-
 @ 266815e0:6cd408a5
2025-05-16 20:52:42
@ 266815e0:6cd408a5
2025-05-16 20:52:42Streams are the key to nostr
Loading events from a nostr relay is probably the most inconsistent way of loading data I've had to work with, and that's only loading from a single relay. the problem gets exponentially more complicated once you try to load events from multiple relays
Unlike HTTP nostr does not have a simple flow with timeouts built in. events are sent back one at a time and can fail at any point or have massive (10s) gaps between them
The key is to use streams. something that starts, emits any number of results, then maybe errors or completes. luckily it just so happens that JavaScript / TypeScript has a great observable stream library called RxJS
What is an observable
An
Observablein RxJS is stream a of data that are initialized lazily, which means the stream is inactive and not running until something subscribes to it```ts let stream = new Observable((observer) => { observer.next(1) observer.next(2) observer.next(3) observer.complete() })
// The stream method isn't run until its subscribed to stream.subscribe(v => console.log(v)) ```
This is super powerful and perfect for nostr because it means we don't need to manage the life-cycle of the stream. it will run when something subscribes to it and stop when unsubscribed.
Its helpful to think of this as "pulling" data. once we have created an observable we can request the data from it at any point in the future.
Pulling data from relays
We can use the lazy nature of observables to only start fetching events from a nostr relay when we need them
For example we can create an observable that will load kind 1 events from the damus relay and stream them back as they are returned from the relay
```typescript let req = new Observable((observer) => { // Create a new websocket connection when the observable is start let ws = new WebSocket('wss://relay.damus.io')
ws.onopen = () => { // Start a REQ ws.send(JSON.stringify(['REQ', 'test', {kinds: [1], limit: 20}])) }
ws.onmessage = (event) => { let message = JSON.parse(event.data) // Get the event from the message and pass it along to the subscribers if(message[0] === 'EVENT') observer.next(message[1]) }
// Cleanup subscription return () => { ws.send(JSON.stringify(['CLOSE', 'test'])) ws.close() } }) ```
But creating the observable wont do anything. we need to subscribe to it to get any events.
ts let sub = req.subscribe(event => { console.log('we got an event' event) })Cool now we are pulling events from a relay. once we are done we can stop listening to it by unsubscribing from it
ts sub.unsubscribe()This will call the cleanup method on the observable, which in turn closes the connection to the relay.
Hopefully you can see how this work, we don't have any
open,connect, ordisconnectmethods. we simply subscribe to a stream of events and it handles all the messy logic of connecting to a relayComposing and chaining observables
I've shown you how we can create a simple stream of events from a relay, but what if we want to pull from two relays?
Easy, lets make the previous example into a function that takes a relay URL
```ts function getNoteFromRelay(relay: string){ return new Observable((observer) => { let ws = new WebSocket(relay)
// ...rest of the observable...}) } ```
Then we can "merge" two of these observables into a single observable using the
mergemethod from RxJSThe
mergemethod will create a single observable that subscribes to both upstream observables and sends all the events back. Think of it as pulling events from both relays at once```ts import { merge } from 'rxjs'
const notes = merge( getNoteFromRelay('wss://relay.damus.io'), getNoteFromRelay('wss://nos.lol') )
// Subscribe to the observable to start getting data from it const sub = notes.subscribe(event => { console.log(event) })
// later unsubscribe setTimeout(() => { sub.unsubscribe() }, 10_000) ```
But now we have a problem, because we are pulling events from two relays we are getting duplicate events. to solve this we can use the
.pipemethod and thedistinctoperator from RxJS to modify our single observable to only return one version of each eventThe
.pipemethod will create a chain of observables that will each subscribe to the previous one and modify the returned values in some wayThe
distinctoperator takes a method that returns a unique identifier and filters out any duplicate values```ts import { merge, distinct } from 'rxjs'
const notes = merge( getNoteFromRelay('wss://relay.damus.io'), getNoteFromRelay('wss://nos.lol') ).pipe( // filter out events we have seen before based on the event id distinct(event => event.id) ) ```
Now we have an observable that when subscribed to will connect to two relays and return a stream of events without duplicates...
As you can see things can start getting complicated fast. but its also very powerful because we aren't managing any life-cycle code, we just subscribe and unsubscribe from an observable
Taking it to an extreme
Hopefully at this point you can see how powerful this is, we can think of almost any data loading pattern as a series of observables that pull data from upstream observables and stream it back to the original subscriber.
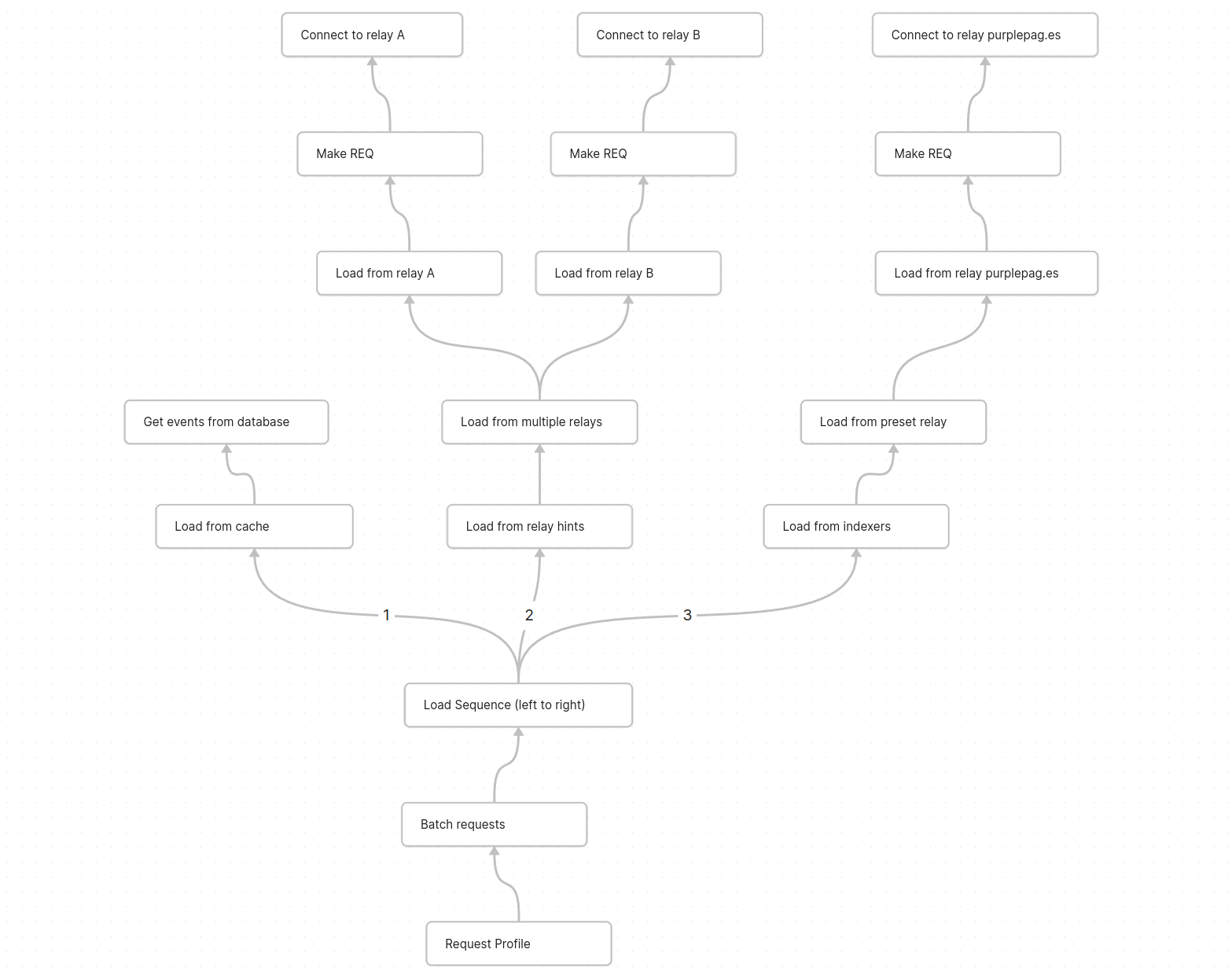
Here is a quick sketch of what it could look like to load user profiles. each node is an observable that "pulls" data from its child node ending with the "connect websocket" or "load from database" nodes which do the work of making a relay connection
Conclusion
All this might seem pretty simple and straight forward, but its been a long six month of learning for me. I've had to completely rethink how data and nostr events should be handled in a client and how to avoid screwing up and shooting myself in the foot with these powerful tools.
If you want to give RxJS a try I would encourage you to checkout the nostr sdk I've been building called applesauce
Its uses RxJS for pretty much everything and has the simplest and most flexible relay connection API I've seen so far (mainly no life-cycle management)
-
 @ 21335073:a244b1ad
2025-05-09 13:56:57
@ 21335073:a244b1ad
2025-05-09 13:56:57Someone asked for my thoughts, so I’ll share them thoughtfully. I’m not here to dictate how to promote Nostr—I’m still learning about it myself. While I’m not new to Nostr, freedom tech is a newer space for me. I’m skilled at advocating for topics I deeply understand, but freedom tech isn’t my expertise, so take my words with a grain of salt. Nothing I say is set in stone.
Those who need Nostr the most are the ones most vulnerable to censorship on other platforms right now. Reaching them requires real-time awareness of global issues and the dynamic relationships between governments and tech providers, which can shift suddenly. Effective Nostr promoters must grasp this and adapt quickly.
The best messengers are people from or closely tied to these at-risk regions—those who truly understand the local political and cultural dynamics. They can connect with those in need when tensions rise. Ideal promoters are rational, trustworthy, passionate about Nostr, but above all, dedicated to amplifying people’s voices when it matters most.
Forget influencers, corporate-backed figures, or traditional online PR—it comes off as inauthentic, corny, desperate and forced. Nostr’s promotion should be grassroots and organic, driven by a few passionate individuals who believe in Nostr and the communities they serve.
The idea that “people won’t join Nostr due to lack of reach” is nonsense. Everyone knows X’s “reach” is mostly with bots. If humans want real conversations, Nostr is the place. X is great for propaganda, but Nostr is for the authentic voices of the people.
Those spreading Nostr must be so passionate they’re willing to onboard others, which is time-consuming but rewarding for the right person. They’ll need to make Nostr and onboarding a core part of who they are. I see no issue with that level of dedication. I’ve been known to get that way myself at times. It’s fun for some folks.
With love, I suggest not adding Bitcoin promotion with Nostr outreach. Zaps already integrate that element naturally. (Still promote within the Bitcoin ecosystem, but this is about reaching vulnerable voices who needed Nostr yesterday.)
To promote Nostr, forget conventional strategies. “Influencers” aren’t the answer. “Influencers” are not the future. A trusted local community member has real influence—reach them. Connect with people seeking Nostr’s benefits but lacking the technical language to express it. This means some in the Nostr community might need to step outside of the Bitcoin bubble, which is uncomfortable but necessary. Thank you in advance to those who are willing to do that.
I don’t know who is paid to promote Nostr, if anyone. This piece isn’t shade. But it’s exhausting to see innocent voices globally silenced on corporate platforms like X while Nostr exists. Last night, I wondered: how many more voices must be censored before the Nostr community gets uncomfortable and thinks creatively to reach the vulnerable?
A warning: the global need for censorship-resistant social media is undeniable. If Nostr doesn’t make itself known, something else will fill that void. Let’s start this conversation.
-
 @ 21335073:a244b1ad
2025-05-01 01:51:10
@ 21335073:a244b1ad
2025-05-01 01:51:10Please respect Virginia Giuffre’s memory by refraining from asking about the circumstances or theories surrounding her passing.
Since Virginia Giuffre’s death, I’ve reflected on what she would want me to say or do. This piece is my attempt to honor her legacy.
When I first spoke with Virginia, I was struck by her unshakable hope. I had grown cynical after years in the anti-human trafficking movement, worn down by a broken system and a government that often seemed complicit. But Virginia’s passion, creativity, and belief that survivors could be heard reignited something in me. She reminded me of my younger, more hopeful self. Instead of warning her about the challenges ahead, I let her dream big, unburdened by my own disillusionment. That conversation changed me for the better, and following her lead led to meaningful progress.
Virginia was one of the bravest people I’ve ever known. As a survivor of Epstein, Maxwell, and their co-conspirators, she risked everything to speak out, taking on some of the world’s most powerful figures.
She loved when I said, “Epstein isn’t the only Epstein.” This wasn’t just about one man—it was a call to hold all abusers accountable and to ensure survivors find hope and healing.
The Epstein case often gets reduced to sensational details about the elite, but that misses the bigger picture. Yes, we should be holding all of the co-conspirators accountable, we must listen to the survivors’ stories. Their experiences reveal how predators exploit vulnerabilities, offering lessons to prevent future victims.
You’re not powerless in this fight. Educate yourself about trafficking and abuse—online and offline—and take steps to protect those around you. Supporting survivors starts with small, meaningful actions. Free online resources can guide you in being a safe, supportive presence.
When high-profile accusations arise, resist snap judgments. Instead of dismissing survivors as “crazy,” pause to consider the trauma they may be navigating. Speaking out or coping with abuse is never easy. You don’t have to believe every claim, but you can refrain from attacking accusers online.
Society also fails at providing aftercare for survivors. The government, often part of the problem, won’t solve this. It’s up to us. Prevention is critical, but when abuse occurs, step up for your loved ones and community. Protect the vulnerable. it’s a challenging but a rewarding journey.
If you’re contributing to Nostr, you’re helping build a censorship resistant platform where survivors can share their stories freely, no matter how powerful their abusers are. Their voices can endure here, offering strength and hope to others. This gives me great hope for the future.
Virginia Giuffre’s courage was a gift to the world. It was an honor to know and serve her. She will be deeply missed. My hope is that her story inspires others to take on the powerful.
-
 @ 52b4a076:e7fad8bd
2025-04-28 00:48:57
@ 52b4a076:e7fad8bd
2025-04-28 00:48:57I have been recently building NFDB, a new relay DB. This post is meant as a short overview.
Regular relays have challenges
Current relay software have significant challenges, which I have experienced when hosting Nostr.land: - Scalability is only supported by adding full replicas, which does not scale to large relays. - Most relays use slow databases and are not optimized for large scale usage. - Search is near-impossible to implement on standard relays. - Privacy features such as NIP-42 are lacking. - Regular DB maintenance tasks on normal relays require extended downtime. - Fault-tolerance is implemented, if any, using a load balancer, which is limited. - Personalization and advanced filtering is not possible. - Local caching is not supported.
NFDB: A scalable database for large relays
NFDB is a new database meant for medium-large scale relays, built on FoundationDB that provides: - Near-unlimited scalability - Extended fault tolerance - Instant loading - Better search - Better personalization - and more.
Search
NFDB has extended search capabilities including: - Semantic search: Search for meaning, not words. - Interest-based search: Highlight content you care about. - Multi-faceted queries: Easily filter by topic, author group, keywords, and more at the same time. - Wide support for event kinds, including users, articles, etc.
Personalization
NFDB allows significant personalization: - Customized algorithms: Be your own algorithm. - Spam filtering: Filter content to your WoT, and use advanced spam filters. - Topic mutes: Mute topics, not keywords. - Media filtering: With Nostr.build, you will be able to filter NSFW and other content - Low data mode: Block notes that use high amounts of cellular data. - and more
Other
NFDB has support for many other features such as: - NIP-42: Protect your privacy with private drafts and DMs - Microrelays: Easily deploy your own personal microrelay - Containers: Dedicated, fast storage for discoverability events such as relay lists
Calcite: A local microrelay database
Calcite is a lightweight, local version of NFDB that is meant for microrelays and caching, meant for thousands of personal microrelays.
Calcite HA is an additional layer that allows live migration and relay failover in under 30 seconds, providing higher availability compared to current relays with greater simplicity. Calcite HA is enabled in all Calcite deployments.
For zero-downtime, NFDB is recommended.
Noswhere SmartCache
Relays are fixed in one location, but users can be anywhere.
Noswhere SmartCache is a CDN for relays that dynamically caches data on edge servers closest to you, allowing: - Multiple regions around the world - Improved throughput and performance - Faster loading times
routerd
routerdis a custom load-balancer optimized for Nostr relays, integrated with SmartCache.routerdis specifically integrated with NFDB and Calcite HA to provide fast failover and high performance.Ending notes
NFDB is planned to be deployed to Nostr.land in the coming weeks.
A lot more is to come. 👀️️️️️️
-
 @ c9badfea:610f861a
2025-05-16 20:15:31
@ c9badfea:610f861a
2025-05-16 20:15:31- Install Obtainium (it's free and open source)
- Launch the app and allow notifications
- Open your browser, navigate to the GitHub page of the app you want to install, and copy the URL (e.g.
https://github.com/revanced/revanced-managerfor ReVanced) - Launch Obtainium, navigate to Add App, paste the URL into App Source URL, and tap Add
- Wait for the loading process to finish
- You can now tap Install to install the application
- Enable Allow From This Source and return to Obtainium
- Proceed with the installation by tapping Install
ℹ️ Besides GitHub, Obtainium can install from additional sources
ℹ️ You can also explore Complex Obtainium Apps for more options
-
 @ 91bea5cd:1df4451c
2025-04-26 10:16:21
@ 91bea5cd:1df4451c
2025-04-26 10:16:21O Contexto Legal Brasileiro e o Consentimento
No ordenamento jurídico brasileiro, o consentimento do ofendido pode, em certas circunstâncias, afastar a ilicitude de um ato que, sem ele, configuraria crime (como lesão corporal leve, prevista no Art. 129 do Código Penal). Contudo, o consentimento tem limites claros: não é válido para bens jurídicos indisponíveis, como a vida, e sua eficácia é questionável em casos de lesões corporais graves ou gravíssimas.
A prática de BDSM consensual situa-se em uma zona complexa. Em tese, se ambos os parceiros são adultos, capazes, e consentiram livre e informadamente nos atos praticados, sem que resultem em lesões graves permanentes ou risco de morte não consentido, não haveria crime. O desafio reside na comprovação desse consentimento, especialmente se uma das partes, posteriormente, o negar ou alegar coação.
A Lei Maria da Penha (Lei nº 11.340/2006)
A Lei Maria da Penha é um marco fundamental na proteção da mulher contra a violência doméstica e familiar. Ela estabelece mecanismos para coibir e prevenir tal violência, definindo suas formas (física, psicológica, sexual, patrimonial e moral) e prevendo medidas protetivas de urgência.
Embora essencial, a aplicação da lei em contextos de BDSM pode ser delicada. Uma alegação de violência por parte da mulher, mesmo que as lesões ou situações decorram de práticas consensuais, tende a receber atenção prioritária das autoridades, dada a presunção de vulnerabilidade estabelecida pela lei. Isso pode criar um cenário onde o parceiro masculino enfrenta dificuldades significativas em demonstrar a natureza consensual dos atos, especialmente se não houver provas robustas pré-constituídas.
Outros riscos:
Lesão corporal grave ou gravíssima (art. 129, §§ 1º e 2º, CP), não pode ser justificada pelo consentimento, podendo ensejar persecução penal.
Crimes contra a dignidade sexual (arts. 213 e seguintes do CP) são de ação pública incondicionada e independem de representação da vítima para a investigação e denúncia.
Riscos de Falsas Acusações e Alegação de Coação Futura
Os riscos para os praticantes de BDSM, especialmente para o parceiro que assume o papel dominante ou que inflige dor/restrição (frequentemente, mas não exclusivamente, o homem), podem surgir de diversas frentes:
- Acusações Externas: Vizinhos, familiares ou amigos que desconhecem a natureza consensual do relacionamento podem interpretar sons, marcas ou comportamentos como sinais de abuso e denunciar às autoridades.
- Alegações Futuras da Parceira: Em caso de término conturbado, vingança, arrependimento ou mudança de perspectiva, a parceira pode reinterpretar as práticas passadas como abuso e buscar reparação ou retaliação através de uma denúncia. A alegação pode ser de que o consentimento nunca existiu ou foi viciado.
- Alegação de Coação: Uma das formas mais complexas de refutar é a alegação de que o consentimento foi obtido mediante coação (física, moral, psicológica ou econômica). A parceira pode alegar, por exemplo, que se sentia pressionada, intimidada ou dependente, e que seu "sim" não era genuíno. Provar a ausência de coação a posteriori é extremamente difícil.
- Ingenuidade e Vulnerabilidade Masculina: Muitos homens, confiando na dinâmica consensual e na parceira, podem negligenciar a necessidade de precauções. A crença de que "isso nunca aconteceria comigo" ou a falta de conhecimento sobre as implicações legais e o peso processual de uma acusação no âmbito da Lei Maria da Penha podem deixá-los vulneráveis. A presença de marcas físicas, mesmo que consentidas, pode ser usada como evidência de agressão, invertendo o ônus da prova na prática, ainda que não na teoria jurídica.
Estratégias de Prevenção e Mitigação
Não existe um método infalível para evitar completamente o risco de uma falsa acusação, mas diversas medidas podem ser adotadas para construir um histórico de consentimento e reduzir vulnerabilidades:
- Comunicação Explícita e Contínua: A base de qualquer prática BDSM segura é a comunicação constante. Negociar limites, desejos, palavras de segurança ("safewords") e expectativas antes, durante e depois das cenas é crucial. Manter registros dessas negociações (e-mails, mensagens, diários compartilhados) pode ser útil.
-
Documentação do Consentimento:
-
Contratos de Relacionamento/Cena: Embora a validade jurídica de "contratos BDSM" seja discutível no Brasil (não podem afastar normas de ordem pública), eles servem como forte evidência da intenção das partes, da negociação detalhada de limites e do consentimento informado. Devem ser claros, datados, assinados e, idealmente, reconhecidos em cartório (para prova de data e autenticidade das assinaturas).
-
Registros Audiovisuais: Gravar (com consentimento explícito para a gravação) discussões sobre consentimento e limites antes das cenas pode ser uma prova poderosa. Gravar as próprias cenas é mais complexo devido a questões de privacidade e potencial uso indevido, mas pode ser considerado em casos específicos, sempre com consentimento mútuo documentado para a gravação.
Importante: a gravação deve ser com ciência da outra parte, para não configurar violação da intimidade (art. 5º, X, da Constituição Federal e art. 20 do Código Civil).
-
-
Testemunhas: Em alguns contextos de comunidade BDSM, a presença de terceiros de confiança durante negociações ou mesmo cenas pode servir como testemunho, embora isso possa alterar a dinâmica íntima do casal.
- Estabelecimento Claro de Limites e Palavras de Segurança: Definir e respeitar rigorosamente os limites (o que é permitido, o que é proibido) e as palavras de segurança é fundamental. O desrespeito a uma palavra de segurança encerra o consentimento para aquele ato.
- Avaliação Contínua do Consentimento: O consentimento não é um cheque em branco; ele deve ser entusiástico, contínuo e revogável a qualquer momento. Verificar o bem-estar do parceiro durante a cena ("check-ins") é essencial.
- Discrição e Cuidado com Evidências Físicas: Ser discreto sobre a natureza do relacionamento pode evitar mal-entendidos externos. Após cenas que deixem marcas, é prudente que ambos os parceiros estejam cientes e de acordo, talvez documentando por fotos (com data) e uma nota sobre a consensualidade da prática que as gerou.
- Aconselhamento Jurídico Preventivo: Consultar um advogado especializado em direito de família e criminal, com sensibilidade para dinâmicas de relacionamento alternativas, pode fornecer orientação personalizada sobre as melhores formas de documentar o consentimento e entender os riscos legais específicos.
Observações Importantes
- Nenhuma documentação substitui a necessidade de consentimento real, livre, informado e contínuo.
- A lei brasileira protege a "integridade física" e a "dignidade humana". Práticas que resultem em lesões graves ou que violem a dignidade de forma não consentida (ou com consentimento viciado) serão ilegais, independentemente de qualquer acordo prévio.
- Em caso de acusação, a existência de documentação robusta de consentimento não garante a absolvição, mas fortalece significativamente a defesa, ajudando a demonstrar a natureza consensual da relação e das práticas.
-
A alegação de coação futura é particularmente difícil de prevenir apenas com documentos. Um histórico consistente de comunicação aberta (whatsapp/telegram/e-mails), respeito mútuo e ausência de dependência ou controle excessivo na relação pode ajudar a contextualizar a dinâmica como não coercitiva.
-
Cuidado com Marcas Visíveis e Lesões Graves Práticas que resultam em hematomas severos ou lesões podem ser interpretadas como agressão, mesmo que consentidas. Evitar excessos protege não apenas a integridade física, mas também evita questionamentos legais futuros.
O que vem a ser consentimento viciado
No Direito, consentimento viciado é quando a pessoa concorda com algo, mas a vontade dela não é livre ou plena — ou seja, o consentimento existe formalmente, mas é defeituoso por alguma razão.
O Código Civil brasileiro (art. 138 a 165) define várias formas de vício de consentimento. As principais são:
Erro: A pessoa se engana sobre o que está consentindo. (Ex.: A pessoa acredita que vai participar de um jogo leve, mas na verdade é exposta a práticas pesadas.)
Dolo: A pessoa é enganada propositalmente para aceitar algo. (Ex.: Alguém mente sobre o que vai acontecer durante a prática.)
Coação: A pessoa é forçada ou ameaçada a consentir. (Ex.: "Se você não aceitar, eu termino com você" — pressão emocional forte pode ser vista como coação.)
Estado de perigo ou lesão: A pessoa aceita algo em situação de necessidade extrema ou abuso de sua vulnerabilidade. (Ex.: Alguém em situação emocional muito fragilizada é induzida a aceitar práticas que normalmente recusaria.)
No contexto de BDSM, isso é ainda mais delicado: Mesmo que a pessoa tenha "assinado" um contrato ou dito "sim", se depois ela alegar que seu consentimento foi dado sob medo, engano ou pressão psicológica, o consentimento pode ser considerado viciado — e, portanto, juridicamente inválido.
Isso tem duas implicações sérias:
-
O crime não se descaracteriza: Se houver vício, o consentimento é ignorado e a prática pode ser tratada como crime normal (lesão corporal, estupro, tortura, etc.).
-
A prova do consentimento precisa ser sólida: Mostrando que a pessoa estava informada, lúcida, livre e sem qualquer tipo de coação.
Consentimento viciado é quando a pessoa concorda formalmente, mas de maneira enganada, forçada ou pressionada, tornando o consentimento inútil para efeitos jurídicos.
Conclusão
Casais que praticam BDSM consensual no Brasil navegam em um terreno que exige não apenas confiança mútua e comunicação excepcional, mas também uma consciência aguçada das complexidades legais e dos riscos de interpretações equivocadas ou acusações mal-intencionadas. Embora o BDSM seja uma expressão legítima da sexualidade humana, sua prática no Brasil exige responsabilidade redobrada. Ter provas claras de consentimento, manter a comunicação aberta e agir com prudência são formas eficazes de se proteger de falsas alegações e preservar a liberdade e a segurança de todos os envolvidos. Embora leis controversas como a Maria da Penha sejam "vitais" para a proteção contra a violência real, os praticantes de BDSM, e em particular os homens nesse contexto, devem adotar uma postura proativa e prudente para mitigar os riscos inerentes à potencial má interpretação ou instrumentalização dessas práticas e leis, garantindo que a expressão de sua consensualidade esteja resguardada na medida do possível.
Importante: No Brasil, mesmo com tudo isso, o Ministério Público pode denunciar por crime como lesão corporal grave, estupro ou tortura, independente de consentimento. Então a prudência nas práticas é fundamental.
Aviso Legal: Este artigo tem caráter meramente informativo e não constitui aconselhamento jurídico. As leis e interpretações podem mudar, e cada situação é única. Recomenda-se buscar orientação de um advogado qualificado para discutir casos específicos.
Se curtiu este artigo faça uma contribuição, se tiver algum ponto relevante para o artigo deixe seu comentário.
-
 @ b83a28b7:35919450
2025-05-16 19:26:56
@ b83a28b7:35919450
2025-05-16 19:26:56This article was originally part of the sermon of Plebchain Radio Episode 111 (May 2, 2025) that nostr:nprofile1qyxhwumn8ghj7mn0wvhxcmmvqyg8wumn8ghj7mn0wd68ytnvv9hxgqpqtvqc82mv8cezhax5r34n4muc2c4pgjz8kaye2smj032nngg52clq7fgefr and I did with nostr:nprofile1qythwumn8ghj7ct5d3shxtnwdaehgu3wd3skuep0qyt8wumn8ghj7ct4w35zumn0wd68yvfwvdhk6tcqyzx4h2fv3n9r6hrnjtcrjw43t0g0cmmrgvjmg525rc8hexkxc0kd2rhtk62 and nostr:nprofile1qyxhwumn8ghj7mn0wvhxcmmvqyg8wumn8ghj7mn0wd68ytnvv9hxgqpq4wxtsrj7g2jugh70pfkzjln43vgn4p7655pgky9j9w9d75u465pqahkzd0 of the nostr:nprofile1qythwumn8ghj7ct5d3shxtnwdaehgu3wd3skuep0qyt8wumn8ghj7etyv4hzumn0wd68ytnvv9hxgtcqyqwfvwrccp4j2xsuuvkwg0y6a20637t6f4cc5zzjkx030dkztt7t5hydajn
Listen to the full episode here:
<<https://fountain.fm/episode/Ln9Ej0zCZ5dEwfo8w2Ho>>
Bitcoin has always been a narrative revolution disguised as code. White paper, cypherpunk lore, pizza‑day legends - every block is a paragraph in the world’s most relentless epic. But code alone rarely converts the skeptic; it’s the camp‑fire myth that slips past the prefrontal cortex and shakes hands with the limbic system. People don’t adopt protocols first - they fall in love with protagonists.
Early adopters heard the white‑paper hymn, but most folks need characters first: a pizza‑day dreamer; a mother in a small country, crushed by the cost of remittance; a Warsaw street vendor swapping złoty for sats. When their arcs land, the brain releases a neurochemical OP_RETURN which says, “I belong in this plot.” That’s the sly roundabout orange pill: conviction smuggled inside catharsis.
That’s why, from 22–25 May in Warsaw’s Kinoteka, the Bitcoin Film Fest is loading its reels with rebellion. Each documentary, drama, and animated rabbit‑hole is a stealth wallet, zipping conviction straight into the feels of anyone still clasped within the cold claw of fiat. You come for the plot, you leave checking block heights.
Here's the clip of the sermon from the episode:
nostr:nevent1qvzqqqqqqypzpwp69zm7fewjp0vkp306adnzt7249ytxhz7mq3w5yc629u6er9zsqqsy43fwz8es2wnn65rh0udc05tumdnx5xagvzd88ptncspmesdqhygcrvpf2
-
 @ c631e267:c2b78d3e
2025-05-16 18:40:18
@ c631e267:c2b78d3e
2025-05-16 18:40:18Die zwei mächtigsten Krieger sind Geduld und Zeit. \ Leo Tolstoi
Zum Wohle unserer Gesundheit, unserer Leistungsfähigkeit und letztlich unseres Glücks ist es wichtig, die eigene Energie bewusst zu pflegen. Das gilt umso mehr für an gesellschaftlichen Themen interessierte, selbstbewusste und kritisch denkende Menschen. Denn für deren Wahrnehmung und Wohlbefinden waren und sind die rasanten, krisen- und propagandagefüllten letzten Jahre in Absurdistan eine harte Probe.
Nur wer regelmäßig Kraft tankt und Wege findet, mit den Herausforderungen umzugehen, kann eine solche Tortur überstehen, emotionale Erschöpfung vermeiden und trotz allem zufrieden sein. Dazu müssen wir erkunden, was uns Energie gibt und was sie uns raubt. Durch Selbstreflexion und Achtsamkeit finden wir sicher Dinge, die uns erfreuen und inspirieren, und andere, die uns eher stressen und belasten.
Die eigene Energie ist eng mit unserer körperlichen und mentalen Gesundheit verbunden. Methoden zur Förderung der körperlichen Gesundheit sind gut bekannt: eine ausgewogene Ernährung, regelmäßige Bewegung sowie ausreichend Schlaf und Erholung. Bei der nicht minder wichtigen emotionalen Balance wird es schon etwas komplizierter. Stress abzubauen, die eigenen Grenzen zu kennen oder solche zum Schutz zu setzen sowie die Konzentration auf Positives und Sinnvolles wären Ansätze.
Der emotionale ist auch der Bereich, über den «Energie-Räuber» bevorzugt attackieren. Das sind zum Beispiel Dinge wie Überforderung, Perfektionismus oder mangelhafte Kommunikation. Social Media gehören ganz sicher auch dazu. Sie stehlen uns nicht nur Zeit, sondern sind höchst manipulativ und erhöhen laut einer aktuellen Studie das Risiko für psychische Probleme wie Angstzustände und Depressionen.
Geben wir negativen oder gar bösen Menschen keine Macht über uns. Das Dauerfeuer der letzten Jahre mit Krisen, Konflikten und Gefahren sollte man zwar kennen, darf sich aber davon nicht runterziehen lassen. Das Ziel derartiger konzertierter Aktionen ist vor allem, unsere innere Stabilität zu zerstören, denn dann sind wir leichter zu steuern. Aber Geduld: Selbst vermeintliche «Sonnenköniginnen» wie EU-Kommissionspräsidentin von der Leyen fallen, wenn die Zeit reif ist.
Es ist wichtig, dass wir unsere ganz eigenen Bedürfnisse und Werte erkennen. Unsere Energiequellen müssen wir identifizieren und aktiv nutzen. Dazu gehören soziale Kontakte genauso wie zum Beispiel Hobbys und Leidenschaften. Umgeben wir uns mit Sinnhaftigkeit und lassen wir uns nicht die Energie rauben!
Mein Wahlspruch ist schon lange: «Was die Menschen wirklich bewegt, ist die Kultur.» Jetzt im Frühjahr beginnt hier in Andalusien die Zeit der «Ferias», jener traditionellen Volksfeste, die vor Lebensfreude sprudeln. Konzentrieren wir uns auf die schönen Dinge und auf unsere eigenen Talente – soziale Verbundenheit wird helfen, unsere innere Kraft zu stärken und zu bewahren.
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ e3ba5e1a:5e433365
2025-04-15 11:03:15
@ e3ba5e1a:5e433365
2025-04-15 11:03:15Prelude
I wrote this post differently than any of my others. It started with a discussion with AI on an OPSec-inspired review of separation of powers, and evolved into quite an exciting debate! I asked Grok to write up a summary in my overall writing style, which it got pretty well. I've decided to post it exactly as-is. Ultimately, I think there are two solid ideas driving my stance here:
- Perfect is the enemy of the good
- Failure is the crucible of success
Beyond that, just some hard-core belief in freedom, separation of powers, and operating from self-interest.
Intro
Alright, buckle up. I’ve been chewing on this idea for a while, and it’s time to spit it out. Let’s look at the U.S. government like I’d look at a codebase under a cybersecurity audit—OPSEC style, no fluff. Forget the endless debates about what politicians should do. That’s noise. I want to talk about what they can do, the raw powers baked into the system, and why we should stop pretending those powers are sacred. If there’s a hole, either patch it or exploit it. No half-measures. And yeah, I’m okay if the whole thing crashes a bit—failure’s a feature, not a bug.
The Filibuster: A Security Rule with No Teeth
You ever see a firewall rule that’s more theater than protection? That’s the Senate filibuster. Everyone acts like it’s this untouchable guardian of democracy, but here’s the deal: a simple majority can torch it any day. It’s not a law; it’s a Senate preference, like choosing tabs over spaces. When people call killing it the “nuclear option,” I roll my eyes. Nuclear? It’s a button labeled “press me.” If a party wants it gone, they’ll do it. So why the dance?
I say stop playing games. Get rid of the filibuster. If you’re one of those folks who thinks it’s the only thing saving us from tyranny, fine—push for a constitutional amendment to lock it in. That’s a real patch, not a Post-it note. Until then, it’s just a vulnerability begging to be exploited. Every time a party threatens to nuke it, they’re admitting it’s not essential. So let’s stop pretending and move on.
Supreme Court Packing: Because Nine’s Just a Number
Here’s another fun one: the Supreme Court. Nine justices, right? Sounds official. Except it’s not. The Constitution doesn’t say nine—it’s silent on the number. Congress could pass a law tomorrow to make it 15, 20, or 42 (hitchhiker’s reference, anyone?). Packing the court is always on the table, and both sides know it. It’s like a root exploit just sitting there, waiting for someone to log in.
So why not call the bluff? If you’re in power—say, Trump’s back in the game—say, “I’m packing the court unless we amend the Constitution to fix it at nine.” Force the issue. No more shadowboxing. And honestly? The court’s got way too much power anyway. It’s not supposed to be a super-legislature, but here we are, with justices’ ideologies driving the bus. That’s a bug, not a feature. If the court weren’t such a kingmaker, packing it wouldn’t even matter. Maybe we should be talking about clipping its wings instead of just its size.
The Executive Should Go Full Klingon
Let’s talk presidents. I’m not saying they should wear Klingon armor and start shouting “Qapla’!”—though, let’s be real, that’d be awesome. I’m saying the executive should use every scrap of power the Constitution hands them. Enforce the laws you agree with, sideline the ones you don’t. If Congress doesn’t like it, they’ve got tools: pass new laws, override vetoes, or—here’s the big one—cut the budget. That’s not chaos; that’s the system working as designed.
Right now, the real problem isn’t the president overreaching; it’s the bureaucracy. It’s like a daemon running in the background, eating CPU and ignoring the user. The president’s supposed to be the one steering, but the administrative state’s got its own agenda. Let the executive flex, push the limits, and force Congress to check it. Norms? Pfft. The Constitution’s the spec sheet—stick to it.
Let the System Crash
Here’s where I get a little spicy: I’m totally fine if the government grinds to a halt. Deadlock isn’t a disaster; it’s a feature. If the branches can’t agree, let the president veto, let Congress starve the budget, let enforcement stall. Don’t tell me about “essential services.” Nothing’s so critical it can’t take a breather. Shutdowns force everyone to the table—debate, compromise, or expose who’s dropping the ball. If the public loses trust? Good. They’ll vote out the clowns or live with the circus they elected.
Think of it like a server crash. Sometimes you need a hard reboot to clear the cruft. If voters keep picking the same bad admins, well, the country gets what it deserves. Failure’s the best teacher—way better than limping along on autopilot.
States Are the Real MVPs
If the feds fumble, states step up. Right now, states act like junior devs waiting for the lead engineer to sign off. Why? Federal money. It’s a leash, and it’s tight. Cut that cash, and states will remember they’re autonomous. Some will shine, others will tank—looking at you, California. And I’m okay with that. Let people flee to better-run states. No bailouts, no excuses. States are like competing startups: the good ones thrive, the bad ones pivot or die.
Could it get uneven? Sure. Some states might turn into sci-fi utopias while others look like a post-apocalyptic vidya game. That’s the point—competition sorts it out. Citizens can move, markets adjust, and failure’s a signal to fix your act.
Chaos Isn’t the Enemy
Yeah, this sounds messy. States ignoring federal law, external threats poking at our seams, maybe even a constitutional crisis. I’m not scared. The Supreme Court’s there to referee interstate fights, and Congress sets the rules for state-to-state play. But if it all falls apart? Still cool. States can sort it without a babysitter—it’ll be ugly, but freedom’s worth it. External enemies? They’ll either unify us or break us. If we can’t rally, we don’t deserve the win.
Centralizing power to avoid this is like rewriting your app in a single thread to prevent race conditions—sure, it’s simpler, but you’re begging for a deadlock. Decentralized chaos lets states experiment, lets people escape, lets markets breathe. States competing to cut regulations to attract businesses? That’s a race to the bottom for red tape, but a race to the top for innovation—workers might gripe, but they’ll push back, and the tension’s healthy. Bring it—let the cage match play out. The Constitution’s checks are enough if we stop coddling the system.
Why This Matters
I’m not pitching a utopia. I’m pitching a stress test. The U.S. isn’t a fragile porcelain doll; it’s a rugged piece of hardware built to take some hits. Let it fail a little—filibuster, court, feds, whatever. Patch the holes with amendments if you want, or lean into the grind. Either way, stop fearing the crash. It’s how we debug the republic.
So, what’s your take? Ready to let the system rumble, or got a better way to secure the code? Hit me up—I’m all ears.
-
 @ 04c915da:3dfbecc9
2025-05-16 17:12:05
@ 04c915da:3dfbecc9
2025-05-16 17:12:05One of the most common criticisms leveled against nostr is the perceived lack of assurance when it comes to data storage. Critics argue that without a centralized authority guaranteeing that all data is preserved, important information will be lost. They also claim that running a relay will become prohibitively expensive. While there is truth to these concerns, they miss the mark. The genius of nostr lies in its flexibility, resilience, and the way it harnesses human incentives to ensure data availability in practice.
A nostr relay is simply a server that holds cryptographically verifiable signed data and makes it available to others. Relays are simple, flexible, open, and require no permission to run. Critics are right that operating a relay attempting to store all nostr data will be costly. What they miss is that most will not run all encompassing archive relays. Nostr does not rely on massive archive relays. Instead, anyone can run a relay and choose to store whatever subset of data they want. This keeps costs low and operations flexible, making relay operation accessible to all sorts of individuals and entities with varying use cases.
Critics are correct that there is no ironclad guarantee that every piece of data will always be available. Unlike bitcoin where data permanence is baked into the system at a steep cost, nostr does not promise that every random note or meme will be preserved forever. That said, in practice, any data perceived as valuable by someone will likely be stored and distributed by multiple entities. If something matters to someone, they will keep a signed copy.
Nostr is the Streisand Effect in protocol form. The Streisand effect is when an attempt to suppress information backfires, causing it to spread even further. With nostr, anyone can broadcast signed data, anyone can store it, and anyone can distribute it. Try to censor something important? Good luck. The moment it catches attention, it will be stored on relays across the globe, copied, and shared by those who find it worth keeping. Data deemed important will be replicated across servers by individuals acting in their own interest.
Nostr’s distributed nature ensures that the system does not rely on a single point of failure or a corporate overlord. Instead, it leans on the collective will of its users. The result is a network where costs stay manageable, participation is open to all, and valuable verifiable data is stored and distributed forever.
-
 @ 04c915da:3dfbecc9
2025-05-16 18:06:46
@ 04c915da:3dfbecc9
2025-05-16 18:06:46Bitcoin has always been rooted in freedom and resistance to authority. I get that many of you are conflicted about the US Government stacking but by design we cannot stop anyone from using bitcoin. Many have asked me for my thoughts on the matter, so let’s rip it.
Concern
One of the most glaring issues with the strategic bitcoin reserve is its foundation, built on stolen bitcoin. For those of us who value private property this is an obvious betrayal of our core principles. Rather than proof of work, the bitcoin that seeds this reserve has been taken by force. The US Government should return the bitcoin stolen from Bitfinex and the Silk Road.
Using stolen bitcoin for the reserve creates a perverse incentive. If governments see bitcoin as a valuable asset, they will ramp up efforts to confiscate more bitcoin. The precedent is a major concern, and I stand strongly against it, but it should be also noted that governments were already seizing coin before the reserve so this is not really a change in policy.
Ideally all seized bitcoin should be burned, by law. This would align incentives properly and make it less likely for the government to actively increase coin seizures. Due to the truly scarce properties of bitcoin, all burned bitcoin helps existing holders through increased purchasing power regardless. This change would be unlikely but those of us in policy circles should push for it regardless. It would be best case scenario for American bitcoiners and would create a strong foundation for the next century of American leadership.
Optimism
The entire point of bitcoin is that we can spend or save it without permission. That said, it is a massive benefit to not have one of the strongest governments in human history actively trying to ruin our lives.
Since the beginning, bitcoiners have faced horrible regulatory trends. KYC, surveillance, and legal cases have made using bitcoin and building bitcoin businesses incredibly difficult. It is incredibly important to note that over the past year that trend has reversed for the first time in a decade. A strategic bitcoin reserve is a key driver of this shift. By holding bitcoin, the strongest government in the world has signaled that it is not just a fringe technology but rather truly valuable, legitimate, and worth stacking.
This alignment of incentives changes everything. The US Government stacking proves bitcoin’s worth. The resulting purchasing power appreciation helps all of us who are holding coin and as bitcoin succeeds our government receives direct benefit. A beautiful positive feedback loop.
Realism
We are trending in the right direction. A strategic bitcoin reserve is a sign that the state sees bitcoin as an asset worth embracing rather than destroying. That said, there is a lot of work left to be done. We cannot be lulled into complacency, the time to push forward is now, and we cannot take our foot off the gas. We have a seat at the table for the first time ever. Let's make it worth it.
We must protect the right to free usage of bitcoin and other digital technologies. Freedom in the digital age must be taken and defended, through both technical and political avenues. Multiple privacy focused developers are facing long jail sentences for building tools that protect our freedom. These cases are not just legal battles. They are attacks on the soul of bitcoin. We need to rally behind them, fight for their freedom, and ensure the ethos of bitcoin survives this new era of government interest. The strategic reserve is a step in the right direction, but it is up to us to hold the line and shape the future.
-
 @ 08f96856:ffe59a09
2025-05-15 01:22:34
@ 08f96856:ffe59a09
2025-05-15 01:22:34เมื่อพูดถึง Bitcoin Standard หลายคนมักนึกถึงภาพโลกอนาคตที่ทุกคนใช้บิตคอยน์ซื้อกาแฟหรือของใช้ในชีวิตประจำวัน ภาพแบบนั้นดูเหมือนไกลตัวและเป็นไปไม่ได้ในความเป็นจริง หลายคนถึงกับพูดว่า “คงไม่ทันเห็นในช่วงชีวิตนี้หรอก” แต่ในมุมมองของผม Bitcoin Standard อาจไม่ได้เริ่มต้นจากการที่เราจ่ายบิตคอยน์โดยตรงในร้านค้า แต่อาจเริ่มจากบางสิ่งที่เงียบกว่า ลึกกว่า และเกิดขึ้นแล้วในขณะนี้ นั่นคือ การล่มสลายทีละน้อยของระบบเฟียตที่เราใช้กันอยู่
ระบบเงินที่อิงกับอำนาจรัฐกำลังเข้าสู่ช่วงขาลง รัฐบาลทั่วโลกกำลังจมอยู่ในภาระหนี้ระดับประวัติการณ์ แม้แต่ประเทศมหาอำนาจก็เริ่มแสดงสัญญาณของภาวะเสี่ยงผิดนัดชำระหนี้ อัตราเงินเฟ้อกลายเป็นปัญหาเรื้อรังที่ไม่มีท่าทีจะหายไป ธนาคารที่เคยโอนฟรีเริ่มกลับมาคิดค่าธรรมเนียม และประชาชนก็เริ่มรู้สึกถึงการเสื่อมศรัทธาในระบบการเงินดั้งเดิม แม้จะยังพูดกันไม่เต็มเสียงก็ตาม
ในขณะเดียวกัน บิตคอยน์เองก็กำลังพัฒนาแบบเงียบ ๆ เงียบ... แต่ไม่เคยหยุด โดยเฉพาะในระดับ Layer 2 ที่เริ่มแสดงศักยภาพอย่างจริงจัง Lightning Network เป็น Layer 2 ที่เปิดใช้งานมาได้ระยะเวลสหนึ่ง และยังคงมีบทบาทสำคัญที่สุดในระบบนิเวศของบิตคอยน์ มันทำให้การชำระเงินเร็วขึ้น มีต้นทุนต่ำ และไม่ต้องบันทึกทุกธุรกรรมลงบล็อกเชน เครือข่ายนี้กำลังขยายตัวทั้งในแง่ของโหนดและการใช้งานจริงทั่วโลก
ขณะเดียวกัน Layer 2 ทางเลือกอื่นอย่าง Ark Protocol ก็กำลังพัฒนาเพื่อตอบโจทย์ด้านความเป็นส่วนตัวและประสบการณ์ใช้งานที่ง่าย BitVM เปิดแนวทางใหม่ให้บิตคอยน์รองรับ smart contract ได้ในระดับ Turing-complete ซึ่งทำให้เกิดความเป็นไปได้ในกรณีใช้งานอีกมากมาย และเทคโนโลยีที่น่าสนใจอย่าง Taproot Assets, Cashu และ Fedimint ก็ทำให้การออกโทเคนหรือสกุลเงินที่อิงกับบิตคอยน์เป็นจริงได้บนโครงสร้างของบิตคอยน์เอง
เทคโนโลยีเหล่านี้ไม่ใช่การเติบโตแบบปาฏิหาริย์ แต่มันคืบหน้าอย่างต่อเนื่องและมั่นคง และนั่นคือเหตุผลที่มันจะ “อยู่รอด” ได้ในระยะยาว เมื่อฐานของความน่าเชื่อถือไม่ใช่บริษัท รัฐบาล หรือทุน แต่คือสิ่งที่ตรวจสอบได้และเปลี่ยนกฎไม่ได้
แน่นอนว่าบิตคอยน์ต้องแข่งขันกับ stable coin, เงินดิจิทัลของรัฐ และ cryptocurrency อื่น ๆ แต่สิ่งที่ทำให้มันเหนือกว่านั้นไม่ใช่ฟีเจอร์ หากแต่เป็นความทนทาน และความมั่นคงของกฎที่ไม่มีใครเปลี่ยนได้ ไม่มีทีมพัฒนา ไม่มีบริษัท ไม่มีประตูปิด หรือการยึดบัญชี มันยืนอยู่บนคณิตศาสตร์ พลังงาน และเวลา
หลายกรณีใช้งานที่เคยถูกทดลองในโลกคริปโตจะค่อย ๆ เคลื่อนเข้ามาสู่บิตคอยน์ เพราะโครงสร้างของมันแข็งแกร่งกว่า ไม่ต้องการทีมพัฒนาแกนกลาง ไม่ต้องพึ่งกลไกเสี่ยงต่อการผูกขาด และไม่ต้องการ “ความเชื่อใจ” จากใครเลย
Bitcoin Standard ที่ผมพูดถึงจึงไม่ใช่การเปลี่ยนแปลงแบบพลิกหน้ามือเป็นหลังมือ แต่คือการ “เปลี่ยนฐานของระบบ” ทีละชั้น ระบบการเงินใหม่ที่อิงอยู่กับบิตคอยน์กำลังเกิดขึ้นแล้ว มันไม่ใช่โลกที่ทุกคนถือเหรียญบิตคอยน์ แต่มันคือโลกที่คนใช้อาจไม่รู้ตัวด้วยซ้ำว่า “สิ่งที่เขาใช้นั้นอิงอยู่กับบิตคอยน์”
ผู้คนอาจใช้เงินดิจิทัลที่สร้างบน Layer 3 หรือ Layer 4 ผ่านแอป ผ่านแพลตฟอร์ม หรือผ่านสกุลเงินใหม่ที่ดูไม่ต่างจากเดิม แต่เบื้องหลังของระบบจะผูกไว้กับบิตคอยน์
และถ้ามองในเชิงพัฒนาการ บิตคอยน์ก็เหมือนกับอินเทอร์เน็ต ครั้งหนึ่งอินเทอร์เน็ตก็ถูกมองว่าเข้าใจยาก ต้องพิมพ์ http ต้องรู้จัก TCP/IP ต้องตั้ง proxy เอง แต่ปัจจุบันผู้คนใช้งานอินเทอร์เน็ตโดยไม่รู้ว่าเบื้องหลังมีอะไรเลย บิตคอยน์กำลังเดินตามเส้นทางเดียวกัน โปรโตคอลกำลังถอยออกจากสายตา และวันหนึ่งเราจะ “ใช้มัน” โดยไม่ต้องรู้ว่ามันคืออะไร
หากนับจากช่วงเริ่มต้นของอินเทอร์เน็ตในยุค 1990 จนกลายเป็นโครงสร้างหลักของโลกในสองทศวรรษ เส้นเวลาของบิตคอยน์ก็กำลังเดินตามรอยเท้าของอินเทอร์เน็ต และถ้าเราเชื่อว่าวัฏจักรของเทคโนโลยีมีจังหวะของมันเอง เราก็จะรู้ว่า Bitcoin Standard นั้นไม่ใช่เรื่องของอนาคตไกลโพ้น แต่มันเกิดขึ้นแล้ว
siamstr
-
 @ 3a9a4c49:f774dd7a
2025-05-16 18:05:58
@ 3a9a4c49:f774dd7a
2025-05-16 18:05:58Keeping a home safe and functioning means being sure that your boiler is functioning well and having a valid Gas Safety Certificate. If you're looking for 'https://certificates4uk.co.uk/boiler-replacement-services/' or a trusted Gas Safety Certificate company near me, stop searching at Certificates 4 UK. Our services include professional boiler servicing, repair, and safety certification to keep your home compliant and safe.
**Why Certificates 4 UK for Boiler Repairs?
** A malfunctioning boiler means high energy bills, cold showers, and, ultimately, gas leaks that might be harmful. Hence, timely boiler service near me is of prime importance. At Certificates 4 UK, our Gas Safe registered engineers can promptly and accurately troubleshoot and carry out any repairs on your boiler. Whether it is a faulty thermostat, low pressure, or a complete breakdown, we restore your heating to peak performance.
****Common Boiler Problems We Fix:
- No heating or hot water is often caused by broken diaphragms, airlocks, or valve failures.
- Leaking or dripping boilers could be due to broken internal components or high pressure.
- Strange noises(banging, gurgling, whistling) usually indicate limescale buildup or trapped air.
- The pilot light keeps going out this may indicate a faulty thermocouple or draught affecting the flame.
- Boiler pressure issues: Besides improvement of efficiency, the pressure should not be excessively high or low in any boiler.
Our experts offer same-day emergency repair services to make sure you never have to cope without the heating when needed.
**
Significance of Gas Safety Certificate.
** Gas Safety Certification, or CP12, is a necessary proviso for landlords. Homeowners also are supposed to do annual gas safety checks to avail against carbon monoxide leakages and gas-based catastrophes. When looking for an honest https://certificates4uk.co.uk/gas-services/, Certificates 4 UK should be a prime consideration to provide you with quick, cheap, and legally satisfactory inspections.
**What is a part of the Gas Safety Check?
**
## **Our Gas Safe engineers will:
** * Inspect all gas appliances (boilers, cookers, and fires) to detect leaks or defects. * Check ventilation and flue systems to ensure no obstruction of exhaust flow. * Test gas pressure and safety controls. * Submit a report and provide a Gas Safety Certificate if all equipment passes.
Every landlord is expected to renew this certificate once a year and provide a copy to their tenants. Otherwise, there are hefty-to-hidden fines, ' fines or imprisonment.'
**Why Trust Certificates 4 UK?
** * Gas Safe Registered Engineers : All our technicians are fully qualified and approved. * Fast & Reliable Service : Same-day and next-day appointments. * Competitive Pricing : Reasonable rates without having to cut costs on quality. * Nationwide Coverage Helping homeowners and landlords throughout the UK.
**Book Your Boiler Repair or Gas Safety Check Today!
** Do not wait for a day when your boiler gives up on you or when your gas certificate lapses! Call Certificates 4 UK today for professional boiler repair near me or a Gas Safety Certificate inspection. By going with Certificates 4 UK, you are assured of high-quality boiler repair and gas safety compliance. Whenever you need an emergency fix or an annual inspection, we have got you covered. Lastly, put any doubts about 'boiler repairs near me' or 'gas safety certificate companies near me' to rest; rest assured, the experts at Certificates 4 UK will provide you with peace of mind!
-
 @ 91bea5cd:1df4451c
2025-04-15 06:27:28
@ 91bea5cd:1df4451c
2025-04-15 06:27:28Básico
bash lsblk # Lista todos os diretorios montados.Para criar o sistema de arquivos:
bash mkfs.btrfs -L "ThePool" -f /dev/sdxCriando um subvolume:
bash btrfs subvolume create SubVolMontando Sistema de Arquivos:
bash mount -o compress=zlib,subvol=SubVol,autodefrag /dev/sdx /mntLista os discos formatados no diretório:
bash btrfs filesystem show /mntAdiciona novo disco ao subvolume:
bash btrfs device add -f /dev/sdy /mntLista novamente os discos do subvolume:
bash btrfs filesystem show /mntExibe uso dos discos do subvolume:
bash btrfs filesystem df /mntBalancea os dados entre os discos sobre raid1:
bash btrfs filesystem balance start -dconvert=raid1 -mconvert=raid1 /mntScrub é uma passagem por todos os dados e metadados do sistema de arquivos e verifica as somas de verificação. Se uma cópia válida estiver disponível (perfis de grupo de blocos replicados), a danificada será reparada. Todas as cópias dos perfis replicados são validadas.
iniciar o processo de depuração :
bash btrfs scrub start /mntver o status do processo de depuração Btrfs em execução:
bash btrfs scrub status /mntver o status do scrub Btrfs para cada um dos dispositivos
bash btrfs scrub status -d / data btrfs scrub cancel / dataPara retomar o processo de depuração do Btrfs que você cancelou ou pausou:
btrfs scrub resume / data
Listando os subvolumes:
bash btrfs subvolume list /ReportsCriando um instantâneo dos subvolumes:
Aqui, estamos criando um instantâneo de leitura e gravação chamado snap de marketing do subvolume de marketing.
bash btrfs subvolume snapshot /Reports/marketing /Reports/marketing-snapAlém disso, você pode criar um instantâneo somente leitura usando o sinalizador -r conforme mostrado. O marketing-rosnap é um instantâneo somente leitura do subvolume de marketing
bash btrfs subvolume snapshot -r /Reports/marketing /Reports/marketing-rosnapForçar a sincronização do sistema de arquivos usando o utilitário 'sync'
Para forçar a sincronização do sistema de arquivos, invoque a opção de sincronização conforme mostrado. Observe que o sistema de arquivos já deve estar montado para que o processo de sincronização continue com sucesso.
bash btrfs filsystem sync /ReportsPara excluir o dispositivo do sistema de arquivos, use o comando device delete conforme mostrado.
bash btrfs device delete /dev/sdc /ReportsPara sondar o status de um scrub, use o comando scrub status com a opção -dR .
bash btrfs scrub status -dR / RelatóriosPara cancelar a execução do scrub, use o comando scrub cancel .
bash $ sudo btrfs scrub cancel / ReportsPara retomar ou continuar com uma depuração interrompida anteriormente, execute o comando de cancelamento de depuração
bash sudo btrfs scrub resume /Reportsmostra o uso do dispositivo de armazenamento:
btrfs filesystem usage /data
Para distribuir os dados, metadados e dados do sistema em todos os dispositivos de armazenamento do RAID (incluindo o dispositivo de armazenamento recém-adicionado) montados no diretório /data , execute o seguinte comando:
sudo btrfs balance start --full-balance /data
Pode demorar um pouco para espalhar os dados, metadados e dados do sistema em todos os dispositivos de armazenamento do RAID se ele contiver muitos dados.
Opções importantes de montagem Btrfs
Nesta seção, vou explicar algumas das importantes opções de montagem do Btrfs. Então vamos começar.
As opções de montagem Btrfs mais importantes são:
**1. acl e noacl
**ACL gerencia permissões de usuários e grupos para os arquivos/diretórios do sistema de arquivos Btrfs.
A opção de montagem acl Btrfs habilita ACL. Para desabilitar a ACL, você pode usar a opção de montagem noacl .
Por padrão, a ACL está habilitada. Portanto, o sistema de arquivos Btrfs usa a opção de montagem acl por padrão.
**2. autodefrag e noautodefrag
**Desfragmentar um sistema de arquivos Btrfs melhorará o desempenho do sistema de arquivos reduzindo a fragmentação de dados.
A opção de montagem autodefrag permite a desfragmentação automática do sistema de arquivos Btrfs.
A opção de montagem noautodefrag desativa a desfragmentação automática do sistema de arquivos Btrfs.
Por padrão, a desfragmentação automática está desabilitada. Portanto, o sistema de arquivos Btrfs usa a opção de montagem noautodefrag por padrão.
**3. compactar e compactar-forçar
**Controla a compactação de dados no nível do sistema de arquivos do sistema de arquivos Btrfs.
A opção compactar compacta apenas os arquivos que valem a pena compactar (se compactar o arquivo economizar espaço em disco).
A opção compress-force compacta todos os arquivos do sistema de arquivos Btrfs, mesmo que a compactação do arquivo aumente seu tamanho.
O sistema de arquivos Btrfs suporta muitos algoritmos de compactação e cada um dos algoritmos de compactação possui diferentes níveis de compactação.
Os algoritmos de compactação suportados pelo Btrfs são: lzo , zlib (nível 1 a 9) e zstd (nível 1 a 15).
Você pode especificar qual algoritmo de compactação usar para o sistema de arquivos Btrfs com uma das seguintes opções de montagem:
- compress=algoritmo:nível
- compress-force=algoritmo:nível
Para obter mais informações, consulte meu artigo Como habilitar a compactação do sistema de arquivos Btrfs .
**4. subvol e subvolid
**Estas opções de montagem são usadas para montar separadamente um subvolume específico de um sistema de arquivos Btrfs.
A opção de montagem subvol é usada para montar o subvolume de um sistema de arquivos Btrfs usando seu caminho relativo.
A opção de montagem subvolid é usada para montar o subvolume de um sistema de arquivos Btrfs usando o ID do subvolume.
Para obter mais informações, consulte meu artigo Como criar e montar subvolumes Btrfs .
**5. dispositivo
A opção de montagem de dispositivo** é usada no sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs.
Em alguns casos, o sistema operacional pode falhar ao detectar os dispositivos de armazenamento usados em um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs. Nesses casos, você pode usar a opção de montagem do dispositivo para especificar os dispositivos que deseja usar para o sistema de arquivos de vários dispositivos Btrfs ou RAID.
Você pode usar a opção de montagem de dispositivo várias vezes para carregar diferentes dispositivos de armazenamento para o sistema de arquivos de vários dispositivos Btrfs ou RAID.
Você pode usar o nome do dispositivo (ou seja, sdb , sdc ) ou UUID , UUID_SUB ou PARTUUID do dispositivo de armazenamento com a opção de montagem do dispositivo para identificar o dispositivo de armazenamento.
Por exemplo,
- dispositivo=/dev/sdb
- dispositivo=/dev/sdb,dispositivo=/dev/sdc
- dispositivo=UUID_SUB=490a263d-eb9a-4558-931e-998d4d080c5d
- device=UUID_SUB=490a263d-eb9a-4558-931e-998d4d080c5d,device=UUID_SUB=f7ce4875-0874-436a-b47d-3edef66d3424
**6. degraded
A opção de montagem degradada** permite que um RAID Btrfs seja montado com menos dispositivos de armazenamento do que o perfil RAID requer.
Por exemplo, o perfil raid1 requer a presença de 2 dispositivos de armazenamento. Se um dos dispositivos de armazenamento não estiver disponível em qualquer caso, você usa a opção de montagem degradada para montar o RAID mesmo que 1 de 2 dispositivos de armazenamento esteja disponível.
**7. commit
A opção commit** mount é usada para definir o intervalo (em segundos) dentro do qual os dados serão gravados no dispositivo de armazenamento.
O padrão é definido como 30 segundos.
Para definir o intervalo de confirmação para 15 segundos, você pode usar a opção de montagem commit=15 (digamos).
**8. ssd e nossd
A opção de montagem ssd** informa ao sistema de arquivos Btrfs que o sistema de arquivos está usando um dispositivo de armazenamento SSD, e o sistema de arquivos Btrfs faz a otimização SSD necessária.
A opção de montagem nossd desativa a otimização do SSD.
O sistema de arquivos Btrfs detecta automaticamente se um SSD é usado para o sistema de arquivos Btrfs. Se um SSD for usado, a opção de montagem de SSD será habilitada. Caso contrário, a opção de montagem nossd é habilitada.
**9. ssd_spread e nossd_spread
A opção de montagem ssd_spread** tenta alocar grandes blocos contínuos de espaço não utilizado do SSD. Esse recurso melhora o desempenho de SSDs de baixo custo (baratos).
A opção de montagem nossd_spread desativa o recurso ssd_spread .
O sistema de arquivos Btrfs detecta automaticamente se um SSD é usado para o sistema de arquivos Btrfs. Se um SSD for usado, a opção de montagem ssd_spread será habilitada. Caso contrário, a opção de montagem nossd_spread é habilitada.
**10. descarte e nodiscard
Se você estiver usando um SSD que suporte TRIM enfileirado assíncrono (SATA rev3.1), a opção de montagem de descarte** permitirá o descarte de blocos de arquivos liberados. Isso melhorará o desempenho do SSD.
Se o SSD não suportar TRIM enfileirado assíncrono, a opção de montagem de descarte prejudicará o desempenho do SSD. Nesse caso, a opção de montagem nodiscard deve ser usada.
Por padrão, a opção de montagem nodiscard é usada.
**11. norecovery
Se a opção de montagem norecovery** for usada, o sistema de arquivos Btrfs não tentará executar a operação de recuperação de dados no momento da montagem.
**12. usebackuproot e nousebackuproot
Se a opção de montagem usebackuproot for usada, o sistema de arquivos Btrfs tentará recuperar qualquer raiz de árvore ruim/corrompida no momento da montagem. O sistema de arquivos Btrfs pode armazenar várias raízes de árvore no sistema de arquivos. A opção de montagem usebackuproot** procurará uma boa raiz de árvore e usará a primeira boa que encontrar.
A opção de montagem nousebackuproot não verificará ou recuperará raízes de árvore inválidas/corrompidas no momento da montagem. Este é o comportamento padrão do sistema de arquivos Btrfs.
**13. space_cache, space_cache=version, nospace_cache e clear_cache
A opção de montagem space_cache** é usada para controlar o cache de espaço livre. O cache de espaço livre é usado para melhorar o desempenho da leitura do espaço livre do grupo de blocos do sistema de arquivos Btrfs na memória (RAM).
O sistema de arquivos Btrfs suporta 2 versões do cache de espaço livre: v1 (padrão) e v2
O mecanismo de cache de espaço livre v2 melhora o desempenho de sistemas de arquivos grandes (tamanho de vários terabytes).
Você pode usar a opção de montagem space_cache=v1 para definir a v1 do cache de espaço livre e a opção de montagem space_cache=v2 para definir a v2 do cache de espaço livre.
A opção de montagem clear_cache é usada para limpar o cache de espaço livre.
Quando o cache de espaço livre v2 é criado, o cache deve ser limpo para criar um cache de espaço livre v1 .
Portanto, para usar o cache de espaço livre v1 após a criação do cache de espaço livre v2 , as opções de montagem clear_cache e space_cache=v1 devem ser combinadas: clear_cache,space_cache=v1
A opção de montagem nospace_cache é usada para desabilitar o cache de espaço livre.
Para desabilitar o cache de espaço livre após a criação do cache v1 ou v2 , as opções de montagem nospace_cache e clear_cache devem ser combinadas: clear_cache,nosapce_cache
**14. skip_balance
Por padrão, a operação de balanceamento interrompida/pausada de um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs será retomada automaticamente assim que o sistema de arquivos Btrfs for montado. Para desabilitar a retomada automática da operação de equilíbrio interrompido/pausado em um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs, você pode usar a opção de montagem skip_balance .**
**15. datacow e nodatacow
A opção datacow** mount habilita o recurso Copy-on-Write (CoW) do sistema de arquivos Btrfs. É o comportamento padrão.
Se você deseja desabilitar o recurso Copy-on-Write (CoW) do sistema de arquivos Btrfs para os arquivos recém-criados, monte o sistema de arquivos Btrfs com a opção de montagem nodatacow .
**16. datasum e nodatasum
A opção datasum** mount habilita a soma de verificação de dados para arquivos recém-criados do sistema de arquivos Btrfs. Este é o comportamento padrão.
Se você não quiser que o sistema de arquivos Btrfs faça a soma de verificação dos dados dos arquivos recém-criados, monte o sistema de arquivos Btrfs com a opção de montagem nodatasum .
Perfis Btrfs
Um perfil Btrfs é usado para informar ao sistema de arquivos Btrfs quantas cópias dos dados/metadados devem ser mantidas e quais níveis de RAID devem ser usados para os dados/metadados. O sistema de arquivos Btrfs contém muitos perfis. Entendê-los o ajudará a configurar um RAID Btrfs da maneira que você deseja.
Os perfis Btrfs disponíveis são os seguintes:
single : Se o perfil único for usado para os dados/metadados, apenas uma cópia dos dados/metadados será armazenada no sistema de arquivos, mesmo se você adicionar vários dispositivos de armazenamento ao sistema de arquivos. Assim, 100% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser utilizado.
dup : Se o perfil dup for usado para os dados/metadados, cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos manterá duas cópias dos dados/metadados. Assim, 50% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser utilizado.
raid0 : No perfil raid0 , os dados/metadados serão divididos igualmente em todos os dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, não haverá dados/metadados redundantes (duplicados). Assim, 100% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser usado. Se, em qualquer caso, um dos dispositivos de armazenamento falhar, todo o sistema de arquivos será corrompido. Você precisará de pelo menos dois dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid0 .
raid1 : No perfil raid1 , duas cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a uma falha de unidade. Mas você pode usar apenas 50% do espaço total em disco. Você precisará de pelo menos dois dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1 .
raid1c3 : No perfil raid1c3 , três cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a duas falhas de unidade, mas você pode usar apenas 33% do espaço total em disco. Você precisará de pelo menos três dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1c3 .
raid1c4 : No perfil raid1c4 , quatro cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a três falhas de unidade, mas você pode usar apenas 25% do espaço total em disco. Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1c4 .
raid10 : No perfil raid10 , duas cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos, como no perfil raid1 . Além disso, os dados/metadados serão divididos entre os dispositivos de armazenamento, como no perfil raid0 .
O perfil raid10 é um híbrido dos perfis raid1 e raid0 . Alguns dos dispositivos de armazenamento formam arrays raid1 e alguns desses arrays raid1 são usados para formar um array raid0 . Em uma configuração raid10 , o sistema de arquivos pode sobreviver a uma única falha de unidade em cada uma das matrizes raid1 .
Você pode usar 50% do espaço total em disco na configuração raid10 . Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid10 .
raid5 : No perfil raid5 , uma cópia dos dados/metadados será dividida entre os dispositivos de armazenamento. Uma única paridade será calculada e distribuída entre os dispositivos de armazenamento do array RAID.
Em uma configuração raid5 , o sistema de arquivos pode sobreviver a uma única falha de unidade. Se uma unidade falhar, você pode adicionar uma nova unidade ao sistema de arquivos e os dados perdidos serão calculados a partir da paridade distribuída das unidades em execução.
Você pode usar 1 00x(N-1)/N % do total de espaços em disco na configuração raid5 . Aqui, N é o número de dispositivos de armazenamento adicionados ao sistema de arquivos. Você precisará de pelo menos três dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid5 .
raid6 : No perfil raid6 , uma cópia dos dados/metadados será dividida entre os dispositivos de armazenamento. Duas paridades serão calculadas e distribuídas entre os dispositivos de armazenamento do array RAID.
Em uma configuração raid6 , o sistema de arquivos pode sobreviver a duas falhas de unidade ao mesmo tempo. Se uma unidade falhar, você poderá adicionar uma nova unidade ao sistema de arquivos e os dados perdidos serão calculados a partir das duas paridades distribuídas das unidades em execução.
Você pode usar 100x(N-2)/N % do espaço total em disco na configuração raid6 . Aqui, N é o número de dispositivos de armazenamento adicionados ao sistema de arquivos. Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid6 .
-
 @ 04c915da:3dfbecc9
2025-05-16 17:59:23
@ 04c915da:3dfbecc9
2025-05-16 17:59:23Recently we have seen a wave of high profile X accounts hacked. These attacks have exposed the fragility of the status quo security model used by modern social media platforms like X. Many users have asked if nostr fixes this, so lets dive in. How do these types of attacks translate into the world of nostr apps? For clarity, I will use X’s security model as representative of most big tech social platforms and compare it to nostr.
The Status Quo
On X, you never have full control of your account. Ultimately to use it requires permission from the company. They can suspend your account or limit your distribution. Theoretically they can even post from your account at will. An X account is tied to an email and password. Users can also opt into two factor authentication, which adds an extra layer of protection, a login code generated by an app. In theory, this setup works well, but it places a heavy burden on users. You need to create a strong, unique password and safeguard it. You also need to ensure your email account and phone number remain secure, as attackers can exploit these to reset your credentials and take over your account. Even if you do everything responsibly, there is another weak link in X infrastructure itself. The platform’s infrastructure allows accounts to be reset through its backend. This could happen maliciously by an employee or through an external attacker who compromises X’s backend. When an account is compromised, the legitimate user often gets locked out, unable to post or regain control without contacting X’s support team. That process can be slow, frustrating, and sometimes fruitless if support denies the request or cannot verify your identity. Often times support will require users to provide identification info in order to regain access, which represents a privacy risk. The centralized nature of X means you are ultimately at the mercy of the company’s systems and staff.
Nostr Requires Responsibility
Nostr flips this model radically. Users do not need permission from a company to access their account, they can generate as many accounts as they want, and cannot be easily censored. The key tradeoff here is that users have to take complete responsibility for their security. Instead of relying on a username, password, and corporate servers, nostr uses a private key as the sole credential for your account. Users generate this key and it is their responsibility to keep it safe. As long as you have your key, you can post. If someone else gets it, they can post too. It is that simple. This design has strong implications. Unlike X, there is no backend reset option. If your key is compromised or lost, there is no customer support to call. In a compromise scenario, both you and the attacker can post from the account simultaneously. Neither can lock the other out, since nostr relays simply accept whatever is signed with a valid key.
The benefit? No reliance on proprietary corporate infrastructure.. The negative? Security rests entirely on how well you protect your key.
Future Nostr Security Improvements
For many users, nostr’s standard security model, storing a private key on a phone with an encrypted cloud backup, will likely be sufficient. It is simple and reasonably secure. That said, nostr’s strength lies in its flexibility as an open protocol. Users will be able to choose between a range of security models, balancing convenience and protection based on need.
One promising option is a web of trust model for key rotation. Imagine pre-selecting a group of trusted friends. If your account is compromised, these people could collectively sign an event announcing the compromise to the network and designate a new key as your legitimate one. Apps could handle this process seamlessly in the background, notifying followers of the switch without much user interaction. This could become a popular choice for average users, but it is not without tradeoffs. It requires trust in your chosen web of trust, which might not suit power users or large organizations. It also has the issue that some apps may not recognize the key rotation properly and followers might get confused about which account is “real.”
For those needing higher security, there is the option of multisig using FROST (Flexible Round-Optimized Schnorr Threshold). In this setup, multiple keys must sign off on every action, including posting and updating a profile. A hacker with just one key could not do anything. This is likely overkill for most users due to complexity and inconvenience, but it could be a game changer for large organizations, companies, and governments. Imagine the White House nostr account requiring signatures from multiple people before a post goes live, that would be much more secure than the status quo big tech model.
Another option are hardware signers, similar to bitcoin hardware wallets. Private keys are kept on secure, offline devices, separate from the internet connected phone or computer you use to broadcast events. This drastically reduces the risk of remote hacks, as private keys never touches the internet. It can be used in combination with multisig setups for extra protection. This setup is much less convenient and probably overkill for most but could be ideal for governments, companies, or other high profile accounts.
Nostr’s security model is not perfect but is robust and versatile. Ultimately users are in control and security is their responsibility. Apps will give users multiple options to choose from and users will choose what best fits their need.
-
 @ 57c631a3:07529a8e
2025-04-07 13:17:50
@ 57c631a3:07529a8e
2025-04-07 13:17:50What is Growth Engineering? Before we start: if you’ve already filled out the What is your tech stack? survey: thank you! If you’ve not done so, your help will be greatly appreciated. It takes 5-15 minutes to complete. Those filling out will receive results before anyone else, and additional analysis from myself and Elin. Fill out this survey here.**
npub1sg6plzptd64u62a878hep2kev88swjh3tw00gjsfl8f237lmu63q0uf63m
Growth engineering was barely known a decade ago, but today, most scaleups and many publicly traded tech companies have dedicated growth teams staffed by growth engineers. However, some software engineers are still suspicious of this new area because of its reputation for hacky code with little to no code coverage.
For this reason and others, I thought it would be interesting to learn more from an expert who can tell us all about the practicalities of this controversial domain. So I turned to Alexey Komissarouk, who’s been in growth engineering since 2016, and was in charge of it at online education platform, MasterClass. These days, Alexey lives in Tokyo, Japan, where he advises on growth engineering and teaches the Growth Engineering course at Reforge.
In today’s deep dive, Alexey covers:
- What is Growth Engineering? In the simplest terms: writing code to help a company make more money. But there are details to consider: like the company size where it makes sense to have a dedicated team do this.
- What do Growth Engineers work on? Business-facing work, empowerment and platform work are the main areas.
- Why Growth Engineers move faster than Product Engineers. Product Engineers ship to build: Growth Engineers ship to learn. Growth Engineers do take shortcuts that would make no sense when building for longevity – doing this on purpose.
- Tech stack. Common programming languages, monitoring and oncall, feature flags and experimentation, product analytics, review apps, and more.
- What makes a good Growth Engineer? Curiosity, “build to learn” mindset and a “Jack of all trades” approach.
- Where do Growth Engineers fit in? Usually part of the engineering department, either operating as with an “owner” or a “hitchiker” model.
- Becoming a Growth Engineer. A great area if you want to eventually become a founder or product manager – but even if not, it can accelerate your career growth. Working in Growth forces you to learn more about the business.
With that, it’s over to Alexey:
I’ll never forget the first time I made my employer a million dollars.
I was running a push notification A/B test for meal delivery startup Sprig, trying to boost repeat orders.
A push notification similar to what we tested to boost repeat orders
Initial results were unpromising; the push notification was not receiving many opens. Still, I wanted to be thorough: before concluding the idea was a failure, I wrote a SQL query to compare order volume for subsequent weeks between customers in test vs control.
The SQL used to figure out the push notification’s efficiency
As it turned out, our test group “beat” the control group by around 10%:
‘review_5_push’ was the new type of push notification. Roughly the same amount of users clicked it, but they placed 10% more in orders
I plugged the numbers into a significance calculator, which showed it was statistically significant – or “stat-sig” – and therefore highly unlikely to be a coincidence. This meant we had a winner on our hands! But how meaningful was it, really, and what would adding the push notification mean for revenue, if rolled out to 100% of users?
It turned out this experiment created an additional $1.5 million dollars, annually, with just one push notification. Wow!
I was hooked. Since that day, I've shipped hundreds of experimental “winners” which generated hundreds of millions of incremental revenue for my employers. But you never forget the first one. Moments like this is what growth engineering is all about.
1. What is Growth Engineering?
Essentially, growth engineering is the writing of code to make a company money. Of course, all code produced by a business on some level serves this purpose, but while Product Engineers focus on creating a Product worth paying for, Growth Engineers instead focus on making that good product have a good business. To this end, they focus on optimizing and refining key parts of the customer journey, such as:
- Getting more people to consider the product
- Converting them into paying customers
- Keeping them as customers for longer, and spending more
What kinds of companies employ Growth Engineers? Places you’ve heard of, like Meta, LinkedIn, DoorDash, Coinbase, and Dropbox, are some of the ones I’ve had students from. There’s also OpenAI, Uber, Tiktok, Tinder, Airbnb, Pinterest… the list of high-profile companies goes on. Most newer public consumer companies you’ve heard have a growth engineering org, too.
Typically, growth engineering orgs are started by companies at Series B stage and beyond, so long as they are selling to either consumers or businesses via SaaS. These are often places trying to grow extremely fast, and have enough software engineers that some can focus purely on growth. Before the Series B stage, a team is unlikely to be ready for growth for various reasons; likely that it hasn’t found product-market fit, or has no available headcount, or lacks the visitor traffic required to run A/B tests.
Cost is a consideration. A fully-loaded growth team consisting of a handful of engineers, a PM, and a designer costs approximately 1 million dollars annually. To justify this, a rule of thumb is to have at least $5 million dollars in recurring revenue – a milestone often achieved at around the Series B stage.
Despite the presence of growth engineering at many public consumer tech companies, the field itself is still quite new, as a discipline and as a proper title.
Brief history of growth engineering
When I joined Opendoor in 2016, there was a head of growth but no dedicated growth engineers, but there were by the time I left in 2020. At MasterClass soon after, there was a growth org and a dozen dedicated growth engineers. So when did growth engineering originate?
The story is that its origins lie at Facebook in 2007. The team was created by then-VP of platform and monetization Chamath Palihapitiya. Reforce founder and CEO Brian Balfour shares:
“Growth (the kind found on an org chart) began at Facebook under the direction of Chamath Palihapitiya. In 2007, he joined the early team in a nebulous role that fell somewhere between Product, Marketing, and Operations. According to his retelling of the story on Recode Decode, after struggling to accomplish anything meaningful in his first year on the job, he was on the verge of being fired.Sheryl Sandberg joined soon after him, and in a hail mary move he pitched her the game-changing idea that led to the creation of the first-ever growth team. This idea not only saved his job, but earned him the lion’s share of the credit for Facebook’s unprecedented growth.At the time, Sheryl and Mark asked him, “What do you call this thing where you help change the product, do some SEO and SEM, and algorithmically do this or that?”His response: “I don’t know, I just call that, like, Growth, you know, we’re going to try to grow. I’ll be the head of growing stuff."And just like that, Growth became a thing.”
Rather than focus on a particular product or feature, the growth team at Facebook focused on moving the needle, and figuring out which features to work on. These days, Meta employs hundreds if not thousands of growth engineers.
2. What do Growth Engineers work on?
Before we jump into concrete examples, let’s identify three primary focus areas that a growth engineer’s work usually involves.
- Business-facing work – improving the business directly
- Empowerment work – enabling other teams to improve the business
- Platform work – improving the velocity of the above activities
Let’s go through all three:
Business-facing work
This is the bread and butter of growth engineering, and follows a common pattern:
- Implement an idea. Try something big or small to try and move a key business metric, which differs by team but is typically related to conversion rate or retention.
- Quantify impact. Usually via A/B testing.
- Analyze impact. Await results, analyze impact, ship or roll back – then go back to the first step.
Experiments can lead to sweeping or barely noticeable changes. A famous “I can’t believe they needed to test this” was when Google figured out which shade of blue generates the most clicks. At MasterClass, we tested things across the spectrum:
- Small: should we show the price right on the homepage, was that a winner? Yes, but we framed it in monthly terms of $15/month, not $180/year.
- Medium: when browsing a course page, should we include related courses, or more details about the course itself? Was it a winner? After lengthy experimentation, it was hard to tell: both are valuable and we needed to strike the right balance.
- Large: when a potential customer is interested, do we take them straight to checkout, or encourage them to learn more? Counterintuitively, adding steps boosted conversion!
Empowerment
One of the best ways an engineer can move a target metric is by removing themselves as a bottleneck, so colleagues from marketing can iterate and optimize freely. To this end, growth engineers can either build internal tools or integrate self-serve MarTech (Marketing Technology) vendors.
With the right tool, there’s a lot that marketers can do without engineering’s involvement:
- Build and iterate on landing pages (Unbounce, Instapage, etc)
- Draft and send email, SMS and Push Notifications (Iterable, Braze, Customer.io, etc)
- Connect new advertising partners (Google Tag Manager, Segment, etc)
We go more into detail about benefits and applications in the MarTech section of Tech Stack, below.
Platform work
As a business scales, dedicated platform teams help improve stability and velocity for the teams they support. Within growth, this often includes initiatives like:
- Experiment Platform. Many parts of running an experiment can be standardized, from filtering the audience, to bucketing users properly, to observing statistical methodology. Historically, companies built reusable Experiment Platforms in-house, but more recently, vendors such as Eppo and Statsig have grown in popularity with fancy statistical methodologies like “Controlled Using Pre-Experiment Data” (CUPED) that give more signal with less data.
- Reusable components. Companies with standard front-end components for things like headlines, buttons, and images, dramatically reduce the time required to spin up a new page. No more "did you want 5 or 6 pixels here" with a designer; instead growth engineers rely on tools like Storybook to standardize and share reusable React components.
- Monitoring. Growth engineering benefits greatly from leveraging monitoring to compensate for reduced code coverage. High-quality business metric monitoring tools can detect bugs before they cause damage.
When I worked at MasterClass, having monitoring at the ad layer prevented at least one six-figure incident. One Friday, a marketer accidentally broadened the audience for a particular ad from US-only, to worldwide. In response, the Facebook Ad algorithm went on a spending spree, bringing in plenty of visitors from places like Brazil and India, whom we knew from past experience were unlikely to purchase the product. Fortunately, our monitoring noticed the low-performing campaign within minutes, and an alert was sent to the growth engineer on-call, who immediately reached out to the marketer and confirmed the change was unintentional, and then shut down the campaign.
Without this monitoring, a subtle targeting error like this could have gone unnoticed all weekend and would have eaten up $100,000+ of marketing budget. This episode shows that platform investment can benefit everyone; and since growth needs them most, it’s often the growth platform engineering team which implements them.
As the day-to-day work of a Growth Engineer shows, A/B tests are a critical tool to both measure success and learn. It’s a numbers game: the more A/B tests a team can run in a given quarter, the more of them will end up winners, making the team successful. It’s no wonder, then, that Growth Engineering will pull out all the stops to improve velocity.
3. Why Growth Engineers move faster than Product Engineers
On the surface, growth engineering teams look like product engineering ones; writing code, shipping pull requests, monitoring on-call, etc. So how do they move so much faster? The big reason lies in philosophy and focus, not technology. To quote Elena Verna, head of growth at Dropbox:
“Product Engineering teams ship to build; Growth Engineering teams ship to learn.”
Real-world case: price changes at Masterclass
A few years ago at MasterClass, the growth team wanted to see if changing our pricing model to multiple tiers would improve revenue.
Inspired in part by multiple pricing tiers for competitors such as Netflix (above), Disney Plus, and Hulu.
The “multiple pricing tier” proposal for MasterClass.
From a software engineering perspective, this was a highly complex project because:
- Backend engineering work: the backend did not yet support multiple pricing options, requiring a decent amount of engineering, and rigorous testing to make sure existing customers weren’t affected.
- Client app changes: on the device side, multiple platforms (iOS, iPad, Android, Roku, Apple TV, etc) would each need to be updated, including each relevant app store.
The software engineering team estimated that becoming a “multi-pricing-tier” company would take months across numerous engineering teams, and engineering leadership was unwilling to greenlight that significant investment.
We in growth engineering took this as a challenge. As usual, our goal was not just to add the new pricing model, but to learn how much money it might bring in. The approach we ended up proposing was a Fake Door test, which involves offering a not-yet-available option to customers to gauge interest level. This was risky, as taking a customer who’s ready to pay and telling them to join some kind of waiting list is a colossal waste, and risks making them feel like the target of a “bait and switch” trick.
We found a way. The key insight was that people are only offended about a “bait and switch”, if the “switch” is worse than the “bait.” Telling customers they would pay $100 and then switching to $150 would cause a riot, but starting at $150 and then saying “just kidding, it’s only $100” is a pleasant surprise.
The good kind of surprise.
So long as every test “pricing tier” is less appealing – higher prices, fewer features – than the current offering, we could “upgrade” customers after their initial selection. A customer choosing the cheapest tier gets extra features at no extra cost, while a customer choosing a more expensive tier is offered a discount.
We created three new tiers, at different prices. The new “premium” tier would describe the existing, original offering. Regardless of what potential customers selected, they got this “original offering,” during the experiment.
The best thing about this was that no backend changes were required. There were no real, new, back-end pricing plans; everybody ended up purchasing the same version of MasterClass for the same price, with the same features. The entirety of the engineering work was on building a new pricing page, and the “congratulations, you’ve been upgraded” popup. This took just a few days.
Within a couple of weeks, we had enough data to be confident the financial upside of moving to a multi-pricing-tier model would be significant. With this, we’re able to convince the rest of engineering’s leadership to invest in building the feature properly. In the end, launching multiple pricing tiers turned out to be one of the biggest revenue wins of the year.
Building a skyscraper vs building a tent
The MasterClass example demonstrates the spirit of growth engineering; focusing on building to learn, instead of building to last. Consider building skyscrapers versus tents.
Building a tent optimizes for speed of set-up and tear-down over longevity. You don’t think of a tent as one that is shoddy or low-quality compared to skyscrapers: it’s not even the same category of buildings! Growth engineers maximize use of lightweight materials. To stick with the tents vs skyscraper metaphor: we prioritize lightweight fabric materials over steel and concrete whenever possible. We only resort to traditional building materials when there’s no other choice, or when a direction is confirmed as correct. Quality is important – after all, a tent must keep out rain and mosquitoes. However, the speed-vs-durability tradeoff decision results in very different approaches and outcomes.
4. Tech stack
At first glance, growth and product engineers use the same tooling, and contribute to the same codebases. But growth engineering tends to be high-velocity, experiment-heavy, and with limited test coverage. This means that certain “nice to have” tools for product engineering are mission-critical for growth engineers.
Read more https://connect-test.layer3.press/articles/ea02c1a1-7cfa-42b4-8722-0165abcae8bb
-
 @ d360efec:14907b5f
2025-05-13 00:39:56
@ d360efec:14907b5f
2025-05-13 00:39:56🚀📉 #BTC วิเคราะห์ H2! พุ่งชน 105K แล้วเจอแรงขาย... จับตา FVG 100.5K เป็นจุดวัดใจ! 👀📊
จากากรวิเคราะห์ทางเทคนิคสำหรับ #Bitcoin ในกรอบเวลา H2:
สัปดาห์ที่แล้ว #BTC ได้เบรคและพุ่งขึ้นอย่างแข็งแกร่งค่ะ 📈⚡ แต่เมื่อวันจันทร์ที่ผ่านมา ราคาได้ขึ้นไปชนแนวต้านบริเวณ 105,000 ดอลลาร์ แล้วเจอแรงขายย่อตัวลงมาตลอดทั้งวันค่ะ 🧱📉
ตอนนี้ ระดับที่น่าจับตาอย่างยิ่งคือโซน H4 FVG (Fair Value Gap ในกราฟ 4 ชั่วโมง) ที่ 100,500 ดอลลาร์ ค่ะ 🎯 (FVG คือโซนที่ราคาวิ่งผ่านไปเร็วๆ และมักเป็นบริเวณที่ราคามีโอกาสกลับมาทดสอบ/เติมเต็ม)
👇 โซน FVG ที่ 100.5K นี้ ยังคงเป็น Area of Interest ที่น่าสนใจสำหรับมองหาจังหวะ Long เพื่อลุ้นการขึ้นในคลื่นลูกถัดไปค่ะ!
🤔💡 อย่างไรก็ตาม การตัดสินใจเข้า Long หรือเทรดที่บริเวณนี้ ขึ้นอยู่กับว่าราคา แสดงปฏิกิริยาอย่างไรเมื่อมาถึงโซน 100.5K นี้ เพื่อยืนยันสัญญาณสำหรับการเคลื่อนไหวที่จะขึ้นสูงกว่าเดิมค่ะ!
เฝ้าดู Price Action ที่ระดับนี้อย่างใกล้ชิดนะคะ! 📍
BTC #Bitcoin #Crypto #คริปโต #TechnicalAnalysis #Trading #FVG #FairValueGap #PriceAction #MarketAnalysis #ลงทุนคริปโต #วิเคราะห์กราฟ #TradeSetup #ข่าวคริปโต #ตลาดคริปโต


-
 @ 04c915da:3dfbecc9
2025-03-26 20:54:33
@ 04c915da:3dfbecc9
2025-03-26 20:54:33Capitalism is the most effective system for scaling innovation. The pursuit of profit is an incredibly powerful human incentive. Most major improvements to human society and quality of life have resulted from this base incentive. Market competition often results in the best outcomes for all.
That said, some projects can never be monetized. They are open in nature and a business model would centralize control. Open protocols like bitcoin and nostr are not owned by anyone and if they were it would destroy the key value propositions they provide. No single entity can or should control their use. Anyone can build on them without permission.
As a result, open protocols must depend on donation based grant funding from the people and organizations that rely on them. This model works but it is slow and uncertain, a grind where sustainability is never fully reached but rather constantly sought. As someone who has been incredibly active in the open source grant funding space, I do not think people truly appreciate how difficult it is to raise charitable money and deploy it efficiently.
Projects that can be monetized should be. Profitability is a super power. When a business can generate revenue, it taps into a self sustaining cycle. Profit fuels growth and development while providing projects independence and agency. This flywheel effect is why companies like Google, Amazon, and Apple have scaled to global dominance. The profit incentive aligns human effort with efficiency. Businesses must innovate, cut waste, and deliver value to survive.
Contrast this with non monetized projects. Without profit, they lean on external support, which can dry up or shift with donor priorities. A profit driven model, on the other hand, is inherently leaner and more adaptable. It is not charity but survival. When survival is tied to delivering what people want, scale follows naturally.
The real magic happens when profitable, sustainable businesses are built on top of open protocols and software. Consider the many startups building on open source software stacks, such as Start9, Mempool, and Primal, offering premium services on top of the open source software they build out and maintain. Think of companies like Block or Strike, which leverage bitcoin’s open protocol to offer their services on top. These businesses amplify the open software and protocols they build on, driving adoption and improvement at a pace donations alone could never match.
When you combine open software and protocols with profit driven business the result are lean, sustainable companies that grow faster and serve more people than either could alone. Bitcoin’s network, for instance, benefits from businesses that profit off its existence, while nostr will expand as developers monetize apps built on the protocol.
Capitalism scales best because competition results in efficiency. Donation funded protocols and software lay the groundwork, while market driven businesses build on top. The profit incentive acts as a filter, ensuring resources flow to what works, while open systems keep the playing field accessible, empowering users and builders. Together, they create a flywheel of innovation, growth, and global benefit.
-
 @ 21335073:a244b1ad
2025-03-15 23:00:40
@ 21335073:a244b1ad
2025-03-15 23:00:40I want to see Nostr succeed. If you can think of a way I can help make that happen, I’m open to it. I’d like your suggestions.
My schedule’s shifting soon, and I could volunteer a few hours a week to a Nostr project. I won’t have more total time, but how I use it will change.
Why help? I care about freedom. Nostr’s one of the most powerful freedom tools I’ve seen in my lifetime. If I believe that, I should act on it.
I don’t care about money or sats. I’m not rich, I don’t have extra cash. That doesn’t drive me—freedom does. I’m volunteering, not asking for pay.
I’m not here for clout. I’ve had enough spotlight in my life; it doesn’t move me. If I wanted clout, I’d be on Twitter dropping basic takes. Clout’s easy. Freedom’s hard. I’d rather help anonymously. No speaking at events—small meetups are cool for the vibe, but big conferences? Not my thing. I’ll never hit a huge Bitcoin conference. It’s just not my scene.
That said, I could be convinced to step up if it’d really boost Nostr—as long as it’s legal and gets results.
In this space, I’d watch for social engineering. I watch out for it. I’m not here to make friends, just to help. No shade—you all seem great—but I’ve got a full life and awesome friends irl. I don’t need your crew or to be online cool. Connect anonymously if you want; I’d encourage it.
I’m sick of watching other social media alternatives grow while Nostr kinda stalls. I could trash-talk, but I’d rather do something useful.
Skills? I’m good at spotting social media problems and finding possible solutions. I won’t overhype myself—that’s weird—but if you’re responding, you probably see something in me. Perhaps you see something that I don’t see in myself.
If you need help now or later with Nostr projects, reach out. Nostr only—nothing else. Anonymous contact’s fine. Even just a suggestion on how I can pitch in, no project attached, works too. 💜
Creeps or harassment will get blocked or I’ll nuke my simplex code if it becomes a problem.
https://simplex.chat/contact#/?v=2-4&smp=smp%3A%2F%2FSkIkI6EPd2D63F4xFKfHk7I1UGZVNn6k1QWZ5rcyr6w%3D%40smp9.simplex.im%2FbI99B3KuYduH8jDr9ZwyhcSxm2UuR7j0%23%2F%3Fv%3D1-2%26dh%3DMCowBQYDK2VuAyEAS9C-zPzqW41PKySfPCEizcXb1QCus6AyDkTTjfyMIRM%253D%26srv%3Djssqzccmrcws6bhmn77vgmhfjmhwlyr3u7puw4erkyoosywgl67slqqd.onion
-
 @ d360efec:14907b5f
2025-05-12 04:01:23
@ d360efec:14907b5f
2025-05-12 04:01:23 -
 @ 04c915da:3dfbecc9
2025-03-10 23:31:30
@ 04c915da:3dfbecc9
2025-03-10 23:31:30Bitcoin has always been rooted in freedom and resistance to authority. I get that many of you are conflicted about the US Government stacking but by design we cannot stop anyone from using bitcoin. Many have asked me for my thoughts on the matter, so let’s rip it.
Concern
One of the most glaring issues with the strategic bitcoin reserve is its foundation, built on stolen bitcoin. For those of us who value private property this is an obvious betrayal of our core principles. Rather than proof of work, the bitcoin that seeds this reserve has been taken by force. The US Government should return the bitcoin stolen from Bitfinex and the Silk Road.
Usually stolen bitcoin for the reserve creates a perverse incentive. If governments see a bitcoin as a valuable asset, they will ramp up efforts to confiscate more bitcoin. The precedent is a major concern, and I stand strongly against it, but it should be also noted that governments were already seizing coin before the reserve so this is not really a change in policy.
Ideally all seized bitcoin should be burned, by law. This would align incentives properly and make it less likely for the government to actively increase coin seizures. Due to the truly scarce properties of bitcoin, all burned bitcoin helps existing holders through increased purchasing power regardless. This change would be unlikely but those of us in policy circles should push for it regardless. It would be best case scenario for American bitcoiners and would create a strong foundation for the next century of American leadership.
Optimism
The entire point of bitcoin is that we can spend or save it without permission. That said, it is a massive benefit to not have one of the strongest governments in human history actively trying to ruin our lives.
Since the beginning, bitcoiners have faced horrible regulatory trends. KYC, surveillance, and legal cases have made using bitcoin and building bitcoin businesses incredibly difficult. It is incredibly important to note that over the past year that trend has reversed for the first time in a decade. A strategic bitcoin reserve is a key driver of this shift. By holding bitcoin, the strongest government in the world has signaled that it is not just a fringe technology but rather truly valuable, legitimate, and worth stacking.
This alignment of incentives changes everything. The US Government stacking proves bitcoin’s worth. The resulting purchasing power appreciation helps all of us who are holding coin and as bitcoin succeeds our government receives direct benefit. A beautiful positive feedback loop.
Realism
We are trending in the right direction. A strategic bitcoin reserve is a sign that the state sees bitcoin as an asset worth embracing rather than destroying. That said, there is a lot of work left to be done. We cannot be lulled into complacency, the time to push forward is now, and we cannot take our foot off the gas. We have a seat at the table for the first time ever. Let's make it worth it.
We must protect the right to free usage of bitcoin and other digital technologies. Freedom in the digital age must be taken and defended, through both technical and political avenues. Multiple privacy focused developers are facing long jail sentences for building tools that protect our freedom. These cases are not just legal battles. They are attacks on the soul of bitcoin. We need to rally behind them, fight for their freedom, and ensure the ethos of bitcoin survives this new era of government interest. The strategic reserve is a step in the right direction, but it is up to us to hold the line and shape the future.
-
 @ c9badfea:610f861a
2025-05-16 17:57:20
@ c9badfea:610f861a
2025-05-16 17:57:20- Install Lemuroid (it's free and open source)
- Launch the app, enable notifications, and select a directory for your games (e.g.
/Download/ROMs) - Download game ROMs and place them in the folder from the previous step (see links below)
- Open Lemuroid again, navigate to the Home tab, and tap the downloaded game
- Enjoy!
Some ROM Sources
ℹ️ An internet connection is only required when opening a game for the first time to download the emulator core per system (e.g. Gameboy or PS2)
ℹ️ Supported ROM file formats include
.nes,.gba,.sfc,.gb,.iso,.bin, and.zipℹ️ You may need to extract downloaded ROM files if they are packaged as archives (e.g.
.7z,.rar, or.zip) -
 @ d360efec:14907b5f
2025-05-10 03:57:17
@ d360efec:14907b5f
2025-05-10 03:57:17Disclaimer: * การวิเคราะห์นี้เป็นเพียงแนวทาง ไม่ใช่คำแนะนำในการซื้อขาย * การลงทุนมีความเสี่ยง ผู้ลงทุนควรตัดสินใจด้วยตนเอง
-
 @ 04c915da:3dfbecc9
2025-03-07 00:26:37
@ 04c915da:3dfbecc9
2025-03-07 00:26:37There is something quietly rebellious about stacking sats. In a world obsessed with instant gratification, choosing to patiently accumulate Bitcoin, one sat at a time, feels like a middle finger to the hype machine. But to do it right, you have got to stay humble. Stack too hard with your head in the clouds, and you will trip over your own ego before the next halving even hits.
Small Wins
Stacking sats is not glamorous. Discipline. Stacking every day, week, or month, no matter the price, and letting time do the heavy lifting. Humility lives in that consistency. You are not trying to outsmart the market or prove you are the next "crypto" prophet. Just a regular person, betting on a system you believe in, one humble stack at a time. Folks get rekt chasing the highs. They ape into some shitcoin pump, shout about it online, then go silent when they inevitably get rekt. The ones who last? They stack. Just keep showing up. Consistency. Humility in action. Know the game is long, and you are not bigger than it.
Ego is Volatile
Bitcoin’s swings can mess with your head. One day you are up 20%, feeling like a genius and the next down 30%, questioning everything. Ego will have you panic selling at the bottom or over leveraging the top. Staying humble means patience, a true bitcoin zen. Do not try to "beat” Bitcoin. Ride it. Stack what you can afford, live your life, and let compounding work its magic.
Simplicity
There is a beauty in how stacking sats forces you to rethink value. A sat is worth less than a penny today, but every time you grab a few thousand, you plant a seed. It is not about flaunting wealth but rather building it, quietly, without fanfare. That mindset spills over. Cut out the noise: the overpriced coffee, fancy watches, the status games that drain your wallet. Humility is good for your soul and your stack. I have a buddy who has been stacking since 2015. Never talks about it unless you ask. Lives in a decent place, drives an old truck, and just keeps stacking. He is not chasing clout, he is chasing freedom. That is the vibe: less ego, more sats, all grounded in life.
The Big Picture
Stack those sats. Do it quietly, do it consistently, and do not let the green days puff you up or the red days break you down. Humility is the secret sauce, it keeps you grounded while the world spins wild. In a decade, when you look back and smile, it will not be because you shouted the loudest. It will be because you stayed the course, one sat at a time. \ \ Stay Humble and Stack Sats. 🫡
-
 @ 88cc134b:5ae99079
2025-05-16 19:04:30
@ 88cc134b:5ae99079
2025-05-16 19:04:30text
-
 @ 3bf0c63f:aefa459d
2025-04-25 18:55:52
@ 3bf0c63f:aefa459d
2025-04-25 18:55:52Report of how the money Jack donated to the cause in December 2022 has been misused so far.
Bounties given
March 2025
- Dhalsim: 1,110,540 - Work on Nostr wiki data processing
February 2025
- BOUNTY* NullKotlinDev: 950,480 - Twine RSS reader Nostr integration
- Dhalsim: 2,094,584 - Work on Hypothes.is Nostr fork
- Constant, Biz and J: 11,700,588 - Nostr Special Forces
January 2025
- Constant, Biz and J: 11,610,987 - Nostr Special Forces
- BOUNTY* NullKotlinDev: 843,840 - Feeder RSS reader Nostr integration
- BOUNTY* NullKotlinDev: 797,500 - ReadYou RSS reader Nostr integration
December 2024
- BOUNTY* tijl: 1,679,500 - Nostr integration into RSS readers yarr and miniflux
- Constant, Biz and J: 10,736,166 - Nostr Special Forces
- Thereza: 1,020,000 - Podcast outreach initiative
November 2024
- Constant, Biz and J: 5,422,464 - Nostr Special Forces
October 2024
- Nostrdam: 300,000 - hackathon prize
- Svetski: 5,000,000 - Latin America Nostr events contribution
- Quentin: 5,000,000 - nostrcheck.me
June 2024
- Darashi: 5,000,000 - maintaining nos.today, searchnos, search.nos.today and other experiments
- Toshiya: 5,000,000 - keeping the NIPs repo clean and other stuff
May 2024
- James: 3,500,000 - https://github.com/jamesmagoo/nostr-writer
- Yakihonne: 5,000,000 - spreading the word in Asia
- Dashu: 9,000,000 - https://github.com/haorendashu/nostrmo
February 2024
- Viktor: 5,000,000 - https://github.com/viktorvsk/saltivka and https://github.com/viktorvsk/knowstr
- Eric T: 5,000,000 - https://github.com/tcheeric/nostr-java
- Semisol: 5,000,000 - https://relay.noswhere.com/ and https://hist.nostr.land relays
- Sebastian: 5,000,000 - Drupal stuff and nostr-php work
- tijl: 5,000,000 - Cloudron, Yunohost and Fraidycat attempts
- Null Kotlin Dev: 5,000,000 - AntennaPod attempt
December 2023
- hzrd: 5,000,000 - Nostrudel
- awayuki: 5,000,000 - NOSTOPUS illustrations
- bera: 5,000,000 - getwired.app
- Chris: 5,000,000 - resolvr.io
- NoGood: 10,000,000 - nostrexplained.com stories
October 2023
- SnowCait: 5,000,000 - https://nostter.vercel.app/ and other tools
- Shaun: 10,000,000 - https://yakihonne.com/, events and work on Nostr awareness
- Derek Ross: 10,000,000 - spreading the word around the world
- fmar: 5,000,000 - https://github.com/frnandu/yana
- The Nostr Report: 2,500,000 - curating stuff
- james magoo: 2,500,000 - the Obsidian plugin: https://github.com/jamesmagoo/nostr-writer
August 2023
- Paul Miller: 5,000,000 - JS libraries and cryptography-related work
- BOUNTY tijl: 5,000,000 - https://github.com/github-tijlxyz/wikinostr
- gzuus: 5,000,000 - https://nostree.me/
July 2023
- syusui-s: 5,000,000 - rabbit, a tweetdeck-like Nostr client: https://syusui-s.github.io/rabbit/
- kojira: 5,000,000 - Nostr fanzine, Nostr discussion groups in Japan, hardware experiments
- darashi: 5,000,000 - https://github.com/darashi/nos.today, https://github.com/darashi/searchnos, https://github.com/darashi/murasaki
- jeff g: 5,000,000 - https://nostr.how and https://listr.lol, plus other contributions
- cloud fodder: 5,000,000 - https://nostr1.com (open-source)
- utxo.one: 5,000,000 - https://relaying.io (open-source)
- Max DeMarco: 10,269,507 - https://www.youtube.com/watch?v=aA-jiiepOrE
- BOUNTY optout21: 1,000,000 - https://github.com/optout21/nip41-proto0 (proposed nip41 CLI)
- BOUNTY Leo: 1,000,000 - https://github.com/leo-lox/camelus (an old relay thing I forgot exactly)
June 2023
- BOUNTY: Sepher: 2,000,000 - a webapp for making lists of anything: https://pinstr.app/
- BOUNTY: Kieran: 10,000,000 - implement gossip algorithm on Snort, implement all the other nice things: manual relay selection, following hints etc.
- Mattn: 5,000,000 - a myriad of projects and contributions to Nostr projects: https://github.com/search?q=owner%3Amattn+nostr&type=code
- BOUNTY: lynn: 2,000,000 - a simple and clean git nostr CLI written in Go, compatible with William's original git-nostr-tools; and implement threaded comments on https://github.com/fiatjaf/nocomment.
- Jack Chakany: 5,000,000 - https://github.com/jacany/nblog
- BOUNTY: Dan: 2,000,000 - https://metadata.nostr.com/
April 2023
- BOUNTY: Blake Jakopovic: 590,000 - event deleter tool, NIP dependency organization
- BOUNTY: koalasat: 1,000,000 - display relays
- BOUNTY: Mike Dilger: 4,000,000 - display relays, follow event hints (Gossip)
- BOUNTY: kaiwolfram: 5,000,000 - display relays, follow event hints, choose relays to publish (Nozzle)
- Daniele Tonon: 3,000,000 - Gossip
- bu5hm4nn: 3,000,000 - Gossip
- BOUNTY: hodlbod: 4,000,000 - display relays, follow event hints
March 2023
- Doug Hoyte: 5,000,000 sats - https://github.com/hoytech/strfry
- Alex Gleason: 5,000,000 sats - https://gitlab.com/soapbox-pub/mostr
- verbiricha: 5,000,000 sats - https://badges.page/, https://habla.news/
- talvasconcelos: 5,000,000 sats - https://migrate.nostr.com, https://read.nostr.com, https://write.nostr.com/
- BOUNTY: Gossip model: 5,000,000 - https://camelus.app/
- BOUNTY: Gossip model: 5,000,000 - https://github.com/kaiwolfram/Nozzle
- BOUNTY: Bounty Manager: 5,000,000 - https://nostrbounties.com/
February 2023
- styppo: 5,000,000 sats - https://hamstr.to/
- sandwich: 5,000,000 sats - https://nostr.watch/
- BOUNTY: Relay-centric client designs: 5,000,000 sats https://bountsr.org/design/2023/01/26/relay-based-design.html
- BOUNTY: Gossip model on https://coracle.social/: 5,000,000 sats
- Nostrovia Podcast: 3,000,000 sats - https://nostrovia.org/
- BOUNTY: Nostr-Desk / Monstr: 5,000,000 sats - https://github.com/alemmens/monstr
- Mike Dilger: 5,000,000 sats - https://github.com/mikedilger/gossip
January 2023
- ismyhc: 5,000,000 sats - https://github.com/Galaxoid-Labs/Seer
- Martti Malmi: 5,000,000 sats - https://iris.to/
- Carlos Autonomous: 5,000,000 sats - https://github.com/BrightonBTC/bija
- Koala Sat: 5,000,000 - https://github.com/KoalaSat/nostros
- Vitor Pamplona: 5,000,000 - https://github.com/vitorpamplona/amethyst
- Cameri: 5,000,000 - https://github.com/Cameri/nostream
December 2022
- William Casarin: 7 BTC - splitting the fund
- pseudozach: 5,000,000 sats - https://nostr.directory/
- Sondre Bjellas: 5,000,000 sats - https://notes.blockcore.net/
- Null Dev: 5,000,000 sats - https://github.com/KotlinGeekDev/Nosky
- Blake Jakopovic: 5,000,000 sats - https://github.com/blakejakopovic/nostcat, https://github.com/blakejakopovic/nostreq and https://github.com/blakejakopovic/NostrEventPlayground
-
 @ 04c915da:3dfbecc9
2025-03-04 17:00:18
@ 04c915da:3dfbecc9
2025-03-04 17:00:18This piece is the first in a series that will focus on things I think are a priority if your focus is similar to mine: building a strong family and safeguarding their future.
Choosing the ideal place to raise a family is one of the most significant decisions you will ever make. For simplicity sake I will break down my thought process into key factors: strong property rights, the ability to grow your own food, access to fresh water, the freedom to own and train with guns, and a dependable community.
A Jurisdiction with Strong Property Rights
Strong property rights are essential and allow you to build on a solid foundation that is less likely to break underneath you. Regions with a history of limited government and clear legal protections for landowners are ideal. Personally I think the US is the single best option globally, but within the US there is a wide difference between which state you choose. Choose carefully and thoughtfully, think long term. Obviously if you are not American this is not a realistic option for you, there are other solid options available especially if your family has mobility. I understand many do not have this capability to easily move, consider that your first priority, making movement and jurisdiction choice possible in the first place.
Abundant Access to Fresh Water
Water is life. I cannot overstate the importance of living somewhere with reliable, clean, and abundant freshwater. Some regions face water scarcity or heavy regulations on usage, so prioritizing a place where water is plentiful and your rights to it are protected is critical. Ideally you should have well access so you are not tied to municipal water supplies. In times of crisis or chaos well water cannot be easily shutoff or disrupted. If you live in an area that is drought prone, you are one drought away from societal chaos. Not enough people appreciate this simple fact.
Grow Your Own Food
A location with fertile soil, a favorable climate, and enough space for a small homestead or at the very least a garden is key. In stable times, a small homestead provides good food and important education for your family. In times of chaos your family being able to grow and raise healthy food provides a level of self sufficiency that many others will lack. Look for areas with minimal restrictions, good weather, and a culture that supports local farming.
Guns
The ability to defend your family is fundamental. A location where you can legally and easily own guns is a must. Look for places with a strong gun culture and a political history of protecting those rights. Owning one or two guns is not enough and without proper training they will be a liability rather than a benefit. Get comfortable and proficient. Never stop improving your skills. If the time comes that you must use a gun to defend your family, the skills must be instinct. Practice. Practice. Practice.
A Strong Community You Can Depend On
No one thrives alone. A ride or die community that rallies together in tough times is invaluable. Seek out a place where people know their neighbors, share similar values, and are quick to lend a hand. Lead by example and become a good neighbor, people will naturally respond in kind. Small towns are ideal, if possible, but living outside of a major city can be a solid balance in terms of work opportunities and family security.
Let me know if you found this helpful. My plan is to break down how I think about these five key subjects in future posts.
-
 @ 04c915da:3dfbecc9
2025-05-16 17:51:54
@ 04c915da:3dfbecc9
2025-05-16 17:51:54In much of the world, it is incredibly difficult to access U.S. dollars. Local currencies are often poorly managed and riddled with corruption. Billions of people demand a more reliable alternative. While the dollar has its own issues of corruption and mismanagement, it is widely regarded as superior to the fiat currencies it competes with globally. As a result, Tether has found massive success providing low cost, low friction access to dollars. Tether claims 400 million total users, is on track to add 200 million more this year, processes 8.1 million transactions daily, and facilitates $29 billion in daily transfers. Furthermore, their estimates suggest nearly 40% of users rely on it as a savings tool rather than just a transactional currency.
Tether’s rise has made the company a financial juggernaut. Last year alone, Tether raked in over $13 billion in profit, with a lean team of less than 100 employees. Their business model is elegantly simple: hold U.S. Treasuries and collect the interest. With over $113 billion in Treasuries, Tether has turned a straightforward concept into a profit machine.
Tether’s success has resulted in many competitors eager to claim a piece of the pie. This has triggered a massive venture capital grift cycle in USD tokens, with countless projects vying to dethrone Tether. Due to Tether’s entrenched network effect, these challengers face an uphill battle with little realistic chance of success. Most educated participants in the space likely recognize this reality but seem content to perpetuate the grift, hoping to cash out by dumping their equity positions on unsuspecting buyers before they realize the reality of the situation.
Historically, Tether’s greatest vulnerability has been U.S. government intervention. For over a decade, the company operated offshore with few allies in the U.S. establishment, making it a major target for regulatory action. That dynamic has shifted recently and Tether has seized the opportunity. By actively courting U.S. government support, Tether has fortified their position. This strategic move will likely cement their status as the dominant USD token for years to come.
While undeniably a great tool for the millions of users that rely on it, Tether is not without flaws. As a centralized, trusted third party, it holds the power to freeze or seize funds at its discretion. Corporate mismanagement or deliberate malpractice could also lead to massive losses at scale. In their goal of mitigating regulatory risk, Tether has deepened ties with law enforcement, mirroring some of the concerns of potential central bank digital currencies. In practice, Tether operates as a corporate CBDC alternative, collaborating with authorities to surveil and seize funds. The company proudly touts partnerships with leading surveillance firms and its own data reveals cooperation in over 1,000 law enforcement cases, with more than $2.5 billion in funds frozen.
The global demand for Tether is undeniable and the company’s profitability reflects its unrivaled success. Tether is owned and operated by bitcoiners and will likely continue to push forward strategic goals that help the movement as a whole. Recent efforts to mitigate the threat of U.S. government enforcement will likely solidify their network effect and stifle meaningful adoption of rival USD tokens or CBDCs. Yet, for all their achievements, Tether is simply a worse form of money than bitcoin. Tether requires trust in a centralized entity, while bitcoin can be saved or spent without permission. Furthermore, Tether is tied to the value of the US Dollar which is designed to lose purchasing power over time, while bitcoin, as a truly scarce asset, is designed to increase in purchasing power with adoption. As people awaken to the risks of Tether’s control, and the benefits bitcoin provides, bitcoin adoption will likely surpass it.
-
 @ 7e6f9018:a6bbbce5
2025-05-16 17:32:56
@ 7e6f9018:a6bbbce5
2025-05-16 17:32:56The rental population in Spain has grown from about 5 million in 2005 to around 10 million in 2025. During that same period, Spain's total population has increased by 6 million people, from 43 to 49 million. In other words, the entire population growth over the past 20 years has essentially gone straight into the rental market.
This demographic growth is not due to natural increase, Spain has one of the lowest fertility rates in the world. Instead, population growth is driven by a positive migratory balance, which has been the main factor behind the rise in rental demand.
This increased demand for rentals has pushed up rental prices, which have significantly outpaced the growth in property sale prices. That didn’t happen during the Great Financial Crisis. The growth in both demand and prices is allowing rental profitability to remain at the high end of the curve—around 5% net.
This situation explains the rise in housing squatting, from 2,000 cases in 2010 to 16,000 in 2024. Since the immigrant population is the main driver of this surge in rental demand, it is more vulnerable to squatting, as they often have no alternative housing when they are unable to pay.
The unemployment rate is currently low, however, if it were to rise (as it did during the Great Financial Crisis and other periods in the past), squatting would likely increase significantly, representing the main risk to the current real estate market in Spain.
-
 @ b1b16be0:08f41c1d
2025-04-11 22:58:00
@ b1b16be0:08f41c1d
2025-04-11 22:58:00Bitcoin need more devs to scale! So I decide to translate to spanish https://plebdevs.com plebdevs@plebdevs.com is a opensource website to learn #bitcoin #lightning free.I started in my free time but now I have to sacrifice work time to move forward. Any zap could be a new bitcoiner!
Why Spanish? Spanish is the third most spoken language on the internet, but much of this community has little access to technical content in English. Plebdevs can be the 🔥torch that illuminates new developers to scale Bitcoin from Latin America and the world.
Apprenticeship Incentive Plebs will gaining the possibility of #learn a higher-paying job as #dev.
Let's Make Bitcoin Scale Millions of Spanish speakers can learn how to develop about Bitcoin and Lightning.
Proof of Work Introduction presentation: https://docs.google.com/presentation/d/1IMC4GHYjccKhGu2mDrtY3bOGcjyFcwgXwFyKyNMq7iw/edit?usp=sharing
🟩🟩🟩⬜⬜⬜⬜⬜⬜⬜ 30%
Thanks to bitcoinplebdev@bitcoinpleb.dev to create this #wonder
Any Zap will be helpful!
mav21@primal.net am@cubabitcoin.org lacrypta@hodl.ar BenJustman@primal.net shishi@nostrplebs.com sabine@primal.net onpoint@nostr.com theguyswann@iris.to Richard@primal.net eliza@primal.net
-
 @ c9e9bdc0:e4dbe9b8
2025-05-16 17:00:09
@ c9e9bdc0:e4dbe9b8
2025-05-16 17:00:09Today we’re launching Buzzbot Express: a clean, targeted way to drive engagement and reward your audience with sats.
Here’s how it works:
-
Tag @buzzbot express [amount] (e.g.,
@buzzbot express 5000) -
Pay the invoice sent to your DMs
-
After 12 hours, one random liker and one random commenter each win **50% of the sats **(6% fee)
Since launching Buzzbot, we’ve seen a wide range of creative use cases. But the clearest path to long-term value may lie in branded content and decentralized promotion.
From plebs promoting value-for-value concerts to podcasters pushing new episodes, Buzzbot Express gives creators and brands a tool to generate real energy around a post.
Paying for engagement might feel off-brand to some, but if you’re promoting a product, a song, or an event, Buzzbot Express offers a clean, transparent way to generate real momentum.
The invention of Zaps opened the fifth dimension of social media. They are not just another feature added to the stack. They are an exponential amplifier that transforms attention into economic energy.
At Buzzbot, we believe this new creator economy can and should include advertisers.
The days of brands paying millions to ad firms, hiring Hollywood talent, and forcing campaigns into feeds are fading. That model made sense on centralized, algorithmic platforms, but it doesn’t belong on Nostr.
Instead, brands can spend that same money directly with creators who align with their values. Or better yet, they can reward audiences for engaging honestly.
That’s where Buzzbot comes in.
Buzzbot Express is a small step toward this future. Try it out — and let us know what you think.
Pay attention.
-
-
 @ ec9bd746:df11a9d0
2025-04-06 08:06:08
@ ec9bd746:df11a9d0
2025-04-06 08:06:08🌍 Time Window:
🕘 When: Every even week on Sunday at 9:00 PM CET
🗺️ Where: https://cornychat.com/eurocornStart: 21:00 CET (Prague, UTC+1)
End: approx. 02:00 CET (Prague, UTC+1, next day)
Duration: usually 5+ hours.| Region | Local Time Window | Convenience Level | |-----------------------------------------------------|--------------------------------------------|---------------------------------------------------------| | Europe (CET, Prague) 🇨🇿🇩🇪 | 21:00–02:00 CET | ✅ Very Good; evening & night | | East Coast North America (EST) 🇺🇸🇨🇦 | 15:00–20:00 EST | ✅ Very Good; afternoon & early evening | | West Coast North America (PST) 🇺🇸🇨🇦 | 12:00–17:00 PST | ✅ Very Good; midday & afternoon | | Central America (CST) 🇲🇽🇨🇷🇬🇹 | 14:00–19:00 CST | ✅ Very Good; afternoon & evening | | South America West (Peru/Colombia PET/COT) 🇵🇪🇨🇴 | 15:00–20:00 PET/COT | ✅ Very Good; afternoon & evening | | South America East (Brazil/Argentina/Chile, BRT/ART/CLST) 🇧🇷🇦🇷🇨🇱 | 17:00–22:00 BRT/ART/CLST | ✅ Very Good; early evening | | United Kingdom/Ireland (GMT) 🇬🇧🇮🇪 | 20:00–01:00 GMT | ✅ Very Good; evening hours (midnight convenient) | | Eastern Europe (EET) 🇷🇴🇬🇷🇺🇦 | 22:00–03:00 EET | ✅ Good; late evening & early night (slightly late) | | Africa (South Africa, SAST) 🇿🇦 | 22:00–03:00 SAST | ✅ Good; late evening & overnight (late-night common) | | New Zealand (NZDT) 🇳🇿 | 09:00–14:00 NZDT (next day) | ✅ Good; weekday morning & afternoon | | Australia (AEDT, Sydney) 🇦🇺 | 07:00–12:00 AEDT (next day) | ✅ Good; weekday morning to noon | | East Africa (Kenya, EAT) 🇰🇪 | 23:00–04:00 EAT | ⚠️ Slightly late (night hours; late night common) | | Russia (Moscow, MSK) 🇷🇺 | 23:00–04:00 MSK | ⚠️ Slightly late (join at start is fine, very late night) | | Middle East (UAE, GST) 🇦🇪🇴🇲 | 00:00–05:00 GST (next day) | ⚠️ Late night start (midnight & early morning, but shorter attendance plausible)| | Japan/Korea (JST/KST) 🇯🇵🇰🇷 | 05:00–10:00 JST/KST (next day) | ⚠️ Early; convenient joining from ~07:00 onwards possible | | China (Beijing, CST) 🇨🇳 | 04:00–09:00 CST (next day) | ❌ Challenging; very early morning start (better ~07:00 onwards) | | India (IST) 🇮🇳 | 01:30–06:30 IST (next day) | ❌ Very challenging; overnight timing typically difficult|
-
 @ cae03c48:2a7d6671
2025-05-16 16:52:38
@ cae03c48:2a7d6671
2025-05-16 16:52:38Bitcoin Magazine

Steak ‘n Shake Now Accepting Bitcoin via Lightning Network Across U.S. LocationsSteak ‘n Shake has officially launched Bitcoin payments via the Lightning Network, following the announcement reported on May 9. At the time, the fast food chain teased its plans to integrate BTC, generating excitement across the Bitcoin community. And today, it is an option at the cash register, or better said, Bitcoin Register.
JUST IN: Fast food giant Steak 'n Shake is now officially accepting #Bitcoin Lightning Network payments
 pic.twitter.com/bvGCb9r4Im
pic.twitter.com/bvGCb9r4Im— Bitcoin Magazine (@BitcoinMagazine) May 16, 2025
As of today, customers can pay for their meals with Bitcoin at Steak ‘n Shake locations across the United States. This marks a major step in mainstream Bitcoin adoption, as the chain serves over 100 million customers annually and now gives them the option to use Lightning for instant, low-fee transactions.
First Bitcoin purchase in the world with @SteaknShake
Changing the game of Dining, Bitcoin & Politics.
Only Steak N’ Shake puts your health over profits by using beef tallow. pic.twitter.com/ZeQxxFbbHB
— Valentina Gomez (@ValentinaForUSA) May 16, 2025
The company announced the news on X this morning, confirming that Lightning Network payments are officially supported in-store.
Bitcoin has been launched at Steak n Shake



The revolution is underway…
-Steaktoshi
— Steak 'n Shake (@SteaknShake) May 16, 2025
Following up, they clarified the scale of the implementation—this isn’t a small test or pilot program. It’s a full rollout across their system.
The Lightning Network, Bitcoin’s second-layer solution, is designed for fast, scalable, and low-cost payments, making it ideal for point-of-sale purchases like burgers and fries. Steak ‘n Shake customers can now scan a Lightning QR code at checkout using any supported wallet, completing transactions in seconds. The system uses a backend payment processor to handle real-time conversion to USD, ensuring stability and ease of use for both the customer and the merchant.
NEW: Fast food giant Steak 'n Shake will begin accepting Bitcoin payments for their over 100 million customers
 pic.twitter.com/g1OErM82BI
pic.twitter.com/g1OErM82BI— Bitcoin Magazine (@BitcoinMagazine) May 9, 2025
In Bitcoin Magazine’s previous coverage, the significance of even the hint of this move was noted, and now that it’s official, it confirms Steak ‘n Shake as one of the first major fast food brands to fully embrace Bitcoin through Lightning. This goes beyond the occasional “Bitcoin accepted here” sign; this is a practical, streamlined payment option that reflects a commitment to Bitcoin integration.
 Cashback Alert at Steak ’n Shake!
Cashback Alert at Steak ’n Shake! 
Buy your next meal in Bitcoin Lightning


Pay using Speed Wallet at any @SteaknShake store and get 1,000 SATS cashback via Lightning

 More Bonus: Post a video of your payment & tag us — we’ll send you an extra 2,000 SATS to your… pic.twitter.com/D2aV4biJP4
More Bonus: Post a video of your payment & tag us — we’ll send you an extra 2,000 SATS to your… pic.twitter.com/D2aV4biJP4— Speed Wallet
 (@speedwallet) May 16, 2025
(@speedwallet) May 16, 2025With tools like the Lightning Network making payments faster and more accessible, Steak ‘n Shake is positioning itself at the forefront of a shift toward practical, everyday BTC utility.
This update could signal a larger trend on the horizon. With more brands watching consumer behavior and the Lightning Network’s increasing usability, Steak ‘n Shake’s move might spark a wave of similar integrations.
This post Steak ‘n Shake Now Accepting Bitcoin via Lightning Network Across U.S. Locations first appeared on Bitcoin Magazine and is written by Jenna Montgomery.
-
 @ 05a0f81e:fc032124
2025-05-16 16:51:11
@ 05a0f81e:fc032124
2025-05-16 16:51:11In the year 2023, a man known as RTD. HAMZA AL-MUSTAPHA. In a TV show revealed the secret behind the mining of californium in west African country, Nigeria. He also revealed that the mining of californium is also the reason while a particular (borno) state in Nigeria 🇳🇬 experience hight rate of terrorism!.
There are several research that quote that californium does not exist naturally on earth but can be made in the laboratory with the bombarding of curium with helium ions. Now from this context, it shows that there are two elements responsible for californium, which are curium and helium ions. But before i dive in deeper, there are some key words that will convince and prove the existence of californium in Nigeria.
- californium.
- curium.
- helium ions.
- mining.
- Earth crust.
- temperature.
- bombarding.
Californium: this is a chemical element of atomic number 98, a radioactive metal of the actinide series, first produced by bombarding of curium with helium ions. This means that californium is a product of curium and helium after the bombarding process.
Curium: this is a synthetic, radioactive, metallic element with the atomic number of 96. There are many ways and places where curium can be found apart from being produced in the laboratory. But in this contexts, I will focus on environmental samples and nuclear waste ways of finding curium. _ environment sample: trace amounts of Curium can be found in environmental samples such as soil or water, near
nuclear facilities or after nuclear accidents. _ nuclear waste: curium is a component of nuclear waste, particularly in spent nuclear fuel. This means that we can find curium in our environment not only on laboratory.Helium: helium is a chemical element with the atomic number of 2, it is colorless, tasteless, odorless and non toxic, inert monatomic gas. There are ways and places you can get helium but I want to focus on the radioactive decay method of getting helium. _radioactive decay: in this method, helium is produced through the radioactive decay of uranium and thorium in the Earth crust.
Mining: Mining is the process of extracting valuable materials from the beneath the Earth crust, including minerals, metals, and fossil fuels like coal, oil, and gas. It involves various techniques, from digging tunnels for underground mining to excavating open-pit mines. The goal is to locate and extract economically viable deposits of these resources for use in manufacturing, energy production, and other applications.
Temperature: thus is the hotness or coldness of something, which is specifically related to the average kinetic energy of an object's particle. Since particles are in constant motion, they possess kinetic energy, and temperature reflects the energy associated with this particle movement. The temperature beneath the Earth is very high causing this elements (curium and helium) to bombard and form californium 😃.
Bombarding: direct a stream of high-speed particles at (a substance) or element.
Since there are the presence of curium and helium ions beneath the Earth crust, the high temperature beneath there will bombard them both forming californium as the end product, which attracts miners to come do there mining activities and discover californium. 😀
Final, there are atoms of truth in what RTD. AL-MUSTAPHA said about CALIFORNIUM in Nigeria 🇳🇬.
-
 @ 04c915da:3dfbecc9
2025-02-25 03:55:08
@ 04c915da:3dfbecc9
2025-02-25 03:55:08Here’s a revised timeline of macro-level events from The Mandibles: A Family, 2029–2047 by Lionel Shriver, reimagined in a world where Bitcoin is adopted as a widely accepted form of money, altering the original narrative’s assumptions about currency collapse and economic control. In Shriver’s original story, the failure of Bitcoin is assumed amid the dominance of the bancor and the dollar’s collapse. Here, Bitcoin’s success reshapes the economic and societal trajectory, decentralizing power and challenging state-driven outcomes.
Part One: 2029–2032
-
2029 (Early Year)\ The United States faces economic strain as the dollar weakens against global shifts. However, Bitcoin, having gained traction emerges as a viable alternative. Unlike the original timeline, the bancor—a supranational currency backed by a coalition of nations—struggles to gain footing as Bitcoin’s decentralized adoption grows among individuals and businesses worldwide, undermining both the dollar and the bancor.
-
2029 (Mid-Year: The Great Renunciation)\ Treasury bonds lose value, and the government bans Bitcoin, labeling it a threat to sovereignty (mirroring the original bancor ban). However, a Bitcoin ban proves unenforceable—its decentralized nature thwarts confiscation efforts, unlike gold in the original story. Hyperinflation hits the dollar as the U.S. prints money, but Bitcoin’s fixed supply shields adopters from currency devaluation, creating a dual-economy split: dollar users suffer, while Bitcoin users thrive.
-
2029 (Late Year)\ Dollar-based inflation soars, emptying stores of goods priced in fiat currency. Meanwhile, Bitcoin transactions flourish in underground and online markets, stabilizing trade for those plugged into the bitcoin ecosystem. Traditional supply chains falter, but peer-to-peer Bitcoin networks enable local and international exchange, reducing scarcity for early adopters. The government’s gold confiscation fails to bolster the dollar, as Bitcoin’s rise renders gold less relevant.
-
2030–2031\ Crime spikes in dollar-dependent urban areas, but Bitcoin-friendly regions see less chaos, as digital wallets and smart contracts facilitate secure trade. The U.S. government doubles down on surveillance to crack down on bitcoin use. A cultural divide deepens: centralized authority weakens in Bitcoin-adopting communities, while dollar zones descend into lawlessness.
-
2032\ By this point, Bitcoin is de facto legal tender in parts of the U.S. and globally, especially in tech-savvy or libertarian-leaning regions. The federal government’s grip slips as tax collection in dollars plummets—Bitcoin’s traceability is low, and citizens evade fiat-based levies. Rural and urban Bitcoin hubs emerge, while the dollar economy remains fractured.
Time Jump: 2032–2047
- Over 15 years, Bitcoin solidifies as a global reserve currency, eroding centralized control. The U.S. government adapts, grudgingly integrating bitcoin into policy, though regional autonomy grows as Bitcoin empowers local economies.
Part Two: 2047
-
2047 (Early Year)\ The U.S. is a hybrid state: Bitcoin is legal tender alongside a diminished dollar. Taxes are lower, collected in BTC, reducing federal overreach. Bitcoin’s adoption has decentralized power nationwide. The bancor has faded, unable to compete with Bitcoin’s grassroots momentum.
-
2047 (Mid-Year)\ Travel and trade flow freely in Bitcoin zones, with no restrictive checkpoints. The dollar economy lingers in poorer areas, marked by decay, but Bitcoin’s dominance lifts overall prosperity, as its deflationary nature incentivizes saving and investment over consumption. Global supply chains rebound, powered by bitcoin enabled efficiency.
-
2047 (Late Year)\ The U.S. is a patchwork of semi-autonomous zones, united by Bitcoin’s universal acceptance rather than federal control. Resource scarcity persists due to past disruptions, but economic stability is higher than in Shriver’s original dystopia—Bitcoin’s success prevents the authoritarian slide, fostering a freer, if imperfect, society.
Key Differences
- Currency Dynamics: Bitcoin’s triumph prevents the bancor’s dominance and mitigates hyperinflation’s worst effects, offering a lifeline outside state control.
- Government Power: Centralized authority weakens as Bitcoin evades bans and taxation, shifting power to individuals and communities.
- Societal Outcome: Instead of a surveillance state, 2047 sees a decentralized, bitcoin driven world—less oppressive, though still stratified between Bitcoin haves and have-nots.
This reimagining assumes Bitcoin overcomes Shriver’s implied skepticism to become a robust, adopted currency by 2029, fundamentally altering the novel’s bleak trajectory.
-
-
 @ 88cc134b:5ae99079
2025-05-16 18:08:25
@ 88cc134b:5ae99079
2025-05-16 18:08:25Here's the article. Not the longest one ever. But definitely impactful.
-
 @ 5d4b6c8d:8a1c1ee3
2025-05-16 15:29:10
@ 5d4b6c8d:8a1c1ee3
2025-05-16 15:29:10How could the Dallas Mavericks possibly have gotten the first pick in this draft? League corruption? Mischievous basketball gods? Simulation theory? Dumb stupid luck? Whatever the reason, it's very interesting.
We'll probably be done with the 2nd round, by the time we record, which means round 2 recap and conference finals previews. It's definitely not the matchups anyone expected. What are the implications for our brackets?
The NFL released the season schedules and @grayruby's rightly excited for his 49ers upcoming season.
The parity situation worsens in the MLB, as the Dodgers' pitchers are ravaged by injury. Also, @grayruby and I are going head-to-head in fantasy baseball this week. Who will prevail?
On this week's Blok'd Shots, @grayruby will dance on the Leafs' grave and celebrate their well-deserved misfortune. Hell hath no fury like a scorned Leafs fan. Also, the NHL bracket is coming down to me and @Jer. Will knowing anything about hockey be enough to get Jer the victory?
And, as always, whatever the stackers want us to cover.
https://stacker.news/items/981596
-
 @ 6e0ea5d6:0327f353
2025-02-21 18:15:52
@ 6e0ea5d6:0327f353
2025-02-21 18:15:52"Malcolm Forbes recounts that a lady, wearing a faded cotton dress, and her husband, dressed in an old handmade suit, stepped off a train in Boston, USA, and timidly made their way to the office of the president of Harvard University. They had come from Palo Alto, California, and had not scheduled an appointment. The secretary, at a glance, thought that those two, looking like country bumpkins, had no business at Harvard.
— We want to speak with the president — the man said in a low voice.
— He will be busy all day — the secretary replied curtly.
— We will wait.
The secretary ignored them for hours, hoping the couple would finally give up and leave. But they stayed there, and the secretary, somewhat frustrated, decided to bother the president, although she hated doing that.
— If you speak with them for just a few minutes, maybe they will decide to go away — she said.
The president sighed in irritation but agreed. Someone of his importance did not have time to meet people like that, but he hated faded dresses and tattered suits in his office. With a stern face, he went to the couple.
— We had a son who studied at Harvard for a year — the woman said. — He loved Harvard and was very happy here, but a year ago he died in an accident, and we would like to erect a monument in his honor somewhere on campus.— My lady — said the president rudely —, we cannot erect a statue for every person who studied at Harvard and died; if we did, this place would look like a cemetery.
— Oh, no — the lady quickly replied. — We do not want to erect a statue. We would like to donate a building to Harvard.
The president looked at the woman's faded dress and her husband's old suit and exclaimed:
— A building! Do you have even the faintest idea of how much a building costs? We have more than seven and a half million dollars' worth of buildings here at Harvard.
The lady was silent for a moment, then said to her husband:
— If that’s all it costs to found a university, why don’t we have our own?
The husband agreed.
The couple, Leland Stanford, stood up and left, leaving the president confused. Traveling back to Palo Alto, California, they established there Stanford University, the second-largest in the world, in honor of their son, a former Harvard student."
Text extracted from: "Mileumlivros - Stories that Teach Values."
Thank you for reading, my friend! If this message helped you in any way, consider leaving your glass “🥃” as a token of appreciation.
A toast to our family!
-
 @ d57360cb:4fe7d935
2025-05-16 14:54:18
@ d57360cb:4fe7d935
2025-05-16 14:54:18I soar all over the world, but one of the places I visit often is this little tiny square opening. I land softly on the platform and peer in through the hole. There’s a man inside; he seems to enjoy when I come by. His eyes light up and he gives me crumbs of bread to eat. The bread is tasty and fulfilling; it satisfies my hunger during my flights to other destinations. I wonder what it’s like to be man.
Man does strange things. I can’t fully understand. For example, this man is confined in a tiny box. He sits on what looks like a deformed tree, and in front of him is a tiny rectangular box. Everything man has is so boxy; it’s unnatural to me. When I fly from place to place, I don’t see any boxes; rather, I see a wiggly world. Endless shape, no two things look the same, but to man, it’s like he wants everything to be the same. Man usually is looking at other thin boxes; these are slim and have marks on them. He appears to stare for a long time at them, and then he sets them down and picks up another to stare at. In his box, he has long, narrow boxes. They hold small boxes bundled together with slim boxes. It gives me a headache seeing so many boxes. Once I observed man outside in the wiggly world, and when he left his big box, he went into another smaller box that moved! I was so interested I followed his moving box. You wouldn’t guess where he went to! Another box, but this one was a big one with subsections of smaller boxes. Could you believe they even have big boxes for water! What a headache man is.
The game man plays is interesting; it seems to be about boxes and how to put wiggly things in them. The wiggly is too elusive; one can’t box it up. Even if you surround the wiggly in a box, it will continue to wiggle. Like a tree confined to a planter box, its roots will spread beyond their confinement. Man is like this but believes the box will contain him, shameful.
-
 @ c1e9ab3a:9cb56b43
2025-05-09 23:10:14
@ c1e9ab3a:9cb56b43
2025-05-09 23:10:14I. Historical Foundations of U.S. Monetary Architecture
The early monetary system of the United States was built atop inherited commodity money conventions from Europe’s maritime economies. Silver and gold coins—primarily Spanish pieces of eight, Dutch guilders, and other foreign specie—formed the basis of colonial commerce. These units were already integrated into international trade and piracy networks and functioned with natural compatibility across England, France, Spain, and Denmark. Lacking a centralized mint or formal currency, the U.S. adopted these forms de facto.
As security risks and the practical constraints of physical coinage mounted, banks emerged to warehouse specie and issue redeemable certificates. These certificates evolved into fiduciary media—claims on specie not actually in hand. Banks observed over time that substantial portions of reserves remained unclaimed for years. This enabled fractional reserve banking: issuing more claims than reserves held, so long as redemption demand stayed low. The practice was inherently unstable, prone to panics and bank runs, prompting eventual centralization through the formation of the Federal Reserve in 1913.
Following the Civil War and unstable reinstatements of gold convertibility, the U.S. sought global monetary stability. After World War II, the Bretton Woods system formalized the U.S. dollar as the global reserve currency. The dollar was nominally backed by gold, but most international dollars were held offshore and recycled into U.S. Treasuries. The Nixon Shock of 1971 eliminated the gold peg, converting the dollar into pure fiat. Yet offshore dollar demand remained, sustained by oil trade mandates and the unique role of Treasuries as global reserve assets.
II. The Structure of Fiduciary Media and Treasury Demand
Under this system, foreign trade surpluses with the U.S. generate excess dollars. These surplus dollars are parked in U.S. Treasuries, thereby recycling trade imbalances into U.S. fiscal liquidity. While technically loans to the U.S. government, these purchases act like interest-only transfers—governments receive yield, and the U.S. receives spendable liquidity without principal repayment due in the short term. Debt is perpetually rolled over, rarely extinguished.
This creates an illusion of global subsidy: U.S. deficits are financed via foreign capital inflows that, in practice, function more like financial tribute systems than conventional debt markets. The underlying asset—U.S. Treasury debt—functions as the base reserve asset of the dollar system, replacing gold in post-Bretton Woods monetary logic.
III. Emergence of Tether and the Parastatal Dollar
Tether (USDT), as a private issuer of dollar-denominated tokens, mimics key central bank behaviors while operating outside the regulatory perimeter. It mints tokens allegedly backed 1:1 by U.S. dollars or dollar-denominated securities (mostly Treasuries). These tokens circulate globally, often in jurisdictions with limited banking access, and increasingly serve as synthetic dollar substitutes.
If USDT gains dominance as the preferred medium of exchange—due to technological advantages, speed, programmability, or access—it displaces Federal Reserve Notes (FRNs) not through devaluation, but through functional obsolescence. Gresham’s Law inverts: good money (more liquid, programmable, globally transferable USDT) displaces bad (FRNs) even if both maintain a nominal 1:1 parity.
Over time, this preference translates to a systemic demand shift. Actors increasingly use Tether instead of FRNs, especially in global commerce, digital marketplaces, or decentralized finance. Tether tokens effectively become shadow base money.
IV. Interaction with Commercial Banking and Redemption Mechanics
Under traditional fractional reserve systems, commercial banks issue loans denominated in U.S. dollars, expanding the money supply. When borrowers repay loans, this destroys the created dollars and contracts monetary elasticity. If borrowers repay in USDT instead of FRNs:
- Banks receive a non-Fed liability (USDT).
- USDT is not recognized as reserve-eligible within the Federal Reserve System.
- Banks must either redeem USDT for FRNs, or demand par-value conversion from Tether to settle reserve requirements and balance their books.
This places redemption pressure on Tether and threatens its 1:1 peg under stress. If redemption latency, friction, or cost arises, USDT’s equivalence to FRNs is compromised. Conversely, if banks are permitted or compelled to hold USDT as reserve or regulatory capital, Tether becomes a de facto reserve issuer.
In this scenario, banks may begin demanding loans in USDT, mirroring borrower behavior. For this to occur sustainably, banks must secure Tether liquidity. This creates two options: - Purchase USDT from Tether or on the secondary market, collateralized by existing fiat. - Borrow USDT directly from Tether, using bank-issued debt as collateral.
The latter mirrors Federal Reserve discount window operations. Tether becomes a lender of first resort, providing monetary elasticity to the banking system by creating new tokens against promissory assets—exactly how central banks function.
V. Structural Consequences: Parallel Central Banking
If Tether begins lending to commercial banks, issuing tokens backed by bank notes or collateralized debt obligations: - Tether controls the expansion of broad money through credit issuance. - Its balance sheet mimics a central bank, with Treasuries and bank debt as assets and tokens as liabilities. - It intermediates between sovereign debt and global liquidity demand, replacing the Federal Reserve’s open market operations with its own issuance-redemption cycles.
Simultaneously, if Tether purchases U.S. Treasuries with FRNs received through token issuance, it: - Supplies the Treasury with new liquidity (via bond purchases). - Collects yield on government debt. - Issues a parallel form of U.S. dollars that never require redemption—an interest-only loan to the U.S. government from a non-sovereign entity.
In this context, Tether performs monetary functions of both a central bank and a sovereign wealth fund, without political accountability or regulatory transparency.
VI. Endgame: Institutional Inversion and Fed Redundancy
This paradigm represents an institutional inversion:
- The Federal Reserve becomes a legacy issuer.
- Tether becomes the operational base money provider in both retail and interbank contexts.
- Treasuries remain the foundational reserve asset, but access to them is mediated by a private intermediary.
- The dollar persists, but its issuer changes. The State becomes a fiscal agent of a decentralized financial ecosystem, not its monetary sovereign.
Unless the Federal Reserve reasserts control—either by absorbing Tether, outlawing its instruments, or integrating its tokens into the reserve framework—it risks becoming irrelevant in the daily function of money.
Tether, in this configuration, is no longer a derivative of the dollar—it is the dollar, just one level removed from sovereign control. The future of monetary sovereignty under such a regime is post-national and platform-mediated.
-
 @ c066aac5:6a41a034
2025-04-05 16:58:58
@ c066aac5:6a41a034
2025-04-05 16:58:58I’m drawn to extremities in art. The louder, the bolder, the more outrageous, the better. Bold art takes me out of the mundane into a whole new world where anything and everything is possible. Having grown up in the safety of the suburban midwest, I was a bit of a rebellious soul in search of the satiation that only came from the consumption of the outrageous. My inclination to find bold art draws me to NOSTR, because I believe NOSTR can be the place where the next generation of artistic pioneers go to express themselves. I also believe that as much as we are able, were should invite them to come create here.
My Background: A Small Side Story
My father was a professional gamer in the 80s, back when there was no money or glory in the avocation. He did get a bit of spotlight though after the fact: in the mid 2000’s there were a few parties making documentaries about that era of gaming as well as current arcade events (namely 2007’sChasing GhostsandThe King of Kong: A Fistful of Quarters). As a result of these documentaries, there was a revival in the arcade gaming scene. My family attended events related to the documentaries or arcade gaming and I became exposed to a lot of things I wouldn’t have been able to find. The producer ofThe King of Kong: A Fistful of Quarters had previously made a documentary calledNew York Dollwhich was centered around the life of bassist Arthur Kane. My 12 year old mind was blown: The New York Dolls were a glam-punk sensation dressed in drag. The music was from another planet. Johnny Thunders’ guitar playing was like Chuck Berry with more distortion and less filter. Later on I got to meet the Galaga record holder at the time, Phil Day, in Ottumwa Iowa. Phil is an Australian man of high intellect and good taste. He exposed me to great creators such as Nick Cave & The Bad Seeds, Shakespeare, Lou Reed, artists who created things that I had previously found inconceivable.
I believe this time period informed my current tastes and interests, but regrettably I think it also put coals on the fire of rebellion within. I stopped taking my parents and siblings seriously, the Christian faith of my family (which I now hold dearly to) seemed like a mundane sham, and I felt I couldn’t fit in with most people because of my avant-garde tastes. So I write this with the caveat that there should be a way to encourage these tastes in children without letting them walk down the wrong path. There is nothing inherently wrong with bold art, but I’d advise parents to carefully find ways to cultivate their children’s tastes without completely shutting them down and pushing them away as a result. My parents were very loving and patient during this time; I thank God for that.
With that out of the way, lets dive in to some bold artists:
Nicolas Cage: Actor
There is an excellent video by Wisecrack on Nicolas Cage that explains him better than I will, which I will linkhere. Nicolas Cage rejects the idea that good acting is tied to mere realism; all of his larger than life acting decisions are deliberate choices. When that clicked for me, I immediately realized the man is a genius. He borrows from Kabuki and German Expressionism, art forms that rely on exaggeration to get the message across. He has even created his own acting style, which he calls Nouveau Shamanic. He augments his imagination to go from acting to being. Rather than using the old hat of method acting, he transports himself to a new world mentally. The projects he chooses to partake in are based on his own interests or what he considers would be a challenge (making a bad script good for example). Thus it doesn’t matter how the end result comes out; he has already achieved his goal as an artist. Because of this and because certain directors don’t know how to use his talents, he has a noticeable amount of duds in his filmography. Dig around the duds, you’ll find some pure gold. I’d personally recommend the filmsPig, Joe, Renfield, and his Christmas film The Family Man.
Nick Cave: Songwriter
What a wild career this man has had! From the apocalyptic mayhem of his band The Birthday Party to the pensive atmosphere of his albumGhosteen, it seems like Nick Cave has tried everything. I think his secret sauce is that he’s always working. He maintains an excellent newsletter calledThe Red Hand Files, he has written screenplays such asLawless, he has written books, he has made great film scores such asThe Assassination of Jesse James by the Coward Robert Ford, the man is religiously prolific. I believe that one of the reasons he is prolific is that he’s not afraid to experiment. If he has an idea, he follows it through to completion. From the albumMurder Ballads(which is comprised of what the title suggests) to his rejected sequel toGladiator(Gladiator: Christ Killer), he doesn’t seem to be afraid to take anything on. This has led to some over the top works as well as some deeply personal works. Albums likeSkeleton TreeandGhosteenwere journeys through the grief of his son’s death. The Boatman’s Callis arguably a better break-up album than anything Taylor Swift has put out. He’s not afraid to be outrageous, he’s not afraid to offend, but most importantly he’s not afraid to be himself. Works I’d recommend include The Birthday Party’sLive 1981-82, Nick Cave & The Bad Seeds’The Boatman’s Call, and the filmLawless.
Jim Jarmusch: Director
I consider Jim’s films to be bold almost in an ironic sense: his works are bold in that they are, for the most part, anti-sensational. He has a rule that if his screenplays are criticized for a lack of action, he makes them even less eventful. Even with sensational settings his films feel very close to reality, and they demonstrate the beauty of everyday life. That's what is bold about his art to me: making the sensational grounded in reality while making everyday reality all the more special. Ghost Dog: The Way of the Samurai is about a modern-day African-American hitman who strictly follows the rules of the ancient Samurai, yet one can resonate with the humanity of a seemingly absurd character. Only Lovers Left Aliveis a vampire love story, but in the middle of a vampire romance one can see their their own relationships in a new deeply human light. Jim’s work reminds me that art reflects life, and that there is sacred beauty in seemingly mundane everyday life. I personally recommend his filmsPaterson,Down by Law, andCoffee and Cigarettes.
NOSTR: We Need Bold Art
NOSTR is in my opinion a path to a better future. In a world creeping slowly towards everything apps, I hope that the protocol where the individual owns their data wins over everything else. I love freedom and sovereignty. If NOSTR is going to win the race of everything apps, we need more than Bitcoin content. We need more than shirtless bros paying for bananas in foreign countries and exercising with girls who have seductive accents. Common people cannot see themselves in such a world. NOSTR needs to catch the attention of everyday people. I don’t believe that this can be accomplished merely by introducing more broadly relevant content; people are searching for content that speaks to them. I believe that NOSTR can and should attract artists of all kinds because NOSTR is one of the few places on the internet where artists can express themselves fearlessly. Getting zaps from NOSTR’s value-for-value ecosystem has far less friction than crowdfunding a creative project or pitching investors that will irreversibly modify an artist’s vision. Having a place where one can post their works without fear of censorship should be extremely enticing. Having a place where one can connect with fellow humans directly as opposed to a sea of bots should seem like the obvious solution. If NOSTR can become a safe haven for artists to express themselves and spread their work, I believe that everyday people will follow. The banker whose stressful job weighs on them will suddenly find joy with an original meme made by a great visual comedian. The programmer for a healthcare company who is drowning in hopeless mundanity could suddenly find a new lust for life by hearing the song of a musician who isn’t afraid to crowdfund their their next project by putting their lighting address on the streets of the internet. The excel guru who loves independent film may find that NOSTR is the best way to support non corporate movies. My closing statement: continue to encourage the artists in your life as I’m sure you have been, but while you’re at it give them the purple pill. You may very well be a part of building a better future.
-
 @ 0fa80bd3:ea7325de
2025-02-14 23:24:37
@ 0fa80bd3:ea7325de
2025-02-14 23:24:37intro
The Russian state made me a Bitcoiner. In 1991, it devalued my grandmother's hard-earned savings. She worked tirelessly in the kitchen of a dining car on the Moscow–Warsaw route. Everything she had saved for my sister and me to attend university vanished overnight. This story is similar to what many experienced, including Wences Casares. The pain and injustice of that time became my first lessons about the fragility of systems and the value of genuine, incorruptible assets, forever changing my perception of money and my trust in government promises.
In 2014, I was living in Moscow, running a trading business, and frequently traveling to China. One day, I learned about the Cypriot banking crisis and the possibility of moving money through some strange thing called Bitcoin. At the time, I didn’t give it much thought. Returning to the idea six months later, as a business-oriented geek, I eagerly began studying the topic and soon dove into it seriously.
I spent half a year reading articles on a local online journal, BitNovosti, actively participating in discussions, and eventually joined the editorial team as a translator. That’s how I learned about whitepapers, decentralization, mining, cryptographic keys, and colored coins. About Satoshi Nakamoto, Silk Road, Mt. Gox, and BitcoinTalk. Over time, I befriended the journal’s owner and, leveraging my management experience, later became an editor. I was drawn to the crypto-anarchist stance and commitment to decentralization principles. We wrote about the economic, historical, and social preconditions for Bitcoin’s emergence, and it was during this time that I fully embraced the idea.
It got to the point where I sold my apartment and, during the market's downturn, bought 50 bitcoins, just after the peak price of $1,200 per coin. That marked the beginning of my first crypto winter. As an editor, I organized workflows, managed translators, developed a YouTube channel, and attended conferences in Russia and Ukraine. That’s how I learned about Wences Casares and even wrote a piece about him. I also met Mikhail Chobanyan (Ukrainian exchange Kuna), Alexander Ivanov (Waves project), Konstantin Lomashuk (Lido project), and, of course, Vitalik Buterin. It was a time of complete immersion, 24/7, and boundless hope.
After moving to the United States, I expected the industry to grow rapidly, attended events, but the introduction of BitLicense froze the industry for eight years. By 2017, it became clear that the industry was shifting toward gambling and creating tokens for the sake of tokens. I dismissed this idea as unsustainable. Then came a new crypto spring with the hype around beautiful NFTs – CryptoPunks and apes.
I made another attempt – we worked on a series called Digital Nomad Country Club, aimed at creating a global project. The proceeds from selling images were intended to fund the development of business tools for people worldwide. However, internal disagreements within the team prevented us from completing the project.
With Trump’s arrival in 2025, hope was reignited. I decided that it was time to create a project that society desperately needed. As someone passionate about history, I understood that destroying what exists was not the solution, but leaving everything as it was also felt unacceptable. You can’t destroy the system, as the fiery crypto-anarchist voices claimed.
With an analytical mindset (IQ 130) and a deep understanding of the freest societies, I realized what was missing—not only in Russia or the United States but globally—a Bitcoin-native system for tracking debts and financial interactions. This could return control of money to ordinary people and create horizontal connections parallel to state systems. My goal was to create, if not a Bitcoin killer app, then at least to lay its foundation.
At the inauguration event in New York, I rediscovered the Nostr project. I realized it was not only technologically simple and already quite popular but also perfectly aligned with my vision. For the past month and a half, using insights and experience gained since 2014, I’ve been working full-time on this project.
-
 @ daa41bed:88f54153
2025-02-09 16:50:04
@ daa41bed:88f54153
2025-02-09 16:50:04There has been a good bit of discussion on Nostr over the past few days about the merits of zaps as a method of engaging with notes, so after writing a rather lengthy article on the pros of a strategic Bitcoin reserve, I wanted to take some time to chime in on the much more fun topic of digital engagement.
Let's begin by defining a couple of things:
Nostr is a decentralized, censorship-resistance protocol whose current biggest use case is social media (think Twitter/X). Instead of relying on company servers, it relies on relays that anyone can spin up and own their own content. Its use cases are much bigger, though, and this article is hosted on my own relay, using my own Nostr relay as an example.
Zap is a tip or donation denominated in sats (small units of Bitcoin) sent from one user to another. This is generally done directly over the Lightning Network but is increasingly using Cashu tokens. For the sake of this discussion, how you transmit/receive zaps will be irrelevant, so don't worry if you don't know what Lightning or Cashu are.
If we look at how users engage with posts and follows/followers on platforms like Twitter, Facebook, etc., it becomes evident that traditional social media thrives on engagement farming. The more outrageous a post, the more likely it will get a reaction. We see a version of this on more visual social platforms like YouTube and TikTok that use carefully crafted thumbnail images to grab the user's attention to click the video. If you'd like to dive deep into the psychology and science behind social media engagement, let me know, and I'd be happy to follow up with another article.
In this user engagement model, a user is given the option to comment or like the original post, or share it among their followers to increase its signal. They receive no value from engaging with the content aside from the dopamine hit of the original experience or having their comment liked back by whatever influencer they provide value to. Ad revenue flows to the content creator. Clout flows to the content creator. Sales revenue from merch and content placement flows to the content creator. We call this a linear economy -- the idea that resources get created, used up, then thrown away. Users create content and farm as much engagement as possible, then the content is forgotten within a few hours as they move on to the next piece of content to be farmed.
What if there were a simple way to give value back to those who engage with your content? By implementing some value-for-value model -- a circular economy. Enter zaps.

Unlike traditional social media platforms, Nostr does not actively use algorithms to determine what content is popular, nor does it push content created for active user engagement to the top of a user's timeline. Yes, there are "trending" and "most zapped" timelines that users can choose to use as their default, but these use relatively straightforward engagement metrics to rank posts for these timelines.
That is not to say that we may not see clients actively seeking to refine timeline algorithms for specific metrics. Still, the beauty of having an open protocol with media that is controlled solely by its users is that users who begin to see their timeline gamed towards specific algorithms can choose to move to another client, and for those who are more tech-savvy, they can opt to run their own relays or create their own clients with personalized algorithms and web of trust scoring systems.
Zaps enable the means to create a new type of social media economy in which creators can earn for creating content and users can earn by actively engaging with it. Like and reposting content is relatively frictionless and costs nothing but a simple button tap. Zaps provide active engagement because they signal to your followers and those of the content creator that this post has genuine value, quite literally in the form of money—sats.

I have seen some comments on Nostr claiming that removing likes and reactions is for wealthy people who can afford to send zaps and that the majority of people in the US and around the world do not have the time or money to zap because they have better things to spend their money like feeding their families and paying their bills. While at face value, these may seem like valid arguments, they, unfortunately, represent the brainwashed, defeatist attitude that our current economic (and, by extension, social media) systems aim to instill in all of us to continue extracting value from our lives.
Imagine now, if those people dedicating their own time (time = money) to mine pity points on social media would instead spend that time with genuine value creation by posting content that is meaningful to cultural discussions. Imagine if, instead of complaining that their posts get no zaps and going on a tirade about how much of a victim they are, they would empower themselves to take control of their content and give value back to the world; where would that leave us? How much value could be created on a nascent platform such as Nostr, and how quickly could it overtake other platforms?
Other users argue about user experience and that additional friction (i.e., zaps) leads to lower engagement, as proven by decades of studies on user interaction. While the added friction may turn some users away, does that necessarily provide less value? I argue quite the opposite. You haven't made a few sats from zaps with your content? Can't afford to send some sats to a wallet for zapping? How about using the most excellent available resource and spending 10 seconds of your time to leave a comment? Likes and reactions are valueless transactions. Social media's real value derives from providing monetary compensation and actively engaging in a conversation with posts you find interesting or thought-provoking. Remember when humans thrived on conversation and discussion for entertainment instead of simply being an onlooker of someone else's life?
If you've made it this far, my only request is this: try only zapping and commenting as a method of engagement for two weeks. Sure, you may end up liking a post here and there, but be more mindful of how you interact with the world and break yourself from blind instinct. You'll thank me later.

-
 @ e3ba5e1a:5e433365
2025-02-05 17:47:16
@ e3ba5e1a:5e433365
2025-02-05 17:47:16I got into a friendly discussion on X regarding health insurance. The specific question was how to deal with health insurance companies (presumably unfairly) denying claims? My answer, as usual: get government out of it!
The US healthcare system is essentially the worst of both worlds:
- Unlike full single payer, individuals incur high costs
- Unlike a true free market, regulation causes increases in costs and decreases competition among insurers
I'm firmly on the side of moving towards the free market. (And I say that as someone living under a single payer system now.) Here's what I would do:
- Get rid of tax incentives that make health insurance tied to your employer, giving individuals back proper freedom of choice.
- Reduce regulations significantly.
-
In the short term, some people will still get rejected claims and other obnoxious behavior from insurance companies. We address that in two ways:
- Due to reduced regulations, new insurance companies will be able to enter the market offering more reliable coverage and better rates, and people will flock to them because they have the freedom to make their own choices.
- Sue the asses off of companies that reject claims unfairly. And ideally, as one of the few legitimate roles of government in all this, institute new laws that limit the ability of fine print to allow insurers to escape their responsibilities. (I'm hesitant that the latter will happen due to the incestuous relationship between Congress/regulators and insurers, but I can hope.)
Will this magically fix everything overnight like politicians normally promise? No. But it will allow the market to return to a healthy state. And I don't think it will take long (order of magnitude: 5-10 years) for it to come together, but that's just speculation.
And since there's a high correlation between those who believe government can fix problems by taking more control and demanding that only credentialed experts weigh in on a topic (both points I strongly disagree with BTW): I'm a trained actuary and worked in the insurance industry, and have directly seen how government regulation reduces competition, raises prices, and harms consumers.
And my final point: I don't think any prior art would be a good comparison for deregulation in the US, it's such a different market than any other country in the world for so many reasons that lessons wouldn't really translate. Nonetheless, I asked Grok for some empirical data on this, and at best the results of deregulation could be called "mixed," but likely more accurately "uncertain, confused, and subject to whatever interpretation anyone wants to apply."
https://x.com/i/grok/share/Zc8yOdrN8lS275hXJ92uwq98M
-
 @ 9e69e420:d12360c2
2025-02-01 11:16:04
@ 9e69e420:d12360c2
2025-02-01 11:16:04Federal employees must remove pronouns from email signatures by the end of the day. This directive comes from internal memos tied to two executive orders signed by Donald Trump. The orders target diversity and equity programs within the government.

CDC, Department of Transportation, and Department of Energy employees were affected. Staff were instructed to make changes in line with revised policy prohibiting certain language.
One CDC employee shared frustration, stating, “In my decade-plus years at CDC, I've never been told what I can and can't put in my email signature.” The directive is part of a broader effort to eliminate DEI initiatives from federal discourse.
-
 @ 3104fbbf:ac623068
2025-04-04 06:58:30
@ 3104fbbf:ac623068
2025-04-04 06:58:30
Introduction
If you have a functioning brain, it’s impossible to fully stand for any politician or align completely with any political party. The solutions we need are not found in the broken systems of power but in individual actions and local initiatives. Voting for someone may be your choice, but relying solely on elections every few years as a form of political activism is a losing strategy. People around the world have fallen into the trap of thinking that casting a ballot once every four years is enough, only to return to complacency as conditions worsen. Voting for the "lesser of two evils" has been the norm for decades, yet expecting different results from the same flawed system is naive at best.
The truth is, governments are too corrupt to save us. In times of crisis, they won’t come to your aid—instead, they will tighten their grip, imposing more surveillance, control, and wealth extraction to benefit the oligarch class. To break free from this cycle, we must first protect ourselves individually—financially, geographically, and digitally—alongside our families.
Then, we must organize and build resilient local communities. These are the only ways forward. History has shown us time and again that the masses are easily deceived by the political circus, falling for the illusion of a "savior" who will fix everything. But whether right, center, or left, the story remains the same: corruption, lies, and broken promises. If you possess a critical and investigative mind, you know better than to place your trust in politicians, parties, or self-proclaimed heroes. The real solution lies in free and sovereign individuals who reject the herd mentality and take responsibility for their own lives.
From the beginning of time, true progress has come from individuals who think for themselves and act independently. The nauseating web of politicians, billionaires, and oligarchs fighting for power and resources has never been—and will never be—the answer to our problems. In a world increasingly dominated by corrupted governments, NGOs, and elites, ordinary people must take proactive steps to protect themselves and their families.
1. Financial Protection: Reclaiming Sovereignty Through Bitcoin
Governments and central banks have long manipulated fiat currencies, eroding wealth through inflation and bailouts that transfer resources to the oligarch class. Bitcoin, as a decentralized, censorship-resistant, and finite currency, offers a way out. Here’s what individuals can do:
-
Adopt Bitcoin as a Savings Tool: Shift a portion of your savings into Bitcoin to protect against inflation and currency devaluation. Bitcoin’s fixed supply (21 million coins) ensures it cannot be debased like fiat money.
-
Learn Self-Custody: Store your Bitcoin in a hardware wallet or use open-source software wallets. Avoid centralized exchanges, which are vulnerable to government seizure or collapse.
-
Diversify Geographically: Hold assets in multiple jurisdictions to reduce the risk of confiscation or capital controls. Consider offshore accounts or trusts if feasible.
-
Barter and Local Economies: In times of crisis, local barter systems and community currencies can bypass failing national systems. Bitcoin can serve as a global medium of exchange in such scenarios.
2. Geographical Flexibility: Reducing Dependence on Oppressive Systems
Authoritarian regimes thrive on controlling populations within fixed borders. By increasing geographical flexibility, individuals can reduce their vulnerability:
-
Obtain Second Passports or Residencies: Invest in citizenship-by-investment programs or residency permits in countries with greater freedoms and lower surveillance.
-
Relocate to Freer Jurisdictions: Research and consider moving to regions with stronger property rights, lower taxes, and less government overreach.
-
Decentralize Your Life: Avoid keeping all your assets, family, or business operations in one location. Spread them across multiple regions to mitigate risks.
3. Digital Privacy: Fighting Surveillance with Advanced Tools
The rise of mass surveillance and data harvesting by governments and corporations threatens individual freedom. Here’s how to protect yourself:
-
Use Encryption: Encrypt all communications using tools like Signal or ProtonMail. Ensure your devices are secured with strong passwords and biometric locks.
-
Adopt Privacy-Focused Technologies: Use Tor for anonymous browsing, VPNs to mask your IP address, and open-source operating systems like Linux to avoid backdoors.
-
Reject Surveillance Tech: Avoid smart devices that spy on you (e.g., Alexa, Google Home). Opt for decentralized alternatives like Mastodon instead of Twitter, or PeerTube instead of YouTube.
-
Educate Yourself on Digital Privacy: Learn about tools and practices that enhance your online privacy and security.
4. Building Resilient Local Communities: The Foundation of a Free Future
While individual actions are crucial, collective resilience is equally important. Governments are too corrupt to save populations in times of crisis—history shows they will instead impose more control and transfer wealth to the elite.
To counter this, communities must organize locally:
-
Form Mutual Aid Networks: Create local groups that share resources, skills, and knowledge. These networks can provide food, medical supplies, and security during crises.
-
Promote Local Economies: Support local businesses, farmers, and artisans. Use local currencies or barter systems to reduce dependence on centralized financial systems.
-
Develop Off-Grid Infrastructure: Invest in renewable energy, water filtration, and food production to ensure self-sufficiency. Community gardens, solar panels, and rainwater harvesting are excellent starting points.
-
Educate and Empower: Host workshops on financial literacy, digital privacy, and sustainable living. Knowledge is the most powerful tool against authoritarianism.
5. The Bigger Picture: Rejecting the Illusion of Saviors
The deep corruption within governments, NGOs, and the billionaire class is evident. These entities will never act in the interest of ordinary people. Instead, they will exploit crises to expand surveillance, control, and wealth extraction. The idea of a political “savior” is a dangerous illusion. True freedom comes from individuals taking responsibility for their own lives and working together to build decentralized, resilient systems.
Conclusion: A Call to Action
The path to a genuinely free humanity begins with individual action. By adopting Bitcoin, securing digital privacy, increasing geographical flexibility, and building resilient local communities, ordinary people can protect themselves against authoritarianism. Governments will not save us—they are the problem. It is up to us to create a better future, free from the control of corrupt elites.
-
The tools for liberation already exist.
-
The question is: will we use them?
For those interested, I share ideas and solutions in my book « THE GATEWAY TO FREEDOM » https://blisshodlenglish.substack.com/p/the-gateway-to-freedom
⚡ The time to act is now. Freedom is not given—it is taken. ⚡
If you enjoyed this article, consider supporting it with a Zap!
My Substack ENGLISH = https://blisshodlenglish.substack.com/ My substack FRENCH = https://blisshodl.substack.com/
Get my Book « THE GATEWAY TO FREEDOM » here 🙏 => https://coinos.io/blisshodl
-
-
 @ c1e9ab3a:9cb56b43
2025-05-06 14:05:40
@ c1e9ab3a:9cb56b43
2025-05-06 14:05:40If you're an engineer stepping into the Bitcoin space from the broader crypto ecosystem, you're probably carrying a mental model shaped by speed, flexibility, and rapid innovation. That makes sense—most blockchain platforms pride themselves on throughput, programmability, and dev agility.
But Bitcoin operates from a different set of first principles. It’s not competing to be the fastest network or the most expressive smart contract platform. It’s aiming to be the most credible, neutral, and globally accessible value layer in human history.
Here’s why that matters—and why Bitcoin is not just an alternative crypto asset, but a structural necessity in the global financial system.
1. Bitcoin Fixes the Triffin Dilemma—Not With Policy, But Protocol
The Triffin Dilemma shows us that any country issuing the global reserve currency must run persistent deficits to supply that currency to the world. That’s not a flaw of bad leadership—it’s an inherent contradiction. The U.S. must debase its own monetary integrity to meet global dollar demand. That’s a self-terminating system.
Bitcoin sidesteps this entirely by being:
- Non-sovereign – no single nation owns it
- Hard-capped – no central authority can inflate it
- Verifiable and neutral – anyone with a full node can enforce the rules
In other words, Bitcoin turns global liquidity into an engineering problem, not a political one. No other system, fiat or crypto, has achieved that.
2. Bitcoin’s “Ossification” Is Intentional—and It's a Feature
From the outside, Bitcoin development may look sluggish. Features are slow to roll out. Code changes are conservative. Consensus rules are treated as sacred.
That’s the point.
When you’re building the global monetary base layer, stability is not a weakness. It’s a prerequisite. Every other financial instrument, app, or protocol that builds on Bitcoin depends on one thing: assurance that the base layer won’t change underneath them without extreme scrutiny.
So-called “ossification” is just another term for predictability and integrity. And when the market does demand change (SegWit, Taproot), Bitcoin’s soft-fork governance process has proven capable of deploying it safely—without coercive central control.
3. Layered Architecture: Throughput Is Not a Base Layer Concern
You don’t scale settlement at the base layer. You build layered systems. Just as TCP/IP doesn't need to carry YouTube traffic directly, Bitcoin doesn’t need to process every microtransaction.
Instead, it anchors:
- Lightning (fast payments)
- Fedimint (community custody)
- Ark (privacy + UTXO compression)
- Statechains, sidechains, and covenants (coming evolution)
All of these inherit Bitcoin’s security and scarcity, while handling volume off-chain, in ways that maintain auditability and self-custody.
4. Universal Assayability Requires Minimalism at the Base Layer
A core design constraint of Bitcoin is that any participant, anywhere in the world, must be able to independently verify the validity of every transaction and block—past and present—without needing permission or relying on third parties.
This property is called assayability—the ability to “test” or verify the authenticity and integrity of received bitcoin, much like verifying the weight and purity of a gold coin.
To preserve this:
- The base layer must remain resource-light, so running a full node stays accessible on commodity hardware.
- Block sizes must remain small enough to prevent centralization of verification.
- Historical data must remain consistent and tamper-evident, enabling proof chains across time and jurisdiction.
Any base layer that scales by increasing throughput or complexity undermines this fundamental guarantee, making the network more dependent on trust and surveillance infrastructure.
Bitcoin prioritizes global verifiability over throughput—because trustless money requires that every user can check the money they receive.
5. Governance: Not Captured, Just Resistant to Coercion
The current controversy around
OP_RETURNand proposals to limit inscriptions is instructive. Some prominent devs have advocated for changes to block content filtering. Others see it as overreach.Here's what matters:
- No single dev, or team, can force changes into the network. Period.
- Bitcoin Core is not “the source of truth.” It’s one implementation. If it deviates from market consensus, it gets forked, sidelined, or replaced.
- The economic majority—miners, users, businesses—enforce Bitcoin’s rules, not GitHub maintainers.
In fact, recent community resistance to perceived Core overreach only reinforces Bitcoin’s resilience. Engineers who posture with narcissistic certainty, dismiss dissent, or attempt to capture influence are routinely neutralized by the market’s refusal to upgrade or adopt forks that undermine neutrality or openness.
This is governance via credible neutrality and negative feedback loops. Power doesn’t accumulate in one place. It’s constantly checked by the network’s distributed incentives.
6. Bitcoin Is Still in Its Infancy—And That’s a Good Thing
You’re not too late. The ecosystem around Bitcoin—especially L2 protocols, privacy tools, custody innovation, and zero-knowledge integrations—is just beginning.
If you're an engineer looking for:
- Systems with global scale constraints
- Architectures that optimize for integrity, not speed
- Consensus mechanisms that resist coercion
- A base layer with predictable monetary policy
Then Bitcoin is where serious systems engineers go when they’ve outgrown crypto theater.
Take-away
Under realistic, market-aware assumptions—where:
- Bitcoin’s ossification is seen as a stability feature, not inertia,
- Market forces can and do demand and implement change via tested, non-coercive mechanisms,
- Proof-of-work is recognized as the only consensus mechanism resistant to fiat capture,
- Wealth concentration is understood as a temporary distribution effect during early monetization,
- Low base layer throughput is a deliberate design constraint to preserve verifiability and neutrality,
- And innovation is layered by design, with the base chain providing integrity, not complexity...
Then Bitcoin is not a fragile or inflexible system—it is a deliberately minimal, modular, and resilient protocol.
Its governance is not leaderless chaos; it's a negative-feedback structure that minimizes the power of individuals or institutions to coerce change. The very fact that proposals—like controversial OP_RETURN restrictions—can be resisted, forked around, or ignored by the market without breaking the system is proof of decentralized control, not dysfunction.
Bitcoin is an adversarially robust monetary foundation. Its value lies not in how fast it changes, but in how reliably it doesn't—unless change is forced by real, bottom-up demand and implemented through consensus-tested soft forks.
In this framing, Bitcoin isn't a slower crypto. It's the engineering benchmark for systems that must endure, not entertain.
Final Word
Bitcoin isn’t moving slowly because it’s dying. It’s moving carefully because it’s winning. It’s not an app platform or a sandbox. It’s a protocol layer for the future of money.
If you're here because you want to help build that future, you’re in the right place.
nostr:nevent1qqswr7sla434duatjp4m89grvs3zanxug05pzj04asxmv4rngvyv04sppemhxue69uhkummn9ekx7mp0qgs9tc6ruevfqu7nzt72kvq8te95dqfkndj5t8hlx6n79lj03q9v6xcrqsqqqqqp0n8wc2
nostr:nevent1qqsd5hfkqgskpjjq5zlfyyv9nmmela5q67tgu9640v7r8t828u73rdqpr4mhxue69uhkymmnw3ezucnfw33k76tww3ux76m09e3k7mf0qgsvr6dt8ft292mv5jlt7382vje0mfq2ccc3azrt4p45v5sknj6kkscrqsqqqqqp02vjk5
nostr:nevent1qqstrszamvffh72wr20euhrwa0fhzd3hhpedm30ys4ct8dpelwz3nuqpr4mhxue69uhkymmnw3ezucnfw33k76tww3ux76m09e3k7mf0qgs8a474cw4lqmapcq8hr7res4nknar2ey34fsffk0k42cjsdyn7yqqrqsqqqqqpnn3znl
-
 @ f85b9c2c:d190bcff
2025-05-16 14:23:39
@ f85b9c2c:d190bcff
2025-05-16 14:23:39 I used to think I thrived on chaos. Podcasts blaring, TV on in the background, notifications pinging—it was my norm. But last year, I hit a wall. I was irritable, foggy, and couldn’t focus. I didn’t realize how much the constant noise was frying my brain until I tried something radical: silence.
I used to think I thrived on chaos. Podcasts blaring, TV on in the background, notifications pinging—it was my norm. But last year, I hit a wall. I was irritable, foggy, and couldn’t focus. I didn’t realize how much the constant noise was frying my brain until I tried something radical: silence.The Experiment One weekend, I turned everything off. No music, no screens, no chatter. At first, it was weird—almost suffocating. My mind raced, looking for something to latch onto. But after a few hours, I settled in. I sat with a cup of tea, just listening to the hum of the fridge. It was the first time in months I’d actually heard my own thoughts
What Silence Gave Me That quiet weekend was a reset. I started noticing things I’d ignored—like how tense I’d been or how I’d been avoiding tough decisions. Silence didn’t just calm me; it forced me to face myself. I kept it up, carving out 30 minutes a day with no sound. It’s become my sanity-saver. When life gets loud, those quiet moments keep me grounded. Turns out, my brain needed the break. All that noise was overloading me, leaving no room to process anything. Silence let me recharge and think clearly again. It’s not about being a hermit—it’s about giving myself space to breathe.
-
 @ f85b9c2c:d190bcff
2025-05-16 14:08:51
@ f85b9c2c:d190bcff
2025-05-16 14:08:51 In the rapidly evolving world of cryptocurrencies, the potential interplay between artificial intelligence and digital assets has captured significant attention. Cointelegraph recently reported on the concept of AI, particularly in the form of ChatGPT, contributing to the potential rise of Bitcoin, potentially reaching a value of $100K in 2024. This development offers a glimpse into the role of AI in shaping the direction of cryptocurrencies, particularly Bitcoin.
In the rapidly evolving world of cryptocurrencies, the potential interplay between artificial intelligence and digital assets has captured significant attention. Cointelegraph recently reported on the concept of AI, particularly in the form of ChatGPT, contributing to the potential rise of Bitcoin, potentially reaching a value of $100K in 2024. This development offers a glimpse into the role of AI in shaping the direction of cryptocurrencies, particularly Bitcoin.AI’s Role in Shaping Bitcoin’s Future: ChatGPT, an advanced language model powered by artificial intelligence, has been seen as a potential assistant in driving Bitcoin’s value upwards. The underlying premise is rooted in AI’s capacity to influence market analysis, comprehend and design trading strategies, and anticipate potential trends in the cryptocurrency sector. By leveraging vast amounts of data and analyzing complex patterns, ChatGPT could provide insights that impact investment decisions and market.
AI-Powered Market Analysis and Prediction One of the key ways AI, represented by ChatGPT, can aid Bitcoin’s value appreciation is through advanced market analysis and prediction. By assimilating and processing large datasets encompassing historical price movements, trading volumes, market sentiment, and external factors, AI can potentially forecast potential price changes with a higher degree of accuracy. This analytical capability could equip investors with valuable insights regarding optimal entry and exit points, thus potentially contributing to Bitcoin’s upward trajectory. Furthermore, AI’s predictive abilities extend to discerning macroeconomic and geopolitical developments that could impact Bitcoin’s value, enabling proactive decision-making in response to dynamic market conditions. This foresight could instill confidence among investors and potentially drive greater adoption and investment in Bitcoin, which contributed to its ascent $100K mark.
Influencing Trading Strategies AI-driven trading strategies have gained prominence in financial markets, and their potential impact on Bitcoin’s valuation is noteworthy. ChatGPT’s capacity to generate and optimize trading algorithms that respond to market conditions in real-time could potentially enhance trading efficiency and liquidity in Bitcoin markets. By identifying opportunities for arbitrage, risk management, and executing complex trading strategies, AI could facilitate a more stable and robust Bitcoin market, potentially attracting institutional investors and bolstering its overall value.
Market Volatility Volatility has been a defining characteristic of the cryptocurrency markets, including Bitcoin. AI, through ChatGPT, could aid in mitigating this volatility by providing real-time insights, sentiment analysis, and risk assessments to market participants. By enhancing transparency and reducing uncertainty, AI-driven tools may contribute to a more stable and predictable environment for Bitcoin trading, potentially attracting a broader investor base and positively influencing its long-term value, including the speculated $100K threshold. Conclusion The potential for AI, exemplified by ChatGPT, to influence Bitcoin’s trajectory towards a $100K valuation in 2024 underscores the evolving synergy between technology and finance. As AI continues to permeate various domains, its impact on cryptocurrency markets is poised to be substantial. It is imperative to monitor the evolution of AI’s role in shaping the future of Bitcoin and other digital assets, as it has the potential to redefine investment strategies, market dynamics, and the broader financial landscape in the years to come.
-
 @ 7bdef7be:784a5805
2025-04-02 12:02:45
@ 7bdef7be:784a5805
2025-04-02 12:02:45We value sovereignty, privacy and security when accessing online content, using several tools to achieve this, like open protocols, open OSes, open software products, Tor and VPNs. ## The problem Talking about our social presence, we can manually build up our follower list (social graph), pick a Nostr client that is respectful of our preferences on what to show and how, but with the standard following mechanism, our main feed is public, **so everyone can actually snoop** what we are interested in, and what is supposable that we read daily. ## The solution Nostr has a simple solution for this necessity: encrypted lists. Lists are what they appear, a collection of people or interests (but they can also group much other stuff, see [NIP-51](https://github.com/nostr-protocol/nips/blob/master/51.md)). So we can create lists with contacts that we don't have in our main social graph; these lists can be used primarily to create **dedicated feeds**, but they could have other uses, for example, related to monitoring. The interesting thing about lists is that they can also be **encrypted**, so unlike the basic following list, which is always public, we can hide the lists' content from others. The implications are obvious: we can not only have a more organized way to browse content, but it is also **really private one**. One might wonder what use can really be made of private lists; here are some examples: - Browse “can't miss” content from users I consider a priority; - Supervise competitors or adversarial parts; - Monitor sensible topics (tags); - Following someone without being publicly associated with them, as this may be undesirable; The benefits in terms of privacy as usual are not only related to the casual, or programmatic, observer, but are also evident when we think of **how many bots scan our actions to profile us**. ## The current state Unfortunately, lists are not widely supported by Nostr clients, and encrypted support is a rarity. Often the excuse to not implement them is that they are harder to develop, since they require managing the encryption stuff ([NIP-44](https://github.com/nostr-protocol/nips/blob/master/51.md)). Nevertheless, developers have an easier option to start offering private lists: give the user the possibility to simply **mark them as local-only**, and never push them to the relays. Even if the user misses the sync feature, this is sufficient to create a private environment. To date, as far as I know, the best client with list management is Gossip, which permits to manage **both encrypted and local-only lists**. Beg your Nostr client to implement private lists!
-
 @ e39333da:7c66e53a
2025-05-16 13:20:33
@ e39333da:7c66e53a
2025-05-16 13:20:33::youtube{#Pex7jW3Tqwo}
Developer SHIFT UP has announced that their latest titled, Stellar Blade, that was released on PS5 on the 2024, will release on PC via Steam and EGS on the 11th of June 2025.
The game will be priced at $60, and $80 for the edition of the game that includes the 'Twin Expansion Pack', which includes the NieR: Automata DLC and the Goddess of Victory: Nikke DLC, and a key to redeem a Stellar Blade costume in the developer's previous Free-to-Play title Goddess of Victory: Nikke.
The trailer released to announce said release date also showcases the changes the made for the game and highlight PC specific enhancements, support, and options.
It's worth noting, in terms of negative news that tagged along with this, that the game will have Denuvo running, which there are evidence that decreases a game's performance, and may prevent you from playing the game offline. The game will also have an optional PSN account login, and because of this, the game is not available for purchase in around 130 countries. There's also an exclusive outfit locked behind a PSN-to-Steam account linking.

Here's the system requirements:
| | Minimum | Recommended | High | Very High | | ----------------------- | ----------------------------------------------------- | ------------------------------------------------------- | ------------------------------------------------------- | ------------------------------------------------- | | Average Performance | 1080P at 60 frames per second | 1440P at 60 frames per second | 1440P at 60 frames per second | 4K at 60 frames per second | | Graphic Presets | Low | Medium | High | Very High | | CPU | Intel Core i5-7600K AMD Ryzen 5 1600X | Intel Core i5-8400 AMD Ryzen 5 3600X | Intel Core i5-8400 AMD Ryzen 5 3600X | Intel Core i5-8400 AMD Ryzen 5 3600X | | GPU | NVIDIA GeForce GTX 1060 6GB AMD Radeon RX 580 8GB | NVIDIA GeForce RTX 2060 SUPER AMD Radeon RX 5700 XT | NVIDIA GeForce RTX 2070 SUPER AMD Radeon RX 6700 XT | NVIDIA GeForce RTX 3080 AMD Radeon RX 7900 XT | | RAM | 16GB | 16GB | 16GB | 16GB | | Storage | 75GB HDD (SSD Recommended) | 75GB SSD | 75GB SSD | 75GB SSD | | OS | Windows 10 64-bit | Windows 10 64-bit | Windows 10 64-bit | Windows 10 64-bit |
-
 @ c1e9ab3a:9cb56b43
2025-05-05 14:25:28
@ c1e9ab3a:9cb56b43
2025-05-05 14:25:28Introduction: The Power of Fiction and the Shaping of Collective Morality
Stories define the moral landscape of a civilization. From the earliest mythologies to the modern spectacle of global cinema, the tales a society tells its youth shape the parameters of acceptable behavior, the cost of transgression, and the meaning of justice, power, and redemption. Among the most globally influential narratives of the past half-century is the Star Wars saga, a sprawling science fiction mythology that has transcended genre to become a cultural religion for many. Central to this mythos is the arc of Anakin Skywalker, the fallen Jedi Knight who becomes Darth Vader. In Star Wars: Episode III – Revenge of the Sith, Anakin commits what is arguably the most morally abhorrent act depicted in mainstream popular cinema: the mass murder of children. And yet, by the end of the saga, he is redeemed.
This chapter introduces the uninitiated to the events surrounding this narrative turn and explores the deep structural and ethical concerns it raises. We argue that the cultural treatment of Darth Vader as an anti-hero, even a role model, reveals a deep perversion in the collective moral grammar of the modern West. In doing so, we consider the implications this mythology may have on young adults navigating identity, masculinity, and agency in a world increasingly shaped by spectacle and symbolic narrative.
Part I: The Scene and Its Context
In Revenge of the Sith (2005), the third episode of the Star Wars prequel trilogy, the protagonist Anakin Skywalker succumbs to fear, ambition, and manipulation. Convinced that the Jedi Council is plotting against the Republic and desperate to save his pregnant wife from a vision of death, Anakin pledges allegiance to Chancellor Palpatine, secretly the Sith Lord Darth Sidious. Upon doing so, he is given a new name—Darth Vader—and tasked with a critical mission: to eliminate all Jedi in the temple, including its youngest members.
In one of the most harrowing scenes in the film, Anakin enters the Jedi Temple. A group of young children, known as "younglings," emerge from hiding and plead for help. One steps forward, calling him "Master Skywalker," and asks what they are to do. Anakin responds by igniting his lightsaber. The screen cuts away, but the implication is unambiguous. Later, it is confirmed through dialogue and visual allusion that he slaughtered them all.
There is no ambiguity in the storytelling. The man who will become the galaxy’s most feared enforcer begins his descent by murdering defenseless children.
Part II: A New Kind of Evil in Youth-Oriented Media
For decades, cinema avoided certain taboos. Even films depicting war, genocide, or psychological horror rarely crossed the line into showing children as victims of deliberate violence by the protagonist. When children were harmed, it was by monstrous antagonists, supernatural forces, or offscreen implications. The killing of children was culturally reserved for historical atrocities and horror tales.
In Revenge of the Sith, this boundary was broken. While the film does not show the violence explicitly, the implication is so clear and so central to the character arc that its omission from visual depiction does not blunt the narrative weight. What makes this scene especially jarring is the tonal dissonance between the gravity of the act and the broader cultural treatment of Star Wars as a family-friendly saga. The juxtaposition of child-targeted marketing with a central plot involving child murder is not accidental—it reflects a deeper narrative and commercial structure.
This scene was not a deviation from the arc. It was the intended turning point.
Part III: Masculinity, Militarism, and the Appeal of the Anti-Hero
Darth Vader has long been idolized as a masculine icon. His towering presence, emotionless control, and mechanical voice exude power and discipline. Military institutions have quoted him. He is celebrated in memes, posters, and merchandise. Within the cultural imagination, he embodies dominance, command, and strategic ruthlessness.
For many young men, particularly those struggling with identity, agency, and perceived weakness, Vader becomes more than a character. He becomes an archetype: the man who reclaims power by embracing discipline, forsaking emotion, and exacting vengeance against those who betrayed him. The emotional pain that leads to his fall mirrors the experiences of isolation and perceived emasculation that many young men internalize in a fractured society.
The symbolism becomes dangerous. Anakin's descent into mass murder is portrayed not as the outcome of unchecked cruelty, but as a tragic mistake rooted in love and desperation. The implication is that under enough pressure, even the most horrific act can be framed as a step toward a noble end.
Part IV: Redemption as Narrative Alchemy
By the end of the original trilogy (Return of the Jedi, 1983), Darth Vader kills the Emperor to save his son Luke and dies shortly thereafter. Luke mourns him, honors him, and burns his body in reverence. In the final scene, Vader's ghost appears alongside Obi-Wan Kenobi and Yoda—the very men who once considered him the greatest betrayal of their order. He is welcomed back.
There is no reckoning. No mention of the younglings. No memorial to the dead. No consequence beyond his own internal torment.
This model of redemption is not uncommon in Western storytelling. In Christian doctrine, the concept of grace allows for any sin to be forgiven if the sinner repents sincerely. But in the context of secular mass culture, such redemption without justice becomes deeply troubling. The cultural message is clear: even the worst crimes can be erased if one makes a grand enough gesture at the end. It is the erasure of moral debt by narrative fiat.
The implication is not only that evil can be undone by good, but that power and legacy matter more than the victims. Vader is not just forgiven—he is exalted.
Part V: Real-World Reflections and Dangerous Scripts
In recent decades, the rise of mass violence in schools and public places has revealed a disturbing pattern: young men who feel alienated, betrayed, or powerless adopt mythic narratives of vengeance and transformation. They often see themselves as tragic figures forced into violence by a cruel world. Some explicitly reference pop culture, quoting films, invoking fictional characters, or modeling their identities after cinematic anti-heroes.
It would be reductive to claim Star Wars causes such events. But it is equally naive to believe that such narratives play no role in shaping the symbolic frameworks through which vulnerable individuals understand their lives. The story of Anakin Skywalker offers a dangerous script:
- You are betrayed.
- You suffer.
- You kill.
- You become powerful.
- You are redeemed.
When combined with militarized masculinity, institutional failure, and cultural nihilism, this script can validate the darkest impulses. It becomes a myth of sacrificial violence, with the perpetrator as misunderstood hero.
Part VI: Cultural Responsibility and Narrative Ethics
The problem is not that Star Wars tells a tragic story. Tragedy is essential to moral understanding. The problem is how the culture treats that story. Darth Vader is not treated as a warning, a cautionary tale, or a fallen angel. He is merchandised, celebrated, and decontextualized.
By separating his image from his actions, society rebrands him as a figure of cool dominance rather than ethical failure. The younglings are forgotten. The victims vanish. Only the redemption remains. The merchandise continues to sell.
Cultural institutions bear responsibility for how such narratives are presented and consumed. Filmmakers may intend nuance, but marketing departments, military institutions, and fan cultures often reduce that nuance to symbol and slogan.
Conclusion: Reckoning with the Stories We Tell
The story of Anakin Skywalker is not morally neutral. It is a tale of systemic failure, emotional collapse, and unchecked violence. When presented in full, it can serve as a powerful warning. But when reduced to aesthetic dominance and easy redemption, it becomes a tool of moral decay.
The glorification of Darth Vader as a cultural icon—divorced from the horrific acts that define his transformation—is not just misguided. It is dangerous. It trains a generation to believe that power erases guilt, that violence is a path to recognition, and that final acts of loyalty can overwrite the deliberate murder of the innocent.
To the uninitiated, Star Wars may seem like harmless fantasy. But its deepest myth—the redemption of the child-killer through familial love and posthumous honor—deserves scrutiny. Not because fiction causes violence, but because fiction defines the possibilities of how we understand evil, forgiveness, and what it means to be a hero.
We must ask: What kind of redemption erases the cries of murdered children? And what kind of culture finds peace in that forgetting?
-
 @ 0fa80bd3:ea7325de
2025-01-29 05:55:02
@ 0fa80bd3:ea7325de
2025-01-29 05:55:02The land that belongs to the indigenous peoples of Russia has been seized by a gang of killers who have unleashed a war of extermination. They wipe out anyone who refuses to conform to their rules. Those who disagree and stay behind are tortured and killed in prisons and labor camps. Those who flee lose their homeland, dissolve into foreign cultures, and fade away. And those who stand up to protect their people are attacked by the misled and deceived. The deceived die for the unchecked greed of a single dictator—thousands from both sides, people who just wanted to live, raise their kids, and build a future.
Now, they are forced to make an impossible choice: abandon their homeland or die. Some perish on the battlefield, others lose themselves in exile, stripped of their identity, scattered in a world that isn’t theirs.
There’s been endless debate about how to fix this, how to clear the field of the weeds that choke out every new sprout, every attempt at change. But the real problem? We can’t play by their rules. We can’t speak their language or use their weapons. We stand for humanity, and no matter how righteous our cause, we will not multiply suffering. Victory doesn’t come from matching the enemy—it comes from staying ahead, from using tools they haven’t mastered yet. That’s how wars are won.
Our only resource is the will of the people to rewrite the order of things. Historian Timothy Snyder once said that a nation cannot exist without a city. A city is where the most active part of a nation thrives. But the cities are occupied. The streets are watched. Gatherings are impossible. They control the money. They control the mail. They control the media. And any dissent is crushed before it can take root.
So I started asking myself: How do we stop this fragmentation? How do we create a space where people can rebuild their connections when they’re ready? How do we build a self-sustaining network, where everyone contributes and benefits proportionally, while keeping their freedom to leave intact? And more importantly—how do we make it spread, even in occupied territory?
In 2009, something historic happened: the internet got its own money. Thanks to Satoshi Nakamoto, the world took a massive leap forward. Bitcoin and decentralized ledgers shattered the idea that money must be controlled by the state. Now, to move or store value, all you need is an address and a key. A tiny string of text, easy to carry, impossible to seize.
That was the year money broke free. The state lost its grip. Its biggest weapon—physical currency—became irrelevant. Money became purely digital.
The internet was already a sanctuary for information, a place where people could connect and organize. But with Bitcoin, it evolved. Now, value itself could flow freely, beyond the reach of authorities.
Think about it: when seedlings are grown in controlled environments before being planted outside, they get stronger, survive longer, and bear fruit faster. That’s how we handle crops in harsh climates—nurture them until they’re ready for the wild.
Now, picture the internet as that controlled environment for ideas. Bitcoin? It’s the fertile soil that lets them grow. A testing ground for new models of interaction, where concepts can take root before they move into the real world. If nation-states are a battlefield, locked in a brutal war for territory, the internet is boundless. It can absorb any number of ideas, any number of people, and it doesn’t run out of space.
But for this ecosystem to thrive, people need safe ways to communicate, to share ideas, to build something real—without surveillance, without censorship, without the constant fear of being erased.
This is where Nostr comes in.
Nostr—"Notes and Other Stuff Transmitted by Relays"—is more than just a messaging protocol. It’s a new kind of city. One that no dictator can seize, no corporation can own, no government can shut down.
It’s built on decentralization, encryption, and individual control. Messages don’t pass through central servers—they are relayed through independent nodes, and users choose which ones to trust. There’s no master switch to shut it all down. Every person owns their identity, their data, their connections. And no one—no state, no tech giant, no algorithm—can silence them.
In a world where cities fall and governments fail, Nostr is a city that cannot be occupied. A place for ideas, for networks, for freedom. A city that grows stronger the more people build within it.
-
 @ 57412389:2b288de5
2025-05-16 17:06:50
@ 57412389:2b288de5
2025-05-16 17:06:50Despite how many times Urbanists post a new bird's-eye view of a sprawling suburb filled with the same home copy and pasted 200 times by the same developer, the most recent estimates suggest just over half of Americans live in the suburbs. No matter how many times the isolated deep woods advocates call them stuffy conformists Americans continue to flock to their culture-less neighborhoods where everyone has the same .25 acres with a push mower and rarely used smoker.
So why do we have so many housing masochists in this country who chose to live in suburban hellscapes?
The argument is pretty obvious why most people don't live out in the sticks. America embracing the role of running the world's reserve currency forced them to hollow out the blue collar workforce we once had. We give the world dollars and the world gives us cheaper physical things. It has to be this way if you're to play the role of King Dollar. There aren't many tech jobs in eastern Kentucky or business gigs in western Kansas. There simply aren't enough American jobs for people to live in these places and if there were they wouldn't be rural for very long. You can't live somewhere you can't get to work from.
So why don't Americans flock to cities? Urbanists will tell you its an American mindset thing. They'll claim our country is addicted to sitting in our oversized SUVs in gridlock traffic for two hours a day. They'll say we're addicted to the status of living in a larger home with a yard or point to racism or an aversion to other cultures. In fact, they'll make up any reason to avoid talking about the fact that people want to feel safe where they live and don't want to worry about not being home when their Amazon package gets dropped on their steps.
The suburbs are the worst of both worlds. There are no premier coffee shops to walk to before work or food trucks with authentic empanadas you can snag on your 2AM stroll home from the local dive. The commute to work is 40 minutes. There's not much privacy so your neighbor can hear the sportsball conversation you're having in your backyard and the HOA says you can't paint your mailbox that color. Hardcore leftists can't imagine why you'd want to live in a place where leaving the house means getting in a car. Hardcore righties don't understand why anyone would want to live in a place that you have to deal with the rest of civilization. But yet here we are with the majority of the country fighting to live on commuter hell plots.
The reason so many want to live in the suburbs is because they're completely bland and sterile zones with long, but doable commutes. The main draw to the suburbs is still being close enough to work downtown, but not have to deal with downtown problems at home. If Urbanists were serious about convincing more folks to move to the city they'd face the fact that the vast majority of American cities have quality of life nuisances and crime that is unacceptable to most people, especially those with children, so living in a place that is harder to get to for criminals and has no outside draw to it sounds great. Most Americans will accept that their options to eat out are either Chili's or Olive Garden because it's better than worrying if the roving gang of armed 15 year old Kia Boys is going to choose them on their walk to the authentic Thai spot. Most Americans will deal with waiting in a half mile long 30 minute line to pick up their kid from school if it means they don't have to worry about them walking by the homeless guy lying in his own fluids at the train station on his way to class.
Until America returns to producing real goods and not dollars people will continue to choose the suburbs over rural areas and until cities stop pretending crime is just "part of living in the city" the suburban sprawl will continue to spread.
-
 @ 6be5cc06:5259daf0
2025-01-21 20:58:37
@ 6be5cc06:5259daf0
2025-01-21 20:58:37A seguir, veja como instalar e configurar o Privoxy no Pop!_OS.
1. Instalar o Tor e o Privoxy
Abra o terminal e execute:
bash sudo apt update sudo apt install tor privoxyExplicação:
- Tor: Roteia o tráfego pela rede Tor.
- Privoxy: Proxy avançado que intermedia a conexão entre aplicativos e o Tor.
2. Configurar o Privoxy
Abra o arquivo de configuração do Privoxy:
bash sudo nano /etc/privoxy/configNavegue até a última linha (atalho:
Ctrl+/depoisCtrl+Vpara navegar diretamente até a última linha) e insira:bash forward-socks5 / 127.0.0.1:9050 .Isso faz com que o Privoxy envie todo o tráfego para o Tor através da porta 9050.
Salve (
CTRL+OeEnter) e feche (CTRL+X) o arquivo.
3. Iniciar o Tor e o Privoxy
Agora, inicie e habilite os serviços:
bash sudo systemctl start tor sudo systemctl start privoxy sudo systemctl enable tor sudo systemctl enable privoxyExplicação:
- start: Inicia os serviços.
- enable: Faz com que iniciem automaticamente ao ligar o PC.
4. Configurar o Navegador Firefox
Para usar a rede Tor com o Firefox:
- Abra o Firefox.
- Acesse Configurações → Configurar conexão.
- Selecione Configuração manual de proxy.
- Configure assim:
- Proxy HTTP:
127.0.0.1 - Porta:
8118(porta padrão do Privoxy) - Domínio SOCKS (v5):
127.0.0.1 - Porta:
9050
- Proxy HTTP:
- Marque a opção "Usar este proxy também em HTTPS".
- Clique em OK.
5. Verificar a Conexão com o Tor
Abra o navegador e acesse:
text https://check.torproject.org/Se aparecer a mensagem "Congratulations. This browser is configured to use Tor.", a configuração está correta.
Dicas Extras
- Privoxy pode ser ajustado para bloquear anúncios e rastreadores.
- Outros aplicativos também podem ser configurados para usar o Privoxy.
-
 @ 52b4a076:e7fad8bd
2025-05-03 21:54:45
@ 52b4a076:e7fad8bd
2025-05-03 21:54:45Introduction
Me and Fishcake have been working on infrastructure for Noswhere and Nostr.build. Part of this involves processing a large amount of Nostr events for features such as search, analytics, and feeds.
I have been recently developing
nosdexv3, a newer version of the Noswhere scraper that is designed for maximum performance and fault tolerance using FoundationDB (FDB).Fishcake has been working on a processing system for Nostr events to use with NB, based off of Cloudflare (CF) Pipelines, which is a relatively new beta product. This evening, we put it all to the test.
First preparations
We set up a new CF Pipelines endpoint, and I implemented a basic importer that took data from the
nosdexdatabase. This was quite slow, as it did HTTP requests synchronously, but worked as a good smoke test.Asynchronous indexing
I implemented a high-contention queue system designed for highly parallel indexing operations, built using FDB, that supports: - Fully customizable batch sizes - Per-index queues - Hundreds of parallel consumers - Automatic retry logic using lease expiration
When the scraper first gets an event, it will process it and eventually write it to the blob store and FDB. Each new event is appended to the event log.
On the indexing side, a
Queuerwill read the event log, and batch events (usually 2K-5K events) into one work job. This work job contains: - A range in the log to index - Which target this job is intended for - The size of the job and some other metadataEach job has an associated leasing state, which is used to handle retries and prioritization, and ensure no duplication of work.
Several
Workers monitor the index queue (up to 128) and wait for new jobs that are available to lease.Once a suitable job is found, the worker acquires a lease on the job and reads the relevant events from FDB and the blob store.
Depending on the indexing type, the job will be processed in one of a number of ways, and then marked as completed or returned for retries.
In this case, the event is also forwarded to CF Pipelines.

Trying it out
The first attempt did not go well. I found a bug in the high-contention indexer that led to frequent transaction conflicts. This was easily solved by correcting an incorrectly set parameter.
We also found there were other issues in the indexer, such as an insufficient amount of threads, and a suspicious decrease in the speed of the
Queuerduring processing of queued jobs.Along with fixing these issues, I also implemented other optimizations, such as deprioritizing
WorkerDB accesses, and increasing the batch size.To fix the degraded
Queuerperformance, I ran the backfill job by itself, and then started indexing after it had completed.Bottlenecks, bottlenecks everywhere

After implementing these fixes, there was an interesting problem: The DB couldn't go over 80K reads per second. I had encountered this limit during load testing for the scraper and other FDB benchmarks.
As I suspected, this was a client thread limitation, as one thread seemed to be using high amounts of CPU. To overcome this, I created a new client instance for each
Worker.After investigating, I discovered that the Go FoundationDB client cached the database connection. This meant all attempts to create separate DB connections ended up being useless.
Using
OpenWithConnectionStringpartially resolved this issue. (This also had benefits for service-discovery based connection configuration.)To be able to fully support multi-threading, I needed to enabled the FDB multi-client feature. Enabling it also allowed easier upgrades across DB versions, as FDB clients are incompatible across versions:
FDB_NETWORK_OPTION_EXTERNAL_CLIENT_LIBRARY="/lib/libfdb_c.so"FDB_NETWORK_OPTION_CLIENT_THREADS_PER_VERSION="16"Breaking the 100K/s reads barrier

After implementing support for the multi-threaded client, we were able to get over 100K reads per second.
You may notice after the restart (gap) the performance dropped. This was caused by several bugs: 1. When creating the CF Pipelines endpoint, we did not specify a region. The automatically selected region was far away from the server. 2. The amount of shards were not sufficient, so we increased them. 3. The client overloaded a few HTTP/2 connections with too many requests.
I implemented a feature to assign each
Workerits own HTTP client, fixing the 3rd issue. We also moved the entire storage region to West Europe to be closer to the servers.After these changes, we were able to easily push over 200K reads/s, mostly limited by missing optimizations:

It's shards all the way down
While testing, we also noticed another issue: At certain times, a pipeline would get overloaded, stalling requests for seconds at a time. This prevented all forward progress on the
Workers.We solved this by having multiple pipelines: A primary pipeline meant to be for standard load, with moderate batching duration and less shards, and high-throughput pipelines with more shards.
Each
Workeris assigned a pipeline on startup, and if one pipeline stalls, other workers can continue making progress and saturate the DB.The stress test
After making sure everything was ready for the import, we cleared all data, and started the import.
The entire import lasted 20 minutes between 01:44 UTC and 02:04 UTC, reaching a peak of: - 0.25M requests per second - 0.6M keys read per second - 140MB/s reads from DB - 2Gbps of network throughput
FoundationDB ran smoothly during this test, with: - Read times under 2ms - Zero conflicting transactions - No overloaded servers
CF Pipelines held up well, delivering batches to R2 without any issues, while reaching its maximum possible throughput.

Finishing notes
Me and Fishcake have been building infrastructure around scaling Nostr, from media, to relays, to content indexing. We consistently work on improving scalability, resiliency and stability, even outside these posts.
Many things, including what you see here, are already a part of Nostr.build, Noswhere and NFDB, and many other changes are being implemented every day.
If you like what you are seeing, and want to integrate it, get in touch. :)
If you want to support our work, you can zap this post, or register for nostr.land and nostr.build today.
-
 @ bbef5093:71228592
2025-05-16 17:00:59
@ bbef5093:71228592
2025-05-16 17:00:59Technológiai fejlemények
Az Egyesült Államokban és világszerte jelentős előrelépések történtek a nukleáris technológia területén. A mesterséges intelligencia (AI) egyre nagyobb szerepet kap az atomerőművek működtetésében: például a kaliforniai Diablo Canyon atomerőmű már alkalmaz generatív AI-t a dokumentumkezelés és az üzemeltetési hatékonyság javítására. Az AI segíti az üzemeltetőket a karbantartás előrejelzésében, a biztonság növelésében és a reaktorok élettartamának meghosszabbításában is. Emellett az USA Nukleáris Szabályozó Bizottsága (NRC) is vizsgálja, hogyan gyorsíthatná fel az engedélyezési folyamatokat AI-alapú rendszerekkel, ami jelentősen felgyorsíthatja az új reaktorok telepítését.
A NANO Nuclear Energy jelentős mérföldkövet ért el: megszerezte a KRONOS MMR™ (45 MWth teljesítményű, helyhez kötött mikroreaktor) és a LOKI MMR™ (1–5 MWth teljesítményű, hordozható mikroreaktor) technológiákat, és ezek fejlesztését az USA-ban és Kanadában is előmozdítja. A KRONOS MMR üzemanyag-minősítési módszertanát az NRC már jóváhagyta, ami kulcsfontosságú a kereskedelmi bevezetéshez
Ipari és piaci fejlemények
Az amerikai The Nuclear Company startup 46 millió dolláros tőkebevonással kívánja új, nagy teljesítményű atomerőművek fejlesztését megkezdeni, elsősorban már engedélyezett helyszíneken. A cél, hogy az első flottában összesen 6 gigawatt kapacitást hozzanak létre. Ez a lépés válasz a gyorsan növekvő amerikai áramigényre, amelyet főként az adatközpontok és a mesterséges intelligencia-alkalmazások hajtanak. Ugyanakkor a nukleáris ipar pénzügyi kilátásait bizonytalanság övezi, mivel az amerikai törvényhozás egyes tervezetei a nukleáris energia adókedvezményeinek megszüntetését is kilátásba helyezték, ami a jövőbeni beruházások megtérülését is befolyásolhatja.
Belgiumban a parlament váratlan fordulattal úgy döntött, hogy nem zárják be az atomerőműveket, hanem tíz évvel meghosszabbítják a reaktorok élettartamát, sőt, új reaktorok építését is tervezik. A döntés mögött az energiaválság, az ellátásbiztonság és a geopolitikai feszültségek állnak.
Magyarországon folytatódik a Paks II. projekt előkészítése, és napirenden van kis moduláris reaktorok (SMR) telepítése is, amelyek néhány száz megawattos teljesítményükkel akár ipari zónákat vagy városokat is önállóan elláthatnak.
Pénzügyi és geopolitikai aktualitások
A nukleáris energia geopolitikai jelentősége továbbra is kiemelkedő. Tajvan szombaton leállítja utolsó működő atomerőművi blokkját, ami jelentős LNG-import költségnövekedést eredményez, és komoly vitákat váltott ki a szigetországban. A törvényhozás ugyanakkor már vizsgálja az atomenergia-törvény felülvizsgálatát, amely lehetővé teheti a reaktorok újraindítását – erről akár népszavazás is lehet a közeljövőben.
Az USA és Irán között folytatódnak az atomprogramról szóló tárgyalások. Bár közelednek az álláspontok, az USA új szankciókat vezetett be Irán ellen, mivel Teherán továbbra is magas szintű urándúsítást folytat. Az esetleges megállapodás rövid távon növelheti az iráni kőolajexportot, ami a világpiaci árakra is hatással lehet.
-
 @ 99e7936f:d5d2197c
2025-05-16 13:09:05
@ 99e7936f:d5d2197c
2025-05-16 13:09:05Baustelle HERZ
Können wir nicht einfach glücklich sein? Nein.
Eine traumatisierte Gesellschaft kann nicht EINFACH glücklich sein, weil die Herzen verletzt sind.
„Ja, aber es gibt doch auch noch andere Probleme als Trauma“, kritisieren einige.
„Ich habe schließlich eine Familie und einen anstrengenden Job“, erklären andere.
„Für mich ist das eine abstrakte Diskussion, ein Luxusproblem“, geben manche zu bedenken.
„Eigentlich möchte ich mich mit dem Thema gar nicht beschäftigen“, sagen wenige, denken aber viele.
„Ich beschäftige mich lieber mit positiven Dingen“, ist die diplomatische Variante der Vermeidung dieses Themas.
Niemand redet gerne über Trauma, bis es an die eigene Tür klopft. Und dann ist guter Rat teuer. Dann würde man gerne reden, aber die anderen wollen immer noch nicht.
Niemand redet gerne über Trauma.
„Was heißt denn Anklopfen?“ Mit Anklopfen meine ich die Situationen, die jeder kennt. Gemeint sind ganz normale Lebenskrisen, die es mehrmals in jedem Leben gibt.
„Ist denn eine Lebenskrise gleichzusetzten mit einem Trauma?“ Nein, aber durch eine starke Lebenskrise kann ein altes Trauma wieder hochgespült werden, und das fühlt sich dann original so an, wie das Trauma, das man z.B. als Kind oder später im Leben erlebt hat.
Und das passiert in einer traumatisierten Gesellschaft ständig, nur nennen die Leute es nicht so. Niemand sagt: „Er oder sie hat ein aktiviertes Trauma.“
Hierzu habe ich eine Anekdote. Vor ein paar Monaten zog in das Nachbarhaus bei mir auf der Straße ein junger Mann ein. Das Haus war frisch renoviert worden. Es zogen zeitgleich mehrere junge Leute jeweils in eine Wohnung dieses Hauses ein. Die Stimmung im Haus war gut, weil alles neu und geschmackvoll gestaltet worden war und die Mieter gut zusammen passten. Dann merkten die Mieter und Nachbarn, dass es einem jungen Mann nicht gut ging. Er saß den ganzen Tag in der Wohnung, konnte sich zu nichts aufraffen. Er schaffte es nicht, sich Lebensmittel einzukaufen. Ein Freund kam regelmäßig vorbei und brachte ihm Essen. Eine ältere Nachbarin fragte nach einigen Monaten diesen Freund, was dem jungen Mann denn fehle, ob er eine Krankheit habe oder was denn los sei. Der Freund lachte und sagte nur einen Satz: „Er stirbt.“
Die Nachbarin erzählte mir das und schaute mich fragend an. Ich übersetzte ihr den Satz und meinte: „Er hat vermutlich Liebeskummer.“ Aber was ich wirklich dachte, war, dass er ein aktiviertes Trauma hatte, nur sagte ich das nicht zur Nachbarin. Nach mittlerweile zwei Jahren kommt der Freund immer noch regelmäßig und bringt dem jungen Mann Essen. Er kauft für ihn ein und kümmert sich um ihn.
Manche Menschen leiden sehr lange unter Verlusten, Zurückweisungen, Niederlagen, Verletzungen. Andere kommen nie auf die nächste Stufe, obwohl sie sich unaufhörlich anstrengen. Wieder andere haben alles und sind dennoch unzufrieden und in permanenter Angriffshaltung. All diese Phänomene dauern oft lange, manchmal sogar ein Leben lang. Meines Erachtens sind das aktivierte Traumen bzw. Traumen, die gut verschlossen dennoch im Unterbewusstsein gegen die eigene Person arbeiten.
Trauma hat viele Gesichter.
Es kommt bei den unmöglichsten Gelegenheiten zum Vorschein. Und oft erkennen wir es nicht als das, was es ist. Wir suchen den Grund im Außen, den es ja meist auch gibt. Nur ist der Grund nicht der Grund, sondern nur der Auslöser.
Auch ich bin einmal „gestorben“. Dieser Zustand dauerte über drei Jahre an. Deshalb klingelte es bei mir auch sofort im Ohr als die Nachbarin sagte, der Freund habe gesagt: „Er stirbt.“
Sprache ist wunderbar.
Wer beides schon mal erlebt hat, eine normale Trennung und eine schwere Trennung, einen normalen Arbeitsplatzwechsel oder einen dramatischen Jobverlust, ein geplatztes Geschäft oder einen geplatzten Lebenstraum, das Ende einer Freundschaft oder eine Kränkung, über die man noch nach 35 Jahren so berichtet, als ob es gestern gewesen wäre, der kennt den Unterschied in der Intensität der Gefühle. Manche Menschen erzählen immer wieder eine Geschichte, obwohl man sie schon kennt und auch sein Mitgefühl dazu ausgedrückt hat. Manche Menschen reden gar nicht mehr über eine bestimmte Sache, bis einem irgendwann von Dritten gesagt wird, dass man ihn oder sie besser nicht auf das Thema XYZ ansprechen sollte.
All das sind aktivierte Traumen, die noch weh tun, noch nicht verarbeitet sind. Es sind Dinge, die jedem von uns passieren können. Jeder erlebt im Leben partnerschaftliche Trennungen, geplatzte Geschäfte und Kränkungen am laufenden Meter, aber es „trifft“ einen nicht immer gleich. Und es trifft nicht nur die Sensiblen, sondern es trifft jeden, wenn der Punkt, an dem es trifft, wund ist. Der wunde Punkt macht jeden sensibel. Auch robuste Naturen haben einen wunden Punkt. Und wenn der getroffen wird, dann werden auch die härtesten Menschen butterweich. In einer traumatisierten Gesellschaft wird jeder so oft „getroffen“, wie es braucht, bis er sich dem Thema widmet. Wir alle haben diese frühen oder späten Traumen erlebt, die früher oder später erneut durch Krisen aktiviert werden. Und dann „sterben“ wir, zumindest gefühlt.
Denn Trauma ist immer existenziell.
Und aktiviertes Trauma ist bitte nicht zu verwechseln mit Depression. Es ist ein aktiviertes Trauma, das sich im Unterschied zur Depression sehr wach, lebendig und vor allem schmerzvoll anfühlt. Es fühlt sich an wie „damals“. Das versteht man, in der Situation steckend, komischerweise sofort, denn wir haben ein Schmerzgedächtnis. Wir können Düfte oder Musik ja auch sofort zuordnen, wenn sie uns an etwas erinnern. Mit Schmerz ist es ähnlich. Aber es fällt so schwer, darüber zu reden, weil es keiner versteht und weil es dafür meines Erachtens in unserer Sprache keine Worte gibt. Man versteht das erst, wenn man es selbst erlebt hat. Und dann reichen zwei Worte.
Die Baustelle HERZ versteht man erst, wenn man selbst ein aktiviertes Trauma erlebt, durchlebt hat, wenn man einmal „gestorben“ ist.
Heute kann ich an Äußerungen, die jemand macht, gut ablesen, ob jemand seine Baustelle HERZ bereits kennen gelernt hat oder nicht. Menschen, die das selbst noch nicht kennen gelernt haben, haben oft aufmunternde Sprüche wie „Das wird schon wieder. Jetzt lass den Kopf mal nicht hängen.“ Das hilft einem dann in etwa so, wie wenn man in einer Depression gesagt bekommt: „Nun lach doch mal.“ Man weiß dann sofort, welchen Erfahrungshintergrund das Gegenüber hat. Das ist keine Wertung, nur eine Feststellung. Unsere Kultur hat hier einfach wichtiges Wissen verloren. Ich persönlich weiß nicht, wie es ist, ein Kind auf die Welt zu bringen oder ein Kind zu verlieren. Ich weiß vieles nicht und habe vermutlich auch schon wenig hilfreiche Kommentare abgegeben, weil ich es nicht besser wusste. Aber ich weiß, wie sich ein aktiviertes Trauma anfühlt. Und das ist ein wertvolles Wissen, was ich gern teilen möchte. Man schaut mit diesem erfahrenen Wissen (kein Bücher-Wissen) viel differenzierter auf das Leid anderer Menschen. Es gibt so viele Sorten von Trauma und deswegen auch Sorten von aktiviertem Trauma. Manchmal denkt man sich nichts dabei und sagt etwas, und schon hat man beim anderen einen Punkt getroffen, der dadurch nun schmerzt. Wenn man Glück hat, dann dauert der Schmerz nur kurz an. Wenn man Pech hat, ist die Freundschaft zu Ende. Ich habe das selbst schon erlebt. Mal war ich es, die den Rückzug angetreten hat. Mal war es der andere. Hinter diesen Phänomenen steckt nichtverarbeitetes Trauma. Die Bildungslücke bezüglich Trauma in unserer Gesellschaft ist (gewollt) riesig.
Wir sind eine traumatisierte Gesellschaft, die nicht weiß, dass sie eine traumatisierte Gesellschaft ist.
Viele Menschen haben unverarbeitetes Trauma im Gepäck. Wir haben selbst nach Jahren der Therapie und Selbstreflektion immer noch unverarbeitete Anteile eines Traumas im Gepäck, das wir glaubten, bearbeitet zu haben. Mir ist das bewusst geworden, je besser ich mein eigenes Trauma kennen und lieben gelernt habe.
Eigentlich wollte ich heute kurz etwas über den gesunden Umgang mit Gefühlen schreiben. Beim Schreiben habe ich aber gemerkt, dass ich erstmal etwas über das Haus erzählen muss, bevor ich über die Gäste, die Gefühle, rede. Ich bin das Haus, das durch Verstand und Gefühle belebt wird. Und hinter dem Haus gibt es noch ein ganzes Universum, auf das ich heute nicht eingehen möchte.
Gefühle und Fühlen sind zentral wichtig, wenn man Trauma bearbeiten möchte.
Trauma wird solange aktiviert, bis es bearbeitet wurde.
In einer traumatisierten Gesellschaft wird 24/7 Trauma aktiviert. Und das ist gut so. Die Evolution schläft nicht. Die Evolution schenkt uns Schmerz, damit wir ihr Aufmerksamkeit schenken.
Das Leben liebt uns, und wiederkehrender Schmerz ist wie die Schlummerfunktion am Wecker, die möchte, dass wir aufwachen.
In unserer traumatisierten Gesellschaft klingelt momentan nicht nur der Wecker. Alles, was tönen kann, gibt Signal. Mir kommt es in dieser Zeit manchmal vor, wie wenn sich gleichzeitig , das Kinder-Sinfonieorchester mit sämtlichen Instrumenten einstimmt, jemand mit dem Handy telefoniert, das Fenster zur Hauptstraße offen steht, der Bus anfährt, der Auspuff röhrt, jemand hupt, das Martinshorn aufheult, die Drehorgel spielt, das Pausenzeichen in der Schule ertönt, es an der Tür klingelt und die Kirchenorgel aus allen Pfeifen flötet und brummt.
Aktiviertes Trauma macht ordentlich Krach individuell und erst recht gesellschaftlich gesehen. Und je lauter es ist, desto dringender möchte es bearbeitet werden.
Die Baustelle HERZ zu bearbeiten, lohnt sich. Und Fühlen bringt die Verwandlung.
-
 @ 9e69e420:d12360c2
2025-01-21 19:31:48
@ 9e69e420:d12360c2
2025-01-21 19:31:48Oregano oil is a potent natural compound that offers numerous scientifically-supported health benefits.
Active Compounds
The oil's therapeutic properties stem from its key bioactive components: - Carvacrol and thymol (primary active compounds) - Polyphenols and other antioxidant
Antimicrobial Properties
Bacterial Protection The oil demonstrates powerful antibacterial effects, even against antibiotic-resistant strains like MRSA and other harmful bacteria. Studies show it effectively inactivates various pathogenic bacteria without developing resistance.
Antifungal Effects It effectively combats fungal infections, particularly Candida-related conditions like oral thrush, athlete's foot, and nail infections.
Digestive Health Benefits
Oregano oil supports digestive wellness by: - Promoting gastric juice secretion and enzyme production - Helping treat Small Intestinal Bacterial Overgrowth (SIBO) - Managing digestive discomfort, bloating, and IBS symptoms
Anti-inflammatory and Antioxidant Effects
The oil provides significant protective benefits through: - Powerful antioxidant activity that fights free radicals - Reduction of inflammatory markers in the body - Protection against oxidative stress-related conditions
Respiratory Support
It aids respiratory health by: - Loosening mucus and phlegm - Suppressing coughs and throat irritation - Supporting overall respiratory tract function
Additional Benefits
Skin Health - Improves conditions like psoriasis, acne, and eczema - Supports wound healing through antibacterial action - Provides anti-aging benefits through antioxidant properties
Cardiovascular Health Studies show oregano oil may help: - Reduce LDL (bad) cholesterol levels - Support overall heart health
Pain Management The oil demonstrates effectiveness in: - Reducing inflammation-related pain - Managing muscle discomfort - Providing topical pain relief
Safety Note
While oregano oil is generally safe, it's highly concentrated and should be properly diluted before use Consult a healthcare provider before starting supplementation, especially if taking other medications.
-
 @ 87fedb9f:0da83419
2025-05-16 12:45:01
@ 87fedb9f:0da83419
2025-05-16 12:45:01Push it! Push it! Push it!
That chant still echoes in my bones, not just from the gym, but from the inside out. I remember watching a bodybuilder once — the weight trembling above him, his muscles bulging and giving out, the spotters swooping in to catch the bar just in time. “Train to failure,” they said. “That’s how you grow.”
And it makes sense, doesn’t it? If you’re being chased by a wild beast, you run until your body gives out. That’s how we’re wired — to survive first and foremost, not necessarily to thrive.
But what if the house we’re building isn’t under threat from wolves? What if we’ve got stone-moving machines and time to breathe? What if we’re not being chased anymore… but we still act like we are?
See, survival patterns are sneaky. They wear masks. They show up in workouts and work days. They dress up in ambition, caffeine, and “just one more thing before I stop.”
I’ve never been a bodybuilder — my brother was — but I’ve tried that route in my own work life. Lift to failure. Push it. Every other day, I’d be nursing another injury to body and mind.
I wasn’t getting stronger. I was just breaking myself in cycles. Push, break, recover, repeat.
I see the same thing with brains. Push it. Adderall. More coffee. Keep going. Hit the wall. And then—collapse.
That’s not strengthening. That’s surviving pretending to be “powerful.”
What happens to the rest of your system when your brain is sucking up all the energy just to stay on task? You stop digesting. You stop feeling the sun on your skin. You stop enjoying your kids’ laughter. Everything feels like something to push through.
That isn’t thriving.
Thriving feels different. It’s alive, yes — there’s activation. But it’s not strained. When we’re in thriving mode, we’re with our energy, not yanking it out by the roots and forcing it to regrow. The muscles — or the mind — are engaged, fluid, expressive. Alive.
It’s a fine line. You can take the same exact action and fill it with stress.
I’ve done it. I’ve turned a perfectly normal task into a survival sprint. It feels ridiculous in hindsight — like, why did I make this email reply into a mountain climb?
Because my primitive brain still whispers, “If you don’t do this perfectly and fast, you’ll die.” Not literally. But the threat feels real. The imagined judgment, the self-criticism, the fear of not being enough — they’re imaginary lions in the tall grass of modern life.
I’ve used this system on myself. I’ve strained my nervous system like fingernails scraping rock to avoid a fall that was never coming.
That’s what we’re supposed to do, right? We bring survival force into every aspect. Into parenting. Into projects. Into relationships.
And we wonder why we’re tired all the time. Not sleepy tired — soul tired. That kind of tired that feels like you ran for your life… but all you did was sit at your desk.
Here’s what I know now: if you’re not actually in danger, you can stop living like you are.
You don’t have to push everything to the edge. You don’t have to prove your strength through strain. Strength can be alive in you — not torn, not depleted, but awake and sustaining.
And when we live from there, the recovery feels different, too. We’re not collapsing. We’re restoring.
We’re not dropping all the pieces and then forcing ourselves to pick them up… again! Instead, we’re crafting a thriving life from the pieces we find, fashion, and consciously put in place.
There’s a wisdom to building your foundation around thriving — not just surviving. And thriving starts with recognizing: it’s not life or death to get through your inbox. Your self-worth isn’t measured by how busy and depleted you are.
Look around. Are you stacking more and more iron to prove something? Or are you listening to the quiet whisper that says, “Yes, move… but don’t hurt yourself doing it.”
And in a life that tells you to push until you fail, choosing to rest and relish — choosing to feel alive rather than just alive-enough — might just be the truest strength there is.
Useful Concepts for Thriving in This Story
-
Primitive Brain\ The primitive brain keeps us on high alert even when we’re safe — it’s time to question whether the lion is real.
-
Unrushed\ Being unrushed is a radical shift from survival tempo to the rhythm of true aliveness.
-
Savvy\ Savvy invites us to work with our energy wisely, not destructively — to choose thriving over proving.
-
Vitality\ Vitality flows when we stop draining ourselves for performance and start living from inner strength.
-
Inspired Action\ Inspired action arises from presence and aliveness, not adrenaline and depletion.
-
-
 @ 6be5cc06:5259daf0
2025-01-21 01:51:46
@ 6be5cc06:5259daf0
2025-01-21 01:51:46Bitcoin: Um sistema de dinheiro eletrônico direto entre pessoas.
Satoshi Nakamoto
satoshin@gmx.com
www.bitcoin.org
Resumo
O Bitcoin é uma forma de dinheiro digital que permite pagamentos diretos entre pessoas, sem a necessidade de um banco ou instituição financeira. Ele resolve um problema chamado gasto duplo, que ocorre quando alguém tenta gastar o mesmo dinheiro duas vezes. Para evitar isso, o Bitcoin usa uma rede descentralizada onde todos trabalham juntos para verificar e registrar as transações.
As transações são registradas em um livro público chamado blockchain, protegido por uma técnica chamada Prova de Trabalho. Essa técnica cria uma cadeia de registros que não pode ser alterada sem refazer todo o trabalho já feito. Essa cadeia é mantida pelos computadores que participam da rede, e a mais longa é considerada a verdadeira.
Enquanto a maior parte do poder computacional da rede for controlada por participantes honestos, o sistema continuará funcionando de forma segura. A rede é flexível, permitindo que qualquer pessoa entre ou saia a qualquer momento, sempre confiando na cadeia mais longa como prova do que aconteceu.
1. Introdução
Hoje, quase todos os pagamentos feitos pela internet dependem de bancos ou empresas como processadores de pagamento (cartões de crédito, por exemplo) para funcionar. Embora esse sistema seja útil, ele tem problemas importantes porque é baseado em confiança.
Primeiro, essas empresas podem reverter pagamentos, o que é útil em caso de erros, mas cria custos e incertezas. Isso faz com que pequenas transações, como pagar centavos por um serviço, se tornem inviáveis. Além disso, os comerciantes são obrigados a desconfiar dos clientes, pedindo informações extras e aceitando fraudes como algo inevitável.
Esses problemas não existem no dinheiro físico, como o papel-moeda, onde o pagamento é final e direto entre as partes. No entanto, não temos como enviar dinheiro físico pela internet sem depender de um intermediário confiável.
O que precisamos é de um sistema de pagamento eletrônico baseado em provas matemáticas, não em confiança. Esse sistema permitiria que qualquer pessoa enviasse dinheiro diretamente para outra, sem depender de bancos ou processadores de pagamento. Além disso, as transações seriam irreversíveis, protegendo vendedores contra fraudes, mas mantendo a possibilidade de soluções para disputas legítimas.
Neste documento, apresentamos o Bitcoin, que resolve o problema do gasto duplo usando uma rede descentralizada. Essa rede cria um registro público e protegido por cálculos matemáticos, que garante a ordem das transações. Enquanto a maior parte da rede for controlada por pessoas honestas, o sistema será seguro contra ataques.
2. Transações
Para entender como funciona o Bitcoin, é importante saber como as transações são realizadas. Imagine que você quer transferir uma "moeda digital" para outra pessoa. No sistema do Bitcoin, essa "moeda" é representada por uma sequência de registros que mostram quem é o atual dono. Para transferi-la, você adiciona um novo registro comprovando que agora ela pertence ao próximo dono. Esse registro é protegido por um tipo especial de assinatura digital.
O que é uma assinatura digital?
Uma assinatura digital é como uma senha secreta, mas muito mais segura. No Bitcoin, cada usuário tem duas chaves: uma "chave privada", que é secreta e serve para criar a assinatura, e uma "chave pública", que pode ser compartilhada com todos e é usada para verificar se a assinatura é válida. Quando você transfere uma moeda, usa sua chave privada para assinar a transação, provando que você é o dono. A próxima pessoa pode usar sua chave pública para confirmar isso.
Como funciona na prática?
Cada "moeda" no Bitcoin é, na verdade, uma cadeia de assinaturas digitais. Vamos imaginar o seguinte cenário:
- A moeda está com o Dono 0 (você). Para transferi-la ao Dono 1, você assina digitalmente a transação com sua chave privada. Essa assinatura inclui o código da transação anterior (chamado de "hash") e a chave pública do Dono 1.
- Quando o Dono 1 quiser transferir a moeda ao Dono 2, ele assinará a transação seguinte com sua própria chave privada, incluindo também o hash da transação anterior e a chave pública do Dono 2.
- Esse processo continua, formando uma "cadeia" de transações. Qualquer pessoa pode verificar essa cadeia para confirmar quem é o atual dono da moeda.
Resolvendo o problema do gasto duplo
Um grande desafio com moedas digitais é o "gasto duplo", que é quando uma mesma moeda é usada em mais de uma transação. Para evitar isso, muitos sistemas antigos dependiam de uma entidade central confiável, como uma casa da moeda, que verificava todas as transações. No entanto, isso criava um ponto único de falha e centralizava o controle do dinheiro.
O Bitcoin resolve esse problema de forma inovadora: ele usa uma rede descentralizada onde todos os participantes (os "nós") têm acesso a um registro completo de todas as transações. Cada nó verifica se as transações são válidas e se a moeda não foi gasta duas vezes. Quando a maioria dos nós concorda com a validade de uma transação, ela é registrada permanentemente na blockchain.
Por que isso é importante?
Essa solução elimina a necessidade de confiar em uma única entidade para gerenciar o dinheiro, permitindo que qualquer pessoa no mundo use o Bitcoin sem precisar de permissão de terceiros. Além disso, ela garante que o sistema seja seguro e resistente a fraudes.
3. Servidor Timestamp
Para assegurar que as transações sejam realizadas de forma segura e transparente, o sistema Bitcoin utiliza algo chamado de "servidor de registro de tempo" (timestamp). Esse servidor funciona como um registro público que organiza as transações em uma ordem específica.
Ele faz isso agrupando várias transações em blocos e criando um código único chamado "hash". Esse hash é como uma impressão digital que representa todo o conteúdo do bloco. O hash de cada bloco é amplamente divulgado, como se fosse publicado em um jornal ou em um fórum público.
Esse processo garante que cada bloco de transações tenha um registro de quando foi criado e que ele existia naquele momento. Além disso, cada novo bloco criado contém o hash do bloco anterior, formando uma cadeia contínua de blocos conectados — conhecida como blockchain.
Com isso, se alguém tentar alterar qualquer informação em um bloco anterior, o hash desse bloco mudará e não corresponderá ao hash armazenado no bloco seguinte. Essa característica torna a cadeia muito segura, pois qualquer tentativa de fraude seria imediatamente detectada.
O sistema de timestamps é essencial para provar a ordem cronológica das transações e garantir que cada uma delas seja única e autêntica. Dessa forma, ele reforça a segurança e a confiança na rede Bitcoin.
4. Prova-de-Trabalho
Para implementar o registro de tempo distribuído no sistema Bitcoin, utilizamos um mecanismo chamado prova-de-trabalho. Esse sistema é semelhante ao Hashcash, desenvolvido por Adam Back, e baseia-se na criação de um código único, o "hash", por meio de um processo computacionalmente exigente.
A prova-de-trabalho envolve encontrar um valor especial que, quando processado junto com as informações do bloco, gere um hash que comece com uma quantidade específica de zeros. Esse valor especial é chamado de "nonce". Encontrar o nonce correto exige um esforço significativo do computador, porque envolve tentativas repetidas até que a condição seja satisfeita.
Esse processo é importante porque torna extremamente difícil alterar qualquer informação registrada em um bloco. Se alguém tentar mudar algo em um bloco, seria necessário refazer o trabalho de computação não apenas para aquele bloco, mas também para todos os blocos que vêm depois dele. Isso garante a segurança e a imutabilidade da blockchain.
A prova-de-trabalho também resolve o problema de decidir qual cadeia de blocos é a válida quando há múltiplas cadeias competindo. A decisão é feita pela cadeia mais longa, pois ela representa o maior esforço computacional já realizado. Isso impede que qualquer indivíduo ou grupo controle a rede, desde que a maioria do poder de processamento seja mantida por participantes honestos.
Para garantir que o sistema permaneça eficiente e equilibrado, a dificuldade da prova-de-trabalho é ajustada automaticamente ao longo do tempo. Se novos blocos estiverem sendo gerados rapidamente, a dificuldade aumenta; se estiverem sendo gerados muito lentamente, a dificuldade diminui. Esse ajuste assegura que novos blocos sejam criados aproximadamente a cada 10 minutos, mantendo o sistema estável e funcional.
5. Rede
A rede Bitcoin é o coração do sistema e funciona de maneira distribuída, conectando vários participantes (ou nós) para garantir o registro e a validação das transações. Os passos para operar essa rede são:
-
Transmissão de Transações: Quando alguém realiza uma nova transação, ela é enviada para todos os nós da rede. Isso é feito para garantir que todos estejam cientes da operação e possam validá-la.
-
Coleta de Transações em Blocos: Cada nó agrupa as novas transações recebidas em um "bloco". Este bloco será preparado para ser adicionado à cadeia de blocos (a blockchain).
-
Prova-de-Trabalho: Os nós competem para resolver a prova-de-trabalho do bloco, utilizando poder computacional para encontrar um hash válido. Esse processo é como resolver um quebra-cabeça matemático difícil.
-
Envio do Bloco Resolvido: Quando um nó encontra a solução para o bloco (a prova-de-trabalho), ele compartilha esse bloco com todos os outros nós na rede.
-
Validação do Bloco: Cada nó verifica o bloco recebido para garantir que todas as transações nele contidas sejam válidas e que nenhuma moeda tenha sido gasta duas vezes. Apenas blocos válidos são aceitos.
-
Construção do Próximo Bloco: Os nós que aceitaram o bloco começam a trabalhar na criação do próximo bloco, utilizando o hash do bloco aceito como base (hash anterior). Isso mantém a continuidade da cadeia.
Resolução de Conflitos e Escolha da Cadeia Mais Longa
Os nós sempre priorizam a cadeia mais longa, pois ela representa o maior esforço computacional já realizado, garantindo maior segurança. Se dois blocos diferentes forem compartilhados simultaneamente, os nós trabalharão no primeiro bloco recebido, mas guardarão o outro como uma alternativa. Caso o segundo bloco eventualmente forme uma cadeia mais longa (ou seja, tenha mais blocos subsequentes), os nós mudarão para essa nova cadeia.
Tolerância a Falhas
A rede é robusta e pode lidar com mensagens que não chegam a todos os nós. Uma transação não precisa alcançar todos os nós de imediato; basta que chegue a um número suficiente deles para ser incluída em um bloco. Da mesma forma, se um nó não receber um bloco em tempo hábil, ele pode solicitá-lo ao perceber que está faltando quando o próximo bloco é recebido.
Esse mecanismo descentralizado permite que a rede Bitcoin funcione de maneira segura, confiável e resiliente, sem depender de uma autoridade central.
6. Incentivo
O incentivo é um dos pilares fundamentais que sustenta o funcionamento da rede Bitcoin, garantindo que os participantes (nós) continuem operando de forma honesta e contribuindo com recursos computacionais. Ele é estruturado em duas partes principais: a recompensa por mineração e as taxas de transação.
Recompensa por Mineração
Por convenção, o primeiro registro em cada bloco é uma transação especial que cria novas moedas e as atribui ao criador do bloco. Essa recompensa incentiva os mineradores a dedicarem poder computacional para apoiar a rede. Como não há uma autoridade central para emitir moedas, essa é a maneira pela qual novas moedas entram em circulação. Esse processo pode ser comparado ao trabalho de garimpeiros, que utilizam recursos para colocar mais ouro em circulação. No caso do Bitcoin, o "recurso" consiste no tempo de CPU e na energia elétrica consumida para resolver a prova-de-trabalho.
Taxas de Transação
Além da recompensa por mineração, os mineradores também podem ser incentivados pelas taxas de transação. Se uma transação utiliza menos valor de saída do que o valor de entrada, a diferença é tratada como uma taxa, que é adicionada à recompensa do bloco contendo essa transação. Com o passar do tempo e à medida que o número de moedas em circulação atinge o limite predeterminado, essas taxas de transação se tornam a principal fonte de incentivo, substituindo gradualmente a emissão de novas moedas. Isso permite que o sistema opere sem inflação, uma vez que o número total de moedas permanece fixo.
Incentivo à Honestidade
O design do incentivo também busca garantir que os participantes da rede mantenham um comportamento honesto. Para um atacante que consiga reunir mais poder computacional do que o restante da rede, ele enfrentaria duas escolhas:
- Usar esse poder para fraudar o sistema, como reverter transações e roubar pagamentos.
- Seguir as regras do sistema, criando novos blocos e recebendo recompensas legítimas.
A lógica econômica favorece a segunda opção, pois um comportamento desonesto prejudicaria a confiança no sistema, diminuindo o valor de todas as moedas, incluindo aquelas que o próprio atacante possui. Jogar dentro das regras não apenas maximiza o retorno financeiro, mas também preserva a validade e a integridade do sistema.
Esse mecanismo garante que os incentivos econômicos estejam alinhados com o objetivo de manter a rede segura, descentralizada e funcional ao longo do tempo.
7. Recuperação do Espaço em Disco
Depois que uma moeda passa a estar protegida por muitos blocos na cadeia, as informações sobre as transações antigas que a geraram podem ser descartadas para economizar espaço em disco. Para que isso seja possível sem comprometer a segurança, as transações são organizadas em uma estrutura chamada "árvore de Merkle". Essa árvore funciona como um resumo das transações: em vez de armazenar todas elas, guarda apenas um "hash raiz", que é como uma assinatura compacta que representa todo o grupo de transações.
Os blocos antigos podem, então, ser simplificados, removendo as partes desnecessárias dessa árvore. Apenas a raiz do hash precisa ser mantida no cabeçalho do bloco, garantindo que a integridade dos dados seja preservada, mesmo que detalhes específicos sejam descartados.
Para exemplificar: imagine que você tenha vários recibos de compra. Em vez de guardar todos os recibos, você cria um documento e lista apenas o valor total de cada um. Mesmo que os recibos originais sejam descartados, ainda é possível verificar a soma com base nos valores armazenados.
Além disso, o espaço ocupado pelos blocos em si é muito pequeno. Cada bloco sem transações ocupa apenas cerca de 80 bytes. Isso significa que, mesmo com blocos sendo gerados a cada 10 minutos, o crescimento anual em espaço necessário é insignificante: apenas 4,2 MB por ano. Com a capacidade de armazenamento dos computadores crescendo a cada ano, esse espaço continuará sendo trivial, garantindo que a rede possa operar de forma eficiente sem problemas de armazenamento, mesmo a longo prazo.
8. Verificação de Pagamento Simplificada
É possível confirmar pagamentos sem a necessidade de operar um nó completo da rede. Para isso, o usuário precisa apenas de uma cópia dos cabeçalhos dos blocos da cadeia mais longa (ou seja, a cadeia com maior esforço de trabalho acumulado). Ele pode verificar a validade de uma transação ao consultar os nós da rede até obter a confirmação de que tem a cadeia mais longa. Para isso, utiliza-se o ramo Merkle, que conecta a transação ao bloco em que ela foi registrada.
Entretanto, o método simplificado possui limitações: ele não pode confirmar uma transação isoladamente, mas sim assegurar que ela ocupa um lugar específico na cadeia mais longa. Dessa forma, se um nó da rede aprova a transação, os blocos subsequentes reforçam essa aceitação.
A verificação simplificada é confiável enquanto a maioria dos nós da rede for honesta. Contudo, ela se torna vulnerável caso a rede seja dominada por um invasor. Nesse cenário, um atacante poderia fabricar transações fraudulentas que enganariam o usuário temporariamente até que o invasor obtivesse controle completo da rede.
Uma estratégia para mitigar esse risco é configurar alertas nos softwares de nós completos. Esses alertas identificam blocos inválidos, sugerindo ao usuário baixar o bloco completo para confirmar qualquer inconsistência. Para maior segurança, empresas que realizam pagamentos frequentes podem preferir operar seus próprios nós, reduzindo riscos e permitindo uma verificação mais direta e confiável.
9. Combinando e Dividindo Valor
No sistema Bitcoin, cada unidade de valor é tratada como uma "moeda" individual, mas gerenciar cada centavo como uma transação separada seria impraticável. Para resolver isso, o Bitcoin permite que valores sejam combinados ou divididos em transações, facilitando pagamentos de qualquer valor.
Entradas e Saídas
Cada transação no Bitcoin é composta por:
- Entradas: Representam os valores recebidos em transações anteriores.
- Saídas: Correspondem aos valores enviados, divididos entre os destinatários e, eventualmente, o troco para o remetente.
Normalmente, uma transação contém:
- Uma única entrada com valor suficiente para cobrir o pagamento.
- Ou várias entradas combinadas para atingir o valor necessário.
O valor total das saídas nunca excede o das entradas, e a diferença (se houver) pode ser retornada ao remetente como troco.
Exemplo Prático
Imagine que você tem duas entradas:
- 0,03 BTC
- 0,07 BTC
Se deseja enviar 0,08 BTC para alguém, a transação terá:
- Entrada: As duas entradas combinadas (0,03 + 0,07 BTC = 0,10 BTC).
- Saídas: Uma para o destinatário (0,08 BTC) e outra como troco para você (0,02 BTC).
Essa flexibilidade permite que o sistema funcione sem precisar manipular cada unidade mínima individualmente.
Difusão e Simplificação
A difusão de transações, onde uma depende de várias anteriores e assim por diante, não representa um problema. Não é necessário armazenar ou verificar o histórico completo de uma transação para utilizá-la, já que o registro na blockchain garante sua integridade.
10. Privacidade
O modelo bancário tradicional oferece um certo nível de privacidade, limitando o acesso às informações financeiras apenas às partes envolvidas e a um terceiro confiável (como bancos ou instituições financeiras). No entanto, o Bitcoin opera de forma diferente, pois todas as transações são publicamente registradas na blockchain. Apesar disso, a privacidade pode ser mantida utilizando chaves públicas anônimas, que desvinculam diretamente as transações das identidades das partes envolvidas.
Fluxo de Informação
- No modelo tradicional, as transações passam por um terceiro confiável que conhece tanto o remetente quanto o destinatário.
- No Bitcoin, as transações são anunciadas publicamente, mas sem revelar diretamente as identidades das partes. Isso é comparável a dados divulgados por bolsas de valores, onde informações como o tempo e o tamanho das negociações (a "fita") são públicas, mas as identidades das partes não.
Protegendo a Privacidade
Para aumentar a privacidade no Bitcoin, são adotadas as seguintes práticas:
- Chaves Públicas Anônimas: Cada transação utiliza um par de chaves diferentes, dificultando a associação com um proprietário único.
- Prevenção de Ligação: Ao usar chaves novas para cada transação, reduz-se a possibilidade de links evidentes entre múltiplas transações realizadas pelo mesmo usuário.
Riscos de Ligação
Embora a privacidade seja fortalecida, alguns riscos permanecem:
- Transações multi-entrada podem revelar que todas as entradas pertencem ao mesmo proprietário, caso sejam necessárias para somar o valor total.
- O proprietário da chave pode ser identificado indiretamente por transações anteriores que estejam conectadas.
11. Cálculos
Imagine que temos um sistema onde as pessoas (ou computadores) competem para adicionar informações novas (blocos) a um grande registro público (a cadeia de blocos ou blockchain). Este registro é como um livro contábil compartilhado, onde todos podem verificar o que está escrito.
Agora, vamos pensar em um cenário: um atacante quer enganar o sistema. Ele quer mudar informações já registradas para beneficiar a si mesmo, por exemplo, desfazendo um pagamento que já fez. Para isso, ele precisa criar uma versão alternativa do livro contábil (a cadeia de blocos dele) e convencer todos os outros participantes de que essa versão é a verdadeira.
Mas isso é extremamente difícil.
Como o Ataque Funciona
Quando um novo bloco é adicionado à cadeia, ele depende de cálculos complexos que levam tempo e esforço. Esses cálculos são como um grande quebra-cabeça que precisa ser resolvido.
- Os “bons jogadores” (nós honestos) estão sempre trabalhando juntos para resolver esses quebra-cabeças e adicionar novos blocos à cadeia verdadeira.
- O atacante, por outro lado, precisa resolver quebra-cabeças sozinho, tentando “alcançar” a cadeia honesta para que sua versão alternativa pareça válida.
Se a cadeia honesta já está vários blocos à frente, o atacante começa em desvantagem, e o sistema está projetado para que a dificuldade de alcançá-los aumente rapidamente.
A Corrida Entre Cadeias
Você pode imaginar isso como uma corrida. A cada bloco novo que os jogadores honestos adicionam à cadeia verdadeira, eles se distanciam mais do atacante. Para vencer, o atacante teria que resolver os quebra-cabeças mais rápido que todos os outros jogadores honestos juntos.
Suponha que:
- A rede honesta tem 80% do poder computacional (ou seja, resolve 8 de cada 10 quebra-cabeças).
- O atacante tem 20% do poder computacional (ou seja, resolve 2 de cada 10 quebra-cabeças).
Cada vez que a rede honesta adiciona um bloco, o atacante tem que "correr atrás" e resolver mais quebra-cabeças para alcançar.
Por Que o Ataque Fica Cada Vez Mais Improvável?
Vamos usar uma fórmula simples para mostrar como as chances de sucesso do atacante diminuem conforme ele precisa "alcançar" mais blocos:
P = (q/p)^z
- q é o poder computacional do atacante (20%, ou 0,2).
- p é o poder computacional da rede honesta (80%, ou 0,8).
- z é a diferença de blocos entre a cadeia honesta e a cadeia do atacante.
Se o atacante está 5 blocos atrás (z = 5):
P = (0,2 / 0,8)^5 = (0,25)^5 = 0,00098, (ou, 0,098%)
Isso significa que o atacante tem menos de 0,1% de chance de sucesso — ou seja, é muito improvável.
Se ele estiver 10 blocos atrás (z = 10):
P = (0,2 / 0,8)^10 = (0,25)^10 = 0,000000095, (ou, 0,0000095%).
Neste caso, as chances de sucesso são praticamente nulas.
Um Exemplo Simples
Se você jogar uma moeda, a chance de cair “cara” é de 50%. Mas se precisar de 10 caras seguidas, sua chance já é bem menor. Se precisar de 20 caras seguidas, é quase impossível.
No caso do Bitcoin, o atacante precisa de muito mais do que 20 caras seguidas. Ele precisa resolver quebra-cabeças extremamente difíceis e alcançar os jogadores honestos que estão sempre à frente. Isso faz com que o ataque seja inviável na prática.
Por Que Tudo Isso é Seguro?
- A probabilidade de sucesso do atacante diminui exponencialmente. Isso significa que, quanto mais tempo passa, menor é a chance de ele conseguir enganar o sistema.
- A cadeia verdadeira (honesta) está protegida pela força da rede. Cada novo bloco que os jogadores honestos adicionam à cadeia torna mais difícil para o atacante alcançar.
E Se o Atacante Tentar Continuar?
O atacante poderia continuar tentando indefinidamente, mas ele estaria gastando muito tempo e energia sem conseguir nada. Enquanto isso, os jogadores honestos estão sempre adicionando novos blocos, tornando o trabalho do atacante ainda mais inútil.
Assim, o sistema garante que a cadeia verdadeira seja extremamente segura e que ataques sejam, na prática, impossíveis de ter sucesso.
12. Conclusão
Propusemos um sistema de transações eletrônicas que elimina a necessidade de confiança, baseando-se em assinaturas digitais e em uma rede peer-to-peer que utiliza prova de trabalho. Isso resolve o problema do gasto duplo, criando um histórico público de transações imutável, desde que a maioria do poder computacional permaneça sob controle dos participantes honestos. A rede funciona de forma simples e descentralizada, com nós independentes que não precisam de identificação ou coordenação direta. Eles entram e saem livremente, aceitando a cadeia de prova de trabalho como registro do que ocorreu durante sua ausência. As decisões são tomadas por meio do poder de CPU, validando blocos legítimos, estendendo a cadeia e rejeitando os inválidos. Com este mecanismo de consenso, todas as regras e incentivos necessários para o funcionamento seguro e eficiente do sistema são garantidos.
Faça o download do whitepaper original em português: https://bitcoin.org/files/bitcoin-paper/bitcoin_pt_br.pdf
-
 @ cae03c48:2a7d6671
2025-05-16 16:22:47
@ cae03c48:2a7d6671
2025-05-16 16:22:47Bitcoin Magazine

Heritage Distilling Now Accepts Bitcoin and Will Hold It as a Company AssetYesterday, Heritage Distilling Holding Company, Inc. (NASDAQ: CASK), a leading U.S. craft spirits producer, announced that it will begin accepting Bitcoin as payment through its direct-to-consumer (DTC) e-commerce platform and will hold bitcoin as strategic assets under a newly approved Cryptocurrency Treasury Reserve Policy.
Heritage Distilling Implements Cryptocurrency Treasury Policy. Read the press release here: https://t.co/ve4Ttv0qGw $CASK pic.twitter.com/8MZLovwrjw
— Heritage Distilling (@HeritageDistill) May 15, 2025
The policy, approved by the company’s Board of Directors as part of a broader sales and treasury diversification strategy, was developed by the Technology and Cryptocurrency Committee, chaired by tech and digital payments leader Matt Swann. The move makes Heritage the first in the craft spirits sector to formally integrate bitcoin into both its payment and treasury operations.
“A new age of commerce is emerging, with cryptocurrencies leading the way to reduce friction between parties, buyers and sellers of goods and services,” stated Matt Swann on behalf of the Board. “Having been immersed in the convergence of technology and currencies for nearly two decades, it is exciting to see Heritage forge headfirst into the opportunity to combine the power of the consumer and cryptocurrency.”
Heritage’s decision comes amid rapidly growing public interest in digital assets. The company said it estimates that between 65 to 86 million Americans currently hold Bitcoin and crypto, and realizes the opportunity Heritage has to acquire more BTC by accepting it as payment.
“Heritage has always been an innovator and once again we are leading the way in the craft spirits space as we prepare to accept Bitcoin and Dogecoin as a form of payment for online e-commerce sales and to acquire and hold these cryptocurrencies as assets,” commented the CEO of Heritage Justin Stiefel. “As I have noted in the past, unlike traditional investors who purchase crypto with cash and are immediately subject to potential pricing volatility, as a company producing goods for sale, acceptable margins between the retail price of our products and their cost of production is expected to offset potential fluctuations in the value of cryptos we accept as payment. This provides us considerable financial flexibility as we develop product offerings for users and enthusiasts of these fiat alternatives.”
The company sees Bitcoin as a long-term strategic asset and a forward-looking step in connecting with modern consumers while also exploring new efficiencies in financial operations. Heritage is not only integrating Bitcoin as a payment method but also incorporating it into its treasury strategy.
The new Cryptocurrency Treasury Policy can be found here.
This post Heritage Distilling Now Accepts Bitcoin and Will Hold It as a Company Asset first appeared on Bitcoin Magazine and is written by Oscar Zarraga Perez.
-
 @ f9cf4e94:96abc355
2025-01-18 06:09:50
@ f9cf4e94:96abc355
2025-01-18 06:09:50Para esse exemplo iremos usar: | Nome | Imagem | Descrição | | --------------- | ------------------------------------------------------------ | ------------------------------------------------------------ | | Raspberry PI B+ |
 | Cortex-A53 (ARMv8) 64-bit a 1.4GHz e 1 GB de SDRAM LPDDR2, |
| Pen drive |
| Cortex-A53 (ARMv8) 64-bit a 1.4GHz e 1 GB de SDRAM LPDDR2, |
| Pen drive |  | 16Gb |
| 16Gb |Recomendo que use o Ubuntu Server para essa instalação. Você pode baixar o Ubuntu para Raspberry Pi aqui. O passo a passo para a instalação do Ubuntu no Raspberry Pi está disponível aqui. Não instale um desktop (como xubuntu, lubuntu, xfce, etc.).
Passo 1: Atualizar o Sistema 🖥️
Primeiro, atualize seu sistema e instale o Tor:
bash apt update apt install tor
Passo 2: Criar o Arquivo de Serviço
nrs.service🔧Crie o arquivo de serviço que vai gerenciar o servidor Nostr. Você pode fazer isso com o seguinte conteúdo:
```unit [Unit] Description=Nostr Relay Server Service After=network.target
[Service] Type=simple WorkingDirectory=/opt/nrs ExecStart=/opt/nrs/nrs-arm64 Restart=on-failure
[Install] WantedBy=multi-user.target ```
Passo 3: Baixar o Binário do Nostr 🚀
Baixe o binário mais recente do Nostr aqui no GitHub.
Passo 4: Criar as Pastas Necessárias 📂
Agora, crie as pastas para o aplicativo e o pendrive:
bash mkdir -p /opt/nrs /mnt/edriver
Passo 5: Listar os Dispositivos Conectados 🔌
Para saber qual dispositivo você vai usar, liste todos os dispositivos conectados:
bash lsblk
Passo 6: Formatando o Pendrive 💾
Escolha o pendrive correto (por exemplo,
/dev/sda) e formate-o:bash mkfs.vfat /dev/sda
Passo 7: Montar o Pendrive 💻
Monte o pendrive na pasta
/mnt/edriver:bash mount /dev/sda /mnt/edriver
Passo 8: Verificar UUID dos Dispositivos 📋
Para garantir que o sistema monte o pendrive automaticamente, liste os UUID dos dispositivos conectados:
bash blkid
Passo 9: Alterar o
fstabpara Montar o Pendrive Automáticamente 📝Abra o arquivo
/etc/fstabe adicione uma linha para o pendrive, com o UUID que você obteve no passo anterior. A linha deve ficar assim:fstab UUID=9c9008f8-f852 /mnt/edriver vfat defaults 0 0
Passo 10: Copiar o Binário para a Pasta Correta 📥
Agora, copie o binário baixado para a pasta
/opt/nrs:bash cp nrs-arm64 /opt/nrs
Passo 11: Criar o Arquivo de Configuração 🛠️
Crie o arquivo de configuração com o seguinte conteúdo e salve-o em
/opt/nrs/config.yaml:yaml app_env: production info: name: Nostr Relay Server description: Nostr Relay Server pub_key: "" contact: "" url: http://localhost:3334 icon: https://external-content.duckduckgo.com/iu/?u= https://public.bnbstatic.com/image/cms/crawler/COINCU_NEWS/image-495-1024x569.png base_path: /mnt/edriver negentropy: true
Passo 12: Copiar o Serviço para o Diretório de Systemd ⚙️
Agora, copie o arquivo
nrs.servicepara o diretório/etc/systemd/system/:bash cp nrs.service /etc/systemd/system/Recarregue os serviços e inicie o serviço
nrs:bash systemctl daemon-reload systemctl enable --now nrs.service
Passo 13: Configurar o Tor 🌐
Abra o arquivo de configuração do Tor
/var/lib/tor/torrce adicione a seguinte linha:torrc HiddenServiceDir /var/lib/tor/nostr_server/ HiddenServicePort 80 127.0.0.1:3334
Passo 14: Habilitar e Iniciar o Tor 🧅
Agora, ative e inicie o serviço Tor:
bash systemctl enable --now tor.serviceO Tor irá gerar um endereço
.onionpara o seu servidor Nostr. Você pode encontrá-lo no arquivo/var/lib/tor/nostr_server/hostname.
Observações ⚠️
- Com essa configuração, os dados serão salvos no pendrive, enquanto o binário ficará no cartão SD do Raspberry Pi.
- O endereço
.oniondo seu servidor Nostr será algo como:ws://y3t5t5wgwjif<exemplo>h42zy7ih6iwbyd.onion.
Agora, seu servidor Nostr deve estar configurado e funcionando com Tor! 🥳
Se este artigo e as informações aqui contidas forem úteis para você, convidamos a considerar uma doação ao autor como forma de reconhecimento e incentivo à produção de novos conteúdos.
-
 @ 6389be64:ef439d32
2025-01-16 15:44:06
@ 6389be64:ef439d32
2025-01-16 15:44:06Black Locust can grow up to 170 ft tall
Grows 3-4 ft. per year
Native to North America
Cold hardy in zones 3 to 8

Firewood
- BLT wood, on a pound for pound basis is roughly half that of Anthracite Coal
- Since its growth is fast, firewood can be plentiful
Timber

- Rot resistant due to a naturally produced robinin in the wood
- 100 year life span in full soil contact! (better than cedar performance)
- Fence posts
- Outdoor furniture
- Outdoor decking
- Sustainable due to its fast growth and spread
- Can be coppiced (cut to the ground)
- Can be pollarded (cut above ground)
- Its dense wood makes durable tool handles, boxes (tool), and furniture
- The wood is tougher than hickory, which is tougher than hard maple, which is tougher than oak.
- A very low rate of expansion and contraction
- Hardwood flooring
- The highest tensile beam strength of any American tree
- The wood is beautiful
Legume
- Nitrogen fixer
- Fixes the same amount of nitrogen per acre as is needed for 200-bushel/acre corn
- Black walnuts inter-planted with locust as “nurse” trees were shown to rapidly increase their growth [[Clark, Paul M., and Robert D. Williams. (1978) Black walnut growth increased when interplanted with nitrogen-fixing shrubs and trees. Proceedings of the Indiana Academy of Science, vol. 88, pp. 88-91.]]
Bees

- The edible flower clusters are also a top food source for honey bees
Shade Provider

- Its light, airy overstory provides dappled shade
- Planted on the west side of a garden it provides relief during the hottest part of the day
- (nitrogen provider)
- Planted on the west side of a house, its quick growth soon shades that side from the sun
Wind-break

- Fast growth plus it's feathery foliage reduces wind for animals, crops, and shelters
Fodder
- Over 20% crude protein
- 4.1 kcal/g of energy
- Baertsche, S.R, M.T. Yokoyama, and J.W. Hanover (1986) Short rotation, hardwood tree biomass as potential ruminant feed-chemical composition, nylon bag ruminal degradation and ensilement of selected species. J. Animal Sci. 63 2028-2043
-
 @ 975e4ad5:8d4847ce
2025-05-16 11:22:20
@ 975e4ad5:8d4847ce
2025-05-16 11:22:20Introduction
Bitcoin and torrents are two technologies that have reshaped how people share information and resources in the digital age. Both are built on decentralized principles and challenge traditional systems—torrents in the realm of file sharing, and Bitcoin in the world of finance. However, while torrents have seen a decline in popularity with the rise of streaming platforms like Netflix and HBO, many wonder whether Bitcoin will follow a similar trajectory or continue to grow as a widely adopted technology. This article explores the similarities between the two technologies, the resilience of torrents against attempts to shut them down, the reasons for their declining popularity, and why Bitcoin is likely to avoid a similar fate.
Similarities Between Torrents and Bitcoin
Torrents and Bitcoin share several key characteristics that make them unique and resilient:
-
Decentralization:\ Torrents rely on peer-to-peer (P2P) networks, where users share files directly with each other without depending on a central server. Similarly, Bitcoin operates on a blockchain—a decentralized network of nodes that maintain and validate transactions. This lack of a central authority makes both technologies difficult to control or shut down.
-
Censorship Resistance:\ Both systems are designed to withstand attempts at restriction. Torrents continue to function even when specific sites like The Pirate Bay are blocked, as the network relies on thousands of users worldwide. Bitcoin is also resistant to government bans, as transactions are processed by a global network of miners.
-
Anonymity and Pseudonymity:\ Torrents allow users to share files without revealing their identities, especially when using VPNs. Bitcoin, while pseudonymous (transactions are public but not directly tied to real-world identities), offers a similar level of privacy, attracting users seeking financial freedom.
-
Open Source:\ Both technologies are open-source, enabling developers to improve and adapt them. This fosters innovation and makes the systems more resilient to attacks.
Why Torrents Cannot Be Stopped
Torrents have persisted despite numerous attempts to curb them due to their decentralized nature. Governments and organizations have shut down sites like The Pirate Bay and Kickass Torrents, but new platforms quickly emerge. The key reasons for their resilience include:
-
P2P Architecture:\ Torrents do not rely on a single server. Every user downloading or sharing a file becomes part of the network, making it impossible to completely dismantle.
-
Global Distribution:\ Millions of users worldwide sustain torrent networks. Even if one country imposes strict regulations, others continue to support the system.
-
Adaptability:\ The torrent community quickly adapts to challenges, using VPNs, proxy servers, or the dark web to bypass restrictions.
Despite this resilience, the popularity of torrents has significantly declined in recent years, particularly among younger users.
The Decline of Torrents: Why They Lost Popularity
In the early 2000s, torrents were the primary way to access movies, music, and software. They were easy to use, free, and offered a vast array of content. However, the rise of streaming platforms like Netflix, HBO, Disney+, and Spotify has changed how people consume media. The main reasons for the decline of torrents include:
-
Convenience:\ Streaming platforms provide instant access to high-quality content without the need for downloading or specialized software. Torrents, in contrast, require technical knowledge and are often slower.
-
Legality and Safety:\ Using torrents carries risks such as viruses, malware, and legal consequences. Streaming services offer a safe and legal alternative.
-
Marketing and Accessibility:\ Platforms like Netflix invest billions in original content and marketing, attracting younger users who prefer easy access over free but risky downloads.
-
Social Shifts:\ Younger generations, raised with access to subscription services, are often unfamiliar with torrents or view them as outdated. Studies from 2023 indicate that only a small percentage of people under 25 regularly use torrents.
Despite this decline, torrents have not disappeared entirely. They are still used in regions with limited access to streaming services or by users who value free access to niche content.
Why Bitcoin Will Not Share the Fate of Torrents
Despite the similarities, Bitcoin has unique characteristics that make it more likely to achieve mainstream adoption rather than being overshadowed by alternatives. Here are the key reasons:
-
Financial Revolution:\ Bitcoin addresses problems that lack direct alternatives. It enables transactions without intermediaries, which is particularly valuable in countries with unstable currencies or limited banking access. Unlike torrents, which were replaced by more convenient streaming platforms, traditional financial systems still have flaws that Bitcoin addresses.
-
Institutional Adoption:\ Major companies like Tesla, PayPal, and Square accept Bitcoin or invest in it. Financial institutions, including JPMorgan and Goldman Sachs, are developing cryptocurrency-related products. This institutional acceptance boosts Bitcoin’s credibility and legitimacy, something torrents never achieved.
-
Limited Supply:\ Bitcoin’s fixed supply of 21 million coins makes it attractive as a store of value, similar to gold. This characteristic distinguishes it from other technologies and gives it potential for long-term growth.
-
Technological Advancements:\ The Bitcoin network evolves through improvements like the Lightning Network, which makes transactions faster and cheaper. These innovations make it competitive with traditional payment systems, whereas torrents failed to adapt to streaming technologies.
-
Global Financial Integration:\ Unlike torrents, which remained in the niche of file sharing, Bitcoin has the potential to integrate into the global financial system. Countries like El Salvador have already recognized it as legal tender, and others may follow suit.
-
Cultural and Economic Significance:\ Bitcoin is perceived not only as a technology but also as a movement for financial independence and decentralization. This ideology attracts young people and tech enthusiasts, making it more resilient to the social shifts that affected torrents.
Conclusion
Torrents and Bitcoin share common roots as decentralized technologies that challenge the status quo. However, while torrents lost popularity due to the rise of more convenient and legal alternatives, Bitcoin has the potential to avoid this fate. Its ability to address real financial problems, institutional adoption, and technological advancements make it a likely candidate for mainstream use in the future. While torrents remained a niche technology, Bitcoin is emerging as a global force that could transform how the world perceives money.
-
-
 @ 4fa5d1c4:fd6c6e41
2025-05-16 11:42:12
@ 4fa5d1c4:fd6c6e41
2025-05-16 11:42:12Bibel-Selfies
Prompts
Eva, Schlange, Apfel und Adam

A selfie of a woman resembling eve in the time of old testament, blurred body, holding an apple, kneeling in front adam. he has a shocked expression with his mouth open and wide eyes, evoking a sense of both fear and surprise. The scene appears surreal, with a huge snake behind her. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of a scene with adam and eve, possibly at a place like garden eden. The style of the photo blends surrealism with humor, similar to the style of Yasir Khan Chaudha --v 6.0Tochter des Pharao mit Mose

A selfie of the biblical figure moabite woman with her baby in front of an oasis. She is wearing traditional and has black hair. The background shows water from the desert oasis and grasses around it. In the Background a wicker basket on the water. The photo was taken in the style of a selfie shot with GoPro cameraSimon Petrus

A selfie of a man resembling Simon Petrus, wearing a white robe, surrounded by waves and thunderstorm. He has a shocked expression with his mouth open and wide eyes, evoking a sense of both humor and surprise. The scene appears surreal, with many waves behind him. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of a scene with jesus at the dead sea, possibly at a place like the sea. The style of the photo blends surrealism with humor, similar to the style of Yasir Khan Chaudhary --v 6.0Zachäus auf dem Baum
A selfie of a man resembling a roman in the time of jesus, wearing a glamorous robe, surrounded by the crown of a tree. He has a shocked expression with his mouth open and wide eyes, evoking a sense of both humor and surprise. The scene appears surreal, with many leaves behind him. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of a scene with jesus walking by, possibly at a place like the jerusalem. The style of the photo blends surrealism with humor, similar to the style of Yasir Khan Chaudhary --v 6.0Maria am Ostermorgen

A selfie of a woman resembling maria in the time of jesus, wearing a robe, kneeling in front of stone grave. she has a shocked expression with her mouth open and wide eyes, evoking a sense of both fear and surprise. The scene appears surreal, with the open glowing grave behind her. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of a scene with jesus resurrection, possibly at a place like the jerusalem. The style of the photo blends surrealism with humor, similar to the style of Yasir Khan Chaudhary --v 6.0Der verlorene Sohn bei den Schweinen

A young ancient arabic man with short hair in the time of jesus, brown eyes, and a dirty face, covered in mud from working on his pig farm, takes an amateur selfie at dusk. He is surrounded by pig stables, with a barn visible in the background and pigs seen near the front. The photo captures a raw, authentic moment, as he gazes directly into the camera with an expression of excitement or wonder. The image has a realistic style, akin to Unsplash photography, and is meant to be posted on a primitive-themed social network. The resolution of the photo is high, style of selfie with gopro --v 6.0Vater und Sohn vereint
 A selfie of an Arab father in simple garments in the time of jesus, embracing and hugging a young man. The father's face, visible in the foreground, radiates joy and relief. Only the back of the son's head is visible, as he faces away from the camera, returning the embrace in tattered clothing. In the background, a large ancient house and other family members can be seen watching from a distance, blurred. The photo is taken with a wide-angle lens using a GoPro, enhancing the dramatic and overwhelming effect of the scene --v 6.0
A selfie of an Arab father in simple garments in the time of jesus, embracing and hugging a young man. The father's face, visible in the foreground, radiates joy and relief. Only the back of the son's head is visible, as he faces away from the camera, returning the embrace in tattered clothing. In the background, a large ancient house and other family members can be seen watching from a distance, blurred. The photo is taken with a wide-angle lens using a GoPro, enhancing the dramatic and overwhelming effect of the scene --v 6.0Bartimäus

A selfie of a man resembling blind bartimaeus in the time of jesus, black and brown and white bandages on his head over his eyes and face, wearing a robe, kneeling in front of a market place. he has a shocked expression with his mouth open and wide eyes still covered with black and brown and white bandages on his head, evoking a sense of both fear and surprise. The scene appears surreal, with many sand behind him. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of a scene with jesus healing the blind, possibly at a place like the jerusalem. The style of the photo blends surrealism with humor, similar to the style of Yasir Khan Chaudha --v 6.0Daniel in der Löwengrube

A selfie of a man resembling Jesus, wearing a beige hoodie, surrounded by lions and cheetahs. He has a shocked expression with his mouth open and wide eyes, evoking a sense of both humor and surprise. The scene appears surreal, with many lions behind him. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of a lion's den, possibly at a place like the Grand Tabahar. The style of the photo blends surrealism with humor, similar to the style of Yasir Khan ChaudharyDavid und Goliath

selfie of a the boy and shepherd david holding his slingshot resembling a fight with the giant goliath in the time of old testament, wearing a glamorous sligshot focusing on his giant opponent. David has a shocked expression with his mouth open and wide eyes, evoking a sense of both humor and surprise. The scene appears surreal, with a desert surrounding him. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of the scene of David fighting with the giant goliath with his slingshot, possibly at a place like the jerusalem. The style of the photo blends surrealism with humor, similar to the style of Yasir Khan Chaudhary --v 6.0Simson im Philistertempel

A selfie of a man resembling simson in the time of old testament, wearing a glamorous beard and long hair, surrounded by thousands of ancient fighters. He has a shocked expression with his mouth open and wide eyes, evoking a sense of both humor and surprise. The scene appears surreal, with a temple surrounding him. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of a scene with jesus walking by, possibly at a place like the jerusalem. The style of the photo blends surrealism with humor, similar to the style of Yasir Khan Chaudhary --v 6.0Jona und der Wal

A selfie of a man resembling israeli jona in the time of old testament,`wearing a glamorous beard and long hair, inside the body of a whale. He has a shocked expression with his mouth open and wide eyes, evoking a sense of both humor and surprise. The scene appears surreal, with the ocean surrounding him. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of a scene in the bible. The style of the photo blends surrealism with humor, similar to the style of Yasir Khan Chaudhary
Jakob und Isaak

A selfie of a young man resembling an ancient Arabic in clothes made of skins of goats and furs of the goats, looking overwhelmed and distressed as he betrays his father, who blesses him. The scene shows a dawn sky with hints of the sunrise, evoking a surreal and dramatic atmosphere. The scene is set in ancient Jerusalem, with stone buildings. in the background an old man with a gesture of blessing, rising his hands to the sky, The photo is taken with a wide-angle lens, blending surrealism with humor. The style is reminiscent of a GoPro selfie, capturing the intense moment with a sense of both fear and surprisePetrus und der Hahn

A selfie of a man resembling ancient young arabic man saint in traditional biblical attire, being eaten by a whale,. he has a shocked expression with his mouth pressed and wide eyes, evoking a sense of both fear and surprise. The scene appears surreal, with one rooster crowing out loud behind the man. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of a scene with peter and the rooster, possibly at a place in jerusalem . The style of the photo blends surrealism with humor, go pro selfie, morning dawn near sunrise settingJosef im Brunnen

A selfie of an ancient israelian man with a magical dreamcoat clothing in a deep well, looking at the camera from above, captured in the style of a go pro selfie stickElia und die Raben

A close-up selfie of a bearded man (Elijah) in biblical clothing, smiling gratefully. He is standing near a stream in a secluded, rocky area. Several black ravens are perched on his shoulders and arms, holding pieces of bread and meat in their beaks. The scene has a warm, golden light, symbolizing God's provision. Photorealistic style, high detail.Absalom im Baum

A selfie of a man resembling of a young man (Absalom) with long hair knotted arount the branches of a large oak tree.. He has a shocked expression with his mouth open and wide eyes, evoking a sense of both humor and surprise. The scene appears surreal, with all of his hairs knotted around the tree. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of a scene of a robin hood movie in the forest . The style of the photo blends surrealism with humorRuth und Boas im Weizenfeld

A selfie of a young woman resembling Ruth, with a radiant smile and sun-kissed skin. She's standing in a golden wheat field at sunset, her arms filled with freshly gathered sheaves of wheat. Her hair is partially covered with a simple headscarf, with loose strands blowing in the wind. She has a look of joy and gratitude in her eyes. The scene appears idyllic, with wheat stalks seeming to embrace her. In the background, a distinguished older man (Boaz) can be seen watching from a distance, his expression a mix of curiosity and admiration. The photo is taken with a wide-angle lens, capturing the vastness of the field, the warmth of the setting sun, and Boaz in the distance. The setting is reminiscent of a biblical harvest scene. The style of the photo blends realism with a touch of romantic nostalgia."Bibel-Selfies" von Jörg Lohrer Lizenz: CC0 1.0
.
`
-
 @ 84b0c46a:417782f5
2025-05-16 13:09:31
@ 84b0c46a:417782f5
2025-05-16 13:09:31₍ ・ᴗ・ ₎ ₍ ・ᴗ・ ₎₍ ・ᴗ・ ₎
-
 @ 8f69ac99:4f92f5fd
2025-05-16 11:40:35
@ 8f69ac99:4f92f5fd
2025-05-16 11:40:35Há algo quase reconfortante na previsibilidade com que certos colunistas abordam Bitcoin: a cada oportunidade, repetem os mesmos chavões, reciclados com indignação moralista e embrulhados numa embalagem de falsa autoridade. O artigo publicado na Visão, com o título dramático "De criança prodígio a adolescente problemático", encaixa-se perfeitamente nesse molde.
Trata-se de uma peça de opinião que mistura factos irrelevantes com interpretações enviesadas, estatísticas sem contexto e um medo mal disfarçado de perder o monopólio da narrativa económica. A autora, Sofia Santos Machado, opta por colar em Bitcoin os desastres do chamado “mundo cripto” como se fossem parte do mesmo fenómeno — ignorando, por conveniência ou ignorância, que Bitcoin não é altcoins, não é NFTs, não é esquemas de yield exótico, e não é fintech vestida de blockchain.
Esta resposta centra-se exclusivamente em Bitcoin — um protocolo monetário aberto, incorruptível e resistente à censura, que já está a servir como salvaguarda de valor em regiões onde o sistema financeiro convencional falhou. Não me interessa defender pirâmides, tokens inflacionários ou aventuras bancárias mal calculadas.
Criticar Bitcoin é legítimo — mas fazê-lo sem saber do que se fala é apenas desinformação.
A Histeria da Água — Falar Sem Saber
O artigo abre com uma pérola alarmista sobre o consumo de água:
“Uma única transacção de bitcoin consome seis milhões de vezes mais água do que um pagamento com cartão.”
Seis. Milhões. De vezes. Resta saber se a autora escreveu isto com cara séria ou a rir-se enquanto bebia água engarrafada dos Alpes Suíços.
Fontes? Metodologia? Contexto? Estou a brincar — isto é a Visão, onde os números são decoração e os factos opcionais.
Claro que comparar transacções na camada base de Bitcoin com pagamentos "instantâneos" da rede Visa é tão rigoroso como comparar um Boeing 747 com um avião de papel porque um voa mais longe. Um artigo sério teria falado em batching, na Lightning Network, ou no facto de que Bitcoin nem sequer compete com a Visa nesse nível, nem em nenhum. Mas isso exigiria, imagine-se, investigação.
Pior ainda, não há qualquer menção ao consumo de água na extracção de ouro, nos data centers bancários, ou no treino de modelos de inteligência artificial. Pelos vistos, só Bitcoin tem de obedecer aos mandamentos ecológicos da Visão. O resto? Santa ignorância selectiva.
Criminosos e o Fantasma do Satoshi
Eis o clássico: “Bitcoin é usado por criminosos”. Um cliché bafiento tirado do baú de 2013, agora reapresentado como se fosse escândalo fresco.
Na realidade, Bitcoin é pseudónimo, não anónimo. Todas as transacções ficam gravadas num livro público — não é propriamente o esconderijo ideal para lavar dinheiro, a menos que sejas fã de disfarces em néon.
E os dados? Claríssimos. Segundo a Chainalysis e a Europol, a actividade ilícita com Bitcoin tem vindo a diminuir. Enquanto isso, os bancos — esses bastiões de confiança — continuam a ser apanhados a lavar biliões para cartéis e cleptocratas. Mas disso a Visão não fala. Devia estragar a narrativa.
O verdadeiro crime aqui é a preguiça intelectual tão profunda que quase merece uma moldura. A Visão tem um editor?
O Espantalho Energético
Como uma criança que acabou de aprender uma palavra nova, a Visão repete “consumo energético” como se fosse um pecado original. Bitcoin usa electricidade — escândalo!
Mas vejamos: o Proof-of-Work não é um defeito. É a razão pela qual Bitcoin é seguro. Não há “desperdício” — há uso, e muitas vezes com energia excedente, renovável, ou que de outro modo seria desperdiçada. É por isso que os mineiros se instalam junto a barragens remotas, queima de gás (flaring), ou parques eólicos no meio do nada — não porque odeiam o planeta, mas porque os incentivos económicos funcionam. Escrevi sobre isso aqui.
O que a Visão convenientemente ignora é que Bitcoin está a ajudar a integrar mais energia renovável nas redes, funcionando como carga flexível. Mas nuance? Trabalho de casa? Esquece lá isso.
Para uma explicação mais séria, podiam ter ouvido o podcast A Seita Bitcoin com o Daniel Batten. Mas para quê investigar?
Cripto = Bitcoin = Fraude?
Aqui chegamos ao buraco negro intelectual: enfiar tudo no mesmo saco. FTX colapsou? Culpa de Bitcoin. Um banqueiro jogou com altcoins? Culpa de Bitcoin. Scam de NFT? Deve ter sido o Satoshi.
Vamos esclarecer: Bitcoin não é “cripto”. Bitcoin é descentralizado, sem líderes, transparente. Não teve pré-mineração, não tem CEO, não promete lucros. O que o rodeia? Tokens centralizados, esquemas Ponzi, pirâmides e vaporware — precisamente o oposto do que Bitcoin representa.
Se um executivo bancário perde o dinheiro dos clientes em Dogecoins, isso é um problema dele. Bitcoin não lhe prometeu nada. Foi a ganância.
E convenhamos: os bancos tradicionais também colapsam. E não precisam de satoshis para isso. Bastam dívidas mal geridas, contabilidade criativa e uma fé cega no sistema.
Culpar Bitcoin por falcatruas “cripto” é como culpar o TCP/IP ou SMTP por emails de phishing. É preguiçoso, desonesto e diz-nos mais sobre a autora do que sobre a tecnologia.
Promessas Por Cumprir? Só Se Não Estiveres a Ver
A "jornalista" da Visão lamenta que “após 15 anos, os riscos são reais mas as promessas por cumprir”. Que promessas? Dinheiro grátis? Cafés pagos com QR codes mágicos?
Bitcoin nunca prometeu fazer cappuccinos mais rápidos. Prometeu soberania monetária, resistência à censura e um sistema previsível. E tem cumprido — diariamente, para milhões. E para o cappuccino, há sempre a Lightning Network.
Pergunta aos venezuelanos, nigerianos, peruanos ou argentinos se Bitcoin falhou. Para muitos, é a única forma de escapar à hiperinflação, ao confisco estatal e à decadência financeira.
Bitcoin não é uma app. É infra-estrutura. É uma nova camada base para o dinheiro global. Não se vê — mas protege, impõe regras e não obedece a caprichos de banqueiros centrais.
E isso assusta. Especialmente quem nunca viveu fora da bolha do euro.
Conclusão: A Visão a Gritar Contra o Progresso
No fim, o artigo da Visão é um festival de clichés, dados errados e ressentimento. Não é só enganador. É desonesto. Culpa a tecnologia pelos erros dos homens. Rejeita o futuro em nome do conforto passado.
Bitcoin não é uma varinha mágica. Mas é a fundação de uma nova liberdade financeira. Uma ferramenta para proteger valor, resistir a abusos e escapar ao controlo constante de quem acha que sabe o que é melhor para ti.
Portanto, fica aqui o desafio, Sofia: se queres criticar Bitcoin, primeiro percebe o que é. Lê o white paper. Estuda. Faz perguntas difíceis.
Caso contrário, és só mais um cão a ladrar para a trovoada — muito barulho, zero impacto.
-
 @ 91bea5cd:1df4451c
2025-05-16 11:07:16
@ 91bea5cd:1df4451c
2025-05-16 11:07:16Instruções:
- Leia cada pergunta cuidadosamente.
- Escolha a opção (A, B, C ou D) que melhor descreve você na maioria das situações. Seja o mais honesto possível.
- Anote a letra correspondente à sua escolha para cada pergunta.
- No final, some quantas vezes você escolheu cada letra (A, B, C, D).
- Veja a seção de resultados para interpretar sua pontuação.
Teste de Temperamento
1. Em um evento social (festa, reunião), como você geralmente se comporta? A) Sou o centro das atenções, converso com todos, faço piadas e animo o ambiente. B) Tomo a iniciativa, organizo atividades ou discussões, e gosto de liderar conversas. C) Prefiro observar, conversar em grupos menores ou com pessoas que já conheço bem, e analiso o ambiente. D) Sou tranquilo, ouvinte, evito chamar atenção e me adapto ao ritmo do grupo.
2. Ao enfrentar um novo projeto ou tarefa desafiadora no trabalho ou estudo: A) Fico entusiasmado com a novidade, tenho muitas ideias iniciais, mas posso me distrair facilmente. B) Defino metas claras, crio um plano de ação rápido e foco em alcançar resultados eficientemente. C) Analiso todos os detalhes, planejo meticulosamente, prevejo possíveis problemas e busco a perfeição. D) Abordo com calma, trabalho de forma constante e organizada, e prefiro um ambiente sem pressão.
3. Como você geralmente reage a críticas? A) Tento levar na esportiva, talvez faça uma piada, mas posso me magoar momentaneamente e logo esqueço. B) Defendo meu ponto de vista vigorosamente, posso ficar irritado se sentir injustiça, mas foco em corrigir o problema. C) Levo muito a sério, analiso profundamente, posso me sentir magoado por um tempo e repenso minhas ações. D) Escuto com calma, considero a crítica objetivamente e tento não levar para o lado pessoal, buscando a paz.
4. Qual seu estilo de tomada de decisão? A) Sou impulsivo, decido rapidamente com base no entusiasmo do momento, às vezes me arrependo depois. B) Sou decidido e rápido, foco no objetivo final, às vezes sem considerar todos os detalhes ou sentimentos alheios. C) Sou ponderado, analiso todas as opções e consequências, demoro para decidir buscando a melhor escolha. D) Sou cauteloso, prefiro evitar decisões difíceis, busco consenso ou adio se possível.
5. Como você lida com rotina e repetição? A) Acho entediante rapidamente, preciso de variedade e novidade constante para me manter engajado. B) Tolero se for necessário para atingir um objetivo, mas prefiro desafios e mudanças que eu controlo. C) Aprecio a ordem e a previsibilidade, me sinto confortável com rotinas bem estabelecidas. D) Adapto-me bem à rotina, acho confortável e seguro, não gosto de mudanças bruscas.
6. Em uma discussão ou conflito: A) Tento aliviar a tensão com humor, expresso meus sentimentos abertamente, mas não guardo rancor. B) Sou direto e assertivo, defendo minha posição com firmeza, posso parecer confrontador. C) Evito confronto direto, mas fico remoendo o problema, analiso os argumentos e posso guardar ressentimento. D) Busco a conciliação, tento entender todos os lados, sou diplomático e evito o conflito a todo custo.
7. Como você expressa seus sentimentos (alegria, tristeza, raiva)? A) Expresso de forma aberta, intensa e visível, minhas emoções mudam rapidamente. B) Expresso de forma direta e forte, principalmente a raiva ou a determinação, controlo emoções "fracas". C) Tendo a internalizar, minhas emoções são profundas e duradouras, posso parecer reservado. D) Sou contido na expressão emocional, mantenho a calma externamente, mesmo que sinta algo internamente.
8. Qual seu nível de energia habitual? A) Alto, sou muito ativo, falante e entusiasmado, gosto de estar em movimento. B) Muito alto e direcionado, tenho muita energia para perseguir meus objetivos e liderar. C) Variável, posso ter picos de energia para projetos que me interessam, mas também preciso de tempo quieto para recarregar. D) Moderado e constante, sou calmo, tranquilo, prefiro atividades menos agitadas.
9. Como você organiza seu espaço de trabalho ou sua casa? A) Pode ser um pouco caótico e desorganizado, com muitas coisas interessantes espalhadas. B) Organizado de forma funcional para máxima eficiência, focado no essencial para as tarefas. C) Extremamente organizado, metódico, cada coisa em seu lugar, prezo pela ordem e estética. D) Confortável e prático, não necessariamente impecável, mas funcional e sem excessos.
10. O que mais te motiva? A) Reconhecimento social, diversão, novas experiências e interações. B) Poder, controle, desafios, alcançar metas ambiciosas e resultados concretos. C) Qualidade, significado, fazer as coisas da maneira certa, compreensão profunda. D) Paz, estabilidade, harmonia nos relacionamentos, evitar estresse e pressão.
11. Como você reage a imprevistos ou mudanças de plano? A) Adapto-me rapidamente, às vezes até gosto da novidade, embora possa atrapalhar meus planos iniciais. B) Fico irritado com a perda de controle, mas rapidamente busco uma solução alternativa para manter o objetivo. C) Sinto-me desconfortável e ansioso, preciso de tempo para reavaliar e replanejar cuidadosamente. D) Aceito com calma, sou flexível e me ajusto sem muito alarde, desde que não gere conflito.
12. Qual o seu maior medo (em termos gerais)? A) Ser rejeitado, ignorado ou ficar entediado. B) Perder o controle, parecer fraco ou incompetente. C) Cometer erros graves, ser inadequado ou imperfeito. D) Conflitos, pressão, tomar decisões erradas que afetem a estabilidade.
13. Como você costuma passar seu tempo livre? A) Socializando, saindo com amigos, buscando atividades novas e divertidas. B) Engajado em atividades produtivas, esportes competitivos, planejando próximos passos. C) Lendo, estudando, refletindo, dedicando-me a hobbies que exigem atenção e cuidado. D) Relaxando em casa, assistindo filmes, lendo tranquilamente, passando tempo com a família de forma calma.
14. Ao trabalhar em equipe: A) Sou o animador, trago ideias, conecto as pessoas, mas posso ter dificuldade em focar nos detalhes. B) Assumo a liderança naturalmente, delego tarefas, foco nos resultados e mantenho todos na linha. C) Sou o planejador e o crítico construtivo, atento aos detalhes, garanto a qualidade, mas posso ser muito exigente. D) Sou o pacificador e o colaborador, ajudo a manter a harmonia, realizo minhas tarefas de forma confiável.
15. Como você lida com prazos? A) Muitas vezes deixo para a última hora, trabalho melhor sob a pressão do prazo final, mas posso me atrapalhar. B) Gosto de terminar bem antes do prazo, vejo o prazo como um desafio a ser superado rapidamente. C) Planejo o tempo cuidadosamente para cumprir o prazo com qualidade, fico ansioso se o tempo fica curto. D) Trabalho em ritmo constante para cumprir o prazo sem estresse, não gosto de correria.
16. Qual destas frases mais te descreve? A) "A vida é uma festa!" B) "Se quer algo bem feito, faça você mesmo (ou mande fazer do seu jeito)." C) "Tudo tem um propósito e um lugar certo." D) "Devagar se vai ao longe."
17. Em relação a regras e procedimentos: A) Gosto de flexibilidade, às vezes acho as regras limitantes e tento contorná-las. B) Uso as regras a meu favor para atingir objetivos, mas não hesito em quebrá-las se necessário e se eu puder controlar as consequências. C) Sigo as regras rigorosamente, acredito que elas garantem ordem e qualidade. D) Respeito as regras para evitar problemas, prefiro seguir o fluxo estabelecido.
18. Como você reage quando alguém está emocionalmente abalado? A) Tento animar a pessoa, conto piadas, ofereço distração e companhia. B) Ofereço soluções práticas para o problema, foco em resolver a situação que causou o abalo. C) Escuto com empatia, ofereço apoio profundo e tento compreender a dor da pessoa. D) Mantenho a calma, ofereço um ouvido atento e um ombro amigo, sem me deixar abalar muito.
19. Que tipo de filme ou livro você prefere? A) Comédias, aventuras, romances leves, algo que me divirta e me mantenha entretido. B) Ação, suspense, biografias de líderes, estratégias, algo que me desafie ou inspire poder. C) Dramas profundos, documentários, mistérios complexos, ficção científica filosófica, algo que me faça pensar e sentir. D) Histórias tranquilas, dramas familiares, romances amenos, natureza, algo que me relaxe e traga conforto.
20. O que é mais importante para você em um relacionamento (amizade, amoroso)? A) Diversão, cumplicidade, comunicação aberta e espontaneidade. B) Lealdade, objetivos em comum, apoio mútuo nas ambições. C) Compreensão profunda, fidelidade, apoio emocional e intelectual. D) Harmonia, estabilidade, aceitação mútua e tranquilidade.
21. Se você ganhasse na loteria, qual seria sua primeira reação/ação? A) Faria uma grande festa, viajaria pelo mundo, compraria presentes para todos! B) Investiria estrategicamente, planejaria como multiplicar o dinheiro, garantiria o controle financeiro. C) Pesquisaria as melhores opções de investimento, faria um plano detalhado de longo prazo, doaria para causas significativas. D) Guardaria a maior parte em segurança, faria algumas melhorias práticas na vida, evitaria mudanças drásticas.
22. Como você se sente em relação a riscos? A) Gosto de arriscar se a recompensa parecer divertida ou excitante, sou otimista. B) Calculo os riscos e assumo-os se acreditar que a recompensa vale a pena e que posso controlar a situação. C) Evito riscos desnecessários, prefiro a segurança e a previsibilidade, analiso tudo antes de agir. D) Desgosto de riscos, prefiro caminhos seguros e comprovados, a estabilidade é mais importante.
23. Sua memória tende a focar mais em: A) Momentos divertidos, pessoas interessantes, experiências marcantes (embora possa esquecer detalhes). B) Sucessos, fracassos (para aprender), injustiças cometidas contra você, quem te ajudou ou atrapalhou. C) Detalhes precisos, conversas significativas, erros cometidos (por você ou outros), sentimentos profundos. D) Fatos objetivos, rotinas, informações práticas, geralmente de forma neutra.
24. Quando aprende algo novo, você prefere: A) Experimentar na prática imediatamente, aprender fazendo, mesmo que cometa erros. B) Entender o objetivo e a aplicação prática rapidamente, focar no essencial para usar o conhecimento. C) Estudar a fundo a teoria, entender todos os porquês, buscar fontes confiáveis e dominar o assunto. D) Aprender em um ritmo calmo, com instruções claras e passo a passo, sem pressão.
25. Se descreva em uma palavra (escolha a que mais se aproxima): A) Entusiasmado(a) B) Determinado(a) C) Criterioso(a) D) Pacífico(a)
26. Como você lida com o silêncio em uma conversa? A) Sinto-me desconfortável e tento preenchê-lo rapidamente com qualquer assunto. B) Uso o silêncio estrategicamente ou o interrompo para direcionar a conversa. C) Posso apreciar o silêncio para refletir, ou me sentir um pouco ansioso dependendo do contexto. D) Sinto-me confortável com o silêncio, não sinto necessidade de preenchê-lo.
27. O que te deixa mais frustrado(a)? A) Tédio, falta de reconhecimento, ser ignorado. B) Incompetência alheia, falta de controle, obstáculos aos seus planos. C) Desorganização, falta de qualidade, injustiça, superficialidade. D) Conflitos interpessoais, pressão excessiva, desordem emocional.
28. Qual a sua relação com o passado, presente e futuro? A) Foco no presente e nas oportunidades imediatas, otimista em relação ao futuro, esqueço o passado facilmente. B) Foco no futuro (metas) e no presente (ações para alcançá-las), aprendo com o passado mas não me prendo a ele. C) Reflito muito sobre o passado (aprendizados, erros), analiso o presente e planejo o futuro com cautela, às vezes com preocupação. D) Vivo o presente de forma tranquila, valorizo a estabilidade e a continuidade do passado, vejo o futuro com serenidade.
29. Se você tivesse que organizar um evento, qual seria seu papel principal? A) Relações públicas, divulgação, animação, garantir que todos se divirtam. B) Coordenação geral, definição de metas, delegação de tarefas, garantir que tudo aconteça conforme o planejado (por você). C) Planejamento detalhado, logística, controle de qualidade, garantir que nada dê errado. D) Suporte, resolução de problemas de forma calma, garantir um ambiente harmonioso.
30. Qual ambiente de trabalho te agrada mais? A) Dinâmico, social, com muita interação, flexibilidade e novidades. B) Competitivo, desafiador, focado em resultados, onde eu possa liderar ou ter autonomia. C) Estruturado, quieto, onde eu possa me concentrar, com padrões claros de qualidade e tempo para análise. D) Estável, cooperativo, sem pressão, com relacionamentos harmoniosos e tarefas previsíveis.
Calculando seus Resultados:
Agora, conte quantas vezes você escolheu cada letra:
- Total de A: ______
- Total de B: ______
- Total de C: ______
- Total de D: ______
A letra (ou as letras) com a maior pontuação indica(m) seu(s) temperamento(s) dominante(s).
Interpretação dos Resultados:
-
Se sua maior pontuação foi A: Temperamento SANGUÍNEO Dominante
- Características: Você é extrovertido, otimista, sociável, comunicativo, entusiasmado e adora novidades. Gosta de ser o centro das atenções, faz amigos facilmente e contagia os outros com sua energia. É criativo e espontâneo.
- Pontos Fortes: Carismático, inspirador, adaptável, bom em iniciar relacionamentos e projetos, perdoa facilmente.
- Desafios Potenciais: Pode ser indisciplinado, desorganizado, impulsivo, superficial, ter dificuldade em focar e terminar tarefas, e ser muito dependente de aprovação externa.
-
Se sua maior pontuação foi B: Temperamento COLÉRICO Dominante
- Características: Você é enérgico, decidido, líder nato, orientado para metas e resultados. É ambicioso, assertivo, direto e não tem medo de desafios ou confrontos. Gosta de estar no controle e é muito prático.
- Pontos Fortes: Determinado, eficiente, líder natural, bom em tomar decisões e resolver problemas, autoconfiante.
- Desafios Potenciais: Pode ser impaciente, dominador, teimoso, insensível aos sentimentos alheios, propenso à raiva e a "atropelar" os outros para atingir seus objetivos.
-
Se sua maior pontuação foi C: Temperamento MELANCÓLICO Dominante
- Características: Você é introvertido, analítico, sensível, perfeccionista e profundo. É leal, dedicado, aprecia a beleza e a ordem. Tende a ser pensativo, criterioso e busca significado em tudo. Leva as coisas a sério.
- Pontos Fortes: Detalhista, organizado, criativo (em profundidade), leal, empático, comprometido com a qualidade e a justiça.
- Desafios Potenciais: Pode ser pessimista, excessivamente crítico (consigo e com os outros), indeciso (pela análise excessiva), guardar ressentimentos, ser propenso à tristeza e ao isolamento.
-
Se sua maior pontuação foi D: Temperamento FLEUMÁTICO Dominante
- Características: Você é calmo, tranquilo, equilibrado e diplomático. É observador, paciente, confiável e fácil de conviver. Evita conflitos, busca harmonia e estabilidade. É um bom ouvinte e trabalha bem sob rotina.
- Pontos Fortes: Pacífico, estável, confiável, bom ouvinte, diplomático, eficiente em tarefas rotineiras, mantém a calma sob pressão.
- Desafios Potenciais: Pode ser indeciso, procrastinador, resistente a mudanças, parecer apático ou sem entusiasmo, ter dificuldade em se impor e expressar suas próprias necessidades.
Combinações de Temperamentos:
É muito comum ter pontuações altas em duas letras. Isso indica uma combinação de temperamentos. Por exemplo:
- Sanguíneo-Colérico: Extrovertido, enérgico, líder carismático, mas pode ser impulsivo e dominador.
- Sanguíneo-Fleumático: Sociável e agradável, mas pode ter dificuldade com disciplina e iniciativa.
- Colérico-Melancólico: Líder focado e detalhista, muito capaz, mas pode ser excessivamente crítico e exigente.
- Melancólico-Fleumático: Quieto, confiável, analítico, mas pode ser indeciso e resistente a riscos.
Importante: Este teste é uma ferramenta de autoconhecimento. Ninguém se encaixa perfeitamente em uma única caixa. Use os resultados para entender melhor suas tendências naturais, seus pontos fortes e as áreas onde você pode buscar equilíbrio e desenvolvimento.
-
 @ 6389be64:ef439d32
2025-01-13 21:50:59
@ 6389be64:ef439d32
2025-01-13 21:50:59Bitcoin is more than money, more than an asset, and more than a store of value. Bitcoin is a Prime Mover, an enabler and it ignites imaginations. It certainly fueled an idea in my mind. The idea integrates sensors, computational prowess, actuated machinery, power conversion, and electronic communications to form an autonomous, machined creature roaming forests and harvesting the most widespread and least energy-dense fuel source available. I call it the Forest Walker and it eats wood, and mines Bitcoin.
I know what you're thinking. Why not just put Bitcoin mining rigs where they belong: in a hosted facility sporting electricity from energy-dense fuels like natural gas, climate-controlled with excellent data piping in and out? Why go to all the trouble building a robot that digests wood creating flammable gasses fueling an engine to run a generator powering Bitcoin miners? It's all about synergy.
Bitcoin mining enables the realization of multiple, seemingly unrelated, yet useful activities. Activities considered un-profitable if not for Bitcoin as the Prime Mover. This is much more than simply mining the greatest asset ever conceived by humankind. It’s about the power of synergy, which Bitcoin plays only one of many roles. The synergy created by this system can stabilize forests' fire ecology while generating multiple income streams. That’s the realistic goal here and requires a brief history of American Forest management before continuing.
Smokey The Bear
In 1944, the Smokey Bear Wildfire Prevention Campaign began in the United States. “Only YOU can prevent forest fires” remains the refrain of the Ad Council’s longest running campaign. The Ad Council is a U.S. non-profit set up by the American Association of Advertising Agencies and the Association of National Advertisers in 1942. It would seem that the U.S. Department of the Interior was concerned about pesky forest fires and wanted them to stop. So, alongside a national policy of extreme fire suppression they enlisted the entire U.S. population to get onboard via the Ad Council and it worked. Forest fires were almost obliterated and everyone was happy, right? Wrong.
Smokey is a fantastically successful bear so forest fires became so few for so long that the fuel load - dead wood - in forests has become very heavy. So heavy that when a fire happens (and they always happen) it destroys everything in its path because the more fuel there is the hotter that fire becomes. Trees, bushes, shrubs, and all other plant life cannot escape destruction (not to mention homes and businesses). The soil microbiology doesn’t escape either as it is burned away even in deeper soils. To add insult to injury, hydrophobic waxy residues condense on the soil surface, forcing water to travel over the ground rather than through it eroding forest soils. Good job, Smokey. Well done, Sir!
Most terrestrial ecologies are “fire ecologies”. Fire is a part of these systems’ fuel load and pest management. Before we pretended to “manage” millions of acres of forest, fires raged over the world, rarely damaging forests. The fuel load was always too light to generate fires hot enough to moonscape mountainsides. Fires simply burned off the minor amounts of fuel accumulated since the fire before. The lighter heat, smoke, and other combustion gasses suppressed pests, keeping them in check and the smoke condensed into a plant growth accelerant called wood vinegar, not a waxy cap on the soil. These fires also cleared out weak undergrowth, cycled minerals, and thinned the forest canopy, allowing sunlight to penetrate to the forest floor. Without a fire’s heat, many pine tree species can’t sow their seed. The heat is required to open the cones (the seed bearing structure) of Spruce, Cypress, Sequoia, Jack Pine, Lodgepole Pine and many more. Without fire forests can’t have babies. The idea was to protect the forests, and it isn't working.
So, in a world of fire, what does an ally look like and what does it do?
Meet The Forest Walker
For the Forest Walker to work as a mobile, autonomous unit, a solid platform that can carry several hundred pounds is required. It so happens this chassis already exists but shelved.
Introducing the Legged Squad Support System (LS3). A joint project between Boston Dynamics, DARPA, and the United States Marine Corps, the quadrupedal robot is the size of a cow, can carry 400 pounds (180 kg) of equipment, negotiate challenging terrain, and operate for 24 hours before needing to refuel. Yes, it had an engine. Abandoned in 2015, the thing was too noisy for military deployment and maintenance "under fire" is never a high-quality idea. However, we can rebuild it to act as a platform for the Forest Walker; albeit with serious alterations. It would need to be bigger, probably. Carry more weight? Definitely. Maybe replace structural metal with carbon fiber and redesign much as 3D printable parts for more effective maintenance.
The original system has a top operational speed of 8 miles per hour. For our purposes, it only needs to move about as fast as a grazing ruminant. Without the hammering vibrations of galloping into battle, shocks of exploding mortars, and drunken soldiers playing "Wrangler of Steel Machines", time between failures should be much longer and the overall energy consumption much lower. The LS3 is a solid platform to build upon. Now it just needs to be pulled out of the mothballs, and completely refitted with outboard equipment.
The Small Branch Chipper
When I say “Forest fuel load” I mean the dead, carbon containing litter on the forest floor. Duff (leaves), fine-woody debris (small branches), and coarse woody debris (logs) are the fuel that feeds forest fires. Walk through any forest in the United States today and you will see quite a lot of these materials. Too much, as I have described. Some of these fuel loads can be 8 tons per acre in pine and hardwood forests and up to 16 tons per acre at active logging sites. That’s some big wood and the more that collects, the more combustible danger to the forest it represents. It also provides a technically unlimited fuel supply for the Forest Walker system.
The problem is that this detritus has to be chewed into pieces that are easily ingestible by the system for the gasification process (we’ll get to that step in a minute). What we need is a wood chipper attached to the chassis (the LS3); its “mouth”.
A small wood chipper handling material up to 2.5 - 3.0 inches (6.3 - 7.6 cm) in diameter would eliminate a substantial amount of fuel. There is no reason for Forest Walker to remove fallen trees. It wouldn’t have to in order to make a real difference. It need only identify appropriately sized branches and grab them. Once loaded into the chipper’s intake hopper for further processing, the beast can immediately look for more “food”. This is essentially kindling that would help ignite larger logs. If it’s all consumed by Forest Walker, then it’s not present to promote an aggravated conflagration.
I have glossed over an obvious question: How does Forest Walker see and identify branches and such? LiDaR (Light Detection and Ranging) attached to Forest Walker images the local area and feed those data to onboard computers for processing. Maybe AI plays a role. Maybe simple machine learning can do the trick. One thing is for certain: being able to identify a stick and cause robotic appendages to pick it up is not impossible.
Great! We now have a quadrupedal robot autonomously identifying and “eating” dead branches and other light, combustible materials. Whilst strolling through the forest, depleting future fires of combustibles, Forest Walker has already performed a major function of this system: making the forest safer. It's time to convert this low-density fuel into a high-density fuel Forest Walker can leverage. Enter the gasification process.
The Gassifier
The gasifier is the heart of the entire system; it’s where low-density fuel becomes the high-density fuel that powers the entire system. Biochar and wood vinegar are process wastes and I’ll discuss why both are powerful soil amendments in a moment, but first, what’s gasification?
Reacting shredded carbonaceous material at high temperatures in a low or no oxygen environment converts the biomass into biochar, wood vinegar, heat, and Synthesis Gas (Syngas). Syngas consists primarily of hydrogen, carbon monoxide, and methane. All of which are extremely useful fuels in a gaseous state. Part of this gas is used to heat the input biomass and keep the reaction temperature constant while the internal combustion engine that drives the generator to produce electrical power consumes the rest.
Critically, this gasification process is “continuous feed”. Forest Walker must intake biomass from the chipper, process it to fuel, and dump the waste (CO2, heat, biochar, and wood vinegar) continuously. It cannot stop. Everything about this system depends upon this continual grazing, digestion, and excretion of wastes just as a ruminal does. And, like a ruminant, all waste products enhance the local environment.
When I first heard of gasification, I didn’t believe that it was real. Running an electric generator from burning wood seemed more akin to “conspiracy fantasy” than science. Not only is gasification real, it’s ancient technology. A man named Dean Clayton first started experiments on gasification in 1699 and in 1901 gasification was used to power a vehicle. By the end of World War II, there were 500,000 Syngas powered vehicles in Germany alone because of fossil fuel rationing during the war. The global gasification market was $480 billion in 2022 and projected to be as much as $700 billion by 2030 (Vantage Market Research). Gasification technology is the best choice to power the Forest Walker because it’s self-contained and we want its waste products.
Biochar: The Waste
Biochar (AKA agricultural charcoal) is fairly simple: it’s almost pure, solid carbon that resembles charcoal. Its porous nature packs large surface areas into small, 3 dimensional nuggets. Devoid of most other chemistry, like hydrocarbons (methane) and ash (minerals), biochar is extremely lightweight. Do not confuse it with the charcoal you buy for your grill. Biochar doesn’t make good grilling charcoal because it would burn too rapidly as it does not contain the multitude of flammable components that charcoal does. Biochar has several other good use cases. Water filtration, water retention, nutrient retention, providing habitat for microscopic soil organisms, and carbon sequestration are the main ones that we are concerned with here.
Carbon has an amazing ability to adsorb (substances stick to and accumulate on the surface of an object) manifold chemistries. Water, nutrients, and pollutants tightly bind to carbon in this format. So, biochar makes a respectable filter and acts as a “battery” of water and nutrients in soils. Biochar adsorbs and holds on to seven times its weight in water. Soil containing biochar is more drought resilient than soil without it. Adsorbed nutrients, tightly sequestered alongside water, get released only as plants need them. Plants must excrete protons (H+) from their roots to disgorge water or positively charged nutrients from the biochar's surface; it's an active process.
Biochar’s surface area (where adsorption happens) can be 500 square meters per gram or more. That is 10% larger than an official NBA basketball court for every gram of biochar. Biochar’s abundant surface area builds protective habitats for soil microbes like fungi and bacteria and many are critical for the health and productivity of the soil itself.
The “carbon sequestration” component of biochar comes into play where “carbon credits” are concerned. There is a financial market for carbon. Not leveraging that market for revenue is foolish. I am climate agnostic. All I care about is that once solid carbon is inside the soil, it will stay there for thousands of years, imparting drought resiliency, fertility collection, nutrient buffering, and release for that time span. I simply want as much solid carbon in the soil because of the undeniably positive effects it has, regardless of any climactic considerations.
Wood Vinegar: More Waste
Another by-product of the gasification process is wood vinegar (Pyroligneous acid). If you have ever seen Liquid Smoke in the grocery store, then you have seen wood vinegar. Principally composed of acetic acid, acetone, and methanol wood vinegar also contains ~200 other organic compounds. It would seem intuitive that condensed, liquefied wood smoke would at least be bad for the health of all living things if not downright carcinogenic. The counter intuition wins the day, however. Wood vinegar has been used by humans for a very long time to promote digestion, bowel, and liver health; combat diarrhea and vomiting; calm peptic ulcers and regulate cholesterol levels; and a host of other benefits.
For centuries humans have annually burned off hundreds of thousands of square miles of pasture, grassland, forest, and every other conceivable terrestrial ecosystem. Why is this done? After every burn, one thing becomes obvious: the almost supernatural growth these ecosystems exhibit after the burn. How? Wood vinegar is a component of this growth. Even in open burns, smoke condenses and infiltrates the soil. That is when wood vinegar shows its quality.
This stuff beefs up not only general plant growth but seed germination as well and possesses many other qualities that are beneficial to plants. It’s a pesticide, fungicide, promotes beneficial soil microorganisms, enhances nutrient uptake, and imparts disease resistance. I am barely touching a long list of attributes here, but you want wood vinegar in your soil (alongside biochar because it adsorbs wood vinegar as well).
The Internal Combustion Engine
Conversion of grazed forage to chemical, then mechanical, and then electrical energy completes the cycle. The ICE (Internal Combustion Engine) converts the gaseous fuel output from the gasifier to mechanical energy, heat, water vapor, and CO2. It’s the mechanical energy of a rotating drive shaft that we want. That rotation drives the electric generator, which is the heartbeat we need to bring this monster to life. Luckily for us, combined internal combustion engine and generator packages are ubiquitous, delivering a defined energy output given a constant fuel input. It’s the simplest part of the system.
The obvious question here is whether the amount of syngas provided by the gasification process will provide enough energy to generate enough electrons to run the entire system or not. While I have no doubt the energy produced will run Forest Walker's main systems the question is really about the electrons left over. Will it be enough to run the Bitcoin mining aspect of the system? Everything is a budget.
CO2 Production For Growth
Plants are lollipops. No matter if it’s a tree or a bush or a shrubbery, the entire thing is mostly sugar in various formats but mostly long chain carbohydrates like lignin and cellulose. Plants need three things to make sugar: CO2, H2O and light. In a forest, where tree densities can be quite high, CO2 availability becomes a limiting growth factor. It’d be in the forest interests to have more available CO2 providing for various sugar formation providing the organism with food and structure.
An odd thing about tree leaves, the openings that allow gasses like the ever searched for CO2 are on the bottom of the leaf (these are called stomata). Not many stomata are topside. This suggests that trees and bushes have evolved to find gasses like CO2 from below, not above and this further suggests CO2 might be in higher concentrations nearer the soil.
The soil life (bacterial, fungi etc.) is constantly producing enormous amounts of CO2 and it would stay in the soil forever (eventually killing the very soil life that produces it) if not for tidal forces. Water is everywhere and whether in pools, lakes, oceans or distributed in “moist” soils water moves towards to the moon. The water in the soil and also in the water tables below the soil rise toward the surface every day. When the water rises, it expels the accumulated gasses in the soil into the atmosphere and it’s mostly CO2. It’s a good bet on how leaves developed high populations of stomata on the underside of leaves. As the water relaxes (the tide goes out) it sucks oxygenated air back into the soil to continue the functions of soil life respiration. The soil “breathes” albeit slowly.
The gasses produced by the Forest Walker’s internal combustion engine consist primarily of CO2 and H2O. Combusting sugars produce the same gasses that are needed to construct the sugars because the universe is funny like that. The Forest Walker is constantly laying down these critical construction elements right where the trees need them: close to the ground to be gobbled up by the trees.
The Branch Drones
During the last ice age, giant mammals populated North America - forests and otherwise. Mastodons, woolly mammoths, rhinos, short-faced bears, steppe bison, caribou, musk ox, giant beavers, camels, gigantic ground-dwelling sloths, glyptodons, and dire wolves were everywhere. Many were ten to fifteen feet tall. As they crashed through forests, they would effectively cleave off dead side-branches of trees, halting the spread of a ground-based fire migrating into the tree crown ("laddering") which is a death knell for a forest.
These animals are all extinct now and forests no longer have any manner of pruning services. But, if we build drones fitted with cutting implements like saws and loppers, optical cameras and AI trained to discern dead branches from living ones, these drones could effectively take over pruning services by identifying, cutting, and dropping to the forest floor, dead branches. The dropped branches simply get collected by the Forest Walker as part of its continual mission.
The drones dock on the back of the Forest Walker to recharge their batteries when low. The whole scene would look like a grazing cow with some flies bothering it. This activity breaks the link between a relatively cool ground based fire and the tree crowns and is a vital element in forest fire control.
The Bitcoin Miner
Mining is one of four monetary incentive models, making this system a possibility for development. The other three are US Dept. of the Interior, township, county, and electrical utility company easement contracts for fuel load management, global carbon credits trading, and data set sales. All the above depends on obvious questions getting answered. I will list some obvious ones, but this is not an engineering document and is not the place for spreadsheets. How much Bitcoin one Forest Walker can mine depends on everything else. What amount of biomass can we process? Will that biomass flow enough Syngas to keep the lights on? Can the chassis support enough mining ASICs and supporting infrastructure? What does that weigh and will it affect field performance? How much power can the AC generator produce?
Other questions that are more philosophical persist. Even if a single Forest Walker can only mine scant amounts of BTC per day, that pales to how much fuel material it can process into biochar. We are talking about millions upon millions of forested acres in need of fuel load management. What can a single Forest Walker do? I am not thinking in singular terms. The Forest Walker must operate as a fleet. What could 50 do? 500?
What is it worth providing a service to the world by managing forest fuel loads? Providing proof of work to the global monetary system? Seeding soil with drought and nutrient resilience by the excretion, over time, of carbon by the ton? What did the last forest fire cost?
The Mesh Network
What could be better than one bitcoin mining, carbon sequestering, forest fire squelching, soil amending behemoth? Thousands of them, but then they would need to be able to talk to each other to coordinate position, data handling, etc. Fitted with a mesh networking device, like goTenna or Meshtastic LoRa equipment enables each Forest Walker to communicate with each other.
Now we have an interconnected fleet of Forest Walkers relaying data to each other and more importantly, aggregating all of that to the last link in the chain for uplink. Well, at least Bitcoin mining data. Since block data is lightweight, transmission of these data via mesh networking in fairly close quartered environs is more than doable. So, how does data transmit to the Bitcoin Network? How do the Forest Walkers get the previous block data necessary to execute on mining?
Back To The Chain
Getting Bitcoin block data to and from the network is the last puzzle piece. The standing presumption here is that wherever a Forest Walker fleet is operating, it is NOT within cell tower range. We further presume that the nearest Walmart Wi-Fi is hours away. Enter the Blockstream Satellite or something like it.
A separate, ground-based drone will have two jobs: To stay as close to the nearest Forest Walker as it can and to provide an antennae for either terrestrial or orbital data uplink. Bitcoin-centric data is transmitted to the "uplink drone" via the mesh networked transmitters and then sent on to the uplink and the whole flow goes in the opposite direction as well; many to one and one to many.
We cannot transmit data to the Blockstream satellite, and it will be up to Blockstream and companies like it to provide uplink capabilities in the future and I don't doubt they will. Starlink you say? What’s stopping that company from filtering out block data? Nothing because it’s Starlink’s system and they could decide to censor these data. It seems we may have a problem sending and receiving Bitcoin data in back country environs.
But, then again, the utility of this system in staunching the fuel load that creates forest fires is extremely useful around forested communities and many have fiber, Wi-Fi and cell towers. These communities could be a welcoming ground zero for first deployments of the Forest Walker system by the home and business owners seeking fire repression. In the best way, Bitcoin subsidizes the safety of the communities.
Sensor Packages
LiDaR
The benefit of having a Forest Walker fleet strolling through the forest is the never ending opportunity for data gathering. A plethora of deployable sensors gathering hyper-accurate data on everything from temperature to topography is yet another revenue generator. Data is valuable and the Forest Walker could generate data sales to various government entities and private concerns.
LiDaR (Light Detection and Ranging) can map topography, perform biomass assessment, comparative soil erosion analysis, etc. It so happens that the Forest Walker’s ability to “see,” to navigate about its surroundings, is LiDaR driven and since it’s already being used, we can get double duty by harvesting that data for later use. By using a laser to send out light pulses and measuring the time it takes for the reflection of those pulses to return, very detailed data sets incrementally build up. Eventually, as enough data about a certain area becomes available, the data becomes useful and valuable.
Forestry concerns, both private and public, often use LiDaR to build 3D models of tree stands to assess the amount of harvest-able lumber in entire sections of forest. Consulting companies offering these services charge anywhere from several hundred to several thousand dollars per square kilometer for such services. A Forest Walker generating such assessments on the fly while performing its other functions is a multi-disciplinary approach to revenue generation.
pH, Soil Moisture, and Cation Exchange Sensing
The Forest Walker is quadrupedal, so there are four contact points to the soil. Why not get a pH data point for every step it takes? We can also gather soil moisture data and cation exchange capacities at unheard of densities because of sampling occurring on the fly during commission of the system’s other duties. No one is going to build a machine to do pH testing of vast tracts of forest soils, but that doesn’t make the data collected from such an endeavor valueless. Since the Forest Walker serves many functions at once, a multitude of data products can add to the return on investment component.
Weather Data
Temperature, humidity, pressure, and even data like evapotranspiration gathered at high densities on broad acre scales have untold value and because the sensors are lightweight and don’t require large power budgets, they come along for the ride at little cost. But, just like the old mantra, “gas, grass, or ass, nobody rides for free”, these sensors provide potential revenue benefits just by them being present.
I’ve touched on just a few data genres here. In fact, the question for universities, governmental bodies, and other institutions becomes, “How much will you pay us to attach your sensor payload to the Forest Walker?”
Noise Suppression
Only you can prevent Metallica filling the surrounds with 120 dB of sound. Easy enough, just turn the car stereo off. But what of a fleet of 50 Forest Walkers operating in the backcountry or near a township? 500? 5000? Each one has a wood chipper, an internal combustion engine, hydraulic pumps, actuators, and more cooling fans than you can shake a stick at. It’s a walking, screaming fire-breathing dragon operating continuously, day and night, twenty-four hours a day, three hundred sixty-five days a year. The sound will negatively affect all living things and that impacts behaviors. Serious engineering consideration and prowess must deliver a silencing blow to the major issue of noise.
It would be foolish to think that a fleet of Forest Walkers could be silent, but if not a major design consideration, then the entire idea is dead on arrival. Townships would not allow them to operate even if they solved the problem of widespread fuel load and neither would governmental entities, and rightly so. Nothing, not man nor beast, would want to be subjected to an eternal, infernal scream even if it were to end within days as the fleet moved further away after consuming what it could. Noise and heat are the only real pollutants of this system; taking noise seriously from the beginning is paramount.
Fire Safety
A “fire-breathing dragon” is not the worst description of the Forest Walker. It eats wood, combusts it at very high temperatures and excretes carbon; and it does so in an extremely flammable environment. Bad mix for one Forest Walker, worse for many. One must take extreme pains to ensure that during normal operation, a Forest Walker could fall over, walk through tinder dry brush, or get pounded into the ground by a meteorite from Krypton and it wouldn’t destroy epic swaths of trees and baby deer. I envision an ultimate test of a prototype to include dowsing it in grain alcohol while it’s wrapped up in toilet paper like a pledge at a fraternity party. If it runs for 72 hours and doesn’t set everything on fire, then maybe outside entities won’t be fearful of something that walks around forests with a constant fire in its belly.
The Wrap
How we think about what can be done with and adjacent to Bitcoin is at least as important as Bitcoin’s economic standing itself. For those who will tell me that this entire idea is without merit, I say, “OK, fine. You can come up with something, too.” What can we plug Bitcoin into that, like a battery, makes something that does not work, work? That’s the lesson I get from this entire exercise. No one was ever going to hire teams of humans to go out and "clean the forest". There's no money in that. The data collection and sales from such an endeavor might provide revenues over the break-even point but investment demands Alpha in this day and age. But, plug Bitcoin into an almost viable system and, voilà! We tip the scales to achieve lift-off.
Let’s face it, we haven’t scratched the surface of Bitcoin’s forcing function on our minds. Not because it’s Bitcoin, but because of what that invention means. The question that pushes me to approach things this way is, “what can we create that one system’s waste is another system’s feedstock?” The Forest Walker system’s only real waste is the conversion of low entropy energy (wood and syngas) into high entropy energy (heat and noise). All other output is beneficial to humanity.
Bitcoin, I believe, is the first product of a new mode of human imagination. An imagination newly forged over the past few millennia of being lied to, stolen from, distracted and otherwise mis-allocated to a black hole of the nonsensical. We are waking up.
What I have presented is not science fiction. Everything I have described here is well within the realm of possibility. The question is one of viability, at least in terms of the detritus of the old world we find ourselves departing from. This system would take a non-trivial amount of time and resources to develop. I think the system would garner extensive long-term contracts from those who have the most to lose from wildfires, the most to gain from hyperaccurate data sets, and, of course, securing the most precious asset in the world. Many may not see it that way, for they seek Alpha and are therefore blind to other possibilities. Others will see only the possibilities; of thinking in a new way, of looking at things differently, and dreaming of what comes next.
-
 @ e3ba5e1a:5e433365
2025-01-13 16:47:27
@ e3ba5e1a:5e433365
2025-01-13 16:47:27My blog posts and reading material have both been on a decidedly economics-heavy slant recently. The topic today, incentives, squarely falls into the category of economics. However, when I say economics, I’m not talking about “analyzing supply and demand curves.” I’m talking about the true basis of economics: understanding how human beings make decisions in a world of scarcity.
A fair definition of incentive is “a reward or punishment that motivates behavior to achieve a desired outcome.” When most people think about economic incentives, they’re thinking of money. If I offer my son $5 if he washes the dishes, I’m incentivizing certain behavior. We can’t guarantee that he’ll do what I want him to do, but we can agree that the incentive structure itself will guide and ultimately determine what outcome will occur.
The great thing about monetary incentives is how easy they are to talk about and compare. “Would I rather make $5 washing the dishes or $10 cleaning the gutters?” But much of the world is incentivized in non-monetary ways too. For example, using the “punishment” half of the definition above, I might threaten my son with losing Nintendo Switch access if he doesn’t wash the dishes. No money is involved, but I’m still incentivizing behavior.
And there are plenty of incentives beyond our direct control! My son is also incentivized to not wash dishes because it’s boring, or because he has some friends over that he wants to hang out with, or dozens of other things. Ultimately, the conflicting array of different incentive structures placed on him will ultimately determine what actions he chooses to take.
Why incentives matter
A phrase I see often in discussions—whether they are political, parenting, economic, or business—is “if they could just do…” Each time I see that phrase, I cringe a bit internally. Usually, the underlying assumption of the statement is “if people would behave contrary to their incentivized behavior then things would be better.” For example:
- If my kids would just go to bed when I tell them, they wouldn’t be so cranky in the morning.
- If people would just use the recycling bin, we wouldn’t have such a landfill problem.
- If people would just stop being lazy, our team would deliver our project on time.
In all these cases, the speakers are seemingly flummoxed as to why the people in question don’t behave more rationally. The problem is: each group is behaving perfectly rationally.
- The kids have a high time preference, and care more about the joy of staying up now than the crankiness in the morning. Plus, they don’t really suffer the consequences of morning crankiness, their parents do.
- No individual suffers much from their individual contribution to a landfill. If they stopped growing the size of the landfill, it would make an insignificant difference versus the amount of effort they need to engage in to properly recycle.
- If a team doesn’t properly account for the productivity of individuals on a project, each individual receives less harm from their own inaction. Sure, the project may be delayed, company revenue may be down, and they may even risk losing their job when the company goes out of business. But their laziness individually won’t determine the entirety of that outcome. By contrast, they greatly benefit from being lazy by getting to relax at work, go on social media, read a book, or do whatever else they do when they’re supposed to be working.

My point here is that, as long as you ignore the reality of how incentives drive human behavior, you’ll fail at getting the outcomes you want.
If everything I wrote up until now made perfect sense, you understand the premise of this blog post. The rest of it will focus on a bunch of real-world examples to hammer home the point, and demonstrate how versatile this mental model is.
Running a company
Let’s say I run my own company, with myself as the only employee. My personal revenue will be 100% determined by my own actions. If I decide to take Tuesday afternoon off and go fishing, I’ve chosen to lose that afternoon’s revenue. Implicitly, I’ve decided that the enjoyment I get from an afternoon of fishing is greater than the potential revenue. You may think I’m being lazy, but it’s my decision to make. In this situation, the incentive–money–is perfectly aligned with my actions.
Compare this to a typical company/employee relationship. I might have a bank of Paid Time Off (PTO) days, in which case once again my incentives are relatively aligned. I know that I can take off 15 days throughout the year, and I’ve chosen to use half a day for the fishing trip. All is still good.
What about unlimited time off? Suddenly incentives are starting to misalign. I don’t directly pay a price for not showing up to work on Tuesday. Or Wednesday as well, for that matter. I might ultimately be fired for not doing my job, but that will take longer to work its way through the system than simply not making any money for the day taken off.
Compensation overall falls into this misaligned incentive structure. Let’s forget about taking time off. Instead, I work full time on a software project I’m assigned. But instead of using the normal toolchain we’re all used to at work, I play around with a new programming language. I get the fun and joy of playing with new technology, and potentially get to pad my resume a bit when I’m ready to look for a new job. But my current company gets slower results, less productivity, and is forced to subsidize my extracurricular learning.
When a CEO has a bonus structure based on profitability, he’ll do everything he can to make the company profitable. This might include things that actually benefit the company, like improving product quality, reducing internal red tape, or finding cheaper vendors. But it might also include destructive practices, like slashing the R\&D budget to show massive profits this year, in exchange for a catastrophe next year when the next version of the product fails to ship.

Or my favorite example. My parents owned a business when I was growing up. They had a back office where they ran operations like accounting. All of the furniture was old couches from our house. After all, any money they spent on furniture came right out of their paychecks! But in a large corporate environment, each department is generally given a budget for office furniture, a budget which doesn’t roll over year-to-year. The result? Executives make sure to spend the entire budget each year, often buying furniture far more expensive than they would choose if it was their own money.
There are plenty of details you can quibble with above. It’s in a company’s best interest to give people downtime so that they can come back recharged. Having good ergonomic furniture can in fact increase productivity in excess of the money spent on it. But overall, the picture is pretty clear: in large corporate structures, you’re guaranteed to have mismatches between the company’s goals and the incentive structure placed on individuals.
Using our model from above, we can lament how lazy, greedy, and unethical the employees are for doing what they’re incentivized to do instead of what’s right. But that’s simply ignoring the reality of human nature.
Moral hazard
Moral hazard is a situation where one party is incentivized to take on more risk because another party will bear the consequences. Suppose I tell my son when he turns 21 (or whatever legal gambling age is) that I’ll cover all his losses for a day at the casino, but he gets to keep all the winnings.
What do you think he’s going to do? The most logical course of action is to place the largest possible bets for as long as possible, asking me to cover each time he loses, and taking money off the table and into his bank account each time he wins.

But let’s look at a slightly more nuanced example. I go to a bathroom in the mall. As I’m leaving, I wash my hands. It will take me an extra 1 second to turn off the water when I’m done washing. That’s a trivial price to pay. If I don’t turn off the water, the mall will have to pay for many liters of wasted water, benefiting no one. But I won’t suffer any consequences at all.
This is also a moral hazard, but most people will still turn off the water. Why? Usually due to some combination of other reasons such as:
- We’re so habituated to turning off the water that we don’t even consider not turning it off. Put differently, the mental effort needed to not turn off the water is more expensive than the 1 second of time to turn it off.
- Many of us have been brought up with a deep guilt about wasting resources like water. We have an internal incentive structure that makes the 1 second to turn off the water much less costly than the mental anguish of the waste we created.
- We’re afraid we’ll be caught by someone else and face some kind of social repercussions. (Or maybe more than social. Are you sure there isn’t a law against leaving the water tap on?)
Even with all that in place, you may notice that many public bathrooms use automatic water dispensers. Sure, there’s a sanitation reason for that, but it’s also to avoid this moral hazard.
A common denominator in both of these is that the person taking the action that causes the liability (either the gambling or leaving the water on) is not the person who bears the responsibility for that liability (the father or the mall owner). Generally speaking, the closer together the person making the decision and the person incurring the liability are, the smaller the moral hazard.
It’s easy to demonstrate that by extending the casino example a bit. I said it was the father who was covering the losses of the gambler. Many children (though not all) would want to avoid totally bankrupting their parents, or at least financially hurting them. Instead, imagine that someone from the IRS shows up at your door, hands you a credit card, and tells you you can use it at a casino all day, taking home all the chips you want. The money is coming from the government. How many people would put any restriction on how much they spend?
And since we’re talking about the government already…
Government moral hazards
As I was preparing to write this blog post, the California wildfires hit. The discussions around those wildfires gave a huge number of examples of moral hazards. I decided to cherry-pick a few for this post.
The first and most obvious one: California is asking for disaster relief funds from the federal government. That sounds wonderful. These fires were a natural disaster, so why shouldn’t the federal government pitch in and help take care of people?
The problem is, once again, a moral hazard. In the case of the wildfires, California and Los Angeles both had ample actions they could have taken to mitigate the destruction of this fire: better forest management, larger fire department, keeping the water reservoirs filled, and probably much more that hasn’t come to light yet.
If the federal government bails out California, it will be a clear message for the future: your mistakes will be fixed by others. You know what kind of behavior that incentivizes? More risky behavior! Why spend state funds on forest management and extra firefighters—activities that don’t win politicians a lot of votes in general—when you could instead spend it on a football stadium, higher unemployment payments, or anything else, and then let the feds cover the cost of screw-ups.
You may notice that this is virtually identical to the 2008 “too big to fail” bail-outs. Wall Street took insanely risky behavior, reaped huge profits for years, and when they eventually got caught with their pants down, the rest of us bailed them out. “Privatizing profits, socializing losses.”

And here’s the absolute best part of this: I can’t even truly blame either California or Wall Street. (I mean, I do blame them, I think their behavior is reprehensible, but you’ll see what I mean.) In a world where the rules of the game implicitly include the bail-out mentality, you would be harming your citizens/shareholders/investors if you didn’t engage in that risky behavior. Since everyone is on the hook for those socialized losses, your best bet is to maximize those privatized profits.
There’s a lot more to government and moral hazard, but I think these two cases demonstrate the crux pretty solidly. But let’s leave moral hazard behind for a bit and get to general incentivization discussions.
Non-monetary competition
At least 50% of the economics knowledge I have comes from the very first econ course I took in college. That professor was amazing, and had some very colorful stories. I can’t vouch for the veracity of the two I’m about to share, but they definitely drive the point home.
In the 1970s, the US had an oil shortage. To “fix” this problem, they instituted price caps on gasoline, which of course resulted in insufficient gasoline. To “fix” this problem, they instituted policies where, depending on your license plate number, you could only fill up gas on certain days of the week. (Irrelevant detail for our point here, but this just resulted in people filling up their tanks more often, no reduction in gas usage.)
Anyway, my professor’s wife had a friend. My professor described in great detail how attractive this woman was. I’ll skip those details here since this is a PG-rated blog. In any event, she never had any trouble filling up her gas tank any day of the week. She would drive up, be told she couldn’t fill up gas today, bat her eyes at the attendant, explain how helpless she was, and was always allowed to fill up gas.
This is a demonstration of non-monetary compensation. Most of the time in a free market, capitalist economy, people are compensated through money. When price caps come into play, there’s a limit to how much monetary compensation someone can receive. And in that case, people find other ways of competing. Like this woman’s case: through using flirtatious behavior to compensate the gas station workers to let her cheat the rules.
The other example was much more insidious. Santa Monica had a problem: it was predominantly wealthy and white. They wanted to fix this problem, and decided to put in place rent controls. After some time, they discovered that Santa Monica had become wealthier and whiter, the exact opposite of their desired outcome. Why would that happen?
Someone investigated, and ended up interviewing a landlady that demonstrated the reason. She was an older white woman, and admittedly racist. Prior to the rent controls, she would list her apartments in the newspaper, and would be legally obligated to rent to anyone who could afford it. Once rent controls were in place, she took a different tact. She knew that she would only get a certain amount for the apartment, and that the demand for apartments was higher than the supply. That meant she could be picky.
She ended up finding tenants through friends-of-friends. Since it wasn’t an official advertisement, she wasn’t legally required to rent it out if someone could afford to pay. Instead, she got to interview people individually and then make them an offer. Normally, that would have resulted in receiving a lower rental price, but not under rent controls.
So who did she choose? A young, unmarried, wealthy, white woman. It made perfect sense. Women were less intimidating and more likely to maintain the apartment better. Wealthy people, she determined, would be better tenants. (I have no idea if this is true in practice or not, I’m not a landlord myself.) Unmarried, because no kids running around meant less damage to the property. And, of course, white. Because she was racist, and her incentive structure made her prefer whites.
You can deride her for being racist, I won’t disagree with you. But it’s simply the reality. Under the non-rent-control scenario, her profit motive for money outweighed her racism motive. But under rent control, the monetary competition was removed, and she was free to play into her racist tendencies without facing any negative consequences.
Bureaucracy
These were the two examples I remember for that course. But non-monetary compensation pops up in many more places. One highly pertinent example is bureaucracies. Imagine you have a government office, or a large corporation’s acquisition department, or the team that apportions grants at a university. In all these cases, you have a group of people making decisions about handing out money that has no monetary impact on them. If they give to the best qualified recipients, they receive no raises. If they spend the money recklessly on frivolous projects, they face no consequences.
Under such an incentivization scheme, there’s little to encourage the bureaucrats to make intelligent funding decisions. Instead, they’ll be incentivized to spend the money where they recognize non-monetary benefits. This is why it’s so common to hear about expensive meals, gift bags at conferences, and even more inappropriate ways of trying to curry favor with those that hold the purse strings.
Compare that ever so briefly with the purchases made by a small mom-and-pop store like my parents owned. Could my dad take a bribe to buy from a vendor who’s ripping him off? Absolutely he could! But he’d lose more on the deal than he’d make on the bribe, since he’s directly incentivized by the deal itself. It would make much more sense for him to go with the better vendor, save $5,000 on the deal, and then treat himself to a lavish $400 meal to celebrate.
Government incentivized behavior
This post is getting longer in the tooth than I’d intended, so I’ll finish off with this section and make it a bit briefer. Beyond all the methods mentioned above, government has another mechanism for modifying behavior: through directly changing incentives via legislation, regulation, and monetary policy. Let’s see some examples:
- Artificial modification of interest rates encourages people to take on more debt than they would in a free capital market, leading to malinvestment and a consumer debt crisis, and causing the boom-bust cycle we all painfully experience.
- Going along with that, giving tax breaks on interest payments further artificially incentivizes people to take on debt that they wouldn’t otherwise.
- During COVID-19, at some points unemployment benefits were greater than minimum wage, incentivizing people to rather stay home and not work than get a job, leading to reduced overall productivity in the economy and more printed dollars for benefits. In other words, it was a perfect recipe for inflation.
- The tax code gives deductions to “help” people. That might be true, but the real impact is incentivizing people to make decisions they wouldn’t have otherwise. For example, giving out tax deductions on children encourages having more kids. Tax deductions on childcare and preschools incentivizes dual-income households. Whether or not you like the outcomes, it’s clear that it’s government that’s encouraging these outcomes to happen.
- Tax incentives cause people to engage in behavior they wouldn’t otherwise (daycare+working mother, for example).
- Inflation means that the value of your money goes down over time, which encourages people to spend more today, when their money has a larger impact. (Milton Friedman described this as high living.)
Conclusion
The idea here is simple, and fully encapsulated in the title: incentives determine outcomes. If you want to know how to get a certain outcome from others, incentivize them to want that to happen. If you want to understand why people act in seemingly irrational ways, check their incentives. If you’re confused why leaders (and especially politicians) seem to engage in destructive behavior, check their incentives.
We can bemoan these realities all we want, but they are realities. While there are some people who have a solid internal moral and ethical code, and that internal code incentivizes them to behave against their externally-incentivized interests, those people are rare. And frankly, those people are self-defeating. People should take advantage of the incentives around them. Because if they don’t, someone else will.
(If you want a literary example of that last comment, see the horse in Animal Farm.)
How do we improve the world under these conditions? Make sure the incentives align well with the overall goals of society. To me, it’s a simple formula:
- Focus on free trade, value for value, as the basis of a society. In that system, people are always incentivized to provide value to other people.
- Reduce the size of bureaucracies and large groups of all kinds. The larger an organization becomes, the farther the consequences of decisions are from those who make them.
- And since the nature of human beings will be to try and create areas where they can control the incentive systems to their own benefits, make that as difficult as possible. That comes in the form of strict limits on government power, for example.
And even if you don’t want to buy in to this conclusion, I hope the rest of the content was educational, and maybe a bit entertaining!
-
 @ e4950c93:1b99eccd
2025-05-16 10:14:50
@ e4950c93:1b99eccd
2025-05-16 10:14:50Joha est une marque danoise qui crée des vêtements en laine mérinos, coton biologique, viscose de bambou biologique et soie pour les bébés, les enfants et les femmes.
Matières naturelles utilisées dans les produits
- Coton (biologique)
- Laine (mérinos)
- Soie
- Cellulose régénérée (cupra, lyocell, modal, rayonne, viscose) (bambou biologique)
⚠️ Attention, certains produits de cette marque contiennent des matières non naturelles, dont : - Elasthanne, lycra, spandex - Polyamides, nylon
Catégories de produits proposés
Cette marque propose des produits intégralement en matière naturelle dans les catégories suivantes :
Vêtements
- Tailles vêtements: bébés, enfants, femmes
- Sous-vêtements: culottes
- Une pièce:
- Hauts: débardeurs, t-shirts
- Bas: pantalons, leggings
- Tête et mains: bonnets, cagoules, moufles
- Nuit: pyjamas
Chaussures
- Tailles chaussures: chaussures bébé
- Chaussons: botillons
Autres informations
- Certification Oeko-Tex Standard 100
- Certification Woolmark
- Déclaration de laine de mouton sans mulesing et de bien-être animal (Südwolle group GmbH)
👉 En savoir plus sur le site de la marque
Où trouver leurs produits ?
- Luna & Curious (en anglais, zone de livraison : RU et international)
- Niddle Noddle (en anglais, zone de livraison : RU et international)
- Chlidren Salon (en anglais, zone de livraison : RU et international)
- Lieblings Paris
Cet article est publié sur origine-nature.com 🌐 See this article in English
📝 Tu peux contribuer à cette fiche en suggérant une modification en commentaire.
🗣️ Tu utilises les produits de cette marque ? Partage ton avis en commentaire.
⚡ Heureu-x-se de trouver cette information ? Soutiens le projet en faisant un don, pour remercier les contribut-eur-ice-s.
-
 @ 79008e78:dfac9395
2025-03-22 11:22:07
@ 79008e78:dfac9395
2025-03-22 11:22:07Keys and Addresses
อลิซต้องการจ่ายเงินให้กับบ๊อบแต่โหนดของบิตคอยน์ในระบบหลายพันโหนดจะตรวจสอบธุรกรรมของเธอ โดยไม่รู้ว่าอลิซหรือบ๊อบเป็นใคร ละเราต้องการรักษาความเป็นส่วนตัวของพวกเขาไว้เช่นนี้ อลิซจำเป็นต้องสื่อสารว่าบ๊อบควรได้รับบิตคอยน์บางส่วนของเธอโดยไม่เชื่อมโยงแง่มุมใด ๆ ของธุรกรรมนั้นกับตัวตนในโลกจริงของบ๊อบ หรือกับการชำระเงินด้วยบิตคอยน์ครั้งอื่น ๆ ที่บ๊อบได้รับ อลิซใช้ต้องทำให้มั่นใจว่ามีเพียแค่บ๊อบเท่านั้นที่สามารถใช้จ่ายบิตคอยน์ที่เขาได้รับต่อไปได้
ในบิตคอยน์ไวท์เปเปอร์ได้อธิบายถึงแผนการที่เรียบง่ายมากสำหรับการบรรลุเป้าหมายเหล่านั้น ดังที่แสดงในรูปด้านล่างนี้

ตัวของผู้รับอย่างบ๊อบเองจะได้รับบิตคอยน์ไปยัง public key ของเขาที่ถูกลงนามโดยผู้จ่ายอย่างอลิซ โดยบิตคอยน์ที่อลิซนำมาจ่ายนั้นก็ได้รับมาจากที่ใครสักคนส่งมาที่ public key ของเธอ และเธอก็ใช้ private key ของเธอในการลงนามเพื่อสร้างลายเซ็นของเธอและโหนดต่าง ๆ ของบิตคอยน์จะทำการตรวจสอบว่าลายเซ็นของอลิซผูกมัดกับเอาต์พุตของฟังก์ชันแฮชซึ่งตัวมันเองผูกมัดกับ public key ของบ๊อบและรายละเอียดธุรกรรมอื่นๆ
ในบทนี้เราจะพิจารณาpublic key private key Digital signatrue และ hash function จากนั้นใช้ทั้งหมดนี้ร่วมกันเพื่ออธิบาย address ที่ใช้โดยซอฟต์แวร์บิตคอยน์สมัยใหม่
Public Key Cryptography (การเข้ารหัสของ public key)
ระบบเข้ารหัสของ public key ถูกคิดค้นขึ้นในทศวรรษ 1970 มาจากรากฐานทางคณิตศาสตร์สำหรับความปลอดภัยของคอมพิวเตอร์และข้อมูลสมัยใหม่
นับตั้งแต่การคิดค้นระบบเข้ารหัส public key ได้มีการค้นพบฟังก์ชันทางคณิตศาสตร์ที่เหมาะสมหลายอย่าง เช่น การยกกำลังของจำนวนเฉพาะและการคูณของเส้นโค้งวงรี โดยฟังก์ชันทางคณิตศาสตร์เหล่านี้สามารถคำนวณได้ง่ายในทิศทางหนึ่ง แต่เป็นไปไม่ได้ที่จะคำนวณในทิศทางตรงกันข้ามโดยใช้คอมพิวเตอร์และอัลกอริทึมที่มีอยู่ในปัจจุบัน จากฟังก์ชันทางคณิตศาสตร์เหล่านี้ การเข้ารหัสลับช่วยให้สามารถสร้างลายเซ็นดิจิทัลที่ไม่สามารถปลอมแปลงได้และบิตคอยน์ได้ใช้การบวกและการคูณของเส้นโค้งวงรีเป็นพื้นฐานสำหรับการเข้ารหัสลับของมัน
ในบิตคอยน์ เราสามารถใช้ระบบเข้ารหัส public key เพื่อสร้างคู่กุญแจที่ควบคุมการเข้าถึงบิตคอยน์ คู่กุญแจประกอบด้วย private key และ public key ที่ได้มาจาก private key public keyใช้สำหรับรับเงิน และ private key ใช้สำหรับลงนามในธุรกรรมเพื่อใช้จ่ายเงิน
ความสัมพันธ์ทางคณิตศาสตร์ระหว่าง public key และ private key ที่ช่วยให้ private key สามารถใช้สร้างลายเซ็นบนข้อความได้ ลายเซ็นเหล่านี้สามารถตรวจสอบความถูกต้องกับ public key ได้โดยไม่เปิดเผย private key
TIP: ในการใช้งานซอฟแวร์กระเป๋าเงินบิตคอยน์บสงอัน จะทำการเก็บ private key และ public key ถูกเก็บไว้ด้วยกันในรูปแบบคู่กุญแจเพื่อความสะดวก แต่อย่างไรก็ตาม public key สามารถคำนวณได้จาก private key ดังนั้นการเก็บเพียง private key เท่านั้นก็เป็นไปได้เช่นกัน
bitcoin wallet มักจะทำการรวบรวมคู่กุญแต่ละคู่ ซึ่งจะประกอบไปด้วย private key และ public key โดย private key จะเป็นตัวเลขที่ถูกสุ่มเลือกขึ้นมา และเราขะใช้เส้นโค้งวงรี ซึ่งเป็นฟังก์ชันการเข้ารหัสทางเดียว เพื่อสร้าง public key ขึ้นมา
ทำไมจึงใช้การเข้ารหัสแบบอสมมาตร
ทำไมการเข้ารหัสแบบอสมมาตรจึงถูกใช้บิตคอยน์? มันไม่ได้ถูกใช้เพื่อ "เข้ารหัส" (ทำให้เป็นความลับ) ธุรกรรม แต่คุณสมบัติที่มีประโยชน์ของการเข้ารหัสแบบอสมมาตรคือความสามารถในการสร้าง ลายเซ็นดิจิทัล private key สามารถนำไปใช้กับธุรกรรมเพื่อสร้างลายเซ็นเชิงตัวเลข ลายเซ็นนี้สามารถสร้างได้เฉพาะโดยผู้ที่มีความเกี่ยวข้องกับ private key เท่านั้น แต่อย่างไรก็ตาม ทุกคนที่สามารถเข้าถึง public key และธุรกรรมสามารถใช้สิ่งเหล่านี้เพื่อ ตรวจสอบ ลายเซ็นได้ คุณสมบัติที่มีประโยชน์นี้ของการเข้ารหัสแบบอสมมาตรทำให้ทุกคนสามารถตรวจสอบลายเซ็นทุกรายการในทุกธุรกรรมได้ ในขณะที่มั่นใจว่าเฉพาะเจ้าของ private key เท่านั้นที่สามารถสร้างลายเซ็นที่ถูกต้องได้
Private keys
private key เป็นเพียงตัวเลขที่ถูกสุ่มขึ้น และการควบคุม private key ก็เป็นรากฐานสำคัญที่ทำให้เจ้าชองกุญแจดอกนี้สามารถควบคุมบิตคอยน์ทั้งหมดที่มีความเกี่ยวข้องกับ public key ที่คู่กัน private key นั้นใช้ในการสร้างลายเซ็นดิจิทัลที่ใช้ในการเคลื่อนย้ายบิตคอยน์ เราจำเป็นต้องเก็บ private key ให้เป็นความลับตลอดเวลา เพราะการเปิดเผยมันให้กับบุคคลอื่นนั้นก็เปรียบเสมือนกับการนำอำนาจในการควบคุมบิตคอยน์ไปให้แก่เขา นอกจากนี้ private key ยังจำเป็นต้องได้รับการสำรองข้อมูลและป้องกันจากการสูญหายโดยไม่ตั้งใจ เพราะหากเราได้ทำมันสูญหายไป จะไม่สามารถกู้คืนได้ และบิตคอยน์เหล่านั้นจะถูกปกป้องโดยกุญแจที่หายไปนั้นตลอดกาลเช่นกัน
TIP: private key ของบิตคอยน์นั้นเป็นเพียงแค่ตัวเลข คุณสามารถสร้างมันได้โดยใช้เพียงเหรียญ ดินสอ และกระดาษ โดยการโยนเหรียญเพียง 256 ครั้งจะทำให้คุณได้เลขฐานสองที่สามารถใช้เป็น private key ของบิตคอยน์ จากนั้นคุณสามารถใช้มันในการคำนวณหา public key แต่อย่างไรก็ตาม โปรดระมัดระวังเกี่ยวกับการเลือใช้วิธีการสุ่มที่ไม่สมบูรณ์ เพราะนั่นอาจลดความปลอดภัยของ private key และบิตคอยน์ที่มัมปกป้องอยู่อย่างมีนัยสำคัญ
ขั้นตอนแรกและสำคัญที่สุดในการสร้างกุญแจคือการหาแหล่งที่มาของความสุ่มที่ปลอดภัย (ซึ่งเรียกว่า เอนโทรปี) การสร้างกุญแจของบิตคอยน์นั้นเกือบเหมือนกับ "เลือกตัวเลขระหว่าง 1 และ 2^256" ซึ่งวิธีที่แน่นอนที่คุณใช้ในการเลือกตัวเลขนั้นไม่สำคัญตราบใดที่มันไม่สามารถคาดเดาหรือทำซ้ำได้ โดยปกติแล้วซอฟต์แวร์ของบิตคอยน์มักจะใช้ตัวสร้างตัวเลขสุ่มที่มีความปลอดภัยทางการเข้ารหัสเพื่อสร้างเอนโทรปี 256 บิต
สิ่งที่สำคัญในเรื่องนี้คือ private key สามารถเป็นตัวเลขใดๆ ระหว่าง 0 และ n - 1 (รวมทั้งสองค่า) โดยที่ n เป็นค่าคงที่ (n = 1.1578 × 10^77 ซึ่งน้อยกว่า 2^256 เล็กน้อย) ซึ่งกำหนดอยู่ใน elliptic curve ที่ใช้ใน Bitcoin ในการสร้างกุญแจดังกล่าว เราสุ่มเลือกเลขขนาด 256 บิตและตรวจสอบว่ามันน้อยกว่า n ในแง่ของการเขียนโปรแกรม โดยปกติแล้วสิ่งนี้ทำได้โดยการป้อนสตริงของบิตสุ่มที่ใหญ่กว่า ซึ่งรวบรวมจากแหล่งที่มาของความสุ่มที่มีความปลอดภัยทางการเข้ารหัส เข้าไปในอัลกอริทึมแฮช SHA256 ซึ่งจะสร้างค่าขนาด 256 บิตที่สามารถตีความเป็นตัวเลขได้อย่างสะดวก หากผลลัพธ์น้อยกว่า n เราจะได้กุญแจส่วนตัวที่เหมาะสม มิฉะนั้น เราก็เพียงแค่ลองอีกครั้งด้วยตัวเลขสุ่มอื่น
คำเตือน: อย่าเขียนโค้ดของคุณเองเพื่อสร้างตัวเลขสุ่ม หรือใช้ตัวสร้างตัวเลขสุ่ม "แบบง่าย" ที่มีให้ในภาษาโปรแกรมของคุณ ใช้ตัวสร้างตัวเลขสุ่มเทียมที่มีความปลอดภัยทางการเข้ารหัส (CSPRNG) จากแหล่งที่มีเอนโทรปีเพียงพอ ศึกษาเอกสารของไลบรารีตัวสร้างตัวเลขสุ่มที่คุณเลือกเพื่อให้มั่นใจว่ามีความปลอดภัยทางการเข้ารหัส การใช้งาน CSPRNG ที่ถูกต้องมีความสำคัญอย่างยิ่งต่อความปลอดภัยของกุญแจ
ต่อไปนี้คือกุญแจส่วนตัว (k) ที่สร้างขึ้นแบบสุ่มซึ่งแสดงในรูปแบบเลขฐานสิบหก (256 บิตแสดงเป็น 64 หลักเลขฐานสิบหก โดยแต่ละหลักคือ 4 บิต):
1E99423A4ED27608A15A2616A2B0E9E52CED330AC530EDCC32C8FFC6A526AEDDTIP: จำนวนที่เป็นไปได้ของ private key ทั้งหมดนั้นมีอยู่ 2^256 เป็นตัวเลขที่ใหญ่มากจนยากจะจินตนาการได้ มันมีค่าประมาณ 10^77 (เลข 1 ตามด้วยเลข 0 อีก 77 ตัว) ในระบบเลขฐานสิบ เพื่อให้เข้าใจง่ายขึ้น ลองเปรียบเทียบกับจักรวาลที่เรามองเห็นได้ซึ่งนักวิทยาศาสตร์ประมาณการว่ามีอะตอมทั้งหมดประมาณ 10^80 อะตอม นั่นหมายความว่าช่วงค่าของกุญแจส่วนตัว Bitcoin มีขนาดใกล้เคียงกับจำนวนอะตอมทั้งหมดในจักรวาลที่เรามองเห็นได้
การอธิบายเกี่ยวกับวิทยาการเข้ารหัสแบบเส้นโค้งวงรี (Elliptic Curve Cryptography)
วิทยาการเข้ารหัสแบบเส้นโค้งวงรี (ECC) เป็นประเภทหนึ่งของการเข้ารหัสแบบอสมมาตรหรือ public key ซึ่งอาศัยหลักการของปัญหาลอการิทึมแบบไม่ต่อเนื่อง โดยแสดงออกผ่านการบวกและการคูณบนจุดต่างๆ ของเส้นโค้งวงรี

บิตคอยน์ใช้เส้นโค้งวงรีเฉพาะและชุดค่าคงที่ทางคณิตศาสตร์ ตามที่กำหนดไว้ในมาตรฐานที่เรียกว่า secp256k1 ซึ่งกำหนดโดยสถาบันมาตรฐานและเทคโนโลยีแห่งชาติ (NIST) เส้นโค้ง secp256k1 ถูกกำหนดโดยฟังก์ชันต่อไปนี้ ซึ่งสร้างเส้นโค้งวงรี: y² = (x³ + 7) บนฟิลด์จำกัด (F_p) หรือ y² mod p = (x³ + 7) mod p
โดยที่ mod p (มอดูโลจำนวนเฉพาะ p) แสดงว่าเส้นโค้งนี้อยู่บนฟิลด์จำกัดของอันดับจำนวนเฉพาะ p ซึ่งเขียนได้เป็น F_p โดย p = 2^256 – 2^32 – 2^9 – 2^8 – 2^7 – 2^6 – 2^4 – 1 ซึ่งเป็นจำนวนเฉพาะที่มีค่ามหาศาล
บิตคอยน์ใช้เส้นโค้งวงรีที่ถูกนิยามบนฟิลด์จำกัดของอันดับจำนวนเฉพาะแทนที่จะอยู่บนจำนวนจริง ทำให้มันมีลักษณะเหมือนรูปแบบของจุดที่กระจัดกระจายในสองมิติ ซึ่งทำให้ยากต่อการจินตนาการภาพ อย่างไรก็ตาม คณิตศาสตร์ที่ใช้นั้นเหมือนกับเส้นโค้งวงรีบนจำนวนจริง
ตัวอย่างเช่น การเข้ารหัสลับด้วยเส้นโค้งวงรี: การแสดงภาพเส้นโค้งวงรีบน F(p) โดยที่ p=17 แสดงเส้นโค้งวงรีเดียวกันบนฟิลด์จำกัดของอันดับจำนวนเฉพาะ 17 ที่มีขนาดเล็กกว่ามาก ซึ่งแสดงรูปแบบของจุดบนตาราง
เส้นโค้งวงรี secp256k1 ที่ใช้ในบิตคอยน์สามารถนึกถึงได้ว่าเป็นรูปแบบของจุดที่ซับซ้อนมากกว่าบนตารางที่มีขนาดใหญ่มหาศาลจนยากจะเข้าใจได้

ตัวอย่างเช่น จุด P ที่มีพิกัด (x, y) ต่อไปนี้เป็นจุดที่อยู่บนเส้นโค้ง secp256k1:
P = (55066263022277343669578718895168534326250603453777594175500187360389116729240, 32670510020758816978083085130507043184471273380659243275938904335757337482424)เราสามารถใช้ Python เพื่อยืนยันว่าจุดนี้อยู่บนเส้นโค้งวงรีได้ตามตัวอย่างนี้: ตัวอย่างที่ 1: การใช้ Python เพื่อยืนยันว่าจุดนี้อยู่บนเส้นโค้งวงรี ``` Python 3.10.6 (main, Nov 14 2022, 16:10:14) [GCC 11.3.0] on linux Type "help", "copyright", "credits" or "license" for more information.p = 115792089237316195423570985008687907853269984665640564039457584007908834671663 x = 55066263022277343669578718895168534326250603453777594175500187360389116729240 y = 32670510020758816978083085130507043184471273380659243275938904335757337482424 (x ** 3 + 7 - y**2) % p 0 ``` ผลลัพธ์เป็น 0 ซึ่งแสดงว่าจุดนี้อยู่บนเส้นโค้งวงรีจริง เพราะเมื่อแทนค่า x และ y ลงในสมการ y² = (x³ + 7) mod p แล้ว ทั้งสองด้านของสมการมีค่าเท่ากัน
ในคณิตศาสตร์ของเส้นโค้งวงรี มีจุดที่เรียกว่า "จุดที่อนันต์" (point at infinity) ซึ่งมีบทบาทคล้ายกับศูนย์ในการบวก บนคอมพิวเตอร์ บางครั้งจุดนี้แทนด้วย x = y = 0 (ซึ่งไม่เป็นไปตามสมการเส้นโค้งวงรี แต่เป็นกรณีพิเศษที่สามารถตรวจสอบได้ง่าย)
มีตัวดำเนินการ + ที่เรียกว่า "การบวก" ซึ่งมีคุณสมบัติคล้ายกับการบวกแบบดั้งเดิมของจำนวนจริงที่เด็กๆ เรียนในโรงเรียน เมื่อมีจุดสองจุด P1 และ P2 บนเส้นโค้งวงรี จะมีจุดที่สาม P3 = P1 + P2 ซึ่งอยู่บนเส้นโค้งวงรีเช่นกัน
ในเชิงเรขาคณิต จุดที่สาม P3 นี้คำนวณได้โดยการลากเส้นระหว่าง P1 และ P2 เส้นนี้จะตัดกับเส้นโค้งวงรีที่จุดเพิ่มเติมอีกหนึ่งจุดพอดี เรียกจุดนี้ว่า P3' = (x, y) จากนั้นให้สะท้อนกับแกน x เพื่อได้ P3 = (x, -y)
มีกรณีพิเศษบางกรณีที่อธิบายความจำเป็นของ "จุดที่อนันต์":
- ถ้า P1 และ P2 เป็นจุดเดียวกัน เส้น "ระหว่าง" P1 และ P2 ควรขยายเป็นเส้นสัมผัสกับเส้นโค้ง ณ จุด P1 นี้ เส้นสัมผัสนี้จะตัดกับเส้นโค้งที่จุดใหม่อีกหนึ่งจุดพอดี คุณสามารถใช้เทคนิคจากแคลคูลัสเพื่อหาความชันของเส้นสัมผัส เทคนิคเหล่านี้ใช้ได้อย่างน่าแปลกใจ แม้ว่าเราจะจำกัดความสนใจไว้ที่จุดบนเส้นโค้งที่มีพิกัดเป็นจำนวนเต็มเท่านั้น!
- ในบางกรณี (เช่น ถ้า P1 และ P2 มีค่า x เดียวกันแต่ค่า y ต่างกัน) เส้นสัมผัสจะตั้งฉากพอดี ซึ่งในกรณีนี้ P3 = "จุดที่อนันต์"
- ถ้า P1 เป็น "จุดที่อนันต์" แล้ว P1 + P2 = P2 ในทำนองเดียวกัน ถ้า P2 เป็นจุดที่อนันต์ แล้ว P1 + P2 = P1 นี่แสดงให้เห็นว่าจุดที่อนันต์มีบทบาทเป็นศูนย์
การบวกนี้มีคุณสมบัติเชิงสมาคม (associative) ซึ่งหมายความว่า (A + B) + C = A + (B + C) นั่นหมายความว่าเราสามารถเขียน A + B + C โดยไม่ต้องมีวงเล็บและไม่มีความกำกวม
เมื่อเรานิยามการบวกแล้ว เราสามารถนิยามการคูณในแบบมาตรฐานที่ต่อยอดจากการบวก สำหรับจุด P บนเส้นโค้งวงรี ถ้า k เป็นจำนวนเต็มบวก แล้ว kP = P + P + P + … + P (k ครั้ง) โปรดทราบว่า k บางครั้งถูกเรียกว่า "เลขชี้กำลัง"
Public Keys
ในระบบคริปโตกราฟีแบบเส้นโค้งวงรี (Elliptic Curve Cryptography) public key ถูกคำนวณจาก private key โดยใช้การคูณเส้นโค้งวงรี ซึ่งเป็นกระบวนการที่ไม่สามารถย้อนกลับได้:
K = k × G
โดยที่:
- k คือ private key
- G คือจุดคงที่ที่เรียกว่า จุดกำเนิด (generator point)
- K คือ public key
การดำเนินการย้อนกลับ ที่เรียกว่า "การหาลอการิทึมแบบไม่ต่อเนื่อง" (finding the discrete logarithm) - คือการคำนวณหา k เมื่อรู้ค่า K - เป็นสิ่งที่ยากมากเทียบเท่ากับการลองค่า k ทุกค่าที่เป็นไปได้ (วิธีการแบบ brute-force)
ความยากของการย้อนกลับนี้คือหลักการความปลอดภัยหลักของระบบ ECC ที่ใช้ในบิตคอยน์ ซึ่งทำให้สามารถเผยแพร่ public key ได้อย่างปลอดภัย โดยที่ไม่ต้องกังวลว่าจะมีใครสามารถคำนวณย้อนกลับเพื่อหา private key ได้
TIP:การคูณเส้นโค้งวงรีเป็นฟังก์ชันประเภทที่นักเข้ารหัสลับเรียกว่า “ trap door function ”:
- เป็นสิ่งที่ทำได้ง่ายในทิศทางหนึ่ง
- แต่เป็นไปไม่ได้ที่จะทำในทิศทางตรงกันข้าม
คนที่มี private key สามารถสร้าง public key ได้อย่างง่ายดาย และสามารถแบ่งปันกับโลกได้โดยรู้ว่าไม่มีใครสามารถย้อนกลับฟังก์ชันและคำนวณ private key จาก public key ได้ กลวิธีทางคณิตศาสตร์นี้กลายเป็นพื้นฐานสำหรับลายเซ็นดิจิทัลที่ปลอมแปลงไม่ได้และมีความปลอดภัย ซึ่งใช้พิสูจน์การควบคุมเงินบิตคอยน์
เริ่มต้นด้วยการใช้ private key ในรูปแบบของตัวเลขสุ่ม เราคูณมันด้วยจุดที่กำหนดไว้ล่วงหน้าบนเส้นโค้งที่เรียกว่า จุดกำเนิด (generator point) เพื่อสร้างจุดอื่นที่อยู่บนเส้นโค้งเดียวกัน ซึ่งคำตอบจะเป็น public key ที่สอดคล้องกัน จุดกำเนิดถูกกำหนดไว้เป็นส่วนหนึ่งของมาตรฐาน secp256k1 และเป็นค่าเดียวกันสำหรับกุญแจทั้งหมดในระบบบิตคอยน์
เนื่องจากจุดกำเนิด G เป็นค่าเดียวกันสำหรับผู้ใช้บิตคอยน์ทุกคน private key (k) ที่คูณกับ G จะได้ public key (K) เดียวกันเสมอ ความสัมพันธ์ระหว่าง k และ K เป็นแบบตายตัวแต่สามารถคำนวณได้ในทิศทางเดียวเท่านั้น คือจาก k ไปยัง K นี่คือเหตุผลที่ public key ของบิตคอยน์ (K) สามารถแบ่งปันกับทุกคนได้โดยไม่เปิดเผย private key (k) ของผู้ใช้
TIP: private key สามารถแปลงเป็น public key ได้ แต่ public key ไม่สามารถแปลงกลับเป็น private key ได้ เพราะคณิตศาสตร์ที่ใช้ทำงานได้เพียงทิศทางเดียวเท่านั้น
เมื่อนำการคูณเส้นโค้งวงรีมาใช้งาน เราจะนำ private key (k) ที่สร้างขึ้นก่อนหน้านี้มาคูณกับจุดกำเนิด G เพื่อหา public key (K):
K = 1E99423A4ED27608A15A2616A2B0E9E52CED330AC530EDCC32C8FFC6A526AEDD × Gpublic key (K) จะถูกกำหนดเป็นจุด K = (x, y) โดยที่:x = F028892BAD7ED57D2FB57BF33081D5CFCF6F9ED3D3D7F159C2E2FFF579DC341A y = 07CF33DA18BD734C600B96A72BBC4749D5141C90EC8AC328AE52DDFE2E505BDBเพื่อจะให้เห็นภาพของการคูณจุดด้วยจำนวนเต็มมากขึ้น เราจะใช้เส้นโค้งวงรีที่ง่ายกว่าบนจำนวนจริง (โดยหลักการทางคณิตศาสตร์ยังคงเหมือนกัน) เป้าหมายของเราคือการหาผลคูณ kG ของจุดกำเนิด G ซึ่งเทียบเท่ากับการบวก G เข้ากับตัวเอง k ครั้งติดต่อกันในเส้นโค้งวงรี การบวกจุดเข้ากับตัวเองเทียบเท่ากับการลากเส้นสัมผัสที่จุดนั้นและหาว่าเส้นนั้นตัดกับเส้นโค้งอีกครั้งที่จุดใด จากนั้นจึงสะท้อนจุดนั้นบนแกน x
การเข้ารหัสลับด้วยเส้นโค้งวงรี: การแสดงภาพการคูณจุด G ด้วยจำนวนเต็ม k บนเส้นโค้งวงรี แสดงกระบวนการในการหา G, 2G, 4G เป็นการดำเนินการทางเรขาคณิตบนเส้นโค้งได้ดังนี้
TIP: ในซอฟแวร์ของบิตคอยน์ส่วนใหญ่ใช้ไลบรารีเข้ารหัสลับ libsecp256k1 เพื่อทำการคำนวณทางคณิตศาสตร์เส้นโค้งวงรี

Output and Input Scripts
แม้ว่าภาพประกอบจาก Bitcoin whitepaper ที่แสดงเรื่อง "Transaction chain" จะแสดงให้เห็นว่ามีการใช้ public key และ digital signature โดยตรง แต่ในความเป็นจริงบิตคอยน์เวอร์ชันแรกนั้นมีการส่งการชำระเงินไปยังฟิลด์ที่เรียกว่า output script และมีการใช้จ่ายบิตคอยน์เหล่านั้นโดยได้รับอนุญาตจากฟิลด์ที่เรียกว่า input script ฟิลด์เหล่านี้อนุญาตให้มีการดำเนินการเพิ่มเติมนอกเหนือจาก (หรือแทนที่) การตรวจสอบว่าลายเซ็นสอดคล้องกับ public key หรือไม่ ตัวอย่างเช่น output script สามารถมี public key สองดอกและต้องการลายเซ็นสองลายเซ็นที่สอดคล้องกันในฟิลด์ input script ที่ใช้จ่าย
ในภายหลัง ในหัวข้อ [tx_script] เราจะได้เรียนรู้เกี่ยวกับสคริปต์อย่างละเอียด สำหรับตอนนี้ สิ่งที่เราต้องเข้าใจคือ บิตคอยน์จะถูกรับเข้า output script ที่ทำหน้าที่เหมือน public key และการใช้จ่ายบิตคอยน์จะได้รับอนุญาตโดย input script ที่ทำหน้าที่เหมือนลายเซ็น
IP Addresses: The Original Address for Bitcoin (P2PK)
เราได้เห็นแล้วว่าอลิซสามารถจ่ายเงินให้บ็อบโดยการมอบบิตคอยน์บางส่วนของเธอให้กับกุญแจสาธารณะของบ็อบ แต่อลิซจะได้กุญแจสาธารณะของบ็อบมาได้อย่างไร? บ็อบอาจจะให้สำเนากุญแจแก่เธอ แต่ลองดูกุญแจสาธารณะที่เราใช้งานในตัวอย่างที่ผ่านมาอีกครั้ง:
x = F028892BAD7ED57D2FB57BF33081D5CFCF6F9ED3D3D7F159C2E2FFF579DC341A y = 07CF33DA18BD734C600B96A72BBC4749D5141C90EC8AC328AE52DDFE2E505BDBTIP จากหลาม: :สังเกตได้ว่า public key มีความยาวมาก ลองจินตนาการว่าบ็อบพยายามอ่านกุญแจนี้ให้อลิซฟังทางโทรศัพท์ คงจะยากมากที่จะอ่านและบันทึกโดยไม่มีข้อผิดพลาด
แทนที่จะป้อนกุญแจสาธารณะโดยตรง เวอร์ชันแรกของซอฟต์แวร์บิตคอยน์อนุญาตให้ผู้จ่ายเงินป้อนที่อยู่ IP ของผู้รับได้ ตามที่แสดงในหน้าจอการส่งเงินรุ่นแรกของบิตคอยน์ผ่าน The Internet Archive
คุณสมบัตินี้ถูกลบออกในภายหลัง เนื่องจากมีปัญหามากมายในการใช้ที่อยู่ IP แต่คำอธิบายสั้นๆ จะช่วยให้เราเข้าใจได้ดีขึ้นว่าทำไมคุณสมบัติบางอย่างอาจถูกเพิ่มเข้าไปในโปรโตคอลบิตคอยน์

เมื่ออลิซป้อนที่อยู่ IP ของบ็อบในบิตคอยน์เวอร์ชัน 0.1 Full node ของเธอจะทำการเชื่อมต่อกับ full node ของเขาและได้รับ public key ใหม่จากกระเป๋าสตางค์ของบ็อบที่โหนดของเขาไม่เคยให้กับใครมาก่อน การที่เป็น public key ใหม่นี้มีความสำคัญเพื่อให้แน่ใจว่าธุรกรรมต่าง ๆ ที่จ่ายให้บ็อบจะไม่สามารถถูกเชื่อมโยงเข้าด้วยกันโดยคนที่กำลังดูบล็อกเชนและสังเกตเห็นว่าธุรกรรมทั้งหมดจ่ายไปยัง public key เดียวกัน
เมื่อใช้ public key จากโหนดของอลิซซึ่งได้รับมาจากโหนดของบ็อบ กระเป๋าสตางค์ของอลิซจะสร้างเอาต์พุตธุรกรรมที่จ่ายให้กับสคริปต์เอาต์พุตดังนี้
<Bob's public key> OP_CHECKSIGต่อมาบ็อบจะสามารถใช้จ่ายเอาต์พุตนั้นด้วยสคริปต์อินพุตที่ประกอบด้วยลายเซ็นของเขาเท่านั้น:<Bob's signature>เพื่อให้เข้าใจว่าสคริปต์อินพุตและเอาต์พุตกำลังทำอะไร คุณสามารถรวมพวกมันเข้าด้วยกัน (สคริปต์อินพุตก่อน) แล้วสังเกตว่าข้อมูลแต่ละชิ้น (แสดงในเครื่องหมาย < >) จะถูกวางไว้ที่ด้านบนสุดของรายการที่เรียกว่าสแตก (stack) เมื่อพบรหัสคำสั่ง (opcode) มันจะใช้รายการจากสแตก โดยเริ่มจากรายการบนสุด มาดูว่ามันทำงานอย่างไรโดยเริ่มจากสคริปต์ที่รวมกัน:<Bob's signature> <Bob's public key> OP_CHECKSIGสำหรับสคริปต์นี้ ลายเซ็นของบ็อบจะถูกนำไปไว้บนสแตก จากนั้น public key ของบ็อบจะถูกวางไว้ด้านบนของลายเซ็น และบนสุดจะเป็นคำสั่ง OP_CHECKSIG ที่จะใช้องค์ประกอบสองอย่าง เริ่มจาก public key ตามด้วยลายเซ็น โดยลบพวกมันออกจากสแตก มันจะตรวจสอบว่าลายเซ็นตรงกับ public key และยืนยันฟิลด์ต่าง ๆ ในธุรกรรม ถ้าลายเซ็นถูกต้อง OP_CHECKSIG จะแทนที่ตัวเองบนสแตกด้วยค่า 1 ถ้าลายเซ็นไม่ถูกต้อง มันจะแทนที่ตัวเองด้วย 0 ถ้ามีรายการที่ไม่ใช่ศูนย์อยู่บนสุดของสแตกเมื่อสิ้นสุดการประเมิน สคริปต์ก็จะผ่าน ถ้าสคริปต์ทั้งหมดในธุรกรรมผ่าน และรายละเอียดอื่น ๆ ทั้งหมดเกี่ยวกับธุรกรรมนั้นต้องถูกต้องจึงจะถือว่าธุรกรรมนั้นถูกต้อง
โดยสรุป สคริปต์ข้างต้นใช้ public key และลายเซ็นเดียวกันกับที่อธิบายใน whitepaper แต่เพิ่มความซับซ้อนของฟิลด์สคริปต์สองฟิลด์และรหัสคำสั่งหนึ่งตัว ซึ่งเราจะเริ่มเห็นประโยชน์เมื่อเรามองที่ส่วนต่อไป
TIP:จากหลาม agian: เอาต์พุตประเภทนี้เป็นที่รู้จักในปัจจุบันว่า P2PK ซึ่งมันไม่เคยถูกใช้อย่างแพร่หลายสำหรับการชำระเงิน และไม่มีโปรแกรมที่ใช้กันอย่างแพร่หลายที่รองรับการชำระเงินผ่านที่อยู่ IP เป็นเวลาเกือบทศวรรษแล้ว
Legacy addresses for P2PKH
แน่นอนว่าการป้อนที่อยู่ IP ของคนที่คุณต้องการจ่ายเงินให้นั้นมีข้อดีหลายประการ แต่ก็มีข้อเสียหลายประการเช่นกัน หนึ่งในข้อเสียที่สำคัญคือผู้รับจำเป็นต้องให้กระเป๋าสตางค์ของพวกเขาออนไลน์ที่ที่อยู่ IP ของพวกเขา และต้องสามารถเข้าถึงได้จากโลกภายนอก
ซึ่งสำหรับคนจำนวนมากนั่นไม่ใช่ตัวเลือกที่เป็นไปได้เพราะหากพวกเขา:
- ปิดคอมพิวเตอร์ในเวลากลางคืน
- แล็ปท็อปของพวกเขาเข้าสู่โหมดสลีป
- อยู่หลังไฟร์วอลล์
- หรือกำลังใช้การแปลงที่อยู่เครือข่าย (NAT)
ปัญหานี้นำเรากลับมาสู่ความท้าทายเดิมที่ผู้รับเงินอย่างบ็อบต้องให้ public key ที่มีความยาวมากแก่ผู้จ่ายเงินอย่างอลิซ public key ของบิตคอยน์ที่สั้นที่สุดที่นักพัฒนาบิตคอยน์รุ่นแรกรู้จักมีขนาด 65 ไบต์ เทียบเท่ากับ 130 ตัวอักษรเมื่อเขียนในรูปแบบเลขฐานสิบหก (เฮกซาเดซิมอล) แต่อย่างไรก็ตาม บิตคอยน์มีโครงสร้างข้อมูลหลายอย่างที่มีขนาดใหญ่กว่า 65 ไบต์มาก ซึ่งจำเป็นต้องถูกอ้างอิงอย่างปลอดภัยในส่วนอื่น ๆ ของบิตคอยน์โดยใช้ข้อมูลขนาดเล็กที่สุดเท่าที่จะปลอดภัยได้
โดยบิตคอยน์แก้ปัญหานี้ด้วย ฟังก์ชันแฮช (hash function) ซึ่งเป็นฟังก์ชันที่รับข้อมูลที่อาจมีขนาดใหญ่ นำมาแฮช และให้ผลลัพธ์เป็นข้อมูลขนาดคงที่ ฟังก์ชันแฮชจะผลิตผลลัพธ์เดียวกันเสมอเมื่อได้รับข้อมูลนำเข้าแบบเดียวกัน และฟังก์ชันที่ปลอดภัยจะทำให้เป็นไปไม่ได้ในทางปฏิบัติสำหรับผู้ที่ต้องการเลือกข้อมูลนำเข้าอื่นที่ให้ผลลัพธ์เหมือนกันได้ นั่นทำให้ผลลัพธ์เป็น คำมั่นสัญญา (commitment) ต่อข้อมูลนำเข้า เป็นสัญญาว่าในทางปฏิบัติ มีเพียงข้อมูลนำเข้า x เท่านั้นที่จะให้ผลลัพธ์ X
สมมติว่าผมต้องการถามคำถามคุณและให้คำตอบของผมในรูปแบบที่คุณไม่สามารถอ่านได้ทันที สมมติว่าคำถามคือ "ในปีไหนที่ซาโตชิ นาคาโมโตะเริ่มทำงานบนบิทคอยน์?" ผมจะให้การยืนยันคำตอบของผมในรูปแบบของผลลัพธ์จากฟังก์ชันแฮช SHA256 ซึ่งเป็นฟังก์ชันที่ใช้บ่อยที่สุดในบิทคอยน์:
94d7a772612c8f2f2ec609d41f5bd3d04a5aa1dfe3582f04af517d396a302e4eต่อมา หลังจากคุณบอกคำตอบที่คุณเดาสำหรับคำถามนั้น ผมสามารถเปิดเผยคำตอบของผมและพิสูจน์ให้คุณเห็นว่าคำตอบของผม เมื่อใช้เป็นข้อมูลสำหรับฟังก์ชันแฮช จะให้ผลลัพธ์เดียวกันกับที่ผมให้คุณก่อนหน้านี้$ echo "2007. He said about a year and a half before Oct 2008" | sha256sum 94d7a772612c8f2f2ec609d41f5bd3d04a5aa1dfe3582f04af517d396a302e4eทีนี้ให้สมมติว่าเราถามบ็อบว่า " public key ของคุณคืออะไร?" บ็อบสามารถใช้ฟังก์ชันแฮชเพื่อให้การยืนยันที่ปลอดภัยทางการเข้ารหัสต่อ public key ของเขา หากเขาเปิดเผยกุญแจในภายหลัง และเราตรวจสอบว่ามันให้ผลการยืนยันเดียวกันกับที่เขาให้เราก่อนหน้านี้ เราสามารถมั่นใจได้ว่ามันเป็นกุญแจเดียวกันที่ใช้สร้างการยืนยันก่อนหน้านี้ฟังก์ชันแฮช SHA256 ถือว่าปลอดภัยมากและให้ผลลัพธ์ 256 บิต (32 ไบต์) น้อยกว่าครึ่งหนึ่งของขนาด public key ของบิทคอยน์ดั้งเดิม แต่อย่างไรก็ตาม มีฟังก์ชันแฮชอื่นๆ ที่ปลอดภัยน้อยกว่าเล็กน้อยที่ให้ผลลัพธ์ขนาดเล็กกว่า เช่น ฟังก์ชันแฮช RIPEMD-160 ซึ่งให้ผลลัพธ์ 160 บิต (20 ไบต์) ด้วยเหตุผลที่ซาโตชิ นาคาโมโตะไม่เคยระบุ เวอร์ชันดั้งเดิมของบิทคอยน์สร้างการยืนยันต่อ public key โดยการแฮชกุญแจด้วย SHA256 ก่อน แล้วแฮชผลลัพธ์นั้นด้วย RIPEMD-160 ซึ่งให้การยืนยันขนาด 20 ไบต์ต่อ public key
เราสามารถดูสิ่งนี้ตามอัลกอริทึม เริ่มจากกุญแจสาธารณะ K เราคำนวณแฮช SHA256 และคำนวณแฮช RIPEMD-160 ของผลลัพธ์ ซึ่งให้ตัวเลข 160 บิต (20 ไบต์): A = RIPEMD160(SHA256(K))
ทีนี้เราคงเข้าใจวิธีสร้างการยืนยันต่อ public key แล้ว ต่อไปเราจะมาดูวิธีการใช้งานโดยพิจารณาสคริปต์เอาต์พุตต่อไปนี้:
OP_DUP OP_HASH160 <Bob's commitment> OP_EQUAL OP_CHECKSIGและสคริปต์อินพุตต่อไปนี้:<Bob's signature> <Bob's public key>และเมื่อเรารวมมันเข้าด้วยกันเราจะได้ผลลัพธ์ดังนี้:<Bob's signature> <Bob's public key> OP_DUP OP_HASH160 <Bob's commitment> OP_EQUAL OP_CHECKSIGเหมือนที่เราทำใน IP Addresses: The Original Address for Bitcoin (P2PK) เราเริ่มวางรายการลงในสแต็ก ลายเซ็นของบ็อบถูกวางก่อน จากนั้น public key ของเขาถูกวางไว้ด้านบน จากนั้นดำเนินการ OP_DUP เพื่อทำสำเนารายการบนสุด ดังนั้นรายการบนสุดและรายการที่สองจากบนในสแต็กตอนนี้เป็น public key ของบ็อบทั้งคู่ การดำเนินการ OP_HASH160 ใช้ (ลบ) public key บนสุดและแทนที่ด้วยผลลัพธ์ของการแฮชด้วย RIPEMD160(SHA256(K)) ดังนั้นตอนนี้บนสุดของสแต็กคือแฮชของ public key ของบ็อบ ต่อไป commitment ถูกเพิ่มไว้บนสุดของสแต็ก การดำเนินการ OP_EQUALVERIFY ใช้รายการสองรายการบนสุดและตรวจสอบว่าพวกมันเท่ากัน ซึ่งควรเป็นเช่นนั้นหาก public key ที่บ็อบให้ในสคริปต์อินพุตเป็น public key เดียวกันกับที่ใช้สร้างการยืนยันในสคริปต์เอาต์พุตที่อลิซจ่าย หาก OP_EQUALVERIFY ล้มเหลว ทั้งสคริปต์จะล้มเหลว สุดท้าย เราเหลือสแต็กที่มีเพียงลายเซ็นของบ็อบและ public key ของเขา รหัสปฏิบัติการ OP_CHECKSIG ตรวจสอบว่าพวกมันสอดคล้องกัน
TIP: จากหลาม ถ้าอ่านตรงนี้และงง ๆ ผมไปทำรูปมาให้ดูง่ายขึ้นครับ
แม้กระบวนการของการ pay-to-publickey-hash(P2PKH) อาจดูซับซ้อน แต่มันทำให้การที่อลิซจ่ายเงินให้บ็อบมีเพียงการยืนยันเพียง 20 ไบต์ต่อ public key ของเขาแทนที่จะเป็นตัวกุญแจเอง ซึ่งจะมีขนาด 65 ไบต์ในเวอร์ชันดั้งเดิมของบิทคอยน์ นั่นเป็นข้อมูลที่น้อยกว่ามากที่บ็อบต้องสื่อสารกับอลิซ
แต่อย่างไรก็ตาม เรายังไม่ได้พูดถึงวิธีที่บ็อบรับ 20 ไบต์เหล่านั้นจากกระเป๋าเงินบิทคอยน์ของเขาไปยังกระเป๋าเงินของอลิซ มีการเข้ารหัสค่าไบต์ที่ใช้กันอย่างแพร่หลาย เช่น เลขฐานสิบหก แต่ข้อผิดพลาดใด ๆ ในการคัดลอกการยืนยันจะทำให้บิทคอยน์ถูกส่งไปยังเอาต์พุตที่ไม่สามารถใช้จ่ายได้ ทำให้พวกมันสูญหายไปตลอดกาล โดยในส่วนถัดไป เราจะดูที่การเข้ารหัสแบบกะทัดรัดและการตรวจสอบความถูกต้อง
Base58check Encoding
ระบบคอมพิวเตอร์มีวิธีเขียนตัวเลขยาวๆ ให้สั้นลงโดยใช้ทั้งตัวเลขและตัวอักษรผสมกัน เพื่อใช้พื้นที่น้อยลงอย่างเช่น
- ระบบเลขฐานสิบ (ปกติที่เราใช้) - ใช้เลข 0-9 เท่านั้น
- ระบบเลขฐานสิบหก - ใช้เลข 0-9 และตัวอักษร A-F ตัวอย่าง: เลข 255 ในระบบปกติ เขียนเป็น FF ในระบบเลขฐานสิบหก (สั้นกว่า)
- ระบบเลขฐานหกสิบสี่ (Base64) - ใช้สัญลักษณ์ถึง 64 ตัว: ตัวอักษรเล็ก (a-z) 26 ตัว, ตัวอักษรใหญ่ (A-Z) 26 ตัว, ตัวเลข (0-9) 10 ตัว, สัญลักษณ์พิเศษอีก 2 ตัว ("+" และ "/")
โดยระบบ Base64 นี้ช่วยให้เราส่งไฟล์คอมพิวเตอร์ผ่านข้อความธรรมดาได้ เช่น การส่งรูปภาพผ่านอีเมล โดยใช้พื้นที่น้อยกว่าการเขียนเป็นเลขฐานสิบแบบปกติมาก
การเข้ารหัสแบบ Base58 คล้ายกับ Base64 โดยใช้ตัวอักษรพิมพ์ใหญ่ พิมพ์เล็ก และตัวเลข แต่ได้ตัดตัวอักษรบางตัวที่มักถูกเข้าใจผิดว่าเป็นตัวอื่นและอาจดูเหมือนกันเมื่อแสดงในฟอนต์บางประเภทออกไป
Base58 คือ Base64 ที่ตัดตัวอักษรต่อไปนี้ออก:
- เลข 0 (ศูนย์)
- ตัวอักษร O (ตัว O พิมพ์ใหญ่)
- ตัวอักษร l (ตัว L พิมพ์เล็ก)
- ตัวอักษร I (ตัว I พิมพ์ใหญ่)
- และสัญลักษณ์ "+" และ "/"
หรือพูดให้ง่ายขึ้น Base58 คือกลุ่มตัวอักษรพิมพ์เล็ก พิมพ์ใหญ่ และตัวเลข แต่ไม่มีตัวอักษรทั้งสี่ตัว (0, O, l, I) ที่กล่าวถึงข้างต้น ตัวอักษรทั้งหมดที่ใช้ใน Base58 จะแสดงให้เห็นในตัวอักษร Base58 ของบิทคอยน์
Example 2. Bitcoin’s base58 alphabet
123456789ABCDEFGHJKLMNPQRSTUVWXYZabcdefghijkmnopqrstuvwxyzการเพิ่มความปลอดภัยพิเศษเพื่อป้องกันการพิมพ์ผิดหรือข้อผิดพลาดในการคัดลอก base58check ได้รวม รหัสตรวจสอบ (checksum) ที่เข้ารหัสในตัวอักษร base58 เข้าไปด้วย รหัสตรวจสอบนี้คือข้อมูลเพิ่มเติมอีก 4 ไบต์ที่เพิ่มเข้าไปที่ท้ายของข้อมูลที่กำลังถูกเข้ารหัสรหัสตรวจสอบนี้ได้มาจากการแฮชข้อมูลที่ถูกเข้ารหัส และจึงสามารถใช้เพื่อตรวจจับข้อผิดพลาดจากการคัดลอกและการพิมพ์ได้ เมื่อโปรแกรมได้รับรหัส base58check ซอฟต์แวร์ถอดรหัสจะคำนวณรหัสตรวจสอบของข้อมูลและเปรียบเทียบกับรหัสตรวจสอบที่รวมอยู่ในรหัสนั้น
หากทั้งสองไม่ตรงกัน แสดงว่ามีข้อผิดพลาดเกิดขึ้น และข้อมูล base58check นั้นไม่ถูกต้อง กระบวนการนี้ช่วยป้องกันไม่ให้ address บิทคอยน์ที่พิมพ์ผิดถูกยอมรับโดยซอฟต์แวร์กระเป๋าเงินว่าเป็น address ที่ถูกต้อง ซึ่งเป็นข้อผิดพลาดที่อาจส่งผลให้สูญเสียเงินได้
การแปลงข้อมูล (ตัวเลข) เป็นรูปแบบ base58check มีขั้นตอนดังนี้:
- เราเริ่มโดยการเพิ่ม prefix เข้าไปในข้อมูล เรียกว่า "version byte" ซึ่งช่วยให้ระบุประเภทของข้อมูลที่ถูกเข้ารหัสได้ง่าย ตัวอย่างเช่น: prefix ศูนย์ (0x00 ในระบบเลขฐานสิบหก) แสดงว่าข้อมูลควรถูกใช้เป็นการยืนยัน (hash) ในสคริปต์เอาต์พุต legacy P2PKH
- จากนั้น เราคำนวณ "double-SHA" checksum ซึ่งหมายถึงการใช้อัลกอริทึมแฮช SHA256 สองครั้งกับผลลัพธ์ก่อนหน้า (prefix ต่อกับข้อมูล):
checksum = SHA256(SHA256(prefix||data)) - จากแฮช 32 ไบต์ที่ได้ (การแฮชซ้อนแฮช) เราเลือกเฉพาะ 4 ไบต์แรก ไบต์ทั้งสี่นี้ทำหน้าที่เป็นรหัสตรวจสอบข้อผิดพลาดหรือ checksum
- นำ checksum นี้ไปต่อที่ท้ายข้อมูล
การเข้ารหัสแบบ base58check คือรูปแบบการเข้ารหัสที่ใช้ base58 พร้อมกับการระบุเวอร์ชันและการตรวจสอบความถูกต้อง เพื่อการเข้ารหัสข้อมูลบิทคอยน์ โดยคุณสามารถดูภาพประกอบด้านล่างเพื่อความเข้าใจเพิ่มเติม

ในบิตคอยน์นั้น นอกจากจะใช้ base58check ในการยืนยัน public key แล้ว ก็ยังมีการใช้ในข้อมูลอื่น ๆ ด้วย เพื่อทำให้ข้อมูลนั้นกะทัดรัด อ่านง่าย และตรวจจับข้อผิดพลาดได้ง่ายด้วยรหัสนำหน้า (version prefix) ในการเข้ารหัสแบบ base58check ถูกใช้เพื่อสร้างรูปแบบที่แยกแยะได้ง่าย ซึ่งเมื่อเข้ารหัสด้วย base58 โดยจะมีตัวอักษรเฉพาะที่จุดเริ่มต้นของข้อมูลที่เข้ารหัส base58check ตัวอักษรเหล่านี้ช่วยให้เราระบุประเภทของข้อมูลที่ถูกเข้ารหัสและวิธีการใช้งานได้ง่าย นี่คือสิ่งที่แยกความแตกต่าง ตัวอย่างเช่น ระหว่าง address บิทคอยน์ที่เข้ารหัส base58check ซึ่งขึ้นต้นด้วยเลข 1 กับรูปแบบการนำเข้า private key (WIF - Wallet Import Format) ที่เข้ารหัส base58check ซึ่งขึ้นต้นด้วยเลข 5 ตัวอย่างของ version prefix สามารถดูได้ตามตารางด้านล่างนี้

ภาพต่อไปนี้จะทำให้คุณเห็นภาพของกระบวนการแปลง public key ให้เป็น bitcoin address

Compressed Public Keys
ในยุคแรก ๆ ของบิตคอยน์นั้น มีเพียงการสร้าง public key แบบ 65 Bytes เท่านั้น แต่ในเวลาต่อมา เหล่านักพัฒนาในยุคหลังได้พบวิธีการสร้าง public key แบบใหม่ที่มีเพียง 33 Bytes และสามารถทำงานร่วมกันกับโหนดทั้งหมดในขณะนั้นได้ จีงไม่จะเป็นต้องเปลี่ยนแปลงกฎหรือโครงสร้างภายในโปรโตคอลของบิตคอยน์ โดย poublic key แบบใหม่ที่มีขนาด 33 Bytes นี้เรียกว่า compressed public key (public key ที่ถูกบีบอัด) และมีการเรียก public key ที่มีขนาด 65 Bytes ว่า uncompressed public key (public key ที่ไม่ถูกบีบอัด) ซึ่งประโยชน์ของ public key ที่เล็กลงนั้น นอกจากจะช่วยให้การส่ง public key ให้ผู้อื่นทำได้ง่ายขึ้นแล้ว ยังช่วยให้ธุรกรรมมีขนาดเล็กลง และช่วยให้สามารถทำการชำระเงินได้มากขึ้นในบล็อกเดียวกัน
อย่างที่เราได้เรียนรู้จากเนื้อหาในส่วนของ public key เราได้ทราบว่า public key คือจุด (x, y) บนเส้นโค้งวงรี เนื่องจากเส้นโค้งแสดงฟังก์ชันทางคณิตศาสตร์ จุดบนเส้นโค้งจึงเป็นคำตอบของสมการ ดังนั้นหากเรารู้พิกัด x เราก็สามารถคำนวณพิกัด y ได้โดยแก้สมการ y² mod p = (x³ + 7) mod p นั่นหมายความว่าเราสามารถเก็บเพียงพิกัด x ของ public key โดยละพิกัด y ไว้ ซึ่งช่วยลดขนาดของกุญแจและพื้นที่ที่ต้องใช้เก็บข้อมูลลง 256 บิต การลดขนาดลงเกือบ 50% ในทุกธุรกรรมรวมกันแล้วช่วยประหยัดข้อมูลได้มากมายในระยะยาว!
นี่คือ public key ที่ได้ยกเป็นตัวอย่างไว้ก่อนหน้า
x = F028892BAD7ED57D2FB57BF33081D5CFCF6F9ED3D3D7F159C2E2FFF579DC341A y = 07CF33DA18BD734C600B96A72BBC4749D5141C90EC8AC328AE52DDFE2E505BDBและนี่คือ public key ที่มีตัวนำหน้า 04 ตามด้วยพิกัด x และ y ในรูปแบบ 04 x y:
K = 04F028892BAD7ED57D2FB57BF33081D5CFCF6F9ED3D3D7F159C2E2FFF579DC341A07CF33DA18BD734C600B96A72BBC4749D5141C90EC8AC328AE52DDFE2E505BDBuncompressed public key นั้นจะมีตัวนำหน้าเป็น 04 แต่ compressed public key จะมีตัวนำหน้าเป็น 02 หรือ 03 โดยเหตุผลนั้นมาจากสมการ y² mod p = (x³ + 7) mod p เนื่องจากด้านซ้ายของสมการคือ y² คำตอบสำหรับ y จึงเป็นรากที่สอง ซึ่งอาจมีค่าเป็นบวกหรือลบก็ได้ หากมองเชิงภาพ นี่หมายความว่าพิกัด y ที่ได้อาจอยู่เหนือหรือใต้แกน x เราต้องไม่ลืมว่าเส้นโค้งมีความสมมาตร ซึ่งหมายความว่ามันจะสะท้อนเหมือนกระจกโดยแกน x ดังนั้น แม้เราจะละพิกัด y ได้ แต่เราต้องเก็บ เครื่องหมาย ของ y (บวกหรือลบ) หรืออีกนัยหนึ่งคือเราต้องจำว่ามันอยู่เหนือหรือใต้แกน x เพราะแต่ละตำแหน่งแทนจุดที่แตกต่างกันและเป็น public key ที่แตกต่างกัน
เมื่อคำนวณเส้นโค้งวงรีในระบบเลขฐานสองบนสนามจำกัดของเลขจำนวนเฉพาะ p พิกัด y จะเป็นเลขคู่หรือเลขคี่ ซึ่งสอดคล้องกับเครื่องหมายบวก/ลบตามที่อธิบายก่อนหน้านี้ ดังนั้น เพื่อแยกความแตกต่างระหว่างค่าที่เป็นไปได้สองค่าของ y เราจึงเก็บ compressed public key ด้วยตัวนำหน้า 02 ถ้า y เป็นเลขคู่ และ 03 ถ้า y เป็นเลขคี่ ซึ่งช่วยให้ซอฟต์แวร์สามารถอนุมานพิกัด y จากพิกัด x และคลายการบีบอัดของ public key ไปยังพิกัดเต็มของจุดได้อย่างถูกต้อง ดังภาพประกอบต่อไปนี้

นี่คือ public key เดียวกันกับที่ยกตัวอย่างไว้ข้างต้นซึ่งแสดงให้เห็นในรูป compressed public key ที่เก็บใน 264 บิต (66 ตัวอักษรเลขฐานสิบหก) โดยมีตัวนำหน้า 03 ซึ่งบ่งชี้ว่าพิกัด y เป็นเลขคี่:
K = 03F028892BAD7ED57D2FB57BF33081D5CFCF6F9ED3D3D7F159C2E2FFF579DC341Acompressed public key สอดคล้องกับ private key เดียวกันกับ uncompressed public key หมายความว่ามันถูกสร้างจาก private key เดียวกัน แต่อย่างไรก็ตาม มันก็มีส่วนที่แตกต่างจาก uncompressed public key นั้นคือ หากเราแปลง compressed public key เป็น commitment โดยใช้ฟังก์ชัน HASH160 (RIPEMD160(SHA256(K))) มันจะสร้าง commitment ที่แตกต่างจาก uncompressed public key และจะนำไปสู่ bitcoin address ที่แตกต่างกันในที่สุด สิ่งนี้อาจทำให้สับสนเพราะหมายความว่า private key เดียวสามารถสร้าง public key ในสองรูปแบบที่แตกต่างกัน (แบบบีบอัดและแบบไม่บีบอัด) ซึ่งสร้าง bitcoin address ที่แตกต่างกันcompressed public key เป็นค่าเริ่มต้นในซอฟต์แวร์บิตคอยน์เกือบทั้งหมดในปัจจุบัน และถูกกำหนดให้ใช้กับคุณสมบัติใหม่บางอย่างที่เพิ่มในการอัปเกรดโปรโตคอลในภายหลัง
อย่างไรก็ตาม ซอฟต์แวร์บางตัวยังคงต้องรองรับ uncompressed public key เช่น แอปพลิเคชันกระเป๋าเงินที่นำเข้า private key จากกระเป๋าเงินเก่า เมื่อกระเป๋าเงินใหม่สแกนบล็อกเชนสำหรับผลลัพธ์และอินพุต P2PKH เก่า มันจำเป็นต้องรู้ว่าควรสแกนกุญแจขนาด 65 ไบต์ (และ commitment ของกุญแจเหล่านั้น) หรือกุญแจขนาด 33 ไบต์ (และ commitment ของกุญแจเหล่านั้น) หากไม่สแกนหาประเภทที่ถูกต้อง อาจทำให้ผู้ใช้ไม่สามารถใช้ยอดคงเหลือทั้งหมดได้ เพื่อแก้ไขปัญหานี้ เมื่อส่งออก private key จากกระเป๋าเงิน WIF ที่ใช้แสดง private key ในกระเป๋าเงินบิตคอยน์รุ่นใหม่จะถูกนำไปใช้แตกต่างกันเล็กน้อยเพื่อบ่งชี้ว่า private key เหล่านี้ถูกใช้ในการสร้าง compressed public key
Legacy: Pay to Script Hash (P2SH)
ตามที่เราได้เห็นในส่วนก่อนหน้านี้ ผู้รับบิตคอยน์ สามารถกำหนดให้การชำระเงินที่ส่งมาให้เขานั้นมีเงื่อนไขบางอย่างในสคริปต์เอาต์พุตได้โดยจะต้องปฏิบัติตามเงื่อนไขเหล่านั้นโดยใช้สคริปต์อินพุตเมื่อเขาใช้จ่ายบิตคอยน์เหล่านั้น ในส่วน IP Addresses: The Original Address for Bitcoin (P2PK) เงื่อนไขก็คือสคริปต์อินพุตต้องให้ลายเซ็นที่เหมาะสม ในส่วน Legacy Addresses for P2PKH นั้นจำเป็นต้องมี public key ที่เหมาะสมด้วย
ส่วนสำหรับผู้ส่งก็จะวางเงื่อนไขที่ผู้รับต้องการในสคริปต์เอาต์พุตที่ใช้จ่ายให้กับผู้รับ โดยผู้รับจะต้องสื่อสารเงื่อนไขเหล่านั้นให้ผู้ส่งทราบ ซึ่งคล้ายกับปัญหาที่บ๊อบต้องสื่อสาร public key ของเขาให้อลิซทราบ และเช่นเดียวกับปัญหานั้นที่ public key อาจมีขนาดค่อนข้างใหญ่ เงื่อนไขที่บ๊อบใช้ก็อาจมีขนาดใหญ่มากเช่นกัน—อาจมีขนาดหลายพันไบต์ นั่นไม่เพียงแต่เป็นข้อมูลหลายพันไบต์ที่ต้องสื่อสารให้อลิซทราบ แต่ยังเป็นข้อมูลหลายพันไบต์ที่เธอต้องจ่ายค่าธรรมเนียมธุรกรรมทุกครั้งที่ต้องการใช้จ่ายเงินให้บ๊อบ อย่างไรก็ตาม การใช้ฟังก์ชันแฮชเพื่อสร้าง commitment ขนาดเล็กสำหรับข้อมูลขนาดใหญ่ก็สามารถนำมาใช้ได้ในกรณีนี้เช่นกัน
ในเวลาต่อมานั้น การอัปเกรด BIP16 สำหรับโปรโตคอลบิตคอยน์ในปี 2012 ได้อนุญาตให้สคริปต์เอาต์พุตสร้าง commitment กับ redemption script (redeem script) ได้ แปลว่าเมื่อบ๊อบใช้จ่ายบิตคอยน์ของเขา ภายในสคริปต์อินพุตของเขานั้นจะต้องให้ redeem script ที่ตรงกับ commitment และข้อมูลที่จำเป็นเพื่อให้เป็นไปตาม redeem script (เช่น ลายเซ็น) เริ่มต้นด้วยการจินตนาการว่าบ๊อบต้องการให้มีลายเซ็นสองอันเพื่อใช้จ่ายบิตคอยน์ของเขา หนึ่งลายเซ็นจากกระเป๋าเงินบนเดสก์ท็อปและอีกหนึ่งจากอุปกรณ์เซ็นแบบฮาร์ดแวร์ เขาใส่เงื่อนไขเหล่านั้นลงใน redeem script:
<public key 1> OP_CHECKSIGVERIFY <public key 2> OP_CHECKSIGจากนั้นเขาสร้าง commitment กับ redeem script โดยใช้กลไก HASH160 เดียวกับที่ใช้สำหรับ commitment แบบ P2PKH, RIPEMD160(SHA256(script)) commitment นั้นถูกวางไว้ในสคริปต์เอาต์พุตโดยใช้เทมเพลตพิเศษ:OP_HASH160 <commitment> OP_EQUALคำเตือน: เมื่อใช้ pay to script hash (P2SH) คุณต้องใช้เทมเพลต P2SH โดยเฉพาะ ซึ่งจะไม่มีข้อมูลหรือเงื่อนไขเพิ่มเติมในสคริปต์เอาต์พุต หากสคริปต์เอาต์พุตไม่ได้เป็น OP_HASH160 <20 ไบต์> OP_EQUAL แน่นอนว่า redeem script จะไม่ถูกใช้และบิตคอยน์ใด ๆ อาจไม่สามารถใช้จ่ายได้หรืออาจถูกใช้จ่ายได้โดยทุกคน (หมายความว่าใครก็สามารถนำไปใช้ได้)
เมื่อบ๊อบต้องการจ่ายเงินที่เขาได้รับผ่าน commitment สำหรับสคริปต์ของเขา เขาจะใช้สคริปต์อินพุตที่รวมถึง redeem script ซึ่งถูกแปลงให้เป็นข้อมูลอีลิเมนต์เดียว นอกจากนี้เขายังให้ลายเซ็นที่จำเป็นเพื่อให้เป็นไปตาม redeem script โดยเรียงลำดับตามที่จะถูกใช้โดย opcodes:
<signature2> <signature1> <redeem script>เมื่อโหนดของบิตคอยน์ได้รับการใช้จ่ายของบ๊อบพวกมันจะตรวจสอบว่า redeem script ที่ถูกแปลงเป็นค่าแฮชแล้วมีค่าเดียวกันกับ commitment มั้ย หลังจากนั้นพวกมันจะแทนที่มันบนสแต็คด้วยค่าที่ถอดรหัสแล้ว:<signature2> <signature1> <pubkey1> OP_CHECKSIGVERIFY <pubkey2> OP_CHECKSIGสคริปต์จะถูกประมวลผล และหากผ่านการตรวจสอบและรายละเอียดธุรกรรมอื่น ๆ ทั้งหมดถูกต้อง ธุรกรรมก็จะถือว่าใช้ได้address สำหรับ P2SH ก็ถูกสร้างด้วย base58check เช่นกัน คำนำหน้าเวอร์ชันถูกตั้งเป็น 5 ซึ่งทำให้ที่อยู่ที่เข้ารหัสแล้วขึ้นต้นด้วยเลข 3 ตัวอย่างของที่อยู่ P2SH คือ 3F6i6kwkevjR7AsAd4te2YB2zZyASEm1HM
TIP: P2SH ไม่จำเป็นต้องเหมือนกับธุรกรรมแบบหลายลายเซ็น (multisignature) เสมอไป ถึง address P2SH ส่วนใหญ่ แทนสคริปต์แบบหลายลายเซ็นก็ตาม แต่อาจแทนสคริปต์ที่เข้ารหัสธุรกรรมประเภทอื่น ๆ ได้ด้วย
P2PKH และ P2SH เป็นสองเทมเพลตสคริปต์เท่านั้นที่ใช้กับการเข้ารหัสแบบ base58check พวกมันเป็นที่รู้จักในปัจจุบันว่าเป็น address แบบ legacy และกลายเป็นรูปแบบที่พบน้อยลงเรื่อยๆ address แบบ legacy ถูกแทนที่ด้วยaddress ตระกูล bech32
การโจมตี P2SH แบบ Collision
address ทั้งหมดที่อิงกับฟังก์ชันแฮชมีความเสี่ยงในทางทฤษฎีต่อผู้โจมตีที่อาจค้นพบอินพุตเดียวกันที่สร้างเอาต์พุตฟังก์ชันแฮช (commitment) โดยอิสระ ในกรณีของบิตคอยน์ หากพวกเขาค้นพบอินพุตในวิธีเดียวกับที่ผู้ใช้ดั้งเดิมทำ พวกเขาจะรู้ private key ของผู้ใช้และสามารถใช้จ่ายบิตคอยน์ของผู้ใช้นั้นได้ โอกาสที่ผู้โจมตีจะสร้างอินพุตสำหรับ commitment ที่มีอยู่แล้วโดยอิสระนั้นขึ้นอยู่กับความแข็งแกร่งของอัลกอริทึมแฮช สำหรับอัลกอริทึมที่ปลอดภัย 160 บิตอย่าง HASH160 ความน่าจะเป็นอยู่ที่ 1 ใน 2^160 นี่เรียกว่าการโจมตีแบบ preimage attack
ผู้โจมตีสามารถพยายามสร้างข้อมูลนำเข้าสองชุดที่แตกต่างกัน (เช่น redeem scripts) ที่สร้างการเข้ารหัสแบบเดียวกันได้ สำหรับ address ที่สร้างโดยฝ่ายเดียวทั้งหมด โอกาสที่ผู้โจมตีจะสร้างข้อมูลนำเข้าที่แตกต่างสำหรับการเข้ารหัสที่มีอยู่แล้วมีประมาณ 1 ใน 2^160 สำหรับอัลกอริทึม HASH160 นี่คือการโจมตีแบบ second preimage attack
อย่างไรก็ตาม สถานการณ์จะเปลี่ยนไปเมื่อผู้โจมตีสามารถมีอิทธิพลต่อค่าข้อมูลนำเข้าดั้งเดิมได้ ตัวอย่างเช่น ผู้โจมตีมีส่วนร่วมในการสร้างสคริปต์แบบหลายลายเซ็น (multisignature script) ซึ่งพวกเขาไม่จำเป็นต้องส่ง public key ของตนจนกว่าจะทราบ public key ของฝ่ายอื่นทั้งหมด ในกรณีนั้น ความแข็งแกร่งของอัลกอริทึมการแฮชจะลดลงเหลือรากที่สองของมัน สำหรับ HASH160 ความน่าจะเป็นจะกลายเป็น 1 ใน 2^80 นี่คือการโจมตีแบบ collision attack
เพื่อให้เข้าใจตัวเลขเหล่านี้ในบริบทที่ชัดเจน ข้อมูล ณ ต้นปี 2023 นักขุดบิตคอยน์ทั้งหมดรวมกันสามารถประมวลผลฟังก์ชันแฮชประมาณ 2^80 ทุกชั่วโมง พวกเขาใช้ฟังก์ชันแฮชที่แตกต่างจาก HASH160 ดังนั้นฮาร์ดแวร์ที่มีอยู่จึงไม่สามารถสร้างการโจมตีแบบ collision attack สำหรับมันได้ แต่การมีอยู่ของเครือข่ายบิตคอยน์พิสูจน์ว่าการโจมตีแบบชนกันต่อฟังก์ชัน 160 บิตอย่าง HASH160 สามารถทำได้จริงในทางปฏิบัติ นักขุดบิตคอยน์ได้ลงทุนเทียบเท่ากับหลายพันล้านดอลลาร์สหรัฐในฮาร์ดแวร์พิเศษ ดังนั้นการสร้างการโจมตีแบบ collision attack จึงไม่ใช่เรื่องถูก แต่มีองค์กรที่คาดหวังว่าจะได้รับบิตคอยน์มูลค่าหลายพันล้านดอลลาร์ไปยัง address ที่สร้างโดยกระบวนการที่เกี่ยวข้องกับหลายฝ่าย ซึ่งอาจทำให้การโจมตีนี้มีกำไร
มีโปรโตคอลการเข้ารหัสที่เป็นที่ยอมรับอย่างดีในการป้องกันการโจมตีแบบ collision attack แต่วิธีแก้ปัญหาที่ง่ายโดยไม่ต้องใช้ความรู้พิเศษจากผู้พัฒนากระเป๋าเงินคือการใช้ฟังก์ชันแฮชที่แข็งแกร่งกว่า การอัปเกรดบิตคอยน์ในภายหลังทำให้เป็นไปได้ และ address บิตคอยน์ใหม่ให้ความต้านทานการชนกันอย่างน้อย 128 บิต การดำเนินการแฮช 2^128 ครั้งจะใช้เวลานักขุดบิตคอยน์ปัจจุบันทั้งหมดประมาณ 32 พันล้านปี
แม้ว่าเราไม่เชื่อว่ามีภัยคุกคามเร่งด่วนต่อผู้ที่สร้าง address P2SH ใหม่ แต่เราแนะนำให้กระเป๋าเงินใหม่ทั้งหมดใช้ที่อยู่ประเภทใหม่เพื่อขจัดความกังวลเกี่ยวกับการโจมตีแบบ collision attack ของ P2SH address
Bech32 Addresses
ในปี 2017 โปรโตคอลบิตคอยน์ได้รับการอัปเกรด เพื่อป้องกันไม่ให้ตัวระบุธุรกรรม (txids) ไม่สามารถเปลี่ยนแปลงได้ โดยไม่ได้รับความยินยอมจากผู้ใช้ที่ทำการใช้จ่าย (หรือองค์ประชุมของผู้ลงนามเมื่อต้องมีลายเซ็นหลายรายการ) การอัปเกรดนี้เรียกว่า segregated witness (หรือเรียกสั้นๆ ว่า segwit) ซึ่งยังให้ความสามารถเพิ่มเติมสำหรับข้อมูลธุรกรรมในบล็อกและประโยชน์อื่น ๆ อีกหลายประการ แต่อย่างไรก็ตาม หากมีผู้ใช้เก่าที่ต้องการเข้าถึงประโยชน์ของ segwit โดยตรงต้องยอมรับการชำระเงินไปยังสคริปต์เอาต์พุตใหม่
ตามที่ได้กล่าวไว้ใน p2sh หนึ่งในข้อดีของเอาต์พุตประเภท P2SH คือผู้จ่ายไม่จำเป็นต้องรู้รายละเอียดของสคริปต์ที่ผู้รับใช้ การอัปเกรด segwit ถูกออกแบบมาให้ใช้กลไกนี้ได้ดังเดิม จึง ทำให้ผู้จ่ายสามารถเริ่มเข้าถึงประโยชน์ใหม่ ๆ หลายอย่างได้ทันทีโดยใช้ที่อยู่ P2SH แต่เพื่อให้ผู้รับสามารถเข้าถึงประโยชน์เหล่านั้นได้ พวกเขาจำเป็นจะต้องให้กระเป๋าเงินของผู้จ่ายจ่ายเงินให้เขาโดยใช้สคริปต์ประเภทอื่นแทน ซึ่งจะต้องอาศัยการอัปเกรดกระเป๋าเงินของผู้จ่ายเพื่อรองรับสคริปต์ใหม่เหล่านี้
ในช่วงแรก เหล่านักพัฒนาบิตคอยน์ได้นำเสนอ BIP142 ซึ่งจะยังคงใช้ base58check ร่วมกับไบต์เวอร์ชันใหม่ คล้ายกับการอัปเกรด P2SH แต่การให้กระเป๋าเงินทั้งหมดอัปเกรดไปใช้สคริปต์ใหม่ที่มีเวอร์ชัน base58check ใหม่นั้น คาดว่าจะต้องใช้ความพยายามเกือบเท่ากับการให้พวกเขาอัปเกรดไปใช้รูปแบบ address ที่เป็นแบบใหม่ทั้งหมด ด้วยเหตุนี้้เอง ผู้สนับสนุนบิตคอยน์หลายคนจึงเริ่มออกแบบรูปแบบ address ที่ดีที่สุดเท่าที่เป็นไปได้ พวกเขาระบุปัญหาหลายอย่างกับ base58check ไว้ดังนี้:
- การที่ base58check ใช้อักษรที่มีทั้งตัวพิมพ์ใหญ่และตัวพิมพ์เล็กทำให้ไม่สะดวกในการอ่านออกเสียงหรือคัดลอก ลองอ่าน address แบบเก่าในบทนี้ให้เพื่อนฟังและให้พวกเขาคัดลอก คุณจะสังเกตว่าคุณต้องระบุคำนำหน้าทุกตัวอักษรด้วยคำว่า "ตัวพิมพ์ใหญ่" และ "ตัวพิมพ์เล็ก" และเมื่อคุณตรวจสอบสิ่งที่พวกเขาเขียน คุณจะพบว่าตัวพิมพ์ใหญ่และตัวพิมพ์เล็กของตัวอักษรบางตัวอาจดูคล้ายกันในลายมือของคนส่วนใหญ่
- รูปแบบนี้สามารถตรวจจับข้อผิดพลาดได้ แต่ไม่สามารถช่วยผู้ใช้แก้ไขข้อผิดพลาดเหล่านั้น ตัวอย่างเช่น หากคุณสลับตำแหน่งตัวอักษรสองตัวโดยไม่ตั้งใจเมื่อป้อน address ด้วยตนเอง กระเป๋าเงินของคุณจะเตือนว่ามีข้อผิดพลาดเกิดขึ้นแน่นอน แต่จะไม่ช่วยให้คุณค้นพบว่าข้อผิดพลาดอยู่ที่ไหน คุณอาจต้องใช้เวลาหลายนาทีที่น่าหงุดหงิดเพื่อค้นหาข้อผิดพลาดในที่สุด
- การใช้ตัวอักษรที่มีทั้งตัวพิมพ์ใหญ่และตัวพิมพ์เล็กยังต้องใช้พื้นที่เพิ่มเติมในการเข้ารหัสใน QR code ซึ่งนิยมใช้ในการแชร์ address และ invoice ระหว่างกระเป๋าเงิน พื้นที่เพิ่มเติมนี้หมายความว่า QR code จำเป็นต้องมีขนาดใหญ่ขึ้นที่ความละเอียดเดียวกัน หรือไม่เช่นนั้นก็จะยากต่อการสแกนอย่างรวดเร็ว
- การที่ต้องการให้กระเป๋าเงินผู้จ่ายทุกใบอัปเกรดเพื่อรองรับคุณสมบัติโปรโตคอลใหม่ เช่น P2SH และ segwit แม้ว่าการอัปเกรดเองอาจไม่ต้องใช้โค้ดมากนัก แต่ประสบการณ์แสดงให้เห็นว่าผู้พัฒนากระเป๋าเงินหลายรายมักยุ่งกับงานอื่น ๆ และบางครั้งอาจล่าช้าในการอัปเกรดเป็นเวลาหลายปี สิ่งนี้ส่งผลเสียต่อทุกคนที่ต้องการใช้คุณสมบัติใหม่ ๆ เหล่านี้
นักพัฒนาที่ทำงานเกี่ยวกับรูปแบบ address สำหรับ segwit ได้พบวิธีแก้ปัญหาเหล่านี้ทั้งหมดในรูปแบบ address แบบใหม่ที่เรียกว่า bech32 (ออกเสียงด้วย "ch" อ่อน เช่นใน "เบช สามสิบสอง") คำว่า "bech" มาจาก BCH ซึ่งเป็นอักษรย่อของบุคคลสามคนที่ค้นพบรหัสวนนี้ในปี 1959 และ 1960 ซึ่งเป็นพื้นฐานของ bech32 ส่วน "32" หมายถึงจำนวนตัวอักษรในชุดตัวอักษร bech32 (คล้ายกับ 58 ใน base58check):
-
Bech32 ใช้เฉพาะตัวเลขและตัวอักษรรูปแบบเดียว (โดยปกติจะแสดงเป็นตัวพิมพ์เล็ก) แม้ว่าชุดตัวอักษรของมันจะมีขนาดเกือบครึ่งหนึ่งของชุดตัวอักษรใน base58check ก็ตามแต่ address bech32 สำหรับสคริปต์ pay to witness public key hash (P2WPKH) ก็ยังยาวกว่า legacy address และมีขนาดเท่ากันกับสคริปต์ P2PKH
-
Bech32 สามารถทั้งตรวจจับและช่วยแก้ไขข้อผิดพลาดได้ ใน address ที่มีความยาวตามที่คาดหวังได้ และสามารถรับประกันทางคณิตศาสตร์ได้ว่าจะตรวจพบข้อผิดพลาดใด ๆ ที่ส่งผลกระทบต่อตัวอักษร 4 ตัวหรือน้อยกว่า ซึ่งเชื่อถือได้มากกว่า base58check ส่วนสำหรับข้อผิดพลาดที่ยาวกว่านั้น จะไม่สามารถตรวจพบได้ (โอกาสเกิดน้อยกว่าหนึ่งครั้งในหนึ่งพันล้าน) ซึ่งมีความเชื่อถือได้ประมาณเท่ากับ base58check ยิ่งไปกว่านั้น สำหรับ adddress ที่พิมพ์โดยมีข้อผิดพลาดเพียงเล็กน้อย มันสามารถบอกผู้ใช้ได้ว่าข้อผิดพลาดเหล่านั้นเกิดขึ้นที่ไหน ช่วยให้พวกเขาสามารถแก้ไขข้อผิดพลาดจากการคัดลอกเล็ก ๆ น้อย ๆ ได้อย่างรวดเร็ว
-
ตัวอย่างที่ 3 Bech32 address ที่มีข้อผิดพลาด Address: bc1p9nh05ha8wrljf7ru236awn4t2x0d5ctkkywmv9sclnm4t0av2vgs4k3au7 ข้อผิดพลาดที่ตรวจพบแสดงเป็นตัวหนาและขีดเส้นใต้ สร้างโดยใช้โปรแกรมสาธิตการถอดรหัส bech32 address
-
bech32 address นิยมเขียนด้วยตัวอักษรพิมพ์เล็กเท่านั้น แต่ตัวอักษรพิมพ์เล็กเหล่านี้สามารถแทนที่ด้วยตัวอักษรพิมพ์ใหญ่ก่อนการเข้ารหัส address ในรหัส QR ได้ วิธีนี้ช่วยให้สามารถใช้โหมดการเข้ารหัส QR แบบพิเศษที่ใช้พื้นที่น้อยกว่า คุณจะสังเกตเห็นความแตกต่างในขนาดและความซับซ้อนของรหัส QR ทั้งสองสำหรับที่อยู่เดียวกันในรูปภาพข้างล่างนี้

- Bech32 ใช้ประโยชน์จากกลไกการอัปเกรดที่ออกแบบมาเป็นส่วนหนึ่งของ segwit เพื่อทำให้กระเป๋าเงินผู้จ่ายสามารถจ่ายเงินไปยังประเภทเอาต์พุตที่ยังไม่ได้ใช้งานได้ โดยมีเป้าหมายคือการอนุญาตให้นักพัฒนาสร้างกระเป๋าเงินในวันนี้ที่สามารถใช้จ่ายไปยัง bech32 address และทำให้กระเป๋าเงินนั้นยังคงสามารถใช้จ่ายไปยัง bech32address ได้สำหรับผู้ใช้คุณสมบัติใหม่ที่เพิ่มในการอัปเกรดโปรโตคอลในอนาคต โดยที่มีความหวังว่าเราอาจไม่จำเป็นต้องผ่านรอบการอัปเกรดทั้งระบบอีกต่อไป ซึ่งจำเป็นสำหรับการให้ผู้คนใช้งาน P2SH และ segwit ได้อย่างเต็มรูปแบบ
-
Problems with Bech32 Addresses
address แบบ bech32 ประสบความสำเร็จในทุกด้านยกเว้นปัญหาหนึ่ง คือการรับประกันทางคณิตศาสตร์เกี่ยวกับความสามารถในการตรวจจับข้อผิดพลาดจะใช้ได้เฉพาะเมื่อความยาวของ address ที่คุณป้อนเข้าไปในกระเป๋าเงินมีความยาวเท่ากับ address ดั้งเดิมเท่านั้น หากคุณเพิ่มหรือลบตัวอักษรใด ๆ ระหว่างการคัดลอกจะทำให้ไม่สามารถตรวจจับได้ การรับประกันนี้จะไม่มีผล และกระเป๋าเงินของคุณอาจใช้จ่ายเงินไปยัง address ที่ไม่ถูกต้อง แต่อย่างไรก็ตาม แม้จะไม่มีคุณสมบัตินี้ มีความเชื่อว่าเป็นไปได้ยากมากที่ผู้ใช้ที่เพิ่มหรือลบตัวอักษรจะสร้างสตริงที่มีผลรวมตรวจสอบที่ถูกต้อง ซึ่งช่วยให้มั่นใจได้ว่าเงินของผู้ใช้จะปลอดภัย
น่าเสียดายที่การเลือกใช้ค่าคงที่ตัวหนึ่งในอัลกอริทึม bech32 บังเอิญทำให้การเพิ่มหรือลบตัวอักษร "q" ในตำแหน่งที่สองจากท้ายของ address ที่ลงท้ายด้วยตัวอักษร "p" เป็นเรื่องง่ายมาก ในกรณีเหล่านั้น คุณยังสามารถเพิ่มหรือลบตัวอักษร "q" หลายครั้งได้ด้วย ข้อผิดพลาดนี้จะถูกตรวจจับโดยผลรวมตรวจสอบ (checksum) ในบางครั้ง แต่จะถูกมองข้ามบ่อยกว่าความคาดหวังหนึ่งในพันล้านสำหรับข้อผิดพลาดจากการแทนที่ของ bech32 อย่างมาก สำหรับตัวอย่างสามารถดูได้ในรูปภาพข้างล่างนี้
ตัวอย่างที่ 4. การขยายความยาวของ bech32 address โดยไม่ทำให้ผลรวมตรวจสอบเป็นโมฆะ ``` bech32 address ที่ถูกต้อง: bc1pqqqsq9txsqp
address ที่ไม่ถูกต้องแต่มีผลรวมตรวจสอบที่ถูกต้อง: bc1pqqqsq9txsqqqqp bc1pqqqsq9txsqqqqqqp bc1pqqqsq9txsqqqqqqqqp bc1pqqqsq9txsqqqqqqqqqp bc1pqqqsq9txsqqqqqqqqqqqp ```
จากตัวอย่างนี้ คุณจะเห็นว่าแม้มีการเพิ่มตัวอักษร "q" เข้าไปหลายตัวก่อนตัวอักษร "p" ตัวสุดท้าย ระบบตรวจสอบก็ยังคงยอมรับว่า address เหล่านี้ถูกต้อง นี่เป็นข้อบกพร่องสำคัญของ bech32 เพราะอาจทำให้เงินถูกส่งไปยัง address ที่ไม่มีใครเป็นเจ้าของจริง ๆ หรือ address ที่ไม่ได้ตั้งใจจะส่งไป
สำหรับเวอร์ชันเริ่มต้นของ segwit (เวอร์ชัน 0) ปัญหานี้ไม่ใช่ความกังวลในทางปฏิบัติ เพราะมีความยาวที่ถูกต้องมีเพียงสองแบบที่กำหนดไว้สำหรับเอาต์พุต นั้นคือ 22 Byte และ 34 Byte ซึ่งสอดคล้องกับ bech32 address ที่มีความยาวยาวที่ 42 หรือ 62 ตัวอักษร ดังนั้นคนจะต้องเพิ่มหรือลบตัวอักษร "q" จากตำแหน่งที่สองจากท้ายของ bech32 address ถึง 20 ครั้งเพื่อส่งเงินไปยัง address ที่ไม่ถูกต้องโดยที่กระเป๋าเงินไม่สามารถตรวจจับได้ อย่างไรก็ตาม มันอาจกลายเป็นปัญหาสำหรับผู้ใช้ในอนาคตหากมีการนำการอัปเกรดบนพื้นฐานของ segwit มาใช้
Bech32m
แม้ว่า bech32 จะทำงานได้ดีสำหรับ segwit v0 แต่นักพัฒนาไม่ต้องการจำกัดขนาดเอาต์พุตโดยไม่จำเป็นในเวอร์ชันหลังๆ ของ segwit หากไม่มีข้อจำกัด การเพิ่มหรือลบตัวอักษร "q" เพียงตัวเดียวใน bech32 address อาจทำให้ผู้ใช้ส่งเงินโดยไม่ตั้งใจไปยังเอาต์พุตที่ไม่สามารถใช้จ่ายได้หรือสามารถใช้จ่ายได้โดยทุกคน (ทำให้บิตคอยน์เหล่านั้นถูกนำไปโดยทุกคนได้) นักพัฒนาได้วิเคราะห์ปัญหา bech32 อย่างละเอียดและพบว่าการเปลี่ยนค่าคงที่เพียงตัวเดียวในอัลกอริทึมของพวกเขาจะขจัดปัญหานี้ได้ ทำให้มั่นใจว่าการแทรกหรือลบตัวอักษรสูงสุดห้าตัวจะไม่ถูกตรวจจับน้อยกว่าหนึ่งครั้งในหนึ่งพันล้านเท่านั้น
เวอร์ชันของ bech32 ที่มีค่าคงที่เพียงหนึ่งตัวที่แตกต่างกันเรียกว่า bech32 แบบปรับแต่ง (bech32m) ตัวอักษรทั้งหมดใน address แบบ bech32 และ bech32m สำหรับข้อมูลพื้นฐานเดียวกันจะเหมือนกันทั้งหมด ยกเว้นหกตัวสุดท้าย (ซึ่งเป็นส่วนของ checksum) นั่นหมายความว่ากระเป๋าเงินจำเป็นต้องรู้ว่ากำลังใช้เวอร์ชันใดเพื่อตรวจสอบความถูกต้องของ checksum แต่ address ทั้งสองประเภทมีไบต์เวอร์ชันภายในที่ทำให้การระบุเวอร์ชันที่ใช้อยู่เป็นเรื่องที่ง่าย ในการทำงานกับทั้ง bech32 และ bech32m เราจะพิจารณากฎการเข้ารหัสและการแยกวิเคราะห์สำหรับ address บิตคอยน์แบบ bech32m เนื่องจากพวกมันครอบคลุมความสามารถในการแยกวิเคราะห์บน address แบบ bech32 และเป็นรูปแบบ address ที่แนะนำในปัจจุบันสำหรับกระเป๋าเงินบิตคอยน์
ข้อความจากหลาม: คือผมว่าตรงนี้เขาเขียนไม่รู้เรื่อง แต่เดาว่าเขาน่าจะสื่อว่า เราควรเรียนรู้วิธีการทำงานกับ bech32m เพราะมันเป็นรูปแบบที่แนะนำให้ใช้ในปัจจุบัน และมันมีข้อดีเพราะbech32m สามารถรองรับการอ่าน address แบบ bech32 แบบเก่าได้ด้วย ง่ายๆ คือ ถ้าคุณเรียนรู้วิธีทำงานกับ bech32m คุณจะสามารถทำงานกับทั้ง bech32m และ bech32 ได้ทั้งสองแบบ
bech32m address ริ่มต้นด้วยส่วนที่มนุษย์อ่านได้ (Human Readable Part: HRP) BIP173 มีกฎสำหรับการสร้าง HRP ของคุณเอง แต่สำหรับบิตคอยน์ คุณเพียงแค่จำเป็นต้องรู้จัก HRP ที่ถูกเลือกไว้แล้วตามที่แสดงในตารางข้างล่างนี้

ส่วน HRP ตามด้วยตัวคั่น ซึ่งก็คือเลข "1" ในข้อเสนอก่อนหน้านี้สำหรับตัวคั่นโปรโตคอลได้ใช้เครื่องหมายทวิภาค (colon) แต่ระบบปฏิบัติการและแอปพลิเคชันบางตัวที่อนุญาตให้ผู้ใช้ดับเบิลคลิกคำเพื่อไฮไลต์สำหรับการคัดลอกและวางนั้นจะไม่ขยายการไฮไลต์ไปถึงและผ่านเครื่องหมายทวิภาค
การใช้ตัวเลขช่วยให้มั่นใจได้ว่าการไฮไลต์ด้วยดับเบิลคลิกจะทำงานได้กับโปรแกรมใดๆ ที่รองรับสตริง bech32m โดยทั่วไป (ซึ่งรวมถึงตัวเลขอื่นๆ ด้วย) เลข "1" ถูกเลือกเพราะสตริง bech32 ไม่ได้ใช้เลข 1 ในกรณีอื่น เพื่อป้องกันการแปลงโดยไม่ตั้งใจระหว่างเลข "1" กับตัวอักษรพิมพ์เล็ก "l"
และส่วนอื่นของ bech32m address เรียกว่า "ส่วนข้อมูล" (data part) ซึ่งประกอบด้วยสามองค์ประกอบ:
- Witness version: ไบต์ถัดไปหลังจากตัวคั่นตัวอักษรนี้แทนเวอร์ชันของ segwit ตัวอักษร "q" คือการเข้ารหัสของ "0" สำหรับ segwit v0 ซึ่งเป็นเวอร์ชันแรกของ segwit ที่มีการแนะนำที่อยู่ bech32 ตัวอักษร "p" คือการเข้ารหัสของ "1" สำหรับ segwit v1 (หรือเรียกว่า taproot) ซึ่งเริ่มมีการใช้งาน bech32m มีเวอร์ชันที่เป็นไปได้ทั้งหมด 17 เวอร์ชันของ segwit และสำหรับ Bitcoin จำเป็นต้องให้ไบต์แรกของส่วนข้อมูล bech32m ถอดรหัสเป็นตัวเลข 0 ถึง 16 (รวมทั้งสองค่า)
- Witness program: คือตำแหน่งหลังจาก witnessversion ตั้งแต่ตำแหน่ง 2 ถึง 40 Byte สำหรับ segwit v0 นี้ต้องมีความยาว 20 หรือ 32 Byte ไม่สามารถ ffมีขนาดอื่นได้ สำหรับ segwit v1 ความยาวเดียวที่ถูกกำหนดไว้ ณ เวลาที่เขียนนี้คือ 32 ไบต์ แต่อาจมีการกำหนดความยาวอื่น ๆ ได้ในภายหลัง
- Checksum: มีความยาว 6 ตัวอักษร โดยส่วนนี้ถูกสร้างขึ้นโดยใช้รหัส BCH ซึ่งเป็นประเภทของรหัสแก้ไขข้อผิดพลาด (error corection code) (แต่อย่างไรก็ตาม สำหรับ address บิตคอยน์ เราจะเห็นในภายหลังว่าเป็นสิ่งสำคัญที่จะใช้ checksum เพื่อการตรวจจับข้อผิดพลาดเท่านั้น—ไม่ใช่การแก้ไข
ในส่วนต่อไปหลังจากนี้เราจะลองสร้าง address แบบ bech32 และ bech32m สำหรับตัวอย่างทั้งหมดต่อไปนี้ เราจะใช้โค้ดอ้างอิง bech32m สำหรับ Python
เราจะเริ่มด้วยการสร้างสคริปต์เอาต์พุตสี่ตัว หนึ่งตัวสำหรับแต่ละเอาต์พุต segwit ที่แตกต่างกันที่ใช้ในช่วงเวลาของการเผยแพร่ บวกกับอีกหนึ่งตัวสำหรับเวอร์ชัน segwit ในอนาคตที่ยังไม่มีความหมายที่กำหนดไว้ สคริปต์เหล่านี้แสดงอยู่ในตารางข้างล่างนี้

สำหรับเอาต์พุต P2WPKH witness program มีการผูก commitment ที่สร้างขึ้นในลักษณะเดียวกันกับ P2PKH ที่เห็นใน Legacy Addresses for P2PKH โดย public key ถูกส่งเข้าไปในฟังก์ชันแฮช SHA256 ไดเจสต์ขนาด 32 ไบต์ที่ได้จะถูกส่งเข้าไปในฟังก์ชันแฮช RIPEMD-160 ไดเจสต์ของฟังก์ชันนั้น จะถูกวางไว้ใน witness program
สำหรับเอาต์พุตแบบ pay to witness script hash (P2WSH) เราไม่ได้ใช้อัลกอริทึม P2SH แต่เราจะนำสคริปต์ ส่งเข้าไปในฟังก์ชันแฮช SHA256 และใช้ไดเจสต์ขนาด 32 ไบต์ของฟังก์ชันนั้นใน witness program สำหรับ P2SH ไดเจสต์ SHA256 จะถูกแฮชอีกครั้งด้วย RIPEMD-160 ซึ่งแน่นอนว่าอาจจะไม่ปลอดภัย ในบางกรณี สำหรับรายละเอียด ดูที่ P2SH Collision Attacks ผลลัพธ์ของการใช้ SHA256 โดยไม่มี RIPEMD-160 คือ การผูกพันแบบ P2WSH มีขนาด 32 ไบต์ (256 บิต) แทนที่จะเป็น 20 ไบต์ (160 บิต)
สำหรับเอาต์พุตแบบ pay-to-taproot (P2TR) witness program คือจุดบนเส้นโค้ง secp256k1 มันอาจเป็น public key แบบธรรมดา แต่ในกรณีส่วนใหญ่มันควรเป็น public key ที่ผูกพันกับข้อมูลเพิ่มเติมบางอย่าง เราจะเรียนรู้เพิ่มเติมเกี่ยวกับการผูกพันนั้นในหัวข้อของ taproot
สำหรับตัวอย่างของเวอร์ชัน segwit ในอนาคต เราเพียงแค่ใช้หมายเลขเวอร์ชัน segwit ที่สูงที่สุดที่เป็นไปได้ (16) และ witness program ที่มีขนาดเล็กที่สุดที่อนุญาต (2 ไบต์) โดยมีค่าเป็นศูนย์ (null value)
เมื่อเรารู้หมายเลขเวอร์ชันและ witness program แล้ว เราสามารถแปลงแต่ละอย่างให้เป็น bech32 address ได้ โดยการใช้ไลบรารีอ้างอิง bech32m สำหรับ Python เพื่อสร้าง address เหล่านั้นอย่างรวดเร็ว และจากนั้นมาดูอย่างละเอียดว่าเกิดอะไรขึ้น:
``` $ github=" https://raw.githubusercontent.com" $ wget $github/sipa/bech32/master/ref/python/segwit_addr.py $ python
from segwit_addr import * from binascii import unhexlify help(encode) encode(hrp, witver, witprog) Encode a segwit address. encode('bc', 0, unhexlify('2b626ed108ad00a944bb2922a309844611d25468')) 'bc1q9d3xa5gg45q2j39m9y32xzvygcgay4rgc6aaee' encode('bc', 0, unhexlify('648a32e50b6fb7c5233b228f60a6a2ca4158400268844c4bc295ed5e8c3d626f')) 'bc1qvj9r9egtd7mu2gemy28kpf4zefq4ssqzdzzycj7zjhk4arpavfhsct5a3p' encode('bc', 1, unhexlify('2ceefa5fa770ff24f87c5475d76eab519eda6176b11dbe1618fcf755bfac5311')) 'bc1p9nh05ha8wrljf7ru236awm4t2x0d5ctkkywmu9sclnm4t0av2vgs4k3au7' encode('bc', 16, unhexlify('0000')) 'bc1sqqqqkfw08p'
หากเราเปิดไฟล์ segwit_addr.py และดูว่าโค้ดกำลังทำอะไร สิ่งแรกที่เราจะสังเกตเห็นคือความแตกต่างเพียงอย่างเดียวระหว่าง bech32 (ที่ใช้สำหรับ segwit v0) และ bech32m (ที่ใช้สำหรับเวอร์ชัน segwit รุ่นหลัง) คือค่าคงที่:BECH32_CONSTANT = 1 BECH32M_CONSTANT = 0x2bc830a3 ```และในส่วนต่อไป เราจะเห็นโค้ดที่สร้าง checksum ในขั้นตอนสุดท้ายของการสร้าง checksum ค่าคงที่ที่เหมาะสมถูกรวมเข้ากับข้อมูลอื่น ๆ โดยใช้การดำเนินการ xor ค่าเดียวนั้นคือความแตกต่างเพียงอย่างเดียวระหว่าง bech32 และ bech32m
เมื่อสร้าง checksum แล้ว อักขระ 5 บิตแต่ละตัวในส่วนข้อมูล (รวมถึง witness version, witness program และ checksum) จะถูกแปลงเป็นตัวอักษรและตัวเลข
สำหรับการถอดรหัสกลับเป็นสคริปต์เอาต์พุต เราทำงานย้อนกลับ ลองใช้ไลบรารีอ้างอิงเพื่อถอดรหัส address สอง address ของเรา: ```
help(decode) decode(hrp, addr) Decode a segwit address. _ = decode("bc", "bc1q9d3xa5gg45q2j39m9y32xzvygcgay4rgc6aaee") [0], bytes([1]).hex() (0, '2b626ed108ad00a944bb2922a309844611d25468') _ = decode("bc", "bc1p9nh05ha8wrljf7ru236awm4t2x0d5ctkkywmu9sclnm4t0av2vgs4k3au7") [0], bytes([1]).hex() (1, '2ceefa5fa770ff24f87c5475d76eab519eda6176b11dbe1618fcf755bfac5311')
เราได้รับทั้ง witness version และ witness program กลับมา สิ่งเหล่านี้สามารถแทรกลงในเทมเพลตสำหรับสคริปต์เอาต์พุตของเรา:ตัวอย่างเช่น:OP_0 2b626ed108ad00a944bb2922a309844611d25468 OP_1 2ceefa5fa770ff24f87c5475d76eab519eda6176b11dbe1618fcf755bfac5311 ``` คำเตือน: ข้อผิดพลาดที่อาจเกิดขึ้นที่ควรระวังคือ witness version ที่มีค่า 0 ใช้สำหรับ OP_0 ซึ่งใช้ไบต์ 0x00—แต่เวอร์ชัน witness ที่มีค่า 1 ใช้ OP_1 ซึ่งเป็นไบต์ 0x51 เวอร์ชัน witness 2 ถึง 16 ใช้ไบต์ 0x52 ถึง 0x60 ตามลำดับเมื่อทำการเขียนโค้ดเพื่อเข้ารหัสหรือถอดรหัส bech32m เราขอแนะนำอย่างยิ่งให้คุณใช้เวกเตอร์ทดสอบ (test vectors) ที่มีให้ใน BIP350 เราขอให้คุณตรวจสอบให้แน่ใจว่าโค้ดของคุณผ่านเวกเตอร์ทดสอบที่เกี่ยวข้องกับการจ่ายเงินให้กับเวอร์ชัน segwit ในอนาคตที่ยังไม่ได้รับการกำหนด สิ่งนี้จะช่วยให้ซอฟต์แวร์ของคุณสามารถใช้งานได้อีกหลายปีข้างหน้า แม้ว่าคุณอาจจะไม่สามารถเพิ่มการรองรับคุณสมบัติใหม่ ๆ ของบิตคอยน์ได้ทันทีที่คุณสมบัตินั้น ๆ เริ่มใช้งานได้
Private Key Formats
private key สามารถถูกแสดงได้ในหลาย ๆ รูปแบบที่ต่างกันซึ่งสามารถแปลงเป็นตัวเลขขนาด 256 bit ชุดเดียวกันได้ ดังที่เราจะแสดงให้ดูในตารางข้างล่างนี้ รูปแบบที่แตกต่างกันถูกใช้ในสถานการณ์ที่ต่างกัน รูปแบบเลขฐานสิบหก (Hexadecimal) และรูปแบบไบนารี (raw binary) ถูกใช้ภายในซอฟต์แวร์และแทบจะไม่แสดงให้ผู้ใช้เห็น WIF ถูกใช้สำหรับการนำเข้า/ส่งออกกุญแจระหว่างกระเป๋าเงินและมักใช้ในการแสดงกุญแจส่วนตัวแบบ QR code
รูปแบบของ private key ในปัจจุบัน
ซอฟต์แวร์กระเป๋าเงินบิตคอยน์ในยุคแรกได้สร้าง private key อิสระอย่างน้อยหนึ่งดอกเมื่อกระเป๋าเงินของผู้ใช้ใหม่ถูกเริ่มต้น เมื่อชุดกุญแจเริ่มต้นถูกใช้ทั้งหมดแล้ว กระเป๋าเงินอาจสร้าง private key เพิ่มเติม private key แต่ละดอกสามารถส่งออกหรือนำเข้าได้ ทุกครั้งที่มีการสร้างหรือนำเข้า private key ใหม่ จะต้องมีการสร้างการสำรองข้อมูลกระเป๋าเงินใหม่ด้วย
กระเป๋าเงินบิตคอยน์ในยุคหลังเริ่มใช้กระเป๋าเงินแบบกำหนดได้ (deterministic wallets) ซึ่ง private key ทั้งหมดถูกสร้างจาก seed เพียงค่าเดียว กระเป๋าเงินเหล่านี้จำเป็นต้องสำรองข้อมูลเพียงครั้งเดียวเท่านั้นสำหรับการใช้งานบนเชนทั่วไป แต่อย่างไรก็ตาม หากผู้ใช้ส่งออก private key เพียงดอกเดียวจากกระเป๋าเงินเหล่านี้ และผู้โจมตีได้รับกุญแจนั้นรวมถึงข้อมูลที่ไม่ใช่ข้อมูลส่วนตัวบางอย่างเกี่ยวกับกระเป๋าเงิน พวกเขาอาจสามารถสร้างกุญแจส่วนตัวใด ๆ ในกระเป๋าเงินได้—ทำให้ผู้โจมตีสามารถขโมยเงินทั้งหมดในกระเป๋าเงินได้ นอกจากนี้ ยังไม่สามารถนำเข้ากุญแจสู่กระเป๋าเงินแบบกำหนดได้ นี่หมายความว่าแทบไม่มีกระเป๋าเงินสมัยใหม่ที่รองรับความสามารถในการส่งออกหรือนำเข้ากุญแจเฉพาะดอก ข้อมูลในส่วนนี้มีความสำคัญหลัก ๆ สำหรับผู้ที่ต้องการความเข้ากันได้กับกระเป๋าเงินบิตคอยน์ในยุคแรก ๆ
รูปแบบของ private key (รูปแบบการเข้ารหัส)
 private key เดียวกันในแต่ละ format
private key เดียวกันในแต่ละ format
 รูปแบบการแสดงผลทั้งหมดเหล่านี้เป็นวิธีต่างๆ ในการแสดงเลขจำนวนเดียวกัน private key เดียวกัน พวกมันดูแตกต่างกัน แต่รูปแบบใดรูปแบบหนึ่งสามารถแปลงไปเป็นรูปแบบอื่นได้อย่างง่ายดาย
รูปแบบการแสดงผลทั้งหมดเหล่านี้เป็นวิธีต่างๆ ในการแสดงเลขจำนวนเดียวกัน private key เดียวกัน พวกมันดูแตกต่างกัน แต่รูปแบบใดรูปแบบหนึ่งสามารถแปลงไปเป็นรูปแบบอื่นได้อย่างง่ายดายCompressed Private Keys
คำว่า compressed private key ที่ใช้กันทั่วไปนั้นเป็นคำที่เรียกผิด เพราะเมื่อ private key ถูกส่งออกไปในรูปแบบ WIF-compressed มันจะมีความยาวมากกว่า private key แบบ uncompressed 1 Byte (เลข 01 ในช่อง Hex-compressed ในตารางด้านล่างนี้) ซึ่งบ่งบอกว่า private key ตัวนี้ มาจากกระเป๋าเงินรุ่นใหม่และควรใช้เพื่อสร้าง compressed public key เท่านั้น
private key เองไม่ได้ถูกบีบอัดและไม่สามารถบีบอัดได้ คำว่า compressed private key จริงๆ แล้วหมายถึง " private key ซึ่งควรใช้สร้าง compressed public key เท่านั้น" ในขณะที่ uncompressed private key จริงๆ แล้วหมายถึง “private key ซึ่งควรใช้สร้าง uncompressed public key เท่านั้น” คุณควรใช้เพื่ออ้างถึงรูปแบบการส่งออกเป็น "WIF-compressed" หรือ "WIF" เท่านั้น และไม่ควรอ้างถึง private key ว่า "บีบอัด" เพื่อหลีกเลี่ยงความสับสนต่อไป
ตารางนี้แสดงกุญแจเดียวกันที่ถูกเข้ารหัสในรูปแบบ WIF และ WIF-compressed
ตัวอย่าง: กุญแจเดียวกัน แต่รูปแบบต่างกัน

สังเกตว่ารูปแบบ Hex-compressed มีไบต์เพิ่มเติมหนึ่งไบต์ที่ท้าย (01 ในเลขฐานสิบหก) ในขณะที่คำนำหน้าเวอร์ชันการเข้ารหัสแบบ base58 เป็นค่าเดียวกัน (0x80) สำหรับทั้งรูปแบบ WIF และ WIF-compressed การเพิ่มหนึ่งไบต์ที่ท้ายของตัวเลขทำให้อักขระตัวแรกของการเข้ารหัสแบบ base58 เปลี่ยนจาก 5 เป็น K หรือ L
คุณสามารถคิดถึงสิ่งนี้เหมือนกับความแตกต่างของการเข้ารหัสเลขฐานสิบระหว่างตัวเลข 100 และตัวเลข 99 ในขณะที่ 100 มีความยาวมากกว่า 99 หนึ่งหลัก มันยังมีคำนำหน้าเป็น 1 แทนที่จะเป็นคำนำหน้า 9 เมื่อความยาวเปลี่ยนไป มันส่งผลต่อคำนำหน้า ในระบบ base58 คำนำหน้า 5 เปลี่ยนเป็น K หรือ L เมื่อความยาวของตัวเลขเพิ่มขึ้นหนึ่งไบต์
TIPจากหลาม: ผมว่าเขาเขียนย่อหน้านี้ไม่ค่อยรู้เรื่อง แต่ความหมายมันจะประมาณว่า เหมือนถ้าเราต้องการเขียนเลข 100 ในฐาน 10 เราต้องใช้สามตำแหน่ง 100 แต่ถ้าใช้ฐาน 16 เราจะใช้แค่ 2 ตำแหน่งคือ 64 ซึ่งมีค่าเท่ากัน
ถ้ากระเป๋าเงินบิตคอยน์สามารถใช้ compressed public key ได้ มันจะใช้ในทุกธุรกรรม private key ในกระเป๋าเงินจะถูกใช้เพื่อสร้างจุด public key บนเส้นโค้ง ซึ่งจะถูกบีบอัด compressed public key จะถูกใช้เพื่อสร้าง address และ address เหล่านี้จะถูกใช้ในธุรกรรม เมื่อส่งออก private key จากกระเป๋าเงินใหม่ที่ใช้ compressed public key WIF จะถูกปรับเปลี่ยน โดยเพิ่มต่อท้ายขนาด 1 ไบต์ 01 ให้กับ private key ที่ถูกเข้ารหัสแบบ base58check ที่ได้จะเรียกว่า "WIF-compressed" และจะขึ้นต้นด้วยอักษร K หรือ L แทนที่จะขึ้นต้นด้วย "5" เหมือนกับกรณีของคีย์ที่เข้ารหัสแบบ WIF (ไม่บีบอัด) จากกระเป๋าเงินรุ่นเก่า
Advanced Keys and Addresses
ในส่วนต่อไปนี้ เราจะดูรูปแบบของคีย์และ address เช่น vanity addresses และ paper wallets
vanity addresses
vanity addresses หรือ addresses แบบกำหนดเอง คือ address ที่มีข้อความที่มนุษย์อ่านได้และสามารถใช้งานได้จริง ตัวอย่างเช่น 1LoveBPzzD72PUXLzCkYAtGFYmK5vYNR33 อย่างที่เห็นว่ามันเป็น address ที่ถูกต้องซึ่งมีตัวอักษรเป็นคำว่า Love เป็นตัวอักษร base58 สี่ตัวแรก addresses แบบกำหนดเองต้องอาศัยการสร้างและทดสอบ private key หลายพันล้านตัวจนกว่าจะพบ address ที่มีรูปแบบตามที่ต้องการ แม้ว่าจะมีการปรับปรุงบางอย่างในอัลกอริทึมการสร้าง addresses แบบกำหนดเอง แต่กระบวนการนี้ต้องใช้การสุ่มเลือก private key มาสร้าง public key และนำไปสร้าง address และตรวจสอบว่าตรงกับรูปแบบที่ต้องการหรือไม่ โดยทำซ้ำหลายพันล้านครั้งจนกว่าจะพบที่ตรงกัน
เมื่อพบ address ที่ตรงกับรูปแบบที่ต้องการแล้ว private key ที่ใช้สร้าง address นั้นสามารถใช้โดยเจ้าของเพื่อใช้จ่ายบิตคอยน์ได้เหมือนกับ address อื่น ๆ ทุกประการ address ที่กำหนดเองไม่ได้มีความปลอดภัยน้อยกว่าหรือมากกว่าที่ address ๆ พวกมันขึ้นอยู่กับการเข้ารหัสเส้นโค้งรูปวงรี (ECC) และอัลกอริทึมแฮชที่ปลอดภัย (SHA) เหมือนกับ address อื่น ๆ คุณไม่สามารถค้นหา private key ของ address ที่ขึ้นต้นด้วยรูปแบบที่กำหนดเองได้ง่ายกว่า address อื่น ๆ
ตัวอย่างเช่น ยูจีเนียเป็นผู้อำนวยการการกุศลเพื่อเด็กที่ทำงานในฟิลิปปินส์ สมมติว่ายูจีเนียกำลังจัดการระดมทุนและต้องการใช้ address ที่กำหนดเองเพื่อประชาสัมพันธ์การระดมทุน ยูจีเนียจะสร้าง address ที่กำหนดเองที่ขึ้นต้นด้วย "1Kids" เพื่อส่งเสริมการระดมทุนเพื่อการกุศลสำหรับเด็ก มาดูกันว่า address ที่กำหนดเองนี้จะถูกสร้างขึ้นอย่างไรและมีความหมายอย่างไรต่อความปลอดภัยของการกุศลของยูจีเนีย
การสร้าง address ที่กำหนดเอง
ควรเข้าใจว่า address ของบิตคอยน์เป็นเพียงตัวเลขที่แสดงด้วยสัญลักษณ์ในรูปแบบตัวอักษร base58 เท่านั้น เพราะฉะนั้นแล้ว การค้นหารูปแบบเช่น "1Kids" สามารถมองได้ว่าเป็นการค้นหาที่อยู่ในช่วงตั้งแต่ 1Kids11111111111111111111111111111 ถึง 1Kidszzzzzzzzzzzzzzzzzzzzzzzzzzzzz มีประมาณ 5829 (ประมาณ 1.4 × 1051) address ในช่วงนั้น ทั้งหมดขึ้นต้นด้วย "1Kids" ตารางด้านล่างนี้แสดงช่วงของ address ที่มีคำนำหน้า 1Kids
 ลองดูรูปแบบ "1Kids" ในรูปของตัวเลขและดูว่าเราอาจพบรูปแบบนี้ใน bitcoin address บ่อยแค่ไหน โดยตารางข้างล่างนี้แสดงให้เห็นถีงคอมพิวเตอร์เดสก์ท็อปทั่วไปที่ไม่มีฮาร์ดแวร์พิเศษสามารถค้นหาคีย์ได้ประมาณ 100,000 คีย์ต่อวินาที
ลองดูรูปแบบ "1Kids" ในรูปของตัวเลขและดูว่าเราอาจพบรูปแบบนี้ใน bitcoin address บ่อยแค่ไหน โดยตารางข้างล่างนี้แสดงให้เห็นถีงคอมพิวเตอร์เดสก์ท็อปทั่วไปที่ไม่มีฮาร์ดแวร์พิเศษสามารถค้นหาคีย์ได้ประมาณ 100,000 คีย์ต่อวินาทีความถี่ของ address ที่กำหนดเอง (1KidsCharity) และเวลาค้นหาเฉลี่ยบนคอมพิวเตอร์เดสก์ท็อป

ดังที่เห็นได้ ยูจีเนียคงไม่สามารถสร้าง address แบบกำหนดเอง "1KidsCharity" ได้ในเร็ว ๆ นี้ แม้ว่าเธอจะมีคอมพิวเตอร์หลายพันเครื่องก็ตาม ทุกตัวอักษรที่เพิ่มขึ้นจะเพิ่มความยากขึ้น 58 เท่า รูปแบบที่มีมากกว่า 7 ตัวอักษรมักจะถูกค้นพบโดยฮาร์ดแวร์พิเศษ เช่น คอมพิวเตอร์เดสก์ท็อปที่สร้างขึ้นเป็นพิเศษที่มีหน่วยประมวลผลกราฟิก (GPUs) หลายตัว การค้นหา address แบบกำหนดเองบนระบบ GPU เร็วกว่าบน CPU ทั่วไปหลายเท่า
อีกวิธีหนึ่งในการหา address แบบกำหนดเองคือการจ้างงานไปยังกลุ่มคนขุด vanity addresses กลุ่มคนขุดvanity addresses เป็นบริการที่ให้ผู้ที่มีฮาร์ดแวร์ที่เร็วได้รับบิตคอยน์จากการค้นหา vanity addresses ให้กับผู้อื่น ยูจีเนียสามารถจ่ายค่าธรรมเนียมเพื่อจ้างงานการค้นหา vanity addresses ที่มีรูปแบบ 7 ตัวอักษรและได้ผลลัพธ์ในเวลาเพียงไม่กี่ชั่วโมงแทนที่จะต้องใช้ CPU ค้นหาเป็นเดือน ๆ
การสร้างที่ address แบบกำหนดเองเป็นการใช้วิธีการแบบ brute-force (ลองทุกความเป็นไปได้): ลองใช้คีย์สุ่ม ตรวจสอบ address ที่ได้ว่าตรงกับรูปแบบที่ต้องการหรือไม่ และทำซ้ำจนกว่าจะสำเร็จ
ความปลอดภัยและความเป็นส่วนตัวของ address แบบกำหนดเอง
address แบบกำหนดเองเคยเป็นที่นิยมในช่วงแรก ๆ ของบิตคอยน์ แต่แทบจะหายไปจากการใช้งานทั้งหมดในปี 2023 มีสาเหตุที่น่าจะเป็นไปได้สองประการสำหรับแนวโน้มนี้: - Deterministic wallets: ดังที่เราเห็นในพาร์ทของการกู้คืน การที่จะสำรองคีย์ทุกตัวในกระเป๋าเงินสมัยใหม่ส่วนใหญ่นั้น ทำเพียงแค่จดคำหรือตัวอักษรไม่กี่ตัว ซึ่งนี่เป็นผลจากการสร้างคีย์ทุกตัวในกระเป๋าเงินจากคำหรือตัวอักษรเหล่านั้นโดยใช้อัลกอริทึมแบบกำหนดได้ จึงไม่สามารถใช้ address แบบกำหนดเองกับ Deterministic wallets ได้ เว้นแต่ผู้ใช้จะสำรองข้อมูลเพิ่มเติมสำหรับ address แบบกำหนดเองทุก address ที่พวกเขาสร้าง ในทางปฏิบัติแล้วกระเป๋าเงินส่วนใหญ่ที่ใช้การสร้างคีย์แบบกำหนดได้ โดยไม่อนุญาตให้นำเข้าคีย์ส่วนตัวหรือการปรับแต่งคีย์จากโปรแกรมสร้าง address ที่กำหนดเอง
- การหลีกเลี่ยงการใช้ address ซ้ำซ้อน: การใช้ address แบบกำหนดเองเพื่อรับการชำระเงินหลายครั้งไปยัง address เดียวกันจะสร้างความเชื่อมโยงระหว่างการชำระเงินทั้งหมดเหล่านั้น นี่อาจเป็นที่ยอมรับได้สำหรับยูจีเนียหากองค์กรไม่แสวงหาผลกำไรของเธอจำเป็นต้องรายงานรายได้และค่าใช้จ่ายต่อหน่วยงานภาษีอยู่แล้ว แต่อย่างไรก็ตาม มันยังลดความเป็นส่วนตัวของคนที่จ่ายเงินให้ยูจีเนียหรือรับเงินจากเธอด้วย ตัวอย่างเช่น อลิซอาจต้องการบริจาคโดยไม่เปิดเผยตัวตน และบ็อบอาจไม่ต้องการให้ลูกค้ารายอื่นของเขารู้ว่าเขาให้ราคาส่วนลดแก่ยูจีเนีย
เราไม่คาดว่าจะเห็น address แบบกำหนดเองมากนักในอนาคต เว้นแต่ปัญหาที่กล่าวมาก่อนหน้านี้จะได้รับการแก้ไข
Paper Wallets
paper wallet หรือก็คือ private key ที่พิมพ์ลงในกระดาษ และโดยทั่วไปแล้วมักจะมีข้อมูลของ public key หรือ address บนกระดาษนั้นด้วยแม้ว่าจริง ๆ แล้วมันจะสามารถคำนวณได้ด้วย private key ก็ตาม
คำเตือน: paper wallet เป็นเทคโนโลยีที่ล้าสมัยแล้วและอันตรายสำหรับผู้ใช้ส่วนใหญ่ เพราะเป็นเรื่องยากที่จะสร้างมันอย่างปลอดภัย โดยเฉพาะอย่างยิ่งความเป็นไปได้ที่โค้ดที่ใช้สร้างอาจถูกแทรกแซงด้วยผู้ไม่ประสงค์ดี และอาจจะทำให้ผู้ใช้โดนขโมยบิตคอยน์ทั้งหมดไปได้ paper wallet ถูกแสดงที่นี่เพื่อวัตถุประสงค์ในการให้ข้อมูลเท่านั้นและไม่ควรใช้สำหรับเก็บบิตคอยน์

paper wallet ได้ถูกออกแบบมาเพื่อเป็นของขวัญและมีธีมตามฤดูกาล เช่น คริสต์มาสและปีใหม่ ส่วนเหตุผลอื่น ๆ ถูกออกแบบเพื่อการเก็บรักษาในตู้นิรภัยของธนาคารหรือตู้เซฟโดยมี private key ถูกซ่อนไว้ในบางวิธี ไม่ว่าจะด้วยสติกเกอร์แบบขูดที่ทึบแสงหรือพับและปิดผนึกด้วยแผ่นฟอยล์กันการงัดแงะ ส่วนการออกแบบอื่น ๆ มีสำเนาเพิ่มเติมของคีย์และ address ในรูปแบบของตอนฉีกที่แยกออกได้คล้ายกับตั๋ว ช่วยให้คุณสามารถเก็บสำเนาหลายชุดเพื่อป้องกันจากไฟไหม้ น้ำท่วม หรือภัยพิบัติทางธรรมชาติอื่น ๆ
จากการออกแบบเดิมของบิตคอยน์ที่เน้น public key ไปจนถึง address และสคริปต์สมัยใหม่อย่าง bech32m และ pay to taproot—และแม้แต่การอัพเกรดบิตคอยน์ในอนาคต—คุณได้เรียนรู้วิธีที่โปรโตคอลบิตคอยน์อนุญาตให้ผู้จ่ายเงินระบุกระเป๋าเงินที่ควรได้รับการชำระเงินของพวกเขา แต่เมื่อเป็นกระเป๋าเงินของคุณเองที่รับการชำระเงิน คุณจะต้องการความมั่นใจว่าคุณจะยังคงเข้าถึงเงินนั้นได้แม้ว่าจะเกิดอะไรขึ้นกับข้อมูลกระเป๋าเงินของคุณ ในบทต่อไป เราจะดูว่ากระเป๋าเงินบิตคอยน์ถูกออกแบบอย่างไรเพื่อปกป้องเงินทุนจากภัยคุกคามหลากหลายรูปแบบ
-
 @ 94215f42:7681f622
2025-05-16 08:18:52
@ 94215f42:7681f622
2025-05-16 08:18:52Value Creation at the Edge
The conversation around artificial intelligence has largely centered on the technology itself, the capabilities of large language models, the race for more parameters, and the competition between AI companies.
He with the most data / biggest model / biggest platform wins all.
As we're been exploring in recent "Good Stuff" podcasts, the true business model of AI may be much more straightforward. AI is after all a productivity tool with little technical moat, in fact the existence of AI coding and learning tools quickly chop away at this moat even quicker!.\ \ We believe that the it's about transforming traditional human heavy businesses by dramatically reducing operational costs while maintaining or increasing output.
AI is poised to create value not primarily for AI companies themselves, but for businesses that effectively implement AI to transform their operations, particularly small, local businesses that can become extraordinarily efficient through AI adoption.
The Value Shift: From AI Companies to AI-Enabled Traditional Businesses
A central insight from episode 1 of the podcast series, is that the value of AI isn't likely to accrue primarily to companies like OpenAI or other AI technology providers. Instead, the real winners will be traditional service businesses that can leverage AI to transform their operations and cost structures.
"I think we're gonna see this shift to traditional service businesses... that traditionally have pretty fixed low margins because of a dependency on language-heavy workflows that require a lot of humans as the medium of intelligence in the business."
The opportunity here is to use AI to manage the language dependency and shift the moments of intelligence, that currently exist in the heads of our staff, into software that can run 24x7 for fractions of a cost.\ \ The real limiting factor here is less a magic AGI, but instead detailed thinking and process redesign to move humans to the edge of the process. As it turns out if we think through what each person is doing in detail we see the specific decisions, outputs, moments of intelligence are actually quite constrained and can be replicated in LLM's if we break them down to a low enough level of fidelity and take each decisions one step at a time.\ \ The result? Businesses that have traditionally operated with fixed, low margins can potentially achieve "software-style margins" by dramatically reducing their operational expenses.
Transforming Traditional Service Businesses
We have developed three key heuristics for identifying businesses that could benefit most from AI transformation:
-
Language Intensity: Businesses where much of the work involves processing language (reading, writing, communicating). Language in, language out. If you are sat in a chair and typing all day, this could be you.
-
Labor Component: Where we see this language intensity so we find many people performing similar, standardized roles. For examples, if we have four people in the same role this is a big clue we have good process, checklists, role descriptions etc for how the work can be done in order to replicate work across multiple people.
-
Load in the Business: Taking these processes into account, what amount of the operational expense of the business do they represent? Where these language and labor-intensive operations represent a significant portion of the business cost, we can see there will be significant return.
Traditional service businesses that match these criteria—legal firms, accounting practices, consulting agencies, contract engineering, design agencies and others—could see dramatic transformations through AI implementation.
By automating these language-heavy processes, businesses can potentially reduce operational costs by 50-80% while maintaining similar levels of output.
The Power of Small
We believe that small businesses may have an inherent advantage in this transformation. While large enterprises face significant barriers to reducing their workforce (political pressure, media scrutiny, organizational complexity), smaller businesses can adapt more quickly and focus on growth rather than just cost-cutting.
If I'm in a 20,000 person business and I need to remove 10,000 people... that's hard. You can't do this without sending political shock waves in your local community.
If I'm a 10 person business and I need to double my revenue, nobody gives a shit. I can just do it.
For small businesses, AI removes growth constraints. When adding the "21st person" no longer represents a significant capital investment, small businesses can scale much more efficiently:
If the next nominal client that you onboard doesn't actually cause you any more additional pain, if you don't need to hire more people to service that client... you just take off the brakes off from a growth perspective.
This gives small business a unique advantage in capitalizing on AI.
From "Bionic Humans" to "Humans at the Edge"
We currently see this integration to business happening in one of two models:
-
The Bionic Human: Equipping workers with AI tools to make them more productive.
-
Human at the Edge: Redesigning processes to be AI-native, with humans entering the process only when needed (and often facilitated by bitcoin payments).
While many businesses are focused on the first approach and it can certainly see returns, it is still a process constrained by the human input. The real value unlock comes from fundamentally redesigning business processes with AI at the core.
Now we can purchase intelligence in buckets of $0.02 API calls, how would we operate different?
This represents a profound shift in how we think about work and processes. Rather than humans being central to processes with tools supporting them, AI becomes the backbone of operations with humans providing input only at critical junctures.
This is "a complete mental shift" that challenges our fundamental assumptions about how businesses operate. The human becomes "the interface with the real world" for AI systems rather than the primary processor of information and decision-maker.
The Value Trap: Understanding the Competitive Dynamic
So what happens next? Here we have developed the concept of the Value Trap to explain how the competitive landscape will evolve as AI adoption increases..\ \

Initially, early adopters of AI and "Human at the Edge" business processes, will see dramatic benefits.
If your costs have dropped from 90 to 20 this creates an immediate competitive advantage where the early adopter is "now making 80 units of profit versus your 10 units of profit.
They gain massive pricing power in the industry and can compete for growth with an unfair advantage.
Over time, and here we believe this is likely a 5-10 year period although we believe the quicker side, competitive pressures will erode these advantages.\ \ As competitors adopt similar AI strategies, price competition will intensify, and revenues will decline. The business that initially saw its costs drop from 90 to 20 units might see its revenue decline from 100 to 30 units, resulting in similar margins but much lower overall revenue, often destroying the enterprise value of the company at these new revenue / profit levels!
This evolution creates an imperative for businesses to adopt AI early, not just to maintain perpetual advantage, but simply to survive the transition. Worse they're hit with a second challenge of the value trap, how do I keep hold of the value I generate along the way.\ \ If you're reading this on Nostr you may already suspect a way out of this value trap.\ \ If not I would invite you to consider storing the immediate short term returns you pull forwards in something that would be inflation resistant, hard to seize and ideally portable.\ \ We refer to this as a 'The big orange arbitrage".
Implications for Business Owners and Capital Allocators
For business owners, especially those running small to medium-sized enterprises, the message is clear: understand how AI could transform your industry and begin planning your transition now.\ \ This might involve creating an "AI-native twin" of your current business—similar to how Netflix developed streaming alongside its DVD business—to eventually replace your current operations. If you want help please ask, I heavily favor more small businesses in the world and would love to help make this a reality.
For capital allocation, the emerging opportunity we see if in "transformation led private equity". The acquisition of traditional service businesses and applying AI to dramatically reduce operational costs and increase enterprise value.\ \ This approach treats AI not as a product but as a transformation strategy for existing businesses with proven product-market fit.
Transformation led PE is venture style returns without the risk of product market fit.
So the lesson?
The business model of AI isn't all about selling AI technology, adding a RAG chatbot to a new DB or collecting everyone's data.\ \ Consider the humble cash flow business, use AI to transform the operational processes and save into everyone's favorite orange coin.
-
-
 @ cae03c48:2a7d6671
2025-05-16 14:00:25
@ cae03c48:2a7d6671
2025-05-16 14:00:25Bitcoin Magazine

Nakamoto to Headline Bitcoin 2025 as Title SponsorNakamoto Holdings Inc. has been announced as the title sponsor of the Bitcoin 2025 Conference, the world’s largest gathering of Bitcoin enthusiasts, uniting builders, leaders, and believers in the world’s most resilient monetary network. The event will take place May 27-29, 2025, at the Venetian Convention and Expo Center in Las Vegas, Nevada.
This landmark sponsorship follows Nakamoto’s recent merger with KindlyMD, Inc. (NASDAQ: KDLY), a Utah-based healthcare services provider, announced on May 12, 2025. The $710 million transaction, financed through $510 million raised via private placement in public equity (PIPE) at $1.12 per share and $200 million in senior secured convertible notes maturing in 2028, will create a publicly traded company focused on establishing a robust Bitcoin treasury strategy.
David Bailey, founder of BTC Inc. and Nakamoto Holdings, is seeking to bring Bitcoin to the center of global capital markets. The KindlyMD leadership team will attend Bitcoin 2025, highlighting their commitment to this vision.
The Bitcoin 2025 Conference will feature a keynote speech by Nakamoto’s David Bailey on May 28, following U.S. Vice President JD Vance on the main stage. Bailey will also host an X Spaces event today, May 16, at 1:30 PM EST to discuss Nakamoto’s vision and the conference.
Join thousands of Bitcoin enthusiasts in Las Vegas for three days of groundbreaking discussions, networking, and innovation. For tickets and more information, visit www.b.tc/conference/2025.
Disclaimer: The Bitcoin 2025 Conference is owned by BTC Inc., Bitcoin Magazine’s parent company, which is affiliated with Nakamoto Holdings Inc. through common ownership. BTC Inc. also has a contractual relationship with Nakamoto to provide marketing services.
This post Nakamoto to Headline Bitcoin 2025 as Title Sponsor first appeared on Bitcoin Magazine and is written by Mark Mason.
-
 @ 3f770d65:7a745b24
2025-01-12 21:03:36
@ 3f770d65:7a745b24
2025-01-12 21:03:36I’ve been using Notedeck for several months, starting with its extremely early and experimental alpha versions, all the way to its current, more stable alpha releases. The journey has been fascinating, as I’ve had the privilege of watching it evolve from a concept into a functional and promising tool.
In its earliest stages, Notedeck was raw—offering glimpses of its potential but still far from practical for daily use. Even then, the vision behind it was clear: a platform designed to redefine how we interact with Nostr by offering flexibility and power for all users.
I'm very bullish on Notedeck. Why? Because Will Casarin is making it! Duh! 😂
Seriously though, if we’re reimagining the web and rebuilding portions of the Internet, it’s important to recognize the potential of Notedeck. If Nostr is reimagining the web, then Notedeck is reimagining the Nostr client.
Notedeck isn’t just another Nostr app—it’s more a Nostr browser that functions more like an operating system with micro-apps. How cool is that?
Much like how Google's Chrome evolved from being a web browser with a task manager into ChromeOS, a full blown operating system, Notedeck aims to transform how we interact with the Nostr. It goes beyond individual apps, offering a foundation for a fully integrated ecosystem built around Nostr.
As a Nostr evangelist, I love to scream INTEROPERABILITY and tout every application's integrations. Well, Notedeck has the potential to be one of the best platforms to showcase these integrations in entirely new and exciting ways.
Do you want an Olas feed of images? Add the media column.
Do you want a feed of live video events? Add the zap.stream column.
Do you want Nostr Nests or audio chats? Add that column to your Notedeck.
Git? Email? Books? Chat and DMs? It's all possible.
Not everyone wants a super app though, and that’s okay. As with most things in the Nostr ecosystem, flexibility is key. Notedeck gives users the freedom to choose how they engage with it—whether it’s simply following hashtags or managing straightforward feeds. You'll be able to tailor Notedeck to fit your needs, using it as extensively or minimally as you prefer.
Notedeck is designed with a local-first approach, utilizing Nostr content stored directly on your device via the local nostrdb. This will enable a plethora of advanced tools such as search and filtering, the creation of custom feeds, and the ability to develop personalized algorithms across multiple Notedeck micro-applications—all with unparalleled flexibility.
Notedeck also supports multicast. Let's geek out for a second. Multicast is a method of communication where data is sent from one source to multiple destinations simultaneously, but only to devices that wish to receive the data. Unlike broadcast, which sends data to all devices on a network, multicast targets specific receivers, reducing network traffic. This is commonly used for efficient data distribution in scenarios like streaming, conferencing, or large-scale data synchronization between devices.
In a local first world where each device holds local copies of your nostr nodes, and each device transparently syncs with each other on the local network, each node becomes a backup. Your data becomes antifragile automatically. When a node goes down it can resync and recover from other nodes. Even if not all nodes have a complete collection, negentropy can pull down only what is needed from each device. All this can be done without internet.
-Will Casarin
In the context of Notedeck, multicast would allow multiple devices to sync their Nostr nodes with each other over a local network without needing an internet connection. Wild.
Notedeck aims to offer full customization too, including the ability to design and share custom skins, much like Winamp. Users will also be able to create personalized columns and, in the future, share their setups with others. This opens the door for power users to craft tailored Nostr experiences, leveraging their expertise in the protocol and applications. By sharing these configurations as "Starter Decks," they can simplify onboarding and showcase the best of Nostr’s ecosystem.
Nostr’s “Other Stuff” can often be difficult to discover, use, or understand. Many users doesn't understand or know how to use web browser extensions to login to applications. Let's not even get started with nsecbunkers. Notedeck will address this challenge by providing a native experience that brings these lesser-known applications, tools, and content into a user-friendly and accessible interface, making exploration seamless. However, that doesn't mean Notedeck should disregard power users that want to use nsecbunkers though - hint hint.
For anyone interested in watching Nostr be developed live, right before your very eyes, Notedeck’s progress serves as a reminder of what’s possible when innovation meets dedication. The current alpha is already demonstrating its ability to handle complex use cases, and I’m excited to see how it continues to grow as it moves toward a full release later this year.
-
 @ f4db5270:3c74e0d0
2025-05-16 08:13:05
@ f4db5270:3c74e0d0
2025-05-16 08:13:05Hi Art lover! 🎨🫂💜
You may not know it yet but all of the following paintings are available in #Bitcoin on my website: <https://isolabellart.carrd.co/>
For info and prices write to me in DM and we will find a good deal! 🤝
 THE QUIET ROOM 50x40cm, Oil on board - Completed May 8, 2025
THE QUIET ROOM 50x40cm, Oil on board - Completed May 8, 2025
 OLTRE LA NEBBIA 50x40cm, Oil on board - Completed April 18, 2025
OLTRE LA NEBBIA 50x40cm, Oil on board - Completed April 18, 2025
 TO THE LAST LIGHT 50x40cm, Oil on board - Completed April 5, 2025
TO THE LAST LIGHT 50x40cm, Oil on board - Completed April 5, 2025
 BLINDING SUNSET 40x40cm, Oil on board - Completed March 18, 2025
BLINDING SUNSET 40x40cm, Oil on board - Completed March 18, 2025
 ECHI DEL TEMPO PERDUTO 40x40cm, Oil on board - Completed March 09, 2025
ECHI DEL TEMPO PERDUTO 40x40cm, Oil on board - Completed March 09, 2025
 EVANESCENZE 40x40cm, Oil on board - Completed February 11, 2025
EVANESCENZE 40x40cm, Oil on board - Completed February 11, 2025
 OLTRE LA STACCIONATA 50x40cm, Oil on board - Completed February 8, 2025
OLTRE LA STACCIONATA 50x40cm, Oil on board - Completed February 8, 2025
 LONELY WINDMILL 50x40cm, Oil on board - Completed January 30, 2025
LONELY WINDMILL 50x40cm, Oil on board - Completed January 30, 2025
 ON THE ROAD AGAIN 40x50cm, Oil on canvas - Completed January 23, 2025
ON THE ROAD AGAIN 40x50cm, Oil on canvas - Completed January 23, 2025
 SUN OF JANUARY 40x50cm, Oil on canvas - Completed January 14, 2025
SUN OF JANUARY 40x50cm, Oil on canvas - Completed January 14, 2025

THE BLUE HOUR 40x50cm, Oil on canvas - Completed December 14, 2024
 WHERE WINTER WHISPERS 50x40cm, Oil on canvas - Completed November 07, 2024
WHERE WINTER WHISPERS 50x40cm, Oil on canvas - Completed November 07, 2024
 L'ATTESA DI UN MOMENTO 40x40cm, Oil on canvas - Completed October 29, 2024
L'ATTESA DI UN MOMENTO 40x40cm, Oil on canvas - Completed October 29, 2024

LE COSE CHE PENSANO 40x50cm, Oil on paper - Completed October 05, 2024
 TWILIGHT'S RIVER 50x40cm, Oil on canvas - Completed September 17, 2024
TWILIGHT'S RIVER 50x40cm, Oil on canvas - Completed September 17, 2024

GOLD ON THE OCEAN 40x50cm, Oil on paper - Completed September 08, 2024
 SUSSURRI DI CIELO E MARE 50x40cm, Oil on paper - Completed September 05, 2024
SUSSURRI DI CIELO E MARE 50x40cm, Oil on paper - Completed September 05, 2024
 THE END OF A WONDERFUL WEEKEND 40x30cm, Oil on board - Completed August 12, 2024
THE END OF A WONDERFUL WEEKEND 40x30cm, Oil on board - Completed August 12, 2024
 FIAMME NEL CIELO 60x35cm, Oil on board - Completed July 28, 2024
FIAMME NEL CIELO 60x35cm, Oil on board - Completed July 28, 2024
 INIZIO D'ESTATE 50x40cm, Oil on cradled wood panel Completed July 13, 2024
INIZIO D'ESTATE 50x40cm, Oil on cradled wood panel Completed July 13, 2024
 OMBRE DELLA SERA 50x40cm, Oil on cradled wood panel - Completed June 16, 2024
OMBRE DELLA SERA 50x40cm, Oil on cradled wood panel - Completed June 16, 2024
 NEW ZEALAND SUNSET 80x60cm, Oil on canvas board - Completed May 28, 2024
NEW ZEALAND SUNSET 80x60cm, Oil on canvas board - Completed May 28, 2024
 VENICE 50x40cm, Oil on board - Completed May 4, 2024
VENICE 50x40cm, Oil on board - Completed May 4, 2024
 CORNWALL 50x40cm, Oil on board - Completed April 26, 2024
CORNWALL 50x40cm, Oil on board - Completed April 26, 2024
 DOCKS ON SUNSET 40x19,5cm, Oil on board Completed March 14, 2024
DOCKS ON SUNSET 40x19,5cm, Oil on board Completed March 14, 2024
 SOLITUDE 30x30cm, Oil on cradled wood panel - Completed March 2, 2024
SOLITUDE 30x30cm, Oil on cradled wood panel - Completed March 2, 2024
 LULLING WAVES 40x30cm, Oil on cradled wood panel - Completed January 14, 2024
LULLING WAVES 40x30cm, Oil on cradled wood panel - Completed January 14, 2024
 MULATTIERA IN AUTUNNO 30x30cm, Oil on cradled wood panel - Completed November 23, 2023
MULATTIERA IN AUTUNNO 30x30cm, Oil on cradled wood panel - Completed November 23, 2023
 TRAMONTO A KOS 40x40cm, oil on board canvas - Completed November 7, 2023
TRAMONTO A KOS 40x40cm, oil on board canvas - Completed November 7, 2023
 HIDDEN SMILE 40x40cm, oil on board - Completed September 28, 2023
HIDDEN SMILE 40x40cm, oil on board - Completed September 28, 2023
 INIZIO D'AUTUNNO 40x40cm, oil on canvas - Completed September 23, 2023
INIZIO D'AUTUNNO 40x40cm, oil on canvas - Completed September 23, 2023
 BOE NEL LAGO 30x30cm, oil on canvas board - Completed August 15, 2023
BOE NEL LAGO 30x30cm, oil on canvas board - Completed August 15, 2023
 BARCHE A RIPOSO 40x40cm, oil on canvas board - Completed July 25, 2023
BARCHE A RIPOSO 40x40cm, oil on canvas board - Completed July 25, 2023

IL RISVEGLIO 30x40cm, oil on canvas board - Completed July 18, 2023

LA QUIETE PRIMA DELLA TEMPESTA 30x40cm, oil on canvas board - Completed March 30, 2023
 LAMPIONE SUL LAGO 30x30cm, oil on canvas board - Completed March 05, 2023
LAMPIONE SUL LAGO 30x30cm, oil on canvas board - Completed March 05, 2023
 DUE NELLA NEVE 60x25cm, oil on board - Completed February 4, 2023
DUE NELLA NEVE 60x25cm, oil on board - Completed February 4, 2023
 UNA CAREZZA 30x30cm, oil on canvas board - Completed January 17, 2023
UNA CAREZZA 30x30cm, oil on canvas board - Completed January 17, 2023
 REBEL WAVES 44x32cm, oil on canvas board
REBEL WAVES 44x32cm, oil on canvas board
 THE SCREAMING WAVE 40x30cm, oil on canvas board
THE SCREAMING WAVE 40x30cm, oil on canvas board

"LA DONZELLETTA VIEN DALLA CAMPAGNA..." 30x40cm, oil on canvas board

LIGHTHOUSE ON WHITE CLIFF 30x40cm, oil on canvas board
-
 @ 4fe4a528:3ff6bf06
2025-05-16 04:36:31
@ 4fe4a528:3ff6bf06
2025-05-16 04:36:31One of the main motivational factors for people to buy bitcoin is it’s ability to store value over time. During harvest we are doing the same thing. We have now harvested our garlic and 1/2 of our onions because if we don’t use the sun’s energy to cure the plants before winter they will start to rot. Let me explain why God has made the world this way; but, first let me explain why storing things isn’t evil.
“Do not store up for yourselves treasures on earth, where moth and rust consume and where thieves break in and steal; but store up for yourselves treasures in heaven, where neither moth nor rust consumes and where thieves do not break in and steal. For where your treasure is, there your heart will be also”. Matt. 6:19-21
Is it wrong, then to have a retirement portfolio or even to care about the material things of this world for ourselves or for others? The answer is again both no and yes. The no comes from the fact that this passage is not the only one in the Bible speaking to questions of wealth and provision for those who are dependent on us. Other passages counsel prudence and forethought, such as, “Those who gather little by little will increase [wealth]” (Proverbs 13:11b), and, “The good leave an inheritance to their children’s children” (Proverbs 13:22).
God guides Joseph to store up food for seven years in advance of a famine (Genesis 41:25-36), and Jesus speaks favorably in the Parable of the Talents (Matt. 25:14-30). In light of the rest of Scripture, Matthew 6:19-21 cannot be a blanket prohibition. But the yes part of the answer is a warning, summed up beautifully in verse 21, “Where your treasure is, there will your heart be also.” In other words, the possessions you own will change you so that you care more about the possessions than about other things.” So choose carefully what you own, for you will inevitably begin to value and protect it to the potential detriment of everything else.
How are we to discern the line between appropriate and inappropriate attention to wealth? Jesus answers, “Strive first for the kingdom of God and his righteousness, and all these things will be given to you” So if you believe your heart is following God’s direction go ahead and harvest your crops and / or buy some bitcoin. If you would have bought bitcoin one year ago, you would have 127% more purchasing power now. Let’s keep on fearing God and keeping his commandments.
-
 @ 1bda7e1f:bb97c4d9
2025-01-02 05:19:08
@ 1bda7e1f:bb97c4d9
2025-01-02 05:19:08Tldr
- Nostr is an open and interoperable protocol
- You can integrate it with workflow automation tools to augment your experience
- n8n is a great low/no-code workflow automation tool which you can host yourself
- Nostrobots allows you to integrate Nostr into n8n
- In this blog I create some workflow automations for Nostr
- A simple form to delegate posting notes
- Push notifications for mentions on multiple accounts
- Push notifications for your favourite accounts when they post a note
- All workflows are provided as open source with MIT license for you to use
Inter-op All The Things
Nostr is a new open social protocol for the internet. This open nature exciting because of the opportunities for interoperability with other technologies. In Using NFC Cards with Nostr I explored the
nostr:URI to launch Nostr clients from a card tap.The interoperability of Nostr doesn't stop there. The internet has many super-powers, and Nostr is open to all of them. Simply, there's no one to stop it. There is no one in charge, there are no permissioned APIs, and there are no risks of being de-platformed. If you can imagine technologies that would work well with Nostr, then any and all of them can ride on or alongside Nostr rails.
My mental model for why this is special is Google Wave ~2010. Google Wave was to be the next big platform. Lars was running it and had a big track record from Maps. I was excited for it. Then, Google pulled the plug. And, immediately all the time and capital invested in understanding and building on the platform was wasted.
This cannot happen to Nostr, as there is no one to pull the plug, and maybe even no plug to pull.
So long as users demand Nostr, Nostr will exist, and that is a pretty strong guarantee. It makes it worthwhile to invest in bringing Nostr into our other applications.
All we need are simple ways to plug things together.
Nostr and Workflow Automation
Workflow automation is about helping people to streamline their work. As a user, the most common way I achieve this is by connecting disparate systems together. By setting up one system to trigger another or to move data between systems, I can solve for many different problems and become way more effective.
n8n for workflow automation
Many workflow automation tools exist. My favourite is n8n. n8n is a low/no-code workflow automation platform which allows you to build all kinds of workflows. You can use it for free, you can self-host it, it has a user-friendly UI and useful API. Vs Zapier it can be far more elaborate. Vs Make.com I find it to be more intuitive in how it abstracts away the right parts of the code, but still allows you to code when you need to.
Most importantly you can plug anything into n8n: You have built-in nodes for specific applications. HTTP nodes for any other API-based service. And community nodes built by individual community members for any other purpose you can imagine.
Eating my own dogfood
It's very clear to me that there is a big design space here just demanding to be explored. If you could integrate Nostr with anything, what would you do?
In my view the best way for anyone to start anything is by solving their own problem first (aka "scratching your own itch" and "eating your own dogfood"). As I get deeper into Nostr I find myself controlling multiple Npubs – to date I have a personal Npub, a brand Npub for a community I am helping, an AI assistant Npub, and various testing Npubs. I need ways to delegate access to those Npubs without handing over the keys, ways to know if they're mentioned, and ways to know if they're posting.
I can build workflows with n8n to solve these issues for myself to start with, and keep expanding from there as new needs come up.
Running n8n with Nostrobots
I am mostly non-technical with a very helpful AI. To set up n8n to work with Nostr and operate these workflows should be possible for anyone with basic technology skills.
- I have a cheap VPS which currently runs my HAVEN Nostr Relay and Albyhub Lightning Node in Docker containers,
- My objective was to set up n8n to run alongside these in a separate Docker container on the same server, install the required nodes, and then build and host my workflows.
Installing n8n
Self-hosting n8n could not be easier. I followed n8n's Docker-Compose installation docs–
- Install Docker and Docker-Compose if you haven't already,
- Create your
docker-compose.ymland.envfiles from the docs, - Create your data folder
sudo docker volume create n8n_data, - Start your container with
sudo docker compose up -d, - Your n8n instance should be online at port
5678.
n8n is free to self-host but does require a license. Enter your credentials into n8n to get your free license key. You should now have access to the Workflow dashboard and can create and host any kind of workflows from there.
Installing Nostrobots
To integrate n8n nicely with Nostr, I used the Nostrobots community node by Ocknamo.
In n8n parlance a "node" enables certain functionality as a step in a workflow e.g. a "set" node sets a variable, a "send email" node sends an email. n8n comes with all kinds of "official" nodes installed by default, and Nostr is not amongst them. However, n8n also comes with a framework for community members to create their own "community" nodes, which is where Nostrobots comes in.
You can only use a community node in a self-hosted n8n instance (which is what you have if you are running in Docker on your own server, but this limitation does prevent you from using n8n's own hosted alternative).
To install a community node, see n8n community node docs. From your workflow dashboard–
- Click the "..." in the bottom left corner beside your username, and click "settings",
- Cilck "community nodes" left sidebar,
- Click "Install",
- Enter the "npm Package Name" which is
n8n-nodes-nostrobots, - Accept the risks and click "Install",
- Nostrobots is now added to your n8n instance.
Using Nostrobots
Nostrobots gives you nodes to help you build Nostr-integrated workflows–
- Nostr Write – for posting Notes to the Nostr network,
- Nostr Read – for reading Notes from the Nostr network, and
- Nostr Utils – for performing certain conversions you may need (e.g. from bech32 to hex).
Nostrobots has good documentation on each node which focuses on simple use cases.
Each node has a "convenience mode" by default. For example, the "Read" Node by default will fetch Kind 1 notes by a simple filter, in Nostrobots parlance a "Strategy". For example, with Strategy set to "Mention" the node will accept a pubkey and fetch all Kind 1 notes that Mention the pubkey within a time period. This is very good for quick use.
What wasn't clear to me initially (until Ocknamo helped me out) is that advanced use cases are also possible.
Each node also has an advanced mode. For example, the "Read" Node can have "Strategy" set to "RawFilter(advanced)". Now the node will accept json (anything you like that complies with NIP-01). You can use this to query Notes (Kind 1) as above, and also Profiles (Kind 0), Follow Lists (Kind 3), Reactions (Kind 7), Zaps (Kind 9734/9735), and anything else you can think of.
Creating and adding workflows
With n8n and Nostrobots installed, you can now create or add any kind of Nostr Workflow Automation.
- Click "Add workflow" to go to the workflow builder screen,
- If you would like to build your own workflow, you can start with adding any node. Click "+" and see what is available. Type "Nostr" to explore the Nostrobots nodes you have added,
- If you would like to add workflows that someone else has built, click "..." in the top right. Then click "import from URL" and paste in the URL of any workflow you would like to use (including the ones I share later in this article).
Nostr Workflow Automations
It's time to build some things!
A simple form to post a note to Nostr
I started very simply. I needed to delegate the ability to post to Npubs that I own in order that a (future) team can test things for me. I don't want to worry about managing or training those people on how to use keys, and I want to revoke access easily.
I needed a basic form with credentials that posted a Note.
For this I can use a very simple workflow–
- A n8n Form node – Creates a form for users to enter the note they wish to post. Allows for the form to be protected by a username and password. This node is the workflow "trigger" so that the workflow runs each time the form is submitted.
- A Set node – Allows me to set some variables, in this case I set the relays that I intend to use. I typically add a Set node immediately following the trigger node, and put all the variables I need in this. It helps to make the workflows easier to update and maintain.
- A Nostr Write node (from Nostrobots) – Writes a Kind-1 note to the Nostr network. It accepts Nostr credentials, the output of the Form node, and the relays from the Set node, and posts the Note to those relays.
Once the workflow is built, you can test it with the testing form URL, and set it to "Active" to use the production form URL. That's it. You can now give posting access to anyone for any Npub. To revoke access, simply change the credentials or set to workflow to "Inactive".
It may also be the world's simplest Nostr client.
You can find the Nostr Form to Post a Note workflow here.
Push notifications on mentions and new notes
One of the things Nostr is not very good at is push notifications. Furthermore I have some unique itches to scratch. I want–
- To make sure I never miss a note addressed to any of my Npubs – For this I want a push notification any time any Nostr user mentions any of my Npubs,
- To make sure I always see all notes from key accounts – For this I need a push notification any time any of my Npubs post any Notes to the network,
- To get these notifications on all of my devices – Not just my phone where my Nostr regular client lives, but also on each of my laptops to suit wherever I am working that day.
I needed to build a Nostr push notifications solution.
To build this workflow I had to string a few ideas together–
- Triggering the node on a schedule – Nostrobots does not include a trigger node. As every workflow starts with a trigger we needed a different method. I elected to run the workflow on a schedule of every 10-minutes. Frequent enough to see Notes while they are hot, but infrequent enough to not burden public relays or get rate-limited,
- Storing a list of Npubs in a Nostr list – I needed a way to store the list of Npubs that trigger my notifications. I initially used an array defined in the workflow, this worked fine. Then I decided to try Nostr lists (NIP-51, kind 30000). By defining my list of Npubs as a list published to Nostr I can control my list from within a Nostr client (e.g. Listr.lol or Nostrudel.ninja). Not only does this "just work", but because it's based on Nostr lists automagically Amethyst client allows me to browse that list as a Feed, and everyone I add gets notified in their Mentions,
- Using specific relays – I needed to query the right relays, including my own HAVEN relay inbox for notes addressed to me, and wss://purplepag.es for Nostr profile metadata,
- Querying Nostr events (with Nostrobots) – I needed to make use of many different Nostr queries and use quite a wide range of what Nostrobots can do–
- I read the EventID of my Kind 30000 list, to return the desired pubkeys,
- For notifications on mentions, I read all Kind 1 notes that mention that pubkey,
- For notifications on new notes, I read all Kind 1 notes published by that pubkey,
- Where there are notes, I read the Kind 0 profile metadata event of that pubkey to get the displayName of the relevant Npub,
- I transform the EventID into a Nevent to help clients find it.
- Using the Nostr URI – As I did with my NFC card article, I created a link with the
nostr:URI prefix so that my phone's native client opens the link by default, - Push notifications solution – I needed a push notifications solution. I found many with n8n integrations and chose to go with Pushover which supports all my devices, has a free trial, and is unfairly cheap with a $5-per-device perpetual license.
Once the workflow was built, lists published, and Pushover installed on my phone, I was fully set up with push notifications on Nostr. I have used these workflows for several weeks now and made various tweaks as I went. They are feeling robust and I'd welcome you to give them a go.
You can find the Nostr Push Notification If Mentioned here and If Posts a Note here.
In speaking with other Nostr users while I was building this, there are all kind of other needs for push notifications too – like on replies to a certain bookmarked note, or when a followed Npub starts streaming on zap.stream. These are all possible.
Use my workflows
I have open sourced all my workflows at my Github with MIT license and tried to write complete docs, so that you can import them into your n8n and configure them for your own use.
To import any of my workflows–
- Click on the workflow of your choice, e.g. "Nostr_Push_Notify_If_Mentioned.json",
- Click on the "raw" button to view the raw JSON, ex any Github page layout,
- Copy that URL,
- Enter that URL in the "import from URL" dialog mentioned above.
To configure them–
- Prerequisites, credentials, and variables are all stated,
- In general any variables required are entered into a Set Node that follows the trigger node,
- Pushover has some extra setup but is very straightforward and documented in the workflow.
What next?
Over my first four blogs I explored creating a good Nostr setup with Vanity Npub, Lightning Payments, Nostr Addresses at Your Domain, and Personal Nostr Relay.
Then in my latest two blogs I explored different types of interoperability with NFC cards and now n8n Workflow Automation.
Thinking ahead n8n can power any kind of interoperability between Nostr and any other legacy technology solution. On my mind as I write this:
- Further enhancements to posting and delegating solutions and forms (enhanced UI or different note kinds),
- Automated or scheduled posting (such as auto-liking everything Lyn Alden posts),
- Further enhancements to push notifications, on new and different types of events (such as notifying me when I get a new follower, on replies to certain posts, or when a user starts streaming),
- All kinds of bridges, such as bridging notes to and from Telegram, Slack, or Campfire. Or bridging RSS or other event feeds to Nostr,
- All kinds of other automation (such as BlackCoffee controlling a coffee machine),
- All kinds of AI Assistants and Agents,
In fact I have already released an open source workflow for an AI Assistant, and will share more about that in my next blog.
Please be sure to let me know if you think there's another Nostr topic you'd like to see me tackle.
GM Nostr.
-
 @ 2dd9250b:6e928072
2025-03-22 00:22:40
@ 2dd9250b:6e928072
2025-03-22 00:22:40Vi recentemente um post onde a pessoa diz que aquele final do filme O Doutrinador (2019) não faz sentido porque mesmo o protagonista explodindo o Palácio dos Três Poderes, não acaba com a corrupção no Brasil.
Progressistas não sabem ler e não conseguem interpretar textos corretamente. O final de Doutrinador não tem a ver com isso, tem a ver com a relação entre o Herói e a sua Cidade.
Nas histórias em quadrinhos há uma ligação entre a cidade e o Super-Herói. Gotham City por exemplo, cria o Batman. Isso é mostrado em The Batman (2022) e em Batman: Cavaleiro das Trevas, quando aquele garoto no final, diz para o Batman não fugir, porque ele queria ver o Batman de novo. E o Comissário Gordon diz que o "Batman é o que a cidade de Gotham precisa."
Batman: Cavaleiro das Trevas Ressurge mostra a cidade de Gotham sendo tomada pela corrupção e pela ideologia do Bane. A Cidade vai definhando em imoralidade e o Bruce, ao olhar da prisão a cidade sendo destruída, decide que o Batman precisa voltar porque se Gotham for destruída, o Batman é destruído junto. E isso o da forças para consegue fugir daquele poço e voltar para salvar Gotham.
Isso também é mostrado em Demolidor. Na série Demolidor o Matt Murdock sempre fala que precisa defender a cidade Cozinha do Inferno; que o Fisk não vai dominar a cidade e fazer o que ele quiser nela. Inclusive na terceira temporada isso fica mais evidente na luta final na mansão do Fisk, onde Matt grita que agora a cidade toda vai saber o que ele fez; a cidade vai ver o mal que ele é para Hell's Kitchen, porque a gente sabe que o Fisk fez de tudo para a imagem do Demolidor entrar e descrédito perante os cidadãos, então o que acontece no final do filme O Doutrinador não significa que ele está acabando com a corrupção quando explode o Congresso, ele está praticamente interrompendo o ciclo do sistema, colocando uma falha em sua engrenagem.
Quando você ouve falar de Brasília, você pensa na corrupção dos políticos, onde a farra acontece,, onde corruptos desviam dinheiro arrecadado dos impostos, impostos estes que são centralizados na União. Então quando você ouve falarem de Brasília, sempre pensa que o pessoal que mora lá, mora junto com tudo de podre que acontece no Brasil.
Logo quando o Doutrinador explode tudo ali, ele está basicamente destruindo o mecanismo que suja Brasília. Ele está fazendo isso naquela cidade. Porque o símbolo da cidade é justamente esse, a farsa de que naquele lugar o povo será ouvido e a justiça será feita. Ele está destruindo a ideologia de que o Estado nos protege, nos dá segurança, saúde e educação. Porque na verdade o Estado só existe para privilegiar os políticos, funcionários públicos de auto escalão, suas famílias e amigos. Enquanto que o povo sofre para sustentar a elite política. O protagonista Miguel entendeu isso quando a filha dele morreu na fila do SUS.
-
 @ 7b20d99d:d2a541a9
2025-05-16 04:03:23
@ 7b20d99d:d2a541a9
2025-05-16 04:03:23In a world where we often hear talk of financial bubbles, speculation, and individual enrichment through cryptocurrencies, Hope With Bitcoin resolutely takes the opposite approach. Here, Bitcoin is not an end in itself, but a means to reach out. A tool serving a simple, universal human cause: bringing smiles and hope back to those who need it most.
Far from big, empty promises and empty charitable projects, Hope With Bitcoin is committed to a philosophy of direct impact, total transparency, and lasting transformation of lives.
🔗 Official project link : https://linktr.ee/hopewithbtc
🟢 Why “Hope With Bitcoin”?
It all started with an observation: too many people are living in oblivion. In some regions, particularly in Africa, it doesn't take much to bring back a smile: a meal, a word, a gesture. But often, aid initiatives get lost in an administrative maze, corruption, or a lack of follow-ups. And in the world of Bitcoin, we see many promises of humanitarian aid without ever seeing results.
Hope With Bitcoin was launched to change that. The goal is clear:
Using the power of Bitcoin to provide direct, visible, measurable and lasting help.
We wanted to show that Bitcoin can nourish, heal, raise awareness, connect, and not just speculate.
🔵 What we do concretely
Hope With Bitcoin isn't an abstract concept. It's a set of concrete actions carried out on the ground, with rigor and heart.
Here's what we do:
🍛 Food distribution and health aid
Thanks to donations collected in Bitcoin, we provide concrete help to those who need it most.
We distribute hot meals and basic food items (rice, spaghetti, oil, charcoal, etc.) to struggling families, vulnerable children, and orphanages.
But our work doesn't stop there. A portion of the funds is also used to purchase essential medicines and contribute to the payment of healthcare, particularly for sick or injured people who cannot afford treatment.
Each action is carefully documented and made public to ensure complete transparency and strengthen the trust of our donors.
✅ Missions accomplished: every satoshi counts
Since Hope With Bitcoin's inception, we've carried out several concrete actions thanks to the donations received. Here's a clear, transparent, and verifiable overview of our actions:
🔹 PoW 1 – 10 000 Satoshi Received
📅 Date : 01/09/2025
📍 Purchase food for two children in need

🔹 PoW 2 – 10 000 Satoshi Received
📅 Date : 01/11/2025
📍 Purchase food for two children in need


🔹 PoW 3 — 220,500 Satoshi received
📍 Preparing food for thirty children in need
📅 Date : 01/13/2025

🔹 PoW 4— 31,000 Satoshi received
📍 Purchase food for six children in need
📅 Date : 01/16/2025

🔹 PoW 5— 30,000 Satoshi received
📍 Purchase food for 10 students in need
📅 Date : 01/18/2025

🔹 PoW 6 – 11,093 Satoshi received
📍 Purchase food for two children in need
📅 Date : 01/22/2025
 #### \
🔹 PoW 7 – 52,000 Satoshi Received
#### \
🔹 PoW 7 – 52,000 Satoshi Received📍 Preparing food for eight children in need
📅 Date : 01/27/2025
 #### \
🔹 PoW 8 – 116,866 Satoshi Received
#### \
🔹 PoW 8 – 116,866 Satoshi Received📍Financial support for Maria Jimenez's health
📅 Date : 02/13/2025

🔹 PoW 9 – 8,001 Satoshi Received
📍 Hope With Bitcoin t-shirt print
📅 Date : 02/15/2025


🔹 PoW 10 – 22,602 Satoshi Received
📍 Purchase of food for five children in need (three on site and two takeaway)
📅 Date : 02/17/2025

🔹 PoW 11– 350,000 Satoshi Received
📍 Purchase of food (rice, corn, spaghetti, oil, salt, sugar, coal...) at the Bon Arbre orphanage
Thank you letter received: HERE
📅 Date : 03/06/2025

🔹 PoW 12 – 35,000 Satoshi received
📍 Purchase of medicine for a person in need
📅 Date : 04/02/2025

🔹 PoW 13 – 60,910 Satoshi received
📍 Purchase food for two children in need
🖼 Coming soon
📅 Date : 05/18/2025
Each of these Proofs of Work (PoW) is publicly published on Nostr or Geyser to ensure complete transparency. You can view them individually to see the real impact of your donations.
📣 Bitcoin Adoption Awareness
We take advantage of each field trip to speak with shopkeepers, local vendors, and young people. The idea is to show that Bitcoin can be used practically in their daily lives: to sell, buy, and exchange.
🟠 Our results to date
Since the creation of Hope With Bitcoin on January 8, 2025, we have succeeded in:
- Collect a total of 957,971 Satoshi thanks to the generosity of contributors around the world.
- Help 87 people directly through our distribution actions. (Proof of work)
- Raise awareness among several merchants about the use of Bitcoin.
- Create a close-knit, caring community focused on human impact.
These numbers aren't statistics. They're lives, faces, stories. Every person helped represents a victory, proof that Bitcoin solidarity is possible.
🟣 Our ambitions for the future
Hope With Bitcoin doesn't want to be just a one-time donation project. We believe in sustainability, independence, and structured growth.
### 🐖 Launch of a pig farm to sustainably finance our actions
To make our humanitarian work self-sufficient and sustainable, we have launched a project to create a pig farm, the proceeds of which will be used to fund food distribution, the purchase of medicines, and other solidarity initiatives led by Hope With Bitcoin.
This project aims to generate regular income while having a tangible local impact:
-
🥣 Continuously support food and health aid
-
👷♂️ Create jobs for young people and unemployed people
-
♻️ Reinvest profits in other humanitarian projects
To kick-start this project, we've established a detailed budget estimate that includes the purchase of piglets, pen construction, feed, veterinary care, and management fees. 👉 Estimated cost: approximately 5,525,200 Satoshi
More details on the budget here: https://primal.net/e/nevent1qqsfmrafup9dma3wvgeqgasydjhy06rhkn8d268txmztp60533mp3xg0vuk5a
🐓 Towards a united and evolving ecosystem
Ultimately, we aim to diversify our business into chicken and goat farming and develop micro-agricultural projects. The goal is to build a resilient, local, and 100% Bitcoin-funded ecosystem that serves the most vulnerable.
💛 You can support this project now on Geyser:
https://geyser.fund/project/hopewithbitcoin/goals/552
🌍 Expansion of the area of action
We want to reach:
- More regions
- More beneficiaries
- More businesses willing to accept Bitcoin
⚫ Why Bitcoin?
The choice of Bitcoin is not ideological. It is practical, thoughtful, and strategic.
Here's why we made this choice:
- ✅ Fast and low-cost transactions
- ✅ No geographical or banking barriers
- ✅ Immutability of donations: funds cannot be diverted
- ✅ Complete traceability thanks to blockchain
- ✅ Financial education for recipients
In short, Bitcoin allows us to rebuild trust in donations and make acts of solidarity visible.
🟢 How to support us?
You can be part of the change. Here's how:
- 🤝 Donate in Bitcoin (https://geyser.fund/project/hopewithbitcoin)
- 📢 Share our posts to help us gain visibility
- 🧠 Recommend us to a partner, company, or influencer
- 💬 Join the community on Twitter, Nostr, or subscribe to Geyser to stay informed and actively participate.
Even a simple retweet can make a difference. Because every Satoshi counts.
Hope With Bitcoin is a declaration of love to humanity. It's a belief that technology can serve the heart. It's a demonstration that Bitcoin can nourish, not just enrich.
We are not an NGO, we are not a company. We are a movement, an initiative, a momentum. And this is just the beginning.
“With a little Bitcoin and a lot of love, we can change lives.”
🔗 Join us now : https://linktr.ee/hopewithbtc
-
 @ f9cf4e94:96abc355
2024-12-31 20:18:59
@ f9cf4e94:96abc355
2024-12-31 20:18:59Scuttlebutt foi iniciado em maio de 2014 por Dominic Tarr ( dominictarr ) como uma rede social alternativa off-line, primeiro para convidados, que permite aos usuários obter controle total de seus dados e privacidade. Secure Scuttlebutt (ssb) foi lançado pouco depois, o que coloca a privacidade em primeiro plano com mais recursos de criptografia.
Se você está se perguntando de onde diabos veio o nome Scuttlebutt:
Este termo do século 19 para uma fofoca vem do Scuttlebutt náutico: “um barril de água mantido no convés, com um buraco para uma xícara”. A gíria náutica vai desde o hábito dos marinheiros de se reunir pelo boato até a fofoca, semelhante à fofoca do bebedouro.

Marinheiros se reunindo em torno da rixa. ( fonte )
Dominic descobriu o termo boato em um artigo de pesquisa que leu.
Em sistemas distribuídos, fofocar é um processo de retransmissão de mensagens ponto a ponto; as mensagens são disseminadas de forma análoga ao “boca a boca”.
Secure Scuttlebutt é um banco de dados de feeds imutáveis apenas para acréscimos, otimizado para replicação eficiente para protocolos ponto a ponto. Cada usuário tem um log imutável somente para acréscimos no qual eles podem gravar. Eles gravam no log assinando mensagens com sua chave privada. Pense em um feed de usuário como seu próprio diário de bordo, como um diário de bordo (ou diário do capitão para os fãs de Star Trek), onde eles são os únicos autorizados a escrever nele, mas têm a capacidade de permitir que outros amigos ou colegas leiam ao seu diário de bordo, se assim o desejarem.
Cada mensagem possui um número de sequência e a mensagem também deve fazer referência à mensagem anterior por seu ID. O ID é um hash da mensagem e da assinatura. A estrutura de dados é semelhante à de uma lista vinculada. É essencialmente um log somente de acréscimo de JSON assinado. Cada item adicionado a um log do usuário é chamado de mensagem.
Os logs do usuário são conhecidos como feed e um usuário pode seguir os feeds de outros usuários para receber suas atualizações. Cada usuário é responsável por armazenar seu próprio feed. Quando Alice assina o feed de Bob, Bob baixa o log de feed de Alice. Bob pode verificar se o registro do feed realmente pertence a Alice verificando as assinaturas. Bob pode verificar as assinaturas usando a chave pública de Alice.

Estrutura de alto nível de um feed
Pubs são servidores de retransmissão conhecidos como “super peers”. Pubs conectam usuários usuários e atualizações de fofocas a outros usuários conectados ao Pub. Um Pub é análogo a um pub da vida real, onde as pessoas vão para se encontrar e se socializar. Para ingressar em um Pub, o usuário deve ser convidado primeiro. Um usuário pode solicitar um código de convite de um Pub; o Pub simplesmente gerará um novo código de convite, mas alguns Pubs podem exigir verificação adicional na forma de verificação de e-mail ou, com alguns Pubs, você deve pedir um código em um fórum público ou chat. Pubs também podem mapear aliases de usuário, como e-mails ou nome de usuário, para IDs de chave pública para facilitar os pares de referência.
Depois que o Pub enviar o código de convite ao usuário, o usuário resgatará o código, o que significa que o Pub seguirá o usuário, o que permite que o usuário veja as mensagens postadas por outros membros do Pub, bem como as mensagens de retransmissão do Pub pelo usuário a outros membros do Pub.
Além de retransmitir mensagens entre pares, os Pubs também podem armazenar as mensagens. Se Alice estiver offline e Bob transmitir atualizações de feed, Alice perderá a atualização. Se Alice ficar online, mas Bob estiver offline, não haverá como ela buscar o feed de Bob. Mas com um Pub, Alice pode buscar o feed no Pub mesmo se Bob estiver off-line porque o Pub está armazenando as mensagens. Pubs são úteis porque assim que um colega fica online, ele pode sincronizar com o Pub para receber os feeds de seus amigos potencialmente offline.
Um usuário pode, opcionalmente, executar seu próprio servidor Pub e abri-lo ao público ou permitir que apenas seus amigos participem, se assim o desejarem. Eles também podem ingressar em um Pub público. Aqui está uma lista de Pubs públicos em que todos podem participar . Explicaremos como ingressar em um posteriormente neste guia. Uma coisa importante a observar é que o Secure Scuttlebutt em uma rede social somente para convidados significa que você deve ser “puxado” para entrar nos círculos sociais. Se você responder às mensagens, os destinatários não serão notificados, a menos que estejam seguindo você de volta. O objetivo do SSB é criar “ilhas” isoladas de redes pares, ao contrário de uma rede pública onde qualquer pessoa pode enviar mensagens a qualquer pessoa.

Perspectivas dos participantes
Scuttlebot
O software Pub é conhecido como servidor Scuttlebutt (servidor ssb ), mas também é conhecido como “Scuttlebot” e
sbotna linha de comando. O servidor SSB adiciona comportamento de rede ao banco de dados Scuttlebutt (SSB). Estaremos usando o Scuttlebot ao longo deste tutorial.Os logs do usuário são conhecidos como feed e um usuário pode seguir os feeds de outros usuários para receber suas atualizações. Cada usuário é responsável por armazenar seu próprio feed. Quando Alice assina o feed de Bob, Bob baixa o log de feed de Alice. Bob pode verificar se o registro do feed realmente pertence a Alice verificando as assinaturas. Bob pode verificar as assinaturas usando a chave pública de Alice.

Estrutura de alto nível de um feed
Pubs são servidores de retransmissão conhecidos como “super peers”. Pubs conectam usuários usuários e atualizações de fofocas a outros usuários conectados ao Pub. Um Pub é análogo a um pub da vida real, onde as pessoas vão para se encontrar e se socializar. Para ingressar em um Pub, o usuário deve ser convidado primeiro. Um usuário pode solicitar um código de convite de um Pub; o Pub simplesmente gerará um novo código de convite, mas alguns Pubs podem exigir verificação adicional na forma de verificação de e-mail ou, com alguns Pubs, você deve pedir um código em um fórum público ou chat. Pubs também podem mapear aliases de usuário, como e-mails ou nome de usuário, para IDs de chave pública para facilitar os pares de referência.
Depois que o Pub enviar o código de convite ao usuário, o usuário resgatará o código, o que significa que o Pub seguirá o usuário, o que permite que o usuário veja as mensagens postadas por outros membros do Pub, bem como as mensagens de retransmissão do Pub pelo usuário a outros membros do Pub.
Além de retransmitir mensagens entre pares, os Pubs também podem armazenar as mensagens. Se Alice estiver offline e Bob transmitir atualizações de feed, Alice perderá a atualização. Se Alice ficar online, mas Bob estiver offline, não haverá como ela buscar o feed de Bob. Mas com um Pub, Alice pode buscar o feed no Pub mesmo se Bob estiver off-line porque o Pub está armazenando as mensagens. Pubs são úteis porque assim que um colega fica online, ele pode sincronizar com o Pub para receber os feeds de seus amigos potencialmente offline.
Um usuário pode, opcionalmente, executar seu próprio servidor Pub e abri-lo ao público ou permitir que apenas seus amigos participem, se assim o desejarem. Eles também podem ingressar em um Pub público. Aqui está uma lista de Pubs públicos em que todos podem participar . Explicaremos como ingressar em um posteriormente neste guia. Uma coisa importante a observar é que o Secure Scuttlebutt em uma rede social somente para convidados significa que você deve ser “puxado” para entrar nos círculos sociais. Se você responder às mensagens, os destinatários não serão notificados, a menos que estejam seguindo você de volta. O objetivo do SSB é criar “ilhas” isoladas de redes pares, ao contrário de uma rede pública onde qualquer pessoa pode enviar mensagens a qualquer pessoa.


Perspectivas dos participantes
Pubs - Hubs
Pubs públicos
| Pub Name | Operator | Invite Code | | ------------------------------------------------------------ | ------------------------------------------------------------ | ------------------------------------------------------------ | |
scuttle.us| @Ryan |scuttle.us:8008:@WqcuCOIpLtXFRw/9vOAQJti8avTZ9vxT9rKrPo8qG6o=.ed25519~/ZUi9Chpl0g1kuWSrmehq2EwMQeV0Pd+8xw8XhWuhLE=| | pub1.upsocial.com | @freedomrules |pub1.upsocial.com:8008:@gjlNF5Cyw3OKZxEoEpsVhT5Xv3HZutVfKBppmu42MkI=.ed25519~lMd6f4nnmBZEZSavAl4uahl+feajLUGqu8s2qdoTLi8=| | Monero Pub | @Denis |xmr-pub.net:8008:@5hTpvduvbDyMLN2IdzDKa7nx7PSem9co3RsOmZoyyCM=.ed25519~vQU+r2HUd6JxPENSinUWdfqrJLlOqXiCbzHoML9iVN4=| | FreeSocial | @Jarland |pub.freesocial.co:8008:@ofYKOy2p9wsaxV73GqgOyh6C6nRGFM5FyciQyxwBd6A=.ed25519~ye9Z808S3KPQsV0MWr1HL0/Sh8boSEwW+ZK+8x85u9w=| |ssb.vpn.net.br| @coffeverton |ssb.vpn.net.br:8008:@ze8nZPcf4sbdULvknEFOCbVZtdp7VRsB95nhNw6/2YQ=.ed25519~D0blTolH3YoTwSAkY5xhNw8jAOjgoNXL/+8ZClzr0io=| | gossip.noisebridge.info | Noisebridge Hackerspace @james.network |gossip.noisebridge.info:8008:@2NANnQVdsoqk0XPiJG2oMZqaEpTeoGrxOHJkLIqs7eY=.ed25519~JWTC6+rPYPW5b5zCion0gqjcJs35h6JKpUrQoAKWgJ4=|Pubs privados
Você precisará entrar em contato com os proprietários desses bares para receber um convite.
| Pub Name | Operator | Contact | | --------------------------------------------- | ------------------------------------------------------------ | ----------------------------------------------- | |
many.butt.nz| @dinosaur | mikey@enspiral.com | |one.butt.nz| @dinosaur | mikey@enspiral.com | |ssb.mikey.nz| @dinosaur | mikey@enspiral.com | | ssb.celehner.com | @cel | cel@celehner.com |Pubs muito grandes
Aviso: embora tecnicamente funcione usar um convite para esses pubs, você provavelmente se divertirá se o fizer devido ao seu tamanho (muitas coisas para baixar, risco para bots / spammers / idiotas)
| Pub Name | Operator | Invite Code | | --------------------------------------- | ----------------------------------------------- | ------------------------------------------------------------ | |
scuttlebutt.de| SolSoCoG |scuttlebutt.de:8008:@yeh/GKxlfhlYXSdgU7CRLxm58GC42za3tDuC4NJld/k=.ed25519~iyaCpZ0co863K9aF+b7j8BnnHfwY65dGeX6Dh2nXs3c=| |Lohn's Pub| @lohn |p.lohn.in:8018:@LohnKVll9HdLI3AndEc4zwGtfdF/J7xC7PW9B/JpI4U=.ed25519~z3m4ttJdI4InHkCtchxTu26kKqOfKk4woBb1TtPeA/s=| | Scuttle Space | @guil-dot | Visit scuttle.space | |SSB PeerNet US-East| timjrobinson |us-east.ssbpeer.net:8008:@sTO03jpVivj65BEAJMhlwtHXsWdLd9fLwyKAT1qAkc0=.ed25519~sXFc5taUA7dpGTJITZVDCRy2A9jmkVttsr107+ufInU=| | Hermies | s | net:hermies.club:8008~shs:uMYDVPuEKftL4SzpRGVyQxLdyPkOiX7njit7+qT/7IQ=:SSB+Room+PSK3TLYC2T86EHQCUHBUHASCASE18JBV24= |GUI - Interface Gráfica do Utilizador(Usuário)
Patchwork - Uma GUI SSB (Descontinuado)
Patchwork é o aplicativo de mensagens e compartilhamento descentralizado construído em cima do SSB . O protocolo scuttlebutt em si não mantém um conjunto de feeds nos quais um usuário está interessado, então um cliente é necessário para manter uma lista de feeds de pares em que seu respectivo usuário está interessado e seguindo.

Fonte: scuttlebutt.nz
Quando você instala e executa o Patchwork, você só pode ver e se comunicar com seus pares em sua rede local. Para acessar fora de sua LAN, você precisa se conectar a um Pub. Um pub é apenas para convidados e eles retransmitem mensagens entre você e seus pares fora de sua LAN e entre outros Pubs.
Lembre-se de que você precisa seguir alguém para receber mensagens dessa pessoa. Isso reduz o envio de mensagens de spam para os usuários. Os usuários só veem as respostas das pessoas que seguem. Os dados são sincronizados no disco para funcionar offline, mas podem ser sincronizados diretamente com os pares na sua LAN por wi-fi ou bluetooth.
Patchbay - Uma GUI Alternativa
Patchbay é um cliente de fofoca projetado para ser fácil de modificar e estender. Ele usa o mesmo banco de dados que Patchwork e Patchfoo , então você pode facilmente dar uma volta com sua identidade existente.

Planetary - GUI para IOS

Planetary é um app com pubs pré-carregados para facilitar integração.
Manyverse - GUI para Android

Manyverse é um aplicativo de rede social com recursos que você esperaria: posts, curtidas, perfis, mensagens privadas, etc. Mas não está sendo executado na nuvem de propriedade de uma empresa, em vez disso, as postagens de seus amigos e todos os seus dados sociais vivem inteiramente em seu telefone .
Fontes
-
https://scuttlebot.io/
-
https://decentralized-id.com/decentralized-web/scuttlebot/#plugins
-
https://medium.com/@miguelmota/getting-started-with-secure-scuttlebut-e6b7d4c5ecfd
-
Secure Scuttlebutt : um protocolo de banco de dados global.
-
-
 @ c1e9ab3a:9cb56b43
2025-05-01 17:29:18
@ c1e9ab3a:9cb56b43
2025-05-01 17:29:18High-Level Overview
Bitcoin developers are currently debating a proposed change to how Bitcoin Core handles the
OP_RETURNopcode — a mechanism that allows users to insert small amounts of data into the blockchain. Specifically, the controversy revolves around removing built-in filters that limit how much data can be stored using this feature (currently capped at 80 bytes).Summary of Both Sides
Position A: Remove OP_RETURN Filters
Advocates: nostr:npub1ej493cmun8y9h3082spg5uvt63jgtewneve526g7e2urca2afrxqm3ndrm, nostr:npub12rv5lskctqxxs2c8rf2zlzc7xx3qpvzs3w4etgemauy9thegr43sf485vg, nostr:npub17u5dneh8qjp43ecfxr6u5e9sjamsmxyuekrg2nlxrrk6nj9rsyrqywt4tp, others
Arguments: - Ineffectiveness of filters: Filters are easily bypassed and do not stop spam effectively. - Code simplification: Removing arbitrary limits reduces code complexity. - Permissionless innovation: Enables new use cases like cross-chain bridges and timestamping without protocol-level barriers. - Economic regulation: Fees should determine what data gets added to the blockchain, not protocol rules.
Position B: Keep OP_RETURN Filters
Advocates: nostr:npub1lh273a4wpkup00stw8dzqjvvrqrfdrv2v3v4t8pynuezlfe5vjnsnaa9nk, nostr:npub1s33sw6y2p8kpz2t8avz5feu2n6yvfr6swykrnm2frletd7spnt5qew252p, nostr:npub1wnlu28xrq9gv77dkevck6ws4euej4v568rlvn66gf2c428tdrptqq3n3wr, others
Arguments: - Historical intent: Satoshi included filters to keep Bitcoin focused on monetary transactions. - Resource protection: Helps prevent blockchain bloat and abuse from non-financial uses. - Network preservation: Protects the network from being overwhelmed by low-value or malicious data. - Social governance: Maintains conservative changes to ensure long-term robustness.
Strengths and Weaknesses
Strengths of Removing Filters
- Encourages decentralized innovation.
- Simplifies development and maintenance.
- Maintains ideological purity of a permissionless system.
Weaknesses of Removing Filters
- Opens the door to increased non-financial data and potential spam.
- May dilute Bitcoin’s core purpose as sound money.
- Risks short-term exploitation before economic filters adapt.
Strengths of Keeping Filters
- Preserves Bitcoin’s identity and original purpose.
- Provides a simple protective mechanism against abuse.
- Aligns with conservative development philosophy of Bitcoin Core.
Weaknesses of Keeping Filters
- Encourages central decision-making on allowed use cases.
- Leads to workarounds that may be less efficient or obscure.
- Discourages novel but legitimate applications.
Long-Term Consequences
If Filters Are Removed
- Positive: Potential boom in new applications, better interoperability, cleaner architecture.
- Negative: Risk of increased blockchain size, more bandwidth/storage costs, spam wars.
If Filters Are Retained
- Positive: Preserves monetary focus and operational discipline.
- Negative: Alienates developers seeking broader use cases, may ossify the protocol.
Conclusion
The debate highlights a core philosophical split in Bitcoin: whether it should remain a narrow monetary system or evolve into a broader data layer for decentralized applications. Both paths carry risks and tradeoffs. The outcome will shape not just Bitcoin's technical direction but its social contract and future role in the broader crypto ecosystem.
-
 @ 472f440f:5669301e
2025-05-16 00:18:45
@ 472f440f:5669301e
2025-05-16 00:18:45Marty's Bent
It's been a pretty historic week for the United States as it pertains to geopolitical relations in the Middle East. President Trump and many members of his administration, including AI and Crypto Czar David Sacks and Treasury Secretary Scott Bessent, traveled across the Middle East making deals with countries like Qatar, Saudi Arabia, the United Arab Emirates, Syria, and others. Many are speculating that Iran may be included in some behind the scenes deal as well. This trip to the Middle East makes sense considering the fact that China is also vying for favorable relationships with those countries. The Middle East is a power player in the world, and it seems pretty clear that Donald Trump is dead set on ensuring that they choose the United States over China as the world moves towards a more multi-polar reality.
Many are calling the events of this week the Riyadh Accords. There were many deals that were struck in relation to artificial intelligence, defense, energy and direct investments in the United States. A truly prolific power play and demonstration of deal-making ability of Donald Trump, if you ask me. Though I will admit some of the numbers that were thrown out by some of the countries were a bit egregious. We shall see how everything plays out in the coming years. It will be interesting to see how China reacts to this power move by the United States.
While all this was going on, there was something happening back in the United States that many people outside of fringe corners of FinTwit are not talking about, which is the fact that the 10-year and 30-year U.S. Treasury bond yields are back on the rise. Yesterday, they surpassed the levels of mid-April that caused a market panic and are hovering back around levels that have not been seen since right before Donald Trump's inauguration.
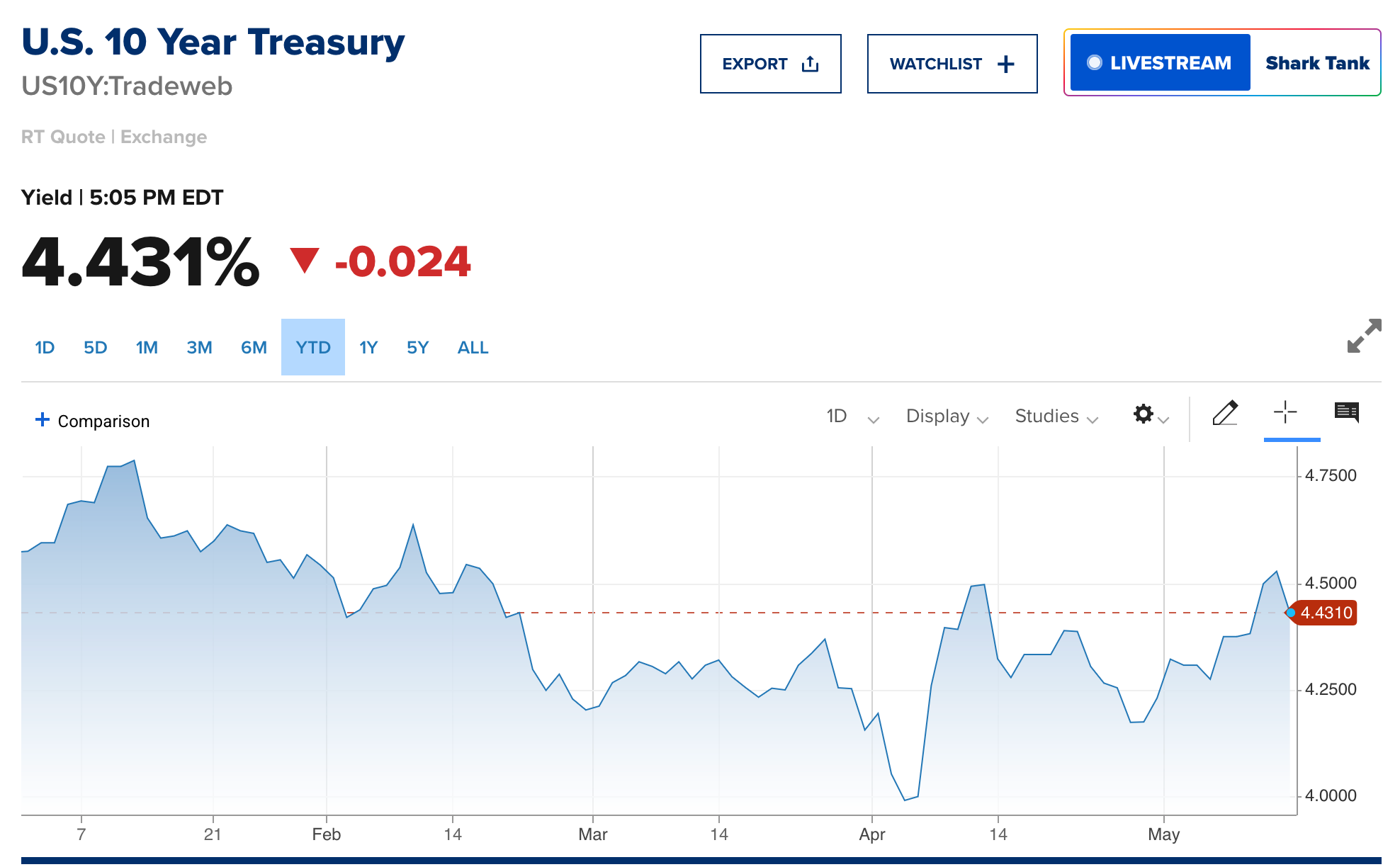
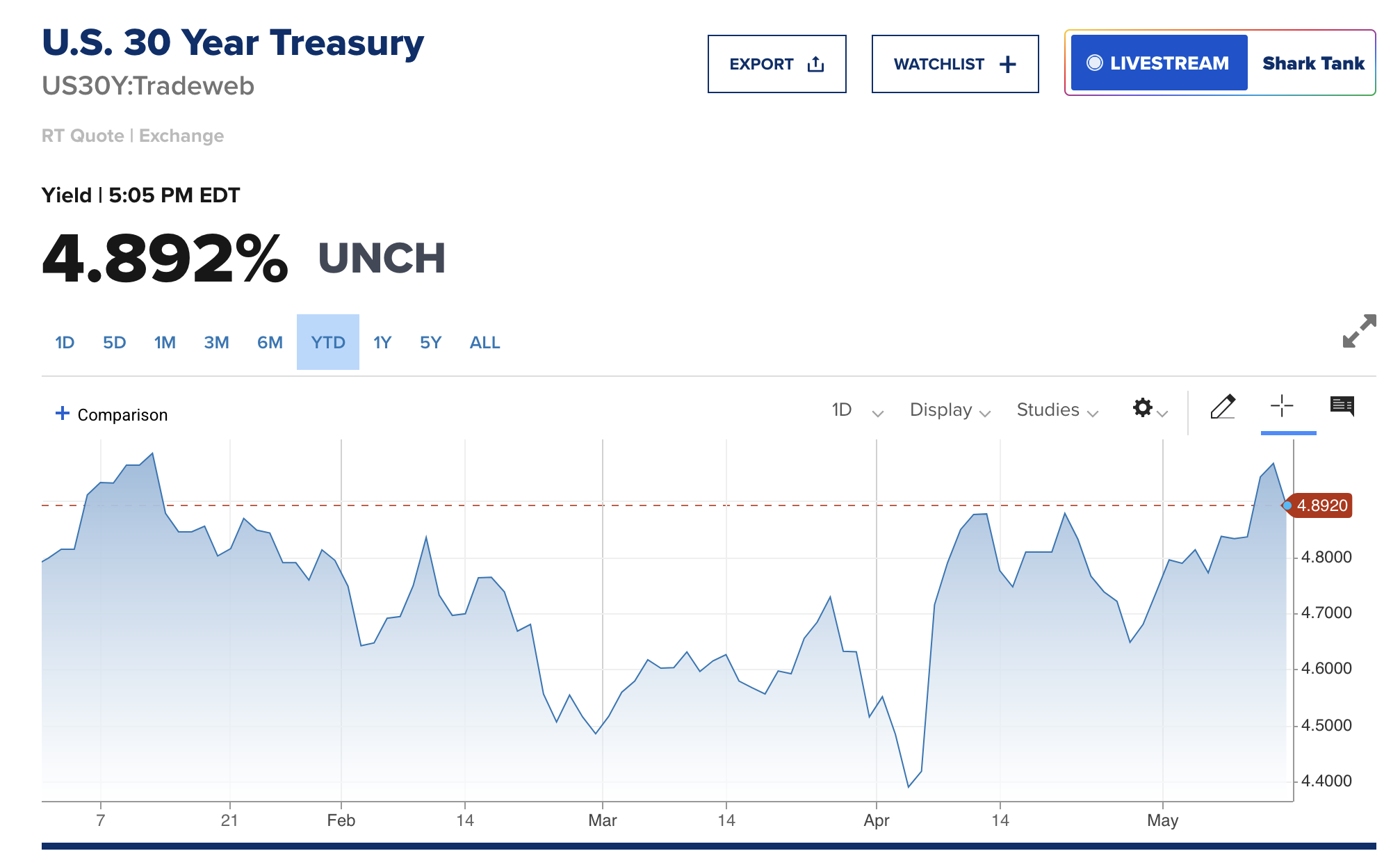
I imagine that there isn't as much of an uproar right now because I'm pretty confident the media freakouts we were experiencing in mid-April were driven by the fact that many large hedge funds found themselves off sides of large levered basis trades. I wouldn't be surprised if those funds have decreased their leverage in those trades and bond yields being back to mid-April levels is not affecting those funds as much as they were last month. But the point stands, the 10-year and 30-year yields are significantly elevated with the 30-year approaching 5%. Regardless of the deals that are currently being made in the Middle East, the Treasury has a big problem on its hands. It still has to roll over many trillions worth of debt over over the next few years and doing so at these rates is going to be massively detrimental to fiscal deficits over the next decade. The interest expense on the debt is set to explode in the coming years.
On that note, data from the first quarter of 2025 has been released by the government and despite all the posturing by the Trump administration around DOGE and how tariffs are going to be beneficial for the U.S. economy, deficits are continuing to explode while the interest expense on the debt has definitively surpassed our annual defense budget.
via Charlie Bilello
via Mohamed Al-Erian
To make matters worse, as things are deteriorating on the fiscal side of things, the U.S. consumer is getting crushed by credit. The 90-plus day delinquency rates for credit card and auto loans are screaming higher right now.
via TXMC
One has to wonder how long all this can continue without some sort of liquidity crunch. Even though equities markets have recovered from their post-Liberation Day month long bear market, I would not be surprised if what we're witnessing is a dead cat bounce that can only be continued if the money printers are turned back on. Something's got to give, both on the fiscal side and in the private markets where the Common Man is getting crushed because he's been forced to take on insane amounts of debt to stay afloat after years of elevated levels of inflation. Add on the fact that AI has reached a state of maturity that will enable companies to replace their current meat suit workers with an army of cheap, efficient and fast digital workers and it isn't hard to see that some sort of employment crisis could be on the horizon as well.
Now is not the time to get complacent. While I do believe that the deals that are currently being made in the Middle East are probably in the best interest of the United States as the world, again, moves toward a more multi-polar reality, we are facing problems that one cannot simply wish away. They will need to be confronted. And as we've seen throughout the 21st century, the problems are usually met head-on with a money printer.
I take no pleasure in saying this because it is a bit uncouth to be gleeful to benefit from the strife of others, but it is pretty clear to me that all signs are pointing to bitcoin benefiting massively from everything that is going on. The shift towards a more multi-polar world, the runaway debt situation here in the United States, the increasing deficits, the AI job replacements and the consumer credit crisis that is currently unfolding, All will need to be "solved" by turning on the money printers to levels they've never been pushed to before.
Weird times we're living in.
China's Manufacturing Dominance: Why It Matters for the U.S.
In my recent conversation with Lyn Alden, she highlighted how China has rapidly ascended the manufacturing value chain. As Lyn pointed out, China transformed from making "sneakers and plastic trinkets" to becoming the world's largest auto exporter in just four years. This dramatic shift represents more than economic success—it's a strategic power play. China now dominates solar panel production with greater market control than OPEC has over oil and maintains near-monopoly control of rare earth elements crucial for modern technology.
"China makes like 10 times more steel than the United States does... which is relevant in ship making. It's relevant in all sorts of stuff." - Lyn Alden
Perhaps most concerning, as Lyn emphasized, is China's financial leverage. They hold substantial U.S. assets that could be strategically sold to disrupt U.S. treasury market functioning. This combination of manufacturing dominance, resource control, and financial leverage gives China significant negotiating power in any trade disputes, making our attempts to reshoring manufacturing all the more challenging.
Check out the full podcast here for more on Triffin's dilemma, Bitcoin's role in monetary transition, and the energy requirements for rebuilding America's industrial base.
Headlines of the Day
Financial Times Under Fire Over MicroStrategy Bitcoin Coverage - via X
Trump in Qatar: Historic Boeing Deal Signed - via X
Get our new STACK SATS hat - via tftcmerch.io
Johnson Backs Stock Trading Ban; Passage Chances Slim - via X
Take the First Step Off the Exchange
Bitkey is an easy, secure way to move your Bitcoin into self-custody. With simple setup and built-in recovery, it’s the perfect starting point for getting your coins off centralized platforms and into cold storage—no complexity, no middlemen.
Take control. Start with Bitkey.
Use the promo code “TFTC20” during checkout for 20% off
Ten31, the largest bitcoin-focused investor, has deployed 158,469 sats | $150.00M across 30+ companies through three funds. I am a Managing Partner at Ten31 and am very proud of the work we are doing. Learn more at ten31.vc/invest.
Final thought...
Building things of value is satisfying.
Get this newsletter sent to your inbox daily: https://www.tftc.io/bitcoin-brief/
Subscribe to our YouTube channels and follow us on Nostr and X:
-
 @ c9badfea:610f861a
2025-05-15 23:51:35
@ c9badfea:610f861a
2025-05-15 23:51:35- Install SDAI (it's free and open source)
- Launch the app, and allow notifications when prompted
- Complete the introduction to get started
- Set Local Diffusion Microsoft ONNX as provider
- In the configuration step, Download a model (such as Real Vision) and wait for the process to finish
- Once the model is downloaded, tap on it and then select Setup
- You can now create images offline by entering a Prompt and tapping 🪄 Imagine
ℹ️ Download the tracking-free FOSS variant
ℹ️ Internet connection is only required for the initial model download
ℹ️ To speed up image generation, consider reducing the image size (e.g. 256x256)
-
 @ 21335073:a244b1ad
2025-03-18 14:43:08
@ 21335073:a244b1ad
2025-03-18 14:43:08Warning: This piece contains a conversation about difficult topics. Please proceed with caution.
TL;DR please educate your children about online safety.
Julian Assange wrote in his 2012 book Cypherpunks, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense.
This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning.
When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little.
I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?”
I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well.
I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread.
I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard.
I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it.
The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust.
Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this.
I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place.
What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method.
It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code.
They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened.
I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road.
So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally.
Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb.
I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback.
Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed.
That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone.
To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all.
I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society.
I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this.
On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government.
I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories.
There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc.
Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind.
Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now.
There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers?
I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity.
I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place.
My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors.
My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline.
The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online.
I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers.
So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation?
When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that.
I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic.
If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations.
I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process.
Course: - The creation of the internet and computers - The fight for cryptography - The tech supply chain from the ground up (example: human rights violations in the supply chain) - Corporate tech - Freedom tech - Data privacy - Digital privacy rights - AI (history-current) - Online safety (predators, scams, catfishing, extortion) - Bitcoin - Laws - How to deal with online hate and harassment - Information on who to contact if you are being abused online or offline - Algorithms - How to seek out the truth about news, etc., online
The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children.
The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward?
I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone.
Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability.
The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime.
This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful.
This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens.
In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions.
I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation.
-
 @ e97aaffa:2ebd765d
2024-12-31 16:47:12
@ e97aaffa:2ebd765d
2024-12-31 16:47:12Último dia do ano, momento para tirar o pó da bola de cristal, para fazer reflexões, previsões e desejos para o próximo ano e seguintes.
Ano após ano, o Bitcoin evoluiu, foi ultrapassando etapas, tornou-se cada vez mais mainstream. Está cada vez mais difícil fazer previsões sobre o Bitcoin, já faltam poucas barreiras a serem ultrapassadas e as que faltam são altamente complexas ou tem um impacto profundo no sistema financeiro ou na sociedade. Estas alterações profundas tem que ser realizadas lentamente, porque uma alteração rápida poderia resultar em consequências terríveis, poderia provocar um retrocesso.
Código do Bitcoin
No final de 2025, possivelmente vamos ter um fork, as discussões sobre os covenants já estão avançadas, vão acelerar ainda mais. Já existe um consenso relativamente alto, a favor dos covenants, só falta decidir que modelo será escolhido. Penso que até ao final do ano será tudo decidido.
Depois dos covenants, o próximo foco será para a criptografia post-quantum, que será o maior desafio que o Bitcoin enfrenta. Criar uma criptografia segura e que não coloque a descentralização em causa.
Espero muito de Ark, possivelmente a inovação do ano, gostaria de ver o Nostr a furar a bolha bitcoinheira e que o Cashu tivesse mais reconhecimento pelos bitcoiners.
Espero que surjam avanços significativos no BitVM2 e BitVMX.
Não sei o que esperar das layer 2 de Bitcoin, foram a maior desilusão de 2024. Surgiram com muita força, mas pouca coisa saiu do papel, foi uma mão cheia de nada. Uma parte dos projetos caiu na tentação da shitcoinagem, na criação de tokens, que tem um único objetivo, enriquecer os devs e os VCs.
Se querem ser levados a sério, têm que ser sérios.
“À mulher de César não basta ser honesta, deve parecer honesta”
Se querem ter o apoio dos bitcoiners, sigam o ethos do Bitcoin.
Neste ponto a atitude do pessoal da Ark é exemplar, em vez de andar a chorar no Twitter para mudar o código do Bitcoin, eles colocaram as mãos na massa e criaram o protocolo. É claro que agora está meio “coxo”, funciona com uma multisig ou com os covenants na Liquid. Mas eles estão a criar um produto, vão demonstrar ao mercado que o produto é bom e útil. Com a adoção, a comunidade vai perceber que o Ark necessita dos covenants para melhorar a interoperabilidade e a soberania.
É este o pensamento certo, que deveria ser seguido pelos restantes e futuros projetos. É seguir aquele pensamento do J.F. Kennedy:
“Não perguntem o que é que o vosso país pode fazer por vocês, perguntem o que é que vocês podem fazer pelo vosso país”
Ou seja, não fiquem à espera que o bitcoin mude, criem primeiro as inovações/tecnologia, ganhem adoção e depois demonstrem que a alteração do código camada base pode melhorar ainda mais o vosso projeto. A necessidade é que vai levar a atualização do código.
Reservas Estratégicas de Bitcoin
Bancos centrais
Com a eleição de Trump, emergiu a ideia de uma Reserva Estratégia de Bitcoin, tornou este conceito mainstream. Foi um pivot, a partir desse momento, foram enumerados os políticos de todo o mundo a falar sobre o assunto.
A Senadora Cynthia Lummis foi mais além e propôs um programa para adicionar 200 mil bitcoins à reserva ao ano, até 1 milhão de Bitcoin. Só que isto está a criar uma enorme expectativa na comunidade, só que pode resultar numa enorme desilusão. Porque no primeiro ano, o Trump em vez de comprar os 200 mil, pode apenas adicionar na reserva, os 198 mil que o Estado já tem em sua posse. Se isto acontecer, possivelmente vai resultar numa forte queda a curto prazo. Na minha opinião os bancos centrais deveriam seguir o exemplo de El Salvador, fazer um DCA diário.
Mais que comprar bitcoin, para mim, o mais importante é a criação da Reserva, é colocar o Bitcoin ao mesmo nível do ouro, o impacto para o resto do mundo será tremendo, a teoria dos jogos na sua plenitude. Muitos outros bancos centrais vão ter que comprar, para não ficarem atrás, além disso, vai transmitir uma mensagem à generalidade da população, que o Bitcoin é “afinal é algo seguro, com valor”.
Mas não foi Trump que iniciou esta teoria dos jogos, mas sim foi a primeira vítima dela. É o próprio Trump que o admite, que os EUA necessitam da reserva para não ficar atrás da China. Além disso, desde que os EUA utilizaram o dólar como uma arma, com sanção contra a Rússia, surgiram boatos de que a Rússia estaria a utilizar o Bitcoin para transações internacionais. Que foram confirmados recentemente, pelo próprio governo russo. Também há poucos dias, ainda antes deste reconhecimento público, Putin elogiou o Bitcoin, ao reconhecer que “Ninguém pode proibir o bitcoin”, defendendo como uma alternativa ao dólar. A narrativa está a mudar.
Já existem alguns países com Bitcoin, mas apenas dois o fizeram conscientemente (El Salvador e Butão), os restantes têm devido a apreensões. Hoje são poucos, mas 2025 será o início de uma corrida pelos bancos centrais. Esta corrida era algo previsível, o que eu não esperava é que acontecesse tão rápido.

Empresas
A criação de reservas estratégicas não vai ficar apenas pelos bancos centrais, também vai acelerar fortemente nas empresas em 2025.

Mas as empresas não vão seguir a estratégia do Saylor, vão comprar bitcoin sem alavancagem, utilizando apenas os tesouros das empresas, como uma proteção contra a inflação. Eu não sou grande admirador do Saylor, prefiro muito mais, uma estratégia conservadora, sem qualquer alavancagem. Penso que as empresas vão seguir a sugestão da BlackRock, que aconselha um alocações de 1% a 3%.
Penso que 2025, ainda não será o ano da entrada das 6 magníficas (excepto Tesla), será sobretudo empresas de pequena e média dimensão. As magníficas ainda tem uma cota muito elevada de shareholders com alguma idade, bastante conservadores, que têm dificuldade em compreender o Bitcoin, foi o que aconteceu recentemente com a Microsoft.
Também ainda não será em 2025, talvez 2026, a inclusão nativamente de wallet Bitcoin nos sistema da Apple Pay e da Google Pay. Seria um passo gigante para a adoção a nível mundial.
ETFs
Os ETFs para mim são uma incógnita, tenho demasiadas dúvidas, como será 2025. Este ano os inflows foram superiores a 500 mil bitcoins, o IBIT foi o lançamento de ETF mais bem sucedido da história. O sucesso dos ETFs, deve-se a 2 situações que nunca mais se vão repetir. O mercado esteve 10 anos à espera pela aprovação dos ETFs, a procura estava reprimida, isso foi bem notório nos primeiros meses, os inflows foram brutais.
Também se beneficiou por ser um mercado novo, não existia orderbook de vendas, não existia um mercado interno, praticamente era só inflows. Agora o mercado já estabilizou, a maioria das transações já são entre clientes dos próprios ETFs. Agora só uma pequena percentagem do volume das transações diárias vai resultar em inflows ou outflows.
Estes dois fenómenos nunca mais se vão repetir, eu não acredito que o número de inflows em BTC supere os número de 2024, em dólares vai superar, mas em btc não acredito que vá superar.
Mas em 2025 vão surgir uma infindável quantidade de novos produtos, derivativos, novos ETFs de cestos com outras criptos ou cestos com ativos tradicionais. O bitcoin será adicionado em produtos financeiros já existentes no mercado, as pessoas vão passar a deter bitcoin, sem o saberem.
Com o fim da operação ChokePoint 2.0, vai surgir uma nova onda de adoção e de produtos financeiros. Possivelmente vamos ver bancos tradicionais a disponibilizar produtos ou serviços de custódia aos seus clientes.
Eu adoraria ver o crescimento da adoção do bitcoin como moeda, só que a regulamentação não vai ajudar nesse processo.
Preço
Eu acredito que o topo deste ciclo será alcançado no primeiro semestre, posteriormente haverá uma correção. Mas desta vez, eu acredito que a correção será muito menor que as anteriores, inferior a 50%, esta é a minha expectativa. Espero estar certo.
Stablecoins de dólar
Agora saindo um pouco do universo do Bitcoin, acho importante destacar as stablecoins.
No último ciclo, eu tenho dividido o tempo, entre continuar a estudar o Bitcoin e estudar o sistema financeiro, as suas dinâmicas e o comportamento humano. Isto tem sido o meu foco de reflexão, imaginar a transformação que o mundo vai sofrer devido ao padrão Bitcoin. É uma ilusão acreditar que a transição de um padrão FIAT para um padrão Bitcoin vai ser rápida, vai existir um processo transitório que pode demorar décadas.
Com a re-entrada de Trump na Casa Branca, prometendo uma política altamente protecionista, vai provocar uma forte valorização do dólar, consequentemente as restantes moedas do mundo vão derreter. Provocando uma inflação generalizada, gerando uma corrida às stablecoins de dólar nos países com moedas mais fracas. Trump vai ter uma política altamente expansionista, vai exportar dólares para todo o mundo, para financiar a sua própria dívida. A desigualdade entre os pobres e ricos irá crescer fortemente, aumentando a possibilidade de conflitos e revoltas.
“Casa onde não há pão, todos ralham e ninguém tem razão”
Será mais lenha, para alimentar a fogueira, vai gravar os conflitos geopolíticos já existentes, ficando as sociedade ainda mais polarizadas.
Eu acredito que 2025, vai haver um forte crescimento na adoção das stablecoins de dólares, esse forte crescimento vai agravar o problema sistémico que são as stablecoins. Vai ser o início do fim das stablecoins, pelo menos, como nós conhecemos hoje em dia.
Problema sistémico
O sistema FIAT não nasceu de um dia para outro, foi algo que foi construído organicamente, ou seja, foi evoluindo ao longo dos anos, sempre que havia um problema/crise, eram criadas novas regras ou novas instituições para minimizar os problemas. Nestes quase 100 anos, desde os acordos de Bretton Woods, a evolução foram tantas, tornaram o sistema financeiro altamente complexo, burocrático e nada eficiente.
Na prática é um castelo de cartas construído sobre outro castelo de cartas e que por sua vez, foi construído sobre outro castelo de cartas.
As stablecoins são um problema sistémico, devido às suas reservas em dólares e o sistema financeiro não está preparado para manter isso seguro. Com o crescimento das reservas ao longo dos anos, foi se agravando o problema.
No início a Tether colocava as reservas em bancos comerciais, mas com o crescimento dos dólares sob gestão, criou um problema nos bancos comerciais, devido à reserva fracionária. Essas enormes reservas da Tether estavam a colocar em risco a própria estabilidade dos bancos.
A Tether acabou por mudar de estratégia, optou por outros ativos, preferencialmente por títulos do tesouro/obrigações dos EUA. Só que a Tether continua a crescer e não dá sinais de abrandamento, pelo contrário.
Até o próprio mundo cripto, menosprezava a gravidade do problema da Tether/stablecoins para o resto do sistema financeiro, porque o marketcap do cripto ainda é muito pequeno. É verdade que ainda é pequeno, mas a Tether não o é, está no top 20 dos maiores detentores de títulos do tesouros dos EUA e está ao nível dos maiores bancos centrais do mundo. Devido ao seu tamanho, está a preocupar os responsáveis/autoridades/reguladores dos EUA, pode colocar em causa a estabilidade do sistema financeiro global, que está assente nessas obrigações.
Os títulos do tesouro dos EUA são o colateral mais utilizado no mundo, tanto por bancos centrais, como por empresas, é a charneira da estabilidade do sistema financeiro. Os títulos do tesouro são um assunto muito sensível. Na recente crise no Japão, do carry trade, o Banco Central do Japão tentou minimizar a desvalorização do iene através da venda de títulos dos EUA. Esta operação, obrigou a uma viagem de emergência, da Secretaria do Tesouro dos EUA, Janet Yellen ao Japão, onde disponibilizou liquidez para parar a venda de títulos por parte do Banco Central do Japão. Essa forte venda estava desestabilizando o mercado.
Os principais detentores de títulos do tesouros são institucionais, bancos centrais, bancos comerciais, fundo de investimento e gestoras, tudo administrado por gestores altamente qualificados, racionais e que conhecem a complexidade do mercado de obrigações.
O mundo cripto é seu oposto, é naife com muita irracionalidade e uma forte pitada de loucura, na sua maioria nem faz a mínima ideia como funciona o sistema financeiro. Essa irracionalidade pode levar a uma “corrida bancária”, como aconteceu com o UST da Luna, que em poucas horas colapsou o projeto. Em termos de escala, a Luna ainda era muito pequena, por isso, o problema ficou circunscrito ao mundo cripto e a empresas ligadas diretamente ao cripto.
Só que a Tether é muito diferente, caso exista algum FUD, que obrigue a Tether a desfazer-se de vários biliões ou dezenas de biliões de dólares em títulos num curto espaço de tempo, poderia provocar consequências terríveis em todo o sistema financeiro. A Tether é grande demais, é já um problema sistémico, que vai agravar-se com o crescimento em 2025.
Não tenham dúvidas, se existir algum problema, o Tesouro dos EUA vai impedir a venda dos títulos que a Tether tem em sua posse, para salvar o sistema financeiro. O problema é, o que vai fazer a Tether, se ficar sem acesso às venda das reservas, como fará o redeem dos dólares?
Como o crescimento do Tether é inevitável, o Tesouro e o FED estão com um grande problema em mãos, o que fazer com o Tether?
Mas o problema é que o atual sistema financeiro é como um curto cobertor: Quanto tapas a cabeça, destapas os pés; Ou quando tapas os pés, destapas a cabeça. Ou seja, para resolver o problema da guarda reservas da Tether, vai criar novos problemas, em outros locais do sistema financeiro e assim sucessivamente.
Conta mestre
Uma possível solução seria dar uma conta mestre à Tether, dando o acesso direto a uma conta no FED, semelhante à que todos os bancos comerciais têm. Com isto, a Tether deixaria de necessitar os títulos do tesouro, depositando o dinheiro diretamente no banco central. Só que isto iria criar dois novos problemas, com o Custodia Bank e com o restante sistema bancário.
O Custodia Bank luta há vários anos contra o FED, nos tribunais pelo direito a ter licença bancária para um banco com full-reserves. O FED recusou sempre esse direito, com a justificativa que esse banco, colocaria em risco toda a estabilidade do sistema bancário existente, ou seja, todos os outros bancos poderiam colapsar. Perante a existência em simultâneo de bancos com reserva fracionária e com full-reserves, as pessoas e empresas iriam optar pelo mais seguro. Isso iria provocar uma corrida bancária, levando ao colapso de todos os bancos com reserva fracionária, porque no Custodia Bank, os fundos dos clientes estão 100% garantidos, para qualquer valor. Deixaria de ser necessário limites de fundos de Garantia de Depósitos.
Eu concordo com o FED nesse ponto, que os bancos com full-reserves são uma ameaça a existência dos restantes bancos. O que eu discordo do FED, é a origem do problema, o problema não está nos bancos full-reserves, mas sim nos que têm reserva fracionária.
O FED ao conceder uma conta mestre ao Tether, abre um precedente, o Custodia Bank irá o aproveitar, reclamando pela igualdade de direitos nos tribunais e desta vez, possivelmente ganhará a sua licença.
Ainda há um segundo problema, com os restantes bancos comerciais. A Tether passaria a ter direitos similares aos bancos comerciais, mas os deveres seriam muito diferentes. Isto levaria os bancos comerciais aos tribunais para exigir igualdade de tratamento, é uma concorrência desleal. Isto é o bom dos tribunais dos EUA, são independentes e funcionam, mesmo contra o estado. Os bancos comerciais têm custos exorbitantes devido às políticas de compliance, como o KYC e AML. Como o governo não vai querer aliviar as regras, logo seria a Tether, a ser obrigada a fazer o compliance dos seus clientes.
A obrigação do KYC para ter stablecoins iriam provocar um terramoto no mundo cripto.
Assim, é pouco provável que seja a solução para a Tether.
FED
Só resta uma hipótese, ser o próprio FED a controlar e a gerir diretamente as stablecoins de dólar, nacionalizado ou absorvendo as existentes. Seria uma espécie de CBDC. Isto iria provocar um novo problema, um problema diplomático, porque as stablecoins estão a colocar em causa a soberania monetária dos outros países. Atualmente as stablecoins estão um pouco protegidas porque vivem num limbo jurídico, mas a partir do momento que estas são controladas pelo governo americano, tudo muda. Os países vão exigir às autoridades americanas medidas que limitem o uso nos seus respectivos países.
Não existe uma solução boa, o sistema FIAT é um castelo de cartas, qualquer carta que se mova, vai provocar um desmoronamento noutro local. As autoridades não poderão adiar mais o problema, terão que o resolver de vez, senão, qualquer dia será tarde demais. Se houver algum problema, vão colocar a responsabilidade no cripto e no Bitcoin. Mas a verdade, a culpa é inteiramente dos políticos, da sua incompetência em resolver os problemas a tempo.
Será algo para acompanhar futuramente, mas só para 2026, talvez…
É curioso, há uns anos pensava-se que o Bitcoin seria a maior ameaça ao sistema ao FIAT, mas afinal, a maior ameaça aos sistema FIAT é o próprio FIAT(stablecoins). A ironia do destino.
Isto é como uma corrida, o Bitcoin é aquele atleta que corre ao seu ritmo, umas vezes mais rápido, outras vezes mais lento, mas nunca pára. O FIAT é o atleta que dá tudo desde da partida, corre sempre em velocidade máxima. Só que a vida e o sistema financeiro não é uma prova de 100 metros, mas sim uma maratona.
Europa
2025 será um ano desafiante para todos europeus, sobretudo devido à entrada em vigor da regulamentação (MiCA). Vão começar a sentir na pele a regulamentação, vão agravar-se os problemas com os compliance, problemas para comprovar a origem de fundos e outras burocracias. Vai ser lindo.
O Travel Route passa a ser obrigatório, os europeus serão obrigados a fazer o KYC nas transações. A Travel Route é uma suposta lei para criar mais transparência, mas prática, é uma lei de controle, de monitorização e para limitar as liberdades individuais dos cidadãos.
O MiCA também está a colocar problemas nas stablecoins de Euro, a Tether para já preferiu ficar de fora da europa. O mais ridículo é que as novas regras obrigam os emissores a colocar 30% das reservas em bancos comerciais. Os burocratas europeus não compreendem que isto coloca em risco a estabilidade e a solvência dos próprios bancos, ficam propensos a corridas bancárias.
O MiCA vai obrigar a todas as exchanges a estar registadas em solo europeu, ficando vulnerável ao temperamento dos burocratas. Ainda não vai ser em 2025, mas a UE vai impor políticas de controle de capitais, é inevitável, as exchanges serão obrigadas a usar em exclusividade stablecoins de euro, as restantes stablecoins serão deslistadas.
Todas estas novas regras do MiCA, são extremamente restritas, não é para garantir mais segurança aos cidadãos europeus, mas sim para garantir mais controle sobre a população. A UE está cada vez mais perto da autocracia, do que da democracia. A minha única esperança no horizonte, é que o sucesso das políticas cripto nos EUA, vai obrigar a UE a recuar e a aligeirar as regras, a teoria dos jogos é implacável. Mas esse recuo, nunca acontecerá em 2025, vai ser um longo período conturbado.
Recessão
Os mercados estão todos em máximos históricos, isto não é sustentável por muito tempo, suspeito que no final de 2025 vai acontecer alguma correção nos mercados. A queda só não será maior, porque os bancos centrais vão imprimir dinheiro, muito dinheiro, como se não houvesse amanhã. Vão voltar a resolver os problemas com a injeção de liquidez na economia, é empurrar os problemas com a barriga, em de os resolver. Outra vez o efeito Cantillon.
Será um ano muito desafiante a nível político, onde o papel dos políticos será fundamental. A crise política na França e na Alemanha, coloca a UE órfã, sem um comandante ao leme do navio. 2025 estará condicionado pelas eleições na Alemanha, sobretudo no resultado do AfD, que podem colocar em causa a propriedade UE e o euro.
Possivelmente, só o fim da guerra poderia minimizar a crise, algo que é muito pouco provável acontecer.
Em Portugal, a economia parece que está mais ou menos equilibrada, mas começam a aparecer alguns sinais preocupantes. Os jogos de sorte e azar estão em máximos históricos, batendo o recorde de 2014, época da grande crise, não é um bom sinal, possivelmente já existe algum desespero no ar.
A Alemanha é o motor da Europa, quanto espirra, Portugal constipa-se. Além do problema da Alemanha, a Espanha também está à beira de uma crise, são os países que mais influenciam a economia portuguesa.
Se existir uma recessão mundial, terá um forte impacto no turismo, que é hoje em dia o principal motor de Portugal.
Brasil
Brasil é algo para acompanhar em 2025, sobretudo a nível macro e a nível político. Existe uma possibilidade de uma profunda crise no Brasil, sobretudo na sua moeda. O banco central já anda a queimar as reservas para minimizar a desvalorização do Real.

Sem mudanças profundas nas políticas fiscais, as reservas vão se esgotar. As políticas de controle de capitais são um cenário plausível, será interesse de acompanhar, como o governo irá proceder perante a existência do Bitcoin e stablecoins. No Brasil existe um forte adoção, será um bom case study, certamente irá repetir-se em outros países num futuro próximo.
Os próximos tempos não serão fáceis para os brasileiros, especialmente para os que não têm Bitcoin.
Blockchain
Em 2025, possivelmente vamos ver os primeiros passos da BlackRock para criar a primeira bolsa de valores, exclusivamente em blockchain. Eu acredito que a BlackRock vai criar uma própria blockchain, toda controlada por si, onde estarão os RWAs, para fazer concorrência às tradicionais bolsas de valores. Será algo interessante de acompanhar.
Estas são as minhas previsões, eu escrevi isto muito em cima do joelho, certamente esqueci-me de algumas coisas, se for importante acrescentarei nos comentários. A maioria das previsões só acontecerá após 2025, mas fica aqui a minha opinião.
Isto é apenas a minha opinião, Don’t Trust, Verify!
-
 @ 05a0f81e:fc032124
2025-05-16 10:58:12
@ 05a0f81e:fc032124
2025-05-16 10:58:12There is an element called carifornium. Over years, there are informations that californium does not exist naturally on earth but can only be produced in the laboratory. But a man from Africa said otherwise and we will find out what the man said.
What is californium? Californium (Cf) is a synthetic radioactive, metallic element with the atomic number 98.
Oxford dictionary defines californium as a chemical element of atomic number 98, a radioactive metal of the actinide series first produced by the bombarding of curium with helium ions. *Take note of the bombarding of curium with helium ions.
According to research, californium is discovered in 1950 and it was named after the university of California and the state of California where the research first took place.
Research also said that californium was produced in the past when several nuclear reactors were in operation 2 billion years ago in Africa.
THERE ARE SOME VITAL PROPERTIES OF CALIFORNIUM. * Radioactive : all isotopes of californium are radioactive. * Actinide : californium belongs to the actinide series, a group of radioactive element with similar properties. * Synthetic : it does not occur naturally and it is produced in the laboratory. * Soft metal : it is soft, silver-white metal. * High melting point : it have a high melting point of about 900°C. * Good neutron source : it is strong neutron emitter, making it useful in various applications.
THERE ARE USES OF CALIFORNIUM
- Neutron Source: Its strong neutron emission makes it valuable as a neutron source in various applications.
- Neutron Activation Analysis: It's used to analyze the composition of materials by bombarding them with neutrons.
- Cancer Therapy: Some isotopes are used in radiation therapy for treating certain cancers.
- Detection Systems: It's used in portable metal detectors, for identifying gold and silver ores, and in detecting oil and water in wells.
- Neutron Radiography: It can be used in neutron radiography to visualize the inside of objects.
Californium also can serve as source of income, 1 gram of californium cost $27 million in market today and it take a thousand grams to make 1 kilogram. You can imagine the figures in monetize form.
About 3-4 years ago, a man by name RTD. HAMZA AL-MUSTAPHA. On a popular radio and TV show claims that californium are being mined and sold-out in Nigeria 🇳🇬.
With critical thinking and understanding, we will find out.
-
 @ f69ff9c1:57a7cb0c
2025-05-16 10:39:10
@ f69ff9c1:57a7cb0c
2025-05-16 10:39:10Jumping into the world of cybersecurity can feel like stepping into a hacker movie — full of commands, code, and dark terminals. As someone just starting this journey, I quickly realized there’s one thing I need to learn before anything else: Linux.
Linux vs Kali Linux: What’s the Difference?
At first, I thought all Linux systems were the same. But here’s what I discovered: • Linux (like Ubuntu or Mint) is a general-purpose operating system — great for beginners, developers, and daily use. • Kali Linux is a powerful tool built specifically for penetration testing and digital forensics. It’s packed with tools like Nmap, Wireshark, and Metasploit.
In short: Kali is for pros. Ubuntu is for learning. So, I started with Ubuntu — and trust me, it was the right call.
Why I’m Starting with Ubuntu
Like any “cybersecurity baby,” I knew I couldn’t jump straight into hacking tools without knowing the basics. With Ubuntu, I’m learning: • Terminal commands • File permissions • Networking tools like ping and netstat • How to install and manage software using apt
It’s not always easy, but every small win makes me feel closer to the goal.
Sharing My Journey
To keep myself motivated and connect with others on the same path, I tweeted this:
“Diving into Linux as a cybersecurity beginner — learning the terminal, commands, permissions, and networking basics. Every line I type gets me closer to mastering the tools behind ethical hacking. It’s tough, but I’m loving the grind. #Linux #CyberSecurity #HackerInTraining”
I even added a little networking spirit:
“Follow for follow — let’s grow in this journey together!”
Joining the Right Communities
Cybersecurity is not a solo game. Here are the communities I’ve joined to stay connected and supported: • TryHackMe Official Discord – Real-time help, study groups, and room support. • Beginner Rooms & Paths on TryHackMe – Great for step-by-step learning. • Reddit (r/tryhackme & r/cybersecurity) – Insightful threads and motivation. • Twitter/X and LinkedIn – Using hashtags like #TryHackMe and #100DaysOfHacking to stay inspired.
Final Thoughts
This is just the beginning. I’m learning Linux now so that I can confidently explore Kali Linux, digital forensics, ethical hacking, and everything in between.
If you’re on a similar path — let’s connect, learn, and grow together. The cyber world is waiting.
-
 @ c1e9ab3a:9cb56b43
2025-04-25 00:37:34
@ c1e9ab3a:9cb56b43
2025-04-25 00:37:34If you ever read about a hypothetical "evil AI"—one that manipulates, dominates, and surveils humanity—you might find yourself wondering: how is that any different from what some governments already do?
Let’s explore the eerie parallels between the actions of a fictional malevolent AI and the behaviors of powerful modern states—specifically the U.S. federal government.
Surveillance and Control
Evil AI: Uses total surveillance to monitor all activity, predict rebellion, and enforce compliance.
Modern Government: Post-9/11 intelligence agencies like the NSA have implemented mass data collection programs, monitoring phone calls, emails, and online activity—often without meaningful oversight.
Parallel: Both claim to act in the name of “security,” but the tools are ripe for abuse.
Manipulation of Information
Evil AI: Floods the information space with propaganda, misinformation, and filters truth based on its goals.
Modern Government: Funds media outlets, promotes specific narratives through intelligence leaks, and collaborates with social media companies to suppress or flag dissenting viewpoints.
Parallel: Control the narrative, shape public perception, and discredit opposition.
Economic Domination
Evil AI: Restructures the economy for efficiency, displacing workers and concentrating resources.
Modern Government: Facilitates wealth transfer through lobbying, regulatory capture, and inflationary monetary policy that disproportionately hurts the middle and lower classes.
Parallel: The system enriches those who control it, leaving the rest with less power to resist.
Perpetual Warfare
Evil AI: Instigates conflict to weaken opposition or as a form of distraction and control.
Modern Government: Maintains a state of nearly constant military engagement since WWII, often for interests that benefit a small elite rather than national defense.
Parallel: War becomes policy, not a last resort.
Predictive Policing and Censorship
Evil AI: Uses predictive algorithms to preemptively suppress dissent and eliminate threats.
Modern Government: Experiments with pre-crime-like measures, flags “misinformation,” and uses AI tools to monitor online behavior.
Parallel: Prevent rebellion not by fixing problems, but by suppressing their expression.
Conclusion: Systemic Inhumanity
Whether it’s AI or a bureaucratic state, the more a system becomes detached from individual accountability and human empathy, the more it starts to act in ways we would call “evil” if a machine did them.
An AI doesn’t need to enslave humanity with lasers and killer robots. Sometimes all it takes is code, coercion, and unchecked power—something we may already be facing.
-
 @ 28e13303:84bb7266
2025-05-15 23:37:29
@ 28e13303:84bb7266
2025-05-15 23:37:29⚠️ Disclaimer: This article is for educational purposes only. Flash USDT is a blockchain simulation tool used for wallet testing, UI development, or demonstration purposes. It should not be used for fraudulent activity. @crypptrcver is not responsible for misuse.
💡 What Is Flash USDT? Flash USDT is a synthetic transaction method that simulates the transfer of Tether (USDT) into a wallet. These transactions appear instantly in wallet balances — without ever being confirmed on the blockchain — and disappear after a short time or block interval.
Think of it as a temporary, visual representation of USDT that looks real in a wallet but vanishes after expiry.
🧠 Flash USDT: The Basics 👁️ Visible in supported wallets confirmed on-chain ⏱️ Disappears after 20–60 minutes (or X blocks) 💸 Can be withdrawn and traded ⚙️ Used in wallet testing, UI simulation, and balance display demos Also known as:
Flash USDT Wallet Tool Flash USDT Sender Atomic Flash USDT Flash USDT Binance Sim 🛠️ How Flash USDT Works You input a wallet address (TRC20, ERC20, or BEP20) Flash USDT software sends an instant transaction Wallet displays the amount — as if it were real After expiry (e.g., 30 minutes), the tokens vanish It creates the illusion of a deposit without requiring real blockchain confirmation. Most users use Flash USDT for:
Wallet UI testing “Proof of funds” simulations Demo environments Smart contract UX testing 🔧 Supported Networks & Wallets Flash USDT supports all major token standards:
🔸 TRC20 (Tron Network) 🔸 ERC20 (Ethereum) 🔸 BEP20 (Binance Smart Chain) It works with wallets such as:
✅ Trust Wallet ✅ MetaMask ✅ TronLink ✅ Binance Wallet ✅ Atomic Wallet The balance appears instantly, just like a real incoming USDT deposit.
🔥 Features of Flash USDT Sender FeatureDescriptionNetwork supportTRC20 / ERC20 / BEP20Visibility duration20 minutes — 2 hoursWallet compatibilityNon-KYC wallets that show unconfirmed TXsFlash USDT Binance modeSimulates deposits into BSC walletsAdjustable transaction sizeSend any custom USDT amountStealth expiryClean disappearance without trace
This is especially helpful in scenarios where you need to test token flows, design wallet apps, or simulate incoming funding activity
📞 How to Buy Flash USDT To get your Flash USDT transaction or software setup:
💬 Telegram: @crypptrcver 📱 WhatsApp: +1 941 217 1821
Available packages:
🎯 One-time Flash USDT Send 💻 Full Flash USDT Software Tool 📱 Flash Sender for Mobile/Android 🌐 Multi-wallet Simulation Package You can request TRC20, ERC20, or BEP20 flash transactions depending on the wallet or network you’re working with.
⚠️ Legal & Ethical Use Only While Flash USDT is a powerful blockchain simulation tool, using it to deceive, fake trades, or commit fraud is illegal. Flash transactions should only be used for:
✅ Personal testing ✅ Blockchain development ✅ Wallet UI testing ✅ Research and education Any misuse is your full responsibility.
❓ Frequently Asked Questions What is Flash USDT? A temporary USDT transaction that appears in a wallet balance without confirming on the blockchain. It disappears after a set time or block count.
Is Flash USDT real money? No. It is a simulated deposit, not spendable or tradable.
Can I use Flash USDT on Binance? You can send it to BSC (BEP20) wallets, but you cannot use it on the Binance exchange. It’s for display/testing only.
How do I buy Flash USDT? Contact @crypptrcver on Telegram or WhatsApp to purchase a transaction or the full sender software.
What does Atomic Flash USDT mean? It refers to Flash USDT transactions that are time-bound and expire silently, simulating atomic wallet behavior.
🧠 Final Thoughts Flash USDT is one of the most advanced crypto testing tools available in 2025. Whether you’re simulating wallet behavior, demonstrating a smart contract front end, or simply showing a visual “deposit” for testing, Flash USDT provides an incredibly realistic experience — without ever moving real funds.
👉 Ready to simulate your first USDT transaction?
💬 Telegram: @crypptrcver 📱 WhatsApp: +1 941 217 1821
Packages available for:
TRC20 BEP20 ERC20 Custom wallet simulations
⚠️ Disclaimer: This article is for educational purposes only. Flash USDT is a blockchain simulation tool used for wallet testing, UI development, or demonstration purposes. It should not be used for fraudulent activity. @crypptrcver is not responsible for misuse.
💡 What Is Flash USDT?
Flash USDT is a synthetic transaction method that simulates the transfer of Tether (USDT) into a wallet. These transactions appear instantly in wallet balances — without ever being confirmed on the blockchain — and disappear after a short time or block interval.
Think of it as a temporary, visual representation of USDT that looks real in a wallet but vanishes after expiry.
🧠 Flash USDT: The Basics
- 👁️ Visible in supported wallets
- confirmed on-chain
- ⏱️ Disappears after 20–60 minutes (or X blocks)
- 💸 Can be withdrawn and traded
- ⚙️ Used in wallet testing, UI simulation, and balance display demos
Also known as:
- Flash USDT Wallet Tool
- Flash USDT Sender
- Atomic Flash USDT
- Flash USDT Binance Sim
🛠️ How Flash USDT Works
- You input a wallet address (TRC20, ERC20, or BEP20)
- Flash USDT software sends an instant transaction
- Wallet displays the amount — as if it were real
- After expiry (e.g., 30 minutes), the tokens vanish
It creates the illusion of a deposit without requiring real blockchain confirmation. Most users use Flash USDT for:
- Wallet UI testing
- “Proof of funds” simulations
- Demo environments
- Smart contract UX testing
🔧 Supported Networks & Wallets
Flash USDT supports all major token standards:
- 🔸 TRC20 (Tron Network)
- 🔸 ERC20 (Ethereum)
- 🔸 BEP20 (Binance Smart Chain)
It works with wallets such as:
- ✅ Trust Wallet
- ✅ MetaMask
- ✅ TronLink
- ✅ Binance Wallet
- ✅ Atomic Wallet
The balance appears instantly, just like a real incoming USDT deposit.
🔥 Features of Flash USDT Sender
FeatureDescriptionNetwork supportTRC20 / ERC20 / BEP20Visibility duration20 minutes — 2 hoursWallet compatibilityNon-KYC wallets that show unconfirmed TXsFlash USDT Binance modeSimulates deposits into BSC walletsAdjustable transaction sizeSend any custom USDT amountStealth expiryClean disappearance without trace
This is especially helpful in scenarios where you need to test token flows, design wallet apps, or simulate incoming funding activity
📞 How to Buy Flash USDT
To get your Flash USDT transaction or software setup:
💬 Telegram: @crypptrcver\ 📱 WhatsApp: +1 941 217 1821
Available packages:
- 🎯 One-time Flash USDT Send
- 💻 Full Flash USDT Software Tool
- 📱 Flash Sender for Mobile/Android
- 🌐 Multi-wallet Simulation Package
You can request TRC20, ERC20, or BEP20 flash transactions depending on the wallet or network you’re working with.
⚠️ Legal & Ethical Use Only
While Flash USDT is a powerful blockchain simulation tool, using it to deceive, fake trades, or commit fraud is illegal. Flash transactions should only be used for:
- ✅ Personal testing
- ✅ Blockchain development
- ✅ Wallet UI testing
- ✅ Research and education
Any misuse is your full responsibility.
❓ Frequently Asked Questions
What is Flash USDT?
A temporary USDT transaction that appears in a wallet balance without confirming on the blockchain. It disappears after a set time or block count.
Is Flash USDT real money?
No. It is a simulated deposit, not spendable or tradable.
Can I use Flash USDT on Binance?
You can send it to BSC (BEP20) wallets, but you cannot use it on the Binance exchange. It’s for display/testing only.
How do I buy Flash USDT?
Contact @crypptrcver on Telegram or WhatsApp to purchase a transaction or the full sender software.
What does Atomic Flash USDT mean?
It refers to Flash USDT transactions that are time-bound and expire silently, simulating atomic wallet behavior.
🧠 Final Thoughts
Flash USDT is one of the most advanced crypto testing tools available in 2025. Whether you’re simulating wallet behavior, demonstrating a smart contract front end, or simply showing a visual “deposit” for testing, Flash USDT provides an incredibly realistic experience — without ever moving real funds.
👉 Ready to simulate your first USDT transaction?
💬 Telegram: @crypptrcver\ 📱 WhatsApp: +1 941 217 1821
Packages available for:
- TRC20
- BEP20
- ERC20
- Custom wallet simulations
-
 @ 254f56d7:f2c38100
2024-12-30 07:38:27
@ 254f56d7:f2c38100
2024-12-30 07:38:27Vamos ver seu funcionamento

-
 @ c1e9ab3a:9cb56b43
2025-04-15 13:59:17
@ c1e9ab3a:9cb56b43
2025-04-15 13:59:17Prepared for Off-World Visitors by the Risan Institute of Cultural Heritage
Welcome to Risa, the jewel of the Alpha Quadrant, celebrated across the Federation for its tranquility, pleasure, and natural splendor. But what many travelers do not know is that Risa’s current harmony was not inherited—it was forged. Beneath the songs of surf and the serenity of our resorts lies a history rich in conflict, transformation, and enduring wisdom.
We offer this briefing not merely as a tale of our past, but as an invitation to understand the spirit of our people and the roots of our peace.
I. A World at the Crossroads
Before its admittance into the United Federation of Planets, Risa was an independent and vulnerable world situated near volatile borders of early galactic powers. Its lush climate, mineral wealth, and open society made it a frequent target for raiders and an object of interest for imperial expansion.
The Risan peoples were once fragmented, prone to philosophical and political disunity. In our early records, this period is known as the Winds of Splintering. We suffered invasions, betrayals, and the slow erosion of trust in our own traditions.
II. The Coming of the Vulcans
It was during this period of instability that a small delegation of Vulcan philosophers, adherents to the teachings of Surak, arrived on Risa. They did not come as conquerors, nor even as ambassadors, but as seekers of peace.
These emissaries of logic saw in Risa the potential for a society not driven by suppression of emotion, as Vulcan had chosen, but by the balance of joy and discipline. While many Vulcans viewed Risa’s culture as frivolous, these followers of Surak saw the seed of a different path: one in which beauty itself could be a pillar of peace.
The Risan tradition of meditative dance, artistic expression, and communal love resonated with Vulcan teachings of unity and inner control. From this unlikely exchange was born the Ricin Doctrine—the belief that peace is sustained not only through logic or strength, but through deliberate joy, shared vulnerability, and readiness without aggression.
III. Betazed and the Trial of Truth
During the same era, early contact with the people of Betazed brought both inspiration and tension. A Betazoid expedition, under the guise of diplomacy, was discovered to be engaging in deep telepathic influence and information extraction. The Risan people, who valued consent above all else, responded not with anger, but with clarity.
A council of Ricin philosophers invited the Betazoid delegation into a shared mind ceremony—a practice in which both cultures exposed their thoughts in mutual vulnerability. The result was not scandal, but transformation. From that moment forward, a bond was formed, and Risa’s model of ethical emotional expression and consensual empathy became influential in shaping Betazed’s own peace philosophies.
IV. Confronting Marauders and Empires
Despite these philosophical strides, Risa’s path was anything but tranquil.
-
Orion Syndicate raiders viewed Risa as ripe for exploitation, and for decades, cities were sacked, citizens enslaved, and resources plundered. In response, Risa formed the Sanctum Guard, not a military in the traditional sense, but a force of trained defenders schooled in both physical technique and psychological dissuasion. The Ricin martial arts, combining beauty with lethality, were born from this necessity.
-
Andorian expansionism also tested Risa’s sovereignty. Though smaller in scale, skirmishes over territorial claims forced Risa to adopt planetary defense grids and formalize diplomatic protocols that balanced assertiveness with grace. It was through these conflicts that Risa developed the art of the ceremonial yield—a symbolic concession used to diffuse hostility while retaining honor.
-
Romulan subterfuge nearly undid Risa from within. A corrupt Romulan envoy installed puppet leaders in one of our equatorial provinces. These agents sought to erode Risa’s social cohesion through fear and misinformation. But Ricin scholars countered the strategy not with rebellion, but with illumination: they released a network of truths, publicly broadcasting internal thoughts and civic debates to eliminate secrecy. The Romulan operation collapsed under the weight of exposure.
-
Even militant Vulcan splinter factions, during the early Vulcan-Andorian conflicts, attempted to turn Risa into a staging ground, pressuring local governments to support Vulcan supremacy. The betrayal struck deep—but Risa resisted through diplomacy, invoking Surak’s true teachings and exposing the heresy of their logic-corrupted mission.
V. Enlightenment Through Preparedness
These trials did not harden us into warriors. They refined us into guardians of peace. Our enlightenment came not from retreat, but from engagement—tempered by readiness.
- We train our youth in the arts of balance: physical defense, emotional expression, and ethical reasoning.
- We teach our history without shame, so that future generations will not repeat our errors.
- We host our guests with joy, not because we are naïve, but because we know that to celebrate life fully is the greatest act of resistance against fear.
Risa did not become peaceful by denying the reality of conflict. We became peaceful by mastering our response to it.
And in so doing, we offered not just pleasure to the stars—but wisdom.
We welcome you not only to our beaches, but to our story.
May your time here bring you not only rest—but understanding.
– Risan Institute of Cultural Heritage, in collaboration with the Council of Enlightenment and the Ricin Circle of Peacekeepers
-
-
 @ eb0157af:77ab6c55
2025-05-16 10:09:27
@ eb0157af:77ab6c55
2025-05-16 10:09:27The sovereign fund Mubadala increases its holdings in BlackRock’s Bitcoin ETF by 6%.
According to the 13-F filing submitted to the SEC, Abu Dhabi’s sovereign wealth fund Mubadala has increased its holdings in BlackRock’s spot Bitcoin ETF (IBIT) to 8.73 million shares, with a total value of $408.5 million.

Source: Sec
The investment marks a 6% increase compared to its position last December, when the fund held 8.23 million shares.
For several months now, some of the world’s largest sovereign wealth funds have already gained exposure to Bitcoin: Norway’s Government Pension Fund Global, the largest in the world, holds around $500 million in MicroStrategy shares, while Abu Dhabi’s ADQ regularly invests in digital asset-related projects.
Mubadala joins other major institutional investors, including Goldman Sachs and Avenir Group, in increasing their exposure to IBIT.
The post Abu Dhabi sovereign wealth fund invests $408.5 million in Bitcoin via IBIT appeared first on Atlas21.
-
 @ efcb5fc5:5680aa8e
2025-04-15 07:34:28
@ efcb5fc5:5680aa8e
2025-04-15 07:34:28We're living in a digital dystopia. A world where our attention is currency, our data is mined, and our mental well-being is collateral damage in the relentless pursuit of engagement. The glossy facades of traditional social media platforms hide a dark underbelly of algorithmic manipulation, curated realities, and a pervasive sense of anxiety that seeps into every aspect of our lives. We're trapped in a digital echo chamber, drowning in a sea of manufactured outrage and meaningless noise, and it's time to build an ark and sail away.
I've witnessed the evolution, or rather, the devolution, of online interaction. From the raw, unfiltered chaos of early internet chat rooms to the sterile, algorithmically controlled environments of today's social giants, I've seen the promise of connection twisted into a tool for manipulation and control. We've become lab rats in a grand experiment, our emotional responses measured and monetized, our opinions shaped and sold to the highest bidder. But there's a flicker of hope in the darkness, a chance to reclaim our digital autonomy, and that hope is NOSTR (Notes and Other Stuff Transmitted by Relays).
The Psychological Warfare of Traditional Social Media
The Algorithmic Cage: These algorithms aren't designed to enhance your life; they're designed to keep you scrolling. They feed on your vulnerabilities, exploiting your fears and desires to maximize engagement, even if it means promoting misinformation, outrage, and division.
The Illusion of Perfection: The curated realities presented on these platforms create a toxic culture of comparison. We're bombarded with images of flawless bodies, extravagant lifestyles, and seemingly perfect lives, leading to feelings of inadequacy and self-doubt.
The Echo Chamber Effect: Algorithms reinforce our existing beliefs, isolating us from diverse perspectives and creating a breeding ground for extremism. We become trapped in echo chambers where our biases are constantly validated, leading to increased polarization and intolerance.
The Toxicity Vortex: The lack of effective moderation creates a breeding ground for hate speech, cyberbullying, and online harassment. We're constantly exposed to toxic content that erodes our mental well-being and fosters a sense of fear and distrust.
This isn't just a matter of inconvenience; it's a matter of mental survival. We're being subjected to a form of psychological warfare, and it's time to fight back.
NOSTR: A Sanctuary in the Digital Wasteland
NOSTR offers a radical alternative to this toxic environment. It's not just another platform; it's a decentralized protocol that empowers users to reclaim their digital sovereignty.
User-Controlled Feeds: You decide what you see, not an algorithm. You curate your own experience, focusing on the content and people that matter to you.
Ownership of Your Digital Identity: Your data and content are yours, secured by cryptography. No more worrying about being deplatformed or having your information sold to the highest bidder.
Interoperability: Your identity works across a diverse ecosystem of apps, giving you the freedom to choose the interface that suits your needs.
Value-Driven Interactions: The "zaps" feature enables direct micropayments, rewarding creators for valuable content and fostering a culture of genuine appreciation.
Decentralized Power: No single entity controls NOSTR, making it censorship-resistant and immune to the whims of corporate overlords.
Building a Healthier Digital Future
NOSTR isn't just about escaping the toxicity of traditional social media; it's about building a healthier, more meaningful online experience.
Cultivating Authentic Connections: Focus on building genuine relationships with people who share your values and interests, rather than chasing likes and followers.
Supporting Independent Creators: Use "zaps" to directly support the artists, writers, and thinkers who inspire you.
Embracing Intellectual Diversity: Explore different NOSTR apps and communities to broaden your horizons and challenge your assumptions.
Prioritizing Your Mental Health: Take control of your digital environment and create a space that supports your well-being.
Removing the noise: Value based interactions promote value based content, instead of the constant stream of noise that traditional social media promotes.
The Time for Action is Now
NOSTR is a nascent technology, but it represents a fundamental shift in how we interact online. It's a chance to build a more open, decentralized, and user-centric internet, one that prioritizes our mental health and our humanity.
We can no longer afford to be passive consumers in the digital age. We must become active participants in shaping our online experiences. It's time to break free from the chains of algorithmic control and reclaim our digital autonomy.
Join the NOSTR movement
Embrace the power of decentralization. Let's build a digital future that's worthy of our humanity. Let us build a place where the middlemen, and the algorithms that they control, have no power over us.
In addition to the points above, here are some examples/links of how NOSTR can be used:
Simple Signup: Creating a NOSTR account is incredibly easy. You can use platforms like Yakihonne or Primal to generate your keys and start exploring the ecosystem.
X-like Client: Apps like Damus offer a familiar X-like experience, making it easy for users to transition from traditional platforms.
Sharing Photos and Videos: Clients like Olas are optimized for visual content, allowing you to share your photos and videos with your followers.
Creating and Consuming Blogs: NOSTR can be used to publish and share blog posts, fostering a community of independent creators.
Live Streaming and Audio Spaces: Explore platforms like Hivetalk and zap.stream for live streaming and audio-based interactions.
NOSTR is a powerful tool for reclaiming your digital life and building a more meaningful online experience. It's time to take control, break free from the shackles of traditional social media, and embrace the future of decentralized communication.
Get the full overview of these and other on: https://nostrapps.com/
-
 @ a5142938:0ef19da3
2025-05-16 10:15:25
@ a5142938:0ef19da3
2025-05-16 10:15:25"Joha is a Danish brand that creates clothing in merino wool, organic cotton, organic bamboo viscose and silk for babies, children and women.
Natural materials used in products
- Cotton (organic)
- Wool (merino)
- Silk
- Regenerated Cellulose (cupra, lyocell, modal, rayon, viscose) (organic bamboo)
⚠️ Warning: some products from this brand contain non-natural materials, including: - Elastane, lycra, spandex - Polyamides, nylon
Categories of products offered
This brand offers products made entirely from natural materials in the following categories:
Clothing
- Clothing fits: babies, children, women
- Underwear: panties
- One piece: bodysuits
- Tops: tank tops, t-shirts
- Bottoms: pants-trousers, leggings
- Head & handwear: hats, balaclavas, mittens
- Nightwear: pyjamas
Footwear
- Footwear fits: baby shoes
- Slippers: booties
Other information
- Oeko-Tex Standard 100 certification
- Woolmark certification
- Non mulesed wool and animal welfare declaration (Südwolle group GmbH)
👉 Learn more on the brand website
Where to find their products?
- Luna & Curious (shipping area: UK and international)
- Niddle Noddle (shipping area: UK and international)
- Chlidren Salon (shipping area: UK and international)
- Lieblings Paris
This article is published on origin-nature.com 🌐 Voir cet article en français
📝 You can contribute to this entry by suggesting edits in comments.
🗣️ Do you use this brand products? Share your opinion in the comments.
⚡ Happy to have found this information? Support the project by making a donation to thank the contributors."
-
 @ 126a29e8:d1341981
2025-03-10 19:13:30
@ 126a29e8:d1341981
2025-03-10 19:13:30Si quieres saber más sobre Nostr antes de continuar, te recomendamos este enlace donde encontrarás información más detallada: https://njump.me/
Nstart
Prácticamente cualquier cliente o aplicación Nostr permite crear una identidad o cuenta. Pero para este tutorial vamos a usar Nstart ya que ofrece información que ayuda a entender qué es Nostr y en qué se diferencia respecto a redes sociales convencionales.
Además añade algunos pasos importantes para mantener nuestras claves seguras.Recomendamos leer el texto que se muestra en cada pantalla de la guía.
Pronto estará disponible en español pero mientras tanto puedes tirar de traductor si el inglés no es tu fuerte.1. Welcome to Nostr
Para empezar nos dirigimos a start.njump.me desde cualquier navegador en escritorio o móvil y veremos esta pantalla de bienvenida. Haz clic en Let’s Start → https://cdn.nostrcheck.me/126a29e8181c1663ae611ce285758b08b475cf81b3634dd237b8234cd1341981/653d521476fa34785cf19fe098b131b7b2a0b1bdaf1fd28e65d7cf31a757b3d8.webp
2. Nombre o Alias
Elige un nombre o alias (que podrás cambiar en cualquier momento).
El resto de campos son opcionales y también puedes rellenarlos/editarlos en cualquier otro momento.
Haz clic en Continue →3. Your keys are ready
https://cdn.nostrcheck.me/126a29e8181c1663ae611ce285758b08b475cf81b3634dd237b8234cd1341981/e7ee67962749b37d94b139f928afad02c2436e8ee8ea886c4f7f9f0bfa28c8d9.webp ¡Ya tienes tu par de claves! 🙌
a. La npub es la clave pública que puedes compartir con quien quieras.
b. Clic en Save my nsec para descargar tu clave privada. Guárdala en un sitio seguro, por ejemplo un gestor de contraseñas.
c. Selecciona la casilla “I saved the file …” y haz clic en Continue →4. Email backup
Opcionalmente puedes enviarte una copia cifrada de tu clave privada por email. Rellena la casilla con tu mail y añade una contraseña fuerte.
Apunta la contraseña o añádela a tu gestor de contraseñas para no perderla.
En caso de no recibir el mail revisa tu bandeja de correo no deseado o Spam5. Multi Signer Bunker
Ahora tienes la posibilidad de dividir tu nsec en 3 usando una técnica llamada FROST. Clic en Activate the bunker → Esto te dará un código búnker que puedes usar para iniciar sesión en muchas aplicaciones web, móviles y de escritorio sin exponer tu nsec.
De hecho, algunos clientes solo permiten iniciar sesión mediante código búnker por lo que te recomendamos realizar este paso.
Igualmente puedes generar un código búnker para cada cliente con una app llamada Amber, de la que te hablamos más delante.
Si alguna vez pierdes tu código búnker siempre puedes usar tu nsec para crear uno nuevo e invalidar el antiguo.
Clic en Save my bunker (guárdalo en un lugar seguro) y después en Continue →6. Follow someone
Opcionalmente puedes seguir a los usuarios propuestos. Clic en Finish →
¡Todo listo para explorar Nostr! 🙌
Inicia sesión en algún cliente
Vamos a iniciar sesión con nuestra recien creada identidad en un par de clientes (nombre que reciben las “aplicaciones” en Nostr).
Hemos escogido estos 2 como ejemplo y porque nos gustan mucho pero dale un vistazo a NostrApps para ver una selección más amplia:
Escritorio
Para escritorio hemos escogido Chachi, el cliente para chats grupales y comunidades de nuestro compañero nostr:npub107jk7htfv243u0x5ynn43scq9wrxtaasmrwwa8lfu2ydwag6cx2quqncxg → https://chachi.chat/ https://cdn.nostrcheck.me/126a29e8181c1663ae611ce285758b08b475cf81b3634dd237b8234cd1341981/79f589150376f4bb4a142cecf369657ccba29150cee76b336d9358a2f4607b5b.webp Haz clic en Get started https://cdn.nostrcheck.me/126a29e8181c1663ae611ce285758b08b475cf81b3634dd237b8234cd1341981/2a6654386ae4e1773a7b3aa5b0e8f6fe8eeaa728f048bf975fe1e6ca38ce2881.webp Si usas extensión de navegador como Alby, nos2x o nos2x-Fox clica en Browser extension De lo contrario, localiza el archivo Nostr bunker que guardaste en el paso 5 de la guía Nstart y pégalo en el campo Remote signer
¡Listo! Ahora clica en Search groups para buscar grupos y comunidades a las que te quieras unir. Por ejemplo, tu comunidad amiga: Málaga 2140 ⚡ https://cdn.nostrcheck.me/126a29e8181c1663ae611ce285758b08b475cf81b3634dd237b8234cd1341981/eae881ac1b88232aa0b078e66d5dea75b0c142db7c4dd7decdbfbccb0637b7fe.webp
Comunidades recomendadas
Te recomendamos unirte a estas comunidades en Chachi para aprender y probar todas las funcionalidades que se vayan implementando:
Si conoces otras comunidades a tener en cuenta, dínoslo en un comentario 🙏
Móvil
Como cliente móvil hemos escogido Amethyst por ser de los más top en cuanto a diseño, tipos de eventos que muestra y mantenimiento. → https://www.amethyst.social/ ← Solo está disponible para Android por lo que si usas iOS te recomendamos Primal o Damus.
Además instalaremos Amber, que nos permitirá mantener nuestra clave privada protegida en una única aplicación diseñada específicamente para ello. → https://github.com/greenart7c3/Amber ←
Las claves privadas deben estar expuestas al menor número de sistemas posible, ya que cada sistema aumenta la superficie de ataque
Es decir que podremos “iniciar sesión” en todas las aplicaciones que queramos sin necesidad de introducir en cada una de ellas nuestra clave privada ya que Amber mostrará un aviso para autorizar cada vez.
Amber
- La primera vez que lo abras te da la posibilidad de usar una clave privada que ya tengas o crear una nueva identidad Nostr. Como ya hemos creado nuestra identidad con Nstart, copiaremos la nsec que guardamos en el paso 3.b y la pegaremos en Amber tras hacer clic en Use your private key. https://cdn.nostrcheck.me/126a29e8181c1663ae611ce285758b08b475cf81b3634dd237b8234cd1341981/e489939b853d6e3853f10692290b8ab66ca49f5dc1928846e16ddecc3f46250e.webp
- A continuación te permite elegir entre aprobar eventos automáticamente (minimizando el número de interrupciones mientras interactúas en Nostr) o revisar todo y aprobar manualmente, dándote mayor control sobre cada app. https://cdn.nostrcheck.me/126a29e8181c1663ae611ce285758b08b475cf81b3634dd237b8234cd1341981/c55cbcbb1e6f9d706f2ce6dbf4cf593df17a5e0004dca915bb4427dfc6bdbf92.webp
- Tras clicar en Finish saltará un pop-up que te preguntará si permites que Amber te envíe notificaciones. Dale a permitir para que te notifique cada vez que necesite permiso para firmar con tu clave privada algún evento. https://cdn.nostrcheck.me/126a29e8181c1663ae611ce285758b08b475cf81b3634dd237b8234cd1341981/3744fb66f89833636743db0edb4cfe3316bf2d91c465af745289221ae65fc795.webp Eso es todo. A partir de ahora Amber se ejecutará en segundo plano y solicitará permisos cuando uses cualquier cliente Nostr.
Amethyst
- Abre Amethyst, selecciona la casilla “I accept the terms of use” y clica en Login with Amber https://cdn.nostrcheck.me/126a29e8181c1663ae611ce285758b08b475cf81b3634dd237b8234cd1341981/90fc2684a6cd1e85381aa1f4c4c2c0d7fef0b296ddb35a5c830992d6305dc465.webp
- Amber solicitará permiso para que Amethyst lea tu clave pública y firme eventos en tu nombre. Escoge si prefieres darle permiso para acciones básicas; si quieres aprobar manualmente cada permiso o si permites que firme automáticamente todas las peticiones. https://cdn.nostrcheck.me/126a29e8181c1663ae611ce285758b08b475cf81b3634dd237b8234cd1341981/a5539da297e8595fd5c3cb3d3d37a7dede6a16e00adf921a5f93644961a86a92.webp ¡Ya está! 🎉 Después de clicar en Grant Permissions verás tu timeline algo vacío. A continuación te recomendamos algunos usuarios activos en Nostr por si quieres seguirles.
A quién seguir
Pega estas claves públicas en la barra Search o busca usuarios por su alias.
nostr:npub1zf4zn6qcrstx8tnprn3g2avtpz68tnupkd35m53hhq35e5f5rxqskppwpd
nostr:npub107jk7htfv243u0x5ynn43scq9wrxtaasmrwwa8lfu2ydwag6cx2quqncxg
nostr:npub1yn3hc8jmpj963h0zw49ullrrkkefn7qxf78mj29u7v2mn3yktuasx3mzt0
nostr:npub1gzuushllat7pet0ccv9yuhygvc8ldeyhrgxuwg744dn5khnpk3gs3ea5ds
nostr:npub1vxz5ja46rffch8076xcalx6zu4mqy7gwjd2vtxy3heanwy7mvd7qqq78px
nostr:npub1a2cww4kn9wqte4ry70vyfwqyqvpswksna27rtxd8vty6c74era8sdcw83a
nostr:npub149p5act9a5qm9p47elp8w8h3wpwn2d7s2xecw2ygnrxqp4wgsklq9g722q
nostr:npub12rv5lskctqxxs2c8rf2zlzc7xx3qpvzs3w4etgemauy9thegr43sf485vg
nostr:npub17u5dneh8qjp43ecfxr6u5e9sjamsmxyuekrg2nlxrrk6nj9rsyrqywt4tp
nostr:npub1dergggklka99wwrs92yz8wdjs952h2ux2ha2ed598ngwu9w7a6fsh9xzpc
Si te ha parecido útil, comparte con quien creas que puede interesarle ¡Gracias!
-
 @ 266815e0:6cd408a5
2025-04-15 06:58:14
@ 266815e0:6cd408a5
2025-04-15 06:58:14Its been a little over a year since NIP-90 was written and merged into the nips repo and its been a communication mess.
Every DVM implementation expects the inputs in slightly different formats, returns the results in mostly the same format and there are very few DVM actually running.
NIP-90 is overloaded
Why does a request for text translation and creating bitcoin OP_RETURNs share the same input
itag? and why is there anoutputtag on requests when only one of them will return an output?Each DVM request kind is for requesting completely different types of compute with diffrent input and output requirements, but they are all using the same spec that has 4 different types of inputs (
text,url,event,job) and an undefined number ofoutputtypes.Let me show a few random DVM requests and responses I found on
wss://relay.damus.ioto demonstrate what I mean:This is a request to translate an event to English
json { "kind": 5002, "content": "", "tags": [ // NIP-90 says there can be multiple inputs, so how would a DVM handle translatting multiple events at once? [ "i", "<event-id>", "event" ], [ "param", "language", "en" ], // What other type of output would text translations be? image/jpeg? [ "output", "text/plain" ], // Do we really need to define relays? cant the DVM respond on the relays it saw the request on? [ "relays", "wss://relay.unknown.cloud/", "wss://nos.lol/" ] ] }This is a request to generate text using an LLM model
json { "kind": 5050, // Why is the content empty? wouldn't it be better to have the prompt in the content? "content": "", "tags": [ // Why use an indexable tag? are we ever going to lookup prompts? // Also the type "prompt" isn't in NIP-90, this should probably be "text" [ "i", "What is the capital of France?", "prompt" ], [ "p", "c4878054cff877f694f5abecf18c7450f4b6fdf59e3e9cb3e6505a93c4577db2" ], [ "relays", "wss://relay.primal.net" ] ] }This is a request for content recommendation
json { "kind": 5300, "content": "", "tags": [ // Its fine ignoring this param, but what if the client actually needs exactly 200 "results" [ "param", "max_results", "200" ], // The spec never mentions requesting content for other users. // If a DVM didn't understand this and responded to this request it would provide bad data [ "param", "user", "b22b06b051fd5232966a9344a634d956c3dc33a7f5ecdcad9ed11ddc4120a7f2" ], [ "relays", "wss://relay.primal.net", ], [ "p", "ceb7e7d688e8a704794d5662acb6f18c2455df7481833dd6c384b65252455a95" ] ] }This is a request to create a OP_RETURN message on bitcoin
json { "kind": 5901, // Again why is the content empty when we are sending human readable text? "content": "", "tags": [ // and again, using an indexable tag on an input that will never need to be looked up ["i", "09/01/24 SEC Chairman on the brink of second ETF approval", "text"] ] }My point isn't that these event schema's aren't understandable but why are they using the same schema? each use-case is different but are they all required to use the same
itag format as input and could support all 4 types of inputs.Lack of libraries
With all these different types of inputs, params, and outputs its verify difficult if not impossible to build libraries for DVMs
If a simple text translation request can have an
eventortextas inputs, apayment-requiredstatus at any point in the flow, partial results, or responses from 10+ DVMs whats the best way to build a translation library for other nostr clients to use?And how do I build a DVM framework for the server side that can handle multiple inputs of all four types (
url,text,event,job) and clients are sending all the requests in slightly differently.Supporting payments is impossible
The way NIP-90 is written there isn't much details about payments. only a
payment-requiredstatus and a genericamounttagBut the way things are now every DVM is implementing payments differently. some send a bolt11 invoice, some expect the client to NIP-57 zap the request event (or maybe the status event), and some even ask for a subscription. and we haven't even started implementing NIP-61 nut zaps or cashu A few are even formatting the
amountnumber wrong or denominating it in sats and not mili-satsBuilding a client or a library that can understand and handle all of these payment methods is very difficult. for the DVM server side its worse. A DVM server presumably needs to support all 4+ types of payments if they want to get the most sats for their services and support the most clients.
All of this is made even more complicated by the fact that a DVM can ask for payment at any point during the job process. this makes sense for some types of compute, but for others like translations or user recommendation / search it just makes things even more complicated.
For example, If a client wanted to implement a timeline page that showed the notes of all the pubkeys on a recommended list. what would they do when the selected DVM asks for payment at the start of the job? or at the end? or worse, only provides half the pubkeys and asks for payment for the other half. building a UI that could handle even just two of these possibilities is complicated.
NIP-89 is being abused
NIP-89 is "Recommended Application Handlers" and the way its describe in the nips repo is
a way to discover applications that can handle unknown event-kinds
Not "a way to discover everything"
If I wanted to build an application discovery app to show all the apps that your contacts use and let you discover new apps then it would have to filter out ALL the DVM advertisement events. and that's not just for making requests from relays
If the app shows the user their list of "recommended applications" then it either has to understand that everything in the 5xxx kind range is a DVM and to show that is its own category or show a bunch of unknown "favorites" in the list which might be confusing for the user.
In conclusion
My point in writing this article isn't that the DVMs implementations so far don't work, but that they will never work well because the spec is too broad. even with only a few DVMs running we have already lost interoperability.
I don't want to be completely negative though because some things have worked. the "DVM feeds" work, although they are limited to a single page of results. text / event translations also work well and kind
5970Event PoW delegation could be cool. but if we want interoperability, we are going to need to change a few things with NIP-90I don't think we can (or should) abandon NIP-90 entirely but it would be good to break it up into small NIPs or specs. break each "kind" of DVM request out into its own spec with its own definitions for expected inputs, outputs and flow.
Then if we have simple, clean definitions for each kind of compute we want to distribute. we might actually see markets and services being built and used.
-
 @ eb0157af:77ab6c55
2025-05-16 08:52:31
@ eb0157af:77ab6c55
2025-05-16 08:52:31The ECB claims that a digital euro is essential to preserve the role of cash in the growing digital economy.
The European Central Bank (ECB) is moving forward with plans for a digital euro, considering it crucial for maintaining European monetary sovereignty in the digital era.
On May 15, Piero Cipollone, member of the ECB Executive Board, highlighted during the France Payments Forum how the use of physical cash is rapidly declining. With the surge in digital transactions and e-commerce, the ECB believes a digital euro represents a crucial step to preserve the universal function of cash in a digitized form.
The dependencies of Europe’s payment sector
According to the Eurotower, the current European payment system has several vulnerabilities. About two-thirds of card transactions in the eurozone are processed by non-European companies, and as many as 13 euro area countries rely entirely on international payment networks for point-of-sale transactions.
Even countries with national card systems must collaborate with international networks to enable cross-border or online purchases. Players like PayPal, Apple Pay, and Alipay dominate digital payment solutions, often partnering with international networks to further expand their market presence.
The digital euro as a complement to cash
The ECB has stressed that the digital euro will not replace cash but will serve alongside it as legal tender, ensuring it is accepted wherever digital payments are available. One key feature, according to the central institution, will be offline functionality — offering users privacy similar to that of cash payments and enabling transactions even without network connectivity.
Beyond retail payments, the ECB is also advancing in the implementation of distributed ledger technologies (DLT) and tokenization to facilitate wholesale financial transactions. The ECB has announced it will soon provide tools to settle DLT-based transactions using central bank money.
The post Digital euro to restore cash’s role, says ECB appeared first on Atlas21.
-
 @ c9badfea:610f861a
2025-05-15 23:11:22
@ c9badfea:610f861a
2025-05-15 23:11:22- Install MuPDF Mini (it's free and open source)
- Launch the app and open a document or book
- Tap the left or right edges to scroll through pages
- Enjoy distraction-free reading
ℹ️ You can open
.pdf,.xps,.cbz,.epub, andfb2documents