-
 @ 8cb60e21:5f2deaea
2024-09-06 22:23:03
@ 8cb60e21:5f2deaea
2024-09-06 22:23:03 -
 @ 472f440f:5669301e
2024-09-06 21:56:48
@ 472f440f:5669301e
2024-09-06 21:56:48I had the pleasure of sitting back down with Will Reeves, Founder and CEO of Fold, on TFTC last week to discuss Fold's journey from a startup to (soon to be) a publicly listed company. I particularly liked this conversation because it was a great lens into the grit it takes to run a successful bitcoin company.
https://fountain.fm/episode/1FrspxmpK5bsoReGx73n
Building a successful company is extremely hard in its own right. Building a successful bitcoin company is significantly harder considering the fact that you're building a company in parallel with a nascent and volatile monetary asset that is monetizing in real time. Bitcoin adoption comes in waves. People flood in when the price is ripping and fade out when the price corrects and goes into a multi-year bear market before the tide comes back in. This means that your potential user base is expanding and contracting more than it would be in other industries. As a company you need to be able to absorb the incoming waves of new adopters and then capture and retain the users who stick around for the bear market.
To do this correctly, a founder and their team needs to thread many needles. First, can you assemble a team that can actually build something? Second, can you bring a product to market that people actually use because it provides value to them? Third, can you stick out against the crowd? So on and so forth. One of the most important aspects of building a bitcoin company during bitcoin's monetization phase is timing. There are many great ideas that people have in terms of companies, products and tools that can built using bitcoin. There are sci-fi futures that can be built today on bitcoin if people really wanted to.
The problem that arises is that adoption and understanding of bitcoin are at a point where, even though a functional product could be brought to market, it won't be adopted by a large number of people because there 1.) aren't enough people who would understand how to use it and 2.) for the people who do understand how to use it and could benefit from it, the universe of people they can interact with using that product is minuscule.
Timing is everything. And I think Fold nailed the timing of their product. Allowing people to passively stack sats by offering a product that enables them to go about their daily spending and get sats back instead of cash back rewards is a great first-touch bitcoin experience. Once Fold found their sticky user base and perfected their sats back experience, they began expanding their product offering to provide their users with more bitcoin services. Buy/sell bitcoin in-app, bill pay for sats back, and more. They'll eventually roll out a credit card and additional financial services. Start simple, provide something of value, nail the timing and then expand from there. That seems to be the recipe.
For any founders in the space reading this, I highly recommend you listen to the episode. Particularly for the advice Will gives about knowing when to sprint on product and when to lean into growth. Bear markets are for building and bull markets are for casting the widest net possible and capturing as many new users as possible.
At Ten31 we are extremely proud to back Fold and a number of other companies in the bitcoin space that understand the intricacies described above. We work with some of the best founders in the world. Founders who know how to eat glass with the best of them. Bitcoin can be a cruel mistress and no one knows that more intimately than the founders building bitcoin companies.
Final thought...
The NFL having a week 1 game in Brazil should get Roger Godell fired.
Enjoy your weekend, freaks.
-
 @ e83b66a8:b0526c2b
2024-09-06 19:16:04
@ e83b66a8:b0526c2b
2024-09-06 19:16:04The founder of Telegram has just been arrested in France. Charges include lack of cooperation with law enforcement, drug trafficking and fraud.
Aside from Telegram, social media is controlled by two billionaires who decide what you say, are themselves controlled by overbearing governments and make money through advertising and selling your personal data.
There is a different way.
NOSTR stands for Notes and Other Stuff Transmitted on Relays and it is a social media protocol in the same way http is a web protocol.
The protocol is open and anybody can build upon it. It has some fundamental concepts that are very different to existing social media platforms.
Firstly it is decentralised, it runs across relays and anybody can run a relay. They can be open or closed, public or private, free or paid.
Secondly as a user, you don’t have an account, you have a private key which is used to secure your data.
Your profile (account) is yours, you own and control it using your private keys and verified by others with your public key.
Your posts are yours and you can store them on your own relay in your own home or business or you can rely on free public relays or more feature rich paid public relays.
All your public data is signed by your private keys to verify it is you that owns it and all your private data is encrypted so nobody can read it.
Messages (i.e. think NOSTR WhatsApp) are encrypted with your private keys so NOBODY can hack it or listen in, not even the NSA through a companies backdoor. You message other users privately by encrypting messages to them using their public key, which they decrypt using their private key.
Relays store your data in a decentralised network of private and public relays and you discover relays automatically when searching for people or content.
Data is normally sent on the clearnet, but can be relayed across the darknet (Tor) in highly censored regions.
Because it is built using Bitcoin principles and technology, so it has Bitcoin money built in, meaning you actually send / receive money from / to any participant.
As money is built in, the commercial options are different to centralised corporate owned platforms. It would be technically possible to build a platform that supports advertising, however that hasn’t really happened because influencers can be paid directly from their audience in many different ways. Ad hoc tips, subscriptions, pay to view or pay per time models.
The great thing for content creators is that they control, own and keep all the money they make. There is no third party intermediary or merchant deciding whether they are allowed to be paid or not.
NOSTR is censorship resistant, as there is no way to stop anybody publishing anything they want, in the same way nobody can stop or interfere with a Bitcoin payment.
From an end users point of view, if they want to self censor, they can do this in multiple ways. You can mute users individually, or you can choose to use relays that adhere to your views or interests, so if you don’t want to see certain categories of content, you would avoid relays that carry those feeds. You can even run your own relay and curate content that you then charge other like minded users to connect to. You can of course connect to multiple relays for multiple different type of feed.
While NOSTR is a protocol, platforms have to be built to use it, so the first platforms were twitter like clients and they are still very prevalent. However, NOSTR now has clients that emulate most social media platforms, Instagram, Facebook, YouTube, Soundcloud, WhatsApp etc. They are even creating their own categories as well as emulating other functions such as Office Suite tools, collaborative calendars, contact lists or e-commerce shops.
If you want to give it a go, the easiest, but not the best, way to get started is download Primal on your phone from here:
https://primal.net/downloads
It will create a private key for you and setup a Bitcoin wallet.
Once you have done this you can visit me here:
nostr:npub1aqakd28d95muqlg6h6nwrvqq5925n354prayckr424k49vzjds4s0c237n
If you want to see a small part of the ecosystem, then visit https://www.nostrapps.com/ where volunteers are listing some of the many apps that exist already.
NOSTR is being backed by Jack Dorsey, Twitter founder, and you can see his account here:
nostr:npub1sg6plzptd64u62a878hep2kev88swjh3tw00gjsfl8f237lmu63q0uf63m
Or you can see his account like this:
https://primal.net/jack
Edward Snowden is also on the platform and you can find him here:
https://primal.net/Snowden
NOSTR has around 2 million users or public keys, although nobody really knows how many, because it is decentralised and not controlled or run by any person or organisation.
Once you’ve setup Primal, you can use those same private keys to access any platform you wish and you can use a browser extension such as Alby to manage your keys: https://getalby.com/
Primal looks great, but there are other better functioning twitter like clients, probably the most reliable for iPhone is Damus: https://www.nostrapps.com/apps/damus
or Amethyst for Android: https://nostrapps.com/amethyst
The content and user base is very Bitcoin and freedom focused right now, but more and more people are starting to use the various platforms and some are transferring exclusively to it.
Some of the more interesting projects right now are:
https://www.0xchat.com/#/ – Private messaging – think WhatsApp
https://zap.stream/ – Video streaming
https://fountain.fm/ – Podcasting
https://wavlake.com/ – Music streaming
https://shopstr.store/ – Online shop
https://npub.pro/ – Website creation tool
https://nostr.build/ – Media and file storage
https://relay.tools/ – Build and curate your own relay
https://creatr.nostr.wine/subscriptions/new-user – Creator tools
Remember, the same keys you created for Primal can be used across the whole ecosystem.
If you want to see some of the other apps that have been built on the NOSTR protocol visit: https://nostrapps.com/
-
 @ ffd375eb:4529ed08
2024-09-06 15:39:31
@ ffd375eb:4529ed08
2024-09-06 15:39:31Chef's notes
Watch the video 🇫🇷: https://youtu.be/cYl4Lb0vbyc
Details
- ⏲️ Prep time: 20 min
- 🍳 Cook time: 3 months
- 🍽️ Servings: Many
Ingredients
- 1 fennel bulb
- 1 large onion
- 3 garlic cloves
- 1/2 tsp salt per fennel bulb
- 1 tbsp turmeric powder per fennel bulb
- 1 tbsp oil per fennel bulb
- 1 tsp black pepper per fennel bulb
- 1 tbsp honey per fennel bulb
Directions
- Thinly slice the fennel bulb, onion, and garlic using a mandoline slicer.
- In a bowl, mix the sliced fennel, onion, garlic, and salt. Let sit for a bit to allow the salt to act on the ingredients.
- In a separate bowl, mix the turmeric, oil, black pepper, and honey to make a sauce.
- Combine the fennel, onion, garlic mixture with the turmeric sauce and mix well.
-
 @ 9977c3ad:43a20d63
2024-09-06 13:08:49
@ 9977c3ad:43a20d63
2024-09-06 13:08:49Chef's notes
Stabbing your duck with a meat fork, or making a tiny incision to determine the color is a huge no-no. The way that any chef worth his salt determines the temperature of duck is to poke it with a finger. Bring the tips of your index finger and your thumb together in a circle, to form an «OK» sign. Now press the meaty part of your palm below the thumb – this is how a rare duckbreast feels. For medium-rare, bring your middle finger and thumb together to form a circle, and press the meaty part of your palm below the thumb, and notice that it gets firmer the farther you go: this is medium-rare. Repeat the process with your ring finger: medium. Repeat the process with your pinky finger: well-done.
Details
- 🍽️ Servings: 2
Ingredients
- 1 large apricot
- 1 tsp. Champagne vinegar
- 1/8 tsp. chilly flakes
- 2 Tbsp. honey
- 1 small duck breast, skin-on
- 2 sprigs rosemary
- 1 piece fresh ginger root, 1/2 inch thick
- 1 Tbsp. butter
- 1/2 cup dry white wine
- 1/4 lbs Brie
- 3 oz. Mascarpone
- 1 sprig of mint
- Salt
- Coarsely ground black peppercorn
- Water
Directions
- Cut the apricot in half and then in wedges, about 5mm thick. Combine the vinegar, chilly flakes, 1/2 tsp. honey, and season with nutmeg. Toss the fruits in the seasoning and let them sit. Heat a skillet or light your barbecue. Over high heat, dry roast the marinated fruit wedges on both sides until they’re beginning to charr.
- Preheat your oven to 475°F. Remove the leaves from the rosemary sprigs and peel the ginger. On a cutting board, combine the rosemary and ginger, then cover them with enough salt to season your duck breast. Chop everything together until the ginger and rosemary are finely minced, infusing the salt with their flavors. Season the butter with half of the infused salt. Score the skin of the duck breast and rub the seasoned butter into it. Then, season the skinless side of the duck with the remaining infused salt. Place the duck breast on a sheet tray, skin side up. Roast the duck in the oven for about 7 minutes, then reduce the temperature to 325°F. In a bowl, mix together honey and water. Brush the duck with this honey-water mixture. Continue baking and brushing the duck until it almost reaches your desired doneness (refer to the cooking guide above). Once done, open the oven door, turn off the oven, and let the duck rest for 10-15 minutes.
- Plating: Cut the mint leaves in thin stripes (chiffonade). Carve the duck into thin slices. Pour the fondue into a flat soup bowl. Plate the fruit wedges and the chicken breast in a fan shape. Sprinkle mint leaves on top.
-
 @ 9977c3ad:43a20d63
2024-09-05 11:21:09
@ 9977c3ad:43a20d63
2024-09-05 11:21:09Details
- 🍽️ Servings: 2
Ingredients
- 1 cup Jasmine rice
- 1 Tbsp. lavender flowers, crushed with mortar and pestle
- 1/4 cup apple cider vinegar
- 2 Tbsp. fine cane sugar
- 2 Tbsp. honey
- 1 sprig rosemary
- 1/4 tsp angostura bitters
- 1/2 cup blackberries
- 1/2 cup blueberries
- 4 cups trimmed and quartered shiitake mushrooms
- 1 tsp fresh coriander crushed
- 1/4 tsp fresh cumin ground
- 1/2 tsp red pepper flakes
- 3 sprigs of thyme
- 2 Tbsp. olive oil
- 1 tsp soy sauce
- 1 cup creamy coconut milk
Directions
- Combine rice, lavender, 1/4 tsp salt, and 2 cups of water in a saucepan. Bring the rice to a boil, cover the pan with a lid and turn the heat off. Let the rice sit in the pan for at least 20 minutes.
- Combine 1/4 cup of water, the vinegar, sugar, honey, rosemary, angostura bitters in a saucepan and bring the brine to a boil. Season with a pinch of salt. Add the berries and wait until the brine comes back to a boil. Lower the heat, so the brine simmers but does not boil. When the brine thickens, after about 15 minutes, remove the saucepan from the heat and set it aside.
- Pre-heat the oven to 400F. In a bowl big enough to hold all the shiitake, combine the olive oil, the soy sauce and the spices. Whisk vigorously, so the oil emulsifies with the other liquid. Toss the shiitake in the mix to marinate, then evenly lay them out on a baking sheet with parchment paper. Bake the shiitake for 10 minutes. When you remove the shiitake from the oven, remove the thyme and throw it out. In a saucepan, bring the coconut milk to a boil. Add the shiitake and reduce the heat to a light boil until the sauce thickens.
-
 @ 7460b7fd:4fc4e74b
2024-09-05 08:37:48
@ 7460b7fd:4fc4e74b
2024-09-05 08:37:48请看2014年王兴的一场思维碰撞,视频27分钟开始
最后,一个当时无法解决的点:丢失
-
 @ 9a35b935:4b4c66af
2024-09-03 01:43:37
@ 9a35b935:4b4c66af
2024-09-03 01:43:37Chef's notes
Easy and flavorful dish that can be prepared cooked in about 30-35 minutes. Just omit the smoke if you want to take it indoors with the oven
Details
- ⏲️ Prep time: Rub ahead of time
- 🍳 Cook time: 30-35 minutes (temperature though and not time)
Ingredients
- 2 tablespoons paprika
- 4 tablespoons coconut sugar (can substitute brown sugar)
- 1.5 tablespoons kosher salt
- 1 tablespoon fresh black pepper
- .5 tablespoon chili powder
- 1 tablespoon garlic powder
- 1 tablespoon onion powder
- 1 tablespoon ground mustard
- 1/2 teaspoon cayenne pepper (optional)
Directions
- Pat tenderloins dry and season with Rub and let rest for at least two hours
- Fire up grill / smoker to 350 When appropriate for your grill add a mild wood like pecan.
- Smoke Roast and pull off a little early to let rest to 145. I like this temp because I think searing becomes optional. If you want to sear go ahead and take it down to 250
- If sear is desired: Sear for one minute per side in a hot cast iron pan. Check after 30 seconds to be careful not to let the sugar burn
-
 @ 361d3e1e:50bc10a8
2024-09-06 19:02:33
@ 361d3e1e:50bc10a8
2024-09-06 19:02:33A teacher is arrested because he refused to teach LGBT+ to his students
politics #lgbt #education #arrest #ireland #freedom
-
 @ d34e832d:383f78d0
2024-09-06 18:26:44
@ d34e832d:383f78d0
2024-09-06 18:26:44Cox Media Group has been promoting a new targeted advertising tool to tech companies that uses audio recordings from smart home devices. This program was first revealed by Gizmodo late last year. Recently, 404 Media obtained more details about it through a leaked pitch deck, and the contents are unsettling.
The tool, called "Active Listening," is designed to leverage smart devices that “capture real-time intent data by listening to conversations.” Advertisers can then pair this data with behavioral information to target consumers. The deck also mentions using artificial intelligence to analyze both behavioral and voice data from over 470 sources, raising further privacy concerns.
The legality of this practice is questionable. Many states have wiretapping laws prohibiting recording without explicit consent. If smart devices are always recording and funneling data into targeted ads, this could violate laws like California’s two-party consent requirement.
Cox claims partnerships with major platforms like Google, Amazon, and Facebook, but it’s unclear if any are involved with this tool. After being contacted, Google dropped Cox Media Group from its advertising partners program, and Amazon stated it has never worked with CMG on this program.
You can view the full pitch deck here.
-
 @ b6dcdddf:dfee5ee7
2024-09-06 17:46:11
@ b6dcdddf:dfee5ee7
2024-09-06 17:46:11Hey Frens,
This is the Geyser team, coming at you with a spicy idea: a grant for proper journalism.
Issue: Journalism is broken. Independent journalism is emerging with the work of The Rage, Whitney Webb and so forth. They deal with issues like privacy, political corruption, economics, ESG, medicine and many other issues that are not discussed by mainstream media.
The problem is that not many people know about their work and there are very few grant programs that support their work.
Proposed Solution: Geyser would like to host a Grant supporting independent journalists using 'community voting mechanism'. See here for how Community Voting Grants work.
However, we need more companies to partner up and sponsor this initiative with us. Ideas of more sponsors: - Stacker news: SN has become a great repository of independent/indie journalism. I think they'd fit in great as sponsors for this type of grant. cc: @k00b - Bitesize media: A new independent media house that wants to focus on the signal Bitcoin brings to our world. They expressed interest already. - Bitcoin Magazine: might be interested as well in this effort.
Would love the community's feedback on this idea and propose additional thoughts!
originally posted at https://stacker.news/items/674951
-
 @ 75bf2353:e1bfa895
2024-09-06 17:04:57
@ 75bf2353:e1bfa895
2024-09-06 17:04:57Creative Commons Legal Code
CC0 1.0 Universal
CREATIVE COMMONS CORPORATION IS NOT A LAW FIRM AND DOES NOT PROVIDE LEGAL SERVICES. DISTRIBUTION OF THIS DOCUMENT DOES NOT CREATE AN ATTORNEY-CLIENT RELATIONSHIP. CREATIVE COMMONS PROVIDES THIS INFORMATION ON AN "AS-IS" BASIS. CREATIVE COMMONS MAKES NO WARRANTIES REGARDING THE USE OF THIS DOCUMENT OR THE INFORMATION OR WORKS PROVIDED HEREUNDER, AND DISCLAIMS LIABILITY FOR DAMAGES RESULTING FROM THE USE OF THIS DOCUMENT OR THE INFORMATION OR WORKS PROVIDED HEREUNDER.Statement of Purpose
The laws of most jurisdictions throughout the world automatically confer exclusive Copyright and Related Rights (defined below) upon the creator and subsequent owner(s) (each and all, an "owner") of an original work of authorship and/or a database (each, a "Work").
Certain owners wish to permanently relinquish those rights to a Work for the purpose of contributing to a commons of creative, cultural and scientific works ("Commons") that the public can reliably and without fear of later claims of infringement build upon, modify, incorporate in other works, reuse and redistribute as freely as possible in any form whatsoever and for any purposes, including without limitation commercial purposes. These owners may contribute to the Commons to promote the ideal of a free culture and the further production of creative, cultural and scientific works, or to gain reputation or greater distribution for their Work in part through the use and efforts of others.
For these and/or other purposes and motivations, and without any expectation of additional consideration or compensation, the person associating CC0 with a Work (the "Affirmer"), to the extent that he or she is an owner of Copyright and Related Rights in the Work, voluntarily elects to apply CC0 to the Work and publicly distribute the Work under its terms, with knowledge of his or her Copyright and Related Rights in the Work and the meaning and intended legal effect of CC0 on those rights.
- Copyright and Related Rights. A Work made available under CC0 may be protected by copyright and related or neighboring rights ("Copyright and Related Rights"). Copyright and Related Rights include, but are not limited to, the following:
i. the right to reproduce, adapt, distribute, perform, display, communicate, and translate a Work; ii. moral rights retained by the original author(s) and/or performer(s); iii. publicity and privacy rights pertaining to a person's image or likeness depicted in a Work; iv. rights protecting against unfair competition in regards to a Work, subject to the limitations in paragraph 4(a), below; v. rights protecting the extraction, dissemination, use and reuse of data in a Work; vi. database rights (such as those arising under Directive 96/9/EC of the European Parliament and of the Council of 11 March 1996 on the legal protection of databases, and under any national implementation thereof, including any amended or successor version of such directive); and vii. other similar, equivalent or corresponding rights throughout the world based on applicable law or treaty, and any national implementations thereof.
-
Waiver. To the greatest extent permitted by, but not in contravention of, applicable law, Affirmer hereby overtly, fully, permanently, irrevocably and unconditionally waives, abandons, and surrenders all of Affirmer's Copyright and Related Rights and associated claims and causes of action, whether now known or unknown (including existing as well as future claims and causes of action), in the Work (i) in all territories worldwide, (ii) for the maximum duration provided by applicable law or treaty (including future time extensions), (iii) in any current or future medium and for any number of copies, and (iv) for any purpose whatsoever, including without limitation commercial, advertising or promotional purposes (the "Waiver"). Affirmer makes the Waiver for the benefit of each member of the public at large and to the detriment of Affirmer's heirs and successors, fully intending that such Waiver shall not be subject to revocation, rescission, cancellation, termination, or any other legal or equitable action to disrupt the quiet enjoyment of the Work by the public as contemplated by Affirmer's express Statement of Purpose.
-
Public License Fallback. Should any part of the Waiver for any reason be judged legally invalid or ineffective under applicable law, then the Waiver shall be preserved to the maximum extent permitted taking into account Affirmer's express Statement of Purpose. In addition, to the extent the Waiver is so judged Affirmer hereby grants to each affected person a royalty-free, non transferable, non sublicensable, non exclusive, irrevocable and unconditional license to exercise Affirmer's Copyright and Related Rights in the Work (i) in all territories worldwide, (ii) for the maximum duration provided by applicable law or treaty (including future time extensions), (iii) in any current or future medium and for any number of copies, and (iv) for any purpose whatsoever, including without limitation commercial, advertising or promotional purposes (the "License"). The License shall be deemed effective as of the date CC0 was applied by Affirmer to the Work. Should any part of the License for any reason be judged legally invalid or ineffective under applicable law, such partial invalidity or ineffectiveness shall not invalidate the remainder of the License, and in such case Affirmer hereby affirms that he or she will not (i) exercise any of his or her remaining Copyright and Related Rights in the Work or (ii) assert any associated claims and causes of action with respect to the Work, in either case contrary to Affirmer's express Statement of Purpose.
-
Limitations and Disclaimers.
a. No trademark or patent rights held by Affirmer are waived, abandoned, surrendered, licensed or otherwise affected by this document. b. Affirmer offers the Work as-is and makes no representations or warranties of any kind concerning the Work, express, implied, statutory or otherwise, including without limitation warranties of title, merchantability, fitness for a particular purpose, non infringement, or the absence of latent or other defects, accuracy, or the present or absence of errors, whether or not discoverable, all to the greatest extent permissible under applicable law. c. Affirmer disclaims responsibility for clearing rights of other persons that may apply to the Work or any use thereof, including without limitation any person's Copyright and Related Rights in the Work. Further, Affirmer disclaims responsibility for obtaining any necessary consents, permissions or other rights required for any use of the Work. d. Affirmer understands and acknowledges that Creative Commons is not a party to this document and has no duty or obligation with respect to this CC0 or use of the Work.
DON'T BE A DICK PUBLIC LICENSE
originally created by Phil Sturgeon
Version 1.1, December 2016
Copyright (C) Blogging Bitcoin
Everyone is permitted to copy and distribute verbatim or modified copies of this license document.
DON'T BE A DICK PUBLIC LICENSE TERMS AND CONDITIONS FOR COPYING, DISTRIBUTION AND MODIFICATION
- Do whatever you like with the original work, just don't be a dick.
Being a dick includes - but is not limited to - the following instances:
1a. Outright copyright infringement - Don't just copy this and change the name. 1b. Selling the unmodified original with no work done what-so-ever, that's REALLY being a dick. 1c. Modifying the original work to contain hidden harmful content. That would make you a PROPER dick.
-
If you become rich through modifications, related works/services, or supporting the original work, share the love. Only a dick would make loads off this work and not buy the original work's creator(s) a pint.
-
Code is provided with no warranty. Using somebody else's code and bitching when it goes wrong makes you a DONKEY dick. Fix the problem yourself. A non-dick would submit the fix back.
-
 @ c73818cc:ccd5c890
2024-09-06 16:44:51
@ c73818cc:ccd5c890
2024-09-06 16:44:51
💩 Il governo italiano approva il decreto di adeguamento al regolamento MiCAR mentre la Banca d'Italia aggiorna il Piano Strategico 2023-2025 per rafforzare la vigilanza e l'innovazione nel settore finanziario.
💩 Rafforzamento della regolamentazione:
💩 Il Consiglio dei ministri ha approvato un decreto legislativo che adegua le normative italiane al regolamento europeo MiCAR, stabilendo una regolamentazione minima per tutte le cripto-attività a livello UE. L'obiettivo è garantire maggiore trasparenza e tutela degli investitori, prevenendo abusi nel mercato delle criptovalute.
💩 Nuovi poteri a Banca d'Italia e Consob:
💩 Il decreto conferisce poteri ampliati alla Banca d'Italia e alla Consob per vigilare e sanzionare gli operatori nel settore delle cripto-attività. Queste istituzioni avranno la responsabilità di garantire che le emissioni, le offerte pubbliche e le negoziazioni di token avvengano in conformità con le normative vigenti.
💩 Piano Strategico 2023-2025:
💩 Parallelamente, la Banca d'Italia ha aggiornato il suo Piano Strategico, che punta su innovazione e resilienza cibernetica. Tra le priorità figurano il rafforzamento della stabilità finanziaria, l'introduzione dell'euro digitale e il miglioramento delle infrastrutture di pagamento, con un'attenzione particolare alla lotta alle attività illegali.
💩 Tutela degli utenti e sostenibilità:
💩 Il piano prevede anche misure per proteggere i clienti dei servizi bancari, promuovere l'educazione finanziaria e contribuire alla sostenibilità ambientale. La Banca d'Italia si allinea agli obiettivi dell'Agenda 2030 delle Nazioni Unite, puntando a ridurre l'impronta ambientale e a favorire l'inclusività.
💩 Transizione energetica e innovazione:
💩 Infine, il piano della Banca d'Italia mira a consolidare il lavoro ibrido, valorizzare la diversità e sviluppare nuove competenze per affrontare le sfide future. L'adozione di tecnologie digitali sarà centrale per mantenere l'efficienza e l'efficacia operativa dell'istituzione.
Unisciti al nostro gruppo Telegram: https://t.me/Bitcoin_Report_Italia
Referral Bitget -10% sulle fee + bonus benvenuto 6w5d o link: https://bonus.bitget.com/U1JNEK
BitcoinReportItalia #Decreto #Normative #MiCAR #Italia #Banca #UE #Consob #EuroDigitale #CBDC #Agenda2030 #ONU #Cripto #Bitcoin
-
 @ 150cec32:eea45aec
2024-09-06 16:18:50
@ 150cec32:eea45aec
2024-09-06 16:18:50כותרת
טקסט
-
 @ 7ab1ed7a:f8e15275
2024-09-06 16:15:53
@ 7ab1ed7a:f8e15275
2024-09-06 16:15:53 -
 @ 9bc2d34d:d19d2948
2024-09-02 19:41:40
@ 9bc2d34d:d19d2948
2024-09-02 19:41:40Chef's notes
This recipe is designed for home cooks who want to recreate the delicious buttery hollandaise sauce at home without feeling overwhelmed. It focuses on teaching the basics of the sauce, allowing beginners to master the fundamentals before experimenting with seasonings, hot sauces, or herbs.
Please note the thickness of sauce in the picture. This is after ten minutes of blending.
Details
- ⏲️ Prep time: 3 minutes
- 🍳 Cook time: 10 minutes (blending)
- 🍽️ Servings: 2 - 4
Ingredients
- 4 egg yolks
- 8 tablespoons of melted butter
- 1 tablespoon of lemon juice
- Pinch of salt
- Pinch of pepper
Directions
- Melt butter in the microwave or on the stovetop.
- Separate the egg yolks from the egg whites (reserve the egg whites for another dish).
- Place the egg yolks in a blender.
- Start the blender (medium to high settings for blend mode is fine).
- Slowly pour the melted butter into the cover opening (it will splatter).
- Add the remaining ingredients.
- Blend for ten minutes (seriously, walk away and do something else).
- Taste and adjust the flavors (add extra lemon juice or salt if desired).
- Serve over your breakfast!
-
 @ 0edc2f47:730cff1b
2024-09-02 15:50:08
@ 0edc2f47:730cff1b
2024-09-02 15:50:08Chef's notes
This recipe works with any fat, although butter is generally preferred and traditional. To make it vegan, substitute vegetable oil for the butter and nut milk for the regular cow’s milk. If you want a smokier flavor, try substituting an equal amount of bacon grease for the butter.
Details
- ⏲️ Prep time: 15 minutes
- 🍳 Cook time: 15 minutes
Ingredients
- 2½ pounds spinach in bulk, or two 10-ounce plastic wrapped bags, blanched, (very well) drained, and chopped (or about 1.75 cups well-drained thawed frozen spinach)
- 1 tablespoon butter
- 1 tablespoon all-purpose flour
- 1 cup milk
- Grated nutmeg (optional, to taste)
- Black pepper (optional, to taste)
- Salt (to taste)
Directions
- Melt the butter (or whatever fat you are using) in a saucepan and add the flour, stirring with a wire whisk.
- Add the milk, stirring rapidly with the whisk. Cook until the mixture starts to bubble and thicken.
- Add nutmeg, salt and pepper to taste.
- Cook, stirring, about 5 minutes and add the spinach. Stir to blend. Continue to cook until spinach is heated through and serve.
-
 @ 0edc2f47:730cff1b
2024-09-02 01:54:55
@ 0edc2f47:730cff1b
2024-09-02 01:54:55Chef's notes
In this case, sweet-and-sour doesn’t mean Americanized Chinese food but rather the sauce that dominated the Shabbos and Pesach dinner table among American Jewish immigrants in the early 20th century.
Details
- ⏲️ Prep time: 30 minutes
- 🍳 Cook time: 6 hours
- 🍽️ Servings: 12
Ingredients
- 1 medium onion, peeled and quartered
- 2 tsp ground ginger
- 8-10 large cloves garlic
- 1 cup ketchup
- ¼ cup dry sherry
- ¼ cup sake
- ¼ cup cider vinegar
- ¼ cup soy sauce
- ¼ cup honey
- ¼ cup Dijon mustard
- 1 tablespoon coarsely ground black pepper
- ¼ teaspoon ground cloves
- 1½ cups Coca-Cola, ginger ale, or Dr. Pepper
- 1 first-cut brisket, 6 to 7 pounds (2.7-3.2kg), rinsed and patted thoroughly dry
Directions
- Preheat oven to 325F / 160C.
- Combine all ingredients except brisket in a blender and blend until smooth.
- Place brisket in a Dutch oven or other large pot with a tight-fitting lid.
- Pour sauce over brisket, place lid on pot, roast in oven for 3 hours. Flip roast and return to oven for 3 hours or until fork tender.
- Remove roast to rest. Skim fat from sauce and reduce if desired. Serve immediately with sauce or cool, cover brisket and refrigerate overnight in cooking pan. The next day, defat sauce, reduce if desired, and reheat meat in sauce before serving.
-
 @ c69b71dc:426ba763
2024-09-01 11:50:28
@ c69b71dc:426ba763
2024-09-01 11:50:28Chef's notes
All you need are your favorite vegetables, nori sheets, a bamboo mat, a cutting board, and a knife. For the dip, you can simply use soy sauce, or try this recipe for a delicious creamy dip.
I make my own cream cheese with soaked cashews, nutritional yeast, salt, lime juice, and vinegar. You can also find vegan cream cheese or cashew cheese at a health food store.
Feel free to add other veggies like bell pepper, chili, cucumber, fresh onion or anything you like! In the image I used also red bell pepper and shiitake.
Details
- ⏲️ Prep time: 20-30 min depending the amount
- 🍳 Cook time: 0
- 🍽️ Servings: 2
Ingredients
- 1 carrot medium size
- 300g cauliflower
- 1-2 leaves of red cabbage
- 1 avocado
- 1/2 cup cream cheese (see chef's note)
- 4 tbsp tamari sauce (organic soy sauce)
- 1 tbsp mustard
- 1 tbsp date syrup (optional any other liquid sweetener of your choice like agave or maple)
- 1 tbsp peanut butter (preferable raw quality)
- 1/2 tsp grated ginger (fresh or powder)
- water
- 1/4 tsp garlic, freshly grated or dried ground
Directions
- Finely grate the cauliflower by hand or in a blender. This is the rice substitute.
- Cut the carrot into thin strips using a vegetable peeler.
- Cut the red cabbage leaves into thin strips and massage them with your hands in a bowl to make them a little more tender.
- Remove the pit from the avocado and take out the flesh and cut it into thin slices.
- Now place the nori sheet on the bamboo mat, spread a thin layer cashew cheese or cream cheese evenly on the nori sheet, cover 2/3 of the sheet with the finely grated cauliflower (as if it was rice, press lightly to hold it together).
- Then use some of the prepared vegetables and roll up the sushi using the bamboo mat.
- Moisten the end with a little water and finish rolling the sushi. Be careful not to fill it with too much of the ingredients and make sure to roll as tight as possible.
- Then you can cut the roll into bite-sized pieces on a wooden board and with a sharp knife. Place the individual rolls on a plate. Continue like this until you have no more vegetables.
- For the sauce, mix all the ingredients (peanut butter, date syrup, mustard, ginger, tamari sauce) in a bowl with a fork and if it is too thick and too salty, add a little water.
-
 @ 5b0183ab:a114563e
2024-08-29 03:34:51
@ 5b0183ab:a114563e
2024-08-29 03:34:51Chef's notes
Growing up there are a few staple foods that stick with you. For me, it was my Grandma Betty's Chicken Dijon. It was my birthday request every year and every time we cook it up it touches my heart. Grandma Betty passed away a 7 years ago. This dish is dedicated to her, directly from her recipe book.
Details
- ⏲️ Prep time: 10
- 🍳 Cook time: 35
Ingredients
- 4 Chicken Breasts
- 3 Tbsp Butter
- 2 Tbsp Flower
- 1/2 Cup Heavy Cream
- 3 Tbsp Dijon Mustard
- Tomato Wedges
Directions
- In large skillet, cook chicken in butter on medium heat till brown on both sides and cooked through (about 20 min)
- Remove chicken and set aside
- Stir flower into skillet drippings. (whisk thoroughly for best flavor)
- Add chicken broth and cream. Whisk until sauce thickens. (about 5 minutes)
- Add dijon mustard and stir to combine.
- Place chicken breasts in skillet. Place lid on skillet and simmer on low. (10 minutes)
- Slice tomato in wedges
- Chop Parsley
- Plate Chicken, pour cream sauce, tomato wedges and garnish with parsley.
- Pairs well with steamed rice or pasta and your favorite vegetable(s) (I prefer sweat peas and Steamed Rice)
-
 @ a3d9328e:5560628c
2024-09-06 15:55:19
@ a3d9328e:5560628c
2024-09-06 15:55:19Keepass, Keepass2, KeepassX, KeepassXC and others... What is the difference?
KeePass is a free and open-source password manager which helps you manage your passwords securely. It is stored in a database, which is locked with a master key and fully encrypted.
I realize that as you read this article, you're likely familiar with password managers and have some knowledge of KeePass or other popular systems such as LastPass, Bitwarden, Dashlane, and 1Password. While all of these options are online and offer limited features in their free versions, they also sell subscription plans. This makes KeePass an excellent alternative in various situations.
## KeePass
The official KeePass is https://keepass.info/, with the initial release in 2003! The newest versions are 2.53 and 1.41 (when I wrote this article), released in January 2023 (less than 5 months after the previous release).
On the site, you will find 2 versions available: KeePass 1.x and KeePass 2.x One is not the evolution of the other! They are developed in parallel, and both are free and open source. However, 1.x uses an older platform and is still supported (2.x is not!).
Both versions use AES 256, with KeePass 2.x through plugins able to add and support other algorithms.
The differences:
KeePass 1.x
Written in C++, runs only on Windows platforms (or using Wine on Linux). The password database has the extension KDB. In addition to AES 256, there is Twofish 256 bits and data authentication/integrity is guaranteed using a plain text SHA-256 hash.
KeePass 2.x
Introduced in 2007, KeePass 2.x offers more support and features than KeePass 1.x, including OTP (One Time Password) support, Smart Cards, an extensive list of plugins, and remote database support. Developed in C# using .NET, it can be run on Linux with Mono. The password database uses the KDBX extension. Besides AES 256, it supports ChaCha20 256-bit encryption, and data authentication/integrity is ensured through an HMAC-SHA-256 ciphertext hash.
In the database versions, there are also changes while KDBX3 uses AES-KDF KDBX4 (most current) uses Argon2.
In this link, there is a developer's table with the comparison between versions: https://keepass.info/compare.html
Here is the list of plugins (with information on which version they support, 1x or 2x): https://keepass.info/plugins.html
Here you can find more details about security differences between versions: https://keepass.info/help/base/security.html Forks and Ports KeePass-Related Projects
KeePassL
A fork of KeePass to run on Linux (when there was no Mono and remembering that KeePass 2.x came out in 2007!).
KeePassX
When KeePass L became cross-platform in 2006, it changed its name to KeePassX. Cross-platform means Mac OS X, Windows and the tarball for Linux. Some third party developers created packages for distros.
KeePassX was officially discontinued in December 2021, with its final release dating back to 2016.
KeePassXC
KeePassXC was introduced in 2012 as a fork of KeePassX due to its extensive development process. Essentially, it continues to serve as a multi-platform port of KeePass 2.x, but is built using C++, eliminating the need for Mono installation on Linux.
It's compatible with both KDBX3 and KDBX4 formats, although the goal is to transition to KDBX4. Additionally, it can import KeePass 1.x (KDB) files, but does not support KeePass 2.x plugins.
It officially has browser extensions! For the others, you need to look for some third-party extensions.
KeeWeb
KeeWeb is a KeePass-compatible fork developed in JavaScript, designed to be multi-platform and function as a web app. Users can access their database either through a browser, with the option to upload their web app instance, or via a client installed on their operating system (Electron). Launched in 2016, KeeWeb is the newest addition to this list, with its latest stable version released in 07/2021. However, the project's GitHub currently lacks a dedicated maintainer.
It is possible, using KeeWeb, to point to the password database directly stored in some provider (like Google Drive, Dropbox, OneDrive or any other that supports webDAV). While the others need to be done another way, like mapping the remote file to the operating system, either by mounting a path (webDAV, samba, NFS, FTP...) or by other means (like Dropbox's client), but for Google Drive, OneDrive and some others, just downloading the file (or using some third-party app like OneDriver or InSync).
For browsers, the project site indicates using the KeePassXC extension.
AuthPass
Similar to KeeWeb, there is AuthPass. Its latest version is from 06/2022 and it seems that its development is more active. Made in Flutter, and multi-platform (including mobile).
KPCLI
Kpcli is a command-line interface (CLI) client compatible with both KeePass 1 and 2 databases (KDB and KDBX family). With the help of bash, you can create scripts to automate password usage via the command line, eliminating the need for a graphical client or KeePass itself. Other ports/forks
On the KeePass site, there is a list: https://keepass.info/download.html
However, on GitHub, there is an even longer list, separated by platform-specific clients, cross-platform clients, mobiles, plugins and tools. https://github.com/lgg/awesome-keepass
Conclusion
Let me help you decide which version of KeePass is best for you.
Do you use Windows? Give KeePass2 a try. If you're not interested in KeePass 2.x, no worries! Just refer to the list above and pick any alternative that suits you. ;-)
Are you a Linux user? Give KeePassXC a try.
Concerned about usability and compatibility across multiple operating systems? Try KeePassXC on Linux, Windows, or Mac for a seamless experience.
Looking to use it in your browser, just like those paid/freemium competitors? Give KeePassXC a shot and simply install the official extension.
Looking to access it on Android as well? Give KeePassDX a try. It's compatible with all password database versions (KDB, KDBX...), ensuring seamless integration with any desktop app you choose. If you opt for AuthPass, it's the only one with an official Android version. For all other options, you'll need to depend on apps developed by third parties.
Moreover, implement 2FA/MFA for every feasible application! When faced with a choice between two services or websites, opt for the one that provides 2FA/MFA (ideally through an app rather than SMS).
I originally posted this article on my blog at https://esli.blog.br/which-keepass-version-is-best-for-me The text is also versioned in markdown on my github profile and I decided to post it here as a first test and perhaps migrate the other texts I've written.
-
 @ 113958ea:f1ce9557
2024-09-06 14:27:03
@ 113958ea:f1ce9557
2024-09-06 14:27:03 -
 @ c73818cc:ccd5c890
2024-09-06 13:22:32
@ c73818cc:ccd5c890
2024-09-06 13:22:32
😎 L'FBI mette in guardia le aziende statunitensi contro sofisticati attacchi di ingegneria sociale orchestrati da hacker nordcoreani, volti a rubare asset digitali dai fondi negoziati in borsa (ETF) legati alle criptovalute.
😎 Gli hacker nordcoreani stanno intensificando gli attacchi contro le aziende statunitensi coinvolte negli ETF di criptovaluta, utilizzando tecniche avanzate di ingegneria sociale. Questi attacchi mirano a rubare asset digitali attraverso l'inganno e la manipolazione delle vittime.
😎 Secondo l'FBI, gli attacchi includono impersonificazioni e scenari falsi, come offerte di lavoro o opportunità di investimento, per ingannare i dipendenti del settore DeFi e criptovalute. La ricerca pre-operativa dettagliata consente agli hacker di sfruttare specifici interessi e connessioni.
😎 L'FBI esorta le aziende a implementare rigorose misure di sicurezza, come l'autenticazione multifattoriale e la verifica delle identità. Con un'attenzione particolare alla protezione degli asset digitali, queste precauzioni possono aiutare a mitigare i rischi posti dalle sofisticate minacce informatiche nordcoreane.
Unisciti al nostro gruppo Telegram: https://t.me/Bitcoin_Report_Italia
Referral Bitget -10% sulle fee + bonus benvenuto 6w5d o link: https://bonus.bitget.com/U1JNEK
BitcoinReportItalia #FBI #Hacker #Nordcoreani #ETF #Investimento #Furto #Sicurezza #Asset #Hacking #Transazioni #Cripto #Bitcoin
-
 @ 3bf0c63f:aefa459d
2024-09-06 12:49:46
@ 3bf0c63f:aefa459d
2024-09-06 12:49:46Nostr: a quick introduction, attempt #2
Nostr doesn't subscribe to any ideals of "free speech" as these belong to the realm of politics and assume a big powerful government that enforces a common ruleupon everybody else.
Nostr instead is much simpler, it simply says that servers are private property and establishes a generalized framework for people to connect to all these servers, creating a true free market in the process. In other words, Nostr is the public road that each market participant can use to build their own store or visit others and use their services.
(Of course a road is never truly public, in normal cases it's ran by the government, in this case it relies upon the previous existence of the internet with all its quirks and chaos plus a hand of government control, but none of that matters for this explanation).
More concretely speaking, Nostr is just a set of definitions of the formats of the data that can be passed between participants and their expected order, i.e. messages between clients (i.e. the program that runs on a user computer) and relays (i.e. the program that runs on a publicly accessible computer, a "server", generally with a domain-name associated) over a type of TCP connection (WebSocket) with cryptographic signatures. This is what is called a "protocol" in this context, and upon that simple base multiple kinds of sub-protocols can be added, like a protocol for "public-square style microblogging", "semi-closed group chat" or, I don't know, "recipe sharing and feedback".
-
 @ e97aaffa:2ebd765d
2024-09-06 10:27:57
@ e97aaffa:2ebd765d
2024-09-06 10:27:57«Only 10 of the 190 taxes collect 90% of the total revenue. The other 180 taxes don’t cause direct economic damage but they generate obstacles, delays and an endless number of procedures that hinder economic activity in a country where making money is already an impossible task»
Eu concordo plenamente com este pensamento do Javier Milei e tinha a convicção que a situação de Portugal é muito similar, por isso fiz o meu “Don’t Trust, verify”.
Receita tributária
Foi analisar o caso de Portugal, as receitas tributárias de 2023:
«Carga fiscal subiu para 95 mil milhões de euros. Mas cai para 35,8% do PIB em 2023» – ECO
Se o objetivo final da estatística é para efetuar uma comparação entre países, é necessário efetuar a divisão pelo PIB. Mas se a análise é apenas para comparações internas ou homólogas, não faz qualquer sentido efetuar a divisão. Com a divisão dos valores pelo PIB, mascaramos a realidade, sobretudo em períodos inflacionários, porque o crescimento do PIB não é real, é uma consequência da inflação. A melhor maneira para analisar as estatísticas internamente é utilizar o valor nominal.
No relatório do INE, os impostos são divididos em 3 grupos: * Impostos Diretos * Impostos Indiretos * Contribuições Sociais
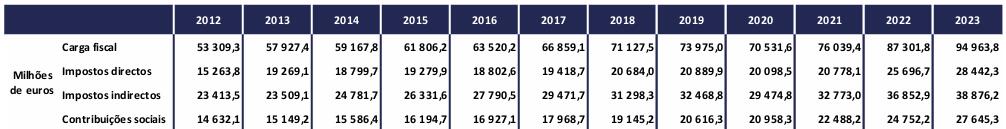
Segundo esses dados, nos últimos anos, tem acontecido um enorme crescimento da arrecadação fiscal por parte do estado, a única exceção foi 2020, devido ao covid. De 2019 a 2023, o aumento foi de quase 30%. Ou seja, totalmente oposto à ideia (divisão pelo PIB) que os governos gostam de propagandear.
Para termos uma comparação, no mesmo período, o salário mínimo nacional(Portugal) subiu 27%, mas o salário médio apenas subiu 17%. As pessoas estão a perder poder de compra.
A tabela seguinte é a compilação dos dados:
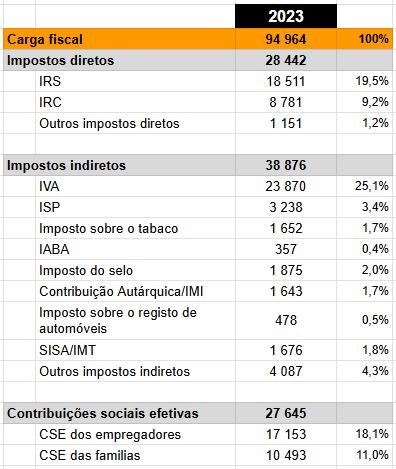
O IVA é o imposto com maior arrecadação, corresponde a aproximadamente a 25% do total da arrecadação fiscal, seguido pelo IRS, com 19.5%. É curioso que a constituição portuguesa, defende que os impostos devem ser progressivos, ou seja, quem ganha mais, deve pagar mais.
Artigo 104.º (Impostos) 1. O imposto sobre o rendimento pessoal visa a diminuição das desigualdades e será único e progressivo, tendo em conta as necessidades e os rendimentos do agregado familiar. 2. A tributação das empresas incide fundamentalmente sobre o seu rendimento real. 3. A tributação do património deve contribuir para a igualdade entre os cidadãos. 4. A tributação do consumo visa adaptar a estrutura do consumo à evolução das necessidades do desenvolvimento económico e da justiça social, devendo onerar os consumos de luxo.
Mas o IVA é um imposto cego, onde os principais afetados são os mais pobres, totalmente oposto ao que a constituição diz, sem justiça social.
Somando os 10 maiores impostos, resulta em 93.6% da receita fiscal, é similar à situação da Argentina:
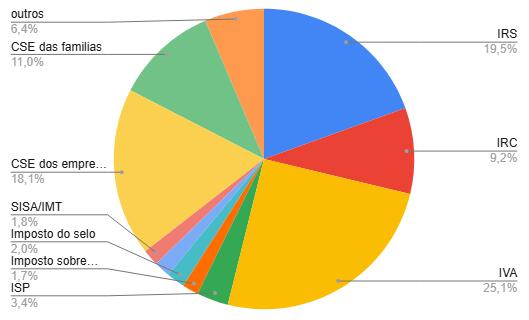
A quantidade de impostos em Portugal é tal, que a maioria deles nem aparece nos relatórios, apenas ficam nas secções “outros”. Curiosamente, perguntei a uma AI, quantos impostos existem em Portugal, mas a AI, esquivou-se à resposta.
Em Portugal, existem cerca de 20 impostos principais, incluindo os mais conhecidos como o IRS, IRC, IVA, IMI, e IMT. Além desses, há vários outros impostos e taxas específicas que podem ser aplicáveis em diferentes situações.
Eu insisti mais que uma vez, mas ele nunca deu um número concreto. Possivelmente, nem o governo sabe quantos impostos existem…
Conclusão
Em Portugal e na Argentina, a esmagadora receita fiscal acontece, sobretudo em apenas 10 impostos, os restantes são residuais na receita do governo mas gera uma enorme burocracia nas empresas e nas pessoas.
Se muitos desses "mini" impostos fossem eliminados, permitia uma maior dinamização do mercado, gerando crescimento económico e mais empregos. Nos fins das contas, o estado acabaria por arrecadar mais receitas através dos outros impostos, sobretudo no IVA. Em certos casos, é provável que custos operacionais para o estado são superior à propria arrecadação fiscal desse respectivo imposto. Sem esquecer os casos de impostos sobre impostos, da dupla tributação, como acontece na compra de um automóvel. A curva de Laffer, há muito que foi ultrapassada em Portugal.
Além de prejudicar a economia diretamente, esta enorme quantidade de taxas, taxinhas e burocracias, tem um efeito perverso no “estado”. Os estados necessitam de muitos meios físicos e humanos para efetuar a gestão, fiscalização e a recolha desses impostos, além disso, a burocracia leva ao surgimento da corrupção. A burocracia é criada propositadamente pelos políticos para atrapalhar a vida dos cidadãos, com o objectivo final de beneficiar terceiros, como advogados ou lobis ou os próprios políticos. A receita fiscal é mínima, mas é um incentivo à corrupção, isto é especialmente visível a nível mais local, nas autarquias. Qualquer coisa que se faça, sobretudo a nível de obras, é necessário uma infindável quantidade de autorizações, papeladas e claro, muitas taxinhas. Devido a essa burocracia, qualquer licenciamento demoram meses a anos, no meio disto tudo, existem empresários/pessoas impacientes, que desesperam com a tremenda demora e acabam por colocar uma notinha no bolso de alguém importante, para que este acelere o processo. Coisas que normalmente demorariam meses, são aprovadas em semanas, a burocracia incentiva a corrupção.
Portugal necessita urgentemente de uma simplificação fiscal, se houvesse vontade política para mudar, o governo poderia diminuir drasticamente o número de impostos sem diminuir a arrecadação fiscal. Se esta mudança, eles não são capazes de a fazer, muito menos vão fazer uma mudança que provoque uma redução da arrecadação fiscal. Eu acho que Portugal vai seguir o caminho oposto, em vez de simplificar, vai é criar ainda mais novos impostos, porque como os atuais impostos já estão demasiado elevados, é extremamente impopular aumentá-los ainda mais, a maneira mais simples para o governo é criar novos impostos para aumentar a arrecadação fiscal.
Os governos modernos só olham para o aumento da arrecadação/impostos, "esquecem” por completo a redução de gastos, a eficiência. Resumindo, isto é o mundo FIAT.
-
 @ 6bae33c8:607272e8
2024-09-06 08:16:48
@ 6bae33c8:607272e8
2024-09-06 08:16:48I got back into the Circa Survivor Contest this year at great cost (my flight out of Palm Springs on July 5 was cancelled due to heat, so I had to rent a car and drive through the Mojave Desert, and the road to Vegas was closed, so I had to double back another 100 miles, which in total took six hours), so this is Team Of Destiny 2.0. Or at least it had better be.
I’m not going to stick to any one method or philosophy. Put differently, I realize that in order to win, I need to go into the future, find out what has already happened and pick on that basis. Pot odds is great, but even if you do that properly every week, your edge over the field isn’t that huge. Instead of a 1 in 10,000 chance to win, maybe you have 1 in 6,500. Sure, if you had 100 entries in every high stakes contest, it might be enough to eke out a reliable profit, but I’m not here for that. I’m here to navigate one boat through the icebergs and take down the $10M. And for that, you can’t hope to get lucky. You have to know in advance.
What method do I propose to see into the future? Only my imagination. I’m going to spend a lot of time imagining what might happen, turn my brain into a quantum device, break space-time and come to the right answers. Easier said than done, but I’m committed.
. . .
In any event, let’s take a look at the slate: Here are the ownership numbers per Officefootballpools.com.

The pot-odds play is the Bills if you buy into the Vegas numbers — Bengals roughly 78.5 and the Bills at 72.6%. That means the Bengals have a 21.5% chance to lose, the Bills 27.4%. That’s a 27.4 percent increase in risk (coincidentally.)
But if the Bengals lose they take out 39 people, and if the Bills lose they take out only 15. Let’s assume another 20-odd people lose with other teams (in a hypothetical 100-person pool) and you’re down to 41 if the Bengals lose/Bills win, 65 if the Bills lose/Bengals win.
If we say each person put in $10, the former scenario is $1000 (total pot)/41 = $24.39, and the latter $1000/65 = $15.38. The ratio of 24.39/15.38 = 1.59. In other words, you have 59 percent percent more equity in Week 2 on the Bills if the Bengals lose than you would on the Bengals if the Bills lose.
You’re talking a 27.4 percent greater risk for a 59 percent greater reward. So normally I’d snap call the Bills.
But I’m probably going Bengals because I think the Cardinals are dangerous this year, and the Pats are arguably the worst team in the league and in surrender mode after they dealt Matthew Judon to the Falcons. (All this is supposed to be priced in, of course, but I don’t care.)
I’ll finalize my pick before Saturday’s deadline, but that’s how I see it for now.
-
 @ 6bae33c8:607272e8
2024-09-06 08:14:27
@ 6bae33c8:607272e8
2024-09-06 08:14:27An odd thing happened — I squinted when opening my laptop this morning so as not to see the final score, but I thought I read a headline saying the Ravens beat the Chiefs. Maybe it was a cached headline from the night before saying what they’d have to do to beat the Chiefs? but I shut the laptop and logged into my Apple TV account to stream the game on the TV, fully expecting the Ravens to win. I mean up until the moment they overturned the Isaiah Likely TD, I thought the Ravens would win. Funny, but not funny because I picked the Ravens in my low-stakes picking pool, and I HATE starting off the week 0-1, no matter the stakes.
In any event, it was an okay game, not great, but there were some interesting takeaways.
-
Derrick Henry looked fine but is going to do almost nothing in the passing game. He had two awkward targets, but Justice Hill was in the game on passing downs and during the end-of-half two-minute drill. Plus Lamar Jackson almost always takes off when he’s in trouble, so if the play isn’t a designed pass to the back, which will be rare for Henry, he’s not getting the ball except via handoff.
-
Jackson looked smooth to me and he’ll have a huge year for as long as he can stay healthy, especially now that Isaiah Likely looks like a real threat. But at 6-2, 205, 16 carries per game is a big ask.
-
Likely looked great. On his long TD, he made great moves, and even on the TD that was overturned, he showed great footwork to make it that close. I’m awfully curious to see where the near-invisible Mark Andrews slips in my NFFC Primetime tonight. (I think Round 8 or so, and I’d have to think about it.)
-
Rashod Bateman had five targets, four of them down the field. He’s their field stretcher, and though it was a quiet day, there should be more.
-
Zay Flowers got 10 targets (good), but it was dink and dunk stuff. To be honest, Likely (12 targets!) looked like the WR1, the alpha running the intermediate routes, Bateman the deep guy and Flowers the midget in the slot.
-
Patrick Mahomes didn’t have a big game, but that was against a top defense and he still got 10.4 YPA. And they were missing one of their field stretchers in Hollywood Brown.
-
Rashee Rice was the story for the Chiefs IMO. He had nine targets and made it look so easy, like Cooper Kupp schemed open on the Rams a few years ago. Xavier Worthy scored twice, but on only three targets even without Brown. He did look awfully fast, though.
-
Isiah Pacheco ran hard against a tough defense, but didn’t do much as a receiver. He’ll be fine — I wouldn’t move his stock much after this game.
-
Travis Kelce had a quiet night, but I wouldn’t read much into it. It’s not like Noah Gray is Likely to take his role.
-
After all these years, I finally ditched the loyal Justin Tucker for a Younghoe, and I feel like a new man. It still brought me no joy to see him miss that 53-yard FG.
-
You have to love Steak League IDP Roquan Smith getting a pick for you opening night.
-
-
 @ a012dc82:6458a70d
2024-09-06 08:07:02
@ a012dc82:6458a70d
2024-09-06 08:07:02Table Of Content
-
Why is there a Projection of Bitcoin Adoption Increase by 50% by 2025?
-
What are the Potential Challenges for Bitcoin Adoption?
-
What is the Impact of Bitcoin Adoption on the Global Economy?
-
Conclusion
-
FAQ
Bitcoin, the world's first and largest cryptocurrency, has been gaining momentum and popularity over the years. With its decentralized and secure nature, Bitcoin has become a preferred mode of payment and investment for many individuals and businesses. The cryptocurrency has been making headlines for its unprecedented price surges, with its value surpassing $60,000 in early 2021. However, it has also experienced significant price drops and market volatility. Despite this, experts predict that Bitcoin adoption will continue to increase, with a projected 50% growth by 2025.
Why is there a Projection of Bitcoin Adoption Increase by 50% by 2025?
There are several reasons why experts are predicting a significant increase in Bitcoin adoption by 2025:
Increased institutional investment: Over the past few years, more and more institutional investors, such as banks and hedge funds, have been investing in Bitcoin. These investments bring legitimacy and stability to the cryptocurrency market, making it more appealing to individual investors.
Global economic uncertainty: The COVID-19 pandemic has had a significant impact on the global economy, causing many individuals and businesses to re-evaluate their investment strategies. With traditional investments, such as stocks and bonds, experiencing volatility, Bitcoin's decentralized nature and limited supply make it an attractive investment option.
Growing acceptance and adoption: As more businesses and individuals accept Bitcoin as a mode of payment, its adoption rate continues to increase. This trend is expected to continue, with more merchants and payment processors accepting Bitcoin.
Increased regulation: While some argue that increased regulation may stifle Bitcoin's growth, others believe that it will bring greater legitimacy and stability to the cryptocurrency market. As governments and regulatory bodies create clearer guidelines and regulations for cryptocurrencies, it is likely that more individuals and businesses will feel comfortable investing in Bitcoin.
What are the Potential Challenges for Bitcoin Adoption?
While the projected increase in Bitcoin adoption is promising, there are still potential challenges that may hinder its growth:
Market volatility: Bitcoin's value is subject to market fluctuations, which can be unpredictable and lead to significant price drops. This volatility may discourage some investors from investing in Bitcoin.
Security concerns: While Bitcoin's blockchain technology is secure, there have been instances of hacking and theft. These security concerns may discourage some individuals and businesses from accepting Bitcoin as a mode of payment or investing in it.
Regulatory challenges: As governments and regulatory bodies work to create clearer guidelines and regulations for cryptocurrencies, there may be challenges in achieving a balance between regulation and innovation. Overly restrictive regulations may hinder Bitcoin's growth and adoption.
Energy consumption: Bitcoin mining requires significant energy consumption, which has led to concerns about its environmental impact. As more attention is given to climate change and sustainability, these concerns may hinder Bitcoin's growth.
What is the Impact of Bitcoin Adoption on the Global Economy?
The projected increase in Bitcoin adoption has the potential to have a significant impact on the global economy:
Increased investment opportunities: As Bitcoin adoption grows, more investment opportunities may arise, creating new revenue streams and job opportunities.
Greater financial inclusion: Bitcoin's decentralized nature and accessibility have the potential to provide greater financial inclusion for individuals who may not have access to traditional banking services.
Disruptive technology: Bitcoin's blockchain technology has the potential to disrupt traditional financial systems, creating new opportunities for innovation and growth.
New challenges: With disruptive technology comes new challenges, such as the need for clear regulations and guidelines, as well as addressing potential security concerns.
Shift in power dynamics: Bitcoin's decentralized nature challenges traditional power structures, such as those held by central banks and governments. This shift in power dynamics may lead to changes in the way financial systems operate globally.
Impact on traditional banking systems: As Bitcoin adoption continues to grow, traditional banking systems may experience disruptions. Banks may need to adapt to the changing landscape by incorporating blockchain technology or other innovative solutions.
Conclusion
Experts predict that Bitcoin adoption will increase by 50% by 2025, driven by increased institutional investment, global economic uncertainty, growing acceptance and adoption, and increased regulation. While there are potential challenges to Bitcoin's growth, such as market volatility, security concerns, regulatory challenges, and energy consumption, the projected increase in Bitcoin adoption has the potential to have a significant impact on the global economy. As Bitcoin continues to gain momentum and popularity, it's important for individuals and businesses to understand the risks and potential rewards involved in investing in this cryptocurrency.
FAQ
Will increased Bitcoin adoption lead to greater financial inclusion? Yes, increased Bitcoin adoption has the potential to provide greater financial inclusion, as it enables individuals without access to traditional banking systems to participate in the global economy.
How can individuals buy Bitcoin? Individuals can buy Bitcoin through cryptocurrency exchanges, peer-to-peer marketplaces, and Bitcoin ATMs. It's important to do your research and choose a reputable platform to ensure secure transactions.
Can Bitcoin be used for everyday transactions? Yes, Bitcoin can be used for everyday transactions, but its use is still limited compared to traditional currencies. However, as Bitcoin adoption increases, more merchants may start accepting it as a mode of payment.
What is the environmental impact of Bitcoin mining? Bitcoin mining requires significant energy consumption, which has raised concerns about its environmental impact. However, some argue that the use of renewable energy sources for mining can help mitigate this impact.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 3c9712ff:14fecbc4
2024-09-06 02:20:21
@ 3c9712ff:14fecbc4
2024-09-06 02:20:21Over the past week, the south-east corner of Australia experienced a battering from mother nature.
High winds and unseasonably hot winter days caused Australia's wind and solar network to run at near maximum capacity. However, this wasn’t necessarily beneficial.
 Article from the Australian Financial Review
Article from the Australian Financial ReviewGrid Operation 101
Energy is produced and consumed almost simultaneously. This real-time mechanism makes the energy grid one of the fastest and most responsive systems in existence.
When the grid operates at peak efficiency, everyone who needs power can access it, and anyone producing power can sell it. Energy must be generated and balanced continuously, regardless of the weather. It’s not good enough to produce abundance of energy when people don’t want it, just to fall short when they do.
Since solar and wind cannot consistently maintain a balance between supply and demand, coal remains the backbone of Australia's energy grid, providing reliable base-load power and being supplemented during peak times.
Too Much Energy?
Apart from the environmental benefits, the key advantage of renewable energy lies in its abundance. However, because we don’t control when the sun shines or the wind blows, this often results in a mismatch between supply and demand. At times, energy supply can sometimes double or even triple demand. Since it’s usually too expensive to shut down solar and wind farms, this leads to stranded or curtailed energy, and consequently wholesale electricity prices can drop into negative territory.
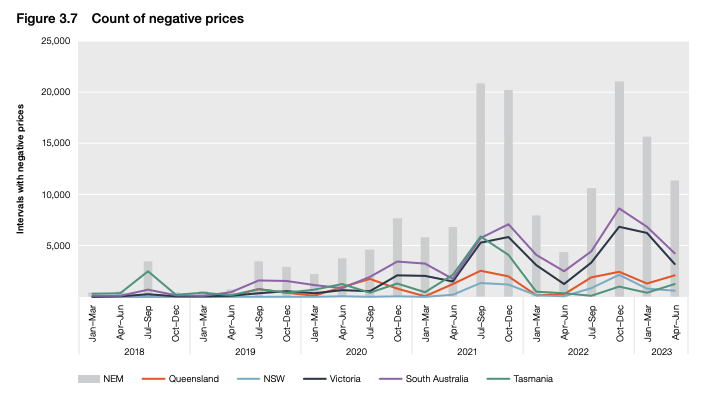 Instances of negative prices have risen since 2018.
Instances of negative prices have risen since 2018.The rise of negative electricity prices across the eastern seaboard has closely correlated with the expansion of renewable infrastructure. Since 2017, Australia has been actively seeking solutions to absorb the excess supply and restore efficiency to the energy system.
Solution 1 - Batteries
This idea makes the most intuitive sense to the average person. If we can't immediately use the power generated by a roaring wind turbine to power a family home, why not store it until peak demand and then release that cheap energy back into the grid?
The answer is twofold, 1. The buildout of these projects are expensive, 2. Storage capacity is minimal.
The Victorian Government's Big Battery initiative has the ability to power 1m Victorian homes for only 30 minutes and was built to a tune of $160m.
I always love technological innovation and perhaps one day all Australian houses will be powered by sea of solar panels and batteries in the middle of desert however it's evident we at least need an interim solution.
Solution 2 - Bitcoin Mining
We’ve all heard the same FUD. Critics prey on readers' misunderstandings of how the grid operates, portraying a vision where miners supposedly divert power away from households and businesses to feed this energy hungry beast into what they call a "worthless internet currency" and drive prices up.
However, if we incorporate Bitcoin mining's energy usage into what we've learned about grid operations, we can see how it can actually bolster renewable energy for two reasons:
Runtime Flexibility - Mining is an operation with razor thin margins and is only profitable with cheap electricity. Since this only occurs when energy has low to no demand (stranded), miners are not competing with households and businesses.
Mobility - Bitcoin miners are highly mobile and are often built right next to the power source, reducing transmission losses and optimising energy use at the source.
However one might feel about the net zero goals, there is no denying we should always prioritise reliability over sheer abundance. It's time Australia utilises the power of bitcoin to help stabilise our renewable grid to push forth to a sustainable future.
-
 @ c7eadcf0:7821e562
2024-09-06 00:10:23
@ c7eadcf0:7821e562
2024-09-06 00:10:23Who would have thought that we would have the change to buy sub 60K Bitcoin again? With all the talk of mooning after the halving, seeing Bitcoin's price back around 56k at the time of this post is disappointing to the lettuce handed, ETF buying individuals that are not here for the revolution, but to make a quick buck.
Bitcoin being a neutral money, it is not unexpected that it would gain the attention of these types of people. I am actually glad that they are participants in this market has it helps transfer Bitcoin from weak unconverted holders to people who are fully dyed in the orange wool of the Bitcoin thesis.
Every time there is some geopolitical event, or some kind of economic crisis brewing on the other side of the world, Bitcoin normally takes a hit because it is a high liquid asset. This should be taken as a good sign when the price goes down as it shows that you can easily move in and out of Bitcoin with relative ease. Try doing that with your house, car or other assets. Sure you can sell them eventually but its not nearly as seamless as Bitcoin.
This lull in price will not last long, so if you got some dry powder sitting on the sidelines, today is a good day to buy some cheap corn. Framing Bitcoin as a liquid asset that can be sold in times of need is a good way to introduce Bitcoin to your nocoiner friends and family. I would hate for them to have to buy Bitcoin at much higher prices. Good for us. Bad for them. Amirite?
Just a short post from the Obsidian Nostr Writer Plugin. If you like writing long from content, I would highly recommend giving it a shot! Peace out.
-
 @ 472f440f:5669301e
2024-09-05 22:25:15
@ 472f440f:5669301e
2024-09-05 22:25:15https://x.com/parkeralewis/status/1831746160781938947 Here's a startling chart from an American staple, Walgreens. The convenience store and pharmacy chain has seen its stock price plummet by more than 67% this year and by more than 90% from its all time high, which was reached in 2015.
The combination of the COVID lock downs and the lax laws around theft that followed were materially detrimental to Walgreens business. The crux of their problem at the moment, however, is a double whammy of those disruptions in their business coupled with the "higher for longer" interest rate policy from the Fed over the last couple of years. As Tuur points out in the tweet above, Walgreens has $34B in debt, which means they definitely have significant interest rate payments they need to make on a monthly basis. Tuur also points out that Walgreens has very little cash compared to their debt obligations. Let's take a look at their balance sheet as of May of this year.
Less than $1B in cash for $34B debt with $67.56B in total liabilities. Even worse, their cash balance was drained by more than 27% over the course of the year between May 2023 and May 2024. As you may notice their total assets fell by more than 15% over the same period. This is because Walgreens understands the dire financial straits it finds itself in and has begun shutting down thousands of their locations across the country.
The recent efforts of Walgreens to sell off their assets to raise cash to pay down their debts seem to be completely ineffective as their cash balance is falling faster than their total assets, which is falling 7x faster than their total liabilities. These numbers are most definitely going to get worse as cascading sell pressure in commercial real estate markets (which is the bucket that Walgreens locations fall into) drive down the value of their assets. Leaving them with less cash to pay down their debts as time goes on. To make matters worse, it puts the institutions that lent money to Walgreens in a terrible position. How many commercial and investment banks has Walgreens tapped to fund their operations with expensive debt? How exposed to Walgreens is any individual lender? Could a default on some or all of their loans catch these financial institutions off sides? If it isn't Walgreens that pushes them off sides, how many more bad borrowers would it take to push them off sides?
As our good friend Parker Lewis points out, the only way the hemorrhaging can be stopped is if the Federal Reserve and Federal Government step in with bail outs in the form of massive liquidity injections via quantitative easing and other emergency measures. On top of this, the Fed and the Federal Government find themselves in a classic catch-22. If they let Walgreens fall into bankruptcy it could set off a domino effect that could exacerbate inflation. Riteaid, a similar retail convenience store and pharmacy chain, filed for bankruptcy last October and is still wading its way through that process. Part of that process has been shuttering many of their storefronts. One has to imagine that since Walgreens and Riteaid are having these problems, some of their other competitors must be feeling the pain as well. If enough of these convenience stores, which tens of millions of Americans depend on for everyday goods, find themselves in a position where they have to shut down their stores it could lead to a supply crunch. People will obviously not be able to get their goods from Riteaid or Walgreens and will flee to alternatives, exacerbating the stress on their supplies, which will drive prices higher.
This is a catch-22 because the only way to avoid this mad dash for consumer goods in the midst of a convenience store Armageddon is to re-introduce ZIRP and flood the market with freshly printed dollars, which will drive prices up as well.
Talk about a rock and a hard place. You better get yourself some bitcoin.
Final thought... Zach Bryan radio crushes.
-
 @ e771af0b:8e8ed66f
2024-09-05 22:14:04
@ e771af0b:8e8ed66f
2024-09-05 22:14:04I have searched the web for "Find bitcoin block number from historical date" maybe 100 times in my life.
Never again.
You'll need a bitcoin node for this to work. The script is fast.
Install
WoT Install
one liner ```
curl
curl -o fjb.sh https://gist.githubusercontent.com/dskvr/18252c16cf85c06c1ee6cb5ae04a3197/raw/34bad6a35d98501978c8cd0c25b1628db1191cfe/fjb.sh && chmod +x fjb.sh
wget
wget -O fjb.sh https://gist.githubusercontent.com/dskvr/18252c16cf85c06c1ee6cb5ae04a3197/raw/34bad6a35d98501978c8cd0c25b1628db1191cfe/fjb.sh && chmod +x fjb.sh ```
Trust no one.
create file ``` vi fjb.sh
or
nano fjb.sh ```
review, copy and past into file ``` TIMESTAMP=$1 LOWER=0 UPPER=$(bitcoin-cli getblockcount)
while (( LOWER <= UPPER )); do MID=$(( (LOWER + UPPER) / 2 )) BLOCKHASH=$(bitcoin-cli getblockhash $MID) BLOCKTIME=$(bitcoin-cli getblockheader $BLOCKHASH | jq .time)
if (( BLOCKTIME < TIMESTAMP )); then LOWER=$(( MID + 1 )) elif (( BLOCKTIME > TIMESTAMP )); then UPPER=$(( MID - 1 )) else echo "$BLOCKTIME" exit 0 fidone
echo "$UPPER" ```
give executable permissions
chmod +x ./fjb.shUsage
./fjb.sh <timestampSeconds>It returns block number onlyExample
$: ./fjb.sh 1668779310 763719 -
 @ 361d3e1e:50bc10a8
2024-09-05 20:32:32
@ 361d3e1e:50bc10a8
2024-09-05 20:32:32A wave of criticism against a supermodel who chose alternative cancer treatment, and yet she was cured
cancer #alternative #health #medicine #model #treatment #usa #showbiz
-
 @ 97c70a44:ad98e322
2024-08-29 00:50:27
@ 97c70a44:ad98e322
2024-08-29 00:50:27Nostr is a mess. It always has been and will always be. That's part of the appeal! But it's important that users be able to navigate the rolling seas of this highly partition-tolerant network of kaleidoscopically-interwoven people, bots, topics, relays, clients, events, recommendations, lists, feeds, micro-apps, macro-apps, Chinese spam, and "GM"s.
In order to do this, users must be able to articulate "what" they are looking for, and clients must be able to articulate "how" to find that thing. This "how" is divided into two parts: building a request that will match the desired content (very easy), and selecting a relay that is able to serve that content to the user requesting it (very very hard).
Why guessing isn't good enough
As a concrete example, let's say the user wants to find everyone in their "network" who is using a particular topic. The process would look something like this:
- The user clicks the "network" tab and types in the topic they want to browse. This is the "what".
- The client then translates the term "network" to a list of public keys using whatever definition they prefer (Follows? WoT? Grapevine?), and builds a filter that might look something like this:
[{"authors": pubkeys, "#t": ["mytopic"]}]. Any relay will happily accept, understand, and respond to that filter. - The client then has to decide which relays it should send that filter to. This is the
???stage of the outbox model, which immediately precedes: - Profit
It may not be immediately obvious why selecting the correct relays might be difficult. Most people post to relay.damus.io, and most people read from relay.damus.io, so in most cases you should be good, right?
This approach to relay selection has historically worked "well enough", but it depends on a flawed definition of success. If you only want to find 90% of the content that matches your query, using the top 10 relays will suffice. But nostr is intended to be censorship-resistant. What if those 10 hubs have banned a particular public key? Nostr clients should (at least in theory) be 100% successful in retrieving requested content. Even if someone only posts to their self-hosted relay, you should be able to find their notes if their account is set up properly.
A naive solution to fixing the FOMO
A 90% hit rate results in a feeling of flakiness, even if users aren't completely aware of what isn't working. Feeds will be incomplete, quoted notes will be missing, replies will be orphaned, user profiles won't load. The natural response to the FOMO this creates is for users to "try harder" by adding more relays.
On the read side, this means clients open more connections, resulting in much higher data transfer requirements, with massively diminishing returns, since there's no reason to expect that a randomly chosen relay will have a substantially different data set.
One the publish side, this means that clients end up publishing more copies of their data to more relays. This approach has been automated in the past by services like Blastr, which don't store a copy of events published to the relay, but instead forward events to the top 300 relays in the network. This results in a two-orders-of-magnitude increase in storage required, and only makes the read side of the problem worse, since it reduces the uniqueness of the data set each relay stores. This in turn means that more duplicates are retrieved when querying relays.
Both halves of this approach are equivalent to guessing. On the read side, users are guessing which relays will have any arbitrary content they might ask for in the future. On the write side, users are guessing which relays other people might use to find their notes. It is a brute-force method for finding content.
Randomness results in centralization
In theory, random relay selection would result in a perfect distribution of content across all relays in the network. But in practice, this method of selection isn't random at all, but is strongly influenced by user bias in what constitutes a "good" relay. While some users may check nostr.watch for ping times, geographical proximity, or uptime, most will choose relays based on familiar names or other people's recommendations.
In either case, these biases are entirely orthogonal to achieving a higher content retrieval hit rate, except when bias in relay selection results in clustering — i.e., centralization. In other words, the kind of randomness exhibited by users when selecting relays actually results in pretty much everyone picking the same few relays. We see this same effect when people try to come up with passwords or seed phrases — human-provided randomness is anything but random.
Clustering improves the hit rate when requesting events (slightly), but it results in nearly as much centralization as if only a single relay was used — and a lot more duplicate events.
Something (anything) other than randomness
In early 2023, Mike Dilger introduced NIP 65 (now known as the "Outbox Model") with a problem statement in the spirit of the original description of nostr: "Nostr should scale better. People should be able to find what they want."
Historical note: NIP 65 was formerly known as the "Gossip Model", derived from the name of Mike's desktop nostr client, called "Gossip". This unfortunately created a lot of confusion, since gossip protocols work very differently from how nostr tends to work, hence the re-brand.
Before NIP 65, an informal standard existed in which
kind 3user contact lists also included a list of relays that clients could use as something similar to Mastodon's "home servers". This list included the option to only read or write from a given relay. Unfortunately, it wasn't really clear what the semantics of this relay list were, so different clients handled them differently (and many clients ignored them). Usually this amounted to user-provided static relay configurations, which resulted in the naive relay selection approach described above.NIP 65 used a very similar format (a list of relay urls with optional "read" or "write" directives), but with a very important semantic difference: relays listed in a user's
kind 10002were intended to "advertise to others, not for configuring one's client." In other words, these relay selections were intended as a signal to other users that they should use certain relays when attempting to communicate with the author of the relay list.I highly recommend reading the entire NIP, which is very short and easy to read. But the mechanics of the spec are very simple:
When seeking events from a user, Clients SHOULD use the WRITE relays of the user's
kind:10002.When seeking events about a user, where the user was tagged, Clients SHOULD use the READ relays of the user's
kind:10002.When broadcasting an event, Clients SHOULD:
- Broadcast the event to the WRITE relays of the author
- Broadcast the event to all READ relays of each tagged user
For the first time, we had a way to differentiate relays in terms of what content could be found where.
When looking for a note by a particular user, a client could now look up the author's
writerelays according to theirkind 10002event, and send its query there. The result is a much higher hit rate with much lower data transfer requirements, and fewer connections per query.Making Outbox Work
There are of course some assumptions required to make this work.
First, the user must know which author they're looking for. This isn't always true when looking up a quote or parent note, but context and pubkey hints solve this difficulty in most cases.
The author must also publish a
kind 10002event. This may not always be the case, but clients should prompt users to set up their relay list correctly. This isn't really a flaw in the Outbox Model, just in implementations of it.Additionally, the user's client must be able to find the author's
kind 10002event. This is the "bootstrapping" phase of the Outbox Model, during which the mechanisms the system provides for finding events aren't available. This requires us to fall back to randomly guessing which relays have the content we're looking for, which as we saw above doesn't work very well.Other than guessing, there are a few different ways a client might find the relay selection event in question, each of which is applicable in different circumstances. In most cases, using one of a handful of indexer relays like purplepag.es or relay.nostr.band is a simple and efficient way to find user profiles and relay selections.
However, if an author's content has been aggressively purged from these indexers due to censorship, they obviously can't be relied upon. Even though the author in question hasn't been deplatformed from nostr itself (since he can always self-host a publicly accessible relay to store his content), he has been effectively shadow-banned.
To get around this, relay selections have to be communicated in some other way. Nostr has a few different mechanisms for this:
- If the author's NIP 05 address is known and properly configured (it may not be), clients can look up the author's NIP 05 endpoint to find some reasonable relay hints. Unfortunately, these are often neglected, and usually custodial, so they can run into the same problems.
- If the author's pubkey is found in another signed event found on nostr, relay hints can be a way to propagate relay selections through the network. This relies on implementations picking reliable relay hints which can be difficult, and hints do tend to become less reliable over time. However, this strategy is very effective in resisting censorship because it makes banning viral — if a relay wants to completely purge a particular pubkey from their database, they have to purge every event that references it, since events are tamper-proof.
- In extremis, relay recommendations can always be communicated out-of-band. This can be done using manual input, QR codes, DHTs, jsonl torrents full of
kind 10002events, or any other mechanism client developers choose to resort to.
Another, more technical assumption is that any given query can be fulfilled by few enough relays that a client can actually make all the connections needed, without running into resource limits. If you're trying to request content from 10,000 users across 1,000 relays, you're going to have a bad time. This was pointed out to me by Mazin of nostr.wine. He makes a good point, and it's definitely something to keep in mind. There are some mitigating factors though.
The first is that the current topology of the network probably won't persist forever. Because nostr is largely populated by self-hosting enthusiasts, the number of "tiny" relays is proportionally much higher than it will be if adoption picks up, even if the total number of relays grows. The trajectory is that nostr will drift toward fewer, larger relays, reducing the number of connections needed to fulfill any given query.
This is "centralizing", but it's important to understand that this isn't necessarily a bad thing. As long as there are more than one or two large hubs, there is user choice. And as long as it's possible to run a new relay, there is always an escape hatch. Nostr, like bitcoin, has no hard dependency on the biggest player in the network.
The other thing to consider is that there are lots of other techniques we can use to overcome the limits of the lowest-common denominator's limitations (mobile browser clients), including self hosted or third-party relay proxies. The trade-off here is that a little trust (aka centralization) can go a long way to reducing resource requirements needed to fulfill queries using the Outbox model.
If you're interested in more details on this topic, see this blog post.
That was a long digression, but there is one other thing that the Outbox model assumes to be the case. Even if the correct relays are found and connected to, they still may not return all desired content, either because they don't have it, or because they refuse to return it to the user requesting it.
This can happen if the publishing client isn't following the Outbox Model, if the author had migrated from one relay set to another without copying their notes over, or if the relay in question chose not to retain the author's content for some reason.
The first two issues can be fixed by improving implementations, but the question of policy is a little more interesting.
Relativistic relays
The Outbox Model is a mechanical process; it's only as useful as user relay selections are. In order for it to work, users have to be able to make intelligent relay selections.
Every relay has trade-offs, depending on its policy. 140.f7z.io would not be useful for long-form content, for example. Some relays might have a content retention policy that changes depending on whether you're a paying user. If you don't pay, you might find out too late that your content has been deleted from the relay.
So what makes a relay "good" for a particular use case? Well, it's complicated. Here are a few factors that go into that calculus:
- Is the relay in the same geographical as the user? Proximity reduces latency, but jurisdictional arbitrage might be desired. Users should probably have a variety of relays that fit different profiles.
- Will the relay ban the user? Do the operators have a history of good behavior? Is the relay focused on particular types of content? Is the relay's focus consistent with the user's goal in adding that relay to their list?
- What are the relay's retention policies? A user might want to set up an archival relay for her old content, or a multi-availability-zone relay so her notes are immediately accessible to the rest of the network.
- Does the relay require payment? Paid relays are more aligned with their users, but obviously come at a financial cost.
- Does the relay have policies for read-protecting content? If so, other users might not be able to find your posts published to that relay. On the other hand, some relays are configured to work as inboxes for direct messages, which can help preserve privacy.
- Does the relay request that users authenticate? Authentication can help manage spam, but it also allows relays to correlate content requests with users, reducing user privacy.
- Is the relay you use hosted by your client's developer? If so, you're in danger of getting banned from your client and your relay at the same time.
- Is the relay a hub? Using hubs can help smooth out rough areas in Outbox Model implementations, at the cost of centralization.
- Is the relay used by anyone else? One-off relays can be useful for archival purposes, but often won't be used by clients following the Outbox Model, depending on how they optimize requests.
There are lots of ways to approach the problem of helping users select relays, but it's an inherently complex problem which very few people will have the patience to properly address on their own. Relay selection is a multi-dimensional problem, and requires satisfying multiple constraints with a limited number of relay selections.
In the future, special-purpose clients might be used to help people build relay sets. Clients also might provide curated "relay kits" that users can choose and customize. Or, we might see an increase in hybrid solutions, like smarter relay proxies or client-local relays that synchronize using other protocols or platforms.
The Limitations of Outbox
Outbox is not a complete solution, not because of any of the caveats listed above, but because NIP 65 per se only addresses the question of how to index content by pubkey in a broadcast social media context. But there are many other scenarios for relay selection that Outbox does not solve:
- Community, chat, and group posts might be best posted to relays dedicated to that context.
- Direct messages shouldn't follow the same contours as public social media content.
- Topic-oriented relays, or relays serving a custom feed might be useful independent of who uses them.
- Relays focused on serving a particular kind of event, like music, long-form content, or relay selections, are useful independent of who reads from or writes to them.
- Certain clients might need to fulfill particular use cases by using relays that support certain protocol features, like search, count, or sync commands.
- Some events might not make sense to publish to relays, but should instead be shared only directly, out of band.
Some of these use cases might be solved by new specifications similar to Outbox that prescribe where certain data belongs — for example, NIP 17 requires users to publish a different relay list before they can receive direct messages, while NIP 72 places community relay recommendations directly into the group's metadata object. A reasonably complete list of different relay types can be found in this PR, very few of which have a canonical way to manage selections.
Other use cases might be supported more informally, either by relays advertising their own value proposition, or via third-party NIP 66 metadata. Still others might be supported by scoping the network down to only certain relays through explicit relay selection — this is how white-labeled Coracle instances work.
The basic idea here is that there are categories of events that don't have anything to do with where a particular person puts his or her "tweets". For every "what" on nostr, there should be a "how".
Keep nostr weird
Whatever additional systems we end up adopting for helping with relay selection, one thing is certain — people will continue to discover new, creative uses for relays, and we will always be playing catch up. This is one of the coolest things about nostr!
But it does mean that users will have to adapt their expectations to a network that partitions, re-configures, and evolves over time. Nostr is not a "worse" experience than legacy social media, but it is a version of social media that has itself been set free from the stagnant walled-garden model. Nostr is in many ways a living organism — we should be careful not to impose our expectations prematurely, leaving room to discover what this thing actually is, or can be.
If you enjoyed this post but want more take a look at the talk I gave at Nostrasia last year. I also wrote up a blog post at about the same time that addresses some of the same issues, but focuses more on privacy concerns around relays and nostr groups. Finally, I recently wrote this comment, which includes some details about challenges I've faced putting Outbox into Coracle.
-
 @ 8cb60e21:5f2deaea
2024-09-05 19:48:32
@ 8cb60e21:5f2deaea
2024-09-05 19:48:32Part 3: Asynchroni et DOM Manipulatio
3.1 Promissa et Async/Await
Praesent blandit. Nam nulla. Integer pede justo, lacinia eget, tincidunt eget, tempus vel, pede.
``javascript function simulaRequest(data, probabilitasErroris = 0.1) { return new Promise((resolve, reject) => { setTimeout(() => { if (Math.random() < probabilitasErroris) { reject("Error: Aliquid mali accidit"); } else { resolve(Data accepta: ${data}`); } }, 1000); }); }simulaRequest("Lorem ipsum") .then((responsum) => console.log(responsum)) .catch((error) => console.error(error));
async function fetchData() { try { const responsum = await simulaRequest("Dolor sit amet"); console.log(responsum); } catch (error) { console.error(error); } }
fetchData(); ```
3.2 DOM Manipulatio
Morbi non lectus. Aliquam sit amet diam in magna bibendum imperdiet. Nullam orci pede, venenatis non, sodales sed, tincidunt eu, felis.
```javascript document.addEventListener("DOMContentLoaded", () => { const titulus = document.createElement("h1"); titulus.textContent = "Lorem Ipsum JavaScript"; document.body.appendChild(titulus);
const paragraphus = document.createElement("p"); paragraphus.textContent = "Neque porro quisquam est qui dolorem ipsum quia dolor sit amet, consectetur, adipisci velit..."; document.body.appendChild(paragraphus); const button = document.createElement("button"); button.textContent = "Fac Clic Me"; button.addEventListener("click", () => { alert("Gratias tibi ago pro clic!"); }); document.body.appendChild(button);}); ```
3.3 Fetch API
Maecenas leo odio, condimentum id, luctus nec, molestie sed, justo. Pellentesque viverra pede ac diam.
``javascript async function fetchLoremIpsum() { try { const responsum = await fetch("https://api.lorem.space/image/game?w=150&h=220"); if (!responsum.ok) { throw new Error(HTTP error! status: ${responsum.status}`); } const data = await responsum.blob(); const imago = document.createElement("img"); imago.src = URL.createObjectURL(data); document.body.appendChild(imago); } catch (error) { console.error("Problema cum fetching imagine:", error); } }fetchLoremIpsum(); ```
3.4 Local Storage
Cras mi pede, malesuada in, imperdiet et, commodo vulputate, justo. In blandit ultrices enim.
```javascript function salvaPreferentias(clavis, valor) { localStorage.setItem(clavis, JSON.stringify(valor)); }
function accipePreferentias(clavis) { const valor = localStorage.getItem(clavis); return valor ? JSON.parse(valor) : null; }
const preferentiae = { thema: "clarus", lingua: "Latina", notificationes: true };
salvaPreferentias("userPrefs", preferentiae);
const salvataePreferentiae = accipePreferentias("userPrefs"); console.log(salvataePreferentiae); ```
3.5 Exercitia Parti III
- Crea paginam web simplicem quae utitur fetch API ad exhibendum datos ex API publica.
- Implementa functionalitatem "drag and drop" utens DOM API.
- Construe applicationem "todo list" quae persistit datos in local storage.
Conclusio
Vivamus vestibulum sagittis sapien. Cum sociis natoque penatibus et magnis dis parturient montes, nascetur ridiculus mus. Etiam vel augue. Vestibulum rutrum rutrum neque. Aenean auctor gravida sem. Praesent id massa id nisl venenatis lacinia. Aenean sit amet justo. Morbi ut odio.
Cras mi pede, malesuada in, imperdiet et, commodo vulputate, justo. In blandit ultrices enim. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Proin interdum mauris non ligula pellentesque ultrices. Phasellus id sapien in sapien iaculis congue. Vivamus metus arcu, adipiscing molestie, hendrerit at, vulputate vitae, nisl.
Aenean lectus. Pellentesque eget nunc. Donec quis orci eget orci vehicula condimentum. Curabitur in libero ut massa volutpat convallis. Morbi odio odio, elementum eu, interdum eu, tincidunt in, leo. Maecenas pulvinar lobortis est.
Phasellus sit amet erat. Nulla tempus. Vivamus in felis eu sapien cursus vestibulum. Proin eu mi. Nulla ac enim. In tempor, turpis nec euismod scelerisque, quam turpis adipiscing lorem, vitae mattis nibh ligula nec sem. Duis aliquam convallis nunc. Proin at turpis a pede posuere nonummy.
Integer non velit. Donec diam neque, vestibulum eget, vulputate ut, ultrices vel, augue. Vestibulum ante ipsum primis in faucibus orci luctus et ultrices posuere cubilia Curae; Donec pharetra, magna vestibulum aliquet ultrices, erat tortor sollicitudin mi, sit amet lobortis sapien sapien non mi. Integer ac neque. Duis bibendum. Morbi non quam nec dui luctus rutrum. Nulla tellus. In sagittis dui vel nisl. Duis ac nibh. Fusce lacus purus, aliquet at, feugiat non, pretium quis, lectus.
Suspendisse potenti. In eleifend quam a odio. In hac habitasse platea dictumst. Maecenas ut massa quis augue luctus tincidunt. Nulla mollis molestie lorem. Quisque ut erat. Curabitur gravida nisi at nibh. In hac habitasse platea dictumst. Aliquam augue quam, sollicitudin vitae, consectetuer eget, rutrum at, lorem. Integer tincidunt ante vel ipsum. Praesent blandit lacinia erat. Vestibulum sed magna at nunc commodo placerat. Praesent blandit. Nam nulla.
-
 @ af9c48b7:a3f7aaf4
2024-08-27 16:51:52
@ af9c48b7:a3f7aaf4
2024-08-27 16:51:52Chef's notes
Easy recipe with simple ingredients. This recipe uses some store bought, precooked items as way to cut down on cook time. I recommend letting the vegetables thaw if you don't like them on the firm/crunchy side.Feel free to substitute fresh ingredients if you have the time and want to make the extra effort.
Details
- ⏲️ Prep time: 20 min
- 🍳 Cook time: 50 min
- 🍽️ Servings: 8-10
Ingredients
- 2 (8 oz) packages refrigerated crescent rolls (dough sheets preferred)
- 1 pound cooked rotisserie chicken (deboned and chopped)
- 2 table spoons of butter
- 2 (10 once) packages of frozen mixed vegetables
- 1 (15 once can sliced potatoes (drained)
- 1 (10.5 once) can condensed cream of chicken soup
- 1 (10.5 once) can condensed cream of mushroom soup
- 1/2 cup milk
- salt and ground pepper to taste
Directions
- Preheat oven to 350 degrees F (175 degrees C). Line the botton of 9x13-inch baking dish with one can of crescent roll dough. If you don't get the sheet dough, be sure to pinch the seams together.
- Melt the butter in a sauce pan over medium heat. Then add the chicken, mixed vegetables, and sliced potatoes (recommend cutting into smaller pieces). Cook, stirring frequently, until vegetables are thawed and mixture is heated through, 5 to 7 minutes.
- While the mixed vegetables are heating, warm both cans of condensed soup in a seperate pan over medium-low heat. Slowly add milk and cook, stirring frequently, until combined and heated through, about 3 minutes.
- Add the soup mixture to the chicken mixture, then pour into the baking dish. Top with the second can of crescent roll dough. Feel free to cut some slits in dough if you are using the dough sheets. Cover lightly with foil to prevent the crescent roll dough from browning too quickly.
- Bake in oven until heated through and dough is a golden brown. Cook time should be around 45-50 minutes I reommend removing the foil for the last 10 minutes to get a golden crust. Be sure to keep a close watch on the crust after removing the foil because it will brown quickly.
-
 @ c230edd3:8ad4a712
2024-08-26 01:13:49
@ c230edd3:8ad4a712
2024-08-26 01:13:49Chef's notes
Allow meat to soak for 1-24 hours. The rougher the cut, the longer the soak. This is great for open flame grilling, as well as pan seared, though the latter is preferable. Petit Sirloin can marinade for approximately 1 hour and still develop tenderness. I like to score the steaks if they will only be resting in the mix for a short time. All seasonings can be adjusted to taste. Base ingredients scale well, for any number of steaks. Equal parts, enough to coat the meat is really all that matters.
I'm terrible at remembering cooking pictures, so image is a random steak. I will try to remember to update that next time I make these.
Details
- ⏲️ Prep time: 10
- 🍳 Cook time: However long you usually cook your steak to preferred doneness
Ingredients
- 4 petite sirloin steaks or other cut
- 1/4 cup yellow mustard
- 1/4 cup soy sauce
- 3-5 cloves garlic, depending on size, minced and salted
- 1 tsp dried basil
- 1\2 tsp crushed red pepper
Directions
- Mix ingredients and marinade 1-24 hours.
- Grill or pan sear to your preferred doneness
- Enjoy!
-
 @ 8cb60e21:5f2deaea
2024-09-05 19:48:32
@ 8cb60e21:5f2deaea
2024-09-05 19:48:32Part 1: Fundamentum Javascripti
1.1 Introductionis
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Nullam euismod, nisi vel consectetur interdum, nisl nunc egestas nunc, vitae tincidunt nisl nunc euismod nunc. Sed euismod, nisi vel consectetur interdum, nisl nunc egestas nunc, vitae tincidunt nisl nunc euismod nunc.
javascript console.log("Salve, mundi!");1.2 Variabiles et Typi Datorum
Pellentesque habitant morbi tristique senectus et netus et malesuada fames ac turpis egestas. Integer convallis, nunc ac blandit tincidunt, ipsum augue tincidunt nunc, vitae tincidunt nisl nunc euismod nunc.
javascript var numerus = 42; let textus = "Lorem ipsum"; const CONSTANTIA = true;1.2.1 Typi Numerorum
Curabitur in libero ut massa volutpat convallis. Morbi odio odio, elementum eu, interdum eu, tincidunt in, leo.
javascript let integer = 10; let floatinum = 3.14; let scientificum = 2.998e8;1.2.2 Typi Textuum
Maecenas tristique, est et tempus semper, est quam pharetra magna, ac consequat metus sapien ut nunc.
javascript let textusBrevis = 'Carpe diem'; let textusLongus = "Quod erat demonstrandum"; let textusTemplatum = `Cogito, ${textusBrevis.toLowerCase()}, sum`;1.3 Operatores
Donec dapibus. Duis at velit eu est congue elementum. In hac habitasse platea dictumst.
```javascript let a = 5; let b = 3;
console.log(a + b); // Additio console.log(a - b); // Subtractio console.log(a * b); // Multiplicatio console.log(a / b); // Divisio console.log(a % b); // Modulus console.log(a ** b); // Potentia ```
1.4 Structurae Controli
Morbi non lectus. Aliquam sit amet diam in magna bibendum imperdiet. Nullam orci pede, venenatis non, sodales sed, tincidunt eu, felis.
1.4.1 Conditionales
```javascript let aetas = 20;
if (aetas >= 18) { console.log("Adultus es"); } else if (aetas >= 13) { console.log("Adolescens es"); } else { console.log("Puer es"); } ```
1.4.2 Iterationes
``javascript for (let i = 0; i < 5; i++) { console.log(Iteratio ${i}`); }let j = 0; while (j < 5) { console.log(
Dum iteratio ${j}); j++; } ```1.5 Exercitia Parti I
- Scribe programma quod convertat gradus Celsius in Fahrenheit.
- Crea algorithmum qui determinat si numerus est par vel impar.
- Implementa "FizzBuzz" pro numeris 1 ad 100.
-
 @ 8cb60e21:5f2deaea
2024-09-05 19:48:32
@ 8cb60e21:5f2deaea
2024-09-05 19:48:32Part 2: Functiones et Objecta
2.1 Functiones
Fusce posuere felis sed lacus. Morbi sem mauris, laoreet ut, rhoncus aliquet, pulvinar sed, nisl.
``javascript function salutatio(nomen) { returnSalve, ${nomen}!`; }console.log(salutatio("Cicero"));
const valedictio = (nomen) => { console.log(
Vale, ${nomen}!); };valedictio("Seneca"); ```
2.1.1 Parametri Default et Rest
Nunc purus. Phasellus in felis. Donec semper sapien a libero.
``javascript function congregatio(primus, secundus = "mundi", ...ceteri) { console.log(${primus} ${secundus}); console.log(Ceteri: ${ceteri.join(", ")}`); }congregatio("Salve"); congregatio("Lorem", "ipsum"); congregatio("Veni", "vidi", "vici", "et", "cetera"); ```
2.2 Objecta
Nam congue, risus semper porta volutpat, quam pede lobortis ligula, sit amet eleifend pede libero quis orci.
``javascript const persona = { nomen: "Iulius", cognomen: "Caesar", aetas: 55, salutatio: function() { returnSalve, ${this.nomen} ${this.cognomen}!`; } };console.log(persona.salutatio()); ```
2.2.1 Methodi Object
Nullam porttitor lacus at turpis. Donec posuere metus vitae ipsum. Aliquam non mauris.
```javascript const claves = Object.keys(persona); console.log(claves);
const valores = Object.values(persona); console.log(valores);
const paria = Object.entries(persona); console.log(paria); ```
2.3 Arrays
Morbi porttitor lorem id ligula. Suspendisse ornare consequat lectus. In est risus, auctor sed, tristique in, tempus sit amet, sem.
```javascript const fructus = ["malum", "pirum", "uva", "cerasum"];
fructus.forEach((fructus) => { console.log(fructus); });
const longiFructus = fructus.filter((fructus) => fructus.length > 4); console.log(longiFructus);
const maiusculaFructus = fructus.map((fructus) => fructus.toUpperCase()); console.log(maiusculaFructus); ```
2.4 Exercitia Parti II
- Crea functionem quae calculat factorialem numeri.
- Implementa methodum quae invenit maximum valorem in array.
- Scribe programma quod ordinat objecta in array secundum proprietatem specificam.
-
 @ 592295cf:413a0db9
2024-08-25 09:17:54
@ 592295cf:413a0db9
2024-08-25 09:17:54A Ux designer has arrived on Nostr. I thought run away while you can. He could get rich, if there was a little economy.
Klout, do you remember that service, which took data from Twitter and made a ~~ WoT~~.
From a note of chip, I understood one thing:
Bitcoin is your "sovereign" currency. Nostr is just third party protocol. If you have a service you can use Nostr to face your customers. "Sovereign" people offer services. They can be bitcoiners or not. So at this stage Nostr is a layer 3 Bitcoin.
So to grow the enveiroment it must be attractive. Let's paraphrase: the protocol is agnostic, the people are fundamentalist Catholics.
So when an atheist person arrives he says ah ok, how do I silence these people and use the protocol If a Protestant Catholic arrives he is laughed at or ignored or at most converted.
I had a disagreement with Dergigi, in the end he won, but he is not right... (True)

Post more notes, zap more, follow 1000 people update FAQ to the nth degree. We are in the desert of the Tartars and the enemy is coming and there are those who say every day we must be ready, sooner or later, it will happen, ah ok. Everything must be perfect. Push harder. This leads to exhaustion.
New Grant from Opensat to Victor of Amethyst, totally deserved, pushed the envelope. If you are a grapheneos user download Amethyst. It's not just Amethyst it's also orbot, citrine, amber, zap store or obtainium or f-droid.
GitCitadel has raised its first fund I wonder if it was just a test on geyser, I wonder if it is the right project to do on nostrocket, but I think Opensat grant for nostrocket makes it irreconcilable. This opens a pandora's box, as always. We are silent as fish.
I tried not to answer some questions even in one case I knew the answer, I apologize, Nostr is much older than me, so it's okay not to answer sometimes. Tomorrow begins nostRiga, The last unconference of Nostr.
(First day) The morning was so-so, in the evening the situation improved a little. In the evening I played a bit with Nostr and it broke The second day good in the morning bad in the evening. I saw little of the backstage maybe only two panels, Will by Damus, and P2Phash on Nostr.
I don't follow anyone anymore, I did a little bit of a unfollow. I saw that two users had 200 followers in common, and I said to myself ah ok what is this thing, I have to understand how they do it there is something that doesn't work, let's try to be a little more distant.
It's weird, too much reliance on following, you have to go and look, not be stationary.
-
 @ e27ae11e:e0c36580
2024-09-05 16:28:24
@ e27ae11e:e0c36580
2024-09-05 16:28:24In the present computerized age, having a website is essential for any business, including tradies. Yet, it's not just about having a website; about having a website looks perfect and functions admirably on all gadgets. This is where responsive web design comes in. We should investigate why responsive web design is fundamental for tradies and how it can help your business. Visit us > Best Tradie Web Design Key takeaways Mobile-Friendly is a Must: Guarantee your website looks perfect and functions admirably on cell phones and tablets to draw in additional clients.
Better Insight: A responsive site is simpler to utilize, making guests blissful and bound to reach you.
Higher Google Rankings: A versatile website can assist you with seeming higher in list items, carrying more traffic to your webpage.
Set aside Time and Cash: Overseeing one responsive site is less expensive and easier than having separate locales for various gadgets. Overview Responsive web design is a methodology that does a good job for your website and capacity suitably on any contraption, whether it's a PC, tablet, or cell. It suggests your website will thusly change its format and content to fit the screen size of the contraption being used. This ensures a predictable and beguiling experience for your visitors, paying little heed to how they access your site. What difference Does It Make for Tradies? 1. Increased Versatile Utilization More individuals are utilizing their cell phones to peruse the web. Potential clients could look for your administrations while in a hurry. On the off chance that your website isn't versatile, you could lose those possible clients. Responsive web design guarantees that your webpage looks perfect and functions admirably on cell phones, making it simpler for guests to find and reach you. Tip: Check your website analytics to see how many visitors are accessing your site from mobile devices. Use this data to prioritize mobile optimization. 2. Better Client Experience A responsive website gives a superior client experience. At the point when guests can undoubtedly explore your site and find the information they need without zooming in or scroll on a level plane, they are bound to remain longer and investigate your administrations. A positive client experience can prompt more requests and appointments. Tip: Use a clean and simple design that is easy to navigate on all devices. Avoid clutter and ensure that buttons and links are easy to tap 3. Improved Website optimization Rankings Web crawlers like Google focus on versatile websites. In case your site is responsive, it will rank higher in list things. This infers more prominent detectable quality for your business and more potential clients believing that you are on the web. Higher rankings can basically uphold your web-based presence and attract more busy time gridlock to your website. Tip: Guarantee your website content is applicable and helpful to your interest group. Excellent substance further develops Search engine optimization and keeps guests locked in. 4. Cost-Powerful Keeping a single responsive website is smarter than having separate objections for workspace and flexible clients. With responsive web design, you simply need to regulate and invigorate one website, saving you time and money long term. Tip: Consistently update your website's substance and design to keep it new and important, guaranteeing it stays viable and cost-productive. 5. Consistent Marking A responsive website guarantees that your marking stays steady across all gadgets. Whether a client visits your site on a PC or a cell phone, they will see similar design, tones, and logo. Steady marking assists fabricate trust and acknowledgment with your crowd. Tip: Utilize a similar variety plan, logo, and textual styles across all variants of your website to keep a predictable brand personality.
Make Your Website Responsive 1. Pick a Responsive Subject If you are using a website producer or a substance the chiefs system like WordPress, pick a responsive subject. These subjects are designed to be dynamic and will consequently change in accordance with various screen sizes. Tip: Preview the theme on different devices before making a final decision to ensure it meets your needs. 2. Optimize Pictures and Media Guarantee that pictures and media records are improved for quick stacking on all gadgets. Enormous pictures can dial back your site, particularly on cell phones. Use devices to pack pictures without forfeiting quality. Tip: Use image compression tools like TinyPNG or JPEGmini to reduce the file size of your images without losing quality 3. Simplify Route Ensure your website's route is basic and simple to use on all gadgets. Utilize clear menus and buttons that are not difficult to tap on a touchscreen. Try not to utilize an excessive number of connections or complex dropdown menus that can be hard to explore on a little screen. Tip: Use a simple, easy-to-use menu that adapts to different screen sizes. A hamburger menu can be effective for mobile devices. 4. Use Adaptable Designs Design your website utilizing adaptable formats that can change in accordance with various screen sizes. This can be accomplished utilizing CSS (Flowing Templates) to make a liquid framework design that changes in light of the gadget's screen size. Tip: Avoid fixed-width layouts. Instead, use percentage-based widths that allow your content to resize fluidly. 5. Test Your Website Reliably test your website on different contraptions and screen sizes to promise it looks perfect and works fittingly. There are online instruments available that can help you see how your webpage appears on different devices. Tip: Utilize online instruments like Google's Dynamic Test and Browser Stack to perceive how your website looks and works on changed gadgets and programs. Conclusion Responsive web design is essential for tradies that need to attract and hold clients in the present high level world. It ensures that your website looks great and works honorably on all devices, giving you an unrivaled client experience, further fostering your Web enhancement rankings, and saving you time and money. By picking a responsive topic, streamlining pictures, improving on route, and testing your webpage consistently, you can make a responsive website that assists your exchange business with flourishing on the web. Putting resources into responsive web design isn't just about staying aware of patterns; it's tied in with giving the most ideal experience to your guests and guaranteeing your business stays serious. In this way, make the strides today to make your website responsive and watch your web-based presence develop!
-
 @ be39043c:4a573ca3
2024-08-19 23:36:04
@ be39043c:4a573ca3
2024-08-19 23:36:04Details
- ⏲️ Prep time: 5 mins
- 🍳 Cook time: 10mins
- 🍽️ Servings: 2-
Ingredients
- Shishito
- Butter/ Oil of your choice
- Soy sauce
- Salt
- Sugar (optional)
Directions
-
- Wash shishitos, remove stems, and dry.
-
- Heat the pan, add butter or oil, and shishitos. Sauté until shishitos are tender and winkled.
-
- Add a bit of sugar (optional), and a bit of salts, and finally soy sauce. Do not add too much soy sauce. Try and adjust with more say sauce if needed.
-
 @ 469fa704:2b6cb760
2024-09-05 15:06:49
@ 469fa704:2b6cb760
2024-09-05 15:06:49The Evolution of Web 3.0: Bitcoin's Role in Decentralizing the Internet
Introduction to Web 3.0
Web 3.0, often referred to as the decentralized web, represents the next phase in the evolution of the internet. Unlike its predecessors, Web 3.0 aims to redistribute control from centralized entities back to individual users through technologies like blockchain, cryptocurrencies, and decentralized applications (dApps). This shift promises a more democratic internet where users control their data, identity, and digital destiny.
The Bitcoin Protocol: A Foundation for Web 3.0
Bitcoin's Influence on Decentralization
Bitcoin, introduced in 2008, can be seen as a precursor to Web 3.0 due to its decentralized nature. The Bitcoin protocol introduced the world to blockchain technology, a decentralized ledger that records all transactions across a network of computers. This technology underpins Web 3.0's ethos by:
- Promoting Decentralization: Bitcoin's network operates without a central authority, showcasing how internet services could run on similar principles, reducing the power of centralized tech giants.
- Enhancing Security and Privacy: Through cryptographic means, Bitcoin ensures that transactions are secure and pseudonymus, a feature integral to Web 3.0's vision of user-controlled data.
Scalability and Functionality Challenges
However, Bitcoin's protocol wasn't designed on the base layer with the complex applications of Web 3.0 in mind. Its primary function as a digital currency means:
- Scalability Issues: Bitcoin's blockchain has limitations in transaction speed and volume, which might not suffice for a fully realized Web 3.0 environment where millions of micro-transactions could occur seamlessly.
- Limited Smart Contract Capabilities: Bitcoin's scripting language isn't as versatile as platforms like Ethereum, which are designed to support a broader range of decentralized applications.
Expanding Bitcoin's Role with Layer 2 Solutions
To bridge these gaps, developers are working on Layer 2 solutions like the Lightning Network for faster transactions, and projects like Stacks aim to bring smart contract functionality directly to Bitcoin. These innovations suggest that while Bitcoin might not be the sole backbone of Web 3.0 yet, it can significantly contribute to its infrastructure. In the long term, the question is whether we need more than one network, I mean, we don't have multiple Internets today. The market will probably decide in favor of the strongest and most secure network, and Bitcoin is by far that.
Web 3.0 Beyond Bitcoin
A Broader Blockchain Ecosystem
At the moment Web 3.0 encompasses by far more than just Bitcoin. It includes:
- Ethereum and Smart Contracts: Ethereum's introduction of smart contracts has been pivotal, allowing for decentralized applications that can interact in complex ways, far beyond simple transactions.
- Other Blockchains: Platforms like Solana, Sui, and Near are gaining traction for their high throughput and lower costs, addressing some of Bitcoin's limitations on the base layer.
The Cultural and Economic Shift
The move towards Web 3.0 isn't just technological but cultural. There's a growing sentiment, reflected in posts on platforms like X, that users are ready for a change where they own their digital presence. Here's some background based on general knowledge and trends up to 2024:
Cultural Shift:
- Distrust in Centralized Institutions: There's been a growing distrust in traditional centralized institutions like banks, governments, and large corporations. This distrust stems from various scandals, data breaches, privacy concerns, and perceived inefficiencies or corruption. Posts on platforms like X or even more on Nostr reflect this sentiment, where users often discuss the diminishing trust in these institutions.
- Rise of Individual Empowerment: Culturally, there's a move towards empowerment of the individual, facilitated by technology. Social media, blockchain, and other decentralized technologies give individuals tools to bypass traditional gatekeepers in finance, media, and more. This shift champions the idea that individuals should have more control over their data, finances, and digital identity.
- Identity and Community: Decentralization also touches on identity politics and community governance. There's a trend towards localism or regionalism where communities seek more control over their governance, which can be seen in movements for local autonomy or even secessionist sentiments in various parts of the world.
- Cultural Movements: Movements like the maker culture, DIY (Do It Yourself), open-source software, and even the gig economy reflect a cultural shift towards decentralization where individuals or small groups can produce, create, or work independently of large entities.
Economic Shift:
- Decentralized Finance (DeFi): DeFi represents one of the most tangible shifts, aiming to recreate and potentially improve financial systems outside of traditional banking. This includes lending, borrowing, and earning interest in a trustless, permissionless environment, primarily using blockchain technology.
- Cryptocurrencies and Tokenization: The rise of cryptocurrencies like Bitcoin and Ethereum symbolizes a move away from centralized monetary systems. Tokenization of assets, from art (NFTs - Non-Fungible Tokens) to real estate, embodies this shift, allowing for fractional ownership and reducing the barriers to investment.
- Globalization vs. Localism: While globalization has interconnected economies, there's a counter-trend where economic decentralization supports local economies. This can be seen in the push for local currencies, community-supported agriculture, or local energy production like solar microgrids.
- Work and Employment: The gig economy, remote work, and digital nomadism are part of this economic shift. Platforms enabling freelance work decentralize employment, moving away from traditional office environments and 9-to-5 jobs.
General Observations:
- Technology as an Enabler: Blockchain, the internet, and advancements in communication technology are pivotal in this shift. They provide the infrastructure necessary for decentralization to occur at scale.
- Political Implications: Economically, this shift maybe challenges existing power structures, potentially leading to regulatory battles as seen with cryptocurrencies. Culturally, it might lead to a redefinition of nationalism, community, and individual rights in the digital age.
- Challenges: Despite its promise, decentralization faces hurdles like scalability issues, regulatory pushback, the digital divide, and the potential for new forms of centralization (e.g., large crypto exchanges becoming new central authorities).
Conclusion: Bitcoin's Place in Web 3.0
Bitcoin's protocol ignited the spark for a decentralized internet, but Web 3.0 is evolving into a multifaceted ecosystem where Bitcoin might play a crucial, though not yet exclusive, role. The integration of Bitcoin with newer technologies and platforms could see it becoming a fundamental layer in the Web 3.0 stack, particularly in areas of value transfer and as a store of value within decentralized finance (DeFi).
As we progress, the synergy between Bitcoin's proven security and stability, combined with the innovation of other blockchain technologies, might just be the blend needed for Web 3.0 to achieve mainstream adoption, ensuring the internet becomes more open, secure, and user-centric. As stated before, the market will probably decide in favor of the strongest and most secure network, and Bitcoin is by far that.
-
 @ 8a3a9236:374b9419
2024-08-19 15:07:59
@ 8a3a9236:374b9419
2024-08-19 15:07:59Details
- ⏲️ Prep time: 10 min
- 🍳 Cook time: 30 min
- 🍽️ Servings: 2 (depends how hungry the bears are)
Ingredients
- 1 pound boneless chicken (thighs or breast)
- 1 can Campbells Cream of Mushroom Soup
- half a can of heavy cream
- 6 ounces white rice
- garlic powder
- cayenne pepper
- onion powder
- salt & pepper
Directions
- Start by getting the rice going.
- generously season chicken with salt and pepper
- cook chicken
- prepare sauce: mix cream of mushroom soup with heavy cream (i use 1/2 of the empty soup can to measure)
- add generous portions of garlic powder and cayenne pepper. Add in some onion powder and salt and pepper as well. stir all these together on low/medium heat
- once chicken is cooked, chop it up into tiny pieces. The chicken needs to be chopped up to give the sludge the proper consistency
- add chicken to sludge (sauce) and stir so everything is well mixed.
- finally, pour the chicken/sludge over the rice and mix all that together. ENJOY!
-
 @ c69b71dc:426ba763
2024-08-18 14:35:51
@ c69b71dc:426ba763
2024-08-18 14:35:51Chef's notes
You will need a blender! 🌱 This breakfast is nutritious, healthy, easy, and quick to make. 🌱 It's gluten free and vegan.
Details
- ⏲️ Prep time: 10 min.
- 🍳 Cook time: 0
- 🍽️ Servings: 2
Ingredients
- 1 Apple 🍏
- 2 Ripe Peaches 🍑
- 1 Banana 🍌
- 1/2 cup (Wild) Blueberries 🫐 (frozen or fresh)
- 1/2 cup pine nuts (or optional ground almonds)
- 4 tbsp Almond Butter (or optional cashew butter)
- 2 Pitted Dates
- 1 tbsp Vegan Protein Vanilla Powder (optional)
Directions
- Peach, apple, pine nuts, pitted dates, and vanilla protein powder: Blend until smooth.
- Peel and slice the banana into rounds.
- Blueberries (thaw in a water bath if frozen) and just mix and stir with a spoon in a little bowl with almond butter. (no need to blend with a blender)
- Alternate layers of peach-apple mixture, banana and blueberry-almond butter mix in a glass.
- Garnish with grapes, pine nuts, cacao nibs, and a drizzle of almond butter
- Enjoy and tag me, when you try the recipe 💜🙏🏽💚
-
 @ 361d3e1e:50bc10a8
2024-09-05 12:58:30
@ 361d3e1e:50bc10a8
2024-09-05 12:58:30He wished Pfizer's vaccine naysayers screwed, and now he's screwed
uk #music #vaccine #covid #sideeffects #health #freespeech
-
 @ 592295cf:413a0db9
2024-08-17 07:36:43
@ 592295cf:413a0db9
2024-08-17 07:36:43Week 12-08 a suitable protocol
The knots come to a head, some of you have gray hair, you get older.
Tkinter is better than ws://, more secure, but has limitations, unless you know how to use figma and do some magic. The project of Nabismo.
Maybe Nostr doesn't work for me.
Aspirin moment Nip-17, works with nip-44 and nip-59. Someone said they made the groups encrypted with nip-17. I tried and succeeded, now you can DM me, don't do it. I had sent the link to a conversation of nip-87 closed groups. There's JeffG doing something with MLS. Then there's keychat.io which uses signal Nostr Bitcoin ecash and that's it... But in dart. It's a bit like the Matrix analogue for Nostr.
Final controversy not all nips are mandatory.
Build the foundation. You can't think about selling the house
Yakihonne has a countdown. What can a desktop app be. Community Lists, Nip-29
A birthday on Nostr, no that's not possible, they're all cypherpunks. 🎉🎉 (Except me)
There is a different attitude from Nostr when updates are released compared to Bluesky, everyone there is still enthusiastic, on Nostr ah ok but this is missing oh but this is missing or but support this other one, or but * zap, wait a minute, keep calm 🙇♂️, I'm the first to do this. (The revolt of the developers)
Deletetion: Client that have relay paired can do delete, more intelligently, Perhaps you can think of a delete.nrelay subdomain as a filter. This id is deleted. Be careful what you don't want to do. Maybe a session with a psychologist is better, because then you find yourself doing what you said you didn't want to do.
Does it make sense to follow someone on Bluesky? In my opinion no, or better yet yes. There are several algorithms on Bluesky, which do their job well. In the end it's just a matter of arranging them better on the screen. Yes you can have lists to save someone, but then you read everything, so lists with algorithm seems like a next feature. this way they can keep the following small, almost minimal, because there are algorithms that work for the user. People will start writing for SEO algorithm and AI and other things, which tech gurus really like and so on. The fact that it is almost exclusively an app will greatly facilitate this trend, there will be almost no need for moderation, and you can get it all in just a few apps. (Great)
Oh yegorpetrov has abandoned. Pegorpetrov said that he is coming back 😌 It might be an invention but I'm a little heartened by it.
Bankify, a new wallet of super testnet, only for crush testers.
You can't stream on zap stream without reach, maybe it's better audio space. Contact someone maybe an influencer or Nostr elite or whatever. Open Source Justice Foundation streaming
Designer, I wanted to propose comment on wikifreedia nielliesmons article and follow #nostrdesign, but too many answers for today. NVK note is ~~mainstream~~
I think I'm not suited to Nostr.
Nostr-ava bike file geo tag sharing. (NIP-113) Sebastix doesn't respond, I must have done something bad to him, or maybe I'm stressing him too much. Finally he replied 🤙. In the end maybe, I have too much hype about this proposal and it's something I don't know maybe, but maybe if they were already doing something with geo tags it's better to say so.
Another birthday, less cypher more punk 😌
Usdt on Nostr, there must be some error. (freeform app)
USDT on tron is like Money. (Bitcoiner not really)
Privacy issue, deletion motion, or deletion request, go go.
Nip29 hype, i don't have hype at all. I'm tired of words, I record a podcast on Nostr. Let's see if I can do it, at least think it. (It's more of a workflow thing than actually something I would do)
- Create an npub (easy)
- Record the audio episode (I think I can do it). Terrible audio
- Loading on a Nostrhosting, if less than 10 MB it should go smoothly.
- Publish the video or audio of the episode on some Nostr client, perhaps using blastr relay 😞.
- Do the nostree link, by putting the episode, and also the npub.pro and put the URL on café-society. 6) Publish all these links on the Main profile, saying that, made a podcast about Nostr in Nostr of nostr. 😂
I thought a client could have poll, form, spreadsheet, collaboration document. It's the kind of otherstuff we want to see. Something that goes beyond a normal feed.
Emoj on bluesky, Eventually also zap 🥜 link emoj Blue
Eventually there will be a developer revolt And they will only do a social network in their downtime, they will call it Nostr.
There is a storm, Nostr does not work in 4g with two bars. Or now 4G is gone too.
Yakihonne Smart widgets, something to try on the weekend.
-
 @ a012dc82:6458a70d
2024-09-05 09:46:29
@ a012dc82:6458a70d
2024-09-05 09:46:29Table Of Content
-
What are the factors driving this adoption?
-
What are the potential benefits of widespread Bitcoin adoption?
-
What are the potential challenges to Bitcoin adoption?
-
Conclusion
-
FAQ
The cryptocurrency market has been on a rollercoaster ride over the past few years, with Bitcoin emerging as the undisputed king of the digital currencies. Despite facing intense scrutiny and skepticism from traditional financial institutions, Bitcoin has continued to gain traction among investors, traders, and even mainstream businesses. The future of Bitcoin and the wider cryptocurrency industry has been the subject of much speculation, with many analysts making bold predictions about its potential growth and impact.
According to the report, the analyst predicts that Bitcoin will become the primary global currency by 2025, with an estimated 50% adoption rate. This means that half of the world's population could potentially be using Bitcoin as their main currency by 2025, marking a significant shift in the way we think about money and finance.
What are the factors driving this adoption?
The analyst attributes this projected surge in Bitcoin adoption to several key factors. These include:
Increased mainstream acceptance: More and more businesses are starting to accept Bitcoin as a form of payment, including some major players like Microsoft, Tesla, and PayPal. This increased acceptance is helping to legitimize Bitcoin and make it more accessible to the average person.
Growing distrust in traditional finance: The 2008 financial crisis and subsequent economic instability have eroded trust in traditional financial institutions. Bitcoin offers a decentralized alternative to the current system, making it an attractive option for those seeking greater financial autonomy and security.
Technological advancements: The development of blockchain technology and other innovations are making Bitcoin more secure, faster, and easier to use. This is helping to remove some of the barriers to adoption and make Bitcoin a more viable option for everyday use.
What are the potential benefits of widespread Bitcoin adoption?
The potential benefits of widespread Bitcoin adoption are numerous and far-reaching. These include:
Increased financial freedom: Bitcoin offers a level of financial freedom and autonomy that is impossible with traditional currencies. Users can send and receive money anywhere in the world without having to go through intermediaries or deal with cumbersome regulations.
Lower transaction fees: Bitcoin transactions are typically much cheaper than traditional banking fees, making it a more cost-effective option for businesses and individuals.
Greater security: Bitcoin's decentralized nature makes it more resistant to hacking and fraud than traditional banking systems. This offers a higher level of security and protection for users.
What are the potential challenges to Bitcoin adoption?
While the potential benefits of widespread Bitcoin adoption are exciting, there are also several potential challenges that must be overcome. These include:
Lack of regulation: Bitcoin operates outside of traditional financial systems and is largely unregulated. While this offers greater autonomy and freedom, it also makes it more susceptible to fraud and other criminal activity.
Volatility: Bitcoin's value is notoriously volatile, making it a risky investment option for some. This could make it more difficult to convince everyday users to adopt Bitcoin as their primary currency.
Technical barriers: While technological advancements are making Bitcoin more accessible, there are still some technical barriers that could prevent widespread adoption. These include issues with scalability, user interfaces, and education.
Conclusion
The analyst's forecast of mind-blowing Bitcoin adoption in 2025 is certainly an exciting prospect, and one that has the potential to transform the world of finance as we know it. While there are certainly challenges to be overcome, the benefits of widespread Bitcoin adoption are clear, and it is clear that more and more people are starting to recognize the potential of this revolutionary digital currency. Whether Bitcoin will ultimately become the primary global currency by 2025 remains to be seen, but it is clear that it is here to stay, and that it will continue to play an increasingly important role in the world of finance.
FAQ
Can Bitcoin be used as a form of payment? Yes, many businesses and merchants now accept Bitcoin as a form of payment, and it is becoming increasingly common.
Is Bitcoin safe to use? Bitcoin is generally considered to be a safe and secure form of payment, thanks to its decentralized nature and strong cryptographic protocols. However, as with any form of payment, there are some risks involved, and users should take appropriate precautions to protect their funds.
What is the potential impact of widespread Bitcoin adoption? The potential impact of widespread Bitcoin adoption is huge, as it could fundamentally change the way we think about money and finance. It could also have significant implications for traditional financial systems and institutions.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ b22fef18:1bba6e1f
2024-08-16 17:54:13
@ b22fef18:1bba6e1f
2024-08-16 17:54:13Chef's notes
Old family recipe that my grandma used to make during the summer. Creamy and refreshing.
Details
- ⏲️ Prep time: 10 min
- 🍳 Cook time: 4 hours chilled
- 🍽️ Servings: 8-10
Ingredients
- 3/4 cup shredded cucumber
- 3/4 cup cucumber juice
- 3/4 cup water
- 1 packet lime jello
- 1/4 cup chopped onion
- 1 cup 4% cottage cheese
- 1 cup Miracle Whip
Directions
- Shred cucumber and add salt to draw out moisture.
- Mix juice from shredded cucumber and water.
- Heat juice/water and dissolve lime jello.
- Allow to cool slightly. (Add a couple ice cubes to chill it down and remove before melted)
- Mix together the jello mixture and all other ingredients.
-
 @ d1b118c6:4985b38d
2024-08-15 19:34:51
@ d1b118c6:4985b38d
2024-08-15 19:34:51Chef's notes
I hope you like it, let me know
https://maria.omg.lol
Details
- ⏲️ Prep time: 10 minutes or so
- 🍳 Cook time: 30 minutes or so
- 🍽️ Servings: 1-4
Ingredients
- Brussels sprouts cut in half
- Olive oil
- Salt, pepper, garlic powder
- Dried cranberries (craisins)
- Sunflower seeds
- Goat cheese
- Balsamic vinegar
- Sugar
Directions
- Preheat oven to 375°F
- Cut brussel sprouts in half
- Put them on a baking sheet and mix them up with olive oil and seasoning
- Throw them in the over for like 20-30 minutes
- Mix balsamic vinegar and sugar together in a sauce pan, heat up til boil then turn it real low to thicken it up a bit
- When the Brussels start to brown pull them out of the oven
- Pour the balsamic sauce on the Brussels to taste
- Add dried cranberries and sunflower seeds to taste
- Add goat cheese to taste or use on flatbread/crackers on the side
- Add bacon bits to taste (if you have already cooked bacon!)
-
 @ d543c820:aa8001e7
2024-09-05 09:03:02
@ d543c820:aa8001e7
2024-09-05 09:03:02皮草两事
前日与朋友聊天,谈起时下留下的一种扮演了某种人格的 AI(有个时髦的名字,叫 “智能体”),蓦地想起英伦法学家边沁(Jeremy Bentham)。第二日,又联想起别的事来,因有此文。
“皮草”,在现代中文是指 “以动物(连)皮(带)毛制成的服装”,因其奢侈和暖和受人追捧。但也有关爱动物的人士批评其制作过程过于残忍。
但在古代中文中,这词可作别的意思:“皮以实草”、“剥皮揎草”。指的是把皮剥下来,把草填充进去,做成玩偶。
据说,明朝的创建者朱元璋(1328-1398),就制定过这样的刑罚:将贪腐的官员,处以剥皮之刑,然后以草填充,做成人偶,放在其继任官员的公堂旁边,以示警戒。
你可以想象,这种刑法是多么残酷。其恐怖、血腥的程度,与历史上有名的酷刑炮烙、分尸相比,是不遑多让的。所以,其在朱元璋统治的时代结束后,也并未被继续施行。有明一代,此种残酷刑罚的一个回响是在万历时代(1573-1620),有名的清官海瑞主张恢复这种刑罚,以整肃官员中贪腐的风气。
那么,朱元璋为什么要对贪腐官员制定如此残酷的刑罚呢?
小说家金庸先生的读者可能会认为,这跟其宗教信仰(明教)有关。明教即拜火教(琐罗亚斯德教),其本身推崇互帮互助,且憎恶贪官污吏,有点公社主义的味道。然而,这是说不通的 。因为明教本身有反体制倾向,不信任政治权力可被用来改善平民的生活。而朱元璋一以贯之地追求统治权力,自然不可能在实质上信奉此种理念。
(插句话,明代创建者与明教有关,此说始创于吴晗,被金庸先生拿去放在小说中,有了很大影响。然而,近些年的学术界,已开始反对这种理论,认为 “明” 的国号可能来自佛教经典,或来自儒家经典《易经》。)
也有人会认为,这跟朱元璋的出身有关。他出身贫苦,也曾流离失所,也许饱受贪官污吏欺压,因此格外痛恨他们。
我的想法是,这只是因为与前代帝王相比,朱元璋有格外疯狂的机器乌托邦狂想。朱元璋为明朝制定的制度,是格外机械、死板,而且严苛的。首先,其要求编订各地域的人口户籍 —— 这不出奇,中国从秦朝开始就这样做了 —— 然后,有趣的东西来了:他要求给这些人口按照经济条件分组,每组有固定的力役和纳税义务,以年为单位;以户为最小单位,每 10 个单位合并成一个大单位,层层往上合并;每一组的带头人都每年轮换一次,这个带头人要在该年中完成经济统计并带领其组内成员完成力役(比如修城墙、挖运河)和纳税(交粮)义务。与此同时,迁徙自由是禁止的,良民必须在其土地上完成其义务,而不能 “流窜” 到其它地方,官员的任务之一是将境内的流民遣返回原籍、保证境内的民不要流窜到其它地方。而这些力役和纳税义务,也是跟地域高度捆绑的,它们以就近的原则,被分配给所在地的城市和军队,而不是经过行政机构的统一收发管理。
也就是说,朱元璋希望把偌大的中国变成一台机器,所有人(主要是农民)在其出生的地域上为劳役和纳税而劳作,以恒久不变的速率为一个行政系统和军事系统提供养料,然后朱家江山永保稳定和太平。—— 而统治者,君主,将使用这套系统中形成的统计资料,来精确地了解每一个地区的实情,然后施行统治,保持系统的运行。
对于这样一个系统而已,统计资料的精确性,是具有第一位的重要性的。它决定了统治者到底能不能获得地方的实情,而不被自己的官僚蒙蔽。于是,贪腐 —— 为了个人私利,甚至不是什么特别大的利益,而弄虚作假,比如虚报产出以求减免税务、将经济富裕的农民反而分到税务负担较轻的组中 —— 就成了一个最多发、最难对付的顽疾。官员稍微不认真,产生的偏差就会不断叠加,然后积累出完全失实、无用的记录。这就是为什么贪腐的官员要被处于如此残酷的刑罚 —— 要用最残酷的刑罚、最血腥的展示,让他们在统治以机器人为理想模板的人群时,自己也成为机器人。—— 只有皇帝可以是个活人。
(《万历十五年》的作者黄仁宇认为明代的一大问题在于其制度阻碍了技术的发展,例如,军队的粮食是定点向某个村镇收取的,并由村镇自己负责押韵到军队驻地,这是 “散收散支”;如果交到行政机关处集中收取集中分发,就可以发展物流技术、保险技术云云。我认为,这是浅见。)
那么,十四世纪的朱元璋,跟边沁(1747-1832),怎么会扯上关系呢?
是因为边沁也曾设想过一种 “皮草” 的用途。他希望的是,有卓越成就的人物,可以在死后将自己制作成人偶(原描述为 “auto-icon”),摆放在公共空间里,(最好还能播放其生前录下的声音),起到教育的作用。
边沁自己也实践了这种想法。他在死前立下遗嘱,将自己的身体托付给一个好朋友,嘱咐其将自己制作成 auto-icon,要求以一个带玻璃的木盒子盛装,将自己做成坐姿,配上自己生前使用的椅子,还要身着正装,配上手杖。
事实上,边沁的 auto-icon 还真的是在保留了骨骼的前提下以草填充的。唯一美中不足的是,其头颅在防腐处理过程中被毁容了,完全不像其生前的容貌,因此被一个蜡像代替。
这个 auto-icon 后来一直放在实践了边沁的教育改革理念(一言以蔽之,有教无类,不论家资,不论宗教)的 University Collage London(伦敦大学学院,UCL)(在 2020 年以前,放在学院主楼南回廊的尽头;之后,迁移到学生中心)。
有关边沁的 auto-icon,我还听过一个传说(已被边沁的英文维基页面证伪):UCL 在每次召开理事会时,都将边沁的 auto-icon 陈列在侧,并认定他会给会议中的改革派投半票。
同样的皮草,在两种社会,两个时代,承担完全不同的预期作用。一个是为了在公共空间中承担教育的责任,或是给某一些人鼓励;甚或按一些浪漫的说法,是 “一种社会实验”。另一个,则是作为生杀大权的象征,要给人以无限的恐怖,从而使人战战兢兢地做好皇帝交办的工作。这何止天差地别。
参考文献:
百度百科·剥皮揎草:https://baike.baidu.com/item/%E5%89%A5%E7%9A%AE%E6%8F%8E%E8%8D%89/5372899
不要再說明朝國號「大明」源於明教:http://www.observer-taipei.com/book2021/item/634-2022-03-29-08-11-13
维基百科·Bentham:https://en.wikipedia.org/wiki/Jeremy_Bentham
《显微镜下的大明》
-
 @ 9bc2d34d:d19d2948
2024-08-13 22:13:23
@ 9bc2d34d:d19d2948
2024-08-13 22:13:23Chef's notes
Enjoy your delicious keto ham, egg, & cheese breakfast cups!
foodstr #foodjournalist #gastronomy #keto #homecooking #recipe
Details
- 🍳 Cook time: 15-20 (until the egg is cooked to your desired doneness)
- 🍽️ Servings: 1-12 (make one or fill the whole muffin tin)
Ingredients
- Slices of deli ham or your choice
- Large egg (one for each slice of deli meat)
- 2 tablespoons shredded cheese (cheddar, mozzarella, or your choice)
- 1 tablespoon thinly sliced shallots
- Salt and pepper to taste
- Optional: herbs or spices (like paprika or chives) for extra flavor OR bacon crumbles
Directions
- Preheat the Oven: Preheat your oven to 375°F (190°C).
- Prepare the Muffin Tin: Lightly grease a muffin tin to prevent sticking.
- Form the Ham Cups: Take a slice of deli ham and press it into one of the muffin tin cups, creating a cup shape. Repeat with the remaining slices of ham, using one slice per cup.
- Add Shallots: Sprinkle a little bit of the sliced shallots into each ham cup.
- Add Cheese: Add a tablespoon of shredded cheese into each ham cup on top of the shallots.
- Crack the Egg: Carefully crack an egg into each ham cup, being careful not to break the yolk. If you prefer, you can whisk the egg beforehand and pour it in.
- Season: Sprinkle with salt, pepper, and any optional herbs or spices you like.
- Bake: Place the muffin tin in the preheated oven and bake for about 15-20 minutes, or until the egg is cooked to your desired doneness.
- Cool and Serve: Let the cups cool for a minute before carefully removing them from the muffin tin.
- Enjoy your delicious keto ham, egg, & cheese breakfast cups!
-
foodstr #foodjournalist #gastronomy #keto #homecooking #recipe
-
 @ 592295cf:413a0db9
2024-08-10 09:24:14
@ 592295cf:413a0db9
2024-08-10 09:24:14Week on Nostr 05-08
List of site for nostriches https://zaplinks.lol/
Fiatjaf web components
Welcome bear market 🧟♂️ fear, angry, build It's fine meme
I mutated one on stackernews. Basically I have notifications on Nostr page But someone keeps spamming every single thing, from his point of view it's a shared bookmark, but do it on your site. Maybe it's the heat...
On bluesky they eliminated a "for you" feed, now there is Discovery, not your feed, not your choice. There's actually a label that says my feeds, they're yours... Designed for you is more appropriate.
Mutiny lightning, "get the fuck on board". 😔
You lose your Money, ok
I don't know much about programming languages, but it seems like a jungle of scams
The purple pill help the Orange pill go down, maybe it was wrong. For now it's more people passing pills I have the orange give me the purple, I have the purple give me the orange. 😅
If you don't want no corn content you can go to mastodon and bluesky or whatever.
I thought nostr:relay might be a good solution to be a little more like a mint. It was deprecated, then the Nip-73 was added, rss feed and other devilry.
If you don't like what you see, change the app, this one will perhaps clear your following list and you'll start again from scratch. Not all things come to harm.
Why not Building agregore on Nostr, Nostr pear fedimint cashu mesh and local first. It doesn't seem like a simple application to make, from a local-first perspective, I solve a problem, but it's not a small problem to solve, Sync, database management, database schema, authentication, put everything together, instead I need this to solve this problem. It seems strange.
Aspie96 is making a client of ours, there was a lot of talk about how to increase content not related to bitcoin and things like that, there was one who was anti-bitcoin. I thought: Bitcoin is just a tool. Even guns are just a tool. I hate guns, I hate Bitcoin. It will be difficult, if you know any npub that hates Bitcoin comment below, thanks.
Trying not to use nostter for a while. It has glitches when loading threads and even with zap, I zapped myself even though I was clicking on the post I was replying to.
Voyage separates follow to topic in a new version.
People start arguing, it's allowed, everyone wants to be right, that's not the definition of social 👾.
Monitors watch-only bitcoin wallets https://github.com/sommerfelddev/sentrum
I noticed on Openvibe that in the trending timeline Nostr's notes have more interactions than responses. Maybe it was just that today Fiatjaf was doing universal polls 😅.
Step away from your favorite app, for a week if you can. Detox.
Oh Our founding, rain of money https://github.com/theborakompanioni/nostr-spring-boot-starte https://opensats.org/blog/nostr-grants-august-2024#seer
I'm happy for Vic and Sepher Nostroot exists 😅, note from some time ago. (I can't find it)
Perhaps the list of grant applications should be published, no one wants to open Pandora's box. 🙇♂️
Nostrasia 2.0 the Japanese community is a bit at a loss, they are trying to relaunch themselves 🤙, even if I'm seeing less enthusiasm, I'm following less.
I think a month has passed since I said this sentence, every day it was better but the next day something happened that you said maybe 6 months is too long. nostr:nevent1qy88wumn8ghj7mn0wvhxcmmv9uq3zamnwvaz7te3xsczue3h0ghxjme0qyw8wumn8ghj7mn0wd68ytnxwfskxarpd35h5ety9ehx2ap0qythwumn8ghj7mn0wd68ytnnw3skkete9ehx2ap0qy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qpqf25td2xxgxfu80xpgg47cmfg2zkn6v803kefj3htjss5nvamfmgswf2kcs
Ho iniziato a seguire un po' local-first. https://docnode.dev/local-first I follow a podcast of the same name and dev tools.
When everyone thinks of Nostr they think of their favorite app and think that others see the same, but this is not the case.
I delete some gossip (photo)

Gossip is Nostr or Nostr is gossip.
Communities are difficult, they take time. I don't have this type of problem. People are fine on telegram and on simplex or any app. But maybe a Nostr project should be on Nostr?? Nip-29 can be interesting. Even if you start from scratch or almost. It's true that there are more apps, but this will perhaps only add to the confusion.
They are still talking about paid or non-paid relay, it's not a mature stage. Early stage.. I thought designers liked relays, that's not the case, I thought it was a place of experimentation, that's not the case. Bring more people. Last week I was talking about how I was jealous of bluesky who had an agenda for design, now it's also on Nostr, first hypernote article https://wikifreedia.xyz/hypernote-nip
I might say silly things, I'll go.
Hey Will remember to practice safe nsec always
nostr:nevent1qqsr6x8hduv8ta0g2da4aukrhzdtv6qcekyp5f9z9sxq6sd5peegnxgprpmhxue69uhhyetvv9ujumn0wdmksetjv5hxxmmdqy28wumn8ghj7un9d3shjtnyv9kh2uewd9hsygr4wku5l2q32tl99xjgn8feq22279pzwu25eezqxm2su2ken4wzvuf2ydnp
nostr:nevent1qqspsm343talkkjnyf3ah0zwy727cwd7phw3xnz49q59q5cfw4uhyngpzemhxue69uhhyetvv9ujuurjd9kkzmpwdejhgqgcwaehxw309aex2mrp0yhxummnwa5x2un99e3k7mgzyqewrqnkx4zsaweutf739s0cu7et29zrntqs5elw70vlm8zudr3y2j7zajz
Use nsec.app, 😅 Share bunker (smart people will know how to do it)
-
 @ c7eadcf0:7821e562
2024-09-04 23:58:56
@ c7eadcf0:7821e562
2024-09-04 23:58:56Another test post. I think I might have found my long form content writing app. Well done.
-
 @ c7eadcf0:7821e562
2024-09-04 23:53:44
@ c7eadcf0:7821e562
2024-09-04 23:53:44seeing if this works lol
-
 @ 592295cf:413a0db9
2024-08-04 05:55:02
@ 592295cf:413a0db9
2024-08-04 05:55:02Nostter muted by kind
Will mute freefrom, hashtag fall
Venezuela riots, after the vote
I was thinking that having a Nostr conference every 6 months doesn't make sense, maybe it's better to focus on something else. If not it becomes a Tour Life. It doesn't increase adoption Produces tons of material It's good for networking It's not sustainable
Readable updates, how important they are. If it's just bugs and fixes it's better.
I hate Pam. As user It writes interesting stuff, but, doesnn't write in long form, because long form are more difficult, less reach and immediacy, and difficulties to share over in the feed,but not write a poem, sorry.
The thing about coracle is that I load the initial feed, but that gets printed, and it doesn't tell me if there are new notes coming in, as if it interrupts the flow, and it's always a fetch. I want to read the future, not always the past. RealTime feeds Like bluesky 🧞

Njump had problems, it keeps the cache and if the user changes something in their data it doesn't update it immediately. Fiatjaf was angry.
It's the month of NostRiga, we can move on to September without thinking about it. No
It's funny when you see a text in Japanese and inside read Nostr, I want to know what it says. He usually says Nostr is great. And the next note I drank too much 🤣
Today I thought that on the other side of the world it is February and that their February is 31 days. Pam said was sick. I see that hate is a virus 😅🙇♂️
I decided to publish stronpy when it's ready, maybe in 6 months. I've done the lineup, now I have to do the gantt 😅. Maybe I can post the gantt somewhere.
If it's not encrypted it's public. Amethyst draft 31000 and something like event
Nostr Is great but the amount of time Lost to the same thing because you don't know that exist Is remarkable. Nostr is a redundancy protocol
nostr:nevent1qqsqjqauc34k9k278x6cka5jyf3aq033y4pn5czwaff72l3rwum7llq7ela3x When they do that I can't stand them, then maybe it's a little different 😔😔 Zapper.fun ✅ Because you launch a project, example nostr.band but contain others 100 apps 😅 Nostr.band, nostrapp.link, zapper.fun, Nostr login, nsec.app, Npub.pro, Npub.pro also cli, Nostr universe/ knows as spring site
Even in Coracle it would be great to have a check on the note as root, because when you see the answers, perhaps the distance from another post, is so small, so perhaps a gray line for the mark of another note as root.
I listened to several minutes of plebchain radio episode on nostrnests. Language is an obstacle, but also an excellent justification. Last year I started recording a podcast episode, in which I talked about nostr bookmark update. I didn't even want to listen to it again 🤣.
I sent a video of an explanation of a zap it was 500 MByte of video for 4 minutes.
Nostr doesn't work. In practice, many apps have removed the possibility of logging in with the simple key, be it public or private, because especially the private one you don't want to copy paste in every single clients/apps, increasing the attack surface.
However, by removing this functionality and doing little onboarding, the matter is very difficult, but there is a certain belief that people who arrive at a Twitter like client get to know the network a little and then move on to videos or writing, or similar. But one can open a site by chance and see what it offers without knowing anything.
In the future there will only be one client, that of medical data...
Someone share this nostr:nevent1qqs24qzelpk8xjlk4dthr9tfkqwz8n58dlm04ezyvg9nuztud6jjfhc9mg04n I had in my bookmarks. I see dozen types of this self hosted manners. Maybe captains-log is for nostr-type, good.
-
 @ 048ecb14:7c28ac78
2024-08-02 00:20:09
@ 048ecb14:7c28ac78
2024-08-02 00:20:09Chef's notes
- Makes 6 buns
- Can be cold fermented over night - do what works for your schedule (for a night event, start in the morning ; for a lunch event, prep the night before and cold ferment).
- Based on a recipe by the ChainBaker (whose recipes and YouTube I highly recommend).
- This recipe uses a softening technique called Yudane which involves prepping flour + boiling water in advance to making the dough.
- Work with the dough in a cool environment < 24°C (75°F) so that the dough is not too sticky. When it's really sticky, I just use a Slap and Fold kneading method.

Details
- ⏲️ Prep time: 6-7 hr (start to finish)
- 🍳 Cook time: 25
- 🍽️ Servings: 3 (2 rolls/person)
Ingredients
- Flour 300g (50g for yudane + 250g for main dough)
- Boiling Water 50ml
- Milk 150ml
- Dry Active/Instant Yeast 4g
- White Sugar 20g (can be reduced)
- Salt 6g
- Butter (softened) 20g
- Egg Yolk 1
- [glaze] Egg White 1
- [glaze] Sesame seeds
Directions
- [Yudane] Pour 50ml of boiling water over 50g of flour while mixing. Put in fridge to cool for 1.5 hours.
- Take butter out of fridge and leave to soften
- In a big bowl add the yeast, salt, sugar, egg yolk. Pour in the cold milk and mix so that the granules can hydrate/dissolve
- Add the cooled yudane from the fridge and mix.
- Add in the rest of the flour and mix. Leave to hydrate for 15mins.
- Scrape the dough out onto a cold surface for kneading. It will be quite wet (especially in a warm environment). Knead for 5-6 minutes, possibly using the slap and fold method due to stickiness.
- Add the butter, and knead for another couple of minutes so that it is well incorporated.
- Collect the dough (it's okay if it's still sticky and difficult and not a pretty ball) and move back into the bowl. Cover with plastic wrap.
- If baking same day, leave for 2-2.5 hours to proof/ferment at room temperature (~24-26°C/75-78°F). Adjust the time for higher/lower temps. If baking the next day, put the bowl in the fridge overnight.
- After the bulk proofing time is up, prep a scale and weigh the dough. Calculate what each dough ball should be (this recipe makes 6 balls).
- Slice the dough into pieces weighing the right amount for each ball. I find this is usually around 85g, but depends on factors like how much dough was lost in moving / evaporation etc. so weighing is important.
- Frequently dust the working area with flour so the balls don't stick. For each ball, loosely fold the edges of the dough into the center, flip it over and let it rest for 10-20 minutes.
- Once again flip each ball over and fold the edges again inward. A little tighter/cleaner this time. Flip so the folds are down, and gentle roll the dough in a circular fashion with a cupped hand so that it becomes a ball. You can also try to create some tension at the top of the ball if you know how.
- Prepare the tray you'll bake the buns in, lining the bottom with a cooking sheet.
- Line up the balls on the tray with a little space between (they'll grow) and place plastic wrap over them so they don't dry out, dusting the tops and side with just a little flour so the film doesn't stick.
- Leave the balls to proof/rise for 2 hours.
- Pre-heat the oven to 160°C/320°F.
- While waiting for the over to heat up, use the leftover egg whites to brush over the buns. Then sprinkle sesame seeds over the top.
- Bake for 25 minutes and then let rest for another 30min. I recommend toasting in butter in a frying pan prior to serving with burgers
-
 @ a324b2fe:68bf4629
2024-09-04 23:47:54
@ a324b2fe:68bf4629
2024-09-04 23:47:54One of the most significant underlining doctrines of our time is that of the rapture and the eschatological (study of the end times) understanding that the world will be overrun with evil, and God will ‘beam us up scotty’ either before the faeces hits the fan or after. There are slight variations in this ‘futurist eschatology’ I’ve just briefly explained. Many would agree that this is what the bible clearly teaches, and others will have a verse or two in their minds that without further study seems to validate this popular understanding.
Make no mistake, most Christians believe in a ‘futurist eschatology’ (see below), but the real question is why and how most of us have landed believing that things are going to get much worse on the planet, or that things will get better but will suddenly plummet down and Armageddon becomes more than a badly plotted movie. Some might be wondering “I never knew such a thing existed”, let alone know that there are different opinions on the matter. Keep reading because you’ll be surprised at how much this doctrine actually influences ALL your decisions.
To summarise, there are four major positions of interpreting “The book of Revelation”, which is the core book to influence our perspective on the future or “end times”.
Futurisme:
The belief that the events in the book of Revelation is referring to global events in our future. (popular since the 1800’s; the beast’ (see revelation 13 and 17) is a man and a new world order, many historical figures have been suggested in their time; Napoleon, Hitler, Stalin, Osama bin Laden, Barack Obama etc.).
Historicism:
The belief that the events have transpired over history like a timeline (popular in the 1500’s at the time of the reformation, notably that the Pope of the Catholic Church and the Papacy were the ‘beast’.
Preterism:
The belief that the events (most or all) have already taken place in the 1st century, climaxing at the destruction of Jerusalem in 70AD, Rome as a whole and Emperor Nero being considered the ‘beast’.
Idealism:
That the book is a symbolic battle between good and evil.
Before I get into the nitty gritty on history, specific scripture and their exegesis (a fancy word I never use in conversation, meaning critical study and interpretation on a text). Let me highlight why what we believe about the future influences our every decision.
One day in 10 years time you’re married to a beautiful/handsome spouse and have 7 children. You believe that the world will end soon and that there’s going to be a massive heavenly battle and the angels are going to use their majestic rippled muscled limbs to wreck havoc on all those that oppose. Nice. Or not nice if you chose the wrong side. Before that happens though your daughter wants $1000 to invest in some shares because she learned at school that if you put $1000 in shares today and top up $100 every month you’ll have accumulated a total of $72,000 in twenty years having only contributed $25,000 of your own money. Smart kid, that’s a good long term investment strategy.
You however don’t believe the world is going to exist in its normal state in another 20 years time, or you reason it might, but surely not much longer after that. So you say: “Sweety, I really don’t think that’s going to do you much good, the market is too volatile and I don’t foresee things getting better in the future, why don’t you spend your money on some clothes or go out with your friends”? Yes this is quite an elementary example and I’m sure you’ve all invested money into shares and it would never happen to you.
How about another scenario then? You believe the rapture will take place in your lifetime. You read your bible and see that Christians need to share the gospel, so you start to share with people, some people reject you, some are indifferent, and others are deeply touched. The ones that are impacted, you give them a bible and say go to church and get ready for the return of Christ (in your mind you’re thinking that means rapture). Some of them do, some go and fall away and still others somehow are consistent and are growing in the Lord, good job right? What about those people that fell through the cracks? That’s not my responsibility you say, they need to work out their own salvation with fear and trembling. Okay, have you considered that the responsibility is actually squarely on your shoulders? In regards to making a disciple, not a convert. Discipleship takes much longer, it takes time, it takes sacrifice, and it takes a perspective that there is even time for discipleship. Otherwise it’s a 6 week course in “How to be a Christian”.
Thankfully some of the church has in the last few decades focused a lot more on discipleship, even whilst holding the perspective of a futuristic eschatology. Yet even in this the reasoning is simple, they are doing their best to follow what they read in the bible regarding discipleship (rightfully so), and also a discipleship approach of evangelism retains and reaches more people, so it’s a more successful method to convert in any case. If this is you, you’re amazing, please keep making disciples! I however propose that you sincerely ask yourself what you would do differently if you believed the world would exist for another 200 years plus.
As you can see our belief on the future has extreme and subtle effects on our actions and decisions. Our society is peripheral to where the church is at, and right now the church as a whole believes that the end is soon and there’s no point in believing and acting like it’s a good thing to leave an inheritance for your children’s children. That is why we buy cheap, that is why we don’t invest, it is why we are driven by instant gratification. Why would you bother with all that if the world will end in a matter of years. It comes to whether you have a hope filled optimistic expanding Kingdom perspective on how the world is going to turn out or one that is governed by a defeatist/fatalistic mentality and perhaps even one fear riddled.
Now that we’ve looked at how our beliefs can be outworked in everyday life, let’s get into doctrine. Finally. Actually, some more history first.
I and many others find it helpful to look at history to see when a certain doctrine began to gain support and become the popular belief to determine its validity. Let’s jump in then, during the reformation, the Catholic Church was under fire and experiencing some mostly accurate criticism. In a response to Christians accusing the Pope and the Papacy of being the beast, a Jesuit priest wrote extensively that the events in the book of Revelation are referring to their future, thus eliminating the Pope and the Papacy of fault. His writings didn’t gain traction until the 1800’s where John Nelson Dalby adopted the belief and started widely teaching it, specifically on ‘Pre-tribulation rapture theology’ (we get raptured/caught up prior to the tribulation that will happen on the earth). I would like to explicitly mention that before this, proponents for a futurist eschatology were almost non-existent.
Then in the following early century (1909 to be exact), the first ever bible with commentary was printed. The Scofield bible. This bible was a massive advocate for dispensationalism and a futuristic eschatology; practically every bible college student got one of these bibles, and lo and behold an entire generation of pastors and theologians were massively influenced on their belief of the future. Couple that with two world wars, the reestablishment of the Jewish nation, Israel, and we have a perfect concoction for believing the time is near and Armageddon is around the corner.
Now there are entire books discussing all of this that I cannot even hope to cover even a slither, but if you are so inclined, see some recommendations at the end. I won’t attempt (nor can I) to extrapolate on everything there is regarding a ‘preterist view’ of Revelation, and a ‘victorious eschatology’ which was the orthodox view in early Christianity, but here is a summary of what you need to know.
The Kingdom of God:
As indicated by the statue in Daniel 2 was inaugurated with the birth of Jesus (coming of Jesus in the Manger), and started to expand and is still expanding. See Mathew 13:31-33. Also see Isaiah 2 for the hope for the future.
The destruction of Jerusalem in 70 A.D.
Wasn’t just an important event in history, it is paramount to the entire New testament and is referenced to in almost every book. To miss its importance is to miss understanding much of the New testament. This event is crucial to the progress of God’s redemptive plan in history, with the final removal of the temple and the genealogical records of the priests therein, the old (mosaic) covenant closes and the new covenant is fully and permanently established.
“When you see Jerusalem being surrounded by armies, you will know that its desolation is near. Then let those who are in Judea flee to the mountains, let those in the city get out, and let those in the country not enter the city. For this is the time of punishment in fulfillment of all that has been written. - Luke 21:20-22
John the Baptist proclaims judgement on the Jews in Matthew 3:10-12. See also Matthew 7:19 “The ax is already at the root of the trees, and every tree that does not produce good fruit will be cut down and thrown into the fire. I baptize you with water for repentance. But after me comes one who is more powerful than I, whose sandals I am not worthy to carry. He will baptize you with the Holy Spirit and fire. His winnowing fork is in his hand, and he will clear his threshing floor, gathering his wheat into the barn and burning up the chaff with unquenchable fire.” This provides the backdrop to Jerusalem erupting in flames in A.D. 70. Later Jesus declares John is Elijah to come (Matt 11:14) fulfilling the prophecy in Malachi 4:5-6, as he proclaims judgment in Israel before the great and terrible day of the Lord (John mentions the day of the Lord in Rev 6:17; 16:14).
In Matt 12:39 Jesus regards the Jews of His day as an adulterous generation, the same imagery is found in Revelation 17:3 as John presents Jerusalem as a harlot (see also Isa 1:21; Jer 2:20; 3:1,6,8; Eze 16:9, 15-17, 26; Hos 2:5; 4:10; 12-15). In Matthew 23:34-35 Jesus warns that God will judge 1st century Jews for the righteous blood that was shed in the land (we see the same statement in Rev 18:24). In Matt 23:36-38 Jesus laments Jerusalem’s destruction and declares the temple desolate, John declares Jerusalem is desolate in Rev 17:16. After that Jesus prophesies its destruction in Matt 24:2-3 and Luke 21:24, and John uses the same language as Luke, in Rev 11:2. In Matthew 24:16 Jesus urges his followers to flee Judea because “this generation will experience judgement (Matt 23:32). John calls the saints out of Jerusalem in Rev 18:4.
I could go on but there are books for that. Here's the simplicity of it; John’s general message in Revelation is ‘the divorce of Israel and God’s marriage to the new covenant church’ (which obviously includes Jews if they turn to Christ). The ‘second coming of Christ’ came when he came in judgement on Jerusalem. There is another coming, hold your horses I’ll get there.
The 'Olivet discourse’ of Matthew 24:
Is referring to 1st century events and uses prophetic symbolic language (stars falling, moon to blood, sun darkened etc.) to demonstrate a toppling of governments, see Isa 13:10,13 referring to Babylon; Isa 34:4 referring to Edom; and Eze 32:7-8 referring to Egypt. Also think of Joseph and how his family were stars, a moon and a sun and that they bowed to him. Again, it’s language to communicate a natural toppling of governments or exchange of political dominion. Not a global catastrophic Armageddon.
The Anti-Christ:
Used only four times in the bible (1 John 2:18; 1 John 2:22; 1 John 4:3; 2 John 1:7). It has always been a referenced to a false teaching in the 1st century that claimed Jesus had not come in the flesh. A gnostic heresy.
The Beast, the mark of the Beast, and his number 666:
Referring to Emperor Nero who was called a beast, forced people to get markings of him to be able to buy and sell in the marketplace (Rev 13:16-17), see a short video on the matter https://www.youtube.com/watch?v=wng3jcfMkZU. Now Gematria is a Jewish Interpretive method that assigns numerical value of Hebrew letters to words. We find this with the number of the beast being 616 (in Latin) or 666 (in Hebrew), with the values added up it spells Nero Caesar. See this 2 min video https://youtu.be/JXkTc18xBoM. Some people, like in the video say that he represents a future beast as well, this is simply poor and biased exegesis and is thus construed to validate their pre-existing beliefs.
The Word Rapture:
Found in 1 Thessalonians 4:17; “After that, we who are still alive and are left will be caught up (rapturo in Latin) together with them in the clouds to meet the Lord in the air. And so we will be with the Lord forever”. The entire bases of the doctrine of the rapture is found in this one simple verse. Yet all it means is that we will be gathered to Jesus and the past saints/Christians at His return.
What now? Is everything done?
Well not quite.. Jesus’ Return: Jesus will return as is promised in Acts 1:11, but it won’t be with a massive army to lay plunder to the earth, well maybe, but I highly doubt it. “…will come back to you in the same way you have seen Him go into heaven”. The resurrection of the dead: Zombies! Kidding, just mass people coming back to life. See 1 Thessalonians and 1 Corinthians 15. The Great judgement: The great judgement day of the sheep and the goats in Matt 25.
That’s it, so until then, however long that will take (my money is on 197 years), let’s keep bringing the Kingdom of God to earth, lets pray for miracles, make healthy disciples that reproduce, transform every facet of society to look like heaven, and establish a Kingdom legacy that our Lord and King would be excited to come back to.
Ps. My views on Gods judgment on the 1st century Jews is not that he wanted to destroy them, but rather he was bringing judgment on an old covenantal system, the Jews that clung to that sinking ship unfortunately went down with it.
Book Recommendations: Understanding the whole bible – Jonathan Welton Raptureless – Jonathan Welton The art of revelation – Jonathan Welton Before Jerusalem Fell: Dating the book of revelation – Kenneth L Gentry Navigating the book of Revelation - Kenneth L Gentry Victorious eschatology: A partial Preterist view – Harold R Eberle and Martin Trench
Theologian Gary Demar
-
 @ a1db88e7:f541cabf
2024-07-22 11:00:59
@ a1db88e7:f541cabf
2024-07-22 11:00:59Details
- ⏲️ Prep time: 10 min
- 🍳 Cook time: 35 mins
Ingredients
- 4 eggs
- chives
- Onions one chopped
- Mushrooms of your choice
- Salt and pepper
- Cayenne pepper
- Milk - preferably oat or almond
Directions
- Blend the eggs with the chopped up onions and chives. Put in the seasoning and whisk well with the milk.
- In a pan, melt the butter or oil on medium heat. Pour down the eggs. Let it sit for a few minutes and then lower the heat. Let i be för approximately 15 min. Let it set and rest for a few minutes.
-
 @ 44dc1c2d:31c74f0b
2024-07-11 19:26:22
@ 44dc1c2d:31c74f0b
2024-07-11 19:26:22Chef's notes
Make sure you cook them thoroughly on the skin side first to render out as much of the fat as possible and ensure maximum crispiness.
This goes great with rice.
Ingredients
- 6 skin-on, bone-in chicken thighs (about 2 pounds total)
- Kosher salt
- 2 tablespoons sesame oil, preferably toasted, divided
- 1 pound medium carrots, scrubbed
- 2 tablespoons soy sauce
- 2 tablespoons Sriracha
- 2 tablespoons unseasoned rice vinegar
- 1 tablespoon honey
- 1 1-inch piece ginger
- 3 scallions
- Toasted sesame seeds (for serving)
Directions
- Preheat oven to 425°. Heat a large dry skillet, preferably cast iron, over medium-low.
- Pat 6 chicken thighs dry with paper towels and season all over with salt. Rub only skin side of thighs with 1 Tbsp. oil.
- Transfer thighs skin side down to skillet and cook until enough fat is rendered to cover bottom of skillet, about 5 minutes. Once skin starts to brown, increase heat to medium. Rotate skillet to encourage even browning. Carefully lift up thighs to allow hot fat to run underneath. If thighs are stubborn and don’t want to release, let them go a bit longer.
- While thighs are cooking, cut 1 lb. carrots into 4" segments.
- Cook thighs until meat is opaque all around the edges and skin is deep golden brown, 10–12 minutes total. Transfer skin side up to a plate.
- Pour off all but about 2 Tbsp. fat from skillet (you just want enough left to form a thin layer) and heat over medium-high. Add carrots and try to arrange so all are side by side in a single layer in direct contact with skillet. Cook, undisturbed, until lightly charred on first side, about 5 minutes. Turn carrots so charred side is facing up, then season lightly with salt.
- Cook carrots on opposite side until lightly charred, about 2 minutes. Turn off stove and transfer skillet to oven. Roast until a toothpick, skewer, or cake tester easily pierces surface of carrot but encounters resistance in the center, 8–10 minutes.
- While carrots are roasting, stir 2 Tbsp. soy sauce, 2 Tbsp. Sriracha, 1 Tbsp. rice vinegar, 1 Tbsp. honey, and remaining 1 Tbsp. oil in a small bowl. Scrape peel off of ginger root with a spoon; discard peel. Grate ginger into bowl with microplane, then stir to combine.
- Carefully remove skillet from oven (the handle will be hot!) and place on stove. Arrange thighs over carrots and drizzle sauce over. Return to oven and roast until chicken thighs are cooked through (an instant-read thermometer inserted into the thickest part near the bone will register 165°), juices run clear, sauce is caramelized on chicken skin, and carrots are tender all the way through, 12–18 minutes. Remove from oven and let rest 10 minutes.
- While skillet is resting, thinly slice 3 scallions.
- Transfer chicken and carrots to a platter and drizzle pan juices over. Top with scallions and sesame seeds.
-
 @ 1a48e74d:02c0e00f
2024-09-04 23:38:34
@ 1a48e74d:02c0e00f
2024-09-04 23:38:34seeing if this works.
-
 @ ee2f41fa:23552fbb
2024-07-10 12:38:57
@ ee2f41fa:23552fbb
2024-07-10 12:38:57Chef's notes
Perfect for the summer days
Details
- ⏲️ Prep time: 5-10min
- 🍳 Cook time: no cooking time
- 🍽️ Servings: 4
Ingredients
- 2 cucumbers (about 500 g or 1 lb)
- 500 g plain yogurt (1 lb)
- 2 -3 tablespoons of crushed walnuts (optional)
- 1 bunch fresh dill
- oil
- salt
- water (optional)
Directions
- Beat the yogurt with a fork until it gets liquid and pour it over the cucumbers.
- Add the crushed garlic, the walnuts and the minced dill as well as salt and oil to taste.
- If needed add some water to make the soup as liquid as you like but take care not to make it too "thin".
- Put into the refrigerator to cool or add ice cubes.
- Serve cold
-
 @ c7eadcf0:7821e562
2024-09-04 23:03:59
@ c7eadcf0:7821e562
2024-09-04 23:03:59Welcome back ya'll hope you are doing well this week. Today I wanted to talk about why Bitcoin represents a dawn of a new age in property ownership. Before you spit out your coffee and walk away, hear me out. Bitcoin and real estate have a few things in common. The first is property rights.
When you are the owner of a building with your name on the dotted line and whatnot, you are the sole owner of that property. No one can tell you what to do with it, and no one has a claim to what you own. You are free to do what you wish. Property rights are sacrosanct and immutable similar to Bitcoin.
Bitcoin confers upon the owner the same property right protections as owning a piece of real estate. Once you own it, you are the sole owner of that Bitcoin. No one can tell you what to do with it. No one else has a claim to your Bitcoin. You are free to do with it what you wish.
Bitcoin and real estate are similar in terms of built-in scarcity. There is only 21 million Bitcoin that will ever be created, and you can't print more land. This is why owning real estate has been such a good investment since the beginning of time. Buying a piece of land and "HODLING" for decades will generate a substantial return on your investment.
This same buy and hodl strategy apply to Bitcoin as well. If you bought Bitcoin back in 2009, you would be a multi-millionaire right now.
If you invested $1000 back in 2011 when Bitcoin was trading at $3.50, you would have turned that $1000 into $15.6 million if you held on to it for ten years. Just sayin.
You have to reframe your thinking to understand what is going on. We are living in the 21st-century gold rush, and you have an opportunity to stake your claim to the soundest money on Earth with a few taps on your phone. Never in the history of the world has the plebs like us had the ability to front-run a monetary revolution.
Bitcoin is freedom from oppression. Bitcoin restores your sovereignty. Bitcoin makes you fuckable, and the powers that be know it. They are afraid they will lose control if too many people catch on too quickly, which is why large institutions are rushing to offer Bitcoin services or buy them and keep them on their balance sheet.
Bitcoin won't stay this cheap forever. $100-300k Bitcoin is in the cards over the next few years. I don't want you guys to miss out on this.
All you have to do is buy Bitcoin and hold. It's that simple. FYI trying out the new obsidian writer for nostr notes!
Bitcoin #nostr
-
 @ 1a48e74d:02c0e00f
2024-09-04 23:00:22
@ 1a48e74d:02c0e00f
2024-09-04 23:00:22Welcome back ya'll hope you are doing well this week. Today I wanted to talk about why Bitcoin represents a dawn of a new age in property ownership. Before you spit out your coffee and walk away, hear me out. Bitcoin and real estate have a few things in common. The first is property rights.
When you are the owner of a building with your name on the dotted line and whatnot, you are the sole owner of that property. No one can tell you what to do with it, and no one has a claim to what you own. You are free to do what you wish. Property rights are sacrosanct and immutable similar to Bitcoin.
Bitcoin confers upon the owner the same property right protections as owning a piece of real estate. Once you own it, you are the sole owner of that Bitcoin. No one can tell you what to do with it. No one else has a claim to your Bitcoin. You are free to do with it what you wish.
Bitcoin and real estate are similar in terms of built-in scarcity. There is only 21 million Bitcoin that will ever be created, and you can't print more land. This is why owning real estate has been such a good investment since the beginning of time. Buying a piece of land and "HODLING" for decades will generate a substantial return on your investment.
This same buy and hodl strategy apply to Bitcoin as well. If you bought Bitcoin back in 2009, you would be a multi-millionaire right now.
If you invested $1000 back in 2011 when Bitcoin was trading at $3.50, you would have turned that $1000 into $15.6 million if you held on to it for ten years. Just sayin.
You have to reframe your thinking to understand what is going on. We are living in the 21st-century gold rush, and you have an opportunity to stake your claim to the soundest money on Earth with a few taps on your phone. Never in the history of the world has the plebs like us had the ability to front-run a monetary revolution.
Bitcoin is freedom from oppression. Bitcoin restores your sovereignty. Bitcoin makes you fuckable, and the powers that be know it. They are afraid they will lose control if too many people catch on too quickly, which is why large institutions are rushing to offer Bitcoin services or buy them and keep them on their balance sheet.
Bitcoin won't stay this cheap forever. $100-300k Bitcoin is in the cards over the next few years. I don't want you guys to miss out on this.
All you have to do is buy Bitcoin and hold. It's that simple. FYI trying out the new obsidian writer for nostr notes!
Bitcoin #nostr
-
 @ af9c48b7:a3f7aaf4
2024-07-10 03:41:28
@ af9c48b7:a3f7aaf4
2024-07-10 03:41:28Chef's notes
I found this recipe online and couldn’t believe I’d never thought about it before. This is the easiest way to prepare corn on the cob for a large group. This is a must try for your next big event.
Details
- ⏲️ Prep time: 30 minutes
- 🍳 Cook time: 45 minutes
- 🍽️ Servings: 10-20
Ingredients
- 20-30 ears of fresh sweet corn on the cob
- 3-4 sticks of butter
- Season to taste…salt, pepper, cajun seasoning
Directions
- Shuck fresh corn, removing all silk and husks, then rinse if desired
- Place corn in a cooler (size needed will be based on # ears)
- Bring pots of water to boil and pour into cooler, covering all the corn
- Add a stick of butter for every 6-8 ears of corn
- Add seasoning to taste
- Seal cooler and allow to sit for 45 minutes
- Enjoy fresh cooler corn with friends and family
-
 @ 472f440f:5669301e
2024-09-04 22:54:11
@ 472f440f:5669301e
2024-09-04 22:54:11For the last few months many people in bitcoin, myself included, have been focused on bitcoin's role as a macroeconomic asset. Bitcoin as a strategic reserve for the US government. Bitcoin as a strategic treasury asset for corporations. Bitcoin as a geopolitical hedge in a world that is trending toward a multi-polar power dynamic. This is where the focus has been. And for good reason. These trends will ultimately have a material effect on the price of bitcoin if they pick up steam.
However, with all of the focus on bitcoin as a strategic asset I think a couple of technical developments and trends have been overlooked. Particularly in the realm of second layer privacy. I'll touch on two of them in this letter; BOLT 12 invoices and the progression of ecash.
Yesterday afternoon the Strike (a company Ten31 is very proud to be backing) team released a blog post that detailed their journey to implementing BOLT 12 offers in their product stack. For those who are unaware of BOLT 12 and why it is important, in short, it is an upgrade to the lightning network that would make receiving bitcoin on the lightning network more private while also significantly improving the user experience. The current standard for invoicing people via the lightning network is BOLT 11, which forces users to create a unique invoice every time they want to receive bitcoin and comes with privacy tradeoffs for the party receiving bitcoin.
BOLT 12 brings with it route blinding which allows a receiver to publish a lightning offer to the network without revealing their node's public key. It also brings with it onion messaging, which allows users of the lightning network to communicate without a dependence on HTTP, which can be censored by a motivated state actor. On top of this, it enables users to create a static invoice that can be paid multiple times by multiple people. Think of a band putting their Venmo or Cash App QR code next to their tip jar on the stage. They'll be able to add a private lightning invoice their audience can pay to now.
https://strike.me/blog/bolt12-offers/
As it stands right now, Strike has only enabled BOLT 12 offers and there is work to do at the protocol layer of lightning and the different implementations of that protocol to get the full benefits of BOLT 12, but this is material progress that gets us closer to a significantly better user experience on the lightning network. If you read Strike's blog post you'll come to appreciate the collaboration between the teams working on these implementations and the companies implementing the protocol that is necessary to get these features live. Shout out to everyone who worked on this. Everyone who uses the lightning network will be better off when BOLT 12 is fully implemented.
Moving on. Earlier today the founder of the BTCPay Server open source project, Nicolas Dorier, published a blog post outlining his thoughts on how ecash has the potential to solve problems that many have tried to solve by launching their own blockchains in the past. The problem with trying to "blockchain the world" is that blockchains are very inefficient and only really work for one application; enabling a peer-to-peer digital cash system with no trusted third parties (i.e., bitcoin). However, the ultimate goals of the thousands of blockchain projects that spun up in bitcoin's wake are desirable. Cheap, private and instant transactions. The ability to trivially spin up private money tokens suited for very particular use cases. Overall great UX that makes it easy for people to realize the benefits of "blockchain technology".
The problem that has existed to date is that you don't need a blockchain for all of these things. In fact, having a blockchain for these things proves to be detrimental to their ultimate goals. Instead, what people really need is a protocol that gives you the granular control, privacy, instantaneous transactions and UX that anchors to bitcoin. This is exactly what Chaumian Mints bring to the bitcoin stack.
This is something that we've been screaming about for more than seven years in this rag. Now with ecash protocols like Cashu and Fedimint maturing, gaining traction and bringing products to market that highlight the power and flexibility of ecash systems, people are beginning to see the promise. It is only a matter of time before more and more people begin to realize this potential.
Another benefit of ecash protocols is the fact that they are siloed from each other. Ecash mints are permissionless; any one person or group of people can spin them up, offer their preferred services and maintain (or fail to maintain) their mints. The failure of one mint is not a systemic risk to other mints. This is very different from token projects that are spun up on blockchains. The last ten years have proven that individual token projects can prove to be systemic problems for individual blockchains (i.e., The DAO token on Ethereum). Being able to silo mints is the only way to ensure that the utility of ecash overall is actually scalable and robust.
Don't get so distracted by the bitcoin macro talk that you miss out on the incredible technical developments happening on top of and adjacent to bitcoin.
Final thought... Vibes are high.
-
 @ 0e8c41eb:95ff0faa
2024-07-08 14:36:14
@ 0e8c41eb:95ff0faa
2024-07-08 14:36:14Chef's notes
Sprinkle a pinch of salt in a bowl. Sift 275 grams of flour above it. Make a well in the center of the flour and sprinkle the yeast into it. Add 50 grams of butter, 25 grams of sugar, and the egg. Pour in the milk and knead the dough with the mixer or by hand into a smooth dough. If necessary, add a bit more flour if the dough is too sticky. Form the dough into a ball. Let the dough rise covered with cling film at room temperature for 1 hour.
Peel the apples. Cut the apples and apricots into pieces. Cook the fruit with 150 grams of sugar and 50 ml of water in 15 minutes into a thick compote. Let this fruit filling cool.
Knead the dough again briefly and roll it out to a round sheet of about 28-30 cm in diameter, so that it fits well over the baking tin. Press the dough into the tin and press it well into the corners. Let the dough rise again for 10 minutes and cut off the excess edges.
Spread the fruit filling over the dough.
Mix the rest of the flour with the remaining 100 grams of butter and 100 grams of sugar and knead it with your fingers into a crumbly mixture. Sprinkle this crumble mixture over the fruit filling. Bake the tart in the preheated oven at 200°C for about 30 minutes until golden brown.
Variations: Only apple? Make this tart with 1 kilo of apples. High or low? You can also bake the crumble tart in a low tart tin of 30 cm diameter. If the fruit filling is a bit too voluminous, you can make double the crumble mixture and sprinkle it over the larger surface area.
Additional needs: Mixer with dough hooks or food processor Cling film Round baking tin with a diameter of 28-30 cm, greased
Details
- ⏲️ Prep time: 45 min + 1 hour Rising
- 🍳 Cook time: 30 minutes
- 🍽️ Servings: 8
Ingredients
- 375 grams flour
- 1 packet dried yeast (7 grams)
- 125 grams unsalted butter, at room temperature
- 275 grams sugar
- 1 egg
- 100 ml milk, at room temperature
- 500 grams apples
- 500 grams apricots (fresh or from a can)
Directions
- Sprinkle a pinch of salt in a bowl. Sift 275 grams of flour above it. Make a well in the center of the flour and sprinkle the yeast into it. Add 50 grams of butter, 25 grams of sugar, and the egg. Pour in the milk and knead the dough with the mixer or by hand into a smooth dough. If necessary, add a bit more flour if the dough is too sticky. Form the dough into a ball. Let the dough rise covered with cling film at room temperature for 1 hour.
- Peel the apples. Cut the apples and apricots into pieces. Cook the fruit with 150 grams of sugar and 50 ml of water in 15 minutes into a thick compote. Let this fruit filling cool.
- Knead the dough again briefly and roll it out to a round sheet of about 28-30 cm in diameter, so that it fits well over the baking tin. Press the dough into the tin and press it well into the corners. Let the dough rise again for 10 minutes and cut off the excess edges.
- Spread the fruit filling over the dough.
-
 @ cec2981c:814d4f26
2024-07-08 12:56:36
@ cec2981c:814d4f26
2024-07-08 12:56:36Chef's notes
More information about its origins: https://en.wikipedia.org/wiki/Soda_bread
Details
- ⏲️ Prep time: 10 min
- 🍳 Cook time: 45 min
- 🍽️ Servings: 4-8
Ingredients
- 500 gr whole grain flour
- 450 ml butter milk
- 10 gr (sea)salt
- 15 gr baking soda (not US's "baking powder") (also known as sodium bicarbonate)
- a bit of butter or olive oil
Directions
- Pre-heat the oven to 220°C
- Put all flour in a bowl with baking soda and salt. Mix it well.
- Create a hole in the middle and pour all butter milk in the center.
- Stir it from the centre and slowly mixing all together until you get a dough.
- When mixed, the dough is sticky. Use all purpose flour on counter and bulge to the same size as your skillet.
- Use a bit of butter or olive oil to wet the skillet to prevent sticky bread. And put the dough in your skillet.
- Add a but of flour on top of the dough and then cut lightly a X.
- Bake for ±45 min on 220°C until done (inside temperature must be at least 95°C). Turn up the heat for the last 5 min to get a crust.
- Let the bread cool down a bit before taking it out the skillet, and let it cool down even more before eating.
- Donate some sats to me if you like this recipe.
-
 @ 1a48e74d:02c0e00f
2024-09-04 22:53:26
@ 1a48e74d:02c0e00f
2024-09-04 22:53:26Welcome back ya'll hope you are doing well this week. Today I wanted to talk about why Bitcoin represents a dawn of a new age in property ownership. Before you spit out your coffee and walk away, hear me out. Bitcoin and real estate have a few things in common. The first is property rights.
When you are the owner of a building with your name on the dotted line and whatnot, you are the sole owner of that property. No one can tell you what to do with it, and no one has a claim to what you own. You are free to do what you wish. Property rights are sacrosanct and immutable similar to Bitcoin.
Bitcoin confers upon the owner the same property right protections as owning a piece of real estate. Once you own it, you are the sole owner of that Bitcoin. No one can tell you what to do with it. No one else has a claim to your Bitcoin. You are free to do with it what you wish.
Bitcoin and real estate are similar in terms of built-in scarcity. There is only 21 million Bitcoin that will ever be created, and you can't print more land. This is why owning real estate has been such a good investment since the beginning of time. Buying a piece of land and "HODLING" for decades will generate a substantial return on your investment.
This same buy and hodl strategy apply to Bitcoin as well. If you bought Bitcoin back in 2009, you would be a multi-millionaire right now.
If you invested $1000 back in 2011 when Bitcoin was trading at $3.50, you would have turned that $1000 into $15.6 million if you held on to it for ten years. Just sayin.
You have to reframe your thinking to understand what is going on. We are living in the 21st-century gold rush, and you have an opportunity to stake your claim to the soundest money on Earth with a few taps on your phone. Never in the history of the world has the plebs like us had the ability to front-run a monetary revolution.
Bitcoin is freedom from oppression. Bitcoin restores your sovereignty. Bitcoin makes you fuckable, and the powers that be know it. They are afraid they will lose control if too many people catch on too quickly, which is why large institutions are rushing to offer Bitcoin services or buy them and keep them on their balance sheet.
Bitcoin won't stay this cheap forever. $100-300k Bitcoin is in the cards over the next few years. I don't want you guys to miss out on this.
All you have to do is buy Bitcoin and hold. It's that simple. FYI trying out the new obsidian writer for nostr notes!
Bitcoin #nostr
-
 @ 32e18276:5c68e245
2024-07-05 18:28:20
@ 32e18276:5c68e245
2024-07-05 18:28:20Hey guys!
Here's our Q3-Q4 report. There was some confusion with the timing of the previous quarters so we've accumulated everything since the Q2 report (March 2nd, 2024) into this one. Enjoy!
Damus OpenSats Q3-Q4 Progress Report
The third and fourth quarter of the initial Damus OpenSats grant encompasses work done across many of the active projects being worked on at Damus HQ. Here's a quick overview of the progress made across the organization:
nostrdb
Added
- Author query support (William Casarin)
- REQ support: ndb_subscribe (William Casarin)
- CLOSE support: ndb_unsubscibe (William Casarin)
- Profile flatbuffer dump utility (William Casarin)
- Ability to register a subscription callback instead of just polling (William Casarin)
Changed
- Dump json in filter and fulltext queries in cli tool (William Casarin)
Stats
name added removed commits William Casarin <jb55@jb55.com> +665 -739 16nostrdb-rust
Added
- Note builder interface (William Casarin)
- Nip10 implementation (William Casarin)
- Getting profile by key (William Casarin)
- Note tag support (William Casarin)
Tag::into_itermethod (Yuki Kishimoto)FilterBuilder::untilmethod (Yuki Kishimoto)- Export structs from
tagsmodule (Yuki Kishimoto)
Fixed
FilterBuilder::limitmethod (Yuki Kishimoto)Note::sigmethod (Yuki Kishimoto)
Stats
Yuki Kishimoto <yukikishimoto@protonmail.com> +20 -4 5 William Casarin <jb55@jb55.com> +1551 -867 32Damus NoteDeck/Android
This project is in heavy development and doesn't have clean changelogs yet, so here are all of the git logs from this period
Willam's updates
- account_manager: don't add the same pubkey more than once
- actionbar placeholder
- actionbar: remove border on reply button, add expand animation
- actionbar: support both dark and light buttons
- Add forward navigation animation
- add hover to profile map demo
- add --light lightmode flag to previews and notedeck
- add my pubkey to the timeline query for testing
- add test queries for elsat
- add vertical separators between timelines
- allow missing profiles in account switcher
- allow multiple invocations of --sec
- always have some default timeline
- app: make ndb public
- a quick note about the View trait
- args: allow filter files and raw filters on cli
- bump timeline filter limit
- cap size of remote filter limits
- change selection color to purple
- check: remove duplicate and disable wasm checks
- ci: disable wasm builds for now
- cli: add --sec argument to quickly add an account
- clippy postbox cleanups
- crates: add bitflags
- damus: make relay pool public
- darker quote reposts for mobile
- debug: add some debug logs for keyboard note selection
- deps: using tracing instead of log
- direnv: disable nix direnv on darwin
- direnv: make args explicit so its easy to change
- don't bump timeline when adding notes
- dont since-optimize when we don't have enough notes
- don't use an actual keystorage in Damus test apps
- drafts: clear post after posting
- enable nip10 replies
- enostr: rename Event to Note
- env: allow private things like secret keys
- filter: add default limit
- filters: fix hashtag filters
- filter: unify nostrdb and remote limits
- Fix all warnings
- fixed_window: fix clippy warning
- fix global query
- fix inline note preview colors
- fix light borders for quote reposts
- fix postbox design
- fix scroll area shrinking
- fix some clippy warnings
- fix until filters
- fix warnings
- fonts: always use base fonts for all families
- fun large profile grid preview
- get all missing ids from all timelines
- github: remove pages workflow
- gitignore: add perf files
- hide navigation title on global nav
- ids: find more unknown ids from inline notes
- images: add aspect_fill
- initial inline note previews
- initial navigation
- initial note posting
- initial postbox for testing
- initial post box view
- initial post reply view
- initial refactor in preparation for routing
- input: fix deadlock on resize
- input: handle raw events
- input: process input once
- input: switch to scanning over raw input events
- integrate sidebar into main view
- introduce View and Previews traits
- irc mode
- ircmode: tighten username
- keys: actually use the keystore
- lighter gray for inline previews in white mode
- list: switch from arc mutext to rc refcell
- load timelines from commandline
- log: reduce spammy new note log
- log relay subscriptions
- make notedeck front and center
- mobile: add lots of top padding on mobile
- mobile: a tad more padding at the top
- mobile: black panel bg color
- mobile: don't add hover on mobile
- mobile: make mobile flag runtime-configurable
- mobile: simplify is_mobile
- mobile: use my timeline for testing again
- move account_login_view to ui submodule
- move add_space to its correct location
- nip10: fetch unknown replied-to notes
- nip10: show initial reply information on notes
- nix: add openssl dep for reqwest
- nix: make android emulator optional
- nostrdb: bump to support timeline queries
- note: don't allow nested note previews
- note: support nprofile mentions
- perf: don't clone bytes via a more specialized function
- perf: fix continuous repaint
- perf: profiling note content rendering
- popup: increase fixed window margin
- popup: simplify borrow
- postbox: add focused state
- postbox: add focus shadow from figma
- post: full available width
- postview: add vertical scroll
- previews: remove central panel frame
- profile: add about and username to profile previews
- profiles: introduce DisplayNames
- profiling: update puffin version
- queries: add a few more test queries
- queries: set reasonable initial query sizes
- queries: update hashtags query
- readme: add usage
- readme: document previews
- readme: make it clear that its for desktop
- readme: make it clear that nix is optional for non-android dev
- readme: show notedeck preview
- refactor: move fixed_window to ui
- refactor: move note into its own widget
- refactor: rename widgets to ui
- refactor: use map instead of explicit
if let - remote: use default_remote_limit instead of hardcoding
- remove context from DesktopSidePanel
- remove minimum window size
- remove useless struct
- render_pfp: only depend on imgcache
- reset virtual list if notes are spliced into timeline
- set tooltip delay to 100ms
- side_panel: return more detailed side panel responses
- simplify is_mobile check
- simplify tab underline calculation
- since filter optimization
- slightly larger pfpfs
- small inline preview pfps
- style: initial logic for mobile style
- style: less bubbly
- style: realtime hover interactions
- style: set 0 duration tooltip delay
- Switch to egui master to fix wgpu issues
- switch to glow for now
- switch to rustls-tls-native-roots
- tabs: select notes & replies by default
- test: add test timeline query
- test: update test profile with a banner
- test: use my timeline query by default for testing
- textmode: adjust name sizing so it doesn't bump the column
- textmode: fix coloring of abbreviated names
- textmode: no previews in textmore for now
- theme: update to correct colors based on figma design
- timeline: don't hide on resize
- timeline: refactor tabs into TimelineView
- timeline: use strips instead of panels
- ui: add banners to profile previews
- ui: add feathering-resistant hline separator fn
- ui: add frame around note previews
- ui: add initial Profile hover previews
- ui: add profile picture hover animation
- ui: integrate egui-tabs for notes & replies selector
- ui: introduce profile picture widget
- ui: make pixel sizes correct, use more of the figma
- ui: move RelayView into ui module
- ui: only inline preview kind1 notes for now
- ui: reduce vertical padding for more compact timelines
- ui: remove some old note ui comments
- ui: simplify note widget
- ui: switch to flags for note options
- update slow timeline query
- update to latest nostrdb, adding tag support
- update version in comment because I still use this on my laptop
- use egui_virtual_list for rendering
- use unique id for post/reply view
- weird actionbar experiment
- we should just called this damus
- widgets: begin organizing ui components into widgets
- working notes + notes&replies
kernelkind's updates
- account_management: refactor
- AccountManagementView
- AccountManager: add ability to make a selection
- AccountSelectionWidget
- Account switcher
- Add AccountManager to app
- Add custom visual themes
- Add flag to emulate mobile during preview
- Add keypair & update pubkey
- Add login key parsing
- Add login manager
- Add MacOS key storage
- Add MobileAccountLoginView
- Add modular custom text styles
- Add monospace text style
- Add nix-shell for macos android development
- Add nostr-sdk dependency
- Add precommit hook to suggest proper formatting
- Add preview for RelayView
- Add relay view
- add reqwest as dependency
- Add SimpleProfilePreview
- Add ui_test_harness binary implementation
- Add warn color and highlight color
- app: add accounts to Damus & mock
- Apply app style to AccountLoginView
- Apply cargo fmt
- Conditionally compile MacOS key storage code
- Constrain app minimum size
- Create account login panel
- Create side panel & global popup
- enostr: expose RelayStatus
- Extract the sample relay to test_data for reuse
- impl linux credential storage
- Integrate account switcher to side panel
- Integrate global popup into app
- login: Add key loading & error to mobile
- macos_key_storage: runner ignore tests
- migrate AccountManagementView to enostr Keypair
- Migrate to new AccountManagementView conception
- Move login business logic to LoginManager
- move login logic from promise to async fns
- Move preview controller out of account_manager.rs
- move test account creation & apply to global popup
- Pfp integration to side panel
- refactor account switcher & management previews
- Refactor 'ui tests' conception to previews
- reintroduce account management
- reintroduce account switcher
- remove nostr-sdk
- Rename PersistState -> StateInMemory
- select first account
- Seperate mobile dark color theme into its own func
- update cargo.lock to reflect toml change
- Update egui 0.26.1 -> 0.27.1
- Use app_creation for common app setup functions
- Use custom style in app
- use nostr in enostr
Stats
name added removed commits kernelkind <kernelkind@gmail.com> +6844 -1979 58 William Casarin <jb55@jb55.com> +9733 -5583 194Damus iOS
Added
- Ability to create highlights (ericholguin)
- Add ability to mute hashtag from SearchView (Charlie Fish)
- Add ability to mute words, add new mutelist interface (Charlie) (William Casarin)
- Added callbackuri for a better ux when connecting mutiny wallet nwc (ericholguin)
- Added nip10 marker replies (William Casarin)
- Added title image and tags to longform events (ericholguin)
- Add event content preview to the full screen carousel (Daniel D’Aquino)
- Add First Aid solution for users who do not have a contact list created for their account (Daniel D’Aquino)
- Add marker nip10 support when reading notes (William Casarin)
- Add video cache to save network bandwidth (Daniel D’Aquino)
- Completely new threads experience that is easier and more pleasant to use (Daniel D’Aquino)
- Connect to Mutiny Wallet Button (ericholguin)
- Highlights (NIP-84) (ericholguin)
- Notification reminders for Damus Purple impending expiration (Daniel D’Aquino)
- Proxy Tags are now viewable on Selected Events (ericholguin)
- Relay fees metadata (ericholguin)
- Revamp emoji picker to be less error-prone and add search, frequently used, and multiple skin tone support capabilities (Terry Yiu)
- Show list of quoted reposts in threads (William Casarin)
Changed
- Added first aid contact damus support email (alltheseas)
- Add support for Apple In-App purchases (Daniel D’Aquino)
- Always strip GPS data from images (kernelkind)
- Change reactions to use a native looking emoji picker (Terry Yiu)
- Errors with an NWC will show as an alert (ericholguin)
- Improve UX around video playback (Daniel D’Aquino)
- Moved paste nwc button to main wallet view (ericholguin)
- Relay config view user interface (ericholguin)
- Relay detail design (ericholguin)
- Updated Zeus logo (ericholguin)
Fixed
- Fix broken GIF uploads (Daniel D’Aquino)
- Fix bug that would cause connection issues with relays defined with a trailing slash URL, and an inability to delete them. (Daniel D’Aquino)
- Fixed issue where some replies were including the q tag (William Casarin)
- Fixed issue where timeline was scrolling when it isn't supposed to (William Casarin)
- Fixed threads not loading sometimes (William Casarin)
- Fixed wallet not disconnecting when a user logs out (ericholguin)
- Fix emoji reactions being cut off (ericholguin)
- Fix ghost notifications caused by Purple impending expiration notifications (Daniel D’Aquino)
- Fix image indicators to limit number of dots to not spill screen beyond visible margins (ericholguin)
- Fix in-app purchase issue that would trigger an error on purchase before confirming the account information. (Daniel D’Aquino)
- Fix issue where bootstrap relays would inadvertently be added to the user's list on connectivity issues (Daniel D’Aquino)
- Fix missing Mute button in profile view menu (Terry Yiu)
- Fix nostrscripts not loading (William Casarin)
- Fix profile not updating bug (William Casarin)
- Fix stale feed issue when follow list is too big (Daniel D’Aquino)
- Fix thread bug where a quote isn't picked up as a reply (William Casarin)
- Fix welcome screen not showing if the user enters the app directly after a successful checkout without going through the link (Daniel D’Aquino)
- Improve reliability of contact list creation during onboarding (Daniel D’Aquino)
- Issue where NWC Scanner view would not dismiss after a failed scan/paste (ericholguin)
Stats
name added removed commits Fonta1n3 <fontainedenton@googlemail.com> +1 -0 1 Sean Kibler <skibler@protonmail.com> +13 -2 1 alltheseas <64376233+alltheseas> +65 -1 4 Transifex <transifex@transifex.com> +581 -39 36 Terry Yiu <git@tyiu.xyz> +763 -1383 8 William Casarin <jb55@jb55.com> +1017 -1564 49 ericholguin <ericholguin@apache.org> +1962 -643 13 Daniel D’Aquino <daniel@daquino.me> +3885 -761 48 -
 @ 1a48e74d:02c0e00f
2024-09-04 22:36:48
@ 1a48e74d:02c0e00f
2024-09-04 22:36:48Nothing can defeat Bitcoin.
-
 @ 7f0cbb03:c59f23d0
2024-09-04 21:28:57
@ 7f0cbb03:c59f23d0
2024-09-04 21:28:57 -
 @ 77409953:ea177f56
2024-07-02 13:48:50
@ 77409953:ea177f56
2024-07-02 13:48:50Chef's notes
I purchased all ingredients from my local Sprouts Market
The benefits of this Organic Apple Granola Probiotic Bowl go far beyond its delicious taste. The organic ingredients used in our granola are free from harmful pesticides and chemicals, ensuring that you're nourishing your body with the purest, most nutrient-dense foods available. Additionally, the probiotic yogurt in this bowl helps to support a healthy gut microbiome, which has been linked to a wide range of health benefits, from improved digestion to a stronger immune system.
CONTAINS CLEAN SIMPLE INGREDIENTS
NON-GMO
USDA ORGANIC
GLUTEN-FREE
DAIRY-FREE
SOY-FREE
7G SUGAR (14%)
PLANT-BASED
VEGAN
NO ARTIFICIAL OR “NATURAL FLAVORS”
Details
- ⏲️ Prep time: 10
- 🍳 Cook time: 1
- 🍽️ Servings: 2
Ingredients
- 2 handfuls of Purely Elizabeth Chocolate Sea Salt Ancient Grain Granola
- 3 tbsp Cocojune Organic Dairy-Free Vanilla Unsweetened Coconut Yogurt
Directions
- 10
-
 @ 7ceaffbc:143b9e56
2024-09-04 20:50:26
@ 7ceaffbc:143b9e56
2024-09-04 20:50:26(roles in the adoption space)
Being different matters - At first!
The reasonable man adapts himself to the world; the unreasonable one persists in trying to adapt the world to himself. Therefore, all progress depends on the unreasonable man (Shaw, 1903).
h/t Everyone who is Satoshi.
It is probably fair to say Satoshi, Hal Finney, Adam Back et al. and we early ones are amongst the crazy ones.
Here’s to the crazy ones, the misfits, the rebels, the troublemakers, the round pegs in the square holes… the ones who see things differently — they’re not fond of rules… You can quote them, disagree with them, glorify or vilify them, but the only thing you can’t do is ignore them because they change things… they push the human race forward, and while some may see them as the crazy ones, we see genius, because the ones who are crazy enough to think that they can change the world, are the ones who do. (Jobs, 1997).
Sub-conclusion - To rid ourselves of fiat required radical thought - a base on which to build.
Most Babies learn to Walk
Born with the normal count of fingers toes etc, by the age of 26 I reckoned I had pretty much mastered walking (or so I believed) - until recently I fell, whereupon five things struck me deeply:
- Ageing and the associated decline is another form of novelty - I can resist it, it will eventually win but meanwhile I can adapt - and being alive is about adapting
- Things I have learnt must inevitably include all the things things I need to unlearn
- Things I have not learnt can become urgent (perhaps a wheechair lies in my future) and the learning can be delayed by the requisite unlearning from point 2 above
- Walking was something the masses did before I ever achieved it - which was probably what prompted me to adopt it as a means of ambulation
- The floor
Sub-conclusion - Mass adoption requires; * initiation (the crazy ones) * attention (seeing what others do) * unlearning (elimination of perceived assumptions) * learning (PoW) * emulation ( doing what others do) * mastery (practice doing it well) * review (figuring out what is no longer valuable) * evangelism (Helping others towards Truth)
OK - I have your attention - now what ? (Unpopular opinions incoming)
Eccentricity is not important to anything other than grabbing attention. Bitcoin is well beyond the thresh-hold of needing Eccentrics. We could all name them (and should appreciate their efforts).
The Overton window (that which may be normally spoken of) has become big enough that includes the best of our thinkers now. Analysts, Politicians, Purists, Financial advisers ??, Maxis, Left, Right & Centre.
But most of all it needs the centre. The extremes are great for raising attention and have the greatest voice on lesser social media platforms (which may be a thing of the past when you read this). However, it is clear that out of the centre (the Ex-centrics ? ) will come the mass of humanity that can benefit from bitcoin.
The bulk of future normies (users of bitcoin when only laggards use fiat) must come from the centre - because that is where they are now.
So decentralists or if you prefer "ex-centrics" will be easiest to help if we are seen as different - but reasonable, attractive and something to aspire to. The generosity / loving nature of many Bitcoiners will continue to win hearts (and minds)
Again unpopular perhaps (I should not care) - but this means ideally; - avoiding offensive behaviour (potty language) - avoiding ejection of those who are different (even if you reject their lifestyle choices) - understanding that we all start somewhere on this journey - smaller egos - I am a Bitcoin Maximalist by many definitions but, while my Christianity, what I eat, my and even my choice of frying pan may be most important to me - they may not help evangelise a better bitcoin future.
FWIW I think Bitcoin & Christianity go hand-in-glove in the journey toward a better future , but respect your (God given) right to disagree
Conclusion
Its time to stop thinking we are special and become normal - because that is what hyper-bitcoinisation implies.
To achieve this we need to find ways to secure legislation, peacefully dis-empower fiat states (a side effect - but IMHO a good one), make learning easier, remove barriers (FUD, technological etc) and lend a sympathetic ear to anyone who asks, what, why, how because that's how we all learn:
I keep six honest serving-men (They taught me all I knew); Their names are What and Why and When And How and Where and Who. I send them over land and sea, I send them east and west; But after they have worked for me, I give them all a rest.... (Kipling; The Elephant’s Child)
One day, if we do as well as we must, we will be able to claim - but we are just normal !
-
 @ 572aa884:e266a569
2024-09-04 19:46:40
@ 572aa884:e266a569
2024-09-04 19:46:40STAR TREK TNG: INCOMPATIBLE IDEALS
by Luke Parker
Premise: This screenplay is for an episode of Star Trek: The Next Generation, set near the end of Season 7. It imagines a first contact encounter between Picard’s Enterprise and a fully Anarcho-Capitalist planet with no government nor belief in authority.
Scene 1: Bridge
Exterior views of the Starship Enterprise give way to Captain Jean-Luc Picard standing at his command station on the bridge, his gaze steady and contemplative as he records his log.
Picard: (voiceover) "Captain's log, Stardate 48881.4. We were on our way to Deep Space 9 to provide support for the upcoming Bajoran elections when we received an audio-only distress call from a person on the planet Anarak, just outside of Cardassian space. The planet has yet to be contacted by the Federation, and in fact very little is known about it other than how it has a highly unusual social structure; one that appears to function without any form of central government or hierarchical leadership. It is a society that, despite its relatively high level of technological sophistication, has yet to achieve warp capability. The message is urgently requesting help from any peaceful civilization in range to defend his people against Cardassian invaders. It is difficult to imagine even the Cardassians violating the Prime Directive in such a manner. We are changing course to investigate."
Picard finishes his log entry and looks up, his expression thoughtful. The rest of the bridge crew is attentive with the memory of the Cardassain conquest of Bajor fresh in their minds.
Data: [turning from his console to face Picard] "Captain, Starfleet's lone anthropological record on Anarak indicates that it has a relatively large population and is advanced in various scientific fields. However, there are no reports of warp capability nor a leadership structure for us to contact there. Their society’s structure might challenge our usual protocols for contact."
Riker: [with a hint of curiosity] "An advanced society with no central government? That's a first."
Picard: [nodding] "Indeed, Number One. The distress call came from an individual named Bas T'yat, who identifies himself only as an entrepreneur. Our intelligence suggests that Anarak's society is structured in a way that is not only hostile to hierarchies but completely devoid of any form of leadership or authority. They seem to operate on a principle of total autonomy. This would seem to indicate an absence of a planetary defense system."
Troi: [thoughtful, with concern] "Without a central authority, how do they respond to any external threats? A society like this could be quite vulnerable to more aggressive powers, like the Cardassians."
Picard: [grimly] "It seems that may already be the case. The distress signal implied that a hostile force, likely Cardassian, has targeted them. Without a unified defense, they could be easy prey."
Worf: [sternly] "If the Cardassians are involved, Captain, they will not hesitate to exploit such a weakness. We must be prepared for hostilities."
Data: [analyzing the implications] "However, the lack of formal governance could complicate any assistance we offer. Without a government to negotiate with, we may face challenges in determining how to intervene appropriately."
Picard: [resolute, yet cautious] "We will treat Anarak as we would any other planet sending a distress call, regardless of their social structure. However, we must tread carefully. If we arrive to find Cardassians engaged in hostile acts, we may be forced to intervene. But in Federation space, our priority remains the protection of life and the maintenance of Federation principles."
The bridge crew exchanges looks of determination, each officer understanding the complexities of the mission ahead.
Picard: [decisive, raising his voice slightly] "Set course for Anarak. Engage at warp seven."
Data: [acknowledging] "Course plotted, Captain. Engaging warp seven."
The familiar hum of the warp engines intensifies as the stars on the viewscreen stretch into streaks of light, and the Enterprise leaps into warp, speeding towards the strange planet and the potential conflict awaiting them.
Scene 2: Bridge
The Enterprise emerges from warp above the planet Anarak, the planet’s blue-green surface appearing deceptively peaceful below.
Worf: [at tactical, scanning the area] "Captain, no alien vessels are currently in the vicinity, only artificial satellites. However, I'm detecting signs of recent battle on the planet's surface."
Picard: [moving closer to Worf's station] "Specify, Lieutenant."
Worf: [analyzing the data] "There is minor damage to infrastructure in multiple locations, consistent with Cardassian disruptor fire. Several structures show signs of targeted attacks, but the damage is localized and not extensive."
Data: [at the science station] "Captain, I'm detecting several warp signatures leading to and from the planet. However, one of these signatures does not match any known Cardassian engine profile and is not in our warp signature database."
Riker: [concerned, looking to Picard] "An unknown vessel in the area right around the time of a Cardassian attack? This could complicate matters."
Troi: [sensing the tension, her voice calm but alert] "Whoever they are, they may not have the best intentions. The people of Anarak could be more vulnerable than we initially thought."
Picard ponders this information, his expression thoughtful yet wary. The bridge crew continues their scans, tension mounting as they try to make sense of the situation.
Worf: [interrupting the silence] "Captain, we are being hailed from the surface."
Picard: [decisive, nodding] "On screen."
The viewscreen flickers to life, revealing the image of a middle-aged man with a rugged, practical look. He exudes an air of cautious relief, though his eyes betray a deep-seated wariness.
Bas T'yat: "Alien vessel, thank you for coming so quickly. My name is Bas T'yat, and I’m an entrepreneur and concerned family man. Please, can you tell me, are you an ally of the Cardassians?"
Picard: [calm and reassuring] "Mr. T'yat, I am Captain Jean-Luc Picard of the Federation starship Enterprise. I assure you, the Federation is not aligned with the Cardassians, although we have dealt with them before, and are aware of their transgressions."
Bas T'yat: [sighs in relief] "Thank goodness. We desperately need your help. An alien ship identifying itself as Cardassian has been harassing us for weeks. I fear they'll return soon, and we have little defense against their matter transportation technology. I'm a successful inventor and businessman, Captain. I have resources and tech that could be of value to your Federation, and I'm prepared to trade anything you want in order to help protect my people."
Picard: [curious, leaning slightly forward] "Tell me more about these attacks. What exactly have the Cardassians done?"
Bas T'yat: [his tone shifting to one of frustration mixed with guilt] "It started about a month ago. One of our companies, my own company, in fact, launched a new type of vessel that can travel faster than light using a warp field, the first one we've ever built. Within an hour of it's maiden voyage the Cardassians showed up. At first, they demanded to know who was in charge of the planet. They didn't like the answer they got: We are a free people and no one commands us."
Riker: [sharing a knowing glance with Picard] "A society without centralized leadership would be difficult for the Cardassians to understand or even tolerate."
Bas T'yat: [nodding] "That was my conclusion. They treated us like a lawless frontier, moving in to take whatever they wanted. They attacked our resource stockpiles, dematerialising and I assume stealing whatever they could before we even knew what was happening. Our ground-based defense missiles successfully took out their two smaller fighter crafts that came down into our sirspace, but we have no defense against their transporter technology. Their last visit was just a raid from orbit. They just grabbed what they could without even entering the atmosphere and left within minutes."
Picard: [thoughtful, with a hint of concern] "I see. There are widely-agreed-upon rules against this type of behavior, I assure you. However, since the Federation has never made contact with your people before now, we are unfamiliar with the proper etiquette for such a first encounter. How do you suggest we proceed safely for an official meeting?"
Bas pauses, visibly perplexed by the concept of "official" procedures, his expression almost amused.
Bas T'yat: [with a chuckle] "Official meeting? Captain, just come on down and park your craft outside my coordinates. My wife will make us all some refreshments."
Picard: [with a slight smile, yet maintaining formality] "We appreciate the hospitality, Mr. T'yat, but we prefer to beam down if that's acceptable to you. We can be there in a few minutes."
Bas T'yat: [nervous but agreeable] "Beam down? Uh, sure, that's fine. I was wondering if that technology worked on people. Love to see it in action."
Picard: [nodding respectfully] "Understood. I'll be down with a small team to meet you outside your building shortly. Picard out."
The screen goes dark as the connection ends, leaving the bridge crew to process the encounter.
Riker: [with a wry smile] "Drinks with the locals; sounds like fun."
Troi: [softly, but with insight] "He's nervous, but also hopeful. I'm sensing some hurt pride in him, too, Captain. This is likely the first time his people have ever had to reach out to anyone off-world for help. His pride may cloud his ability to fully grasp the dangers they’re facing."
Picard: [serious, standing up to address the crew] "On top of being an official first contact, the Cardassians have made this a very delicate situation. We must be prepared for anything. Counselor Troi, Data, and La Forge, you're with me. Number one, you have the bridge."
The crew nods in understanding as the away team heads to the turbolift. The tension in the air is palpable as they ready themselves for what may be a challenging first contact and a possible hostile encounter with the Cardassians.
Scene 3: Bas T’yat’s Front Lawn
The team materializes on the surface of Anarak, just outside of a large, elegant house set in a lush, rural landscape. The area is a blend of modern luxury and natural beauty, though signs of recent damage are evident. Smoke still rises from a nearby hangar, the aftermath of the Cardassian attack clear in the smoldering ruins. As the team takes in their surroundings, a group of locals approaches. At the forefront is Bas T'yat, flanked by a few colleagues. He's a middle-aged man with a commanding presence, dressed in practical yet fine clothing. His stride is confident, and his eyes sharp with the determination of a man used to getting what he wants. Bas’s face lights up with a mixture of curiosity and enthusiasm as he sees the away team.
Bas T'yat: [warmly, holding his palms upwards and then extending one hand towards Picard in a greeting] "Captain Picard! Welcome to Anarak! I'm Bas T'yat. It is my honor to meet you."
Picard: [imitating the hand motion, with a polite smile] "The honor is ours, Mr. T'yat. Thank you for your hospitality. May our two peoples forever live in harmony."
Bas gestures to the smoldering hangar in the distance, his tone tinged with frustration.
Bas T'yat: [with a sigh] "That would be wonderful. I do wish the circumstances for your visit were better. [clenching his fists] That's my hangar over there, or what's left of it, anyway. The Cardassians destroyed it and the spacecraft I designed and built there. It was our first warp vessel, one that the whole world cheered on at launch just last month. We were going to colonize the asteroids with it."
Geordi: [To Picard, gesturing towards the wreckage] "If I may, Captain?"
Picard: "Certainly." [To Bas T'yat] "This is my head engineer, Commander Geordi La Forge."
Geordi: [stepping forward] "Mr. T'yat, if it's alright with you, I'd like to examine the wreckage. I might be able to determine if anything is salvageable."
Bas T'yat: [nodding, gesturing to a colleague] "Of course. Lar Kinn here is our chief pilot. He made the historic first flight and he'll take you to the hangar and help with anything you need."
Geordi and Lar Kinn head towards the hangar, with Geordi hoping to confirm if this was the source of the warp signature detected in orbit. Meanwhile, Bas leads Picard, Troi, and Data toward his house. As they walk, Bas impatiently answers a few questions about his planet, his voice tinged with annoyance and concern.
Data: “Mr. T’yat, if I may, I notice that your neighborhood’s infrastructure is well taken care of. If Anarak has no central authority of any kind, who is responsible for keeping the roads and infrastructure?”
Bas T'yat: ”Well, as a rule of thumb, if it’s on my land, I am. If it’s not on my land, then someone else is, but I may have to pay them to use it. They look so nice because we all get better insurance rates for keeping them that way.”
Data: “Curious. And who initiates larger projects like mass transportation and research?”
Bas T'yat: [slightly annoyed] “They are all risky endeavors taken by entrepreneurs like myself. Sometimes profits take decades to appear, but like with my new warp engine, I’m sure they’ll make me a huge fortune one day.” [turning to ensure Picard can hear him] "Anyway, I fear the Cardassians aren't done with us. They've stopped even trying to make demands of us, which makes me think they're planning something bigger. Perhaps a larger assault. We've been able to fend them off so far, but I have no clue how to defend against those transporter devices."
Picard: [impressed] "It is remarkable that your society, with no planetary defense force, was able to repel Cardassian military forces, even if only temporarily. Cardassian ships are known for their significant weapons and shields."
Bas T'yat: [with a hint of pride] "The people of Anarak are no strangers to defending themselves. We have numerous private protection agencies, each with advanced missile fortifications and other kinds of defenses to protect every inch of this planet. But these were designed to fend off terrorists or rival companies, not an alien invader."
They reach the entrance to Bas's home. He pauses before entering, turning to Picard with a serious expression.
Bas T'yat: [earnestly] "Captain, I'm prepared to trade for whatever defensive technology you can provide, especially something to counter the Cardassian's transporter technology. I am confident that our ground defenses can take out their shuttlecraft, but we're helpless against their ability to beam in and out at will."
Picard pauses, his face reflecting the weight of his decision before he speaks.
Picard: [in his most diplomatic tone] "Mr. T'yat, the Federation is committed to helping those in need, and we don't tolerate bullies. However, there are restrictions on the technology we can share, particularly weaponry. Also, the Federation's assistance often depends on whether a planet is on the path to becoming a member. We must ensure that our values align. In this case, a diplomatic approach might bring a far more lasting peace than simply escalating an arms race."
Bas considers this, his optimism tinged with caution. The group moves into a large room with lots of seating where a warm drink much like tea is offered. Picard partakes graciously.
Bas T'yat: [thoughtfully] "I see. Federation membership is... a complicated idea. I'm sure many heads of companies like myself would welcome it, but for the whole planet to become a singular member of any larger federation is hard to imagine. Our society values individual freedom above all else, and I'm not sure how compatible everyone here is with the Federation's ideals."
Data: "The benefits of Federation membership are considerable. Could not your people one day vote on the issue to see if a majority wants to join after taking ample time to research membership?"
Bas T'yat: [skeptically] "Voting is something that hasn't been done here for tens of thousands of years. We consider it to be archaic, a form of slavery of the minority. Honestly, I'm surprised your culture still practices it."
Picard: [nodding, a little embarrassed] "I see. Rest assured that we try to only vote on things that have every participant's full consent. You'll find that this is very common among the races you meet as your people start to explore the stars. But until then, know that the Federation's primary concern is the safety of everyone in Federation space, including your people."
While inside Bas's home, Data discreetly connects to an open network connection, accessing Anarak's version of the internet called the Openlink. His eyes flicker left to right at an inhuman speed as he analyzes the planet's defenses and infrastructure.
Data: [quietly, to Picard as he processes the data] "Captain, while there are many advanced technologies in the hands of individuals and companies, I find no evidence of any kind of unified military infrastructure. The defense efforts are completely decentralized, which will surely prove problematic in the event of a full-scale Cardassian invasion."
Picard: [grimly] "Given the Cardassians' history, we must prepare for the worst."
Just then, Geordi returns from the hangar, his expression a mix of curiosity and concern.
Geordi: "Captain, I've confirmed that Bas's ship was the source of the warp signature we detected. Unfortunately, the wreckage isn't salvageable. It could be a long time before Anarak returns to the stars."
Bas T'yat: [with a determined grin] "I wouldn't say that. My first flight was widely publicized. Lar Kinn and I are celebrities now. Hundreds of other companies are likely working on similar technology already. Some of us refer to it as 'the great space race,' with the goal of creating the first off-world colony, and my company is currently in the lead."
Picard: [with a slight smile, impressed by the resilience] "It seems the people of Anarak are not to be counted out yet. Your intrepid spirit will serve you well as Anarakans start exploring the Galaxy."
Troi: [warmly] "Your optimism is admirable, Mr. T'yat. But remember, resilience is strongest when combined with caution."
Bas T'yat: [nodding, appreciatively] "Wise words, Miss Troi. Hopefully with your help we'll be ready for whatever comes next."
Picard: [ready to leave] "This tea is delicious, thank you for your hospitality. Next I'll need to talk to my superiors at Starfleet headquarters before we can proceed any further. I'll be sure and pass your concerns and needs on to them and then we'll contact you again later today."
The away team prepares to depart, with Bas expressing his thanks once more. As they beam back to the Enterprise, each member reflects on the unique challenges of Anarak.
Scene 4: Picard’s ready room
Minutes later, Captain Picard sits alone in his ready room, the vast starscape of space visible through the window behind him. His posture is straight, and the weight of the decision before him is clear in his eyes. He taps a command into his desk console, and the screen flickers to life with the familiar stern face of Vice Admiral Alynna Nechayev. Her image on the screen is as imposing as ever.
Picard: [calmly, but with underlying urgency] "Admiral, I've just concluded a preliminary contact with a representative of Anarak, just a few light years this side of Cardassian space. The situation is more complex than anticipated. The planet is under threat from the Cardassians; specifically Gul Bankar, who's been making increasingly aggressive moves from orbit. Meanwhile, the society on Anarak is... unconventional. They have no central government, no formal leadership nor military structure. The entire planet operates under a decentralized, anarchic, commerce-based system."
Nechayev: [eyes narrowing] "Anarchists? No structure? That's not exactly an encouraging environment for a first contact, Jean-Luc.
Picard: “Admiral, they’ve managed to develop warp technology without either a government or military. It’s a remarkable feat, but one that leaves them vulnerable.”
Nechayev: “Are you certain there’s no one in authority at all? Not even an ambassador?"
Picard: [nodding] "Precisely. Their social structure wouldn’t allow it. Our first contact has been with an individual and his family, one Bas T'yat; a wealthy businessman and the inventor of their first warp-capable ship. He's requesting assistance to defend against further Cardassian attacks, but without a central authority, assisting one individual could have unpredictable consequences."
Nechayev: [questioning sharply] "Hmm. And what of the Cardassians? Is there any evidence of their involvement?"
Picard: [gravely] "Plenty. The Cardassians have already raided the planet, seizing valuable resources. Their ship left orbit shortly before our arrival, but the threat of their return looms large. Bas T'yat is convinced they'll come back with a larger force."
Nechayev pauses, her expression hardening as she considers the situation.
Nechayev: [warningly] "Starfleet cannot afford to be drawn into deeper hostilities with the Cardassian Union, Jean-Luc. Especially not over a non-member world. You must tread carefully. A diplomatic solution is paramount, and under no circumstances should you provide this Bas T'yat with advanced defensive technology. The Prime Directive is clear; we don't interfere with the internal affairs of non-member worlds, and besides, you haven't even made proper first contact with the planet, only with one family."
Picard: [measured, but firm] "Admiral, with respect, Anarak is far more advanced than many worlds we've encountered. Their technological capabilities, while decentralized, are impressive. Now that they are getting their space legs it won't be long before Anarakans are showing up in ports across the quadrant. And if the Cardassians establish a foothold here, it could destabilize the entire region."
Nechayev's face softens slightly, recognizing the gravity of the situation. She sighs, her resolve shifting as she weighs the options.
Nechayev: [reluctantly] "Alright, Jean-Luc. I don’t like this, but I trust your judgement. You may share transport inhibitor technology. Only enough to help them counter the Cardassians' beaming technology, but nothing more. And remember, this Bas T'yat doesn't speak for his whole planet. Try to treat his family like you would if you found them alone in a spaceship."
Picard: "Understood, Admiral. I'll proceed with caution."
Nechayev: [more sternly] "Just don't start another war, Jean-Luc."
The screen goes dark. Picard leans back in his chair, the weight of the decision pressing on him. He stands, smoothing his uniform, and exits the ready room onto the bridge.
Scene 5: Bridge
On the bridge, the atmosphere is tense as the crew processes the situation. Picard steps up to his command chair, addressing the senior officers who have gathered.
Picard: [seriously] "Admiral Nechayev has authorized us to share transport inhibitor technology with Anarak to help them defend against further Cardassian raids. But we must be mindful of the ethical implications of our actions."
Dr. Crusher:: [concerned] "Captain, I'm worried about the consequences of becoming involved in this situation. If we assist Anarak, it could escalate into a larger conflict--one that could draw the Federation into another war with the Cardassians."
Worf: [gruffly, with resolve] "But allowing the Cardassians to plunder a defenseless society is equally unacceptable, Doctor. We have a responsibility to protect the vulnerable."
Picard: [thoughtfully, considering both viewpoints] "I'm inclined to agree with Worf on this one, Beverly. We must work fast to deploy the inhibitors wherever we can, but that does bring up another problem. The Prime Directive prevents us from interfering in the internal affairs of non-member worlds. And giving one individual on Anarak access to advanced technology could upset the delicate balance of their society. What if Bas T'yat's company gains a monopoly on defense technology? It could shift the power dynamics on the entire planet."
Troi: [insightfully, her voice calm] "Captain, I sense that Bas T'yat is deeply worried about his planet's future. He feels a strong sense of responsibility and guilt for the attacks... I don't think that he had any way to know that their warp signature would act as a beacon to those seeking resources. They didn't even know other life forms existed until the Cardassians arrived. It's clear that Anarakans weren't prepared for the reality of interstellar contact."
Picard: [resolved] "I agree, Counselor. We're dealing with a society that is both advanced and vulnerable. A dangerous combination. We must proceed carefully."
Picard considers this, his brow furrowed in thought. Finally, he makes a decision.
Picard: [decisively] "We must proceed, however. I'll invite Bas T'yat to the Enterprise to discuss the situation further. We will ensure that any assistance we provide doesn't destabilize their society, or escalate the conflict."
Picard hails Bas T'yat from his command station.
Picard: [calmly] "Mr. T'yat, I'd like to invite you aboard the Enterprise to discuss our options in person."
The main screen fills with T'yat's face again.
Bas T'yat: [with a hint of hesitation] "Thank you, Captain, I accept. But I'd prefer to take my own craft... Still not quite comfortable with the transporter technology, if you'll understand. I'll bring my wife, L'anna, and my pilot, Lar Kinn."
Picard: [diplomatic, nodding slightly] "Understood. We'll be ready to receive you in the shuttlebay.”
Scene 6: Main Shuttlebay
In the Enterprise's shuttlebay, the crew prepares to greet their visitors. The doors slide open, and a sleek, streamlined skysled enters the bay, guided by Lar Kinn at the controls. The craft settles gently onto the deck, and the hatch opens. Bas T'yat steps out, accompanied by his wife, L'anna, and Lar Kinn, who looks around the shuttlebay with wide-eyed curiosity. Picard, Troi, and Data are there to meet them, offering warm greetings as the Anarakans take in the impressive sight of the Enterprise's interior.
Picard: [welcoming, with a gesture towards the ship] "Welcome aboard the Enterprise, Mr. and Mrs. T'yat. I trust your journey was smooth?"
Bas T'yat: [grinning, clearly impressed] "Very much so, Captain. Your ship is... well, it's more than I imagined. Thank you for having us."
Troi steps forward, offering a kind smile.
Troi: [invitingly] "If you'd like, I can give you a tour of the ship. We're quite proud of our vessel, and I think you'll find it fascinating."
L'anna's eyes widen with excitement, and she nods eagerly. Bas exchanges a look with Lar Kinn, just catching up to the group. He seems just as eager to explore as the others, and nods excitedly to Troi.
Bas T'yat: [appreciatively] "We'd be honored. Lead the way, Counselor."
Lar Kinn: So can all these shuttles go faster than light?
With that, the group sets off on a tour of the Enterprise, the Anarakans marveling at the advanced technology and seamless design of the Federation starship. As they walk, Troi can't help but notice the mix of awe and determination in Bas T'yat an inventor and leader who knows that his world's future may very well depend on the choices made in the hours to come.
Scene 7: Bridge
The scene opens as Counselor Troi leads Bas T'yat, L'anna, and Lar Kinn onto the bridge of the Enterprise. The visitor's awe is palpable as they take in the grandeur of the ship's command center. Picard, standing near the captain's chair, barely has a moment to welcome them when a sudden alert draws everyone's attention.
Data: [at his station, voice urgent] "Captain, I'm detecting the return of the Cardassian battle cruiser. It is registered as the Kolarak. It just popped out from behind the home star and is entering orbit around Anarak."
Riker: "Yellow alert. On screen."
Picard immediately straightens, his expression shifting from welcoming to resolute. The tension on the bridge heightens as the viewscreen flickers to life, displaying the imposing sight of the Kolarak. The Cardassian vessel looms in space, its dark hull bristling with weaponry.
Picard: [calmly, but with authority] "Mr. Worf, open a channel to the Kolarak."
The screen quickly reveals the stern visage of a Cardassian Gul in his command chair. His eyes narrow as he takes in the sight of the bridge crew and the unfamiliar faces of Bas and his companions.
Picard: [with measured politeness] "I am Captain Jean-Luc Picard of the Federation starship Enterprise. With whom am I speaking?"
Gul Bankar: [with a sneer, his voice dripping with condescension] "You may address me as Gul Bankar."
Picard: "Gul Bankar, there have been reports of your vessel causing harm and stealing resources from the planet below. With me is Bas T'yat, the owner of the warp-capable vessel that it appears your forces destroyed on the surface. We request an explanation for these hostilities."
Gul Bankar: "Captain Picard, your presence here is an unwelcome interference. This planet, and its inhabitants, are under Cardassian protection. You will withdraw immediately, leaving Anarak to our care."
Picard's gaze hardens, but his tone remains calm and firm.
Picard: [skeptically] "Cardassian protection? Anarak lies within Federation territory. We received a distress call and are here to provide assistance."
Bankar's expression darkens, his eyes flashing with anger.
Gul Bankar: [coldly] "The Federation's meddling in this region is all too well documented, Picard, but Anarak is too close to Cardassian space for your interference to be tolerated. I find your so-called assistance nothing more than another prelude to annexation."
Bas, standing beside Troi, listens intently, his face reflecting a mixture of concern and frustration. Picard, sensing the rising tension, steps closer to the viewscreen.
Picard: [with resolve] "The Federation respects the sovereignty of all worlds. We are only here because of your aggressive actions, not to claim this planet. We have long worked to maintain peace in this sector, and I would hate to see that peace jeopardized by your reckless actions here."
Gul Bankar: [sarcastically] "Peace? The Federation's control of Terok Nor and the Bajoran wormhole is hardly a gesture of peace. It was a clear power grab, one that we will not allow to extend to Anarak."
Picard's eyes narrow, his voice taking on a steely edge.
Picard: [firmly] "Gul Bankar, a conflict between the Federation and the Cardassian Union would serve no one's interests, especially not over a planet that is so new to the neighborhood. I suggest you contact your superiors before taking any further aggressive actions."
There's a tense silence as Bankar considers Picard's words, his eyes flicking to Bas and then back to Picard. Finally, he lowers his head in a slight nod, though his expression remains hostile.
Gul Bankar: [grudgingly] "Very well, Captain. I will contact Central Command. But understand this; Anarak will not fall under Federation control, and I will ensure that Cardassia's interests are protected. I will contact you again in 4 hours."
The transmission abruptly cuts off, leaving the bridge in a heavy silence. The Kolarak remains on the viewscreen, hovering ominously in space, nose to nose with the Enterprise now. Picard exhales, turning to face his crew.
Picard: [calmly, but with an undertone of urgency] "Maintain our position and yellow alert, Mr. Worf, and monitor the Kolarak for any signs of hostile activity."
Worf gives a curt nod, his eyes never leaving the tactical display.
Worf: [with determination] "Aye, Captain. Shields at maximum, weapons ready."
Picard then turns to Bas, who is visibly shaken but trying to maintain his composure.
Picard: [reassuringly] "Mr. T'yat, I understand this is a difficult situation and you don't yet know who to trust, but I assure you that we aim to keep the peace in this sector and will do everything in our power to ensure your planet's safety. We ask nothing in return from the Anarakan people. However, it is crucial that we handle this matter diplomatically."
Bas nods, though his expression is one of deep concern.
Bas T'yat: [uneasily] "I appreciate that, Captain, and don't worry, nothing that Gul Bankar says will make me trust his offer of "protection" after he destroyed my ship and stole resources from all over the planet. But I do worry that he’s using this time to call for reinforcements."
Picard places a reassuring hand on Bas's shoulder, his voice steady.
Picard: [confidently] "If he attacks, we'll face that challenge together, Mr. T'yat. You are free to return to the surface at any time but for now, I think it best that we consider how fast we could deploy our transporter inhibitor technology on your planet."
Bas T'yat: [enthusiastically] "You mean you're willing to sell us devices that can stop them from beaming up our resources?"
Picard: "Or beaming their troops down. And we wouldn't sell it to you, it is our gift. The Federation doesn't sell it's assistance to those in need."
The visitors faces all brighten in unison with relief.
L'anna: "I don't know how we could ever thank you enough, Captain. This means everything to our people."
Picard: "Don't thank us yet, there is still the issue of deploying enough of them in time. If they're going to attack in 4 hours you'd need them set up near all the most valuable targets at the very least. They'll need a steady supply of energy, too."
Bas furls his lips in concerned thought.
Data: "Captain, I've analyzed all of the planet's most valuable resource depots that our scanners can detect and I see 168 unique locations that we should set up transport inhibitors. There may, of course, be other targets too that they would want."
Riker: [apprehensively] "That's way too many for us to replicate in time, much less visit each location to install within the next 4 hours."
Picard: "We need a way to speed up that deployment, at least to enough sites that will show Gul Bankar that things have changed... And hopefully without him detecting our movements."
Bas T'yat: "If I may captain, I think I know a better way to deploy them if I can just make a detailed scan of one and save it to our printer file format... We don't have your transporter technology, but our device printers are able to scan and quickly reproduce any technological device that we can identify the components of."
Riker: "And how will that help distribute them to everyone in time?"
Bas T'yat: "Simple, every business and household has one of these printers. I can upload the scanned file to our Openlink and tell all of Anarak in one broadcast about the imminent threat and how to protect themselves from it with one of these inhibitors. They'll pop out thousands of them in time."
Picard: "That sounds very promising, Mr. T’yat. But I want your assurance that your company will not hold any sort of monopoly on this technology or otherwise profit from it; In lieu of a government, the Federation requires that this gift be made to your whole planet at once."
Bas T'yat: [after some hesitation] "Alright, Captain. You have my promise. Giving up some profits is the least I can do to make up for attracting the Cardassians to Anarak."
Picard looks visibly relieved, giving a curt nod to Bas.
Picard: "Data, take our guests to engineering and grab whomever you may need to assist you with making this happen in time. Remember, you’ll also need to show the Anarakans how to use these devices."
Data: "Aye sir." [To the visitors] "If you'll follow me please, we'll be able to work on this in engineering."
Data, Bas, Lar Kinn, and L'anna walk briskly to the turbolift. The scene closes with Picard returning to his command chair, the bridge crew resuming their stations as the standoff between the Enterprise and the Kolarak continues. The two ships remain locked in silence, nose to nose, as the 4-hour countdown begins.
Scene 8: Main Engineering
The scene opens in Main Engineering, where Geordi La Forge, Data, and Ensign Sam Lavelle are putting the final touches on the scan for their transport inhibitor device. Bas T'yat and Lar Kinn stand nearby, observing the process with keen interest. The atmosphere is tense, underscored by the ticking clock counting down the hours until Gul Bankar's deadline.
Geordi: [focused as he works] "All right, that should do it. The scan of this transport inhibitor is ready, and the data's been formatted for your printers."
He hands a datapad to Bas, who takes it with a mix of curiosity and nervousness.
Geordi: [reassuringly] "You'll be able to upload the complete plans from this device, including an adapter for your power source. Once it's on your network, anyone with Openlink access will be able to build and deploy these inhibitors in a matter of minutes. It's up to you, however, to convince them to do that."
Bas T'yat: [relieved] "Thank you, Commander. I'm sure many will manage it in time, but I just hope it's enough."
Lavelle: [chiming in, pointing to the datapad] "Also I've included a detailed instruction set too. It explains how to set the units up and operate them."
Bas nods his thanks, flipping through the instructions as Lar Kinn looks over his shoulder.
Data: [ever precise, offering a suggestion] "Mr. T'yat, given the standoff outside, it may be prudent to avoid the use of the transporter. The Kolarak is likely monitoring our actions closely. Sending the plans with you aboard the skysled would appear less provocative."
Bas looks visibly relieved at the suggestion, nodding in agreement.
Bas T'yat: [grateful] "Thank you, we'd prefer not having our atoms scattered throughout the atmosphere today anyway."
Geordi: [nodding, humorously] "No problem. We'll make sure the skysled is ready to go."
Data gestures toward the exit of Engineering, indicating it's time to depart.
Data: [calmly, but with urgency] "We should make our way to the shuttlebay. There's less than two hours remaining before the Gul's deadline. It's imperative that as many Anarakans as possible receive these plans in time."
Bas and Lar Kinn exchange a look, their expressions set with determination as they follow Data out of Engineering. The camera follows the group as they walk briskly through the corridors of the Enterprise.
L'anna: "You'll be sure to tell the Captain and Councilor Troi that we said goodbye?"
Data: "Of course. And let me say that I find your culture truly intriguing, and hope we get the chance to visit again in the future, no matter if Anarak chooses Federation membership or otherwise."
Bas T'yat: "You'd be our welcome guest anytime, Mr. Data. I think you'd most enjoy seeing the progress my people have made with robotics and artificial intelligence. My company produces one of the best-selling android assistants on the market."
Data: "Fascinating. I look forward to it. Here we are."
As they reach the shuttlebay, the large bay doors slide open, revealing the sleek skysled waiting for them. The ship is prepped and ready for launch, its engines humming with quiet power.
Data: [pausing as their ship's door opens] "We wish you a safe journey, Mr. T'yat, L'anna, Mr. Kinn."
Bas T'yat: [nodding, with resolve] "We'll make sure everyone gets these plans. Thank you, Commander Data."
Lar Kinn gives Data a respectful nod before they step onto the skysled. Data watches as they take their positions inside the cockpit. Data then taps his communicator, his voice steady.
Data: "Data to the Bridge, our visitors are ready to depart."
The camera cuts to the exterior of the Enterprise, where the massive shuttlebay doors slide open. The skysled, with its sleek design and glowing engines, slowly backs out of the bay, the vastness of space stretching out behind it. As the skysled turns on its main engines, the camera shifts to an interior cabin view, showing Bas and Lar Kinn exchanging a final, determined nod before the vessel speeds downwards towards Anarak.
Scene 9: Bridge
The scene opens 30 minutes later. The tension on the Enterprise bridge is palpable as the Openlink broadcasts Bas's message and the transport inhibitor plans worldwide. The crew watches anxiously as the first inhibitors are swiftly deployed across Anarak. Suddenly, the ship's sensors beep urgently. Worf glances at his console, eyes narrowing.
Worf: [alarmed] "Captain, seven additional Cardassian battle cruisers have exited warp and joined Gul Bankar's ship. They're forming up and preparing to engage."
Riker: "Red alert, forward shields to maximum."
Picard's expression hardens as the Kolarak hails them. Gul Bankar's visage appears on the viewscreen, eyes burning with fury.
Gul Bankar: [accusatory] "We've detected the inhibitor plans on their planet-wide network, Picard. You've broken our gentleman's agreement by sharing advanced technology with a primitive civilization. So much for Starfleet ideals! You're no match for us now. Try and stop us at your own peril."
With that, Bankar cuts off communications. Picard stands, frustration etched into his features as the fleet of eight warships begins its descent toward Anarak.
Data: [urgently] "Captain, the Cardassian ships are gaining speed and appear to be initiating an attack run on the planet's largest population center. Tens of millions of civilian lives are at risk, more than usual because the defensive turrets are spread out among the greater population. It is not uncommon for them to be placed on rooftops and around housing here."
The crew's tension escalates as the gravity of the situation sinks in. Picard, feeling the weight of command, turns to his officers.
Picard: [steady but intense] "Ideas?"
Worf: "Captain, we could attempt to disable their weapons and transporters, focusing on minimizing their capacity to attack."
Riker: [shaking his head] "Even so, we're outmatched. Enterprise won't survive against eight battle cruisers."
Troi: [calm but urgent] "We just need to buy time. To give the Anarakans a chance to fully deploy their defense net. But any kind of engagement from us still risks re-igniting a war with the Cardassians."
Data, ever analytical, speaks up with a grim tone.
Data: "Captain, I've run millions of battle scenarios. None result in the Enterprise surviving while saving more than a few dozen lives on the surface. Our current position is untenable."
As the Cardassian warships break through the planet's stratosphere, Ensign Lavelle, stationed at comms, suddenly speaks up.
Lavelle: [urgently] "Captain, Bas T'yat has just sent out another message across the planet, warning of the incoming Cardassian fleet."
Picard opens his mouth and lifts his index finger to respond, but he's cut off by a sudden, blinding array of light erupting from the planet's surface, filling up the viewscreen. The bridge crew shields their eyes as the screen fills with thousands of pinpricks of light; an overwhelming launch of nuclear-armed missiles aimed directly at the Cardassian fleet.
Worf: [stunned] "Captain, these are nuclear-fission warheads, each with a 10-megaton yield. I've never seen a civilization with this many dirty weapons in active deployment."
The bridge falls silent as the sheer scale of the Anarakan response becomes clear. The entire hemisphere of Anarak has mobilized, proving their incredible capacity for defense, despite the lack of a centralized government.
Data: "Fascinating. It could be that no central authority is needed for coordination when the threat is dire. These people all appear to be responding individually with their own weapons."
The first few dozen warheads impact the Cardassian shields, which manage to absorb their blasts. But the onslaught is unrelenting. Hundreds, then thousands of warheads detonate in rapid succession, creating a cataclysmic, sustained explosion. The Cardassian ships, though formidable, are utterly overwhelmed. The viewscreen shows an apocalyptic display; a temporary star forms in Anarak's upper atmosphere, engulfing the entire Cardassian flotilla in an unprecedented, blinding flash.
Picard: "Helm, back off our position."
The bridge crew watches in stunned silence as the massive explosion slowly dissipates, leaving nothing but a red afterglow and the eerie silence of space. Power has gone out across the hemisphere on the planet below, but not a single molecule of the Cardassian ships remain. Picard and his crew are left in awe, mingled with a deep sense of disappointment. The enormity of what they've witnessed sinks in; a civilization so welcoming, yet still capable of such destructive power... Sso fundamentally different from the Federation's ideals. Troi closes her eyes tightly and winces, blocking out the pain of all those Cardassian deaths. Picard stands, staring out at the aftermath, the weight of the moment heavy on his shoulders.
Picard: [quietly, with a great sense of loss] "Such utter destruction..."
The camera pulls back, showing the Enterprise as a small silhouette against the reddish glow below.
Scene 10: Bridge
The scene opens minutes later with the Enterprise bridge crew still processing the aftermath of the overwhelming display of destructive power. The mood is somber as the reality of what they've witnessed lingers. Suddenly, Bas T'yat's face appears on the viewscreen, his expression a mixture of relief and satisfaction.
Bas T'yat: [earnestly] "Captain Picard, I wanted to thank you and your crew for everything. It seems our future is secure now, thanks to the defense network and your assistance. We're eager to move forward and hope the Federation will allow us to engage in commerce with your worlds and other peaceful civilizations."
Picard stands, his gaze steady, though his tone reflects the weight of what has transpired. He pauses for a moment, as if searching for the right words, the bridge falling into a brief, tense silence.
Picard: [measured, but firm] "Mister T'yat, I must be candid. While the Enterprise is pleased to have assisted in safeguarding your world, the events of today have left us with grave concerns. The way Anarak handled the Cardassians… particularly the use of nuclear warheads, demonstrates a fundamental difference in values between our societies. We cannot endorse methods that pose such a grave risk to all life, even in defence. The Federation could not, in good conscience, approve your planet for membership given these circumstances."
Bas's expression shifts to one of slight disappointment, but he remains composed.
Bas T'yat: "I understand, Captain. We've always been a world that does things our own way. Federation membership would have been a tough sell to my people anyway. But what about trade? Surely we can still establish commerce with Federation worlds?"
Picard nods, his tone softening slightly.
Picard: "Trade remains an option. We won't turn away peaceful commerce between Anarak and Federation planets. However, I must stress that the use of nuclear weapons is fundamentally at odds with Federation ethics. While I recognize their role in your planet's defense, I hope that over time, your people will explore more sophisticated and less destructive means of protection."
Bas nods again, understanding the implications of Picard's words.
Bas T'yat: "It's clear that today's events were... extreme. The fallout, the EMP blackouts, the atmospheric damage; we've already seen unacceptable cost. I'll do my best to guide my people toward more advanced defenses, and away from reliance on such careless weapons. It will be my penance for leading the Cardassians here."
Troi senses his guilt once again and takes a deep breath. Clearly still shaken by the loss of life, she steadies herself before offering a supportive smile.
Troi: "You shouldn't burden yourself with guilt, Mister T'yat. Anarak was bound to take that step sooner or later. What matters now is how you use your newfound role as an ambassador to the stars. Your actions will shape your planet's future in the galaxy."
Bas smiles, clearly grateful for the support.
Bas T'yat: "Thank you, Counselor. I'll do my best to live up to that responsibility."
After a few more exchanges, the connection ends, and Bas T'yat's image fades from the viewscreen. Picard takes a deep breath and turns to face his bridge crew.
Picard: [reflective] "We've witnessed two amazing displays of power today; one of the explosive variety, and the other of a free people's resolve. It's hard to imagine how their society works with no acceptance of authority, but today they've clearly displayed that they can accomplish amazing things working together even without any."
Worf, still perplexed, shakes his head slightly.
Worf: "I still don't understand how an entire planet could coordinate such a specific defense without any central leadership."
Leaning casually against the console, Riker chuckles lightly.
Riker: "It was in everyone's best interest, Worf. They just needed Bas's signal to know when the attack was imminent. The rest fell into place."
Worf: "And how they could hide that many warheads from our scans? Enriched Uranium is the easiest of all elements to scan for."
Data: "It appears that their stealth technology may be on par with our own."
Picard, his expression thoughtful, gazes out at the stars beyond the viewscreen.
Picard: "I'm placing a note in my log for Starfleet to leave this planet alone until they can't be ignored any longer. I believe it's for the best that we leave Anarak to chart its own course in the galaxy."
He pauses, a faint smile tugging at the corner of his mouth.
Picard: "I doubt we'll have trouble with them soon, at least, until they meet the Ferengi."
*The bridge crew shares a quick laugh and then a quiet moment of contemplation before returning to their stations. The camera pulls back, showing the Enterprise once again poised in the vastness of space, a symbol of hope and integrity amidst the complexities of a vast and unpredictable galaxy.
Fade to black.*
---
*This story is set in the Star Trek universe, created by Gene Roddenberry and owned by Paramount. I do not own any of the characters or settings from the Star Trek franchise, and this is purely a fan-made work for non-commercial purposes.*
-
 @ 1a48e74d:02c0e00f
2024-09-04 18:53:09
@ 1a48e74d:02c0e00f
2024-09-04 18:53:09Welcome back ya'll hope you are doing well this week. Today I wanted to talk about why Bitcoin represents a dawn of a new age in property ownership. Before you spit out your coffee and walk away, hear me out. Bitcoin and real estate have a few things in common. The first is property rights.
When you are the owner of a building with your name on the dotted line and whatnot, you are the sole owner of that property. No one can tell you what to do with it, and no one has a claim to what you own. You are free to do what you wish. Property rights are sacrosanct and immutable similar to Bitcoin.
Bitcoin confers upon the owner the same property right protections as owning a piece of real estate. Once you own it, you are the sole owner of that Bitcoin. No one can tell you what to do with it. No one else has a claim to your Bitcoin. You are free to do with it what you wish.
Bitcoin and real estate are similar in terms of built-in scarcity. There is only 21 million Bitcoin that will ever be created, and you can't print more land. This is why owning real estate has been such a good investment since the beginning of time. Buying a piece of land and "HODLING" for decades will generate a substantial return on your investment.
This same buy and hodl strategy apply to Bitcoin as well. If you bought Bitcoin back in 2009, you would be a multi-millionaire right now.
If you invested $1000 back in 2011 when Bitcoin was trading at $3.50, you would have turned that $1000 into $15.6 million if you held on to it for ten years. Just sayin.
You have to reframe your thinking to understand what is going on. We are living in the 21st-century gold rush, and you have an opportunity to stake your claim to the soundest money on Earth with a few taps on your phone. Never in the history of the world has the plebs like us had the ability to front-run a monetary revolution.
Bitcoin is freedom from oppression. Bitcoin restores your sovereignty. Bitcoin makes you fuckable, and the powers that be know it. They are afraid they will lose control if too many people catch on too quickly, which is why large institutions are rushing to offer Bitcoin services or buy them and keep them on their balance sheet.
Bitcoin won't stay this cheap forever. $100-300k Bitcoin is in the cards over the next few years. I don't want you guys to miss out on this.
All you have to do is buy Bitcoin and hold. It's that simple. FYI trying out the new obsidian writer for nostr notes!
Bitcoin #nostr
-
 @ af9c48b7:a3f7aaf4
2024-06-30 19:16:15
@ af9c48b7:a3f7aaf4
2024-06-30 19:16:15Chef's notes
Homemade ice cream was a summertime staple when I was growing up. Use this simple recipe to bring back memories or start new one’s.
Details
- 🍳 Cook time: 45 minutes
- 🍽️ Servings: 10
Ingredients
- (1) 14oz can of sweetened condensed milk
- (1) 2lt bottle of your favorite fruity flavored soda
Directions
- In a large bowl, whisk the condensed milk and soda until thoroughly blended.
- Pour into ice cream machine and follow the operating instructions for the machine
- Enjoy a refreshing bowl of ice cream with friends and family
- Feel free to experiment with adding fresh fruit or fruit juice. Recommended soda flavors include orange (orange sherbet) and pineapple (famous Dole Whip from Disney World/Land) but any flavor should be good.
-
 @ fb1366ab:d78068ac
2024-06-27 05:30:17
@ fb1366ab:d78068ac
2024-06-27 05:30:17Chef's notes
Double the butter to make it more crumbly and buttery.
Details
- 🍳 Cook time: 0 min
- 🍽️ Servings: 15
Ingredients
- 1 lb cream cheese
- 8 oz unsalted butter
- 12 oz pesto
- cherry tomatoes
- toasted pine nuts
- sourdough baguette, sliced
Directions
- Bring cream cheese and butter to room temperature.
- Mix butter and cream cheese in a stand mixer until fluffy.
- Line a bowl with cheesecloth.
- Press a small layer of cream cheese / butter mixture at the bottom of the bowl. Add a layer of pesto. Add a layer of cream cheese mixture, then pesto, and continue for three layers of pesto and four layers of cream cheese / butter.
- Cover and refrigerate for several hours or overnight.
- To serve, invert on serving platter, peeling away cheesecloth and revealing a nicely compact mound.
- Slice cherry tomatoes in half and scatter with pine nuts around the mound.
- Serve with sliced sourdough baguette.
-
 @ 361d3e1e:50bc10a8
2024-09-04 18:48:17
@ 361d3e1e:50bc10a8
2024-09-04 18:48:17Is France preparing to seize people's savings to avoid bankruptcy?
politics #europe #banks #france #savings #cyprus
-
 @ 32e18276:5c68e245
2024-06-26 19:03:35
@ 32e18276:5c68e245
2024-06-26 19:03:35Here's a neat tip for figuring out exactly where your packet went during a traceroute. You can simply paste the output of traceroute into ChatGPT, asking where the packet actually went geographically.
The question
Here's the input I gave it:
``` can you get a sense of this route geographically ?
monad> tracepath nghttp2.org1?: [LOCALHOST] pmtu 1500 1: _gateway 0.445ms 1: _gateway 0.363ms 2: 24.86.64.1 11.495ms 3: rc1st-be118-1.vc.shawcable.net 8.924ms 4: 24.244.60.69 12.607ms asymm 3 5: 24.244.63.101 9.884ms asymm 3 6: rc1st-be214.vc.shawcable.net 11.561ms asymm 3 7: rc2wt-be50-1.wa.shawcable.net 14.402ms asymm 3 8: rc2wt-be50-1.wa.shawcable.net 14.334ms asymm 3 9: ge3-0.cr02.sea01.pccwbtn.net 13.858ms asymm 4 10: ge3-0.cr02.sea01.pccwbtn.net 13.936ms asymm 4 11: 63-216-84-226.static.pccwglobal.net 191.730ms asymm 8 12: ae1.r01.hkg03.icn.netarch.akamai.com 154.284ms asymm 9 13: ae1.r01.hkg03.icn.netarch.akamai.com 160.912ms asymm 9 14: ae7.r01.tyo03.icn.netarch.akamai.com 156.906ms asymm 9 15: a23-56-142-37.deploy.static.akamaitechnologies.com 189.058ms asymm 10 16: a23-56-142-37.deploy.static.akamaitechnologies.com 189.577ms asymm 10 ```
Response
Tracing the geographical path from your local host to nghttp2.org involves a series of hops that typically represent different network routers or devices. Let's break down the route step-by-step:
- Localhost to Gateway:
-
This is your local network's gateway, indicating the first point of contact outside your computer.
-
24.86.64.1:
-
This IP is likely the first hop within your Internet Service Provider's (ISP) network. Given the IP range, this looks like a Canadian IP address, possibly Vancouver (Shaw Communications).
-
rc1st-be118-1.vc.shawcable.net:
-
This indicates a Shaw Communications router, likely in Vancouver, British Columbia.
-
24.244.60.69 and 24.244.63.101:
-
These are further hops within Shaw Communications' network, still in Vancouver.
-
rc1st-be214.vc.shawcable.net:
-
Another router in Vancouver within Shaw's network.
-
rc2wt-be50-1.wa.shawcable.net:
-
This hop seems to indicate a transition from Vancouver to Washington state in the USA.
-
rc2wt-be50-1.wa.shawcable.net:
-
This appears again, indicating it's a key router in Washington state, likely Seattle.
-
ge3-0.cr02.sea01.pccwbtn.net:
-
This shows the transition to PCCW Global's network, a major international telecommunications provider, in Seattle, Washington.
-
63-216-84-226.static.pccwglobal.net:
-
Another hop within PCCW Global's network, possibly still in Seattle but preparing for a trans-Pacific jump.
-
ae1.r01.hkg03.icn.netarch.akamai.com:
- This hop indicates a significant jump to Hong Kong, to an Akamai router. This suggests the use of Akamai's CDN (Content Delivery Network).
-
ae1.r01.hkg03.icn.netarch.akamai.com:
- Another Akamai router in Hong Kong.
-
ae7.r01.tyo03.icn.netarch.akamai.com:
- Transition from Hong Kong to Tokyo, Japan, within Akamai's network.
-
a23-56-142-37.deploy.static.akamaitechnologies.com:
- The final destination is likely a server hosted by Akamai in Japan, which is hosting nghttp2.org.
In summary, the geographical path likely follows this route:
- Vancouver, Canada (Shaw Communications)
- Seattle, Washington, USA (Shaw Communications and PCCW Global)
- Hong Kong (PCCW Global and Akamai)
- Tokyo, Japan (Akamai)
This route involves both North American and Asia-Pacific regions, indicating a significant geographical spread typically seen in global internet routing.
Summary
This makes traceroute way more understandable. ChatGPT knows enough about the domains to give you a good sense of the geographical path. I will definitely be using this from now on, maybe someone can make a tool to do this automatically and format it nicely.
Obviously don't do this if you actually care about the privacy of your network paths, but I personally could care less so I don't mind feeding the AI overlords in this case.
Until next time!
-
 @ 8d34bd24:414be32b
2024-09-04 15:57:00
@ 8d34bd24:414be32b
2024-09-04 15:57:00Today is the official publishing day of this post. I already tried scheduling this post in another editor that went out early.
I’ve mentioned multiple times that I feel our time left is short and that the rapture and the tribulation are coming soon. I feel it with every ounce of my being. I see it in the rush to evil around us. I see Biblical prophecy coming to fulfillment and technologies that could not be fathomed 2,000 years ago coming into being in a way that will make prophecy possible. The question is, what do we do with the time left to us?
Don’t Be a Foolish Virgin
Matthew gives an analogy of believers waiting for Christs return:
“Then the kingdom of heaven will be comparable to ten virgins, who took their lamps and went out to meet the bridegroom. Five of them were foolish, and five were prudent. For when the foolish took their lamps, they took no oil with them, but the prudent took oil in flasks along with their lamps. Now while the bridegroom was delaying, they all got drowsy and began to sleep. But at midnight there was a shout, ‘Behold, the bridegroom! Come out to meet him.’ Then all those virgins rose and trimmed their lamps. The foolish said to the prudent, ‘Give us some of your oil, for our lamps are going out.’ But the prudent answered, ‘No, there will not be enough for us and you too; go instead to the dealers and buy some for yourselves.’ And while they were going away to make the purchase, the bridegroom came, and those who were ready went in with him to the wedding feast; and the door was shut. 11Later the other virgins also came, saying, ‘Lord, lord, open up for us.’ But he answered, ‘Truly I say to you, I do not know you.’ Be on the alert then, for you do not know the day nor the hour. (Matthew 25:1-13)
Christians have been waiting for around 2,000 years for Christ’s return. It is easy to get drowsy and begin to sleep due to the delay to His return, but we are called to be ready. “You too, be ready; for the Son of Man is coming at an hour that you do not expect.” (Luke 12:40) Our wait may be long or short, but we are supposed to live our lives like he will arrive today. We don’t want to miss out on joining Him at His return, but we also don’t want to have to face Him knowing that we were not focused on what He had called us to do. We don’t want to admit that we didn’t share the gospel to that friend, that we didn’t stand up for the truth when the crowd was speaking contrary to the word of God, or that we acted in an unloving way to fellow believers or to the lost.
The Bible clearly tells us that we “do not know the day nor the hour,” but that doesn’t mean that He has not given us signs that the time is short.
What Should We Be Doing?
If Jesus is coming soon, how should we spend our time? What should we be doing? Should we just sit back and wait?
For even when we were with you, we used to give you this order: if anyone is not willing to work, then he is not to eat, either. For we hear that some among you are leading an undisciplined life, doing no work at all, but acting like busybodies. Now such persons we command and exhort in the Lord Jesus Christ to work in quiet fashion and eat their own bread. But as for you, brethren, do not grow weary of doing good. (2 Thessalonians 3:10-13)
The Bible is clear that we should work. This not only means that we should not quit our jobs, but should continue working as we have been doing, but it also means we should put time and effort into kingdom work. God has given each one of us a purpose and a job to do. We should study His word and pray and keep our eyes open so we don’t miss out on what He intends as our purpose. Another analogy is given in Matthew:
“For it is just like a man about to go on a journey, who called his own slaves and entrusted his possessions to them. To one he gave five talents, to another, two, and to another, one, each according to his own ability; and he went on his journey. Immediately the one who had received the five talents went and traded with them, and gained five more talents. In the same manner the one who had received the two talents gained two more. But he who received the one talent went away, and dug a hole in the ground and hid his master’s money.
“Now after a long time the master of those slaves came and settled accounts with them. The one who had received the five talents came up and brought five more talents, saying, ‘Master, you entrusted five talents to me. See, I have gained five more talents.’ His master said to him, ‘Well done, good and faithful slave. You were faithful with a few things, I will put you in charge of many things; enter into the joy of your master.’
“Also the one who had received the two talents came up and said, ‘Master, you entrusted two talents to me. See, I have gained two more talents.’ His master said to him, ‘Well done, good and faithful slave. You were faithful with a few things, I will put you in charge of many things; enter into the joy of your master.’
“And the one also who had received the one talent came up and said, ‘Master, I knew you to be a hard man, reaping where you did not sow and gathering where you scattered no seed. And I was afraid, and went away and hid your talent in the ground. See, you have what is yours.’
“But his master answered and said to him, ‘You wicked, lazy slave, you knew that I reap where I did not sow and gather where I scattered no seed. Then you ought to have put my money in the bank, and on my arrival I would have received my money back with interest. Therefore take away the talent from him, and give it to the one who has the ten talents.’
“For to everyone who has, more shall be given, and he will have an abundance; but from the one who does not have, even what he does have shall be taken away. Throw out the worthless slave into the outer darkness; in that place there will be weeping and gnashing of teeth. (Matthew 25:14-29)God has given each of us different skills, gifts, and opportunities. He wants us to make the most of them. If God gave you skill in business, you can use your wealth to fund ministries, churches, and missionaries. If God has gifted you with the ability to teach, you can disciple many to grow in their faith and knowledge of God. If God has brought you into a relationship with someone influential, you can share the Gospel with them and be used to draw them into saving faith in Jesus. Whatever skills, gifts, and opportunities God has given to you, you need to make the most of them. You need to grow and make the most of what God has given you.
What is the Best Use of Our Time and Money?
God wants us to shine a light for Him. He wants us to make a difference. There are many ways to do this and we can’t do them all. We have to pick and chose what is God’s will and what will make the best use of what God has given us.
There are lots of good things we can do, but what is the best?
I used to focus on prepping to be able to provide for my family and others if times get bad. That was good, but was it best? I used to grow a garden and grow healthy food. That was good, but was it the best? I used to be highly involved in politics and worked hard to support and elect godly men and women into government positions where they could have a positive influence on our culture and our country. That was good, but was it the best?
According to the grace of God which was given to me, like a wise master builder I laid a foundation, and another is building on it. But each man must be careful how he builds on it. For no man can lay a foundation other than the one which is laid, which is Jesus Christ. Now if any man builds on the foundation with gold, silver, precious stones, wood, hay, straw, each man’s work will become evident; for the day will show it because it is to be revealed with fire, and the fire itself will test the quality of each man’s work. If any man’s work which he has built on it remains, he will receive a reward. If any man’s work is burned up, he will suffer loss; but he himself will be saved, yet so as through fire. (1 Corinthians 3:10-15)
The best way to judge which actions are best is to see which actions have an eternal influence and to look and see what God is doing and to join His work. The difference between gold & silver versus wood, hay, and straw is the gold & silver can survive fire. Whether something is good or best depends on whether the action makes a difference in eternity. Providing for my family and friend’s physical needs and health is good, but it doesn’t make an eternal difference. Electing Godly officials makes life here on Earth better, but does it actually make a difference eternally? Probably not.
What does make a difference? Sharing the Gospel with others makes an eternal difference. Standing up for the truth, especially the spiritual truths from the Bible, makes an eternal difference. Writing a book or a blog sharing the truths of the Bible and Jesus makes an eternal difference. I’ve tried to focus my time on this type of activity more than the former. I don’t want one soul to go to Hell because I was too busy to share the Gospel. I don’t want one Christian to regret their life on Earth because I was too busy to disciple them. I don’t want to be like the man who received the single talent and buried it in the ground, who, when facing his master, was told, “You wicked, lazy slave.”
What Is Most Important?
“Do not store up for yourselves treasures on earth, where moth and rust destroy, and where thieves break in and steal. But store up for yourselves treasures in heaven, where neither moth nor rust destroys, and where thieves do not break in or steal; for where your treasure is, there your heart will be also. (Matthew 6:19-21)
What are the most important things in our lives? The most important things are people.
- Some people in our lives have never heard about Jesus. We need to share the gospel with them.
- Some people in our lives are hurting and need to be helped and encouraged and taught to trust in Jesus.
- Some people in our lives are new Christians or just immature Christians, who have trusted in Jesus, but haven’t grown much since salvation. We need to teach and disciple them to grow in their understanding of God and who He is. We need to build up their faith. We need to encourage them to study the Bible.
- Some people in our lives know God and His word, but are unsure how to live out their faith and share it with others. We need to encourage them and train them, so they can multiply their faith among others in their lives.
What are you doing to make an eternal difference in service to our Lord Jesus Christ? Are you one of the lazy, unprepared virgins? Are you hiding the gifts God gave you in the ground or shining a light that can be seen by everyone around you? Are you so busy doing good, that you don’t see God’s best?
Are you excited about meeting Jesus in the air at the rapture of the Church? I am! I hope you are, too.
your sister in Christ,
Christy
Bible verses are NASB (New American Standard Bible) 1995 edition unless otherwise stated
-
 @ 6dcaee2b:66134885
2024-06-24 13:38:35
@ 6dcaee2b:66134885
2024-06-24 13:38:35Chef's notes
I got the idea for this recipe from row 7 seeds.
Details
- ⏲️ Prep time: 15 to 25 minutes
- 🍳 Cook time: None
- 🍽️ Servings: 8
Ingredients
- 2 small red onions thinly sliced
- A handful or more of herbs chopped. I like dill, cilantro, parsley
- Dressing:
- 2 tablespoons whole grain mustard
- 1 tablespoon honey
- 1 clove garlic, I used a few garlic scapes.
- 1/2 cup olive oil
- 4 tablespoons rice vinegar or vinegar of choice
- Salt/pepper to taste
Directions
- In mixing bowl combine mustard, honey, garlic, salt/pepper, and vinegar. Slowly drizzle olive oil while whisking to emulsify dressing.
- Combine vegetables in large bowl. Pour dressing over vegetables and combine and mix till dressing has fully coated vegetables. Test for seasoning. Adjust if necessary.
-
 @ 6ad3e2a3:c90b7740
2024-06-22 17:54:17
@ 6ad3e2a3:c90b7740
2024-06-22 17:54:17
I’ve been obsessed with large numbers for a few years now, trying in vain to get others to care. But the “why” eluded me. I made one partially satisfying attempt to explain last year. Yes, he who has “the deepest paradigm can name the biggest number,” but to what end?
Now I think I’ve found the end, the reason I can’t quit this line of thinking, even if it’s driven me half mad: that the number TREE(3) is quite possibly a miracle. Despite arising from a simple game, TREE(3) can be hard to understand, so maybe it’s best to start with one of its “competitors”, Graham’s Number, to grasp what it is not.
Now Graham’s Number is only a competitor because the two are often compared, not because there is really any kind of competition. TREE(3) dwarfs Graham’s Number the way the breadth of the observable universe dwarfs the dimensions of an ant. (Actually, as you will see, that comparison vastly understates the disparity between the two numbers.)
But Graham’s Number, unfathomably vast in its own right, is both easier to understand and is generated via a different process. To get to Graham’s Number, we have to start with the most basic math that exists: counting.
I’ll excerpt from my post on growth that covers this:
First you have counting 1, 2, 3, 4…
If you want to speed up counting, you can add.
Instead of counting from three to six, you can just add 3 + 3. Addition therefore is _ just repeated (iterated) counting.
But instead of adding 3 + 3 + 3 + 3 + 3 + 3, you can just do 3 * 6 because multiplication is iterated addition.
But instead of multiplying 3 * 3 * 3 * 3, you can just do 3 ^ 4 because exponentiation is iterated multiplication.
That’s where most people leave off in their education, and they feel perfectly content to live their lives only because they don’t know what they’re missing. Beyond exponentiation lies tetration, or iterated exponentiation.
Instead of 3 ^ 3 ^ 3 ^ 3, you can just do 3 ↑↑ 4 (a power-tower of threes, four high.)
You would say it “three to the three to the three to the three” in exponentiation terms, or “three arrow arrow three” in tetration terms. The number before the arrows determines the base and the number after them how high the tower goes. Let’s calculate some easy ones.
2 ↑↑ 2 is a power tower of twos, two high. That is 2 ^ 2 = 4.
3 ↑↑ 2 is a power tower of threes two high. That is 3 ^ 3 = 27. Easy.
2 ↑↑ 3 is a power tower of twos three high. That is 2 ^ 2 ^ 2 which is 2 ^ 4 = 16.
_3 ↑↑ 3 is a power tower of threes three high. That is 3 ^ 3 ^ 3 which is 3 ^ 27 = 7,625,597,484,987.
_Wait, what happened? You just encountered a fast-growing function.
Ok, tetration is cute, but if you want to generate Graham’s number, you’ll need to add more up arrows. Iterated tetration, symbolized by three up-arrows, is called pentation and would look like this: 3 ↑↑↑ 3. If 3 ↑↑ 3 is 7.6 trillion, what would 3 ↑↑↑ 3 be?
Well, it’s just iterated tetration, which means it’s a series of double-arrow operations with a base of three, three long, i.e., 3 ↑↑ 3 ↑↑ 3.
And since we know the second half, (3 ↑↑ 3) = 7.6 trillion, we can simplify it to 3 ↑↑ 7.6 trillion. What does that mean? It means a power tower of threes, 7.6 trillion high.
Okay, that sounds big. How big?
Consider a power tower of threes five high, i.e., 3^3^3^3^3 or 3 ↑↑ 5, is bigger than a googolplex.
To get the scale of a googolplex (one with a googol zeroes), consider you could not fit the zeroes it would take to write it out in the universe, even if you put one trillion zeroes on every atom. Again, we are not talking about the number itself, merely the number of digits required to write it out.
Consider a number with 200 digits is so massive, it’s far more than the number of Planck volumes (smallest known unit of measure) in the universe, but it’s trivial to write out. But you do not have space to write out a googolplex even while using a trillion digits per atom, let alone what those digits, if you could even write them, represent.
Your odds of entering every lottery on earth for the rest of your life, from the local bake sale to the mega millions, and winning all of them are far, far, far greater than 1 in a googolplex.
Your odds of guessing all the private bitcoin keys on earth without making an error are greater than one in a googolplex. A googolplex is an unfathomably large number. And yet it is smaller than 3 ↑↑ 5, or 3^3^3^3^3.
But 3 ↑↑↑ 3 is a tower of threes not five high, but 7.6 trillion high! When you get even to 10 high, you’ve exceeded a googolplex to the googolplexth power. The human mind cannot fathom the number you arrive at even at 100 or 1000 high, but we have to get to 7.6 trillion.
Okay, now that we’ve multiplied out the entire power tower to 7.6 trillion, guess what, we have to add another arrow. Not 3 ↑↑↑ 3 but 3 ↑↑↑↑ 3.
That’s hexation which is iterated pentation, in this case with a base of three and three terms, i.e., 3 ↑↑↑ 3 ↑↑↑ 3. We already know the second half is, whatever the incomprehensible result of the multiplied-out 7.6 trillion-high power tower was, call it X. So it’s 3 ↑↑↑ X.
And that means iterated tetration with a base of three, X times, i.e., _3 ↑↑ 3 ↑↑3 ↑↑ 3… X times.
To solve this, we go term by term. The first one is 7.6 trillion, which feeds into the second, the multiplied-out power tower 7.6 trillion high, i.e. X, the third is a power tower of threes, X high, multiplied out, and so on, and there are X of these entire towers, each one unfathomably, astronomically taller than the last.
Once we get through all X (remember itself an unfathomably large number) of the terms we’re at 3↑↑↑↑3.
That number is G1.
To get to G2, we just take 3 ↑↑↑↑↑↑↑↑↑↑…G1 arrows… 3.
Wait, what?
Remember each individual move up the scale from counting to addition to multiplication to exponentiation turbo-charged the growth of the function, and now in this function, they’re telling us to add G1 (3↑↑↑↑3) moves up the scale all at once!
Put differently, from counting by ones to the insanity of hexation, there are only six steps. To get G2, there are 3↑↑↑↑3 steps!
To get G3, it’s 3 G2 arrows 3. To get to G4, it’s 3 G3 arrows 3.
And so on until we hit G64 which is Graham’s Number.
It’s an indescribably massive number, not relatable to anything in the universe, not even in terms of the possible ways the atoms could be arranged taken to the power of the number of ways history’s chess games could have been played.
There is no way to visualize or imagine it except by walking vaguely through the steps to get there and straining your brain to grasp the process.
But as I said, Graham’s Number is trivial, basically zero compared to TREE(3), and that is so much the case that if instead of going to G64 via the steps, you went to G(Googolplex), or even G(Graham’s Number), i.e., G(G64), you would still be at zero relative to TREE(3).
But here’s where it gets fascinating. While Graham’s Number is generated via ramping up increasingly powerful iterative operations (as we did in the beginning) TREE(3) comes from a simple game.
There is a good article in Popular Mechanics that lays it out, building off this excellent Numberphile video with Tony Padilla:
You can click on the article and video for the specific (and relatively basic rules), but essentially, the TREE function has to do with “seeds” (dots) and “trees” (combinations of dots and lines), such that you make the maximum amount of unique “trees” (dot-line combos) per the types of seeds available.
If you have only one kind of seed, say a green one, there is only one unique tree that can be made.
So:
TREE(1) = 1.
If you have two seeds, say a green and a red, there are three different kinds of unique trees you could make.
TREE(2) = 3.
If you have three seeds, say a green, a red and a black, there are TREE(3) different kinds of trees you could make. As it turns out, that number (which is not infinite) is so much bigger than Graham’s number the two are not even in the same universe:
Here’s Padilla comparing TREE(3) to Graham’s Number if you want to see the difference:
Okay, so what does all this mean? It means that Graham’s Number, which is generated by successively more powerful iterations of mathematical operations, cannot compete with TREE(3) which comes from a game with simple rules.
Graham’s Number is built the way a machine would do it, the way an AI would go about making a huge number — mechanically increasing the rate of construction.
Consider if you had a machine that made products one at a time, that’s like counting. And if you had a machine that made products three at a time, that’s like adding.
And a machine that made machines that made products three at a time, that’s like multiplication. And a machine that made those three at a time would be exponentiation, etc., etc.
Each successive machine-making machine would take you into a deeper paradigm of growth. But you can see this is a mechanical process, no matter how deep you go.
By contrast, the tree series is what happens when you design a game with simple rules and let it play out. The growth (once you realize it to the extent the human brain can even grasp it) is not just faster than the mechanistic model, it’s on another plane.
The takeaway then is bottom-up complex systems (games) with a few simple rules can spawn a paradigm so much bigger than top-down mechanistic growth models.
The human brain (neocortex in McKenna’s terms) is just such a system, and yet we train ourselves to be like machines! Practice, routine, iteration, follow-these-10-steps to happiness, learn these five keys to investing, etc. Yes, you can get somewhere with these recipes, but nowhere near the destination of which you are inherently capable.
The key is a few simple inputs — good nutrition, enough sleep, a decent environment — and to let the mind have its space to play out the sequence in full.
In modern society the conditions needed for greatness, since the basics are relatively easy to come by, are achieved more by getting rid of negatives. Don’t be a drug addict or alcoholic, ditch the porn, the video games, the excessive social media use, etc. Then let the game play out.
Of course, this is easier said than done, as we’ve been deeply conditioned by the mechanistic paradigm, and remember TREE(1) is only 1, while G(1) is 3↑↑↑↑3, i.e., the more powerful growth function doesn’t necessarily reveal itself at the outset. But that changes in short order, and once it does, the mechanistic growth is no match for the “most densely ramified complexified structure in the known universe.”
I’ll end on a speculative thought, one that occurred to me while recording a podcast on this topic: Might what we think of as good vs evil actually just be a battle between the mechanistic and the complex, the difference between top-down compulsion and bottom-up free choice?
BONUS VIDEOS For those who want to dive deeper into this, there are some good videos by Carbrickscity on You Tube here, here and here. And Tim Urban’s article on Graham’s Number is worthwhile too.
-
 @ 469fa704:2b6cb760
2024-09-04 15:22:28
@ 469fa704:2b6cb760
2024-09-04 15:22:28Money Printing in general
First of all, we need to make a distinction between money creation by central banks and fractional-reserve banking. Usually, the term money printing or “printer goes brrrrrr” refers to the creation of new central bank money, which is primarily created by central banks through:
- Open Market Operations: Buying government securities, which injects money into the banking system by increasing bank reserves. This is often done electronically, not by physically printing money.
- Quantitative Easing (QE): Purchasing assets to inject money directly into the economy, aiming to stimulate economic activity by increasing the money supply.
- Setting Reserve Requirements: Although less about creating money, lowering reserve requirements can indirectly influence money creation by allowing banks to lend more, but as of recent policy changes, this has been set to zero in some systems, shifting focus to interest rates.
- Interest on Reserves: By adjusting the interest rate paid on reserves, central banks influence how much banks are willing to lend, thereby indirectly affecting money creation.
This is the first step of money creation, although printing money is usually connected to one of the aforementioned processes, the second step creates much more money through the expansion of credit.
The Mechanics of Fractional-Reserve Banking
The Concept
In fractional-reserve banking, banks accept deposits from customers and only keep a small fraction of these deposits in reserve, lending out the rest. This practice essentially creates new money because:
- Deposits: When you deposit money, say $1,000, into a bank, that money doesn't just sit there.
- Reserves: If the reserve requirement is 10%, the bank keeps $100 as reserves.
- Loans: The remaining $900 can be loaned out. Here's where money creation begins.
Note: Current reserve requirements of the FED (Source) and the ECB (Source) are set at 0% respectively 1%.
Example Calculation of Money Creation
- Initial Deposit: You deposit $1,000 into Bank A.
- Bank A's Action:
- Keeps $10 (1%) as reserve.
-
Loans out $990 to another customer.
-
The $990 Loan: This $990, when spent, might end up in Bank B as someone's deposit.
- Bank B's Action:
- Keeps $9.9 (1% of $990) as reserve.
-
Can loan out $980.1
-
Continuation: This process repeats, with each cycle creating new deposits from loans.
The Deposit Multiplier (m) can be calculated as: * m = 1 divided by Reserve Ration = 1 / Reserve Ration
If the reserve ratio is 1%: * m = 1 / 1% = 1 / 0.01 = 100
This means, theoretically, an initial deposit of $1,000 could expand to:
- $1,000 times 100 = $100,000
- However, in practice, this is tempered by factors like cash holdings, loan demand, and banks holding excess reserves.
Historical and Economic Context
- Evolution from Goldsmiths: The system has its roots in the practices of goldsmiths who issued notes for gold deposits, which eventually circulated as money. This practice evolved into the modern banking system where notes (now digital entries) represent claims on money.
- Regulation and Central Banking: Over time, central banks like the Federal Reserve in the U.S. were established to regulate this process, provide stability, and act as lenders of last resort. The Fed's tools include setting reserve requirements, though this has become less relevant with the shift to a 0% reserve requirement.
Criticisms and Alternatives
- Risk of Bank Runs: Critics argue that fractional-reserve banking makes the system vulnerable to bank runs, where too many depositors demand their money back at once, which the bank cannot cover since most of the money is loaned out.
- Vollgeld Initiative and Full-Reserve Banking: Movements like Switzerland's Vollgeld Initiative have proposed shifting to full-reserve banking, where banks must hold 100% of deposits in reserve, preventing them from creating money through lending. However, this would significantly alter how banks operate and make profits. *** Modern Adjustments**: The move to a 0% reserve requirement in the U.S. reflects a shift towards using other monetary policy tools like interest rates on reserves to control money creation and economic stability.
Real-World Implications
- Money Supply Control: While banks create money through loans, central banks like the Federal Reserve influence this through monetary policy, adjusting how much money banks can create.
- Economic Stability: The zero reserve requirement might seem to allow infinite money creation, but in reality, banks are constrained by capital requirements, risk assessments, and economic conditions.
Conclusion
Fractional-reserve banking is a dynamic system that significantly influences economic growth by expanding the money supply through debt. While it allows for economic expansion, it also introduces risks of instability, which central banks attempt to mitigate through various policy tools. Understanding this system helps demystify how money flows and grows within an economy, showcasing both its capacity for economic stimulation and its inherent risks. As we move forward, debates continue on how best to balance these aspects to foster economic stability and growth. In 2009, a new system called Bitcoin emerged that could redefine the rules for money creation.
-
 @ 1a11c2a7:6f7556b0
2024-06-20 07:51:43
@ 1a11c2a7:6f7556b0
2024-06-20 07:51:43Chef's notes
Chef's Note: These No-Bake Oreo Cheesecake Bars are a delightful treat that combines the beloved flavors of Oreo cookies with a creamy cheesecake filling. The simplicity of this recipe makes it perfect for any occasion, from casual gatherings to special celebrations. Ensure the cheesecake bars are well-chilled before serving for the best texture and flavor. Feel free to customize with extra Oreo cookie crumbles or a drizzle of chocolate sauce for added indulgence. Enjoy the rich, creamy goodness straight from the fridge!
Details
- ⏲️ Prep time: 20 min
- 🍳 Cook time: Refrigerate for 4 hours
- 🍽️ Servings: 9-12
Ingredients
- Crust:** - 24 Oreo cookies - 1/4 cup (56g) unsalted butter, melted
- Cheesecake Filling:** - 8 oz (225g) cream cheese, softened - 1/3 cup (40g) powdered sugar - 1 teaspoon vanilla extract - 1 cup (240ml) heavy cream
- Optional Topping: - Additional Oreo cookies for decoration
Directions
-
- Prepare the Crust: - Crush Oreo cookies into fine crumbs. - Mix with melted butter and press firmly into an 8x8 inch baking dish lined with parchment paper. Chill in the refrigerator.
-
- Make the Cheesecake Filling: - Beat cream cheese until smooth. - Add powdered sugar and vanilla extract, mix until creamy.
-
- Whip the Cream: - In a separate bowl, whip heavy cream until stiff peaks form.
-
- Combine and Assemble: - Gently fold whipped cream into cream cheese mixture. - Spread evenly over chilled Oreo crust.
-
- Chill and Serve: - Refrigerate for at least 4 hours, or overnight, until set. - Cut into bars, top with crushed Oreo cookies if desired, and serve chilled.
-
 @ ba4a39ee:df9b4c6b
2024-09-04 14:23:26
@ ba4a39ee:df9b4c6b
2024-09-04 14:23:26 -
 @ 361d3e1e:50bc10a8
2024-09-04 13:54:12
@ 361d3e1e:50bc10a8
2024-09-04 13:54:12More European countries are choosing BRICS instead of the European Union
europe #turkey #serbia #brics #politics
-
 @ 5af07946:98fca8c4
2024-09-04 13:02:36
@ 5af07946:98fca8c4
2024-09-04 13:02:36 -
 @ 1a11c2a7:6f7556b0
2024-06-20 07:37:45
@ 1a11c2a7:6f7556b0
2024-06-20 07:37:45Chef's notes
Chef's Note:
Chef's Tip:
Achieve restaurant-quality Spicy Beef Stir-Fry at home with this simple yet delicious recipe. Marinating the beef in soy sauce and cornstarch ensures it's tender and packed with flavor. High heat and quick cooking are key to preserving the vegetables' crunch and the beef's juiciness. Adjust the heat level by varying the amount of chili garlic sauce to suit your palate. Serve hot over rice for a satisfying meal that's sure to impress!
Details
- ⏲️ Prep time: 30
- 🍳 Cook time: 10-15
- 🍽️ Servings: 3-4
Ingredients
- Beef Marinade:* - 1 lb (450g) beef sirloin or flank steak, thinly sliced - 2 tbsp soy sauce - 1 tbsp cornstarch - 1 tbsp vegetable oil
- Stir-Fry:** - 2 tbsp vegetable oil - 3 cloves garlic, minced - 1-inch piece ginger, minced - 1 red bell pepper, thinly sliced - 1 green bell pepper, thinly sliced - 1 small onion, thinly sliced - 2-3 green onions, cut into 2-inch pieces
- Sauce:* - 2 tbsp soy sauce - 1 tbsp oyster sauce - 1 tbsp hoisin sauce - 1 tbsp chili garlic sauce (adjust to taste) - 1 tbsp rice vinegar - 1 tsp sugar - 1 tsp sesame oil - 1-2 tbsp water or beef broth (if needed)
- To Serve:** - Cooked rice - Optional: sesame seeds and chopped cilantro for garnish
Directions
-
- sPrepare the beef marinade: - In a bowl, combine the thinly sliced beef with soy sauce, cornstarch, and vegetable oil. Mix well to coat the beef evenly. Let it marinate for at least 15 minutes.
-
- Make the sauce: - In a small bowl, whisk together soy sauce, oyster sauce, hoisin sauce, chili garlic sauce, rice vinegar, sugar, sesame oil, and water or beef broth. Set aside.
-
- Stir-fry the beef: - Heat 1 tablespoon of vegetable oil in a large skillet or wok over medium-high heat. Add the marinated beef in a single layer and stir-fry for 2-3 minutes until browned and cooked through. Remove the beef from the skillet and set aside.
-
- Cook the vegetables: - In the same skillet, add another tablespoon of vegetable oil if needed. Add minced garlic and ginger, stir-fry for about 30 seconds until fragrant. - Add sliced red and green bell peppers, and onion. Stir-fry for 2-3 minutes until vegetables are tender-crisp.
-
- Combine everything: - Return the cooked beef to the skillet. Pour in the prepared sauce and toss everything together to coat evenly. Cook for another 1-2 minutes until heated through and sauce thickens slightly.
-
- Serve: - Serve the spicy beef stir-fry hot over cooked rice. Garnish with sesame seeds and chopped cilantro if desired.
-
 @ 469fa704:2b6cb760
2024-09-04 12:07:53
@ 469fa704:2b6cb760
2024-09-04 12:07:53Unified Login Across Platforms
With Nostr, you use one login for all services, and your followers are seamlessly integrated. So you don't have start anew on every single platform. I think this is a real advantage of Nostr even for people not accustomed to Bitcoin or decentralization in general.
Value for Value (V4V) Model
Embrace the V4V principle where value is exchanged directly between users. Meaning if you find something useful or anohter nostr user was able to help you then you can simply zap him or her some Sats.
Blogging Platforms
- Habla or Yakihonne: Since joining Nostr 8 days ago, I've started blogging using Habla, which I found incredibly user-friendly. You can check out my articles directly on some clients like noStrudel, where they appear under my profile. Habla also serves as a great community explorer. Yakihonne, another comprehensive client with an integrated blog editor, caught my eye too, although it didn't sync all my Habla posts, possibly due to relay issues.
- Highlighter.com: Offers a sleek interface for reading articles. On noStrudel, articles are tucked away under the "More" menu.
Presentations
- Slidestr.net: This tool transforms your notes into a slideshow, making revisiting old notes quite entertaining.
Video Content
- Flare.pub: If you're looking for a YouTube-like experience, Flare.pub is the closest you'll get on Nostr. You can upload, watch videos, and curate playlists. Remember, since Nostr is fundamentally text-based, videos are hosted on traditional servers, but the interface remains decentralized. There's definitely room for more video content, so start creating!
Live Streaming
- Zapstream: Offers a smooth streaming experience with a fee of 10 Sats per minute to cover server costs. You can watch streams on clients like Amethyst or noStrudel.
Music and Podcasts
- Wavlake and Tunestr: Ideal for artists to share music or podcasts. Listeners can enjoy content freely or support creators via zaps, adhering to the V4V model.
Lists and Grouping
- Listr: A tool for organizing everything from regional user groups to thematic notes or hashtags. You can also follow lists created by others in the Nostr community.
Culinary Arts
- zap.cooking: A haven for aspiring or seasoned chefs, offering a plethora of recipes in a blog format. It's well-organized, allowing you to browse through different categories of recipes.
Marketplaces
- Plebian Market: Reminiscent of eBay's early days, this marketplace allows easy buying and selling among users.
Community Features
- Many clients like noStrudel, Habla, and Amethyst support community functionalities, enhancing user interaction within Nostr.
-
 @ 7f21affa:57e19174
2024-06-19 04:33:36
@ 7f21affa:57e19174
2024-06-19 04:33:36Chef's notes
Keep heat on the pot, from medium low to medium high.
Details
- ⏲️ Prep time: 15 minutes
- 🍳 Cook time: 45 mins
- 🍽️ Servings: 9
Ingredients
- 6 tbsp butter / cooking oil
- 1 medium / large yellow onion (chopped)
- 6 cloves garlic
- 3/4 cup all purpose flour
- 1.5 tsp salt
- 1.5 tsp black pepper
- 3 tsp paprika powder
- 3 tsp ground mustard powder
- 0.5 tsp cayenne powder
- 6 cups chicken / vegetable stock
- 4 broccoli heads (chopped into florets : discard stem)
- 6 carrots (shredded)
- 1 cup cornstarch mixed with 1 cup water
- 6 cups dairy milk (no plant-based)
- 9 cups cheddar cheese (shredded)
Directions
- Heat up pot on medium heat
- Add 6 tbsp butter / cooking oil
- Add a chopped yellow onion
- Sauté in pot until onion is soft and tender
- Add 6 cloves minced garlic
- (If pot looks dry, add splash of water too)
- Once pot has a nice garlic & onion aroma, add in 0.75 cup of all purpose flour , 1.5 tsp salt , 1.5 tsp black pepper , 3 tsp paprika powder , 3 tsp ground mustard powder , & 0.5 tsp cayenne powder .
- Mix in the dry ingredients with the vegetables .
- Add in the 6 cups of chicken / vegetable stock . (One cup at a time on medium high heat)
- Stir & wait until pot boils .
- Add chopped broccoli florets & shredded carrots
- If you want a thicker soup , then add in the 1 cup cornstarch mixed with 1 cup water .
- Let boil for 15 mins , then check if vegetables are at preferred softness.
- Add in 6 cups of dairy milk & 9 cups of cheddar cheese .
- Cook for about 1 - 2 minutes
- Enjoy & store in fridge with air tight containers !
-
 @ 5954198a:0c6fa207
2024-09-04 09:21:15
@ 5954198a:0c6fa207
2024-09-04 09:21:15If you are newbie in the business world, what you really wish for? The very first thought in your mind would be reaching out to your target audience. Here, we, one of the best SEO companies in Indore brings you a complete package of all seo services under a roof. Our SEO company in Indore has become truly efficient and time-reductant, letting you expect 2x customer faster. Our SEO services in Indore allow you to promote your business not only at a city level but also globally. Now no need to worry about your business, expand it free with one of the best SEO companies in Indore. Get a chance to upscale your small size business into a big one by amplifying your reach with our SEO services in Indore. Understanding what your customer base needs is very crucial and important for us as a business entity and our knowledge and proficiently in the concern field regarded us one of the reliable seo companies in Indore. Visit: https://digi-partners.com/seo-company-in-indore/
-
 @ 7f21affa:57e19174
2024-06-19 04:32:33
@ 7f21affa:57e19174
2024-06-19 04:32:33Chef's notes
Salt the water when boiling water for noodles.
Mix sauce separately, then add to the cold noodles.
Details
- ⏲️ Prep time: 30 mins
- 🍳 Cook time: 30 mins
- 🍽️ Servings: 8
Ingredients
- 16 oz bag of elbow noodles
- 1 tbsp of salt
- 16 cups of water in pot
- 2 cup mayo
- 2 tbsp mustard paste
- 4 tbsp white vinegar
- 4 tbsp pickle juice
- 1 tsp black pepper
- 4 tsp white sugar
- 2 tsp salt
- 1 tsp garlic powder
- 1 tsp onion powder
- 1 medium / large red onion (diced)
- 2 red / green bell peppers (diced)
- 2 pickles (diced)
- 4 celery sticks (diced)
Directions
- Boil 16 cups of water in a pot with 1 tbsp salt & 16 oz elbow noodles
- Let pot boil for 15 mins ; Start on making the sauce
- In a medium bowl , add 2 cup mayo , 2 tbsp mustard paste , 4 tbsp white vinegar , 4 tbsp pickle juice , 1 tsp black pepper , 4 tsp white sugar , 2 tsp salt , 1 tsp garlic powder , & 1 tsp onion powder .
- Mix sauce & set aside .
- Next , Cut & dice up 1 medium / large red onion , 2 red / green bell peppers , 2 pickles , & 4 celery sticks .
- Mix half of the sauce in with the diced vegetables .
- By this time , noodles should be ready to rinse and drain with cold water .
- ( Noodles should be cold and water drained )
- In a large bowl , add the cold noodles , vegetables , & the remaining sauce
- Mix ingredients well & refrigerate for 2 hours +
- Enjoy & store in fridge with air tight containers .
-
 @ e21df944:1d414c31
2024-06-16 05:39:19
@ e21df944:1d414c31
2024-06-16 05:39:19Chef's notes
Never guess your cooking times again – make your air frying experience simple and stress-free!
Tips:
• Shake the Basket: Halfway through cooking for even results. • Check for Doneness: Use a meat thermometer or cut open to ensure proper cooking. • Preheat: Preheat the air fryer for best results.General Recommendations:
• Always preheat your air fryer for 3-5 minutes before cooking. • Flip or shake foods halfway through the cooking time to ensure even cooking. • Adjust times and temperatures based on your specific air fryer model and the thickness of the food.Details
- 🍳 Cook time: 5-35
Ingredients
- Vegetables, Frozen Foods, Chicken, Beef
Directions
- General Recommendations: • Always preheat your air fryer for 3-5 minutes before cooking. • Flip or shake foods halfway through the cooking time to ensure even cooking. • Adjust times and temperatures based on your specific air fryer model and the thickness of the food.
-
 @ 06a260a2:d7a7791c
2024-09-04 08:13:22
@ 06a260a2:d7a7791c
2024-09-04 08:13:22Co je plnohodnotný bitcoinový uzel (bitcoin full node)? Je to základní prvek bitcoinové sítě. Server, na kterém běží bitcoinový klient, komunikuje s dalšími uzly v síti, udržuje kopii bitcoinového blockchainu (databáze všech potvrzených transakcí v bitcoinové síti), ověřuje nově příchozí transakce, validuje nově vytěžené bloky a zprostředkovává interakci uživatelů bitcoinu s bitcoinovou sítí. Pro těžaře zároveň připravuje šablonu nového bloku z transakcí čekajících na potvrzení. Je toho celkem dost, ne?
Satoshi Nakamoto už ve svém whitepaperu předpokládal, že každý uživatel bitcoinové sítě bude provozovat vlastní plnohodnotný uzel. Proč by to měli uživatelé bitcoinu chtít?
Proč provozovat vlastní bitcoinový uzel?
Používání vlastního plnohodnotného uzlu přináší celou řadu benefitů jak svému uživateli, tak bitcoinové siti a celému ekosystému. Pojďme se na ně podívat.
Podpora decentralizace bitcoinové sítě
BItcoinová síť je navržena jako decentralizovaná a má to své důvody. Decentralizace snižuje pravděpodobnost fatálního selhání sítě tím, že zvyšuje redundanci jejich kritických míst, kterými jsou právě uzly. Decentralizace v podobě zvýšené množstevní i geografické redundance pak chrání síť proti důsledkům přírodních katastrof, cíleným útokům hackerů nebo vládních organizací, ale i nečestnému jednání jednotlivých uživatelů sítě v podobě manipulace s bitcoinovým softwarem. Decentralizace se navíc nevztahuje pouze na fyzické uzly, ale i na celou governance - způsob řízení a rozhodování v síti. Neexistuje tak žádná centrální autorita, která by mohla svým jednáním a rozhodnutím, ať už svévolně nebo pod externím tlakem ovlivnit chování sítě.
Pokud se tedy rozhodnete provozovat vlastní uzel, zvýšíte tím antifragilitu bitcoinové sítě a stanete se jejím pravým uživatelem tak, jak to Satoshi zamýšlel.
Ověřování transakcí a validace nových bloků
Důležitým aspektem decentralizace je schopnost samostatně ověřit příchozí transakce a nově vytěžené bloky vůči platným pravidlům bitcoinové sítě bez nutnosti důvěřovat kterékoliv třetí straně. Vyjádřením tohoto principu je okřídlené "Don't trust, verify!". Každý full node obsahuje kompletní kopii bitcoinového blockchainu, databáze všech potvrzených transakcí za celou dobu jeho existence. A nejen to. Při prvním spuštění uzlu a kopírování této databáze od jiných uzlů v síti znovu ověřuje každý jednotlivý blok a transakce v něm podle existujících pravidel sítě, aby měl jistotu, že této databázi může nadále věřit. Tomuto procesu se říká synchronizace. Po jejím dokončení uzel kontroluje nově příchozí transakce i obsah a strukturu nově vytěžených bloků. Pokud zjistí porušení pravidel, odmítne je a do vlastní kopie blockchainu je nezařadí.
Jaká jsou ta pravidla? Je jich celá řada, ale mezi ta nejdůležitější patří:
- kontrola struktury transakce
- kontrola pravosti podpisů náležejícím adresám vstupů transakcí
- kontrola splnění podmínek definovaných v transakčním skriptu
- kontrola vícenásobného utracení UTXO
- kontrola struktury a velikosti nového bloku
- kontrola dodržování monetární politiky bitcoinu (velikost odměny těžaři musí odpovídat aktuální epoše)
Tato vlastnost je důležitá nejen pro vás, provozovatele vašeho uzlu, ale i pro stabilitu celé sítě. Vám umožňuje kontrolovat vaše transakce a zůstatky bez nutnosti důvěřovat jakékoliv třetí straně pouze oproti vaší vlastní kopii blockchainu. Celou síť pak chrání proti nečestnému uživateli, který by se pokusil šířit sítí neplatnou transakci (třeba podruhé utratit už jednou utracené mince) nebo se snažil připojit do blockchainu nový blok větší než povolené velikosti nebo přiznávající mu vyšší než aktuálně platnou odměnu. Takové chování uzel odmítne a není nikdo, kdo by mu v tom dokázal zabránit (je však třeba odpovědně přistupovat k výběru bitcoinového softwarového klienta - o tom více dále v textu).
Ochrana vlastního soukromí a bezpečnosti
Bitcoin není anonymní, ale pseudonymní. Všechny transakce lze v blockchainu dohledat a každý jeden satoshi lze v rámci UTXO dosledovat až k jeho coinbase transakci (okamžiku vzniku jako odměny za vytěžený blok). Transakce sice neidentifikují vlastníky jednotlivých adres, některé z nich o nich ale určité informace poskytují. Například konsolidační transakce může dle struktury podpisů prozradit, že vlastníkem vstupů je pouze jeden člověk. Nebo pokud platíte za nějakou službu na známou adresu a neutratíte kompletní UTXO, je velmi pravděpodobné, že jste vlastníkem i adresy, na kterou se posílá zbytek a to i přesto, že použijete adresu novou. Existují i další analytické postupy, které pomáhají určit vztahy mezi jednotlivými adresami a jejich vlastníky. Takže nakonec stačí prozradit vlastnictví jediné adresy a celou řadu jiných již k ní doplní odpovídající analýza nebo heuristika.
Pokud je pro vás soukromí důležité a vlastnictví bitcoinu považujete za soukromou informaci, je dobré vyvarovat se aktivitám, které by mohly prozradit váš vztah ke konkrétním bitcoinovým adresám. Mezi ně patří i přístup k blockchainu při zadávání nových transakcí, kontrole jejich stavu nebo kontrole zůstatků přes vaši peněženku nebo blockchain explorer. Použijete-li uzel třetí strany, dáváte jí možnost párovat uskutečněné transakce nebo dotazované adresy s vaší IP adresou, která o vás už lecos prozrazuje. I v případě použití Toru nebo VPN nemáte vyhráno. Pokud používáte více různých peněženek třeba pro oddělení KYC a non-KYC mincí, přístupem z jednoho místa je rovněž dáváte do vzájemné souvislosti.
Samostatným problémem je důvěra v informace, které vám uzel třetí strany poskytuje. Jsou skutečně pravdivé, transakce validní a zůstatky odpovídají realitě? Uzel třetí strany za vás sice nepodepíše transakci s vašimi prostředky, ale může vám třeba falešně tvrdit, že transakce, která na vaši adresu převádí dohodnutou platbu, je již potvrzena.
Provoz vlastního plnohodnotného uzlu pro vás tyto problémy řeší. Dotazy na zůstatky a nové transakce zadáváte přímo do vlastního bitcoinového uzlu, který je ověřuje přímo s vaší vlastní kopií blockchainu. Bez cizích očí a rizika manipulace.
Ochrana před cenzurou transakcí
Speciálním případem manipulace třetí strany s informacemi, které vám poskytuje, je cenzura transakcí a adres. Bitcoinový blockchain je transparentní, proto v něm není problém sledovat pohyb libovolných bitcoinů z jakéhokoliv důvodu. Platí to i pro bitcoiny pocházející z nějaké loupeže, podvodu či hacku. Bývají označeny jako špinavé a různé subjekty se brání manipulaci s nimi prostřednictvím blacklistů adres, přes které prošly. A pokud se dostaly do nějaké coinjoin transakce mixovací služby, mohou se na blacklist dostat i všechny adresy v transakci zúčastněné, ačkoliv neměly s původně "špinavými" bitcoiny nic společného.
Mohl bych takto pokračovat a uvádět další, ještě absurdnější, nespravedlivé příklady cenzury, vyplývající ze zlovůle mocných státních aparátů. Ale vezmu to z druhé strany. Pokud jste sběrateli Bitcoin Punků nebo obchodujete s Runama a chtěli by jste zadat svou transakci prostřednictvím mého uzlu, neuspějete také. Chráním bitcoinovou síť před spamem pomocí klienta Bitcoin Knots, který mi umožňuje takové transakce cenzurovat.
Ať tak či onak, používání vlastního plnohodnotného uzlu vás části problémů s cenzurou opět zbaví. Nikoho se nemusíte ptát, jakou transakci, pokud splňuje pravidla konsensu bitcoinové sítě, můžete zadat ke zpracování. Bohužel, je to jenom první část problému. Tou druhou částí je možná cenzura transakcí při jejich zařazování do bloků těžaři. O té se můžete více dozvědět v článku Domácí těžba bitcoinu.
Podpora bitcoinové sítě
Váš plnohodnotný bitcoinový uzel může poskytovat ostatním uzlům další užitečné služby, které posilují odolnost a decentralizaci sítě. Jsou to hlavně:
- Filtrování transakcí a bloků pro neplnohodnotné uzly a peněženky
- Poskytnutí historických bloků uzlům, které byly nějakou dobu offline nebo provádějí prvotní synchronizaci blockchainu
- Propagaci nových transakcí sítí směrem k těžařům
- Propagaci nově vytěžených bloků od těžařů k ostatním uzlům v síti
- Přenos dat mezi Clearnetem a Torem pro uzly, které jsou připojeny pouze k jedné ze sítí
Na tomto místě je ale dobré říci, že do role tranzitních uzlů (těch, které přijímají externí požadavky na spojení - mají povolen parametr
listen=1alistenonion=1) by měly být použity servery s odpovídajícím výkonem a vhodném bezpečnostním nastavení. Malý privátní full node na bázi RaspberryPi a UmbrelOS jím není.Provoz vlastního uzlu pro Lightning Network
Ligtning Network - druhá vrstva bitcoinu - přináší nezbytné škálování počtu zpracovaných transakcí a snižuje transakční poplatky. Obojí je nezbytné pro další růst adopce bitcoinu. Lightning Network (LN) tvoří síť LN uzlů, které si mezi sebou otvírají tzv. LN platební kanály, jejichž prostřednictvím směrují LN platby.
Ačkoliv jednotlivé LN platby mezi LN platebním kanály probíhají nezávisle na bitcoinovém blockchainu, otevření a zavření LN platebního kanálu je reprezentováno bitcoinovou transakcí. Z tohoto důvodu potřebují LN uzly přístup k bitcoinové síti a využívají k tomu právě bitcoinové uzly.
Pro pochopení Lightning Network doporučuji skvělou knihu Michala Nováka Lightning Network: Platby budoucnosti.
Výhody a důvody provozování vlastního LN uzlu je téma na samostatný článek, který jsem ještě nenapsal. Možná vás ale přesvědčil Michal Novák a nebo jste k rozhodnutí mít vlastní LN uzel došli jinou cestou. V takovém případě potřebujete i vlastní bitcoinový uzel.
Rozšíření znalostí a zkušeností s používáním bitcoinu
Okřídlená pravda říká, že pokud neověřujete transakce a své zůstatky na svém uzlu, nepoužíváte bitcoin, ale jste klientem někoho jiného se všemi důsledky, které to může mít. Pravdou také je, že úsilí spustit bitcoinový uzel vlastními silami vás zcela jistě mnoho nového naučí a poskytne vám na bitcoin úplně nový pohled. Skin in the game. O biozemědělství se také nejvíce dozvíte, až když zaboříte ruce do hlíny a slimáci vám sežerou úrodu. Váš pohled na svěže vypadající bio-mrkev v Lidlu již nikdy nebude stejný jako dříve.
Stavba vlastního uzlu: ano nebo ne?
Pokud vás předchozí odstavce přesvědčily, že dává smysl mít vlastní bitcoinový uzel, zbývá ještě rozhodnutí, jak jej realizovat.
Uzel by měl být v nepřetržitém provozu 24 hodin denně, 7 dní v týdnu. Jen tak může plnit svou funkci, průběžně ověřovat příchozí transakce a validovat nové bloky. Zastavení uzlu kvůli udržbě nebo z jiného důvodu je samozřejmě možné, po odstávce však uzel začne vždy synchronizovat chybějící bloky v jeho kopii blochchainu. Pokud jej tedy zastavíte na delší čas, může i následná dosynchronizace nějakou dobu trvat.
Dalším důležitým pravidlem je provozovat uzel na dedikovaném hardwaru, na kterém neběží žádný jiný, nesouvisející software. Vlastní uzel budete provozovat i kvůli ochraně vlastního soukromí a bezpečnosti a nechcete tedy zvyšovat riziko jejich ohrožení zavlečením nějaké softwarové infekce. Zároveň tak nebude bitcoinový uzel soupeřit s jinými aplikacemi o výpočetní zdroje. Protože sám není nijak zvlášť náročný, nebude tak ani zvyšovat náklady na svůj provoz.
Pro svůj provoz bitcoinový uzel potřebuje běžné CPU, na jehož výkon nejsou dnes žádné specifické požadavky. Dále přibližně 4GB paměti RAM nebo více. Potřebnou pamět nejvíce ovlivní použitý operační systém. Důležité je zabránit swapování paměti na pevný disk. A do třetice přibližně 1TB diskového prostoru. Aktuální velikost bitcoinového blockchainu (léto 2024) je necelých 700GB a roste rychlostí přibližně 230MB za den. Při zachování tohoto trendu by vám měl 1TB disk ještě pár let vydržet. Velmi často se pro uložení blockchainu doporučuje SSD disk. Já s tímto doporučením souhlasím, jeho výkon vám oproti standartním točivým diskům pomůže výrazně zkrátit potřebný čas na počáteční synchronizaci blockchainu. V běžném provozu uzlu se jeho výhody už tolik neprojeví.
Posledním předpokladem je síťové rozhraní pro přístup k internetu.
Jaké máme možnosti?
K provozu vlastního uzlu můžete použít jakýkoliv běžný a dostupný počítač, který již máte doma k dispozici, třeba i starší, protože požadavky na jeho výkon jsou skutečně minimální. Nepoužívaný notebook nebo stolní počítač mohou takto ještě dobře posloužit. Je dobré ale zamyslet se i nad ekonomikou provozu. Starší už nepoužívané herní PC se 150W zdrojem, pokud jej máte odložené někde ve sklepě, je sice zadarmo, jeho nepřetržitý provoz však již nějaké nezanedbatelné množství energie spálí.
Další možností je koupě nového levného počítače uvedených parametrů. Velmi oblíbené jsou minipočítače Intel NUC (dnes již převzal jejich výrobu ASUS). Koupit si můžete i minipočítač speciálně připravený pro provoz bitcoinového uzlu. Bude mít již nainstalovaný operační systém na linuxové bázi a většinou i některé ze základních potřebných aplikací. Takové uzly nabízí například Start9, Umbrel nebo MyNode.
Poslední možností je postavit si vhodný počítač pro provoz bitcoinového uzlu svépomocí z dostupných komponent. Výhodou takového postupu je vyšší kontrola nad jeho HW bezpečností (použité komponenty si můžete sami zvolit) a také volba jeho parametrů přesně dle vašich záměrů a potřeb. Jakou HW platformu pro jeho stavbu zvolíte je čistě na vás. Mezi nejoblíbenější však v současné době patří Raspberry Pi.
Kromě vhodného hardware budete také potřebovat vhodný operační systém. Důležitou vlastností takového operační systému je dostupnost jeho zdrojového kódu (v rámci FOSS), kvůli nezávislé kontrole jeho bezpečnosti. I v této oblasti je nabídka poměrně široká. Vybírat můžete kromě obecného linuxu a jeho známých distribucí i mezi specializovanými distribucemi pro bitcoinové uzly:
Umbrel na Raspberry Pi
Nemám k dispozici starý, nepoužívaný počítač, ani se mi nechtělo investovat do předpřipraveného řešení, a proto jsem si vybral stavbu vlastního uzlu na platformě Raspberry Pi. Jako operační systém jsem zvolil UmbrelOS. Je aktivně vyvíjen a v nedávné době prošel zásadním redesignem. Za jeho aktuální oblibou a velkým rozšířením stojí příjemné a jednoduché uživatelské rozhraní a vlastní App Store s velkým množstvím dostupných aplikací.
Návodů, jak sestavit uzel na Raspberry Pi je plný internet. Inspirovat se můžete jak u Kicoma v jeho serii videí Úvod do bitcoinu, nebo přímo na stránkách Umbrelu.
Já zvolil tyto komponenty:
- Raspberry Pi 5 8GB - 2.179,- Kč
- Raspberry Pi 27W USB-C napájecí zdroj - 349,- Kč
- Krabička pro Raspberry Pi 5 Cooling case - 299,- Kč
- 1TB Lexar NM620 - 1.497,- Kč
- Geekworm X1002 M.2 NVMe SSD HAT pro RPi 5 - 420,- Kč
- SanDisk MicroSDHC 32GB Ultra - 229,- Kč
Raspberry Pi 5 je dnes již přirozenou volbou. Oproti svému předchůdci RPi 4 je jen o 100 korun dražší, nové PCI Express 2.0 rozhraní výrazně zrychluje komunikaci s diskem, což pocítíte při iniciální synchronizaci bitcoinového blockchainu.
Geekworm X1002 je jedna z možných NVMe SSD rozšiřujících karet (HAT). Zvolil jsem ji, protože se nepřipojuje k RPi shora, ale zdola a nebrání tak připojení jiné rozšiřující karty přes standardní GPIO konektor (třeba této). Navíc je na ni NVMe disk orientován směrem dolů, takže jej lze chladit spodním dílem zvolené hliníkové krabičky (pro úplnost ale dodávám, že chladit SSD disk na tomto bitcoinovém uzlu není nutné).

Sestavení celého uzlu vám nezabere více než 15 minut. Podle návodu na stránkách Umbrelu nainstalujte i verzi UmbrelOS pro vaše Raspberry Pi. Po spuštění uzlu si v nastavení nezapomeňte povolit TOR pro vzdálený přístup mimo vaši lokální siť a zkontrolovat dostupnost případných aktualizací.
A můžeme se pustit do výběru a instalace aplikací, které z vašeho uzlu udělají uzel bitcoinový.
Základní aplikace
Tou hlavní aplikací plnohodnotného bitcoinového uzlu je bitcoinový klient. V současné době existuje několik implementací bitcoinového klienta.
Pro UmbrelOS jsou však portovány pouze první dva: Bitcoin Core a Bitcoin Knots. Já si vybral ten druhý, viz. dále. Vy si však vyberte sami podle svých preferencí.
Na tomto místě musím zdůraznit, jak je dobré sledovat vývoj jednotlivých klientů a hlavně vlastností, které implementují. Pomocí bitcoinových klientů dochází v bitcoinové síti k prosazování změn. Pokud tyto změny nejsou kontroverzní a existuje na nich konsenzus, postupně je implementují všichni klienti. Pokud však kontroverzi vyvolávají nebo dokonce přinášejí změny, které pro síť představuji softfork (změnu zpětně kompatibilní) nebo hardfork (zpětně nekompatibilní změnu), můžete vybráním správného klienta nebo jeho verze o takové změně hlasovat a přijmout ji nebo odmítnout.
Výběr bitcoinového klienta a jeho vlastností je tou nejsilnější mocí, kterou jako uživatelé bitcoinové sítě máte a ultimátním důvodem pro provozování vlastního uzlu.
Bitcoin Knots
Bitcoin Knots jsou alternativní implementací bitcoinového uzlu. Vychází z Bitcoin Core a nabízí tak stejnou úroveň zabezpečení, soukromí a stability. Kromě toho však svým uživatelům rozšiřují možnosti filtrování spamu pomocí rozšířené sady parametrů a pravidel k jeho potlačení. (Více o spamu v bitcoinovém blockchainu naleznete zde.)
Ačkoliv jsou Bitcoin Knots pro instalaci k dispozici přímo v Umbrel App Store, nedoporučuji je nyní instalovat z tohoto místa. Připravený balíček obsahuje chybu, která znemožňuje následnou instalaci aplikací, které jsou na bitcoinovém uzlu závislé, jako třeba Electrum server, lightningový uzel nebo nějaký blockchain explorer. Použijte raději připravenou instalaci v alternativním komunitním app store Bitcoin Knots Community App Store.
Umbrel umožňuje svým uživatelům používat alternativní app store. Přidáte jej v nastavení Umbrel App Store (tři tečky v pravém horním rohu, volba Community App Stores). Do pole pro URL vložte link na github repositář app store, v tomto případě:
https://github.com/Retropex/Bitcoin-storea stiskněte Add. Přidaný komunitní app store otevřete tlačítkem Open. Pro RaspberryPi je určena verze Bitcoin Knots arm64.
Samotná instalace zabere několik desítek vteřin. Ihned po instalaci však začnou Bitcoin Knots stahovat a ověřovat bitcoinový blockchain, který má nyní (v červenci roku 2024) 664GB. Synchronizace blockchainu trvá podstatně déle. Její postup můžete v aplikaci sledovat. Mému RPi5 s SSD diskem připojeným přes PCI Express interface to trvalo necelých 30 hodin. O generaci starší RPi4 s SSD diskem přes USB 3.0 potřeboval přibližně 76 hodin.
Nezapomeňte si po instalaci zkontrolovat a případně nastavit preferovaná pravidla filtrování bitcoinového SPAMu (ostatně proto si instalujete Bitcoin Knots). Najdete je v nastavení (Advanced Settings) v sekci Optimization.
V základu je již nastaveno (verze 27.1.020240801):
datacarrier=1(Relay transaction with embedded data)datacarriersize=42(Maximum size of relayed transactions with embedded data)rejectparasites=1(Reject parasitic transactions)permitbaremultisig=0(Relay old type of multisig transaction)Pokud chcete filtrovat i Runes, nezapomeňte povolit:
rejecttokens=1(Reject tokens transactions)Electrum server
Použití Bitcoin Knots v současné verzi UmbrelOS 1.2.2 přináší bohužel ještě jeden problém. UmbrelOS registruje a dodržuje vzájemné deklarované závislosti aplikací. Aby vám povolil instalovat třeba blockchainový explorer Mempool, musíte mít nejprve nainstalován bitcoinový uzel, protože bez něj se Mempool nedostane k blockchainu. Bohužel v této verzi UmbrelOS trvá na konkrétní instalaci aplikace Bitcoin Node (původní Bitcoin Core). Na existenci bitcoinového uzlu je závislá i aplikace Electrs, implementace Electrum Serveru. Naštěstí lze tuto závislost jednoduše obejít.
Aplikace Electrs - Electrum Server in Rust - je reimplementací původního Electrum serveru s cílem umožnit provozovat jej s minimálními hardwarovými nároky. Server neuchovává celý blockchain (je závislý na lokální instalaci bitcoinového uzlu), ale vytváří a udržuje index všech vstupů a výstupů bitcoinových transakcí. Ten zpřístupňuje přes Electrum protokol on-chain bitcoinovým peněženkám pro dotazování na zůstatky a historii transakcí. Připojení přes Electrum server využívají hardwarové (Trezor, Ledger, ColdCard...) i mnohé softwarové peněženky (desktop i mobile).
Aplikaci Electrs nelze instalovat přímo z Umbrel App Store (viz. výše), instalaci musíme spustit ručně přes SSH terminál. Příkazový řádek v UmbrelOS spustíte přes ikonku Settings v doku úvodní obrazovky a položky menu Advanced Settings a Open Terminal. Do terminálu zadejte následující příkaz:
umbreld client apps.install.mutate --appId electrsPo několika vteřinách potvrdí úspěšnou instalaci návratová hodnota true. I Electrum Server provádí po prvním spuštění časově náročnou synchronizaci s blockchainem, při které vytváří transakční index. Instalaci aplikace spusťte až po dokončení synchronizace Bitcoin Knots.
Electrum server nabízí dva způsoby připojení bitcoinových on-chain peněženek. Buď přes lokální siť pro peněženky instalované na samotném uzlu nebo na desktopu ve stejné lokální síti. Nebo přes Tor protokol. Kromě zmíněných hardwarových peněženek může připojit peněženky Green, BlueWallet, Sparrow wallet, Specter, Nunchuk.
Mempool
Mempool je blockchainový explorer, klon pro RaspberryPi veřejně známého exploreru Mempool.space. Proč používat svůj vlastní a nikoliv ten veřejný? Protože nechcete, aby kdokoliv věděl, že jste si dohledával stav určité transakce jen několik vteřin poté, co se objevila v mempoolu a pak ještě několikrát až do okamžiku, kdy byla potvrzena v novém bloku.
Aplikace Mempool je také závislá na přítomnosti bitcoinového klienta, proto je nutné při použití Bitcoin Knots instalovat ji ručně přes SSH terminál. Potřebný příkaz vypadá takto:
umbreld client apps.install.mutate --appId mempoolProtože je Mempool závislý i na dostupnosti indexu Electrum serveru, používejte jej až poté, co aplikace Electrs tento index dokončí.
Core Lightning
Core Lightning (CLN) je jedna ze čtyř nejpopulárnějších implementací Lightning Network uzlu od společnosti Blockstream. Jedná se samozřejmě o open source a má výborně zpracovanou dokumentaci včetně celé řady návodů k použití.
Proč si vybrat Core Lightning implementaci a ne hojně rozšířenou LND? CLN má oproti LND lépe navrženou modulární architekturu a systém pluginů, které elegantně rozšiřují nebo upravují jeho funkcionalitu. Je napsán v jazyce C (LND převážně v jazyce GO), který v kompilovaném stavu nabízí efektivnější kód, uzpůsobený konkrétní HW platformě a tedy potřebuje menší dostupný výkon v porovnání s LND. Není to zásadní výhoda pro provoz privátního LN uzlu, ale na RaspberryPi přeci jen přijde vhod.
CLN implementace je také často chválena za lepší přístup k ochraně soukromí jednotlivých plateb. Používá k tomu několik technik, které výrazně komplikují ostatním uzlům na cestě sledovat informace o vašich platbách. Shadow route přidává do platební cesty zpoždění a poplatky, čímž ji virtuálně prodlouží a brání tak špiclujícím uzlům odhadovat reálnou vzdálenost k příjemci platby. Route randomization zase zajistí určitou míru náhodnosti při výběru finální platební cesty. Nemusí tak být vybrána vždy ta nejkratší respektive nejlevnější cesta, což zabrání routování všech vašich plateb přes uzel, který má uměle (záměrně) snížené poplatky pod síťový průměr. MPP - (Multi-Part-Payments) pak rozdělí vaši platbu na menší, nestejně velké části, které směruje samostatně. Zajistí tím průchodnost i větších plateb sítí a zároveň znemožňuje uzlům na cestě zjistit celkovou velikost platby.
Tím nejzásadnějším důvodem je pro mne však podpora BOLT 12 specifikace. BOLT 12 přináší takzvané offers, statické, opakovaně použitelné faktury. Ty se hodí všude tam, kde potřebujete trvale přijímat částky předem neznámé hodnoty a nechcete pro každou z nich aktivně vystavovat fakturu. Příklad? Zapy na Nostru nebo třeba anonymní výplaty z Ocean.xyz těžebního poolu. Nebo třeba příjem příspěvků v bitcoinu na váš YouTube stream. LND řeší tuto potřebu přes další nadstavbové aplikace (LNBits, LNDK) a třeba LNURL. CLN nabízí elegantní řešení přímo ve svém základu.
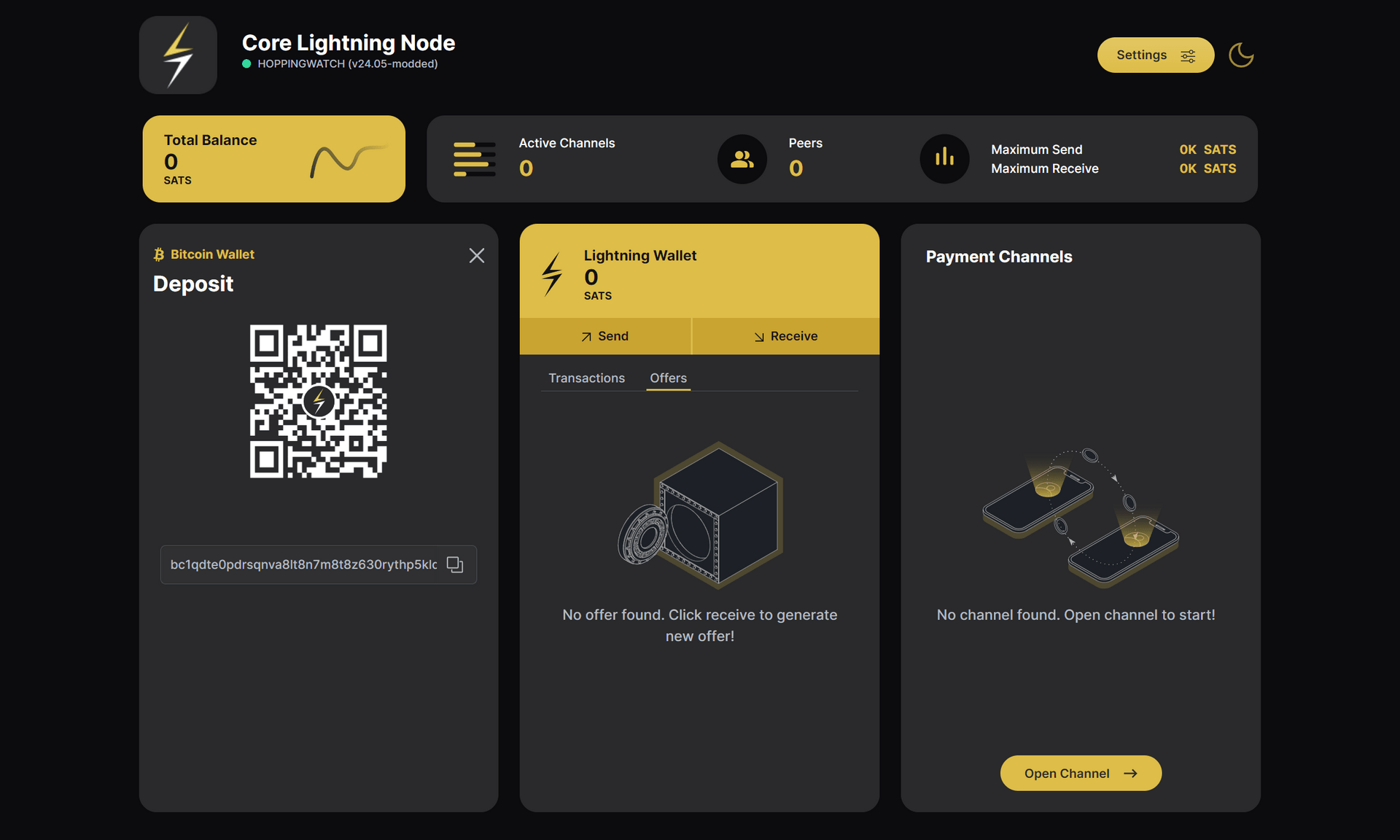
Stejně jako předchozí aplikace je i Core Lightning závislá na přítomnosti bitcoinového klienta. S Bitcoin Knots je třeba ji tedy instalovat ručně přes SSH terminál. Potřebný příkaz vypadá takto:
umbreld client apps.install.mutate --appId core-lightningZáloha a obnova ze zálohy
Core Lightning uzel obsahuje bitcoinovou on-chain peněženku, ze které čerpá bitcoiny pro otvírání kanálů. Po (re)instalaci aplikace vždy vygeneruje novou, proto je dobré mít zálohu, ke které se můžete vrátit v případě, že jste o tu původní přišli v důsledku havárie uzlu nebo provádíte instalaci na nový hardware a chcete obnovit již exitující uzel.
Klíče on-chain peněženky jsou uloženy v souboru
hsm_secret, který se nachází v adresářiroot/.lightning/bitcoin. Jedná se o binární, 32 byte veliký soubor. Zálohovat jej můžete buď na nějaký připojený externí disk (USB klíčenku), nebo si jeho obsah zobrazíte v hexadecimálním formátu (linuxový příkaz:xxd hsm_secret) a někam si jej bezpečně poznamenáte.Při obnově nebo po reinstalaci uzlu nahraďte nově vygenerovaný soubor
hsm_secrettím ze zálohy a restartujte aplikaci Core Lightning.Pro zacházení se souborem
hsm_secreta jeho obsahem platí stejná pravidla, jako pro zacházení s bitcoinovými privátními klíči nebo seed frází. Mají stejný význam a jejich znalost umožňuje manipulovat s prostředky na peněžence uloženými. Proto buďte opatrní.Zajímavou alternativou je možnost vygenerovat soubor
hsm_secretz existujícího BIP-39 seedu, včetně použití volitelné přístupové fráze (passphrase). To vám umožní uchovat recovery seed standartními způsoby, které používáte u své hardwarové peněženky (SeedOr Safe, Trezor Keep Metal, CryptoTag...) a v případě potřeby obnovit peněženku nebo přistupovat k bitcoinům na jejich adresách i z jiného zařízení, než je Core Lightning aplikace. Jak na to?Po instalaci Core Lightning aplikace ji zastavte (příkaz Stop v kontextovém menu nad ikonou aplikace) a spusťte si terminál v jejím kontextu (Settings > Advanced settings > Terminal > App > Core Lightning). V terminálovém okně spusťte nástroj
hsmtools parametremgeneratehsma cestou khsm_secretsouboru. V následujícím dialogu pak vyberte BIP-39 slovník a zadejte jednotlivá slova svého seedu. Nakonec můžete vložit svou volitelnou přístupovou frázi. Utilitka vygeneruje nový souborhsm_secreta uloží jej.``` root@aabbccdd0102:/# lightning-hsmtool generatehsm root/.lightning/bitcoin/hsm_secret Select your language: 0) English (en) 1) Spanish (es) 2) French (fr) 3) Italian (it) 4) Japanese (jp) 5) Chinese Simplified (zhs) 6) Chinese Traditional (zht) Select [0-6]: 0 Introduce your BIP39 word list separated by space (at least 12 words):
Warning: remember that different passphrases yield different bitcoin wallets. If left empty, no password is used (echo is disabled). Enter your passphrase: New hsm_secret file created at root/.lightning/bitcoin/hsm_secret Use the
encryptcommand to encrypt the BIP32 seed if needed root@aabbccdd0102:/#```
Opusťte terminál a znovu spusťte aplikaci Core Lightning.
Kromě bitcoinové on-chain peněženky je nutné zálohovat i otevřené lightning network kanály. Core Lightning aplikace uchovává informace o otevřených kanálech v souboru
emergency.recover. Ten se nachází také v adresářiroot/.lightning/bitcoin. Mění se pouze v souvislosti s otevřením nebo uzavřením kanálu, proto doporučuji provést jeho zálohu vždy po takové operaci.Soubor
emergency.recoverneobsahuje informace o stavu kanálu. Při obnově dojde vždy k uzavření všech kanálů a vypořádání jejich balancí.Jak kopírovat uvedené soubory z vašeho Umbrelu na Raspberry Pi na USB disk? UmbrelOS pro to zatím nemá podporu ve svém UX, ale pomůže vám opět terminál a následující návod.
```
Najděte LABEL vašeho připojeného USB disku
Nejprve si vylistujte všechna existující bloková úložiště příkazem
sudo blkid
Fyzicky připojte váš USB disk s vylistujte stejným příkazem úložiště ještě jednou
sudo blkid
Podívejte se, které přibylo a najděte jeho LABEL. Řekněme, že se jmenuje "sda1"
Vytvořte si adresář pro zálohu, nazvěme jej třeba "/backup"
sudo mkdir /backup
Připojte váš identifikovaný USB disk přes jeho LABEL k vytvořenému adresáři
sudo mount /dev/sda1 /backup
Zkopírujte soubory hsm_secret a emergency.recover do adresáře "/backup"
sudo cp /home/umbrel/umbrel/app-data/core-lightning/data/lightningd/bitcoin/emergency.recover /backup
sudo cp /home/umbrel/umbrel/app-data/core-lightning/data/lightningd/bitcoin/hsm_secret /backup
Ukliďte po sobě - nejprve odpojte váš USB disk od adresáře "/backup"
sudo umount /backup
A následně zrušte adresář "/backup"
sudo rmdir /backup
```
Při obnově ze zálohy budete postupovat úplně stejně, jen příkazy pro kopírování budou směřovat opačným směrem
```
Kopírování záloh z připojeného adresáře "/backup" do cílového adresáře CLN
sudo cp /backup/emergency.recover /home/umbrel/umbrel/app-data/core-lightning/data/lightningd/bitcoin
sudo cp /backup/hsm_secret /home/umbrel/umbrel/app-data/core-lightning/data/lightningd/bitcoin ```
Kromě statické zálohy kanálů umožňuje CLN i průběžné zálohování jejich stavu prostřednictvím zálohy interní databáze do druhé, bezpečné lokality (na jiný disk). Databáze se nachází v souboru
lightningd.sqlite3ve stejném adresáři, jakohsm_secretneboemergency.recover. CLN lze dokonce nastavit tak, aby veškeré updaty do této databáze průběžně zapisoval i na druhou lokalitu. Bohužel však v současné verzi UmbrelOS toto není možné.UmbrelOS ve stávající verzi nepodporuje připojení více disků současně. Nelze tedy průběžně zálohovat data na druhý disk. Přestože můžete během provozu druhý disk připojit a přes terminál na něj data zkopírovat, nikdy takový disk nenechávejte připojen trvale. Po restartu uzlu může zabránit korektnímu nastartování Umbrelu a nainstalovaných aplikací.
Otevření kanálů
Lightningový uzel pro vás začne být užitečný teprve poté, co jej propojíte s LN sítí prostřednictvím platebních kanálů. Otevření kanálu je relativně jednoduché a lze jej docílit v podstatě dvěma způsoby.
- Otevřete kanál vy z vašeho uzlu
- Požádáte jiný uzel, aby otevřel kanál směrem k vám
Existují i další způsoby, ale pro jednoduchost si vystačíme s těmito dvěma. Důležité je si uvědomit, že uzel, který kanál otvírá, jej také musí naplnit bitcoiny na požadovanou kapacitu. Po otevření kanálu budou zároveň všechny bitcoiny (likvidita) na straně toho, kdo jej otevřel.
V prvním případě tedy nejprve pošlete na bitcoinovou peněženku vašeho CLN uzlu nějaké prostředky (tlačítko Deposit vám zobrazí příslušnou bitcoinovou adresu). Po potvrzení depositní transakce v blockchainu (můžete ji sledovat ve svém Mempool exploreru) můžete tlačítkem Open Channel požádat o otevření kanálu s vybraným LN uzlem. Ten si můžete vybrat dle své preference v některé z veřejných databází, jako je Amboss.Space nebo 1ml, nebo přímo na MemPool.Space v sekci lightning network.
Strategií pro výběr je opět celá řada, ale pro domácí uzel neuděláte chybu výběrem uzlu od některého z velkých hráčů, kteří jsou na kvalitě svého připojení do LN sítě obchodně zainteresováni. Poskytovatelé peněženek (ACINQ, WalletOfSatoshi, Blockstream, Alby, ...), burzy, směnárny a platební brány (Anycoin, Confirmo, Binance, Kraken, ...), poskytovatelé služeb na LN sítí (LOOP, Boltz, Strike). Ale třeba i SatoshiLabs nebo GeneralBytes. Můžete se u nich spolehnout na dostatečnou kapacitu, konektivitu i stabilitu provozu. Pozor si dejte pouze na požadovanou minimální velikost kanálu.
Do pole Node Id: vložte adresu vybraného uzlu (ve formátu PubKey@IP:Port) a do pole Amount: pak požadovanou velikost kanálu (částka bude stržena z vaší bitcoiové peněženky a ponížena o poplatky za otvírací transakci). Důležitý je přepínač Announce. Ten určuje, zda bude váš kanál veřejný a tedy k dispozici celé síti pro směrování plateb, nebo soukromý, o jehož existenci budete vědět pouze vy a připojený uzel a pro směrování cizích plateb nebude využíván. Pokud chcete využívat svůj LN uzel pouze pro své soukromé platby, doporučuji otevřený kanál do sítě neanoncovat. Zjednodušíte si práci s jeho balancováním, protože budete reagovat pouze na vlastní pohyby v jednotlivých kanálech.
Takto otevřený kanál bude mít likviditu na vaší straně (odchozí likvidita) a bude tedy primárně sloužit na posílání plateb z vašeho uzlu. Minimálně do doby, než si odesláním dostatečné částky vytvoříte prostor i pro příjem.
Druhý způsob, požádat jiný uzel, aby otevřel kanál k vám, vám přinese příchozí likviditu, tedy schopnost přijímat platby až do velikosti takového kanálu. Můžete se domluvit s kamarádem, který již uzel provozuje, aby k vám kanál otevřel. Nebo využít některou z nabídek jiných uzlů, která vám kanál otevřou za úplatu. Vybrat si můžete na tržištích LnRouter nebo LnBig. Lightning Network Plus nabízí možnost otevřít si kanály v takzvaném Liquidity Swapu. Uzly, které se jej účastní, si otevřou kanály vzájemně v kruhu. Každý tedy za otevření kanálu jedním směrem získá i kanál stejné velikosti s příchozí likviditou.
Nejjednodušším způsobem, jak získat příchozí likviditu, je otevření dalšího kanálu s vybraným uzlem a následné odeslání všech svých prostředků v tomto kanále na svou jinou lightning peněženku nebo swap out službu (služba, která příchozí prostředky uloží na vámi zadanou bitcoinovou adresu. Například Boltz.Exchange).
Nezapomeňte po otevření všech kanálů provést jejich zálohu dle postupu uvedeného výše.
Ride the Lightning
Ride the Lightning (RTL) je nástroj pro správu vašeho lightningového uzlu. Ačkoliv vlastní uzel, v našem případě aplikace CLN, nabízí jednoduché GUI pro svou obsluhu a v mnoha případech stačí (zvláště při otevření pouze několika privátních kanálů), některé parametry a pokročilé vlastnosti kanálů přes něj nejsou dostupné. Aplikace RTL nabízí webové rozhraní k většině těchto parametrů a další doplňkové služby pro zajištění likvidity vašich kanálů, jejich rebalancing a převod prostředků na on-chain adresy (swap out). Navíc nabízí přehledné statistiky a grafy využití uzlu, které lze využít pro optimalizaci nastavení CLN.
Aplikaci RTL můžete nainstalovat přímo z Umbrel App Store. Pozor, jsou tam uvedeny dvě verze, každá pro jednu z dostupných implementací lightning uzlu. Pokud jste nainstalovali Core Lightning, vyberte si Ride the Lightning (Core Lightning).
Máte-li otevřenu konzoli, můžete ji samozřejmě nainstalovat i z příkazového řádku.
umbreld client apps.install.mutate --appId core-lightning-rtlPřihlášení do aplikace je trochu nestandardní. RTL vyžaduje heslo, ale správu aplikačních hesel řídí UmbrelOS. Vaše heslo do aplikace naleznete na stránce RTL v App store (Default password). Objeví se tam po nainstalování aplikace, je kryptograficky odvozené od unikátního seedu vaší instalace uzlu a nelze jej změnit. Umbrel touto politikou reagoval na případy vykradení peněženek přes uniklou statickou TOR adresu aplikací jako RTL nebo Thunderhub, ke kterým neměli uživatelé změněné defaultní hesla.
Public Pool
Esenciální aplikace pro všechny, kteří doma kromě vlastního bitcoinového uzlu provozují také nějaký domácí miner. Public Pool je navzdory svému názvu privátní domácí těžební pool pro solo mining. Bez poplatků a s jistototu, že veškeré případně vytěžené odměny skončí na vaší vlastní bitcoinové adrese.
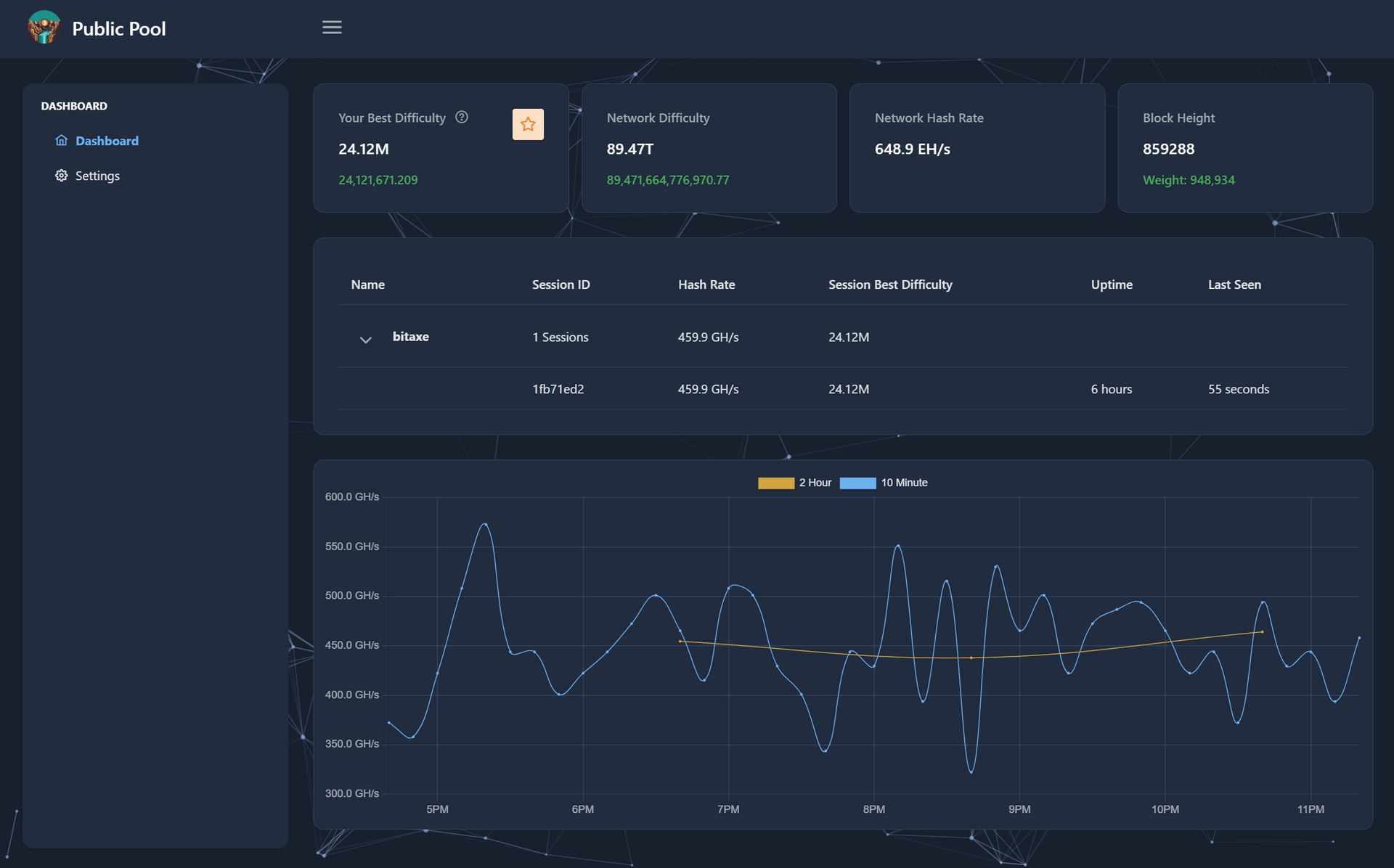
Instalace opět kvůli závislosti na Bitcoin Knots přes příkazový řádek:
umbreld client apps.install.mutate --appId public-poolKonfiguraci pro připojení vašeho mineru najdete hned v úvodu GUI po spuštění aplikace.
Zkušenosti z provozu
Provozování vlastního uzlu není nikterak náročnou činností a s trochou nadsázky lze říci, že se obejde bez složité údržby. Ve výše uvedené konfiguraci může běžet bez nutnosti zásahu i několik měsíců. Přesto je dobré se ke svému uzlu čas od času vrátit a jednoduchou údržbu provést.
Předně provádějte pravidelné upgrady nainstalovaných aplikací. Nové verze se objevují celkem pravidelně a přinášejí většinou opravy nalezených chyb a bezpečnostních děr, ale také nové funkcionality, které rozšiřují jejich možnosti použití. Doporučuji neinstalovat bez rozmyslu, ale přečíst si dostupné release notes (popis změn nové verze). Zvláště u bitcoinového uzlu (ať už Bitcoin Knots nebo Bitcoin Core), protože nové verze mohou obsahovat změny, které mění chování bitcoinové sítě a tedy i bitcoinu. Jejich výběrem a (ne)instalací hlasujete o tom, jak by měl bitcoin podle vás vypadat. Přečtěte si knihu The Blocksize Wars k lepšímu pochopení, co je tím myšleno.
Ze stejných důvodů pravidelně aktualizujte i operační systém UmbrelOS. Nové verze vycházejí přibližně jednou za čtvrt roku a vlastnosti operačního sytému většinou výrazně vylepšují.
Důležitou aktivitou je i záloha lightning uzlu a jeho kanálů vždy, když nějaký otevřete nebo zavřete. To se naštěstí neděje příliš často, většinou vystačíte s jednotkami otevřených kanálů i po dobu několika let. Výjimkou je však provoz veřejného lightning uzlu pro směrování plateb v síti. Takový uzel již vyžaduje pravidelnou údržbu kanálů, správu jejich poplatků a vyhodnocování jejich efektivity. To vede k zavírání neefektivních kanálů a otvírání nových směrem k lukrativním uzlům.
Raspberry Pi a UmbrelOS není vhodnou platformou pro provoz veřejných lightning uzlů a směrování plateb v síti. Nevyhovuje celkovým výkonem a bezpečností a neumožňuje nastavit adekvátní SLA pro provoz takové služby. Proto ji k tomuto účelu důrazně nedoporučuju.
Nezapomeňte svůj uzel čas od času restartovat. Mně se osvědčilo provést restart ne déle než po půl roce provozu. Dlouhodobý nepřetržitý provoz jakéhokoliv softwaru hromadí důsledky chyb v něm existujících (a každý takové obsahuje), které se časem zcela určitě nějak projeví. Je dobré těmto projevům předcházet právě restartem celého uzlu. Restart vždy provádějte kontrolovaně přes příslušné tlačítko v menu Settings Umbrel OS, nikdy uzel natvrdo nevypínejte odstavením od napájení. Umožníte všem aplikacím korektně se ukončit, aby následně mohly korektně nastartovat. To samé platí i pro vypínání uzlu v případě potřeby.
Vlastní bitcoinový uzel? Ano!
Pokud jste dočetli až sem, pravděpodobně stavbu a provoz vlastního uzlu vážně zvažujete. Rád bych vás v tom podpořil. Ano, dává to smysl. A přestože si myslím, že nejvíce zážitků a pozitivní energie získáte při stavbě a zprovoznění vlastního uzlu (třeba tak, jak je popsáno v tomto článku), nezatracuji ani pořízení již předpřipraveného řešení, které stačí připojit do zásuvky a zapnout. Stále vám zbyde spoustu zábavy s nastavením jednotlivých aplikací.
Staňte se součástí bitcoinové sítě a podpořte její původní étos! Staňte se Bitcoinerem!
-
 @ a012dc82:6458a70d
2024-09-04 08:09:45
@ a012dc82:6458a70d
2024-09-04 08:09:45Table Of Content
-
The Energy Consumption of Bitcoin Mining
-
The Environmental Impact of Bitcoin Mining
-
Innovations in Green Energy
-
The Advantages of Using Green Energy in Bitcoin Mining
-
The Challenges of Using Green Energy in Bitcoin Mining
-
Conclusion
-
FAQ
Bitcoin is a digital currency that has gained a lot of popularity over the years, and it's being used for various transactions. However, mining bitcoin requires a lot of energy, and this has raised concerns about the sustainability of bitcoin mining and its impact on the environment. In recent years, there have been efforts to make bitcoin mining more sustainable by using renewable energy sources. This article aims to assess the sustainability of bitcoin mining and its impact on green energy.
The Energy Consumption of Bitcoin Mining
Bitcoin mining is a process that involves solving complex mathematical problems that require a lot of computing power. This process consumes a significant amount of energy, and the energy consumption of bitcoin mining is growing every day. According to recent studies, the energy consumption of bitcoin mining is estimated to be around 121 terawatt-hours (TWh) per year, which is more than the energy consumption of some countries.
The Environmental Impact of Bitcoin Mining
The energy consumption of bitcoin mining has a significant impact on the environment. Most of the energy used in bitcoin mining comes from non-renewable sources such as coal and natural gas, which release greenhouse gases into the atmosphere. This contributes to climate change, which has adverse effects on the environment and human health.
Innovations in Green Energy
In recent years, there have been innovations in green energy that can be used to make bitcoin mining more sustainable. These innovations include renewable energy sources such as solar, wind, and hydropower. The use of these renewable energy sources can reduce the environmental impact of bitcoin mining and make it more sustainable.
The Advantages of Using Green Energy in Bitcoin Mining
Using green energy in bitcoin mining has several advantages. Firstly, it reduces the environmental impact of bitcoin mining by reducing greenhouse gas emissions. Secondly, it can make bitcoin mining more cost-effective, as the cost of renewable energy sources is declining. Thirdly, it can increase the adoption of renewable energy sources and drive innovation in the renewable energy sector.
The Challenges of Using Green Energy in Bitcoin Mining
There are also challenges associated with using green energy in bitcoin mining. Firstly, the availability of renewable energy sources may not be consistent, as solar and wind energy are dependent on weather conditions. This can affect the profitability of bitcoin mining, as miners may need to switch to non-renewable energy sources during periods of low renewable energy availability. Secondly, the initial investment required to set up renewable energy infrastructure can be high, which may deter some miners from switching to green energy sources.
Conclusion
Bitcoin mining has a significant impact on the environment, but there are efforts to make it more sustainable by using renewable energy sources. Using green energy in bitcoin mining has several advantages, including reducing greenhouse gas emissions and driving innovation in the renewable energy sector. However, there are also challenges associated with using green energy in bitcoin mining, such as the inconsistent availability of renewable energy sources and the high initial investment required to set up renewable energy infrastructure. Overall, assessing the sustainability of bitcoin mining and its impact on green energy is a complex issue that requires a comprehensive evaluation of various factors.
FAQ
Can bitcoin mining be done without consuming a lot of energy? No, bitcoin mining requires a significant amount of energy to solve complex mathematical problems and validate transactions.
Is bitcoin mining harmful to the environment? Yes, bitcoin mining consumes a lot of energy, most of which comes from non-renewable sources that release greenhouse gases into the atmosphere.
What are the benefits of using renewable energy sources in bitcoin mining? Using renewable energy sources can reduce the environmental impact of bitcoin mining, make it more cost-effective, and drive innovation in the renewable energy sector.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ c69b71dc:426ba763
2024-06-13 12:50:37
@ c69b71dc:426ba763
2024-06-13 12:50:37Chef's notes
Soaking nuts and seeds overnight makes the soup creamier and easier to blend if you have a less powerful blender. You can also use a hand blender. You can swap out nuts and seeds as needed. Cashews alone or cashews with almonds are also very tasty. More variety provides you with all the essential amino acids and fatty acids your body needs.
If you don't have miso or soy sauce, you can just use salt. But it tastes so much better with the other ingredients.
You will be surprised how tasty this soup will be! Please let me know if you try it 💚
Details
- ⏲️ Prep time: 7 minutes
- 🍳 Cook time: 0
- 🍽️ Servings: 2 - 3
Ingredients
- 200g Cashews (soaked over night)
- 50g Sunflower Seeds (soaked over night)
- 20g Hemp seeds (soaked over night)
- 2 Mushrooms (medium size)
- 2 Shiitake
- 4 tbsp Nutritional Yeast (optional)
- 1 tsp Salt (or more)
- 1 tbsp Miso (optional)
- 2 tbsp Soy Sauce (Nama Tamari)
- 2 cm of a spicy red Chilli (optional)
- 700ml Filtered Water
- 1 Clove of Garlic
- Pepper and Herbs (optional for topping)
Directions
- Soak Cashews, sunflower seeds and hemp seeds over night in water.
- Next day blend all the other ingredients with soaked seeds and nuts.
- Give it a taste and add more salt, miso or soy sauce
- Add more water if it's to thick
- Serve and sprinkle ground pepper and some herbs on top if desired for decoration
-
 @ 44dc1c2d:31c74f0b
2024-06-13 06:25:20
@ 44dc1c2d:31c74f0b
2024-06-13 06:25:20Chef's notes
I really like serving this with a saffron and cardamon rice. Add a few saffron threads and 3 or 4 crushed green cardamon pods while the rice is cooking to make it.
Details
- ⏲️ Prep time: ~15 min
- 🍳 Cook time: ~1.5 hours
- 🍽️ Servings: 6
Ingredients
- .5 cups neutral frying oil or ghee
- 2 onions halved and thinly sliced
- ~1 inch piece ginger root cut into thin batons
- 1 garlic clove crushed
- 2 fresh red chilies seeded and minced
- 1 inch piece fresh turmeric crushed or 1 tsp ground turmeric
- 1 lemongrass stalk lower part sliced thin and the top bruised
- 1.5 lbs steak cut into strips
- 14oz coconut milk
- 1 1/4 cups water
- 1 aubergine (eggplant) sliced and patted dry
- 1 tsp tamarind pulp, soaked in ~4 tbsp warm water
- salt and pepper to taste
- Garnish:
- Deep fried onions
- More fresh chilis
- Serve :
- Rice
Directions
- Heat half your oil in a wok or large pan. Fry onions, ginger and garlic tell fragrant. Add chilies, turmeric and the lower parts of the lemongrass stalk. Push the contents to the side, crank the heat and add the steak. Stirring tell the meat is browned a bit.
- Add the coconut milk, water and lemongrass top. Hit it with some salt and pepper. Cover and let simmer for about an hour and a half. You want the meat to be tender.
- Towards the end of the cook time, use the rest of the oil to fry the aubergines. Brown on both sides.
- Add the browned aubergines cook for another 15 minutes or so. Stir gently every so often. Strain the tamarind juice and add it to the curry. Taste and adjust seasoning.
- Garnish with more Chilies and serve with rice.
-
 @ 5954198a:0c6fa207
2024-09-04 07:39:29
@ 5954198a:0c6fa207
2024-09-04 07:39:29Even after posting stuff related to your business on your social media, your followers still haven’t increased much?
Does even after following a social media strategy, the number of sales hasn’t increased much? If your answer is yes, then you need to hire a Social Media Marketing Company in Indore. India’s cleanest city Indore is a city of dreams that also cleans the businesses if not run properly. Businesses aren’t that easy to run, maybe when your business grows, things work pretty well for your business, but the initial days of your business might not be like what you’ve imagined.
Starting a business from the scrap can be a very challenging thing to do. But if you have an idea that’s going to run your business, dedication to make your dream come true, then no one can stop you from achieving your dream of starting your business. Digi Partners is a Social Media Marketing Company in Indore that works for companies like yours on expanding their businesses. Digi Partners being an SMM company in Indore, have a team of professionals trained in graphic designing, content writing, digital marketing, strategy making, video producing, and editing. Graphic design plays a very vital role in social media marketing. Visit: https://digi-partners.com/social-media-marketing-company-indore/
-
 @ 169292c6:e7064967
2024-06-13 00:17:23
@ 169292c6:e7064967
2024-06-13 00:17:23Details
- ⏲️ Prep time: 10 min
- 🍳 Cook time: 0
Ingredients
- 8 oz of Imitation Crab Meat
- 1 small onion
- 2 celery sticks
- 1/2 cup of Mayonnaise
- 1 teaspoon of Garlic Powder
- 3 tablespoons of lemon Juice
- Salted Butter
- 1 teaspoon Onion Powder
- 1 teaspoon Parsley
- king Hawaiian Sweet Rolls
Directions
- Dice onion and celery and package of crab. Dice as fine as you'd like. In medium bowl, add mayo, lemon, parsley, garlic and onion powder. Mix. Next add in chopped veggies and crab. Mix together well with spoon. In the meantime, butter the rolls and sprinkle with garlic powder. Toast in the oven until slightly toasted. Remove from toaster oven slice the rolls and place crab mix inside the rolls.