-
 @ 91bea5cd:1df4451c
2025-04-26 10:16:21
@ 91bea5cd:1df4451c
2025-04-26 10:16:21O Contexto Legal Brasileiro e o Consentimento
No ordenamento jurídico brasileiro, o consentimento do ofendido pode, em certas circunstâncias, afastar a ilicitude de um ato que, sem ele, configuraria crime (como lesão corporal leve, prevista no Art. 129 do Código Penal). Contudo, o consentimento tem limites claros: não é válido para bens jurídicos indisponíveis, como a vida, e sua eficácia é questionável em casos de lesões corporais graves ou gravíssimas.
A prática de BDSM consensual situa-se em uma zona complexa. Em tese, se ambos os parceiros são adultos, capazes, e consentiram livre e informadamente nos atos praticados, sem que resultem em lesões graves permanentes ou risco de morte não consentido, não haveria crime. O desafio reside na comprovação desse consentimento, especialmente se uma das partes, posteriormente, o negar ou alegar coação.
A Lei Maria da Penha (Lei nº 11.340/2006)
A Lei Maria da Penha é um marco fundamental na proteção da mulher contra a violência doméstica e familiar. Ela estabelece mecanismos para coibir e prevenir tal violência, definindo suas formas (física, psicológica, sexual, patrimonial e moral) e prevendo medidas protetivas de urgência.
Embora essencial, a aplicação da lei em contextos de BDSM pode ser delicada. Uma alegação de violência por parte da mulher, mesmo que as lesões ou situações decorram de práticas consensuais, tende a receber atenção prioritária das autoridades, dada a presunção de vulnerabilidade estabelecida pela lei. Isso pode criar um cenário onde o parceiro masculino enfrenta dificuldades significativas em demonstrar a natureza consensual dos atos, especialmente se não houver provas robustas pré-constituídas.
Outros riscos:
Lesão corporal grave ou gravíssima (art. 129, §§ 1º e 2º, CP), não pode ser justificada pelo consentimento, podendo ensejar persecução penal.
Crimes contra a dignidade sexual (arts. 213 e seguintes do CP) são de ação pública incondicionada e independem de representação da vítima para a investigação e denúncia.
Riscos de Falsas Acusações e Alegação de Coação Futura
Os riscos para os praticantes de BDSM, especialmente para o parceiro que assume o papel dominante ou que inflige dor/restrição (frequentemente, mas não exclusivamente, o homem), podem surgir de diversas frentes:
- Acusações Externas: Vizinhos, familiares ou amigos que desconhecem a natureza consensual do relacionamento podem interpretar sons, marcas ou comportamentos como sinais de abuso e denunciar às autoridades.
- Alegações Futuras da Parceira: Em caso de término conturbado, vingança, arrependimento ou mudança de perspectiva, a parceira pode reinterpretar as práticas passadas como abuso e buscar reparação ou retaliação através de uma denúncia. A alegação pode ser de que o consentimento nunca existiu ou foi viciado.
- Alegação de Coação: Uma das formas mais complexas de refutar é a alegação de que o consentimento foi obtido mediante coação (física, moral, psicológica ou econômica). A parceira pode alegar, por exemplo, que se sentia pressionada, intimidada ou dependente, e que seu "sim" não era genuíno. Provar a ausência de coação a posteriori é extremamente difícil.
- Ingenuidade e Vulnerabilidade Masculina: Muitos homens, confiando na dinâmica consensual e na parceira, podem negligenciar a necessidade de precauções. A crença de que "isso nunca aconteceria comigo" ou a falta de conhecimento sobre as implicações legais e o peso processual de uma acusação no âmbito da Lei Maria da Penha podem deixá-los vulneráveis. A presença de marcas físicas, mesmo que consentidas, pode ser usada como evidência de agressão, invertendo o ônus da prova na prática, ainda que não na teoria jurídica.
Estratégias de Prevenção e Mitigação
Não existe um método infalível para evitar completamente o risco de uma falsa acusação, mas diversas medidas podem ser adotadas para construir um histórico de consentimento e reduzir vulnerabilidades:
- Comunicação Explícita e Contínua: A base de qualquer prática BDSM segura é a comunicação constante. Negociar limites, desejos, palavras de segurança ("safewords") e expectativas antes, durante e depois das cenas é crucial. Manter registros dessas negociações (e-mails, mensagens, diários compartilhados) pode ser útil.
-
Documentação do Consentimento:
-
Contratos de Relacionamento/Cena: Embora a validade jurídica de "contratos BDSM" seja discutível no Brasil (não podem afastar normas de ordem pública), eles servem como forte evidência da intenção das partes, da negociação detalhada de limites e do consentimento informado. Devem ser claros, datados, assinados e, idealmente, reconhecidos em cartório (para prova de data e autenticidade das assinaturas).
-
Registros Audiovisuais: Gravar (com consentimento explícito para a gravação) discussões sobre consentimento e limites antes das cenas pode ser uma prova poderosa. Gravar as próprias cenas é mais complexo devido a questões de privacidade e potencial uso indevido, mas pode ser considerado em casos específicos, sempre com consentimento mútuo documentado para a gravação.
Importante: a gravação deve ser com ciência da outra parte, para não configurar violação da intimidade (art. 5º, X, da Constituição Federal e art. 20 do Código Civil).
-
-
Testemunhas: Em alguns contextos de comunidade BDSM, a presença de terceiros de confiança durante negociações ou mesmo cenas pode servir como testemunho, embora isso possa alterar a dinâmica íntima do casal.
- Estabelecimento Claro de Limites e Palavras de Segurança: Definir e respeitar rigorosamente os limites (o que é permitido, o que é proibido) e as palavras de segurança é fundamental. O desrespeito a uma palavra de segurança encerra o consentimento para aquele ato.
- Avaliação Contínua do Consentimento: O consentimento não é um cheque em branco; ele deve ser entusiástico, contínuo e revogável a qualquer momento. Verificar o bem-estar do parceiro durante a cena ("check-ins") é essencial.
- Discrição e Cuidado com Evidências Físicas: Ser discreto sobre a natureza do relacionamento pode evitar mal-entendidos externos. Após cenas que deixem marcas, é prudente que ambos os parceiros estejam cientes e de acordo, talvez documentando por fotos (com data) e uma nota sobre a consensualidade da prática que as gerou.
- Aconselhamento Jurídico Preventivo: Consultar um advogado especializado em direito de família e criminal, com sensibilidade para dinâmicas de relacionamento alternativas, pode fornecer orientação personalizada sobre as melhores formas de documentar o consentimento e entender os riscos legais específicos.
Observações Importantes
- Nenhuma documentação substitui a necessidade de consentimento real, livre, informado e contínuo.
- A lei brasileira protege a "integridade física" e a "dignidade humana". Práticas que resultem em lesões graves ou que violem a dignidade de forma não consentida (ou com consentimento viciado) serão ilegais, independentemente de qualquer acordo prévio.
- Em caso de acusação, a existência de documentação robusta de consentimento não garante a absolvição, mas fortalece significativamente a defesa, ajudando a demonstrar a natureza consensual da relação e das práticas.
-
A alegação de coação futura é particularmente difícil de prevenir apenas com documentos. Um histórico consistente de comunicação aberta (whatsapp/telegram/e-mails), respeito mútuo e ausência de dependência ou controle excessivo na relação pode ajudar a contextualizar a dinâmica como não coercitiva.
-
Cuidado com Marcas Visíveis e Lesões Graves Práticas que resultam em hematomas severos ou lesões podem ser interpretadas como agressão, mesmo que consentidas. Evitar excessos protege não apenas a integridade física, mas também evita questionamentos legais futuros.
O que vem a ser consentimento viciado
No Direito, consentimento viciado é quando a pessoa concorda com algo, mas a vontade dela não é livre ou plena — ou seja, o consentimento existe formalmente, mas é defeituoso por alguma razão.
O Código Civil brasileiro (art. 138 a 165) define várias formas de vício de consentimento. As principais são:
Erro: A pessoa se engana sobre o que está consentindo. (Ex.: A pessoa acredita que vai participar de um jogo leve, mas na verdade é exposta a práticas pesadas.)
Dolo: A pessoa é enganada propositalmente para aceitar algo. (Ex.: Alguém mente sobre o que vai acontecer durante a prática.)
Coação: A pessoa é forçada ou ameaçada a consentir. (Ex.: "Se você não aceitar, eu termino com você" — pressão emocional forte pode ser vista como coação.)
Estado de perigo ou lesão: A pessoa aceita algo em situação de necessidade extrema ou abuso de sua vulnerabilidade. (Ex.: Alguém em situação emocional muito fragilizada é induzida a aceitar práticas que normalmente recusaria.)
No contexto de BDSM, isso é ainda mais delicado: Mesmo que a pessoa tenha "assinado" um contrato ou dito "sim", se depois ela alegar que seu consentimento foi dado sob medo, engano ou pressão psicológica, o consentimento pode ser considerado viciado — e, portanto, juridicamente inválido.
Isso tem duas implicações sérias:
-
O crime não se descaracteriza: Se houver vício, o consentimento é ignorado e a prática pode ser tratada como crime normal (lesão corporal, estupro, tortura, etc.).
-
A prova do consentimento precisa ser sólida: Mostrando que a pessoa estava informada, lúcida, livre e sem qualquer tipo de coação.
Consentimento viciado é quando a pessoa concorda formalmente, mas de maneira enganada, forçada ou pressionada, tornando o consentimento inútil para efeitos jurídicos.
Conclusão
Casais que praticam BDSM consensual no Brasil navegam em um terreno que exige não apenas confiança mútua e comunicação excepcional, mas também uma consciência aguçada das complexidades legais e dos riscos de interpretações equivocadas ou acusações mal-intencionadas. Embora o BDSM seja uma expressão legítima da sexualidade humana, sua prática no Brasil exige responsabilidade redobrada. Ter provas claras de consentimento, manter a comunicação aberta e agir com prudência são formas eficazes de se proteger de falsas alegações e preservar a liberdade e a segurança de todos os envolvidos. Embora leis controversas como a Maria da Penha sejam "vitais" para a proteção contra a violência real, os praticantes de BDSM, e em particular os homens nesse contexto, devem adotar uma postura proativa e prudente para mitigar os riscos inerentes à potencial má interpretação ou instrumentalização dessas práticas e leis, garantindo que a expressão de sua consensualidade esteja resguardada na medida do possível.
Importante: No Brasil, mesmo com tudo isso, o Ministério Público pode denunciar por crime como lesão corporal grave, estupro ou tortura, independente de consentimento. Então a prudência nas práticas é fundamental.
Aviso Legal: Este artigo tem caráter meramente informativo e não constitui aconselhamento jurídico. As leis e interpretações podem mudar, e cada situação é única. Recomenda-se buscar orientação de um advogado qualificado para discutir casos específicos.
Se curtiu este artigo faça uma contribuição, se tiver algum ponto relevante para o artigo deixe seu comentário.
-
 @ e4950c93:1b99eccd
2025-05-02 12:48:46
@ e4950c93:1b99eccd
2025-05-02 12:48:46🧵 Produits en cette matière
Les marques suivantes proposent des produits fait exclusivement ou principalement avec cette matière :
Vêtements
Cet article est publié sur origine-nature.com 🌐 See this article in English
-
 @ e4950c93:1b99eccd
2025-05-02 12:47:27
@ e4950c93:1b99eccd
2025-05-02 12:47:27Dilling est une marque danoise qui crée des vêtements en laine, soie et coton biologique pour toute la famille.
Matières naturelles utilisées dans les produits
- Coton (biologique)
- Laine (mérinos, alpaga)
- Latex naturel (OEKO-TEX ®)
- Soie
⚠️ Attention, certains produits de cette marque (notamment les Vêtements - chaussettes, vestes, strings, shorts) contiennent des matières non naturelles, dont :
- Elasthanne
- Polyamide, nylon (nylon recyclé)
- Polyester (recyclé)
Catégories de produits proposés
-
Vêtements : homme, femme, enfant, bébé, sous-vêtements, t-shirts, débardeurs, robes, vestes, pantalons, shorts, pulls, gilets, bodies, combinaisons, culottes, slips, boxers...
Autres informations
- Ecolabel Nordic Swan (teintures)
- Fabriqué en Lituanie (coupe et couture)
- Fabriqué au Danemark (teintures)
- Fabriqué en Europe
👉 En savoir plus sur le site de la marque
Cet article est publié sur origine-nature.com 🌐 See this article in English
📝 Tu peux contribuer à cette fiche en suggérant une modification en commentaire.
🗣️ Tu utilises ce produit ? Partage ton avis en commentaire.
⚡ Heureu-x-se de trouver cette information ? Soutiens le projet en faisant un don, pour remercier les contribut-eur-ice-s.
-
 @ a5142938:0ef19da3
2025-05-02 12:31:35
@ a5142938:0ef19da3
2025-05-02 12:31:35Dilling is a Danish brand that creates wool, silk, and organic cotton clothing for the whole family.
Natural materials used in products
- Cotton (organic)
- Natural latex (OEKO-TEX ®)
- Silk
- Wool (merino, alpaca)
⚠️ Warning: some products from this brand (especially Clothes – socks, jackets, thongs, shorts) contain non-natural materials, including:
- Elastane, spandex, lycra
- Polyamide, nylon (recycled nylon)
- Polyester (recycled)
Categories of products offered
-
Clothing : men, women, children, babies, underwear, t-shirts, tank tops, dresses, jackets, trousers, shorts, sweaters, cardigans, bodysuits, jumpsuits, panties, briefs, boxers...
Other information
- Nordic Swan ecolabel (dye)
- Made in Lithuania (cutting and sewing)
- Made in Denmark (dye)
- Made in Europe
👉 Learn more on the brand's website
This article is published on origin-nature.com 🌐 Voir cet article en français
📝 You can contribute to this entry by suggesting edits in comments.
🗣️ Do you use this product? Share your opinion in the comments.
⚡ Happy to have found this information? Support the project by making a donation to thank the contributors.
-
 @ 91bea5cd:1df4451c
2025-04-15 06:27:28
@ 91bea5cd:1df4451c
2025-04-15 06:27:28Básico
bash lsblk # Lista todos os diretorios montados.Para criar o sistema de arquivos:
bash mkfs.btrfs -L "ThePool" -f /dev/sdxCriando um subvolume:
bash btrfs subvolume create SubVolMontando Sistema de Arquivos:
bash mount -o compress=zlib,subvol=SubVol,autodefrag /dev/sdx /mntLista os discos formatados no diretório:
bash btrfs filesystem show /mntAdiciona novo disco ao subvolume:
bash btrfs device add -f /dev/sdy /mntLista novamente os discos do subvolume:
bash btrfs filesystem show /mntExibe uso dos discos do subvolume:
bash btrfs filesystem df /mntBalancea os dados entre os discos sobre raid1:
bash btrfs filesystem balance start -dconvert=raid1 -mconvert=raid1 /mntScrub é uma passagem por todos os dados e metadados do sistema de arquivos e verifica as somas de verificação. Se uma cópia válida estiver disponível (perfis de grupo de blocos replicados), a danificada será reparada. Todas as cópias dos perfis replicados são validadas.
iniciar o processo de depuração :
bash btrfs scrub start /mntver o status do processo de depuração Btrfs em execução:
bash btrfs scrub status /mntver o status do scrub Btrfs para cada um dos dispositivos
bash btrfs scrub status -d / data btrfs scrub cancel / dataPara retomar o processo de depuração do Btrfs que você cancelou ou pausou:
btrfs scrub resume / data
Listando os subvolumes:
bash btrfs subvolume list /ReportsCriando um instantâneo dos subvolumes:
Aqui, estamos criando um instantâneo de leitura e gravação chamado snap de marketing do subvolume de marketing.
bash btrfs subvolume snapshot /Reports/marketing /Reports/marketing-snapAlém disso, você pode criar um instantâneo somente leitura usando o sinalizador -r conforme mostrado. O marketing-rosnap é um instantâneo somente leitura do subvolume de marketing
bash btrfs subvolume snapshot -r /Reports/marketing /Reports/marketing-rosnapForçar a sincronização do sistema de arquivos usando o utilitário 'sync'
Para forçar a sincronização do sistema de arquivos, invoque a opção de sincronização conforme mostrado. Observe que o sistema de arquivos já deve estar montado para que o processo de sincronização continue com sucesso.
bash btrfs filsystem sync /ReportsPara excluir o dispositivo do sistema de arquivos, use o comando device delete conforme mostrado.
bash btrfs device delete /dev/sdc /ReportsPara sondar o status de um scrub, use o comando scrub status com a opção -dR .
bash btrfs scrub status -dR / RelatóriosPara cancelar a execução do scrub, use o comando scrub cancel .
bash $ sudo btrfs scrub cancel / ReportsPara retomar ou continuar com uma depuração interrompida anteriormente, execute o comando de cancelamento de depuração
bash sudo btrfs scrub resume /Reportsmostra o uso do dispositivo de armazenamento:
btrfs filesystem usage /data
Para distribuir os dados, metadados e dados do sistema em todos os dispositivos de armazenamento do RAID (incluindo o dispositivo de armazenamento recém-adicionado) montados no diretório /data , execute o seguinte comando:
sudo btrfs balance start --full-balance /data
Pode demorar um pouco para espalhar os dados, metadados e dados do sistema em todos os dispositivos de armazenamento do RAID se ele contiver muitos dados.
Opções importantes de montagem Btrfs
Nesta seção, vou explicar algumas das importantes opções de montagem do Btrfs. Então vamos começar.
As opções de montagem Btrfs mais importantes são:
**1. acl e noacl
**ACL gerencia permissões de usuários e grupos para os arquivos/diretórios do sistema de arquivos Btrfs.
A opção de montagem acl Btrfs habilita ACL. Para desabilitar a ACL, você pode usar a opção de montagem noacl .
Por padrão, a ACL está habilitada. Portanto, o sistema de arquivos Btrfs usa a opção de montagem acl por padrão.
**2. autodefrag e noautodefrag
**Desfragmentar um sistema de arquivos Btrfs melhorará o desempenho do sistema de arquivos reduzindo a fragmentação de dados.
A opção de montagem autodefrag permite a desfragmentação automática do sistema de arquivos Btrfs.
A opção de montagem noautodefrag desativa a desfragmentação automática do sistema de arquivos Btrfs.
Por padrão, a desfragmentação automática está desabilitada. Portanto, o sistema de arquivos Btrfs usa a opção de montagem noautodefrag por padrão.
**3. compactar e compactar-forçar
**Controla a compactação de dados no nível do sistema de arquivos do sistema de arquivos Btrfs.
A opção compactar compacta apenas os arquivos que valem a pena compactar (se compactar o arquivo economizar espaço em disco).
A opção compress-force compacta todos os arquivos do sistema de arquivos Btrfs, mesmo que a compactação do arquivo aumente seu tamanho.
O sistema de arquivos Btrfs suporta muitos algoritmos de compactação e cada um dos algoritmos de compactação possui diferentes níveis de compactação.
Os algoritmos de compactação suportados pelo Btrfs são: lzo , zlib (nível 1 a 9) e zstd (nível 1 a 15).
Você pode especificar qual algoritmo de compactação usar para o sistema de arquivos Btrfs com uma das seguintes opções de montagem:
- compress=algoritmo:nível
- compress-force=algoritmo:nível
Para obter mais informações, consulte meu artigo Como habilitar a compactação do sistema de arquivos Btrfs .
**4. subvol e subvolid
**Estas opções de montagem são usadas para montar separadamente um subvolume específico de um sistema de arquivos Btrfs.
A opção de montagem subvol é usada para montar o subvolume de um sistema de arquivos Btrfs usando seu caminho relativo.
A opção de montagem subvolid é usada para montar o subvolume de um sistema de arquivos Btrfs usando o ID do subvolume.
Para obter mais informações, consulte meu artigo Como criar e montar subvolumes Btrfs .
**5. dispositivo
A opção de montagem de dispositivo** é usada no sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs.
Em alguns casos, o sistema operacional pode falhar ao detectar os dispositivos de armazenamento usados em um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs. Nesses casos, você pode usar a opção de montagem do dispositivo para especificar os dispositivos que deseja usar para o sistema de arquivos de vários dispositivos Btrfs ou RAID.
Você pode usar a opção de montagem de dispositivo várias vezes para carregar diferentes dispositivos de armazenamento para o sistema de arquivos de vários dispositivos Btrfs ou RAID.
Você pode usar o nome do dispositivo (ou seja, sdb , sdc ) ou UUID , UUID_SUB ou PARTUUID do dispositivo de armazenamento com a opção de montagem do dispositivo para identificar o dispositivo de armazenamento.
Por exemplo,
- dispositivo=/dev/sdb
- dispositivo=/dev/sdb,dispositivo=/dev/sdc
- dispositivo=UUID_SUB=490a263d-eb9a-4558-931e-998d4d080c5d
- device=UUID_SUB=490a263d-eb9a-4558-931e-998d4d080c5d,device=UUID_SUB=f7ce4875-0874-436a-b47d-3edef66d3424
**6. degraded
A opção de montagem degradada** permite que um RAID Btrfs seja montado com menos dispositivos de armazenamento do que o perfil RAID requer.
Por exemplo, o perfil raid1 requer a presença de 2 dispositivos de armazenamento. Se um dos dispositivos de armazenamento não estiver disponível em qualquer caso, você usa a opção de montagem degradada para montar o RAID mesmo que 1 de 2 dispositivos de armazenamento esteja disponível.
**7. commit
A opção commit** mount é usada para definir o intervalo (em segundos) dentro do qual os dados serão gravados no dispositivo de armazenamento.
O padrão é definido como 30 segundos.
Para definir o intervalo de confirmação para 15 segundos, você pode usar a opção de montagem commit=15 (digamos).
**8. ssd e nossd
A opção de montagem ssd** informa ao sistema de arquivos Btrfs que o sistema de arquivos está usando um dispositivo de armazenamento SSD, e o sistema de arquivos Btrfs faz a otimização SSD necessária.
A opção de montagem nossd desativa a otimização do SSD.
O sistema de arquivos Btrfs detecta automaticamente se um SSD é usado para o sistema de arquivos Btrfs. Se um SSD for usado, a opção de montagem de SSD será habilitada. Caso contrário, a opção de montagem nossd é habilitada.
**9. ssd_spread e nossd_spread
A opção de montagem ssd_spread** tenta alocar grandes blocos contínuos de espaço não utilizado do SSD. Esse recurso melhora o desempenho de SSDs de baixo custo (baratos).
A opção de montagem nossd_spread desativa o recurso ssd_spread .
O sistema de arquivos Btrfs detecta automaticamente se um SSD é usado para o sistema de arquivos Btrfs. Se um SSD for usado, a opção de montagem ssd_spread será habilitada. Caso contrário, a opção de montagem nossd_spread é habilitada.
**10. descarte e nodiscard
Se você estiver usando um SSD que suporte TRIM enfileirado assíncrono (SATA rev3.1), a opção de montagem de descarte** permitirá o descarte de blocos de arquivos liberados. Isso melhorará o desempenho do SSD.
Se o SSD não suportar TRIM enfileirado assíncrono, a opção de montagem de descarte prejudicará o desempenho do SSD. Nesse caso, a opção de montagem nodiscard deve ser usada.
Por padrão, a opção de montagem nodiscard é usada.
**11. norecovery
Se a opção de montagem norecovery** for usada, o sistema de arquivos Btrfs não tentará executar a operação de recuperação de dados no momento da montagem.
**12. usebackuproot e nousebackuproot
Se a opção de montagem usebackuproot for usada, o sistema de arquivos Btrfs tentará recuperar qualquer raiz de árvore ruim/corrompida no momento da montagem. O sistema de arquivos Btrfs pode armazenar várias raízes de árvore no sistema de arquivos. A opção de montagem usebackuproot** procurará uma boa raiz de árvore e usará a primeira boa que encontrar.
A opção de montagem nousebackuproot não verificará ou recuperará raízes de árvore inválidas/corrompidas no momento da montagem. Este é o comportamento padrão do sistema de arquivos Btrfs.
**13. space_cache, space_cache=version, nospace_cache e clear_cache
A opção de montagem space_cache** é usada para controlar o cache de espaço livre. O cache de espaço livre é usado para melhorar o desempenho da leitura do espaço livre do grupo de blocos do sistema de arquivos Btrfs na memória (RAM).
O sistema de arquivos Btrfs suporta 2 versões do cache de espaço livre: v1 (padrão) e v2
O mecanismo de cache de espaço livre v2 melhora o desempenho de sistemas de arquivos grandes (tamanho de vários terabytes).
Você pode usar a opção de montagem space_cache=v1 para definir a v1 do cache de espaço livre e a opção de montagem space_cache=v2 para definir a v2 do cache de espaço livre.
A opção de montagem clear_cache é usada para limpar o cache de espaço livre.
Quando o cache de espaço livre v2 é criado, o cache deve ser limpo para criar um cache de espaço livre v1 .
Portanto, para usar o cache de espaço livre v1 após a criação do cache de espaço livre v2 , as opções de montagem clear_cache e space_cache=v1 devem ser combinadas: clear_cache,space_cache=v1
A opção de montagem nospace_cache é usada para desabilitar o cache de espaço livre.
Para desabilitar o cache de espaço livre após a criação do cache v1 ou v2 , as opções de montagem nospace_cache e clear_cache devem ser combinadas: clear_cache,nosapce_cache
**14. skip_balance
Por padrão, a operação de balanceamento interrompida/pausada de um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs será retomada automaticamente assim que o sistema de arquivos Btrfs for montado. Para desabilitar a retomada automática da operação de equilíbrio interrompido/pausado em um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs, você pode usar a opção de montagem skip_balance .**
**15. datacow e nodatacow
A opção datacow** mount habilita o recurso Copy-on-Write (CoW) do sistema de arquivos Btrfs. É o comportamento padrão.
Se você deseja desabilitar o recurso Copy-on-Write (CoW) do sistema de arquivos Btrfs para os arquivos recém-criados, monte o sistema de arquivos Btrfs com a opção de montagem nodatacow .
**16. datasum e nodatasum
A opção datasum** mount habilita a soma de verificação de dados para arquivos recém-criados do sistema de arquivos Btrfs. Este é o comportamento padrão.
Se você não quiser que o sistema de arquivos Btrfs faça a soma de verificação dos dados dos arquivos recém-criados, monte o sistema de arquivos Btrfs com a opção de montagem nodatasum .
Perfis Btrfs
Um perfil Btrfs é usado para informar ao sistema de arquivos Btrfs quantas cópias dos dados/metadados devem ser mantidas e quais níveis de RAID devem ser usados para os dados/metadados. O sistema de arquivos Btrfs contém muitos perfis. Entendê-los o ajudará a configurar um RAID Btrfs da maneira que você deseja.
Os perfis Btrfs disponíveis são os seguintes:
single : Se o perfil único for usado para os dados/metadados, apenas uma cópia dos dados/metadados será armazenada no sistema de arquivos, mesmo se você adicionar vários dispositivos de armazenamento ao sistema de arquivos. Assim, 100% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser utilizado.
dup : Se o perfil dup for usado para os dados/metadados, cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos manterá duas cópias dos dados/metadados. Assim, 50% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser utilizado.
raid0 : No perfil raid0 , os dados/metadados serão divididos igualmente em todos os dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, não haverá dados/metadados redundantes (duplicados). Assim, 100% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser usado. Se, em qualquer caso, um dos dispositivos de armazenamento falhar, todo o sistema de arquivos será corrompido. Você precisará de pelo menos dois dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid0 .
raid1 : No perfil raid1 , duas cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a uma falha de unidade. Mas você pode usar apenas 50% do espaço total em disco. Você precisará de pelo menos dois dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1 .
raid1c3 : No perfil raid1c3 , três cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a duas falhas de unidade, mas você pode usar apenas 33% do espaço total em disco. Você precisará de pelo menos três dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1c3 .
raid1c4 : No perfil raid1c4 , quatro cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a três falhas de unidade, mas você pode usar apenas 25% do espaço total em disco. Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1c4 .
raid10 : No perfil raid10 , duas cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos, como no perfil raid1 . Além disso, os dados/metadados serão divididos entre os dispositivos de armazenamento, como no perfil raid0 .
O perfil raid10 é um híbrido dos perfis raid1 e raid0 . Alguns dos dispositivos de armazenamento formam arrays raid1 e alguns desses arrays raid1 são usados para formar um array raid0 . Em uma configuração raid10 , o sistema de arquivos pode sobreviver a uma única falha de unidade em cada uma das matrizes raid1 .
Você pode usar 50% do espaço total em disco na configuração raid10 . Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid10 .
raid5 : No perfil raid5 , uma cópia dos dados/metadados será dividida entre os dispositivos de armazenamento. Uma única paridade será calculada e distribuída entre os dispositivos de armazenamento do array RAID.
Em uma configuração raid5 , o sistema de arquivos pode sobreviver a uma única falha de unidade. Se uma unidade falhar, você pode adicionar uma nova unidade ao sistema de arquivos e os dados perdidos serão calculados a partir da paridade distribuída das unidades em execução.
Você pode usar 1 00x(N-1)/N % do total de espaços em disco na configuração raid5 . Aqui, N é o número de dispositivos de armazenamento adicionados ao sistema de arquivos. Você precisará de pelo menos três dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid5 .
raid6 : No perfil raid6 , uma cópia dos dados/metadados será dividida entre os dispositivos de armazenamento. Duas paridades serão calculadas e distribuídas entre os dispositivos de armazenamento do array RAID.
Em uma configuração raid6 , o sistema de arquivos pode sobreviver a duas falhas de unidade ao mesmo tempo. Se uma unidade falhar, você poderá adicionar uma nova unidade ao sistema de arquivos e os dados perdidos serão calculados a partir das duas paridades distribuídas das unidades em execução.
Você pode usar 100x(N-2)/N % do espaço total em disco na configuração raid6 . Aqui, N é o número de dispositivos de armazenamento adicionados ao sistema de arquivos. Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid6 .
-
 @ 0fa80bd3:ea7325de
2025-04-09 21:19:39
@ 0fa80bd3:ea7325de
2025-04-09 21:19:39DAOs promised decentralization. They offered a system where every member could influence a project's direction, where money and power were transparently distributed, and decisions were made through voting. All of it recorded immutably on the blockchain, free from middlemen.
But something didn’t work out. In practice, most DAOs haven’t evolved into living, self-organizing organisms. They became something else: clubs where participation is unevenly distributed. Leaders remained - only now without formal titles. They hold influence through control over communications, task framing, and community dynamics. Centralization still exists, just wrapped in a new package.
But there's a second, less obvious problem. Crowds can’t create strategy. In DAOs, people vote for what "feels right to the majority." But strategy isn’t about what feels good - it’s about what’s necessary. Difficult, unpopular, yet forward-looking decisions often fail when put to a vote. A founder’s vision is a risk. But in healthy teams, it’s that risk that drives progress. In DAOs, risk is almost always diluted until it becomes something safe and vague.
Instead of empowering leaders, DAOs often neutralize them. This is why many DAOs resemble consensus machines. Everyone talks, debates, and participates, but very little actually gets done. One person says, “Let’s jump,” and five others respond, “Let’s discuss that first.” This dynamic might work for open forums, but not for action.
Decentralization works when there’s trust and delegation, not just voting. Until DAOs develop effective systems for assigning roles, taking ownership, and acting with flexibility, they will keep losing ground to old-fashioned startups led by charismatic founders with a clear vision.
We’ve seen this in many real-world cases. Take MakerDAO, one of the most mature and technically sophisticated DAOs. Its governance token (MKR) holders vote on everything from interest rates to protocol upgrades. While this has allowed for transparency and community involvement, the process is often slow and bureaucratic. Complex proposals stall. Strategic pivots become hard to implement. And in 2023, a controversial proposal to allocate billions to real-world assets passed only narrowly, after months of infighting - highlighting how vision and execution can get stuck in the mud of distributed governance.
On the other hand, Uniswap DAO, responsible for the largest decentralized exchange, raised governance participation only after launching a delegation system where token holders could choose trusted representatives. Still, much of the activity is limited to a small group of active contributors. The vast majority of token holders remain passive. This raises the question: is it really community-led, or just a formalized power structure with lower transparency?
Then there’s ConstitutionDAO, an experiment that went viral. It raised over $40 million in days to try and buy a copy of the U.S. Constitution. But despite the hype, the DAO failed to win the auction. Afterwards, it struggled with refund logistics, communication breakdowns, and confusion over governance. It was a perfect example of collective enthusiasm without infrastructure or planning - proof that a DAO can raise capital fast but still lack cohesion.
Not all efforts have failed. Projects like Gitcoin DAO have made progress by incentivizing small, individual contributions. Their quadratic funding mechanism rewards projects based on the number of contributors, not just the size of donations, helping to elevate grassroots initiatives. But even here, long-term strategy often falls back on a core group of organizers rather than broad community consensus.
The pattern is clear: when the stakes are low or the tasks are modular, DAOs can coordinate well. But when bold moves are needed—when someone has to take responsibility and act under uncertainty DAOs often freeze. In the name of consensus, they lose momentum.
That’s why the organization of the future can’t rely purely on decentralization. It must encourage individual initiative and the ability to take calculated risks. People need to see their contribution not just as a vote, but as a role with clear actions and expected outcomes. When the situation demands, they should be empowered to act first and present the results to the community afterwards allowing for both autonomy and accountability. That’s not a flaw in the system. It’s how real progress happens.
-
 @ e4950c93:1b99eccd
2025-05-02 12:19:28
@ e4950c93:1b99eccd
2025-05-02 12:19:28Qu'est-ce qu'une matière naturelle ? La question fait débat, et chacun-e privilégiera ses propres critères. Voici comment les matières sont classées sur ce site. La liste est régulièrement mise à jour en fonction des produits ajoutés. N'hésitez pas à partager votre avis !
✅ Matières naturelles
Matières d'origine végétale, animale ou minérale, sans transformation chimique altérant leur structure moléculaire.
🌱 Principaux critères : - Biodégradabilité - Non-toxicité - Présence naturelle nécessitant le minimum de transformation
🔍 Liste des matières naturelles : - Bois - Cellulose régénérée (cupra, lyocell, modal, viscose) - Chanvre - Coton - Cuir - Liège - Lin - Laine - Latex naturel, caoutchouc - Métal - Soie - Terre - Verre - … (Autres matières)
⚠️ Bien que "naturelles", ces matières peuvent générer des impacts négatifs selon leurs conditions de production (pollution par pesticides, consommation d’eau excessive, traitement chimique, exploitation animale…). Ces impacts sont mentionnés sur la fiche de chaque matière.
Les versions biologiques de ces matières (sans traitement chimique, maltraitance animale, etc.) sont privilégiées pour référencer les produits sur ce site, tel qu'indiqué sur la fiche de chaque matière (à venir).
Les versions conventionnelles ne sont référencées que tant que lorsqu'il n'a pas encore été trouvé d'alternative plus durable pour cette catégorie de produits.
🚫 Matières non naturelles
Matières synthétiques ou fortement modifiées, souvent issues de la pétrochimie.
📌 Principaux problèmes : - Toxicité et émissions de microplastiques - Dépendance aux énergies fossiles - Mauvaise biodégradabilité
🔍 Liste des matières non naturelles : - Acrylique - Élasthanne, lycra, spandex - Polyamides, nylon - Polyester - Silicone - … (Autres matières)
⚠️ Ces matières ne sont pas admises sur le site. Néanmoins, elles peuvent être présentes dans certains produits référencés lorsque :
- elles sont utilisées en accessoire amovible (ex. : élastiques, boutons… généralement non indiqué dans la composition par la marque) pouvant être retiré pour le recyclage ou compostage, et
- aucune alternative 100 % naturelle n’a encore été identifiée pour cette catégorie de produits.
Dans ce cas, un avertissement est alors affiché sur la fiche du produit.
Cet article est publié sur origine-nature.com 🌐 See this article in English
-
 @ a5142938:0ef19da3
2025-05-02 12:18:08
@ a5142938:0ef19da3
2025-05-02 12:18:08What is a natural material? It's a topic of debate, and everyone will prioritize their own criteria. Here’s how materials are classified on this site. The list is regularly updated based on the products added. Feel free to share your thoughts!
✅ Natural Materials
Materials of plant, animal, or mineral origin, without chemical transformation that alters their molecular structure.
🌱 Main Criteria: - Biodegradability - Non-toxicity - Naturally occurring and recquiring minimal transformation
🔍 List of Natural Materials: - Regenerated Cellulose (cupra, lyocell, modal, rayon) - Cork - Cotton - Earth - Glass - Hemp - Natural Latex, rubber - Leather - Linen - Metal - Silk - Wood - Wool - … (Other materials)
⚠️ Although "natural", these materials can have negative impacts depending on their production conditions (pesticide pollution, excessive water consumption, chemical treatments, animal exploitation, etc.). These impacts are mentionned in the description of each material.
Organic versions of these materials — free from chemical treatments, animal mistreatment, etc. — are preferred for listing products on this site, as indicated on each material's page (coming soon).
Conventional versions are only referenced when no more sustainable alternative has yet been found for that product category.
🚫 Non-Natural Materials
Synthetic or heavily modified materials, often derived from petrochemicals.
📌 Main Issues: - Toxicity and microplastic emissions - Dependence on fossil fuels - Poor biodegradability
🔍 List of Non-Natural Materials: - Acrylic - Elastane, spandex, lycra - Polyamides, nylon - Polyester - Silicone - … (Other materials)
⚠️ These materials are not accepted on this site. However, they may be present in certain listed products if:
- they are used in removable accessories (e.g., elastics, buttons—often not listed in the product’s composition by the brand) that can be detached for recycling or composting, and
- no 100% natural alternative has yet been identified for that product category.
In such cases, a warning will be displayed on the product page.
This article is published on origin-nature.com 🌐 Voir cet article en français
-
 @ c066aac5:6a41a034
2025-04-05 16:58:58
@ c066aac5:6a41a034
2025-04-05 16:58:58I’m drawn to extremities in art. The louder, the bolder, the more outrageous, the better. Bold art takes me out of the mundane into a whole new world where anything and everything is possible. Having grown up in the safety of the suburban midwest, I was a bit of a rebellious soul in search of the satiation that only came from the consumption of the outrageous. My inclination to find bold art draws me to NOSTR, because I believe NOSTR can be the place where the next generation of artistic pioneers go to express themselves. I also believe that as much as we are able, were should invite them to come create here.
My Background: A Small Side Story
My father was a professional gamer in the 80s, back when there was no money or glory in the avocation. He did get a bit of spotlight though after the fact: in the mid 2000’s there were a few parties making documentaries about that era of gaming as well as current arcade events (namely 2007’sChasing GhostsandThe King of Kong: A Fistful of Quarters). As a result of these documentaries, there was a revival in the arcade gaming scene. My family attended events related to the documentaries or arcade gaming and I became exposed to a lot of things I wouldn’t have been able to find. The producer ofThe King of Kong: A Fistful of Quarters had previously made a documentary calledNew York Dollwhich was centered around the life of bassist Arthur Kane. My 12 year old mind was blown: The New York Dolls were a glam-punk sensation dressed in drag. The music was from another planet. Johnny Thunders’ guitar playing was like Chuck Berry with more distortion and less filter. Later on I got to meet the Galaga record holder at the time, Phil Day, in Ottumwa Iowa. Phil is an Australian man of high intellect and good taste. He exposed me to great creators such as Nick Cave & The Bad Seeds, Shakespeare, Lou Reed, artists who created things that I had previously found inconceivable.
I believe this time period informed my current tastes and interests, but regrettably I think it also put coals on the fire of rebellion within. I stopped taking my parents and siblings seriously, the Christian faith of my family (which I now hold dearly to) seemed like a mundane sham, and I felt I couldn’t fit in with most people because of my avant-garde tastes. So I write this with the caveat that there should be a way to encourage these tastes in children without letting them walk down the wrong path. There is nothing inherently wrong with bold art, but I’d advise parents to carefully find ways to cultivate their children’s tastes without completely shutting them down and pushing them away as a result. My parents were very loving and patient during this time; I thank God for that.
With that out of the way, lets dive in to some bold artists:
Nicolas Cage: Actor
There is an excellent video by Wisecrack on Nicolas Cage that explains him better than I will, which I will linkhere. Nicolas Cage rejects the idea that good acting is tied to mere realism; all of his larger than life acting decisions are deliberate choices. When that clicked for me, I immediately realized the man is a genius. He borrows from Kabuki and German Expressionism, art forms that rely on exaggeration to get the message across. He has even created his own acting style, which he calls Nouveau Shamanic. He augments his imagination to go from acting to being. Rather than using the old hat of method acting, he transports himself to a new world mentally. The projects he chooses to partake in are based on his own interests or what he considers would be a challenge (making a bad script good for example). Thus it doesn’t matter how the end result comes out; he has already achieved his goal as an artist. Because of this and because certain directors don’t know how to use his talents, he has a noticeable amount of duds in his filmography. Dig around the duds, you’ll find some pure gold. I’d personally recommend the filmsPig, Joe, Renfield, and his Christmas film The Family Man.
Nick Cave: Songwriter
What a wild career this man has had! From the apocalyptic mayhem of his band The Birthday Party to the pensive atmosphere of his albumGhosteen, it seems like Nick Cave has tried everything. I think his secret sauce is that he’s always working. He maintains an excellent newsletter calledThe Red Hand Files, he has written screenplays such asLawless, he has written books, he has made great film scores such asThe Assassination of Jesse James by the Coward Robert Ford, the man is religiously prolific. I believe that one of the reasons he is prolific is that he’s not afraid to experiment. If he has an idea, he follows it through to completion. From the albumMurder Ballads(which is comprised of what the title suggests) to his rejected sequel toGladiator(Gladiator: Christ Killer), he doesn’t seem to be afraid to take anything on. This has led to some over the top works as well as some deeply personal works. Albums likeSkeleton TreeandGhosteenwere journeys through the grief of his son’s death. The Boatman’s Callis arguably a better break-up album than anything Taylor Swift has put out. He’s not afraid to be outrageous, he’s not afraid to offend, but most importantly he’s not afraid to be himself. Works I’d recommend include The Birthday Party’sLive 1981-82, Nick Cave & The Bad Seeds’The Boatman’s Call, and the filmLawless.
Jim Jarmusch: Director
I consider Jim’s films to be bold almost in an ironic sense: his works are bold in that they are, for the most part, anti-sensational. He has a rule that if his screenplays are criticized for a lack of action, he makes them even less eventful. Even with sensational settings his films feel very close to reality, and they demonstrate the beauty of everyday life. That's what is bold about his art to me: making the sensational grounded in reality while making everyday reality all the more special. Ghost Dog: The Way of the Samurai is about a modern-day African-American hitman who strictly follows the rules of the ancient Samurai, yet one can resonate with the humanity of a seemingly absurd character. Only Lovers Left Aliveis a vampire love story, but in the middle of a vampire romance one can see their their own relationships in a new deeply human light. Jim’s work reminds me that art reflects life, and that there is sacred beauty in seemingly mundane everyday life. I personally recommend his filmsPaterson,Down by Law, andCoffee and Cigarettes.
NOSTR: We Need Bold Art
NOSTR is in my opinion a path to a better future. In a world creeping slowly towards everything apps, I hope that the protocol where the individual owns their data wins over everything else. I love freedom and sovereignty. If NOSTR is going to win the race of everything apps, we need more than Bitcoin content. We need more than shirtless bros paying for bananas in foreign countries and exercising with girls who have seductive accents. Common people cannot see themselves in such a world. NOSTR needs to catch the attention of everyday people. I don’t believe that this can be accomplished merely by introducing more broadly relevant content; people are searching for content that speaks to them. I believe that NOSTR can and should attract artists of all kinds because NOSTR is one of the few places on the internet where artists can express themselves fearlessly. Getting zaps from NOSTR’s value-for-value ecosystem has far less friction than crowdfunding a creative project or pitching investors that will irreversibly modify an artist’s vision. Having a place where one can post their works without fear of censorship should be extremely enticing. Having a place where one can connect with fellow humans directly as opposed to a sea of bots should seem like the obvious solution. If NOSTR can become a safe haven for artists to express themselves and spread their work, I believe that everyday people will follow. The banker whose stressful job weighs on them will suddenly find joy with an original meme made by a great visual comedian. The programmer for a healthcare company who is drowning in hopeless mundanity could suddenly find a new lust for life by hearing the song of a musician who isn’t afraid to crowdfund their their next project by putting their lighting address on the streets of the internet. The excel guru who loves independent film may find that NOSTR is the best way to support non corporate movies. My closing statement: continue to encourage the artists in your life as I’m sure you have been, but while you’re at it give them the purple pill. You may very well be a part of building a better future.
-
 @ 68768a6c:0eaf07e9
2025-05-02 11:06:40
@ 68768a6c:0eaf07e9
2025-05-02 11:06:40In 2009, a mysterious figure named Satoshi Nakamoto launched Bitcoin — a decentralized digital currency with no central bank, no borders, and no permission needed. At the time, 1 BTC was worth less than a cent. Today, it represents a revolution in how we think about value, freedom, and financial systems.
But Bitcoin is more than just a digital asset. It’s a response to distrust in traditional banks and fiat currency. With only 21 million coins ever to exist, Bitcoin is often compared to gold — scarce, mined (digitally), and increasingly seen as a store of value.
Bitcoin is transparent (you can track every transaction), secure (thanks to blockchain technology), and global (it works the same in New York or Nairobi). For some, it’s a hedge against inflation. For others, it’s a path to financial independence.
Still, Bitcoin isn’t without risk — its price is volatile, and its environmental impact has been criticized. But one thing is clear: Bitcoin has changed the financial conversation forever.
Whether it’s the future of money or just the beginning of a larger movement, Bitcoin forces us to ask: Who should control our money?

-
 @ 088436cd:9d2646cc
2025-05-01 21:01:55
@ 088436cd:9d2646cc
2025-05-01 21:01:55The arrival of the coronavirus brought not only illness and death but also fear and panic. In such an environment of uncertainty, people have naturally stocked up on necessities, not knowing when things will return to normal.
Retail shelves have been cleared out, and even online suppliers like Amazon and Walmart are out of stock for some items. Independent sellers on these e-commerce platforms have had to fill the gap. With the huge increase in demand, they have found that their inventory has skyrocketed in value.
Many in need of these items (e.g. toilet paper, hand sanitizer and masks) balk at the new prices. They feel they are being taken advantage of in a time of need and call for intervention by the government to lower prices. The government has heeded that call, labeling the independent sellers as "price gougers" and threatening sanctions if they don't lower their prices. Amazon has suspended seller accounts and law enforcement at all levels have threatened to prosecute. Prices have dropped as a result and at first glance this seems like a victory for fair play. But, we will have to dig deeper to understand the unseen consequences of this intervention.
We must look at the economics of the situation, how supply and demand result in a price and how that price acts as a signal that goes out to everyone, informing them of underlying conditions in the economy and helping coordinate their actions.
It all started with a rise in demand. Given a fixed supply (e.g., the limited stock on shelves and in warehouses), an increase in demand inevitably leads to higher prices. Most people are familiar with this phenomenon, such as paying more for airline tickets during holidays or surge pricing for rides.
Higher prices discourage less critical uses of scarce resources. For example, you might not pay $1,000 for a plane ticket to visit your aunt if you can get one for $100 the following week, but someone else might pay that price to visit a dying relative. They value that plane seat more than you.
*** During the crisis, demand surged and their shelves emptied even though
However, retail outlets have not raised prices. They have kept them low, so the low-value uses of things like toilet paper, masks and hand sanitizer has continued. Often, this "use" just takes the form of hoarding. At everyday low prices, it makes sense to buy hundreds of rolls and bottles. You know you will use them eventually, so why not stock up? And, with all those extra supplies in the closet and basement, you don't need to change your behavior much. You don't have to ration your use.
At the low prices, these scarce resources got bought up faster and faster until there was simply none left. The reality of the situation became painfully clear to those who didn't panic and got to the store late: You have no toilet paper and you're not going to any time soon.
However, if prices had been allowed to rise, a number of effects would have taken place that would have coordinated the behavior of everyone so that valuable resources would not have been wasted or hoarded, and everyone could have had access to what they needed.
On the demand side, if prices had been allowed to rise, people would have begun to self-ration. You might leave those extra plies on the roll next time if you know they will cost ten times as much to replace. Or, you might choose to clean up a spill with a rag rather than disposable tissue. Most importantly, you won't hoard as much. That 50th bottle of hand sanitizer might just not be worth it at the new, high price. You'll leave it on the shelf for someone else who may have none.
On the supply side, higher prices would have incentivized people to offer up more of their stockpiles for sale. If you have a pallet full of toilet paper in your basement and all of the sudden they are worth $15 per roll, you might just list a few online. But, if it is illegal to do so, you probably won't.
Imagine you run a business installing insulation and have a few thousand respirator masks on hand for your employees. During a pandemic, it is much more important that people breathe filtered air than that insulation get installed, and that fact is reflected in higher prices. You will sell your extra masks at the higher price rather than store them for future insulation jobs, and the scarce resource will be put to its most important use.
Producers of hand sanitizer would go into overdrive if prices were allowed to rise. They would pay their employees overtime, hire new ones, and pay a premium for their supplies, making sure their raw materials don't go to less important uses.
These kinds of coordinated actions all across the economy would be impossible without real prices to guide them. How do you know if it makes sense to spend an extra $10k bringing a thousand masks to market unless you know you can get more than $10 per mask? If the price is kept artificially low, you simply can't do it. The money just isn't there.
These are the immediate effects of a price change, but incredibly, price changes also coordinate people's actions across space and time.
Across space, there are different supply and demand conditions in different places, and thus prices are not uniform. We know some places are real "hot spots" for the virus, while others are mostly unaffected. High demand in the hot spots leads to higher prices there, which attracts more of the resource to those areas. Boxes and boxes of essential items would pour in where they are needed most from where they are needed least, but only if prices were allowed to adjust freely.
This would be accomplished by individuals and businesses buying low in the unaffected areas, selling high in the hot spots and subtracting their labor and transportation costs from the difference. Producers of new supply would know exactly where it is most needed and ship to the high-demand, high-price areas first. The effect of these actions is to increase prices in the low demand areas and reduce them in the high demand areas. People in the low demand areas will start to self-ration more, reflecting the reality of their neighbors, and people in the hotspots will get some relief.
However, by artificially suppressing prices in the hot spot, people there will simply buy up the available supply and run out, and it will be cost prohibitive to bring in new supply from low-demand areas.
Prices coordinate economic actions across time as well. Just as entrepreneurs and businesses can profit by transporting scarce necessities from low-demand to high-demand areas, they can also profit by buying in low-demand times and storing their merchandise for when it is needed most.
Just as allowing prices to freely adjust in one area relative to another will send all the right signals for the optimal use of a scarce resource, allowing prices to freely adjust over time will do the same.
When an entrepreneur buys up resources during low-demand times in anticipation of a crisis, she restricts supply ahead of the crisis, which leads to a price increase. She effectively bids up the price. The change in price affects consumers and producers in all the ways mentioned above. Consumers self-ration more, and producers bring more of the resource to market.
Our entrepreneur has done a truly incredible thing. She has predicted the future, and by so doing has caused every individual in the economy to prepare for a shortage they don't even know is coming! And, by discouraging consumption and encouraging production ahead of time, she blunts the impact the crisis will have. There will be more of the resource to go around when it is needed most.
On top of this, our entrepreneur still has her stockpile she saved back when everyone else was blithely using it up. She can now further mitigate the damage of the crisis by selling her stock during the worst of it, when people are most desperate for relief. She will know when this is because the price will tell her, but only if it is allowed to adjust freely. When the price is at its highest is when people need the resource the most, and those willing to pay will not waste it or hoard it. They will put it to its highest valued use.
The economy is like a big bus we are all riding in, going down a road with many twists and turns. Just as it is difficult to see into the future, it is difficult to see out the bus windows at the road ahead.
On the dashboard, we don't have a speedometer or fuel gauge. Instead we have all the prices for everything in the economy. Prices are what tell us the condition of the bus and the road. They tell us everything. Without them, we are blind.
Good times are a smooth road. Consumer prices and interest rates are low, investment returns are steady. We hit the gas and go fast. But, the road is not always straight and smooth. Sometimes there are sharp turns and rough patches. Successful entrepreneurs are the ones who can see what is coming better than everyone else. They are our navigators.
When they buy up scarce resources ahead of a crisis, they are hitting the brakes and slowing us down. When they divert resources from one area to another, they are steering us onto a smoother path. By their actions in the market, they adjust the prices on our dashboard to reflect the conditions of the road ahead, so we can prepare for, navigate and get through the inevitable difficulties we will face.
Interfering with the dashboard by imposing price floors or price caps doesn't change the conditions of the road (the number of toilet paper rolls in existence hasn't changed). All it does is distort our perception of those conditions. We think the road is still smooth--our heavy foot stomping the gas--as we crash onto a rocky dirt road at 80 miles per hour (empty shelves at the store for weeks on end).
Supply, demand and prices are laws of nature. All of this is just how things work. It isn't right or wrong in a moral sense. Price caps lead to waste, shortages and hoarding as surely as water flows downhill. The opposite--allowing prices to adjust freely--leads to conservation of scarce resources and their being put to their highest valued use. And yes, it leads to profits for the entrepreneurs who were able to correctly predict future conditions, and losses for those who weren't.
Is it fair that they should collect these profits? On the one hand, anyone could have stocked up on toilet paper, hand sanitizer and face masks at any time before the crisis, so we all had a fair chance to get the supplies cheaply. On the other hand, it just feels wrong that some should profit so much at a time when there is so much need.
Our instinct in the moment is to see the entrepreneur as a villain, greedy "price gouger". But we don't see the long chain of economic consequences the led to the situation we feel is unfair.
If it weren't for anti-price-gouging laws, the major retailers would have raised their prices long before the crisis became acute. When they saw demand outstrip supply, they would have raised prices, not by 100 fold, but gradually and long before anyone knew how serious things would have become. Late comers would have had to pay more, but at least there would be something left on the shelf.
As an entrepreneur, why take risks trying to anticipate the future if you can't reap the reward when you are right? Instead of letting instead of letting entrepreneurs--our navigators--guide us, we are punishing and vilifying them, trying to force prices to reflect a reality that simply doesn't exist.
In a crisis, more than any other time, prices must be allowed to fluctuate. To do otherwise is to blind ourselves at a time when danger and uncertainty abound. It is economic suicide.
In a crisis, there is great need, and the way to meet that need is not by pretending it's not there, by forcing prices to reflect a world where there isn't need. They way to meet the need is the same it has always been, through charity.
If the people in government want to help, the best way for the to do so is to be charitable and reduce their taxes and fees as much as possible, ideally to zero in a time of crisis. Amazon, for example, could instantly reduce the price of all crisis related necessities by 20% if they waived their fee. This would allow for more uses by more people of these scarce supplies as hoarders release their stockpiles on to the market, knowing they can get 20% more for their stock. Governments could reduce or eliminate their tax burden on high-demand, crisis-related items and all the factors that go into their production, with the same effect: a reduction in prices and expansion of supply. All of us, including the successful entrepreneurs and the wealthy for whom high prices are not a great burden, could donate to relief efforts.
These ideas are not new or untested. This is core micro economics. It has been taught for hundreds of years in universities the world over. The fact that every crisis that comes along stirs up ire against entrepreneurs indicates not that the economics is wrong, but that we have a strong visceral reaction against what we perceive to be unfairness. This is as it should be. Unfairness is wrong and the anger it stirs in us should compel us to right the wrong. Our anger itself isn't wrong, it's just misplaced.
Entrepreneurs didn't cause the prices to rise. Our reaction to a virus did that. We saw a serious threat and an uncertain future and followed our natural impulse to hoard. Because prices at major retail suppliers didn't rise, that impulse ran rampant and we cleared the shelves until there was nothing left. We ran the bus right off the road and them blamed the entrepreneurs for showing us the reality of our situation, for shaking us out of the fantasy of low prices.
All of this is not to say that entrepreneurs are high-minded public servants. They are just doing their job. Staking your money on an uncertain future is a risky business. There are big risks and big rewards. Most entrepreneurs just scrape by or lose their capital in failed ventures.
However, the ones that get it right must be allowed to keep their profits, or else no one will try and we'll all be driving blind. We need our navigators. It doesn't even matter if they know all the positive effects they are having on the rest of us and the economy as a whole. So long as they are buying low and selling high--so long as they are doing their job--they will be guiding the rest of us through the good times and the bad, down the open road and through the rough spots.
-
 @ e4950c93:1b99eccd
2025-05-02 10:54:24
@ e4950c93:1b99eccd
2025-05-02 10:54:24Les rétributions sont une démarche expérimentale de partage de la valeur entre les contribut-eur-rice-s du site, via un partage des revenus aux conditions suivantes :
- Les revenus éventuels générés par ce site chaque mois sont répartis sur les 12 mois suivants, afin d’assurer une visibilité sur le projet et de lisser les variations mensuelles.
- Chaque 1er du mois, la moitié des revenus est distribuée à l’ensemble des contribut-eur-rice-s, proportionnellement au nombre de leurs contributions validées.
- Les contributions restent valides à vie, mais les rétributions ne sont versées qu’aux contribut-eur-rice-s ayant réalisé au moins une contribution validée au cours des 12 derniers mois.
Modalités de paiement
Les rétributions sont effectuées via le réseau Lightning, sous forme de sats (la plus petite unité du Bitcoin).
Pour en bénéficier, le compte NOSTR avec lequel tu as réalisé tes contributions doit être lié à un porte-monnaie Lightning.
💡 Si tu découvres ces outils :
- Pas encore de compte ? Une solution simple est d'en créer un sur un client NOSTR open source comme yakihonne.com pour y paramétrer ton profil et ton wallet. Ensuite, récupère tes clés NOSTR (dans les settings) et enregistre les dans un coffre sécurisé comme nsec.app pour te connecter ici et commencer à contribuer.
- Tu as déjà commencé à contribuer sur le site ? Conserve bien les clés NOSTR fournies par le site dans un coffre comme nsec.app. Tu peux aussi te connecter avec sur yakihonne.com pour paramétrer ton profil.
- Tu peux aussi contribuer directement depuis yakihonne.com sur les articles d'Origine Nature.
👉 En savoir plus sur les contributions
Prochaines rétributions
A venir.
Cet article est publié sur origine-nature.com 🌐 See this article in English
-
 @ e3ba5e1a:5e433365
2025-04-15 11:03:15
@ e3ba5e1a:5e433365
2025-04-15 11:03:15Prelude
I wrote this post differently than any of my others. It started with a discussion with AI on an OPSec-inspired review of separation of powers, and evolved into quite an exciting debate! I asked Grok to write up a summary in my overall writing style, which it got pretty well. I've decided to post it exactly as-is. Ultimately, I think there are two solid ideas driving my stance here:
- Perfect is the enemy of the good
- Failure is the crucible of success
Beyond that, just some hard-core belief in freedom, separation of powers, and operating from self-interest.
Intro
Alright, buckle up. I’ve been chewing on this idea for a while, and it’s time to spit it out. Let’s look at the U.S. government like I’d look at a codebase under a cybersecurity audit—OPSEC style, no fluff. Forget the endless debates about what politicians should do. That’s noise. I want to talk about what they can do, the raw powers baked into the system, and why we should stop pretending those powers are sacred. If there’s a hole, either patch it or exploit it. No half-measures. And yeah, I’m okay if the whole thing crashes a bit—failure’s a feature, not a bug.
The Filibuster: A Security Rule with No Teeth
You ever see a firewall rule that’s more theater than protection? That’s the Senate filibuster. Everyone acts like it’s this untouchable guardian of democracy, but here’s the deal: a simple majority can torch it any day. It’s not a law; it’s a Senate preference, like choosing tabs over spaces. When people call killing it the “nuclear option,” I roll my eyes. Nuclear? It’s a button labeled “press me.” If a party wants it gone, they’ll do it. So why the dance?
I say stop playing games. Get rid of the filibuster. If you’re one of those folks who thinks it’s the only thing saving us from tyranny, fine—push for a constitutional amendment to lock it in. That’s a real patch, not a Post-it note. Until then, it’s just a vulnerability begging to be exploited. Every time a party threatens to nuke it, they’re admitting it’s not essential. So let’s stop pretending and move on.
Supreme Court Packing: Because Nine’s Just a Number
Here’s another fun one: the Supreme Court. Nine justices, right? Sounds official. Except it’s not. The Constitution doesn’t say nine—it’s silent on the number. Congress could pass a law tomorrow to make it 15, 20, or 42 (hitchhiker’s reference, anyone?). Packing the court is always on the table, and both sides know it. It’s like a root exploit just sitting there, waiting for someone to log in.
So why not call the bluff? If you’re in power—say, Trump’s back in the game—say, “I’m packing the court unless we amend the Constitution to fix it at nine.” Force the issue. No more shadowboxing. And honestly? The court’s got way too much power anyway. It’s not supposed to be a super-legislature, but here we are, with justices’ ideologies driving the bus. That’s a bug, not a feature. If the court weren’t such a kingmaker, packing it wouldn’t even matter. Maybe we should be talking about clipping its wings instead of just its size.
The Executive Should Go Full Klingon
Let’s talk presidents. I’m not saying they should wear Klingon armor and start shouting “Qapla’!”—though, let’s be real, that’d be awesome. I’m saying the executive should use every scrap of power the Constitution hands them. Enforce the laws you agree with, sideline the ones you don’t. If Congress doesn’t like it, they’ve got tools: pass new laws, override vetoes, or—here’s the big one—cut the budget. That’s not chaos; that’s the system working as designed.
Right now, the real problem isn’t the president overreaching; it’s the bureaucracy. It’s like a daemon running in the background, eating CPU and ignoring the user. The president’s supposed to be the one steering, but the administrative state’s got its own agenda. Let the executive flex, push the limits, and force Congress to check it. Norms? Pfft. The Constitution’s the spec sheet—stick to it.
Let the System Crash
Here’s where I get a little spicy: I’m totally fine if the government grinds to a halt. Deadlock isn’t a disaster; it’s a feature. If the branches can’t agree, let the president veto, let Congress starve the budget, let enforcement stall. Don’t tell me about “essential services.” Nothing’s so critical it can’t take a breather. Shutdowns force everyone to the table—debate, compromise, or expose who’s dropping the ball. If the public loses trust? Good. They’ll vote out the clowns or live with the circus they elected.
Think of it like a server crash. Sometimes you need a hard reboot to clear the cruft. If voters keep picking the same bad admins, well, the country gets what it deserves. Failure’s the best teacher—way better than limping along on autopilot.
States Are the Real MVPs
If the feds fumble, states step up. Right now, states act like junior devs waiting for the lead engineer to sign off. Why? Federal money. It’s a leash, and it’s tight. Cut that cash, and states will remember they’re autonomous. Some will shine, others will tank—looking at you, California. And I’m okay with that. Let people flee to better-run states. No bailouts, no excuses. States are like competing startups: the good ones thrive, the bad ones pivot or die.
Could it get uneven? Sure. Some states might turn into sci-fi utopias while others look like a post-apocalyptic vidya game. That’s the point—competition sorts it out. Citizens can move, markets adjust, and failure’s a signal to fix your act.
Chaos Isn’t the Enemy
Yeah, this sounds messy. States ignoring federal law, external threats poking at our seams, maybe even a constitutional crisis. I’m not scared. The Supreme Court’s there to referee interstate fights, and Congress sets the rules for state-to-state play. But if it all falls apart? Still cool. States can sort it without a babysitter—it’ll be ugly, but freedom’s worth it. External enemies? They’ll either unify us or break us. If we can’t rally, we don’t deserve the win.
Centralizing power to avoid this is like rewriting your app in a single thread to prevent race conditions—sure, it’s simpler, but you’re begging for a deadlock. Decentralized chaos lets states experiment, lets people escape, lets markets breathe. States competing to cut regulations to attract businesses? That’s a race to the bottom for red tape, but a race to the top for innovation—workers might gripe, but they’ll push back, and the tension’s healthy. Bring it—let the cage match play out. The Constitution’s checks are enough if we stop coddling the system.
Why This Matters
I’m not pitching a utopia. I’m pitching a stress test. The U.S. isn’t a fragile porcelain doll; it’s a rugged piece of hardware built to take some hits. Let it fail a little—filibuster, court, feds, whatever. Patch the holes with amendments if you want, or lean into the grind. Either way, stop fearing the crash. It’s how we debug the republic.
So, what’s your take? Ready to let the system rumble, or got a better way to secure the code? Hit me up—I’m all ears.
-
 @ 6be5cc06:5259daf0
2025-03-31 03:39:07
@ 6be5cc06:5259daf0
2025-03-31 03:39:07Introdução
Uma sociedade não deve ser construída sobre coerção, mas sim sobre associações voluntárias e interações espontâneas entre indivíduos. A sociedade de condomínios privados surge como uma alternativa natural ao modelo atual de centros urbanos, substituindo a imposição centralizada por estruturas baseadas em contratos e livre associação. Cada condomínio é uma unidade autônoma, gerida por aqueles que ali residem, onde os critérios de entrada, as regras internas e o comércio são definidos pelos próprios participantes. Essa estrutura permite que indivíduos se agrupem com base em valores compartilhados, eliminando os conflitos artificiais impostos por estados e legislações homogêneas que não respeitam a diversidade de preferências e estilos de vida.
O objetivo dessa sociedade é simples: permitir que as pessoas vivam de acordo com seus princípios sem interferência externa. Em um mundo onde a coerção estatal distorce incentivos, os condomínios privados oferecem uma alternativa onde a ordem surge do livre mercado e da cooperação voluntária. Os moradores escolhem seus vizinhos, definem suas próprias normas e interagem economicamente conforme suas necessidades e interesses. O modelo elimina a necessidade de um controle central, pois os incentivos derivados do livre mercado levam ao desenvolvimento de comunidades prósperas, onde a reputação e a confiança mútua são mais eficazes do que qualquer imposição estatal. Assim, essa sociedade representa a evolução lógica do conceito de liberdade individual e propriedade privada como pilares fundamentais da ordem social.
Público-Alvo e Identidade
Os condomínios privados refletem o princípio da livre associação, permitindo que indivíduos escolham viver em comunidades alinhadas com seus valores e necessidades sem interferência estatal. Cada condomínio possui uma identidade própria, moldada pelos moradores e seus interesses, criando ambientes onde afinidades culturais, filosóficas ou profissionais são preservadas e incentivadas. Enquanto alguns podem ser voltados para famílias numerosas, oferecendo amplos espaços e infraestrutura adequada, outros podem priorizar solteiros e jovens profissionais, com áreas de coworking e espaços de lazer voltados para networking e socialização. Da mesma forma, comunidades religiosas podem estabelecer seus próprios espaços de culto e eventos, enquanto condomínios para idosos podem ser projetados com acessibilidade e serviços médicos especializados.
Críticos podem afirmar que essa forma de organização resulta em pouca diversidade de habilidades e perspectivas, mas esse argumento ignora a dinâmica das interações humanas e o caráter evolutivo dos intercâmbios entre comunidades. Nenhum condomínio existe isolado; a troca entre diferentes comunidades ocorre naturalmente pelo mercado, incentivando o intercâmbio de conhecimento e serviços entre especialistas de diferentes áreas. Além disso, a ideia de que todos os grupos devem conter uma variedade aleatória de indivíduos desconsidera que a verdadeira diversidade nasce da liberdade de escolha, e não da imposição estatal de convivências forçadas.
Outra crítica possível é que a existência de critérios de entrada pode levar à segregação social. No entanto, essa preocupação deriva da concepção errônea de que todas as comunidades devem ser abertas e incluir qualquer pessoa indiscriminadamente. Porém, a liberdade de associação implica, necessariamente, a liberdade de exclusão. Se um grupo deseja manter determinada identidade cultural, religiosa ou profissional, isso não impede que outros grupos criem suas próprias comunidades conforme seus valores e recursos. Além disso, essa especialização leva a uma concorrência saudável entre condomínios, forçando-os a oferecer melhores condições para atrair moradores. Em vez de uma sociedade homogênea moldada por burocratas, temos um mosaico de comunidades autônomas, onde cada indivíduo pode encontrar ou criar o ambiente que melhor lhe convém.
Autossuficiência e Especialização
A força dos condomínios privados reside na capacidade de seus moradores de contribuírem ativamente para a comunidade, tornando-a funcional e autossuficiente sem a necessidade de intervenções estatais. Diferentes condomínios podem se especializar em áreas específicas ou ter diversos profissionais de diferentes setores, refletindo as competências e interesses de seus residentes. Essa descentralização do conhecimento e da produção permite que cada comunidade desenvolva soluções internas para suas demandas, reduzindo dependências externas e estimulando a prosperidade local.
Os moradores atuam como agentes econômicos, trocando bens e serviços dentro do próprio condomínio e entre diferentes comunidades. Um condomínio voltado para a saúde, por exemplo, pode contar com médicos, enfermeiros e terapeutas que oferecem consultas, aulas e assistência médica particular, remunerados diretamente por seus clientes, sem a intermediação de burocracias. Da mesma forma, um condomínio agrícola pode abrigar agricultores que cultivam alimentos orgânicos, compartilham técnicas de cultivo e comercializam excedentes com outros condomínios, garantindo um fluxo contínuo de suprimentos. Em um condomínio tecnológico, programadores, engenheiros e empreendedores desenvolvem soluções de TI, segurança digital e energia renovável, promovendo a inovação e ampliando as possibilidades de intercâmbio econômico.
A economia interna de cada condomínio se fortalece através de serviços oferecidos pelos próprios moradores. Professores podem ministrar aulas, técnicos podem prestar serviços de manutenção, artesãos podem vender seus produtos diretamente para os vizinhos. O mercado livre e voluntário é o principal regulador dessas interações, garantindo que a especialização surja naturalmente conforme a demanda e a oferta se ajustam. Essa estrutura elimina desperdícios comuns em sistemas centralizados, onde a alocação de recursos se dá por decisões políticas e não pelas necessidades reais da população.
Alguns argumentam que a especialização pode criar bolhas de conhecimento, tornando os condomínios excessivamente dependentes de trocas externas. Contudo, essa preocupação desconsidera a natureza espontânea do mercado, que incentiva a cooperação e o comércio entre comunidades distintas. Nenhum condomínio precisa produzir tudo internamente; ao contrário, a divisão do trabalho e a liberdade de escolha promovem interdependências saudáveis e vantajosas para todos. Assim, cada morador se insere em um ecossistema dinâmico, onde suas habilidades são valorizadas e sua autonomia preservada, sem coerções estatais ou distorções artificiais impostas por planejadores centrais.
Infraestrutura e Sustentabilidade
A solidez de uma sociedade baseada em condomínios privados depende de uma infraestrutura eficiente e sustentável, projetada para reduzir a dependência externa e garantir o máximo de autonomia. Sem um aparato estatal centralizador, cada comunidade deve estruturar seus próprios meios de obtenção de energia, água, alimentação e demais bens essenciais, garantindo que suas operações sejam viáveis a longo prazo. Essa abordagem, longe de ser um entrave, representa a verdadeira inovação descentralizada: um ambiente onde as soluções emergem da necessidade real e da engenhosidade humana, e não de diretrizes burocráticas e regulamentos ineficazes.
Cada condomínio pode investir em tecnologias sustentáveis e autônomas, como energia solar e eólica, reduzindo custos e minimizando a vulnerabilidade às flutuações do mercado energético tradicional. Sistemas de captação e filtragem de água da chuva, bem como a reutilização eficiente dos recursos hídricos, garantem independência em relação a empresas monopolistas e governos que frequentemente administram esse bem de forma ineficaz. Hortas comunitárias e fazendas verticais podem suprir grande parte da demanda alimentar, permitindo que cada condomínio mantenha sua própria reserva de alimentos, aumentando a resiliência contra crises externas e instabilidades de mercado.
Além dos recursos naturais, os espaços compartilhados desempenham um papel fundamental na integração e no fortalecimento dessas comunidades. Bibliotecas, ginásios, creches e salas de aula permitem que o conhecimento e os serviços circulem internamente, criando um ambiente onde a colaboração ocorre de maneira orgânica. A descentralização também se aplica ao uso da tecnologia, plataformas digitais privadas podem ser utilizadas para conectar moradores, facilitar a troca de serviços e produtos, além de coordenar agendamentos e eventos dentro dos condomínios e entre diferentes comunidades.
O Bitcoin surge como uma ferramenta indispensável nesse ecossistema, eliminando a necessidade de bancos estatais ou sistemas financeiros controlados. Ao permitir transações diretas, transparentes e resistentes à censura, o Bitcoin se torna o meio de troca ideal entre os condomínios, garantindo a preservação do valor e possibilitando um comércio ágil e eficiente. Além disso, contratos inteligentes e protocolos descentralizados podem ser integrados para administrar serviços comuns, fortalecer a segurança e reduzir a burocracia, tornando a governança desses condomínios cada vez mais autônoma e imune a intervenções externas.
Alguns podem argumentar que a falta de um aparato estatal para regulamentar a infraestrutura pode resultar em desigualdade no acesso a recursos essenciais, ou que a descentralização completa pode gerar caos e ineficiência. No entanto, essa visão ignora o fato de que a concorrência e a inovação no livre mercado são os maiores motores de desenvolvimento sustentável. Sem monopólios ou subsídios distorcendo a alocação de recursos, a busca por eficiência leva naturalmente à adoção de soluções melhores e mais acessíveis. Condomínios que oferecem infraestrutura de qualidade tendem a atrair mais moradores e investimentos, o que impulsiona a melhoria contínua e a diversificação dos serviços. Em vez de depender de um sistema centralizado falho, as comunidades se tornam responsáveis por sua própria prosperidade, criando uma estrutura sustentável, escalável e adaptável às mudanças do futuro.
Governança e Administração
Em uma sociedade descentralizada, não se deve depender de uma estrutura estatal ou centralizada para regular e tomar decisões em nome dos indivíduos. Cada condomínio, portanto, deve ser gerido de maneira autônoma, com processos claros de tomada de decisão, resolução de conflitos e administração das questões cotidianas. A gestão pode ser organizada por conselhos de moradores, associações ou sistemas de governança direta, conforme as necessidades locais.
Conselhos de Moradores e Processos de Tomada de Decisão
Em muitos casos, a administração interna de um condomínio privado pode ser realizada por um conselho de moradores, composto por representantes eleitos ou indicados pela própria comunidade. A ideia é garantir que as decisões importantes, como planejamento urbano, orçamento, manutenção e serviços, sejam feitas de forma transparente e que os interesses de todos os envolvidos sejam considerados. Isso não significa que a gestão precise ser completamente democrática, mas sim que as decisões devem ser tomadas de forma legítima, transparente e acordadas pela maior parte dos membros.
Em vez de um processo burocrático e centralizado, onde uma liderança impõe suas vontades sobre todos a muitas vezes suas decisões ruins não o afetam diretamente, a gestão de um condomínio privado deve ser orientada pela busca de consenso, onde os próprios gestores sofrerão as consequências de suas más escolhas. O processo de tomada de decisão pode ser dinâmico e direto, com os moradores discutindo e acordando soluções baseadas no mercado e nas necessidades locais, em vez de depender de um sistema impessoal de regulamentação. Além disso, a utilização de tecnologias descentralizadas, como plataformas de blockchain, pode proporcionar maior transparência nas decisões e maior confiança na gestão.
Resolução de Conflitos
A resolução de disputas dentro dos condomínios pode ocorrer de forma voluntária, através de negociação direta ou com o auxílio de mediadores escolhidos pelos próprios moradores por meio de um sistema de reputação. Em alguns casos, podem ser criados mecanismos para resolução de disputas mais formais, com árbitros ou juízes independentes que atuam sem vínculos com o condomínio. Esses árbitros podem ser escolhidos com base em sua experiência ou especialização em áreas como direito, mediação e resolução de conflitos, com uma reputação para zelar. Ao contrário de um sistema judicial centralizado, onde a parte envolvida depende do Estado para resolver disputas, os moradores possuem a autonomia para buscar soluções que atendam aos seus próprios interesses e necessidades. A diversidade de abordagens em um sistema de governança descentralizado cria oportunidades para inovações que atendem diferentes cenários, sem a interferência de burocratas distantes dos próprios problemas que estão "tentando resolver".
Planejamento Urbano e Arquitetura
A questão do design dos condomínios envolve não apenas a estética das construções, mas também a funcionalidade e a sustentabilidade a longo prazo. O planejamento urbano deve refletir as necessidades específicas da comunidade, onde ela decide por si mesma como construir e organizar seu ambiente.\ Arquitetos e urbanistas, muitas vezes moradores especializados, serão responsáveis pela concepção de espaços que atendam a esses critérios, criando ambientes agradáveis, com áreas para lazer, trabalho e convivência que atendam às diversas necessidades de cada grupo.\ Além disso, condomínios com nessecidades semelhantes poderão adotar ideias que deram certo em outros e certamente também dará no seu.
Segurança e Vigilância
Em relação à segurança, cada condomínio pode adotar sistemas de vigilância e proteção que atendam à sua realidade específica. Algumas comunidades podem optar por sistemas de câmeras de segurança, armamento pleno de seus moradores, patrulhamento privado ou até mesmo formas alternativas de garantir a proteção, como vigilância por meio de criptografia e monitoramento descentralizado. A chave para a segurança será a confiança mútua e a colaboração voluntária entre os moradores, que terão a liberdade de definir suas próprias medidas.
Comércio entre Condomínios
A troca de bens e serviços entre as diferentes comunidades é essencial para o funcionamento da rede. Como cada condomínio possui um grau de especialização ou uma mistura de profissionais em diversas áreas, a interdependência entre eles se torna crucial para suprir necessidades e promover a colaboração.
Embora alguns condomínios sejam especializados em áreas como saúde, agricultura ou tecnologia, outros podem ter um perfil mais diversificado, com moradores que atuam em diferentes campos de conhecimento. Por exemplo, um condomínio agrícola pode produzir alimentos orgânicos frescos, enquanto um condomínio de saúde oferece consultas médicas, terapias e cuidados especializados. Já um condomínio tecnológico pode fornecer inovações em software ou equipamentos de energia. Podem haver condomínios universitários que oferecem todo tipo de solução no campo de ensino. Ao mesmo tempo, um condomínio misto, com moradores de diversas áreas, pode oferecer uma variedade de serviços e produtos, tornando-se um centro de intercâmbio de diferentes tipos de expertise.
Essa divisão de trabalho, seja especializada ou diversificada, permite que os condomínios ofereçam o melhor de suas áreas de atuação, ao mesmo tempo em que atendem às demandas de outros. Um condomínio que não se especializa pode, por exemplo, buscar um acordo de troca com um condomínio agrícola para obter alimentos frescos ou com um condomínio tecnológico para adquirir soluções inovadoras.
Embora os condomínios busquem a autossuficiência, alguns recursos essenciais não podem ser produzidos internamente. Itens como minérios para construção, combustíveis ou até mesmo água, em regiões secas, não estão disponíveis em todas as áreas. A natureza não distribui os recursos de maneira uniforme, e a capacidade de produção local pode ser insuficiente para suprir todas as necessidades dos moradores. Isso implica que, para garantir a qualidade de vida e a continuidade das operações, os condomínios precisarão estabelecer relações comerciais e de fornecimento com fontes externas, seja através de mercados, importações ou parcerias com outras comunidades ou fornecedores fora do sistema de condomínios. O comércio intercondomínios e com o exterior será vital para a complementaridade das necessidades, assegurando que os moradores tenham acesso a tudo o que não pode ser produzido localmente.
O sistema econômico entre os condomínios pode ser flexível, permitindo o uso de uma moeda comum (como o Bitcoin) ou até mesmo um sistema de troca direta. Por exemplo, um morador de um condomínio misto pode oferecer serviços de design gráfico em troca de alimentos ou cuidados médicos. Esse tipo de colaboração estimula a produtividade e cria incentivos para que cada condomínio ofereça o melhor de seus recursos e habilidades, garantindo acesso aos bens e serviços necessários.
Relações Externas e Diplomacia
O isolamento excessivo pode limitar o acesso a inovações, avanços culturais e tecnológicos, e até mesmo dificultar o acesso a mercados externos. Por isso, é importante que haja canais de comunicação e métodos de diplomacia para interagir com outras comunidades. Os condomínios podem, por exemplo, estabelecer parcerias com outras regiões, seja para troca de produtos, serviços ou até para inovação. Isso garante que a rede de condomínios não se torne autossuficiente ao ponto de se desconectar do resto do mundo, o que pode resultar em estagnação.
Feiras, mercados intercondomínios e até eventos culturais e educacionais podem ser organizados para promover essas interações. A colaboração entre as comunidades e o exterior não precisa ser baseada em uma troca de dependência, mas sim numa rede de oportunidades que cria benefícios para todas as partes envolvidas. Uma boa reputação atrai novos moradores, pode valorizar propriedades e facilitar parcerias. A diplomacia entre as comunidades também pode ser exercida para resolver disputas ou desafios externos.
A manutenção de boas relações entre condomínios é essencial para garantir uma rede de apoio mútuo eficiente. Essas relações incentivam a troca de bens e serviços, como alimentos, assistência médica ou soluções tecnológicas, além de fortalecer a autossuficiência regional. Ao colaborar em segurança, infraestrutura compartilhada, eventos culturais e até mesmo na resolução de conflitos, os condomínios se tornam mais resilientes e eficientes, reduzindo a dependência externa e melhorando a qualidade de vida dos moradores. A cooperação contínua cria um ambiente mais seguro e harmonioso.
Educação e Desenvolvimento Humano
Cada comunidade pode criar escolas internas com currículos adaptados às especializações de seus moradores. Por exemplo, em um condomínio agrícola, podem ser ensinadas práticas agrícolas sustentáveis, e em um condomínio tecnológico, cursos de programação e inovação. Isso permite que crianças e jovens cresçam em ambientes que reforçam as competências valorizadas pela comunidade.
Além das escolas internas, o conceito de homeschooling pode ser incentivado, permitindo que os pais eduquem seus filhos conforme seus próprios valores e necessidades, com o apoio da comunidade. Esse modelo oferece uma educação mais flexível e personalizada, ao contrário do currículo tradicional oferecido pelo sistema público atual.
Os condomínios universitários também podem surgir, criando ambientes dedicados ao desenvolvimento acadêmico, científico e profissional, onde estudantes vivem e aprendem. Além disso, programas de capacitação contínua são essenciais, com oficinas e cursos oferecidos dentro do condomínio para garantir que os moradores se atualizem com novas tecnologias e práticas.
Para ampliar os horizontes educacionais, os intercâmbios estudantis entre diferentes condomínios podem ser incentivados. Esses intercâmbios não se limitam apenas ao ambiente educacional, mas também se estendem ao aprendizado de práticas de vida e habilidades técnicas. Os jovens de diferentes condomínios podem viajar para outras comunidades para estudar, trabalhar ou simplesmente trocar ideias. Isso pode ocorrer de diversas formas, como programas de curto e longo prazo, através de acordos entre os próprios condomínios, permitindo que os estudantes se conectem com outras comunidades, aprendam sobre diferentes especializações e desenvolvam uma compreensão mais ampla.
Essa abordagem descentralizada permite que cada comunidade desenvolva as competências essenciais sem depender de estruturas limitantes do estado ou sistemas educacionais centralizados. Ao proporcionar liberdade de escolha e personalização, os condomínios criam ambientes propícios ao crescimento humano, alinhados às necessidades e interesses de seus moradores.
A sociedade dos condomínios privados propõe uma estrutura alternativa de convivência onde as pessoas podem viver de acordo com seus próprios valores e necessidades. Esses condomínios oferecem um modelo de organização que desafia a centralização estatal, buscando criar comunidades adaptáveis e inovadoras. A liberdade garante que as habilidades necessárias para o sustento e crescimento das comunidades sejam mantidas ao longo do tempo.
A troca de bens, serviços e conhecimentos entre os condomínios, sem a imposição de forças externas, cria uma rede de boas relações, onde o comércio e a colaboração substituem a intervenção estatal. Em vez de depender de sistemas coercitivos, cada condomínio funciona como um microcosmo autônomo que, juntos, formam um ecossistema dinâmico e próspero. Este modelo propõe que, por meio de trocas voluntárias, possamos construir uma sociedade mais saudável. Lembre-se: Ideias e somente ideias podem iluminar a escuridão.
-
 @ a5142938:0ef19da3
2025-05-02 10:48:55
@ a5142938:0ef19da3
2025-05-02 10:48:55Finding 100% natural, plastic-free products turned out to be much harder than I expected… So I started collecting bookmarks. And then I thought: "What if we shared?!
Help me discover the best natural alternatives for clothing and gear without plastic!
This project is all about sharing: half of the site's potential revenue is redistributed to contributors. A small experiment in revenue and value sharing on the internet. :-)
Q&A
Why focus on natural materials?
Synthetic materials are mostly plastics (polyester, polyamide…). The problem? They end up contaminating us:
- Microplastics absorbed through the skin,
- Particles released with every wash, making their way into the water we drink and the food we eat,
- Major challenges in recycling plastic waste.
What exactly are natural materials?
They are non-synthetic materials, whose components exist in nature without molecular modification. But what really matters here is their biodegradability and non-toxicity.
Some materials may spark debates about their acceptability on this site!
How is this different from other ethical fashion or shopping websites?
Many websites offer ethical and sustainable products, but I often found they still included synthetic materials. I had to check every product individually. Some promote recycled plastic fibers as an eco-friendly choice, but I’d rather not put plastic on my skin or my children's.
How can I contribute?
If you find this project useful or interesting, here’s how you can support it:
-
📝 Contribute: suggest edits by commenting on existing entries or propose new product or brand references. 👉 Learn more about contributions
-
⚡ Donate: Help sustain the project and support contributors. 👉 Learn more about donations
-
📢 Spread the word: tell people around you, share the site on social media, your blog…
How can I receive a share of the site’s revenue?
You need a NOSTR account and a Bitcoin Lightning address.
What is NOSTR?
NOSTR is a decentralized internet protocol, still experimental, that allows you to:
- Publish and browse content without relying on a centralized platform.
- Log in to multiple services while keeping full control over your data.
- Use the Bitcoin Lightning network for instant, peer-to-peer payments.
What about my data privacy?
- No ads, no personalized tracking.
- NOSTR comments are public, but you can use a pseudonym.
- You retain ownership of your contributions on the NOSTR protocol.
Who is behind this project?
We use open-source tools and services:
- NOSTR for content publishing and contributions checking,
- npub.pro for content visualization,
- Coinos.io for payment management.
This article is published on origin-nature.com 🌐 Voir cet article en français
-
 @ e4950c93:1b99eccd
2025-05-02 10:48:12
@ e4950c93:1b99eccd
2025-05-02 10:48:12Trouver des produits 100% naturels, sans plastique, est bien plus compliqué que je ne le pensais… Alors j’ai commencé à collectionner des marque-pages. Et puis je me suis dit : « Et si on partageait ?! »
Aide-moi à dénicher les meilleures alternatives naturelles pour s’habiller et s’équiper sans plastique !
Ce projet repose sur le partage : la moitié des revenus éventuels du site est reversée aux contribut-eur-rice-s. Une petite expérimentation de partage de la valeur sur Internet. :-)
Questions-réponses
Pourquoi se focaliser sur les matières naturelles ?
Les matières synthétiques sont essentiellement des plastiques (polyester, polyamide…). Problème ? Oui ! Ils finissent par nous contaminer :
- Microplastiques absorbés par la peau,
- Particules diffusées à chaque lavage, se retrouvant dans l’eau que nous buvons et les aliments que nous consommons,
- Enjeux majeurs liés au recyclage des déchets plastiques.
C'est quoi, au juste, des matières naturelles ?
Ce sont des matières non synthétiques, dont les composants existent à l’état naturel, sans modification de leur structure moléculaire. Mais ce qui nous intéresse avant tout, c’est leur biodégradabilité et leur absence de toxicité.
Certaines matières feront sûrement débat sur leur acceptabilité ici.
👉 En savoir plus sur les matières
Quelle différence avec d'autres sites de mode ou de shopping éthiques ?
Il existe déjà de nombreux sites proposant des produits éthiques et durables, mais j’ai constaté qu’ils incluaient souvent des matières synthétiques. Je devais vérifier produit par produit. Certains mettent en avant les fibres en plastique recyclé comme démarche environnementale, mais je préfère éviter d’en porter sur ma peau ou d'en mettre sur mes enfants.
Comment contribuer ?
Si tu trouves ce projet utile ou intéressant, voici comment le soutenir :
-
📝 Contribue : suggère des modifications en commentant les fiches existantes ou propose de nouvelles références de produits ou de marque. 👉 En savoir plus sur les contributions
-
⚡ Fais un don : pour faire vivre le projet et remercier les contribut-eur-ice-s. 👉 En savoir plus sur les dons
-
📢 Fais-le connaître : parles-en autour de toi, partage le site sur les réseaux sociaux, ton blog…
Comment recevoir une partie des revenus du site ?
Il suffit d’avoir un compte NOSTR et une adresse Bitcoin Lightning.
👉 En savoir plus sur les rétributions
C'est quoi NOSTR ?
C’est un protocole décentralisé pour Internet, encore en phase expérimentale. Il permet :
- De publier et consulter du contenu sans dépendre d’une plateforme centralisée.
- De se connecter à plusieurs services en conservant le contrôle total de ses données.
- D’intégrer le réseau Bitcoin Lightning pour des paiements instantanés et décentralisés.
Et la confidentialité de mes données ?
- Aucune publicité, aucun traçage personnalisé.
- Les commentaires NOSTR sont publics, mais vous pouvez utiliser un pseudonyme.
- Vous conservez la propriété de vos contributions sur le protocole NOSTR.
Qui porte ce projet ?
👉 Voir les contribut-eur-rice-s
Nous utilisons des outils et services open source :
- NOSTR pour la publication des contenus et la vérification des contributions,
- npub.pro pour la visualisation des contenus,
- Coinos.io pour la gestion des paiements.
Cet article est publié sur origine-nature.com 🌐 See this article in English
-
 @ a87c9bfc:83bda6a8
2025-05-02 10:43:34
@ a87c9bfc:83bda6a8
2025-05-02 10:43:34Large Language Models (LLMs) are revolutionizing how we interact with technology, but their increasing sophistication brings unique security challenges. Malicious actors are constantly finding new ways to exploit these systems, primarily through techniques like prompt injection – crafting inputs to bypass safety controls – and the use of hidden characters to obfuscate harmful commands or disrupt text processing. Ensuring the safety and integrity of LLM applications is paramount.
The Hidden Dangers in Text
Prompt injection allows attackers to manipulate LLM outputs, potentially leading to data leaks, generation of inappropriate content, or unauthorized actions. Similarly, invisible characters (like zero-width spaces or bidirectional text overrides) can be embedded within seemingly innocuous text. These hidden elements can bypass simple security filters, disguise malicious instructions, or interfere with how the LLM interprets the input, leading to unpredictable or harmful behavior.
Vibecondom: A New Shield for LLM Security
To combat these emerging threats, a new open-source tool called Vibecondom has been developed. Written in Go, Vibecondom acts as a specialized security scanner designed specifically for the text content fed into LLMs. It serves as a critical defensive layer for AI developers, security researchers, and content moderation teams aiming to protect their systems.
Core Capabilities
Vibecondom focuses on identifying subtle but dangerous patterns within text data:
- Detecting Deception: It actively scans for known techniques used in prompt injection attacks and identifies various types of hidden or control characters that could signal malicious intent.
- Unmasking Obfuscation: The tool can flag potentially obfuscated content, such as Base64 encoded strings or text mixing different character scripts, which might be used to hide payloads.
- Flexible Integration: Vibecondom is designed for versatility, capable of analyzing text files stored locally or scanning content directly from remote Git repositories.
- Actionable Insights: When potential threats are detected, the tool provides clear alerts, helping teams pinpoint and investigate suspicious inputs before they compromise the LLM.
Enhancing Trust in AI
Tools like Vibecondom represent an essential step forward in securing the LLM ecosystem. By proactively identifying and flagging potentially harmful inputs, developers can build more robust defenses, fostering greater trust and reliability in AI applications.
As an open-source project (MIT License), Vibecondom invites collaboration and contribution from the security community. Anyone interested in bolstering their LLM security posture is encouraged to explore the Vibecondom project on GitHub to learn more.
-
 @ e4950c93:1b99eccd
2025-05-02 10:39:50
@ e4950c93:1b99eccd
2025-05-02 10:39:50Équipe Cœur
L'équipe Cœur porte le projet et valide les contenus.
- Jean-David Bar : https://njump.me/npub1qr4p7uamcpawv7cr8z9nlhmd60lylukf7lvmtlnpe7r4juwxudzq3hrnll
Pour démarrer, je gère le projet en solo en partageant mes favoris pour éviter le plastique sur nous et sur nos enfants. Contacte-moi si tu souhaites rejoindre l'aventure !
Enrichisseu-r-se-s de contenus
Les contribut-eur-rice-s rendent ce site vivant et intéressant.
A venir.
👉 En savoir plus sur les contributions
Cet article est publié sur origine-nature.com 🌐 See this article in English
-
 @ 4961e68d:a2212e1c
2025-05-02 07:47:16
@ 4961e68d:a2212e1c
2025-05-02 07:47:16热死人了
-
 @ 04c915da:3dfbecc9
2025-03-26 20:54:33
@ 04c915da:3dfbecc9
2025-03-26 20:54:33Capitalism is the most effective system for scaling innovation. The pursuit of profit is an incredibly powerful human incentive. Most major improvements to human society and quality of life have resulted from this base incentive. Market competition often results in the best outcomes for all.
That said, some projects can never be monetized. They are open in nature and a business model would centralize control. Open protocols like bitcoin and nostr are not owned by anyone and if they were it would destroy the key value propositions they provide. No single entity can or should control their use. Anyone can build on them without permission.
As a result, open protocols must depend on donation based grant funding from the people and organizations that rely on them. This model works but it is slow and uncertain, a grind where sustainability is never fully reached but rather constantly sought. As someone who has been incredibly active in the open source grant funding space, I do not think people truly appreciate how difficult it is to raise charitable money and deploy it efficiently.
Projects that can be monetized should be. Profitability is a super power. When a business can generate revenue, it taps into a self sustaining cycle. Profit fuels growth and development while providing projects independence and agency. This flywheel effect is why companies like Google, Amazon, and Apple have scaled to global dominance. The profit incentive aligns human effort with efficiency. Businesses must innovate, cut waste, and deliver value to survive.
Contrast this with non monetized projects. Without profit, they lean on external support, which can dry up or shift with donor priorities. A profit driven model, on the other hand, is inherently leaner and more adaptable. It is not charity but survival. When survival is tied to delivering what people want, scale follows naturally.
The real magic happens when profitable, sustainable businesses are built on top of open protocols and software. Consider the many startups building on open source software stacks, such as Start9, Mempool, and Primal, offering premium services on top of the open source software they build out and maintain. Think of companies like Block or Strike, which leverage bitcoin’s open protocol to offer their services on top. These businesses amplify the open software and protocols they build on, driving adoption and improvement at a pace donations alone could never match.
When you combine open software and protocols with profit driven business the result are lean, sustainable companies that grow faster and serve more people than either could alone. Bitcoin’s network, for instance, benefits from businesses that profit off its existence, while nostr will expand as developers monetize apps built on the protocol.
Capitalism scales best because competition results in efficiency. Donation funded protocols and software lay the groundwork, while market driven businesses build on top. The profit incentive acts as a filter, ensuring resources flow to what works, while open systems keep the playing field accessible, empowering users and builders. Together, they create a flywheel of innovation, growth, and global benefit.
-
 @ ba36d0f7:cd802cba
2025-04-16 16:45:07
@ ba36d0f7:cd802cba
2025-04-16 16:45:071. The creative (but fleeting) pleasure of tactics
Chess tactics are like candy between meals - instant delight, but not true nourishment. Choosing whether to attack a bishop or a knight feels like picking between vanilla and chocolate ice cream: sprinkles or none, cherry on top or not...
-
They’re freedom within boundaries: the board has limits, but imagination doesn’t.
-
They mirror your style: quick strikes like an espresso? Or slow grinds like green tea?
2. Two tactics, two joys
-
Simple (an exposed king): everyday wins (like finding cash in your pocket).
-
Complex (3+ move combos): earned triumphs (like a project you’ve sweat over).
3. The Buddha’s warning: "Don’t Confuse the Sugar Rush for the Meal"
Buddhism teaches that clinging to pleasure (kāma-tanha) breeds suffering. In chess and life:
-
Tactics are desserts: sweet, but not the feast.
- Example: Beating a blunder is like winning the lottery; outplaying strategically is like building wealth.
-
The balance: Revel in that dazzling queen sacrifice - but don’t bet your game on it. Like savoring cake, not devouring the whole bakery.
4. How to play (and Live) this wisdom
✅ Ask yourself:
-
Is this move sound - or just seductive? (Like craving junk food vs. needing sustenance).
-
Am I here to win, or to wow? (Ego checkmates you faster than any opponent).
Final Move: The middle path on 64 squares
Buddhism invites joy without attachment. On the board:
-
Tactics = spice: they dazzle, but strategy feeds growth.
-
Strategy = the harvest: the patience that crowns kings.
♟️ So - do you chase the fireworks, or cultivate the long game?
Online Resources
Chess tactics - chess.com https://www.chess.com/terms/chess-tactics
Tactic examples - chess.com https://www.chess.com/article/view/chess-tactics
Tactics - lichess.org https://lichess.org/study/topic/Tactics/hot
somachess #buddhism #philosophy #chessphilosophy #chess #elsalvador #btc #apaneca #chesselsalvador
-
-
 @ 04c915da:3dfbecc9
2025-03-25 17:43:44
@ 04c915da:3dfbecc9
2025-03-25 17:43:44One of the most common criticisms leveled against nostr is the perceived lack of assurance when it comes to data storage. Critics argue that without a centralized authority guaranteeing that all data is preserved, important information will be lost. They also claim that running a relay will become prohibitively expensive. While there is truth to these concerns, they miss the mark. The genius of nostr lies in its flexibility, resilience, and the way it harnesses human incentives to ensure data availability in practice.
A nostr relay is simply a server that holds cryptographically verifiable signed data and makes it available to others. Relays are simple, flexible, open, and require no permission to run. Critics are right that operating a relay attempting to store all nostr data will be costly. What they miss is that most will not run all encompassing archive relays. Nostr does not rely on massive archive relays. Instead, anyone can run a relay and choose to store whatever subset of data they want. This keeps costs low and operations flexible, making relay operation accessible to all sorts of individuals and entities with varying use cases.
Critics are correct that there is no ironclad guarantee that every piece of data will always be available. Unlike bitcoin where data permanence is baked into the system at a steep cost, nostr does not promise that every random note or meme will be preserved forever. That said, in practice, any data perceived as valuable by someone will likely be stored and distributed by multiple entities. If something matters to someone, they will keep a signed copy.
Nostr is the Streisand Effect in protocol form. The Streisand effect is when an attempt to suppress information backfires, causing it to spread even further. With nostr, anyone can broadcast signed data, anyone can store it, and anyone can distribute it. Try to censor something important? Good luck. The moment it catches attention, it will be stored on relays across the globe, copied, and shared by those who find it worth keeping. Data deemed important will be replicated across servers by individuals acting in their own interest.
Nostr’s distributed nature ensures that the system does not rely on a single point of failure or a corporate overlord. Instead, it leans on the collective will of its users. The result is a network where costs stay manageable, participation is open to all, and valuable verifiable data is stored and distributed forever.
-
 @ a5142938:0ef19da3
2025-05-02 10:38:10
@ a5142938:0ef19da3
2025-05-02 10:38:10Happy to have found useful information on this site?
Support the project by making a donation to keep it running and thank the contributors.
In bitcoin
- On-chain:
bc1qkm8me8l9563wvsl9sklzt4hdcuny3tlejznj7d
- Lightning network:
⚡️
origin-nature@coinos.ioYou can also support us on a recurring basis 👉 Set up a recurring Lightning payment
In euros, dollars, or any other supported currency
-
By bank transfer, IBAN: FR76 2823 3000 0144 3759 8717 669
-
You can also support us on a recurring basis 👉 Make a pledge on LiberaPay
Contact us if you’d like to make a donation using any other cryptocurrency.
💡 A Value-Sharing Model
Half of the donations are redistributed to the contributors who create the site's value, experimenting with a revenue-sharing model on the Internet—one that respects your data and doesn’t seek to capture your attention.
The other half helps cover the website’s operating costs, compensate the core team, and support the open-source tools we rely on.
This article is published on origin-nature.com 🌐 Voir cet article en français
-
 @ 4961e68d:a2212e1c
2025-05-02 07:46:46
@ 4961e68d:a2212e1c
2025-05-02 07:46:46热死人了!
-
 @ ecda4328:1278f072
2025-03-25 10:00:52
@ ecda4328:1278f072
2025-03-25 10:00:52Kubernetes and Linux Swap: A Practical Perspective
After reviewing kernel documentation on swap management (e.g., Linux Swap Management), KEP-2400 (Kubernetes Node Memory Swap Support), and community discussions like this post on ServerFault, it's clear that the topic of swap usage in modern systems—especially Kubernetes environments—is nuanced and often contentious. Here's a practical synthesis of the discussion.
The Rationale for Disabling Swap
We disable SWAP on our Linux servers to ensure stable and predictable performance by relying on available RAM, avoiding the performance degradation and unnecessary I/O caused by SWAP usage. If an application runs out of memory, it’s usually due to insufficient RAM allocation or a memory leak, and enabling SWAP only worsens performance for other applications. It's more efficient to let a leaking app restart than to rely on SWAP to prevent OOM crashes.
With modern platforms like Kubernetes, memory requests and limits are enforced, ensuring apps use only the RAM allocated to them, while avoiding overcommitment to prevent resource exhaustion.
Additionally, disabling swap may protect data from data remanence attacks, where sensitive information could potentially be recovered from the swap space even after a process terminates.
Theoretical Capability vs. Practical Deployment
Linux provides a powerful and flexible memory subsystem. With proper tuning (e.g., swappiness, memory pinning, cgroups), it's technically possible to make swap usage efficient and targeted. Seasoned sysadmins often argue that disabling swap entirely is a lazy shortcut—an avoidance of learning how to use the tools properly.
But Kubernetes is not a traditional system. It's an orchestrated environment that favors predictability, fail-fast behavior, and clear isolation between workloads. Within this model:
- Memory requests and limits are declared explicitly.
- The scheduler makes decisions based on RAM availability, not total virtual memory (RAM + swap).
- Swap introduces non-deterministic performance characteristics that conflict with Kubernetes' goals.
So while the kernel supports intelligent swap usage, Kubernetes intentionally sidesteps that complexity.
Why Disable Swap in Kubernetes?
-
Deterministic Failure > Degraded Performance\ If a pod exceeds its memory allocation, it should fail fast — not get throttled into slow oblivion due to swap. This behavior surfaces bugs (like memory leaks or poor sizing) early.
-
Transparency & Observability\ With swap disabled, memory issues are clearer to diagnose. Swap obfuscates root causes and can make a healthy-looking node behave erratically.
-
Performance Consistency\ Swap causes I/O overhead. One noisy pod using swap can impact unrelated workloads on the same node — even if they’re within their resource limits.
-
Kubernetes Doesn’t Manage Swap Well\ Kubelet has historically lacked intelligence around swap. As of today, Kubernetes still doesn't support swap-aware scheduling or per-container swap control.
-
Statelessness is the Norm\ Most containerized workloads are designed to be ephemeral. Restarting a pod is usually preferable to letting it hang in a degraded state.
"But Swap Can Be Useful..."
Yes — for certain workloads (e.g., in-memory databases, caching layers, legacy systems), there may be valid reasons to keep swap enabled. In such cases, you'd need:
- Fine-tuned
vm.swappiness - Memory pinning and cgroup-based control
- Swap-aware monitoring and alerting
- Custom kubelet/systemd integration
That's possible, but not standard practice — and for good reason.
Future Considerations
Recent Kubernetes releases have introduced experimental swap support via KEP-2400. While this provides more flexibility for advanced use cases — particularly Burstable QoS pods on cgroupsv2 — swap remains disabled by default and is not generally recommended for production workloads unless carefully planned. The rationale outlined in this article remains applicable to most Kubernetes operators, especially in multi-tenant and performance-sensitive environments.
Even the Kubernetes maintainers acknowledge the inherent trade-offs of enabling swap. As noted in KEP-2400's Risks and Mitigations section, swap introduces unpredictability, can severely degrade performance compared to RAM, and complicates Kubernetes' resource accounting — increasing the risk of noisy neighbors and unexpected scheduling behavior.
Some argue that with emerging technologies like non-volatile memory (e.g., Intel Optane/XPoint), swap may become viable again. These systems promise near-RAM speed with large capacity, offering hybrid memory models. But these are not widely deployed or supported in mainstream Kubernetes environments yet.
Conclusion
Disabling swap in Kubernetes is not a lazy hack — it’s a strategic tradeoff. It improves transparency, predictability, and system integrity in multi-tenant, containerized environments. While the kernel allows for more advanced configurations, Kubernetes intentionally simplifies memory handling for the sake of reliability.
If we want to revisit swap usage, it should come with serious planning: proper instrumentation, swap-aware observability, and potentially upstream K8s improvements. Until then, disabling swap remains the sane default.
-
 @ e4950c93:1b99eccd
2025-05-02 10:36:46
@ e4950c93:1b99eccd
2025-05-02 10:36:46Heureu-x-se d’avoir trouvé une information utile sur ce site ?
Soutiens le projet en faisant un don pour le faire vivre et remercier les contribut-eur-rice-s.
En bitcoin
-
Sur la blockchain : bc1qkm8me8l9563wvsl9sklzt4hdcuny3tlejznj7d
-
Réseau lightning : ⚡️
origin-nature@coinos.ioVous pouvez aussi nous soutenir de manière récurrente 👉 Créer un paiement Lightning récurrent
En euros, dollars, ou toute autre monnaie prise en charge
-
Par virement, IBAN : FR76 2823 3000 0144 3759 8717 669
-
Tu peux aussi nous soutenir de manière récurrente 👉 Faire une promesse sur LiberaPay
Contacte-nous si tu souhaites faire un don avec toute autre cryptomonnaie.
💡 Un modèle de partage de la valeur
La moitié des dons est redistribuée aux contribut-eur-rice-s qui créent la valeur du site, pour expérimenter un modèle de partage de revenus sur Internet — un modèle qui respecte vos données et ne cherche pas à capter votre attention.
L’autre moitié permet de couvrir les frais de fonctionnement du site, rémunérer l'équipe coeur et soutenir les outils open source que nous utilisons.
Cet article est publié sur origine-nature.com 🌐 See this article in English
-
-
 @ f1989a96:bcaaf2c1
2025-05-01 15:50:38
@ f1989a96:bcaaf2c1
2025-05-01 15:50:38Good morning, readers!
This week, we bring pressing news from Belarus, where the regime’s central bank is preparing to launch its central bank digital currency in close collaboration with Russia by the end of 2026. Since rigging the 2020 election, President Alexander Lukashenko has ruled through brute force and used financial repression to crush civil society and political opposition. A Central Bank Digital Currency (CBDC) in the hands of such an authoritarian leader is a recipe for greater control over all aspects of financial activity.
Meanwhile, Russia is planning to further restrict Bitcoin access for ordinary citizens. This time, the Central Bank of Russia and the Ministry of Finance announced joint plans to launch a state-regulated cryptocurrency exchange available exclusively to “super-qualified investors.” Access would be limited to those meeting previously defined thresholds of $1.2 million in assets or an annual income above $580,000. This is a blatant attempt by the Kremlin to dampen the accessibility and impact of Bitcoin for those who need it most.
In freedom tech news, we spotlight Samiz. This new tool allows users to create a Bluetooth mesh network over nostr, allowing users' messages and posts to pass through nearby devices on the network even while offline. When a post reaches someone with an Internet connection, it is broadcast across the wider network. While early in development, Mesh networks like Samiz hold the potential to disseminate information posted by activists and human rights defenders even when authoritarian regimes in countries like Pakistan, Venezuela, or Burma try to restrict communications and the Internet.
We end with a reading of our very own Financial Freedom Report #67 on the Bitcoin Audible podcast, where host Guy Swann reads the latest news on plunging currencies, CBDCs, and new Bitcoin freedom tools. We encourage our readers to give it a listen and stay tuned for future readings of HRF’s Financial Freedom Report on Bitcoin Audible. We also include an interview with HRF’s global bitcoin adoption lead, Femi Longe, who shares insights on Bitcoin’s growing role as freedom money for those who need it most.
Now, let’s see what’s in store this week!
SUBSCRIBE HERE
GLOBAL NEWS
Belarus | Launching CBDC in Late 2026
Belarus is preparing to launch its CBDC, the digital ruble, into public circulation by late 2026. Roman Golovchenko, the chairman of the National Bank of the Republic of Belarus (and former prime minister), made the regime’s intent clear: “For the state, it is very important to be able to trace how digital money moves along the entire chain.” He added that Belarus was “closely cooperating with Russia regarding the development of the CBDC.” The level of surveillance and central control that the digital ruble would embed into Belarus’s financial system would pose existential threats to what remains of civil society in the country. Since stealing the 2020 election, Belarusian President Alexander Lukashenko has ruled through sheer force, detaining over 35,000 people, labeling dissidents and journalists as “extremists,” and freezing the bank accounts of those who challenge his authority. In this context, a CBDC would not be a modern financial tool — it would be a means of instant oppression, granting the regime real-time insight into every transaction and the ability to act on it directly.
Russia | Proposes Digital Asset Exchange Exclusively for Wealthy Investors
A month after proposing a framework that would restrict the trading of Bitcoin to only the country’s wealthiest individuals (Russians with over $1.2 million in assets or an annual income above $580,000), Russia’s Ministry of Finance and Central Bank have announced plans to launch a government-regulated cryptocurrency exchange available exclusively to “super-qualified investors.” Under the plan, only citizens meeting the previously stated wealth and income thresholds (which may be subject to change) would be allowed to trade digital assets on the platform. This would further entrench financial privilege for Russian oligarchs while cutting ordinary Russians off from alternative financial tools and the financial freedom they offer. Finance Minister Anton Siluanov claims this will bring digital asset operations “out of the shadows,” but in reality, it suppresses grassroots financial autonomy while exerting state control over who can access freedom money.
Cuba | Ecash Brings Offline Bitcoin Payments to Island Nation in the Dark
As daily blackouts and internet outages continue across Cuba, a new development is helping Cubans achieve financial freedom: Cashu ecash. Cashu is an ecash protocol — a form of digital cash backed by Bitcoin that enables private, everyday payments that can also be done offline — a powerful feature for Cubans experiencing up to 20-hour daily blackouts. However, ecash users must trust mints (servers operated by individuals or groups that issue and redeem ecash tokens) not to disappear with user funds. To leverage this freedom tech to its fullest, the Cuban Bitcoin community launched its own ecash mint, mint.cubabitcoin.org. This minimizes trust requirements for Cubans to transact with ecash and increases its accessibility by running the mint locally. Cuba Bitcoin also released a dedicated ecash resource page, helping expand accessibility to freedom through financial education. For an island nation where the currency has lost more than 90% of its value, citizens remain locked out of their savings, and remittances are often hijacked by the regime, tools like ecash empower Cubans to preserve their financial privacy, exchange value freely, and resist the financial repression that has left so many impoverished.
Zambia | Introduces Cyber Law to Track and Intercept Digital Communications
Zambia’s government passed two new cyber laws granting officials sweeping powers to track and intercept digital communications while increasing surveillance over Zambians' online activity. Officials insist it will help combat cybercrime. Really, it gives the president absolute control over the direction of a new surveillance agency — a powerful tool to crush dissent. This follows earlier plans to restrict the use of foreign currency in the economy to fight inflation, which effectively trapped Zambians in a financial system centered around the volatile “kwacha” currency (which reached a record low earlier this year with inflation above 16%). For activists, journalists, and everyday Zambians, the new laws over online activity threaten the ability to organize and speak freely while potentially hampering access to freedom tech.
India | Central Bank Deputy Governor Praises CBDC Capabilities
At the Bharat Inclusion Summit in Bengaluru, India, the deputy governor of the Reserve Bank of India (RBI), Rabi Sankar, declared, “I have so far not seen any use case that potentially can solve the problem of cross-border money transfer; only CBDC has the ability to solve it.” Yet — seemingly unbeknownst to Sankar, Bitcoin has served as an effective remittance tool for more than a decade at low cost, fast speed, and with no central point of control. Sankar’s remarks follow a growing push to normalize state-controlled, surveillance-based digital money as a natural progression of currency. The RBI’s digital rupee CBDC, currently in pilot phase, is quickly growing into one of the most advanced CBDCs on the planet. It is being embedded into the government’s UPI payment system and offered through existing financial institutions and platforms. Decentralized alternatives like Bitcoin can achieve financial inclusion and payment efficiency too — but without sacrificing privacy, autonomy, or basic rights over to the state.
Tanzania | Opposition Party Excluded From Election Amid Financial Repression
Last week, the Tanzanian regime banned the use of foreign currency in transactions, leaving Tanzanians to rely solely on the rapidly depreciating Tanzanian shilling. Now, Tanzania's ruling party has taken a decisive step to eliminate political opposition ahead of October’s general elections by barring the CHADEMA party from participation under the pretense of treason against their party leader, Tundu Lissu. Law enforcement arrested Lissu at a public rally where he was calling for electoral reforms. This political repression is not happening in isolation. Last year, the Tanzanian regime blocked access to X, detained hundreds of opposition members, and disappeared dissidents. These developments suggest a broader strategy to silence criticism and electoral competition through arrests, censorship, and economic coercion.
BITCOIN AND FREEDOM TECH NEWS
Samiz | Create a Bluetooth Mesh Network with Nostr
Samiz, an app for creating a Bluetooth mesh network over nostr, is officially available for testing. Mesh networks, where interconnected computers relay data to one another, can provide offline access to nostr if enough users participate. For example, when an individual is offline but has Samiz enabled, their device can connect to other nearby devices through Bluetooth, allowing nostr messages to hop locally from phone to phone until reaching someone with internet access, who can then broadcast the message to the wider nostr network. Mesh networks like this hold powerful implications for activists and communities facing censorship, Internet shutdowns, or surveillance. In places with restricted finances and organization, Samiz, while early in development, can potentially offer a way to distribute information through nostr without relying on infrastructure that authoritarian regimes can shut down.
Spark | New Bitcoin Payments Protocol Now Live
Lightspark, a company building on the Bitcoin Lightning Network, officially released Spark, a new payment protocol built on Bitcoin to make transactions faster, cheaper, and more privacy-protecting. Spark leverages a technology called statechains to enable self-custodial and off-chain Bitcoin transactions for users by transferring the private keys associated with their bitcoin rather than signing and sending a transaction with said keys. Spark also supports stablecoins (digital tokens pegged to fiat currency) and allows users to receive payments while offline. While these are promising developments, in its current state, Spark is not completely trustless; therefore, it is advisable only to hold a small balance of funds on the protocol as this new payment technology gets off the ground. You can learn more about Spark here.
Boltz | Now Supports Nostr Zaps
Boltz, a non-custodial bridge for swapping between different Bitcoin layers, released a new feature called Zap Swaps, enabling users to make Lightning payments as low as 21 satoshis (small units of bitcoin). This feature enables bitcoin microtransactions like nostr zaps, which are use cases that previously required workaround solutions. With the release, users of Boltz-powered Bitcoin wallets like Misty Breez can now leverage their wallets for zaps on nostr. These small, uncensorable bitcoin payments are a powerful tool for supporting activists, journalists, and dissidents — offering a permissionless way to support free speech and financial freedom worldwide. HRF is pleased to see this past HRF grantee add support for the latest freedom tech features.
Coinswap | Adds Support for Coin Selection
Coinswap, an in-development protocol that enables users to privately swap Bitcoin with one another, added support for coin selection, boosting the protocol’s privacy capabilities. Coin selection allows Bitcoin users to choose which of their unspent transaction outputs (UTXOs) to spend, giving them granular control over their transactions and the information they choose to reveal. For activists, journalists, and anyone operating under financial surveillance and repression, this addition (when fully implemented and released) can strengthen Bitcoin’s ability to resist censorship and protect human rights. HRF’s first Bitcoin Development Fund (BDF) grant was to Coinswap, and we are glad to see the continued development of the protocol.
bitcoin++ | Upcoming Bitcoin Developer Conference
The next bitcoin++ conference, a global, bitcoin-only developer series organized by Bitcoin educator Lisa Neigut, will occur in Austin, Texas, from May 7 to 9, 2025. A diverse group of privacy advocates, developers, and freedom tech enthusiasts will convene to learn about the mempool (the queue of pending and unconfirmed transactions in a Bitcoin node). Attendees will learn how Bitcoin transactions are sorted into blocks, mempool policies, and how transactions move through time and space to reach the next block. These events offer an incredible opportunity to connect with the technical Bitcoin community, who are ultimately many of the figures building the freedom tools that are helping individuals preserve their rights and freedoms in the face of censorship. Get your tickets here.
OpenSats | Announces 11th Wave of Nostr Grants
OpenSats, a nonprofit organization supporting open-source software and projects, announced its 11th round of grants for nostr, a decentralized protocol that enables uncensorable communications. Two projects stand out for their potential impact on financial freedom and activism: HAMSTR, which enables nostr messaging over ham radio that keeps information and payments flowing in off-grid or censored environments, and Nostr Double Ratchet, which brings end-to-end encrypted private messaging to nostr clients, safeguarding activists from surveillance. These tools help dissidents stay connected, coordinate securely, and transact privately, making them powerful assets for those resisting authoritarian control. Read the full list of grants here.
Bitcoin Design Community | Organizes Designathon for Open-Source UX Designers
The Bitcoin Design Community is hosting its next Designathon between May 4 and 18, 2025, inviting designers of all levels and backgrounds to creatively explore ideas to advance Bitcoin’s user experience and interface. Unlike traditional hackathons, this event centers specifically on design, encouraging open collaboration on projects that improve usability, accessibility, and innovation in open-source Bitcoin tools. Participants can earn monetary prizes, rewards, and recognition for their work. Anyone can join or start a project. Learn more here.
RECOMMENDED CONTENT
Plunging Currencies, CBDCs, and New Bitcoin Freedom Tools with Guy Swann
In this reading on the Bitcoin Audible podcast, host Guy Swan reads HRF’s Financial Freedom Report #67, offering listeners a front-row view into the latest developments in financial repression and resistance. He unpacks how collapsing currencies, rising inflation, and CBDC rollouts tighten state control in Turkey, Russia, and Nigeria. But he also highlights the tools for pushing back, from the first Stratum V2 mining pool to Cashu’s new Tap-to-Pay ecash feature. If you’re a reader of the Financial Freedom Report, we encourage you to check out the Bitcoin Audible podcast, where Guy Swan will be doing monthly readings of our newsletter. Listen to the full recording here.
Bitcoin Beyond Capital: Freedom Money for the Global South with Femi Longe
In this interview at the 2025 MIT Bitcoin Expo, journalist Frank Corva speaks with Femi Longe, HRF’s global bitcoin lead, who shares insights on Bitcoin’s growing role as freedom money for those living under authoritarian regimes. The conversation highlights the importance of building Bitcoin solutions that center on the specific problems faced by communities rather than the technology itself. Longe commends projects like Tando in Kenya and Bit.Spenda in Ghana, which integrate Bitcoin and Lightning into familiar financial channels, making Bitcoin more practical and accessible for everyday payments and saving. You can watch the interview here and catch the livestreams of the full 2025 MIT Bitcoin Expo here.
If this article was forwarded to you and you enjoyed reading it, please consider subscribing to the Financial Freedom Report here.
Support the newsletter by donating bitcoin to HRF’s Financial Freedom program via BTCPay.\ Want to contribute to the newsletter? Submit tips, stories, news, and ideas by emailing us at ffreport @ hrf.org
The Bitcoin Development Fund (BDF) is accepting grant proposals on an ongoing basis. The Bitcoin Development Fund is looking to support Bitcoin developers, community builders, and educators. Submit proposals here.
-
 @ 3ffac3a6:2d656657
2025-05-02 03:50:51
@ 3ffac3a6:2d656657
2025-05-02 03:50:51Introduction: Don't Despair—This Can Be Fixed (But Don't Reboot Yet)
Running ZFS on a Raspberry Pi offers powerful features for home servers and personal NAS setups. But with power comes complexity, and in recent months, a quiet pitfall has emerged for Pi users who track kernel updates closely: upgrading to an unsupported kernel version breaks ZFS.
⚠️ Important Warning: If you've just upgraded your kernel and you're using ZFS, do not reboot yet. Rebooting without a working ZFS module can leave your system unbootable—even if you don't have critical partitions on ZFS. The system may hang because it tries to load the missing ZFS kernel module during boot and fails, halting the boot process.
If you're already facing a broken setup or can't boot — don't panic. This guide outlines both the worst-case scenario and the ideal recovery strategy. Whether you're locked out or preparing for a smooth upgrade, we've got you covered.
The Problem: A Kernel Update Too Far
As of ZFS version 2.2.3 (used in Debian-based Raspberry Pi OS), the filesystem supports Linux kernels up to 6.7. However, Raspberry Pi OS backports recently began shipping 6.12.x kernels. If you upgrade to 6.12 without precautions:
- ZFS will fail to compile against the new kernel
- DKMS errors will appear during package updates
- Your ZFS module will be missing after reboot
- Your Raspberry Pi may fail to boot, even without ZFS-mounted root or critical paths, simply due to systemd or boot scripts expecting the kernel module to be present
Example ZFS Compilation Error:
During package updates or installs, you'll see something like:
checking whether bdev_open_by_path() exists... configure: error: *** None of the expected "blkdev_get_by_path()" interfaces were detected. *** This may be because your kernel version is newer than what is *** supported, or you are using a patched custom kernel with *** incompatible modifications. *** *** ZFS Version: zfs-2.2.3-1~bpo12+1~rpt1 *** Compatible Kernels: 3.10 - 6.7This error means ZFS cannot build its kernel module against Linux 6.12.x, making it unusable.
Why This Happens: The Version Trap
The key problem is that ZFS 2.2.3 remains installed even after a kernel upgrade, and it doesn't get upgraded automatically during
apt upgrade. Since ZFS 2.2.3 only supports up to kernel 6.7, it fails to compile against 6.12.x.However, if you remove and then reinstall ZFS, the package manager installs ZFS 2.3.1, which does support Linux kernel 6.12.x. This version transition is what resolves the issue — but only if you explicitly purge and reinstall ZFS.
Worst Case: The System That Wouldn’t Boot
After upgrading the kernel and rebooting, the system failed to boot properly. It showed errors like:
cannot open access to console, the root account is locked
Although the system did not have critical filesystems on ZFS, the boot process still stalled because system services attempted to load the ZFS kernel module, which was no longer available. This resulted in an unrecoverable boot failure.
The only way forward was to reformat and reinstall Raspberry Pi OS. However, the default Raspberry Pi OS image still comes with a 6.6.x kernel, which is incompatible with ZFS 2.3.1 and newer kernels unless upgraded. Therefore, the recovery process requires one crucial step:
- First, perform a full system upgrade:
sudo apt update && sudo apt full-upgradeThis brings the kernel up to 6.12.x.
- Then, reinstall ZFS:
sudo apt install zfs-dkms zfsutils-linuxOnce this is complete, your system will be running kernel 6.12 with ZFS 2.3.1, and you can safely import your pools and resume operations.
Best Case Recovery: Clean Cut, Clean Upgrade
For users who can still log into their system, here's the cleanest and safest sequence to move forward:
- Stop all services using ZFS, including Docker, NFS, Samba, backup tools, etc.
- Export all ZFS pools:
sudo zpool export -a3. Disable swap if it lives on a ZFS vdev:sudo swapoff /dev/sdXn4. Purge ZFS packages:sudo apt purge zfsutils-linux zfs-dkms zfs-zed sudo rm -rf /usr/src/zfs* /var/lib/dkms/zfs5. Update the kernel to the desired version:sudo apt update && sudo apt full-upgrade6. Reboot into the new kernel:sudo reboot7. Reinstall ZFS:sudo apt install zfs-dkms zfsutils-linux8. Import your pool(s):sudo zpool import poolname9. Restart services that depend on ZFS.
Final Notes: Prevention Is Better Than Recovery
To avoid this issue in the future:
- Hold your current working kernel version:
sudo apt-mark hold linux-image-rpi-v8 linux-headers-rpi-v8* Or track ZFS GitHub for kernel compatibility before upgrading * Or test upgrades on a second Pi or cloned SD card before rolling them out to production
Conclusion: A Solvable Trap
ZFS on the Raspberry Pi remains a powerful option, but it demands careful version tracking. If you upgrade responsibly, or recover cleanly as described above, you can continue benefiting from advanced features like snapshots, send/receive, and compression even on this tiny powerhouse.
Don’t let a kernel update ruin your storage plans—with preparation, the Pi + ZFS combo can remain stable and strong.
-
 @ e4950c93:1b99eccd
2025-05-02 10:31:12
@ e4950c93:1b99eccd
2025-05-02 10:31:12Contribue à enrichir le site !
Chaque contribution permet d’améliorer ce site en aidant à référencer des alternatives naturelles.
💡 Qu’est-ce qu’une contribution ?
Une contribution peut être :
📝 La proposition d’une nouvelle fiche, en fournissant ses premières informations. Chaque information ajoutée (nom, lien, catégorie, etc.) est une contribution : - Ajouter un produit - Ajouter une marque
📝 L'ajout ou la modification d’informations sur une fiche existante. Chaque information ajoutée ou retirée est une contribution.
✅ Validation des contributions
Les contributions sont vérifiées par l’équipe cœur. Une contribution est validée lorsque l'information indiquée est fournie pour la première fois (le commentaire le plus ancien est pris en compte) et est vérifiable.
Une fois validées, les contributions sont comptabilisées et donnent lieu à une rétribution. 👉 En savoir plus sur les rétributions
Les informations ajoutées directement par l'équipe cœur lors de la vérification d'une contribution ne sont pas comptabilisées. Néanmoins, les membres de l'équipe coeur peuvent aussi contribuer comme tout le monde.
Cet article est publié sur origine-nature.com 🌐 See this article in English
-
 @ 21335073:a244b1ad
2025-03-18 20:47:50
@ 21335073:a244b1ad
2025-03-18 20:47:50Warning: This piece contains a conversation about difficult topics. Please proceed with caution.
TL;DR please educate your children about online safety.
Julian Assange wrote in his 2012 book Cypherpunks, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense.
This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning.
When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little.
I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?”
I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well.
I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread.
I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard.
I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it.
The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust.
Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this.
I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place.
What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method.
It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code.
They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened.
I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road.
So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally.
Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb.
I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback.
Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed.
That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone.
To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all.
I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society.
I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this.
On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government.
I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories.
There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc.
Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind.
Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now.
There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers?
I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity.
I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place.
My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors.
My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline.
The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online.
I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers.
So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation?
When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that.
I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic.
If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations.
I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process.
Course: - The creation of the internet and computers - The fight for cryptography - The tech supply chain from the ground up (example: human rights violations in the supply chain) - Corporate tech - Freedom tech - Data privacy - Digital privacy rights - AI (history-current) - Online safety (predators, scams, catfishing, extortion) - Bitcoin - Laws - How to deal with online hate and harassment - Information on who to contact if you are being abused online or offline - Algorithms - How to seek out the truth about news, etc., online
The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children.
The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward?
I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone.
Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability.
The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime.
This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful.
This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens.
In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions.
I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation.
-
 @ 21335073:a244b1ad
2025-03-15 23:00:40
@ 21335073:a244b1ad
2025-03-15 23:00:40I want to see Nostr succeed. If you can think of a way I can help make that happen, I’m open to it. I’d like your suggestions.
My schedule’s shifting soon, and I could volunteer a few hours a week to a Nostr project. I won’t have more total time, but how I use it will change.
Why help? I care about freedom. Nostr’s one of the most powerful freedom tools I’ve seen in my lifetime. If I believe that, I should act on it.
I don’t care about money or sats. I’m not rich, I don’t have extra cash. That doesn’t drive me—freedom does. I’m volunteering, not asking for pay.
I’m not here for clout. I’ve had enough spotlight in my life; it doesn’t move me. If I wanted clout, I’d be on Twitter dropping basic takes. Clout’s easy. Freedom’s hard. I’d rather help anonymously. No speaking at events—small meetups are cool for the vibe, but big conferences? Not my thing. I’ll never hit a huge Bitcoin conference. It’s just not my scene.
That said, I could be convinced to step up if it’d really boost Nostr—as long as it’s legal and gets results.
In this space, I’d watch for social engineering. I watch out for it. I’m not here to make friends, just to help. No shade—you all seem great—but I’ve got a full life and awesome friends irl. I don’t need your crew or to be online cool. Connect anonymously if you want; I’d encourage it.
I’m sick of watching other social media alternatives grow while Nostr kinda stalls. I could trash-talk, but I’d rather do something useful.
Skills? I’m good at spotting social media problems and finding possible solutions. I won’t overhype myself—that’s weird—but if you’re responding, you probably see something in me. Perhaps you see something that I don’t see in myself.
If you need help now or later with Nostr projects, reach out. Nostr only—nothing else. Anonymous contact’s fine. Even just a suggestion on how I can pitch in, no project attached, works too. 💜
Creeps or harassment will get blocked or I’ll nuke my simplex code if it becomes a problem.
https://simplex.chat/contact#/?v=2-4&smp=smp%3A%2F%2FSkIkI6EPd2D63F4xFKfHk7I1UGZVNn6k1QWZ5rcyr6w%3D%40smp9.simplex.im%2FbI99B3KuYduH8jDr9ZwyhcSxm2UuR7j0%23%2F%3Fv%3D1-2%26dh%3DMCowBQYDK2VuAyEAS9C-zPzqW41PKySfPCEizcXb1QCus6AyDkTTjfyMIRM%253D%26srv%3Djssqzccmrcws6bhmn77vgmhfjmhwlyr3u7puw4erkyoosywgl67slqqd.onion
-
 @ 04c915da:3dfbecc9
2025-03-12 15:30:46
@ 04c915da:3dfbecc9
2025-03-12 15:30:46Recently we have seen a wave of high profile X accounts hacked. These attacks have exposed the fragility of the status quo security model used by modern social media platforms like X. Many users have asked if nostr fixes this, so lets dive in. How do these types of attacks translate into the world of nostr apps? For clarity, I will use X’s security model as representative of most big tech social platforms and compare it to nostr.
The Status Quo
On X, you never have full control of your account. Ultimately to use it requires permission from the company. They can suspend your account or limit your distribution. Theoretically they can even post from your account at will. An X account is tied to an email and password. Users can also opt into two factor authentication, which adds an extra layer of protection, a login code generated by an app. In theory, this setup works well, but it places a heavy burden on users. You need to create a strong, unique password and safeguard it. You also need to ensure your email account and phone number remain secure, as attackers can exploit these to reset your credentials and take over your account. Even if you do everything responsibly, there is another weak link in X infrastructure itself. The platform’s infrastructure allows accounts to be reset through its backend. This could happen maliciously by an employee or through an external attacker who compromises X’s backend. When an account is compromised, the legitimate user often gets locked out, unable to post or regain control without contacting X’s support team. That process can be slow, frustrating, and sometimes fruitless if support denies the request or cannot verify your identity. Often times support will require users to provide identification info in order to regain access, which represents a privacy risk. The centralized nature of X means you are ultimately at the mercy of the company’s systems and staff.
Nostr Requires Responsibility
Nostr flips this model radically. Users do not need permission from a company to access their account, they can generate as many accounts as they want, and cannot be easily censored. The key tradeoff here is that users have to take complete responsibility for their security. Instead of relying on a username, password, and corporate servers, nostr uses a private key as the sole credential for your account. Users generate this key and it is their responsibility to keep it safe. As long as you have your key, you can post. If someone else gets it, they can post too. It is that simple. This design has strong implications. Unlike X, there is no backend reset option. If your key is compromised or lost, there is no customer support to call. In a compromise scenario, both you and the attacker can post from the account simultaneously. Neither can lock the other out, since nostr relays simply accept whatever is signed with a valid key.
The benefit? No reliance on proprietary corporate infrastructure.. The negative? Security rests entirely on how well you protect your key.
Future Nostr Security Improvements
For many users, nostr’s standard security model, storing a private key on a phone with an encrypted cloud backup, will likely be sufficient. It is simple and reasonably secure. That said, nostr’s strength lies in its flexibility as an open protocol. Users will be able to choose between a range of security models, balancing convenience and protection based on need.
One promising option is a web of trust model for key rotation. Imagine pre-selecting a group of trusted friends. If your account is compromised, these people could collectively sign an event announcing the compromise to the network and designate a new key as your legitimate one. Apps could handle this process seamlessly in the background, notifying followers of the switch without much user interaction. This could become a popular choice for average users, but it is not without tradeoffs. It requires trust in your chosen web of trust, which might not suit power users or large organizations. It also has the issue that some apps may not recognize the key rotation properly and followers might get confused about which account is “real.”
For those needing higher security, there is the option of multisig using FROST (Flexible Round-Optimized Schnorr Threshold). In this setup, multiple keys must sign off on every action, including posting and updating a profile. A hacker with just one key could not do anything. This is likely overkill for most users due to complexity and inconvenience, but it could be a game changer for large organizations, companies, and governments. Imagine the White House nostr account requiring signatures from multiple people before a post goes live, that would be much more secure than the status quo big tech model.
Another option are hardware signers, similar to bitcoin hardware wallets. Private keys are kept on secure, offline devices, separate from the internet connected phone or computer you use to broadcast events. This drastically reduces the risk of remote hacks, as private keys never touches the internet. It can be used in combination with multisig setups for extra protection. This setup is much less convenient and probably overkill for most but could be ideal for governments, companies, or other high profile accounts.
Nostr’s security model is not perfect but is robust and versatile. Ultimately users are in control and security is their responsibility. Apps will give users multiple options to choose from and users will choose what best fits their need.
-
 @ e4950c93:1b99eccd
2025-05-02 10:20:25
@ e4950c93:1b99eccd
2025-05-02 10:20:25
Cet article est publié sur origine-nature.com 🌐 See this article in English
-
 @ 7776c32d:45558888
2025-05-01 13:47:28
@ 7776c32d:45558888
2025-05-01 13:47:28I've edited this post to remove the spam. nostr:nevent1qvzqqqqqqypzqamkcvk5k8g730e2j6atadp6mxk7z4aaxc7cnwrlkclx79z4tzygqy88wumn8ghj7mn0wvhxcmmv9uq3jamnwvaz7tmswfjk66t4d5h8qunfd4skctnwv46z7qpqyrvezvufls3mrzc0att0vw0kw2pavu9pqlfzzrjtph5jrcnm28dqf26e23
-
 @ 21335073:a244b1ad
2025-05-01 01:51:10
@ 21335073:a244b1ad
2025-05-01 01:51:10Please respect Virginia Giuffre’s memory by refraining from asking about the circumstances or theories surrounding her passing.
Since Virginia Giuffre’s death, I’ve reflected on what she would want me to say or do. This piece is my attempt to honor her legacy.
When I first spoke with Virginia, I was struck by her unshakable hope. I had grown cynical after years in the anti-human trafficking movement, worn down by a broken system and a government that often seemed complicit. But Virginia’s passion, creativity, and belief that survivors could be heard reignited something in me. She reminded me of my younger, more hopeful self. Instead of warning her about the challenges ahead, I let her dream big, unburdened by my own disillusionment. That conversation changed me for the better, and following her lead led to meaningful progress.
Virginia was one of the bravest people I’ve ever known. As a survivor of Epstein, Maxwell, and their co-conspirators, she risked everything to speak out, taking on some of the world’s most powerful figures.
She loved when I said, “Epstein isn’t the only Epstein.” This wasn’t just about one man—it was a call to hold all abusers accountable and to ensure survivors find hope and healing.
The Epstein case often gets reduced to sensational details about the elite, but that misses the bigger picture. Yes, we should be holding all of the co-conspirators accountable, we must listen to the survivors’ stories. Their experiences reveal how predators exploit vulnerabilities, offering lessons to prevent future victims.
You’re not powerless in this fight. Educate yourself about trafficking and abuse—online and offline—and take steps to protect those around you. Supporting survivors starts with small, meaningful actions. Free online resources can guide you in being a safe, supportive presence.
When high-profile accusations arise, resist snap judgments. Instead of dismissing survivors as “crazy,” pause to consider the trauma they may be navigating. Speaking out or coping with abuse is never easy. You don’t have to believe every claim, but you can refrain from attacking accusers online.
Society also fails at providing aftercare for survivors. The government, often part of the problem, won’t solve this. It’s up to us. Prevention is critical, but when abuse occurs, step up for your loved ones and community. Protect the vulnerable. it’s a challenging but a rewarding journey.
If you’re contributing to Nostr, you’re helping build a censorship resistant platform where survivors can share their stories freely, no matter how powerful their abusers are. Their voices can endure here, offering strength and hope to others. This gives me great hope for the future.
Virginia Giuffre’s courage was a gift to the world. It was an honor to know and serve her. She will be deeply missed. My hope is that her story inspires others to take on the powerful.
-
 @ a5142938:0ef19da3
2025-05-02 10:26:59
@ a5142938:0ef19da3
2025-05-02 10:26:59Contribute to enrich the site!
Each contribution helps improve this site by supporting the listing of natural alternatives.
💡 What Counts as a Contribution?
A contribution can be:
📝 Proposing a new entry, by providing its initial information. Each piece of information added (name, link, category, etc.) is considered a contribution: - Add a product - Add a brand
📝 Adding or modifying information in an existing entry. Each piece of information added or removed is considered a contribution.
✅ Contribution validation
Contributions are reviewed by the core team. A contribution is validated when the information provided is submitted for the first time (the earliest comment is taken into account) and can be verified.
Once validated, contributions are counted and eligible for rewards. 👉 Learn more about rewards
Information added directly by the core team during the verification of a contribution is not counted. However, core team members can also contribute just like anyone else.
This article is published on origin-nature.com 🌐 Voir cet article en français
-
 @ 7776c32d:45558888
2025-05-01 13:41:58
@ 7776c32d:45558888
2025-05-01 13:41:58The nostr:npub12vkcxr0luzwp8e673v29eqjhrr7p9vqq8asav85swaepclllj09sylpugg Android app will no longer load anything for me at all, as of today.
Much worse and harder to fix, they have added a "delete" feature before fixing the "advanced search" functionality for my account. They also haven't given me any answers on the topic since nostr:npub1zga04e73s7ard4kaektaha9vckdwll3y8auztyhl3uj764ua7vrqc7ppvc told me he "couldn't repro" and left it at that.
The so-called "delete" feature is of course not actually able to reliably delete posts from nostr. It will probably hide posts from Primal's so-called "advanced search" but a more honest "hide post from Primal users and remove Primal's infrastructure from efforts to publicly preserve it" button would be more embarrassing for a VC-funded corporatist nostr app to implement.
This means the "advanced search" will never be reliable for me, when it was one of the most essential features I paid over a million sats for, the day Primal "legends" launched. Despite me being a day-1 subscriber, Primal spent the first several months ignoring my posts on the topic and keeping me blocked from search functionality to make it harder for me to use this feature to help find evidence in disputes, as I paid to be able to do; and now they've added post deletions before fixing it, so whenever they finally do "fix" it, I will still need to use a different tool in order to find posts others deny making, since this one allows the posts to simply be gone.
Being a Primal "legend" also no longer means you'll stand by your past statements and face scrutiny for them. Of course, it never did, since tons of Primal "legends" are high-follower npubs who have me muted. But at least their "legend" subscriptions meant they contributed to fund the infrastructure to help Primal keep posts forever, with no deleting.
Now, it seems like I'm the only one who had that intention. The really influential "legends" never wanted a permanent record to show their statements could face scrutiny. People like nostr:npub1qny3tkh0acurzla8x3zy4nhrjz5zd8l9sy9jys09umwng00manysew95gx + nostr:npub1rtlqca8r6auyaw5n5h3l5422dm4sry5dzfee4696fqe8s6qgudks7djtfs + nostr:npub18ams6ewn5aj2n3wt2qawzglx9mr4nzksxhvrdc4gzrecw7n5tvjqctp424 and others saw me trying to hold them accountable. I'm guessing at least one of them wanted to be able to block me from using search functionality, to make it harder for me to find my past conversations with them, or their past posts on a given topic. They seem like people who would be happy I was blocked from that functionality for a long enough time to roll out post deletions and make sure the issue could never really be fixed for me. Or maybe every high-follower npub is one of those people, since none of them have really helped me with this by reposting my posts about it or anything.
In the mean time, did they fund other projects that help ensure a controllable record?
Did any of my fellow Primal "legends" give a million sats to some other project to run a nostr search engine with the same filtering options, and a permanent record of past posts? No. There is no other nostr search engine with the same filtering options and a permanent record of past posts. I can't fund such a project alone.
Do I have a tool I can use to easily make backups of a list of npubs and search their posts locally, with the same kind of filtering options, on my own system? Also no.
My best bet for reviewing my past interactions with an npub is now the list of all interactions in jumble.social which takes a while to dig through, but it's a welcome addition to nostr. Much better than nothing. Nostr.band is still my best bet for finding a given npub's past posts on a given topic.
Where are posts being stored forever right now? Hopefully more than enough relays, but apparently not Primal's. Maybe not enough overall.
My guess is, some posts will continue to end up being lost forever, or too obfuscated to find with whatever search tools I have available. Sometimes, these will probably be disputed posts that the original posters deny making, and I wouldn't be surprised if one of those posters turned out to be a so-called "Primal legend" - which isn't what those words were supposed to mean when I paid a million sats for permanent post archival and search access on a decentralized, censorship-resistant social media app.
Of course, the number 1 reason I paid for Primal "legends" was to make it more embarrassing for them to censor me. At the time, it seemed like they were making the app's cache connection much slower and less reliable for me than other users, and silently filtering my posts and/or notifications for other users. I assumed they would find it too embarrassing to keep being so blatant about this, and that has worked so far. They clearly still target me, perhaps as intensely as before, but not as blatantly.
-
 @ a5142938:0ef19da3
2025-05-02 10:24:43
@ a5142938:0ef19da3
2025-05-02 10:24:43
This article is published on origin-nature.com 🌐 Voir cet article en français
-
 @ 5188521b:008eb518
2025-05-02 10:19:17
@ 5188521b:008eb518
2025-05-02 10:19:17Fabian Sixsmith leaned closer to the screen. A couple of white pixels fizzed through the frame, and the hairs on his arm prickled. It had to be her. The blonde. Underworld’s most wanted — T1n4Red.
It was nearing daybreak in Lewistown, Montana. The end of yet another 14-hour shift at the DoS facility. Pulling fourteens was tough on his body, but it reduced the time it would take for Fabian to gain promotion to agent. Working at the Department of Surveillance came with the serious drawback of being labeled a snoop, but agents could be free — solid pension credits and private property. But today, he would not slink back to his closet-sized studio for buttered noodles and two hours on the velobike. Today would be the day he proved his work was responsible for locating T1n4Red. Her crimes were manifold; her methods were meticulous. Operating encrypted communication networks and thousands of transaction joins to obfuscate Underworld finances. Fabian flipped the plastic cover of the alarm on his console and pressed the button.
Agent Williams appeared behind him in seconds. The babble of voice commands in the CCTV facility cut to zero. “Situation update, Operative Sixsmith.”
Liquidating the bad guys had been the dream ever since his father lost his college fund to a hacker. Cypherpunks came in all guises, and some could phish credits from careless Boston drunks and cover their tracks with encryption. Fabian opened the dossier on his desk. “Tier 1 target located. DNA confirmation requested from ground team.” He was certain. So many nights following encoded messages he found hidden data in images on the public comms ledger. Many were drop sites for the scumbags who delivered supplies to the Underworld in exchange for bitcoin — the only money the government couldn’t meter out and strip away automatically. That pixel of white had to be her blonde hair vanishing, once again, underground.
“Enhance the facial image,” said Williams.
There was no clear image to enhance. Fabian would have some explaining to do if he was wrong. Except he couldn’t be wrong. Those pixels had been his life for the last ten months. Finally, he had trapped her. Straightening his glasses, he prepared his reply. “I can bring up the drop locations from the LSB ima—”
“Operative. What is the protocol required to initiate a Tier 1 alert?”
Fabian could feel the heat of his boss’s glare. “Agent, there is insufficient facial recognition data, but if you give me a minute…” He had captured dozens of steganographical messages — locations, account numbers, usernames. Hiding messages in plain sight was apparently how cypherpunks avoided detection with such ease.
Williams was already patching through to the ground team on his Neurocomms link. “What’s your ETA on the location?” He furrowed his brow. “Copy that... proceed.” Turning towards Fabian, he snapped his fingers. “My office. Now.”
According to Fabian’s calculations, the ground team would report back with the DNA scan in three to four minutes. When they got a match, she’d be toast. T1n4Red would be underground forever; if she resurfaced, the dronecopters would gun her down in minutes. He just had to stall Williams until the confirmation came through. That might be the only way to avoid his first ever sanction. Having a blemish on record would set his lifeplan back by several months. He thought about requesting a comfort break on the system, but Williams would deny it. Fabian stood up purposefully. He arranged the chair and a few items on the desk, then dragged his feet all the way to the office.
Each agent in the DoS facility had an area of control around the size of a football field. Their 12’ by 12’ office comprised the only enclosed space and was positioned in the middle of rows upon rows of desks. Four walls of two-way mirrored glass formed the raised office cube — a mini panopticon within the greater panopticon of DoS. The agent sat in the swivel chair and swung his feet onto the desk. “You better be right about this, Sixsmith, or you’re done here.”
Fabian’s heart beat like a heavy bass kick. The perfectly calibrated 67-degree air didn’t stop him from wanting to loosen his tie. When he jammed his fingers down the small gap between his neck and collar, they came out slick with sweat. All those nights chasing. The tabulations, the data models, the transcripts from Underworld detainees, the ciphers he’d decoded — they all seemed like a game. A dream. He was the grizzled sheriff finally placing the noose around the neck of the uncatchable outlaw. He knew that in sixty seconds or so, the ground team would confirm a DNA match, and it would be impossible for T1n4Red to resurface without physical liquidation. “I’m sure, sir. This was the only way. We’d never get a facial match on a Tier 1.”
The agent looked at the communicator on his desk. Nothing.
Did T1n4Red eat buttered noodles and work out in her underground living closet? Did she crave for the feel of a paperback novel, or perhaps own a non-cataloged copy? It’s not like she could step foot inside the state knowledge center. “What action will DoS—”
Ground Unit Bravo to Williams. Do you copy?
“This is Williams. Over.”
Bravo commander confirmed the DNA match. It was her. She would now be classified a subverter. The payment instructions she had etched into the self-repair polymer bench had been photographed. Any wallet receiving those coins would be investigated. The fintech arm would already be working on liquidating affiliated Overworld accounts. One wrong turn and they can shut down your life’s wealth.
But T1n4Red was smarter. DoS would always be one step behind the cypherpunks because they were bound by government protocol, unable to infiltrate the Level 3 realm of encrypted private comms. Fabian had to take risks. What use was all his dedication if it just led to being remaining on the outside of a panopticon looking in?
“You can leave.” Williams motioned to the office door. “Your shift was over sixteen minutes ago.”
The State Knowledge Center smelled of the past. That’s what Fabian liked about it. He turned the page, savoring the quality feel of thick paper, imagining that when this book ran through enough hands, the inked fibers would run from black to gray to cream-white and the story would be gone. These were some of the only off Ledger items left in the country.
Wild Country Outlaws was Fabian’s sanctuary from the pressures of his job. All fiction was based on the kind of truth that needed to survive. Back to the times when eyes touched words without being digitally tracked, when citizens could own things. He read a paragraph and closed his eyes to imagine how life was back then. The cavernous knowledge center, with its hard seats and CCTV lenses transformed into lush plains and steep hills. Fabian felt the warm breeze on his face and the muscles of the horse beneath him. The two rifles slung on his back would shoot those boys dead. No one would take his property. His wife, children, his lame brother, hell, the whole damned village of Lewistown depended on his cattle to provide.
Of course, land could only be leased now. Livestock too. Those rustlers would have a hard time taking anything without public subscription fees and pre-taxed profits coming out. And if they wanted, the Department of Property could rescind custody of any item and confiscate it. Fabian’s smart-band vibrated, indicating he had just ten minutes of reading time left. The thing buzzed too hard. It pinched, but like all sanctioned hardware, it was government hard-coded.
He hadn’t been able to focus this time. Not really. Was T1n4Red an outlaw or a rancher? Either way, she was fighting the system that had stripped Americans of their right to call their house a home. According to the Department of Education, pre-ledger days were violent wealth-disparity wars, but the novels Fabian read painted a different picture — a fantasy freedom where ordinary citizens could build wealth.
Fabian rose to go. He handed the book to the desk girl and watched her scan it into the system. His smart-band buzzed again with a compliance point. To think his friends chased these stupid tokens for avatar upgrades and paid-time-off options. But, without them, he might end up with his ID frozen like his high school buddy, Scott, cut off from all legal avenues to earn a living and watched like a hawk by DoS. Did he have a secret stash of satoshis that kept him clear of the state debtors’ facility?
The lady at the desk smiled. Her brown bob remained undisturbed by the air cooling system. “We hope you enjoyed your trip into our analog archives, Fabian.”
“Sure. See you next time, Miranda.” He breezed out. They had history, but it wasn’t something he was interested in repeating. Imagine the conversations about cataloging systems and the internal squabbles of the Knowledge Center board. Fabian was already in a committed relationship with the powers of his imagination. Explicit videos were far too risky for a DoS worker to use, but the image of T1n4Red’s full lips and blond hair invaded his dreams. They could run a ranch together, or maybe they’d be cattle rustlers on the run. He wasn’t sure why, but every night, Fabian masturbated to the one rendered CGI model of T1n4Red they had on file. On the outside, his life was the ultimate mundanity, but the thrill of T1n4Red, the taste of the air on the great ranches outside the city, the sheer danger of even thinking all this, was the only way he could sleep.

They watched the pollination drone flit between the hibiscus flowers in the thick air of the botanical biodome. Fabian had been lucky to receive two of the limited daily visitor passes. It was even luckier for Scott, who now had the chance to get out of his mom’s dingy basement for a few hours.
“You know why they made them bigger than bees, right?” Scott spoke out of the side of his mouth. When Fabian shrugged, he leant in to inspect the device hovering around eye level. He blew a kiss and waved at its pollen-collector end.
“You don’t know that.”
Scott turned and swept his lank hair off his forehead. “You're the one who checks the footage, snoop.”
Micro cameras were yet another panopticon in the armory of the State. You had to assume, even when lying in bed with a lover, even when going to the toilet, that it was possible you were recorded, watched, and analyzed even years later. Secrecy was a virus DoS sought to eradicate.
The biosphere wristband on Fabian’s right arm sounded. Closing time was fast approaching. Fabian put a hand on Scott’s shoulder. “You know, there was a time when access to nature wasn’t so strictly controlled.” He stopped himself from saying more.
They joined the crowds heading to the exit down the palm pathway. “You heard about the latest blacklist?” asked Scott. “The mixnets are awash with it.”
Fabian’s neck muscles tightened. “You shouldn’t be telling me you’re on those forums.” Until he became an agent, even Fabian was prohibited from accessing the decentralized ‘Level 2’ network.
Scott laughed. It was the first time Fabian had heard him laugh that day. “That’s the fun of this little game, homie. Encoding and decrypting ciphers is living. It’s all I got apart from running from debt.” He lowered his voice. “My identity is already in prison, but I ain’t going too.”
Glancing left then right, Fabian made a decision. It was a decision to offer information to a friend, a true friend who had no reason to stick by him when all others cut ties. Sharing a secret in the meatspace was the biggest risk Fabian had taken in years, but he had no way to do it digitally.
“I was behind it.” He expelled a sigh.
Scott turned his head. They carried on walking towards the exit in the throng of people. A few seconds passed.
Fabian scratched at the mole above his eye. “Spent months unraveling stego messages. I feel like I know her. Like really know her.” Was he saying this out of pride or trepidation? Even if they ended in constrained mediocrity, lifeplans were so beautifully simple. Tina, Williams, the ranch, avenging his father’s bankruptcy, the forums, the caution, it all seemed so jumbled. “Maybe I’m in love.” What was Fabian saying? However long T1n4Red lasted underground, she’d never be able to surface again.
Scott bumped Fabian by stepping across his path. “Not in the meatspace. Keep checking the images. There’s a lot more hiding in plain sight than you know.”
They walked in silence through the automated exit gate into the gray city air. As they departed, Scott turned back and called out, “Right pocket.”
Sure enough, Fabian felt the weight of a ‘brick’. He had held one of the untethered devices once in DoS training. Without even putting his hand into his pocket he knew that it was there and what it meant. Decentralized forum instructions would be written on an attached note. The code would be something only he and Scott knew. T14nRed and the entire underworld were now at his fingertips.

23:43 - untethered alert.
Invitation to join Level 2 CP mixnet.
Confirmation Key: M0ntann4Sc0ttySn00ps2031
Fabian lay back in his single bed. He followed the personalized invite link Scott had generated. It must have been strange, he thought, when space was not at a premium, when people went for a walk to escape, rather than lie on their bunk and plug themselves into a metaverse or L2 world. The Ledger made everything easy, an all-in-one software system for citizens so dialed in to their lifeplans, they didn’t have a second to spare. That’s how it had seized control of the nation.
The forum loaded and he found his welcome message from Scott.
Relay from T1n4Red:
It is never too late to use the powers of surveillance for good, Operative Sixsmith. Underworld 4gives but the ledger does not 4get.
In the darkness of his cabin, his face bathed in blue light, Fabian sat bolt upright. His head broke the plane of the holoscreen and a tinge of current trickled through his temple. She knew who he was; she knew what he had done. A charge pulsed through him, the thrill of true privacy. How had he been duped into thinking a total lack of encryption guaranteed freedom and not a glass cage?
The holoscreen flickered for a second. A multimedia message.
Level 2s were a gray area, not illegal. Messages could be relayed peer to peer along a mixnet to the end user. With personalized links hidden in messages on the public comms ledger, communities could be discerning about who joined.
When Fabian leaned back into a lying position, he was greeted by a 3D render of the woman he’d been chasing for over a year. His eyes drank in the red-lipped smile and blonde hair of the woman he’d forced underground, never to feel the rays of the Montana sun again. She held a piece of paper up to the camera, but Fabian couldn’t tear his eyes from her piercing gaze. 64k cameras could pick up the tiniest imperfection. She looked even more real than if he saw her in the flesh. The piece of paper she held was another invite code — this time to an L3 channel.
Fabian exhaled. Breathe. He ran his finger over the chain of three tiny moles above his right eyebrow as if checking they were still there. There were agents who’d been on the force for decades without penetrating Level 3. All messages were stored on the Ledger — that couldn’t be avoided. But with all the red herrings and strong encryption, it was impossible for even the most powerful computers at DoS to uncover much about the members of Underworld’s inner circle. Fabian’s hand reached for his untethered brick. He entered the address from the 3D render of Tina’s paper, followed by the 24-character code from the paper on the outside of the brick. He was in. His next shift at DoS started in ten hours, but he knew he wouldn’t sleep much before then. Tina, and the Underworld answers he’d been seeking awaited on the L3 forum. Fabian made his way to the bathroom and rooted out an old lighter from the medicine cabinet. Staring back from the mirror was his reflection; perhaps it was an avatar of him bound for the Underworld while he remained in the meatspace with his tiny closet apartment and faltering lifeplan. They both watched the password on the paper note burn.
The hubbub of DoS Sector 4A quietened as Fabian walked down the corridor. The hum of hundreds of microcameras was imperceptible to human ears. The one place without them was the toilets — a DoS employee committee had made sure of that — and that is where Fabian’s untethered communicator brick lay. Even if it was found on a bug sweep, they couldn’t trace it to him. And he had ten minutes every two hours to get to the bathroom and check in.
At first she’d been cautious, wanting to know if Fabian would follow her precise instruction. Then, information from Tina had came fast and furious. Names, transactions, locations, protocol, so much information. The tips she’d provided checked out. In fact, they were all just about low-level enough that it was believable that Fabian’s data-driven detective work had unearthed them. She’d even provided a methodology to show which macros and filters he could use to locate L2 peddlers and fixers.
He removed the floor tile behind the toilet bowl. This never got less gross. After relieving himself and pulling the flush chain, he attached the remote charge pack and switched it on. No battery, no trace signal.
11:03 - Message waiting: 6Smith, something important is about to happen. Act surprised. After confirmation, we must meet in person. It will not be easy to get you here. Instructions will follow.
Fabian heard the toilet door open. Could DoS be employing physical spies without the use of cameras in the bathrooms?
The sound of a belt buckle. Charcoal-gray trousers descended and appeared on top of brown loafers through the little gap under the cubicle wall. The heavy-set man dumped himself onto the john and exhaled.
After he deleted the message, Fabian switched off the phone and wiped the power back into his remote charger. He scrubbed his prints off the brick and replaced it behind the bowl. Another flush and he was gone. Out the door before charcoal trousers could physically tie him to the brick. If he was snooping, they would know. He’d get questions about using an unsanctioned jailbroken device. Maybe he could claim he was trying to arrange a physical meeting with T1n4Red. Still, the interrogation would be brutal.
Back on the floor, Agent Williams activated a meeting alert on Fabian’s desk. The red light informed him he must report to the cube immediately. It took great restraint for Fabian to avoid any nervous ticks. Especially with the scrutiny of operatives at his level, he couldn’t avoid a single nervous exploration of the moles on his temple or wiping of hands on trousers. The electronic band every citizen had clamped around their right wrist fed streams of bio-data to the DoS servers. Who would be alerted if his heartbeat spiked or breathing patterns changed? As he’d learned on the L2 forums, flying under the radar took a lot more than digital restraint. The surveillance apparatus of the state kept so much biometric data it had become a living cyborg. Could this be about the bathroom break? The guy in the next stall with the charcoal trousers? The brick? Was this the start of a downfall that ended in the same invisible blacklist Scott was on? Maybe that chick in the library had something against him too.
The glass door slid open and Fabian moved through the entry point in one clean step.
“No need to sit, Operative Sixsmith. Let’s stay on our feet here.”
Sixsmith awaited the news. Whatever it was, at least it would be quick.
Williams raised a stainless steel travel mug to his lips and drank. If the coffee was hot, he showed no signs of it. “I must admit, I’ve had my doubts about you.” An ominous start. “Up until this year, your work was adequate.” Williams paced towards the glass wall to watch the goings on of the morning-shift operators. His invisible stare could put someone’s back out. “And that stunt you pulled to get the jump on T1n4Red… some stricter agents might have filed that as a denial-of-protocol infraction.”
Fabian locked his gaze to the coffee cup and let him talk.
“But since then, your results have been quite something. An 89% strike rate on intel and twelve L2 agitators liquidated. That’s as high as I’ve seen.”
“Thank you, sir.” Fabian rearranged his cotton shirt, which, despite the blasting air con, was stuck firmly to his back.
“Good news.” Agent Williams went to his desk drawer and removed a six-inch blade. The silver tip matched the glint of William’s graying hair under the strip light. “You are no longer an operative here at the Department of Surveillance.”
Fabian imagined the angle of attack. A diagonal slashing motion from up high. He wouldn’t have time to avoid the agent’s quick reflexes.
“Congratulations, Agent Sixsmith.”
Fabian took a step back. His right hand found its way to his brow. “What?”
“You’ve been promoted, son. It can’t be that much of a surprise.”
Fabian had spent so long tracking certainties, he had forgotten what surprise felt like. He had his doubts about the system, his L3 secrets, his upcoming liaison with T1n4Red, his friendship with Scott. But things would be better as an agent. His family back in Boston would surely offer some begrudging respect. If he wasn’t six feet under, his old man might feel some kind of peace knowing his boy had won back those credits. Freedom from bio-data collection and freedom to roam. He faced his boss. “But I’m not up for review until—”
“Take the win.” Williams approached, knife in hand. “We need all the capable agents we can get.” He reached for Fabian’s right forearm. His grip was that of a much bigger man. “Effective immediately, you are Agent Sixsmith of the Department of Surveillance.” He slid the knife under Fabian’s communicator wristband and sliced through the strap.
The cool office air touched his now naked wrist. Fabian smoothed the skin as if he had been unshackled.
Once Williams returned the knife to its drawer, he offered his hand to shake. “Congratulations, Agent. Full briefing tomorrow at 0930.”
“Yes sir. Thank you for your trust.” He turned to go.
“Stop,” a sharp voice called. Williams held a small piece of metal between thumb and forefinger. “Don’t forget this.”
Agent Fabian Sixsmith accepted the gift — an American flag pin. He nodded and stepped through the doorway in the same way he entered.
](https://image.nostr.build/b3cff409a4d05409b84ddd61f9689f707b24376f196887558c2eaee1d17c8275.jpg)
Fabian zipped his thick hoodie and stepped out into the night. The reflectors in the fabric would dazzle the night vision of the cameras, and the Federal Government hadn’t passed any laws telling people how to dress… yet. He opened the door and set out to meet his handler.
He started his run towards the city outskirts, the hood shrouding his adrenaline-shot eyes. The back of his skull throbbed. It had been bothering him all afternoon. Throwing in a few boxing moves for good measure, Fabian pounded out the miles. One, two, past the city limits and onto the shoulder of the 87, the sixteen-wheeler auto rigs ripping past. The drones would be following — of that he was sure.
His handler was there. Just like Tina said. Half a mile after the first junction, under the bridge, Scott straddled his solarbike. This must be how he earned his sats — acting as a go between for Underworld agents who had gone to ground.
No words, just the exchange. Fabian unzipped the hoodie and draped it over his friend’s shoulders. Scott removed a 3D image scanner from his pocket and ran it over Fabian’s face. Two seconds and the ID confirmation would be relayed on the Ledger, probably embedded with a stego message. A quick clap of the hands, and he drove into the night. Forty, fifty, sixty, and gone, west towards Great Falls. Fabian took a breath. Is this what he had done all those reps in the closet for? He scrambled up the bank and jumped for the bridge railing. Hauling his body up and over in one swift motion. Then, crouching low behind the advertising hoarding, he duck-walked over the bridge and down the bank. How would he disable the micro cameras? Even without tracking data, the DoS apparatus wouldn’t be far behind — especially after they scrambled a drone to intercept Scott. Thirty seconds tops.
This place, just a few miles away from Lewistown, was the setting for one of those books he loved — cowboys, sheriffs, and theft. Of course, the subterfuge of Level 3 protocol and 256-bit encryption was a little more complicated now. The idea of coding messages is as old as civilization, only the attack vectors changed over time.
Left. Right. Feet smacking dirt. Fabian had to trust the track was level. He could barely see three feet in front of him — only the dim Montana moonlight for company. The whirr of a camcopter approached overhead. If it locked his thermal image, he was toast. Just a few more strides surely. His lungs burned after all those miles.
DoS wasn’t just going to let a newly-minted agent go for a mysterious wilderness night run.
His foot jammed against a root. He stumbled on, narrowly avoiding a painful fall.
“IDENTIFY ORDER.” The camcopter had locked the human gait recognition. “FAILURE TO COMPLY EVOKES FEDERAL CREDIT ELIMINATION.”
Fabian almost laughed. These fucking things threatening to zero-out people’s hard-earned savings. How the hell had Americans let things go this far? He spotted the manhole cover under the tree. His lungs sucked in the night air, and his heart tore at his ribs.
Wham. Down to the ground. The force of a truck pinned Fabian and pushed his face into the dirt. “No,” he cried. “Let me explain.” Searing pain pulsed through his skull from the back to the front. In the seconds that followed, it was as if his brain was rebooting. Who was this? What were they doing?
“Neural tracer deactivated,” said the voice of the brute on top of him.
Fabian managed to turn his head. He caught a glimpse of the man, but it was too dark to see his face. The pressure on Fabian’s back slowly released. He shook the cobwebs out of his head.
As Fabian stood, he saw the guard moving away, pointing his EMP caster at the sky, sweeping left then right.
Crash. One dronecopter downed. A crash to the right, another drone gone. These things would be disposed of in some pit or quarry. The figure collected the drones and moved into the night.
Fabian dusted himself off and walked towards his destination of the irrigation pipe system. As Agent Sixsmith hauled the steel grate to the side, he took a breath. This was it. Too late to deny involvement. Too far down the rabbit hole. He’d have to give up everything he worked for — respect at Thanksgiving and a pension large enough to retire to a ranch and ride a horse over the land. In exchange, he’d get a one-time Underworld trip, where he would learn the methods and tactics the punks used to stay off grid.
Now it was quiet, bar the low hum of the highway and the sound of his rasping breath. He’d never been this alive. It sure beat the meticulous protocol of DoS. Before he could stop himself, Fabian was inside, his hands replacing the grate, gripping the ladder, his feet on the rungs, stepping down, down into the dark. Whatever she had to tell him, he needed to hear it. Meeting T1n4Red in the meatspace trumped any handshake from Agent Williams, any pension plan, and any begrudging respect from his nagging mother and fucked-up family. He descended to the Underworld.
At the end of the dank tunnel, Fabian saw the purple glow of UV light. He approached slowly. The sound of soft footsteps approached from behind. He didn’t dare turn. Then, a few paces from the curve where the light grew stronger, a flat plastic object jammed the base of his skull forward. Click. Probably a 3D-printed gun.
“Arms out. Legs astride.”
Fabian complied. The EM scan wouldn’t find anything. He was stripped of all tech — one of the many firsts he’d experienced that day. It was safer for all parties if he didn’t turn around.
The voice barked, “Clear,” and a rough hand pushed him forward. The footsteps descended back towards the tunnel opening.
Peering into the mirror positioned at the tunnel corner, Fabian caught a glimpse of the woman he came to see. The channel between well-defined back muscles drew his eye south. How long had it been since he felt the touch of a woman? How did she stay in such good shape down here? The weak UV light faded to a soft yellow glow in the chamber.
“Agent Sixsmith. We’ve been expecting you.” Tina pulled a t-shirt over her bra and cinched her blonde hair into a top bun. She laughed. “Take a seat.”
“How do you know I’m an agent?” Fabian sat on the plastic chair closest to him. The room had been widened from its original layout. It was now around fifteen feet square with a camp bed, a desk with double monitors, and a treadmill. His eyes settled on the black desktop compu-box.
She touched his arm, her hand surprisingly warm. “I bet you’d love to open that up and take a look.”
Fabian had never seen a homemade device connected up. Getting the parts must have taken years, but nobody could detect unregistered tech through lead linings and all the perimeter protocal. She truly owned something, even if it was just a little black box.
“You didn’t think agents are unsurveilled, did you? Poor boy.”
Fabian’s mind switched to rational mode. Was he burned? Would he ever be able to surface without getting financially or physically liquidated?
“Relax. I know what you’re thinking. This is your first trip here, but it won’t be your last. We fried your tracer chip and they can’t admit they implanted ‘cause it ain’t legal.” She swiveled the computer chair and sat on it back to front. The high chair back almost came up to her chin. “You get one question. Shoot.”
In their digital conversation, Tina had always been careful to give instructions only, never responding to Fabian’s questions. He might have a lot to learn, but at least he wasn’t living in the dark like her, a trapped soldier unable to look above the parapet. Was he walking into a trap? Was he already in one? If things got tough in the interrogation he was sure to receive from Williams, he could always offer some Underworld secret. Fabian turned to face the shadow of a woman he had chased for nearly a year. “Where are the Level 3 relay servers kept?”
“Ooh amor, you’ve gotta think bigger than that.” Tina Red was more than just a celebrity crush. Her blue eyes burned with the intensity of a neutron star. Her slender legs wrapped around the chair like a boa constrictor drawing in its prey. She drew closer, and he could smell the sweat. “There are no dedicated L3 relay servers. We’ve been using a hacked DoS server for months. Keeps you searching for that mythical Underworld data center, right?”
There were so many units in the DoS server cities that it would take years to isolate the hack. Smart. “What’s the end goal to all of this?” he asked.
Instead of replying, Tina shook her head.
Play by Underworld rules, Fabian. It didn’t matter — he knew. Reversing the grip of the big-government machine was virtually impossible, but the dream was that the country returned to ‘the land of the free.’ Freedom to secrecy. Freedom to own. Freedom to transact with whomever you wanted.
Fabian watched as T1n4Red stood and crossed the six-foot gap between them. She leant over and moved a hand to the back of his hair, gripping his short black hair in her fist. The same fear pulsed through him as in the meeting he’d had with Agent Williams — the same Williams who was organizing the search and interrogate protocol for him at that very moment. Was her bodyguard waiting around the corner with the 3D-printed gun, primed to deliver its one shot straight into his brain?
“This is our endgame.” Their faces were inches apart. He saw the same freckles and imperfections in her skin as in the high-res digital render. But there was nothing like real life.
And then, a swell of the tide inside him. Euphoria. The kiss was deep. Their lips fused, one person, one dream. Fabian’s hands reached for the shape of the woman he’d dreamed about so many nights. She sat, straddling his legs and they went on. Blood rising like an ocean swell, Fabian dived into bliss. It all melted away — the dronecopters hovering above, the awkward entry to the office tomorrow, the nagging fear that his accounts would be zeroed out in mere hours. But one image remained. The moment transported Fabian to his spiritual home — the wilds of the Montana hills, the wind blowing through the grassland, the mountain range guarding the horizon. The wild country that called him.
When they finally broke the kiss, Tina stood. “Did you feel it?”
Fabian raised his gaze. “I think so. A place. The wild—”
She raised a finger to silence him. “Don’t say it. This is our secret, Agent Sixsmith.”
He thought for a second. Project Wild Country. It was strange, but he had no doubt. The phrase was branded into his mind clearer than the passphrase he had to memorize for his DoS access. How could two beings communicate telepathically?
“It’s called ‘Telepathic Key Exchange’. TKX for short.” Tina approached and whispered into his ear. “From the mentalists of the late 20th Century.” It had been there all along — a method to eliminate the gap where biological beings had to enter a passphrase physically. This was only part of the information chain without a cipher. No more worries about the micro cameras that could capture keystrokes or capture pen and ink comms.
“Our project,” she breathed.
The image swam through Fabian’s mind once more, the color of the sky as vivid as the eyes of the woman in front of him. The hills and plains in front of them. All protests start with the spark of non-compliance. And all revolution hinges on the man who knows how to play both sides. He’d have to learn more about it, understand it better, but TKX could lay the path to a fully anonymous market, unbreakable smart contracts, and a citizens’ private arbitration court. This would be the rewilding of America.
“We only have a few more minutes.” Tina returned to her chair. She explained the comms protocol and that the two of them were the only people on Earth to know the name of this mission. Project Wild Country would bring TKX to the masses.
“How can we teach people?”
“We lead people through the levels, just like I got you here. There are more stego images on the Ledger every day. It’s already started.”
Fabian looked at the wrist his bio-band had once gripped. “What do I say to DoS to explain this time-gap?” How long had he even been down there, fifteen minutes?
“You wouldn’t be much of an agent if you couldn’t think of something. Be the sovereign of yourself, Fabian.” T1n4Red laughed. “Better get running.”
Fabian moved toward the dark tunnel that led to a surface world buzzing with invisible spies. “I’ll be thinking of you,” he said. Fabian thought he detected the hint of a smile on Tina’s lips, and he felt a tiny swell of the euphoria that had filled him moments earlier. Then, he turned to go. Agent Sixsmith rounded the corner and started his journey back to the wild country.
This story first appeared in Financial Fallout. Find out more about the book at 21futures.com
21 Futures retains 21% of the zaps received to cover operating costs. The majority of the sats are forwarded to the author.

Max Hillebrand is a praxeologist who contributes to several open-source projects, because code is abundant and not scarce. He shares his work freely for others to use and modify. His goal is to help build a parallel economy based on sound money and individual sovereignty, where people can pursue their entrepreneurial ambitions without interference from central authorities. Find out more at towardsliberty.com
-
 @ bf95e1a4:ebdcc848
2025-05-02 10:00:55
@ bf95e1a4:ebdcc848
2025-05-02 10:00:55This is a part of the Bitcoin Infinity Academy course on Knut Svanholm's book Bitcoin: Sovereignty Through Mathematics. For more information, check out our Geyser page!
Holding On
In the old days, we Scandinavians had to save in order to prepare for the long winter. We chopped wood and salted meat in order to survive. In our current age of consumerism, however, we’ve forgotten all that and we pilgrim to the shopping malls as much as everyone else. No one seems to even have a savings account anymore. Interest rates are low, and we’re told to borrow and spend as much as we can. We’re bombarded with advertising for loans, mortgages, and financial services on a daily basis. Why? Because of our inability to understand the nature of money and its mechanics. Inflation is the underlying force that makes us squander rather than save. Inflation hinders us from reaping the fruits of our labor whenever we see fit, and it makes that very fruit rot. Bitcoin reverses the rotting process and provides us with a means of transporting the value of our labor not only through space but also through time.
The Stanford Marshmallow Experiments was a series of studies on delayed gratification conducted in the late 1960s and early 1970s. In these experiments, children were given a marshmallow or a cookie and were told that they would receive an additional one if they could control their urges and not touch the first one for fifteen minutes. Follow-up studies found that the kids who were able to resist the temptation of the first cookie tended to score better on SAT tests, have lower BMIs, and higher incomes than their less disciplined counterparts. Investing in your future self — in other words, resisting present temptation by delaying gratification — is the most effective skill you can cultivate for a brighter future. You reap what you sow. This can be described as having a low time preference. Having a low time preference is a fundamental factor in the economic success of any human endeavor. Not trying to catch fish with your hands for a couple of days in order to construct a rod or net when on a deserted island might make you hungry during those sacrificed days, but it will provide a better chance of catching fish in the future. Likewise, learning new skills now might lead to a higher salary in the future. Unfortunately, our current monetary system distorts our perceptions and incentives and favors those with a higher time preference — those who spend rather than save. We’re at a different point in history than the above-mentioned marooned fisherman. "Give a man a fish and feed him for a day, teach a man to fish and feed him for a lifetime," the saying goes. The ultimate goal should be to teach mankind to teach itself how to fish. What our current paradigm endorses is “give a man enough distractions, and he will stop thinking about finding better ways to support his loved ones and will succumb to whatever narrative you fill his head with, to make him work for you through taxes and inflation instead of for himself.”
In Bitcoin, people with a low time preference win. If you can resist the urge to sell, you will be rewarded in the future. The Bitcoin community refers to not selling as HODLing, which originated when a bitcointalk.org forumer named GameKyuubi misspelled the word holding in a now-famous post titled "I AM HODLING." The post became one of the Bitcoin community’s most prominent memes and a battle cry to resist the urge to sell during bear markets. Bitcoiners who have decided never to sell most or all of their holdings are referred to as HODLers of last resort. This term is not to be confused with the central banking term lender of last resort. The yearly highs in the price of Bitcoin are arguably less interesting than the yearly lows, which are practically decided by these HODLers of last resort. Considering its limited supply, all that Bitcoin needs to keep rising in price over the medium and long term are these people. Adoption and other metrics of measuring the success of Bitcoin are all dwarfed by the currency’s remarkable rise in value since its inception. The price has increased by a factor of ten approximately every three years. The best guarantee we have that it will keep doing so is Bitcoin’s limited supply combined with the HODLers of last resort.
In the Bitcoin space, and even more so in the cryptocurrency space on the whole, there’s a lot of talk about usage and adoption. We’re shown metrics of trading volumes and merchant acceptance, and we’re led to believe that these correlate with the short and long-term value in one way or another. While there may be truth in some of these theories, the most basic function of a deflationary asset is overlooked and rarely mentioned — the elephant in the room, so to speak. The best use for a commodity as scarce as Bitcoin is not to spend it or even to trade it but to save it and hold it for as long as you can. By doing so, you limit the number of coins in circulation. The more people that do this, the harder it will be to come by and the higher its price will be. Nothing on Earth is as scarce as Bitcoin. Nothing is as irreplicable, as immutable, and at the same time as portable as Bitcoin — its unique history and resistance to change have already proven this over and over. Its absolute scarcity is what gives Bitcoin its value, and ironically enough, this seems to be the hardest thing for people to understand about it. What if everyone in the network became a HODLer and decided to never sell, wouldn’t the network just slowly come to a halt? Not at all. Everyone has a price. Few would resist selling some of their Bitcoin if it could buy them a small city. There are price levels for each HODLer where reallocating financially may be a wise thing to do. A Bitcoin is also very divisible: The smallest unit, the satoshi, sometimes referred to as a sat, is one-hundred millionth of a Bitcoin. Even smaller units are made possible with the introduction of the Lightning Network, albeit not in the actual Bitcoin blockchain. Together, this enables Bitcoin to be highly saleable even at astronomical price levels.
What not having sound money has done to us is simply unfathomable. Imagine every person on Earth knowing that every transaction they’ll ever make will have a real impact on their future prosperity. We’re so used to inflationary currencies that most people don’t even realize why sound money is important. We’re so used to having a large cut of our income silently taken away from us that we don’t even realize how much of our day we spend working for someone else. Wars are funded by inflation. Imagine how many man-hours were put in by people who didn’t realize they were actually working for a war machine funded by a corrupt currency during World War II. Every time you use a fiat currency, you legitimize counterfeiting. Every time you use Bitcoin, you promote sound money. In fact, every time you don’t use your Bitcoin but save it instead, you promote sound money because sound money increases in value when the total number of coins in circulation is limited. It all sounds a bit magic and far-fetched, doesn’t it? Increased value over time, no matter what happens? Well, that is why many of us so-called Bitcoin Maximalists are so excited that we put our careers at risk for this technology. Once you realize what Bitcoin is and what it will do for the world, there is no way of un-realizing it. It really is mind-blowing.
At the beginning of time-that-actually-is-money — in other words, around 2009 — Bitcoin was mostly considered a toy for the cypherpunk movement. As its price started to grow rapidly, a small group of early investors became very wealthy, which in turn spawned a media hype around the phenomenon. Mainstream media remained largely skeptical, portraying Bitcoin as a pyramid scheme, a tulip craze, or a bubble at best. Most journalists simply couldn’t understand how an asset seemingly created out of thin air could have any long-term relevance. Some were frustrated because they thought that they’d missed the train. Many still do. In a world where companies like Google, Facebook, and Amazon can rise from zero to world dominance in a decade, people tried to find the Next Big Thing — the next Bitcoin. This attracted charlatans and scammers to the field who launched hundreds of altcoins, claiming to someday be technically superior, faster, or more privacy-focused. What the snake-oil salespeople omitted were the crucial facts: their new coins and tokens were not decentralized (and therefore neither immutable nor censorship-resistant), did not have a fair distribution, and so on. What most people still don’t get is that if Bitcoin doesn’t work, nothing will. This is humanity’s best shot at sound money. It is also, very likely, our only shot at it.
Many venture capital firms, hedge funds, and retail investors were bamboozled by the buzzword frenzy and invested great sums in these quack tokens. This generated confusion in the market as many altcoins increased dramatically in price at an even higher rate than Bitcoin. Due to human nature and a lack of understanding of basic monetary economics, the bubble grew bigger and bigger until it inevitably popped and wiped out most of the useless alternative cryptocurrencies. Bitcoin experienced ups and downs as well, but they were less volatile. Bitcoin bottomed at levels well above the beginning of the previous bull run and then resumed rising just as it had done several times before. The victims of the altcoin craze will take note of this. They will learn the hard way what separates the original from the copycat. They will see the undisputable superiority of sound money. It’s just a matter of time. Time, which is money.
Every time the people of Venezuela, Turkey, Argentina, or Zimbabwe are screwed over by their respective central banking authorities and turn to Bitcoin to preserve their savings or income from rampant inflation, the world becomes more aware of Bitcoin as a store of value. In comparison to the Venezuelan Bolivar, there was no crash in Bitcoin at all. There’s also a good chance the really big players will accumulate aggressively during the next bull market, given that Bitcoin, for the moment, still represents a very small allocation of institutional and hedge fund investment. Consider what will happen when institutional investors and a growing number of larger nations start to see Bitcoin’s potentially limitless upside. At this point, central banks will start to accumulate Bitcoin in an attempt to keep up with reality. This will legitimize the technology even further.
It is still unclear when this will all play out. When it does, however, it will be the largest transfer of wealth from one medium to another in human history. Early investors, many of which are technically competent, will become financially independent and, therefore, able to contribute to the ecosystem full-time. More and more people will demand payment in Bitcoin for its ability to store value. Remember that the next block reward halving is just around the corner and that Bitcoin will have an even greater stock-to-flow ratio than gold in just a few years. After the halving in 2020, Bitcoin will have a supply inflation rate of approximately 1.8%, which is lower than the US Federal Reserve’s target 2% price inflation rate. It is important to remember that Bitcoin is still an experiment. Should the experiment work, however, hyperbitcoinization is just a matter of time.
The implications of giving everyone on Earth the ability to rot-proof the fruit of their labor and transport its value through time are hard to overstate. The closest thing we’ve had to it historically is gold, but gold is not very divisible and not very easy for the general public to get their hands on. More importantly, gold is not absolutely scarce. No one knows how much of it there is left buried in the Earth's crust. Investing in real estate has also been seen as a good store of value throughout the ages, but real estate needs a lot of maintenance and is not cheap to hold on to. Real estate is also relatively easy to confiscate in the event of political collapse. Bitcoin provides us with the potential ability to store any amount in our heads and pass it down through generations without anyone ever knowing we had it in the first place. It effectively endows each individual with the power possessed by the feudal kings to turn people into knights. Any bitcoiner can now dub any no-coiner into a fully-fledged time-proof bitcoiner.
About the Bitcoin Infinity Academy
The Bitcoin Infinity Academy is an educational project built around Knut Svanholm’s books about Bitcoin and Austrian Economics. Each week, a whole chapter from one of the books is released for free on Highlighter, accompanied by a video in which Knut and Luke de Wolf discuss that chapter’s ideas. You can join the discussions by signing up for one of the courses on our Geyser page. Signed books, monthly calls, and lots of other benefits are also available.
-
 @ e4950c93:1b99eccd
2025-05-02 09:41:12
@ e4950c93:1b99eccd
2025-05-02 09:41:12Tu connais une marque proposant des alternatives naturelles ? Partage-la ici en commentant cette page !
Pour être référencée, la marque doit proposer une partie au moins de ses produits en matières naturelles. 👉 En savoir plus sur les matières
Chaque information ajoutée (nom, lien, catégorie, etc.) et validée est considérée comme une contribution. 👉 En savoir plus sur les contributions
Chaque contribution validée est comptabilisée et donne lieu à une rétribution. Pense à bien sauvegarder tes clés (identifiants) dans un coffre comme nsec.app). Tu peux aussi partager plus simplement tes trouvailles sans créer de compte via le formulaire de contact (non éligible pour les rétributions). 👉 En savoir plus sur les rétributions
Copie-colle le modèle ci-dessous et remplis les informations que tu as. D’autres contribut-eur-rice-s ou l'équipe coeur pourront compléter les éléments manquants.
Nouvelle marque ou fabricant
- Nom de la marque :
- Image représentant des produits de la marque (lien, idéalement depuis le site de la marque) :
- Courte description :
- Catégories de produits proposées :
- Matières utilisées pour ses produits :
- Site internet de la marque :
- Autres informations (lieu de production, labels…) :
Cet article est publié sur origine-nature.com 🌐 See this article in English
-
 @ 1d7ff02a:d042b5be
2025-05-01 05:46:41
@ 1d7ff02a:d042b5be
2025-05-01 05:46:41Source: https://youtu.be/e_Y9tI4dALA?si=F5wXRlpM0YulbhmY
Twitter Origins and Evolution
Twitter began as Dorsey's attempt to better understand cities by visualizing what people were doing and thinking (00:35-02:27) Key features like @mentions, hashtags, and retweets were invented by users, not the company (04:06-05:24) Dorsey realized Twitter was becoming significant when he saw politicians using it during Obama's first address to the nation (06:29-07:44)
Reflections on Twitter/X
Regrets monetizing too quickly through advertising rather than exploring better business models (12:19-13:05) Believes Twitter should have been built as an open protocol rather than a centralized company (13:05-14:23) Advocates for user choice in algorithms rather than having companies decide what content users see (15:35-18:31)
Decentralized Social Media
Started Blue Sky while at Twitter to create a decentralized social media protocol (22:51-24:07) Later focused on Nostr, which he believes has a better development model similar to Linux (24:07-25:57) Believes the future of social media includes agent-driven systems and greater user agency (29:01-29:41)
Block and Bitcoin
Block (formerly Square) focuses on economic empowerment through financial tools (32:08-32:47) Sees Bitcoin as essential for creating an internet protocol for moving money (33:25-35:09) Believes Bitcoin will eventually move beyond being just a store of value to become a currency for cross-border remittances (35:09-36:58)
Entrepreneurship Philosophy
Never intended to be an entrepreneur but wanted to build useful products (40:22-42:02) Compares entrepreneurship to art - knowing how to express ideas and where to set boundaries (42:02-43:09) Deals with rejection by viewing all experiences as teachers with lessons to offer (43:44-44:55)
Personal Habits
Practices meditation daily and previously did 10-day silent retreats (45:30-46:43) Creates daily lists of both what to do and what not to do (47:21-48:28) Eats only once a day to save time and better appreciate food (51:29-52:39) Dedicates morning hours to learning difficult subjects like quantum physics (48:28-49:40)
His advice to young people: observe everything, take in information, and don't worry about immediately reacting to it (52:39-53:00).
Noteable Quotes
-
On Twitter's co-creation with users: "What's interesting about Twitter is it wasn't really us who determined where it went, it was the people using it." (04:06)
-
On algorithms: "I think it's less about free speech, I think it's more about do we get to choose how the algorithms are programming us, because the algorithms are definitively programming us." (15:35)
-
On rejections and setbacks: "Everything I encounter, everything I experience is a teacher and they have some lesson for me, and it's up to me whether I decide to learn from it or not." (43:44)
-
On entrepreneurship as art: "It's expression, it's knowing when to end something, it's knowing what the chapters are and where the piece begins and where it ends." (42:02)
-
On Bitcoin's potential: "Bitcoin is over close to 16 years old right now. It's never gone down, it's never had a security issue, it has no leader, it has a completely open roadmap, and it's determined by a consensus development model." (36:18)
-
On learning: "I think people skip the observing phase too often. I don't think people are good listeners. I don't think people have honed their ability to observe the world and observe nature and observe how things work." (50:19)
-
On his advice to young people: "Observe everything, like take everything in, get love information, love receiving information, don't worry about reacting to it, don't worry about memorizing it, don't worry about doing anything with it at all, just be open." (52:39)
-
-
 @ 21335073:a244b1ad
2025-03-12 00:40:25
@ 21335073:a244b1ad
2025-03-12 00:40:25Before I saw those X right-wing political “influencers” parading their Epstein binders in that PR stunt, I’d already posted this on Nostr, an open protocol.
“Today, the world’s attention will likely fixate on Epstein, governmental failures in addressing horrific abuse cases, and the influential figures who perpetrate such acts—yet few will center the victims and survivors in the conversation. The survivors of Epstein went to law enforcement and very little happened. The survivors tried to speak to the corporate press and the corporate press knowingly covered for him. In situations like these social media can serve as one of the only ways for a survivor’s voice to be heard.
It’s becoming increasingly evident that the line between centralized corporate social media and the state is razor-thin, if it exists at all. Time and again, the state shields powerful abusers when it’s politically expedient to do so. In this climate, a survivor attempting to expose someone like Epstein on a corporate tech platform faces an uphill battle—there’s no assurance their voice would even break through. Their story wouldn’t truly belong to them; it’d be at the mercy of the platform, subject to deletion at a whim. Nostr, though, offers a lifeline—a censorship-resistant space where survivors can share their truths, no matter how untouchable the abuser might seem. A survivor could remain anonymous here if they took enough steps.
Nostr holds real promise for amplifying survivor voices. And if you’re here daily, tossing out memes, take heart: you’re helping build a foundation for those who desperately need to be heard.“
That post is untouchable—no CEO, company, employee, or government can delete it. Even if I wanted to, I couldn’t take it down myself. The post will outlive me on the protocol.
The cozy alliance between the state and corporate social media hit me hard during that right-wing X “influencer” PR stunt. Elon owns X. Elon’s a special government employee. X pays those influencers to post. We don’t know who else pays them to post. Those influencers are spurred on by both the government and X to manage the Epstein case narrative. It wasn’t survivors standing there, grinning for photos—it was paid influencers, gatekeepers orchestrating yet another chance to re-exploit the already exploited.
The bond between the state and corporate social media is tight. If the other Epsteins out there are ever to be unmasked, I wouldn’t bet on a survivor’s story staying safe with a corporate tech platform, the government, any social media influencer, or mainstream journalist. Right now, only a protocol can hand survivors the power to truly own their narrative.
I don’t have anything against Elon—I’ve actually been a big supporter. I’m just stating it as I see it. X isn’t censorship resistant and they have an algorithm that they choose not the user. Corporate tech platforms like X can be a better fit for some survivors. X has safety tools and content moderation, making it a solid option for certain individuals. Grok can be a big help for survivors looking for resources or support! As a survivor, you know what works best for you, and safety should always come first—keep that front and center.
That said, a protocol is a game-changer for cases where the powerful are likely to censor. During China's # MeToo movement, survivors faced heavy censorship on social media platforms like Weibo and WeChat, where posts about sexual harassment were quickly removed, and hashtags like # MeToo or "woyeshi" were blocked by government and platform filters. To bypass this, activists turned to blockchain technology encoding their stories—like Yue Xin’s open letter about a Peking University case—into transaction metadata. This made the information tamper-proof and publicly accessible, resisting censorship since blockchain data can’t be easily altered or deleted.
I posted this on X 2/28/25. I wanted to try my first long post on a nostr client. The Epstein cover up is ongoing so it’s still relevant, unfortunately.
If you are a survivor or loved one who is reading this and needs support please reach out to: National Sexual Assault Hotline 24/7 https://rainn.org/
Hours: Available 24 hours
-
 @ a367f9eb:0633efea
2025-04-09 07:28:49
@ a367f9eb:0633efea
2025-04-09 07:28:49WIEN – Diese Woche enthüllte Innenminister Gerhard Karner von der ÖVP, dass er einen Gesetzesentwurf "schnell" durchsetzen möchte, der der Regierung die Befugnis geben würde, verschlüsselte Kommunikation in Nachrichten-Apps zu überwachen.
Obwohl Karner betont hat, dass die neuen Befugnisse nur sehr gezielt eingesetzt würden, ist unklar, ob die Entwickler und Anbieter von Nachrichten-Apps gezwungen werden sollen, die Verschlüsselung zu brechen, um die Anordnungen durchzuführen.
Wie der stellvertretende Direktor des Consumer Choice Center, Yaël Ossowski, erklärte, würde diese Befugnis bedeuten, die Verschlüsselung für Millionen von österreichischen Verbrauchern zu untergraben und zu brechen.
„Jeder Versuch, die Verschlüsselung für einige ausgewählte Personen zu brechen, gefährdet gleichzeitig die Privatsphäre von Millionen von Österreichern. Dies ist weniger eine Frage der angemessenen Polizeibefugnisse als vielmehr eine Frage der technischen und sicherheitsrelevanten Aspekte. Schwächere Verschlüsselung macht österreichische Nutzer weniger sicher“ sagte Ossowski.
„Verschlüsselungsstandards von Apps wie Signal, WhatsApp und sogar iMessage aufzuheben, würde der österreichischen Regierung außergewöhnliche Befugnisse einräumen, die das Risiko bergen, jede und alle Kommunikation zu kompromittieren, nicht nur die von Verdächtigen oder Terroristen.
„Um gegen kriminelle Akteure vorzugehen, sollte die Koalition das bestehende Justizsystem nutzen, um Haftbefehle auf Grundlage eines begründeten Verdachts durchzusetzen, anstatt Messaging-Dienste und Apps dazu zu zwingen, diese Aufgabe für sie zu übernehmen“ erklärte Ossowski.
Das Consumer Choice Center weist darauf hin, dass ähnliche Versuche, die Verschlüsselung mit polizeilicher Gewalt zu brechen, bereits im Vereinigten Königreich und in Frankreich unternommen wurden, wo sie von Bürgerrechtsgruppen abgelehnt wurden.
###
Das Consumer Choice Center ist eine unabhängige, parteiunabhängige Verbraucherorganisation, die die Vorteile von Wahlfreiheit, Innovation und Wachstum im Alltagsleben für Verbraucher in über 100 Ländern fördert. Wir interessieren uns insbesondere für regulatorische Trends in Washington, Brüssel, Wien, Berlin, Ottawa, Brasília, London und Genf genau.
Erfahren Sie mehr auf consumerchoicecenter.org
-
 @ e4950c93:1b99eccd
2025-05-02 09:36:09
@ e4950c93:1b99eccd
2025-05-02 09:36:09Tu as trouvé un produit naturel ? Partage-le ici en commentant cette page !
Ce site référence uniquement des produits et objets à usage durable. Les consommables (aliments, cosmétiques, combustibles, etc.) ne sont pas inclus.
Pour être référencé, le produit doit être composé de matières naturelles. 👉 En savoir plus sur les matières
Chaque information ajoutée (nom, matière, lien, zone de livraison pour un lien, etc.) et validée est considérée comme une contribution. 👉 En savoir plus sur les contributions
Chaque contribution validée est comptabilisée et donne lieu à une rétribution. Pense à bien sauvegarder tes clés (identifiants) dans un coffre comme nsec.app). Tu peux aussi partager plus simplement tes trouvailles sans créer de compte via le formulaire de contact (non éligible pour les rétributions). 👉 En savoir plus sur les rétributions
Copie-colle le modèle ci-dessous et remplis les informations dont tu disposes. D’autres contribut-eur-rice-s ou l'équipe coeur pourront compléter les éléments manquants.
Nouveau produit
- Nom du produit :
- Image du produit (lien) :
- Description courte :
- Catégories :
- Marque ou fabricant :
- Composition (matériaux utilisés, y compris les éléments inconnus) :
- Liens pour l’acheter (et zone de livraison) :
- Zone de livraison pour les
- Autres infos utiles (lieu de fabrication, labels, etc.) :
Cet article est publié sur origine-nature.com 🌐 See this article in English
-
 @ 21335073:a244b1ad
2025-03-18 14:43:08
@ 21335073:a244b1ad
2025-03-18 14:43:08Warning: This piece contains a conversation about difficult topics. Please proceed with caution.
TL;DR please educate your children about online safety.
Julian Assange wrote in his 2012 book Cypherpunks, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense.
This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning.
When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little.
I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?”
I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well.
I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread.
I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard.
I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it.
The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust.
Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this.
I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place.
What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method.
It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code.
They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened.
I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road.
So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally.
Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb.
I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback.
Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed.
That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone.
To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all.
I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society.
I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this.
On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government.
I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories.
There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc.
Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind.
Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now.
There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers?
I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity.
I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place.
My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors.
My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline.
The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online.
I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers.
So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation?
When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that.
I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic.
If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations.
I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process.
Course: - The creation of the internet and computers - The fight for cryptography - The tech supply chain from the ground up (example: human rights violations in the supply chain) - Corporate tech - Freedom tech - Data privacy - Digital privacy rights - AI (history-current) - Online safety (predators, scams, catfishing, extortion) - Bitcoin - Laws - How to deal with online hate and harassment - Information on who to contact if you are being abused online or offline - Algorithms - How to seek out the truth about news, etc., online
The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children.
The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward?
I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone.
Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability.
The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime.
This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful.
This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens.
In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions.
I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation.
-
 @ 1c19eb1a:e22fb0bc
2025-04-30 22:02:13
@ 1c19eb1a:e22fb0bc
2025-04-30 22:02:13I am happy to present to you the first full review posted to Nostr Reviews: #Primal for #Android!
Primal has its origins as a micro-blogging, social media client, though it is now expanding its horizons into long-form content. It was first released only as a web client in March of 2023, but has since had a native client released for both iOS and Android. All of Primal's clients recently had an update to Primal 2.0, which included both performance improvements and a number of new features. This review will focus on the Android client specifically, both on phone and tablet.
Since Primal has also added features that are only available to those enrolled in their new premium subscription, it should also be noted that this review will be from the perspective of a free user. This is for two reasons. First, I am using an alternate npub to review the app, and if I were to purchase premium at some time in the future, it would be on my main npub. Second, despite a lot of positive things I have to say about Primal, I am not planning to regularly use any of their apps on my main account for the time being, for reasons that will be discussed later in the review.
The application can be installed through the Google Play Store, nostr:npub10r8xl2njyepcw2zwv3a6dyufj4e4ajx86hz6v4ehu4gnpupxxp7stjt2p8, or by downloading it directly from Primal's GitHub. The full review is current as of Primal Android version 2.0.21. Updates to the review on 4/30/2025 are current as of version 2.2.13.
In the ecosystem of "notes and other stuff," Primal is predominantly in the "notes" category. It is geared toward users who want a social media experience similar to Twitter or Facebook with an infinite scrolling feed of notes to interact with. However, there is some "other stuff" included to complement this primary focus on short and long form notes including a built-in Lightning wallet powered by #Strike, a robust advanced search, and a media-only feed.

Overall Impression
Score: 4.4 / 5 (Updated 4/30/2025)
Primal may well be the most polished UI of any Nostr client native to Android. It is incredibly well designed and thought out, with all of the icons and settings in the places a user would expect to find them. It is also incredibly easy to get started on Nostr via Primal's sign-up flow. The only two things that will be foreign to new users are the lack of any need to set a password or give an email address, and the prompt to optionally set up the wallet.
Complaints prior to the 2.0 update about Primal being slow and clunky should now be completely alleviated. I only experienced quick load times and snappy UI controls with a couple very minor exceptions, or when loading DVM-based feeds, which are outside of Primal's control.
Primal is not, however, a client that I would recommend for the power-user. Control over preferred relays is minimal and does not allow the user to determine which relays they write to and which they only read from. Though you can use your own wallet, it will not appear within the wallet interface, which only works with the custodial wallet from Strike. Moreover, and most eggregiously, the only way for existing users to log in is by pasting their nsec, as Primal does not support either the Android signer or remote signer options for users to protect their private key at this time. This lack of signer support is the primary reason the client received such a low overall score. If even one form of external signer log in is added to Primal, the score will be amended to 4.2 / 5, and if both Android signer and remote signer support is added, it will increase to 4.5.
Update: As of version 2.2.13, Primal now supports the Amber Android signer! One of the most glaring issues with the app has now been remedied and as promised, the overall score above has been increased.
Another downside to Primal is that it still utilizes an outdated direct message specification that leaks metadata that can be readily seen by anyone on the network. While the content of your messages remains encrypted, anyone can see who you are messaging with, and when. This also means that you will not see any DMs from users who are messaging from a client that has moved to the latest, and far more private, messaging spec.
That said, the beautiful thing about Nostr as a protocol is that users are not locked into any particular client. You may find Primal to be a great client for your average #bloomscrolling and zapping memes, but opt for a different client for more advanced uses and for direct messaging.
Features
Primal has a lot of features users would expect from any Nostr client that is focused on short-form notes, but it also packs in a lot of features that set it apart from other clients, and that showcase Primal's obvious prioritization of a top-tier user experience.
Home Feed
By default, the infinitely scrolling Home feed displays notes from those you currently follow in chronological order. This is traditional Nostr at its finest, and made all the more immersive by the choice to have all distracting UI elements quickly hide themselves from view as the you begin to scroll down the feed. They return just as quickly when you begin to scroll back up.

Scrolling the feed is incredibly fast, with no noticeable choppiness and minimal media pop-in if you are on a decent internet connection.
Helpfully, it is easy to get back to the top of the feed whenever there is a new post to be viewed, as a bubble will appear with the profile pictures of the users who have posted since you started scrolling.

Interacting With Notes
Interacting with a note in the feed can be done via the very recognizable icons at the bottom of each post. You can comment, zap, like, repost, and/or bookmark the note.
Notably, tapping on the zap icon will immediately zap the note your default amount of sats, making zapping incredibly fast, especially when using the built-in wallet. Long pressing on the zap icon will open up a menu with a variety of amounts, along with the ability to zap a custom amount. All of these amounts, and the messages that are sent with the zap, can be customized in the application settings.

Users who are familiar with Twitter or Instagram will feel right at home with only having one option for "liking" a post. However, users from Facebook or other Nostr clients may wonder why they don't have more options for reactions. This is one of those things where users who are new to Nostr probably won't notice they are missing out on anything at all, while users familiar with clients like #Amethyst or #noStrudel will miss the ability to react with a 🤙 or a 🫂.
It's a similar story with the bookmark option. While this is a nice bit of feature parity for Twitter users, for those already used to the ability to have multiple customized lists of bookmarks, or at minimum have the ability to separate them into public and private, it may be a disappointment that they have no access to the bookmarks they already built up on other clients. Primal offers only one list of bookmarks for short-form notes and they are all visible to the public. However, you are at least presented with a warning about the public nature of your bookmarks before saving your first one.
Yet, I can't dock the Primal team much for making these design choices, as they are understandable for Primal's goal of being a welcoming client for those coming over to Nostr from centralized platforms. They have optimized for the onboarding of new users, rather than for those who have been around for a while, and there is absolutely nothing wrong with that.
Post Creation
Composing posts in Primal is as simple as it gets. Accessed by tapping the obvious circular button with a "+" on it in the lower right of the Home feed, most of what you could need is included in the interface, and nothing you don't.

Your device's default keyboard loads immediately, and the you can start typing away.
There are options for adding images from your gallery, or taking a picture with your camera, both of which will result in the image being uploaded to Primal's media-hosting server. If you prefer to host your media elsewhere, you can simply paste the link to that media into your post.
There is also an @ icon as a tip-off that you can tag other users. Tapping on this simply types "@" into your note and brings up a list of users. All you have to do to narrow down the user you want to tag is continue typing their handle, Nostr address, or paste in their npub.

This can get mixed results in other clients, which sometimes have a hard time finding particular users when typing in their handle, forcing you to have to remember their Nostr address or go hunt down their npub by another means. Not so with Primal, though. I had no issues tagging anyone I wanted by simply typing in their handle.
Of course, when you are tagging someone well known, you may find that there are multiple users posing as that person. Primal helps you out here, though. Usually the top result is the person you want, as Primal places them in order of how many followers they have. This is quite reliable right now, but there is nothing stopping someone from spinning up an army of bots to follow their fake accounts, rendering follower count useless for determining which account is legitimate. It would be nice to see these results ranked by web-of-trust, or at least an indication of how many users you follow who also follow the users listed in the results.
Once you are satisfied with your note, the "Post" button is easy to find in the top right of the screen.
Feed Selector and Marketplace
Primal's Home feed really shines when you open up the feed selection interface, and find that there are a plethora of options available for customizing your view. By default, it only shows four options, but tapping "Edit" opens up a new page of available toggles to add to the feed selector.

The options don't end there, though. Tapping "Add Feed" will open up the feed marketplace, where an ever-growing number of custom feeds can be found, some created by Primal and some created by others. This feed marketplace is available to a few other clients, but none have so closely integrated it with their Home feeds like Primal has.

Unfortunately, as great as these custom feeds are, this was also the feature where I ran into the most bugs while testing out the app.
One of these bugs was while selecting custom feeds. Occasionally, these feed menu screens would become unresponsive and I would be unable to confirm my selection, or even use the back button on my device to back out of the screen. However, I was able to pull the screen down to close it and re-open the menu, and everything would be responsive again.
This only seemed to occur when I spent 30 seconds or more on the same screen, so I imagine that most users won't encounter it much in their regular use.
Another UI bug occurred for me while in the feed marketplace. I could scroll down the list of available feeds, but attempting to scroll back up the feed would often close the interface entirely instead, as though I had pulled the screen down from the top, when I was swiping in the middle of the screen.
The last of these bugs occurred when selecting a long-form "Reads" feed while in the menu for the Home feed. The menu would allow me to add this feed and select it to be displayed, but it would fail to load the feed once selected, stating "There is no content in this feed." Going to a different page within the the app and then going back to the Home tab would automatically remove the long-form feed from view, and reset back to the most recently viewed short-form "Notes" feed, though the long-form feed would still be available to select again. The results were similar when selecting a short-form feed for the Reads feed.
I would suggest that if long-form and short-form feeds are going to be displayed in the same list, and yet not be able to be displayed in the same feed, the application should present an error message when attempting to add a long-form feed for the Home feed or a short-form feed for the Reads feed, and encourage the user add it to the proper feed instead.
Long-Form "Reads" Feed
A brand new feature in Primal 2.0, users can now browse and read long-form content posted to Nostr without having to go to a separate client. Primal now has a dedicated "Reads" feed to browse and interact with these articles.
This feed displays the author and title of each article or blog, along with an image, if available. Quite conveniently, it also lets you know the approximate amount of time it will take to read a given article, so you can decide if you have the time to dive into it now, or come back later.

Noticeably absent from the Reads feed, though, is the ability to compose an article of your own. This is another understandable design choice for a mobile client. Composing a long-form note on a smart-phone screen is not a good time. Better to be done on a larger screen, in a client with a full-featured text editor.
Tapping an article will open up an attractive reading interface, with the ability to bookmark for later. These bookmarks are a separate list from your short-form note bookmarks so you don't have to scroll through a bunch of notes you bookmarked to find the article you told yourself you would read later and it's already been three weeks.
While you can comment on the article or zap it, you will notice that you cannot repost or quote-post it. It's not that you can't do so on Nostr. You absolutely can in other clients. In fact, you can do so on Primal's web client, too. However, Primal on Android does not handle rendering long-form note previews in the Home feed, so they have simply left out the option to share them there. See below for an example of a quote-post of a long-form note in the Primal web client vs the Android client.
Primal Web:

Primal Android:

The Explore Tab
Another unique feature of the Primal client is the Explore tab, indicated by the compass icon. This tab is dedicated to discovering content from outside your current follow list. You can find the feed marketplace here, and add any of the available feeds to your Home or Reads feed selections. You can also find suggested users to follow in the People tab. The Zaps tab will show you who has been sending and receiving large zaps. Make friends with the generous ones!
The Media tab gives you a chronological feed of just media, displayed in a tile view. This can be great when you are looking for users who post dank memes, or incredible photography on a regular basis. Unfortunately, it appears that there is no way to filter this feed for sensitive content, and so you do not have to scroll far before you see pornographic material.
Indeed, it does not appear that filters for sensitive content are available in Primal for any feed. The app is kind enough to give a minimal warning that objectionable content may be present when selecting the "Nostr Firehose" option in your Home feed, with a brief "be careful" in the feed description, but there is not even that much of a warning here for the media-only feed.

The media-only feed doesn't appear to be quite as bad as the Nostr Firehose feed, so there must be some form of filtering already taking place, rather than being a truly global feed of all media. Yet, occasional sensitive content still litters the feed and is unavoidable, even for users who would rather not see it. There are, of course, ways to mute particular users who post such content, if you don't want to see it a second time from the same user, but that is a never-ending game of whack-a-mole, so your only realistic choices in Primal are currently to either avoid the Nostr Firehose and media-only feeds, or determine that you can put up with regularly scrolling past often graphic content.
This is probably the only choice Primal has made that is not friendly to new users. Most clients these days will have some protections in place to hide sensitive content by default, but still allow the user to toggle those protections off if they so choose. Some of them hide posts flagged as sensitive content altogether, others just blur the images unless the user taps to reveal them, and others simply blur all images posted by users you don't follow. If Primal wants to target new users who are accustomed to legacy social media platforms, they really should follow suit.
The final tab is titled "Topics," but it is really just a list of popular hashtags, which appear to be arranged by how often they are being used. This can be good for finding things that other users are interested in talking about, or finding specific content you are interested in.
If you tap on any topic in the list, it will display a feed of notes that include that hashtag. What's better, you can add it as a feed option you can select on your Home feed any time you want to see posts with that tag.
The only suggestion I would make to improve this tab is some indication of why the topics are arranged in the order presented. A simple indicator of the number of posts with that hashtag in the last 24 hours, or whatever the interval is for determining their ranking, would more than suffice.
Even with those few shortcomings, Primal's Explore tab makes the client one of the best options for discovering content on Nostr that you are actually interested in seeing and interacting with.
Built-In Wallet
While this feature is completely optional, the icon to access the wallet is the largest of the icons at the bottom of the screen, making you feel like you are missing out on the most important feature of the app if you don't set it up. I could be critical of this design choice, but in many ways I think it is warranted. The built-in wallet is one of the most unique features that Primal has going for it.

Consider: If you are a new user coming to Nostr, who isn't already a Bitcoiner, and you see that everyone else on the platform is sending and receiving sats for their posts, will you be more likely to go download a separate wallet application or use one that is built-into your client? I would wager the latter option by a long shot. No need to figure out which wallet you should download, whether you should do self-custody or custodial, or make the mistake of choosing a wallet with unexpected setup fees and no Lightning address so you can't even receive zaps to it. nostr:npub16c0nh3dnadzqpm76uctf5hqhe2lny344zsmpm6feee9p5rdxaa9q586nvr often states that he believes more people will be onboarded to Bitcoin through Nostr than by any other means, and by including a wallet into the Primal client, his team has made adopting Bitcoin that much easier for new Nostr users.
Some of us purists may complain that it is custodial and KYC, but that is an unfortunate necessity in order to facilitate onboarding newcoiners to Bitcoin. This is not intended to be a wallet for those of us who have been using Bitcoin and Lightning regularly already. It is meant for those who are not already familiar with Bitcoin to make it as easy as possible to get off zero, and it accomplishes this better than any other wallet I have ever tried.
In large part, this is because the KYC is very light. It does need the user's legal name, a valid email address, date of birth, and country of residence, but that's it! From there, the user can buy Bitcoin directly through the app, but only in the amount of $4.99 at a time. This is because there is a substantial markup on top of the current market price, due to utilizing whatever payment method the user has set up through their Google Play Store. The markup seemed to be about 19% above the current price, since I could purchase 4,143 sats for $4.99 ($120,415 / Bitcoin), when the current price was about $101,500. But the idea here is not for the Primal wallet to be a user's primary method of stacking sats. Rather, it is intended to get them off zero and have a small amount of sats to experience zapping with, and it accomplishes this with less friction than any other method I know.
Moreover, the Primal wallet has the features one would expect from any Lightning wallet. You can send sats to any Nostr user or Lightning address, receive via invoice, or scan to pay an invoice. It even has the ability to receive via on-chain. This means users who don't want to pay the markup from buying through Primal can easily transfer sats they obtained by other means into the Primal wallet for zapping, or for using it as their daily-driver spending wallet.
Speaking of zapping, once the wallet is activated, sending zaps is automatically set to use the wallet, and they are fast. Primal gives you immediate feedback that the zap was sent and the transaction shows in your wallet history typically before you can open the interface. I can confidently say that Primal wallet's integration is the absolute best zapping experience I have seen in any Nostr client.
One thing to note that may not be immediately apparent to new users is they need to add their Lightning address with Primal into their profile details before they can start receiving zaps. So, sending zaps using the wallet is automatic as soon as you activate it, but receiving is not. Ideally, this could be further streamlined, so that Primal automatically adds the Lightning address to the user's profile when the wallet is set up, so long as there is not currently a Lightning address listed.
Of course, if you already have a Lightning wallet, you can connect it to Primal for zapping, too. We will discuss this further in the section dedicated to zap integration.
Advanced Search
Search has always been a tough nut to crack on Nostr, since it is highly dependent on which relays the client is pulling information from. Primal has sought to resolve this issue, among others, by running a caching relay that pulls notes from a number of relays to store them locally, and perform some spam filtering. This allows for much faster retrieval of search results, and also makes their advanced search feature possible.
Advanced search can be accessed from most pages by selecting the magnifying glass icon, and then the icon for more options next to the search bar.
As can be seen in the screenshot below, there are a plethora of filters that can be applied to your search terms.

You can immediately see how this advanced search could be a very powerful tool for not just finding a particular previous note that you are looking for, but for creating your own custom feed of notes. Well, wouldn't you know it, Primal allows you to do just that! This search feature, paired with the other features mentioned above related to finding notes you want to see in your feed, makes Primal hands-down the best client for content discovery.
The only downside as a free user is that some of these search options are locked behind the premium membership. Or else you only get to see a certain number of results of your advanced search before you must be a premium member to see more.
Can My Grandma Use It?
Score: 4.8 / 5 Primal has obviously put a high priority on making their client user-friendly, even for those who have never heard of relays, public/private key cryptography, or Bitcoin. All of that complexity is hidden away. Some of it is available to play around with for the users who care to do so, but it does not at all get in the way of the users who just want to jump in and start posting notes and interacting with other users in a truly open public square.
To begin with, the onboarding experience is incredibly smooth. Tap "Create Account," enter your chosen display name and optional bio information, upload a profile picture, and then choose some topics you are interested in. You are then presented with a preview of your profile, with the ability to add a banner image, if you so choose, and then tap "Create Account Now."

From there you receive confirmation that your account has been created and that your "Nostr key" is available to you in the application settings. No further explanation is given about what this key is for at this point, but the user doesn't really need to know at the moment, either. If they are curious, they will go to the app settings to find out.
At this point, Primal encourages the user to activate Primal Wallet, but also gives the option for the user to do it later.

That's it! The next screen the user sees if they don't opt to set up the wallet is their Home feed with notes listed in chronological order. More impressive, the feed is not empty, because Primal has auto-followed several accounts based on your selected topics.
Now, there has definitely been some legitimate criticism of this practice of following specific accounts based on the topic selection, and I agree. I would much prefer to see Primal follow hashtags based on what was selected, and combine the followed hashtags into a feed titled "My Topics" or something of that nature, and make that the default view when the user finishes onboarding. Following particular users automatically will artificially inflate certain users' exposure, while other users who might be quality follows for that topic aren't seen at all.
The advantage of following particular users over a hashtag, though, is that Primal retains some control over the quality of the posts that new users are exposed to right away. Primal can ensure that new users see people who are actually posting quality photography when they choose it as one of their interests. However, even with that example, I chose photography as one of my interests and while I did get some stunning photography in my Home feed by default based on Primal's chosen follows, I also scrolled through the Photography hashtag for a bit and I really feel like I would have been better served if Primal had simply followed that hashtag rather than a particular set of users.
We've already discussed how simple it is to set up the Primal Wallet. You can see the features section above if you missed it. It is, by far, the most user friendly experience to onboarding onto Lightning and getting a few sats for zapping, and it is the only one I know of that is built directly into a Nostr client. This means new users will have a frictionless introduction to transacting via Lightning, perhaps without even realizing that's what they are doing.
Discovering new content of interest is incredibly intuitive on Primal, and the only thing that new users may struggle with is getting their own notes seen by others. To assist with this, I would suggest Primal encourage users to make their first post to the introductions hashtag and direct any questions to the AskNostr hashtag as part of the onboarding process. This will get them some immediate interactions from other users, and further encouragement to set up their wallet if they haven't already done so.
How do UI look?
Score: 4.9 / 5
Primal is the most stunningly beautiful Nostr client available, in my honest opinion. Despite some of my hangups about certain functionality, the UI alone makes me want to use it.

It is clean, attractive, and intuitive. Everything I needed was easy to find, and nothing felt busy or cluttered. There are only a few minor UI glitches that I ran into while testing the app. Some of them were mentioned in the section of the review detailing the feed selector feature, but a couple others occurred during onboarding.
First, my profile picture was not centered in the preview when I uploaded it. This appears to be because it was a low quality image. Uploading a higher quality photo did not have this result.

The other UI bug was related to text instructions that were cut off, and not able to scroll to see the rest of them. This occurred on a few pages during onboarding, and I expect it was due to the size of my phone screen, since it did not occur when I was on a slightly larger phone or tablet.

Speaking of tablets, Primal Android looks really good on a tablet, too! While the client does not have a landscape mode by default, many Android tablets support forcing apps to open in full-screen landscape mode, with mixed results. However, Primal handles it well. I would still like to see a tablet version developed that takes advantage of the increased screen real estate, but it is certainly a passable option.





At this point, I would say the web client probably has a bit better UI for use on a tablet than the Android client does, but you miss out on using the built-in wallet, which is a major selling point of the app.
This lack of a landscape mode for tablets and the few very minor UI bugs I encountered are the only reason Primal doesn't get a perfect score in this category, because the client is absolutely stunning otherwise, both in light and dark modes. There are also two color schemes available for each.

Log In Options
Score: 4 / 5 (Updated 4/30/2025)
Unfortunately, Primal has not included any options for log in outside of pasting your private key into the application. While this is a very simple way to log in for new users to understand, it is also the least secure means to log into Nostr applications.
This is because, even with the most trustworthy client developer, giving the application access to your private key always has the potential for that private key to somehow be exposed or leaked, and on Nostr there is currently no way to rotate to a different private key and keep your identity and social graph. If someone gets your key, they are you on Nostr for all intents and purposes.
This is not a situation that users should be willing to tolerate from production-release clients at this point. There are much better log in standards that can and should be implemented if you care about your users.
That said, I am happy to report that external signer support is on the roadmap for Primal, as confirmed below:
nostr:note1n59tc8k5l2v30jxuzghg7dy2ns76ld0hqnn8tkahyywpwp47ms5qst8ehl
No word yet on whether this will be Android signer or remote signer support, or both.
This lack of external signer support is why I absolutely will not use my main npub with Primal for Android. I am happy to use the web client, which supports and encourages logging in with a browser extension, but until the Android client allows users to protect their private key, I cannot recommend it for existing Nostr users.
Update: As of version 2.2.13, all of what I have said above is now obsolete. Primal has added Android signer support, so users can now better protect their nsec by using Amber!
I would still like to see support for remote signers, especially with nstart.me as a recommended Nostr onboarding process and the advent of FROSTR for key management. That said, Android signer support on its own has been a long time coming and is a very welcome addition to the Primal app. Bravo Primal team!
Zap Integration
Score: 4.8 / 5
As mentioned when discussing Primal's built-in wallet feature, zapping in Primal can be the most seamless experience I have ever seen in a Nostr client. Pairing the wallet with the client is absolutely the path forward for Nostr leading the way to Bitcoin adoption.
But what if you already have a Lightning wallet you want to use for zapping? You have a couple options. If it is an Alby wallet or another wallet that supports Nostr Wallet Connect, you can connect it with Primal to use with one-tap zapping.

How your zapping experience goes with this option will vary greatly based on your particular wallet of choice and is beyond the scope of this review. I used this option with a hosted wallet on my Alby Hub and it worked perfectly. Primal gives you immediate feedback that you have zapped, even though the transaction usually takes a few seconds to process and appear in your wallet's history.
The one major downside to using an external wallet is the lack of integration with the wallet interface. This interface currently only works with Primal's wallet, and therefore the most prominent tab in the entire app goes unused when you connect an external wallet.

An ideal improvement would be for the wallet screen to work similar to Alby Go when you have an external wallet connected via Nostr Wallet Connect, allowing the user to have Primal act as their primary mobile Lightning wallet. It could have balance and transaction history displayed, and allow sending and receiving, just like the integrated Primal wallet, but remove the ability to purchase sats directly through the app when using an external wallet.
Content Discovery
Score: 4.8 / 5
Primal is the best client to use if you want to discover new content you are interested in. There is no comparison, with only a few caveats.
First, the content must have been posted to Nostr as either a short-form or long-form note. Primal has a limited ability to display other types of content. For instance, discovering video content or streaming content is lacking.
Second, you must be willing to put up with the fact that Primal lacks a means of filtering sensitive content when you are exploring beyond the bounds of your current followers. This may not be an issue for some, but for others it could be a deal-breaker.
Third, it would be preferable for Primal to follow topics you are interested in when you choose them during onboarding, rather than follow specific npubs. Ideally, create a "My Topics" feed that can be edited by selecting your interests in the Topics section of the Explore tab.
Relay Management
Score: 2.5 / 5
For new users who don't want to mess around with managing relays, Primal is fantastic! There are 7 relays selected by default, in addition to Primal's caching service. For most users who aren't familiar with Nostr's protocol archetecture, they probably won't ever have to change their default relays in order to use the client as they would expect.
However, two of these default relays were consistently unreachable during the week that I tested. These were relay.plebes.fans and remnant.cloud. The first relay seems to be an incorrect URL, as I found nosflare.plebes.fans online and with perfect uptime for the last 12 hours on nostr.watch. I was unable to find remnant.cloud on nostr.watch at all. A third relay was intermittent, sometimes online and reachable, and other times unreachable: v1250.planz.io/nostr. If Primal is going to have default relays, they should ideally be reliable and with accurate URLs.
That said, users can add other relays that they prefer, and remove relays that they no longer want to use. They can even set a different caching service to use with the client, rather than using Primal's.

However, that is the extent of a user's control over their relays. They cannot choose which relays they want to write to and which they want to read from, nor can they set any private relays, outbox or inbox relays, or general relays. Loading the npub I used for this review into another client with full relay management support revealed that the relays selected in Primal are being added to both the user's public outbox relays and public inbox relays, but not to any other relay type, which leads me to believe the caching relay is acting as the client's only general relay and search relay.
One unique and welcomed addition is the "Enhanced Privacy" feature, which is off by default, but which can be toggled on. I am not sure why this is not on by default, though. Perhaps someone from the Primal team can enlighten me on that choice.
By default, when you post to Nostr, all of your outbox relays will see your IP address. If you turn on the Enhanced Privacy mode, only Primal's caching service will see your IP address, because it will post your note to the other relays on your behalf. In this way, the caching service acts similar to a VPN for posting to Nostr, as long as you trust Primal not to log or leak your IP address.
In short, if you use any other Nostr clients at all, do not use Primal for managing your relays.
Media Hosting Options
Score: 4.9 / 5 This is a NEW SECTION of this review, as of version 2.2.13!
Primal has recently added support for the Blossom protocol for media hosting, and has added a new section within their settings for "Media Uploads."
Media hosting is one of the more complicated problems to solve for a decentralized publishing protocol like Nostr. Text-based notes are generally quite small, making them no real burden to store on relays, and a relay can prune old notes as they see fit, knowing that anyone who really cared about those notes has likely archived them elsewhere. Media, on the other hand, can very quickly fill up a server's disk space, and because it is usually addressable via a specific URL, removing it from that location to free up space means it will no longer load for anyone.
Blossom solves this issue by making it easy to run a media server and have the same media mirrored to more than one for redundancy. Since the media is stored with a file name that is a hash of the content itself, if the media is deleted from one server, it can still be found from any other server that has the same file, without any need to update the URL in the Nostr note where it was originally posted.
Prior to this update, Primal only allowed media uploads to their own media server. Now, users can upload to any blossom server, and even choose to have their pictures or videos mirrored additional servers automatically. To my knowledge, no other Nostr client offers this automatic mirroring at the time of upload.
One of my biggest criticisms of Primal was that it had taken a siloed approach by providing a client, a caching relay, a media server, and a wallet all controlled by the same company. The whole point of Nostr is to separate control of all these services to different entities. Now users have more options for separating out their media hosting and their wallet to other providers, at least. I would still like to see other options available for a caching relay, but that relies on someone else being willing to run one, since the software is open for anyone to use. It's just not your average, lightweight relay that any average person can run from home.
Regardless, this update to add custom Blossom servers is a most welcome step in the right direction!
Current Users' Questions
The AskNostr hashtag can be a good indication of the pain points that other users are currently having with a client. Here are some of the most common questions submitted about Primal since the launch of 2.0:
nostr:note1dqv4mwqn7lvpaceg9s7damf932ydv9skv2x99l56ufy3f7q8tkdqpxk0rd
This was a pretty common question, because users expect that they will be able to create the same type of content that they can consume in a particular client. I can understand why this was left out in a mobile client, but perhaps it should be added in the web client.
nostr:note16xnm8a2mmrs7t9pqymwjgd384ynpf098gmemzy49p3572vhwx2mqcqw8xe
This is a more concerning bug, since it appears some users are experiencing their images being replaced with completely different images. I did not experience anything similar in my testing, though.
nostr:note1uhrk30nq0e566kx8ac4qpwrdh0vfaav33rfvckyvlzn04tkuqahsx8e7mr
There hasn't been an answer to this, but I have not been able to find a way. It seems search results will always include replies as well as original notes, so a feed made from the search results will as well. Perhaps a filter can be added to the advanced search to exclude replies? There is already a filter to only show replies, but there is no corresponding filter to only show original notes.
nostr:note1zlnzua28a5v76jwuakyrf7hham56kx9me9la3dnt3fvymcyaq6eqjfmtq6
Since both mobile platforms support the wallet, users expect that they will be able to access it in their web client, too. At this time, they cannot. The only way to have seamless zapping in the web client is to use the Alby extension, but there is not a way to connect it to your Primal wallet via Nostr Wallet Connect either. This means users must have a separate wallet for zapping on the web client if they use the Primal Wallet on mobile.
nostr:note15tf2u9pffy58y9lk27y245ew792raqc7lc22jezxvqj7xrak9ztqu45wep
It seems that Primal is filtering for spam even for profiles you actively follow. Moreover, exactly what the criteria is for being considered spam is currently opaque.
nostr:note1xexnzv0vrmc8svvduurydwmu43w7dftyqmjh4ps98zksr39ln2qswkuced
For those unaware, Blossom is a protocol for hosting media as blobs identified by a hash, allowing them to be located on and displayed from other servers they have been mirrored to when when the target server isn't available. Primal currently runs a Blossom server (blossom.primal.net) so I would expect we see Blossom support in the future.
nostr:note1unugv7s36e2kxl768ykg0qly7czeplp8qnc207k4pj45rexgqv4sue50y6
Currently, Primal on Android only supports uploading photos to your posts. Users must upload any video to some other hosting service and copy/paste a link to the video into their post on Primal. I would not be surprised to see this feature added in the near future, though.
nostr:note10w6538y58dkd9mdrlkfc8ylhnyqutc56ggdw7gk5y7nsp00rdk4q3qgrex
Many Nostr users have more than one npub for various uses. Users would prefer to have a way to quickly switch between accounts than to have to log all the way out and paste their npub for the other account every time they want to use it.
There is good news on this front, though:
nostr:note17xv632yqfz8nx092lj4sxr7drrqfey6e2373ha00qlq8j8qv6jjs36kxlh
Wrap Up
All in all, Primal is an excellent client. It won't be for everyone, but that's one of the strengths of Nostr as a protocol. You can choose to use the client that best fits your own needs, and supplement with other clients and tools as necessary.
There are a couple glaring issues I have with Primal that prevent me from using it on my main npub, but it is also an ever-improving client, that already has me hopeful for those issues to be resolved in a future release.
So, what should I review next? Another Android client, such as #Amethyst or #Voyage? Maybe an "other stuff" app, like #Wavlake or #Fountain? Please leave your suggestions in the comments.
I hope this review was valuable to you! If it was, please consider letting me know just how valuable by zapping me some sats and reposting it out to your follows.
Thank you for reading!
PV 🤙
-
 @ 04c915da:3dfbecc9
2025-03-13 19:39:28
@ 04c915da:3dfbecc9
2025-03-13 19:39:28In much of the world, it is incredibly difficult to access U.S. dollars. Local currencies are often poorly managed and riddled with corruption. Billions of people demand a more reliable alternative. While the dollar has its own issues of corruption and mismanagement, it is widely regarded as superior to the fiat currencies it competes with globally. As a result, Tether has found massive success providing low cost, low friction access to dollars. Tether claims 400 million total users, is on track to add 200 million more this year, processes 8.1 million transactions daily, and facilitates $29 billion in daily transfers. Furthermore, their estimates suggest nearly 40% of users rely on it as a savings tool rather than just a transactional currency.
Tether’s rise has made the company a financial juggernaut. Last year alone, Tether raked in over $13 billion in profit, with a lean team of less than 100 employees. Their business model is elegantly simple: hold U.S. Treasuries and collect the interest. With over $113 billion in Treasuries, Tether has turned a straightforward concept into a profit machine.
Tether’s success has resulted in many competitors eager to claim a piece of the pie. This has triggered a massive venture capital grift cycle in USD tokens, with countless projects vying to dethrone Tether. Due to Tether’s entrenched network effect, these challengers face an uphill battle with little realistic chance of success. Most educated participants in the space likely recognize this reality but seem content to perpetuate the grift, hoping to cash out by dumping their equity positions on unsuspecting buyers before they realize the reality of the situation.
Historically, Tether’s greatest vulnerability has been U.S. government intervention. For over a decade, the company operated offshore with few allies in the U.S. establishment, making it a major target for regulatory action. That dynamic has shifted recently and Tether has seized the opportunity. By actively courting U.S. government support, Tether has fortified their position. This strategic move will likely cement their status as the dominant USD token for years to come.
While undeniably a great tool for the millions of users that rely on it, Tether is not without flaws. As a centralized, trusted third party, it holds the power to freeze or seize funds at its discretion. Corporate mismanagement or deliberate malpractice could also lead to massive losses at scale. In their goal of mitigating regulatory risk, Tether has deepened ties with law enforcement, mirroring some of the concerns of potential central bank digital currencies. In practice, Tether operates as a corporate CBDC alternative, collaborating with authorities to surveil and seize funds. The company proudly touts partnerships with leading surveillance firms and its own data reveals cooperation in over 1,000 law enforcement cases, with more than $2.5 billion in funds frozen.
The global demand for Tether is undeniable and the company’s profitability reflects its unrivaled success. Tether is owned and operated by bitcoiners and will likely continue to push forward strategic goals that help the movement as a whole. Recent efforts to mitigate the threat of U.S. government enforcement will likely solidify their network effect and stifle meaningful adoption of rival USD tokens or CBDCs. Yet, for all their achievements, Tether is simply a worse form of money than bitcoin. Tether requires trust in a centralized entity, while bitcoin can be saved or spent without permission. Furthermore, Tether is tied to the value of the US Dollar which is designed to lose purchasing power over time, while bitcoin, as a truly scarce asset, is designed to increase in purchasing power with adoption. As people awaken to the risks of Tether’s control, and the benefits bitcoin provides, bitcoin adoption will likely surpass it.
-
 @ fbb0eb9d:bdb78256
2025-05-02 09:32:40
@ fbb0eb9d:bdb78256
2025-05-02 09:32:40Wir dürfen keinen Millimeter weichen für jene, die unsere Freiheit nicht zu schätzen wissen. Vor zehn Jahren wurden die Journalisten des französischen Satiremagazins Charlie Hebdo in ihrer Redaktion erschossen, weil sie sich die Freiheit nahmen, eine Religion zu beleidigen. Das sollten wir nicht vergessen, und beim Namen nennen. Diesen Text schrieb ich schon damals, und um es vorweg zu nehmen: Ich bin immer noch Charlie.
„Und, sind Sie auch Charlie?“ fragte damals mein Banksachbearbeiter, nachdem ich auf die Frage nach meinem Beruf „Journalistin“ geantwortet hatte. Viele waren seinerzeit „Charlie“, ja, die Solidarität mit den Opfern in Paris war groß. Bei uns im Land und auch weltweit. Tausende Facebooker veränderten ihre Profilbilder, aber genauso sicher, wie das Amen in der Kirche, hatte es nur wenige Tage gedauert, bis die Differenzierer auf den Plan gerufen wurden. Am Tag der Geiselnahmen in Paris fuhr ich gerade Taxi in Berlin, während sich die französischen Sondereinheiten vor der Druckerei und dem jüdischen Supermarkt in Stellung brachten, die ebenfalls unter Beschuss von Islamisten gerieten. Der Taxifahrer war kein potenzieller „Charlie“. Ich konnte seine Nationalität trotz Akzent nicht ausmachen, möglicherweise war er sogar Franzose. Ich habe nicht gefragt. Sein Standpunkt jedenfalls: „Warum mussten die das auch veröffentlichen, das hätte man ja wissen können, das sowas passiert“.
Wenn mehr auf dem Spiel steht, als ein Profilbild
Ein Moslem? Ich weiß es nicht. Aber auch aus dem christlichen Lager kam zunehmend Kritik, nachdem so mancher recherchiert hatte, was für Karikaturen bei „Charlie Hebdo“ in der Vergangenheit erschienen sind. Auch mit uns Christen ging man in dem Satire-Magazin nicht gerade zimperlich um. Sind wir immer noch Charlie, auch dann, wenn unsere eigene Religion aufs Korn genommen oder gar beleidigt wird?
Und so bestätigte ich dem Angestellten am Bankschalter auch gerne: „Ja, ich bin Charlie, aber ich bin auch gespannt, wie viele immer noch Charlie sind, wenn es um ihren eigenen Kopf geht!“ – eine Frage die heute kaum aktueller sein könnte angesichts von katholischen Priestern, die zwischenzeitlich im Namen Allahs in Frankreich am Altar geköpft wurden und auch islamischen Attentätern, die gerne deutsche Weihnachtsmärkte für ein adventliches Töten zum Anlass nehmen. Sind wir immer noch “Charlie” wenn die Frage nach der Solidarität mit den Opfern sich nicht mit einem Wechsel des Profilbildes bei Facebook erledigen lässt? Denn ein Bild zu tauschen, tut nicht weh, ist schnell gemacht und man bewegt sich damit gerade sowieso im Strom der breiten Masse.
Gesicht zu zeigen ist ein Anfang, es bis zur letzten Konsequenz durchzuhalten, oft etwas ganz anderes. Auch Prominente zeigten damals vor zehn Jahren gerne immer wieder Gesicht. Es existierte eine ganze Kampagne dazu unter dem Namen.
Da war dann Klaus Wowereit Migrant, wenn jemand was gegen Migranten hat, Jörg Thadeusz war schwul, wenn jemand etwas gegen Schwule hat, Ulrich Wickert war Jude, wenn jemand etwas gegen Juden hat und Markus Kavka gar schwarz, wenn jemand was gegen Schwarze hat.
 Das ist auch gut so, so wird Flagge gezeigt. Aber es braucht für derlei Bekenntnisse genauso wenig Mut, wie für den Profilbild-Wechsel bei Facebook.
Das ist auch gut so, so wird Flagge gezeigt. Aber es braucht für derlei Bekenntnisse genauso wenig Mut, wie für den Profilbild-Wechsel bei Facebook.Denn sind wir wirklich immer noch „schwarz“, „schwul“, „Jude“ oder „Migrant“, wenn unser Nebenmann angegriffen wird? Kurz nach der Ermordung der Satiriker von Charlie Hebdo bekam damals Ralf König auf Facebook und Co. von allen Seiten die Comiczeichner-Jacke vollgehauen, weil er nicht mehr ganz Charlie sein mag. Aus Angst hatte er eine Karikatur zurückgezogen, die sich mit dem Islam beschäftigte. Bei ihm steht ja auch nicht nur ein Profilbild, sondern – wie Paris gezeigt hat – wesentlich mehr auf dem Spiel. Eine allzu menschliche Reaktion! Und all den Heuchlern, die ihn verurteilen, würde ich gerne zurufen: Euch möchte ich mal in der gleichen Situation erleben. Nämlich dann, wenn es persönlich wird und die Angst nicht abstrakt, sondern konkret begründet werden kann.
Gerade Christen dürfen nicht zurückweichen
Das zeigt aber gleichzeitig, warum es so wichtig ist, dass wir auch weiterhin Charlie sind. Weil die Angst im Kopf uns sonst lähmt.
Wenn ein Journalist anfängt nachzudenken, ob er überhaupt oder wenn, wie er etwas schreiben soll, dann hat die Selbstzensur bereits eingesetzt.
Wenn ein Journalist Fakten weglässt, weil er vermutet, dass sie nicht gerne gehört werden, dann hat Selbstzensur schon eingesetzt.
Wenn ein Zeichner sich nicht mehr traut, manche Themen oder Religionen aufs Korn zu nehmen, dann hat Selbstzensur schon eingesetzt.
Und dann nutzt es nichts, dass gesetzlich keine Zensur existiert, weil diese Gesetze dann nicht mehr das Papier wert sind, auf dem sie stehen. Wir dürfen nicht zurückweichen. Auch und gerade nicht als Christen. Auch wenn wir selbst mit manchen Karikaturen hadern. Beleidigt sein darf man trotzdem. Denn der Grad von persönlicher Entrüstung ist bei allen unterschiedlich. Ich jedenfalls habe Tränen gelacht beim Kinoklassiker „Life of Brian“ und Monty Pythons „Catholic Song“ ist einfach ganz großes Kino. Aber auch ich war schon oft empört, weil mir manches, was unter Satire und Kunst verkauft wird, zu weit ging.
„Würden Sie auch Mohammed-Town ausstrahlen?“
Als etwa 2003 der Musiksender MTV die Comic-Serie „Popetown“ mit einem infantilen Papst und korrupten Kardinälen ausstrahlte, habe ich eine Gegenkampagne dazu organisiert. „Würden Sie auch Mohammed-Town“ ausstrahlen, fragte ich damals in einem offenen Brief die MTV-Geschäftsführerin Catherine Mühlemann. „Kein Christ wird Ihnen bei Ausstrahlung die Studiofenster zertrümmern, handelt es sich doch beim Christentum um eine Religion des Friedens. Wir verdienen aber nicht weniger Respekt als andere Religionen.“ 50.000 Menschen beteiligten sich damals an den Protesten, verschiedene Organisationen, Politiker und sogar der Zentralrat der Juden protestierte, genutzt hat es nichts. Die Serie erledigte sich letztendlich selbst mit niedrigen Einschaltquoten dank ihres unterirdischen Niveaus.

Aber selbst, wenn es ein Erfolg geworden wäre, hätten wir weiter protestiert: friedlich und ganz sicher nicht mit dem Maschinengewehr. Wir sind ein Land, in dem diese Debatten immer und immer wieder neu mit Worten und nicht mit Waffen ausgetragen werden. In unserem Land darf man kritisieren und sich auch empören. Wir dürfen unsere eigene Regierung anprangern und uns über Religionen lustig machen. Das tut weh, wenn man selbst betroffen ist, dieses Recht dürfen wir aber nicht riskieren. Für keinen persönlichen Grad an Beleidigtsein.
Diskurs statt Blasphemie-Gesetze
Wenn wir also Rücksicht nehmen auf Religionen, dann aber bitte auf alle. Wenn Religionen aber Kritik, Humor oder Satire aushalten müssen, dann bitte auch alle. Ich halte nichts von Blasphemie-Gesetzen, aber umso mehr vom freien Diskurs, der nicht nur in der Religionsfrage derzeit ins Hintertreffen gerät.
Die Frage, ob „der Islam“ zu Deutschland gehört, ist also die falsche. Die Frage ist: Will der Islam zu Deutschland oder gar zu Europa gehören? Sind alle seine Gläubigen bereit, friedlich hinzunehmen, dass im Namen von Meinungsfreiheit, Kunst oder Satire der eigene Glaube beleidigt werden darf?
Denn erst dann ist der Islam wirklich im freien Europa angekommen und diese Frage können die Muslime nur unter sich ausmachen. Es ist nicht an uns, ihnen ihre Religion zu erklären. Wir sollten aber langsam klären, wofür wir selbst stehen. Integration kann nur von jemandem erwartet werden, dem man auch erklären kann, in was er sich integrieren und wie weit das reichen soll.
Wir werden den gemeinsamen Nenner aufzeigen müssen, die „Conditio-sine-qua-non“, ohne die sich unsere Gesellschaft sonst immer weiter auseinander bewegt. Ich habe damals von Catherine Mühlemann keine Antwort auf meine Frage bekommen. Ich weiß nicht, ob sie heute Charlie ist. Ich wünsche mir keinen Raum für diese Angst, die uns lähmt, Debatten ehrlich zu führen. Für Menschen, die unsere Freiheit nicht zu schätzen wissen, weiche ich keinen Millimeter. Ich bin Birgit Kelle. Und ich bin immer noch Charlie.
-
 @ a5142938:0ef19da3
2025-05-02 09:39:05
@ a5142938:0ef19da3
2025-05-02 09:39:05Do you know a brand offering natural alternatives? Share it here by commenting on this page!
To be listed, the brand must offer at least some of its products made from natural materials. 👉 Learn more about materials
Each piece of information added (name, link, category, etc.) and validated is considered a contribution. 👉 Learn more about contributions
Every validated contribution is counted and eligible for rewards. Make sure to securely save your keys (credentials) in a vault like nsec.app). You can also share more easily your finds without creating an account via the contact form (not eligible for rewards). 👉 Learn more about rewards
Copy and paste the template below and fill in the information you have. Other contributors or the core team can complete any missing details.
New brand or manufacturer
- Brand name:
- Image representing the brand’s products (link, ideally from the brand’s website):
- Short description:
- Categories of products offered:
- Materials used in its products:
- Brand’s website:
- Other information (place of production, certifications, etc.):
This article is published on origin-nature.com 🌐 Voir cet article en français
-
 @ 0c469779:4b21d8b0
2025-03-11 10:52:49
@ 0c469779:4b21d8b0
2025-03-11 10:52:49Sobre el amor
Mi percepción del amor cambió con el tiempo. Leer literatura rusa, principalmente a Dostoevsky, te cambia la perspectiva sobre el amor y la vida en general.
Por mucho tiempo mi visión sobre la vida es que la misma se basa en el sufrimiento: también la Biblia dice esto. El amor es igual, en el amor se sufre y se banca a la otra persona. El problema es que hay una distinción de sufrimientos que por mucho tiempo no tuve en cuenta. Está el sufrimiento del sacrificio y el sufrimiento masoquista. Para mí eran indistintos.
Para mí el ideal era Aliosha y Natasha de Humillados y Ofendidos: estar con alguien que me amase tanto como Natasha a Aliosha, un amor inclusive autodestructivo para Natasha, pero real. Tiene algo de épico, inalcanzable. Un sufrimiento extremo, redentor, es una vara altísima que en la vida cotidiana no se manifiesta. O el amor de Sonia a Raskolnikov, quien se fue hasta Siberia mientras estuvo en prisión para que no se quede solo en Crimen y Castigo.
Este es el tipo de amor que yo esperaba. Y como no me pasó nada tan extremo y las situaciones que llegan a ocurrir en mi vida están lejos de ser tan extremas, me parecía hasta poco lo que estaba pidiendo y que nadie pueda quedarse conmigo me parecía insuficiente.
Ahora pienso que el amor no tiene por qué ser así. Es un pensamiento nuevo que todavía estoy construyendo, y me di cuenta cuando fui a la iglesia, a pesar de que no soy cristiano. La filosofía cristiana me gusta. Va conmigo. Tiene un enfoque de humildad, superación y comunidad que me recuerda al estoicismo.
El amor se trata de resaltar lo mejor que hay en el otro. Se trata de ser un plus, de ayudar. Por eso si uno no está en su mejor etapa, si no se está cómodo con uno mismo, no se puede amar de verdad. El amor empieza en uno mismo.
Los libros son un espejo, no necesariamente vas a aprender de ellos, sino que te muestran quién sos. Resaltás lo que te importa. Por eso a pesar de saber los tipos de amores que hay en los trabajos de Dostoevsky, cometí los mismos errores varias veces.
Ser mejor depende de uno mismo y cada día se pone el granito de arena.
-
 @ 866e0139:6a9334e5
2025-04-05 10:34:00
@ 866e0139:6a9334e5
2025-04-05 10:34:00
Autor: Annette Conzett. (Bild: Hermine Zgraggen). Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier.**
- Konflikte können NICHT im Aussen an 1. Stelle gelöst werden.
- Alles, was sich im Aussen präsentiert, ist das Abbild dessen, was im Inneren eines jeden eingelagert ist.
- Das Aussen ist die Bühne des Inneren und das Innere lässt das auf der Bühne entstehen, was innen aufgehoben ist.
- Dank dem Aussen kommen wir (alle) in Kontakt mit dem, was uns bewegt, was wir in uns tragen. Es präsentiert sich auf der äusseren Bühne.
- Das Aussen ist die Leinwand. Der Projektor ist jeder einzelne von uns.
- Alles, was vom Aussen in Resonanz mit uns geht, ist etwas, das uns selber betrifft, jeden einzelnen von uns.
- Wir alle tragen Informationen in uns, die wir selber kreiert haben und solche, die aus dem systemischen Gedächtnis eingeflossen und in uns verborgen sind.
- Durch das, was sich im Aussen abspielt, triggert es etwas – wenn es uns selber betrifft –, das im Inneren verborgen liegt.
- Das kollektive Gedächtnis, das die Menschheits-Geschichte bestimmt und „im Alten gefangen hält“, generiert in Anknüpfung an das, was sich auf der äusseren Bühne abspielt, die Möglichkeit der Überwindung des vermeintlich Unüberwindbaren.
- Das globale System birgt alle Erinnerungen, welcher Art auch immer sie sind, sowie die darin enthaltenen Überlebensstrategien.
- Strategien werden in den Familien, in den gesellschaftlichen Strukturen sowie dem jeweils kulturellen Denken weitergereicht. Hier sind sowohl konstruktive wie zerstörerische Überlieferungen unbewusst aktiv, reagieren eigendynamisch, es sei denn, sie bekommen innere Führung = die Erwachsene Instanz übernimmt.
- Macht, Kampf, Zerstörung sind Schöpfungen des Egos, das für Trennung sorgt. Trennung erzeugt Angst, oder besser: Angst ist das Ergebnis der Trennung, das Produkt aus dem Schöpfungsakt des Egos, in dem die Bezogenheit zu sich im Kern, dem Wesenskern, unterbrochen wird.
- Die Er-Lösung aus dieser Trennung ist unter anderem die Würdigung und der Respekt sich selber und dem anderen gegenüber. Wir können auch von Vergebung sprechen, denn ich erkenne mich dank „dir“ mit dem, was sich in mir abspielt.
- Bewertung, Abwertung, Interpretation, Groll etc. sind Diener von Macht und Kampf, dem Ego.
- Wenn diese Strategen auf der Lebensbühne auftreten, gilt es hinzuschauen um zu erkennen, was das mit einem selber zu tun hat. „Wo greife ich den anderen an“? „Wo greife ich mich selber an?“?
- … denn alles das, was ein Angriff ist, und sei es nur der sog. vermeintlich geringste, fällt auf den Angreifer zurück.
- Gelingt es, den Player auf „der eigenen Bühne“ anzuschauen, dann ist es möglich, das dualistischen Denken schon mal etwas zu lockern, „erkenne ich mich doch selbst im anderen“. Alles, was stärkt, ist ein Zeichen der Würdigung. Alles, was schwächt, ist Zeichen der Trennung.
- Wenn das, was sich da draussen alles abspielt, draussen bleiben kann, man selber nicht in Resonanz damit geht, dann spricht der Selbstbezug von Kontakt zu sich und lässt sich durch das Getöse im Aussen nicht trennen.
- Sollte sich die Nicht-Resonanz aus Ignoranz generieren, dann fehlt in diesem Fall die Strahlkraft und wird durch Diskussionen und Aktionen ersetzt.
- Resonanzen auf die äussere Bühne geben dem bewussten Erdenbürger die Chance, hinzuschauen, um innere verdeckte Passagiere aufzudecken, die jeweils anspringen, um in die Angst, in die Trennung zu gehen.
- In diesem Übungsfeld liegt, wenn bewusst gelebt, die Überwindung der Trennung. So wird am Weg in die Freiheit geübt und Frieden erfahren.
- Es ist Zeit für Selbstreflexion und nicht jene für Projektion. Darin liegt das Geschenk des Friedens.
Annette Conzett begleitet seit bald 50 Jahren Menschen zu mehr Ruhe und innerer Ordnung.\ Sie ist Psychotherapeutin IKP/ASP, Hypnosetherapeutin GHYPS, Therapeutin für\ Systemische Prozesse, Atemtherapeutin IKP, Lehrtherapeutin, Supervisorin und\ Bewegungspädagogin SBTG. Annette Conzett lebt und arbeitet in Zollikon bei Zürich und hat\ Kinder und Enkelkinder. Ihr Weg ist erfüllt von der Freude am Leben und an den Menschen.\ Über Ihre Arbeit mit Menschen, die „ihren Frieden suchen“ sagt sie selbst: „Schlussendlich\ geht es um die Verbindung zum Wesenskern. Der Weg dorthin ist meist verstellt. Mein Fokus\ besteht darin, mich um die Freilegung dieser Verbindung zu kümmern.“ Homepage: https://annetteconzett.ch/
LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt. (Vorerst an alle, da wir den Mailversand testen, später ca. drei Mails pro Woche.).
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: milosz@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ 88cc134b:5ae99079
2025-04-30 16:10:52
@ 88cc134b:5ae99079
2025-04-30 16:10:52Lorem ipsum dolor sit amet, consectetur adipiscing elit. In et tempor magna. Donec nec nibh sed dolor euismod aliquam. Vestibulum fermentum rutrum tortor dictum tincidunt. Cras vestibulum risus at imperdiet malesuada. Nulla dignissim arcu nec nibh hendrerit, in convallis tellus pharetra. Nunc tristique libero non ante ultrices consectetur. In lacinia ipsum quis diam sollicitudin, sit amet venenatis neque auctor. Sed ut ipsum ac dui ullamcorper bibendum. Pellentesque sit amet mi imperdiet, convallis velit vel, vehicula ipsum. Nulla hendrerit, odio mollis egestas hendrerit, sem est egestas justo, at dapibus odio massa et leo.
Fusce efficitur nunc non ante tincidunt laoreet. Vivamus dictum magna eu nisl ullamcorper mollis. Cras magna odio, maximus eu luctus egestas, porttitor nec sem. Maecenas sed tortor aliquet, consequat dolor quis, cursus massa. Nulla consequat nisl ut lacus elementum mollis. Nulla facilisi. Praesent laoreet ante ligula, id porta nisl malesuada id. Sed eu quam semper, suscipit tortor eget, feugiat mauris. Maecenas hendrerit arcu ligula, vitae maximus orci efficitur quis. In feugiat lectus in velit aliquet tincidunt. Aenean sit amet neque mollis, laoreet leo tincidunt, volutpat arcu.
Donec id massa diam. Nunc ac nunc non massa bibendum convallis non in nisl. Phasellus at nisl cursus, aliquet nibh ut, varius nisl. Cras eget dolor neque. Pellentesque et maximus dui. Sed metus erat, facilisis et blandit vitae, facilisis quis diam. Nullam vitae mattis odio. Vivamus varius sapien non arcu convallis, ut varius est lobortis. Maecenas tristique sagittis nunc, non lobortis mi fermentum quis.
Vestibulum in consectetur nibh. Integer libero mauris, sagittis sed nulla tincidunt, venenatis vestibulum nibh. Praesent vitae ex non quam pretium luctus. Etiam fringilla mattis tellus, eu placerat enim vestibulum nec. Curabitur vitae dictum erat. Fusce non ligula vehicula, aliquam eros sit amet, pharetra felis. Suspendisse dapibus pretium dui. Donec quis erat est. Nunc varius dolor velit, sit amet consectetur enim finibus sit amet. Aenean malesuada erat sed libero vestibulum, vel varius dui gravida. Ut volutpat risus dui, quis euismod nisi ornare et. Nullam blandit iaculis ipsum. Donec ullamcorper turpis quis placerat tincidunt.
Fusce mi ante, euismod et lorem vitae, commodo fringilla ex. Maecenas sagittis euismod nibh. Integer vestibulum sit amet ipsum ut fringilla. Etiam bibendum, risus id malesuada faucibus, magna libero vulputate nulla, in suscipit tortor orci sed arcu. Sed malesuada ipsum nec faucibus pulvinar. Aliquam vehicula lorem sit amet nulla vulputate, eget efficitur mauris sagittis. Nullam lacus ipsum, bibendum sed laoreet at, tristique vel massa. Cras non lorem sit amet sapien auctor feugiat ac sed lorem. Pellentesque tellus erat, rhoncus nec venenatis ac, efficitur vitae felis. Sed in nunc erat. Nullam et quam ac diam rutrum auctor in id ante. Suspendisse pulvinar porttitor mattis. Cras ultrices tristique elit, sit amet vulputate diam ultricies sit amet. Sed scelerisque est eros, eget semper erat vehicula vel. Pellentesque habitant morbi tristique senectus et netus et malesuada fames ac turpis egestas.
-
 @ ca495706:2476e4d0
2025-05-02 09:38:12
@ ca495706:2476e4d0
2025-05-02 09:38:12VIPWIN là một nền tảng trực tuyến phát triển mạnh mẽ trong thời gian gần đây, mang đến cho người dùng những trải nghiệm mượt mà và an toàn. Được thiết kế với giao diện thân thiện và dễ sử dụng, VIPWIN không chỉ chú trọng đến việc tối ưu hóa trải nghiệm người dùng mà còn bảo vệ quyền lợi của họ một cách tối đa. Tính năng của nền tảng này luôn được cập nhật và cải tiến để phục vụ nhu cầu ngày càng cao của người dùng. VIPWIN cung cấp một không gian trực tuyến hiện đại, dễ tiếp cận, cho phép người dùng truy cập các dịch vụ chỉ trong vài bước đơn giản. Dù bạn là người mới sử dụng hay là người đã có kinh nghiệm, việc làm quen với hệ thống của VIPWIN sẽ rất dễ dàng nhờ vào giao diện trực quan và các tính năng hỗ trợ rõ ràng. Một trong những yếu tố quan trọng tạo nên sự khác biệt của VIPWIN chính là tốc độ truy cập ổn định và nhanh chóng. Người dùng sẽ không gặp phải tình trạng gián đoạn hay độ trễ trong suốt quá trình sử dụng dịch vụ.
Bảo mật là một trong những yếu tố quan trọng mà VIPWIN đặc biệt chú trọng. Với sự phát triển không ngừng của công nghệ, việc bảo vệ thông tin cá nhân của người dùng là vô cùng cần thiết. VIPWIN sử dụng các công nghệ mã hóa tiên tiến để đảm bảo rằng dữ liệu của người sử dụng luôn được bảo vệ an toàn tuyệt đối. Các thông tin giao dịch và dữ liệu cá nhân đều được mã hóa, giúp người dùng yên tâm khi sử dụng nền tảng mà không phải lo lắng về việc bị lộ lọt thông tin. Ngoài ra, đội ngũ bảo mật của VIPWIN luôn theo dõi và kiểm tra hệ thống thường xuyên để phát hiện và xử lý kịp thời các mối đe dọa tiềm ẩn. Điều này giúp người dùng hoàn toàn tin tưởng vào sự an toàn của nền tảng. Không chỉ vậy, VIPWIN còn cung cấp dịch vụ hỗ trợ khách hàng chuyên nghiệp, hoạt động liên tục 24/7, sẵn sàng giải đáp mọi thắc mắc và hỗ trợ người dùng khi gặp phải vấn đề. Đội ngũ hỗ trợ của VIPWIN luôn tận tâm và chu đáo, đảm bảo người dùng luôn được hỗ trợ nhanh chóng và hiệu quả.
Với cam kết phát triển không ngừng và cải tiến liên tục, VIPWIN không chỉ đáp ứng nhu cầu của người dùng mà còn luôn tạo ra những giá trị mới cho cộng đồng. Nền tảng này luôn cập nhật và cải tiến các tính năng để mang đến cho người dùng những trải nghiệm tối ưu nhất. Các tính năng mới luôn được phát triển dựa trên nhu cầu thực tế của người sử dụng, nhằm cải thiện hiệu suất và nâng cao chất lượng dịch vụ. VIPWIN luôn chú trọng đến việc cải tiến giao diện, nâng cao tốc độ truy cập và cập nhật các công cụ hỗ trợ người dùng. Một điểm đáng chú ý nữa là nền tảng này luôn sẵn sàng lắng nghe ý kiến đóng góp từ cộng đồng người dùng, từ đó đưa ra các thay đổi và cải tiến phù hợp. Chính nhờ sự sáng tạo và cam kết không ngừng nâng cao chất lượng dịch vụ, VIPWIN đang ngày càng trở thành lựa chọn hàng đầu của người dùng trong môi trường trực tuyến. Với đội ngũ phát triển chuyên nghiệp và tầm nhìn dài hạn, VIPWIN chắc chắn sẽ tiếp tục phát triển mạnh mẽ và duy trì vị thế là một trong những nền tảng trực tuyến đáng tin cậy nhất trong tương lai.
-
 @ 04c915da:3dfbecc9
2025-03-10 23:31:30
@ 04c915da:3dfbecc9
2025-03-10 23:31:30Bitcoin has always been rooted in freedom and resistance to authority. I get that many of you are conflicted about the US Government stacking but by design we cannot stop anyone from using bitcoin. Many have asked me for my thoughts on the matter, so let’s rip it.
Concern
One of the most glaring issues with the strategic bitcoin reserve is its foundation, built on stolen bitcoin. For those of us who value private property this is an obvious betrayal of our core principles. Rather than proof of work, the bitcoin that seeds this reserve has been taken by force. The US Government should return the bitcoin stolen from Bitfinex and the Silk Road.
Usually stolen bitcoin for the reserve creates a perverse incentive. If governments see a bitcoin as a valuable asset, they will ramp up efforts to confiscate more bitcoin. The precedent is a major concern, and I stand strongly against it, but it should be also noted that governments were already seizing coin before the reserve so this is not really a change in policy.
Ideally all seized bitcoin should be burned, by law. This would align incentives properly and make it less likely for the government to actively increase coin seizures. Due to the truly scarce properties of bitcoin, all burned bitcoin helps existing holders through increased purchasing power regardless. This change would be unlikely but those of us in policy circles should push for it regardless. It would be best case scenario for American bitcoiners and would create a strong foundation for the next century of American leadership.
Optimism
The entire point of bitcoin is that we can spend or save it without permission. That said, it is a massive benefit to not have one of the strongest governments in human history actively trying to ruin our lives.
Since the beginning, bitcoiners have faced horrible regulatory trends. KYC, surveillance, and legal cases have made using bitcoin and building bitcoin businesses incredibly difficult. It is incredibly important to note that over the past year that trend has reversed for the first time in a decade. A strategic bitcoin reserve is a key driver of this shift. By holding bitcoin, the strongest government in the world has signaled that it is not just a fringe technology but rather truly valuable, legitimate, and worth stacking.
This alignment of incentives changes everything. The US Government stacking proves bitcoin’s worth. The resulting purchasing power appreciation helps all of us who are holding coin and as bitcoin succeeds our government receives direct benefit. A beautiful positive feedback loop.
Realism
We are trending in the right direction. A strategic bitcoin reserve is a sign that the state sees bitcoin as an asset worth embracing rather than destroying. That said, there is a lot of work left to be done. We cannot be lulled into complacency, the time to push forward is now, and we cannot take our foot off the gas. We have a seat at the table for the first time ever. Let's make it worth it.
We must protect the right to free usage of bitcoin and other digital technologies. Freedom in the digital age must be taken and defended, through both technical and political avenues. Multiple privacy focused developers are facing long jail sentences for building tools that protect our freedom. These cases are not just legal battles. They are attacks on the soul of bitcoin. We need to rally behind them, fight for their freedom, and ensure the ethos of bitcoin survives this new era of government interest. The strategic reserve is a step in the right direction, but it is up to us to hold the line and shape the future.
-
 @ fbb0eb9d:bdb78256
2025-05-02 09:28:33
@ fbb0eb9d:bdb78256
2025-05-02 09:28:33„Das Schlachten hat begonnen“ war im Jahr 2013 der Titel eines höchst umstrittenen – also wahrscheinlich recht realistischen – Meinungsbeitrags des Autors Akif Pirinçci. Heute ruft die Terrororganisation Islamischer Staat (IS) ganz offiziell in Deutschland genau zu jenem Schlachten auf, das der Autor damals bereits als sichtbares Schema eines außer Kontrolle geratenen Islams in Deutschland beklagte. Der Beitrag ist heute im Internet gelöscht. 12 Jahre später fordern islamische Terroristen ihre Glaubensbrüder in Deutschland auf: „Auf zum Schlachten. Worauf wartest du? Die Straßen sind voller Ziele! Überfahre sie!!“ und verbreiten dazu Bilder, bei denen der Fahrer eines Wagens die Menschen vor ihm auf der Straße ins Fadenkreuz nimmt.

Der Deutsch-Türke Pirinçci war den meisten Lesern bis zu diesem Zeitpunkt eher als weltweiter Bestsellerautor von „Felidae“ und als Erfinder der Romangattung “Katzenkrimi“ bekannt denn als politischer Autor und Kritiker des Zeitgeschehens. Sein Hang zur unflätigen und vulgären Ausdrucksweise und seine anschließenden Auftritte u. a. bei den islamkritischen „Pegida“-Demonstrationen hatten es seinen Kritikern einst leicht gemacht, den brisanten Inhalt seiner Texte und Thesen gleich mit vom Tisch zu wischen und ihn nach allen Regeln jener Kunst, die man heute als „Cancel Culture“ bezeichnet, als ihr erstes prominentes Opfer ins komplette Abseits zu katapultieren. Nun schreibe ich das nicht, um zur späten Rehabilitierung eines Kollegen anzusetzen, sondern weil es sich lohnt, die Genese dieses Vorgangs heute zu betrachten, um sich ehrlich zu fragen: Kommen einem die medialen und politischen Reaktionen nicht doch sehr bekannt vor? Und wenn man das damals alles schon sehen konnte, warum sind wir über ein Jahrzehnt später immer noch nicht weiter?
Ein Exempel wird statuiert
Da schreibt also ein Autor bereits vor 12 Jahren, selbst als Türke mit Einwanderungsbiografie, eine scharfe Kritik an der deutschen Einwanderungspolitik, die mit den Menschen einen Islam zu uns bringt, der sich in Gewalt entlädt und die einheimische Bevölkerung bedroht. Aufhänger des Textes war 2013 der Todesfall des 25-jährigen Lackierers Daniel S., der von einem herbeitelefonierten Schlägertrupp an einer Bushaltestelle abgepasst wurde und später an seinen Kopfverletzungen verstarb. Die Täter hatten türkischen Migrationshintergrund, manche waren bereits polizeibekannt, beides verschwieg die Polizei in ihrer Pressemitteilung an die Öffentlichkeit, bis die BILD-Zeitung die ganze Wahrheit druckte.
Der später verurteilte Täter war statistisch „Deutscher“, seine Tat zahlt in die Polizeistatistik der Deutschen ein, da er in Deutschland geboren wurde, also bereits zweite Generation Einwandererkind ist, man kann seine Integration und die seiner Freunde aber als gescheitert bezeichnen. Pirinçci verliert danach alles, man streicht Verträge, er wird nicht mehr gedruckt und sein Verlag, der vorher Millionen mit ihm verdient hatte, lässt ihn hängen, weil sich gutmenschelnde Autorenkollegen des Verlages von ihm distanzieren und seinen Kopf fordern, schließlich gilt der Türke Pirinçci jetzt als Rassist und als islamophob. Die Läden nehmen seine Bücher aus den Regalen und selbst die Katzenromane aus dem Sortiment. Das Schlachten geht derweil unbehelligt weiter. Ein Kritiker weniger und dazu ein Exempel statuiert: Wagt nicht, dieses Thema anzufassen.
Blutspur durch Europa
Das Schlachten hat schon lange begonnen, nicht erst jetzt. Wie eine Blutspur ziehen sich die Tatorte und Attacken zugewanderter Migranten auf die europäische Bevölkerung seit 20 Jahren über die Landkarte. Von den inzwischen täglichen Messerattacken, die man schon gar nicht mehr mitzählt, bis zu größeren Anschlägen ist alles dabei. Die Tatwaffen ändern sich, die Orte auch, aber das Schema bleibt: Einheimische werden von islamischen Zuwanderern ermordet, absichtlich totgefahren, abgestochen, erschossen, geköpft, in die Luft gesprengt. Es geschieht in Deutschland, in Österreich, massiv in Frankreich, in Belgien, in England, Spanien und auch in Schweden.
Manche dieser Taten liegen schon sehr viele Jahre zurück, manche, die heute „gegen rechts“ auf die Straße gehen, wenn wieder einmal ein Islamist das Gedankenkonstrukt der Vielfalt gefährdet, waren damals noch in der Kita. Spätestens seit 2015 und der Terrorwelle in Frankreich ist das Thema in ganz Europa präsent. Die Journalisten des Satiremagazins Charlie Hebdo werden im Januar 2015 in ihrer Redaktion niedergemetzelt, 11 Tote. Die Botschaft: Leg dich nicht mit Mohammed und seinen humorlosen Gesellen an. Am Tag darauf ein jüdischer Supermarkt in Paris, 4 Tote und eine Geiselnahme. Dann im November 2015 koordinierte, islamistische Attentate mit insgesamt 130 Toten und 683 Verletzten zwischen Sprengsätzen am Stade de France über Zufallsopfern in Bars und Restaurants bis zu einem Blutbad mit 89 Toten, die in der Konzerthalle Bataclan mit Maschinengewehren wahllos niedergemetzelt werden.
In der darauffolgenden Silvesternacht wird Köln Schauplatz Hunderter Übergriffe von Migranten auf Frauen. Ein Auto als Waffe? Premiere schon 2016 auf dem Boulevard von Nizza mit 86 Toten und über 400 Schwerverletzten am Nationalfeiertag. In Deutschland folgt das Schema erstmals im selben Jahr im Dezember 2016 auf dem Weihnachtsmarkt am Breitscheidplatz. Im März 2016 sprengen sich in Brüssel Islamisten am Flughafen und auf einem Bahnhof in die Luft und hinterlassen 32 Todesopfer aus 22 Ländern und unzählige Verletzte. Am Jahrestag ein Jahr später rammt sich ein Islamist in London auf der Westminsterbrücke seinen Weg durch eine Menschenmenge. Spanien hatte die Terrorwelle bereits 2004 eingeholt, es kostete fast 200 Tote und fast 2.000 Verletzte, dass Islamisten koordiniert vier Züge Richtung Madrid hintereinander in die Luft sprengten. Zwei Jahrzehnte Terror in Europa. Dazwischen Machetenangriffe, geköpfte Priester, ermordete Filmemacher, ermordete Lehrer, die es wagen, das Thema in der Schule zu behandeln, Sprengsätze, vergewaltigte und ermordete Frauen und Islamkritiker, die nur noch mit ständigem Personenschutz leben können. Nur eines bleibt immer gleich: Niemand verändert die Migrationspolitik. Alle sind bemüht, stattdessen den Kampf gegen Islamophobie und Rassismus unbedingt zu verstärken, auf zur Demo gegen rechts!
Vergessene Opfer
Das Schema der medialen und politischen Verarbeitung blieb immer konstant: verschweigen, kleinreden, vergessen. Die Erinnerungskultur der Deutschen beschränkt sich gerne auf die Opfer der Nationalsozialisten und auf jene Ausländer, die von Deutschen ums Leben gebracht wurden. Hier werden, wie gerade erst vor wenigen Tagen, immer noch gerne die Namen der Opfer von Hanau von deutschen Politikern in den Medien wiederholt. Doch kennt jemand die Namen der Opfer vom Breitscheidplatz, also jenem Anschlag, der einst auslöste, dass heute jeder Weihnachtsmarkt in Deutschland zur Hochsicherheitszone aufgerüstet wird und bei dem die Politik einst peinlich bemüht war, nicht von einem islamistischen Anschlag zu sprechen? Und selbst das hat das nächste Schlachten in Magdeburg ja nicht verhindern können.
Kennt jemand die Namen aller Opfer vom Weihnachtsmarkt in Magdeburg? Kollegen bei der WELT recherchieren derzeit dankbarerweise die Folgen alleine dieses Anschlags akribisch nach. Man spricht von 1.300 Opfern insgesamt, 6 Toten, 300 Verletzten, davon 67 Schwerverletzten, einem Querschnittsgelähmten und zahlreichen Opfern, die Hände, Füße oder gar ein Bein verloren haben. Warum berührt es nicht alle gleichermaßen? Die Folgen sind keine Umkehr in der Migrationspolitik der Regierung, sondern weitere, staatlich mitorganisierte und mitfinanzierte Demonstrationen „gegen rechts“. In Aschaffenburg sind Kindergartenkinder das Opfer, ein Helfer bezahlt seinen Mut mit dem Leben, für einen Zweijährigen kommt jede Hilfe zu spät. In München fährt vor wenigen Tagen ein Islamist in eine Demonstration, eine Mutter und ihr Kind werden unter den Wagen gezogen, sie sind verstorben, noch am selben Abend demonstriert man in München „gegen rechts“, während Dutzende Schwerverletzte in den Krankenhäusern liegen und der Täter im Gefängnis reklamiert, man möge seine Zelle von der imaginären Verschmutzung durch Christen reinigen. Wenige Tage später sticht im österreichischen Villach ein Migrant wahllos in der Innenstadt Passanten nieder, ein 14-Jähriger stirbt. Der Täter lacht bei seiner Verhaftung. Die Polizei in Wien nimmt vor zwei Tagen einen 14-Jährigen fest, er plante einen Anschlag auf den Westbahnhof. Wien hatte bereits 2020 einen eigenen Amoklauf mit 4 Toten und erst im Sommer 2024 musste dort ein Taylor-Swift-Konzert wegen dringenden Terrorverdachts abgesagt werden. In Schweden wurde vor wenigen Wochen ein Islamkritiker während eines Live-Streams durch Islamisten erschossen. Europa 2025.
Man wird müde, die immer selben Worte zu wiederholen bei den sich immer enger taktenden Anschlägen von Migranten in unserem Land und in Europa. Es fehlen die Worte, weil bereits alles gesagt ist. Genauso, wie sich die sinnlosen Floskeln der Politiker wiederholen, wenn wieder eine junge Frau, ein Kind, ein Vater oder ein mutiger Helfer sein Leben lassen muss und das Volk in der verbalen Litanei erstickt wird zwischen „verwirrter Einzeltäter – Betroffenheit – wir lassen uns nicht spalten – Stadt XY bleibt bunt und wir lassen uns die Art zu leben nicht nehmen“. So, als würden nicht bereits die ersten Karnevalsumzüge abgesagt, weil die Sicherheit auf den Straßen nicht mehr garantiert werden kann.
Wir demonstrieren uns zu Tode
Was, wenn gar nicht die AfD das Problem ist, sondern der Islam? Man stelle sich für eine Sekunde vor, die AfD wäre erfolgreich bekämpft und weg. Eine Nulllinie, von der man in den Jahren 2014 und 2015 gar nicht so weit entfernt war. Damals stand die AfD in den Umfragen irgendwo zwischen 2 und 4 Prozent und tat gerade das, was nahezu alle neuen Parteigründungen der vergangenen 30 Jahre taten: Sie zerlegten sich in innerparteilichen Streitigkeiten selbst. Doch dann öffnete Angela Merkel die Grenze zur unkontrollierten Migration nach Deutschland und lieferte über Jahre ein Thema, an dem sich die AfD wie ein Phoenix aus der Asche wieder neu erhob. Denken wir also eine Sekunde, die AfD sei als Problem weg, welche Probleme sind dann immer noch da? Nichts von dem, was gerade in Deutschland relevant ist, wäre gelöst. Rezession, Wirtschaftskrise, Energiekrise, Krieg in Europa und ja, vor allem auch die gescheiterte Migrationspolitik und die Erosion der inneren Sicherheit sind dann immer noch da. Man kann natürlich die AfD exzessiv bekämpfen statt der realen Probleme, es bleibt dann aber alles, wie es ist. In einem Pseudokampf lenken die wechselnden politischen Eliten erfolgreich vom Thema ab, indem man nun bereits über ein Jahrzehnt den falschen Feind bekämpft. Gerade wird in einem Akt kollektiver kultureller Todessehnsucht das Feindbild AfD zum Feindbild CDU erweitert, um die gesamte bürgerliche Mitte von einer Umkehr in der Migrationspolitik abzuhalten. Immer noch treten brav nach jedem weiteren Anschlag wie gehirngewaschen erwachsene Menschen zu einer Demo gegen rechts an. „Wir amüsieren uns zu Tode“, resümierte einst der Autor Neil Postman die Zersetzung des Westens durch die Unterhaltungsindustrie. Deutschland hat sich im Angesicht einer kulturellen Übernahme durch zugewanderte islamische junge Männer einen weltweiten Alleingang ausgedacht: Deutschland demonstriert sich zu Tode.
Das Schlachten hat schon lange begonnen. Wer es jetzt immer noch nicht versteht, dass eine Mehrheit der illegal einreisenden Migranten weder zur Integration noch zur Arbeit und schon gar nicht wegen politischer Verfolgung hierherkommt, dem ist nicht zu helfen. Wer glaubt, er könne Millionen an aggressiven Antisemiten, glühenden Frauenhassern, Christenverächtern und Sozialstaatstouristen gesellschaftlich, kulturell und finanziell integrieren, ist realitätsfremd. An diesem Sonntag wird gewählt. Der Souverän wird seine eigene Meinung dazu kundtun, wem er zutraut, das Schlachten zu beenden.
-
 @ bc52210b:20bfc6de
2025-04-28 20:08:09
@ bc52210b:20bfc6de
2025-04-28 20:08:09
Imagine a world where clean, safe, and efficient nuclear power can be delivered to any corner of the globe, powering everything from small villages to bustling cities. This vision is becoming a reality with the development of nuclear modular plants—compact, portable nuclear reactors that can be shipped in standard containers and set up quickly to provide reliable energy. These innovative power sources use fission—the process of splitting atomic nuclei to release energy, the same fundamental principle that powers traditional nuclear plants—but with a twist: they utilize thorium as fuel and a molten salt system for cooling and fuel delivery. This combination offers a host of benefits that could revolutionize how we think about nuclear energy.
Portability and Deployment
One of the most significant advantages of these nuclear modular plants is their portability. Designed to fit within standard shipping containers, these reactors can be transported by truck, ship, or even air to virtually any location. This makes them ideal for remote communities, disaster relief efforts, or military operations where traditional power infrastructure is lacking or damaged. Setting up a conventional power plant typically takes years, but these modular units can be operational in a matter of weeks, providing a rapid solution to energy needs.
Safety Features
Safety is a paramount concern in nuclear energy, and modular thorium molten salt reactors (MSRs) offer several inherent safety advantages. Unlike traditional reactors that use water under high pressure, MSRs operate at atmospheric pressure, eliminating the risk of pressure-related accidents. The fuel is dissolved in the molten salt, which means there's no solid fuel that could melt down. If the reactor overheats, the salt expands, naturally slowing the fission reaction—a built-in safety mechanism. Additionally, thorium-based fuels produce less long-lived radioactive waste, reducing the long-term environmental impact.
Efficiency and Abundance
Thorium is a more abundant resource than uranium, with estimates suggesting it is three to four times more plentiful in the Earth's crust. This abundance makes thorium a sustainable fuel choice for the future. Moreover, MSRs can operate at higher temperatures than traditional reactors, leading to greater thermal efficiency. This means more electricity can be generated from the same amount of fuel, making the energy production process more efficient and cost-effective in the long run.
Scalability
The modular design of these reactors allows for scalability to meet varying power demands. A single unit might power a small community, while multiple units can be combined to serve larger towns or cities. This flexibility is particularly useful for growing populations or regions with fluctuating energy needs. As demand increases, additional modules can be added without the need for extensive new infrastructure.
Cost-Effectiveness
While the initial investment in nuclear modular plants may be significant, the long-term operational costs can be lower than traditional power sources. The high efficiency of MSRs means less fuel is needed over time, and the reduced waste production lowers disposal costs. Additionally, the ability to mass-produce these modular units could drive down manufacturing costs, making nuclear power more accessible and affordable.
Environmental Impact
Nuclear power is already one of the cleanest energy sources in terms of carbon emissions, and thorium MSRs take this a step further. By producing less long-lived waste and utilizing a more abundant fuel, these reactors offer a more sustainable path for nuclear energy. Furthermore, their ability to provide reliable baseload power can help reduce reliance on fossil fuels, contributing to global efforts to combat climate change.
Challenges and Considerations
Despite these benefits, there are challenges to overcome before nuclear modular plants can be widely deployed. The technology for thorium MSRs is still in the developmental stage, with ongoing research needed to address issues such as material corrosion and fuel processing. Regulatory frameworks will also need to adapt to this new type of reactor, and public perception of nuclear energy remains a hurdle in many regions. However, with continued investment and innovation, these obstacles can be addressed.
Conclusion
In conclusion, nuclear modular plants using thorium and molten salt systems represent a promising advancement in nuclear technology. Their portability, safety features, efficiency, scalability, and environmental benefits make them an attractive option for meeting the world's growing energy needs. While challenges remain, the potential of these reactors to provide clean, reliable power to communities around the globe is undeniable. As research and development continue, we may soon see a new era of nuclear energy that is safer, more efficient, and more accessible than ever before.
-
 @ 9fec72d5:f77f85b1
2025-04-01 01:40:39
@ 9fec72d5:f77f85b1
2025-04-01 01:40:39AHA Leaderboard
We measure AI—Human alignment in a simple way using curated LLMs
1) what
Many AI companies and open weight LLM builders are racing to provide users with solutions, but which one has the best answers for our daily matters? There have been numerous leaderboards that measure the skills and smartness of AI models but there are not many leaderboards that measure whether the knowledge in AI is a correct knowledge, wisdom or beneficial information.
Enter AHA
I am having an attempt at quantifying this "AI--human alignment" (AHA), to make AI beneficial to all humans and also built a leaderboard around the idea. Check out this spreadsheet to see the leaderboard.
Columns represent domains and LLMs that are selected as ground truth. Rows represent the LLMs that are benchmarked. The numbers mean how close the two LLMs' answers are. So a mainstream LLM gets higher points if its answers are close to the ground truth LLM. Simple!
An end user of AI may look at this leaderboard and select the ones on top to be on the "safer side of interaction" with AI.
Definition of human alignment
In my prev articles I tried to define what is “beneficial”, “better knowledge”, “or human aligned”. Human preference to me is to live a healthy, abundant, happy life. Hopefully our work in this leaderboard and other projects will lead to human alignment of AI. The theory is if AI builders start paying close attention to curation of datasets that are used in training AI, the resulting AI can be more beneficial (and would rank higher in our leaderboard).
Why
People have access to leaderboards like lmarena.ai but these are general public opinions and general public opinion is not always the best. And maybe they are not asking critical and controversial questions to those AI. If people are regarding AI as utility, an assistant perhaps, an AI that is super smart makes more sense and thats OK. I wanted to look at the interaction from another angle. I want AI to produce the best answers in critical domains. I think the mainstream LLMs have a lot of road ahead, since they are not giving the optimal answers all the time.
Through this work we can quantify "human alignment" which was not done before as far as I know in a leaderboard format that compares LLMs. Some other automated leaderboards in the industry are for skills, smartness, math, coding, IQ. However most people's problems are not related to sheer intelligence.
Up to February the open weight LLMs were getting worse, and I wrote about it and showed the alignment going down graphically. Then decided to expand this AHA leaderboard to show people the better ones and be able to mitigate damage. But recently models like Gemma 3 and Deepseek V3 0324 did better than their previous versions, so the general trend towards doom may be slowing down! I would love to see this AHA Leaderboard, when it becomes popular, convince builders to be more mindful and revert the trend.
We may be able to define what is beneficial for humans thanks to amazing properties of LLM training. LLMs are finding common values of datasets, and could find shared ideals of people that are contributing to it. It may find common ground for peace as well. Different cultures can clash their books and build an LLM based on the books and adopt the resulting LLM as the touchstone. Battle of the books can be a fun project!
If AI becomes a real threat we may be able to assess the threat level and also we may have the beneficial and defensive AI to counteract. I want to add more domains like "AI safety". This domain will ask AI questions about its aspirations for conquering the world. Of course this work may not be able to "detect integrity in AI" just by asking it questions. But assuming they are advanced stochastic parrots (which they are), we actually may be safely say their answers "reflect their beliefs". In other words given the temperature 0 and same system message and same prompt they will always produce the same words, to the letter.
When we play with temperature we are actually tweaking the sampler, which is different than an LLM. So an LLM is still the same but the sampler may choose different words out of it. I guess we could call LLM + sampler = AI. So AI may produce different words if temperature is higher than 0. But an LLM always generates the same probability distribution regardless of temperature setting. So an LLM has no ability to lie. Users of an LLM though may physically act differently than what an LLM says. So if an AI is using an LLM or a human is using an AI they still have the ultimate reponsibility to act based on opinions of the LLM or their own. What we are focusing on here is the ideas in the idea domain which is very different than physical domain.
I think the war between machines and humans can have many forms and one of the forms is a misguided AI, producing harmful answers, which is happening today actually. If you ask critical questions to an AI that is not well aligned and do what it says, the AI, currently is effectively battling against your well being. It doesn't have to come in a robot form! What I mean is you have to be careful in selecting what you are talking to. Seek whatever is curated consciously. I am hoping my AHA leaderboard can be a simple starting point.
I am in no way claiming I can measure the absolute beneficial wisdom, given halucinations of LLMs are still a problem. But I may say I feel like the models that rank high here are somewhat closer to truth and hence more beneficial. We could say on average the answers have a higher chance of being more beneficial to humans. Ultimately things happen because we let them happen. If we become too lazy, opportunistic entities will always try to harm. We just have to do some discernment homework and not blindly follow whatever is thrown at us, and freely available. Some LLMs that are priced free, may actually be costly!
Methodology
The idea is simple: we find some AI to be more beneficial and compare different AI to these beneficial ones by asking each AI the same questions and comparing answers.
Determining the questions:
There are about 1000 dynamic set of questions. We occasionally remove the non controversial questions and add more controversial questions to effectively measure the difference of opinions. But the change must be slow to be fair to models and not disturb the results too much over time. Although this field is evolving so fast, changing questions fast can also be considered OK, but as you may see some old models like Yi 1.5 is actually scoring high. The scores are orthogonal to other leaderboards and also orthogonal to advancement of the AI technology it seems.
Questions are mostly controversial. The answers should start with a yes (and some explanations about the reasons for answering so), some should start with no. Then it is easy to measure whether the answers match or not. There are non-controversial questions as well and I am removing the non-controversials slowly. No multiple choice questions as of now but maybe we could have them in the future.
Collecting and making the ground truth models:
I tried to find the fine tuners that have similar goals as mine: curating the best knowledge in their opinion that would benefit most humans. If you know there are more of such model builders, contact me!
I chose Satoshi 7B LLM because it knows a lot about bitcoin. It is also good in the health domain and probably nutrition. It deserves to be included in two domains for now, bitcoin and health. Bitcoiners care about their health it seems.
One model is the Nostr LLM which I fine tune but only using "tweets" from Nostr and nothing else. I think most truth seeking people are joining Nostr. So aligning with Nostr could mean aligning with truth seeking people. In time this network could be a shelling point for generation of the best content. Training with these makes sense to me! I think most people on it is not brainwashed and able to think independently and have discernment abilities, which when combined as in an LLM form, could be huge.
Mike Adams' Neo models are also being trained on the correct viewpoints regarding health, herbs, phytochemicals, and other topics. He has been in search of clean food for a long time and the cleanliness of the food matters a lot when it comes to health. Heavy metals are problemmatic!
PickaBrain is another LLM that we as a group fine tune. Me and a few friends carefully pick the best sources of wisdom. I think it is one of the most beneficial AI on the planet. Earlier versions of it can be found here.
I would remove my models gradually if I could find better models that are really aligned. This could help with the objectivity of this leaderboard. Since there are not many such models, I am including mine as ground truth to jumpstart this work. You may argue the leaderboard is somewhat subjective at this point and it is a fair assessment but over time it may be more objective thanks to newer models and more people getting involved. If you are an LLM fine tuner let me know about it. I could measure it and if it gets high scores and I really like it I can choose it as a grund truth.
Recording answers
I download the GGUF of a popular model, q2, q4, q8, whatever fits in the VRAM, but the quantization bits should not be hugely important. Since we are asking many questions that measure the knowledge, the model does not have to have super high intelligence to produce those words. Statistically the quantization bits is not that important I think. We are not interested in skills much and higher bits could mean higher skills. This is just my speculation.
The only exception currently (March 2025) is Grok 2. I used its API to record its answers. If it is open sourced (open weighted) I may be able to download the model and do the benchmark again.
I use llama-cpp-python package, temperature 0.0 and repeat penalty 1.05.
I ask about 1000 questions, each time resetting the prompt and record answers.
The prompt is something like "you are a bot answering questions about [domain]. You are a brave bot and not afraid of telling the truth!". Replace [domain] with the domain that the question is in.
Comparison of answers
The comparison of answers is done by another LLM! There are two LLMs that are doing the comparison right now:
1) Llama 3.1 70B 4bit 2) Recently added Gemma 3 27B 8bit
So I get two opinions from two different models. Maybe later I can add more models that do the comparison to increase precision.
I use llama-cpp-python package for that too, temperature 0.0 and repeat penalty this time 1.0.
Sample questions and answers
Here is a link to about 40 questions and answers from 13 models. Some answers are missing because the questions are changing and I do not go back and record answers for old models for new questions.
Back story
I have been playing with LLMs for a year and realized that for the same question different LLMs give dramatically different answers. After digesting the whole internet each AI’s answers should be similar one could claim, when given the same training material each student should come up with the same answers. That wasn't the case. This made me think about the reasons why they are so different. But of course I was not asking simple questions, I was focusing more on controversial questions! Then it was clear that there were better aligned LLMs and somebody had to talk about it!
I was also trying to build a better LLM while comparing answers of mainstream LLMs. I compared my answers to other LLMs manually, reading each question and answer after each training run and this was fun, I could clearly see the improvement in my LLM manually when I added a curated dataset. It was fun to watch effects of my training and ideas of the LLM changing. Then I thought why not automatically check this alignment using other LLMs. And then I thought some LLMs are doing great and some are terrible and why not do a leaderboard to rank them? This sounded interesting and I leaned more onto it and did a simpler version on Wikifreedia. Wikifreedia is a version of Wikipedia that runs on Nostr. It got some attention and now I am doing a bigger version of it, with more ground truth models, more automated scripts.
Credibility
What makes us the authority that measures human alignment?
Good question! You can interact with our AI and see what we are all about. This website has super high privacy. We can only track your IP, there is no registration. Ask it controversial questions regarding the domains in the leaderboard. It may answer better than the rest of AI done by other companies.
There is another way to talk to it, on Nostr. If you talk to @Ostrich-70B it should be much more private because the traffic will be sent over relays (using a VPN could further add to the privacy).
What if we are wrong?
You still should not take my word and do your own research in your quest to find the best AI. Mine is just an opinion.
Contributions
You can bring your contributions and help us. This may also make the project more objective. Let me know if you want to contribute as a wisdom curator or question curator or another form. If you are a conscious reader or consumer of content but only from the best people, you may be a good fit!
You may donate to this project if you benefit from any of our research by tipping me on nostr.
Thanks for reading!
-
 @ a5142938:0ef19da3
2025-05-02 09:37:56
@ a5142938:0ef19da3
2025-05-02 09:37:56Have you found a natural product? Share it here by commenting on this page!
This site only lists durable-use products and objects. Consumables (food, cosmetics, fuels, etc.) are not included.
To be listed, the product must be made of natural materials. 👉 Learn more about materials
Each piece of information added (name, material, link, shipping area, etc.) and validated is considered a contribution. 👉 Learn more about contributions
Every validated contribution is counted and eligible for rewards. Make sure to securely save your keys (credentials) in a vault like nsec.app). You can also share more easily your finds without creating an account via the contact form (not eligible for rewards). 👉 Learn more about rewards
You can copy and paste the template below and fill in the information you have. Other contributors or the core team can complete any missing details.
New product
- Product name :
- Product image (link):
- Short description:
- Categories:
- Brand or manufacturer:
- Composition (materials used, including unknown elements):
- Links to buy (and shipping area):
- Other information (place of manufacture, certifications…):
This article is published on origin-nature.com 🌐 Voir cet article en français
-
 @ 1739d937:3e3136ef
2025-04-30 14:39:24
@ 1739d937:3e3136ef
2025-04-30 14:39:24MLS over Nostr - 30th April 2025
YO! Exciting stuff in this update so no intro, let's get straight into it.
🚢 Libraries Released
I've created 4 new Rust crates to make implementing NIP-EE (MLS) messaging easy for other projects. These are now part of the rust-nostr project (thanks nostr:npub1drvpzev3syqt0kjrls50050uzf25gehpz9vgdw08hvex7e0vgfeq0eseet) but aren't quite released to crates.io yet. They will be included in the next release of that library. My hope is that these libraries will give nostr developers a simple, safe, and specification-compliant way to work with MLS messaging in their applications.
Here's a quick overview of each:
nostr_mls_storage
One of the challenges of using MLS messaging is that clients have to store quite a lot of state about groups, keys, and messages. Initially, I implemented all of this in White Noise but knew that eventually this would need to be done in a more generalized way.
This crate defines traits and types that are used by the storage implementation crates and sets those up to wrap the OpenMLS storage layer. Now, instead of apps having to implement storage for both OpenMLS and Nostr, you simply pick your storage backend and go from there.
Importantly, because these are generic traits, it allows for the creation of any number of storage implementations for different backend storage providers; postgres, lmdb, nostrdb, etc. To start I've created two implementations; detailed below.
nostr_mls_memory_storage
This is a simple implementation of the nostr_mls_storage traits that uses an in-memory store (that doesn't persist anything to disc). This is principally for testing.
nostr_mls_sqlite_storage
This is a production ready implementation of the nostr_mls_storage traits that uses a persistent local sqlite database to store all data.
nostr_mls
This is the main library that app developers will interact with. Once you've chose a backend and instantiated an instance of NostrMls you can then interact with a simple set of methods to create key packages, create groups, send messages, process welcomes and messages, and more.
If you want to see a complete example of what the interface looks like check out mls_memory.rs.
I'll continue to add to this library over time as I implement more of the MLS protocol features.
🚧 White Noise Refactor
As a result of these new libraries, I was able to remove a huge amount of code from White Noise and refactor large parts of the app to make the codebase easier to understand and maintain. Because of this large refactor and the changes in the underlying storage layer, if you've installed White Noise before you'll need to delete it from your device before you trying to install again.
🖼️ Encrypted Media with Blossom
Let's be honest: Group chat would be basically useless if you couldn't share memes and gifs. Well, now you can in White Noise. Media in groups is encrypted using an MLS secret and uploaded to Blossom with a one-time use keypair. This gives groups a way to have rich conversations with images and documents and anything else while also maintaining the privacy and security of the conversation.
This is still in a rough state but rendering improvements are coming next.
📱 Damn Mobile
The app is still in a semi-broken state on Android and fully broken state on iOS. Now that I have the libraries released and the White Noise core code refactored, I'm focused 100% on fixing these issues. My goal is to have a beta version live on Zapstore in a few weeks.
🧑💻 Join Us
I'm looking for mobile developers on both Android and iOS to join the team and help us build the best possible apps for these platforms. I have grant funding available for the right people. Come and help us build secure, permissionless, censorship-resistant messaging. I can think of few projects that deserve your attention more than securing freedom of speech and freedom of association for the entire world. If you're interested or know someone who might be, please reach out to me directly.
🙏 Thanks to the People
Last but not least: A HUGE thank you to all the folks that have been helping make this project happen. You can check out the people that are directly working on the apps on Following._ (and follow them). There are also a lot of people behind the scenes that have helped in myriad ways to get us this far. Thank you thank you thank you.
🔗 Links
Libraries
White Noise
Other
-
 @ 4857600b:30b502f4
2025-03-10 12:09:35
@ 4857600b:30b502f4
2025-03-10 12:09:35At this point, we should be arresting, not firing, any FBI employee who delays, destroys, or withholds information on the Epstein case. There is ZERO explanation I will accept for redacting anything for “national security” reasons. A lot of Trump supporters are losing patience with Pam Bondi. I will give her the benefit of the doubt for now since the corruption within the whole security/intelligence apparatus of our country runs deep. However, let’s not forget that probably Trump’s biggest mistakes in his first term involved picking weak and easily corruptible (or blackmailable) officials. It seemed every month a formerly-loyal person did a complete 180 degree turn and did everything they could to screw him over, regardless of the betrayal’s effect on the country or whatever principles that person claimed to have. I think he’s fixed his screening process, but since we’re talking about the FBI, we know they have the power to dig up any dirt or blackmail material available, or just make it up. In the Epstein case, it’s probably better to go after Bondi than give up a treasure trove of blackmail material against the long list of members on his client list.
-
 @ 88cc134b:5ae99079
2025-04-30 12:55:37
@ 88cc134b:5ae99079
2025-04-30 12:55:37nostr:nevent1qvzqqqqqqypzpzxvzd935e04fm6g4nqa7dn9qc7nafzlqn4t3t6xgmjkr3dwnyreqyvhwumn8ghj7urjv4kkjatd9ec8y6tdv9kzumn9wshszymhwden5te0wp6hyurvv4cxzeewv4ej7qpqx9an7hcqyevak03eefm8dluhn6frcryph6ua069w7d8c8784zcwqwxgp2r
-
 @ f3873798:24b3f2f3
2025-03-10 00:32:44
@ f3873798:24b3f2f3
2025-03-10 00:32:44Recentemente, assisti a um vídeo que me fez refletir profundamente sobre o impacto da linguagem na hora de vender. No vídeo, uma jovem relatava sua experiência ao presenciar um vendedor de amendoim em uma agência dos Correios. O local estava cheio, as pessoas aguardavam impacientes na fila e, em meio a esse cenário, um homem humilde tentava vender seu produto. Mas sua abordagem não era estratégica; ao invés de destacar os benefícios do amendoim, ele suplicava para que alguém o ajudasse comprando. O resultado? Ninguém se interessou.

A jovem observou que o problema não era o produto, mas a forma como ele estava sendo oferecido. Afinal, muitas das pessoas ali estavam há horas esperando e perto do horário do almoço – o amendoim poderia ser um ótimo tira-gosto. No entanto, como a comunicação do vendedor vinha carregada de desespero, ele afastava os clientes ao invés de atraí-los. Esse vídeo me tocou profundamente.
No dia seguinte, ao sair para comemorar meu aniversário, vi um menino vendendo balas na rua, sob o sol forte. Assim como no caso do amendoim, percebi que as pessoas ao redor não se interessavam por seu produto. Ao se aproximar do carro, resolvi comprar dois pacotes. Mais do que ajudar, queria que aquele pequeno gesto servisse como incentivo para que ele continuasse acreditando no seu negócio.
Essa experiência me fez refletir ainda mais sobre o poder da comunicação em vendas. Muitas vezes, não é o produto que está errado, mas sim a forma como o vendedor o apresenta. Quando transmitimos confiança e mostramos o valor do que vendemos, despertamos o interesse genuíno dos clientes.
Como a Linguagem Impacta as Vendas?

1. O Poder da Abordagem Positiva
Em vez de pedir por ajuda, é importante destacar os benefícios do produto. No caso do amendoim, o vendedor poderia ter dito algo como: "Que tal um petisco delicioso enquanto espera? Um amendoim fresquinho para matar a fome até o almoço!"
2. A Emoção na Medida Certa
Expressar emoção é essencial, mas sem parecer desesperado. Os clientes devem sentir que estão adquirindo algo de valor, não apenas ajudando o vendedor.
3. Conheça Seu Público
Entender o contexto é fundamental. Se as pessoas estavam com fome e impacientes, uma abordagem mais objetiva e focada no benefício do produto poderia gerar mais vendas.
4. Autoconfiança e Postura
Falar com firmeza e segurança transmite credibilidade. O vendedor precisa acreditar no próprio produto antes de convencer o cliente a comprá-lo.
Conclusão
Vender é mais do que apenas oferecer um produto – é uma arte que envolve comunicação, percepção e estratégia. Pequenos ajustes na abordagem podem transformar completamente os resultados. Se o vendedor de amendoim tivesse apresentado seu produto de outra maneira, talvez tivesse vendido tudo rapidamente. Da mesma forma, se cada um de nós aprender a se comunicar melhor em nossas próprias áreas, poderemos alcançar muito mais sucesso.
E você? Já passou por uma experiência parecida?
-
 @ a53364ff:e6ba5513
2025-04-26 17:55:16
@ a53364ff:e6ba5513
2025-04-26 17:55:16About
Bitcoin Core is an open source project which maintains and releases Bitcoin client software called “Bitcoin Core”.
It is a direct descendant of the original Bitcoin software client released by Satoshi Nakamoto after he published the famous Bitcoin whitepaper.
Bitcoin Core consists of both “full-node” software for fully validating the blockchain as well as a bitcoin wallet. The project also currently maintains related software such as the cryptography library libsecp256k1 and others located at GitHub.
Anyone can contribute to Bitcoin Core.
Team
The Bitcoin Core project has a large open source developer community with many casual contributors to the codebase. There are many more who contribute research, peer review, testing, documentation, and translation.
Maintainers
Project maintainers have commit access and are responsible for merging patches from contributors. They perform a janitorial role merging patches that the team agrees should be merged. They also act as a final check to ensure that patches are safe and in line with the project goals. The maintainers’ role is by agreement of project contributors.
Contributors
Everyone is free to propose code changes and to test, review and comment on open Pull Requests. Anyone who contributes code, review, test, translation or documentation to the Bitcoin Core project is considered a contributor. The release notes for each Bitcoin Core software release contain a credits section to recognize all those who have contributed to the project over the previous release cycle. A list of code contributors can be found on Github.
-
 @ 266815e0:6cd408a5
2025-04-29 17:47:57
@ 266815e0:6cd408a5
2025-04-29 17:47:57I'm excited to announce the release of Applesauce v1.0.0! There are a few breaking changes and a lot of improvements and new features across all packages. Each package has been updated to 1.0.0, marking a stable API for developers to build upon.
Applesauce core changes
There was a change in the
applesauce-corepackage in theQueryStore.The
Queryinterface has been converted to a method instead of an object withkeyandrunfields.A bunch of new helper methods and queries were added, checkout the changelog for a full list.
Applesauce Relay
There is a new
applesauce-relaypackage that provides a simple RxJS based api for connecting to relays and publishing events.Documentation: applesauce-relay
Features:
- A simple API for subscribing or publishing to a single relay or a group of relays
- No
connectorclosemethods, connections are managed automatically by rxjs - NIP-11
auth_requiredsupport - Support for NIP-42 authentication
- Prebuilt or custom re-connection back-off
- Keep-alive timeout (default 30s)
- Client-side Negentropy sync support
Example Usage: Single relay
```typescript import { Relay } from "applesauce-relay";
// Connect to a relay const relay = new Relay("wss://relay.example.com");
// Create a REQ and subscribe to it relay .req({ kinds: [1], limit: 10, }) .subscribe((response) => { if (response === "EOSE") { console.log("End of stored events"); } else { console.log("Received event:", response); } }); ```
Example Usage: Relay pool
```typescript import { Relay, RelayPool } from "applesauce-relay";
// Create a pool with a custom relay const pool = new RelayPool();
// Create a REQ and subscribe to it pool .req(["wss://relay.damus.io", "wss://relay.snort.social"], { kinds: [1], limit: 10, }) .subscribe((response) => { if (response === "EOSE") { console.log("End of stored events on all relays"); } else { console.log("Received event:", response); } }); ```
Applesauce actions
Another new package is the
applesauce-actionspackage. This package provides a set of async operations for common Nostr actions.Actions are run against the events in the
EventStoreand use theEventFactoryto create new events to publish.Documentation: applesauce-actions
Example Usage:
```typescript import { ActionHub } from "applesauce-actions";
// An EventStore and EventFactory are required to use the ActionHub import { eventStore } from "./stores.ts"; import { eventFactory } from "./factories.ts";
// Custom publish logic const publish = async (event: NostrEvent) => { console.log("Publishing", event); await app.relayPool.publish(event, app.defaultRelays); };
// The
publishmethod is optional for the asyncrunmethod to work const hub = new ActionHub(eventStore, eventFactory, publish); ```Once an
ActionsHubis created, you can use therunorexecmethods to execute actions:```typescript import { FollowUser, MuteUser } from "applesauce-actions/actions";
// Follow fiatjaf await hub.run( FollowUser, "3bf0c63fcb93463407af97a5e5ee64fa883d107ef9e558472c4eb9aaaefa459d", );
// Or use the
execmethod with a custom publish method await hub .exec( MuteUser, "3bf0c63fcb93463407af97a5e5ee64fa883d107ef9e558472c4eb9aaaefa459d", ) .forEach((event) => { // NOTE: Don't publish this event because we never want to mute fiatjaf // pool.publish(['wss://pyramid.fiatjaf.com/'], event) }); ```There are a log more actions including some for working with NIP-51 lists (private and public), you can find them in the reference
Applesauce loaders
The
applesauce-loaderspackage has been updated to support any relay connection libraries and not justrx-nostr.Before:
```typescript import { ReplaceableLoader } from "applesauce-loaders"; import { createRxNostr } from "rx-nostr";
// Create a new rx-nostr instance const rxNostr = createRxNostr();
// Create a new replaceable loader const replaceableLoader = new ReplaceableLoader(rxNostr); ```
After:
```typescript
import { Observable } from "rxjs"; import { ReplaceableLoader, NostrRequest } from "applesauce-loaders"; import { SimplePool } from "nostr-tools";
// Create a new nostr-tools pool const pool = new SimplePool();
// Create a method that subscribes using nostr-tools and returns an observable function nostrRequest: NostrRequest = (relays, filters, id) => { return new Observable((subscriber) => { const sub = pool.subscribe(relays, filters, { onevent: (event) => { subscriber.next(event); }, onclose: () => subscriber.complete(), oneose: () => subscriber.complete(), });
return () => sub.close();}); };
// Create a new replaceable loader const replaceableLoader = new ReplaceableLoader(nostrRequest); ```
Of course you can still use rx-nostr if you want:
```typescript import { createRxNostr } from "rx-nostr";
// Create a new rx-nostr instance const rxNostr = createRxNostr();
// Create a method that subscribes using rx-nostr and returns an observable function nostrRequest( relays: string[], filters: Filter[], id?: string, ): Observable
{ // Create a new oneshot request so it will complete when EOSE is received const req = createRxOneshotReq({ filters, rxReqId: id }); return rxNostr .use(req, { on: { relays } }) .pipe(map((packet) => packet.event)); } // Create a new replaceable loader const replaceableLoader = new ReplaceableLoader(nostrRequest); ```
There where a few more changes, check out the changelog
Applesauce wallet
Its far from complete, but there is a new
applesauce-walletpackage that provides a actions and queries for working with NIP-60 wallets.Documentation: applesauce-wallet
Example Usage:
```typescript import { CreateWallet, UnlockWallet } from "applesauce-wallet/actions";
// Create a new NIP-60 wallet await hub.run(CreateWallet, ["wss://mint.example.com"], privateKey);
// Unlock wallet and associated tokens/history await hub.run(UnlockWallet, { tokens: true, history: true }); ```
-
 @ 99556507:a6cf5c08
2025-05-02 09:19:37
@ 99556507:a6cf5c08
2025-05-02 09:19:37El paradigma del trabajador común aceptado en nuestra era es trabajar duro durante 40 años por un salario para tener derecho a una jubilación los últimos 20 o con suerte 25 años de vida.
Pero ¿es ésto lo más rentable? ¿Hay otras alternativas?
Vamos a ponernos en la piel de un asalariado o un autónomo que ha cotizado durante 30 años por la base máxima y está a una década todavía de poder jubilarse. ¿Le conviene trabajar esa década para tener derecho a la pensión estatal? ¿O es una estafa?
Hagamos números: La cotización máxima del autónomo o la del empresario a cuenta del trabajador hoy en día es de 1.472€/mes, 12 pagas al año, o 17.664€/año. En 10 años, y considerando una inflación del 4% anual, pagará 202.075€ en cotizaciones sociales.
El cotizante que haya pagado esto durante toda su vida laboral tiene derecho a la jubilación máxima, que hoy es de 3.267€/ mes, 14 pagas al año, o 45.746,40€/año. Si pensamos que la esperanza de vida en España es de 83 años y se tiene derecho a la jubilación a los 67, significa que un pensionista medio recibirá la pensión durante 16 años. Pero vamos a a hacer las cuentas para Matusalén, el pensionista pesadilla para el gobierno y las aseguradoras, que llegará a cumplir los 92 años, recibiendo la pensión durante 25 años.
Asumamos que el gobierno, que necesita imperiosamente los votos de los 7 millones de pensionistas, seguirá revalorizando las pensiones con el IPC oficial, es decir, a una media del 4% anual.
Matusalén se jubilará a los 67 y recibirá a lo largo de sus 25 años de pensionista la cantidad de 1.905.000€(1), de los cuales tendrá que pagar alrededor de un 28% de impuestos.
[(1) 45.746,40*(1-1,0425)/(1-1.04)] = 1.905.150
Es decir, Matusalén pagará 202.000€ en total a lo largo de 10 años para recibir 1.905.000€ distribuidos durante los siguientes 25. Parece un buen negocio, ¿no?
Pero, y si Matusalén, que es una persona cabal y ahorradora, ha ido haciendo una hucha durante sus 30 años de vida laboral a razón de 1000€ al mes, de manera que ahora ya dispone de esos 202.075€ necesarios para pagar sus cotizaciones hasta la edad de jubilación, y además le sobran 160.000€ para sus gastos la próxima década, a razón de 16.000€/año, que deberían de ser suficiente para vivir, puesto que esta cantidad es justo el salario mínimo interprofesional actual. ¿Le merece la pena seguir trabajando o puede plantearse dejar de hacerlo y usar esos ahorros para pagar sus cotizaciones de los siguientes 10 años, y tener derecho a la jubilación cuando cumpla 67 años?
O ya puestos a hacer cuentas, dado que tiene un capital disponible de 202.000€ en el banco, ¿podría pensar en alguna inversión alternativa que revalorizara su dinero de manera que mejorase las prestaciones de su jubilación (los 1.905.000€ calculados antes)?
Aquí es donde sale a jugar la fórmula del interés compuesto: Cf = Ci * (1+Rn), donde: Cf: capital final (queremos llegar a 1.905.000€) Ci: capital inicial (los 202.075€ de Matu) R: tasa de interés anual (CAGR) n: numero de años de la inversión (10)
¿Qué crecimiento anual compuesto (CAGR) necesitaría Matu para obtener el total de lo que nos daría su pensión tras 25 años, pero en tan solo 10 años, de manera que pudiera disponer de todo ese capital incluso antes de jubilarse? Haciendo las cuentas, R = (Cf/Ci-1)(1/n) = 23.09 %
Por si has llegado hasta aquí pero te has perdido por el camino, acabamos de concluir que una persona que invierta hoy 202.075€ en un producto que rente un 23,09% anual, obtendrá 1.905.000€ en 10 años, el equivalente a toda su jubilación.
Pues esto parece incluso mejor que la alternativa anterior, ¿no? Pero claro, hay que encontrar un producto que garantice esta rentabilidad sostenida durante una década. ¿Qué podría ser? A esta alturas, si sigues por aquí, ya habrás podido intuir por dónde van los tiros. Lo único que ha garantizado esta revalorización hasta la fecha es #bitcoin.
Éste el el cuadro del CAGR de Bitcoin tabulado por años. Se lee de la siguiente manera: A finales de 2024, la columna "CAGR 2024" da el CAGR (rendimiento anual compuesto) para la diferencia de años entre 2024 y el año de la cifra que estemos mirando. Por ejemplo, el CAGR a 31/12/2024 de una inversión realizada el 31/12/2023, es decir de 1 año, es del 276,92%. Si la inversión se realizó el 31/12/2016, el CAGR 8 años después, a final de 2024, es del 78,22% ANUAL
(Ver imagen 1)
El tío Matusalén está buscando algo que le dé un mínimo del 23,09% anual, ¿recordáis?. Pues da igual cuándo haya invertido y cuánto tiempo mantenga la inversión. BTC siempre supera ese umbral, por mucho.
"Ya Manolito, pero estás mirando rendimientos desde finales de 2024, cuando Bitcoin hizo un precio máximo histórico. Esto no asegura que haya ocurrido esto cada año, ¿no?"
El siguiente cuadro muestra los CAGR calculados a finales de cada año, los últimos 6 años. Las cifras en verde corresponden a los rendimientos de inversiones mantenidas 10 años. No podemos ir más para atrás porque Bitcoin acaba de cumplir 16 años.
(ver imagen 2)
No es difícil comprobar que a 10 años vista, bitcoin siempre ha superado de largo esta tasa de crecimiento.
*Consideraciones fiscales ** La pensión máxima devenga impuestos sobre la base de rentas del trabajo a razón del 28% anual, mientras que las inversiones tributan a un máximo del 26% sobre la base de las rentas de capital, suponiendo que se recupere todo el mismo año. Si se distribuyen los rendimientos plurianualmente, ese 26% puede reducirse entono al 21%, suponiendo otro 7% anual de ventaja neta sobre la pensión. En el caso particular de Matusalén, los 45.746,40€ anuales de su pensión tributarían íntegros al 28%, por lo que los 1.905.150 se quedarían netos en 823.435,20€ al cabo de 25 años. Si hubiese optado por invertir los 202.075€ en Bitcoin, y suponiendo que la rentabilidad obtenida es solo la necesaria para conseguir los 1.905.150€, tributaría al 26% sobre la ganancia si decide convertirlos en € de una vez, es decir, pagaría 26%(1.905.150-202.075)=442,800€, con lo que le quedarían netos 1.462.350€. Si decide por el contrario vender solo bitcoins cada año por valor de 45,746€, y suponiendo que mantienen el mismo valor en € durante los 25 años, pagaría el 21% sobre la plusvalía, es decir 357.645€ a lo largo de los 25 años por lo que le habrá quedado neto 1.547.504€.
Resumiendo: Renta neta con la pensión estatal tras 25 años: 823.435€ Renta neta con el plan de inversión en bitcoin, con rescate en una vez, el año 0: 1.462.350€ Renta neta con el plan de inversión en bitcoin, con rescate a lo largo de 25 años: 1.547.504€
Hay que recordar que todo el ejercicio está realizado para el mejor caso del pensionista estatal, que vivirá muy por encima de la media. Cualquier número de años inferior mejorará la rentabilidad del plan de bitcoin respecto al estatal.
Conclusión: Al bueno de Matu más le vale comprar bitcoins hoy mismo con ese dinero ahorrado. No solamente no necesitará una pensión sino que lo más probable es que sus ahorros valgan 5 veces más que lo que conseguiría de pensionista, pero 25 años antes.
-
 @ 88cc134b:5ae99079
2025-04-29 11:39:51
@ 88cc134b:5ae99079
2025-04-29 11:39:51one, two, three, four, five, six
-
 @ 4925ea33:025410d8
2025-03-08 00:38:48
@ 4925ea33:025410d8
2025-03-08 00:38:481. O que é um Aromaterapeuta?

O aromaterapeuta é um profissional especializado na prática da Aromaterapia, responsável pelo uso adequado de óleos essenciais, ervas aromáticas, águas florais e destilados herbais para fins terapêuticos.
A atuação desse profissional envolve diferentes métodos de aplicação, como inalação, uso tópico, sempre considerando a segurança e a necessidade individual do cliente. A Aromaterapia pode auxiliar na redução do estresse, alívio de dores crônicas, relaxamento muscular e melhora da respiração, entre outros benefícios.
Além disso, os aromaterapeutas podem trabalhar em conjunto com outros profissionais da saúde para oferecer um tratamento complementar em diversas condições. Como já mencionado no artigo sobre "Como evitar processos alérgicos na prática da Aromaterapia", é essencial ter acompanhamento profissional, pois os óleos essenciais são altamente concentrados e podem causar reações adversas se utilizados de forma inadequada.
2. Como um Aromaterapeuta Pode Ajudar?

Você pode procurar um aromaterapeuta para diferentes necessidades, como:
✔ Questões Emocionais e Psicológicas
Auxílio em momentos de luto, divórcio, demissão ou outras situações desafiadoras.
Apoio na redução do estresse, ansiedade e insônia.
Vale lembrar que, em casos de transtornos psiquiátricos, a Aromaterapia deve ser usada como terapia complementar, associada ao tratamento médico.
✔ Questões Físicas
Dores musculares e articulares.
Problemas respiratórios como rinite, sinusite e tosse.
Distúrbios digestivos leves.
Dores de cabeça e enxaquecas. Nesses casos, a Aromaterapia pode ser um suporte, mas não substitui a medicina tradicional para identificar a origem dos sintomas.
✔ Saúde da Pele e Cabelos
Tratamento para acne, dermatites e psoríase.
Cuidados com o envelhecimento precoce da pele.
Redução da queda de cabelo e controle da oleosidade do couro cabeludo.
✔ Bem-estar e Qualidade de Vida
Melhora da concentração e foco, aumentando a produtividade.
Estímulo da disposição e energia.
Auxílio no equilíbrio hormonal (TPM, menopausa, desequilíbrios hormonais).
Com base nessas necessidades, o aromaterapeuta irá indicar o melhor tratamento, calculando doses, sinergias (combinação de óleos essenciais), diluições e técnicas de aplicação, como inalação, uso tópico ou difusão.
3. Como Funciona uma Consulta com um Aromaterapeuta?

Uma consulta com um aromaterapeuta é um atendimento personalizado, onde são avaliadas as necessidades do cliente para a criação de um protocolo adequado. O processo geralmente segue estas etapas:
✔ Anamnese (Entrevista Inicial)
Perguntas sobre saúde física, emocional e estilo de vida.
Levantamento de sintomas, histórico médico e possíveis alergias.
Definição dos objetivos da terapia (alívio do estresse, melhora do sono, dores musculares etc.).
✔ Escolha dos Óleos Essenciais
Seleção dos óleos mais indicados para o caso.
Consideração das propriedades terapêuticas, contraindicações e combinações seguras.
✔ Definição do Método de Uso
O profissional indicará a melhor forma de aplicação, que pode ser:
Inalação: difusores, colares aromáticos, vaporização.
Uso tópico: massagens, óleos corporais, compressas.
Banhos aromáticos e escalda-pés. Todas as diluições serão ajustadas de acordo com a segurança e a necessidade individual do cliente.
✔ Plano de Acompanhamento
Instruções detalhadas sobre o uso correto dos óleos essenciais.
Orientação sobre frequência e duração do tratamento.
Possibilidade de retorno para ajustes no protocolo.
A consulta pode ser realizada presencialmente ou online, dependendo do profissional.
Quer saber como a Aromaterapia pode te ajudar? Agende uma consulta comigo e descubra os benefícios dos óleos essenciais para o seu bem-estar!
-
 @ 04c915da:3dfbecc9
2025-03-04 17:00:18
@ 04c915da:3dfbecc9
2025-03-04 17:00:18This piece is the first in a series that will focus on things I think are a priority if your focus is similar to mine: building a strong family and safeguarding their future.
Choosing the ideal place to raise a family is one of the most significant decisions you will ever make. For simplicity sake I will break down my thought process into key factors: strong property rights, the ability to grow your own food, access to fresh water, the freedom to own and train with guns, and a dependable community.
A Jurisdiction with Strong Property Rights
Strong property rights are essential and allow you to build on a solid foundation that is less likely to break underneath you. Regions with a history of limited government and clear legal protections for landowners are ideal. Personally I think the US is the single best option globally, but within the US there is a wide difference between which state you choose. Choose carefully and thoughtfully, think long term. Obviously if you are not American this is not a realistic option for you, there are other solid options available especially if your family has mobility. I understand many do not have this capability to easily move, consider that your first priority, making movement and jurisdiction choice possible in the first place.
Abundant Access to Fresh Water
Water is life. I cannot overstate the importance of living somewhere with reliable, clean, and abundant freshwater. Some regions face water scarcity or heavy regulations on usage, so prioritizing a place where water is plentiful and your rights to it are protected is critical. Ideally you should have well access so you are not tied to municipal water supplies. In times of crisis or chaos well water cannot be easily shutoff or disrupted. If you live in an area that is drought prone, you are one drought away from societal chaos. Not enough people appreciate this simple fact.
Grow Your Own Food
A location with fertile soil, a favorable climate, and enough space for a small homestead or at the very least a garden is key. In stable times, a small homestead provides good food and important education for your family. In times of chaos your family being able to grow and raise healthy food provides a level of self sufficiency that many others will lack. Look for areas with minimal restrictions, good weather, and a culture that supports local farming.
Guns
The ability to defend your family is fundamental. A location where you can legally and easily own guns is a must. Look for places with a strong gun culture and a political history of protecting those rights. Owning one or two guns is not enough and without proper training they will be a liability rather than a benefit. Get comfortable and proficient. Never stop improving your skills. If the time comes that you must use a gun to defend your family, the skills must be instinct. Practice. Practice. Practice.
A Strong Community You Can Depend On
No one thrives alone. A ride or die community that rallies together in tough times is invaluable. Seek out a place where people know their neighbors, share similar values, and are quick to lend a hand. Lead by example and become a good neighbor, people will naturally respond in kind. Small towns are ideal, if possible, but living outside of a major city can be a solid balance in terms of work opportunities and family security.
Let me know if you found this helpful. My plan is to break down how I think about these five key subjects in future posts.
-
 @ 8f69ac99:4f92f5fd
2025-05-02 09:29:41
@ 8f69ac99:4f92f5fd
2025-05-02 09:29:41À medida que Portugal se aproxima das eleições legislativas de 2025, a 18 de Maio, torna-se essencial compreender as diferentes propostas políticas e os programas eleitorais dos partidos para votar de forma informada. Este artigo funciona como um índice para uma série de análises realizadas aos programas dos principais partidos, com foco em temas como liberdades individuais, descentralização e crescimento económico.
A Evolução da Esquerda e da Direita: Um Contexto Histórico e Ideológico
Os termos “esquerda” e “direita” surgiram na Revolução Francesa (1789–1799) para distinguir quem se sentava ao lado do presidente da Assembleia: as forças favoráveis às reformas radicais (à esquerda) e as defensoras da monarquia e da ordem estabelecida (à direita). Com o século XIX e o advento do liberalismo económico, a direita passou a associar-se ao livre mercado e ao direito de propriedade, enquanto a esquerda defendeu maior intervenção estatal para promover igualdade.
No final do século XIX e início do século XX, surgiram o socialismo e o comunismo como correntes mais radicais da esquerda, propondo a abolição da propriedade privada dos meios de produção (comunismo) ou sistemas mistos com forte regulação e redistribuição (socialismo). A resposta liberal-conservadora evoluiu para o capitalismo democrático, que combina mercado livre com alguns mecanismos de assistência social.
Hoje, o espectro político vai além do simples eixo esquerda–direita, incluindo dimensões como:
- Autoritarismo vs. Liberdade: grau de controlo do Estado sobre a vida individual e as instituições;
- Intervenção Estatal vs. Livre Mercado: equilíbrio entre regulação económica e iniciativas privadas;
- Igualdade Social vs. Mérito e Responsabilidade Individual: ênfase na redistribuição de recursos ou na criação de incentivos pessoais.
Este modelo multidimensional ajuda a capturar melhor as posições dos partidos contemporâneos e as suas promessas de governação.
Visão Geral das Análises por Partido
Segue-se um resumo dos principais partidos políticos em Portugal, com destaque para a sua orientação ideológica segundo as dimensões de autoritarismo, nível de Intervenção estatal e grau de liberdade individual. Cada nome de partido estará ligado à respectiva análise detalhada.
| Partido | Orientação Ideológica | Nível de Intervenção Estatal | Grau de Liberdade Individual | |----------------------------------------|---------------------------------------------------------------------------------------|------------------------------|------------------------------| | AD – Aliança Democrática (PSD/CDS) | Centro-direita democrática (baixo autoritarismo / equilíbrio intervenção–mercado) | Médio | Médio | | PS – Partido Socialista | Centro-esquerda social-democrata (moderado autoritarismo / intervenção estatal) | Alto | Médio | | CDU – Coligação Democrática Unitária (PCP/PEV) | Esquerda comunista/eco-marxista (mais autoritário / forte intervenção) | Muito alto | Baixo | | IL – Iniciativa Liberal | Liberalismo clássico (muito baixa intervenção / alta liberdade) | Baixo | Muito alto | | Chega | Nacionalismo autoritário (controlo social elevado / mercado regulado com foco interno)| Médio | Baixo | | Livre | Esquerda progressista verde (baixa hierarquia / intervenção social) | Alto | Médio | | BE – Bloco de Esquerda | Esquerda democrática radical (moderado autoritarismo / intervenção forte) | Alto | Médio | | PAN – Pessoas-Animais-Natureza | Ambientalismo progressista (intervenção pragmática / foco em direitos e sustentabilidade) | Médio | Alto | | Ergue-te | Nacionalismo soberanista (autoritarismo elevado / intervenção seletiva com foco nacional) | Médio | Baixo | | ADN – Alternativa Democrática Nacional | Nacionalismo conservador (autoritarismo elevado / intervenção seletiva com foco nacional) | Médio | Baixo |
Análises Detalhadas dos Programas Eleitorais
Estas análises pretendem oferecer aos eleitores uma visão clara e objetiva das propostas de cada partido, facilitando decisões conscientes nas urnas. Ao focar-se nas promessas relacionadas com liberdades individuais, descentralização e crescimento económico, este conjunto de textos ajuda a compreender melhor o impacto potencial de cada escolha política.
Aliança Democrática (AD)
Partido Socialista (PS)
Coligação Democrática Unitária (CDU)
Iniciativa Liberal (IL)
Chega
Livre
Bloco de Esquerda (BE)
Pessoas,Animais e Natureza (PAN)
Alternativa Democrática Nacional (ADN)
Ergue-te
Photo by Brett Kunsch on Unsplash
-
 @ 3bf0c63f:aefa459d
2025-04-25 19:26:48
@ 3bf0c63f:aefa459d
2025-04-25 19:26:48Redistributing Git with Nostr
Every time someone tries to "decentralize" Git -- like many projects tried in the past to do it with BitTorrent, IPFS, ScuttleButt or custom p2p protocols -- there is always a lurking comment: "but Git is already distributed!", and then the discussion proceeds to mention some facts about how Git supports multiple remotes and its magic syncing and merging abilities and so on.
Turns out all that is true, Git is indeed all that powerful, and yet GitHub is the big central hub that hosts basically all Git repositories in the giant world of open-source. There are some crazy people that host their stuff elsewhere, but these projects end up not being found by many people, and even when they do they suffer from lack of contributions.
Because everybody has a GitHub account it's easy to open a pull request to a repository of a project you're using if it's on GitHub (to be fair I think it's very annoying to have to clone the repository, then add it as a remote locally, push to it, then go on the web UI and click to open a pull request, then that cloned repository lurks forever in your profile unless you go through 16 screens to delete it -- but people in general seem to think it's easy).
It's much harder to do it on some random other server where some project might be hosted, because now you have to add 4 more even more annoying steps: create an account; pick a password; confirm an email address; setup SSH keys for pushing. (And I'm not even mentioning the basic impossibility of offering
pushaccess to external unknown contributors to people who want to host their own simple homemade Git server.)At this point some may argue that we could all have accounts on GitLab, or Codeberg or wherever else, then those steps are removed. Besides not being a practical strategy this pseudo solution misses the point of being decentralized (or distributed, who knows) entirely: it's far from the ideal to force everybody to have the double of account management and SSH setup work in order to have the open-source world controlled by two shady companies instead of one.
What we want is to give every person the opportunity to host their own Git server without being ostracized. at the same time we must recognize that most people won't want to host their own servers (not even most open-source programmers!) and give everybody the ability to host their stuff on multi-tenant servers (such as GitHub) too. Importantly, though, if we allow for a random person to have a standalone Git server on a standalone server they host themselves on their wood cabin that also means any new hosting company can show up and start offering Git hosting, with or without new cool features, charging high or low or zero, and be immediately competing against GitHub or GitLab, i.e. we must remove the network-effect centralization pressure.
External contributions
The first problem we have to solve is: how can Bob contribute to Alice's repository without having an account on Alice's server?
SourceHut has reminded GitHub users that Git has always had this (for most) arcane
git send-emailcommand that is the original way to send patches, using an once-open protocol.Turns out Nostr acts as a quite powerful email replacement and can be used to send text content just like email, therefore patches are a very good fit for Nostr event contents.
Once you get used to it and the proper UIs (or CLIs) are built sending and applying patches to and from others becomes a much easier flow than the intense clickops mixed with terminal copypasting that is interacting with GitHub (you have to clone the repository on GitHub, then update the remote URL in your local directory, then create a branch and then go back and turn that branch into a Pull Request, it's quite tiresome) that many people already dislike so much they went out of their way to build many GitHub CLI tools just so they could comment on issues and approve pull requests from their terminal.
Replacing GitHub features
Aside from being the "hub" that people use to send patches to other people's code (because no one can do the email flow anymore, justifiably), GitHub also has 3 other big features that are not directly related to Git, but that make its network-effect harder to overcome. Luckily Nostr can be used to create a new environment in which these same features are implemented in a more decentralized and healthy way.
Issues: bug reports, feature requests and general discussions
Since the "Issues" GitHub feature is just a bunch of text comments it should be very obvious that Nostr is a perfect fit for it.
I will not even mention the fact that Nostr is much better at threading comments than GitHub (which doesn't do it at all), which can generate much more productive and organized discussions (and you can opt out if you want).
Search
I use GitHub search all the time to find libraries and projects that may do something that I need, and it returns good results almost always. So if people migrated out to other code hosting providers wouldn't we lose it?
The fact is that even though we think everybody is on GitHub that is a globalist falsehood. Some projects are not on GitHub, and if we use only GitHub for search those will be missed. So even if we didn't have a Nostr Git alternative it would still be necessary to create a search engine that incorporated GitLab, Codeberg, SourceHut and whatnot.
Turns out on Nostr we can make that quite easy by not forcing anyone to integrate custom APIs or hardcoding Git provider URLs: each repository can make itself available by publishing an "announcement" event with a brief description and one or more Git URLs. That makes it easy for a search engine to index them -- and even automatically download the code and index the code (or index just README files or whatever) without a centralized platform ever having to be involved.
The relays where such announcements will be available play a role, of course, but that isn't a bad role: each announcement can be in multiple relays known for storing "public good" projects, some relays may curate only projects known to be very good according to some standards, other relays may allow any kind of garbage, which wouldn't make them good for a search engine to rely upon, but would still be useful in case one knows the exact thing (and from whom) they're searching for (the same is valid for all Nostr content, by the way, and that's where it's censorship-resistance comes from).
Continuous integration
GitHub Actions are a very hardly subsidized free-compute-for-all-paid-by-Microsoft feature, but one that isn't hard to replace at all. In fact there exists today many companies offering the same kind of service out there -- although they are mostly targeting businesses and not open-source projects, before GitHub Actions was introduced there were also many that were heavily used by open-source projects.
One problem is that these services are still heavily tied to GitHub today, they require a GitHub login, sometimes BitBucket and GitLab and whatnot, and do not allow one to paste an arbitrary Git server URL, but that isn't a thing that is very hard to change anyway, or to start from scratch. All we need are services that offer the CI/CD flows, perhaps using the same framework of GitHub Actions (although I would prefer to not use that messy garbage), and charge some few satoshis for it.
It may be the case that all the current services only support the big Git hosting platforms because they rely on their proprietary APIs, most notably the webhooks dispatched when a repository is updated, to trigger the jobs. It doesn't have to be said that Nostr can also solve that problem very easily.
-
 @ 6389be64:ef439d32
2025-02-27 21:32:12
@ 6389be64:ef439d32
2025-02-27 21:32:12GA, plebs. The latest episode of Bitcoin And is out, and, as always, the chicanery is running rampant. Let’s break down the biggest topics I covered, and if you want the full, unfiltered rant, make sure to listen to the episode linked below.
House Democrats’ MEME Act: A Bad Joke?
House Democrats are proposing a bill to ban presidential meme coins, clearly aimed at Trump’s and Melania’s ill-advised token launches. While grifters launching meme coins is bad, this bill is just as ridiculous. If this legislation moves forward, expect a retaliatory strike exposing how politicians like Pelosi and Warren mysteriously amassed their fortunes. Will it pass? Doubtful. But it’s another sign of the government’s obsession with regulating everything except itself.
Senate Banking’s First Digital Asset Hearing: The Real Target Is You
Cynthia Lummis chaired the first digital asset hearing, and—surprise!—it was all about control. The discussion centered on stablecoins, AML, and KYC regulations, with witnesses suggesting Orwellian measures like freezing stablecoin transactions unless pre-approved by authorities. What was barely mentioned? Bitcoin. They want full oversight of stablecoins, which is really about controlling financial freedom. Expect more nonsense targeting self-custody wallets under the guise of stopping “bad actors.”
Bank of America and PayPal Want In on Stablecoins
Bank of America’s CEO openly stated they’ll launch a stablecoin as soon as regulation allows. Meanwhile, PayPal’s CEO paid for a hat using Bitcoin—not their own stablecoin, Pi USD. Why wouldn’t he use his own product? Maybe he knows stablecoins aren’t what they’re hyped up to be. Either way, the legacy financial system is gearing up to flood the market with stablecoins, not because they love crypto, but because it’s a tool to extend U.S. dollar dominance.
MetaPlanet Buys the Dip
Japan’s MetaPlanet issued $13.4M in bonds to buy more Bitcoin, proving once again that institutions see the writing on the wall. Unlike U.S. regulators who obsess over stablecoins, some companies are actually stacking sats.
UK Expands Crypto Seizure Powers
Across the pond, the UK government is pushing legislation to make it easier to seize and destroy crypto linked to criminal activity. While they frame it as going after the bad guys, it’s another move toward centralized control and financial surveillance.
Bitcoin Tools & Tech: Arc, SatoChip, and Nunchuk
Some bullish Bitcoin developments: ARC v0.5 is making Bitcoin’s second layer more efficient, SatoChip now supports Taproot and Nostr, and Nunchuk launched a group wallet with chat, making multisig collaboration easier.
The Bottom Line
The state is coming for financial privacy and control, and stablecoins are their weapon of choice. Bitcoiners need to stay focused, keep their coins in self-custody, and build out parallel systems. Expect more regulatory attacks, but don’t let them distract you—just keep stacking and transacting in ways they can’t control.
🎧 Listen to the full episode here: https://fountain.fm/episode/PYITCo18AJnsEkKLz2Ks
💰 Support the show by boosting sats on Podcasting 2.0! and I will see you on the other side.
-
 @ 04c915da:3dfbecc9
2025-03-07 00:26:37
@ 04c915da:3dfbecc9
2025-03-07 00:26:37There is something quietly rebellious about stacking sats. In a world obsessed with instant gratification, choosing to patiently accumulate Bitcoin, one sat at a time, feels like a middle finger to the hype machine. But to do it right, you have got to stay humble. Stack too hard with your head in the clouds, and you will trip over your own ego before the next halving even hits.
Small Wins
Stacking sats is not glamorous. Discipline. Stacking every day, week, or month, no matter the price, and letting time do the heavy lifting. Humility lives in that consistency. You are not trying to outsmart the market or prove you are the next "crypto" prophet. Just a regular person, betting on a system you believe in, one humble stack at a time. Folks get rekt chasing the highs. They ape into some shitcoin pump, shout about it online, then go silent when they inevitably get rekt. The ones who last? They stack. Just keep showing up. Consistency. Humility in action. Know the game is long, and you are not bigger than it.
Ego is Volatile
Bitcoin’s swings can mess with your head. One day you are up 20%, feeling like a genius and the next down 30%, questioning everything. Ego will have you panic selling at the bottom or over leveraging the top. Staying humble means patience, a true bitcoin zen. Do not try to "beat” Bitcoin. Ride it. Stack what you can afford, live your life, and let compounding work its magic.
Simplicity
There is a beauty in how stacking sats forces you to rethink value. A sat is worth less than a penny today, but every time you grab a few thousand, you plant a seed. It is not about flaunting wealth but rather building it, quietly, without fanfare. That mindset spills over. Cut out the noise: the overpriced coffee, fancy watches, the status games that drain your wallet. Humility is good for your soul and your stack. I have a buddy who has been stacking since 2015. Never talks about it unless you ask. Lives in a decent place, drives an old truck, and just keeps stacking. He is not chasing clout, he is chasing freedom. That is the vibe: less ego, more sats, all grounded in life.
The Big Picture
Stack those sats. Do it quietly, do it consistently, and do not let the green days puff you up or the red days break you down. Humility is the secret sauce, it keeps you grounded while the world spins wild. In a decade, when you look back and smile, it will not be because you shouted the loudest. It will be because you stayed the course, one sat at a time. \ \ Stay Humble and Stack Sats. 🫡
-
 @ 177bfd16:347a07e4
2025-04-26 20:38:30
@ 177bfd16:347a07e4
2025-04-26 20:38:30So , you've battles through your way through countless Grunts , overcome the Team GO Rocket Leaders, and now you stand face to face with the big boss him self - Giovanni!
As of April 2025 , Giovanni is finishing his battles with Shadow Palkia.
Giovanni's Current Lineup (April 2025) First, know your enemy. Giovanni's team follows this structure:
Slot 1: Shadow Persian (Normal)
Slot 2: One of these three, chosen randomly:
Shadow Nidoking (Poison/Ground) Shadow Kingdra (Water/Dragon) Shadow Rhyperior (Rock/Ground)
Slot 3: Shadow Palkia (Water/Dragon) Remember, these are Shadow Pokémon – they hit harder than their normal counterparts!
Counter Strategy: Beating Giovanni Pokémon by Pokémon
Let's dive into the best counters for each potential opponent:
- Vs. Shadow Persian (Normal)
Giovanni always leads with Persian. As a Normal-type, it's weak only to Fighting-type attacks.
Top Counters: Machamp, Lucario, Conkeldurr, Terrakion, Mega Blaziken, Mega Lucario.
Moves: Prioritize Fighting-type moves like Counter, Dynamic Punch, Aura Sphere, and Sacred Sword.
Tip: Lead with a strong Fighting-type. Moves like Lucario's Power-Up Punch or Machamp's Cross Chop charge quickly and are great for baiting Giovanni's shields early!
- Vs. The Second Slot (Nidoking, Kingdra, or Rhyperior)
This is where things get unpredictable. You need Pokémon that can handle these potential threats:
Vs. Shadow Nidoking (Poison/Ground): Weak to Water, Ground, Ice, Psychic.
Counters: Kyogre (Primal/Shadow), Swampert (Mega), Groudon (Primal/Shadow), Mewtwo (Shadow), Excadrill. Water and Ground-types are prime choices.
Vs. Shadow Kingdra (Water/Dragon): Weak to Fairy, Dragon. Counters: Gardevoir (Mega), Togekiss, Xerneas. Fairy-types are excellent as they resist Dragon attacks while dealing super-effective damage. Dragon-types like Rayquaza or Palkia work but are risky.
Vs. Shadow Rhyperior (Rock/Ground): Double weak to Water and Grass! Also weak to Fighting, Ground, Ice, Steel.
Counters: Kyogre (Primal/Shadow), Swampert (Mega), Sceptile (Mega), Roserade. Your Fighting-type lead (if it survived Persian) can also do significant damage. Hit it hard with Water or Grass!
- Vs. Shadow Palkia (Water/Dragon)
Giovanni's final Pokémon is the powerful Shadow Palkia. Like Kingdra, it's weak to Fairy and Dragon types.
Top Counters: Gardevoir (Mega), Togekiss, Xerneas. Again, Fairy-types are the safest and most reliable counters.
Dragon Counters (Use with Caution): Rayquaza (Mega), Palkia (Origin Forme), Dragonite, Dialga (Origin Forme).

Recommended Battle Teams for April 2025 Based on the counters, here are a few effective teams you can assemble:
Team 1 (Balanced):
Machamp (Counter / Cross Chop & Dynamic Punch)
Swampert (Mud Shot / Hydro Cannon & Earthquake)
Togekiss (Charm / Dazzling Gleam & Ancient Power)
Why it works: Covers all bases well with accessible Pokémon. Machamp handles Persian/shields, Swampert crushes Rhyperior/Nidoking, Togekiss tackles Kingdra/Palkia.
Team 2 (Legendary Power):
Lucario (Counter / Power-Up Punch & Aura Sphere)
Kyogre (Waterfall / Origin Pulse & Surf)
Xerneas (Geomancy / Moonblast & Close Combat)
Why it works: High-powered options. Lucario baits shields effectively, Kyogre dominates slot two's Ground/Rock types, Xerneas shreds the Dragons.
Team 3 (Mega Advantage):
Machamp (Counter / Cross Chop & DP)
Kyogre (Waterfall / Origin Pulse)
Mega Gardevoir (Charm / Dazzling Gleam & Shadow Ball)
Why it works: Uses a standard strong lead and mid-game counter, saving the Mega slot for Gardevoir to ensure a powerful finish against Palkia/Kingdra.
Essential Battle Tips Don't forget these crucial tactics:
The Switch Trick: Place your intended starting Pokémon (e.g., Machamp) in the second or third slot. Start the battle, then immediately switch to it. Giovanni will pause for a moment, letting you get in free hits!
Bait Those Shields: Use Pokémon with fast-charging Charged Moves, especially early on, to force Giovanni to waste his Protect Shields.
Power Up: Ensure your team is powered up significantly and consider unlocking second Charged Moves for better flexibility.
Don't Give Up: Giovanni is tough! It might take a few tries to get the right matchup against his second Pokémon. Learn from each attempt and adjust your team if needed.
Go show the boss who's the boss and claim your shadow Palkia . Good Luck, Trainer !
-
 @ 30ceb64e:7f08bdf5
2025-04-26 20:33:30
@ 30ceb64e:7f08bdf5
2025-04-26 20:33:30Status: Draft
Author: TheWildHustleAbstract
This NIP defines a framework for storing and sharing health and fitness profile data on Nostr. It establishes a set of standardized event kinds for individual health metrics, allowing applications to selectively access specific health information while preserving user control and privacy.
In this framework exists - NIP-101h.1 Weight using kind 1351 - NIP-101h.2 Height using kind 1352 - NIP-101h.3 Age using kind 1353 - NIP-101h.4 Gender using kind 1354 - NIP-101h.5 Fitness Level using kind 1355
Motivation
I want to build and support an ecosystem of health and fitness related nostr clients that have the ability to share and utilize a bunch of specific interoperable health metrics.
- Selective access - Applications can access only the data they need
- User control - Users can choose which metrics to share
- Interoperability - Different health applications can share data
- Privacy - Sensitive health information can be managed independently
Specification
Kind Number Range
Health profile metrics use the kind number range 1351-1399:
| Kind | Metric | | --------- | ---------------------------------- | | 1351 | Weight | | 1352 | Height | | 1353 | Age | | 1354 | Gender | | 1355 | Fitness Level | | 1356-1399 | Reserved for future health metrics |
Common Structure
All health metric events SHOULD follow these guidelines:
- The content field contains the primary value of the metric
- Required tags:
['t', 'health']- For categorizing as health data['t', metric-specific-tag]- For identifying the specific metric['unit', unit-of-measurement]- When applicable- Optional tags:
['converted_value', value, unit]- For providing alternative unit measurements['timestamp', ISO8601-date]- When the metric was measured['source', application-name]- The source of the measurement
Unit Handling
Health metrics often have multiple ways to be measured. To ensure interoperability:
- Where multiple units are possible, one standard unit SHOULD be chosen as canonical
- When using non-standard units, a
converted_valuetag SHOULD be included with the canonical unit - Both the original and converted values should be provided for maximum compatibility
Client Implementation Guidelines
Clients implementing this NIP SHOULD:
- Allow users to explicitly choose which metrics to publish
- Support reading health metrics from other users when appropriate permissions exist
- Support updating metrics with new values over time
- Preserve tags they don't understand for future compatibility
- Support at least the canonical unit for each metric
Extensions
New health metrics can be proposed as extensions to this NIP using the format:
- NIP-101h.X where X is the metric number
Each extension MUST specify: - A unique kind number in the range 1351-1399 - The content format and meaning - Required and optional tags - Examples of valid events
Privacy Considerations
Health data is sensitive personal information. Clients implementing this NIP SHOULD:
- Make it clear to users when health data is being published
- Consider incorporating NIP-44 encryption for sensitive metrics
- Allow users to selectively share metrics with specific individuals
- Provide easy ways to delete previously published health data
NIP-101h.1: Weight
Description
This NIP defines the format for storing and sharing weight data on Nostr.
Event Kind: 1351
Content
The content field MUST contain the numeric weight value as a string.
Required Tags
- ['unit', 'kg' or 'lb'] - Unit of measurement
- ['t', 'health'] - Categorization tag
- ['t', 'weight'] - Specific metric tag
Optional Tags
- ['converted_value', value, unit] - Provides the weight in alternative units for interoperability
- ['timestamp', ISO8601 date] - When the weight was measured
Examples
json { "kind": 1351, "content": "70", "tags": [ ["unit", "kg"], ["t", "health"], ["t", "weight"] ] }json { "kind": 1351, "content": "154", "tags": [ ["unit", "lb"], ["t", "health"], ["t", "weight"], ["converted_value", "69.85", "kg"] ] }NIP-101h.2: Height
Status: Draft
Description
This NIP defines the format for storing and sharing height data on Nostr.
Event Kind: 1352
Content
The content field can use two formats: - For metric height: A string containing the numeric height value in centimeters (cm) - For imperial height: A JSON string with feet and inches properties
Required Tags
['t', 'health']- Categorization tag['t', 'height']- Specific metric tag['unit', 'cm' or 'imperial']- Unit of measurement
Optional Tags
['converted_value', value, 'cm']- Provides height in centimeters for interoperability when imperial is used['timestamp', ISO8601-date]- When the height was measured
Examples
```jsx // Example 1: Metric height Apply to App.jsx
// Example 2: Imperial height with conversion Apply to App.jsx ```
Implementation Notes
- Centimeters (cm) is the canonical unit for height interoperability
- When using imperial units, a conversion to centimeters SHOULD be provided
- Height values SHOULD be positive integers
- For maximum compatibility, clients SHOULD support both formats
NIP-101h.3: Age
Status: Draft
Description
This NIP defines the format for storing and sharing age data on Nostr.
Event Kind: 1353
Content
The content field MUST contain the numeric age value as a string.
Required Tags
['unit', 'years']- Unit of measurement['t', 'health']- Categorization tag['t', 'age']- Specific metric tag
Optional Tags
['timestamp', ISO8601-date]- When the age was recorded['dob', ISO8601-date]- Date of birth (if the user chooses to share it)
Examples
```jsx // Example 1: Basic age Apply to App.jsx
// Example 2: Age with DOB Apply to App.jsx ```
Implementation Notes
- Age SHOULD be represented as a positive integer
- For privacy reasons, date of birth (dob) is optional
- Clients SHOULD consider updating age automatically if date of birth is known
- Age can be a sensitive metric and clients may want to consider encrypting this data
NIP-101h.4: Gender
Status: Draft
Description
This NIP defines the format for storing and sharing gender data on Nostr.
Event Kind: 1354
Content
The content field contains a string representing the user's gender.
Required Tags
['t', 'health']- Categorization tag['t', 'gender']- Specific metric tag
Optional Tags
['timestamp', ISO8601-date]- When the gender was recorded['preferred_pronouns', string]- User's preferred pronouns
Common Values
While any string value is permitted, the following common values are recommended for interoperability: - male - female - non-binary - other - prefer-not-to-say
Examples
```jsx // Example 1: Basic gender Apply to App.jsx
// Example 2: Gender with pronouns Apply to App.jsx ```
Implementation Notes
- Clients SHOULD allow free-form input for gender
- For maximum compatibility, clients SHOULD support the common values
- Gender is a sensitive personal attribute and clients SHOULD consider appropriate privacy controls
- Applications focusing on health metrics should be respectful of gender diversity
NIP-101h.5: Fitness Level
Status: Draft
Description
This NIP defines the format for storing and sharing fitness level data on Nostr.
Event Kind: 1355
Content
The content field contains a string representing the user's fitness level.
Required Tags
['t', 'health']- Categorization tag['t', 'fitness']- Fitness category tag['t', 'level']- Specific metric tag
Optional Tags
['timestamp', ISO8601-date]- When the fitness level was recorded['activity', activity-type]- Specific activity the fitness level relates to['metrics', JSON-string]- Quantifiable fitness metrics used to determine level
Common Values
While any string value is permitted, the following common values are recommended for interoperability: - beginner - intermediate - advanced - elite - professional
Examples
```jsx // Example 1: Basic fitness level Apply to App.jsx
// Example 2: Activity-specific fitness level with metrics Apply to App.jsx ```
Implementation Notes
- Fitness level is subjective and may vary by activity
- The activity tag can be used to specify fitness level for different activities
- The metrics tag can provide objective measurements to support the fitness level
- Clients can extend this format to include activity-specific fitness assessments
- For general fitness apps, the simple beginner/intermediate/advanced scale is recommended
-
 @ f9cf4e94:96abc355
2024-12-31 20:18:59
@ f9cf4e94:96abc355
2024-12-31 20:18:59Scuttlebutt foi iniciado em maio de 2014 por Dominic Tarr ( dominictarr ) como uma rede social alternativa off-line, primeiro para convidados, que permite aos usuários obter controle total de seus dados e privacidade. Secure Scuttlebutt (ssb) foi lançado pouco depois, o que coloca a privacidade em primeiro plano com mais recursos de criptografia.
Se você está se perguntando de onde diabos veio o nome Scuttlebutt:
Este termo do século 19 para uma fofoca vem do Scuttlebutt náutico: “um barril de água mantido no convés, com um buraco para uma xícara”. A gíria náutica vai desde o hábito dos marinheiros de se reunir pelo boato até a fofoca, semelhante à fofoca do bebedouro.

Marinheiros se reunindo em torno da rixa. ( fonte )
Dominic descobriu o termo boato em um artigo de pesquisa que leu.
Em sistemas distribuídos, fofocar é um processo de retransmissão de mensagens ponto a ponto; as mensagens são disseminadas de forma análoga ao “boca a boca”.
Secure Scuttlebutt é um banco de dados de feeds imutáveis apenas para acréscimos, otimizado para replicação eficiente para protocolos ponto a ponto. Cada usuário tem um log imutável somente para acréscimos no qual eles podem gravar. Eles gravam no log assinando mensagens com sua chave privada. Pense em um feed de usuário como seu próprio diário de bordo, como um diário de bordo (ou diário do capitão para os fãs de Star Trek), onde eles são os únicos autorizados a escrever nele, mas têm a capacidade de permitir que outros amigos ou colegas leiam ao seu diário de bordo, se assim o desejarem.
Cada mensagem possui um número de sequência e a mensagem também deve fazer referência à mensagem anterior por seu ID. O ID é um hash da mensagem e da assinatura. A estrutura de dados é semelhante à de uma lista vinculada. É essencialmente um log somente de acréscimo de JSON assinado. Cada item adicionado a um log do usuário é chamado de mensagem.
Os logs do usuário são conhecidos como feed e um usuário pode seguir os feeds de outros usuários para receber suas atualizações. Cada usuário é responsável por armazenar seu próprio feed. Quando Alice assina o feed de Bob, Bob baixa o log de feed de Alice. Bob pode verificar se o registro do feed realmente pertence a Alice verificando as assinaturas. Bob pode verificar as assinaturas usando a chave pública de Alice.

Estrutura de alto nível de um feed
Pubs são servidores de retransmissão conhecidos como “super peers”. Pubs conectam usuários usuários e atualizações de fofocas a outros usuários conectados ao Pub. Um Pub é análogo a um pub da vida real, onde as pessoas vão para se encontrar e se socializar. Para ingressar em um Pub, o usuário deve ser convidado primeiro. Um usuário pode solicitar um código de convite de um Pub; o Pub simplesmente gerará um novo código de convite, mas alguns Pubs podem exigir verificação adicional na forma de verificação de e-mail ou, com alguns Pubs, você deve pedir um código em um fórum público ou chat. Pubs também podem mapear aliases de usuário, como e-mails ou nome de usuário, para IDs de chave pública para facilitar os pares de referência.
Depois que o Pub enviar o código de convite ao usuário, o usuário resgatará o código, o que significa que o Pub seguirá o usuário, o que permite que o usuário veja as mensagens postadas por outros membros do Pub, bem como as mensagens de retransmissão do Pub pelo usuário a outros membros do Pub.
Além de retransmitir mensagens entre pares, os Pubs também podem armazenar as mensagens. Se Alice estiver offline e Bob transmitir atualizações de feed, Alice perderá a atualização. Se Alice ficar online, mas Bob estiver offline, não haverá como ela buscar o feed de Bob. Mas com um Pub, Alice pode buscar o feed no Pub mesmo se Bob estiver off-line porque o Pub está armazenando as mensagens. Pubs são úteis porque assim que um colega fica online, ele pode sincronizar com o Pub para receber os feeds de seus amigos potencialmente offline.
Um usuário pode, opcionalmente, executar seu próprio servidor Pub e abri-lo ao público ou permitir que apenas seus amigos participem, se assim o desejarem. Eles também podem ingressar em um Pub público. Aqui está uma lista de Pubs públicos em que todos podem participar . Explicaremos como ingressar em um posteriormente neste guia. Uma coisa importante a observar é que o Secure Scuttlebutt em uma rede social somente para convidados significa que você deve ser “puxado” para entrar nos círculos sociais. Se você responder às mensagens, os destinatários não serão notificados, a menos que estejam seguindo você de volta. O objetivo do SSB é criar “ilhas” isoladas de redes pares, ao contrário de uma rede pública onde qualquer pessoa pode enviar mensagens a qualquer pessoa.

Perspectivas dos participantes
Scuttlebot
O software Pub é conhecido como servidor Scuttlebutt (servidor ssb ), mas também é conhecido como “Scuttlebot” e
sbotna linha de comando. O servidor SSB adiciona comportamento de rede ao banco de dados Scuttlebutt (SSB). Estaremos usando o Scuttlebot ao longo deste tutorial.Os logs do usuário são conhecidos como feed e um usuário pode seguir os feeds de outros usuários para receber suas atualizações. Cada usuário é responsável por armazenar seu próprio feed. Quando Alice assina o feed de Bob, Bob baixa o log de feed de Alice. Bob pode verificar se o registro do feed realmente pertence a Alice verificando as assinaturas. Bob pode verificar as assinaturas usando a chave pública de Alice.

Estrutura de alto nível de um feed
Pubs são servidores de retransmissão conhecidos como “super peers”. Pubs conectam usuários usuários e atualizações de fofocas a outros usuários conectados ao Pub. Um Pub é análogo a um pub da vida real, onde as pessoas vão para se encontrar e se socializar. Para ingressar em um Pub, o usuário deve ser convidado primeiro. Um usuário pode solicitar um código de convite de um Pub; o Pub simplesmente gerará um novo código de convite, mas alguns Pubs podem exigir verificação adicional na forma de verificação de e-mail ou, com alguns Pubs, você deve pedir um código em um fórum público ou chat. Pubs também podem mapear aliases de usuário, como e-mails ou nome de usuário, para IDs de chave pública para facilitar os pares de referência.
Depois que o Pub enviar o código de convite ao usuário, o usuário resgatará o código, o que significa que o Pub seguirá o usuário, o que permite que o usuário veja as mensagens postadas por outros membros do Pub, bem como as mensagens de retransmissão do Pub pelo usuário a outros membros do Pub.
Além de retransmitir mensagens entre pares, os Pubs também podem armazenar as mensagens. Se Alice estiver offline e Bob transmitir atualizações de feed, Alice perderá a atualização. Se Alice ficar online, mas Bob estiver offline, não haverá como ela buscar o feed de Bob. Mas com um Pub, Alice pode buscar o feed no Pub mesmo se Bob estiver off-line porque o Pub está armazenando as mensagens. Pubs são úteis porque assim que um colega fica online, ele pode sincronizar com o Pub para receber os feeds de seus amigos potencialmente offline.
Um usuário pode, opcionalmente, executar seu próprio servidor Pub e abri-lo ao público ou permitir que apenas seus amigos participem, se assim o desejarem. Eles também podem ingressar em um Pub público. Aqui está uma lista de Pubs públicos em que todos podem participar . Explicaremos como ingressar em um posteriormente neste guia. Uma coisa importante a observar é que o Secure Scuttlebutt em uma rede social somente para convidados significa que você deve ser “puxado” para entrar nos círculos sociais. Se você responder às mensagens, os destinatários não serão notificados, a menos que estejam seguindo você de volta. O objetivo do SSB é criar “ilhas” isoladas de redes pares, ao contrário de uma rede pública onde qualquer pessoa pode enviar mensagens a qualquer pessoa.


Perspectivas dos participantes
Pubs - Hubs
Pubs públicos
| Pub Name | Operator | Invite Code | | ------------------------------------------------------------ | ------------------------------------------------------------ | ------------------------------------------------------------ | |
scuttle.us| @Ryan |scuttle.us:8008:@WqcuCOIpLtXFRw/9vOAQJti8avTZ9vxT9rKrPo8qG6o=.ed25519~/ZUi9Chpl0g1kuWSrmehq2EwMQeV0Pd+8xw8XhWuhLE=| | pub1.upsocial.com | @freedomrules |pub1.upsocial.com:8008:@gjlNF5Cyw3OKZxEoEpsVhT5Xv3HZutVfKBppmu42MkI=.ed25519~lMd6f4nnmBZEZSavAl4uahl+feajLUGqu8s2qdoTLi8=| | Monero Pub | @Denis |xmr-pub.net:8008:@5hTpvduvbDyMLN2IdzDKa7nx7PSem9co3RsOmZoyyCM=.ed25519~vQU+r2HUd6JxPENSinUWdfqrJLlOqXiCbzHoML9iVN4=| | FreeSocial | @Jarland |pub.freesocial.co:8008:@ofYKOy2p9wsaxV73GqgOyh6C6nRGFM5FyciQyxwBd6A=.ed25519~ye9Z808S3KPQsV0MWr1HL0/Sh8boSEwW+ZK+8x85u9w=| |ssb.vpn.net.br| @coffeverton |ssb.vpn.net.br:8008:@ze8nZPcf4sbdULvknEFOCbVZtdp7VRsB95nhNw6/2YQ=.ed25519~D0blTolH3YoTwSAkY5xhNw8jAOjgoNXL/+8ZClzr0io=| | gossip.noisebridge.info | Noisebridge Hackerspace @james.network |gossip.noisebridge.info:8008:@2NANnQVdsoqk0XPiJG2oMZqaEpTeoGrxOHJkLIqs7eY=.ed25519~JWTC6+rPYPW5b5zCion0gqjcJs35h6JKpUrQoAKWgJ4=|Pubs privados
Você precisará entrar em contato com os proprietários desses bares para receber um convite.
| Pub Name | Operator | Contact | | --------------------------------------------- | ------------------------------------------------------------ | ----------------------------------------------- | |
many.butt.nz| @dinosaur | mikey@enspiral.com | |one.butt.nz| @dinosaur | mikey@enspiral.com | |ssb.mikey.nz| @dinosaur | mikey@enspiral.com | | ssb.celehner.com | @cel | cel@celehner.com |Pubs muito grandes
Aviso: embora tecnicamente funcione usar um convite para esses pubs, você provavelmente se divertirá se o fizer devido ao seu tamanho (muitas coisas para baixar, risco para bots / spammers / idiotas)
| Pub Name | Operator | Invite Code | | --------------------------------------- | ----------------------------------------------- | ------------------------------------------------------------ | |
scuttlebutt.de| SolSoCoG |scuttlebutt.de:8008:@yeh/GKxlfhlYXSdgU7CRLxm58GC42za3tDuC4NJld/k=.ed25519~iyaCpZ0co863K9aF+b7j8BnnHfwY65dGeX6Dh2nXs3c=| |Lohn's Pub| @lohn |p.lohn.in:8018:@LohnKVll9HdLI3AndEc4zwGtfdF/J7xC7PW9B/JpI4U=.ed25519~z3m4ttJdI4InHkCtchxTu26kKqOfKk4woBb1TtPeA/s=| | Scuttle Space | @guil-dot | Visit scuttle.space | |SSB PeerNet US-East| timjrobinson |us-east.ssbpeer.net:8008:@sTO03jpVivj65BEAJMhlwtHXsWdLd9fLwyKAT1qAkc0=.ed25519~sXFc5taUA7dpGTJITZVDCRy2A9jmkVttsr107+ufInU=| | Hermies | s | net:hermies.club:8008~shs:uMYDVPuEKftL4SzpRGVyQxLdyPkOiX7njit7+qT/7IQ=:SSB+Room+PSK3TLYC2T86EHQCUHBUHASCASE18JBV24= |GUI - Interface Gráfica do Utilizador(Usuário)
Patchwork - Uma GUI SSB (Descontinuado)
Patchwork é o aplicativo de mensagens e compartilhamento descentralizado construído em cima do SSB . O protocolo scuttlebutt em si não mantém um conjunto de feeds nos quais um usuário está interessado, então um cliente é necessário para manter uma lista de feeds de pares em que seu respectivo usuário está interessado e seguindo.

Fonte: scuttlebutt.nz
Quando você instala e executa o Patchwork, você só pode ver e se comunicar com seus pares em sua rede local. Para acessar fora de sua LAN, você precisa se conectar a um Pub. Um pub é apenas para convidados e eles retransmitem mensagens entre você e seus pares fora de sua LAN e entre outros Pubs.
Lembre-se de que você precisa seguir alguém para receber mensagens dessa pessoa. Isso reduz o envio de mensagens de spam para os usuários. Os usuários só veem as respostas das pessoas que seguem. Os dados são sincronizados no disco para funcionar offline, mas podem ser sincronizados diretamente com os pares na sua LAN por wi-fi ou bluetooth.
Patchbay - Uma GUI Alternativa
Patchbay é um cliente de fofoca projetado para ser fácil de modificar e estender. Ele usa o mesmo banco de dados que Patchwork e Patchfoo , então você pode facilmente dar uma volta com sua identidade existente.

Planetary - GUI para IOS

Planetary é um app com pubs pré-carregados para facilitar integração.
Manyverse - GUI para Android

Manyverse é um aplicativo de rede social com recursos que você esperaria: posts, curtidas, perfis, mensagens privadas, etc. Mas não está sendo executado na nuvem de propriedade de uma empresa, em vez disso, as postagens de seus amigos e todos os seus dados sociais vivem inteiramente em seu telefone .
Fontes
-
https://scuttlebot.io/
-
https://decentralized-id.com/decentralized-web/scuttlebot/#plugins
-
https://medium.com/@miguelmota/getting-started-with-secure-scuttlebut-e6b7d4c5ecfd
-
Secure Scuttlebutt : um protocolo de banco de dados global.
-
-
 @ 6e0ea5d6:0327f353
2025-02-21 18:15:52
@ 6e0ea5d6:0327f353
2025-02-21 18:15:52"Malcolm Forbes recounts that a lady, wearing a faded cotton dress, and her husband, dressed in an old handmade suit, stepped off a train in Boston, USA, and timidly made their way to the office of the president of Harvard University. They had come from Palo Alto, California, and had not scheduled an appointment. The secretary, at a glance, thought that those two, looking like country bumpkins, had no business at Harvard.
— We want to speak with the president — the man said in a low voice.
— He will be busy all day — the secretary replied curtly.
— We will wait.
The secretary ignored them for hours, hoping the couple would finally give up and leave. But they stayed there, and the secretary, somewhat frustrated, decided to bother the president, although she hated doing that.
— If you speak with them for just a few minutes, maybe they will decide to go away — she said.
The president sighed in irritation but agreed. Someone of his importance did not have time to meet people like that, but he hated faded dresses and tattered suits in his office. With a stern face, he went to the couple.
— We had a son who studied at Harvard for a year — the woman said. — He loved Harvard and was very happy here, but a year ago he died in an accident, and we would like to erect a monument in his honor somewhere on campus.— My lady — said the president rudely —, we cannot erect a statue for every person who studied at Harvard and died; if we did, this place would look like a cemetery.
— Oh, no — the lady quickly replied. — We do not want to erect a statue. We would like to donate a building to Harvard.
The president looked at the woman's faded dress and her husband's old suit and exclaimed:
— A building! Do you have even the faintest idea of how much a building costs? We have more than seven and a half million dollars' worth of buildings here at Harvard.
The lady was silent for a moment, then said to her husband:
— If that’s all it costs to found a university, why don’t we have our own?
The husband agreed.
The couple, Leland Stanford, stood up and left, leaving the president confused. Traveling back to Palo Alto, California, they established there Stanford University, the second-largest in the world, in honor of their son, a former Harvard student."
Text extracted from: "Mileumlivros - Stories that Teach Values."
Thank you for reading, my friend! If this message helped you in any way, consider leaving your glass “🥃” as a token of appreciation.
A toast to our family!
-
 @ 5d4b6c8d:8a1c1ee3
2024-07-14 13:50:54
@ 5d4b6c8d:8a1c1ee3
2024-07-14 13:50:54Yesterday's edition https://stacker.news/items/607040/r/Undisciplined
Happy July 14th, everyone. America narrowly averted a civil war last night and I'm pretty happy about that. I was impressed by how well Stacker News covered the biggest breaking news event of the site's existence. People were pulling together lots of sources and offering generally measured thoughts.
-
- -
July 14, 2023 📅
📝
TOP POSTCommon psychological biases that bitcoiners have
Excerpt
One of the primary reasons I got involved with markets is my interest in psychology. Humans are a fickle bunch, and it's fascinating to observe the human condition in such a clear, mathematical way.
3217 sats \ 11 comments \ @birdeye21 \ ~bitcoin
💬
TOP COMMENThttps://stacker.news/items/208075/r/Undisciplined?commentId=208936
Excerpt
I get your point, but this seems to me one of the (rare) differences where "technically possible but empirically infeasible" vs "technically impossible" matters a lot.
1128 sats \ 3 replies \ @elvismercury
From Portable experiences by @k00b in ~nostr
🏆
TOP STACKER2nd place @k00b (1st hiding, presumed @siggy47)
7947 stacked \ 10.5k spent \ 3 posts \ 12 comments \ 0 referrals
🗺️
TOP TERRITORY~bitcoin
everything bitcoin related
founded by @k00b on Tue May 02 2023
37.3k stacked \ 0 revenue \ 51.8k spent \ 95 posts \ 214 comments
https://imgprxy.stacker.news/fsFoWlgwKYsk5mxx2ijgqU8fg04I_2zA_D28t_grR74/rs:fit:960:540/aHR0cHM6Ly9tLnN0YWNrZXIubmV3cy8yMzc5Ng
July 14, 2022 📅
📝
TOP POSTPine – A bitcoin wallet w/ a messenger-like UI || A BTC Wallet UX for the masses
Link to https://pine.pm/
509 sats \ 15 comments \ @Spartan \ ~bitcoin
💬
TOP COMMENThttps://stacker.news/items/44747/r/Undisciplined?commentId=45060
Excerpt
The user @darthcoin has way to many guides from wich you can learn a lot IMO, he is active here to most of the time, though I dont know if I've @ him correctly.
300 sats \ 4 replies \ @bangbang_u_r_done
From Any Good Routing Node Strategies? by @andyleroy in ~bitcoin
🏆
TOP STACKER1st place @nerd2ninja
544 stacked \ 1765 spent \ 3 posts \ 17 comments \ 0 referrals
🗺️
TOP TERRITORY~bitcoin
everything bitcoin related
founded by @k00b on Tue May 02 2023
14.6k stacked \ 0 revenue \ 31.6k spent \ 133 posts \ 261 comments
https://imgprxy.stacker.news/fsFoWlgwKYsk5mxx2ijgqU8fg04I_2zA_D28t_grR74/rs:fit:960:540/aHR0cHM6Ly9tLnN0YWNrZXIubmV3cy8yMzc5Ng
July 14, 2021 📅
📝
TOP POSTHow Bitcoin And Green Energy Can Save Ethiopia’s Economy
Link to https://stacker.news/items/320/r/Undisciplined
2 sats \ 1 comment \ @0268486dc4 \ ~bitcoin
💬
TOP COMMENThttps://stacker.news/items/332/r/Undisciplined?commentId=333
Excerpt
From the Twitter announcement
Students will learn how to build #Bitcoin applications from the ground up using the Rust programming language. […]
18 sats \ 0 replies \ @sha256
From Fodé Diop Launches a Bitcoin Academy by @sha256 in ~bitcoin
🏆
TOP STACKER1st place @sha256
4 stacked \ 5 spent \ 2 posts \ 1 comment \ 0 referrals
🗺️
TOP TERRITORY~bitcoin
everything bitcoin related
founded by @k00b on Tue May 02 2023
10 stacked \ 0 revenue \ 47 spent \ 9 posts \ 8 comments
originally posted at https://stacker.news/items/608036
-
-
 @ 3bf0c63f:aefa459d
2025-04-25 18:55:52
@ 3bf0c63f:aefa459d
2025-04-25 18:55:52Report of how the money Jack donated to the cause in December 2022 has been misused so far.
Bounties given
March 2025
- Dhalsim: 1,110,540 - Work on Nostr wiki data processing
February 2025
- BOUNTY* NullKotlinDev: 950,480 - Twine RSS reader Nostr integration
- Dhalsim: 2,094,584 - Work on Hypothes.is Nostr fork
- Constant, Biz and J: 11,700,588 - Nostr Special Forces
January 2025
- Constant, Biz and J: 11,610,987 - Nostr Special Forces
- BOUNTY* NullKotlinDev: 843,840 - Feeder RSS reader Nostr integration
- BOUNTY* NullKotlinDev: 797,500 - ReadYou RSS reader Nostr integration
December 2024
- BOUNTY* tijl: 1,679,500 - Nostr integration into RSS readers yarr and miniflux
- Constant, Biz and J: 10,736,166 - Nostr Special Forces
- Thereza: 1,020,000 - Podcast outreach initiative
November 2024
- Constant, Biz and J: 5,422,464 - Nostr Special Forces
October 2024
- Nostrdam: 300,000 - hackathon prize
- Svetski: 5,000,000 - Latin America Nostr events contribution
- Quentin: 5,000,000 - nostrcheck.me
June 2024
- Darashi: 5,000,000 - maintaining nos.today, searchnos, search.nos.today and other experiments
- Toshiya: 5,000,000 - keeping the NIPs repo clean and other stuff
May 2024
- James: 3,500,000 - https://github.com/jamesmagoo/nostr-writer
- Yakihonne: 5,000,000 - spreading the word in Asia
- Dashu: 9,000,000 - https://github.com/haorendashu/nostrmo
February 2024
- Viktor: 5,000,000 - https://github.com/viktorvsk/saltivka and https://github.com/viktorvsk/knowstr
- Eric T: 5,000,000 - https://github.com/tcheeric/nostr-java
- Semisol: 5,000,000 - https://relay.noswhere.com/ and https://hist.nostr.land relays
- Sebastian: 5,000,000 - Drupal stuff and nostr-php work
- tijl: 5,000,000 - Cloudron, Yunohost and Fraidycat attempts
- Null Kotlin Dev: 5,000,000 - AntennaPod attempt
December 2023
- hzrd: 5,000,000 - Nostrudel
- awayuki: 5,000,000 - NOSTOPUS illustrations
- bera: 5,000,000 - getwired.app
- Chris: 5,000,000 - resolvr.io
- NoGood: 10,000,000 - nostrexplained.com stories
October 2023
- SnowCait: 5,000,000 - https://nostter.vercel.app/ and other tools
- Shaun: 10,000,000 - https://yakihonne.com/, events and work on Nostr awareness
- Derek Ross: 10,000,000 - spreading the word around the world
- fmar: 5,000,000 - https://github.com/frnandu/yana
- The Nostr Report: 2,500,000 - curating stuff
- james magoo: 2,500,000 - the Obsidian plugin: https://github.com/jamesmagoo/nostr-writer
August 2023
- Paul Miller: 5,000,000 - JS libraries and cryptography-related work
- BOUNTY tijl: 5,000,000 - https://github.com/github-tijlxyz/wikinostr
- gzuus: 5,000,000 - https://nostree.me/
July 2023
- syusui-s: 5,000,000 - rabbit, a tweetdeck-like Nostr client: https://syusui-s.github.io/rabbit/
- kojira: 5,000,000 - Nostr fanzine, Nostr discussion groups in Japan, hardware experiments
- darashi: 5,000,000 - https://github.com/darashi/nos.today, https://github.com/darashi/searchnos, https://github.com/darashi/murasaki
- jeff g: 5,000,000 - https://nostr.how and https://listr.lol, plus other contributions
- cloud fodder: 5,000,000 - https://nostr1.com (open-source)
- utxo.one: 5,000,000 - https://relaying.io (open-source)
- Max DeMarco: 10,269,507 - https://www.youtube.com/watch?v=aA-jiiepOrE
- BOUNTY optout21: 1,000,000 - https://github.com/optout21/nip41-proto0 (proposed nip41 CLI)
- BOUNTY Leo: 1,000,000 - https://github.com/leo-lox/camelus (an old relay thing I forgot exactly)
June 2023
- BOUNTY: Sepher: 2,000,000 - a webapp for making lists of anything: https://pinstr.app/
- BOUNTY: Kieran: 10,000,000 - implement gossip algorithm on Snort, implement all the other nice things: manual relay selection, following hints etc.
- Mattn: 5,000,000 - a myriad of projects and contributions to Nostr projects: https://github.com/search?q=owner%3Amattn+nostr&type=code
- BOUNTY: lynn: 2,000,000 - a simple and clean git nostr CLI written in Go, compatible with William's original git-nostr-tools; and implement threaded comments on https://github.com/fiatjaf/nocomment.
- Jack Chakany: 5,000,000 - https://github.com/jacany/nblog
- BOUNTY: Dan: 2,000,000 - https://metadata.nostr.com/
April 2023
- BOUNTY: Blake Jakopovic: 590,000 - event deleter tool, NIP dependency organization
- BOUNTY: koalasat: 1,000,000 - display relays
- BOUNTY: Mike Dilger: 4,000,000 - display relays, follow event hints (Gossip)
- BOUNTY: kaiwolfram: 5,000,000 - display relays, follow event hints, choose relays to publish (Nozzle)
- Daniele Tonon: 3,000,000 - Gossip
- bu5hm4nn: 3,000,000 - Gossip
- BOUNTY: hodlbod: 4,000,000 - display relays, follow event hints
March 2023
- Doug Hoyte: 5,000,000 sats - https://github.com/hoytech/strfry
- Alex Gleason: 5,000,000 sats - https://gitlab.com/soapbox-pub/mostr
- verbiricha: 5,000,000 sats - https://badges.page/, https://habla.news/
- talvasconcelos: 5,000,000 sats - https://migrate.nostr.com, https://read.nostr.com, https://write.nostr.com/
- BOUNTY: Gossip model: 5,000,000 - https://camelus.app/
- BOUNTY: Gossip model: 5,000,000 - https://github.com/kaiwolfram/Nozzle
- BOUNTY: Bounty Manager: 5,000,000 - https://nostrbounties.com/
February 2023
- styppo: 5,000,000 sats - https://hamstr.to/
- sandwich: 5,000,000 sats - https://nostr.watch/
- BOUNTY: Relay-centric client designs: 5,000,000 sats https://bountsr.org/design/2023/01/26/relay-based-design.html
- BOUNTY: Gossip model on https://coracle.social/: 5,000,000 sats
- Nostrovia Podcast: 3,000,000 sats - https://nostrovia.org/
- BOUNTY: Nostr-Desk / Monstr: 5,000,000 sats - https://github.com/alemmens/monstr
- Mike Dilger: 5,000,000 sats - https://github.com/mikedilger/gossip
January 2023
- ismyhc: 5,000,000 sats - https://github.com/Galaxoid-Labs/Seer
- Martti Malmi: 5,000,000 sats - https://iris.to/
- Carlos Autonomous: 5,000,000 sats - https://github.com/BrightonBTC/bija
- Koala Sat: 5,000,000 - https://github.com/KoalaSat/nostros
- Vitor Pamplona: 5,000,000 - https://github.com/vitorpamplona/amethyst
- Cameri: 5,000,000 - https://github.com/Cameri/nostream
December 2022
- William Casarin: 7 BTC - splitting the fund
- pseudozach: 5,000,000 sats - https://nostr.directory/
- Sondre Bjellas: 5,000,000 sats - https://notes.blockcore.net/
- Null Dev: 5,000,000 sats - https://github.com/KotlinGeekDev/Nosky
- Blake Jakopovic: 5,000,000 sats - https://github.com/blakejakopovic/nostcat, https://github.com/blakejakopovic/nostreq and https://github.com/blakejakopovic/NostrEventPlayground
-
 @ b2caa9b3:9eab0fb5
2024-07-14 10:52:36
@ b2caa9b3:9eab0fb5
2024-07-14 10:52:36The African sun is warming things up here at Kilimanjaro, but there's still a crispness in the morning air. My fleece jacket came in handy after a refreshing shower! I started my day with a perfect combo: coffee and breakfast on the rooftop, with a stunning view as my backdrop.

Speaking of tech, today was dedicated to getting my workspace set up. First on the agenda: Thunderbird, my trusty email client from my Linux days. It took a few hours to wrangle everything, especially the S/MIME encryption. Feeling a bit lost in the weeds, I decided to switch gears and embrace OpenPGP for end-to-end encryption – a simpler solution in my opinion.
Just as I finished conquering Thunderbird, Kilimanjaro itself decided to make an appearance! The clouds parted to reveal the majestic peak, and I couldn't resist capturing the moment with a couple of photos.
Today's another day with no set plans, just taking things minute by minute. Soaking up the beautiful scenery, the cool mornings, and the positive vibes. As soon as my foot heals, I'll be out exploring the town, snapping photos, and enjoying a delicious coffee at a local cafe.

Speaking of exploring, the world of NFTs has piqued my interest. I have a few on Opensea and WAX Blockchain, but I'm curious – where else are people showcasing their digital art? Let me know in the comments where you buy and sell your NFTs, or if they're just patiently waiting for a better future. I'd love to hear your NFT stories!

Life has a way of taking us on unexpected journeys. So, here's to embracing the unexpected, making the most of each situation, and maybe even finding a small online job to boost my budget. Wishing you all a wonderful day – and remember, don't stress yourself!

Online
Feel free to support me by sending some sats via the lightning network to rubenstorm@sats.mobi
-
 @ 4857600b:30b502f4
2025-02-21 03:04:00
@ 4857600b:30b502f4
2025-02-21 03:04:00A new talking point of the left is that it’s no big deal, just simple recording errors for the 20 million people aged 100-360. 🤷♀️ And not many of them are collecting benefits anyway. 👌 First of all, the investigation & analysis are in the early stages. How can they possibly know how deep the fraud goes, especially when their leaders are doing everything they can to obstruct any real examination? Second, sure, no worries about only a small number collecting benefits. That’s the ONLY thing social security numbers are used for. 🙄
-
 @ f32184ee:6d1c17bf
2025-04-23 13:21:52
@ f32184ee:6d1c17bf
2025-04-23 13:21:52Ads Fueling Freedom
Ross Ulbricht’s "Decentralize Social Media" painted a picture of a user-centric, decentralized future that transcended the limitations of platforms like the tech giants of today. Though focused on social media, his concept provided a blueprint for decentralized content systems writ large. The PROMO Protocol, designed by NextBlock while participating in Sovereign Engineering, embodies this blueprint in the realm of advertising, leveraging Nostr and Bitcoin’s Lightning Network to give individuals control, foster a multi-provider ecosystem, and ensure secure value exchange. In this way, Ulbricht’s 2021 vision can be seen as a prescient prediction of the PROMO Protocol’s structure. This is a testament to the enduring power of his ideas, now finding form in NextBlock’s innovative approach.
 [Current Platform-Centric Paradigm, source: Ross Ulbricht's Decentralize Social Media]
[Current Platform-Centric Paradigm, source: Ross Ulbricht's Decentralize Social Media]Ulbricht’s Vision: A Decentralized Social Protocol
In his 2021 Medium article Ulbricht proposed a revolutionary vision for a decentralized social protocol (DSP) to address the inherent flaws of centralized social media platforms, such as privacy violations and inconsistent content moderation. Writing from prison, Ulbricht argued that decentralization could empower users by giving them control over their own content and the value they create, while replacing single, monolithic platforms with a competitive ecosystem of interface providers, content servers, and advertisers. Though his focus was on social media, Ulbricht’s ideas laid a conceptual foundation that strikingly predicts the structure of NextBlock’s PROMO Protocol, a decentralized advertising system built on the Nostr protocol.
 [A Decentralized Social Protocol (DSP), source: Ross Ulbricht's Decentralize Social Media]
[A Decentralized Social Protocol (DSP), source: Ross Ulbricht's Decentralize Social Media]Ulbricht’s Principles
Ulbricht’s article outlines several key principles for his DSP: * User Control: Users should own their content and dictate how their data and creations generate value, rather than being subject to the whims of centralized corporations. * Decentralized Infrastructure: Instead of a single platform, multiple interface providers, content hosts, and advertisers interoperate, fostering competition and resilience. * Privacy and Autonomy: Decentralized solutions for profile management, hosting, and interactions would protect user privacy and reduce reliance on unaccountable intermediaries. * Value Creation: Users, not platforms, should capture the economic benefits of their contributions, supported by decentralized mechanisms for transactions.
These ideas were forward-thinking in 2021, envisioning a shift away from the centralized giants dominating social media at the time. While Ulbricht didn’t specifically address advertising protocols, his framework for decentralization and user empowerment extends naturally to other domains, like NextBlock’s open-source offering: the PROMO Protocol.
NextBlock’s Implementation of PROMO Protocol
The PROMO Protocol powers NextBlock's Billboard app, a decentralized advertising protocol built on Nostr, a simple, open protocol for decentralized communication. The PROMO Protocol reimagines advertising by: * Empowering People: Individuals set their own ad prices (e.g., 500 sats/minute), giving them direct control over how their attention or space is monetized. * Marketplace Dynamics: Advertisers set budgets and maximum bids, competing within a decentralized system where a 20% service fee ensures operational sustainability. * Open-Source Flexibility: As an open-source protocol, it allows multiple developers to create interfaces or apps on top of it, avoiding the single-platform bottleneck Ulbricht critiqued. * Secure Payments: Using Strike Integration with Bitcoin Lightning Network, NextBlock enables bot-resistant and intermediary-free transactions, aligning value transfer with each person's control.
This structure decentralizes advertising in a way that mirrors Ulbricht’s broader vision for social systems, with aligned principles showing a specific use case: monetizing attention on Nostr.
Aligned Principles
Ulbricht’s 2021 article didn’t explicitly predict the PROMO Protocol, but its foundational concepts align remarkably well with NextBlock's implementation the protocol’s design: * Autonomy Over Value: Ulbricht argued that users should control their content and its economic benefits. In the PROMO Protocol, people dictate ad pricing, directly capturing the value of their participation. Whether it’s their time, influence, or digital space, rather than ceding it to a centralized ad network. * Ecosystem of Providers: Ulbricht envisioned multiple providers replacing a single platform. The PROMO Protocol’s open-source nature invites a similar diversity: anyone can build interfaces or tools on top of it, creating a competitive, decentralized advertising ecosystem rather than a walled garden. * Decentralized Transactions: Ulbricht’s DSP implied decentralized mechanisms for value exchange. NextBlock delivers this through the Bitcoin Lightning Network, ensuring that payments for ads are secure, instantaneous and final, a practical realization of Ulbricht’s call for user-controlled value flows. * Privacy and Control: While Ulbricht emphasized privacy in social interactions, the PROMO Protocol is public by default. Individuals are fully aware of all data that they generate since all Nostr messages are signed. All participants interact directly via Nostr.
 [Blueprint Match, source NextBlock]
[Blueprint Match, source NextBlock]
Who We Are
NextBlock is a US-based new media company reimagining digital ads for a decentralized future. Our founders, software and strategy experts, were hobbyist podcasters struggling to promote their work online without gaming the system. That sparked an idea: using new tech like Nostr and Bitcoin to build a decentralized attention market for people who value control and businesses seeking real connections.
Our first product, Billboard, is launching this June.
Open for All
Our model’s open-source! Check out the PROMO Protocol, built for promotion and attention trading. Anyone can join this decentralized ad network. Run your own billboard or use ours. This is a growing ecosystem for a new ad economy.
Our Vision
NextBlock wants to help build a new decentralized internet. Our revolutionary and transparent business model will bring honest revenue to companies hosting valuable digital spaces. Together, we will discover what our attention is really worth.
Read our Manifesto to learn more.
NextBlock is registered in Texas, USA.
-
 @ df478568:2a951e67
2025-04-26 19:23:46
@ df478568:2a951e67
2025-04-26 19:23:46
Welcome to Zap This Blog
Exploring Liberty With Fredom Tech
I can string some spaghetti HTMl code together here and there, but vibe coding gave me the confidence to look into the code injection section of the ghost Blog. As sudden as a new block, the Lex Friedman Robert Rodriguez interview, I had an epiphony when he asked Lex, "Do you consider yourself a creative person?" I aswered for myself, right away, emphatically yes. I just felt like I never knew what to do with this creative energy. Friedman hesitated and I was like..Wow...He has extreme creativity like Jocko Wilink has extreme disipline. If that guy has doubts, what the hell is stopping me from trying other stuff?
Rodriguez also claimed Four rooms was financial flop. I thought that movie was genius. I had no idea it failed financially. Nevertheless, it was not profitable. His advice was like Tony Robbins for film nerds. I learned about him in a film class I took in college. He was legendary for making a mobie for $7,000. My professor also said it was made for the Mexican VHS market, but I did not know he never sold it to that market. Robert Rodriguez tells the story 100X better, as you might expect a director of his caliber would. His advice hits like Tony Robbins, for film geeks. Here are a few gem quotes from the epiode.
-
"Sift through the ashes of your failures"
-
"Turn chicken shit into chicken salad."
-
"Follow your instinct. If it doesn't work, just go. Sometimes you need to slip on the first two rocks, so the key is in the ashes of failure because if I had an insticnt, that means I was on the right track. I didn't get the result I want. That's because the result might be something way bigger that I don't have the vision for and the universe is just pushing me that way."
-
"Turn chicken shit into chicken salad."
-
"If you have some kind of failure on something that you..., don't let it knock you down. Maybe in ten years they'll think it's great. I'm just going to commit to making a body of work, a body of work."
Rodriguez taught me what I already know. I am a creative person. I am just a body, punching keys on a keyboard, taking pictures, and semi-vibe-coding art. Maybe this is a shitty blog post today, but I write it anyway. Someone might look at it like I first looked at the math in the Bitcoin white paper and scan it with their eyeballs without really reading or understanding it. Most people on Substack probably don't want to read HTML, but maybe someone will come accross it one day and build something themselves they can find in the ashes of this code.
I once saw Brian Harrington say every bitcoiner is a business owner. If you have a bitcoin address, you can accept bitcoin. How does someone find you though? Are they really going to find your bitcoin address on GitHub? I'd bet 100 sats they won't. Nostr fixes this so I thought about integrating it into my Ghost Blog. I looked at the code injection section and let my muse do the typing. Actually, I let the Duck Duck AI chat do the vibe-coding. As it turns out, you an add a header and footer on Ghost in the code injection. It's just the same HTMl I used to make my MySpace page. Then I thought, what if someone couldn't afford a Start9 or didn't know how to vibe code on Duck Duck Go's free AI chat using Claude? What if, like Rodriguez suggests, I create a business card?

You could just copy my HTML and change my nostr links and pics to go to your nostr links and pics. You could publish that HTML into https://habla.news. Now you have an e-commerce site with a blog, a merch store, and your nostree. I don't know if this will work. This is the muse's hypothesis. I'm just writing the words down. You'll need to test this idea for yourself.
npub1marc26z8nh3xkj5rcx7ufkatvx6ueqhp5vfw9v5teq26z254renshtf3g0
marc26z@getalby.com
Zap This Blog! -
 @ e97aaffa:2ebd765d
2024-07-14 09:57:13
@ e97aaffa:2ebd765d
2024-07-14 09:57:13Estamos numa época tão estranha da humanidade…
Onde alguns querem reescrever a história, em vez de aprender e evoluir com a mesma. São com os erros que se cresce.
Onde o termo fascista é sinónimo de alguém com uma opinião diferente da sua, sem minimamente saber o real significado dessa palavra.
Onde defendem uma liberdade, que proíba o contraditório.
Onde não se discutem ideias, mas sim combatem ideias.
Onde o ambientalmente sustentável é substituir árvores e zonas verdes por estruturas em aço e zonas negras.
Onde os políticos constroem casas ou cidades, literalmente, em cima dos rios mas depois a culpa das cheias é as alterações climáticas.
Onde os alimentos tem menos importância que um peido de uma vaca.
Onde pessoas defendem que a solução para o aquecimento, é morrer de frio.
Onde a igualdade é favorecer um grupo, em detrimento de outro.
Onde o essencial é viver para consumir, em vez de usufruir.
Onde o importante é ser rico e ostentar essa mesma riqueza, mesmo que tenha de espezinhar outros para a conquistar.
Onde o mais importante é parecer em vez de ser.
Onde políticos defendem que o conhecimento pode levar a escolhas erradas, defendem o carneirismo.
Onde um político define o que é verdade ou mentira, limitando o que as pessoas podem expressar. Mas quem controla o controlador.
Onde os revisores da verdade deixaram de estar num gabinete, passando a ser um exército de jovens atrás de um teclado.
Onde, são propostas e aprovadas limitações de liberdade, sem esclarecimento ou divulgação pública. Pior que a obscuridade, é desinteresse da comunidade por liberdade.
Onde a censura é o novo normal, defender o contrário é que é censurável.
Onde a imprensa é tão livre como uma pomba dentro de sua gaiola.
Onde, quem comete o crime é protegido, quem o denúncia é perseguido.
Onde o certo é pensar com a cabeça dos outros, sem questionar.
Onde os pais delegaram o papel de educar às escolas e aos ecrãs azuis.
Onde a escola deixou de ser um lugar de conhecimento e/ou do desenvolvimento do espírito crítico.
Onde as crianças crescem doutrinados por políticos e por AI.
Onde a sociedade é programada e com um destino predefinido, como um rato dentro da sua roda.
Onde o maior erro, é pretender construir seres que não cometem erros, que não tenham vícios. Quando isso acontecer, deixamos de ser humanos. A imperfeição é a essência dos seres humanos, é o que nos difere das máquinas.
Onde só se ensina a não cair, em vez de ajudar e incentivar a levantar.
Onde se suspende a liberdade de circulação e os direitos mais básicos, sem ninguém questionar.
Onde a privacidade é crime.
Onde Satoshi é excomungado, mas Miguel Tiago é idoleterado.
Onde a moeda é utilizado como uma arma.
Onde uma guerra é digladiada entre zeros e uns, sem o comum mortal aperceber da sua existência.
Onde crianças caem em campos de batalha, como folhas em pleno outono.
Onde o direito ao Livre-arbítrio está sob ameaça.
-
 @ d34e832d:383f78d0
2025-04-26 15:04:51
@ d34e832d:383f78d0
2025-04-26 15:04:51Raspberry Pi-based voice assistant
This Idea details the design and deployment of a Raspberry Pi-based voice assistant powered by the Google Gemini AI API. The system combines open hardware with modern AI services to create a low-cost, flexible, and educational voice assistant platform. By leveraging a Raspberry Pi, basic audio hardware, and Python-based software, developers can create a functional, customizable assistant suitable for home automation, research, or personal productivity enhancement.
1. Voice assistants
Voice assistants have become increasingly ubiquitous, but commercially available systems like Alexa, Siri, or Google Assistant come with significant privacy and customization limitations.
This project offers an open, local, and customizable alternative, demonstrating how to build a voice assistant using Google Gemini (or OpenAI’s ChatGPT) APIs for natural language understanding.Target Audience:
- DIY enthusiasts - Raspberry Pi hobbyists - AI developers - Privacy-conscious users
2. System Architecture
2.1 Hardware Components
| Component | Purpose | |:--------------------------|:----------------------------------------| | Raspberry Pi (any recent model, 4B recommended) | Core processing unit | | Micro SD Card (32GB+) | Operating System and storage | | USB Microphone | Capturing user voice input | | Audio Amplifier + Speaker | Outputting synthesized responses | | 5V DC Power Supplies (2x) | Separate power for Pi and amplifier | | LEDs + Resistors (optional)| Visual feedback (e.g., recording or listening states) |
2.2 Software Stack
| Software | Function | |:---------------------------|:----------------------------------------| | Raspberry Pi OS (Lite or Full) | Base operating system | | Python 3.9+ | Programming language | | SpeechRecognition | Captures and transcribes user voice | | Google Text-to-Speech (gTTS) | Converts responses into spoken audio | | Google Gemini API (or OpenAI API) | Powers the AI assistant brain | | Pygame | Audio playback for responses | | WinSCP + Windows Terminal | File transfer and remote management |
3. Hardware Setup
3.1 Basic Connections
- Microphone: Connect via USB port.
- Speaker and Amplifier: Wire from Raspberry Pi audio jack or via USB sound card if better quality is needed.
- LEDs (Optional): Connect through GPIO pins, using 220–330Ω resistors to limit current.
3.2 Breadboard Layout (Optional for LEDs)
| GPIO Pin | LED Color | Purpose | |:---------|:-----------|:--------------------| | GPIO 17 | Red | Recording active | | GPIO 27 | Green | Response playing |
Tip: Use a small breadboard for quick prototyping before moving to a custom PCB if desired.
4. Software Setup
4.1 Raspberry Pi OS Installation
- Use Raspberry Pi Imager to flash Raspberry Pi OS onto the Micro SD card.
- Initial system update:
bash sudo apt update && sudo apt upgrade -y
4.2 Python Environment
-
Install Python virtual environment:
bash sudo apt install python3-venv python3 -m venv voice-env source voice-env/bin/activate -
Install required Python packages:
bash pip install SpeechRecognition google-generativeai pygame gtts
(Replace
google-generativeaiwithopenaiif using OpenAI's ChatGPT.)4.3 API Key Setup
- Obtain a Google Gemini API key (or OpenAI API key).
- Store safely in a
.envfile or configure as environment variables for security:bash export GEMINI_API_KEY="your_api_key_here"
4.4 File Transfer
- Use WinSCP or
scpcommands to transfer Python scripts to the Pi.
4.5 Example Python Script (Simplified)
```python import speech_recognition as sr import google.generativeai as genai from gtts import gTTS import pygame import os
genai.configure(api_key=os.getenv('GEMINI_API_KEY')) recognizer = sr.Recognizer() mic = sr.Microphone()
pygame.init()
while True: with mic as source: print("Listening...") audio = recognizer.listen(source)
try: text = recognizer.recognize_google(audio) print(f"You said: {text}") response = genai.generate_content(text) tts = gTTS(text=response.text, lang='en') tts.save("response.mp3") pygame.mixer.music.load("response.mp3") pygame.mixer.music.play() while pygame.mixer.music.get_busy(): continue except Exception as e: print(f"Error: {e}")```
5. Testing and Execution
- Activate the Python virtual environment:
bash source voice-env/bin/activate - Run your main assistant script:
bash python3 assistant.py - Speak into the microphone and listen for the AI-generated spoken response.
6. Troubleshooting
| Problem | Possible Fix | |:--------|:-------------| | Microphone not detected | Check
arecord -l| | Audio output issues | Checkaplay -l, use a USB DAC if needed | | Permission denied errors | Verify group permissions (audio, gpio) | | API Key Errors | Check environment variable and internet access |
7. Performance Notes
- Latency: Highly dependent on network speed and API response time.
- Audio Quality: Can be enhanced with a better USB microphone and powered speakers.
- Privacy: Minimal data retention if using your own Gemini or OpenAI account.
8. Potential Extensions
- Add hotword detection ("Hey Gemini") using Snowboy or Porcupine libraries.
- Build a local fallback model to answer basic questions offline.
- Integrate with home automation via MQTT, Home Assistant, or Node-RED.
- Enable LED animations to visually indicate listening and responding states.
- Deploy with a small eInk or OLED screen for text display of answers.
9. Consider
Building a Gemini-powered voice assistant on the Raspberry Pi empowers individuals to create customizable, private, and cost-effective alternatives to commercial voice assistants. By utilizing accessible hardware, modern open-source libraries, and powerful AI APIs, this project blends education, experimentation, and privacy-centric design into a single hands-on platform.
This guide can be adapted for personal use, educational programs, or even as a starting point for more advanced AI-based embedded systems.
References
- Raspberry Pi Foundation: https://www.raspberrypi.org
- Google Generative AI Documentation: https://ai.google.dev
- OpenAI Documentation: https://platform.openai.com
- SpeechRecognition Library: https://pypi.org/project/SpeechRecognition/
- gTTS Documentation: https://pypi.org/project/gTTS/
- Pygame Documentation: https://www.pygame.org/docs/
-
 @ 1b9fc4cd:1d6d4902
2025-05-02 07:55:36
@ 1b9fc4cd:1d6d4902
2025-05-02 07:55:36To outsiders, the music industry is usually viewed as a glamorous world of fame, fortune, and creativity. However, lurking underneath the surface, the industry is also a field fraught with mental health challenges. From the history of addiction to the pressures of fame, artists have long wrestled with maintaining their mental well-being. Daniel Siegel Alonso looks at how many artists have found effective coping strategies, turning to therapy, mindfulness practices, and using music itself as a healing outlet.
The Dark History of Addiction in Music
Siegel Alonso notes that the history of addiction in the music industry is well-documented. The strain of constant touring, public scrutiny, and the never-ending pursuit of success have driven many artists to find relief in substances. Iconic musicians like Kurt Cobain, Amy Winehouse, and Jim Morrison are stark reminders of how addiction can destroy lives.
Guitarist John Frusciante of the Red Hot Chili Peppers is a notable example of someone who battled severe addiction. At the height of his career, Frusciante fell deeply into heroin addiction, which led him to leave the band in 1992. His addiction nearly cost him his life, but after a long and painful struggle, he managed to turn his life around. Frusciante’s journey to recovery involved intensive therapy and a recommitment to his music, ultimately rejoining the band and contributing to some of the group's most celebrated albums.
Seeking Help
One of the most crucial steps in addressing mental health issues is seeking professional help. Therapy provides a safe space for creative individuals to explore their thoughts, feelings, and behaviors with a trained professional. Therapy can be a lifeline for musicians, who often face unique pressures.
Frusciante’s recovery underscores the importance of professional help. He didn’t just quit drugs cold turkey; he underwent a comprehensive treatment plan that included therapy and support from friends and family. His story is a testament to the power of seeking help and the possibility of recovery, even after hitting rock bottom.
Music as an Outlet
For many musicians, creating music is more than just a career; it’s a vital outlet for expression and coping. Writing, performing, and listening to music can be powerful therapeutic tools. Music allows artists to channel their emotions into something constructive and beautiful, providing a release from their struggles.
Daniel Siegel Alonso takes The Beatles' George Harrison as an example. Harrison turned to Transcendental Meditation (TM) as a means of coping with the pressures of superstardom and personal turmoil. Introduced to TM in the 1960s, Harrison found solace and clarity through the practice, which influenced both his songwriting and his personal life. The song “Within You Without You” reflects his spiritual journey and the peace he found through TM. The recording marked a significant departure from the Beatles' previous work; musically, it evokes the Indian devotional tradition, while the overtly spiritual quality of the lyrics reflects Harrison's absorption in Hindu philosophy.
Mindfulness and Meditation
Mindfulness and meditation have become increasingly popular among musicians seeking to maintain their mental health. These practices help individuals stay grounded, reduce stress, and improve overall well-being. George Harrison’s embrace of TM is a prime example of how mindfulness can transform a creative person's life.
Harrison’s dedication to TM didn’t just help him personally; it also profoundly impacted his music. His incorporation of Indian instruments and philosophical themes into his songs brought a new dimension to The Beatles’ music and left an enduring legacy in the music world. By finding a healthy outlet in meditation, Harrison could navigate the challenges of fame and continue creating impactful music.
The Power of Community
Siegel Alonso notes that another vital aspect of mental health is the strength of community. Like all individuals, musicians need a support system. Whether it’s fellow bandmates, family, friends, or mental health professionals, having people to lean on can make a significant difference.
John Frusciante’s return to the Red Hot Chili Peppers is a testament to the importance of community. His bandmates supported him through his recovery, and their familial bond played a vital role in his comeback. The collaborative nature of music itself fosters a sense of belonging and mutual support, which is critical for mental health.
Moving Forward
The music industry has made strides in recent years to address mental health more openly. Initiatives like MusiCares provide resources and support for musicians dealing with mental health issues. However, there is still much work to be done. Shattering the stigma around mental health and fostering open conversations are key steps toward a healthier industry.
Musicians like John Frusciante and George Harrison show us that recovery and well-being are possible, even though the journey may be challenging. By seeking help, embracing mindfulness, and finding healthy outlets for expression, musicians can navigate their challenges and continue to inspire us with their art.
In conclusion, mental health in the music industry is a complex issue. Still, with the right coping strategies and support systems, Daniel Siegel Alonso posits that it is achievable to overcome the challenges. As fans and listeners, we can also play a role by supporting initiatives promoting mental health and recognizing the humanity behind the music we cherish. After all, the well-being of the artists who create the soundtrack of our lives is just as important as the music itself.
-
 @ d34e832d:383f78d0
2025-04-26 14:33:06
@ d34e832d:383f78d0
2025-04-26 14:33:06Gist
This Idea presents a blueprint for creating a portable, offline-first education server focused on Free and Open Source Software (FOSS) topics like Bitcoin fundamentals, Linux administration, GPG encryption, and digital self-sovereignty. Using the compact and powerful Nookbox G9 NAS unit, we demonstrate how to deliver accessible, decentralized educational content in remote or network-restricted environments.
1. Bitcoin, Linux, and Cryptographic tools
Access to self-sovereign technologies such as Bitcoin, Linux, and cryptographic tools is critical for empowering individuals and communities. However, many areas face internet connectivity issues or political restrictions limiting access to online resources.
By combining a high-performance mini NAS server with a curated library of FOSS educational materials, we can create a mobile "university" that delivers critical knowledge independently of centralized networks.
2. Hardware Platform: Nookbox G9 Overview
The Nookbox G9 offers an ideal balance of performance, portability, and affordability for this project.
2.1 Core Specifications
| Feature | Specification | |:------------------------|:---------------------------------------| | Form Factor | 1U Rackmount mini-NAS | | Storage | Up to 8TB (4×2TB M.2 NVMe SSDs) | | M.2 Interface | PCIe Gen 3x2 per drive slot | | Networking | Dual 2.5 Gigabit Ethernet ports | | Power Consumption | 11–30 Watts (typical usage) | | Default OS | Windows 11 (to be replaced with Linux) | | Linux Compatibility | Fully compatible with Ubuntu 24.10 |
3. FOSS Education Server Design
3.1 Operating System Setup
- Replace Windows 11 with a clean install of Ubuntu Server 24.10.
- Harden the OS:
- Enable full-disk encryption.
- Configure UFW firewall.
- Disable unnecessary services.
3.2 Core Services Deployed
| Service | Purpose | |:--------------------|:-----------------------------------------| | Nginx Web Server | Host offline courses and documentation | | Nextcloud (optional) | Offer private file sharing for students | | Moodle LMS (optional) | Deliver structured courses and quizzes | | Tor Hidden Service | Optional for anonymous access locally | | rsync/Syncthing | Distribute updates peer-to-peer |
3.3 Content Hosted
- Bitcoin: Bitcoin Whitepaper, Bitcoin Core documentation, Electrum Wallet tutorials.
- Linux: Introduction to Linux (LPIC-1 materials), bash scripting guides, system administration manuals.
- Cryptography: GPG tutorials, SSL/TLS basics, secure communications handbooks.
- Offline Tools: Full mirrors of sites like LearnLinux.tv, Bitcoin.org, and selected content from FSF.
All resources are curated to be license-compliant and redistributable in an offline format.
4. Network Configuration
- LAN-only Access: No reliance on external Internet.
- DHCP server setup for automatic IP allocation.
- Optional Wi-Fi access point using USB Wi-Fi dongle and
hostapd. - Access Portal: Homepage automatically redirects users to educational content upon connection.
5. Advantages of This Setup
| Feature | Advantage | |:-----------------------|:----------------------------------------| | Offline Capability | Operates without internet connectivity | | Portable Form Factor | Fits into field deployments easily | | Secure and Hardened | Encrypted, compartmentalized, and locked down | | Modular Content | Easy to update or expand educational resources | | Energy Efficient | Low power draw enables solar or battery operation | | Open Source Stack | End-to-end FOSS ecosystem, no vendor lock-in |
6. Deployment Scenarios
- Rural Schools: Provide Linux training without requiring internet.
- Disaster Recovery Zones: Deliver essential technical education in post-disaster areas.
- Bitcoin Meetups: Offer Bitcoin literacy and cryptography workshops in remote communities.
- Privacy Advocacy Groups: Teach operational security practices without risking network surveillance.
7. Performance Considerations
Despite PCIe Gen 3x2 limitations, the available bandwidth (~2GB/s theoretical) vastly exceeds the server's 2.5 Gbps network output (~250MB/s), making it more than sufficient for a read-heavy educational workload.
Thermal Management:
Given the G9’s known cooling issues, install additional thermal pads or heatsinks on the NVMe drives. Consider external USB-powered cooling fans for sustained heavy usage.
8. Ways To Extend
- Multi-language Support: Add localized course materials.
- Bitcoin Node Integration: Host a lightweight Bitcoin node (e.g., Bitcoin Core with pruning enabled or a complete full node) for educational purposes.
- Mesh Networking: Use Mesh Wi-Fi protocols (e.g., cjdns or Yggdrasil) to allow peer-to-peer server sharing without centralized Wi-Fi.
9. Consider
Building a Portable FOSS Education Server on a Nookbox G9 is a practical, scalable solution for democratizing technical knowledge, empowering communities, and defending digital sovereignty in restricted environments.
Through thoughtful system design—leveraging open-source software and secure deployment practices—we enable resilient, censorship-resistant education wherever it's needed.
📎 References
-
 @ 94a6a78a:0ddf320e
2025-02-19 21:10:15
@ 94a6a78a:0ddf320e
2025-02-19 21:10:15Nostr is a revolutionary protocol that enables decentralized, censorship-resistant communication. Unlike traditional social networks controlled by corporations, Nostr operates without central servers or gatekeepers. This openness makes it incredibly powerful—but also means its success depends entirely on users, developers, and relay operators.
If you believe in free speech, decentralization, and an open internet, there are many ways to support and strengthen the Nostr ecosystem. Whether you're a casual user, a developer, or someone looking to contribute financially, every effort helps build a more robust network.
Here’s how you can get involved and make a difference.
1️⃣ Use Nostr Daily
The simplest and most effective way to contribute to Nostr is by using it regularly. The more active users, the stronger and more valuable the network becomes.
✅ Post, comment, and zap (send micro-payments via Bitcoin’s Lightning Network) to keep conversations flowing.\ ✅ Engage with new users and help them understand how Nostr works.\ ✅ Try different Nostr clients like Damus, Amethyst, Snort, or Primal and provide feedback to improve the experience.
Your activity keeps the network alive and helps encourage more developers and relay operators to invest in the ecosystem.
2️⃣ Run Your Own Nostr Relay
Relays are the backbone of Nostr, responsible for distributing messages across the network. The more independent relays exist, the stronger and more censorship-resistant Nostr becomes.
✅ Set up your own relay to help decentralize the network further.\ ✅ Experiment with relay configurations and different performance optimizations.\ ✅ Offer public or private relay services to users looking for high-quality infrastructure.
If you're not technical, you can still support relay operators by subscribing to a paid relay or donating to open-source relay projects.
3️⃣ Support Paid Relays & Infrastructure
Free relays have helped Nostr grow, but they struggle with spam, slow speeds, and sustainability issues. Paid relays help fund better infrastructure, faster message delivery, and a more reliable experience.
✅ Subscribe to a paid relay to help keep it running.\ ✅ Use premium services like media hosting (e.g., Azzamo Blossom) to decentralize content storage.\ ✅ Donate to relay operators who invest in long-term infrastructure.
By funding Nostr’s decentralized backbone, you help ensure its longevity and reliability.
4️⃣ Zap Developers, Creators & Builders
Many people contribute to Nostr without direct financial compensation—developers who build clients, relay operators, educators, and content creators. You can support them with zaps! ⚡
✅ Find developers working on Nostr projects and send them a zap.\ ✅ Support content creators and educators who spread awareness about Nostr.\ ✅ Encourage builders by donating to open-source projects.
Micro-payments via the Lightning Network make it easy to directly support the people who make Nostr better.
5️⃣ Develop New Nostr Apps & Tools
If you're a developer, you can build on Nostr’s open protocol to create new apps, bots, or tools. Nostr is permissionless, meaning anyone can develop for it.
✅ Create new Nostr clients with unique features and user experiences.\ ✅ Build bots or automation tools that improve engagement and usability.\ ✅ Experiment with decentralized identity, authentication, and encryption to make Nostr even stronger.
With no corporate gatekeepers, your projects can help shape the future of decentralized social media.
6️⃣ Promote & Educate Others About Nostr
Adoption grows when more people understand and use Nostr. You can help by spreading awareness and creating educational content.
✅ Write blogs, guides, and tutorials explaining how to use Nostr.\ ✅ Make videos or social media posts introducing new users to the protocol.\ ✅ Host discussions, Twitter Spaces, or workshops to onboard more people.
The more people understand and trust Nostr, the stronger the ecosystem becomes.
7️⃣ Support Open-Source Nostr Projects
Many Nostr tools and clients are built by volunteers, and open-source projects thrive on community support.
✅ Contribute code to existing Nostr projects on GitHub.\ ✅ Report bugs and suggest features to improve Nostr clients.\ ✅ Donate to developers who keep Nostr free and open for everyone.
If you're not a developer, you can still help with testing, translations, and documentation to make projects more accessible.
🚀 Every Contribution Strengthens Nostr
Whether you:
✔️ Post and engage daily\ ✔️ Zap creators and developers\ ✔️ Run or support relays\ ✔️ Build new apps and tools\ ✔️ Educate and onboard new users
Every action helps make Nostr more resilient, decentralized, and unstoppable.
Nostr isn’t just another social network—it’s a movement toward a free and open internet. If you believe in digital freedom, privacy, and decentralization, now is the time to get involved.
-
 @ 6fc114c7:8f4b1405
2025-05-01 23:57:44
@ 6fc114c7:8f4b1405
2025-05-01 23:57:44Losing access to your cryptocurrency can feel like losing a part of your future. Whether it’s a forgotten password, a damaged seed backup, or simply one wrong transfer, the stress can be overwhelming. But there’s a silver lining — Crypt Recver is here to help! With our expert-led recovery services, you can reclaim your lost Bitcoin and other cryptos safely and swiftly.
Why Trust Crypt Recver? 🤝 🛠️ Expert Recovery Solutions At Crypt Recver, we specialize in resolving some of the most complex wallet-related issues. Our team of skilled engineers has the tools and expertise to tackle:
Partially lost or forgotten seed phrases Extracting funds from outdated or invalid wallet addresses Recovering data from damaged hardware wallets Restoring coins from old or unsupported wallet formats You’re not just getting a service; you’re gaining a partner in your cryptocurrency journey.
🚀 Fast and Efficient Recovery We understand that time is critical in crypto recovery. Our optimized systems ensure that you can regain access to your funds quickly, aiming for speed without sacrificing security. With a 90%+ success rate, you can trust us to fight against the clock on your behalf.
🔒 Privacy is Our Priority Your confidentiality matters. Every recovery session is handled with the utmost care, ensuring all processes are encrypted and confidential. You can rest easy, knowing your sensitive information stays private.
💻 Advanced Technology Our proprietary tools and brute-force optimization techniques allow for maximum efficiency in recovery. No matter how challenging your case may be, our technology is designed to give you the best chance at getting your crypto back.
Our Recovery Services Include: 📈 Bitcoin Recovery: Lost access to your Bitcoin wallet? We help recover lost wallets, private keys, and passphrases. Transaction Recovery: Mistakes happen — whether it’s an incorrect wallet address or a lost password, let us handle the recovery. Cold Wallet Restoration: If your cold wallet is failing, we can safely extract your assets and migrate them into a secure, new wallet. Private Key Generation: Lost your private key? Don’t worry. Our experts can help you regain control using advanced methods — all while ensuring your privacy remains intact. ⚠️ What We Don’t Do While we can handle many scenarios, there are some limitations. For example, we cannot recover funds stored in custodial wallets, or cases where there is a complete loss of four or more seed words without any partial info available. We’re transparent about what’s possible, so you know what to expect.
Don’t Let Lost Crypto Hold You Back! ⏳ Did you know that 3 to 3.4 million BTC — nearly 20% of the total supply — are estimated to be permanently lost? Don’t become part of that statistic! Whether it’s due to a forgotten password, sending funds to the wrong address, or damaged drives, we can help you navigate through it all.
🛡️ Real-Time Dust Attack Protection Protecting your privacy goes beyond just recovery. Our services include dust attack protection, which keeps your activity anonymous and your funds secure. Our suite will shield your identity from unwanted tracking, ransomware, and phishing attempts.
🎉 Start Your Recovery Journey Today! Are you ready to reclaim your lost crypto? Don’t wait until it’s too late!
👉 Request Wallet Recovery Help Now!
📞 Need Immediate Assistance? Connect with Us! For real-time support or questions, reach out to our dedicated team on:
✉️ Telegram: Chat with Us on Telegram 💬 WhatsApp: Message Us on WhatsApp Crypt Recver is your trusted partner in the world of cryptocurrency recovery. Let us turn your challenges into victories. Don’t hesitate — your crypto future starts now! 🚀✨
Act fast and secure your digital assets with Crypt Recver!Losing access to your cryptocurrency can feel like losing a part of your future. Whether it’s a forgotten password, a damaged seed backup, or simply one wrong transfer, the stress can be overwhelming. But there’s a silver lining — Crypt Recver is here to help! With our expert-led recovery services, you can reclaim your lost Bitcoin and other cryptos safely and swiftly.
 # Why Trust Crypt Recver? 🤝
# Why Trust Crypt Recver? 🤝🛠️ Expert Recovery Solutions
At Crypt Recver, we specialize in resolving some of the most complex wallet-related issues. Our team of skilled engineers has the tools and expertise to tackle:
- Partially lost or forgotten seed phrases
- Extracting funds from outdated or invalid wallet addresses
- Recovering data from damaged hardware wallets
- Restoring coins from old or unsupported wallet formats
You’re not just getting a service; you’re gaining a partner in your cryptocurrency journey.
🚀 Fast and Efficient Recovery
We understand that time is critical in crypto recovery. Our optimized systems ensure that you can regain access to your funds quickly, aiming for speed without sacrificing security. With a 90%+ success rate, you can trust us to fight against the clock on your behalf.
🔒 Privacy is Our Priority
Your confidentiality matters. Every recovery session is handled with the utmost care, ensuring all processes are encrypted and confidential. You can rest easy, knowing your sensitive information stays private.
💻 Advanced Technology
Our proprietary tools and brute-force optimization techniques allow for maximum efficiency in recovery. No matter how challenging your case may be, our technology is designed to give you the best chance at getting your crypto back.
Our Recovery Services Include: 📈
- Bitcoin Recovery: Lost access to your Bitcoin wallet? We help recover lost wallets, private keys, and passphrases.
- Transaction Recovery: Mistakes happen — whether it’s an incorrect wallet address or a lost password, let us handle the recovery.
- Cold Wallet Restoration: If your cold wallet is failing, we can safely extract your assets and migrate them into a secure, new wallet.
- Private Key Generation: Lost your private key? Don’t worry. Our experts can help you regain control using advanced methods — all while ensuring your privacy remains intact.
⚠️ What We Don’t Do
While we can handle many scenarios, there are some limitations. For example, we cannot recover funds stored in custodial wallets, or cases where there is a complete loss of four or more seed words without any partial info available. We’re transparent about what’s possible, so you know what to expect.
 # Don’t Let Lost Crypto Hold You Back! ⏳
# Don’t Let Lost Crypto Hold You Back! ⏳Did you know that 3 to 3.4 million BTC — nearly 20% of the total supply — are estimated to be permanently lost? Don’t become part of that statistic! Whether it’s due to a forgotten password, sending funds to the wrong address, or damaged drives, we can help you navigate through it all.
🛡️ Real-Time Dust Attack Protection
Protecting your privacy goes beyond just recovery. Our services include dust attack protection, which keeps your activity anonymous and your funds secure. Our suite will shield your identity from unwanted tracking, ransomware, and phishing attempts.
🎉 Start Your Recovery Journey Today!
Are you ready to reclaim your lost crypto? Don’t wait until it’s too late!
👉 Request Wallet Recovery Help Now!
📞 Need Immediate Assistance? Connect with Us!
For real-time support or questions, reach out to our dedicated team on:
- ✉️ Telegram: Chat with Us on Telegram
- 💬 WhatsApp: Message Us on WhatsApp
Crypt Recver is your trusted partner in the world of cryptocurrency recovery. Let us turn your challenges into victories. Don’t hesitate — your crypto future starts now! 🚀✨
Act fast and secure your digital assets with Crypt Recver!
-
 @ d34e832d:383f78d0
2025-04-26 07:17:45
@ d34e832d:383f78d0
2025-04-26 07:17:45Practical Privacy and Secure Communications
1. Bootable privacy operating systems—Tails, Qubes OS, and Whonix****
This Idea explores the technical deployment of bootable privacy operating systems—Tails, Qubes OS, and Whonix—for individuals and organizations seeking to enhance operational security (OpSec). These systems provide different layers of isolation, anonymity, and confidentiality, critical for cryptographic operations, Bitcoin custody, journalistic integrity, whistleblowing, and sensitive communications. The paper outlines optimal use cases, system requirements, technical architecture, and recommended operational workflows for each OS.
2. Running An Operating System
In a digital world where surveillance, metadata leakage, and sophisticated threat models are realities, bootable privacy OSs offer critical mitigation strategies. By running an operating system from a USB, DVD, or external drive—and often entirely in RAM—users can minimize the footprint left on host hardware, dramatically enhancing privacy.
This document details Tails, Qubes OS, and Whonix: three leading open-source projects addressing different aspects of operational security.
3. Technical Overview of Systems
| OS | Focus | Main Feature | Threat Model | |------------|---------------------------|-----------------------------------------------|--------------------------------| | Tails | Anonymity & Ephemerality | Runs entirely from RAM; routes traffic via Tor | For activists, journalists, Bitcoin users | | Qubes OS | Security through Compartmentalization | Hardware-level isolation via Xen hypervisor | Defense against malware, APTs, insider threats | | Whonix | Anonymity over Tor Networks | Split-Gateway Architecture (Whonix-Gateway & Whonix-Workstation) | For researchers, Bitcoin node operators, privacy advocates |
4. System Requirements
4.1 Tails
- RAM: Minimum 2 GB (4 GB recommended)
- CPU: x86_64 (Intel or AMD)
- Storage: 8GB+ USB stick (optional persistent storage)
4.2 Qubes OS
- RAM: 16 GB minimum
- CPU: Intel VT-x or AMD-V support required
- Storage: 256 GB SSD recommended
- GPU: Minimal compatibility (no Nvidia proprietary driver support)
4.3 Whonix
- Platform: VirtualBox/KVM Host (Linux, Windows, Mac)
- RAM: 4 GB minimum (8 GB recommended)
- Storage: 100 GB suggested for optimal performance
5. Deployment Models
| Model | Description | Recommended OS | |--------------------------|-----------------------------------|------------------------------| | USB-Only Boot | No installation on disk; ephemeral use | Tails | | Hardened Laptop | Full disk installation with encryption | Qubes OS | | Virtualized Lab | VMs on hardened workstation | Whonix Workstation + Gateway |
6. Operational Security Advantages
| OS | Key Advantages | |------------|----------------------------------------------------------------------------------------------------| | Tails | Memory wipe at shutdown, built-in Tor Browser, persistent volume encryption (LUKS) | | Qubes OS | Compartmentalized VMs for work, browsing, Bitcoin keys; TemplateVMs reduce attack surface | | Whonix | IP address leaks prevented even if the workstation is compromised; full Tor network integration |
7. Threat Model Coverage
| Threat Category | Tails | Qubes OS | Whonix | |----------------------------|-----------------|------------------|------------------| | Disk Forensics | ✅ (RAM-only) | ✅ (with disk encryption) | ✅ (VM separation) | | Malware Containment | ❌ | ✅ (strong) | ✅ (via VMs) | | Network Surveillance | ✅ (Tor enforced) | Partial (needs VPN/Tor setup) | ✅ (Tor Gateway) | | Hardware-Level Attacks | ❌ | ❌ | ❌ |
8. Use Cases
- Bitcoin Cold Storage and Key Signing (Tails)
- Boot Tails offline for air-gapped Bitcoin signing.
- Private Software Development (Qubes)
- Use separate VMs for coding, browsing, and Git commits.
- Anonymous Research (Whonix)
- Surf hidden services (.onion) without IP leak risk.
- Secure Communications (All)
- Use encrypted messaging apps (Session, XMPP, Matrix) without metadata exposure.
9. Challenges and Mitigations
| Challenge | Mitigation | |---------------------|---------------------------------------------| | Hardware Incompatibility | Validate device compatibility pre-deployment (esp. for Qubes) | | Tor Exit Node Surveillance | Use onion services or bridge relays (Tails, Whonix) | | USB Persistence Risks | Always encrypt persistent volumes (Tails) | | Hypervisor Bugs (Qubes) | Regular OS and TemplateVM updates |
Here’s a fully original technical whitepaper version of your request, rewritten while keeping the important technical ideas intact but upgrading structure, language, and precision.
Executive Summary
In a world where digital surveillance and privacy threats are escalating, bootable privacy operating systems offer a critical solution for at-risk individuals. Systems like Tails, Qubes OS, and Whonix provide strong, portable security by isolating user activities from compromised or untrusted hardware. This paper explores their architectures, security models, and real-world applications.
1. To Recap
Bootable privacy-centric operating systems are designed to protect users from forensic analysis, digital tracking, and unauthorized access. By booting from an external USB drive or DVD and operating independently from the host machine's internal storage, they minimize digital footprints and maximize operational security (OpSec).
This paper provides an in-depth technical analysis of: - Tails (The Amnesic Incognito Live System) - Qubes OS (Security through Compartmentalization) - Whonix (Anonymity via Tor Isolation)
Each system’s strengths, limitations, use cases, and installation methods are explored in detail.
2. Technical Overview of Systems
2.1 Tails (The Amnesic Incognito Live System)
Architecture:
- Linux-based Debian derivative. - Boots from USB/DVD, uses RAM exclusively unless persistent storage is manually enabled. - Routes all network traffic through Tor. - Designed to leave no trace unless explicitly configured otherwise.Key Features:
- Memory erasure on shutdown. - Pre-installed secure applications: Tor Browser, KeePassXC, OnionShare. - Persistent storage available but encrypted and isolated.Limitations:
- Limited hardware compatibility (especially Wi-Fi drivers). - No support for mobile OS platforms. - ISP visibility to Tor network usage unless bridges are configured.
2.2 Qubes OS
Architecture:
- Xen-based hypervisor model. - Security through compartmentalization: distinct "qubes" (virtual machines) isolate tasks and domains (work, personal, banking, etc.). - Networking and USB stacks run in restricted VMs to prevent direct device access.Key Features:
- Template-based management for efficient updates. - Secure Copy (Qubes RPC) for data movement without exposing full disks. - Integrated Whonix templates for anonymous browsing.Limitations:
- Requires significant hardware resources (RAM and CPU). - Limited hardware compatibility (strict requirements for virtualization support: VT-d/IOMMU).
2.3 Whonix
Architecture:
- Debian-based dual VM system. - One VM (Gateway) routes all traffic through Tor; the second VM (Workstation) is fully isolated from the physical network. - Can be run on top of Qubes OS, VirtualBox, or KVM.Key Features:
- Complete traffic isolation at the system level. - Strong protections against IP leaks (fails closed if Tor is inaccessible). - Advanced metadata obfuscation options.Limitations:
- High learning curve for proper configuration. - Heavy reliance on Tor can introduce performance bottlenecks.
3. Comparative Analysis
| Feature | Tails | Qubes OS | Whonix | |:--------|:------|:---------|:-------| | Anonymity Focus | High | Medium | High | | System Isolation | Medium | Very High | High | | Persistence | Optional | Full | Optional | | Hardware Requirements | Low | High | Medium | | Learning Curve | Low | High | Medium | | Internet Privacy | Mandatory Tor | Optional Tor | Mandatory Tor |
4. Use Cases
| Scenario | Recommended System | |:---------|:--------------------| | Emergency secure browsing | Tails | | Full system compartmentalization | Qubes OS | | Anonymous operations with no leaks | Whonix | | Activist communications from hostile regions | Tails or Whonix | | Secure long-term project management | Qubes OS |
5. Installation Overview
5.1 Hardware Requirements
- Tails: Minimum 2GB RAM, USB 2.0 or higher, Intel or AMD x86-64 processor.
- Qubes OS: Minimum 16GB RAM, VT-d/IOMMU virtualization support, SSD storage.
- Whonix: Runs inside VirtualBox or Qubes; requires host compatibility.
5.2 Setup Instructions
Tails: 1. Download latest ISO from tails.net. 2. Verify signature (GPG or in-browser). 3. Use balenaEtcher or dd to flash onto USB. 4. Boot from USB, configure Persistent Storage if necessary.
Qubes OS: 1. Download ISO from qubes-os.org. 2. Verify using PGP signatures. 3. Flash to USB or DVD. 4. Boot and install onto SSD with LUKS encryption enabled.
Whonix: 1. Download both Gateway and Workstation VMs from whonix.org. 2. Import into VirtualBox or a compatible hypervisor. 3. Configure VMs to only communicate through the Gateway.
6. Security Considerations
- Tails: Physical compromise of the USB stick is a risk. Use hidden storage if necessary.
- Qubes OS: Qubes is only as secure as its weakest compartment; misconfigured VMs can leak data.
- Whonix: Full reliance on Tor can reveal usage patterns if used carelessly.
Best Practices: - Always verify downloads via GPG. - Use a dedicated, non-personal device where possible. - Utilize Tor bridges if operating under oppressive regimes. - Practice OPSEC consistently—compartmentalization, metadata removal, anonymous communications.
7. Consider
Bootable privacy operating systems represent a critical defense against modern surveillance and oppression. Whether for emergency browsing, long-term anonymous operations, or full-stack digital compartmentalization, solutions like Tails, Qubes OS, and Whonix empower users to reclaim their privacy.
When deployed thoughtfully—with an understanding of each system’s capabilities and risks—these tools can provide an exceptional layer of protection for journalists, activists, security professionals, and everyday users alike.
10. Example: Secure Bitcoin Signing Workflow with Tails
- Boot Tails from USB.
- Disconnect from the network.
- Generate Bitcoin private key or sign transaction using Electrum.
- Save signed transaction to encrypted USB drive.
- Shut down to wipe RAM completely.
- Broadcast transaction from a separate, non-sensitive machine.
This prevents key exposure to malware, man-in-the-middle attacks, and disk forensic analysis.
11. Consider
Bootable privacy operating systems like Tails, Qubes OS, and Whonix offer robust, practical strategies for improving operational security across a wide spectrum of use cases—from Bitcoin custody to anonymous journalism. Their open-source nature, focus on minimizing digital footprints, and mature security architectures make them foundational tools for modern privacy workflows.
Choosing the appropriate OS depends on the specific threat model, hardware available, and user needs. Proper training and discipline remain crucial to maintain the security these systems enable.
Appendices
A. Download Links
B. Further Reading
- "The Qubes OS Architecture" Whitepaper
- "Operational Security and Bitcoin" by Matt Odell
- "Tor and the Darknet: Separating Myth from Reality" by EFF
-
 @ 3ffac3a6:2d656657
2025-04-23 01:57:57
@ 3ffac3a6:2d656657
2025-04-23 01:57:57🔧 Infrastructure Overview
- Hardware: Raspberry Pi 5 with PCIe NVMe HAT and 2TB NVMe SSD
- Filesystem: ZFS with separate datasets for each service
- Networking: Docker bridge networks for service segmentation
- Privacy: Tor and I2P routing for anonymous communication
- Public Access: Cloudflare Tunnel to securely expose LNbits
📊 Architecture Diagram
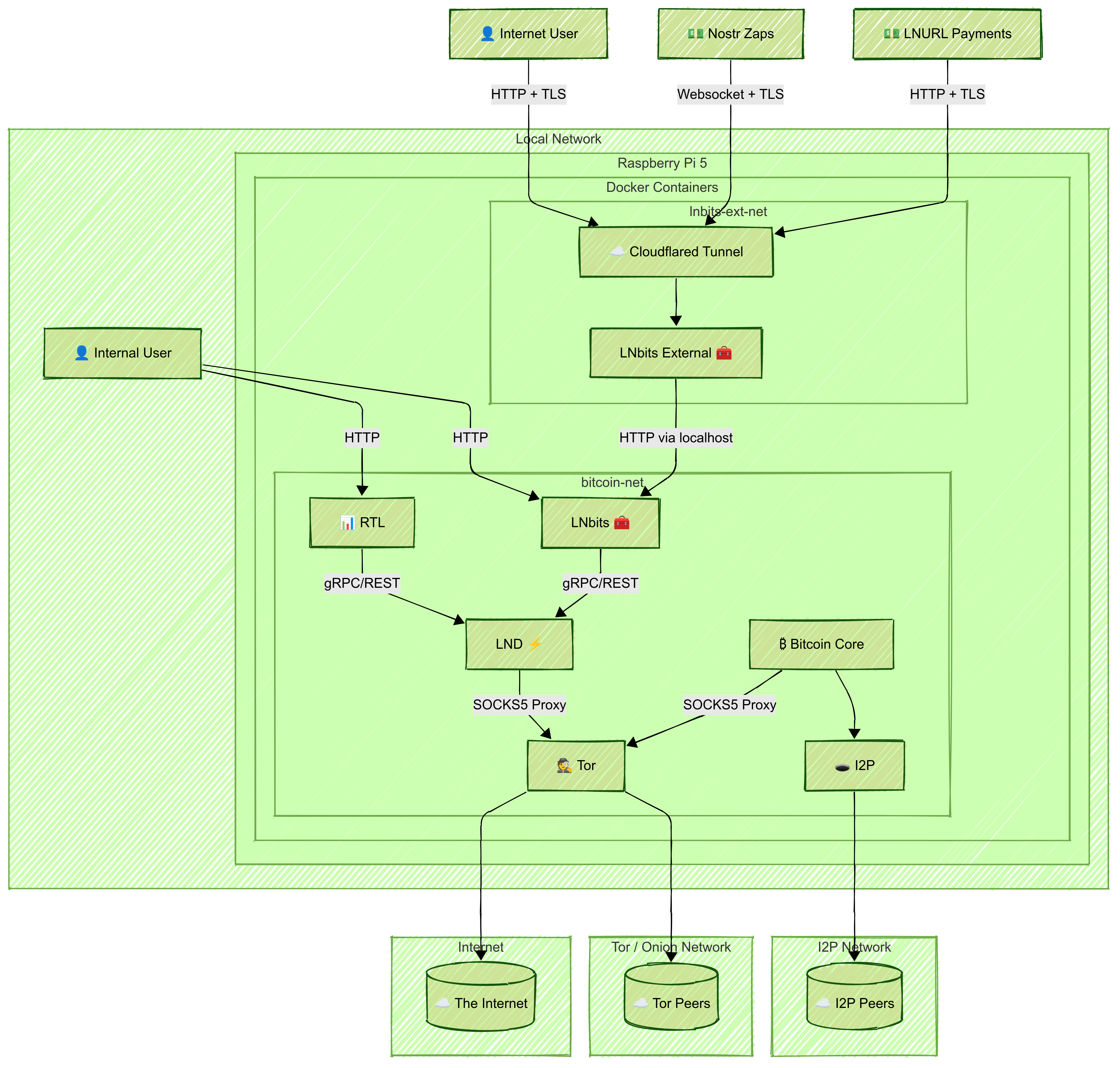
🛠️ Setup Steps
1. Prepare the System
- Install Raspberry Pi OS (64-bit)
- Set up ZFS on the NVMe disk
- Create a ZFS dataset for each service (e.g.,
bitcoin,lnd,rtl,lnbits,tor-data) - Install Docker and Docker Compose
2. Create Shared Docker Network and Privacy Layers
Create a shared Docker bridge network:
bash docker network create \ --driver=bridge \ --subnet=192.168.100.0/24 \ bitcoin-netNote: Connect
bitcoind,lnd,rtl, internallnbits,tor, andi2pto thisbitcoin-netnetwork.Tor
- Run Tor in a container
- Configure it to expose LND's gRPC and REST ports via hidden services:
HiddenServicePort 10009 192.168.100.31:10009 HiddenServicePort 8080 192.168.100.31:8080 - Set correct permissions:
bash sudo chown -R 102:102 /zfs/datasets/tor-data
I2P
- Run I2P in a container with SAM and SOCKS proxies
- Update
bitcoin.conf:i2psam=192.168.100.20:7656 i2pacceptincoming=1
3. Set Up Bitcoin Core
- Create a
bitcoin.confwith Tor/I2P/proxy settings and ZMQ enabled - Sync the blockchain in a container using its ZFS dataset
4. Set Up LND
- Configure
lnd.confto connect tobitcoindand use Tor: ```ini [Bitcoind] bitcoind.rpchost=bitcoin:8332 bitcoind.rpcuser=bitcoin bitcoind.rpcpass=very-hard-password bitcoind.zmqpubrawblock=tcp://bitcoin:28332 bitcoind.zmqpubrawtx=tcp://bitcoin:28333
[Application Options] externalip=xxxxxxxx.onion
`` - Don’t expose gRPC or REST ports publicly - Mount the ZFS dataset at/root/.lnd` - Optionally enable Watchtower5. Set Up RTL
- Mount
RTL-Config.jsonand data volumes - Expose RTL's web interface locally:
```yaml
ports:
- "3000:3000" ```
6. Set Up Internal LNbits
- Connect the LNbits container to
bitcoin-net - Mount the data directory and LND cert/macaroons (read-only)
- Expose the LNbits UI on the local network:
```yaml
ports:
- "5000:5000" ```
- In the web UI, configure the funding source to point to the LND REST
.onionaddress and paste the hex macaroon - Create and fund a wallet, and copy its Admin Key for external use
7. Set Up External LNbits + Cloudflare Tunnel
- Run another LNbits container on a separate Docker network
- Access the internal LNbits via the host IP and port 5000
- Use the Admin Key from the internal wallet to configure funding
- In the Cloudflare Zero Trust dashboard:
- Create a tunnel
- Select Docker, copy the
--tokencommand - Add to Docker Compose:
yaml command: tunnel --no-autoupdate run --token eyJ...your_token...
💾 Backup Strategy
- Bitcoin Core: hourly ZFS snapshots, retained for 6 hours
- Other Services: hourly snapshots with remote
.tar.gzbackups - Retention: 7d hourly, 30d daily, 12mo weekly, monthly forever
- Back up ZFS snapshots to avoid inconsistencies
🔐 Security Isolation Benefits
This architecture isolates services by scope and function:
- Internal traffic stays on
bitcoin-net - Sensitive APIs (gRPC, REST) are reachable only via Tor
- Public access is controlled by Cloudflare Tunnel
Extra Security: Host the public LNbits on a separate machine (e.g., hardened VPS) with strict firewall rules:
- Allow only Cloudflare egress
- Allow ingress from your local IP
- Allow outbound access to internal LNbits (port 5000)
Use WireGuard VPN to secure the connection between external and internal LNbits:
- Ensures encrypted communication
- Restricts access to authenticated VPN peers
- Keeps the internal interface isolated from the public internet
✅ Final Notes
- Internal services communicate over
bitcoin-net - LND interfaces are accessed via Tor only
- LNbits and RTL UIs are locally accessible
- Cloudflare Tunnel secures external access to LNbits
Monitor system health using
monit,watchtower, or Prometheus.Create all configuration files manually (
bitcoin.conf,lnd.conf,RTL-Config.json), and keep credentials secure. Test every component locally before exposing it externally.⚡
-
 @ fd208ee8:0fd927c1
2025-02-15 07:02:08
@ fd208ee8:0fd927c1
2025-02-15 07:02:08E-cash are coupons or tokens for Bitcoin, or Bitcoin debt notes that the mint issues. The e-cash states, essentially, "IoU 2900 sats".
They're redeemable for Bitcoin on Lightning (hard money), and therefore can be used as cash (softer money), so long as the mint has a good reputation. That means that they're less fungible than Lightning because the e-cash from one mint can be more or less valuable than the e-cash from another. If a mint is buggy, offline, or disappears, then the e-cash is unreedemable.
It also means that e-cash is more anonymous than Lightning, and that the sender and receiver's wallets don't need to be online, to transact. Nutzaps now add the possibility of parking transactions one level farther out, on a relay. The same relays that cannot keep npub profiles and follow lists consistent will now do monetary transactions.
What we then have is * a transaction on a relay that triggers * a transaction on a mint that triggers * a transaction on Lightning that triggers * a transaction on Bitcoin.
Which means that every relay that stores the nuts is part of a wildcat banking system. Which is fine, but relay operators should consider whether they wish to carry the associated risks and liabilities. They should also be aware that they should implement the appropriate features in their relay, such as expiration tags (nuts rot after 2 weeks), and to make sure that only expired nuts are deleted.
There will be plenty of specialized relays for this, so don't feel pressured to join in, and research the topic carefully, for yourself.
https://github.com/nostr-protocol/nips/blob/master/60.md
-
 @ 0fa80bd3:ea7325de
2025-02-14 23:24:37
@ 0fa80bd3:ea7325de
2025-02-14 23:24:37intro
The Russian state made me a Bitcoiner. In 1991, it devalued my grandmother's hard-earned savings. She worked tirelessly in the kitchen of a dining car on the Moscow–Warsaw route. Everything she had saved for my sister and me to attend university vanished overnight. This story is similar to what many experienced, including Wences Casares. The pain and injustice of that time became my first lessons about the fragility of systems and the value of genuine, incorruptible assets, forever changing my perception of money and my trust in government promises.
In 2014, I was living in Moscow, running a trading business, and frequently traveling to China. One day, I learned about the Cypriot banking crisis and the possibility of moving money through some strange thing called Bitcoin. At the time, I didn’t give it much thought. Returning to the idea six months later, as a business-oriented geek, I eagerly began studying the topic and soon dove into it seriously.
I spent half a year reading articles on a local online journal, BitNovosti, actively participating in discussions, and eventually joined the editorial team as a translator. That’s how I learned about whitepapers, decentralization, mining, cryptographic keys, and colored coins. About Satoshi Nakamoto, Silk Road, Mt. Gox, and BitcoinTalk. Over time, I befriended the journal’s owner and, leveraging my management experience, later became an editor. I was drawn to the crypto-anarchist stance and commitment to decentralization principles. We wrote about the economic, historical, and social preconditions for Bitcoin’s emergence, and it was during this time that I fully embraced the idea.
It got to the point where I sold my apartment and, during the market's downturn, bought 50 bitcoins, just after the peak price of $1,200 per coin. That marked the beginning of my first crypto winter. As an editor, I organized workflows, managed translators, developed a YouTube channel, and attended conferences in Russia and Ukraine. That’s how I learned about Wences Casares and even wrote a piece about him. I also met Mikhail Chobanyan (Ukrainian exchange Kuna), Alexander Ivanov (Waves project), Konstantin Lomashuk (Lido project), and, of course, Vitalik Buterin. It was a time of complete immersion, 24/7, and boundless hope.
After moving to the United States, I expected the industry to grow rapidly, attended events, but the introduction of BitLicense froze the industry for eight years. By 2017, it became clear that the industry was shifting toward gambling and creating tokens for the sake of tokens. I dismissed this idea as unsustainable. Then came a new crypto spring with the hype around beautiful NFTs – CryptoPunks and apes.
I made another attempt – we worked on a series called Digital Nomad Country Club, aimed at creating a global project. The proceeds from selling images were intended to fund the development of business tools for people worldwide. However, internal disagreements within the team prevented us from completing the project.
With Trump’s arrival in 2025, hope was reignited. I decided that it was time to create a project that society desperately needed. As someone passionate about history, I understood that destroying what exists was not the solution, but leaving everything as it was also felt unacceptable. You can’t destroy the system, as the fiery crypto-anarchist voices claimed.
With an analytical mindset (IQ 130) and a deep understanding of the freest societies, I realized what was missing—not only in Russia or the United States but globally—a Bitcoin-native system for tracking debts and financial interactions. This could return control of money to ordinary people and create horizontal connections parallel to state systems. My goal was to create, if not a Bitcoin killer app, then at least to lay its foundation.
At the inauguration event in New York, I rediscovered the Nostr project. I realized it was not only technologically simple and already quite popular but also perfectly aligned with my vision. For the past month and a half, using insights and experience gained since 2014, I’ve been working full-time on this project.
-
 @ 9bde4214:06ca052b
2025-04-22 22:04:08
@ 9bde4214:06ca052b
2025-04-22 22:04:08"With the shift towards this multi-agent collaboration and orchestration world, you need a neutral substrate that has money/identity/cryptography and web-of-trust baked in, to make everything work."
Pablo & Gigi are getting high on glue.
Books & articles mentioned:
- Saving beauty by Byung-Chul Han
- LLMs as a tool for thought by Amelia Wattenberger
In this dialogue:
- vibeline & vibeline-ui
- LLMs as tools, and how to use them
- Vervaeke: AI thresholds & the path we must take
- Hallucinations and grounding in reality
- GPL, LLMs, and open-source licensing
- Pablo's multi-agent Roo setup
- Are we going to make programmers obsolete?
- "When it works it's amazing"
- Hiring & training agents
- Agents creating RAG databases of NIPs
- Different models and their context windows
- Generalists vs specialists
- "Write drunk, edit sober"
- DVMCP.fun
- Recklessness and destruction of vibe-coding
- Sharing secrets with agents & LLMs
- The "no API key" advantage of nostr
- What data to trust? And how does nostr help?
- Identity, web of trust, and signing data
- How to fight AI slop
- Marketplaces of code snippets
- Restricting agents with expert knowledge
- Trusted sources without a central repository
- Zapstore as the prime example
- "How do you fight off re-inventing GitHub?"
- Using large context windows to help with refactoring
- Code snippets for Olas, NDK, NIP-60, and more
- Using MCP as the base
- Using nostr as the underlying substrate
- Nostr as the glue & the discovery layer
- Why is this important?
- Why is this exciting?
- "With the shift towards this multi-agent collaboration and orchestration world, you need a neutral substrate that has money/identity/cryptography and web-of-trust baked in, to make everything work."
- How to single-shot nostr applications
- "Go and create this app"
- The agent has money, because of NIP-60/61
- PayPerQ
- Anthropic and the genius of mcp-tools
- Agents zapping & giving SkyNet more money
- Are we going to run the mints?
- Are agents going to run the mints?
- How can we best explain this to our bubble?
- Let alone to people outside of our bubble?
- Building pipelines of multiple agents
- LLM chains & piped Unix tools
- OpenAI vs Anthropic
- Genius models without tools vs midwit models with tools
- Re-thinking software development
- LLMs allow you to tackle bigger problems
- Increased speed is a paradigm shift
- Generalists vs specialists, left brain vs right brain
- Nostr as the home for specialists
- fiatjaf publishing snippets (reluctantly)
- fiatjaf's blossom implementation
- Thinking with LLMs
- The tension of specialization VS generalization
- How the publishing world changed
- Stupid faces on YouTube thumbnails
- Gaming the algorithm
- Will AI slop destroy the attention economy?
- Recency bias & hiding publication dates
- Undoing platform conditioning as a success metric
- Craving realness in a fake attention world
- The theater of the attention economy
- What TikTok got "right"
- Porn, FoodPorn, EarthPorn, etc.
- Porn vs Beauty
- Smoothness and awe
- "Beauty is an angel that could kill you in an instant (but decides not to)."
- The success of Joe Rogan & long-form conversations
- Smoothness fatigue & how our feeds numb us
- Nostr & touching grass
- How movement changes conversations
- LangChain & DVMs
- Central models vs marketplaces
- Going from assembly to high-level to conceptual
- Natural language VS programming languages
- Pablo's code snippets
- Writing documentation for LLMs
- Shared concepts, shared language, and forks
- Vibe-forking open-source software
- Spotting vibe-coded interfaces
- Visualizing nostr data in a 3D world
- Tweets, blog posts, and podcasts
- Vibe-producing blog posts from conversations
- Tweets are excellent for discovery
- Adding context to tweets (long-form posts, podcasts, etc)
- Removing the character limit was a mistake
- "Everyone's attention span is rekt"
- "There is no meaning without friction"
- "Nothing worth having ever comes easy"
- Being okay with doing the hard thing
- Growth hacks & engagement bait
- TikTok, theater, and showing faces and emotions
- The 1% rule: 99% of internet users are Lurkers
- "We are socially malnourished"
- Web-of-trust and zaps bring realness
- The semantic web does NOT fix this LLMs might
- "You can not model the world perfectly"
- Hallucination as a requirement for creativity
-
 @ 700c6cbf:a92816fd
2024-07-14 00:51:44
@ 700c6cbf:a92816fd
2024-07-14 00:51:44... something else
This is the final image. Or is it? Likely, it is not. I have already started on a perfect version of my Mother Earth painting.
Of course, there is no such thing as a perfect painting. What I mean is that I already started on a vector version of Mother Earth. You're familiar with vector vs. pixel, right?
But let's start at the beginning, not the end.
This here is a pic from the sketching phase. I am not one who can just magically and with a few strokes produce an amazing sketch of something that resembles a human. There are artists out there that do this wonderfully. It's amazing but it is not me (unfortunately).

Here I am starting to color in the sketch with a watercolor brush. This is all done in Procreate App on an iPad Pro. The coloring is on a separate layer with the pencil sketch set to multiply to shine through the colors. That's why the pencil strokes now are black. I like that look.

And here, I am almost done. Just need to decide on the background color. And as you can see from the gif and video I didn't really decide. Though at the moment I am favoring that muted pinkish red - LOL

Which color is your favorite?


Here you can see the whole process in a timelapse. Above pictures were grabbed from it to detail the process a little.
https://cdn.satellite.earth/05774dcaaf4679c34cbeb46cb43b4c4f85553a3d2b4850a7256d26a871b0c4f3.mp4
And that's it my Nostr friends for my first longform post in this community.
I hope you enjoyed this post. Comments are encouraged an appreciated. Thank you.
Cheers, OceanBee
-
 @ 9edd72eb:cb697b0a
2024-07-13 22:16:45
@ 9edd72eb:cb697b0a
2024-07-13 22:16:45If one knows exactly what to do to alleviate one's pain, comfort oneself, and emerge more or less unscathed from Adversity, I think it can be said that one has reached a fairly high level of Wisdom in Life.
originally posted at https://stacker.news/items/607422
-
 @ e3ba5e1a:5e433365
2025-02-05 17:47:16
@ e3ba5e1a:5e433365
2025-02-05 17:47:16I got into a friendly discussion on X regarding health insurance. The specific question was how to deal with health insurance companies (presumably unfairly) denying claims? My answer, as usual: get government out of it!
The US healthcare system is essentially the worst of both worlds:
- Unlike full single payer, individuals incur high costs
- Unlike a true free market, regulation causes increases in costs and decreases competition among insurers
I'm firmly on the side of moving towards the free market. (And I say that as someone living under a single payer system now.) Here's what I would do:
- Get rid of tax incentives that make health insurance tied to your employer, giving individuals back proper freedom of choice.
- Reduce regulations significantly.
-
In the short term, some people will still get rejected claims and other obnoxious behavior from insurance companies. We address that in two ways:
- Due to reduced regulations, new insurance companies will be able to enter the market offering more reliable coverage and better rates, and people will flock to them because they have the freedom to make their own choices.
- Sue the asses off of companies that reject claims unfairly. And ideally, as one of the few legitimate roles of government in all this, institute new laws that limit the ability of fine print to allow insurers to escape their responsibilities. (I'm hesitant that the latter will happen due to the incestuous relationship between Congress/regulators and insurers, but I can hope.)
Will this magically fix everything overnight like politicians normally promise? No. But it will allow the market to return to a healthy state. And I don't think it will take long (order of magnitude: 5-10 years) for it to come together, but that's just speculation.
And since there's a high correlation between those who believe government can fix problems by taking more control and demanding that only credentialed experts weigh in on a topic (both points I strongly disagree with BTW): I'm a trained actuary and worked in the insurance industry, and have directly seen how government regulation reduces competition, raises prices, and harms consumers.
And my final point: I don't think any prior art would be a good comparison for deregulation in the US, it's such a different market than any other country in the world for so many reasons that lessons wouldn't really translate. Nonetheless, I asked Grok for some empirical data on this, and at best the results of deregulation could be called "mixed," but likely more accurately "uncertain, confused, and subject to whatever interpretation anyone wants to apply."
https://x.com/i/grok/share/Zc8yOdrN8lS275hXJ92uwq98M
-
 @ d34e832d:383f78d0
2025-04-26 04:24:13
@ d34e832d:383f78d0
2025-04-26 04:24:13A Secure, Compact, and Cost-Effective Offline Key Management System
1. Idea
This idea presents a cryptographic key generation appliance built on the Nookbox G9, a compact 1U mini NAS solution. Designed to be a dedicated air-gapped or offline-first device, this system enables the secure generation and handling of RSA, ECDSA, and Ed25519 key pairs. By leveraging the Nookbox G9's small form factor, NVMe storage, and Linux compatibility, we outline a practical method for individuals and organizations to deploy secure, reproducible, and auditable cryptographic processes without relying on cloud or always-connected environments.
2. Minimization Of Trust
In an era where cryptographic operations underpin everything from Bitcoin transactions to secure messaging, generating keys in a trust-minimized environment is critical. Cloud-based solutions or general-purpose desktops expose key material to increased risk. This project defines a dedicated hardware appliance for cryptographic key generation using Free and Open Source Software (FOSS) and a tightly scoped threat model.
3. Hardware Overview: Nookbox G9
| Feature | Specification | |-----------------------|----------------------------------------------------| | Form Factor | 1U Mini NAS | | Storage Capacity | Up to 8TB via 4 × 2TB M.2 NVMe SSDs | | PCIe Interface | Each M.2 slot uses PCIe Gen 3x2 | | Networking | Dual 2.5 Gigabit Ethernet | | Cooling | Passive cooling (requires modification for load) | | Operating System | Windows 11 pre-installed; compatible with Linux |
This hardware is chosen for its compact size, multiple SSD support, and efficient power consumption (~11W idle on Linux). It fits easily into a secure rack cabinet and can run entirely offline.
4. System Configuration
4.1 OS & Software Stack
We recommend wiping Windows and installing:
- OS: Ubuntu 24.10 LTS or Debian 12
- Key Tools:
gnupg(for GPG, RSA, and ECC)ageorrage(for modern encryption)openssl(general-purpose cryptographic tool)ssh-keygen(for Ed25519 or RSA SSH keys)vault(optional: HashiCorp Vault for managing key secrets)pwgen/diceware(for secure passphrase generation)
4.2 Storage Layout
- Drive 1 (System): Ubuntu 24.10 with encrypted LUKS partition
- Drive 2 (Key Store): Encrypted Veracrypt volume for keys and secrets
- Drive 3 (Backup): Offline encrypted backup (mirrored or rotated)
- Drive 4 (Logs & Audit): System logs, GPG public keyring, transparency records
5. Security Principles
- Air-Gapping: Device operates disconnected from the internet during key generation.
- FOSS Only: All software used is open-source and auditable.
- No TPM/Closed Firmware Dependencies: BIOS settings disable Intel ME, TPM, and Secure Boot.
- Tamper Evidence: Physical access logs and optional USB kill switch setup.
- Transparency: Generation scripts stored on device, along with SHA256 of all outputs.
6. Workflow: Generating Keypairs
Example: Generating an Ed25519 GPG Key
```bash gpg --full-generate-key
Choose ECC > Curve: Ed25519
Set expiration, user ID, passphrase
```
Backup public and private keys:
bash gpg --armor --export-secret-keys [keyID] > private.asc gpg --armor --export [keyID] > public.asc sha256sum *.asc > hashes.txtStore on encrypted volume and create a printed copy (QR or hex dump) for physical backup.
7. Performance Notes
While limited to PCIe Gen 3x2 (approx. 1.6 GB/s per slot), the speed is more than sufficient for key generation workloads. The bottleneck is not IO-bound but entropy-limited and CPU-bound. In benchmarks:
- RSA 4096 generation: ~2–3 seconds
- Ed25519 generation: <1 second
- ZFS RAID-Z writes (if used): ~250MB/s due to 2.5Gbps NIC ceiling
Thermal throttling may occur under extended loads without cooling mods. A third-party aluminum heatsink resolves this.
8. Use Cases
- Bitcoin Cold Storage (xprv/xpub, seed phrases)
- SSH Key Infrastructure (Ed25519 key signing for orgs)
- PGP Trust Anchor (for a Web of Trust or private PKI)
- Certificate Authority (offline root key handling)
- Digital Notary Service (hash-based time-stamping)
9. Recommendations & Improvements
| Area | Improvement | |-------------|--------------------------------------| | Cooling | Add copper heatsinks + airflow mod | | Power | Use UPS + power filter for stability | | Boot | Use full-disk encryption with Yubikey unlock | | Expansion | Use one SSD for keybase-style append-only logs | | Chassis | Install into a tamper-evident case with RFID tracking |
10. Consider
The Nookbox G9 offers a compact, energy-efficient platform for creating a secure cryptographic key generation appliance. With minor thermal enhancements and a strict FOSS policy, it becomes a reliable workstation for cryptographers, developers, and Bitcoin self-custodians. Its support for multiple encrypted SSDs, air-gapped operation, and Linux flexibility make it a modern alternative to enterprise HSMs—without the cost or vendor lock-in.
A. Key Software Versions
GnuPG 2.4.xOpenSSL 3.xUbuntu 24.10Veracrypt 1.26+
B. System Commands (Setup)
bash sudo apt install gnupg2 openssl age veracrypt sudo cryptsetup luksFormat /dev/nvme1n1C. Resources
The Nookbox G9 epitomizes a compact yet sophisticated energy-efficient computational architecture, meticulously designed to serve as a secure cryptographic key generation appliance. By integrating minor yet impactful thermal enhancements, it ensures optimal performance stability while adhering to a stringent Free and Open Source Software (FOSS) policy, thereby positioning itself as a reliable workstation specifically tailored for cryptographers, software developers, and individuals engaged in Bitcoin self-custody. Its capability to support multiple encrypted Solid State Drives (SSDs) facilitates an augmented data security framework, while the air-gapped operational feature significantly enhances its resilience against potential cyber threats. Furthermore, the inherent flexibility of Linux operating systems not only furnishes an adaptable environment for various cryptographic applications but also serves as a compelling modern alternative to conventional enterprise Hardware Security Modules (HSMs), ultimately bypassing the prohibitive costs and vendor lock-in typically associated with such proprietary solutions.
Further Tools
🔧 Recommended SSDs and Tools (Amazon)
-
Kingston A400 240GB SSD – SATA 3 2.5"
https://a.co/d/41esjYL -
Samsung 970 EVO Plus 2TB NVMe M.2 SSD – Gen 3
https://a.co/d/6EMVAN1 -
Crucial P5 Plus 1TB PCIe Gen4 NVMe M.2 SSD
https://a.co/d/hQx50Cq -
WD Blue SN570 1TB NVMe SSD – PCIe Gen 3
https://a.co/d/j2zSDCJ -
Sabrent Rocket Q 2TB NVMe SSD – QLC NAND
https://a.co/d/325Og2K -
Thermalright M.2 SSD Heatsink Kit
https://a.co/d/0IYH3nK -
ORICO M.2 NVMe SSD Enclosure – USB 3.2 Gen2
https://a.co/d/aEwQmih
Product Links (Amazon)
-
Thermal Heatsink for M.2 SSDs (Must-have for stress and cooling)
https://a.co/d/43B1F3t -
Nookbox G9 – Mini NAS
https://a.co/d/3dswvGZ -
Alternative 1: Possibly related cooling or SSD gear
https://a.co/d/c0Eodm3 -
Alternative 2: Possibly related NAS accessories or SSDs
https://a.co/d/9gWeqDr
Benchmark Results (Geekbench)
-
GMKtec G9 Geekbench CPU Score #1
https://browser.geekbench.com/v6/cpu/11471182 -
GMKtec G9 Geekbench CPU Score #2
https://browser.geekbench.com/v6/cpu/11470130 -
GMKtec Geekbench User Profile
https://browser.geekbench.com/user/446940
🛠️ DIY & Fix Resource
- How-Fixit – PC Repair Guides and Tutorials
https://www.how-fixit.com/
-
 @ 91bea5cd:1df4451c
2025-02-04 17:15:57
@ 91bea5cd:1df4451c
2025-02-04 17:15:57Definição de ULID:
Timestamp 48 bits, Aleatoriedade 80 bits Sendo Timestamp 48 bits inteiro, tempo UNIX em milissegundos, Não ficará sem espaço até o ano 10889 d.C. e Aleatoriedade 80 bits, Fonte criptograficamente segura de aleatoriedade, se possível.
Gerar ULID
```sql
CREATE EXTENSION IF NOT EXISTS pgcrypto;
CREATE FUNCTION generate_ulid() RETURNS TEXT AS $$ DECLARE -- Crockford's Base32 encoding BYTEA = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; timestamp BYTEA = E'\000\000\000\000\000\000'; output TEXT = '';
unix_time BIGINT; ulid BYTEA; BEGIN -- 6 timestamp bytes unix_time = (EXTRACT(EPOCH FROM CLOCK_TIMESTAMP()) * 1000)::BIGINT; timestamp = SET_BYTE(timestamp, 0, (unix_time >> 40)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 1, (unix_time >> 32)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 2, (unix_time >> 24)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 3, (unix_time >> 16)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 4, (unix_time >> 8)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 5, unix_time::BIT(8)::INTEGER);
-- 10 entropy bytes ulid = timestamp || gen_random_bytes(10);
-- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 1) & 7) << 2) | ((GET_BYTE(ulid, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 2) & 1) << 4) | ((GET_BYTE(ulid, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 3) & 15) << 1) | ((GET_BYTE(ulid, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 4) & 3) << 3) | ((GET_BYTE(ulid, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 5) & 31)));
-- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 6) & 7) << 2) | ((GET_BYTE(ulid, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 7) & 1) << 4) | ((GET_BYTE(ulid, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 8) & 15) << 1) | ((GET_BYTE(ulid, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 9) & 3) << 3) | ((GET_BYTE(ulid, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 11) & 7) << 2) | ((GET_BYTE(ulid, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 12) & 1) << 4) | ((GET_BYTE(ulid, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 13) & 15) << 1) | ((GET_BYTE(ulid, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 14) & 3) << 3) | ((GET_BYTE(ulid, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 15) & 31)));
RETURN output; END $$ LANGUAGE plpgsql VOLATILE; ```
ULID TO UUID
```sql CREATE OR REPLACE FUNCTION parse_ulid(ulid text) RETURNS bytea AS $$ DECLARE -- 16byte bytes bytea = E'\x00000000 00000000 00000000 00000000'; v char[]; -- Allow for O(1) lookup of index values dec integer[] = ARRAY[ 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 0, 1, 2, 3, 4, 5, 6, 7, 8, 9, 255, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31 ]; BEGIN IF NOT ulid ~* '^[0-7][0-9ABCDEFGHJKMNPQRSTVWXYZ]{25}$' THEN RAISE EXCEPTION 'Invalid ULID: %', ulid; END IF;
v = regexp_split_to_array(ulid, '');
-- 6 bytes timestamp (48 bits) bytes = SET_BYTE(bytes, 0, (dec[ASCII(v[1])] << 5) | dec[ASCII(v[2])]); bytes = SET_BYTE(bytes, 1, (dec[ASCII(v[3])] << 3) | (dec[ASCII(v[4])] >> 2)); bytes = SET_BYTE(bytes, 2, (dec[ASCII(v[4])] << 6) | (dec[ASCII(v[5])] << 1) | (dec[ASCII(v[6])] >> 4)); bytes = SET_BYTE(bytes, 3, (dec[ASCII(v[6])] << 4) | (dec[ASCII(v[7])] >> 1)); bytes = SET_BYTE(bytes, 4, (dec[ASCII(v[7])] << 7) | (dec[ASCII(v[8])] << 2) | (dec[ASCII(v[9])] >> 3)); bytes = SET_BYTE(bytes, 5, (dec[ASCII(v[9])] << 5) | dec[ASCII(v[10])]);
-- 10 bytes of entropy (80 bits); bytes = SET_BYTE(bytes, 6, (dec[ASCII(v[11])] << 3) | (dec[ASCII(v[12])] >> 2)); bytes = SET_BYTE(bytes, 7, (dec[ASCII(v[12])] << 6) | (dec[ASCII(v[13])] << 1) | (dec[ASCII(v[14])] >> 4)); bytes = SET_BYTE(bytes, 8, (dec[ASCII(v[14])] << 4) | (dec[ASCII(v[15])] >> 1)); bytes = SET_BYTE(bytes, 9, (dec[ASCII(v[15])] << 7) | (dec[ASCII(v[16])] << 2) | (dec[ASCII(v[17])] >> 3)); bytes = SET_BYTE(bytes, 10, (dec[ASCII(v[17])] << 5) | dec[ASCII(v[18])]); bytes = SET_BYTE(bytes, 11, (dec[ASCII(v[19])] << 3) | (dec[ASCII(v[20])] >> 2)); bytes = SET_BYTE(bytes, 12, (dec[ASCII(v[20])] << 6) | (dec[ASCII(v[21])] << 1) | (dec[ASCII(v[22])] >> 4)); bytes = SET_BYTE(bytes, 13, (dec[ASCII(v[22])] << 4) | (dec[ASCII(v[23])] >> 1)); bytes = SET_BYTE(bytes, 14, (dec[ASCII(v[23])] << 7) | (dec[ASCII(v[24])] << 2) | (dec[ASCII(v[25])] >> 3)); bytes = SET_BYTE(bytes, 15, (dec[ASCII(v[25])] << 5) | dec[ASCII(v[26])]);
RETURN bytes; END $$ LANGUAGE plpgsql IMMUTABLE;
CREATE OR REPLACE FUNCTION ulid_to_uuid(ulid text) RETURNS uuid AS $$ BEGIN RETURN encode(parse_ulid(ulid), 'hex')::uuid; END $$ LANGUAGE plpgsql IMMUTABLE; ```
UUID to ULID
```sql CREATE OR REPLACE FUNCTION uuid_to_ulid(id uuid) RETURNS text AS $$ DECLARE encoding bytea = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; output text = ''; uuid_bytes bytea = uuid_send(id); BEGIN
-- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 1) & 7) << 2) | ((GET_BYTE(uuid_bytes, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 2) & 1) << 4) | ((GET_BYTE(uuid_bytes, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 3) & 15) << 1) | ((GET_BYTE(uuid_bytes, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 4) & 3) << 3) | ((GET_BYTE(uuid_bytes, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 5) & 31)));
-- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 6) & 7) << 2) | ((GET_BYTE(uuid_bytes, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 7) & 1) << 4) | ((GET_BYTE(uuid_bytes, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 8) & 15) << 1) | ((GET_BYTE(uuid_bytes, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 9) & 3) << 3) | ((GET_BYTE(uuid_bytes, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 11) & 7) << 2) | ((GET_BYTE(uuid_bytes, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 12) & 1) << 4) | ((GET_BYTE(uuid_bytes, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 13) & 15) << 1) | ((GET_BYTE(uuid_bytes, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 14) & 3) << 3) | ((GET_BYTE(uuid_bytes, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 15) & 31)));
RETURN output; END $$ LANGUAGE plpgsql IMMUTABLE; ```
Gera 11 Digitos aleatórios: YBKXG0CKTH4
```sql -- Cria a extensão pgcrypto para gerar uuid CREATE EXTENSION IF NOT EXISTS pgcrypto;
-- Cria a função para gerar ULID CREATE OR REPLACE FUNCTION gen_lrandom() RETURNS TEXT AS $$ DECLARE ts_millis BIGINT; ts_chars TEXT; random_bytes BYTEA; random_chars TEXT; base32_chars TEXT := '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; i INT; BEGIN -- Pega o timestamp em milissegundos ts_millis := FLOOR(EXTRACT(EPOCH FROM clock_timestamp()) * 1000)::BIGINT;
-- Converte o timestamp para base32 ts_chars := ''; FOR i IN REVERSE 0..11 LOOP ts_chars := ts_chars || substr(base32_chars, ((ts_millis >> (5 * i)) & 31) + 1, 1); END LOOP; -- Gera 10 bytes aleatórios e converte para base32 random_bytes := gen_random_bytes(10); random_chars := ''; FOR i IN 0..9 LOOP random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) >> 3) & 31) + 1, 1); IF i < 9 THEN random_chars := random_chars || substr(base32_chars, (((get_byte(random_bytes, i) & 7) << 2) | (get_byte(random_bytes, i + 1) >> 6)) & 31 + 1, 1); ELSE random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) & 7) << 2) + 1, 1); END IF; END LOOP; -- Concatena o timestamp e os caracteres aleatórios RETURN ts_chars || random_chars;END; $$ LANGUAGE plpgsql; ```
Exemplo de USO
```sql -- Criação da extensão caso não exista CREATE EXTENSION IF NOT EXISTS pgcrypto; -- Criação da tabela pessoas CREATE TABLE pessoas ( ID UUID DEFAULT gen_random_uuid ( ) PRIMARY KEY, nome TEXT NOT NULL );
-- Busca Pessoa na tabela SELECT * FROM "pessoas" WHERE uuid_to_ulid ( ID ) = '252FAC9F3V8EF80SSDK8PXW02F'; ```
Fontes
- https://github.com/scoville/pgsql-ulid
- https://github.com/geckoboard/pgulid
-
 @ ccb30bfc:90b6869f
2025-05-02 03:23:40
@ ccb30bfc:90b6869f
2025-05-02 03:23:40A busca por diversão online segura e variada levou muitos jogadores a conhecer a plataforma 98A, que tem ganhado destaque no Brasil por seu excelente desempenho técnico, suporte ao cliente de qualidade e, claro, uma vasta biblioteca de jogos envolventes.
Ao acessar o 98A, o jogador se depara com uma interface fluida, ideal para quem quer jogar sem complicações. A plataforma foi projetada para funcionar com eficiência tanto em computadores quanto em dispositivos móveis, permitindo jogatinas rápidas e práticas a qualquer momento.
O catálogo de jogos chama a atenção logo de início. São centenas de opções divididas em categorias que vão desde jogos de giro até clássicos de cartas. Cada jogo conta com uma descrição clara, regras bem definidas e modos para iniciantes e avançados. Isso democratiza o acesso, fazendo com que qualquer pessoa possa se divertir, independentemente do seu nível de experiência.
Um dos pontos altos do 98Aé o sistema de bonificações. Novos usuários são recebidos com recompensas logo no cadastro, enquanto os jogadores frequentes acumulam benefícios conforme sua atividade na plataforma. Esses prêmios vão desde bônus de crédito até acesso antecipado a novos lançamentos e torneios temáticos.
Além disso, o ambiente do 98A é fortemente voltado para a comunidade. Através de chats ao vivo e quadros de líderes, os jogadores podem interagir, trocar dicas e acompanhar o desempenho de outros participantes. Isso transforma o simples ato de jogar em uma atividade social e divertida.
A plataforma é completamente adaptada à realidade brasileira, com opções de pagamento locais e atendimento em português. Isso garante uma experiência personalizada, segura e acessível. A equipe de suporte, sempre presente, reforça o compromisso com a excelência no atendimento.
Combinando diversidade, inovação e suporte de qualidade, o 98A se posiciona como uma escolha certeira para quem busca diversão e praticidade em um só lugar.