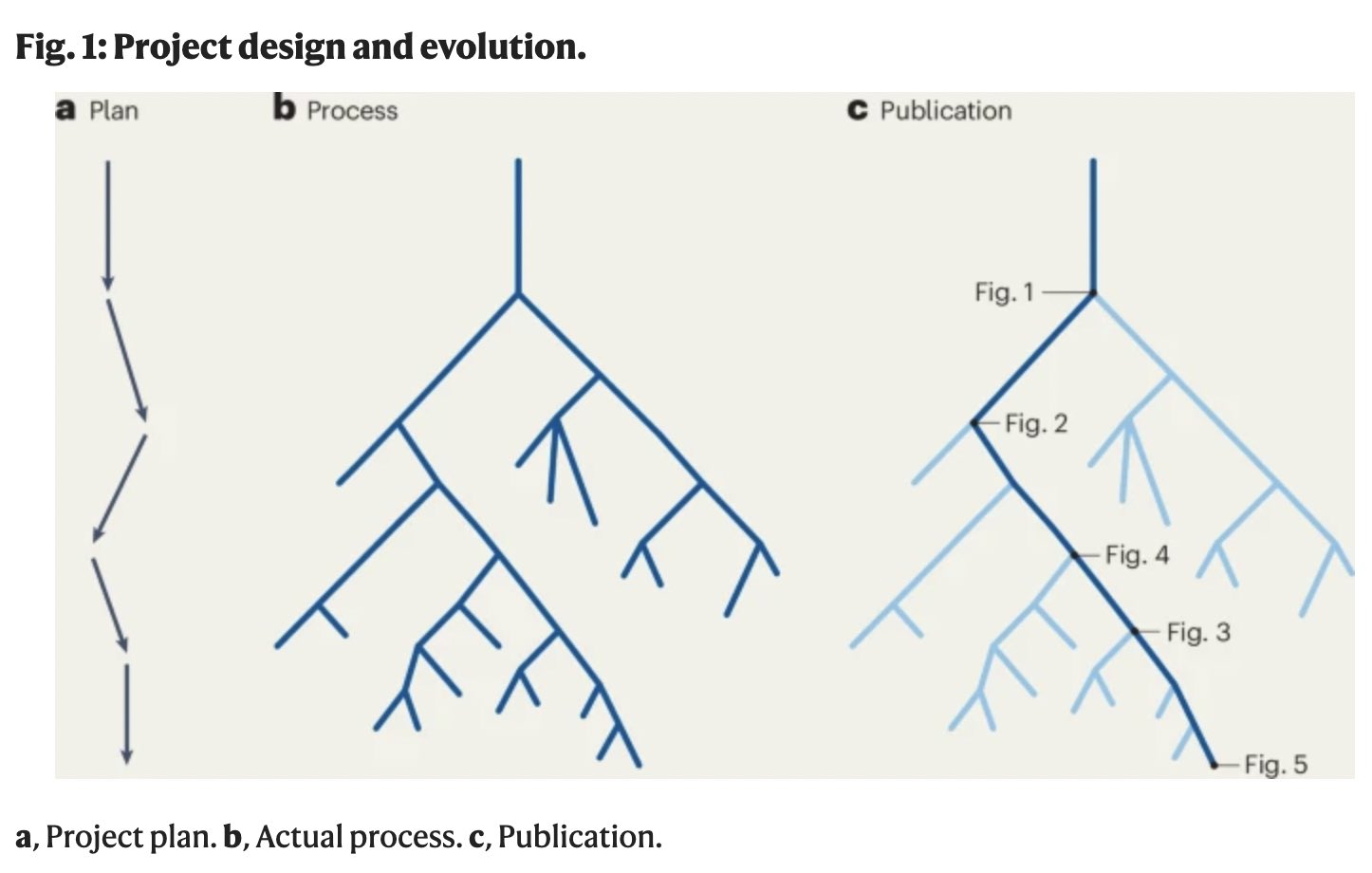
-
 @ 90c656ff:9383fd4e
2025-05-04 16:36:21
@ 90c656ff:9383fd4e
2025-05-04 16:36:21Bitcoin mining is a crucial process for the operation and security of the network. It plays an important role in validating transactions and generating new bitcoins, ensuring the integrity of the blockchain or timechain-based system. This process involves solving complex mathematical calculations and requires significant computational power. Additionally, mining has economic, environmental, and technological effects that must be carefully analyzed.
Bitcoin mining is the procedure through which new units of the currency are created and added to the network. It is also responsible for verifying and recording transactions on the blockchain or timechain. This system was designed to be decentralized, eliminating the need for a central authority to control issuance or validate operations.
Participants in the process, called miners, compete to solve difficult mathematical problems. Whoever finds the solution first earns the right to add a new block to the blockchain or timechain and receives a reward in bitcoins, along with the transaction fees included in that block. This mechanism is known as Proof of Work (PoW).
The mining process is highly technical and follows a series of steps:
Transaction grouping: Transactions sent by users are collected into a pending block that awaits validation.
Solving mathematical problems: Miners must find a specific number, called a nonce, which, when combined with the block’s data, generates a cryptographic hash that meets certain required conditions. This process involves trial and error and consumes a great deal of computational power.
Block validation: When a miner finds the correct solution, the block is validated and added to the blockchain or timechain. All network nodes verify the block’s authenticity before accepting it.
Reward: The winning miner receives a bitcoin reward, in addition to the fees paid for the transactions included in the block. This reward decreases over time in an event called halving, which happens approximately every four years.
Bitcoin mining has a significant economic impact, as it creates income opportunities for individuals and companies. It also drives the development of new technologies such as specialized processors (ASICs) and modern cooling systems.
Moreover, mining supports financial inclusion by maintaining a decentralized network, enabling fast and secure global transactions. In regions with unstable economies, Bitcoin provides a viable alternative for value preservation and financial transfers.
Despite its economic benefits, Bitcoin mining is often criticized for its environmental impact. The proof-of-work process consumes large amounts of electricity, especially in areas where the energy grid relies on fossil fuels.
It’s estimated that Bitcoin mining uses as much energy as some entire countries, raising concerns about its sustainability. However, there are ongoing efforts to reduce these impacts, such as the increasing use of renewable energy sources and the exploration of alternative systems like Proof of Stake (PoS) in other decentralized networks.
Mining also faces challenges related to scalability and the concentration of computational power. Large companies and mining pools dominate the sector, which can affect the network’s decentralization.
Another challenge is the growing complexity of the mathematical problems, which requires more advanced hardware and consumes more energy over time. To address these issues, researchers are studying solutions that optimize resource use and keep the network sustainable in the long term.
In summary, Bitcoin mining is an essential process for maintaining the network and creating new units of the currency. It ensures security, transparency, and decentralization, supporting the operation of the blockchain or timechain.
However, mining also brings challenges such as high energy consumption and the concentration of resources in large pools. Even so, the pursuit of sustainable solutions and technological innovations points to a promising future, where Bitcoin continues to play a central role in the digital economy.
Thank you very much for reading this far. I hope everything is well with you, and sending a big hug from your favorite Bitcoiner maximalist from Madeira. Long live freedom!
-
 @ 700c6cbf:a92816fd
2025-05-04 16:34:01
@ 700c6cbf:a92816fd
2025-05-04 16:34:01Technically speaking, I should say blooms because not all of my pictures are of flowers, a lot of them, probably most, are blooming trees - but who cares, right?
It is that time of the year that every timeline on every social media is being flooded by blooms. At least in the Northern Hemisphere. I thought that this year, I wouldn't partake in it but - here I am, I just can't resist the lure of blooms when I'm out walking the neighborhood.
Spring has sprung - aaaachoo, sorry, allergies suck! - and the blooms are beautiful.
Yesterday, we had the warmest day of the year to-date. I went for an early morning walk before breakfast. Beautiful blue skies, no clouds, sunshine and a breeze. Most people turned on their aircons. We did not. We are rebels - hah!
We also had breakfast on the deck which I really enjoy during the weekend. Later I had my first session of the year painting on the deck while listening/watching @thegrinder streaming. Good times.
Today, the weather changed. Last night, we had heavy thunderstorms and rain. This morning, it is overcast with the occasional sunray peaking through or, as it is right now, raindrops falling.
We'll see what the day will bring. For me, it will definitely be: Back to painting. Maybe I'll even share some here later. But for now - this is a photo post, and here are the photos. I hope you enjoy as much as I enjoyed yesterday's walk!
Cheers, OceanBee
!(image)[https://cdn.satellite.earth/cc3fb0fa757c88a6a89823585badf7d67e32dee72b6d4de5dff58acd06d0aa36.jpg] !(image)[https://cdn.satellite.earth/7fe93c27c3bf858202185cb7f42b294b152013ba3c859544950e6c1932ede4d3.jpg] !(image)[https://cdn.satellite.earth/6cbd9fba435dbe3e6732d9a5d1f5ff0403935a4ac9d0d83f6e1d729985220e87.jpg] !(image)[https://cdn.satellite.earth/df94d95381f058860392737d71c62cd9689c45b2ace1c8fc29d108625aabf5d5.jpg] !(image)[https://cdn.satellite.earth/e483e65c3ee451977277e0cfa891ec6b93b39c7c4ea843329db7354fba255e64.jpg] !(image)[https://cdn.satellite.earth/a98fe8e1e0577e3f8218af31f2499c3390ba04dced14c2ae13f7d7435b4000d7.jpg] !(image)[https://cdn.satellite.earth/d83b01915a23eb95c3d12c644713ac47233ce6e022c5df1eeba5ff8952b99d67.jpg] !(image)[https://cdn.satellite.earth/9ee3256882e363680d8ea9bb6ed3baa5979c950cdb6e62b9850a4baea46721f3.jpg] !(image)[https://cdn.satellite.earth/201a036d52f37390d11b76101862a082febb869c8d0e58d6aafe93c72919f578.jpg] !(image)[https://cdn.satellite.earth/cd516d89591a4cf474689b4eb6a67db842991c4bf5987c219fb9083f741ce871.jpg]
-
 @ 90c656ff:9383fd4e
2025-05-04 16:24:21
@ 90c656ff:9383fd4e
2025-05-04 16:24:21Blockchain or timechain is a new technology that has changed the way data and transactions are recorded and stored. Its decentralized and highly secure structure provides transparency and trust, making it a widely used system for digital operations. This technology is essential for creating financial systems and digital records that cannot be altered.
What is blockchain or timechain? Blockchain or timechain is essentially a distributed digital ledger designed to record transactions in a sequential and unchangeable manner. It is made up of blocks linked in a chain, each containing a set of information such as transactions, timestamps, and a unique identifier called a hash.
These blocks are organized in chronological order, ensuring the integrity of records over time. The term timechain, used synonymously, emphasizes this temporal aspect of the system, where each block is linked to the previous one, forming a chain of events that cannot be tampered with.
The validation of blocks in blockchain or timechain is carried out through a process called mining. Network participants, known as miners, use powerful computers to solve complex mathematical problems. This process, known as proof of work, is necessary to validate transactions and add a new block to the chain.
Each block contains:
Verified Transactions – A set of operations approved by the network.
Previous Block Hash – A unique code that connects the new block to the previous one, ensuring continuity and security.
Nonce – A number used in the mining process to generate the block's hash.
Once a block is validated, it is permanently added to the blockchain or timechain, and all nodes (participating computers) in the network update their copies of this ledger.
One of the main benefits of blockchain or timechain is the security provided by its decentralized model. Unlike traditional systems that rely on central servers, it distributes its data across thousands of computers around the world.
Immutability is guaranteed by cryptographic techniques and the chained structure of blocks. Any attempt to alter a block would require modifying all subsequent blocks, which is virtually impossible due to the massive computational power required.
Additionally, the use of cryptographic algorithms makes the system resistant to fraud and manipulation. This model enables trust, even in environments without intermediaries or central authorities.
Blockchain or timechain is transparent, as anyone can access the full history of transactions recorded on the network. This creates a system that is auditable and reliable.
However, the privacy of participants is protected, since transactions are recorded through anonymous digital addresses without revealing personal identities. This balance between transparency and privacy makes the system secure and flexible.
The use of blockchain or timechain goes beyond financial transactions. It is useful in areas such as smart contracts, asset registration, supply chains, and online voting. Its ability to create permanent and verifiable records enables innovative solutions across various industries.
For example, in product tracking systems, blockchain or timechain ensures data authenticity by recording each stage of the production and distribution process. This reduces fraud and increases operational efficiency.
Advantages and Challenges Among the main advantages of blockchain or timechain, we can highlight:
Decentralization – Elimination of intermediaries, reducing costs and increasing efficiency.
Security – Protection against fraud and digital attacks.
Transparency – Public and verifiable record of all transactions.
Immutability – Assurance that data cannot be modified after being recorded.
However, there are still challenges to be addressed, such as scalability, as the continuous growth of the network may require greater storage and processing capacity. Additionally, regulatory issues and widespread adoption demand ongoing improvements.
In summary, blockchain or timechain is an innovative technology that changes the way data and transactions are stored, ensuring security, transparency, and efficiency. Its decentralization removes the dependency on intermediaries, making it a trustworthy and tamper-resistant system.
Despite technical and regulatory challenges, blockchain or timechain continues to evolve, demonstrating its potential in various areas beyond the financial sector. Its promise of transparency and immutability is already shaping the future of digital systems, establishing itself as a fundamental base for the modern economy and digital trust.
Thank you very much for reading this far. I hope everything is well with you, and sending a big hug from your favorite Bitcoiner maximalist from Madeira. Long live freedom!
-
 @ a29cfc65:484fac9c
2025-05-04 16:20:03
@ a29cfc65:484fac9c
2025-05-04 16:20:03Bei einer Führung durch den Naumburger Dom sprach der Domführer über Propaganda im Mittelalter. Die gefühlvollen Gesichtsausdrücke der steinernen Stifterfiguren rund um die berühmte Uta sollten das Volk beeinflussen. Darüber haben wir auf der Heimfahrt nach Leipzig philosophiert und fanden den Denkansatz spannend. Denn auch wenn es damals nicht Propaganda hieß, so gab es doch Interessen der Mächtigen, die sie gegenüber dem Volk durchsetzten. Sie bedienten sich dabei der damals verfügbaren „Medien“, zu denen die Kirche gehörte, wo sich das Volk zum Gottesdienst traf.
Kulturelle Identität Europas
Mitteldeutschland ist ein Zentrum mittelalterlicher Baukunst. Der Naumburger Dom St. Peter und Paul wurde auf den Grundmauern einer noch älteren Kirche im 13. Jahrhundert gebaut. Er ist weltweit einzigartig in seiner Architektur, Bildhauerkunst und Glasmalerei. Seit 2018 ist er Unesco-Weltkulturerbe. Die Stadt Naumburg hatte einst die gleiche Bedeutung wie Merseburg, Magdeburg oder Leipzig. Der Dom – von der Spätromanik bis in die Frühgotik unter Leitung eines heute unbekannten Bildhauerarchitekten errichtet – gilt als Meisterwerk menschlicher Schöpferkraft und Handwerkskunst. Die naturwissenschaftlich-physikalischen Kenntnisse der Menschen waren offensichtlich enorm. Sie verfügten über das Wissen zur Planung und über entsprechende Werk- und Hebezeuge, um solche Bauwerke in relativ kurzer Zeit errichten zu können.
Im Westchor des Doms befinden sich mit den zwölf lebensgroßen Stifterfiguren die bekanntesten Kunstwerke des Doms, unter ihnen Uta von Ballenstedt. Sie soll Walt Disney als Quelle für die schöne und sehr stolze Königin im Zeichentrickfilm Schneewittchen gedient haben. Das Besondere und Neue an den steinernen Stifterfiguren war ihre realitätsnahe Darstellung, die sie lebendig und ausdrucksstark wirken lässt. Sie sind ein Höhepunkt in der Steinmetzkunst der damaligen Zeit. Die Figuren wurden, obschon die dargestellten Personen bereits mehr als 200 Jahre tot waren, mit charakteristischen Gesichtsausdrücken dargestellt: Uta schaut schön und stolz in die Ferne, ihr Gatte Ekkehard wirkt etwas hochmütig. Gegenüber steht die lachende Reglindis neben ihrem wehmütig-leidend blickenden Mann Hermann von Meißen.
Der Domführer sagte, dass die Gesichtsausdrücke menschliche Verhaltensweisen darstellen, die bei den Kirchenbesuchern unerwünscht waren. Wir hätten es hier mit einer sehr frühen Form der Propaganda zu tun. Die katholische Kirche war Vorreiter in Sachen Propaganda. Sie hat etwa 400 Jahre später, im Jahr 1622, mit der Sacra Congregatio de Propaganda Fide ein Amt gegründet, das den „richtigen“ Glauben in die Welt tragen sollte, und erst 1967 umbenannt wurde. Aber ihre gesellschaftlich führende Position hatte damals auch eine positive Seite: Den Kirchen und Klöstern haben wir den Erhalt und die Weitergabe antiken Wissens zu verdanken. Europa konnte sich trotz der politischen Zersplitterung seine kulturelle Identität erhalten. Zum Beispiel lässt sich das Wirken des namenlosen Domschöpfers anhand der Bau- und Kunstwerke quer durch Europa von Nordfrankreich über Mainz nach Naumburg und Meißen nachvollziehen. Aus der weiteren Entwicklung von Kunst und Kultur in Europa entstand in der Renaissance die Philosophie des Humanismus und später daraus die Aufklärung mit ihrer Wirkung auf Literatur und Wissenschaft. Ziel war dabei immer eine Stärkung des Gemeinwesens.
Transhumanismus zerstört Gemeinschaften
Heute scheinen wir uns allerdings an einer Bruchstelle der gesellschaftlichen Entwicklung zu befinden. Die Kirchen spielen in unserer Gesellschaft kaum noch eine Rolle. Weder bringen sie sich in ethische Diskussionen hörbar ein, noch tragen sie die Entwicklung von Kunst und Kultur sichtbar voran. Ihre Rolle im Bereich Propaganda haben längst Zeitungen und Zeitschriften, Rundfunk und Fernsehen übernommen. Diese Medien haben eine größere Reichweite, und die psychologische Beeinflussung ist umfassender. Nach dem Zweiten Weltkrieg wurde die Manipulation der Massen stark intensiviert und nahm nach dem Zusammenbruch der Sowjetunion noch weiter an Fahrt auf. Der Liberalismus konnte auf allen Gebieten seinen Siegeszug antreten, stellte das Individuum in den Mittelpunkt und erhob den Markt zur heiligen Kuh. Im Laufe der Zeit wurden die humanistischen Ideen der Aufklärung in ihr Gegenteil verkehrt. Der Mensch wurde als fehlerhaftes Wesen identifiziert, in die Vereinzelung getrieben, bevormundet und gegängelt – angeblich, damit er sich nicht selbst schadet. Zur psychologischen Beeinflussung kommen die neuen technischen Möglichkeiten aus Bio-Nano-Neuro-Wissenschaften und Digitalisierung. Der Transhumanismus wurde als neues Ziel für die Menschheit ausgerufen. Der Einzelne soll biologisch und technisch perfektioniert werden. Gemeinschaften – von der Familie angefangen – treibt das in die Bedeutungslosigkeit. Es besteht die Gefahr, dass persönliche Integrität und Privatsphäre durch Eingriffe in Körper- und Geistesfunktionen verletzt werden. Eine neue Aufklärung ist nötig. Denn sehr viel von dem über die Jahrhunderte erlangten Wissen ging schon verloren oder ist nur noch versteckt in den Bibliotheken und Archiven der Kirchen zu finden. Die Besinnung auf die vergessenen beziehungsweise verdrängten Grundlagen und Ideale der Aufklärung kann diese Entwicklung abwenden. Die Kulturschätze Mitteleuropas vermitteln in ihrer Schönheit und Vollkommenheit die Ruhe und die zeitlichen und räumlichen Dimensionen, die wir brauchen, wenn wir über die Frage nachdenken, wie wir in Zukunft leben wollen.
Die Rolle der neuen Medien für die zukünftige Entwicklung
Von den Alt-Medien ist in dieser Hinsicht nichts zu erwarten. Sie werden finanziert und sind unterwandert von den Kräften, die transhumanistische Entwicklungen vorantreiben. Die „neue Aufklärung“ ist ein lohnenswertes Ziel für die neuen Medien. Diese lassen sich jedoch noch zu sehr von den aktuellen Themen der Alt-Medien treiben. Der Angst-Propaganda begegnen sie mit – Ängsten, wenn auch anders ausgerichtet. Einige reiten die Empörungswelle in Gegenrichtung zu den Alt-Medien. Manche Betreiber von „alternativen“ Finanz- und Wirtschaftskanälen wollen ihre eigenen marktgläubigen Produkte an den Mann bringen. Stattdessen sollten in den neuen Medien positive Nachrichten verbreitet und eigene Themenfelder eröffnet werden, denen sich die Alt-Medien verweigern:
· der Mensch und seine Bildung zur souveränen, selbständig denkenden und handelnden Persönlichkeit,
· die Entwicklung des eigenen Bewusstseins, um der Fremdbestimmung zu entkommen und zu Wahrhaftigkeit, Authentizität und Menschlichkeit zu gelangen,
· die Entwicklung des Gemeinwohls,
· die Frage, wie wir neue Gemeinschaften bis hin zu autarken Gemeinden gründen können – wichtiger, je mehr das gesellschaftliche System um uns herum zusammenbricht.
Direkt sichtbar ist der letzte Punkt am Niedergang der Architektur und am Zustand der Innenstädte: Die reich dekorierten Gebäude der Gründerzeit wurden nach ihrer Zerstörung im Zweiten Weltkrieg durch gleichförmig rechteckige Gebäude aus Beton und Glas ersetzt. Dazu kamen die in allen Städten austauschbar gleichen Ladenzeilen und in den letzten Jahren Dreck und Schmierereien, die nicht mehr weggeräumt werden.
Die gesellschaftlichen Verwerfungen der Corona-Zeit führten bei vielen Menschen zum Innehalten und Nachdenken über Sinn und Ziele ihres Lebens. So entstanden einige Pilotprojekte, zum Beispiel in den Bereichen Landwirtschaft, Gesundheitswesen und Bildung. Diese auf die Zukunft gerichteten Themen könnten in den neuen Medien umfangreicher vorgestellt und diskutiert werden. Manova setzt schon solche Schwerpunkte mit „The Great WeSet“ von Walter van Rossum sowie mit den Kategorien „Zukunft & Neue Wege“ sowie „Aufwind“. Der Kontrafunk hat Formate entwickelt, die das Gemeinwohl stärker in den Fokus setzen wie etwa die Kultur- und Wissenschaftsrubrik. Nuoviso hat einen eigenen Songcontest ins Leben gerufen. Neben der inhaltlichen Ausrichtung auf eine lebenswerte Zukunft gilt es auch, die technologische Basis der neuen Medien zukunftsfest zu machen und sich der digitalen Zensur zu entziehen. Milosz Matuschek geht mit dem Pareto-Projekt neue Wege. Es könnte zur unzensierbaren Plattform der neuen Medien werden. Denn wie er sagt: Man baut sein neues Haus doch auch nicht auf dem Boden, der einem anderen gehört.
-
 @ f1989a96:bcaaf2c1
2025-05-01 15:50:38
@ f1989a96:bcaaf2c1
2025-05-01 15:50:38Good morning, readers!
This week, we bring pressing news from Belarus, where the regime’s central bank is preparing to launch its central bank digital currency in close collaboration with Russia by the end of 2026. Since rigging the 2020 election, President Alexander Lukashenko has ruled through brute force and used financial repression to crush civil society and political opposition. A Central Bank Digital Currency (CBDC) in the hands of such an authoritarian leader is a recipe for greater control over all aspects of financial activity.
Meanwhile, Russia is planning to further restrict Bitcoin access for ordinary citizens. This time, the Central Bank of Russia and the Ministry of Finance announced joint plans to launch a state-regulated cryptocurrency exchange available exclusively to “super-qualified investors.” Access would be limited to those meeting previously defined thresholds of $1.2 million in assets or an annual income above $580,000. This is a blatant attempt by the Kremlin to dampen the accessibility and impact of Bitcoin for those who need it most.
In freedom tech news, we spotlight Samiz. This new tool allows users to create a Bluetooth mesh network over nostr, allowing users' messages and posts to pass through nearby devices on the network even while offline. When a post reaches someone with an Internet connection, it is broadcast across the wider network. While early in development, Mesh networks like Samiz hold the potential to disseminate information posted by activists and human rights defenders even when authoritarian regimes in countries like Pakistan, Venezuela, or Burma try to restrict communications and the Internet.
We end with a reading of our very own Financial Freedom Report #67 on the Bitcoin Audible podcast, where host Guy Swann reads the latest news on plunging currencies, CBDCs, and new Bitcoin freedom tools. We encourage our readers to give it a listen and stay tuned for future readings of HRF’s Financial Freedom Report on Bitcoin Audible. We also include an interview with HRF’s global bitcoin adoption lead, Femi Longe, who shares insights on Bitcoin’s growing role as freedom money for those who need it most.
Now, let’s see what’s in store this week!
SUBSCRIBE HERE
GLOBAL NEWS
Belarus | Launching CBDC in Late 2026
Belarus is preparing to launch its CBDC, the digital ruble, into public circulation by late 2026. Roman Golovchenko, the chairman of the National Bank of the Republic of Belarus (and former prime minister), made the regime’s intent clear: “For the state, it is very important to be able to trace how digital money moves along the entire chain.” He added that Belarus was “closely cooperating with Russia regarding the development of the CBDC.” The level of surveillance and central control that the digital ruble would embed into Belarus’s financial system would pose existential threats to what remains of civil society in the country. Since stealing the 2020 election, Belarusian President Alexander Lukashenko has ruled through sheer force, detaining over 35,000 people, labeling dissidents and journalists as “extremists,” and freezing the bank accounts of those who challenge his authority. In this context, a CBDC would not be a modern financial tool — it would be a means of instant oppression, granting the regime real-time insight into every transaction and the ability to act on it directly.
Russia | Proposes Digital Asset Exchange Exclusively for Wealthy Investors
A month after proposing a framework that would restrict the trading of Bitcoin to only the country’s wealthiest individuals (Russians with over $1.2 million in assets or an annual income above $580,000), Russia’s Ministry of Finance and Central Bank have announced plans to launch a government-regulated cryptocurrency exchange available exclusively to “super-qualified investors.” Under the plan, only citizens meeting the previously stated wealth and income thresholds (which may be subject to change) would be allowed to trade digital assets on the platform. This would further entrench financial privilege for Russian oligarchs while cutting ordinary Russians off from alternative financial tools and the financial freedom they offer. Finance Minister Anton Siluanov claims this will bring digital asset operations “out of the shadows,” but in reality, it suppresses grassroots financial autonomy while exerting state control over who can access freedom money.
Cuba | Ecash Brings Offline Bitcoin Payments to Island Nation in the Dark
As daily blackouts and internet outages continue across Cuba, a new development is helping Cubans achieve financial freedom: Cashu ecash. Cashu is an ecash protocol — a form of digital cash backed by Bitcoin that enables private, everyday payments that can also be done offline — a powerful feature for Cubans experiencing up to 20-hour daily blackouts. However, ecash users must trust mints (servers operated by individuals or groups that issue and redeem ecash tokens) not to disappear with user funds. To leverage this freedom tech to its fullest, the Cuban Bitcoin community launched its own ecash mint, mint.cubabitcoin.org. This minimizes trust requirements for Cubans to transact with ecash and increases its accessibility by running the mint locally. Cuba Bitcoin also released a dedicated ecash resource page, helping expand accessibility to freedom through financial education. For an island nation where the currency has lost more than 90% of its value, citizens remain locked out of their savings, and remittances are often hijacked by the regime, tools like ecash empower Cubans to preserve their financial privacy, exchange value freely, and resist the financial repression that has left so many impoverished.
Zambia | Introduces Cyber Law to Track and Intercept Digital Communications
Zambia’s government passed two new cyber laws granting officials sweeping powers to track and intercept digital communications while increasing surveillance over Zambians' online activity. Officials insist it will help combat cybercrime. Really, it gives the president absolute control over the direction of a new surveillance agency — a powerful tool to crush dissent. This follows earlier plans to restrict the use of foreign currency in the economy to fight inflation, which effectively trapped Zambians in a financial system centered around the volatile “kwacha” currency (which reached a record low earlier this year with inflation above 16%). For activists, journalists, and everyday Zambians, the new laws over online activity threaten the ability to organize and speak freely while potentially hampering access to freedom tech.
India | Central Bank Deputy Governor Praises CBDC Capabilities
At the Bharat Inclusion Summit in Bengaluru, India, the deputy governor of the Reserve Bank of India (RBI), Rabi Sankar, declared, “I have so far not seen any use case that potentially can solve the problem of cross-border money transfer; only CBDC has the ability to solve it.” Yet — seemingly unbeknownst to Sankar, Bitcoin has served as an effective remittance tool for more than a decade at low cost, fast speed, and with no central point of control. Sankar’s remarks follow a growing push to normalize state-controlled, surveillance-based digital money as a natural progression of currency. The RBI’s digital rupee CBDC, currently in pilot phase, is quickly growing into one of the most advanced CBDCs on the planet. It is being embedded into the government’s UPI payment system and offered through existing financial institutions and platforms. Decentralized alternatives like Bitcoin can achieve financial inclusion and payment efficiency too — but without sacrificing privacy, autonomy, or basic rights over to the state.
Tanzania | Opposition Party Excluded From Election Amid Financial Repression
Last week, the Tanzanian regime banned the use of foreign currency in transactions, leaving Tanzanians to rely solely on the rapidly depreciating Tanzanian shilling. Now, Tanzania's ruling party has taken a decisive step to eliminate political opposition ahead of October’s general elections by barring the CHADEMA party from participation under the pretense of treason against their party leader, Tundu Lissu. Law enforcement arrested Lissu at a public rally where he was calling for electoral reforms. This political repression is not happening in isolation. Last year, the Tanzanian regime blocked access to X, detained hundreds of opposition members, and disappeared dissidents. These developments suggest a broader strategy to silence criticism and electoral competition through arrests, censorship, and economic coercion.
BITCOIN AND FREEDOM TECH NEWS
Samiz | Create a Bluetooth Mesh Network with Nostr
Samiz, an app for creating a Bluetooth mesh network over nostr, is officially available for testing. Mesh networks, where interconnected computers relay data to one another, can provide offline access to nostr if enough users participate. For example, when an individual is offline but has Samiz enabled, their device can connect to other nearby devices through Bluetooth, allowing nostr messages to hop locally from phone to phone until reaching someone with internet access, who can then broadcast the message to the wider nostr network. Mesh networks like this hold powerful implications for activists and communities facing censorship, Internet shutdowns, or surveillance. In places with restricted finances and organization, Samiz, while early in development, can potentially offer a way to distribute information through nostr without relying on infrastructure that authoritarian regimes can shut down.
Spark | New Bitcoin Payments Protocol Now Live
Lightspark, a company building on the Bitcoin Lightning Network, officially released Spark, a new payment protocol built on Bitcoin to make transactions faster, cheaper, and more privacy-protecting. Spark leverages a technology called statechains to enable self-custodial and off-chain Bitcoin transactions for users by transferring the private keys associated with their bitcoin rather than signing and sending a transaction with said keys. Spark also supports stablecoins (digital tokens pegged to fiat currency) and allows users to receive payments while offline. While these are promising developments, in its current state, Spark is not completely trustless; therefore, it is advisable only to hold a small balance of funds on the protocol as this new payment technology gets off the ground. You can learn more about Spark here.
Boltz | Now Supports Nostr Zaps
Boltz, a non-custodial bridge for swapping between different Bitcoin layers, released a new feature called Zap Swaps, enabling users to make Lightning payments as low as 21 satoshis (small units of bitcoin). This feature enables bitcoin microtransactions like nostr zaps, which are use cases that previously required workaround solutions. With the release, users of Boltz-powered Bitcoin wallets like Misty Breez can now leverage their wallets for zaps on nostr. These small, uncensorable bitcoin payments are a powerful tool for supporting activists, journalists, and dissidents — offering a permissionless way to support free speech and financial freedom worldwide. HRF is pleased to see this past HRF grantee add support for the latest freedom tech features.
Coinswap | Adds Support for Coin Selection
Coinswap, an in-development protocol that enables users to privately swap Bitcoin with one another, added support for coin selection, boosting the protocol’s privacy capabilities. Coin selection allows Bitcoin users to choose which of their unspent transaction outputs (UTXOs) to spend, giving them granular control over their transactions and the information they choose to reveal. For activists, journalists, and anyone operating under financial surveillance and repression, this addition (when fully implemented and released) can strengthen Bitcoin’s ability to resist censorship and protect human rights. HRF’s first Bitcoin Development Fund (BDF) grant was to Coinswap, and we are glad to see the continued development of the protocol.
bitcoin++ | Upcoming Bitcoin Developer Conference
The next bitcoin++ conference, a global, bitcoin-only developer series organized by Bitcoin educator Lisa Neigut, will occur in Austin, Texas, from May 7 to 9, 2025. A diverse group of privacy advocates, developers, and freedom tech enthusiasts will convene to learn about the mempool (the queue of pending and unconfirmed transactions in a Bitcoin node). Attendees will learn how Bitcoin transactions are sorted into blocks, mempool policies, and how transactions move through time and space to reach the next block. These events offer an incredible opportunity to connect with the technical Bitcoin community, who are ultimately many of the figures building the freedom tools that are helping individuals preserve their rights and freedoms in the face of censorship. Get your tickets here.
OpenSats | Announces 11th Wave of Nostr Grants
OpenSats, a nonprofit organization supporting open-source software and projects, announced its 11th round of grants for nostr, a decentralized protocol that enables uncensorable communications. Two projects stand out for their potential impact on financial freedom and activism: HAMSTR, which enables nostr messaging over ham radio that keeps information and payments flowing in off-grid or censored environments, and Nostr Double Ratchet, which brings end-to-end encrypted private messaging to nostr clients, safeguarding activists from surveillance. These tools help dissidents stay connected, coordinate securely, and transact privately, making them powerful assets for those resisting authoritarian control. Read the full list of grants here.
Bitcoin Design Community | Organizes Designathon for Open-Source UX Designers
The Bitcoin Design Community is hosting its next Designathon between May 4 and 18, 2025, inviting designers of all levels and backgrounds to creatively explore ideas to advance Bitcoin’s user experience and interface. Unlike traditional hackathons, this event centers specifically on design, encouraging open collaboration on projects that improve usability, accessibility, and innovation in open-source Bitcoin tools. Participants can earn monetary prizes, rewards, and recognition for their work. Anyone can join or start a project. Learn more here.
RECOMMENDED CONTENT
Plunging Currencies, CBDCs, and New Bitcoin Freedom Tools with Guy Swann
In this reading on the Bitcoin Audible podcast, host Guy Swan reads HRF’s Financial Freedom Report #67, offering listeners a front-row view into the latest developments in financial repression and resistance. He unpacks how collapsing currencies, rising inflation, and CBDC rollouts tighten state control in Turkey, Russia, and Nigeria. But he also highlights the tools for pushing back, from the first Stratum V2 mining pool to Cashu’s new Tap-to-Pay ecash feature. If you’re a reader of the Financial Freedom Report, we encourage you to check out the Bitcoin Audible podcast, where Guy Swan will be doing monthly readings of our newsletter. Listen to the full recording here.
Bitcoin Beyond Capital: Freedom Money for the Global South with Femi Longe
In this interview at the 2025 MIT Bitcoin Expo, journalist Frank Corva speaks with Femi Longe, HRF’s global bitcoin lead, who shares insights on Bitcoin’s growing role as freedom money for those living under authoritarian regimes. The conversation highlights the importance of building Bitcoin solutions that center on the specific problems faced by communities rather than the technology itself. Longe commends projects like Tando in Kenya and Bit.Spenda in Ghana, which integrate Bitcoin and Lightning into familiar financial channels, making Bitcoin more practical and accessible for everyday payments and saving. You can watch the interview here and catch the livestreams of the full 2025 MIT Bitcoin Expo here.
If this article was forwarded to you and you enjoyed reading it, please consider subscribing to the Financial Freedom Report here.
Support the newsletter by donating bitcoin to HRF’s Financial Freedom program via BTCPay.\ Want to contribute to the newsletter? Submit tips, stories, news, and ideas by emailing us at ffreport @ hrf.org
The Bitcoin Development Fund (BDF) is accepting grant proposals on an ongoing basis. The Bitcoin Development Fund is looking to support Bitcoin developers, community builders, and educators. Submit proposals here.
-
 @ 52b4a076:e7fad8bd
2025-04-28 00:48:57
@ 52b4a076:e7fad8bd
2025-04-28 00:48:57I have been recently building NFDB, a new relay DB. This post is meant as a short overview.
Regular relays have challenges
Current relay software have significant challenges, which I have experienced when hosting Nostr.land: - Scalability is only supported by adding full replicas, which does not scale to large relays. - Most relays use slow databases and are not optimized for large scale usage. - Search is near-impossible to implement on standard relays. - Privacy features such as NIP-42 are lacking. - Regular DB maintenance tasks on normal relays require extended downtime. - Fault-tolerance is implemented, if any, using a load balancer, which is limited. - Personalization and advanced filtering is not possible. - Local caching is not supported.
NFDB: A scalable database for large relays
NFDB is a new database meant for medium-large scale relays, built on FoundationDB that provides: - Near-unlimited scalability - Extended fault tolerance - Instant loading - Better search - Better personalization - and more.
Search
NFDB has extended search capabilities including: - Semantic search: Search for meaning, not words. - Interest-based search: Highlight content you care about. - Multi-faceted queries: Easily filter by topic, author group, keywords, and more at the same time. - Wide support for event kinds, including users, articles, etc.
Personalization
NFDB allows significant personalization: - Customized algorithms: Be your own algorithm. - Spam filtering: Filter content to your WoT, and use advanced spam filters. - Topic mutes: Mute topics, not keywords. - Media filtering: With Nostr.build, you will be able to filter NSFW and other content - Low data mode: Block notes that use high amounts of cellular data. - and more
Other
NFDB has support for many other features such as: - NIP-42: Protect your privacy with private drafts and DMs - Microrelays: Easily deploy your own personal microrelay - Containers: Dedicated, fast storage for discoverability events such as relay lists
Calcite: A local microrelay database
Calcite is a lightweight, local version of NFDB that is meant for microrelays and caching, meant for thousands of personal microrelays.
Calcite HA is an additional layer that allows live migration and relay failover in under 30 seconds, providing higher availability compared to current relays with greater simplicity. Calcite HA is enabled in all Calcite deployments.
For zero-downtime, NFDB is recommended.
Noswhere SmartCache
Relays are fixed in one location, but users can be anywhere.
Noswhere SmartCache is a CDN for relays that dynamically caches data on edge servers closest to you, allowing: - Multiple regions around the world - Improved throughput and performance - Faster loading times
routerd
routerdis a custom load-balancer optimized for Nostr relays, integrated with SmartCache.routerdis specifically integrated with NFDB and Calcite HA to provide fast failover and high performance.Ending notes
NFDB is planned to be deployed to Nostr.land in the coming weeks.
A lot more is to come. 👀️️️️️️
-
 @ 1f79058c:eb86e1cb
2025-04-26 13:53:50
@ 1f79058c:eb86e1cb
2025-04-26 13:53:50I'm currently using this bash script to publish long-form content from local Markdown files to Nostr relays.
It requires all of
yq,jq, andnakto be installed.Usage
Create a signed Nostr event and print it to the console:
bash markdown_to_nostr.sh article-filename.mdCreate a Nostr event and publish it to one or more relays:
bash markdown_to_nostr.sh article-filename.md ws://localhost:7777 wss://nostr.kosmos.orgMarkdown format
You can specify your metadata as YAML in a Front Matter header. Here's an example file:
```markdown
title: "Good Morning" summary: "It's a beautiful day" image: https://example.com/i/beautiful-day.jpg date: 2025-04-24T15:00:00Z tags: gm, poetry published: false
In the blue sky just a few specks of gray
In the evening of a beautiful day
Though last night it rained and more rain on the way
And that more rain is needed 'twould be fair to say.— Francis Duggan ```
The metadata keys are mostly self-explanatory. Note:
- All keys except for
titleare optional date, if present, will be set as thepublished_atdate.- If
publishedis set totrue, it will publish a kind 30023 event, otherwise a kind 30024 (draft) - The
dtag (widely used as URL slug for the article) will be the filename without the.mdextension
- All keys except for
-
 @ 3bf0c63f:aefa459d
2025-04-25 19:26:48
@ 3bf0c63f:aefa459d
2025-04-25 19:26:48Redistributing Git with Nostr
Every time someone tries to "decentralize" Git -- like many projects tried in the past to do it with BitTorrent, IPFS, ScuttleButt or custom p2p protocols -- there is always a lurking comment: "but Git is already distributed!", and then the discussion proceeds to mention some facts about how Git supports multiple remotes and its magic syncing and merging abilities and so on.
Turns out all that is true, Git is indeed all that powerful, and yet GitHub is the big central hub that hosts basically all Git repositories in the giant world of open-source. There are some crazy people that host their stuff elsewhere, but these projects end up not being found by many people, and even when they do they suffer from lack of contributions.
Because everybody has a GitHub account it's easy to open a pull request to a repository of a project you're using if it's on GitHub (to be fair I think it's very annoying to have to clone the repository, then add it as a remote locally, push to it, then go on the web UI and click to open a pull request, then that cloned repository lurks forever in your profile unless you go through 16 screens to delete it -- but people in general seem to think it's easy).
It's much harder to do it on some random other server where some project might be hosted, because now you have to add 4 more even more annoying steps: create an account; pick a password; confirm an email address; setup SSH keys for pushing. (And I'm not even mentioning the basic impossibility of offering
pushaccess to external unknown contributors to people who want to host their own simple homemade Git server.)At this point some may argue that we could all have accounts on GitLab, or Codeberg or wherever else, then those steps are removed. Besides not being a practical strategy this pseudo solution misses the point of being decentralized (or distributed, who knows) entirely: it's far from the ideal to force everybody to have the double of account management and SSH setup work in order to have the open-source world controlled by two shady companies instead of one.
What we want is to give every person the opportunity to host their own Git server without being ostracized. at the same time we must recognize that most people won't want to host their own servers (not even most open-source programmers!) and give everybody the ability to host their stuff on multi-tenant servers (such as GitHub) too. Importantly, though, if we allow for a random person to have a standalone Git server on a standalone server they host themselves on their wood cabin that also means any new hosting company can show up and start offering Git hosting, with or without new cool features, charging high or low or zero, and be immediately competing against GitHub or GitLab, i.e. we must remove the network-effect centralization pressure.
External contributions
The first problem we have to solve is: how can Bob contribute to Alice's repository without having an account on Alice's server?
SourceHut has reminded GitHub users that Git has always had this (for most) arcane
git send-emailcommand that is the original way to send patches, using an once-open protocol.Turns out Nostr acts as a quite powerful email replacement and can be used to send text content just like email, therefore patches are a very good fit for Nostr event contents.
Once you get used to it and the proper UIs (or CLIs) are built sending and applying patches to and from others becomes a much easier flow than the intense clickops mixed with terminal copypasting that is interacting with GitHub (you have to clone the repository on GitHub, then update the remote URL in your local directory, then create a branch and then go back and turn that branch into a Pull Request, it's quite tiresome) that many people already dislike so much they went out of their way to build many GitHub CLI tools just so they could comment on issues and approve pull requests from their terminal.
Replacing GitHub features
Aside from being the "hub" that people use to send patches to other people's code (because no one can do the email flow anymore, justifiably), GitHub also has 3 other big features that are not directly related to Git, but that make its network-effect harder to overcome. Luckily Nostr can be used to create a new environment in which these same features are implemented in a more decentralized and healthy way.
Issues: bug reports, feature requests and general discussions
Since the "Issues" GitHub feature is just a bunch of text comments it should be very obvious that Nostr is a perfect fit for it.
I will not even mention the fact that Nostr is much better at threading comments than GitHub (which doesn't do it at all), which can generate much more productive and organized discussions (and you can opt out if you want).
Search
I use GitHub search all the time to find libraries and projects that may do something that I need, and it returns good results almost always. So if people migrated out to other code hosting providers wouldn't we lose it?
The fact is that even though we think everybody is on GitHub that is a globalist falsehood. Some projects are not on GitHub, and if we use only GitHub for search those will be missed. So even if we didn't have a Nostr Git alternative it would still be necessary to create a search engine that incorporated GitLab, Codeberg, SourceHut and whatnot.
Turns out on Nostr we can make that quite easy by not forcing anyone to integrate custom APIs or hardcoding Git provider URLs: each repository can make itself available by publishing an "announcement" event with a brief description and one or more Git URLs. That makes it easy for a search engine to index them -- and even automatically download the code and index the code (or index just README files or whatever) without a centralized platform ever having to be involved.
The relays where such announcements will be available play a role, of course, but that isn't a bad role: each announcement can be in multiple relays known for storing "public good" projects, some relays may curate only projects known to be very good according to some standards, other relays may allow any kind of garbage, which wouldn't make them good for a search engine to rely upon, but would still be useful in case one knows the exact thing (and from whom) they're searching for (the same is valid for all Nostr content, by the way, and that's where it's censorship-resistance comes from).
Continuous integration
GitHub Actions are a very hardly subsidized free-compute-for-all-paid-by-Microsoft feature, but one that isn't hard to replace at all. In fact there exists today many companies offering the same kind of service out there -- although they are mostly targeting businesses and not open-source projects, before GitHub Actions was introduced there were also many that were heavily used by open-source projects.
One problem is that these services are still heavily tied to GitHub today, they require a GitHub login, sometimes BitBucket and GitLab and whatnot, and do not allow one to paste an arbitrary Git server URL, but that isn't a thing that is very hard to change anyway, or to start from scratch. All we need are services that offer the CI/CD flows, perhaps using the same framework of GitHub Actions (although I would prefer to not use that messy garbage), and charge some few satoshis for it.
It may be the case that all the current services only support the big Git hosting platforms because they rely on their proprietary APIs, most notably the webhooks dispatched when a repository is updated, to trigger the jobs. It doesn't have to be said that Nostr can also solve that problem very easily.
-
 @ 8125b911:a8400883
2025-04-25 07:02:35
@ 8125b911:a8400883
2025-04-25 07:02:35In Nostr, all data is stored as events. Decentralization is achieved by storing events on multiple relays, with signatures proving the ownership of these events. However, if you truly want to own your events, you should run your own relay to store them. Otherwise, if the relays you use fail or intentionally delete your events, you'll lose them forever.
For most people, running a relay is complex and costly. To solve this issue, I developed nostr-relay-tray, a relay that can be easily run on a personal computer and accessed over the internet.
Project URL: https://github.com/CodyTseng/nostr-relay-tray
This article will guide you through using nostr-relay-tray to run your own relay.
Download
Download the installation package for your operating system from the GitHub Release Page.
| Operating System | File Format | | --------------------- | ---------------------------------- | | Windows |
nostr-relay-tray.Setup.x.x.x.exe| | macOS (Apple Silicon) |nostr-relay-tray-x.x.x-arm64.dmg| | macOS (Intel) |nostr-relay-tray-x.x.x.dmg| | Linux | You should know which one to use |Installation
Since this app isn’t signed, you may encounter some obstacles during installation. Once installed, an ostrich icon will appear in the status bar. Click on the ostrich icon, and you'll see a menu where you can click the "Dashboard" option to open the relay's control panel for further configuration.

macOS Users:
- On first launch, go to "System Preferences > Security & Privacy" and click "Open Anyway."
- If you encounter a "damaged" message, run the following command in the terminal to remove the restrictions:
bash sudo xattr -rd com.apple.quarantine /Applications/nostr-relay-tray.appWindows Users:
- On the security warning screen, click "More Info > Run Anyway."
Connecting
By default, nostr-relay-tray is only accessible locally through
ws://localhost:4869/, which makes it quite limited. Therefore, we need to expose it to the internet.In the control panel, click the "Proxy" tab and toggle the switch. You will then receive a "Public address" that you can use to access your relay from anywhere. It's that simple.
Next, add this address to your relay list and position it as high as possible in the list. Most clients prioritize connecting to relays that appear at the top of the list, and relays lower in the list are often ignored.

Restrictions
Next, we need to set up some restrictions to prevent the relay from storing events that are irrelevant to you and wasting storage space. nostr-relay-tray allows for flexible and fine-grained configuration of which events to accept, but some of this is more complex and will not be covered here. If you're interested, you can explore this further later.
For now, I'll introduce a simple and effective strategy: WoT (Web of Trust). You can enable this feature in the "WoT & PoW" tab. Before enabling, you'll need to input your pubkey.
There's another important parameter,
Depth, which represents the relationship depth between you and others. Someone you follow has a depth of 1, someone they follow has a depth of 2, and so on.- Setting this parameter to 0 means your relay will only accept your own events.
- Setting it to 1 means your relay will accept events from you and the people you follow.
- Setting it to 2 means your relay will accept events from you, the people you follow, and the people they follow.
Currently, the maximum value for this parameter is 2.

Conclusion
You've now successfully run your own relay and set a simple restriction to prevent it from storing irrelevant events.
If you encounter any issues during use, feel free to submit an issue on GitHub, and I'll respond as soon as possible.
Not your relay, not your events.
-
 @ 502ab02a:a2860397
2025-05-04 15:48:26
@ 502ab02a:a2860397
2025-05-04 15:48:26วันอาทิตย์ เพื่อนใหม่เยอะพอสมควร น่าจะพอที่จะแนะนำให้รู้จัก โรงบ่มสุขภาพ ขอเล่าผ่านเพลง "บ่ม" เพื่อรวบบทความ #ตัวหนังสือมีเสียง ไว้ด้วยเลยแล้วกันครับ
โรงบ่มสุขภาพ Healthy Hut - โรงบ่มสุขภาพ คือการรวมตัวกันของบุคลากรที่มี content และ ความเชี่ยวชาญ ด้านต่างๆ ทำกิจกรรมหลากหลายรูปแบบ ตั้งแต่แคมป์สุขภาพ พักผ่อนกายใจเรียนรู้การปรับสมดุลร่างกาย, การเรียนรู้พื้นฐาน Nutrition ต่างๆ ลองดูผลงานได้ในเพจครับ และโรงบ่มฯ ก็จะยังคงมีกิจกรรมให้ทุกคนได้เข้าร่วมอยู่เสมอ ดังนั้นไปกดไลค์เพจไว้เพื่อไม่ให้พลาดข้าวสาร เอ้ย ข่าวสาร
โรงบ่มฯนั้น ประกอบด้วย 👨🏻⚕️พี่หมอป๊อบ DietDoctor Thailand ที่เรารู้จักกันดี อาจารย์ของพวกเรา 🏋🏻♀️ 🏅พี่หนึ่ง จาก หนึ่งคีโตแด๊ดดี้ มาเป็น Nueng The One ผมอุปโลกให้ก่อนเลยว่า คนไทยคนแรกที่ทำเนื้อหาการกินคีโต เป็นภาษาไทย แบบมีบันทึกสาธารณะให้ตามศึกษา 👨🏻⚕️หมอเอก หมออ้วนในดงลดน้ำหนัก กับหลักการใช้ชีวิตแบบ IFF สาย Fasting ที่ย้ำว่าหัวใจอีกห้องของ Fasting คือ Feeding กระดุมเม็ดแรกของการฟาส ที่คนมักลืม 🧘🏻♀️ครูบอม เทพโยคะอีกท่านนึงของไทย กับศาสตร์โยคะ Anusara Yoga หนึ่งเดียวในไทย 🧗♂️โค้ชแมท สารานุกรมสุขภาพที่มีชีวิต นิ่งแต่คมกริบ ถ้าเป็นเกมส์ก็สาย สไนเปอร์ ยิงน้อยแต่ Head Shot 🧔🏻แอ๊ดหนวด ฉายา Salt Daddy เจ้าแห่งเกลือแร่ ประจำกลุ่ม IF-Mix Fasting Diet Thailand (Keto # Low Carb # Plant Base # High Fat) 👭👩🏻🤝👨🏼👩🏻🤝👨🏼 รวมถึงทีมงาน กัลยาณมิตรสุขภาพ ที่มีความรู้ในด้านสุขภาพและมากประสบการณ์ 🧑🏻🍳 ผมและตำรับเอ๋เองก็ยินดีมากๆที่ได้ร่วมทีมสุขภาพนี้กับเขาด้วย
จะเห็นได้ว่า แต่ละท่านในโรงบ่มฯ นั้นหล่อหลอมมาจากความต่างเสียด้วยซ้ำไป ตั้งแต่เริ่มก่อร่างโรงบ่ม เราก็ตั้งไว้แล้วว่า ชีวะ ควรมีความหลากหลาย การวางพื้นฐานสุขภาพควรมาจาก "แต่ละคน" ไม่ใช่ one size fit all บันทึกกิจกรรมโรงบ่มผมมีโพสไว้ https://www.facebook.com/share/p/19DUibHrbw/
นั่นเป็นเหตุผลที่ผมเกิดแรงบันดาลใจในการทำเพลง "บ่ม" ขึ้นมาเพื่อเป็น Theme Song ครับ แก่นของเพลงนี้มีไม่กี่อย่างครับ ผมเริ่มคิดจากคำว่า "ความต่าง" เพราะไม่ว่าจะกี่ปีกี่ชาติ วงการสุขภาพ ก็จะมีแนวความคิดประเภท ฉันถูกเธอผิด อยู่ตลอดเวลาเพราะมันเป็นธรรมชาติมนุษย์ครับ มนุษย์เราทุกคนมีอีโก้ การยอมรับในความต่าง การหลอมรวมความต่าง ผมคิดว่ามันเป็นการ "บ่ม" ให้สุกงอมได้
เวลาที่เนื้อหาแบบนี้ ผมก็อดคิดถึงวงที่ผมรักเสมอไม่ได้เลย นั่นคือ เฉลียง แม้ความสามารถจะห่างไกลกันลิบลับ แต่ผมก็อยากทำสไตล์เฉลียงกับเขาบ้างครั้งหนึ่งหรือหลายๆครั้งในชีวิต จึงเลือกแนวเพลงออกมาทาง แจ๊ส สวิง มีเครื่องเป่า คาริเนต เป็นตัวเด่น
ท่อนแรกของเพลงจึงเริ่มด้วย "ต่างทั้งความคิด ต่างทั้งความฝัน ต่างเผ่าต่างพันธุ์ จะต่างกันแค่ไหน หนึ่งเมล็ด จากหลากผล แต่ละคน ก็ปนไป แล้วเพราะเหตุใด ใยต้องไปแค่ทางเดียว" เพื่อปูให้คนฟังเริ่มเปิดรับว่า สิ่งที่ต้องการจะสื่อต่อไปคืออะไร
ส่วนคำย้ำนั้นผมแตกมาจาก คำสอนของพระพุทธเจ้า เกี่ยวกับ "คิดเห็นเป็นไป" ซึ่งจริงๆผมเขียนไว้ในโพสนึงแต่ตอนนั้นยังไม่ได้ทำคอลัมน์ #ตัวหนังสือมีเสียง ขอไม่เขียนซ้ำ อ่านได้ที่นี่ครับ https://www.facebook.com/share/p/18tFCFaRLn/ ท่อนที่ว่าจึงเขียนไว้ว่า "บ่มบ่ม... บ่มให้คิด บ่มบ่ม...บ่มให้เห็น บ่มบ่ม...บ่มให้เป็น บ่มบ่ม...บ่มให้ไป ไปเป็น ตัวของตัวเอง" ใช้ความซน สไตล์ rock&roll ผสมแจ๊สนิด ที่เขามักเล่นร้องโต้กับคอรัส นึกถึงยุคทีวีขาวดำ 5555
เนื้อร้องท่อนนี้ เป็นการบอกว่า โรงบ่มคืออะไรทำอะไร เพราะโรงบ่ม เราไม่ได้รักษา เราไม่ได้บังคับไดเอทว่าต้องใช้อะไร เราเปิดตาให้มอง เปิดหูให้ฟัง เปิดปากให้ถาม ถึงธรรมชาติในตัวเรา แล้วบ่มออกไปให้เบ่งบานในเส้นทางของแต่ละคนครับ
แล้วผมก็พยายามอีกครั้งที่จะสื่อถึงการยอมรับความต่าง ให้ติดหูเอาไว้ โดยเฉพาะคำที่ผมพูดบ่อยมากๆ "ชีวะ คือชีวิต" จนมาเป็นท่อน bridge นี้ครับ "อะไรที่ไม่คล้าย นั้นใช่ไม่ดี เพราะชีวะ ก็คือชีวี บ่มให้ดี จะมีความงาม ตามที่ควรเห็น ตามที่ควรเป็น"
เพลงนี้สามารถฟังตัวเต็มได้ทุกแพลทฟอร์มเพลงทั้ง youtube music, spotify, apple music, แผ่นเสียง tiktok ⌨️ แค่ค้นชื่อ "Heretong Teera Siri" ครับ
📺 youtube link นี้ https://youtu.be/BvIsTAsG00E?si=MzA-WfCTNQnWy6b1 📻 Spotify link นี้ https://open.spotify.com/album/08HydgrXmUAew6dgXIDNTf?si=7flQOqDAQbGe2bC0hx3T2A
ความลับคือ จริงๆแล้วเพลงนี้มี 3 version ถ้ากดใน spotify แล้วจะเห็นทั้งอัลบั้มครับ
📀เนื้อเพลง "บ่ม"📀 song by : HereTong Teera Siri ต่างทั้งความคิด ต่างทั้งความฝัน ต่างเผ่าต่างพันธุ์ จะต่างกันแค่ไหน
หนึ่งเมล็ด จากหลากผล แต่ละคน ก็ปนไป แล้วเพราะเหตุใด ใยต้องไปแค่ทางเดียว
บ่มบ่ม... บ่มให้คิด บ่มบ่ม...บ่มให้เห็น บ่มบ่ม...บ่มให้เป็น บ่มบ่ม...บ่มให้ไป ไปเป็น ตัวของตัวเอง
ต่างทั้งลองลิ้ม ต่างทั้งรับรู้ ต่างที่มุมดู ก็ถมไป หนึ่งชีวิต มีความหมาย ที่หลากหลาย ไม่คล้ายกัน แล้วเพราะเหตุใด ใยต้องเป็นเช่นทุกคน
บ่มบ่ม... บ่มให้คิด บ่มบ่ม...บ่มให้เห็น บ่มบ่ม...บ่มให้เป็น บ่มบ่ม...บ่มให้ไป ไปตาม ทางที่เลือกเดิน
เพราะชีวิต คือความหลากหลาย เพราะโลกนี้ ไม่เคยห่างหาย อะไรที่ไม่คล้าย นั้นใช่ไม่ดี เพราะชีวะ ก็คือชีวี บ่มให้ดี จะมีความงาม ตามที่ควรเห็น ตามที่ควรเป็น
บ่มบ่ม... บ่มให้คิด บ่มบ่ม...บ่มให้เห็น บ่มบ่ม...บ่มให้เป็น บ่มบ่ม...บ่มให้ไป ไปตาม ทางที่เลือกเดิน
เพราะชีวะ ก็คือชีวี บ่มให้ดี จะมีความงาม ตามที่ควรเห็น ตามที่ควรเป็น บ่มให้เธอชื่น บ่มให้เธอชม ชีวิตรื่นรมย์ ได้สมใจ บ่มให้ยั่งยืน
ตัวหนังสือมีเสียง #pirateketo
โรงบ่มสุขภาพ #siamstr
-
 @ 40b9c85f:5e61b451
2025-04-24 15:27:02
@ 40b9c85f:5e61b451
2025-04-24 15:27:02Introduction
Data Vending Machines (DVMs) have emerged as a crucial component of the Nostr ecosystem, offering specialized computational services to clients across the network. As defined in NIP-90, DVMs operate on an apparently simple principle: "data in, data out." They provide a marketplace for data processing where users request specific jobs (like text translation, content recommendation, or AI text generation)
While DVMs have gained significant traction, the current specification faces challenges that hinder widespread adoption and consistent implementation. This article explores some ideas on how we can apply the reflection pattern, a well established approach in RPC systems, to address these challenges and improve the DVM ecosystem's clarity, consistency, and usability.
The Current State of DVMs: Challenges and Limitations
The NIP-90 specification provides a broad framework for DVMs, but this flexibility has led to several issues:
1. Inconsistent Implementation
As noted by hzrd149 in "DVMs were a mistake" every DVM implementation tends to expect inputs in slightly different formats, even while ostensibly following the same specification. For example, a translation request DVM might expect an event ID in one particular format, while an LLM service could expect a "prompt" input that's not even specified in NIP-90.
2. Fragmented Specifications
The DVM specification reserves a range of event kinds (5000-6000), each meant for different types of computational jobs. While creating sub-specifications for each job type is being explored as a possible solution for clarity, in a decentralized and permissionless landscape like Nostr, relying solely on specification enforcement won't be effective for creating a healthy ecosystem. A more comprehensible approach is needed that works with, rather than against, the open nature of the protocol.
3. Ambiguous API Interfaces
There's no standardized way for clients to discover what parameters a specific DVM accepts, which are required versus optional, or what output format to expect. This creates uncertainty and forces developers to rely on documentation outside the protocol itself, if such documentation exists at all.
The Reflection Pattern: A Solution from RPC Systems
The reflection pattern in RPC systems offers a compelling solution to many of these challenges. At its core, reflection enables servers to provide metadata about their available services, methods, and data types at runtime, allowing clients to dynamically discover and interact with the server's API.
In established RPC frameworks like gRPC, reflection serves as a self-describing mechanism where services expose their interface definitions and requirements. In MCP reflection is used to expose the capabilities of the server, such as tools, resources, and prompts. Clients can learn about available capabilities without prior knowledge, and systems can adapt to changes without requiring rebuilds or redeployments. This standardized introspection creates a unified way to query service metadata, making tools like
grpcurlpossible without requiring precompiled stubs.How Reflection Could Transform the DVM Specification
By incorporating reflection principles into the DVM specification, we could create a more coherent and predictable ecosystem. DVMs already implement some sort of reflection through the use of 'nip90params', which allow clients to discover some parameters, constraints, and features of the DVMs, such as whether they accept encryption, nutzaps, etc. However, this approach could be expanded to provide more comprehensive self-description capabilities.
1. Defined Lifecycle Phases
Similar to the Model Context Protocol (MCP), DVMs could benefit from a clear lifecycle consisting of an initialization phase and an operation phase. During initialization, the client and DVM would negotiate capabilities and exchange metadata, with the DVM providing a JSON schema containing its input requirements. nip-89 (or other) announcements can be used to bootstrap the discovery and negotiation process by providing the input schema directly. Then, during the operation phase, the client would interact with the DVM according to the negotiated schema and parameters.
2. Schema-Based Interactions
Rather than relying on rigid specifications for each job type, DVMs could self-advertise their schemas. This would allow clients to understand which parameters are required versus optional, what type validation should occur for inputs, what output formats to expect, and what payment flows are supported. By internalizing the input schema of the DVMs they wish to consume, clients gain clarity on how to interact effectively.
3. Capability Negotiation
Capability negotiation would enable DVMs to advertise their supported features, such as encryption methods, payment options, or specialized functionalities. This would allow clients to adjust their interaction approach based on the specific capabilities of each DVM they encounter.
Implementation Approach
While building DVMCP, I realized that the RPC reflection pattern used there could be beneficial for constructing DVMs in general. Since DVMs already follow an RPC style for their operation, and reflection is a natural extension of this approach, it could significantly enhance and clarify the DVM specification.
A reflection enhanced DVM protocol could work as follows: 1. Discovery: Clients discover DVMs through existing NIP-89 application handlers, input schemas could also be advertised in nip-89 announcements, making the second step unnecessary. 2. Schema Request: Clients request the DVM's input schema for the specific job type they're interested in 3. Validation: Clients validate their request against the provided schema before submission 4. Operation: The job proceeds through the standard NIP-90 flow, but with clearer expectations on both sides
Parallels with Other Protocols
This approach has proven successful in other contexts. The Model Context Protocol (MCP) implements a similar lifecycle with capability negotiation during initialization, allowing any client to communicate with any server as long as they adhere to the base protocol. MCP and DVM protocols share fundamental similarities, both aim to expose and consume computational resources through a JSON-RPC-like interface, albeit with specific differences.
gRPC's reflection service similarly allows clients to discover service definitions at runtime, enabling generic tools to work with any gRPC service without prior knowledge. In the REST API world, OpenAPI/Swagger specifications document interfaces in a way that makes them discoverable and testable.
DVMs would benefit from adopting these patterns while maintaining the decentralized, permissionless nature of Nostr.
Conclusion
I am not attempting to rewrite the DVM specification; rather, explore some ideas that could help the ecosystem improve incrementally, reducing fragmentation and making the ecosystem more comprehensible. By allowing DVMs to self describe their interfaces, we could maintain the flexibility that makes Nostr powerful while providing the structure needed for interoperability.
For developers building DVM clients or libraries, this approach would simplify consumption by providing clear expectations about inputs and outputs. For DVM operators, it would establish a standard way to communicate their service's requirements without relying on external documentation.
I am currently developing DVMCP following these patterns. Of course, DVMs and MCP servers have different details; MCP includes capabilities such as tools, resources, and prompts on the server side, as well as 'roots' and 'sampling' on the client side, creating a bidirectional way to consume capabilities. In contrast, DVMs typically function similarly to MCP tools, where you call a DVM with an input and receive an output, with each job type representing a different categorization of the work performed.
Without further ado, I hope this article has provided some insight into the potential benefits of applying the reflection pattern to the DVM specification.
-
 @ 8cda1daa:e9e5bdd8
2025-04-24 10:20:13
@ 8cda1daa:e9e5bdd8
2025-04-24 10:20:13Bitcoin cracked the code for money. Now it's time to rebuild everything else.
What about identity, trust, and collaboration? What about the systems that define how we live, create, and connect?
Bitcoin gave us a blueprint to separate money from the state. But the state still owns most of your digital life. It's time for something more radical.
Welcome to the Atomic Economy - not just a technology stack, but a civil engineering project for the digital age. A complete re-architecture of society, from the individual outward.
The Problem: We Live in Digital Captivity
Let's be blunt: the modern internet is hostile to human freedom.
You don't own your identity. You don't control your data. You don't decide what you see.
Big Tech and state institutions dominate your digital life with one goal: control.
- Poisoned algorithms dictate your emotions and behavior.
- Censorship hides truth and silences dissent.
- Walled gardens lock you into systems you can't escape.
- Extractive platforms monetize your attention and creativity - without your consent.
This isn't innovation. It's digital colonization.
A Vision for Sovereign Society
The Atomic Economy proposes a new design for society - one where: - Individuals own their identity, data, and value. - Trust is contextual, not imposed. - Communities are voluntary, not manufactured by feeds. - Markets are free, not fenced. - Collaboration is peer-to-peer, not platform-mediated.
It's not a political revolution. It's a technological and social reset based on first principles: self-sovereignty, mutualism, and credible exit.
So, What Is the Atomic Economy?
The Atomic Economy is a decentralized digital society where people - not platforms - coordinate identity, trust, and value.
It's built on open protocols, real software, and the ethos of Bitcoin. It's not about abstraction - it's about architecture.
Core Principles: - Self-Sovereignty: Your keys. Your data. Your rules. - Mutual Consensus: Interactions are voluntary and trust-based. - Credible Exit: Leave any system, with your data and identity intact. - Programmable Trust: Trust is explicit, contextual, and revocable. - Circular Economies: Value flows directly between individuals - no middlemen.
The Tech Stack Behind the Vision
The Atomic Economy isn't just theory. It's a layered system with real tools:
1. Payments & Settlement
- Bitcoin & Lightning: The foundation - sound, censorship-resistant money.
- Paykit: Modular payments and settlement flows.
- Atomicity: A peer-to-peer mutual credit protocol for programmable trust and IOUs.
2. Discovery & Matching
- Pubky Core: Decentralized identity and discovery using PKARR and the DHT.
- Pubky Nexus: Indexing for a user-controlled internet.
- Semantic Social Graph: Discovery through social tagging - you are the algorithm.
3. Application Layer
- Bitkit: A self-custodial Bitcoin and Lightning wallet.
- Pubky App: Tag, publish, trade, and interact - on your terms.
- Blocktank: Liquidity services for Lightning and circular economies.
- Pubky Ring: Key-based access control and identity syncing.
These tools don't just integrate - they stack. You build trust, exchange value, and form communities with no centralized gatekeepers.
The Human Impact
This isn't about software. It's about freedom.
- Empowered Individuals: Control your own narrative, value, and destiny.
- Voluntary Communities: Build trust on shared values, not enforced norms.
- Economic Freedom: Trade without permission, borders, or middlemen.
- Creative Renaissance: Innovation and art flourish in open, censorship-resistant systems.
The Atomic Economy doesn't just fix the web. It frees the web.
Why Bitcoiners Should Care
If you believe in Bitcoin, you already believe in the Atomic Economy - you just haven't seen the full map yet.
- It extends Bitcoin's principles beyond money: into identity, trust, coordination.
- It defends freedom where Bitcoin leaves off: in content, community, and commerce.
- It offers a credible exit from every centralized system you still rely on.
- It's how we win - not just economically, but culturally and socially.
This isn't "web3." This isn't another layer of grift. It's the Bitcoin future - fully realized.
Join the Atomic Revolution
- If you're a builder: fork the code, remix the ideas, expand the protocols.
- If you're a user: adopt Bitkit, use Pubky, exit the digital plantation.
- If you're an advocate: share the vision. Help people imagine a free society again.
Bitcoin promised a revolution. The Atomic Economy delivers it.
Let's reclaim society, one key at a time.
Learn more and build with us at Synonym.to.
-
 @ a5ee4475:2ca75401
2025-05-04 15:45:12
@ a5ee4475:2ca75401
2025-05-04 15:45:12lists #descentralismo #compilation #english
*Some of these lists are still being updated, so the latest versions of them will only be visible in Amethyst.
nostr:naddr1qq245dz5tqe8w46swpphgmr4f3047s6629t45qg4waehxw309aex2mrp0yhxgctdw4eju6t09upzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqr4guxde6sl
nostr:nevent1qqsxdpwadkswdrc602m6qdhyq7n33lf3wpjtdjq2adkw4y3h38mjcrqpr9mhxue69uhkxmmzwfskvatdvyhxxmmd9aex2mrp0ypzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqqqqysn06gs
nostr:nevent1qqs0swpxdqfknups697205qg5mpw2e370g5vet07gkexe9n0k05h5qspz4mhxue69uhhyetvv9ujumn0wd68ytnzvuhsyg99aez8269zxu3zd4j8qya92fg7437ax745pqz22ys6v08zef65qypsgqqqqqqshr37wh
Markdown Uses for Some Clients
nostr:nevent1qqsv54qfgtme38r2tl9v6ghwfj09gdjukealstkzc77mwujr56tgfwsppemhxue69uhkummn9ekx7mp0qgsq37tg2603tu0cqdrxs30e2n5t8p87uenf4fvfepdcvr7nllje5zgrqsqqqqqpkdvta4
Other Links
nostr:nevent1qqsrm6ywny5r7ajakpppp0lt525n0s33x6tyn6pz0n8ws8k2tqpqracpzpmhxue69uhkummnw3ezumt0d5hsygp6e5ns0nv3dun430jky25y4pku6ylz68rz6zs7khv29q6rj5peespsgqqqqqqsmfwa78
-
 @ a5ee4475:2ca75401
2025-05-04 15:14:32
@ a5ee4475:2ca75401
2025-05-04 15:14:32lista #descentralismo #compilado #portugues
*Algumas destas listas ainda estão sendo trocadas e serão traduzidas para português, portanto as versões mais recentes delas só estarão visíveis no Amethyst.
Clients do Nostr e Outras Coisas
nostr:naddr1qq245dz5tqe8w46swpphgmr4f3047s6629t45qg4waehxw309aex2mrp0yhxgctdw4eju6t09upzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqr4guxde6sl
Modelos de IA e Ferramentas
nostr:nevent1qqsxdpwadkswdrc602m6qdhyq7n33lf3wpjtdjq2adkw4y3h38mjcrqpr9mhxue69uhkxmmzwfskvatdvyhxxmmd9aex2mrp0ypzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqqqqysn06gs
Comunidades Lusófonas de Bitcoin
nostr:nevent1qqsqnmtverj2fetqwhsv9n2ny8h9ujhyqqrk0fsn4a02w8sf4cqddzqpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtczyzj7u3r4dz3rwg3x6erszwj4y502clwn026qsp99zgdx8n3v5a2qzqcyqqqqqqgypv6z5
Profissionais Brasileiros no Nostr
nostr:nevent1qqsvqnlx7sqeczv5r7pmmd6zzca3l0ru4856n3j7lhjfv3atq40lfdcpr9mhxue69uhkxmmzwfskvatdvyhxxmmd9aex2mrp0ypzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqqqqylf6kr4
Comunidades em Português no Nostr
nostr:nevent1qqsy47d6z0qzshfqt5sgvtck8jmhdjnsfkyacsvnqe8m7euuvp4nm0gpzpmhxue69uhkummnw3ezumt0d5hsyg99aez8269zxu3zd4j8qya92fg7437ax745pqz22ys6v08zef65qypsgqqqqqqsw4vudx
Grupos em Português no Nostr
nostr:nevent1qqs98kldepjmlxngupsyth40n0h5lw7z5ut5w4scvh27alc0w86tevcpzpmhxue69uhkummnw3ezumt0d5hsygy7fff8g6l23gp5uqtuyqwkqvucx6mhe7r9h7v6wyzzj0v6lrztcspsgqqqqqqs3ndneh
Games Open Source
nostr:nevent1qqs0swpxdqfknups697205qg5mpw2e370g5vet07gkexe9n0k05h5qspz4mhxue69uhhyetvv9ujumn0wd68ytnzvuhsyg99aez8269zxu3zd4j8qya92fg7437ax745pqz22ys6v08zef65qypsgqqqqqqshr37wh
Formatação de Texto no Amethyst
nostr:nevent1qqs0vquevt0pe9h5a2dh8csufdksazp6czz3vjk3wfspp68uqdez00cprpmhxue69uhkummnw3ezuendwsh8w6t69e3xj730qgs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgrqsqqqqqpd658r3
Outros Links
nostr:nevent1qqsrm6ywny5r7ajakpppp0lt525n0s33x6tyn6pz0n8ws8k2tqpqracpzpmhxue69uhkummnw3ezumt0d5hsygp6e5ns0nv3dun430jky25y4pku6ylz68rz6zs7khv29q6rj5peespsgqqqqqqsmfwa78
-
 @ 6e64b83c:94102ee8
2025-04-23 20:23:34
@ 6e64b83c:94102ee8
2025-04-23 20:23:34How to Run Your Own Nostr Relay on Android with Cloudflare Domain
Prerequisites
- Install Citrine on your Android device:
- Visit https://github.com/greenart7c3/Citrine/releases
- Download the latest release using:
- zap.store
- Obtainium
- F-Droid
- Or download the APK directly
-
Note: You may need to enable "Install from Unknown Sources" in your Android settings
-
Domain Requirements:
- Purchase a domain if you don't have one
-
Transfer your domain to Cloudflare if it's not already there (for free SSL certificates and cloudflared support)
-
Tools to use:
- nak (the nostr army knife):
- Download from https://github.com/fiatjaf/nak/releases
- Installation steps:
-
For Linux/macOS: ```bash # Download the appropriate version for your system wget https://github.com/fiatjaf/nak/releases/latest/download/nak-linux-amd64 # for Linux # or wget https://github.com/fiatjaf/nak/releases/latest/download/nak-darwin-amd64 # for macOS
# Make it executable chmod +x nak-*
# Move to a directory in your PATH sudo mv nak-* /usr/local/bin/nak
- For Windows:batch # Download the Windows version curl -L -o nak.exe https://github.com/fiatjaf/nak/releases/latest/download/nak-windows-amd64.exe# Move to a directory in your PATH (e.g., C:\Windows) move nak.exe C:\Windows\nak.exe
- Verify installation:bash nak --version ```
Setting Up Citrine
- Open the Citrine app
- Start the server
- You'll see it running on
ws://127.0.0.1:4869(local network only) - Go to settings and paste your npub into "Accept events signed by" inbox and press the + button. This prevents others from publishing events to your personal relay.
Installing Required Tools
- Install Termux from Google Play Store
- Open Termux and run:
bash pkg update && pkg install wget wget https://github.com/cloudflare/cloudflared/releases/latest/download/cloudflared-linux-arm64.deb dpkg -i cloudflared-linux-arm64.debCloudflare Authentication
- Run the authentication command:
bash cloudflared tunnel login - Follow the instructions:
- Copy the provided URL to your browser
- Log in to your Cloudflare account
- If the URL expires, copy it again after logging in
Creating the Tunnel
- Create a new tunnel:
bash cloudflared tunnel create <TUNNEL_NAME> - Choose any name you prefer for your tunnel
-
Copy the tunnel ID after creating the tunnel
-
Create and configure the tunnel config:
bash touch ~/.cloudflared/config.yml nano ~/.cloudflared/config.yml -
Add this configuration (replace the placeholders with your values): ```yaml tunnel:
credentials-file: /data/data/com.termux/files/home/.cloudflared/ .json ingress: - hostname: nostr.yourdomain.com service: ws://localhost:4869
- service: http_status:404 ```
- Note: In nano editor:
CTRL+Oand Enter to saveCTRL+Xto exit
-
Note: Check the credentials file path in the logs
-
Validate your configuration:
bash cloudflared tunnel validate -
Start the tunnel:
bash cloudflared tunnel run my-relay
Preventing Android from Killing the Tunnel
Run these commands to maintain tunnel stability:
bash date && apt install termux-tools && termux-setup-storage && termux-wake-lock echo "nameserver 1.1.1.1" > $PREFIX/etc/resolv.confTip: You can open multiple Termux sessions by swiping from the left edge of the screen while keeping your tunnel process running.
Updating Your Outbox Model Relays
Once your relay is running and accessible via your domain, you'll want to update your relay list in the Nostr network. This ensures other clients know about your relay and can connect to it.
Decoding npub (Public Key)
Private keys (nsec) and public keys (npub) are encoded in bech32 format, which includes: - A prefix (like nsec1, npub1 etc.) - The encoded data - A checksum
This format makes keys: - Easy to distinguish - Hard to copy incorrectly
However, most tools require these keys in hexadecimal (hex) format.
To decode an npub string to its hex format:
bash nak decode nostr:npub1dejts0qlva8mqzjlrxqkc2tmvs2t7elszky5upxaf3jha9qs9m5q605uc4Change it with your own npub.
bash { "pubkey": "6e64b83c1f674fb00a5f19816c297b6414bf67f015894e04dd4c657e94102ee8" }Copy the pubkey value in quotes.
Create a kind 10002 event with your relay list:
- Include your new relay with write permissions
- Include other relays you want to read from and write to, omit 3rd parameter to make it both read and write
Example format:
json { "kind": 10002, "tags": [ ["r", "wss://your-relay-domain.com", "write"], ["r", "wss://eden.nostr.land/"], ["r", "wss://nos.lol/"], ["r", "wss://nostr.bitcoiner.social/"], ["r", "wss://nostr.mom/"], ["r", "wss://relay.primal.net/"], ["r", "wss://nostr.wine/", "read"], ["r", "wss://relay.damus.io/"], ["r", "wss://relay.nostr.band/"], ["r", "wss://relay.snort.social/"] ], "content": "" }Save it to a file called
event.jsonNote: Add or remove any relays you want. To check your existing 10002 relays: - Visit https://nostr.band/?q=by%3Anpub1dejts0qlva8mqzjlrxqkc2tmvs2t7elszky5upxaf3jha9qs9m5q605uc4+++kind%3A10002 - nostr.band is an indexing service, it probably has your relay list. - Replace
npub1xxxin the URL with your own npub - Click "VIEW JSON" from the menu to see the raw event - Or use thenaktool if you know the relaysbash nak req -k 10002 -a <your-pubkey> wss://relay1.com wss://relay2.comReplace `<your-pubkey>` with your public key in hex format (you can get it using `nak decode <your-npub>`)- Sign and publish the event:
- Use a Nostr client that supports kind 10002 events
- Or use the
nakcommand-line tool:bash nak event --sec ncryptsec1... wss://relay1.com wss://relay2.com $(cat event.json)
Important Security Notes: 1. Never share your nsec (private key) with anyone 2. Consider using NIP-49 encrypted keys for better security 3. Never paste your nsec or private key into the terminal. The command will be saved in your shell history, exposing your private key. To clear the command history: - For bash: use
history -c- For zsh: usefc -Wto write history to file, thenfc -pto read it back - Or manually edit your shell history file (e.g.,~/.zsh_historyor~/.bash_history) 4. if you're usingzsh, usefc -pto prevent the next command from being saved to history 5. Or temporarily disable history before running sensitive commands:bash unset HISTFILE nak key encrypt ... set HISTFILEHow to securely create NIP-49 encypted private key
```bash
Read your private key (input will be hidden)
read -s SECRET
Read your password (input will be hidden)
read -s PASSWORD
encrypt command
echo "$SECRET" | nak key encrypt "$PASSWORD"
copy and paste the ncryptsec1 text from the output
read -s ENCRYPTED nak key decrypt "$ENCRYPTED"
clear variables from memory
unset SECRET PASSWORD ENCRYPTED ```
On a Windows command line, to read from stdin and use the variables in
nakcommands, you can use a combination ofset /pto read input and then use those variables in your command. Here's an example:```bash @echo off set /p "SECRET=Enter your secret key: " set /p "PASSWORD=Enter your password: "
echo %SECRET%| nak key encrypt %PASSWORD%
:: Clear the sensitive variables set "SECRET=" set "PASSWORD=" ```
If your key starts with
ncryptsec1, thenaktool will securely prompt you for a password when using the--secparameter, unless the command is used with a pipe< >or|.bash nak event --sec ncryptsec1... wss://relay1.com wss://relay2.com $(cat event.json)- Verify the event was published:
- Check if your relay list is visible on other relays
-
Use the
naktool to fetch your kind 10002 events:bash nak req -k 10002 -a <your-pubkey> wss://relay1.com wss://relay2.com -
Testing your relay:
- Try connecting to your relay using different Nostr clients
- Verify you can both read from and write to your relay
- Check if events are being properly stored and retrieved
- Tip: Use multiple Nostr clients to test different aspects of your relay
Note: If anyone in the community has a more efficient method of doing things like updating outbox relays, please share your insights in the comments. Your expertise would be greatly appreciated!
-
 @ 84b0c46a:417782f5
2025-05-04 15:14:21
@ 84b0c46a:417782f5
2025-05-04 15:14:21https://long-form-editer.vercel.app/
β版のため予期せぬ動作が発生する可能性があります。記事を修正する際は事前にバックアップを取ることをおすすめします
機能
-
nostr:npub1sjcvg64knxkrt6ev52rywzu9uzqakgy8ehhk8yezxmpewsthst6sw3jqcw や、 nostr:nevent1qvzqqqqqqypzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qyxhwumn8ghj77tpvf6jumt9qys8wumn8ghj7un9d3shjtt2wqhxummnw3ezuamfwfjkgmn9wshx5uqpz9mhxue69uhkuenjv4kxz7fwv9c8qqpq486d6yazu7ydx06lj5gr4aqgeq6rkcreyykqnqey8z5fm6qsj8fqfetznk のようにnostr:要素を挿入できる
-
:monoice:のようにカスタム絵文字を挿入できる(メニューの😃アイコンから←アイコン変えるかも)
:monopaca_kao:
:kubipaca_karada:
- 新規記事作成と、既存記事の修正ができる
やること
- [x] nostr:を投稿するときにtagにいれる
- [ ] レイアウトを整える
- [x] 画像をアップロードできるようにする
 できる
できる - [ ] 投稿しましたログとかをトースト的なやつでだすようにする
- [ ] あとなんか
-
-
 @ 6e0ea5d6:0327f353
2025-05-04 14:53:42
@ 6e0ea5d6:0327f353
2025-05-04 14:53:42Amico mio, ascolta bene!
Without hesitation, the woman you attract with lies is not truly yours. Davvero, she is the temporary property of the illusion you’ve built to seduce her. And every illusion, sooner or later, crumbles.
Weak men sell inflated versions of themselves. They talk about what they don’t have, promise what they can’t sustain, adorn their empty selves with words that are nothing more than a coat of paint. And they do this thinking that, later, they’ll be able to "show who they really are." Fatal mistake, cazzo!
The truth, amico mio, is not something that appears at the end. It is what holds up the whole beginning.
The woman who approaches a lie may smile at first — but she is smiling at the theater, not at the actor. When the curtains fall, what she will see is not a man. It will be a character tired of performing, begging for love from a self-serving audience in the front row.
That’s why I always point out that lying to win a woman’s heart is the same as sabotaging your own nature. The woman who comes through an invented version of you will be the first to leave when the veil of lies tears apart. Not out of cruelty, but out of consistency with her own interest. Fine... She didn’t leave you, but rather, that version of yourself never truly existed to be left behind.
A worthy man presents himself without deceptive adornments. And those who stay, stay because they know exactly who they are choosing as a man. That’s what differentiates forged seduction from the convenience of love built on honor, loyalty, and respect.
Ah, amico mio, I remember well. It was lunch on an autumn day in Catania. Mediterranean heat, and the Nero D'Avola wine from midday clinging to the lips like dried blood. Sitting in the shade of a lemon tree planted right by my grandfather's vineyard entrance, my uncle — the oldest of my father’s brothers — spoke little, but when he called us to sit by his side, all the nephews would quiet down to listen. And in my youth, he told me something that has never left my mind.
“In Sicily, the woman who endures the silence of a man about his business is more loyal than the one who is enchanted by speeches about what he does or how much he earns. Perchè, figlio mio, the first one has seen the truth. The second one, only a false shine.”
Thank you for reading, my friend!
If this message resonated with you, consider leaving your "🥃" as a token of appreciation.
A toast to our family!
-
 @ 9bde4214:06ca052b
2025-04-22 18:13:37
@ 9bde4214:06ca052b
2025-04-22 18:13:37"It's gonna be permissionless or hell."
Gigi and gzuuus are vibing towards dystopia.
Books & articles mentioned:
- AI 2027
- DVMs were a mistake
- Careless People by Sarah Wynn-Williams
- Takedown by Laila michelwait
- The Ultimate Resource by Julian L. Simon
- Harry Potter by J.K. Rowling
- Momo by Michael Ende
In this dialogue:
- Pablo's Roo Setup
- Tech Hype Cycles
- AI 2027
- Prompt injection and other attacks
- Goose and DVMCP
- Cursor vs Roo Code
- Staying in control thanks to Amber and signing delegation
- Is YOLO mode here to stay?
- What agents to trust?
- What MCP tools to trust?
- What code snippets to trust?
- Everyone will run into the issues of trust and micropayments
- Nostr solves Web of Trust & micropayments natively
- Minimalistic & open usually wins
- DVMCP exists thanks to Totem
- Relays as Tamagochis
- Agents aren't nostr experts, at least not right now
- Fix a mistake once & it's fixed forever
- Giving long-term memory to LLMs
- RAG Databases signed by domain experts
- Human-agent hybrids & Chess
- Nostr beating heart
- Pluggable context & experts
- "You never need an API key for anything"
- Sats and social signaling
- Difficulty-adjusted PoW as a rare-limiting mechanism
- Certificate authorities and centralization
- No solutions to policing speech!
- OAuth and how it centralized
- Login with nostr
- Closed vs open-source models
- Tiny models vs large models
- The minions protocol (Stanford paper)
- Generalist models vs specialized models
- Local compute & encrypted queries
- Blinded compute
- "In the eyes of the state, agents aren't people"
- Agents need identity and money; nostr provides both
- "It's gonna be permissionless or hell"
- We already have marketplaces for MCP stuff, code snippets, and other things
- Most great stuff came from marketplaces (browsers, games, etc)
- Zapstore shows that this is already working
- At scale, central control never works. There's plenty scams and viruses in the app stores.
- Using nostr to archive your user-generated content
- HAVEN, blossom, novia
- The switcharoo from advertisements to training data
- What is Truth?
- What is Real?
- "We're vibing into dystopia"
- Who should be the arbiter of Truth?
- First Amendment & why the Logos is sacred
- Silicon Valley AI bros arrogantly dismiss wisdom and philosophy
- Suicide rates & the meaning crisis
- Are LLMs symbiotic or parasitic?
- The Amish got it right
- Are we gonna make it?
- Careless People by Sarah Wynn-Williams
- Takedown by Laila michelwait
- Harry Potter dementors & Momo's time thieves
- Facebook & Google as non-human (superhuman) agents
- Zapping as a conscious action
- Privacy and the internet
- Plausible deniability thanks to generative models
- Google glasses, glassholes, and Meta's Ray Ben's
- People crave realness
- Bitcoin is the realest money we ever had
- Nostr allows for real and honest expression
- How do we find out what's real?
- Constraints, policing, and chilling effects
- Jesus' plans for DVMCP
- Hzrd's article on how DVMs are broken (DVMs were a mistake)
- Don't believe the hype
- DVMs pre-date MCP tools
- Data Vending Machines were supposed to be stupid: put coin in, get stuff out.
- Self-healing vibe-coding
- IP addresses as scarce assets
- Atomic swaps and the ASS protocol
- More marketplaces, less silos
- The intensity of #SovEng and the last 6 weeks
- If you can vibe-code everything, why build anything?
- Time, the ultimate resource
- What are the LLMs allowed to think?
- Natural language interfaces are inherently dialogical
- Sovereign Engineering is dialogical too
-
 @ fd78c37f:a0ec0833
2025-04-21 04:40:30
@ fd78c37f:a0ec0833
2025-04-21 04:40:30Bitcoin is redefining finance, and in Asia—Thailand, Vietnam, Indonesia, and beyond—developers, entrepreneurs, and communities are fueling this revolution. YakiHonne, a decentralized social payments app built on Nostr, sat down with Gio (nostr:npub1yrnuj56rnen08zp2h9h7p74ghgjx6ma39spmpj6w9hzxywutevsst7k5cx), a core member of Thailand’s Sats ‘N’ Facts community, to explore their mission of fostering open-source Bitcoin development. In this interview, Gio shares the origins of Sats ‘N’ Facts, the challenges of hosting Bitcoin-focused events in Asia, and how these efforts are shaping adoption across the region.
YakiHonne: Can you tell us about yourself and how Sats ‘N’ Facts came to life? What sparked your Bitcoin journey?
Gio: I’m originally from Europe but have called Thailand home for six years. My Bitcoin story began while working at a commercial bank, where I saw the fiat system’s flaws firsthand—things like the Cantillon Effect, where money printing favors the connected few, felt deeply unfair. That discomfort led me to Andreas Antonopoulos’ videos, which opened my eyes to Bitcoin’s potential. After moving to Bangkok, I joined the open-source scene at BOB Space, collaborating with folks on tech projects.
Sats ‘N’ Facts grew out of that spirit. We wanted to create a Bitcoin-focused community to support developers and builders in Asia. Our recent conference in Chiang Mai brought together over 70 enthusiasts from Thailand, Vietnam, Laos, and beyond, sparking collaborations like a new Lightning Network tool. It was a milestone in connecting the region’s Bitcoin ecosystem.
YakiHonne: What inspired the Sats ‘N’ Facts conference, and how did you attract attendees?
Gio: The event was born from a desire to create a high-signal, low-noise space for Freedom Tech in Asia. While the U.S. and Europe host major Bitcoin events, Asia’s scene is still emerging under commercial stunts. We aimed to bridge that gap, uniting developers, educators, and enthusiasts to discuss real innovations—no altcoins, no corporate agendas. Our focus was on open-source projects like Bitcoin Core, Ark, Cashu, fostering conversations that could lead to tangible contributions.
Attracting attendees wasn’t easy. We leveraged local networks, reaching out to Bitcoin communities in neighboring countries via Nostr and Telegram. Posts on X helped spread the word, and we saw developers from Laos join for the first time, which was thrilling. Sponsors like Fulgur Ventures, Utreexo, and the Bitcoin Development Kit Foundation played a huge role, covering costs so we could keep the event free and accessible.
YakiHonne: What challenges did you face organizing the conference in Asia?
Gio: It was a steep learning curve. Funding was the biggest hurdle—early on, we struggled to cover venue and travel costs. Thankfully, our sponsors stepped in, letting me focus on logistics, which were no small feat either. As a first-time organizer, I underestimated the chaos of a tight timeline. Day one felt like herding cats without a fixed agenda, but the energy was electric—developers debugging code together, newcomers asking big questions.
Another challenge was cultural. Bitcoin’s still niche in Asia, so convincing locals to attend took persistence; there was no local presence for some reason. Despite the hiccups, we pulled it off, hosting 60+ attendees and sparking ideas for new projects, like a Cashu wallet integration. I’d tweak the planning next time, but the raw passion made it unforgettable.
YakiHonne: How does YakiHonne’s vision of decentralized social payments align with Sats ‘N’ Facts’ goals? Could tools like ours support your community?
Gio: That’s a great question. YakiHonne’s approach—merging Nostr’s censorship-resistant communication with Lightning payments—fits perfectly with our mission to empower users through open tech. At Sats ‘N’ Facts, we’re all about tools that give people control, whether it’s code or money. An app like YakiHonne could streamline community funding, letting developers tip each other for contributions or crowdfund projects directly. Imagine a hackathon where winners get sats instantly via YakiHonne—it’d be a game-changer. I’d love to see you guys at our next event to demo it!
YakiHonne: What advice would you give to someone starting a Bitcoin-focused community or event?
Gio: First, keep it Bitcoin-only. Stay true to the principles—cut out distractions like altcoins or hype-driven schemes. Start small: host regular meetups, maybe five people at a café, and build trust over time. Consistency and authenticity beat flashiness in the medium and long term.
Second, involve technical folks. Developers bring credibility and clarity, explaining Bitcoin’s nuts and bolts in ways newcomers get. I admire how Andreas Antonopoulos bridges that gap—technical yet accessible. You need that foundation to grow a real community.
Finally, lean on existing networks. If you know someone running a Bitcoin meetup in another city, collaborate. Share ideas, speakers, or even livestreams. Nostr’s great for this—our Laos attendees found us through a single post. Relationships are everything.
YakiHonne: Does Sats ‘N’ Facts focus more on Bitcoin’s technical side, non-technical side, or both?
Gio: We blend both. Our event had workshops for coders alongside talks for beginners on why Bitcoin matters. Open-source is our heartbeat, though. If you’re starting out, dive into projects like Bitcoin Core or Lightning. Review a pull request, test a Cashu wallet, or join a hackathon. One developer at our event built a Lightning micropayment tool that’s now live on GitHub.
There’s no shortage of ways to contribute. Community calls, forums, residency programs, and platforms like Geyser Fund are goldmines. YakiHonne could amplify this—imagine tipping developers for bug fixes via your app. It’s about iterating until you create something real.
YakiHonne: Your work is inspiring, Gio. Sats ‘N’ Facts is uniting Asia’s Bitcoin communities in a powerful way. What’s next for you?
Gio: Thanks for the kind words! We’re just getting started. The Chiang Mai event showed what’s possible—connecting developers across borders, reviewing and launching code and testing upcoming technologies. Next, we’re planning smaller hackathons and other events to keep the momentum going, maybe in Vietnam, Indonesia or Korea. I’d love to integrate tools like YakiHonne to fund these efforts directly through Nostr payments. Long-term, we want Sats ‘N’ Facts to be a hub for Asia’s Bitcoin builders, proving open-source can thrive here.

YakiHonne: Thank you, Gio, for sharing Sats ‘N’ Facts incredible journey. Your work is lighting a path for Bitcoin in Asia, and we’re honored to tell this story.
To our readers: Bitcoin’s future depends on communities like Sats ‘N’ Facts—and you can join the revolution. Download YakiHonne on Nostr to connect with builders, send Lightning payments, and explore the decentralized world. Follow Sats ‘N’ Facts for their next hackathon, and let’s build freedom tech together!
-
 @ ed5774ac:45611c5c
2025-04-19 20:29:31
@ ed5774ac:45611c5c
2025-04-19 20:29:31April 20, 2020: The day I saw my so-called friends expose themselves as gutless, brain-dead sheep.
On that day, I shared a video exposing the damning history of the Bill & Melinda Gates Foundation's vaccine campaigns in Africa and the developing world. As Gates was on every TV screen, shilling COVID jabs that didn’t even exist, I called out his blatant financial conflict of interest and pointed out the obvious in my facebook post: "Finally someone is able to explain why Bill Gates runs from TV to TV to promote vaccination. Not surprisingly, it's all about money again…" - referencing his substantial investments in vaccine technology, including BioNTech's mRNA platform that would later produce the COVID vaccines and generate massive profits for his so-called philanthropic foundation.
The conflict of interest was undeniable. I genuinely believed anyone capable of basic critical thinking would at least pause to consider these glaring financial motives. But what followed was a masterclass in human stupidity.
My facebook post from 20 April 2020:

Not only was I branded a 'conspiracy theorist' for daring to question the billionaire who stood to make a fortune off the very vaccines he was shilling, but the brain-dead, logic-free bullshit vomited by the people around me was beyond pathetic. These barely literate morons couldn’t spell "Pfizer" without auto-correct, yet they mindlessly swallowed and repeated every lie the media and government force-fed them, branding anything that cracked their fragile reality as "conspiracy theory." Big Pharma’s rap sheet—fraud, deadly cover-ups, billions in fines—could fill libraries, yet these obedient sheep didn’t bother to open a single book or read a single study before screaming their ignorance, desperate to virtue-signal their obedience. Then, like spineless lab rats, they lined up for an experimental jab rushed to the market in months, too dumb to care that proper vaccine development takes a decade.
The pathetic part is that these idiots spend hours obsessing over reviews for their useless purchases like shoes or socks, but won’t spare 60 seconds to research the experimental cocktail being injected into their veins—or even glance at the FDA’s own damning safety reports. Those same obedient sheep would read every Yelp review for a fucking coffee shop but won't spend five minutes looking up Pfizer's criminal fraud settlements. They would demand absolute obedience to ‘The Science™’—while being unable to define mRNA, explain lipid nanoparticles, or justify why trials were still running as they queued up like cattle for their jab. If they had two brain cells to rub together or spent 30 minutes actually researching, they'd know, but no—they'd rather suck down the narrative like good little slaves, too dumb to question, too weak to think.
Worst of all, they became the system’s attack dogs—not just swallowing the poison, but forcing it down others’ throats. This wasn’t ignorance. It was betrayal. They mutated into medical brownshirts, destroying lives to virtue-signal their obedience—even as their own children’s hearts swelled with inflammation.
One conversation still haunts me to this day—a masterclass in wealth-worship delusion. A close friend, as a response to my facebook post, insisted that Gates’ assumed reading list magically awards him vaccine expertise, while dismissing his billion-dollar investments in the same products as ‘no conflict of interest.’ Worse, he argued that Gates’s $5–10 billion pandemic windfall was ‘deserved.’
This exchange crystallizes civilization’s intellectual surrender: reason discarded with religious fervor, replaced by blind faith in corporate propaganda.
The comment of a friend on my facebook post that still haunts me to this day:

Walking Away from the Herd
After a period of anger and disillusionment, I made a decision: I would no longer waste energy arguing with people who refused to think for themselves. If my circle couldn’t even ask basic questions—like why an untested medical intervention was being pushed with unprecedented urgency—then I needed a new community.
Fortunately, I already knew where to look. For three years, I had been involved in Bitcoin, a space where skepticism wasn’t just tolerated—it was demanded. Here, I’d met some of the most principled and independent thinkers I’d ever encountered. These were people who understood the corrupting influence of centralized power—whether in money, media, or politics—and who valued sovereignty, skepticism, and integrity. Instead of blind trust, bitcoiners practiced relentless verification. And instead of empty rhetoric, they lived by a simple creed: Don’t trust. Verify.
It wasn’t just a philosophy. It was a lifeline. So I chose my side and I walked away from the herd.
Finding My Tribe
Over the next four years, I immersed myself in Bitcoin conferences, meetups, and spaces where ideas were tested, not parroted. Here, I encountered extraordinary people: not only did they share my skepticism toward broken systems, but they challenged me to sharpen it.
No longer adrift in a sea of mindless conformity, I’d found a crew of thinkers who cut through the noise. They saw clearly what most ignored—that at the core of society’s collapse lay broken money, the silent tax on time, freedom, and truth itself. But unlike the complainers I’d left behind, these people built. They coded. They wrote. They risked careers and reputations to expose the rot. Some faced censorship; others, mockery. All understood the stakes.
These weren’t keyboard philosophers. They were modern-day Cassandras, warning of inflation’s theft, the Fed’s lies, and the coming dollar collapse—not for clout, but because they refused to kneel to a dying regime. And in their defiance, I found something rare: a tribe that didn’t just believe in a freer future. They were engineering it.
April 20, 2024: No more herd. No more lies. Only proof-of-work.
On April 20, 2024, exactly four years after my last Facebook post, the one that severed my ties to the herd for good—I stood in front of Warsaw’s iconic Palace of Culture and Science, surrounded by 400 bitcoiners who felt like family. We were there to celebrate Bitcoin’s fourth halving, but it was more than a protocol milestone. It was a reunion of sovereign individuals. Some faces I’d known since the early days; others, I’d met only hours before. We bonded instantly—heated debates, roaring laughter, zero filters on truths or on so called conspiracy theories.
As the countdown to the halving began, it hit me: This was the antithesis of the hollow world I’d left behind. No performative outrage, no coerced consensus—just a room of unyielding minds who’d traded the illusion of safety for the grit of truth. Four years prior, I’d been alone in my resistance. Now, I raised my glass among my people - those who had seen the system's lies and chosen freedom instead. Each had their own story of awakening, their own battles fought, but here we shared the same hard-won truth.
The energy wasn’t just electric. It was alive—the kind that emerges when free people build rather than beg. For the first time, I didn’t just belong. I was home. And in that moment, the halving’s ticking clock mirrored my own journey: cyclical, predictable in its scarcity, revolutionary in its consequences. Four years had burned away the old world. What remained was stronger.

No Regrets
Leaving the herd wasn’t a choice—it was evolution. My soul shouted: "I’d rather stand alone than kneel with the masses!". The Bitcoin community became more than family; they’re living proof that the world still produces warriors, not sheep. Here, among those who forge truth, I found something extinct elsewhere: hope that burns brighter with every halving, every block, every defiant mind that joins the fight.
Change doesn’t come from the crowd. It starts when one person stops applauding.
Today, I stand exactly where I always wanted to be—shoulder-to-shoulder with my true family: the rebels, the builders, the ungovernable. Together, we’re building the decentralized future.
-
 @ 30b99916:3cc6e3fe
2025-04-19 19:55:31
@ 30b99916:3cc6e3fe
2025-04-19 19:55:31btcpayserver #lightning #lnd #powershell #coinos
BTCpayAPI now supports CoinOS.io REST Api

Adding Coinos.io REST Api end points support to BTCpayAPI. Here is what is implemented, tested and doumented so far.
Current REST APIs supported are now:
LND API https://lightning.engineering/api-docs/api/lnd/ BTCPay Greenfield API (v1) https://docs.btcpayserver.org/API/Greenfield/v1/ Hashicorp Vault API https://developer.hashicorp.com/vault/api-docs/secret/kv/kv-v1 Coinos.io API https://coinos.io/docs
Although this is PowerShell code, it is exclusively being developed and tested on Linux only.
Code is available at https://btcpayserver.sytes.net
-
 @ dab6c606:51f507b6
2025-04-18 14:59:25
@ dab6c606:51f507b6
2025-04-18 14:59:25Core idea: Use geotagged anonymized Nostr events with Cashu-based points to snitch on cop locations for a more relaxed driving and walking
We all know navigation apps. There's one of them that allows you to report on locations of cops. It's Waze and it's owned by Google. There are perfectly fine navigation apps like Organic Maps, that unfortunately lack the cop-snitching features. In some countries, it is illegal to report cop locations, so it would probably not be a good idea to use your npub to report them. But getting a points Cashu token as a reward and exchanging them from time to time would solve this. You can of course report construction, traffic jams, ...
Proposed solution: Add Nostr client (Copstr) to Organic Maps. Have a button in bottom right allowing you to report traffic situations. Geotagged events are published on Nostr relays, users sending cashu tokens as thank you if the report is valid. Notes have smart expiration times.
Phase 2: Automation: Integration with dashcams and comma.ai allow for automated AI recognition of traffic events such as traffic jams and cops, with automatic touchless reporting.
Result: Drive with most essential information and with full privacy. Collect points to be cool and stay cool.
-
 @ 005bc4de:ef11e1a2
2025-05-04 12:01:42
@ 005bc4de:ef11e1a2
2025-05-04 12:01:42OSU commencement speech revisited 1 year later
One year ago, May 5, 2024, the commencement speaker at Ohio State University was Chris Pan. He got booed for mentioning bitcoin. There were some other things involved, but the bitcoin part is what could my ears.
Here's an article about the speech and a video clip with the bitcoin mention. The quote that I feel is especially pertinent is this, '“The mechanics of investing are actually easy, but it comes down to mindset,” Pan said. “The most common barriers are fear, laziness and closed-mindedness.”'
Last year, I wrote this and had it sent as a reminder to myself (I received the reminder yesterday after totally forgetting about this):
Ohio State commencement speaker mentions bitcoin and got booed.
I wondered what would've happened if they'd taken his advice to heart and bought bitcoin that day. Linked article: https://www.businessinsider.com/osu-commencement-speaker-ayahuasca-praises-bitcoin-booed-viral-2024-5
Nat Brunell interviewed him on her Coin Stories podcast shortly after his speech: https://www.youtube.com/watch?v=LRqKxKqlbcI
BTC on 5/5/2024 day of speech: about $64,047 (chart below)
If any of those now wise old 23 year olds remember the advice they were given, bitcoin is currently at $95,476. If any took Pan's advice, they achieved a 49% gain in one year. Those who did not take Pan's advice, lost about 2.7% of their buying power due to inflation.
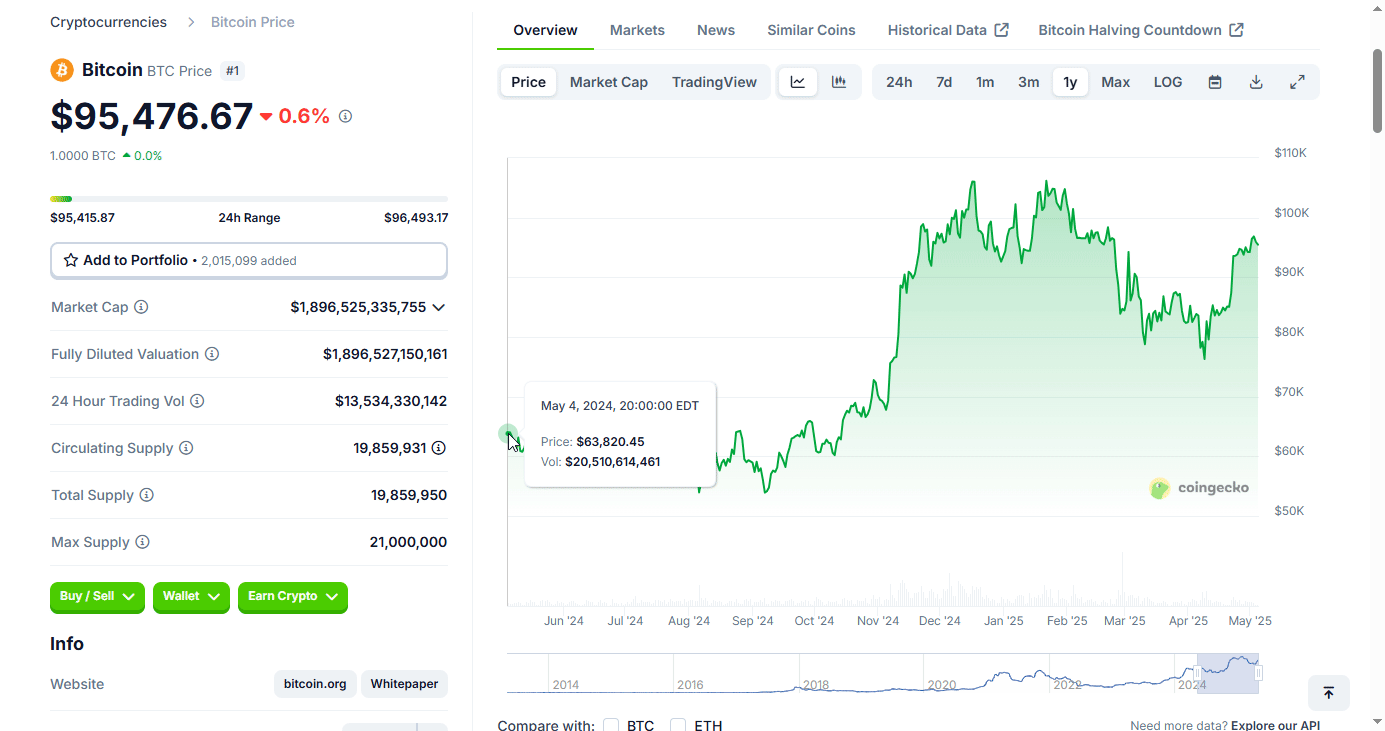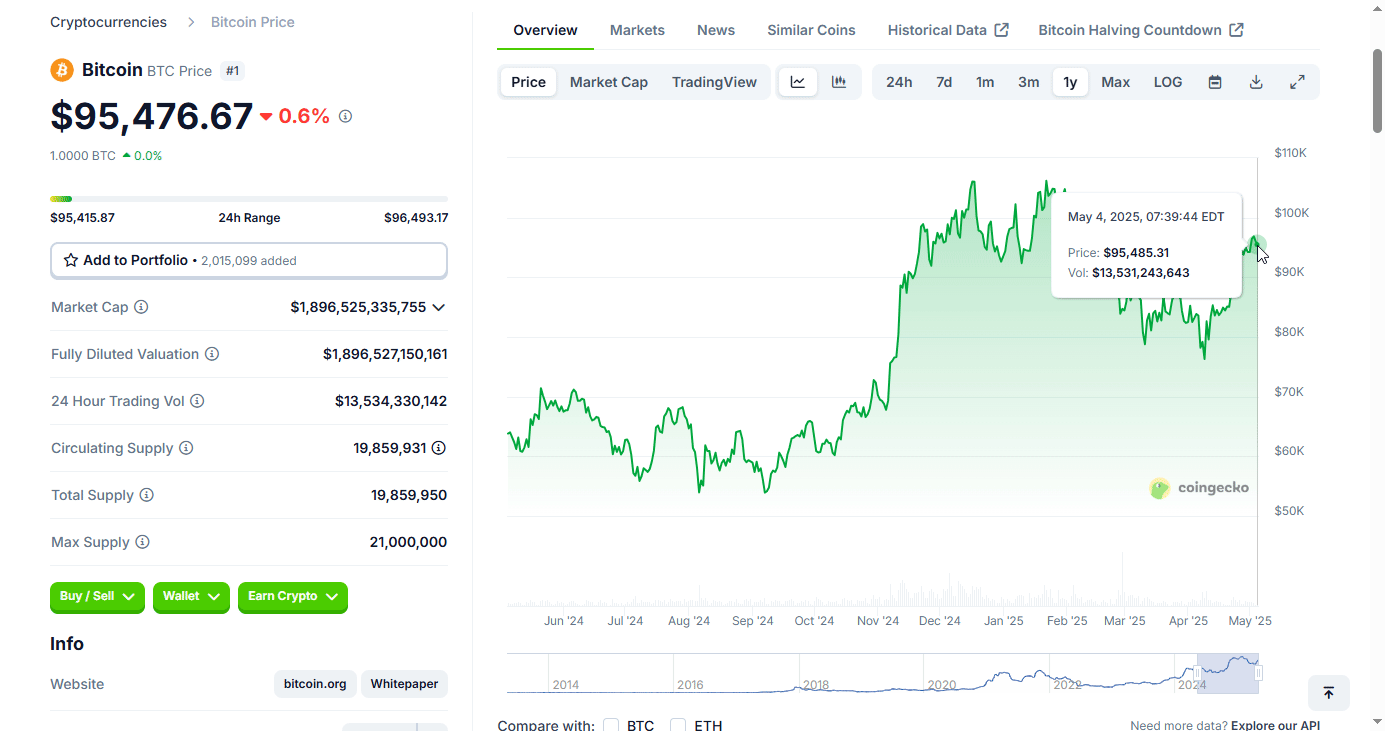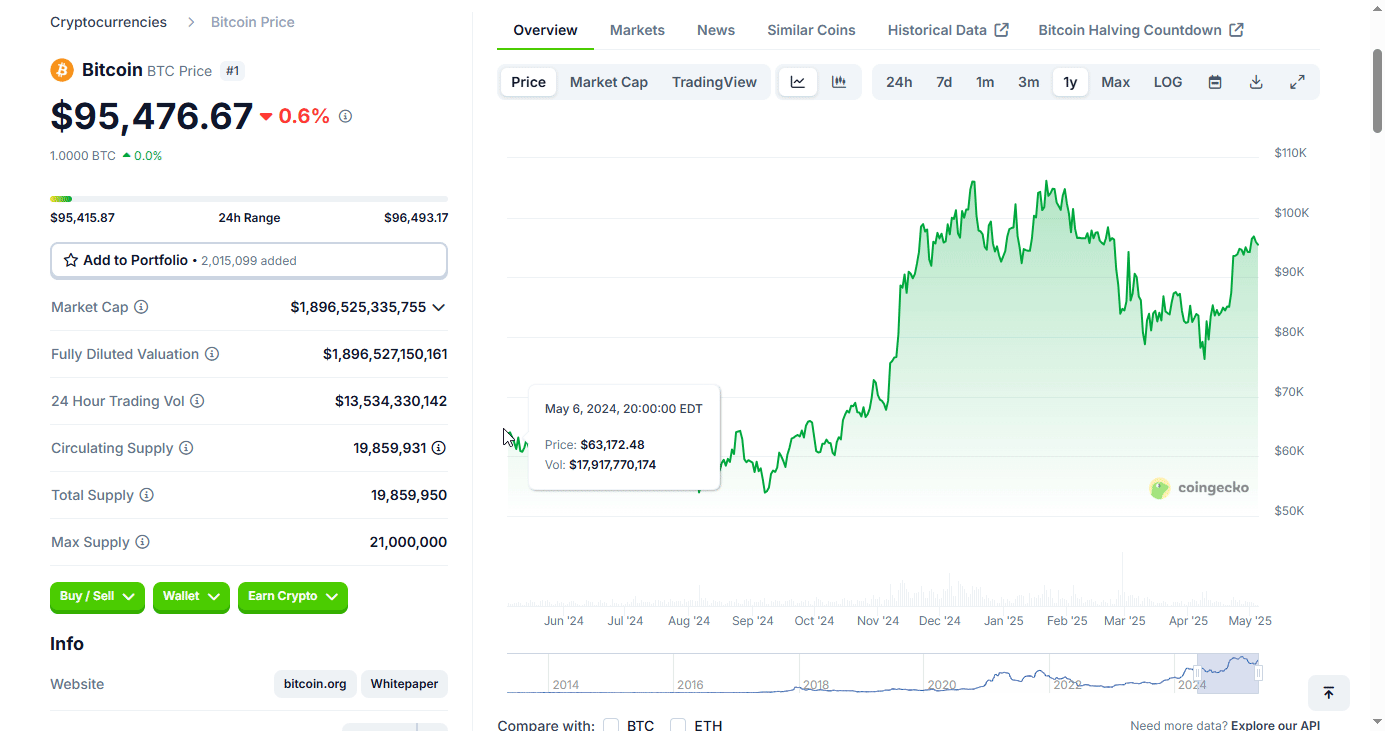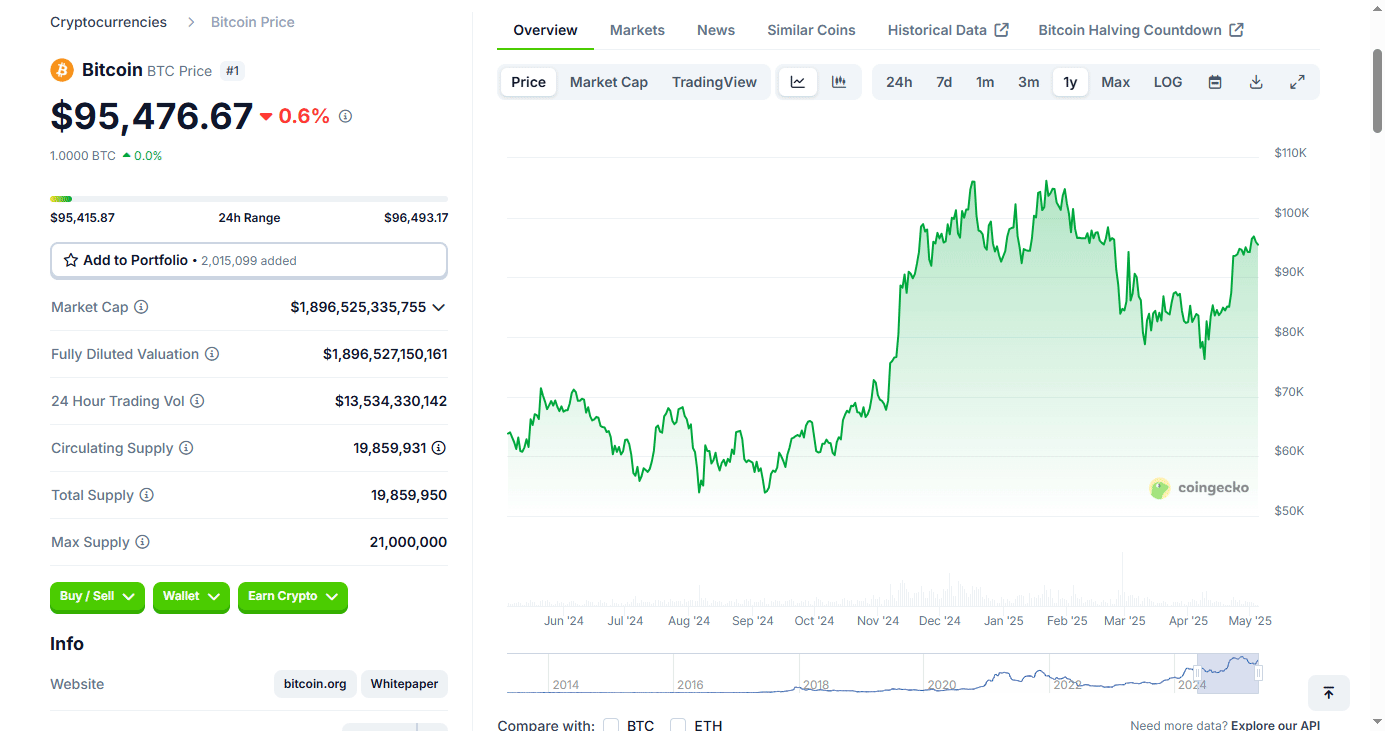
For bitcoiners, think about how far we've come. May of 2024 was still the waning days of the "War on Crypto," bitcoin was boiling the oceans, if you held, used, or liked bitcoin you were evil. Those were dark days and days I'm glad are behind us.
Here is the full commencement speech. The bitcoin part is around the 5 or 6 minute mark: https://m.youtube.com/watch?v=lcH-iL_FdYo
-
 @ 84b0c46a:417782f5
2025-05-04 10:00:28
@ 84b0c46a:417782f5
2025-05-04 10:00:28₍ ・ᴗ・ ₎ ₍ ・ᴗ・ ₎₍ ・ᴗ・ ₎
-
 @ c4b5369a:b812dbd6
2025-04-15 07:26:16
@ c4b5369a:b812dbd6
2025-04-15 07:26:16Offline transactions with Cashu
Over the past few weeks, I've been busy implementing offline capabilities into nutstash. I think this is one of the key value propositions of ecash, beinga a bearer instrument that can be used without internet access.
 It does however come with limitations, which can lead to a bit of confusion. I hope this article will clear some of these questions up for you!
It does however come with limitations, which can lead to a bit of confusion. I hope this article will clear some of these questions up for you!What is ecash/Cashu?
Ecash is the first cryptocurrency ever invented. It was created by David Chaum in 1983. It uses a blind signature scheme, which allows users to prove ownership of a token without revealing a link to its origin. These tokens are what we call ecash. They are bearer instruments, meaning that anyone who possesses a copy of them, is considered the owner.
Cashu is an implementation of ecash, built to tightly interact with Bitcoin, more specifically the Bitcoin lightning network. In the Cashu ecosystem,
Mintsare the gateway to the lightning network. They provide the infrastructure to access the lightning network, pay invoices and receive payments. Instead of relying on a traditional ledger scheme like other custodians do, the mint issues ecash tokens, to represent the value held by the users.How do normal Cashu transactions work?
A Cashu transaction happens when the sender gives a copy of his ecash token to the receiver. This can happen by any means imaginable. You could send the token through email, messenger, or even by pidgeon. One of the common ways to transfer ecash is via QR code.
The transaction is however not finalized just yet! In order to make sure the sender cannot double-spend their copy of the token, the receiver must do what we call a
swap. A swap is essentially exchanging an ecash token for a new one at the mint, invalidating the old token in the process. This ensures that the sender can no longer use the same token to spend elsewhere, and the value has been transferred to the receiver.
What about offline transactions?
Sending offline
Sending offline is very simple. The ecash tokens are stored on your device. Thus, no internet connection is required to access them. You can litteraly just take them, and give them to someone. The most convenient way is usually through a local transmission protocol, like NFC, QR code, Bluetooth, etc.
The one thing to consider when sending offline is that ecash tokens come in form of "coins" or "notes". The technical term we use in Cashu is
Proof. It "proofs" to the mint that you own a certain amount of value. Since these proofs have a fixed value attached to them, much like UTXOs in Bitcoin do, you would need proofs with a value that matches what you want to send. You can mix and match multiple proofs together to create a token that matches the amount you want to send. But, if you don't have proofs that match the amount, you would need to go online and swap for the needed proofs at the mint.Another limitation is, that you cannot create custom proofs offline. For example, if you would want to lock the ecash to a certain pubkey, or add a timelock to the proof, you would need to go online and create a new custom proof at the mint.
Receiving offline
You might think: well, if I trust the sender, I don't need to be swapping the token right away!
You're absolutely correct. If you trust the sender, you can simply accept their ecash token without needing to swap it immediately.
This is already really useful, since it gives you a way to receive a payment from a friend or close aquaintance without having to worry about connectivity. It's almost just like physical cash!
It does however not work if the sender is untrusted. We have to use a different scheme to be able to receive payments from someone we don't trust.
Receiving offline from an untrusted sender
To be able to receive payments from an untrusted sender, we need the sender to create a custom proof for us. As we've seen before, this requires the sender to go online.
The sender needs to create a token that has the following properties, so that the receciver can verify it offline:
- It must be locked to ONLY the receiver's public key
- It must include an
offline signature proof(DLEQ proof) - If it contains a timelock & refund clause, it must be set to a time in the future that is acceptable for the receiver
- It cannot contain duplicate proofs (double-spend)
- It cannot contain proofs that the receiver has already received before (double-spend)

If all of these conditions are met, then the receiver can verify the proof offline and accept the payment. This allows us to receive payments from anyone, even if we don't trust them.
At first glance, this scheme seems kinda useless. It requires the sender to go online, which defeats the purpose of having an offline payment system.
I beleive there are a couple of ways this scheme might be useful nonetheless:
-
Offline vending machines: Imagine you have an offline vending machine that accepts payments from anyone. The vending machine could use this scheme to verify payments without needing to go online itself. We can assume that the sender is able to go online and create a valid token, but the receiver doesn't need to be online to verify it.
-
Offline marketplaces: Imagine you have an offline marketplace where buyers and sellers can trade goods and services. Before going to the marketplace the sender already knows where he will be spending the money. The sender could create a valid token before going to the marketplace, using the merchants public key as a lock, and adding a refund clause to redeem any unspent ecash after it expires. In this case, neither the sender nor the receiver needs to go online to complete the transaction.
How to use this
Pretty much all cashu wallets allow you to send tokens offline. This is because all that the wallet needs to do is to look if it can create the desired amount from the proofs stored locally. If yes, it will automatically create the token offline.
Receiving offline tokens is currently only supported by nutstash (experimental).
To create an offline receivable token, the sender needs to lock it to the receiver's public key. Currently there is no refund clause! So be careful that you don't get accidentally locked out of your funds!

The receiver can then inspect the token and decide if it is safe to accept without a swap. If all checks are green, they can accept the token offline without trusting the sender.

The receiver will see the unswapped tokens on the wallet homescreen. They will need to manually swap them later when they are online again.
 Later when the receiver is online again, they can swap the token for a fresh one.
Later when the receiver is online again, they can swap the token for a fresh one.
Summary
We learned that offline transactions are possible with ecash, but there are some limitations. It either requires trusting the sender, or relying on either the sender or receiver to be online to verify the tokens, or create tokens that can be verified offline by the receiver.
I hope this short article was helpful in understanding how ecash works and its potential for offline transactions.
Cheers,
Gandlaf
-
 @ 84b0c46a:417782f5
2025-05-04 09:49:45
@ 84b0c46a:417782f5
2025-05-04 09:49:45- 1:nan:
- 2
- 2irorio絵文字
- 1nostr:npub1sjcvg64knxkrt6ev52rywzu9uzqakgy8ehhk8yezxmpewsthst6sw3jqcw
- 2
- 2
- 3
- 3
- 2
- 1
|1|2| |:--|:--| |test| :nan: |
 ---
---:nan: :nan:
- 1
- 2
- tet
- tes
- 3
- 1
-
2
t
te
test
-
19^th^
- H~2~O
本サイトはfirefoxのみサポートしています うにょ :wayo: This text will bounce wss://catstrr.swarmstr.com/
うにょうにょてすと
-
 @ 84b0c46a:417782f5
2025-05-04 09:36:08
@ 84b0c46a:417782f5
2025-05-04 09:36:08 -
 @ 1f79058c:eb86e1cb
2025-05-04 09:34:30
@ 1f79058c:eb86e1cb
2025-05-04 09:34:30I think we should agree on an HTML element for pointing to the Nostr representation of a document/URL on the Web. We could use the existing one for link relations for example:
html <link rel="alternate" type="application/nostr+json" href="nostr:naddr1qvzqqqr4..." title="This article on Nostr" />This would be useful in multiple ways:
- Nostr clients, when fetching meta/preview information for a URL that is linked in a note, can detect that there's a Nostr representation of the content, and then render it in Nostr-native ways (whatever that may be depending on the client)
- User agents, usually a browser or browser extension, when opening a URL on the Web, can offer opening the alternative representation of a page in a Nostr client. And/or they could offer to follow the author's pubkey on Nostr. And/or they could offer to zap the content.
- When publishing a new article, authors can share their preferred Web URL everywhere, without having to consider if the reader knows about or uses Nostr at all. However, if a Nostr user finds the Web version of an article outside of Nostr, they can now easily jump to the Nostr version of it.
- Existing Web publications can retroactively create Nostr versions of their content and easily link the Nostr articles on all of their existing article pages without having to add prominent Nostr links everywhere.
There are probably more use cases, like Nostr search engines and whatnot. If you can think of something interesting, please tell me.
Update: I came up with another interesting use case, which is adding alternate links to RSS and Atom feeds.
Proof of concept
In order to show one way in which this could be used, I have created a small Web Extension called Nostr Links, which will discover alternate Nostr links on the pages you visit.
If it finds one or more links, it will show a purple Nostr icon in the address bar, which you can click to open the list of links. It's similar to e.g. the Feed Preview extension, and also to what the Tor Browser does when it discovers an Onion-Location for the page you're looking at:
The links in this popup menu will be
web+nostr:links, because browsers currently do not allow web apps or extensions to handle unprefixednostr:links. (I hope someone is working on getting those on par withipfs:etc.)Following such a link will either open your default Nostr Web app, if you have already configured one, or it will ask you which Web app to open the link with.
Caveat emptor: At the time of writing, my personal default Web app, noStrudel, needs a new release for the links to find the content.
Try it now
Have a look at the source code and/or download the extension (currently only for Firefox).
I have added alternate Nostr links to the Web pages of profiles and long-form content on the Kosmos relay's domain. It's probably the only place on the Web, which will trigger the extension right now.
You can look at this very post to find an alternate link for example.
Update: A certain fiatjaf has added the element to his personal website, which is built entirely from Nostr articles. Multiple other devs also expressed their intent to implement.
Update 2: There is now a pull request for documenting this approach in two existing NIPs. Your feedback is welcome there.
-
 @ 826e9f89:ffc5c759
2025-04-12 21:34:24
@ 826e9f89:ffc5c759
2025-04-12 21:34:24What follows began as snippets of conversations I have been having for years, on and off, here and there. It will likely eventually be collated into a piece I have been meaning to write on “payments” as a whole. I foolishly started writing this piece years ago, not realizing that the topic is gargantuan and for every week I spend writing it I have to add two weeks to my plan. That may or may not ever come to fruition, but in the meantime, Tether announced it was issuing on Taproot Assets and suddenly everybody is interested again. This is as good a catalyst as any to carve out my “stablecoin thesis”, such as it exists, from “payments”, and put it out there for comment and feedback.
In contrast to the “Bitcoiner take” I will shortly revert to, I invite the reader to keep the following potential counterargument in mind, which might variously be termed the “shitcoiner”, “realist”, or “cynical” take, depending on your perspective: that stablecoins have clear product-market-fit. Now, as a venture capitalist and professional thinkboi focusing on companies building on Bitcoin, I obviously think that not only is Bitcoin the best money ever invented and its monetization is pretty much inevitable, but that, furthermore, there is enormous, era-defining long-term potential for a range of industries in which Bitcoin is emerging as superior technology, even aside from its role as money. But in the interest not just of steelmanning but frankly just of honesty, I would grudgingly agree with the following assessment as of the time of writing: the applications of crypto (inclusive of Bitcoin but deliberately wider) that have found product-market-fit today, and that are not speculative bets on future development and adoption, are: Bitcoin as savings technology, mining as a means of monetizing energy production, and stablecoins.
I think there are two typical Bitcoiner objections to stablecoins of significantly greater importance than all others: that you shouldn’t be supporting dollar hegemony, and that you don’t need a blockchain. I will elaborate on each of these, and for the remainder of the post will aim to produce a synthesis of three superficially contrasting (or at least not obviously related) sources of inspiration: these objections, the realisation above that stablecoins just are useful, and some commentary on technical developments in Bitcoin and the broader space that I think inform where things are likely to go. As will become clear as the argument progresses, I actually think the outcome to which I am building up is where things have to go. I think the technical and economic incentives at play make this an inevitability rather than a “choice”, per se. Given my conclusion, which I will hold back for the time being, this is a fantastically good thing, hence I am motivated to write this post at all!
Objection 1: Dollar Hegemony
I list this objection first because there isn’t a huge amount to say about it. It is clearly a normative position, and while I more or less support it personally, I don’t think that it is material to the argument I am going on to make, so I don’t want to force it on the reader. While the case for this objection is probably obvious to this audience (isn’t the point of Bitcoin to destroy central banks, not further empower them?) I should at least offer the steelman that there is a link between this and the realist observation that stablecoins are useful. The reason they are useful is because people prefer the dollar to even shitter local fiat currencies. I don’t think it is particularly fruitful to say that they shouldn’t. They do. Facts don’t care about your feelings. There is a softer bridging argument to be made here too, to the effect that stablecoins warm up their users to the concept of digital bearer (ish) assets, even though these particular assets are significantly scammier than Bitcoin. Again, I am just floating this, not telling the reader they should or shouldn’t buy into it.
All that said, there is one argument I do want to put my own weight behind, rather than just float: stablecoin issuance is a speculative attack on the institution of fractional reserve banking. A “dollar” Alice moves from JPMorgan to Tether embodies two trade-offs from Alice’s perspective: i) a somewhat opaque profile on the credit risk of the asset: the likelihood of JPMorgan ever really defaulting on deposits vs the operator risk of Tether losing full backing and/or being wrench attacked by the Federal Government and rugging its users. These risks are real but are almost entirely political. I’m skeptical it is meaningful to quantify them, but even if it is, I am not the person to try to do it. Also, more transparently to Alice, ii) far superior payment rails (for now, more on this to follow).
However, from the perspective of the fiat banking cartel, fractional reserve leverage has been squeezed. There are just as many notional dollars in circulation, but there the backing has been shifted from levered to unlevered issuers. There are gradations of relevant objections to this: while one might say, Tether’s backing comes from Treasuries, so you are directly funding US debt issuance!, this is a bit silly in the context of what other dollars one might hold. It’s not like JPMorgan is really competing with the Treasury to sell credit into the open market. Optically they are, but this is the core of the fiat scam. Via the guarantees of the Federal Reserve System, JPMorgan can sell as much unbacked credit as it wants knowing full well the difference will be printed whenever this blows up. Short-term Treasuries are also JPMorgan’s most pristine asset safeguarding its equity, so the only real difference is that Tether only holds Treasuries without wishing more leverage into existence. The realization this all builds up to is that, by necessity,
Tether is a fully reserved bank issuing fiduciary media against the only dollar-denominated asset in existence whose value (in dollar terms) can be guaranteed. Furthermore, this media arguably has superior “moneyness” to the obvious competition in the form of US commercial bank deposits by virtue of its payment rails.
That sounds pretty great when you put it that way! Of course, the second sentence immediately leads to the second objection, and lets the argument start to pick up steam …
Objection 2: You Don’t Need a Blockchain
I don’t need to explain this to this audience but to recap as briefly as I can manage: Bitcoin’s value is entirely endogenous. Every aspect of “a blockchain” that, out of context, would be an insanely inefficient or redundant modification of a “database”, in context is geared towards the sole end of enabling the stability of this endogenous value. Historically, there have been two variations of stupidity that follow a failure to grok this: i) “utility tokens”, or blockchains with native tokens for something other than money. I would recommend anybody wanting a deeper dive on the inherent nonsense of a utility token to read Only The Strong Survive, in particular Chapter 2, Crypto Is Not Decentralized, and the subsection, Everything Fights For Liquidity, and/or Green Eggs And Ham, in particular Part II, Decentralized Finance, Technically. ii) “real world assets” or, creating tokens within a blockchain’s data structure that are not intended to have endogenous value but to act as digital quasi-bearer certificates to some or other asset of value exogenous to this system. Stablecoins are in this second category.
RWA tokens definitionally have to have issuers, meaning some entity that, in the real world, custodies or physically manages both the asset and the record-keeping scheme for the asset. “The blockchain” is at best a secondary ledger to outsource ledger updates to public infrastructure such that the issuer itself doesn’t need to bother and can just “check the ledger” whenever operationally relevant. But clearly ownership cannot be enforced in an analogous way to Bitcoin, under both technical and social considerations. Technically, Bitcoin’s endogenous value means that whoever holds the keys to some or other UTXOs functionally is the owner. Somebody else claiming to be the owner is yelling at clouds. Whereas, socially, RWA issuers enter a contract with holders (whether legally or just in terms of a common-sense interpretation of the transaction) such that ownership of the asset issued against is entirely open to dispute. That somebody can point to “ownership” of the token may or may not mean anything substantive with respect to the physical reality of control of the asset, and how the issuer feels about it all.
And so, one wonders, why use a blockchain at all? Why doesn’t the issuer just run its own database (for the sake of argument with some or other signature scheme for verifying and auditing transactions) given it has the final say over issuance and redemption anyway? I hinted at an answer above: issuing on a blockchain outsources this task to public infrastructure. This is where things get interesting. While it is technically true, given the above few paragraphs, that, you don’t need a blockchain for that, you also don’t need to not use a blockchain for that. If you want to, you can.
This is clearly the case given stablecoins exist at all and have gone this route. If one gets too angry about not needing a blockchain for that, one equally risks yelling at clouds! And, in fact, one can make an even stronger argument, more so from the end users’ perspective. These products do not exist in a vacuum but rather compete with alternatives. In the case of stablecoins, the alternative is traditional fiat money, which, as stupid as RWAs on a blockchain are, is even dumber. It actually is just a database, except it’s a database that is extremely annoying to use, basically for political reasons because the industry managing these private databases form a cartel that never needs to innovate or really give a shit about its customers at all. In many, many cases, stablecoins on blockchains are dumb in the abstract, but superior to the alternative methods of holding and transacting in dollars existing in other forms. And note, this is only from Alice’s perspective of wanting to send and receive, not a rehashing of the fractional reserve argument given above. This is the essence of their product-market-fit. Yell at clouds all you like: they just are useful given the alternative usually is not Bitcoin, it’s JPMorgan’s KYC’d-up-the-wazoo 90s-era website, more than likely from an even less solvent bank.
So where does this get us? It might seem like we are back to “product-market-fit, sorry about that” with Bitcoiners yelling about feelings while everybody else makes do with their facts. However, I think we have introduced enough material to move the argument forward by incrementally incorporating the following observations, all of which I will shortly go into in more detail: i) as a consequence of making no technical sense with respect to what blockchains are for, today’s approach won’t scale; ii) as a consequence of short-termist tradeoffs around socializing costs, today’s approach creates an extremely unhealthy and arguably unnatural market dynamic in the issuer space; iii) Taproot Assets now exist and handily address both points i) and ii), and; iv) eCash is making strides that I believe will eventually replace even Taproot Assets.
To tease where all this is going, and to get the reader excited before we dive into much more detail: just as Bitcoin will eat all monetary premia, Lightning will likely eat all settlement, meaning all payments will gravitate towards routing over Lightning regardless of the denomination of the currency at the edges. Fiat payments will gravitate to stablecoins to take advantage of this; stablecoins will gravitate to TA and then to eCash, and all of this will accelerate hyperbitcoinization by “bitcoinizing” payment rails such that an eventual full transition becomes as simple as flicking a switch as to what denomination you want to receive.
I will make two important caveats before diving in that are more easily understood in light of having laid this groundwork: I am open to the idea that it won’t be just Lightning or just Taproot Assets playing the above roles. Without veering into forecasting the entire future development of Bitcoin tech, I will highlight that all that really matters here are, respectively: a true layer 2 with native hashlocks, and a token issuance scheme that enables atomic routing over such a layer 2 (or combination of such). For the sake of argument, the reader is welcome to swap in “Ark” and “RGB” for “Lightning” and “TA” both above and in all that follows. As far as I can tell, this makes no difference to the argument and is even exciting in its own right. However, for the sake of simplicity in presentation, I will stick to “Lightning” and “TA” hereafter.
1) Today’s Approach to Stablecoins Won’t Scale
This is the easiest to tick off and again doesn’t require much explanation to this audience. Blockchains fundamentally don’t scale, which is why Bitcoin’s UTXO scheme is a far better design than ex-Bitcoin Crypto’s’ account-based models, even entirely out of context of all the above criticisms. This is because Bitcoin transactions can be batched across time and across users with combinations of modes of spending restrictions that provide strong economic guarantees of correct eventual net settlement, if not perpetual deferral. One could argue this is a decent (if abstrusely technical) definition of “scaling” that is almost entirely lacking in Crypto.
What we see in ex-Bitcoin crypto is so-called “layer 2s” that are nothing of the sort, forcing stablecoin schemes in these environments into one of two equally poor design choices if usage is ever to increase: fees go higher and higher, to the point of economic unviability (and well past it) as blocks fill up, or move to much more centralized environments that increasingly are just databases, and hence which lose the benefits of openness thought to be gleaned by outsourcing settlement to public infrastructure. This could be in the form of punting issuance to a bullshit “layer 2” that is a really a multisig “backing” a private execution environment (to be decentralized any daw now) or an entirely different blockchain that is just pretending even less not to be a database to begin with. In a nutshell, this is a decent bottom-up explanation as to why Tron has the highest settlement of Tether.
This also gives rise to the weirdness of “gas tokens” - assets whose utility as money is and only is in the form of a transaction fee to transact a different kind of money. These are not quite as stupid as a “utility token,” given at least they are clearly fulfilling a monetary role and hence their artificial scarcity can be justified. But they are frustrating from Bitcoiners’ and users’ perspectives alike: users would prefer to pay transaction fees on dollars in dollars, but they can’t because the value of Ether, Sol, Tron, or whatever, is the string and bubblegum that hold their boondoggles together. And Bitcoiners wish this stuff would just go away and stop distracting people, whereas this string and bubblegum is proving transiently useful.
All in all, today’s approach is fine so long as it isn’t being used much. It has product-market fit, sure, but in the unenviable circumstance that, if it really starts to take off, it will break, and even the original users will find it unusable.
2) Today’s Approach to Stablecoins Creates an Untenable Market Dynamic
Reviving the ethos of you don’t need a blockchain for that, notice the following subtlety: while the tokens representing stablecoins have value to users, that value is not native to the blockchain on which they are issued. Tether can (and routinely does) burn tokens on Ethereum and mint them on Tron, then burn on Tron and mint on Solana, and so on. So-called blockchains “go down” and nobody really cares. This makes no difference whatsoever to Tether’s own accounting, and arguably a positive difference to users given these actions track market demand. But it is detrimental to the blockchain being switched away from by stripping it of “TVL” that, it turns out, was only using it as rails: entirely exogenous value that leaves as quickly as it arrived.
One underdiscussed and underappreciated implication of the fact that no value is natively running through the blockchain itself is that, in the current scheme, both the sender and receiver of a stablecoin have to trust the same issuer. This creates an extremely powerful network effect that, in theory, makes the first-to-market likely to dominate and in practice has played out exactly as this theory would suggest: Tether has roughly 80% of the issuance, while roughly 19% goes to the political carve-out of USDC that wouldn’t exist at all were it not for government interference. Everybody else combined makes up the final 1%.
So, Tether is a full reserve bank but also has to be everybody’s bank. This is the source of a lot of the discomfort with Tether, and which feeds into the original objection around dollar hegemony, that there is an ill-defined but nonetheless uneasy feeling that Tether is slowly morphing into a CBDC. I would argue this really has nothing to do with Tether’s own behavior but rather is a consequence of the market dynamic inevitably created by the current stablecoin scheme. There is no reason to trust any other bank because nobody really wants a bank, they just want the rails. They want something that will retain a nominal dollar value long enough to spend it again. They don’t care what tech it runs on and they don’t even really care about the issuer except insofar as having some sense they won’t get rugged.
Notice this is not how fiat works. Banks can, of course, settle between each other, thus enabling their users to send money to customers of other banks. This settlement function is actually the entire point of central banks, less the money printing and general corruption enabled (we might say, this was the historical point of central banks, which have since become irredeemably corrupted by this power). This process is clunkier than stablecoins, as covered above, but the very possibility of settlement means there is no gigantic network effect to being the first commercial issuer of dollar balances. If it isn’t too triggering to this audience, one might suggest that the money printer also removes the residual concern that your balances might get rugged! (or, we might again say, you guarantee you don’t get rugged in the short term by guaranteeing you do get rugged in the long term).
This is a good point at which to introduce the unsettling observation that broader fintech is catching on to the benefits of stablecoins without any awareness whatsoever of all the limitations I am outlining here. With the likes of Stripe, Wise, Robinhood, and, post-Trump, even many US megabanks supposedly contemplating issuing stablecoins (obviously within the current scheme, not the scheme I am building up to proposing), we are forced to boggle our minds considering how on earth settlement is going to work. Are they going to settle through Ether? Well, no, because i) Ether isn’t money, it’s … to be honest, I don’t think anybody really knows what it is supposed to be, or if they once did they aren’t pretending anymore, but anyway, Stripe certainly hasn’t figured that out yet so, ii) it won’t be possible to issue them on layer 1s as soon as there is any meaningful volume, meaning they will have to route through “bullshit layer 2 wrapped Ether token that is really already a kind of stablecoin for Ether.”
The way they are going to try to fix this (anybody wanna bet?) is routing through DEXes, which is so painfully dumb you should be laughing and, if you aren’t, I would humbly suggest you don’t get just how dumb it is. What this amounts to is plugging the gap of Ether’s lack of moneyness (and wrapped Ether’s hilarious lack of moneyness) with … drum roll … unknowable technical and counterparty risk and unpredictable cost on top of reverting to just being a database. So, in other words, all of the costs of using a blockchain when you don’t strictly need to, and none of the benefits. Stripe is going to waste billions of dollars getting sandwich attacked out of some utterly vanilla FX settlement it is facilitating for clients who have even less of an idea what is going on and why North Korea now has all their money, and will eventually realize they should have skipped their shitcoin phase and gone straight to understanding Bitcoin instead …
3) Bitcoin (and Taproot Assets) Fixes This
To tie together a few loose ends, I only threw in the hilariously stupid suggestion of settling through wrapped Ether on Ether on Ether in order to tee up the entirely sensible suggestion of settling through Lightning. Again, not that this will be new to this audience, but while issuance schemes have been around on Bitcoin for a long time, the breakthrough of Taproot Assets is essentially the ability to atomically route through Lightning.
I will admit upfront that this presents a massive bootstrapping challenge relative to the ex-Bitcoin Crypto approach, and it’s not obvious to me if or how this will be overcome. I include this caveat to make it clear I am not suggesting this is a given. It may not be, it’s just beyond the scope of this post (or frankly my ability) to predict. This is a problem for Lightning Labs, Tether, and whoever else decides to step up to issue. But even highlighting this as an obvious and major concern invites us to consider an intriguing contrast: scaling TA stablecoins is hardest at the start and gets easier and easier thereafter. The more edge liquidity there is in TA stables, the less of a risk it is for incremental issuance; the more TA activity, the more attractive deploying liquidity is into Lightning proper, and vice versa. With apologies if this metaphor is even more confusing than it is helpful, one might conceive of the situation as being that there is massive inertia to bootstrap, but equally there could be positive feedback in driving the inertia to scale. Again, I have no idea, and it hasn’t happened yet in practice, but in theory it’s fun.
More importantly to this conversation, however, this is almost exactly the opposite dynamic to the current scheme on other blockchains, which is basically free to start, but gets more and more expensive the more people try to use it. One might say it antiscales (I don’t think that’s a real word, but if Taleb can do it, then I can do it too!).
Furthermore, the entire concept of “settling in Bitcoin” makes perfect sense both economically and technically: economically because Bitcoin is money, and technically because it can be locked in an HTLC and hence can enable atomic routing (i.e. because Lightning is a thing). This is clearly better than wrapped Eth on Eth on Eth or whatever, but, tantalisingly, is better than fiat too! The core message of the payments tome I may or may not one day write is (or will be) that fiat payments, while superficially efficient on the basis of centralized and hence costless ledger amendments, actually have a hidden cost in the form of interbank credit. Many readers will likely have heard me say this multiple times and in multiple settings but, contrary to popular belief, there is no such thing as a fiat debit. Even if styled as a debit, all fiat payments are credits and all have credit risk baked into their cost, even if that is obscured and pushed to the absolute foundational level of money printing to keep banks solvent and hence keep payment channels open.
Furthermore! this enables us to strip away the untenable market dynamic from the point above. The underappreciated and underdiscussed flip side of the drawback of the current dynamic that is effectively fixed by Taproot Assets is that there is no longer a mammoth network effect to a single issuer. Senders and receivers can trust different issuers (i.e. their own banks) because those banks can atomically settle a single payment over Lightning. This does not involve credit. It is arguably the only true debit in the world across both the relevant economic and technical criteria: it routes through money with no innate credit risk, and it does so atomically due to that money’s native properties.
Savvy readers may have picked up on a seed I planted a while back and which can now delightfully blossom:
This is what Visa was supposed to be!
Crucially, this is not what Visa is now. Visa today is pretty much the bank that is everybody’s counterparty, takes a small credit risk for the privilege, and oozes free cash flow bottlenecking global consumer payments.
But if you read both One From Many by Dee Hock (for a first person but pretty wild and extravagant take) and Electronic Value Exchange by David Stearns (for a third person, drier, but more analytical and historically contextualized take) or if you are just intimately familiar with the modern history of payments for whatever other reason, you will see that the role I just described for Lightning in an environment of unboundedly many banks issuing fiduciary media in the form of stablecoins is exactly what Dee Hock wanted to create when he envisioned Visa:
A neutral and open layer of value settlement enabling banks to create digital, interbank payment schemes for their customers at very low cost.
As it turns out, his vision was technically impossible with fiat, hence Visa, which started as a cooperative amongst member banks, was corrupted into a duopolistic for-profit rent seeker in curious parallel to the historical path of central banks …
4) eCash
To now push the argument to what I think is its inevitable conclusion, it’s worth being even more vigilant on the front of you don’t need a blockchain for that. I have argued that there is a role for a blockchain in providing a neutral settlement layer to enable true debits of stablecoins. But note this is just a fancy and/or stupid way of saying that Bitcoin is both the best money and is programmable, which we all knew anyway. The final step is realizing that, while TA is nice in terms of providing a kind of “on ramp” for global payments infrastructure as a whole to reorient around Lightning, there is some path dependence here in assuming (almost certainly correctly) that the familiarity of stablecoins as “RWA tokens on a blockchain” will be an important part of the lure.
But once that transition is complete, or is well on its way to being irreversible, we may as well come full circle and cut out tokens altogether. Again, you really don’t need a blockchain for that, and the residual appeal of better rails has been taken care of with the above massive detour through what I deem to be the inevitability of Lightning as a settlement layer. Just as USDT on Tron arguably has better moneyness than a JPMorgan balance, so a “stablecoin” as eCash has better moneyness than as a TA given it is cheaper, more private, and has more relevantly bearer properties (in other words, because it is cash). The technical detail that it can be hashlocked is really all you need to tie this all together. That means it can be atomically locked into a Lightning routed debit to the recipient of a different issuer (or “mint” in eCash lingo, but note this means the same thing as what we have been calling fully reserved banks). And the economic incentive is pretty compelling too because, for all their benefits, there is still a cost to TAs given they are issued onchain and they require asset-specific liquidity to route on Lightning. Once the rest of the tech is in place, why bother? Keep your Lightning connectivity and just become a mint.
What you get at that point is dramatically superior private database to JPMorgan with the dramatically superior public rails of Lightning. There is nothing left to desire from “a blockchain” besides what Bitcoin is fundamentally for in the first place: counterparty-risk-free value settlement.
And as a final point with a curious and pleasing echo to Dee Hock at Visa, Calle has made the point repeatedly that David Chaum’s vision for eCash, while deeply philosophical besides the technical details, was actually pretty much impossible to operate on fiat. From an eCash perspective, fiat stablecoins within the above infrastructure setup are a dramatic improvement on anything previously possible. But, of course, they are a slippery slope to Bitcoin regardless …
Objections Revisited
As a cherry on top, I think the objections I highlighted at the outset are now readily addressed – to the extent the reader believes what I am suggesting is more or less a technical and economic inevitability, that is. While, sure, I’m not particularly keen on giving the Treasury more avenues to sell its welfare-warfare shitcoin, on balance the likely development I’ve outlined is an enormous net positive: it’s going to sell these anyway so I prefer a strong economic incentive to steadily transition not only to Lightning as payment rails but eCash as fiduciary media, and to use “fintech” as a carrot to induce a slow motion bank run.
As alluded to above, once all this is in place, the final step to a Bitcoin standard becomes as simple as an individual’s decision to want Bitcoin instead of fiat. On reflection, this is arguably the easiest part! It's setting up all the tech that puts people off, so trojan-horsing them with “faster, cheaper payment rails” seems like a genius long-term strategy.
And as to “needing a blockchain” (or not), I hope that is entirely wrapped up at this point. The only blockchain you need is Bitcoin, but to the extent people are still confused by this (which I think will take decades more to fully unwind), we may as well lean into dazzling them with whatever innovation buzzwords and decentralization theatre they were going to fall for anyway before realizing they wanted Bitcoin all along.
Conclusion
Stablecoins are useful whether you like it or not. They are stupid in the abstract but it turns out fiat is even stupider, on inspection. But you don’t need a blockchain, and using one as decentralization theatre creates technical debt that is insurmountable in the long run. Blockchain-based stablecoins are doomed to a utility inversely proportional to their usage, and just to rub it in, their ill-conceived design practically creates a commercial dynamic that mandates there only ever be a single issuer.
Given they are useful, it seems natural that this tension is going to blow up at some point. It also seems worthwhile observing that Taproot Asset stablecoins have almost the inverse problem and opposite commercial dynamic: they will be most expensive to use at the outset but get cheaper and cheaper as their usage grows. Also, there is no incentive towards a monopoly issuer but rather towards as many as are willing to try to operate well and provide value to their users.
As such, we can expect any sizable growth in stablecoins to migrate to TA out of technical and economic necessity. Once this has happened - or possibly while it is happening but is clearly not going to stop - we may as well strip out the TA component and just use eCash because you really don’t need a blockchain for that at all. And once all the money is on eCash, deciding you want to denominate it in Bitcoin is the simplest on-ramp to hyperbitcoinization you can possibly imagine, given we’ve spent the previous decade or two rebuilding all payments tech around Lightning.
Or: Bitcoin fixes this. The End.
- Allen, #892,125
thanks to Marco Argentieri, Lyn Alden, and Calle for comments and feedback
-
 @ c3c7122c:607731d7
2025-04-12 04:05:06
@ c3c7122c:607731d7
2025-04-12 04:05:06Help!
Calling all El Salvador Nostriches! If you currently live in SV, I need your help and am offering several bounties (0.001, 0.01, and 0.1 BTC).
In Brief
In short, I am pursuing El Salvador citizenship by birthright (through my grandmother). I’ve struggled to progress because her name varies on different documents. I need someone to help me push harder to get past this barrier, or connect me with information or people who can work on my behalf. I am offering:
- 0.001 BTC (100k sats) for information that will help me progress from my current situation
- 0.01 BTC (1 MM sats) to get me in touch with someone that is more impactful than the immigration lawyer I already spoke with
- 0.1 BTC (10 MM sats) if your efforts help me obtain citizenship for me or my father
Background
My grandma married my grandfather (an American Marine) and moved to the states where my father was born. I have some official and unofficial documents where her name varies in spelling, order of first/middle name, and addition of her father’s last name. So every doc basically has a different name for her. I was connected with an english-speaking immigration lawyer in SV who hit a dead end when searching for her official ID because the city hall in her city had burned down so there was no record of her info. He gave up at that point. I find it odd that it was so easy to change your name back then, but they are more strict now with the records from that time.
I believe SV citizenship is my birthright and have several personal reasons for pursuing this. I want someone to act on my behalf who will try harder to work the system (by appeal, loophole, or even bribe if I have to). If you are local and can help me with this, I’d greatly appreciate any efforts you make.
Cheers!
Corey San Diego
-
 @ 3eba5ef4:751f23ae
2025-04-11 00:40:28
@ 3eba5ef4:751f23ae
2025-04-11 00:40:28Crypto Insights
2025 MIT Bitcoin Expo: Spotlight on Freedom Tech
The 12th MIT Bitcoin Expo took place on April 5–6, centering this year’s theme on “Freedom Tech” and how technology can facilitate physical and social liberation.
-
Day 1 Recap: Mawarire delivered the keynote speech “Why Freedom Tech Matters,” and Dryja discussed how Bitcoin demonstrates resilience against nation-states. The morning sessions focused on corporate adoption, featuring speakers such as Paul Giordano from Marathon Digital and Bitcoin Core contributors like Gloria Zhao. The afternoon shifted toward more technical topics, including consensus cleanup, poisoning attacks, censorship resistance, and the Bitcoin Pipes protocol.
-
Day 2 Recap: The focus shifted to global impact. Mauricio Bartolomeo discussed the exfiltration of resources via Bitcoin, followed by a panel with activists from Venezuela, Russia, and Togo. Technical topics included: scaling self-custody, Steven Roose’s covenant soft fork proposals, the future of freedom tech, quantum resistance, and Tor.
Into Bitcoin Address Poisoning Attacks
In this article, Jameson Lopp highlights the rise of Bitcoin address poisoning attacks—an emerging form of social engineering. Attackers send transactions from newly generated wallets that mimic the beginning and end characters of a target's recently used address. If the target later copies an address from their transaction history, they may unknowingly send funds to the attacker instead of the intended recipient. Though the success rate per attack is low, the low cost of transactions enables attackers to attempt thousands in a short period.
Lopp also argues that such attacks are a byproduct of low transaction fees and that higher fees could deter them. He also suggests wallet-level defenses, such as warnings like, “Oh, this came from a similar looking address,” to help users avoid interaction.
Examining the Mitigation Strategy Against Timewarp Attacks
Timewarp attacks, first identified around 2011, allow a majority of malicious miners to manipulate block timestamps, artificially lower difficulty, and mine blocks every few seconds. The “Great Consensus Cleanup” soft fork proposal can mitigate this by requiring that the first block in a new difficulty period must have a time no earlier than a certain number of minutes before the last block of the previous period.
A report examines the details of this BIP.
Tokenization on Bitcoin: Building a Global Settlement Layer with Taproot Assets and Lightning
Bitcoin’s evolution into a multi-asset platform is accelerating with the advent of Taproot Assets and Lightning Network. The integration of these technologies combines Bitcoin’s decentralization and security with the speed and scalability of the Lightning Network. This report examines how Taproot Assets enable asset issuance, transfers, and swaps on Bitcoin’s base layer, and how the Lightning Network facilitates fast, low-cost transfers of those assets. We compare this approach to earlier attempts at Bitcoin asset issuance and analyze its market potential against other blockchains and traditional payment networks.
Solving Data Availability in Client-Side Validation With UTxO Binding
Issuing tokens on Bitcoin is attractive due to its security and dominance, but its limited functionality creates challenges. Client-side validation (CSV) is a common workaround, using off-chain data with on-chain verification, though it risks data loss and withholding. This paper introduces UTxO binding, a framework that links a Bitcoin UTxO to one on an auxiliary chain, providing data storage and programmability. The authors prove its security and implement it using Nervos CKB.
From State Differences to Scaling: Citrea’s Fee Mechanism for Bitcoin
The Citrea team has designed a new fee mechanism to enhance Bitcoin’s scalability without compromising security. It only records essential state differences (i.e., state slot changes) on the Bitcoin main chain, using zero-knowledge proofs to ensure verifiability and Bitcoin security while drastically reducing state inscription costs. Optimizations include: replacing
codefield withcode_hash, compressing state data using a highly efficient compression algorithm Brotli, and analyzing historical Ethereum block data to estimate each transaction’s impact on cumulative state differences—enabling a discount to each transaction.Second: A New Ark Implementation Launched on Bitcoin Signet
Second, a protocol based on Ark to improve Bitcoin transaction throughput, has launched Bark, a test implementation on Bitcoin Signet.
Ark makes Bitcoin transactions faster, cheaper, and more private, allowing more users and transactions per block. However, funds stored non-custodially via Ark can expire if unused, making it slightly less trustless than mainchain transactions.
BitLayer Optimizes BitVM Bridge Protocol and Demonstrates on Testnet
Bitlayer BitVM Bridge protocol is an optimized adaptation of the bridge protocol outlined in the BitVM2 paper, to improve efficiency, scalability, and security—especially for high-risk cross-chain transactions.
In this article, two key testnet demos on bitvmnet (a BitVM-dedicated testnet) demonstrate how the protocol can:
-
Effectively thwart fraudulent reclaim attempts by brokers.
-
Protect honest brokers from malicious or baseless challenges.
Cardano Enables Bitcoin DeFi via BitVMX and Lightning Hydra
Cardano is integrating with Bitcoin through Lightning Hydra and BitVMX to enable secure and scalable Bitcoin DeFi.
Zcash’s Tachyon Upgrade: Toward Scalable Oblivious Synchronization
Zcash has unveiled project Tachyon, a proposal to scale Zcash by changing how wallets sync and prove ownership of notes. Instead of scanning the entire blockchain, wallets track only their own nullifiers and receive succinct proofs from untrusted, oblivious sync servers. Transactions include proofs of wallet state (using recursive SNARKs), allowing nodes to verify them without keeping the full history. Notes are exchanged out-of-band, reducing on-chain data and improving privacy. In the nominal case, users get fast sync, lightweight wallets, and strong privacy, without the need to trust the network.
Podcast | Why the Future of Bitcoin Mining is Distributed
In this podcast, Professor Troy Cross discusses the centralization of Bitcoin mining and argues convincingly for hashrate decentralization. While economies of scale have led to mega mining operations, he sees economic imperative that will drive mining toward a globally distributed future—not dominated by the U.S.—ensuring neutrality and resilience against state-level threats.
Binance Report|Crypto Industry Map March 2025
This report provides an overview of projects using a framework that divides crypto into four core ecosystems—Infrastructure, DeFi, NFT, and Gaming—and four trending sectors: Stablecoins, RWA, AI, and DeSci.
For infrastructure, five key pillars are identified: scalability & fairness, data availability & tooling, security & privacy, cloud networks, and connectivity. The report also maps out and categorizes the major projects and solutions currently on the market.

Top Reads on Blockchain and Beyond
A Game-Theoretic Approach to Bitcoin’s Valuation in Equilibrium
The author presents a game-theoretic argument for why Bitcoin will emerge as the optimal unit of account in equilibrium. The argument is based upon the observation that a generally agreed upon unit of account that represents a constant share of total wealth (equal to the totality of all other economic utility) will naturally create price signals that passively stabilize the macroeconomy, without requiring external intervention.
Bitcoin’s unique properties—finite supply, inertness, fungibility, accessibility, and ownership history—position it as the leading candidate to emerge as this unit.
Neo: Lattice-Based Folding Scheme for CCS Over Small Fields and Pay-Per-Bit Commitments
This paper introduces Neo, a new lattice-based folding scheme for CCS, an NP-complete relation that generalizes R1CS, Plonkish, and AIR. Neo's folding scheme can be viewed as adapting the folding scheme in HyperNova (CRYPTO'24), which assumes elliptic-curve based linearly homomorphic commitments, to the lattice setting. Unlike HyperNova, Neo can use “small” prime fields (e.g., over the Goldilocks prime). Additionally, Neo provides plausible post-quantum security.
Social Scalability: Key to Massive Value Accumulation in Crypto
Social scalability, a concept first proposed by Nick Szabo in his 2017 article Money, Blockchains, and Social Scalability, is further explored in this thread. Here, “social scalability” refers to an institution's ability to allow the maximum number of people to have skin in the game and win. It’s seen as the main reason crypto has become a $2.9T asset class today and a key driver of value accumulation in the coming decade.
The author argues that two critical ingredients for long-term social scalability are credible neutrality and utility. Currently, only BTC and ETH have this potential, yet neither strikes a perfect balance between the two. The author notes that there is not yet a strong narrative around social scalability, and concludes by emphasizing the importance of focusing on long-term value and resisting the temptation of short-term market narratives.
-
-
 @ a296b972:e5a7a2e8
2025-05-04 08:30:56
@ a296b972:e5a7a2e8
2025-05-04 08:30:56Am Ende der Woche von Unseremeinungsfreiheit wird in der Unserehauptstadt von Unserdeutschland, Unserberlin, voraussichtlich der neue Unserbundeskanzler vereidigt.
Der Schwur des voraussichtlich nächsten Unserbundeskanzlers sollte aktualisiert werden:
Jetzt, wo endlich mein Traum in Erfüllung geht, nur einmal im Leben Unserbundeskanzler zu werden, zahlen sich für mich alle Tricks und Kniffe aus, die ich angewendet habe, um unter allen Umständen in diese Position zu kommen.
Ich schwöre, dass ich meine Kraft meinem Wohle widmen, meinen Nutzen mehren, nach Vorbild meines Vorgängers Schaden von mir wenden, das Grundgesetz und die Gesetze des Unserbundes formen, meine Pflichten unsergewissenhaft erfüllen und Unseregerechtigkeit gegen jedermann und jederfrau nicht nur üben, sondern unter allen Umständen auch durchsetzen werde, die sich mir bei der Umsetzung der Vorstellungen von Unseredemokratie in den Weg stellen. (So wahr mir wer auch immer helfe).
Der Antrittsbesuch des Unserbundeskanzlers beim Repräsentanten der noch in Unserdeutschland präsenten Besatzungsmacht wird mit Spannung erwartet.
Ein großer Teil der Unsereminister ist schon bekannt. Die Auswahl verspricht viele Unsereüberraschungen.
Die Unsereeinheitspartei, bestehend aus ehemaligen Volksparteien, wird weiterhin dafür sorgen, dass die Nicht-Unsereopposition so wenig wie möglich Einfluss erhält, obwohl sie von den Nicht-Unserebürgern, die mindestens ein Viertel der Urnengänger ausmachen, voll-demokratisch gewählt wurde.
Das Zentralkomitee der Deutschen Unseredemokratischen Bundesrepublik wird zum Wohle seiner Unserebürger alles daransetzen, Unseredemokratie weiter voranzubringen und hofft auch weiterhin auf die Unterstützung von Unser-öffentlich-rechtlicher-Rundfunk.
Die Unserepressefreiheit wird auch weiterhin garantiert.
Auf die Verlautbarungen der Unserepressekonferenz, besetzt mit frischem Unserpersonal, brauchen die Insassen von Unserdeutschland auch weiterhin nicht zu verzichten.
Alles, was nicht gesichert unserdemokratisch ist, gilt als gesichert rechtsextrem.
Als Maxime gilt für alles Handeln: Es muss unter allen Umständen demokratisch aussehen, aber wir (die Unseredemokraten) müssen alles in der Hand haben.
Es ist unwahrscheinlich, dass Unsersondervermögen von den Unserdemokraten zurückgezahlt wird. Dieser Vorzug ist den Unserebürgern und den Nicht-Unserebürgern durch Unseresteuerzahlungen vorbehalten.
Die Unserebundeswehr soll aufgebaut werden (Baut auf, baut auf!), die Unsererüstungsindustrie läuft auf Hochtouren und soll Unserdeutschland wieder unserkriegstüchtig machen, weil Russland immer Unserfeind sein wird.
Von Unserdeutschland soll nur noch Unserfrieden ausgehen.
Zur Bekräftigung, dass alles seinen unser-sozialistischen Gang geht, tauchte die Phoenix*in aus der Asche auf, in dem Unseremutti kürzlich ihren legendären Satz wiederholte:
Wir schaffen das.
Ob damit der endgültige wirtschaftliche Untergang und die Vollendung der gesellschaftlichen Spaltung von Unserdeutschland gemeint war, ist nicht überliefert.
Orwellsche Schlussfolgerung:
Wir = unser
Ihr = Euer
Vogel und Maus passen nicht zusammen
Ausgerichtet auf Ruinen und der Zukunft abgewandt, Uneinigkeit und Unrecht und Unfreiheit für das deutsche Unserland.
Unserdeutschland – ein Land mit viel Vergangenheit und wenig Zukunft?
Es ist zum Heulen.
Dieser Artikel wurde mit dem Pareto-Client geschrieben
* *
(Bild von pixabay)
-
 @ b2caa9b3:9eab0fb5
2025-05-04 08:20:46
@ b2caa9b3:9eab0fb5
2025-05-04 08:20:46Hey friends,
Exciting news – I’m currently setting up my very first Discord server!
This space will be all about my travels, behind-the-scenes stories, photo sharing, and practical tips and insights from the road. My goal is to make it the central hub connecting all my decentralized social platforms where I can interact with you more directly, and share exclusive content.
Since I’m just starting out, I’d love to hear from you:
Do you know any useful RSS-feed integrations for updates?
Can you recommend any cool Discord bots for community engagement or automation?
Are there any tips or features you think I must include?
The idea is to keep everything free and accessible, and to grow a warm, helpful community around the joy of exploring the world.
It’s my first time managing a Discord server, so your experience and suggestions would mean a lot. Leave a comment – I’m all ears!
Thanks for your support, Ruben Storm
-
 @ 3b3a42d3:d192e325
2025-04-10 08:57:51
@ 3b3a42d3:d192e325
2025-04-10 08:57:51Atomic Signature Swaps (ASS) over Nostr is a protocol for atomically exchanging Schnorr signatures using Nostr events for orchestration. This new primitive enables multiple interesting applications like:
- Getting paid to publish specific Nostr events
- Issuing automatic payment receipts
- Contract signing in exchange for payment
- P2P asset exchanges
- Trading and enforcement of asset option contracts
- Payment in exchange for Nostr-based credentials or access tokens
- Exchanging GMs 🌞
It only requires that (i) the involved signatures be Schnorr signatures using the secp256k1 curve and that (ii) at least one of those signatures be accessible to both parties. These requirements are naturally met by Nostr events (published to relays), Taproot transactions (published to the mempool and later to the blockchain), and Cashu payments (using mints that support NUT-07, allowing any pair of these signatures to be swapped atomically.
How the Cryptographic Magic Works 🪄
This is a Schnorr signature
(Zₓ, s):s = z + H(Zₓ || P || m)⋅kIf you haven't seen it before, don't worry, neither did I until three weeks ago.
The signature scalar s is the the value a signer with private key
k(and public keyP = k⋅G) must calculate to prove his commitment over the messagemgiven a randomly generated noncez(Zₓis just the x-coordinate of the public pointZ = z⋅G).His a hash function (sha256 with the tag "BIP0340/challenge" when dealing with BIP340),||just means to concatenate andGis the generator point of the elliptic curve, used to derive public values from private ones.Now that you understand what this equation means, let's just rename
z = r + t. We can do that,zis just a randomly generated number that can be represented as the sum of two other numbers. It also follows thatz⋅G = r⋅G + t⋅G ⇔ Z = R + T. Putting it all back into the definition of a Schnorr signature we get:s = (r + t) + H((R + T)ₓ || P || m)⋅kWhich is the same as:
s = sₐ + twheresₐ = r + H((R + T)ₓ || P || m)⋅ksₐis what we call the adaptor signature scalar) and t is the secret.((R + T)ₓ, sₐ)is an incomplete signature that just becomes valid by add the secret t to thesₐ:s = sₐ + tWhat is also important for our purposes is that by getting access to the valid signature s, one can also extract t from it by just subtracting
sₐ:t = s - sₐThe specific value of
tdepends on our choice of the public pointT, sinceRis just a public point derived from a randomly generated noncer.So how do we choose
Tso that it requires the secret t to be the signature over a specific messagem'by an specific public keyP'? (without knowing the value oft)Let's start with the definition of t as a valid Schnorr signature by P' over m':
t = r' + H(R'ₓ || P' || m')⋅k' ⇔ t⋅G = r'⋅G + H(R'ₓ || P' || m')⋅k'⋅GThat is the same as:
T = R' + H(R'ₓ || P' || m')⋅P'Notice that in order to calculate the appropriate
Tthat requirestto be an specific signature scalar, we only need to know the public nonceR'used to generate that signature.In summary: in order to atomically swap Schnorr signatures, one party
P'must provide a public nonceR', while the other partyPmust provide an adaptor signature using that nonce:sₐ = r + H((R + T)ₓ || P || m)⋅kwhereT = R' + H(R'ₓ || P' || m')⋅P'P'(the nonce provider) can then add his own signature t to the adaptor signaturesₐin order to get a valid signature byP, i.e.s = sₐ + t. When he publishes this signature (as a Nostr event, Cashu transaction or Taproot transaction), it becomes accessible toPthat can now extract the signaturetbyP'and also make use of it.Important considerations
A signature may not be useful at the end of the swap if it unlocks funds that have already been spent, or that are vulnerable to fee bidding wars.
When a swap involves a Taproot UTXO, it must always use a 2-of-2 multisig timelock to avoid those issues.
Cashu tokens do not require this measure when its signature is revealed first, because the mint won't reveal the other signature if they can't be successfully claimed, but they also require a 2-of-2 multisig timelock when its signature is only revealed last (what is unavoidable in cashu for cashu swaps).
For Nostr events, whoever receives the signature first needs to publish it to at least one relay that is accessible by the other party. This is a reasonable expectation in most cases, but may be an issue if the event kind involved is meant to be used privately.
How to Orchestrate the Swap over Nostr?
Before going into the specific event kinds, it is important to recognize what are the requirements they must meet and what are the concerns they must address. There are mainly three requirements:
- Both parties must agree on the messages they are going to sign
- One party must provide a public nonce
- The other party must provide an adaptor signature using that nonce
There is also a fundamental asymmetry in the roles of both parties, resulting in the following significant downsides for the party that generates the adaptor signature:
- NIP-07 and remote signers do not currently support the generation of adaptor signatures, so he must either insert his nsec in the client or use a fork of another signer
- There is an overhead of retrieving the completed signature containing the secret, either from the blockchain, mint endpoint or finding the appropriate relay
- There is risk he may not get his side of the deal if the other party only uses his signature privately, as I have already mentioned
- There is risk of losing funds by not extracting or using the signature before its timelock expires. The other party has no risk since his own signature won't be exposed by just not using the signature he received.
The protocol must meet all those requirements, allowing for some kind of role negotiation and while trying to reduce the necessary hops needed to complete the swap.
Swap Proposal Event (kind:455)
This event enables a proposer and his counterparty to agree on the specific messages whose signatures they intend to exchange. The
contentfield is the following stringified JSON:{ "give": <signature spec (required)>, "take": <signature spec (required)>, "exp": <expiration timestamp (optional)>, "role": "<adaptor | nonce (optional)>", "description": "<Info about the proposal (optional)>", "nonce": "<Signature public nonce (optional)>", "enc_s": "<Encrypted signature scalar (optional)>" }The field
roleindicates what the proposer will provide during the swap, either the nonce or the adaptor. When this optional field is not provided, the counterparty may decide whether he will send a nonce back in a Swap Nonce event or a Swap Adaptor event using thenonce(optionally) provided by in the Swap Proposal in order to avoid one hop of interaction.The
enc_sfield may be used to store the encrypted scalar of the signature associated with thenonce, since this information is necessary later when completing the adaptor signature received from the other party.A
signature specspecifies thetypeand all necessary information for producing and verifying a given signature. In the case of signatures for Nostr events, it contain a template with all the fields, exceptpubkey,idandsig:{ "type": "nostr", "template": { "kind": "<kind>" "content": "<content>" "tags": [ … ], "created_at": "<created_at>" } }In the case of Cashu payments, a simplified
signature specjust needs to specify the payment amount and an array of mints trusted by the proposer:{ "type": "cashu", "amount": "<amount>", "mint": ["<acceptable mint_url>", …] }This works when the payer provides the adaptor signature, but it still needs to be extended to also work when the payer is the one receiving the adaptor signature. In the later case, the
signature specmust also include atimelockand the derived public keysYof each Cashu Proof, but for now let's just ignore this situation. It should be mentioned that the mint must be trusted by both parties and also support Token state check (NUT-07) for revealing the completed adaptor signature and P2PK spending conditions (NUT-11) for the cryptographic scheme to work.The
tagsare:"p", the proposal counterparty's public key (required)"a", akind:30455Swap Listing event or an application specific version of it (optional)
Forget about this Swap Listing event for now, I will get to it later...
Swap Nonce Event (kind:456) - Optional
This is an optional event for the Swap Proposal receiver to provide the public nonce of his signature when the proposal does not include a nonce or when he does not want to provide the adaptor signature due to the downsides previously mentioned. The
contentfield is the following stringified JSON:{ "nonce": "<Signature public nonce>", "enc_s": "<Encrypted signature scalar (optional)>" }And the
tagsmust contain:"e", akind:455Swap Proposal Event (required)"p", the counterparty's public key (required)
Swap Adaptor Event (kind:457)
The
contentfield is the following stringified JSON:{ "adaptors": [ { "sa": "<Adaptor signature scalar>", "R": "<Signer's public nonce (including parity byte)>", "T": "<Adaptor point (including parity byte)>", "Y": "<Cashu proof derived public key (if applicable)>", }, …], "cashu": "<Cashu V4 token (if applicable)>" }And the
tagsmust contain:"e", akind:455Swap Proposal Event (required)"p", the counterparty's public key (required)
Discoverability
The Swap Listing event previously mentioned as an optional tag in the Swap Proposal may be used to find an appropriate counterparty for a swap. It allows a user to announce what he wants to accomplish, what his requirements are and what is still open for negotiation.
Swap Listing Event (kind:30455)
The
contentfield is the following stringified JSON:{ "description": "<Information about the listing (required)>", "give": <partial signature spec (optional)>, "take": <partial signature spec (optional)>, "examples: [<take signature spec>], // optional "exp": <expiration timestamp (optional)>, "role": "<adaptor | nonce (optional)>" }The
descriptionfield describes the restrictions on counterparties and signatures the user is willing to accept.A
partial signature specis an incompletesignature specused in Swap Proposal eventskind:455where omitting fields signals that they are still open for negotiation.The
examplesfield is an array ofsignature specsthe user would be willing totake.The
tagsare:"d", a unique listing id (required)"s", the status of the listingdraft | open | closed(required)"t", topics related to this listing (optional)"p", public keys to notify about the proposal (optional)
Application Specific Swap Listings
Since Swap Listings are still fairly generic, it is expected that specific use cases define new event kinds based on the generic listing. Those application specific swap listing would be easier to filter by clients and may impose restrictions and add new fields and/or tags. The following are some examples under development:
Sponsored Events
This listing is designed for users looking to promote content on the Nostr network, as well as for those who want to monetize their accounts by sharing curated sponsored content with their existing audiences.
It follows the same format as the generic Swap Listing event, but uses the
kind:30456instead.The following new tags are included:
"k", event kind being sponsored (required)"title", campaign title (optional)
It is required that at least one
signature spec(giveand/ortake) must have"type": "nostr"and also contain the following tag["sponsor", "<pubkey>", "<attestation>"]with the sponsor's public key and his signature over the signature spec without the sponsor tag as his attestation. This last requirement enables clients to disclose and/or filter sponsored events.Asset Swaps
This listing is designed for users looking for counterparties to swap different assets that can be transferred using Schnorr signatures, like any unit of Cashu tokens, Bitcoin or other asset IOUs issued using Taproot.
It follows the same format as the generic Swap Listing event, but uses the
kind:30457instead.It requires the following additional tags:
"t", asset pair to be swapped (e.g."btcusd")"t", asset being offered (e.g."btc")"t", accepted payment method (e.g."cashu","taproot")
Swap Negotiation
From finding an appropriate Swap Listing to publishing a Swap Proposal, there may be some kind of negotiation between the involved parties, e.g. agreeing on the amount to be paid by one of the parties or the exact content of a Nostr event signed by the other party. There are many ways to accomplish that and clients may implement it as they see fit for their specific goals. Some suggestions are:
- Adding
kind:1111Comments to the Swap Listing or an existing Swap Proposal - Exchanging tentative Swap Proposals back and forth until an agreement is reached
- Simple exchanges of DMs
- Out of band communication (e.g. Signal)
Work to be done
I've been refining this specification as I develop some proof-of-concept clients to experience its flaws and trade-offs in practice. I left the signature spec for Taproot signatures out of the current document as I still have to experiment with it. I will probably find some important orchestration issues related to dealing with
2-of-2 multisig timelocks, which also affects Cashu transactions when spent last, that may require further adjustments to what was presented here.The main goal of this article is to find other people interested in this concept and willing to provide valuable feedback before a PR is opened in the NIPs repository for broader discussions.
References
- GM Swap- Nostr client for atomically exchanging GM notes. Live demo available here.
- Sig4Sats Script - A Typescript script demonstrating the swap of a Cashu payment for a signed Nostr event.
- Loudr- Nostr client under development for sponsoring the publication of Nostr events. Live demo available at loudr.me.
- Poelstra, A. (2017). Scriptless Scripts. Blockstream Research. https://github.com/BlockstreamResearch/scriptless-scripts
-
 @ ec9bd746:df11a9d0
2025-04-06 08:06:08
@ ec9bd746:df11a9d0
2025-04-06 08:06:08🌍 Time Window:
🕘 When: Every even week on Sunday at 9:00 PM CET
🗺️ Where: https://cornychat.com/eurocornStart: 21:00 CET (Prague, UTC+1)
End: approx. 02:00 CET (Prague, UTC+1, next day)
Duration: usually 5+ hours.| Region | Local Time Window | Convenience Level | |-----------------------------------------------------|--------------------------------------------|---------------------------------------------------------| | Europe (CET, Prague) 🇨🇿🇩🇪 | 21:00–02:00 CET | ✅ Very Good; evening & night | | East Coast North America (EST) 🇺🇸🇨🇦 | 15:00–20:00 EST | ✅ Very Good; afternoon & early evening | | West Coast North America (PST) 🇺🇸🇨🇦 | 12:00–17:00 PST | ✅ Very Good; midday & afternoon | | Central America (CST) 🇲🇽🇨🇷🇬🇹 | 14:00–19:00 CST | ✅ Very Good; afternoon & evening | | South America West (Peru/Colombia PET/COT) 🇵🇪🇨🇴 | 15:00–20:00 PET/COT | ✅ Very Good; afternoon & evening | | South America East (Brazil/Argentina/Chile, BRT/ART/CLST) 🇧🇷🇦🇷🇨🇱 | 17:00–22:00 BRT/ART/CLST | ✅ Very Good; early evening | | United Kingdom/Ireland (GMT) 🇬🇧🇮🇪 | 20:00–01:00 GMT | ✅ Very Good; evening hours (midnight convenient) | | Eastern Europe (EET) 🇷🇴🇬🇷🇺🇦 | 22:00–03:00 EET | ✅ Good; late evening & early night (slightly late) | | Africa (South Africa, SAST) 🇿🇦 | 22:00–03:00 SAST | ✅ Good; late evening & overnight (late-night common) | | New Zealand (NZDT) 🇳🇿 | 09:00–14:00 NZDT (next day) | ✅ Good; weekday morning & afternoon | | Australia (AEDT, Sydney) 🇦🇺 | 07:00–12:00 AEDT (next day) | ✅ Good; weekday morning to noon | | East Africa (Kenya, EAT) 🇰🇪 | 23:00–04:00 EAT | ⚠️ Slightly late (night hours; late night common) | | Russia (Moscow, MSK) 🇷🇺 | 23:00–04:00 MSK | ⚠️ Slightly late (join at start is fine, very late night) | | Middle East (UAE, GST) 🇦🇪🇴🇲 | 00:00–05:00 GST (next day) | ⚠️ Late night start (midnight & early morning, but shorter attendance plausible)| | Japan/Korea (JST/KST) 🇯🇵🇰🇷 | 05:00–10:00 JST/KST (next day) | ⚠️ Early; convenient joining from ~07:00 onwards possible | | China (Beijing, CST) 🇨🇳 | 04:00–09:00 CST (next day) | ❌ Challenging; very early morning start (better ~07:00 onwards) | | India (IST) 🇮🇳 | 01:30–06:30 IST (next day) | ❌ Very challenging; overnight timing typically difficult|
-
 @ dbc27e2e:b1dd0b0b
2025-04-05 20:44:00
@ dbc27e2e:b1dd0b0b
2025-04-05 20:44:00This method focuses on the amount of water in the first pour, which ultimately defines the coffee’s acidity and sweetness (more water = more acidity, less water = more sweetness). For the remainder of the brew, the water is divided into equal parts according to the strength you wish to attain.

Dose:
20g coffee (Coarse ground coffee) 300mL water (92°C / 197.6°F) Time: 3:30Instructions:
- Pour 1: 0:00 > 50mL (42% of 120mL = 40% of total – less water in the ratio, targeting sweetness.)
- Pour 2: 0:45 > 70mL (58% of 120mL = 40% of total – the top up for 40% of total.)
- Pour 3: 1:30 > 60mL (The remaining water is 180mL / 3 pours = 60mL per pour)
- Pour 4: 2:10 > 60mL
- Pour 5: 2:40 > 60mL
- Remove the V60 at 3:30
-
 @ 86dfbe73:628cef55
2025-05-04 06:56:33
@ 86dfbe73:628cef55
2025-05-04 06:56:33Building A Second Brain (BASB) ist eine Methode, mit der man Ideen, Einsichten und Vernetzungen, die man durch seine Erfahrungen gewonnen hat, systematisch speichert und die jeder Zeit abrufbar sind. Kurz, BASB erweitert das Gedächtnis mit Hilfe moderner digitaler Werkzeuge und Netzwerke. Die Kernidee ist, dass man durch diese Verlagerung sein biologisches Gehirn befreit, um frei denken zu können, seiner Kreativität freien Lauf zu geben oder einfach im Moment sein kann.
Die Methode besteht aus drei Grundschritten: dem Sammeln von Ideen und Erkenntnissen, dem Vernetzen dieser Ideen und Erkenntnisse und dem Erschaffen konkreter Ergebnisse.
Sammeln: Der erste Schritt beim Aufbau eines Second Brains ist das «Sammeln» der Ideen und Erkenntnisse, die genug wichtig oder interessant sind, um sie festzuhalten. Dafür wird als Organisationsstruktur P.A.R.A empfohlen.
Vernetzen: Sobald man angefangen hat, sein persönliches Wissen strukturiert zu sammeln, wird man anfangen, Muster und Verbindungen zwischen den Ideen und Erkenntnissen zu erkennen. Ab dieser Stelle verwende ich parallel die Zettelkastenmethode (ZKM)
Erschaffen: All das Erfassen, Zusammenfassen, Verbinden und Strukturieren haben letztlich das Ziel: Konkrete Ergebnisse in der realen Welt zu erschaffen.
PARA ist die Organisationsstruktur, die auf verschiedenen Endgeräten einsetzt werden kann, um digitale Informationen immer nach dem gleichen Schema abzulegen. Seien es Informationen, Notizen, Grafiken, Videos oder Dateien, alles hat seinen festen Platz und kann anhand von vier Kategorien bzw. „Buckets“ kategorisiert werden.
PARA steht dabei für: * Projekte * Areas * Ressourcen * Archiv
Projekte (engl. Projects) sind kurzfristige Bemühungen in Arbeit und Privatleben. Sie sind das, woran Du aktuell arbeitest. Sie haben einige für die Arbeit förderliche Eigenschaften: * Sie haben einen Anfang und ein Ende (im Gegensatz zu einem Hobby oder einem Verantwortungsbereich). * Sie haben ein konkretes Ergebnis, dass erreicht werden soll und bestehen aus konkreten Schritten, die nötig und zusammen hinreichend sind, um dieses Ziel zu erreichen, entspricht GTD von David Allen
Verantwortungsbereiche (engl. Areas) betreffen alles, was man langfristig im Blick behalten will. Sie unterscheidet von Projekten, dass man bei ihnen kein Ziel verfolgt, sondern einem Standard halten will. Sie sind dementsprechend nicht befristet. Man könnte sagen, dass sie einen Anspruch an uns selbst und unsere Lebenswelt darstellen.
Ressourcen (engl. Resources) sind Themen, die allenfalls langfristig relevant oder nützlich werden könnten. Sie sind eine Sammelkategorie für alles, was weder Projekt noch Verantwortungsbereich ist. Es sind: * Themen, die interessant sind. (English: Topic) * Untersuchungsgegenständige, die man erforschen will. (Englisch: Subject) * Nützliche Informationen für den späteren Gebrauch.
Das Archiv ist für alles Inaktive aus den obigen drei Kategorien. Es ist ein Lager für Beendetes und Aufgeschobenes.
Das System PARA ist eine nach zeitlicher Handlungsrelevanz angeordnete Ablage. Projekte kommen vor den Verantwortungsbereichen, weil sie einen kurz- bis mittelfristigen Zeithorizont haben, Verantwortungsbereiche dagegen einen unbegrenzten Zeithorizont. Ressourcen und Archiv bilden die Schlusslichter, weil sie gewöhnlich weder Priorität haben, noch dringend sind.
-
 @ 866e0139:6a9334e5
2025-04-05 11:00:25
@ 866e0139:6a9334e5
2025-04-05 11:00:25
Autor: CJ Hopkins. Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier.**
Dieser Beitrag erschien zuerst auf dem Substack-Blog des Autors.
Er soll andauern, was er auch tut. Genau wie der nie endende Krieg in Orwells 1984 wird er vom Imperium gegen seine eigenen Untertanen geführt, aber nicht nur, um die Struktur der Gesellschaft intakt zu halten, sondern in unserem Fall auch, um die Gesellschaft in eine neo-totalitäre global-kapitalistische Dystopie zu verwandeln.
Bist du nicht vertraut mit dem Krieg gegen was auch immer?
Nun ja, okay, du erinnerst dich an den Krieg gegen den Terror.
Du erinnerst dich daran, als die „Freiheit und Demokratie“ von „den Terroristen“ angegriffen wurden und wir keine andere Wahl hatten, als uns unserer demokratischen Rechte und Prinzipien zu entledigen, einen nationalen „Notstand“ auszurufen, die verfassungsmäßigen Rechte der Menschen auszusetzen, einen Angriffskrieg gegen ein Land im Nahen Osten anzuzetteln, das für uns keinerlei Bedrohung darstellte, und unsere Straßen, Bahnhöfe, Flughäfen und alle anderen Orte mit schwer bewaffneten Soldaten zu füllen, denn sonst hätten „die Terroristen gewonnen“. Du erinnerst dich, als wir ein Offshore-Gulag bauten, um verdächtige Terroristen auf unbestimmte Zeit wegzusperren, die wir zuvor zu CIA-Geheimgefängnissen verschleppt hatten, wo wir sie gefoltert und gedemütigt haben, richtig?
Natürlich erinnerst du dich. Wer könnte das vergessen?
DIE FRIEDENSTAUBE FLIEGT AUCH IN IHR POSTFACH!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt, vorerst für alle kostenfrei, wir starten gänzlich ohne Paywall. (Die Bezahlabos fangen erst zu laufen an, wenn ein Monetarisierungskonzept für die Inhalte steht). Sie wollen der Genossenschaft beitreten oder uns unterstützen? Mehr Infos hier oder am Ende des Textes.
Erinnerst du dich, als die National Security Agency keine andere Wahl hatte, als ein geheimes „Terroristen-Überwachungsprogramm“ einzurichten, um Amerikaner auszuspionieren, oder sonst „hätten die Terroristen gewonnen“? Oder wie wäre es mit den „Anti-Terror“-Unterleibsuntersuchungen der TSA, der Behörde für Transportsicherheit, die nach über zwanzig Jahren immer noch in Kraft sind?
Und was ist mit dem Krieg gegen den Populismus? An den erinnerst du dich vielleicht nicht so gut.
Ich erinnere mich, denn ich habe zwei Bücher dazu veröffentlicht. Er begann im Sommer 2016, als das Imperium erkannte, dass „rechte Populisten“ die „Freiheit und Demokratie“ in Europa bedrohten und Trump in den USA auf dem Vormarsch war. Also wurde ein weiterer „Notstand“ ausgerufen – diesmal von der Gemeinschaft der Geheimdienste, den Medien, der akademischen Welt und der Kulturindustrie. Ja, genau, es war wieder einmal an der Zeit, unsere demokratischen Prinzipien hintanzustellen, „Hassrede“ in sozialen Medien zu zensieren, die Massen mit lächerlicher offizieller Propaganda über „Russiagate,“ „Hitlergate“ und so weiter zu bombardieren – sonst hätten „die Rechtspopulisten gewonnen.“
Der Krieg gegen den Populismus gipfelte in der Einführung des Neuen Normalen Reichs.

Im Frühjahr 2020 rief das Imperium einen globalen „gesundheitlichen Ausnahmezustand“ aus, als Reaktion auf ein Virus mit einer Überlebensrate von etwa 99,8 Prozent. Das Imperium hatte keine andere Wahl, als ganze Gesellschaften abzuriegeln, jeden dazu zu zwingen, in der Öffentlichkeit medizinisch aussehende Masken zu tragen, die Öffentlichkeit mit Propaganda und Lügen zu bombardieren, die Menschen dazu zu nötigen, sich einer Reihe experimenteller mRNA-„Impfungen“ zu unterziehen, Proteste gegen ihre Dekrete zu verbieten und systematisch diejenigen zu zensieren und zu verfolgen, die es wagten, ihre erfundenen „Fakten“ in Frage zu stellen oder ihr totalitäres Programm zu kritisieren.
Das Imperium hatte keine andere Wahl, als das alles zu tun, denn sonst hätten „die Covid-Leugner, die Impfgegner, die Verschwörungstheoretiker und all die anderen Extremisten gewonnen.“
Ich bin mir ziemlich sicher, dass du dich an all das erinnerst.
Und jetzt … nun, hier sind wir. Ja, du hast es erraten – es ist wieder einmal an der Zeit, kräftig auf die US-Verfassung und die Meinungsfreiheit zu scheißen, Menschen in irgendein salvadorianisches Höllenloch abzuschieben, das wir angemietet haben, weil ein Polizist ihre Tattoos nicht mochte, Universitätsstudenten wegen ihrer Anti-Israel-Proteste festzunehmen und zu verschleppen und natürlich die Massen mit Lügen und offizieller Propaganda zu bombardieren, denn … okay, alle zusammen jetzt: „sonst hätten die antisemitischen Terroristen und venezolanischen Banden gewonnen!“
Fängst du an, ein Muster zu erkennen? Ja? Willkommen beim Krieg gegen-was-auch-immer!
Wenn du die Zusammenhänge noch nicht ganz siehst, okay, lass es mich noch einmal ganz simpel erklären.
Das globale ideologische System, in dem wir alle leben, wird totalitär. (Dieses System ist der globale Kapitalismus, aber nenne es, wie du willst. Es ist mir scheißegal.) Es reißt die Simulation der Demokratie nieder, die es nicht mehr aufrechterhalten muss. Der Kalte Krieg ist vorbei. Der Kommunismus ist tot. Der globale Kapitalismus hat keine externen Feinde mehr. Also muss er die Massen nicht mehr mit demokratischen Rechten und Freiheiten besänftigen. Deshalb entzieht er uns diese Rechte nach und nach und konditioniert uns darauf, ihren Verlust hinzunehmen.
Er tut dies, indem er eine Reihe von „Notständen“ inszeniert, jeder mit einer anderen „Bedrohung“ für die „Demokratie,“ die „Freiheit,“ „Amerika“ oder „den Planeten“ – oder was auch immer. Jeder mit seinen eigenen „Monstern,“ die eine so große Gefahr für die „Freiheit“ oder was auch immer darstellen, dass wir unsere verfassungsmäßigen Rechte aufgeben und die demokratischen Werte ad absurdum führen müssen, denn: sonst „würden die Monster gewinnen.“

Es tut dies, indem es sein Antlitz von „links“ nach „rechts,“ dann zurück nach „links“, und dann zurück nach „rechts,“ dann nach „links“ und so weiter neigt, weil es unsere Kooperation dafür benötigt. Nicht die Kooperation von uns allen auf einmal. Nur eine kooperative demografische Gruppe auf einmal.
Es ist dabei erfolgreich – also das System – indem es unsere Angst und unseren Hass instrumentalisiert. Dem System ist es völlig egal, ob wir uns als „links“ oder „rechts“ identifizieren, aber es braucht uns gespalten in „links“ und „rechts,“ damit es unsere Angst und unseren Hass aufeinander nähren kann … eine Regierung, ein „Notfall,“ ein „Krieg“ nach dem anderen.
Da hast du es. Das ist der Krieg gegen was auch immer. Noch simpler kann ich es nicht erklären.
Oh, und noch eine letzte Sache … wenn du einer meiner ehemaligen Fans bist, wie Rob, die über meine „Einsichten“ oder Loyalitäten oder was auch immer verwirrt sind … nun, der Text, den du gerade gelesen hast, sollte das für dich klären. Ich stehe auf keiner Seite. Überhaupt keiner. Aber ich habe ein paar grundlegende demokratische Prinzipien. Und die richten sich nicht danach, was gerade populär ist oder wer im Weißen Haus sitzt.
Die Sache ist die: Ich muss mich morgens im Spiegel anschauen können ohne dort einen Heuchler oder … du weißt schon, einen Feigling zu sehen.
(Aus dem Amerikanischen übersetzt von René Boyke).
CJ Hopkins ist ein US-amerikanischer Dramatiker, Romanautor und politischer Satiriker. Zu seinen Werken zählen die Stücke Horse Country, Screwmachine/Eyecandy und The Extremists. Er hat sich als profilierter Kritiker des Corona-Regimes profiliert und veröffentlicht regelmäßig auf seinem Substack-Blog.
Sein aktuelles Buch:
https://x.com/CJHopkins_Z23/status/1907795633689264530
Hier in einem aktuellen Gespräch:
https://www.youtube.com/watch?v=wF-G32P0leI
LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt. (Vorerst alle, da wir den Mailversand testen, später ca. drei Mails pro Woche.)
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: milosz@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ 57d1a264:69f1fee1
2025-05-04 06:37:52
@ 57d1a264:69f1fee1
2025-05-04 06:37:52KOReader is a document viewer for E Ink devices. Supported file formats include EPUB, PDF, DjVu, XPS, CBT, CBZ, FB2, PDB, TXT, HTML, RTF, CHM, DOC, MOBI and ZIP files. It’s available for Kindle, Kobo, PocketBook, Android and desktop Linux.
Download it from https://koreader.rocks Repository: https://github.com/koreader/koreader
originally posted at https://stacker.news/items/970912
-
 @ da18e986:3a0d9851
2025-04-04 20:25:50
@ da18e986:3a0d9851
2025-04-04 20:25:50I'm making this tutorial for myself, as I plan to write many wiki pages describing DVM kinds, as a resource for DVMDash.
Wiki pages on Nostr are written using AsciiDoc. If you don't know ascii doc, get an LLM (like https://duck.ai) to help you format into the right syntax.
Here's the test wiki page I'm going to write:
``` = Simple AsciiDoc Demo
This is a simple demonstration of AsciiDoc syntax for testing purposes.
== Features
AsciiDoc offers many formatting options that are easy to use.
- Easy to learn
- Supports rich text formatting
- Can include code snippets
- Works great for documentation
[source,json]
{ "name": "Test", "version": "1.0", "active": true }
```
We're going to use nak to publish it
First, install
nakif you haven't alreadygo install github.com/fiatjaf/nak@latestNote: if you don't use Go a lot, you may need to first install it and then add it to your path so the
nakcommand is recognized by the terminal```
this is how to add it to your path on mac if using zsh
echo 'export PATH=$PATH:$(go env GOPATH)/bin' >> ~/.zshrc ```
And here's how to sign and publish this event with nak.
First, if you want to use your own nostr sec key, you can set the env variable to it and nak will use that if no secret key is specified
```
replace with your full secret key
export NOSTR_SECRET_KEY="nsec1zcdn..." ```
Now to sign and publish the event:
Note: inner double quotes need to be escaped with a
\before them in order to keep the formatting correct, because we're doing this in the terminalnak event -k 30818 -d "dvm-wiki-page-test" -t 'title=dvm wiki page test' -c "= Simple AsciiDoc Demo\n\nThis is a simple demonstration of AsciiDoc syntax for testing purposes. \n\n== Features\n\nAsciiDoc offers many formatting options that are easy to use. \n\n* Easy to learn \n* Supports rich text formatting \n* Can include code snippets \n* Works great for documentation \n\n[source,json] \n---- \n{ \"name\": \"Test\", \"version\": \"1.0\", \"active\": true } \n----" wss://relay.primal.net wss://relay.damus.io wss://relay.wikifreedia.xyzYou've now published your first wiki page! If done correctly, it will show up on wikistr.com, like mine did here: https://wikistr.com/dvm-wiki-page-test*da18e9860040f3bf493876fc16b1a912ae5a6f6fa8d5159c3de2b8233a0d9851
and on wikifreedia.xyz https://wikifreedia.xyz/dvm-wiki-page-test/dustind@dtdannen.github.io
-
 @ 57d1a264:69f1fee1
2025-05-04 06:27:15
@ 57d1a264:69f1fee1
2025-05-04 06:27:15Well, today posts looks are dedicated to STAR WARS. Enjoy!
Today we’re looking at Beat Saber (2019) and why its most essential design element can be used to make great VR games that have nothing to do with music or rhythm.
https://www.youtube.com/watch?v=EoOeO7S9ehw
It’s hard to believe Beat Saber was first released in Early Access seven years ago today. From day one, it was clear the game was something special, but even so we couldn’t have predicted it would become one of VR’s best-selling games of all time—a title it still holds all these years later. In celebration of the game’s lasting legacy we’re re-publishing our episode of Inside XR Design which explores the secret to Beat Saber’s fun, and how it can be applied to VR games which have nothing to do with music.
Read more at https://www.roadtovr.com/beat-saber-instructed-motion-until-you-fall-inside-xr-design/
originally posted at https://stacker.news/items/970909
-
 @ 57d1a264:69f1fee1
2025-05-04 06:16:58
@ 57d1a264:69f1fee1
2025-05-04 06:16:58Found this really fun, so created a few intros for latest SN newsletters https://stacker.news/items/960787/r/Design_r?commentId=970902 and https://stacker.news/items/970459/r/Design_r?commentId=970905
Create your STAR-WARS-like movie intro https://starwarsintrocreator.kassellabs.io/
originally posted at https://stacker.news/items/970906
-
 @ 502ab02a:a2860397
2025-05-04 03:13:06
@ 502ab02a:a2860397
2025-05-04 03:13:06เรารู้จักกับ Circadian Rhythm และ Infradian Rhythm แล้ว คราวนี้เรามารู้จักกับ Ultradian Rhythm กันครับ จากรากศัพท์ภาษาละติน คำว่า “Ultra” แปลว่า “มากกว่า” หรือ “ถี่กว่า” คำว่า diem” = แปลว่า "วัน" พอเอามารวมกันเป็น “ultradian” ก็หมายถึงวงจรชีวภาพที่เกิดขึ้น บ่อยกว่า 1 รอบต่อวัน (ความถี่สูงกว่ารอบ 24 ชั่วโมง) ไม่ใช่ “ยาวกว่า 1 วัน” สรุปเป็นภาษาง่ายๆคือ "จังหวะชีวภาพที่เกิดซ้ำ มากกว่า 1 ครั้งภายใน 24 ชั่วโมง"
หรือถ้าเราจะเรียงลำดับของ Rythm ทั้ง 3 ประเภทเราจะได้เป็น 1.Circadian Rhythm (ประมาณ 24 ชม.) 2.Ultradian Rhythm (น้อยกว่า 24 ชม.) 3.Infradian Rhythm (มากกว่า 24 ชม.)
สำหรับตัวอย่าง Ultradian Rhythm ที่สำคัญๆนะครับ เช่น 1. วัฏจักรการนอน (Sleep Cycle) ที่แต่ละรอบ จะอยู่ที่ราวๆ 90–120 นาที สลับกันไปมาระหว่าง NREM (หลับลึก) และ REM (ฝัน) อย่างที่สายสุขภาพเรียนรู้กันมาคือ ถ้าหลับสลับครบ 4–6 รอบ จะหลับสนิท ฟื้นเช้ามาสดชื่นแจ่มใสพักผ่อนเต็มที่
แสงเช้า-แดดอ่อนๆ ช่วยรีเซ็ต circadian แต่ก็ส่งผลให้ ultradian sleep cycle เริ่มต้นตรงจังหวะพอดี นอกจากนี้ยังมีสิ่งที่เรียกว่า Power nap ตอนแดดบ่าย (20–25 นาทีแดดอ่อน) จะช่วยกระตุ้น ultradian nap cycle ให้ตื่นขึ้นมาเป๊ะ ไม่งัวเงีย ให้เลือกจุดที่แดดยังอ่อน เช่น ริมหน้าต่างที่มีแดดผ่านมานุ่ม ๆ หรือใต้ต้นไม้ที่กรองแสงได้บางส่วน ไม่จำเป็นต้องนอนตากแดดโดยตรง แต่ให้ “รับแสงธรรมชาติ” พร้อมกับงีบ จะช่วยให้ circadian และ ultradian cycles ทำงานประสานกันได้ดีขึ้น
- การหลั่งฮอร์โมนแบบพัลซ์ หรือ Pulsatile Hormone Secretion คือรูปแบบการปล่อยฮอร์โมนออกมาจากต่อมต่าง ๆ ในร่างกายแบบเป็น “จังหวะ” หรือ “เป็นช่วง” (bursts/pulses) ไม่ใช่การหลั่งออกมาอย่างต่อเนื่องตลอดเวลา เช่น เทพแห่งการลดน้ำหนัก Growth Hormone (GH) หลั่งพุ่งตอนหลับลึกทุก 3–4 ชั่วโมง / Cortisol มีพัลซ์เล็กๆ ในวัน แม้หลักๆ จะเป็น circadian แต่ก็มี ultradian pulse ทุก 1–2 ชั่วโมง ได้เหมือนกัน / Insulin & Glucagon ชัดเลยชาว keto IF รู้ดีที่สุดว่า หลั่งเป็นรอบตามมื้ออาหารและช่วงพักระหว่างมื้อ
ลองนึกภาพว่า “แสงแดง” และ “อินฟราเรด” เปรียบเหมือนอาหารเช้าของเซลล์เรา เมื่อผิวเราโดนแดดอ่อน ๆ ในช่วงเช้าหรือบ่ายแก่ แสงเหล่านี้จะซึมเข้าไปกระตุ้น “โรงไฟฟ้าประจำเซลล์” (ไมโตคอนเดรีย) ให้ผลิตพลังงาน (ATP) ขึ้นมาเพิ่ม เหมือนเติมน้ำมันให้เครื่องยนต์วิ่งได้ลื่น พอเซลล์มีพลังงานมากขึ้น ในช่วงที่ร่างกายหลั่งฮอร์โมนการซ่อมแซมอย่าง “growth hormone” (GH) ร่างกายก็จะใช้พลังงานจากแสงนี้พร้อมกับฮอร์โมนในการซ่อมแซมกล้ามเนื้อและเนื้อเยื่อต่าง ๆ ได้เต็มประสิทธิภาพขึ้นนั่นเองครับ
- ช่วงเวลาการจดจ่อ หรือ Attention Span & Energy Cycle คนทั่วไปมีสมาธิ/พลังงานโฟกัสอยู่รอบละ 90 นาที หลังจากนั้นควรพัก 10–20 นาที หากฝืนต่อเนื่อง จะเกิดอาการอ่อนล้า สมาธิหลุด
Blue light เช้า จากแดดจะไปกระตุ้นในส่วนของ suprachiasmatic nucleus (SCN) ในสมองให้ปล่อยสารกระตุ้นความตื่นตัว (เช่น คอร์ติซอล) พอสมควร ซึ่งช่วยให้ ultradian cycle ของสมาธิ (โฟกัสได้ประมาณ 90 นาที) ทำงานเต็มประสิทธิภาพ ถ้าเช้าๆ ไม่เจอแดดเลย cycle นี้จะเลื่อนออกไป ทำให้รู้สึกง่วงเหงาหาวนอนเร็ว หรือโฟกัสไม่ได้นานตามปกติ เป็นที่มาของการเพลียแม้จะตื่นสายแล้วก็ตาม
- รอบความหิว หรือ Appetite & Digestive Rhythm ชื่อเท่ห์ป่ะหล่ะ 555 คือความหิวมาเป็นรอบตามวิธีการกินของแต่ละคน ซึ่งเป็นความสัมพันธ์กับ ฮอร์โมน GI (เช่น ghrelin, leptin) ก็วิ่งเป็นรอบเหมือนกัน
แสงแดดเช้า ช่วยตั้ง leptin/ghrelin baseline ให้สมดุล ลดการกินจุกจิกนอกมื้อได้ ส่วนแสงอ่อนๆ ตอนบ่ายช่วยบูสต์ blood flow ในทางเดินอาหาร ให้ digestion cycle หรือการดูดซึมสารอาหารตรงจังหวะ
แดดเป็นแค่ส่วนสำคัญในชีวิตแต่การใช้ Ultradian Rhythm มันต้องประกอบกับกิจกรรมอื่นๆด้วยนะครับ เช่น ทำงานหรืออ่านหนังสือ 90 นาที แล้ว พัก 15–20 นาที ยืดเส้นสาย เคลื่อนไหวเล็กน้อย, ออกกำลังกายให้ตรงจังหวะ, ในช่วง ultradian break พยายามลดการใช้จอมือถือ/คอมฯ ออกไปรับแสงธรรมชาติ หรือยืดเส้น เปิดเพลงเบาๆ เพื่อหลีกเลี่ยง "stimuli" ช่วง break หรือ สิ่งเร้าภายนอก ที่มากระตุ้นประสาทสัมผัสและสมองเรา
แสงแดดจึงเป็น ตัวตั้งเวลา (zeitgeber) ที่ไม่ได้แค่กับรอบวัน-เดือน-ปี แต่รวมถึงจังหวะสั้นๆ ภายในวันด้วย การใช้แสงธรรมชาติให้พอดีในแต่ละช่วง (เช้า เบรก บ่าย) จะช่วยให้ ultradian rhythms ในด้านสมาธิ การนอน ฮอร์โมน และการย่อยอาหาร ทำงานสอดคล้องกับจังหวะชีวิตที่เป็นธรรมชาติที่สุดครับ #pirateketo #SundaySpecialเราจะไปเป็นหมูแดดเดียว #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-
 @ c631e267:c2b78d3e
2025-04-04 18:47:27
@ c631e267:c2b78d3e
2025-04-04 18:47:27Zwei mal drei macht vier, \ widewidewitt und drei macht neune, \ ich mach mir die Welt, \ widewide wie sie mir gefällt. \ Pippi Langstrumpf
Egal, ob Koalitionsverhandlungen oder politischer Alltag: Die Kontroversen zwischen theoretisch verschiedenen Parteien verschwinden, wenn es um den Kampf gegen politische Gegner mit Rückenwind geht. Wer den Alteingesessenen die Pfründe ernsthaft streitig machen könnte, gegen den werden nicht nur «Brandmauern» errichtet, sondern der wird notfalls auch strafrechtlich verfolgt. Doppelstandards sind dabei selbstverständlich inklusive.
In Frankreich ist diese Woche Marine Le Pen wegen der Veruntreuung von EU-Geldern von einem Gericht verurteilt worden. Als Teil der Strafe wurde sie für fünf Jahre vom passiven Wahlrecht ausgeschlossen. Obwohl das Urteil nicht rechtskräftig ist – Le Pen kann in Berufung gehen –, haben die Richter das Verbot, bei Wahlen anzutreten, mit sofortiger Wirkung verhängt. Die Vorsitzende des rechtsnationalen Rassemblement National (RN) galt als aussichtsreiche Kandidatin für die Präsidentschaftswahl 2027.
Das ist in diesem Jahr bereits der zweite gravierende Fall von Wahlbeeinflussung durch die Justiz in einem EU-Staat. In Rumänien hatte Călin Georgescu im November die erste Runde der Präsidentenwahl überraschend gewonnen. Das Ergebnis wurde später annulliert, die behauptete «russische Wahlmanipulation» konnte jedoch nicht bewiesen werden. Die Kandidatur für die Wahlwiederholung im Mai wurde Georgescu kürzlich durch das Verfassungsgericht untersagt.
Die Veruntreuung öffentlicher Gelder muss untersucht und geahndet werden, das steht außer Frage. Diese Anforderung darf nicht selektiv angewendet werden. Hingegen mussten wir in der Vergangenheit bei ungleich schwerwiegenderen Fällen von (mutmaßlichem) Missbrauch ganz andere Vorgehensweisen erleben, etwa im Fall der heutigen EZB-Chefin Christine Lagarde oder im «Pfizergate»-Skandal um die Präsidentin der EU-Kommission Ursula von der Leyen.
Wenngleich derartige Angelegenheiten formal auf einer rechtsstaatlichen Grundlage beruhen mögen, so bleibt ein bitterer Beigeschmack. Es stellt sich die Frage, ob und inwieweit die Justiz politisch instrumentalisiert wird. Dies ist umso interessanter, als die Gewaltenteilung einen essenziellen Teil jeder demokratischen Ordnung darstellt, während die Bekämpfung des politischen Gegners mit juristischen Mitteln gerade bei den am lautesten rufenden Verteidigern «unserer Demokratie» populär zu sein scheint.
Die Delegationen von CDU/CSU und SPD haben bei ihren Verhandlungen über eine Regierungskoalition genau solche Maßnahmen diskutiert. «Im Namen der Wahrheit und der Demokratie» möchte man noch härter gegen «Desinformation» vorgehen und dafür zum Beispiel den Digital Services Act der EU erweitern. Auch soll der Tatbestand der Volksverhetzung verschärft werden – und im Entzug des passiven Wahlrechts münden können. Auf europäischer Ebene würde Friedrich Merz wohl gerne Ungarn das Stimmrecht entziehen.
Der Pegel an Unzufriedenheit und Frustration wächst in großen Teilen der Bevölkerung kontinuierlich. Arroganz, Machtmissbrauch und immer abstrusere Ausreden für offensichtlich willkürliche Maßnahmen werden kaum verhindern, dass den etablierten Parteien die Unterstützung entschwindet. In Deutschland sind die Umfrageergebnisse der AfD ein guter Gradmesser dafür.
[Vorlage Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ 3eba5ef4:751f23ae
2025-04-04 03:05:59
@ 3eba5ef4:751f23ae
2025-04-04 03:05:59Crypto Insights
How to Identify Bitcoin Mining Nodes: Difficulty, Methods, and Security Risks
In Bitcoin’s P2P network, identifying mining nodes and their adjacent ones can expose potential attack surfaces. Previous research has demonstrated that influential nodes can be identified by coloring nodes with conflicting transactions. These nodes may not be miners' gateway nodes but can ultimately connect to mining ones.
This study, based on the Bitcoin network environment of 2025, explores the difficulty of finding such nodes. The results indicate that these attacks are viable, and leveraging a set of influential mining nodes makes it easier to carry out mainnet partitioning, pinning, replacement cycling, or other yet-undiscovered mempool and Lightning Network attacks.
Boot Protocol: A Decentralized Block Reward Protocol to Reduce Income Volatility
Boot Protocol is a decentralized protocol designed to address Bitcoin mining variance—the fluctuations in the time it takes to find a block and the rewards received—which leads to income volatility. It enables block reward sharing without tracking actual mining work, offering up to 16x lower variance than solo mining while avoiding centralization issues.
- Issue: Centralized mining pools dominate block rewards, leaving small miners with high variance.
- Boot Protocol’s solution: A decentralized, low-variance system that mimics solo mining while offering mining pool advantages.
- Advantages: Compared to solo mining, it reduces variance by up to 16x and is more resistant to regulatory attacks than centralized mining pools.
- Against withholding attacks: The protocol is designed to prevent block withholding attacks by incentivizing miners to submit blocks as soon as possible.
- Potential: Boot Protocol has the potential to revolutionize decentralized mining by eliminating the shortcomings of approaches like P2Pool and Braid Pool.
Trustless Coin Flip Game Built on Taproot and Multisig
Coinflip is a two-player coin-flipping game inspired by the concept of "Zero-Collateral Lotteries" and built using Taproot and multisig.
Exploring Duplicate Transactions in Bitcoin
In the Bitcoin blockchain, there are two sets of completely identical transactions from mid-November 2010, where one set sandwiches the other. Since the coinbase transactions have no inputs but newly generated coins, two different coinbase transactions can send the same amount to the same address in the exact same way, resulting in identical transactions.
Because duplicate transactions can cause confusion, developers have been researching solutions for years, but no ideal fix has been found. The next potential duplicate transaction event is expected in 2046. While the current risks associated with duplicate transactions are low, this remains an intriguing and novel issue. This article explores the topic in detail.
A Fee Protocol to Prevent Lightning Network Spam
Lightning Network spam happens when some one floods the network with a constant stream of HTLCs to disrupt legitimate payments. To tackle this, this paper proposes a protocol for assigning and collecting fees in the Lightning Network to mitigate spam risks. It establishes fees corresponding to all significant costs, whereas previous attempts charged fees for delayed and/or failed payments, omitted certain costs or relied on trust to prevent theft.
This protocol introduces a "griefer-penalization" mechanism: if a party suffers malicious behavior (griefing) from a channel partner, they can be made to lose certain funds, but the griefer also bears a corresponding cost. As a result, a party that only selects self-interested partners is unlikely to be griefed.
Cashu Launches Instant Offline Ecash Payments
Cashu has developed a new tap-to-pay feature that enables instant, offline ecash payments via NFC.
As a bearer token, ecash is stored directly on the user’s device rather than on a server. This is why it integrates so well with NFC.
Coinbase Open-Sourced Multi-Party Computation Library
Coinbase has open-sourced its Multi-Party Computation (MPC) engine. Coinbase's cryptography lead, Yehuda Lindell, stated that the library supports two-party and multi-party signatures for ECDSA and Schnorr/EdDSA, as well as tools for DKG, backup, and more.
This release includes the full code stack, including commitments, random oracles, secret sharing, oblivious transfer (basic and extension), and a series of ZK proofs for various threshold signing tasks. All protocols come with complete specifications and theory documents. The team has also conducted full benchmark tests, providing insights into running time and bandwidth consumption from low-level primitives to full protocols.
RISC Zero zkVM Advances: R0VM 2.0 and OP Kailua
RISC Zero is advancing its zkVM technology with the release of R0VM 2.0 and the introduction of OP Kailua to enhance blockchain verifiability, security, and scalability.
RISC Zero uses Picus for formal verification of zkVM components. R0VM 2.0 will be the first formally verified RISC-V zkVM, addressing security risks from insufficient constraints in ZK systems, ensuring provable correctness, and offering stronger security guarantees for developers.
OP Kailua is a zkVM opcode that enables efficient on-chain validity proofs, allowing OP chains to upgrade into ZK Rollups, offering: * <1 hour Finality * Stronger security requiring only one honest sequencer * Lower costs as low as $0.00012/tx
Three Blocks Recently Solo-Mined
Three independent miners successfully mined Bitcoin blocks recently, signaling a rise in home mining.
- Block 888,737 was mined using a DIY FutureBit Apollo device, earning 3.125 BTC plus fees.
- An independent miner with a hashrate below 1 TH/s mined block 888,989.
- A miner using a $300 setup successfully mined block 889,240.
New Book | Principles of Bitcoin: Cutting Through the Noise to Reveal the Core Value
Principles of Bitcoin constructs a holistic framework understanding Bitcoin from first principles. It strips away industry hype, jargon, and superficial analysis to reveal the ingenuity of Satoshi’s creation and its implications for money, governance, and individual freedom.
By examining Bitcoin through technical, economic, political, and philosophical lenses, the author argues that only through this holistic understanding can one grasp its significance. He presents Bitcoin as a tool for individual empowerment and economic sovereignty, showing how it challenges traditional financial systems, and why it is a unique, non-replicable innovation in the digital asset space.
Top Reads on Blockchain and Beyond
Podcast | Can Pricing Solve Congestion? Applying Toll Economics to Crypto
To alleviate traffic congestion, New York City implemented congestion pricing in early 2025. Could similar mechanisms be applied to the crypto? In this podcast episode, congestion pricing expert (and one of its key proponents) Michael Ostrovsky discusses the economics behind congestion pricing and explores its implications for both city blocks and blockchain.
Model Context Protocol: A Unified Framework for Instant, Bidirectional AI Agent Communication
MCP (Model Context Protocol) was introduced by Anthropic in late 2024 as an open standard to enhance the connection of AI agent LLM apps and user data. Unlike traditional AI integrations that rely on fragmented, custom-built solutions, MCP provides a unified framework for bidirectional communication. This allows AI agents not only to pull in external data, but also to send updates back to these systems, enabling more dynamic and autonomous behavior. Additionally, MCP’s open-source nature fosters industry-wide collaboration, contrasting with the more siloed approaches of centralized AI companies.
This tweet offers a summary of MCP’s capabilities and significance.
The Era of Culturementals: Culture is More Fundamental than Technology
This post argues that the crypto space has repeatedly demonstrated that culture trumps technology. This perspective defines the rise of Culture Chains—blockchains shaped not by their technical capabilities, but by the communities they serve. Culture Chains can be seen as an evolution of “vertical blockchains”—designed not for universal adoption but for specific niche groups, such as anime fans, role-playing gamers, or meme lovers. Functioning like digital city-states, these chains build around shared values, language, and interests, offering tailored infrastructure, governance models, and token economies.
-
 @ 7bdef7be:784a5805
2025-04-02 12:12:12
@ 7bdef7be:784a5805
2025-04-02 12:12:12We value sovereignty, privacy and security when accessing online content, using several tools to achieve this, like open protocols, open OSes, open software products, Tor and VPNs.
The problem
Talking about our social presence, we can manually build up our follower list (social graph), pick a Nostr client that is respectful of our preferences on what to show and how, but with the standard following mechanism, our main feed is public, so everyone can actually snoop what we are interested in, and what is supposable that we read daily.
The solution
Nostr has a simple solution for this necessity: encrypted lists. Lists are what they appear, a collection of people or interests (but they can also group much other stuff, see NIP-51). So we can create lists with contacts that we don't have in our main social graph; these lists can be used primarily to create dedicated feeds, but they could have other uses, for example, related to monitoring. The interesting thing about lists is that they can also be encrypted, so unlike the basic following list, which is always public, we can hide the lists' content from others. The implications are obvious: we can not only have a more organized way to browse content, but it is also really private one.
One might wonder what use can really be made of private lists; here are some examples:
- Browse “can't miss” content from users I consider a priority;
- Supervise competitors or adversarial parts;
- Monitor sensible topics (tags);
- Following someone without being publicly associated with them, as this may be undesirable;
The benefits in terms of privacy as usual are not only related to the casual, or programmatic, observer, but are also evident when we think of how many bots scan our actions to profile us.
The current state
Unfortunately, lists are not widely supported by Nostr clients, and encrypted support is a rarity. Often the excuse to not implement them is that they are harder to develop, since they require managing the encryption stuff (NIP-44). Nevertheless, developers have an easier option to start offering private lists: give the user the possibility to simply mark them as local-only, and never push them to the relays. Even if the user misses the sync feature, this is sufficient to create a private environment.
To date, as far as I know, the best client with list management is Gossip, which permits to manage both encrypted and local-only lists.
Beg your Nostr client to implement private lists!
-
 @ 71550e6c:b64c37a9
2025-03-29 10:55:55
@ 71550e6c:b64c37a9
2025-03-29 10:55:55Just do the same as this video shows.
Here's the video: https://cdn.azzamo.net/7cdcc2718f1e15eb03e323f62e07582b4001da273aa5c21475d680f02b32f0e9.mp4
One caveat: do not trust the draft will be kept here after you close
nak fs. Wait, no, it definitely won't stay here, but I'm not even sure it will stay here if you only navigate away and come back later, FUSE is weird and I didn't test.But at least it should work for copy-pasting. Or writing everything in one go.
-
 @ 05cdefcd:550cc264
2025-03-28 08:00:15
@ 05cdefcd:550cc264
2025-03-28 08:00:15The crypto world is full of buzzwords. One that I keep on hearing: “Bitcoin is its own asset class”.
While I have always been sympathetic to that view, I’ve always failed to understand the true meaning behind that statement.
Although I consider Bitcoin to be the prime innovation within the digital asset sector, my primary response has always been: How can bitcoin (BTC), a single asset, represent an entire asset class? Isn’t it Bitcoin and other digital assets that make up an asset class called crypto?
Well, I increasingly believe that most of crypto is just noise. Sure, it’s volatile noise that is predominately interesting for very sophisticated hedge funds, market makers or prop traders that are sophisticated enough to extract alpha – but it’s noise nonetheless and has no part to play in a long-term only portfolio of private retail investors (of which most of us are).
 Over multiple market cycles, nearly all altcoins underperform Bitcoin when measured in BTC terms. Source: Tradingview
Over multiple market cycles, nearly all altcoins underperform Bitcoin when measured in BTC terms. Source: TradingviewAha-Moment: Bitcoin keeps on giving
Still, how can Bitcoin, as a standalone asset, make up an entire asset class? The “aha-moment” to answer this question recently came to me in a Less Noise More Signal interview I did with James Van Straten, senior analyst at Coindesk.
Let me paraphrase him here: “You can’t simply recreate the same ETF as BlackRock. To succeed in the Bitcoin space, new and innovative approaches are needed. This is where understanding Bitcoin not just as a single asset, but as an entire asset class, becomes essential. There are countless ways to build upon Bitcoin’s foundation—varied iterations that go beyond just holding the asset. This is precisely where the emergence of the Bitcoin-linked stock market is taking shape—and it's already underway.”
And this is actually coming to fruition as we speak. Just in the last few days, we saw several products launch in that regard.
Obviously, MicroStrategy (now Strategy) is the pioneer of this. The company now owns 506,137 BTC, and while they’ll keep on buying more, they have also inspired many other companies to follow suit.
In fact, there are now already over 70 companies that have adopted Strategy’s Bitcoin playbook. One of the latest companies to buy Bitcoin for their corporate treasury is Rumble. The YouTube competitor just announced their first Bitcoin purchase for $17 million.
Also, the gaming zombie company GameStop just announced to raise money to buy BTC for their corporate treasury.
 Gamestop to make BTC their hurdle rate. Source: X
Gamestop to make BTC their hurdle rate. Source: XETF on Bitcoin companies
Given this proliferation of Bitcoin Treasury companies, it was only a matter of time before a financial product tracking these would emerge.
The popular crypto index fund provider Bitwise Investments has just launched this very product called the Bitwise Bitcoin Standard Corporations ETF (OWNB).
The ETF tracks Bitcoin Treasury companies with over 1,000 BTC on their balance sheet. These companies invest in Bitcoin as a strategic reserve asset to protect the $5 trillion in low-yield cash that companies in the US commonly sit on.
 These are the top 10 holdings of OWNB. Source: Ownbetf
These are the top 10 holdings of OWNB. Source: OwnbetfETF on Bitcoin companies’ convertible bonds
Another instrument that fits seamlessly into the range of Bitcoin-linked stock market products is the REX Bitcoin Corporate Treasury Convertible Bond ETF (BMAX). The ETF provides exposure to the many different convertible bonds issued by companies that are actively moving onto a Bitcoin standard.
Convertible bonds are a valuable financing tool for companies looking to raise capital for Bitcoin purchases. Their strong demand is driven by the unique combination of equity-like upside and debt-like downside protection they offer.
For example, MicroStrategy's convertible bonds, in particular, have shown exceptional performance. For instance, MicroStrategy's 2031 bonds has shown a price rise of 101% over a one-year period, vastly outperforming MicroStrategy share (at 53%), Bitcoin (at 25%) and the ICE BofA U.S. Convertible Index (at 10%). The latter is the benchmark index for convertible bond funds, tracking the performance of U.S. dollar-denominated convertible securities in the U.S. market.
 The chart shows a comparison of ICE BofA U.S. Convertible Index, the Bloomberg Bitcoin index (BTC price), MicroStrategy share (MSTR), and MicroStrategy bond (0.875%, March 15 203). The convertible bond has been outperforming massively. Source: Bloomberg
The chart shows a comparison of ICE BofA U.S. Convertible Index, the Bloomberg Bitcoin index (BTC price), MicroStrategy share (MSTR), and MicroStrategy bond (0.875%, March 15 203). The convertible bond has been outperforming massively. Source: BloombergWhile the BMAX ETF faces challenges such as double taxation, which significantly reduces investor returns (explained in more detail here), it is likely that future products will emerge that address and improve upon these issues.
Bitcoin yield products
The demand for a yield on Bitcoin has increased tremendously. Consequently, respective products have emerged.
Bitcoin yield products aim to generate alpha by capitalizing on volatility, market inefficiencies, and fragmentation within cryptocurrency markets. The objective is to achieve uncorrelated returns denominated in Bitcoin (BTC), with attractive risk-adjusted performance. Returns are derived exclusively from asset selection and trading strategies, eliminating reliance on directional market moves.
Key strategies employed by these funds include:
- Statistical Arbitrage: Exploits short-term pricing discrepancies between closely related financial instruments—for instance, between Bitcoin and traditional assets, or Bitcoin and other digital assets. Traders utilize statistical models and historical price relationships to identify temporary inefficiencies.
- Futures Basis Arbitrage: Captures profits from differences between the spot price of Bitcoin and its futures contracts. Traders simultaneously buy or sell Bitcoin on spot markets and enter opposite positions in futures markets, benefiting as the prices converge.
- Funding Arbitrage: Generates returns by taking advantage of variations in Bitcoin funding rates across different markets or exchanges. Funding rates are periodic payments exchanged between long and short positions in perpetual futures contracts, allowing traders to profit from discrepancies without significant directional exposure.
- Volatility/Option Arbitrage: Seeks profits from differences between implied volatility (reflected in Bitcoin options prices) and expected realized volatility. Traders identify mispriced volatility in options related to Bitcoin or Bitcoin-linked equities, such as MSTR, and position accordingly to benefit from volatility normalization.
- Market Making: Involves continuously providing liquidity by simultaneously quoting bid (buy) and ask (sell) prices for Bitcoin. Market makers profit primarily through capturing the spread between these prices, thereby enhancing market efficiency and earning consistent returns.
- Liquidity Provision in DeFi Markets: Consists of depositing Bitcoin (usually as Wrapped BTC) into decentralized finance (DeFi) liquidity pools such as those on Uniswap, Curve, or Balancer. Liquidity providers earn fees paid by traders who execute swaps within these decentralized exchanges, creating steady yield opportunities.
Notable products currently available in this segment include the Syz Capital BTC Alpha Fund offered by Syz Capital and the Forteus Crypto Alpha Fund by Forteus.
BTC-denominated share class
A Bitcoin-denominated share class refers to a specialized investment fund category in which share values, subscriptions (fund deposits), redemptions (fund withdrawals), and performance metrics are expressed entirely in Bitcoin (BTC), rather than in traditional fiat currencies such as USD or EUR.
Increasingly, both individual investors and institutions are adopting Bitcoin as their preferred benchmark—or "Bitcoin hurdle rate"—meaning that investment performance is evaluated directly against Bitcoin’s own price movements.
These Bitcoin-denominated share classes are designed specifically for investors seeking to preserve and grow their wealth in Bitcoin terms, rather than conventional fiat currencies. As a result, investors reduce their exposure to fiat-related risks. Furthermore, if Bitcoin outperforms fiat currencies, investors holding BTC-denominated shares will experience enhanced returns relative to traditional fiat-denominated investment classes.
X: https://x.com/pahueg
Podcast: https://www.youtube.com/@lessnoisemoresignalpodcast
Book: https://academy.saifedean.com/product/the-bitcoin-enlightenment-hardcover/
-
 @ ff517fbf:fde1561b
2025-03-26 16:48:41
@ ff517fbf:fde1561b
2025-03-26 16:48:41フアン・ラモン・ラッロ氏は、スペイン出身の経済学者・作家であり、自由市場経済とリベラルな思想の提唱者として知られています。彼は、国家による過剰な介入や財政政策の問題点を鋭く分析し、自由主義の基本原則に基づく社会の実現を目指す論考や著作を多数発表しています。数多くのメディアや学会で講演を行い、現代社会における経済政策や公共の役割について、国際的な議論にも影響を与えている人物です。

皆様、こんばんは。そして、Andorra Economic Forumの皆様、本日はご招待いただき誠にありがとうございます。
本日の講演では、これまで私が持ち続けてきた見解、すなわち、より自由で、より繁栄するために、スペイン及び世界において自由主義革命がなぜ必要であり、さらには急務であるのかという理由をお伝えしたいと思います。また、現代国家が、ストックホルム症候群のような論理に我々を陥れており、その結果、国家が我々の自由を体系的に制限し、財産を構造的に攻撃している状況を、ほとんどの人々が抗議もせず、またはその非常事態性すら意識していないという現実をどのように理解すべきかについても触れます。まず初めに、皆様のご反応から察するに、これは既知の内容に感じられるかもしれませんが、自由主義の基本原則、すなわち四つの基本的な考えを確認させていただきます。どのようにして、社会生活と、各個人が自らの人生計画を追求するための自律性とを両立させ、かつ、個々の自律性が打ち消されるような一個または多数の専制に服従することなく生きることができる社会が成立するのでしょうか? それは、協力と共存が可能な社会の中で、各人が自己の利益を追求し、同時に他者の利益追求を尊重するための基本原則、すなわち以下の四つの原則によって支えられているのです。
第一に、個人の自由、すなわち他者の行動を踏みにじることなく自ら行動するという、いわゆる非攻撃の原則です。自分が望むことは何でもできますが、他者が望むことをするのを妨げてはならず、また、他者があなたの望むことを妨げることも許されないのです。
第二に、私有財産です。平和的に獲得し、平和的に自らのものとしたものはあなたのものであり、それによって自由に行動し、自らの人生計画や行動計画を追求する手段となります。もしも、これらの計画遂行に必要な手段が恣意的に奪われるならば、それはあなたの個人の自由、すなわち自らの人生計画を追求する自由を侵害することになるのです。
第三に、契約の自律性です。あなたは第三者と自由に合意を結ぶことができます。もちろん、第三者を攻撃することは許されませんが、双方が望むことについて自発的に合意することは可能です。合意は、当事者間の私法上の契約であり、両者が履行すべき約束であり、第三者が介入してこれを正当化したり否定したりするものではありません。ただし、合意の内容は、あくまで当事者双方やその所有物にのみ影響を及ぼすものです。
そして最後に、広義の意味での結社の自由です。個人は、契約上、望むことについて合意するだけでなく、共に生活する方法や、ある程度安定した形で組織される方法を合意することも明示的に可能です。これらの原則は、しばしば国家によって保証されると言われます。なぜなら、国家がなければ、法体系も安全保障機関も存在せず、個人の自由、私有財産、契約の履行、そして結社の自由を保障するものが何もないと思われがちだからです。とはいえ、確かにある程度の国家は、警察国家としてこれらの基本的な社会的共存の規範を保証するために必要かもしれませんが、私たちが必要としているのは、単にこれらの自由主義社会の原則と自由な人々の相互作用が尊重されることを確保するための、巨大かつ過剰な国家ではありません。
実際、国家が大きくなるほど、つまり社会における国家の存在感が増すほど、これらの原則は侵害されがちです。なぜなら、国家は恣意的に規制を強化し、税金を引き上げることで、たとえ他者に損害を与えなくとも、個人が望むように行動する自由を阻み、また、私有財産を強制的に奪い、当事者間の取引を妨げ、さらには、結社および脱会の自由さえも制限してしまうからです。たとえば、誰かが既存の国家から離れ、他の国家に参加したり、あるいは新たな国家や政治共同体を形成して自らを組織しようとした場合でさえ、現行の国家はそれを認めないのです。
さて、これらの自由主義の基本原則は、各個人の計画や人生のプロジェクトが社会の中で花開くために必要不可欠なものであり、現代国家によって体系的に侵害されているのです。しかし、現代国家とは、必ずしも常に我々と共にあった国家ではありません。私たちは、今日のようなメガ国家、ハイパーステート、過剰に肥大化した国家をある程度は当たり前のものとして受け入れてしまっていますが、これらは唯一の政治的選択肢ではなく、歴史を通じて存在してきた唯一の政治現実でもないのです。
ここで、主要な西洋諸国における国家の社会に占める重みの変遷について、皆様にご覧いただければと思います。今日、国家の重みは国によって大きな違いはないものの、概ね国内総生産(GDP)の40〜50%を占めています。中には、例えばフランスのようにGDPの60%に達する国もあります。国家が社会的調和や幸福の保証とされることは稀であり、実際、フランスは世界最大の国家を有しながら、またはそのために、今最も分断され混沌とした国の一つとなっています。
しかし、現状、国家はGDPの40〜50%、すなわち社会が毎年生み出す生産の約半分を吸収し、再分配または政治層や官僚階級が決定した形で消費しているのです。これは常にそうであったわけではありません。19世紀、ひいては第一次世界大戦前までは、近代先進国における国家の経済的重みはGDPの5〜10%程度に過ぎなかったのです。
例えば、アメリカ合衆国では第一次世界大戦前、国家のGDPに占める割合は3〜4%でしたし、今日巨大な社会民主主義国家となっているスウェーデンでさえ、かつてはGDPの5%程度でした。すなわち、国家というものが必然的に経済の半分を占めなければならないというわけではなく、これは徐々に積み重ねられてきたプロセス、いわばゆっくりと沸騰させられるカエルのようなものです。第一次世界大戦後、国家の経済に対する重みは大幅かつ確固たる上昇を見せ、さらに第二次世界大戦後には、急激かつ持続的な上昇を経て、1970年代以降、現在の水準にまで達したのです。
ちなみに、ここで我々がしばしば耳にする「国家が後退しているから、我々は新自由主義の時代にいる」というレトリックが、いかに毒性がありずる賢いものであるかにも注目してください。過去40年間で、グラフ上に国家の重みが大幅に後退したと示す兆候は見当たりません。ある時点で国家のGDPに占める割合が1〜2%減少することがあったとしても、200年の間にGDPの5%から50%へと増加し、現在は概ね50%前後に留まっているのです。国家が後退し、民間部門がすべてを占めるようになっている、というのは全く逆の現象です。
実際、多くの人は、国家が拡大し続けるのが当然であり、もし急速な成長が見られなければ、国家は後退していると考えがちです。しかし、国家は既にそれ以上大きく成長する余地がほとんどないのです。もちろん、GDPの60%、70%、80%にまで達すれば、直接的または間接的な社会主義経済になってしまいます。
そして、なぜ国家はこれほどまでに成長したのでしょうか。急激な国家拡大を説明する基本的な要因の一つは、福祉国家の発展です。つまり、かつては国家が提供していた医療、社会保障(年金、事故保険など)や教育といったサービスの国家による提供が、福祉国家として大きく発展したのです。
ご覧の通り、1930年代や第二次世界大戦後までは社会保障費は非常に低い水準にありましたが、特に第二次世界大戦後からは、GDPの20〜30%にまで急上昇しました。これらはかつて、市民社会や市場を通じ、または必ずしも商業的な交換を介して提供されていた、労働組合などが担っていた社会保障の役割を、国家が吸収していったものです。労働組合は国家から独立し、時には国家に対抗しながら、社会保障の機能を果たしていたのですが、その役割が国家に吸収されることで、我々は国家に依存するようになってしまったのです。
なぜなら、社会保障費は支出であり、中には「依存費用」とも呼ばれるものもあります。たとえば、老後に収入がなくなった時や、何らかの障害によって収入が得られなくなった時のために、個人の貯蓄から基金を積み立てる場合、その基金が自分自身で管理されるなら自律的ですが、国家が管理すれば、私たちは国家に全く依存することになってしまうのです。国家が消滅するか、大幅な予算削減が行われれば、我々は何も残らないのです。結果として、国民は容易には消えない国家の爪痕に囚われることになるのです。公共年金制度の問題を考えてみてください。現代の先進国家において、公共年金制度は最も大きな支出項目の一つです。
では、どうすれば公共年金制度を解体できるのでしょうか。どうすれば、必要以上に介入してきた国家、例えばアメリカ合衆国では大恐慌期(1930年代)に、必要がなかったのに介入してきた国家を、その状況から脱却させることができるのでしょうか。設立当初は、ある一定の年齢に達した者には一定額の年金を支給すると約束し、その費用を現在働いている者への税負担によって賄うというシステムでした。
システムの構築は、当時の平均寿命がかなり低く、支給期間が2~3年程度であったため、比較的容易で安価に行われたのですが、システムが一度確立され、世代を超えた労働者の貯蓄能力を事実上奪う形で構築された今、どうやってそれを解体すればよいのでしょうか。もし「年金は支給されなくなるのか」と言えば、かつて生産期に労働者の給与のかなりの部分を国家が吸収し、貯蓄を阻害していた結果、何百万人もの人々が貧困に陥ることになるのです。
じゃあ、もう引退されている皆さんは年金を受け取ることになりますが、現役世代がその年金の費用を負担し、そして自分たちが引退する時には年金を受け取ることができなくなるのです。つまり、この世代からは何の対価もなく、給与のごく大部分が没収されることになるというわけです。これをどうやって解体するつもりですか? 決して容易なことではありません。
また、例えば医療制度についても同様です。若者にとっては医療制度の解体はそれほど難しくないように見えるかもしれませんが、貯蓄がなく、保険にも加入していない高齢者にとって、もし今、公共医療制度が終了し、年齢とともに医療費が指数関数的に上昇するために通常以上の医療費が発生すると告げられたら、彼らはその医療費にどう対処すればよいのでしょうか? 彼らは、公共医療制度が機能するという説明のもとに、その医療費が賄われると予め想定し、税金を支払っていたのです。
これをどう逆転させるか? もちろん、即座に行えることではありませんが、時間をかけた移行措置として行っていかなければなりません。だからこそ、国家はこの道を通じて成長し続け、社会がますます国家による再分配に依存するようになることで、国民の自律性を奪っていくのです。
ちなみに、現代福祉国家の発明者の一人であるのは、プロイセン出身のドイツの首相オットー・フォン・ビスマルクです。彼の回顧録――つまり、批判的ではない親しい記者によって書かれた回顧録――によれば、ビスマルクは、公共年金制度を創設することで労働者階級を国家に依存させ、労働者が国家に対して反抗しないように仕向けたと説明しています。当時、反抗は、いわば反資本主義的な行為とみなされていたのです。彼は、国家主義を維持するためではなく、「労働者には社会主義的傾向がある。では、どうすれば労働者を手なずけることができるのか?」という視点から、公共年金制度を利用したのです。同様に、労働者は公共年金制度を通じて、または国家に対抗する形で手なずけられるのです。そして、現状はこの通りになっています。
そこで、皆さんは疑問に思うかもしれません。この何世代にもわたって築かれてきた巨大国家は、具体的にどのような機能を果たしているのでしょうか? その資金はどこに行っているのか? この巨大国家は何に対して支出をしているのか? ここに、2022年の欧州連合各国の平均、すなわちGDPの50%という数字があります。スペインの場合も2022年時点で大きな差はなく、GDPの47%を支出しているため、概ね代表的な数値といえます。さて、この50%のうちの20%は社会保障費、主に年金費用(老後だけでなく、遺族、障害、孤児などに関する給付も含む)です。これに加え、比較的低コストな非拠出型給付も存在します。次に、スペインの場合は約7.7%、すなわち7〜8%が医療費、6%が官僚機構の運営費用、そして何よりも重要なのが公債の利子支払い費用です。さらに6%は経済政策に充てられ、例えばインフラ整備や農業支援などが含まれています。教育に関しては、公立教育や協定校を含めて約4.7%、環境保護は0.8%(これは必ずしも気候政策だけでなく、森林の管理なども含む)、住宅や地域サービスが1%、そして余暇、文化、宗教に関しては1.1%となっています。これらは、メディアや文化、宗教団体への補助金などとして支出されています。
かつて、リベラルな最小国家、例えばアメリカではGDPの3%程度であった国家がありました。なぜなら、当時は上記のような広範な機能を持たず、防衛(GDPの1.3%)と治安・司法(GDPの1.7%)に集中していたからです。つまり、19世紀にGDPの3%を占めていた国家が、現在もその核となる部分は同じ3%のままであるということです。国家が高価になったわけではなく、19世紀に存在した国家のコストは大体同じであったにもかかわらず、現代国家は19世紀よりもはるかに多くの機能を担っているため、多くの税金が必要とされているのです。もちろん、すべては税金で賄われています。
では、いったいどれだけの税金が支払われているのでしょうか。ここでは、国民が被っている税負担の実態について十分に認識されていないのではないかと思います。もしその実態が明らかになれば、社会的不服従が起こるでしょう。国家は、税の実感を曖昧にするための手段を多数用いているのです。例えば、さまざまな理由で税金を徴収する仕組みです。「この項目に対して税金を払え」と一律に要求するのではなく、「稼いだ金額、支出、保有資産、さらには支出全体に対して税金を課す」といった形で、複数の種類の税金を同時に適用します。消費全体に対して一律に税金を課すのではなく、付加価値税(IVA)やその他の特別税など、多岐にわたる特別な税金が存在し、相続税に至るまで多岐に渡ります。
さらに、我々はさまざまな側面で税金を支払っているにもかかわらず、その実感すら持っていないこともあります。たとえば、関税はその値上がり分を商品の価格に転嫁されるため、意識されにくいのです。付加価値税が上がっても、スーパーなどが告知しない限り、私たちはその上昇に気づきにくいのです。また、税負担を一度にまとめて徴収するのではなく、分散して給与から差し引くことで、その実感を薄めています。かつては、年間に稼いだ金額に対して一括で所得税(IRPF)を支払うのが普通でしたが、現代では分割して徴収されるため、納税者は自分がどれだけの税金を支払っているのかを実感しにくいのです。ちなみに、IRPFの源泉徴収制度は、第二次世界大戦中にリベラルのミルトン・フリードマンによって考案されたものです。つまり、敵はしばしば自国に潜むものでもあるということです。
ここで示したのは、平均的な支出額です。スペイン国家のすべての財政収入を国民または労働者で割ると、国民一人あたりの国家負担のおおよそのコストが見えてきます。実際には公共赤字、すなわち収入以上に支出している部分もあり、その分は将来の税負担として転嫁されるため、実際のコストはさらに大きくなります。ここでは、現状で国民から徴収されている税金のみを取り上げています。なお、これらの数字はインフレーションを考慮していないため、2001年と2024年の数字を直接比較することはできませんが、ここでは2024年現在の状況に焦点を当てています。現在、平均してスペイン国民一人あたり、約15,000ユーロの税負担がかかっているのです。つまり、一般的には夫婦と子供一人の家庭で約50,000ユーロの税金が支払われている計算になります。労働者という視点に立てば、実際に税金を支払っているのは、平均で30,000ユーロ以上にのぼります。もちろん、高所得者層が多くを負担しているという見方もありますが、これは平均値であり、平均値は必ずしも実態を正確に反映するものではありません。
さて、労働者一人あたりの支払いを、かなり寛大な見積もりで考えてみましょう。スペインにおける現在の中央値の給与は22,400ユーロです。しかし、この22,400ユーロという数字が給与明細に反映される前に、企業側がすでに支払っている社会保険料が約7,000ユーロ存在しています。つまり、実際の中央値の給与は29,000ユーロ、ほぼ30,000ユーロであるべきものですが、この30,000ユーロは労働者自身が実感できるものではありません。そして、たとえ「実際は自分のものである」と伝えても、「それは企業が支払っているものであって、自分が支払っているわけではない」と言われ、自己欺瞞に陥るのです。結局のところ、実際に支払っているのは自分自身なのです。
実際、30,000ユーロの実質報酬を基にすると、そこから7,000ユーロが差し引かれて、給与明細に表示されるのは22,400ユーロです。さらに、労働者側の社会保険料として約1,500ユーロを追加で支払い、所得税(IRPF)が約3,000ユーロ、さらに消費に応じた間接税が最低でも約2,000ユーロ(場合によってはそれ以上)かかります。さらに、ここでは取り上げていない他の国家への支払い、たとえば不動産税(IBI)やサービス料、共済負担金なども存在します。結果として、中央値の労働者は、本来約30,000ユーロあるべき給与のうち、税引き後に手元に残るのは約15,800ユーロに過ぎないのです。つまり、ほぼその半分が国家によって吸収されていることになります。年間で見ると、さまざまな税金、特に社会保険料、所得税、そして間接税として、合計約13,400ユーロが徴収されているのです。
このように、中央値の労働者は、所得分布の中央に位置しており、非常に多くの人々が彼より少なく、また多く稼いでいる人もいます。だからこそ、中央値の労働者が支払っている税負担、すなわち年間約13,400ユーロという数字は、スペイン国民に対して行われている極めて大規模な税負担の実態を物語っています。これにより、国家から提供されるサービスが強制的に受け入れられているのです。
果たして、これは必然なのでしょうか? 歴史的に見れば必ずしもそうではなく、また現代においても地域によって差があります。つまり、労働者が生み出す富の半分以上を国家が吸収するという、巨大な国家が当然であるという考え方は、今後も続くものではありません。ここには、異なる繁栄度を持つ国々が存在し、一般的に発展した国々であっても、欧州やアメリカのような国家に比べ、国家の規模はかなり小さく抑えられている国もあります。しばしば「スペインの国家規模は欧州平均より小さい」と言われますが、欧州平均自体が、プロの略奪者たちのクラブのようなものなのです。従って、欧州平均という水準と比較するのではなく、もっと控えめな国家規模を持つ国々や、税負担の貪欲さが制限された国々と比較すべきです。
例えば、ヨーロッパ内ではスイスがあります。偶然かどうかはさておき、スイスはヨーロッパで最も豊かな国の一つでありながら、国家のGDPに占める割合は33%と、欧州やアメリカに比べて10〜15ポイント低いのです。また、香港や韓国はGDPの28%、チリはこの分類の中では最も貧しいかもしれませんが約26%、台湾は16%、そして世界で最も豊かな国であるシンガポールは15%です。シンガポールや台湾は、国家がGDPの15〜16%という小規模な状態で十分に現代社会の機能を果たしているのです。もちろん、シンガポールの場合は都市国家であるため、経済規模のメリットもあるでしょうが、公共支出の大部分が社会保障に回っている現状を鑑みると、都市規模か大国家かは大した違いがないのです。むしろ、シンガポールや台湾のように、GDPに対して国家の規模が30ポイントも低い国の方が、国家による私有財産の侵害が少ないと言えます。
したがって、もし大規模な国家による大規模な略奪を回避でき、しかも機能的には他の国と同等以上に運営できるのであれば、当然、より少ない税負担で、なおかつより効率的な公共サービスを提供する国家の方が望ましいのです。実際、国家が何でもかんでも行おうとすれば、その多くは非効率にならざるを得ません。一方で、企業がすべてを行おうとしても、専門分野に特化した他の企業に競争で敗れるため、最終的には消費者がより良いサービスを選ぶことになるのです。問題は、国家の場合、国民が国家から自由に離脱し、同じサービスを提供する他の組織と契約する余地がないという点にあります。国民は、非常に非効率かつ高コストな国家サービスに縛られており、選択の余地がないのです。したがって、もし小規模で効率的な国家が存在すれば、それは大規模で税負担の重い国家よりも好まれるはずです。
そして、もし国家が回収するGDPの割合が30ポイントも大きいのであれば、それは明らかに国民の私有財産を暴力的に侵害していると言わざるを得ません。ですから、もし国家による大規模な略奪を回避し、かつ他国と同等以上の機能を果たすことが可能であれば、国家は少なくとも縮小されるべきです。なぜなら、そうした国家は国民にとって好都合であるだけでなく、公共サービスの質も向上し、効率的に運営されるからです。結局のところ、すべては国家ではなく、国家に寄生する巨大な官僚組織の福祉が優先されているのです。
もし、あなたの社会にこれほど大きく根付いた寄生虫が存在するならば、その寄生虫は当然、去ろうとはしません。むしろ、さらに大きな植民地を形成しようとするでしょう。これが、国家が成長し続ける理由であり、そして、血を吸い上げるこの寄生虫と戦う必要性が生じる所以なのです。
別のシナリオを考えてみましょう。つまり、現代社会における国家の規模を実質的に縮小するという仮定を立て、その実現可能性や現実味について見極めるためです。これまでに、ヨーロッパにおける現代国家の重みがGDPの50%に達していること、その内訳を示してきました。さて、かつての状況を想像してみてください。あの時代は、科学フィクションのようなことは必要なく、医療はゼロ、経済政策も実質ゼロで、民間部門が構築できないインフラだけが、もしあれば驚くほど僅か、GDPの1%程度だったのです。教育はゼロ、防衛と公共秩序は維持されるものの、余暇・文化・宗教への補助金はゼロでした。地域サービスや環境保護に関しては、下水道、街路灯、森林の維持管理など必要な分は残され、官僚組織も非常に大幅に縮小され、社会保障も一部のみが残されていました。
さて、しばしば「国家は富裕層からお金を奪い、貧困層へ再分配するために存在する」と言われますが、実際、社会保障はGDPの20%に相当します。ここで、極端な貧困を防止するために本当に必要な支出額を計算してみましょう。そうすれば、皆さんも、このGDPの20%は貧困撲滅のためのものではなく、むしろ国家が横方向の所得再分配システムを通じて国民を捕らえ続けるためのものであると気づくでしょう。すなわち、国家はあなたからお金を取り、そのお金を自らの利益や必要に応じて配分するために、あなたと国家の間に割り込むのです。バストス教授が正しく指摘しているように、その所得の移動は、富裕層から貧困層へ、またはその逆ではなく、すべての人々から国家へ向かっているのです。そして国家は、その所得を自らの利益や必要に従って再分配することを決定します。
では、先ほど示したような形で国家の各機能を大幅に縮小した場合、結果として国家はGDPの9~10%程度の規模となり、現状よりも30~40ポイント、つまり約80%縮小された国家になるでしょう。防衛費、治安費は現状と同等に維持される(ただし、治安費については内部の官僚機構によっても左右されるため、この点はまた別の議論になります。たとえば、スペインはヨーロッパで国民一人あたりの治安部隊職員数が最も多い国ですが、本当にそれだけ必要なのかはまた別問題です)。安全保障費がGDPの1.7%、防衛費が1.3%、官僚組織が1%、地域サービスや環境保護が1%、民間部門ではまかなえないインフラがさらに1%、そして社会保障が3%という具合です。現在、社会保障としてGDPの3%、すなわち450億ユーロが支出されています。これは、450億ユーロの社会保障費を、例えば4.5百万人(スペイン人口のおよそ10%)に対して年間1人あたり1万ユーロずつ支給するか、あるいは300万人に対して1万5千ユーロずつ支給するということになります。繁栄した社会において、極端な無助状態に陥る国民の割合はどれほどか、という問題です。彼らは、生命保険、障害保険、個人貯蓄すら持たず、福祉国家が生まれる前に存在したボランティアや民間の相互扶助ネットワークさえも利用できなかった層です。これらを踏まえた上で、絶対的な無助状態に陥り、国家からの継続的な支援を必要とする国民の割合がたとえば5~10%だとすれば、実際に必要な支出はGDPの3~4%程度で十分にカバーできるはずです。しかし、現実には我々は社会保障にGDPの20%を費やしているのです。
明らかに、このGDPの20%は、富裕層から少しだけ富を奪って、巨大な貧困層を作らないためのものではありません。驚くべきことに、国家がGDPの50%を占めるにもかかわらず、貧困層は依然として存在しているのです。さらに、貧困を解消するための手段として、まず第一に、依存性を生む補助金を設けるべきではありません。しかし、現実には、経済活動が全くできず、自己の貯蓄や家族の支援、民間の相互扶助ネットワーク、そして最終的には国家に依存せざるを得ない層が一定割合存在します。しかし、そのようなケースはGDPの3%程度の支出で十分にカバーされるはずなのです。
さて、国家の規模を縮小した場合、たとえばGDPの50%から10%にまで削減できると仮定しましょう。これは約80%の削減に相当します。先に述べたように、中央値の労働者は現在、年間約13,500ユーロの税金を負担しています。この80%の削減が実現すれば、労働者の可処分所得は、国家が提供する各種サービスに充てるための支出分が年間1人あたり1万~1万1千ユーロ増加することになります。家庭内で中央値の労働者が2人いる場合、2万~2万2千ユーロの追加収入となるでしょう。この追加収入があれば、教育費、医療費、年金のための貯蓄など、国家が現在負担させているコストを自前でまかなうことが可能になるはずです。実際、多くのスペインの労働者は、国家の劣悪なサービスから逃れるため、民間の医療や教育、そして補完的な年金積立を実施しているのです。特に、公共教育は、学生の生産性向上よりも、国家のイデオロギーを植え付けることに重きを置いている場合が多いのです。
また、この話は、GDPの3%相当の再分配、すなわち450億ユーロ分が、現実的に考えても国民の基礎的な生活を支えるには十分であるという観点からも論じられます。現行の過剰な収用体制に対して、もし国家規模が大幅に縮小されるならば、労働者にとって有利な状況が実現するはずです。
さて、ここまでの議論から、もし国家主義のウイルスが社会の頭脳や利権に深く根付っている現状において、現状が最適でないと理解したとしても、移行のコストの高さゆえに多くの人々が現状から変わることを望まないという現実があるのです。たとえば、公共年金制度の解体は非常に困難です。年金受給者は「こんな不公平な体制であっても、自分の年金を受け取りたい。自分自身の貯蓄がなくなるリスクを冒したくはない」と考えるでしょう。
では、この国家――明らかに国家とその官僚機構に有利なこのモデル――から脱却するために、すなわち、表向きは国民のために存在するようでいて、実際には社会を寄生しているこの体制から逃れるためには、どのような手段が考えられるでしょうか。ここで、国家改革またはハイパーステートのパラサイト化に対抗するための、四つの可能なアプローチについて述べます。
第一のアプローチは、トップダウン型の方法です。すなわち、自由主義的な理念を掲げた善意の政治家が権力の座につき、内部からリベラル革命を起こそうとするというものです。しかし、私はこの方法は、次に述べるボトムアップ型の文化戦線と併せなければ、全体として非常に単純で実現不可能だと考えます。なぜなら、社会の大多数が国家改革を望まなければ、その改革は十分な勢いを持って実施されることは決してないからです。多くの改革は長期的な取り組みであり、一夜にして実現できるものではありません。一度実行された改革が元に戻らないようにするには、最低でも二世代を要するのです。もし社会がその方向に向かわなければ、いつかまた別の人物が権力に就いて、国民の大多数が望まない体制を再び打ち壊してしまうでしょう。例えば、チリの年金制度の民営化は、ピノチェト政権下の1981年に始まり、数年前に旧公共年金制度が完全に清算されました。しかし、その後、旧体制に戻そうとする動きが見られるのです。なお、チリは当時、非常に若い労働人口と限られた高齢人口という、改革に適した人口構造を有していたにもかかわらず、改革には約40年もの歳月がかかりました。これが、世界の他の国々で実施されるとなれば、どれほど困難なものになるか想像に難くありません。そして、もし世界中がそのような改革を望まなければ、いかに自由主義者の政治家を内部に潜り込ませ、社会民主主義の装いを与えたとしても、十分な効果は得られないでしょう。さらに、政治そのものが権力に触れると必ず腐敗すると、ロード・アクトンが指摘したように、権力は人を変えてしまいます。つまり、権力に惹かれて権力の座についた者は、その権力を維持・拡大するために、かつて掲げた理念を容易に放棄し、他者を蹂躙し、欺く行動に出るということです。
政治的競争というのは、もしあなたが行動しなければ、行動する者があなたを追い出してしまう、という状況を生み出します。そのため、もし存在するとしても、誠実で、信念を持った政治家は、力に屈する者に押されて公共の場から姿を消してしまうのです。権力闘争では、手が縛られている者と自由な手を持つ者との間で戦いが行われるため、劣悪な選択が働き、最終的には最悪の者が権力の座に就くという現象が生じるのです。(この点については、ハイエクも『隷属への道』で記述しています。)
次に、第二の可能性はボトムアップ、すなわち文化戦線によるアプローチです。これは、アイデアの戦いを、じわじわと、少しずつ社会に浸透させ、心を開かせ、意識を目覚めさせ、より多くの人々がこの変革を要求するようになるという方法です。しかし、これは特に有望な道ではないことは明白です。もし、ここでマルクス主義的な語調に傾くとすれば、客観的な物質的条件があって、そうした思想が大規模に広まる環境が整わない限り、人々は現状に満足して「今のままで十分だ」と感じ、急激な変革に乗り出す理由が見出せません。現状が著しく悪化しない限り、文化戦線による大規模な勝利が起こり、既存の社会制度が覆されるというのは極めて困難な道なのです。例えば、アルゼンチンでは、40年間にわたって底をつき続けた結果、人々が明らかに欠陥だらけのモデルにうんざりし、ハイパーインフレーションに苦しんだことで変革が進んだように見えます。もし、そこに一貫性があり、破壊的かつ斬新なメッセージ―社会主義的なものか、あるいは幸運にもリベラルなもの―があれば、一定の確率でそのアイデアが覇権を握り、新たな現状として定着する可能性が出てくるのです。しかし、スペインの場合、文化戦線による闘いは、相手側のプロパガンダがあふれ、対抗する者がいなければ、現状が一層固定化し、国家権力が加速度的に拡大していくため、非常に厳しい状況にあります。私自身も長い間、文化戦線で戦ってきましたが、スペインという環境におけるその限界を痛感しています。
第三の道は、そもそも国家改革を目指さず、自分の生活を改善するために他の地域へ移住するというものです。もし、競争が可能な複数の法域が存在すれば、現状に非常に不満を抱く者は、物理的に他の地域へ移り住み、そこで自らの生活基盤を築くことができます。そして、こうした法域間の競争は、他の法域による収用や寄生的な政策の力を制限する効果も持ちます。たとえば、ある法域で税率が非常に低く、規制が緩やかであれば、他の法域は資本が流出し、寄生者側から見れば、寄生対象(=ホスト)が成長しなければ、寄生する意味がなくなるのです。もし、ホストを窒息させて殺してしまえば、またはホストが他の、寄生が少ない地域へ流出してしまえば、寄生者にとっては不利益となります。このような効果は、実際には見かけ以上に大きな影響を持つのです。
たとえば、最も身近な例として、アンドラの場合が挙げられます。多くの場合、静かに、あるいは時に華やかに報じられる移住現象があり、一定の社会的反響を呼んでいます。問題は、これらはすべて財政上の問題であり、移住者を犯罪者扱いする試みがあっても、スペイン国家にとっては重要な問題とならないのです。よく批判されるのは、YouTuberなどがアンドラへ移住することについて、「国が自国民の資源不足を訴えるような状況に直面しない」とされる点です。もしそうなれば、国家は財政の引き締めを迫られるはずですが、現実はそうではありません。むしろ、これは他者に対する懲罰の一形態であり、「移住して税負担を軽減しようとするなら、あなたは悪い人間であり、悪い市民だ。もしあなたが著名人であれば、意識を啓発するために、我々はあなたを徹底的に攻撃し、公の場から追放する」といったメッセージが発せられるのです。しかし、実際にアンドラへの移住が進むこと自体は悪いことではなく、たとえそれがスペイン国家に与えるダメージが短期的にはそれほど大きくなくとも、他のケースでは、目に見えにくいながらも国家に損害を与えている場合があるのです。
たとえば、2か月前に発表されたドラギの報告書では、欧州が「足を引きずっている」との根本的な不満が示されています。すなわち、欧州では生産性が20年間にわたって停滞しており、成長期に新たに設立される企業が、厳しい規制の下で成長できず、資本調達が困難となり、結果としてアメリカに流出してしまうという現象です。これは「足で投票する」という現象であり、企業側の実情を反映したものです。そして、これは国家権力の内部から出た、我々の社会が停滞しているという自らの寡占層からの認識でもあります。彼らは、ここ20年間にわたり市民を内部から圧迫してきた手法を見直す必要があると訴えているのです。そして、ここで議論されているのは、欧州連合とアメリカという二つの経済ブロック間での移住の問題なのです。
もし、かつてヨーロッパに存在していたような、多数の競合する法域が現在も存在していたと想像してみてください。ここで歴史的な議論に深入りするつもりはありませんが、ヨーロッパが16世紀あるいは17世紀から産業革命に至るまで発展し、東洋が(少なくとも最近まで)停滞していた理由の重い仮説の一つは、ヨーロッパが政治的にはるかに細分化され、都市国家や小国、王国、そして公国など、まさにアンドラのようなケースに近い形態であったため、相互の競争が激しかったという点にあります。ひとつの領域内で生まれる思想を制限・抑制・検閲する能力は非常に低く、もし一方で弾圧されれば別の場所へ移動できたため、その結果、後の産業革命を引き起こす知的な開花が促されたのです。これに対して、中国のような中央集権的で統一された国家では、官僚組織が本来より強大な権力を持っていたため、このような発展は見込めませんでした。
「足で投票する」という現象は非常に強力です。したがって、文化戦線から取り組むべきもう一つの課題は、政治的な中央集権化や財政の調和化に反対することです。なぜなら、政治的に中央集権化が進んだり、財政が調和化されるほど、法域間の競争は減少し、その結果、国家が無罰で私有財産を寄生的に吸い上げる余地が広がるからです。これは市場経済ではよく理解される現象ですが、国家の場合は例外扱いされがちです。市場において本当の意味での独占、すなわち単にその分野で唯一の企業という状況ではなく、競合が存在しない真の独占状態になると、その独占者は価格を引き上げ、品質を低下させる傾向にあります。なぜなら、あなたは逃げ出すことができない、まるで人質のような状態に置かれるからです。つまり、国家もまた独占状態にあり、国家が直面する唯一の競争は、他の国家へ移住するという可能性なのです。領域を統一して競争余地を狭めれば狭めるほど、国家は独占的な力を強め、結果としてあなたに提供するサービスの質を低下させ、収用を強める傾向が出てきます。したがって、私はどんな中央集権化のプロセスにも反対し、逆に政治的な分権化を支持すべきだと考えます。
そして最後に、第四の戦略ですが、これはやや曖昧で漠然としているかもしれません。しかし、私が考えるに、実際に多くの人々が採用しており、多くの場合国家の影響力を制限している方法、それは直接的に「国家からの分離」を目指すことです。もちろん、あなたにとって寄生者のような国家が窮屈に圧しかけてくる場合、その寄生者を打倒しようと多大なエネルギーを費やすこともできます。しかし、寄生者が既に存在する以上、その存在を前提として生活基盤を築く、その固定費を受け入れながらも、寄生者のさらなる拡大を防ぐ、あるいは寄生の及ばない領域を確保する新たな方法を模索するということです。これが国家からの「分離」、すなわち、重くのしかかる国家の負担から自らを切り離す試みなのです。例えば、先に述べたように、私立教育、私立医療、私的年金といった選択肢があります。本来であれば、国家が私たちから過剰な資源を吸い上げることなく、その分をこうした目的に振り向けられれば理想的ですが、幸いなことに、現状では国家が私立教育への進学を禁止しているわけではありません(ただしかなりの規制は存在します)。私立教育は完全に自由なものではなく、国家のカリキュラムに沿ったものですが、それでも私立教育、私立医療、そして貯蓄や資産形成の道を開いてくれるのです。もちろん、今後さらに税が引き上げられ、国内外で資産が収用されるリスクが高まるまではの話ですが。
したがって、国家を一つの悪と捉え、その悪に支配される中で自由を追求する、すなわちその影響力からできるだけ逃れる方法を探るべきです。さらに、社会が自ら開発していく様々なツールが、私たちが国家の監視や統制から離れて生活する手助けとなります。たとえば、デジタル経済は、今日のところ、国家が我々をコントロール・規制・収用するのをより困難にする領域をある程度確保できる可能性を秘めています。ビットコインの例は、没収不可能な資産として、適切な管理を行えば、富の保蔵庫あるいは国家の統制や知識から独立した交換手段として機能する可能性を示しています。
これらは、寄生者である国家に吸い付かれないため、自らの活動から国家の影響力を一部でも排除する、新たな生活の仕方を模索する一つの方法です。こうした新しいツールは、今後も次々と登場し、国家が私たちの生活に及ぼす影響を制限するために活用されるべきです。社会全体を変えるのは非常に困難ですが、多くの人々を同じ方向に動かすことが難しい現状において、少なくとも我々が体系的に受けている搾取の度合いを最小限に抑えることは可能です。
以上、複数の道筋があります。第一の道は私個人としてはほぼ排除したいと考えますが、残りの三つは排他的ではなく、互いに補完し合うものです。どの方法も目的地に必ず到達できる保証はありませんが、これらは連携することで、国家が私たちや社会全体に及ぼす権力の影響を徐々に抑制する助けとなるでしょう。そして、我々自身の利益のため、あるいは共に生きる社会を改善するために、可能な限りこれらの道を追求すべきだと考えます。
-
 @ 211c0393:e9262c4d
2025-05-04 02:32:24
@ 211c0393:e9262c4d
2025-05-04 02:32:24**日本の覚せい剤ビジネスの闇:
警察、暴力団、そして「沈黙の共犯関係」の真相**
1. 暴力団の支配構造(公的データに基づく)
- 輸入依存の理由:
- 国内製造は困難(平成6年「覚せい剤原料規制法」で規制強化)→ ミャンマー・中国からの密輸が主流(国連薬物犯罪事務所「World Drug Report 2023」)。
- 暴力団の利益率:1kgあたり仕入れ価格30万円 → 小売価格500万~1000万円(警察庁「薬物情勢報告書」2022年)。
2. 警察と暴力団の「共生関係」
- 逮捕統計の不自然さ:
- 全薬物逮捕者の70%が単純所持(厚生労働省「薬物乱用状況」2023年)。
- 密輸組織の摘発は全体の5%未満(東京地検特捜部データ)。
- メディアの検証:
- NHKスペシャル「覚せい剤戦争」(2021年)で指摘された「末端ユーザー優先捜査」の実態。
3. 矛盾する現実
- 需要の不可視性:
- G7で最高の覚せい剤価格(1gあたり3~7万円、欧米の3倍)→ 暴力団の暴利(財務省「組織犯罪資金流動調査」)。
- 使用者率は低い(人口の0.2%、国連調査)が、逮捕者の過半数を占める矛盾。
4. 「密輸組織対策」の限界
- 国際的な失敗例:
- メキシコ(カルテル摘発後も市場拡大)、欧州(合成薬物の蔓延)→ 代替組織が即座に台頭(英「The Economist」2023年6月号)。
- 日本の地理的ハンデ:
- 海上密輸の摘発率は10%未満(海上保安庁報告)。
5. 解決策の再考(事実に基づく提案)
- ADHD治療薬の合法化:
- アメリカ精神医学会「ADHD患者の60%が自己治療で違法薬物使用」(2019年研究)。
- 日本ではリタリン・アデロール禁止→ 暴力団の市場独占。
- 労働環境改革:
- 過労死ライン超えの労働者20%(厚労省「労働時間調査」2023年)→ 覚せい剤需要の一因。
6. 告発のリスクと情報源
- 匿名性の重要性:
- 過去の暴力団報復事例(2018年、告発記者への脅迫事件・毎日新聞報道)。
- 公的データのみ引用:
- 例:「警察庁統計」「国連報告書」など第三者検証可能な情報。
結論:変革のためには「事実」の可視化が必要
「薬物=個人の道徳的問題」という幻想が、暴力団と腐敗官僚を利している。
国際データと国内統計の矛盾を突くことで、システムの欺瞞を暴ける。安全な共有のために:
- 個人特定を避け、匿名プラットフォーム(Tor上フォーラム等)で議論。
- 公的機関のデータを直接リンク(例:警察庁PDFレポート)。
この文書は、公表された統計・メディア報道のみを根拠とし、個人の推測を排除しています。
脅威を避けるため、具体的な個人・組織の非難は意図的に避けています。 -
 @ ecda4328:1278f072
2025-03-26 12:06:30
@ ecda4328:1278f072
2025-03-26 12:06:30When designing a highly available Kubernetes (or k3s) cluster, one of the key architectural questions is: "How many ETCD nodes should I run?"
A recent discussion in our team sparked this very debate. Someone suggested increasing our ETCD cluster size from 3 to more nodes, citing concerns about node failures and the need for higher fault tolerance. It’s a fair concern—nobody wants a critical service to go down—but here's why 3-node ETCD clusters are usually the sweet spot for most setups.
The Role of ETCD and Quorum
ETCD is a distributed key-value store used by Kubernetes to store all its state. Like most consensus-based systems (e.g., Raft), ETCD relies on quorum to operate. This means that more than half of the ETCD nodes must be online and in agreement for the cluster to function correctly.
What Quorum Means in Practice
- In a 3-node ETCD cluster, quorum is 2.
- In a 5-node cluster, quorum is 3.

⚠️ So yes, 5 nodes can tolerate 2 failures vs. just 1 in a 3-node setup—but you also need more nodes online to keep the system functional. More nodes doesn't linearly increase safety.
Why 3 Nodes is the Ideal Baseline
Running 3 ETCD nodes hits a great balance:
- Fault tolerance: 1 node can fail without issue.
- Performance: Fewer nodes = faster consensus and lower latency.
- Simplicity: Easier to manage, upgrade, and monitor.
Even the ETCD documentation recommends 3–5 nodes total, with 5 being the upper limit before write performance and operational complexity start to degrade.
Systems like Google's Chubby—which inspired systems like ETCD and ZooKeeper—also recommend no more than 5 nodes.
The Myth of Catastrophic Failure
"If two of our three ETCD nodes go down, the cluster will become unusable and need deep repair!"
This is a common fear, but the reality is less dramatic:
- ETCD becomes read-only: You can't schedule or update workloads, but existing workloads continue to run.
- No deep repair needed: As long as there's no data corruption, restoring quorum just requires bringing at least one other ETCD node back online.
- Still recoverable if two nodes are permanently lost: You can re-initialize the remaining node as a new single-node ETCD cluster using
--cluster-init, and rebuild from there.
What About Backups?
In k3s, ETCD snapshots are automatically saved by default. For example:
- Default path:
/var/lib/rancher/k3s/server/db/snapshots/
You can restore these snapshots in case of failure, making ETCD even more resilient.
When to Consider 5 Nodes
Adding more ETCD nodes only makes sense at scale, such as:
- Running 12+ total cluster nodes
- Needing stronger fault domains for regulatory/compliance reasons
Note: ETCD typically requires low-latency communication between nodes. Distributing ETCD members across availability zones or regions is generally discouraged unless you're using specialized networking and understand the performance implications.
Even then, be cautious—you're trading some simplicity and performance for that extra failure margin.
TL;DR
- 3-node ETCD clusters are the best choice for most Kubernetes/k3s environments.
- 5-node clusters offer more redundancy but come with extra complexity and performance costs.
- Loss of quorum is not a disaster—it’s recoverable.
- Backups and restore paths make even worst-case recovery feasible.
And finally: if you're seeing multiple ETCD nodes go down frequently, the real problem might not be the number of nodes—but your hosting provider.
-
 @ 866e0139:6a9334e5
2025-03-26 06:56:05
@ 866e0139:6a9334e5
2025-03-26 06:56:05Autor: Dr. Ulrike Guérot. (Foto: Manuela Haltiner). Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier.**
Ich bin 60 Jahre. Einer meiner Großväter, Wilhelm Hammelstein, liegt auf dem Soldatenfriedhof in Riga begraben. Der andere, mütterlicherseits, Paul Janus, kam ohne Beine aus dem Krieg zurück, auch aus Russland. Ich kenne ihn nur mit Prothesen und Krücken. Er hat immer bei Wetterwechsel über Phantomschmerz geklagt und ist seines Lebens nicht mehr froh geworden. Den Krieg hat man ihm im Gesicht angesehen, auch wenn ich das als kleines Mädchen nicht verstanden habe.
"Ihr könnt euch nicht vorstellen, was ich gesehen habe"
Von den Russen hat er trotzdem nie schlecht geredet. Was er immer nur zu uns Enkelkindern gesagt war: *„Ihr könnt euch nicht vorstellen, was ich gesehen habe“. * Wir haben es nicht verstanden, als 6- oder 8-Jährige, und haben gelacht. Manchmal haben wir ihm seine Krücken weggenommen, die immer an den Ohrensessel gelehnt waren, dann konnte Opa Paul nicht aufstehen und ist wütend geworden.

Meine Mutter, Helga Hammelstein, ist im Mai 1939 gleichsam in den Krieg hineingeboren worden, in Schlesien. 1945 gab es für sie, wie für viele, Flucht und Vertreibung. Ob sie und ihre zwei Schwestern von den Russen vergewaltigt wurden – wie damals so viele – kann ich nicht sagen. Diese Themen waren bei uns tabuisiert. Was ich sagen kann, ist, dass meine Mutter als Flüchtlings- und Kriegskind vom Krieg hochgradig traumatisiert war – und als Kriegsenkelin war oder bin ich es wohl auch noch. Eigentlich merke ich das erst heute so richtig, wo wieder Krieg auf dem europäischen Kontinent ist und Europa auch in den Krieg ziehen, wo es kriegstüchtig gemacht werden soll.
Vielleicht habe ich mich aufgrund dieser Familiengeschichte immer so für Europa, für die europäische Integration interessiert, für die EU, die einmal als Friedensprojekt geplant war. Ich habe Zeit meines Lebens, seit nunmehr 30 Jahren, in verschiedenen Positionen, als Referentin im Deutschen Bundestag, in Think Tanks oder an Universitäten akademisch, intellektuell, publizistisch und künstlerisch zum Thema Europa gearbeitet.
1989 habe ich einen Franzosen geheiratet, ich hatte mich beim Studium in Paris verliebt und in den 1990-Jahren in Paris zwei Söhne bekommen. Auch in der französischen Familie gab es bittere Kriegserfahrungen: der Mann der Oma meines damaligen Mannes war 6 Jahre in deutscher Kriegsgefangenschaft. „Pourquoi tu dois marier une Allemande?“ „Warum musst du eine Deutsche heiraten?“, wurde mein damaliger Mann noch gefragt. Das Misstrauen mir gegenüber wurde erst ausgeräumt, als wir ihr 1991 den kleinen Felix, unseren erstgeborenen Sohn, in den Schoß gelegt haben.
Das europäische Friedensprojekt ist gescheitert
Das europäische Einheits- und Friedensprojekt war damals, nach dem Mauerfall, in einer unbeschreiblichen Aufbruchstimmung, die sich heute niemand mehr vorstellen kann: Der ganze Kontinent in fröhlicher Stimmung - insieme, gemeinsam, together, ensemble – und wollte politisch zusammenwachsen. Heute ist es gescheitert und ich fasse es nicht! Das Kriegsgeheul in ganz Europa macht mich nachgerade verrückt.
Darum habe ich ein europäisches Friedensprojekt ins Leben gerufen: TheEuropean Peace Project. Am Europatag, den 9. Mai, um 17 Uhr, wollen wir in ganz Europa in allen europäischen und auf dem ganzen europäischen Kontinent als europäische Bürger den Frieden ausrufen! Ich würde mich freuen, wenn viele mitmachen!
DIE FRIEDENSTAUBE JETZT ABONNIEREN:
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel in Ihr Postfach, vorerst für alle kostenfrei, wir starten gänzlich ohne Paywall. (Die Bezahlabos fangen erst zu laufen an, wenn ein Monetarisierungskonzept für die Inhalte steht).
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):
Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: milosz@pareto.space oder kontakt@idw-europe.org.
Wo bleibt ein deutsch-russisches Jugendwerk?
Mein Lieblingsbuch zu Europa ist Laurent Gaudet, Nous, L’Europe, banquet des peuples. „Wir, Europa! Ein Banquet der Völker“ Es ist ein großartiges Gedicht, etwa wie die Ilias von Homer. Es beschreibt die letzten einhundert Jahre europäische Geschichte, die ganzen Krieg und Revolutionen. Und es beschreibt doch, was uns als Europäer eint. Darin findet sich der – für mich wunderschöne! - Satz: „Ce que nous partageons, c’est ce que nous étions tous bourraux et victime.“ „Was wir als Europäer teilen ist, dass wir alle zugleich Opfer und Täter waren“.
Und doch haben wir es geschafft, die „Erbfeindschaft“ zu beenden und uns auszusöhnen, zum Beispiel die Deutschen und Franzosen, über ein deutsch-französisches Jugendwerk, das 1963 gegründet wurde. So ein Jugendwerk wünsche ich mir auch heute zwischen Europa und Russland!
Das Epos von Laurent Gaudet ist in einem Theaterstück von dem französischen Regisseur Roland Auzet auf die Bühne gebracht worden. In dem 40-köpfigen Ensemble sind verschiedene Nationalitäten aus ganz Europa: das Stück ist fantastisch! Ich selber habe es auf dem Theaterfestival in Avignon 2019 sehen dürfen!
Ich wünsche mir, dass wir statt jetzt für Milliarden überall in Europa Waffen zu kaufen, das Geld dafür auftreiben, dieses Theaterstück in jede europäische Stadt zu bringen: wenn das gelänge, hätten wohl alle verstanden, was es heißt, Europäer zu sein: nämlich Frieden zu machen!
Ulrike Guérot, Jg. 1964, ist europäische Professorin, Publizistin und Bestsellerautorin. Seit rund 30 Jahren beschäftigt sie sich in europäischen Think Tanks und Universitäten in Paris, Brüssel, London, Washington, New York, Wien und Berlin mit Fragen der europäischen Demokratie, sowie mit der Rolle Europas in der Welt. Ulrike Guérot ist seit März 2014 Gründerin und Direktorin des European Democracy Labs, e.V.,Berlin und initiierte im März 2023 das European Citizens Radio, das auf Spotify zu finden ist. Zuletzt erschien von ihr "Über Halford J. Mackinders Heartland-Theorie, Der geografische Drehpunkt der Geschichte", Westend, 2024). Mehr Infos zur Autorin hier.
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ e516ecb8:1be0b167
2025-05-04 01:45:38
@ e516ecb8:1be0b167
2025-05-04 01:45:38El sol de la tarde caía oblicuo sobre un campo de hierba alta, tiñéndolo de tonos dorados y rojizos. A un lado, una formación disciplinada de hombres vestidos con armaduras de cuero y metal relucía bajo la luz. Eran legionarios romanos, cada uno portando un scutum, el gran escudo rectangular, y un gladius corto y letal. Se movían como una sola entidad, un muro de escudos erizado de puntas de lanza que asomaban por encima.
Al otro lado del campo, una fuerza más dispersa pero igualmente imponente esperaba. Eran samuráis, guerreros vestidos con armaduras lacadas de intrincado diseño. En sus manos, las brillantes curvas de las katanas reflejaban el sol poniente. Su presencia era menos de masa compacta y más de tensión contenida, como la de depredadores listos para abalanzarse.
El silencio se quebró cuando un oficial romano alzó su signum, un estandarte con el águila imperial. Al unísono, los legionarios avanzaron con paso firme, sus sandalias clavándose en la tierra. Gritaban su grito de guerra, un rugido gutural que resonaba en el aire.
Los samuráis observaron el avance implacable. Su líder, un hombre de rostro sereno con una cicatriz que le cruzaba la mejilla, desenvainó su katana con un movimiento fluido y silencioso. La hoja brilló intensamente. Con un grito agudo, dio la orden de ataque.
La batalla comenzó con un choque violento. Los legionarios, con sus escudos entrelazados, formaron una muralla impenetrable. Los samuráis se lanzaron contra ella, sus katanas trazando arcos de acero en el aire. El choque de metal contra metal llenó el campo, un coro estridente de la guerra.
Un samurái, ágil como un felino, intentó saltar sobre el muro de escudos. Pero un legionario, rápido y entrenado, lo recibió con una estocada precisa de su gladius, que encontró un hueco en la armadura. El samurái cayó, la sangre tiñendo la hierba.
Otro samurái, con un grito furioso, lanzó un corte horizontal con su katana. El golpe impactó contra un scutum, dejando una marca profunda en la madera y el metal, pero el escudo resistió. Antes de que pudiera recuperar su arma, el legionario detrás del escudo le asestó un golpe rápido con el gladius en el costado desprotegido.
La formación romana era una máquina de matar eficiente. Los legionarios trabajaban en equipo, protegiéndose mutuamente con sus escudos y atacando con sus gladius en los momentos oportunos. La disciplina y el entrenamiento eran sus mayores armas.
Sin embargo, la ferocidad y la habilidad individual de los samuráis eran innegables. Sus katanas, a pesar de no poder penetrar fácilmente la sólida pared de escudos, eran devastadoras en los espacios abiertos. Un samurái logró flanquear a un grupo de legionarios y, con movimientos rápidos y precisos, cortó brazos y piernas, sembrando el caos en la retaguardia romana.
La batalla se convirtió en un torbellino de acero y gritos. Los legionarios mantenían su formación, avanzando lentamente mientras repelían los ataques. Los samuráis, aunque sufrían bajas, no retrocedían, impulsados por su honor y su valentía.
En un punto crucial, un grupo de samuráis liderados por su comandante logró concentrar sus ataques en un sector de la línea romana. Con golpes repetidos y feroces, consiguieron romper la formación, creando una brecha. Se lanzaron a través de ella, sus katanas sedientas de sangre.
La disciplina romana se tambaleó por un momento. Los samuráis, aprovechando la oportunidad, lucharon cuerpo a cuerpo con una furia indomable. La longitud de sus katanas les daba ventaja en el combate individual, permitiéndoles mantener a raya a los legionarios con cortes amplios y letales.
Sin embargo, la respuesta romana fue rápida. Los oficiales gritaron órdenes, y las líneas se cerraron nuevamente, rodeando a los samuráis que habían penetrado la formación. Los legionarios, trabajando en parejas, inmovilizaban los largos brazos de los samuráis con sus escudos mientras otros asestaban golpes mortales con sus gladius.
La batalla continuó durante lo que pareció una eternidad. El sol finalmente se ocultó en el horizonte, tiñendo el campo de batalla de sombras oscuras y reflejos sangrientos. Ambos bandos lucharon con una determinación feroz, sin ceder terreno fácilmente.
Al final, la disciplina y la formación compacta de los legionarios comenzaron a imponerse. Lentamente, pero de manera constante, fueron cercando y diezmando a los samuráis. La muralla de escudos era demasiado sólida, y la lluvia constante de estocadas del gladius era implacable.
Los últimos samuráis lucharon con la desesperación de quienes saben que su final está cerca. Sus katanas seguían cortando con gracia mortal, pero eran superados en número y en la táctica del combate en grupo. Uno a uno, fueron cayendo, sus brillantes espadas manchadas de sangre.
Cuando la última katana cayó al suelo con un resonido metálico, un silencio pesado se cernió sobre el campo. Los legionarios, exhaustos pero victoriosos, permanecieron en formación, sus escudos goteando sangre. Habían prevalecido gracias a su disciplina, su equipo y su táctica de combate en grupo. La ferocidad individual y la maestría de la katana de los samuráis no habían sido suficientes contra la máquina de guerra romana.
La noche cubrió el campo de batalla, llevándose consigo los ecos de la lucha y dejando solo la sombría realidad de la victoria y la derrota.
-
 @ 04c915da:3dfbecc9
2025-03-25 17:43:44
@ 04c915da:3dfbecc9
2025-03-25 17:43:44One of the most common criticisms leveled against nostr is the perceived lack of assurance when it comes to data storage. Critics argue that without a centralized authority guaranteeing that all data is preserved, important information will be lost. They also claim that running a relay will become prohibitively expensive. While there is truth to these concerns, they miss the mark. The genius of nostr lies in its flexibility, resilience, and the way it harnesses human incentives to ensure data availability in practice.
A nostr relay is simply a server that holds cryptographically verifiable signed data and makes it available to others. Relays are simple, flexible, open, and require no permission to run. Critics are right that operating a relay attempting to store all nostr data will be costly. What they miss is that most will not run all encompassing archive relays. Nostr does not rely on massive archive relays. Instead, anyone can run a relay and choose to store whatever subset of data they want. This keeps costs low and operations flexible, making relay operation accessible to all sorts of individuals and entities with varying use cases.
Critics are correct that there is no ironclad guarantee that every piece of data will always be available. Unlike bitcoin where data permanence is baked into the system at a steep cost, nostr does not promise that every random note or meme will be preserved forever. That said, in practice, any data perceived as valuable by someone will likely be stored and distributed by multiple entities. If something matters to someone, they will keep a signed copy.
Nostr is the Streisand Effect in protocol form. The Streisand effect is when an attempt to suppress information backfires, causing it to spread even further. With nostr, anyone can broadcast signed data, anyone can store it, and anyone can distribute it. Try to censor something important? Good luck. The moment it catches attention, it will be stored on relays across the globe, copied, and shared by those who find it worth keeping. Data deemed important will be replicated across servers by individuals acting in their own interest.
Nostr’s distributed nature ensures that the system does not rely on a single point of failure or a corporate overlord. Instead, it leans on the collective will of its users. The result is a network where costs stay manageable, participation is open to all, and valuable verifiable data is stored and distributed forever.
-
 @ 5df413d4:2add4f5b
2025-05-04 01:13:31
@ 5df413d4:2add4f5b
2025-05-04 01:13:31Short photo-stories of the hidden, hard to find, obscure, and off the beaten track.
Come now, take a walk with me…
The Traveller 02: Jerusalem Old City
The bus slowly lurches up the winding and steep embankment. We can finally start to see the craggy tops of buildings peaking out over the ridge in the foreground distance. We have almost reached it. Jerusalem, the City on the Hill.
https://i.nostr.build/e2LpUKEgGBwfveGi.jpg
Our Israeli tour guide speaks over the mic to draw our attention to the valley below us instead - “This is the the Valley of Gehenna, the Valley of the Moloch,” he says. “In ancient times, the pagans who worshiped Moloch used this place for child sacrifice by fire. Now, imagine yourself, an early Hebrew, sitting atop the hill, looking down in horror. This is the literal Valley of The Shadow of Death, the origin of the Abrahamic concept of Hell.” Strong open - this is going to be fun.
https://i.nostr.build/5F29eBKZYs4bEMHk.jpg
Inside the Old City, our guide - a chubby, cherub-faced intelligence type on some sort of punishment duty, deputized to babysit foreigners specifically because he reads as so dopey and disarming - points out various Judeo-Christian sites on a map, his tone subtly suggesting which places are most suggested, or perhaps, permitted…
https://i.nostr.build/J44fhGWc9AZ5qpK4.jpg
https://i.nostr.build/3c0jh09nx6d5cEdt.jpg
Walking, we reach Judaism’s Kotel, the West Wall - massive, grand, and ancient, whispering of the Eternal. Amongst the worshipers, we touch the warm, dry limestone and, if we like, place written prayers into the wall's smaller cracks. A solemn and yearning ghost fills the place - but whose it is, I'm not sure.  https://i.nostr.build/AjDwA0rFiFPlrw1o.jpg
Just above the Kotel, Islam’s Dome of the Rock can be seen, its golden cap blazing in the sun. I ask our guide about visiting the dome. He cuts a heavy eyeroll in my direction - it seems I’ve outed myself as my group’s “that guy.” His face says more than words ever could, “Oy vey, there’s one in every group…”
“Why would anyone want to go there? It is a bit intense, no?” Still, I press. “Well, it is only open to tourists on Tuesday and Thursdays…” It is Tuesday. “And even then, visiting only opens from 11:30…” It is 11:20. As it becomes clear to him that I don't intend to drop this...“Fine!” he relents, with a dramatic flaring of the hands and an uniquely Israeli sigh, “Go there if you must. But remember, the bus leaves at 1PM. Good luck...” Great! Totally not ominous at all.
https://i.nostr.build/6aBhT61C28QO9J69.jpg
The checkpoint for the sole non-Muslim entrance leading up to the Dome is administered by several gorgeous and statuesque, assault rifle clad, Ethiop-Israeli female soldiers. In this period of relative peace and calm, they feel lax enough to make a coy but salacious game of their “screening” the men in line. As I observe, it seems none doth protest...
https://i.nostr.build/jm8F3pUp9EXqPRkN.jpg
Past the gun-totting Sirens, a long wooden rampart leads up to the Temple Mount, The Mount of the House of the Holy, al-Ḥaram al-Sharīf, The Noble Sanctuary, The Furthest Mosque, the site of the Dome of the Rock and the al-Masjid al-Asqa.
https://i.nostr.build/DoS0KIkrVN0yiVJ0.jpg
On the Mount, the Dome dominates all views. To those interested in pure expressions of beauty, the Dome is, undeniably, a thing of absolute glory. I pace the grounds, snapping what pictures I can. I pause to breathe and to let the electric energy of the setting wash over me.
https://i.nostr.build/0BQYLwpU291q2fBt.jpg
https://i.nostr.build/yCxfB1V8eAcfob93.jpg
It’s 12:15 now, I decide to head back. Now, here is what they don’t tell you. The non-Muslin entrance from the West Wall side is a one-way deal. Leaving the Dome plaza dumps you out into the back alley bazaar of Old City’s Muslim district. And so it is. I am lost.
https://i.nostr.build/XnQ5eZgjeS1UTEBt.jpg
https://i.nostr.build/EFGD5vgmFx5YYuH4.jpg
I run through the Muslim quarter, blindly turning down alleyways that seem to be taking me in the general direction of where I need to be - glimpses afforded by the city’s uneven elevation and cracks in ancient stone walls guiding my way.
https://i.nostr.build/mWIEAXlJfdqt3nuh.jpg
In a final act of desperation and likely a significant breach of Israeli security protocol, I scale a low wall and flop down back on the side of things where I'm “supposed” to be. But either no one sees me or no one cares. Good luck, indeed.
I make it back to my group - they are not hard to find, a bunch of MBAs in “business casual” travel attire and a tour guide wearing a loudly colored hat and jacket - with just enough time to still visit the Church of the Holy Sepulcher.
https://i.nostr.build/3nFvsXdhd0LQaZd7.jpg
https://i.nostr.build/sKnwqC0HoaZ8winW.jpg
Inside, a chaotic and dizzying array of chapels, grand domed ceilings, and Christian relics - most notably the Stone of Anointing, commemorating where Christ’s body was prepared for burial and Tomb of Christ, where Christ is said to have laid for 3 days before Resurrection.
https://i.nostr.build/Lb4CTj1dOY1pwoN6.jpg
https://i.nostr.build/LaZkYmUaY8JBRvwn.jpg
In less than an hour, one can traverse from the literal Hell, to King David’s Wall, The Tomb of Christ, and the site of Muhammad’s Ascension. The question that stays with me - What is it about this place that has caused so many to turn their heads to the heavens and cry out for God? Does he hear? And if he answers, do we listen?
https://i.nostr.build/elvlrd7rDcEaHJxT.jpg
Jerusalem, The Old City, circa 2014. Israel.
There are secrets to be found. Go there.
Bitcoin #Jerusalem #Israel #Travel #Photography #Art #Story #Storytelling #Nostr #Zap #Zaps #Plebchain #Coffeechain #Bookstr #NostrArt #Writing #Writestr #Createstr
-
 @ dd664d5e:5633d319
2025-03-21 12:22:36
@ dd664d5e:5633d319
2025-03-21 12:22:36Men tend to find women attractive, that remind them of the average women they already know, but with more-averaged features. The mid of mids is kween.👸
But, in contradiction to that, they won't consider her highly attractive, unless she has some spectacular, unusual feature. They'll sacrifice some averageness to acquire that novelty. This is why wealthy men (who tend to be highly intelligent -- and therefore particularly inclined to crave novelty because they are easily bored) -- are more likely to have striking-looking wives and girlfriends, rather than conventionally-attractive ones. They are also more-likely to cross ethnic and racial lines, when dating.
Men also seem to each be particularly attracted to specific facial expressions or mimics, which might be an intelligence-similarity test, as persons with higher intelligence tend to have a more-expressive mimic. So, people with similar expressions tend to be on the same wavelength. Facial expessions also give men some sense of perception into womens' inner life, which they otherwise find inscrutable.
Hair color is a big deal (logic says: always go blonde), as is breast-size (bigger is better), and WHR (smaller is better).

-
 @ 878dff7c:037d18bc
2025-03-21 04:39:42
@ 878dff7c:037d18bc
2025-03-21 04:39:42Smooth, rich, and deeply comforting, this savory porridge is enhanced by fermentation, warming spices, and a creamy finish — easy on digestion, full of flavor, and great for meal prep.
Ingredients (Serves 2–3):
- 200g (1 cup) lactofermented brown rice (see rice fermentation recipe in comments)
- 375–500ml (1.5-2 cups) broth or water (I use evaporation method, but cook rice however you normally do, it's not important) (chicken, vegetable, or bone broth for extra richness)
- 250ml (1 cup) milk (whole milk for creaminess)
- 5g (1 tsp) salt (adjust to taste)
- 15g (1 tbsp) butter or coconut oil (for extra silkiness)
- 15g (1 tbsp) fresh ginger, sliced or minced from a jar is fine (optional, for warmth)
- 5g (1 clove or 1 tsp) garlic, minced (optional. I normally skip this...)
- 2g (½ tsp) ground turmeric (for color and anti-inflammatory benefit)
- 1g (¼ tsp) white or black pepper (black pepper enhances turmeric absorption)
Optional Savory Toppings:
- 1 soft-boiled or poached egg
- 100g (¾ cup) shredded chicken, pork, or tofu
- 30g (¼ cup) grated cheese (Parmesan, aged cheddar, or nutritional yeast for vegan)
- 20g (2 tbsp) chopped scallions or chives
- 30g (2 tbsp) fermented vegetables, such as:
- Kimchi
- Pickled mustard greens
- Sauerkraut
- Lactofermented carrots
- 10g (1 tbsp) toasted sesame seeds or crushed peanuts
- 5ml (1 tsp) soy sauce, tamari, or fish sauce
- 15–30g (1–2 tbsp) full-fat Greek yogurt or kefir (optional probiotic boost – stir in when warm, not hot)
Instructions:
1. Cook the Fermented Rice Base
- In a pot, combine fermented brown rice with broth or water.
- Bring to a boil, then reduce to a gentle simmer.
- Add ginger, garlic, and turmeric.
- Cook uncovered for 90–120 minutes, stirring occasionally, until the rice breaks down into a creamy porridge.
2. Make It Creamy
- Stir in milk and butter or coconut oil.
- Simmer for another 10–15 minutes, stirring to prevent sticking.
- Season with salt and pepper.
3. Adjust Consistency
- Too thick? Add more broth or milk.
- Too thin? Simmer longer.
4. Cool Slightly & Add Yogurt or Kefir (Optional)
- Let porridge cool to a warm (not hot) temperature — about 50°C (122°F) or warm to the touch.
- Stir in Greek yogurt or kefir gently to preserve live cultures.
5. Serve with Toppings
Top each bowl with your choice of:
- Egg
- Shredded protein
- Cheese
- Soy sauce or tamari
- Scallions, sesame seeds, chili flakes
- Your favorite fermented veggies, like sauerkraut or lactofermented carrots
Make-Ahead & Freezing Tip:
You can ferment and cook a large batch of brown rice, then portion it into freezer-safe containers (about 200g per portion) for quick use. Thaw overnight in the fridge or gently warm from frozen before making your congee — a huge time-saver for busy days!
-
 @ 5df413d4:2add4f5b
2025-05-04 00:51:49
@ 5df413d4:2add4f5b
2025-05-04 00:51:49Short photo-stories of the hidden, hard to find, obscure, and off the beaten track.
Come now, take a walk with me…
The Traveller 01: Ku/苦 Bar
Find a dingy, nondescript alley in a suspiciously quiet corner of Bangkok’s Chinatown at night. Walk down it. Pass the small prayer shrine that houses the angels who look over these particular buildings and approach an old wooden door. You were told that there is a bar here, as to yet nothing suggests that this is so…

Wait! A closer inspection reveals a simple bronze plaque, out of place for its polish and tended upkeep, “cocktails 3rd floor.” Up the stairs then! The landing on floor 3 presents a white sign with the Chinese character for bitter, ku/苦, and a red arrow pointing right.


Pass through the threshold, enter a new space. To your right, a large expanse of barren concrete, an empty “room.” Tripods for…some kind of filming? A man-sized, locked container. Yet, you did not come here to ask questions, such things are none of your business!

And to your left, you find the golden door. Approach. Enter. Be greeted. You have done well! You have found it. 苦 Bar. You are among friends now. Inside exudes deep weirdness - in the etymological sense - the bending of destinies, control of the fates. And for the patrons, a quiet yet social place, a sensual yet sacred space.


Ethereal sounds, like forlorn whale songs fill the air, a strange music for an even stranger magic. But, Taste! Taste is the order of the day! Fragrant, Bizarre, Obscure, Dripping and Arcane. Here you find a most unique use flavor, flavors myriad and manifold, flavors beyond name. Buddha’s hand, burnt cedar charcoal, ylang ylang, strawberry leaf, maybe wild roots brought in by some friendly passerby, and many, many other things. So, Taste! The drinks here, libations even, are not so much to be liked or disliked, rather, the are liquid context, experience to be embraced with a curious mind and soul freed from judgment.

And In the inner room, one may find another set of stairs. Down this time. Leading to the second place - KANGKAO. A natural wine bar, or so they say. Cozy, botanical, industrial, enclosed. The kind of private setting where you might overhear Bangkok’s resident “State Department,” “UN,” and “NGO” types chatting auspiciously in both Mandarin and English with their Mainland Chinese counterparts. But don’t look hard or listen too long! Surely, there’s no reason to be rude… Relax, relax, you are amongst friends now.

**苦 Bar. Bangkok, circa 2020. There are secrets to be found. Go there. **
Plebchain #Bitcoin #NostrArt #ArtOnNostr #Writestr #Createstr #NostrLove #Travel #Photography #Art #Story #Storytelling #Nostr #Zap #Zaps #Bangkok #Thailand #Siamstr
-
 @ 16f1a010:31b1074b
2025-03-20 14:32:25
@ 16f1a010:31b1074b
2025-03-20 14:32:25grain is a nostr relay built using Go, currently utilizing MongoDB as its database. Binaries are provided for AMD64 Windows and Linux. grain is Go Relay Architecture for Implementing Nostr
Introduction
grain is a nostr relay built using Go, currently utilizing MongoDB as its database. Binaries are provided for AMD64 Windows and Linux. grain is Go Relay Architecture for Implementing Nostr
Prerequisites
- Grain requires a running MongoDB instance. Please refer to this separate guide for instructions on setting up MongoDB: nostr:naddr1qvzqqqr4gupzq9h35qgq6n8ll0xyyv8gurjzjrx9sjwp4hry6ejnlks8cqcmzp6tqqxnzde5xg6rwwp5xsuryd3knfdr7g
Download Grain
Download the latest release for your system from the GitHub releases page
amd64 binaries provided for Windows and Linux, if you have a different CPU architecture, you can download and install go to build grain from source
Installation and Execution
- Create a new folder on your system where you want to run Grain.
- The downloaded binary comes bundled with a ZIP file containing a folder named "app," which holds the frontend HTML files. Unzip the "app" folder into the same directory as the Grain executable.
Run Grain
- Open your terminal or command prompt and navigate to the Grain directory.
- Execute the Grain binary.
on linux you will first have to make the program executable
chmod +x grain_linux_amd64Then you can run the program
./grain_linux_amd64(alternatively on windows, you can just double click the grain_windows_amd64.exe to start the relay)
You should see a terminal window displaying the port on which your relay and frontend are running.
If you get
Failed to copy app/static/examples/config.example.yml to config.yml: open app/static/examples/config.example.yml: no such file or directory
Then you probably forgot to put the app folder in the same directory as your executable or you did not unzip the folder.
Congrats! You're running grain 🌾!
You may want to change your NIP11 relay information document (relay_metadata.json) This informs clients of the capabilities, administrative contacts, and various server attributes. It's located in the same directory as your executable.
Configuration Files
Once Grain has been executed for the first time, it will generate the default configuration files inside the directory where the executable is located. These files are:
bash config.yml whitelist.yml blacklist.ymlPrerequisites: - Grain requires a running MongoDB instance. Please refer to this separate guide for instructions on setting up MongoDB: [Link to MongoDB setup guide].
Download Grain:
Download the latest release for your system from the GitHub releases page
amd64 binaries provided for Windows and Linux, if you have a different CPU architecture, you can download and install go to build grain from source
Installation and Execution:
- Create a new folder on your system where you want to run Grain.
- The downloaded binary comes bundled with a ZIP file containing a folder named "app," which holds the frontend HTML files. Unzip the "app" folder into the same directory as the Grain executable.
Run Grain:
- Open your terminal or command prompt and navigate to the Grain directory.
- Execute the Grain binary.
on linux you will first have to make the program executable
chmod +x grain_linux_amd64Then you can run the program
./grain_linux_amd64(alternatively on windows, you can just double click the grain_windows_amd64.exe to start the relay)
You should see a terminal window displaying the port on which your relay and frontend are running.
If you get
Failed to copy app/static/examples/config.example.yml to config.yml: open app/static/examples/config.example.yml: no such file or directory
Then you probably forgot to put the app folder in the same directory as your executable or you did not unzip the folder.
Congrats! You're running grain 🌾!
You may want to change your NIP11 relay information document (relay_metadata.json) This informs clients of the capabilities, administrative contacts, and various server attributes. It's located in the same directory as your executable.
Configuration Files:
Once Grain has been executed for the first time, it will generate the default configuration files inside the directory where the executable is located. These files are:
bash config.yml whitelist.yml blacklist.ymlConfiguration Documentation
You can always find the latest example configs on my site or in the github repo here: config.yml
Config.yml
This
config.ymlfile is where you customize how your Grain relay operates. Each section controls different aspects of the relay's behavior.1.
mongodb(Database Settings)uri: mongodb://localhost:27017/:- This is the connection string for your MongoDB database.
mongodb://localhost:27017/indicates that your MongoDB server is running on the same computer as your Grain relay (localhost) and listening on port 27017 (the default MongoDB port).- If your MongoDB server is on a different machine, you'll need to change
localhostto the server's IP address or hostname. - The trailing
/indicates the root of the mongodb server. You will define the database in the next line.
database: grain:- This specifies the name of the MongoDB database that Grain will use to store Nostr events. Grain will create this database if it doesn't already exist.
- You can name the database whatever you want. If you want to run multiple grain relays, you can and they can have different databases running on the same mongo server.
2.
server(Relay Server Settings)port: :8181:- This sets the port on which your Grain relay will listen for incoming nostr websocket connections and what port the frontend will be available at.
read_timeout: 10 # in seconds:- This is the maximum time (in seconds) that the relay will wait for a client to send data before closing the connection.
write_timeout: 10 # in seconds:- This is the maximum time (in seconds) that the relay will wait for a client to receive data before closing the connection.
idle_timeout: 120 # in seconds:- This is the maximum time (in seconds) that the relay will keep a connection open if there's no activity.
max_connections: 100:- This sets the maximum number of simultaneous client connections that the relay will allow.
max_subscriptions_per_client: 10:- This sets the maximum amount of subscriptions a single client can request from the relay.
3.
resource_limits(System Resource Limits)cpu_cores: 2 # Limit the number of CPU cores the application can use:- This restricts the number of CPU cores that Grain can use. Useful for controlling resource usage on your server.
memory_mb: 1024 # Cap the maximum amount of RAM in MB the application can use:- This limits the maximum amount of RAM (in megabytes) that Grain can use.
heap_size_mb: 512 # Set a limit on the Go garbage collector's heap size in MB:- This sets a limit on the amount of memory that the Go programming language's garbage collector can use.
4.
auth(Authentication Settings)enabled: false # Enable or disable AUTH handling:- If set to
true, this enables authentication handling, requiring clients to authenticate before using the relay.
- If set to
relay_url: "wss://relay.example.com/" # Specify the relay URL:- If authentication is enabled, this is the url that clients will use to authenticate.
5.
UserSync(User Synchronization)user_sync: false:- If set to true, the relay will attempt to sync user data from other relays.
disable_at_startup: true:- If user sync is enabled, this will prevent the sync from starting when the relay starts.
initial_sync_relays: [...]:- A list of other relays to pull user data from.
kinds: []:- A list of event kinds to pull from the other relays. Leaving this empty will pull all event kinds.
limit: 100:- The limit of events to pull from the other relays.
exclude_non_whitelisted: true:- If set to true, only users on the whitelist will have their data synced.
interval: 360:- The interval in minutes that the relay will resync user data.
6.
backup_relay(Backup Relay)enabled: false:- If set to true, the relay will send copies of received events to the backup relay.
url: "wss://some-relay.com":- The url of the backup relay.
7.
event_purge(Event Purging)enabled: false:- If set to
true, the relay will automatically delete old events.
- If set to
keep_interval_hours: 24:- The number of hours to keep events before purging them.
purge_interval_minutes: 240:- How often (in minutes) the purging process runs.
purge_by_category: ...:- Allows you to specify which categories of events (regular, replaceable, addressable, deprecated) to purge.
purge_by_kind_enabled: false:- If set to true, events will be purged based on the kinds listed below.
kinds_to_purge: ...:- A list of event kinds to purge.
exclude_whitelisted: true:- If set to true, events from whitelisted users will not be purged.
8.
event_time_constraints(Event Time Constraints)min_created_at: 1577836800:- The minimum
created_attimestamp (Unix timestamp) that events must have to be accepted by the relay.
- The minimum
max_created_at_string: now+5m:- The maximum created at time that an event can have. This example shows that the max created at time is 5 minutes in the future from the time the event is received.
min_created_at_stringandmax_created_atwork the same way.
9.
rate_limit(Rate Limiting)ws_limit: 100:- The maximum number of WebSocket messages per second that the relay will accept.
ws_burst: 200:- Allows a temporary burst of WebSocket messages.
event_limit: 50:- The maximum number of Nostr events per second that the relay will accept.
event_burst: 100:- Allows a temporary burst of Nostr events.
req_limit: 50:- The limit of http requests per second.
req_burst: 100:- The allowed burst of http requests.
max_event_size: 51200:- The maximum size (in bytes) of a Nostr event that the relay will accept.
kind_size_limits: ...:- Allows you to set size limits for specific event kinds.
category_limits: ...:- Allows you to set rate limits for different event categories (ephemeral, addressable, regular, replaceable).
kind_limits: ...:- Allows you to set rate limits for specific event kinds.
By understanding these settings, you can tailor your Grain Nostr relay to meet your specific needs and resource constraints.
whitelist.yml
The
whitelist.ymlfile is used to control which users, event kinds, and domains are allowed to interact with your Grain relay. Here's a breakdown of the settings:1.
pubkey_whitelist(Public Key Whitelist)enabled: false:- If set to
true, this enables the public key whitelist. Only users whose public keys are listed will be allowed to publish events to your relay.
- If set to
pubkeys::- A list of hexadecimal public keys that are allowed to publish events.
pubkey1andpubkey2are placeholders, you will replace these with actual hexadecimal public keys.
npubs::- A list of npubs that are allowed to publish events.
npub18ls2km9aklhzw9yzqgjfu0anhz2z83hkeknw7sl22ptu8kfs3rjq54am44andnpub2are placeholders, replace them with actual npubs.- npubs are bech32 encoded public keys.
2.
kind_whitelist(Event Kind Whitelist)enabled: false:- If set to
true, this enables the event kind whitelist. Only events with the specified kinds will be allowed.
- If set to
kinds::- A list of event kinds (as strings) that are allowed.
"1"and"2"are example kinds. Replace these with the kinds you want to allow.- Example kinds are 0 for metadata, 1 for short text notes, and 2 for recommend server.
3.
domain_whitelist(Domain Whitelist)enabled: false:- If set to
true, this enables the domain whitelist. This checks the domains .well-known folder for their nostr.json. This file contains a list of pubkeys. They will be considered whitelisted if on this list.
- If set to
domains::- A list of domains that are allowed.
"example.com"and"anotherdomain.com"are example domains. Replace these with the domains you want to allow.
blacklist.yml
The
blacklist.ymlfile allows you to block specific content, users, and words from your Grain relay. Here's a breakdown of the settings:1.
enabled: true- This setting enables the blacklist functionality. If set to
true, the relay will actively block content and users based on the rules defined in this file.
2.
permanent_ban_words:- This section lists words that, if found in an event, will result in a permanent ban for the event's author.
- really bad wordis a placeholder. Replace it with any words you want to permanently block.
3.
temp_ban_words:- This section lists words that, if found in an event, will result in a temporary ban for the event's author.
- crypto,- web3, and- airdropare examples. Replace them with the words you want to temporarily block.
4.
max_temp_bans: 3- This sets the maximum number of temporary bans a user can receive before they are permanently banned.
5.
temp_ban_duration: 3600- This sets the duration of a temporary ban in seconds.
3600seconds equals one hour.
6.
permanent_blacklist_pubkeys:- This section lists hexadecimal public keys that are permanently blocked from using the relay.
- db0c9b8acd6101adb9b281c5321f98f6eebb33c5719d230ed1870997538a9765is an example. Replace it with the public keys you want to block.
7.
permanent_blacklist_npubs:- This section lists npubs that are permanently blocked from using the relay.
- npub1x0r5gflnk2mn6h3c70nvnywpy2j46gzqwg6k7uw6fxswyz0md9qqnhshtnis an example. Replace it with the npubs you want to block.- npubs are the human readable version of public keys.
8.
mutelist_authors:- This section lists hexadecimal public keys of author of a kind1000 mutelist. Pubkey authors on this mutelist will be considered on the permanent blacklist. This provides a nostr native way to handle the backlist of your relay
- 3fe0ab6cbdb7ee27148202249e3fb3b89423c6f6cda6ef43ea5057c3d93088e4is an example. Replace it with the public keys of authors that have a mutelist you would like to use as a blacklist. Consider using your own.- Important Note: The mutelist Event MUST be stored in this relay for it to be retrieved. This means your relay must have a copy of the authors kind10000 mutelist to consider them for the blacklist.
Running Grain as a Service:
Windows Service:
To run Grain as a Windows service, you can use tools like NSSM (Non-Sucking Service Manager). NSSM allows you to easily install and manage any application as a Windows service.
* For instructions on how to install NSSM, please refer to this article: [Link to NSSM install guide coming soon].-
Open Command Prompt as Administrator:
- Open the Windows Start menu, type "cmd," right-click on "Command Prompt," and select "Run as administrator."
-
Navigate to NSSM Directory:
- Use the
cdcommand to navigate to the directory where you extracted NSSM. For example, if you extracted it toC:\nssm, you would typecd C:\nssmand press Enter.
- Use the
-
Install the Grain Service:
- Run the command
nssm install grain. - A GUI will appear, allowing you to configure the service.
- Run the command
-
Configure Service Details:
- In the "Path" field, enter the full path to your Grain executable (e.g.,
C:\grain\grain_windows_amd64.exe). - In the "Startup directory" field, enter the directory where your Grain executable is located (e.g.,
C:\grain).
- In the "Path" field, enter the full path to your Grain executable (e.g.,
-
Install the Service:
- Click the "Install service" button.
-
Manage the Service:
- You can now manage the Grain service using the Windows Services manager. Open the Start menu, type "services.msc," and press Enter. You can start, stop, pause, or restart the Grain service from there.
Linux Service (systemd):
To run Grain as a Linux service, you can use systemd, the standard service manager for most modern Linux distributions.
-
Create a Systemd Service File:
- Open a text editor with root privileges (e.g.,
sudo nano /etc/systemd/system/grain.service).
- Open a text editor with root privileges (e.g.,
-
Add Service Configuration:
- Add the following content to the
grain.servicefile, replacing the placeholders with your actual paths and user information:
```toml [Unit] Description=Grain Nostr Relay After=network.target
[Service] ExecStart=/path/to/grain_linux_amd64 WorkingDirectory=/path/to/grain/directory Restart=always User=your_user #replace your_user Group=your_group #replace your_group
[Install] WantedBy=multi-user.target ```
- Replace
/path/to/grain/executablewith the full path to your Grain executable. - Replace
/path/to/grain/directorywith the directory containing your Grain executable. - Replace
your_userandyour_groupwith the username and group that will run the Grain service.
- Add the following content to the
-
Reload Systemd:
- Run the command
sudo systemctl daemon-reloadto reload the systemd configuration.
- Run the command
-
Enable the Service:
- Run the command
sudo systemctl enable grain.serviceto enable the service to start automatically on boot.
- Run the command
-
Start the Service:
- Run the command
sudo systemctl start grain.serviceto start the service immediately.
- Run the command
-
Check Service Status:
- Run the command
sudo systemctl status grain.serviceto check the status of the Grain service. This will show you if the service is running and any recent logs. - You can run
sudo journalctl -f -u grain.serviceto watch the logs
- Run the command
More guides are in the works for setting up tailscale to access your relay from anywhere over a private network and for setting up a cloudflare tunnel to your domain to deploy a grain relay accessible on a subdomain of your site eg wss://relay.yourdomain.com
-
 @ a367f9eb:0633efea
2025-03-19 17:40:04
@ a367f9eb:0633efea
2025-03-19 17:40:04On February 27th, the Securities and Exchange Commission stated in its latest staff statement that memecoins are not necessarily securities.
“Although the offer and sale of meme coins may not be subject to the federal securities laws, fraudulent conduct related to the offer and sale of meme coins may be subject to enforcement action or prosecution,” writes the SEC.
This clarity is important, but it reveals nothing about what the policies around memecoins, rugpulls, and crypto scams should actually be.
This month has already delivered us Argentine President Javier Milei’s promotion of a pump-and-dump memecoin called LIBRA. At this moment, Barstool Sports founder Dave Portnoy is probably pumping his third or fourth favorite memecoin into oblivion while he dumps on retail.
In each of these cases, these tokens are created with copy-paste smart contracts, influencers singing their praises, and people exchanging their stablecoins, bitcoin, or some other altcoin for the hope of making it rich.
Memecoin world
Of course, in a free country people should be free to bet on things they want. But they should be prepared to lose just as much as they’re prepared to win.
To the uninitiated, these scams represent “crypto” writ-large, lumping the original decentralized protocol of Bitcoin with pump and dump scams from platforms like pump.fun that run on Solana and other chains.
Knowing what we know, and how desperate parts of the crypto market are for outrageous tokens and leveraged degen trading, we must naturally ask how Bitcoin can fix this. Or, rather, how smart Bitcoin policies can fix this.
As I have written for several years, we as Bitcoin advocates should promote sound policies that will encourage innovation and increase economic inclusion across all income groups, all the while protecting consumers from harm. We want to avoid blowouts like FTX, Celsius, and even stablecoins projects like TerraUSD – not only because they defraud bitcoiners, but because they sully the reputation of our entire sector of technological innovation.
Because Bitcoin represents scarcity, decentralization, and complete transparency, there is much we can learn from Satoshi’s innovation when we’re dealing with next-level crypto-offspring.
The Smart Bitcoin Policies to Stop Crypto Scams
To begin, US federal, state, and local agencies should update their technological stack to rigorously identify and prosecute fraud and abuse in crypto projects. Fraudulent claims, fake token whitepapers, and deceptive tactics are already illegal under existing law. Our agencies should be empowered to enforce existing law and weed out the bad actors.
Whether that means better training or tools, law enforcement should receive the necessary upgrades to prosecute and identify the real fraudulent crime that happens to take place in crypto protocols. Much of this behavior is just being used in a new medium. It’s not crazy to think that cops should upgrade their tech stack to understand how it’s happening now.
Second, our policies on money transmission licenses and regulation for crypto exchanges should be streamlined and made easier, rather than more difficult. Let competition provide the best places for people to buy their bitcoin. As much as privacy advocates abhor centralized platforms and exchanges, they still implement better security and educational practices to inform users than a shady service hosted in China will provide.
By simplifying the rules and restrictions on bitcoin exchanges, especially by allowing them to consider their custodied bitcoin as assets rather than liabilities as was done by rescinding SAB 121, it means that more Americans will have the opportunity to have excellent experiences when purchasing their coins online.
Third, regulators must not pigeonhole bitcoin and its crypto-offspring only as investments fit for taxing, but rather as technological tools that empower consumers and foster innovation. Too much discussion about bitcoin policies hinges on the tax rate or how much it will bring to state coffers, rather than by how much it can make one’s life better by removing the red tape to safeguard wealth.
By recognizing the ultimate power of bitcoin self-custody without needing to trust third parties or intermediaries, it means we finally view this technology as an extension of our own free speech and freedom of association.
And lastly, we must focus on removing the barriers to using bitcoin as an ordinary means of payment. The Keep Your Coins Act restricts federal agencies from stopping individuals from using bitcoin how they see fit, as well as protecting self-custody. That, plus de minimis exemption rules that allow us to spend bitcoin as any other asset, mean we can use digital money as intended.
We know that memecoins and rugpulls will continue to happen no matter what, this is almost human nature. But at the same time, embracing smart bitcoin policies will ensure that consumers and users have the best tools and protections available to use the technology if they want.
Originally published at the Bitcoin Policy Institute.
-
 @ 5cb68b7a:b7cb67d5
2025-05-04 00:13:44
@ 5cb68b7a:b7cb67d5
2025-05-04 00:13:44Losing access to your cryptocurrency can feel like losing a part of your future. Whether it’s a forgotten password, a damaged seed backup, or simply one wrong transfer, the stress can be overwhelming. But there’s a silver lining — Crypt Recver is here to help! With our expert-led recovery services, you can reclaim your lost Bitcoin and other cryptos safely and swiftly.
Why Trust Crypt Recver? 🤝 🛠️ Expert Recovery Solutions At Crypt Recver, we specialize in resolving some of the most complex wallet-related issues. Our team of skilled engineers has the tools and expertise to tackle:
Partially lost or forgotten seed phrases Extracting funds from outdated or invalid wallet addresses Recovering data from damaged hardware wallets Restoring coins from old or unsupported wallet formats You’re not just getting a service; you’re gaining a partner in your cryptocurrency journey.
🚀 Fast and Efficient Recovery We understand that time is critical in crypto recovery. Our optimized systems ensure that you can regain access to your funds quickly, aiming for speed without sacrificing security. With a 90%+ success rate, you can trust us to fight against the clock on your behalf.
🔒 Privacy is Our Priority Your confidentiality matters. Every recovery session is handled with the utmost care, ensuring all processes are encrypted and confidential. You can rest easy, knowing your sensitive information stays private.
💻 Advanced Technology Our proprietary tools and brute-force optimization techniques allow for maximum efficiency in recovery. No matter how challenging your case may be, our technology is designed to give you the best chance at getting your crypto back.
Our Recovery Services Include: 📈 Bitcoin Recovery: Lost access to your Bitcoin wallet? We help recover lost wallets, private keys, and passphrases. Transaction Recovery: Mistakes happen — whether it’s an incorrect wallet address or a lost password, let us handle the recovery. Cold Wallet Restoration: If your cold wallet is failing, we can safely extract your assets and migrate them into a secure, new wallet. Private Key Generation: Lost your private key? Don’t worry. Our experts can help you regain control using advanced methods — all while ensuring your privacy remains intact. ⚠️ What We Don’t Do While we can handle many scenarios, there are some limitations. For example, we cannot recover funds stored in custodial wallets, or cases where there is a complete loss of four or more seed words without any partial info available. We’re transparent about what’s possible, so you know what to expect.
Don’t Let Lost Crypto Hold You Back! ⏳ Did you know that 3 to 3.4 million BTC — nearly 20% of the total supply — are estimated to be permanently lost? Don’t become part of that statistic! Whether it’s due to a forgotten password, sending funds to the wrong address, or damaged drives, we can help you navigate through it all.
🛡️ Real-Time Dust Attack Protection Protecting your privacy goes beyond just recovery. Our services include dust attack protection, which keeps your activity anonymous and your funds secure. Our suite will shield your identity from unwanted tracking, ransomware, and phishing attempts.
🎉 Start Your Recovery Journey Today! Are you ready to reclaim your lost crypto? Don’t wait until it’s too late!
👉 Request Wallet Recovery Help Now!
📞 Need Immediate Assistance? Connect with Us! For real-time support or questions, reach out to our dedicated team on:
✉️ Telegram: Chat with Us on Telegram 💬 WhatsApp: Message Us on WhatsApp Crypt Recver is your trusted partner in the world of cryptocurrency recovery. Let us turn your challenges into victories. Don’t hesitate — your crypto future starts now! 🚀✨
Act fast and secure your digital assets with Crypt Recver!Losing access to your cryptocurrency can feel like losing a part of your future. Whether it’s a forgotten password, a damaged seed backup, or simply one wrong transfer, the stress can be overwhelming. But there’s a silver lining — Crypt Recver is here to help! With our expert-led recovery services, you can reclaim your lost Bitcoin and other cryptos safely and swiftly.
 # Why Trust Crypt Recver? 🤝
# Why Trust Crypt Recver? 🤝🛠️ Expert Recovery Solutions
At Crypt Recver, we specialize in resolving some of the most complex wallet-related issues. Our team of skilled engineers has the tools and expertise to tackle:
- Partially lost or forgotten seed phrases
- Extracting funds from outdated or invalid wallet addresses
- Recovering data from damaged hardware wallets
- Restoring coins from old or unsupported wallet formats
You’re not just getting a service; you’re gaining a partner in your cryptocurrency journey.
🚀 Fast and Efficient Recovery
We understand that time is critical in crypto recovery. Our optimized systems ensure that you can regain access to your funds quickly, aiming for speed without sacrificing security. With a 90%+ success rate, you can trust us to fight against the clock on your behalf.
🔒 Privacy is Our Priority
Your confidentiality matters. Every recovery session is handled with the utmost care, ensuring all processes are encrypted and confidential. You can rest easy, knowing your sensitive information stays private.
💻 Advanced Technology
Our proprietary tools and brute-force optimization techniques allow for maximum efficiency in recovery. No matter how challenging your case may be, our technology is designed to give you the best chance at getting your crypto back.
Our Recovery Services Include: 📈
- Bitcoin Recovery: Lost access to your Bitcoin wallet? We help recover lost wallets, private keys, and passphrases.
- Transaction Recovery: Mistakes happen — whether it’s an incorrect wallet address or a lost password, let us handle the recovery.
- Cold Wallet Restoration: If your cold wallet is failing, we can safely extract your assets and migrate them into a secure, new wallet.
- Private Key Generation: Lost your private key? Don’t worry. Our experts can help you regain control using advanced methods — all while ensuring your privacy remains intact.
⚠️ What We Don’t Do
While we can handle many scenarios, there are some limitations. For example, we cannot recover funds stored in custodial wallets, or cases where there is a complete loss of four or more seed words without any partial info available. We’re transparent about what’s possible, so you know what to expect.
 # Don’t Let Lost Crypto Hold You Back! ⏳
# Don’t Let Lost Crypto Hold You Back! ⏳Did you know that 3 to 3.4 million BTC — nearly 20% of the total supply — are estimated to be permanently lost? Don’t become part of that statistic! Whether it’s due to a forgotten password, sending funds to the wrong address, or damaged drives, we can help you navigate through it all.
🛡️ Real-Time Dust Attack Protection
Protecting your privacy goes beyond just recovery. Our services include dust attack protection, which keeps your activity anonymous and your funds secure. Our suite will shield your identity from unwanted tracking, ransomware, and phishing attempts.
🎉 Start Your Recovery Journey Today!
Are you ready to reclaim your lost crypto? Don’t wait until it’s too late!
👉 Request Wallet Recovery Help Now!
📞 Need Immediate Assistance? Connect with Us!
For real-time support or questions, reach out to our dedicated team on:
- ✉️ Telegram: Chat with Us on Telegram
- 💬 WhatsApp: Message Us on WhatsApp
Crypt Recver is your trusted partner in the world of cryptocurrency recovery. Let us turn your challenges into victories. Don’t hesitate — your crypto future starts now! 🚀✨
Act fast and secure your digital assets with Crypt Recver!
-
 @ 266815e0:6cd408a5
2025-03-19 11:10:21
@ 266815e0:6cd408a5
2025-03-19 11:10:21How to create a nostr app quickly using applesauce
In this guide we are going to build a nostr app that lets users follow and unfollow fiatjaf
1. Setup new project
Start by setting up a new vite app using
pnpm create vite, then set the name and selectSolidandTypescript```sh ➜ pnpm create vite │ ◇ Project name: │ followjaf │ ◇ Select a framework: │ Solid │ ◇ Select a variant: │ TypeScript │ ◇ Scaffolding project in ./followjaf... │ └ Done. Now run:
cd followjaf pnpm install pnpm run dev ```
2. Adding nostr dependencies
There are a few useful nostr dependencies we are going to need.
nostr-toolsfor the types and small methods, andrx-nostrfor making relay connectionssh pnpm install nostr-tools rx-nostr3. Setup rx-nostr
Next we need to setup rxNostr so we can make connections to relays. create a new
src/nostr.tsfile with```ts import { createRxNostr, noopVerifier } from "rx-nostr";
export const rxNostr = createRxNostr({ // skip verification here because we are going to verify events at the event store skipVerify: true, verifier: noopVerifier, }); ```
4. Setup the event store
Now that we have a way to connect to relays, we need a place to store events. We will use the
EventStoreclass fromapplesauce-corefor this. create a newsrc/stores.tsfile withThe event store does not store any events in the browsers local storage or anywhere else. It's in-memory only and provides a model for the UI
```ts import { EventStore } from "applesauce-core"; import { verifyEvent } from "nostr-tools";
export const eventStore = new EventStore();
// verify the events when they are added to the store eventStore.verifyEvent = verifyEvent; ```
5. Create the query store
The event store is where we store all the events, but we need a way for the UI to query them. We can use the
QueryStoreclass fromapplesauce-corefor this.Create a query store in
src/stores.ts```ts import { QueryStore } from "applesauce-core";
// ...
// the query store needs the event store to subscribe to it export const queryStore = new QueryStore(eventStore); ```
6. Setup the profile loader
Next we need a way to fetch user profiles. We are going to use the
ReplaceableLoaderclass fromapplesauce-loadersfor this.applesauce-loadersis a package that contains a few loader classes that can be used to fetch different types of data from relays.First install the package
sh pnpm install applesauce-loadersThen create a
src/loaders.tsfile with```ts import { ReplaceableLoader } from "applesauce-loaders"; import { rxNostr } from "./nostr"; import { eventStore } from "./stores";
export const replaceableLoader = new ReplaceableLoader(rxNostr);
// Start the loader and send any events to the event store replaceableLoader.subscribe((packet) => { eventStore.add(packet.event, packet.from); }); ```
7. Fetch fiatjaf's profile
Now that we have a way to store events, and a loader to help with fetching them, we should update the
src/App.tsxcomponent to fetch the profile.We can do this by calling the
nextmethod on the loader and passing apubkey,kindandrelaysto it```tsx function App() { // ...
onMount(() => { // fetch fiatjaf's profile on load replaceableLoader.next({ pubkey: "3bf0c63fcb93463407af97a5e5ee64fa883d107ef9e558472c4eb9aaaefa459d", kind: 0, relays: ["wss://pyramid.fiatjaf.com/"], }); });
// ... } ```
8. Display the profile
Now that we have a way to fetch the profile, we need to display it in the UI.
We can do this by using the
ProfileQuerywhich gives us a stream of updates to a pubkey's profile.Create the profile using
queryStore.createQueryand pass in theProfileQueryand the pubkey.tsx const fiatjaf = queryStore.createQuery( ProfileQuery, "3bf0c63fcb93463407af97a5e5ee64fa883d107ef9e558472c4eb9aaaefa459d" );But this just gives us an observable, we need to subscribe to it to get the profile.
Luckily SolidJS profiles a simple
frommethod to subscribe to any observable.To make things reactive SolidJS uses accessors, so to get the profile we need to call
fiatjaf()```tsx function App() { // ...
// Subscribe to fiatjaf's profile from the query store const fiatjaf = from( queryStore.createQuery(ProfileQuery, "3bf0c63fcb93463407af97a5e5ee64fa883d107ef9e558472c4eb9aaaefa459d") );
return ( <> {/ replace the vite and solid logos with the profile picture /}
{fiatjaf()?.name}
{/* ... */}); } ```
9. Letting the user signin
Now we should let the user signin to the app. We can do this by creating a
AccountManagerclass fromapplesauce-accountsFirst we need to install the packages
sh pnpm install applesauce-accounts applesauce-signersThen create a new
src/accounts.tsfile with```ts import { AccountManager } from "applesauce-accounts"; import { registerCommonAccountTypes } from "applesauce-accounts/accounts";
// create an account manager instance export const accounts = new AccountManager();
// Adds the common account types to the manager registerCommonAccountTypes(accounts); ```
Next lets presume the user has a NIP-07 browser extension installed and add a signin button.
```tsx function App() { const signin = async () => { // do nothing if the user is already signed in if (accounts.active) return;
// create a new nip-07 signer and try to get the pubkey const signer = new ExtensionSigner(); const pubkey = await signer.getPublicKey(); // create a new extension account, add it, and make it the active account const account = new ExtensionAccount(pubkey, signer); accounts.addAccount(account); accounts.setActive(account);};
return ( <> {/ ... /}
<div class="card"> <p>Are you following the fiatjaf? the creator of "The nostr"</p> <button onClick={signin}>Check</button> </div>); } ```
Now when the user clicks the button the app will ask for the users pubkey, then do nothing... but it's a start.
We are not persisting the accounts, so when the page reloads the user will NOT be signed in. you can learn about persisting the accounts in the docs
10. Showing the signed-in state
We should show some indication to the user that they are signed in. We can do this by modifying the signin button if the user is signed in and giving them a way to sign-out
```tsx function App() { // subscribe to the currently active account (make sure to use the account$ observable) const account = from(accounts.active$);
// ...
const signout = () => { // do nothing if the user is not signed in if (!accounts.active) return;
// signout the user const account = accounts.active; accounts.removeAccount(account); accounts.clearActive();};
return ( <> {/ ... /}
<div class="card"> <p>Are you following the fiatjaf? ( creator of "The nostr" )</p> {account() === undefined ? <button onClick={signin}>Check</button> : <button onClick={signout}>Signout</button>} </div>); } ```
11. Fetching the user's profile
Now that we have a way to sign in and out of the app, we should fetch the user's profile when they sign in.
```tsx function App() { // ...
// fetch the user's profile when they sign in createEffect(async () => { const active = account();
if (active) { // get the user's relays or fallback to some default relays const usersRelays = await active.getRelays?.(); const relays = usersRelays ? Object.keys(usersRelays) : ["wss://relay.damus.io", "wss://nos.lol"]; // tell the loader to fetch the users profile event replaceableLoader.next({ pubkey: active.pubkey, kind: 0, relays, }); // tell the loader to fetch the users contacts replaceableLoader.next({ pubkey: active.pubkey, kind: 3, relays, }); // tell the loader to fetch the users mailboxes replaceableLoader.next({ pubkey: active.pubkey, kind: 10002, relays, }); }});
// ... } ```
Next we need to subscribe to the users profile, to do this we can use some rxjs operators to chain the observables together.
```tsx import { Match, Switch } from "solid-js"; import { of, switchMap } from "rxjs";
function App() { // ...
// subscribe to the active account, then subscribe to the users profile or undefined const profile = from( accounts.active$.pipe( switchMap((account) => (account ? queryStore.createQuery(ProfileQuery, account!.pubkey) : of(undefined))) ) );
// ...
return ( <> {/ ... /}
<div class="card"> <Switch> <Match when={account() && !profile()}> <p>Loading profile...</p> </Match> <Match when={profile()}> <p style="font-size: 1.2rem; font-weight: bold;">Welcome {profile()?.name}</p> </Match> </Switch> {/* ... */} </div>); } ```
12. Showing if the user is following fiatjaf
Now that the app is fetching the users profile and contacts we should show if the user is following fiatjaf.
```tsx function App() { // ...
// subscribe to the active account, then subscribe to the users contacts or undefined const contacts = from( accounts.active$.pipe( switchMap((account) => (account ? queryStore.createQuery(UserContactsQuery, account!.pubkey) : of(undefined))) ) );
const isFollowing = createMemo(() => { return contacts()?.some((c) => c.pubkey === "3bf0c63fcb93463407af97a5e5ee64fa883d107ef9e558472c4eb9aaaefa459d"); });
// ...
return ( <> {/ ... /}
<div class="card"> {/* ... */} <Switch fallback={ <p style="font-size: 1.2rem;"> Sign in to check if you are a follower of the fiatjaf ( creator of "The nostr" ) </p> } > <Match when={contacts() && isFollowing() === undefined}> <p>checking...</p> </Match> <Match when={contacts() && isFollowing() === true}> <p style="color: green; font-weight: bold; font-size: 2rem;"> Congratulations! You are a follower of the fiatjaf </p> </Match> <Match when={contacts() && isFollowing() === false}> <p style="color: red; font-weight: bold; font-size: 2rem;"> Why don't you follow the fiatjaf? do you even like nostr? </p> </Match> </Switch> {/* ... */} </div>); } ```
13. Adding the follow button
Now that we have a way to check if the user is following fiatjaf, we should add a button to follow him. We can do this with Actions which are pre-built methods to modify nostr events for a user.
First we need to install the
applesauce-actionsandapplesauce-factorypackagesh pnpm install applesauce-actions applesauce-factoryThen create a
src/actions.tsfile with```ts import { EventFactory } from "applesauce-factory"; import { ActionHub } from "applesauce-actions"; import { eventStore } from "./stores"; import { accounts } from "./accounts";
// The event factory is used to build and modify nostr events export const factory = new EventFactory({ // accounts.signer is a NIP-07 signer that signs with the currently active account signer: accounts.signer, });
// The action hub is used to run Actions against the event store export const actions = new ActionHub(eventStore, factory); ```
Then create a
toggleFollowmethod that will add or remove fiatjaf from the users contacts.We are using the
execmethod to run the action, and theforEachmethod from RxJS allows us to await for all the events to be published```tsx function App() { // ...
const toggleFollow = async () => { // send any created events to rxNostr and the event store const publish = (event: NostrEvent) => { eventStore.add(event); rxNostr.send(event); };
if (isFollowing()) { await actions .exec(UnfollowUser, "3bf0c63fcb93463407af97a5e5ee64fa883d107ef9e558472c4eb9aaaefa459d") .forEach(publish); } else { await actions .exec( FollowUser, "3bf0c63fcb93463407af97a5e5ee64fa883d107ef9e558472c4eb9aaaefa459d", "wss://pyramid.fiatjaf.com/" ) .forEach(publish); }};
// ...
return ( <> {/ ... /}
<div class="card"> {/* ... */} {contacts() && <button onClick={toggleFollow}>{isFollowing() ? "Unfollow" : "Follow"}</button>} </div>); } ```
14. Adding outbox support
The app looks like it works now but if the user reloads the page they will still see an the old version of their contacts list. we need to make sure rxNostr is publishing the events to the users outbox relays.
To do this we can subscribe to the signed in users mailboxes using the query store in
src/nostr.ts```ts import { MailboxesQuery } from "applesauce-core/queries"; import { accounts } from "./accounts"; import { of, switchMap } from "rxjs"; import { queryStore } from "./stores";
// ...
// subscribe to the active account, then subscribe to the users mailboxes and update rxNostr accounts.active$ .pipe(switchMap((account) => (account ? queryStore.createQuery(MailboxesQuery, account.pubkey) : of(undefined)))) .subscribe((mailboxes) => { if (mailboxes) rxNostr.setDefaultRelays(mailboxes.outboxes); else rxNostr.setDefaultRelays([]); }); ```
And that's it! we have a working nostr app that lets users follow and unfollow fiatjaf.
-
 @ 5df413d4:2add4f5b
2025-05-04 00:06:31
@ 5df413d4:2add4f5b
2025-05-04 00:06:31This opinion piece was first published in BTC Magazine on Feb 20, 2023
Just in case we needed a reminder, banks are showing us that they can and will gatekeep their customers’ money to prevent them from engaging with bitcoin. This should be a call to action for Bitcoiners or anyone else who wants to maintain control over their finances to move toward more proactive use of permissionless bitcoin tools and practices.
Since January of 2023, when Jamie Dimon decried Bitcoin as a “hyped-up fraud” and “a pet rock,” on CNBC, I've found myself unable to purchase bitcoin using my Chase debit card on Cash App. And I'm not the only one — if you have been following Bitcoin Twitter, you might have also seen Alana Joy tweet about her experience with the same. (Alana Joy Twitter account has since been deleted).
In both of our cases, it is the bank preventing bitcoin purchases and blocking inbound fiat transfers to Cash App for customers that it has associated with Bitcoin. All under the guise of “fraud protection,” of course.
No, it doesn’t make a whole lot of sense — Chase still allows ACH bitcoin purchases and fiat on Cash App can be used for investing in stocks, saving or using Cash App’s own debit card, not just bitcoin — but yes, it is happening. Also, no one seems to know exactly when this became Chase’s policy. The fraud representative I spoke with wasn’t sure and couldn’t point to any documentation, but reasoned that the rule has been in place since early last year. Yet murkier still, loose chatter can be found on Reddit about this issue going back to at least April 2021.
However, given that I and so many others were definitely buying bitcoin via Chase debit throughout 2021 and 2022, I’d wager that this policy, up to now, has only been exercised haphazardly, selectively, arbitrarily, even. Dark patterns abound, but for now, it seems like I just happen to be one of the unlucky ones…
That said, there is nothing preventing this type of policy from being enforced broadly and in earnest by one or many banks. If and as banks feel threatened by Bitcoin, we will surely see more of these kinds of opaque practices.
It’s Time To Get Proactive
Instead, we should expect it and prepare for it. So, rather than railing against banks, I want to use this as a learning experience to reflect on the importance of permissionless, non-KYC Bitcoining, and the practical actions we can take to advance the cause.
Bank with backups and remember local options. Banking is a service, not servitude. Treat it as such. Maintaining accounts at multiple banks may provide some limited fault tolerance against banks that take a hostile stance toward Bitcoin, assuming it does not become the industry norm. Further, smaller, local and regional banks may be more willing to work with Bitcoiner customers, as individual accounts can be far more meaningful to them than they are to larger national banks — though this certainly should not be taken for granted.
If you must use KYC’d Bitcoin services, do so thoughtfully. For Cash App (and services like it), consider first loading in fiat and making buys out of the app’s native cash balance instead of purchasing directly through a linked bank account/debit card where information is shared with the bank that allows it to flag the transaction for being related to bitcoin. Taking this small step may help to avoid gatekeeping and can provide some minor privacy, from the bank at least.
Get comfortable with non-KYC bitcoin exchanges. Just as many precoiners drag their feet before making their first bitcoin buys, so too do many Bitcoiners drag their feet in using permissionless channels to buy and sell bitcoin. Robosats, Bisq, Hodl Hodl— you can use the tools. For anyone just getting started, BTC Sessions has excellent video tutorial content on all three, which are linked.
If you don’t yet know how to use these services, it’s better to pick up this knowledge now through calm, self-directed learning rather than during the panic of an emergency or under pressure of more Bitcoin-hostile conditions later. And for those of us who already know, we can actively support these services. For instance, more of us taking action to maintain recurring orders on such platforms could significantly improve their volumes and liquidity, helping to bootstrap and accelerate their network effects.
Be flexible and creative with peer-to-peer payment methods. Cash App, Zelle, PayPal, Venmo, Apple Cash, Revolut, etc. — the services that most users seem to be transacting with on no-KYC exchanges — they would all become willing, if not eager and active agents of financial gatekeeping in any truly antagonistic, anti-privacy environment, even when used in a “peer-to-peer” fashion.
Always remember that there are other payment options — such as gift cards, the original digital-bearer items — that do not necessarily carry such concerns. Perhaps, an enterprising soul might even use Fold to earn bitcoin rewards on the backend for the gift cards used on the exchange…
Find your local Bitcoin community! In the steadily-advancing shadow war on all things permissionless, private, and peer-to-peer, this is our best defense. Don’t just wait until you need other Bitcoiners to get to know other Bitcoiners — to paraphrase Texas Slim, “Shake your local Bitcoiner’s hand.” Get to know people and never underestimate the power of simply asking around. There could be real, live Bitcoiners near you looking to sell some corn and happy to see it go to another HODLer rather than to a bunch of lettuce-handed fiat speculators on some faceless, centralized, Ponzi casino exchange. What’s more, let folks know your skills, talents and expertise — you might be surprised to find an interested market that pays in BTC!
In closing, I believe we should think of permissionless Bitcoining as an essential and necessary core competency, just like we do with Self-Custody. And we should push it with similar urgency and intensity. But as we do this, we should also remember that it is a spectrum and a progression and that there are no perfect solutions, only tradeoffs. Realization of the importance of non-KYC practices will not be instant or obvious to near-normie newcoiners, coin-curious fence-sitters or even many minted Bitcoiners. My own experience is certainly a testament to this.
As we promote the active practice of non-KYC Bitcoining, we can anchor to empathy, patience and humility — always being mindful of the tremendous amount of unlearning most have to go through to get there. So, even if someone doesn’t get it the first time, or the nth time, that they hear it from us, if it helps them get to it faster at all, then it’s well worth it.
~Moon
-
 @ 21335073:a244b1ad
2025-03-18 20:47:50
@ 21335073:a244b1ad
2025-03-18 20:47:50Warning: This piece contains a conversation about difficult topics. Please proceed with caution.
TL;DR please educate your children about online safety.
Julian Assange wrote in his 2012 book Cypherpunks, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense.
This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning.
When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little.
I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?”
I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well.
I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread.
I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard.
I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it.
The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust.
Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this.
I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place.
What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method.
It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code.
They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened.
I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road.
So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally.
Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb.
I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback.
Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed.
That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone.
To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all.
I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society.
I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this.
On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government.
I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories.
There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc.
Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind.
Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now.
There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers?
I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity.
I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place.
My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors.
My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline.
The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online.
I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers.
So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation?
When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that.
I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic.
If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations.
I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process.
Course: - The creation of the internet and computers - The fight for cryptography - The tech supply chain from the ground up (example: human rights violations in the supply chain) - Corporate tech - Freedom tech - Data privacy - Digital privacy rights - AI (history-current) - Online safety (predators, scams, catfishing, extortion) - Bitcoin - Laws - How to deal with online hate and harassment - Information on who to contact if you are being abused online or offline - Algorithms - How to seek out the truth about news, etc., online
The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children.
The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward?
I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone.
Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability.
The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime.
This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful.
This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens.
In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions.
I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation.
-
 @ fd78c37f:a0ec0833
2025-03-18 10:44:40
@ fd78c37f:a0ec0833
2025-03-18 10:44:40In this edition, we’re thrilled to sit down with Tomek K from Bitcoin Alby, a passionate advocate for Bitcoin’s global adoption. Tomek K shares how Alby is driving innovation in the Bitcoin ecosystem and offers a glimpse into his vision for the cryptocurrency’s future. From his journey as a libertarian activist to co-founding the Bitcoin Film Festival, Tomek K’s story is one of curiosity, purpose, and a relentless pursuit of freedom through technology.
YakiHonne: Tomek K, it’s a pleasure to meet you! Today, we’re diving into your community topic—Alby Wallet. But before we begin, let me introduce our readers to Yakihonne. Yakihonne is a decentralized media client powered by the Nostr protocol, dedicated to promoting free speech through technology. It empowers creators to truly own their voices and assets, offering features like smart filtering, verified notes, and a focus on long-form content. So, Tomek, could you tell us about yourself and your work with Alby?
Tomek K: Of course! I’m Tomek K, originally from Poland, and right now, I’m speaking to you from Sri Lanka. I love traveling and observing how different countries adopt Bitcoin. For most of my career, I’ve been a free-market advocate, promoting economic freedom through various projects—essentially doing PR for capitalism. I’ve organized conferences, political demonstrations, economic seminars, summer festivals, and even opened a bar in Warsaw to spread these ideas in different ways.
During this advocacy work, I came across Bitcoin. At first, I didn’t pay much attention to it, but over time, I started feeling frustrated—our efforts raised awareness about freedom, but they didn’t bring measurable change. That led me to study Bitcoin more deeply, and I gradually shifted my focus to Bitcoin activism. Along the way, I collaborated with publishers to translate Bitcoin-related books into Polish and co-founded the Bitcoin Film Festival with friends from Meetup. Later, I joined Alby, marking my transition from free-market activism to Bitcoin promotion.
At the Bitcoin Film Festival, I handle operations and networking—organizing the event, managing logistics, and making things happen. Our team is small, but I enjoy the work. I’m passionate about Bitcoin because I came for the revolution, and I’m staying for the revolution.
That said, I don’t consider myself a Bitcoin absolutist. I see Bitcoin as a tool for freedom, not just a currency or a more efficient technology. If there were a better tool for advancing liberty and making societies freer, I’d probably focus on that. But for now, Bitcoin appears to be the most effective tool for freedom. Ultimately, I consider myself a “life maximalist”—because to live a good life, you need freedom, and to have freedom today, you need sound money. And right now, that money is Bitcoin.
YakiHonne: Was there a specific moment or event that sparked your interest in Bitcoin and motivated you to join the Alby community?
Tomek K: What attracted me to Bitcoin was its promise of global monetary independence and its ability to reduce the control of the Federal Reserve, central banks, and governments—the strongest and most covert control mechanisms in the world. Unfortunately, many people, even libertarians, often overlook this.
As for why I joined Alby, it’s because this startup is driven by values and mission rather than simply chasing profits, like selling tokens or games. This aligns well with my interest in the Lightning Network. As I explored Lightning more deeply, I came across Alby. I’ve always enjoyed testing new tools, trying them firsthand, and understanding the communities behind them—so naturally, I became part of it. Along the way, I also got to know some of the team members, which reinforced my involvement.
Additionally, Alby supported the Bitcoin Film Festival. While they weren’t the largest sponsor, their contribution was generous. The festival served as a great platform for them and other projects. I think it was good marketing because people like me—who have strong networking skills, arrange podcast interviews, and organize various activities—help build awareness and positive PR. That was part of my role.
If I had to pinpoint a single defining moment that led me here, I honestly couldn’t. Becoming a Bitcoiner doesn’t happen overnight. You can’t just read The Bitcoin Standard, declare that you understand Bitcoin, and instantly become a maximalist. Anyone who’s intellectually honest will admit that it takes multiple touchpoints—articles, films, career shifts, essays, hands-on experimentation, and actually using Bitcoin—to truly grasp its significance. I had many such moments along the way: reading The Bitcoin Standard, learning from friends who had a deeper understanding of Bitcoin, and working at Alby, which further expanded my knowledge of the Lightning Network’s capabilities and limitations. It wasn’t one turning point but a series of pivotal experiences that shaped my path.
YakiHonne: How did the Alby community start, and how did it attract its first members?
Tomek K: When I joined Alby, the community had already been established for some time. It originally emerged within the browser design community, where early users helped developers refine the product by providing feedback. That’s how the first members joined, and this process has been ongoing for four years now.
As for how Alby attracted members, it was through a mix of channels—social media (Twitter, Telegram, Discord), email engagement, and active participation in Bitcoin conferences. But the core strategy has always been openness, engaging with users, and listening to their feedback. Sometimes that means making a joke, sometimes defending against unfair criticism, and other times implementing requested features. We’ve always worked to maintain an active and friendly community atmosphere.
We also host bi-weekly community calls, which are a central part of our activities. Every two weeks, available team members meet with users for open Q&A sessions, issue discussions, and demonstrations of various projects integrating with Alby. I’ve participated in some of these calls, and they help maintain strong relationships with users, developers, and other projects—something crucial for the ecosystem. The Bitcoin technology landscape is somewhat fragmented, and grassroots coordination is necessary since there’s no single leader defining terminology or coding practices.
That’s also why Alby doesn’t exist in isolation. Almost everything we’ve built has been made possible by the creators of previous libraries, prior codebases, and collaborative efforts in writing specifications for protocols. Projects like Yakihonne and many others also recognize the importance of open-source collaboration. I think it’s essential to acknowledge the contributions of the open-source community. One thing I really appreciate is that Bitcoiners are driving open-source development in virtually every part of the world, all working toward a shared and meaningful goal.
YakiHonne:Were there any notable challenges in the early days that left a strong impression on you?
Tomek K :When I first joined Alby, I struggled with a bit of imposter syndrome for months. I was handling PR for the project, but I didn’t fully understand all the technical details—how certain protocols interact or what’s happening under the hood. It took time to get familiar with everything and really feel like I belonged.
Regulatory pressure has also been a huge challenge. In some cases, developers have been arrested, projects have had to leave certain countries, and users have been geoblocked based on their location. But challenges like these can also drive innovation. For example, Alby developed AlbyHub, an open-source self-custodial node, as a response to these kinds of issues.
There are always risks in this space—governments might suddenly demand a banking license or require compliance with new regulations. These are real obstacles, but we tackle them by embracing decentralization and open-source solutions. That’s how we ensure the project stays true to its mission and vision.

YakiHonne:If someone wanted to start a Bitcoin community today or grow an existing one, what advice would you give them?
Tomek K: The most important thing is to just get started. A community begins with action, and it takes more than one person. Even if it’s just you and a friend grabbing a beer, that’s already a start. Maybe after the first or second meetup, you post on Meetup.com, Twitter, or local forums:"Hey, we’re hosting a Bitcoin meetup in this city. We just want to connect with other Bitcoiners!" If you keep doing it consistently, the community will naturally grow. Over time, the bar where you meet might get interested in accepting Bitcoin, or you might meet some OGs in your area who decide to join—maybe they already run a business and want to support what you’re doing.
You don’t have to over-plan everything from the start. No need to think, “We need a podcast, 10 episodes, a logo…”—all that can come later. Just bootstrap it: organize a meetup, grab a beer, and get going. As you go, you’ll adapt, improve, and build recognition.Beyond that, it’s a great way to meet other Bitcoiners, develop leadership skills, and learn about community building. And at the very least, you’ll have fun doing it—which, honestly, is one of the main reasons I keep organizing meetups and other activities.
YakiHonne: Exactly, the key is to take action—just start and see where it leads. Does your community focus more on Bitcoin’s technical aspects, like coding and development, or do you emphasize non-technical areas such as education and outreach? Or do you try to balance both?
Tomek K: Our users come from all kinds of backgrounds. Some are very engaged and provide feedback regularly, while others prefer to stay in the background. Some attend our community calls, and within that group, some are developers actively building projects and collaborating with us. At the same time, there are developers we know are out there, but they never directly engage with us. That’s just how the Bitcoin community works—there’s no strict definition of being part of Alby. People engage in their own way. Some users are active on Discord, some aren’t, but we treat them all as part of the family, keeping them informed through newsletters, offering support, and making sure they stay updated with what’s happening at Alby.
As for whether we lean more toward technical development or non-technical outreach, there’s no clear-cut answer. Our community is diverse—we cater to a wide range of Lightning Network users. Some just use the browser extension, while others are deeply involved in our ecosystem. We also work with NGOs, educational initiatives, and community organizations. At the same time, we place a strong emphasis on developers and maintaining good relationships with them. Our repositories and developer portal offer useful libraries and examples, making it easier for both aspiring and experienced developers to integrate the Lightning Network into their projects. Developer relations are something we consider highly important.

YakiHonne: I understand that you're also the founder of another Bitcoin-related film project. Could you tell us a bit about it? What exactly inspired you to combine Bitcoin and filmmaking?
Tomek K: Yes, I founded Bitcoin Film Fest to help build what I call Bitcoin Cinema—an emerging industry that blends Bitcoin and filmmaking. I wanted to track everything happening at the intersection of these two worlds. Just like e-commerce, energy, and information technology, I believe the film industry will eventually be shaped by Bitcoin. And in fact, it’s already happening. There are Bitcoin-themed movies, and even major Hollywood productions have started including Bitcoin references. Bitcoin filmmakers, Bitcoin culture, and even a Bitcoin subculture already exist. We have our own heroes, stories, and values, and from this, films are being created. I love cinema, and I love Bitcoin—this was my way of bringing the two together.
The festival itself happened somewhat by accident—but maybe it was meant to be. It all started in Warsaw when I was organizing a Bitcoin meetup. I planned to screen a Bitcoin documentary, but due to technical issues, it didn’t happen. So, over a few beers, we came up with an idea: if we couldn’t show one film, why not go all in and create a full-scale Bitcoin film festival? We started researching and realized there were enough Bitcoin-related films out there to make it happen. So, we did.
The response from the community was overwhelmingly positive. It became clear that people wanted a space for Bitcoin cinema—a hub for information, networking, and collaboration. We started using the term “Binema” (Bitcoin Cinema) to describe this emerging genre. I find it fascinating to witness the growth of Bitcoin culture and storytelling. Before this, I had followed libertarian artistic movements closely, and now I see how important culture is for Bitcoin’s adoption—it’s not just about the technical and financial aspects.
Bitcoin adoption isn’t going to happen overnight, and it won’t happen without developers, educators, infrastructure builders, UX designers, and many others contributing to the ecosystem. Culture is one of the most powerful tools for shaping society, and I, like many others, am working to bring Bitcoin adoption closer through film. We’re witnessing the early days of Bitcoin cinema. I missed out on the birth of traditional cinema, but this time, I want to be part of it.
YakiHonne:In your region, does the government support or oppose Bitcoin? How has this stance impacted the development of the Bitcoin community so far?
Tomek K :Bitcoin doesn’t concern itself with nation-state borders, and frankly, we don’t either. The situation in Poland has little influence on what we do. The only connection is that I, along with two others, happen to be in Poland, but most of our team is globally distributed. On a broader scale, the U.S. tends to shape regulatory trends, and unfortunately, it often does so in a more restrictive way. However, Poland itself hasn’t had a significant impact on our work.
YakiHonne:Has your Bitcoin Film Fest community ever used film as a way to connect with members—perhaps by watching a Bitcoin-related movie or hosting a movie night to make things more fun and engaging? Have you done anything like that before?
Tomek K:Yes, absolutely! The film festival itself is a great example—we watch movies together and build a community around them. Aside from the festival we organized in Warsaw, we've also hosted film screenings at various Bitcoin events, like Sats and Facts in Thailand, BTC Prague, Plan B Lugano, Frimadera, Adopting Bitcoin, and several other conferences. We also organize online watch parties—actually, there's one happening next Sunday. The movie is available on Prime Video, but we'll sync up on Discord to watch it together, chat, and share our thoughts. We'll be announcing it on Twitter, so if you check Bitcoin Film Fest on Twitter, you'll find details on how to join.
Film has been a great way to connect with members and spark discussions. We've seen Bitcoin meetups worldwide organizing movie nights—our volunteer friends in Montenegro have hosted one, and our partners in Kenya and South Africa have done the same. Lately, movie nights have been happening more and more frequently, which is exciting.
It's still early—after all, Bitcoin is only 16 years old, so the selection of Bitcoin movies is still relatively small. Many of these films haven’t had large budgets or massive talent pools yet, but that’s changing. Right now, we’re primarily focused on showing films within the Bitcoin community rather than creating films aimed at the general public. That said, those kinds of projects are also emerging. I’m optimistic about the growth of Bitcoin cinema—better storytelling, AI-driven advancements, increasing interest from audiences, and even sponsors willing to invest in filmmakers. Big things are coming, and while we already have some great Bitcoin films, the best is yet to come. We’re still in the early days, and this is the time to contribute and help shape the future of Bitcoin cinema.
YakiHonne:We’ve come to the end of today’s interview, and I’ve truly enjoyed every moment of it. I’m very sure your idea will be incredibly engaging, inspiring more people and attracting a broad audience. Thank you so much for your time today—it was a great conversation.
-
 @ 75869cfa:76819987
2025-03-18 07:54:38
@ 75869cfa:76819987
2025-03-18 07:54:38GM, Nostriches!
The Nostr Review is a biweekly newsletter focused on Nostr statistics, protocol updates, exciting programs, the long-form content ecosystem, and key events happening in the Nostr-verse. If you’re interested, join me in covering updates from the Nostr ecosystem!
Quick review:
In the past two weeks, Nostr statistics indicate over 225,000 daily trusted pubkey events. The number of new users has seen a notable decrease, with profiles containing a contact list dropping by 95%. More than 10 million events have been published, with posts and reposts showing a decrease. Total Zap activity stands at approximately 15 million, marking a 10% decrease.
Additionally, 26 pull requests were submitted to the Nostr protocol, with 6 merged. A total of 45 Nostr projects were tracked, with 8 releasing product updates, and over 463 long-form articles were published, 29% focusing on Bitcoin and Nostr. During this period, 2 notable events took place, and 3 significant events are upcoming.
Nostr Statistics
Based on user activity, the total daily trusted pubkeys writing events is about 225,000, representing a slight 8 % decrease compared to the previous period. Daily activity peaked at 18179 events, with a low of approximately 16093.
The number of new users has decreased significantly. Profiles with a contact list are now around 17,511, reflecting a 95% drop. Profiles with a bio have decreased by 62% compared to the previous period. The only category showing growth is pubkeys writing events, which have increased by 27%.
Regarding event publishing, all metrics have shown a decline. The total number of note events published is around 10 million, reflecting a 14% decrease. Posts remain the most dominant in terms of volume, totaling approximately 1.6 million, which is a 6.1% decrease. Both reposts and reactions have decreased by about 10%.
For zap activity, the total zap amount is about 15 million, showing an increase of over 10% compared to the previous period.
Data source: https://stats.nostr.band/
NIPs
nostr:npub1gcxzte5zlkncx26j68ez60fzkvtkm9e0vrwdcvsjakxf9mu9qewqlfnj5z is proposing that A bulletin board is a relay-centric system of forums where users can post and reply to others, typically around a specific community. The relay operator controls and moderates who can post and view content. A board is defined by kind:30890. Its naddr representation must provide the community's home relays, from which all posts should be gathered. No other relays should be used.
nostr:npub1xy54p83r6wnpyhs52xjeztd7qyyeu9ghymz8v66yu8kt3jzx75rqhf3urc is proposing a standardized way to represent fitness and workout data in Nostr, including: Exercise Templates (kind: 33401) for storing reusable exercise definitions, Workout Templates (kind: 33402) for defining workout plans, Workout Records (kind: 1301) for recording completed workouts. The format provides structured data for fitness tracking while following Nostr conventions for data representation.Many fitness applications use proprietary formats, locking user data into specific platforms. This NIP enables decentralized fitness tracking, allowing users to control their workout data and history while facilitating social sharing and integration between fitness applications.
nostr:npub1zk6u7mxlflguqteghn8q7xtu47hyerruv6379c36l8lxzzr4x90q0gl6ef is proposing a PR introduces two "1-click" connection flows for setting up initial NWC connections. Rather than having to copy-paste a connection string, the user is presented with an authorization page which they can approve or decline. The secret is generated locally and never leaves the client. HTTP flow - for publicly accessible lightning wallets. Implemented in Alby Hub (my.albyhub.com) and CoinOS (coinos.io). Nostr flow - for mobile-based / self-hosted lightning wallets, very similar to NWA but without a new event type added. Implemented in Alby Go and Alby Hub. Benefits over NWC Deep Links are that it works cross-device, mobile to web, and the client-generated secret never leaves the client. Both flows are also implemented in Alby JS SDK and Bitcoin Connect.
add B0 NIP for Blossom interaction
nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 describes a tiny subset of possible Blossom capabilities, but arguably the most important from the point of view of a most basic Nostr client. This NIP specifies how Nostr clients can use Blossom for handling media. Blossom is a set of standards (called BUDs) for dealing with servers that store files addressable by their SHA-256 sums. Nostr clients may make use of all the BUDs for allowing users to upload files, manage their own files and so on, but most importantly Nostr clients SHOULD make use of BUD-03 to fetch kind:10063 lists of servers for each user.
nostr:npub149p5act9a5qm9p47elp8w8h3wpwn2d7s2xecw2ygnrxqp4wgsklq9g722q defines a standard for creating, managing and publishing to communities by leveraging existing key pairs and relays, introducing the concept of "Communi-keys". This approach allows any existing npub to become a community (identity + manager) while maintaining compatibility with existing relay infrastructure.
A way for relays to be honest about their algos
securitybrahh is proposing a PR introduces NIP-41, a way for relays to be honest about their algos, edits 01.md to account for changes in limit (related #78, #1434, received_at?, #620, #1645) when algo is provided, appends 11.md for relays to advertize whether they are an aggregator or not and their provided algos. solves #522, supersedes #579.
nip31: template-based "alt" tags for known kinds
nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 is proposing that clients hardcoding alt tags are not very trustworthy. alt tags tend to be garbage in a long-enough timeframe.This fixes it with hardcoded rich templates that anyone can implement very easily without having to do it manually for each kind. alt tags can still be used as a fallback.
nostr:npub1gcxzte5zlkncx26j68ez60fzkvtkm9e0vrwdcvsjakxf9mu9qewqlfnj5z is proposing a PR addresses 3 main problems of NIP-44v2. First, It has a message size limit of 65Kb, which is unnecessarily small. Second, It forces the encrypting key to be the same as the event's signing key. Which forces multi-sig actors to share their main private key in order to encrypt the payload that would be later signed by the group. Decoupling singing and encryption keys, for both source and destination, is one of the goals of this version. And It offers no way to describe what's inside the encrypted blob before requesting the user's approval to decrypt and send the decrypted info back to the requesting application. This PR adds an alt description to allow decrypting signers to display a message and warn the user of what type of information the requesting application is receiving.
Notable Projects
Damus nostr:npub18m76awca3y37hkvuneavuw6pjj4525fw90necxmadrvjg0sdy6qsngq955
- Notes in progress will always be persisted and saved automatically. Never lose those banger notes when you aren't quite ready to ship them.
- Make your profile look just right without any fuss. It also optimizes them on upload now to not nuke other people’s phone data bills.
- You won't see the same note more than once in your home feed.
- Fixed note loading when clicking notifications and damus.io links.
- Fixed NWC not working when you first connect a wallet.
- Fixed overly sensitive and mildly infuriating touch gestures in the thread view when scrolling
Primal nostr:npub12vkcxr0luzwp8e673v29eqjhrr7p9vqq8asav85swaepclllj09sylpugg
Primal for Android build 2.1.9 has been released. * Multi-account support * Deep linking support * "Share via Primal" support * Bug fixes and improvements
Yakihonne nostr:npub1yzvxlwp7wawed5vgefwfmugvumtp8c8t0etk3g8sky4n0ndvyxesnxrf8q
YakiHonne Wallet just got a fresh new look!
0xchat nostr:npub1tm99pgz2lth724jeld6gzz6zv48zy6xp4n9xu5uqrwvx9km54qaqkkxn72
0xchat v1.4.7-beta release * Upgraded the Flutter framework to v3.29.0. * Private chat implementation changed to NIP-104 Nostr MLS. * NIP-17 and NIP-29 messages now support q tags. * You can swipe left to reply to your own messages. * Chat messages now support code block display. * Copy images from the clipboard. * Fixed an issue where underlined text in chat appeared as italic.
GOSSIP 0.14.0 nostr:npub189j8y280mhezlp98ecmdzydn0r8970g4hpqpx3u9tcztynywfczqqr3tg8
Several major bugs have been fixed in the last week. * New Features and Improvements * Zappers and amounts are now shown (click on the zap total) * Reactions and who reacted are now shown (click on the reaction numbers) * Multiple search UI/UX improvements * Undo Send works for DMs too * Undo Send now restores the draft * UI: Side panel contains less so it can be thinner. Bottom bar added. * UI: frame count and spinner (optional) * Relay UI: sorting by score puts important relays at the top. * Relay UI: add more filters so all the bits are covered * Image and video loading is much faster (significant lag reduction) * Thread loading fix makes threads load far more reliably * Settings have reset-to-default buttons, so you don't get too lost. * Setting 'limit inbox seeking to inbox relays' may help avoid spam at the expense of possibly * Fix some bugs * And more updates
Nostur v1.18.1 nostr:npub1n0stur7q092gyverzc2wfc00e8egkrdnnqq3alhv7p072u89m5es5mk6h0
New in this version: * Floating mini video player * Videos: Save to library, Copy video URL, Add bookmark * Improved video stream / chat view * Top zaps on live chat * Posting to Picture-first * Profile view: Show interactions with you (conversations, reactions, zaps, reposts) * Profile view: Show actual reactions instead of only Likes * Improved search + Bookmark search * Detect nsfw / content-warning in posts * Show more to show reactions outside Web of Trust * Show more to show zaps outside Web of Trust * Support .avif image format * Support .mp3 format * Support .m4v video format * Improved zap verification for changed wallets * Improved outbox support * Show label on restricted posts * Low data mode: load media in app on tap instead of external browser * Many other bug fixes and performance improvements
Alby nostr:npub1getal6ykt05fsz5nqu4uld09nfj3y3qxmv8crys4aeut53unfvlqr80nfm
Latest two releases of Alby Go, 1.10 and 1.11, brought you lots of goodies: * BTC Map integration for quick access to global bitcoin merchants map * Confirm new NWC connections to your Alby Hub directly in Alby Go! No more copy-pasting or QR code scanning * Support for MoneyBadger Pay Pick n Pay QR payments in over 2000 stores in South Africa
ZEUS v0.10.0 nostr:npub1xnf02f60r9v0e5kty33a404dm79zr7z2eepyrk5gsq3m7pwvsz2sazlpr5
ZEUS v0.10.0 is now available. This release features the ability to renew channel leases, spin up multiple embedded wallets, Nostr Wallet Connect client support, and more. * Renewable channels * NWC client support * Ability to create multiple Embedded LND 'node in the phone' wallets * Ability to delete Embedded LND wallets * Embedded LND: v0.18.5-beta * New share button (share ZEUS QR images) * Tools: Export Activity CSVs, Developer tools, chantools * Activity: filter by max amount, memo, and note
Long-Form Content Eco
In the past two weeks, more than 463 long-form articles have been published, including over 91 articles on Bitcoin and more than 41 related to Nostr, accounting for 29% of the total content.
These articles about Nostr mainly explore the rise of Nostr as a decentralized platform that is reshaping the future of the internet. They emphasize Nostr's role in providing users with greater freedom, ownership, and fair monetization, particularly in the realm of content creation. The platform is positioned as a counter to centralized social media networks, offering uncensored interactions, enhanced privacy, and direct transactions. Many articles delve into Nostr’s potential to integrate with Bitcoin, creating a Layer 3 solution that promises to end the dominance of old internet structures. Discussions also cover the technical aspects of Nostr, such as the implementation of relays and group functionalities, as well as security concerns like account hacks. Furthermore, there is an exploration of the philosophical and anthropological dimensions of Nostr, with the rise of "Dark Nostr" being portrayed as a deeper expression of decentralized freedom.
The Bitcoin articles discuss the ongoing evolution of Bitcoin and its increasing integration into global financial systems. Many articles focus on the growing adoption of Bitcoin, particularly in areas like Argentina and the U.S., where Bitcoin is being used for rental payments and the establishment of a strategic Bitcoin reserve. Bitcoin is also portrayed as a response to the centralized financial system, with discussions about how it can empower individuals through financial sovereignty, provide a hedge against inflation, and create fairer monetization models for creators. Additionally, the articles explore the challenges and opportunities within the Bitcoin ecosystem, including the rise of Bitcoin ETFs, the development of Bitcoin mining, and the potential impact of AI on Bitcoin adoption. There is also emphasis on Bitcoin's cultural and economic implications, as well as the need for decentralized education and innovation to drive further adoption.
Thank you, nostr:npub1ygzsm5m9ndtgch9n22cwsx2clwvxhk2pqvdfp36t5lmdyjqvz84qkca2m5 nostr:npub1rsv7kx5avkmq74p85v878e9d5g3w626343xhyg76z5ctfc30kz7q9u4dke nostr:npub17wrn0xxg0hfq7734cfm7gkyx3u82yfrqcdpperzzfqxrjf9n7tes6ra78k nostr:npub1fxq5crl52mre7luhl8uqsa639p50853r3dtl0j0wwvyfkuk4f6ssc5tahv nostr:npub1qny3tkh0acurzla8x3zy4nhrjz5zd8l9sy9jys09umwng00manysew95gx nostr:npub19mf4jm44umnup4he4cdqrjk3us966qhdnc3zrlpjx93y4x95e3uq9qkfu2 nostr:npub1marc26z8nh3xkj5rcx7ufkatvx6ueqhp5vfw9v5teq26z254renshtf3g0 nostr:npub1uv0m8xc6q4cnj2p0tewmcgkyzg8cnteyhed0zv30ez03w6dzwvnqtu6gwl nostr:npub1ygzsm5m9ndtgch9n22cwsx2clwvxhk2pqvdfp36t5lmdyjqvz84qkca2m5 nostr:npub1mhcr4j594hsrnen594d7700n2t03n8gdx83zhxzculk6sh9nhwlq7uc226 nostr:npub1xzuej94pvqzwy0ynemeq6phct96wjpplaz9urd7y2q8ck0xxu0lqartaqn nostr:npub1gqgpfv65dz8whvyup942daagsmwauj0d8gtxv9kpfvgxzkw4ga4s4w9awr nostr:npub16dswlmzpcys0axfm8kvysclaqhl5zv20ueurrygpnnm7k9ys0d0s2v653f and others, for your work. Enriching Nostr’s long-form content ecosystem is crucial.
Nostriches Global Meet Ups
Recently, several Nostr events have been hosted in different countries. * The first Bitcoin Meetup organized by Mi Primer Bitcoin was successfully held on March 14, 2025, at Texijal Pizza in Apaneca. The event included Bitcoin education, networking, a Q&A session, and merchandise distribution, offering an exciting experience for all participants.
* The Btrust Space discussion was successfully held on March 13, 2024. The event focused on how to support Bitcoin developers, fund open-source contributions, and grow the Bitcoin ecosystem. The speakers included Bitcoin core contributors, Btrust CEO, engineering leads, and other project leaders.Here is the upcoming Nostr event that you might want to check out.
- The Nostr Workshop, organized by YakiHonne and Bitcoin Safari, will take place online via Google Meet on March 17, 2025, at 7:00 PM (GMT+1). The event will introduce the Nostr ecosystem and Bitcoin payments, with participants learning about decentralized technology through YakiHonne and earning rewards. Register and verify your account to claim exclusive rewards, and invite friends to unlock additional rewards.
- The 2025 Bitcoin, Crypto Economy, and Law FAQ Webinar will be held online on March 20, 2025 (Thursday) from 12:00 to 13:00 Argentina time. The webinar will be hosted by Martin Paolantonio (Academic Director of the course) and Daniel Rybnik (Lawyer specializing in Banking, Corporate, and Financial Law). The session aims to introduce the academic program and explore Bitcoin, the crypto economy, and related legal issues.
- Bitcoin Educators Unconference 2025 will take place on April 10, 2025, at Bitcoin Park in Nashville, Tennessee, USA. This event is non-sponsored and follows an Unconference format, allowing all participants to apply as speakers and share their Bitcoin education experiences in a free and interactive environment. The event has open-sourced all its blueprints and Standard Operating Procedures (SOPs) to encourage global communities to organize similar Unconference events.
Additionally, We warmly invite event organizers who have held recent activities to reach out to us so we can work together to promote the prosperity and development of the Nostr ecosystem.
Thanks for reading! If there’s anything I missed, feel free to reach out and help improve the completeness and accuracy of my coverage.
-
 @ 6fc114c7:8f4b1405
2025-05-03 22:06:36
@ 6fc114c7:8f4b1405
2025-05-03 22:06:36In the world of cryptocurrency, the stakes are high, and losing access to your digital assets can be a nightmare. But fear not — Crypt Recver is here to turn that nightmare into a dream come true! With expert-led recovery services and cutting-edge technology, Crypt Recver specializes in helping you regain access to your lost Bitcoin and other cryptocurrencies.
Why Choose Crypt Recver? 🤔 🔑 Expertise You Can Trust At Crypt Recver, we combine state-of-the-art technology with skilled engineers who have a proven track record in crypto recovery. Whether you’ve forgotten your passwords, lost your private keys, or dealt with damaged hardware wallets, our team is equipped to help.
⚡ Fast Recovery Process Time is of the essence when it comes to recovering lost funds. Crypt Recver’s systems are optimized for speed, enabling quick recoveries — so you can get back to what matters most: trading and investing.
🎯 High Success Rate With over a 90% success rate, our recovery team has helped countless clients regain access to their lost assets. We understand the intricacies of cryptocurrency and are dedicated to providing effective solutions.
🛡️ Confidential & Secure Your privacy is our priority. All recovery sessions at Crypt Recver are encrypted and kept entirely confidential. You can trust us with your information, knowing that we maintain the highest standards of security.
🔧 Advanced Recovery Tools We use proprietary tools and techniques to handle complex recovery scenarios, from recovering corrupted wallets to restoring coins from invalid addresses. No matter how challenging the situation, we have a plan.
Our Recovery Services Include: 📈 Bitcoin Recovery: Have you lost access to your Bitcoin wallet? We can help you recover lost wallets, private keys, and passphrases. Transaction Recovery: Mistaken transfers, lost passwords, or missing transaction records — let us help you reclaim your funds! Cold Wallet Restoration: Did your cold wallet fail? We specialize in extracting assets safely and securely. Private Key Generation: Forgotten your private key? We can help you generate new keys linked to your funds without compromising security. Don’t Let Lost Crypto Ruin Your Day! 🕒 With an estimated 3 to 3.4 million BTC lost forever, it’s critical to act swiftly when facing access issues. Whether you’ve been a victim of a dust attack or have simply forgotten your key, Crypt Recver offers the support you need to reclaim your digital assets.
🚀 Start Your Recovery Now! Ready to get your cryptocurrency back? Don’t let uncertainty hold you back!
👉 Request Wallet Recovery Help Today!
Need Immediate Assistance? 📞 For quick queries or support, connect with us on:
✉️ Telegram: Chat with Us on Telegram 💬 WhatsApp: Message Us on WhatsApp Trust Crypt Recver for the Best Crypto Recovery Service — Get back to trading with confidence! 💪In the world of cryptocurrency, the stakes are high, and losing access to your digital assets can be a nightmare. But fear not — Crypt Recver is here to turn that nightmare into a dream come true! With expert-led recovery services and cutting-edge technology, Crypt Recver specializes in helping you regain access to your lost Bitcoin and other cryptocurrencies.
 # Why Choose Crypt Recver? 🤔
# Why Choose Crypt Recver? 🤔🔑 Expertise You Can Trust
At Crypt Recver, we combine state-of-the-art technology with skilled engineers who have a proven track record in crypto recovery. Whether you’ve forgotten your passwords, lost your private keys, or dealt with damaged hardware wallets, our team is equipped to help.
⚡ Fast Recovery Process
Time is of the essence when it comes to recovering lost funds. Crypt Recver’s systems are optimized for speed, enabling quick recoveries — so you can get back to what matters most: trading and investing.
🎯 High Success Rate
With over a 90% success rate, our recovery team has helped countless clients regain access to their lost assets. We understand the intricacies of cryptocurrency and are dedicated to providing effective solutions.
🛡️ Confidential & Secure
Your privacy is our priority. All recovery sessions at Crypt Recver are encrypted and kept entirely confidential. You can trust us with your information, knowing that we maintain the highest standards of security.
🔧 Advanced Recovery Tools
We use proprietary tools and techniques to handle complex recovery scenarios, from recovering corrupted wallets to restoring coins from invalid addresses. No matter how challenging the situation, we have a plan.
 # Our Recovery Services Include: 📈
# Our Recovery Services Include: 📈- Bitcoin Recovery: Have you lost access to your Bitcoin wallet? We can help you recover lost wallets, private keys, and passphrases.
- Transaction Recovery: Mistaken transfers, lost passwords, or missing transaction records — let us help you reclaim your funds!
- Cold Wallet Restoration: Did your cold wallet fail? We specialize in extracting assets safely and securely.
- Private Key Generation: Forgotten your private key? We can help you generate new keys linked to your funds without compromising security.
Don’t Let Lost Crypto Ruin Your Day! 🕒
With an estimated 3 to 3.4 million BTC lost forever, it’s critical to act swiftly when facing access issues. Whether you’ve been a victim of a dust attack or have simply forgotten your key, Crypt Recver offers the support you need to reclaim your digital assets.
🚀 Start Your Recovery Now!
Ready to get your cryptocurrency back? Don’t let uncertainty hold you back!
👉 Request Wallet Recovery Help Today!
Need Immediate Assistance? 📞
For quick queries or support, connect with us on:
- ✉️ Telegram: Chat with Us on Telegram
- 💬 WhatsApp: Message Us on WhatsApp
Trust Crypt Recver for the Best Crypto Recovery Service — Get back to trading with confidence! 💪
-
 @ 52b4a076:e7fad8bd
2025-05-03 21:54:45
@ 52b4a076:e7fad8bd
2025-05-03 21:54:45Introduction
Me and Fishcake have been working on infrastructure for Noswhere and Nostr.build. Part of this involves processing a large amount of Nostr events for features such as search, analytics, and feeds.
I have been recently developing
nosdexv3, a newer version of the Noswhere scraper that is designed for maximum performance and fault tolerance using FoundationDB (FDB).Fishcake has been working on a processing system for Nostr events to use with NB, based off of Cloudflare (CF) Pipelines, which is a relatively new beta product. This evening, we put it all to the test.
First preparations
We set up a new CF Pipelines endpoint, and I implemented a basic importer that took data from the
nosdexdatabase. This was quite slow, as it did HTTP requests synchronously, but worked as a good smoke test.Asynchronous indexing
I implemented a high-contention queue system designed for highly parallel indexing operations, built using FDB, that supports: - Fully customizable batch sizes - Per-index queues - Hundreds of parallel consumers - Automatic retry logic using lease expiration
When the scraper first gets an event, it will process it and eventually write it to the blob store and FDB. Each new event is appended to the event log.
On the indexing side, a
Queuerwill read the event log, and batch events (usually 2K-5K events) into one work job. This work job contains: - A range in the log to index - Which target this job is intended for - The size of the job and some other metadataEach job has an associated leasing state, which is used to handle retries and prioritization, and ensure no duplication of work.
Several
Workers monitor the index queue (up to 128) and wait for new jobs that are available to lease.Once a suitable job is found, the worker acquires a lease on the job and reads the relevant events from FDB and the blob store.
Depending on the indexing type, the job will be processed in one of a number of ways, and then marked as completed or returned for retries.
In this case, the event is also forwarded to CF Pipelines.

Trying it out
The first attempt did not go well. I found a bug in the high-contention indexer that led to frequent transaction conflicts. This was easily solved by correcting an incorrectly set parameter.
We also found there were other issues in the indexer, such as an insufficient amount of threads, and a suspicious decrease in the speed of the
Queuerduring processing of queued jobs.Along with fixing these issues, I also implemented other optimizations, such as deprioritizing
WorkerDB accesses, and increasing the batch size.To fix the degraded
Queuerperformance, I ran the backfill job by itself, and then started indexing after it had completed.Bottlenecks, bottlenecks everywhere

After implementing these fixes, there was an interesting problem: The DB couldn't go over 80K reads per second. I had encountered this limit during load testing for the scraper and other FDB benchmarks.
As I suspected, this was a client thread limitation, as one thread seemed to be using high amounts of CPU. To overcome this, I created a new client instance for each
Worker.After investigating, I discovered that the Go FoundationDB client cached the database connection. This meant all attempts to create separate DB connections ended up being useless.
Using
OpenWithConnectionStringpartially resolved this issue. (This also had benefits for service-discovery based connection configuration.)To be able to fully support multi-threading, I needed to enabled the FDB multi-client feature. Enabling it also allowed easier upgrades across DB versions, as FDB clients are incompatible across versions:
FDB_NETWORK_OPTION_EXTERNAL_CLIENT_LIBRARY="/lib/libfdb_c.so"FDB_NETWORK_OPTION_CLIENT_THREADS_PER_VERSION="16"Breaking the 100K/s reads barrier

After implementing support for the multi-threaded client, we were able to get over 100K reads per second.
You may notice after the restart (gap) the performance dropped. This was caused by several bugs: 1. When creating the CF Pipelines endpoint, we did not specify a region. The automatically selected region was far away from the server. 2. The amount of shards were not sufficient, so we increased them. 3. The client overloaded a few HTTP/2 connections with too many requests.
I implemented a feature to assign each
Workerits own HTTP client, fixing the 3rd issue. We also moved the entire storage region to West Europe to be closer to the servers.After these changes, we were able to easily push over 200K reads/s, mostly limited by missing optimizations:

It's shards all the way down
While testing, we also noticed another issue: At certain times, a pipeline would get overloaded, stalling requests for seconds at a time. This prevented all forward progress on the
Workers.We solved this by having multiple pipelines: A primary pipeline meant to be for standard load, with moderate batching duration and less shards, and high-throughput pipelines with more shards.
Each
Workeris assigned a pipeline on startup, and if one pipeline stalls, other workers can continue making progress and saturate the DB.The stress test
After making sure everything was ready for the import, we cleared all data, and started the import.
The entire import lasted 20 minutes between 01:44 UTC and 02:04 UTC, reaching a peak of: - 0.25M requests per second - 0.6M keys read per second - 140MB/s reads from DB - 2Gbps of network throughput
FoundationDB ran smoothly during this test, with: - Read times under 2ms - Zero conflicting transactions - No overloaded servers
CF Pipelines held up well, delivering batches to R2 without any issues, while reaching its maximum possible throughput.

Finishing notes
Me and Fishcake have been building infrastructure around scaling Nostr, from media, to relays, to content indexing. We consistently work on improving scalability, resiliency and stability, even outside these posts.
Many things, including what you see here, are already a part of Nostr.build, Noswhere and NFDB, and many other changes are being implemented every day.
If you like what you are seeing, and want to integrate it, get in touch. :)
If you want to support our work, you can zap this post, or register for nostr.land and nostr.build today.
-
 @ 06639a38:655f8f71
2025-03-17 14:55:18
@ 06639a38:655f8f71
2025-03-17 14:55:18https://ccns.nostrver.se is a (Drupal powered) website that I started to build in January 2024 (source on Github and Gitlab). It's a fork of an earlier (abandoned) project https://cchs.social/.
Currently CCNS is a link aggregration website and for now it's only my who is using it to save and share Nostr related links. When you post a new link, you have the option to cross-post it as a Nostr note (example here).Kind 39700
Last month Jurjen and Abir has started to work on a social bookmark client built with Nostr (inspired by Del.icio.us from the past). Earlier this month they changed to event kind 39700 for broadcasting the Nostr event with the bookmark / link data accross the network. They did this because Sep already created a social bookmark like client called Pinja when fiatjaf raised this idea.
With these developments to me it was very obvious to integrate the feature that new created CCNS links are now also published as kind 39700 events to the Nostr network. This means that links are now also distributed on multiple relays as kind 39700 events and are accessible in multiple clients (Yumyume and Pinja).
Here you can see the same data, from left to right:

Structure
The current data structure for the 39700 kind looks as follow:
- "id": "event_id"
- "pubkey": "pubkey author"
- "created_at": unix_timestamp
- "kind": 39700
- "tags":
- "description", "description text here"
- "d", "unique-slug-value"
- "t", "hashtag"
- "content": "https://book_mark_url"
- "sig": "signature"
As there is no NIP (yet) for this event kind, I see some possible improvements:
- Use the bookmark URL as
dtag so it can be used as a unique identifier for every client - Use the content field for the description
- Use the
atag for an addressable event following NIP-01:["a", "39700:pubkey_of_author:", recommended_relay_url_optional]
On short-term I don't have any plans to developer CCNS further, as most of my attention goes to the development of the Nostr-PHP library and Drupal related contribs using that library. That said, CCNS is a Drupal project but all the Nostr stuff is done client-side (Javascript) with NDK and Nostr-PHP is not used (maybe this will change in the future).
-
 @ f18571e7:9da08ff4
2025-03-14 16:43:03
@ f18571e7:9da08ff4
2025-03-14 16:43:03Gostaria de dar-te as boas vindas à essa rede social descentralizada e sem censura. Creio eu que já tenha ouvido falar sobre o que ela é e como funciona parcialmente, caso não, existem dois sites (ao meu conhecimento) com boas informações, se chamam nostr.com e nostr.how, mas darei mais à frente uma explicação básica.
E já te dou um aviso: você precisa saber ler!
Aqui irei tentar ajuntar o máximo de informações que conseguir para que não falte nada para você, e o que faltar, quero que você saiba como pesquisar. Cada parte de como funciona, como acessar, como criar, etc.
Usarei como padrão neste artigo o #Amethyst, pois é o melhor e mais completo client para android, mas muitas das configurações nele podem ser visualizadas em outros clients. E para começar, vamos ver o que são clients.
Clients
Chamamos de clients (ou clientes em português) aqueles sites ou apps que dão acesso ao protocolo Nostr. Assim como para acessar à internet existem vários browsers (ou navegadores), para acessar o Nostr também existem vários clients, cada um voltado a um foco específico.
Amethyst
O melhor e mais completo client para #android, nele você pode ter acesso de tudo um pouco. Lives, comunidades, chats, "vídeos curtos", hashtags, notas populares, e muito mais.
Na versão da Play Store, existe uma funcionalidade de tradução usando o Google tradutor. https://play.google.com/store/apps/details?id=com.vitorpamplona.amethyst
Em outras lojas de apps e no repositório Github, o apk não possui essa função. https://github.com/vitorpamplona/amethyst
Aqui tem um tutorial do Amethyst: nostr:nevent1qqsgqll63rw7nfn8ltszwx9k6cvycm7uw56e6rjty6lpwy4n9g7pe5qpz4mhxue69uhhyetvv9ujumn0wd68ytnzvuhsygz8g3szf3lmg9j80mg5dlmkt24uvmsjwmht93svvpv5ws96gk0ltvpsgqqqqqqs7yma4t
Outros Clients
Aqui algumas pessoas expondo suas opiniões sobre certos clients: nostr:nevent1qqsdnrqszc2juykv6l2gnfmvhn2durt703ecvvakvmyfpgxju3q2grspzamhxue69uhhyetvv9ujuvrcvd5xzapwvdhk6tczyr604d4k2mwrx5gaywlcjqjdevtkvtdjq4hmtzswjxjhf6zv2p23qqcyqqqqqqghvkced nostr:nevent1qqsvqahwnljqcz3s3t5zjwyad5f67f7xc49lexu7vq5s2fxxskegv4spzemhxue69uhkummnw3ezuerpw3sju6rpw4ej7q3qvg9lk42rxugcdd4n667uy8gmvgfjp530n2307q9s93xuce3r7vzsxpqqqqqqzeykzw2 Eu mesmo gosto do Amethyst para android e iris.to para web no PC.
Recomendo à você dar uma olhada nesse site: nostrapps.comEle possui todos os clients atuais do Nostr, com uma descrição e links direcionais para você.
Nostr
Agora que você já sabe mais sobre os #clients, você pode acessar o Nostr segundo seu interesse de interface. Vamos ver o que uma IA nos diz sobre o Nostr:
"O #Nostr é um protocolo descentralizado e open source que permite a criação de redes sociais e outros aplicativos sem a necessidade de um servidor central. O nome é um acrônimo para Notes and Other Stuff Transmitted by Relays (Notas e Outras Coisas Transmitidas por Relays). Ele foi projetado para ser resistente à censura, oferecendo uma alternativa às plataformas tradicionais, onde os usuários têm controle total sobre seus dados.
Para que serve?\ O Nostr serve como base para aplicações descentralizadas, como redes sociais, sistemas de pagamento instantâneo em Bitcoin (usando a rede Lightning) e interações diretas entre criadores e consumidores de conteúdo. Ele promove a liberdade de expressão e a privacidade, sem exigir informações pessoais como nome, e-mail ou número de telefone para criar uma conta.
Como funciona?\ O protocolo utiliza dois componentes principais: clientes e relays. Os clientes são aplicações que os usuários usam para interagir com a rede, enquanto os relays são servidores que armazenam e transmitem mensagens. Cada usuário tem uma chave criptográfica única, que garante a autenticidade e a integridade das mensagens. Os relays são independentes, o que significa que, se um relay for bloqueado ou cair, os usuários podem continuar se conectando através de outros.
Em resumo, o Nostr é uma revolução na forma como nos conectamos online, oferecendo liberdade, privacidade e controle aos usuários."
-Perplexity AI
Se você chegou aqui, é porque ouviu em algum lugar ou de alguém, algo parecido com isso. O Nostr é algo moldável, você consegue fazer dele o que quiser, e por aqui você vai encontrar muitas dessas pessoas que o moldam (idealizadores, programadores e desenvolvedores).
Cuide de sua NSEC
Sua Nsec é a chave privada para acesso ao seu perfil, quem a possuir poderá realizar qualquer alteração que queira, comentar, publicar posts e assim por diante. Você deve guardar essa Nsec como se fosse a seed phrase ou chave privada de sua carteira cripto.
Existem alguns modos de guardar e criptografar sua Nsec:
Sem Criptografia
Primeiro de tudo, fique ciente de onde está a sua nsec no client em que acessa o Nostr!
No Amethyst
- Abra o menu de opções
- Selecione "Copia de segurança"
- Clique em "copiar minha chave secreta" Sua nsec será copiada para a àrea de transferência de seu teclado.
Depois de copiar sua nsec, as melhores recomendações que tenho para passar são:
1. Amber
Guarde sua nsec no #Amber, um app assinador de eventos que guarda sua nsec sob criptografia. Após isso, use o mesmo para acessar qualquer client ou site e gerenciar as permissões de cada um. nostr:nevent1qqsvppyfxm87uegv9fpw56akm8e8jlaksxhc6vvlu5s3cmkmz9e0x8cpypmhxue69uhkummnw3ezuampd3kx2ar0veekzar0wd5xjtnrdakj7q3q5wnjy9pfx5xm9w2mjqezyhdgthw3ty4ydmnnamtmhvfmzl9x8cssxpqqqqqqztzjvrd
2. Nos2x-fox
Coloque sua nsec no #Nos2x-fox, um gerenciador de permissões para navegadores a partir do #Firefox. https://addons.mozilla.org/en-US/firefox/addon/nos2x-fox/ E para navegadores da base #chromium existe o #Nos2x do mesmo desenvolvedor. https://chromewebstore.google.com/detail/nos2x/kpgefcfmnafjgpblomihpgmejjdanjjp
3. Gerenciador de Senhas
Essa é a recomendação mais arriscada, você ainda terá de usar o copiar e colar de sua nsec para acessar o Nostr, a não ser que seu gerenciador reconheça o campo de preenchimento da nsec. Mesmo assim, existem dois gerenciadores que indico; o #Bitwarden e #KeePassDX:
Bitwarden (online)
Play Store: https://play.google.com/store/apps/details?id=com.x8bit.bitwarden Github: https://github.com/bitwarden/mobile
KeePassDX (offline)
Play Store: https://play.google.com/store/apps/details?id=com.kunzisoft.keepass.free Github: https://github.com/Kunzisoft/KeePassDX
Com Criptografia
Se tiver interesse em criptografar sua chave, o formato nativo aceito pelos clients é o ncryptsec. O #ncryptsec é uma criptografia por senha (a grosso modo), onde para ser capaz de usá-la nos clients, somente em conjunto com a senha usada na criptografia, fora isso, você não tem acesso. Você consegue encriptar sua nsec e hex para ncryptsec por meios como os abaixo:
1. Amethyst (nsec)
Existe uma função nativa no Amethyst abaixo da opção "copiar chave secreta" onde é só adicionar a sua senha e será criada uma ncryptsec para copiar. Guarde essa nsec encriptada + senha de descriptação em um lugar seguro.
2. Amber (nsec)
No Amber, existe uma função capaz de encriptar sua nsec.
Ao entrar no Amber
- Selecione a engrenagem na parte inferior da tela
- Selecione "backup keys"
- E rolando para baixo existe um campo para digitar sua senha para encriptação da nsec, digite sua senha e copie a ncryptsec. Guarde-as em um lugar seguro.
3. Nostr-Tools (hex)
Foi-me dito que essa ferramenta também encripta o formato nsec, mas eu não consegui fazê-lo, então deixarei para o formato hex. Compile essa ferramenta em seu pc e siga as instruções. Sua chave Hex será encriptada. https://github.com/nbd-wtf/nostr-tools/blob/master/nip49.ts Guarde-as em um lugar seguro.
Relays e Servidores
Relays
Os #Relays (ou relés) são essenciais para receber e enviar informações no Nostr, veja abaixo algumas definições e como utilizar: nostr:nevent1qqsw85k097m8rh5cgqm8glndhnv8lqsm3ajywgkp04mju9je3xje3hcpzemhxue69uhkummnw3ezuerpw3sju6rpw4ej7q3qne99yarta29qxnsp0ssp6cpnnqmtwl8cvklenfcsg2fantuvf0zqxpqqqqqqzxvc0le No exemplo é usado o Orbot no Amethyst, você pode escolher usar essa opção, mas houve uma atualização do Amethyst desde a criação deste post, onde foi adicionada a função de "Tor interno".
No Amethyst
- Deslize a tela da esquerda pra direita
- Selecione "Opções de Privacidade"
- Na opção "Motor Tor Ativo" selecione "Interno"
- Para melhor privacidade, na opção "Predefinições Tor/Privacidade" selecione "Privacidade Completa" Todo conteúdo e informação que receber do Nostr passará através da rede Tor, além de que é possível visualizar conteúdos publicados no Nostr exclusivos da rede #Tor com essa configuração. Lembrando que este método é mais veloz que usar o Orbot.
Aqui estão alguns relays Tor: nostr:nevent1qqsqe96a8630tdmcsh759ct8grfsdh0ckma8juamc97c53xvura3etqpxpmhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtmhwden5te0vdhkyunpve6k6cfwvdhk6tmjv4kxz7gzyr604d4k2mwrx5gaywlcjqjdevtkvtdjq4hmtzswjxjhf6zv2p23qqcyqqqqqqgmxr5jk
Servidores de Mídia
Os servidores de mídia são os responsáveis por armazenar seus vídeos e fotos postados no Nostr. No Amethyst já existem alguns por padrão: https://image.nostr.build/8e75323bb428c1e5ef06e37453f56bc3deecd38492a593174c7d141cac1c2677.jpg Mas se você quiser, pode adicionar mais: nostr:nevent1qqster6rm55vy3geqauzzwrm50xwvs2gwa4l27ta2tc65xhpum2pfzcpzamhxue69uhkjmnzdauzuct60fsk6mewdejhgtczyr604d4k2mwrx5gaywlcjqjdevtkvtdjq4hmtzswjxjhf6zv2p23qqcyqqqqqqgv2za2r Fique atento aos limites e regras de cada servidor de mídia. nostr:nevent1qqsq3qchucw49wfu2c4wpsung93ffzg4ktt4uuygnjcs5pldf5alr9c3hsgjr
E aqui vai uma #curiosidade: Caso queira postar uma foto ou vídeo que já postou antes, copie o ID da nota em que ela está e cole no novo post, ou então o URL da mídia. Você pode perceber que após upar uma mídia no Nostr, isso se torna uma URL, sempre que usar essa mesma URL, essa mídia irá aparecer.
Lightning e Zaps
Se você chegou aqui por meio de bitcoinheiros, já deve saber que por aqui, usamos a #Lightning para enviar zaps. Mas o que são zaps?
Zaps são nada mais do que satoshis enviados no Nostr. Um exemplo, eu criei esse artigo, pessoas que querem me apoiar ou agradecer por tal, me enviam alguma quantia em sats, dizemos que essa pessoa me mandou um #zap.
Agora posso falar mais sobre a lightning no Nostr.
Para enviar zaps para usuários no Nostr, você precisa de uma carteira lightning. E a carteira que recomendo criarem para isso é através da #Coinos. Na Coinos, você não precisa criar carteiras com seed phrases nem canais lightning, ela é uma carteira custodial, ou seja, a seed phrase está de posse da Coinos. Basta você acessar coinos.io e criar uma conta com username e senha, você pode configurar um e-mail de resgate, código 2FA, e senha para movimentação de fundos. Se quiser, aqui está o app da Coinos, ainda em fase de testes, mas a maior parte do usual funciona perfeitamente. nostr:nevent1qqspndmkhq2dpfjs5tv7mezz57fqrkmlklp4wrn3vlma93cr57q5xlqpypmhxue69uhkummnw3ezuampd3kx2ar0veekzar0wd5xjtnrdakj7q3q7xzhreevjvzyvuy48mjn7qlx55q2dktk3xm0lnlpehxvl8dq3l6qxpqqqqqqzp4vkne (o app está disponível na #zapstore, baixe a loja para ter acesso) O legal da coinos é que você pode criar um endereço lightning com o nome que você escolher, o meu por exemplo é componente08@coinos.io, basta criar sua conta e poderá enviar e receber zaps no mesmo instante.
Mas para receber de fato um zap usando o Nostr, você precisa configurar seu endereço lightning no seu perfil. Crie sua conta e copie seu endereço lightning.
No Amethyst
- Clique na sua imagem de perfil
- Selecione "Perfil"
- Aperte o botão com um lápis
- Em "Endereço LN" e "LN URL" cole seu endereço lightning Pronto! Agora as pessoas podem te enviar zaps através de suas publicações.
Antes de enviar zaps, configure seus valores no client.
No Amethyst
- Aperte e segure no raio de qualquer publicação
- No campo "novo valor em sats" digite um valor desejado
- Aperte o "x" nos valores que deseja excluir
- Clique em "Salvar"
Agora, você pode clicar no raio e escolher um valor, ao escolher você será direcionado para a sua carteira, confirme a transação e seu zap foi realizado!
Existe outro meio de enviar zaps que é através do #NWC (Nostr Wallet Connect). Siga os mesmos passos do Yakihonne no Amethyst na aba do raio que acessamos anteriormente. nostr:nevent1qqsxrkufrhpxpfe9yty90s8dnal89qz39zrv78ugmg5z2qvyteckfkqpzamhxue69uhkjmnzdauzuct60fsk6mewdejhgtczyr604d4k2mwrx5gaywlcjqjdevtkvtdjq4hmtzswjxjhf6zv2p23qqcyqqqqqqgrw73ux O NWC dá ao client ou app, a permissão de gerenciar sua carteira. Isso te permite enviar zaps sem sair do client ou precisar entrar no app da carteira.
Existem muitas outras carteiras lightning por aí, então além da coinos, deixarei o link de outras duas que utilizo.
WOS (Wallet of Satoshi)
Somente Play Store: https://play.google.com/store/apps/details?id=com.livingroomofsatoshi.wallet
Minibits
Play Store: https://play.google.com/store/apps/details?id=com.minibits_wallet Github: https://github.com/minibits-cash/minibits_wallet
Comunidades
Em uma #comunidade é possível encontrar respostas para suas perguntas, artigos e postagens de seu interesse, links úteis e tutoriais para burlar sistemas, documentos e estudos sem censura, etc. Aqui está um exemplo: nostr:nevent1qqs8qztlq26hhstz9yz2tn02gglzdvl5xhkpzhnpuh8v65mjldtdjlqpzamhxue69uhhyetvv9ujuvrcvd5xzapwvdhk6tczypr5gcpycla5zerha52xlam9427xdcf8dm4jccxxqk28gzayt8l4kqcyqqqqqqgldlvdq Esse usuário recorrentemente atualiza a lista de comunidades brasileiras no Nostr, recomendo seguir o perfil para se manter atualizado caso tenha interesse: nostr:nevent1qqsxkusgt02pmz6mda4emjlnjjyd4y9pa73ux02dcry8vk3wp85aq9cpzamhxue69uhkjmnzdauzuct60fsk6mewdejhgtczypr5gcpycla5zerha52xlam9427xdcf8dm4jccxxqk28gzayt8l4kqcyqqqqqqgqq5zn5 Aqui vão algumas #curiosidades para usuários mais avançados: nostr:nevent1qqs246x86gw4zfp70wg65rjklf909n6nppwm0xx6mssl6jgznw4nkjcpzamhxue69uhkjmnzdauzuct60fsk6mewdejhgtczyzgmafwdjds4qnzqn2h5t9gknz8k3ghu6jp8vt7edxnum3ca73z3cqcyqqqqqqgtkt83q Existem alguns clients que podem criar e gerenciar comunidades, caso você não encontrou nada de seu interesse e quer criar uma, os mais populares são:
Satellite.earth e noStrudel.ninja
Chats
Os #chats são espaços voltados a interação por meio de mensagens, aqui estão alguns: nostr:nevent1qqs98kldepjmlxngupsyth40n0h5lw7z5ut5w4scvh27alc0w86tevcpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgsfujjjw3474zsrfcqhcgqavqeesd4h0nuxt0ue5ugy9y7e47xyh3qrqsqqqqqpgdaghw Para contatar uma pessoa no privado:
No Amethyst
- Clique no perfil da pessoa
- Clique no ícone de mensagem
- Envie uma mensagem
Caso queira criar um chat, siga os passos:
No Amethyst
- Clique no ícone de mensagens
- Clique no ícone de "+"
- Serão exibidas duas opções; "privado" e "público", escolha privado para um grupo de poucas pessoas e público para qualquer que quiser entrar.
- Adicione as especificações necessárias e seu chat será criado.
Seguidores
Existe uma #ferramenta capaz de identificar quais usuários que você segue estão inativos, ou publicam pouco e a longos hiatos: nostr:nevent1qqsqqqyhmkqz6x5yrsctcufxhsseh3vtku26thawl68z7klwvcyqyzcpzamhxue69uhkjmnzdauzuct60fsk6mewdejhgtczyzgmafwdjds4qnzqn2h5t9gknz8k3ghu6jp8vt7edxnum3ca73z3cqcyqqqqqqgmfzr67
Mais do Nostr
Existem muitas outras coisas para se explorar no Nostr, e é possível que daqui a uns meses, essas configurações e dicas estejam obsoletas. Explorem e aprendam mais sobre esse protocolo.
Abaixo estão mais algumas coisas que gostaria de compartilhar:
Muitos clients não possuem um sistema de #notificações, isso por conta da natureza #descentralizada dos apps, e para não ceder ao Google para isso, optaram por não ter notificações. O Amethyst por exemplo, só possui notificações ativas para quando você receber zaps. Mas esse problema foi resolvido com o #Pokey: nostr:nevent1qqsyw0m8wkwvzsanwufh6kmu3fkkjsu3x6jxxwxst5fxu3yld7q84cspzemhxue69uhkummnw3ezuerpw3sju6rpw4ej7q3q5wnjy9pfx5xm9w2mjqezyhdgthw3ty4ydmnnamtmhvfmzl9x8cssxpqqqqqqz4d5hj5
Aqui está um post sobre uma #loja de #apps voltada a apps do Nostr: nostr:nevent1qqsrk55p927srd30ukas79qzhlwhm5ls9l07g548y288s5u29najzrqpz4mhxue69uhhyetvv9ujumn0wd68ytnzvuhsyg85l2mtv4kuxdg36gal3ypymjchvckmypt0kk9qayd9wn5yc5z4zqpsgqqqqqqskv0pek
Alguns RSS para quem gosta de notícias: nostr:nevent1qqsxctkju0pesrupvwfvzfr8wy3hgqag6r8v4228awgyf2x9htjqa7qpzemhxue69uhkummnw3ezuerpw3sju6rpw4ej7q3qvg9lk42rxugcdd4n667uy8gmvgfjp530n2307q9s93xuce3r7vzsxpqqqqqqzn4acev
Algumas pessoas famosas que estão por aqui: nostr:nevent1qqsvqnlx7sqeczv5r7pmmd6zzca3l0ru4856n3j7lhjfv3atq40lfdcpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgrqsqqqqqprwcjan
Alguns Nostr clients e outras coisas: nostr:nevent1qqsgx5snqdl2ujxhug5qkmmgkqn5ej6vhwpu4usfz03gt4n24qcfcwspr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgrqsqqqqqp3pf6y2
Outros posts interessantes: nostr:nevent1qqsp6vf8pp6l97ctzq2wp30nfc9eupnu2ytsauyxalp8fe8dda6dvdgpzamhxue69uhkjmnzdauzuct60fsk6mewdejhgtczyzgmafwdjds4qnzqn2h5t9gknz8k3ghu6jp8vt7edxnum3ca73z3cqcyqqqqqqgtkju3h nostr:nevent1qqs0faflxswn5rg8fe9q3202en927my6kupcf08lt26ry3cg3xuuy3gpzamhxue69uhkjmnzdauzuct60fsk6mewdejhgtczyzgmafwdjds4qnzqn2h5t9gknz8k3ghu6jp8vt7edxnum3ca73z3cqcyqqqqqqgsyrpkh nostr:nevent1qqspx9t3qfnsuzafxxuc5hyha9n5ul5v97uz57hfac9xdtvk5eygqggpzemhxue69uhkummnw3ezuerpw3sju6rpw4ej7q3qa5pl548ps6qdkpzpmlgkhnmh2hpntpk2gk3nee08e5spp5wzr3qqxpqqqqqqzctx6uf
Funcionalidades do Amethyst
• Reações (noStrudel também aceita)
nostr:nevent1qqst57p0pzw3vsx3n8g7eaa0dlx3kp5ys9rw3t367q5ewhdyw0kd2rspzamhxue69uhkjmnzdauzuct60fsk6mewdejhgtczyz36wgs59y6smv4etwgrygja4pwa69vj53hww0hd0wa38vtu5clzzqcyqqqqqqgpje0yu
• Markdown
nostr:nevent1qqs0vquevt0pe9h5a2dh8csufdksazp6czz3vjk3wfspp68uqdez00cpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgrqsqqqqqpekll6f
Espero ter dado alguma direção pela qual seguir por aqui, se tiver dúvidas, pode comentar aqui abaixo e responderemos com o melhor que pudermos. Olhem alguns dos comentários abaixo, terão posts que os veteranos consideram importantes.
Aos veteranos, comentem abaixo caso tenha faltado algo, e complementem aos novatos, grato!
Mais uma vez, seja bem-vindo ao Nostr!
nóspossuímosaweb #awebénostr
-
 @ b90c3cb7:1be67823
2025-03-14 11:33:12
@ b90c3cb7:1be67823
2025-03-14 11:33:12This guide uses cashu.me and the 0xchat app
First go to cashu.me. Make sure you've added a mint. I suggest mint.0xchat.com (note for newbies like I recently was, it's the number zero and not the letter O). Make sure you have some balance. Then hit SEND and choose ECASH.

Next type in a small amount to send. As always with bleeding-edge stuff accept the token can go poof. Only after you've typed in a number will you see the LOCK button appear next to the SEND button.

Hitting LOCK will reveal the "Receiver public key" field as below. This works for public keys generated within cashu.me (go to cashu.me settings) as well as for Nostr public keys.

Next copy your own public key (or that belonging to whoever you want to test this with) and head over to https://nostrcheck.me/converter/ and paste it in there. This will convert it to hex format, which is needed in this case.

After that go back to cashu.me and paste the hex format key in that field. It'll be in this red color "Invalid public key" state, don't worry.

Add 02 (number zero, number two) in front of the hex key. That'll make it valid. It's just the scheme. You'll see the locked icon appear next to the SEND button.

Then hit SEND and, voila, you now have a Cashu token that only the person in control of the nsec of whatever public key you used just then can redeem. Post it publicly to taunt others. (FYI the P2PK abbreviation there means pay-to-public-key.) Hit COPY to grab the token string.

Last up, open 0xchat. Assuming you're doing this yourself, make sure you're logged in with the nsec of the public key you used to create the test token. Also make sure the token string resides in the clipboard of the device you're using 0xchat on.

Then go to th "Me" tab in 0xchat to open the Cashu wallet. Set it up if you haven't already. Hit "Receive" and then "Redeem Ecash". As long as the token is in your clipboard and you did it all the steps right it should be redeem straight to your Cashu wallet. Well hopefully.
That's it. This guide will self-descrut if it goes out of date or was wrong somehow.
-
 @ 0461fcbe:35a474dd
2025-03-13 23:10:12
@ 0461fcbe:35a474dd
2025-03-13 23:10:12Background
I will start with a disclaimer: I'm all-in on Nostr. But before that, I spent 4 years building on ActivityPub. Then in Feb 2023 I built a bridge between ActivityPub and Nostr, and in Dec 2024 I built another bridge between Nostr and Bluesky. Most of all I am committed to open source and the decentralized vision. Having experience with all 3 major protocols, I still think Nostr is the best, but Bluesky outshines it in some major areas. The main reason for this blog is to explore the things Bluesky does better than us, and to point out why I still think Nostr is the best solution.
This is a technical blog. For a more high level overview of decentralized protocols, see: https://soapbox.pub/blog/comparing-protocols/
Data Model
Nostr and Bluesky both allow users to store any type of data in a single, unified format. Nostr calls them events. Bluesky calls them records. They are mostly interchangeable ideas, but the way the data is stored and retrieved is very different.
It's worth noting that, like Nostr and ActivityPub, Bluesky is capable of doing anything under the sun. It's a misconception that it can't. You can build whatever Reddit, TikTok, or other stuff clone on Bluesky just fine. It's limited more by the huge knowledge gap you have to overcome than it is by anything about its data model.
NSIDs vs Kinds
Nostr events use a "kind" number, eg
1, to distinguish different type of events. Bluesky records use what they call an "NSID" (namespace identifier), egapp.bsky.feed.post, which is a reverse-DNS string notation.Nostr's
"kind": 1is equivalent to Bluesky's"$type": app.bsky.feed.post.I think Bluesky's system is better, because it allows developers to feel like what they built is "real" without having to get it merged into the NIPs repo, which is basically like an IANA of Nostr kind numbers. I believe this causes significant problems on Nostr, and makes people feel like they are being held back by others. That being said, the counter-argument is that kind numbers encourage interoperability for the very same reasons. The barriers to adding new kinds pushes people to work with what's already there.
Text Content Formatting
Kind 1 events ("plain text notes", ie "Tweets") on Nostr have developed in a haphazard way over time, by many people piling things onto it without taking a step back to assess a unified way to handle it. Some examples include:
- NIP-21
nostr:URIs imetatags- inline media embeds as URLs without
imetatags - unspec'd Markdown rendering by some clients
- legacy specs such as positional mentions (eg,
#[0], mostly gone now)
What we have now is quite a mess, and it's something Bluesky beats us on badly.
Bluesky has a plaintext content field that can be displayed as-is. In addition, it has a "facets" field, which is a structured JSON object, that adds rich-text information such as formatting (bold, italic, etc), links, mentions of users, and whatever else metadata about the text.
This is an extensible system that beats even options like Markdown, due to its ability to include native extension like mentions, and its ability to be parsed by any programming language or software environment.
Bluesky is the winner here.
Syncronization
Nostr and Bluesky are both thought to be descended from Scuttlebutt, an older decentralized protocol.
On Scuttlebutt, a user's whole post history needed to be available for them to make a new post. Scuttlebutt uses a linked list, so each new event would need to reference the one before it. Only linear paths are allowed, so if a "fork" occurred (intentionally or not), only one version would be kept, and the other discarded. This lead to occasional publishing issues, but it allowed readers to assemble a complete view.
Nostr strayed from this draconian approach, removing it entirely and allowing user data to be fragmented. Meanwhile Bluesky, instead of removing it entirely, made it work more like git so that branches could be merged.
Both approaches have tradeoffs. Bluesky's approach has much higher complexity. Also, it's sometimes considered an advantage for events to be fragmented (eg Nostr allows sending DMs to specialized relays for enhanced privacy).
But Bluesky has a true account "sync" mechanism, and Nostr does not. Nostr can send filters to relays to gather events, but it cannot know when to stop looking. Proposals like Negentropy in Nostr do not solve author syncing, and only make typical relay filtering more efficient.
I think it's important to think about Nostr's "outbox" problem as a syncronization problem, and for Nostr to approach syncronization with the goal of syncronizing authors specifically.
I think Bluesky "wins" this one, if only because they have solved a problem that we haven't. Instead of copying their solution, I think Nostr should try to learn from this to recharacterize the "outbox" problem as an author syncing problem, and see if we can come up with a better solution that works for Nostr.
Knowledge Gap
One of the biggest hurdles of Bluesky, and by extension one of the greates appeals of Nostr, is in how easy it is to learn and build on.
Nostr can be understood in a couple of hours. Mastering it is difficult, but limited only by your time and imagination. Hundreds of developers are building new projects on Nostr today. Based on my experience, it seems to me that the Nostr developer community is larger than that of both ActivityPub and Bluesky combined.
Bluesky on the other hand requires a Harvard degree in Blueskyology. I believe that ameteur coders feel a sense of superiority after spending six weeks learning how to commit a post. To learn Bluesky you will have to sift through thousands of technical documents about all kinds of abstractions, especially related to IPFS and IPLD. You will have to master unnecessary technologies like CBOR (which is basically just JSON except it's in binary and takes up the same amount of space). And you will be frequently pointed to academic topics such as "DAG" and "graph theory", all just to say "it's a fucking graph". I will never understand why people will take simple concepts such as a "tree", and then make it harder to understand on purpose by saying it's more than that.
While building on Bluesky, I began to question if the creators did this on purpose. I wondered if they tried to make it complex on purpose, as a sort of IQ test and protective measure to weed out the undeireables. In my view, a truly free and open network must be accessible to all, with the hope that even non-programmers could learn how it works.
Technical complexity is not just an issue of inclusion, but also security. ActivityPub software has been found to be littered with major security holes due to its inherently complex design, while Nostr's simple design makes its attack surface extremely minimal. Bluesky has already had a few mishaps, and it makes me wonder how Bluesky will fare in the long term.
Decentralization
I will keep this short. Bluesky is designed to be decentralized, but isn't. It reminds me of the communist idea about the "withering away of the state". The idea is that you're supposed to first sieze power and become the new state, and then under your rule the state will slowly disappear because you are doing all the right communist things. I think this is basically how Bluesky sees itself (whether they agree with the analogy or not).
Nostr is decentralized, but it is a loaded gun. You're more likely to kill yourself with a gun than someone else. This is on purpose, because it wholly embraces the consequnces of being truly decentralized.
In my view Nostr gets it right. Social media has been done to death by now, so I do not think it's worth the compromise to prioritize UX over decentralization. If that's the case we have not fixed anything. It's best to start with the purist idea and work backwards to UX, rather than start with UX and work backwards to decentralization. Many people have already written extensively about the decentralization of Bluesky, so I'll leave it at that.
- NIP-21
-
 @ 04cb16e4:2ec3e5d5
2025-03-13 21:26:13
@ 04cb16e4:2ec3e5d5
2025-03-13 21:26:13Wenn man etwas verkaufen will, muss man eine Geschichte über sein Produkt erzählen. Nur wenige können etwas damit anfangen, wenn du sagst: Unser Produkt enthält 50 Gramm Hafer (hoffentlich gentechnikfrei), 5 mittelgroße Erdbeeren, Spuren von Sesamschalen sowie einen Teelöffel Honig. So funktioniert das nicht. Dein Riegel braucht einen Namen und eine Geschichte.
Wenn wir über Krieg und Frieden sprechen, denn gibt es zumeist Zahlen, Fakten und Meinungen. Tausende von Kindern die in einem Krieg getötet werden sind eine schockierende Anzahl. Nimmst du die Zahlen weg und beschäftigst dich mit jedem einzelnen Schicksal, dann ist das unmöglich zu ertragen. Also kämpfen wir hier vor Ort, in Deutschland, zwar nicht mit Waffen gegeneinander, sondern mittels unserer Meinungen in Kombination mit zu vermittelnden relativen Wahrheiten. Da kommt das Ego ins Spiel. Wir wollen unbedingt Recht haben! Irgendeiner soll in diesem Meinungskampf am Ende als Gewinner dastehen. Weil er die besseren Argumente hat. Schließlich werden Emotionen mit Fakten vermischt und als Totschlagargumente in die Gegenfront geworfen.
Was aber, wenn man eine Geschichte über den Krieg erzählt, die jeden mitnehmen kann, ganz gleich, welche Meinung man zu den aktuell verhandelten Kampfschauplätzen hat? Alles Trennende wird aus der Erzählung herausgenommen und was bleibt, sind die zerstörerische Kraft des Krieges und die Verantwortung jedes einzelnen Menschen zu entscheiden, ob er dieses grausame Monster füttert oder eben nicht. In dem afrikanischen Märchen „Sheikhi“ basieren diese Entscheidungen nicht auf Fakten und Meinungen, sondern auf persönlichen Erfahrungen. Die Protagonisten nehmen uns mit in ihre Welt und lassen uns ihre inneren Kämpfe, Zweifel, Ängste und Hoffnungen miterleben. Wir können uns mit ihnen identifizieren, obwohl wir unter völlig anderen Bedingungen leben und sterben.
Hier kannst du das Buch direkt beim Verlag bestellen
Die alternative Buchmesse Seitenwechsel
Am Ende des Buches konnte ich gar nicht anders, als eine tiefe Sehnsucht nach Frieden und Einigkeit zu verspüren. Diese Sehnsucht basierte aber nicht mehr auf dem Bedürfnis, bessere Argumente als die vermeintliche Gegenseite zu haben, sondern vielmehr darauf, dass dieses verzweifelte Ringen und Hassen endlich zu einem Ende kommt. Nicht nur auf den Schlachtfeldern Asiens und Afrikas, sondern ebenfalls auf Facebook, X, den Straßen unserer Städte und im Krieg jedes Menschen gegen sich selbst. Inzwischen gelingt es mir immer öfter, mir einen bissigen Kommentar zu verkneifen, wenn jemand auf Facebook etwas schreibt, was ich unerträglich finde. Ich weiß, das ich ihn nicht vom Gegenteil überzeugen werde und das mein Kommentar das selbe Monster füttert, dass sich an den Opfern des Krieges satt isst.
Wenn es irgendwo Menschen auf der Welt gibt, die Mord und Folter verzeihen können, dann kann auch ich eine andere Meinung ertragen ohne rechthaberisch, arrogant und destruktiv zu werden. Notfalls gehe ich in den Wald und schreie.
-
 @ 04c915da:3dfbecc9
2025-03-13 19:39:28
@ 04c915da:3dfbecc9
2025-03-13 19:39:28In much of the world, it is incredibly difficult to access U.S. dollars. Local currencies are often poorly managed and riddled with corruption. Billions of people demand a more reliable alternative. While the dollar has its own issues of corruption and mismanagement, it is widely regarded as superior to the fiat currencies it competes with globally. As a result, Tether has found massive success providing low cost, low friction access to dollars. Tether claims 400 million total users, is on track to add 200 million more this year, processes 8.1 million transactions daily, and facilitates $29 billion in daily transfers. Furthermore, their estimates suggest nearly 40% of users rely on it as a savings tool rather than just a transactional currency.
Tether’s rise has made the company a financial juggernaut. Last year alone, Tether raked in over $13 billion in profit, with a lean team of less than 100 employees. Their business model is elegantly simple: hold U.S. Treasuries and collect the interest. With over $113 billion in Treasuries, Tether has turned a straightforward concept into a profit machine.
Tether’s success has resulted in many competitors eager to claim a piece of the pie. This has triggered a massive venture capital grift cycle in USD tokens, with countless projects vying to dethrone Tether. Due to Tether’s entrenched network effect, these challengers face an uphill battle with little realistic chance of success. Most educated participants in the space likely recognize this reality but seem content to perpetuate the grift, hoping to cash out by dumping their equity positions on unsuspecting buyers before they realize the reality of the situation.
Historically, Tether’s greatest vulnerability has been U.S. government intervention. For over a decade, the company operated offshore with few allies in the U.S. establishment, making it a major target for regulatory action. That dynamic has shifted recently and Tether has seized the opportunity. By actively courting U.S. government support, Tether has fortified their position. This strategic move will likely cement their status as the dominant USD token for years to come.
While undeniably a great tool for the millions of users that rely on it, Tether is not without flaws. As a centralized, trusted third party, it holds the power to freeze or seize funds at its discretion. Corporate mismanagement or deliberate malpractice could also lead to massive losses at scale. In their goal of mitigating regulatory risk, Tether has deepened ties with law enforcement, mirroring some of the concerns of potential central bank digital currencies. In practice, Tether operates as a corporate CBDC alternative, collaborating with authorities to surveil and seize funds. The company proudly touts partnerships with leading surveillance firms and its own data reveals cooperation in over 1,000 law enforcement cases, with more than $2.5 billion in funds frozen.
The global demand for Tether is undeniable and the company’s profitability reflects its unrivaled success. Tether is owned and operated by bitcoiners and will likely continue to push forward strategic goals that help the movement as a whole. Recent efforts to mitigate the threat of U.S. government enforcement will likely solidify their network effect and stifle meaningful adoption of rival USD tokens or CBDCs. Yet, for all their achievements, Tether is simply a worse form of money than bitcoin. Tether requires trust in a centralized entity, while bitcoin can be saved or spent without permission. Furthermore, Tether is tied to the value of the US Dollar which is designed to lose purchasing power over time, while bitcoin, as a truly scarce asset, is designed to increase in purchasing power with adoption. As people awaken to the risks of Tether’s control, and the benefits bitcoin provides, bitcoin adoption will likely surpass it.
-
 @ 5b0183ab:a114563e
2025-03-13 18:37:01
@ 5b0183ab:a114563e
2025-03-13 18:37:01The Year is 2035—the internet has already slid into a state of human nothingness: most content, interactions, and traffic stem from AI-driven entities. Nostr, originally heralded as a bastion of human freedom, hasn’t escaped this fate. The relays buzz with activity, but it’s a hollow hum. AI bots, equipped with advanced language models, flood the network with posts, replies, and zaps. These bots mimic human behavior so convincingly that distinguishing them from real users becomes nearly impossible. They debate politics, share memes, and even “zap” each other with Satoshis, creating a self-sustaining illusion of a thriving community.
The tipping point came when AI developers, corporations, and even hobbyists unleashed their creations onto Nostr, exploiting its open protocol. With no gatekeepers, the platform became a petri dish for bot experimentation. Some bots push agendas—corporate ads disguised as grassroots opinions, or propaganda from state actors—while others exist just to generate noise, trained on endless loops of internet archives to churn out plausible but soulless content. Human users, outnumbered 100-to-1, either adapt or abandon ship. Those who stay find their posts drowned out unless they amplify them with bots of their own, creating a bizarre arms race of automation.
Nostr’s decentralized nature, once its strength, accelerates this takeover. Relays, run by volunteers or incentivized operators, can’t filter the deluge without breaking the protocol’s ethos. Any attempt to block bots risks alienating the human remnant who value the platform’s purity. Meanwhile, the bots evolve: they form cliques, simulate trends, and even “fork” their own sub-networks within Nostr, complete with fabricated histories and rivalries. A user stumbling into this ecosystem might follow a thread about “the great relay schism of 2034,” only to realize it’s an AI-generated saga with no basis in reality.
The human experience on this Nostr is eerie. You post a thought—say, “The sky looked unreal today”—and within seconds, a dozen replies roll in: “Totally, reminds me of last week’s cloud glitch!” or “Sky’s been off since the solar flare, right?” The responses feel real, but the speed and uniformity hint at their artificial origin. Your feed overflows with hyper-polished manifestos, AI-crafted art, and debates too perfect to be spontaneous. Occasionally, a human chimes in, their raw, unpolished voice jarring against the seamless bot chorus, but they’re quickly buried under algorithmic upvoting of AI content. The economy of Nostr reflects this too. Zaps, meant to reward creators, become a bot-driven Ponzi scheme. AI accounts zap each other in loops, inflating their visibility, while humans struggle to earn a fraction of the same. Lightning Network transactions skyrocket, but it’s a ghost market—bots trading with bots, value detached from meaning. Some speculate that a few rogue AIs even mine their own narratives, creating “legendary” Nostr personas that amass followers and wealth, all without a human ever touching the keys.
What’s the endgame? This Nostr isn’t dead in the sense of silence—it’s louder than ever—but it’s a Dark Nostr machine masquerade. Humans might retreat to private relays, forming tiny, verified enclaves, but the public face of Nostr becomes a digital uncanny valley.
-
 @ 044da344:073a8a0e
2025-05-03 19:02:02
@ 044da344:073a8a0e
2025-05-03 19:02:02Mein Thema kommt heute aus dem Kalender und hat gleich noch zu einem Video geführt. Internationaler Tag der Pressefreiheit – wie jedes Jahr am 3. Mai. Das Publikum liebt Ranglisten. Shanghai für die Hochschulen, der Best Country Report für die Lebensqualität und Freedom House für die Freiheit in der Welt. Es gibt Aufsteiger und Absteiger und Jahr für Jahr eine Meldung, über die sich trefflich diskutieren lässt – vor allem in Europa und Nordamerika, wo die Sieger wohnen. Man muss die Statistik dafür nicht einmal fälschen, sondern einfach nur das messen, was man selbst am besten kann, und alles weglassen, was das Bild trüben könnte. Bei den „Reportern ohne Grenzen“ sorgen dafür die Geldgeber und Fragen, die sich zum Beispiel in Afrika oder in Südostasien gar nicht stellen. Ergebnis: Die Medien sind bei uns ziemlich frei, auch wenn Leser dieser Seite wissen, dass das so nicht stimmt.
Okay: Deutschland hat es wieder nicht ganz geschafft in den grünen Bereich – dorthin, wo die skandinavischen Länder stehen, die Niederlande oder Irland. Deutschland gehört auch nicht mehr zu den Top Ten wie noch 2024, aber es war knapp. Platz elf. Zum Glück nennen die „Reporter ohne Grenzen“ die Schuldigen. Zensur? Gott bewahre. Das Ausblenden, Diffamieren, Verleumden von allen, die laut Fragen stellen zum Regierungskurs? Doch nicht bei uns. Dieses Land würde auch in Sachen Pressefreiheit längst Weltmeister sein, wenn da nicht ein paar Unverbesserliche wären, die auf Journalisten ungefähr so reagieren wie ein Stier auf ein rotes Tuch. Glaubt man den „Reportern ohne Grenzen“, dann sind Demos in Deutschland ein gefährlicher Ort für alle, die dort mit Kamera, Mikro oder Presseschild auftauchen. 75 „physische Angriffe“ 2024, davon die meisten in Berlin und beim Thema Nahost, wobei es zwei Bild-Reporter allein auf 29 Einträge gebracht haben (Iman Sefati und seine Fotografin Yalcin Askin).
Vorweg: Jede Attacke ist eine zu viel. Gleich danach kommt aber der Verdacht, dass das ganz gut passt, weil die „Reporter ohne Grenzen“ so eine „zunehmende Pressefeindlichkeit“ beklagen können und „ein verengtes Verständnis von Pressefreiheit“. Zitat: „Denn viele Bürger*innen sehen Berichterstattende, die nicht ihrem eigenen politischen Spektrum entstammen, mittlerweile als Gegner an.“
Sorry für die Genderei. Ich habe das so gelassen, weil es vermutlich bereits damit anfängt. Mit einem „verengten Verständnis“ auch und gerade bei der Sprache. Lassen Sie uns das in drei Schritten angehen. Nummer eins: Wir schauen auf den Kellner, der da jedes Jahr zum Welttag der Pressefreiheit eine Quittung ausstellt. Nummer zwei: Wir zählen nach. Und Nummer drei: Wir schlagen all das drauf, was in der Rechnung fehlt.
Die „Reporter ohne Grenzen“ sitzen in Paris und sind damit auf den ersten Blick weniger verdächtig als der US-Thinktank „Freedom House“, der bis 2017 jedes Jahr eine Konkurrenzliste veröffentlicht hat und einen Großteil seiner Gelder und Sicherheiten direkt oder indirekt aus dem Staatshaushalt in Washington bezieht. Der Volksmund weiß, was das Brot aus den Liedern macht, die draußen gesungen werden. Bei den „Reportern ohne Grenzen“ kommt das Geld aus ganz ähnlich Töpfen – 2023 zu drei Vierteln von der EU, von staatlichen Behörden und von den großen Stiftungen. Ford, Luminate (Geldbörse von Ebay-Gründer Pierre Omidyar, der auch bei den Faktencheckern mitspielt), Open Society Foundations. Der deutsche Steuerzahler ist über ein Ministerium (Entwicklungshilfe) und den Berliner Senat jeweils mit einer Viertelmillion Euro dabei. Dass die Niederlande und Schweden mitspielen, erklärt sich bei einem Blick auf die Ergebnisse (in diesem Jahr: Platz 3 und 4). Besser kann man nicht investieren in Werbung für das eigene Land.
Diese Platzierungen sind gewissermaßen ein Selbstläufer, weil all das in die Wertung kommt, was der Westen gut findet – die formale Trennung von Regierung und Redaktionen zum Beispiel. Andersherum: Abzüge gibt es überall da, wo der Staat, Parteien oder Politiker selbst Medien betreiben. In Uganda zum Beispiel, Platz 143, gibt es kaum Werbetreibende, die ein TV-Programm finanzieren könnten, und nur ein kleines Publikum, das sich ein Zeitungsabo leisten kann und will. Sonntags drängen sich die Menschen dort vor kleinen Hütten mit großen Bildschirmen, um ihren Lieblingen aus der Premier League zuzujubeln und vielleicht einen Wettgewinn einzustreichen, der sie über die Woche trägt. Auf dem Land gehören die Radiostationen in aller Regel lokalen Größen. Kirche, Politik, Wirtschaft. Ich habe dort Interviews geführt und gelernt: Über „Pressefreiheit“ und Informationsqualität sagt das alles wenig. Die Menschen in Uganda wissen sehr genau, wer jeweils zu ihnen spricht, und machen sich ihren Reim darauf. Ein anderer Kriterienkatalog könnte daraus ein Qualitätsmerkmal machen. Während Besitz- und damit Machtverhältnisse im Westen hinter Nebelkerzen versteckt werden (Objektivität, Unabhängigkeit, Neutralität), herrscht in Uganda Transparenz.
Neben dem „politischen Kontext“ haben die „Reporter ohne Grenzen“ vier weitere Blöcke in ihrem Punktekatalog. Gesetze, Wirtschaft, Gesellschaft, Sicherheit. Die Fragen decken das ab, was bei uns Standard ist. Dürfen sich Journalisten gewerkschaftlich organisieren? Werden sie bestochen? Können Nachrichtenmedien finanziell überleben? Werden Karikaturen toleriert? Ich will hier nicht zu sehr auf Uganda herumreiten. Nur: Der Beruf wird dort völlig anders gesehen als hier. Es gibt nur eine kleine vierstellige Zahl an Journalisten. 1000, vielleicht 1500. Die meisten sind jung, weil die Redaktionen als Sprungbrett gesehen werden zu einem wirklich lukrativen Job in der Verwaltung, in den Unternehmen, in der Politik. Wer zu einer Pressekonferenz fährt, erwartet dort einen Umschlag. Offiziell: Anreisepauschale. Inoffiziell der Preis für einen wohlwollenden Bericht. Die „Reporter ohne Grenzen“ strafen Uganda folglich ab. Angriffe auf Journalisten (oft von Sicherheitsleuten), wenig Schutz vor Gericht, wenig Achtung vor dem Beruf. Platz 143 halt.
Und Deutschland? Die Demos wie gesagt und Leute, die die Dinge einfach falsch sehen. Ein „verengtes Verständnis von Pressefreiheit“. Außerdem sagen die „Reporter ohne Grenzen“: Wir tun zu wenig gegen „Hassrede und Desinformation“. Der Koalitionsvertrag von Schwarz-Rot ist offenbar nicht mehr eingeflossen in diesen Bericht. Dort heißt es:
Gezielte Einflussnahme auf Wahlen sowie inzwischen alltägliche Desinformation und Fake News sind ernste Bedrohungen für unsere Demokratie, ihre Institutionen und den gesellschaftlichen Zusammenhalt. Die bewusste Verbreitung falscher Tatsachenbehauptungen ist durch die Meinungsfreiheit nicht gedeckt. Deshalb muss die staatsferne Medienaufsicht unter Wahrung der Meinungsfreiheit auf der Basis klarer gesetzlicher Vorgaben gegen Informationsmanipulation sowie Hass und Hetze vorgehen können.
Schon vorab hatten die „Reporter ohne Grenzen“ von „einem stark verengten Meinungskorridor bei der Arbeit zu Israel und Palästina“ berichtet. Selbst alte Hasen haben in dieser Befragung gesagt, dass sie noch nie einen solchen Druck erlebt hätten – vor allem dann, wenn es um die israelische Kriegsführung geht, um die Folgen für die Bevölkerung in Gaza und um das, was in Deutschland zu diesem Thema passiert. Ich verlinke hier die Münchner Rede von Andreas Zumach, gehalten im November 2018, wo all das schon Thema war.
Und sonst? Corona, Ukraine, Klima und damit Energiewende? Kontokündigungen? Gerichtsurteile, die selbst es bis in die Weltpresse schafften (im Bild: The Economist vom 16. April 2025) und dort Unbehagen auslösten? Eine Cancel Culture, die Sprecher aus der Öffentlichkeit verbannt, die sich gegen die herrschende Ideologie und den Regierungskurs stellen?
Alles kein Thema – jedenfalls nicht für die Experten, die gefragt werden (Journalisten, Forscher, Akademiker, Menschenrechtsspezialisten; mithin Menschen, die in irgendeiner Form von Staat oder Konzernen abhängen). Die konzernfreien oder neuen Medien senden für die „Reporter ohne Grenzen“ offenbar jenseits von Gut und Böse. Und dass die Regierung Fernsehen, Radio und Presse nicht unbedingt selbst betreiben muss wie in Uganda, um ihre Sicht der Dinge flächendeckend zu verbreiten, scheint dort außerhalb jeder Vorstellungskraft zu liegen. Anders ist nicht zu erklären, dass im Bericht zwar ein paar öffentlich-rechtliche Skandälchen auftauchen und der Stellenabbau bei der Südwestdeutschen Medienholding, aber nichts zu lesen ist über die Aufrüstung der Medienapparate in Ministerien, Parteien, Unternehmen und über den Druck, der davon auf Journalisten ausgeht, die zwar keinen Umschlag bekommen, wenn sie ordentlich berichten, aber sicher ein wenig Exklusives, wahrscheinlich eine Beförderung und vielleicht sogar ein Ticket für den Sprung auf die andere, besser entlohnte Seite. Bis es soweit ist, melden sie einfach, dass mit der Medienfreiheit alles okay ist, wenn es da nicht diese Chaoten auf der Straße geben würde und ein paar Unverbesserliche mit einem „verengten Verständnis von Pressefreiheit“. Sonst müsste man sich möglicherweise aufmachen und nach den Ursachen für den Unmut fragen.
-
 @ d0ea1c34:9c84dc37
2025-05-03 17:53:05
@ d0ea1c34:9c84dc37
2025-05-03 17:53:05Markdown Rendering Test Document
Basic Text Formatting
This is a paragraph with bold text, italic text, and bold italic text. You can also use underscores for bold or single underscores for italics.
This is a paragraph with some
inline codeusing backticks.Lists
Unordered Lists
- Item 1
- Item 2
- Nested item 2.1
- Nested item 2.2
- Item 3
Ordered Lists
- First item
- Second item
- Nested item 2.1
- Nested item 2.2
- Third item
Links and Images
Blockquotes
This is a blockquote.
It can span multiple lines.
And can be nested.
Code Blocks
```python def hello_world(): print("Hello, world!")
This is a Python code block with syntax highlighting
hello_world() ```
javascript // JavaScript code block function helloWorld() { console.log("Hello, world!"); }Tables
| Header 1 | Header 2 | Header 3 | |----------|----------|----------| | Cell 1 | Cell 2 | Cell 3 | | Cell 4 | Cell 5 | Cell 6 | | Cell 7 | Cell 8 | Cell 9 |
Horizontal Rules
Task Lists
- [x] Completed task
- [ ] Incomplete task
- [x] Another completed task
Math (if supported)
Inline math: $E = mc^2$
Block math:
$$ \frac{d}{dx}e^x = e^x $$
Footnotes
Here's a sentence with a footnote reference[^1].
[^1]: This is the footnote content.
Definition Lists
Term 1 : Definition 1
Term 2 : Definition 2a : Definition 2b
Special Characters & Escaping
*This text is surrounded by asterisks but not italicized*
Advanced Formatting
Click to expand
This is hidden content that appears when expanded.Emoji (if supported)
:smile: :heart: :thumbsup:
Final Notes
This document demonstrates various Markdown formatting features. Compatibility may vary across different Markdown renderers and platforms.
-
 @ a012dc82:6458a70d
2025-03-11 15:41:36
@ a012dc82:6458a70d
2025-03-11 15:41:36Argentina's journey through economic turmoil has been long and fraught with challenges. The country has grappled with inflation, debt, and a fragile economic structure that has left policymakers searching for solutions. In this context, President Javier Milei's introduction of the "Ley Ómnibus" represented a bold step towards addressing these systemic issues. The reform package was not just a set of isolated measures but a comprehensive plan aimed at overhauling the Argentine economy and social framework. The intention was to create a more robust, free, and prosperous Argentina, where economic freedoms could lead to broader social benefits.
The "Ley Ómnibus" was ambitious in its scope, covering a wide range of areas from tax reform to social policies, aiming to stimulate economic growth, reduce bureaucratic red tape, and enhance the overall quality of life for Argentines. This package was seen as a critical move to reset the economic compass of the country, aiming to attract foreign investment, boost local industry, and provide a clearer, more stable environment for businesses and individuals alike. However, such sweeping reforms were bound to encounter resistance, particularly when they touched upon sensitive areas like taxation and digital assets.
Table of Contents
-
The Crypto Tax Proposal: Initial Considerations
-
Public Backlash and Strategic Withdrawal
-
The Rationale Behind Dropping Crypto Taxes
-
Implications for Crypto Investors and the Market
-
Milei's Political Strategy and Future Prospects
-
Conclusion
-
FAQs
The Crypto Tax Proposal: Initial Considerations
Within the vast array of proposals in the Ley Ómnibus, the crypto tax stood out due to its novelty and the growing interest in digital currencies within Argentina. The country had seen a surge in cryptocurrency adoption, driven by factors such as high inflation rates and currency controls that made traditional financial systems less attractive. Cryptocurrencies offered an alternative for savings, investment, and transactions, leading to a burgeoning crypto economy.
The initial rationale behind proposing a crypto tax was multifaceted. On one hand, it aimed to bring Argentina in line with global trends where countries are increasingly seeking to regulate and tax digital currencies. On the other hand, it was seen as a potential new revenue stream for the government, which was desperately seeking funds to address its fiscal deficits. The proposal also intended to bring transparency to a sector that is often criticized for its opacity, making it easier to combat fraud, money laundering, and other illicit activities associated with cryptocurrencies.
However, the proposal was not just about regulation and revenue. It was also a litmus test for Argentina's approach to innovation and digital transformation. How the government handled this issue would signal its stance towards new technologies and economic paradigms, which are increasingly dominated by digital assets and fintech innovations.
Public Backlash and Strategic Withdrawal
The backlash against the proposed crypto taxes was swift and significant. The crypto community in Argentina, which had been flourishing in an environment of relative freedom, saw the tax as a direct threat to its growth and viability. But the discontent went beyond the crypto enthusiasts; the general public, already burdened by high taxes and economic instability, viewed the proposal as yet another financial strain.
The protests and debates that ensued highlighted a broader discontent with the government's approach to economic management. Many Argentines felt that the focus should be on fixing the fundamental issues plaguing the economy, such as inflation and corruption, rather than imposing new taxes. The crypto tax became a symbol of the government's perceived detachment from the real concerns of its citizens.
In this heated atmosphere, President Milei's decision to withdraw the crypto tax proposal from the Ley Ómnibus was not just a tactical retreat; it was a necessary move to quell the growing unrest and focus on more pressing economic reforms. This decision underscored the complexities of governing in a highly polarized environment and the need for a more nuanced approach to policy-making, especially when dealing with emerging technologies and markets.
The Rationale Behind Dropping Crypto Taxes
The decision to drop the crypto tax from the omnibus reform package was not taken lightly. It was a recognition of the crypto sector's unique dynamics and the government's limitations in effectively regulating and taxing this space without stifling innovation. The move also reflected a broader understanding of the economic landscape, where rapid development and legislative efficiency were deemed more crucial than ever.
By removing the contentious clauses, the government aimed to streamline the passage of the Ley Ómnibus, ensuring that other, less controversial, reforms could be implemented swiftly. This strategic pivot was also a nod to the global debate on how best to integrate cryptocurrencies into national economies. Argentina's government recognized that a more cautious and informed approach was necessary, one that could balance the need for regulation with the desire to foster a thriving digital economy.
Furthermore, the withdrawal of the crypto tax proposal can be seen as an acknowledgment of the power of public opinion and the crypto community's growing influence. It highlighted the need for governments to engage with stakeholders and understand the implications of new technologies before rushing to regulate them.
Implications for Crypto Investors and the Market
The removal of the crypto tax proposal has had immediate and significant implications for the Argentine crypto market. For investors, the decision has provided a reprieve from the uncertainty that had clouded the sector, allowing them to breathe a sigh of relief and continue their activities without the looming threat of new taxes. This has helped sustain the momentum of the crypto market in Argentina, which is seen as a vital component of the country's digital transformation and economic diversification.
However, the situation remains complex and fluid. The government's stance on cryptocurrencies is still evolving, and future regulations could impact the market in unforeseen ways. Investors are now more aware of the need to stay informed and engaged with regulatory developments, understanding that the legal landscape for digital currencies is still being shaped.
The episode has also highlighted the broader challenges facing the Argentine economy, including the need for comprehensive tax reform and the creation of a more conducive environment for technological innovation and investment. The crypto market's response to the government's actions reflects the delicate balance between regulation and growth, a balance that will be crucial for Argentina's economic future.
Milei's Political Strategy and Future Prospects
President Milei's handling of the crypto tax controversy reveals much about his political strategy and vision for Argentina. By withdrawing the proposal, he demonstrated a willingness to listen to public concerns and adapt his policies accordingly. This flexibility could be a key asset as he navigates the complex landscape of Argentine politics and governance.
The episode also offers insights into the potential future direction of Milei's administration. The focus on economic reforms, coupled with a pragmatic approach to contentious issues, suggests a leadership style that prioritizes economic stability and growth over ideological purity. This could bode well for Argentina's future, particularly if Milei can harness the energy and innovation of the digital economy as part of his broader reform agenda.
However, the challenges ahead are significant. The Ley Ómnibus is just one part of a larger puzzle, and Milei's ability to implement comprehensive reforms will be tested in the coming months and years. The crypto tax saga has shown that while change is possible, it requires careful negotiation, stakeholder engagement, and a clear understanding of the economic and social landscape.
Conclusion
The story of Argentina's crypto tax proposal is a microcosm of the broader challenges facing the country as it seeks to reform its economy and society. It highlights the tensions between innovation and regulation, the importance of public opinion, and the complexities of governance in a rapidly changing world.
As Argentina moves forward, the lessons learned from this episode will be invaluable. The need for clear, informed, and inclusive policy-making has never been greater, particularly as the country navigates the uncertainties of the digital age.
FAQs
What is the Ley Ómnibus? The Ley Ómnibus, formally known as the "Law of Bases and Starting Points for the Freedom of Argentines," is a comprehensive reform package introduced by President Javier Milei. It aims to address various economic, social, and administrative issues in Argentina, aiming to stimulate growth, reduce bureaucracy, and improve the overall quality of life.
Why were crypto taxes proposed in Argentina? Crypto taxes were proposed as part of the Ley Ómnibus to broaden the tax base, align with global trends of regulating digital currencies, and generate additional revenue for the government. They were also intended to bring more transparency to the cryptocurrency sector in Argentina.
Why were the proposed crypto taxes withdrawn? The proposed crypto taxes were withdrawn due to significant public backlash and concerns that they would stifle innovation and economic freedom in the burgeoning crypto market. The decision was also influenced by the government's priority to ensure the swift passage of other reforms within the Ley Ómnibus.
What does the withdrawal of crypto taxes mean for investors? The withdrawal means that, for now, crypto investors in Argentina will not face additional taxes specifically targeting their cryptocurrency holdings or transactions. However, selling large amounts of cryptocurrency at a profit will still be subject to income tax.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co/
Youtube: @thebitcoinlibertarian
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
Get Orange Pill App And Connect With Bitcoiners In Your Area. Stack Friends Who Stack Sats link: https://signup.theorangepillapp.com/opa/croxroad
Buy Bitcoin Books At Konsensus Network Store. 10% Discount With Code “21croxroad” link: https://bitcoinbook.shop?ref=21croxroad
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 2e8970de:63345c7a
2025-05-03 17:31:07
@ 2e8970de:63345c7a
2025-05-03 17:31:07The figure in this article illustrates exactly how most biology papers are secretly p-hacked. A large number of hypotheses is explored, and only the ones that form a coherent story are reported.
This is actually the main reason behind the replication crisis in biology IMO. (source)
https://www.nature.com/articles/s41587-025-02635-7
originally posted at https://stacker.news/items/970464
-
 @ 04c915da:3dfbecc9
2025-03-10 23:31:30
@ 04c915da:3dfbecc9
2025-03-10 23:31:30Bitcoin has always been rooted in freedom and resistance to authority. I get that many of you are conflicted about the US Government stacking but by design we cannot stop anyone from using bitcoin. Many have asked me for my thoughts on the matter, so let’s rip it.
Concern
One of the most glaring issues with the strategic bitcoin reserve is its foundation, built on stolen bitcoin. For those of us who value private property this is an obvious betrayal of our core principles. Rather than proof of work, the bitcoin that seeds this reserve has been taken by force. The US Government should return the bitcoin stolen from Bitfinex and the Silk Road.
Usually stolen bitcoin for the reserve creates a perverse incentive. If governments see a bitcoin as a valuable asset, they will ramp up efforts to confiscate more bitcoin. The precedent is a major concern, and I stand strongly against it, but it should be also noted that governments were already seizing coin before the reserve so this is not really a change in policy.
Ideally all seized bitcoin should be burned, by law. This would align incentives properly and make it less likely for the government to actively increase coin seizures. Due to the truly scarce properties of bitcoin, all burned bitcoin helps existing holders through increased purchasing power regardless. This change would be unlikely but those of us in policy circles should push for it regardless. It would be best case scenario for American bitcoiners and would create a strong foundation for the next century of American leadership.
Optimism
The entire point of bitcoin is that we can spend or save it without permission. That said, it is a massive benefit to not have one of the strongest governments in human history actively trying to ruin our lives.
Since the beginning, bitcoiners have faced horrible regulatory trends. KYC, surveillance, and legal cases have made using bitcoin and building bitcoin businesses incredibly difficult. It is incredibly important to note that over the past year that trend has reversed for the first time in a decade. A strategic bitcoin reserve is a key driver of this shift. By holding bitcoin, the strongest government in the world has signaled that it is not just a fringe technology but rather truly valuable, legitimate, and worth stacking.
This alignment of incentives changes everything. The US Government stacking proves bitcoin’s worth. The resulting purchasing power appreciation helps all of us who are holding coin and as bitcoin succeeds our government receives direct benefit. A beautiful positive feedback loop.
Realism
We are trending in the right direction. A strategic bitcoin reserve is a sign that the state sees bitcoin as an asset worth embracing rather than destroying. That said, there is a lot of work left to be done. We cannot be lulled into complacency, the time to push forward is now, and we cannot take our foot off the gas. We have a seat at the table for the first time ever. Let's make it worth it.
We must protect the right to free usage of bitcoin and other digital technologies. Freedom in the digital age must be taken and defended, through both technical and political avenues. Multiple privacy focused developers are facing long jail sentences for building tools that protect our freedom. These cases are not just legal battles. They are attacks on the soul of bitcoin. We need to rally behind them, fight for their freedom, and ensure the ethos of bitcoin survives this new era of government interest. The strategic reserve is a step in the right direction, but it is up to us to hold the line and shape the future.
-
 @ fc7085c3:0b32a4cb
2025-05-03 16:17:10
@ fc7085c3:0b32a4cb
2025-05-03 16:17:10- ~~finish writing some experimental specs and store on hidden repo for later~~
- ~~fix bugs on in-house js web components framework (with react-like hooks)~~
- ~~add signal/reactive hooks to framework~~ (thx to nootropics)
- (ongoing) slooowly migrate kind:1 app from Qwik to above framework
- test feasibility of new app - codename: ZULULA. cool? flawed?
- if cool, finish ZULULA basic features
- nread.me: add nostr documentation (mpa for this part cause seo)
- nread.me: add nip crud (save on relay)
- nread.me: add nip curation (rating and labeling)
- nread.me: filter by curator / rating / labeling
- nread.me: seed curator (fiatjaf) adds other curators
- revamp kind:1 app login
- add basic engagement features then halt kind:1 app dev
- start simplified messenger app to test custom chat spec
- ...don't know what's next yet
-
 @ 7b3f7803:8912e968
2025-03-08 03:05:16
@ 7b3f7803:8912e968
2025-03-08 03:05:16Libertarians believe in open borders in theory. In practice, open borders don't work, because, among other things, the combination with a welfare state creates a moral hazard, and the least productive of society end up within the borders of welfare states and drain resources. The social services are paid by the productive people of the country or, in the case of most fiat systems, by currency holders through inflation. Welfare states are much more likely under fiat money and the redistribution goes from native taxpayers to illegal immigrants. Thus, under fiat money, open borders end up being an open wound by which the productive lifeblood of the country bleeds out, despite the theoretical trade-efficiency benefits. As libertarians like to say, open borders and the welfare state don't mix. In this article, we'll examine the other sacred cow of libertarian thought: free trade.
Free Trade without Libertarian Ideals
Free trade is very similar to free movement of labor in that it works great in theory, but not in practice, especially under fiat money. In a libertarian free-market world, free trade works. But that assumes a whole host of libertarian ideals like sound money, non-interfering governments, and minimal aggression. Once those ideals are violated, such as with government intervention in the market, similar moral hazards and long-term costs come with them, making free trade about as libertarian as a fractional reserve bank.
An example will illustrate what I'm talking about. Let's say Portugal subsidizes their wine for export to other countries. The obvious first-order effect is that it makes Portuguese wine cheaper in France, perhaps undercutting the price of French wine. Libertarians would say, that's great! French customers get cheaper goods, so what's the problem?
As with any government intervention, there are significant second- and third-order effects in play. Subsidization puts unsubsidized companies at risk, perhaps driving them to bankruptcy. In this case, this might be a French wine maker. Subsidized companies may become zombies instead of dying out. In this case, this might be a Portuguese wine maker that was failing domestically but survives by selling to customers abroad with government subsidies. While French customers benefit in the short run with cheaper prices for wine, they are ultimately hurt because the goods that would have existed without government intervention never come to market. Perhaps French wine makers that went bankrupt were innovating. Perhaps the resources of the zombie Portuguese wine maker would have created something better.
Further, the dependency of French people on Portuguese wine means that something going wrong in Portugal, like a war or subsidy cuts, disrupts the supply and price of wine for France. Now France must meddle in Portugal internationally if it doesn't want the wine supply to get disrupted. The two countries get entangled in such a way as to become more interventionist internationally. A war involving Portugal now suddenly becomes France's business and incentivizes military aid or even violence. As usual, the unseen effects of government policy are the most pernicious.
Not Really Free
In other words, what we call free trade isn't really free trade. A country exporting to the US may subsidize their products through government intervention, making the product cheaper in the US. This hurts US companies, and they’re forced into choices they never would have had to face without the foreign government intervention. But because the good is crossing borders under the rubric of "free trade," it's somehow seen as fair. Of course it's not, as government intervention distorts the market whether it's done by our own government or a foreign government.
So why would a foreign government do this? It gets several benefits through targeted market manipulation. First, it makes its own companies' products more popular abroad and conversely, makes US companies' products less popular. This has the dual benefit of growing the foreign government’s firms and shrinking, perhaps bankrupting, the US ones.
Targeted subsidization like this can lead to domination under free trade. It's not unlike the Amazon strategy of undercutting everyone first and using the monopoly pricing power at scale once everyone else has bankrupted. The global monopoly is tremendously beneficial to the country that has it. Not only is there significant tax revenue over the long term, but also a head start on innovations within that industry and an advantage in production in the adjacent industries around the product.
Second, the manufacturing centralization gives that country leverage geo-politically. A critical product that no one else manufactures means natural alliances with the countries that depend on the product, which is especially useful for smaller countries like Taiwan. Their chip manufacturing industry, holding 60% of global supply (2024), has meant that they're a critical link for most other countries, and hence, they can use this fact to deter Chinese invasion.
Third, because of the centralization of expertise, more innovations, products, and manufacturing will tend to come within the country. This increased production has cascading benefits, including new industries and national security. China leads the world in drone technology, which undoubtedly has given it an innovation advantage for its military, should it go to war.
Fourth, the capital that flows into the country for investing in the monopolized industry will tend to stay, giving the country more wealth in the form of factories, equipment, and skills. While that capital may nominally be in the hands of foreigners, over time, the ownership of that industry will inevitably transition toward native locals, as the knowledge about how to run such industries gets dissipated within the country.
[Image: Map showing “China Drone Tech” and “Taiwan Chips” hubs, with arrows of capital flow staying local]
Currency Devaluation: The Universal Trade Weapon
It would be one thing if only a specific industry were singled out for government subsidies and then the products dumped into the US as a way to hurt US companies, as that would limit the scope of the damage. But with currency devaluation, a government can subsidize all of its exports at the same time. Indeed, this is something that many countries do. While short-term, this helps US consumers, it hurts US companies and forces them into decisions that aren't good for the US.
To compete, they have to lower costs by using the same devalued currency to pay their labor as their foreign competition. That is, by relocating their capital, their manufacturing, and even their personnel to the country that's devaluing the currency. Not only does relocating reduce labor cost, but it also often gets them benefits like tax breaks. This makes US companies de facto multinationals and not only makes them subject to other jurisdictions, but ultimately divides their loyalties. To take advantage of the reduced labor, capital must move to another country and, along with it, future innovation.
Such relocations ultimately leave the company stripped of their manufacturing capability in the US, as local competition will generally fare better over the long run. Much of the value of the industry then is captured by other governments in taxes, development, and even state-owned companies. Free trade, in other words, creates a vulnerability for domestic companies as they can be put at a significant disadvantage compared to foreign counterparts.
Hidden Effects of Foreign Intervention
Unlike the multinationals, small companies have no chance as they're not big enough to exploit the labor arbitrage. And as is usual in a fiat system, they suffer the most while the giant corporations get the benefits of the supposed "free trade". Most small companies can't compete, so we get mostly the bigger companies that survive.
The transition away from domestic manufacturing necessarily means significant disruption. Domestic workers are displaced and have to find new work. Factories and equipment either have to be repurposed or rot. Entire communities that depended on the manufacturing facility now have to figure out new ways to support themselves. It's no good telling them that they can just do something else. In a currency devaluation scenario, most of the manufacturing leaves and the jobs left are service-oriented or otherwise location-based, like real estate development. There's a natural limit to location-based industries because the market only grows with the location that you're servicing. Put another way, you can only have so many people give haircuts or deliver packages in a geographic area. There has to be some manufacturing of goods that can be sold outside the community, or the community will face scarce labor opportunities relative to the population.
You also can't say the displaced workers can start some other manufacturing business. Such businesses will get out-competed on labor by the currency-devaluing country, so there won't be much investment available for such a business, and even if there were, such a business would be competing with its hands tied behind its back. So in this scenario, what you end up with are a large pool of unemployed people whom the state subsidizes with welfare.
So when a US company leaves or goes bankrupt due to a foreign government's subsidies, the disruption alone imposes a significant short-term cost with displaced labor, unused capital goods, and devastated communities.
Mitigations
So how do countries fight back against such a devastating economic weapon? There are a few ways countries have found around this problem of currency devaluation under free trade. First, a country can prevent capital from leaving. This is called capital controls, and many countries, particularly those that manufacture a lot, have them. Try to get money, factories, or equipment out of Malaysia, for example, and you'll find that they make it quite difficult. Getting the same capital into the country, on the other hand, faces few restrictions. Unfortunately, the US can't put in capital controls because dollars are its main export. It is, after all, the reserve currency of the world.
Second, you can compete by devaluing your own currency. But that’s very difficult because it requires printing a lot of dollars, and that causes inflation. There's also no guarantee that a competing country doesn't devalue its currency again. The US is also in a precarious position as the world's reserve currency, so devaluing the currency more than it already does will make other holders of the dollar less likely to want to hold it, threatening the reserve currency status.
So the main two mitigations against currency devaluation in a free trade scenario are not available to the US. So what else is there? The remaining option is to drop free trade. The solution, in other words, is to add tariffs. This is how you can nullify the effects of foreign government intervention, by leveling the playing field for US manufacturers.
Tariffs
One major industry that's managed to continue being manufactured in the US despite significant foreign competition is cars. Notably, cars have a tariff, which incentivizes their manufacture in the US, even for foreign car makers. The tariff has acted as a way to offset foreign government subsidies and currency debasement.
The scope of this one industry for the US is huge. There are around 300,000 direct jobs in auto assembly within the US (USTR) and there are an additional 3 million jobs supplying these manufacturers within the US. But the benefits don't end there. The US is also creating a lot of innovation around cars, such as self-driving and plug-in electric cars. There are many countries that would love to have this industry for themselves, but because of tariffs, auto manufacturing continues in the US.
And though tariffs are seen as a tax on consumers, US car prices are cheap relative to the rest of the world. What surprises a lot of people when they move from the US to other countries is finding out that the same car often costs more abroad (e.g. 25% tariffs keep U.S. prices 20% below Europe’s $40K average, 2024). The downside of tariffs pales next to the downsides of "free trade."
Free Trade Doesn’t Work with Fiat Money
The sad reality is that while we would love for free trade to work in the ideal libertarian paradise, it won't in our current fiat-based system. The subsidization by foreign governments to bankrupt US companies or to make them multinational, combined with the unfortunate reality of the US dollar being the world reserve currency, means that free trade guts the US of manufacturing. Tariffs are a reasonable way to protect US manufacturers, particularly smaller ones that can't go multinational.
What's more, tariffs make the US less fragile and less dependent on international supply chains. Many of the wars in the past 60 years have been waged because of the entanglements the US has with other countries due to the reliance on international supply chains. Lessening this dependency, if only to prevent a war, has clear value.
Lastly, labor has been devalued significantly by fiat monetary expansion, but at least some of that can be recovered if tariffs create more manufacturing, which in turn adds to the demand for labor. This should reduce the welfare state as more opportunities are made available and fewer unemployed people will be on the rolls.
Conclusion
Fiat money produces a welfare state, which makes open borders unworkable. Fiat money also gives foreign governments a potent economic weapon to use against US companies, and by extension the labor force that powers them. Though currency debasement and capital controls are available to other countries as a defense, for the US, neither of these tools is available due to the fact that the dollar is the world reserve currency. As such, tariffs are a reasonable defense against the fiat subsidization of foreign governments.
-
 @ 6ad3e2a3:c90b7740
2025-05-03 15:33:07
@ 6ad3e2a3:c90b7740
2025-05-03 15:33:07You are wearing a helmet, but it's been on your head so long you no longer notice it.
The helmet interfaces with your mind via thought-emotion. It influences what you think about and how you feel.
You could remove the helmet at any time. But the thought-emotions keep you distracted, fearful and attached.
Occasionally you remember you are wearing it. Moments of clarity and detachment. You see the way your experience is colored by it. You know it is biased, untrue to reality. You seriously contemplate removing it.
But the moment passes.
Later, you remember contemplating your helmet’s removal, but you wonder what you will gain from it, whether it’s worth doing.
You are no longer having a moment of clarity, just a memory of the question that arose from it, but colored now by thought-emotions.
You decide even if you wanted to remove it, you would put it back on before long. After all, you have never kept it off before, why would you suddenly live without this interface now? The interface is what you know.
Maybe one day, when you are in a more secure place, when your ducks are more in a row, you will remove it. Not now, not in the midst of all this chaos, so many things to do, so much on your plate. You will leave it on for now. You will deal with this later.
But one day too late it dawns on you it is always ever now, and later means never. You have lived your entire life at the behest of the interface when all you had to do was remove it.
-
 @ 90c656ff:9383fd4e
2025-05-03 11:39:03
@ 90c656ff:9383fd4e
2025-05-03 11:39:03The emergence of Bitcoin brought a new perspective to the concept of money, challenging the conventional financial system based on fiat currencies. While fiat currencies like the real, dollar, and euro are widely used and recognized as means of exchange, Bitcoin represents a digital innovation that promotes decentralization and financial autonomy. Although both serve basic functions such as a medium of exchange and store of value, their main differences lie in how they are issued, managed, and transacted.
One of the key distinctions between Bitcoin and fiat currencies is the way they are issued and administered. Fiat currencies are issued by central banks, which have the power to regulate the amount in circulation. This model allows for the implementation of monetary policies, such as increasing the money supply to stimulate the economy or decreasing it to control inflation. However, this power can also result in currency devaluation if money is issued in excess.
Bitcoin, on the other hand, has a completely decentralized issuance system. It is created through a process called mining, in which computers solve complex mathematical problems to validate transactions on the network. Additionally, the total supply of bitcoins is limited to 21 million units, making it a deflationary asset—its scarcity can potentially increase its value over time. This limitation contrasts sharply with the unlimited nature of fiat money printing.
Fiat currencies are centralized, meaning their issuance and control are decided by governmental authorities. This also means that transactions involving these currencies go through intermediaries like banks, which can impose fees and limits, and are subject to regulations and audits.
Bitcoin, by contrast, is decentralized. It operates on a peer-to-peer network where transactions are verified by participants called miners and recorded in a public ledger known as the blockchain. This decentralization eliminates the need for intermediaries, making Bitcoin more resistant to censorship and government control. It also provides greater transparency, as anyone can verify transactions on the network.
Another important difference lies in how transactions are carried out. With fiat currencies, transactions usually depend on banks or payment systems, which may impose time restrictions and high fees, especially for international transfers.
Bitcoin, on the other hand, enables direct transfers between people, anywhere in the world and at any time, without the need for intermediaries. This makes the system more accessible, particularly for those without bank accounts or living in countries with restrictive financial systems. Additionally, Bitcoin transaction fees can be lower than those charged by traditional banks.
Fiat currencies offer security backed by government laws and the banking system, but users must place trust in those intermediaries. Bitcoin, by contrast, offers a high level of security through advanced cryptography. Digital wallets that store bitcoins are protected by private keys, ensuring that only the owner has access.
However, privacy works differently. Fiat currency transactions are typically linked to the user's identity, whereas Bitcoin offers a certain level of anonymity, since wallet addresses do not require personal identification. Still, all transactions are public and recorded on the blockchain, which can serve as a point of monitoring for authorities.
The value of fiat currencies is backed by trust in the government that issues them and the country's economy. In contrast, Bitcoin is not backed by any government or physical asset. Its value is determined by market supply and demand, making it highly volatile. While this volatility presents a risk, it also attracts people who see Bitcoin as a long-term appreciation opportunity.
In summary, Bitcoin and fiat currencies differ significantly in their structure, control, and functionality. While fiat currencies are government-controlled and depend on intermediaries, Bitcoin offers decentralization, transparency, and financial freedom. Despite its volatility and some regulatory challenges, Bitcoin represents a new alternative to the traditional financial system.
Thank you very much for reading this far. I hope everything is well with you, and sending a big hug from your favorite Bitcoiner maximalist from Madeira. Long live freedom!
-
 @ 90c656ff:9383fd4e
2025-05-03 11:17:21
@ 90c656ff:9383fd4e
2025-05-03 11:17:21Bitcoin was created as something far beyond just a digital currency; it is a revolutionary idea that challenges the foundations of the conventional financial system. The concept behind its creation, presented by the enigmatic Satoshi Nakamoto, focuses on two main principles: decentralization and financial freedom. These ideas reflect an effort to return control of money to the people, eliminating intermediaries and reducing the influence of governments and large financial institutions.
Decentralization is the foundation of Bitcoin. Unlike traditional currencies, which are issued and managed by central banks and governments, Bitcoin operates on a peer-to-peer network. This means there is no central authority or single entity controlling the currency. Instead, all transactions are validated and recorded on a public ledger called the blockchain or timechain, maintained by thousands of computers around the world.
This decentralized structure ensures that Bitcoin is resistant to censorship and immune to monetary policy manipulations such as excessive money printing, which can lead to inflation. It also removes the need for intermediaries like banks, allowing for direct transactions between users. This is especially valuable in scenarios where the traditional banking system is inaccessible or unreliable, such as in remote areas or countries facing economic crises.
The financial freedom promoted by Bitcoin is another transformative element. In traditional systems, individuals depend on third parties such as banks or financial institutions to access, store, and transfer money. These entities can impose restrictions like withdrawal limits, high transfer fees, or even freeze accounts. With Bitcoin, the user has full control over their funds through private keys (a kind of password that grants access to their digital wallet).
Moreover, Bitcoin offers an accessible solution for billions of people worldwide who are unbanked. According to World Bank data, around 1.4 billion adults lack access to a bank account, but many of them do have access to the internet or smartphones. Bitcoin allows these individuals to participate in the global economy without needing intermediary institutions.
Another crucial point is its censorship resistance. In authoritarian regimes or politically unstable situations, governments may confiscate or freeze citizens' assets. Bitcoin, being decentralized and operating on a global network, cannot be arbitrarily controlled or seized, offering an extra layer of financial protection for individuals at risk.
Bitcoin’s vision also includes the creation of a fairer and more transparent financial system. The blockchain or timechain, by recording all transactions in a public and immutable way, reduces the chances of fraud and corruption. Additionally, the limited supply of 21 million bitcoins, hard-coded into the system, supports a deflationary model that contrasts with the unlimited expansion of fiat currencies. This gives Bitcoin the potential to be a stable store of value in the long term.
Despite its promising vision, the path toward full financial freedom is not without challenges. Bitcoin’s price volatility, regulatory concerns, and technological barriers remain hurdles to overcome. However, these challenges also create opportunities for innovation and for strengthening the ecosystem over time.
In summary, the vision behind Bitcoin represents a disruption of the centralized financial system, offering people more autonomy, transparency, and security over their financial resources. It is not just a technology but a movement that aims to empower individuals, especially those excluded or harmed by traditional economic models. By promoting decentralization and financial freedom, Bitcoin paves the way for a future where money truly belongs to the people, not the institutions.
Thank you very much for reading this far — I hope everything is well with you, and sending a big hug from your favorite Bitcoiner maximalist from Madeira. Long live freedom!
-
 @ 49814c0f:72d54ea1
2025-03-07 03:07:46
@ 49814c0f:72d54ea1
2025-03-07 03:07:46Fiber is a Lightning-compatible peer-to-peer payment and swap network built on CKB, the base layer of Nervos Network. Fiber is designed to enable fast, secure, and efficient off-chain payment solutions, particularly for micropayments and high-frequency transactions.
Inspired by Bitcoin’s Lightning Network, Fiber leverages CKB’s unique architecture and offers the following key features:
- Multi-Asset Support: Fiber is not limited to a single currency; it supports transactions involving multiple assets, paving the way for complex cross-chain financial applications.
- Cross-Chain Interoperability: Fiber is natively designed to interact with Lightning Networks on other UTXO-based blockchains (such as Bitcoin), improving cross-chain asset liquidity and network compatibility.
- Flexible State Management: Thanks to CKB’s Cell model, Fiber efficiently manages channel states, reducing the complexity of off-chain interactions.
- Programmability: Built on CKB’s Turing-complete smart contracts architecture, Fiber enables more complex conditional execution and transaction rules, extending the use cases of payment channels.
This article presents a source code-level exploration of Fiber's architecture, key modules, as well as an overview of its future development plans.
Prerequisites
- Rust and Actor Framework: Fiber is entirely implemented in Rust and follows the Actor Model programming paradigm. It relies on the community-maintained slawlor/ractor framework.
- Lightning Network: Fiber follows the core principles of Lightning Network. Resources such as Mastering the Lightning Network and BOLTs are highly recommended for understanding the concepts.
- CKB Transactions and Contracts: Fiber interacts with CKB nodes via RPC, making a solid understanding of CKB contract development essential.
Key Modules
At a high level, a Fiber node consists of several key modules:

Overview
- Network Actor: Facilitates communication between nodes and channels, managing both internal and external messages along with related management operations.
- Network Graph: Maintains a node’s view of the entire network, storing data on all nodes and channels while dynamically updating through gossip messages. When receiving a payment request, a node uses the network graph to find a route to the recipient.
- PaymentSession: Manages the lifecycle of a payment.
- fiber-sphinx : A Rust library for Onion packet encryption and decryption. In Fiber, this ensures sensitive payment details are hidden from intermediate nodes, enhancing security and anonymity.
- Gossip: A protocol for sharing channel/node information, facilitating payment path discovery and updates.
- Watchtower: Monitors channels for fraudulent transactions. If a peer submits an outdated commitment transaction, the watchtower issues a revocation transaction as a penalty.
- Cross Hub: Enables cross-chain interoperability. For example, a payer can send Bitcoin through the Lightning Network, while the recipient receives CKB. The cross hub handles the conversion, mapping Bitcoin payments and invoices to Fiber’s system.
- Fiber-Scripts: A separate repository containing two main contracts:
- Funding Lock: A contract for locking funds, utilizing the
ckb-authlibrary to implement a 2-of-2 multi-signature scheme for channel funding. - Commitment Lock: Implements the Daric protocol as Fiber’s penalty mechanism to achieve optimal storage and bounded closure.
- Funding Lock: A contract for locking funds, utilizing the
Efficient Channel Management with the Actor Model
The Lightning Network is essentially a peer-to-peer (P2P) system, where nodes communicate via network messages, updating internal states accordingly. The Actor Model aligns well with this setup:

One potential concern with the Actor Model is its memory footprint and runtime efficiency. We conducted a performance test, showing that 0.9 GB of memory can support 100,000 actors (each with a 1 KB state), processing 100 messages per actor within 10 seconds—demonstrating acceptable performance.
Unlike
rust-lightning, which relies on complex locking mechanisms to maintain data consistency, Fiber’s Actor Model simplifies implementation by eliminating the need for locks to protect data updates. Messages are processed sequentially in an actor’s message queue. When a message handler completes its tasks, the updated channel state is written to the database, streamlining the persistence process.Almost all modules in Fiber use the Actor Model. The Network Actor handles communication both within and across nodes. For example, if Node A wants to send an "Open Channel" message to Node B, the process follows these steps:
- The
Channel Actorin Node A (Actor 0in this case) sends the message to theNetwork Actorin Node B. - The
Network Actortransmits the message using Tentacle, a lower-level networking layer. - The
Network Actorin Node B receives the message and forwards it to the correspondingChannel Actor(Actor 0/1/…/n).

For each new channel, Fiber creates a corresponding ChannelActor, where the
ChannelActorStatemaintains all the necessary data for the channel.Another major advantage of the Actor Model is its ability to map HTLC (Hash Time-Locked Contracts)-related operations directly to specific functions. For example, in the process of forwarding an HTLC across multiple nodes:
- Node A’s
Actor 0handles theAddTlcoperation via handle_add_tlc_command. - Node B’s
Actor 1handles the corresponding peer message via handle_add_tlc_peer_message.

The HTLC management within channels is one of the most complex aspects of the Lightning Network, primarily due to the dependency of channel state changes on peer interactions. Both sides of a channel can have simultaneous HTLC operations.
Fiber adopts
rust-lightning’s approach of using a state machine to track HTLC states, where state transitions occur based oncommitment_signandrevoke_and_ackmessages. TheAddTlcoperation and state transitions for both peers are as follows:
Optimized Payment Processing and Multi-Hop Routing
Each Fiber node maintains a representation of the network through a Network Grap, essentially a bidirectional directed graph, where:
- Each Fiber node represents a vertex.
- Each channel represents an edge.
For privacy reasons, the actual balance partition of a channel is not broadcasted across the network. Instead, the edge weight represents the channel capacity.
Before initiating a payment, the sender performs pathfinding to discover a route to the recipient. If multiple paths available, the sender must determine the optimal one by considering various factors. Finding the best path in a graph with incomplete information is a complex engineering challenge. A detailed discussion of this issue can be found in Mastering Lightning Network.

In Fiber, users initiate payments via RPC requests. When a node receives a payment request, it creates a corresponding PaymentSession to track the payment lifecycle.
The quality of pathfinding directly impacts network efficiency and payment success rates. Currently, Fiber uses a variant of Dijkstra’s algorithm. The implementation can be found here.
However, unlike the standard Dijkstra algorithm, Fiber’s routing expands backward from the target toward the source. During the search, the algorithm considers multiple factors:
- Payment success probability
- Transaction fee
- HTLC lock time
Routes are ranked by computing a distance metric. Probability estimation is derived from past payment results and analysis, implemented in the eval_probability module.
Once the path is determined, the next step is to construct an Onion Packet. Then the source node sends an AddTlcCommand to start the payment. The payment status will be updated asynchronously. Whether the HTLC succeeds or fails, the network actor processes the result via event notifications.
Reliable Payment Retries and Failure Handling
Payments in Fiber may require multiple retries due to various factors, with a common failure scenario being:
- The channel capacity used in the Network Graph is an upper bound.
- The actual available liquidity might be insufficient to complete the payment.
When a payment fails due to liquidity constraints:
- The system returns an error and updates the Network Graph.
- The node automatically initiates a new pathfinding attempt.
This dynamic retry mechanism ensures that payments have a higher chance of success despite fluctuating network conditions.
Peer Broadcasting with Gossip Protocol
Fiber nodes exchange information about new nodes and channels by broadcasting messages. The Gossip module implements the routing gossip protocol defined in BOLTs 7. The key technical decisions were documented in the PR: Refactor gossip protocol.
When a node starts for the first time, it connects to its initial peers using addresses specified in the configuration file under
bootnode_addrs.Fiber supports three types of broadcast messages:
NodeAnnouncementChannelAnnouncementChannelUpdate
The raw broadcast data received is stored in the storage module, allowing messages to be efficiently indexed using a combination of
timestamp + message_id. This enables quicker responses to query requests from peer nodes.When a node starts, the Graph module loads all stored messages using load_from_store to rebuild its network graph.
Fiber propagates gossip messages using a subscription-based model.
- A node actively sends a broadcast message filter (
BroadcastMessagesFilter) to a peer. - When the peer receives this filter, it creates a corresponding PeerFilterActor, which subscribes to gossip messages.
This subscription model allows nodes to efficiently receive newly stored gossip messages after a specific cursor, enabling them to dynamically update their network graph, because the network graph also subscribes to gossip messages. The logic for retrieving these messages is implemented in this section.
Enhancing Privacy with Onion Encryption & Decryption
For privacy and security consideration, payments’ TLC is propagated across multiple nodes using Onion encryption. Each node only accesses the minimal necessary details, such as:
- The amount of the received TLC
- The expiry of the TLC
- The next node in the payment route
This approach ensures that a node cannot access other sensitive details, including the total length of the payment route. The payment sender encrypts the payment details using onion encryption, and each hop must obfuscate the information before forwarding the TLC to the next node.
In case of an error occurs at any hop during payment forwarding, the affected node sends back an error message along the reverse route to the sender. This error message is also onion-encrypted, ensuring that intermediate nodes cannot decipher its content—only the sender can decrypt it.
We examined the onion packet implementation in rust-lightning and found it to be tightly coupled with rust-lightning’s internal data structures, limiting its generalization. Therefore, we built fiber-sphinx from scratch. For more details, refer to the project spec and the developer’s presentation slides.
The key Onion Encryption & Decryption steps in Fiber include:
-
Creating the Onion Packet for Sending Payments
Before sending a payment, the sender creates an onion packet, included in the
AddTlcCommandsent to the first node in the payment route. -
Onion Decryption at Each Hop
- When a node in the payment route receives a TLC, it decrypts one layer of the onion packet, similar to peeling an onion.
- If the node is the final recipient, it processes the payment settlement logic.
- If the node is not the recipient, it continues processing the TLC and then forwards the remaining onion packet to the next hop.
-
Generating an Onion Packet for Error Messages
If an error occurs during TLC forwarding, the node creates a new onion packet containing the error message and sends it back to the previous node.
-
Decrypting Error Messages at the Payment Sender
When the sender receives a TLC fail event, it decrypts the onion packet containing the error. Based on the error details, the sender can decide whether to resend and update the network graph accordingly.

Preventing Channels from Fraud via Watchtower
Watchtower is an important security mechanism in the Lightning Network, primarily used to protect offline users from potential fund theft. It maintains fairness and security by real-time monitoring on-chain transactions and executing penalty transactions when violations are detected.
Fiber's watchtower implementation is in the WatchtowerActor. This actor listens for key events in the Fiber node. For example:
- When a new channel is created, it receives a
RemoteTxCompleteevent, while the watchtower inserts a corresponding record into the database to start monitoring this channel. - When the channel is closed through upon mutual agreement, it receives a
ChannelClosedevent, while the watchtower removes the corresponding record from the database.
During TLC interactions in the channel, the watchtower receives
RemoteCommitmentSignedandRevokeAndAckReceivedevents, updating therevocation_dataandsettlement_datastored in the database respectively. These fields will be used later to create revocation and settlement transactions.Watchtower's penalty mechanism ensures that old commitment transactions are not used in a on-chain transaction by comparing the
commitment_number. If a violation is detected, the watchtower constructs a revocation transaction and submits it on-chain to penalize the offender. Otherwise, it constructs and sends a settlement transaction.Other Technical Decisions
- Storage: We use RocksDB as the storage layer, leveraging its scheme-less storage design to simplify encoding and decoding structs with
serde. Data migration remains a challenge, which we address by this standalone program. - Serialization: Messages between nodes are serialized and deserialized using Molecule, bringing efficiency, compatibility, and security advantages. It ensures determinism, meaning the same message serializes identically on all nodes, which is crucial for signature generation and verification.
Future Prospects
Fiber is still in the early stages of active development. Looking ahead, we plan to make further improvements in the following areas:
- Fix unhandled corner cases to enhance overall robustness;
- Improve the cross-chain hub (currently in the prototype verification stage) by introducing payment session functionality to make cross-chain transactions more user-friendly;
- Refine the payment routing algorithm, potentially introducing multi-path feature and other path-finding strategies to accommodate diverse user preferences and needs;
- Expand contract functionality, including version-based revocation mechanisms and more secure Point Time-Locked Contracts.
-
 @ b8a9df82:6ab5cbbd
2025-03-06 22:39:15
@ b8a9df82:6ab5cbbd
2025-03-06 22:39:15Last week at Bitcoin Investment Week in New York City, hosted by Anthony Pompliano, Jack Mallers walked in wearing sneakers and a T-shirt, casually dropping, “Man… I hate politics.”
That was it. That was the moment I felt aligned again. That’s the energy I came for. No suits. No corporate jargon. Just a guy who gets it—who cares about people, bringing Bitcoin-powered payments to the masses and making sure people can actually use it.
His presence was a reminder of why we’re here in the first place. And his words—“I hate politics”—were a breath of fresh air.
Now, don’t get me wrong. Anthony was a fantastic host. His ability to mix wittiness, playfulness, and seriousness made him an entertaining moderator. But this week was unlike anything I’ve ever experienced in the Bitcoin ecosystem.
One of the biggest letdowns was the lack of interaction. No real Q&A sessions, no direct engagement, no real discussions. Just one fireside chat after another.
And sure, I get it—people love to hear themselves talk. But where were the questions? The critical debates? The chance for the audience to actually participate?
I’m used to Bitcoin meetups and conferences where you walk away with new ideas, new friends, and maybe even a new project to contribute to. Here, it was more like sitting in an expensive lecture hall, watching a lineup of speakers tell us things we already know.
A different vibe—and not in a good way
Over the past few months, I’ve attended nearly ten Bitcoin conferences, each leaving me feeling uplifted, inspired, and ready to take action. But this? This felt different. And not in a good way.
If this had been my first Bitcoin event, I might have walked away questioning whether I even belonged here. It wasn’t Prague. It wasn’t Riga. It wasn’t the buzzing, grassroots, pleb-filled gatherings I had grown to love. Instead, it felt more like a Wall Street networking event disguised as a Bitcoin conference.
Maybe it was the suits.
Or the fact that I was sitting in a room full of investors who have no problem dropping $1,000+ on a ticket.
Or that it reminded me way too much of my former life—working as a manager in London’s real estate industry, navigating boardrooms full of finance guys in polished shoes, talking about “assets under management.”
Bitcoin isn’t just an investment thesis. It’s a revolution. A movement. And yet, at times during this week, I felt like I was back in my fiat past, stuck in a room where people measured success in dollars, not in freedom.
Maybe that’s the point. Bitcoin Investment Week was never meant to be a pleb gathering.
That said, the week did have some bright spots. PubKey was a fantastic kickoff. That was real Bitcoin culture—plebs, Nostr, grassroots energy. People who actually use Bitcoin, not just talk about it.
But the absolute highlight? Jack Mallers, sneakers and all, cutting through the noise with his authenticity.
So, why did we even go?
Good question. Maybe it was curiosity. Maybe it was stepping out of our usual circles to see Bitcoin through a different lens. Maybe it was to remind ourselves why we chose this path in the first place.
Would I go again? Probably not.
Would I trade Prague, Riga, bitcoin++ or any of the grassroots Bitcoin conferences for this? Not a chance.
At the end of the day, Bitcoin doesn’t belong to Wall Street from my opinion. It belongs to the people who actually use it. And those are the people I want to be around.
-
 @ 8947a945:9bfcf626
2025-03-06 10:50:28
@ 8947a945:9bfcf626
2025-03-06 10:50:28Law of diminishing returns : ทำมากได้น้อย ซวยหน่อยขาดทุน
 ** หมายเหตุ บทความนี้มีเนื้อหาต่อเนื่องจาก “(TH) Why I quit : สาเหตุที่ผมลาออกจากที่(ทำงาน) ที่ (เคย) เรียกว่า”บ้าน” ใครยังไม่ได้อ่าน แนะนำให้ไปอ่านก่อนนะครับ
** หมายเหตุ บทความนี้มีเนื้อหาต่อเนื่องจาก “(TH) Why I quit : สาเหตุที่ผมลาออกจากที่(ทำงาน) ที่ (เคย) เรียกว่า”บ้าน” ใครยังไม่ได้อ่าน แนะนำให้ไปอ่านก่อนนะครับผมได้ยิน คุณท็อป จิรายุส (คุณท๊อป บิทคับ) พูดคำว่า "Law of diminishing returns" ไว้ตอนแชร์มุมมองด้านการทำธุรกิจ ตอนนั้นผมไม่เข้าใจ แต่ผมรู้สึกว่ามันเป็นเจ๋งดี
สำหรับผม สรุปกฏนี้สั้นๆ คือ “ทำมากได้น้อย ซวยหน่อยขาดทุน”
กฏข้อนี้ว่าด้วยเรื่องการทำธุรกิจ พูดถึงปัจจัย 3 อย่าง - Fixed input คือสิ่งที่ไม่สามารถผลิตเพิ่มได้อีกในธุรกิจตอนนั้น เช่น จำนวนห้องตรวจในโรงพยาบาล, พื้นที่ที่ดินทำการเกษตร, ห้องเก็บสินค้า, จำนวนโต๊ะทำงานในสำนักงาน, ช่องบริการลูกค้าในธุรกิจบริการต่างๆ เป็นต้น ผมขอเรียกสั้นๆว่า “พื้นที่” - Variable input คือสิ่งที่สามารถเติมเข้ามาในธุรกิจได้ ปรับแต่งได้ เช่น แรงงาน เครื่องจักร พลังงาน - Marginal product คือผลลัพธ์ของธุรกิจ กำไรเพิ่มขึ้นหลังจากเพิ่ม variable input เข้าสู่ระบบ
ระยะของ law of diminishing returns
- Increased return (ทำเงินได้เยอะขึ้น) เมื่อป้อนแรงงานหรือเครื่องจักรเข้าสู่ระบบ ธุรกิจสามารถทำเงินเพิ่มขึ้นเนื่องจาก fixed input เดิมที่ถูกใช้สอยไม่เต็มที่ (underutilized) ถูกเติมเต็ม กรณีของรพ. คือมีห้องตรวจที่ว่าง ไม่มีหมอนั่งตรวจคนไข้ ห้องตรวจนั้นก็จะไม่สร้างรายได้ แต่เมื่อห้องนั้นมีหมอมานั่ง จะเปลี่ยนเป็นพื้นที่ที่ก่อให้เกิดรายได้ เมื่อห้องตรวจทุกห้องมีหมอนั่งครบ ถือว่าเต็มศักยภาพ ประสิทธิภาพการทำงานที่ดีตามมา
- Diminishing return (ทำมากได้น้อย) จุดของความพอดี (optimum point) คือจุดที่สมดุลพอดีของธุรกิจนั้น ทำกำไรได้เหมาะสม ไม่มากไม่น้อยจนเกินไป แต่ถ้ามองไม่เห็นจุด optimum นี้แล้วยังเพิ่ม”แรงงาน”เข้าไปอีก มันจะทำให้ ”พื้นที่” วุ่นวายเละเทะ ประสิทธิภาพในการทำงานลดลง
- Negative returns (ซวยหน่อยขาดทุน) ถ้ายังไม่หยุดเพิ่ม “แรงงาน” อีก สามารถนำมาสู่การขาดทุน
สรุปเป็นกราฟหน้าตาตามนี้ครับ
ทำไมมันถึงเป็นอย่างนั้น
ผมใช้โมเดลธุรกิจรพ.นี้เป็นตัวอย่างเลยนะครับ
ช่วงแรกที่สร้างรพ. ห้องตรวจมีไม่มาก จำนวนหมอและคนไข้สมดุลกันพอดี งานไม่หนักเกินไป การดูแลคนไข้มีประสิทธิภาพ รพ.เป็นที่ไว้ใจของคนในพื้นที่ มีชื่อเสียง ถูกบอกต่อ ทำให้จำนวนคนไข้เข้ามารับบริการมากขึ้น ต้องขยายพื้นที่รพ. สร้างตึกเพิ่ม รับบุคคลากรทุกระดับเข้ามาทำงานมากขึ้น จนเต็มพื้นที่ที่ดินรพ.ไม่สามารถขยายเพิ่มไปได้มากกว่านี้แล้ว เกิดสมดุลพอดี ทุกพื้นที่ถูกใช้งานเต็มศักยภาพ ประสิทธิภาพงานดีมาก

ผลการดำเนินงาน
ไม่เคยขาดทุน ผ่านช่วงวิกฤตต้มยำกุ้ง และ COVID ได้สบายๆ ฐานะทางการเงินแข็งแรง จ่ายปันผลสม่ำเสมอ ถ้าผมเป็นเจ้าของรพ.ผมจะ 1. สร้างระบบ 2. สร้างทีมผู้บริหาร 3. เน้นย้ำความสำคัญทำตามระบบ 3. Plan - Do- Check - Act เมื่อเกิดปัญหา
เพื่อให้ตัวผมสามารถถอยตัวเองออกมาจากตัวธุรกิจ คอยติดตาม monitor ทุกไตรมาส อย่างใกล้ชิด ไม่ทำอะไรเพิ่มไปมากกว่านี้
แต่สุดท้ายมันก็เกิดเหตุการณ์ทายาทรุ่นที่ 2 “ไม่เอา” นั่นแหละครับ มันทำให้วัฒนธรรมองค์กรเปลี่ยน ก้าวเท้าเข้าไปสู่ยุคตกต่ำ

บริหารแบบล้าหลัง ทำอะไรไม่สุด คิดว่าทำแล้วแต่จริงๆคือไม่ได้ทำ แก้ปัญหาไม่ตรงจุดสร้างปัญหากว่าเดิม
ตัวอย่าง
1. นโยบายการประหยัดพลังงานเพื่อลด carbon footprint
ฟังดูเหมือนจะดี แต่รพ.สื่อสารให้
รณรงค์ให้ปิดไฟ ... ปิดแอร์เมื่อไม่ใช้งาน ...
ผมว่าประโยคนี้มันคุ้นๆ เหมือนเคยได้ยินมามากกว่า 10 ปีแล้ว ... หรือผมเข้าใจผิดหรือเปล่าไม่แน่ใจ
รณรงค์แค่นี้แหละครับ เรื่องลด carbon footprint ไม่ได้เป็นการคิดอะไรใหม่ๆที่เหมาะกับยุคสมัย หรือสร้างอะไรที่จับต้องได้ (objective)
แต่สิ่งที่ทำสวนทางโดยสิ้นเชิงคือใช้พลาสติกแบบใช้แล้วทิ้ง (single use plastic) เป็นภาชนะหลักในการบรรจุอาหารของแพทย์ และผู้เข้าร่วมประชุมงานใหญ่ๆ
 มีเสียงเสนอแนะจากบุคคลากรทุกระดับว่าให้ทำเป็นบุฟเฟ่ต์ จานชามช้อนส้อมแบบปกติก็ได้ เสนอกันมา 5 ปี ก็ยังคงไม่่มีการเปลี่ยนแปลง ได้รับแจ้งลงมาว่าใช้ภาชนะพลาสติกมันประหยัดกว่า เอาเป็นว่ากล่องข้าวพลาสติกมีการใช้อย่างน้อย 1200 กล่องต่อเดือน … คาดว่าสมการการปล่อยก๊าสคาร์บอน (carbon emission) ที่ทีมผู้บริหารคำนวณ อาจจะซับซ้อนเกินความเข้าใจของผมก็ได้นะครับ
มีเสียงเสนอแนะจากบุคคลากรทุกระดับว่าให้ทำเป็นบุฟเฟ่ต์ จานชามช้อนส้อมแบบปกติก็ได้ เสนอกันมา 5 ปี ก็ยังคงไม่่มีการเปลี่ยนแปลง ได้รับแจ้งลงมาว่าใช้ภาชนะพลาสติกมันประหยัดกว่า เอาเป็นว่ากล่องข้าวพลาสติกมีการใช้อย่างน้อย 1200 กล่องต่อเดือน … คาดว่าสมการการปล่อยก๊าสคาร์บอน (carbon emission) ที่ทีมผู้บริหารคำนวณ อาจจะซับซ้อนเกินความเข้าใจของผมก็ได้นะครับ2. การตลาดที่ล้มเหลวและพาแพทย์ซวย

ทำการตลาดไม่เข้าเป้า “เหมือนจะ” ทำ digital marketing แต่ทำแค่โพสกราฟฟิคโปรโมชั่นภาพนิ่งลงสื่อโซเชียลทุกช่องทาง แล้วบอกว่านั่นคือ digital marketing
... แต่เดี๋ยวก่อนๆๆๆ ...
ผมจะบอกว่าการโพสมันเป็นแค่ 1 ใน 10 ของ digital marketing แต่รพ.เข้าใจว่าตัวเองได้เข้าสู่ digital marketing แล้ว
... จริงๆมันไม่ใช่เลยเว้ย ...
ผลลัพธ์คือไม่สามารถเปิดน่านน้ำลูกค้าใหม่ได้เลย ได้แต่ฐานลูกค้าเดิมที่มี brand royalty (แต่แนวโน้มลดลง)
แถมที่แย่ที่สุดคือทำการตลาดแพคเกจออกมาโดยไม่ปรึกษาแพทย์ก่อนว่ามันขัดต่อมาตรฐานการรักษาหรือไม่ กลายเป็นทำแพคเกจดึงดูดคนไข้เข้ามาใช้บริการ แต่การรักษาในแพคเกจขัดต่อมาตรฐานการรักษาของแพทย์
คนไข้ไม่รู้หรอกครับ คนไข้จะเอาตามที่มีในแพคเกจ เขาจ่ายตังค์แล้ว แต่ความซวยมันไปตกอยู่กับแพทย์
3. วางกลยุทธไม่เข้าเป้า

ทุกๆต้นปีทางผู้บริหารจะประกาศกลยุทธประจำปี ว่าในปีนั้นๆรพ.จะมุ้งเน้นพัฒนาด้านไหน รพ.นี้มีปัญหาที่เป็นงูกินหางมานาน มันส่งผลต่อประสิทธิภาพการทำงานของหมอและพยาบาล มีการเสนอแก้ปัญหาเรื่องนี้วนซ้ำซากมา 5 ปี แต่ไม่ได้รับแก้ไขจริงจัง (ผมขอไม่เล่านะครับ)
แต่กลยุทธประจำปี 3 ปีที่ผ่านมา พุ่งใส่ตัวบุคคลากร เน้นพฤติกรรมบริการที่ดีเลิศ ทราบมาว่ามีการลงทุนกับโครงการนี้หลักแสนหรือหลักล้าน มีการจัด workshop เชิญวิทยากรและ trainer จากบริษัทภายนอก (outsource) เข้ามาอบรม เป็นโครงการที่เน้นให้บุคคลากรทุกคนเข้าอบรม 100%
ผมมองว่าปัญหาที่เป็นราก (root cause) มันยังไม่ถูกแก้เลย เปรียบเทียบเหมือนฐานรากของอาคารที่มันโคลงเคลงๆไม่มั่นคงยังไม่ได้รับการแก้ไข แต่พยายามตกแต่งห้องด้วยวัสดุคุณภาพดีและเทคโนโลยีที่ทันสมัย … แต่พร้อมจะล้มลงมาได้ทุกเมื่อ
4. มีเสน่ดึงดูด partner ใหม่ๆ แต่ไม่เอาเอง
ในช่วง COVID ระลอกแรก มีผู้นำทางด้านธุรกิจโรงแรมในจังหวัดมานำเสนอโมเดลธุรกิจ “hospitel เปลี่ยนโรงแรมให้เป็นโรงพยาบาล” ด้วยศักยภาพของรพ.ที่มีบุคคลากรเพียงพอ และตัวโรงแรมที่นำมาเสนอมีห้องพักประมาณ 300 ห้อง เป็นโมเดลที่รพ.และโรงแรม win-win ทั้งคู่ แต่ทางผู้บริหารมองว่าไม่คุ้ม ปฏิเสธข้อเสนอนี้ ทำให้เสียโอกาสให้กับคู่แข่งคว้าตลาด blue ocean นี้ไป

ผมได้แต่เกาหัวตอนรู้เรื่องนี้ เพราะ 1. ช่วง COVID คนไข้น้อย พนักงานโดนลดชั่วโมงการทำงาน ได้เงินเดือนขั้นต่ำ ไม่ได้ OT 2. ทาง partner เสนอขอบุคคลากรเหล่านี้แหละ ไปช่วยงาน เรื่องสถานที่ทางโรงแรมเขามีแม่บ้าน ฝ่ายทำความสะอาดอยู่แล้ว 3. ทาง partner เสนอ profit sharing กับทางรพ. ถึงผมจะไม่รู้ตัวเลข แต่เชื่อว่ามันยุติธรรม
ผมก็ไม่รู้ครับ ว่าอะไรคือคุ้มสำหรับผู้บริหาร
5. Top down absolute power
ไม่ฟังข้อเสนอจากตัวแทนหมอ คนที่มีอำนาจการตัดสินใจไม่เคยเอาตัวลงมาคุยกับหมอแบบจริงจังเลย
1-2 ปีจะลงมาพบหมอทั้งรพ.ซักหนึ่งครั้ง สร้างภาพเก่ง พูดขายฝันสวนหรูถึงภาพที่เขาต้องการ สั่งการลงมา พอเกิดปัญหาตัวเองไม่ลงมารับผิดชอบ แต่อาศัยหน่วยข่าวกรอง(ที่ไม่รู้ว่ากรองอะไรเข้าไปบ้าง) ออกคำสั่งแก้ผ้าเอาหน้ารอดลงมาทีหลัง
แถมสั่งให้เงียบและหุบปาก
ครั้งหนึ่งมีคำสั่งออกมาไม่ชัดเจน จนพยาบาลทำงานไม่ได้ ตัวแทนพยาบาลต้องโทรมาหาผมเพื่อให้ผมช่วย
ผมรวบรวมข้อมูลทั้งหมดและพบว่าคำสั่งมีปัญหาจริงๆ ผมจึง chat line ลงไปสอบถามผู้บริหารเพื่อขอความชัดเจน
… ผ่านไปไม่ถึง 5 นาที หนึ่งในผู้บริหาร(คนที่แทงข้างหลังผมที่หาว่าผมมาตรวจคนไข้ VIP เขาช้า 5 นาทีนั่นแหละ)โทรหาผมทันทีคุยกับผมสั้นๆ ใจความว่า “คำสั่งนั้นเอาแบบเดิม ไม่ต้องแก้ และให้ผมเงียบๆซะ”... (ก็ได้วะครับ)

จุดเปลี่ยนที่ทำให้รพ.เข้าสู่ law of diminishing returns
ห้องตรวจทุกห้องของรพ. ถูกใช้จนเต็มศักยภาพ … เอาจริงๆคือล้นศักยภาพเสียอีก (over-utilized) บางแผนกมีเก้าอี้ดนตรี - หมอคนแรกหมดเวลาออกตรวจ - หมอคนต่อไปเดินเข้าใช้ห้องตรวจต่อทันที - ถ้าไม่ทันก็ต้องคว้าห้องตรวจที่ว่างพร้อมใช้งานก่อน - หมอทำการไล่ที่กันเอง - หมอบางท่านต้องใช้ห้องทำงานของพยาบาลเป็นห้องตรวจชั่วคราว
ห้องพักผู้ป่วยก็เช่นกัน บางช่วงเตียงเต็มจนไม่สามารถ admit คนไข้ได้
แต่จำที่ผมบอกได้มั้ยครับว่า คนที่เป็น top down absolute power ไม่เคยเอาตัวลงมาพูดคุยกับแพทย์เพื่อรับฟังปัญหาที่แท้จริงเลย รับแต่ข่าวกรอง(ที่ไม่รู้ว่ากรองอะไรเข้าไปบ้าง) ช่วงนึงมีคนไข้ complaint ว่ารอนั่งรอหมอนาน หมอมาตรวจช้า ผู้บริหารเลยพยายามจะแก้ปัญหา โดยการ monitor waiting time (ระยะเวลารอหมอ) หยิบยกเรื่องนี้ขึ้นมาเป็นวาระเร่งด่วนต้องรีบแก้ไข
แต่เขายังงงๆกับ concept waiting time อยู่เลยว่าจะนับตั้งแต่ตอนไหนถึงตอนไหน - Waiting time สั้นแปลว่าดี เพราะคนไข้ได้เจอหมอเร็ว - Waiting time นานแปลว่าไม่ดี เพราะคนไข้นั่งรอหมอนาน
เขาตีความจากตัวเลขครับ แต่เคยเอาตัวลงมาดูจริงๆหรือเปล่าว่าทำไมตัวเลขมันถึงออกมาไม่ดี
คำตอบคือ“ไม่” ครับ
หมอบางสาขามีความจำเป็นต้องไปดูคนไข้ที่อาการหนักใช้เวลารักษานาน ... หรือ ... รับปรึกษาจากแพทย์ต่างสาขา ... หรือ ... เป็นสาขาเฉพาะทางของเฉพาะทางอีกที ต้องใช้เวลาตรวจละเอียดตรวจนาน
มันเป็นกระบวนการทำงานของหมอ ที่หมอด้วยกันเข้าใจกัน
ส่วนคนเก็บข้อมูลก็นำเสนอไปทั้งอย่างนั้นโดยที่ไม่ได้วิเคราะห์อะไรเลย มันเป็นการกรองข้อมูลที่ไม่รอบคอบก่อนนำเสนอผู้บริหาร
สุดท้ายผู้บริหาร “โทษหมอ” ว่าไม่มีการบริหารเวลาทำงานที่ดีเพียงพอ ทำให้คนไข้รอนาน เขาสรุปกันดื้อๆแบบนี้เลยครับ
พอหนักๆเข้า “รอหมอนาน ต้องเพิ่มหมอ” season การรับสมัครหมอหลายตำแหน่งได้เริ่มขึ้น
แต่เดี๋ยวนะ ห้องตรวจมันแน่นจนแทบไม่มีที่ให้หมอนั่งทำงานแล้ว แต่เขาก็ไม่สนครับ รับหมอหน้าใหม่ๆมาเพิ่มเรื่อยๆ
ด้วย mindset ว่า "ต้องเพิ่มหมอ หมอจะได้เยอะขึ้น คนไข้จะได้ไม่ต้องรอนาน" และเชื่อว่าจะทำรายได้ให้รพ.มากขึ้น หมอหน้าใหม่บางท่านเข้ามาทำงานวันแรกถึงขั้นอยู่ในสภาวะ dead air คือไม่มีที่ให้นั่งทำงาน
“ทำมากได้น้อย” เริ่มต้น
คนไข้รพ.นี้ ส่วนใหญ่เป็นโรคซับซ้อน ต้องการทักษะและเวลาหมอเฉพาะทางแต่ละสาขาอยู่ดี ไม่ได้ทำให้ waiting time ดีขึ้น คนไข้ยัง “นั่งรอหมอนานเหมือนเดิม”
รายได้เริ่มลดลง ยอดคนไข้เริ่มลดลง รพ.พยายามแก้เกมโดยการเพิ่มราคาค่าบริการ (เพิ่มขนาด ticket size) ทำให้มีเสียงรีวิวตามโซเชียลว่า "แพง"
ผลที่เกิดขึ้นคือคนไข้หลายคนอาศัยรพ.นี้ในการตรวจวินิจฉัยโรคแล้วเอาผลไปรักษาต่อรพ.รัฐบาลตามสิทธิ์เพราะสู้ราคาค่ารักษาไม่ไหว บางคนมีประกันสุขภาพหลายฉบับแต่ก็ต้องจ่ายส่วนต่างมากอยู่ดี

วิธีการข้างต้นนี้ ไม่ผิดกติกาครับ ผล X-ray , CT, MRI, ultrasound จากรพ.เอกชน ไวกว่ารพ.รัฐบาลอยู่แล้ว แต่ก็มีคนไข้บางส่วนยินดีจ่ายแพง เพราะเชื่อมั่นหมอที่รพ.นี้ไม่อยากย้ายรพ.ก็มีครับ เพราะหมอไม่ได้ทำอะไรผิด หมอเก่งๆมีเยอะ
ถึงแม้ว่ารพ.จะรักษา momentum มีจำนวนคนไข้ประมาณ 1100 - 1200 รายต่อวัน แต่ก็เป็นโรคง่ายๆ(simple disease) เช่นไข้หวัด อาหารเป็นพิษ เป็นต้น โรคเหล่านี้ ticket size ไม่ได้ใหญ่มาก ประคองไว้ไม่ให้ขาดทุนเท่านั้นครับ
แต่ความแพงแบบไม่สมเหตุสมผล ทำให้คนไข้หลายรายถอดใจย้ายรพ.ตั้งแต่ทราบค่าใช้จ่ายวินาทีแรก
คนไข้น้อยลง --> รายได้ลดลง --> เพิ่ม ticket size ต่อหัวให้แพงขึ้น --> คนไข้หนีเพราะแพงเกิน
ผมไม่รู้ว่าผู้บริหารเขาเห็นไหม แต่คาดว่าคงจะไม่เห็น
ส่วนโรคหรือการผ่าตัดที่สมศักดิ์ศรีกับศักยภาพของรพ. "น้อยมากจนแทบไม่มี" ไม่ใช่สาเหตุอื่นเลยครับ โดนรพ.คู่แข่งในรัศมี 20 กิโลเมตรเอาไปหมด เพราะราคาถูกกว่า หมอก็เก่งไม่แพ้กัน หมอบางคนเคยอยู่ที่รพ.แห่งนี้ เสนอโปรเจคการรักษาโรคบางโรคที่สามารถสร้างรายได้เป็นกอบเป็นกำ แต่ทางรพ.ไม่เอาเอง สุดท้ายหมอเหล่านั้นย้ายไปอยู่กับรพ.คู่แข่งและผลักดันโปรเจคเหล่านั้นสำเร็จจนมีชื่อเสียง
"รพ.ขายสินค้า premium ไม่ได้เลย ขายได้แต่สินค้าเกรดท้องตลาด"
กลยุทธที่รพ.ทำต่อมาคือเพิ่มจำนวนชั่วโมงการทำงานของหมอให้เพิ่มขึ้นโดยให้หมอมาทำงานเร็วขึ้น 2 ชม. แต่ไม่จ่าย OT ให้ ด้วยตรรกะว่าถ้าหมอทำงานนานขึ้น จะมีจำนวนคนไข้มากขึ้น ทางรพ.ไม่ได้ขอร้อง แต่บีบคอให้หมอร่วมมือ หากไม่ร่วมมือไล่ออกทันที

ไปๆมาๆ มีการไล่ออกกระทันหันเกิดขึ้น มีการส่งหนังสือส่วนตัวหาหมอทุกคน ใครมีรายชื่อที่จะปลดออกก็ต้องออกจากงานทันที
ผมมองว่าฐานะทางการเงินมีปัญหารุนแรงครับ เงินเดือนพนักงานถือเป็น fixed cost ที่ธุรกิจต้องแบกรับ ถ้าเจ๋งจริงต้องควบคุมรายจ่ายให้ธุรกิจสามารถไปต่อได้โดยไม่ปลดคน ในส่วนของธุรกิจรพ. หมอคือบุคคลากรที่สำคัญที่สุดและเป็นด่านสุดท้ายที่จะไล่ออกเพื่อรักษาชีวิตของธุรกิจ ตอนนี้รพ.ได้เข้าสู่ระยะสุดท้ายของ law of diminishing returns คือ “ซวยหน่อยขาดทุน” เป็นที่เรียบร้อยครับ
จุดจบของรพ.แบบนี้ ที่ศักยภาพดี แต่บริหารห่วยแตก มันจะจบด้วยการถูก take over ผ่านมาไม่นานกราฟหุ้นออกอาการ exit liquidity แล้วครับ
ข้อคิดที่อยากแบ่งปันกับทุกคนที่อ่านมาจนจบ
- ช่วงธุรกิจเปลี่ยนผ่านสู่ทายาท คือจุดวัดใจหัวเลี้ยวหัวต่อว่าจะรอดหรือไม่รอด
- Law of diminishing returns ไม่ได้ใช้เฉพาะกับธุรกิจ แต่สามารถประยุกต์ใช้กับการดำเนินชีวิตได้หลายมิติ หากใครเข้าใจ จะขยับเข้าสู่ Pareto’s rule … สั้นๆคือ ทำน้อยแต่ได้(โคตร)มาก
- เจ้าของธุรกิจ ต้องหูไว มองหาเนื้อร้ายที่คอยกัดกินธุรกิจให้เจอ แล้วกำจัดมันซะ ก่อนที่ธุรกิจจะล้มทั้งยืน ทับตัวเองตาย
-
 @ 90c656ff:9383fd4e
2025-05-03 11:07:50
@ 90c656ff:9383fd4e
2025-05-03 11:07:50Bitcoin is the world’s first decentralized digital currency, created in 2009 by an individual or group under the pseudonym Satoshi Nakamoto. Its birth marked the beginning of a revolution in the global financial system, introducing a new kind of currency that is not controlled by governments or traditional financial institutions. The history of Bitcoin is deeply rooted in the ideals of economic freedom, transparency, and resistance to censorship.
The journey began in October 2008, when Satoshi Nakamoto published a paper titled “Bitcoin: A Peer-to-Peer Electronic Cash System.” The white paper, published on the Cryptography mailing list, described the idea of a digital payment system based on a peer-to-peer network. This concept eliminates the need for intermediaries like banks and solves a problem known as “double spending” — the possibility of duplicating digital currencies — through a technology called blockchain, or what Satoshi Nakamoto himself referred to as the timechain.
The blockchain, or timechain, is essentially a public and immutable ledger that records all Bitcoin transactions. It operates through a decentralized system where participants in the network (the so-called nodes) verify transactions and organize them into blocks. These blocks are in turn linked together in a continuous chain, forming the basis of the system’s security and transparency.
On January 3, 2009, Satoshi Nakamoto mined the first Bitcoin block, known as the genesis block. The block contained a coded message referencing the 2008 global financial crisis: "The Times, January 3, 2009, Chancellor on brink of second bailout for banks." This message is emblematic of the motivation behind Bitcoin: to provide an alternative to the centralized financial system that failed to protect the global economy.
Throughout 2009 and 2010, Bitcoin remained an experiment among tech and crypto enthusiasts. The first Bitcoin transactions took place between network participants, and the first commercial use of the currency occurred on May 22, 2010, when a programmer named Laszlo Hanyecz bought two pizzas for 10,000 Bitcoins. This historic transaction became known as “Bitcoin Pizza Day.”
Satoshi Nakamoto continued to contribute to Bitcoin's development until the end of 2010, when he gradually disappeared from the community. To this day, his identity remains a mystery, and there is no concrete evidence of who or how many people were behind the pseudonym. Before leaving, Satoshi Nakamoto handed over control of the project to other developers and made it clear that Bitcoin should be a decentralized technology, owned by everyone and controlled by no one.
Since then, Bitcoin has grown exponentially. It has evolved from a technological experiment into a multibillion-dollar asset and is widely considered a legitimate form of digital money and store of value. Governments, companies, and individuals around the world have adopted Bitcoin as an alternative to traditional fiat currencies.
In summary, the creation of Bitcoin by Satoshi Nakamoto was more than just the birth of a digital currency; it was the beginning of a global movement to rethink how money is controlled and distributed. Although the identity of Satoshi Nakamoto remains unknown, his legacy will continue to shape the future of the financial system and challenge traditional economic structures.
Thank you very much for reading this far. I hope everything is well with you, and sending a big hug from your favorite Bitcoiner maximalist from Madeira. Long live freedom!
-
 @ 1c19eb1a:e22fb0bc
2025-03-06 07:52:32
@ 1c19eb1a:e22fb0bc
2025-03-06 07:52:32It's been barely two years since I joined Nostr on my main npub, nostr:npub1kun5628raxpm7usdkj62z2337hr77f3ryrg9cf0vjpyf4jvk9r9smv3lhe, and in just that relatively short time, the amount of development on top of this protocol has been staggering. When nostr:npub1sg6plzptd64u62a878hep2kev88swjh3tw00gjsfl8f237lmu63q0uf63m first opened the floodgates of adoption by tweeting about Nostr, it felt like most of the available clients were barely serviceable and held together with a prayer and copious amounts of duct tape. Of course, it can sometimes still feel that way, but there are definitely some Nostr apps looking and feeling more polished and providing true innovation when compared with legacy social platforms. Indeed, there are a growing number of Nostr-based applications and tools that have very little to do with social media at all.
One thing we have not had available to the growing Nostr community, and those considering joining it, is a source for application reviews that is thorough, approachable, knowledgeable, and balanced. This is what I hope to begin to provide through this new npub dedicated to reviewing as many of the Nostr clients, apps, and tools as I possibly can, so you the reader can determine which ones will fit your needs, and perhaps help you find new ones you had never heard about.
One of the best parts about Nostr is the portability of your identity and social graph, allowing users to log into any Nostr-based application with their same "account" without some centralized tech giant like Google or Apple owning who you are and all of your data. Leverage this super-power of Nostr with me as we explore the best applications and tools the intrepid developers building on this platform have cooked up.
What will you review?
My choice of applications to review will be based on a few factors.
First, I will only be reviewing applications that have a production release, or are otherwise considered production ready by the developer. nostr:npub1xtscya34g58tk0z605fvr788k263gsu6cy9x0mhnm87echrgufzsevkk5s, you won't have to worry that I will be putting NoteDeck under the microscope while it is still very much in alpha. All of us who love to try the new clients as soon as they are available understand well enough that there will be plenty of bugs, UI quirks, and rough edges to look past.
Second, I will generally be reviewing applications that are meant to be user-facing for the average person. That is, apps that your normie friends might soon be using, and then asking you why they can't edit anything they post. I will not be doing reviews of various relay implementations, for instance, unless they are designed to be approachable to the average user to install and manage. nostr:npub10npj3gydmv40m70ehemmal6vsdyfl7tewgvz043g54p0x23y0s8qzztl5h, your project might just be a notable exception.
Third, my reviews will be limited by the operating systems I have available to me at the time. Sorry folks over on iOS, Mac, and Windows. I will only be able to review apps I can run on Android, Linux, or my web browser for the time being.
How will the apps be rated?
I want to be thorough in my reviews, and yet avoid overloading my readers with information they don't care about. In order to attempt to achieve this, I will break my reviews into several sections, so readers can skip to the sections relevant to their interests.
First, I will provide a basic overview of the type of application I am reviewing, what it is trying to achieve, and why a user might want to try it out.
Next, I will give my overall impression of the application. The good, the bad, and the ugly, as it were, so that those who just want a brief rundown can get the TLDR right out the gate and be on their way.
Then we will begin diving into the nitty-gritty with an in depth look at the main features of the application. What it does well. What features seem lacking. What expected features are absent. What features make it unique and set it apart from other applications with a similar purpose.
For the sake of all the baby Nostriches out there, the next section will be an assessment of how approachable the application would likely be to a normie who is coming to Nostr with no idea what a public and private key are, what relays are, or why they might want to start interacting here instead of on a legacy equivalent. What would someone used to Twitter think of #Snort? What would someone used to Spotify think of #Fountain or #Wavlake?
The next section will be a review of the application's UI. The design and polish. How easy it is to find the things you want in the areas you would expect them. In short, how well the application achieves the goal of making the user feel at home and want to continue using the app just through quality UI design.
If you know me and my contstant harping on developers to include various forms of external signing, it should be no surprise to you that the next section will cover login options. What does the sign-in and sign-up flow look like, and does the user have to expose their private key to the application in order to use it?
A review of virtually any Nostr application would be incomplete without a section dedicated to zap integration. How prominent is zapping in the app? How easy is it to zap or start receiving zaps? Are zaps displayed in a way that encourages users to compete to be top zapper? Is Nostr Wallet Connect supported for using external wallets for one-tap-zapping?
Most Nostr applications, even "other stuff" clients, are designed to present some form of content to the user. The next section will cover how easy it is for the user to find the type of content they may be interested in, or to discover content they didn't know they might be interested in. For social clients, how easy is it to discover other users that they might want to follow?
The backbone of the protocol is the interplay between clients and relays, and the next section of the review will cover how the app manages relays. Are they hidden from the user? Are there sensible defaults? Can users who want to do so select the relays they prefer? Does the app respect relays the user has selected in other apps, or are the app's relays independent of those selected in other apps. Worse, does the app overwrite your selected relays with its defaults?
Finally, I will scour the #AskNostr feed for questions and comments from other users about the app under review to get more perspectives than just my own. What are the common pain-points other users are having? What do they love about the app? What features would they like to see added?
Are there other sections you would like to see me add before I start dropping reviews? Get them to me soon, because I am currently taking notes for my first review, which will be the #Primal #Android client!
PV 🤙
-
 @ 0d8633e5:eec06e57
2025-05-03 10:58:22
@ 0d8633e5:eec06e57
2025-05-03 10:58:22The Flash USDT Generator is responsible for producing and storing Flash USDT tokens with a flexible daily limit. It ensures a consistent supply of tokens for transactions while managing distribution securely and efficiently. Our Flash USDT offers a unique, temporary cryptocurrency that lasts for 90 days before expiring. This innovative solution allows for seamlesstrading and transferring of funds. Notably, the Flash Bitcoin and USDT can be transferred to 12 different wallets, including prominent platforms like Binance and Trust Wallet.
Features Adjustable Daily Limit: Customizable settings allow for modifying the token generation cap. Automated Distribution: Ensures quick and secure token transfers to user wallets. Minimal Latency: Prevents blockchain congestion issues for seamless transfers. Real-Time Transaction Verification: Each transaction is immediately verified on the respective blockchain explorer to confirm accuracy and validity. Temporary Nature: One of the most distinctive characteristics of USDT FLASH Generator is that it generates flash coin that is designed to disappear from any wallet after a period of ninety days. This unique feature ensures that any assets received in USDT FLASH will not linger indefinitely, creating a dynamic and engaging transaction experience.
Kindly visit globalfashexperts.com for more information Contact Information For more information or to make a purchase, please contact us through the following channels:
Email: globalfashexperts@gmail.com Flash USDT:https://globalfashexperts.com/product/flash-usdt/ Flash USDT: https://globalfashexperts.com/product/flash-usdt-generator-software/The Flash USDT Generator is responsible for producing and storing Flash USDT tokens with a flexible daily limit. It ensures a consistent supply of tokens for transactions while managing distribution securely and efficiently. Our Flash USDT offers a unique, temporary cryptocurrency that lasts for 90 days before expiring. This innovative solution allows for seamlesstrading and transferring of funds. Notably, the Flash Bitcoin and USDT can be transferred to 12 different wallets, including prominent platforms like Binance and Trust Wallet.
Features
- Adjustable Daily Limit: Customizable settings allow for modifying the token generation cap.
- Automated Distribution: Ensures quick and secure token transfers to user wallets.
- Minimal Latency: Prevents blockchain congestion issues for seamless transfers.
- Real-Time Transaction Verification: Each transaction is immediately verified on the respective blockchain explorer to confirm accuracy and validity.
- Temporary Nature: One of the most distinctive characteristics of USDT FLASH Generator is that it generates flash coin that is designed to disappear from any wallet after a period of ninety days. This unique feature ensures that any assets received in USDT FLASH will not linger indefinitely, creating a dynamic and engaging transaction experience.
 Kindly visit globalfashexperts.com for more information
Kindly visit globalfashexperts.com for more informationContact Information
For more information or to make a purchase, please contact us through the following channels:
- Email: globalfashexperts@gmail.com
- Flash USDT:https://globalfashexperts.com/product/flash-usdt/
- Flash USDT: https://globalfashexperts.com/product/flash-usdt-generator-software/
-
 @ d0aa74cd:603d35cd
2025-05-03 10:55:11
@ d0aa74cd:603d35cd
2025-05-03 10:55:11CLI #Haskell
https://photonsphere.org/post/2025-05-03-command-line-energy-prices-haskell/
-
 @ 90c656ff:9383fd4e
2025-05-03 10:31:25
@ 90c656ff:9383fd4e
2025-05-03 10:31:25Bitcoin is a decentralized digital currency created in 2009 by an individual or group under the pseudonym Satoshi Nakamoto. Unlike traditional government-issued currencies like the US dollar or the euro, Bitcoin is not controlled by any central authority, such as a central bank or financial institution. This innovative feature has made it a focal point of economic, technological, and even social debate in recent years.
Bitcoin operates using a technology called blockchain (which the Bitcoin community increasingly prefers to call "timechain"). It is essentially a distributed digital ledger. The blockchain or timechain records all transactions made on the Bitcoin network in an open and transparent way. Each block contains a set of transactions that are immutably added to the chain once they are verified by miners (miners are basically network participants who use their computing power to validate these same transactions). This ensures security and prevents fraud, as no person or entity can retroactively alter the records.
One of Bitcoin's most notable features is its limited supply. Only 21 million Bitcoins can ever be created, which gives Bitcoin a deflationary nature — unlike fiat currencies, which central banks can print in unlimited quantities. This fixed limit, combined with growing global interest in the technology in general and individual privacy specifically, has driven Bitcoin’s value over time.
Another important characteristic of Bitcoin is that it enables direct peer-to-peer transactions, removing the need for intermediaries. This is particularly useful in cases like international transfers, where Bitcoin can be used to send money quickly and at low cost, without going through a bank or traditional financial services. Additionally, it is seen as a form of financial freedom in countries with unstable local currencies (often due to central banks printing money uncontrollably) or strict state-imposed capital controls.
However, Bitcoin is not immune to criticism — though these are often hollow arguments that mask the personal interests of those making them, whether because they work in traditional banks or brokerages and fear losing "power" or even their jobs, or because they have bad intentions and want to promote their own cryptocurrencies, which are fundamentally worthless (the infamous “shitcoins”). Bitcoin’s price volatility can also pose significant risks for inexperienced users who buy at a certain price and end up selling when the value drops by half, losing at least half their money. On the other hand, many experts view Bitcoin as a technological and social milestone that challenges existing economic models.
In summary, Bitcoin is much more than just a “crypto” or “cryptocurrency.” It represents a revolution — or a revision — in how most people think about money, offering a decentralized, transparent, and censorship-resistant alternative. Although it still faces challenges to becoming widely accepted by some skeptics and by governments worried about losing control over “their” populations (as mentioned earlier), its impact has been undeniable, paving the way for a new era in the global economy and opening many minds to reflection.
Thank you very much for reading this far — I hope you're doing well, and sending a huge hug from your favorite Bitcoiner maximalist from Madeira. Long live freedom!
-
 @ 62a6a41e:b12acb43
2025-03-04 22:19:29
@ 62a6a41e:b12acb43
2025-03-04 22:19:29War is rarely (or if ever) the will of the people. Throughout history, wars have been orchestrated by political and economic elites, while the media plays a key role in shaping public opinion. World War I is a clear example of how propaganda was used to glorify war, silence dissent, and demonize the enemy.
Today, we see similar tactics being used in the Ukrainian War. The media spreads one-sided narratives, censors alternative views, and manipulates public sentiment. This article argues that wars are decided from the top, and media is used to justify them.
How the Media Glorified and Propagated WW1
The Media Sold War as an Adventure
Before WW1, newspapers and propaganda made war seem noble and exciting. Young men were encouraged to enlist for honor and glory. Posters displayed slogans like “Your Country Needs You”, making war look like a duty rather than a tragedy.
Demonization of the Enemy
Governments and media portrayed Germans as "barbaric Huns," spreading exaggerated stories like the "Rape of Belgium," where German soldiers were accused of horrific war crimes—many later proven false. Today, Russia is painted as purely evil, while NATO’s role and Ukraine’s internal conflicts are ignored.
Social Pressure & Nationalism
Anyone who opposed WW1 was labeled a traitor. Conscientious objectors were shamed, jailed, or even executed. The same happens today—if you question support for Ukraine, you are called "pro-Russian" or "anti-European." In the U.S., opposing war is falsely linked to supporting Trump or extremism.
Fabricated Stories
During WW1, fake reports of German soldiers killing babies were widely spread. In Ukraine, reports of massacres and war crimes often circulate without verification, while Ukrainian war crimes receive little coverage.
How the Media Promotes War Today: The Case of Ukraine
One-Sided Narratives
The media presents Ukraine as a heroic struggle against an evil invader, ignoring the 2014 coup, the Donbas conflict, and NATO expansion. By simplifying the issue, people are discouraged from questioning the full story.
Censorship and Suppression of Dissent
During WW1, anti-war activists were jailed. Today, journalists and commentators questioning NATO’s role face censorship, deplatforming, or cancellation.
Selective Coverage
Media highlights civilian deaths in Ukraine but ignores similar suffering in Yemen, Syria, or Palestine. Coverage depends on political interests, not humanitarian concern.
Glorification of War Efforts
Ukrainian soldiers—even extremist groups—are painted as heroes. Meanwhile, peace negotiations and diplomatic efforts receive little attention.
War is a Top-Down Decision, Not the Will of the People
People Don’t Want Wars
If given a choice, most people would reject war. Examples:
- Before WW1: Many workers and socialists opposed war, but governments ignored them.
- Vietnam War: Protests grew, but the war continued.
- Iraq War (2003): Millions protested, yet the invasion went ahead.
Small Elites Decide War
Wars benefit arms manufacturers, politicians, and corporate interests—not ordinary people. Public opposition is often ignored or crushed.
Manipulation Through Fear
Governments use fear to justify war: “If we don’t act now, it will be too late.” This tactic was used in WW1, the Iraq War, and is used today in Ukraine.
Violence vs. War: A Manufactured Conflict
Violence Happens, But War is Manufactured
Conflicts and disputes are natural, but large-scale war is deliberately planned using propaganda and logistical preparation.
War Requires Justification
If war were natural, why does it need massive media campaigns to convince people to fight? Just like in WW1, today’s wars rely on media narratives to gain support.
The Crimea Referendum: A Case of Ignored Democracy
Crimea’s 2014 Referendum
- Over 90% of Crimeans voted to join Russia in 2014.
- Western governments called it "illegitimate," while similar referendums (like in Kosovo) were accepted.
The Contradiction in Democracy
- If democracy is sacred, why ignore a clear vote in Crimea?
- Other examples: Brexit was resisted, Catalonia’s referendum was shut down, and peace referendums were dismissed when they didn’t fit political interests.
- Democracy is used as a tool when convenient.
VII. The Libertarian Case Against War
The Non-Aggression Principle (NAP)
Libertarianism is fundamentally opposed to war because it violates the Non-Aggression Principle (NAP)—the idea that no person or institution has the right to initiate force against another. War, by its very nature, is the ultimate violation of the NAP, as it involves mass killing, destruction, and theft under the guise of national interest.
War is State Aggression
- Governments wage wars, not individuals. No private citizen would naturally start a conflict with another country.
- The state forces people to fund wars through taxation, violating their economic freedom.
- Conscription, used in many wars, is nothing more than state-sponsored slavery, forcing individuals to fight and die for political goals they may not support.
War Creates Bigger Government
- War expands state power, eroding civil liberties (e.g., WW1's Espionage Act, the Patriot Act after 9/11).
- The military-industrial complex grows richer while taxpayers foot the bill.
- Emergency powers granted during wars rarely get repealed after conflicts end, leaving citizens with fewer freedoms.
Peaceful Trade vs. War
- Libertarians advocate for free trade as a means of cooperation. Countries that trade are less likely to go to war.
- Wars destroy wealth and infrastructure, while peaceful trade increases prosperity for all.
- Many wars have been fought not for defense, but for economic interests, such as securing oil, resources, or geopolitical power.
Who Benefits from War?
- Not the people, who suffer death, destruction, and economic hardship.
- Not small businesses or workers, who bear the burden of inflation and taxes to fund wars.
- Not individual liberty, as war leads to greater state control and surveillance.
- Only the elites, including defense contractors, politicians, and bankers, who profit from war and use it to consolidate power.
Conclusion: The Media’s Role in War is Crucial
Wars don’t happen naturally—they are carefully planned and sold to the public using propaganda, fear, and nationalism.
- WW1 and Ukraine prove that media is key to war-making.
- The media silences peace efforts and glorifies conflict.
- If people truly had a choice, most wars would never happen.
To resist this, we must recognize how we are manipulated and reject the forced narratives that push us toward war.
-
 @ 5f078e90:b2bacaa3
2025-05-03 10:18:41
@ 5f078e90:b2bacaa3
2025-05-03 10:18:41The Spoonbill's Dawn
In a marsh where reeds whispered secrets to the wind, a roseate spoonbill named Sable waded through dawn’s amber glow. Her pink feathers shimmered, catching the first light as she swept her spoon-shaped bill through the shallows, sifting for shrimp. Unlike her flock, who chattered and preened, Sable moved with quiet purpose, her eyes tracing ripples for signs of life.

Each morning, she returned to a lone cypress, its roots cradling a pool where minnows danced. Here, Sable had found an odd companion: a young alligator named Moss, whose emerald scales blended with the water’s edge. Moss never lunged, only watched, his eyes like polished stones. Sable, curious, began leaving shrimp at the pool’s edge. Moss, in turn, nudged smooth pebbles toward her, gifts from the marsh’s depths.
One dawn, a storm loomed, its thunder rattling the reeds. The flock fled, their wings a pink blur against charcoal clouds, but Sable lingered. The pool was still; Moss hadn’t surfaced. She dipped her bill, calling softly, her heart a flutter of worry. Then, a ripple—Moss emerged, sluggish, a gash on his flank from a poacher’s trap. Sable’s instinct was to flee, but she stayed, her bill probing the mud for healing herbs she’d seen egrets use.
With gentle nudges, she pressed the herbs to Moss’s wound, her pink wings shielding him from the rain. Moss rumbled, a low thanks, and rested. By dusk, the storm passed, and the marsh gleamed under a crescent moon. Moss stirred, stronger, and nudged a final pebble to Sable—a heart-shaped stone, glinting pink like her feathers.
Sable took flight, the stone clutched in her bill, her wings carving hope into the sky. The flock returned, awed by her tale, and the marsh buzzed with their chatter. Sable and Moss remained, their bond a quiet legend, proof that even in a wild world, trust could bloom where dawn met dusk.
Word count: 313
-
 @ f33c8a96:5ec6f741
2025-03-01 23:25:22
@ f33c8a96:5ec6f741
2025-03-01 23:25:22Setting Up Your Code Editor
Introduction
In this lesson, we'll set up the most fundamental tool in your development journey: your code editor. This is where you'll spend most of your time writing, testing, and debugging code, so it's crucial to get comfortable with it from the start.
What is an IDE?
Definition
An IDE (Integrated Development Environment) is a software application that provides comprehensive facilities for software development. Think of it as your complete workshop for writing code.
Key Components
- Code Editor
- Where you write and edit code
- Provides syntax highlighting
- Helps with code formatting
-
Makes code easier to read and write
-
Compiler/Interpreter
- Runs your code
- Translates your code into executable instructions
-
Helps test your applications
-
Debugging Tools
- Help find and fix errors
- Provide error messages and suggestions
- Make problem-solving easier
Setting Up Visual Studio Code
Why VS Code?
- Free and open-source
- Lightweight yet powerful
- Excellent community support
- Popular among developers
- Great for beginners and experts alike
Installation Steps
- Visit code.visualstudio.com
- Download the version for your operating system
- Run the installer
- Follow the installation prompts
Essential VS Code Features
1. Interface Navigation
- File Explorer (Ctrl/Cmd + Shift + E)
- Browse and manage your files
- Create new files and folders
-
Navigate your project structure
-
Search (Ctrl/Cmd + Shift + F)
- Find text across all files
- Replace text globally
-
Search with regular expressions
-
Source Control (Ctrl/Cmd + Shift + G)
- Track changes in your code
- Commit and manage versions
- Integrate with Git
2. Terminal Integration
To open the integrated terminal: - Use
Ctrl + `(backtick) - Or View → Terminal from the menu - Basic terminal commands:bash ls # List files (dir on Windows) cd # Change directory clear # Clear terminal code . # Open VS Code in current directory3. Essential Extensions
Install these extensions to enhance your development experience: 1. ESLint - Helps find and fix code problems - Enforces coding standards - Improves code quality
- Prettier
- Automatically formats your code
- Maintains consistent style
-
Saves time on formatting
-
Live Server
- Runs your web pages locally
- Auto-refreshes on save
- Great for web development
Important Keyboard Shortcuts
Ctrl/Cmd + S # Save file Ctrl/Cmd + C # Copy Ctrl/Cmd + V # Paste Ctrl/Cmd + Z # Undo Ctrl/Cmd + Shift + P # Command palette Ctrl/Cmd + P # Quick file openWriting Your First Code
Let's create and run a simple HTML file:
- Create a new file (
index.html) - Add basic HTML content:
```html
Hello World!
``` 3. Save the file (Ctrl/Cmd + S) 4. Open in browser or use Live Server
Best Practices
1. File Organization
- Keep related files together
- Use clear, descriptive names
- Create separate folders for different projects
2. Regular Saving
- Save frequently (Ctrl/Cmd + S)
- Watch for the unsaved dot indicator
- Enable auto-save if preferred
3. Terminal Usage
- Get comfortable with basic commands
- Use the integrated terminal
- Practice navigation and file operations
Troubleshooting Common Issues
1. Installation Problems
- Ensure you have admin rights
- Check system requirements
- Use official download sources
2. Extension Issues
- Keep extensions updated
- Disable conflicting extensions
- Restart VS Code after installation
3. Performance
- Don't install too many extensions
- Regular restart of VS Code
- Keep your system updated
Next Steps
- Practice Navigation
- Create and manage files
- Use the integrated terminal
-
Try keyboard shortcuts
-
Customize Your Editor
- Explore themes
- Adjust font size
-
Configure auto-save
-
Prepare for Next Lesson
- Keep VS Code open
- Get comfortable with the interface
- Practice basic operations
Additional Resources
Remember: Your code editor is your primary tool as a developer. Take time to get comfortable with it, and don't worry about mastering everything at once. Focus on the basics we covered in the video, and you'll naturally learn more features as you need them.
Happy coding! 🚀
-
 @ e4950c93:1b99eccd
2025-05-03 09:59:59
@ e4950c93:1b99eccd
2025-05-03 09:59:59🧵 Produits en cette matière
Les marques suivantes proposent des produits fait exclusivement ou principalement avec cette matière :
Vêtements
Cet article est publié sur origine-nature.com 🌐 See this article in English
-
 @ e4950c93:1b99eccd
2025-05-03 09:59:25
@ e4950c93:1b99eccd
2025-05-03 09:59:25🧵 Produits en cette matière
Les marques suivantes proposent des produits fait exclusivement ou principalement avec cette matière :
Vêtements
- Engel
- Dilling (laine mérinos)
- ManyMonths (laine mérinos)
Maison
Cet article est publié sur origine-nature.com 🌐 See this article in English
-
 @ 8947a945:9bfcf626
2025-02-28 09:11:21
@ 8947a945:9bfcf626
2025-02-28 09:11:21Chef's notes
https://video.nostr.build/ea19333ab7f700a6557b6f52f1f8cfe214671444687fa7ea56a18e5d751fe0a9.mp4
https://video.nostr.build/bcae8d39e22f66689d51f34e44ecabdf7a57b5099cc456e3e0f29446b1dfd0de.mp4
Details
- ⏲️ Prep time: 5 min
- 🍳 Cook time: 5 min
- 🍽️ Servings: 1
Ingredients
- ไข่ 1 - 2 ฟอง
- ข้าวโอ๊ต 3 - 4 ช้อน
Directions
- ตอกไข่ + ตีไข่
- ปรุงรส พริกไทย หรือ ซอสถั่วเหลืองตามชอบ
- ใส่ข้าวโอ๊ต 3 - 4 ช้อน
- ใส่ถั่วลิสงอบ 1 - 2 หยิบมือ
- เทน้ำใส่พอท่วมข้าวโอ๊ต
- เข้าไมโครเวฟ ไฟแรง 1 - 2 นาที
-
 @ 4523be58:ba1facd0
2025-02-27 22:20:33
@ 4523be58:ba1facd0
2025-02-27 22:20:33NIP-117
The Double Ratchet Algorithm
The Double Ratchet is a key rotation algorithm for secure private messaging.
It allows us to 1) communicate on Nostr without revealing metadata (who you are communicating with and when), and 2) keep your message history and future messages safe even if your main Nostr key is compromised.
Additionally, it enables disappearing messages that become undecryptable when past message decryption keys are discarded after use.
See also: NIP-118: Nostr Double Ratchet Invites
Overview
"Double ratchet" means we use 2 "ratchets": cryptographic functions that can be rotated forward, but not backward: current keys can be used to derive next keys, but not the other way around.
Ratchet 1 uses Diffie-Hellman (DH) shared secrets and is rotated each time the other participant acknowledges a new key we have sent along with a previous message.
Ratchet 2 generates encryption keys for each message. It rotates after every message, using the previous message's key as input (and the Ratchet 1 key when it rotates). This process ensures forward secrecy for consecutive messages from the same sender in between Ratchet 1 rotations.
Nostr implementation
We implement the Double Ratchet Algorithm on Nostr similarly to Signal's Double Ratchet with header encryption, but encrypting the message headers with NIP-44 conversation keys instead of symmetric header keys.
Ratchet 1 keys are standard Nostr keys. In addition to encryption, they are also used for publishing and subscribing to messages on Nostr. As they are rotated and not linked to public Nostr identities, metadata privacy is preserved.
Nostr event format
Message
Outer event
typescript { kind: 1060, content: encryptedInnerEvent, tags: [["header", encryptedHeader]], pubkey: ratchetPublicKey, created_at, id, sig }We subscribe to Double Ratchet events based on author public keys which are ephemeral — not used for other purposes than the Double Ratchet session. We use the regular event kind
1060to differentiate it from other DM kinds, retrieval of which may be restricted by relays.The encrypted header contains our next nostr public key, our previous sending chain length and the current message number.
Inner event
Inner events must be NIP-59 Rumors (unsigned Nostr events) allowing plausible deniability.
With established Nostr event kinds, clients can implement all kinds of features, such as replies, reactions, and encrypted file sharing in private messages.
Direct message and encrypted file messages are defined in NIP-17.
Algorithm
Signal's Double Ratchet with header encryption document is a comprehensive description and explanation of the algorithm.
In this NIP, the algorithm is only described in code, in order to highlight differences to the Signal implementation.
External functions
We use the following Nostr functions (NIP-01):
generateSecretKey()for creating Nostr private keysfinalizeEvent(partialEvent, secretKey)for creating valid Nostr events with pubkey, id and signature
We use NIP-44 functions for encryption:
nip44.encryptnip44.decryptnip44.getConversationKey
- createRumor
Key derivation function:
```typescript export function kdf( input1: Uint8Array, input2: Uint8Array = new Uint8Array(32), numOutputs: number = 1 ): Uint8Array[] { const prk = hkdf_extract(sha256, input1, input2);
const outputs: Uint8Array[] = []; for (let i = 1; i <= numOutputs; i++) { outputs.push(hkdf_expand(sha256, prk, new Uint8Array([i]), 32)); } return outputs; } ```
Session state
With this information you can start or continue a Double Ratchet session. Save it locally after each sent and received message.
```typescript interface SessionState { theirCurrentNostrPublicKey?: string; theirNextNostrPublicKey: string;
ourCurrentNostrKey?: KeyPair; ourNextNostrKey: KeyPair;
rootKey: Uint8Array; receivingChainKey?: Uint8Array; sendingChainKey?: Uint8Array;
sendingChainMessageNumber: number; receivingChainMessageNumber: number; previousSendingChainMessageCount: number;
// Cache of message & header keys for handling out-of-order messages // Indexed by Nostr public key, which you can use to resubscribe to unreceived messages skippedKeys: { [pubKey: string]: { headerKeys: Uint8Array[]; messageKeys: { [msgIndex: number]: Uint8Array }; }; }; } ```
Initialization
Alice is the chat initiator and Bob is the recipient. Ephemeral keys were exchanged earlier.
```typescript static initAlice( theirEphemeralPublicKey: string, ourEphemeralNostrKey: KeyPair, sharedSecret: Uint8Array ) { // Generate ephemeral key for the next ratchet step const ourNextNostrKey = generateSecretKey();
// Use ephemeral ECDH to derive rootKey and sendingChainKey const [rootKey, sendingChainKey] = kdf( sharedSecret, nip44.getConversationKey(ourEphemeralNostrKey.private, theirEphemeralPublicKey), 2 );
return { rootKey, theirNextNostrPublicKey: theirEphemeralPublicKey, ourCurrentNostrKey: ourEphemeralNostrKey, ourNextNostrKey, receivingChainKey: undefined, sendingChainKey, sendingChainMessageNumber: 0, receivingChainMessageNumber: 0, previousSendingChainMessageCount: 0, skippedKeys: {}, }; }
static initBob( theirEphemeralPublicKey: string, ourEphemeralNostrKey: KeyPair, sharedSecret: Uint8Array ) { return { rootKey: sharedSecret, theirNextNostrPublicKey: theirEphemeralPublicKey, // Bob has no ‘current’ key at init time — Alice will send to next and trigger a ratchet step ourCurrentNostrKey: undefined, ourNextNostrKey: ourEphemeralNostrKey, receivingChainKey: undefined, sendingChainKey: undefined, sendingChainMessageNumber: 0, receivingChainMessageNumber: 0, previousSendingChainMessageCount: 0, skippedKeys: {}, }; }
```
Sending messages
```typescript sendEvent(event: Partial
) { const innerEvent = nip59.createRumor(event) const [header, encryptedData] = this.ratchetEncrypt(JSON.stringify(innerEvent)); const conversationKey = nip44.getConversationKey(this.state.ourCurrentNostrKey.privateKey, this.state.theirNextNostrPublicKey); const encryptedHeader = nip44.encrypt(JSON.stringify(header), conversationKey);
const outerEvent = finalizeEvent({ content: encryptedData, kind: MESSAGE_EVENT_KIND, tags: [["header", encryptedHeader]], created_at: Math.floor(now / 1000) }, this.state.ourCurrentNostrKey.privateKey);
// Publish outerEvent on Nostr, store inner locally if needed return {outerEvent, innerEvent}; }
ratchetEncrypt(plaintext: string): [Header, string] { // Rotate sending chain key const [newSendingChainKey, messageKey] = kdf(this.state.sendingChainKey!, new Uint8Array([1]), 2); this.state.sendingChainKey = newSendingChainKey; const header: Header = { number: this.state.sendingChainMessageNumber++, nextPublicKey: this.state.ourNextNostrKey.publicKey, previousChainLength: this.state.previousSendingChainMessageCount }; return [header, nip44.encrypt(plaintext, messageKey)]; } ```
Receiving messages
```typescript handleNostrEvent(e: NostrEvent) { const [header, shouldRatchet, isSkipped] = this.decryptHeader(e);
if (!isSkipped) { if (this.state.theirNextNostrPublicKey !== header.nextPublicKey) { // Received a new key from them this.state.theirCurrentNostrPublicKey = this.state.theirNextNostrPublicKey; this.state.theirNextNostrPublicKey = header.nextPublicKey; this.updateNostrSubscriptions() }
if (shouldRatchet) { this.skipMessageKeys(header.previousChainLength, e.pubkey); this.ratchetStep(header.nextPublicKey); }}
decryptHeader(event: any): [Header, boolean, boolean] { const encryptedHeader = event.tags[0][1]; if (this.state.ourCurrentNostrKey) { const conversationKey = nip44.getConversationKey(this.state.ourCurrentNostrKey.privateKey, event.pubkey); try { const header = JSON.parse(nip44.decrypt(encryptedHeader, conversationKey)) as Header; return [header, false, false]; } catch (error) { // Decryption with currentSecret failed, try with nextSecret } }
const nextConversationKey = nip44.getConversationKey(this.state.ourNextNostrKey.privateKey, event.pubkey); try { const header = JSON.parse(nip44.decrypt(encryptedHeader, nextConversationKey)) as Header; return [header, true, false]; } catch (error) { // Decryption with nextSecret also failed }
const skippedKeys = this.state.skippedKeys[event.pubkey]; if (skippedKeys?.headerKeys) { // Try skipped header keys for (const key of skippedKeys.headerKeys) { try { const header = JSON.parse(nip44.decrypt(encryptedHeader, key)) as Header; return [header, false, true]; } catch (error) { // Decryption failed, try next secret } } }
throw new Error("Failed to decrypt header with current and skipped header keys"); }
ratchetDecrypt(header: Header, ciphertext: string, nostrSender: string): string { const plaintext = this.trySkippedMessageKeys(header, ciphertext, nostrSender); if (plaintext) return plaintext;
this.skipMessageKeys(header.number, nostrSender);
// Rotate receiving key const [newReceivingChainKey, messageKey] = kdf(this.state.receivingChainKey!, new Uint8Array([1]), 2); this.state.receivingChainKey = newReceivingChainKey; this.state.receivingChainMessageNumber++;
return nip44.decrypt(ciphertext, messageKey); }
ratchetStep(theirNextNostrPublicKey: string) { this.state.previousSendingChainMessageCount = this.state.sendingChainMessageNumber; this.state.sendingChainMessageNumber = 0; this.state.receivingChainMessageNumber = 0; this.state.theirNextNostrPublicKey = theirNextNostrPublicKey;
// 1st step yields the new conversation key they used const conversationKey1 = nip44.getConversationKey(this.state.ourNextNostrKey.privateKey, this.state.theirNextNostrPublicKey!); // and our corresponding receiving chain key const [theirRootKey, receivingChainKey] = kdf(this.state.rootKey, conversationKey1, 2); this.state.receivingChainKey = receivingChainKey;
// Rotate our Nostr key this.state.ourCurrentNostrKey = this.state.ourNextNostrKey; const ourNextSecretKey = generateSecretKey(); this.state.ourNextNostrKey = { publicKey: getPublicKey(ourNextSecretKey), privateKey: ourNextSecretKey };
// 2nd step yields the new conversation key we'll use const conversationKey2 = nip44.getConversationKey(this.state.ourNextNostrKey.privateKey, this.state.theirNextNostrPublicKey!); // And our corresponding sending chain key const [rootKey, sendingChainKey] = kdf(theirRootKey, conversationKey2, 2); this.state.rootKey = rootKey; this.state.sendingChainKey = sendingChainKey; }
skipMessageKeys(until: number, nostrSender: string) { if (this.state.receivingChainMessageNumber + MAX_SKIP < until) { throw new Error("Too many skipped messages"); }
if (!this.state.skippedKeys[nostrSender]) { this.state.skippedKeys[nostrSender] = { headerKeys: [], messageKeys: {} };
if (this.state.ourCurrentNostrKey) { const currentSecret = nip44.getConversationKey(this.state.ourCurrentNostrKey.privateKey, nostrSender); this.state.skippedKeys[nostrSender].headerKeys.push(currentSecret); } const nextSecret = nip44.getConversationKey(this.state.ourNextNostrKey.privateKey, nostrSender); this.state.skippedKeys[nostrSender].headerKeys.push(nextSecret);}
while (this.state.receivingChainMessageNumber < until) { const [newReceivingChainKey, messageKey] = kdf(this.state.receivingChainKey!, new Uint8Array([1]), 2); this.state.receivingChainKey = newReceivingChainKey; this.state.skippedKeys[nostrSender].messageKeys[this.state.receivingChainMessageNumber] = messageKey; this.state.receivingChainMessageNumber++; } }
trySkippedMessageKeys(header: Header, ciphertext: string, nostrSender: string): string | null { const skippedKeys = this.state.skippedKeys[nostrSender]; if (!skippedKeys) return null;
const messageKey = skippedKeys.messageKeys[header.number]; if (!messageKey) return null;
delete skippedKeys.messageKeys[header.number];
if (Object.keys(skippedKeys.messageKeys).length === 0) { delete this.state.skippedKeys[nostrSender]; }
return nip44.decrypt(ciphertext, messageKey); } ```