-
 @ 502ab02a:a2860397
2025-04-13 01:38:46
@ 502ab02a:a2860397
2025-04-13 01:38:46อะไรคือ Heliotherapy
ถ้าลองหลับตา แล้วนึกถึงคนยุโรปยุคต้นศตวรรษที่ 20 ที่กำลังนอนอาบแดดบนภูเขา ห่มผ้าขนหนูบาง ๆ เปิดผิวให้พระอาทิตย์ลูบไล้ เฮียกำลังนึกถึงภาพของการรักษาโรคอย่างหนึ่งที่เรียกว่า Heliotherapy หรือ การบำบัดด้วยแสงอาทิตย์ ซึ่งเคยเป็นหนึ่งในศาสตร์ทางการแพทย์ที่ถูกยอมรับอย่างเป็นทางการ โดยเฉพาะในยุคที่ยังไม่มี “ยาปฏิชีวนะ”
Heliotherapy ไม่ได้เกิดจากความงมงาย แต่จากหลักฐานจริงจัง โดยเฉพาะผลงานของ ดร.ออกุสต์ โรลเลอร์ (Dr. Auguste Rollier) แพทย์ชาวสวิตเซอร์แลนด์ ผู้บุกเบิกการใช้แสงแดดรักษาผู้ป่วยวัณโรคกระดูกอย่างได้ผลในช่วงต้นศตวรรษที่ 20 เขาก่อตั้ง “โรงพยาบาลแห่งแสงอาทิตย์” บนเทือกเขาแอลป์ โดยให้ผู้ป่วยขึ้นไปอยู่ในที่สูงกว่า 1,500 เมตรเหนือระดับน้ำทะเล แล้วเปิดรับแสงแดดอย่างเป็นระบบ
ที่น่าสนใจคือ โรลเลอร์มีข้อกำหนดชัดเจนว่า ห้ามผู้ป่วยใส่แว่นกันแดดเด็ดขาด เพราะ “ดวงตา” คือหนึ่งในอวัยวะสำคัญที่ต้องรับรังสี UV เพื่อนำข้อมูลไปกระตุ้นต่อมไพเนียลในสมอง ส่งผลต่อวงจรชีวภาพ ฮอร์โมน และระบบภูมิคุ้มกันทั้งหมด ถ้าเราอาบแดดแต่ใส่แว่นดำ เท่ากับปิดประตูสำคัญของระบบบำบัดจากธรรมชาติ
แต่ถ้าย้อนกลับไปก่อนหน้านั้นอีกนิด เราจะเจอ “ต้นฉบับของแนวคิดแสงบำบัด” อยู่ที่ ดร.นีลส์ ฟินเซน (Dr. Niels Ryberg Finsen) นายแพทย์ชาวเดนมาร์ก ผู้ได้รับ รางวัลโนเบลสาขาสรีรวิทยาหรือการแพทย์ ในปี ค.ศ. 1903 จากการใช้แสงสว่างในการรักษาโรค Lupus vulgaris ซึ่งเป็นวัณโรคชนิดเรื้อรังที่แสดงออกบนผิวหนัง โดยเขาออกแบบอุปกรณ์ “Finsen Lamp” เพื่อฉายแสงตรงเข้าไปรักษาเซลล์ผิวโดยเฉพาะ และถือเป็นบิดาแห่ง Phototherapy ยุคใหม่
ทำไมแค่ “แดด” ถึงมีฤทธิ์บำบัด? แสงแดดคือคลังยาแห่งธรรมชาติอย่างแท้จริง เพราะประกอบด้วยรังสี UV หลายชนิด โดยเฉพาะ UVB ที่กระตุ้นให้ผิวหนังสร้าง วิตามินดี (Vitamin D3) ซึ่งมีบทบาทเสมือนฮอร์โมนที่ควบคุมระบบภูมิคุ้มกัน การอักเสบ และการดูดซึมแร่ธาตุต่าง ๆ เช่น แคลเซียมและแมกนีเซียม
แต่แดดไม่ได้มีแค่ UV แสงแดดในช่วงเช้ายังเต็มไปด้วยคลื่นแสงสีแดงและอินฟราเรดใกล้ (Near Infrared Light) ซึ่งมีบทบาทสำคัญในการซ่อมแซมไมโทคอนเดรีย—the powerhouse of the cell และช่วยกระตุ้นการหลั่งไนตริกออกไซด์ในหลอดเลือด ทำให้ระบบไหลเวียนโลหิตดีขึ้น ความดันสมดุลขึ้น และฟื้นฟูอวัยวะลึก ๆ ได้อย่างเงียบ ๆ
พูดง่าย ๆ คือ แดดเช้า = เติมแบตชีวภาพ ยิ่งแสงอาทิตย์กระทบผิวเราผ่าน “ดวงตาเปล่า” (โดยไม่ใส่แว่นกันแดดในช่วงเช้า) ก็ยิ่งช่วย “รีเซ็ตนาฬิกาชีวภาพ” ให้เราตื่นตรงเวลา หลับลึกขึ้น และเพิ่มการหลั่งเมลาโทนินในตอนค่ำโดยอัตโนมัติ
ในโลกที่คนวิ่งหาฮอร์โมนจากขวด การนอนตากแดด 10–20 นาทีต่อวัน กลับกลายเป็นเวทมนตร์ราคาถูกที่เรามองข้าม
และงานวิจัยจาก มหาวิทยาลัยเอดินบะระ (University of Edinburgh) ประเทศสกอตแลนด์ ก็ได้ยืนยันว่า แสงแดดมีส่วนช่วยลดความดันโลหิตได้จริง โดยไม่จำเป็นต้องพึ่งวิตามินดีเลยด้วยซ้ำ เพราะเมื่อแสงยูวีจากดวงอาทิตย์สัมผัสผิวหนัง จะกระตุ้นให้เกิดการปลดปล่อย “ไนตริกออกไซด์” (Nitric Oxide) จากชั้นผิวเข้าสู่ระบบหมุนเวียนโลหิต ซึ่งมีผลทำให้หลอดเลือดขยายตัว ความดันโลหิตลดลง และลดความเสี่ยงโรคหัวใจอย่างเห็นผล
นี่แปลว่าแสงแดดไม่เพียงแค่สว่าง แต่มันกำลัง “พูดภาษาเคมี” กับร่างกายเราอย่างเงียบ ๆ ทุกเช้า
ในยุคที่การแพทย์พัฒนาไปสุดทาง เทคโนโลยีผ่าตัดทำได้ถึงระดับนาโนเมตร กลับมีหมอบางคนหันกลับมาบอกว่า “คุณแค่ต้องออกไปรับแดดเช้า” เพื่อให้ร่างกายฟื้นตัวดีกว่าการพึ่งยาเพียงอย่างเดียว ดีไหมหล่ะ แต่ขอโทษทีคุณหมอที่บอกให้ไปตากแดดช่างมีน้อยเหลือเกินเมื่อดูในภาพรวม
Heliotherapy จึงไม่ใช่แค่การอาบแดด แต่คือการกลับไปเชื่อมโยงกับวงจรธรรมชาติ เหมือนคนโบราณที่เคารพดวงอาทิตย์ เพราะเขารู้ว่าพระอาทิตย์ไม่เคยหลอกเรา
ขณะที่ fiat ผลิตเม็ดสีสังเคราะห์และวิตามินปลอม ๆ พระอาทิตย์กลับให้ของจริง โดยไม่เรียกเก็บภาษีด้วย
ใครมีเวลา วันนี้เฮียขอชวนไปยืนรับแสงเช้า 10 นาที ไม่ต้องทำอะไร แค่ยืนเฉย ๆ ให้แสงซึมเข้าตา ซึมลงผิว แล้วฟังเสียงเงียบของร่างกายที่กำลังซ่อมแซมตัวเอง เงียบจนเราอาจได้ยินเสียงหัวใจบอกว่า "ขอบคุณนะ ที่ออกมารับแดดกับฉัน" #SundaySpecialเราจะไปเป็นหมูแดดเดียว #pirateketo #ตำรับเอ๋
-
 @ f6488c62:c929299d
2025-04-13 01:34:27
@ f6488c62:c929299d
2025-04-13 01:34:27ที่มาของเหรียญ BABY
Babylon (BABY) คือโปรเจกต์บล็อกเชนที่เกิดขึ้นเพื่อตอบโจทย์ความต้องการในการเชื่อมโยง Bitcoin เข้ากับระบบ Proof-of-Stake (PoS) โดย Babylon Chain ชูจุดแข็งด้านการนำ Bitcoin มาใช้ในการสเตค (staking) เพื่อเสริมความปลอดภัยให้กับเครือข่าย PoS และแอปพลิเคชันแบบกระจายศูนย์ (DApps) อื่นๆ
โครงการนี้ก่อตั้งโดยกลุ่มนักวิจัยจากมหาวิทยาลัยที่มีความเชี่ยวชาญด้านบล็อกเชน และได้รับการสนับสนุนจากนักลงทุนรายใหญ่ เช่น Binance Labs, Polychain Capital, และ IDG Capital โดยในช่วงต้นปี 2025 Babylon ได้เปิดตัวเครือข่ายเลเยอร์ 1 ชื่อ “Genesis” ซึ่งอนุญาตให้ผู้ถือครอง BTC นำเหรียญมาสเตคโดยไม่ต้องแปลงเป็นโทเคนอื่น
สถานการณ์ล่าสุดของเหรียญ BABY
ณ วันที่ 13 เมษายน 2025 ราคาเหรียญ BABY อยู่ที่ประมาณ $0.142 USD หรือตีเป็นเงินบาทราว 5.04 บาท ซึ่งลดลงประมาณ 14.5% จากจุดสูงสุดตลอดกาล (ATH) ที่ $0.1661 ซึ่งเกิดขึ้นเมื่อวันที่ 12 เมษายน 2025 ที่ผ่านมา
การปรับฐานในช่วงสั้นๆ หลังจากพุ่งขึ้นแรง เป็นสิ่งที่พบได้ทั่วไปในตลาดคริปโต โดยเฉพาะกับเหรียญที่เพิ่งได้รับกระแสความนิยมจากการเปิดตัวหรือข่าวเชิงบวก
วิเคราะห์แนวโน้มทางเทคนิค (Technical Analysis)
ในภาพรวมระยะสั้น: • แนวรับที่น่าจับตา อยู่ที่บริเวณ $0.130 – $0.135 ซึ่งเป็นจุดที่มีแรงซื้อกลับเข้ามาหลายครั้ง • แนวต้านสำคัญ อยู่ที่บริเวณ $0.160 – $0.166 หากทะลุขึ้นไปได้อีกครั้ง จะเป็นการยืนยันแนวโน้มขาขึ้นในระยะกลาง • อินดิเคเตอร์อย่าง RSI (Relative Strength Index) เริ่มลดลงจากโซน overbought (เหนือ 70) ซึ่งแสดงถึงการพักตัวของราคา แต่ยังอยู่ในแดน bullish • MACD ยังอยู่เหนือเส้นศูนย์ แสดงว่าแนวโน้มยังไม่เป็นขาลงโดยสมบูรณ์
สรุป
เหรียญ BABY เป็นโปรเจกต์ที่มีพื้นฐานแข็งแรง และอยู่ในกระแสของการเชื่อมโยง Bitcoin เข้ากับโลก DeFi ผ่านระบบ PoS ซึ่งถือเป็นไอเดียที่น่าจับตามอง แนวโน้มราคาระยะสั้นอาจมีการพักฐานหลังแตะจุดสูงสุด แต่หากสามารถยืนเหนือแนวรับและกลับขึ้นไปทดสอบแนวต้านได้อีกครั้ง มีโอกาสสูงที่จะเข้าสู่รอบขาขึ้นใหม่
บทความนี้ ใช้ ai ในการช่วยค้นหาข้อมูล ผิดถูกประการใด ขอ อภัย และขอคำชี้แนะจากทุกท่านไว้ด้วยนะครับ อย่างไรก็ตาม นักลงทุนควรระมัดระวังความผันผวนและติดตามข่าวสารจากทาง Babylon อย่างใกล้ชิด
-
 @ 5d4b6c8d:8a1c1ee3
2025-04-13 00:49:08
@ 5d4b6c8d:8a1c1ee3
2025-04-13 00:49:08Yesterday, I posted about the NBA Bracket Challenge that we're doing with Global Sports Central.
Today we're revealing that the grand prize is a Blockstream JADE cold wallet.
We've also decided on a 1k sats buy-in. Now that's a great expected value!
Follow Global Sports Central on nostr to stay up to date on competition details.
originally posted at https://stacker.news/items/941901
-
 @ 5d4b6c8d:8a1c1ee3
2025-04-13 00:35:13
@ 5d4b6c8d:8a1c1ee3
2025-04-13 00:35:13@cryotosensei, is this right?
originally posted at https://stacker.news/items/941895
-
 @ 0ef78f78:1cc6bede
2025-04-12 23:21:18
@ 0ef78f78:1cc6bede
2025-04-12 23:21:18In a world of relentless change and mounting political chaos, developing a carefully reasoned worldview feels both urgent and indispensable. Modern existence throws us into a tempest of technological leaps, ethical dilemmas, and existential questions, pressing us to find clarity amid the chaos. Philosophy rises to meet this challenge—not as a leisurely diversion, but as a disciplined effort to probe truth and cultivate wisdom.
This blog sets out to invite readers to wrestle with life’s big questions and their relevance now. My aim is to unpack foundational concepts with precision, tying them to the realities of our time. This space is for serious reflection—rigorous yet accessible—where we can scrutinize the beliefs that steer our lives.
Philosophy as Theory Making About Theories I’ve always been struck by an idea from Wilfred Sellars: philosophy is about crafting theories about our theories. It’s a process of stepping back to examine the very frameworks we use to make sense of the world. As Sellars put it, “The aim of philosophy, abstractly formulated, is to understand how things in the broadest possible sense of the term hang together in the broadest possible sense of the term.” To me, this captures philosophy’s essence—it’s not just about asking what we believe, but why we believe it, and how those beliefs hold together. We all operate with answers to life’s deepest questions, whether we’ve thought them through or not, and they form the silent foundation of our worldview.
Here are some of the questions philosophy urges us to confront:
What gives human life its purpose? Are our choices genuinely free, or shaped by unseen forces? How do we discern right from wrong? Is certain knowledge possible, or is truth forever out of reach? What lies beyond death? Is there an ultimate reality or higher power? What makes a life meaningful? These aren’t idle musings—they quietly shape how we act, what we value, and how we see the world. As Socrates cautioned, an unexamined life risks being lived without purpose or understanding. Philosophy, as theory making about theories, pushes us to take charge of our beliefs, testing and refining them through reason.
Why This Matters Now Today, the need for this kind of reflection is sharper than ever. We’re awash in information and clashing viewpoints, each vying for our allegiance. Meanwhile, breakthroughs like artificial intelligence, biotechnology, and global connectivity force us to rethink what it means to be human. How do we stay human when machines rival our abilities? How do we judge right and wrong in a world of endless options?
Philosophy equips us to tackle these questions with clarity. It teaches us to pause, question what we assume, and construct thoughtful answers to the problems we face. By engaging in this theory-making process, we gain insight into both the world and ourselves.
Come Along for the Ride This blog is an open call to dive into these ideas together. In the posts to come, I’ll explore philosophical concepts and their real-world stakes, hoping to stir curiosity and conversation. I’m not here to hand out final answers, but to deepen our grasp of the questions—and maybe inspire us to live with more intention.
Philosophy is a journey of discovery, blending intellectual rigor with an embrace of complexity. As we go forward, I’d love for you to join me in this exploration—one that offers not just understanding, but a more deliberate way of being.
-
 @ 8671a6e5:f88194d1
2025-04-12 23:04:34
@ 8671a6e5:f88194d1
2025-04-12 23:04:34
intro
Full disclosure : I bought multiple bitcoin art items to support artists
Bitcoin has absorbed old tropes from finance, tech, and economics, fundamentally reshaping how we think about money. But Bitcoin art? It should be a companion on the journey to a Bitcoin standard. Yet it doesn’t even seem to be trying. Every artistic movement worth its salt needs something to push against—to rebel, to spark thought, to provoke, or at the very least, to represent a technical or methodological leap forward in its field.
Pointillism comes to mind as an example in painting.
In this piece, I take a brief stroll into the subjective realm of art, specifically exploring art in the Bitcoin space—if such a thing truly exists. Some people might not like it, but as someone who has created modern art myself, I can confidently say that artists will emerge stronger from this transitional phase of Bitcoin art, whatever this era may be called later.
The art corner You know the drill. You visit any Bitcoin conference and there’s the obligatory “art corner” or gallery. Funny, wasn’t it just a few years back that a single decent artwork was a rarity needing a proper place for being shown tot he public? Now, every conference (small or big) needs this curated space, crammed with artists all vying for a sliver of attention.
And what do you usually find? A collection of the utterly predictable, the profoundly uninspired, the tiresomely repetitive, and anything but artistically groundbreaking amidst some exceptional pieces that will be snatched up almost immediately.
The themes are often so worn out, they’re practically a self-parody version of bitcoin art:
Animals holding signs (with of course… bitcoin logos)

Whales, dolphins, and the aquatic crew: The go-to, utterly drained metaphor for Bitcoin wealth, rendered in every conceivable medium with sea creatures.
Majestic vistas with bitcoin slogans: Think inspirational landscapes defaced with inscriptions or cryptic (not really) messages.
Women cradling blocks: Because apparently, nothing screams "Bitcoin" like a woman clutching a perfectly geometric cube. Bonus points if there are more painted women on a canvas, than actual women at the event.
Coins, coins, and more coins: Gold, silver, pixelated, abstract – just in case anyone forgot Bitcoin isn't a physical trinket.
Collages of Bitcoin celebs and memes: Why bother with originality when you can just mash up some social posts?
Reheated classics with an orange filter: Slap some orange highlights and a Bitcoin logo on a famous painting, and voilà! “Bitcoin art.” Bitcoin Pop-art, Bitcoin punk, Bitcoin collages…
It’s like the whole Bitcoin art scene is endlessly regurgitating the same tired ideas, and pouring a lot of time and effort in being just a fancy washing machine of orange t-shirts.
Most of it—not all, mind you, as there are people with exceptional thought and even more exceptional work—is no more than Bitcoin-themed art. By "theme," I mean the color orange or a “B,” much like you’d see M&M’s-themed coffee mugs, M&M’s t-shirts, or M&M’s-themed playing cards.
Now, let’s be clear: this isn’t about slagging off the artists themselves. I know how hard it is to thrive in this space, and I also learned about the time and effort put in to any work (the perception of the artwork has nothing to do with this at all!)
The dedication and passion within the bitcoin art scene are undeniable. Making art in a niche like Bitcoin is a tough gig (and often a thankless one, given the whole value-4-value thing seems perpetually broken). They deserve respect for putting themselves out there, doing the work and trying to make their passion work.
Many genuinely believe in what they’re creating, even if not everyone is convinced or will like a work of art. However, a lot of them are chasing a mirage, much like those hoping for an oasis of Bitcoin jobs in the desert. Many artists dream of turning their art into a business or a career move, and some even try to make a full-time living from it. That’s admirable, but I’m convinced it’s often a ruse, where your money, time, and effort dress up someone else’s business ideas and sense of branding. In my opinion, the real art movement in Bitcoin has yet to take off. It will need people with great ideas, motivation, know-how, and effort, for sure!
So I repeat the issue isn’t the individuals, the artists; it’s the collective creative stagnation that comes from clamoring to the general interest of this perceived “bitcoiner” as an audience.
Target < B > Audience
Only, this audience is usually not the target audience for the artworks itself. Art needs to have room to inspire, be free and relay an idea (even if that idea challenges another idea). That can’t be done to a target audience that just wants to sell their stuff to each other at a conference (see my piece on Bitcoin conferences for that) neither can it be a target audience that even is too cheap to buy a ticket and freeloads themselves into an conference.
Bitcoin is supposed to be revolutionary, yet so much of its art (or perceived art) feels like a tacked-on commercial necessity or, worse, a desperate attempt at self-validation. Most of it is just a perpetual branding motion from a non-existing marketing team.
The target audience is usually even worse. Not knowing what they’re looking at, out of their element and knowing they should and could support the artists and their work. A lot is depending on why this audience is wandering through a conference gallery in the first place.
If most people at a conference are the usuals, the sellers, the company people, then they're used to seeing these artists and their art pieces. No one is amazed anymore. Which is in fact a sad thing to happen.
I can't imagine how incredibly hard it must be to try to sell something as bitcoin art to this kind of audience, while trying to believe that a B-logo on an excerpt of the whitepaper is worth the effort. (I don’t think it is, but tastes differ, some people prefer a Whopper over a nice steak dinner)
Signaling “membership” in the bitcoin community is important to some, and they do that through hats, t-shirts, pins and hoodies, not buying a bitcoin artwork.
Art is inherently subjective, fluid, and deeply personal.
I love Kusama’s polka dots, someone else might be into Herman Brood’s chaotic paintings, and someone else might get all nostalgic over an Anton Pieck candy store drawings.
The contradiction Bitcoin: The hardest money ever created. Objectively verifiable. Math-based. Impersonal. Code.
The clash is between feeling and finance, between cold emotionless, hard numbers and warm, beating hearts.

That’s why it's always a bit surreal to see people that sit in a conference room, go from a deep dive into Lightning Network scalability or Bitcoin’s code ossification; and see them wandering through an “art gallery” filled with pieces that are the polar opposite of anything remotely code-related. The cold hearts walk amongst the works of warmth. The trustless math calculates their steps and starts to look at something that’s exposed to a public of that’s not there for the art, but the mimicking of such a think in their setting makes them have their own élan, grandeur. It feels forced. And to me, it feels even wrong to see people walk out of a conference room, right into the art gallery… where they’re usually stroll around out of boredom or just as a form of a break. It’s almost disrespectful, and I feel art needs its own place, the right setting. And that setting is definitely not a bitcoin conference.
You see tech and finance folks just standing there, at these art corners looking at the art pieces like cows watching a drone show.
You feel this subtle pressure to act like it’s profound, even though it rarely is. But you’re there, so you play along with the charade as well. It’s miserable to see. Certainly when some people are more interested in buying the piece of mind of the artist, the way of life or a glimmer of independence they’re missing themselves.
I believe bitcoin art is rarely bought for anything else than capturing the reality and authenticity of the artists. Artists know that. And they sell that authenticity (out) to eat, drink, sleep and pay their rent. Authenticity can be double spent, unlike the hard money asset where it’s supposedly all about. Artists have very big blocks.
It’s a bit like that hyped-up restaurant that turns out to be serving dressed-up bar food, but you’re with friends, so you pretend that $35 hors d'oeuvre doesn’t taste suspiciously like steamed shoe laces. Theaters are sometimes food bars or galleries. Proof of fart Then there’s the awkward issue of selling this stuff. How do you, as an artist, “comment on” or “complete” an asset in an artistic way, while that asset appreciates by an average of 40 to 70% a year?
Buying traditional art as an investment is one thing, driven by aesthetics or emotional connection. But buying Bitcoin art with Bitcoin? That’s a financial decision triggering regret (almost for sure). Think about it: 0.1 BTC spent on a canvas today, isn’t just a fixed one-time cost; it’s a future opportunity cost.
That same Bitcoin could be worth significantly more in a few years. The artwork, not so much, not even a Picasso painting or a Hokusai manages that kind of annual return. So, unless you’re head-over-heels for the piece (or the artist), buying Bitcoin art with Bitcoin is almost certainly a bad trade financially – though, so is buying that fancy coffee machine you'll use twice or getting a diamond ring for you loved one.
Of course, this isn't a definitive argument against it (it's subjective, remember). But it's a factor, just one element. People who buy art to lock it away into a vault aren't the same folks milling around a Bitcoin conference, presumably. But still.
Purpose
Historically, in the West at least, art served many purposes: glorifying churches, telling stories to the illiterate, and expressing the full spectrum of human emotion (pain, regret, doubt, madness, etc.). There was always a demand, whether from religious institutions, the populace, or a desire for education and status. The demand rarely came from onlookers or passive walk-ins. You can only walk in after the demand has been met. The real commanding force in Bitcoin art isn’t the financial types in suits or the grifter with a few stickers who got into the conference for free and smells like weed. The demand comes from people who love to cultivate the branding to propel themselves forward.
In Bitcoin? None of that. There’s little genuine demand, I’d argue. The demand seems mostly driven by the artists themselves wanting to participate. Which, in itself, makes the act of creation worthwhile for them. But the audience demand feels… manufactured. Nobody wakes up thinking: “.. I sure hope there’s a Bitcoin art gallery at this conference...”
This low-to-nonexistent demand, however, presents a massive opportunity to actually impress. Low expectations mean impact is easier to achieve in a lasting way. But that impact evaporates fast if all the visitors get is the same old themes with some orange varnish or a monkey holding a sign.
"Proof of work" isn’t enough here; we already have that in the bitcoin network. Bitcoin art need "proof of thought". Sure, Bitcoin artists put in the hours. Their work is literally proof of effort. But effort alone doesn’t equal value – originality does. Copying Warhol, Mondrian, or Van Gogh and slapping a Bitcoin twist on it isn’t the high level of creativity that can pull art lovers in (and even make them bitcoiners); on the contrary it’s opportunism. And in a space that seems to thrive on recycling successful (or at least visible or temporary cool) ideas, genuine artistic innovation is a rare beast.
Bitcoin art could be so much more. And yes that’s subjective, but at the same time, … walk around at any art gallery and be honest with yourself as a person and buy what you really like, support the artists and the scene, and at the same time realize you’re playing dress up.
There should be so much more, as a separate art movement. It could delve into the philosophy of decentralization, the tension between digital scarcity and creativity, the profound societal shifts Bitcoin is triggering. Instead, we’re mostly drowning in kitsch and thinly veiled cash grabs. The Bitcoin art world doesn’t need more bodies; it needs better minds. We don’t need bigger blocks, we don’t need blocks at all!
The uncomfortable truth is that many Bitcoin artists are here chasing opportunities, just like the rest of us. But spotting an opportunity doesn’t magically transform you into an artist.
I could “find the opportunity” to be a star in the hypothetical Bitcoin basketball league, being one of the first to join. But compared to the global pool of professional basketball talent, I’d likely be laughably bad. I’m not even tall enough to reach most pro players’ armpits, let alone dunk. Yet, in òur tiny Bitcoin league WBBF (World Bitcoin Basketball Federation), I’d be a legend, an OG, demanding respect for my early participation and best-dunk-champion. Just like some Bitcoin artists seem to expect accolades for a weak, orange-tinted imitation of 1960s pop art.

I wouldn’t cut it in any real basketball club, probably not even the lowest amateur league, considering my limited knowledge of the rules. Do you have to run back to the center? Can you tackle other players? Is snatching the ball mid-dribble legal? No clue.
But I could hang around the basketball scene a bit, soak up the jargon, maybe buy a sports drink for a better player to glean some knowledge, and then clumsily mimic their moves while still being terrible at dribbling. I’de buy the right shoes as well. To fit in. Just like bitcoiners buy the right t-shirts.
The same principle applies to some Bitcoin musicians and other creatives. Being the only one doing something – be it Bitcoin-themed sculptures, paintings, sci-fi, or whale graffiti murals – doesn’t automatically make you a leading figure. It just makes you… the only one. Being the sole sci-fi filmmaker in Bangladesh makes you the top of your national field, sure, but it doesn’t make you the next Kubrick. Likewise, airbrushing an orange “B” on a canvas doesn’t turn you into the next Georgia O’Keeffe.
The Bitcoin world thrives on competition and proof of work. Perhaps it’s high time Bitcoin art did the same. We need a battle of ideas, experiments, and genuine insights, not just more orange paint, paragraphs of the white paper and some copper wires.
The genuinely sad part is the sheer effort many of the artists pour into their work! But there’s a limit to how much you can make people want to buy an art piece simply because it has a Bitcoin theme. Go beyond that.
Get real
Real Bitcoin art, in whatever form it takes, will command a high valuation because it will be scarce, original, and have Bitcoin not just as a subject, but woven into its very fabric. That form (and there will be many), in my opinion, is still waiting to be discovered. And I’m fairly certain it won’t be found in a conference gallery, where bored artists sit next to their work, politely nodding at every bloke who wants to sound knowledgeable about art for five minutes or tries to make himself look like a big shot. Because let’s face it, I’ve yet to meet a Bitcoiner with a genuine understanding of art history or a truly discerning eye.
Some starting points, perhaps (just my two cents) :
Art that embodies decentralization itself, inviting audience participation and co-creation, mirroring Bitcoin’s ethos but yet to be fully realized in the art world. Including consensus.
Art that incorporates distributed consensus or a rotating "proof of work" concept in its creation or presentation.
Purely mathematical art forms that resonate with Bitcoin’s underlying principles.
The possibilities are vast. Or maybe, just maybe, Bitcoin itself is our art, and we don’t need all this orange-tinged stuff cluttering up galleries nobody asked for.
And why not paint blocks holding women, instead of women holding blocks? Or why not have inflation-resistant art? Or math-based art that isn’t even possible to show on a canvas?
On that subject, the author of this piece enjoys making art as well and conducted a small experiment. I've performed a "life performance" approximately three times now, which I consider pure Bitcoin art. This was an action, not a physical object. It demonstrated work I personally delivered as “a miner” (function in this art piece), and during the process, people could verify it and even received my block subsidy (effort). So far, only one person has recognized this art form; the rest were unaware. Since it's an action, not an object, it's intangible unless you witnessed it. This is my way of saying, "you are the artist." According to the bitcoin ethos.
Interestingly enough, other people, even those involved in Bitcoin art themselves (!), didn't see it. This amused me because, much like the early weeks of Bitcoin's network growth, many initially failed to recognize its potential. Perhaps this parallel should be enough for us all to understand the true nature of Bitcoin art.
The Artistic Dare:
Here’s a challenge, not to your wallet, but to your creative soul: conceive and execute a piece of art that embodies the spirit and principles of Bitcoin in a way that is genuinely original, thought-provoking, and resonates beyond the immediate Bitcoin echo chamber. Forget the predictable iconography. Dig deeper.
If you can create something truly compelling, something that makes us see Bitcoin – or art – in a new light, then you’ve truly created Bitcoin art. And then comes the extra real challenge: finding someone who can and would pay for it, and at the same time “gets it”.
The main challenge is creating real art—a path, a genre—where a standalone Bitcoin art gallery can thrive outside the conferences and the small echo chamber of the “what do you sell?” crowd.
Don’t sell your dreams and authenticity to bored traders or bitcoin consultants. It’s like serving the finest wine to a bunch of alcoholics in a bar at 4 am.
Playing it safe with themes and artworks that can’t cross into the real art scene (even the underground art scene, let alone the corporate art) will not be as long-lived as bitcoin itself. Trying to spark interest from art lovers in general, will be the killer app, and will make bitcoin art into a movement. And that’s what we all need to make it art,… the pieces can’t exist without the movement. I hope someone will get the right spark, idea and fire going.
But until then we’ll be stuck with people painting a chimpanzee holding a glittering Bitcoin logo and chatting with any dude that wants to feel like someone at a conference.
Good luck.
AVB
-
 @ a0381e98:5f5d71de
2025-04-12 21:38:12
@ a0381e98:5f5d71de
2025-04-12 21:38:12Trong thời đại mà công nghệ số ngày càng phát triển mạnh mẽ và thói quen tiêu dùng nội dung trực tuyến không ngừng thay đổi, B29 nổi lên như một điểm đến lý tưởng dành cho những ai đang tìm kiếm sự khác biệt, tính cá nhân hóa và một trải nghiệm số thực sự đáng nhớ. Nền tảng này không chỉ gây ấn tượng bởi giao diện hiện đại, tinh gọn, mà còn nhờ vào cấu trúc hệ thống thông minh được thiết kế nhằm tối ưu hóa toàn bộ hành trình trải nghiệm của người dùng. Mỗi yếu tố – từ tốc độ truy cập, độ mượt mà của thao tác cho đến khả năng tương thích với nhiều thiết bị – đều được tối ưu ở mức cao nhất, giúp B29 trở thành lựa chọn ưu tiên hàng đầu cho người dùng hiện đại luôn đề cao sự tiện lợi và hiệu quả. Không dừng lại ở việc cung cấp một giao diện đẹp, B29 còn tạo nên không gian để người dùng thực sự tương tác, khám phá, và tận hưởng những nội dung hấp dẫn, được chọn lọc kỹ lưỡng, phù hợp với mọi phong cách cá nhân.
Điểm sáng lớn nhất của B29 chính là sự đổi mới không ngừng và tư duy phát triển bền vững, không chạy theo xu hướng một cách máy móc mà chọn lọc để cải tiến có chiều sâu. Những cập nhật định kỳ không chỉ mang đến sự mới mẻ, mà còn góp phần nâng cao trải nghiệm tổng thể, biến mỗi lần truy cập thành một cơ hội để khám phá điều gì đó mới lạ và đầy tiềm năng. Dù là người dùng mới bắt đầu hay người đã có kinh nghiệm lâu năm, B29 luôn có khả năng làm hài lòng nhờ vào sự linh hoạt, thân thiện và thông minh trong cách thiết kế tính năng. Bên cạnh đó, đội ngũ hỗ trợ của B29 không chỉ phản hồi nhanh chóng mà còn thực sự thấu hiểu nhu cầu của người dùng, tạo ra một hệ sinh thái nơi bạn không bao giờ cảm thấy đơn độc trên hành trình số của mình. Chính nhờ sự tận tâm này, B29 không chỉ giữ chân người dùng mà còn xây dựng được niềm tin – một giá trị ngày càng hiếm thấy trong thế giới kỹ thuật số đầy cạnh tranh.
Hơn cả một nền tảng thông thường, B29 chủ động định hình một cộng đồng người dùng năng động và có định hướng rõ ràng về trải nghiệm số lành mạnh. Bằng cách tích hợp những công cụ hỗ trợ như quản lý thời gian, kiểm soát mức độ tương tác và tùy chỉnh không gian sử dụng, B29 giúp mỗi cá nhân xây dựng thói quen sử dụng bền vững và phù hợp với nhịp sống hiện đại. Không gian cộng đồng của B29 cũng đóng vai trò quan trọng trong việc kết nối người dùng – nơi mọi người có thể chia sẻ trải nghiệm, học hỏi kỹ năng và tạo ra những mối quan hệ tích cực dựa trên nền tảng công nghệ. Đây không chỉ là một nơi để tiêu khiển hay giải trí đơn thuần, mà là môi trường lý tưởng để phát triển bản thân, rèn luyện tư duy và kết nối với những người cùng chí hướng. Trong thế giới số rộng lớn, B29 như một ngọn đèn dẫn lối – không phô trương nhưng vững vàng, không ồn ào nhưng luôn hiện diện – mang đến cho người dùng một điểm tựa an toàn, thú vị và đầy cảm hứng.
-
 @ a0381e98:5f5d71de
2025-04-12 21:37:25
@ a0381e98:5f5d71de
2025-04-12 21:37:25Trong kỷ nguyên số nơi mà tốc độ, sự tiện lợi và trải nghiệm người dùng đóng vai trò then chốt, BongVIP đã nhanh chóng khẳng định vị thế là một nền tảng giải trí hàng đầu nhờ vào khả năng kết hợp hoàn hảo giữa công nghệ hiện đại và tính cá nhân hóa sâu sắc. BongVIP không đơn thuần chỉ là nơi để người dùng truy cập và khám phá nội dung, mà còn là một hệ sinh thái số nơi mỗi cá nhân được khuyến khích thể hiện bản thân, vận dụng trí tuệ và chiến lược trong môi trường thân thiện và đầy cảm hứng. Ngay khi bước vào, người dùng sẽ nhận thấy giao diện được thiết kế gọn gàng, thẩm mỹ và tối ưu cho mọi thiết bị, giúp cho việc trải nghiệm trở nên mượt mà, linh hoạt và thoải mái trong từng thao tác. Bên cạnh đó, tốc độ xử lý cực nhanh và khả năng tương thích đa nền tảng giúp BongVIP luôn sẵn sàng phục vụ người dùng mọi lúc mọi nơi, bất kể bạn đang ở đâu hay đang sử dụng thiết bị gì.
BongVip không chỉ nổi bật bởi giao diện mà còn gây ấn tượng mạnh với cách xây dựng nội dung và trải nghiệm tương tác thông minh, kích thích sự sáng tạo và phản xạ nhạy bén của người dùng. Với hệ thống hoạt động được cập nhật định kỳ và liên tục đổi mới, người dùng không bao giờ cảm thấy nhàm chán bởi luôn có những thử thách mới mẻ, các tính năng độc đáo và sự kiện thú vị chờ đón. Điều này giúp nền tảng giữ được sự tươi mới, đồng thời tạo ra cảm giác khám phá không ngừng, khiến mỗi lần truy cập đều là một trải nghiệm mới. Đặc biệt, BongVIP rất chú trọng đến yếu tố hỗ trợ khách hàng, với đội ngũ chăm sóc chuyên nghiệp, thân thiện và phản hồi nhanh chóng. Đây là một phần quan trọng giúp người dùng cảm thấy an tâm, tin tưởng và gắn bó lâu dài với nền tảng. Không chỉ đơn giản là một dịch vụ trực tuyến, BongVIP đang từng bước trở thành bạn đồng hành lý tưởng trong hành trình tìm kiếm cảm hứng và sự khác biệt của hàng ngàn người dùng mỗi ngày.
Một trong những điểm tạo nên giá trị lâu dài của BongVIP chính là cách mà nền tảng định hình cộng đồng và khuyến khích thói quen sử dụng có trách nhiệm. Người dùng tại đây không chỉ đơn thuần tham gia để tiêu khiển mà còn có cơ hội học hỏi, kết nối và phát triển kỹ năng cá nhân trong một môi trường năng động, tích cực. BongVIP hỗ trợ các tính năng quản lý thời gian, tự điều chỉnh mức độ tương tác và duy trì sự cân bằng giữa thế giới số và cuộc sống thực, góp phần thúc đẩy lối sống lành mạnh và bền vững. Đồng thời, sự kết nối trong cộng đồng người dùng cũng là yếu tố không thể thiếu, khi mọi người có thể giao lưu, chia sẻ kinh nghiệm và đồng hành cùng nhau trên hành trình khám phá những nội dung thú vị và độc đáo. BongVIP không chỉ là điểm đến cho nhu cầu giải trí chất lượng, mà còn là nơi truyền cảm hứng, nơi mỗi cá nhân được trân trọng, được thể hiện và được kết nối với một thế giới số thông minh, văn minh và đầy nhân văn.
-
 @ a0381e98:5f5d71de
2025-04-12 21:36:25
@ a0381e98:5f5d71de
2025-04-12 21:36:2588BET mang đến một trải nghiệm giải trí kỹ thuật số hoàn toàn khác biệt, nơi mà công nghệ, tốc độ và sự tối ưu được kết hợp một cách hoàn hảo để phục vụ cho nhu cầu ngày càng cao của người dùng hiện đại. Ngay từ những giây đầu tiên truy cập, bạn sẽ cảm nhận được sự tinh tế trong giao diện được thiết kế một cách chuyên nghiệp, dễ sử dụng và tối ưu cho mọi thiết bị, từ máy tính cho đến điện thoại thông minh. Mỗi thao tác lướt, nhấn, chuyển đổi giữa các nội dung đều diễn ra mượt mà, không gián đoạn, phản ánh trình độ công nghệ cao và khả năng vận hành ổn định của hệ thống. Nhưng điều làm nên bản sắc riêng của 88BET chính là cách nền tảng này đưa người dùng vào một thế giới tương tác sống động, nơi bạn không chỉ thư giãn mà còn được rèn luyện tư duy, khả năng quan sát và phản xạ nhạy bén trong từng thử thách mang tính chiến lược. Đây không chỉ là một nơi để giải trí, mà là một sân chơi trí tuệ hiện đại, nơi mọi phản ứng và quyết định đều mang lại cảm giác hứng khởi và thử thách.
Với sứ mệnh không ngừng nâng cao chất lượng dịch vụ, 88BET liên tục đổi mới và cập nhật nội dung để phù hợp với nhu cầu và thị hiếu đang thay đổi nhanh chóng của người dùng. Hệ thống không chỉ phong phú về nội dung mà còn đa dạng về hình thức, mang đến nhiều lựa chọn cho từng cá nhân – từ những người yêu thích khám phá đến những ai ưa thích sự cạnh tranh và thử thách. Mỗi tính năng được tích hợp đều mang tính ứng dụng cao và có chiều sâu, cho phép người dùng tự do điều chỉnh trải nghiệm theo sở thích riêng. Đồng thời, đội ngũ chăm sóc khách hàng được đào tạo bài bản, chuyên nghiệp và luôn sẵn sàng hỗ trợ 24/7 là một điểm mạnh lớn của 88BET, đảm bảo rằng mọi thắc mắc hay khó khăn đều được xử lý nhanh chóng và hiệu quả. Không gian thân thiện, dịch vụ tận tâm và tinh thần cầu tiến đã tạo nên một hệ sinh thái bền vững, thu hút và giữ chân người dùng trong hành trình dài lâu.
Ngoài ra, 88BET còn chú trọng đặc biệt đến việc xây dựng một cộng đồng người dùng văn minh, có trách nhiệm và chủ động. Nền tảng cung cấp các công cụ giúp người dùng theo dõi, kiểm soát thời gian và cách thức tương tác để đảm bảo sự cân bằng giữa giải trí và cuộc sống cá nhân. Điều này không chỉ thể hiện sự chuyên nghiệp trong cách vận hành, mà còn cho thấy 88BET đang hướng tới giá trị bền vững và lâu dài. Cộng đồng người dùng tại đây không chỉ là những cá nhân đơn lẻ mà còn là một tập thể gắn bó, cùng chia sẻ kinh nghiệm, giao lưu ý tưởng và hỗ trợ nhau phát triển. Với sự đầu tư nghiêm túc vào chất lượng và trải nghiệm người dùng, 88BET không đơn thuần là một nền tảng giải trí – mà là nơi hội tụ của những con người năng động, hiện đại và dẫn đầu xu hướng kỹ thuật số. Đây là điểm đến lý tưởng cho những ai đang tìm kiếm một trải nghiệm giải trí đẳng cấp, sáng tạo và khác biệt trong thế giới số ngày nay.
-
 @ 39cc53c9:27168656
2025-04-09 07:59:33
@ 39cc53c9:27168656
2025-04-09 07:59:33Know Your Customer is a regulation that requires companies of all sizes to verify the identity, suitability, and risks involved with maintaining a business relationship with a customer. Such procedures fit within the broader scope of anti-money laundering (AML) and counterterrorism financing (CTF) regulations.
Banks, exchanges, online business, mail providers, domain registrars... Everyone wants to know who you are before you can even opt for their service. Your personal information is flowing around the internet in the hands of "god-knows-who" and secured by "trust-me-bro military-grade encryption". Once your account is linked to your personal (and verified) identity, tracking you is just as easy as keeping logs on all these platforms.
Rights for Illusions
KYC processes aim to combat terrorist financing, money laundering, and other illicit activities. On the surface, KYC seems like a commendable initiative. I mean, who wouldn't want to halt terrorists and criminals in their tracks?
The logic behind KYC is: "If we mandate every financial service provider to identify their users, it becomes easier to pinpoint and apprehend the malicious actors."
However, terrorists and criminals are not precisely lining up to be identified. They're crafty. They may adopt false identities or find alternative strategies to continue their operations. Far from being outwitted, many times they're several steps ahead of regulations. Realistically, KYC might deter a small fraction – let's say about 1% ^1 – of these malefactors. Yet, the cost? All of us are saddled with the inconvenient process of identification just to use a service.
Under the rhetoric of "ensuring our safety", governments and institutions enact regulations that seem more out of a dystopian novel, gradually taking away our right to privacy.
To illustrate, consider a city where the mayor has rolled out facial recognition cameras in every nook and cranny. A band of criminals, intent on robbing a local store, rolls in with a stolen car, their faces obscured by masks and their bodies cloaked in all-black clothes. Once they've committed the crime and exited the city's boundaries, they switch vehicles and clothes out of the cameras' watchful eyes. The high-tech surveillance? It didn’t manage to identify or trace them. Yet, for every law-abiding citizen who merely wants to drive through the city or do some shopping, their movements and identities are constantly logged. The irony? This invasive tracking impacts all of us, just to catch the 1% ^1 of less-than-careful criminals.
KYC? Not you.
KYC creates barriers to participation in normal economic activity, to supposedly stop criminals. ^2
KYC puts barriers between many users and businesses. One of these comes from the fact that the process often requires multiple forms of identification, proof of address, and sometimes even financial records. For individuals in areas with poor record-keeping, non-recognized legal documents, or those who are unbanked, homeless or transient, obtaining these documents can be challenging, if not impossible.
For people who are not skilled with technology or just don't have access to it, there's also a barrier since KYC procedures are mostly online, leaving them inadvertently excluded.
Another barrier goes for the casual or one-time user, where they might not see the value in undergoing a rigorous KYC process, and these requirements can deter them from using the service altogether.
It also wipes some businesses out of the equation, since for smaller businesses, the costs associated with complying with KYC norms—from the actual process of gathering and submitting documents to potential delays in operations—can be prohibitive in economical and/or technical terms.
You're not welcome
Imagine a swanky new club in town with a strict "members only" sign. You hear the music, you see the lights, and you want in. You step up, ready to join, but suddenly there's a long list of criteria you must meet. After some time, you are finally checking all the boxes. But then the club rejects your membership with no clear reason why. You just weren't accepted. Frustrating, right?
This club scenario isn't too different from the fact that KYC is being used by many businesses as a convenient gatekeeping tool. A perfect excuse based on a "legal" procedure they are obliged to.
Even some exchanges may randomly use this to freeze and block funds from users, claiming these were "flagged" by a cryptic system that inspects the transactions. You are left hostage to their arbitrary decision to let you successfully pass the KYC procedure. If you choose to sidestep their invasive process, they might just hold onto your funds indefinitely.
Your identity has been stolen
KYC data has been found to be for sale on many dark net markets^3. Exchanges may have leaks or hacks, and such leaks contain very sensitive data. We're talking about the full monty: passport or ID scans, proof of address, and even those awkward selfies where you're holding up your ID next to your face. All this data is being left to the mercy of the (mostly) "trust-me-bro" security systems of such companies. Quite scary, isn't it?
As cheap as $10 for 100 documents, with discounts applying for those who buy in bulk, the personal identities of innocent users who passed KYC procedures are for sale. ^3
In short, if you have ever passed the KYC/AML process of a crypto exchange, your privacy is at risk of being compromised, or it might even have already been compromised.
(they) Know Your Coins
You may already know that Bitcoin and most cryptocurrencies have a transparent public blockchain, meaning that all data is shown unencrypted for everyone to see and recorded forever. If you link an address you own to your identity through KYC, for example, by sending an amount from a KYC exchange to it, your Bitcoin is no longer pseudonymous and can then be traced.
If, for instance, you send Bitcoin from such an identified address to another KYC'ed address (say, from a friend), everyone having access to that address-identity link information (exchanges, governments, hackers, etc.) will be able to associate that transaction and know who you are transacting with.
Conclusions
To sum up, KYC does not protect individuals; rather, it's a threat to our privacy, freedom, security and integrity. Sensible information flowing through the internet is thrown into chaos by dubious security measures. It puts borders between many potential customers and businesses, and it helps governments and companies track innocent users. That's the chaos KYC has stirred.
The criminals are using stolen identities from companies that gathered them thanks to these very same regulations that were supposed to combat them. Criminals always know how to circumvent such regulations. In the end, normal people are the most affected by these policies.
The threat that KYC poses to individuals in terms of privacy, security and freedom is not to be neglected. And if we don’t start challenging these systems and questioning their efficacy, we are just one step closer to the dystopian future that is now foreseeable.
Edited 20/03/2024 * Add reference to the 1% statement on Rights for Illusions section to an article where Chainalysis found that only 0.34% of the transaction volume with cryptocurrencies in 2023 was attributable to criminal activity ^1
-
 @ 826e9f89:ffc5c759
2025-04-12 21:34:24
@ 826e9f89:ffc5c759
2025-04-12 21:34:24What follows began as snippets of conversations I have been having for years, on and off, here and there. It will likely eventually be collated into a piece I have been meaning to write on “payments” as a whole. I foolishly started writing this piece years ago, not realizing that the topic is gargantuan and for every week I spend writing it I have to add two weeks to my plan. That may or may not ever come to fruition, but in the meantime, Tether announced it was issuing on Taproot Assets and suddenly everybody is interested again. This is as good a catalyst as any to carve out my “stablecoin thesis”, such as it exists, from “payments”, and put it out there for comment and feedback.
In contrast to the “Bitcoiner take” I will shortly revert to, I invite the reader to keep the following potential counterargument in mind, which might variously be termed the “shitcoiner”, “realist”, or “cynical” take, depending on your perspective: that stablecoins have clear product-market-fit. Now, as a venture capitalist and professional thinkboi focusing on companies building on Bitcoin, I obviously think that not only is Bitcoin the best money ever invented and its monetization is pretty much inevitable, but that, furthermore, there is enormous, era-defining long-term potential for a range of industries in which Bitcoin is emerging as superior technology, even aside from its role as money. But in the interest not just of steelmanning but frankly just of honesty, I would grudgingly agree with the following assessment as of the time of writing: the applications of crypto (inclusive of Bitcoin but deliberately wider) that have found product-market-fit today, and that are not speculative bets on future development and adoption, are: Bitcoin as savings technology, mining as a means of monetizing energy production, and stablecoins.
I think there are two typical Bitcoiner objections to stablecoins of significantly greater importance than all others: that you shouldn’t be supporting dollar hegemony, and that you don’t need a blockchain. I will elaborate on each of these, and for the remainder of the post will aim to produce a synthesis of three superficially contrasting (or at least not obviously related) sources of inspiration: these objections, the realisation above that stablecoins just are useful, and some commentary on technical developments in Bitcoin and the broader space that I think inform where things are likely to go. As will become clear as the argument progresses, I actually think the outcome to which I am building up is where things have to go. I think the technical and economic incentives at play make this an inevitability rather than a “choice”, per se. Given my conclusion, which I will hold back for the time being, this is a fantastically good thing, hence I am motivated to write this post at all!
Objection 1: Dollar Hegemony
I list this objection first because there isn’t a huge amount to say about it. It is clearly a normative position, and while I more or less support it personally, I don’t think that it is material to the argument I am going on to make, so I don’t want to force it on the reader. While the case for this objection is probably obvious to this audience (isn’t the point of Bitcoin to destroy central banks, not further empower them?) I should at least offer the steelman that there is a link between this and the realist observation that stablecoins are useful. The reason they are useful is because people prefer the dollar to even shitter local fiat currencies. I don’t think it is particularly fruitful to say that they shouldn’t. They do. Facts don’t care about your feelings. There is a softer bridging argument to be made here too, to the effect that stablecoins warm up their users to the concept of digital bearer (ish) assets, even though these particular assets are significantly scammier than Bitcoin. Again, I am just floating this, not telling the reader they should or shouldn’t buy into it.
All that said, there is one argument I do want to put my own weight behind, rather than just float: stablecoin issuance is a speculative attack on the institution of fractional reserve banking. A “dollar” Alice moves from JPMorgan to Tether embodies two trade-offs from Alice’s perspective: i) a somewhat opaque profile on the credit risk of the asset: the likelihood of JPMorgan ever really defaulting on deposits vs the operator risk of Tether losing full backing and/or being wrench attacked by the Federal Government and rugging its users. These risks are real but are almost entirely political. I’m skeptical it is meaningful to quantify them, but even if it is, I am not the person to try to do it. Also, more transparently to Alice, ii) far superior payment rails (for now, more on this to follow).
However, from the perspective of the fiat banking cartel, fractional reserve leverage has been squeezed. There are just as many notional dollars in circulation, but there the backing has been shifted from levered to unlevered issuers. There are gradations of relevant objections to this: while one might say, Tether’s backing comes from Treasuries, so you are directly funding US debt issuance!, this is a bit silly in the context of what other dollars one might hold. It’s not like JPMorgan is really competing with the Treasury to sell credit into the open market. Optically they are, but this is the core of the fiat scam. Via the guarantees of the Federal Reserve System, JPMorgan can sell as much unbacked credit as it wants knowing full well the difference will be printed whenever this blows up. Short-term Treasuries are also JPMorgan’s most pristine asset safeguarding its equity, so the only real difference is that Tether only holds Treasuries without wishing more leverage into existence. The realization this all builds up to is that, by necessity,
Tether is a fully reserved bank issuing fiduciary media against the only dollar-denominated asset in existence whose value (in dollar terms) can be guaranteed. Furthermore, this media arguably has superior “moneyness” to the obvious competition in the form of US commercial bank deposits by virtue of its payment rails.
That sounds pretty great when you put it that way! Of course, the second sentence immediately leads to the second objection, and lets the argument start to pick up steam …
Objection 2: You Don’t Need a Blockchain
I don’t need to explain this to this audience but to recap as briefly as I can manage: Bitcoin’s value is entirely endogenous. Every aspect of “a blockchain” that, out of context, would be an insanely inefficient or redundant modification of a “database”, in context is geared towards the sole end of enabling the stability of this endogenous value. Historically, there have been two variations of stupidity that follow a failure to grok this: i) “utility tokens”, or blockchains with native tokens for something other than money. I would recommend anybody wanting a deeper dive on the inherent nonsense of a utility token to read Only The Strong Survive, in particular Chapter 2, Crypto Is Not Decentralized, and the subsection, Everything Fights For Liquidity, and/or Green Eggs And Ham, in particular Part II, Decentralized Finance, Technically. ii) “real world assets” or, creating tokens within a blockchain’s data structure that are not intended to have endogenous value but to act as digital quasi-bearer certificates to some or other asset of value exogenous to this system. Stablecoins are in this second category.
RWA tokens definitionally have to have issuers, meaning some entity that, in the real world, custodies or physically manages both the asset and the record-keeping scheme for the asset. “The blockchain” is at best a secondary ledger to outsource ledger updates to public infrastructure such that the issuer itself doesn’t need to bother and can just “check the ledger” whenever operationally relevant. But clearly ownership cannot be enforced in an analogous way to Bitcoin, under both technical and social considerations. Technically, Bitcoin’s endogenous value means that whoever holds the keys to some or other UTXOs functionally is the owner. Somebody else claiming to be the owner is yelling at clouds. Whereas, socially, RWA issuers enter a contract with holders (whether legally or just in terms of a common-sense interpretation of the transaction) such that ownership of the asset issued against is entirely open to dispute. That somebody can point to “ownership” of the token may or may not mean anything substantive with respect to the physical reality of control of the asset, and how the issuer feels about it all.
And so, one wonders, why use a blockchain at all? Why doesn’t the issuer just run its own database (for the sake of argument with some or other signature scheme for verifying and auditing transactions) given it has the final say over issuance and redemption anyway? I hinted at an answer above: issuing on a blockchain outsources this task to public infrastructure. This is where things get interesting. While it is technically true, given the above few paragraphs, that, you don’t need a blockchain for that, you also don’t need to not use a blockchain for that. If you want to, you can.
This is clearly the case given stablecoins exist at all and have gone this route. If one gets too angry about not needing a blockchain for that, one equally risks yelling at clouds! And, in fact, one can make an even stronger argument, more so from the end users’ perspective. These products do not exist in a vacuum but rather compete with alternatives. In the case of stablecoins, the alternative is traditional fiat money, which, as stupid as RWAs on a blockchain are, is even dumber. It actually is just a database, except it’s a database that is extremely annoying to use, basically for political reasons because the industry managing these private databases form a cartel that never needs to innovate or really give a shit about its customers at all. In many, many cases, stablecoins on blockchains are dumb in the abstract, but superior to the alternative methods of holding and transacting in dollars existing in other forms. And note, this is only from Alice’s perspective of wanting to send and receive, not a rehashing of the fractional reserve argument given above. This is the essence of their product-market-fit. Yell at clouds all you like: they just are useful given the alternative usually is not Bitcoin, it’s JPMorgan’s KYC’d-up-the-wazoo 90s-era website, more than likely from an even less solvent bank.
So where does this get us? It might seem like we are back to “product-market-fit, sorry about that” with Bitcoiners yelling about feelings while everybody else makes do with their facts. However, I think we have introduced enough material to move the argument forward by incrementally incorporating the following observations, all of which I will shortly go into in more detail: i) as a consequence of making no technical sense with respect to what blockchains are for, today’s approach won’t scale; ii) as a consequence of short-termist tradeoffs around socializing costs, today’s approach creates an extremely unhealthy and arguably unnatural market dynamic in the issuer space; iii) Taproot Assets now exist and handily address both points i) and ii), and; iv) eCash is making strides that I believe will eventually replace even Taproot Assets.
To tease where all this is going, and to get the reader excited before we dive into much more detail: just as Bitcoin will eat all monetary premia, Lightning will likely eat all settlement, meaning all payments will gravitate towards routing over Lightning regardless of the denomination of the currency at the edges. Fiat payments will gravitate to stablecoins to take advantage of this; stablecoins will gravitate to TA and then to eCash, and all of this will accelerate hyperbitcoinization by “bitcoinizing” payment rails such that an eventual full transition becomes as simple as flicking a switch as to what denomination you want to receive.
I will make two important caveats before diving in that are more easily understood in light of having laid this groundwork: I am open to the idea that it won’t be just Lightning or just Taproot Assets playing the above roles. Without veering into forecasting the entire future development of Bitcoin tech, I will highlight that all that really matters here are, respectively: a true layer 2 with native hashlocks, and a token issuance scheme that enables atomic routing over such a layer 2 (or combination of such). For the sake of argument, the reader is welcome to swap in “Ark” and “RGB” for “Lightning” and “TA” both above and in all that follows. As far as I can tell, this makes no difference to the argument and is even exciting in its own right. However, for the sake of simplicity in presentation, I will stick to “Lightning” and “TA” hereafter.
1) Today’s Approach to Stablecoins Won’t Scale
This is the easiest to tick off and again doesn’t require much explanation to this audience. Blockchains fundamentally don’t scale, which is why Bitcoin’s UTXO scheme is a far better design than ex-Bitcoin Crypto’s’ account-based models, even entirely out of context of all the above criticisms. This is because Bitcoin transactions can be batched across time and across users with combinations of modes of spending restrictions that provide strong economic guarantees of correct eventual net settlement, if not perpetual deferral. One could argue this is a decent (if abstrusely technical) definition of “scaling” that is almost entirely lacking in Crypto.
What we see in ex-Bitcoin crypto is so-called “layer 2s” that are nothing of the sort, forcing stablecoin schemes in these environments into one of two equally poor design choices if usage is ever to increase: fees go higher and higher, to the point of economic unviability (and well past it) as blocks fill up, or move to much more centralized environments that increasingly are just databases, and hence which lose the benefits of openness thought to be gleaned by outsourcing settlement to public infrastructure. This could be in the form of punting issuance to a bullshit “layer 2” that is a really a multisig “backing” a private execution environment (to be decentralized any daw now) or an entirely different blockchain that is just pretending even less not to be a database to begin with. In a nutshell, this is a decent bottom-up explanation as to why Tron has the highest settlement of Tether.
This also gives rise to the weirdness of “gas tokens” - assets whose utility as money is and only is in the form of a transaction fee to transact a different kind of money. These are not quite as stupid as a “utility token,” given at least they are clearly fulfilling a monetary role and hence their artificial scarcity can be justified. But they are frustrating from Bitcoiners’ and users’ perspectives alike: users would prefer to pay transaction fees on dollars in dollars, but they can’t because the value of Ether, Sol, Tron, or whatever, is the string and bubblegum that hold their boondoggles together. And Bitcoiners wish this stuff would just go away and stop distracting people, whereas this string and bubblegum is proving transiently useful.
All in all, today’s approach is fine so long as it isn’t being used much. It has product-market fit, sure, but in the unenviable circumstance that, if it really starts to take off, it will break, and even the original users will find it unusable.
2) Today’s Approach to Stablecoins Creates an Untenable Market Dynamic
Reviving the ethos of you don’t need a blockchain for that, notice the following subtlety: while the tokens representing stablecoins have value to users, that value is not native to the blockchain on which they are issued. Tether can (and routinely does) burn tokens on Ethereum and mint them on Tron, then burn on Tron and mint on Solana, and so on. So-called blockchains “go down” and nobody really cares. This makes no difference whatsoever to Tether’s own accounting, and arguably a positive difference to users given these actions track market demand. But it is detrimental to the blockchain being switched away from by stripping it of “TVL” that, it turns out, was only using it as rails: entirely exogenous value that leaves as quickly as it arrived.
One underdiscussed and underappreciated implication of the fact that no value is natively running through the blockchain itself is that, in the current scheme, both the sender and receiver of a stablecoin have to trust the same issuer. This creates an extremely powerful network effect that, in theory, makes the first-to-market likely to dominate and in practice has played out exactly as this theory would suggest: Tether has roughly 80% of the issuance, while roughly 19% goes to the political carve-out of USDC that wouldn’t exist at all were it not for government interference. Everybody else combined makes up the final 1%.
So, Tether is a full reserve bank but also has to be everybody’s bank. This is the source of a lot of the discomfort with Tether, and which feeds into the original objection around dollar hegemony, that there is an ill-defined but nonetheless uneasy feeling that Tether is slowly morphing into a CBDC. I would argue this really has nothing to do with Tether’s own behavior but rather is a consequence of the market dynamic inevitably created by the current stablecoin scheme. There is no reason to trust any other bank because nobody really wants a bank, they just want the rails. They want something that will retain a nominal dollar value long enough to spend it again. They don’t care what tech it runs on and they don’t even really care about the issuer except insofar as having some sense they won’t get rugged.
Notice this is not how fiat works. Banks can, of course, settle between each other, thus enabling their users to send money to customers of other banks. This settlement function is actually the entire point of central banks, less the money printing and general corruption enabled (we might say, this was the historical point of central banks, which have since become irredeemably corrupted by this power). This process is clunkier than stablecoins, as covered above, but the very possibility of settlement means there is no gigantic network effect to being the first commercial issuer of dollar balances. If it isn’t too triggering to this audience, one might suggest that the money printer also removes the residual concern that your balances might get rugged! (or, we might again say, you guarantee you don’t get rugged in the short term by guaranteeing you do get rugged in the long term).
This is a good point at which to introduce the unsettling observation that broader fintech is catching on to the benefits of stablecoins without any awareness whatsoever of all the limitations I am outlining here. With the likes of Stripe, Wise, Robinhood, and, post-Trump, even many US megabanks supposedly contemplating issuing stablecoins (obviously within the current scheme, not the scheme I am building up to proposing), we are forced to boggle our minds considering how on earth settlement is going to work. Are they going to settle through Ether? Well, no, because i) Ether isn’t money, it’s … to be honest, I don’t think anybody really knows what it is supposed to be, or if they once did they aren’t pretending anymore, but anyway, Stripe certainly hasn’t figured that out yet so, ii) it won’t be possible to issue them on layer 1s as soon as there is any meaningful volume, meaning they will have to route through “bullshit layer 2 wrapped Ether token that is really already a kind of stablecoin for Ether.”
The way they are going to try to fix this (anybody wanna bet?) is routing through DEXes, which is so painfully dumb you should be laughing and, if you aren’t, I would humbly suggest you don’t get just how dumb it is. What this amounts to is plugging the gap of Ether’s lack of moneyness (and wrapped Ether’s hilarious lack of moneyness) with … drum roll … unknowable technical and counterparty risk and unpredictable cost on top of reverting to just being a database. So, in other words, all of the costs of using a blockchain when you don’t strictly need to, and none of the benefits. Stripe is going to waste billions of dollars getting sandwich attacked out of some utterly vanilla FX settlement it is facilitating for clients who have even less of an idea what is going on and why North Korea now has all their money, and will eventually realize they should have skipped their shitcoin phase and gone straight to understanding Bitcoin instead …
3) Bitcoin (and Taproot Assets) Fixes This
To tie together a few loose ends, I only threw in the hilariously stupid suggestion of settling through wrapped Ether on Ether on Ether in order to tee up the entirely sensible suggestion of settling through Lightning. Again, not that this will be new to this audience, but while issuance schemes have been around on Bitcoin for a long time, the breakthrough of Taproot Assets is essentially the ability to atomically route through Lightning.
I will admit upfront that this presents a massive bootstrapping challenge relative to the ex-Bitcoin Crypto approach, and it’s not obvious to me if or how this will be overcome. I include this caveat to make it clear I am not suggesting this is a given. It may not be, it’s just beyond the scope of this post (or frankly my ability) to predict. This is a problem for Lightning Labs, Tether, and whoever else decides to step up to issue. But even highlighting this as an obvious and major concern invites us to consider an intriguing contrast: scaling TA stablecoins is hardest at the start and gets easier and easier thereafter. The more edge liquidity there is in TA stables, the less of a risk it is for incremental issuance; the more TA activity, the more attractive deploying liquidity is into Lightning proper, and vice versa. With apologies if this metaphor is even more confusing than it is helpful, one might conceive of the situation as being that there is massive inertia to bootstrap, but equally there could be positive feedback in driving the inertia to scale. Again, I have no idea, and it hasn’t happened yet in practice, but in theory it’s fun.
More importantly to this conversation, however, this is almost exactly the opposite dynamic to the current scheme on other blockchains, which is basically free to start, but gets more and more expensive the more people try to use it. One might say it antiscales (I don’t think that’s a real word, but if Taleb can do it, then I can do it too!).
Furthermore, the entire concept of “settling in Bitcoin” makes perfect sense both economically and technically: economically because Bitcoin is money, and technically because it can be locked in an HTLC and hence can enable atomic routing (i.e. because Lightning is a thing). This is clearly better than wrapped Eth on Eth on Eth or whatever, but, tantalisingly, is better than fiat too! The core message of the payments tome I may or may not one day write is (or will be) that fiat payments, while superficially efficient on the basis of centralized and hence costless ledger amendments, actually have a hidden cost in the form of interbank credit. Many readers will likely have heard me say this multiple times and in multiple settings but, contrary to popular belief, there is no such thing as a fiat debit. Even if styled as a debit, all fiat payments are credits and all have credit risk baked into their cost, even if that is obscured and pushed to the absolute foundational level of money printing to keep banks solvent and hence keep payment channels open.
Furthermore! this enables us to strip away the untenable market dynamic from the point above. The underappreciated and underdiscussed flip side of the drawback of the current dynamic that is effectively fixed by Taproot Assets is that there is no longer a mammoth network effect to a single issuer. Senders and receivers can trust different issuers (i.e. their own banks) because those banks can atomically settle a single payment over Lightning. This does not involve credit. It is arguably the only true debit in the world across both the relevant economic and technical criteria: it routes through money with no innate credit risk, and it does so atomically due to that money’s native properties.
Savvy readers may have picked up on a seed I planted a while back and which can now delightfully blossom:
This is what Visa was supposed to be!
Crucially, this is not what Visa is now. Visa today is pretty much the bank that is everybody’s counterparty, takes a small credit risk for the privilege, and oozes free cash flow bottlenecking global consumer payments.
But if you read both One From Many by Dee Hock (for a first person but pretty wild and extravagant take) and Electronic Value Exchange by David Stearns (for a third person, drier, but more analytical and historically contextualized take) or if you are just intimately familiar with the modern history of payments for whatever other reason, you will see that the role I just described for Lightning in an environment of unboundedly many banks issuing fiduciary media in the form of stablecoins is exactly what Dee Hock wanted to create when he envisioned Visa:
A neutral and open layer of value settlement enabling banks to create digital, interbank payment schemes for their customers at very low cost.
As it turns out, his vision was technically impossible with fiat, hence Visa, which started as a cooperative amongst member banks, was corrupted into a duopolistic for-profit rent seeker in curious parallel to the historical path of central banks …
4) eCash
To now push the argument to what I think is its inevitable conclusion, it’s worth being even more vigilant on the front of you don’t need a blockchain for that. I have argued that there is a role for a blockchain in providing a neutral settlement layer to enable true debits of stablecoins. But note this is just a fancy and/or stupid way of saying that Bitcoin is both the best money and is programmable, which we all knew anyway. The final step is realizing that, while TA is nice in terms of providing a kind of “on ramp” for global payments infrastructure as a whole to reorient around Lightning, there is some path dependence here in assuming (almost certainly correctly) that the familiarity of stablecoins as “RWA tokens on a blockchain” will be an important part of the lure.
But once that transition is complete, or is well on its way to being irreversible, we may as well come full circle and cut out tokens altogether. Again, you really don’t need a blockchain for that, and the residual appeal of better rails has been taken care of with the above massive detour through what I deem to be the inevitability of Lightning as a settlement layer. Just as USDT on Tron arguably has better moneyness than a JPMorgan balance, so a “stablecoin” as eCash has better moneyness than as a TA given it is cheaper, more private, and has more relevantly bearer properties (in other words, because it is cash). The technical detail that it can be hashlocked is really all you need to tie this all together. That means it can be atomically locked into a Lightning routed debit to the recipient of a different issuer (or “mint” in eCash lingo, but note this means the same thing as what we have been calling fully reserved banks). And the economic incentive is pretty compelling too because, for all their benefits, there is still a cost to TAs given they are issued onchain and they require asset-specific liquidity to route on Lightning. Once the rest of the tech is in place, why bother? Keep your Lightning connectivity and just become a mint.
What you get at that point is dramatically superior private database to JPMorgan with the dramatically superior public rails of Lightning. There is nothing left to desire from “a blockchain” besides what Bitcoin is fundamentally for in the first place: counterparty-risk-free value settlement.
And as a final point with a curious and pleasing echo to Dee Hock at Visa, Calle has made the point repeatedly that David Chaum’s vision for eCash, while deeply philosophical besides the technical details, was actually pretty much impossible to operate on fiat. From an eCash perspective, fiat stablecoins within the above infrastructure setup are a dramatic improvement on anything previously possible. But, of course, they are a slippery slope to Bitcoin regardless …
Objections Revisited
As a cherry on top, I think the objections I highlighted at the outset are now readily addressed – to the extent the reader believes what I am suggesting is more or less a technical and economic inevitability, that is. While, sure, I’m not particularly keen on giving the Treasury more avenues to sell its welfare-warfare shitcoin, on balance the likely development I’ve outlined is an enormous net positive: it’s going to sell these anyway so I prefer a strong economic incentive to steadily transition not only to Lightning as payment rails but eCash as fiduciary media, and to use “fintech” as a carrot to induce a slow motion bank run.
As alluded to above, once all this is in place, the final step to a Bitcoin standard becomes as simple as an individual’s decision to want Bitcoin instead of fiat. On reflection, this is arguably the easiest part! It's setting up all the tech that puts people off, so trojan-horsing them with “faster, cheaper payment rails” seems like a genius long-term strategy.
And as to “needing a blockchain” (or not), I hope that is entirely wrapped up at this point. The only blockchain you need is Bitcoin, but to the extent people are still confused by this (which I think will take decades more to fully unwind), we may as well lean into dazzling them with whatever innovation buzzwords and decentralization theatre they were going to fall for anyway before realizing they wanted Bitcoin all along.
Conclusion
Stablecoins are useful whether you like it or not. They are stupid in the abstract but it turns out fiat is even stupider, on inspection. But you don’t need a blockchain, and using one as decentralization theatre creates technical debt that is insurmountable in the long run. Blockchain-based stablecoins are doomed to a utility inversely proportional to their usage, and just to rub it in, their ill-conceived design practically creates a commercial dynamic that mandates there only ever be a single issuer.
Given they are useful, it seems natural that this tension is going to blow up at some point. It also seems worthwhile observing that Taproot Asset stablecoins have almost the inverse problem and opposite commercial dynamic: they will be most expensive to use at the outset but get cheaper and cheaper as their usage grows. Also, there is no incentive towards a monopoly issuer but rather towards as many as are willing to try to operate well and provide value to their users.
As such, we can expect any sizable growth in stablecoins to migrate to TA out of technical and economic necessity. Once this has happened - or possibly while it is happening but is clearly not going to stop - we may as well strip out the TA component and just use eCash because you really don’t need a blockchain for that at all. And once all the money is on eCash, deciding you want to denominate it in Bitcoin is the simplest on-ramp to hyperbitcoinization you can possibly imagine, given we’ve spent the previous decade or two rebuilding all payments tech around Lightning.
Or: Bitcoin fixes this. The End.
- Allen, #892,125
thanks to Marco Argentieri, Lyn Alden, and Calle for comments and feedback
-
 @ 04cb16e4:2ec3e5d5
2025-04-12 19:21:48
@ 04cb16e4:2ec3e5d5
2025-04-12 19:21:48Meine erste "Begegnung" mit Ulrike hatte ich am 21. März 2022 - dank Amazon konnte ich das Ereignis noch exakt nachvollziehen. Es war eines meiner ersten (Lockdown) kritischen Bücher, die ich in dieser Zeit in die Hände bekam - noch nach Thomas Röper (das war mein Einstieg) aber vor Daniele Ganser. Insofern war es mir möglich, das, was dann folgte für die Autorin, live und in Farbe mit zu verfolgen:
"Wer sich in die Öffentlichkeit traut, kann sich dort ganz schnell eine blutige Nase holen. Dieselben Medien, die eine Person heute glorifizieren, stellen sie morgen an den Pranger. Sie verteilen und entziehen Reputation, fördern und zerstören Karrieren. Das Medium selbst bleibt jedoch immer auf der Siegerseite. Die Gesetze von Marktorientierung und zynisch-ideologisierter Machtausübung gelten für Rundfunk und Fernsehen ebenso wie für die Printmedien - von RTL bis ARD und ZDF, von der BILD über die taz bis zur ZEIT.
»Das Phänomen Guérot« legt genau diesen Vorgang detailliert offen: Der MENSCH Ulrike Guérot ist in der Realität nicht die dämonische Figur, als die sie hingestellt worden ist. Aber an ihr kristallisiert sich genau dieser menschenverachtende Prozess heraus, der bis heute andauert."
Im Herbst 2022 habe ich durch den ersten Vortrag von Daniele Ganser in Falkensee nicht nur Zugang zu einer für mich neuen und anderen Welt bekommen, ab da hat sich eigentlich auch für mich mein Leben komplett auf den Kopf gestellt. Die Weichen wurden zwar schon vorher gestellt, aber nun war es endgültig und es gab kein zurück mehr. Die Planung für das erste Symposium Falkensee war in meinem Kopf geboren und die MenschheitsFamilie entstand als Ort, der virtuell das vereinen sollte, was Daniele an Spiritualität, Menschlichkeit und Friedenswillen in mir freigesetzt hat. Es war sozusagen eine Energie, die nun stetig floß und einen Trichter gefunden hat, in dem sie wirksam werden und sich entfalten konnte. Insofern haben wir auch etwas gemeinsam - Ulrike und ich. Wir sind zu der Zeit auf einen Zug aufgesprungen, der unser Leben veränderte - der uns zwang, alte Wege zu verlassen und neue Wege zu beschreiten. Sowohl beruflich, als auch privat. Und auch das canceln und entfernt werden ist eine Erfahrung, die wir beide teilen. Vielleicht war es deswegen mein erster Gedanke im Herbst 2022, Ulrike Guérot zu meinem 1. Symposium nach Falkensee einzuladen. Das es dann erst beim 2. Anlauf wirklich geklappt hat, hatte auch mit den Höhen und Tiefen des Lebens in dieser Zeit zu tun gehabt.
Nun ist sie zum 2. Mal dabei - denn wer könnte das Thema "Europa" bei einem so wichtigen und hochaktuellen Thema besser vertreten und beleuchten als Ulrike Guérot? Es geht um Geschichte, es geht um Nationalitäten, es geht um Gemeinsamkeiten und um das, was uns hier im Herzen zusammenhält, was unsere Ziele und unsere Befindlichkeiten sind, es geht um Verantwortung und es geht vor allen Dingen um Frieden! Denn dafür steht Europa - für einen Kontinent, der es geschafft hat, trotz aller Gegensätze und Konflikte, die in Jahrhunderten kriegerisch aufgetragen wurden, eine neuen und besonderen Frieden zu finden und zu installieren:
"Völkerrechtlich legt der Westfälische Frieden den oder zumindest einen Grundstein für ein modernes Prinzip: Die Gleichberechtigung souveräner Staaten, unabhängig von ihrer Macht und Größe. Noch heute spricht die Politikwissenschaft, insbesondere die realistische Schule (Henry Kissinger), deshalb vom „Westphalian System“. Durch die Garantien der großen europäischen Mächte erweist sich dieser Frieden als stabilisierendes Element für die weitere Entwicklung in Europa. Noch bis zum Ende des 18. Jahrhunderts wird er immer wieder als Referenz für nachfolgende Friedensschlüsse herangezogen."
Es ging damals um viel und es geht heute um das Überleben auf einem Kontinent, der es eigentlich besser wissen sollte. Wir dürfen gespannt sein, was wir in diesem Vortrag von Ulrike auf dem Symposium Falkensee am 27. April 2025 für Lösungen finden, um wieder zu einer Ordnung und zu einem System der friedlichen Koexistenz zurückfinden zu können, ohne schwarz und weiß und mit all den Facetten, die das Leben uns so bietet:
"Es ging nicht mehr um das Ausfechten religiöser Wahrheiten, sondern um geregelte Verfahren, die es möglich machten, mit konkurrierenden religiösen Wahrheiten, die nach wie vor nebeneinander und unversöhnlich bestanden, auf friedliche Weise umzugehen. Deutlich wurde das nicht zuletzt, als der Papst in einer offiziellen Note scharf gegen den Friedensschluss protestierte, weil er die Rechte der katholischen Seite leichtfertig aufgegeben sah. Die katholischen Beteiligten des Abkommens hielt dies nicht von der Unterzeichnung ab - ein religiöser Schiedsrichter wurde in Sachen Krieg und Frieden nicht mehr akzeptiert."
-
 @ 7bdef7be:784a5805
2025-04-02 12:37:35
@ 7bdef7be:784a5805
2025-04-02 12:37:35The following script try, using nak, to find out the last ten people who have followed a
target_pubkey, sorted by the most recent. It's possibile to shortensearch_timerangeto speed up the search.```
!/usr/bin/env fish
Target pubkey we're looking for in the tags
set target_pubkey "6e468422dfb74a5738702a8823b9b28168abab8655faacb6853cd0ee15deee93"
set current_time (date +%s) set search_timerange (math $current_time - 600) # 24 hours = 86400 seconds
set pubkeys (nak req --kind 3 -s $search_timerange wss://relay.damus.io/ wss://nos.lol/ 2>/dev/null | \ jq -r --arg target "$target_pubkey" ' select(. != null and type == "object" and has("tags")) | select(.tags[] | select(.[0] == "p" and .[1] == $target)) | .pubkey ' | sort -u)
if test -z "$pubkeys" exit 1 end
set all_events "" set extended_search_timerange (math $current_time - 31536000) # One year
for pubkey in $pubkeys echo "Checking $pubkey" set events (nak req --author $pubkey -l 5 -k 3 -s $extended_search_timerange wss://relay.damus.io wss://nos.lol 2>/dev/null | \ jq -c --arg target "$target_pubkey" ' select(. != null and type == "object" and has("tags")) | select(.tags[][] == $target) ' 2>/dev/null)
set count (echo "$events" | jq -s 'length') if test "$count" -eq 1 set all_events $all_events $events endend
if test -n "$all_events" echo -e "Last people following $target_pubkey:" echo -e ""
set sorted_events (printf "%s\n" $all_events | jq -r -s ' unique_by(.id) | sort_by(-.created_at) | .[] | @json ') for event in $sorted_events set npub (echo $event | jq -r '.pubkey' | nak encode npub) set created_at (echo $event | jq -r '.created_at') if test (uname) = "Darwin" set follow_date (date -r "$created_at" "+%Y-%m-%d %H:%M") else set follow_date (date -d @"$created_at" "+%Y-%m-%d %H:%M") end echo "$follow_date - $npub" endend ```
-
 @ e1147cac:bbcd354e
2025-04-12 19:17:03
@ e1147cac:bbcd354e
2025-04-12 19:17:03My everyday activity
r
petrinet ;startDay () -> working ;stopDay working -> () ;startPause working -> paused ;endPause paused -> working ;goSmoke working -> smoking ;endSmoke smoking -> working ;startEating working -> eating ;stopEating eating -> working ;startCall working -> onCall ;endCall onCall -> working ;startMeeting working -> inMeetinga ;endMeeting inMeeting -> working ;logTask working -> working -
 @ a296b972:e5a7a2e8
2025-04-12 19:12:54
@ a296b972:e5a7a2e8
2025-04-12 19:12:54So sehr der Gedanke auch verlockend ist, es ist leider nicht möglich, den Staat durch Steuerzahlungsverweigerung auszuhungern, obwohl die absurde, generationenübergreifende Sonderverschuldung geradezu danach schreit. Das hysterische Herbeireden einer Bedrohung durch Russland wird durch die Steuerzahler zwangsfinanziert. Die zu melkende Kuh kann nicht aus ihrem Stall ausbrechen. Nach wie vor gibt es Menschen, die ihre Steuererklärung fristgerecht abgeben möchten, die sich daraus ergebende Steuerschuld jedoch auf einem Notar-Anderkonto so lange parken wollen, bis die Vertreter der deutschen Kakistokratie mit totalitären, faschistischen, kommunistischen, bolschewistischen und sozialistischen Strömungen, zu lebenslangem Sozialdienst in Senioren-Residenzen (oder lieber nicht) verdonnert wurden oder sich ihre Spuren in selbstloser Aufopferung für Unseredemokratie in der Ukraine verloren haben.
Sobald eine Regierung, die zuerst zu beweisen hätte, dass sie bei Verstand ist und ihr Ohr wieder am Willen des Volkes hat, würden diese eingefrorenen Gelder des Souveräns von demselben für mit ihm abgestimmte Projekte zugunsten des Gemeinwohls freigegeben werden. Ein Mitspracherecht der Bevölkerung ist dringend notwendig und laut Grundgesetz auch möglich! Denunzierungsportale und staatlich geförderte NGOs gehörten sicher nicht dazu.
Auch, wenn mit allen Mitteln versucht wird, der demokratischen Grundordnung durch verhaltensauffällig-denkeingeschränkte Ideologinnen und Ideologen den größtmöglichen Schaden, den selbige als solchen nicht erkennen wollen, zuzufügen, gibt es dennoch Möglichkeiten des Widerstands.
Derzeit könnte hilfreich sein:
So viele wie möglich distanzieren sich so weit wie möglich von allen staatlichen Institutionen und bedienen das vom Alt-Parteien-Kartell missbrauchte System nur noch im geringst möglichen Maß.
Es sollte jede Möglichkeit genutzt werden, mit legalen Mitteln Sand ins Getriebe zu streuen.
Es ist die demokratische Pflicht des Souveräns, NEIN zu sagen, wo immer er denkt, dass Freiheit und Demokratie in Gefahr sind. Wer mit offenen Augen durch das Land geht, findet Gründe genug. Zu bestimmen, was Lüge ist, ist nicht Aufgabe der Politik. Dieses Vorgehen gleicht betreutem Denken innerhalb eines vorbestimmten Korridors für ein entmündigtes Volk. Antrieb ist das unbedingte Festhalten an der Macht, die in weiten Teilen längst keinen Rückhalt mehr in der Bevölkerung und sogar innerhalb der Parteien selbst hat.
Zur Erinnerung: Die Meinungsfreiheit schließt auch Lügen ein. Die hier oft aus der Schublade geholte „Nazi-Keule“ dient vor allem der Rechtfertigung der politischen Vorgaben und missbraucht so die Achtung vor den Gräueltaten in der vorläufig dunkelsten Zeit der deutschen Geschichte. Es gibt Anzeichen dafür, sich in Sachen Machtmissbrauch dieser so weit wie möglich anzunähern.
Es ist die demokratische Pflicht zu sagen „ICH MACHE DA NICHT MIT“, wenn politische Entscheidungen getroffen werden, die sich einer friedlichen Einigung und in Konflikten, diplomatischen Verhandlungen, entgegenstellen.
Es ist ein Friedensgebot aller Mütter und Väter, klar und deutlich anzusagen:
„NEIN, MEINE SÖHNE UND TÖCHTER GEB ICH NICHT HER!“
Die Gehirnwäsche und Propaganda-Beschallung durch die Medienkartelle in Funk, Fernsehen und Presse sind zu meiden, wie eine hochansteckende Hauterkrankung bei gleichzeitiger Vergiftung der inneren Organe.
Zahlungen sollten, wo immer es möglich ist, in bar erfolgen. Dies sollte so als Notwendigkeit verinnerlicht werden, wie das Ein- und Ausatmen.
Ein Aufruf zu öffentlichen Protestbekundungen hat derzeit wenig Sinn, da es die deutsche Mentalität nicht hergibt, das Bedürfnis zu spüren, in Massen auf die Straße zu gehen. In anderen europäischen Staaten sieht das anders aus. Besonders beeindruckend jüngst die Friedensaufrufe in Rom mit Menschenmengen, von denen man in Deutschland nur träumen kann.
Die Realität zeigt, dass für eine Veränderung die breite Masse in Deutschland momentan nicht zu gewinnen ist. Zu tief steckt der Deutsche Michel mit seiner German Angst in den Seelen. Daher ist es zunächst die Aufgabe der kritischen, wachen und Dummschwätz-immunen Menschen, einen „Wandel zur Vernunft und eine Abkehr vom Wahnsinn“ herbeizuführen.
Es ist die Zeit gekommen, dass so viele wie möglich, dem Regime, die wohlverdiente, größtmögliche Verachtung, für die Aushöhlung der Demokratie, die massive Einschränkung der Rede- und Meinungsfreiheit, die zu oft systemkonforme Rechtsprechung, die Ausweitung der Spaltung und das Vergessen-machen-wollen der deutschen Geschichte, entgegenbringen.
Was Deutschland fehlt, ist Einigkeit und Recht und Freiheit.
Sollte es, derzeit noch wider Erwarten, dennoch dazu kommen, dass der bereits vorhandene friedliche Widerstand eine wachsende Kraft erzeugen könnte, die Weitere dazu veranlasst, sich ihrer Kraft als der Souverän dieses einst ertragbar-demokratischen Staates wieder bewusst zu werden, wäre ein Generalstreik zu organisieren, um die Macht wieder dahin zu befördern, wo sie hingehört: Nämlich zu den Bürgerinnen und Bürgern eines Landes, das weitgehend vergessen hat, dass seine Ahnen die Demokratie mit ihrem Blut erkämpft haben und dass die Demokratie kein Dauergeschenk ist, für das man sich nie wieder einzusetzen hat. Die derzeitigen Machthaber haben ihren Auftrag zum Wohle des deutschen Volkes tätig zu sein offensichtlich vergessen. Man muss sie dringend wieder daran erinnern, wofür sie gewählt wurden: Die Interessen des Volkes umzusetzen und nicht ihre Vorstellungen davon. In ihrer Überheblichkeit glauben sie zu wissen, was gut für das Volk ist. Leider wissen sie es nicht!
Eine Einordnung als „Hass und Hetze“ durch das deutsch-orwellsche Wahrheitsministerium verbietet sich, da dies die perfiden Maßnahmen im Dritten Reich zu Unrecht relativieren würden.
Die Menschlichkeit gebietet, den verirrten Geistern in Entscheiderpositionen Mitgefühl entgegenzubringen, da sie in gutem Glauben und der Überzeugung sind, nur Gutes zum Wohle des deutschen Volkes, schadenabwendend zu vollbringen. Grund ist die Ideologie, von der sie gar nicht merken (oder es nicht merken wollen), dass sie in ihr gefangen sind.
Nachgeschlagen in einem deutschen Herkunftswörterbuch von 2001 kommt das Wort „Delegitimation“ noch gar nicht vor. Diese Neuschöpfung scheint, durch die politische Kaste entstanden, der Notwendigkeit geschuldet zu sein, kritische Stimmen mundtot machen zu wollen. Sie dient einzig und allein als Totschlagargument. Jeder, der seine demokratische Pflicht wahrnimmt, politische Entscheidungen zu hinterfragen und Kritik auszusprechen, trägt zur lebendigen Debattenkultur bei und hält damit die in einer Demokratie innewohnende Meinungsfreiheit hoch. Kritik, und sei sie noch so scharf, als Delegitimation zu bezeichnen, spricht eher von einer charakterlichen Fehlbildung und Ungeeignetheit für ein politisches Amt in einer Demokratie, als dass sie Respekt vor der Meinungsäußerung des Souveräns zeigt. Gleichzeitig entlarvt die Erfindung des Begriffes Delegitimation, anstelle von Zensur (das wäre zu offensichtlich), durch ihrer Realitätsferne, die fehlende politische Wirkungskraft, so dass man nicht mehr anders weiter weiß, als sich von der Demokratie entfernend, totalitär anmutender Mittel bedienen zu müssen.
Mit den Mitteln der Freiheit sind die Menschen in der Lage, diese armen Politiker-Seelen von ihrem Leiden zu befreien. Ein Besinnen auf die christliche Kultur des Abendlandes kann hier sehr hilfreich sein. Ein Erinnern an die europäische Kultur und Geschichte ebenso.
Dass viele Menschen die legitimen Mittel der Freiheit derzeit nicht nutzen, liegt vielleicht daran, dass das, was ihnen bisher als Freiheit verkauft wurde, aus menschlicher Sicht gar keine Freiheit ist. Die Auswahl in einem 5 Meter langen Yoghurt-Regal ist keine Freiheit! Vielleicht haben viele Menschen sogar Angst vor wirklicher, innerer Freiheit, weil da eine große innere Leere ist, die mit eigener Persönlichkeit durch individuelle, charakterliche Eigenschaften auszufüllen wäre. Man kann diesen Menschen noch nicht einmal einen Vorwurf daraus machen, weil das Bildungssystem gar kein Interesse daran hat, zu viele Menschen heranzubilden, die die Demokratie-Simulation durchschauen.
Es scheint, als würde man mit allen Mitteln versuchen, den jahrhundertealten geschichtlichen Faden Deutschlands und Europas durchschneiden zu wollen und den dunklen Teil der deutschen Geschichte ausklammernd dazu zu missbrauchen, den fortgeschrittenen Wahnsinn zu legitimieren.
Dieser Beitrag wurde mit dem Pareto-Client geschrieben.
-
 @ c8d8587e:3d5cb2ba
2025-04-12 19:06:13
@ c8d8587e:3d5cb2ba
2025-04-12 19:06:13My everyday activity25555555
This template is just for demo needs.
petrinet ;startDay () -> working ;stopDay working -> () ;startPause working -> paused ;endPause paused -> working ;goSmoke working -> smoking ;endSmoke smoking -> working ;startEating working -> eating ;stopEating eating -> working ;startCall working -> onCall ;endCall onCall -> working ;startMeeting working -> inMeetinga ;endMeeting inMeeting -> working ;logTask working -> working -
 @ becd9821:e4cd2082
2025-04-12 18:49:02
@ becd9821:e4cd2082
2025-04-12 18:49:02My everyday activity1111111
This template is just for demo needs.
petrinet ;startDay () -> working ;stopDay working -> () ;startPause working -> paused ;endPause paused -> working ;goSmoke working -> smoking ;endSmoke smoking -> working ;startEating working -> eating ;stopEating eating -> working ;startCall working -> onCall ;endCall onCall -> working ;startMeeting working -> inMeetinga ;endMeeting inMeeting -> working ;logTask working -> working -
 @ fbf0e434:e1be6a39
2025-04-12 18:04:10
@ fbf0e434:e1be6a39
2025-04-12 18:04:10Hackathon 概要
Hack The Grid — Level 2 是 LUKSO 推出的四级创作者项目的第二阶段,重点在于开发mini去中心化应用程序(dApps)。本阶段共有 70 名注册开发者参与,最终审批了 41 个 BUIDL 项目。该阶段鼓励参与者在 AI 代理、社交 DeFi、创作者货币化及游戏化等领域创新,致力于将 Universal Profiles 打造成集数字身份、社交互动与创造力于一体的多功能空间。
活动于 2025 年 2 月至 4 月开展,总资金池达 150,000 LYX,分配至各个级别。参与者可在多个阶段远程参与,1 至 3 级的成功项目将在第 4 级的社区资助轮中获得额外支持。
黑客松日程包含办公时间与学习会议,通过前期获奖者的见解为参赛者提供帮助。除技术实验外,活动还营造了协作开发环境,展现了去中心化应用程序创建的潜力,培育了生态系统中的创新。Hack The Grid 凸显了开发者社区的积极参与以及值得关注的项目贡献。
Hackathon 获奖者
ORIGIN GRANTS 奖项获奖作品
在第2级类别中,两个项目因其技术创新和对生态系统目标的对齐获得了Origin Grants的认可。
- Hiraeth Mini App: 此应用程序将区块链交易转变为基于NFT的数字文物,通过独特的表现形式捕捉各链上的历史叙事。
- Multisend - Defolio: MultiSend 提供了一种简化的方法,用于在单个交易中在 LUKSO 区块链上执行多个代币和NFT的转移,提高了资产管理的效率。
这些获奖项目以其对智能合约安全性、用户友好的界面、技术执行以及对 LUKSO 社区的价值增值而闻名。每位Origin Grant获奖者将获得价值$2,250的LYX,其中70%会提前发放,剩余金额取决于实现以采用为重点的KPI。获奖者还有机会进军第4级——社区资助轮,通过二次方融资获得额外的$24,000 LYX。
完整项目列表,请访问 DoraHacks。
关于组织者
LUKSO
LUKSO 是一家专注于区块链解决方案的技术导向型组织,专注于数字生活方式和创意经济。它因其在区块链基础设施领域的贡献而获得认可,并在开发增强用户中心身份和数字所有权的应用程序中扮演重要角色。该组织在创建Universal Profiles方面起了重要作用,促进了数字平台之间的无缝交互。目前,LUKSO 旨在扩大区块链在日常数字体验中的角色,优先考虑安全性和可访问性,以此为技术领域内多样化的用户群体服务。
-
 @ fbf0e434:e1be6a39
2025-04-12 18:02:06
@ fbf0e434:e1be6a39
2025-04-12 18:02:06Hackathon 概述
Innovate on Creator Network #Creathon 圆满落幕,116 位注册开发者中有 44 个项目获批。此次黑客松的主要目标是借助去中心化应用程序(dApps),在去中心化金融(DeFi)、非同质化代币(NFTs)、游戏及社会影响等领域,强化 Creator Network 生态系统。活动于 2025 年 1 月 19 日至 2 月 24 日期间举办,设置了 1,250 USDT 的奖金池,将颁发给十名获奖者,其中前三名的奖金在 200 美元至 300 美元之间。
在此次黑客松中展示的项目,通过创新性和功能性,展现了对 Creator Network 生态系统的潜在影响。这些项目如今有机会进一步融入平台并获得支持。活动极大地吸引了开发者参与,参与者们利用了 Creator Network 的开发工具和测试网。这一举措标志着,在通过创新技术方案拓展 Creator Network 能力及强化其生态系统方面,迈出了重要一步。
Hackathon 获奖者
Creator Network 奖项获奖者
- DeFi Connect Credit: 在Creator Testnet Network上运作的去中心化交易所,通过提供代币交换、锁定、深度流动性和投票机制来增强去中心化和流动性管理,提高DeFi解决方案。
- Lumoswap: 基于Creatorchain的去中心化交易所,提供快速、安全且用户友好的交易体验。它解决了DeFi生态系统中交易速度和安全性等关键问题。
- Sendtokens: 一个具备自我保管功能的加密货币钱包,通过简化交易和提高用户体验,解决了与冗长钱包地址和界面可用性相关的常见挑战。
- Tokens: 该平台简化了加密货币代币的创建,提供在去中心化环境中高效管理和部署的工具,确保即时可见性和实用性。
- ProtectedPay: 一个多链DeFi平台,促进安全交易和群组支付。它整合了储蓄功能,以在区块链网络中增强安全性和便利性。
- AuditFi_Creator: 利用AI技术为智能合约提供即时链上审计报告,从而加强Creator Network生态系统中的信任和安全性。
关于所有项目的详细信息,请访问 Hackathon 详情页 。
组织者信息
Creator Network
Creator Network 是一家以技术为核心的组织,专注于区块链解决方案。它因开发增强区块链互操作性和安全性的去中心化平台而闻名。该组织已经推出了多个项目,旨在改善数字资产管理和智能合约功能。Creator Network 致力于扩展区块链的可访问性,促进数字生态系统的透明度。
-
 @ f5369849:f34119a0
2025-04-12 17:54:45
@ f5369849:f34119a0
2025-04-12 17:54:45Hackathon Overview
The Innovate on Creator Network #Creathon concluded successfully with 44 projects approved out of 116 registered developers. The primary focus of this hackathon was to enhance the Creator Network ecosystem through decentralized applications (dApps) in areas such as decentralized finance (DeFi), non-fungible tokens (NFTs), gaming, and social impact. Held from January 19 to February 24, 2025, the event featured a $1,250 USDT prize pool, awarded to ten winners, with the top three prizes ranging from $200 to $300.
Projects showcased during the hackathon highlighted their potential impact on the Creator Network ecosystem through innovation and functionality. These projects now have opportunities for further integration and support within the platform.
The event significantly engaged developers, with participants utilizing Creator Network’s development tools and testnet. This initiative represents a step forward in expanding the Creator Network's capabilities and enhancing its ecosystem through innovative technical solutions.
Hackathon Winners
Creator Network Prize Winners
- DeFi Connect Credit: A decentralized exchange operating on the Creator Testnet Network, which enhances DeFi solutions by offering features like token swapping, locking, deep liquidity, and a voting mechanism to improve decentralization and liquidity management.
- Lumoswap: A decentralized exchange on Creatorchain, providing a fast, secure, and user-friendly trading experience. It addresses critical issues such as transaction speed and security within the DeFi ecosystem.
- Sendtokens: A self-custody cryptocurrency wallet that enhances transaction simplicity and user experience, tackling common challenges related to lengthy wallet addresses and interface usability.
- Tokens: This platform simplifies cryptocurrency token creation, providing tools for efficient management and deployment within a decentralized environment, ensuring immediate visibility and utility.
- ProtectedPay: A multi-chain DeFi platform facilitating secure transactions and group payments. It incorporates savings features to enhance security and convenience across blockchain networks.
- AuditFi_Creator: Utilizes AI technology to deliver instant on-chain audit reports for smart contracts, thereby strengthening trust and security within the Creator Network ecosystem.
For additional details on all projects, visit Hackathon Projects.
Organizer Information
Creator Network
Creator Network is a technology-centric organization specializing in blockchain solutions. It is recognized for developing decentralized platforms that enhance blockchain interoperability and security. The organization has launched numerous projects aimed at improving digital asset management and smart contract functionality.
-
 @ f5369849:f34119a0
2025-04-12 17:54:36
@ f5369849:f34119a0
2025-04-12 17:54:36Hackathon Summary
Hack The Grid — Level 2 is the second phase of a four-level builder program launched by LUKSO, focusing on the development of mini decentralized applications (dApps). This phase saw participation from 70 registered hackers, resulting in the approval of 41 BUIDLs. It encouraged participants to innovate in areas such as AI agents, social DeFi, creator monetization, and gamification. The hackathon aims to evolve Universal Profiles into versatile spaces that integrate digital identity, social engagement, and creativity.
The event spanned from February to April 2025, offering a total funding pool of $150,000 in LYX, distributed across the various levels. Participants could engage remotely at multiple stages, with successful projects from Levels 1 to 3 becoming eligible for additional support in Level 4's Community Grants Round.
The hackathon schedule featured office hours and learning sessions with insights from previous winners to aid participants. Beyond technological experimentation, the event fostered a collaborative development environment, demonstrating the potential for decentralized application creation and fostering innovation within the ecosystem. Hack The Grid highlighted significant participation and noteworthy project contributions from the developer community.
Hackathon Winners
ORIGIN GRANTS Prize Winners
Two projects in the Level 2 category were awarded Origin Grants, recognizing their technical innovation and alignment with the ecosystem's objectives.
Hiraeth Mini App: This application transforms blockchain transactions into NFT-based digital artifacts, capturing historical narratives across various chains through distinctive representations.
Multisend - Defolio: MultiSend offers a streamlined method for executing multiple token and NFT transfers on the LUKSO blockchain within a single transaction, improving efficiency in asset management.
The winning projects are noted for their focus on smart contract security, user-friendly interface, technical execution, and value addition to the LUKSO community. Each Origin Grant winner receives $2,250 in LYX, with 70% disbursed upfront and the remainder dependent on achieving adoption-focused KPIs. Winners also have the opportunity to progress to Level 4—the Community Grants Round—where an additional $24,000 in LYX is available through quadratic funding.
For a full list of projects, visit DoraHacks.
About the Organizer
LUKSO
LUKSO is a technology-oriented organization specializing in blockchain solutions with a focus on digital lifestyle and creative economies. It plays a significant role in developing applications that enhance user-centric identity and digital ownership. The organization was instrumental in creating Universal Profiles, facilitating seamless interactions across digital platforms. Currently, LUKSO aims to expand the blockchain's role in everyday digital experiences, prioritizing security and accessibility for a diverse user base within the technology landscape.
-
 @ f57bac88:6045161e
2025-04-12 17:52:45
@ f57bac88:6045161e
2025-04-12 17:52:45پازل فناوری: ساختاری بیپایان
اینترنت و فناوری مثل موجوداتی زندهاند؛ همواره در حال رشد، تغییر و دگرگونی. برای سادهسازی، فرض میکنیم این پازل از سه بخش اصلی تشکیل شده:\ تکههای فعال (آنچه اکنون در دسترس ماست)،\ تکههای در حال توسعه (آنچه در راه است)، و\ تکههای خالی (آنچه جایش حس میشود).\ در ادامه، هر تکه را با جزئیات بررسی میکنم تا هیچ بخشی از این پازل از قلم نیفتد.
تکههای فعال: ستونهای دنیای دیجیتال امروز
این تکهها پایههای فناوری و اینترنت امروزیاند که بدون آنها، زندگی مدرن قابلتصور نیست. تا بهار ۱۴۰۴، این بخشها به بلوغ رسیدهاند و هر روز در حال استفادهاند:
-
شبکههای نوری پرسرعت: کابلهایی که دادهها را با سرعت بالا منتقل میکنند و اینترنتی پایدار و سریع را به خانهها و شهرها رساندهاند.
-
نسل پنجم ارتباطات سیار: فناوری ارتباطی جدیدی که با سرعت بالا و زمان پاسخدهی بسیار کم، ابزارهای هوشمند را به هم متصل میکند.
-
اینترنت ماهوارهای: پروژههایی که اتصال اینترنت را به دورافتادهترین نقاط کره زمین میبرند.
-
رایانش ابری: خدماتی بر پایهی سرورهای اینترنتی که ذخیرهسازی و پردازش دادهها را آسان کردهاند.
-
شبکههای اجتماعی دیجیتال: فضاهایی که گفتوگو، اشتراکگذاری و ارتباط را به بستر اینترنت آوردهاند.
-
بازرگانی الکترونیکی: فروشگاهها و بازارهایی که خرید و فروش را به شکل آنلاین و جهانی ممکن کردهاند.
-
ابزارهای جستوجوی اینترنتی: موتورهایی که در کسری از ثانیه، اطلاعات سراسر دنیا را در اختیارمان میگذارند.
-
پخش اینترنتی محتوا: سامانههایی که فیلم، موسیقی و ویدیو را به صورت آنلاین و لحظهای ارائه میدهند.
-
برنامههای تلفن همراه: نرمافزارهایی که تجربهی دیجیتال را شخصی، سریع و قابلحمل کردهاند.
-
ابزارهای هوشمند خانگی: وسایلی که با اتصال به اینترنت، خانه را خودکار و هوشمند میکنند.
-
هوش رایانهای: سامانههایی که توانایی درک، تحلیل و تصمیمگیری را به فناوری دادهاند.
-
یادگیری ماشینی: شیوههایی که رایانه از دادهها آموخته و نتایج بهتری ارائه میدهد.
-
تحلیل دادههای عظیم: بررسی حجم زیادی از اطلاعات برای کشف الگوها و تصمیمگیری بهتر.
-
امنیت فضای مجازی: ابزارهایی برای محافظت از دادهها و سیستمها در برابر تهدیدها.
-
زنجیرهی بلوکی: فناوریای برای انجام تراکنشهای امن و شفاف بدون واسطه.
-
پولهای دیجیتال: ارزهایی که مفهوم پول را وارد دنیای رایانهای کردهاند.
-
واقعیت مجازی: فناوریای که با استفاده از نمایشگرهای ویژه، افراد را وارد دنیایی شبیهسازیشده میکند.
-
واقعیت افزوده: افزودن اطلاعات دیجیتال به دنیای واقعی از طریق نمایشگرها یا گوشی همراه.
-
خانههای هوشمند: سامانههایی که با یک لمس، نور و گرمای خانه را مدیریت میکنند.
-
فناوریهای پوشیدنی: ابزارهایی که بر بدن پوشیده میشوند و سلامت و فعالیت ما را پایش میکنند.
این تکهها، ستونهای اصلی پازلاند که هر روز با آنها سر و کار داریم، ولی هنوز جای پیشرفت دارند، از امنیت بهتر تا دسترسی برابرتر.
تکههای در حال توسعه: نوآوریهایی در آستانهی شکوفایی
این بخش، آیندهی نزدیک و دور فناوری را به تصویر میکشد؛ تکههایی که در آزمایشگاهها و پروژههای پژوهشی در حال شکلگیریاند و بهزودی به پازل افزوده میشوند:
-
نسل ششم ارتباطات سیار: ارتباطاتی با سرعتی فراتر از نسل پنجم.
-
رایانش کوانتومی: رایانههایی که بر پایهی قوانین فیزیک کوانتوم، مسائل بسیار پیچیده را در لحظه حل میکنند.
-
پردازش در لبهی شبکه: انتقال بخشی از محاسبات به نزدیکترین نقطه به محل تولید داده برای کاهش تأخیر و مصرف انرژی.
-
وسایل نقلیهی بدون راننده: خودروهایی که با کمک هوش رایانهای و حسگرها، بهتنهایی حرکت میکنند.
-
رابط مغز و ماشین: فناوریای که فعالیتهای مغزی را به رایانهها و دستگاهها متصل میکند.
-
شبکههای هوشمند انرژی: سامانههایی برای مدیریت بهینهی مصرف برق و منابع انرژی.
-
پزشکی دیجیتال پیشرفته: بهرهگیری از فناوری برای تشخیص و درمان بهتر، مانند جراحی رباتیک یا تحلیل دادههای سلامت.
-
مواد واکنشپذیر: موادی که با تغییر شرایط محیطی واکنش نشان میدهند، مانند پارچههایی که ترمیم میشوند.
-
هوش فراگیر رایانهای: هوشی که میتواند همچون انسان در زمینههای مختلف فکر کند و خلاق باشد.
این تکهها نویدبخش آیندهای هیجانانگیزند، اما هنوز نیاز به زمان، سرمایهگذاری و زیرساخت دارند تا کامل شوند.
تکههای خالی: خلأهایی که باید پر شوند
این بخش، جاهایی را نشان میدهد که هنوز کامل ساخته نشدهاند یا نیاز به توجه ویژه دارند. این تکهها، چالشها و فرصتهای آیندهاند:
-
دسترسی برابر به اینترنت برای همه: فراهم کردن اینترنت پرسرعت در همهجا، حتی مناطق دورافتاده.
-
حفاظت کامل از حریم خصوصی: فناوریهایی که جلوی هر نوع سوءاستفاده از اطلاعات شخصی را بگیرند.
-
تأمین انرژی پایدار برای فناوری: بهرهگیری از منابع انرژی پاک برای تأمین نیازهای روزافزون.
-
قوانین جهانی هماهنگ در زمینه فناوری: مقررات مشترکی که هماهنگی جهانی را ممکن کنند.
-
بازیافت کامل تجهیزات دیجیتال: فرآیندهایی برای بازیافت زبالههای الکترونیکی بدون آسیب به محیط زیست.
-
هوش مصنوعی مسئول و منصفانه: سامانههایی که تصمیمهایی بدون تبعیض و ناعادلانه میگیرند.
-
شبکههایی مقاوم در برابر سانسور: ارتباطاتی که دولتها یا نهادها نتوانند آنها را محدود کنند.
-
زیرساختهای مقاوم در برابر بلایا: سامانههایی که حتی در شرایط بحرانی همچنان فعال بمانند.
-
آموزش دیجیتال همگانی: آموزشهایی که برای همه، در هر سطح و سن، قابلدسترس باشد.
-
ارتباط با فضا و سیارات دیگر: فناوریهایی برای برقراری ارتباط بین زمین و نقاط دوردست فضایی.
این تکهها خلأهاییاند که پر شدنشان میتواند کل تصویر را دگرگون کند.
تصویر نهایی: پازلی که هرگز کامل نمیشود؟
پازل فناوری، با سه دستهی فعال، در حال توسعه و خالی، ساختاری پویاست. هر تکهی تازهای که افزوده میشود، ممکن است به تکههای دیگری نیاز پیدا کند. مثلاً فناوری پول دیجیتال، بحثهایی تازه دربارهی قوانین مالی یا امنیت دیجیتالی به دنبال آورده. یا رشد هوش رایانهای، نیاز به بحثهای اخلاقی را مطرح کرده است.
امروز، بخش بزرگی از پازل سر جایش قرار گرفته، اما آینده، پر از ناشناختههاست. از رایانههای کوانتومی گرفته تا خودروهای بدون راننده، از خلأهای دسترسی برابر تا دغدغههای امنیتی، همگی ما را به تفکر، تلاش و انتخابهایی مهم فرا میخوانند.
شما چه فکر میکنید؟\ کدام تکه از این پازل از دید شما مهمتر است؟\ فکر میکنید چه چیزی هنوز از قلم افتاده؟\ نظرات خودتان را بنویسید تا این پازل را با هم کاملتر کنیم.
منابع
-
Simplilearn. 25 New Technology Trends for 2025: An overview of emerging technology trends in 2025.
-
GeeksforGeeks. Top 25 New Technology Trends in 2025: In-depth analysis of developing technologies.
-
Forbes. Top 10 Technology Trends For 2025: Key trend predictions by Forbes experts.
-
NKTelco. Internet Trends to Watch in 2025: A look at the future of internet and connectivity.
-
-
 @ 7d33ba57:1b82db35
2025-04-12 15:14:35
@ 7d33ba57:1b82db35
2025-04-12 15:14:35Pisa, in Tuscany, is world-famous for its iconic Leaning Tower, but this riverside city offers much more than a fun photo op. With Romanesque architecture, student energy (thanks to its prestigious university), and charming piazzas, Pisa makes a great day trip—or a surprisingly rewarding overnight stay.
🌟 Must-See in Pisa
1️⃣ The Leaning Tower of Pisa (Torre Pendente)
- Built in the 12th century and leaning ever since due to soft soil
- Climb the spiral staircase (about 300 steps) for sweeping views of the city
- Best photo time? Early morning or golden hour for softer light
2️⃣ Piazza dei Miracoli (Square of Miracles)
- A UNESCO World Heritage Site and home to:
- The Cathedral (Duomo di Pisa) – Beautiful Romanesque façade
- The Baptistery – The largest in Italy, with amazing acoustics
- The Camposanto Monumentale – A peaceful cemetery with frescoes and ancient tombs
3️⃣ Walk Along the Arno River
- Quiet and atmospheric, especially at sunset
- Great way to escape the crowds around the tower and see the colorful riverside buildings
4️⃣ Explore the Historic Center
- Visit Piazza dei Cavalieri, once the political heart of Pisa
- Check out Scuola Normale Superiore, one of Italy’s most elite universities
- Wander through narrow medieval streets lined with shops and cafés
🍕 What to Eat in Pisa
- Cecina – A savory chickpea pancake, usually eaten as street food
- Torta co’ bischeri – A traditional chocolate and rice tart
- Pisan-style pasta with gamey meats or wild boar ragù
- Pair with local wines from the Colline Pisane

🎯 Quick Tips for Visiting
✅ Pisa is very walkable—comfortable shoes are your best friend
✅ The Leaning Tower is popular—book climb tickets online in advance
✅ It’s an easy day trip from Florence or Lucca by train (about 1 hour)
✅ Stay for the evening to enjoy Pisa’s local vibe once day-trippers leave -
 @ 4898fe02:4ae46cb0
2025-04-12 14:29:49
@ 4898fe02:4ae46cb0
2025-04-12 14:29:49Directory
📖 Day 1 - In the Beginning, an Idea...\ 📖 Day 2 - When Money Dies\ 📖 Day 3 - One Coin to Rule them All\ 📖 Day 4 - Transacting Adversarially pt. 1\ 📖 Day 5 - Transacting Adversarially pt. 2\ 📖 Day 6 - Not your Keys not your Coin\ 📖 Day 7 - The Seventh Day
Foreword
This is more than a curated list of articles.
This is more than a guide.
It is not a how-to or tutorial.
This is the first unschooled course syllabus and it is based entirely on the peer-reviewed work published by Stackers.
In undertaking such work as building a beginners course in bitcoin, one might stop and appreciate the plethora of other Bitcoin courses that live in the blogs of various company sites, such as those you will find on exchanges, wallet providers and the like. These are great, but the spirit of Bitcoin is in its community, so why not learn from the community directly?
Course Intro
What you will find below is a selection of some of the best that has been written by the thriving community on Stacker News. It is being referred to here as a course syllabus for the reason that it is intended to be used as a guide that you can follow as you take your first steps into the rabbit hole. Exploring new spaces online, especially those surrounding Bitcoin, can be intimidating and anxiety inducing, so rest easy and let this syllabus be your guide.
Included are a carefully selected list articles, spread across seven days of learning. Each day also has included the learning outcomes for that day and post-reading reflections.
It is recommended you come ready to learn, with a note-taking implement/software and an open mind. Feel free to share your responses to the questions in the comments. The discussion questions are obviously optional, but have been written with the purpose of prompting further engagement in the materials.
Target Audience
This particular Unschooled course is geared toward the intellectually curious and self-directed (much like later iterations will be).
No prior knowledge of Bitcoin is required as the course has been designed to suit the absolute bitcoin initiate.
Expected outcomes
By the end of the seven-days, learners will have
- developed an awareness of peer to peer electronic cash
- engaged some of the philosophical currents in the Bitcoin community
- analyzed the quesiton: why Bitcoin not crypto?
- reflected on the important concepts in Bitcoin such as wallets, UTXO's, Nodes and Lightning Network
- answered the question: what is KYC and AML?
- seen the relevance of the phrase "not your keys, not your bitcoin"
A Final note by way of Introduction
The course is designed to familiarize you with the technology that you will ultimately use to interact with the Bitcoin network, not to give investment advice. It is recommended that you finish the course before making any financial decisions, as there is important insight to be gained in all seven days.
Lastly, nothing stated herein is intended as financial advice.
Let's begin!
-
 @ fd78c37f:a0ec0833
2025-04-01 11:49:06
@ fd78c37f:a0ec0833
2025-04-01 11:49:06In this edition, we invited Keypleb, the founder of Bitcoin Indonesia, to share how he built the Bitcoin community in Indonesia, overcoming challenges like member turnover and venue selection, while driving the adoption and growth of Bitcoin.
YakiHonne: Welcome, Keypleb. Before we begin, let me briefly introduce YakiHonne. YakiHonne is a decentralized media client built on Nostr—a protocol designed to empower freedom of speech through technology. It enables creators to own their voices and assets while offering innovative tools like smart widgets, verified notes, and support for long-form content. We focus on free speech and free media by user privacy and data to be protected. So before starting the interview, I'd like to hear about yourself and your community.
Keypleb:My name is Keypleb, though it’s a pseudonym—a name I use to respect privacy. I'm a co-founder of Bitcoin Indonesia, Bitcoin House Bali, and Code Orange, a new developer school we launched at a conference just a few days ago. We focus on driving adoption through meetups, hackathons, and technical workshops. I'll dive into more details later, but that's a brief overview. I'm based in Bali now, though I travel a lot and consider myself quite nomadic. Great to be here.
YakiHonne: What sparked your interest in Bitcoin and what motivated you to create a community on Bitcoin?
Keypleb:I first got interested in Bitcoin because it solved a specific problem. At the time, I didn’t know exactly what the solution was, but the problem was that I couldn’t afford a home. Back in 2019, I was living in London, and a two-bedroom apartment was £600,000, which was insanely expensive. First-time buyers like myself simply couldn’t afford it. Why was it so expensive? Why was buying a house so hard? During the COVID lockdown, I had more time on my hands and started listening to Michael Saylor on a Bitcoin podcast, where he talked about how the system is rigged, and that’s why people work hard but still can’t afford a house. That really resonated with me. So I started looking for a community, but unfortunately, there wasn’t one.. Keypleb:After moving to Bali, I attended a lot of crypto meetups, especially scammy altcoin ones, thinking, “There has to be a solution.” But none of them resonated with me. There was no sense of freedom, and no real discussion about inflation resistance. I remembered a podcast from Dea Reskita, an Indonesian host who’s pretty well-known online. I reached out to her and said, “ you’ve got to help me. I’m surrounded by all these shitcoiners, and I can’t take it anymore. I need a real community. Is anything happening?” She replied, “Yes, something is happening. We should restart these meetups next month.” And that’s how it all began. Keypleb:There’s also another story about how we started Bitcoin House and how Bitcoin in Asia came to be, but maybe I’ll save that for later. Anyway, the spark of interest came from Bitcoin solving a real problem, and my drive to keep going came from the lack of quality meetups. Now, we’ve hosted 31 meetups, launched Bitcoin House and Code Orange, and the movement is growing rapidly.

YakiHonne: That’s such an amazing story—going from being on the brink of homelessness to creating something so impactful, and keeping it running every day, bringing new people into the journey. It’s truly inspiring. I’m curious about how the community started. How did you manage to attract members and build a strong community? What challenges did you face along the way?
Keypleb:It all started with our first meetup at the end of 2022, which was two and a half years ago now. At that time, we sent out an email to a group from a previous database, and the first meetup had around 20 people, which was a good start. However, problems quickly arose as people started dropping off, and the community lacked retention. In Bali, people come and go, usually staying for no more than two months, leading to a lack of long-term participation. This became one of our challenges: how to attract more people and, more importantly, get the same people to keep coming back. While I've been coming back for two and a half years, not everyone is able to return as often, and that has been a real challenge. Keypleb:Actually, I should also mention how I met my co-founders—Marius, Diana, and Dimas. We met at the 2023 Indonesia Bitcoin Conference. As time went on, we kept hosting meetups and had a lot of fun each time, though the locations kept changing. One of the initial challenges was that we didn't realize the importance of having a fixed meetup location. We changed venues several times before we realized that having a consistent location is crucial. If anyone wants to run a meetup, it's best to always choose a fixed location. We learned this through trial and error, but now it's no longer an issue. Keypleb:Since the conference, my co-founders and I have been working together, consistently putting in the effort. This is why our community has grown so large—so far, we are hosting 31 monthly meetups, 6 of which are in Bali. This means there is a bitcoin meetup almost every day on a regular basis. We've also established Bitcoin House Bali, a physical space, and the movement is growing rapidly. Without this movement, the region would face many challenges, including inflation and heavy censorship. It all started from just one meetup.
 YakiHonne: It's amazing to see how you met your co-founders and how you’ve built something incredible that continues to grow today. What advice would you give to someone looking to start a successful Bitcoin community right now?
YakiHonne: It's amazing to see how you met your co-founders and how you’ve built something incredible that continues to grow today. What advice would you give to someone looking to start a successful Bitcoin community right now?Keypleb:First, one very important piece of advice is to ensure that every meetup is held at the same location regularly. We realized this challenge through trial and error. To help others who are interested, we’ve published our meetup guide on GitHub, where everyone can check it out. For example, meetups should be held regularly, ideally once a month, or even once a week. In Chiang Mai, the Bitcoin meetup starts every Thursday at 7 PM, and everyone knows the time and location, making it easy to join without having to look up the next meetup. Keypleb:Additionally, our meetup structure is very simple. First, we do a round of introductions where everyone shares their name, where they’re from, and what Bitcoin means to them. This usually takes about 15 minutes. Then, we discuss three main questions: First, why do we need Bitcoin? The discussion typically focuses on two main issues Bitcoin addresses: inflation and censorship;Secondly, how to buy Bitcoin? We usually ask who wants to buy some Bitcoin, and then we do a small purchase together and conduct a P2P trade to demonstrate how easy it is to buy Bitcoin. Lastly, how to store Bitcoin? We introduce self-custody and show how to use hardware wallets (like Trezor), explaining the concept of the 12 words and private keys. Keypleb:The whole meetup usually wraps up in about an hour, after which people can continue socializing at Bitcoin House or wherever the meetup is taking place. In short, keeping the meetup simple and efficient, and ensuring a fixed location for each event, are key factors in building a successful community.
YakiHonne: What's the major approach? Is it more technical, or do you focus on non-technical aspects, or do you cover both?
Keypleb:Our approach includes both technical and non-technical content. Initially, our meetups were completely non-technical, just casual gatherings for people to socialize. Over time, however, we've evolved to incorporate more technical content. Keypleb:Out of the 31 monthly regular meetups we host, most of them have been non-technical, simply regular gatherings held at the same time and place according to our meetup guide. For example, we host the “Bitcoin for Beginners” meetup, which is designed for newcomers and takes place every second Friday of the month at 5 PM at the Bitcoin House Bali. This is entirely non-technical. Additionally, every Wednesday at Bitcoin House, we host the “My First Bitcoin” course. While the course touches on some technical aspects, such as seed phrases and backups, it’s still beginner-friendly and not too technical. The course runs for 10 weeks, and we plan to offer it in the local language at Bali University to help the local community better understand Bitcoin. Keypleb:On the other hand, we also offer highly technical content. We launched a new program called “Code Orange,” which is specifically designed for developers and programmers. We use the “Decoding Bitcoin” website, created by Jamal, which is a learning platform for developers. Many developer schools, like Code Orange, use this resource. Additionally, we host “Code Orange” meetups where we dive into the technical aspects of Bitcoin, such as how mining works and how to prevent single points of failure. Keypleb:We also organize technical workshops, such as “How to Defend Against a Five-Dollar Wrench Attack,” which is closely related to security. Recently, there have been some kidnapping incidents in Bali, and many people are concerned about their Bitcoin being stolen. To address this, we plan to hold a workshop on how to protect Bitcoin against such attacks. Additionally, we host hackathons and other high-tech events, and we just completed a very successful beginner-level hackathon. Keypleb:In summary, our community caters to everyone, from beginners to technical experts. For beginners, we offer easy-to-understand, non-technical content, while for experienced Bitcoiners, we provide in-depth technical material.
 YakiHonne: It's great to approach it in both ways, so everyone gets their own "piece of the cake."Now, I'd like to dive into the technical side. What advice would you give to technically inclined individuals or organizations looking to contribute to the Bitcoin ecosystem? How should they approach the technical aspects of Bitcoin if they want to get involved?
YakiHonne: It's great to approach it in both ways, so everyone gets their own "piece of the cake."Now, I'd like to dive into the technical side. What advice would you give to technically inclined individuals or organizations looking to contribute to the Bitcoin ecosystem? How should they approach the technical aspects of Bitcoin if they want to get involved?Keypleb:I have some additional advice. First, technical individuals can sign up for the “Decoding Bitcoin” course that starts on 18th March 2025 or join our “Code Orange” program and participate in the end-of-year hackathon. If they are technically proficient, this will be a great opportunity. “Decoding Bitcoin” is great for beginners, but it’s also useful for technical individuals. If someone is very skilled, they can start contributing code right away. If they find the course too easy, they can skip it and dive directly into more advanced projects. Additionally, Bitshala and Chaincode Labs offer advanced courses, which more technically advanced individuals can choose to pursue.
 Keypleb:Additionally, it's worth mentioning that the Bitcoin Dev Project has a great platform where technical individuals can find “Good First Issue” or open-source projects to start contributing code. You'll learn about the philosophy behind Bitcoin and why it's more meaningful than other “shitcoins.” Once you’ve taken enough “orange pills” (the philosophy and technology of Bitcoin), you can dive deeper into Bitcoin core development and potentially start coding in C++. If you're interested, you can join specific projects like Nostr, Fedimint or E-Cash.
Keypleb:Additionally, it's worth mentioning that the Bitcoin Dev Project has a great platform where technical individuals can find “Good First Issue” or open-source projects to start contributing code. You'll learn about the philosophy behind Bitcoin and why it's more meaningful than other “shitcoins.” Once you’ve taken enough “orange pills” (the philosophy and technology of Bitcoin), you can dive deeper into Bitcoin core development and potentially start coding in C++. If you're interested, you can join specific projects like Nostr, Fedimint or E-Cash.YakiHonne: I’d like to move on to the next question: How do you see Bitcoin communities evolving as technology progresses, particularly in areas like scalability, privacy, and adaptability to other systems? Keypleb:I believe the Bitcoin community will continue to evolve, and it has already made incredible progress. Two and a half years ago, we started alone in Bali, with just ourselves. We began in the official phase and have had numerous conversations throughout the year. For example, we are now starting a Bitcoin club at a university in Bali; we just need to find a passionate, driven “Bitcoin maximalist,” and the Bitcoin club will begin. Like what our friends did in Banyuwangi, Indonesia, these clubs could eventually evolve into Bitcoin houses.
Keypleb:Regarding privacy and scalability, the community is making strides. We’re big fans of Fedi, which builds on top of the Fedimint protocol and uses e-cash to scale Bitcoin while improving privacy. Fedi low fees and high privacy potential give Bitcoin great opportunities in this area. Keypleb:As for Bitcoin's compatibility with fiat systems, although Bitcoin payments are illegal in some countries like Indonesia, smart developers across Southeast Asia are working on legal solutions. For example, there's a website called Pleb QR that works in Thailand, allowing you to pay in fiat via the Lightning Network. Koral is another app specifically for Indonesia. These kinds of testing products already exist and are physically possible, but we’re just waiting on regulations. My influential friends are actively lobbying the government for adoption. Keypleb:In summary, privacy, scalability, and compatibility with fiat systems are all works in progress, and they will continue to evolve positively. There will be more meetups, more wallet downloads, and more adoption—there’s no doubt about that.
YakiHonne: You mentioned the concept of cross-country issues, so I have one last question: How is the government’s stance on Bitcoin? Is the political climate supportive or against Bitcoin? How do you see the government's approach to Bitcoin in your community or environment?
Keypleb:This reminds me of a person, Jeff Booth, who once said, “We are them, the government is made up of us.” In Indonesia, many politicians actually support Bitcoin, and many of them mine Bitcoin themselves. When money is involved, the incentive is strong, and politicians naturally like to make more money. As a result, Indonesia has a large Bitcoin mining scene. However, overall, the Indonesian government is against Bitcoin, as seen in their ban on Bitcoin payments. The 2011 currency law states that any currency other than the Indonesian Rupiah (IDR) cannot be used, and violators can face up to one year in prison or a fine. This means you cannot pay with US dollars, lira, euros, pesos or pounds. Keypleb:This shows that the government’s legal system is somewhat fragile. It’s understandable that the government is concerned about disruptive technologies like Bitcoin, especially with such a fragile fiat system. Indonesia has also seen many arrests. In 2016, Bank Indonesia issued a letter announcing a crackdown on cryptocurrency payments. Those involved in paying in Bitcoin had their funds seized, and the police cooperated in shutting down businesses accepting Bitcoin payments in the cities. While this isn't very friendly, it does highlight the fragility of the existing system. We also believe that a new executive order may be introduced in the future, similar to when President Roosevelt in 1933 ordered Americans to hand over all their gold with his Executive Order 6102. If it happened before, it could happen again. Keypleb:Therefore, we predict that Bitcoin custody could become a legal issue, which is one of the reasons we blur the faces of participants at every meetup. We need to protect the community from any potential risks. But overall, we remain optimistic. Despite the government ban, the ideology of Bitcoin is unstoppable, and its spread cannot be stopped. So, we are very optimistic about the future.
YakiHonne: I think almost every government around the world, even in Africa, faces similar issues with Bitcoin. Some governments might want Bitcoin but hesitate to openly accept it due to the fear of it undermining the traditional financial system, which, of course, could eventually happen. But hopefully, as the new generation comes into power, we'll see more Bitcoin-friendly governments. So, thank you so much for sharing your insights and advice. I really appreciate your time and the valuable input you've provided.
Keypleb:I'm really glad this conversation enlightened me. I enjoyed it a lot, and it made me reflect on how much work we're doing and how valuable it is. There are a lot of problems out there, with censorship being the biggest one, followed by inflation, which is also a major issue depending on the region. But Bitcoin is open, the community is growing, and people are fighting against censorship and internet shutdowns in places like Indonesia and beyond. The movement is definitely growing. So, I'm very happy to be here and have this chat. Thanks again.
Bitcoin Indonesia nostr: nostr:npub1y4qd2zhtn05gnsaaq5xfejzfk4a32638tx6gpp9g8k6e42g9d66qaxhcr3
Keypleb nostr: nostr:npub190trvg63e6tyqlwlj6lccqpftx76lckj25c006vwx3dzvdl88yxs2nyqdx
-
 @ 73dc15e0:b7a84244
2025-04-12 14:24:06
@ 73dc15e0:b7a84244
2025-04-12 14:24:06プロローグ
童貞こと薄(すすき) 仙人(せんにん)29歳。ここに眠る。「RIP」。29年間ずっと不運だった。親が仙人なんて名前を付けるから。学校では薄い仙人で「はげ仙人」なんてよばれるし、会社は倒産し、家は燃え、さっきトラックで引かれたところだ。そして、今「自称邪心」に次の魔王になってほしいと頼まれている。
―「なんで俺がそんなことしなきゃいけないのだ。」
「君には普通の人間よりも欲が何倍も大きい。ほんとは君の世界では収まらないぐらいだよ。」
―「異世界に行くのはいいとして、なんで魔王なんだ?」
「一つは、さっきも言った通り、君の欲は大きい。二つ目はもうすぐ現魔王がいなくなるからだよ。」
―「勇者にでも殺されたか?」
「いや、勇者と魔王が結婚した。」
―「は?」意味がわからない。勇者は魔王を倒すものではないのか?
「いなくなるというよりは魔王をやめるという表現のほうが正しかったかな。」
邪神によると勇者と魔王が結婚し、現魔王は魔王をやめるので、勇者と魔王の子供に転生し、次の新たな魔王になってほしいとのことだった。
人族と魔族(エルフ、ドワーフ、悪魔など)がこの世界にはあり、人族は聖神、魔族は
邪神が保護しているそうで、人と魔族は大昔から敵対しているそうだ。
聖神は魔族を忌み嫌っているので、魔族を統べる物がいなくなればいつ人族が襲ってくるかわからない。
人族には個別スキル(怪力、俊足など)には一般スキルと固有スキルがある。
固有スキルは世界に一人しかもっておらず、使用者が死ぬと新しく生まれてきた誰かがその固有スキルを手にする。固有スキルは5000万人に1人ぐらいの割合だそうだ。
一般スキルは固有スキルと違い、スキルがかぶることはよくあるそうだ。
魔族は種族スキルがある。種族スキルとはその種族が全員同じスキルをもっている。
魔族は固有スキルや個別スキルがない代わり人よりも各ステータスが高い。
俺は邪神に恩恵を3つもらった。一つは「超再生」。これは怪我や魔力、体力を瞬時に再生させてくれるチート能力だ。2つ目は「代償」腕や心臓などの代償をつくることによって自分を強化したり、新しく武器を作ることができる。この能力は一つ目の「超再生」と組み合わせることでバグをうみだすことができる。3つ目は「入れ替え」これは、さわったことのある物や人との場所を入れ替えることができる。
この三つの恩恵で異世界を俺は生き抜いてやる。
-
 @ 71550e6c:b64c37a9
2025-03-29 10:55:55
@ 71550e6c:b64c37a9
2025-03-29 10:55:55Just do the same as this video shows.
Here's the video: https://cdn.azzamo.net/7cdcc2718f1e15eb03e323f62e07582b4001da273aa5c21475d680f02b32f0e9.mp4
One caveat: do not trust the draft will be kept here after you close
nak fs. Wait, no, it definitely won't stay here, but I'm not even sure it will stay here if you only navigate away and come back later, FUSE is weird and I didn't test.But at least it should work for copy-pasting. Or writing everything in one go.
-
 @ f1e78daa:124e0e56
2025-04-12 14:13:41
@ f1e78daa:124e0e56
2025-04-12 14:13:41今日はテストです。
-
 @ f1e78daa:124e0e56
2025-04-12 14:02:20
@ f1e78daa:124e0e56
2025-04-12 14:02:20プロローグ
童貞こと薄(すすき) 仙人(せんにん)29歳。ここに眠る。「RIP」。29年間ずっと不運だった。親が仙人なんて名前を付けるから。学校では薄い仙人で「はげ仙人」なんてよばれるし、会社は倒産し、家は燃え、さっきトラックで引かれたところだ。そして、今「自称邪心」に次の魔王になってほしいと頼まれている。
―「なんで俺がそんなことしなきゃいけないのだ。」
「君には普通の人間よりも欲が何倍も大きい。ほんとは君の世界では収まらないぐらいだよ。」
―「異世界に行くのはいいとして、なんで魔王なんだ?」
「一つは、さっきも言った通り、君の欲は大きい。二つ目はもうすぐ現魔王がいなくなるからだよ。」
―「勇者にでも殺されたか?」
「いや、勇者と魔王が結婚した。」
―「は?」意味がわからない。勇者は魔王を倒すものではないのか?
「いなくなるというよりは魔王をやめるという表現のほうが正しかったかな。」
邪神によると勇者と魔王が結婚し、現魔王は魔王をやめるので、勇者と魔王の子供に転生し、次の新たな魔王になってほしいとのことだった。
人族と魔族(エルフ、ドワーフ、悪魔など)がこの世界にはあり、人族は聖神、魔族は
邪神が保護しているそうで、人と魔族は大昔から敵対しているそうだ。
聖神は魔族を忌み嫌っているので、魔族を統べる物がいなくなればいつ人族が襲ってくるかわからない。
人族には個別スキル(怪力、俊足など)には一般スキルと固有スキルがある。
固有スキルは世界に一人しかもっておらず、使用者が死ぬと新しく生まれてきた誰かがその固有スキルを手にする。固有スキルは5000万人に1人ぐらいの割合だそうだ。
一般スキルは固有スキルと違い、スキルがかぶることはよくあるそうだ。
魔族は種族スキルがある。種族スキルとはその種族が全員同じスキルをもっている。
魔族は固有スキルや個別スキルがない代わり人よりも各ステータスが高い。
俺は邪神に恩恵を3つもらった。一つは「超再生」。これは怪我や魔力、体力を瞬時に再生させてくれるチート能力だ。2つ目は「代償」腕や心臓などの代償をつくることによって自分を強化したり、新しく武器を作ることができる。この能力は一つ目の「超再生」と組み合わせることでバグをうみだすことができる。3つ目は「入れ替え」これは、さわったことのある物や人との場所を入れ替えることができる。
この三つの恩恵で異世界を俺は生き抜いてやる。
-
 @ a60e79e0:1e0e6813
2025-03-28 08:47:35
@ a60e79e0:1e0e6813
2025-03-28 08:47:35This is a long form note of a post that lives on my Nostr educational website Hello Nostr.
When most people stumble across Nostr, they see is as a 'decentralized social media alternative' — something akin to Twitter (X), but free from corporate control. But the full name, "Notes and Other Stuff Transmitted by Relays", gives a clue that there’s more to it than just posting short messages. The 'notes' part is easy to grasp because it forms almost everyone's first touch point with the protocol. But the 'other stuff'? That’s where Nostr really gets exciting. The 'other stuff' is all the creative and experimental things people are building on Nostr, beyond simple text based notes.
Every action on Nostr is an event, a like, a post, a profile update, or even a payment. The 'Kind' is what specifies the purpose of each event. Kinds are the building blocks of how information is categorized and processed on the network, and the most popular become part of higher lever specification guidelines known as Nostr Implementation Possibility - NIP. A NIP is a document that defines how something in Nostr should work, including the rules, standards, or features. NIPs define the type of 'other stuff' that be published and displayed by different styles of client to meet different purposes.
Nostr isn’t locked into a single purpose. It’s a foundation for whatever 'other stuff' you can dream up.
Types of Other Stuff
The 'other stuff' name is intentionally vague. Why? Because the possibilities of what can fall under this category are quite literally limitless. In the short time since Nostr's inception, the number of sub-categories that have been built on top of the Nostr's open protocol is mind bending. Here are a few examples:
- Long-Form Content: Think blog posts or articles. NIP-23.
- Private Messaging: Encrypted chats between users. NIP-04.
- Communities: Group chats or forums like Reddit. NIP-72
- Marketplaces: People listing stuff for sale, payable with zaps. NIP-15
- Zaps: Value transfer over the Lightning Network. NIP57

Popular 'Other Stuff' Clients
Here's a short list of some of the most recent and popular apps and clients that branch outside of the traditional micro-blogging use case and leverage the openness, and interoperability that Nostr can provide.
Blogging (Long Form Content)
- Habla - Web app for Nostr based blogs
- Highlighter - Web app that enables users to highlight, store and share content
Group Chats
- Chachi Chat - Relay-based (NIP-29) group chat client
- 0xchat - Mobile based secure chat
- Flotilla - Web based chat app built for self-hosted communities
- Nostr Nests - Web app for audio chats
- White Noise - Mobile based secure chat
Marketplaces
- Shopstr - Permissionless marketplace for web
- Plebeian Market - Permissionless marketplace for web
- LNBits Market - Permissionless marketplace for your node
- Mostro - Nostr based Bitcoin P2P Marketplace
Photo/Video
Music
- Fountain - Podcast app with Nostr features
- Wavlake - A music app supporting the value-for-value ecosystem
Livestreaming
- Zap.stream - Nostr native live streams
Misc
- Wikifreedia - Nostr based Wikipedia alternative
- Wikistr - Nostr based Wikipedia alternative
- Pollerama - Nostr based polls
- Zap Store - The app store powered by your social graph
The 'other stuff' in Nostr is what makes it special. It’s not just about replacing Twitter or Facebook, it’s about building a decentralized ecosystem where anything from private chats to marketplaces can thrive. The beauty of Nostr is that it’s a flexible foundation. Developers can dream up new ideas and build them into clients, and the relays just keep humming along, passing the data around. It’s still early days, so expect the 'other stuff' to grow wilder and weirder over time!
You can explore the evergrowing 'other stuff' ecosystem at NostrApps.com, Nostr.net and Awesome Nostr.
-
 @ f1e78daa:124e0e56
2025-04-12 14:01:15
@ f1e78daa:124e0e56
2025-04-12 14:01:15プロローグ
童貞こと薄(すすき) 仙人(せんにん)29歳。ここに眠る。「RIP」。29年間ずっと不運だった。親が仙人なんて名前を付けるから。学校では薄い仙人で「はげ仙人」なんてよばれるし、会社は倒産し、家は燃え、さっきトラックで引かれたところだ。そして、今「自称邪心」に次の魔王になってほしいと頼まれている。
―「なんで俺がそんなことしなきゃいけないのだ。」
「君には普通の人間よりも欲が何倍も大きい。ほんとは君の世界では収まらないぐらいだよ。」
―「異世界に行くのはいいとして、なんで魔王なんだ?」
「一つは、さっきも言った通り、君の欲は大きい。二つ目はもうすぐ現魔王がいなくなるからだよ。」
―「勇者にでも殺されたか?」
「いや、勇者と魔王が結婚した。」
―「は?」意味がわからない。勇者は魔王を倒すものではないのか?
「いなくなるというよりは魔王をやめるという表現のほうが正しかったかな。」
邪神によると勇者と魔王が結婚し、現魔王は魔王をやめるので、勇者と魔王の子供に転生し、次の新たな魔王になってほしいとのことだった。
人族と魔族(エルフ、ドワーフ、悪魔など)がこの世界にはあり、人族は聖神、魔族は
邪神が保護しているそうで、人と魔族は大昔から敵対しているそうだ。
聖神は魔族を忌み嫌っているので、魔族を統べる物がいなくなればいつ人族が襲ってくるかわからない。
人族には個別スキル(怪力、俊足など)には一般スキルと固有スキルがある。
固有スキルは世界に一人しかもっておらず、使用者が死ぬと新しく生まれてきた誰かがその固有スキルを手にする。固有スキルは5000万人に1人ぐらいの割合だそうだ。
一般スキルは固有スキルと違い、スキルがかぶることはよくあるそうだ。
魔族は種族スキルがある。種族スキルとはその種族が全員同じスキルをもっている。
魔族は固有スキルや個別スキルがない代わり人よりも各ステータスが高い。
俺は邪神に恩恵を3つもらった。一つは「超再生」。これは怪我や魔力、体力を瞬時に再生させてくれるチート能力だ。2つ目は「代償」腕や心臓などの代償をつくることによって自分を強化したり、新しく武器を作ることができる。この能力は一つ目の「超再生」と組み合わせることでバグをうみだすことができる。3つ目は「入れ替え」これは、さわったことのある物や人との場所を入れ替えることができる。
この三つの恩恵で異世界を俺は生き抜いてやる。
-
 @ 6a6be47b:3e74e3e1
2025-04-12 12:13:13
@ 6a6be47b:3e74e3e1
2025-04-12 12:13:13Hi frens! How's your weekend starting? I'm just finishing a newblog entry 🖋️on my website and I'm going to be selling a few things on my Ko-fi shop 🛍️.
Before I post everything, I wanted to share a special treat with my Nostr family:
🎁 I've created two beautiful postcard-sized (148mm x 210mm or 5.83 in x 8.27 in)artworks inspired by Holy Week. Here they are:
Palm Day
 Resurrection Day
Resurrection Day

✉️ If you'd like one, just DM me with your email address, and I'll send it your way! Zaps are always appreciated and help keep me going. 🙏
❤️ This is big thank you to you my frens Have fun and stay safe
✝️ This is an INSTANT DIGITAL DOWNLOAD, no physical item will be shipped to you.
✝️ The frames and accessories in the listing images are not included.
🚨 DISCLAIMER 🚨
❤️ Copyright Retention: I, the artist, retain full copyright of all original artwork, even after the digital print is purchased.
❤️ Limited License: The digital print provides a limited, non-transferable license for personal use only. It is not intended for commercial use or resale.
❤️ No Reproduction Rights: The purchase of this digital print does not grant any rights to reproduce, distribute, or create derivative works based on the design.
🚨 By proceeding with the purchase of this digital print, you acknowledge and agree to these terms. 🚨
-
 @ fa4be169:e335db0e
2025-04-12 11:51:14
@ fa4be169:e335db0e
2025-04-12 11:51:14sdadknjsdjasdfsdkfdfsdfsd
-
 @ fa4be169:e335db0e
2025-04-12 11:51:13
@ fa4be169:e335db0e
2025-04-12 11:51:13sdadknjsdjasdfsdkfdfsdfsd
-
 @ d5c3d063:4d1159b3
2025-04-12 11:21:59
@ d5c3d063:4d1159b3
2025-04-12 11:21:59เศรษฐศาสตร์ออสเตรียนคืออะไร?
แนวคิดที่รัฐไม่อยากให้คุณเข้าใจ
ของแพงขึ้นทุกปี แต่ไม่มีใครบอกเราว่า...ใครกันแน่ คือคนที่ทำให้มันเกิดขึ้น ?
คุณทำงานหนักขึ้นแต่กลับรู้สึกว่าได้ “น้อยลง” แล้วก็ถูกบอกให้เชื่อว่า “ทั้งหมดนี้เป็นเรื่องของตลาด” ว่าเป็นเพราะพ่อค้าโก่งราคา เป็นเพราะต้นทุนสูง เป็นเพราะคนไม่ขยัน หรือเพราะเงินไม่พอในระบบ จากนั้นรัฐก็เข้ามา พิมพ์เงิน แจกเงิน ออกกฎหมายควบคุมราคา หรือไม่ก็ดันดอกเบี้ยต่ำลงเพื่อให้คนใช้จ่ายมากขึ้น ซึ่งทั้งหมดนี้ดูเหมือนจะช่วยในระยะสั้น แต่มันกลับทำให้ทุกอย่างเละเทะในระยะยาวยิ่งขึ้นอีก แล้วคำถามก็เกิดขึ้นว่า จริง ๆ แล้ว…ปัญหามาจากตลาดจริงหรือ? หรือเราทั้งหมดกำลังติดอยู่ใน “ระบบที่มีใครบางคนกำลังควบคุม” โดยที่เราไม่เคยมีโอกาสตั้งคำถามเลยว่า มันควรถูกควบคุมตั้งแต่แรกไหม
ความจริงที่เก่ากว่าร้อยปี
นี่คือจุดเริ่มต้นของการตั้งคำถามที่นำไปสู่สิ่งที่เรียกว่า “เศรษฐศาสตร์ออสเตรียน” หรือ Austrian Economics แนวคิดที่ดูเหมือนใหม่ในยุคนี้ แต่แท้จริงแล้ว...มันคือความจริงเก่าที่เคยถูกลืม เศรษฐศาสตร์ออสเตรียนเชื่อว่า มนุษย์คือผู้กระทำที่มีเหตุผล ราคาคือผลลัพธ์ของการแลกเปลี่ยนอย่างเสรี และตลาดจะสมดุลได้ด้วยตัวของมันเอง ถ้าไม่มีใครไปบิดเบือนมัน แต่สิ่งที่น่าทึ่งยิ่งกว่านั้นคือ แนวคิดนี้ไม่ได้เพิ่งเกิดขึ้นแค่เมื่อร้อยปีก่อน ไม่ได้เกิดที่เวียนนา หรือห้องวิจัยเศรษฐศาสตร์ใด ๆ แต่มันมีรากเหง้ามาจากการตั้งคำถามของมนุษย์ตั้งแต่สองพันปีก่อนแล้ว
ปรัชญาเสรีภาพจากอดีตที่ถูกลืม
โสเครติสเคยตั้งคำถามกับสิ่งที่รัฐบอกว่า “ถูกต้อง” อย่างเงียบ ๆ ผ่านการเสนอให้เลิกรองเท้าไซส์เดียวที่บังคับใช้ทั้งประเทศ เพราะเขารู้ว่าไม่มีอะไรที่เหมาะกับทุกคนเสมอไป เขาไม่ได้แค่คัดค้านรองเท้า แต่เขากำลังคัดค้าน “ความจริงที่ถูกยัดเยียด” โดยรัฐ ภายใต้ชื่อของ “ความดีส่วนรวม” สิ่งที่โสเครติสทำ ไม่ใช่การจลาจล ไม่ใช่การปฏิเสธทุกอย่าง แต่เป็นการชี้ให้เห็นว่า ความจริงไม่ควรถูกนิยามโดยคนกลุ่มเดียว และความเข้าใจของมนุษย์ ควรเกิดจาก “การตั้งคำถามอย่างมีเหตุผล” ไม่ใช่การยอมรับอย่างเชื่อฟัง นี่คือแก่นกลางของสิ่งที่นักเศรษฐศาสตร์ออสเตรียนเชื่อว่าราคาควรเกิดจากการตัดสินใจเสรีของผู้คนในตลาด ไม่ใช่จากสูตรหรือคำสั่งของเจ้าหน้าที่รัฐที่อ้างว่า “รู้ดีที่สุด” ข้ามมาที่แนวคิดสโตอิก (Stoicism) ซึ่งถือเป็นอีกหนึ่งแนวคิดรากฐานของปรัชญาตะวันตก ลัทธินี้ไม่ได้สอนให้คนยอมจำนนต่อโชคชะตา แต่กลับเชื่อว่า อิสรภาพที่แท้จริงคือการควบคุมตัวเอง ไม่ใช่การรอให้รัฐหรือใครมาชี้ทางชีวิตให้เรา พวกเขาเชื่อใน “ธรรมชาติของมนุษย์” และการรับผิดชอบต่อการเลือกของตัวเอง ไม่ใช่การโยนภาระให้กับนโยบายรัฐ ปรัชญาสโตอิกเห็นว่า ความสงบในชีวิตไม่ใช่สิ่งที่รัฐสามารถแจกจ่ายได้ แต่เป็นผลจากความสามารถในการตัดสินใจภายใต้เหตุผลและการยอมรับว่าโลกนั้นไม่แน่นอน เปรียบเสมือนแนวคิดของเศรษฐศาสตร์ออสเตรียนที่ไม่พยายามควบคุมตลาดให้แน่นอน แต่ยอมรับว่าความไม่แน่นอนคือธรรมชาติของเศรษฐกิจ และมนุษย์จะตัดสินใจได้ดีที่สุดในสภาพแวดล้อมที่ไม่มีใครกดทับ ข้ามฟากมายังตะวันออก แนวคิดของ “เต๋า” (Taoism) ของเหล่าจื่อก็พูดในภาษาที่ต่างกัน แต่ด้วยจิตวิญญาณเดียวกัน เต๋าเชื่อว่าทุกสิ่งมีหนทางธรรมชาติของมัน (เต๋า) และยิ่งเราพยายามควบคุมสิ่งที่เราไม่เข้าใจ โลกก็ยิ่งปั่นป่วน เต๋าเรียกภาวะสมดุลว่า “อู๋เว่ย” หรือ “การไม่ฝืน” เมื่อปล่อยให้สิ่งต่าง ๆ เป็นไปตามหนทางของมัน มันจะคืนสมดุลของตัวเองโดยไม่ต้องมีใครไปควบคุม แนวคิดนี้สะท้อนกับสิ่งที่นักเศรษฐศาสตร์ออสเตรียนชี้ไว้ว่า ตลาดไม่ใช่สิ่งที่ควบคุมได้จากเบื้องบน หากแต่เป็นผลรวมของการเลือกของผู้คนนับล้าน ที่ตอบสนองต่อความเปลี่ยนแปลงอย่างเป็นธรรมชาติ หากปล่อยให้เป็นไป มันจะหาสมดุลของมันเอง เพราะในที่สุดแล้ว ไม่ว่าจะจากฝั่งตะวันตกหรือตะวันออก เส้นทางของอิสรภาพทั้งหมดก็นำมาสู่จุดเดียวกันการไม่ฝืนธรรมชาติของมนุษย์ และนั่นคือหัวใจของเศรษฐศาสตร์ออสเตรียน
จากนักบวชสเปน...สู่กรุงเวียนนา
ในอีกฟากของยุโรป ย้อนกลับไปตั้งแต่ศตวรรษที่ 16 กลุ่มนักบวชสายคาทอลิกที่รู้จักกันในชื่อ Late Scholastics จากมหาวิทยาลัย Salamanca ประเทศสเปน ได้เริ่มต้นการปฏิวัติความคิดบางอย่างที่ “ล้ำยุคเกินไปสำหรับยุคของเขา” พวกเขาเฝ้าสังเกตพฤติกรรมของผู้คนจริง ๆ ไม่ใช่ทฤษฎีที่ลอยอยู่บนตำรา และพบว่า มูลค่าของสิ่งของไม่ใช่สิ่งที่คงที่ตายตัว แต่มันเปลี่ยนไปตามมุมมอง ความต้องการ และสถานการณ์ของแต่ละคน พวกเขาคือผู้บุกเบิกแนวคิด “มูลค่าเชิงอัตวิสัย” (Subjective Value) ก่อนที่ Carl Menger จะสรุปมันไว้ในศตวรรษที่ 19 และคือคนกลุ่มแรกที่เข้าใจว่า ราคาคือผลของการประเมินคุณค่าภายในใจมนุษย์ ไม่ใช่ผลจากต้นทุนการผลิตหรือคำสั่งจากรัฐ นอกจากเรื่องมูลค่า พวกเขายังตั้งข้อสังเกตถึง ผลเสียของการพิมพ์เงินมากเกินไป และเตือนว่าเงินเฟ้อไม่ได้เป็นปรากฏการณ์ที่ลึกลับ แต่คือสิ่งที่รัฐ “สร้างขึ้นเอง” ผ่านการออกเหรียญเกิน, ลดค่ามาตรฐานโลหะ, หรือควบคุมอัตราแลกเปลี่ยนเพื่อผลประโยชน์เฉพาะกลุ่ม ที่น่าทึ่งคือ พวกเขาเสนอความคิดแบบเดียวกับที่ Mises และ Rothbard จะพูดอีกหลายร้อยปีให้หลังว่า... หน้าที่ของนักเศรษฐศาสตร์ที่แท้จริง ไม่ใช่เสนอวิธีควบคุมผู้คน แต่คือการบอกให้รัฐรู้ว่า “อะไรที่มันไม่มีสิทธิ์ทำ” พวกเขาไม่เพียงวิจารณ์การเก็บภาษีแบบไร้เหตุผล แต่ยังคัดค้านกฎหมายควบคุมราคา การผูกขาดโดยพระราชวงศ์ และการใช้กฎหมายในการแทรกแซงกลไกตลาด ที่สำคัญ พวกเขามองเห็นว่า ธุรกิจและตลาดเสรี ไม่ใช่สิ่งที่น่ารังเกียจเหมือนที่อำนาจนิยมหลายยุคพยายามทำให้เป็น แต่คือกระบวนการธรรมชาติที่ผู้คนแลกเปลี่ยนกันอย่างสมัครใจ เพื่อสร้างความมั่งคั่งร่วมกัน ทั้งหมดนี้เกิดขึ้นภายใต้หมวกของ “นักบวช” ไม่ใช่นักเศรษฐศาสตร์ แต่งานของพวกเขาได้วางรากฐานให้กับสิ่งที่ Rothbard ยกย่องว่าเป็น “นักเศรษฐศาสตร์ตัวจริงกลุ่มแรกในประวัติศาสตร์” และพวกเขานี่เอง...คือผู้จุดประกายปรัชญาเศรษฐศาสตร์สายตลาดเสรีที่ต่อมาจะกลายเป็น “สายออสเตรียน”
Carl Menger: ผู้จุดไฟแห่งความเข้าใจใหม่
ในปี 1871 Carl Menger หยิบแนวคิดเหล่านี้มาต่อยอด ด้วยหนังสือชื่อ Principles of Economics เขาได้เปลี่ยนวิธีมองโลกของทั้งวงการเศรษฐศาสตร์ เขาเขียนไว้อย่างเรียบง่ายแต่ลึกซึ้งว่า...
“มูลค่าไม่ใช่สิ่งที่อยู่ในตัวสินค้าด้วยตัวมันเอง แต่มันเกิดจากการตัดสินของมนุษย์ผู้มีเหตุผลในการใช้ทรัพยากร” – Carl Menger, 1871
แนวคิดนี้เรียกว่า “มูลค่าเชิงอัตวิสัย” (Subjective Value) ซึ่งปฏิวัติความเข้าใจด้านเศรษฐศาสตร์ที่เคยคิดว่ามูลค่าเป็นผลลัพธ์ของแรงงานหรือวัตถุดิบ เขาอธิบายว่า มูลค่าของสิ่งของไม่ได้เกิดจากต้นทุนหรือแรงงาน แต่มาจากความต้องการเฉพาะเวลาของผู้คนในสถานการณ์เฉพาะที่แตกต่างกัน เขาเสนอว่าเงินไม่ควรเกิดจากคำสั่งของรัฐ แต่มาจากการที่ผู้คนเลือกใช้สิ่งที่แลกเปลี่ยนได้ดีที่สุด จนกลายเป็นเงินโดยธรรมชาติ
เขาวางรากฐานให้เศรษฐศาสตร์กลายเป็น “ศาสตร์ของการเลือก” มากกว่าจะเป็น “ศาสตร์ของตัวเลข” ในมุมมองของเขา เศรษฐศาสตร์ไม่ใช่เรื่องของการสะสมข้อมูล แต่คือการทำความเข้าใจ “มนุษย์” ที่มีเป้าหมาย มีทางเลือก และเลือกการกระทำตามเหตุผลของตนเอง นี่คือจุดเริ่มต้นของเศรษฐศาสตร์แบบอิงพฤติกรรมมนุษย์ ซึ่งกลายมาเป็นแก่นกลางของเศรษฐศาสตร์ออสเตรียน
หลังจาก Carl Menger วางรากฐานสำคัญไว้ ศิษย์ผู้สืบทอดแนวคิดของเขาอย่าง Eugen Böhm-Bawerk ได้ขยายความเข้าใจนั้นให้ลึกขึ้นอีกระดับ โดยเฉพาะในเรื่องของ ทุน, ดอกเบี้ย, และ มิติเวลาของการผลิต Böhm-Bawerk อธิบายว่า อัตราดอกเบี้ยไม่ใช่สิ่งที่รัฐควรกำหนด แต่มันสะท้อนพฤติกรรมของมนุษย์ที่มี “ระดับความเห็นแก่เวลา” แตกต่างกัน คนที่ยอมรอ เพื่อให้ได้ผลตอบแทนในอนาคต คือคนที่มี Time Preference ต่ำ ขณะที่คนที่อยากได้ตอนนี้ ย่อมต้องยอมจ่ายเพิ่ม นี่คือธรรมชาติของดอกเบี้ยในตลาดเสรี เขายังแสดงให้เห็นว่า ทุนไม่ได้มีลักษณะ “ก้อนเดียว” แต่เป็นโครงสร้างซับซ้อนที่กินเวลาและสัมพันธ์กับกระบวนการผลิตในโลกจริง มันคือความเข้าใจเศรษฐกิจในแบบที่รัฐไม่สามารถ "จัดการจากบนลงล่าง" ได้เลย F.A. Hayek หนึ่งในศิษย์สายตรงของแนวคิดนี้ ขยายต่อโดยชี้ว่า ข้อมูลที่จำเป็นในการตัดสินใจทางเศรษฐกิจไม่ได้ถูกรวมไว้ในสมองของเจ้าหน้าที่ธนาคารกลางหรือรัฐมนตรีคลัง แต่กระจายอยู่ในพฤติกรรมของคนธรรมดาทุกคนในระบบเศรษฐกิจ และเมื่อมีใครพยายามควบคุมมันจากศูนย์กลาง นั่นแหละคือจุดเริ่มของการบิดเบือน
การควบคุมตลาดคือจุดเริ่มของการทำลายเสรีภาพ
เศรษฐศาสตร์สำนักออสเตรียนจึงไม่มองว่า "ตลาด" คืออะไรที่ซับซ้อนเกินเข้าใจ แต่มองว่ามันคือภาพสะท้อนของชีวิตมนุษย์จริง ๆ คนที่ซื้อกาแฟตอนเช้า คนที่ไม่ซื้อของที่คิดว่าแพงไป คนที่เลือกเก็บเงินไว้ใช้ในอนาคต พฤติกรรมเหล่านี้คือเศรษฐกิจจริง ๆ ที่เกิดขึ้นทุกวัน และนั่นคือเหตุผลที่ไม่มีใครควรไปควบคุมมัน Ludwig von Mises ยืนยันว่าการพิมพ์เงินโดยรัฐไม่ใช่นโยบายเศรษฐกิจ แต่คือการปล้นอย่างถูกกฎหมาย เขาแสดงผ่านทฤษฎี “regression theorem” ว่า เงินที่แท้จริงต้องมีจุดเริ่มจากตลาดเสรีเสมอ และเมื่อรัฐพยายามสร้างเงินจากความว่างเปล่า สุดท้ายมันจะทำลายมูลค่าทุกอย่างในระบบ แนวคิดเรื่อง “Time Preference” หรือความเห็นแก่เวลา ก็เป็นหนึ่งในแกนสำคัญที่ Mises และ Böhm-Bawerk พูดถึงว่า มนุษย์มักให้คุณค่ากับปัจจุบันมากกว่าอนาคต เมื่อระบบการเงินเอื้อให้ใช้เงินง่าย ใช้เร็ว แต่ไม่มีแรงจูงใจให้เก็บหรือลงทุนระยะยาว สังคมจะค่อย ๆ กลายเป็นสังคมบริโภค และสูญเสียวัฒนธรรมของความยั่งยืน นั่นคือเหตุผลว่าทำไมคนจึงยอมรูดบัตรก่อน เก็บเงินทีหลัง และทำให้ระบบการเงินทั้งระบบ...เร่งให้เราใช้จ่ายแบบไม่ยั้งคิด Murray Rothbard คือผู้ที่นำแนวคิดทั้งหมดนี้มาขยายให้ถึงที่สุด เขาไม่เพียงแต่วิเคราะห์ว่าอะไรทำให้เศรษฐกิจล่ม แต่ยังเชื่อมมันกับหลักปรัชญาธรรมชาติ โดยวางรากฐานว่า หากรัฐไม่มีสิทธิ์บังคับร่างกายของเรา มันก็ไม่มีสิทธิ์บังคับทรัพย์สินของเราเช่นกัน เขาอธิบายว่า การแทรกแซงทุกรูปแบบของรัฐ ล้วนเป็นการทำลายเสรีภาพของการเลือกในระดับรากฐาน
แล้วเราทำอะไรได้ ?
คำตอบของออสเตรียนไม่ใช่ “รอให้รัฐฉลาดขึ้น” แต่คือ “หยุดให้รัฐยุ่งมากเกินไปตั้งแต่แรก” ตลอดประวัติศาสตร์ เราเห็นมาแล้วว่ารัฐสามารถพิมพ์เงินจนเงินเฟ้อ ยึดทองคำของประชาชน เปลี่ยนระบบการเงินโดยไม่ขอความเห็นจากผู้ใช้ และในโลกปัจจุบัน มีสิ่งหนึ่งที่สะท้อนแนวคิดนี้ได้จริงที่สุด นั่นคือบิตคอยน์ บิตคอยน์ไม่ได้เป็นแค่เงินสดดิจิทัล แต่มันคือ “เงินที่รัฐพิมพ์เพิ่มไม่ได้” ไม่มีใครเปลี่ยนกติกากลางเกม ไม่มีธนาคารกลาง ไม่มีใครควบคุมอัตราเงินเฟ้อด้วยปลายนิ้ว มีเพียงผู้ใช้ที่ยินยอมแลกเปลี่ยนกันอย่างเสรี บิตคอยน์คือเศรษฐศาสตร์ออสเตรียนในรูปธรรม คือคำประกาศของเสรีภาพทางการเงินในยุคดิจิทัล
เศรษฐศาสตร์ออสเตรียนจึงไม่ใช่แค่เศรษฐศาสตร์ทางเลือก แต่มันคือวิธีมองมนุษย์อย่างเคารพ เข้าใจ และยอมรับว่าเราทุกคนต่างมีเหตุผล มีความต้องการ มีจุดมุ่งหมาย และควรมีเสรีภาพในการตัดสินใจด้วยตนเอง มันคือแนวคิดที่กล้าบอกว่ารัฐไม่ได้รู้ดีที่สุด และคนธรรมดาไม่ควรถูกบังคับให้เล่นในระบบที่พวกเขาไม่เคยเลือกกติกาได้เอง
มันไม่ใช่แค่แนวคิดใหม่ แต่มันคือความจริงเก่า ที่โลกเคยลืม และกำลังกลับมา…เพื่อทวงคืน “อิสรภาพ” ที่หายไปจากกระเป๋าเงินของเรา ทั้งหมดนี้จึงเป็นเหตุผลว่า ทำไม “เศรษฐศาสตร์สำนักออสเตรียน” ไม่ได้เป็นแค่ทางเลือกของเศรษฐกิจ แต่มันคือ “อาวุธทางความคิด” สำหรับคนที่ไม่ยอมจำนนให้ใครควบคุมชีวิต
อ้างอิง Menger, Carl. Principles of Economics. 1871. Böhm-Bawerk, Eugen von. Positive Theory of Capital. 1889. Mises, Ludwig von. The Theory of Money and Credit. 1912. Hayek, Friedrich A. The Use of Knowledge in Society. 1945. Rothbard, Murray N. For a New Liberty: The Libertarian Manifesto. 1973. Ammous, Saifedean. The Bitcoin Standard: The Decentralized Alternative to Central Banking. 2018. Mises Institute. “Promoting teaching and research in the Austrian school of economics.” Rothbard, Murray N. An Austrian Perspective on the History of Economic Thought, Volume I. Ludwig von Mises Institute, 2006.
Siamstr
-
 @ 2e8970de:63345c7a
2025-04-12 10:27:01
@ 2e8970de:63345c7a
2025-04-12 10:27:01This week I read up on what's currently happening to kids and their relationship to social media and smartphones. Especially the following thw pieces of media: The Ezra Klein Show: ‘Our Kids Are the Least Flourishing Generation We Know Of’ interview with Jonathan Haidt and his book on the topic:
https://www.youtube.com/watch?v=RN2GhPal4qA
And the podcast Search Engine 'What’s actually on teenagers’ phones? ' and a documentary tv show on the topic where teenagers show their phone screens to their parents as a social experiment
https://www.searchengine.show/whats-actually-on-teenagers-phones/
Yes yes, both are outlets that are clearly progressive partisan. But this topic really is a non partisan topic. Don't click away yet.
Here are my key takeaways on the topic:
How kids spend their time
- For most of human history kids and teenagers spend their time with other kids. And especially not only their exact same age: also with kids a few years older and younger. This is obviously a lot less now that kids are almost exclusively online. When kids play outside and have other kids that are 2y older as rolemodels and look out for other kids that are 2y younger that obviously changes something in their upbringing and how they learn to behave in social connections. What changes about personality of humans when whole generations did not have this experience?
- Kids spend more and more time with their parents. This might be surprising in a story that is primarily about less and less socializing. But parents are more and more of the opinion that the most important goal in parenting is spending "quality time" with their kids. But is this true? Shouldn't they spend time with peers instead?
- The offline world is online now. In the tv show referenced in the podcast the filmcrew also got insight what teenagers do on gettogethers and partys. It was a surprising sight. Everyone is used to being filmed all the time. A boy jumped off a building, another kid took drugs and ended up in the hospital. But haven't teenagers always done stupid shit? The key difference is the boy did not jump off a building because he was a stupid teenager having fun. He did it to go viral online. What a bleak bleak new world.
- Younger than you expect. Did you know that 40% of 2yo own a tablet/ipad? I still remember the outrage of 10yo owning non-smart phones. The topic is still on but now it's babys. Also elementary school aged kids are almost surely all confronted with softcore porn and violence regularly. You can almost expect a child of this age have also seen hardcore porn and extreme violence. This really begs the question why we as a society still count if a Marvel movie has 1 or 2 f-words - what a ludicrous contrast.
- What happens on the phone is a secret. Kids have almost all the behavior to not talk about what happens on their phones. To some extent this is normal, to some extent this is also a big mystery how this developed. Your teenage daughter will not tell you when she looks bulimia, eating disorders, and superhuman women influencers all the time. Your 7yo will not tell you that they looked at disturbing violence gore content. Most mysteriously: even 3yo often already know this behaviour to hide their phone screens when playing phone games. How do they learn this? It is indeed a mystery.
Gender divide
Young girls and young boys have very different experiences here. Boys do still spend time with gaming and voicechats together. Young girls time online is very different. It is mostly alone. It is instagram pictures of unattainable lifestyle and looks.
The loss of common values
Jonathan Haidt had an interesting insight on the interplay of smartphones and the decline of religiosity here. The decline of religiosity in the west is obviously nothing new, it predates smartphones. But social media confronts kids with a whole world of different people and different values. So, a secularized world might not derive its values from religion anymore but a secularized world with local communities might still create consensus on values. But a secularized world where culture happens globally does not anymore. kids increasingly say they have no meaning or goals in life. In the interview Jonathan Haidt lists many statistics on this topic that you can look at from many angles but overall this is the trend.
An overaching concept in probably all value sets from liberal cities to arch conservative societies was some concept of social status. Maybe in an Amish village social status came from having a dozen children. Maybe in turbo leftist circles social status came from having an art exhibition.... you get the idea, the specifics do not matter. For teenagers this social status is synonymous with likes and followers. You, as a kid, will probably never have a million followers and therefore in this new world social status is unattainable.
This is of course very oversimplified. But you see how the world changed overnight when smartphones happened.
The concept of "Pacts"
If phones are so bad, just give it to them at an older age! Not so fast cowboy.
Kids with smartphones are less depressed, less anxious, more social, get more exercise, & experience less cyberbullying than kids w/out smartphones
https://x.com/ENBrown/status/1909257644499480973
The problem here is of course that kids without phones are social outcasts. This is even worse than the phones themselves.
The solution that has become really popular post covid is the concept of pacts. A few parents from one neighborhood and/or one school year come together and make a pact to not give their kids phones until a certain age.
Depressingly, Jonathan Haidt analysis found that these pacts don't work that well: It's only a trend in what is upper middle class anyway. Statistically many parents "break" under the pressure before the year has arrived. And lastly, they only seem to work when the size of the pact is like 10 kids or bigger.
Conclusion
I encourage you all the watch the interview and or listen to the podcast. The world changed a lot and we are barely talking about it.
originally posted at https://stacker.news/items/941383
-
 @ 7d33ba57:1b82db35
2025-04-12 09:27:34
@ 7d33ba57:1b82db35
2025-04-12 09:27:34Florence (Firenze) is where art, history, and passion collide in the most graceful way. As the birthplace of the Renaissance, it’s a city steeped in creativity—from Michelangelo’s David to Brunelleschi’s dome—and yet, it also lives in the little things: the smell of espresso, the sound of church bells, and golden sunsets over the Arno. Compact, walkable, and overflowing with beauty, Florence stirs something deep.
🌟 Must-See Highlights in Florence
1️⃣ The Duomo & Brunelleschi’s Dome
- The Cathedral of Santa Maria del Fiore dominates the skyline with its red-tiled dome
- Climb to the top (463 steps!) for breathtaking views of the city and Tuscan hills
- Don’t miss the baptistery’s golden doors—aka the “Gates of Paradise”
2️⃣ Uffizi Gallery
- One of the most famous art museums in the world
- Home to masterpieces by Botticelli (The Birth of Venus), da Vinci, Michelangelo, and Caravaggio
- Book timed-entry tickets—lines can be intense!
3️⃣ Ponte Vecchio
- Florence’s iconic medieval bridge, lined with goldsmiths and jewelers
- Great photo spot—especially at sunrise or golden hour
4️⃣ Michelangelo’s David at the Accademia
- The original, larger-than-life marble David is a powerful sight in person
- Also check out Michelangelo’s unfinished “Prisoners,” still emerging from stone
5️⃣ Boboli Gardens & Pitti Palace
- Cross the Arno to explore lush gardens, sculptures, and royal vibes
- Offers a peaceful break from the city streets and great panoramic views
🍷 What to Eat & Drink in Florence
- Bistecca alla Fiorentina – A legendary T-bone steak, grilled rare
- Ribollita – A hearty Tuscan soup with bread, beans, and vegetables
- Crostini with chicken liver pâté – Classic local starter
- Cantucci with Vin Santo – Almond biscuits dipped in sweet dessert wine
- Pair it all with a glass of Chianti Classico or Brunello di Montalcino
✨ Local Gems to Discover
- Piazzale Michelangelo – Sunset views that will stay with you forever
- San Lorenzo Market – Leather goods, food stalls, and local flair
- Santa Croce Basilica – Tombs of Michelangelo, Galileo, Machiavelli
- Oltrarno neighborhood – Artisans, cool cafés, and a slower, bohemian vibe
🎯 Florence Travel Tips
✅ Most sights are walkable—comfortable shoes are a must
✅ The city is busiest from late spring to early fall—visit in shoulder seasons if you can
✅ Museums are closed on Mondays
✅ Make restaurant reservations—especially for dinner at popular spots -
 @ da0b9bc3:4e30a4a9
2025-04-12 09:08:53
@ da0b9bc3:4e30a4a9
2025-04-12 09:08:53Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/941336
-
 @ 3644865c:09dbf9fb
2025-04-12 07:34:32
@ 3644865c:09dbf9fb
2025-04-12 07:34:32In a world where centralized platforms dominate communication and finance, Nostr and Bitcoin emerge as beacons of hope, paving the way for decentralized freedom. These technologies embody the principles of sovereignty, transparency, and community empowerment, redefining how we connect, transact, and share knowledge.
UNVEILING THE POWER OF NOSTR AND BITCOIN At its core, Nostr is more than a decentralized protocol—it’s a revolution in how we communicate. By eliminating central points of control, it ensures censorship-resistant messaging and true ownership of content. Bitcoin, on the other hand, is the ultimate sound money—a financial system that empowers individuals to take control of their wealth without intermediaries. Together, these innovations form a powerful alliance, addressing key challenges like privacy, identity, and trust.
Imagine a world where your voice is never silenced, your wealth is secure, and your interactions are free from surveillance. This is the promise of Nostr and Bitcoin, a future that prioritizes individual freedom over institutional control.
STORIES OF DECENTRALIZED SUCCESS Around the globe, individuals and communities are using Nostr and Bitcoin to challenge the status quo. Activists in oppressive regimes rely on Nostr to share their stories without fear of censorship. Artists and creators are embracing Bitcoin’s Lightning Network to receive direct support from fans, bypassing exploitative platforms. These stories showcase the transformative power of freedom tech, inspiring others to join the movement.
Consider the impact of a creator who can directly connect with their audience through Nostr, receiving instant zaps via Bitcoin. This not only supports their work but also strengthens the ecosystem, proving that decentralized technologies are not just theoretical—they are practical solutions for real-world problems.
FUELING THE FREEDOM REVOLUTION As a community, we hold the responsibility to build and showcase the capabilities of Nostr and Bitcoin. By contributing to the ecosystem—whether through coding, creating content, or simply zapping—we demonstrate the tangible benefits of decentralized freedom.
Zapping isn’t just a tip; it’s a statement. It says,I believe in your work, and I’m investing in a future built on trust and sovereignty. Each zap strengthens the foundation of freedom tech, encouraging innovation and collaboration.
-
 @ 04c915da:3dfbecc9
2025-03-26 20:54:33
@ 04c915da:3dfbecc9
2025-03-26 20:54:33Capitalism is the most effective system for scaling innovation. The pursuit of profit is an incredibly powerful human incentive. Most major improvements to human society and quality of life have resulted from this base incentive. Market competition often results in the best outcomes for all.
That said, some projects can never be monetized. They are open in nature and a business model would centralize control. Open protocols like bitcoin and nostr are not owned by anyone and if they were it would destroy the key value propositions they provide. No single entity can or should control their use. Anyone can build on them without permission.
As a result, open protocols must depend on donation based grant funding from the people and organizations that rely on them. This model works but it is slow and uncertain, a grind where sustainability is never fully reached but rather constantly sought. As someone who has been incredibly active in the open source grant funding space, I do not think people truly appreciate how difficult it is to raise charitable money and deploy it efficiently.
Projects that can be monetized should be. Profitability is a super power. When a business can generate revenue, it taps into a self sustaining cycle. Profit fuels growth and development while providing projects independence and agency. This flywheel effect is why companies like Google, Amazon, and Apple have scaled to global dominance. The profit incentive aligns human effort with efficiency. Businesses must innovate, cut waste, and deliver value to survive.
Contrast this with non monetized projects. Without profit, they lean on external support, which can dry up or shift with donor priorities. A profit driven model, on the other hand, is inherently leaner and more adaptable. It is not charity but survival. When survival is tied to delivering what people want, scale follows naturally.
The real magic happens when profitable, sustainable businesses are built on top of open protocols and software. Consider the many startups building on open source software stacks, such as Start9, Mempool, and Primal, offering premium services on top of the open source software they build out and maintain. Think of companies like Block or Strike, which leverage bitcoin’s open protocol to offer their services on top. These businesses amplify the open software and protocols they build on, driving adoption and improvement at a pace donations alone could never match.
When you combine open software and protocols with profit driven business the result are lean, sustainable companies that grow faster and serve more people than either could alone. Bitcoin’s network, for instance, benefits from businesses that profit off its existence, while nostr will expand as developers monetize apps built on the protocol.
Capitalism scales best because competition results in efficiency. Donation funded protocols and software lay the groundwork, while market driven businesses build on top. The profit incentive acts as a filter, ensuring resources flow to what works, while open systems keep the playing field accessible, empowering users and builders. Together, they create a flywheel of innovation, growth, and global benefit.
-
 @ 866e0139:6a9334e5
2025-04-12 07:01:52
@ 866e0139:6a9334e5
2025-04-12 07:01:52
Autor: Jürgen Müller. Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier.**
Um Demokratie und edle moralische Werte soll es im Krieg gehen, wenn man den Verlautbarungen unserer selbsternannten politischen und intellektuellen Elite glauben soll. Wenn man auf all die Kriege der letzten Jahrhunderte und Jahrtausende zurückblickt, dürfte sich jedoch ein realitätsnaher Blick ergeben. Darum ging es nie. Es geht um Geld.
„So mir nix dir nix fangt ma doch koan Kriag o. Do geht's oiwai um so was, ob's jetz a Holz is oder was anders..." Übersetzt: Es geht ums Holz, so soll der Vater des bayerischen Schriftstellers Oskar Maria Graf seinem Sohn diese verdichtete Lebensweisheit weitergegeben haben. Holz könne dabei auch einen anderen Namen haben wie etwa wohl Geld, Macht und geostrategische Interessen – wobei sich letztere ebenfalls in Geld übersetzen lassen. Die Essenz des Krieges ist Geld.
Was aber, wenn selbst der Krieg einen anderen Namen hat? Was, wenn man den Bevölkerungen in den wohlstandsverwöhnten westlichen Ländern keinen Krieg zumuten kann, weil sie zwar Kriege auf der ganzen Welt führen, um ihrer imperialistischen Lebensweise frönen zu können, es aber nicht ohne weiteres mit sich machen ließen, mit Krieg überzogen zu werden? Was, wenn aber der Krieg genau dorthin gebracht werden müsste, wo sehr viel zu holen ist, weil man zwar bisher den Rahm abgeschöpft hat, dies jedoch im Endstadium des Kapitalismus nicht mehr für diejenigen ausreicht, zu denen der stete Fluss an Vermögenskonzentration entgegen der Schwerkraft fließt – nach oben? Dann führt man Krieg unter einem anderen Namen.
„There's class warfare, all right, but it's my class, the rich class, that's making war, and we're winning", so ein Ausspruch des US-Oligarchen und Finanzmoguls Warren Buffet (neudeutsch „Philanthrop“). Zu Deutsch: „Es herrscht Klassenkrieg, richtig, aber es ist meine Klasse, die Klasse der Reichen, die Krieg führt, und wir gewinnen."
Biosicherheit ist Kriegsrecht
Das Zitat stammt noch aus der Zeit vor der Finanzkrise, mit der dieser Klassenkampf sichtbar wurde. Es folgte eine unvorstellbare Umverteilung und Privatisierung von öffentlichem Vermögen. Krieg mag man dies vielleicht noch nicht nennen. Mit Krieg verbindet man Tod, Leid und Zerstörung. Mit guter Begründung ließe sich dann jedoch die Behauptung aufstellen, dass sich die westlichen Gesellschaften seit dem Beginn der Coronakrise im Jahr 2020 selbst in einem Krieg befinden.
Biosicherheit ist Kriegsrecht. Ein General wurde in Deutschland an die Spitze der militärischen Spezial-Operation gestellt. Das Gesundheitswesen wurde militarisiert. Dies ist insofern konsequent, da man offen kommuniziert, dass man sich in einem Krieg befände, auch wenn man das wahre Ziel der Kriegshandlungen dadurch verschleierte. Rund um den Globus ließen die Regierungen westlicher Staaten verlautbaren, dass man sich im Krieg gegen das Virus oder einen unsichtbaren Feind befände. Beispiele:
Emmanuel Macron (Frankreich): „Nous sommes en guerre."
Donald Trump (USA): „We're at war. We're fighting an invisible enemy...I'm a wartime president."
Boris Johnson (Großbritannien): „We must act like any wartime government."
Pedro Sánchez (Spanien): „Nos enfrentamos a una guerra contra un enemigo invisible."
Für diese Kriegsrhetorik findet man Beispiele in vielen Ländern durch deren seinerzeitige Regierungschefs. Wer die Coronakrise bewusst erlebt hat, konnte die Kriegsführung beobachten. Sie richtete sich jedoch nicht gegen ein Virus, sondern gegen die Bevölkerung und deren Grund- und Menschenrechte, die in westlichen Gesellschaften eigentlich stets als unveräußerlich deklariert worden waren. Und sie kulminierte darin, dass die Bevölkerungen unter gewaltigem Druck mit einer Biowaffe gespritzt wurden, für deren Produktion eine regelrechte Rüstungsindustrie hochgezogen wurde. Anders als als Biowaffe sollte dies nicht mehr bezeichnet werden, nachdem nun nach jahrelangem Abwiegeln sogar Regierungslinie und Allgemeinwissen zu werden scheint, dass das Virus aus einem Labor stammt und Ergebnis einer Gain-of-Function-Forschung, mithin der Biowaffenforschung ist. Was aber sollte dann der genetische Impfstoff anderes sein, der den Körper derart umprogrammiert, dass er das, was das Virus für manche gefährlich macht, dort produziert, wo es bei den meisten Menschen überhaupt nicht hinkäme, und dort gewaltige Schäden anrichtet bis hin zum Tod?
Wenn man zu diesem Schluss kommt, kann man dies auch dahingehend übersetzen, dass die Regierungen ihre eigene Bevölkerung mit einer verheerenden Biowaffe angegriffen haben und dabei sogar so weit gegangen sind, den Nürnberger Kodex zu brechen. Wie groß die Zahl der Opfer sein wird, wird sich erst rückblickend betrachten lassen, aber bei objektiver Beobachtung wird man bereits jetzt zu dem Schluss kommen, dass die Schäden gigantisch sind.
Wir sind bereits im Krieg
Aktuell läuft in Europa die Kriegsrhetorik auf Hochtouren. Bis 2029 will man kriegstüchtig sein. Man ist geneigt, sich zu fragen, was das werden soll, dem Gegner mitzuteilen, was man bis wann vorhat. Gewaltige Schuldenpakete werden aufgenommen, um dieses vermeintliche Ziel zu erreichen. Die Aktienkurse von Rüstungsherstellern gehen durch die Decke. In Deutschland herrscht ein komplettes Kriegsparlament ohne relevante Widerworte. Sogar ein nach seiner Auflösung und darauf folgender Neuwahl längst nicht mehr demokratisch legitimierter Bundestag kann eine Verfassungsänderung zu Gunsten gigantischer Kriegskredite verabschieden, und eine Mehrheit scheint das gut zu finden.
Völlig unklar ist, ob es zu einem Krieg kommen wird. Warum sollte Putin Deutschland angreifen und warum sollte er damit warten bis 2029? Oder spekuliert man gar darauf, dass bis dahin jemand anderes in Russland das Sagen hat, der nicht so besonnen auf die ständigen Provokationen reagiert, wie dies Putin in der Vergangenheit getan hat? Die Bevölkerung wurde in der Coronakrise konditioniert. Der Staat wird umgebaut zu einem totalitären System. Das alles kann eine Vorbereitung für einen Krieg sein, der in einer liberalen Demokratie undenkbar wäre. Nicht umsonst laufen aktuell Vorbereitungen, die Meinungsfreiheit weiter einzuschränken, legitime Meinungsäußerungen zu kriminalisieren und den Bürgern weitere Kontrolle über die Exekutive zu entziehen, wie es der Vorstoß zur Abschaffung des Informationsfreiheitsgesetzes andeutet. Wenn man Krieg will, braucht man ein totalitäres System. Deshalb wird das, was wir an Einschränkung der Meinungsfreiheit während Corona erlebt haben, um das Coronaregime zu ermöglichen, nur ein lauer Vorgeschmack gewesen sein. Denn einen Krieg mit Waffen verstehen die Menschen besser als einen Krieg mit Biowaffen. Da wird man die Zügel anziehen müssen, was ohnehin sinnvoll ist, denn irgendwann wird sich auch der seit 5 Jahren gegen die Bevölkerungen geführte Krieg nicht mehr verdecken lassen.
DIE FRIEDENSTAUBE FLIEGT AUCH IN IHR POSTFACH!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt, vorerst für alle kostenfrei, wir starten gänzlich ohne Paywall. (Die Bezahlabos fangen erst zu laufen an, wenn ein Monetarisierungskonzept für die Inhalte steht). Sie wollen der Genossenschaft beitreten oder uns unterstützen? Mehr Infos hier oder am Ende des Textes.
Das Kriegstrommeln ist daher durchaus ernst zu nehmen, aber es überlagert den Kriegszustand, in dem wir uns längst befinden, und stellt die Frage, ob es wirklich den großen Krieg für das braucht, was man auch so durch eine Politik der Angst erreichen kann.
Corona, Krieg, Klima. Virus, Putin, CO2. Das Narrativ ist egal, der Feind ist austauschbar. Die Angst ist es nicht. Sie ist das Feuer, das die Geld-Destillerie am Laufen hält und den Destillationsprozess überhaupt erst ermöglicht. Die kleinen Kriegsgewinnler betreiben Heimdestillerien. Sie impfen, betreiben Testzentren, kaufen Rheinmetallaktien. Natürlich gibt es auch etwas größere Schwarzbrennereien, die mit Maskengeschäften, Auftragsreden oder Beratungsjobs während und nach der Politkarriere Millionen verdienen und gerne auch Insiderwissen nutzen. Aber das wirklich große Geschäft wird in den professionellen Großdestillerien gemacht, deren Eigentümer kaum jemand kennt.
Die Coronakrise und der Krieg lassen sich nicht voneinander trennen. Die Mechanismen sind dieselben. Die Akteure überschneiden sich zum Teil. Die Gräben, die man in der Gesellschaft während Corona aufgerissen hat, werden nun vielleicht ganz real zu Schützengräben.
Letztendlich ist es zum Geldverdienen jedoch egal, ob ein Land durch Waffen zerstört wird, an denen man verdienen kann, um das Land danach wieder aufzubauen, woran man erneut gut verdienen kann. Oder ob man die Gesundheit von Menschen mit „Impfstoffen" zerstört, an denen man gut verdient, um im Nachgang an der Behandlung der ramponierten Gesundheit zu verdienen. In ähnlicher Weise dürfte es sich mit der Klimapolitik verhalten. Aber das scheint noch arg abstrakt zu sein.
Aufarbeitung der Coronapolitik als friedenssichernde Maßnahme
Die kritische gesellschaftliche Debatte dreht sich meist nur um Symptome. Die unkritische, die in den Leitmedien zu finden ist, scheut sogar dies. An den Kern des Problems geht auch der kritische Teil der Gesellschaft kaum, weil er vom herrlichsten Empörungsmanagement abgelenkt wird, das jemals in Think-Tanks ersonnen wurde.
Einen kurzen Augenblick gab es vor gut einem Jahr, nachdem Paul Schreyer die damals noch weitgehend geschwärzten und von ihm herausgeklagten RKI-Protokolle veröffentlicht hatte. Bereits in der Überschrift hat er mit seiner Erfahrung die wirklich wichtige Schlagzeile herausdestilliert: Es sollte hochskaliert werden. Ohne einen Grund sollte ein Grundrechtemassaker angerichtet werden. Der Blick wurde auf die wesentlichen Fragen gelenkt – auch auf den militärischen Charakter. Wenige Wochen später wurde das RKI-Leak veröffentlicht. Das mag zwar gewaltige historische und juristische Bedeutung haben, verwässerte jedoch die aktuell notwendige Diskussion auf Unwesentliches wie etwa die Untauglichkeit einer Maskenpflicht im Alltag.
Erst wenn die Menschen verstehen, was mit ihnen gemacht wurde und welche Mechanismen dazu führten, dass sie selbst ihre Kinder mit etwas spritzen ließen, das über mehrere Jahre Entzündungsreaktionen im Körper anheizt, Autoimmunerkrankungen und Krebs auslösen kann und bereits in vielen Fällen zum Tod führte, werden sie die Größe des Verbrechens erkennen können. Denn wer hätte seine Kinder mit dieser Substanz spritzen lassen, wenn ihm Vorstehendes gesagt worden wäre, was selbst nur ein Teil der erschütternden Wahrheit ist. Vermutlich fast niemand.
Es sind gut bekannte, aber inzwischen durch die Möglichkeiten der Digitalisierung stark verfeinerte Mechanismen, die ein derartiges Verhalten ermöglichen. Die kognitive Kriegsführung, die Jonas Tögel in seinem gleichnamigen Buch beschreibt, ist längst Realität. Was man in der Coronakrise und in den Nachwirkungen bis heute erleben konnte, ist mit diesem Begriff gut beschrieben.
Jürgen Müller ist verheiratet und Vater von Zwillings-Jungs. Er ist Rechtsanwalt und Insolvenzverwalter. In den vergangenen 10 Jahren hat er ehrenamtlich viel bewirkt und einige Vereine gegründet, die er mit Beginn der Coronakrise auf einmal „auf der anderen Seite" vorfand. Da er weiterhin auf seinem Fundament von Grundrechten und Demokratie, Ökologie, Frieden und Gerechtigkeit stand, gründete er, als die Verhältnisse eskalierten, den Verein Kinderrechte Jetzt e.V., um Kindern und Jugendlichen eine freie Impfentscheidung zu ermöglichen. Mit seinen Mitstreitern gründete er zudem in München das „Wir-Gemeinsam-Bündnis", das u.a. die öffentlichen Debattenräume, das Lebenselixier der Demokratie, wiederbeleben und eine Aufarbeitung der Coronakrise bewirken will. Er ist Mitorganisator im deutschlandweiten Friedensbündnis „Macht Frieden!", dem es gelang, im Jahr 2023 in München mit rund 25.000 Teilnehmern die erste große lagerübergreifende Friedensdemo seit vielen Jahren zu organisieren. Seine Homepage: www.indikativ.jetzt
LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt. (Vorerst alle, da wir den Mailversand testen, später ca. drei Mails pro Woche.)
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: milosz@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ 6b3780ef:221416c8
2025-03-26 18:42:00
@ 6b3780ef:221416c8
2025-03-26 18:42:00This workshop will guide you through exploring the concepts behind MCP servers and how to deploy them as DVMs in Nostr using DVMCP. By the end, you'll understand how these systems work together and be able to create your own deployments.
Understanding MCP Systems
MCP (Model Context Protocol) systems consist of two main components that work together:
- MCP Server: The heart of the system that exposes tools, which you can access via the
.listTools()method. - MCP Client: The interface that connects to the MCP server and lets you use the tools it offers.
These servers and clients can communicate using different transport methods:
- Standard I/O (stdio): A simple local connection method when your server and client are on the same machine.
- Server-Sent Events (SSE): Uses HTTP to create a communication channel.
For this workshop, we'll use stdio to deploy our server. DVMCP will act as a bridge, connecting to your MCP server as an MCP client, and exposing its tools as a DVM that anyone can call from Nostr.
Creating (or Finding) an MCP Server
Building an MCP server is simpler than you might think:
- Create software in any programming language you're comfortable with.
- Add an MCP library to expose your server's MCP interface.
- Create an API that wraps around your software's functionality.
Once your server is ready, an MCP client can connect, for example, with
bun index.js, and then call.listTools()to discover what your server can do. This pattern, known as reflection, makes Nostr DVMs and MCP a perfect match since both use JSON, and DVMs can announce and call tools, effectively becoming an MCP proxy.Alternatively, you can use one of the many existing MCP servers available in various repositories.
For more information about mcp and how to build mcp servers you can visit https://modelcontextprotocol.io/
Setting Up the Workshop
Let's get hands-on:
First, to follow this workshop you will need Bun. Install it from https://bun.sh/. For Linux and macOS, you can use the installation script:
curl -fsSL https://bun.sh/install | bash-
Choose your MCP server: You can either create one or use an existing one.
-
Inspect your server using the MCP inspector tool:
bash npx @modelcontextprotocol/inspector build/index.js arg1 arg2This will: - Launch a client UI (default: http://localhost:5173)
- Start an MCP proxy server (default: port 3000)
-
Pass any additional arguments directly to your server
-
Use the inspector: Open the client UI in your browser to connect with your server, list available tools, and test its functionality.
Deploying with DVMCP
Now for the exciting part – making your MCP server available to everyone on Nostr:
-
Navigate to your MCP server directory.
-
Run without installing (quickest way):
npx @dvmcp/bridge -
Or install globally for regular use:
npm install -g @dvmcp/bridge # or bun install -g @dvmcp/bridgeThen run using:bash dvmcp-bridge
This will guide you through creating the necessary configuration.
Watch the console logs to confirm successful setup – you'll see your public key and process information, or any issues that need addressing.
For the configuration, you can set the relay as
wss://relay.dvmcp.fun, or use any other of your preferenceTesting and Integration
- Visit dvmcp.fun to see your DVM announcement.
- Call your tools and watch the responses come back.
For production use, consider running dvmcp-bridge as a system service or creating a container for greater reliability and uptime.
Integrating with LLM Clients
You can also integrate your DVMCP deployment with LLM clients using the discovery package:
-
Install and use the
@dvmcp/discoverypackage:bash npx @dvmcp/discovery -
This package acts as an MCP server for your LLM system by:
- Connecting to configured Nostr relays
- Discovering tools from DVMCP servers
-
Making them available to your LLM applications
-
Connect to specific servers or providers using these flags: ```bash # Connect to all DVMCP servers from a provider npx @dvmcp/discovery --provider npub1...
# Connect to a specific DVMCP server npx @dvmcp/discovery --server naddr1... ```
Using these flags, you wouldn't need a configuration file. You can find these commands and Claude desktop configuration already prepared for copy and paste at dvmcp.fun.
This feature lets you connect to any DVMCP server using Nostr and integrate it into your client, either as a DVM or in LLM-powered applications.
Final thoughts
If you've followed this workshop, you now have an MCP server deployed as a Nostr DVM. This means that local resources from the system where the MCP server is running can be accessed through Nostr in a decentralized manner. This capability is powerful and opens up numerous possibilities and opportunities for fun.
You can use this setup for various use cases, including in a controlled/local environment. For instance, you can deploy a relay in your local network that's only accessible within it, exposing all your local MCP servers to anyone connected to the network. This setup can act as a hub for communication between different systems, which could be particularly interesting for applications in home automation or other fields. The potential applications are limitless.
However, it's important to keep in mind that there are security concerns when exposing local resources publicly. You should be mindful of these risks and prioritize security when creating and deploying your MCP servers on Nostr.
Finally, these are new ideas, and the software is still under development. If you have any feedback, please refer to the GitHub repository to report issues or collaborate. DVMCP also has a Signal group you can join. Additionally, you can engage with the community on Nostr using the #dvmcp hashtag.
Useful Resources
- Official Documentation:
- Model Context Protocol: modelcontextprotocol.org
-
DVMCP.fun: dvmcp.fun
-
Source Code and Development:
- DVMCP: github.com/gzuuus/dvmcp
-
DVMCP.fun: github.com/gzuuus/dvmcpfun
-
MCP Servers and Clients:
- Smithery AI: smithery.ai
- MCP.so: mcp.so
-
Glama AI MCP Servers: glama.ai/mcp/servers
Happy building!
- MCP Server: The heart of the system that exposes tools, which you can access via the
-
 @ 3b2218fc:5a1784e2
2025-04-12 06:22:36
@ 3b2218fc:5a1784e2
2025-04-12 06:22:36A indústria de entretenimento online tem evoluído rapidamente nos últimos anos, oferecendo aos jogadores uma variedade de opções para se divertir e se envolver com plataformas digitais. Uma das mais recentes e inovadoras opções é a NNNBet, uma plataforma online que tem conquistado a atenção de jogadores do Brasil e de várias partes do mundo. Neste artigo, vamos explorar o que torna a NNNBet uma escolha popular, com foco em sua introdução ao mercado, a variedade de jogos disponíveis e a experiência proporcionada aos seus usuários.
Introdução à NNNBet: Uma Plataforma de Entretenimento Digital para Todos A NNNBet é uma plataforma digital criada para oferecer uma experiência única de entretenimento, com um amplo portfólio de jogos que atende a uma variedade de gostos e preferências. O site é moderno, acessível e fácil de navegar, permitindo que os jogadores encontrem rapidamente os jogos que mais os interessam. Além disso, a plataforma conta com uma interface intuitiva, adaptada para diversos dispositivos, garantindo que todos os jogadores, independentemente de estarem usando um desktop, tablet ou smartphone, possam desfrutar de uma navegação fluida.
A segurança e a confiabilidade são aspectos fundamentais para a Nnnbet . A plataforma é comprometida com a proteção dos dados dos seus usuários e oferece transações seguras, além de implementar tecnologias de criptografia de última geração para garantir a privacidade dos jogadores. Este compromisso com a segurança é essencial para a construção de uma relação de confiança com os jogadores.
Além disso, a NNNBet oferece diversos métodos de pagamento, incluindo opções populares no Brasil, como cartões de crédito, transferências bancárias e carteiras digitais. Isso facilita o processo de depósitos e retiradas, proporcionando uma experiência sem complicações.
A Variedade de Jogos: Diversão sem Limites A NNNBet se destaca pela diversidade de jogos que oferece aos seus usuários. O portfólio da plataforma é constantemente atualizado, trazendo novas opções para que os jogadores possam se divertir a qualquer momento. Desde opções de sorte e habilidade até jogos com mecânicas mais complexas, há algo para todos os tipos de jogador.
Uma das categorias mais populares na NNNBet são os jogos de habilidade, onde os jogadores podem testar seus conhecimentos e estratégias. Esses jogos exigem atenção e inteligência, proporcionando uma experiência emocionante. A plataforma também oferece jogos de sorte, que são perfeitos para quem deseja uma experiência mais simples e rápida, com resultados imprevisíveis que podem levar a grandes vitórias.
Os jogadores também podem experimentar jogos de apostas esportivas, onde podem tentar prever o resultado de eventos esportivos ao redor do mundo. As opções são variadas, incluindo futebol, basquete, tênis, entre outros, oferecendo uma experiência dinâmica e empolgante para os fãs de esportes.
Para quem prefere um pouco mais de emoção, a NNNBet também conta com jogos de cartas e roleta, trazendo a experiência clássica de apostas para o mundo digital. Estes jogos oferecem uma jogabilidade envolvente, onde a interação social com outros jogadores e a tensão de cada rodada tornam a experiência mais imersiva.
Experiência do Jogador: Uma Jornada Inesquecível A experiência do jogador é, sem dúvida, um dos pontos fortes da NNNBet. A plataforma se esforça para criar uma jornada única para cada usuário, oferecendo um ambiente amigável e acolhedor. Ao acessar o site, os jogadores são recebidos com uma interface limpa e intuitiva, que facilita a navegação e a escolha dos jogos desejados.
Além disso, a NNNBet investe em um suporte ao cliente de alta qualidade. A plataforma oferece atendimento via chat ao vivo, e-mail e outras formas de comunicação, garantindo que os jogadores possam resolver qualquer problema ou tirar dúvidas com rapidez e eficiência. A equipe de suporte é treinada para fornecer respostas rápidas e precisas, sempre buscando oferecer a melhor experiência possível.
Outro ponto importante é a experiência de jogabilidade. A NNNBet se dedica a garantir que seus jogos sejam não apenas divertidos, mas também justos e equilibrados. Para isso, a plataforma utiliza tecnologia de ponta para garantir que todos os resultados sejam aleatórios e baseados em um sistema imparcial, sem favorecimento a nenhum jogador. Isso oferece uma sensação de confiança para os usuários, que podem desfrutar dos jogos com a certeza de que estão participando de uma competição justa.
A plataforma também possui diversas promoções e bônus que são atualizados regularmente. Os jogadores podem aproveitar essas ofertas para maximizar suas chances de sucesso e tornar sua experiência ainda mais gratificante. Além disso, a NNNBet oferece um programa de fidelidade para os jogadores mais assíduos, proporcionando benefícios exclusivos como bônus adicionais e acesso a eventos especiais.
Conclusão: NNNBet, A Escolha Certa para os Amantes de Entretenimento Digital Com uma plataforma moderna, segura e acessível, a NNNBet se apresenta como uma excelente opção para quem busca diversão e entretenimento digital de qualidade. Sua diversidade de jogos, que vai de apostas esportivas a jogos de habilidade e sorte, garante que todos os tipos de jogadores encontrem algo de seu interesse. A experiência do usuário é aprimorada por um atendimento ao cliente eficiente e por um ambiente justo e seguro para jogar.
Se você está em busca de uma plataforma inovadora, com jogos envolventes e uma experiência personalizada, a NNNBet é uma excelente escolha. Ao se inscrever e explorar o vasto portfólio de jogos, você descobrirá por que tantos jogadores estão adotando essa plataforma como seu principal destino de entretenimento online.
-
 @ b2d670de:907f9d4a
2025-03-25 20:17:57
@ b2d670de:907f9d4a
2025-03-25 20:17:57This guide will walk you through setting up your own Strfry Nostr relay on a Debian/Ubuntu server and making it accessible exclusively as a TOR hidden service. By the end, you'll have a privacy-focused relay that operates entirely within the TOR network, enhancing both your privacy and that of your users.
Table of Contents
- Prerequisites
- Initial Server Setup
- Installing Strfry Nostr Relay
- Configuring Your Relay
- Setting Up TOR
- Making Your Relay Available on TOR
- Testing Your Setup]
- Maintenance and Security
- Troubleshooting
Prerequisites
- A Debian or Ubuntu server
- Basic familiarity with command line operations (most steps are explained in detail)
- Root or sudo access to your server
Initial Server Setup
First, let's make sure your server is properly set up and secured.
Update Your System
Connect to your server via SSH and update your system:
bash sudo apt update sudo apt upgrade -ySet Up a Basic Firewall
Install and configure a basic firewall:
bash sudo apt install ufw -y sudo ufw allow ssh sudo ufw enableThis allows SSH connections while blocking other ports for security.
Installing Strfry Nostr Relay
This guide includes the full range of steps needed to build and set up Strfry. It's simply based on the current version of the
DEPLOYMENT.mddocument in the Strfry GitHub repository. If the build/setup process is changed in the repo, this document could get outdated. If so, please report to me that something is outdated and check for updated steps here.Install Dependencies
First, let's install the necessary dependencies. Each package serves a specific purpose in building and running Strfry:
bash sudo apt install -y git build-essential libyaml-perl libtemplate-perl libregexp-grammars-perl libssl-dev zlib1g-dev liblmdb-dev libflatbuffers-dev libsecp256k1-dev libzstd-devHere's why each dependency is needed:
Basic Development Tools: -
git: Version control system used to clone the Strfry repository and manage code updates -build-essential: Meta-package that includes compilers (gcc, g++), make, and other essential build toolsPerl Dependencies (used for Strfry's build scripts): -
libyaml-perl: Perl interface to parse YAML configuration files -libtemplate-perl: Template processing system used during the build process -libregexp-grammars-perl: Advanced regular expression handling for Perl scriptsCore Libraries for Strfry: -
libssl-dev: Development files for OpenSSL, used for secure connections and cryptographic operations -zlib1g-dev: Compression library that Strfry uses to reduce data size -liblmdb-dev: Lightning Memory-Mapped Database library, which Strfry uses for its high-performance database backend -libflatbuffers-dev: Memory-efficient serialization library for structured data -libsecp256k1-dev: Optimized C library for EC operations on curve secp256k1, essential for Nostr's cryptographic signatures -libzstd-dev: Fast real-time compression algorithm for efficient data storage and transmissionClone and Build Strfry
Clone the Strfry repository:
bash git clone https://github.com/hoytech/strfry.git cd strfryBuild Strfry:
bash git submodule update --init make setup-golpe make -j2 # This uses 2 CPU cores. Adjust based on your server (e.g., -j4 for 4 cores)This build process will take several minutes, especially on servers with limited CPU resources, so go get a coffee and post some great memes on nostr in the meantime.
Install Strfry
Install the Strfry binary to your system path:
bash sudo cp strfry /usr/local/binThis makes the
strfrycommand available system-wide, allowing it to be executed from any directory and by any user with the appropriate permissions.Configuring Your Relay
Create Strfry User
Create a dedicated user for running Strfry. This enhances security by isolating the relay process:
bash sudo useradd -M -s /usr/sbin/nologin strfryThe
-Mflag prevents creating a home directory, and-s /usr/sbin/nologinprevents anyone from logging in as this user. This is a security best practice for service accounts.Create Data Directory
Create a directory for Strfry's data:
bash sudo mkdir /var/lib/strfry sudo chown strfry:strfry /var/lib/strfry sudo chmod 755 /var/lib/strfryThis creates a dedicated directory for Strfry's database and sets the appropriate permissions so that only the strfry user can write to it.
Configure Strfry
Copy the sample configuration file:
bash sudo cp strfry.conf /etc/strfry.confEdit the configuration file:
bash sudo nano /etc/strfry.confModify the database path:
```
Find this line:
db = "./strfry-db/"
Change it to:
db = "/var/lib/strfry/" ```
Check your system's hard limit for file descriptors:
bash ulimit -HnUpdate the
nofilessetting in your configuration to match this value (or set to 0):```
Add or modify this line in the config (example if your limit is 524288):
nofiles = 524288 ```
The
nofilessetting determines how many open files Strfry can have simultaneously. Setting it to your system's hard limit (or 0 to use the system default) helps prevent "too many open files" errors if your relay becomes popular.You might also want to customize your relay's information in the config file. Look for the
infosection and update it with your relay's name, description, and other details.Set ownership of the configuration file:
bash sudo chown strfry:strfry /etc/strfry.confCreate Systemd Service
Create a systemd service file for managing Strfry:
bash sudo nano /etc/systemd/system/strfry.serviceAdd the following content:
```ini [Unit] Description=strfry relay service
[Service] User=strfry ExecStart=/usr/local/bin/strfry relay Restart=on-failure RestartSec=5 ProtectHome=yes NoNewPrivileges=yes ProtectSystem=full LimitCORE=1000000000
[Install] WantedBy=multi-user.target ```
This systemd service configuration: - Runs Strfry as the dedicated strfry user - Automatically restarts the service if it fails - Implements security measures like
ProtectHomeandNoNewPrivileges- Sets resource limits appropriate for a relayEnable and start the service:
bash sudo systemctl enable strfry.service sudo systemctl start strfryCheck the service status:
bash sudo systemctl status strfryVerify Relay is Running
Test that your relay is running locally:
bash curl localhost:7777You should see a message indicating that the Strfry relay is running. This confirms that Strfry is properly installed and configured before we proceed to set up TOR.
Setting Up TOR
Now let's make your relay accessible as a TOR hidden service.
Install TOR
Install TOR from the package repositories:
bash sudo apt install -y torThis installs the TOR daemon that will create and manage your hidden service.
Configure TOR
Edit the TOR configuration file:
bash sudo nano /etc/tor/torrcScroll down to wherever you see a commented out part like this: ```
HiddenServiceDir /var/lib/tor/hidden_service/
HiddenServicePort 80 127.0.0.1:80
```
Under those lines, add the following lines to set up a hidden service for your relay:
HiddenServiceDir /var/lib/tor/strfry-relay/ HiddenServicePort 80 127.0.0.1:7777This configuration: - Creates a hidden service directory at
/var/lib/tor/strfry-relay/- Maps port 80 on your .onion address to port 7777 on your local machine - Keeps all traffic encrypted within the TOR networkCreate the directory for your hidden service:
bash sudo mkdir -p /var/lib/tor/strfry-relay/ sudo chown debian-tor:debian-tor /var/lib/tor/strfry-relay/ sudo chmod 700 /var/lib/tor/strfry-relay/The strict permissions (700) are crucial for security as they ensure only the debian-tor user can access the directory containing your hidden service private keys.
Restart TOR to apply changes:
bash sudo systemctl restart torMaking Your Relay Available on TOR
Get Your Onion Address
After restarting TOR, you can find your onion address:
bash sudo cat /var/lib/tor/strfry-relay/hostnameThis will output something like
abcdefghijklmnopqrstuvwxyz234567.onion, which is your relay's unique .onion address. This is what you'll share with others to access your relay.Understanding Onion Addresses
The .onion address is a special-format hostname that is automatically generated based on your hidden service's private key.
Your users will need to use this address with the WebSocket protocol prefix to connect:
ws://youronionaddress.onionTesting Your Setup
Test with a Nostr Client
The best way to test your relay is with an actual Nostr client that supports TOR:
- Open your TOR browser
- Go to your favorite client, either on clearnet or an onion service.
- Check out this list of nostr clients available over TOR.
- Add your relay URL:
ws://youronionaddress.onionto your relay list - Try posting a note and see if it appears on your relay
- In some nostr clients, you can also click on a relay to get information about it like the relay name and description you set earlier in the stryfry config. If you're able to see the correct values for the name and the description, you were able to connect to the relay.
- Some nostr clients also gives you a status on what relays a note was posted to, this could also give you an indication that your relay works as expected.
Note that not all Nostr clients support TOR connections natively. Some may require additional configuration or use of TOR Browser. E.g. most mobile apps would most likely require a TOR proxy app running in the background (some have TOR support built in too).
Maintenance and Security
Regular Updates
Keep your system, TOR, and relay updated:
```bash
Update system
sudo apt update sudo apt upgrade -y
Update Strfry
cd ~/strfry git pull git submodule update make -j2 sudo cp strfry /usr/local/bin sudo systemctl restart strfry
Verify TOR is still running properly
sudo systemctl status tor ```
Regular updates are crucial for security, especially for TOR which may have security-critical updates.
Database Management
Strfry has built-in database management tools. Check the Strfry documentation for specific commands related to database maintenance, such as managing event retention and performing backups.
Monitoring Logs
To monitor your Strfry logs:
bash sudo journalctl -u strfry -fTo check TOR logs:
bash sudo journalctl -u tor -fMonitoring logs helps you identify potential issues and understand how your relay is being used.
Backup
This is not a best practices guide on how to do backups. Preferably, backups should be stored either offline or on a different machine than your relay server. This is just a simple way on how to do it on the same server.
```bash
Stop the relay temporarily
sudo systemctl stop strfry
Backup the database
sudo cp -r /var/lib/strfry /path/to/backup/location
Restart the relay
sudo systemctl start strfry ```
Back up your TOR hidden service private key. The private key is particularly sensitive as it defines your .onion address - losing it means losing your address permanently. If you do a backup of this, ensure that is stored in a safe place where no one else has access to it.
bash sudo cp /var/lib/tor/strfry-relay/hs_ed25519_secret_key /path/to/secure/backup/locationTroubleshooting
Relay Not Starting
If your relay doesn't start:
```bash
Check logs
sudo journalctl -u strfry -e
Verify configuration
cat /etc/strfry.conf
Check permissions
ls -la /var/lib/strfry ```
Common issues include: - Incorrect configuration format - Permission problems with the data directory - Port already in use (another service using port 7777) - Issues with setting the nofiles limit (setting it too big)
TOR Hidden Service Not Working
If your TOR hidden service is not accessible:
```bash
Check TOR logs
sudo journalctl -u tor -e
Verify TOR is running
sudo systemctl status tor
Check onion address
sudo cat /var/lib/tor/strfry-relay/hostname
Verify TOR configuration
sudo cat /etc/tor/torrc ```
Common TOR issues include: - Incorrect directory permissions - TOR service not running - Incorrect port mapping in torrc
Testing Connectivity
If you're having trouble connecting to your service:
```bash
Verify Strfry is listening locally
sudo ss -tulpn | grep 7777
Check that TOR is properly running
sudo systemctl status tor
Test the local connection directly
curl --include --no-buffer localhost:7777 ```
Privacy and Security Considerations
Running a Nostr relay as a TOR hidden service provides several important privacy benefits:
-
Network Privacy: Traffic to your relay is encrypted and routed through the TOR network, making it difficult to determine who is connecting to your relay.
-
Server Anonymity: The physical location and IP address of your server are concealed, providing protection against denial-of-service attacks and other targeting.
-
Censorship Resistance: TOR hidden services are more resilient against censorship attempts, as they don't rely on the regular DNS system and can't be easily blocked.
-
User Privacy: Users connecting to your relay through TOR enjoy enhanced privacy, as their connections are also encrypted and anonymized.
However, there are some important considerations:
- TOR connections are typically slower than regular internet connections
- Not all Nostr clients support TOR connections natively
- Running a hidden service increases the importance of keeping your server secure
Congratulations! You now have a Strfry Nostr relay running as a TOR hidden service. This setup provides a resilient, privacy-focused, and censorship-resistant communication channel that helps strengthen the Nostr network.
For further customization and advanced configuration options, refer to the Strfry documentation.
Consider sharing your relay's .onion address with the Nostr community to help grow the privacy-focused segment of the network!
If you plan on providing a relay service that the public can use (either for free or paid for), consider adding it to this list. Only add it if you plan to run a stable and available relay.
-
 @ 3b2218fc:5a1784e2
2025-04-12 06:21:23
@ 3b2218fc:5a1784e2
2025-04-12 06:21:23No universo das plataformas de entretenimento digital, poucas conseguem se destacar pela inovação, variedade e qualidade dos serviços como o 5ubet. Com uma abordagem centrada no jogador e na experiência imersiva, o 5ubet se apresenta como uma plataforma versátil, onde a diversão e as emoções estão ao alcance de um clique. Neste artigo, exploraremos a introdução da plataforma, as opções de jogos disponíveis e a experiência única proporcionada aos jogadores.
Introdução ao 5ubet O 5ubet é uma plataforma de entretenimento online que oferece uma gama diversificada de opções para os jogadores que buscam uma experiência completa e divertida no mundo virtual. Com um design moderno e uma interface amigável, o 5ubet se destaca por sua facilidade de navegação e pela confiabilidade de seus serviços. Ao acessar o site ou o aplicativo, os jogadores são recebidos por um ambiente intuitivo e organizado, onde podem escolher entre diversas categorias de jogos, desde os mais clássicos até os mais inovadores.
A plataforma se orgulha de trabalhar com as melhores tecnologias do mercado, garantindo uma experiência fluida, segura e, acima de tudo, divertida. A confiança e a transparência são pilares fundamentais para o 5ubet, que implementa sistemas de segurança de ponta para proteger as informações pessoais e financeiras dos jogadores. Além disso, a plataforma conta com suporte ao cliente disponível 24/7, pronto para ajudar os jogadores com quaisquer dúvidas ou problemas.
Ao longo do tempo, o 5ubet tem se consolidado como uma das principais opções para quem busca diversão e entretenimento online, com uma proposta diferenciada que valoriza a experiência do usuário e oferece uma vasta gama de alternativas para quem deseja se aventurar no mundo dos jogos digitais.
Os Jogos do 5ubet: Diversão Sem Limites Quando se fala em opções de jogo, o 5ubet não deixa a desejar. A plataforma oferece uma extensa coleção de jogos que atendem a todos os gostos e preferências. Seja você fã de ação, estratégia, ou apenas busca um passatempo divertido, no 5ubet há algo para todos.
A seção de jogos de habilidade, por exemplo, é perfeita para os jogadores que desejam colocar suas competências à prova. Aqui, é possível encontrar títulos que exigem raciocínio lógico, estratégia e tomada de decisões rápidas. Para aqueles que preferem uma experiência mais relaxante, o 5ubet também oferece jogos casuais, com mecânicas simples e intuitivas, ideais para descontrair após um longo dia de trabalho.
Os jogos de competição são outro destaque da plataforma. Se você é fã de desafios em tempo real, vai adorar as opções que o 5ubet disponibiliza, com partidas emocionantes contra outros jogadores ao redor do mundo. Esses jogos não só testam suas habilidades, mas também oferecem a emoção da vitória e a adrenalina da competição.
Para quem busca novidades, o 5ubet está sempre atualizando seu portfólio com novos lançamentos, incorporando as tendências do mercado e oferecendo jogos inovadores que mantêm os jogadores engajados. Os gráficos de alta qualidade, a jogabilidade fluida e as mecânicas envolventes são elementos que tornam a experiência de jogar no 5ubet única e inesquecível.
A Experiência do Jogador no 5ubet O que realmente distingue o 5ubet das demais plataformas de entretenimento online é a experiência do jogador. Desde o momento em que você acessa a plataforma até o final de sua sessão de jogo, cada detalhe é pensado para garantir que o usuário tenha uma jornada agradável e empolgante.
A interface do 5ubet é intuitiva e fácil de usar, com menus bem organizados que permitem ao jogador navegar entre as diferentes categorias de jogos com facilidade. A plataforma também é compatível com diversos dispositivos, incluindo smartphones e tablets, garantindo que você possa jogar onde estiver, sem perder a qualidade da experiência.
Além disso, a plataforma do 5ubet é altamente personalizada. O sistema aprende com as preferências do jogador e oferece recomendações de jogos baseadas no histórico de atividades e nos interesses individuais. Isso cria uma experiência personalizada, onde o jogador sempre encontra algo novo para jogar e explorar.
Outro ponto importante é o sistema de recompensas e promoções do 5ubet. Ao longo de sua jornada na plataforma, o jogador tem a oportunidade de participar de eventos exclusivos, receber bônus e aproveitar ofertas especiais que tornam a experiência ainda mais emocionante. Essas promoções são uma excelente maneira de aumentar as chances de vitória e proporcionar um toque extra de diversão.
A comunidade de jogadores também é um aspecto importante do 5ubet. O sistema de chat ao vivo e as funções de interação social permitem que os jogadores se conectem, compartilhem dicas, estratégias e até mesmo formem equipes para desafios em grupo. Essa interação cria um ambiente de amizade e colaboração, tornando a experiência ainda mais gratificante.
Conclusão O 5ubet é uma plataforma que se destaca pela sua diversidade, inovação e foco na experiência do jogador. Com uma ampla gama de jogos, uma interface intuitiva e uma abordagem personalizada, oferece aos usuários um ambiente seguro, divertido e emocionante. Seja você um jogador experiente ou um iniciante, o 5ubet é o lugar ideal para quem busca entretenimento de qualidade e uma experiência única no mundo dos jogos online.
-
 @ 502ab02a:a2860397
2025-04-12 02:40:22
@ 502ab02a:a2860397
2025-04-12 02:40:22เริ่มจากบรอกโคลี แล้วขยายผลไปสู่ระดับโลก
หลายประเทศในเอเชีย แอฟริกา ละตินอเมริกา ตกอยู่ในสภาพ “จนหนี้หัวโต” ทั้งจากวิกฤตเศรษฐกิจหรือปัญหาสภาพภูมิอากาศ แล้วใครกันล่ะเข้ามาช่วย?
ชื่อที่ได้ยินบ่อยคือ IMF (กองทุนการเงินระหว่างประเทศ) World Bank (ธนาคารโลก) WTO (องค์การการค้าโลก) FAO (องค์การอาหารและการเกษตรของ UN)
ฟังดูเหมือนองค์กรการกุศล แต่เบื้องหลังคือกลไกที่ “แลกข้าวกับกฎหมาย” โดยเฉพาะเมื่อประเทศยากจนขอเงินกู้หรือขอเข้าเป็นสมาชิกข้อตกลงการค้า พวกเขาจะถูก “บังคับกลายๆ” ให้ต้องแก้กฎหมายภายในประเทศให้สอดคล้องกับ UPOV 1991
ตัวอย่างชัดๆ กันครับเช่น 1. แอฟริกาใต้ / กานา / เคนยา ถูกกดดันจาก World Bank ให้ปรับกฎหมายคุ้มครองพันธุ์พืช ไม่งั้นจะไม่อนุมัติเงินช่วยเหลือสำหรับเกษตรกรรมและการศึกษา 2.ฟิลิปปินส์ / เวียดนาม / อินโดนีเซีย ต้องรับเงื่อนไข UPOV 1991 เพื่อเข้า FTA กับ EU หรือสหรัฐฯ ถ้าไม่ยอม? ข้าว ข้าวโพด หรือสินค้าเกษตรอื่นๆ จะเข้าไปขายไม่ได้ 3.เม็กซิโก เคยต่อสู้กับ Monsanto เรื่องสิทธิในการปลูกข้าวโพดดั้งเดิม แต่สุดท้ายโดน “ตีท้ายครัว” ด้วย FTA กับสหรัฐที่ฝัง UPOV 1991 มาแบบแนบเนียน
ปี 2561 รัฐบาลบางประเทศพยายาม “รีบแก้กฎหมายพันธุ์พืช” ให้สอดคล้องกับ UPOV 1991 เพื่อปูทางเข้าสู่ CPTPP ซึ่งเป็นข้อตกลงการค้าเสรีระดับภูมิภาคที่มีประเทศร่ำรวยอยู่เต็มไปหมด
ข้อเรียกร้องจาก CPTPP คือ -ต้อง ห้ามเกษตรกรเก็บพันธุ์ไว้ใช้ซ้ำโดยไม่ได้รับอนุญาต -ต้อง คุ้มครองพันธุ์พืชที่พัฒนาขึ้นโดยบริษัทเอกชน 20-25 ปี -ต้อง เปิดทางให้บริษัทต่างชาติเข้ามาจดทะเบียนพันธุ์พืชในประเทศได้โดยง่าย
เสียงค้านจึงดังกระหึ่มจากเกษตรกร นักวิชาการ และภาคประชาสังคม นำโดยเครือข่ายเกษตรกรรมยั่งยืน กลุ่มรักษ์พันธุ์ข้าว จนนายกรัฐมนตรีในขณะนั้นต้องออกมาประกาศ “พักเรื่องนี้ไว้ก่อน” แต่ถึงวันนี้... ก็ยังไม่มีการยืนยันว่าจะ “ล้มเลิกโดยสิ้นเชิง”
รู้หรือไม่ว่า บริษัทพันธุ์พืชที่ใหญ่ที่สุดในโลกไม่ใช่คนปลูกข้าว แต่มาจาก “บริษัทยา” และ “บริษัทเคมี”!!!
Bayer (เยอรมนี) ที่ควบรวม Monsanto Corteva (สหรัฐฯ) แยกตัวจาก DowDuPont Syngenta (สวิตเซอร์แลนด์) ที่ตอนนี้เป็นของบริษัทจีน ChemChina
3 บริษัทนี้ครองตลาดพันธุ์พืชดัดแปลงพันธุกรรม (GMO) และพันธุ์ลูกผสมทั่วโลก และผลักดัน UPOV 1991 แบบดุดันผ่านองค์กรเช่น ISF (International Seed Federation)
องค์กรเหล่านี้พวกเขาไม่ได้ปล้นด้วยปืน แต่ใช้ สัญญา พวกเขาไม่ได้เผาไร่ แต่ “จดสิทธิบัตร” สิ่งที่ไม่ควรเป็นของใคร และสิ่งที่พวกเขาต้องการ ไม่ใช่แค่ข้าวโพดหรือถั่วเหลือง แต่คือ “สิทธิในการออกแบบอาหารทั้งโลก” ในแบบที่คนตัวเล็ก... ต้องจ่ายค่าเช่ากินข้าว ทุกปี ตลอดชีวิต
จากปัญหาเหล่านี้ก็เลยเกิดแนวคิดที่เรียกว่า Seed Sovereignty ซึ่งมองว่าเมล็ดพันธุ์เป็นสมบัติร่วมของมนุษยชาติ ไม่ควรถูกครอบครองแบบผูกขาด และเกษตรกรควรมีสิทธิในการ
-เก็บเมล็ดพันธุ์ -แลกเปลี่ยน -ปรับปรุง -ใช้งานซ้ำ โดยไม่ต้องขออนุญาตใครตอนต่อไปเรามาคุยเรื่อง UPOV 1991 กันครับ
#pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก
-
 @ 3b2218fc:5a1784e2
2025-04-12 06:20:37
@ 3b2218fc:5a1784e2
2025-04-12 06:20:37Nos últimos anos, a indústria de jogos online tem vivido um crescimento emocionante e acelerado. Entre as várias plataformas que surgiram, A188 se destaca como um espaço inovador e completo, ideal para jogadores de todos os níveis. Se você é um jogador experiente ou está começando a explorar o mundo dos jogos online, A188 oferece um ambiente fácil de usar, imersivo e diversificado, projetado para atender a todos os gostos.
A188 é mais do que apenas uma plataforma de jogos online; é um hub global onde os entusiastas podem se conectar, interagir e aproveitar diversas opções de entretenimento. A plataforma oferece uma combinação imbatível de ação ao vivo, jogabilidade em tempo real e inovação digital, criada para proporcionar uma experiência excepcional aos jogadores.
O que torna a A188 realmente única é sua dedicação em oferecer uma experiência fluida em diferentes dispositivos. Se você está jogando no smartphone, tablet ou desktop, a plataforma é otimizada para todos os tamanhos de tela, garantindo que você não perca nem um momento de seu jogo favorito. Além disso, ela possui uma interface responsiva que permite aos usuários navegar facilmente entre as seções, desde a navegação pelos jogos até a realização de depósitos e retiradas seguras.
A188 garante que os jogadores tenham uma experiência agradável ao fornecer tempos de carregamento rápidos, gráficos de alta qualidade e uma ampla seleção de opções de entretenimento. De simulações de esportes a jogos de estratégia e sequências de ação imersivas, a plataforma tem algo para todos. A A188 também atualiza constantemente sua biblioteca de jogos, garantindo que sempre haja algo novo e emocionante para os jogadores descobrirem.
A segurança é outro pilar do serviço da A188. A plataforma utiliza tecnologias de criptografia de ponta, garantindo que as informações pessoais e financeiras dos jogadores estejam sempre protegidas. Seja ao realizar um depósito ou simplesmente ao interagir com outros jogadores, a A188 assegura que seus dados estejam seguros, proporcionando tranquilidade enquanto você se diverte.
O atendimento ao cliente é mais uma área em que a A188 se destaca. Com uma equipe de suporte disponível 24 horas por dia, sete dias por semana, os jogadores podem rapidamente resolver qualquer dúvida ou problema que possam ter. Se você precisar de ajuda com a gestão da conta ou tiver questões sobre um jogo específico, a equipe de suporte está sempre pronta para ajudar.
Em termos de acessibilidade, a plataforma da A188 oferece suporte a vários idiomas e moedas, tornando-a ideal para jogadores de todo o mundo. É verdadeiramente uma comunidade internacional, onde pessoas de diferentes partes do mundo podem se conectar e aproveitar os jogos juntos. A plataforma também adota políticas de jogo justo, garantindo que todos os jogadores sejam tratados de maneira igual e justa, o que contribui para uma experiência ainda mais positiva.
-
 @ c3c7122c:607731d7
2025-04-12 04:05:06
@ c3c7122c:607731d7
2025-04-12 04:05:06Help!
Calling all El Salvador Nostriches! If you currently live in SV, I need your help and am offering several bounties (0.001, 0.01, and 0.1 BTC).
In Brief
In short, I am pursuing El Salvador citizenship by birthright (through my grandmother). I’ve struggled to progress because her name varies on different documents. I need someone to help me push harder to get past this barrier, or connect me with information or people who can work on my behalf. I am offering:
- 0.001 BTC (100k sats) for information that will help me progress from my current situation
- 0.01 BTC (1 MM sats) to get me in touch with someone that is more impactful than the immigration lawyer I already spoke with
- 0.1 BTC (10 MM sats) if your efforts help me obtain citizenship for me or my father
Background
My grandma married my grandfather (an American Marine) and moved to the states where my father was born. I have some official and unofficial documents where her name varies in spelling, order of first/middle name, and addition of her father’s last name. So every doc basically has a different name for her. I was connected with an english-speaking immigration lawyer in SV who hit a dead end when searching for her official ID because the city hall in her city had burned down so there was no record of her info. He gave up at that point. I find it odd that it was so easy to change your name back then, but they are more strict now with the records from that time.
I believe SV citizenship is my birthright and have several personal reasons for pursuing this. I want someone to act on my behalf who will try harder to work the system (by appeal, loophole, or even bribe if I have to). If you are local and can help me with this, I’d greatly appreciate any efforts you make.
Cheers!
Corey San Diego
-
 @ 04c915da:3dfbecc9
2025-03-25 17:43:44
@ 04c915da:3dfbecc9
2025-03-25 17:43:44One of the most common criticisms leveled against nostr is the perceived lack of assurance when it comes to data storage. Critics argue that without a centralized authority guaranteeing that all data is preserved, important information will be lost. They also claim that running a relay will become prohibitively expensive. While there is truth to these concerns, they miss the mark. The genius of nostr lies in its flexibility, resilience, and the way it harnesses human incentives to ensure data availability in practice.
A nostr relay is simply a server that holds cryptographically verifiable signed data and makes it available to others. Relays are simple, flexible, open, and require no permission to run. Critics are right that operating a relay attempting to store all nostr data will be costly. What they miss is that most will not run all encompassing archive relays. Nostr does not rely on massive archive relays. Instead, anyone can run a relay and choose to store whatever subset of data they want. This keeps costs low and operations flexible, making relay operation accessible to all sorts of individuals and entities with varying use cases.
Critics are correct that there is no ironclad guarantee that every piece of data will always be available. Unlike bitcoin where data permanence is baked into the system at a steep cost, nostr does not promise that every random note or meme will be preserved forever. That said, in practice, any data perceived as valuable by someone will likely be stored and distributed by multiple entities. If something matters to someone, they will keep a signed copy.
Nostr is the Streisand Effect in protocol form. The Streisand effect is when an attempt to suppress information backfires, causing it to spread even further. With nostr, anyone can broadcast signed data, anyone can store it, and anyone can distribute it. Try to censor something important? Good luck. The moment it catches attention, it will be stored on relays across the globe, copied, and shared by those who find it worth keeping. Data deemed important will be replicated across servers by individuals acting in their own interest.
Nostr’s distributed nature ensures that the system does not rely on a single point of failure or a corporate overlord. Instead, it leans on the collective will of its users. The result is a network where costs stay manageable, participation is open to all, and valuable verifiable data is stored and distributed forever.
-
 @ f3873798:24b3f2f3
2025-04-11 22:43:43
@ f3873798:24b3f2f3
2025-04-11 22:43:43Durante décadas, ouvimos que o Brasil era o "país do futuro". Uma terra rica, com imenso potencial humano e natural, destinada a se tornar uma grande potência e referência para o mundo. Essa ideia, repetida em discursos políticos e publicações internacionais, alimentou gerações com esperança. Mas o tempo passou — e esse futuro promissor parece nunca chegar.
Na prática, o que vemos é um ciclo de promessas não cumpridas, problemas sociais profundos e um povo muitas vezes desiludido. Apesar do potencial imenso, o Brasil enfrenta barreiras estruturais e culturais que dificultam seu pleno desenvolvimento. E é justamente sobre isso que precisamos refletir.
A raiz dos nossos desafios
Não há como ter jeito sem que haja um enfrentamento com seriedade aos problemas que estão na base da nossa sociedade. Um dos maiores entraves é a precariedade da educação, tanto no acesso quanto na qualidade. Em muitas regiões, o estudo ainda é visto como perda de tempo, algo que não contribui para o sustento imediato da família. Mesmo com incentivos governamentais, o desempenho das escolas é baixo. Em vez de formar cidadãos críticos e profissionais capacitados, muitas vezes vemos instituições focadas em ideologias ou agendas desconectadas da realidade do aluno.
Outro ponto sensível é a estrutura familiar. Em áreas onde faltam referências morais, espirituais e sociais, o ambiente familiar pode se tornar disfuncional, com casos extremos de abusos e ausência total de valores básicos. Nesses contextos, a ausência de instituições que promovem virtudes e limites — como a Igreja, por exemplo — faz diferença. Não se trata de impor uma religião, mas de reconhecer o papel histórico que a fé teve (e ainda tem) na construção de uma base ética e civilizatória.
A falta de valores basilares e estrutura para a promoção da relações em sociedade, faz do ambiente escolar um local sem propósito, onde são depositados crianças para serem expostas a um convívio forçado com estranhos sem nenhum preparo familiar, e sendo muitas vezes subentendido pelos profissionais educadores como dever da família, no entanto tal estrutura foi corrompida e devido o combate a religião pelos veículos midiáticos.
O papel da cultura e da moralidade
A cultura brasileira também tem sido afetada por uma inversão de valores. Virtudes como honestidade, humildade e dedicação são muitas vezes vistas com desdém, enquanto comportamentos imprudentes e hedonistas são exaltados. Essa distorção enfraquece a sociedade e prejudica qualquer tentativa de avanço coletivo.
A elite intelectual e política, por sua vez, parece muitas vezes mais preocupada com interesses próprios do que com o bem comum. Muitos aderem a ideias que, em vez de promover a soberania e a autonomia nacional, aprofundam nossa dependência e fragilidade como país.
Existe saída?
Sim, existe. Mas não será simples — e muito menos rápida. O Brasil precisa de uma mudança profunda de mentalidade. Isso inclui:
Resgatar o valor da família e da formação moral;
Investir de verdade em uma educação que liberte, que forme e que inspire;
Incentivar a produção científica e tecnológica local;
Valorizar o trabalho árduo, a persistência e o compromisso com a verdade.
Também é preciso reconhecer que o desenvolvimento de uma nação não é apenas econômico, mas também espiritual e cultural. Mesmo que você não seja religioso, é possível entender que a construção de uma sociedade mais justa exige princípios, virtudes e limites. Sem isso, qualquer progresso será frágil e passageiro.
O Brasil tem jeito? Sim. Mas depende de nós — da nossa capacidade de enxergar com coragem onde estamos falhando, e da nossa disposição para agir com sabedoria, verdade e esperança.
-
 @ 10fe3f70:3489c810
2025-04-12 03:53:36
@ 10fe3f70:3489c810
2025-04-12 03:53:36contract-drafting #agreement-drafting #learn-drafting #keep-learning
I am a lawyer and a teacher. I am interested in learning new things every day.
I am from India, and have studied in a reputed law school in Delhi. I have long experience of working as in-house counsels to some reputed organisations.
My present goal is to teach drafting of contracts. What I will teach is some basic skills required by students to draft contracts.
I did some freelance online teaching during Covid Pandemic, and found that students are very interested in learning the craft. But, I also understood that they may not have enough free time to learn due to busy schedule.
If you are interested, you can access my curated playlist on Youtube
Keep watching this space, if you wish to know more...
Lessons on Contract Drafting
- Contract Drafting - An Introduction
- ...
-
 @ d0aa74cd:603d35cd
2025-04-11 20:24:40
@ d0aa74cd:603d35cd
2025-04-11 20:24:40Experimenting with cat package examples.
Gleam #Gleamlang #cat #Haskell
https://photonsphere.org/post/2025-04-11-gleam-cat/
-
 @ 2ed3596e:98b4cc78
2025-04-11 20:13:03
@ 2ed3596e:98b4cc78
2025-04-11 20:13:03Americans can now instantly sell bitcoin directly from their Lightning Wallets. The same auto conversion Bitcoin Well Customers are used for instantly and conveniently selling bitcoin from self-custody now has a Lightning option ready in the Sell bitcoin page of your Bitcoin Well account.
Adding the ability to sell bitcoin from the Lightning Network underscores our commitment to enabling you to get the most out of the freedom and independence Bitcoin has to offer. No longer must you rely on giving up custody of your bitcoin or navigate complicated trading interfaces for fast and convenient sales! Just send sats and receive dollars – Lightning fast.
Selling sats from the Lightning Network is quick and easy:
- From your Bitcoin Well account, go to Sell bitcoin and enter the amount of dollars you want
- Choose your bank, select “Lightning” and then generate a Lightning Invoice
- Pay the Lightning invoice and we’ll send dollars to your bank account
Here are detailed steps to guide you on how to sell sats from the Lightning Network 👇
Get your Lightning Invoice
Navigate to your Sell bitcoin page, enter the amount of dollars you wish to receive, set your destination bank account and select “Lightning”.
 Tap ‘Generate invoice’ to create a Lightning invoice. This Lightning invoice will be for the exact amount of sats you need to send for the amount of dollars you want to receive.
Tap ‘Generate invoice’ to create a Lightning invoice. This Lightning invoice will be for the exact amount of sats you need to send for the amount of dollars you want to receive.Send sats to your Lightning Invoice
To instantly sell bitcoin for dollars, simply pay the Lightning Invoice from your Lightning wallet. You can do this by scanning the QR code or by tapping the QR code to copy + paste the invoice into your Lightning wallet. Once received (basically instantly), we automatically convert received sats into dollars and send the dollars to your selected bank account. No waiting for confirmations, no mining fees and no complicated trading interfaces. Just sats in, dollars out. Lightning fast ⚡️
 ## What is the Lightning Network?
## What is the Lightning Network?The Lightning Network is a second-layer protocol built on top of Bitcoin. It enables fast, cheap, and private bitcoin payments, perfect for small transactions and daily use. Think of it like the relationship between the credit card network and the banking system. While Bitcoin’s base layer is optimized for security, Lightning is optimized for frequent or small, cheap and private payments for everyday transactions — instantly and without bloating the blockchain. The Lightning Network makes it much more convenient to use bitcoin in everyday life, bringing you closer to replacing your bank with bitcoin.
Currently, sats on the Lightning Network cannot be directly sent to an on-chain bitcoin wallet, and vice versa. However, that won’t remain true for Bitcoin Well accounts for long…
Why Does the Lightning Network Matter?
The Lightning Network helps bitcoin reach its full potential as everyday money. While Bitcoin’s base chain is perfect for storing value, it’s not always practical for everyday payments or quick, small transactions. Lightning fills that gap — it’s fast, inexpensive, and built for a world where people use bitcoin as easily as cash. Bitcoin is the future of money. Lightning makes it usable today. We love Lightning, and have some exciting additional products coming that will shock you!
Earn sats over the Lightning Network
Earn sats when you refer your friends! When you add your Lightning Payment address from your personal Lightning Wallet to your Referral page, every time someone you referred transacts on the portal, you get a kickback paid in sats! Of course, we never custody your bitcoin, even when you get a Lightning referral reward! All bitcoin is always sent straight to your wallet. ⚡\ \ Haven’t signed up with Bitcoin Well yet? Sign up here and embrace the Bitcoin Standard.
About Bitcoin Well
Bitcoin Well exists to enable independence. We do this by coupling the convenience of modern banking, with the benefits of bitcoin. In other words, we want to make it easy to use bitcoin in self-custody.
We are publicly traded (and love it when our customers become shareholders!) and hold ourselves to a high standard of enabling life on a Bitcoin standard. If you want to learn more about Bitcoin Well, please visit our website or reach out!
-
 @ eba786d8:8d3dc09c
2025-04-12 03:39:49
@ eba786d8:8d3dc09c
2025-04-12 03:39:49Seminode is transforming supply chains into efficient information networks. Manufacturers and distributors rely on outdated technology, excel and email, which greatly hinders visibility and information flow between parties. Trading applications on an open standard layer will enable companies to transact quickly and securely, making supply chains more resilient to future disruptions.
We are looking for OEMs to partner with us on in-house proof of concepts. We promise we will work our ass off to make you money and save you time.
Oh..and if anyone can get in touch with jack or anyone at Block, we would love to help power their supply chain.
Ryan
posting from comet - 4/11/25 -
 @ 27dd78c2:66ffe658
2025-03-25 17:12:08
@ 27dd78c2:66ffe658
2025-03-25 17:12:08In an age where ‘run clubs’ are getting more popular than ‘night clubs’, it’s exciting to see a Nostr-based sovereign fitness tracker hit the scene: Enter Runstr.club!
Runstr has emerged as a game-changer, redefining how runners connect, track progress, and stay motivated. For Bitcoin Runners, a movement that advocates sovereignty of one’s wealth, while improving one’s health, Runstr.club presents an exciting platform of choice to record your proof-of-work, take ownership of your personal data, and selectively engage with your social graph.
What is Runstr.club?
Runstr.club is a platform that’s being built to grow the proof-of-work community, with plans to offer interactive leaderboards, challenges, and social engagement. Unlike traditional running apps that focus purely on statistics, Runstr.club puts emphasis on camaraderie, motivation, and shared goals. It’s the Strava alternative that values ownership of your data, interoperability between platforms, and privacy as standard.
Why Runstr.club is a Great Fit for Bitcoin Runners
Bitcoin Runners isn’t just about proof-of-work; it’s about promoting freedom tech, decentralisation, and self-sovereignty principles that align closely with the ethos of Runstr.club.
Here’s why this platform is a great match for our movement:
- Community-Driven & Decentralised Spirit
Bitcoin Runners thrives on grassroots adoption and community participation, much like Runstr.club’s organic and community-focused model. Unlike corporate-owned fitness platforms that prioritise monetisation, Runstr.club is designed to empower runners, keeping the experience authentic and meaningful.
- Privacy-First Approach
One of the key concerns for bitcoiners is privacy. Mainstream fitness platforms harvest user data for profit, but Runstr.club offers a privacy-first alternative. This makes it an excellent choice for runners who value sovereignty in the digital age.
- The Advantage of Nostr Over Centralised Run Tracking Tools
Most mainstream running apps, like Strava or Nike Run Club, rely on centralised platforms that control user data, impose restrictions, and often monetise user activity. Runstr.club, however, is built on Nostr, a decentralised protocol that enables users to interact without getting trapped inside a walled garden.
With Nostr, runners benefit from:
-
True ownership of their data – no risk of platforms selling or misusing personal running history.
-
Resilience against censorship – no arbitrary bans or content moderation dictated by a 'shadowy suit'.
-
Interoperability – seamless integration with other Nostr-based applications, keeping data fluid and accessible across different platforms.
-
Peer-to-peer connectivity – allowing runners to share progress, create challenges, and stay engaged independent of big tech.
For Bitcoin Runners, Nostr’s decentralised nature aligns perfectly with the principles of sovereignty, freedom, and privacy.
- Gamification & Challenges
Runstr.club has engaging challenges and decentralised leaderboards on its roadmap. Whether you’re stacking sats through running-related bitcoin challenges or simply competing with fellow bitcoiners for fun, the platform will add an extra layer of engagement to every run. We would love to see such features come to life!
Conclusion
Runstr.club is more than just a running tracker—it’s a Nostr, bitcoin, and fitness onboarding community-driven movement. By embracing platforms that respect privacy, encourage competition, and foster community, we stay true to our values while pushing our limits as runners.
Let’s take this to the next level - be sure to follow Runstr on Nostr!
Run free. Stay sovereign. Stack zaps!
We’re shilling this open-source initiative out of genuine appreciation for both its vision and the dedicated team behind it.
-
 @ eba786d8:8d3dc09c
2025-04-12 03:39:25
@ eba786d8:8d3dc09c
2025-04-12 03:39:25Seminode is transforming supply chains into efficient information networks. Manufacturers and distributors rely on outdated technology, excel and email, which greatly hinders visibility and information flow between parties. Trading applications on an open standard layer will enable companies to transact quickly and securely, making supply chains more resilient to future disruptions.
We are looking for OEMs to partner with us on in-house proof of concepts. We promise we will work our ass off to make you money and save you time.
Oh..and if anyone can get in touch with jack or anyone at Block, we would love to help power their supply chain.
Ryan
posting from comet - 4/11/25 -
 @ fd06f542:8d6d54cd
2025-04-12 03:16:30
@ fd06f542:8d6d54cd
2025-04-12 03:16:30What is Nostr?
Nostr is a simple, open protocol that enables global, decentralized, and censorship-resistant social media.
nostr 是 去中心化的 抗审查的社交媒体。
去中心化,其实就是多中心化,这里中心就是relay 服务器。现在的nostr 网络上有很多relay服务器可以存储信息。 * 短文,就是写类似微博,朋友圈什么的。 * 长文,可以写长博客,写书什么的。 * 图片 和 视频 ,nostr社区有专门的 图片和视频服务器很多都是免费的,按照nostr协议上传即可。
Simple
The protocol is based on very simple & flexible event objects (which are passed around as plain JSON) and uses standard elliptic-curve cryptography for keys and signing. The only supported transport is websockets connections from clients to relays. This makes it easy to write clients and relays and promotes software diversity.
nostr的协议非常简单,客户端通过 event 的格式(json)打包通过websocket 和relay服务器交互。
将一个 短文传到 relay服务器,很多relay服务器都 无需任何权限。任何人都可以上传获取读取服务器内容。
协议中是通过加密签名的,因此发布者拥有每个event的所有权,是可以证实的。
Verifiable
Because Nostr accounts are based on public-key cryptography it's easy to verify messages were really sent by the user in question.
nostr的账户是基于密码学生成的,用户无需邮件和手机注册; 也许无需到任何服务器去注册。 这一点 非常的具有吸引力,就像每个人的BTC账户一样。非常的自由,让用户感觉的无比的的快捷。
!> 以上两点是深深吸引 nostr用户的地方。自由,而不伤害第三方。
Nostr: a quick introduction, attempt by fiatjaf
Nostr doesn't have a material existence, it is not a website or an app. Nostr is just a description what kind of messages each computer can send to the others and vice-versa. It's a very simple thing, but the fact that such description exists allows different apps to connect to different servers automatically, without people having to talk behind the scenes or sign contracts or anything like that.
When you use a Nostr client that is what happens, your client will connect to a bunch of servers, called relays, and all these relays will speak the same "language" so your client will be able to publish notes to them all and also download notes from other people.
That's basically what Nostr is: this communication layer between the client you run on your phone or desktop computer and the relay that someone else is running on some server somewhere. There is no central authority dictating who can connect to whom or even anyone who knows for sure where each note is stored.
If you think about it, Nostr is very much like the internet itself: there are millions of websites out there, and basically anyone can run a new one, and there are websites that allow you to store and publish your stuff on them.
The added benefit of Nostr is that this unified "language" that all Nostr clients speak allow them to switch very easily and cleanly between relays. So if one relay decides to ban someone that person can switch to publishing to others relays and their audience will quickly follow them there. Likewise, it becomes much easier for relays to impose any restrictions they want on their users: no relay has to uphold a moral ground of "absolute free speech": each relay can decide to delete notes or ban users for no reason, or even only store notes from a preselected set of people and no one will be entitled to complain about that.
There are some bad things about this design: on Nostr there are no guarantees that relays will have the notes you want to read or that they will store the notes you're sending to them. We can't just assume all relays will have everything — much to the contrary, as Nostr grows more relays will exist and people will tend to publishing to a small set of all the relays, so depending on the decisions each client takes when publishing and when fetching notes, users may see a different set of replies to a note, for example, and be confused.
Another problem with the idea of publishing to multiple servers is that they may be run by all sorts of malicious people that may edit your notes. Since no one wants to see garbage published under their name, Nostr fixes that by requiring notes to have a cryptographic signature. This signature is attached to the note and verified by everybody at all times, which ensures the notes weren't tampered (if any part of the note is changed even by a single character that would cause the signature to become invalid and then the note would be dropped). The fix is perfect, except for the fact that it introduces the requirement that each user must now hold this 63-character code that starts with "nsec1", which they must not reveal to anyone. Although annoying, this requirement brings another benefit: that users can automatically have the same identity in many different contexts and even use their Nostr identity to login to non-Nostr websites easily without having to rely on any third-party.
To conclude: Nostr is like the internet (or the internet of some decades ago): a little chaotic, but very open. It is better than the internet because it is structured and actions can be automated, but, like in the internet itself, nothing is guaranteed to work at all times and users many have to do some manual work from time to time to fix things. Plus, there is the cryptographic key stuff, which is painful, but cool.
诞生blog
https://fiatjaf.com/nostr.html
The simplest open protocol that is able to create a censorship-resistant global "social" network once and for all.
It doesn't rely on any trusted central server, hence it is resilient; it is based on cryptographic keys and signatures, so it is tamperproof; it does not rely on P2P techniques, therefore it works. ...
-
 @ 220522c2:61e18cb4
2025-03-25 16:05:27
@ 220522c2:61e18cb4
2025-03-25 16:05:27draftoptionalAbstract
This NIP defines a new event kind for sharing and storing code snippets. Unlike regular text notes (
kind:1), code snippets have specialized metadata like language, extension, and other code-specific attributes that enhance discoverability, syntax highlighting, and improved user experience.Event Kind
This NIP defines
kind:1337as a code snippet event.The
.contentfield contains the actual code snippet text.Optional Tags
-
filename- Filename of the code snippet -
l- Programming language name (lowercase). Examples: "javascript", "python", "rust" -
extension- File extension (without the dot). Examples: "js", "py", "rs" -
description- Brief description of what the code does -
runtime- Runtime or environment specification (e.g., "node v18.15.0", "python 3.11") -
license- License under which the code is shared (e.g., "MIT", "GPL-3.0", "Apache-2.0") -
dep- Dependency required for the code to run (can be repeated) -
repo- Reference to a repository where this code originates
Format
```json {
"id": "<32-bytes lowercase hex-encoded SHA-256 of the the serialized event data>",
"pubkey": "<32-bytes lowercase hex-encoded public key of the event creator>",
"created_at":
, "kind": 1337,
"content": "function helloWorld() {\n console.log('Hello, Nostr!');\n}\n\nhelloWorld();",
"tags": [
["l", "javascript"], ["extension", "js"], ["filename", "hello-world.js"], ["description", "A basic JavaScript function that prints 'Hello, Nostr!' to the console"], ["runtime", "node v18.15.0"], ["license", "MIT"], ["repo", "https://github.com/nostr-protocol/nostr"]],
"sig": "<64-bytes signature of the id>"
} ```
Client Behavior
Clients that support this NIP SHOULD:
-
Display code snippets with proper syntax highlighting based on the language.
-
Allow copying the full code snippet with a single action.
-
Render the code with appropriate formatting, preserving whitespace and indentation.
-
Display the language and extension prominently.
-
Provide "run" functionality for supported languages when possible.
-
Display the description (if available) as part of the snippet presentation.
Clients MAY provide additional functionality such as:
-
Code editing capabilities
-
Forking/modifying snippets
-
Creating executable environments based on the runtime/dependencies
-
Downloading the snippet as a file using the provided extension
-
Sharing the snippet with attribution
References
nip #grownostr
-
-
 @ a60e79e0:1e0e6813
2025-03-23 16:10:10
@ a60e79e0:1e0e6813
2025-03-23 16:10:10**This is a long form note test of a post that lives on my Nostr educational website Hello Nostr **
In early 2025, social media is the most common use case for Nostr (and probably the reason you're reading this). Nostr is SO much more than just social media, but that's where the bulk of the activity is, and is what I'm focusing on in this post. Even though the protocol is still so young, that has not prevented an explosion of excellent social media focused clients that predominantly coalesce around the Twitter (X) style feed, containing shorter form content, often with images, and the ability to comment, like and share.
This first steps guide showcases one of the most polished and simplest examples of such a client, Primal. Primal is a cross platform app, that also works on your computer too. The steps that follow are demonstrated on iPhone, but should be identical for Android users. There may be some topics of concepts here that are new to you, to learn more about them, check out our Nostr 101 to learn more about Nostr basics and why it matters.
You can and should explore all of the other options available to you, that's the beauty of Nostr, you're free to choose how and where to interact with your social network. No lock in. No walled gardens. True freedom.

Getting Started
-
Go to your app store and download Primal to your Android or iPhone
-
Open Primal and choose Create Account. Choose your public display name and add a short bio about yourself.
- Select your chosen interests from the list provided. This will bootstrap your feed and auto-follow a number of accounts so that your feed is not completely empty when starting out.
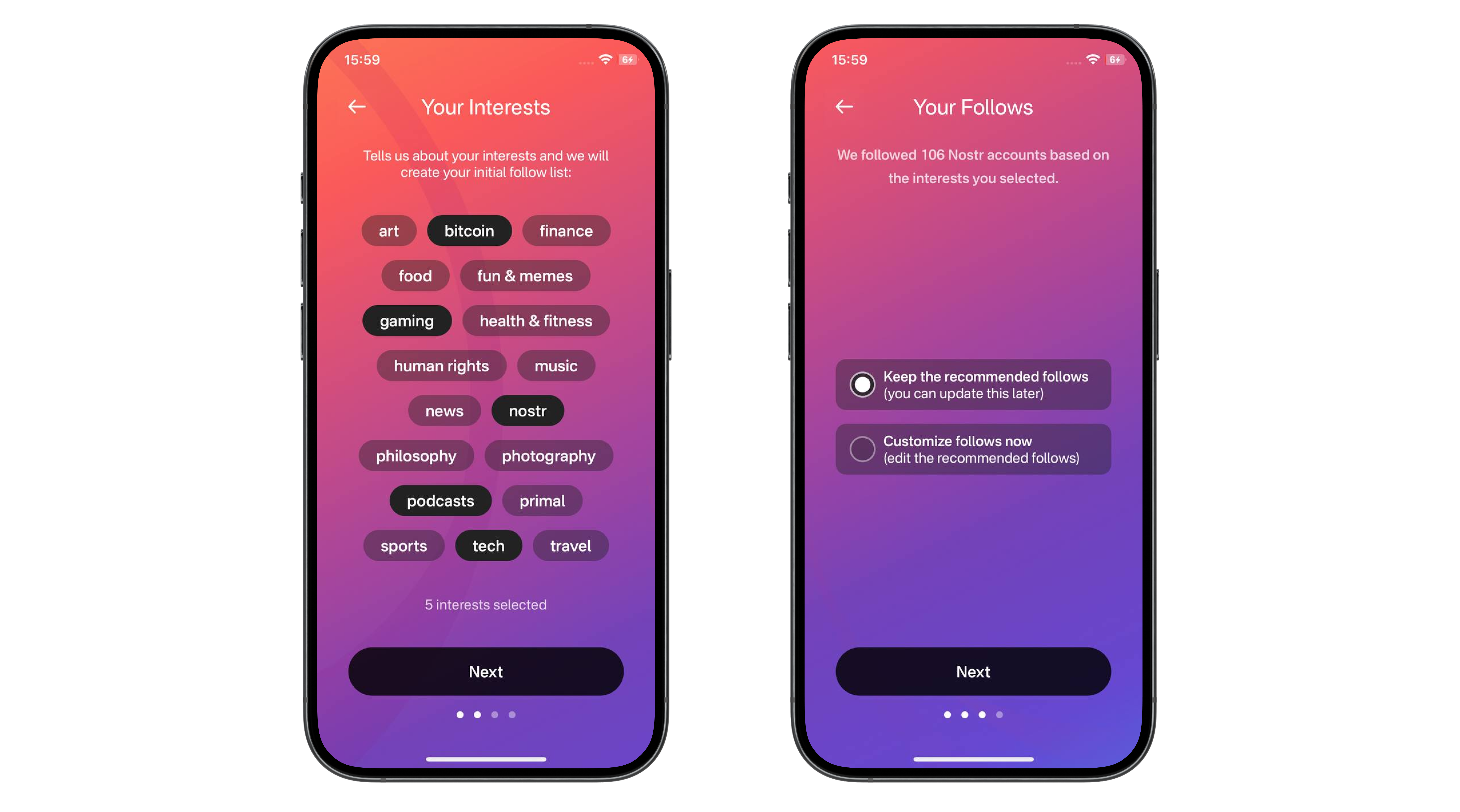
- Review your account info and tap Create Account Now. Take note of the fact that 'Your Nostr Key is available in your Account Settings'. We'll revisit this shortly.
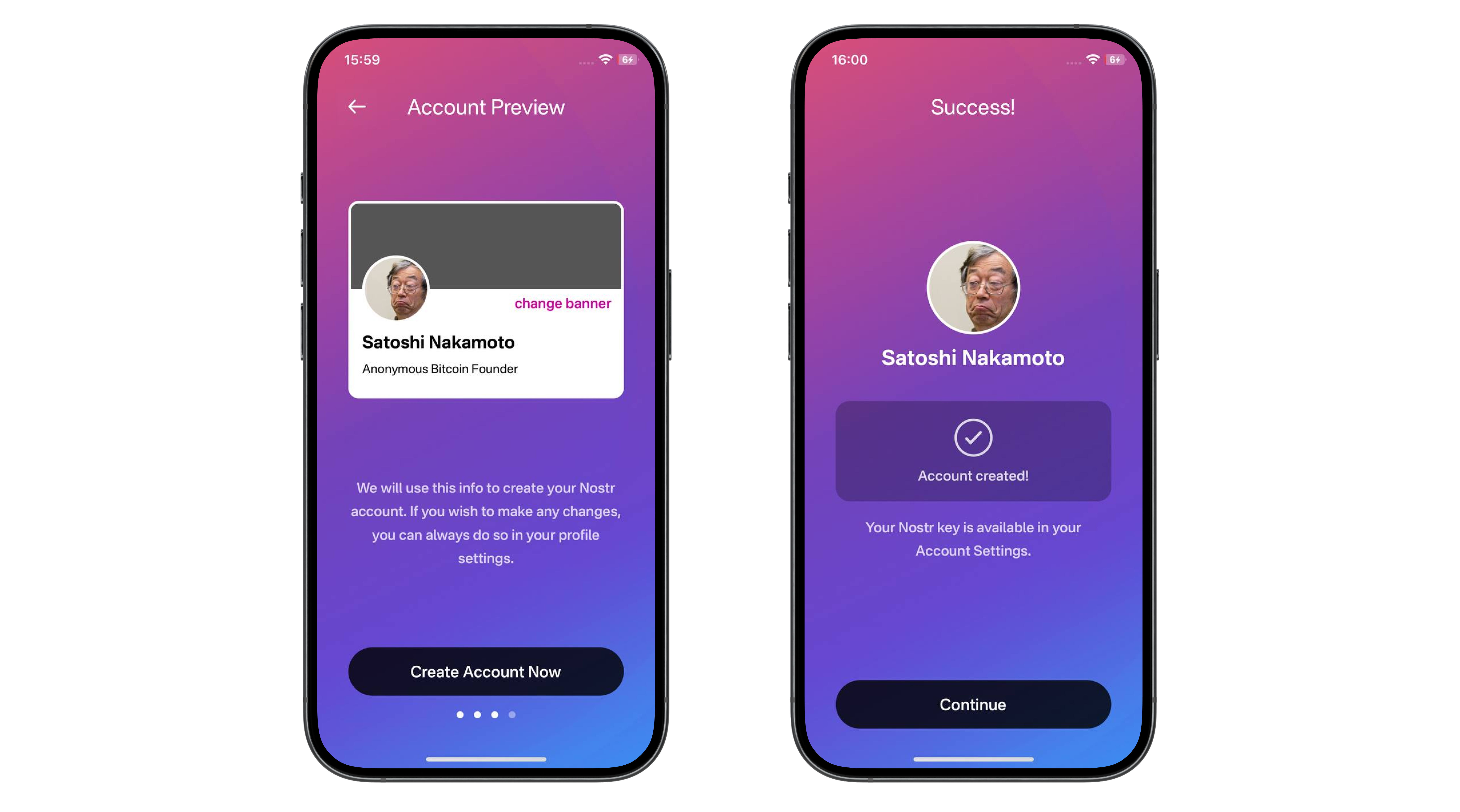
- Next is an optional step of activating the wallet feature within Primal. Having a wallet within your social client enables you to send and receive value (known as 'Zaps') in the form of Bitcoin. On Facebook and Twitter you can like a post, but it means much more to send someone fractions of a penny (or more if you like) to show your appreciation for their insights. You'll need to provide some personal information to enable the wallet, including an email address.
Using the internal wallet and purchasing sats with your credit card will tie your Nostr identity to your real ID. Think very carefully before carrying out this step.
Learn more in the detailed section at the end of this post.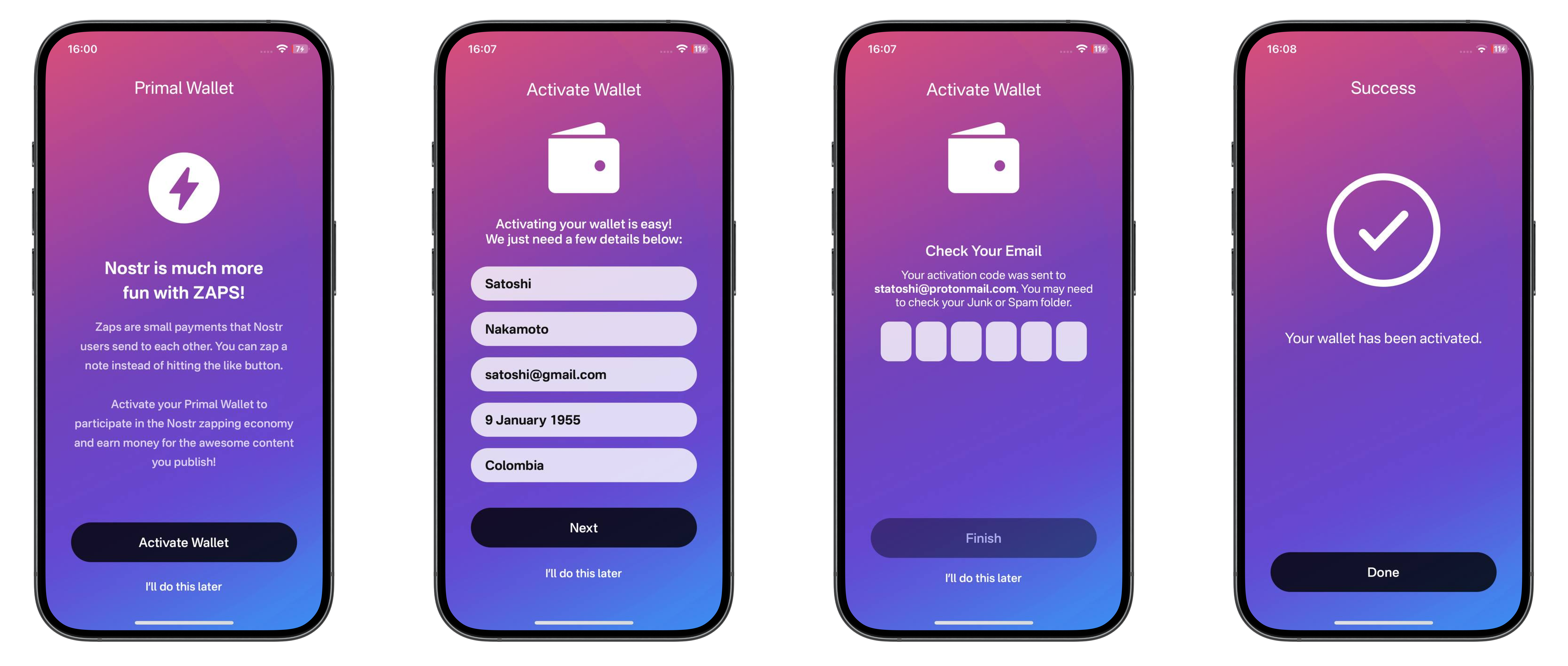
- That's it, you're now set up and ready to start sharing your thoughts, feelings and memes with the world via a decentralized and censorship resistant social network. To post your first note and say hello to the Nostr world, tap the + in the bottom right corner.
- If you activated the wallet at step 5, you might want to deposit some Bitcoin in there to allow you to send some value to your friends. There are three main ways to do this:
- Post some awesome content and have people send you value in the form of 'Zaps'
- Send some Bitcoin from a wallet you already have
- Purchase some directly within Primal
The latter is made very simple thanks to the in-app purchase feature, which allows you to purchase a small amount with the card you likely already have connected to your Apple/Google account. All you need to do is tap 'Buy Sats Now'.
- Next, let's look at the different feeds available on our home screen. Tap 'Latest' at the top of the screen and you can toggle between three different types of home feeds, great for discovering new people and content.
- Let's assume you already have some friends on Nostr and want to find and follow them. Tap the search icon in the top right corner, the enter the name of the person you want to follow. Once on their profile, simply tap the 'Follow' button.
- So you found a friend and want to start interacting with them so they know you made it over to Nostr. Simply find a note you like and choose from the different types of interactions available. From left to right they are:
- Comment
- Zap (send value from your wallet to theirs)
- Like
- Repost
- Bookmark
When Zapping, a single tap will send a tiny amount of 42 sats. If you want to send more, or a custom amount, tap and hold the zap button to bring up a selector menu. All default zap amounts are configurable in the app settings page.

- After you've started posting and interacting with others, you'll likely receive some notifications to tell you. Notifications can be filtered into interaction types.
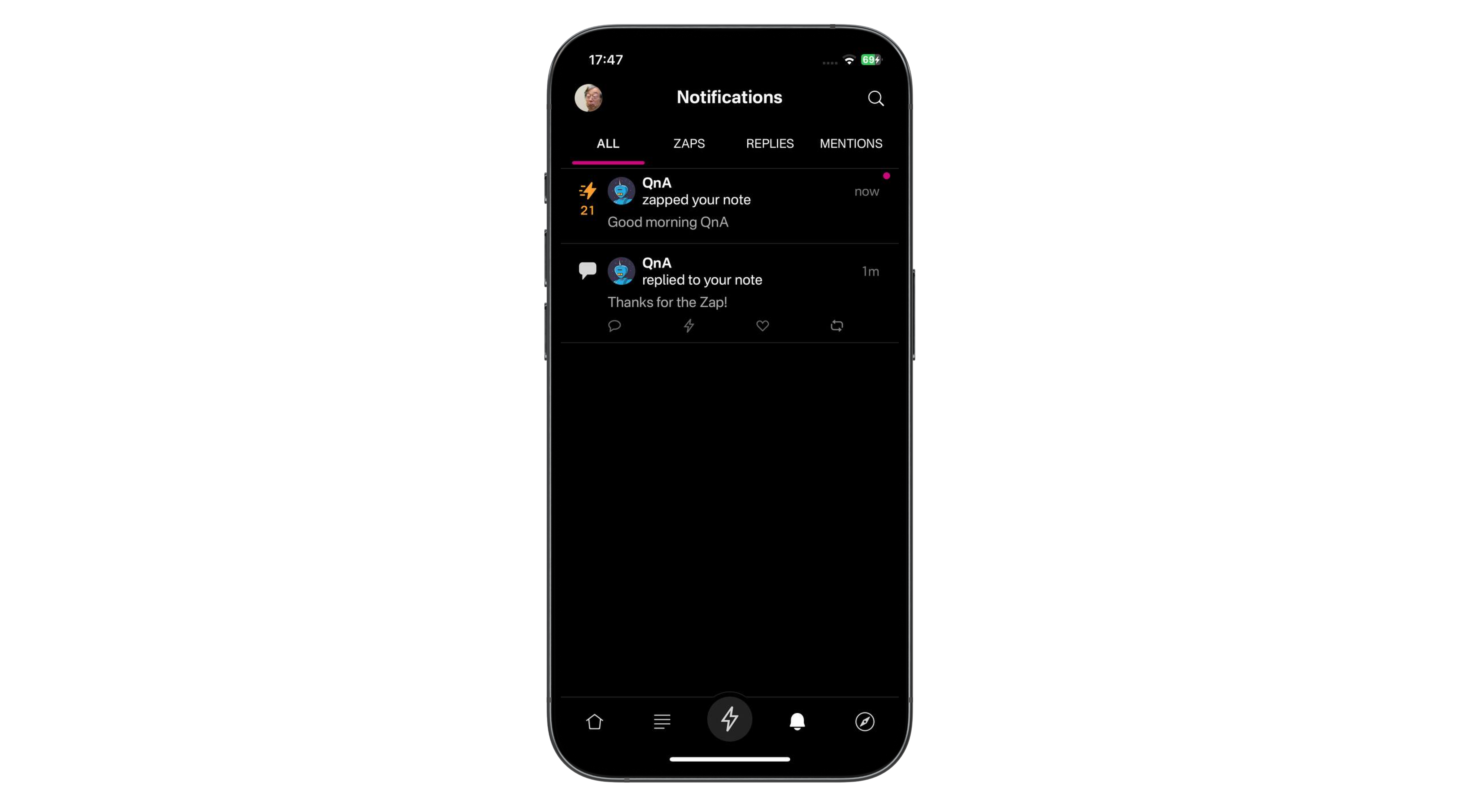
- Another great way to find more people to follow and interact with is to use the discover page. To open it, tap the compass in the bottom right corner of the screen. Here you'll be able to browse different types of pre-built feeds, trending profiles, notes with large zaps and extra topics.
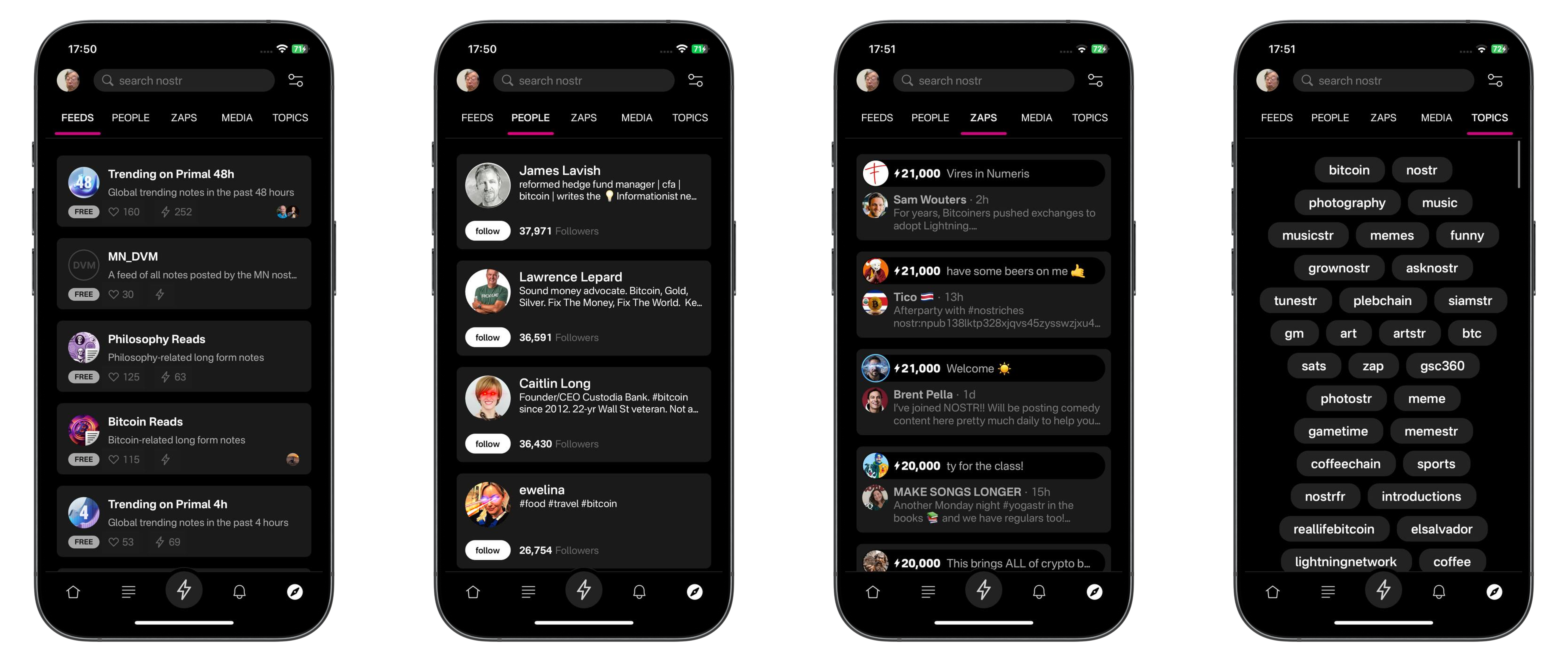
The Important Part
You might have noticed that throughout that setup, you were not asked for a unique username, nor were you asked for a password. So how the hell is this secure? What happens if you log out? Is your account lost forever?
This is where Nostr really starts to shine. Just like in Bitcoin or other cryptocurrencies, your Nostr account is protected by a 'Private Key'. Anyone with knowledge of the private key can access your account in any Nostr client. No private key, no access. So let's make sure you have a backup copy of it, so you can still recover access to your account in the event you lose your phone!
Tap on your profile image in the top left of the screen. Then tap Settings > Keys. Here you'll see two keys, one public and one private. Your public key is how people find you on Nostr. It is often referred to by its more technical name 'nPub' which is the prefix if the key itself. Your public key is designed to be exactly that, public!
Your private key is sometimes referred to by its technical name 'nSec' which is also the prefix of the key. Copy your private key and paste it somewhere safe and secure, in a location accessible independently from your phone, and only by you.
If you were to lose your phone, or accidentally delete the Primal app, now all you'd need to do is head back to step 1 above and choose Sign In. You'd then be asked to paste your private key, after which your profile and content would be magically restored.
Your private key can be imported into any other Nostr social client for the same result.
Things to Consider
This post has one primary focus - To get you from zero to posting and zapping in the quickest time and with the least friction. To achieve this, there are some trade-offs made that you should be aware of.
Custodial Wallet
The built in wallet is a custodial one. This means that the funds within are ultimately controlled by the developers behind Primal. They may be good actors, but you should approach the amount of money you maintain inside this wallet accordingly. If your wallet balance ever gets to a balance that makes you uncomfortable, you should send a good chunk of it out to another Bitcoin wallet where you control the keys. I recommend Phoenix or Zeus.
Those sats are never truly yours until you withdraw them to a self-custodial wallet
Wallet Privacy
If you choose to top up the wallet using the convenient in-app purchase method, you will tie that small amount of Bitcoin ownership to your Nostr account. If you Nostr account is literally your name, you might not have an issue with this, but often times people like to remain pseudonymous online. If you fall into that category, using your credit card to deposit Bitcoin into your Nostr account is not a good idea.
Android users of Primal can use an advanced technology called Nostr Wallet Connect (NWC) to connect an external Lightning wallet to their Nostr account in Primal. We'll cover this in a subsequent post.
Your private key allows you to take your profile and social network to any other client
If you found this post useful, please share it with your peers and consider following and zapping me on Nostr. If you write to me and let me know that you found me via this post, I'll be sure to Zap you back! ⚡️
-
-
 @ c230edd3:8ad4a712
2025-04-11 16:02:15
@ c230edd3:8ad4a712
2025-04-11 16:02:15Chef's notes
Wildly enough, this is delicious. It's sweet and savory.
(I copied this recipe off of a commercial cheese maker's site, just FYI)
I hadn't fully froze the ice cream when I took the picture shown. This is fresh out of the churner.
Details
- ⏲️ Prep time: 15 min
- 🍳 Cook time: 30 min
- 🍽️ Servings: 4
Ingredients
- 12 oz blue cheese
- 3 Tbsp lemon juice
- 1 c sugar
- 1 tsp salt
- 1 qt heavy cream
- 3/4 c chopped dark chocolate
Directions
- Put the blue cheese, lemon juice, sugar, and salt into a bowl
- Bring heavy cream to a boil, stirring occasionally
- Pour heavy cream over the blue cheese mix and stir until melted
- Pour into prepared ice cream maker, follow unit instructions
- Add dark chocolate halfway through the churning cycle
- Freeze until firm. Enjoy.
-
 @ 1c19eb1a:e22fb0bc
2025-03-21 15:48:32
@ 1c19eb1a:e22fb0bc
2025-03-21 15:48:32For our first edition of #Nostrversity, we'll be diving into Nostr Wallet Connect, or #NWC; a handy means of connecting a #Lightning wallet to your favorite #Nostr app that quickly became the standard and is now an essential part of onboarding to Nostr for any new user who wants to experience the magic of zaps. Yet NWC enables so much more than just one-tap-zapping, as we will see when we look a little closer at how it works under the hood.
Lightning History on Nostr
Back in the wild-west days of Nostr, before nostr:npub1xtscya34g58tk0z605fvr788k263gsu6cy9x0mhnm87echrgufzsevkk5s invented zaps, Bitcoin psychopaths were already sending sats to one another over Nostr. However, the way we had to do it back then was by going into our Lightning wallet, selecting "receive," inputting an amount we wanted, and copy/pasting an invoice from the wallet into our Nostr note, then hope someone was willing to pay it. And the payment side was just as cumbersome, requiring manually copying the invoice from your Nostr client, pasting it into a Lightning wallet so you could see how much the other user wanted, and then deciding if you were even willing to send it.
It didn't take long before Nostr clients, particularly on mobile, started rendering Lightning invoices in a convenient format that showed the invoice amount and a "Pay" button, that would prompt the user to open a Lightning wallet. This took out a decent amount of friction for the sender, but it was still just as big a hassle for the receiver.
Then zaps came along, and soon everyone had the ability to send sats to any other user when they found value in the content they posted. At least, any other user that added their Lightning address to their profile and whose Lightning wallet provider supported sending a "paid" receipt to a Nostr relay. Receiver friction had been virtually eliminated and the sats began to flow. Nostr also became the de facto directory for Bitcoiner payment addresses. If you heard nostr:npub1a2cww4kn9wqte4ry70vyfwqyqvpswksna27rtxd8vty6c74era8sdcw83a say something brilliant on a podcast, you could just look her up on any Nostr client with zaps and send some sats her way as a thank you.
Enter the zapathon, a community event with one purpose: break nostr:npub1hcwcj72tlyk7thtyc8nq763vwrq5p2avnyeyrrlwxrzuvdl7j3usj4h9rq by zapping each other so much it was effectively a DDOS attack. Sure, it was a stress test on other wallets too, but most users were on Wallet of Satoshi because it was the easiest way to get a Lightning address with a mobile wallet.
It was a ton of fun flinging sats around as fast as your fingers would let you! However, a new friction point was soon discovered from trying to zap so frequently. Every time you tapped the zap icon in your Nostr client, you had to wait for your wallet to open and present the invoice to approve payment, then switch back to your Nostr client to zap the next note. Not a big deal when you only send a zap occasionally, but when trying to zap every note in your feed, it adds a significant amount of time and extra clicks. In fact, this small amount of friction, whether you realize it or not, often acts as just enough of a barrier to zapping that you will choose not to zap a post you found some value in, just because of the extra 5 seconds it takes to load into your wallet app, approve the payment, and switch back to your Nostr client.
Wouldn't it be amazing if we could have one-tap-zaps?
I can't recall if there were any other methods by which this was achieved, but the method that caught on was developed and released into the wild by nostr:npub1getal6ykt05fsz5nqu4uld09nfj3y3qxmv8crys4aeut53unfvlqr80nfm, who called it Nostr Wallet Connect. At that time (March of 2023), Alby was a custodial Lightning wallet for your web browser, and while you could connect your own node to it using LNDHub, most people just stuck with their custodial option since it came with a Lightning address. Nostr Wallet Connect was, at that time, a way to connect your Alby wallet to a Nostr client.
I am not certain which client was the first to support NWC, but I know that #Amethyst was pretty early on, and it was an instant success. Users could get a "connection string" from Alby, paste it into Amethyst, and zap with a single tap of their finger. Just like zaps themselves had eliminated the friction for receiving payments via Lightning for anyone with a Lightning address, Nostr Wallet Connect had eliminated the friction for sending payments. No more wasted seconds switching back and forth between Nostr client and wallet app, just tap and zap sent, tap again and another zap gone.
Of course, this meant that it was all too easy to send way more sats out of your wallet than you intended. This was solved by the ability to set budgets, so your wallet would cut you off once you reached the max amount you had set for yourself.
Because Alby had made Nostr Wallet Connect open source and part of the Nostr protocol, it didn't take long before more and more clients started adding support for it. Users demanded it and wouldn't shut up about it until it was added. Other wallet providers also saw the value of including it. Now it is simply expected, and any wallet that doesn't include it won't attract Nostr users.
Notably, Wallet of Satoshi went from being the most popular wallet among Nostr users to being a rare and quaint throwback to a bygone era, because they never integrated NWC and they pulled away from serving anyone in the U.S. out of fear of regulation under the Biden administration.
So we arrive at the state of Lightning on Nostr today, with Lightning addresses in our profiles for receiving zaps, and Nostr Wallet Connect for sending, and hard pressed to find Nostr clients that don't support both.
So... How does it work?
All of that history is great, but you're here to learn how this technology works. What is happening behind the scenes when you tap that little ⚡️ icon and sats seem to magically leave your Lightning wallet and show up on your screen as a zap underneath the latest nostr:npub1lrnvvs6z78s9yjqxxr38uyqkmn34lsaxznnqgd877j4z2qej3j5s09qnw5 meme, without you having to fiddle around with any Lightning invoices at all?
It's really quite simple, in the end. Your wallet communicating with your Nostr client using a Nostr relay in the middle, the same way you communicate with other Nostr users by saving notes to a relay that they can retrieve them from.
First, your Nostr client has to know how to "tag" your wallet, and on which relay to send it notes. This is why you need to get a "connection string" from your wallet to paste into your Nostr client. This string has all the information that is needed for your Nostr client to know how to communicate with your wallet, and for your wallet to be sure that the payment requests are authorized by you.
Let's take a look at an example connection string:
nostr+walletconnect://b889ff5b1513b641e2a139f661a661364979c5beee91842f8f0ef42ab558e9d4?relay=wss%3A%2F%2Frelay.damus.io&secret=71a8c14c1407c113601079c4302dab36460f0ccd0ad506f1f2dc73b5100e4f3cLooks like a bunch of gobbledygook, right? We'll break down each of its parts and see what it does.
nostr+walletconnect://This portion just defines the type of information that follows it. Because the string starts with this marker, any software reading it will know that what follows is information on how to communicate with a Lightning wallet, so long as it has been programmed to recognize it.
b889ff5b1513b641e2a139f661a661364979c5beee91842f8f0ef42ab558e9d4This section is just a public key, the same as an npub. In fact, it can be readily converted to an npub if you want using nostr:npub1zdr58j526qsrkdjhcg9xs60xfutqeey2ucugms04efnlx3spnmns2eqha9's key converter. It's a nostr identity just like yours or mine, but you won't find any GM posts or catstr pictures in its note history. It's only posting special note types used by NWC. This public key belongs to your Lightning wallet, and just like you can have multiple npubs for each of your alter egos, your wallet creates a separate public key to use with each new app you want to connect it to. Or at least it should. The Nostr client you use will tag your wallet in notes it creates by using this public key.
relay=wss%3A%2F%2Frelay.damus.ioThis section is probably easily recognizable. It's the same as typing
relay=wss://relay.damus.io, except that it has to use%3A%2F%2Fin place of://. This tells your Nostr client which relay it needs to use to communicate with your wallet. Hopefully your wallet uses a relay with high up-time, because one of the major ways for NWC to fail is if the relay is down. You also can't use just any relay. It has to accept the note kinds used by NWC, which is why wallets don't typically let their users choose the relay that will be used. You also can't just modify the connection string to use a relay you prefer, even if you know it allows NWC note kinds. This is because it will result in your Nostr client sending requests to your wallet on that relay, but your wallet is not reading from that relay, so it will never receive the requests.secret=71a8c14c1407c113601079c4302dab36460f0ccd0ad506f1f2dc73b5100e4f3cThis is just a Nostr private key. It's an nsec, but in hex format. Your wallet is giving your Nostr client a private key that it must use to sign all of the requests it sends to your wallet. No request signed by any other private key will be answered by your wallet. Your wallet will generate a separate private key for each connection string, allowing you as the user to revoke those connections individually, or set a separate budget for each connection.
When you tap the ⚡️ icon in your Nostr client, it obtains a Lightning invoice from the user's wallet you are trying to zap using their Lightning address. It then creates a note tagging your wallet's public key and requesting payment of that Lightning invoice, signing the note with the private key your wallet generated for it, and writing that note to the specified Nostr relay. Your wallet is constantly checking that relay for new notes and when it sees the payment request signed by an authorized private key, it pays the invoice, so long as it is within the budget you set, and sends out a payment receipt stating it has been paid so your client can light up the zap indicator to show that it was successful. All of this from a single tap of your finger in Amethyst.
More than Zaps
Now that we know the basics of how NWC works, it doesn't take much extrapolation to realize that this communication between wallet and Nostr client could be used for much more than just payment requests. A client could ask for your wallet's balance information, or transaction history, or ask for a lightning invoice. In fact, why does it have to be a Nostr client making those requests at all? Why not a mobile wallet app, or browser extension?
One of the major pieces of friction felt by those who run Lightning nodes is the difficulty of connecting to them remotely in a secure way. nostr:npub1aghreq2dpz3h3799hrawev5gf5zc2kt4ch9ykhp9utt0jd3gdu2qtlmhct and nostr:npub126ntw5mnermmj0znhjhgdk8lh2af72sm8qfzq48umdlnhaj9kuns3le9ll allow for connecting via Tor by default, but that can be painfully slow and unreliable. Anyone who has set up a connection to their node via LND Rest over Tor to their nostr:npub1xnf02f60r9v0e5kty33a404dm79zr7z2eepyrk5gsq3m7pwvsz2sazlpr5 wallet can attest to the frustration of opening their wallet and waiting several seconds for the interface to load, only to receive a timeout notice.
Nostr Wallet Connect has eliminated this issue thanks to Alby Hub and Alby Go. Just create a new connection in Alby Hub, give it a budget, and scan the QR code with Alby Go and you have a fully-functional, mobile Lightning wallet connected to your node at home that loads extremely quickly and reliably, so long as the Nostr relay in-between is up and running.
Now, you may be concerned that the information being passed back and forth on this Nostr relay is incredibly sensitive financial information, especially if balance and transaction history is involved. However, this is not a concern because the content of the notes is fully encrypted. The relay owner, or anyone else with access to read data on that relay, has no idea what information is contained in the messages being sent between wallet provider and Nostr client, or Lightning node and mobile wallet. And because neither npub being used by your wallet provider or your Nostr client is the same as your npub, there is nothing tying the messages to you.
As a result, NWC is quickly becoming an integral piece of Lightning infrastructure, even if those making use of it have no interest in joining Nostr at all.
The Future of NWC
To wrap this up, I'd like to point the reader to recent developments with Nostr Wallet Connect, and other use-cases we could very well see in the near future.
First, NWC may not just be for Lightning. nostr:npub1utx00neqgqln72j22kej3ux7803c2k986henvvha4thuwfkper4s7r50e8 recently revealed that he has a working prototype of on-chain payments via NWC.
nostr:nevent1qvzqqqqqqypzpckv7l8jqspl8u4y54dn9rcduwlrs4v2040nxce0m2h0cunvrj8tqyw8wumn8ghj7un9d3shjtnzd96xxmmfdecxzunt9e3k7mf0qyfhwumn8ghj7am0wsh82arcduhx7mn99uq32amnwvaz7tmjv4kxz7fww468smewdahx2tcqyzswntflhlvuea2uf3035r94azm32frnskk5qp2evj43x6nz6kt9zd7j485
We are already seeing it used with eCash wallets like nostr:npub1kvaln6tm0re4d99q9e4ma788wpvnw0jzkz595cljtfgwhldd75xsj9tkzv. There is no reason we shouldn't expect to see it used with all forms of Bitcoin payments. This could lead to an explosion of available wallet applications for all platforms, since they will simply be an interface for communicating with your node or wallet provider.
NWC can also be used for subscriptions, as alluded to in nostr:npub1utx00neqgqln72j22kej3ux7803c2k986henvvha4thuwfkper4s7r50e8's note above. Before you protest about what an awful monetization model subscriptions are, I generally agree. That said, subscriptions where the user remains in control the entire time, and can unilaterally cancel the subscription at any time, without having to jump through hoops and give explanations about why they no longer want to use the service, is a massive improvement over the current status quo. Remember, NWC allows the user to set a budget for each connection. This means your subscription can't incrementally increase its monthly fee on you. Not without you willingly going into your wallet settings and adjusting the monthly budget, at any rate.
Last one before we close this out: NWC can be used for streaming services where you pay only for what you use, and give yourself a budget. Instead of paying a monthly subscription to Netflix, you could pay per minute that you watch. Previously this could only be done by topping up a wallet controlled by the service itself, the way nostr:npub1v5ufyh4lkeslgxxcclg8f0hzazhaw7rsrhvfquxzm2fk64c72hps45n0v5's wallet worked with streaming sats for Podcasting 2.0. But now NWC is coming to Fountain, and users can bring their own wallet that they control.
The future of NWC is bright, and it extends well beyond zapping memes on Nostr. It's going to open up a world of possibilities for how we can use our sats to stream media, make reoccurring donations, use micro-payments to rent compute, and so much more. I don't know about you, but I am here for it!
-
 @ fd06f542:8d6d54cd
2025-04-12 02:13:35
@ fd06f542:8d6d54cd
2025-04-12 02:13:35 -
 @ e17e9a18:66d67a6b
2025-04-11 14:00:27
@ e17e9a18:66d67a6b
2025-04-11 14:00:27We wrote this album to explain the inspiration behind Mutiny Brewing, and as a way to share the story of Bitcoin and freedom technologies like nostr. Through these songs, we’ve tried to capture every truth that we believe is essential to understand about money, freedom, trust, and human connection in the internet age. It’s our way of making these ideas real and relatable, and we hope it helps others see the power of taking control of their future through the systems we use.
01. "Tomorrow's Prices on Yesterday's Wage" explores the harsh reality of inflation. As central banks inflate the money supply, prices rise faster than wages, leaving us constantly falling behind. People, expecting prices to keep climbing, borrow more to buy sooner, pushing prices even higher in a vicious cycle. You're always a step behind, forced to pay tomorrow's inflated prices with yesterday's stagnant wages.
https://wavlake.com/track/76a6cd02-e876-4a37-b093-1fe919e9eabe
02. "Everybody Works For The Bank" exposes the hidden truth behind our fiat money system. When banks issue loans, they create new money from debt—but you must pay back both the principal and interest. That interest requires even more money, relying on others to borrow, creating an endless cycle of debt. If borrowing slows, the system falters and governments step in, printing more money to keep banks afloat. Ultimately, we’re all working to service debt, chained to the banks.
“Paying back what they create, working till I break” https://wavlake.com/track/4d94cb4b-ff3b-4423-be6a-03e0be8177d6
03. "Let My People Go" references Moses' demand for freedom but directly draws from Proverbs 6:1–5, exposing the danger of debt based money. Every dollar you hold is actually someone else's debt, making you personally liable—held in the hand of your debtor and at risk of their losses, which you ultimately pay for through inflation or higher taxes. As the song says, "The more you try to save it up, the deeper in you get." The wisdom of Proverbs urges immediate action, pleading urgently to escape this trap and free yourself, like a gazelle from a hunter.
https://wavlake.com/track/76214ff1-f8fd-45b0-a677-d9c285b1e7d6
04. "Mutiny Brewing" embodies Friedrich Hayek's insight: "I don't believe we shall ever have good money again before we take it out of the hands of government... we can't take it violently... all we can do is by some sly roundabout way introduce something they can't stop."
Inspired also by the Cypherpunk manifesto's rallying cry, "We will write the code", the song celebrates Bitcoin as exactly that unstoppable solution.
"Not here to break ya, just here to create our own little world where we determine our fate." https://wavlake.com/track/ba767fc8-6afc-4b0d-be64-259b340432f3
05. "Invisible Wealth" is inspired by The Sovereign Individual, a groundbreaking 1990s book that predicted the rise of digital money and explores how the return on violence shaped civilizations. The song references humanity's vulnerability since agriculture began—where stored wealth attracted violence, forcing reliance on larger governments for protection.
Today, digital privacy enabled by cryptography fundamentally changes this dynamic. When wealth is stored privately, secured by cryptographic keys, violence becomes ineffective. As the song emphasizes, "You can't bomb what you can't see." Cryptography dismantles traditional power structures, providing individuals true financial security, privacy, and freedom from exploitation.
“Violence is useless against cryptography” https://wavlake.com/track/648da3cc-d58c-4049-abe0-d22f9e61fef0
06. "Run A Node" is a rallying cry for Bitcoin's decentralisation. At its heart, it's about personal verification and choice: every node is a vote, every check’s a voice. By running the code yourself, you enforce the rules you choose to follow. This is true digital democracy. When everyone participates, there's no room for collusion, and authority comes directly from transparent code rather than blind trust.
"I verify, therefore I do." https://wavlake.com/track/ee11362b-2e84-4631-b05e-df6d8e6797f8
07. "Leverage is a Liar" warns against gambling with your wealth, but beneath the surface, it's a sharp critique of fractional reserve banking. Fractional reserves inflate asset prices, creating the illusion of wealth built on leverage. This system isn't sustainable and inevitably leads to collapse. Real wealth requires sound money, money that can't be inflated. Trying to gain more through leverage only feeds the lie.
"Watch it burn higher and higher—leverage is a liar." https://wavlake.com/track/67f9c39c-c5e1-4e15-b171-f1f5442f29a5
08. "Don't Get Rekt" serves as a stark warning about trusting custodians with your Bitcoin. Highlighting infamous collapses like Mt.Gox, Celsius, and FTX. These modern failures echo the 1933 Executive Order 6102, where the US government forcibly seized citizens' gold, banned its use, and then promptly devalued the currency exchanged for it. History shows clearly: trusting others with your wealth means risking losing it all.
"Your keys, your life, don't forget." https://wavlake.com/track/fbd9b46d-56fc-4496-bc4b-71dec2043705
09. "One Language" critiques the thousands of cryptocurrencies claiming to be revolutionary. Like languages, while anyone can invent one, getting people to actually use it is another story. Most of these cryptos are just affinity scams, centralized towers built on shaky foundations. Drawing from The Bitcoin Standard, the song argues money naturally gravitates toward a single unit, a universal language understood by all. When the dust settles, only genuine, decentralized currency remains.
"One voice speaking loud and clear, the rest will disappear." https://wavlake.com/track/22fb4705-9a01-4f65-9b68-7e8a77406a16
10. "Key To Life" is an anthem dedicated to nostr, the permissionless, unstoppable internet identity protocol. Unlike mainstream social media’s walled gardens, nostr places your identity securely in a cryptographic key, allowing you total control. Every message or action you sign proves authenticity, verifiable by anyone. This ensures censorship resistant communication, crucial for decentralised coordination around Bitcoin, keeping it free from centralised control.
"I got the key that sets me free—my truth is mine, authentically." https://wavlake.com/track/0d702284-88d2-4d3a-9059-960cc9286d3f
11. "Web Of Trust" celebrates genuine human connections built through protocols like nostr, free from corporate algorithms and their manipulative agendas. Instead of top down control, it champions grassroots sharing of information among trusted peers, ensuring truth and authenticity rise naturally. It's about reclaiming our digital lives, building real communities where trust isn't manufactured by machines, but created by people.
"My filter, my future, my choice to make, real connections no one can fake." https://wavlake.com/track/b383d4e2-feba-4d63-b9f6-10382683b54b
12. "Proof Of Work" is an anthem for fair value creation. In Bitcoin, new money is earned through real work, computing power and electricity spent to secure the network. No shortcuts, no favourites. It's a system grounded in natural law: you reap what you sow. Unlike fiat money, which rewards those closest to power and the printing press, Proof of Work ensures rewards flow to those who put in the effort. Paper castles built on easy money will crumble, but real work builds lasting worth.
"Real work makes real worth, that's the law of this earth." https://wavlake.com/track/01bb7327-0e77-490b-9985-b5ff4d4fdcfc
13. "Stay Humble" is a reminder that true wealth isn’t measured in coins or possessions. It’s grounded in the truth that a man’s life does not consist in the abundance of his possessions. Real wealth is the freedom to use your life and time for what is good and meaningful. When you let go of the obsession with numbers, you make room for gratitude, purpose, and peace. It's not about counting coins, it's about counting your blessings.
"Real wealth ain't what you own, it's gratitude that sets the tone." https://wavlake.com/track/3fdb2e9b-2f52-4def-a8c5-c6b3ee1cd194
-
 @ 1c19eb1a:e22fb0bc
2025-03-21 00:34:10
@ 1c19eb1a:e22fb0bc
2025-03-21 00:34:10What is #Nostrversity? It's where you can come to learn about all the great tools, clients, and amazing technology that is being built on #Nostr, for Nostr, or utilized by Nostr, presented in an approachable and non-technical format. If you have ever wondered what Blossom, bunker signing, or Nostr Wallet Connect are, how they work, and how you can put them to work to improve your Nostr experience, this is the place you can read about them without needing a computer-science degree ahead of time.
Between writing full-length reviews, which take a fair amount of time to research, test, and draft, I will post shorter articles with the Nostrversity hashtag to provide a Nostr-native resource to help the community understand and utilize the tools our illustrious developers are building. These articles will be much shorter, and more digestible than my full-length reviews. They will also cover some things that may not be quite ready for prime-time, whereas my reviews will continue to focus on Nostr apps that are production-ready.
Keep an eye out, because Nostr Wallet Connect will be the first topic of study. Take your seats, get out your notepads, and follow along to discover how Nostr Wallet Connect is improving Lightning infrastructure. Hint: It's not just for zaps.
-
 @ fd06f542:8d6d54cd
2025-04-12 01:32:38
@ fd06f542:8d6d54cd
2025-04-12 01:32:38使用nostrbook.com网站
登录和创建用户:
 登录按钮 ,可以粘贴 已有的 nsec....账号,完成登录。
登录按钮 ,可以粘贴 已有的 nsec....账号,完成登录。注册:
 可以点击红标位置 生成你的账户。 “确定” 完成注册。
可以点击红标位置 生成你的账户。 “确定” 完成注册。创建书籍
封面的上传
 创建书籍,可以用 微信截图 后直接 ctrl+v. 粘贴即可。
创建书籍,可以用 微信截图 后直接 ctrl+v. 粘贴即可。或者点击浏览 本地图片文件。
标题和作者
正常填写就可以。 书的作者和上传文件人没有一一绑定。
写书
 创建完成后就可以写书了,写书入口在 登录处 “我的书籍” 。点进去会出现你创建的书籍。选择一本就可以写书了。
创建完成后就可以写书了,写书入口在 登录处 “我的书籍” 。点进去会出现你创建的书籍。选择一本就可以写书了。列出你创建的所有的书籍

点击图标,就可以进入开始写作了。例如《nostrbook站点日记》

如图所示有4个部分
- (1)关闭按钮,点击就退出编辑,这时候他会提示你保存,如果不需要保存退出,点击 “不保存退出”
- (2)
大纲是编写 你书籍的大纲,这个参考 docsify文档 下面会有例子。时间排列是 你所有为本书写的章节。但是有些章节你可能废弃了,或者暂时不想展示,都会存在 时间排列里面,就是按照你编写的时间倒序排列的。草稿是你暂时存储的内容,没有上传到网络,存在你本地浏览器的缓存里面。 - (3)这个部分看到的就是你的章节列表,当让你第一次来的这个地方是空的。
新增章节下一次就会有内容了。 - (4)文件名,是我们存储章节的唯一标识。
readme.md和_sidebar.md是系统默认必须有的。因为docsify技术默认需要这2个。
如何编写大纲
如果你是第一次开始,大纲的界面是这样的。

- 点击
增加大纲 - 点击
查看样例 - 修改系统生成的例子,此时 readme.md是必须的readme 对应的名字你可以自己修改
- 点击提交 就可以完成大纲了。
第二次、点击
更新大纲按钮- [首页](/readme.md) - [国人开发者](/01.md) - [中文用户列表](/02.md)大纲例子,“[]” 内是标题,“()”内是 文件名; 标题是是显示在文章的右侧; 文件名的作用是匹配 ‘新增章节’ 里面的markdown的相匹配关联的。
如何编写一个章节,例如:readme.md
 * 点击
* 点击 新增章节* 填写标题 * 填写内容 * 关键是 填写文件名,需要和大纲里的名字对应 * 提交?> 如果你写的 章节 并没有在大纲里标识名字 ,用户在浏览的时候,左侧的章节并不会出现。
-
 @ fd06f542:8d6d54cd
2025-04-12 01:21:03
@ fd06f542:8d6d54cd
2025-04-12 01:21:03{"coverurl":"https://cdn.nostrcheck.me/fd06f542bc6c06a39881810de917e6c5d277dfb51689a568ad7b7a548d6d54cd/19105641454b483284cf76c42fbdde2ed3f47b1bb2a366a58eaa49630d385027.webp","title":"nostr-examples","author":"nostr-dev"}
-
 @ 5d4b6c8d:8a1c1ee3
2025-04-11 23:56:35
@ 5d4b6c8d:8a1c1ee3
2025-04-11 23:56:35Our yard has a ton of wild onions, so I've been eating lots of fresh green onions with my food and sometimes just chewing on one while I walk around the yard. Other than some mulberries in the fall, our neighborhood doesn't have much other foraging opportunity, but I was reminded of how much I enjoy it.
Other than providing free and fresh snacks, foraging may provide some interesting health benefits, because of xenohormesis.
Xenohormesis is an awesome word that refers to the health benefits of the compounds plants produce when they're subjected to environmental stressors. You may recall my first post in this series about hormesis, which is the health benefits of being subjected to stressors. "Xeno" means "alien" or "foreign", so it's the health benefits derived from other organisms being stressed.
Many compounds like curcumin and resveratrol are the result of xenohormesis, but you don't need to forage to get those benefits. Foraging may provide a distinctly local form of xenohormesis, where our bodies can learn about how to adapt to local environmental stressors from the compounds local plants have produced to deal with those stressors. The idea seems sort of similar to how our immune systems learn from vaccines. Our immune systems observe the adaptive compounds from local plants and learn from them how to deal with those stressors when we encounter them.
I'm sure there was a cool discussion of this on The Darkhorse Podcast, but I couldn't find it.
What are stackers' favorite foods to forage?
originally posted at https://stacker.news/items/941150
-
 @ 16f1a010:31b1074b
2025-03-20 14:32:25
@ 16f1a010:31b1074b
2025-03-20 14:32:25grain is a nostr relay built using Go, currently utilizing MongoDB as its database. Binaries are provided for AMD64 Windows and Linux. grain is Go Relay Architecture for Implementing Nostr
Introduction
grain is a nostr relay built using Go, currently utilizing MongoDB as its database. Binaries are provided for AMD64 Windows and Linux. grain is Go Relay Architecture for Implementing Nostr
Prerequisites
- Grain requires a running MongoDB instance. Please refer to this separate guide for instructions on setting up MongoDB: nostr:naddr1qvzqqqr4gupzq9h35qgq6n8ll0xyyv8gurjzjrx9sjwp4hry6ejnlks8cqcmzp6tqqxnzde5xg6rwwp5xsuryd3knfdr7g
Download Grain
Download the latest release for your system from the GitHub releases page
amd64 binaries provided for Windows and Linux, if you have a different CPU architecture, you can download and install go to build grain from source
Installation and Execution
- Create a new folder on your system where you want to run Grain.
- The downloaded binary comes bundled with a ZIP file containing a folder named "app," which holds the frontend HTML files. Unzip the "app" folder into the same directory as the Grain executable.
Run Grain
- Open your terminal or command prompt and navigate to the Grain directory.
- Execute the Grain binary.
on linux you will first have to make the program executable
chmod +x grain_linux_amd64Then you can run the program
./grain_linux_amd64(alternatively on windows, you can just double click the grain_windows_amd64.exe to start the relay)
You should see a terminal window displaying the port on which your relay and frontend are running.
If you get
Failed to copy app/static/examples/config.example.yml to config.yml: open app/static/examples/config.example.yml: no such file or directory
Then you probably forgot to put the app folder in the same directory as your executable or you did not unzip the folder.
Congrats! You're running grain 🌾!
You may want to change your NIP11 relay information document (relay_metadata.json) This informs clients of the capabilities, administrative contacts, and various server attributes. It's located in the same directory as your executable.
Configuration Files
Once Grain has been executed for the first time, it will generate the default configuration files inside the directory where the executable is located. These files are:
bash config.yml whitelist.yml blacklist.ymlPrerequisites: - Grain requires a running MongoDB instance. Please refer to this separate guide for instructions on setting up MongoDB: [Link to MongoDB setup guide].
Download Grain:
Download the latest release for your system from the GitHub releases page
amd64 binaries provided for Windows and Linux, if you have a different CPU architecture, you can download and install go to build grain from source
Installation and Execution:
- Create a new folder on your system where you want to run Grain.
- The downloaded binary comes bundled with a ZIP file containing a folder named "app," which holds the frontend HTML files. Unzip the "app" folder into the same directory as the Grain executable.
Run Grain:
- Open your terminal or command prompt and navigate to the Grain directory.
- Execute the Grain binary.
on linux you will first have to make the program executable
chmod +x grain_linux_amd64Then you can run the program
./grain_linux_amd64(alternatively on windows, you can just double click the grain_windows_amd64.exe to start the relay)
You should see a terminal window displaying the port on which your relay and frontend are running.
If you get
Failed to copy app/static/examples/config.example.yml to config.yml: open app/static/examples/config.example.yml: no such file or directory
Then you probably forgot to put the app folder in the same directory as your executable or you did not unzip the folder.
Congrats! You're running grain 🌾!
You may want to change your NIP11 relay information document (relay_metadata.json) This informs clients of the capabilities, administrative contacts, and various server attributes. It's located in the same directory as your executable.
Configuration Files:
Once Grain has been executed for the first time, it will generate the default configuration files inside the directory where the executable is located. These files are:
bash config.yml whitelist.yml blacklist.ymlConfiguration Documentation
You can always find the latest example configs on my site or in the github repo here: config.yml
Config.yml
This
config.ymlfile is where you customize how your Grain relay operates. Each section controls different aspects of the relay's behavior.1.
mongodb(Database Settings)uri: mongodb://localhost:27017/:- This is the connection string for your MongoDB database.
mongodb://localhost:27017/indicates that your MongoDB server is running on the same computer as your Grain relay (localhost) and listening on port 27017 (the default MongoDB port).- If your MongoDB server is on a different machine, you'll need to change
localhostto the server's IP address or hostname. - The trailing
/indicates the root of the mongodb server. You will define the database in the next line.
database: grain:- This specifies the name of the MongoDB database that Grain will use to store Nostr events. Grain will create this database if it doesn't already exist.
- You can name the database whatever you want. If you want to run multiple grain relays, you can and they can have different databases running on the same mongo server.
2.
server(Relay Server Settings)port: :8181:- This sets the port on which your Grain relay will listen for incoming nostr websocket connections and what port the frontend will be available at.
read_timeout: 10 # in seconds:- This is the maximum time (in seconds) that the relay will wait for a client to send data before closing the connection.
write_timeout: 10 # in seconds:- This is the maximum time (in seconds) that the relay will wait for a client to receive data before closing the connection.
idle_timeout: 120 # in seconds:- This is the maximum time (in seconds) that the relay will keep a connection open if there's no activity.
max_connections: 100:- This sets the maximum number of simultaneous client connections that the relay will allow.
max_subscriptions_per_client: 10:- This sets the maximum amount of subscriptions a single client can request from the relay.
3.
resource_limits(System Resource Limits)cpu_cores: 2 # Limit the number of CPU cores the application can use:- This restricts the number of CPU cores that Grain can use. Useful for controlling resource usage on your server.
memory_mb: 1024 # Cap the maximum amount of RAM in MB the application can use:- This limits the maximum amount of RAM (in megabytes) that Grain can use.
heap_size_mb: 512 # Set a limit on the Go garbage collector's heap size in MB:- This sets a limit on the amount of memory that the Go programming language's garbage collector can use.
4.
auth(Authentication Settings)enabled: false # Enable or disable AUTH handling:- If set to
true, this enables authentication handling, requiring clients to authenticate before using the relay.
- If set to
relay_url: "wss://relay.example.com/" # Specify the relay URL:- If authentication is enabled, this is the url that clients will use to authenticate.
5.
UserSync(User Synchronization)user_sync: false:- If set to true, the relay will attempt to sync user data from other relays.
disable_at_startup: true:- If user sync is enabled, this will prevent the sync from starting when the relay starts.
initial_sync_relays: [...]:- A list of other relays to pull user data from.
kinds: []:- A list of event kinds to pull from the other relays. Leaving this empty will pull all event kinds.
limit: 100:- The limit of events to pull from the other relays.
exclude_non_whitelisted: true:- If set to true, only users on the whitelist will have their data synced.
interval: 360:- The interval in minutes that the relay will resync user data.
6.
backup_relay(Backup Relay)enabled: false:- If set to true, the relay will send copies of received events to the backup relay.
url: "wss://some-relay.com":- The url of the backup relay.
7.
event_purge(Event Purging)enabled: false:- If set to
true, the relay will automatically delete old events.
- If set to
keep_interval_hours: 24:- The number of hours to keep events before purging them.
purge_interval_minutes: 240:- How often (in minutes) the purging process runs.
purge_by_category: ...:- Allows you to specify which categories of events (regular, replaceable, addressable, deprecated) to purge.
purge_by_kind_enabled: false:- If set to true, events will be purged based on the kinds listed below.
kinds_to_purge: ...:- A list of event kinds to purge.
exclude_whitelisted: true:- If set to true, events from whitelisted users will not be purged.
8.
event_time_constraints(Event Time Constraints)min_created_at: 1577836800:- The minimum
created_attimestamp (Unix timestamp) that events must have to be accepted by the relay.
- The minimum
max_created_at_string: now+5m:- The maximum created at time that an event can have. This example shows that the max created at time is 5 minutes in the future from the time the event is received.
min_created_at_stringandmax_created_atwork the same way.
9.
rate_limit(Rate Limiting)ws_limit: 100:- The maximum number of WebSocket messages per second that the relay will accept.
ws_burst: 200:- Allows a temporary burst of WebSocket messages.
event_limit: 50:- The maximum number of Nostr events per second that the relay will accept.
event_burst: 100:- Allows a temporary burst of Nostr events.
req_limit: 50:- The limit of http requests per second.
req_burst: 100:- The allowed burst of http requests.
max_event_size: 51200:- The maximum size (in bytes) of a Nostr event that the relay will accept.
kind_size_limits: ...:- Allows you to set size limits for specific event kinds.
category_limits: ...:- Allows you to set rate limits for different event categories (ephemeral, addressable, regular, replaceable).
kind_limits: ...:- Allows you to set rate limits for specific event kinds.
By understanding these settings, you can tailor your Grain Nostr relay to meet your specific needs and resource constraints.
whitelist.yml
The
whitelist.ymlfile is used to control which users, event kinds, and domains are allowed to interact with your Grain relay. Here's a breakdown of the settings:1.
pubkey_whitelist(Public Key Whitelist)enabled: false:- If set to
true, this enables the public key whitelist. Only users whose public keys are listed will be allowed to publish events to your relay.
- If set to
pubkeys::- A list of hexadecimal public keys that are allowed to publish events.
pubkey1andpubkey2are placeholders, you will replace these with actual hexadecimal public keys.
npubs::- A list of npubs that are allowed to publish events.
npub18ls2km9aklhzw9yzqgjfu0anhz2z83hkeknw7sl22ptu8kfs3rjq54am44andnpub2are placeholders, replace them with actual npubs.- npubs are bech32 encoded public keys.
2.
kind_whitelist(Event Kind Whitelist)enabled: false:- If set to
true, this enables the event kind whitelist. Only events with the specified kinds will be allowed.
- If set to
kinds::- A list of event kinds (as strings) that are allowed.
"1"and"2"are example kinds. Replace these with the kinds you want to allow.- Example kinds are 0 for metadata, 1 for short text notes, and 2 for recommend server.
3.
domain_whitelist(Domain Whitelist)enabled: false:- If set to
true, this enables the domain whitelist. This checks the domains .well-known folder for their nostr.json. This file contains a list of pubkeys. They will be considered whitelisted if on this list.
- If set to
domains::- A list of domains that are allowed.
"example.com"and"anotherdomain.com"are example domains. Replace these with the domains you want to allow.
blacklist.yml
The
blacklist.ymlfile allows you to block specific content, users, and words from your Grain relay. Here's a breakdown of the settings:1.
enabled: true- This setting enables the blacklist functionality. If set to
true, the relay will actively block content and users based on the rules defined in this file.
2.
permanent_ban_words:- This section lists words that, if found in an event, will result in a permanent ban for the event's author.
- really bad wordis a placeholder. Replace it with any words you want to permanently block.
3.
temp_ban_words:- This section lists words that, if found in an event, will result in a temporary ban for the event's author.
- crypto,- web3, and- airdropare examples. Replace them with the words you want to temporarily block.
4.
max_temp_bans: 3- This sets the maximum number of temporary bans a user can receive before they are permanently banned.
5.
temp_ban_duration: 3600- This sets the duration of a temporary ban in seconds.
3600seconds equals one hour.
6.
permanent_blacklist_pubkeys:- This section lists hexadecimal public keys that are permanently blocked from using the relay.
- db0c9b8acd6101adb9b281c5321f98f6eebb33c5719d230ed1870997538a9765is an example. Replace it with the public keys you want to block.
7.
permanent_blacklist_npubs:- This section lists npubs that are permanently blocked from using the relay.
- npub1x0r5gflnk2mn6h3c70nvnywpy2j46gzqwg6k7uw6fxswyz0md9qqnhshtnis an example. Replace it with the npubs you want to block.- npubs are the human readable version of public keys.
8.
mutelist_authors:- This section lists hexadecimal public keys of author of a kind1000 mutelist. Pubkey authors on this mutelist will be considered on the permanent blacklist. This provides a nostr native way to handle the backlist of your relay
- 3fe0ab6cbdb7ee27148202249e3fb3b89423c6f6cda6ef43ea5057c3d93088e4is an example. Replace it with the public keys of authors that have a mutelist you would like to use as a blacklist. Consider using your own.- Important Note: The mutelist Event MUST be stored in this relay for it to be retrieved. This means your relay must have a copy of the authors kind10000 mutelist to consider them for the blacklist.
Running Grain as a Service:
Windows Service:
To run Grain as a Windows service, you can use tools like NSSM (Non-Sucking Service Manager). NSSM allows you to easily install and manage any application as a Windows service.
* For instructions on how to install NSSM, please refer to this article: [Link to NSSM install guide coming soon].-
Open Command Prompt as Administrator:
- Open the Windows Start menu, type "cmd," right-click on "Command Prompt," and select "Run as administrator."
-
Navigate to NSSM Directory:
- Use the
cdcommand to navigate to the directory where you extracted NSSM. For example, if you extracted it toC:\nssm, you would typecd C:\nssmand press Enter.
- Use the
-
Install the Grain Service:
- Run the command
nssm install grain. - A GUI will appear, allowing you to configure the service.
- Run the command
-
Configure Service Details:
- In the "Path" field, enter the full path to your Grain executable (e.g.,
C:\grain\grain_windows_amd64.exe). - In the "Startup directory" field, enter the directory where your Grain executable is located (e.g.,
C:\grain).
- In the "Path" field, enter the full path to your Grain executable (e.g.,
-
Install the Service:
- Click the "Install service" button.
-
Manage the Service:
- You can now manage the Grain service using the Windows Services manager. Open the Start menu, type "services.msc," and press Enter. You can start, stop, pause, or restart the Grain service from there.
Linux Service (systemd):
To run Grain as a Linux service, you can use systemd, the standard service manager for most modern Linux distributions.
-
Create a Systemd Service File:
- Open a text editor with root privileges (e.g.,
sudo nano /etc/systemd/system/grain.service).
- Open a text editor with root privileges (e.g.,
-
Add Service Configuration:
- Add the following content to the
grain.servicefile, replacing the placeholders with your actual paths and user information:
```toml [Unit] Description=Grain Nostr Relay After=network.target
[Service] ExecStart=/path/to/grain_linux_amd64 WorkingDirectory=/path/to/grain/directory Restart=always User=your_user #replace your_user Group=your_group #replace your_group
[Install] WantedBy=multi-user.target ```
- Replace
/path/to/grain/executablewith the full path to your Grain executable. - Replace
/path/to/grain/directorywith the directory containing your Grain executable. - Replace
your_userandyour_groupwith the username and group that will run the Grain service.
- Add the following content to the
-
Reload Systemd:
- Run the command
sudo systemctl daemon-reloadto reload the systemd configuration.
- Run the command
-
Enable the Service:
- Run the command
sudo systemctl enable grain.serviceto enable the service to start automatically on boot.
- Run the command
-
Start the Service:
- Run the command
sudo systemctl start grain.serviceto start the service immediately.
- Run the command
-
Check Service Status:
- Run the command
sudo systemctl status grain.serviceto check the status of the Grain service. This will show you if the service is running and any recent logs. - You can run
sudo journalctl -f -u grain.serviceto watch the logs
- Run the command
More guides are in the works for setting up tailscale to access your relay from anywhere over a private network and for setting up a cloudflare tunnel to your domain to deploy a grain relay accessible on a subdomain of your site eg wss://relay.yourdomain.com
-
 @ da0b9bc3:4e30a4a9
2025-04-11 23:29:46
@ da0b9bc3:4e30a4a9
2025-04-11 23:29:46Hello Stackers,
I was conversing with my wife over dinner and she asked me, "why do you stack?" and when it really boiled down to it my answer was "I don't know, because I don't like how it is and I hope for a different way".
Some context, we don't have kids, we may not ever have them.
So who are you leaving your legacy to? On the suggestion that BTC won't be mass adopted in our lifetime and BTC is for us to leave to our next generation... Why do you stack?
And a broader question, why do you invest in anything at all?
Appreciate your comments.
Pub 👊
originally posted at https://stacker.news/items/941137
-
 @ caa88a52:6c226a91
2025-04-11 22:58:40
@ caa88a52:6c226a91
2025-04-11 22:58:40Running Nestr!
-
 @ 1bc70a01:24f6a411
2025-04-11 13:50:38
@ 1bc70a01:24f6a411
2025-04-11 13:50:38The heading to be
Testing apps, a tireless quest, Click and swipe, then poke the rest. Crashing bugs and broken flows, Hidden deep where logic goes.
Specs in hand, we watch and trace, Each edge case in its hiding place. From flaky taps to loading spins, The war on regressions slowly wins.
Push the build, review the log, One more fix, then clear the fog. For in each test, truth will unfold— A quiet tale of stable code.
This has been a test. Thanks for tuning in.
- one
- two
- three
Listen a chillTranquility
And leisure
-
 @ da0b9bc3:4e30a4a9
2025-04-11 07:02:54
@ da0b9bc3:4e30a4a9
2025-04-11 07:02:54Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/940429
-
 @ 16f1a010:31b1074b
2025-03-20 14:31:19
@ 16f1a010:31b1074b
2025-03-20 14:31:19Introduction
MongoDB is a popular NoSQL document database, meaning it stores data in flexible, JSON-like documents. This makes it highly scalable and adaptable for various applications. This guide will focus on installing the Community Server edition, which is free and open-source.
This article is designed for beginners and those new to MongoDB, providing a clear and concise walkthrough of the installation process. We will cover installation on both Windows and Linux operating systems.
The official MongoDB documentation on the MongoDB website is very informative and you should be able to follow their guides. This article is written to provide a brief overview and a more streamlined installation experience.
Prerequisites
MongoDB Community Server can be installed and run on a wide range of systems. While specific hardware requirements can vary based on your intended use case and the size of your database, here are the general prerequisites:
- Operating System:
- This guide will cover installation on popular versions of Windows and Linux (specifically Ubuntu/Debian). MongoDB also supports other operating systems, which you can find on the official MongoDB website.
- Storage Space:
- You'll need sufficient disk space to store your database files. The amount of space required will depend on the size of your data. It is recommended to have more storage than you think you will initially need.
- RAM:
- While MongoDB can run with minimal RAM, having more RAM will improve performance, especially for larger databases. The amount of RAM needed will depend on the size of your data.
- Basic System Knowledge:
- Familiarity with using the command line or terminal is helpful, especially for Linux installations.
- Basic understanding of file systems and directories.
Essentially, MongoDB is designed to be flexible and can run on most modern systems. As your data grows, you can always scale your hardware accordingly.
Downloading MongoDB Community Server:
To begin, you'll need to download the MongoDB Community Server installation package.
- Visit the official MongoDB download page: https://www.mongodb.com/try/download/community
On the download page, you'll see options to select the following:
- Version: Choose the desired version of MongoDB. It is generally recommended to select the latest stable release.
- Operating System: Select your operating system (Windows or Linux).
- Package: Select the appropriate package type. For Windows, it will typically be
msi. For Linux, you will choose the package type that aligns with your linux distro. For example.debfor Debian/Ubuntu or.rpmfor RedHat/Fedora.
Once you have made your selections, click the "Download" button to download the installer or package.
Installation on Windows:
Running the Installer:
-
Locate the Downloaded Installer:
- Navigate to the directory where you downloaded the MongoDB
.msiinstaller.
- Navigate to the directory where you downloaded the MongoDB
-
Run the Installer:
- Double-click the
.msifile to start the installation wizard.
- Double-click the
-
Welcome Screen:
- Click "Next" on the welcome screen.
-
License Agreement:
- Read the license agreement, check the "I accept the terms in the License Agreement" box, and click "Next."
-
Setup Type:
- Select "Custom" installation. This allows you to choose the installation location and data directory. Click "Next."
-
Installation Location:
- You can change the default installation directory if desired. Click "Next."
-
Service Configuration:
- You can choose to install MongoDB as a service. It is recommended to install as a service.
- You can also change the "Data Directory" location here. It is recommended to change this to a location such as
C:\data\db. If you do not change it here, you will need to create the data directory manually later. - Click "Next."
-
Ready to Install:
- Click "Install" to begin the installation process.
-
Complete Installation:
- Once the installation is complete, click "Finish."
Setting Environment Variables (Optional but Recommended):
Setting the
PATHenvironment variable allows you to run MongoDB commands from any command prompt window without specifying the full path to the executable.-
Open System Properties:
- Search for "Environment Variables" in the Windows Start menu and select "Edit the system environment variables."
-
Environment Variables:
- In the "System Properties" window, click the "Environment Variables..." button.
-
Edit Path Variable:
- In the "System variables" section, find the "Path" variable and click "Edit."
-
Add MongoDB Bin Directory:
- Click "New" and add the path to the MongoDB
bindirectory. This is typicallyC:\Program Files\MongoDB\Server\<version>\bin, replacing<version>with your installed version. - Click "OK" on all open windows to save the changes.
- Click "New" and add the path to the MongoDB
-
Verify Path:
- Open a new command prompt window and type
mongod --version. If MongoDB is installed correctly and thePATHvariable is set, you should see the MongoDB version information.
- Open a new command prompt window and type
Installation on Linux (Ubuntu/Debian):
These instructions are specifically for Debian-based systems like Ubuntu.
Importing the MongoDB Public GPG Key:
-
Open a Terminal:
- Open your terminal application.
-
Import the GPG Key:
- Run the following command to import the MongoDB public GPG key:
bash wget -qO - [https://www.mongodb.org/static/pgp/server-7.0.asc](https://www.mongodb.org/static/pgp/server-7.0.asc) | sudo apt-key add -- This command downloads the GPG key and adds it to your system's trusted keys. This ensures that the packages you download from the MongoDB repository are authentic.
Adding the MongoDB Repository:
-
Add the Repository:
- Run the following command to add the MongoDB repository to your system's sources list:
bash echo "deb [ arch=amd64,arm64 ] [https://repo.mongodb.org/apt/ubuntu](https://repo.mongodb.org/apt/ubuntu) $(lsb_release -cs)/mongodb-org/7.0 multiverse" | sudo tee /etc/apt/sources.list.d/mongodb-org-7.0.list- This command adds the MongoDB repository to your system's package manager sources. The
$(lsb_release -cs)part automatically determines your Ubuntu/Debian version.
-
Update Package List:
- Run the following command to update your package list:
bash sudo apt update- This command refreshes the package list, including the newly added MongoDB repository.
Installing MongoDB:
-
Install MongoDB:
- Run the following command to install the MongoDB Community Server:
bash sudo apt install mongodb-org- This command downloads and installs the MongoDB packages.
After install, linux and windows should both have a system service already setup from the install process. You can check if it's running on linux with
sudo systemctl status mongod. On Windows, you should see the service running as "MongoDB Server" if you open system services on WindowsBasic MongoDB Commands:
After installing and starting MongoDB, you can use the
mongoshell to interact with your database. Here are some basic commands to get you started:Checking MongoDB Version:
First, let's verify that MongoDB is installed correctly by checking its version:
-
Open a Terminal or Command Prompt:
- Open your terminal (Linux/macOS) or command prompt (Windows).
-
Run
mongosh --version:- Type
mongosh --versionand press Enter. - This command will display the installed MongoDB version if it's correctly installed and in your system's PATH.
- Type
Basic MongoDB Shell Commands:
-
Open the
mongoshShell:- Type
mongoshand press Enter. This will open the MongoDB shell, and you'll see a prompt like>.
- Type
-
Show Databases:
- To see a list of all databases on your MongoDB server, type
show dbsand press Enter. - This will display a list of database names.
- To see a list of all databases on your MongoDB server, type
-
Use a Database:
- To switch to a specific database, type
use <database_name>and press Enter. Replace<database_name>with the name of the database you want to use. - Example:
use mydatabase - If the database doesn't exist, MongoDB will create it when you first store data in it.
- To switch to a specific database, type
-
Show Collections:
- After switching to a database, you can see a list of collections (similar to tables in relational databases) in that database by typing
show collectionsand pressing Enter. - Collections are where you store documents (JSON-like data).
- After switching to a database, you can see a list of collections (similar to tables in relational databases) in that database by typing
Example Session:
```bash
mongosh Current Mongosh Log ID: 6563728637951a37887e2730 Connecting to: mongodb://127.0.0.1:27017/?directConnection=true&serverSelectionTimeoutMS=2000&appName=mongosh Using MongoDB: 7.0.3 Using Mongosh: 2.1.1 For mongosh info see: https://docs.mongodb.com/mongodb-shell/
test> show dbs admin 40 KiB config 72 KiB local 40 KiB test> use mydatabase switched to db mydatabase mydatabase> show collections mydatabase> ```
Conclusion
Congratulations! You have successfully installed and started MongoDB Community Server. You've learned how to download, install, and run MongoDB on both Windows and Linux systems, and you've explored some basic commands to interact with your database.
Now, you might want to try an application like grain, a Nostr relay, which utilizes MongoDB as its database. Learn How to Install grain: nostr:naddr1qvzqqqr4gupzq9h35qgq6n8ll0xyyv8gurjzjrx9sjwp4hry6ejnlks8cqcmzp6tqqxnzde5xg6rqdpnx56rqv34uyz5g4
Remember, this guide covers the basics. There's much more to explore in the world of MongoDB, including advanced querying, indexing, replication, and sharding. Continue exploring the official MongoDB documentation to deepen your knowledge and unlock the full potential of this powerful database.
- Operating System:
-
 @ 502ab02a:a2860397
2025-04-11 18:16:56
@ 502ab02a:a2860397
2025-04-11 18:16:56วันนี้เรามาคุยกันเรื่องที่ว่า บรอกโคลี เข้าร่วมเส้นทางของความ fiat food ยังไงกันครับ
ในอดีตกาล เมล็ดพันธุ์เป็นของสาธารณะ เป็นมรดกของมนุษยชาติที่ส่งต่อจากรุ่นสู่รุ่น ต้นข้าว ต้นถั่ว ต้นผัก ล้วนเติบโตจากธรรมชาติ ผ่านมือของชาวนาอย่างเสรี ไม่มีใครเป็นเจ้าของมันได้ คนอินเดีย คนไทย คนแอฟริกัน ต่างมีเมล็ดพันธุ์ของตนเอง เหมือนมีภาษาท้องถิ่นที่เล่าขานกันรุ่นต่อรุ่น
แต่แล้ววันหนึ่ง โลกเข้าสู่ยุค “Fiat” เมื่ออุตสาหกรรมเกษตรข้ามชาติอย่าง Monsanto, Bayer, Syngenta และ DuPont รวมพลังกันเปลี่ยนสิ่งมีชีวิตให้กลายเป็น “ทรัพย์สิน” เมล็ดพันธุ์ถูกจดสิทธิบัตร เกษตรกรเก็บเมล็ดพันธุ์ไว้ปลูกใหม่ กลับกลายเป็น “อาชญากร”! โลกเปลี่ยนจากการปลูกเพื่อกิน สู่การปลูกเพื่อขึ้นศาล กฎหมายและสิทธิบัตรกลายเป็นเครื่องมือในการควบคุม บริษัทเหล่านี้ใช้กฎหมายทรัพย์สินทางปัญญา เช่น สิทธิบัตรและสิทธิของผู้ปรับปรุงพันธุ์พืช (Plant Breeders' Rights) เพื่อควบคุมเมล็ดพันธุ์ กฎหมายเหล่านี้จำกัดสิทธิของเกษตรกรในการเก็บ ใช้ แลกเปลี่ยน หรือขายเมล็ดพันธุ์ของตนเอง
ปลูกอะไร? ปลูกหนี้? ชาวนาในอินเดียบางรัฐถึงกับฆ่าตัวตาย เพราะซื้อเมล็ดพันธุ์จีเอ็มโอที่มีสิทธิบัตรราคาแพงจากบริษัทเหล่านี้ พวกเขาไม่สามารถเก็บเมล็ดไว้ใช้ปีต่อไป ต้องซื้อใหม่ทุกปี บางครั้งซื้อแล้วปลูกไม่ได้ผล เพราะพันธุ์ไม่เหมาะกับภูมิอากาศของเขา แต่ก็ยังต้องจ่ายหนี้ จ่ายค่าปุ๋ย จ่ายค่าฆ่าแมลงที่บริษัทบอกว่าจำเป็นต่อเมล็ดของมัน ในขณะที่ผู้ที่ไม่ได้เดือดร้อนจากเรื่องนี้ มักบอกว่า ช่วยไม่ได้ไปเลือกซื้อของเขาเอง?
พูดให้เห็นภาพก็คือบริษัทเหล่านี้สร้างระบบแบบ “log in” เหมือนซอฟต์แวร์ ผูกเมล็ดพันธุ์เข้ากับเคมีภัณฑ์ ผูกเคมีเข้ากับกฎหมาย ผูกกฎหมายเข้ากับรัฐบาล และผูกรัฐบาลเข้ากับองค์กรโลกที่เห็น “ความมั่นคงทางอาหาร” เป็นเพียงบรรทัดนึงของ account เราครับ
-ค่าใช้จ่ายที่เพิ่มขึ้น เกษตรกรต้องซื้อเมล็ดพันธุ์ใหม่ทุกฤดูกาลเพราะถูกห้ามไม่ให้เก็บเมล็ดพันธุ์จากผลผลิตเดิม ทำให้ต้นทุนการผลิตสูงขึ้น -การสูญเสียความหลากหลายทางชีวภาพ การเน้นปลูกพืชสายพันธุ์เดียวกันทั่วโลกทำให้พืชท้องถิ่นและสายพันธุ์พื้นเมืองลดลง ซึ่งส่งผลต่อความหลากหลายทางชีวภาพและความยืดหยุ่นของระบบนิเวศ -ความเสี่ยงต่อความมั่นคงทางอาหาร การพึ่งพาเมล็ดพันธุ์จากบริษัทไม่กี่แห่งทำให้ระบบอาหารโลกเสี่ยงต่อการผันผวนของตลาดและการเปลี่ยนแปลงทางการเมือง
บรอกโคลี กับการเป็น Fiat Food ในรูปแบบพืช เริ่มมาจากพืชตระกูลผักกาด เช่น บรอกโคลี กระหล่ำดอก คะน้า และกะหล่ำปลี ถูก “ปรับปรุงพันธุ์” โดยมนุษย์จากบรรพบุรุษเดียวกัน มัสตาร์ดป่า พวกมันไม่สามารถขยายพันธุ์ตามธรรมชาติได้ ต้องอาศัยโรงงานผลิตเมล็ดพันธุ์โดยเฉพาะ และในบางกรณี ไม่มีเมล็ดเลย ต้องขยายพันธุ์โดย “Hybrid Sterility System” บริษัทผู้ผลิตเมล็ดพันธุ์จึงควบคุมได้หมด ใครจะปลูกต้องขออนุญาต ใครจะขายต้องผ่านระบบควบคุม
นั่นแหละ... เข้าคออนเสป Fiat Food ตัวจริง อาหารที่ดูเขียว ดูคลีน ดูดีต่อใจ แต่ไร้ “รากเหง้า” และถูกสร้างขึ้นด้วยอำนาจเหนือธรรมชาติอย่างจงใจ ไม่ใช่ของจากธรรมชาติ ไม่ใช่ของจากพระเจ้าแต่เป็นของจาก “วาระซ่อนเร้น” ที่ซ่อนอยู่ในแสงแฟลชของโฆษณาอาหารคลีน การประเคนข้อดีของความเป็น super food โดยไม่พูดถึงเหรียญอีกด้าน เหรียญด้านมืดของมัน
ดังนั้นก็เลยเกิดสมการ อธิปไตยของเมล็ดพันธุ์ = อิสรภาพของมนุษยชาติ การต่อสู้ครั้งนี้ไม่ใช่แค่เรื่องของเกษตรกรรม แต่มันคือ “การเมืองของชีวิต” เพราะใครก็ตามที่ควบคุมเมล็ดพันธุ์ เขาคือผู้ควบคุมอาหาร และใครควบคุมอาหาร เขาคือผู้ควบคุมโลก การต่อสู้ก็เลยมีองค์กรอย่าง Navdanya ในอินเดีย หรือ La Via Campesina ในลาตินอเมริกา ที่ลุกขึ้นมาปกป้อง “สิทธิในการปลูกของมนุษย์” มีคนขนานนามว่าพวกเขาไม่ใช่นักเกษตร พวกเขาคือนักปฏิวัติ
ดร. วันทนา ศิวะ Vandana Shiva นักฟิสิกส์ชาวอินเดียผู้กลายมาเป็นนักเคลื่อนไหวด้านสิ่งแวดล้อมและอาหาร ผู้ก่อตั้งโรงเรียนเมล็ดพันธุ์พืชนวธัญญะ (Navdanya) ผู้ปกป้องพืชท้องถิ่นจากบริษัทข้ามชาติที่คิดจะเข้ามายึดประชาธิปไตยทางอาหารไปจากมือประชาชน คือตัวอย่างที่ชัดเจนคนหนึ่ง เจ้าของวลี “หากจะยึดครองประเทศจงยึดแหล่งน้ำมัน แต่หากต้องการยึดครองชีวิต จงยึดเมล็ดพันธุ์พืชของพวกเขา”
งานเขียนที่น่าสนใจของเธอคือ Earth Democracy: Justice, Sustainability and Peace ปี 2005 เป็นการออกมาตอบโต้ระบบทุนนิยม ที่มองว่าทุกสิ่งทุกอย่างบนโลกใบนี้มีไว้ขาย เพื่อเก็งกำไร พร้อมทั้งตั้งคำถามว่า หากผืนดินไม่ใช่ของมนุษย์ โลกไม่ได้เป็นสินทรัพย์ น้ำทุกหยด เมล็ดพันธุ์พืชทุกชนิดล้วนเป็นของธรรมชาติ ความคิดของบริษัทที่จะเข้ามาผูกขาดธรรมชาติเป็นสิ่งที่สมควรจริงหรือ
ดังนั้นสรุปๆกันจากที่ผมจั่วไว้ว่า บรอกโคลี อีกตัวแทนแห่ง fiat food นั้นคือประตูบานแรกที่ชักนำให้เราฉุกคิดถึงรูปแบบของ อาหารที่ปลอมตัวมาอยู่ในรูปแบบ real food โดยภาพร่างประมาณนี้ครับ เมล็ดพันธุ์พื้นเมือง เคยเป็นของสาธารณะ → ถูกบริษัท “แปรรูป” เป็นทรัพย์สิน การเก็บเมล็ดพันธุ์ใช้ซ้ำ กลายเป็นสิ่งผิดกฎหมายในหลายประเทศ เกษตรกรกลายเป็นทาส ของระบบ “Fiat Seed” เหมือนเราทุกคนเป็นทาสของ “Fiat Money” บรอกโคลีและผักไฮบริดอื่นๆ คือตัวแทนของการควบคุมระบบอาหารผ่านสายพันธุ์ที่คนทั่วไปปลูกเองไม่ได้ ทางออกที่กลุ่มคนมีความหวังกับมันคือ Seed Sovereignty คืนสิทธิให้ชุมชน เก็บ แบ่ง แลก เปลี่ยนเมล็ดพันธุ์เองได้
การผูกขาดเมล็ดพันธุ์โดยบริษัทยักษ์ใหญ่ส่งผลกระทบต่อเกษตรกรและความมั่นคงทางอาหารอย่างมาก การเคลื่อนไหวเพื่ออธิปไตยทางเมล็ดพันธุ์เป็นสิ่งจำเป็นในการปกป้องสิทธิของเกษตรกรและรักษาความหลากหลายทางชีวภาพของพืชผลในอนาคต ใครกุมเมล็ดพันธุ์ คนนั้นกุมคอหอยมนุษย์ทั้งโลก
อ่านถึงตรงนี้แล้ว นึกถึงพืชอื่นอะไรอีกบ้าง? ทิ้งไว้ให้ตั้งคำถามกันต่อครับ ตอนต่อไปจะว่าด้วยเรื่องของ สนธิสัญญาและกฎหมายต่างๆครับ
แถมให้ดูคลิปการปลูก บรอกโคลี ครับ https://youtu.be/8ZNPTMIEFV8?si=SKZy
ผมเลือกคลิปที่ถ่ายโดย local ไม่ได้เป็น pr film โปรโมทองค์กรใดๆ เพื่อให้เห็นกระบวนการแท้ๆเลยนะครับส่วนคำถามที่ว่า แล้วจะกินอะไรได้ ตอบได้เลยว่า กินได้ทุกอย่างแหละครับ แต่ช่วยรู้ด้วยว่า อย่าไปคิดว่าอะไรเทพ อะไร superfood เลย โลกไม่ได้สวยงามขนาดนั้นครับ เราถึงพยายามชักชวนมาทำให้ local แข็งแรงไง
#PirateKeto #กูต้องรู้มั๊ย #ม้วนหางสิลูก
-
 @ 21335073:a244b1ad
2025-03-20 13:16:22
@ 21335073:a244b1ad
2025-03-20 13:16:22I’d never had the chance to watch Harry Potter on the big screen before. Experiencing the first movie in 3D was nothing short of spectacular. Right from the opening scene with Albus Dumbledore, I was floored—the makeup and costumes were so vivid, it felt like pure magic unfolding before my eyes. It’s clear that real masters of their craft worked behind the scenes, and their artistry shines through. The sets? Absolutely jaw-dropping! The level of detail in Diagon Alley was beyond impressive.
Seeing legends like Alan Rickman as Snape and Maggie Smith as Minerva McGonagall on that massive 3D screen was an unforgettable thrill. The film is packed with phenomenal actors, and it was a joy to catch every tiny eye twitch and subtle nuance of their performances brought to life. It was a mind-blowing experience, and I’d wholeheartedly recommend it to anyone who gets the chance.
Don’t forget to have a little whimsical fun sometimes my friends. 🪄
-
 @ e111a405:fa441558
2025-04-11 17:15:58
@ e111a405:fa441558
2025-04-11 17:15:58Meritocracy without equality is basically a ladder with missing steps, which only the fortunate few can climb. The rest is basically left at the ground to gaze up.
Furthermore, a pure focus on meritocracy can become a weakness if it’s a zero-sum game. While talents thrive in systems that value it, without fairness, you ultimately get exploitation, resentment, or fragility.
Ergo: meritocracy needs to be balanced with equality, and equality needs to be balanced with meritocracy.
In a meritocratic system, you basically need that the fortunate and the able are compassionate towards those less fortunate and able.
If you are more on the libertarian side, you need the fortunate individuals to compete as capitalists and then be socialists within their communities and families.
If you prefer a state, then the state must encourage meritocratic contribution of everyone that is able, to the best of their ability, while balancing it with a fair welfare system that nurtures and supports those less able and fortunate.
I think this is something Germany did historically quite well, but at one point we lost the balance: we lost the culture of merit by putting too much emphasis on equality – even to a point that Germany now cares for millions of non-citizens that never contributed, when it should instead demand these individuals to contribute to the best of their ability.
If we want to have a state, then we don’t want a welfare state, and – I think – we should also not want a pure capitalistic state. We need balance and thus a social meritocracy.
-
 @ 7e538978:a5987ab6
2025-04-10 13:14:04
@ 7e538978:a5987ab6
2025-04-10 13:14:04After five years and over 6,000 commits, LNbits has reached a momentous milestone: Version 1.0.0 is here. LNbits is officially out of beta!
This release represents the five years relentless development, dedication, bug-hunting, feature-building, and community involvement. What started as a lightweight Lightning wallet application for Lightning Network payments has evolved into one of the most versatile, modular, and widely-used Bitcoin tools in the space.
We want to offer a heartfelt thank you to every contributor, developer, tester, and user—from those running LNbits for personal use to the communities and businesses who rely on it every day. Your feedback, bug reports, feature requests, and support have made LNbits what it is today.
🚀 Key Highlights in v1.0.0
- LNbits now at v1.0.0 – the software is stable, hardened, and production-ready.
- Vue 3 migration – a complete frontend overhaul for performance and long-term maintainability.
- WebSocket payments – faster and more efficient, replacing older SSE and long-polling methods.
- New lnbits.sh install script – simplifies setup and local deployment.
- Access Control Lists (ACL) – token-based permissions for powerful role and scope control.
- Admin tools:
- Admin payments overview
- Toggle outgoing payments
- View payments from deleted wallets
- NWC (Nostr Wallet Connect) support
- Login with Nostr or OAuth – expanding integration and authentication options
💱 Fiat & Exchange Upgrades
- Custom exchange providers
- Improved fiat precision
- Wallet-level fiat tracking and labels
- Support for Bitpay and Yadio fiat rate providers
🧑🎨 UI / UX Improvements New Login/Register interface
- Default theme for new users
- Custom background images
- Visual refresh with new themes (including neon and light/dark modes)
- Revamped Pay Invoice dialog and invoice creation
- Custom wallet icons/colours
- CSV export and in-wallet payment filtering
🛠️ Developer Tools & Internal Enhancements Migration to pyjwt, updated to breez-sdk 0.6.6, pyln-client 24.5
- Support for Python 3.10–3.13
- New nodemanager for managing Lightning channels
- Backend refactors, improved database handling, type hinting, and extension logic
- More robust testing and CI support
🩹 Maintenance & Fixes Persistent fix for admin removal bug
- Improved extension handling
- Bug fixes across wallet logic, funding sources, and legacy compatibility
- Dozens of improvements to reliability, performance, and developer experience
🎉 A Huge Thank You
To every developer, translator, tester, UX contributor, node runner, and user: thank you.
LNbits wouldn’t be what it is without your involvement. Whether you've written code, opened issues, translated labels, or simply used it and given feedback—this release is yours too.
Here's to the next chapter!
-
 @ 95cb33b5:f4580cd4
2025-04-11 16:57:35
@ 95cb33b5:f4580cd4
2025-04-11 16:57:35Electrical overloads are a significant concern in residential and commercial settings, often leading to hazardous situations such as fires, equipment damage, and power outages. One effective strategy to mitigate these risks is the installation of additional electrical circuits. By distributing electrical loads more evenly, additional circuits enhance safety, improve system efficiency, and accommodate the growing demand for electrical power in modern infrastructures.
Understanding Electrical Overloads
An electrical overload occurs when the current flowing through a circuit exceeds its designated capacity. This situation typically arises when multiple high-power devices operate simultaneously on a single circuit, drawing more amperage than the wiring can safely handle. Consequences of overloads include overheating of wires, degradation of insulation, and, in severe cases, ignition of fires. Common indicators of an overloaded circuit are:
Flickering or dimming lights
Frequently tripped circuit breakers or blown fuses
Warm or discolored wall plates
Buzzing sounds from outlets or switches
Burning odors emanating from electrical fixtures
Mild shocks or tingling sensations when touching appliances
The Prevalence and Impact of Electrical Fires
Electrical malfunctions are a leading cause of residential fires. According to the Electrical Safety Foundation International (ESFI), home electrical fires account for an estimated 51,000 fires each year, resulting in nearly 500 deaths, more than 1,400 injuries, and $1.3 billion in property damage. These statistics underscore the critical need for preventive measures to address electrical overloads and enhance the safety of electrical systems.
The Role of Additional Circuits in Preventing Overloads
Incorporating additional circuits into an electrical system effectively distributes the electrical load, reducing the likelihood of overloads. This approach involves segmenting the electrical supply into multiple pathways, each dedicated to specific areas or high-power appliances. Benefits of this strategy include:
Enhanced Safety: By preventing excessive current flow through any single circuit, the risk of overheating and potential fires is significantly reduced.
Improved Performance: Appliances and devices operate more efficiently when supplied with adequate power, free from the voltage drops associated with overloaded circuits.
Capacity for Expansion: Additional circuits provide the necessary infrastructure to support new appliances or technological upgrades without compromising the existing system's integrity.
Implementing Additional Circuits: Practical Considerations
When planning to add circuits, several factors must be considered to ensure effectiveness and compliance with safety standards:
Assessment of Current Load: A thorough evaluation of the existing electrical load helps identify circuits that are frequently overloaded and areas where additional circuits are needed.
Professional Installation: Engaging a licensed electrician ensures that new circuits are installed correctly, adhering to local codes and regulations.
Use of Appropriate Materials: Selecting wiring and components that match the intended load capacity is crucial for safety and durability.
Regular Maintenance: Periodic inspections and maintenance of the electrical system help detect and address potential issues before they escalate.
Complementary Measures to Prevent Overloads
In addition to installing extra circuits, other practices can further mitigate the risk of electrical overloads:
Use of Surge Protectors: Surge protectors safeguard sensitive electronics from voltage spikes, which can occur during overload conditions.
Avoidance of Extension Cords for Permanent Use: Relying on extension cords as a permanent solution indicates insufficient outlets and can contribute to overloads. Installing additional outlets or circuits is a safer alternative.
Upgrading Electrical Panels: Older electrical panels may not support the increased load demands of modern appliances. Upgrading to a panel with higher capacity can enhance system safety and performance.
Conclusion The integration of additional electrical circuits is a proactive and effective measure to prevent electrical overloads. By ensuring a balanced distribution of electrical loads, this approach enhances the safety, efficiency, and adaptability of electrical systems. Given the significant number of fires attributed to electrical malfunctions annually, prioritizing such preventive strategies is imperative. Engaging qualified professionals to assess and implement necessary electrical upgrades, including the addition of circuits, is essential in safeguarding property and lives against the hazards of electrical overloads.
-
 @ 21335073:a244b1ad
2025-03-18 20:47:50
@ 21335073:a244b1ad
2025-03-18 20:47:50Warning: This piece contains a conversation about difficult topics. Please proceed with caution.
TL;DR please educate your children about online safety.
Julian Assange wrote in his 2012 book Cypherpunks, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense.
This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning.
When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little.
I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?”
I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well.
I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread.
I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard.
I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it.
The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust.
Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this.
I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place.
What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method.
It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code.
They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened.
I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road.
So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally.
Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb.
I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback.
Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed.
That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone.
To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all.
I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society.
I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this.
On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government.
I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories.
There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc.
Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind.
Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now.
There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers?
I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity.
I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place.
My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors.
My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline.
The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online.
I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers.
So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation?
When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that.
I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic.
If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations.
I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process.
Course: - The creation of the internet and computers - The fight for cryptography - The tech supply chain from the ground up (example: human rights violations in the supply chain) - Corporate tech - Freedom tech - Data privacy - Digital privacy rights - AI (history-current) - Online safety (predators, scams, catfishing, extortion) - Bitcoin - Laws - How to deal with online hate and harassment - Information on who to contact if you are being abused online or offline - Algorithms - How to seek out the truth about news, etc., online
The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children.
The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward?
I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone.
Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability.
The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime.
This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful.
This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens.
In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions.
I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation.
-
 @ 3b3a42d3:d192e325
2025-04-10 08:57:51
@ 3b3a42d3:d192e325
2025-04-10 08:57:51Atomic Signature Swaps (ASS) over Nostr is a protocol for atomically exchanging Schnorr signatures using Nostr events for orchestration. This new primitive enables multiple interesting applications like:
- Getting paid to publish specific Nostr events
- Issuing automatic payment receipts
- Contract signing in exchange for payment
- P2P asset exchanges
- Trading and enforcement of asset option contracts
- Payment in exchange for Nostr-based credentials or access tokens
- Exchanging GMs 🌞
It only requires that (i) the involved signatures be Schnorr signatures using the secp256k1 curve and that (ii) at least one of those signatures be accessible to both parties. These requirements are naturally met by Nostr events (published to relays), Taproot transactions (published to the mempool and later to the blockchain), and Cashu payments (using mints that support NUT-07, allowing any pair of these signatures to be swapped atomically.
How the Cryptographic Magic Works 🪄
This is a Schnorr signature
(Zₓ, s):s = z + H(Zₓ || P || m)⋅kIf you haven't seen it before, don't worry, neither did I until three weeks ago.
The signature scalar s is the the value a signer with private key
k(and public keyP = k⋅G) must calculate to prove his commitment over the messagemgiven a randomly generated noncez(Zₓis just the x-coordinate of the public pointZ = z⋅G).His a hash function (sha256 with the tag "BIP0340/challenge" when dealing with BIP340),||just means to concatenate andGis the generator point of the elliptic curve, used to derive public values from private ones.Now that you understand what this equation means, let's just rename
z = r + t. We can do that,zis just a randomly generated number that can be represented as the sum of two other numbers. It also follows thatz⋅G = r⋅G + t⋅G ⇔ Z = R + T. Putting it all back into the definition of a Schnorr signature we get:s = (r + t) + H((R + T)ₓ || P || m)⋅kWhich is the same as:
s = sₐ + twheresₐ = r + H((R + T)ₓ || P || m)⋅ksₐis what we call the adaptor signature scalar) and t is the secret.((R + T)ₓ, sₐ)is an incomplete signature that just becomes valid by add the secret t to thesₐ:s = sₐ + tWhat is also important for our purposes is that by getting access to the valid signature s, one can also extract t from it by just subtracting
sₐ:t = s - sₐThe specific value of
tdepends on our choice of the public pointT, sinceRis just a public point derived from a randomly generated noncer.So how do we choose
Tso that it requires the secret t to be the signature over a specific messagem'by an specific public keyP'? (without knowing the value oft)Let's start with the definition of t as a valid Schnorr signature by P' over m':
t = r' + H(R'ₓ || P' || m')⋅k' ⇔ t⋅G = r'⋅G + H(R'ₓ || P' || m')⋅k'⋅GThat is the same as:
T = R' + H(R'ₓ || P' || m')⋅P'Notice that in order to calculate the appropriate
Tthat requirestto be an specific signature scalar, we only need to know the public nonceR'used to generate that signature.In summary: in order to atomically swap Schnorr signatures, one party
P'must provide a public nonceR', while the other partyPmust provide an adaptor signature using that nonce:sₐ = r + H((R + T)ₓ || P || m)⋅kwhereT = R' + H(R'ₓ || P' || m')⋅P'P'(the nonce provider) can then add his own signature t to the adaptor signaturesₐin order to get a valid signature byP, i.e.s = sₐ + t. When he publishes this signature (as a Nostr event, Cashu transaction or Taproot transaction), it becomes accessible toPthat can now extract the signaturetbyP'and also make use of it.Important considerations
A signature may not be useful at the end of the swap if it unlocks funds that have already been spent, or that are vulnerable to fee bidding wars.
When a swap involves a Taproot UTXO, it must always use a 2-of-2 multisig timelock to avoid those issues.
Cashu tokens do not require this measure when its signature is revealed first, because the mint won't reveal the other signature if they can't be successfully claimed, but they also require a 2-of-2 multisig timelock when its signature is only revealed last (what is unavoidable in cashu for cashu swaps).
For Nostr events, whoever receives the signature first needs to publish it to at least one relay that is accessible by the other party. This is a reasonable expectation in most cases, but may be an issue if the event kind involved is meant to be used privately.
How to Orchestrate the Swap over Nostr?
Before going into the specific event kinds, it is important to recognize what are the requirements they must meet and what are the concerns they must address. There are mainly three requirements:
- Both parties must agree on the messages they are going to sign
- One party must provide a public nonce
- The other party must provide an adaptor signature using that nonce
There is also a fundamental asymmetry in the roles of both parties, resulting in the following significant downsides for the party that generates the adaptor signature:
- NIP-07 and remote signers do not currently support the generation of adaptor signatures, so he must either insert his nsec in the client or use a fork of another signer
- There is an overhead of retrieving the completed signature containing the secret, either from the blockchain, mint endpoint or finding the appropriate relay
- There is risk he may not get his side of the deal if the other party only uses his signature privately, as I have already mentioned
- There is risk of losing funds by not extracting or using the signature before its timelock expires. The other party has no risk since his own signature won't be exposed by just not using the signature he received.
The protocol must meet all those requirements, allowing for some kind of role negotiation and while trying to reduce the necessary hops needed to complete the swap.
Swap Proposal Event (kind:455)
This event enables a proposer and his counterparty to agree on the specific messages whose signatures they intend to exchange. The
contentfield is the following stringified JSON:{ "give": <signature spec (required)>, "take": <signature spec (required)>, "exp": <expiration timestamp (optional)>, "role": "<adaptor | nonce (optional)>", "description": "<Info about the proposal (optional)>", "nonce": "<Signature public nonce (optional)>", "enc_s": "<Encrypted signature scalar (optional)>" }The field
roleindicates what the proposer will provide during the swap, either the nonce or the adaptor. When this optional field is not provided, the counterparty may decide whether he will send a nonce back in a Swap Nonce event or a Swap Adaptor event using thenonce(optionally) provided by in the Swap Proposal in order to avoid one hop of interaction.The
enc_sfield may be used to store the encrypted scalar of the signature associated with thenonce, since this information is necessary later when completing the adaptor signature received from the other party.A
signature specspecifies thetypeand all necessary information for producing and verifying a given signature. In the case of signatures for Nostr events, it contain a template with all the fields, exceptpubkey,idandsig:{ "type": "nostr", "template": { "kind": "<kind>" "content": "<content>" "tags": [ … ], "created_at": "<created_at>" } }In the case of Cashu payments, a simplified
signature specjust needs to specify the payment amount and an array of mints trusted by the proposer:{ "type": "cashu", "amount": "<amount>", "mint": ["<acceptable mint_url>", …] }This works when the payer provides the adaptor signature, but it still needs to be extended to also work when the payer is the one receiving the adaptor signature. In the later case, the
signature specmust also include atimelockand the derived public keysYof each Cashu Proof, but for now let's just ignore this situation. It should be mentioned that the mint must be trusted by both parties and also support Token state check (NUT-07) for revealing the completed adaptor signature and P2PK spending conditions (NUT-11) for the cryptographic scheme to work.The
tagsare:"p", the proposal counterparty's public key (required)"a", akind:30455Swap Listing event or an application specific version of it (optional)
Forget about this Swap Listing event for now, I will get to it later...
Swap Nonce Event (kind:456) - Optional
This is an optional event for the Swap Proposal receiver to provide the public nonce of his signature when the proposal does not include a nonce or when he does not want to provide the adaptor signature due to the downsides previously mentioned. The
contentfield is the following stringified JSON:{ "nonce": "<Signature public nonce>", "enc_s": "<Encrypted signature scalar (optional)>" }And the
tagsmust contain:"e", akind:455Swap Proposal Event (required)"p", the counterparty's public key (required)
Swap Adaptor Event (kind:457)
The
contentfield is the following stringified JSON:{ "adaptors": [ { "sa": "<Adaptor signature scalar>", "R": "<Signer's public nonce (including parity byte)>", "T": "<Adaptor point (including parity byte)>", "Y": "<Cashu proof derived public key (if applicable)>", }, …], "cashu": "<Cashu V4 token (if applicable)>" }And the
tagsmust contain:"e", akind:455Swap Proposal Event (required)"p", the counterparty's public key (required)
Discoverability
The Swap Listing event previously mentioned as an optional tag in the Swap Proposal may be used to find an appropriate counterparty for a swap. It allows a user to announce what he wants to accomplish, what his requirements are and what is still open for negotiation.
Swap Listing Event (kind:30455)
The
contentfield is the following stringified JSON:{ "description": "<Information about the listing (required)>", "give": <partial signature spec (optional)>, "take": <partial signature spec (optional)>, "examples: [<take signature spec>], // optional "exp": <expiration timestamp (optional)>, "role": "<adaptor | nonce (optional)>" }The
descriptionfield describes the restrictions on counterparties and signatures the user is willing to accept.A
partial signature specis an incompletesignature specused in Swap Proposal eventskind:455where omitting fields signals that they are still open for negotiation.The
examplesfield is an array ofsignature specsthe user would be willing totake.The
tagsare:"d", a unique listing id (required)"s", the status of the listingdraft | open | closed(required)"t", topics related to this listing (optional)"p", public keys to notify about the proposal (optional)
Application Specific Swap Listings
Since Swap Listings are still fairly generic, it is expected that specific use cases define new event kinds based on the generic listing. Those application specific swap listing would be easier to filter by clients and may impose restrictions and add new fields and/or tags. The following are some examples under development:
Sponsored Events
This listing is designed for users looking to promote content on the Nostr network, as well as for those who want to monetize their accounts by sharing curated sponsored content with their existing audiences.
It follows the same format as the generic Swap Listing event, but uses the
kind:30456instead.The following new tags are included:
"k", event kind being sponsored (required)"title", campaign title (optional)
It is required that at least one
signature spec(giveand/ortake) must have"type": "nostr"and also contain the following tag["sponsor", "<pubkey>", "<attestation>"]with the sponsor's public key and his signature over the signature spec without the sponsor tag as his attestation. This last requirement enables clients to disclose and/or filter sponsored events.Asset Swaps
This listing is designed for users looking for counterparties to swap different assets that can be transferred using Schnorr signatures, like any unit of Cashu tokens, Bitcoin or other asset IOUs issued using Taproot.
It follows the same format as the generic Swap Listing event, but uses the
kind:30457instead.It requires the following additional tags:
"t", asset pair to be swapped (e.g."btcusd")"t", asset being offered (e.g."btc")"t", accepted payment method (e.g."cashu","taproot")
Swap Negotiation
From finding an appropriate Swap Listing to publishing a Swap Proposal, there may be some kind of negotiation between the involved parties, e.g. agreeing on the amount to be paid by one of the parties or the exact content of a Nostr event signed by the other party. There are many ways to accomplish that and clients may implement it as they see fit for their specific goals. Some suggestions are:
- Adding
kind:1111Comments to the Swap Listing or an existing Swap Proposal - Exchanging tentative Swap Proposals back and forth until an agreement is reached
- Simple exchanges of DMs
- Out of band communication (e.g. Signal)
Work to be done
I've been refining this specification as I develop some proof-of-concept clients to experience its flaws and trade-offs in practice. I left the signature spec for Taproot signatures out of the current document as I still have to experiment with it. I will probably find some important orchestration issues related to dealing with
2-of-2 multisig timelocks, which also affects Cashu transactions when spent last, that may require further adjustments to what was presented here.The main goal of this article is to find other people interested in this concept and willing to provide valuable feedback before a PR is opened in the NIPs repository for broader discussions.
References
- GM Swap- Nostr client for atomically exchanging GM notes. Live demo available here.
- Sig4Sats Script - A Typescript script demonstrating the swap of a Cashu payment for a signed Nostr event.
- Loudr- Nostr client under development for sponsoring the publication of Nostr events. Live demo available at loudr.me.
- Poelstra, A. (2017). Scriptless Scripts. Blockstream Research. https://github.com/BlockstreamResearch/scriptless-scripts
-
 @ 866e0139:6a9334e5
2025-04-11 16:23:18
@ 866e0139:6a9334e5
2025-04-11 16:23:18
Autor: Jens Fischer Rodrian. Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier.**
In den letzten fünf Jahren wurde mit allen Mitteln versucht, die Menschen auseinanderzutreiben. Egal welches Thema gestreut oder welche Angst geschürt wurde, ob Corona, Ukraine, Gaza, Energiepolitik, Wirtschaft, Gendern oder Klima – immer sollten die Menschen einem vorgegebenen Narrativ folgen anstatt in einen offenen Debattenraum einzutreten und Differenzen auszuhalten, also das zu leben, was eine lebendige Demokratie ausmacht.
Natürlich stellt sich die Frage – ja aber wer hat das denn versucht? Wer hat denn ein Interesse daran, daß Diversität im Sinne von Vielfalt an Meinungen ausgehebelt wird? Dies zu beantworten würde den Rahmen hier sprengen, ist aber mit Verweis auf die Texte von Journalisten wie Milosz Matuschek, Tom-Oliver Regenauer u.v.a. schnell in Erfahrung zu bringen. Fest steht, nicht alle haben bei dem Versuch, die Bevölkerung ruhig und dumm zu halten, mitgemacht.
Der Wahnsinn als Chance
Egal wie laut die Bellizisten in Regierung und Medien ihre Kriegspropaganda in Dauerschleife rausbrüllen, in dem Wahnsinn steckt auch eine Chance. Immer mehr Leute verstehen, daß Deutschland in nahezu allen oben angeführten Themen, falsch abgebogen ist. Wenn es darum geht, seine Kinder für einen irrsinnigen, von den USA und der NATO provozierten Krieg in der Ukraine, zu opfern, werden hoffentlich mehr Menschen erkennen, daß sie verheizt werden sollen. Wichtig ist, daß wir nicht mit der Energie, die man für einen Sprint braucht, an all die Themen ran gehen, sondern uns auf einen Marathonlauf einstellen. Das wissen wir spätestens, seitdem die von Paul Schreyer heraus geklagten RKI Files nicht für die Empörung gesorgt haben, die man hätte erwarten können, obwohl sie klar aufzeigen, daß die Kritiker der Coronamaßnahmen in fast allen Punkten recht behalten sollten. Spätestens dann hätte die bis dahin sehr einseitig berichtende Konzernpresse auf das Thema aufspringen können, ja müssen, ist sie aber nicht. Milosz Matuschek hatte schon sehr früh in der NZZ gefragt: „Was, wenn am Ende ‚die Covidioten‘ Recht haben?“
Dass die Medien jetzt im Gleichschritt die Bevölkerung auf Krieg einstellen wollen (zahlreiche Links sind am Ende des Artikels zu finden), ist an Irrsinn nicht zu überbieten. Caren Miosga, die u.a. schon durch ihr unsägliches Interview mit Exkanzlerkandidat Robert Habeck durch mangelnde Objektivität und Einfältigkeit auffiel, sagte jüngst: „ (...) das lag lange nicht in unserer DNA, da lag Pazifismus. Wie können wir diesen Code schneller überschreiben?“ Die Antwort des Wehrdienstverweigerers und Kriegstreibers Joschka Fischer, sowie seine wirre Einschätzung einer korrupten ukrainischen Regierung und der von Neonazis durchzogenen Paramilitärs, findet Ihr in den Links am Ende des Artikels.
Seit 1945 war es nie so wichtig wie heute, daß wir uns dem entgegenstellen, alle anderen Unstimmigkeiten für den Moment beiseitelegen und gemeinsame Sache machen, denn es geht um alles, es geht um Krieg oder Frieden! Wir sollten keinen Zweifel daran haben, daß die Verantwortlichen, die Menschen mit einem experimentellen Gentherapeutikum „impfen“ auch keine Bedenken haben, die Kinder anderer Eltern in den Krieg zu treiben. Wären die Staatenlenker verpflichtet, ihre eigenen Kinder auch an die Front zu schicken, wäre das Säbelrasseln sofort vorbei – wobei ich mir bei Anton Hofreiter oder Annalena Baerbock gar nicht so sicher bin, sie sind Überzeugungstäter. Letztere fordert allen Ernstes, Russen bei Kriegsgedenken auszuschließen, sie seien per ‚Hausrecht“ zu behandeln. Der geschichtsvergessenen „Noch -Außenministerin“ ist anscheinend entfallen, daß die Russen 25 Millionen Opfer aus dem 2. Weltkrieg zu beklagen und Auschwitz befreit haben.
Das German Foreign Policy schreibt:
„Das Mindset für den Krieg – Bundeswehr-Kommandeure fordern Einstimmung der Bevölkerung auf Kriegssituationen, dringen auf stärkeren ‚Willen zur Selbstbehauptung‘. Bundesregierung arbeitet an ‚Bunker-App‘. CDU- Politiker spekuliert über ‚Spannungsfall‘“.
Um ein Zeichen gegen diesen Irrsinn zu setzen und sowohl auf die drohende Eskalation in der Ukraine wie auch die seit Jahrzehnten andauernde ethnische Säuberung in Palästina hinzuweisen, veranstalten wir am Karfreitag eine Friedensprozession in Dresden. Die Teilnehmerliste und den Text, den man auch unterzeichnen kann, findet Ihr hier im Anhang.
Jeder, der sich für den Frieden stark macht, ist willkommen.
Einer der Teilnehmer ist Tino Eisbrenner, ein Sänger und Friedensaktivist, der sich seit Jahrzehnten für Dialog und ein friedliches Miteinander einsetzt. Er selbst ist immer wieder mit Angriffen von Leuten konfrontiert, die es nicht ertragen, daß er sich beharrlich mit Wort und Musik für den Dialog mit Russland einsetzt. Erst vor Kurzem mußte er sich die inquisitorischen Fragen einer Journalistin gefallen lassen, die eine Art Gesinnungsprüfung durchführte, da ihr zu Ohren gekommen sei, das Bürger besorgt wären, Eisbrenner könne ein Putinfreund sein. Eisbrenner merkte an, daß sicherlich kein Künstler, der in Amerika auftrete oder amerikanische Poeten verehre, dadurch in Verdacht geraten könne, die imperialistische Politik eines amerikanischen Präsidenten zu unterstützen. Hier der Teil seiner Antwort, der die Kraft der Kultur und deren Funktion, Brücken zu bauen, sehr schön zusammenfasst:
„ (...) wenn man als Künstler der Ansicht ist, daß die Kunst, als wesentlichstes Merkmal des Menschseins, Grenzen überfliegen und die Brücken zwischen den Völkern erhalten und pflegen sollte, und dies auf Russland genau wie auf die USA anwendet, muss man sich rechtfertigen? In der Stadt Wolgograd (ehemals Stalingrad) gibt es ein riesiges Mahnmal für die Opfer des Zweiten Weltkrieges. Das Hauptgebäude, unweit der riesigen Grabstätte deutscher Soldaten, ist eine gigantische Kuppel in deren Mitte ein ewiges Feuer brennt. An den Wänden sind zigtausende Namen sowjetischer Bürger eingraviert, die der deutschen Schlacht um Stalingrad zum Opfer fielen. Und aus den Lautsprechern tönen in Dauerschleife die „Träumereien“ von Robert Schumann, einem deutschen Komponisten. Die Kunst, als Brücke zwischen den Völkern. Vielleicht können ihre „besorgten Bürger“ darüber mal in Ruhe nachdenken (...)“
Ich hatte die große Freude, mit Tino gemeinsam einen Song aufzunehmen, den wir beide bei der Friedensprozession in Dresden das erste mal live aufführen werden.
Frieden mit dem Frieden schließen
Frieden fragt nicht wo warst Du gestern\ Frieden fragt nicht wer ist Dein Gott\ Frieden braucht jetzt jeden, mit Herz Verstand und Mut
Frieden geht oft über Grenzen\ Frieden geht, wenn man ihn übersieht\ Frieden braucht jetzt jeden, mit Herz Verstand und Mut
Frieden schweigt wenn Menschen brüllen\ Frieden erstarrt wenn Schüsse fallen\ Frieden braucht jetzt jeden, mit Herz Verstand und Mut
Frieden fragt nicht nach Deinen Eltern\ Frieden stellt sich vor Deine Wut\ Frieden braucht jetzt jeden, mit Herz Verstand und Mut
Wir müßen Frieden mit dem Frieden schließen
Mit Leib und Seele, Tag für Tag\ Frieden braucht Dich jetzt\ Er ist erschöpft und schwer verletzt ****
Kommt zur Friedensprozession!
Unser Orga-Team hat gemeinsam mit Jürgen Fliege den Text für die Friedensprozession am Karfreitag in Dresden verfasst, den man gern auch unterzeichnen kann.
FUNDAMENT FÜR DEN FRIEDEN Mit Dir! Mit uns! Mit allen!
Jenseits jeder politischen Orientierung wollen wir dieser Sehnsucht eine Stimme geben. Denn ein Krieg, ob er nun wie ein Flächenbrand in der Ukraine oder wie in Palästina wütet, verschont immer die Mächtigen. Nie die Ohnmächtigen. Das sehen viele Menschen in unserem Land längst. Wie schon in Jugoslawien und Afghanistan scheint das die Volksvertreter nicht zu interessieren.
Wir alle wollen keinen Krieg. Wir wollen Abrüstung, Frieden und gute Nachbarn sein.
Was sind das nur für Politiker, die im Gleichschritt gegen das Wohl der Völker marschieren? Die Strack-Zimmermanns, Pistorius‘, die Baerbocks, Merz und Kiesewetters, die den Krieg weit nach Russland hineintragen und amerikanische Raketen in Deutschland stationieren wollen, ähnlich wie ihn der Kriegsverbrecher Netanjahu nach Gaza trug. Wer stoppt die Eskalationsspirale des Wahnsinns? Können wir das noch? Wir müssen es versuchen!
Friede sei mit uns allen! Ohne Ausnahme! Darum müssen wir uns vereinen. Versöhnen statt Spalten war einmal eine gute Idee der alten Sozialdemokratie – genau das wollen wir wieder aufgreifen!
Das alles war einmal der Boden, auf dem unser Grundgesetz wuchs. Die Trümmer des Krieges und die Gräber von Millionen Toten verpflichten uns zum Frieden durch Diplomatie.
Wenn Ihr unsere Sehnsucht nach Frieden teilt, dann freuen wir uns sehr, euch in Dresden zu sehen, wo der Feuersturm des 2. Weltkrieges unvergessen bleibt. Am Karfreitag, an dem die Stille das Waffenrasseln um so hörbarer macht.
Nie wieder Antisemitismus! Nie wieder Faschismus! Nie wieder Krieg! Kommt nach Dresden! Bitte!
Das aktuelle Album „Voices for Gaza“ mit 32 Beiträgen findet Ihr hier:
https://protestnoten.de/produkt/voices-for-gaza-doppel-cd/
Mit dabei sind:
Uwe Steimle, Tino Eisbrenner, Jürgen Fliege, Prof. Ulrike Guérot, Yann Song King, Arnulf Rating, Markus Stockhausen, Kilian Forster, Diether Dehm, Jakob Heymann, Jens Fischer Rodrian, Alexa Rodrian, Guido de Gyrich, Dennis DuVall, Prof. Justus Frantz, Reiner Kröhnert
(Links:
- https://taz.de/Sportunterricht-fuer-den-Ernstfall/!6059664/
- https://www.tagesspiegel.de/politik/wir-mussen-uns-auf-krieg-vorbereiten-nato-chef-rutte-fordert-von-deutschland-deutlich-hohere-verteidigungsausgaben-13131001.html
- https://www.faz.net/aktuell/wirtschaft/unternehmen/bundeswehr-bereitet-unternehmen-auf-kriegsfall-vor-operationsplan-deutschland-110118573.html
- https://www.spiegel.de/politik/deutschland/sicherheit-in-deutschland-innenministerium-fuer-zivilschutz-uebungen-an-schulen-a-1680d64e-4a42-4e00-954b-0cb38e315a90
- https://www.facebook.com/henning.rosenbusch/videos/die-pflicht-zur-musterung-brauche-es-wegen-der-gefallenen-und-verwundeten-um-die/1073875391166801/
- https://www.youtube.com/watch?v=juGk0aY5Rdo Fischer bei Miosga
- https://www.tagesspiegel.de/gesellschaft/die-wehrpflicht-sollte-fur-alle-gelten-frauen-ans-gewehr-13480606.html
Jens Fischer Rodrian, geboren 1967 in Pinneberg, ist ein deutscher Musiker, Komponist, Musikproduzent und Dichter. Aufgewachsen nahe Murnau am Staffelsee, entdeckte er früh seine Liebe zur Gitarre. Er studierte in Los Angeles an der Grove School of Music und wurde 1995 Mitglied der Blue Man Group in New York und Boston. Seit 2004 lebt er mit seiner Frau, der Jazzsängerin Alexa Rodrian in Berlin, wo er als musikalischer Leiter der Blue Man Group tätig ist. Neben seiner Arbeit mit Künstlern wie Konstantin Wecker veröffentlichte er mehrere Soloalben und Gedichtbände, darunter „Sich kurz fassen – ach“ (2017) und „Wahn & Sinn“ (2019). Mit seiner Konzertlesung tourt er durch den deutschsprachigen Raum und setzt sich leidenschaftlich für Frieden und Demokratie ein. Zuletzt erschien: „Die Armada der Irren. Künstlerischer Widerstand in pandemischer Zeit“ (2022): Ein Buch mit beiliegender CD, das sich mit gesellschaftlichem Widerstand und der Rolle der Kunst in Krisenzeiten auseinandersetzt. Es enthält Beiträge von verschiedenen Autoren wie Wolfgang Wodarg, Gunnar Kaiser und anderen.
Die Friedenstaube fliegt auch in Ihr Postfach!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt. (Vorerst an alle, da wir den Mailversand testen, später ca. drei Mails pro Woche.).
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: milosz@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ f5369849:f34119a0
2025-04-11 16:16:25
@ f5369849:f34119a0
2025-04-11 16:16:25Hackathon Summary
CoreDAO returned to DoraHacks with another flagship hackathon - Core Global Gaming Hackathon. Out of 231 registered developers, 86 projects were approved, all competing for a share of the $380,000 prize pool. The hackathon fostered the development of games on Bitcoin and the Core platform, emphasizing innovation in decentralized gaming.
By challenging participants to expand the horizons of decentralized game development, the event resulted in a range of innovative entries. It served as a platform for developers to engage with a vibrant community, cultivate creativity, and influence the future trajectory of Web3 gaming.
Significant achievements included the incorporation of Core Chain technology into gaming applications, highlighting distinct methods of utilizing decentralized platforms. The event concluded with a Demo Day on March 24, 2025, during which final projects were showcased and winners were announced. Overall, the hackathon underscored the potential of blockchain technology in gaming and reflected the collaborative spirit among developers seeking to make an impact in the industry.
Hackathon Winners
Hyper Casual Games Prize Winners
- Farming Saga: A strategy and simulation game focused on building an agricultural empire, featuring dynamic challenges and NFT integration to enrich gameplay.
- Zenista: An idle game aimed at providing relaxation through managing a virtual spa, designed to offer self-care experiences.
- Market Magnate: A retail simulation game that integrates blockchain for true asset ownership, emphasizing strategy, creativity, and management.
Social Games PvP (Player vs Player) Prize Winners
- Core Arena: A PvP game enabling the use of any ERC-721 NFT in battles with automated skill assignments, fostering unification among NFT communities and extending project lifecycles.
- Fight For Tcore: A blockchain-based real-time PvP game where players engage in duels and wager TCORE tokens, utilizing smart contracts for decentralized gameplay.
- CoreVerse Battleground: A real-time multiplayer blockchain game that features NFT trading and in-game currency on the Core Blockchain.
Puzzle Games Prize Winners
- Temporal Odyssey: A blockchain-based puzzle game offering NFT rewards for solving puzzles across diverse worlds.
- Dungeon: Features a procedurally generated dungeon-crawling experience, incorporating blockchain elements and allowing players to mint achievements into Dungeon Tokens ($DGN).
- Skateflow: An endless skateboarding game that implements blockchain technology for potential in-game rewards.
For more detailed information on all projects, please visit the Core Gaming Hackathon page.
About the Organizer
Core DAO
The Core blockchain is the first Proof of Stake (PoS) Layer for Bitcoin, pioneering Self-Custodial Bitcoin Staking and hosting the largest Bitcoin DeFi ecosystem. Core transforms Bitcoin into a yield-bearing asset and empowers holders to actively leverage their Bitcoin within a high-performance BTCfi ecosystem.
-
 @ f5369849:f34119a0
2025-04-11 16:07:30
@ f5369849:f34119a0
2025-04-11 16:07:30Hackathon Summary
The Cambrian Hack was a recent online competition designed to engage developers in the development of Node Consensus Networks (NCNs) using the Cambrian SDK and Jito Restaking. The event drew 88 registered developers, culminating in nine impressive projects. Participants concentrated on rapid NCN deployment, exploring applications such as AI coprocessors, oracle networks, and blockchain bridges. The hackathon concluded with prizes awarded to the top three projects, funded by Cambrian and Jito teams. Part of the prize pool included Cambrian Prize NFTs, convertible to Cambrian tokens.
The hackathon underscored the Cambrian SDK's ability to expedite NCN development by streamlining processes, minimizing the need for large teams, and offering pre-built components. Evaluation criteria encompassed technical complexity, market potential, and innovation. The event concluded with the announcement of winners at Solana Apex Cape Town. Cambrian Hack provided developers with opportunities to connect with technology experts, enhance skills through workshops, and contribute to the progression of web3 and the Solana ecosystem.
Hackathon Winners
Cambrian NCN Builder Excellence Prize Winners
- Ping Project: This project strengthens network integrity and manages reward distribution through a decentralized content delivery service employing PoS consensus on the Solana blockchain, and integrating Cambrian SDK and Jito Restaking technology.
- Ant Vault: Utilizes ElizaOS AI agents alongside Cambrian oracles to manage DeFi strategically, providing intelligent solutions to market challenges.
- STABLE-FUNDS: A platform on Solana for creating stablecoins, integrating decentralized oracles and staking mechanisms to connect government-backed securities with DeFi.
Cambrian Ecosystem Innovator Prize Winners
- NebulaCDN: A decentralized content delivery network leveraging Web3 technology to provide efficient and censorship-resistant data distribution.
- Kamui: A cost-effective, secure VRF oracle for Solana, designed to deliver reliable and affordable randomness solutions.
For further details, explore all projects at Cambrian Hack BUIDL.
About the Organizer
Cambrian
Cambrian makes Jito NCN development a breeze, reducing complexity and time requirements in orders of magnitude. Specializing in innovative blockchain applications, the organization has undertaken several projects aimed at enhancing digital infrastructures. Its accomplishments include collaborations with industry leaders to develop secure and efficient blockchain systems. Cambrian is currently expanding its focus on decentralized technology, working to improve both accessibility and security across different platforms. Through its expertise, Cambrian continues to play a significant role in the evolving landscape of technology and blockchain industries.
-
 @ 95cb33b5:f4580cd4
2025-04-11 16:04:01
@ 95cb33b5:f4580cd4
2025-04-11 16:04:01Your wedding day in London is a story waiting to unfold—a stroll through Hyde Park, vows at the historic St. Paul’s Cathedral, and dancing under the stars at a Thames-side venue. But before the "I dos" and the first dance, there’s one detail that sets the scene: your wedding car. In a city where history meets modernity, your choice of wheels isn’t just transportation—it’s the opening act of your love story. Here’s how to find the perfect wedding car in London, whether you’re dreaming of vintage charm or sleek, 21st-century luxury.
- London’s Wedding Car Options: From Vintage Classics to Modern Marvels
London’s diverse vibe means you’re spoiled for choice. Here’s a breakdown of popular picks:
A. Vintage & Classic Cars
Best For: Traditional weddings, history lovers, or couples marrying at landmarks like Kensington Palace.
Top Picks:
Rolls-Royce Phantom (1960s): Timeless elegance with coach doors and a starlight headliner. Bentley S1 (1950s): Polished wood dashboards and leather seats for old-world glam. Austin Princess (Vintage): A British icon perfect for retro-themed weddings.
Cost: £500–£1,500+ for 6–8 hours.
Real-Life Romance: Sarah and James hired a 1950s Bentley for their Westminster Abbey wedding. “It felt like stepping into a royal procession,” Sarah said.
B. Modern Luxury Cars
Best For: Glamorous city weddings or receptions at venues like The Shard.
Top Picks:
Mercedes-Maybach S-Class: Heated massaging seats and ambient lighting.
Tesla Model X: Eco-friendly and futuristic, ideal for green-minded couples.
Range Rover Autobiography: Bold and spacious for urban chic.
Cost: £600–£2,000+ for full-day hire.
Pro Tip: Opt for a car with tinted windows if you’re navigating busy spots like Piccadilly Circus—privacy plus style!
C. Quirky & Unique Rides
Best For: Couples who dare to be different.
Top Picks:
London Black Cab (Decorated): Adorned with flowers for a playful, local twist.
Vintage Double-Decker Bus: Fit your entire bridal party (and a brass band!).
Electric Rickshaw: Zip through Covent Garden for a fun, eco-friendly entrance.
Cost: £200–£800 for shorter hires.
3.2. How to Choose Your London Wedding Car: 5 Key Factors
Don’t get overwhelmed—narrow your options with these tips:
Match Your Wedding Theme:
A vintage Rolls-Royce suits a classic church wedding.
A Tesla Model S pairs with a modern art gallery reception.
Consider Practicality:
Space: Ball gown? Choose a Bentley Mulsanne. Compact? Try a Jaguar E-Type.
Route: Narrow streets in Notting Hill? Avoid stretch limos.
Weatherproofing:
Convertibles are risky in London’s drizzle. Prefer a hardtop or ensure the hire includes a waterproof cover.
Sustainability:
Many companies now offer hybrid or electric cars (e.g., Tesla, BMW i7).
Budget:
Prioritize: Splurge on the ceremony car, then use a simpler ride for the exit.
Pro Tip: “We hired a vintage car for photos and a Tesla for the reception—best of both worlds!” —Laura, Hackney bride.
- Cost of Wedding Car Hire in London: What to Expect
London prices vary wildly, but here’s a rough guide:
Vintage Cars: £500–£1,500+ (includes chauffeur).
Modern Luxury: £600–£2,000+ (Maybachs at the higher end).
Unique Rides: £200–£1,000 (buses or themed vehicles).
Money-Saving Hacks:
Off-Peak Discounts: Book a weekday wedding for 10–20% off.
Bundle Deals: Some companies offer cars + photo booth or floral decor.
Short-Term Hire: Use the car for 3–4 hours (ceremony + photos only).
Watch For Hidden Fees:
Congestion Charge (£15/day for Central London).
Overtime charges (£50–£150/hour).
- Booking Your London Wedding Car: Step-by-Step
Start Early: Book 6–12 months ahead for peak season (June–September).
Read Reviews: Check Google and Hitched.co.uk for reputable companies.
Visit the Garage: Inspect the car in person—avoid surprises!
Confirm Details:
Backup vehicle clause.
Insurance coverage.
Decor permissions (e.g., floral hoops).
Red Flags:
No physical address or vague contracts.
Pressure to pay 100% upfront.
London Pro Tip: Use local companies like London Vintage Car Hire or Prestige Wedding Cars for better rates.
- Unique London Wedding Car Ideas
Make your ride unforgettable with these twists:
Thames-Side Photos: Park your Rolls-Royce near Tower Bridge for iconic shots.
Themed Decor: Add London Underground-inspired signage or Union Jack ribbons.
Surprise Stops: Arrange a quick champagne toast at Primrose Hill for skyline views.
Real-Life Magic: A couple from Camden hired a red London bus to shuttle guests from St. Pancras to their reception. “It was a party on wheels!” they shared.
Key Takeaways
🚗 Diverse Options: London offers everything from vintage Rolls-Royces to eco-friendly Teslas.
💷 Budget Smart: Prioritize, bundle, or book off-peak.
📅 Book Early: Secure your dream car 6–12 months ahead.
🌧️ Plan for Rain: Choose weather-appropriate vehicles.
📸 Photo Ready: Use London landmarks like the Thames or Kensington Gardens as backdrops.
FAQs About Wedding Car Hire in London
Q: How much does a wedding car cost in London?
A: From £200 for a decorated taxi to £2,000+ for a Rolls-Royce Phantom.
Q: Can we drive ourselves?
A: Rarely. Most luxury hires require a licensed chauffeur (and let you relax!).
Q: Are permits needed for photo locations?
A: Yes! Check with your photographer. Westminster Bridge requires permits for professional shoots.
Q: What if our car breaks down?
A: Reputable companies offer backup vehicles. Always ask!
Q: Can we personalize the car?
A: Yes—ribbons, flowers, or temporary decals. Avoid anything adhesive.
Final Thought: Your London Love Story Starts Here
At your wedding the transportation becomes more than just a method of getting from point A to point B but it creates the start of your lifetime story. The wedding car you select will leave an indelible mark in your memories as well as picture album forever because it can be a vintage Bentley near Big Ben or a flower-adorned bus with your friends onboard.
The streets of London will become the perfect backdrop when you choose your cars that trigger your heart's enthusiasm for your future eternal bond. Each romantic tale in this mesmerizing city ought to receive its definitive entrance.
-
 @ 21335073:a244b1ad
2025-03-18 14:23:35
@ 21335073:a244b1ad
2025-03-18 14:23:35Warning: This piece contains a conversation about difficult topics. Please proceed with caution.
TL;DR please educate your children about online safety.
Julian Assange wrote in his 2012 book Cypherpunks, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense.
This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning.
When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little.
I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?”
I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well.
I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread.
I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard.
I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it.
The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust.
Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this.
I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place.
What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method.
It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code.
They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened.
I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road.
So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally.
Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb.
I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback.
Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed.
That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone.
To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all.
I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society.
I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this.
On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government.
I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories.
There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc.
Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind.
Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now.
There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers?
I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity.
I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place.
My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors.
My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline.
The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online.
I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers.
So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation?
When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that.
I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic.
If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations.
I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process.
Course: - The creation of the internet and computers - The fight for cryptography - The tech supply chain from the ground up (example: human rights violations in the supply chain) - Corporate tech - Freedom tech - Data privacy - Digital privacy rights - AI (history-current) - Online safety (predators, scams, catfishing, extortion) - Bitcoin - Laws - How to deal with online hate and harassment - Information on who to contact if you are being abused online or offline - Algorithms - How to seek out the truth about news, etc., online
The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children.
The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward?
I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone.
Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability.
The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime.
This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful.
This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens.
In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions.
I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation.
-
 @ ed84ce10:cccf4c2a
2025-03-18 14:19:19
@ ed84ce10:cccf4c2a
2025-03-18 14:19:19The Evolution of Hackathons: From Offline to Online, Powering Frontier Innovation Worldwide
Throughout the history of open-source platform technology, hackathons have been the launchpads for innovation—fueling breakthroughs, incubating the next generation of startups, and serving as the proving ground for builders. Over the past decade, DoraHacks has led the charge, driving the hacker movement and open-source revolution. We didn’t just witness the evolution of hackathons—we architected it.
The Online Revolution of Hackathons
Before 2020, hackathons were largely stuck in the physical world—you had to be in the room to participate. The idea of a fully online, global hackathon was a pipe dream. Then, DoraHacks.io changed everything. Suddenly, a developer in Africa could win funding from a hackathon hosted by a Silicon Valley company. Geographic barriers collapsed. Today, over 95% of hackathons happen online.
The Infrastructure Revolution: Making Hackathons 10x More Effective
DoraHacks relentlessly iterated on the hackathon model. We built BUIDL pages for real-time project showcases, a world-class hackathon organizer dashboard, MACI-powered decentralized privacy governance, and Grant DAOs that provide ongoing funding. The result? DoraHacks became the ultimate launchpad for hackers and early-stage builders.
The Ecosystem Revolution: Supercharging Open Innovation
DoraHacks became the backbone of Web3 innovation—from Ethereum, Solana, and BNB Chain to the next wave of blockchains like Aptos, Cosmos, Injective, TON, and Sonic. Since 2023, hackathons have expanded beyond crypto—quantum computing, commercial space tech, and AI-driven innovations are now being built on DoraHacks.
Rolling Hackathons and Uninterrupted BUIDLing - the New Standard for Ecosystem Growth
BUIDLs can be created spontaneously at any time. Hosting Hackathons as short-term events held only once or twice a year is not conducive to attracting outstanding Hackers and high-quality projects to join the ecosystem and drive innovation in the long term. To remediate this, Hackathons should be continuous and uninterrupted, serving as a long-term driving force within the developer ecosystem.
Historically, the high organizational costs and substantial resource investments associated with frequent Hackathons meant that most emerging ecosystems couldn't afford to host them regularly. As a result, Hackathons became rare, annual spectacles, and for some projects, an unaffordable luxury. This model severely restricted developers' chances to participate and hindered the ecosystem's ability to innovate consistently. Let's imagine what would happen if an ecosystem held 12 or more Hackathons each year?
- Developers have a clear loyalty incentive: They would know that the ecosystem is committed to supporting and funding excellent developers and projects continuously, which would encourage them to make long-term investments and contribute regularly.
- Missing out is no longer an issue: Even if a developer couldn't attend a particular Hackathon, there would be another one soon, increasing accessibility.
- Accelerated ecosystem innovation: Frequent Hackathons would accelerate ecosystem innovation. Developers would be constantly pushed to explore new directions, significantly boosting the growth rate of the technological ecosystem.
Previously, due to the limitations of costs and organizational difficulties, frequent Hackathons were almost unthinkable. Only ecosystems with sufficient funds like Google and Amazon could afford rolling Hackathons. But now, DoraHacks' upcoming BUIDL AI platform tools are set to change the game. These tools make it possible to organize 12 Hackathons in a year, and even go a step further by enabling the simultaneous hosting of multiple differently-themed Hackathons. This will help emerging ecosystems effectively incentivise developers, expand their technological influence, and increase the number of exceptional BUIDLs (projects) in their ecosystems.
The majority of BUIDLs come about continuously and spontaneously and should be recognized and incentivized promptly, rather than having to wait for the single annual Hackathon.
As the saying goes, "He who wins over developers wins the world." In the highly competitive Web3 space, Hackathons are an effective means of attracting developers, and rolling Hackathons are the best way to achieve this. For an ecosystem to stay competitive, it must ensure that developers always have opportunities to engage and create.
The AI Era of Hackathons: A 10x Opportunity, A 10x Challenge
AI Turns Everyone Into a Hacker
AI has obliterated repetitive work. Building is faster than ever. Anyone, from anywhere, can hack, ship, and scale with AI tools that accelerate ideation, development, and execution. The potential of hackathons in this AI-powered era is 10x bigger than ever before.
But Hackathon Infrastructure Is Stuck in the Past
Despite this massive opportunity, organizing hackathons remains painfully inefficient:
- Most organizations don’t know how to run hackathons effectively.
- Even those who do lack time and resources to do it frequently.
- Ecosystem builders who have the resources can only host one hackathon per year.
The result?
- Hackathons are underutilized, slowing innovation.
- Ecosystem growth is bottlenecked by developer relations (DevRel) teams.
- Many ecosystems fail to maximize the potential of hackathons.
- Low-frequency hackathons waste hacker potential—builders sit idle when they could be shipping.
BUIDL AI: Unlocking the Infinite Potential of Hackathons
We refuse to let inefficiency limit innovation. BUIDL AI is our answer.
DoraHacks is launching BUIDL AI, the AI-powered Hackathon Co-Pilot that automates, scales, and supercharges hackathon organization.
BUIDL AI: The Game-Changing Features
1. Edit and Launch: One-Click Hackathon Deployment
Organizers can now launch a hackathon in minutes by filling in basic details (prizes, themes, workshops, judges, etc.). No tedious manual setup.
2. BUIDL Review: Submission Evaluation (10x Faster)
Traditional hackathons get hundreds of submissions—judging takes hundreds of hours. BUIDL AI changes the game. It automatically scores projects based on completeness, originality, and theme relevance—filtering out low-quality submissions 10x faster than before.
3. Automated Marketing: Instant Hackathon Reports
After the hackathon ends, BUIDL AI auto-generates a full post-event report—highlighting winners, standout projects, and key takeaways—boosting visibility and impact.
4. Seamless Interaction: Smarter Collaboration, No Bottlenecks
BUIDL AI will interact with hackathon organizers to keep organizers in sync, alerting them about new submissions, pending approvals, and participant inquiries in real time. No more dropped balls.
5. Multi-Hackathon Management: Scaling Innovation Without Limits
Before BUIDL AI, running multiple hackathons at once was a logistical nightmare. Now, ecosystem builders can launch and manage multiple hackathons seamlessly, boosting innovation frequency exponentially
The full BUIDL AI Beta version will release on April 15th, but multiple free BUIDL AI features have already been available on DoraHacks.io!
BUIDL AI: The Next Great Leap in Open Innovation
Hackathons aren’t just competitions. They are the birthplace of the next trillion-dollar innovations.
With BUIDL AI, hackathons enter a new era—automated, intelligent, and infinitely scalable. This means more hackers, more builders, and more breakthrough projects than ever before.
At DoraHacks, we believe in an open, hacker-driven future. BUIDL AI is the rocket fuel for that future.
-
 @ fd78c37f:a0ec0833
2025-03-18 10:44:40
@ fd78c37f:a0ec0833
2025-03-18 10:44:40In this edition, we’re thrilled to sit down with Tomek K from Bitcoin Alby, a passionate advocate for Bitcoin’s global adoption. Tomek K shares how Alby is driving innovation in the Bitcoin ecosystem and offers a glimpse into his vision for the cryptocurrency’s future. From his journey as a libertarian activist to co-founding the Bitcoin Film Festival, Tomek K’s story is one of curiosity, purpose, and a relentless pursuit of freedom through technology.
YakiHonne: Tomek K, it’s a pleasure to meet you! Today, we’re diving into your community topic—Alby Wallet. But before we begin, let me introduce our readers to Yakihonne. Yakihonne is a decentralized media client powered by the Nostr protocol, dedicated to promoting free speech through technology. It empowers creators to truly own their voices and assets, offering features like smart filtering, verified notes, and a focus on long-form content. So, Tomek, could you tell us about yourself and your work with Alby?
Tomek K: Of course! I’m Tomek K, originally from Poland, and right now, I’m speaking to you from Sri Lanka. I love traveling and observing how different countries adopt Bitcoin. For most of my career, I’ve been a free-market advocate, promoting economic freedom through various projects—essentially doing PR for capitalism. I’ve organized conferences, political demonstrations, economic seminars, summer festivals, and even opened a bar in Warsaw to spread these ideas in different ways.
During this advocacy work, I came across Bitcoin. At first, I didn’t pay much attention to it, but over time, I started feeling frustrated—our efforts raised awareness about freedom, but they didn’t bring measurable change. That led me to study Bitcoin more deeply, and I gradually shifted my focus to Bitcoin activism. Along the way, I collaborated with publishers to translate Bitcoin-related books into Polish and co-founded the Bitcoin Film Festival with friends from Meetup. Later, I joined Alby, marking my transition from free-market activism to Bitcoin promotion.
At the Bitcoin Film Festival, I handle operations and networking—organizing the event, managing logistics, and making things happen. Our team is small, but I enjoy the work. I’m passionate about Bitcoin because I came for the revolution, and I’m staying for the revolution.
That said, I don’t consider myself a Bitcoin absolutist. I see Bitcoin as a tool for freedom, not just a currency or a more efficient technology. If there were a better tool for advancing liberty and making societies freer, I’d probably focus on that. But for now, Bitcoin appears to be the most effective tool for freedom. Ultimately, I consider myself a “life maximalist”—because to live a good life, you need freedom, and to have freedom today, you need sound money. And right now, that money is Bitcoin.
YakiHonne: Was there a specific moment or event that sparked your interest in Bitcoin and motivated you to join the Alby community?
Tomek K: What attracted me to Bitcoin was its promise of global monetary independence and its ability to reduce the control of the Federal Reserve, central banks, and governments—the strongest and most covert control mechanisms in the world. Unfortunately, many people, even libertarians, often overlook this.
As for why I joined Alby, it’s because this startup is driven by values and mission rather than simply chasing profits, like selling tokens or games. This aligns well with my interest in the Lightning Network. As I explored Lightning more deeply, I came across Alby. I’ve always enjoyed testing new tools, trying them firsthand, and understanding the communities behind them—so naturally, I became part of it. Along the way, I also got to know some of the team members, which reinforced my involvement.
Additionally, Alby supported the Bitcoin Film Festival. While they weren’t the largest sponsor, their contribution was generous. The festival served as a great platform for them and other projects. I think it was good marketing because people like me—who have strong networking skills, arrange podcast interviews, and organize various activities—help build awareness and positive PR. That was part of my role.
If I had to pinpoint a single defining moment that led me here, I honestly couldn’t. Becoming a Bitcoiner doesn’t happen overnight. You can’t just read The Bitcoin Standard, declare that you understand Bitcoin, and instantly become a maximalist. Anyone who’s intellectually honest will admit that it takes multiple touchpoints—articles, films, career shifts, essays, hands-on experimentation, and actually using Bitcoin—to truly grasp its significance. I had many such moments along the way: reading The Bitcoin Standard, learning from friends who had a deeper understanding of Bitcoin, and working at Alby, which further expanded my knowledge of the Lightning Network’s capabilities and limitations. It wasn’t one turning point but a series of pivotal experiences that shaped my path.
YakiHonne: How did the Alby community start, and how did it attract its first members?
Tomek K: When I joined Alby, the community had already been established for some time. It originally emerged within the browser design community, where early users helped developers refine the product by providing feedback. That’s how the first members joined, and this process has been ongoing for four years now.
As for how Alby attracted members, it was through a mix of channels—social media (Twitter, Telegram, Discord), email engagement, and active participation in Bitcoin conferences. But the core strategy has always been openness, engaging with users, and listening to their feedback. Sometimes that means making a joke, sometimes defending against unfair criticism, and other times implementing requested features. We’ve always worked to maintain an active and friendly community atmosphere.
We also host bi-weekly community calls, which are a central part of our activities. Every two weeks, available team members meet with users for open Q&A sessions, issue discussions, and demonstrations of various projects integrating with Alby. I’ve participated in some of these calls, and they help maintain strong relationships with users, developers, and other projects—something crucial for the ecosystem. The Bitcoin technology landscape is somewhat fragmented, and grassroots coordination is necessary since there’s no single leader defining terminology or coding practices.
That’s also why Alby doesn’t exist in isolation. Almost everything we’ve built has been made possible by the creators of previous libraries, prior codebases, and collaborative efforts in writing specifications for protocols. Projects like Yakihonne and many others also recognize the importance of open-source collaboration. I think it’s essential to acknowledge the contributions of the open-source community. One thing I really appreciate is that Bitcoiners are driving open-source development in virtually every part of the world, all working toward a shared and meaningful goal.
YakiHonne:Were there any notable challenges in the early days that left a strong impression on you?
Tomek K :When I first joined Alby, I struggled with a bit of imposter syndrome for months. I was handling PR for the project, but I didn’t fully understand all the technical details—how certain protocols interact or what’s happening under the hood. It took time to get familiar with everything and really feel like I belonged.
Regulatory pressure has also been a huge challenge. In some cases, developers have been arrested, projects have had to leave certain countries, and users have been geoblocked based on their location. But challenges like these can also drive innovation. For example, Alby developed AlbyHub, an open-source self-custodial node, as a response to these kinds of issues.
There are always risks in this space—governments might suddenly demand a banking license or require compliance with new regulations. These are real obstacles, but we tackle them by embracing decentralization and open-source solutions. That’s how we ensure the project stays true to its mission and vision.

YakiHonne:If someone wanted to start a Bitcoin community today or grow an existing one, what advice would you give them?
Tomek K: The most important thing is to just get started. A community begins with action, and it takes more than one person. Even if it’s just you and a friend grabbing a beer, that’s already a start. Maybe after the first or second meetup, you post on Meetup.com, Twitter, or local forums:"Hey, we’re hosting a Bitcoin meetup in this city. We just want to connect with other Bitcoiners!" If you keep doing it consistently, the community will naturally grow. Over time, the bar where you meet might get interested in accepting Bitcoin, or you might meet some OGs in your area who decide to join—maybe they already run a business and want to support what you’re doing.
You don’t have to over-plan everything from the start. No need to think, “We need a podcast, 10 episodes, a logo…”—all that can come later. Just bootstrap it: organize a meetup, grab a beer, and get going. As you go, you’ll adapt, improve, and build recognition.Beyond that, it’s a great way to meet other Bitcoiners, develop leadership skills, and learn about community building. And at the very least, you’ll have fun doing it—which, honestly, is one of the main reasons I keep organizing meetups and other activities.
YakiHonne: Exactly, the key is to take action—just start and see where it leads. Does your community focus more on Bitcoin’s technical aspects, like coding and development, or do you emphasize non-technical areas such as education and outreach? Or do you try to balance both?
Tomek K: Our users come from all kinds of backgrounds. Some are very engaged and provide feedback regularly, while others prefer to stay in the background. Some attend our community calls, and within that group, some are developers actively building projects and collaborating with us. At the same time, there are developers we know are out there, but they never directly engage with us. That’s just how the Bitcoin community works—there’s no strict definition of being part of Alby. People engage in their own way. Some users are active on Discord, some aren’t, but we treat them all as part of the family, keeping them informed through newsletters, offering support, and making sure they stay updated with what’s happening at Alby.
As for whether we lean more toward technical development or non-technical outreach, there’s no clear-cut answer. Our community is diverse—we cater to a wide range of Lightning Network users. Some just use the browser extension, while others are deeply involved in our ecosystem. We also work with NGOs, educational initiatives, and community organizations. At the same time, we place a strong emphasis on developers and maintaining good relationships with them. Our repositories and developer portal offer useful libraries and examples, making it easier for both aspiring and experienced developers to integrate the Lightning Network into their projects. Developer relations are something we consider highly important.

YakiHonne: I understand that you're also the founder of another Bitcoin-related film project. Could you tell us a bit about it? What exactly inspired you to combine Bitcoin and filmmaking?
Tomek K: Yes, I founded Bitcoin Film Fest to help build what I call Bitcoin Cinema—an emerging industry that blends Bitcoin and filmmaking. I wanted to track everything happening at the intersection of these two worlds. Just like e-commerce, energy, and information technology, I believe the film industry will eventually be shaped by Bitcoin. And in fact, it’s already happening. There are Bitcoin-themed movies, and even major Hollywood productions have started including Bitcoin references. Bitcoin filmmakers, Bitcoin culture, and even a Bitcoin subculture already exist. We have our own heroes, stories, and values, and from this, films are being created. I love cinema, and I love Bitcoin—this was my way of bringing the two together.
The festival itself happened somewhat by accident—but maybe it was meant to be. It all started in Warsaw when I was organizing a Bitcoin meetup. I planned to screen a Bitcoin documentary, but due to technical issues, it didn’t happen. So, over a few beers, we came up with an idea: if we couldn’t show one film, why not go all in and create a full-scale Bitcoin film festival? We started researching and realized there were enough Bitcoin-related films out there to make it happen. So, we did.
The response from the community was overwhelmingly positive. It became clear that people wanted a space for Bitcoin cinema—a hub for information, networking, and collaboration. We started using the term “Binema” (Bitcoin Cinema) to describe this emerging genre. I find it fascinating to witness the growth of Bitcoin culture and storytelling. Before this, I had followed libertarian artistic movements closely, and now I see how important culture is for Bitcoin’s adoption—it’s not just about the technical and financial aspects.
Bitcoin adoption isn’t going to happen overnight, and it won’t happen without developers, educators, infrastructure builders, UX designers, and many others contributing to the ecosystem. Culture is one of the most powerful tools for shaping society, and I, like many others, am working to bring Bitcoin adoption closer through film. We’re witnessing the early days of Bitcoin cinema. I missed out on the birth of traditional cinema, but this time, I want to be part of it.
YakiHonne:In your region, does the government support or oppose Bitcoin? How has this stance impacted the development of the Bitcoin community so far?
Tomek K :Bitcoin doesn’t concern itself with nation-state borders, and frankly, we don’t either. The situation in Poland has little influence on what we do. The only connection is that I, along with two others, happen to be in Poland, but most of our team is globally distributed. On a broader scale, the U.S. tends to shape regulatory trends, and unfortunately, it often does so in a more restrictive way. However, Poland itself hasn’t had a significant impact on our work.
YakiHonne:Has your Bitcoin Film Fest community ever used film as a way to connect with members—perhaps by watching a Bitcoin-related movie or hosting a movie night to make things more fun and engaging? Have you done anything like that before?
Tomek K:Yes, absolutely! The film festival itself is a great example—we watch movies together and build a community around them. Aside from the festival we organized in Warsaw, we've also hosted film screenings at various Bitcoin events, like Sats and Facts in Thailand, BTC Prague, Plan B Lugano, Frimadera, Adopting Bitcoin, and several other conferences. We also organize online watch parties—actually, there's one happening next Sunday. The movie is available on Prime Video, but we'll sync up on Discord to watch it together, chat, and share our thoughts. We'll be announcing it on Twitter, so if you check Bitcoin Film Fest on Twitter, you'll find details on how to join.
Film has been a great way to connect with members and spark discussions. We've seen Bitcoin meetups worldwide organizing movie nights—our volunteer friends in Montenegro have hosted one, and our partners in Kenya and South Africa have done the same. Lately, movie nights have been happening more and more frequently, which is exciting.
It's still early—after all, Bitcoin is only 16 years old, so the selection of Bitcoin movies is still relatively small. Many of these films haven’t had large budgets or massive talent pools yet, but that’s changing. Right now, we’re primarily focused on showing films within the Bitcoin community rather than creating films aimed at the general public. That said, those kinds of projects are also emerging. I’m optimistic about the growth of Bitcoin cinema—better storytelling, AI-driven advancements, increasing interest from audiences, and even sponsors willing to invest in filmmakers. Big things are coming, and while we already have some great Bitcoin films, the best is yet to come. We’re still in the early days, and this is the time to contribute and help shape the future of Bitcoin cinema.
YakiHonne:We’ve come to the end of today’s interview, and I’ve truly enjoyed every moment of it. I’m very sure your idea will be incredibly engaging, inspiring more people and attracting a broad audience. Thank you so much for your time today—it was a great conversation.
-
 @ edf0da8b:b2652fa3
2025-03-17 17:28:33
@ edf0da8b:b2652fa3
2025-03-17 17:28:33One remarkable thing the Wim Hof Method stirs in me is that I increasingly feel the desire to connect with pure nature. Now, what does that mean?
You may know that slight feeling of eeriness when looking at deep moving waters or that tiny insecurity when darkness creeps up around you alone among the trees? You are sure there's nothing to worry about. But still, these little old conditioned anxieties, these unreasonable mind scenarios, they keep coming up and make you seek safety.
They are different for everyone, but these anxieties in the foreground are a sign for inner blockages that deprive us from expressing our power and creativity. What's more, they separate us from nature. They suggest, everything around us is potentially dangerous. Is it though?
When practicing the Wim Hof Method, and especially right after the breathing exercises, I can immediately feel a clarity emerging, a stronger awareness of presence in the moment. Anxieties are caringly pushed back to their rightful place, but do not control my actions and no longer dominate my state of being.
And so suddenly, the world view shifts. Eerie deep moving waters become fascinating, the darkness around reveals the beauty of trees casting soft moonlight shadows. I deeply appreciate what is, I want to touch the waters, I want to merge with the shadows, I feel that power. Instead of running away I want to connect with nature. I'm more aware of the present and should danger reveal itself, I have the confidence that I can properly react when it arises. But until then, I can enjoy beauty and connectedness. The powerful shift is from scenarios about potential threats around me to curiosity and beautiful opportunity everywhere.
There are countless great techniques and traditions that guide us to such shifts. But with regular practice, I find the Wim Hof Method to be particularly simple, accessible and effective.
wimhofmethod
-
 @ c1e9ab3a:9cb56b43
2025-04-10 02:55:11
@ c1e9ab3a:9cb56b43
2025-04-10 02:55:11The United States is on the cusp of a historic technological renaissance, often referred to as the Fourth Industrial Revolution. Artificial intelligence, automation, advanced robotics, quantum computing, biotechnology, and clean manufacturing are converging into a seismic shift that will redefine how we live, work, and relate to one another. But there's a critical catch: this transformation depends entirely on the availability of stable, abundant, and inexpensive electricity.
Why Electricity is the Keystone of Innovation
Let’s start with something basic but often overlooked. Every industrial revolution has had an energy driver:
- The First rode the steam engine, powered by coal.
- The Second was electrified through centralized power plants.
- The Third harnessed computing and the internet.
- The Fourth will demand energy on a scale and reliability never seen before.
Imagine a city where thousands of small factories run 24/7 with robotics and AI doing precision manufacturing. Imagine a national network of autonomous vehicles, delivery drones, urban vertical farms, and high-bandwidth communication systems. All of this requires uninterrupted and inexpensive power.
Without it? Costs balloon. Innovation stalls. Investment leaves. And America risks becoming a second-tier economic power in a multipolar world.
So here’s the thesis: If we want to lead the Fourth Industrial Revolution, we must first lead in energy. And nuclear — specifically Gen IV Small Modular Reactors (SMRs) — must be part of that leadership.
The Nuclear Case: Clean, Scalable, Strategic
Let’s debunk the myth: nuclear is not the boogeyman of the 1970s. It’s one of the safest, cleanest, and most energy-dense sources we have.
But traditional nuclear has problems:
- Too expensive to build.
- Too long to license.
- Too bespoke and complex.
Enter Gen IV SMRs:
- Factory-built and transportable.
- Passively safe with walk-away safety designs.
- Scalable in 50–300 MWe increments.
- Ideal for remote areas, industrial parks, and military bases.
But even SMRs will struggle under the current regulatory, economic, and manufacturing ecosystem. To unlock their potential, we need a new national approach.
The Argument for National Strategy
Let’s paint a vision:
SMRs deployed at military bases across the country, secured by trained personnel, powering critical infrastructure, and feeding clean, carbon-free power back into surrounding communities.
SMRs operated by public chartered utilities—not for Wall Street profits, but for stability, security, and public good.
SMRs manufactured by a competitive ecosystem of certified vendors, just like aircraft or medical devices, with standard parts and rapid regulatory approval.
This isn't science fiction. It's a plausible, powerful model. Here’s how we do it.
Step 1: Treat SMRs as a National Security Asset
Why does the Department of Defense spend billions to secure oil convoys and build fuel depots across the world, but not invest in nuclear microgrids that would make forward bases self-sufficient for decades?
Nuclear power is inherently a strategic asset:
- Immune to price shocks.
- Hard to sabotage.
- Decades of stable power from a small footprint.
It’s time to reframe SMRs from an energy project to a national security platform. That changes everything.
Step 2: Create Public-Chartered Operating Companies
We don’t need another corporate monopoly or Wall Street scheme. Instead, let’s charter SMR utilities the way we chartered the TVA or the Postal Service:
- Low-margin, mission-oriented.
- Publicly accountable.
- Able to sign long-term contracts with DOD, DOE, or regional utilities.
These organizations won’t chase quarterly profits. They’ll chase uptime, grid stability, and national resilience.
Step 3: Build a Competitive SMR Industry Like Aerospace
Imagine multiple manufacturers building SMRs to common, certified standards. Components sourced from a wide supplier base. Designs evolving year over year, with upgrades like software and avionics do.
This is how we build:
- Safer reactors
- Cheaper units
- Modular designs
- A real export industry
Airplanes are safe, affordable, and efficient because of scale and standardization. We can do the same with reactors.
Step 4: Anchor SMRs to the Coming Fourth Industrial Revolution
AI, robotics, and distributed manufacturing don’t need fossil fuels. They need cheap, clean, continuous electricity.
- AI datacenters
- Robotic agriculture
- Carbon-free steel and cement
- Direct air capture
- Electric industrial transport
SMRs enable this future. And they decentralize power, both literally and economically. That means jobs in every region, not just coastal tech hubs.
Step 5: Pair Energy Sovereignty with Economic Reform
Here’s the big leap: what if this new energy architecture was tied to a transparent, auditable, and sovereign monetary system?
- Public utilities priced in a new digital dollar.
- Trade policy balanced by low-carbon energy exports.
- Public accounting verified with open ledgers.
This is not just national security. It’s monetary resilience.
The world is moving to multi-polar trade systems. Energy exports and energy reliability will define economic influence. If America leads with SMRs, we lead the conversation.
Conclusion: A Moral and Strategic Imperative
We can either:
- Let outdated fears and bureaucracy stall the future, or...
- Build the infrastructure for clean, secure, and sovereign prosperity.
We have the designs.
We have the talent.
We have the need.What we need now is will.
The Fourth Industrial Revolution will either be powered by us—or by someone else. Let’s make sure America leads. And let’s do it with SMRs, public charter, competitive industry, and national purpose.
It’s time.
This is a call to engineers, legislators, veterans, economists, and every American who believes in building again. SMRs are not just about power. They are about sovereignty, security, and shared prosperity.
Further reading:
nostr:naddr1qqgrjv33xenx2drpve3kxvrp8quxgqgcwaehxw309anxjmr5v4ezumn0wd68ytnhd9hx2tczyrq7n2e62632km9yh6l5f6nykt76gzkxxy0gs6agddr9y95uk445xqcyqqq823cdzc99s
-
 @ 3f482ba8:193dfe17
2025-04-11 15:57:32
@ 3f482ba8:193dfe17
2025-04-11 15:57:32This is a test article
-
 @ 06bc9ab7:427c48f5
2025-03-17 15:46:23
@ 06bc9ab7:427c48f5
2025-03-17 15:46:23Bitcoin Safe - A bitcoin savings wallet for the entire family
Designed for both beginners and power users, Bitcoin Safe combines security with an intuitive user experience. In this article, we dive deep into its features, unique benefits, and the powerful tools that make managing your Bitcoin wallet simple and secure.
Built for Learners
✔️ Step-by-step wallet setup wizard + PDF backup sheets 📄 🧪 Test transactions to ensure all hardware signers are ready 🔑 🛡️ Secure: Hardware signers only – no hot wallet risks 🚫🔥 🌍 Multi-language support: 🇺🇸 🇨🇳 🇪🇸 🇯🇵 🇷🇺 🇵🇹 🇮🇳 🇮🇹 🇫🇷 🇩🇪 🇲🇲 🇰🇷 📁 Address categories for easy organization ☁️ Label and category synchronization, and cloud backup (optional) 💰 Automatic UTXO merging to save on fees ⚡ Fast syncing with Electrum servers, Compact Block Filters coming soon
Built for Power Users
🔐 Supports Coldcard, Bitbox02, Jade, Trezor, Passport, Keystone & many more 🏦 💬 Multi-party multisig chat & PSBT sharing (optional) 📊 Transaction flow diagrams to trace coin movements 🔍 Instant cross-wallet wallet search ⚙️ Set your own electrum server, mempool instance, and nostr relay
Step-by-Step Wallet Setup
Whether you’re setting up a single-signature or multi-signature wallet, the setup wizard guides you every step of the way:

- Single Sig Wizard: Follow the intuitive wizard that walks you through each step. https://youtu.be/m0g6ytYTy0w
Clear instructions paired with hardware signer screen-shots, like the steps for a Coldcard
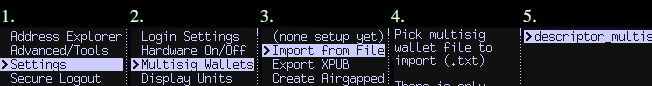
-
Multisig Wizard: The wizard ensures you do all necessary steps for a Multisig wallet in the right order. Afterwards your Multisig is ready to use and all signers are tested. Check out https://bitcoin-safe.org/en/features/setup-multisignature-wallet/
-
PDF Backup: The wizard will also generates 3 PDF backup sheets for a 2-of-3 multisig wallet, so ensure you always have your wallet descriptor together with the seed.
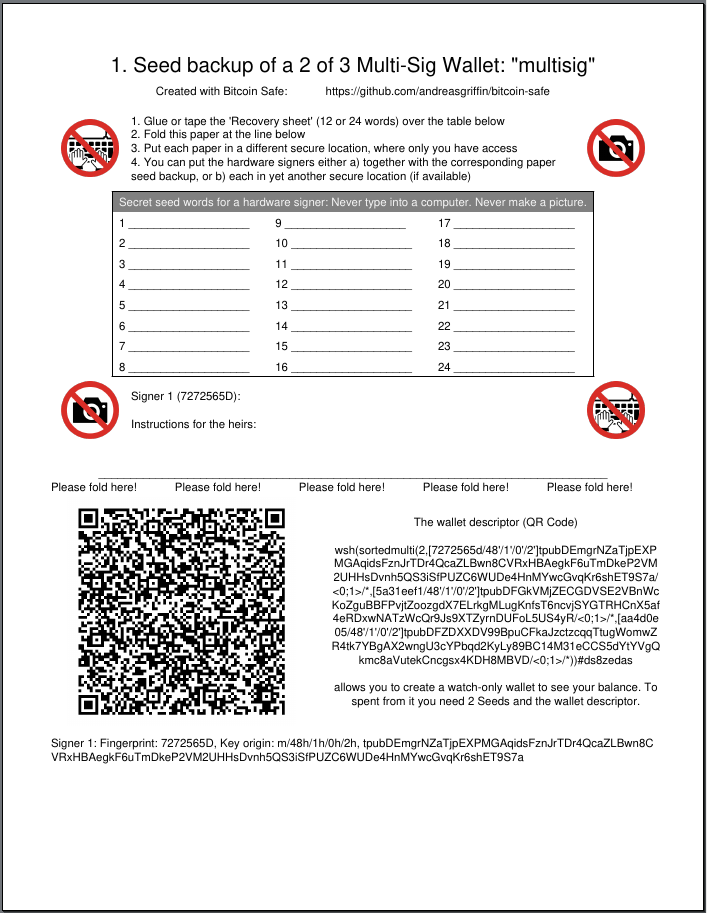
-
Hardware Signer Support: With full support for major hardware signers your keys remain securely offline.
Transaction Visualization
Visualize and navigate your transaction history:
-
Graphical Explorer: An interactive transaction diagram lets you click on inputs and outputs to follow the money flow intuitively.
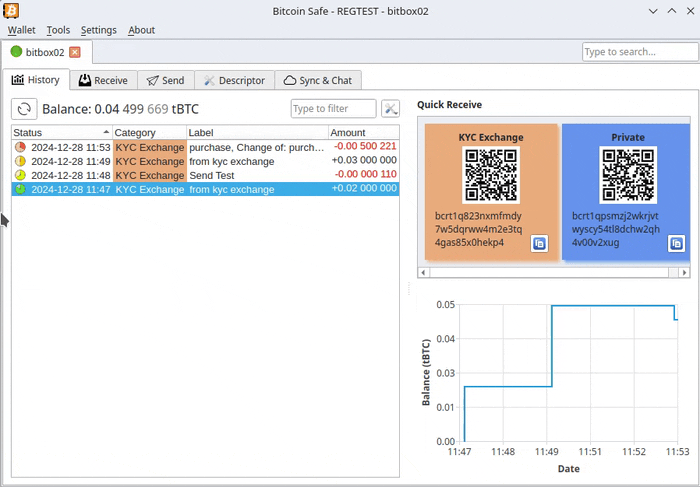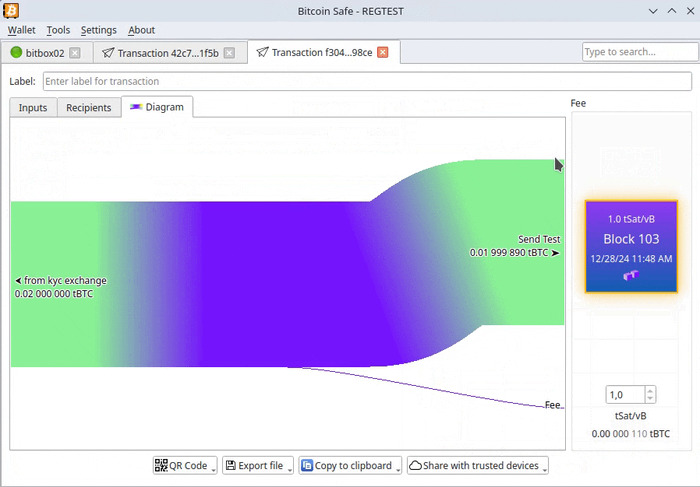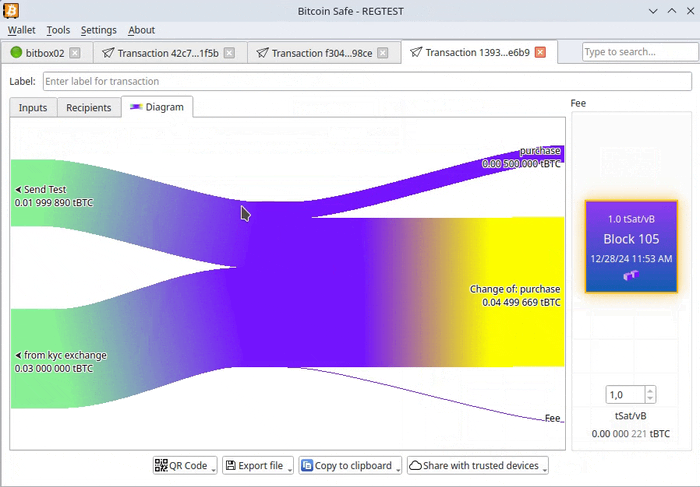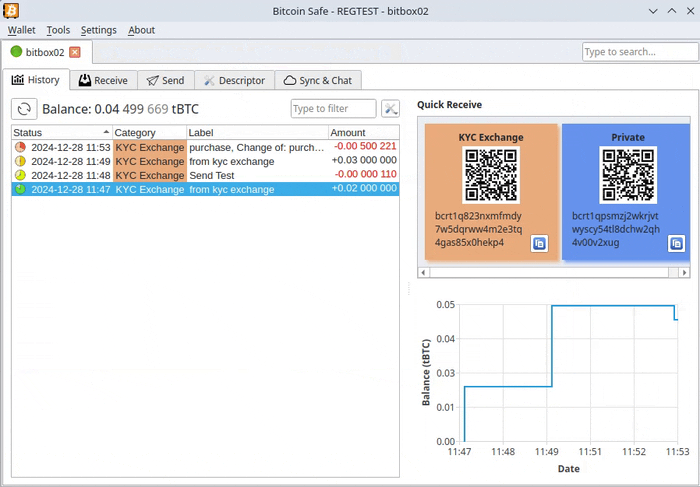
-
Coin Categories: Organize your addresses into distinct coin categories (e.g., “KYC”, “Work”, “Friends”) so Bitcoin Safe automatically selects the correct inputs when creating PSBTs.

It prevents you accidentally linking coin categories when creating a transaction, and warns you if mistakes happened in the past.
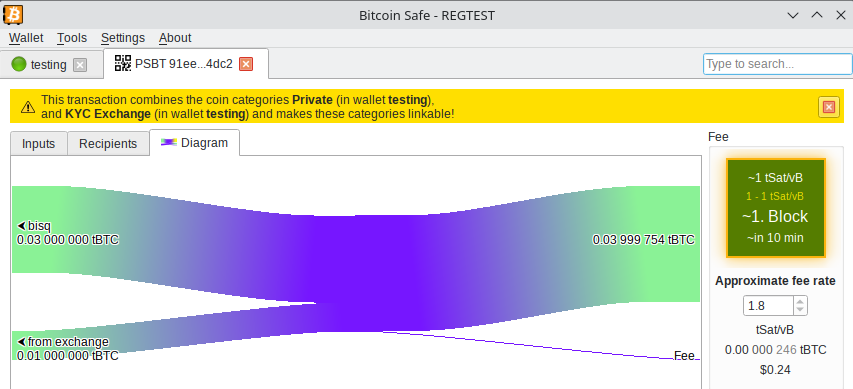
Powerful Wallet Management Tools
- Flexible Fee Selection: Choose fees with one click using an intuitive mempool block preview.
- UTXO Management: Automatically (optional) merge UTXOs when fees are low.
- CSV Table Export: Right click, Drag&Drop, or CTRL+C for immediate CSV export for easy processing in Excel.
- PDF Balance Statement: Export the address balances for easy record keeping on paper.
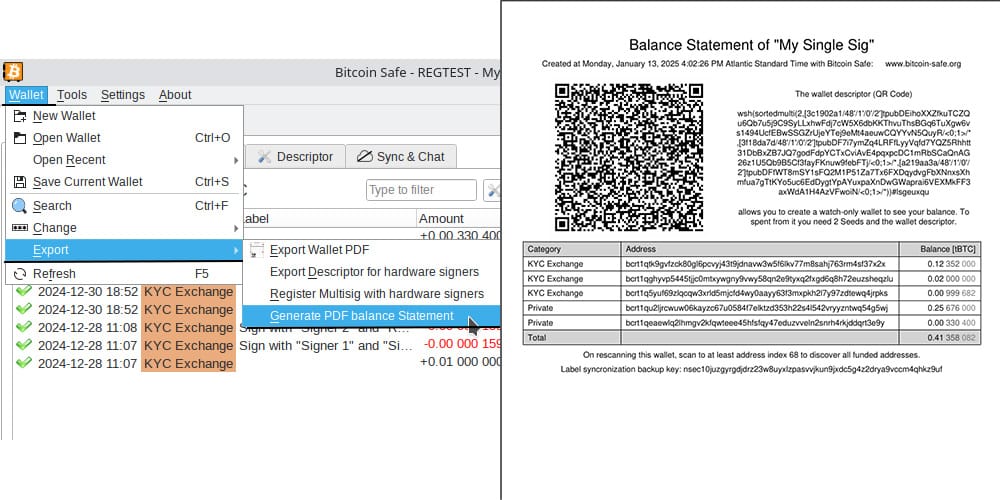
Advanced Features for the Power-User
Sync & Chat is off by default (for the paranoid user), but can be enabled with just one click.
Label Synchronization and Backup
- Seamless Sync: Using encrypted nostr messages, Bitcoin Safe synchronizes your coin categories and labels across multiple devices.
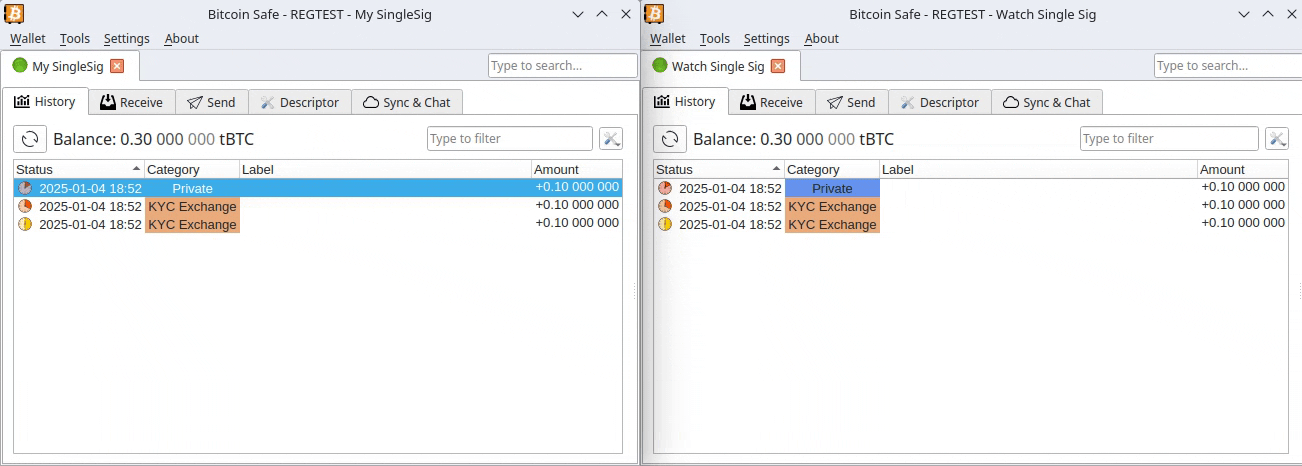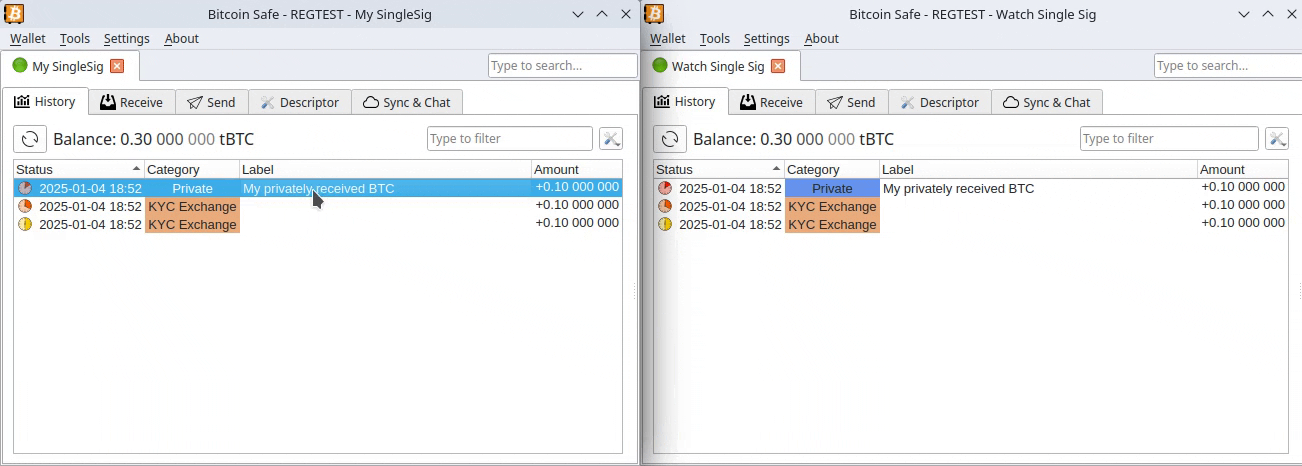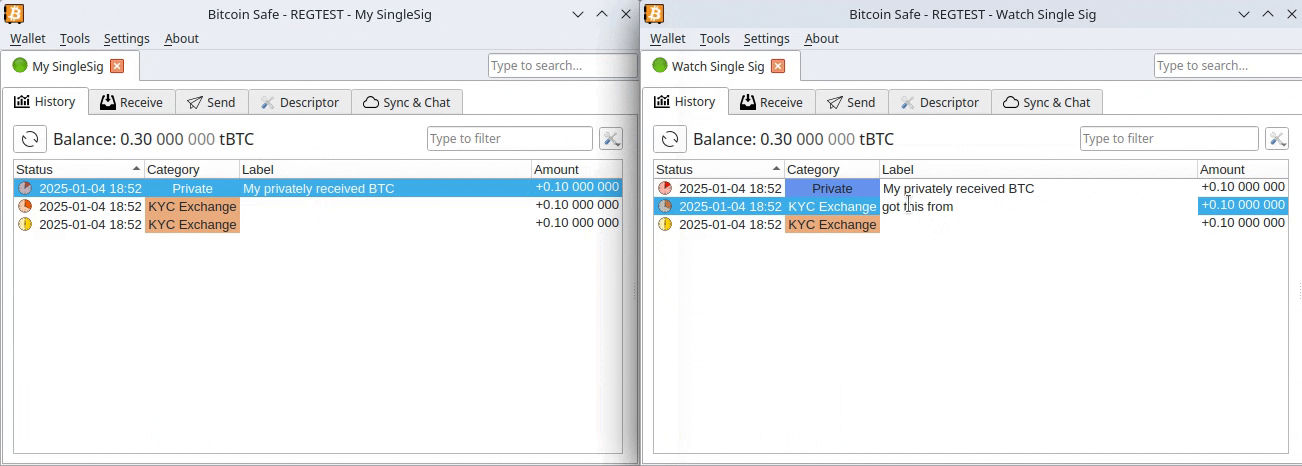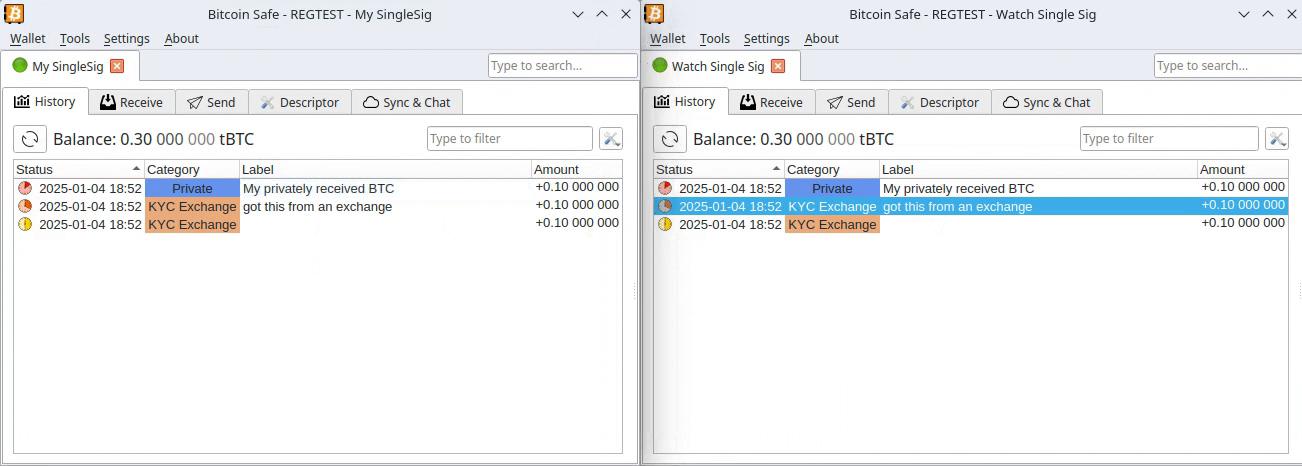
- Easy Backup: A short backup key is all you need to safeguard your coin categories and labels, ensuring your organization remains intact.
Collaborative Multi-party Multisig
- Group Chat Integration: After creating your multisig wallet, Bitcoin Safe offers an encrypted nostr group chat for secure collaboration and one-click PSBT sharing.
- User Authentication: Each participant must authenticate every other user with a simple click, ensuring secure communication.
Watch and Learn: Get Started with Bitcoin Safe
If you’re new to Bitcoin Safe, a short video guide can make all the difference. Learn how to set up your Bitcoin Safe wallet in this detailed walk through:
https://youtu.be/m0g6ytYTy0w
Or see how to verify an address on your hardware singer:
https://youtu.be/h5FkOYj9OT8
Building up a knowledge base: https://bitcoin-safe.org/en/knowledge/
Whats next?
- Compact Block Filters!!! They make electrum servers obsolete.
- Why? Compact Block Filters increase the network privacy dramatically, since you're not asking an electrum server to give you your transactions
- Trade-off: They are a little slower than electrum servers. For a savings wallet like Bitcoin Safe this should be OK.
- How do they work? Simply speaking: They ask normal bitcoin core nodes for a short summary of each block. And if the summary shows a transaction belonging to the wallet, the entire block is then downloaded from the bitcoin core node. The bitcoin core node does not learn however which of the many transactions in the block you were interested in. Read more here and of course in the bip.
- When: 2 weeks 😅. Lots of things need to be done until Bitcoin Safe can use the bdk CBF/kyoto client from rustaceanrob, so keep an eye out for updates and please give feedback when you use Bitcoin Safe.
Stay updated on nostr or on GitHub.
Thank you
A huge thanks goes to nostr:npub10pensatlcfwktnvjjw2dtem38n6rvw8g6fv73h84cuacxn4c28eqyfn34f for supporting this project with a grant and nostr:npub1yrnuj56rnen08zp2h9h7p74ghgjx6ma39spmpj6w9hzxywutevsst7k5cx for the Hackathon prize.
This wallet is only possible because it is building upon other peoples open source work. Most notably
- bdk nostr:nprofile1qqsgkmgkmv63djkxmwvdlyaxx0xtsytvkyyg5fwzmp48pwd30f3jtxspzemhxue69uhhyetvv9ujuurjd9kkzmpwdejhgqg5waehxw309aex2mrp0yhxgctdw4eju6t0qyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqr8vuet
- and especially nostr:npub1thunderat5g552cuy7umk624ct5xe4tpgwr2jcjjq2gc0567wgrqnya79l , nostr:npub1reezn2ctrrg736uqj7mva9lsuwv0kr5asj4vvkwxnrwlhvxf98tsq99ty4 , and nostr:npub1ke470rdgnxg4gjs9cw3tv0dp690wl68f5xak5smflpsksedadd7qtf8jfm for dealing with my many feature requests and questions.
- rustaceanrob building kyoto which implements CBF for BDK; a crucial library and will be able to replace electrum servers for many use cases
- ndk by nostr:nprofile1qqsx3kq3vkgczq9hmfplc28h687py42yvms3zkyxh8nmkvn0vhkyyuspz4mhxue69uhkummnw3ezummcw3ezuer9wchsz9thwden5te0wfjkccte9ejxzmt4wvhxjme0qy88wumn8ghj7mn0wvhxcmmv9u0uehfp
And of course, secure storage of bitcoin is only possible, because of the hardware signer manufacturers. Thanks to nostr:npub1az9xj85cmxv8e9j9y80lvqp97crsqdu2fpu3srwthd99qfu9qsgstam8y8 Coldcard , Coldcard Q , nostr:npub1tg779rlap8t4qm8lpgn89k7mr7pkxpaulupp0nq5faywr8h28llsj3cxmt Bitbox02 , nostr:npub1jg552aulj07skd6e7y2hu0vl5g8nl5jvfw8jhn6jpjk0vjd0waksvl6n8n Blockstream Jade , Trezor Safe, Foundation Passport, Keystone, Ledger, Specter Shield, and many more.
I also want to thank people who gave feedback and helped spread the knowledge of Bitcoin Safe (please forgive me if I forgot to mention you)
- nostr:npub1p5cmlt32vc3jefkl3ymdvm9zk892fsmkq79eq77uvkaqrnyktasqkpkgaw nostr:npub1s07s0h5mwcenfnyagme8shp9trnv964lulgvdmppgenuhtk9p4rsueuk63 nostr:npub18f3g76xc7xs430euwwl9gpn7ue7ux8vmtm9q8htn9s26d8c4neeqdraz3s nostr:npub1mtd7s63xd85ykv09p7y8wvg754jpsfpplxknh5xr0pu938zf86fqygqxas nostr:npub1kysd8m44dhv7ywa75u5z7w2w0gs4t6qzhgvjp555gfknasy3krlqfxde60 nostr:npub185pu2dsgg9d36uvvw7rwuy9aknn8hnknygr7x2yqa60ygvq6r8kqc836k8 nostr:npub1hkcgyqnsuaradq3g5hyvfdekwypc25494nmwggwpygxas7fcs4fst860fu nostr:npub1xsl0msy347vmj8gcpsjum6wwppc4ercvq4xfrhqmek2dqmqm0mtsyf35vx nostr:npub1hxjnw53mhghumt590kgd3fmqme8jzwwflyxesmm50nnapmqdzu7swqagw3 nostr:npub1ke470rdgnxg4gjs9cw3tv0dp690wl68f5xak5smflpsksedadd7qtf8jfm nostr:npub1sk26fxl4fy3vt8m5n0a6aturaql0w20nvh22q0cyaqm28tj7z8ss3lutc9 nostr:npub1r4llq2jcvq4g2tgha5amjz07zk7mrrcj89wllny9xwhhp5zzkklqk4jwja nostr:npub1p9v2zpwl28c0gu0vr2enp3lwdtv29scwpeqsnt0ngqf03vtlyxfqhkae5w nostr:npub1xkym0yaewlz0qfghtt7hjtnu28fxaa5rk3wtcek9d3x3ft2ns3lq775few nostr:npub1r8343wqpra05l3jnc4jud4xz7vlnyeslf7gfsty7ahpf92rhfmpsmqwym8 nostr:npub12zpfs3yq7we83yvypgsrw5f88y2fv780c2kfs89ge5qk6q3sfm7spks880 nostr:npub1yrnuj56rnen08zp2h9h7p74ghgjx6ma39spmpj6w9hzxywutevsst7k5cx https://x.com/91xTx93x2 https://x.com/afilini rustaceanrob
-
 @ 06639a38:655f8f71
2025-03-17 14:55:18
@ 06639a38:655f8f71
2025-03-17 14:55:18https://ccns.nostrver.se is a (Drupal powered) website that I started to build in January 2024 (source on Github and Gitlab). It's a fork of an earlier (abandoned) project https://cchs.social/.
Currently CCNS is a link aggregration website and for now it's only my who is using it to save and share Nostr related links. When you post a new link, you have the option to cross-post it as a Nostr note (example here).Kind 39700
Last month Jurjen and Abir has started to work on a social bookmark client built with Nostr (inspired by Del.icio.us from the past). Earlier this month they changed to event kind 39700 for broadcasting the Nostr event with the bookmark / link data accross the network. They did this because Sep already created a social bookmark like client called Pinja when fiatjaf raised this idea.
With these developments to me it was very obvious to integrate the feature that new created CCNS links are now also published as kind 39700 events to the Nostr network. This means that links are now also distributed on multiple relays as kind 39700 events and are accessible in multiple clients (Yumyume and Pinja).
Here you can see the same data, from left to right:

Structure
The current data structure for the 39700 kind looks as follow:
- "id": "event_id"
- "pubkey": "pubkey author"
- "created_at": unix_timestamp
- "kind": 39700
- "tags":
- "description", "description text here"
- "d", "unique-slug-value"
- "t", "hashtag"
- "content": "https://book_mark_url"
- "sig": "signature"
As there is no NIP (yet) for this event kind, I see some possible improvements:
- Use the bookmark URL as
dtag so it can be used as a unique identifier for every client - Use the content field for the description
- Use the
atag for an addressable event following NIP-01:["a", "39700:pubkey_of_author:", recommended_relay_url_optional]
On short-term I don't have any plans to developer CCNS further, as most of my attention goes to the development of the Nostr-PHP library and Drupal related contribs using that library. That said, CCNS is a Drupal project but all the Nostr stuff is done client-side (Javascript) with NDK and Nostr-PHP is not used (maybe this will change in the future).
-
 @ 5d4b6c8d:8a1c1ee3
2025-04-11 15:23:41
@ 5d4b6c8d:8a1c1ee3
2025-04-11 15:23:41Basketball
March Madness wrapped up with some very exciting games. We'll recap the championship, the contest, and the fun we had at Predyx.
I've also decided how I want to do a similar contest for the NBA Playoffs. Better than that, though, is the Bracket Challenge we'll be doing with Global Sports Central. We also need to update our NBA Predictions and talk about the wild finish in the Western Conference, where multiple playoff teams fired their head coaches.
Football
The NFL Draft is coming up and @grayruby found a very cool new simulator. What are we predicting for the first round?
Also, we're continuing to very much enjoy the Aussie Rules contest and highlights.
The Other Football
UEFA Champions League is back and we're all trying to survive a little longer.
Baseball
Why was half my fantasy roster inactive? Plus, @grayruby wants to overreact to the early season results.
Also, the MLB Survivor Pool is starting up soon.
Hockey
@siggy47's beloved team enters the history books, by allowing Ovi to become the NHL's all-time leading scorer.
Cricket
I fell flat on my face in the T20k contest immediately after mocking @grayruby for doing the same. Oh well, upwards and onwards.
@Coinsreporter is also still running the perpetual CricZap contest, which I continue to do very poorly at. Is it time to inverse Cramer myself?
The Predyx market for the IPL has been one of my favorites.
F1
There are a couple of new F1 markets: Constructor and Driver, for those who may be interested.
Misc
We also need an update on USA vs the world.
Time permitting, I have some thoughts about how new sporting events like Chase might evolve in the sports ecosystem.
Let us know what else you want to hear and we'll endeavor to cover it.
originally posted at https://stacker.news/items/940727
-
 @ b5d34eed:a7475cbf
2025-03-16 20:15:10
@ b5d34eed:a7475cbf
2025-03-16 20:15:10The internet has come a long way since its inception, but let’s be honest—it’s not exactly the utopia of freedom and openness we once imagined. Today, a handful of tech giants control most of our online interactions, from social media to payments. Enter the decentralized web, a movement that’s pushing back against this centralization. At the forefront of this revolution is Nostr, a simple yet powerful protocol that’s redefining how we think about social networking. And when you throw the Lightning Network into the mix, things get even more exciting. Let’s break it all down.
What’s Wrong with the Current Web?
Before we dive into Nostr, let’s talk about why decentralization matters. The internet today is dominated by centralized platforms like Facebook, Twitter (now X), and Instagram. These platforms control what you see, how you interact, and even what you’re allowed to say. They harvest your data, sell it to advertisers, and can ban or silence you at their discretion. It’s a system that prioritizes profit over people.
Centralization also creates single points of failure. If a platform goes down, gets hacked, or decides to shut down, your data and connections disappear overnight. Remember when Twitter had outages, or when Facebook’s servers crashed? Millions of users were left stranded. This isn’t just inconvenient—it’s a fundamental flaw in how we’ve built the web.
Enter Nostr: A Breath of Fresh Air
Nostr, which stands for Notes and Other Stuff Transmitted by Relays, is a decentralized protocol designed to fix these problems. Unlike traditional social media platforms, Nostr doesn’t rely on a central server. Instead, it uses a network of independent relays to transmit messages. Think of it as a decentralized Twitter, but without the corporate overlords.
Here’s why Nostr is a game-changer:
-
No Central Authority: Nostr doesn’t belong to any company or individual. It’s an open protocol, meaning anyone can build apps on top of it or run their own relay. This eliminates the risk of censorship or arbitrary bans.
-
User Control: With Nostr, you own your data. Your posts, messages, and connections are stored locally or on relays you choose. If one relay goes down, you can switch to another without losing anything.
-
Interoperability: Nostr is designed to work across different apps and platforms. This means you’re not locked into a single ecosystem. If you don’t like one Nostr client, you can switch to another without losing your followers or content.
-
Simplicity: Nostr’s protocol is intentionally simple. It doesn’t try to do everything at once, which makes it lightweight and easy to use. This simplicity also makes it more resilient and adaptable.
The Lightning Network: Powering Decentralized Payments
Now, let’s talk about money. One of the coolest things about Nostr is its integration with the Lightning Network, a second-layer payment protocol built on top of Bitcoin. The Lightning Network enables fast, cheap, and scalable transactions, making it perfect for micropayments and tipping.
Here’s why this matters:
-
Monetization Without Ads: Traditional social media platforms rely on ads to make money. This creates a perverse incentive to keep you hooked and harvest your data. With Nostr and the Lightning Network, creators can monetize their content directly through tips or paid subscriptions. No ads, no middlemen—just a direct connection between creators and their audience.
-
Global Payments: The Lightning Network is borderless. Whether you’re tipping a blogger in Nigeria or buying a digital product from someone in Argentina, transactions are instant and cost just a fraction of a cent. This opens up new opportunities for global collaboration and commerce.
-
Censorship-Resistant Money: Just like Nostr resists censorship, the Lightning Network ensures that payments can’t be blocked or controlled by any central authority. This is especially important in regions where financial freedom is under threat.
Why Nostr and the Lightning Network Are a Perfect Match
When you combine Nostr’s decentralized social networking with the Lightning Network’s payment capabilities, you get something truly special. Imagine a social media platform where you can tip your favorite creators, pay for premium content, or even buy goods and services—all without leaving the app. And because both Nostr and the Lightning Network are decentralized, you don’t have to worry about fees, censorship, or corporate interference.
For example, let’s say you’re a musician sharing your work on Nostr. Fans can tip you in Bitcoin via the Lightning Network, or you can sell exclusive content directly to your followers. The money goes straight to you, without a platform taking a cut. This creates a more equitable and sustainable model for creators.
The Bigger Picture: A Decentralized Future
Nostr and the Lightning Network are just two pieces of a much larger puzzle. The decentralized web is about reclaiming control over our online lives—our data, our interactions, and our money. It’s about building a more open, resilient, and user-centric internet.
Of course, decentralization isn’t without its challenges. It can be harder to use than centralized alternatives, and it requires a shift in how we think about technology. But the benefits far outweigh the drawbacks. By embracing protocols like Nostr and the Lightning Network, we can create a web that’s truly by the people, for the people.
Final Thoughts
The decentralized web isn’t just a tech trend—it’s a movement. Nostr and the Lightning Network are proof that we can build better, fairer systems when we prioritize freedom and innovation over profit and control. Whether you’re a creator, a developer, or just someone who’s tired of Big Tech’s grip on your online life, now’s the time to explore what the decentralized web has to offer.
-
-
 @ e516ecb8:1be0b167
2025-04-11 15:07:04
@ e516ecb8:1be0b167
2025-04-11 15:07:04¿Qué es realmente la inflación? Si alguna vez has escuchado que la inflación es “la subida constante de precios”, no estás solo. Hace poco, un economista soltó esa definición en una entrevista, y otro, desde la Fundación para el Progreso (FPP), una institución que suele citar a pensadores como Mises o Hayek, repitió lo mismo. Suena lógico, ¿no? Pero están equivocados. Y ese error, aunque parezca pequeño, puede tener consecuencias catastróficas. Para entender por qué, no hace falta ir muy lejos: miremos a Argentina.
La subida de precios no es la inflación. Es solo el síntoma. La inflación, en esencia, es la pérdida del valor adquisitivo de la moneda. Confundir la causa con el efecto es como tratar una fiebre con un paño frío sin atacar la infección. Y cuando las políticas públicas se basan en esa confusión, el desastre está garantizado.
Argentina: una lección que duele Argentina es el caso de estudio perfecto. Antes de que Javier Milei llegara al poder en diciembre de 2023, la inflación en el país vecino estaba desbocada, alcanzando picos de 211% anual según datos del INDEC. El peronismo, convencido de que el problema eran los precios, implementó medidas como los “Precios Justos”, fijando topes artificiales. ¿Resultado? Escasez total. En un país famoso por su carne, los supermercados se quedaron sin ella. Los productores, enfrentados a costos que subían sin control, preferían exportar antes que vender localmente a precios que no les daban ni para cubrir gastos. Y ahí no terminó la cosa. En lugar de atacar la raíz del problema, el gobierno peronista complicó todo aún más: restringió exportaciones y creó un sistema surrealista de múltiples tipos de dólar (¡hasta uno distinto para Netflix!). Todo porque seguían peleando con el efecto, no con la causa.
¿Por qué los argentinos corrían a ahorrar en dólares y no en pesos? Porque el peso se devaluaba a una velocidad alarmante. Si la inflación fuera solo una cuestión de precios, habría afectado a todas las monedas por igual. Pero no. Como dice Milei una y otra vez, la inflación es un fenómeno monetario: demasiados billetes circulando sin respaldo o una moneda que la gente considera “de segunda” frente a otras.
¿Por qué seguimos repitiendo el error? Entonces, si la inflación es tan claramente un problema del valor de la moneda, ¿por qué seguimos escuchando que es una subida de precios? La respuesta es sencilla: culpar a otros es más fácil. Cuando se vende esa idea, los políticos pueden apuntar con el dedo a empresarios, comerciantes o “especuladores” y lavarse las manos. Es más cómodo que admitir una emisión monetaria irresponsable, un gasto público descontrolado o una pésima gestión económica. Y no faltan economistas, a veces financiados por grupos estatistas o formados en sistemas educativos que promueven esas ideas, que les hacen el coro.
Chile: por un pelo nos salvamos Este malentendido estuvo a punto de colarse en Chile. En el segundo intento de reforma constitucional, impulsado por Chile Vamos en 2023, se propuso que el Banco Central velara por la “estabilidad de precios”, no por la estabilidad del valor de la moneda. Parece un detalle técnico, ¿verdad? Pero no lo es. Ese cambio abría la puerta a políticas que podrían habernos llevado por el mismo camino que Argentina. Por suerte, aunque muchos expertos lo pasaron por alto, la ciudadanía no: la propuesta fue rechazada en las urnas con un contundente “En Contra”.
Nos salvamos, pero no porque nuestros políticos tuvieran las ideas claras. Nos salvamos porque los chilenos dijimos “basta”. Y menos mal, porque en 2024 la inflación en Chile se mantuvo controlada, rondando el 3,5% anual según el Banco Central, lejos del caos argentino. Pero no podemos confiarnos, porque esa inflación sigue siendo alta para nuestros estándares pre-pandémicos o pre-estallido social. El retiro desde las AFP convirtió activos en consumo, en otras palabras aumentó el circulante y todavía batallamos con esa inflación.
No es un “detallito” Cada vez que alguien diga que la inflación es una subida de precios o que la solución está en controlarlos, por favor, corrígelo. No es un error menor. Argentina lleva más de un año intentando salir del pozo que cavó este malentendido. Milei ha dado pasos importantes: transparentó la inflación real, ajustó el tipo de cambio para acercarse al valor de mercado y, aunque la inflación sigue alta (cerca del 50% anual a fines de 2024, según estimaciones), empieza a estabilizarse. Pero el camino es largo, y los costos de este “detallito” los pagan todos los argentinos.
¿Y ahora qué hacemos? La próxima vez que escuches a un político o un experto hablar de inflación como si fuera solo un problema de precios, no te quedes callado. Pregúntales: ¿y el valor de la moneda qué? Comparte esta historia, porque entender la inflación es el primer paso para no repetir los errores del pasado. En Chile esquivamos la bala, pero no podemos bajar la guardia. Los errores pequeños, cuando se trata de economía, terminan costándonos caro.
¿Qué opinas? ¿Crees que Chile aprendió la lección o estamos a un paso de tropezar otra vez? ¡Déja tu comentario y comparte este post si te hizo clic!
-
 @ 21335073:a244b1ad
2025-03-15 23:00:40
@ 21335073:a244b1ad
2025-03-15 23:00:40I want to see Nostr succeed. If you can think of a way I can help make that happen, I’m open to it. I’d like your suggestions.
My schedule’s shifting soon, and I could volunteer a few hours a week to a Nostr project. I won’t have more total time, but how I use it will change.
Why help? I care about freedom. Nostr’s one of the most powerful freedom tools I’ve seen in my lifetime. If I believe that, I should act on it.
I don’t care about money or sats. I’m not rich, I don’t have extra cash. That doesn’t drive me—freedom does. I’m volunteering, not asking for pay.
I’m not here for clout. I’ve had enough spotlight in my life; it doesn’t move me. If I wanted clout, I’d be on Twitter dropping basic takes. Clout’s easy. Freedom’s hard. I’d rather help anonymously. No speaking at events—small meetups are cool for the vibe, but big conferences? Not my thing. I’ll never hit a huge Bitcoin conference. It’s just not my scene.
That said, I could be convinced to step up if it’d really boost Nostr—as long as it’s legal and gets results.
In this space, I’d watch for social engineering. I watch out for it. I’m not here to make friends, just to help. No shade—you all seem great—but I’ve got a full life and awesome friends irl. I don’t need your crew or to be online cool. Connect anonymously if you want; I’d encourage it.
I’m sick of watching other social media alternatives grow while Nostr kinda stalls. I could trash-talk, but I’d rather do something useful.
Skills? I’m good at spotting social media problems and finding possible solutions. I won’t overhype myself—that’s weird—but if you’re responding, you probably see something in me. Perhaps you see something that I don’t see in myself.
If you need help now or later with Nostr projects, reach out. Nostr only—nothing else. Anonymous contact’s fine. Even just a suggestion on how I can pitch in, no project attached, works too. 💜
Creeps or harassment will get blocked or I’ll nuke my simplex code if it becomes a problem.
https://simplex.chat/contact#/?v=2-4&smp=smp%3A%2F%2FSkIkI6EPd2D63F4xFKfHk7I1UGZVNn6k1QWZ5rcyr6w%3D%40smp9.simplex.im%2FbI99B3KuYduH8jDr9ZwyhcSxm2UuR7j0%23%2F%3Fv%3D1-2%26dh%3DMCowBQYDK2VuAyEAS9C-zPzqW41PKySfPCEizcXb1QCus6AyDkTTjfyMIRM%253D%26srv%3Djssqzccmrcws6bhmn77vgmhfjmhwlyr3u7puw4erkyoosywgl67slqqd.onion
-
 @ c3e23eb5:03d7caa9
2025-04-10 00:41:12
@ c3e23eb5:03d7caa9
2025-04-10 00:41:12The issue I have with the term "mesh networks" is that it is associated with a flat network topology. While I love the idea of avoiding hierarchy, this simply doesn't scale.
Data Plane: How the Internet Scales
The internet on the scales because it has a tree like structure. As you can see in the diagram below, global (tier 1) ISPs branch out to national (tier 2) ISPs who in turn branch out to local (tier 3) ISPs. ``` ,-[ Tier 1 ISP (Global) ]─-───────[ Tier 1 ISP (Global) ] / |
/ ▼
[IXP (Global)]═══╦═══[IXP (Global)]
║
Tier 2 ISP (National)◄──────────╗
/ \ ║
▼ ▼ ║
[IXP (Regional)]════╬══[IXP (Regional)] ║
/ \ ║
▼ ▼ ║
Tier 3 ISP (Local) Tier 3 ISP (Local) ║
| | ║
▼ ▼ ▼
[User] [User] [Enterprise]▲ IXPs are physical switch fabrics - members peer directly ▲ Tier 1/2 ISPs provide transit through IXPs but don't control them ```
This structure also reflects in IP addresses, where regional traffic gets routed by regional tiers and global traffic keeps getting passed up through gateways till it reaches the root of the tree. The global ISP then routes the traffic into the correct branch so that it can trickle down to the destination IP at the bottom.
12.0.0.0/8 - Tier 1 manages routing (IANA-allocated) └─12.34.0.0/16 - Tier 2 allocated block (through RIR) └─12.34.56.0/24 - Tier 3 subnet via upstream provider ├─12.34.56.1 Public IP (CGNAT pool) └─192.168.1.1 Private IP (local NAT reuse)Balancing idealism with pragmatism
This approach to scaling is much less idealistic than a flat hierarchy, because it relies on an authority (IANA) to assign the IP ranges to ISPs through Regional Internet Registries (RIRs). Even if this authority wasn't required, the fact that many users rely on few Tier 1 ISPs means that the system is inherently susceptible to sabotage (see 2019 BGP leak incident).
Control Plane: the internet is still described as decentralised
The internet is still described as decentralised because there is a flat hierarchy between
tier 1ISPs at the root of the tree. ``` INTERNET CORE (Tier 1 ISPs)
AT&T (AS7018) <══════════> Deutsche Telekom (AS3320) ║ ╔════════════════════╗ ║ ║ ║ ║ ║ ╚══>║ NTT (AS2914) ║<══╝ ║ ║ ║ ║ ║ ║ ╚═══════> Lumen (AS3356) ║ ║ ╚════╩════════════> Telia (AS1299) ```
The border gateway protocol (BGP) is used to exchange routing information between autonomous systems (ISPs). Each autonomous system is a branch of the "internet tree" and each autonomous system advertises routes to downstream autonomous systems (branches). However, the autonomous systems at the root of the tree also maintain a record of their piers, so that they can forward traffic to the correct peer. Hence, the following is a more complete diagram of the internet:
INTERNET CORE (TIER 1 MESH) ╔══════════════╦═════════════╦════════╦═════════════╗ ║ ║ ║ ║ ║ AT&T (AS7018) <══╬══> Lumen (AS3356) <══╬══> NTT (AS2914) ║ ║ ║ ║ ║ ║ ║ ╚══> Telia (AS1299) <══╝ ║ ║ ╚═══════════════════════════════╝ ║ ║ ╚═> Deutsche Telekom (AS3320) <═╝ ║ TREE HIERARCHY BELOW - MESH ABOVE ║ ▼ [ Tier 1 ISP ]───────────────────┐ / | | / ▼ ▼ [IXP]═══╦═══[IXP] [IXP] ║ ║ ▼ ▼ Tier 2 ISP◄──────────╗ Tier 2 ISP◄───────╗ / \ ║ / \ ║ ▼ ▼ ║ ▼ ▼ ║ [IXP]═╦[IXP] ║ [IXP]═╦[IXP] ║ / \ ║ / \ ║ ▼ ▼ ▼ ▼ ▼ ▼ Tier 3 ISP User Tier 3 ISP EnterpriseSo its a mesh network - whats wrong with that?
In the example above, NTT can only send traffic to Deutsche Telekom via Lumen or AT&T. NTT relies on its peers to maintain a correct record of the IP range that they are responsible for, so that traffic that was intended for Deutsche Telekom doesn't end up in the wrong network. An intentional or even accidental error in an autonomous system's routing tables can be detrimental to the flow of traffic through the network.
Hence, mesh networks require: * Reliability: peers rely on each-other not to fail (e.g., 2019 AWS US-East-1 availability) * Trust: peers must be honest about address ranges (e.g., 2018 BGP hijacking incident) * Central planning: BGP traffic engineering determines which route a packet takes
Application Layer Innovations
Now that we have a rough overview of how the internet is broken, lets think about what can still be done. The flat hierarchy that we associate with mesh networks sounds beautiful, but it doesn't scale. However, the tree-like structure assumes that most participants in the network rely on an authority to give them an address or a range of addresses so that they can communicate.
Overlay networks
Fortunately all it takes to interact with someone on nostr is their public key. The recipients client will render your signed and/or encrypted event no matter how it reaches them. Whether your note reaches them over the internet, over some other network or via a carrier pigeon doesn't matter. nostr:npub1hw6amg8p24ne08c9gdq8hhpqx0t0pwanpae9z25crn7m9uy7yarse465gr is working on a NIP for that and I'm sure he will share an explanation of how it works.
Bitcoin Instead of a Routing Algorithm
Now that we have digital bearer assets (e-cash), users can pay their internet gateway (TollGate) for access to the internet even though they are still offline. Once the TollGate has redeemed the e-cash, it gives the user access to the internet.
Frictionless Switching between ISPs (TollGates)
Legacy internet service providers use KYC money (fiat) to transfer the cost of the infrastructure to their users. However, this means that they are able to identify which packet belongs to which user. The KYC nature of their interaction with the users also makes it difficult for users to switch ISPs when service providers undercut each-other. Internet users who are on e-cash rails can hop between ISPs frictionlessly since they buy small amounts of data frequently in a granular manner.
Users that have access to independent competing TollGates can switch between them freely, so its impossible for any one TollGate to prevent a user from connecting to the internet. The only thing a TollGate can do is attract traffic by providing cheaper and/or faster internet access.
Anyone can arbitrage connectivity
Now that users have non KYC internet, there is nothing stopping them from reselling access to their internet connection. Anyone who has a WiFi router and access to a cheap internet connection can act as a range extender by re-selling access to that gateway for people who aren't able to connect directly.
Now the route that the traffic takes through the network is determined dynamically by the markets. The individual TollGate operators select their gateways and set their prices when they create a business model. The customers select the route that best meets their needs by selecting a gateway for their next purchase.
-
 @ b1b16be0:08f41c1d
2025-04-11 22:58:00
@ b1b16be0:08f41c1d
2025-04-11 22:58:00Bitcoin need more devs to scale! So I decide to translate to spanish https://plebdevs.com plebdevs@plebdevs.com is a opensource website to learn #bitcoin #lightning free.I started in my free time but now I have to sacrifice work time to move forward. Any zap could be a new bitcoiner!
Why Spanish? Spanish is the third most spoken language on the internet, but much of this community has little access to technical content in English. Plebdevs can be the 🔥torch that illuminates new developers to scale Bitcoin from Latin America and the world.
Apprenticeship Incentive Plebs will gaining the possibility of #learn a higher-paying job as #dev.
Let's Make Bitcoin Scale Millions of Spanish speakers can learn how to develop about Bitcoin and Lightning.
Proof of Work Introduction presentation: https://docs.google.com/presentation/d/1IMC4GHYjccKhGu2mDrtY3bOGcjyFcwgXwFyKyNMq7iw/edit?usp=sharing
🟩🟩🟩⬜⬜⬜⬜⬜⬜⬜ 30%
Thanks to bitcoinplebdev@bitcoinpleb.dev to create this #wonder
Any Zap will be helpful!
mav21@primal.net am@cubabitcoin.org lacrypta@hodl.ar BenJustman@primal.net shishi@nostrplebs.com sabine@primal.net onpoint@nostr.com theguyswann@iris.to Richard@primal.net eliza@primal.net
-
 @ 554ab6fe:c6cbc27e
2025-04-09 23:22:16
@ 554ab6fe:c6cbc27e
2025-04-09 23:22:16We all live with our bodies every day, but do we truly experience them? Does this experience of the body have a broader consequence on our interpretation of life and our experience of well-being? The ability to experience the sensations of the body is known as interoception, and mindfulness meditation seems to be a powerful way of enhancing this ability. Enhanced interoception may not just result in a better understanding of the body, but may lead to a general increase in subjective well-being. Furthermore, it also may be indicative of a broader truth about how we can reach a more profound level of consciousness.
In a previous post, I began an exploration into possible reasons why those who meditate claim to achieve an altered form of consciousness. I mentioned that across enlightenment-related research, there is a common experience and interpretation of being one with everything during these altered or heightened states. I proposed that this interpretation of reality was achieved through an improved capability of the brain to process incoming information. The argument stems from the idea that the brain is constantly receiving signals from internal and external stimuli, trying to interpret those signals using previous experiences and predicted models (Seth, 2013). The interpretation created, in part, manifests itself as our conscious reality. I used an analogy of a calm pond to describe a possible consequence of this neuroscientific idea: imagine the brain as this pond, where incoming signals can be thought of as raindrops. When a single raindrop falls upon a pond, the ripples created are distinct. It is incredibly easy to determine how big the raindrop was, where it dropped, and came from, etc. However, if there is a massive rainstorm, then it is almost impossible to interpret all the intersecting ripples, and it is very hard to understand the “information” of each raindrop. This is analogous to how our brains work. The busier the incoming signals, the more difficult it is to interpret the reality of what is happening. This would also be true for the signals within the brain manifested by our thoughts and ruminations. Therefore, the calmer the pond/brain, the clearer and more accurate understanding of our world, and ourselves, is achieved. Meditation may be a method to achieve this heightened state of awareness. I find this idea profoundly interesting, and so my goal is to further explore this idea using scientific evidence as support.
To further explore and verify this idea, I felt it was important to research interoception. If this idea holds water, then it should be observed that meditation allows an individual to achieve a better understanding of incoming stimuli, both internal and external. In this post, I will explore the ability to interpret internal stimuli, which is known as interoception.
A quick note before I continue: As I began researching this topic, I found that the study of interoception was quite complex. The research is constantly evolving, and previous notions are quickly dismissed as the research progresses. Therefore, much of the research presented is speculative, and surely not indicative of definitive truth. Nothing you ever read is definitive of course, but I find that this is especially true here. Regardless, it will adequately depict the fascinating nature of our bodies and the processes involved in interpreting ourselves and reality, hopefully highlighting how important interoception is, and how poorly it is understood.
Understanding the Different Senses
To begin, an outline of our body’s senses is required. Classically speaking, the senses are defined as teloreception (vision and hearing), proprioception (limb position), exteroception (touch), chemoreception (smell and taste), and interoception (sensations from the internal organs)(A. D. Craig, 2002). In this classical definition, sensations of pain, temperature, and itches belonged to the family of touch/exteroception (A. D. Craig, 2002). Therefore, the line between the stimuli from the outside world is clearly defined and separated from the stimuli coming from inside the body. However, more recent findings suggest that temperature, pain, and itch are distinct from touch because they are associated with different neuronal pathways, and the experiences of these sensations seem to rely upon post-processing (A. D. Craig, 2002, 2003). In other words, the experience of these stimuli is more related to the mind than pure touch is. Additionally, interoception is also being redefined. The lamina I spinothalamocortical system is one of the major neuronal pathways that provide the brain with interoceptive signals (A. D. Craig, 2002, 2003). This nerve, across multiple studies, has been shown to not just send signals regarding the organs, but a sense of the condition of the entire body as well (A. D. Craig, 2002). Therefore, interoception encompasses the general feelings we have about the body’s state of being including, but not limited to, thirst, hunger, penile stimulation, exercise/exhaustion, and the condition of our organs such as bladder, stomach, etc. (A. D. B. Craig, 2009). To further complicate things, some researchers have attempted to distinguish between different aspects of interoception (Garfinkel et al., 2015):
• interoceptive accuracy – “Objective accuracy in detecting internal bodily sensations” • interoceptive sensibility – “Self-perceived dispositional tendency to be internally self-focused and interoceptively cognizant” • interoceptive awareness – “Metacognitive awareness of interoceptive accuracy”
Here, the ability to accurately detect signals and the subjective belief of one’s accuracy is differentiated. The interoceptive awareness evaluates if your subjective confidence in your ability to sense the signals coincides with the true ability. Therefore, the mind and our subjective evaluation of our signals are incredibly related to our perceived understanding. For this reason, the neuroscience of interoception should be explored, to gain a better understanding of how it works. The two brain areas that are involved in interoception and that will be discussed here are: the insula and the anterior cingulate cortex (ACC).
Insula
The insula is located deep within the cerebral cortex, and likely plays the most important role in interoception. The insula, especially the anterior portion of the insula, is thought to be involved in bodily and emotional awareness (Giuliani et al., 2011). It plays a major role in interoception and the sensations of internal physical states (Fox et al., 2014; Wolf E. Mehling et al., 2012). Not only is it integral to generating mental images of the internal state, but it is required for the motivation to make reactions based upon the interpretation, which subsequently affect the quality of life and survival (Craig, 2002). Consequentially, it plays a predictive role in awareness and decision-making (Craig, 2009). Therefore, falling in line with the idea that consciousness is the product of the predictive model generating nature of the brain to understanding and interpret incoming stimuli, the insula is thought to be a major seat of human consciousness and awareness of self-hood (Craig, 2009; Fox et al., 2014; Seth, 2013). Already, there is a clear connection between interoception, body awareness, and consciousness within the scientific literature.
Anterior Cingulate Cortex (ACC)
The other brain region heavily involved in interoception is the ACC. Where the insula largely is involved in the processing of the signal, the ACC is more involved with the response to the signal (Craig, 2002). In other words, the insula is related to the limbic sensory cortex, whereas the ACC is associated with the limbic motor cortex (Craig, 2002). Most recent studies have also shown that the ACC and insula are co-activated when a person experiences feelings (Craig, 2002, 2009). For example, both brain regions are involved in the sensation of the intensity and unpleasantness of pain (Grant et al., 2011). This provides further evidence that interoception is both a feeling and a motivation (Craig, 2009). Additionally, this enhances the argument that our interpretations and feelings from our internal environment are there for survival. It supports the idea that our brain is organized in a way that makes predictions, generates a conscious experience, that then elicits a reaction for the continuation of life.
Meditation and Interoception
Interoception involves more than just sensory information. It influences our feelings, and our understanding of our body, self, and the surrounding world. This understanding and experience of the self are seemingly influenced by the practice of meditation. Not only is this idea espoused in the east, but recent research has also indicated that increased mindfulness is correlated with increase interoceptive awareness (de Jong et al., 2016; Farb et al., 2010; Hanley et al., 2017). The exact mechanisms to how this occurs are still unclear. However, fMRI studies have shown that mindfulness meditation seems to increase activation in the insula (Farb et al., 2010). This may indicate that mindfulness promotes neurogenesis in areas that promote interoception. On that same note, the cognitive practices of mindfulness meditation may promote a mental framework that is helpful towards interoception. Mindfulness meditation involves orienting one’s attention to their immediate experience and becoming aware of all incoming stimuli with an open, curious, non-reactive, and non-judgmental interpretation (Bishop et al., 2004). This process helps generate a feeling of safety within the body, and the individual learns to interpret thoughts not as concrete objects of reality, but simply as thoughts that come and go within the mind. Researchers have found evidence to suggest that the non-reactivity obtained through meditation practice is closely linked to the ability to sustain attention towards bodily sensations (Hanley et al., 2017). This concept closely links to the idea that the calmer the mind is, the better the brain can process incoming information. This article brings forward evidence that the brain, with a calmer mind, can process interoceptive information better.
Consciousness
An interesting observation amongst interoceptive research is that an increase in interoceptive awareness is negatively correlated with emotional distress, hence an increase in subjective well-being is achieved (Hanley et al., 2017; W E Mehling et al., 2012). This is further supported by the observation that sadness is correlated with decreased activation of the insula and ACC, the brain regions involved in interoception (Farb et al., 2010). The relationship between the ability to be aware of the internal signals of the body and our mental well-being is very interesting. It suggests that not only does a calm mind generate a greater ability to understand the inner body, but it generates a more positive orientation to said experience. Additionally, it may be possible that this positive outlook spills over into other aspects of life beyond the interpretation of the self. Perhaps the calmer mind generates an accurate and positive outlook on all information received. This is perhaps why those who are expert meditators seem to be so peaceful, loving, and have a feeling of unity amongst everything.
The way we interpret information influences our experience of both ourselves and the world. Being aware of the body and its sensations in a non-judgmental way, creates a general sense of well-being. This may be indicative of a deeper philosophical idea: that the calmer the mind, the more capable the brain can interpret and understand information. This would not only provide a more accurate depiction of reality but provide a more profound understanding of it. Leading to a perspective of the world that is more positive, and potentially more oriented around the idea that we are all one. I cannot claim this is true. Nonetheless, it will be a concept that I will continue to explore. Regardless, it does seem to be the case that mindfulness meditation is capable of increasing interoception and therefore well-being. This being the case, I highly recommend that anyone interested in this topic incorporates mindfulness practice into their life. Reading and thinking about these ideas are all well and good, but to achieve full understanding, one must practice and experience it for themselves.
References
Bishop, S. R., Lau, M., Shapiro, S., Carlson, L., Anderson, N. D., Carmody, J., Segal, Z. v., Abbey, S., Speca, M., Velting, D., & Devins, G. (2004). Mindfulness: A Proposed Operational Definition. Clinical Psychology: Science and Practice, 11(3), 230–241. https://doi.org/10.1093/clipsy.bph077
Craig, A. D. (2002). How do you feel? Nature Review. https://doi.org/10.1177/1359105308095062
Craig, A. D. (2003). Interoception: The sense of the physiological condition of the body. Current Opinion in Neurobiology, 13(4), 500–505. https://doi.org/10.1016/S0959-4388(03)00090-4
Craig, A. D. (2009). How do you feel — now? The anterior insula and human awareness. 10(January).
de Jong, M., Lazar, S. W., Hug, K., Mehling, W. E., Hölzel, B. K., Sack, A. T., Peeters, F., Ashih, H., Mischoulon, D., & Gard, T. (2016). Effects of mindfulness-based cognitive therapy on body awareness in patients with chronic pain and comorbid depression. Frontiers in Psychology, 7(JUN). https://doi.org/10.3389/fpsyg.2016.00967
Farb, N. A. S., Anderson, A. K., Mayberg, H., Bean, J., McKeon, D., & Segal, Z. v. (2010). Minding One’s Emotions: Mindfulness Training Alters the Neural Expression of Sadness. Emotion, 10(1), 25–33. https://doi.org/10.1037/a0017151
Fox, K. C. R., Nijeboer, S., Dixon, M. L., Floman, J. L., Ellamil, M., Rumak, S. P., Sedlmeier, P., & Christoff, K. (2014). Is meditation associated with altered brain structure? A systematic review and meta-analysis of morphometric neuroimaging in meditation practitioners. Neuroscience and Biobehavioral Reviews, 43, 48–73. https://doi.org/10.1016/j.neubiorev.2014.03.016
Garfinkel, S. N., Seth, A. K., Barrett, A. B., Suzuki, K., & Critchley, H. D. (2015). Knowing your own heart: Distinguishing interoceptive accuracy from interoceptive awareness. Biological Psychology, 104, 65–74. https://doi.org/10.1016/j.biopsycho.2014.11.004
Giuliani, N. R., Drabant, E. M., Bhatnagar, R., & Gross, J. J. (2011). Emotion regulation and brain plasticity: Expressive suppression use predicts anterior insula volume. NeuroImage, 58(1), 10–15. https://doi.org/10.1016/J.NEUROIMAGE.2011.06.028
Grant, J. A., Courtemanche, J., & Rainville, P. (2011). A non-elaborative mental stance and decoupling of executive and pain-related cortices predicts low pain sensitivity in Zen meditators. Pain, 152(1), 150–156. https://doi.org/10.1016/j.pain.2010.10.006
Hanley, A. W., Mehling, W. E., & Garland, E. L. (2017). Holding the body in mind: Interoceptive awareness, dispositional mindfulness and psychological well-being. Journal of Psychosomatic Research, 99, 13–20. https://doi.org/10.1016/j.jpsychores.2017.05.014
Mehling, W E, Price, C., Daubenmier, J. J., Acree, M., & Bartmess, E. (2012). The Multidimensional Assessment of Interoceptive Awareness (MAIA). PLoS ONE, 7(11), 48230. https://doi.org/10.1371/journal.pone.0048230
Mehling, Wolf E., Price, C., Daubenmier, J. J., Acree, M., Bartmess, E., & Stewart, A. (2012). The Multidimensional Assessment of Interoceptive Awareness (MAIA). PLoS ONE, 7(11). https://doi.org/10.1371/journal.pone.0048230
Seth, A. K. (2013). Interoceptive inference, emotion, and the embodied self. Trends in Cognitive Sciences, 17(11), 565–573. https://doi.org/10.1016/j.tics.2013.09.007
-
 @ 39cc53c9:27168656
2025-04-09 07:59:35
@ 39cc53c9:27168656
2025-04-09 07:59:35The new website is finally live! I put in a lot of hard work over the past months on it. I'm proud to say that it's out now and it looks pretty cool, at least to me!
Why rewrite it all?
The old kycnot.me site was built using Python with Flask about two years ago. Since then, I've gained a lot more experience with Golang and coding in general. Trying to update that old codebase, which had a lot of design flaws, would have been a bad idea. It would have been like building on an unstable foundation.
That's why I made the decision to rewrite the entire application. Initially, I chose to use SvelteKit with JavaScript. I did manage to create a stable site that looked similar to the new one, but it required Jav aScript to work. As I kept coding, I started feeling like I was repeating "the Python mistake". I was writing the app in a language I wasn't very familiar with (just like when I was learning Python at that mom ent), and I wasn't happy with the code. It felt like spaghetti code all the time.
So, I made a complete U-turn and started over, this time using Golang. While I'm not as proficient in Golang as I am in Python now, I find it to be a very enjoyable language to code with. Most aof my recent pr ojects have been written in Golang, and I'm getting the hang of it. I tried to make the best decisions I could and structure the code as well as possible. Of course, there's still room for improvement, which I'll address in future updates.
Now I have a more maintainable website that can scale much better. It uses a real database instead of a JSON file like the old site, and I can add many more features. Since I chose to go with Golang, I mad e the "tradeoff" of not using JavaScript at all, so all the rendering load falls on the server. But I believe it's a tradeoff that's worth it.
What's new
- UI/UX - I've designed a new logo and color palette for kycnot.me. I think it looks pretty cool and cypherpunk. I am not a graphic designer, but I think I did a decent work and I put a lot of thinking on it to make it pleasant!
- Point system - The new point system provides more detailed information about the listings, and can be expanded to cover additional features across all services. Anyone can request a new point!
- ToS Scrapper: I've implemented a powerful automated terms-of-service scrapper that collects all the ToS pages from the listings. It saves you from the hassle of reading the ToS by listing the lines that are suspiciously related to KYC/AML practices. This is still in development and it will improve for sure, but it works pretty fine right now!
- Search bar - The new search bar allows you to easily filter services. It performs a full-text search on the Title, Description, Category, and Tags of all the services. Looking for VPN services? Just search for "vpn"!
- Transparency - To be more transparent, all discussions about services now take place publicly on GitLab. I won't be answering any e-mails (an auto-reply will prompt to write to the corresponding Gitlab issue). This ensures that all service-related matters are publicly accessible and recorded. Additionally, there's a real-time audits page that displays database changes.
- Listing Requests - I have upgraded the request system. The new form allows you to directly request services or points without any extra steps. In the future, I plan to enable requests for specific changes to parts of the website.
- Lightweight and fast - The new site is lighter and faster than its predecessor!
- Tor and I2P - At last! kycnot.me is now officially on Tor and I2P!
How?
This rewrite has been a labor of love, in the end, I've been working on this for more than 3 months now. I don't have a team, so I work by myself on my free time, but I find great joy in helping people on their private journey with cryptocurrencies. Making it easier for individuals to use cryptocurrencies without KYC is a goal I am proud of!
If you appreciate my work, you can support me through the methods listed here. Alternatively, feel free to send me an email with a kind message!
Technical details
All the code is written in Golang, the website makes use of the chi router for the routing part. I also make use of BigCache for caching database requests. There is 0 JavaScript, so all the rendering load falls on the server, this means it needed to be efficient enough to not drawn with a few users since the old site was reporting about 2M requests per month on average (note that this are not unique users).
The database is running with mariadb, using gorm as the ORM. This is more than enough for this project. I started working with an
sqlitedatabase, but I ended up migrating to mariadb since it works better with JSON.The scraper is using chromedp combined with a series of keywords, regex and other logic. It runs every 24h and scraps all the services. You can find the scraper code here.
The frontend is written using Golang Templates for the HTML, and TailwindCSS plus DaisyUI for the CSS classes framework. I also use some plain CSS, but it's minimal.
The requests forms is the only part of the project that requires JavaScript to be enabled. It is needed for parsing some from fields that are a bit complex and for the "captcha", which is a simple Proof of Work that runs on your browser, destinated to avoid spam. For this, I use mCaptcha.










