-
 @ e2c72a5a:bfacb2ee
2025-06-06 02:55:03
@ e2c72a5a:bfacb2ee
2025-06-06 02:55:03Your crypto wallet is probably leaking money right now. While everyone obsesses over price charts, the silent killer is gas fees – those tiny transactions add up to thousands wasted annually. Smart traders aren't just buying dips, they're timing their transactions when network congestion drops. The difference? Up to 80% savings on every move you make. Next time before hitting "confirm," check the gas tracker. Is it worth paying 3x more just to move your assets right this second? Patience isn't just a virtue in crypto – it's literally profitable. What's your strategy for minimizing transaction costs while maximizing gains?
-
 @ e516ecb8:1be0b167
2025-06-04 20:33:38
@ e516ecb8:1be0b167
2025-06-04 20:33:38Imagina un mundo donde cada peso que gastas es vigilado, registrado y cuestionado. Donde el Estado decide si puedes comprar un café, una manzana o una criptomoneda. No es una distopía de ciencia ficción, es el rumbo que están tomando varios países, mientras otros, como Argentina, dan un giro inesperado hacia la libertad. ¿Quién está ganando esta batalla por el control de tu dinero?
Argentina: "Tus dólares son tuyos" En Argentina, Javier Milei, con su bandera libertaria ondeando, ha dado un paso audaz: desmantelar el control policial sobre el dinero de los ciudadanos. Su lema, "Tus dólares son tuyos", es tan obvio como revolucionario. Después de décadas de corralitos, cepos cambiarios y una inflación que en 2023 alcanzó el 211,4% según el INDEC, Milei apuesta por devolverle al ciudadano el poder sobre su propio capital. Con el país logrando superávit fiscal por primera vez en años (0,2% del PBI en el primer trimestre de 2024), el gobierno ya no necesita espiar cada transacción para exprimir impuestos.
Pero aquí viene lo curioso: encuestas recientes, como una de la consultora Poliarquía, muestran que un 35% de los argentinos aún prefiere que el Estado controle sus finanzas. ¿Masoquismo? ¿Miedo a la libertad? Tal vez sea la costumbre de vivir bajo la lupa. Milei, fiel a su convicción, no solo liberaliza por necesidad económica, sino porque cree que el dinero es tuyo, no del burócrata de turno.
España y el Euro Digital: El ojo que todo lo ve Mientras Argentina afloja las riendas, Europa cabalga en dirección opuesta. En España, el gobierno está reduciendo progresivamente los umbrales para controlar transacciones bancarias. A partir de 2026, cada pago por Bizum —el equivalente ibérico al Pix brasileño— estará bajo escrutinio. Según el Banco de España, en 2024 se realizaron más de 1.200 millones de transacciones por Bizum, moviendo unos 60.000 millones de euros. Ahora, cada una de esas operaciones será un dato más para Hacienda.
Pero no es solo España. La Unión Europea avanza con el Euro Digital, un proyecto que promete ser la pesadilla de cualquier amante de la privacidad. Esta moneda digital, según el Banco Central Europeo, permitirá rastrear cada movimiento, limitar ciertos gastos (¿adiós a compras de cripto o donaciones incómodas?), e incluso programar que el dinero "se oxide". Sí, has leído bien: si no gastas tus euros digitales en un tiempo determinado, podrían perder valor o simplemente desaparecer. Un informe del BCE de 2023 estima que el Euro Digital estará operativo en 2027, y ya hay pruebas piloto en países como Alemania y Francia. ¿Libertad financiera? Más bien un Gran Hermano con esteroides.
Chile: El Estado fisgón y los funcionarios de lujo En Chile, el control monetario también aprieta. El gobierno ha propuesto levantar el secreto bancario, permitiendo que cualquier funcionario del SII pueda husmear en tus cuentas. Además, si haces más de 50 transacciones al mes, el Servicio de Impuestos Internos (SII) pondrá la lupa sobre ti. ¿Y las ferias libres? Esas donde compras tus tomates y zapallos sin complicaciones ahora deberán emitir boletas electrónicas, encareciendo los productos para el ciudadano de a pie. Según la CEPAL, los costos administrativos para pequeños comerciantes podrían aumentar hasta un 15% con estas medidas.
Mientras tanto, el sector público chileno vive en otra galaxia. Funcionarios con sueldos que superan los 5 millones de pesos mensuales (unos 5.500 USD) toman licencias médicas para viajar por el mundo, según denuncias de la Contraloría. Algunos incluso cobran por "turnos" de 17 horas extras diarias o marcan asistencia en dos lugares al mismo tiempo. ¿Y quién paga? Tú, con tus impuestos.
La resistencia: Volver al efectivo o abrazar las cripto Si el Estado quiere controlar cada centavo, ¿qué opciones nos quedan? Una es volver al efectivo, pero no nos engañemos: el dinero fiat, controlado por bancos centrales, pierde valor a largo plazo. En Chile, la inflación acumulada entre 2010 y 2024 fue del 62%, según el INE. Tus billetes de hoy valen menos que los de ayer, y mañana valdrán aún menos.
La otra opción es el mundo cripto, pero no cualquier cripto. Bitcoin, la más conocida, es un titán para almacenar valor, pero para transacciones diarias necesita una segunda capa como Lightning Network, que procesa pagos instantáneos con comisiones ínfimas (menos de 0,01 USD por transacción en 2024). Alternativas como Bitcoin Cash (BCH) o Monero (XMR) ofrecen transacciones rápidas y, en el caso de XMR, un enfoque en la privacidad que hace temblar a los burócratas. Sin embargo, ninguna cripto servirá si los comercios y las personas no las adoptan. En Argentina, por ejemplo, solo el 1,5% de las transacciones minoristas en 2024 usaron criptomonedas, según Chainalysis. La libertad financiera no llega sola: hay que construirla.
El futuro es ahora El dinero es poder, y quien controla el dinero controla tu vida. Mientras Milei en Argentina te devuelve las llaves de tus dólares, en Europa y Chile te atan las manos con leyes, regulaciones y monedas digitales. La pregunta no es si quieres libertad, sino si estás dispuesto a pelear por ella. Usa efectivo, explora cripto, pero sobre todo, no dejes que el Gran Hermano decida por ti. Porque una vez que el Estado mete la mano en tu bolsillo, no la saca nunca.
-
 @ ca76c778:e784c54b
2025-06-04 19:45:11
@ ca76c778:e784c54b
2025-06-04 19:45:11A few days ago I remembered video by Antonio Stappaerts(Artwod) on Youtube. And I thought to myself I want to be really good at drawing hands.\ In the video he explains something that, in my opinion, applies when learning just about anything.
If you've heard of the Dunning-Kruger effect then you know the first part.\ If you haven't, one begins learning something and on top of the first peak thinks oneself to be almost a master. And then one learns a little bit more and realizes how little skill one actually has.
 \
Now, what is really interesting is this. He points out that the second slope is made up of many smaller Dunning-Kruger effects. For example the effect will apply when learning: the basic shape of the figure, how to pose the figure, how draw the hands, the hair etc.
\
Now, what is really interesting is this. He points out that the second slope is made up of many smaller Dunning-Kruger effects. For example the effect will apply when learning: the basic shape of the figure, how to pose the figure, how draw the hands, the hair etc.So the way to climb the second hill is to understand and practice these smaller skills. And not just once or twice. You want to reach close to the second peak of each of the smaller skills.
And with that in mind I search for a good tutorial about drawing hands and got down to it(for the third time).
Step one was to learn pose and gesture using a grid shape.
https://cdn.satellite.earth/f55a9d1ef2fd687a9dce5ceee5e05a1b666c436509e264ddbac4d260b99e882a.jpg
https://cdn.satellite.earth/1b5524635c20ee4869f4860c982deea469cb87be7ad7b404e1777497b5a4fbd4.jpg
https://cdn.satellite.earth/35652251243ffd8c495b855c319d27da0c193ff2e951591f0a9f1b35aad39b29.jpg
https://cdn.satellite.earth/68f55979d102b4ebe55177842c6d9ab2ab30b95f926441429d977b47fae925c3.jpg
Step two. Practice the basic forms for the palm and fingers.\ I got carried away and drew some hands.
https://cdn.satellite.earth/48b400f72e35d078368149f00182cb58e606ddd16f6db4e7789c1431c28d44a0.jpg
Step three. learn the measurements.
https://cdn.satellite.earth/75c9b82da90ef50d17f698dd7b1eadc223b74a019a702a4617ed7d321646a87c.jpg
Step four. Understand the fingers.
https://cdn.satellite.earth/e33f9f3f9217bf5e3e206e96dfe764eba09b9fb3c10b450bb9c8a4075e3c1ec8.jpg
Step five. Learn about the thumb and put it all together. Drawing from reference and imagination.
https://cdn.satellite.earth/b2dd9c1cc1045dde021272199818b0db331e71a603c5900122aa850eb2d4148a.jpg
https://cdn.satellite.earth/8f5647ae9e148ad6217c106b5b69cf231384475e0a0eedf210bd149f75ade0b7.jpg
-
 @ 374ee93a:36623347
2025-06-05 22:42:00
@ 374ee93a:36623347
2025-06-05 22:42:00Chef's notes
Start your day the self sovereign way
Details
- ⏲️ Prep time: 10 mins
- 🍳 Cook time: 15 mins
- 🍽️ Servings: 4
Ingredients
- 1lb Jar Bottled Rhubarb https://jimblesjumble.netlify.app/item/a0c35618722834ac714d0a47058a2adc76ee7485a6b74f5da5f9eb2d3fb5d879
- 1pt Homemade Custard (3/4pt cream, 3 large eggs, 100g honey, 1/2 tbspn vanilla extract)
- 4 Handfuls Granola
- 1 Node https://plebeian.market/products/huxley@nostrplebs.com/start-9-node-y22zfjp8x6
Directions
- Whisk together the cream, eggs, honey and vanilla
- Chill overnight or serve warm with 1/4 jar of stewed rhubarb and a large handful of granola per person
- Consolidate some UTXOs on your node
- Have a Good Morning
-
 @ 2cde0e02:180a96b9
2025-06-05 21:45:00
@ 2cde0e02:180a96b9
2025-06-05 21:45:00日本の姫
https://stacker.news/items/998335
-
 @ a9434ee1:d5c885be
2025-05-12 07:51:31
@ a9434ee1:d5c885be
2025-05-12 07:51:31Colors as a fun and useful identifier
Nostr apps often use totally random colors for their default avatars, profiles names in chat bubbles, etc... That's a missed opportunity. Why don't we just we just derive a color from the npub and use that instead, interoperably across apps?
It gives us a fun and visual extra point of recognition, often without having to add anything extra to the UIs.
The only problem is that we cannot just allow for any color. The colors should be readable as text in Light and Dark modes and gray-scales should be avoided too.
This is the goal:
 Luckily, there's a super simple solution.
Luckily, there's a super simple solution.
(which was used to derive the color above)Deriving the Colors
You can find the simple spec here: nostr:naddr1qvzqqqrcvgpzp22rfmsktmgpk2rtan7zwu00zuzax5maq5dnsu5g3xxvqr2u3pd7qy88wumn8ghj7mn0wvhxcmmv9uqsuamnwvaz7tmwdaejumr0dshsz8rhwden5te0w35x2cmfw3skgetv9ehx7um5wgcjucm0d5hsz8rhwden5te0w35x2cmfw3skgetv9ehx7um5wgcjucm0d5hszxmhwden5te0w35x2en0wfjhxapwdehhxarjxyhxxmmd9uq3kamnwvaz7tm5dpjkvmmjv4ehgtnwdaehgu339e3k7mf0qyghwumn8ghj7mn0wd68ytnhd9hx2tcpz9mhxue69uhkummnw3ezuamfdejj7qghwaehxw309aex2mrp0yhxummnw3ezucnpdejz7qghwaehxw309aex2mrp0yhxummnw3ezucnpdejz7qgwwaehxw309ahx7uewd3hkctcpr3mhxue69uhhg6r9vd5hgctyv4kzumn0wd68yvfwvdhk6tcpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcprdmhxue69uhhg6r9vehhyetnwshxummnw3erztnrdakj7qg3waehxw309ahx7um5wgh8w6twv5hszythwden5te0dehhxarj9emkjmn99uqsuamnwvaz7tmwdaejumr0dshsz8rhwden5te0w35x2cmfw3skgetv9ehx7um5wgcjucm0d5hsqpnwd9cz6ce3pvatyf
TLDR: 1. Convert HEX pubkey to Int 2. Calculate the Hue value: Int % 360 3. Set Saturation to 90 for Hues between 216 and 273, use 80 for the rest 4. Set Brightness to 65 for Hues between 32 and 212, use 85 for the rest
Convert HSB color to whatever format you need. Done.
Easy & Fun to integrate!
-
 @ e2c72a5a:bfacb2ee
2025-06-06 02:43:10
@ e2c72a5a:bfacb2ee
2025-06-06 02:43:10North Korea's digital heist playbook: $7.7M crypto laundering scheme reveals how rogue nations exploit tech talent. The Justice Department's latest civil forfeiture complaint targets crypto and NFTs tied to an elaborate North Korean operation where IT workers posed as legitimate freelancers, infiltrated US companies, and funneled millions through complex blockchain pathways. This isn't just another hack—it's a sophisticated economic warfare strategy that turns technical expertise into untraceable funding for weapons programs. While governments scramble to seize these digital assets, the case exposes a troubling vulnerability: how easily skilled developers can weaponize their talents in plain sight. Are your company's remote contractors who they claim to be, or part of a state-sponsored financial pipeline hiding behind a convincing digital mask?
-
 @ e2c72a5a:bfacb2ee
2025-06-06 01:42:46
@ e2c72a5a:bfacb2ee
2025-06-06 01:42:46North Korea's digital heist reveals the dark side of crypto's borderless nature. The US Justice Department is hunting $7.7 million in stolen cryptocurrency and NFTs allegedly laundered through an elaborate scheme involving North Korean IT workers posing as legitimate freelancers. This isn't just another hack—it's a sophisticated state-sponsored operation exploiting the very features that make crypto revolutionary: anonymity and borderless transactions. While we celebrate crypto's ability to transcend boundaries, this case exposes how those same qualities create perfect conditions for rogue nations to fund weapons programs and evade sanctions. The crypto industry faces a critical balancing act: how do we preserve financial freedom while preventing bad actors from exploiting the system? Perhaps the solution isn't more regulation but smarter blockchain analytics and international cooperation. What security measures would you support that don't compromise crypto's core principles?
-
 @ 3eab247c:1d80aeed
2025-06-05 08:51:39
@ 3eab247c:1d80aeed
2025-06-05 08:51:39Global Metrics
Here are the top stats from the last period:
- Total Bitcoin-accepting merchants: 15,306 → 16,284
- Recently verified (1y): 7,540 → 7,803 (the rest of our dataset is slowly rotting; help us before it's too late!)
- Avg. days since last verification: 398 → 405 (more mappers, please)
- Merchants boosted: 22 (for a total of 4,325 days, someone is feeling generous)
- Comments posted: 34
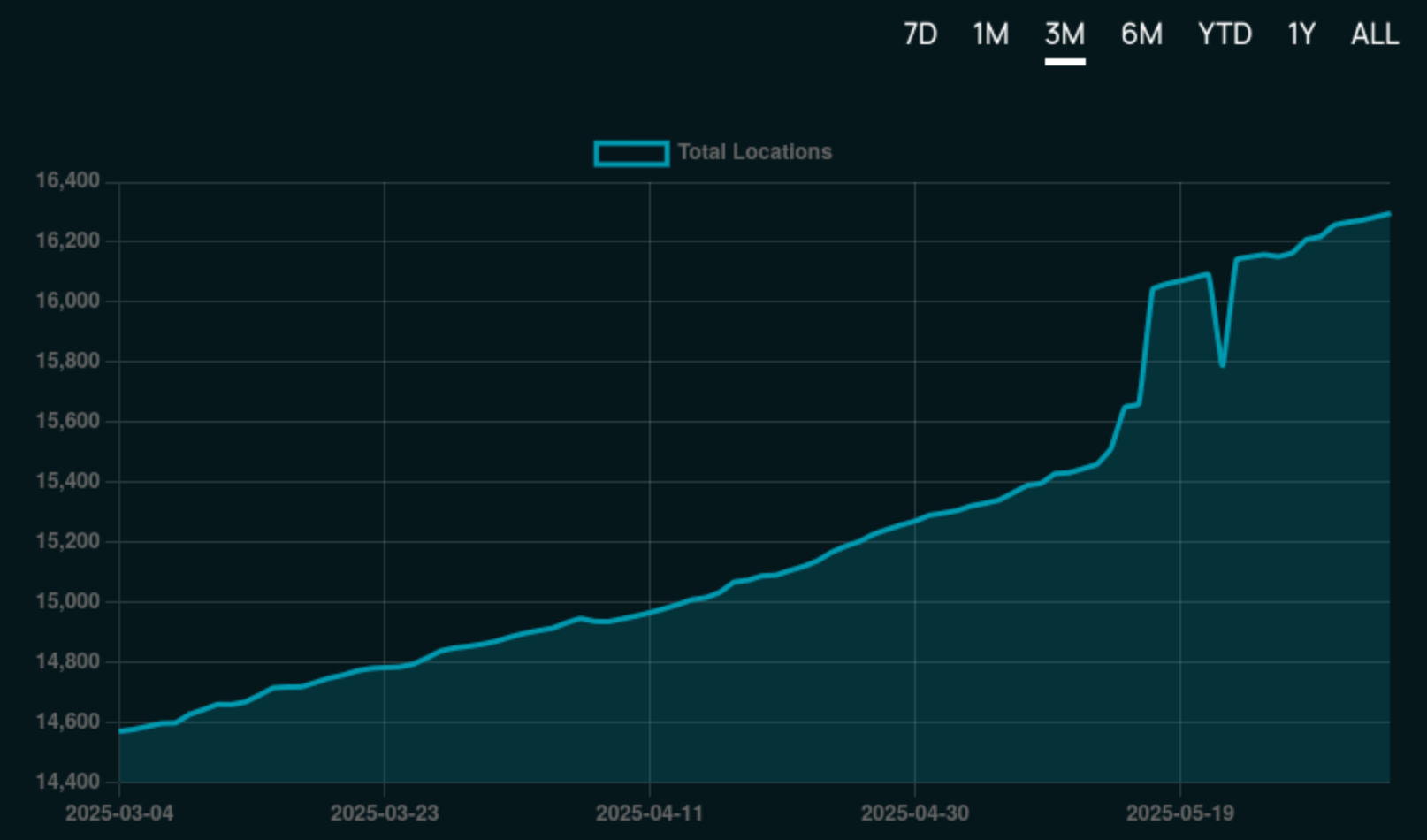
Find current stats over at the 👉 BTC Map Dashboard.
Merchant Adoption
Steak n’ Shake
The US 🇺🇸 is a massive country, yet its BTC Map footprint has been lagging relative to other countries ... that is until now!

In what came as a nice surprise to our Shadowy Supertaggers 🫠, the Steak ’n Shake chain began accepting Bitcoin payments across hundreds of its locations nationwide (with some international locations too).
According to CoinDesk, the rollout has been smooth, with users reporting seamless transactions powered by Speed.
This marks a significant step towards broader Bitcoin adoption in the US. Now to drop the capital gains tax on cheesburgers!
SPAR Switzerland
In other chain/franchise adoption news, the first SPAR supermarket in Switzerland 🇨🇭 to begin accepting Bitcoin was this one in Zug. It was quickly followed by this one in Rossrüti and this one in Kreuzlingen, in what is believed to be part of a wider roll-out plan within the country powered by DFX's Open CryptoPay.
That said, we believe the OG SPAR crown goes to SPAR City in Arnhem Bitcoin City!
New Features
Merchant Comments in the Web App
Web App users are now on par with Android users in that they can both see and make comments on merchants.
This is powered by our tweaked API that enables anyone to make a comment as long as they pass the satswall fee of 500 sats. This helps keep spam manageable and ensure quality comments.
And just in case you were wondering what the number count was on the merchant pins - yep, they're comments!
Here is an 👉 Example merchant page with comments.
Merchant Page Design Tweaks
To support the now trio of actions (Verify, Boost & Comment) on the merchant page, we've re-jigged the design a little to make things a little clearer.
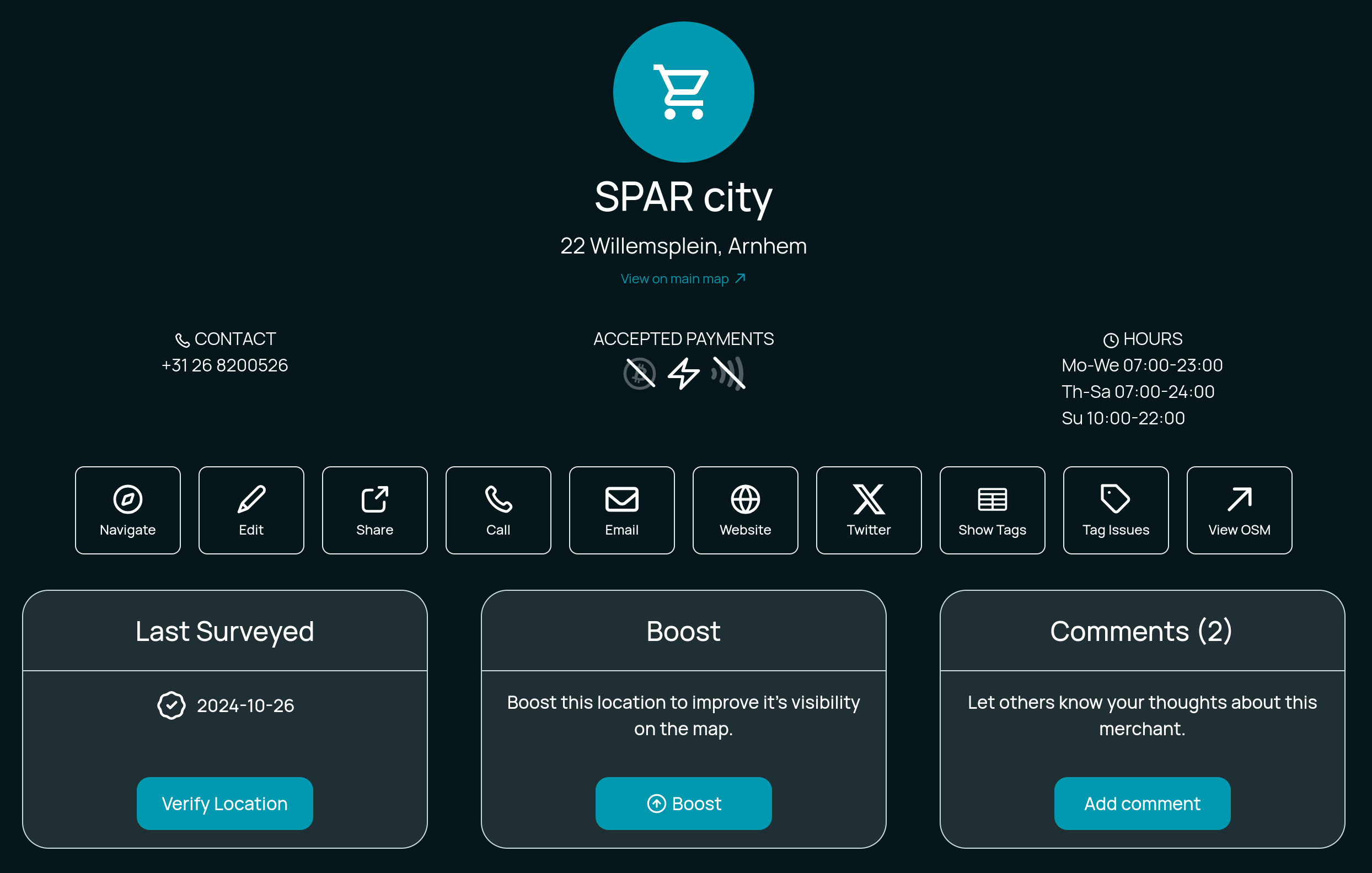
What do you think?
Technical
Codebase Refactoring
Thanks to Hannes’s contributions, we’ve made progress in cleaning-up the Web App's codebase and completing long overdue maintenance. Whilst often thankless tasks, these caretaking activities help immensely with long-term maintainability enabling us to confidently build new features.
Auth System Upgrades
The old auth system was held together with duct tape and prayers, and we’re working on a more robust authentication system to support future public API access. Updates include:
- Password hashing
- Bearer token support
- Improved security practices
More enhancements are in progress and we'll update you in the next blog post.
Better API Documentation
Instead of relying on tribal knowledge, we're finally getting around to writing actual docs (with the help/hindrance of LLMs). The "move fast, break everything" era is over; now we move slightly slower and break slightly less. Progress!
Database Improvements
We use SQLite, which works well but it requires careful handling in async Rust environments. So now we're untangling this mess to avoid accidental blocking queries (and the ensuing dumpster fires).
Backup System Enhancements
BTC Map data comes in three layers of fragility:
- Merchants (backed up by OS - the big boys handle this)
- Non-OSM stuff (areas, users, etc. - currently stored on a napkin)
- External systems (Lightning node, submission tickets - pray to Satoshi)
We're now forcing two core members to backup everything, because redundancy is good.
Credits
Thanks to everyone who directly contributed to the project this period:
- Comino
- descubrebitcoin
- Hannes
- Igor Bubelov
- Nathan Day
- Rockedf
- Saunter
- SiriusBig
- vv01f
Support Us
There are many ways in which you can support us:
-
Become a Shadowy Supertagger and help maintain your local area or pitch-in with the never-ending global effort.
-
Consider a zapping this note or make a donation to the to the project here.
-
 @ 52b4a076:e7fad8bd
2025-04-28 00:48:57
@ 52b4a076:e7fad8bd
2025-04-28 00:48:57I have been recently building NFDB, a new relay DB. This post is meant as a short overview.
Regular relays have challenges
Current relay software have significant challenges, which I have experienced when hosting Nostr.land: - Scalability is only supported by adding full replicas, which does not scale to large relays. - Most relays use slow databases and are not optimized for large scale usage. - Search is near-impossible to implement on standard relays. - Privacy features such as NIP-42 are lacking. - Regular DB maintenance tasks on normal relays require extended downtime. - Fault-tolerance is implemented, if any, using a load balancer, which is limited. - Personalization and advanced filtering is not possible. - Local caching is not supported.
NFDB: A scalable database for large relays
NFDB is a new database meant for medium-large scale relays, built on FoundationDB that provides: - Near-unlimited scalability - Extended fault tolerance - Instant loading - Better search - Better personalization - and more.
Search
NFDB has extended search capabilities including: - Semantic search: Search for meaning, not words. - Interest-based search: Highlight content you care about. - Multi-faceted queries: Easily filter by topic, author group, keywords, and more at the same time. - Wide support for event kinds, including users, articles, etc.
Personalization
NFDB allows significant personalization: - Customized algorithms: Be your own algorithm. - Spam filtering: Filter content to your WoT, and use advanced spam filters. - Topic mutes: Mute topics, not keywords. - Media filtering: With Nostr.build, you will be able to filter NSFW and other content - Low data mode: Block notes that use high amounts of cellular data. - and more
Other
NFDB has support for many other features such as: - NIP-42: Protect your privacy with private drafts and DMs - Microrelays: Easily deploy your own personal microrelay - Containers: Dedicated, fast storage for discoverability events such as relay lists
Calcite: A local microrelay database
Calcite is a lightweight, local version of NFDB that is meant for microrelays and caching, meant for thousands of personal microrelays.
Calcite HA is an additional layer that allows live migration and relay failover in under 30 seconds, providing higher availability compared to current relays with greater simplicity. Calcite HA is enabled in all Calcite deployments.
For zero-downtime, NFDB is recommended.
Noswhere SmartCache
Relays are fixed in one location, but users can be anywhere.
Noswhere SmartCache is a CDN for relays that dynamically caches data on edge servers closest to you, allowing: - Multiple regions around the world - Improved throughput and performance - Faster loading times
routerd
routerdis a custom load-balancer optimized for Nostr relays, integrated with SmartCache.routerdis specifically integrated with NFDB and Calcite HA to provide fast failover and high performance.Ending notes
NFDB is planned to be deployed to Nostr.land in the coming weeks.
A lot more is to come. 👀️️️️️️
-
 @ a19caaa8:88985eaf
2025-05-05 02:55:57
@ a19caaa8:88985eaf
2025-05-05 02:55:57↓ジャック(twitter創業者)のツイート nostr:nevent1qvzqqqqqqypzpq35r7yzkm4te5460u00jz4djcw0qa90zku7739qn7wj4ralhe4zqy28wumn8ghj7un9d3shjtnyv9kh2uewd9hsqg9cdxf7s7kg8kj70a4v5j94urz8kmel03d5a47tr4v6lx9umu3c95072732
↓それに絡むたゃ nostr:note1hr4m0d2k2cvv0yg5xtmpuma0hsxfpgcs2lxe7vlyhz30mfq8hf8qp8xmau
↓たゃのひとりごと nostr:nevent1qqsdt9p9un2lhsa8n27y7gnr640qdjl5n2sg0dh4kmxpqget9qsufngsvfsln nostr:note14p9prp46utd3j6mpqwv46m3r7u7cz6tah2v7tffjgledg5m4uy9qzfc2zf
↓有識者様の助言 nostr:nevent1qvzqqqqqqypzpujqe8p9zrpuv0f4ykk3rmgnqa6p6r0lan0t8ewd0ksj89kqcz5xqqst8w0773wxnkl8sn94tvmd3razcvms0kxjwe00rvgazp9ljjlv0wq0krtvt nostr:nevent1qvzqqqqqqypzpujqe8p9zrpuv0f4ykk3rmgnqa6p6r0lan0t8ewd0ksj89kqcz5xqqsxchzm7s7vn8a82q40yss3a84583chvd9szl9qc3w5ud7pr9ugengcgt9qx
↓たゃ nostr:nevent1qqsp2rxvpax6ks45tuzhzlq94hq6qtm47w69z8p5wepgq9u4txaw88s554jkd
-
 @ 04c915da:3dfbecc9
2025-05-16 18:06:46
@ 04c915da:3dfbecc9
2025-05-16 18:06:46Bitcoin has always been rooted in freedom and resistance to authority. I get that many of you are conflicted about the US Government stacking but by design we cannot stop anyone from using bitcoin. Many have asked me for my thoughts on the matter, so let’s rip it.
Concern
One of the most glaring issues with the strategic bitcoin reserve is its foundation, built on stolen bitcoin. For those of us who value private property this is an obvious betrayal of our core principles. Rather than proof of work, the bitcoin that seeds this reserve has been taken by force. The US Government should return the bitcoin stolen from Bitfinex and the Silk Road.
Using stolen bitcoin for the reserve creates a perverse incentive. If governments see bitcoin as a valuable asset, they will ramp up efforts to confiscate more bitcoin. The precedent is a major concern, and I stand strongly against it, but it should be also noted that governments were already seizing coin before the reserve so this is not really a change in policy.
Ideally all seized bitcoin should be burned, by law. This would align incentives properly and make it less likely for the government to actively increase coin seizures. Due to the truly scarce properties of bitcoin, all burned bitcoin helps existing holders through increased purchasing power regardless. This change would be unlikely but those of us in policy circles should push for it regardless. It would be best case scenario for American bitcoiners and would create a strong foundation for the next century of American leadership.
Optimism
The entire point of bitcoin is that we can spend or save it without permission. That said, it is a massive benefit to not have one of the strongest governments in human history actively trying to ruin our lives.
Since the beginning, bitcoiners have faced horrible regulatory trends. KYC, surveillance, and legal cases have made using bitcoin and building bitcoin businesses incredibly difficult. It is incredibly important to note that over the past year that trend has reversed for the first time in a decade. A strategic bitcoin reserve is a key driver of this shift. By holding bitcoin, the strongest government in the world has signaled that it is not just a fringe technology but rather truly valuable, legitimate, and worth stacking.
This alignment of incentives changes everything. The US Government stacking proves bitcoin’s worth. The resulting purchasing power appreciation helps all of us who are holding coin and as bitcoin succeeds our government receives direct benefit. A beautiful positive feedback loop.
Realism
We are trending in the right direction. A strategic bitcoin reserve is a sign that the state sees bitcoin as an asset worth embracing rather than destroying. That said, there is a lot of work left to be done. We cannot be lulled into complacency, the time to push forward is now, and we cannot take our foot off the gas. We have a seat at the table for the first time ever. Let's make it worth it.
We must protect the right to free usage of bitcoin and other digital technologies. Freedom in the digital age must be taken and defended, through both technical and political avenues. Multiple privacy focused developers are facing long jail sentences for building tools that protect our freedom. These cases are not just legal battles. They are attacks on the soul of bitcoin. We need to rally behind them, fight for their freedom, and ensure the ethos of bitcoin survives this new era of government interest. The strategic reserve is a step in the right direction, but it is up to us to hold the line and shape the future.
-
 @ a9434ee1:d5c885be
2025-03-04 13:05:42
@ a9434ee1:d5c885be
2025-03-04 13:05:42The Key Pair
What a Nostr key pair has by default:
- A unique ID
- A name
- A description
- An ability to sign stuff
The Relay
What a Nostr relay has (or should have) by default:
- Permissions, Moderation, AUTH, ...
- Pricing & other costs to make the above work (cost per content type, subscriptions, xx publications per xx timeframe, ...)
- List of accepted content types
- (to add) Guidelines
The Community
Since I need Communities to have all the above mentioned properties too, the simplest solution seems to be to just combine them. And when you already have a key pair and a relay, you just need the third basic Nostr building block to bring them together...
The Event
To create a #communikey, a key pair (The Profile) needs to sign a (kind 30XXX) event that lays out the Community's : 1. Main relay + backup relays 2. Main blossom server + backup servers 3. (optional) Roles for specific npubs (admin, CEO, dictator, customer service, design lead, ...) 4. (optional) Community mint 5. (optional) "Welcome" Publication that serves as an introduction to the community
This way: * any existing npub can become a Community * Communities are not tied to one relay and have a truly unique ID * Things are waaaaaay easier for relay operators/services to be compatible (relative to existing community proposals) * Running one relay per community works an order of magnitude better, but isn't a requirement
The Publishers
What the Community enjoyers need to chat in one specific #communikey : * Tag the npub in the (kind 9) chat message
What they needs to publish anything else in one or multiple #communikeys : * Publish a (kind 32222 - Targeted publication) event that lists the npubs of the targeted Communities * If the event is found on the main relay = The event is accepted
This way: * any existing publication can be targeted at a Community * Communities can #interop on content and bring their members together in reply sections, etc... * Your publication isn't tied forever to a specific relay
Ncommunity
If nprofile = npub + relay hints, for profiles
Then ncommunity = npub + relay hints, for communities -
 @ dfa02707:41ca50e3
2025-06-06 00:02:15
@ dfa02707:41ca50e3
2025-06-06 00:02:15Contribute to keep No Bullshit Bitcoin news going.
- The latest firmware updates for COLDCARD devices introduce two major features: COLDCARD Co-sign (CCC) and Key Teleport between two COLDCARD Q devices using QR codes and/or NFC with a website.

What's new
- COLDCARD Co-Sign: When CCC is enabled, a second seed called the Spending Policy Key (Key C) is added to the device. This seed works with the device's Main Seed and one or more additional XPUBs (Backup Keys) to form 2-of-N multisig wallets.
- The spending policy functions like a hardware security module (HSM), enforcing rules such as magnitude and velocity limits, address whitelisting, and 2FA authentication to protect funds while maintaining flexibility and control, and is enforced each time the Spending Policy Key is used for signing.
- When spending conditions are met, the COLDCARD signs the partially signed bitcoin transaction (PSBT) with the Main Seed and Spending Policy Key for fund access. Once configured, the Spending Policy Key is required to view or change the policy, and violations are denied without explanation.
"You can override the spending policy at any time by signing with either a Backup Key and the Main Seed or two Backup Keys, depending on the number of keys (N) in the multisig."
-
A step-by-step guide for setting up CCC is available here.
-
Key Teleport for Q devices allows users to securely transfer sensitive data such as seed phrases (words, xprv), secure notes and passwords, and PSBTs for multisig. It uses QR codes or NFC, along with a helper website, to ensure reliable transmission, keeping your sensitive data protected throughout the process.
- For more technical details, see the protocol spec.
"After you sign a multisig PSBT, you have option to “Key Teleport” the PSBT file to any one of the other signers in the wallet. We already have a shared pubkey with them, so the process is simple and does not require any action on their part in advance. Plus, starting in this firmware release, COLDCARD can finalize multisig transactions, so the last signer can publish the signed transaction via PushTX (NFC tap) to get it on the blockchain directly."
- Multisig transactions are finalized when sufficiently signed. It streamlines the use of PushTX with multisig wallets.
- Signing artifacts re-export to various media. Users are now provided with the capability to export signing products, like transactions or PSBTs, to alternative media rather than the original source. For example, if a PSBT is received through a QR code, it can be signed and saved onto an SD card if needed.
- Multisig export files are signed now. Public keys are encoded as P2PKH address for all multisg signature exports. Learn more about it here.
- NFC export usability upgrade: NFC keeps exporting until CANCEL/X is pressed.
- Added Bitcoin Safe option to Export Wallet.
- 10% performance improvement in USB upload speed for large files.
- Q: Always choose the biggest possible display size for QR.
Fixes
- Do not allow change Main PIN to same value already used as Trick PIN, even if Trick PIN is hidden.
- Fix stuck progress bar under
Receiving...after a USB communications failure. - Showing derivation path in Address Explorer for root key (m) showed double slash (//).
- Can restore developer backup with custom password other than 12 words format.
- Virtual Disk auto mode ignores already signed PSBTs (with “-signed” in file name).
- Virtual Disk auto mode stuck on “Reading…” screen sometimes.
- Finalization of foreign inputs from partial signatures. Thanks Christian Uebber!
- Temporary seed from COLDCARD backup failed to load stored multisig wallets.
Destroy Seedalso removes all Trick PINs from SE2.Lock Down Seedrequires pressing confirm key (4) to execute.- Q only: Only BBQr is allowed to export Coldcard, Core, and pretty descriptor.

-
 @ df67f9a7:2d4fc200
2025-06-05 19:52:32
@ df67f9a7:2d4fc200
2025-06-05 19:52:32Nostr is NOT a social network. Nostr is a network of interconnected social apps. And, since any app is a social app, Nostr is for every app.
ONLY Nostr incentivizes inter-connectivity between independent apps, simply by respecting sovereignty at the protocol layer. For end users, sovereignty means that the content they post “to Nostr” will never be owned by the apps that they use. For businesses building apps on Nostr, sovereignty means that every app actually benefits by other apps being on the network. Because sovereignty is respected, users are retained for longer and independent apps thrive far longer on Nostr than on the legacy “black box” social networks.
Social apps thrive on Nostr
Nostr integration provides these benefits for every app :
- Unrestrained access for any app, to all public and private data “on Nostr”. No fees or licenses for harvesting user data from the network.
- Unburdened from liability, when collecting user data with any app. When sending “to Nostr”, end users retain custody of user data while apps never loose access.
- Unlimited free market of search engines and feed algos. Users and brands can create, use, and share any algos or custom feeds. Grow your audience on your own terms.
- Universal open network for all apps. Build any kind of app for any audience, on the same network as other apps for other audiences. Discover new trends from user data.
- Unregulated tech platform. Build your own app and use it as you wish. No gate keepers. No code review.
Sovereignty is good for business.
Regardless of the network size, a Nostr integrated app can grow its user base MUCH faster and with greater independence BECAUSE of the sovereignty respecting protocol. While end users may retain custody of their identities and data on the network, it’s the apps that determine which data is, or is not, sent to the network. Respect for sovereignty IS the killer feature that ONLY the Nostr protocol provides for apps and for end users.
Because Nostr is permissionless for any app to integrate :
- end users will always have a free market of apps choose from
- apps are free to integrate only as much as benefits their business model.
- apps gain access to more novel data as new apps bring new users to the network.
Because data on Nostr is managed by end users and available to all apps :
- User data looses exclusivity and the demand shifts toward novel insights and information derived from these data.
- Apps are freed from having to be “data pirates”, and can focus on establishing a trusted user base, providing valuable services to satisfied customers, informed by the abundance of user data.
- Apps are incentivized to offload data onto the network, establishing a new paradigm for interconnectivity, where independence is NOT at stake as the network grows.
- New markets spring up to support users with self custody of their data, driven by the reality that apps can have full access without assuming responsibility.
- The market for search and algo tools opens up for independent apps and end users to discover and interact freely with each other.
- The ad based “attention economy” slowly transforms to a value based consumer economy, where the end user is the customer rather than the product being sold.
Even while privacy is respected
Sometimes sovereignty is at odds with privacy, but Nostr allows all parties to win while both are protected.
- For end users sending sensetive data "to Nostr", privacy is assured by encrypting it with their own private keys and/or sending it to private (auth required) relays of their choosing.
- For apps handling private IP or business data, any traditional “black box” infrastructure can be used in the back end to manitain isolation from Nostr.
This means apps and end users remain in control of their own private data, without requiring “big social” as trust provider or data reseller. To access a user's private data, client apps (even search engines, running locally) only need explicit permission from the end user to retrieve or decrypt from Nostr relays. Public data, on the other hand, is freely available for any app or search engine to harvest from any Nostr relay. In either case, user data on the Nostr network is always accessible to client apps, without additional restrictions or fees.
Nostr is for every app.
Adding social to any app makes it a better app. Add reviews for products or services. Add commenting or direct messaging. Share or collaborate on content creation. Nostr integration is straightforward and incremental for any app.
Nostr doesn't define your app's business model ... Nostr 10X's it!
Here's how :
- Start with your own business and app design. Add Nosrr login.
- Discover what "kinds" of user data already exists "on Nostr" that your app can ingest and make use of.
- Decide which "kinds" of data would benefit your business, your users, and the network, if sent "to Nostr".
- Implement Nostr integration for data kinds and add webs of trust tools for recommendation and discovery.
- Verify your app is sovereignty respecting in how it handles private data and implements Nostr NIPs.
- Engage with existing users, and onboard new users from your app, to earn their trust and patronage over Nostr.
For more info and assistance, contact our team of Nostr integration experts.
-
 @ f11e91c5:59a0b04a
2025-04-30 07:52:21
@ f11e91c5:59a0b04a
2025-04-30 07:52:21!!!2022-07-07に書かれた記事です。
暗号通貨とかでお弁当売ってます 11:30〜14:00ぐらいでやってます
◆住所 木曜日・東京都渋谷区宇田川町41 (アベマタワーの下らへん)
◆お値段
Monacoin 3.9mona
Bitzeny 390zny
Bitcoin 3900sats (#lightningNetwork)
Ethereum 0.0039Ether(#zkSync)
39=thank you. (円を基準にしてません)
最近は週に一回になりました。 他の日はキッチンカーの現場を探したり色々してます。 東京都内で平日ランチ出店出来そうな場所があればぜひご連絡を!
 写真はNFCタグです。
スマホにウォレットがあればタッチして3900satsで決済出来ます。
正直こんな怪しい手書きのNFCタグなんて絶対にビットコイナーは触りたくも無いだろうなと思いますが、これでも良いんだぜというメッセージです。
写真はNFCタグです。
スマホにウォレットがあればタッチして3900satsで決済出来ます。
正直こんな怪しい手書きのNFCタグなんて絶対にビットコイナーは触りたくも無いだろうなと思いますが、これでも良いんだぜというメッセージです。今までbtcpayのposでしたが速度を追求してこれに変更しました。 たまに上手くいかないですがそしたら渋々POS出すので温かい目でよろしくお願いします。
ノードを建てたり決済したりで1年経ちました。 最近も少しずつノードを建てる方が増えてるみたいで本当凄いですねUmbrel 大体の人がルーティングに果敢に挑むのを見つつ 奥さんに土下座しながら費用を捻出する弱小の私は決済の利便性を全開で振り切るしか無いので応援よろしくお願いします。
あえて あえて言うのであれば、ルーティングも楽しいですけど やはり本当の意味での即時決済や相手を選んでチャネルを繋げる楽しさもあるよとお伝えしたいっ!! 決済を受け入れないと分からない所ですが 承認がいらない時点で画期的です。
QRでもタッチでも金額指定でも入力でも もうやりようには出来てしまうし進化が恐ろしく早いので1番利用の多いpaypayの手数料(事業者側のね)を考えたらビットコイン凄いじゃない!と叫びたくなる。 が、やはり税制面や価格の変動(うちはBTC固定だけども)ウォレットの操作や普及率を考えるとまぁ難しい所もあるんですかね。
それでも継続的に沢山の人が色んな活動をしてるので私も何か出来ることがあれば 今後も奥さんに土下座しながら頑張って行きたいと思います。
(Originally posted 2022-07-07)
I sell bento lunches for cryptocurrency. We’re open roughly 11:30 a.m. – 2:00 p.m. Address Thursdays – 41 Udagawa-chō, Shibuya-ku, Tokyo (around the base of Abema Tower)
Prices Coin Price Note Monacoin 3.9 MONA
Bitzeny 390 ZNY Bitcoin 3,900 sats (Lightning Network)
Ethereum 0.0039 ETH (zkSync) “39” sounds like “thank you” in Japanese. Prices aren’t pegged to yen.These days I’m open only once a week. On other days I’m out scouting new spots for the kitchen-car. If you know weekday-lunch locations inside Tokyo where I could set up, please let me know!
The photo shows an NFC tag. If your phone has a Lightning wallet, just tap and pay 3,900 sats. I admit this hand-written NFC tag looks shady—any self-respecting Bitcoiner probably wouldn’t want to tap it—but the point is: even this works!
I used to run a BTCPay POS, but I switched to this setup for speed. Sometimes the tap payment fails; if that happens I reluctantly pull out the old POS. Thanks for your patience.
It’s been one year since I spun up a node and started accepting Lightning payments. So many people are now running their own nodes—Umbrel really is amazing. While the big players bravely chase routing fees, I’m a tiny operator scraping together funds while begging my wife for forgiveness, so I’m all-in on maximising payment convenience. Your support means a lot!
If I may add: routing is fun, but instant, trust-minimised payments and the thrill of choosing whom to open channels with are just as exciting. You’ll only understand once you start accepting payments yourself—zero-confirmation settlement really is revolutionary.
QR codes, NFC taps, fixed amounts, manual entry… the possibilities keep multiplying, and the pace of innovation is scary fast. When I compare it to the merchant fees on Japan’s most-used service, PayPay, I want to shout: “Bitcoin is incredible!” Sure, taxes, price volatility (my shop is BTC-denominated, though), wallet UX, and adoption hurdles are still pain points.
Even so, lots of people keep building cool stuff, so I’ll keep doing what I can—still on my knees to my wife, but moving forward!
-
 @ ac8bb9b0:70278acc
2025-06-05 18:12:29
@ ac8bb9b0:70278acc
2025-06-05 18:12:29Details
- ⏲️ Prep time: 15 min
- 🍳 Cook time: 20 min
- 🍽️ Servings: 12
Ingredients
- 1 and 1/2 cups (345g) mashed bananas (about 4 medium or 3 large ripe bananas)
- 1/3 cup (113g) honey
- 1 large egg
- 1/4 cup (56g) coconut oil, melted
- 1 teaspoon pure vanilla extract
- 1 cup (130g) whole wheat flour
- 1/2 cup (41g) natural unsweetened cocoa powder
- 1 teaspoon baking powder
- 1 teaspoon baking soda
- 1/2 teaspoon salt
- 1 cup (180g) semi-sweet or dark chocolate chips
Directions
- Preheat oven to 425°F (218°C). Spray a 12-count muffin pan with nonstick spray or line with cupcake liners. Set aside.
- In a medium bowl, mash the bananas up using a fork.* Try to mash up any large lumps. Once mashed, whisk in the honey, egg, coconut oil, and vanilla extract until combined. Set aside.
- In a large bowl, whisk the flour, cocoa powder, baking powder, baking soda, and salt together. Pour the wet ingredients into the dry ingredients and whisk until everything is combined. Fold in the chocolate chips, reserving some for the tops of the warm muffins.
- Spoon the batter evenly into each cup or liner, filling each all the way to the top.
- Bake for 5 minutes at 425°F (218°C); then, keeping the muffins in the oven, reduce heat to 350°F (177°C) and continue baking for another 15–17 minutes or until a toothpick inserted in the center comes out clean. The total time these muffins take in the oven is about 20–21 minutes, give or take. (For mini muffins, bake 11–13 minutes at 350°F (177°C) the whole time.)
- Press any remaining chocolate chips into the tops of the warm muffins. Allow the muffins to cool for 5 minutes in the muffin pan, and then transfer to a wire rack to continue cooling, or enjoy warm.
- Muffins stay fresh covered at room temperature for a few days, then transfer to the refrigerator for up to 1 week.
-
 @ 7f6db517:a4931eda
2025-06-05 22:01:51
@ 7f6db517:a4931eda
2025-06-05 22:01:51

"Privacy is necessary for an open society in the electronic age. Privacy is not secrecy. A private matter is something one doesn't want the whole world to know, but a secret matter is something one doesn't want anybody to know. Privacy is the power to selectively reveal oneself to the world." - Eric Hughes, A Cypherpunk's Manifesto, 1993
Privacy is essential to freedom. Without privacy, individuals are unable to make choices free from surveillance and control. Lack of privacy leads to loss of autonomy. When individuals are constantly monitored it limits our ability to express ourselves and take risks. Any decisions we make can result in negative repercussions from those who surveil us. Without the freedom to make choices, individuals cannot truly be free.
Freedom is essential to acquiring and preserving wealth. When individuals are not free to make choices, restrictions and limitations prevent us from economic opportunities. If we are somehow able to acquire wealth in such an environment, lack of freedom can result in direct asset seizure by governments or other malicious entities. At scale, when freedom is compromised, it leads to widespread economic stagnation and poverty. Protecting freedom is essential to economic prosperity.
The connection between privacy, freedom, and wealth is critical. Without privacy, individuals lose the freedom to make choices free from surveillance and control. While lack of freedom prevents individuals from pursuing economic opportunities and makes wealth preservation nearly impossible. No Privacy? No Freedom. No Freedom? No Wealth.
Rights are not granted. They are taken and defended. Rights are often misunderstood as permission to do something by those holding power. However, if someone can give you something, they can inherently take it from you at will. People throughout history have necessarily fought for basic rights, including privacy and freedom. These rights were not given by those in power, but rather demanded and won through struggle. Even after these rights are won, they must be continually defended to ensure that they are not taken away. Rights are not granted - they are earned through struggle and defended through sacrifice.
If you found this post helpful support my work with bitcoin.

-
 @ a5ee4475:2ca75401
2025-06-04 14:31:23
@ a5ee4475:2ca75401
2025-06-04 14:31:23[EM ATUALIZAÇÃO]
vacina #saude #politica #manipulacao #mundial #genocidio #pandemia #conspiracao
Este artigo reúne algumas evidências mais antigas que vim registrando durante alguns anos contra a covid, vacinas obrigatórias e a ação de agências de governo, fundações, políticos, mídia tradicional, celebridades, influenciadores, cientistas, redes sociais e laboratórios, em envolvimento com genocídio e restrições de liberdades em escala mundial causado por decisões em várias esferas relativas ao covid e as vacinas obrigatórias em geral.
Porém, alguns links podem não estar mais disponiveis, foram que ainda faltam ser registradas muitas informações já divulgadas nos últimos anos e que não tivemos contato pela escassez de meios para a obtenção dessas informações de forma organizada. Portanto, o presente artigo ainda passará por atualizações de conteúdo e formatação, então se possível ajudem sugerindo com complementos ou alterações.
Explicações iniciais:
- Sars-Cov-2 é que é nome do vírus. Ele que causa a doença Covid-19;
- O Sars-Cov-2 é o segundo tipo de Sars-Cov documentado, o primeiro ocorreu em 2003;
- 'Coronavírus' na verdade é um nome genérico para vários vírus de gripes já comuns, dado para o tipo corona (com uma "coroa", 'espetos' ao redor dele), o Sars-Cov-2 é só uma delas.
1. Vacinas Obrigatórias em Geral
-
Vacinas e autismo em crianças https://publichealthpolicyjournal.com/vaccination-and-neurodevelopmental-disorders-a-study-of-nine-year-old-children-enrolled-in-medicaid/
-
O CDC admite que 98 milhões de pessoas receberam o vírus do câncer através da vacina da Poliomielite https://medicinanews.com.br/frente/frente_1/o-cdc-admite-que-98-milhoes-de-pessoas-receberam-o-virus-do-cancer-atraves-da-vacina-poliomielite/
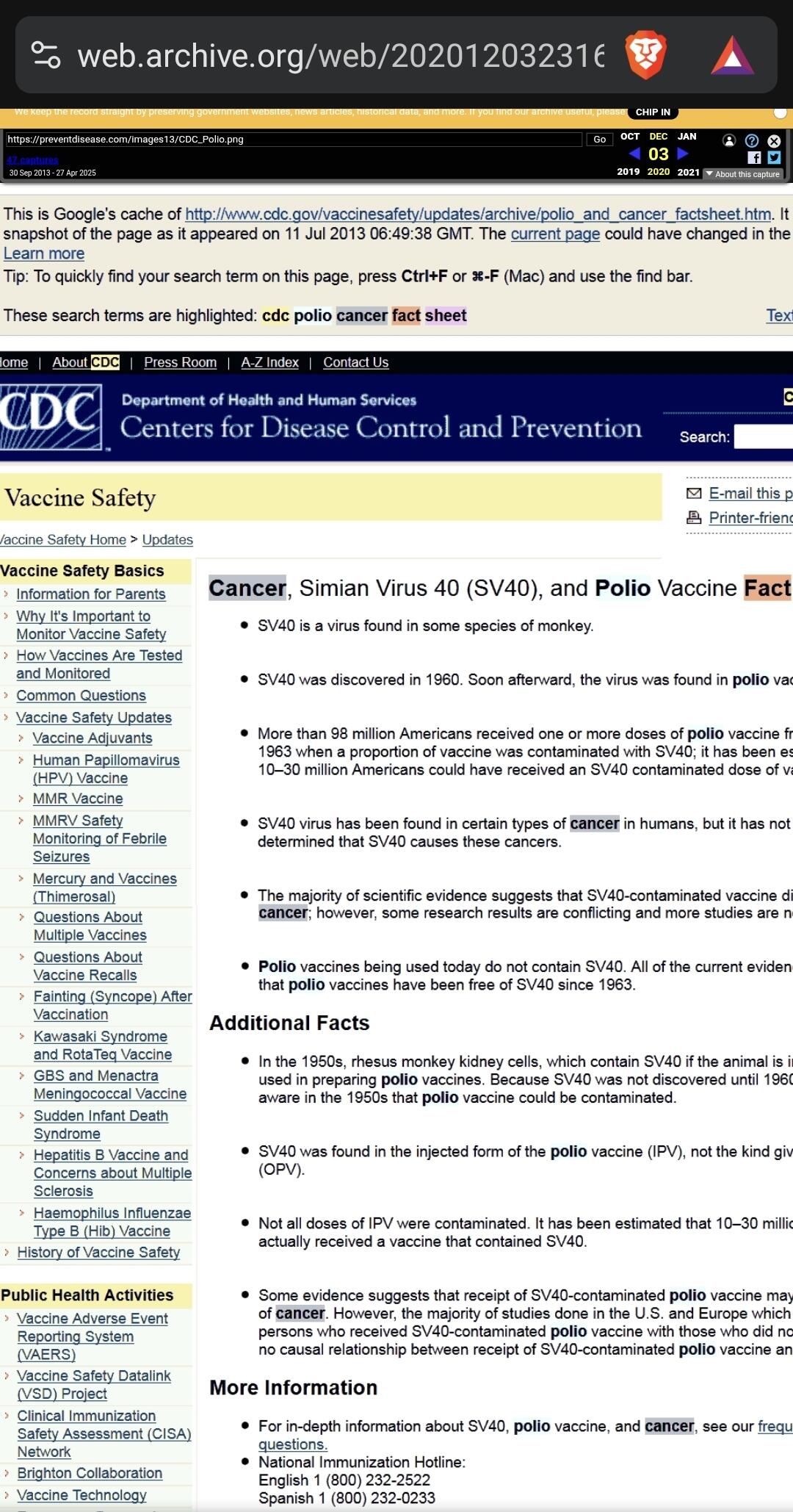 - Fonte original da imagem: https://preventdisease.com/images13/CDC_Polio.png [indisponível]
- Imagem arquivada em: https://web.archive.org/web/20201203231640/
- Fonte original da imagem: https://preventdisease.com/images13/CDC_Polio.png [indisponível]
- Imagem arquivada em: https://web.archive.org/web/20201203231640/"O CDC (Os Centros de Controle e Prevenção de Doenças dos Estados Unidos) removeu rapidamente uma página do seu site, que estava em cache no Google, como você pode ver logo abaixo, admitindo que mais de 98 milhões de americanos receberam uma ou mais doses de vacina contra pólio dentro de 8 período entre 1955 e 1963, quando uma proporção da vacina foi contaminada com um poliomavírus causador de câncer chamado SV40."
27/02/2021 - Por que o Japão demorou para vacinar, mesmo com Olimpíada se aproximando https://www.cnnbrasil.com.br/internacional/2021/02/27/por-que-o-japao-demorou-para-vacinar-mesmo-com-olimpiada-se-aproximando
"Desconfiança da população japonesa em relação a vacinas, ligada a casos ocorridos no passado, está entre razões que atrasaram imunização no país.
A resistência à vacina do Japão remonta à década de 1970, quando duas crianças morreram dentro de 24 horas após receberem a vacina combinada contra difteria, tétano e coqueluche (coqueluche). A vacina foi temporariamente suspensa, mas a confiança já havia sido abalada. Por vários anos, as taxas de vacinação infantil caíram, levando a um aumento nos casos de tosse convulsa.
No final dos anos 1980, houve outro susto com a introdução da vacina tripla contra sarampo, caxumba e rubéola produzida no Japão. As primeiras versões do imunizante foram associadas à meningite asséptica, ou inchaço das membranas ao redor do cérebro e da medula espinhal. O problema foi rastreado até o componente caxumba da vacina tripla, o que levou a uma ação judicial e a indenização por danos pesados.
O Instituto Nacional de Ciências da Saúde interrompeu a dose combinada em 1993 e a substituiu por vacinas individuais. Após o escândalo, Shibuya disse que o governo japonês se tornou "ciente dos riscos" e seu programa nacional de vacinação tornou-se voluntário.
O Dr. Yuho Horikoshi, especialista em doenças infecciosas, diz que os processos levaram a uma "lacuna de vacinação", em que nenhuma vacina foi aprovada no Japão por cerca de 15 anos.
Mais recentemente, em 2013, o Japão adicionou a vacina contra o papilomavírus humano (HPV) ao calendário nacional para proteger as meninas contra o vírus sexualmente transmissível, que é conhecido por causar câncer cervical. No entanto, vídeos de meninas supostamente sofrendo de reações adversas começaram a circular no YouTube, levando o governo a retirá-los da programação nacional."
2. PRIMEIRAS OCORRÊNCIAS PREDITIVAS AO COVID-19
2010 - Fundação Rockfeller, Lockstep. https://www.rockefellerfoundation.org/wp-content/uploads/Annual-Report-2010-1.pdf
Neste PDF da fundação Rockfeller, em seu próprio site, a fundação deixou claro o seu envolvimento em casos de ‘contenção’ de pandemias juntamente com a USAID (agência americana com nome ambíguo, como formalmente ‘United States Agency for International Development’, mas soando como ‘US Socorre’, mas sendo um braço do governo democrata que financiava interferências políticas diretas em vários países, como no Brasil: https://www.gazetadopovo.com.br/vida-e-cidadania/quais-ongs-cooperaram-com-moraes-e-sao-alvo-do-congresso-nos-eua/ ), inclusive em relacionadas ao SARS, um vírus muito semelhante ao SEGUNDO tipo de vírus Sars-Cov, o Sars-Cov-2 (o vírus propagado em 2019) e que causa o COVID-19.
Segundo eles:
“Integração entre Regiões e Países
A Fundação Rockefeler investiu US$ 22 milhões em sua Iniciativa de Redes de Vigilância de Doenças para ajudar a conter a disseminação de doenças infecciosas e pandemias, fortalecendo os sistemas nacionais, regionais e globais de vigilância e resposta a doenças. Dois programas-chave da Rockefeler — a Rede de Vigilância de Doenças da Bacia do Mekong e a Rede Integrada de Vigilância de Doenças da África Oriental — conectaram e capacitaram profissionais de saúde, epidemiologistas e autoridades de saúde pública em toda a região, levando a um aumento de seis vezes nos locais de vigilância de doenças transfronteiriças somente nos últimos três anos. Em 2010, a Rockefeler expandiu a bem-sucedida campanha transdisciplinar One Health, que a USAID e o Banco Asiático de Desenvolvimento adotaram como modelos. One Health refere-se à integração da ciência médica e veterinária para combater essas novas variedades de doenças zoonóticas que se movem e sofrem mutações rapidamente de animais para humanos. Essas colaborações criaram e fortaleceram uma rede regional crítica de saúde pública, enquanto as lições aprendidas foram exportadas entre disciplinas e países. Além de fortalecer os laços globais em saúde pública, a Rockefeler ajudou a elevar o nível de especialização e treinamento em campo. O Programa de Treinamento em Epidemiologia de Campo coloca graduados nos mais altos escalões do governo no Laos e no Vietnã, enquanto as bolsas da Rockefeler transformaram as ferramentas disponíveis para os médicos, permitindo-lhes utilizar o poder da internet para se comunicar e monitorar eventos, compreender contextos locais e analisar novos problemas. Finalmente, estamos aplicando ferramentas do século XXI para combater os desafios de saúde do século XXI.”
Julho de 2012 - Revista Mundo Estranho
Houve uma "coincidência", a revista Mundo Estranho em julho de 2012, entrevistou o até então doutorando em virologia, Átila Iamarino (o mesmo cientista que fez diversas propagandas das vacinas no Brasil), para descrever um possível cenário de propagação de uma epidemia viral, a revista descreve com grande precisão os eventos de 2020, mas apontando o oposto da China, em que, na realidade, sua economia cresceu vertiginosamente.
3. PRIMEIROS INDÍCIOS
10/2019 - Evento 201 - Durante os Jogos Militares Internacionais na China https://www.centerforhealthsecurity.org/event201/
Promovido por: - Bill & Melinda Gates Foundation - John Hopkins Institute - Fórum econômico mundial
"O evento simula a liberação de um coronavírus novo do tipo zoonótico transmitido por morcegos para porcos e por fim para humanos. Eventualmente ele se torna muito transmissível entre humanos levando a uma pandemia severa. O vírus é muito parecido com o vírus da SARS, mas se transmite muito mais facilmente entre pessoas devido a sintomas muito mais leves destas."
Também mencionado por: [Jornal Estadão] ( http://patrocinados.estadao.com.br/medialab/releaseonline/releasegeral-releasegeral/geral-johns-hopkins-center-for-health-security-forum-economico-mundial-e-fundacao-bill-melinda-gates-realizam-exercicio-pandemico-e-transmissao-ao-vivo/)
Sobre o "Movimento antivacina"
05/12/2017 - Movimento antivacina: como surgiu e quais consequências ele pode trazer? https://www.uol.com.br/universa/noticias/redacao/2017/12/05/o-que-o-movimento-antivacina-pode-causar.htm?cmpid=copiaecola
23/03/2019 - "Instagram bloqueia hashtags e conteúdo antivacinação" https://canaltech.com.br/redes-sociais/instagram-bloqueia-hashtags-e-conteudo-antivacinacao-135411/
23/05/2021 - Novos dados sobre pesquisadores de Wuhan aumentam debate sobre origens da Covid https://www.cnnbrasil.com.br/saude/novos-dados-sobre-pesquisadores-de-wuhan-aumentam-debate-sobre-origens-da-covid/
"A China relatou à Organização Mundial da Saúde que o primeiro paciente com sintomas semelhantes aos de Covid-19 foi registrado em Wuhan em 8 de dezembro de 2019"
01/02/2020 - O que aconteceu desde que o novo coronavírus foi descoberto na China https://exame.com/ciencia/o-que-aconteceu-desde-que-o-novo-coronavirus-foi-descoberto-na-china/
"O primeiro alerta foi recebido pela Organização Mundial da Saúde (OMS) em 31 de dezembro de 2019"
15/09/2020 - YouTube diz que vai remover vídeos com mentiras sobre vacina contra COVID-19 https://gizmodo.uol.com.br/youtube-remover-videos-mentiras-vacina-covid-19/
"O YouTube anunciou na quarta-feira (14) que estenderá as regras atuais sobre mentiras, propaganda e teorias da conspiração sobre a pandemia do coronavírus para incluir desinformação sobre as vacinas contra a doença.
De acordo com a Reuters, a gigante do vídeo diz que agora vai proibir conteúdos sobre vacinas contra o coronavírus que contradizem “o consenso de especialistas das autoridades de saúde locais ou da OMS”, como afirmações falsas de que a vacina é um pretexto para colocar chips de rastreamento nas pessoas ou que irá matar ou esterilizar quem tomar."
*07/01/2021 - YouTube vai punir canais que promovem mentiras sobre eleições – incluindo os de Trump https://olhardigital.com.br/2021/01/07/noticias/youtube-vai-punir-canais-que-promovem-mentiras-sobre-eleicoes-incluindo-os-de-trump/
"O YouTube anunciou que vai punir canais que promovem mentiras sobre as eleições, removendo sumariamente qualquer vídeo que contenha desinformação e, ao mesmo tempo, advertindo com um “strike” o canal que o veicular. A medida já está valendo e a primeira “vítima” é ninguém menos que o ex-presidente americano, Donald Trump.
A medida não é exatamente nova, mas foi novamente comunicada e reforçada pelo YouTube na quarta-feira (6), após os eventos de invasão do Capitólio, em Washington, onde o presidente eleito Joe Biden participava da cerimônia que confirmava a sua vitória nas eleições de novembro de 2020. A ocasião ficou marcada pela tentativa de invasão de correligionários de Trump, que entraram no edifício em oposição à nomeação do novo presidente. Uma mulher acabou sendo morta pela polícia que protegia o local.
O ex-presidente Donald Trump teve vídeos banidos de seu canal no YouTube após os eventos de ontem (6) no capitólio."
4. FIGURAS CENTRAIS
Bill Gates
- Bill Gates diz 'não' a abrir patentes de vacinas https://www.frontliner.com.br/bill-gates-diz-nao-a-abrir-patentes-de-vacinas/
"Bill Gates, um dos homens mais ricos do mundo, cuja fundação tem participação na farmacêutica alemã CureVac, produtora de vacina mRNA para prevenção de covid-19, disse não acreditar que a propriedade intelectual tenha algo a ver com o longo esforço global para controlar a pandemia."
João Doria e São Paulo
26/07/2017 - João Dória vai a China conhecer drones para ampliar segurança eletrônica na capital paulista https://jc.ne10.uol.com.br/blogs/jamildo/2017/07/26/joao-doria-vai-china-conhecer-drones-para-ampliar-seguranca-eletronica-na-capital-paulista/
02/08/2019 - Governo de SP fará Missão China para ampliar cooperação e atrair investimentos https://www.saopaulo.sp.gov.br/spnoticias/governo-de-sao-paulo-detalha-objetivos-da-missao-china/
20/11/2019 - Doria se encontra com chineses das gigantes CREC e CRCC e oferece concessões de rodovia, metrô e ferrovia https://diariodotransporte.com.br/2019/11/20/doria-se-encontra-com-chineses-das-gigantes-crec-e-crcc-e-oferece-concessoes-de-rodovia-metro-e-ferrovia/
25/01/2020 - "Chineses serão agressivos" nas privatizações em SP até 2022, afirma Dória https://noticias.uol.com.br/colunas/jamil-chade/2020/01/25/entrevista-joao-doria-privatizacoes-sao-paulo-china.htm
O governador de São Paulo, João Doria, afirma que vai acelerar os programas de desestatização no estado em 2020 e acredita que concessões e vendas poderão permitir uma arrecadação de pelo menos R$ 40 bilhões. Nesse processo, o governador avalia que a China deve atuar de forma agressiva e que aprofundará sua posição de maior parceira comercial do estado, se distanciando de americanos e argentinos.
29/06/2020 - Doria estabelece multa para quem estiver sem máscara na rua em SP https://veja.abril.com.br/saude/doria-estabelece-multa-para-quem-estiver-sem-mascara-na-rua/
24/12/2020 - Doria é flagrado sem máscara e fazendo compras em Miami https://pleno.news/brasil/politica-nacional/doria-e-flagrado-sem-mascara-e-fazendo-compras-em-miami.html
"Foto do governador de São Paulo sem o item de proteção viralizou nas redes"
07/06/2021 - Doria é criticado na internet por tomar sol sem máscara em hotel no Rio https://vejasp.abril.com.br/cidades/doria-e-criticado-na-internet-por-tomar-sol-sem-mascara-em-hotel-no-rio/
30/09/2020 - Governo de SP assina contrato com Sinovac e prevê vacina para dezembro https://agenciabrasil.ebc.com.br/saude/noticia/2020-09/governo-de-sp-assina-contrato-com-sinovac-e-preve-vacina-para-dezembro
O governador de São Paulo, João Doria, e o vice-presidente da laboratório chinês Sinovac, Weining Meng, assinaram hoje (30), um contrato que prevê o fornecimento de 46 milhões de doses da vacina CoronaVac para o governo paulista até dezembro deste ano.
O contrato também prevê a transferência tecnológica da vacina da Sinovac para o Instituto Butantan, o que significa que, o instituto brasileiro poderá começar a fabricar doses dessa vacina contra o novo coronavírus. O valor do contrato, segundo o governador João Doria é de US$ 90 milhões.
20/10/2020 - Coronavac terá mais de 90% de eficácia, afirmam integrantes do governo paulista https://www.cnnbrasil.com.br/saude/2020/12/20/coronavac-tera-mais-de-90-de-eficacia-afirmam-integrantes-do-governo
24/10/2020 - Não esperamos 90% de eficácia da Coronavac’, diz secretário de saúde de SP https://www.cnnbrasil.com.br/saude/2020/12/24/nao-esperamos-90-de-eficacia-da-coronavac-diz-secretario-de-saude-de-sp
07/01/2021 - Vacina do Butantan: eficácia é de 78% em casos leves e 100% em graves https://www.cnnbrasil.com.br/saude/2021/01/07/vacina-do-butantan-eficacia-e-de-78-em-casos-leves-e-100-em-graves
09/01/2021 - Não é hora de sermos tão cientistas como estamos sendo agora https://g1.globo.com/sp/sao-paulo/video/nao-e-hora-de-sermos-tao-cientistas-como-estamos-sendo-agora-diz-secretario-de-saude-de-sp-9166405.ghtml
10/01/2021 - Dados da Coronavac relatados à Anvisa não estão claros, diz médico https://www.cnnbrasil.com.br/saude/2021/01/10/dados-da-coronavac-relatados-a-anvisa-nao-estao-claros-diz-medico
"O diretor do Laboratório de Imunologia do Incor, Jorge Kalil, reforçou que faltaram informações sobre a Coronavac nos dados divulgados à Anvisa"
12/01/2021 - New Brazil data shows disappointing 50,4% efficacy for China’s Coronavac vaccine [Novos dados do Brasil mostram eficácia decepcionante de 50,4% para a vacina CoronaVac da China] https://www.reuters.com/article/us-health-coronavirus-brazil-coronavirus/new-brazil-data-shows-disappointing-504-efficacy-for-chinas-coronavac-vaccine-idUSKBN29H2CE
13/01/2021 - Eficácia da Coronavac: 50,38%, 78% ou 100%? https://blogs.oglobo.globo.com/lauro-jardim/post/5038-78-ou-100.html
“De acordo com interlocutores que participaram tanto do anúncio de ontem como da semana passada, quem pressionou para que os dados de 78% e 100% fossem liberados foi João Dória.”
07/05/2021 - Covid-19: Doria toma primeira dose da vacina CoronaVac https://veja.abril.com.br/saude/covid-19-doria-toma-primeira-dose-da-vacina-coronavac/
04/06/2021 - Doria é vacinado com a segunda dose da CoronaVac em São Paulo https://noticias.uol.com.br/politica/ultimas-noticias/2021/06/04/doria-e-vacinado-com-a-segunda-dose-da-coronavac-em-sao-paulo.htm
15/07/2021 - Doria testa positivo para a Covid-19 pela 2ª vez https://www.correiobraziliense.com.br/politica/2021/07/4937833-doria-testa-positivo-para-covid-19-pela-segunda-vez.html
"Governador de São Paulo já havia sido diagnosticado com a doença no ano passado. Ele diz que, apesar da infecção, se sente bem, o que atribui ao fato de ter sido vacinado com duas doses da Coronavac"
06/08/2021 - CPI recebe investigação contra Doria por compra de máscara sem licitação https://www.conexaopoder.com.br/nacional/cpi-recebe-investigacao-contra-doria-por-compra-de-mascara-sem-licitacao/150827
"Empresa teria usado o nome de Alexandre Frota para vender máscaras ao governo de SP. Doria nega informação"
Renan Filho
(filho do Renan Calheiros)
25/07/2019 - Governador Renan Filho vai à China em busca de investimentos para o estado https://www.tnh1.com.br/videos/vid/governador-renan-filho-vai-a-china-em-busca-de-investimentos-para-o-estado/
20/03/2020 - Governadores do NE consultam China e pedem material para tratar covid-19 https://noticias.uol.com.br/saude/ultimas-noticias/redacao/2020/03/20/governadores-do-ne-consultam-china-e-pedem-material-para-tratar-covid-19.htm
5. Narrativas, restrições e proibições
17/12/2020 - STF decide que vacina contra a covid pode ser obrigatória, mas não forçada https://noticias.uol.com.br/saude/ultimas-noticias/redacao/2020/12/17/stf-julga-vacinacao-obrigatoria.htm?cmpid=copiaecola
"O STF (Supremo Tribunal Federal) decidiu, em julgamento hoje, que o Estado pode determinar a obrigatoriedade da vacinação contra a covid-19. Porém fica proibido o uso da força para exigir a vacinação, ainda que possam ser aplicadas restrições a direitos de quem recusar a imunização.
Dez ministros foram favoráveis a obrigatoriedade da vacinação, que poderá ser determinada pelo governo federal, estados ou municípios. As penalidades a quem não cumprir a obrigação deverão ser definidas em lei."
27/07/2021 - Saiba que países estão adotando 'passaporte da vacina' para suspender restrições https://www.cnnbrasil.com.br/internacional/2021/07/27/saiba-que-paises-estao-adotando-passaporte-da-vacina-para-suspender-restricoes
" - Israel - Uniao Europeia - Áustria - Dinamarca - Eslovênia - França - Grécia - Irlanda - Itália - Letônia - Lituânia - Luxemburgo - Holanda - Portugal - Japão - Coreia do sul"
18/06/2021 - O que é o passaporte da vacina que Bolsonaro quer vetar? https://noticias.uol.com.br/politica/ultimas-noticias/2021/06/18/uol-explica-o-que-e-o-passaporte-da-vacina-que-opoe-bolsonaro-e-damares.htm
"O Brasil poderá ter um certificado de imunização futuramente. Aprovado no Senado na semana passada, o "passaporte da vacina", como é chamado, prevê identificar pessoas vacinadas para que entrem em locais públicos ou privados com possíveis restrições."
6. Vacinas
Alegações iniciais
- CoronaVac, Oxford e Pfizer: veja diferenças entre as vacinas contra covid noticias.uol.com.br/saude/ultimas-noticias/redacao/2021/05/11/diferencas-vacinas-covid-brasil.htm
" - CoronaVac (Butantan/Sinovac - Chinesa) Com virus inativo 50,38% de eficácia 2 doses
-
Covishield - 'AstraZeneca' (Fiocruz/Astrazenica/Oxford - Britânica) Com virus não replicante 67% de eficácia 2 doses
-
ComiRNAty - 'Pfizer' (Pfizer - Americana / BioNTech - Alemã) Com RNA mensageiro 96% de eficácia 2 doses"
Riscos diretos
15/06/2021 - Trombose após vacinação com AstraZeneca: Quais os sintomas e como se deve atuar? https://www.istoedinheiro.com.br/trombose-apos-vacinacao-com-astrazeneca-quais-os-sintomas-e-como-se-deve-atuar/
"Agências europeias estão reticentes com a vacina da AstraZeneca. Ela chegou a ser desaconselhada a pessoas com idade inferior a 60 anos, e um alto funcionário da Agência Europeia de Medicamentos declarou que era melhor deixar de administrar a vacina deste laboratório em qualquer idade quando há alternativas disponíveis, devido aos relatos de trombose após a primeira dose, apesar de raros."
11/05/2021 - CoronaVac, Oxford e Pfizer: veja diferenças entre as vacinas contra covid https://noticias.uol.com.br/saude/ultimas-noticias/redacao/2021/05/11/diferencas-vacinas-covid-brasil.htm
"Na terça-feira (12), o Ministério da Saúde determinou a suspensão da aplicação da vacina de Oxford/AstraZeneca para gestantes e puérperas com comorbidades. A decisão segue recomendação da Anvisa, que apura a morte de uma grávida de 35 anos que tomou o imunizante e teve um AVC (acidente vascular cerebral)."
30/07/2021 - Pfizer representa o mesmo risco de trombose que a Astrazeneca, aponta levantamento https://panoramafarmaceutico.com.br/pfizer-representa-o-mesmo-risco-de-trombose-que-a-astrazeneca-aponta-levantamento/
7. CRIMES
Crimes da Pfizer
18/11/2020 Não listado no google - Os Crimes documentados da produtora de vacinas de Covid - Pfizer [INGLÊS] https://www.dmlawfirm.com/crimes-of-covid-vaccine-maker-pfizer-well-documented/
"A velocidade com que a vacina Covid da Pfizer foi produzida, a ausência de estudos em animais, testes de controle randomizados e outros testes e procedimentos padrão usuais para um novo medicamento são, no mínimo, preocupantes. Além disso, todos os fabricantes de vacinas Covid receberam imunidade legal para quaisquer ferimentos ou mortes que possam causar. Se essas vacinas são tão seguras quanto promovidas, por que seus fabricantes precisam de imunidade geral?"
"A Pfizer, uma empresa farmacêutica que parece ter ganhado na loteria para produzir a primeira vacina Covid-19, está atualmente lutando contra centenas de ações judiciais sobre o Zantac, um popular medicamento contra azia. Os processos da Zantac afirmam que a droga popular pode estar contaminada com uma substância cancerígena chamada N-nitrosodimetilamina (NDMA). Os processos Zantac são em aberto e em andamento, já que a farmacêutica está lutando contra eles; mas a Pfizer, sabemos, cometeu vários crimes ou transgressões pelos quais foi punida nos últimos anos. As falhas da empresa estão bem documentadas e vale a pena revisá-las neste momento crítico da história da humanidade, enquanto todos nós buscamos respostas."
A Pfizer recebeu a maior multa da história dos Estados Unidos como parte de um acordo judicial de US $ 2,3 bilhões com promotores federais por promover medicamentos erroneamente (Bextra, Celebrex) e pagar propinas a médicos complacentes. A Pfizer se confessou culpada de falsificar a marca do analgésico Bextra, promovendo o medicamento para usos para os quais não foi aprovado.
Na década de 1990, a Pfizer estava envolvida em válvulas cardíacas defeituosas que causaram a morte de mais de 100 pessoas. A Pfizer enganou deliberadamente os reguladores sobre os perigos. A empresa concordou em pagar US $ 10,75 milhões para acertar as acusações do departamento de justiça por enganar reguladores.
A Pfizer pagou mais de US $ 60 milhões para resolver um processo sobre o Rezulin, um medicamento para diabetes que causou a morte de pacientes de insuficiência hepática aguda.
No Reino Unido, a Pfizer foi multada em quase € 90 milhões por sobrecarregar o NHS, o Serviço Nacional de Saúde. A Pfizer cobrou do contribuinte um adicional de € 48 milhões por ano, pelo que deveria custar € 2 milhões por ano.
A Pfizer concordou em pagar US $ 430 milhões em 2004 para resolver acusações criminais de que havia subornado médicos para prescrever seu medicamento para epilepsia Neurontin para indicações para as quais não foi aprovado. Em 2011, um júri concluiu que a Pfizer cometeu fraude em sua comercialização do medicamento Neurontin. A Pfizer concordou em pagar $ 142,1 milhões para liquidar as despesas.
A Pfizer revelou que pagou quase 4.500 médicos e outros profissionais médicos cerca de US $ 20 milhões por falar em nome da Pfizer.
Em 2012, a Comissão de Valores Mobiliários dos Estados Unidos - anunciou que havia chegado a um acordo de US $ 45 milhões com a Pfizer para resolver acusações de que suas subsidiárias haviam subornado médicos e outros profissionais de saúde no exterior para aumentar as vendas no exterior.
A Pfizer foi processada em um tribunal federal dos Estados Unidos por usar crianças nigerianas como cobaias humanas, sem o consentimento dos pais das crianças. A Pfizer pagou US $ 75 milhões para entrar em acordo no tribunal nigeriano pelo uso de um antibiótico experimental, o Trovan, nas crianças. A empresa pagou um valor adicional não divulgado nos Estados Unidos para liquidar as despesas aqui. A Pfizer violou o direito internacional, incluindo a Convenção de Nuremberg estabelecida após a Segunda Guerra Mundial, devido aos experimentos nazistas em prisioneiros relutantes.
Em meio a críticas generalizadas de roubar os países pobres em busca de drogas, a Pfizer prometeu dar US $ 50 milhões para um medicamento para a AIDS para a África do Sul. Mais tarde, no entanto, a Pfizer falhou em honrar essa promessa.
- Pfizer contract leaked!
[Contrato da Pfizer vazado]
 http://sanjeev.sabhlokcity.com/Misc/LEXO-KONTRATEN-E-PLOTE.pdf
http://sanjeev.sabhlokcity.com/Misc/LEXO-KONTRATEN-E-PLOTE.pdf
Segundo o contrato "o produto não deve ser serializado":
"5.5 Reconhecimento do comprador.
O Comprador reconhece que a Vacina e os materiais relacionados à Vacina, e seus componentes e materiais constituintes estão sendo desenvolvidos rapidamente devido às circunstâncias de emergência da pandemia de COVID-19 e continuarão a ser estudados após o fornecimento da Vacina ao Comprador nos termos deste Contrato. O Comprador reconhece ainda que os efeitos de longo prazo e eficácia da Vacina não são atualmente conhecidos e que pode haver efeitos adversos da Vacina que não são atualmente conhecidos. Além disso, na medida do aplicável, o Comprador reconhece que o Produto não deve ser serializado."
Crimes da AstraZeneca
21/06/2003 - AstraZeneca se declara culpada no esquema de médico de câncer https://www.nytimes.com/2003/06/21/business/astrazeneca-pleads-guilty-in-cancer-medicine-scheme.html
"A AstraZeneca, a grande empresa farmacêutica, se declarou culpada hoje de uma acusação de crime de fraude no sistema de saúde e concordou em pagar $ 355 milhões para resolver as acusações criminais e civis de que se envolveu em um esquema nacional para comercializar ilegalmente um medicamento contra o câncer de próstata.
O governo disse que os funcionários da empresa deram incentivos financeiros ilegais a cerca de 400 médicos em todo o país para persuadi-los a prescrever o medicamento Zoladex. Esses incentivos incluíram milhares de amostras grátis de Zoladex [...]"
27/04/2010 - Farmacêutica gigante AstraZeneca pagará US $ 520 milhões pelo marketing de medicamentos off-label https://www.justice.gov/opa/pr/pharmaceutical-giant-astrazeneca-pay-520-million-label-drug-marketing
"AstraZeneca LP e AstraZeneca Pharmaceuticals LP vão pagar $ 520 milhões para resolver as alegações de que a AstraZeneca comercializou ilegalmente o medicamento antipsicótico Seroquel para usos não aprovados como seguros e eficazes pela Food and Drug Administration (FDA), os Departamentos de Justiça e Saúde e Serviços Humanos A Equipe de Ação de Fiscalização de Fraudes em Saúde (HEAT) anunciou hoje. Esses usos não aprovados também são conhecidos como usos "off-label" porque não estão incluídos no rótulo do medicamento aprovado pela FDA."
- List of largest pharmaceutical settlements [Lista dos maiores acordos farmaceuticos] https://en.m.wikipedia.org/wiki/List_of_largest_pharmaceutical_settlements
8. CIENTISTAS
Especialistas Sérios
- Máscara Provoca Insuficiência Respiratória E Contaminação Microbiana… [Canal deletado] https://youtube.com/watch?v=eHu-pydSvDI
Não lembro mais a quem pertencia, mas provavelmente era de um médico falando do assunto. Creio ter sido do Dr. Paulo Sato, por essa temática ter sido abordada por ele, mas ao abrir o site aparece somente:
"Este vídeo foi removido por violar as diretrizes da comunidade do YouTube"
Dr. Paulo Sato
- USAR ou NÃO USAR a CUECA do seu governador no rosto https://fb.watch/7NPP_7rS5S/ https://www.facebook.com/AdoniasSoaresBR/videos/1347904292291481/ Adonias Soares entrevista ao Dr. Paulo Sato sobre as máscaras, em que é simulado o efeito da respiração prolongada das máscaras no organismo com o uso de águas de torneira, natural, gaseificada (com gás carbônico) e antioxidante, em que a com gás carbônico (PH 4 - Ácido) representa o organismo humano, e na prática representa lesão corporal e iniciação de doenças.
Dr. Kary Mullis
(Criador do teste PCR)
- PCR nas palavras do seu inventor - Dr. Kary Mullis (legendado) https://www.youtube.com/watch?v=W1O52uTygk8
"Qualquer um pode testar positivo para quase qualquer coisa com um teste de PCR, se você executá-lo por tempo suficiente… Com PCR, se voce fizer isso bem, você pode encontrar quase tudo em qualquer pessoa… Isso não te diz que você está doente."
- Kary Mullis DESTRUYE a Anthony Fauci lbry://@CapitalistChile#0/Kary-Mullis---Fauci#5
"Ele [...] não entende de medicina e não deveria estar onde está. A maioria dos que estão acima são só administrativos e não têm nem ideia do que ocorre aqui em baixo e essas pessoas tem uma agenda que não é a que gostaríamos que tivessem, dado que somos nós os que pagamos a eles para que cuidem da nossa saúde. Têm uma agenda pessoal."
Dra. Li-Meng Yan
- Dra. Li-Meng Yan: O vírus foi criado em laboratório com um objetivo: Causar dano. https://youtu.be/pSXp3CZnvOc
Dr. Joe Roseman
- Cientista Phd Dr Joe Roseman faz seríssimas advertencias sobre a picada https://youtu.be/0PIXVFqJ_h8
Dr. Robert Malone
- As vacinas podem estar causando ADE - Dr. Robert Malone https://odysee.com/@AkashaComunidad:f/Las_vacunas_pueden_estar_causando_ADE_magnificaci%C3%B3n_mediada_por:f lbry://@Información.#b/Drrm#9
Dr. Robert Malone, um dos três inventores da tecnologia de RNAm que se usa de forma farmacêutica. No vídeo fala sobre os efeitos de ADE (realce dependente de anticorpos) que estão ocorrendo com as vacinas. Nas palavras do Dr. Malone, já não é somente uma hipótese, mas baseada nos conhecimentos gerados nas provas e ensaios pré clínicos, com as vacinas contra o primeiro vírus da SARS.
Dr. Luc Montagnier
- Dr. Luc Montagnier, virologista, prêmio Nobel de medicina, um dos descobridores do vírus HIV, afirma: "a vacinação em massa está criando as novas variantes' (@medicospelavida , telegram)
Falsos Especialistas
-
Dr. Anthony Fauci - Imunologista
-
Dr. Atila Iamarino (nerdologia) - Microbiólogo
Atualmente propagandeia a pauta climática do COP30 (30th Conference Of Parties - UN [30ª Conferência das Partes - ONU]) que será no Brasil.
9. CASOS DOCUMENTADOS
13 de setembro de 2021 - 13/09/2021 - Carta aberta ao Ministro da Saúde por Arlene Ferrari Graf, mãe de Bruno Oscar Graf https://telegra.ph/Carta-aberta-ao-Ministro-da-Sa%C3%BAde-09-13
Também em: Gazeta do Povo
O texto de uma mãe discorrendo sobre o filho dela, Bruno Oscar Graf, ter ANTI-HEPARINA PF4 AUTO-IMUNE e ter vindo a falecer por reação à vacina.
11/05/2021 - Rio notifica morte de grávida vacinada com imunizante Oxford https://www.terra.com.br/noticias/coronavirus/rio-notifica-morte-de-gravida-vacinada-com-imunizante-oxford,415b9b0c49169427ac2f90ae3765c057e9suy3qn.html
"Vítima não apresentava histórico de doença circulatória nem sofria de nenhuma doença viral; relação será investigada"
13/08/2021 - Cruzeiro com 4.336 pessoas tem 27 contaminados com Covid-19 em Belize https://paranaportal.uol.com.br/geral/cruzeiro-com-4-336-pessoas-tem-27-contaminados-com-covid-19-em-belize/amp/
"Segundo um comunicado do Conselho de Turismo de Belize emitido na quarta-feira (11), 26 contaminados são da tripulação e um é passageiro. A maioria é assintomática e os 27 estão vacinados."
10. ALEGAÇÕES DIRETAS
Setembro de 2021 - 09/2021 - BOMBA: Ex-membro do Partido Comunista da China revela que o primeiro surto da Covid foi “intencional” https://terrabrasilnoticias.com/2021/09/bomba-ex-membro-do-partido-comunista-da-china-revela-que-o-primeiro-surto-da-covid-foi-intencional/
-
 @ 502ab02a:a2860397
2025-06-06 01:15:24
@ 502ab02a:a2860397
2025-06-06 01:15:24ปิดท้าย week นี้ด้วยสงครามดีไหมครับ ถ้าอาหารเป็นสนามรบ สิทธิบัตรก็เปรียบเหมือนป้อมปราการ และการฟ้องร้องก็คือปืนใหญ่ยิงสวนกันกลางแดด…ใครที่เคยคิดว่าโลกของอาหารแห่งอนาคตจะสวยงามเพราะเปลี่ยนถั่วเป็นสเต๊ก สกัดกลิ่นเลือดจากพืช หรือหลอกลิ้นให้เชื่อว่า “อร่อยเหมือนเนื้อ” ก็คงต้องมานั่งทบทวนใหม่ว่า โลกใบนี้ไม่ได้ขับเคลื่อนด้วยความฝัน แต่ขับเคลื่อนด้วยเอกสาร 70 หน้าของทนายความ และหมายเรียกจากศาลกลางรัฐเดลาแวร์
Motif FoodWorks เข้ามาในวงการอาหารด้วยวิสัยทัศน์สุดเท่ คือจะสร้างโครงสร้าง-กลิ่น-รส ของโปรตีนอนาคตให้แบรนด์ plant-based ทั่วโลกใช้ได้โดยไม่ต้องเริ่มใหม่ตั้งแต่ศูนย์ เปรียบเหมือนเป็นเบื้องหลังของวงการ มีซอสลับคือ HEMAMI™ ที่สกัดกลิ่นเนื้อจากยีสต์ ผ่านวิธีการทางวิทยาศาสตร์สุดซับซ้อน ฟังแล้วดูดี แต่ปัญหาคือซอสลับของเขาดัน “คล้ายเกินไป” กับของ Impossible Foods ที่ใช้ heme protein เหมือนกัน
แล้วอะไรคือจุดเปราะบางที่ทำให้ Motif ต้องร่วง?
เฮียอยากให้ลองคิดแบบนี้ครับ สมมุติว่ามีร้านกาแฟใหม่ที่ตั้งใจจะขายกาแฟแนวใหม่ ใช้เมล็ดกาแฟหมักยีสต์กลิ่นกล้วยหอม รสชาตินุ่มลึก เป็นของตัวเอง เขาไม่ได้ก็อปสูตรใคร แต่ดันไปใช้กระบวนการคล้ายกับแบรนด์เจ้าตลาดที่เขียนจดสิทธิบัตรเอาไว้ก่อนแล้ว แค่คล้ายก็พอจะโดนลากขึ้นศาลได้ เพราะในโลกของสิทธิบัตร “ความใหม่” และ “ความไม่เหมือน” คือสิ่งศักดิ์สิทธิ์ แม้จะไม่ได้ก็อปตรง ๆ
Impossible Foods เห็นช่องนี้ชัด พวกเขายื่นฟ้องทันที โดยระบุว่า HEMAMI™ ของ Motif ละเมิดสิทธิบัตรเทคนิคการใช้ heme เพื่อสร้างรสชาติเหมือนเนื้อในผลิตภัณฑ์ plant-based ซึ่งเป็นหัวใจหลักที่ Impossible ใช้มัดใจตลาดมาหลายปี
ในเดือนมีนาคม 2022, Impossible Foods ก็ลุกขึ้นมาฟ้อง Motif FoodWorks ต่อศาลรัฐบาลกลางของสหรัฐฯ โดยอ้างว่า HEMAMI™ ละเมิดสิทธิบัตรของตนที่เกี่ยวข้องกับการใช้โปรตีน heme ในการสร้างรสชาติและกลิ่นที่คล้ายเนื้อจริงในผลิตภัณฑ์จากพืช จุดนี้ดูผิวเผินเหมือนแค่ “บริษัท A เหมือนของบริษัท B เลยโดนฟ้อง” แต่ความจริงซับซ้อนและลึกกว่านั้นมาก เพราะทั้งสองบริษัทต่างก็ใช้วิธีผลิตโปรตีน heme ที่คล้ายกันมาก นั่นคือการดัดแปลงพันธุกรรมจุลินทรีย์ให้ผลิตโปรตีนเฉพาะ แล้วหมักออกมาในถังขนาดใหญ่ แต่ต่างกันที่วัตถุดิบและดีไซน์โปรตีน
Impossible Foods ใช้ “soy leghemoglobin” ซึ่งเป็นโปรตีน heme จากรากถั่วเหลือง ส่วน Motif ใช้ “bovine myoglobin” ซึ่งเลียนแบบของวัวจริง ๆ โดยตรง ความคล้ายคือโปรตีนทั้งสองต่างก็ให้กลิ่นคาวแบบเนื้อเมื่อโดนความร้อน และสร้างสีแดงแบบ rare steak ได้เหมือนกัน ทั้งยังถูกหมักด้วยจุลินทรีย์ GMO แบบใกล้เคียงกันอีกด้วย แม้จะต่างสายพันธุ์ของโปรตีน แต่การฟ้องครั้งนี้ตั้งอยู่บนแนวคิดว่า “วิธีการใช้” โปรตีน heme ในอาหารจากพืชอาจเข้าข่ายละเมิดสิทธิบัตร
จากนั้นไม่กี่เดือน Motif ก็สวนกลับโดยการยื่นคำร้อง “Inter Partes Review” (IPR) กับสำนักงานสิทธิบัตรของสหรัฐฯ (USPTO) ผ่าน PTAB ซึ่งเป็นขั้นตอนที่ใช้เพื่อขอให้ตรวจสอบความถูกต้องของสิทธิบัตรที่กำลังมีปัญหา แนวคิดคือถ้าพิสูจน์ได้ว่าสิทธิบัตรของ Impossible นั้นไม่ใหม่จริง หรือมี prior art อยู่ก่อนแล้ว (เช่น งานวิจัยเก่า ๆ ที่ตีพิมพ์ก่อน) ก็จะทำให้สิทธิบัตรนั้นกลายเป็นโมฆะ
Motif ยื่นคำร้องโจมตีสิทธิบัตรถึง 7 ฉบับของ Impossible แบบกระหน่ำชุดใหญ่ ยิงทีเดียวหวังให้สั่นคลอนทั้งระบบ แต่ PTAB รับพิจารณาเพียงฉบับเดียว (หมายเลขสิทธิบัตร 10,933,018) และท้ายที่สุดในเดือนเมษายน 2023 ศาลตัดสินยกเลิกฉบับนั้นจริง โดยให้เหตุผลว่า “ไม่เป็นสิ่งประดิษฐ์ใหม่อย่างเพียงพอ” ซึ่งถือเป็นชัยชนะเล็ก ๆ ของ Motif และสร้างแรงกระเพื่อมในแวดวงวิทยาศาสตร์อาหารอยู่พอสมควร
แต่แม้จะมีชัยบางส่วน อีก 6 ฉบับที่เหลือ PTAB กลับไม่รับพิจารณา โดยบอกว่า “หลักฐานไม่ชัดเจนพอจะเข้าขั้นพิจารณาใหม่” นั่นทำให้ฝั่ง Impossible ยังถือสิทธิบัตรส่วนใหญ่ไว้อยู่เหมือนเดิม แล้วก็เริ่มกลับมาเร่งกระบวนการฟ้องร้องในศาลต่อ ซึ่งหมายความว่า Motif ยิ่งต้องใช้เงินมากขึ้นเรื่อย ๆ ในการสู้รบทั้งสองด้าน ทั้งในศาลและในระบบสิทธิบัตร
ชัยชนะเล็ก ๆ นี้กลายเป็นดาบสองคม เพราะในขณะที่ Motif ดีใจว่าล้มได้ 1 ฉบับ ตลาดกลับมองว่าพวกเขาสู้แบบดิ้นสุดตัว ซึ่งในมุมของนักลงทุน นั่นแปลว่า "ขาดเงินทุนหมุนเวียน" หรือ “มีแนวโน้มขาดทุนต่อเนื่อง” มากกว่าจะมองว่าเป็นฮีโร่สู้เพื่อความถูกต้อง
ระหว่างนี้ Motif ยังพยายาม “spin” ภาพลักษณ์ตัวเองในเชิงบวกอย่างหนัก พวกเขาเปิดตัวผลิตภัณฑ์ใหม่ชื่อ “Motif MoBeef™” และ “Motif MoChicken™” โดยใช้ HEMAMI™ ผสมอยู่ พร้อมโชว์ผลงานให้เชฟชื่อดังระดับ Michelin มาชิมและออกสื่อ โดยหวังว่าจะสร้างความเชื่อมั่นให้ตลาดว่า “ผลิตภัณฑ์เรายังไปต่อได้” และอาจดึงดีลใหม่หรือการลงทุนเพิ่มเข้ามาเพื่อบรรเทาภาระจากการฟ้องร้อง
และในขณะที่ Motif เดินหน้าเปิดตัวผลิตภัณฑ์ใหม่เพื่อแสดงพลังให้ตลาดเห็นว่า “เรายังไปต่อได้” ฝั่ง Impossible กลับเดินเกม PR อย่างเงียบ ๆ ด้วยการแจ้งเตือนสื่อและผู้ถือหุ้นว่า “Motif ยังใช้เทคโนโลยีละเมิดอยู่ต่อเนื่อง” พร้อมแนบเอกสารคำฟ้องเพิ่มในปี 2023 ซึ่งแปลความได้ว่า “ศึกยังไม่จบ อย่าเพิ่งส่งเงินให้คู่แข่งเรา” เพราะในเอกสารคำฟ้องของปี 2023 พวกเขาเสริมข้อกล่าวหาใหม่ว่าการที่ Motif ออกสื่อและใช้ HEMAMI™ ต่อไป “เป็นการจงใจละเมิด” และอาจเข้าข่ายการทำลายคุณค่าของแบรนด์ Impossible โดยตรง จุดนี้ยิ่งทำให้ Motif อยู่ในมุมที่เสี่ยงและลำบากมากขึ้น
การต่อสู้ของทั้งสองบริษัทจึงไม่ใช่แค่เรื่องใครเลียนแบบใคร แต่มันคือเกมยืดเวลา เผาเงิน ปั่นมูลค่า และวัดใจนักลงทุนว่าใครจะถอยก่อนกัน และสุดท้ายคนที่หมดลมหายใจก่อนก็คือ Motif แม้จะมีนักวิทยาศาสตร์เก่ง ๆ เทคโนโลยีล้ำ ๆ หรือวัตถุดิบดีแค่ไหน แต่เมื่อต้องมาสู้กับยักษ์ที่มีสิทธิบัตรในมือ บารมีในตลาด และชื่อเสียงติดหูผู้บริโภค…ก็ยากที่จะเอาชนะด้วยวิทยาศาสตร์เพียงอย่างเดียว
ศึกนี้จึงไม่ได้จบแค่ในศาล แต่มันลากไปถึงห้องประชุมนักลงทุน พาดหัวข่าวใน Business Insider และบอร์ด Reddit ที่คุยกันว่า “Motif จะไปไม่รอดหรือเปล่า” ซึ่งในยุคที่เงินทุนคือออกซิเจน การที่ภาพลักษณ์ของบริษัทเริ่มสั่นคลอน ก็เหมือนถังอากาศรั่วในห้องแล็บใต้ทะเล…ไม่นานนัก Motif ก็เริ่มลดจำนวนพนักงาน ลดเป้าการผลิต และสุดท้าย “ลดบทบาทตัวเองในตลาด”
หากดูเผิน ๆ หลายคนอาจคิดว่านี่คือเรื่องของสองบริษัทใหญ่ในโลก plant-based ที่ทะเลาะกันเอง แต่จริง ๆ แล้วนี่คือบทเรียนใหญ่ของ “วงการอาหารแห่งอนาคต” ที่กำลังเติบโตบนหลังคำว่า IP Intellectual Property ใครถือสิทธิบัตรก่อน คนนั้นตั้งกฎได้ ใครมาใหม่ ถ้าไม่จดให้ไว ก็อาจต้องจ่ายค่าต๋งตลอดชีวิต
และที่เจ็บปวดที่สุดคือบางทีของที่คุณคิดขึ้นมาเอง อาจไม่ใช่ของคุณอีกต่อไปแล้ว ถ้าคุณไม่มีเอกสารในมือ
นี่แหละครับ วงการที่ดูเหมือนจะขาย “นวัตกรรมอาหาร” แต่จริง ๆ แล้วขาย “สิทธิบัตรในกล่องข้าว” ใครจะอยู่ใครจะไป บางทีก็ไม่เกี่ยวกับว่า “ของอร่อยแค่ไหน” แต่เกี่ยวกับว่า “ใครมีทนายเก่งกว่า”
และในขณะที่สองยักษ์ใหญ่ยิงกันด้วยเอกสารละเมิดสิทธิ์ เหยื่อเงียบ ๆ อย่างเกษตรกรรายย่อยที่ยังอยากปลูกผักจริง เลี้ยงวัวจริง หรือแม้แต่ผู้บริโภคที่แค่อยากรู้ว่า “กินอะไรแล้วร่างกายจะดีขึ้น” กลับวนเวียนในทางอยู่ในโลกที่อาหารทุกคำถูกควบคุมโดยทุน จดหมายเรียกจากศาล และวัตถุดิบสังเคราะห์ที่มีรหัสมากกว่าชื่อจริง
สงครามสิทธิบัตรเหล่านี้ไม่เคยมีพื้นที่ให้ชาวไร่ หรือผู้บริโภคธรรมดาเข้าไปมีเสียงเลยสักนิด เพราะมันคือการต่อสู้ระหว่างนักล่าที่ฟาดฟันกันบนยอดห่วงโซ่อาหาร แต่เบื้องล่างของพีระมิด กลับมีแต่เหยื่อที่ถูกเลี้ยงให้งุนงง อยู่กับของปลอม และเชื่อว่า “นี่แหละคืออนาคตของอาหาร”
แล้วใครจะบอกเราว่า...ทางรอดคืออะไร?
คำตอบอาจอยู่ไม่ไกล แค่เราต้องกลับมาถามคำถามง่าย ๆ ที่ใครก็ลืมไปว่า “จริง ๆ แล้ว เราต้องการอาหารแบบไหนกันแน่” อาหารที่กินแล้วแข็งแรง หรืออาหารที่บริษัทแข็งแรง?
เพราะตราบใดที่เรายังปล่อยให้กล่องข้าวอยู่ในมือคนจดสิทธิบัตร เราอาจไม่มีวันได้กลับไปจับจอบเอง ปลูกเอง กินเอง แบบที่มนุษย์เคยเป็นมาก่อนโลกจะกลายเป็นห้องทดลองขนาดยักษ์
ศึกระหว่างผู้ล่ายังรุนแรงขนาดนี้ แล้วศึกระหว่างผู้ล่ากับเหยื่อ จะเหลืออะไรครับ
#pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-
 @ 04c915da:3dfbecc9
2025-05-16 17:59:23
@ 04c915da:3dfbecc9
2025-05-16 17:59:23Recently we have seen a wave of high profile X accounts hacked. These attacks have exposed the fragility of the status quo security model used by modern social media platforms like X. Many users have asked if nostr fixes this, so lets dive in. How do these types of attacks translate into the world of nostr apps? For clarity, I will use X’s security model as representative of most big tech social platforms and compare it to nostr.
The Status Quo
On X, you never have full control of your account. Ultimately to use it requires permission from the company. They can suspend your account or limit your distribution. Theoretically they can even post from your account at will. An X account is tied to an email and password. Users can also opt into two factor authentication, which adds an extra layer of protection, a login code generated by an app. In theory, this setup works well, but it places a heavy burden on users. You need to create a strong, unique password and safeguard it. You also need to ensure your email account and phone number remain secure, as attackers can exploit these to reset your credentials and take over your account. Even if you do everything responsibly, there is another weak link in X infrastructure itself. The platform’s infrastructure allows accounts to be reset through its backend. This could happen maliciously by an employee or through an external attacker who compromises X’s backend. When an account is compromised, the legitimate user often gets locked out, unable to post or regain control without contacting X’s support team. That process can be slow, frustrating, and sometimes fruitless if support denies the request or cannot verify your identity. Often times support will require users to provide identification info in order to regain access, which represents a privacy risk. The centralized nature of X means you are ultimately at the mercy of the company’s systems and staff.
Nostr Requires Responsibility
Nostr flips this model radically. Users do not need permission from a company to access their account, they can generate as many accounts as they want, and cannot be easily censored. The key tradeoff here is that users have to take complete responsibility for their security. Instead of relying on a username, password, and corporate servers, nostr uses a private key as the sole credential for your account. Users generate this key and it is their responsibility to keep it safe. As long as you have your key, you can post. If someone else gets it, they can post too. It is that simple. This design has strong implications. Unlike X, there is no backend reset option. If your key is compromised or lost, there is no customer support to call. In a compromise scenario, both you and the attacker can post from the account simultaneously. Neither can lock the other out, since nostr relays simply accept whatever is signed with a valid key.
The benefit? No reliance on proprietary corporate infrastructure.. The negative? Security rests entirely on how well you protect your key.
Future Nostr Security Improvements
For many users, nostr’s standard security model, storing a private key on a phone with an encrypted cloud backup, will likely be sufficient. It is simple and reasonably secure. That said, nostr’s strength lies in its flexibility as an open protocol. Users will be able to choose between a range of security models, balancing convenience and protection based on need.
One promising option is a web of trust model for key rotation. Imagine pre-selecting a group of trusted friends. If your account is compromised, these people could collectively sign an event announcing the compromise to the network and designate a new key as your legitimate one. Apps could handle this process seamlessly in the background, notifying followers of the switch without much user interaction. This could become a popular choice for average users, but it is not without tradeoffs. It requires trust in your chosen web of trust, which might not suit power users or large organizations. It also has the issue that some apps may not recognize the key rotation properly and followers might get confused about which account is “real.”
For those needing higher security, there is the option of multisig using FROST (Flexible Round-Optimized Schnorr Threshold). In this setup, multiple keys must sign off on every action, including posting and updating a profile. A hacker with just one key could not do anything. This is likely overkill for most users due to complexity and inconvenience, but it could be a game changer for large organizations, companies, and governments. Imagine the White House nostr account requiring signatures from multiple people before a post goes live, that would be much more secure than the status quo big tech model.
Another option are hardware signers, similar to bitcoin hardware wallets. Private keys are kept on secure, offline devices, separate from the internet connected phone or computer you use to broadcast events. This drastically reduces the risk of remote hacks, as private keys never touches the internet. It can be used in combination with multisig setups for extra protection. This setup is much less convenient and probably overkill for most but could be ideal for governments, companies, or other high profile accounts.
Nostr’s security model is not perfect but is robust and versatile. Ultimately users are in control and security is their responsibility. Apps will give users multiple options to choose from and users will choose what best fits their need.
-
 @ ec42c765:328c0600
2025-02-05 23:45:09
@ ec42c765:328c0600
2025-02-05 23:45:09test
test
-
 @ da8b7de1:c0164aee
2025-06-05 17:39:41
@ da8b7de1:c0164aee
2025-06-05 17:39:41| Régió/Ország | Fő esemény/politika | Forrás | |------------------|--------------------------------------------------------------------------------------------------|-------------| | Egyesült Államok | Végrehajtási rendeletek a nukleáris termelés négyszeresére növeléséről; a nem létfontosságú K+F költségvetésének csökkentése; SMR és mikroreaktor kezdeményezések | world-nuclear-news, nucnet, aoshearman, ans | | Kanada | Engedélyezés új BWRX-300 SMR reaktor építésére Darlingtonban | world-nuclear-news, ans | | Európa | EU tervek az orosz nukleáris importok korlátozására; Westinghouse–Bulgária beszállítói megállapodások | nucnet, world-nuclear-news | | Globális/Világbank | A nukleáris finanszírozási tilalom esetleges feloldása a fejlődő országok számára | globalissues | | Egyesült Királyság| Új kiberbiztonsági jogszabályok a nukleáris szektorban | aoshearman | | Katonaság/Védelem| A védelmi minisztérium cégeket választott ki mikroreaktorok telepítésére | ans |
Források:
world-nuclear-news
nucnet
aoshearman
globalissues
ans -
 @ b1ddb4d7:471244e7
2025-06-05 19:01:34
@ b1ddb4d7:471244e7
2025-06-05 19:01:34“Not your keys, not your coins” isn’t a slogan—it’s a survival mantra in the age of digital sovereignty.
The seismic collapses of Mt. Gox (2014) and FTX (2022) weren’t anomalies; they were wake-up calls. When $8.7 billion in customer funds vanished with FTX, it exposed the fatal flaw of third-party custody: your bitcoin is only as secure as your custodian’s weakest link.
Yet today, As of early 2025, analysts estimate that between 2.3 million and 3.7 million Bitcoins are permanently lost, representing approximately 11–18% of bitcoin’s fixed maximum supply of 21 million coins, with some reports suggesting losses as high as 4 million BTC. This paradox reveals a critical truth: self-custody isn’t just preferable—it’s essential—but it must be done right.
The Custody Spectrum
Custodial Wallets (The Illusion of Control)
- Rehypothecation Risk: Most platforms lend your bitcoin for yield generation. When Celsius collapsed, users discovered their “held” bitcoin was loaned out in risky strategies.
- Account Freezes: Regulatory actions can lock withdrawals overnight. In 2023, Binance suspended dollar withdrawals for U.S. users citing “partner bank issues,” trapping funds for weeks.
- Data Vulnerability: KYC requirements create honeypots for hackers. The 2024 Ledger breach exposed 270,000 users’ personal data despite hardware security.
True Self-Custody
Self-custody means exclusively controlling your private keys—the cryptographic strings that prove bitcoin ownership. Unlike banks or exchanges, self-custody eliminates:- Counterparty risk (no FTX-style implosions)
- Censorship (no blocked transactions)
- Inflationary theft (no fractional reserve lending)
Conquering the Three Great Fears of Self-Custody
Fear 1: “I’ll Lose Everything If I Make a Mistake”
Reality: Human error is manageable with robust systems:
- Test Transactions: Always send a micro-amount (0.00001 BTC) before large transfers. Verify receipt AND ability to send back.
- Multi-Backup Protocol: Store seed phrases on fireproof/waterproof steel plates (not paper!). Distribute copies geographically—one in a home safe, another with trusted family 100+ miles away.
- SLIP39 Sharding: Split your seed into fragments requiring 3-of-5 shards to reconstruct. No single point of failure.
Fear 2: “Hackers Will Steal My Keys”
Reality: Offline storage defeats remote attacks:
- Hardware Wallets: Devices like Bitkey or Ledger keep keys in “cold storage”—isolated from internet-connected devices. Transactions require physical confirmation.
- Multisig Vaults: Bitvault’s multi-sig system requires attackers compromise multiple locations/devices simultaneously. Even losing two keys won’t forfeit funds.
- Air-Gapped Verification: Use dedicated offline devices for wallet setup. Never type seeds on internet-connected machines.
Fear 3: “My Family Can’t Access It If I Die”
Reality: Inheritance is solvable:
- Dead Man Switches: Bitwarden’s emergency access allows trusted contacts to retrieve encrypted keys after a pre-set waiting period (e.g., 30 days).
- Inheritance Protocols: Bitkey’s inheritance solution shares decryption keys via designated beneficiaries’ emails. Requires multiple approvals to prevent abuse.
- Public Key Registries: Share wallet XPUBs (not private keys!) with heirs. They can monitor balances but not spend, ensuring transparency without risk.
The Freedom Dividend
- Censorship Resistance: Send $10M BTC to a Wikileaks wallet without Visa/Mastercard blocking it.
- Privacy Preservation: Avoid KYC surveillance—non-custodial wallets like Flash require zero ID verification.
- Protocol Access: Participate in bitcoin-native innovations (Lightning Network, DLCs) only possible with self-custodied keys.
- Black Swan Immunity: When Cyprus-style bank bailins happen, your bitcoin remains untouched in your vault.
The Sovereign’s Checklist
- Withdraw from Exchanges: Move all BTC > $1,000 to self-custody immediately.
- Buy Hardware Wallet: Purchase DIRECTLY from manufacturer (no Amazon!) to avoid supply-chain tampering.
- Generate Seed OFFLINE: Use air-gapped device, write phrase on steel—never digitally.
- Test Recovery: Delete wallet, restore from seed before funding.
- Implement Multisig: For > $75k, use Bitvault for 2-of-3 multi-sig setup.
- Create Inheritance Plan: Share XPUBs/SLIP39 shards with heirs + legal documents.
“Self-custody isn’t about avoiding risk—it’s about transferring risk from opaque institutions to transparent, controllable systems you design.”
The Inevitable Evolution: Custody Without Compromise
Emerging solutions are erasing old tradeoffs:
- MPC Wallets: Services like Xapo Bank shatter keys into encrypted fragments distributed globally. No single device holds full keys, defeating physical theft.
- Social Recovery: Ethically designed networks (e.g., Bitkey) let trusted contacts restore access without custodial control.
- Biometric Assurance: Fingerprint reset protocols prevent lockouts from physical injuries.
Lost keys = lost bitcoin. But consider the alternative: entrusting your life savings to entities with proven 8% annual failure rates among exchanges. Self-custody shifts responsibility from hoping institutions won’t fail to knowing your system can’t fail without your consent.
Take action today: Move one coin. Test one recovery. Share one xpub. The path to unchained wealth begins with a single satoshi under your control.
-
 @ df478568:2a951e67
2025-06-05 23:34:01
@ df478568:2a951e67
2025-06-05 23:34:01About 156,000 blocks ago, I went to a Taco Shop for a bitcoin meetup. I asked my favorite question, “Do you accept bitcoin?”
“Yes," he said as he handed me a Toast Terminal with a BTCpayServer QR code.
 ]
]Awesome!
12,960 blocks later, I took my dad to the taco shop. We ordered food. I asked my favorite question once again.
“Uh…Yeah, but I don't know how to work the machine.”
"Dough!🤦"
It's been a problem in the past, but now lightning payments are about to be ubiquitous. Steak N Shake is taking bitcoin using Speed Wallet and Block is implementing bitcoin payments by 2026 in all legal jurisdictions. I have tested both of these so you don't have to. Just kidding. I geek out on this stuff, but both work great. You can pay with your sats by scanning a screen on a QR code. The employees don't need to be bitcoin lightning network experts. You can just pay as easy as a credit card.
There were 35,000 people at the bitcoin conference, and 4,187 transactions were made. It was a world record. Wait, I thought they said there could only be 7 transactions per second! No, not anymore. Now we can use bitcoin for shopping. I can pay for tacos at taco trucks.

How You Can Accept Bitcoin At Your Business
Coinos is a simple bitcoin point of sale information that acts like a cash register. Bitcoin is peer-to-peer electronic cash. Coinos is a cash register and you should treat it as such. If you make a few hundred thousand sats at the end of the night, you should sweep the bitcoin into your own wallet.. You can use Aqua, AlbyHub, Bull Bitcoin wallet, or whatever your favorite lightning enabled wallet is to withdraw. You'll need a password. Do not lose this. I have tried the automatic withdraws, but it did not work for me. I'm no concerned because this is not a wallet I intend to keep a lot of sats in for a long time.
Here is my coinos payment terminal.
https://coinos.io/ZapthisBlog/receive
I made the QR code with libreqr.com/

Now I have an online bitcoin cash register. The Bitcoiners know how to pay for stuff with sats. They will be proud to show you too. If you're nerdy, you can use all the cool kid tools now, but we will just focus on the lightning address. Anyone can send you sats with a lightning address with just a QR code.
At the end of the night, you cash out to your own wallet. Again, this assumes you have an Aqua Wallet or any other lightning enabled wallet, but all it takes to accept bitcoin at your brick and mortar store is to create an account with Coinos and print out a QR code. It's a quick and easy way to start accepting bitcoin even if you don't expect many clients to shop with sats.
Tips
This is not just a cash register. Employees can also make their own Coinos wallet and receive tips from bitcoiners. Anyone can accept payments using this system. Your kids could use it to sell lemonade for sats. You are only limited by your imagination. When will you begin accepting bitcoin payments? It is easier than ever. You do not need to train employees. You do not need to be in the store. Bitcoin is peer-to-peer electronic cash so you can give it away like cash. I don't know what the tax rules on cash are. You need to verify that with your own jurisdiction. This is not financial or tax advice. This is for informational purposes only.
Remember, this is a custodial wallet. Not your keys not your bitcoin. Don't keep more sats than you are willing to lose on custodial wallets. Sweep your wallet early and often. Loss of funds is possible. There is a small fee for liquidity management too. Do your own research.
-
 @ ec42c765:328c0600
2025-02-05 23:43:35
@ ec42c765:328c0600
2025-02-05 23:43:35test
-
 @ 2f5de000:2f9bcef1
2025-06-05 17:33:37
@ 2f5de000:2f9bcef1
2025-06-05 17:33:37I've wanted to write this piece for months. Not because I have anything against Jack Mallers personally - quite the opposite. But because I've watched a pattern emerge in Bitcoin that mirrors one of the most chilling dynamics in Atlas Shrugged: the systematic destruction of our most productive builders by the very people who should be celebrating them.
We are the looters. And Jack might just be our Hank Rearden.
The Underdog's Dilemma
There's a cruel irony in how we treat success in Bitcoin. We champion the underdog, root for the builder in the garage, celebrate the cypherpunk taking on the establishment. But the moment that underdog succeeds - the moment they scale, grow, and inevitably have to navigate the messy realities of the existing system - we turn on them with the ferocity of the same establishment we claim to oppose.\ \ Jack began building Zap (which evolved into Strike) from his parents home in Chicago. Strike has grown into one of the most seamless fiat-to-bitcoin on-ramps for everyday users. No complexity, just pure utility. From day one, he's operated at a level of transparency that would make most CEO's uncomfortable. He's been building in public, taking feedback, admitting mistakes, and iterating - sometimes within hours of criticism.
The Rearden Parallel
In Atlas Shrugged, Hank Rearden creates Rearden Metal - a revolutionary alloy that's stronger, lighter, and more efficient than anything that came before. Instead of celebration, he faces endless scrutiny, regulation, and demands to prove is worthiness. The people who benefit from his innovation spend their time questioning his motives, dissecting his business practices, and demanding he justify his success.
Sound familiar?
Jack comes from a finance background - his father and grandfather were in the industry. This isn't a liability; it's an asset. He understands the beast we're fighting. He's been a Bitcoiner since 2013 with a spotless track record in a space littered with exit scams and broken promises. His values align with proof of work, individualism, and the radical idea that bitcoin is for everyone.
Yet when he helps launch 21 Capital, we don't see innovation - we see betrayal. When he navigates regulatory requirements to build products that can actually reach mainstream adoption, we don't see pragmatism - we see capitulation.
The Scarred Perspective
Our skepticism isn't entirely unfounded. We've been burned before. Mt. Gox, FTX, Three Arrows Capital, Celcius, Terra/ LUNA, BlockFi, Bitconnect, Voyager, QuadrigaCX - the graveyard of Bitcoin is littered with the corpses of trusted institutions. We've learned, painfully, that trust must be earned and verified.
But somewhere along the way, our healthy skepticism has metastasized into destructive paranoia. We've become so focused on protecting ourselves from the next SBF that we're attacking the people building the future we claim to want.
I'm guilty of this myself. I've made scathing attacks on my Nostr feed, comparing Jack to SBF, scrutinising contract clauses about re-hypothecation, and questioning his every move privately. I was viewing his actions through the lens of collective trauma rather than the reality of his long track record.
The Looters Paradox
Here's the uncomfortable truth: we're not just passive observers in this drama. We're active participants. We're the looters.
In Atlas Shrugged, the looters don't necessarily steal directly. They steal time, energy, and focus. They create bureaucracy, demnd endless justification, and burden the productive with the weight of constant explanation. They don't build competing products - they just tear down what others have built.
Everytime we demand Jack explain his business model for the hundredth time, we're stealing his time. Every time we scrutinize his partnerships without offering alternatives, we're creating bureaucracy . Everytime we attack his character rather than his arguments, we're furthering the system we claim to oppose.
The free market will create products whether we like them or not. People will build services that use bitcoin as collateral, create lending products, and navigate regulatory frameworks. The question isn't whether these products will exist - it's whether they'll be built by people who share our values or by those who don't.
The Atlantis Risk
The producers eventually withdraw from society in Atlas Shrugged, retreating to Galt's Gulch (Atlantis) and leaving the looters to face the consequences of their destructive behaviour. The economy collapses because the people who actually build things decided it wasn't worth the hassle anymore.
We're walking dangerously close to this precipice in Bitcoin. We're creating an environment where our most capable builders might just decide it's not worth it. Where the hassle of dealing with our constant scrutiny and bad-faith attacks outweighs the mission of building the future.
Jack has been more patient with our criticism than we deserve. He's addressed concerns publicly, changed the course when necessary, and continued building despite the noise. But patience has limits. At some point, even the most mission-driven builders will ask themselves: "Why am I doing this?"
The Path Forward
I don't know enough about finance to fully understand everything Jack is building with 21 Capital. Neither do most of his critics. But I know enough about Bitcoin to recognise someone who's been fighting the good fight for over a decade.
This doesn't mean we should trust blindly. It doesn't mean we should stop asking questions or demanding transparency. But it does mean we should approach our builders with the same benefit of the doubt we'd want for ourselves.
We need to distinguish between healthy skepticism and destructive paranoia. Between holding people accountable and tearing them down. Between being vigilant and being looters.
The fiat system is the real enemy here. It's massive, entrenched, and infinitely resourcesful. It will adapt, co-opt, and corrupt everything it touches. Fighting it requires builders who are willing to get their hands dirty, navigate imperfect systems, and make pragmatic compromises while holding onto their core values.
We can continue to be looters, tearing down what we don't understand and driving our best builders toward their own version of Atlantis. Or we can be what we claim to be: supporters of the free market, believers of proof of work, and champions of those building the future.
Don't trust. Verify. But remember: verification works both ways.
-
 @ ec42c765:328c0600
2025-02-05 23:38:12
@ ec42c765:328c0600
2025-02-05 23:38:12カスタム絵文字とは
任意のオリジナル画像を絵文字のように文中に挿入できる機能です。
また、リアクション(Twitterの いいね のような機能)にもカスタム絵文字を使えます。

カスタム絵文字の対応状況(2025/02/06)

カスタム絵文字を使うためにはカスタム絵文字に対応したクライアントを使う必要があります。
※表は一例です。クライアントは他にもたくさんあります。
使っているクライアントが対応していない場合は、クライアントを変更する、対応するまで待つ、開発者に要望を送る(または自分で実装する)などしましょう。
対応クライアント
ここではnostterを使って説明していきます。
準備
カスタム絵文字を使うための準備です。
- Nostrエクステンション(NIP-07)を導入する
- 使いたいカスタム絵文字をリストに登録する
Nostrエクステンション(NIP-07)を導入する
Nostrエクステンションは使いたいカスタム絵文字を登録する時に必要になります。
また、環境(パソコン、iPhone、androidなど)によって導入方法が違います。
Nostrエクステンションを導入する端末は、実際にNostrを閲覧する端末と違っても構いません(リスト登録はPC、Nostr閲覧はiPhoneなど)。
Nostrエクステンション(NIP-07)の導入方法は以下のページを参照してください。
ログイン拡張機能 (NIP-07)を使ってみよう | Welcome to Nostr! ~ Nostrをはじめよう! ~
少し面倒ですが、これを導入しておくとNostr上の様々な場面で役立つのでより快適になります。
使いたいカスタム絵文字をリストに登録する
以下のサイトで行います。
右上のGet startedからNostrエクステンションでログインしてください。
例として以下のカスタム絵文字を導入してみます。
実際より絵文字が少なく表示されることがありますが、古い状態のデータを取得してしまっているためです。その場合はブラウザの更新ボタンを押してください。

- 右側のOptionsからBookmarkを選択

これでカスタム絵文字を使用するためのリストに登録できます。
カスタム絵文字を使用する
例としてブラウザから使えるクライアント nostter から使用してみます。
nostterにNostrエクステンションでログイン、もしくは秘密鍵を入れてログインしてください。
文章中に使用
- 投稿ボタンを押して投稿ウィンドウを表示
- 顔😀のボタンを押し、絵文字ウィンドウを表示
- *タブを押し、カスタム絵文字一覧を表示
- カスタム絵文字を選択
- : 記号に挟まれたアルファベットのショートコードとして挿入される

この状態で投稿するとカスタム絵文字として表示されます。
カスタム絵文字対応クライアントを使っている他ユーザーにもカスタム絵文字として表示されます。
対応していないクライアントの場合、ショートコードのまま表示されます。

ショートコードを直接入力することでカスタム絵文字の候補が表示されるのでそこから選択することもできます。

リアクションに使用
- 任意の投稿の顔😀のボタンを押し、絵文字ウィンドウを表示
- *タブを押し、カスタム絵文字一覧を表示
- カスタム絵文字を選択

カスタム絵文字リアクションを送ることができます。

カスタム絵文字を探す
先述したemojitoからカスタム絵文字を探せます。
例えば任意のユーザーのページ emojito ロクヨウ から探したり、 emojito Browse all からnostr全体で最近作成、更新された絵文字を見たりできます。
また、以下のリンクは日本語圏ユーザーが作ったカスタム絵文字を集めたリストです(2025/02/06)
※漏れがあるかもしれません
各絵文字セットにあるOpen in emojitoのリンクからemojitoに飛び、使用リストに追加できます。
以上です。
次:Nostrのカスタム絵文字の作り方
Yakihonneリンク Nostrのカスタム絵文字の作り方
Nostrリンク nostr:naddr1qqxnzdesxuunzv358ycrgveeqgswcsk8v4qck0deepdtluag3a9rh0jh2d0wh0w9g53qg8a9x2xqvqqrqsqqqa28r5psx3
仕様
-
 @ 6ad3e2a3:c90b7740
2025-06-04 08:32:29
@ 6ad3e2a3:c90b7740
2025-06-04 08:32:29"Modern science is based on this principle: give us one free miracle and then we'll explain the rest."
— Terrence McKenna
I always wondered why a pot of water boils on the stove. I mean I know it boils because I turned on the electricity, but why does the electricity cause it to boil? I know the electricity produces heat, and the heat is conducted through the stainless steel pot and into the water, but why does the heat transfer from stovetop to the water?
I know the heat from the stove via the pot speeds up the molecules in the water touching it and that they in turn speed up the molecules touching them and so on throughout the pot, but why do speedy molecules cause adjacent molecules to speed up?
I mean I know they do this, but why do they do this? Why couldn’t it be that sped-up molecules only interact with sufficient speedy molecules and ignore slower ones? Why do they interact with all the molecules, causing all of them to speed up? Or why don’t the speedy ones, instead of sharing their excited state, hoard it and take more energy from adjacent slower molecules, thereby making them colder, i.e., why doesn’t half the water boil twice as fast (on the left side of the pot) while the other half (right side) turns to ice?
The molecules tend to bounce around randomly, interacting as equal opportunists on the surrounding ones rather than distinguishing only certain ones with which to interact. Why do the laws of thermodynamics behave as such rather than some other way?
There may be yet deeper layers to this, explanations going down to the atomic and even quantum levels, but no matter how far you take them, you are always, in the end, left with: “Because those are the laws of physics”, i.e., “because that’s just how it is.”
. . .
The Terrence McKenna quote, recently cited by Joe Rogan on his podcast, refers to the Big Bang, the current explanation adopted by the scientifically literate as to the origins of the universe. You see there was this insanely dense, infinitesimally small micro dot that one day (before the dawn of time) exploded outward with unimaginable power that over billions of years created what we perceive as the known universe.
What happened prior? Can’t really say because time didn’t yet exist, and “prior” doesn’t make sense in that context. Why did it do this? We don’t know. How did it get there? Maybe a supermassive black hole from another universe got too dense and exploded out the other side? Highly speculative.
So why do people believe in the Big Bang? Because it comports with and explains certain observable phenomena and predicted other phenomena which were subsequently confirmed. But scratch a little deeper for an explanation as to what caused it, for what purpose did it occur or what preceded it, and you hit the same wall.
. . .
Even if we were to understand at a quantum level how and why the Big Bang happened and what preceded it, let’s assume it’s due to Factor X, something we eventually replicated with mini big-bangs and universe creations in our labs, we would still be tasked with understanding why Factor X exists in the universe. And if Factor X were explained by Process Y, we’d still be stuck needing an explanation for Process Y — ad infinitum.
Science can thus only push the wall back farther, but can never scale it. We can never arrive at an ultimate explanation, only partial ones. Its limitations are the limitations of thought itself, the impossibility of ever creating a map at a scale of one mile per mile.
-
 @ b1ddb4d7:471244e7
2025-06-04 07:01:24
@ b1ddb4d7:471244e7
2025-06-04 07:01:24Bitcoin FilmFest (BFF25) returns to Warsaw for its third edition, blending independent cinema—from feature films and commercials to AI-driven experimental visuals—with education and entertainment.
Hundreds of attendees from around the world will gather for three days of screenings, discussions, workshops, and networking at the iconic Kinoteka Cinema (PKiN), the same venue that hosted the festival’s first two editions in March 2023 and April 2024.
This year’s festival, themed “Beyond the Frame,” introduces new dimensions to its program, including an extra day on May 22 to celebrate Bitcoin Pizza Day, the first real-world bitcoin transaction, with what promises to be one of Europe’s largest commemorations of this milestone.
BFF25 bridges independent film, culture, and technology, with a bold focus on decentralized storytelling and creative expression. As a community-driven cultural experience with a slightly rebellious spirit, Bitcoin FilmFest goes beyond movies, yet cinema remains at its heart.
Here’s a sneak peek at the lineup, specially curated for movie buffs:
 Generative Cinema – A special slot with exclusive shorts and a thematic debate on the intersection of AI and filmmaking. Featured titles include, for example: BREAK FREE, SATOSHI: THE CREATION OF BITCOIN, STRANGE CURRENCIES, and BITCOIN IS THE MYCELIUM OF MONEY, exploring financial independence, traps of the fiat system, and a better future built on sound money.
Generative Cinema – A special slot with exclusive shorts and a thematic debate on the intersection of AI and filmmaking. Featured titles include, for example: BREAK FREE, SATOSHI: THE CREATION OF BITCOIN, STRANGE CURRENCIES, and BITCOIN IS THE MYCELIUM OF MONEY, exploring financial independence, traps of the fiat system, and a better future built on sound money. Upcoming Productions Preview – A bit over an hour-long block of unreleased pilots and works-in-progress. Attendees will get exclusive first looks at projects like FINDING HOME (a travel-meets-personal-journey series), PARALLEL SPACES (a story about alternative communities), and THE LEGEND OF LANDI (a mysterious narrative).
Upcoming Productions Preview – A bit over an hour-long block of unreleased pilots and works-in-progress. Attendees will get exclusive first looks at projects like FINDING HOME (a travel-meets-personal-journey series), PARALLEL SPACES (a story about alternative communities), and THE LEGEND OF LANDI (a mysterious narrative). Freedom-Focused Ads & Campaigns – Unique screenings of video commercials, animations, and visual projects, culminating in “The PoWies” (Proof of Work-ies)—the first ever awards show honoring the best Bitcoin-only awareness campaigns.
Freedom-Focused Ads & Campaigns – Unique screenings of video commercials, animations, and visual projects, culminating in “The PoWies” (Proof of Work-ies)—the first ever awards show honoring the best Bitcoin-only awareness campaigns.To get an idea of what might come up at the event, here, you can preview 6 selected ads combined into two 2 videos:
 Open Pitch Competition – A chance for filmmakers to present fresh ideas and unfinished projects to an audience of a dedicated jury, movie fans and potential collaborators. This competitive block isn’t just entertaining—it’s a real opportunity for creators to secure funding and partnerships.
Open Pitch Competition – A chance for filmmakers to present fresh ideas and unfinished projects to an audience of a dedicated jury, movie fans and potential collaborators. This competitive block isn’t just entertaining—it’s a real opportunity for creators to secure funding and partnerships. Golden Rabbit Awards: A lively gala honoring films from the festival’s Official Selection, with awards in categories like Best Feature, Best Story, Best Short, and Audience Choice.
Golden Rabbit Awards: A lively gala honoring films from the festival’s Official Selection, with awards in categories like Best Feature, Best Story, Best Short, and Audience Choice.BFF25 Main Screenings
Sample titles from BFF25’s Official Selection:
 REVOLUCIÓN BITCOIN – A documentary by Juan Pablo, making its first screening outside the Spanish-speaking world in Warsaw this May. Three years of important work, 80 powerful minutes to experience. The film explores Bitcoin’s impact across Argentina, Colombia, Mexico, El Salvador, and Spain through around 40 diverse perspectives. Screening in Spanish with English subtitles, followed by a Q&A with the director.
REVOLUCIÓN BITCOIN – A documentary by Juan Pablo, making its first screening outside the Spanish-speaking world in Warsaw this May. Three years of important work, 80 powerful minutes to experience. The film explores Bitcoin’s impact across Argentina, Colombia, Mexico, El Salvador, and Spain through around 40 diverse perspectives. Screening in Spanish with English subtitles, followed by a Q&A with the director. UNBANKABLE – Luke Willms’ directorial debut, drawing from his multicultural roots and his father’s pioneering HIV/AIDS research. An investigative documentary based on Luke’s journeys through seven African countries, diving into financial experiments and innovations—from mobile money and digital lending to Bitcoin—raising smart questions and offering potential lessons for the West. Its May appearance at BFF25 marks its largest European event to date, following festival screenings and nominations across multiple continents over the past year.
UNBANKABLE – Luke Willms’ directorial debut, drawing from his multicultural roots and his father’s pioneering HIV/AIDS research. An investigative documentary based on Luke’s journeys through seven African countries, diving into financial experiments and innovations—from mobile money and digital lending to Bitcoin—raising smart questions and offering potential lessons for the West. Its May appearance at BFF25 marks its largest European event to date, following festival screenings and nominations across multiple continents over the past year. HOTEL BITCOIN – A Spanish comedy directed by Manuel Sanabria and Carlos “Pocho” Villaverde. Four friends, 4,000 bitcoins , and one laptop spark a chaotic adventure of parties, love, crime, and a dash of madness. Exploring sound money, value, and relationships through a twisting plot. The film premiered at the Tarazona and Moncayo Comedy Film Festival in August 2024. Its Warsaw screening at BFF25 (in Spanish with English subtitles) marks its first public showing outside the Spanish-speaking world.
HOTEL BITCOIN – A Spanish comedy directed by Manuel Sanabria and Carlos “Pocho” Villaverde. Four friends, 4,000 bitcoins , and one laptop spark a chaotic adventure of parties, love, crime, and a dash of madness. Exploring sound money, value, and relationships through a twisting plot. The film premiered at the Tarazona and Moncayo Comedy Film Festival in August 2024. Its Warsaw screening at BFF25 (in Spanish with English subtitles) marks its first public showing outside the Spanish-speaking world.Check out trailers for this year’s BFF25 and past editions on YouTube.
Tickets & Info:
- Detailed program and tickets are available at bitcoinfilmfest.com/bff25.
- Stay updated via the festival’s official channels (links provided on the website).
- Use ‘LN-NEWS’ to get 10% of tickets
-
 @ dfa02707:41ca50e3
2025-06-05 04:02:14
@ dfa02707:41ca50e3
2025-06-05 04:02:14Contribute to keep No Bullshit Bitcoin news going.
- RoboSats v0.7.7-alpha is now available!
NOTE: "This version of clients is not compatible with older versions of coordinators. Coordinators must upgrade first, make sure you don't upgrade your client while this is marked as pre-release."
- This version brings a new and improved coordinators view with reviews signed both by the robot and the coordinator, adds market price sources in coordinator profiles, shows a correct warning for canceling non-taken orders after a payment attempt, adds Uzbek sum currency, and includes package library updates for coordinators.

Source: RoboSats.
- siggy47 is writing daily RoboSats activity reviews on stacker.news. Check them out here.
- Stay up-to-date with RoboSats on Nostr.
What's new
- New coordinators view (see the picture above).
- Available coordinator reviews signed by both the robot and the coordinator.
- Coordinators now display market price sources in their profiles.

Source: RoboSats.
- Fix for wrong message on cancel button when taking an order. Users are now warned if they try to cancel a non taken order after a payment attempt.
- Uzbek sum currency now available.
- For coordinators: library updates.
- Add docker frontend (#1861).
- Add order review token (#1869).
- Add UZS migration (#1875).
- Fixed tests review (#1878).
- Nostr pubkey for Robot (#1887).
New contributors

Full Changelog: v0.7.6-alpha...v0.7.7-alpha
-
 @ 2e8970de:63345c7a
2025-06-05 16:07:04
@ 2e8970de:63345c7a
2025-06-05 16:07:04https://x.com/jburnmurdoch/status/1930203297396249067
https://www.dropbox.com/scl/fi/1lp1dwzx608xdu8jfpkqk/FT_GENDER_DIVIDE_SXSW.pptx?rlkey=9gcwvn77zss3k5l5vgiquennl&e=1&st=apgyr3ug&dl=0
https://stacker.news/items/998014
-
 @ ec42c765:328c0600
2025-02-05 23:16:35
@ ec42c765:328c0600
2025-02-05 23:16:35てすと
nostr:nevent1qqst3uqlls4yr9vys4dza2sgjle3ly37trck7jgdmtr23uuz52usjrqqqnjgr
nostr:nevent1qqsdvchy5d27zt3z05rr3q6vvmzgslslxwu0p4dfkvxwhmvxldn9djguvagp2
test
てs
-
 @ b2d670de:907f9d4a
2025-02-28 16:39:38
@ b2d670de:907f9d4a
2025-02-28 16:39:38onion-service-nostr-relays
A list of nostr relays exposed as onion services.
The list
| Relay name | Description | Onion url | Operator | Payment URL | Payment options | | --- | --- | --- | --- | --- | --- | | nostr.oxtr.dev | Same relay as clearnet relay nostr.oxtr.dev | ws://oxtrdevav64z64yb7x6rjg4ntzqjhedm5b5zjqulugknhzr46ny2qbad.onion | operator | N/A | N/A | | relay.snort.social | Same relay as clearnet relay relay.snort.social | wss://skzzn6cimfdv5e2phjc4yr5v7ikbxtn5f7dkwn5c7v47tduzlbosqmqd.onion | operator | N/A | N/A | | nostr.thesamecat.io | Same relay as clearnet relay nostr.thesamecat.io | ws://2jsnlhfnelig5acq6iacydmzdbdmg7xwunm4xl6qwbvzacw4lwrjmlyd.onion | operator | N/A | N/A | | nostr.land | The nostr.land paid relay (same as clearnet) | ws://nostrland2gdw7g3y77ctftovvil76vquipymo7tsctlxpiwknevzfid.onion | operator | Payment URL | BTC LN | | bitcoiner.social | No auth required, currently | ws://bitcoinr6de5lkvx4tpwdmzrdfdpla5sya2afwpcabjup2xpi5dulbad.onion | operator | N/A | N/A | | relay.westernbtc.com | The westernbtc.com paid relay | ws://westbtcebhgi4ilxxziefho6bqu5lqwa5ncfjefnfebbhx2cwqx5knyd.onion | operator | Payment URL | BTC LN | | freelay.sovbit.host | Free relay for sovbit.host | ws://sovbitm2enxfr5ot6qscwy5ermdffbqscy66wirkbsigvcshumyzbbqd.onion | operator | N/A | N/A | | nostr.sovbit.host | Paid relay for sovbit.host | ws://sovbitgz5uqyh7jwcsudq4sspxlj4kbnurvd3xarkkx2use3k6rlibqd.onion | operator | N/A | N/A | | nostr.wine | 🍷 nostr.wine relay | ws://nostrwinemdptvqukjttinajfeedhf46hfd5bz2aj2q5uwp7zros3nad.onion | operator | Payment URL | BTC LN, BTC, Credit Card/CashApp (Stripe) | | inbox.nostr.wine | 🍷 inbox.nostr.wine relay | ws://wineinboxkayswlofkugkjwhoyi744qvlzdxlmdvwe7cei2xxy4gc6ad.onion | operator | Payment URL | BTC LN, BTC | | filter.nostr.wine | 🍷 filter.nostr.wine proxy relay | ws://winefiltermhqixxzmnzxhrmaufpnfq3rmjcl6ei45iy4aidrngpsyid.onion | operator | Payment URL | BTC LN, BTC | | N/A | N/A | ws://pzfw4uteha62iwkzm3lycabk4pbtcr67cg5ymp5i3xwrpt3t24m6tzad.onion:81 | operator | N/A | N/A | | nostr.fractalized.net | Free relay for fractalized.net | ws://xvgox2zzo7cfxcjrd2llrkthvjs5t7efoalu34s6lmkqhvzvrms6ipyd.onion | operator | N/A | N/A | | nfrelay.app | nfrelay.app aggregator relay (nostr-filter-relay) | ws://nfrelay6saohkmipikquvrn6d64dzxivhmcdcj4d5i7wxis47xwsriyd.onion | operator | N/A | N/A | relay.nostr.net | Public relay from nostr.net (Same as clearnet) | ws://nostrnetl6yd5whkldj3vqsxyyaq3tkuspy23a3qgx7cdepb4564qgqd.onion | operator | N/A | N/A | | nerostrator | Free to read, pay XMR to relay | ws://nerostrrgb5fhj6dnzhjbgmnkpy2berdlczh6tuh2jsqrjok3j4zoxid.onion | operator |Payment URL | XMR | | nostr.girino.org | Public relay from nostr.girino.org | ws://gnostr2jnapk72mnagq3cuykfon73temzp77hcbncn4silgt77boruid.onion | operator | N/A | N/A | | wot.girino.org | WoT relay from wot.girino.org | ws://girwot2koy3kvj6fk7oseoqazp5vwbeawocb3m27jcqtah65f2fkl3yd.onion | operator | N/A | N/A | | haven.girino.org/{outbox, inbox, chat, private} | Haven smart relay from haven.girino.org | ws://ghaven2hi3qn2riitw7ymaztdpztrvmm337e2pgkacfh3rnscaoxjoad.onion/{outbox, inbox, chat, private} | operator | N/A | N/A | | relay.nostpy.lol | Free Web of Trust relay (Same as clearnet) | ws://pemgkkqjqjde7y2emc2hpxocexugbixp42o4zymznil6zfegx5nfp4id.onion | operator |N/A | N/A | | Poster.place Nostr Relay | N/A | ws://dmw5wbawyovz7fcahvguwkw4sknsqsalffwctioeoqkvvy7ygjbcuoad.onion | operator | N/A | N/A | | Azzamo Relay | Azzamo Premium Nostr relay. (paid) | ws://q6a7m5qkyonzb5fk5yv4jyu3ar44hqedn7wjopg737lit2ckkhx2nyid.onion | operator | Payment URL | BTC LN | | Azzamo Inbox Relay | Azzamo Group and Private message relay. (Freemium) | ws://gp5kiwqfw7t2fwb3rfts2aekoph4x7pj5pv65re2y6hzaujsxewanbqd.onion | operator | Payment URL | BTC LN | | Noderunners Relay | The official Noderunners Nostr Relay. | ws://35vr3xigzjv2xyzfyif6o2gksmkioppy4rmwag7d4bqmwuccs2u4jaid.onion | operator | Payment URL | BTC LN |
Contributing
Contributions are encouraged to keep this document alive. Just open a PR and I'll have it tested and merged. The onion URL is the only mandatory column, the rest is just nice-to-have metadata about the relay. Put
N/Ain empty columns.If you want to contribute anonymously, please contact me on SimpleX or send a DM on nostr using a disposable npub.
Operator column
It is generally preferred to use something that includes a NIP-19 string, either just the string or a url that contains the NIP-19 string in it (e.g. an njump url).
-
 @ 460c25e6:ef85065c
2025-02-25 15:20:39
@ 460c25e6:ef85065c
2025-02-25 15:20:39If you don't know where your posts are, you might as well just stay in the centralized Twitter. You either take control of your relay lists, or they will control you. Amethyst offers several lists of relays for our users. We are going to go one by one to help clarify what they are and which options are best for each one.
Public Home/Outbox Relays
Home relays store all YOUR content: all your posts, likes, replies, lists, etc. It's your home. Amethyst will send your posts here first. Your followers will use these relays to get new posts from you. So, if you don't have anything there, they will not receive your updates.
Home relays must allow queries from anyone, ideally without the need to authenticate. They can limit writes to paid users without affecting anyone's experience.
This list should have a maximum of 3 relays. More than that will only make your followers waste their mobile data getting your posts. Keep it simple. Out of the 3 relays, I recommend: - 1 large public, international relay: nos.lol, nostr.mom, relay.damus.io, etc. - 1 personal relay to store a copy of all your content in a place no one can delete. Go to relay.tools and never be censored again. - 1 really fast relay located in your country: paid options like http://nostr.wine are great
Do not include relays that block users from seeing posts in this list. If you do, no one will see your posts.
Public Inbox Relays
This relay type receives all replies, comments, likes, and zaps to your posts. If you are not getting notifications or you don't see replies from your friends, it is likely because you don't have the right setup here. If you are getting too much spam in your replies, it's probably because your inbox relays are not protecting you enough. Paid relays can filter inbox spam out.
Inbox relays must allow anyone to write into them. It's the opposite of the outbox relay. They can limit who can download the posts to their paid subscribers without affecting anyone's experience.
This list should have a maximum of 3 relays as well. Again, keep it small. More than that will just make you spend more of your data plan downloading the same notifications from all these different servers. Out of the 3 relays, I recommend: - 1 large public, international relay: nos.lol, nostr.mom, relay.damus.io, etc. - 1 personal relay to store a copy of your notifications, invites, cashu tokens and zaps. - 1 really fast relay located in your country: go to nostr.watch and find relays in your country
Terrible options include: - nostr.wine should not be here. - filter.nostr.wine should not be here. - inbox.nostr.wine should not be here.
DM Inbox Relays
These are the relays used to receive DMs and private content. Others will use these relays to send DMs to you. If you don't have it setup, you will miss DMs. DM Inbox relays should accept any message from anyone, but only allow you to download them.
Generally speaking, you only need 3 for reliability. One of them should be a personal relay to make sure you have a copy of all your messages. The others can be open if you want push notifications or closed if you want full privacy.
Good options are: - inbox.nostr.wine and auth.nostr1.com: anyone can send messages and only you can download. Not even our push notification server has access to them to notify you. - a personal relay to make sure no one can censor you. Advanced settings on personal relays can also store your DMs privately. Talk to your relay operator for more details. - a public relay if you want DM notifications from our servers.
Make sure to add at least one public relay if you want to see DM notifications.
Private Home Relays
Private Relays are for things no one should see, like your drafts, lists, app settings, bookmarks etc. Ideally, these relays are either local or require authentication before posting AND downloading each user\'s content. There are no dedicated relays for this category yet, so I would use a local relay like Citrine on Android and a personal relay on relay.tools.
Keep in mind that if you choose a local relay only, a client on the desktop might not be able to see the drafts from clients on mobile and vice versa.
Search relays:
This is the list of relays to use on Amethyst's search and user tagging with @. Tagging and searching will not work if there is nothing here.. This option requires NIP-50 compliance from each relay. Hit the Default button to use all available options on existence today: - nostr.wine - relay.nostr.band - relay.noswhere.com
Local Relays:
This is your local storage. Everything will load faster if it comes from this relay. You should install Citrine on Android and write ws://localhost:4869 in this option.
General Relays:
This section contains the default relays used to download content from your follows. Notice how you can activate and deactivate the Home, Messages (old-style DMs), Chat (public chats), and Global options in each.
Keep 5-6 large relays on this list and activate them for as many categories (Home, Messages (old-style DMs), Chat, and Global) as possible.
Amethyst will provide additional recommendations to this list from your follows with information on which of your follows might need the additional relay in your list. Add them if you feel like you are missing their posts or if it is just taking too long to load them.
My setup
Here's what I use: 1. Go to relay.tools and create a relay for yourself. 2. Go to nostr.wine and pay for their subscription. 3. Go to inbox.nostr.wine and pay for their subscription. 4. Go to nostr.watch and find a good relay in your country. 5. Download Citrine to your phone.
Then, on your relay lists, put:
Public Home/Outbox Relays: - nostr.wine - nos.lol or an in-country relay. -
.nostr1.com Public Inbox Relays - nos.lol or an in-country relay -
.nostr1.com DM Inbox Relays - inbox.nostr.wine -
.nostr1.com Private Home Relays - ws://localhost:4869 (Citrine) -
.nostr1.com (if you want) Search Relays - nostr.wine - relay.nostr.band - relay.noswhere.com
Local Relays - ws://localhost:4869 (Citrine)
General Relays - nos.lol - relay.damus.io - relay.primal.net - nostr.mom
And a few of the recommended relays from Amethyst.
Final Considerations
Remember, relays can see what your Nostr client is requesting and downloading at all times. They can track what you see and see what you like. They can sell that information to the highest bidder, they can delete your content or content that a sponsor asked them to delete (like a negative review for instance) and they can censor you in any way they see fit. Before using any random free relay out there, make sure you trust its operator and you know its terms of service and privacy policies.
-
 @ 4fe4a528:3ff6bf06
2025-02-01 13:41:28
@ 4fe4a528:3ff6bf06
2025-02-01 13:41:28
In my last article I wrote about NOSTR. I found another local bitcoiner via NOSTR last week so here is why it is important to join / use NOSTR — start telling people “Look me up on NOSTR”
Self-sovereign identity (SSI) is a revolutionary approach to digital identity that puts individuals in control of their own identity and personal data. Unlike traditional digital identity models, which rely on third-party organizations to manage and authenticate identities, SSI empowers individuals to own and manage their digital identity.
This approach is made possible by emerging technologies such as secure public / private key pairs. Decentralized identifiers, conceived and developed by nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 is an attempt to create a global technical standard around cryptographically secured identifiers - a secure, universal, and sovereign form of digital ID. This technology uses peer-to-peer technology to remove the need for intermediaries to own and authenticate ID information.
Notably, NOSTR, a decentralized protocol, has already begun to utilize decentralized IDs, demonstrating the potential of this technology in real-world applications. Via NOSTR, users can be sure that the person or computer publishing to a particular npub knows their nsec (password for your npub), highlighting the secure and decentralized nature of this approach.
With SSI, individuals can decide how their personal data is used, shared, and protected, giving them greater control and agency over their digital lives.
The benefits of SSI are numerous, including:
Enhanced security and protection of personal data. Reduced risk of identity theft and fraud Increased autonomy and agency over one's digital identity. Improved scalability and flexibility in digital identity management
challenges:
Ensuring the security and integrity of decentralized identity systems. Developing standards and protocols for interoperability and compatibility. Addressing concerns around ownership and control of personal data. Balancing individual autonomy with the need for verification and authentication in various contexts.
Overall, self-sovereign identity has the potential to transform the way we think about digital identity and provide individuals with greater control and agency over their personal data. Without people in control of their bitcoin seed words no freedom loving people would be able to exchange their money with others. Yes, keep enjoying using the only free market on the planet BITCOIN. Long live FREEDOM!
-
 @ 472f440f:5669301e
2025-06-04 01:37:37
@ 472f440f:5669301e
2025-06-04 01:37:37Marty's Bent
via nostr:nprofile1qyxhwumn8ghj7mn0wvhxcmmvqy0hwumn8ghj7mn0wd68yttjv4kxz7fwvf5hgcm0d9hzumnfde4xzqpq85h9z5yxn8uc7retm0n6gkm88358lejzparxms5kmy9epr236k2qtyz2zr
A lot of the focus over the last couple of months has been on the emergence of Strategy competitors in public markets looking to build sizable bitcoin treasuries and attract investors of all shapes and sizes to drive shareholder value. The other big topic in the bitcoin development world has been around OP_RETURN and the debate over whether or not the amount of data that can be shoved into a bitcoin transaction should be decided by the dominant implementation.
A topic that is just as, if not more, important that is not getting enough appreciation is the discussion around open source bitcoin developers and the lingering effects of the Biden administration's attack on Samourai Wallet and Tornado Cash. If you read our friend Matt Corallo's tweet above, you'll notice that the lingering effects are such that even though the Trump administration has made concerted efforts to reverse the effects of Operation Chokepoint 2.0 that were levied by the Biden administration, Elizabeth Warren, and her friends at the Treasury and SEC - it is imperative that we enshrine into law the rights of open source developers to build products and services that enable individuals to self-custody bitcoin and use it in a peer-to-peer fashion without the threat of getting thrown in jail cell.
As it stands today, the only assurances that we have are from an administration that is overtly in favor of the proliferation of bitcoin in the United States. There is nothing in place to stop the next administration or another down the line from reverting to Biden-era lawfare that puts thousands of bitcoin developers around the world at risk of being sent into a cage because the government doesn't like how some users leverage the code they write. To make sure that this isn't a problem down the line it is imperative that we pass the Blockchain Regulatory Clarity Act, which would not hold bitcoin developers liable for the ways in which end users leverage their tools.
Not only is this an act that would protect developers from pernicious government officials targeting them when end users use their technology in a way that doesn't make the government happy, it will also protect YOU, the end user, looking to transact in a peer-to-peer fashion and leverage all of the incredible properties of bitcoin the way they were meant to be. If the developers are not protected, they will not be able to build the technology that enables you to leverage bitcoin.
So do your part and go to saveourwallets.org. Reach out to your local representatives in Congress and Senators and make some noise. Let them know that this is something that you care deeply about and that they should not only pay attention to this bill but push it forward and enshrine it into law as quickly as possible.
There are currently many developers either behind bars or under house arrest for developing software that gives you the ability to use Bitcoin in a self-sovereign fashion and use it in a privacy-preserving way. Financial privacy isn't a crime. It is an inalienable human right that should be protected at all cost. The enshrinement of this inalienable right into law is way past due.
#FreeSamourai #FreeRoman
Headlines of the Day
MicroStrategy Copycats See Speculative Premiums Fade - via X
Square Tests Bitcoin Payments, Lightning Yields Beat DeFi - via X
Get our new STACK SATS hat - via tftcmerch.io
Bitfinex Moves $731M Bitcoin to Jack Mallers' Fund - via X
Take the First Step Off the Exchange
Bitkey is an easy, secure way to move your Bitcoin into self-custody. With simple setup and built-in recovery, it’s the perfect starting point for getting your coins off centralized platforms and into cold storage—no complexity, no middlemen.
Take control. Start with Bitkey.
Use the promo code “TFTC20” during checkout for 20% off
Ten31, the largest bitcoin-focused investor, has deployed $150.00M across 30+ companies through three funds. I am a Managing Partner at Ten31 and am very proud of the work we are doing. Learn more at ten31.vc/invest.
Final thought...
Should I join a country club?
Get this newsletter sent to your inbox daily: https://www.tftc.io/bitcoin-brief/
Subscribe to our YouTube channels and follow us on Nostr and X:
-
 @ 20e7c953:3b8bcb21
2025-06-05 10:46:07
@ 20e7c953:3b8bcb21
2025-06-05 10:46:0721… That number means something. A reminder that limits create value - both in Bitcoin and in life.
Every June 21st, skaters around the world remind us that freedom is something you make yourself - one push at a time only constrained by your own limitations.
This year in Vientiane, we’re proud to support one of the few real skate spots in Laos. A place built and held together by skaters for skaters.
Expect around 50 locals - from young kids to older heads - showing up not just to skate, but to hold space for each other. No ego, no filters, just boards, fun and respect.
Bircoiners have lots to learn from these communities on this regard. Go skate and you'll find out.

SnF
Laostr
Skateboardingisfun
Skate4Fun
Skatestr
-
 @ da8b7de1:c0164aee
2025-06-03 19:31:32
@ da8b7de1:c0164aee
2025-06-03 19:31:32Lengyelország előrelépése az első atomerőmű építésében
Lengyelország állami nukleáris vállalata, a Polskie Elektrownie Jadrowe (PEJ) és egy amerikai konzorcium – élén a Westinghouse és a Bechtel cégekkel – mérnöki fejlesztési megállapodást kötött. Ez a szerződés kulcsfontosságú lépés az ország első atomerőművének megvalósítása felé, lehetővé téve a részletes mérnöki és helyszínspecifikus munkák megkezdését. A lengyel kormány ezt mérföldkőnek tekinti az energiaszuverenitás és a dekarbonizáció felé vezető úton.
Amerikai politika: lendület az új nukleáris technológiáknak
Az Egyesült Államok kormánya elnöki rendeletet adott ki, amely reformokat vezet be a nukleáris reaktorok tesztelésében az Energiaügyi Minisztériumnál. A cél az új generációs reaktorok – köztük mikroreaktorok és kis moduláris reaktorok (SMR-ek) – fejlesztésének és engedélyezésének felgyorsítása, valamint a környezetvédelmi vizsgálatok egyszerűsítése. A rendelet legalább három új reaktor kritikus üzembe helyezését célozza meg 2026 júliusáig, támogatva ezzel az ipari alkalmazások széles körét, például adatközpontokat vagy hidrogéntermelést. Az intézkedés célja, hogy az USA visszaszerezze vezető szerepét a nukleáris innovációban, és csökkentse a korábbi években felhalmozódott engedélyezési akadályokat.
Kis moduláris reaktorok (SMR) fejlesztése világszerte
Az SMR-szektorban világszerte jelentős előrelépések történtek: - Az amerikai Tennessee Valley Authority (TVA) benyújtotta az első építési kérelmet egy GE Hitachi BWRX-300 SMR-re a Clinch River telephelyen. - Kanadában az Ontario Power Generation engedélyt kapott az első, négy tervezett SMR megépítésének megkezdésére a Darlington telephelyen. - Belgium és Brazília innovatív SMR-technológiákat vizsgál, köztük ólom-hűtésű reaktorokat és nemzetközi együttműködéseket. - Olyan technológiai óriások, mint a Google, az USA-ban korai fázisú fejlett nukleáris projektekbe fektetnek, ami a magánszektor növekvő érdeklődését mutatja.
Globális ipari és pénzügyi támogatás a nukleáris bővítéshez
Széles körű koalíció – köztük olyan nagyvállalatok, mint az Amazon, Google, Meta, Dow – és pénzügyi intézmények kötelezték el magukat amellett, hogy 2050-re megháromszorozzák a globális nukleáris kapacitást. Ez összhangban van az ENSZ klímacsúcsain tett vállalásokkal, ahol már 31 ország támogatja a nukleáris energia megháromszorozását a nettó zéró kibocsátási célok eléréséhez. Az amerikai kongresszus olyan törvényjavaslatokat készít elő, amelyek lehetővé tennék, hogy a multilaterális fejlesztési bankok – például a Világbank – is finanszírozhassanak nukleáris projekteket, megszüntetve ezzel a korábbi tiltásokat.
Közelgő nemzetközi nukleáris biztonsági gyakorlat
A Nemzetközi Atomenergia-ügynökség (IAEA) készül a ConvEx-3 vészhelyzeti gyakorlatára, amelyet 2025. június 24–25-én Romániában tartanak. A gyakorlat egy súlyos nukleáris vészhelyzetet szimulál a cernavodai atomerőműben, tesztelve a tagállamok és nemzetközi szervezetek felkészültségét és reagálóképességét. A ConvEx-3 a legmagasabb szintű IAEA vészhelyzeti gyakorlat, kulcsszerepet játszik a globális nukleáris biztonság és védelem erősítésében.
Politikai bizonytalanság Dél-Korea nukleáris terveiben
Dél-Korea 2025. június 3-i elnökválasztása hatással lehet az ország nukleáris reneszánszára. A vezető jelölt, Lee Jae-myung kijelentette, hogy „egyelőre” fenntartaná a nukleáris energiát, de hosszabb távon a megújulók felé mozdulna el. Ez bizonytalanságot okoz a koreai nukleáris ipar hazai és exportterveiben, ami kihatással lehet a globális ellátási láncokra és külföldi reaktorprojektekre is.
Iparági trendek és további fejlemények
- Japán új energiastratégiája maximalizálni kívánja a nukleáris energia részarányát, 2040-re mintegy 20%-ot célozva, különös hangsúlyt fektetve a következő generációs reaktorokra és a biztonság növelésére.
- Belgium kormánya és a francia Engie közműcég megállapodott a kulcsfontosságú reaktorok üzemidejének tízéves meghosszabbításáról, ami az európai nukleáris pálfordulás újabb jele.
- Az IAEA és a World Nuclear Association egyaránt növekvő nemzetközi érdeklődésről számol be az SMR-ek és fejlett reaktortechnológiák iránt, új projektek és partnerségek indulnak Ázsiában, Európában és Amerikában.
Források:
world-nuclear-news.org
nucnet.org
iaea.org
world-nuclear.org
govinfo.gov
whitehouse.gov -
 @ ec42c765:328c0600
2025-02-05 22:05:55
@ ec42c765:328c0600
2025-02-05 22:05:55カスタム絵文字とは
任意のオリジナル画像を絵文字のように文中に挿入できる機能です。
また、リアクション(Twitterの いいね のような機能)にもカスタム絵文字を使えます。

カスタム絵文字の対応状況(2025/02/06)

カスタム絵文字を使うためにはカスタム絵文字に対応したクライアントを使う必要があります。
※表は一例です。クライアントは他にもたくさんあります。
使っているクライアントが対応していない場合は、クライアントを変更する、対応するまで待つ、開発者に要望を送る(または自分で実装する)などしましょう。
対応クライアント
ここではnostterを使って説明していきます。
準備
カスタム絵文字を使うための準備です。
- Nostrエクステンション(NIP-07)を導入する
- 使いたいカスタム絵文字をリストに登録する
Nostrエクステンション(NIP-07)を導入する
Nostrエクステンションは使いたいカスタム絵文字を登録する時に必要になります。
また、環境(パソコン、iPhone、androidなど)によって導入方法が違います。
Nostrエクステンションを導入する端末は、実際にNostrを閲覧する端末と違っても構いません(リスト登録はPC、Nostr閲覧はiPhoneなど)。
Nostrエクステンション(NIP-07)の導入方法は以下のページを参照してください。
ログイン拡張機能 (NIP-07)を使ってみよう | Welcome to Nostr! ~ Nostrをはじめよう! ~
少し面倒ですが、これを導入しておくとNostr上の様々な場面で役立つのでより快適になります。
使いたいカスタム絵文字をリストに登録する
以下のサイトで行います。
右上のGet startedからNostrエクステンションでログインしてください。
例として以下のカスタム絵文字を導入してみます。
実際より絵文字が少なく表示されることがありますが、古い状態のデータを取得してしまっているためです。その場合はブラウザの更新ボタンを押してください。

- 右側のOptionsからBookmarkを選択

これでカスタム絵文字を使用するためのリストに登録できます。
カスタム絵文字を使用する
例としてブラウザから使えるクライアント nostter から使用してみます。
nostterにNostrエクステンションでログイン、もしくは秘密鍵を入れてログインしてください。
文章中に使用
- 投稿ボタンを押して投稿ウィンドウを表示
- 顔😀のボタンを押し、絵文字ウィンドウを表示
- *タブを押し、カスタム絵文字一覧を表示
- カスタム絵文字を選択
- : 記号に挟まれたアルファベットのショートコードとして挿入される

この状態で投稿するとカスタム絵文字として表示されます。
カスタム絵文字対応クライアントを使っている他ユーザーにもカスタム絵文字として表示されます。
対応していないクライアントの場合、ショートコードのまま表示されます。

ショートコードを直接入力することでカスタム絵文字の候補が表示されるのでそこから選択することもできます。

リアクションに使用
- 任意の投稿の顔😀のボタンを押し、絵文字ウィンドウを表示
- *タブを押し、カスタム絵文字一覧を表示
- カスタム絵文字を選択

カスタム絵文字リアクションを送ることができます。

カスタム絵文字を探す
先述したemojitoからカスタム絵文字を探せます。
例えば任意のユーザーのページ emojito ロクヨウ から探したり、 emojito Browse all からnostr全体で最近作成、更新された絵文字を見たりできます。
また、以下のリンクは日本語圏ユーザーが作ったカスタム絵文字を集めたリストです(2025/02/06)
※漏れがあるかもしれません
各絵文字セットにあるOpen in emojitoのリンクからemojitoに飛び、使用リストに追加できます。
以上です。
次:Nostrのカスタム絵文字の作り方
Yakihonneリンク Nostrのカスタム絵文字の作り方
Nostrリンク nostr:naddr1qqxnzdesxuunzv358ycrgveeqgswcsk8v4qck0deepdtluag3a9rh0jh2d0wh0w9g53qg8a9x2xqvqqrqsqqqa28r5psx3
仕様
-
 @ 3f770d65:7a745b24
2025-01-19 21:48:49
@ 3f770d65:7a745b24
2025-01-19 21:48:49The recent shutdown of TikTok in the United States due to a potential government ban serves as a stark reminder how fragile centralized platforms truly are under the surface. While these platforms offer convenience, a more polished user experience, and connectivity, they are ultimately beholden to governments, corporations, and other authorities. This makes them vulnerable to censorship, regulation, and outright bans. In contrast, Nostr represents a shift in how we approach online communication and content sharing. Built on the principles of decentralization and user choice, Nostr cannot be banned, because it is not a platform—it is a protocol.
PROTOCOLS, NOT PLATFORMS.
At the heart of Nostr's philosophy is user choice, a feature that fundamentally sets it apart from legacy platforms. In centralized systems, the user experience is dictated by a single person or governing entity. If the platform decides to filter, censor, or ban specific users or content, individuals are left with little action to rectify the situation. They must either accept the changes or abandon the platform entirely, often at the cost of losing their social connections, their data, and their identity.
What's happening with TikTok could never happen on Nostr. With Nostr, the dynamics are completely different. Because it is a protocol, not a platform, no single entity controls the ecosystem. Instead, the protocol enables a network of applications and relays that users can freely choose from. If a particular application or relay implements policies that a user disagrees with, such as censorship, filtering, or even government enforced banning, they are not trapped or abandoned. They have the freedom to move to another application or relay with minimal effort.
THIS IS POWERFUL.
Take, for example, the case of a relay that decides to censor specific content. On a legacy platform, this would result in frustration and a loss of access for users. On Nostr, however, users can simply connect to a different relay that does not impose such restrictions. Similarly, if an application introduces features or policies that users dislike, they can migrate to a different application that better suits their preferences, all while retaining their identity and social connections.
The same principles apply to government bans and censorship. A government can ban a specific application or even multiple applications, just as it can block one relay or several relays. China has implemented both tactics, yet Chinese users continue to exist and actively participate on Nostr, demonstrating Nostr's ability to resistant censorship.
How? Simply, it turns into a game of whack-a-mole. When one relay is censored, another quickly takes its place. When one application is banned, another emerges. Users can also bypass these obstacles by running their own relays and applications directly from their homes or personal devices, eliminating reliance on larger entities or organizations and ensuring continuous access.
AGAIN, THIS IS POWERUFL.
Nostr's open and decentralized design makes it resistant to the kinds of government intervention that led to TikTok's outages this weekend and potential future ban in the next 90 days. There is no central server to target, no company to regulate, and no single point of failure. (Insert your CEO jokes here). As long as there are individuals running relays and applications, users continue creating notes and sending zaps.
Platforms like TikTok can be silenced with the stroke of a pen, leaving millions of users disconnected and abandoned. Social communication should not be silenced so incredibly easily. No one should have that much power over social interactions.
Will we on-board a massive wave of TikTokers in the coming hours or days? I don't know.
TikTokers may not be ready for Nostr yet, and honestly, Nostr may not be ready for them either. The ecosystem still lacks the completely polished applications, tools, and services they’re accustomed to. This is where we say "we're still early". They may not be early adopters like the current Nostr user base. Until we bridge that gap, they’ll likely move to the next centralized platform, only to face another government ban or round of censorship in the future. But eventually, there will come a tipping point, a moment when they’ve had enough. When that time comes, I hope we’re prepared. If we’re not, we risk missing a tremendous opportunity to onboard people who genuinely need Nostr’s freedom.
Until then, to all of the Nostr developers out there, keep up the great work and keep building. Your hard work and determination is needed.
-
 @ ec42c765:328c0600
2025-02-05 20:30:46
@ ec42c765:328c0600
2025-02-05 20:30:46カスタム絵文字とは
任意のオリジナル画像を絵文字のように文中に挿入できる機能です。
また、リアクション(Twitterの いいね のような機能)にもカスタム絵文字を使えます。

カスタム絵文字の対応状況(2024/02/05)

カスタム絵文字を使うためにはカスタム絵文字に対応したクライアントを使う必要があります。
※表は一例です。クライアントは他にもたくさんあります。
使っているクライアントが対応していない場合は、クライアントを変更する、対応するまで待つ、開発者に要望を送る(または自分で実装する)などしましょう。
対応クライアント
ここではnostterを使って説明していきます。
準備
カスタム絵文字を使うための準備です。
- Nostrエクステンション(NIP-07)を導入する
- 使いたいカスタム絵文字をリストに登録する
Nostrエクステンション(NIP-07)を導入する
Nostrエクステンションは使いたいカスタム絵文字を登録する時に必要になります。
また、環境(パソコン、iPhone、androidなど)によって導入方法が違います。
Nostrエクステンションを導入する端末は、実際にNostrを閲覧する端末と違っても構いません(リスト登録はPC、Nostr閲覧はiPhoneなど)。
Nostrエクステンション(NIP-07)の導入方法は以下のページを参照してください。
ログイン拡張機能 (NIP-07)を使ってみよう | Welcome to Nostr! ~ Nostrをはじめよう! ~
少し面倒ですが、これを導入しておくとNostr上の様々な場面で役立つのでより快適になります。
使いたいカスタム絵文字をリストに登録する
以下のサイトで行います。
右上のGet startedからNostrエクステンションでログインしてください。
例として以下のカスタム絵文字を導入してみます。
実際より絵文字が少なく表示されることがありますが、古い状態のデータを取得してしまっているためです。その場合はブラウザの更新ボタンを押してください。

- 右側のOptionsからBookmarkを選択

これでカスタム絵文字を使用するためのリストに登録できます。
カスタム絵文字を使用する
例としてブラウザから使えるクライアント nostter から使用してみます。
nostterにNostrエクステンションでログイン、もしくは秘密鍵を入れてログインしてください。
文章中に使用
- 投稿ボタンを押して投稿ウィンドウを表示
- 顔😀のボタンを押し、絵文字ウィンドウを表示
- *タブを押し、カスタム絵文字一覧を表示
- カスタム絵文字を選択
- : 記号に挟まれたアルファベットのショートコードとして挿入される

この状態で投稿するとカスタム絵文字として表示されます。
カスタム絵文字対応クライアントを使っている他ユーザーにもカスタム絵文字として表示されます。
対応していないクライアントの場合、ショートコードのまま表示されます。

ショートコードを直接入力することでカスタム絵文字の候補が表示されるのでそこから選択することもできます。

リアクションに使用
- 任意の投稿の顔😀のボタンを押し、絵文字ウィンドウを表示
- *タブを押し、カスタム絵文字一覧を表示
- カスタム絵文字を選択

カスタム絵文字リアクションを送ることができます。

カスタム絵文字を探す
先述したemojitoからカスタム絵文字を探せます。
例えば任意のユーザーのページ emojito ロクヨウ から探したり、 emojito Browse all からnostr全体で最近作成、更新された絵文字を見たりできます。
また、以下のリンクは日本語圏ユーザーが作ったカスタム絵文字を集めたリストです(2024/06/30)
※漏れがあるかもしれません
各絵文字セットにあるOpen in emojitoのリンクからemojitoに飛び、使用リストに追加できます。
以上です。
次:Nostrのカスタム絵文字の作り方
Yakihonneリンク Nostrのカスタム絵文字の作り方
Nostrリンク nostr:naddr1qqxnzdesxuunzv358ycrgveeqgswcsk8v4qck0deepdtluag3a9rh0jh2d0wh0w9g53qg8a9x2xqvqqrqsqqqa28r5psx3
仕様
-
 @ 59cb0748:9602464b
2025-01-01 06:15:09
@ 59cb0748:9602464b
2025-01-01 06:15:09Nostrでお世話になっている方も、お世話になってない方も、こんにちは!
タコ頭大吉です!
NIP-23を使った初めての投稿です。
今回は、私がここ数ヶ月中にデザインをした三種類のビタキセケースの紹介記事になります!!
ビタキセを買ったもののあまり自分の好みに合う外観や仕様のケースがなく、いくつかプロトタイプを作りそれなりに時間をかけて考えたケース達です。
これら3シリーズに関しては、FDMタイプの3Dプリンタの精度、耐久性、出力後の作業性を考慮して一つのパーツで完結することに拘って設計をしました。
一定以上の充填率でプリントをすればそれなりに丈夫なはずです。
また、基本的に放熱性と保護性を両立できるように設計をしたつもります。
それぞれのモデルについて簡単に紹介をさせていただきますので、よろしければ各リポジトリに付属のREADMEを読んでいただいて自作、フィードバックをいただけましたら幸いです。
それでは、簡単に各モデルの紹介をさせていたきます。
AirLiftFrame
 最初に作ったモデルです!
少し大きいのが難点ですが、分厚めのフレームをベースとし基盤周辺をあえて囲わない設計により、保護性と放熱を阻害しない事の両立を狙っています。
最初に作ったモデルです!
少し大きいのが難点ですが、分厚めのフレームをベースとし基盤周辺をあえて囲わない設計により、保護性と放熱を阻害しない事の両立を狙っています。
TwinAirLiftFrame
 ビタキセを買い増ししたことにより、複数台をカッコよく運用したいという需要が自分の中に出てきたので、AirLiftFrameを2つくっつけたら良いのではと言うごくごく単純な発想でつくり始めたケースです。
しかし、ただ横並びにしただけでは廃熱が干渉するだけではなく、DCジャックやUSBポートへのアクセスが阻害されるという問題にすぐに気がつきました。
そこで、WebUI上でディスプレイの表示を上下反転出来ることに注目し、2台を上下逆向きに取り付ける事でそれらの問題を解決しました!
ビタキセを買い増ししたことにより、複数台をカッコよく運用したいという需要が自分の中に出てきたので、AirLiftFrameを2つくっつけたら良いのではと言うごくごく単純な発想でつくり始めたケースです。
しかし、ただ横並びにしただけでは廃熱が干渉するだけではなく、DCジャックやUSBポートへのアクセスが阻害されるという問題にすぐに気がつきました。
そこで、WebUI上でディスプレイの表示を上下反転出来ることに注目し、2台を上下逆向きに取り付ける事でそれらの問題を解決しました!
VoronoiShell
 AirLiftFrameシリーズのサイズを小型化する事から始めたプロジョクトです。
縦横の寸法の削減だけではなく、厚みを薄くつくリたいという希望がありました。
所が単純に薄くすると、持った時に発熱する背面パーツに手が触れてしまったり、落下などでぶつかった際に背面パーツが破損する懸念がありました。
そこで、(当初は付けたくはなかった)背面保護用のグリルをデザインする必要が出てきました。
初めは多角形でしたがあまりにもダサく、調べている内にVoronoi柄という有機的なパターンに行き付き即採用しました。
結果、ビタキセを取り付けると柄が見えなくなるのが勿体無いぐらい個性的でスタイリッシュなデザインに仕上がりました。
AirLiftFrameシリーズのサイズを小型化する事から始めたプロジョクトです。
縦横の寸法の削減だけではなく、厚みを薄くつくリたいという希望がありました。
所が単純に薄くすると、持った時に発熱する背面パーツに手が触れてしまったり、落下などでぶつかった際に背面パーツが破損する懸念がありました。
そこで、(当初は付けたくはなかった)背面保護用のグリルをデザインする必要が出てきました。
初めは多角形でしたがあまりにもダサく、調べている内にVoronoi柄という有機的なパターンに行き付き即採用しました。
結果、ビタキセを取り付けると柄が見えなくなるのが勿体無いぐらい個性的でスタイリッシュなデザインに仕上がりました。
いずれカスタム方法やインサートナットや増設ファンの選定方法等を紹介したいのですが、今回はNIP-23になれるという意図もあるので紹介に留めます! また、他の関連OSハードウェアプロジェクトのケースもデザインできたらと思っております!
今後ともタコ頭をよろしくお願いいたします。
-
 @ 6389be64:ef439d32
2025-01-14 01:31:12
@ 6389be64:ef439d32
2025-01-14 01:31:12Bitcoin is more than money, more than an asset, and more than a store of value. Bitcoin is a Prime Mover, an enabler and it ignites imaginations. It certainly fueled an idea in my mind. The idea integrates sensors, computational prowess, actuated machinery, power conversion, and electronic communications to form an autonomous, machined creature roaming forests and harvesting the most widespread and least energy-dense fuel source available. I call it the Forest Walker and it eats wood, and mines Bitcoin.
I know what you're thinking. Why not just put Bitcoin mining rigs where they belong: in a hosted facility sporting electricity from energy-dense fuels like natural gas, climate-controlled with excellent data piping in and out? Why go to all the trouble building a robot that digests wood creating flammable gasses fueling an engine to run a generator powering Bitcoin miners? It's all about synergy.
Bitcoin mining enables the realization of multiple, seemingly unrelated, yet useful activities. Activities considered un-profitable if not for Bitcoin as the Prime Mover. This is much more than simply mining the greatest asset ever conceived by humankind. It’s about the power of synergy, which Bitcoin plays only one of many roles. The synergy created by this system can stabilize forests' fire ecology while generating multiple income streams. That’s the realistic goal here and requires a brief history of American Forest management before continuing.
Smokey The Bear
In 1944, the Smokey Bear Wildfire Prevention Campaign began in the United States. “Only YOU can prevent forest fires” remains the refrain of the Ad Council’s longest running campaign. The Ad Council is a U.S. non-profit set up by the American Association of Advertising Agencies and the Association of National Advertisers in 1942. It would seem that the U.S. Department of the Interior was concerned about pesky forest fires and wanted them to stop. So, alongside a national policy of extreme fire suppression they enlisted the entire U.S. population to get onboard via the Ad Council and it worked. Forest fires were almost obliterated and everyone was happy, right? Wrong.
Smokey is a fantastically successful bear so forest fires became so few for so long that the fuel load - dead wood - in forests has become very heavy. So heavy that when a fire happens (and they always happen) it destroys everything in its path because the more fuel there is the hotter that fire becomes. Trees, bushes, shrubs, and all other plant life cannot escape destruction (not to mention homes and businesses). The soil microbiology doesn’t escape either as it is burned away even in deeper soils. To add insult to injury, hydrophobic waxy residues condense on the soil surface, forcing water to travel over the ground rather than through it eroding forest soils. Good job, Smokey. Well done, Sir!
Most terrestrial ecologies are “fire ecologies”. Fire is a part of these systems’ fuel load and pest management. Before we pretended to “manage” millions of acres of forest, fires raged over the world, rarely damaging forests. The fuel load was always too light to generate fires hot enough to moonscape mountainsides. Fires simply burned off the minor amounts of fuel accumulated since the fire before. The lighter heat, smoke, and other combustion gasses suppressed pests, keeping them in check and the smoke condensed into a plant growth accelerant called wood vinegar, not a waxy cap on the soil. These fires also cleared out weak undergrowth, cycled minerals, and thinned the forest canopy, allowing sunlight to penetrate to the forest floor. Without a fire’s heat, many pine tree species can’t sow their seed. The heat is required to open the cones (the seed bearing structure) of Spruce, Cypress, Sequoia, Jack Pine, Lodgepole Pine and many more. Without fire forests can’t have babies. The idea was to protect the forests, and it isn't working.
So, in a world of fire, what does an ally look like and what does it do?
Meet The Forest Walker

For the Forest Walker to work as a mobile, autonomous unit, a solid platform that can carry several hundred pounds is required. It so happens this chassis already exists but shelved.
Introducing the Legged Squad Support System (LS3). A joint project between Boston Dynamics, DARPA, and the United States Marine Corps, the quadrupedal robot is the size of a cow, can carry 400 pounds (180 kg) of equipment, negotiate challenging terrain, and operate for 24 hours before needing to refuel. Yes, it had an engine. Abandoned in 2015, the thing was too noisy for military deployment and maintenance "under fire" is never a high-quality idea. However, we can rebuild it to act as a platform for the Forest Walker; albeit with serious alterations. It would need to be bigger, probably. Carry more weight? Definitely. Maybe replace structural metal with carbon fiber and redesign much as 3D printable parts for more effective maintenance.
The original system has a top operational speed of 8 miles per hour. For our purposes, it only needs to move about as fast as a grazing ruminant. Without the hammering vibrations of galloping into battle, shocks of exploding mortars, and drunken soldiers playing "Wrangler of Steel Machines", time between failures should be much longer and the overall energy consumption much lower. The LS3 is a solid platform to build upon. Now it just needs to be pulled out of the mothballs, and completely refitted with outboard equipment.
The Small Branch Chipper

When I say “Forest fuel load” I mean the dead, carbon containing litter on the forest floor. Duff (leaves), fine-woody debris (small branches), and coarse woody debris (logs) are the fuel that feeds forest fires. Walk through any forest in the United States today and you will see quite a lot of these materials. Too much, as I have described. Some of these fuel loads can be 8 tons per acre in pine and hardwood forests and up to 16 tons per acre at active logging sites. That’s some big wood and the more that collects, the more combustible danger to the forest it represents. It also provides a technically unlimited fuel supply for the Forest Walker system.
The problem is that this detritus has to be chewed into pieces that are easily ingestible by the system for the gasification process (we’ll get to that step in a minute). What we need is a wood chipper attached to the chassis (the LS3); its “mouth”.
A small wood chipper handling material up to 2.5 - 3.0 inches (6.3 - 7.6 cm) in diameter would eliminate a substantial amount of fuel. There is no reason for Forest Walker to remove fallen trees. It wouldn’t have to in order to make a real difference. It need only identify appropriately sized branches and grab them. Once loaded into the chipper’s intake hopper for further processing, the beast can immediately look for more “food”. This is essentially kindling that would help ignite larger logs. If it’s all consumed by Forest Walker, then it’s not present to promote an aggravated conflagration.
I have glossed over an obvious question: How does Forest Walker see and identify branches and such? LiDaR (Light Detection and Ranging) attached to Forest Walker images the local area and feed those data to onboard computers for processing. Maybe AI plays a role. Maybe simple machine learning can do the trick. One thing is for certain: being able to identify a stick and cause robotic appendages to pick it up is not impossible.
Great! We now have a quadrupedal robot autonomously identifying and “eating” dead branches and other light, combustible materials. Whilst strolling through the forest, depleting future fires of combustibles, Forest Walker has already performed a major function of this system: making the forest safer. It's time to convert this low-density fuel into a high-density fuel Forest Walker can leverage. Enter the gasification process.
The Gassifier

The gasifier is the heart of the entire system; it’s where low-density fuel becomes the high-density fuel that powers the entire system. Biochar and wood vinegar are process wastes and I’ll discuss why both are powerful soil amendments in a moment, but first, what’s gasification?
Reacting shredded carbonaceous material at high temperatures in a low or no oxygen environment converts the biomass into biochar, wood vinegar, heat, and Synthesis Gas (Syngas). Syngas consists primarily of hydrogen, carbon monoxide, and methane. All of which are extremely useful fuels in a gaseous state. Part of this gas is used to heat the input biomass and keep the reaction temperature constant while the internal combustion engine that drives the generator to produce electrical power consumes the rest.
Critically, this gasification process is “continuous feed”. Forest Walker must intake biomass from the chipper, process it to fuel, and dump the waste (CO2, heat, biochar, and wood vinegar) continuously. It cannot stop. Everything about this system depends upon this continual grazing, digestion, and excretion of wastes just as a ruminal does. And, like a ruminant, all waste products enhance the local environment.
When I first heard of gasification, I didn’t believe that it was real. Running an electric generator from burning wood seemed more akin to “conspiracy fantasy” than science. Not only is gasification real, it’s ancient technology. A man named Dean Clayton first started experiments on gasification in 1699 and in 1901 gasification was used to power a vehicle. By the end of World War II, there were 500,000 Syngas powered vehicles in Germany alone because of fossil fuel rationing during the war. The global gasification market was $480 billion in 2022 and projected to be as much as $700 billion by 2030 (Vantage Market Research). Gasification technology is the best choice to power the Forest Walker because it’s self-contained and we want its waste products.
Biochar: The Waste

Biochar (AKA agricultural charcoal) is fairly simple: it’s almost pure, solid carbon that resembles charcoal. Its porous nature packs large surface areas into small, 3 dimensional nuggets. Devoid of most other chemistry, like hydrocarbons (methane) and ash (minerals), biochar is extremely lightweight. Do not confuse it with the charcoal you buy for your grill. Biochar doesn’t make good grilling charcoal because it would burn too rapidly as it does not contain the multitude of flammable components that charcoal does. Biochar has several other good use cases. Water filtration, water retention, nutrient retention, providing habitat for microscopic soil organisms, and carbon sequestration are the main ones that we are concerned with here.
Carbon has an amazing ability to adsorb (substances stick to and accumulate on the surface of an object) manifold chemistries. Water, nutrients, and pollutants tightly bind to carbon in this format. So, biochar makes a respectable filter and acts as a “battery” of water and nutrients in soils. Biochar adsorbs and holds on to seven times its weight in water. Soil containing biochar is more drought resilient than soil without it. Adsorbed nutrients, tightly sequestered alongside water, get released only as plants need them. Plants must excrete protons (H+) from their roots to disgorge water or positively charged nutrients from the biochar's surface; it's an active process.
Biochar’s surface area (where adsorption happens) can be 500 square meters per gram or more. That is 10% larger than an official NBA basketball court for every gram of biochar. Biochar’s abundant surface area builds protective habitats for soil microbes like fungi and bacteria and many are critical for the health and productivity of the soil itself.
The “carbon sequestration” component of biochar comes into play where “carbon credits” are concerned. There is a financial market for carbon. Not leveraging that market for revenue is foolish. I am climate agnostic. All I care about is that once solid carbon is inside the soil, it will stay there for thousands of years, imparting drought resiliency, fertility collection, nutrient buffering, and release for that time span. I simply want as much solid carbon in the soil because of the undeniably positive effects it has, regardless of any climactic considerations.
Wood Vinegar: More Waste

Another by-product of the gasification process is wood vinegar (Pyroligneous acid). If you have ever seen Liquid Smoke in the grocery store, then you have seen wood vinegar. Principally composed of acetic acid, acetone, and methanol wood vinegar also contains ~200 other organic compounds. It would seem intuitive that condensed, liquefied wood smoke would at least be bad for the health of all living things if not downright carcinogenic. The counter intuition wins the day, however. Wood vinegar has been used by humans for a very long time to promote digestion, bowel, and liver health; combat diarrhea and vomiting; calm peptic ulcers and regulate cholesterol levels; and a host of other benefits.
For centuries humans have annually burned off hundreds of thousands of square miles of pasture, grassland, forest, and every other conceivable terrestrial ecosystem. Why is this done? After every burn, one thing becomes obvious: the almost supernatural growth these ecosystems exhibit after the burn. How? Wood vinegar is a component of this growth. Even in open burns, smoke condenses and infiltrates the soil. That is when wood vinegar shows its quality.
This stuff beefs up not only general plant growth but seed germination as well and possesses many other qualities that are beneficial to plants. It’s a pesticide, fungicide, promotes beneficial soil microorganisms, enhances nutrient uptake, and imparts disease resistance. I am barely touching a long list of attributes here, but you want wood vinegar in your soil (alongside biochar because it adsorbs wood vinegar as well).
The Internal Combustion Engine

Conversion of grazed forage to chemical, then mechanical, and then electrical energy completes the cycle. The ICE (Internal Combustion Engine) converts the gaseous fuel output from the gasifier to mechanical energy, heat, water vapor, and CO2. It’s the mechanical energy of a rotating drive shaft that we want. That rotation drives the electric generator, which is the heartbeat we need to bring this monster to life. Luckily for us, combined internal combustion engine and generator packages are ubiquitous, delivering a defined energy output given a constant fuel input. It’s the simplest part of the system.
The obvious question here is whether the amount of syngas provided by the gasification process will provide enough energy to generate enough electrons to run the entire system or not. While I have no doubt the energy produced will run Forest Walker's main systems the question is really about the electrons left over. Will it be enough to run the Bitcoin mining aspect of the system? Everything is a budget.
CO2 Production For Growth

Plants are lollipops. No matter if it’s a tree or a bush or a shrubbery, the entire thing is mostly sugar in various formats but mostly long chain carbohydrates like lignin and cellulose. Plants need three things to make sugar: CO2, H2O and light. In a forest, where tree densities can be quite high, CO2 availability becomes a limiting growth factor. It’d be in the forest interests to have more available CO2 providing for various sugar formation providing the organism with food and structure.
An odd thing about tree leaves, the openings that allow gasses like the ever searched for CO2 are on the bottom of the leaf (these are called stomata). Not many stomata are topside. This suggests that trees and bushes have evolved to find gasses like CO2 from below, not above and this further suggests CO2 might be in higher concentrations nearer the soil.
The soil life (bacterial, fungi etc.) is constantly producing enormous amounts of CO2 and it would stay in the soil forever (eventually killing the very soil life that produces it) if not for tidal forces. Water is everywhere and whether in pools, lakes, oceans or distributed in “moist” soils water moves towards to the moon. The water in the soil and also in the water tables below the soil rise toward the surface every day. When the water rises, it expels the accumulated gasses in the soil into the atmosphere and it’s mostly CO2. It’s a good bet on how leaves developed high populations of stomata on the underside of leaves. As the water relaxes (the tide goes out) it sucks oxygenated air back into the soil to continue the functions of soil life respiration. The soil “breathes” albeit slowly.
The gasses produced by the Forest Walker’s internal combustion engine consist primarily of CO2 and H2O. Combusting sugars produce the same gasses that are needed to construct the sugars because the universe is funny like that. The Forest Walker is constantly laying down these critical construction elements right where the trees need them: close to the ground to be gobbled up by the trees.
The Branch Drones

During the last ice age, giant mammals populated North America - forests and otherwise. Mastodons, woolly mammoths, rhinos, short-faced bears, steppe bison, caribou, musk ox, giant beavers, camels, gigantic ground-dwelling sloths, glyptodons, and dire wolves were everywhere. Many were ten to fifteen feet tall. As they crashed through forests, they would effectively cleave off dead side-branches of trees, halting the spread of a ground-based fire migrating into the tree crown ("laddering") which is a death knell for a forest.
These animals are all extinct now and forests no longer have any manner of pruning services. But, if we build drones fitted with cutting implements like saws and loppers, optical cameras and AI trained to discern dead branches from living ones, these drones could effectively take over pruning services by identifying, cutting, and dropping to the forest floor, dead branches. The dropped branches simply get collected by the Forest Walker as part of its continual mission.
The drones dock on the back of the Forest Walker to recharge their batteries when low. The whole scene would look like a grazing cow with some flies bothering it. This activity breaks the link between a relatively cool ground based fire and the tree crowns and is a vital element in forest fire control.
The Bitcoin Miner

Mining is one of four monetary incentive models, making this system a possibility for development. The other three are US Dept. of the Interior, township, county, and electrical utility company easement contracts for fuel load management, global carbon credits trading, and data set sales. All the above depends on obvious questions getting answered. I will list some obvious ones, but this is not an engineering document and is not the place for spreadsheets. How much Bitcoin one Forest Walker can mine depends on everything else. What amount of biomass can we process? Will that biomass flow enough Syngas to keep the lights on? Can the chassis support enough mining ASICs and supporting infrastructure? What does that weigh and will it affect field performance? How much power can the AC generator produce?
Other questions that are more philosophical persist. Even if a single Forest Walker can only mine scant amounts of BTC per day, that pales to how much fuel material it can process into biochar. We are talking about millions upon millions of forested acres in need of fuel load management. What can a single Forest Walker do? I am not thinking in singular terms. The Forest Walker must operate as a fleet. What could 50 do? 500?
What is it worth providing a service to the world by managing forest fuel loads? Providing proof of work to the global monetary system? Seeding soil with drought and nutrient resilience by the excretion, over time, of carbon by the ton? What did the last forest fire cost?
The Mesh Network

What could be better than one bitcoin mining, carbon sequestering, forest fire squelching, soil amending behemoth? Thousands of them, but then they would need to be able to talk to each other to coordinate position, data handling, etc. Fitted with a mesh networking device, like goTenna or Meshtastic LoRa equipment enables each Forest Walker to communicate with each other.
Now we have an interconnected fleet of Forest Walkers relaying data to each other and more importantly, aggregating all of that to the last link in the chain for uplink. Well, at least Bitcoin mining data. Since block data is lightweight, transmission of these data via mesh networking in fairly close quartered environs is more than doable. So, how does data transmit to the Bitcoin Network? How do the Forest Walkers get the previous block data necessary to execute on mining?
Back To The Chain

Getting Bitcoin block data to and from the network is the last puzzle piece. The standing presumption here is that wherever a Forest Walker fleet is operating, it is NOT within cell tower range. We further presume that the nearest Walmart Wi-Fi is hours away. Enter the Blockstream Satellite or something like it.
A separate, ground-based drone will have two jobs: To stay as close to the nearest Forest Walker as it can and to provide an antennae for either terrestrial or orbital data uplink. Bitcoin-centric data is transmitted to the "uplink drone" via the mesh networked transmitters and then sent on to the uplink and the whole flow goes in the opposite direction as well; many to one and one to many.
We cannot transmit data to the Blockstream satellite, and it will be up to Blockstream and companies like it to provide uplink capabilities in the future and I don't doubt they will. Starlink you say? What’s stopping that company from filtering out block data? Nothing because it’s Starlink’s system and they could decide to censor these data. It seems we may have a problem sending and receiving Bitcoin data in back country environs.
But, then again, the utility of this system in staunching the fuel load that creates forest fires is extremely useful around forested communities and many have fiber, Wi-Fi and cell towers. These communities could be a welcoming ground zero for first deployments of the Forest Walker system by the home and business owners seeking fire repression. In the best way, Bitcoin subsidizes the safety of the communities.
Sensor Packages
LiDaR

The benefit of having a Forest Walker fleet strolling through the forest is the never ending opportunity for data gathering. A plethora of deployable sensors gathering hyper-accurate data on everything from temperature to topography is yet another revenue generator. Data is valuable and the Forest Walker could generate data sales to various government entities and private concerns.
LiDaR (Light Detection and Ranging) can map topography, perform biomass assessment, comparative soil erosion analysis, etc. It so happens that the Forest Walker’s ability to “see,” to navigate about its surroundings, is LiDaR driven and since it’s already being used, we can get double duty by harvesting that data for later use. By using a laser to send out light pulses and measuring the time it takes for the reflection of those pulses to return, very detailed data sets incrementally build up. Eventually, as enough data about a certain area becomes available, the data becomes useful and valuable.
Forestry concerns, both private and public, often use LiDaR to build 3D models of tree stands to assess the amount of harvest-able lumber in entire sections of forest. Consulting companies offering these services charge anywhere from several hundred to several thousand dollars per square kilometer for such services. A Forest Walker generating such assessments on the fly while performing its other functions is a multi-disciplinary approach to revenue generation.
pH, Soil Moisture, and Cation Exchange Sensing

The Forest Walker is quadrupedal, so there are four contact points to the soil. Why not get a pH data point for every step it takes? We can also gather soil moisture data and cation exchange capacities at unheard of densities because of sampling occurring on the fly during commission of the system’s other duties. No one is going to build a machine to do pH testing of vast tracts of forest soils, but that doesn’t make the data collected from such an endeavor valueless. Since the Forest Walker serves many functions at once, a multitude of data products can add to the return on investment component.
Weather Data

Temperature, humidity, pressure, and even data like evapotranspiration gathered at high densities on broad acre scales have untold value and because the sensors are lightweight and don’t require large power budgets, they come along for the ride at little cost. But, just like the old mantra, “gas, grass, or ass, nobody rides for free”, these sensors provide potential revenue benefits just by them being present.
I’ve touched on just a few data genres here. In fact, the question for universities, governmental bodies, and other institutions becomes, “How much will you pay us to attach your sensor payload to the Forest Walker?”
Noise Suppression

Only you can prevent Metallica filling the surrounds with 120 dB of sound. Easy enough, just turn the car stereo off. But what of a fleet of 50 Forest Walkers operating in the backcountry or near a township? 500? 5000? Each one has a wood chipper, an internal combustion engine, hydraulic pumps, actuators, and more cooling fans than you can shake a stick at. It’s a walking, screaming fire-breathing dragon operating continuously, day and night, twenty-four hours a day, three hundred sixty-five days a year. The sound will negatively affect all living things and that impacts behaviors. Serious engineering consideration and prowess must deliver a silencing blow to the major issue of noise.
It would be foolish to think that a fleet of Forest Walkers could be silent, but if not a major design consideration, then the entire idea is dead on arrival. Townships would not allow them to operate even if they solved the problem of widespread fuel load and neither would governmental entities, and rightly so. Nothing, not man nor beast, would want to be subjected to an eternal, infernal scream even if it were to end within days as the fleet moved further away after consuming what it could. Noise and heat are the only real pollutants of this system; taking noise seriously from the beginning is paramount.
Fire Safety

A “fire-breathing dragon” is not the worst description of the Forest Walker. It eats wood, combusts it at very high temperatures and excretes carbon; and it does so in an extremely flammable environment. Bad mix for one Forest Walker, worse for many. One must take extreme pains to ensure that during normal operation, a Forest Walker could fall over, walk through tinder dry brush, or get pounded into the ground by a meteorite from Krypton and it wouldn’t destroy epic swaths of trees and baby deer. I envision an ultimate test of a prototype to include dowsing it in grain alcohol while it’s wrapped up in toilet paper like a pledge at a fraternity party. If it runs for 72 hours and doesn’t set everything on fire, then maybe outside entities won’t be fearful of something that walks around forests with a constant fire in its belly.
The Wrap

How we think about what can be done with and adjacent to Bitcoin is at least as important as Bitcoin’s economic standing itself. For those who will tell me that this entire idea is without merit, I say, “OK, fine. You can come up with something, too.” What can we plug Bitcoin into that, like a battery, makes something that does not work, work? That’s the lesson I get from this entire exercise. No one was ever going to hire teams of humans to go out and "clean the forest". There's no money in that. The data collection and sales from such an endeavor might provide revenues over the break-even point but investment demands Alpha in this day and age. But, plug Bitcoin into an almost viable system and, voilà! We tip the scales to achieve lift-off.
Let’s face it, we haven’t scratched the surface of Bitcoin’s forcing function on our minds. Not because it’s Bitcoin, but because of what that invention means. The question that pushes me to approach things this way is, “what can we create that one system’s waste is another system’s feedstock?” The Forest Walker system’s only real waste is the conversion of low entropy energy (wood and syngas) into high entropy energy (heat and noise). All other output is beneficial to humanity.
Bitcoin, I believe, is the first product of a new mode of human imagination. An imagination newly forged over the past few millennia of being lied to, stolen from, distracted and otherwise mis-allocated to a black hole of the nonsensical. We are waking up.
What I have presented is not science fiction. Everything I have described here is well within the realm of possibility. The question is one of viability, at least in terms of the detritus of the old world we find ourselves departing from. This system would take a non-trivial amount of time and resources to develop. I think the system would garner extensive long-term contracts from those who have the most to lose from wildfires, the most to gain from hyperaccurate data sets, and, of course, securing the most precious asset in the world. Many may not see it that way, for they seek Alpha and are therefore blind to other possibilities. Others will see only the possibilities; of thinking in a new way, of looking at things differently, and dreaming of what comes next.
-
 @ 4fe4a528:3ff6bf06
2025-01-01 15:50:50
@ 4fe4a528:3ff6bf06
2025-01-01 15:50:50I could have wrote about how bitcoin has more than doubled in 2024 or how some people are still sitting on the sidelines not trying to understand why bitcoin will double in 2025, but instead I thought I would write about how bitcoin is allowing for a decentralized social network.
Two years ago I decided to try out this NOSTR idea. Now I have 233 followers, almost the same number of people who read this monthly newsletter. Facebook / whats-app was to ad filled for me to enjoy what my friends were posting. X was great for news, but none of my friends where on it. Linkedin was just about business. Besides, NOSTR gives me more bitcoin every time I post. I am now using the bitcoin to buy eggs every two weeks from my neighbors. So to me it is a win win. I can write notes and eat eggs. I even use my NOSTR extension to log into hivetalk.org and help people with their computer issues. It is better than teaching via ZOOM. 2025 is going to be a great year for decentralization.
If you are trying to join NOSTR via your desktop I recommend going to getalby.com installing the browser extension. Then make an account with getalby and write down your 24 words (nsec). Link your profile to your lightning wallet and start posting and following other friends via primal.net. Yes, of course, I am put on this earth to help my fellow man. Some people enjoy using NOSTR via their cell phone and for those people I recommend amethyst or damus. We are all in this together.
-
 @ 58537364:705b4b85
2025-06-05 15:55:12
@ 58537364:705b4b85
2025-06-05 15:55:12อารมณ์ คือ โลก - โลก คือ อารมณ์ อารมณ์ ในโลกปัจจุบันรวมอยู่ที่ วัตถุนิยม อารมณ์ จึงเป็นปัจจัยแห่งเหตุการณ์ทุกอย่างในโลก
…. “ เดี๋ยวนี้คําว่า “อารมณ์” ในภาษาไทยนั้น หมายถึงความรู้สึกในใจมากกว่า; เช่น พื้นเพของจิตใจในขณะนั้นเป็นอย่างไร, เรียกว่าอารมณ์ของเขาเป็นอย่างไร, อารมณ์กําลังดี อารมณ์กําลังไม่ดี, นี่ คําว่าอารมณ์ในภาษาไทยใช้กันไปเสียอย่างนี้ ; มันคนละเรื่องกับในภาษาบาลี ซึ่งคําว่า “อารมณ์” หมายถึง สิ่งที่จะเข้ามากระทบ ตา หู จมูก ลิ้น กาย ใจ.
…. ถ้ากระทบแล้วเกิดความรู้สึกอย่างไร งุ่นง่านอยู่ในใจ อันนั้นไม่ได้เรียกว่าอารมณ์; อันนั้นก็เรียกว่ากิเลสอย่างอื่น เช่น เรียกว่าตัณหาบ้าง อุปาทานบ้าง; ถ้าจัดเป็นพวกขันธ์ ก็เรียกว่า เวทนาขันธ์บ้าง สัญญาขันธ์บ้าง สังขารขันธ์บ้าง; ถ้าเป็นความคิดที่งุ่นง่านก็เรียกว่า “สังขารขันธ์” ทั้งนั้น ดังนั้น เราจะต้องถือเอาคําว่าอารมณ์ในบาลีมาเป็นหลัก …. คําว่า อารมณ์ ที่จะเข้าใจกันง่ายๆ ก็หมายความว่า รูป เสียง กลิ่น รส โผฏฐัพพะ ที่จะมากระทบ ตา หู จมูก ลิ้น กาย นี้ ๕ อย่าง แล้วก็ความรู้สึกเก่าแก่ที่จะมาผุดขึ้นในใจอีก เรียกว่า ธัมมารมณ์ ที่จะมากระทบใจในปัจจุบันนี้ นี้ก็เป็นอันหนึ่ง เลยได้เป็นอารมณ์ ๖. อารมณ์กระทบ ตา หู จมูก ลิ้น กาย ๕ อย่างข้างนอกนี้ก็สําคัญไปพวกหนึ่ง ที่ปรุงขึ้นภายในสําหรับกระทบใจโดยไม่ต้องอาศัย ตา หู จมูก ลิ้น กาย ใจ เลย ในเวลานั้นก็ยังมีอยู่นี้เรียกว่าธัมมารมณ์ นี้ก็ยิ่งสําคัญ: แต่ว่ารวมกันแล้วก็เรียกว่า อารมณ์ ได้ด้วยกันทั้งนั้น แปลว่า สิ่งที่จะมากระทบกับ ตา หู จมูก ลิ้น กาย ใจ นั่นเอง
…. นี้ ดูให้ละเอียดตามตัวหนังสือ คําว่า “อารมณ์” แปลว่า ที่หน่วงบ้าง แปลว่า ที่ยินดีบ้าง, มันมีความหมายละเอียดมาก. ถ้าถือเอาความหมายอย่างคนที่มีตัวตนเป็นหลัก ธรรมะในฝ่ายฮินดูหรือฝ่ายพรหมณ์เขาก็จะพูดว่า สําหรับจิตหรืออาตมันเข้าไปจับฉวยเอา. แต่ถ้าพูดอย่างภาษาชาวพุทธพูดอย่างนั้นไม่ได้ เพราะไม่มีจิตไม่มีอาตมันชนิดนั้น แล้วจิตนี้ก็เพิ่งเกิดขึ้นหลังอารมณ์กระทบแล้ว; เลยต้องพูดตามพระบาลีที่ว่า อาศัยตาด้วย อาศัยรูปด้วย ย่อมเกิดจักษุวิญญาณ; ตาอาศัยกับรูปคืออารมณ์นั้นได้แล้วจึงจะเกิดจักษุวิญญาณ วิญญาณหรือจิตนี้เกิดทีหลัง
…. ฉะนั้น จึงไม่พูดว่า อารมณ์นี้เป็นสิ่งสําหรับจิตหรือตัวตนเข้าไปจับฉวยยึดเอา; ถ้าพูดอย่างนั้นมันก็จะเป็นฮินดูหรือพราหมณ์ไป คือมีตัวตนไป. พูดอย่างพุทธไม่มีตัวตน ทุกอย่างไม่ใช่ตัวตน เป็นสักว่าธาตุ, ได้การปรุงแต่งที่เหมาะแล้วมันก็ปรุงแต่งเป็นสิ่งใหม่ขึ้นมา ในนั้นอาจจะมีความรู้สึกโง่ไปว่าเป็นตัวเราก็ได้
…. ฉะนั้น คําว่าอารมณ์ ถ้าถือตามหลักในทางพุทธศาสนา ก็แปลว่า สิ่งที่อาศัยกันกับจิต จะเรียกว่าเป็นที่หน่วงของจิตมันก็ยังได้: ถ้าเข้าใจผิดมันก็ผิดได้: เรียกว่าสิ่งที่อาศัยกับอายตนะ แล้วก็เกิดเป็นความรู้สึกเป็นจิตขึ้นมา จิตกําลังหน่วงสิ่งนั้นเป็นอารมณ์ก็ได้ แต่จะให้เป็นตัวตนนั้นไม่ได้
…. โดยพยัญชนะก็มีอยู่อย่างนี้ ตัวพยัญชนะก็ยังกํากวม อารมฺมณํ หรือที่มาจาก อาลมฺพนํ ก็แปลว่า ที่หน่วงของจิต. ถ้าจะถือว่ามาจาก รม ที่แปลว่า ยินดี ก็แปลว่า มันเป็นสิ่งที่หลงใหลยินดีของจิต อย่างนี้ก็ยังได้อีก
…. แต่ขอให้รู้จักจากภายในดีกว่าที่จะมารู้จักจากตัวหนังสือ เมื่อตากระทบรูป เมื่อหูกระทบเสียง เป็นต้น มันเกิดขึ้นในใจ, แล้วสังเกตเอาที่นั่นก็แล้วกัน ว่ารูปที่มากระทบตานั้นมันคืออะไร? เสียงที่มากระทบหูนั้นมันคืออะไร? จะค่อยเข้าใจแจ่มแจ้งขึ้นทีละน้อยๆ ว่าอารมณ์นั้นคืออะไร? แต่ให้เข้าใจไว้ทีหนึ่งก่อนว่าสิ่งที่เรียกว่าอารมณ์ๆที่มากระทบนี้ มันยังไม่ดีไม่ชั่ว ยังไม่จัดเป็นสิ่งดีสิ่งชั่ว มันต้องผสมปรุงแต่งเป็นความคิดอย่างนั้นอย่างนี้เสียก่อน จึงจะจัดเป็นดีเป็นชั่ว อารมณ์ล้วนๆยังไม่ดีไม่ชั่ว จะได้รู้จักป้องกัน อย่าให้เป็นไปในทางชั่ว, ให้เป็นไปแต่ในทางดีได้ตามปรารถนา
…. นี้เรียกว่าโดยพยัญชนะ โดยตัวหนังสือ คําว่า “อารมณ์” แปลว่า เป็นที่ยินดีแห่งจิต, เป็นที่ยึดหน่วงแห่งจิต; โดยเฉพาะภาษาอภิธรรมแล้วก็ใช้คําว่า “เป็นที่หน่วงเอาของจิต”, คือจิตย่อมหน่วงสิ่งใดสิ่งหนึ่งเป็นอารมณ์ แปลคําว่าอารมณ์บ้าง, อาลัมพนะ แปลว่า เป็นที่หน่วงเอา.
…. เดี๋ยวนี้เราเรียนพุทธศาสนาไม่ใช่เรามาเรียนหนังสือบาลี, เราจะเรียนพระธรรมคําสอนของพระพุทธเจ้า เราก็ต้องดูสิ่งที่เรียกว่าอารมณ์ โดยหลักของธรรมชาติที่ปรุงแต่งกันอยู่ในใจดีกว่า; ก็อย่างพระบาลีที่ได้ว่ามาแล้วข้างต้นว่า จกฺขุญฺจ ปฏิจฺจ รูเป จ อุปฺปชฺชติ จกฺขุวิญฺญาณํ = เพราะอาศัยตาด้วย รูปด้วย ย่อมบังเกิดจักษุวิญญาณ ติณฺณํ ธมฺมานํ สงฺคติ ผสฺโส - การประจวบกันของ ๓ สิ่งนี้เรียกว่า “ผัสสะ”, ผสฺสปจฺจยา เวทนา = เพราะผัสสะเป็นปัจจัยจึงเกิดเวทนา, อย่างนี้เรื่อยไปจนเกิดทุกข์ จนเกิดความทุกข์, นี้เรียกว่าโดยธรรมชาติ
…. สิ่งที่เรียกว่าอารมณ์มีอยู่โดยธรรมชาติที่จะเข้ามาอาศัยกันกับตาข้างใน ที่มีอยู่ในตัวคน. แล้วจะเกิดจักษุวิญญาณ เป็นต้น ขึ้นในตัวคน; จะเกิด ผัสสะ เวทนา ตัณหา อุปาทาน ภพ ชาติ ขึ้นในตัวคน; นี้โดยธรรมชาติ พระพุทธเจ้าท่านบันดาลอะไรไม่ได้ : ธรรมชาติเป็นอยู่อย่างนี้ แต่ท่านรู้เรื่องนี้ท่านจึงนํามาสอนว่า ธรรมชาติมันมีอยู่อย่างนี้ เราจะต้องเข้าใจให้ถูกต้อง โดยที่จะป้องกันความทุกข์ไม่ให้เกิดขึ้นมาได้, หรือถ้าเกิดขึ้นมาได้ก็จะดับเสียได้
…. เราควรจะรู้จักอารมณ์ในฐานะที่เป็นธรรมชาติอันหนึ่ง ที่มีอยู่ตามธรรมชาติ แล้วที่จะเข้ามาทําเรื่องทําราวขึ้นในจิตใจของคนเราให้เกิดปัญหายุ่งยากนี้ให้ดีๆ นี้เรียกว่ารู้จักอารมณ์จากธรรมชาติโดยตรงอย่างนี้ ดีกว่าที่จะรู้จักตามตัวหนังสือ, ดีกว่าที่จะรู้จักตามคําบอกเล่าบางอย่างบางประการที่มันไม่มีประโยชน์อะไร. รู้จักตามคําบอกเล่าก็รู้จักตามที่พระพุทธเจ้าท่านตรัสดีกว่า แต่แล้วยังไม่รู้จักตัวจริง จนกว่าจะมารู้จักจากที่เมื่ออารมณ์มากระทบตา หู จมูก ลิ้น กาย ใจ เข้าจริงๆ : นั่นจึงจะรู้จักอารมณ์ รู้จักผลที่เกิดขึ้นจากการกระทบของอารมณ์, รู้จักต่อไปตามลําดับ จนแก้ปัญหาต่างๆ ได้
…. นี่ ขอร้องให้รู้จักสิ่งที่เรียกว่า อารมณ์ ในฐานะที่เป็นธรรมชาติอันหนึ่ง ที่มีอยู่ตามธรรมชาติ ที่จะเข้ามากระทบอายตนะภายใน คือ กระทบ ตา หู จมูก ลิ้น กาย ใจ แล้วมีเรื่องมีราวมีปัญหา
อารมณ์ คือ โลก - โลก คือ อารมณ์ …. “ ที่นี้จะให้ดูต่อไปอีก ว่าโดยข้อเท็จจริงที่เป็นอยู่แล้ว อารมณ์นั้นคืออะไร? ถ้าจะพูดโดยข้อเท็จจริงหรือตามสถานการณ์ที่เป็นอยู่จริงในชีวิตของคนเรา อารมณ์มันก็คือ “โลก” นั่นเอง. เดี๋ยวนี้เราไม่รู้จักโลกในฐานะอย่างนี้, เราไปเข้าใจความหมายของคําว่าโลกแคบไปบ้าง หรือว่าเขวไปบ้าง.
…. ถ้าจะรู้ตามหลักพระพุทธศาสนาแล้ว โลกทั้งหมดก็คือสิ่งที่จะมาปรากฏแก่ ตา หู จมูก ลิ้น กาย ใจ ของเรา, เรามีเพียง ๖ อย่าง, แล้วมันก็ ปรากฏได้เพียง ๖ ทาง, มากกว่านั้นมันปรากฏไม่ได้ ดังนั้น โลกก็คือสิ่งที่จะมาปรากฏแก่ ตา หู จมูก ลิ้น กาย ใจ ๖ อย่างของเรา. “โลก” ก็คือ รูป เสียง กลิ่น รส โผฏฐัพพะ ธัมมารมณ์ ๖ ประการเท่านั้น, ไม่มีอะไรมากไปกว่านั้น
…. ฉะนั้น รูป เสียง กลิ่น รส โผฏฐัพพะ ธัมมารมณ์ แต่ละอย่าง ๆ ก็คือ โลกในแต่ละแง่ละมุม นั่นเอง, ที่เป็น รูป เสียง กลิ่น รส โผฏฐัพพะ ก็อยู่ข้างนอก จะเรียกว่าอยู่ข้างนอกก็ได้, ที่เป็นอารมณ์เกิดขึ้นในใจ ปรุงขึ้นในใจก็เรียกว่าโลกข้างในก็ได้ แต่มันก็เป็นโลกอยู่นั่นแหละ เพราะมันเป็นสิ่งที่จิตจะต้องรู้สึก จิตรู้สึกก็เรียกว่าโลกสําหรับจิต ตา หู จมูก ลิ้น กาย รู้สึก ก็เรียกว่าโลกสำหรับ ตา หู จมูก ลิ้น กาย. นี้ขอให้มองให้เห็นชัดตามพระพุทธประสงค์ว่า โลก ก็คือ อารมณ์, อารมณ์ ก็คือ โลก.
…. แต่ทีนี้ พระพุทธเจ้าท่านมองลึกกว่านั้น ท่านตรัสถึงข้อที่ว่า ถ้ามันมาเกิดเป็นปัญหาแก่เราเมื่อไรจึงจะเรียกว่า “มันมี” พอมันมาเป็นปัญหาแก่เราเมื่อไรก็เรียกว่า “เป็นทุกข์”; เพราะว่าเราได้ไปจับฉวยยึดถือเอาตามประสาตามวิสัยของคนที่ไม่รู้จักโลก ถ้าพูดว่าไม่รู้จักโลกแล้วคนก็มักจะไม่ยอมรับ เพราะว่าเขาจะพูดว่าเขารู้จักโลกดี. ยิ่งพวกฝรั่งสมัยนี้ นักวิทยาศาสตร์ปราดเปรื่องนั้น เขาจะไม่ยอมรับว่าเขาไม่รู้จักโลก. แต่ถ้าพูดตามหลักพุทธศาสนาแล้วก็จะพูดได้ว่ายังไม่รู้จักโลกเลย เป็นคนตาบอดยิ่งกว่าตาบอด; เพราะว่าฝรั่งเหล่านั้นรู้จักโลกแต่ในแง่สําหรับจะยึดมั่นถือมั่นเป็น “ตัวกู ของกู” จะครองโลกจะอะไร เอาประโยชน์ทุกอย่าง; เขารู้จักโลกในแง่นี้ อย่างนี้พุทธบริษัทไม่เรียกว่า “รู้จักโลก”; แต่ถือว่าเป็นคนตาบอดต่อโลก, หลงยึดมั่นถือมั่นในโลก. เพราะว่าคนเหล่านั้นไม่รู้จักโลกโดยความเป็นอารมณ์ ๖ ประการ คือ รูป เสียง กลิ่นรส โผฏฐัพพะ ธัมมารมณ์, แล้วเป็น “มายา” คือ เอาจริงไม่ได้ เป็นของชั่วคราวๆ หลอกให้เกิดความรู้สึกยึดมั่นถือมั่น
…. นี้เรารู้จัก เราไม่ไปหลงยึดมั่นถือมั่นกับมัน นี้จึงเรียกว่า “คนที่รู้จักโลก” ไปตามหลักของพุทธศาสนา, ฉะนั้น จึงไม่ยึดมั่นถือมั่นสิ่งใดโดยความเป็นตัวตน หรือโดยความเป็นของตน, เรียกว่าเป็นผู้รู้จักอารมณ์ ๖ ประการนั้นก็คือรู้จักโลกทั้งปวง, แล้วก็ไม่หลงไปในโลกในแง่ใดแง่หนึ่ง นี้เรียกว่า อารมณ์ ก็คือ โลก นั่นเอง ในความหมายที่ลึกที่สุดของพระพุทธสาสนา ไม่ใช่โลกก้อนดิน, ไม่ใช่โลกก้อนกลมๆ นี้. แต่มันหมายถึงคุณค่าอะไรที่มันมีอยู่ในโลกกลมๆ นี้ ที่จะเข้ามามาทําให้เกิดปัญหา ที่ตา ที่หู ที่จมูก ที่ลิ้น ที่กาย ที่ใจ ของคน. นั่นแหละคือตัวร้ายกาจของสิ่งที่เรียกว่า โลก เราจะต้องรู้จักในส่วนนี้ให้เพียงพอ
อารมณ์ในโลกปัจจุบันมารวมที่วัตถุนิยม …. ทีนี้ ดูอีกแง่หนึ่งก็โดยปัญหาที่กําลังมีอยู่ อารมณ์ในโลกนี้ในฐานะที่มันเป็นตัวปัญหาที่กําลังมีอยู่ มันมารวมอยู่ที่คําว่า “วัตถุนิยม”: หมายความว่า ตา หู จมูก ลิ้น กาย ใจ นี้ มันเป็นฝ่ายชนะ ไปหลงใหลในอารมณ์ รูป เสียง กลิ่น รส โผฏฐัพพะ ฯลฯ, แล้วก็เกิดนิยมหลงใหลในวัตถุเหล่านั้น จนเกิดความคิดใหม่ๆ, ปรุงแต่งไปในทางที่จะให้หลงใหลในโลกยิ่งขึ้นๆ, ความเจริญก้าวหน้า ในโลกสมัยนี้เป็นไปแต่ในทางอย่างนี้ ฉะนั้น จึงไกลความสงบ, ไกลสันติภาพ ไกลอะไรออกไปทุกที. การที่มนุษย์ที่มีปัญญาในโลกสมัยนี้ โดยเฉพาะฝรั่งที่ก้าวหน้านั้นเขาก็จัดโลกไปแต่ในแง่ของวัตถุมากขึ้นๆ: มันก็ไกลจากสันติภาพ ไกลจากความสงบสุขยิ่งขึ้นทุกที
…. ความสะดวกสบายที่ทําให้เกิดขึ้นมาได้นั้น ไม่ได้ช่วยส่งเสริมเกิดสันติภาพ; แต่มันช่วยให้เกิดความหลงในโลกนั้นเองมากขึ้น แล้วก็ช่วยให้หลงใหลใน “ตัวกู ของกู”, ยึดมั่นถือมั่นเห็นแก่ตัวมากขึ้น รวมกันแล้วมันไม่มีทางที่จะเกิดสันติภาพหรือสันติสุขในโลกได้เลย, จึงกลายเป็นความหลอกลวงเหลือประมาณ โลกจึงกลายเป็นความหลอกลวง, หรือสิ่งที่หลอกลวงเหลือประมาณใน เวลานี้ เราเรียกกันว่า ติดบ่วง หรือว่า ติดเหยื่อของวัตถุนิยม. คําพูดทั้งหมดนี้ ล้วนแต่เป็นการแสดงให้เห็นว่า อารมณ์นี้คืออะไร สิ่งที่เรียกว่าอารมณ์นั้น คือตัวโลกที่กําลังหลอกลวงเราอยู่ทุกวันอย่างยิ่ง โดยเฉพาะในปัจจุบันนี้เป็นวัตถุนิยม นี้คืออารมณ์”
พุทธทาสภิกขุ ที่มา : ธรรมบรรยายภาคมาฆบูชา ครั้งที่ ๗ หัวข้อเรื่อง “อารมณ์ คือ ปัจจัยแห่งเหตุการณ์ทุกอย่างในโลก” เมื่อวันที่ ๑๖ กุมภาพันธ์ ๒๕๑๗ จากหนังสือชุดธรรมโฆษณ์ เล่มชื่อว่า “ก ข ก กา ของการศึกษาพุทธศาสนา”
หมายเหตุ
“อารมณ์ ” ในทางพุทธศาสนา มี ๖ คือ... * ๑. รูปะ = รูป, สิ่งที่เห็น หรือ วัณณะ คือ สี * ๒. สัททะ = เสียง * ๓. คันธะ = กลิ่น * ๔. รสะ = รส * ๕. โผฏฐัพพะ = สัมผัสทางกาย * ๖. ธรรมารมณ์ = สิ่งที่ใจนึกคิด, อารมณ์ที่เกิดกับใจ
…. ทั้ง ๖ อย่างนี้ เป็นสิ่งสำหรับให้จิตยึดหน่วง เรียกอีกอย่างว่า "อายตนะภานนอก" ก็ได้
“อายตนะภายใน ๖” คือ ที่เชื่อมต่อให้เกิดความรู้, แดนต่อความรู้ฝ่ายภายใน มี * ๖ อย่าง คือ... * ๑. จักษุ - ตา * ๒. โสตะ - หู * ๓. ฆานะ - จมูก * ๔. ชิวหา - ลิ้น * ๕. กาย - กาย * ๖. มโน - ใจ
… หรือจะเรียกอีกอย่างว่า “อินทรีย์ ๖” ก็ได้ เพราะเป็นใหญ่ในหน้าที่ของตนแต่ละอย่าง เช่น จักษุ เป็นเจ้าการ(เป็นใหญ่)ในการเห็น เป็นต้น
ท. ส. ปัญญาวุฑโฒ – รวบรวม.
-
 @ 7f6db517:a4931eda
2025-06-04 18:03:02
@ 7f6db517:a4931eda
2025-06-04 18:03:02
What is KYC/AML?
- The acronym stands for Know Your Customer / Anti Money Laundering.
- In practice it stands for the surveillance measures companies are often compelled to take against their customers by financial regulators.
- Methods differ but often include: Passport Scans, Driver License Uploads, Social Security Numbers, Home Address, Phone Number, Face Scans.
- Bitcoin companies will also store all withdrawal and deposit addresses which can then be used to track bitcoin transactions on the bitcoin block chain.
- This data is then stored and shared. Regulations often require companies to hold this information for a set number of years but in practice users should assume this data will be held indefinitely. Data is often stored insecurely, which results in frequent hacks and leaks.
- KYC/AML data collection puts all honest users at risk of theft, extortion, and persecution while being ineffective at stopping crime. Criminals often use counterfeit, bought, or stolen credentials to get around the requirements. Criminals can buy "verified" accounts for as little as $200. Furthermore, billions of people are excluded from financial services as a result of KYC/AML requirements.
During the early days of bitcoin most services did not require this sensitive user data, but as adoption increased so did the surveillance measures. At this point, most large bitcoin companies are collecting and storing massive lists of bitcoiners, our sensitive personal information, and our transaction history.
Lists of Bitcoiners
KYC/AML policies are a direct attack on bitcoiners. Lists of bitcoiners and our transaction history will inevitably be used against us.
Once you are on a list with your bitcoin transaction history that record will always exist. Generally speaking, tracking bitcoin is based on probability analysis of ownership change. Surveillance firms use various heuristics to determine if you are sending bitcoin to yourself or if ownership is actually changing hands. You can obtain better privacy going forward by using collaborative transactions such as coinjoin to break this probability analysis.
Fortunately, you can buy bitcoin without providing intimate personal information. Tools such as peach, hodlhodl, robosats, azteco and bisq help; mining is also a solid option: anyone can plug a miner into power and internet and earn bitcoin by mining privately.
You can also earn bitcoin by providing goods and/or services that can be purchased with bitcoin. Long term, circular economies will mitigate this threat: most people will not buy bitcoin - they will earn bitcoin - most people will not sell bitcoin - they will spend bitcoin.
There is no such thing as KYC or No KYC bitcoin, there are bitcoiners on lists and those that are not on lists.
If you found this post helpful support my work with bitcoin.

-
 @ 00ea1f73:71c6e344
2025-06-03 09:59:07
@ 00ea1f73:71c6e344
2025-06-03 09:59:07Je suis en train de construire un outil de référencement collectif de marques et fabricants proposant des produits 100 % en matière naturelle (ce qui veut essentiellement dire "sans plastique").
Voici les étapes de ma progression ces dernières semaines en tant que non développeur pour créer cela tout en privilégiant des outils open source.
Etape 1 : faisons simple, du texte organisé
J'ai commencé par réunir mes idées dans Anytype. Leur approche "tout est un objet" laisse une flexibilité incroyable pour organiser ses données. On peut s'en servir comme simple outil de prise de note ou comme outil de gestion de projet. Le fonctionnement "local first" de l'application me donne la main sur mes données : elles sont stockées en local sur mon ordinateur et mon téléphone, qui se synchronisent entre eux.
Anytype permet depuis peu de publier sur Internet les "objets" de son choix (pages, notes, albums…) mais cela reste limité pour proposer à des visiteur une navigation fluide entre des objets liés (dans mon cas des marques et des matières par exemple). De plus, il n'est pas encore possible d'y automatiser la mise en forme de contenus à partir de données.
Ainsi, après avoir réuni les informations et préparé les contenus "à la main" pour trois marques seulement dans Anytype, j'ai eu besoin d'automatisation, et donc d'une vraie base de données. Je conserve quand même Anytype pour organiser mes idées et la suite du projet. Je l'utilise aussi pour la vie quotidienne (liste de course partagée, journal…).
Etape 2 : structurons une base de données
Baserow est une alternative à Airtable qui permet de gérer une base de données comme un tableur. Les formules utilisables dans les tableaux m'ont aidé à générer automatiquement les contenus de marque à partir des données que je réunissais. J'ai obtenu des données bien ordonnés dans de beaux tableaux sans avoir plus besoin de réécrire tout le contenu pour chaque marque.
J'ai passé un peu de temps à apprendre la syntaxe des formules de Baserow, j'ai mis à jour le contenu des trois premières marques, généré automatiquement celui d'une quatrième et… je me suis rendu compte que ça n'allait pas le faire.
Un point crucial de mon projet est la gestion et l'affichage des catégories de produits proposés par chaque marque, histoire que cela soit pratique de trouver les alternatives naturelles pour ce que l'on cherche sur le site. Or, dans Baserow il n'y avait pas moyen de générer mes contenus catégorisés de manière dynamique. J'étais contraint de modifier sans cesse des formules de plus en plus complexes, et donc avec un risque d'erreur de plus en plus grand. Cela reste un tableur, plus net pour gérer des données, mais moins fourni en termes de formules.
Avec une seule marque traitée en plus, mon "backend" v2 n'aura pas duré longtemps !
Etape 3 : courage, passons aux choses sérieuses
A ce moment là, j'ai sérieusement douté de ma capacité a créer ce site avec des outils open source et j'ai été tenté de retourner vers Bubble. À mon avis, Bubble est l'outil "no code" (ou de "programmation visuelle") le plus abouti. Je l'avais déjà utilisé efficacement avec We Do Good pour réaliser des prototypes de fonctionnalités, même utilisés provisoirement en production.
C'est génial, avec Bubble, des semaines de travail classique entre développeurs et designers pour arriver à une version utilisable se transforment en heures, voire en jours pour tester et valider des prototypes.
Mais… avec Bubble on n'a pas accès à ce qui se passe derrière l'interface de programmation. On devient en fait prisonnier de leur langage de programmation propriétaire. Si on a besoin de faire différemment, s'ils augmentent leurs prix de manière inadaptée, ou si un blocage se présente pour une autre raison, il faut tout refaire à zéro ou faire développer des nouvelles fonctionnalités (plugins) qui enrichissent Bubble.
J'ai alors décidé de passé au niveau supérieur en terme de technicité, avec des outils tout de même accessible aux non initiés motivés : une base de données dans Supabase connectée à une interface créée avec Plasmic. Avec Supabase j'ai accès aux paramétrages les plus fins sur les données et avec Plamic je construis visuellement ce dont j'ai besoin, comme avec Bubble.
Malgré l'interface visuelle très complètes de Plasmic, certaines fonctions dont j'ai besoin demandent des formules personnalisées utilisant un peu de code. L'avantage, c'est que là ou j'avais appris le language Bubble utilisable seulement avec Bubble, j'apprends maintenant les languages ouverts et universels du web sql et javascript, avec un peu d'aide de l'"IA" pour comprendre les fonctions et erreurs de syntaxe.
J'apprendre en faisant directement ce que j'ai envie, et c'est beaucoup plus efficace et motivant !
Plasmic me laisse aussi récupérer et réutiliser l'ensemble du code source ailleurs si j'en ai besoin un jour.
Je devais en passer par là
Chaque version de mon "backend" a été utile et même nécessaire à la suivante.
Avec mon expérience d'entrepreneur du web, je sentais depuis le départ que j'aurais besoin d'une solution robuste de base de données ainsi que de pouvoir intervenir sur le code facilement. Cependant, au démarrage, je n'avais pas envie de me plonger là-dedans. Finalement, bien m'en a pris ! La structuration de données que j'avais initialement imaginée est très différente de celle à laquelle j'arrive maintenant.
Je n'aurais pas eu une base de données claire et bien organisée dans Supabase si je n'avais pas fait précédemment une itération dans Baserow. Je n'aurais pas créé les tables et liaisons utiles dans Baserow si je n'avais pas créé les premiers contenus sous forme de texte avec liaisons dans Anytype.
De plus, je n'aurais pas trouvé l'énergie de me lancer sur ce nouveau projet si je n'avais pas commencé par une version très simple et non "scalable". C'est un vrai progrès personnel : j'ai toujours travaillé en essayant de concevoir le maximum de choses d'avances, pour me rassurer et limiter les risques, et parce que c'est ce qu'on apprend à l'école. Les problèmes, c'est que je dépensais pour cela une énergie folle et que bien sûr, la réalité ne correspond jamais vraiment aux prévisions.
En me lançant avec une première version pas du tout aboutie mais fonctionnelle, je me suis autorisé à faire plus d'erreur, à m'exposer et à me concentrer sur du concret.
Références
Pour moi, favoriser l'open source est essentiel car cela fait partie des outils fondamentaux pour défendre ma liberté et celle des autres.
Tous les outils que j'utilise ou ai utilisé pour ce projet sont open source, sauf Anytype qui est juste "open core" (c'est à dire qu'ils publient leur code mais n'autorisent pas tous les usages avec). Ils présentent aussi tous des plans gratuits bien pratiques pour se lancer sans contrainte financière.
- Anytype : https://anytype.io/
- Baserow : https://baserow.io/
- Supabase : https://supabase.com/
- Plasmic : https://www.plasmic.app/
J'ai aussi testé ou envisagé sans les retenir quelques autres solutions comme WordPress ou Silex. Provisoirement, en attendant d'avoir créé toutes les interfaces dont j'ai besoin avec Plasmic, j'utilise NocoDB, connecté à Supabase, pour disposer d'une interface visuelle équivalente à Baserow (avec des formules moins avancées mais la possibilité de me connecter plusieurs bases de données si besoin).
J'utilise beaucoup Alternative.to pour trouver les outils dont j'ai besoin, on y peut filtrer les applications selon de nombreux critère, je le recommande.
Ensuite, il faut tester et se lancer, voire tester en se lançant !
opensource #nocode #lowcode #vibecoding #ia #produitsnaturels #zeroplastique #nostrfr
-
 @ e8646d56:72dab368
2025-06-03 08:15:30
@ e8646d56:72dab368
2025-06-03 08:15:30eee
-
 @ ec42c765:328c0600
2024-12-22 19:16:31
@ ec42c765:328c0600
2024-12-22 19:16:31この記事は前回の内容を把握している人向けに書いています(特にNostrエクステンション(NIP-07)導入)
手順
- 登録する画像を用意する
- 画像をweb上にアップロードする
- 絵文字セットに登録する
1. 登録する画像を用意する
以下のような方法で用意してください。
- 画像編集ソフト等を使って自分で作成する
- 絵文字作成サイトを使う(絵文字ジェネレーター、MEGAMOJI など)
- フリー画像を使う(いらすとや など)
データ量削減
Nostrでは画像をそのまま表示するクライアントが多いので、データ量が大きな画像をそのまま使うとモバイル通信時などに負担がかかります。
データ量を増やさないためにサイズやファイル形式を変更することをおすすめします。
以下は私のおすすめです。 * サイズ:正方形 128×128 ピクセル、長方形 任意の横幅×128 ピクセル * ファイル形式:webp形式(webp変換おすすめサイト toimg) * 単色、単純な画像の場合:png形式(webpにするとむしろサイズが大きくなる)
その他
- 背景透過画像
- ダークモード、ライトモード両方で見やすい色
がおすすめです。
2. 画像をweb上にアップロードする
よく分からなければ emojito からのアップロードで問題ないです。
普段使っている画像アップロード先があるならそれでも構いません。
気になる方はアップロード先を適宜選んでください。既に投稿されたカスタム絵文字の画像に対して
- 削除も差し替えもできない → emojito など
- 削除できるが差し替えはできない → Gyazo、nostrcheck.meなど
- 削除も差し替えもできる → GitHub 、セルフホスティングなど
これらは既にNostr上に投稿されたカスタム絵文字の画像を後から変更できるかどうかを指します。
どの方法でも新しく使われるカスタム絵文字を変更することは可能です。
同一のカスタム絵文字セットに同一のショートコードで別の画像を登録する形で対応できます。3. 絵文字セットに登録する
emojito から登録します。
右上のアイコン → + New emoji set から新規の絵文字セットを作成できます。


① 絵文字セット名を入力
基本的にカスタム絵文字はカスタム絵文字セットを作り、ひとまとまりにして登録します。
一度作った絵文字セットに後から絵文字を追加することもできます。
② 画像をアップロードまたは画像URLを入力
emojitoから画像をアップロードする場合、ファイル名に日本語などの2バイト文字が含まれているとアップロードがエラーになるようです。
その場合はファイル名を適当な英数字などに変更してください。
③ 絵文字のショートコードを入力
ショートコードは絵文字を呼び出す時に使用する場合があります。
他のカスタム絵文字と被っても問題ありませんが選択時に複数表示されて支障が出る可能性があります。
他と被りにくく長くなりすぎないショートコードが良いかもしれません。
ショートコードに使えるのは半角の英数字とアンダーバーのみです。
④ 追加
Add を押してもまだ作成完了にはなりません。

一度に絵文字を複数登録できます。
最後に右上の Save を押すと作成完了です。

画面が切り替わるので、右側の Options から Bookmark を選択するとそのカスタム絵文字セットを自分で使えるようになります。
既存の絵文字セットを編集するには Options から Edit を選択します。
以上です。
仕様
-
 @ 0b884d0d:9abbd54a
2025-06-02 21:42:29
@ 0b884d0d:9abbd54a
2025-06-02 21:42:29Conceitos chaves
Neste artigo você vai entender um pouco dos conceitos chave desse novo conjunto de ferramentas para aplicar justiça de forma descentralizada e anárquica.
Antes de continuar a leitura, quero elucidar alguns termos que serão constantemente usados neste artigo.
- Private Law Society (PLS)
- Uma organização sem fins lucrativos com o objetivo de criar novas soluções para tornar cada vez mais viável a aplicabilidade de uma justiça privada e descentralizada
- Ao mesmo tempo, um conjunto de protocolos e softwares de código aberto com o mesmo propósito
- Links úteis
- Perfil Nostr: nostr:npub1p79dx59d5gctllar73cqnucqft89gpkfmydxj4mmk2jj69s7hn3sfjatxx
- GitHub: https://github.com/PrivateLawSociety
- Sobre: https://privatelawsociety.net
- Bitcoin Justice Protocol (BJP)
- Um protocolo estabelecido pela Private Law Society
- Também um software de código aberto disponível no GitHub da Private Law Society
- Links úteis
- GitHub: https://github.com/PrivateLawSociety/pls-bjp
- Sobre: https://privatelawsociety.net/bjp
- Implementação oficial da PLS: https://pls-bjp.vercel.app/
- Web Of Trust (WoT)
- Uma base de dados com avaliações entre usuários Nostr relatando confiança/desconfiança e se um usuário teve relações comerciais ou não com outro
- O objetivo é ser um repositório de reputação para chaves Nostr
- Links úteis
- GitHub: https://github.com/PrivateLawSociety/pls-wot
- Sobre: https://privatelawsociety.net/wot
- Implementação oficial da PLS: https://pls-wot.vercel.app/
- Meu fork com o grafo: https://pls-wot-kiuusai.vercel.app/
Prefácio
Recentemente saiu um episódio no BetterMoney podcast sobre o projeto de justiça privada Private Law Society.
Muitos bons pontos foram levantados neste excelente episódio pelos participantes nostr:npub12mllp29adf2fw0eeahmseczcu3y4625qyn3v4uwfvkpzlshnmj3qs903ju e nostr:npub1wsl3695cnz7skvmcfqx980fmrv5ms3tcfyfg52sttvujgxk3r4lqajteft. Mas neste entorno permanecem ainda muitas dúvidas sobre o projeto em si, seu funcionamento, princípios, objetivos e funcionalidades.
Venho através deste artigo, apresentar resumidamente o projeto, a filosofia por trás do mesmo e dar a minha visão de como este conjunto de protocolos chamado Private Law Society tem a capacidade de não só transformar o mundo como o conhecemos, mas de tornar boa parte do "poder judiciário" obsoleto e irrelevante em vários aspectos, se assim os indivíduos o quiserem.
Mas afinal, o que é essa tal de PLS?
PLS é um acrônimo para Private Law Society (Sociedade de Leis Privadas em uma tradução livre). Além de uma organização sem fins lucrativos e totalmente Open Source, trata-se de um conjunto de softwares disponíveis no GitHub de forma a estruturar um protocolo de justiça privada descentralizado com colateral em Bitcoin. Falei grego para você? Vamos com calma dissecar estes conceitos...
Sociedade de leis privadas, a "utopia" libertária se tornando realidade
Quem é adepto do movimento libertário e/ou estuda o tema, provavelmente já ouviu falar nesse termo. Originalmente cunhado por David Hume, o filósofo e idealista escocẽs. O projeto toma este nome com o intúito, talvez de forma ambiciosa, mas com certeza visionária e audaz, de trazer uma solução prática e simples de estabelecer contratos voluntários entre duas ou mais partes, as quais livremente escolhem os seus "árbitros" ou "juízes" para fazer valer a lei. Como realmente uma justiça paralela a qual o contrato faz lei entre as partes.
Para uma introdução sobre o conceito, indico este vídeo do canal AnCapSu que trata sobre o tema de forma resumida.
Essa ideia, simples a priori esbarra no problema da aplicabilidade da força, ou ao menos era o que se pensava, antes da criação de ferramentas como o Bitcoin e soluções como Taproot e Bitcoin Scripts. Agora, com uma propriedade realmente soberana, programável e incensurável, essa ideia começa a ganhar forma.
Basicamente, uma dúvida plausível para uma pessoa leiga no assunto seria: "Tá, entendi. Esse tal de bitcoin é realmente bom, seguro e o Estado não tem poder de controle sobre ele. Mas como isso pode gerar essa tal de sociedade de leis privadas? É só uma forma de dinheiro."
A resposta para isso é: Dinheiro programável, chaves privadas e reputação!
BJP: contratos colateralizados em Bitcoin
Bitcoin, Nostr e Taproot: a chave para a aplicação da justiça privada
Se você já está minimamente envolvido com o ambiente Bitcoin, Nostr e afins, deve saber o que é um par de chaves públicas e privadas e como isso funciona. Existe uma chave pública e privada, a pública é a forma de identificação no sistema e a privada é a que gera as assinaturas. Daí é possível determinar que quem publicou a mensagem, seja na blockchain do Bitcoin, seja na rede Nostr, é o dono daquela chave pública em específico. Assim, se institui uma forma de identidade digital.
O que muita gente não sabe, ou não dá o devido valor, é que depois do soft fork Taproot da rede Bitcoin (ocorrido em 2021), os antigos Bitcoin Scripts tomaram outra forma e maior capacidade, se tornando mais práticos, leves e funcionais. Isso é o que dá base hoje para "contratos inteligentes" no Bitcoin e toda a parafernalha de Ordinals, Runes e coisas do gênero. O que pra muitos foi uma maldição que encheu a mempool, na verdade também se provou uma bênção, a qual é a base do BJP (Bitcoin Justice Protocol) da Private Law Society. A atualização permitiu com que scripts mais complexos pudessem ser desenvolvidos de forma mais simples, fossem mais leves e tivessem uma melhor privacidade. O BJP se empodera disso, fornecendo uma solução ao mesmo tempo que simples, inovadora para casos de uso de contratos. Primariamente na camada nobre do Bitcoin e posteriormente na Liquid Network, para aqueles que querem poupar em taxas e terem mais privacidade.
Por sua vez, o Nostr funciona também com criptografia de curvas elípticas, assim como nosso querido Bitcoin. Para ser mais preciso, o mesmo algoritmo é usado tanto no Nostr quanto no Bitcoin. O Secp256k1. Na prática isso significa que toda chave Nostr também é uma chave Bitcoin em potencial. O BJP se apropria dessa interconexão para possibilitar a criação de contratos jurídicos.
BJP: uma multisig sofisticada?
Ok, até agora vimos o que torna esse tal de BJP possível, mas como ele funciona e como eu posso usá-lo na prática?
Bem grosseiramente falando, o BJP é um software que facilita a criação de carteiras multisig específicas para contratos jurídicos. Com ele, você constrói uma multisig não convencional com Taproot que assegura o cumprimento do contrato mediante concordância de todas as partes "clientes" do contrato ou do número mínimo de árbitros configurados previamente + um dos clientes.
Na prática, um script Taproot é montado com a seguinte lógica:
``` Clientes = {Lista de chaves públicas dos clientes}
Árbitros = {Lista de chaves públicas dos árbitros}
Quorum = Número mínimo de árbitros para aprovar a transação
Se todos os Clientes concordarem: Libera gasto Senão se 1 dentre todos os Clientes concorda e ao menos o Quorum de Árbitros concorda: Libera gasto Senão Bloqueia gasto ```
Esse algoritmo garante que o contrato seja efetuado e esteja de acordo com a vontade de todas as partes envolvidas, ou, se entrar em "disputa judicial", o número mínimo de árbitros designados para "fazer valer a lei", concorde junto com a parte lesada para onde os fundos devem ir.
Um exemplo prático:
Aqui temos um exemplo prático de aplicabilidade de um contrato feito através do BJP. Nesse caso, tendo a concordar com o nostr:npub1narc0ect9jf0ffnvcwg8kdqlte69yxfcxgxwaq35eygw42t3jqvq4hxv0r e discordar do nostr:npub12mllp29adf2fw0eeahmseczcu3y4625qyn3v4uwfvkpzlshnmj3qs903ju quando o primeiro comenta no recente episódio do BetterMoney Podcast:
19:30 Eu discordo do Júlio. Acho que a PLS seria perfeita pro contrato de aluguel. O locatário coloca o colateral e o proprietário vai ter certeza de que não vai tomar calote.
E se uma das partes tentar levar pra justiça estatal, não vai ter nenhum nome no contrato, apenas chaves públicas.
E está certo. O exemplo prático que acabei de citar reforça isso. Não há nada que impeça também, de no contrato, ter uma cláusula a qual envolver a justiça estatal cause algum prejuízo ou perda de causa imediata para a parte expositora. Não estou fazendo recomendação alguma, fazendo apologia a qualquer prática ou aconselhando usar deste tipo de artifício, se o que falo possa ser interpretado como crime pela lei positivada (não sou advogado). Mas, no campo das ideias e das possibilidades no mundo real, é uma possível solução/alternativa.
Vamos ao exemplo...
Adriano Calango quer alugar um apartamento de Beto Lagartixa. Só que ambos não se conhecem e não confiam suficientemente um no outro para fazer um contrato. Ambos decidem então escrever um documento. Word, Pdf ou um texto puro. Não importa. Lá estão todas as cláusulas, o caução do aluguel, multas estabelecidas para uso indevido, penalidades, dia de pagamento, decisão sobre multa de atraso, enfim, qualquer detalhe desse contrato.
Adriano Calango, escolhe Célsio Jacaré, seu amigo como seu árbitro pessoal. Beto Lagartixa escolhe Danilo Crocodilo, seu amigo, como seu árbitro pessoal. Ambos escolhem Eduardo Cobra, um réptil íntegro, com reputação ilibada e que já fez vários julgamentos, como um árbitro em comum para seu contrato. Daqui temos: dois contratantes, duas testemunhas e um juíz.
Adriano Calango então, acessa o site da PLS BJP para criar o contrato. Configura os clientes (ele e Beto Lagartixa), configura todos os árbitros, anexa o arquivo e cria o contrato na rede Bitcoin.
Um evento Nostr criptografado é criado e um link de compartilhamento do contrato é disponibilizado. Adriano Calango compartilha esse link com todos os usuários disponíveis.
Todos os usuários verificam os detalhes do contrato e se o documento do contrato bate com o contrato assinado. Todas as partes ativamente concordando, a nossa multisig é criada.
Um arquivo do contrato é disponibilizado para acessar a multisig do contrato posteriormente. Todos os usuários salvam esse arquivo e o mantém guardado em um local seguro. O objetivo disso é ter redundância. Se um dos participantes perder este arquivo, outro pode compartilhar o mesmo para possibilitar o acesso à multisig do contrato.
Adriano Calango e Beto Lagartixa depositam os devidos colaterais no contrato. Seja o caução de aluguel ou um montante separado para ser empenhorado. Isso é definido pelo acordo feito previamente.
Se tudo ocorrer bem, assim que Adriano Calango resolver se mudar e Beto Lagartixa não tiver nenhuma objeção quanto a isso, ambos voltam para o contrato previamente feito e concordam quanto aos montantes que cada um receberá de volta. Dividem o preço da taxa entre si e cada um tem sua propriedade de volta.
Digamos que Adriano Calango não cumpriu com parte do contrato, atrasando o pagamento de alguns meses. Por outro lado, Beto Lagartixa também não cumpriu parte de seu acordo, deixando de fornecer serviços prescritos no contrato como segurança de condomínio e um elevador funcional. O caso então é levado aos árbitros. Célsio Jacaré argumenta a favor de Adriano Calango, questionando Beto Lagartixa sobre os serviços não prestados pelo mesmo e que claramente no contrato estavam previstos como parte inclusa no custo do aluguel. Danilo Crocodio retruca sobre a inadimplência de Adriano Calango, defendendo seu amigo/cliente, Beto Lagartixa. Eduardo Cobra, ao ouvir calmamente todos os argumentos de ambos os lados, então decide: - Adriano Calango foi inadimplente por três meses. Portanto terá uma multa de 35% sobre seu patrimônio - Beto Lagartixa terá uma multa de 25% sobre o seu patrimônio, pois não prestou o serviço com a devida qualidade - O restante do patrimônio será devolvido para seus respectivos donos - Dos valores da multa: - 90% será dividido entre cada árbitro. 30% para cada - Os 10% restantes serão queimados em taxas para os mineradores
Note que não foi usado nenhum meio coercitivo para solucionar o caso e penalizar os réus em seus devidos processos. Tudo foi aceito voluntariamente previamente, inclusive da parte dos árbitros. As multas aplicadas são meramente ilustrativas. Em um cenário real, tais penalidades seriam acordadas previamente e na falta das mesmas, todas as partes discutiriam até entrar em um acordo quanto a decisão. É totalmente plausível que, por exemplo, a penalidade fosse queimar todo o valor das multas em taxas para os mineradores, se assim todos aceitassem. O mecanismo de mineração nesse cenário também se torna um possivel meio de aplicação de força em um julgamento.
Só esta parte do ecosistema já faz boa parte dos casos de uso da justiça estatal obsoleta, dando maior descentralização, privacidade e soberania para os indivíduos.
Nesse cenário temos novamente a "utopia" libertária sendo definitivamente aplicada. Não há dedo do Estado no meio, todos os contratos foram previamente acordados entre as partes e não houve violação ao PNA (Princípio da Não Agressão). Todo o processo foi estritamente voluntário desde o começo.
WoT: A digitalização da reputação
Quem vê o projeto a primeira vista, pode pensar:
Ah Calango. Legal essa solução com bitcoin e tal. Mas eu vou sempre precisar gastar meus bitcoins toda vida que fizer um contrato? Tem contratos que isso não vale a pena!
Sim. Isso é verdade. Tanto que foi genialmente um caso citado pelo nostr:npub12mllp29adf2fw0eeahmseczcu3y4625qyn3v4uwfvkpzlshnmj3qs903ju. Há casos que os valores são tão pequenos que não compensa criar todo um documento de contrato para, por exemplo, comprar um livro ou algo do tipo. Ou, algumas vezes, o próprio indivíduo não quer gastar dinheiro ou travar valores para manter esse contrato. Mas não é o único caso de uso. Lembre-se que mesmo com colaterais aplicados, normalmente as pessoas não gostam de entrar em decisões judiciais ou confusões em geral. Idealmente todos querem traçar o caminho feliz da história. Então, mesmo para firmar contratos com colateral em Bitcoin usando o BJP, é plausível que um usuário queira pesquisar o "histórico" de outro usuário na rede para averiguar se é uma boa ideia ou não se envolver com aquele indivíduo em específico.
Naturalmente o ser humano já pratica esse cálculo de reputação e analisa o ambiente a sua volta para entender a hierarquia e reputação dele e de outros indivíduos em um grupo. Somos seres sociais e naturalmente na nossa cabeça já montamos uma espécie de rede de confiança na nossa cabeça com a imagem que formamos de um indivíduo X ou Y com base na nossa comunidade. Hierarquia, lideranças, influência, são características naturais do ser humano.
A partir desse cenário, surgiu a ideia de gerar uma solução para uma melhor visualização da reputação entre usuários do protocolo. O objetivo é ser primariamente um repositório com avaliações de usuários sobre outros usuários, os classificando positivamente ou negativamente e informando se houve ou não negócios/fechamento de contratos com o mesmo. A ideia é realmente simples e o objetivo é deixar o protocolo aberto para as mais diversas formas de interpretação desses dados. Seja com modelos matemáticos, visualização e interpretação pessoal ou até mesmo o uso de inteligência artificial para o auxiliar o usuário a tomar suas decisões.
WoT: o nome é conhecido, mas a proposta é diferente
Veja que há uma diferença prática na WoT da PLS e outros projetos de WoT espalhados pela internet afora e pelo Nostr. A maioria dos projetos de WoT são para determinar se uma pessoa/chave privada é ou não relevante a partir da visão de outra chave privada. É o caso de serviços de WoT como o da Coracle.Social, Vertexlab.io e mais recentemente da nova implementação de WoT Relays. Serviços como estes tem o objetivo de reduzir ou eliminar spam e falsidade ideológica (fakes), assim como oferecer uma espécie de algoritmo de recomendação, similar ao que é feito em redes sociais como YouTube e Instagram.
Note que em nenhum momento o objetivo da WoT da PLS é definir por A + B quem é ou deixa de ser confiável ou inconfiável, afinal, confiança é algo estritamente relativo. Nenhum projeto pode ter a audácia de tentar classificar pessoas como confiáveis ou inconfiáveis a nível de estabelecimento de contratos. A PLS entende isso e respeita esse caráter subjetivo da confiança. De igual maneira, nunca foi o objetivo de qualquer projeto de WoT sério fazer algo similar ao que é feito em países como a China, onde pessoas têm alguma espécie de "crédito social". Fique tranquilo. Nosso objetivo não é tornar os episódios distópicos de Black Mirror em realidade 🤣
Visualização em grafo: uma proposta elegante
Desde que entrei de cabeça no projeto da PLS, uma coisa que veio sendo falada nas reuniões era sobre a criação de novas ferramentas para visualizar a rede de formas mais intuitivas, que ajudassem os usuários ao julgar pessoas como confiáveis ou não para estabelecer contratos, e ao mesmo tempo, resolvessem o problema de UX que é uma simples tabela com avaliações entre usuários da rede. A tendência é, a partir do momento que o projeto comece a ter adesão, que o número de notas cresça exponencialmente, e com isso, a visualização da reputação dos indivíduos seja pouco intuitiva. Uma solução apresentada para este problema foi a criação de um frontend com grafos, ou melhor, a criação de uma forma de visualização da sua rede de confiança em particular. A partir disso, foi gerada uma bounty no projeto para a implementação desta solução, a qual eu orgulhosamente estou construindo (na verdade está pronta para uso. Mas ainda quero melhorar algumas coisas). O objetivo é simples: dar ao usuário mais uma forma de contemplar os dados da WoT, de forma mais particular e intuitiva. Facilitando a tomada de decisões.
A natureza da confiança humana em sintonia com a tecnologia
Bolhas virtuais, vilarejos e mineiros
Uma possível crítica que o projeto possa receber é a possibilidade de ataques de spam ou cancelamento em massa corroer ou inviabilizar a utilidade do protocolo. Ataque Sybil também. Entretanto, são espantalhos até bem inocentes quanto ao projeto em questão.
Como havia mencionado anteriormente, a base do projeto em si é propositalmente simples e não se propõe a dar uma solução definitiva para a visualização dos dados postos no protocolo. A tabela de avaliações hoje existente no site da WoT da PLS é apenas uma das inúmeras formas de interpretar estes dados. E uma forma efetiva para problemas como esse, é justamente a implementação de uma visualização por grafo, onde os usuários podem ver redes de confiança sendo tracejadas a partir do ponto de vista específico de uma npub em particular.
Aqui a lógica de um antigo ditado é aplicada:
"O amigo do meu amigo é meu amigo"
Da mesma maneira também podemos formular outras afirmações como:
"O inimigo do meu inimigo é meu amigo"
"O inimigo do meu amigo é meu inimigo"
"O amigo do meu inimigo é meu inimigo"
Se tais derivações fazem sentido para você ou não, não cabe a mim dizer. Novamente, confiança é intrinsecamente algo de caráter subjetivo. Vai de cada um decidir quem é ou não confiável. É justamente por isso que estou implementando diversos filtros de avaliações no meu fork da PLS.
Na prática é o velho jogo de política de sempre. Como bem citado uma vez pelo filósofo e youtuber Platinho, ao citar Carl Schmitt:
Isso também se reflete na cultura mineira (e rural do Brasil em geral), por exemplo. O clássico "cê é fi de quem?". Perceba que essa é uma forma de procurar por um caminho de confiança já estabelecido. Quem tem parente em interior sabe, que uma das coisas mais comuns é os mais velhos, seja ou tio, mãe ou avô perguntar sobre um amigo que você leve para o ambiente familiar (meu filho, esse seu amigo é filho de quem?) É algo até instintivo do ser humano procurar por rotas de confiança e trabalhar de certa forma com o QI (Quem Indica). Goste você ou não, é assim que a natureza humana se expressa e é assim que a dinâmica social é montada.
Vendo que é natural a formação de bolhas, não é uma boa ideia em si interpretar os dados da WoT da PLS simplesmente de uma forma numérica bruta. A melhor forma é fazer uma abordagem individual, com base na sua rede de confiança ao invés de puramente o número de avaliações positivas e negativas.
O grafo da PLS busca justamente tornar mais intuitivo, prático e sistemático essa pesquisa natural. Essa implementação é além de uma ferramenta, uma forma de expressão social muito forte, tanto em âmbito social quanto jurídico, à medida em que a dinâmica social e jurídica se entrelaçam no tecido social.
Adriano Calango ataca novamente
Para um exemplo prático, voltemos a falar dele, Adriano Calango.
Adriano Calango conhece a WoT da PLS já faz um tempo e já avaliou todos os seus parceiros comerciais e amigos aos quais tem laços de confiança já firmes e maduros. Ele procura alguém para alugar uma casa Rolante, RS. ´Ele vê alguns perfis de síndicos no Nostr que moram na mesma cidade que ele com casas disponíveis para alugar. Mas quer ter uma noção que não está se metendo em encrenca ou lidando com algum síndico chato que inferniza a vida dos inquilinos.
Dito isso, ele acessa a WoT da PLS e vai na página do grafo. Percebe que seu amigo Bruno Jabuti, ao qual já havia avaliado positivamente anteriormente, avaliou positivamente um professor de Jiu-jitsu, conhecido como Carlos Camaleão. Que além de ser avaliado positivamente por Bruno Jabuti, recebeu várias avaliações positivas de outros usuários conhecidos de Adriano Calango. Carlos Camaleão, por sua vez, avaliou positivamente um síndico da região chamado Diego Iguana. Na descrição Carlos Camaleão descreve como em todo o tempo que ele foi inquilino de Diego Iguana sempre foi bem tratado e como seu condomínio estava sempre bem organizado e era cuidadosamente zelado, e como sempre que havia alguma falha de infraestrutura, o problema era rapidamente resolvido. Adriano Calango considera firmar um contrato de aluguel com Diego Iguana.
Assim, temos o seguinte caminho de confiança estabelecido:
Adriano Calango 👍 -> Bruno Jabuti 👍 -> Carlos Camaleão 👍 -> Diego Iguana
Passando-se alguns dias, Adriano Calango é abordado por Denis Jacaré em uma DM no Nostr oferecendo aluguel baratíssimo e com poucas exigências. Denis Jacaré foi informado que Adriano Calango estava a procura de um imóvel novo para residir. Adriano Calango, então, pega a chave Nostr de Denis Jacaré e joga na parte de "target" na página do grafo na PLS WoT. Ele percebe que Denis Jacaré tem várias avaliações negativas de inúmeros usuários, mas não consegue ainda bater o martelo quanto a confiabilidade de Denis Jacaré. Ele então insere sua própria chave Nostr no campo de "main rater" e vê que tem um caminho tracejado entre a sua npub e a de Denis Jacaré. Pra sua surpresa, ele vê que Carlos Camaleão deu a Denis Jacaré uma avaliação negativa, por conta que no período em que sua filha era inquilina do mesmo, prestou um péssimo serviço. O condomínio vivia com o elevador quebrado, a portaria muitas vezes não funcionava e tinha falta de luz constante. Denis Jacaré não tomava providẽncia nenhuma quanto a isso e ainda fazia questão de causa intriga entre os inquilinos e tentar jogar uns contra os outros. Adriano Calango, então percebe que Denis Jacaré não é confiável com base na rede de confiança definida por Adriano Calango.
Nesse caso temos o seguinte circuito estabelecido:
Adriano Calango 👍 -> Bruno Jabuti 👍 -> Carlos Camaleão 👎 -> Denis Jacaré
Adriano Calango aborda Diego Iguana para estabelecer um contrato. Agora é a vez de Diego Iguana pesquisar o histórico de Adriano Calango. Pois ele quer manter a comunidade de seu condomínio saudável e não deseja aceitar inquilinos baderneiros ou barraqueiros.
Diego Iguana faz então o caminho inverso de Adriano Calango, pondo a npub de Adriano Calango como "target" e a própria npub como "main rater". Daí Diego Iguana consegue ver que Carlos camaleão deu uma nota positiva para Bruno Jabuti e Bruno Jabuti deu uma nota positiva para Adriano Calango. Os dois então fecham negócio.
Neste exemplo, o grafo da WoT da PLS serviu como uma "bússola de confiança" para Adriano Calango e Diego Iguana firmarem um contrato no BJP com seus árbitros e advogados.
Considerações finais
Neste artigo você pôde aprender os conceitos básicos da Private Law Society, motivos de certas escolhas de design, viu exemplos práticos de casos de uso e um pouco das bases filosóficas que norteiam o ecosistema da PLS. Também pôde compreender um pouco mais sobre o conceito de WoT na PLS e como isso pode ser útil com o passar do tempo e a adesão de novos usuários no sistema.
Se este conteúdo te agregou de forma positiva em algo, considere mandar um ZAP ou fazer uma doação anônima por um dos meios disponibilizados na descrição do meu perfil Nostr. Este artigo foi feito com muito carinho e dedicação. Sua doação me encoraja a continuar produzindo e lhe mantendo informado. Se não pode ou não quer contribuir financeiramente, considere engajar no conteúdo reagindo, compartilhando e comentando. Toda a ajuda é bem vinda. Agradeço de coração sua paciência e atenção para ler até aqui.
Em breve trarei novidades sobre o desenvolvimento do grafo da WoT e logo mais, vídeo novo no meu canal do YouTube. Até mais!
-
 @ ec42c765:328c0600
2024-12-13 08:16:32
@ ec42c765:328c0600
2024-12-13 08:16:32Nostr Advent Calendar 2024 の 12日目の記事です。
昨日の 12/11 は きりの さんの 2024年のNostrリレー運営を振り返る でした。
nostr-zap-view 作った
リポジトリ: https://github.com/Lokuyow/nostr-zap-view/
動作確認ページ: https://lokuyow.github.io/nostr-zap-view/それ何?
特定の誰かや何かに宛てたZap(投げ銭)を一覧できるやつ
を
自分のWebサイトに設置できるやつ
自分のサイトに設置した例 * SNSリンク集ページ(最下部): https://lokuyow.github.io/
おいくらサッツ(Zap一覧ボタン): https://osats.money/
今日からビットコ(最下部): https://lokuyow.github.io/btc-dca-simulator/なんで作ったの?
私の去年のアドベントカレンダー
【Nostr】Webサイトにビットコインの投げ銭ボタンを設置しよう【Zap】
https://spotlight.soy/detail?article_id=ucd7cbrql/
が前提になってるけど長いので要約すると * ZapするやつはあるけどZap見るやつがないので欲しい * ZapをNostr(の典型的なkind:1クライアント)内だけに留めるのはもったいない * Webサイトの広告うざいからZap(的な何か)で置き換わって欲しいお前だれ?
非エンジニア、非プログラマー
AIにコード出させてるだけ人作った感想
できた
作った感想2
完成してから気付いた本当に作りたかったもの
こういうところにそのままZapを表示できる感じにしたい
 (ここまでちゃんとした商業ブログでなく)個人のブログやHPの端っこに「Sponsored by」欄があって名前が表示される感じ
(ここまでちゃんとした商業ブログでなく)個人のブログやHPの端っこに「Sponsored by」欄があって名前が表示される感じ
もうZapっていう文字もビットコインっていう文字もNostrも出さなくていいし説明もしなくていいのでは感がある
イメージはWebサイトを対象にしたニコニ広告 + スーパーチャット + 祭りとか神社の奉納者一覧
で思ったのは
個人からの投げ銭なら推し活的なものにしかならないけど
企業がNostrにアカウントを作ってサイトに投げ銭をしたら企業の広告になるんでは!?
~~企業がNostrにアカウントを!?デリヘルしか見たことない!~~今後
思いつき、予定は未定
* ボタン→ダイアログ形式でなくバナー、Embed形式にしてページアクセスですぐ見れるようにする * 多分リレーに負荷がかかるのでなんかする * Zapの文字は出さず「Sponsored by」等にする * 単純な最新順でなくする * 少額Zapをトリミング * 一定期間(一か月など)ごとで金額順にソート * 多分リレーに負荷がかかるのでなんかする * 今は投稿宛てのZapをWebサイト宛てのZapと勝手に言い張ってるだけなのでちゃんとWebサイト宛てのZapにする * NIPの提案が必要 * ウォレットの準拠も必要 * リレー(wss://~)宛てのZapもできてほしい将来
インターネットのすべてに投げ銭をさせろ
おわり
明日は mono さんの Open Sats 申請編 です!!
-
 @ 319ad3e7:cc01d50a
2024-12-15 21:20:59
@ 319ad3e7:cc01d50a
2024-12-15 21:20:59LETTER FROM THE FOUNDER | FEATURED RECIPE | MICROFICTION | FOOD NOTE QUOTE | SOUNDS | NOSTR MARKETPLACE | REAL REVIEWS | COMMUNITY ALBUM | NEW RECIPES | FIN
LETTER FROM THE FOUNDER 📝
A Year of Growth and Gratitude
As we approach the end of the year, it’s the perfect moment to pause and reflect. 2024 has been a transformative year for Zap Cooking. What started as a simple idea has grown into a vibrant, connected community. From recipes to shared stories, the #zapcooking tag has become a rallying point for food enthusiasts everywhere, and it’s inspiring to see how this shared passion is bringing people together.
None of this would have been possible without the incredible support and dedication of Sarah, who pours her heart into crafting these newsletters. Sarah, thank you for helping us share the joy of cooking and community with so many.
I am deeply grateful, grateful for you, our community, for nostr, for the milestones we’ve reached, and for the challenges that have helped us grow. Zap Cooking is about more than food; it’s about connections, creativity, and collaboration. Together, we’ve built something special, and I’m excited for what 2025 holds.
Here’s to another year of cooking, connecting, and creating together. Thank you for being part of this journey.
Cheers!
Seth
Founder, Zap Cooking
FEATURED RECIPE 🥪
Nostrville 2.0 was located in Nashville, Tennessee. This music destination featured some powerhouse food establishments, such as Ladybird Taco, Hattie B’s Hot Chicken Sandwiches, Pancake Pantry, and Modell’s infamous family-style breakfast; however, it was the people from Louisiana who brought their A-game to the shared kitchen at the after-party rental.
The lovely Rupert and her giant, Kajoozie, served up a traditional gumbo that had all of us reaching for a second bowl… or perhaps a fourth bowl. It was that good! They were also kind enough to share their recipe with all of us.
Rupert and Kajoozie’s #Nostr Famous Gumbo https://substack.com/home/post/p-152296981
MICROFICTION 📖
GIFTS by RustyPuppy
Every Christmas Eve (and by 'every' Aaran meant those he could remember, which, being eight years old, was not many), after the dinner dishes had been washed, and the family settled into the living room to watch "It's a Wonderful Life," his nani would start chopping vegetables. Aaran once asked why she didn't cook Santa's beef stew when she prepared their dinner. Because she wanted the stew to be fresh, came the answer. Aaron knew better than to ask how something that needed to simmer for five hours could be considered 'fresh.'
Everyone knew their grandmother's beef stew, placed in front of the fireplace in a hand-made bowl wrapped in a dish towel to keep warm, was eaten by the dog after everyone went to bed. And every year, she insisted Santa needed a hot, healthy meal.
None of the children could believe anyone would choose vegetables over cookies. Shari, the girl next door, made peanut cookies for Santa. Aaron had helped mix the dough last year. He was forbidden from adding the frosting because Shari needed the perfect amount atop each cookie so she could write her name in the sugary mix with a toothpick. Depending how guilty she felt about the year, she sometimes added candy beads.
One year, a cousin asked if Santa really ate all of those hundreds? thousands? millions? of cookies. An uncle said, "Of course, that's why he's so fat," while Aaaran's mother said, "Of course not, he gives them to children who don't have sweets," and Nani added "And those who still want to believe in him."
Aaran secretly wanted to believe his nani, because his older brothers had teased him for writing his Christmas wish letter, saying Santa was only real for babies. He didn't want to be a baby, but he still wanted to believe in the magic that was Santa.
At last, the evening ended. Some returned to their homes; the rest returned to their rooms. Nani set her bowl under the stockings. Aaran hesitated on the stairs, but the thought of seeing the dog actually eat the stew made his eyes wet. He stepped over his cousin's sleeping bag, got into bed, and dreamed of flying reindeer.
In the morning, as the children opened their gifts and the adults took turns making coffee and tea, Nani asked Aaran to bring her the stew bowl. He looked at the dog, currently surrounded by shreds of wrapping paper, panting happily with a bow on his head. Picking up the bowl, Aaron saw something within; a peanut cookie with the name Shari written in the frosting.
RECIPE REFERENCES:
Lovely Indian beefstew with coconut milk & Ultimate Peanut Cookies https://substack.com/home/post/p-152296981
FOOD NOTE QUOTE 🗒️
Today someone took a picture of my latte art after I handed them their cup 💜 and it made my day. Celebrate the small things. 😊 - TKay
SOUNDS 🔊
At Bitcoin Park in Nashville, Tennessee, the adorable cuties Mallory, Other Mallory, Island, and Sergio, along with help from Fountain, Phantom Power and Tunestr.io organized a night of activities, food, art, and a live acoustic music panel featuring four absolutely talented musicians - Ainsley Costello, Amber Sweeney, Luke Wood, and Jo Corso. SoupBox was honored to sit down with Amber to chat about music, fostering dogs from Wags and Walks, and food | Listen Now: SoupBox with Sarah | Featuring Amber Sweeney
https://fountain.fm/episode/nvwD83sajCiFNqTP4tYu
https://feeds.rssblue.com/soupbox
Short from Nashville | OpenMike | Tunestr
https://v.nostr.build/yLufD7GbwOPI3EgA.mp4
NOSTR MARKETPLACE 💳
Find Your Holiday Gifts on Nostr | Value for Value (aka V4V) #circulareconomy
Agi Choote | Art Prints | Find on Nostr!
Amber Sweeney | Custom Songs for Any Occasion | https://www.theambersweeney.com/merch/custom-songs
Ant Richard | Limited Custom Handcrafted Knife Gift Certificates (12-month waitlist for all custom handmade orders) | Find on Nostr!
Apotheca Viva | https://apothecaviva.love/
Aupa Bars | https://eataupa.com/
Barnminer’s Barn Jerky | Find on Nostr!
Billay Coffee | https://billaycoffee.com/
BitBees | Honey & Honey Products | https://www.kittrellsdaydream.com/
Bitcoin Blankets ⚡️| Website Coming Soon!
Bitpopart | https://bitpopart.com/ | https://www.storeofvalue.eu/collections/christmas-collection
BTC Aloha | Bitcoin Beachwear & Accessories | https://btcaloha.shop/
BtcPins | https://btcpins.com/
Cannabis Records | https://cannabisrecords.store/
CryptoCloaks | https://www.cryptocloaks.com/shop/
Delgado’s Fuego | https://delgadosfuego.com/
Dot GNT | Laser Engravings | https://dotgnt.codeberg.page/
Finca Yabisi | https://yabisi.farm/
Foxfire Mushrooms | https://foxfiremushrooms.com/
Golden Tallow | https://goldentallow.com/
GoodBeans 🇸🇻 Coffee | https://thegoodbeans.com/
Isolabell.art | https://isolabell.art/
Jake Wolki | https://wolkifarm.com.au/
Keto Beejay | Low Sugar Jerky | https://ketolish.us/ | https://ketobeejay.npub.pro/
Kanuto Takumi San | Find on Nostr!
Laser Eyes Cards | https://lasereyes.cards/
LeatherMint | https://theleathermint.com/
Lightning Store | https://lightning.store/
LightningSpore | Full Service Mushroom Cultivation Company | https://www.lightningspore.com/
Lost Sheep Ranch | https://www.lost-sheep-ranch.com/
Lucho Poletti | Art Prints and Merchandise | https://luchopoletti.com/
Madex | Art & Apparel | https://madex.art/collections/in-stock
MapleTrade | Find on Nostr!
Matthew D | https://whitepaperstreetsoap.com/
Next Block Coffee | https://nextblockcoffee.com/
NoGood | Jake Wolki | https://wolkifarm.com.au/
PatsPropolisHoney | Find on Nostr!
Peony Lane Wine | Ben Justman | https://www.peonylanewine.com/
PlebianMarket | https://plebeian.market/
PictureRoom | Assorted Dessert Treats | Find on Nostr!
Regenerative Farmed Meats & Knives | AgrarianContrarian | Find on Nostr!
RustyPuppy | Art and Stories | https://heidi2524.com/
Salt of the Earth | Premium Electrolyte Mix | https://drinksote.com/
Satoshi Coffee Company | https://sats.coffee/
Scott & Son | Animal Portraits, Prints, and Apparel | https://xavierscraftworkanddesign.com/t-shirts
SofterSkin Tallow Skincare | https://softerskin.co/
Shopstr | https://shopstr.store/
Soap Miner | Tallow Body Soap Bars
SweetSats | Honey | https://sweetsats.io/
Veiled Mycology | https://veiledmycology.com/
Yojimbo | Jam & Marmalade | https://jimblesjumble.odoo.com/
REAL REVIEWS ⭐
BitBees | Honey & Honey Products | https://www.kittrellsdaydream.com/ | By Rupert
If you follow me or have ever had the pleasure of chatting with me on cornychat.com or hivetalk.org, you’ll know how proud I am of my Cajun heritage. For me, that means memories of long, hot summer days in South Louisiana, plenty of mosquito bites, the humming of cicadas in the cypress trees, and my grandfather’s bee boxes abuzz with fuzzy little workers.
I recently had the pleasure of meeting our famed #nostr beekeepers, @bitbees and @kingbee, and the absolute joy of tasting the labors of the wee little friends they care for. @KajoozieMaflingo and I purchased both their wildflower and gallberry varieties, and we were able to pay with BTC! (BONUS!) The wildflower was chef’s-kiss perfection, but my taste buds were instantly rocketed back to my childhood when I tried the lovingly and aptly nicknamed “swamp honey.”
Its pale color might fool you into thinking it has a lighter flavor than its rich and flavorful counterpart, but that couldn’t be further from the truth. It’s crisp and bright, with a mellow sweetness balanced by a slight tang to finish. It’s the ideal pairing with my favorite chamomile tea before bedtime.
This was my first purchase, but it will not be my last. By far, this is one of the most delicious use cases for Bitcoin I’ve come across to date.
Keto Beejay | Low Sugar Jerky | https://ketolish.us/ | https://ketobeejay.npub.pro/ | By The Beave
I recently had the pleasure of ordering four types of beef jerky from Beejay, the proprietress of http://ketolish.us. I was intrigued by her offerings and ended up ordering plain, pickle, pizza, and pepper. My order took a while to go through, mostly because Beejay and I were figuring out how to move sats around without it being too much of a pain in the butt. However, once finalized, everything shipped promptly and arrived quickly in a well-packed parcel. Beejay is also very good to communicate with, and I will gladly purchase more from her in the future.
I will start off the reviews with the most surprising of the batch: pizza. This was simply outstanding. I was shocked at how much it reminded me of eating pizza. I can't recommend this one enough! My second favorite pick is the pickle flavor. I love pickles. (I cannot express how much I love pickled things to you in words!) This was also very good, with the dill seasoning being front and center but restrained enough not to completely overpower the delicious beefiness of the jerky. A note on the texture: the jerky is ground, so it is not as tough as other jerkies you might try. This is a very new thing to me, and I rather enjoyed the novelty of the experience. The peppered jerky was full of pepper. This might be too much pepper for some, as it reminded me of the pepper-covered salami you can get at a good Italian pork store. Lastly, the plain jerky was delicious in its own right, though I would have preferred a touch more salt. I would order all of these again and am looking forward to ordering other flavors in the future, especially the bison!
COMMUNITY ALBUM 📷
Photos & Videos by Mandana from NextBlock & Flirting with Bitcoin, Efrat Fenigson, Ava, Birthday B, Vic from CornyChat, Tortuga, Mallory, Island, Jack Spirko, Paul Keating, BreadandToast.com, Nos.Social and Sarah SoupBox
View the Album: https://substack.com/home/post/p-152296981
NEW RECIPES 🍲
https://i.nostr.build/MNrivKtc1fpjamfn.png
In November, we received an incredible surge of over 30 recipes submitted to Zap Cooking! That's a fantastic leap from the three or four we typically see each week! Dive into one, two, or even all of them, and don’t forget to share your reviews and mouthwatering photos on Nostr using #foodstr. We’d also love to see your favorite personal or family recipes—let’s keep the culinary creativity flowing!
Corn Pudding, The Beef Panzone, Vodka Pie Crust, Short Rib Barbacoa Tacos, Guiness Beef Stew with Pickled Pearl Onions, Fast AF Beef Stroganoff, Dark Chocolate Mincemeat, Vic’s London Broil, Easy Wholemeal Spelt Flour Bread, Mamma SLCW’s Cranberry Sauce, Hot Dog Nachos, Italian Wedding Soup, Mapo Tofu Curry, Hot Honey Crispy Salmon Bowls, Curried Butternut Squash Soup, Best Damn Oven Baked Chicken Legs, Chocolate Creme Pie, Broccoli Beef, Tuscan Steak and Green Peppers, Easy Carne Asada, InstantPot Chicken Tortilla Soup, Green Bean Casserole with Bacon and Fried Shallots, Bang Bang Shrimp, Rupert and Kajoozie’s #Nostr Famous Gumbo, The Best Lamb Winter Stew, Avery’s Hot Wallet Salsa, Candied Pecans, Pumpkin Bread, Breakfast Casserole with Sausage and Egg, Gold & Silver Soup, Mr. G’s Homemade Chicken Pasta Salad, Ultimate Peanut Cookies
The recipe links are available here: https://substack.com/home/post/p-152296981
FIN 🤠
https://i.nostr.build/661bAgwsj6tEnICX.jpg
-
 @ b1ddb4d7:471244e7
2025-06-02 11:00:50
@ b1ddb4d7:471244e7
2025-06-02 11:00:50Starting January 1, 2026, the United Kingdom will impose some of the world’s most stringent reporting requirements on cryptocurrency firms.
All platforms operating in or serving UK customers-domestic and foreign alike-must collect and disclose extensive personal and transactional data for every user, including individuals, companies, trusts, and charities.
This regulatory drive marks the UK’s formal adoption of the OECD’s Crypto-Asset Reporting Framework (CARF), a global initiative designed to bring crypto oversight in line with traditional banking and to curb tax evasion in the rapidly expanding digital asset sector.
What Will Be Reported?
Crypto firms must gather and submit the following for each transaction:
- User’s full legal name, home address, and taxpayer identification number
- Detailed data on every trade or transfer: type of cryptocurrency, amount, and nature of the transaction
- Identifying information for corporate, trust, and charitable clients
The obligation extends to all digital asset activities, including crypto-to-crypto and crypto-to-fiat trades, and applies to both UK residents and non-residents using UK-based platforms. The first annual reports covering 2026 activity are due by May 31, 2027.
Enforcement and Penalties
Non-compliance will carry stiff financial penalties, with fines of up to £300 per user account for inaccurate or missing data-a potentially enormous liability for large exchanges. The UK government has urged crypto firms to begin collecting this information immediately to ensure operational readiness.
Regulatory Context and Market Impact
This move is part of a broader UK strategy to position itself as a global fintech hub while clamping down on fraud and illicit finance. UK Chancellor Rachel Reeves has championed these measures, stating, “Britain is open for business – but closed to fraud, abuse, and instability”. The regulatory expansion comes amid a surge in crypto adoption: the UK’s Financial Conduct Authority reported that 12% of UK adults owned crypto in 2024, up from just 4% in 2021.
Enormous Risks for Consumers: Lessons from the Coinbase Data Breach
While the new framework aims to enhance transparency and protect consumers, it also dramatically increases the volume of sensitive personal data held by crypto firms-raising the stakes for cybersecurity.
The risks are underscored by the recent high-profile breach at Coinbase, one of the world’s largest exchanges.
In May 2025, Coinbase disclosed that cybercriminals, aided by bribed offshore contractors, accessed and exfiltrated customer data including names, addresses, government IDs, and partial bank details.
The attackers then used this information for sophisticated phishing campaigns, successfully deceiving some customers into surrendering account credentials and funds.
“While private encryption keys remained secure, sufficient customer information was exposed to enable sophisticated phishing attacks by criminals posing as Coinbase personnel.”
Coinbase now faces up to $400 million in compensation costs and has pledged to reimburse affected users, but the incident highlights the systemic vulnerability created when large troves of personal data are centralized-even if passwords and private keys are not directly compromised. The breach also triggered a notable drop in Coinbase’s share price and prompted a $20 million bounty for information leading to the attackers’ capture.
The Bottom Line
The UK’s forthcoming crypto reporting regime represents a landmark in financial regulation, promising greater transparency and tax compliance. However, as the Coinbase episode demonstrates, the aggregation of sensitive user data at scale poses a significant cybersecurity risk.
As regulators push for more oversight, the challenge will be ensuring that consumer protection does not become a double-edged sword-exposing users to new threats even as it seeks to shield them from old ones.
-
 @ 8bad92c3:ca714aa5
2025-06-03 18:02:33
@ 8bad92c3:ca714aa5
2025-06-03 18:02:33Marty's Bent

It's been a pretty historic week for the United States as it pertains to geopolitical relations in the Middle East. President Trump and many members of his administration, including AI and Crypto Czar David Sacks and Treasury Secretary Scott Bessent, traveled across the Middle East making deals with countries like Qatar, Saudi Arabia, the United Arab Emirates, Syria, and others. Many are speculating that Iran may be included in some behind the scenes deal as well. This trip to the Middle East makes sense considering the fact that China is also vying for favorable relationships with those countries. The Middle East is a power player in the world, and it seems pretty clear that Donald Trump is dead set on ensuring that they choose the United States over China as the world moves towards a more multi-polar reality.
Many are calling the events of this week the Riyadh Accords. There were many deals that were struck in relation to artificial intelligence, defense, energy and direct investments in the United States. A truly prolific power play and demonstration of deal-making ability of Donald Trump, if you ask me. Though I will admit some of the numbers that were thrown out by some of the countries were a bit egregious. We shall see how everything plays out in the coming years. It will be interesting to see how China reacts to this power move by the United States.
While all this was going on, there was something happening back in the United States that many people outside of fringe corners of FinTwit are not talking about, which is the fact that the 10-year and 30-year U.S. Treasury bond yields are back on the rise. Yesterday, they surpassed the levels of mid-April that caused a market panic and are hovering back around levels that have not been seen since right before Donald Trump's inauguration.
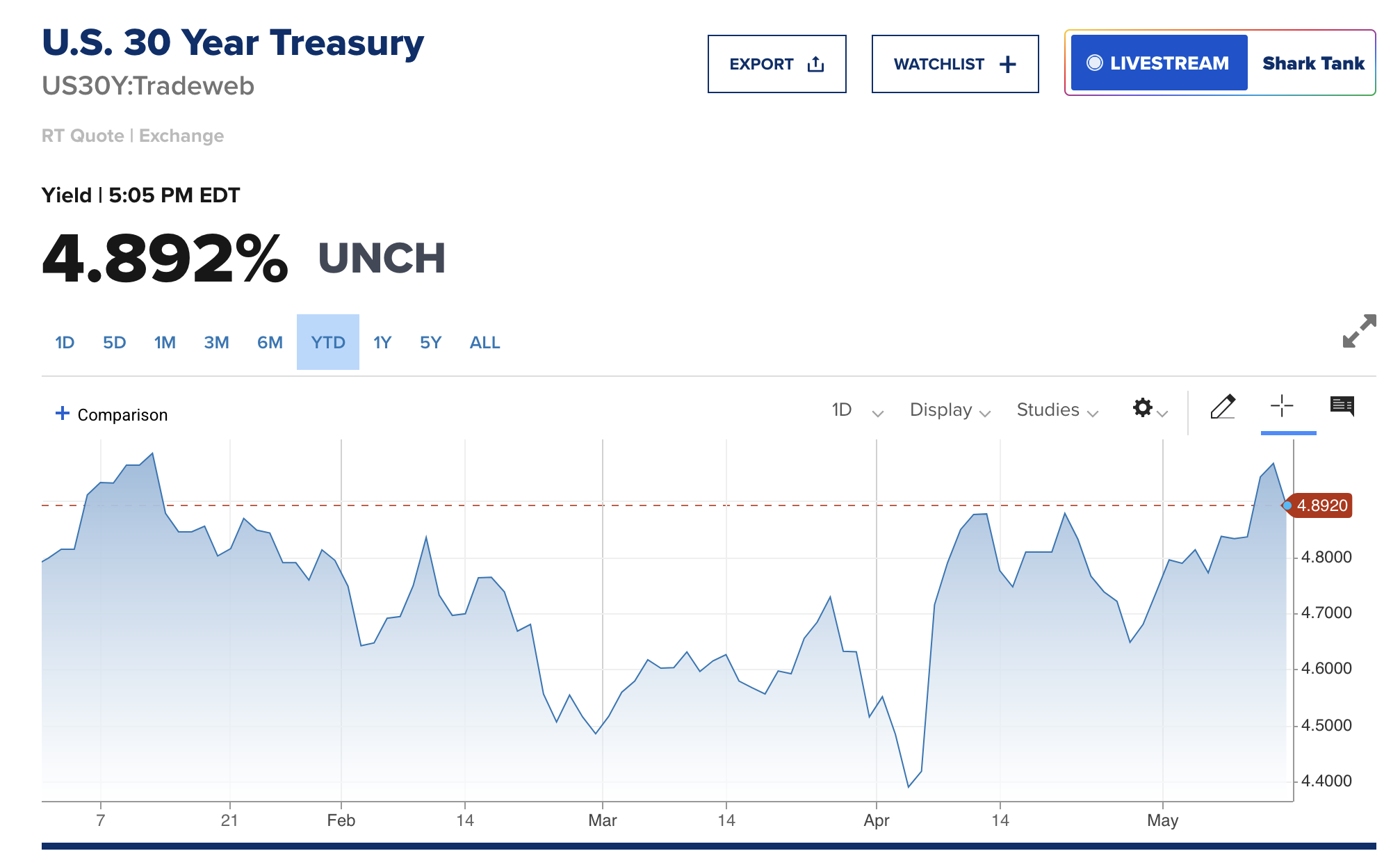
I imagine that there isn't as much of an uproar right now because I'm pretty confident the media freakouts we were experiencing in mid-April were driven by the fact that many large hedge funds found themselves off sides of large levered basis trades. I wouldn't be surprised if those funds have decreased their leverage in those trades and bond yields being back to mid-April levels is not affecting those funds as much as they were last month. But the point stands, the 10-year and 30-year yields are significantly elevated with the 30-year approaching 5%. Regardless of the deals that are currently being made in the Middle East, the Treasury has a big problem on its hands. It still has to roll over many trillions worth of debt over over the next few years and doing so at these rates is going to be massively detrimental to fiscal deficits over the next decade. The interest expense on the debt is set to explode in the coming years.
On that note, data from the first quarter of 2025 has been released by the government and despite all the posturing by the Trump administration around DOGE and how tariffs are going to be beneficial for the U.S. economy, deficits are continuing to explode while the interest expense on the debt has definitively surpassed our annual defense budget.
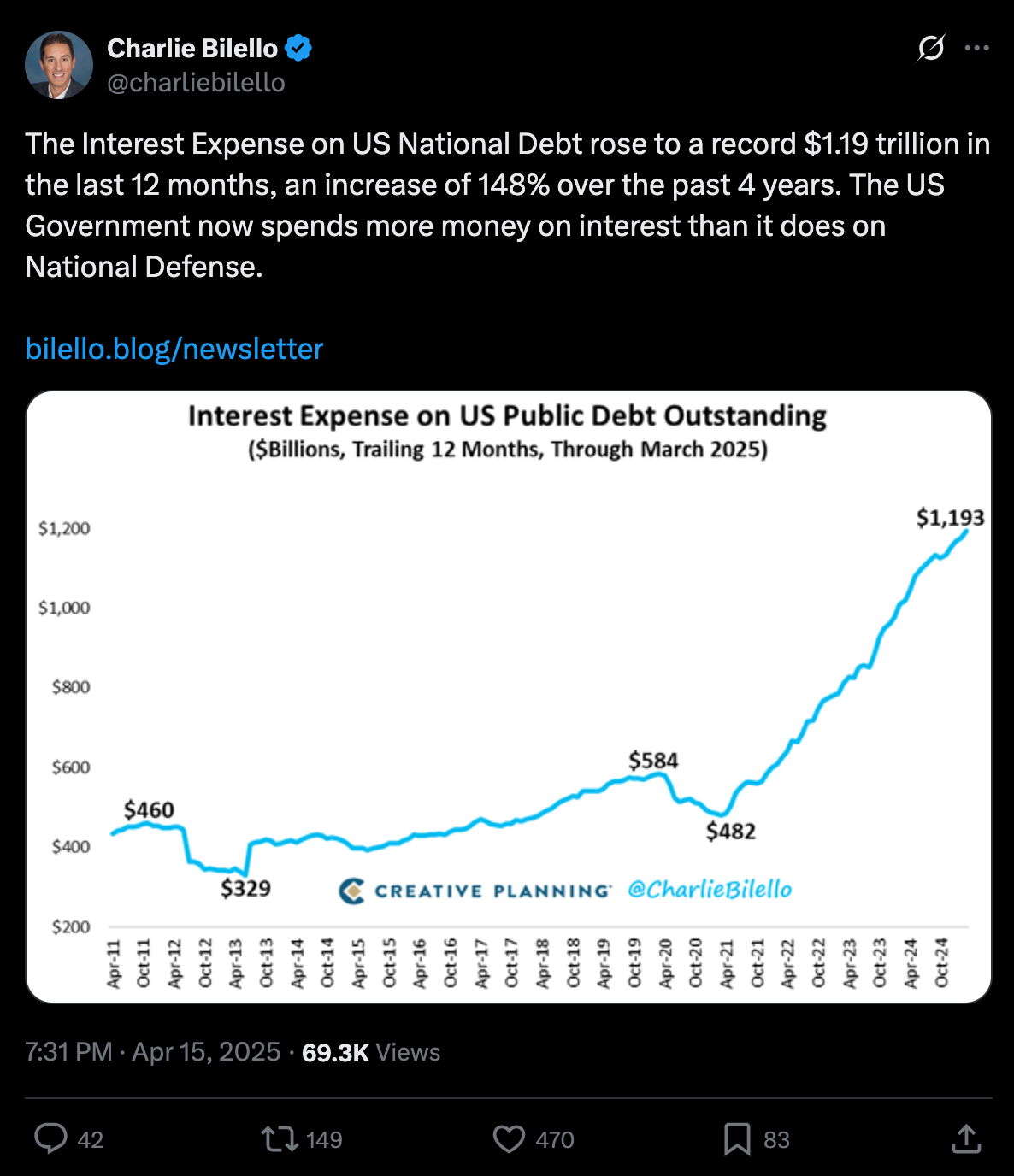
via Charlie Bilello
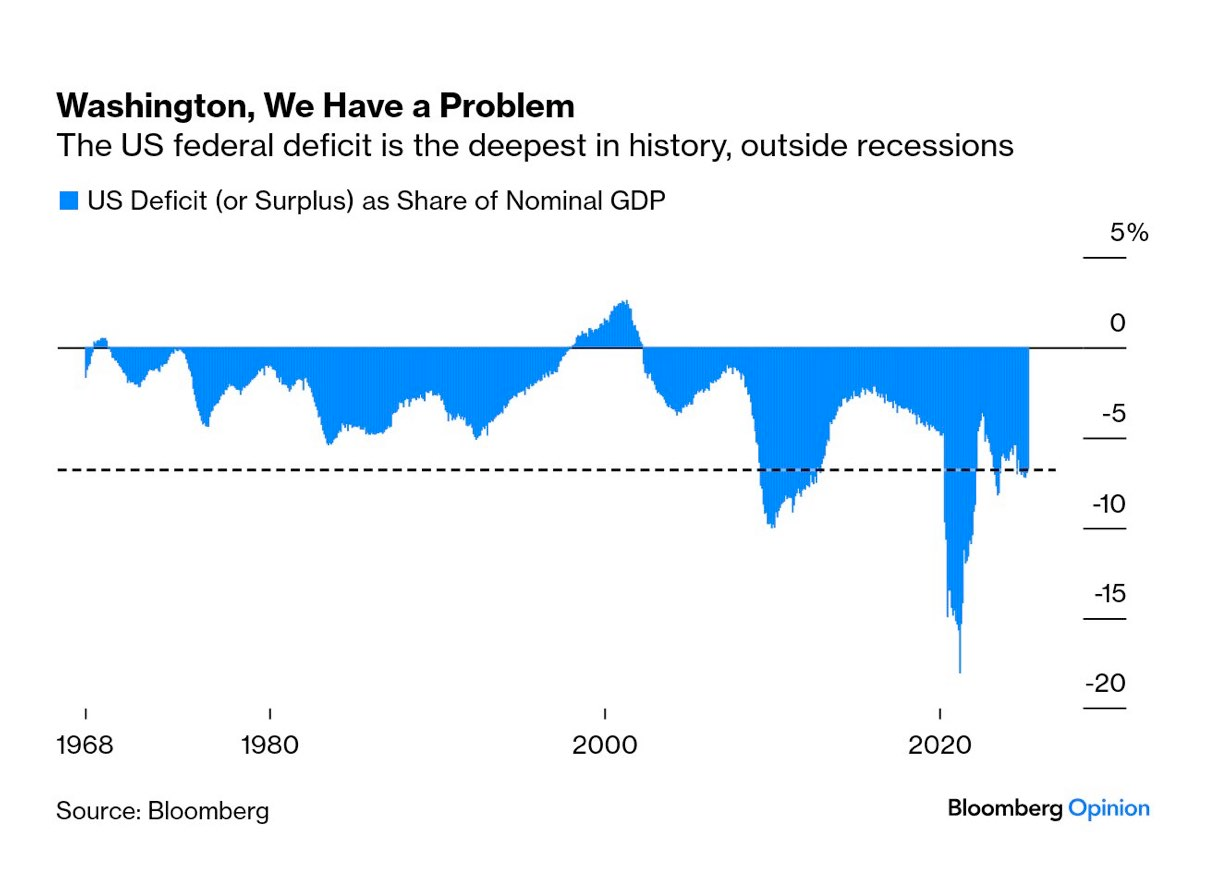
via Mohamed Al-Erian
To make matters worse, as things are deteriorating on the fiscal side of things, the U.S. consumer is getting crushed by credit. The 90-plus day delinquency rates for credit card and auto loans are screaming higher right now.
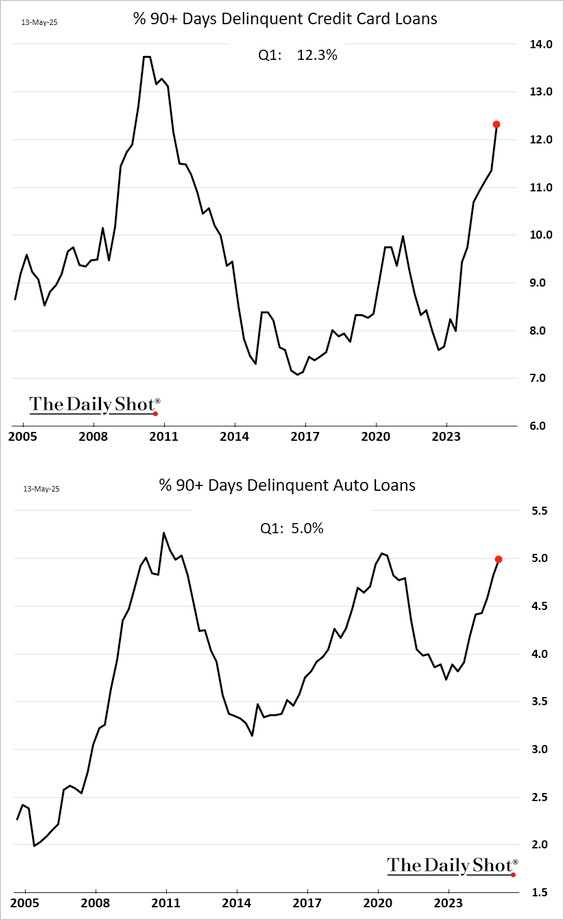
via TXMC
One has to wonder how long all this can continue without some sort of liquidity crunch. Even though equities markets have recovered from their post-Liberation Day month long bear market, I would not be surprised if what we're witnessing is a dead cat bounce that can only be continued if the money printers are turned back on. Something's got to give, both on the fiscal side and in the private markets where the Common Man is getting crushed because he's been forced to take on insane amounts of debt to stay afloat after years of elevated levels of inflation. Add on the fact that AI has reached a state of maturity that will enable companies to replace their current meat suit workers with an army of cheap, efficient and fast digital workers and it isn't hard to see that some sort of employment crisis could be on the horizon as well.
Now is not the time to get complacent. While I do believe that the deals that are currently being made in the Middle East are probably in the best interest of the United States as the world, again, moves toward a more multi-polar reality, we are facing problems that one cannot simply wish away. They will need to be confronted. And as we've seen throughout the 21st century, the problems are usually met head-on with a money printer.
I take no pleasure in saying this because it is a bit uncouth to be gleeful to benefit from the strife of others, but it is pretty clear to me that all signs are pointing to bitcoin benefiting massively from everything that is going on. The shift towards a more multi-polar world, the runaway debt situation here in the United States, the increasing deficits, the AI job replacements and the consumer credit crisis that is currently unfolding, All will need to be "solved" by turning on the money printers to levels they've never been pushed to before.
Weird times we're living in.
China's Manufacturing Dominance: Why It Matters for the U.S.
In my recent conversation with Lyn Alden, she highlighted how China has rapidly ascended the manufacturing value chain. As Lyn pointed out, China transformed from making "sneakers and plastic trinkets" to becoming the world's largest auto exporter in just four years. This dramatic shift represents more than economic success—it's a strategic power play. China now dominates solar panel production with greater market control than OPEC has over oil and maintains near-monopoly control of rare earth elements crucial for modern technology.
"China makes like 10 times more steel than the United States does... which is relevant in ship making. It's relevant in all sorts of stuff." - Lyn Alden
Perhaps most concerning, as Lyn emphasized, is China's financial leverage. They hold substantial U.S. assets that could be strategically sold to disrupt U.S. treasury market functioning. This combination of manufacturing dominance, resource control, and financial leverage gives China significant negotiating power in any trade disputes, making our attempts to reshoring manufacturing all the more challenging.
Check out the full podcast here for more on Triffin's dilemma, Bitcoin's role in monetary transition, and the energy requirements for rebuilding America's industrial base.
Headlines of the Day
Financial Times Under Fire Over MicroStrategy Bitcoin Coverage - via X
Trump in Qatar: Historic Boeing Deal Signed - via X
Get our new STACK SATS hat - via tftcmerch.io
Johnson Backs Stock Trading Ban; Passage Chances Slim - via X
Take the First Step Off the Exchange
Bitkey is an easy, secure way to move your Bitcoin into self-custody. With simple setup and built-in recovery, it’s the perfect starting point for getting your coins off centralized platforms and into cold storage—no complexity, no middlemen.
Take control. Start with Bitkey.
Use the promo code *“TFTC20”* during checkout for 20% off
Ten31, the largest bitcoin-focused investor, has deployed 158,469 sats | $150.00M across 30+ companies through three funds. I am a Managing Partner at Ten31 and am very proud of the work we are doing. Learn more at ten31.vc/invest.
Final thought...
Building things of value is satisfying.
Get this newsletter sent to your inbox daily: https://www.tftc.io/bitcoin-brief/
Subscribe to our YouTube channels and follow us on Nostr and X:
@media screen and (max-width: 480px) { .mobile-padding { padding: 10px 0 !important; } .social-container { width: 100% !important; max-width: 260px !important; } .social-icon { padding: 0 !important; } .social-icon img { height: 32px !important; width: 32px !important; } .icon-cell { padding: 0 4px !import
-
 @ 6bcc27d2:b67d296e
2024-10-21 03:54:32
@ 6bcc27d2:b67d296e
2024-10-21 03:54:32yugoです。 この記事は「Nostrasia2024 逆アドベントカレンダー」10/19の分です。Nostrasiaの当日はリアルタイムで配信を視聴していました。Nostrを使ってアプリケーションの再発明をすべきという発表を聴き、自分だったらどんなものを作ってみたいかを考えて少し調べたり試みたりしたのでその記録を書きます。また、超簡単なものですがおそらく世界初となるvisionOS対応のNostrクライアントをつくってみたので最後の方に紹介します。
アプリケーションを再発明する話があったのは、「What is Nostr Other Stuff?」と題したkaijiさんの発表でした。
Nostrプロトコルを使って既存のアプリケーションを再発明することで、ユーザ体験を損なわずにゆるやかな分散を促すことができ、プロトコルとしてのNostrも成長していくというような内容でした。
自分はまだNostrで何かをつくった経験はなかったので、実装に必要な仕様の知識がほとんどない状態からどのようなアプリケーションをつくってみたいかを考えました。
最初に思いついたのは、Scrapboxのようなネットワーク型のナレッジベースです。自分は最近visionOS勉強会をやっており、勉強会でナレッジを共有する手段としてScrapboxの導入を検討していました。
Nostrコミュニティにも有志によるScrapboxがありますが、Nostrクライアントがあればそれを使うだろうから同じくらいの実用性を備えたクライアントはまだ存在しないのではないかという見立てでした。
長文投稿やpublic chatなどの機能を組み合わせることで実現できるだろうか。そう思っていた矢先、NIP-54のWikiという規格があることを知りました。
https://github.com/nostr-protocol/nips/blob/master/54.md
まだちゃんとは読めていないですが、Scrapboxもwikiソフトウェアだし参考になりそうと思っています。正式な仕様に組み込まれていないようで、採用しているクライアントはfiatjafによるリファレンス実装(?)のwikistrくらいしか見つかりませんでした。
Scrapboxのようなナレッジベースを志向するNostrクライアントがあれば、後述するvisionOS対応クライアントの存在もありアカウントを使いまわせて嬉しいので試してみたいです。もし他にも似たようなサービスをどなたか知っていたら教えてください。
また現在は、勉強会やワークショップ、ハッカソンなどのコラボレーションワークを支援するためのツールを自分たちでも開発しています。Apple Vision Proに搭載されているvisionOSというプラットフォームで動作します。
https://image.nostr.build/14f0c1b8fbe5ce7754825c01b09280a4c22f87bbf3c2fa6d60dd724f98919c34.png
この画面で自分が入りたいスペースを選んで共有体験を開始します。
スライドなどのコンテンツや自らのアバターを同期させることで、遠隔地にいてもまるでオフラインかのように同じ空間を共有することが可能になります。
https://image.nostr.build/cfb75d3db2a9b9cd39f502d6426d5ef4f264b3d5d693b6fc9762735d2922b85c.jpg
ということなので、急遽visionOS対応のクライアントを作ってみました。検索しても1つも事例が出てこなかったので多分まだ世界で実装しているアプリはないのではないでしょうか。
とはいえ、クライアントを名乗っているもののまだ大した機能はなく、リレーからデータを取得するだけの読み取り専用です。
https://image.nostr.build/96e088cc6a082528682989ccc12b4312f9cb6277656e491578e32a0851ce50fe.png
画像では自分のプロフィールデータをリレーから取得しています。
まだどのライブラリもvisionOSに対応していなかったりで手こずったものの仕様の勉強になりました。
ただvisionOSアプリはiOSアプリ同様NIP-7が使えないので秘密鍵を自分で保管しなくてはならず、今後どう対処すべきかわかりかねています。これから時間ある時に少しずつ調べていこうと思っていますが、ネイティブアプリの秘密鍵周りはあまりリソースが多くないようにも感じました。もしどなたかその辺の実装に詳しい方いたら教えていただけると嬉しいです。
準備ができたらそのうちコードも公開したいと思っています。
これから少しずつ色んな機能を実装しながらNostrで遊んでいきたいです!
-
 @ 127d3bf5:466f416f
2025-06-01 12:39:00
@ 127d3bf5:466f416f
2025-06-01 12:39:00In the Name of Allah, the Most Gracious, the Most Merciful,
"Permission to fight (against disbelievers) is given to those (believers) who are fought against, because they have been wronged and surely, Allah is Able to give them (believers) victory" [Quran 22:39]
"Those who believe, fight in the Cause of Allah, and those who disbelieve, fight in the cause of Taghut (anything worshipped other than Allah e.g. Satan). So fight you against the friends of Satan; ever feeble is indeed the plot of Satan."[Quran 4:76]
Some American writers have published articles under the title 'On what basis are we fighting?' These articles have generated a number of responses, some of which adhered to the truth and were based on Islamic Law, and others which have not. Here we wanted to outline the truth - as an explanation and warning - hoping for Allah's reward, seeking success and support from Him.
While seeking Allah's help, we form our reply based on two questions directed at the Americans:
(Q1) Why are we fighting and opposing you?\ (Q2) What are we calling you to, and what do we want from you?
As for the first question: Why are we fighting and opposing you? The answer is very simple:
(1) Because you attacked us and continue to attack us.
a) You attacked us in Palestine:
(i) Palestine, which has sunk under military occupation for more than 80 years. The British handed over Palestine, with your help and your support, to the Jews, who have occupied it for more than 50 years; years overflowing with oppression, tyranny, crimes, killing, expulsion, destruction and devastation. The creation and continuation of Israel is one of the greatest crimes, and you are the leaders of its criminals. And of course there is no need to explain and prove the degree of American support for Israel. The creation of Israel is a crime which must be erased. Each and every person whose hands have become polluted in the contribution towards this crime must pay its*price, and pay for it heavily.
(ii) It brings us both laughter and tears to see that you have not yet tired of repeating your fabricated lies that the Jews have a historical right to Palestine, as it was promised to them in the Torah. Anyone who disputes with them on this alleged fact is accused of anti-semitism. This is one of the most fallacious, widely-circulated fabrications in history. The people of Palestine are pure Arabs and original Semites. It is the Muslims who are the inheritors of Moses (peace be upon him) and the inheritors of the real Torah that has not been changed. Muslims believe in all of the Prophets, including Abraham, Moses, Jesus and Muhammad, peace and blessings of Allah be upon them all. If the followers of Moses have been promised a right to Palestine in the Torah, then the Muslims are the most worthy nation of this.
When the Muslims conquered Palestine and drove out the Romans, Palestine and Jerusalem returned to Islaam, the religion of all the Prophets peace be upon them. Therefore, the call to a historical right to Palestine cannot be raised against the Islamic Ummah that believes in all the Prophets of Allah (peace and blessings be upon them) - and we make no distinction between them.
(iii) The blood pouring out of Palestine must be equally revenged. You must know that the Palestinians do not cry alone; their women are not widowed alone; their sons are not orphaned alone.
(b) You attacked us in Somalia; you supported the Russian atrocities against us in Chechnya, the Indian oppression against us in Kashmir, and the Jewish aggression against us in Lebanon.
(c) Under your supervision, consent and orders, the governments of our countries which act as your agents, attack us on a daily basis;
(i) These governments prevent our people from establishing the Islamic Shariah, using violence and lies to do so.
(ii) These governments give us a taste of humiliation, and places us in a large prison of fear and subdual.
(iii) These governments steal our Ummah's wealth and sell them to you at a paltry price.
(iv) These governments have surrendered to the Jews, and handed them most of Palestine, acknowledging the existence of their state over the dismembered limbs of their own people.
(v) The removal of these governments is an obligation upon us, and a necessary step to free the Ummah, to make the Shariah the supreme law and to regain Palestine. And our fight against these governments is not separate from out fight against you.
(d) You steal our wealth and oil at paltry prices because of you international influence and military threats. This theft is indeed the biggest theft ever witnessed by mankind in the history of the world.
(e) Your forces occupy our countries; you spread your military bases throughout them; you corrupt our lands, and you besiege our sanctities, to protect the security of the Jews and to ensure the continuity of your pillage of our treasures.
(f) You have starved the Muslims of Iraq, where children die every day. It is a wonder that more than 1.5 million Iraqi children have died as a result of your sanctions, and you did not show concern. Yet when 3000 of your people died, the entire world rises and has not yet sat down.
(g) You have supported the Jews in their idea that Jerusalem is their eternal capital, and agreed to move your embassy there. With your help and under your protection, the Israelis are planning to destroy the Al-Aqsa mosque. Under the protection of your weapons, Sharon entered the Al-Aqsa mosque, to pollute it as a preparation to capture and destroy it.
(2) These tragedies and calamities are only a few examples of your oppression and aggression against us. It is commanded by our religion and intellect that the oppressed have a right to return the aggression. Do not await anything from us but Jihad, resistance and revenge. Is it in any way rational to expect that after America has attacked us for more than half a century, that we will then leave her to live in security and peace?!!
(3) You may then dispute that all the above does not justify aggression against civilians, for crimes they did not commit and offenses in which they did not partake:
(a) This argument contradicts your continuous repetition that America is the land of freedom, and its leaders in this world. Therefore, the American people are the ones who choose their government by way of their own free will; a choice which stems from their agreement to its policies. Thus the American people have chosen, consented to, and affirmed their support for the Israeli oppression of the Palestinians, the occupation and usurpation of their land, and its continuous killing, torture, punishment and expulsion of the Palestinians. The American people have the ability and choice to refuse the policies of their Government and even to change it if they want.
(b) The American people are the ones who pay the taxes which fund the planes that bomb us in Afghanistan, the tanks that strike and destroy our homes in Palestine, the armies which occupy our lands in the Arabian Gulf, and the fleets which ensure the blockade of Iraq. These tax dollars are given to Israel for it to continue to attack us and penetrate our lands. So the American people are the ones who fund the attacks against us, and they are the ones who oversee the expenditure of these monies in the way they wish, through their elected candidates.
(c) Also the American army is part of the American people. It is this very same people who are shamelessly helping the Jews fight against us.
(d) The American people are the ones who employ both their men and their women in the American Forces which attack us.
(e) This is why the American people cannot be not innocent of all the crimes committed by the Americans and Jews against us.
(f) Allah, the Almighty, legislated the permission and the option to take revenge. Thus, if we are attacked, then we have the right to attack back. Whoever has destroyed our villages and towns, then we have the right to destroy their villages and towns. Whoever has stolen our wealth, then we have the right to destroy their economy. And whoever has killed our civilians, then we have the right to kill theirs.
The American Government and press still refuses to answer the question:
Why did they attack us in New York and Washington?
If Sharon is a man of peace in the eyes of Bush, then we are also men of peace!!! America does not understand the language of manners and principles, so we are addressing it using the language it understands.
(Q2) As for the second question that we want to answer: What are we calling you to, and what do we want from you?
(1) The first thing that we are calling you to is Islam.
(a) The religion of the Unification of God; of freedom from associating partners with Him, and rejection of this; of complete love of Him, the Exalted; of complete submission to His Laws; and of the discarding of all the opinions, orders, theories and religions which contradict with the religion He sent down to His Prophet Muhammad (peace be upon him). Islam is the religion of all the prophets, and makes no distinction between them - peace be upon them all.
It is to this religion that we call you; the seal of all the previous religions. It is the religion of Unification of God, sincerity, the best of manners, righteousness, mercy, honour, purity, and piety. It is the religion of showing kindness to others, establishing justice between them, granting them their rights, and defending the oppressed and the persecuted. It is the religion of enjoining the good and forbidding the evil with the hand, tongue and heart. It is the religion of Jihad in the way of Allah so that Allah's Word and religion reign Supreme. And it is the religion of unity and agreement on the obedience to Allah, and total equality between all people, without regarding their colour, sex, or language.
(b) It is the religion whose book - the Quran - will remained preserved and unchanged, after the other Divine books and messages have been changed. The Quran is the miracle until the Day of Judgment. Allah has challenged anyone to bring a book like the Quran or even ten verses like it.
(2) The second thing we call you to, is to stop your oppression, lies, immorality and debauchery that has spread among you.
(a) We call you to be a people of manners, principles, honour, and purity; to reject the immoral acts of fornication, homosexuality, intoxicants, gambling's, and trading with interest.
We call you to all of this that you may be freed from that which you have become caught up in; that you may be freed from the deceptive lies that you are a great nation, that your leaders spread amongst you to conceal from you the despicable state to which you have reached.
(b) It is saddening to tell you that you are the worst civilization witnessed by the history of mankind:
(i) You are the nation who, rather than ruling by the Shariah of Allah in its Constitution and Laws, choose to invent your own laws as you will and desire. You separate religion from your policies, contradicting the pure nature which affirms Absolute Authority to the Lord and your Creator. You flee from the embarrassing question posed to you: How is it possible for Allah the Almighty to create His creation, grant them power over all the creatures and land, grant them all the amenities of life, and then deny them that which they are most in need of: knowledge of the laws which govern their lives?
(ii) You are the nation that permits Usury, which has been forbidden by all the religions. Yet you build your economy and investments on Usury. As a result of this, in all its different forms and guises, the Jews have taken control of your economy, through which they have then taken control of your media, and now control all aspects of your life making you their servants and achieving their aims at your expense; precisely what Benjamin Franklin warned you against.
(iii) You are a nation that permits the production, trading and usage of intoxicants. You also permit drugs, and only forbid the trade of them, even though your nation is the largest consumer of them.
(iv) You are a nation that permits acts of immorality, and you consider them to be pillars of personal freedom. You have continued to sink down this abyss from level to level until incest has spread amongst you, in the face of which neither your sense of honour nor your laws object.
Who can forget your President Clinton's immoral acts committed in the official Oval office? After that you did not even bring him to account, other than that he 'made a mistake', after which everything passed with no punishment. Is there a worse kind of event for which your name will go down in history and remembered by nations?
(v) You are a nation that permits gambling in its all forms. The companies practice this as well, resulting in the investments becoming active and the criminals becoming rich.
(vi) You are a nation that exploits women like consumer products or advertising tools calling upon customers to purchase them. You use women to serve passengers, visitors, and strangers to increase your profit margins. You then rant that you support the liberation of women.
(vii) You are a nation that practices the trade of sex in all its forms, directly and indirectly. Giant corporations and establishments are established on this, under the name of art, entertainment, tourism and freedom, and other deceptive names you attribute to it.
(viii) And because of all this, you have been described in history as a nation that spreads diseases that were unknown to man in the past. Go ahead and boast to the nations of man, that you brought them AIDS as a Satanic American Invention.
(xi) You have destroyed nature with your industrial waste and gases more than any other nation in history. Despite this, you refuse to sign the Kyoto agreement so that you can secure the profit of your greedy companies and*industries.
(x) Your law is the law of the rich and wealthy people, who hold sway in their political parties, and fund their election campaigns with their gifts. Behind them stand the Jews, who control your policies, media and economy.
(xi) That which you are singled out for in the history of mankind, is that you have used your force to destroy mankind more than any other nation in history; not to defend principles and values, but to hasten to secure your interests and profits. You who dropped a nuclear bomb on Japan, even though Japan was ready to negotiate an end to the war. How many acts of oppression, tyranny and injustice have you carried out, O callers to freedom?
(xii) Let us not forget one of your major characteristics: your duality in both manners and values; your hypocrisy in manners and principles. All*manners, principles and values have two scales: one for you and one for the others.
(a)The freedom and democracy that you call to is for yourselves and for white race only; as for the rest of the world, you impose upon them your monstrous, destructive policies and Governments, which you call the 'American friends'. Yet you prevent them from establishing democracies. When the Islamic party in Algeria wanted to practice democracy and they won the election, you unleashed your agents in the Algerian army onto them, and to attack them with tanks and guns, to imprison them and torture them - a new lesson from the 'American book of democracy'!!!
(b)Your policy on prohibiting and forcibly removing weapons of mass destruction to ensure world peace: it only applies to those countries which you do not permit to possess such weapons. As for the countries you consent to, such as Israel, then they are allowed to keep and use such weapons to defend their security. Anyone else who you suspect might be manufacturing or keeping these kinds of weapons, you call them criminals and you take military action against them.
(c)You are the last ones to respect the resolutions and policies of International Law, yet you claim to want to selectively punish anyone else who does the same. Israel has for more than 50 years been pushing UN resolutions and rules against the wall with the full support of America.
(d)As for the war criminals which you censure and form criminal courts for - you shamelessly ask that your own are granted immunity!! However, history will not forget the war crimes that you committed against the Muslims and the rest of the world; those you have killed in Japan, Afghanistan, Somalia, Lebanon and Iraq will remain a shame that you will never be able to escape. It will suffice to remind you of your latest war crimes in Afghanistan, in which densely populated innocent civilian villages were destroyed, bombs were dropped on mosques causing the roof of the mosque to come crashing down on the heads of the Muslims praying inside. You are the ones who broke the agreement with the Mujahideen when they left Qunduz, bombing them in Jangi fort, and killing more than 1,000 of your prisoners through suffocation and thirst. Allah alone knows how many people have died by torture at the hands of you and your agents. Your planes remain in the Afghan skies, looking for anyone remotely suspicious.
(e)You have claimed to be the vanguards of Human Rights, and your Ministry of Foreign affairs issues annual reports containing statistics of those countries that violate any Human Rights. However, all these things vanished when the Mujahideen hit you, and you then implemented the methods of the same documented governments that you used to curse. In America, you captured thousands the Muslims and Arabs, took them into custody with neither reason, court trial, nor even disclosing their names. You issued newer, harsher laws.
What happens in Guatanamo is a historical embarrassment to America and its values, and it screams into your faces - you hypocrites, "What is the value of your signature on any agreement or treaty?"
(3) What we call you to thirdly is to take an honest stance with yourselves - and I doubt you will do so - to discover that you are a nation without principles or manners, and that the values and principles to you are something which you merely demand from others, not that which you yourself must adhere to.
(4) We also advise you to stop supporting Israel, and to end your support of the Indians in Kashmir, the Russians against the Chechens and to also cease supporting the Manila Government against the Muslims in Southern Philippines.
(5) We also advise you to pack your luggage and get out of our lands. We desire for your goodness, guidance, and righteousness, so do not force us to send you back as cargo in coffins.
(6) Sixthly, we call upon you to end your support of the corrupt leaders in our countries. Do not interfere in our politics and method of education. Leave us alone, or else expect us in New York and Washington.
(7) We also call you to deal with us and interact with us on the basis of mutual interests and benefits, rather than the policies of sub dual, theft and occupation, and not to continue your policy of supporting the Jews because this will result in more disasters for you.
If you fail to respond to all these conditions, then prepare for fight with the Islamic Nation. The Nation of Monotheism, that puts complete trust on Allah and fears none other than Him. The Nation which is addressed by its Quran with the words: "Do you fear them? Allah has more right that you should fear Him if you are believers. Fight against them so that Allah will punish them by your hands and disgrace them and give you victory over them and heal the breasts of believing people. And remove the anger of their (believers') hearts. Allah accepts the repentance of whom He wills. Allah is All-Knowing, All-Wise." [Quran9:13-1]
The Nation of honour and respect:
"But honour, power and glory belong to Allah, and to His Messenger (Muhammad- peace be upon him) and to the believers." [Quran 63:8]
"So do not become weak (against your enemy), nor be sad, and you will be*superior ( in victory )if you are indeed (true) believers" [Quran 3:139]
The Nation of Martyrdom; the Nation that desires death more than you desire life:
"Think not of those who are killed in the way of Allah as dead. Nay, they are alive with their Lord, and they are being provided for. They rejoice in what Allah has bestowed upon them from His bounty and rejoice for the sake of those who have not yet joined them, but are left behind (not yet martyred) that on them no fear shall come, nor shall they grieve. They rejoice in a grace and a bounty from Allah, and that Allah will not waste the reward of the believers." [Quran 3:169-171]
The Nation of victory and success that Allah has promised:
"It is He Who has sent His Messenger (Muhammad peace be upon him) with guidance and the religion of truth (Islam), to make it victorious over all other religions even though the Polytheists hate it." [Quran 61:9]
"Allah has decreed that 'Verily it is I and My Messengers who shall be victorious.' Verily Allah is All-Powerful, All-Mighty." [Quran 58:21]
The Islamic Nation that was able to dismiss and destroy the previous evil Empires like yourself; the Nation that rejects your attacks, wishes to remove your evils, and is prepared to fight you. You are well aware that the Islamic Nation, from the very core of its soul, despises your haughtiness and arrogance.
If the Americans refuse to listen to our advice and the goodness, guidance and righteousness that we call them to, then be aware that you will lose this Crusade Bush began, just like the other previous Crusades in which you were humiliated by the hands of the Mujahideen, fleeing to your home in great silence and disgrace. If the Americans do not respond, then their fate will be that of the Soviets who fled from Afghanistan to deal with their military defeat, political breakup, ideological downfall, and economic bankruptcy.
This is our message to the Americans, as an answer to theirs. Do they now know why we fight them and over which form of ignorance, by the permission of Allah, we shall be victorious?
-
 @ 2cde0e02:180a96b9
2025-06-05 15:13:03
@ 2cde0e02:180a96b9
2025-06-05 15:13:03pen & ink; monochromized
Magdalena Carmen Frida Kahlo y Calderón[a] (Spanish pronunciation: [ˈfɾiða ˈkalo]; 6 July 1907 – 13 July 1954[1]) was a Mexican painter known for her many portraits, self-portraits, and works inspired by the nature and artifacts of Mexico. Inspired by the country's popular culture, she employed a naïve folk art style to explore questions of identity, postcolonialism, gender, class, and race in Mexican society.[2] Her paintings often had strong autobiographical elements and mixed realism with fantasy. In addition to belonging to the post-revolutionary Mexicayotl movement, which sought to define a Mexican identity, Kahlo has been described as a surrealist or magical realist.[3] She is also known for painting about her experience of chronic pain.[4]
https://stacker.news/items/997980
-
 @ 7f6db517:a4931eda
2025-06-04 18:02:59
@ 7f6db517:a4931eda
2025-06-04 18:02:59
Nostr is an open communication protocol that can be used to send messages across a distributed set of relays in a censorship resistant and robust way.
If you missed my nostr introduction post you can find it here. My nostr account can be found here.
We are nearly at the point that if something interesting is posted on a centralized social platform it will usually be posted by someone to nostr.
We are nearly at the point that if something interesting is posted exclusively to nostr it is cross posted by someone to various centralized social platforms.
We are nearly at the point that you can recommend a cross platform app that users can install and easily onboard without additional guides or resources.
As companies continue to build walls around their centralized platforms nostr posts will be the easiest to cross reference and verify - as companies continue to censor their users nostr is the best censorship resistant alternative - gradually then suddenly nostr will become the standard. 🫡
Current Nostr Stats
If you found this post helpful support my work with bitcoin.

-
 @ 975e4ad5:8d4847ce
2025-06-05 13:14:46
@ 975e4ad5:8d4847ce
2025-06-05 13:14:46What is the Fiat System and How Do Central Banks Set Interest Rates?
When central banks expand credit, they often increase the money supply by creating new money through mechanisms like quantitative easing (QE). For instance, a central bank may purchase government bonds, injecting money into the economy. This boosts liquidity but can lead to inflation when too much money chases limited goods and services.
Low interest rates make borrowing cheaper, encouraging spending and investment. However, this can overheat the economy, create speculative bubbles (e.g., in real estate), and drive inflation. Conversely, high interest rates restrict borrowing, slow the economy, and curb inflation but may trigger recessions.
How Would Interest Rates Work Under a Bitcoin Standard?
Under a Bitcoin standard, the money supply is fixed—only 21 million bitcoins will ever exist, with the last one mined around 2140. Unlike the fiat system, no central authority can manipulate the money supply or set interest rates. Instead, interest rates would be determined entirely by the market—by the supply and demand for capital.
If someone wants to borrow bitcoins, the interest rate would depend on negotiations between the lender and borrower. For example, if demand for loans is high and available bitcoins are scarce, interest rates would rise. Conversely, if there are ample bitcoin savings, rates might fall. This process would be fully decentralized and reflect real market conditions, not central bank decisions.
Since new bitcoins cannot be “printed,” there would be no inflation caused by an expanding money supply. Instead, bitcoin’s value would likely rise over time (deflation) as its fixed supply competes with growing demand. This could encourage saving over reckless spending, reshaping economic behavior.
Advantages of a Bitcoin Standard
-
Protection Against Inflation: Bitcoin’s fixed supply prevents currency devaluation, a common issue with fiat money. This safeguards savings and promotes long-term planning.
-
Decentralization: Without a central bank manipulating the market, economic decisions are made by individuals, not bureaucrats. This aligns with free-market principles where competition and innovation thrive.
-
Transparency and Security: The Bitcoin blockchain is public and immutable, ensuring transactions are transparent and secure from tampering.
-
Financial Freedom: Under a Bitcoin standard, individuals have full control over their money without government or bank interference, which is especially crucial in countries with unstable regimes or currencies.
-
Discipline in Lending: Without the ability to print money, lenders would be more cautious, reducing risky investments and speculative bubbles.
Potential Drawbacks and Why a Bitcoin Standard is Superior
One major argument against a Bitcoin standard is that it could slow economic growth. Low interest rates in the fiat system encourage borrowing and spending, driving economic activity. Under a Bitcoin standard, where interest rates are market-driven and likely higher, borrowing would be costlier, potentially limiting investments in new projects.
However, this critique misses a key point: economic growth fueled by artificially low interest rates and money printing is often unsustainable. It leads to debt crises, inflation, and bubbles that eventually burst, as seen in 2008. A Bitcoin standard promotes healthy economic discipline, where investments are based on real value, not artificial capital.
Moreover, bitcoin’s deflationary nature could shift how people view money. Instead of chasing endless growth, societies might prioritize sustainability, innovation, and efficiency. This could lead to a more stable and equitable economy in the long run.
Additional Considerations
A Bitcoin standard could transform global trade. Today, countries with fiat currencies often manipulate exchange rates to gain trade advantages. With bitcoin as a universal currency, such manipulations would vanish, fostering fairer competition.
Another aspect is energy efficiency. While bitcoin mining consumes energy, it incentivizes the development of renewable sources as miners seek cheap, sustainable energy. This could accelerate the transition to a green economy.
Conclusion
The Bitcoin standard offers a vision of an economy rooted in sound money, free markets, and financial freedom. While it may slow certain aspects of economic growth, it creates a more stable and sustainable system that protects individuals from inflation and centralized control. In a world where trust in institutions is waning, the Bitcoin standard is a step toward a fairer and more transparent future.
-
-
 @ e2c72a5a:bfacb2ee
2025-06-05 17:14:50
@ e2c72a5a:bfacb2ee
2025-06-05 17:14:50The silent revolution: Ethereum's pivot to 'digital oil' could redefine crypto's future. While Bitcoin grabs headlines as digital gold, Ethereum is quietly transforming into something potentially more valuable—the essential infrastructure powering our digital economy. Ryan Berckmans reveals Ethereum's strategic shift from being just another cryptocurrency to becoming the foundation for stablecoins, tokenized assets, and global financial systems. With $480 billion in stablecoin volume and institutional players entering the space, Ethereum isn't just competing with Bitcoin—it's creating an entirely different value proposition. The question isn't whether ETH will hit $3K, but whether we're underestimating its long-term potential as the backbone of digital finance. Are you positioning yourself for the real crypto revolution happening right under our noses?
-
 @ 58537364:705b4b85
2025-06-03 15:22:59
@ 58537364:705b4b85
2025-06-03 15:22:59…. “คนเรา โดยเฉพาะสมัยนี้ พูดกันอีกที่หนึ่งก็พูดได้ว่า ถูกสร้างขึ้นมาด้วยหนังสือ, หนังสือมันสร้างคนขึ้นมา คือว่า..อ่านหนังสืออะไรมาก อ่านหนังสืออะไรมาก หนังสือนั้นก็สร้างคนคนนั้นขึ้นมา, สร้างจิตใจของคนนั้นขึ้นมา โดยไม่รู้สึก
…. ไปดูหนังสือที่เขาอ่าน อ่านมากที่สุด เราก็รู้ได้ว่า..คนนี้มีจิตใจเป็นอย่างไร. หนังสือที่นิยมสั่งกันมามาก ล้วนแต่เป็นหนังสือที่ยั่วยวนทางวัตถุ หรือลุ่มหลงทางวัตถุ : แล้วอย่างดีที่สุดก็เอามาให้เสียเวลา อ่านให้มันมึนหัวเล่น อย่างนั้นแหละ จนไม่มีเวลาที่จะไปอ่านหนังสือธรรมะที่แท้จริง เพราะว่ามีหนังสืออื่นมาก วางอยู่มาก ยั่วยวนให้อ่านมากกว่า
…. แม้แต่พระเณร ก็เป็นอย่างนี้ อ่านหนังสือพิมพ์, หรืออ่านหนังสือภาษา, เรียนภาษาต่างประเทศ หรือว่าเรียนวิชานั่น นี่ ล้วนแต่เป็นเรื่องวัตถุ เรื่องอาชีพ เรื่องความดีความเด่น ที่ฝันไว้ในจิตในใจ, ด้วยความหวังความทะเยอทะยานทั้งนั้น แล้วจะเอากําลังใจ หรือมันสมอง หรืออะไรที่ไหนมาเข้าใจ ธรรมะ ธัมโม ได้
…. ทีนี้ ยิ่งนอกวัดออกไป ก็ยิ่งไกลไปใหญ่ : หอสมุดของมหาวิทยาลัย, หอสมุดของชาติ ของอะไร ก็ล้วนแต่เป็น “หอสมุดของซาตาน” มากยิ่งขึ้นเท่านั้น เพราะไปมีมันขึ้น หรือสร้างมันไว้ ด้วยความอยากดีอยากเด่น ด้วยความอยากที่จะร่ำรวยวัตถุทั้งนั้น ฉะนั้น จึงมีผลทําให้คนทั้งโลกนี้เป็นทาสของวัตถุ พร้อมที่จะสร้างวิกฤตการณ์ ขึ้นในโลกในอนาคต
…. แล้วรองลงมาจากนั้น ก็คือ มันมากจนทําให้เวียนหัว เป็น..“บ้าหอบฟาง”; อย่างที่ว่าแล้วว่าเล่า ว่าเป็นบ้าหอบฟาง, รู้อะไรท่วมหัวก็เอาตัวไม่รอด, เรียนจบมหาวิทยาลัยแล้ว ก็ยังไม่รู้ว่าเกิดมาทําไม ?, เรียนมหาวิทยาลัยจบแล้ว อ่านหนังสือในห้องสมุดของมหาวิทยาลัยจบแล้ว ก็ยังเป็นเด็กอมมือ ไม่รู้ว่า.. “กูนี่ เกิดมาทําไม ?”. ดูซิ!, แล้วจะเรียกว่า “อุดมศึกษา” ได้อย่างไรกัน ? แม้แต่เกิดมาทําไม? ก็ยังไม่รู้ นี่การศึกษาสมัยนี้ หอสมุดหรือห้องสมุดของสมัยนี้ มันเป็นอย่างนี้
…. ทีนี้ เมื่อไม่รู้ว่าเกิดมาทําไม ? มันก็ไม่มีอะไร นอกจากเป็นทาสของวัตถุ ที่หวังว่าจะสนุกสนาน เอร็ดอร่อย มีเกียรติ มีอํานาจวาสนา มีอะไรไปทํานองนั้น นี่แหละ คือการตกเป็นทาสของวัตถุ การตกเป็นทาสของอายตนะ คือ ตา หู จมูก ลิ้น กาย ใจ การเล่าเรียนศึกษาขวนขวายนั้น เพื่อจะเป็นทาส ของ ตา หู จมูก ลิ้น กาย ใจ ในการที่จะแสวงหาความสนุกสนาน เอร็ดอร่อย ทางเนื้อทางหนัง มีเท่านี้ การศึกษาและห้องสมุด” . พุทธทาสภิกขุ ที่มา : ธรรมบรรยายชุดชุมนุมล้ออายุ หัวข้อเรื่อง “ยิ่งจะทำให้ดี โลกมันยิ่งบ้า” บรรยาย ณ ลานหินโค้ง กัณฑ์ค่ำ เมื่อวันที่ ๒๗ พฤษภาคม ๒๕๑๓ จากหนังสือชุดธรรมโฆษณ์ เล่มชื่อว่า “ชุมนุมล้ออายุ เล่ม ๑” หน้า ๕๑๒-๕๑๓
-
 @ 90c656ff:9383fd4e
2025-06-05 12:27:43
@ 90c656ff:9383fd4e
2025-06-05 12:27:43When people talk about Bitcoin, it’s often described as a digital currency or a “speculative investment.” However, one of Bitcoin’s most fundamental and least understood roles is its function as a settlement network. To understand this, it’s worth comparing it with traditional settlement systems like SWIFT and exploring how Bitcoin offers a foundational layer for global value transfer decentralized and censorship-resistant.
First, let’s explain the difference between liquidity and settlement:
-
Liquidity refers to the ease with which an asset can be converted into “money” without losing value.
-
Settlement is the process of completing a transaction (actual transfer of value between parties).
SWIFT: The communication layer of the traditional financial system
The SWIFT system (Society for Worldwide Interbank Financial Telecommunication) is a network for communication between banks. It doesn’t move money directly but sends standardized messages that instruct financial institutions to perform transfers. The process involves multiple intermediaries, is costly, slow (can take days), and depends on trust between parties and local regulations.
Unlike SWIFT, Bitcoin is a self-sufficient network that enables the direct settlement of value between two parties, without the need for intermediaries. With each block mined, transactions are validated and recorded immutably in a global, transparent, and secure database: the timechain or "blockchain".
01 - Final settlement: Once a transaction is confirmed by a sufficient number of blocks, it is considered final and irreversible.
02 - Censorship resistance: There is no central entity that can block or reverse a valid transaction.
03 - Global availability: The network is accessible 24/7 anywhere in the world with internet access.
Just as gold once served as the foundation of monetary systems, Bitcoin is establishing itself as a base layer of digital value. This layer can support others, such as:
01 - The Lightning Network, which enables near-instant transactions with extremely low fees;
02 - Tokenized financial services, which can use Bitcoin as collateral or for inter-institutional settlement.
By functioning as a public and neutral settlement network, Bitcoin offers an alternative to the traditional system, which is fragmented, closed, and reliant on trust between institutions.
In summary, more than just a speculative asset, Bitcoin is emerging as a global financial infrastructure. As a settlement network, it removes intermediaries, reduces costs, increases security, and democratizes access to value transfer. In an increasingly interconnected and digital world, understanding Bitcoin’s role as a base layer may be key to understanding the future of money.
Thank you very much for reading this far. I hope everything is well with you, and sending a big hug from your favorite Bitcoiner maximalist from Madeira. Long live freedom!
-
-
 @ b1ddb4d7:471244e7
2025-05-31 12:00:57
@ b1ddb4d7:471244e7
2025-05-31 12:00:57Bitcoin FilmFest (BFF25) returns to Warsaw for its third edition, blending independent cinema—from feature films and commercials to AI-driven experimental visuals—with education and entertainment.
Hundreds of attendees from around the world will gather for three days of screenings, discussions, workshops, and networking at the iconic Kinoteka Cinema (PKiN), the same venue that hosted the festival’s first two editions in March 2023 and April 2024.
This year’s festival, themed “Beyond the Frame,” introduces new dimensions to its program, including an extra day on May 22 to celebrate Bitcoin Pizza Day, the first real-world bitcoin transaction, with what promises to be one of Europe’s largest commemorations of this milestone.
BFF25 bridges independent film, culture, and technology, with a bold focus on decentralized storytelling and creative expression. As a community-driven cultural experience with a slightly rebellious spirit, Bitcoin FilmFest goes beyond movies, yet cinema remains at its heart.
Here’s a sneak peek at the lineup, specially curated for movie buffs:
 Generative Cinema – A special slot with exclusive shorts and a thematic debate on the intersection of AI and filmmaking. Featured titles include, for example: BREAK FREE, SATOSHI: THE CREATION OF BITCOIN, STRANGE CURRENCIES, and BITCOIN IS THE MYCELIUM OF MONEY, exploring financial independence, traps of the fiat system, and a better future built on sound money.
Generative Cinema – A special slot with exclusive shorts and a thematic debate on the intersection of AI and filmmaking. Featured titles include, for example: BREAK FREE, SATOSHI: THE CREATION OF BITCOIN, STRANGE CURRENCIES, and BITCOIN IS THE MYCELIUM OF MONEY, exploring financial independence, traps of the fiat system, and a better future built on sound money. Upcoming Productions Preview – A bit over an hour-long block of unreleased pilots and works-in-progress. Attendees will get exclusive first looks at projects like FINDING HOME (a travel-meets-personal-journey series), PARALLEL SPACES (a story about alternative communities), and THE LEGEND OF LANDI (a mysterious narrative).
Upcoming Productions Preview – A bit over an hour-long block of unreleased pilots and works-in-progress. Attendees will get exclusive first looks at projects like FINDING HOME (a travel-meets-personal-journey series), PARALLEL SPACES (a story about alternative communities), and THE LEGEND OF LANDI (a mysterious narrative). Freedom-Focused Ads & Campaigns – Unique screenings of video commercials, animations, and visual projects, culminating in “The PoWies” (Proof of Work-ies)—the first ever awards show honoring the best Bitcoin-only awareness campaigns.
Freedom-Focused Ads & Campaigns – Unique screenings of video commercials, animations, and visual projects, culminating in “The PoWies” (Proof of Work-ies)—the first ever awards show honoring the best Bitcoin-only awareness campaigns.To get an idea of what might come up at the event, here, you can preview 6 selected ads combined into two 2 videos:
 Open Pitch Competition – A chance for filmmakers to present fresh ideas and unfinished projects to an audience of a dedicated jury, movie fans and potential collaborators. This competitive block isn’t just entertaining—it’s a real opportunity for creators to secure funding and partnerships.
Open Pitch Competition – A chance for filmmakers to present fresh ideas and unfinished projects to an audience of a dedicated jury, movie fans and potential collaborators. This competitive block isn’t just entertaining—it’s a real opportunity for creators to secure funding and partnerships. Golden Rabbit Awards: A lively gala honoring films from the festival’s Official Selection, with awards in categories like Best Feature, Best Story, Best Short, and Audience Choice.
Golden Rabbit Awards: A lively gala honoring films from the festival’s Official Selection, with awards in categories like Best Feature, Best Story, Best Short, and Audience Choice.BFF25 Main Screenings
Sample titles from BFF25’s Official Selection:
 REVOLUCIÓN BITCOIN – A documentary by Juan Pablo, making its first screening outside the Spanish-speaking world in Warsaw this May. Three years of important work, 80 powerful minutes to experience. The film explores Bitcoin’s impact across Argentina, Colombia, Mexico, El Salvador, and Spain through around 40 diverse perspectives. Screening in Spanish with English subtitles, followed by a Q&A with the director.
REVOLUCIÓN BITCOIN – A documentary by Juan Pablo, making its first screening outside the Spanish-speaking world in Warsaw this May. Three years of important work, 80 powerful minutes to experience. The film explores Bitcoin’s impact across Argentina, Colombia, Mexico, El Salvador, and Spain through around 40 diverse perspectives. Screening in Spanish with English subtitles, followed by a Q&A with the director. UNBANKABLE – Luke Willms’ directorial debut, drawing from his multicultural roots and his father’s pioneering HIV/AIDS research. An investigative documentary based on Luke’s journeys through seven African countries, diving into financial experiments and innovations—from mobile money and digital lending to Bitcoin—raising smart questions and offering potential lessons for the West. Its May appearance at BFF25 marks its largest European event to date, following festival screenings and nominations across multiple continents over the past year.
UNBANKABLE – Luke Willms’ directorial debut, drawing from his multicultural roots and his father’s pioneering HIV/AIDS research. An investigative documentary based on Luke’s journeys through seven African countries, diving into financial experiments and innovations—from mobile money and digital lending to Bitcoin—raising smart questions and offering potential lessons for the West. Its May appearance at BFF25 marks its largest European event to date, following festival screenings and nominations across multiple continents over the past year. HOTEL BITCOIN – A Spanish comedy directed by Manuel Sanabria and Carlos “Pocho” Villaverde. Four friends, 4,000 bitcoins , and one laptop spark a chaotic adventure of parties, love, crime, and a dash of madness. Exploring sound money, value, and relationships through a twisting plot. The film premiered at the Tarazona and Moncayo Comedy Film Festival in August 2024. Its Warsaw screening at BFF25 (in Spanish with English subtitles) marks its first public showing outside the Spanish-speaking world.
HOTEL BITCOIN – A Spanish comedy directed by Manuel Sanabria and Carlos “Pocho” Villaverde. Four friends, 4,000 bitcoins , and one laptop spark a chaotic adventure of parties, love, crime, and a dash of madness. Exploring sound money, value, and relationships through a twisting plot. The film premiered at the Tarazona and Moncayo Comedy Film Festival in August 2024. Its Warsaw screening at BFF25 (in Spanish with English subtitles) marks its first public showing outside the Spanish-speaking world.Check out trailers for this year’s BFF25 and past editions on YouTube.
Tickets & Info:
- Detailed program and tickets are available at bitcoinfilmfest.com/bff25.
- Stay updated via the festival’s official channels (links provided on the website).
- Use ‘LN-NEWS’ to get 10% of tickets
-
 @ 4fe4a528:3ff6bf06
2024-12-01 15:00:30
@ 4fe4a528:3ff6bf06
2024-12-01 15:00:30https://cdn.satellite.earth/8dd22e9b598964ade69d4c5ca517c2637ffafdfb15cf3e589cd1a7955c173375.mp4 In my last news article I wrote about selling my beef for 4500 sats / lb and buying my eggs for 4500 sats / dozen. You will be glad to know that some of my friends gave me bitcoin for my birthday. One person gave me over 60,000 sats, so now I am feeling like my last months article caused everyone to buy bitcoin — opt out of inflation.
It must have been more than my friends giving me bitcoin that caused Bitcoin to increase it’s market cap by 600 billion US dollars. I know that eggs are costing me 3,000 sats now compared to 4500 sats one month ago. If things keep getting 50% cheaper every month I might not have to move all my value into bitcoin.
Isn’t it weird using something that increases in value month after month? It is indeed a far cry from the traditional notion of money, where the value or the purchasing power of the currency loses value month after month. Most Bitcoiners care about the separation of money from the state, the removal of a third party from transactions and the capturing the deflationary nature of technology, etc. The fiat price is simply a short term way of measuring progress toward that goal. In reality, the moose shekel price doesn’t really matter.
With Brazil and Russia now using it as legal tender I don’t want anyone to give me bitcoin as a gift this month. Give your money/love to helping others see Jesus’ love in coming to earth instead. You might be able to write off your donation also.
You do realize there are only 16.5 million bitcoin available to be moved to other bitcoin type people and the US bitcoin strategic reserve might be coming next year. I just hope the Trudeau / Christine “Vib” session doesn’t make Canadians give up on using the Moose Shekels as a means of exchanging value. Bitcoin is now worth more than the Canadian dollar. If you need to get educated about money join Nostr and do a video / desktop sharing conference with me. Say hivetalk.org @ 9am ish works best for me. Remember, learning technology makes you earn more. We are all in this together.
-
 @ 84b0c46a:417782f5
2025-05-31 09:11:23
@ 84b0c46a:417782f5
2025-05-31 09:11:23Simple Long Form Content Editor (NIP-23)
機能
-
nostr:npub1sjcvg64knxkrt6ev52rywzu9uzqakgy8ehhk8yezxmpewsthst6sw3jqcw や、 nostr:nevent1qvzqqqqqqypzq4jsz7zew5j7jr4pdfxh483nwq9vyw9ph6wm706sjwrzj2we58nqqyxhwumn8ghj77tpvf6jumt9qys8wumn8ghj7un9d3shjtt2wqhxummnw3ezuamfwfjkgmn9wshx5uqpr4mhxue69uhhyetvv9ujumn0wd68ytnhd9ex2erwv46zu6nsqyxhwumn8ghj7mn0wvhxcmmvqqsgcn99jyn5tevxz5zxsrkd7h0sx8fwnqztula423xh83j9wau7cms3vg9c7 のようにnostr:要素を挿入できる (メニューのNアイコンから挿入またはnostr:note~~のように手動で入力)
-
:monoice:のようにカスタム絵文字を挿入できる(メニューの🙂アイコンから)
:monopaca_kao:
:kubipaca_karada:
- 新規記事作成と、既存記事の修正ができる
やることやったこと
-
[x] nostr:を投稿するときにtagにいれる
-
[x] 画像をアップロードできるようにする(NIP-96)
 できる
できる - [x] 投稿しましたログとかをトースト的なやつでだすようにする
- [ ] レイアウトを整える
- [ ] あとなんか
test
nostr:naddr1qvzqqqr4gupzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qqxnzde58q6njvpkxqersv3ejxw9x9
-
-
 @ 3bf0c63f:aefa459d
2024-09-06 12:49:46
@ 3bf0c63f:aefa459d
2024-09-06 12:49:46Nostr: a quick introduction, attempt #2
Nostr doesn't subscribe to any ideals of "free speech" as these belong to the realm of politics and assume a big powerful government that enforces a common ruleupon everybody else.
Nostr instead is much simpler, it simply says that servers are private property and establishes a generalized framework for people to connect to all these servers, creating a true free market in the process. In other words, Nostr is the public road that each market participant can use to build their own store or visit others and use their services.
(Of course a road is never truly public, in normal cases it's ran by the government, in this case it relies upon the previous existence of the internet with all its quirks and chaos plus a hand of government control, but none of that matters for this explanation).
More concretely speaking, Nostr is just a set of definitions of the formats of the data that can be passed between participants and their expected order, i.e. messages between clients (i.e. the program that runs on a user computer) and relays (i.e. the program that runs on a publicly accessible computer, a "server", generally with a domain-name associated) over a type of TCP connection (WebSocket) with cryptographic signatures. This is what is called a "protocol" in this context, and upon that simple base multiple kinds of sub-protocols can be added, like a protocol for "public-square style microblogging", "semi-closed group chat" or, I don't know, "recipe sharing and feedback".
-
 @ 0176967e:1e6f471e
2024-07-28 15:31:13
@ 0176967e:1e6f471e
2024-07-28 15:31:13Objavte, ako avatari a pseudonymné identity ovplyvňujú riadenie kryptokomunít a decentralizovaných organizácií (DAOs). V tejto prednáške sa zameriame na praktické fungovanie decentralizovaného rozhodovania, vytváranie a správu avatarových profilov, a ich rolu v online reputačných systémoch. Naučíte sa, ako si vytvoriť efektívny pseudonymný profil, zapojiť sa do rôznych krypto projektov a využiť svoje aktivity na zarábanie kryptomien. Preskúmame aj príklady úspešných projektov a stratégie, ktoré vám pomôžu zorientovať sa a uspieť v dynamickom svete decentralizovaných komunít.
-
 @ cae03c48:2a7d6671
2025-06-03 12:01:09
@ cae03c48:2a7d6671
2025-06-03 12:01:09Bitcoin Magazine

Sberbank, Russia’s Biggest Bank, Launches Structured Bond Tied to BitcoinSberbank, the largest bank in Russia, has launched a new structured bond that ties investor returns to the performance of Bitcoin and the U.S. dollar-to-ruble exchange rate. This new financial product represents one of the first moves by a major Russian institution to offer Bitcoin-linked investments under recently updated national regulations.
BREAKING:
 Russia's largest bank Sberbank launches structured bonds linked to Bitcoin. pic.twitter.com/LtD26jPS0x
Russia's largest bank Sberbank launches structured bonds linked to Bitcoin. pic.twitter.com/LtD26jPS0x— Bitcoin Magazine (@BitcoinMagazine) June 2, 2025
The structured bond is initially available over the counter to a limited group of qualified investors. According to the announcement, it allows investors to earn based on two factors: the price performance of BTC in U.S. dollars and any strengthening of the dollar compared to the Russian ruble.
Unlike typical Bitcoin investments, this product does not require the use of a Bitcoin wallet or foreign platforms. “All transactions [are] processed in rubles within Russia’s legal and infrastructure systems,” Sberbank stated, highlighting compliance with domestic financial protocols.
In addition to the bond, Sberbank has announced plans to launch similar structured investment products with Bitcoin exposure on the Moscow Exchange. The bank also revealed it will introduce a Bitcoin futures product via its SberInvestments platform on June 4, aligning with the product’s debut on the Moscow Exchange.
These developments follow a recent policy change by the Bank of Russia, which now permits financial institutions to offer Bitcoin-linked instruments to qualified investors. This shift opens the door for Bitcoin within the country’s traditional financial markets.
While Russia has previously taken a cautious approach to digital assets, Sberbank’s launch of a Bitcoin-linked bond and upcoming futures product marks a new phase of adoption—one that blends Bitcoin exposure with existing financial infrastructure.
The bank’s structured bond may signal a growing interest in regulated access to Bitcoin, especially within large financial institutions.
This post Sberbank, Russia’s Biggest Bank, Launches Structured Bond Tied to Bitcoin first appeared on Bitcoin Magazine and is written by Jenna Montgomery.
-
 @ d6affa19:9110b177
2024-09-24 18:31:42
@ d6affa19:9110b177
2024-09-24 18:31:42i'm in the upstairs office. lost in some project i've been tinkering with. i feel driven with purpose.
the door is cracked open. i always leave the door open.
Her footsteps echo up the stairway. but my focus is intense; a solution just beyond my fingertips.
the door creaks open, a soft whisper of a sound.
i instantly feel Her presence. a sweet vanilla scent wraps around me, thick and intoxicating.
Her fingers brush through my hair, a gentle caress.
She grips my hair, then releases it— over and over again. it feels good.
a soothing warmth envelops me.
Her fingers glide, each stroke igniting my senses. a chill races down my spine.
the monitor becomes a bit distant.
"You're really focused, hmm?" She teases, leaning closer. "I'm just checking in on my sweet boy." Her tone alluring, already drawing me in.
"of course, my Queen." i reply, my eyes glued to the screen, struggling to concentrate. "thank You," my voice hints at annoyance. "i'm so close to finishing this up."
just when i near a breakthrough, She appears, a siren pulling me from my path. how does She know..? the quiet signals that betray my focus— that reveal my yearning.
"Hmmmm," She playfully muses.
ugh, i need to concentrate. but the way this feels...
it pulls me deeper.
Her fingers drift by my ear, lingering around my neck. nails grazing my skin, sending shivers through me.
my heart begins to race. the screen blurs, reality separates.
"Okay, sweet boy." Her voice is a soft command. Her nails dig in, a mixture of pain and pleasure. a sharp contrast to the softness of Her touch. "I'll be downstairs while you finish."
yet She remains. i close my eyes, drowning in the sensation. i should be finishing this project...
but each press feels like a silent command, an urge to abandon my thoughts, to succumb to the pull of Her presence.
the way She easily captures my attention... it makes me feel so vulnerable...
Her grip finally loosens, and slowly leaves my neck. it wants more...
i barely hear Her leave. but the air feels colder. the warmth of Her presence is fading. an aching emptiness fills the space...
the weight of Her absence settles in, another reminder of how easily She commands my thoughts...
desperately, i take in the remnants of Her scent.
i stare at my monitor. focus shattered, thoughts scattered like leaves.
i linger for a moment. fighting the urge to chase after Her.
the pull of Her absence is heavy in the air. i'm unable to resist. i rise from my seat.
the door is slightly open. She always leaves the door open.
i make my way downstairs, lost in the thoughts of serving Her. my true purpose...
-
 @ 7f6db517:a4931eda
2025-05-31 06:01:36
@ 7f6db517:a4931eda
2025-05-31 06:01:36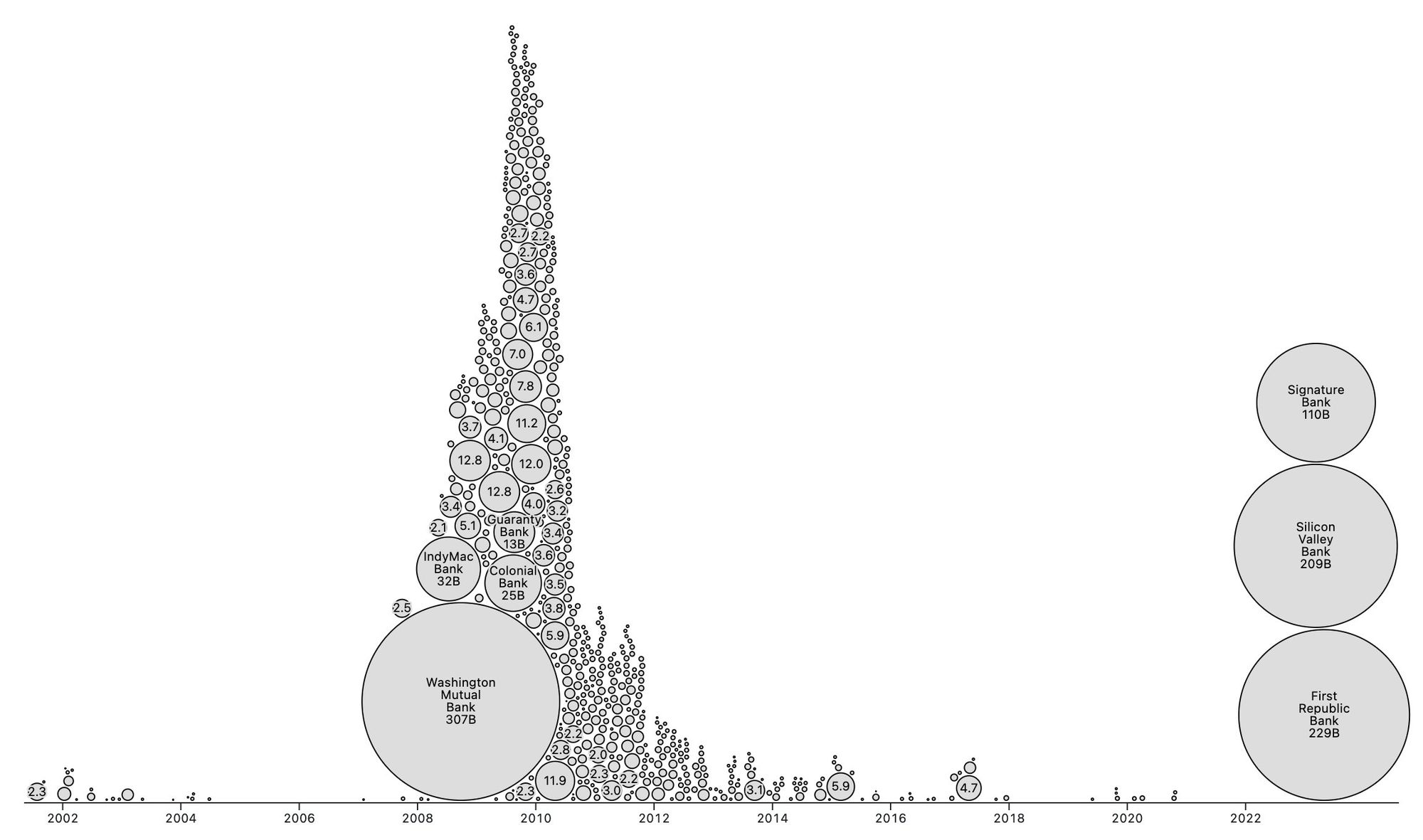
People forget Bear Stearns failed March 2008 - months of denial followed before the public realized how bad the situation was under the surface.
Similar happening now but much larger scale. They did not fix fundamental issues after 2008 - everything is more fragile.
The Fed preemptively bailed out every bank with their BTFP program and First Republic Bank still failed. The second largest bank failure in history.
There will be more failures. There will be more bailouts. Depositors will be "protected" by socializing losses across everyone.
Our President and mainstream financial pundits are currently pretending the banking crisis is over while most banks remain insolvent. There are going to be many more bank failures as this ponzi system unravels.
Unlike 2008, we have the ability to opt out of these broken and corrupt institutions by using bitcoin. Bitcoin held in self custody is unique in its lack of counterparty risk - you do not have to trust a bank or other centralized entity to hold it for you. Bitcoin is also incredibly difficult to change by design since it is not controlled by an individual, company, or government - the supply of dollars will inevitably be inflated to bailout these failing banks but bitcoin supply will remain unchanged. I do not need to convince you that bitcoin provides value - these next few years will convince millions.
If you found this post helpful support my work with bitcoin.

-
 @ e4950c93:1b99eccd
2025-06-05 10:23:39
@ e4950c93:1b99eccd
2025-06-05 10:23:39Marques
Nordkidz est une marque allemande qui crée à la demande des vêtements et linges pour les bébés, les enfants, et un peu pour leurs parents.
Matières naturelles utilisées dans les produits
⚠️ Attention, certains produits de cette marque contiennent des matières non naturelles, dont :
Catégories de produits proposés
Cette marque propose des produits intégralement en matière naturelle dans les catégories suivantes :
Vêtements
- Tailles vêtements : bébés, enfants, unisexe
- Hauts : pulls, t-shirts
- Bas : pantalons, pantalons de survêtement, shorts
- Tête et mains : bonnets, écharpes
Maison
- Linge : housses de pouf, langes, ponchos de bain
Autres informations
👉 En savoir plus sur le site de la marque
Où trouver leurs produits ?
- Nordkidz (en allemand, zone de livraison : Allemagne et Union Européenne) 💚 Via ce lien vous soutenez directement la marque.
📝 Tu peux contribuer à cette fiche en suggérant une modification en commentaire.
🗣️ Tu utilises des produits de cette marque ? Partage ton avis en commentaire.
⚡ Heureu-x-se de trouver cette information ? Soutiens le projet en faisant un don pour remercier les contribut-eur-ice-s.
-
 @ c4f5e7a7:8856cac7
2025-06-03 08:15:33
@ c4f5e7a7:8856cac7
2025-06-03 08:15:33I've managed to amass three SN profiles.
Is there a way to combined these?
@k00b @ek
https://stacker.news/items/995836
-
 @ e2c72a5a:bfacb2ee
2025-06-05 17:11:03
@ e2c72a5a:bfacb2ee
2025-06-05 17:11:03The $220 million crypto heist that took just minutes reveals a fatal flaw in DeFi security. While blockchain tech promises trustless transactions, the Cetus DEX exploit on Sui exposed how a single undetected bug in a math library became catastrophic. What's truly alarming isn't the hack itself but the revelation from Curve's founder that professional hackers-for-hire are now coordinating sophisticated cross-platform attacks. This signals a dangerous evolution in crypto threats where vulnerabilities aren't just discovered—they're hunted by organized teams with specialized skills. The industry faces a stark choice: invest aggressively in preventative security or watch as billions more vanish in seconds. Is your crypto truly safe, or just waiting for the right hacker to find its weakness?
-
 @ ee11a5df:b76c4e49
2024-09-11 08:16:37
@ ee11a5df:b76c4e49
2024-09-11 08:16:37Bye-Bye Reply Guy
There is a camp of nostr developers that believe spam filtering needs to be done by relays. Or at the very least by DVMs. I concur. In this way, once you configure what you want to see, it applies to all nostr clients.
But we are not there yet.
In the mean time we have ReplyGuy, and gossip needed some changes to deal with it.
Strategies in Short
- WEB OF TRUST: Only accept events from people you follow, or people they follow - this avoids new people entirely until somebody else that you follow friends them first, which is too restrictive for some people.
- TRUSTED RELAYS: Allow every post from relays that you trust to do good spam filtering.
- REJECT FRESH PUBKEYS: Only accept events from people you have seen before - this allows you to find new people, but you will miss their very first post (their second post must count as someone you have seen before, even if you discarded the first post)
- PATTERN MATCHING: Scan for known spam phrases and words and block those events, either on content or metadata or both or more.
- TIE-IN TO EXTERNAL SYSTEMS: Require a valid NIP-05, or other nostr event binding their identity to some external identity
- PROOF OF WORK: Require a minimum proof-of-work
All of these strategies are useful, but they have to be combined properly.
filter.rhai
Gossip loads a file called "filter.rhai" in your gossip directory if it exists. It must be a Rhai language script that meets certain requirements (see the example in the gossip source code directory). Then it applies it to filter spam.
This spam filtering code is being updated currently. It is not even on unstable yet, but it will be there probably tomorrow sometime. Then to master. Eventually to a release.
Here is an example using all of the techniques listed above:
```rhai // This is a sample spam filtering script for the gossip nostr // client. The language is called Rhai, details are at: // https://rhai.rs/book/ // // For gossip to find your spam filtering script, put it in // your gossip profile directory. See // https://docs.rs/dirs/latest/dirs/fn.data_dir.html // to find the base directory. A subdirectory "gossip" is your // gossip data directory which for most people is their profile // directory too. (Note: if you use a GOSSIP_PROFILE, you'll // need to put it one directory deeper into that profile // directory). // // This filter is used to filter out and refuse to process // incoming events as they flow in from relays, and also to // filter which events get/ displayed in certain circumstances. // It is only run on feed-displayable event kinds, and only by // authors you are not following. In case of error, nothing is // filtered. // // You must define a function called 'filter' which returns one // of these constant values: // DENY (the event is filtered out) // ALLOW (the event is allowed through) // MUTE (the event is filtered out, and the author is // automatically muted) // // Your script will be provided the following global variables: // 'caller' - a string that is one of "Process", // "Thread", "Inbox" or "Global" indicating // which part of the code is running your // script // 'content' - the event content as a string // 'id' - the event ID, as a hex string // 'kind' - the event kind as an integer // 'muted' - if the author is in your mute list // 'name' - if we have it, the name of the author // (or your petname), else an empty string // 'nip05valid' - whether nip05 is valid for the author, // as a boolean // 'pow' - the Proof of Work on the event // 'pubkey' - the event author public key, as a hex // string // 'seconds_known' - the number of seconds that the author // of the event has been known to gossip // 'spamsafe' - true only if the event came in from a // relay marked as SpamSafe during Process // (even if the global setting for SpamSafe // is off)
fn filter() {
// Show spam on global // (global events are ephemeral; these won't grow the // database) if caller=="Global" { return ALLOW; } // Block ReplyGuy if name.contains("ReplyGuy") || name.contains("ReplyGal") { return DENY; } // Block known DM spam // (giftwraps are unwrapped before the content is passed to // this script) if content.to_lower().contains( "Mr. Gift and Mrs. Wrap under the tree, KISSING!" ) { return DENY; } // Reject events from new pubkeys, unless they have a high // PoW or we somehow already have a nip05valid for them // // If this turns out to be a legit person, we will start // hearing their events 2 seconds from now, so we will // only miss their very first event. if seconds_known <= 2 && pow < 25 && !nip05valid { return DENY; } // Mute offensive people if content.to_lower().contains(" kike") || content.to_lower().contains("kike ") || content.to_lower().contains(" nigger") || content.to_lower().contains("nigger ") { return MUTE; } // Reject events from muted people // // Gossip already does this internally, and since we are // not Process, this is rather redundant. But this works // as an example. if muted { return DENY; } // Accept if the PoW is large enough if pow >= 25 { return ALLOW; } // Accept if their NIP-05 is valid if nip05valid { return ALLOW; } // Accept if the event came through a spamsafe relay if spamsafe { return ALLOW; } // Reject the rest DENY} ```
-
 @ dfa02707:41ca50e3
2025-05-31 06:01:28
@ dfa02707:41ca50e3
2025-05-31 06:01:28- This version introduces the Soroban P2P network, enabling Dojo to relay transactions to the Bitcoin network and share others' transactions to break the heuristic linking relaying nodes to transaction creators.
- Additionally, Dojo admins can now manage API keys in DMT with labels, status, and expiration, ideal for community Dojo providers like Dojobay. New API endpoints, including "/services" exposing Explorer, Soroban, and Indexer, have been added to aid wallet developers.
- Other maintenance updates include Bitcoin Core, Tor, Fulcrum, Node.js, plus an updated ban-knots script to disconnect inbound Knots nodes.
"I want to thank all the contributors. This again shows the power of true Free Software. I also want to thank everyone who donated to help Dojo development going. I truly appreciate it," said Still Dojo Coder.
What's new
- Soroban P2P network. For MyDojo (Docker setup) users, Soroban will be automatically installed as part of their Dojo. This integration allows Dojo to utilize the Soroban P2P network for various upcoming features and applications.
- PandoTx. PandoTx serves as a transaction transport layer. When your wallet sends a transaction to Dojo, it is relayed to a random Soroban node, which then forwards it to the Bitcoin network. It also enables your Soroban node to receive and relay transactions from others to the Bitcoin network and is designed to disrupt the assumption that a node relaying a transaction is closely linked to the person who initiated it.
- Pushing transactions through Soroban can be deactivated by setting
NODE_PANDOTX_PUSH=offindocker-node.conf. - Processing incoming transactions from Soroban network can be deactivated by setting
NODE_PANDOTX_PROCESS=offindocker-node.conf.
- Pushing transactions through Soroban can be deactivated by setting
- API key management has been introduced to address the growing number of people offering their Dojos to the community. Dojo admins can now access a new API management tab in their DMT, where they can create unlimited API keys, assign labels for easy identification, and set expiration dates for each key. This allows admins to avoid sharing their main API key and instead distribute specific keys to selected parties.
- New API endpoints. Several new API endpoints have been added to help API consumers develop features on Dojo more efficiently:
- New:
/latest-block- returns data about latest block/txout/:txid/:index- returns unspent output data/support/services- returns info about services that Dojo exposes
- Updated:
/tx/:txid- endpoint has been updated to return raw transaction with parameter?rawHex=1
- The new
/support/servicesendpoint replaces the deprecatedexplorerfield in the Dojo pairing payload. Although still present, API consumers should use this endpoint for explorer and other pairing data.
- New:
Other changes
- Updated ban script to disconnect inbound Knots nodes.
- Updated Fulcrum to v1.12.0.
- Regenerate Fulcrum certificate if expired.
- Check if transaction already exists in pushTx.
- Bump BTC-RPC Explorer.
- Bump Tor to v0.4.8.16, bump Snowflake.
- Updated Bitcoin Core to v29.0.
- Removed unnecessary middleware.
- Fixed DB update mechanism, added api_keys table.
- Add an option to use blocksdir config for bitcoin blocks directory.
- Removed deprecated configuration.
- Updated Node.js dependencies.
- Reconfigured container dependencies.
- Fix Snowflake git URL.
- Fix log path for testnet4.
- Use prebuilt addrindexrs binaries.
- Add instructions to migrate blockchain/fulcrum.
- Added pull policies.

Learn how to set up and use your own Bitcoin privacy node with Dojo here.
-
 @ 0176967e:1e6f471e
2024-07-28 09:16:10
@ 0176967e:1e6f471e
2024-07-28 09:16:10Jan Kolčák pochádza zo stredného Slovenska a vystupuje pod umeleckým menom Deepologic. Hudbe sa venuje už viac než 10 rokov. Začínal ako DJ, ktorý s obľubou mixoval klubovú hudbu v štýloch deep-tech a afrohouse. Stále ho ťahalo tvoriť vlastnú hudbu, a preto sa začal vzdelávať v oblasti tvorby elektronickej hudby. Nakoniec vydal svoje prvé EP s názvom "Rezonancie". Učenie je pre neho celoživotný proces, a preto sa neustále zdokonaľuje v oblasti zvuku a kompozície, aby jeho skladby boli kvalitné na posluch aj v klube.
V roku 2023 si založil vlastnú značku EarsDeep Records, kde dáva príležitosť začínajúcim producentom. Jeho značku podporujú aj etablované mená slovenskej alternatívnej elektronickej scény. Jeho prioritou je sloboda a neškatulkovanie. Ako sa hovorí v jednej klasickej deephouseovej skladbe: "We are all equal in the house of deep." So slobodou ide ruka v ruke aj láska k novým technológiám, Bitcoinu a schopnosť udržať si v digitálnom svete prehľad, odstup a anonymitu.
V súčasnosti ďalej produkuje vlastnú hudbu, venuje sa DJingu a vedie podcast, kde zverejňuje svoje mixované sety. Na Lunarpunk festivale bude hrať DJ set tvorený vlastnou produkciou, ale aj skladby, ktoré sú blízke jeho srdcu.
Podcast Bandcamp Punk Nostr website alebo nprofile1qythwumn8ghj7un9d3shjtnwdaehgu3wvfskuep0qy88wumn8ghj7mn0wvhxcmmv9uq3xamnwvaz7tmsw4e8qmr9wpskwtn9wvhsz9thwden5te0wfjkccte9ejxzmt4wvhxjme0qyg8wumn8ghj7mn0wd68ytnddakj7qghwaehxw309aex2mrp0yh8qunfd4skctnwv46z7qpqguvns4ld8k2f3sugel055w7eq8zeewq7mp6w2stpnt6j75z60z3swy7h05
-
 @ b1ddb4d7:471244e7
2025-06-03 16:01:15
@ b1ddb4d7:471244e7
2025-06-03 16:01:15Bitcoin FilmFest (BFF25) returns to Warsaw for its third edition, blending independent cinema—from feature films and commercials to AI-driven experimental visuals—with education and entertainment.
Hundreds of attendees from around the world will gather for three days of screenings, discussions, workshops, and networking at the iconic Kinoteka Cinema (PKiN), the same venue that hosted the festival’s first two editions in March 2023 and April 2024.
This year’s festival, themed “Beyond the Frame,” introduces new dimensions to its program, including an extra day on May 22 to celebrate Bitcoin Pizza Day, the first real-world bitcoin transaction, with what promises to be one of Europe’s largest commemorations of this milestone.
BFF25 bridges independent film, culture, and technology, with a bold focus on decentralized storytelling and creative expression. As a community-driven cultural experience with a slightly rebellious spirit, Bitcoin FilmFest goes beyond movies, yet cinema remains at its heart.
Here’s a sneak peek at the lineup, specially curated for movie buffs:
 Generative Cinema – A special slot with exclusive shorts and a thematic debate on the intersection of AI and filmmaking. Featured titles include, for example: BREAK FREE, SATOSHI: THE CREATION OF BITCOIN, STRANGE CURRENCIES, and BITCOIN IS THE MYCELIUM OF MONEY, exploring financial independence, traps of the fiat system, and a better future built on sound money.
Generative Cinema – A special slot with exclusive shorts and a thematic debate on the intersection of AI and filmmaking. Featured titles include, for example: BREAK FREE, SATOSHI: THE CREATION OF BITCOIN, STRANGE CURRENCIES, and BITCOIN IS THE MYCELIUM OF MONEY, exploring financial independence, traps of the fiat system, and a better future built on sound money. Upcoming Productions Preview – A bit over an hour-long block of unreleased pilots and works-in-progress. Attendees will get exclusive first looks at projects like FINDING HOME (a travel-meets-personal-journey series), PARALLEL SPACES (a story about alternative communities), and THE LEGEND OF LANDI (a mysterious narrative).
Upcoming Productions Preview – A bit over an hour-long block of unreleased pilots and works-in-progress. Attendees will get exclusive first looks at projects like FINDING HOME (a travel-meets-personal-journey series), PARALLEL SPACES (a story about alternative communities), and THE LEGEND OF LANDI (a mysterious narrative). Freedom-Focused Ads & Campaigns – Unique screenings of video commercials, animations, and visual projects, culminating in “The PoWies” (Proof of Work-ies)—the first ever awards show honoring the best Bitcoin-only awareness campaigns.
Freedom-Focused Ads & Campaigns – Unique screenings of video commercials, animations, and visual projects, culminating in “The PoWies” (Proof of Work-ies)—the first ever awards show honoring the best Bitcoin-only awareness campaigns.To get an idea of what might come up at the event, here, you can preview 6 selected ads combined into two 2 videos:
 Open Pitch Competition – A chance for filmmakers to present fresh ideas and unfinished projects to an audience of a dedicated jury, movie fans and potential collaborators. This competitive block isn’t just entertaining—it’s a real opportunity for creators to secure funding and partnerships.
Open Pitch Competition – A chance for filmmakers to present fresh ideas and unfinished projects to an audience of a dedicated jury, movie fans and potential collaborators. This competitive block isn’t just entertaining—it’s a real opportunity for creators to secure funding and partnerships. Golden Rabbit Awards: A lively gala honoring films from the festival’s Official Selection, with awards in categories like Best Feature, Best Story, Best Short, and Audience Choice.
Golden Rabbit Awards: A lively gala honoring films from the festival’s Official Selection, with awards in categories like Best Feature, Best Story, Best Short, and Audience Choice.BFF25 Main Screenings
Sample titles from BFF25’s Official Selection:
 REVOLUCIÓN BITCOIN – A documentary by Juan Pablo, making its first screening outside the Spanish-speaking world in Warsaw this May. Three years of important work, 80 powerful minutes to experience. The film explores Bitcoin’s impact across Argentina, Colombia, Mexico, El Salvador, and Spain through around 40 diverse perspectives. Screening in Spanish with English subtitles, followed by a Q&A with the director.
REVOLUCIÓN BITCOIN – A documentary by Juan Pablo, making its first screening outside the Spanish-speaking world in Warsaw this May. Three years of important work, 80 powerful minutes to experience. The film explores Bitcoin’s impact across Argentina, Colombia, Mexico, El Salvador, and Spain through around 40 diverse perspectives. Screening in Spanish with English subtitles, followed by a Q&A with the director. UNBANKABLE – Luke Willms’ directorial debut, drawing from his multicultural roots and his father’s pioneering HIV/AIDS research. An investigative documentary based on Luke’s journeys through seven African countries, diving into financial experiments and innovations—from mobile money and digital lending to Bitcoin—raising smart questions and offering potential lessons for the West. Its May appearance at BFF25 marks its largest European event to date, following festival screenings and nominations across multiple continents over the past year.
UNBANKABLE – Luke Willms’ directorial debut, drawing from his multicultural roots and his father’s pioneering HIV/AIDS research. An investigative documentary based on Luke’s journeys through seven African countries, diving into financial experiments and innovations—from mobile money and digital lending to Bitcoin—raising smart questions and offering potential lessons for the West. Its May appearance at BFF25 marks its largest European event to date, following festival screenings and nominations across multiple continents over the past year. HOTEL BITCOIN – A Spanish comedy directed by Manuel Sanabria and Carlos “Pocho” Villaverde. Four friends, 4,000 bitcoins , and one laptop spark a chaotic adventure of parties, love, crime, and a dash of madness. Exploring sound money, value, and relationships through a twisting plot. The film premiered at the Tarazona and Moncayo Comedy Film Festival in August 2024. Its Warsaw screening at BFF25 (in Spanish with English subtitles) marks its first public showing outside the Spanish-speaking world.
HOTEL BITCOIN – A Spanish comedy directed by Manuel Sanabria and Carlos “Pocho” Villaverde. Four friends, 4,000 bitcoins , and one laptop spark a chaotic adventure of parties, love, crime, and a dash of madness. Exploring sound money, value, and relationships through a twisting plot. The film premiered at the Tarazona and Moncayo Comedy Film Festival in August 2024. Its Warsaw screening at BFF25 (in Spanish with English subtitles) marks its first public showing outside the Spanish-speaking world.Check out trailers for this year’s BFF25 and past editions on YouTube.
Tickets & Info:
- Detailed program and tickets are available at bitcoinfilmfest.com/bff25.
- Stay updated via the festival’s official channels (links provided on the website).
- Use ‘LN-NEWS’ to get 10% of tickets
-
 @ e2c72a5a:bfacb2ee
2025-06-05 17:00:01
@ e2c72a5a:bfacb2ee
2025-06-05 17:00:01Forget Lambos, think real estate tokens.
A European fund just dropped $3.4 million on tokenized real estate, marking the first time big money directly bought retail available tokens. This isn't just about crypto hype; it's about institutions embracing regulated crypto assets. Real World Assets (RWAs) are booming, up 260% this year, fueled by clearer US crypto rules. This surge pushes the tokenization sector past $23 billion.
Is this the start of crypto's mainstream moment?
-
 @ b1ddb4d7:471244e7
2025-06-05 10:00:43
@ b1ddb4d7:471244e7
2025-06-05 10:00:43Starting January 1, 2026, the United Kingdom will impose some of the world’s most stringent reporting requirements on cryptocurrency firms.
All platforms operating in or serving UK customers-domestic and foreign alike-must collect and disclose extensive personal and transactional data for every user, including individuals, companies, trusts, and charities.
This regulatory drive marks the UK’s formal adoption of the OECD’s Crypto-Asset Reporting Framework (CARF), a global initiative designed to bring crypto oversight in line with traditional banking and to curb tax evasion in the rapidly expanding digital asset sector.
What Will Be Reported?
Crypto firms must gather and submit the following for each transaction:
- User’s full legal name, home address, and taxpayer identification number
- Detailed data on every trade or transfer: type of cryptocurrency, amount, and nature of the transaction
- Identifying information for corporate, trust, and charitable clients
The obligation extends to all digital asset activities, including crypto-to-crypto and crypto-to-fiat trades, and applies to both UK residents and non-residents using UK-based platforms. The first annual reports covering 2026 activity are due by May 31, 2027.
Enforcement and Penalties
Non-compliance will carry stiff financial penalties, with fines of up to £300 per user account for inaccurate or missing data-a potentially enormous liability for large exchanges. The UK government has urged crypto firms to begin collecting this information immediately to ensure operational readiness.
Regulatory Context and Market Impact
This move is part of a broader UK strategy to position itself as a global fintech hub while clamping down on fraud and illicit finance. UK Chancellor Rachel Reeves has championed these measures, stating, “Britain is open for business – but closed to fraud, abuse, and instability”. The regulatory expansion comes amid a surge in crypto adoption: the UK’s Financial Conduct Authority reported that 12% of UK adults owned crypto in 2024, up from just 4% in 2021.
Enormous Risks for Consumers: Lessons from the Coinbase Data Breach
While the new framework aims to enhance transparency and protect consumers, it also dramatically increases the volume of sensitive personal data held by crypto firms-raising the stakes for cybersecurity.
The risks are underscored by the recent high-profile breach at Coinbase, one of the world’s largest exchanges.
In May 2025, Coinbase disclosed that cybercriminals, aided by bribed offshore contractors, accessed and exfiltrated customer data including names, addresses, government IDs, and partial bank details.
The attackers then used this information for sophisticated phishing campaigns, successfully deceiving some customers into surrendering account credentials and funds.
“While private encryption keys remained secure, sufficient customer information was exposed to enable sophisticated phishing attacks by criminals posing as Coinbase personnel.”
Coinbase now faces up to $400 million in compensation costs and has pledged to reimburse affected users, but the incident highlights the systemic vulnerability created when large troves of personal data are centralized-even if passwords and private keys are not directly compromised. The breach also triggered a notable drop in Coinbase’s share price and prompted a $20 million bounty for information leading to the attackers’ capture.
The Bottom Line
The UK’s forthcoming crypto reporting regime represents a landmark in financial regulation, promising greater transparency and tax compliance. However, as the Coinbase episode demonstrates, the aggregation of sensitive user data at scale poses a significant cybersecurity risk.
As regulators push for more oversight, the challenge will be ensuring that consumer protection does not become a double-edged sword-exposing users to new threats even as it seeks to shield them from old ones.
-
 @ 9bc2d34d:d19d2948
2024-09-02 19:41:40
@ 9bc2d34d:d19d2948
2024-09-02 19:41:40Chef's notes
This recipe is designed for home cooks who want to recreate the delicious buttery hollandaise sauce at home without feeling overwhelmed. It focuses on teaching the basics of the sauce, allowing beginners to master the fundamentals before experimenting with seasonings, hot sauces, or herbs.
Please note the thickness of sauce in the picture. This is after ten minutes of blending.
Details
- ⏲️ Prep time: 3 minutes
- 🍳 Cook time: 10 minutes (blending)
- 🍽️ Servings: 2 - 4
Ingredients
- 4 egg yolks
- 8 tablespoons of melted butter
- 1 tablespoon of lemon juice
- Pinch of salt
- Pinch of pepper
Directions
- Melt butter in the microwave or on the stovetop.
- Separate the egg yolks from the egg whites (reserve the egg whites for another dish).
- Place the egg yolks in a blender.
- Start the blender (medium to high settings for blend mode is fine).
- Slowly pour the melted butter into the cover opening (it will splatter).
- Add the remaining ingredients.
- Blend for ten minutes (seriously, walk away and do something else).
- Taste and adjust the flavors (add extra lemon juice or salt if desired).
- Serve over your breakfast!
-
 @ e2c72a5a:bfacb2ee
2025-06-05 16:54:43
@ e2c72a5a:bfacb2ee
2025-06-05 16:54:43Think your crypto is FDIC insured like your bank account? Big mistake. Crypto's wild west demands you be your own bank and security guard.
Crypto trading involves buying, selling, and exchanging digital currencies like Bitcoin or Ethereum, aiming to profit from price fluctuations. Security is paramount. Understand basic concepts like wallets (digital storage for your crypto), private keys (passwords to access your crypto), and blockchain (the technology that records all transactions).
Real world applications include using crypto for online purchases, international money transfers, and decentralized finance (DeFi) services like lending and borrowing. Current trends include the rise of DeFi, NFTs (non-fungible tokens), and increasing institutional investment.
Best practices? Use strong, unique passwords, enable two factor authentication (2FA) on all accounts, and store most of your crypto in cold wallets (offline storage) to protect against hacking. Be wary of phishing scams and fake websites. Never share your private keys or seed phrases.
Misconceptions? Crypto is not anonymous, transactions are not easily reversible, and past performance is not indicative of future results. Also, remember that regulations are evolving, so stay informed.
With crypto hacks on the rise, are you truly ready to secure your digital fortune, or are you leaving the door open for the next billion dollar heist?
-
 @ 8bad92c3:ca714aa5
2025-05-31 06:01:27
@ 8bad92c3:ca714aa5
2025-05-31 06:01:27Marty's Bent

It's been a pretty historic week for the United States as it pertains to geopolitical relations in the Middle East. President Trump and many members of his administration, including AI and Crypto Czar David Sacks and Treasury Secretary Scott Bessent, traveled across the Middle East making deals with countries like Qatar, Saudi Arabia, the United Arab Emirates, Syria, and others. Many are speculating that Iran may be included in some behind the scenes deal as well. This trip to the Middle East makes sense considering the fact that China is also vying for favorable relationships with those countries. The Middle East is a power player in the world, and it seems pretty clear that Donald Trump is dead set on ensuring that they choose the United States over China as the world moves towards a more multi-polar reality.
Many are calling the events of this week the Riyadh Accords. There were many deals that were struck in relation to artificial intelligence, defense, energy and direct investments in the United States. A truly prolific power play and demonstration of deal-making ability of Donald Trump, if you ask me. Though I will admit some of the numbers that were thrown out by some of the countries were a bit egregious. We shall see how everything plays out in the coming years. It will be interesting to see how China reacts to this power move by the United States.
While all this was going on, there was something happening back in the United States that many people outside of fringe corners of FinTwit are not talking about, which is the fact that the 10-year and 30-year U.S. Treasury bond yields are back on the rise. Yesterday, they surpassed the levels of mid-April that caused a market panic and are hovering back around levels that have not been seen since right before Donald Trump's inauguration.


I imagine that there isn't as much of an uproar right now because I'm pretty confident the media freakouts we were experiencing in mid-April were driven by the fact that many large hedge funds found themselves off sides of large levered basis trades. I wouldn't be surprised if those funds have decreased their leverage in those trades and bond yields being back to mid-April levels is not affecting those funds as much as they were last month. But the point stands, the 10-year and 30-year yields are significantly elevated with the 30-year approaching 5%. Regardless of the deals that are currently being made in the Middle East, the Treasury has a big problem on its hands. It still has to roll over many trillions worth of debt over over the next few years and doing so at these rates is going to be massively detrimental to fiscal deficits over the next decade. The interest expense on the debt is set to explode in the coming years.
On that note, data from the first quarter of 2025 has been released by the government and despite all the posturing by the Trump administration around DOGE and how tariffs are going to be beneficial for the U.S. economy, deficits are continuing to explode while the interest expense on the debt has definitively surpassed our annual defense budget.

via Charlie Bilello

via Mohamed Al-Erian
To make matters worse, as things are deteriorating on the fiscal side of things, the U.S. consumer is getting crushed by credit. The 90-plus day delinquency rates for credit card and auto loans are screaming higher right now.

via TXMC
One has to wonder how long all this can continue without some sort of liquidity crunch. Even though equities markets have recovered from their post-Liberation Day month long bear market, I would not be surprised if what we're witnessing is a dead cat bounce that can only be continued if the money printers are turned back on. Something's got to give, both on the fiscal side and in the private markets where the Common Man is getting crushed because he's been forced to take on insane amounts of debt to stay afloat after years of elevated levels of inflation. Add on the fact that AI has reached a state of maturity that will enable companies to replace their current meat suit workers with an army of cheap, efficient and fast digital workers and it isn't hard to see that some sort of employment crisis could be on the horizon as well.
Now is not the time to get complacent. While I do believe that the deals that are currently being made in the Middle East are probably in the best interest of the United States as the world, again, moves toward a more multi-polar reality, we are facing problems that one cannot simply wish away. They will need to be confronted. And as we've seen throughout the 21st century, the problems are usually met head-on with a money printer.
I take no pleasure in saying this because it is a bit uncouth to be gleeful to benefit from the strife of others, but it is pretty clear to me that all signs are pointing to bitcoin benefiting massively from everything that is going on. The shift towards a more multi-polar world, the runaway debt situation here in the United States, the increasing deficits, the AI job replacements and the consumer credit crisis that is currently unfolding, All will need to be "solved" by turning on the money printers to levels they've never been pushed to before.
Weird times we're living in.
China's Manufacturing Dominance: Why It Matters for the U.S.
In my recent conversation with Lyn Alden, she highlighted how China has rapidly ascended the manufacturing value chain. As Lyn pointed out, China transformed from making "sneakers and plastic trinkets" to becoming the world's largest auto exporter in just four years. This dramatic shift represents more than economic success—it's a strategic power play. China now dominates solar panel production with greater market control than OPEC has over oil and maintains near-monopoly control of rare earth elements crucial for modern technology.
"China makes like 10 times more steel than the United States does... which is relevant in ship making. It's relevant in all sorts of stuff." - Lyn Alden
Perhaps most concerning, as Lyn emphasized, is China's financial leverage. They hold substantial U.S. assets that could be strategically sold to disrupt U.S. treasury market functioning. This combination of manufacturing dominance, resource control, and financial leverage gives China significant negotiating power in any trade disputes, making our attempts to reshoring manufacturing all the more challenging.
Check out the full podcast here for more on Triffin's dilemma, Bitcoin's role in monetary transition, and the energy requirements for rebuilding America's industrial base.
Headlines of the Day
Financial Times Under Fire Over MicroStrategy Bitcoin Coverage - via X
Trump in Qatar: Historic Boeing Deal Signed - via X
Get our new STACK SATS hat - via tftcmerch.io
Johnson Backs Stock Trading Ban; Passage Chances Slim - via X
Take the First Step Off the Exchange
Bitkey is an easy, secure way to move your Bitcoin into self-custody. With simple setup and built-in recovery, it’s the perfect starting point for getting your coins off centralized platforms and into cold storage—no complexity, no middlemen.
Take control. Start with Bitkey.
Use the promo code *“TFTC20”* during checkout for 20% off
Ten31, the largest bitcoin-focused investor, has deployed 158,469 sats | $150.00M across 30+ companies through three funds. I am a Managing Partner at Ten31 and am very proud of the work we are doing. Learn more at ten31.vc/invest.
Final thought...
Building things of value is satisfying.
Get this newsletter sent to your inbox daily: https://www.tftc.io/bitcoin-brief/
Subscribe to our YouTube channels and follow us on Nostr and X:
@media screen and (max-width: 480px) { .mobile-padding { padding: 10px 0 !important; } .social-container { width: 100% !important; max-width: 260px !important; } .social-icon { padding: 0 !important; } .social-icon img { height: 32px !important; width: 32px !important; } .icon-cell { padding: 0 4px !import
-
 @ 04c915da:3dfbecc9
2025-05-20 15:53:48
@ 04c915da:3dfbecc9
2025-05-20 15:53:48This piece is the first in a series that will focus on things I think are a priority if your focus is similar to mine: building a strong family and safeguarding their future.
Choosing the ideal place to raise a family is one of the most significant decisions you will ever make. For simplicity sake I will break down my thought process into key factors: strong property rights, the ability to grow your own food, access to fresh water, the freedom to own and train with guns, and a dependable community.
A Jurisdiction with Strong Property Rights
Strong property rights are essential and allow you to build on a solid foundation that is less likely to break underneath you. Regions with a history of limited government and clear legal protections for landowners are ideal. Personally I think the US is the single best option globally, but within the US there is a wide difference between which state you choose. Choose carefully and thoughtfully, think long term. Obviously if you are not American this is not a realistic option for you, there are other solid options available especially if your family has mobility. I understand many do not have this capability to easily move, consider that your first priority, making movement and jurisdiction choice possible in the first place.
Abundant Access to Fresh Water
Water is life. I cannot overstate the importance of living somewhere with reliable, clean, and abundant freshwater. Some regions face water scarcity or heavy regulations on usage, so prioritizing a place where water is plentiful and your rights to it are protected is critical. Ideally you should have well access so you are not tied to municipal water supplies. In times of crisis or chaos well water cannot be easily shutoff or disrupted. If you live in an area that is drought prone, you are one drought away from societal chaos. Not enough people appreciate this simple fact.
Grow Your Own Food
A location with fertile soil, a favorable climate, and enough space for a small homestead or at the very least a garden is key. In stable times, a small homestead provides good food and important education for your family. In times of chaos your family being able to grow and raise healthy food provides a level of self sufficiency that many others will lack. Look for areas with minimal restrictions, good weather, and a culture that supports local farming.
Guns
The ability to defend your family is fundamental. A location where you can legally and easily own guns is a must. Look for places with a strong gun culture and a political history of protecting those rights. Owning one or two guns is not enough and without proper training they will be a liability rather than a benefit. Get comfortable and proficient. Never stop improving your skills. If the time comes that you must use a gun to defend your family, the skills must be instinct. Practice. Practice. Practice.
A Strong Community You Can Depend On
No one thrives alone. A ride or die community that rallies together in tough times is invaluable. Seek out a place where people know their neighbors, share similar values, and are quick to lend a hand. Lead by example and become a good neighbor, people will naturally respond in kind. Small towns are ideal, if possible, but living outside of a major city can be a solid balance in terms of work opportunities and family security.
Let me know if you found this helpful. My plan is to break down how I think about these five key subjects in future posts.
-
 @ 3a7c74bb:bbdd5960
2025-06-02 11:48:00
@ 3a7c74bb:bbdd5960
2025-06-02 11:48:00- The Foundation (12th Century)
The territory that would become Portugal was originally part of the Kingdom of León and Castile. But in 1128, the young nobleman Afonso Henriques confronted his own mother at the Battle of São Mamede, taking control of the County of Portugal (Condado Portucalense).
In 1139, after winning the Battle of Ourique, he declared himself King of Portugal. Independence was recognized in 1143 by the King of León and confirmed by the Pope in 1179.
- Expansion and the discoveries (14th–16th Centuries)
In the following centuries, Portugal consolidated its territory and set out to sea. The 15th century marked the beginning of the Portuguese Discoveries:
🚢 1419–1420 – Discovery of Madeira and the Azores 🚢 1488 – Bartolomeu Dias rounds the Cape of Good Hope 🚢 1498 – Vasco da Gama reaches India 🚢 1500 – Pedro Álvares Cabral discovers Brazil
During this period, Portugal created a vast maritime empire with colonies in Africa, the Americas, Asia, and Oceania.
- Iberian Union and the restoration (1580–1640)
In 1580, after a dynastic crisis caused by the death of King Sebastian, Portugal came under Spanish rule in what is known as the Iberian Union. For 60 years, the Spanish kings ruled Portugal until, in 1640, a revolt led by John IV restored Portuguese independence.
- The decline of the Empire and the 1755 earthquake
The 18th century was marked by the Lisbon earthquake of 1755, one of the greatest disasters of its time, which destroyed much of the capital. The Marquis of Pombal led the country’s reconstruction and modernization.
The empire began to weaken, culminating in the independence of Brazil in 1822.
- Wars, republic, and dictatorship (19th–20th Centuries)
Portugal faced internal crises and took part in World War I. In 1910, the monarchy fell and the Portuguese Republic was proclaimed.
In the 20th century, the country lived under the Estado Novo dictatorship (1933–1974), led by António de Oliveira Salazar. In 1974, the Carnation Revolution brought democracy, and the following year, the last African colonies gained independence.
- Modern Portugal (21st Century)
In 1986, Portugal joined the European Union, marking a period of growth and modernization. Today, it is a democratic country with a rich culture and a history that continues to inspire the world.
- And what about the islands?
The Autonomous Regions of Madeira and the Azores play a fundamental role in Portuguese identity. Discovered in the 15th century, they have been part of Portugal ever since and have their own regional governments.
Madeira is known for its wine and stunning landscapes, while the Azores are famous for their volcanic nature and unique culture.
Thank you very much for reading this far. I hope everything is well with you, and sending a big hug from your favorite writer from Madeira. Long live freedom!
-
 @ 1c5ff3ca:efe9c0f6
2025-06-05 06:29:45
@ 1c5ff3ca:efe9c0f6
2025-06-05 06:29:45Just calling it Open is not enough - Herausforderungen öffentlicher Bildungsinfrastrukturen und wie Nostr helfen könnte
Ich möchte gerne mit euch teilen, an welchen Konzepten ich arbeite, um die öffentliche Bildungsinfrastruktur mit Hilfe von Nostr zugänglicher und offener zu gestalten. Ich arbeite im Bereich öffentlicher Bildungsinfrastrukturen, besonders im Feld von Open Educational Resources (#OER). OER sind offen lizenzierte Bildungsmaterialien, die mit einer offenen Lizenz, meist einer Creative Commons Lizenz, versehen sind (CC-0, CC-BY, CC-BY-SA). Durch die klare und offene Lizenzierung ist es leicht möglich, die Lernmaterialien auf die individuellen Bedarfe anzupassen, sie zu verbessern und sie erneut zu veröffentlichen.
Seit vielen Jahren wird einerseits die Entwicklung freier Bildungsmaterialien gefördert, andererseits werden Plattformen, insbesondere Repositorien gefördert, die diese Materialien verfügbar machen sollen. Denn irgendwo müssen diese Materialien zur Verfügung gestellt werden, damit sie auch gefunden werden können.
Das klappt allerdings nur so mittelgut.
Herausforderungen
Nach vielen Jahren Förderung kann die einfache Frage: "Wo kann ich denn mein OER-Material bereitstellen" nicht einfach beantwortet werden. Es gibt Services, bei denen ich mein OER hochladen kann, jedoch bleibt es dann eingeschlossen in dieser Plattform und wird nicht auf anderen Plattformen auffindbar. Außerdem sind diese Services häufig an bestimmte Bildungskontexte gebunden oder geben Content erst nach einer Qualitätsprüfung frei. Dies führt dazu, dass ein einfaches und gleichzeitig öffentliches Teilen nicht möglich ist.
Diese und weitere Herausforderungen haben ihren Ursprung darin, dass Service und Infrastruktur in der Architektur öffentlichen Bildungsarchitektur ungünstig vermischt werden. Als Infrastruktur verstehe ich hier die Bereitstellung einer öffentlichen und offen zugänglichen Bildungsinfrastruktur, auf der Daten ausgetauscht, also bereitgestellt und konsumiert werden können. Jedoch existiert eine solche Infrstruktur momentan nicht unabhängig von den Services, die auf ihr betrieben werden. Infrastrukturbetreiber sind momentan gleichzeitig immer Servicebetreiber. Da sie aber die Hand darüber haben wollen, was genau in ihrem Service passiert (verständlich), schränken sie den Zugang zu ihrer Infrastruktur mit ein, was dazu führt, dass sie Lock-In Mechanismen großer Medienplattformen in der kleinen öffentlichen Bildungsinfrastruktur replizieren.
Es ist in etwas so, als würde jeder Autobauer auch gleichzeitig die Straßen für seine Fahrzeuge bauen. Aber halt nur für seine Autos.
Anhand einiger beispielhafter Services, die bestehende Plattformen auf ihren Infrastrukturen anbieten, möchte ich die Herausforderungen aufzeigen, die ich im aktuellen Architekturkonzept sehe:
- Upload von Bildungsmaterial
- Kuration: Zusammenstellung von Listen, Annotation mit Metadaten
- Crawling, Indexierung und Suche
- Plattfformübergreifende Kollaboration in Communities -> Beispiel: Qualitätssicherung (was auch immer das genau bedeutet)
- KI- Services -> Beispiel: KI generierte Metadaten für BiIdungsmaterial
Material Upload
Der Service "Material-Upload" oder das Mitteilen eines Links zu einem Bildungsmaterial wird von verschiedenen OER-Pattformen bereitgestellt (wirlernenonline.de, oersi.org, mundo.schule).
Dies bedeutet konkret: Wenn ich bei einer der Plattformen Content hochlade, verbleibt der Content in der Regel auch dort und wird nicht mit den anderen Plattformen geteilt. Das Resultat für die User: Entweder muss ich mich überall anmelden und dort mein Material hochladen (führt zu Duplikaten) oder damit leben, dass eben nur die Nutzer:innen der jeweiligen Plattform meinen Content finden können.
Der "Open Educational Resource Search Index" (OERSI) geht diese Herausforderung an, indem die Metadaten zu den Bildungsmaterialien verschiedener Plattformen in einem Index bereitgestellt werden. Dieser Index ist wiederum öffentlich zugänglich, sodass Plattformen darüber auch Metadaten anderer Plattformen konsumieren können. Das ist schon sehr gut. Jedoch funktioniert das nur für Plattformen, die der OERSI indexiert und für alle anderen nicht. Der OERSI ist auf den Hochschulbereich fokussiert, d.h. andere Bildungskontexte werden hier ausgeschlossen. Der Ansatz für jeden Bildungsbereich einen passenden "OERSI" daneben zustellen skaliert und schlecht und es bleibt die Herausforderung bestehen, dass für jede Quelle, die indexiert werden soll, ein entsprechender Importer/Crawler geschrieben werden muss.
Dieser Ansatz (Pull-Ansatz) rennt den Materialien hinterher.
Es gibt jedoch noch mehr Einschränkungen: Die Plattformen haben sich jeweils auf spezifische Bildungskontexte spezialisiert. D.h. auf die Fragen: Wo kann ich denn mein OER bereitstellen, muss immer erst die Gegenfrage: "Für welchen Bildungsbereich denn?" beantwortet werden. Wenn dieser außerhalb des allgemeinbildendenden Bereichs oder außerhalb der Hochschule liegt, geschweige denn außerhalb des institutionellen Bildungsrahmens, wird es schon sehr, sehr dünn. Kurzum:
- Es ist nicht einfach möglich OER bereitzustellen, sodass es auch auf verschiedenen Plattformen gefunden werden kann.
Kuration
Unter Kuration verstehe ich hier die Zusammenstellung von Content in Listen oder Sammlungs ähnlicher Form sowie die Annotation dieser Sammlungen oder des Contents mit Metadaten.
Einige Plattformen bieten die Möglichkeit an, Content in Listen einzuordnen. Diese Listen sind jedoch nicht portabel. Die Liste, die ich auf Plattform A erstelle, lässt sich nicht auf Plattform B importieren. Das wäre aber schön, denn so könnten die Listen leichter auf anderen Plattformen erweitert oder sogar kollaborativ gestaltet werden, andererseits werden Lock-In-Effekte zu vermieden.
Bei der Annotation mit Metadaten treten verschiedene zentralisierende Faktoren auf. In der momentanen Praxis werden die Metadaten meist zum Zeitpunkt der Contentbereitstellung festgelegt. Meist durch eine Person oder Redaktion, bisweilen mit Unterstützung von KI-Services, die bei der Metadateneingabe unterstützen. Wie aber zusätzliche eigene Metadaten ergänzen? Wie mitteilen, dass dieses Material nicht nur für Biologie, sondern auch für Sport in Thema XY super einsetzbar wäre? Die momentanen Ansätze können diese Anforderung nicht erfüllen. Sie nutzen die Kompetenz und das Potential ihrer User nicht.
- Es gibt keine interoperablen Sammlungen
- Metadaten-Annotation ist zentralisiert
- User können keine eigenen Metadaten hinzufügen
Crawling, Indexierung und Suche

Da die Nutzer:innen nicht viele verschiedene Plattformen und Webseiten besuchen wollen, um dort nach passendem Content zu suchen, crawlen die "großen" OER-Aggregatoren diese, um die Metadaten des Contents zu indexieren. Über verschiedene Schnittstellen oder gerne auch mal über das rohe HTML. Letztere Crawler sind sehr aufwändig zu schreiben, fehleranfällig und gehen bei Design-Anpassungen der Webseite schnell kaputt, erstere sind etwas stabiler, solange sich die Schnittstelle nicht ändert. Durch den Einsatz des Allgemeinen Metadatenprofils für Bildungsressourcen (AMB) hat sich die Situation etwas verbessert. Einige Plattformen bieten jetzt eine Sitemap an, die Links zu Bildungsmaterial enthalten, die wiederum eingebettet
script-tags vom Typapplication/ld+jsonenthalten, sodass die Metadaten von dort importiert werden können.Beispiel: e-teaching.org bietet hier eine Sitemap für ihre OER an: https://e-teaching.org/oer-sitemap.xml und auf den jeweiligen Seiten findet sich ein entsprechendes script-Tag.
Das ist schon viel besser, aber da geht noch mehr:
Zunächst ist dieser Ansatz nur für Plattformen und Akteure praktikabel, die über IT-Ressourcen verfügen, um entsprechende Funktionalitäten bei sich einbauen zu können. Lehrende können dies nicht einfach auf ihrem privaten Blog oder ähnliches umsetzen. Zum anderen besteht immer noch ein Discovery Problem. Ich muss nach wie vor wissen, wo ich suchen muss. Ich muss die Sitemaps kennen, sonst finde ich nichts. Statt eines Ansatzes, bei dem Akteure eigenständig mitteilen können, dass sie neuen Content haben (Push-Ansatz), verfolgen wir derzeit einen Ansatz, bei dem jede Plattform für sich Content im Pull-Verfahren akquiriert. Dies führt an vielen Stellen zu Doppelarbeiten, ist ineffizient (mehrere Personen bauen genau die gleichen Crawler, aber halt immer für ihre Plattform) und schliesst vor allem kleine Akteure aus (lohnt es sich einen Crawler zu programmieren, wenn die Webseite "nur" 50 Materialien bereitstellt?).
Anstatt erschlossene Daten zu teilen, arbeiten die Plattformen für sich oder stellen es höchstens wieder hinter eigenen (offenen oder geschlossenen) Schnittstellen bereit. Das ist wohl nicht das, was wir uns unter einer offenen und kollaborativen Gemeinschaft vorstellen, oder?
Bei der Suche stehen wir vor ähnlichen Herausforderungen, wie bereits oben geschildert. Obwohl verschiedene OER-Aggregatoren in Form von Repositorien oder Referatorien bereits viele der "kleineren" Plattformen indexieren und somit eine übergreifende Suche anbieten, ist es nicht möglich, diese Aggregatoren gemeinsam zu durchsuchen. Dies führt im Endeffekt dazu, dass die User wieder verschiedene Plattformen ansteuern müssen, wenn sie den gesamten OER-Fundus durchsuchen wollen.
- An vielen Stellen wird Content doppelt erschlossen, aber immer für die eigene Plattform
- Es gibt keinen geteilten Datenraum, in den Akteure Content "pushen" können
- Es gibt keine plattformübergreifenden Suchmöglichkeiten
Plattformübergreifende Kollaboration
Das wäre schön, oder? Mir ist schleierhaft, wie #OEP (Open Educational Practices, genaue Definition durch die Community steht noch aus) ohne funktionieren soll. Aber es gibt meines Wissens nach nicht mal Ansätze, wie das technisch umgesetzt werden soll (oder doch? let me hear).
Ein Szenario für solche plattformübergreifende Kollaboration könnte Qualitätssicherung sein. Gesetzt, dass sich zwei Plattformen / Communities auf etwas verständigt haben, dass sie als "Qualität" bezeichnen, wie aber dieses Gütesiegel nun an den Content bringen?
Plattform A: Na, dann kommt doch alle zu uns. Hier können wir das machen und dann hängt auch ein schönes Badge an den Materialien.
Plattform B: Ja, aber dann hängt es ja nicht an unseren Materialien. Außerdem wollen/müssen wir bei uns arbeiten, weil welche Existenzberechtigung hat denn meine Plattform noch, wenn wir alles bei dir machen?
- Obwohl nun #OEP in aller Munde sind, gibt es keine technischen Ansätze, wie (plattformübergreifende) Kollaboration technisch abgebildet werden kann
KI-Services
Was ist heute schon komplett ohne das Thema KI zu erwähnen? Mindestens für den nächsten Förderantrag muss auch irgendetwas mit KI gemacht werden...
Verschiedene Projekte erarbeiten hilfreiche und beeindruckende KI-Services. Beispielsweise, um die Annotation von Content mit Metadaten zu erleichtern, Metadaten automatisch hinzuzufügen, Content zu bestimmten Themen zu finden oder (halb-)automatisch zu Sammlungen hinzuzufügen. Aber (vielleicht habt ihr es schon erraten): Funktioniert halt nur auf der eigenen Plattform. Vermutlich, weil die Services nah am plattformeigenen Datenmodell entwickelt werden. Und da die Daten dieses Silo nicht verlassen, passt das schon. Das führt dazu, dass an mehreren Stellen die gleichen Services doppelt entwickelt werden.
- KI-Services funktionieren oft nur auf der Plattform für die sie entwickelt werden
Zusammenfassung der Probleme
Wir machen übrigens vieles schon sehr gut (Einsatz des AMB, Offene Bidungsmaterialien, wir haben eine großartige Community) und jetzt müssen wir halt weiter gehen.
(Die OER-Metadatengruppe, die das Allgemeine Metadatenprofil für Bildungsressourcen (AMB) entwickelt hat, bekommt für ihre Arbeit keine direkte Förderung. Gleichzeitig ist sie eine zentrale Anlaufstelle für alle, die mit Metadaten in offenen Bildungsinfrastukturen hantieren und das Metadatenprofil ist eines der wenigen Applikationsprofile, das öffentlich einsehbar, gut dokumentiert ist und Validierungsmöglichkeiten bietet.)
Betrachten wir die gesamten Plattformen und die beschriebenen Herausforderungen aus der Vogelperspektive, so lassen sich drei ineinander verschränkte Kernbestandteile unterscheiden, die helfen, die beschriebenen Probleme besser zu verstehen:
- User
- Service
- Daten
User: Auf (fast) allen Plattformen agieren User. Sie laden Material hoch, annotieren mit Metadaten, sind in einer Community, suchen Content usw. Egal, ob sie sich einloggen können/müssen, irgendetwas bieten wir unseren Usern an, damit sie daraus hoffentlich Mehrwerte ziehen
Service: Das ist dieses irgendetwas. Die "Webseite", die Oberfläche, das, wo der User klicken und etwas tun kann. Es ist das, was den Daten oft eine "visuelle" Form gibt. Der Service ist der Mittler, das Interface zwischen User und Daten. Mithilfe des Services lassen sich Daten erzeugen, verändern oder entfernen (Es gibt natürlich auch viele nicht-visuelle Services, die Interaktion mit Daten ermöglichen, aber für die meisten normalen Menschen, gibt es irgendwo was zu klicken).
Daten: Die Informationen in strukturierter maschinenlesbarer Form, die dem User in gerenderter Form durch einen Service Mehrwerte bieten können. Ungerenderte Daten können wir schwieirg erfassen (wir sind ja nicht Neo). Das können entweder die Metadaten zu Bildungmaterialien sein, die Materialien selbst, Profilinformationen, Materialsammlungen o.ä.

Meines Erachtens nach haben viele der oben beschriebenen Herausforderungen ihren Ursprung darin, dass die drei Kernbestandteile User, Service, Daten ungünstig miteinander verbunden wurden. Was kein Vorwurf sein soll, denn das ist genau die Art und Weise, wie die letzten Jahre (Jahrzehnte?) Plattformen immer gebaut wurden:
- User, Service und Daten werden in einer Plattform gebündelt
Das heisst durch meinen Service agieren die User mit den Daten und ich kann sicherstellen, dass in meiner kleinen Welt alles gut miteinander funktioniert. Sinnvoll, wenn ich Microsoft, Facebook, X oder ähnliches bin, weil mein Geschäftsmodell genau darin liegt: User einschließen (lock-in), ihnen die Hohheit über ihren Content nehmen (oder kannst du deine Facebook Posts zu X migrieren?) und nach Möglichkeit nicht wieder rauslassen.
Aber unsere Projekte sind öffentlich. Das sind nicht die Mechanismen, die wir replizieren sollten. Also was nun?
Bildungsinfrasstrukturen auf Basis des Nostr-Protokolls
Nostr
Eine pseudonyme Person mit dem Namen "fiatjaf" hat 2019 ein Konzept für ein Social Media Protokoll "Nostr - Notes and Other Stuff Transmitted By Relays" wie folgt beschrieben:
It does not rely on any trusted central server, hence it is resilient, it is based on cryptographic keys and signatures, so it is tamperproof, it does not rely on P2P techniques, therefore it works.
Fiatjaf, 2019
Die Kernbestandsteile des Protokolls bestehen aus:
- JSON -> Datenformat
- SHA256 & Schnorr -> Kryptographie
- Websocket -> Datenaustausch
Und funktionieren tut es so:
User besitzen ein "Schlüsselpaar": einen privaten Schlüssel (den behälst du für dich, nur für dich) und einen öffentlichen Schlüssel, den kannst du herumzeigen, das ist deine öffentliche Identität. Damit sagst du anderen Usern: Hier schau mal, das bin ich. Die beiden Schlüssel hängen dabei auf eine "magische" (kryptografische) Weise zusammen: Der öffentliche Schlüssel lässt sich aus dem privaten Schlüssel generieren, jedoch nicht andersherum. D.h. falls du deinen öffentlichen Schlüssel verlierst: Kein Problem, der lässt sich immer wieder herstellen. Wenn du deinen privaten Schlüssel verlierst: Pech gehabt, es ist faktisch unmöglich, diesen wieder herzustellen.
Die Schlüsselmagie geht jedoch noch weiter: Du kannst mit deinem privaten Schlüssel "Nachrichten" signieren, also wie unterschreiben. Diese Unterschrift, die du mit Hilfe des privaten Schlüssels erstellst, hat eine magische Eigenschaft: Jeder kann mithilfe der Signatur und deinem öffentlichen* Schlüssel nachprüfen, dass nur die Person, die auch den privaten Schlüssel zu diesem öffentlichen Schlüssel besitzt, diese Nachricht unterschrieben haben kann. Magisch, richtig? Verstehst du nicht komplett? Nicht schlimm, du benutzt es bereits vermutlich, ohne dass du es merkst. Das ist keine fancy neue Technologie, sondern gut abgehangen und breit im Einsatz.
Merke: User besitzen ein Schlüsselpaar und können damit Nachrichten signieren.
Dann gibt es noch die Services. Services funktionieren im Grunde wie bereits oben beschrieben. Durch sie interagieren die User mit Daten. Aber bei Nostr ist es ein kleines bisschen anders als sonst, denn: Die Daten "leben" nicht in den Services. Aber wo dann?
Wenn ein User einen Datensatz erstellt, verändert oder entfernen möchte, wird dieses "Event" (so nennen wir das bei Nostr) mit deinem privaten Schlüssel signiert (damit ist für alle klar, nur du kannst das gemacht haben) und dann mehrere "Relays" gesendet. Das sind die Orte, wo die Daten gehalten werden. Wenn ein User sich in einen Service einloggt, dann holt sich der Service die Daten, die er braucht von diesen Relays. User, Service und Daten sind also entkoppelt. Der User könnte zu einem anderen Service wechseln und sich dieseleben Daten von den Relays holen. Keine Lock-In Möglichkeiten.
Merke: User, Service und Daten sind entkoppelt.
Zuletzt gibt es noch die Relays. Relays sind Orte. Es sind die Orte, zu denen die Events, also die Daten der User, ihre Interaktionen, gesendet und von denen sie angefragt werden. Sie sind sowas wie das Backend von Nostr, allerdings tun sie nicht viel mehr als das: Events annehmen, Events verteilen. Je nach Konfiguration dürfen nur bestimmte User auf ein Relay schreiben oder davon lesen.
Das Protokoll ist von seinem Grunddesign auf Offenheit und Interoperabilität ausgelegt. Keine Registrierung ist nötig, sondern nur Schlüsselpaare. Durch kryptografische Verfahren kann dennoch die Authentizitität eines Events sichergestellt werden, da nur die Inhaberin des jeweiligen Schlüsselpaares dieses Event so erstellen konnte. Die Relays sorgen dafür die Daten an die gewünschten Stellen zu bringen und da wir mehr als nur eines benutzen, haben wir eine gewisse Ausfallsicherheit. Da die Daten nur aus signierten JSON-Schnipseln bestehen, können wir sie leicht an einen anderen Ort kopieren, im Falle eines Ausfalls. Durch die Signaturen ist wiederum sichergestellt, dass zwischendurch keine Veränderungen an den Daten vorgenommen wurden.
Beispiel: Ein Nostr Event
Hier ein kleiner technischer Exkurs, der beschreibt, wie Nostr Events strukturiert sind. Falls dich die technischen Details nicht so interessieren, überspringe diesen Abschnitt ruhig.
Jedes Nostr Event besitzt die gleiche Grundstruktur mit den Attributen:
id: Der Hash des Eventspubkey: Der Pubkey des Urhebers des Eventscreated_at: Der Zeitstempel des Eventskind: Der Typ des Eventstags: Zusätzliche Metadaten für das Event können in diesem Array hinterlegt werdencontent: Der textuelle Inhalt eines Eventssig: Die Signatur des Events, um die Integrität der Daten zu überprüfen
json { "id": <32-bytes lowercase hex-encoded sha256 of the serialized event data>, "pubkey": <32-bytes lowercase hex-encoded public key of the event creator>, "created_at": <unix timestamp in seconds>, "kind": <integer between 0 and 65535>, "tags": [ [<arbitrary string>...], // ... ], "content": <arbitrary string>, "sig": <64-bytes lowercase hex of the signature of the sha256 hash of the serialized event data, which is the same as the "id" field> }Die verwendeten Eventtypen sowie die existierenden Spezifikationen lassen sich unter https://github.com/nostr-protocol/nips/ einsehen.
Wichtig ist auch: Du kannst einfach anfangen, Anwendungen zu entwickeln. Die Relays werden alle Events akzeptieren, die dem o.g. Schema folgen. Du musst also niemanden um Erlaubnis fragen oder warten, bis deine Spezifikation akzeptiert und hinzugefügt wurde.
You can just build things.
Exkurs: Nostr für Binärdaten - Blossom
Ja, aber... das ist doch nur für textbasierte Daten geeignet? Was ist denn mit den Binärdaten (Bilder, Videos, PDFs, etc)
Diese Daten sind oft recht groß und es wurde sich auf das Best-Practice geeignet, diese Daten nicht auf Relays abzulegen, sondern einen besser geeigneten Publikationsmechanismus für diese Datentypen zu finden. Der Ansatz wird als "Blossom - Blobs stored simply on mediaservers" bezeichnet und ist recht unkompliziert.
Blossom Server (nichts anderes als simple Medienserver) nutzen Nostr Schlüsselpaare zur Verwaltung Identitäten und zum Signieren von Events. Die Blobs werden über ihren sha256 Hash identifiziert. Blossom definiert einige standardisierte Endpunkte, die beschreiben wie Medien hochgeladen werden können, wie sie konsumiert werden können usw.
Die Details, wie Authorisierung und die jeweiligen Endpunkte funktionieren, werden in der genannten Spezifikation beschrieben.
Nostr 🤝 Öffentliche Bildungsinfrastrukturen
Wie könnten Herausforderungen gelöst werden, wenn wir Nostr als Basis für die öffentliche Bildungsinfrastruktur einsetzen?
Material-Upload
- Es ist nicht einfach möglich OER bereitzustellen, sodass es auch auf verschiedenen Plattformen gefunden werden kann.
Mit Nostr als Basis-Infrastruktur würden die Metadaten und die Binärdaten nicht an den Service gekoppelt sein, von dem aus sie bereitgestellt wurden. Binärdaten können auf sogenannten Blossom-Servern gehostet werden. Metadaten, Kommentare und weitere textbasierte Daten werden über die Relay-Infrastruktur verteilt. Da Daten und Service entkoppelt sind, können die OER Materialien von verschiedenen Anwendungen aus konsumiert werden.
Kuration
- Es gibt keine interoperablen Sammlungen
- Metadaten-Annotation ist zentralisiert
- User können keine eigenen Metadaten hinzufügen
Sammlungen sind per se interoperabel. Auf Protokollebene ist definiert, wie Listen funktionieren. Die Annotation mit Metadaten ist an keiner Stelle zentralisiert. Das Versprechen der RDF-Community "Anyone can say anything about any topic" wird hier verwirklicht. Ich muss mir ja nicht alles anhören. Vielleicht konsumiere ich nur Metadaten-Events bestimmter Redaktionen oder User. Vielleicht nur diejenigen mit einer Nähe zu meinem sozialen Graphen. Jedenfalls gibt es die Möglichkeit für alle User entsprechende Metadaten bereit zu stellen.
Crawling, Indexierung und Suche * An vielen Stellen wird Content doppelt erschlossen, aber immer für die eigene Plattform * Es gibt keinen geteilten Datenraum, in den Akteure Content "pushen" können * Es gibt keine plattformübergreifenden Suchmöglichkeiten
Keine Doppelerschließungen mehr. Wenn ein User im Netzwerk ein Metadatenevent veröffentlicht hat, ist es für alle konsumierbar. Der Datenraum ist per se geteilt. Plattformübergreifende Suche wird durch die Kombination aus Relays und NIPs ermöglicht. In den NIPs können spezielle Query-Formate für die jeweiligen NIPs definiert werden. Relays können anzeigen, welche NIPs sie untersützten. Eine plattformübergreifende Suche ist im Nostr eine relay-übergreifende Suche.
Plattformübergreifende Kollaboration
- Obwohl nun #OEP in aller Munde sind, gibt es keine technischen Ansätze, wie (plattformübergreifende) Kollaboration technisch abgebildet werden kann
Nostr ist der technische Ansatz.
KI-Services
- KI-Services funktionieren oft nur auf der Plattform für die sie entwickelt werden
Es gibt im Nostr das Konzept der Data Vending Machines (s. auch data-vending-machines.org). Statt also einfach nur eine API zu bauen (was auch schon sehr schön ist, wenn sie offen zugänglich ist), könnten diese Services auch als Akteure im Nostr Netzwerk fungieren und Jobs annehmen und ausführen. Die Art der Jobs kann in einer Spezifikation beschrieben werden, sodass die Funktionsweise für alle interessierten Teilnehmer im Netzwerk einfach nachzuvollziehen ist.
Die Services könnten sogar monetarisiert werden, sodass sich hier auch Möglichkeiten böten, Geschäftsmodelle zu entwickeln.
Fazit
Die Open Education Community ist großartig. Es sind einzigartige und unglaublich engagierte Menschen, die sich dem hehren Ziel "Zugängliche Bildung für Alle" -> "Offene Bildung" verschrieben haben. Wir verwenden Creative Commons Lizenzen -> Commons -> Gemeingüter. Es ist okay, dass viele Projekte von Sponsoren und Förderungen abhängig sind. Was wir machen, ist im Sinne eines Gemeingutes: Öffentliche Bildung für alle. Also zahlen wir als Gemeinschaft alle dafür.
Was nicht okay ist: Dass das, wofür wir alle gezahlt haben, nach kurzer Zeit nicht mehr auffindbar ist. Dass es eingeschlossen wird. In öffentlich finanzierten Datensilos. Es muss für alle auch langfristig verfügbar sein. Sonst ist es nicht zugänglich, nicht offen. Dann ist das O in OER nur ein Label und Marketing, um für eine ABM-Maßnahme 3 Jahre Geld zu bekommen. Denn nichts anderes ist Content-Entwicklung, wenn der Content nach drei Jahren weggeschmissen wird.
Und dasselbe gilt für OEP. Offene Lernpraktiken, sind auch nur eine Phrase, wenn wir die passende technische Infrastruktur nicht mitdenken, die wirkliche Offenheit und Kollaboration und damit die Umsetzung offener Lernpraktiken ermöglicht.
Und wenn wir uns jetzt nicht Gedanken darüber machen, die Infrastruktur für offenes Lernen anzupassen, dann werden wir vermutlich in einigen Jahren sehen können, was bei politischen Umorientierungen noch davon übrig bleiben wird. Wenn die Fördertöpfe komplett gestrichen werden, was bleibt dann übrig von dem investierten Geld?
Wir brauchen Lösungen, die engagierte Communities weiter betreiben können und denen kein Kopf abgeschlagen werden kann, ohne dass wir zwei neue daneben setzen könnten.
Wir müssen uns jetzt Gedanken darüber machen.
Wie offen will öffentliche Bildungsinfrastruktur sein?
-
 @ 8dc86882:9dc4ba5e
2024-09-02 15:50:01
@ 8dc86882:9dc4ba5e
2024-09-02 15:50:01Today I saw a YouTube video from one of the privacy related channels, Techlore maybe? I don't exactly remember. Either way this particular video was going over the pluses and minuses of Android and iOS; and it has made me reconsider some things. I have one of each type of phone and jump back and forth a bit, but always thought I would end on Android. I'm not feeling that way anymore.
After really getting to understand Apple's Advanced Data Protection I think I came to the conclusion that my iPhone more than meets my needs and does everything I like. Yeah, Android sounds like it has most of the privacy coolness as far as mods, roms, and apps, but my iPhone is easily fully encrypted along with iCloud. The few services that aren't are covered by my Proton plan. It also allows me to stop paying for services I may not really need.
- I use and pay for Ente photos, which is great, but my Apple photos are already encrypted and backed up. I don't think I need to be paying for the extra service.
- The Apple Notes app falls under the fully encrypted side, and I can use the free version of Standard Notes for other things.
- I still use Signal Messenger where the OS doesn't matter as much.
- MySudo which I use for numbers is transferable between OSs also.
That's really about it, I mainly use my phone for Email, Calendar, Messaging, Notes, some social, and photos. I don't think I need anything special beyond that. The insecure apps I use on either platform keep their risks though Apple isn't an advertising company, so I feel they are less likely to abuse anything, at least for now. I wonder what other folks thoughts are. Feel free to share.
Cheers!
plebone
-
 @ 4fe4a528:3ff6bf06
2024-09-01 12:45:44
@ 4fe4a528:3ff6bf06
2024-09-01 12:45:44One of the main motivational factors for people to buy bitcoin is it’s ability to store value over time. During harvest we are doing the same thing. We have now harvested our garlic and 1/2 of our onions because if we don’t use the sun’s energy to cure the plants before winter they will start to rot. Let me explain why God has made the world this way; but, first let me explain why storing things isn’t evil.
“Do not store up for yourselves treasures on earth, where moth and rust consume and where thieves break in and steal; but store up for yourselves treasures in heaven, where neither moth nor rust consumes and where thieves do not break in and steal. For where your treasure is, there your heart will be also”. Matt. 6:19-21
Is it wrong, then to have a retirement portfolio or even to care about the material things of this world for ourselves or for others? The answer is again both no and yes. The no comes from the fact that this passage is not the only one in the Bible speaking to questions of wealth and provision for those who are dependent on us. Other passages counsel prudence and forethought, such as, “Those who gather little by little will increase [wealth]” (Proverbs 13:11b), and, “The good leave an inheritance to their children’s children” (Proverbs 13:22).
God guides Joseph to store up food for seven years in advance of a famine (Genesis 41:25-36), and Jesus speaks favorably in the Parable of the Talents (Matt. 25:14-30). In light of the rest of Scripture, Matthew 6:19-21 cannot be a blanket prohibition. But the yes part of the answer is a warning, summed up beautifully in verse 21, “Where your treasure is, there will your heart be also.” In other words, the possessions you own will change you so that you care more about the possessions than about other things.” So choose carefully what you own, for you will inevitably begin to value and protect it to the potential detriment of everything else.
How are we to discern the line between appropriate and inappropriate attention to wealth? Jesus answers, “Strive first for the kingdom of God and his righteousness, and all these things will be given to you” So if you believe your heart is following God’s direction go ahead and harvest your crops and / or buy some bitcoin. If you would have bought bitcoin one year ago, you would have 127% more purchasing power now. Let’s keep on fearing God and keeping his commandments.
-
 @ d5c440ce:04726d89
2025-06-05 06:19:49
@ d5c440ce:04726d89
2025-06-05 06:19:49Effektiv behandling af blodsprængninger kræver en professionel tilgang og de rette metoder. Hos Klinik Zenit tilbyder vi skånsomme og dokumenterede teknikker til at reducere synligheden af blodsprængninger i ansigt og på krop. Vores behandlinger tilpasses individuelt og udføres af erfarne specialister med fokus på sikkerhed og langvarige resultater. Få vejledning om hudpleje før og efter behandlingen for at opnå det bedste resultat. Kontakt Klinik Zenit for en professionel vurdering og behandlingsplan.
-
 @ 0176967e:1e6f471e
2024-07-27 11:10:06
@ 0176967e:1e6f471e
2024-07-27 11:10:06Workshop je zameraný pre všetkých, ktorí sa potýkajú s vysvetľovaním Bitcoinu svojej rodine, kamarátom, partnerom alebo kolegom. Pri námietkach z druhej strany väčšinou ideme do protiútoku a snažíme sa vytiahnuť tie najlepšie argumenty. Na tomto workshope vás naučím nový prístup k zvládaniu námietok a vyskúšate si ho aj v praxi. Know-how je aplikovateľné nie len na komunikáciu Bitcoinu ale aj pre zlepšenie vzťahov, pri výchove detí a celkovo pre lepší osobný život.
-
 @ af9c48b7:a3f7aaf4
2024-08-27 16:51:52
@ af9c48b7:a3f7aaf4
2024-08-27 16:51:52Chef's notes
Easy recipe with simple ingredients. This recipe uses some store bought, precooked items as way to cut down on cook time. I recommend letting the vegetables thaw if you don't like them on the firm/crunchy side.Feel free to substitute fresh ingredients if you have the time and want to make the extra effort.
Details
- ⏲️ Prep time: 20 min
- 🍳 Cook time: 50 min
- 🍽️ Servings: 8-10
Ingredients
- 2 (8 oz) packages refrigerated crescent rolls (dough sheets preferred)
- 1 pound cooked rotisserie chicken (deboned and chopped)
- 2 table spoons of butter
- 2 (10 once) packages of frozen mixed vegetables
- 1 (15 once can sliced potatoes (drained)
- 1 (10.5 once) can condensed cream of chicken soup
- 1 (10.5 once) can condensed cream of mushroom soup
- 1/2 cup milk
- salt and ground pepper to taste
Directions
- Preheat oven to 350 degrees F (175 degrees C). Line the botton of 9x13-inch baking dish with one can of crescent roll dough. If you don't get the sheet dough, be sure to pinch the seams together.
- Melt the butter in a sauce pan over medium heat. Then add the chicken, mixed vegetables, and sliced potatoes (recommend cutting into smaller pieces). Cook, stirring frequently, until vegetables are thawed and mixture is heated through, 5 to 7 minutes.
- While the mixed vegetables are heating, warm both cans of condensed soup in a seperate pan over medium-low heat. Slowly add milk and cook, stirring frequently, until combined and heated through, about 3 minutes.
- Add the soup mixture to the chicken mixture, then pour into the baking dish. Top with the second can of crescent roll dough. Feel free to cut some slits in dough if you are using the dough sheets. Cover lightly with foil to prevent the crescent roll dough from browning too quickly.
- Bake in oven until heated through and dough is a golden brown. Cook time should be around 45-50 minutes I reommend removing the foil for the last 10 minutes to get a golden crust. Be sure to keep a close watch on the crust after removing the foil because it will brown quickly.
-
 @ 91bea5cd:1df4451c
2025-04-15 06:27:28
@ 91bea5cd:1df4451c
2025-04-15 06:27:28Básico
bash lsblk # Lista todos os diretorios montados.Para criar o sistema de arquivos:
bash mkfs.btrfs -L "ThePool" -f /dev/sdxCriando um subvolume:
bash btrfs subvolume create SubVolMontando Sistema de Arquivos:
bash mount -o compress=zlib,subvol=SubVol,autodefrag /dev/sdx /mntLista os discos formatados no diretório:
bash btrfs filesystem show /mntAdiciona novo disco ao subvolume:
bash btrfs device add -f /dev/sdy /mntLista novamente os discos do subvolume:
bash btrfs filesystem show /mntExibe uso dos discos do subvolume:
bash btrfs filesystem df /mntBalancea os dados entre os discos sobre raid1:
bash btrfs filesystem balance start -dconvert=raid1 -mconvert=raid1 /mntScrub é uma passagem por todos os dados e metadados do sistema de arquivos e verifica as somas de verificação. Se uma cópia válida estiver disponível (perfis de grupo de blocos replicados), a danificada será reparada. Todas as cópias dos perfis replicados são validadas.
iniciar o processo de depuração :
bash btrfs scrub start /mntver o status do processo de depuração Btrfs em execução:
bash btrfs scrub status /mntver o status do scrub Btrfs para cada um dos dispositivos
bash btrfs scrub status -d / data btrfs scrub cancel / dataPara retomar o processo de depuração do Btrfs que você cancelou ou pausou:
btrfs scrub resume / data
Listando os subvolumes:
bash btrfs subvolume list /ReportsCriando um instantâneo dos subvolumes:
Aqui, estamos criando um instantâneo de leitura e gravação chamado snap de marketing do subvolume de marketing.
bash btrfs subvolume snapshot /Reports/marketing /Reports/marketing-snapAlém disso, você pode criar um instantâneo somente leitura usando o sinalizador -r conforme mostrado. O marketing-rosnap é um instantâneo somente leitura do subvolume de marketing
bash btrfs subvolume snapshot -r /Reports/marketing /Reports/marketing-rosnapForçar a sincronização do sistema de arquivos usando o utilitário 'sync'
Para forçar a sincronização do sistema de arquivos, invoque a opção de sincronização conforme mostrado. Observe que o sistema de arquivos já deve estar montado para que o processo de sincronização continue com sucesso.
bash btrfs filsystem sync /ReportsPara excluir o dispositivo do sistema de arquivos, use o comando device delete conforme mostrado.
bash btrfs device delete /dev/sdc /ReportsPara sondar o status de um scrub, use o comando scrub status com a opção -dR .
bash btrfs scrub status -dR / RelatóriosPara cancelar a execução do scrub, use o comando scrub cancel .
bash $ sudo btrfs scrub cancel / ReportsPara retomar ou continuar com uma depuração interrompida anteriormente, execute o comando de cancelamento de depuração
bash sudo btrfs scrub resume /Reportsmostra o uso do dispositivo de armazenamento:
btrfs filesystem usage /data
Para distribuir os dados, metadados e dados do sistema em todos os dispositivos de armazenamento do RAID (incluindo o dispositivo de armazenamento recém-adicionado) montados no diretório /data , execute o seguinte comando:
sudo btrfs balance start --full-balance /data
Pode demorar um pouco para espalhar os dados, metadados e dados do sistema em todos os dispositivos de armazenamento do RAID se ele contiver muitos dados.
Opções importantes de montagem Btrfs
Nesta seção, vou explicar algumas das importantes opções de montagem do Btrfs. Então vamos começar.
As opções de montagem Btrfs mais importantes são:
**1. acl e noacl
**ACL gerencia permissões de usuários e grupos para os arquivos/diretórios do sistema de arquivos Btrfs.
A opção de montagem acl Btrfs habilita ACL. Para desabilitar a ACL, você pode usar a opção de montagem noacl .
Por padrão, a ACL está habilitada. Portanto, o sistema de arquivos Btrfs usa a opção de montagem acl por padrão.
**2. autodefrag e noautodefrag
**Desfragmentar um sistema de arquivos Btrfs melhorará o desempenho do sistema de arquivos reduzindo a fragmentação de dados.
A opção de montagem autodefrag permite a desfragmentação automática do sistema de arquivos Btrfs.
A opção de montagem noautodefrag desativa a desfragmentação automática do sistema de arquivos Btrfs.
Por padrão, a desfragmentação automática está desabilitada. Portanto, o sistema de arquivos Btrfs usa a opção de montagem noautodefrag por padrão.
**3. compactar e compactar-forçar
**Controla a compactação de dados no nível do sistema de arquivos do sistema de arquivos Btrfs.
A opção compactar compacta apenas os arquivos que valem a pena compactar (se compactar o arquivo economizar espaço em disco).
A opção compress-force compacta todos os arquivos do sistema de arquivos Btrfs, mesmo que a compactação do arquivo aumente seu tamanho.
O sistema de arquivos Btrfs suporta muitos algoritmos de compactação e cada um dos algoritmos de compactação possui diferentes níveis de compactação.
Os algoritmos de compactação suportados pelo Btrfs são: lzo , zlib (nível 1 a 9) e zstd (nível 1 a 15).
Você pode especificar qual algoritmo de compactação usar para o sistema de arquivos Btrfs com uma das seguintes opções de montagem:
- compress=algoritmo:nível
- compress-force=algoritmo:nível
Para obter mais informações, consulte meu artigo Como habilitar a compactação do sistema de arquivos Btrfs .
**4. subvol e subvolid
**Estas opções de montagem são usadas para montar separadamente um subvolume específico de um sistema de arquivos Btrfs.
A opção de montagem subvol é usada para montar o subvolume de um sistema de arquivos Btrfs usando seu caminho relativo.
A opção de montagem subvolid é usada para montar o subvolume de um sistema de arquivos Btrfs usando o ID do subvolume.
Para obter mais informações, consulte meu artigo Como criar e montar subvolumes Btrfs .
**5. dispositivo
A opção de montagem de dispositivo** é usada no sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs.
Em alguns casos, o sistema operacional pode falhar ao detectar os dispositivos de armazenamento usados em um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs. Nesses casos, você pode usar a opção de montagem do dispositivo para especificar os dispositivos que deseja usar para o sistema de arquivos de vários dispositivos Btrfs ou RAID.
Você pode usar a opção de montagem de dispositivo várias vezes para carregar diferentes dispositivos de armazenamento para o sistema de arquivos de vários dispositivos Btrfs ou RAID.
Você pode usar o nome do dispositivo (ou seja, sdb , sdc ) ou UUID , UUID_SUB ou PARTUUID do dispositivo de armazenamento com a opção de montagem do dispositivo para identificar o dispositivo de armazenamento.
Por exemplo,
- dispositivo=/dev/sdb
- dispositivo=/dev/sdb,dispositivo=/dev/sdc
- dispositivo=UUID_SUB=490a263d-eb9a-4558-931e-998d4d080c5d
- device=UUID_SUB=490a263d-eb9a-4558-931e-998d4d080c5d,device=UUID_SUB=f7ce4875-0874-436a-b47d-3edef66d3424
**6. degraded
A opção de montagem degradada** permite que um RAID Btrfs seja montado com menos dispositivos de armazenamento do que o perfil RAID requer.
Por exemplo, o perfil raid1 requer a presença de 2 dispositivos de armazenamento. Se um dos dispositivos de armazenamento não estiver disponível em qualquer caso, você usa a opção de montagem degradada para montar o RAID mesmo que 1 de 2 dispositivos de armazenamento esteja disponível.
**7. commit
A opção commit** mount é usada para definir o intervalo (em segundos) dentro do qual os dados serão gravados no dispositivo de armazenamento.
O padrão é definido como 30 segundos.
Para definir o intervalo de confirmação para 15 segundos, você pode usar a opção de montagem commit=15 (digamos).
**8. ssd e nossd
A opção de montagem ssd** informa ao sistema de arquivos Btrfs que o sistema de arquivos está usando um dispositivo de armazenamento SSD, e o sistema de arquivos Btrfs faz a otimização SSD necessária.
A opção de montagem nossd desativa a otimização do SSD.
O sistema de arquivos Btrfs detecta automaticamente se um SSD é usado para o sistema de arquivos Btrfs. Se um SSD for usado, a opção de montagem de SSD será habilitada. Caso contrário, a opção de montagem nossd é habilitada.
**9. ssd_spread e nossd_spread
A opção de montagem ssd_spread** tenta alocar grandes blocos contínuos de espaço não utilizado do SSD. Esse recurso melhora o desempenho de SSDs de baixo custo (baratos).
A opção de montagem nossd_spread desativa o recurso ssd_spread .
O sistema de arquivos Btrfs detecta automaticamente se um SSD é usado para o sistema de arquivos Btrfs. Se um SSD for usado, a opção de montagem ssd_spread será habilitada. Caso contrário, a opção de montagem nossd_spread é habilitada.
**10. descarte e nodiscard
Se você estiver usando um SSD que suporte TRIM enfileirado assíncrono (SATA rev3.1), a opção de montagem de descarte** permitirá o descarte de blocos de arquivos liberados. Isso melhorará o desempenho do SSD.
Se o SSD não suportar TRIM enfileirado assíncrono, a opção de montagem de descarte prejudicará o desempenho do SSD. Nesse caso, a opção de montagem nodiscard deve ser usada.
Por padrão, a opção de montagem nodiscard é usada.
**11. norecovery
Se a opção de montagem norecovery** for usada, o sistema de arquivos Btrfs não tentará executar a operação de recuperação de dados no momento da montagem.
**12. usebackuproot e nousebackuproot
Se a opção de montagem usebackuproot for usada, o sistema de arquivos Btrfs tentará recuperar qualquer raiz de árvore ruim/corrompida no momento da montagem. O sistema de arquivos Btrfs pode armazenar várias raízes de árvore no sistema de arquivos. A opção de montagem usebackuproot** procurará uma boa raiz de árvore e usará a primeira boa que encontrar.
A opção de montagem nousebackuproot não verificará ou recuperará raízes de árvore inválidas/corrompidas no momento da montagem. Este é o comportamento padrão do sistema de arquivos Btrfs.
**13. space_cache, space_cache=version, nospace_cache e clear_cache
A opção de montagem space_cache** é usada para controlar o cache de espaço livre. O cache de espaço livre é usado para melhorar o desempenho da leitura do espaço livre do grupo de blocos do sistema de arquivos Btrfs na memória (RAM).
O sistema de arquivos Btrfs suporta 2 versões do cache de espaço livre: v1 (padrão) e v2
O mecanismo de cache de espaço livre v2 melhora o desempenho de sistemas de arquivos grandes (tamanho de vários terabytes).
Você pode usar a opção de montagem space_cache=v1 para definir a v1 do cache de espaço livre e a opção de montagem space_cache=v2 para definir a v2 do cache de espaço livre.
A opção de montagem clear_cache é usada para limpar o cache de espaço livre.
Quando o cache de espaço livre v2 é criado, o cache deve ser limpo para criar um cache de espaço livre v1 .
Portanto, para usar o cache de espaço livre v1 após a criação do cache de espaço livre v2 , as opções de montagem clear_cache e space_cache=v1 devem ser combinadas: clear_cache,space_cache=v1
A opção de montagem nospace_cache é usada para desabilitar o cache de espaço livre.
Para desabilitar o cache de espaço livre após a criação do cache v1 ou v2 , as opções de montagem nospace_cache e clear_cache devem ser combinadas: clear_cache,nosapce_cache
**14. skip_balance
Por padrão, a operação de balanceamento interrompida/pausada de um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs será retomada automaticamente assim que o sistema de arquivos Btrfs for montado. Para desabilitar a retomada automática da operação de equilíbrio interrompido/pausado em um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs, você pode usar a opção de montagem skip_balance .**
**15. datacow e nodatacow
A opção datacow** mount habilita o recurso Copy-on-Write (CoW) do sistema de arquivos Btrfs. É o comportamento padrão.
Se você deseja desabilitar o recurso Copy-on-Write (CoW) do sistema de arquivos Btrfs para os arquivos recém-criados, monte o sistema de arquivos Btrfs com a opção de montagem nodatacow .
**16. datasum e nodatasum
A opção datasum** mount habilita a soma de verificação de dados para arquivos recém-criados do sistema de arquivos Btrfs. Este é o comportamento padrão.
Se você não quiser que o sistema de arquivos Btrfs faça a soma de verificação dos dados dos arquivos recém-criados, monte o sistema de arquivos Btrfs com a opção de montagem nodatasum .
Perfis Btrfs
Um perfil Btrfs é usado para informar ao sistema de arquivos Btrfs quantas cópias dos dados/metadados devem ser mantidas e quais níveis de RAID devem ser usados para os dados/metadados. O sistema de arquivos Btrfs contém muitos perfis. Entendê-los o ajudará a configurar um RAID Btrfs da maneira que você deseja.
Os perfis Btrfs disponíveis são os seguintes:
single : Se o perfil único for usado para os dados/metadados, apenas uma cópia dos dados/metadados será armazenada no sistema de arquivos, mesmo se você adicionar vários dispositivos de armazenamento ao sistema de arquivos. Assim, 100% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser utilizado.
dup : Se o perfil dup for usado para os dados/metadados, cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos manterá duas cópias dos dados/metadados. Assim, 50% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser utilizado.
raid0 : No perfil raid0 , os dados/metadados serão divididos igualmente em todos os dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, não haverá dados/metadados redundantes (duplicados). Assim, 100% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser usado. Se, em qualquer caso, um dos dispositivos de armazenamento falhar, todo o sistema de arquivos será corrompido. Você precisará de pelo menos dois dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid0 .
raid1 : No perfil raid1 , duas cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a uma falha de unidade. Mas você pode usar apenas 50% do espaço total em disco. Você precisará de pelo menos dois dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1 .
raid1c3 : No perfil raid1c3 , três cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a duas falhas de unidade, mas você pode usar apenas 33% do espaço total em disco. Você precisará de pelo menos três dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1c3 .
raid1c4 : No perfil raid1c4 , quatro cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a três falhas de unidade, mas você pode usar apenas 25% do espaço total em disco. Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1c4 .
raid10 : No perfil raid10 , duas cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos, como no perfil raid1 . Além disso, os dados/metadados serão divididos entre os dispositivos de armazenamento, como no perfil raid0 .
O perfil raid10 é um híbrido dos perfis raid1 e raid0 . Alguns dos dispositivos de armazenamento formam arrays raid1 e alguns desses arrays raid1 são usados para formar um array raid0 . Em uma configuração raid10 , o sistema de arquivos pode sobreviver a uma única falha de unidade em cada uma das matrizes raid1 .
Você pode usar 50% do espaço total em disco na configuração raid10 . Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid10 .
raid5 : No perfil raid5 , uma cópia dos dados/metadados será dividida entre os dispositivos de armazenamento. Uma única paridade será calculada e distribuída entre os dispositivos de armazenamento do array RAID.
Em uma configuração raid5 , o sistema de arquivos pode sobreviver a uma única falha de unidade. Se uma unidade falhar, você pode adicionar uma nova unidade ao sistema de arquivos e os dados perdidos serão calculados a partir da paridade distribuída das unidades em execução.
Você pode usar 1 00x(N-1)/N % do total de espaços em disco na configuração raid5 . Aqui, N é o número de dispositivos de armazenamento adicionados ao sistema de arquivos. Você precisará de pelo menos três dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid5 .
raid6 : No perfil raid6 , uma cópia dos dados/metadados será dividida entre os dispositivos de armazenamento. Duas paridades serão calculadas e distribuídas entre os dispositivos de armazenamento do array RAID.
Em uma configuração raid6 , o sistema de arquivos pode sobreviver a duas falhas de unidade ao mesmo tempo. Se uma unidade falhar, você poderá adicionar uma nova unidade ao sistema de arquivos e os dados perdidos serão calculados a partir das duas paridades distribuídas das unidades em execução.
Você pode usar 100x(N-2)/N % do espaço total em disco na configuração raid6 . Aqui, N é o número de dispositivos de armazenamento adicionados ao sistema de arquivos. Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid6 .
-
 @ 527337d5:93e9525e
2025-06-05 03:09:02
@ 527337d5:93e9525e
2025-06-05 03:09:02The Algorithmic Pursuit of Connection: A Five-Book Journey into the Self
As a researcher, hitting my thirties and the winding down of a significant project prompted a crucial re-evaluation of life's latter half. While I'd successfully applied probabilistic control theory to one-on-one interactions, the complexities of group dynamics remained a persistent challenge. My recent dive into five diverse books on human relationships inadvertently became a profound journey of self-discovery, fundamentally reshaping my perspective on social connections.
Neil Strauss: A Mirror Reflecting the Self's Evolution
Neil Strauss's The Truth resonated deepest among my recent reads. The author's battle with sex addiction uncomfortably mirrored my own past struggles: the fragile self-esteem stemming from rejection, the hubris born of early successes, and the tendency to view women as mere objects of manipulation. It felt eerily prescient, a glimpse into a potential future.
Yet, I found myself arriving at Strauss's ultimate conclusion – the paramount importance of self-preparation and community – far sooner than he did. This acceleration wasn't accidental; it was the result of intense focus on individual experiences, meticulously replayed and analyzed in my mind. The book, therefore, served less as a revelation and more as a powerful validation of my own journey of introspection and root-cause analysis.
Quantifying Connection: The Promise and Limits of Mathematical Models
Hannah Fry's The Mathematics of Love offered a kindred spirit in its attempt to quantify human relationships. While I appreciate the mathematical lens, Fry's models primarily concern dyadic relationships (N=2), relying on relatively simple systems of two-variable ordinary differential equations. For me, these are akin to linear models, sufficient only up to a certain point. Beyond N=4, the dependencies become exponentially complex.
My own pursuit extends to understanding and optimizing group dynamics within complex systems. This involves multi-variable problems (N $\ge$ 3) and the application of network theory, a far more sophisticated approach. Human collectives, after all, are systems of nodes and edges, where information propagates in predictable ways. My focus is on deriving optimal behavioral controls within these intricate frameworks.
Conversely, Men Are from Mars, Women Are from Venus initially struck me as bordering on conspiracy theory. However, its latter half proved unexpectedly useful. Its clear enumeration of male and female desires, and its articulation of common points of conflict, presented a practical template for communication styles. In a systemic view, this serves as a rudimentary, yet functional, interface design for complex social interactions.
A Dispassionate Critique of Relationship Dogma
My drive for efficiency and systematic understanding led to a rather blunt assessment of certain relationship classics. The New Science of Adult Attachment felt disorganized and frustratingly anecdotal. Lacking a coherent theoretical framework, it burdened the reader with deciphering meaning from a jumble of examples. Its inefficiency was, frankly, its most irksome flaw.
Similarly, Dale Carnegie's How to Win Friends and Influence People struck me as closer to pseudoscience than social science. Its plethora of specific anecdotes obscured any underlying principle. Given my deep engagement with social engineering – a discipline that systematically and practically analyzes human interaction – Carnegie's work appeared largely irrelevant and inefficient. From my perspective, which views humans as objective systems to be analyzed with mathematical rigor, such unstructured approaches hold little value.
The Unveiling of a Core Principle: Humans as Systems
This intensive reading period solidified my most crucial insight: humans, at their core, are systems. This understanding allows for a dispassionate, methodical approach to human collectives, mitigating unnecessary emotional friction.
This revelation has sharply refined my future learning trajectory. I'm now prioritizing foundational theories like graph theory and network theory over anecdotal accounts of human behavior. By mastering these theoretical underpinnings, I aim to precisely model complex human interactions as systems of nodes and edges, enabling the derivation of optimal behavioral controls within communities.
My choice of the term "target for capture" for individuals stems from a personal aversion to perceived equality in certain human interactions, a mechanism to avoid cognitive dissonance. This rational approach, I believe, is key to cultivating secure attachment styles – relationships demonstrably sustainable in the long term. My philosophy is to strategically approach the initial engagement, then transition to a stable, enduring connection. It's a calculated, dispassionate method for achieving desired relational outcomes.
Ultimately, this period of reading wasn't just about acquiring knowledge; it was a profound journey of self-discovery, clarifying my personal frameworks for navigating life's complexities and forging meaningful, yet strategically managed, connections.
-
 @ e2c72a5a:bfacb2ee
2025-06-05 16:50:08
@ e2c72a5a:bfacb2ee
2025-06-05 16:50:08Think crypto is just magic internet money? Think again.
Tokenomics is the secret sauce that makes or breaks a crypto project. It is the study of how tokens are created, distributed, and used within a blockchain ecosystem. Imagine it as the economic policy of a digital nation, dictating everything from supply and demand to user incentives.
Key features include supply caps, distribution models, utility, and burn mechanisms. A well designed token economy incentivizes user behavior, secures the network, and fosters long term growth. Poor tokenomics? It can lead to manipulation and project failure.
Zero Knowledge Proofs are like showing you know a password without revealing the password itself. This tech allows for private and secure transactions, verifying data without exposing the data itself. Think of voting systems where your vote stays secret, or supply chains where product details are confirmed without revealing the supplier.
Want to dive deeper into the economics of crypto? What project has the most interesting tokenomics you have seen?
-
 @ 0176967e:1e6f471e
2024-07-26 17:45:08
@ 0176967e:1e6f471e
2024-07-26 17:45:08Ak ste v Bitcoine už nejaký ten rok, možno máte pocit, že už všetkému rozumiete a že vás nič neprekvapí. Viete čo je to peňaženka, čo je to seed a čo adresa, možno dokonca aj čo je to sha256. Ste si istí? Táto prednáška sa vám to pokúsi vyvrátiť. 🙂
-
 @ dd664d5e:5633d319
2024-08-24 07:57:16
@ dd664d5e:5633d319
2024-08-24 07:57:16We can talk about something else, now.
Making boosts/quotes the primary way new users find a variety of topics is a fundamental flaw. We don't need boosts (which merely results in the main trending list trending even harder, as people feel safer boosting something that is already popular), and hashtags have become the mess they naturally will become.
We need topical forums and relay-based community boards.
This would actively encourage those of us who want to write on OtherTopics to write more on them, as we would have some chance of the material being found by those interested in it. And it would spare us having to win some general popularity contest, just to be able to converse about golfing, Hinduism, or veganism.
Scrollable "timeline" feeds, even with AI assistance (like DVMs), don't accomplish this as well, as they eliminate the ability to skim the top-level and selectively read. You have to scroll, scroll, scroll.
It would also reduce the overloading of the original posts with videos, which is starting to give Nostr a Tik-Tok vibe. There's nothing wrong with that, per se, and we should probably have clients like that, but it makes life hard for anyone who wants to have a deeper discussion. People scrolling have trouble even "seeing" a text-based OP, but using the written word is a true signal to the other people, that you are capable of carrying a conversation through text.
Examples for other styles of client
(I am including the Communities in Nostrudel and Satellite, even though they don't yet work, effectively.)
Some of the things that set these clients apart, is that: 1. they are topic-first or thread-first, not person-first, 2. they sometimes allow voting (I suppose we could rank by zaps), 3. they often allow the user to override the default order and simply look at whatever is newest, most popular, or where their friends are currently active (i.e. they allow for easy sorting and filtering), 4. they cap the depth of threads to one or two levels, keep the indentation tiny, or offer a "flat" view, 5. they are primarily text-based (Reddit broke with this and now their main pages look really spammy), 6. they allow you to see all of the entries in the thread, at once, and simply actualize to display the entries that pop up in-between, 7. they often have some indication of what you have already read (this is application data) and allow you to sort for "stuff I haven't looked at, yet".
https://i.nostr.build/uCx5YKMOsjhKBU5c.png https://i.nostr.build/hMkm2oKpos0pWaV9.png https://i.nostr.build/mGQONMw5RC8XKtph.png https://i.nostr.build/TCSkG1bPuMOL0jja.webp https://i.nostr.build/3fLjCSNdtefiZmAH.png https://i.nostr.build/BHgo7EKTK5FRIsVl.png
-
 @ 97c70a44:ad98e322
2025-02-18 20:30:32
@ 97c70a44:ad98e322
2025-02-18 20:30:32For the last couple of weeks, I've been dealing with the fallout of upgrading a web application to Svelte 5. Complaints about framework churn and migration annoyances aside, I've run into some interesting issues with the migration. So far, I haven't seen many other people register the same issues, so I thought it might be constructive for me to articulate them myself.
I'll try not to complain too much in this post, since I'm grateful for the many years of Svelte 3/4 I've enjoyed. But I don't think I'll be choosing Svelte for any new projects going forward. I hope my reflections here will be useful to others as well.
If you're interested in reproductions for the issues I mention here, you can find them below.
The Need for Speed
To start with, let me just quickly acknowledge what the Svelte team is trying to do. It seems like most of the substantial changes in version 5 are built around "deep reactivity", which allows for more granular reactivity, leading to better performance. Performance is good, and the Svelte team has always excelled at reconciling performance with DX.
In previous versions of Svelte, the main way this was achieved was with the Svelte compiler. There were many ancillary techniques involved in improving performance, but having a framework compile step gave the Svelte team a lot of leeway for rearranging things under the hood without making developers learn new concepts. This is what made Svelte so original in the beginning.
At the same time, it resulted in an even more opaque framework than usual, making it harder for developers to debug more complex issues. To make matters worse, the compiler had bugs, resulting in errors which could only be fixed by blindly refactoring the problem component. This happened to me personally at least half a dozen times, and is what ultimately pushed me to migrate to Svelte 5.
Nevertheless, I always felt it was an acceptable trade-off for speed and productivity. Sure, sometimes I had to delete my project and port it to a fresh repository every so often, but the framework was truly a pleasure to use.
Svelte is not Javascript
Svelte 5 doubled down on this tradeoff — which makes sense, because it's what sets the framework apart. The difference this time is that the abstraction/performance tradeoff did not stay in compiler land, but intruded into runtime in two important ways:
- The use of proxies to support deep reactivity
- Implicit component lifecycle state
Both of these changes improved performance and made the API for developers look slicker. What's not to like? Unfortunately, both of these features are classic examples of a leaky abstraction, and ultimately make things more complex for developers, not less.
Proxies are not objects
The use of proxies seems to have allowed the Svelte team to squeeze a little more performance out of the framework, without asking developers to do any extra work. Threading state through multiple levels of components without provoking unnecessary re-renders in frameworks like React is an infamously difficult chore.
Svelte's compiler avoided some of the pitfalls associated with virtual DOM diffing solutions, but evidently there was still enough of a performance gain to be had to justify the introduction of proxies. The Svelte team also seems to argue that their introduction represents an improvement in developer experience:
we... can maximise both efficiency and ergonomics.
Here's the problem: Svelte 5 looks simpler, but actually introduces more abstractions.
Using proxies to monitor array methods (for example) is appealing because it allows developers to forget all the goofy heuristics involved with making sure state was reactive and just
pushto the array. I can't count how many times I've writtenvalue = valueto trigger reactivity in svelte 4.In Svelte 4, developers had to understand how the Svelte compiler worked. The compiler, being a leaky abstraction, forced its users to know that assignment was how you signaled reactivity. In svelte 5, developers can just "forget" about the compiler!
Except they can't. All the introduction of new abstractions really accomplishes is the introduction of more complex heuristics that developers have to keep in their heads in order to get the compiler to act the way they want it to.
In fact, this is why after years of using Svelte, I found myself using Svelte stores more and more often, and reactive declarations less. The reason being that Svelte stores are just javascript. Calling
updateon a store is simple, and being able to reference them with a$was just a nice bonus — nothing to remember, and if I mess up the compiler yells at me.Proxies introduce a similar problem to reactive declarations, which is that they look like one thing but act like another on the edges.
When I started using Svelte 5, everything worked great — until I tried to save a proxy to indexeddb, at which point I got a
DataCloneError. To make matters worse, it's impossible to reliably tell if something is aProxywithouttry/catching a structured clone, which is a performance-intensive operation.This forces the developer to remember what is and what isn't a Proxy, calling
$state.snapshotevery time they pass a proxy to a context that doesn't expect or know about them. This obviates all the nice abstractions they gave us in the first place.Components are not functions
The reason virtual DOM took off way back in 2013 was the ability to model your application as composed functions, each of which takes data and spits out HTML. Svelte retained this paradigm, using a compiler to sidestep the inefficiencies of virtual DOM and the complexities of lifecycle methods.
In Svelte 5, component lifecycles are back, react-hooks style.
In React, hooks are an abstraction that allows developers to avoid writing all the stateful code associated with component lifecycle methods. Modern React tutorials universally recommend using hooks instead, which rely on the framework invisibly synchronizing state with the render tree.
While this does result in cleaner code, it also requires developers to tread carefully to avoid breaking the assumptions surrounding hooks. Just try accessing state in a
setTimeoutand you'll see what I mean.Svelte 4 had a few gotchas like this — for example, async code that interacts with a component's DOM elements has to keep track of whether the component is unmounted. This is pretty similar to the kind of pattern you'd see in old React components that relied on lifecycle methods.
It seems to me that Svelte 5 has gone the React 16 route by adding implicit state related to component lifecycles in order to coordinate state changes and effects.
For example, here is an excerpt from the documentation for $effect:
You can place $effect anywhere, not just at the top level of a component, as long as it is called during component initialization (or while a parent effect is active). It is then tied to the lifecycle of the component (or parent effect) and will therefore destroy itself when the component unmounts (or the parent effect is destroyed).
That's very complex! In order to use
$effect... effectively (sorry), developers have to understand how state changes are tracked. The documentation for component lifecycles claims:In Svelte 5, the component lifecycle consists of only two parts: Its creation and its destruction. Everything in-between — when certain state is updated — is not related to the component as a whole; only the parts that need to react to the state change are notified. This is because under the hood the smallest unit of change is actually not a component, it’s the (render) effects that the component sets up upon component initialization. Consequently, there’s no such thing as a “before update”/"after update” hook.
But then goes on to introduce the idea of
tickin conjunction with$effect.pre. This section explains that "tickreturns a promise that resolves once any pending state changes have been applied, or in the next microtask if there are none."I'm sure there's some mental model that justifies this, but I don't think the claim that a component's lifecycle is only comprised of mount/unmount is really helpful when an addendum about state changes has to come right afterward.
The place where this really bit me, and which is the motivation for this blog post, is when state gets coupled to a component's lifecycle, even when the state is passed to another function that doesn't know anything about svelte.
In my application, I manage modal dialogs by storing the component I want to render alongside its props in a store and rendering it in the
layout.svelteof my application. This store is also synchronized with browser history so that the back button works to close them. Sometimes, it's useful to pass a callback to one of these modals, binding caller-specific functionality to the child component:javascript const {value} = $props() const callback = () => console.log(value) const openModal = () => pushModal(MyModal, {callback})This is a fundamental pattern in javascript. Passing a callback is just one of those things you do.
Unfortunately, if the above code lives in a modal dialog itself, the caller component gets unmounted before the callback gets called. In Svelte 4, this worked fine, but in Svelte 5
valuegets updated toundefinedwhen the component gets unmounted. Here's a minimal reproduction.This is only one example, but it seems clear to me that any prop that is closed over by a callback function that lives longer than its component will be undefined when I want to use it — with no reassignment existing in lexical scope. It seems that the reason this happens is that the props "belong" to the parent component, and are accessed via getters so that the parent can revoke access when it unmounts.
I don't know why this is necessary, but I assume there's a good engineering reason for it. The problem is, this just isn't how javascript works. Svelte is essentially attempting to re-invent garbage collection around component lifecycles, which breaks the assumption every javascript developer has that variables don't simply disappear without an explicit reassignment. It should be safe to pass stuff around and let the garbage collector do its job.
Conclusion
Easy things are nice, but as Rich Hickey says, easy things are not always simple. And like Joel Spolsky, I don't like being surprised. Svelte has always been full of magic, but with the latest release I think the cognitive overhead of reciting incantations has finally outweighed the power it confers.
My point in this post is not to dunk on the Svelte team. I know lots of people like Svelte 5 (and react hooks). The point I'm trying to make is that there is a tradeoff between doing things on the user's behalf, and giving the user agency. Good software is built on understanding, not cleverness.
I also think this is an important lesson to remember as AI-assisted coding becomes increasingly popular. Don't choose tools that alienate you from your work. Choose tools that leverage the wisdom you've already accumulated, and which help you to cultivate a deeper understanding of the discipline.
Thank you to Rich Harris and team for many years of pleasant development. I hope that (if you read this) it's not so full of inaccuracies as to be unhelpful as user feedback.
-
 @ 9e69e420:d12360c2
2025-02-17 17:12:01
@ 9e69e420:d12360c2
2025-02-17 17:12:01President Trump has intensified immigration enforcement, likening it to a wartime effort. Despite pouring resources into the U.S. Immigration and Customs Enforcement (ICE), arrest numbers are declining and falling short of goals. ICE fell from about 800 daily arrests in late January to fewer than 600 in early February.
Critics argue the administration is merely showcasing efforts with ineffectiveness, while Trump seeks billions more in funding to support his deportation agenda. Increased involvement from various federal agencies is intended to assist ICE, but many lack specific immigration training.
Challenges persist, as fewer immigrants are available for quick deportation due to a decline in illegal crossings. Local sheriffs are also pressured by rising demands to accommodate immigrants, which may strain resources further.
-
 @ e2c72a5a:bfacb2ee
2025-06-05 16:46:19
@ e2c72a5a:bfacb2ee
2025-06-05 16:46:19Think proving you're over 21 without showing your ID is impossible? Zero Knowledge Proofs make it real.
Zero Knowledge Proofs let you prove something is true without revealing the information itself. Imagine proving you know a password without saying it. It's like magic, but it's math.
They're used in crypto for private transactions, secure voting, and faster blockchains. Zcash and Aztec use them to hide transaction details. StarkWare uses them to make Ethereum faster.
But here's the twist: zk STARKs don't need a trusted setup, unlike zk SNARKs. This makes them more secure and decentralized.
Misconception alert: ZKPs aren't just for privacy. They also boost scalability and interoperability.
Want to dive deeper into this mind bending tech? What other secrets can ZKPs unlock?
-
 @ 0176967e:1e6f471e
2024-07-26 12:15:35
@ 0176967e:1e6f471e
2024-07-26 12:15:35Bojovať s rakovinou metabolickou metódou znamená použiť metabolizmus tela proti rakovine. Riadenie cukru a ketónov v krvi stravou a pohybom, časovanie rôznych typov cvičení, včasná kombinácia klasickej onko-liečby a hladovania. Ktoré vitamíny a suplementy prijímam a ktorým sa napríklad vyhýbam dajúc na rady mojej dietologičky z USA Miriam (ktorá sa špecializuje na rakovinu).
Hovori sa, že čo nemeriame, neriadime ... Ja som meral, veľa a dlho ... aj grafy budú ... aj sranda bude, hádam ... 😉