninety-five Theses, and nails this on the church doors in Wittenberg. The theses are also known as the “Disputation on the Power and Efficacy of Indulgences”. He kickstarted a movement with a radical new idea for that time: The separation of the church from the state.
The Catholic Church had become one with the state. Via the means of indulgences, there was an ability to pay for your redemption. The church was corrupted by money, power and politics. The church and indulgences replaced the need for personal responsibility and an individual faith with money and perverse structures.
Reformation Day is a Protestant Christian religious holiday celebrated on 31 October in remembrance of the onset of the Reformation. But the 31st of October is also the day in which Satoshi shared his pamphlet with the world: in 2008 they published the Bitcoin Whitepaper. It kickstarted a movement with a radical new idea for that time: The separation of the money from the state.
But this was not Satoshi’s only hint. Another one is the date of Bitcoin’s Genesis Block: January 3, 2009. It was the day that the idea of the separation of money and the state became reality, more than just an idea in an individual's mind.
Did you know that Maarten Luther was excommunicated from the Catholic Church in 1521 by Pope Leo X for sparking this revolutionary new way of thinking (and being). It happened on January 3 as well. I bet Satoshi Nakamoto knew.
To be fair, this parallel is not new and known by many bitcoiners. But it’s a good introduction to the topic, and after reading “The Air We Breathe: How We All Came to Believe in Freedom, Kindness, Progress, and Equality”, I automatically started to see more parallels between (the early days of) Christianity and todays adoption of Bitcoin. Because it was of course not Maarten Luther who sparked these rebellious thoughts in 1500, but it was Jesus himself approx. 2000 years ago.
Let’s go back from the 1500s to the first decades AD to the beginning of this radical new belief system. During the dominance of the Roman empire in the Mediterranean and much of Europe, Western Asia and North Africa, someone told a story that opposed every mainstream paradigm.
Jesus’ idea was radically different from the belief systems of that day. He preached Freedom, Kindness, Progress, and Equality in a world that was full of Debauchery and Violence, with Gladiator Games, Slavery, Public Crucifixion, and Brutalities. The belief system of that time was not like todays. There were superior races (Greek/Romans over barbarians), superior sexes (man over women), superior classes (free man over slaves) and the concept of justice was more something in the realm of “restoring rights of those that were superior”, than “equality for all, men and women, Greek and barbarian, free and slave”.
Jesus opposed the status quo. It started small and irrelevant; as a counterculture. But it didn’t stay that way.
2. From obscure counterculture to dominant force In “The Air We Breathe”, Scrivener asks the question: “How did the obscure, marginal Jesus movement of the 1st century become the dominant religious force in the Western world in a few centuries?”
Important to know, is that the Christian faith was the opposite of the narrative. Concepts like Freedom, Kindness, Progress, and Equality didn’t exist in the Roman Empire. Human rights neither. Individual rights neither. The emperor was almost de facto God himself.
Early Christians were persecuted for preaching a different story: that God is NOT the ruler of the empire. Jesus preached the separation of politics from God; separating faith from the state. As a result, he was crucified, and many of his followers were killed by Nero (between 54 and 68 AD), Domitian (81–96 AD), Trajan (98–117 AD) and Decius (249–251 AD). This new narrative was a thread for the Roman rulers.
Draw the parallels of how there have been many attempts to “kill” bitcoin, not with physical persecution but with an information war. Not by physical violence, but by misinformation. Bitcoin threatens the status quo, just like Christianity threatened the Roman Empire.
You see?
But how is the obscure movement of Bitcoin in the 20th century becoming the dominant force, similar to the question that Scrivener asked about Christianity? Perhaps the answer lies in the following parallel.
3. Exponential grassroots growth Sociologist Rodney Stark estimates in “The Rise of Christianity” that from the time of the first Easter, the church began growing at a rate of 40% per decade, a modest but relentless 3.4% per year. By the year 300, Christians numbered perhaps 6 million: about a tenth of the empire.
Despite pushbacks, the army of believers continued to grow. Grassroots, peer-to-peer. It was not the state-religion, it was a peaceful army of believers that spread the word, resulting in an exponential growth of its followers. The counterculture became more and more dominant.
You may see what I’m doing here. It was basically the meme that all Bitcoiners know: Gradually, then suddenly. Against the current.
4. Conversion of emperors/politicians In 312 a big change happened: Emperor Constantine converted to Christianity. As Stark writes, "Constantine's conversion would better be seen as a response to the massive exponential wave in progress, not as its cause".
Are we living in that same era, where nation states start to embrace Bitcoin? Where politicians don’t oppose as strongly anymore, but are flirting with the idea of embracing it? And again the parallel: it’s responsive to the exponential wave of progress, not as its cause.
Whether Constantine is Nayib Bukele, Donald Trump, or Milei: it doesn’t matter. It’s the dynamic that matters. The counterculture becomes so dominant, that the “rulers” of the world are wanting to be part of it. Which will be followed by “rules” that favour the ideology, movement, and beliefs.
5. Tolerance and protection for ideology In 313 Constatines Edict of Milan granted freedom to Christians that were remarkable for that time and a model for religious toleration for the coming centuries.
The tide was turning, and by 380 Emperor Theodosius made Christianity Rome's official religion, more than half the population had already converted. In a few short centuries Christianity had gone from radical counterculture to dominant cultural power. This was an extraordinary shift in the church's relationship with the world. The edict expressly grants religious liberty to Christians, who had been the object of special persecution, but also goes even further and grants liberty to all other religions. And then, in 410, the world itself changed.
It changed from grassroots, bottom-up adoption to some kind of nation state adoption. One that was driven by decrees and edicts, instead of the analog cyberhornets of that day. Actually, the ideas of Indulgences were introduced via these Edicts, something that Maarten Luther actually was fighting against in the 1500s.
The world changed from the state-less Christian belief and moved (back) towards a system in which the state and church were connected again. Yes — the Roman Catholic Church. Until the previously mentioned critics during the Reformation.
6. Fall of the empire, end of the status quo When people speak of the fall of the Roman Empire, they usually mean in the 5th century when the western half fell. But there was also an eastern half, known as the Byzantine Empire (with its capital in what is modern-day Istanbul).
How did this relate to the movement that once was Cult, and now suddenly had become Culture?
It was Augustine, the north African bishop (354-430), who laid the foundation for a new philosophical, theological, and legal system. He distinguished between the fragile earthly realm and the eternal heavenly kingdom. Rome was “a city of man”, which fell. But the “city of God” was forever. He continued to separate the Roman Catholic Church from the faith that it once was. This distinction was vital, and it gave rise to the concept of "the secular realm". He planted the first ideas of "the separation of church and state" again, which started to spread throughout Europe during the supposedly "sandy desert" of the Middle Ages.
The parallel and lesson here might be that narratives can be taken over, for the worse. And that it takes centuries to take back the narrative, but/and only after an empire has fallen. Whether we refer to “The Fourth Turning” by William Strauss and Neil Howe or “Changing World Orders” by Ray Dalio. There is something to preserve, and it needs active monitoring and pushbacks!
7. Missionary, spreading the word The way the church sought to spread its influence would become a question that would take many centuries (and many failures) to settle. In the past, empires sought to spread their influence almost always by force. Christianity has been a missionary faith from the beginning. It was for this reason that Pope Gregory the Great sent Augustine to Britain to convert the Anglo-Saxons.
Augustine was commanded by Gregory to use only "gentle means". His goal was persuasion. His method was teaching and preaching. And he was successful, converting King Aethelbert of Kent and becoming the first Archbishop of Canterbury.
You see what I’m talking about again: the parallel is simple. Bitcoin is a similar peaceful revolution, a missionary movement, of those that wish to see their Cult turn into a Culture. “Genle means”, teachings, persuasions. Or in pleb terminology: Orangepilling.
8. Persuasion and education are key Over the next decades and centuries, this movement continued. English Benedictine monk (675-754) Boniface was sent from the previously “barbarian” Britain to “orangepill the East” – in this case the Saxons in the Germanic lands. In the words of his advisor, the Bishop of Winchester, his goal was "to convince them by many documents and arguments". This mission of persuasion and education was largely successful. Today he’s better known as “the Apostle to the Germans". He was killed in The Netherlands (Dokkum).
Boniface kept to a policy of non-violence and non-retaliation, even to the point of death. Another famous writer about this topic, Tom Holland, summarises the lesson we learn from Boniface: "to convert was to educate".
In the following century this lesson was sorely needed by the Frankish king Charles the Great, aka Charlemagne (742-814). Charlemagne's path to power was a brutal one. When the Saxons stood in his way, Charlemagne beheaded 4,500 of them in a single day. There are concrete reasons why "getting medieval" might be associated today with brutality.
Is “Bitcoin as Legal Tender”, whether this is peaceful or violently, the way to go? Are we “getting medieval” with these kind of measures, in order to go from Cult to Culture, from counterculture to dominant culture, in which we lose the true essence of our revolution of separation of the state from the matter?
9. Age of Enlightenment Alcuin of York (735-804), was bold enough to write to Charlemagne directly with his criticism. "A person can be drawn into the faith, not forced into it". Be a lighthouse, not a tugboat!
The church's official teaching would later agree with Alcuin's position. In the 12th century all "harsh means" were forbidden since faith arises from the will, not compulsion. Enlightenment comes through education and persuasion.
There’s work to do. Grassroots. Education. Peer-to-peer. Not directed by politicians, nor opposed by those in power. Through education and persuasion. Rules without rulers. Because eventually, with the Crusades and the Spanish Inquisition, there are stark examples of the church using “harsh means" again. Forcing Bitcoin on people will never be the way: it’s a cheat code to the end goal. In order to succeed, we’ll need to be a missionary.
Final words I don’t want in any way to compare Christianity in itself as a faith, and Bitcoin as a technology, with each other. I enjoyed exploring the sociological phenomena between two countercultures, the grassroots movement and missionary parallels between both of them. Satoshi gave the first assist, with the 31st of October (Whitepaper Day) and the Genesis Block on January 3rd.
Let’s not mix religion with monetary systems, even though there are many similarities between certain movements. That’s not my goal for sharing this brain dump. But let’s learn from the past, from Constatine’s Edict and from Augustine, from Charlemagne (and especially Alcuin of York), from Boniface and from Maarten Luther. And from Satoshi Nakamoto.
-
 @ 2fdae362:c9999539
2025-04-30 22:17:19
@ 2fdae362:c9999539
2025-04-30 22:17:19The architecture you choose for your embedded firmware has long-lasting consequences. It impacts how quickly you can add features, how easily your team can debug and maintain the system, and how confidently you can scale. While main loops and real-time operating systems (RTOS) are common, a third option — the state machine kernel — often delivers the most value in modern embedded development. At Wolff Electronic Design, we’ve used this approach for over 15 years to build scalable, maintainable, and reliable systems across a wide range of industries.
Every embedded system starts with one big decision: how will the firmware be structured?
Many teams default to the familiar—using a simple main loop or adopting a RTOS. But those approaches can introduce unnecessary complexity or long-term maintenance headaches. A third option, often overlooked, is using a state machine kernel—an event-driven framework designed for reactive, real-time systems. Below, we compare the three options head-to-head to help you choose the right architecture for your next project.Comparison Chart
| Approach | Description | Pros | Cons | Best For | |-----------------------|------------------------------------------------------------------------|-------------------------------------------------------------|------------------------------------------------------------|--------------------------------------| | Main Loop | A single, continuous while-loop calling functions in sequence | Simple to implement, low memory usage | Hard to scale, difficult to manage timing and state | Small, simple devices | | RTOS | Multi-threaded system with scheduler, tasks, and preemption | Good for multitasking, robust toolchain support | Thread overhead, complex debugging, race conditions | Systems with multiple async tasks | | State Machine Kernel | Event-driven system with structured state transitions, run in a single thread | Easy to debug, deterministic behavior, scalable and modular | Learning curve, may need rethinking architecture | Reactive systems, clean architecture |
Why the State Machine Kernel Wins
Promotes Innovation Without Chaos
With clear, hierarchical state transitions, your codebase becomes modular and self-documenting — making it easier to prototype, iterate, and innovate without fear of breaking hidden dependencies or triggering bugs.
Prevents Hidden Complexity
Unlike RTOSes, where tasks run in parallel and can create race conditions or timing bugs, state machines run cooperatively in a single-threaded model. This eliminates deadlocks, stack overflows, and debugging nightmares that come with thread-based systems.
Scales Without Becoming Fragile
As features and states are added, the system remains predictable. You don’t have to untangle spaghetti logic or rework your entire loop to support new behaviors — you just add new events and state transitions.
Improves Maintainability and Handoff
Because logic is encapsulated in individual states with defined transitions, the code is easier to understand, test, and maintain. This lowers the cost of onboarding new developers or revisiting the system years later.
At Wolff Electronic Design, we’ve worked with every kind of firmware structure over the past 15+ years. Our go-to for complex embedded systems? A state machine kernel. It gives our clients the flexibility of RTOS-level structure without the bugs, complexity, or overhead. Whether you’re developing restaurant equipment or industrial control systems, this architecture offers a better path forward: clean, maintainable, and built to last.
Learn more about our capabilities here.
design, #methodologies, #quantumleaps, #statemachines
-
 @ 91bea5cd:1df4451c
2025-04-15 06:27:28
@ 91bea5cd:1df4451c
2025-04-15 06:27:28Básico
bash lsblk # Lista todos os diretorios montados.Para criar o sistema de arquivos:
bash mkfs.btrfs -L "ThePool" -f /dev/sdxCriando um subvolume:
bash btrfs subvolume create SubVolMontando Sistema de Arquivos:
bash mount -o compress=zlib,subvol=SubVol,autodefrag /dev/sdx /mntLista os discos formatados no diretório:
bash btrfs filesystem show /mntAdiciona novo disco ao subvolume:
bash btrfs device add -f /dev/sdy /mntLista novamente os discos do subvolume:
bash btrfs filesystem show /mntExibe uso dos discos do subvolume:
bash btrfs filesystem df /mntBalancea os dados entre os discos sobre raid1:
bash btrfs filesystem balance start -dconvert=raid1 -mconvert=raid1 /mntScrub é uma passagem por todos os dados e metadados do sistema de arquivos e verifica as somas de verificação. Se uma cópia válida estiver disponível (perfis de grupo de blocos replicados), a danificada será reparada. Todas as cópias dos perfis replicados são validadas.
iniciar o processo de depuração :
bash btrfs scrub start /mntver o status do processo de depuração Btrfs em execução:
bash btrfs scrub status /mntver o status do scrub Btrfs para cada um dos dispositivos
bash btrfs scrub status -d / data btrfs scrub cancel / dataPara retomar o processo de depuração do Btrfs que você cancelou ou pausou:
btrfs scrub resume / data
Listando os subvolumes:
bash btrfs subvolume list /ReportsCriando um instantâneo dos subvolumes:
Aqui, estamos criando um instantâneo de leitura e gravação chamado snap de marketing do subvolume de marketing.
bash btrfs subvolume snapshot /Reports/marketing /Reports/marketing-snapAlém disso, você pode criar um instantâneo somente leitura usando o sinalizador -r conforme mostrado. O marketing-rosnap é um instantâneo somente leitura do subvolume de marketing
bash btrfs subvolume snapshot -r /Reports/marketing /Reports/marketing-rosnapForçar a sincronização do sistema de arquivos usando o utilitário 'sync'
Para forçar a sincronização do sistema de arquivos, invoque a opção de sincronização conforme mostrado. Observe que o sistema de arquivos já deve estar montado para que o processo de sincronização continue com sucesso.
bash btrfs filsystem sync /ReportsPara excluir o dispositivo do sistema de arquivos, use o comando device delete conforme mostrado.
bash btrfs device delete /dev/sdc /ReportsPara sondar o status de um scrub, use o comando scrub status com a opção -dR .
bash btrfs scrub status -dR / RelatóriosPara cancelar a execução do scrub, use o comando scrub cancel .
bash $ sudo btrfs scrub cancel / ReportsPara retomar ou continuar com uma depuração interrompida anteriormente, execute o comando de cancelamento de depuração
bash sudo btrfs scrub resume /Reportsmostra o uso do dispositivo de armazenamento:
btrfs filesystem usage /data
Para distribuir os dados, metadados e dados do sistema em todos os dispositivos de armazenamento do RAID (incluindo o dispositivo de armazenamento recém-adicionado) montados no diretório /data , execute o seguinte comando:
sudo btrfs balance start --full-balance /data
Pode demorar um pouco para espalhar os dados, metadados e dados do sistema em todos os dispositivos de armazenamento do RAID se ele contiver muitos dados.
Opções importantes de montagem Btrfs
Nesta seção, vou explicar algumas das importantes opções de montagem do Btrfs. Então vamos começar.
As opções de montagem Btrfs mais importantes são:
**1. acl e noacl
**ACL gerencia permissões de usuários e grupos para os arquivos/diretórios do sistema de arquivos Btrfs.
A opção de montagem acl Btrfs habilita ACL. Para desabilitar a ACL, você pode usar a opção de montagem noacl .
Por padrão, a ACL está habilitada. Portanto, o sistema de arquivos Btrfs usa a opção de montagem acl por padrão.
**2. autodefrag e noautodefrag
**Desfragmentar um sistema de arquivos Btrfs melhorará o desempenho do sistema de arquivos reduzindo a fragmentação de dados.
A opção de montagem autodefrag permite a desfragmentação automática do sistema de arquivos Btrfs.
A opção de montagem noautodefrag desativa a desfragmentação automática do sistema de arquivos Btrfs.
Por padrão, a desfragmentação automática está desabilitada. Portanto, o sistema de arquivos Btrfs usa a opção de montagem noautodefrag por padrão.
**3. compactar e compactar-forçar
**Controla a compactação de dados no nível do sistema de arquivos do sistema de arquivos Btrfs.
A opção compactar compacta apenas os arquivos que valem a pena compactar (se compactar o arquivo economizar espaço em disco).
A opção compress-force compacta todos os arquivos do sistema de arquivos Btrfs, mesmo que a compactação do arquivo aumente seu tamanho.
O sistema de arquivos Btrfs suporta muitos algoritmos de compactação e cada um dos algoritmos de compactação possui diferentes níveis de compactação.
Os algoritmos de compactação suportados pelo Btrfs são: lzo , zlib (nível 1 a 9) e zstd (nível 1 a 15).
Você pode especificar qual algoritmo de compactação usar para o sistema de arquivos Btrfs com uma das seguintes opções de montagem:
- compress=algoritmo:nível
- compress-force=algoritmo:nível
Para obter mais informações, consulte meu artigo Como habilitar a compactação do sistema de arquivos Btrfs .
**4. subvol e subvolid
**Estas opções de montagem são usadas para montar separadamente um subvolume específico de um sistema de arquivos Btrfs.
A opção de montagem subvol é usada para montar o subvolume de um sistema de arquivos Btrfs usando seu caminho relativo.
A opção de montagem subvolid é usada para montar o subvolume de um sistema de arquivos Btrfs usando o ID do subvolume.
Para obter mais informações, consulte meu artigo Como criar e montar subvolumes Btrfs .
**5. dispositivo
A opção de montagem de dispositivo** é usada no sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs.
Em alguns casos, o sistema operacional pode falhar ao detectar os dispositivos de armazenamento usados em um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs. Nesses casos, você pode usar a opção de montagem do dispositivo para especificar os dispositivos que deseja usar para o sistema de arquivos de vários dispositivos Btrfs ou RAID.
Você pode usar a opção de montagem de dispositivo várias vezes para carregar diferentes dispositivos de armazenamento para o sistema de arquivos de vários dispositivos Btrfs ou RAID.
Você pode usar o nome do dispositivo (ou seja, sdb , sdc ) ou UUID , UUID_SUB ou PARTUUID do dispositivo de armazenamento com a opção de montagem do dispositivo para identificar o dispositivo de armazenamento.
Por exemplo,
- dispositivo=/dev/sdb
- dispositivo=/dev/sdb,dispositivo=/dev/sdc
- dispositivo=UUID_SUB=490a263d-eb9a-4558-931e-998d4d080c5d
- device=UUID_SUB=490a263d-eb9a-4558-931e-998d4d080c5d,device=UUID_SUB=f7ce4875-0874-436a-b47d-3edef66d3424
**6. degraded
A opção de montagem degradada** permite que um RAID Btrfs seja montado com menos dispositivos de armazenamento do que o perfil RAID requer.
Por exemplo, o perfil raid1 requer a presença de 2 dispositivos de armazenamento. Se um dos dispositivos de armazenamento não estiver disponível em qualquer caso, você usa a opção de montagem degradada para montar o RAID mesmo que 1 de 2 dispositivos de armazenamento esteja disponível.
**7. commit
A opção commit** mount é usada para definir o intervalo (em segundos) dentro do qual os dados serão gravados no dispositivo de armazenamento.
O padrão é definido como 30 segundos.
Para definir o intervalo de confirmação para 15 segundos, você pode usar a opção de montagem commit=15 (digamos).
**8. ssd e nossd
A opção de montagem ssd** informa ao sistema de arquivos Btrfs que o sistema de arquivos está usando um dispositivo de armazenamento SSD, e o sistema de arquivos Btrfs faz a otimização SSD necessária.
A opção de montagem nossd desativa a otimização do SSD.
O sistema de arquivos Btrfs detecta automaticamente se um SSD é usado para o sistema de arquivos Btrfs. Se um SSD for usado, a opção de montagem de SSD será habilitada. Caso contrário, a opção de montagem nossd é habilitada.
**9. ssd_spread e nossd_spread
A opção de montagem ssd_spread** tenta alocar grandes blocos contínuos de espaço não utilizado do SSD. Esse recurso melhora o desempenho de SSDs de baixo custo (baratos).
A opção de montagem nossd_spread desativa o recurso ssd_spread .
O sistema de arquivos Btrfs detecta automaticamente se um SSD é usado para o sistema de arquivos Btrfs. Se um SSD for usado, a opção de montagem ssd_spread será habilitada. Caso contrário, a opção de montagem nossd_spread é habilitada.
**10. descarte e nodiscard
Se você estiver usando um SSD que suporte TRIM enfileirado assíncrono (SATA rev3.1), a opção de montagem de descarte** permitirá o descarte de blocos de arquivos liberados. Isso melhorará o desempenho do SSD.
Se o SSD não suportar TRIM enfileirado assíncrono, a opção de montagem de descarte prejudicará o desempenho do SSD. Nesse caso, a opção de montagem nodiscard deve ser usada.
Por padrão, a opção de montagem nodiscard é usada.
**11. norecovery
Se a opção de montagem norecovery** for usada, o sistema de arquivos Btrfs não tentará executar a operação de recuperação de dados no momento da montagem.
**12. usebackuproot e nousebackuproot
Se a opção de montagem usebackuproot for usada, o sistema de arquivos Btrfs tentará recuperar qualquer raiz de árvore ruim/corrompida no momento da montagem. O sistema de arquivos Btrfs pode armazenar várias raízes de árvore no sistema de arquivos. A opção de montagem usebackuproot** procurará uma boa raiz de árvore e usará a primeira boa que encontrar.
A opção de montagem nousebackuproot não verificará ou recuperará raízes de árvore inválidas/corrompidas no momento da montagem. Este é o comportamento padrão do sistema de arquivos Btrfs.
**13. space_cache, space_cache=version, nospace_cache e clear_cache
A opção de montagem space_cache** é usada para controlar o cache de espaço livre. O cache de espaço livre é usado para melhorar o desempenho da leitura do espaço livre do grupo de blocos do sistema de arquivos Btrfs na memória (RAM).
O sistema de arquivos Btrfs suporta 2 versões do cache de espaço livre: v1 (padrão) e v2
O mecanismo de cache de espaço livre v2 melhora o desempenho de sistemas de arquivos grandes (tamanho de vários terabytes).
Você pode usar a opção de montagem space_cache=v1 para definir a v1 do cache de espaço livre e a opção de montagem space_cache=v2 para definir a v2 do cache de espaço livre.
A opção de montagem clear_cache é usada para limpar o cache de espaço livre.
Quando o cache de espaço livre v2 é criado, o cache deve ser limpo para criar um cache de espaço livre v1 .
Portanto, para usar o cache de espaço livre v1 após a criação do cache de espaço livre v2 , as opções de montagem clear_cache e space_cache=v1 devem ser combinadas: clear_cache,space_cache=v1
A opção de montagem nospace_cache é usada para desabilitar o cache de espaço livre.
Para desabilitar o cache de espaço livre após a criação do cache v1 ou v2 , as opções de montagem nospace_cache e clear_cache devem ser combinadas: clear_cache,nosapce_cache
**14. skip_balance
Por padrão, a operação de balanceamento interrompida/pausada de um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs será retomada automaticamente assim que o sistema de arquivos Btrfs for montado. Para desabilitar a retomada automática da operação de equilíbrio interrompido/pausado em um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs, você pode usar a opção de montagem skip_balance .**
**15. datacow e nodatacow
A opção datacow** mount habilita o recurso Copy-on-Write (CoW) do sistema de arquivos Btrfs. É o comportamento padrão.
Se você deseja desabilitar o recurso Copy-on-Write (CoW) do sistema de arquivos Btrfs para os arquivos recém-criados, monte o sistema de arquivos Btrfs com a opção de montagem nodatacow .
**16. datasum e nodatasum
A opção datasum** mount habilita a soma de verificação de dados para arquivos recém-criados do sistema de arquivos Btrfs. Este é o comportamento padrão.
Se você não quiser que o sistema de arquivos Btrfs faça a soma de verificação dos dados dos arquivos recém-criados, monte o sistema de arquivos Btrfs com a opção de montagem nodatasum .
Perfis Btrfs
Um perfil Btrfs é usado para informar ao sistema de arquivos Btrfs quantas cópias dos dados/metadados devem ser mantidas e quais níveis de RAID devem ser usados para os dados/metadados. O sistema de arquivos Btrfs contém muitos perfis. Entendê-los o ajudará a configurar um RAID Btrfs da maneira que você deseja.
Os perfis Btrfs disponíveis são os seguintes:
single : Se o perfil único for usado para os dados/metadados, apenas uma cópia dos dados/metadados será armazenada no sistema de arquivos, mesmo se você adicionar vários dispositivos de armazenamento ao sistema de arquivos. Assim, 100% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser utilizado.
dup : Se o perfil dup for usado para os dados/metadados, cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos manterá duas cópias dos dados/metadados. Assim, 50% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser utilizado.
raid0 : No perfil raid0 , os dados/metadados serão divididos igualmente em todos os dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, não haverá dados/metadados redundantes (duplicados). Assim, 100% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser usado. Se, em qualquer caso, um dos dispositivos de armazenamento falhar, todo o sistema de arquivos será corrompido. Você precisará de pelo menos dois dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid0 .
raid1 : No perfil raid1 , duas cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a uma falha de unidade. Mas você pode usar apenas 50% do espaço total em disco. Você precisará de pelo menos dois dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1 .
raid1c3 : No perfil raid1c3 , três cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a duas falhas de unidade, mas você pode usar apenas 33% do espaço total em disco. Você precisará de pelo menos três dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1c3 .
raid1c4 : No perfil raid1c4 , quatro cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a três falhas de unidade, mas você pode usar apenas 25% do espaço total em disco. Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1c4 .
raid10 : No perfil raid10 , duas cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos, como no perfil raid1 . Além disso, os dados/metadados serão divididos entre os dispositivos de armazenamento, como no perfil raid0 .
O perfil raid10 é um híbrido dos perfis raid1 e raid0 . Alguns dos dispositivos de armazenamento formam arrays raid1 e alguns desses arrays raid1 são usados para formar um array raid0 . Em uma configuração raid10 , o sistema de arquivos pode sobreviver a uma única falha de unidade em cada uma das matrizes raid1 .
Você pode usar 50% do espaço total em disco na configuração raid10 . Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid10 .
raid5 : No perfil raid5 , uma cópia dos dados/metadados será dividida entre os dispositivos de armazenamento. Uma única paridade será calculada e distribuída entre os dispositivos de armazenamento do array RAID.
Em uma configuração raid5 , o sistema de arquivos pode sobreviver a uma única falha de unidade. Se uma unidade falhar, você pode adicionar uma nova unidade ao sistema de arquivos e os dados perdidos serão calculados a partir da paridade distribuída das unidades em execução.
Você pode usar 1 00x(N-1)/N % do total de espaços em disco na configuração raid5 . Aqui, N é o número de dispositivos de armazenamento adicionados ao sistema de arquivos. Você precisará de pelo menos três dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid5 .
raid6 : No perfil raid6 , uma cópia dos dados/metadados será dividida entre os dispositivos de armazenamento. Duas paridades serão calculadas e distribuídas entre os dispositivos de armazenamento do array RAID.
Em uma configuração raid6 , o sistema de arquivos pode sobreviver a duas falhas de unidade ao mesmo tempo. Se uma unidade falhar, você poderá adicionar uma nova unidade ao sistema de arquivos e os dados perdidos serão calculados a partir das duas paridades distribuídas das unidades em execução.
Você pode usar 100x(N-2)/N % do espaço total em disco na configuração raid6 . Aqui, N é o número de dispositivos de armazenamento adicionados ao sistema de arquivos. Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid6 .
-
 @ 9223d2fa:b57e3de7
2025-04-15 02:54:00
@ 9223d2fa:b57e3de7
2025-04-15 02:54:0012,600 steps
-
 @ bb1c863a:2953c3fb
2025-04-14 22:22:50
@ bb1c863a:2953c3fb
2025-04-14 22:22:50Block Height 892385 11:47 pm Monday, 14 April 2025
In a powerful gesture of support for Bitcoin-aligned education, Blockstream has donated 21 Blockstream Jade hardware wallets to the Consensus21 School — a groundbreaking learning initiative launching its first campus this year on the Mornington Peninsula, just outside Melbourne, Australia.
The donation will place 21 Jades directly into the hands of the first 21 students at the new campus — some as young as five years old — giving them real tools to explore Bitcoin self-custody, digital sovereignty, and privacy-first technology in an age-appropriate and hands-on way.
“The Jade wallets are more than just devices — they’re symbols of freedom, responsibility, and the future of education,” said Kieran Nolan, co-founder of Consensus21. “We’re incredibly grateful to Blockstream for standing behind our mission.”
Real Tools for Real Sovereignty
The Blockstream Jade is a secure, open-source hardware wallet built for Bitcoiners who value freedom, privacy, and independence. These values are embedded deeply into the Consensus21 educational philosophy, which blends Steiner-inspired learning, homeschooling flexibility, and a curriculum rooted in Bitcoin principles like voluntary exchange, decentralization, and self-responsibility.
With the Jades now part of the learning toolkit, Consensus21 learners will be introduced to key concepts like:
- Private key management
- Seed phrase generation and backup
- Multisig wallets
- The importance of self-custody and trust minimization
This is not just about theory — learners will get to use these tools in real-world contexts, preparing them to grow up fluent in the principles of freedom tech.
A Campus, A Vision, A Movement
Launching in 2025, the Mornington Peninsula campus is the pilot site for the broader Consensus21 vision: a distributed, regenerative, and values-aligned network of co-learning spaces, including a future 10-acre farm campus and a registered Steiner school.
The Blockstream donation comes at a pivotal time, as the community transitions from vision to reality. The gift of exactly 21 Blockstream Jades — echoing Bitcoin’s 21 million hard cap — is both a symbolic and practical gesture of support, underscoring the shared commitment between Bitcoin builders and grassroots educators.
Stay Connected
📄 Whitepaper: https://github.com/consensus21school/consensus21school.github.io/blob/main/whitepaper.md
🌐 Website: https://consensus21.school
📝 Nostr: CONSENSUS21@nostrcheck.me
🐦 X (Twitter): https://x.com/Consensus21
-
 @ 3906af02:af15c9f4
2024-12-19 13:40:00
@ 3906af02:af15c9f4
2024-12-19 13:40:00NEW: HRF #Bitcoin Development Fund grants 700 million satoshis to 20 projects worldwide!
https://bitcoinmagazine.com/business/human-rights-foundation-donates-700000000-satoshis-to-fund-bitcoin-development-and-projects
The grants cover decentralized #Bitcoin mining, technical education, decentralized communications, independent media & privacy-enhanced financial solutions for human rights groups, focusing on key regions in Latin America, Asia, and Africa 🌍🌏🌎🎁
Grants include:
🛠️ Stratum V2 Reference Implementation (SRI) decentralizes #Bitcoin mining by allowing nodes create their own block templates, reducing reliance on large pools. Funds will support @bit-aloo’s work on SRI including benchmarking tools, integration tests & codebase maintenance
⛏️ Public Pool makes #Bitcoin mining accessible for low-hash-rate devices, empowering individuals to self-host mining servers & contribute to decentralization. Funds will support hosting costs, hardware upgrades, & operational expenses.
🛠️ Jon Atack, recognized as one of the top all-time contributors to #Bitcoin Core, plays a pivotal role in enhancing Bitcoin’s decentralization and robustness. Funds will empower him to continue his vital contributions to Bitcoin development
👩🏿💻 Naiyoma, the first female #Bitcoin Core developer from Africa. Her work focuses on reviewing pull requests (PRs), addressing bugs through new PRs & improving Bitcoin Core’s codebase. Funds will support her full-time contributions to advancing Bitcoin Core.
🔒 Daniela Brozzoni, a #Bitcoin Core developer who previously contributed to the Bitcoin Development Kit (BDK). This grant will support her full-time contributions to Bitcoin Core reviewing key pull requests (PRs), contributing to new features & improving testing coverage
📱 UX/UI Design for Bitcoin Core by @Michaelhaase will bring the #Bitcoin Core App to mobile enabling users to run nodes, access essential wallet features directly on their phones to improve their financial privacy. Funding will support the project’s design & development.
🚀 Brink, co-founded by Mike Schmidt, supports #Bitcoin protocol engineers with grants and offers training & mentorship to onboard new contributors to open-source development. This grant will support operational expenses
⚡@Tando.me, cofounded by Sabina Gitau, integrates #Bitcoin with Kenya’s M-PESA system, enabling KYC-free, fee-free Lightning payments for everyday transactions for 54 million Kenyans. Funds will help boost Tando’s liquidity, support user growth & drive African expansion.
🌐 YakiHonne, a Nostr client founded by Wendy Ding, supports free speech & promote #Bitcoin payments across 170 countries with innovative functionality & a blend of online & offline events. Funds will support smart widget development, relay improvements & community events.
🌍 SeedSigner Multi-language Support brings accessibility to the open-source SeedSigner hardware wallet, empowering marginalized communities through inexpensive & accessible self-custody. Funds support Ace to deliver a multi-language version of SeedSigner.
🤝 Vexl, cofounded by Lea Petrasova, provides a private, KYC-free, peer-to-peer #Bitcoin trading experience by connecting users to trade through the social graph of their phone contacts. Funds will support expanded adoption in Africa & improvements to the backend infrastructure.
🇮🇳 Tomatech is building developer talent in Goa, India to advance #Bitcoin infrastructure & FOSS projects through training, workshops, & community meetups. Funding will support developer training, the creation of a developer hub, bounties & grants, & general operations.
💾 Krux, open-source firmware that turns generic devices into hardware wallets for secure #Bitcoin self-custody featuring air-gapped operations, key management & backups & support for 10 languages. Funding will support @odudex to advance this project.
🔐 Iris, a #Nostr web client by @MarttiMalmi, which aims to improve protection for metadata & message content, ensuring conversations remain private, especially in surveillant environments. Funding will support hiring an additional developer to expand Iris' features & functionality.
💻 Cashu-ts, the primary Software Development Kit in the @CashuBTC ecosystem developed by @Gandlaf21, simplifies wallet creation, integrates the latest protocol updates & powers popular wallets. Funds will support the developers to maintain & improve this essential library.
🤝 Unify, a Payjoin wallet developed by Fontaine, enhances privacy in #Bitcoin transactions by obscuring transaction histories, crucial for individuals navigating repressive regimes. Funds will support the developer to ship new features & expand compatibility with other wallets.
📢 The Financial Freedom Policy Coalition, led by Venezuelan activist Jorge Jraissati, promotes economic opportunities for people living under authoritarian regimes. Funds will support advocacy missions to educate policymakers on how #Bitcoin supports human rights.
🎓 African UX Bitcoin Bootcamp, led by @MouxDesign, empowered 10 African UX designers with #Bitcoin UX research skills ahead of the Africa Bitcoin Conference & support to test 5 popular Bitcoin products during the conference. Funds cover all program expenses for participants.
📰 No BS Bitcoin delivers ad-free, privacy-focused #Bitcoin news in clear & accessible format, essential for activists & citizens under authoritarian regimes. This grant ensures continued operations, adds an editor & supports Nostr features like Zaps & comments.
📖 Bitcoin History, a research project by Pete Rizzo, documenting key people, events & materials that shaped Bitcoin’s rise as a global monetary & human rights force. Fund will support a researcher to investigate & document stories of Bitcoin’s use against authoritarianism.
🌎 HRF is committed to supporting human rights and financial freedom with #Bitcoin.
If you are working on a #Bitcoin or adjacent freedom tech software (Nostr, eCash, TOR etc), education or adoption project that meets our mandate, submit your application at http://hrf.org/bdfapply 💪
-
 @ 5f078e90:b2bacaa3
2025-04-30 20:26:32
@ 5f078e90:b2bacaa3
2025-04-30 20:26:32Petal's Glow
In a quiet meadow, pink flower blooms named Petal danced under moonlight. Their delicate petals glowed, guiding a weary firefly home. Grateful, the firefly wove light patterns, telling their tale. By dawn, bees hummed Petal’s story, spreading it across the valley. The blooms stood prouder, their rosy hue a symbol of gentle hope.
This is 334 characters, some md, bidirectional-bridge.js used.

-
 @ 6e0ea5d6:0327f353
2025-04-14 15:11:17
@ 6e0ea5d6:0327f353
2025-04-14 15:11:17Ascolta.
We live in times where the average man is measured by the speeches he gives — not by the commitments he keeps. People talk about dreams, goals, promises… but what truly remains is what’s honored in the silence of small gestures, in actions that don’t seek applause, in attitudes unseen — yet speak volumes.
Punctuality, for example. Showing up on time isn’t about the clock. It’s about respect. Respect for another’s time, yes — but more importantly, respect for one’s own word. A man who is late without reason is already running late in his values. And the one who excuses his own lateness with sweet justifications slowly gets used to mediocrity.
Keeping your word is more than fulfilling promises. It is sealing, with the mouth, what the body must later uphold. Every time a man commits to something, he creates a moral debt with his own dignity. And to break that commitment is to declare bankruptcy — not in the eyes of others, but in front of himself.
And debts? Even the small ones — or especially the small ones — are precise thermometers of character. A forgotten sum, an unpaid favor, a commitment left behind… all of these reveal the structure of the inner building that man resides in. He who neglects the small is merely rehearsing for his future collapse.
Life, contrary to what the reckless say, is not built on grand deeds. It is built with small bricks, laid with almost obsessive precision. The truly great man is the one who respects the details — recognizing in them a code of conduct.
In Sicily, especially in the streets of Palermo, I learned early on that there is more nobility in paying a five-euro debt on time than in flaunting riches gained without word, without honor, without dignity.
As they say in Palermo: L’uomo si conosce dalle piccole cose.
So, amico mio, Don’t talk to me about greatness if you can’t show up on time. Don’t talk to me about respect if your word is fickle. And above all, don’t talk to me about honor if you still owe what you once promised — no matter how small.
Thank you for reading, my friend!
If this message resonated with you, consider leaving your "🥃" as a token of appreciation.
A toast to our family!
-
 @ 5f078e90:b2bacaa3
2025-04-30 20:13:35
@ 5f078e90:b2bacaa3
2025-04-30 20:13:35Cactus story
In a sun-scorched desert, a lone cactus named Sage stood tall. Each dawn, she whispered to the wind, sharing tales of ancient rains. One night, a lost coyote curled beneath her spines, seeking shade. Sage offered her last drops of water, saved from a rare storm. Grateful, the coyote sang her story to the stars, and Sage’s legend grew, a beacon of kindness in the arid wild.
This test is between 300 and 500 characters long, started on Nostr to test the bidirectional-bridge script.
It has a bit of markdown included.

-
 @ 7ed7d5c3:6927e200
2024-12-18 00:56:48
@ 7ed7d5c3:6927e200
2024-12-18 00:56:48There was a time when we dared not rustle a whisper. But now we write and read samizdat and, congregating in the smoking rooms of research institutes, heartily complain to each other of all they are muddling up, of all they are dragging us into! There’s that unnecessary bravado around our ventures into space, against the backdrop of ruin and poverty at home; and the buttressing of distant savage regimes; and the kindling of civil wars; and the ill-thought-out cultivation of Mao Zedong (at our expense to boot)—in the end we’ll be the ones sent out against him, and we’ll have to go, what other option will there be? And they put whomever they want on trial, and brand the healthy as mentally ill—and it is always “they,” while we are—helpless.
We are approaching the brink; already a universal spiritual demise is upon us; a physical one is about to flare up and engulf us and our children, while we continue to smile sheepishly and babble:
“But what can we do to stop it? We haven’t the strength.”
We have so hopelessly ceded our humanity that for the modest handouts of today we are ready to surrender up all principles, our soul, all the labors of our ancestors, all the prospects of our descendants—anything to avoid disrupting our meager existence. We have lost our strength, our pride, our passion. We do not even fear a common nuclear death, do not fear a third world war (perhaps we’ll hide away in some crevice), but fear only to take a civic stance! We hope only not to stray from the herd, not to set out on our own, and risk suddenly having to make do without the white bread, the hot water heater, a Moscow residency permit.
We have internalized well the lessons drummed into us by the state; we are forever content and comfortable with its premise: we cannot escape the environment, the social conditions; they shape us, “being determines consciousness.” What have we to do with this? We can do nothing.
But we can do—everything!—even if we comfort and lie to ourselves that this is not so. It is not “they” who are guilty of everything, but we ourselves, only we!
Some will counter: But really, there is nothing to be done! Our mouths are gagged, no one listens to us, no one asks us. How can we make them listen to us?
To make them reconsider—is impossible.
The natural thing would be simply not to reelect them, but there are no re-elections in our country.
In the West they have strikes, protest marches, but we are too cowed, too scared: How does one just give up one’s job, just go out onto the street?
All the other fateful means resorted to over the last century of Russia’s bitter history are even less fitting for us today—true, let’s not fall back on them! Today, when all the axes have hewn what they hacked, when all that was sown has borne fruit, we can see how lost, how drugged were those conceited youths who sought, through terror, bloody uprising, and civil war, to make the country just and content. No thank you, fathers of enlightenment! We now know that the vileness of the means begets the vileness of the result. Let our hands be clean!
So has the circle closed? So is there indeed no way out? So the only thing left to do is wait inertly: What if something just happens by itself?
But it will never come unstuck by itself, if we all, every day, continue to acknowledge, glorify, and strengthen it, if we do not, at the least, recoil from its most vulnerable point.
From lies.
When violence bursts onto the peaceful human condition, its face is flush with self-assurance, it displays on its banner and proclaims: “I am Violence! Make way, step aside, I will crush you!” But violence ages swiftly, a few years pass—and it is no longer sure of itself. To prop itself up, to appear decent, it will without fail call forth its ally—Lies. For violence has nothing to cover itself with but lies, and lies can only persist through violence. And it is not every day and not on every shoulder that violence brings down its heavy hand: It demands of us only a submission to lies, a daily participation in deceit—and this suffices as our fealty.
And therein we find, neglected by us, the simplest, the most accessible key to our liberation: a personal nonparticipation in lies! Even if all is covered by lies, even if all is under their rule, let us resist in the smallest way: Let their rule hold not through me!
And this is the way to break out of the imaginary encirclement of our inertness, the easiest way for us and the most devastating for the lies. For when people renounce lies, lies simply cease to exist. Like parasites, they can only survive when attached to a person.
We are not called upon to step out onto the square and shout out the truth, to say out loud what we think—this is scary, we are not ready. But let us at least refuse to say what we do not think!
This is the way, then, the easiest and most accessible for us given our deep-seated organic cowardice, much easier than (it’s scary even to utter the words) civil disobedience à la Gandhi.
Our way must be: Never knowingly support lies! Having understood where the lies begin (and many see this line differently)—step back from that gangrenous edge! Let us not glue back the flaking scales of the Ideology, not gather back its crumbling bones, nor patch together its decomposing garb, and we will be amazed how swiftly and helplessly the lies will fall away, and that which is destined to be naked will be exposed as such to the world.
And thus, overcoming our timidity, let each man choose: Will he remain a witting servant of the lies (needless to say, not due to natural predisposition, but in order to provide a living for the family, to rear the children in the spirit of lies!), or has the time come for him to stand straight as an honest man, worthy of the respect of his children and contemporaries? And from that day onward he:
· Will not write, sign, nor publish in any way, a single line distorting, so far as he can see, the truth;
· Will not utter such a line in private or in public conversation, nor read it from a crib sheet, nor speak it in the role of educator, canvasser, teacher, actor;
· Will not in painting, sculpture, photograph, technology, or music depict, support, or broadcast a single false thought, a single distortion of the truth as he discerns it;
· Will not cite in writing or in speech a single “guiding” quote for gratification, insurance, for his success at work, unless he fully shares the cited thought and believes that it fits the context precisely;
· Will not be forced to a demonstration or a rally if it runs counter to his desire and his will; will not take up and raise a banner or slogan in which he does not fully believe;
· Will not raise a hand in vote for a proposal which he does not sincerely support; will not vote openly or in secret ballot for a candidate whom he deems dubious or unworthy;
· Will not be impelled to a meeting where a forced and distorted discussion is expected to take place;
· Will at once walk out from a session, meeting, lecture, play, or film as soon as he hears the speaker utter a lie, ideological drivel, or shameless propaganda;
· Will not subscribe to, nor buy in retail, a newspaper or journal that distorts or hides the underlying facts.
This is by no means an exhaustive list of the possible and necessary ways of evading lies. But he who begins to cleanse himself will, with a cleansed eye, easily discern yet other opportunities.
Yes, at first it will not be fair. Someone will have to temporarily lose his job. For the young who seek to live by truth, this will at first severely complicate life, for their tests and quizzes, too, are stuffed with lies, and so choices will have to be made. But there is no loophole left for anyone who seeks to be honest: Not even for a day, not even in the safest technical occupations can he avoid even a single one of the listed choices—to be made in favor of either truth or lies, in favor of spiritual independence or spiritual servility. And as for him who lacks the courage to defend even his own soul: Let him not brag of his progressive views, boast of his status as an academician or a recognized artist, a distinguished citizen or general. Let him say to himself plainly: I am cattle, I am a coward, I seek only warmth and to eat my fill.
For us, who have grown staid over time, even this most moderate path of resistance will be not be easy to set out upon. But how much easier it is than self-immolation or even a hunger strike: Flames will not engulf your body, your eyes will not pop out from the heat, and your family will always have at least a piece of black bread to wash down with a glass of clear water.
Betrayed and deceived by us, did not a great European people—the Czechoslovaks—show us how one can stand down the tanks with bared chest alone, as long as inside it beats a worthy heart?
It will not be an easy path, perhaps, but it is the easiest among those that lie before us. Not an easy choice for the body, but the only one for the soul. No, not an easy path, but then we already have among us people, dozens even, who have for years abided by all these rules, who live by the truth.
And so: We need not be the first to set out on this path, Ours is but to join! The more of us set out together, the thicker our ranks, the easier and shorter will this path be for us all! If we become thousands—they will not cope, they will be unable to touch us. If we will grow to tens of thousands—we will not recognize our country!
But if we shrink away, then let us cease complaining that someone does not let us draw breath—we do it to ourselves! Let us then cower and hunker down, while our comrades the biologists bring closer the day when our thoughts can be read and our genes altered.
And if from this also we shrink away, then we are worthless, hopeless, and it is of us that Pushkin asks with scorn:
Why offer herds their liberation?
............................. Their heritage each generation
The yoke with jingles, and the whip.February 12, 1974
—translated from the Russian by Yermolai Solzhenitsyn
-
 @ 1ef61805:f18312cc
2025-04-13 22:40:49
@ 1ef61805:f18312cc
2025-04-13 22:40:49In today’s increasingly surveilled digital world, privacy and security are paramount. OpSec Academy has taken a major step forward by customizing TailsOS to create OpSecOS, an operating system built with the same focus on anonymity and privacy, but enhanced with a suite of peer-reviewed and battle-tested applications. These applications empower users with decentralised tools, ensuring complete control over their digital lives while maintaining the high standards of security and privacy that OpSec Academy stands for.
In this article, we’ll explore the tools available in OpSec Academy’s custom OpSecOS image, highlighting the new and updated features that enhance security, decentralisation, and privacy.
-
Sparrow Wallet (Version 2.1.3) Sparrow Wallet remains one of the most privacy-conscious Bitcoin wallets available. It provides an advanced suite of features such as multi-signature support, coin control, and hardware wallet integration, which allow users to have complete control over their funds. By integrating Sparrow Wallet into OpSecOS, we ensure that Bitcoin transactions are handled with the highest standards of privacy, all while utilising Tor to anonymise transaction data. Peer-Reviewed & Battle-Tested: Sparrow Wallet has been rigorously tested by the privacy community and has earned a reputation for robustness and security. Its commitment to user privacy makes it one of the most trusted Bitcoin wallets in the ecosystem.
-
Feather Wallet (Version 2.7.0) Feather Wallet is a lightweight yet powerful Bitcoin wallet designed with privacy and simplicity in mind. Featuring Tor support and integration with hardware wallets, Feather Wallet ensures that users' private information remains secure while offering an intuitive user experience. By adding Feather Wallet to OpSecOS, we provide an easy-to-use wallet solution without compromising security. Peer-Reviewed & Battle-Tested: Feather Wallet has undergone thorough peer review and is widely regarded as a secure and privacy-focused option for Bitcoin users. Its simplicity and security features have been battle-tested by users in real-world environments.
-
Liana Wallet (Version 10.0) Liana Wallet is a Bitcoin wallet designed with a strong emphasis on long-term security, recovery, and inheritance. It allows users to set up primary keys for regular spending and recovery keys that activate after a specified period of inactivity, making it ideal for scenarios where funds need to be securely passed on without relying on third-party custodians. The wallet supports advanced features like on-chain timelocks, enabling users to create time-locked backup keys for inheritance planning. Additionally, Liana offers a user-friendly interface with ready-made templates, such as "Simple Inheritance" and "Expanding Multisig," to simplify the wallet setup process. For those seeking a comprehensive solution, the Liana Box Starter Pack includes hardware signing devices, tamper-evident bags, seed phrase storage, and an inheritance letter, providing everything needed to set up a secure and resilient Bitcoin wallet.
-
Snort & Iris (Nostr Clients) For decentralised, secure communication, OpSecOS includes two leading Nostr protocol clients: Snort and Iris. These applications allow users to send and receive messages privately across a peer-to-peer network, eliminating the need for centralised messaging platforms that can compromise privacy. Snort: A minimalist interface for basic, secure messaging.
Iris: A feature-rich client that provides more tools and options for a robust, decentralised messaging experience.
Peer-Reviewed & Battle-Tested: Both Snort and Iris have been reviewed by the community for their security, decentralisation, and resilience. These clients have been battle-tested in real-world environments where privacy and security are non-negotiable, making them trusted tools for secure communications. By including both Snort and Iris, users of OpSecOS have a flexible and secure communication platform that protects their privacy.
-
BIP39 - Ian Coleman’s Tool Managing Bitcoin securely requires careful attention to wallet seed phrases. BIP39 allows users to generate mnemonic seed phrases offline, protecting against online threats. By integrating Ian Coleman's BIP39 tool into OpSecOS, we provide a secure, offline method for generating and managing wallet backups, ensuring users’ funds remain under their control at all times. Peer-Reviewed & Battle-Tested: The BIP39 tool is widely regarded as one of the most secure and trusted methods for generating wallet seed phrases. It has been peer-reviewed by security experts and used in countless real-world scenarios to ensure the safe recovery of cryptocurrency wallets.
-
Mempool.space Mempool.space is a real-time visualisation tool for Bitcoin’s mempool — the collection of unconfirmed transactions awaiting inclusion in the next block. This tool allows users to see transaction fees, network congestion, and block size, helping them optimise their Bitcoin transactions for speed and cost-effectiveness. Mempool.space provides an edge for users who want to monitor Bitcoin’s network activity and ensure that their transactions are processed in the most efficient manner. Peer-Reviewed & Battle-Tested: Mempool.space is used by advanced Bitcoin users, miners, and developers worldwide to monitor and optimise transactions. It has been thoroughly reviewed and is trusted by the community as an indispensable tool for understanding Bitcoin's network dynamics.
**Why These Applications Matter ** The integration of these peer-reviewed and battle-tested applications into OpSecOS transforms it from a privacy-focused operating system into a powerful, decentralised security suite. Each of these tools has been carefully selected to provide users with more control over their digital assets, communications, and privacy. Whether you’re trading Bitcoin, Monero, or engaging in private communications, these tools ensure that you are operating in a trusted, decentralised environment free from surveillance or censorship. These applications, trusted by privacy experts, offer an elevated user experience built on the core principles of decentralisation, security, and privacy. With these tools, users can navigate the digital world with confidence, knowing their activities remain private and under their control.
**New and Improved for 2025 ** While some applications have been updated to the latest, most secure versions, others have been removed to ensure OpSecOS stays focused on delivering the best possible security. We’ve carefully vetted each app to make sure it meets the highest standards for privacy and decentralisation, removing older or less secure applications that could pose risks to our users.
**Conclusion ** OpSec Academy’s custom OpSecOS takes the trusted, privacy-focused foundation of TailsOS and supercharges it with a suite of powerful, peer-reviewed and battle-tested applications. Whether you’re managing your Bitcoin and Monero holdings, engaging in private communications, or ensuring your wallet is securely backed up, OpSecOS provides you with everything you need to operate in a decentralised, secure, and private environment. As surveillance and digital threats continue to grow, OpSecOS remains a vital tool for users looking to protect their privacy and maintain complete control over their digital lives. OpSec Academy is committed to continually improving OpSecOS to meet the evolving demands of privacy-conscious users. With OpSecOS, we provide an enhanced privacy experience that stays true to the principles of decentralisation and operational security.
OpSec Academy offers consultations for individuals or organisations looking to integrate OpSecOS into their security framework. Contact us securely for more information.
-
-
 @ 59b96df8:b208bd59
2025-04-30 19:27:41
@ 59b96df8:b208bd59
2025-04-30 19:27:41Nostr is a decentralized protocol designed to be censorship-resistant.
However, this resilience can sometimes make data synchronization between relays more difficult—though not impossible.In my opinion, Nostr still lacks a few key features to ensure consistent and reliable operation, especially regarding data versioning.
Profile Versions
When I log in to a new Nostr client using my private key, I might end up with an outdated version of my profile, depending on how the client is built or configured.
Why does this happen?
The client fetches my profile data (kind:0 - NIP 1) from its own list of selected relays.
If I didn’t publish the latest version of my profile on those specific relays, the client will only display an older version.Relay List Metadata
The same issue occurs with the relay list metadata (kind:10002 - NIP 65).
When switching to a new client, it's common that my configured relay list isn't properly carried over because it also depends on where the data is fetched.Protocol Change Proposal
I believe the protocol should evolve, specifically regarding how
kind:0(user metadata) andkind:10002(relay list metadata) events are distributed to relays.Relays should be able to build a list of public relays automatically (via autodiscovery), and forward all received
kind:0andkind:10002events to every relay in that list.This would create a ripple effect:
``` Relay A relay list: [Relay B, Relay C]
Relay B relay list: [Relay A, Relay C]
Relay C relay list: [Relay A, Relay B]User A sends kind:0 to Relay A
→ Relay A forwards kind:0 to Relay B
→ Relay A forwards kind:0 to Relay C
→ Relay B forwards kind:0 to Relay A
→ Relay B forwards kind:0 to Relay C → Relay A forwards kind:0 to Relay B
→ etc. ```Solution: Event Encapsulation
To avoid infinite replication loops, the solution could be to wrap the user’s signed event inside a new event signed by the relay, using a dedicated
kind(e.g.,kind:9999).When Relay B receives a
kind:9999event from Relay A, it extracts the original event, checks whether it already exists or if a newer version is present. If not, it adds the event to its database.Here is an example of such encapsulated data:
json { "content": "{\"content\":\"{\\\"lud16\\\":\\\"dolu@npub.cash\\\",\\\"name\\\":\\\"dolu\\\",\\\"nip05\\\":\\\"dolu@dolu.dev\\\",\\\"picture\\\":\\\"!(image)[!(image)[https://pbs.twimg.com/profile_images/1577320325158682626/igGerO9A_400x400.jpg]]\\\",\\\"pubkey\\\":\\\"59b96df8d8b5e66b3b95a3e1ba159750a6edd69bcbba1857aeb652a5b208bd59\\\",\\\"npub\\\":\\\"npub1txukm7xckhnxkwu450sm59vh2znwm45mewaps4awkef2tvsgh4vsf7phrl\\\",\\\"created_at\\\":1688312044}\",\"created_at\":1728233747,\"id\":\"afc3629314aad00f8786af97877115de30c184a25a48440a480bff590a0f9ba8\",\"kind\":0,\"pubkey\":\"59b96df8d8b5e66b3b95a3e1ba159750a6edd69bcbba1857aeb652a5b208bd59\",\"sig\":\"989b250f7fd5d4cfc9a6ee567594c81ee0a91f972e76b61332005fb02aa1343854104fdbcb6c4f77ae8896acd886ab4188043c383e32a6bba509fd78fedb984a\",\"tags\":[]}", "created_at": 1746036589, "id": "efe7fa5844c5c4428fb06d1657bf663d8b256b60c793b5a2c5a426ec773c745c", "kind": 9999, "pubkey": "79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798", "sig": "219f8bc840d12969ceb0093fb62f314a1f2e19a0cbe3e34b481bdfdf82d8238e1f00362791d17801548839f511533461f10dd45cd0aa4e264d71db6844f5e97c", "tags": [] } -
 @ 73dc15e0:b7a84244
2025-04-12 14:24:06
@ 73dc15e0:b7a84244
2025-04-12 14:24:06プロローグ
童貞こと薄(すすき) 仙人(せんにん)29歳。ここに眠る。「RIP」。29年間ずっと不運だった。親が仙人なんて名前を付けるから。学校では薄い仙人で「はげ仙人」なんてよばれるし、会社は倒産し、家は燃え、さっきトラックで引かれたところだ。そして、今「自称邪心」に次の魔王になってほしいと頼まれている。
―「なんで俺がそんなことしなきゃいけないのだ。」
「君には普通の人間よりも欲が何倍も大きい。ほんとは君の世界では収まらないぐらいだよ。」
―「異世界に行くのはいいとして、なんで魔王なんだ?」
「一つは、さっきも言った通り、君の欲は大きい。二つ目はもうすぐ現魔王がいなくなるからだよ。」
―「勇者にでも殺されたか?」
「いや、勇者と魔王が結婚した。」
―「は?」意味がわからない。勇者は魔王を倒すものではないのか?
「いなくなるというよりは魔王をやめるという表現のほうが正しかったかな。」
邪神によると勇者と魔王が結婚し、現魔王は魔王をやめるので、勇者と魔王の子供に転生し、次の新たな魔王になってほしいとのことだった。
人族と魔族(エルフ、ドワーフ、悪魔など)がこの世界にはあり、人族は聖神、魔族は
邪神が保護しているそうで、人と魔族は大昔から敵対しているそうだ。
聖神は魔族を忌み嫌っているので、魔族を統べる物がいなくなればいつ人族が襲ってくるかわからない。
人族には個別スキル(怪力、俊足など)には一般スキルと固有スキルがある。
固有スキルは世界に一人しかもっておらず、使用者が死ぬと新しく生まれてきた誰かがその固有スキルを手にする。固有スキルは5000万人に1人ぐらいの割合だそうだ。
一般スキルは固有スキルと違い、スキルがかぶることはよくあるそうだ。
魔族は種族スキルがある。種族スキルとはその種族が全員同じスキルをもっている。
魔族は固有スキルや個別スキルがない代わり人よりも各ステータスが高い。
俺は邪神に恩恵を3つもらった。一つは「超再生」。これは怪我や魔力、体力を瞬時に再生させてくれるチート能力だ。2つ目は「代償」腕や心臓などの代償をつくることによって自分を強化したり、新しく武器を作ることができる。この能力は一つ目の「超再生」と組み合わせることでバグをうみだすことができる。3つ目は「入れ替え」これは、さわったことのある物や人との場所を入れ替えることができる。
この三つの恩恵で異世界を俺は生き抜いてやる。
-
 @ 866e0139:6a9334e5
2025-04-30 18:47:50
@ 866e0139:6a9334e5
2025-04-30 18:47:50Autor: Ulrike Guérot. Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier.**
Die neuesten Artikel der Friedenstaube gibt es jetzt auch im eigenen Friedenstaube-Telegram-Kanal.
https://www.youtube.com/watch?v=KarwcXKmD3E
Liebe Freunde und Bekannte,
liebe Friedensbewegte,
liebe Dresdener, Dresden ist ja auch eine kriegsgeplagte Stadt,
dies ist meine dritte Rede auf einer Friedensdemonstration innerhalb von nur gut einem halben Jahr: München im September, München im Februar, Dresden im April. Und der Krieg rückt immer näher! Wer sich den „Operationsplan Deutschland über die zivil-militärische Kooperation als wesentlicher Bestandteil der Kriegsführung“ anschaut, dem kann nur schlecht werden zu sehen, wie weit die Kriegsvorbereitungen schon gediehen sind.
Doch bevor ich darauf eingehe, möchte ich mich als erstes distanzieren von dem wieder einmal erbärmlichen Framing dieser Demo als Querfront oder Schwurblerdemo. Durch dieses Framing wurde diese Demo vom Dresdener Marktplatz auf den Postplatz verwiesen, wurden wir geschmäht und wurde die Stadtverwaltung Dresden dazu gebracht, eine „genehmere“ Demo auf dem Marktplatz zuzulassen! Es wäre schön, wenn wir alle - alle! - solche Framings weglassen würden und uns als Friedensbewegte die Hand reichen! Der Frieden im eigenen Haus ist die Voraussetzung für unsere Friedensarbeit. Der Streit in unserem Haus nutzt nur denen, die den Krieg wollen und uns spalten!
Ich möchte hier noch einmal klarstellen, von welcher Position aus ich hier und heute wiederholt auf einer Bühne spreche: Ich spreche als engagierte Bürgerin der Bundesrepublik Deutschland. Ich spreche als Europäerin, die lange Jahre in und an dem einstigen Friedensprojekt EU gearbeitet hat. Ich spreche als Enkelin von zwei Großvätern. Der eine ist im Krieg gefallen, der andere kam ohne Beine zurück. Ich spreche als Tochter einer Mutter, die 1945, als 6-Jährige, unter traumatischen Umständen aus Schlesien vertrieben wurde, nach Delitzsch in Sachsen übrigens. Ich spreche als Mutter von zwei Söhnen, 33 und 31 Jahre, von denen ich nicht möchte, dass sie in einen Krieg müssen. Von dieser, und nur dieser Position aus spreche ich heute zu Ihnen und von keiner anderen! Ich bin nicht rechts, ich bin keine Schwurblerin, ich bin nicht radikal, ich bin keine Querfront.
Als Bürgerin wünsche ich mir – nein, verlange ich! – dass die Bundesrepublik Deutschland sich an ihre gesetzlichen Grundlagen und Vertragstexte hält. Das sind namentlich: Die Friedensklausel des Grundgesetzes aus Art. 125 und 126 GG, dass von deutschem Boden nie wieder Krieg ausgeht. Und der Zwei-plus-Vier-Vertrag, in dem Deutschland 1990 unterschrieben hat, dass es nie an einem bewaffneten Konflikt gegen Russland teilnimmt. Ich schäme mich dafür, dass mein Land dabei ist, vertragsbrüchig zu werden. Ich bitte Friedrich Merz, den designierten Bundeskanzler, keinen Vertragsbruch durch die Lieferung von Taurus-Raketen zu begehen!
Ich bitte ferner darum, dass sich dieses Land an seine didaktischen Vorgaben für Schulen hält, die im immer noch geltenden „Beutelsbacher Konsens“ aus den 1970er Jahren festgelegt wurden. In diesem steht in Artikel I. ein Überwältigungsverbot: „Es ist nicht erlaubt, den Schüler – mit welchen Mitteln auch immer – im Sinne erwünschter Meinungen zu überrumpeln und damit an der Gewinnung eines selbständigen Urteils zu hindern.“ Vor diesem Hintergrund ist es nicht erlaubt, Soldaten oder Gefreite in Schulen zu schicken und für die Bundeswehr zu werben. Vielmehr wäre es geboten, unsere Kinder über Art. 125 & 126 GG und die Friedenspflicht des Landes und seine Geschichte mit Blick auf Russland aufzuklären.
Als Europäerin wünsche ich mir, dass wir die europäische Hymne, Beethovens 9. Sinfonie, ernst nehmen, deren Text da lautet: Alle Menschen werden Brüder. Alle Menschen werden Brüder. Alle! Dazu gehören auch die Russen und natürlich auch die Ukrainer!
Als Europäerin, die in den 1990er Jahren für den großartigen EU-Kommissionspräsidenten Jacques Delors gearbeitet hat, Katholik, Sozialist und Gewerkschafter, wünsche ich mir, dass wir das Versprechen, #Europa ist nie wieder Krieg, ernst nehmen. Wir haben es 70 Jahre lang auf diesem Kontinent erzählt. Die Lügen und die Propaganda, mit der jetzt die Kriegsnotwendigkeit gegen Russland herbeigeredet wird, sind unerträglich. Die EU, Friedensnobelpreisträgerin von 2012, ist dabei – oder hat schon – ihr Ansehen in der Welt verloren. Es ist eine politische Tragödie! Neben ihrem Ansehen ist die EU jetzt dabei, das zivilisatorische Erbe Europas zu verspielen, die civilité européenne, wie der französische Historiker und Marxist, Étienne Balibar es nennt.
Ein Element dieses historischen Erbes ist es, dass uns in Europa eint, dass wir über Jahrhunderte alle zugleich Täter und Opfer gewesen sind. Ce que nous partageons, c’est ce que nous étions tous bourreaux et victimes. So schreibt es der französische Literat Laurent Gaudet in seinem europäischen Epos, L’Europe. Une Banquet des Peuples von 2016.
Das heißt, dass niemand in Europa, niemand – auch die Esten nicht! – das Recht hat, vorgängige Traumata, die die baltischen Staaten unbestrittenermaßen mit Stalin-Russland gehabt haben, zu verabsolutieren, auf die gesamte EU zu übertragen, die EU damit zu blockieren und die Politikgestaltung der EU einseitig auf einen Kriegskurs gegen Russland auszurichten. Ich wende mich mit dieser Feststellung direkt an Kaja Kalles, die Hohe Beauftragte für Sicherheits- und Außenpolitik der EU und hoffe, dass sie diese Rede hört und das Epos von Laurent Gaudet liest.
Es gibt keinen gerechten Krieg! Krieg ist immer nur Leid. In Straßburg, dem Sitz des Europäischen Parlaments, steht auf dem Place de la République eine Statue, eine Frau, die Republik. Sie hält in jedem Arm einen Sohn, einen Elsässer und einen Franzosen, die aus dem Krieg kommen. In der Darstellung der Bronzefigur haben die beiden Soldaten-Männer ihre Uniformen schon ausgezogen und werden von Madame la République gehalten und getröstet. An diesem Denkmal sollten sich alle Abgeordnete des Straßburger Europaparlamentes am 9. Mai versammeln. Ich zitiere noch einmal Cicero: Der ungerechteste Friede ist besser als der gerechteste Krieg. Für den Vortrag dieses Zitats eines der größten Staatsdenker des antiken Roms in einer Fernsehsendung bin ich 2022 mit einem Shitstorm überzogen worden. Allein das ist Ausdruck des Verfalls unserer Diskussionskultur in unfassbarem Ausmaß, ganz besonders in Deutschland.
Als Europäerin verlange ich die Überwindung unserer kognitiven Dissonanz. Wenn schon die New York Times am 27. März 2025 ein 27-seitiges Dossier veröffentlicht, das nicht nur belegt, was man eigentlich schon weiß, aber bisher nicht sagen durfte, nämlich, dass der ukrainisch-russische Krieg ein eindeutiger Stellvertreter-Krieg der USA ist, in der die Ukraine auf monströseste Weise instrumentalisiert wurde – was das Dossier der NYT unumwunden zugibt! – wäre es an der Zeit, die eindeutige Schuldzuweisung an Russland für den Krieg zurückzuziehen und die gezielt verbreitete Russophobie in Europa zu beenden. Anstatt dass – wofür es leider viele Verdachtsmomente gibt – die EU die Friedensverhandlungen in Saudi-Arabien nach Strich und Faden torpediert.
Der französische Philosoph Luc Ferry hat vor ein paar Tagen im prime time französischen Fernsehen ganz klar gesagt, dass der Krieg 2014 nach der Instrumentalisierung des Maidan durch die USA von der West-Ukraine ausging, dass Zelensky diesen Krieg wollte und – mit amerikanischer Rückendeckung – provoziert hat, dass Putin nicht Hitler ist und dass die einzigen mit faschistoiden Tendenzen in der ukrainischen Regierung sitzen. Ich wünschte mir, ein solches Statement wäre auch im Deutschen Fernsehen möglich und danke Richard David Precht, dass er, der noch in den Öffentlich-Rechtlichen Rundfunk vorgelassen wird, an dieser Stelle versucht, etwas Vernunft in die Debatte zu bringen.
Auch ist es gerade als Europäerin nicht hinzunehmen, dass russische Diplomaten von den Feierlichkeiten am 8. Mai 2025 ausgeschlossen werden sollen, ausgerechnet 80 Jahre nach Ende des II. Weltkrieges. Nicht nur sind Feierlichkeiten genau dazu da, sich die Hand zu reichen und den Frieden zu feiern. Doch gerade vor dem Hintergrund von 27 Millionen gefallenen sowjetischen Soldaten ist die Zurückweisung der Russen von den Feierlichkeiten geradezu eklatante Geschichtsvergessenheit.
***
Der Völkerbund hat 1925 die Frage erörtert, warum der I. Weltkrieg noch so lange gedauert hat, obgleich er militärisch bereits 1916 nach Eröffnung des Zweifrontenkrieges zu Lasten des Deutschen Reiches entschieden war. Wir erinnern uns: Für die Niederlage wurden mit der Dolchstoßlegende die jüdischen, kommunistischen und sozialistischen Pazifisten verantwortlich gemacht. Richtig ist, so der Bericht des Völkerbundes von 1925, dass allein die Rüstungsindustrie dafür gesorgt hat, dass der militärisch eigentlich schon entschiedene Krieg noch zwei weitere Jahre als Materialabnutzungs- und Stellungskrieg weiterbetrieben wurde, nur, damit noch ein bisschen Geld verdient werden konnte. Genauso scheint es heute zu sein. Der Krieg ist militärisch entschieden. Er kann und muss sofort beendet werden, und das passiert lediglich deswegen nicht, weil der Westen seine Niederlage nicht zugeben kann. Hochmut aber kommt vor dem Fall, und es darf nicht sein, dass für europäischen Hochmut jeden Tag rund 2000 ukrainische oder russische Soldaten und viele Zivilisten sterben. Die offenbare europäische Absicht, den Krieg jetzt einzufrieren, nur, um ihn 2029/ 2030 wieder zu entfachen, wenn Europa dann besser aufgerüstet ist, ist nur noch zynisch.
Als Kriegsenkelin von Kriegsversehrten, Tochter einer Flüchtlingsmutter und Mutter von zwei Söhnen, deren französischer Urgroßvater 6 Jahre in deutscher Kriegsgefangenschaft war, wünsche ich mir schließlich und zum Abschluss, dass wir die Kraft haben werden, wenn dieser Wahnsinn, den man den europäischen Bürgern gerade aufbürdet, vorbei sein wird, ein neues europäisches Projekt zu erdenken und zu erbauen, in dem Europa politisch geeint ist und es bleibt, aber dezentral, regional, subsidiär, friedlich und neutral gestaltet wird. Also ein Europa jenseits der Strukturen der EU, das bereit ist, die Pax Americana zu überwinden, aus der NATO auszutreten und der multipolaren Welt seine Hand auszustrecken! Unser Europa ist postimperial, postkolonial, groß, vielfältig und friedfertig!
Ulrike Guérot, Jg. 1964, ist europäische Professorin, Publizistin und Bestsellerautorin. Seit rund 30 Jahren beschäftigt sie sich in europäischen Think Tanks und Universitäten in Paris, Brüssel, London, Washington, New York, Wien und Berlin mit Fragen der europäischen Demokratie sowie mit der Rolle Europas in der Welt. Ulrike Guérot ist seit März 2014 Gründerin und Direktorin des European Democracy Lab e.V., Berlin und initiierte im März 2023 das European Citizens Radio, das auf Spotify zu finden ist. Zuletzt erschien von ihr „Über Halford J. Mackinders Heartland-Theorie, Der geografische Drehpunkt der Geschichte“ (Westend, 2024). Mehr Infos zur Autorin hier.
LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt.
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: friedenstaube@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ fd78c37f:a0ec0833
2024-12-11 01:32:23
@ fd78c37f:a0ec0833
2024-12-11 01:32:23Bitcoin, as a decentralized digital currency, is reshaping the global financial landscape, sparking innovation and transformation across various sectors. In South America, Bitcoin communities are emerging as crucial drivers of economic empowerment, financial inclusion, and local technological advancement. This issue will highlight 21 Bitcoin communities from South America, exploring their missions, growth trajectories, and recent developments. By examining these grassroots initiatives, we aim to show how Bitcoin is being leveraged to create sustainable economic ecosystems, foster social progress, and expand access to education and financial tools. Thank you, YakiHonne decentralized media client on Nostr to support people in owning their voice. #iOS #Android, for supporting the publication of the Bitcoin Community Newsletter. Most of the content has been reviewed and confirmed by the South American communities. If there are any omissions, please feel free to reach out to me.
1.Mi Primer Bitcoin nostr:npub17cyatz6z2dzcw6xehtcm9z45m76lde5smxdmyasvs00r4pqv863qrs4ml3 * Introduction My First Bitcoin is a Bitcoin education initiative rooted in the principles of independence, fairness, and community leadership. Originating in El Salvador, it aims to empower individuals and communities by providing open-source educational resources and fostering a decentralized network. Through a commitment to high-quality education, resistance to external influence, and the creation of a global collaborative network, it seeks to spread Bitcoin education to every corner of the world, offering a transparent and transformative model for reshaping traditional financial systems. * Latest Updates Recently, MyfirstBitcoin successfully hosted the fourth Bitcoin Educators Unconference, featuring guests such as nostr:npub1zfgx8v2g0faswd0ry2qn3ay4pvx4jr6q4fw9d0yqalpkyv9hhp0sjccnj5 nostr:npub1rhh9pkmf6l6z7298yg6fgp95rzkmx4j9uxpekn8j73p5k95ck7gsvce7vj attracting around 170 participants and receiving positive feedback. They also held the graduation ceremony in Ilopango, El Salvador, and continued to organize their regular monthly Bitcoin education meetups and Bitcoin game nights. Additionally, MyfirstBitcoin’s Bitcoin Educators Node Network welcomed four new projects from Canada, Nigeria, and the United States. In partnership with Bitcoin Boma, they are launching a free online Bitcoin education course for Malawi in January 2025, aimed at enhancing local Bitcoin knowledge.
- Introduction Bitcoin Beach is a groundbreaking initiative in El Salvador aimed at fostering sustainable local economic development through Bitcoin. The project provides financial services to the community, particularly for those without access to traditional banking. By using Bitcoin for payments, residents can cover everyday expenses such as utility bills, medical costs, and food. Bitcoin Beach leverages the Lightning Network and community collaboration to promote the adoption of Bitcoin both within El Salvador and globally.
- Latest Updates Recently, Bitcoin Beach attended the conference at Bitcoin Lake, where they hosted the Bitcoin Beach Meetup and Bitcoin Beach Festival to support local businesses with Bitcoin. They also invited notable figures such as nostr:npub1q0al05h2uvtj0fp8ww7etl0pdjnkum638ynz9tmku3e522fyvlmqjq04mt Hermann Buhr-Vivier, nostr:npub164xhe3pgcqaj70ls7ls5e4hwlnvl4ttuu8wns99jmwp5z6lwhutsa27wle as podcast guests. The discussions covered a range of impactful topics, including how Bitcoin mining can truly light up rural Africa, how to use Bitcoin to transform small towns in South Africa, and integrating Bitcoin into state-level policies across the United States, among other key areas.
3.Praia Bitcoin Brazil nostr:npub1m3tu3l6y59g2tmackq23v5vgn59u7hu66gxg8xajghz59tqm6xnqk2m888 * Introduction Praia Bitcoin Brazil, located in Jericoacoara, Brazil, is dedicated to creating the country's first Bitcoin circular economy, empowering local residents with financial inclusion. Founded by Fernando Motolese, the project promotes Bitcoin adoption through education, technology, and community-driven initiatives. It has integrated over 40 local businesses into the Bitcoin ecosystem and raised more than 12 BTC through Bitcoin-only crowdfunding. Praia Bitcoin offers self-sovereign financial services and runs programs like the "Bitcoin Smiles" initiative and educational support for children. * Latest Updates Recently, Praia Bitcoin Brazil launched several innovative projects, including the first stage lighting course and free acoustic guitar course funded entirely through Bitcoin crowdfunding. Additionally, Praia Bitcoin successfully hosted the Praia Bitcoin Conference 2024, attracting 10 volunteers, 100 local residents, and 10 new merchants. The conference also sponsored the first music performance paid in Bitcoin and introduced three local courses, all funded via Bitcoin crowdfunding. These initiatives highlight Praia Bitcoin's ongoing efforts to drive Bitcoin adoption and foster local community development.
4.Bitcoin Lake / Lago Bitcoin Guatemala nostr:npub1a4excy7uf9z3mcafvm9cwdr549dl5lpazuvpr2nc550vf27n5a4scqq5k2 * Introduction Bitcoin Lake aims to create a circular economy powered by Bitcoin, providing a novel and accessible solution for unbanked as well as banked merchants in Guatemala. * Latest Updates The Bitcoin Lake community has been actively preparing and promoting a series of innovative initiatives. On November 30 and December 1, Bitcoin Lake successfully hosted its 2024 conference, inviting industry experts such as Ronny Avendaño, co-founder and CEO of the Bitcoin hardware store, and prominent Bitcoin advocate Roman Martínez (chimbera). During the conference, the community also organized creative activities like the coffee workshop and “Be Captain of the Bitcoin Boat”, offering participants an opportunity to dive deeper into Bitcoin and the local economy. Additionally, through partnerships with local merchants, Bitcoin Lake is actively advancing the development of the Bitcoin economy, fostering economic growth and financial inclusion in the community.
5.Bitcoin jungle nostr:npub14f26g7dddy6dpltc70da3pg4e5w2p4apzzqjuugnsr2ema6e3y6s2xv7lu * Introduction Bitcoin Jungle is an open-source community project built on the Bitcoin Lightning Network with the goal of creating a circular Bitcoin economy. The project provides education, resources, and technology to both individuals and businesses. Starting from the Golden Triangle area in Costa Rica (Dominical, Uvita, Ojochal, Platanillo, Tinamaste), it is developing a shining example of what a Bitcoin community can represent. * Latest Updates Recently, the Bitcoin Jungle community has been actively promoting the adoption and use of Bitcoin in Costa Rica, participating in various projects and events. Community members attended the Adopting Bitcoin conference in El Salvador, further advancing global Bitcoin adoption. At the same time, they have been actively supporting children's charity projects and Bitcoin diploma courses, continuously driving Bitcoin education, social responsibility, and community development.
6.Bitcoin Berlín sv * Introduction Bitcoin Berlín sv aimed at creating a financially sovereign town in Berlín, El Salvador, through the implementation of a Bitcoin circular economy. The project seeks to integrate Bitcoin into the local economy by educating residents and businesses about its benefits, promoting the adoption of Bitcoin-based payment systems, and empowering local entrepreneurs with financial education. It also focuses on environmental sustainability, encouraging the use of renewable energy and waste reduction. * Latest Updates Recently, the Bitcoin Berlín sv has been actively promoting the use of Bitcoin by sharing informative articles and supporting the graduation of podcast producer Joel through the BlinkBTC QR code platform, allowing contributions in sats. This initiative not only supports the growth and development of community members but also furthers Bitcoin’s adoption and usage within the community. Additionally, on November 23rd, the community successfully hosted a cultural festival celebrating the local heritage. During the event, all vendors accepted Bitcoin payments, showcasing its practical application in Berlín’s economy. The festival attracted numerous tourists and residents eager to experience Bitcoin payments, further advancing its integration into daily life.
7.Bitcoin embassy San Salvador * Introduction Bitcoin embassy San Salvador is more into promoting Nostr in the region. * Latest Updates Recently, the Bitcoin Embassy San Salvador has been actively promoting the use and adoption of Bitcoin within the community, organizing various events. One of the highlights was the Christmas Toy Drive x Cuarteto Salvación, where toys were purchased using Sats to bring holiday cheer to children in need. The event, held on December 1 at Cuscatlán Park, also featured a special Music Night, attracting a large audience. Additionally, the Embassy hosted an educational gathering for food vendors, aimed at promoting Bitcoin payment systems. During the event, vendors accept Bitcoin payments through tiankii_Tech and blinkbtc platforms, further encouraging local businesses to embrace and adopt Bitcoin payments.
8.ONG Bitcoin Argentina * Introduction ONG Bitcoin Argentina is dedicated to advancing the development and application of decentralized technologies, particularly in the fields of Bitcoin, cryptocurrencies, and blockchain. As a leading organization in this space, the community promotes user protection and the healthy growth of the crypto ecosystem through education, training, and public advocacy. Its mission is to help individuals, businesses, and decision-makers understand and leverage decentralized, transparent, and secure technologies to bring more opportunities and progress to society. ONG Bitcoin Argentina has become a leading force in promoting decentralized technology in Argentina and Latin America. * Latest Updates Recently, ONG Bitcoin Argentina has been actively preparing for the “Moon Party | Despedimos el año ATH (A Todo Hodler)” celebration, set to take place on December 5, 2024. Bitcoin enthusiasts will gather to enjoy exciting activities, including a Lightning Network demonstration and the Fish Bowl Manizesto Bitcoiner art exhibition. In addition, the community has hosted and will host a series of conferences and workshops covering a range of topics, including local digital asset services, Bitcoin as a strategic reserve in the U.S., the reconversion of the Bitcoin and cryptocurrency economy and financial systems, the role of crypto economics in financial system reform, the impact of Bitcoin ETFs on markets, and Bitcoin's influence on global issues, fostering in-depth discussions and development within the crypto industry.
9.La bitcoineta * Introduction La Bitcoineta is an initiative launched by the Argentine community in 2018, designed to promote the adoption and understanding of Bitcoin through a unique and powerful tool: a van and a group of volunteers. This traveling educational project has visited hundreds of towns across Latin America, Africa, and Europe, reaching thousands of people and covering hundreds of thousands of kilometers with the aim of spreading its mission and activities.With its innovative and mobile approach, Bitcoineta has become a globally recognized educational project.
10.Motiv Peru * Introduction Motiv is a non-profit organization founded in 2020, focused on addressing systemic poverty through Bitcoin and innovative projects, aiming to provide better opportunities for survival and prosperity to underserved communities. Its founders, Rich Swisher and Vali Popescu, witnessed firsthand the tragic impact of poverty and lack of basic living conditions in a remote village in the Andes Mountains of Peru, where children were dying due to preventable causes. This inspired them to create Motiv, with the goal of empowering vulnerable populations. By leveraging global support and partnerships, Motiv uses Bitcoin to help local communities break free from poverty and improve their lives, striving to bring positive change and hope to those in need. * Latest Updates Recently, MOTIV Perú has made significant progress in promoting Bitcoin and the circular economy. The organization continues to transform communities across Peru through various initiatives. For example, in the Comas district of Lima, entrepreneurial women are paying for their classes with Bitcoin and learning how to make delicious desserts, further advancing the local circular economy. Additionally, MOTIV Perú held its first Bitcoin training in Carabayllo-Lima, helping Peruvians understand the nature of money and the advantages of Bitcoin. MOTIV is also assisting communities in areas like Tarapoto and Ancon, where locals are using Bitcoin for daily transactions, driving financial freedom and economic empowerment.
11.Montanha bitcoin * Introduction Building a circular economy in Sao thome, Brazil. * Latest Updates Recently, The community has had no recent updates. The latest event dates back to June 2024, highlighting a water contamination incident.
12.Amityage honduras * Introduction Amityage Honduras is the first Bitcoin education center in Honduras, located on Roatán Island in the Prosperá zone. The center's mission is to educate the local community about Bitcoin and spread this knowledge throughout Central America and the Caribbean. It is dedicated to helping businesses on the island adopt Bitcoin as a payment method, teaching children financial literacy, and empowering individuals to achieve financial sovereignty through Bitcoin. The center aims to empower the local community through education and innovation, fostering economic independence and sustainable development. * Latest Updates Recently, Amityage Honduras is actively promoting Bitcoin education by participating in various international Bitcoin events and organizing local courses to help more people understand Bitcoin. Community members took part in significant events such as AdoptingBTC 2024 and BitcoinUnconference, and hosted workshops around the theme of “How to Enter the World of Bitcoin Education.” In Haidmühle, Germany, AmityAge completed a four-day Bitcoin Educators Academy, where the curriculum included topics like using simple analogies to explain Bitcoin and public speaking exercises. Additionally, the community hosted Bitcoin education courses on Roatán Island and provided a free Bitcoin event for beginners at the Crawfish Rock community, further spreading Bitcoin knowledge.
13.Lima - Orange Pill Perú nostr:npub1fw8m5g6nfywmsgqjc66j47jax7jrv8lq46zf7grydjqppc54a8eql47qrx * Introduction Orange Pill Peru is a community-driven initiative dedicated to empowering Peruvians through Bitcoin education. With a focus on transforming the financial landscape, Orange Pill Peru provides resources for individuals to learn about Bitcoin, connect with like-minded enthusiasts, and grow their knowledge through various events and workshops. The community serves as a hub for both beginners and professionals, offering a supportive environment to explore the fundamentals of Bitcoin, its history, and its potential to shape the future of finance. * Latest Updates Recently, there have been no major updates. They actively engage in Bitcoin education and industry updates by sharing and reposting Bitcoin-related content. They support MOTIV Perú's financial freedom education project in the Ancon community in Lima, emphasizing the empowerment of women through Bitcoin. Additionally, the community has shared information about the upcoming Bitcoin Medellin Conference scheduled for January 2025.
14.La Antigua Bitcoin * Introduction La Antigua Bitcoin is a community-based initiative in La Antigua Guatemala, focusing on promoting Bitcoin adoption in local businesses. The community works to create awareness and facilitate the use of Bitcoin as a payment method in various establishments throughout the city. By encouraging merchants to accept Bitcoin, La Antigua Bitcoin aims to integrate cryptocurrency into the everyday economy, driving financial innovation and expanding access to decentralized financial systems within the region. * Latest Updates Recently, the Antigua Bitcoin community has had few updates, with a focus on organizing its first meetup in collaboration with “Run with Bitcoin” on November 24, 2023. The event garnered significant attention within the community, featuring interactions with a special guest. The aim of the event was to further promote Bitcoin adoption in Antigua, Guatemala, and encourage exchange and collaboration between Bitcoin enthusiasts and the local community.
15.Horizonte Bitcoin nostr:npub1wl8u4wfqsdz5m9ey0vvzh4y05mcpk2lm2xhhpw3uzs3878c2mw9sr2ksxk * Introduction Project that aims to contribute to the Bitcoinization of the economy and encourage Entrepreneurship and Decentralization. * Latest Updates Recently, The community has had no recent updates. The latest event dates back to Oct 2024, which shared a message encouraging women to learn more about Bitcoin and connect with others in the field, highlighted a meetup, Satoshe's Lounge, for women, providing a space to learn, discuss, and share knowledge about Bitcoin.
16.Escuelita Bitcoin nostr:npub1awggmqvlw8pa0kp9qq5law8zsvp2a8suztk0357j7e0nt746suwspt7lwx * Introduction Educational Project for Little School. * Latest Updates Recently, the Escuelita Bitcoin team has grown to five members and is actively advancing Bitcoin education and community development. Team members have hosted several workshops in Paraguay and Mexico, spreading Bitcoin knowledge within local communities and encouraging merchants to accept Bitcoin payments, particularly in Ciudad del Este, Paraguay. The team is raising funds through platforms like Geyser. fund and Kuno.anne.media to support the expansion of their educational initiatives and help locals better understand and use Bitcoin. Escuelita Bitcoin also emphasizes privacy education, promoting the use of tools like CakeWallet and Monero. Through collaborations with other organizations and individuals, the team is extending the reach of Bitcoin education, fostering the adoption of Bitcoin in Latin America and emerging markets.
17.Bitcoin é aqui! Rolante/Riozinho-RS-BRASIL nostr:npub168dqt5c8ue3uj8ynlk0lhwalnp7uy39lvzf9tm09wy3htxwmw7qq5nerj4 * Introduction Bitcoin é Aqui! Rolante is located in Rolante, Brazil, and is dedicated to creating a lifestyle and tourism destination where 40% of businesses now accept Bitcoin as a payment method, showcasing the community's success in integrating Bitcoin into the local economy. Residents and visitors can use it to pay for all services, including accommodation, tours, local goods, medical services, and even construction and solar energy equipment. This reflects the practical application and convenience of its use in everyday life, aiming to create a digitally-driven environment powered by Bitcoin. * Latest Updates Recently, the Bitcoin é Aqui! Rolante has been actively promoting the adoption and use of Bitcoin in Brazil and beyond. The community has organized several educational events aimed at spreading basic Bitcoin knowledge and its practical applications in daily life, particularly through online videos and lectures. These efforts help people understand how Bitcoin plays a crucial role in the global financial system. The community has also been actively involved in promoting Bitcoin payments, supporting their adoption by local businesses and in the tourism industry.
18.Bitcoin Forte * Introduction Bitcoin Forte is a voluntary initiative aimed at introducing Bitcoin as a currency to Praia do Forte in Bahia, Brazil. The project provides valuable information about Bitcoin’s importance and encourages local merchants to adopt it as a payment method. By highlighting Bitcoin's international use, simplicity, and security, Bitcoin Forte aims to facilitate its adoption among both tourists and businesses.The community promotes Bitcoin as a stable and controlled currency, helping to avoid systemic price inflation. Bitcoin Forte simplifies the process for businesses by offering tools such as QR codes and the “Satoshi POS Wallet” app, which connects to a merchant’s primary wallet for seamless transactions. * Latest Updates Recently, the community has had no recent updates. The latest event dates back to July 2024, introducing Airbtc, a platform similar to Airbnb, but it only accepts Bitcoin as payment.
19.Bitcoin Paraguay * Introduction Bitcoin Paraguay is a community dedicated to connecting individuals in Paraguay who are interested in Bitcoin, promoting its adoption, and fostering the development of local circular economies. The community’s mission is to increase Bitcoin adoption by collaborating with local businesses and nonprofit organizations, helping to create a more sustainable local economy. Through regular events, talks, and resource sharing, Bitcoin Paraguay provides education and support to its members while actively exploring Bitcoin's application across various sectors in Paraguay. * Latest Updates Recently, the Bitcoin Paraguay community has made significant progress in promoting Bitcoin adoption. On November 5, they successfully hosted the fifth Bitcoin meetup in Asunción, attracting 110 attendees. The event included two Spanish-language presentations and a Lightning Network onboarding training session, with food and drinks available for purchase using Bitcoin. The event was made possible with strong support from sponsors Blink Wallet and Hacking Lives. On November 13, Josef Tetek visited Bitcoin Paraguay to help promote the adoption of Vexl in the country. The community also shared their progress through articles, with Jake, a community member, publishing an article in the Asunción Times on how Bitcoin Paraguay is improving people's lives.
20.Bitcoin Amantikir * Introduction They are starting the first community in the Serra da Mantiqueira to use and extol people about the bitcoin economy. * Latest Updates Recently, the Bitcoin Amantikir community has made significant progress in promoting Bitcoin as a payment method and fostering a circular economy in Santo Antônio do Pinhal. Various businesses, including a pet store, transportation service providers, a hotel, a fruit shop, and a tourist attraction, have started accepting Bitcoin payments. Additionally, the community is organizing a Bitcoin financial education course on December 2nd at Munay Pousada, aimed at helping young people aged 14-18 acquire essential financial knowledge and understand the importance of Bitcoin.
21.La Crypta nostr:npub1rujdpkd8mwezrvpqd2rx2zphfaztqrtsfg6w3vdnljdghs2q8qrqtt9u68 * Introduction La Crypta is an open-source community dedicated to advancing the adoption of the Nostr protocol and Bitcoin through developer-friendly tools and resources. By providing an integrated open-source stack, La Crypta empowers developers to sync with multiple relays, showcase profiles with badges, and facilitate seamless messaging, making it easier to build and utilize decentralized social platforms. Events like hackathons further enhance collaboration and attract new members, fostering innovation in decentralized social media. * Latest Updates LaWallet, their open-source wallet, integrates Bitcoin, Lightning, and Nostr to provide a seamless learning experience. With over 8,000 NFC cards distributed across conferences in regions like Argentina, Brazil, and Spain, LaWallet enables easy adoption while prioritizing user privacy. The wallet’s functionality is now supported by Alby’s official browser extension, further boosting accessibility.
-
 @ a58a2663:87bb2918
2024-12-09 13:39:49
@ a58a2663:87bb2918
2024-12-09 13:39:49- Concluir com minha filha, até o fim de 2025, a leitura da tradução latina de Ursinho Pooh, isto é, Winnie Ille Pu, de Alexander Lenard (1910-1972), poeta, ensaísta e tradutor húngaro que viveu no Brasil. Que texto curioso! Estranho estímulo que me chegou para voltar a estudar latim a sério.

-
Importar mais livros pela Thrift Books e menos pela Loja do Diabo. Seu acervo é excepcional e o frete é mais barato. Às vezes, em menos de duas semanas já estou com o livro em mãos (e olha que resido no Maranhão).
-
Concluir e publicar meu livro Vida após as Universidades. Escrita & criação em velhos & novos contextos de risco, desenvolvimento de algumas ideias que insinuei em Contra a vida intelectual, no que diz respeito ao encerramento de um ciclo histórico de modos de fazer investigação erudita.
-
Rematar o terceiro e último módulo de Convivium - Seminário Permanente de Humanidades, "A Alegoria do Mundo: o Mago, o Filólogo e o Colonizador", embrião de um longo ensaio sobre o "projeto humanista" e as vias de saída da modernidade oferecidas pelo pensamento latino-americano. (As inscrições seguem abertas. Caso queira inscrever-se pagando em bitcoin, me mande um e-mail: camoensiii57@protonmail.com).
-
Defender no primeiro semestre minha tese de doutoramento sobre João Francisco Lisboa (1812-1863), o maior prosador brasileiro de meados do século XIX. Compreender seu Jornal de Tímon implica rever concepções há muitos estabelecidas sobre a formação da literatura brasileira.
-
Escrever pelo menos cinco ensaios de apresentação do pensamento de Vilém Flusser e do que pretendo realizar em FLUSSER_project. A ideia é divulgá-los em inglês e especialmente aqui pelo Nostr.
-
Ler TUDO de Ignacio Gómez de Liaño.
-
Não ceder à tentação de discutir com imbecil.
-
 @ 90de72b7:8f68fdc0
2025-04-30 17:55:30
@ 90de72b7:8f68fdc0
2025-04-30 17:55:30PetriNostr. My everyday activity 30/04
PetriNostr never sleep! This is a demo
petrinet ;startDay () -> working ;stopDay working -> () ;startPause working -> paused ;endPause paused -> working ;goSmoke working -> smoking ;endSmoke smoking -> working ;startEating working -> eating ;stopEating eating -> working ;startCall working -> onCall ;endCall onCall -> working ;startMeeting working -> inMeetinga ;endMeeting inMeeting -> working ;logTask working -> working -
 @ a008def1:57a3564d
2025-04-30 17:52:11
@ a008def1:57a3564d
2025-04-30 17:52:11A Vision for #GitViaNostr
Git has long been the standard for version control in software development, but over time, we has lost its distributed nature. Originally, Git used open, permissionless email for collaboration, which worked well at scale. However, the rise of GitHub and its centralized pull request (PR) model has shifted the landscape.
Now, we have the opportunity to revive Git's permissionless and distributed nature through Nostr!
We’ve developed tools to facilitate Git collaboration via Nostr, but there are still significant friction that prevents widespread adoption. This article outlines a vision for how we can reduce those barriers and encourage more repositories to embrace this approach.
First, we’ll review our progress so far. Then, we’ll propose a guiding philosophy for our next steps. Finally, we’ll discuss a vision to tackle specific challenges, mainly relating to the role of the Git server and CI/CD.
I am the lead maintainer of ngit and gitworkshop.dev, and I’ve been fortunate to work full-time on this initiative for the past two years, thanks to an OpenSats grant.
How Far We’ve Come
The aim of #GitViaNostr is to liberate discussions around code collaboration from permissioned walled gardens. At the core of this collaboration is the process of proposing and applying changes. That's what we focused on first.
Since Nostr shares characteristics with email, and with NIP34, we’ve adopted similar primitives to those used in the patches-over-email workflow. This is because of their simplicity and that they don’t require contributors to host anything, which adds reliability and makes participation more accessible.
However, the fork-branch-PR-merge workflow is the only model many developers have known, and changing established workflows can be challenging. To address this, we developed a new workflow that balances familiarity, user experience, and alignment with the Nostr protocol: the branch-PR-merge model.
This model is implemented in ngit, which includes a Git plugin that allows users to engage without needing to learn new commands. Additionally, gitworkshop.dev offers a GitHub-like interface for interacting with PRs and issues. We encourage you to try them out using the quick start guide and share your feedback. You can also explore PRs and issues with gitplaza.
For those who prefer the patches-over-email workflow, you can still use that approach with Nostr through gitstr or the
ngit sendandngit listcommands, and explore patches with patch34.The tools are now available to support the core collaboration challenge, but we are still at the beginning of the adoption curve.
Before we dive into the challenges—such as why the Git server setup can be jarring and the possibilities surrounding CI/CD—let’s take a moment to reflect on how we should approach the challenges ahead of us.
Philosophy
Here are some foundational principles I shared a few years ago:
- Let Git be Git
- Let Nostr be Nostr
- Learn from the successes of others
I’d like to add one more:
- Embrace anarchy and resist monolithic development.
Micro Clients FTW
Nostr celebrates simplicity, and we should strive to maintain that. Monolithic developments often lead to unnecessary complexity. Projects like gitworkshop.dev, which aim to cover various aspects of the code collaboration experience, should not stifle innovation.
Just yesterday, the launch of following.space demonstrated how vibe-coded micro clients can make a significant impact. They can be valuable on their own, shape the ecosystem, and help push large and widely used clients to implement features and ideas.
The primitives in NIP34 are straightforward, and if there are any barriers preventing the vibe-coding of a #GitViaNostr app in an afternoon, we should work to eliminate them.
Micro clients should lead the way and explore new workflows, experiences, and models of thinking.
Take kanbanstr.com. It provides excellent project management and organization features that work seamlessly with NIP34 primitives.
From kanban to code snippets, from CI/CD runners to SatShoot—may a thousand flowers bloom, and a thousand more after them.
Friction and Challenges
The Git Server
In #GitViaNostr, maintainers' branches (e.g.,
master) are hosted on a Git server. Here’s why this approach is beneficial:- Follows the original Git vision and the "let Git be Git" philosophy.
- Super efficient, battle-tested, and compatible with all the ways people use Git (e.g., LFS, shallow cloning).
- Maintains compatibility with related systems without the need for plugins (e.g., for build and deployment).
- Only repository maintainers need write access.
In the original Git model, all users would need to add the Git server as a 'git remote.' However, with ngit, the Git server is hidden behind a Nostr remote, which enables:
- Hiding complexity from contributors and users, so that only maintainers need to know about the Git server component to start using #GitViaNostr.
- Maintainers can easily swap Git servers by updating their announcement event, allowing contributors/users using ngit to automatically switch to the new one.
Challenges with the Git Server
While the Git server model has its advantages, it also presents several challenges:
- Initial Setup: When creating a new repository, maintainers must select a Git server, which can be a jarring experience. Most options come with bloated social collaboration features tied to a centralized PR model, often difficult or impossible to disable.
-
Manual Configuration: New repositories require manual configuration, including adding new maintainers through a browser UI, which can be cumbersome and time-consuming.
-
User Onboarding: Many Git servers require email sign-up or KYC (Know Your Customer) processes, which can be a significant turn-off for new users exploring a decentralized and permissionless alternative to GitHub.
Once the initial setup is complete, the system works well if a reliable Git server is chosen. However, this is a significant "if," as we have become accustomed to the excellent uptime and reliability of GitHub. Even professionally run alternatives like Codeberg can experience downtime, which is frustrating when CI/CD and deployment processes are affected. This problem is exacerbated when self-hosting.
Currently, most repositories on Nostr rely on GitHub as the Git server. While maintainers can change servers without disrupting their contributors, this reliance on a centralized service is not the decentralized dream we aspire to achieve.
Vision for the Git Server
The goal is to transform the Git server from a single point of truth and failure into a component similar to a Nostr relay.
Functionality Already in ngit to Support This
-
State on Nostr: Store the state of branches and tags in a Nostr event, removing reliance on a single server. This validates that the data received has been signed by the maintainer, significantly reducing the trust requirement.
-
Proxy to Multiple Git Servers: Proxy requests to all servers listed in the announcement event, adding redundancy and eliminating the need for any one server to match GitHub's reliability.
Implementation Requirements
To achieve this vision, the Nostr Git server implementation should:
-
Implement the Git Smart HTTP Protocol without authentication (no SSH) and only accept pushes if the reference tip matches the latest state event.
-
Avoid Bloat: There should be no user authentication, no database, no web UI, and no unnecessary features.
-
Automatic Repository Management: Accept or reject new repositories automatically upon the first push based on the content of the repository announcement event referenced in the URL path and its author.
Just as there are many free, paid, and self-hosted relays, there will be a variety of free, zero-step signup options, as well as self-hosted and paid solutions.
Some servers may use a Web of Trust (WoT) to filter out spam, while others might impose bandwidth or repository size limits for free tiers or whitelist specific npubs.
Additionally, some implementations could bundle relay and blossom server functionalities to unify the provision of repository data into a single service. These would likely only accept content related to the stored repositories rather than general social nostr content.
The potential role of CI / CD via nostr DVMs could create the incentives for a market of highly reliable free at the point of use git servers.
This could make onboarding #GitViaNostr repositories as easy as entering a name and selecting from a multi-select list of Git server providers that announce via NIP89.
!(image)[https://image.nostr.build/badedc822995eb18b6d3c4bff0743b12b2e5ac018845ba498ce4aab0727caf6c.jpg]
Git Client in the Browser
Currently, many tasks are performed on a Git server web UI, such as:
- Browsing code, commits, branches, tags, etc.
- Creating and displaying permalinks to specific lines in commits.
- Merging PRs.
- Making small commits and PRs on-the-fly.
Just as nobody goes to the web UI of a relay (e.g., nos.lol) to interact with notes, nobody should need to go to a Git server to interact with repositories. We use the Nostr protocol to interact with Nostr relays, and we should use the Git protocol to interact with Git servers. This situation has evolved due to the centralization of Git servers. Instead of being restricted to the view and experience designed by the server operator, users should be able to choose the user experience that works best for them from a range of clients. To facilitate this, we need a library that lowers the barrier to entry for creating these experiences. This library should not require a full clone of every repository and should not depend on proprietary APIs. As a starting point, I propose wrapping the WASM-compiled gitlib2 library for the web and creating useful functions, such as showing a file, which utilizes clever flags to minimize bandwidth usage (e.g., shallow clone, noblob, etc.).
This approach would not only enhance clients like gitworkshop.dev but also bring forth a vision where Git servers simply run the Git protocol, making vibe coding Git experiences even better.
song
nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 created song with a complementary vision that has shaped how I see the role of the git server. Its a self-hosted, nostr-permissioned git server with a relay baked in. Its currently a WIP and there are some compatability with ngit that we need to work out.
We collaborated on the nostr-permissioning approach now reflected in nip34.
I'm really excited to see how this space evolves.
CI/CD
Most projects require CI/CD, and while this is often bundled with Git hosting solutions, it is currently not smoothly integrated into #GitViaNostr yet. There are many loosely coupled options, such as Jenkins, Travis, CircleCI, etc., that could be integrated with Nostr.
However, the more exciting prospect is to use DVMs (Data Vending Machines).
DVMs for CI/CD
Nostr Data Vending Machines (DVMs) can provide a marketplace of CI/CD task runners with Cashu for micro payments.
There are various trust levels in CI/CD tasks:
- Tasks with no secrets eg. tests.
- Tasks using updatable secrets eg. API keys.
- Unverifiable builds and steps that sign with Android, Nostr, or PGP keys.
DVMs allow tasks to be kicked off with specific providers using a Cashu token as payment.
It might be suitable for some high-compute and easily verifiable tasks to be run by the cheapest available providers. Medium trust tasks could be run by providers with a good reputation, while high trust tasks could be run on self-hosted runners.
Job requests, status, and results all get published to Nostr for display in Git-focused Nostr clients.
Jobs could be triggered manually, or self-hosted runners could be configured to watch a Nostr repository and kick off jobs using their own runners without payment.
But I'm most excited about the prospect of Watcher Agents.
CI/CD Watcher Agents
AI agents empowered with a NIP60 Cashu wallet can run tasks based on activity, such as a push to master or a new PR, using the most suitable available DVM runner that meets the user's criteria. To keep them running, anyone could top up their NIP60 Cashu wallet; otherwise, the watcher turns off when the funds run out. It could be users, maintainers, or anyone interested in helping the project who could top up the Watcher Agent's balance.
As aluded to earlier, part of building a reputation as a CI/CD provider could involve running reliable hosting (Git server, relay, and blossom server) for all FOSS Nostr Git repositories.
This provides a sustainable revenue model for hosting providers and creates incentives for many free-at-the-point-of-use hosting providers. This, in turn, would allow one-click Nostr repository creation workflows, instantly hosted by many different providers.
Progress to Date
nostr:npub1hw6amg8p24ne08c9gdq8hhpqx0t0pwanpae9z25crn7m9uy7yarse465gr and nostr:npub16ux4qzg4qjue95vr3q327fzata4n594c9kgh4jmeyn80v8k54nhqg6lra7 have been working on a runner that uses GitHub Actions YAML syntax (using act) for the dvm-cicd-runner and takes Cashu payment. You can see example runs on GitWorkshop. It currently takes testnuts, doesn't give any change, and the schema will likely change.
Note: The actions tab on GitWorkshop is currently available on all repositories if you turn on experimental mode (under settings in the user menu).
It's a work in progress, and we expect the format and schema to evolve.
Easy Web App Deployment
For those disapointed not to find a 'Nostr' button to import a git repository to Vercel menu: take heart, they made it easy. vercel.com_import_options.png there is a vercel cli that can be easily called in CI / CD jobs to kick of deployments. Not all managed solutions for web app deployment (eg. netlify) make it that easy.
Many More Opportunities
Large Patches via Blossom
I would be remiss not to mention the large patch problem. Some patches are too big to fit into Nostr events. Blossom is perfect for this, as it allows these larger patches to be included in a blossom file and referenced in a new patch kind.
Enhancing the #GitViaNostr Experience
Beyond the large patch issue, there are numerous opportunities to enhance the #GitViaNostr ecosystem. We can focus on improving browsing, discovery, social and notifications. Receiving notifications on daily driver Nostr apps is one of the killer features of Nostr. However, we must ensure that Git-related notifications are easily reviewable, so we don’t miss any critical updates.
We need to develop tools that cater to our curiosity—tools that enable us to discover and follow projects, engage in discussions that pique our interest, and stay informed about developments relevant to our work.
Additionally, we should not overlook the importance of robust search capabilities and tools that facilitate migrations.
Concluding Thoughts
The design space is vast. Its an exciting time to be working on freedom tech. I encourage everyone to contribute their ideas and creativity and get vibe-coding!
I welcome your honest feedback on this vision and any suggestions you might have. Your insights are invaluable as we collaborate to shape the future of #GitViaNostr. Onward.
Contributions
To conclude, I want to acknowledge some the individuals who have made recent code contributions related to #GitViaNostr:
nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 (gitstr, song, patch34), nostr:npub1useke4f9maul5nf67dj0m9sq6jcsmnjzzk4ycvldwl4qss35fvgqjdk5ks (gitplaza)
nostr:npub1elta7cneng3w8p9y4dw633qzdjr4kyvaparuyuttyrx6e8xp7xnq32cume (ngit contributions, git-remote-blossom),nostr:npub16p8v7varqwjes5hak6q7mz6pygqm4pwc6gve4mrned3xs8tz42gq7kfhdw (SatShoot, Flotilla-Budabit), nostr:npub1ehhfg09mr8z34wz85ek46a6rww4f7c7jsujxhdvmpqnl5hnrwsqq2szjqv (Flotilla-Budabit, Nostr Git Extension), nostr:npub1ahaz04ya9tehace3uy39hdhdryfvdkve9qdndkqp3tvehs6h8s5slq45hy (gnostr and experiments), and others.
nostr:npub1uplxcy63up7gx7cladkrvfqh834n7ylyp46l3e8t660l7peec8rsd2sfek (git-remote-nostr)
Project Management nostr:npub1ltx67888tz7lqnxlrg06x234vjnq349tcfyp52r0lstclp548mcqnuz40t (kanbanstr) Code Snippets nostr:npub1ygzj9skr9val9yqxkf67yf9jshtyhvvl0x76jp5er09nsc0p3j6qr260k2 (nodebin.io) nostr:npub1r0rs5q2gk0e3dk3nlc7gnu378ec6cnlenqp8a3cjhyzu6f8k5sgs4sq9ac (snipsnip.dev)
CI / CD nostr:npub16ux4qzg4qjue95vr3q327fzata4n594c9kgh4jmeyn80v8k54nhqg6lra7 nostr:npub1hw6amg8p24ne08c9gdq8hhpqx0t0pwanpae9z25crn7m9uy7yarse465gr
and for their nostr:npub1c03rad0r6q833vh57kyd3ndu2jry30nkr0wepqfpsm05vq7he25slryrnw nostr:npub1qqqqqq2stely3ynsgm5mh2nj3v0nk5gjyl3zqrzh34hxhvx806usxmln03 and nostr:npub1l5sga6xg72phsz5422ykujprejwud075ggrr3z2hwyrfgr7eylqstegx9z for their testing, feedback, ideas and encouragement.
Thank you for your support and collaboration! Let me know if I've missed you.
-
 @ 6d8e2a24:5faaca4c
2024-11-30 00:07:10
@ 6d8e2a24:5faaca4c
2024-11-30 00:07:10Why do people enjoy pain and a short time pleasure, which could ruin their life and peace?
Why can't people leave their fleshy desires, obsession and pleasures even if it kills them?
Many have become slaves to their obsession having no will of theirs, claiming to be free yet imprisoned by their futility and lust.
We thought we have closed all the doors and windows, turn off the light so no one can see us, least so we thought to ourselves, forgetting our conscience is wide open, and God who sit in heaven watching, like it was never night nor dark, sees through us for he is light ruling over darkness.
The devil working upon our obsession making it a reality. The devil always uses our sinful, lustful desire to trick us given an end vain pleasure
We fall once, down with the guilt and pain of sin, the weight of the burden once thought, destroying the spirit and causing so many pains of regret, low self-esteem, and lack of confidence again.
He comes again not to bring new but to dwell in our past, bringing memories, mistakes, and errors making us feel more guilty and vulnerable, making us feel worthless and hopeless "We are doomed, so we think, God can't help us, our sins are too many; and with that, he finds a way to make us fall again, destroying us slowly till we are empty, having no will (stronghold).
Like a fire 🔥 lit in a bush, small as it is no one thought it could cause so much harm, or rather they thought they could control it or, put it off when they don't need it or, get bizarre.
Anything that has passed infantry allowed to grow is difficult or impossible to control so is a sin when is allowed to grow like a fire covering many areas is hard to put all areas off fast before one knows many areas are damaged many are beyond repairs
Every day we wake up, we plan how our lives, and how we are going to live the day, without the slimmest thought of contention, 'what if'. We do believe we have everything under control, everything planned out, but we forget that we are nothing but a sand timer that runs down so quickly than we thought.
Like the sand timer, our lives fade away gently, piece by piece till we cease to exist, only then, do we understand that we are rebels in this kingdom, not owners for we own nothing, with the dust reaching its last, the heartbeat and craves for more time, then we also understand, that time is never enough and time is so precious and priceless
Why do we always feel as if we have all the time in the world? why do we assume death to be a fairytale or a horror ghost story just to scare us out? Without having a sting.
Every day death proves more eager, the grave is so desperate that it looms looking and searching for any opportunity necessary to sting it stings.
But we are so carried away by life, deceived by what we have, the power, authority, and influence. We feel we are covered, yes we are but only to some certain extent. For life is so spiritual, than we could ever imagine or think of.
The night comes darkness looms over, evil rises, and fear grips one's heart, all wishing for the light. But now is no longer darkness that's so terrifying, but light itself has become as terrifying as the darkness, people wishing to live through the light, now wish the same to live through the night, for in it they find peace and comfort 😢
Why, I ask why, why has light become so terrifying and darkness become more comforting that the people find solace in it?
I came to understand why people find comfort in darkness is because they are afraid of selves afraid of what they have become, darkness does not challenge but rather allows you to wallow in your misery and regret, killing and draining you where no one will correct you or remind you, that you are not good enough, darkness gives you the room to accept who and what you have become, and there and then it echoes is better to die and live in peace than to be alive and live in misery.
Why will one think of death as the only option or think of death as the only solution to peace, is living not joyful, is life not great to live, why will one wish to leave all, family, friends everything, and settle for death?
I came to understand that, the most reason why one tends to choose death over life or loves to behold the warmth of darkness instead of light, is the feeling of emptiness and internal failure even after a significant measure, of material and social success, is a direct result of failure to discover purpose in life and a reason of being, when one loses his peace, joy all that's left or remain is pain, and regret. When a man reaches a stage of emptiness, where nothing else again matters life itself has no meaning, then it's only a test of time before destruction befalls such a person
Even the rich are depressed and frustrated beholding the enticement of the dark, and many try to drink themselves up, to them is the only way to find peace within, why, after so much wealth and achievement yet feel lonely, his greatest friends are alcohol and nights.
If money, riches cant give fulfillment or perfect peace then what can?
-
 @ c4b5369a:b812dbd6
2024-11-24 09:27:12
@ c4b5369a:b812dbd6
2024-11-24 09:27:12How to print your own ecash, using Gandlaf's money printer
To celebrate the recent money printer update, here is a short guide on how to use it.
Step 1: Go to the money printer
Unlike the FED's money printer, this Cashu ecash money printer is openly available. Head over to https://brrr.gandlaf.com to give it a spin.
Select a mint
Choose a mint that should be backing the ecash notes. You have a few different options when choosing a mint:
- Connect to your own mint: Connecting to your own mint is great if you want to be the backer of the ecash notes. It does however require you to have your mint up and running. You can connect to it by typing the mint URL into the input field.
- Connect to a known mint: There are mints that are already indexed on nostr. You can find them by clicking on the `discover more mints` button.
- Connect to any mint you want!: All you need is the mints URL. Just type it into the input bar!
Once you selected a mint, click connect to set up the mint for money printing :

After connecting to the mint, you will have the option to select the currency you want to print. Not all mints support all currencies! The dropdown menu below will show all available currencies the mint offers.
After selecting your preferred currency, click confirm to continue.

In the next step, you will chose the amount that should be printed on each note. Be careful though, because unfortunately not every amount is possible. To preserve mint users privacy ecash mints use fixed coin amounts. This means a specific amount, will be made up from smaller amounts. Today, most cashu mints use power-of-2 amounts.
So if you for example would like to print the amount "100", it would be made up from the coins [64, 32, 4]. The maximum number of coins that can be encoded in a QR code, without the QR code losing its readability is \~4. The money printer will analyze which amounts the mint offers, and show how many coins will be needed.
Below, you will see the calculation of how much the total issuance for this printing cycle will be. Once you are all set, click confirm to continue.

You can now either add the funds for the print via Cashu token or via Lightning. Let's first take a look on how to add funds via Cashu token.
If you select this option, I will assume that you already own ecash from the mint you wish to print the notes. Otherwise, you should move on to the payment by lightning.
You have to make sure that the token you are pasting is from the correct mint, in the correct unit/currency and matches the amount exactly! Otherwise, it will not work.

If you don't own ecash from that mint, you can pay for the print with lightning directly. The only fees that will be charged are Lightning network fees.
Just scan the QR code that is presented to you and wait for the payment to be confirmed.

Once the payment has confirmed, either through Cashu or through Lightning, the print is ready. You can now customize the design you wish to print.
You can select a color, a brand image and a corner image that should be put on the note.
Once you are happy with the design, go ahead and click `Print now! BRRRRRRRRRRR`

This will take you to the print page. You can now print the ecash by pressing `CTRL`+`P`
And that's it! You have now printed your own money. I hope you liked the experience of playing FED for a day.
Be aware! Once scanned and redeemed, the ecash notes become invalid. So they are one-time-use.
If you want to make another print, just refresh the page. It will take you back to the beginning. Your past prints will also be stored in the browser cache, so you can come back to them at a later time, if your printer overheated or something.

Happy printing!
Gandlaf
-
 @ f1e78daa:124e0e56
2025-04-12 14:13:41
@ f1e78daa:124e0e56
2025-04-12 14:13:41今日はテストです。
-
 @ af9d7040:42d05d35
2024-11-14 09:25:34
@ af9d7040:42d05d35
2024-11-14 09:25:34
Oswald: Ruthlessness in the Pursuit of Power and Survival
In Gotham City, Oswald Cobblepot, known as “The Penguin,” lives by the unrelenting rules of the mob: ruthless, without compromise or boundaries. For him, survival demands sheer will, extreme cunning, and coldness. He will do anything to achieve his aims, even betray those closest to him—like his mother, who has profoundly influenced him. His attachment to her is rooted in a twisted, obsessive need for approval, and his ruthlessness is not only a survival strategy but also an expression of his deeply embedded self-centeredness.
The Penguin maneuvers through the shadows of Gotham City with manipulation, deceit, and vengeance, like a serpent coiling around its prey. His every success is built on a disregard for humanity and a relentless thirst for power. Though he appears to show devotion to his mother, this is only another facet of his self-serving nature. He cherishes her only so long as she provides him with a sense of security; the moment she becomes a liability, he discards her without hesitation. This twisted complexity makes him a character who elicits both fascination and repulsion.
The Penguin’s unique blend of cruelty and contradiction separates him from the typical mob character. His ruthless selfishness is rooted in self-preservation. He is capable of manipulating or even betraying those closest to him. His “loyalty” is merely a mask for his unyielding self-interest. This guise of loyalty makes him more isolated and untrustworthy than those around him, ultimately marking him as a true antihero—someone who cannot be trusted and who feels no attachment even to those he holds dear.

Sofia: A Tender Wound in the Cold Reality
In contrast to the Penguin’s dark nature, Sofia, the female lead, presents a softer, yet no less complex character. Like him, she exists within Gotham’s shadows, but she retains a degree of innocence and kindness. Sofia, too, has a damaged side, but hers is gentler, perhaps even curable; her inner nature is resilient and compassionate. The Penguin, however, is wholly different—cold and selfish, with his inner darkness shaping every decision and action. Where Sofia struggles within Gotham’s corruption but maintains her inner light, the Penguin is the opposite, allowing his cruelty to permeate every aspect of his life.
Sofia’s presence is like a quiet undercurrent, casting the Penguin’s icy nature in sharper relief. She occasionally brings light into his shadowed world, though her warmth is ultimately no match for his darkness. Sofia’s compassion exposes the Penguin’s pathological selfishness, and her fleeting kindness only emphasizes his chilling indifference.

The Solitude of a Drifter
With its muted color palette, the film portrays Gotham as a city almost devoid of life, where the clamor of daily existence only serves to conceal an underlying emptiness. The city’s visual loneliness, along with a slow, deliberate narrative and moments of silence, subtly reflects the Penguin’s inner struggle. His journey for power begins with a warped attachment to Gotham, and as the story unfolds, we see him descend into total darkness, losing all semblance of warmth. The scattered plot structure and somber music shape his evolution into a kind of melancholic, fragmented poem.
In this solitude, the director refrains from casting the Penguin in simple moral terms. Like life itself, the narrative is complex and fragmented, juxtaposing Gotham’s wealthy and impoverished neighborhoods to create a blurry psychological divide. In this “ruin” of Gotham, some people drift, some settle, while the Penguin himself wanders, searching for a place to belong. The pacing and cinematography draw the viewer in as though they are walking Gotham’s desolate streets, accompanied by a haunting piano melody.

The Paradox of Power and Loneliness
The Penguin’s loneliness is not merely a result of Gotham’s darkness; it is the byproduct of his dependence on power. His need for control and his fixation on security bind him, like twin shackles, to his misery. He cannot escape his solitude even when perched at the top of Gotham’s hierarchy. His attachment to his mother is merely an extension of his self-interest; he has never truly known love or warmth. His cold and selfish nature is not a choice but an innate part of him, driving him inevitably toward isolation.
The series offers no definitive moral compass nor romanticizes any side. The Penguin’s relationship with Sofia and the sacrifices, betrayals, and suffering they both endure on the road to power seem to reflect the harsh realities of life. Gotham’s “ruinous” stage presents each character grappling with their choices and their costs.

Moving Forward in the Darkness
The allure of The Penguin lies not only in its portrayal of an antihero but also in its exploration of the character’s inner lives. The Penguin’s turbulent life as a mobster intertwines with his attachment to Gotham, echoing those who search for belonging in places that feel forgotten. Sofia’s gentleness and fragile compassion, like a tender blade, continually pierce the Penguin’s illusions about power and loneliness.
The Penguin does not rise to power swiftly; instead, he edges toward a deep, inevitable abyss. The director’s pacing, intense and deliberate, brings the Penguin closer to the heights of power while making his solitude more profound. The Penguin strikes at the heart of adult disillusionment, showing us that the world will not soften simply because we yield. We can only stumble forward in the dark, perhaps even make peace with it.
— Written by @Shaun on November 13, 2024
-
 @ f1e78daa:124e0e56
2025-04-12 14:02:20
@ f1e78daa:124e0e56
2025-04-12 14:02:20プロローグ
童貞こと薄(すすき) 仙人(せんにん)29歳。ここに眠る。「RIP」。29年間ずっと不運だった。親が仙人なんて名前を付けるから。学校では薄い仙人で「はげ仙人」なんてよばれるし、会社は倒産し、家は燃え、さっきトラックで引かれたところだ。そして、今「自称邪心」に次の魔王になってほしいと頼まれている。
―「なんで俺がそんなことしなきゃいけないのだ。」
「君には普通の人間よりも欲が何倍も大きい。ほんとは君の世界では収まらないぐらいだよ。」
―「異世界に行くのはいいとして、なんで魔王なんだ?」
「一つは、さっきも言った通り、君の欲は大きい。二つ目はもうすぐ現魔王がいなくなるからだよ。」
―「勇者にでも殺されたか?」
「いや、勇者と魔王が結婚した。」
―「は?」意味がわからない。勇者は魔王を倒すものではないのか?
「いなくなるというよりは魔王をやめるという表現のほうが正しかったかな。」
邪神によると勇者と魔王が結婚し、現魔王は魔王をやめるので、勇者と魔王の子供に転生し、次の新たな魔王になってほしいとのことだった。
人族と魔族(エルフ、ドワーフ、悪魔など)がこの世界にはあり、人族は聖神、魔族は
邪神が保護しているそうで、人と魔族は大昔から敵対しているそうだ。
聖神は魔族を忌み嫌っているので、魔族を統べる物がいなくなればいつ人族が襲ってくるかわからない。
人族には個別スキル(怪力、俊足など)には一般スキルと固有スキルがある。
固有スキルは世界に一人しかもっておらず、使用者が死ぬと新しく生まれてきた誰かがその固有スキルを手にする。固有スキルは5000万人に1人ぐらいの割合だそうだ。
一般スキルは固有スキルと違い、スキルがかぶることはよくあるそうだ。
魔族は種族スキルがある。種族スキルとはその種族が全員同じスキルをもっている。
魔族は固有スキルや個別スキルがない代わり人よりも各ステータスが高い。
俺は邪神に恩恵を3つもらった。一つは「超再生」。これは怪我や魔力、体力を瞬時に再生させてくれるチート能力だ。2つ目は「代償」腕や心臓などの代償をつくることによって自分を強化したり、新しく武器を作ることができる。この能力は一つ目の「超再生」と組み合わせることでバグをうみだすことができる。3つ目は「入れ替え」これは、さわったことのある物や人との場所を入れ替えることができる。
この三つの恩恵で異世界を俺は生き抜いてやる。
-
 @ c230edd3:8ad4a712
2025-04-30 16:19:30
@ c230edd3:8ad4a712
2025-04-30 16:19:30Chef's notes
I found this recipe on beyondsweetandsavory.com. The site is incredibly ad infested (like most recipe sites) and its very annoying so I'm copying it to Nostr so all the homemade ice cream people can access it without dealing with that mess. I haven't made it yet. Will report back, when I do.
Details
- ⏲️ Prep time: 20 min
- 🍳 Cook time: 55 min
- 🍽️ Servings: 8
Ingredients
- 2 cups heavy cream
- 1 cup 2% milk
- 8 oz dark chocolate, 70%
- ¼ cup Dutch cocoa
- 2 tbsps loose Earl grey tea leaves
- 4 medium egg yolks
- ¾ cup granulated sugar
- ⅛ tsp salt
- ¼ cup dark chocolate, 70% chopped
Directions
- In a double boiler or a bowl set over a saucepan of simmering water, add the cacao solids and ½ cup of heavy cream. Stir chocolate until melted and smooth. Set melted chocolate aside.
- In a heavy saucepan, combine remaining heavy cream, milk, salt and ½ cup of sugar.
- Put the pan over medium heat and let the mixture boil gently to bubbling just around the edges (gentle simmer) and sugar completely dissolved, about 5 minutes. Remove from heat.
- Add the Earl Grey tea leaves and let it steep for 7-8 minutes until the cream has taken on the tea flavor, stirring occasionally and tasting to make sure it’s not too bitter.
- Whisk in Dutch cocoa until smooth. Add in melted chocolate and whisk until smooth.
- In a medium heatproof bowl, whisk the yolks just to break them up and whisk in remaining sugar. Set aside.
- Put the saucepan back on the stove over low heat and let it warm up for 2 minutes.
- Carefully measure out ½ cup of hot cream mixture.
- While whisking the eggs constantly, whisk the hot cream mixture into the eggs until smooth. Continue tempering the eggs by adding another ½ cup of hot cream to the bowl with the yolks.
- Pour the cream-egg mixture back to the saucepan and cook over medium-low heat, stirring constantly until it is thickened and coats the back of a spatula, about 5 minutes.
- Strain the base through a fine-mesh strainer into a clean container.
- Pour the mixture into a 1-gallon Ziplock freezer bag and submerge the sealed bag in an ice bath until cold, about 30 minutes. Refrigerate the ice cream base for at least 4 hours or overnight.
- Pour the ice cream base into the frozen canister of your ice cream machine and follow the manufacturer’s instructions.
- Spin until thick and creamy about 25-30 minutes.
- Pack the ice cream into a storage container, press a sheet of parchment directly against the surface and seal with an airtight lid. Freeze in the coldest part of your freezer until firm, at least 4 hours.
- When ready to serve, scoop the ice cream into a serving bowl and top with chopped chocolate.
-
 @ 1739d937:3e3136ef
2025-04-30 14:39:24
@ 1739d937:3e3136ef
2025-04-30 14:39:24MLS over Nostr - 30th April 2025
YO! Exciting stuff in this update so no intro, let's get straight into it.
🚢 Libraries Released
I've created 4 new Rust crates to make implementing NIP-EE (MLS) messaging easy for other projects. These are now part of the rust-nostr project (thanks nostr:npub1drvpzev3syqt0kjrls50050uzf25gehpz9vgdw08hvex7e0vgfeq0eseet) but aren't quite released to crates.io yet. They will be included in the next release of that library. My hope is that these libraries will give nostr developers a simple, safe, and specification-compliant way to work with MLS messaging in their applications.
Here's a quick overview of each:
nostr_mls_storage
One of the challenges of using MLS messaging is that clients have to store quite a lot of state about groups, keys, and messages. Initially, I implemented all of this in White Noise but knew that eventually this would need to be done in a more generalized way.
This crate defines traits and types that are used by the storage implementation crates and sets those up to wrap the OpenMLS storage layer. Now, instead of apps having to implement storage for both OpenMLS and Nostr, you simply pick your storage backend and go from there.
Importantly, because these are generic traits, it allows for the creation of any number of storage implementations for different backend storage providers; postgres, lmdb, nostrdb, etc. To start I've created two implementations; detailed below.
nostr_mls_memory_storage
This is a simple implementation of the nostr_mls_storage traits that uses an in-memory store (that doesn't persist anything to disc). This is principally for testing.
nostr_mls_sqlite_storage
This is a production ready implementation of the nostr_mls_storage traits that uses a persistent local sqlite database to store all data.
nostr_mls
This is the main library that app developers will interact with. Once you've chose a backend and instantiated an instance of NostrMls you can then interact with a simple set of methods to create key packages, create groups, send messages, process welcomes and messages, and more.
If you want to see a complete example of what the interface looks like check out mls_memory.rs.
I'll continue to add to this library over time as I implement more of the MLS protocol features.
🚧 White Noise Refactor
As a result of these new libraries, I was able to remove a huge amount of code from White Noise and refactor large parts of the app to make the codebase easier to understand and maintain. Because of this large refactor and the changes in the underlying storage layer, if you've installed White Noise before you'll need to delete it from your device before you trying to install again.
🖼️ Encrypted Media with Blossom
Let's be honest: Group chat would be basically useless if you couldn't share memes and gifs. Well, now you can in White Noise. Media in groups is encrypted using an MLS secret and uploaded to Blossom with a one-time use keypair. This gives groups a way to have rich conversations with images and documents and anything else while also maintaining the privacy and security of the conversation.
This is still in a rough state but rendering improvements are coming next.
📱 Damn Mobile
The app is still in a semi-broken state on Android and fully broken state on iOS. Now that I have the libraries released and the White Noise core code refactored, I'm focused 100% on fixing these issues. My goal is to have a beta version live on Zapstore in a few weeks.
🧑💻 Join Us
I'm looking for mobile developers on both Android and iOS to join the team and help us build the best possible apps for these platforms. I have grant funding available for the right people. Come and help us build secure, permissionless, censorship-resistant messaging. I can think of few projects that deserve your attention more than securing freedom of speech and freedom of association for the entire world. If you're interested or know someone who might be, please reach out to me directly.
🙏 Thanks to the People
Last but not least: A HUGE thank you to all the folks that have been helping make this project happen. You can check out the people that are directly working on the apps on Following._ (and follow them). There are also a lot of people behind the scenes that have helped in myriad ways to get us this far. Thank you thank you thank you.
🔗 Links
Libraries
White Noise
Other
-
 @ f1e78daa:124e0e56
2025-04-12 14:01:15
@ f1e78daa:124e0e56
2025-04-12 14:01:15プロローグ
童貞こと薄(すすき) 仙人(せんにん)29歳。ここに眠る。「RIP」。29年間ずっと不運だった。親が仙人なんて名前を付けるから。学校では薄い仙人で「はげ仙人」なんてよばれるし、会社は倒産し、家は燃え、さっきトラックで引かれたところだ。そして、今「自称邪心」に次の魔王になってほしいと頼まれている。
―「なんで俺がそんなことしなきゃいけないのだ。」
「君には普通の人間よりも欲が何倍も大きい。ほんとは君の世界では収まらないぐらいだよ。」
―「異世界に行くのはいいとして、なんで魔王なんだ?」
「一つは、さっきも言った通り、君の欲は大きい。二つ目はもうすぐ現魔王がいなくなるからだよ。」
―「勇者にでも殺されたか?」
「いや、勇者と魔王が結婚した。」
―「は?」意味がわからない。勇者は魔王を倒すものではないのか?
「いなくなるというよりは魔王をやめるという表現のほうが正しかったかな。」
邪神によると勇者と魔王が結婚し、現魔王は魔王をやめるので、勇者と魔王の子供に転生し、次の新たな魔王になってほしいとのことだった。
人族と魔族(エルフ、ドワーフ、悪魔など)がこの世界にはあり、人族は聖神、魔族は
邪神が保護しているそうで、人と魔族は大昔から敵対しているそうだ。
聖神は魔族を忌み嫌っているので、魔族を統べる物がいなくなればいつ人族が襲ってくるかわからない。
人族には個別スキル(怪力、俊足など)には一般スキルと固有スキルがある。
固有スキルは世界に一人しかもっておらず、使用者が死ぬと新しく生まれてきた誰かがその固有スキルを手にする。固有スキルは5000万人に1人ぐらいの割合だそうだ。
一般スキルは固有スキルと違い、スキルがかぶることはよくあるそうだ。
魔族は種族スキルがある。種族スキルとはその種族が全員同じスキルをもっている。
魔族は固有スキルや個別スキルがない代わり人よりも各ステータスが高い。
俺は邪神に恩恵を3つもらった。一つは「超再生」。これは怪我や魔力、体力を瞬時に再生させてくれるチート能力だ。2つ目は「代償」腕や心臓などの代償をつくることによって自分を強化したり、新しく武器を作ることができる。この能力は一つ目の「超再生」と組み合わせることでバグをうみだすことができる。3つ目は「入れ替え」これは、さわったことのある物や人との場所を入れ替えることができる。
この三つの恩恵で異世界を俺は生き抜いてやる。
-
 @ 4e616576:43c4fee8
2025-04-30 13:28:18
@ 4e616576:43c4fee8
2025-04-30 13:28:18asdfasdfsadfaf
-
 @ f3873798:24b3f2f3
2025-04-11 22:43:43
@ f3873798:24b3f2f3
2025-04-11 22:43:43Durante décadas, ouvimos que o Brasil era o "país do futuro". Uma terra rica, com imenso potencial humano e natural, destinada a se tornar uma grande potência e referência para o mundo. Essa ideia, repetida em discursos políticos e publicações internacionais, alimentou gerações com esperança. Mas o tempo passou — e esse futuro promissor parece nunca chegar.
Na prática, o que vemos é um ciclo de promessas não cumpridas, problemas sociais profundos e um povo muitas vezes desiludido. Apesar do potencial imenso, o Brasil enfrenta barreiras estruturais e culturais que dificultam seu pleno desenvolvimento. E é justamente sobre isso que precisamos refletir.
A raiz dos nossos desafios
Não há como ter jeito sem que haja um enfrentamento com seriedade aos problemas que estão na base da nossa sociedade. Um dos maiores entraves é a precariedade da educação, tanto no acesso quanto na qualidade. Em muitas regiões, o estudo ainda é visto como perda de tempo, algo que não contribui para o sustento imediato da família. Mesmo com incentivos governamentais, o desempenho das escolas é baixo. Em vez de formar cidadãos críticos e profissionais capacitados, muitas vezes vemos instituições focadas em ideologias ou agendas desconectadas da realidade do aluno.
Outro ponto sensível é a estrutura familiar. Em áreas onde faltam referências morais, espirituais e sociais, o ambiente familiar pode se tornar disfuncional, com casos extremos de abusos e ausência total de valores básicos. Nesses contextos, a ausência de instituições que promovem virtudes e limites — como a Igreja, por exemplo — faz diferença. Não se trata de impor uma religião, mas de reconhecer o papel histórico que a fé teve (e ainda tem) na construção de uma base ética e civilizatória.
A falta de valores basilares e estrutura para a promoção da relações em sociedade, faz do ambiente escolar um local sem propósito, onde são depositados crianças para serem expostas a um convívio forçado com estranhos sem nenhum preparo familiar, e sendo muitas vezes subentendido pelos profissionais educadores como dever da família, no entanto tal estrutura foi corrompida e devido o combate a religião pelos veículos midiáticos.
O papel da cultura e da moralidade
A cultura brasileira também tem sido afetada por uma inversão de valores. Virtudes como honestidade, humildade e dedicação são muitas vezes vistas com desdém, enquanto comportamentos imprudentes e hedonistas são exaltados. Essa distorção enfraquece a sociedade e prejudica qualquer tentativa de avanço coletivo.
A elite intelectual e política, por sua vez, parece muitas vezes mais preocupada com interesses próprios do que com o bem comum. Muitos aderem a ideias que, em vez de promover a soberania e a autonomia nacional, aprofundam nossa dependência e fragilidade como país.
Existe saída?
Sim, existe. Mas não será simples — e muito menos rápida. O Brasil precisa de uma mudança profunda de mentalidade. Isso inclui:
Resgatar o valor da família e da formação moral;
Investir de verdade em uma educação que liberte, que forme e que inspire;
Incentivar a produção científica e tecnológica local;
Valorizar o trabalho árduo, a persistência e o compromisso com a verdade.
Também é preciso reconhecer que o desenvolvimento de uma nação não é apenas econômico, mas também espiritual e cultural. Mesmo que você não seja religioso, é possível entender que a construção de uma sociedade mais justa exige princípios, virtudes e limites. Sem isso, qualquer progresso será frágil e passageiro.
O Brasil tem jeito? Sim. Mas depende de nós — da nossa capacidade de enxergar com coragem onde estamos falhando, e da nossa disposição para agir com sabedoria, verdade e esperança.
-
 @ 1bc70a01:24f6a411
2025-04-11 13:50:38
@ 1bc70a01:24f6a411
2025-04-11 13:50:38The heading to be
Testing apps, a tireless quest, Click and swipe, then poke the rest. Crashing bugs and broken flows, Hidden deep where logic goes.
Specs in hand, we watch and trace, Each edge case in its hiding place. From flaky taps to loading spins, The war on regressions slowly wins.
Push the build, review the log, One more fix, then clear the fog. For in each test, truth will unfold— A quiet tale of stable code.
This has been a test. Thanks for tuning in.
- one
- two
- three
Listen a chillTranquility
And leisure
-
 @ 4e616576:43c4fee8
2025-04-30 13:27:51
@ 4e616576:43c4fee8
2025-04-30 13:27:51asdfasdf
-
 @ c4f5e7a7:8856cac7
2024-09-27 08:20:16
@ c4f5e7a7:8856cac7
2024-09-27 08:20:16Best viewed on Habla, YakiHonne or Highlighter.
TL;DR
This article explores the links between public, community-driven data sources (such as OpenStreetMap) and private, cryptographically-owned data found on networks such as Nostr.
The following concepts are explored:
- Attestations: Users signalling to their social graph that they believe something to be true by publishing Attestations. These social proofs act as a decentralised verification system that leverages your web-of-trust.
- Proof of Place: An oracle-based system where physical letters are sent to real-world locations, confirming the corresponding digital ownership via cryptographic proofs. This binds physical locations in meatspace with their digital representations in the Nostrverse.
- Check-ins: Foursquare-style check-ins that can be verified using attestations from place owners, ensuring authenticity. This approach uses web-of-trust to validate check-ins and location ownership over time.
The goal is to leverage cryptographic ownership where necessary while preserving the open, collaborative nature of public data systems.
Open Data in a public commons has a place and should not be thrown out with the Web 2.0 bathwater.
Cognitive Dissonance
Ever since discovering Nostr in August of 2022 I've been grappling with how BTC Map - a project that helps bitcoiners find places to spend sats - should most appropriately use this new protocol.
I am assuming, dear reader, that you are somewhat familiar with Nostr - a relatively new protocol for decentralised identity and communication. If you don’t know your nsec from your npub, please take some time to read these excellent posts: Nostr is Identity for the Internet and The Power of Nostr by @max and @lyn, respectively. Nostr is so much more than a short-form social media replacement.
The social features (check-ins, reviews, etc.) that Nostr unlocks for BTC Map are clear and exciting - all your silos are indeed broken - however, something fundamental has been bothering me for a while and I think it comes down to data ownership.
For those unfamiliar, BTC Map uses OpenStreetMap (OSM) as its main geographic database. OSM is centred on the concept of a commons of objectively verifiable data that is maintained by a global community of volunteer editors; a Wikipedia for maps. There is no data ownership; the data is free (as in freedom) and anyone can edit anything. It is the data equivalent of FOSS (Free and Open Source Software) - FOSD if you will, but more commonly referred to as Open Data.
In contrast, Notes and Other Stuff on Nostr (Places in this cartographic context) are explicitly owned by the controller of the private key. These notes are free to propagate, but they are owned.
How do we reconcile the decentralised nature of Nostr, where data is cryptographically owned by individuals, with the community-managed data commons of OpenStreetMap, where no one owns the data?
Self-sovereign Identity
Before I address this coexistence question, I want to talk a little about identity as it pertains to ownership. If something is to be owned, it has to be owned by someone or something - an identity.
All identities that are not self-sovereign are, by definition, leased to you by a 3rd party. You rent your Facebook identity from Meta in exchange for your data. You rent your web domain from your DNS provider in exchange for your money.
Taken to the extreme, you rent your passport from your Government in exchange for your compliance. You are you at the pleasure of others. Where Bitcoin separates money from the state; Nostr separates identity from the state.
Or, as @nvk said recently: "Don't build your house on someone else's land.".
https://i.nostr.build/xpcCSkDg3uVw0yku.png
While we’ve had the tools for self-sovereign digital identity for decades (think PGP keys or WebAuthN), we haven't had the necessary social use cases nor the corresponding social graph to elevate these identities to the mainstream. Nostr fixes this.
Nostr is PGP for the masses and will take cryptographic identities mainstream.
Full NOSTARD?
Returning to the coexistence question: the data on OpenStreetMap isn’t directly owned by anyone, even though the physical entities the data represents might be privately owned. OSM is a data commons.
We can objectively agree on the location of a tree or a fire hydrant without needing permission to observe and record it. Sure, you could place a tree ‘on Nostr’, but why should you? Just because something can be ‘on Nostr’ doesn’t mean it should be.
https://i.nostr.build/s3So2JVAqoY4E1dI.png
There might be a dystopian future where we can't agree on what a tree is nor where it's located, but I hope we never get there. It's at this point we'll need a Wikifreedia variant of OpenStreetMap.
While integrating Nostr identities into OpenStreetMap would be valuable, the current OSM infrastructure, tools, and community already provide substantial benefits in managing this data commons without needing to go NOSTR-native - there's no need to go Full NOSTARD. H/T to @princeySOV for the original meme.
https://i.nostr.build/ot9jtM5cZtDHNKWc.png
So, how do we appropriately blend cryptographically owned data with the commons?
If a location is owned in meatspace and it's useful to signal that ownership, it should also be owned in cyberspace. Our efforts should therefore focus on entities like businesses, while allowing the commons to manage public data for as long as it can successfully mitigate the tragedy of the commons.
The remainder of this article explores how we can:
- Verify ownership of a physical place in the real world;
- Link that ownership to the corresponding digital place in cyberspace.
As a side note, I don't see private key custodianship - or, even worse, permissioned use of Places signed by another identity's key - as any more viable than the rented identities of Web 2.0.
And as we all know, the Second Law of Infodynamics (no citation!) states that:
"The total amount of sensitive information leaked will always increase over time."
This especially holds true if that data is centralised.
Not your keys, not your notes. Not your keys, not your identity.
Places and Web-of-Trust
@Arkinox has been leading the charge on the Places NIP, introducing Nostr notes (kind 37515) that represent physical locations. The draft is well-crafted, with bonus points for linking back to OSM (and other location repositories) via NIP-73 - External Content IDs (championed by @oscar of @fountain).
However, as Nostr is permissionless, authenticity poses a challenge. Just because someone claims to own a physical location on the Internet doesn’t necessarily mean they have ownership or control of that location in the real world.
Ultimately, this problem can only be solved in a decentralised way by using Web-of-Trust - using your social graph and the perspectives of trusted peers to inform your own perspective. In the context of Places, this requires your network to form a view on which digital identity (public key / npub) is truly the owner of a physical place like your local coffee shop.
This requires users to:
- Verify the owner of a Place in cyberspace is the owner of a place in meatspace.
- Signal this verification to their social graph.
Let's look at the latter idea first with the concept of Attestations ...
Attestations
A way to signal to your social graph that you believe something to be true (or false for that matter) would be by publishing an Attestation note. An Attestation note would signify to your social graph that you think something is either true or false.
Imagine you're a regular at a local coffee shop. You publish an Attestation that says the shop is real and the owner behind the Nostr public key is who they claim to be. Your friends trust you, so they start trusting the shop's digital identity too.
However, attestations applied to Places are just a single use case. The attestation concept could be more widely applied across Nostr in a variety of ways (key rotation, identity linking, etc).
Here is a recent example from @lyn that would carry more signal if it were an Attestation:
https://i.nostr.build/lZAXOEwvRIghgFY4.png
Parallels can be drawn between Attestations and transaction confirmations on the Bitcoin timechain; however, their importance to you would be weighted by clients and/or Data Vending Machines in accordance with:
- Your social graph;
- The type or subject of the content being attested and by whom;
- Your personal preferences.
They could also have a validity duration to be temporally bound, which would be particularly useful in the case of Places.
NIP-25 (Reactions) do allow for users to up/downvote notes with optional content (e.g., emojis) and could work for Attestations, but I think we need something less ambiguous and more definitive.
‘This is true’ resonates more strongly than ‘I like this.’.
https://i.nostr.build/s8NIG2kXzUCLcoax.jpg
There are similar concepts in the Web 3 / Web 5 world such as Verified Credentials by tdb. However, Nostr is the Web 3 now and so wen Attestation NIP?
https://i.nostr.build/Cb047NWyHdJ7h5Ka.jpg
That said, I have seen @utxo has been exploring ‘smart contracts’ on nostr and Attestations may just be a relatively ‘dumb’ subset of the wider concept Nostr-native scripting combined with web-of-trust.
Proof of Place
Attestations handle the signalling of your truth, but what about the initial verification itself?
We already covered how this ultimately has to be derived from your social graph, but what if there was a way to help bootstrap this web-of-trust through the use of oracles? For those unfamiliar with oracles in the digital realm, they are simply trusted purveyors of truth.
Introducing Proof of Place, an out–of-band process where an oracle (such as BTC Map) would mail - yes physically mail- a shared secret to the address of the location being claimed in cyberspace. This shared secret would be locked to the public key (npub) making the claim, which, if unlocked, would prove that the associated private key (nsec) has physical access to the location in meatspace.
One way of doing this would be to mint a 1 sat cashu ecash token locked to the npub of the claimant and mail it to them. If they are able to redeem the token then they have cryptographically proven that they have physical access to the location.
Proof of Place is really nothing more than a weighted Attestation. In a web-of-trust Nostrverse, an oracle is simply a npub (say BTC Map) that you weigh heavily for its opinion on a given topic (say Places).
In the Bitcoin world, Proof of Work anchors digital scarcity in cyberspace to physical scarcity (energy and time) in meatspace and as @Gigi says in PoW is Essential:
"A failure to understand Proof of Work, is a failure to understand Bitcoin."
In the Nostrverse, Proof of Place helps bridge the digital and physical worlds.
@Gigi also observes in Memes vs The World that:
"In Bitcoin, the map is the territory. We can infer everything we care about by looking at the map alone."
https://i.nostr.build/dOnpxfI4u7EL2v4e.png
This isn’t true for Nostr.
In the Nostrverse, the map IS NOT the territory. However, Proof of Place enables us to send cryptographic drones down into the physical territory to help us interpret our digital maps. 🤯
Check-ins
Although not a draft NIP yet, @Arkinox has also been exploring the familiar concept of Foursquare-style Check-ins on Nostr (with kind 13811 notes).
For the uninitiated, Check-ins are simply notes that signal the publisher is at a given location. These locations could be Places (in the Nostr sense) or any other given digital representation of a location for that matter (such as OSM elements) if NIP-73 - External Content IDs are used.
Of course, not everyone will be a Check-in enjoyooor as the concept will not sit well with some people’s threat models and OpSec practices.
Bringing Check-ins to Nostr is possible (as @sebastix capably shows here), but they suffer the same authenticity issues as Places. Just because I say I'm at a given location doesn't mean that I am.
Back in the Web 2.0 days, Foursquare mitigated this by relying on the GPS position of the phone running their app, but this is of course spoofable.
How should we approach Check-in verifiability in the Nostrverse? Well, just like with Places, we can use Attestations and WoT. In the context of Check-ins, an Attestation from the identity (npub) of the Place being checked-in to would be a particularly strong signal. An NFC device could be placed in a coffee shop and attest to check-ins without requiring the owner to manually intervene - I’m sure @blackcoffee and @Ben Arc could hack something together over a weekend!
Check-ins could also be used as a signal for bonafide Place ownership over time.
Summary: Trust Your Bros
So, to recap, we have:
Places: Digital representations of physical locations on Nostr.
Check-ins: Users signalling their presence at a location.
Attestations: Verifiable social proofs used to confirm ownership or the truth of a claim.
You can visualise how these three concepts combine in the diagram below:
https://i.nostr.build/Uv2Jhx5BBfA51y0K.jpg
And, as always, top right trumps bottom left! We have:
Level 0 - Trust Me Bro: Anyone can check-in anywhere. The Place might not exist or might be impersonating the real place in meatspace. The person behind the npub may not have even been there at all.
Level 1 - Definitely Maybe Somewhere: This category covers the middle-ground of ‘Maybe at a Place’ and ‘Definitely Somewhere’. In these examples, you are either self-certifying that you have checked-in at an Attested Place or you are having others attest that you have checked-in at a Place that might not even exist IRL.
Level 2 - Trust Your Bros: An Attested Check-in at an Attested Place. Your individual level of trust would be a function of the number of Attestations and how you weigh them within your own social graph.
https://i.nostr.build/HtLAiJH1uQSTmdxf.jpg
Perhaps the gold standard (or should that be the Bitcoin standard?) would be a Check-in attested by the owner of the Place, which in itself was attested by BTC Map?
Or perhaps not. Ultimately, it’s the users responsibility to determine what they trust by forming their own perspective within the Nostrverse powered by web-of-trust algorithms they control. ‘Trust Me Bro’ or ‘Trust Your Bros’ - you decide.
As we navigate the frontier of cryptographic ownership and decentralised data, it’s up to us to find the balance between preserving the Open Data commons and embracing self-sovereign digital identities.
Thanks
With thanks to Arkinox, Avi, Ben Gunn, Kieran, Blackcoffee, Sebastix, Tomek, Calle, Short Fiat, Ben Weeks and Bitcoms for helping shape my thoughts and refine content, whether you know it or not!

