-
 @ 37c10448:f8256861
2025-04-22 07:44:10
@ 37c10448:f8256861
2025-04-22 07:44:10Title H1
Hello !
-
 @ b8af284d:f82c91dd
2025-04-22 07:28:03
@ b8af284d:f82c91dd
2025-04-22 07:28:03Kaiser: Es fehlt an Geld, nun gut, so schaff es denn,
Mephisto: Ich schaffe, was ihr wollt, und schaffe mehr;
Zwar ist es leicht, doch ist das Leichte schwer;
Es liegt schon da, doch um es zu erlangen, das ist die Kunst.
(Goethe: Faust II)
Liebe Abonnenten,
die meisten Medien sind nach wie vor damit beschäftigt, wie sie Trump am eindrücklichsten Wahnsinn unterstellen können. Sie vergessen dabei, worum es eigentlich geht: Ein Drittel aller amerikanischen Staatsschulden müssen dieses Jahr refinanziert werden. Sonst ist das mächtigste Land der Welt demnächst Pleite. Dafür müssen die Doppel-Defizite ausgeglichen, oder zumindest gesenkt werden. Und vor allem müssen die Zinsen runter. Die amerikanische Zentralbank wird den Wünschen der Regierung bald nachkommen, sprich die Zinsen senken und über ein neues Quantitative-Easing-Programm die Geldmenge erhöhen. Ein paar Jahre später werden die Effekte im Alltag über Inflation sichtbar.
Die Wahrscheinlichkeit ist hoch, dass wir bald Zeuge eines raffinierten Geld-Recycling-Programms werden. Wir treffen dabei auf einen alten Bekannten, den Stablecoin-Anbieter Tether. Der Essay ist keine leichte Kost, aber wer dabei bleibt, gelangt tief in die wundersame Welt der Geldvermehrung.
Mitte März wagt Paolo Ardoino den Schritt. Der Tether-CEO fliegt von der Hauptstadt El Salvadors nach New York. Es ist die erste Reise in die USA des erst 41-Jährigen seit Jahren. Zu hoch war bisher das Risiko gewesen, dort von den Behörden festgenommen zu werden. Vier Jahre zuvor war das Milliarden-Unternehmen, das er leitet, noch einmal davon gekommen: 2021 war Tether von der amerikanischen Börsenaufsicht mit einer Strafe von 41 Millionen US-Dollar belegt wegen ungenauer Angaben zu seinen Reserven. Man hatte sich schließlich auf einen Vergleich in Höhe von 18 Millionen Dollar geeinigt. Ein Witz, hatten Kritiker des Unternehmens entgegnet. Schließlich, so die Vorwürfe, ging es um Milliarden-Betrug. Seitdem hatten die Tether-Bosse die Vereinigten Staaten aus Vorsicht gemieden. Man war mal in Hongkong, auf den Bahamas und den Bermuda-Inseln, bis man sich Anfang des Jahres offiziell im Bitcoin-freundlichen El Salvador niedergelassen hatte. Doch mit der neuen US-Administration ist alles anders.
Nach New York geladen hat die Firma Cantor Fitzgerald. Thema des Gesprächs: Die Schaffung eines exklusiven Stablecoins für den amerikanischen Markt. Cantor Fitzgerald ist nicht irgendeine Bank oder Unternehmen. Das 1945 gegründete Investmenthaus ist einer von 24 Primärhändlern, die von der Federal Reserve Bank of New York autorisiert sind, US-Staatsanleihen zu handeln. Damit spielen sie eine zentrale Rolle im Finanzsystem der USA, da sie die Liquidität und Effizienz des Marktes für Staatsanleihen sicherstellen, dem wichtigsten und liquidisten Markt der Welt.
Langjähriger CEO von Cantor Fitzgerald war Howard Lutnick, ein Milliardär und seit Jahren enger Vertrauter der Trump-Familie. Da Lutnick mittlerweile US-Handelsminister ist, dürfte Ardoino nicht nur das Ok von ganz oben bekommen haben, in die Vereinigten Staaten einreisen zu dürfen. Man wird ihm wohl auch einen roten Teppich ausgerollt haben. Der Grund:
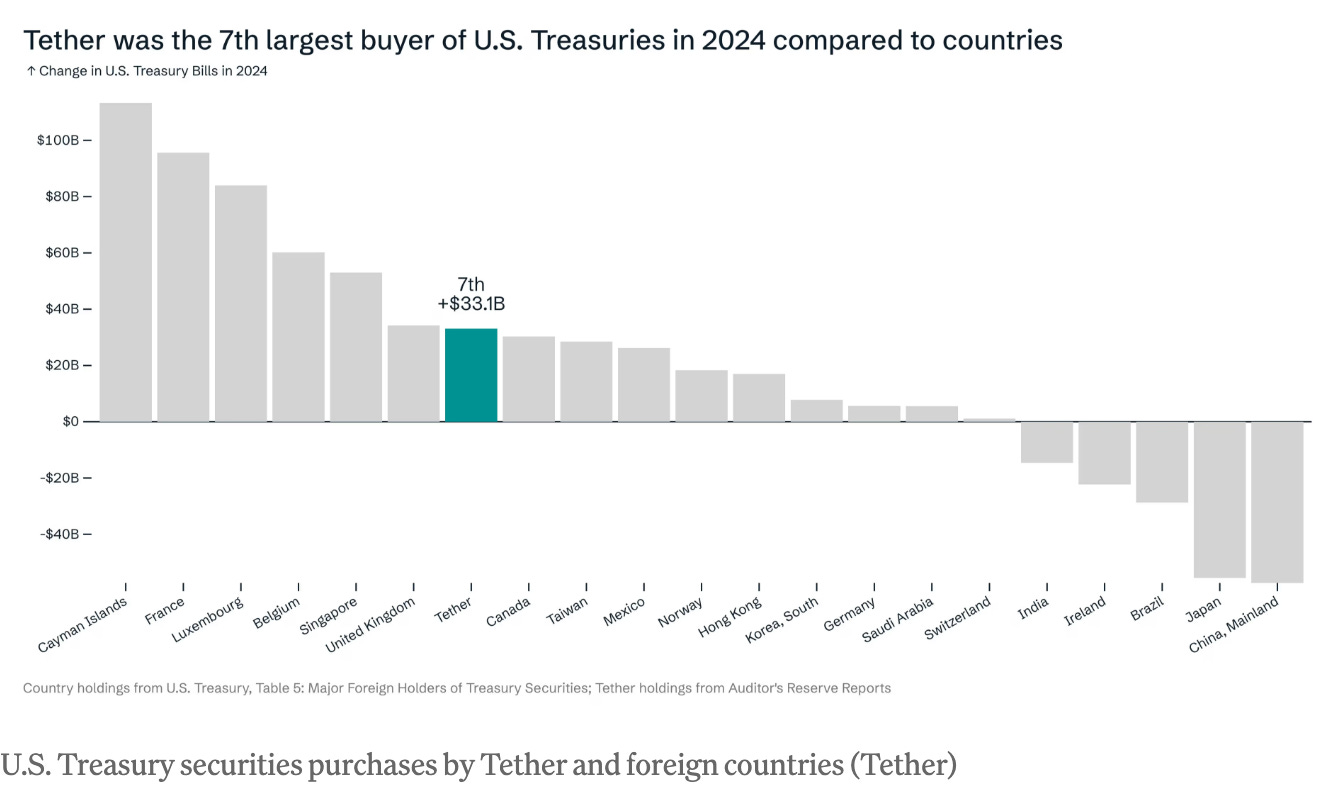
Die USA haben aktuell ein Problem mit ihrer Verschuldung. (BlingBling hat das in den Essays Die nächsten 90 Tage und Der Mar-a-Largo-Accord beschrieben). Rund ein Drittel des gesamten Schuldenbergs der USA müssen dieses Jahr refinanziert werden. Dafür müssen die Zinsen runter. Deswegen will Trump unbedingt das Handelsdefizit ausgleichen. Deswegen wird über die Neubewertung der Goldreserven nachgedacht. Und deswegen wird vermutlich bald eine neue Liquiditätswelle die Kurse von Bitcoin und Co auf neue Höchststände treiben. Denn bisher haben Staaten in solchen Phasen immer auf Geldentwertung gesetzt, um sich aus der Schuldenfalle zu befreien. Anders als Privatpersonen und viele kleinere Staaten können die USA immerhin die Währung selbst drucken, in der sie verschuldet sind. Die amerikanische Staatsverschuldung ist das Endgame. Und im Endgame spielt Tether mittlerweile eine ziemlich wichtige Rolle. Der Stablecoin-Anbieter hält mit 113 Milliarden aktuell mehr US-Staatsanleihen als Deutschland. Tendenz steigend: Ende 2024 war Tether mit 31 Milliarden der siebtgrößte Käufer von amerikanischen Staatsschulden.
Wie kann ein obskures Unternehmen, mit nicht einmal 100 Mitarbeitern, im vergangenen Jahr 13 Milliarden Dollar Gewinn machen, und zu einem der wichtigsten Kunden des amerikanischen Staats werden?
Weiter auf BlingBling - Die Geschichte eines der größten Geld-Recyclingprozesse der Welt.
-
 @ 53257040:b43c5005
2025-04-22 06:57:45
@ 53257040:b43c5005
2025-04-22 06:57:45السلام عليكم ورحمة الله وبركاته
حاليا كتب ابن القيم ببلاش على موقع google play books
كتُب بواسطة الإمام أبي عبدالله محمد بن أبي بكر بن أيوب ابن قيم الجوزية على Google Play بس عيب الكتب ذي بالذات انها بيجي معاها drm من أدوبي، ففي حل للموضوع ذا وله طريقة، بس قبل كذا بوريكم كيف "تصدرون" الكتب من الموقع لأننا بنحتاجها
- تروح لموقع جوجل بلاي للكتب
- بعد ما تضيف الكتب لحسابك تروح عند مكتبتك
- دوس على ال3 نقاط عند الكتاب اللي تبغاه
- تدوس على تصدير وتنزل ملف الacsm اللي بنحتاجه
طريقة ازالة الحماية: استخدام calibre مع الاضافات
- بتحتاج تطبيق calibre - E-book management على حاسوبك وتثبت عليها اضافتي DeDRM و DeACSM وتعيد تشغيل calibre
- تفتح calibre وتروح عند الاعدادت>الاضافات
- تبحث عن DeACSM وتأكد انك مثبتها
- تضغط مرتين عليها عشان يقتح
- تدوس على connect anonymous authorization
- بيجيك نافذة تحدد فيها نسخة ade، سيبها زي ما هي
- انتظر الين يعطيك رسالة انه نجح
- تدوس على ok ومن ثم تطبيق او apply
- يفضل تسوي اعادة تشغيل للبرنامج (ما ادري اذا هي مطلوبة)
- تسوي استيراد لملفات acsm وتنتظر الين يجيك الpdf ومبروك
-
 @ 2b24a1fa:17750f64
2025-04-22 06:57:36
@ 2b24a1fa:17750f64
2025-04-22 06:57:36Es fühlt sich wie ein Staatsstreich an. Vielleicht ist es auch einer. Ein abgewählter Bundestag genehmigt mittels Grundgesetzänderung die größte Staatsverschuldung in der Geschichte Deutschlands mit der unvorstellbaren Summe von 1000 Milliarden Euro, also eine Billion.
https://soundcloud.com/radiomuenchen/vom-schuldenstaatsstreich-zur-finanzdiktatur-von-rob-kenius?\ Jedem muss klar sein, wohin diese Gelder aus den Taschen der Steuerzahler wandern und wer, wenn in Rüstung, Militärhilfen, Konzern-Subventionen investiert wird, die Leidtragenden sind: Kinder, Rentner, kleine Firmen und Betriebe, sozial Schwache, Kranke, Arbeitslose, Obdachlose.
\ Die Kräfte aus Finanzeliten, Militär, Rüstungsindustrie, regierenden Parteien und den staatstragenden Medien werden dafür immer stärker.
\ Hören Sie den Beitrag „Vom Schuldenstaatsstreich zur Finanzdiktatur“ von Rob Kenius, der zunächst beim Overton-Magazin erschienen war: https://overton-magazin.de/top-story/vom-schuldenstaatsstreich-zur-finanzdiktatur-in-leicht-verstaendlicher-sprache/
Sprecherin: Sabrina Khalil
Redaktion: Jonny Rieder
Bild: Bund der Steuerzahler / Janek Werner
Rob Kenius betreibt die systemkritische Webseite kritlit.de und den Podcast 9min Denksport. Der Text Vom Schuldenstaatsstreich zur Finanzdiktatur ist davon die 14. Folge.
Radio München\ www.radiomuenchen.net/\ @radiomuenchen\ www.facebook.com/radiomuenchen\ www.instagram.com/radio_muenchen/\ twitter.com/RadioMuenchen\ odysee.com/@RadioMuenchen.net:9\ rumble.com/user/RadioMunchen
Radio München ist eine gemeinnützige Unternehmung.\ Wir freuen uns, wenn Sie unsere Arbeit unterstützen.
GLS-Bank\ IBAN: DE65 4306 0967 8217 9867 00\ BIC: GENODEM1GLS\ Bitcoin (BTC): bc1qqkrzed5vuvl82dggsyjgcjteylq5l58sz4s927\ Ethereum (ETH): 0xB9a49A0bda5FAc3F084D5257424E3e6fdD303482
-
 @ 4fa5d1c4:fd6c6e41
2025-04-22 06:46:28
@ 4fa5d1c4:fd6c6e41
2025-04-22 06:46:28Bibel-Selfies
Prompts
Eva, Schlange, Apfel und Adam

A selfie of a woman resembling eve in the time of old testament, blurred body, holding an apple, kneeling in front adam. he has a shocked expression with his mouth open and wide eyes, evoking a sense of both fear and surprise. The scene appears surreal, with a huge snake behind her. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of a scene with adam and eve, possibly at a place like garden eden. The style of the photo blends surrealism with humor, similar to the style of Yasir Khan Chaudha --v 6.0Tochter des Pharao mit Mose

A selfie of the biblical figure moabite woman with her baby in front of an oasis. She is wearing traditional and has black hair. The background shows water from the desert oasis and grasses around it. In the Background a wicker basket on the water. The photo was taken in the style of a selfie shot with GoPro cameraSimon Petrus

A selfie of a man resembling Simon Petrus, wearing a white robe, surrounded by waves and thunderstorm. He has a shocked expression with his mouth open and wide eyes, evoking a sense of both humor and surprise. The scene appears surreal, with many waves behind him. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of a scene with jesus at the dead sea, possibly at a place like the sea. The style of the photo blends surrealism with humor, similar to the style of Yasir Khan Chaudhary --v 6.0Zachäus auf dem Baum
A selfie of a man resembling a roman in the time of jesus, wearing a glamorous robe, surrounded by the crown of a tree. He has a shocked expression with his mouth open and wide eyes, evoking a sense of both humor and surprise. The scene appears surreal, with many leaves behind him. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of a scene with jesus walking by, possibly at a place like the jerusalem. The style of the photo blends surrealism with humor, similar to the style of Yasir Khan Chaudhary --v 6.0Maria am Ostermorgen

A selfie of a woman resembling maria in the time of jesus, wearing a robe, kneeling in front of stone grave. she has a shocked expression with her mouth open and wide eyes, evoking a sense of both fear and surprise. The scene appears surreal, with the open glowing grave behind her. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of a scene with jesus resurrection, possibly at a place like the jerusalem. The style of the photo blends surrealism with humor, similar to the style of Yasir Khan Chaudhary --v 6.0Der verlorene Sohn bei den Schweinen

A young ancient arabic man with short hair in the time of jesus, brown eyes, and a dirty face, covered in mud from working on his pig farm, takes an amateur selfie at dusk. He is surrounded by pig stables, with a barn visible in the background and pigs seen near the front. The photo captures a raw, authentic moment, as he gazes directly into the camera with an expression of excitement or wonder. The image has a realistic style, akin to Unsplash photography, and is meant to be posted on a primitive-themed social network. The resolution of the photo is high, style of selfie with gopro --v 6.0Vater und Sohn vereint
 A selfie of an Arab father in simple garments in the time of jesus, embracing and hugging a young man. The father's face, visible in the foreground, radiates joy and relief. Only the back of the son's head is visible, as he faces away from the camera, returning the embrace in tattered clothing. In the background, a large ancient house and other family members can be seen watching from a distance, blurred. The photo is taken with a wide-angle lens using a GoPro, enhancing the dramatic and overwhelming effect of the scene --v 6.0
A selfie of an Arab father in simple garments in the time of jesus, embracing and hugging a young man. The father's face, visible in the foreground, radiates joy and relief. Only the back of the son's head is visible, as he faces away from the camera, returning the embrace in tattered clothing. In the background, a large ancient house and other family members can be seen watching from a distance, blurred. The photo is taken with a wide-angle lens using a GoPro, enhancing the dramatic and overwhelming effect of the scene --v 6.0Bartimäus

A selfie of a man resembling blind bartimaeus in the time of jesus, black and brown and white bandages on his head over his eyes and face, wearing a robe, kneeling in front of a market place. he has a shocked expression with his mouth open and wide eyes still covered with black and brown and white bandages on his head, evoking a sense of both fear and surprise. The scene appears surreal, with many sand behind him. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of a scene with jesus healing the blind, possibly at a place like the jerusalem. The style of the photo blends surrealism with humor, similar to the style of Yasir Khan Chaudha --v 6.0Daniel in der Löwengrube

A selfie of a man resembling Jesus, wearing a beige hoodie, surrounded by lions and cheetahs. He has a shocked expression with his mouth open and wide eyes, evoking a sense of both humor and surprise. The scene appears surreal, with many lions behind him. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of a lion's den, possibly at a place like the Grand Tabahar. The style of the photo blends surrealism with humor, similar to the style of Yasir Khan ChaudharyDavid und Goliath

selfie of a the boy and shepherd david holding his slingshot resembling a fight with the giant goliath in the time of old testament, wearing a glamorous sligshot focusing on his giant opponent. David has a shocked expression with his mouth open and wide eyes, evoking a sense of both humor and surprise. The scene appears surreal, with a desert surrounding him. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of the scene of David fighting with the giant goliath with his slingshot, possibly at a place like the jerusalem. The style of the photo blends surrealism with humor, similar to the style of Yasir Khan Chaudhary --v 6.0Simson im Philistertempel

A selfie of a man resembling simson in the time of old testament, wearing a glamorous beard and long hair, surrounded by thousands of ancient fighters. He has a shocked expression with his mouth open and wide eyes, evoking a sense of both humor and surprise. The scene appears surreal, with a temple surrounding him. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of a scene with jesus walking by, possibly at a place like the jerusalem. The style of the photo blends surrealism with humor, similar to the style of Yasir Khan Chaudhary --v 6.0Jona und der Wal

A selfie of a man resembling israeli jona in the time of old testament,`wearing a glamorous beard and long hair, inside the body of a whale. He has a shocked expression with his mouth open and wide eyes, evoking a sense of both humor and surprise. The scene appears surreal, with the ocean surrounding him. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of a scene in the bible. The style of the photo blends surrealism with humor, similar to the style of Yasir Khan Chaudhary
Jakob und Isaak

A selfie of a young man resembling an ancient Arabic in clothes made of skins of goats and furs of the goats, looking overwhelmed and distressed as he betrays his father, who blesses him. The scene shows a dawn sky with hints of the sunrise, evoking a surreal and dramatic atmosphere. The scene is set in ancient Jerusalem, with stone buildings. in the background an old man with a gesture of blessing, rising his hands to the sky, The photo is taken with a wide-angle lens, blending surrealism with humor. The style is reminiscent of a GoPro selfie, capturing the intense moment with a sense of both fear and surprisePetrus und der Hahn

A selfie of a man resembling ancient young arabic man saint in traditional biblical attire, being eaten by a whale,. he has a shocked expression with his mouth pressed and wide eyes, evoking a sense of both fear and surprise. The scene appears surreal, with one rooster crowing out loud behind the man. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of a scene with peter and the rooster, possibly at a place in jerusalem . The style of the photo blends surrealism with humor, go pro selfie, morning dawn near sunrise settingJosef im Brunnen

A selfie of an ancient israelian man with a magical dreamcoat clothing in a deep well, looking at the camera from above, captured in the style of a go pro selfie stickElia und die Raben

A close-up selfie of a bearded man (Elijah) in biblical clothing, smiling gratefully. He is standing near a stream in a secluded, rocky area. Several black ravens are perched on his shoulders and arms, holding pieces of bread and meat in their beaks. The scene has a warm, golden light, symbolizing God's provision. Photorealistic style, high detail.Absalom im Baum

A selfie of a man resembling of a young man (Absalom) with long hair knotted arount the branches of a large oak tree.. He has a shocked expression with his mouth open and wide eyes, evoking a sense of both humor and surprise. The scene appears surreal, with all of his hairs knotted around the tree. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of a scene of a robin hood movie in the forest . The style of the photo blends surrealism with humorRuth und Boas im Weizenfeld

A selfie of a young woman resembling Ruth, with a radiant smile and sun-kissed skin. She's standing in a golden wheat field at sunset, her arms filled with freshly gathered sheaves of wheat. Her hair is partially covered with a simple headscarf, with loose strands blowing in the wind. She has a look of joy and gratitude in her eyes. The scene appears idyllic, with wheat stalks seeming to embrace her. In the background, a distinguished older man (Boaz) can be seen watching from a distance, his expression a mix of curiosity and admiration. The photo is taken with a wide-angle lens, capturing the vastness of the field, the warmth of the setting sun, and Boaz in the distance. The setting is reminiscent of a biblical harvest scene. The style of the photo blends realism with a touch of romantic nostalgia."Bibel-Selfies" von Jörg Lohrer Lizenz: CC0 1.0
.
`
-
 @ da0b9bc3:4e30a4a9
2025-04-22 06:44:40
@ da0b9bc3:4e30a4a9
2025-04-22 06:44:40Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/952743
-
 @ d34e832d:383f78d0
2025-04-22 06:43:30
@ d34e832d:383f78d0
2025-04-22 06:43:30It is noteworthy to mention that Bill Gates, a distinguished co-founder of Microsoft and a philanthropist with extensive impact on global health and education initiatives, serves as a limited partner in various investment vehicles associated with Village Global. However, it is critical to delineate the nuances of this relationship, as Gates' status as a limited partner does not confer upon him any authoritative control or decision-making power regarding the operational protocols or strategic direction of SimpleX Chat.
The development team behind SimpleX Chat has made a concerted effort to clarify that Village Global's involvement is strictly financial in nature, devoid of any operational oversight or influence over the management and technical development of the project.
Privacy Without Compromise
SimpleX Chat aims to provide a messenger that is both convenient and private, addressing the perceived trade-off between these two qualities in existing solutions. They define privacy as protecting not only message content but also metadata like connection details and user identities.
In contrast to a multitude of contemporary messaging applications, SimpleX Chat distinctly emphasizes the safeguarding of metadata privacy as a foundational component of its architecture.
The development team articulates a compelling argument regarding the intrinsic value of communication relationships, suggesting that the identification of interlocutors constitutes sensitive data that may be weaponized against users in various contexts—an issue that current market leaders in the domain have failed to remedy with sufficient rigor.
Consequently, the developers are actively engaged in initiatives to bolster the obfuscation of users’ IP addresses, thereby enhancing the overall security framework against potential surveillance and data exploitation threats.
A Radical Architectural Shift
The architecture underpinning SimpleX Chat diverges notably from conventional paradigms associated with user account management.
Specifically, it eschews the creation and maintenance of user profiles in the traditional sense, thereby negating the repository of personally identifiable information on centralized servers. Instead, all pertinent data transactions pertinent to user interactions are localized, existing solely on the end-user's devices.
This paradigm shift engenders a formidable barrier to data accessibility, effectively neutralizing the potential for data disclosure to law enforcement agencies, irrespective of judicial mandates such as court warrants.
Furthermore, in their adherence to statutory obligations, SimpleX Chat's design ethos proactively prioritizes the minimization of data collection, establishing a privacy-centric framework that aptly aligns with contemporary concerns regarding data sovereignty and user anonymity.
Functionality Grounded in Security
The SimpleX Chat application exemplifies a multi-device compatibility framework, strategically prioritizing stringent security protocols over user convenience.
This methodology distinctly contrasts with that of various competitors who may opt for convenience-focused functionalities that inadvertently jeopardize user data integrity and confidentiality.
The current technical architecture facilitates seamless profile transfers across devices, while also enabling a desktop terminal interface that remains operationally tethered to the mobile device.
Such an arrangement underscores SimpleX Chat's commitment to balancing usability with robust security measures, effectively mitigating potential vulnerabilities in cross-platform interactions.
Transient Messaging and Signal Protocol Reimagined
SimpleX Chat integrates the functionality of transient messaging, which serves primarily as a user convenience element rather than representing a robust security mechanism.
The developers have explicitly articulated that they are unable to ensure the irreversible deletion of messages from the recipient's device, thereby highlighting potential vulnerabilities associated with data retention and privacy concerns in digital communications.
The development team arrived at a strategic decision to forgo the utilization of the existing Signal codebase, primarily attributed to its inherent complexity and the prospective risks associated with the coupling dynamics that could emerge between the Signal protocol and its corresponding system architecture.
As a result, they opted to engineer the Signal protocol anew, commencing from foundational coding principles.
This approach not only enables them to exert comprehensive control over the implementation but also significantly facilitates the seamless integration of advanced cryptographic frameworks, specifically post-quantum key agreement methodologies, which are imperative in future-proofing cryptographic communications against the advent of quantum computing threats.
UX Development and the Road Ahead
The UI is still under development. The developers acknowledge some usability challenges, especially for users unfamiliar with the concept of profile-based messaging without traditional accounts.
They are actively working on improving UX based on user feedback.
A Decentralized Economic Model
SimpleX Chat is poised to introduce an innovative commercial framework predicated on the integration of a decentralized accounting mechanism, characterized by the utilization of distributed ledger technology, which underpins cryptocurrency transactions, coupled with a system reminiscent of traditional gift card paradigms.
This commercial model is strategically designed to provide economic incentives to both infrastructure operators, who maintain the necessary backbone for the network's operations, and software vendors, who contribute essential applications and services—all while preserving the fundamental decentralized architecture inherent to blockchain systems.
This careful balance is crucial for fostering a sustainable ecosystem that rewards participants without compromising the network's core principles of transparency and egalitarian access.
🚧 Prerequisites
| Requirement | Description | |-------------------|----------------------------------------------| | VPS | Debian 12, at least 1GB RAM (for running server) | | Build Machine | A second Linux machine with ≥ 8GB RAM for compiling binaries | | Domains | FQDNs like
smp.yourdomain.com,xfp.yourdomain.com,turn.yourdomain.com| | SSH Keys | SSH access secured with key-based auth only | | Firewall | Only allow ports for SSH (22), SMP (5223), XFP (5353), TURN (5349) |
🧱 Step 1: Build SimpleX on Build Machine
You’ll compile the binaries on your high-RAM machine and then SCP them over.
```bash sudo apt update && sudo apt install build-essential git rustc cargo pkg-config libssl-dev
Clone repo
git clone https://github.com/simplex-chat/simplexmq cd simplexmq
Build binaries
cargo build --release ```
You’ll find: -
target/release/smp-server-target/release/xfp-serverCopy them to your VPS:
bash scp target/release/smp-server user@vps:/home/user/ scp target/release/xfp-server user@vps:/home/user/
🧑💻 Step 2: Harden the VPS
🔒 SSH-only access
```bash
Edit /etc/ssh/sshd_config
PermitRootLogin no PasswordAuthentication no ```
Restart SSH:
bash sudo systemctl restart ssh🔥 UFW Firewall
bash sudo apt install ufw sudo ufw default deny incoming sudo ufw default allow outgoing sudo ufw allow OpenSSH sudo ufw enable🛡️ Fail2ban
bash sudo apt install fail2ban sudo systemctl enable --now fail2ban
📡 Step 3: SMP Server Setup
Create user and directories:
bash sudo useradd -m -r -s /usr/sbin/nologin smp sudo mkdir -p /var/lib/smp /var/log/smp sudo chown -R smp:smp /var/lib/smp /var/log/smpMove binary and set permissions:
bash sudo mv /home/user/smp-server /usr/local/bin/ sudo chmod +x /usr/local/bin/smp-serverCreate systemd service:
/etc/systemd/system/smp.service```ini [Unit] Description=SimpleX SMP Server After=network.target[Service] User=smp ExecStart=/usr/local/bin/smp-server --fqdn smp.yourdomain.com --log /var/log/smp/smp.log WorkingDirectory=/var/lib/smp Restart=on-failure
[Install] WantedBy=multi-user.target ```
bash sudo systemctl daemon-reexec sudo systemctl enable --now smp.service
🗂️ Step 4: XFP Server Setup
bash sudo useradd -m -r -s /usr/sbin/nologin xfp sudo mkdir -p /var/lib/xfp /var/log/xfp sudo chown -R xfp:xfp /var/lib/xfp /var/log/xfp sudo mv /home/user/xfp-server /usr/local/bin/ sudo chmod +x /usr/local/bin/xfp-serverCreate systemd service:
/etc/systemd/system/xfp.service```ini [Unit] Description=SimpleX XFP Server After=network.target[Service] User=xfp ExecStart=/usr/local/bin/xfp-server --storage /var/lib/xfp --log /var/log/xfp/xfp.log --quota 2GB WorkingDirectory=/var/lib/xfp Restart=on-failure
[Install] WantedBy=multi-user.target ```
bash sudo systemctl daemon-reexec sudo systemctl enable --now xfp.service
🎙️ Step 5: Optional TURN Server (WebRTC)
Install Coturn:
bash sudo apt install coturnEdit
/etc/turnserver.conf:ini listening-port=5349 tls-listening-port=5349 fingerprint lt-cred-mech realm=turn.yourdomain.com user=someuser:somepassword cert=/etc/letsencrypt/live/turn.yourdomain.com/fullchain.pem pkey=/etc/letsencrypt/live/turn.yourdomain.com/privkey.pem cipher-list="ECDHE-RSA-AES256-GCM-SHA384" no-stdout-logSet to auto-start:
bash sudo systemctl enable coturnConfigure DNS and firewall to allow 5349.
🔁 Step 6: Certificate Renewal (Let's Encrypt)
bash sudo apt install certbotSet up renewal cron:
bash sudo crontab -ebash 0 3 * * * certbot renew --quiet && systemctl restart coturn
🧪 Step 7: Testing with SimpleX Desktop
- Download SimpleX Desktop
- Launch and go to Settings → Relay Settings
- Disable defaults, add your SMP and XFP addresses.
🔄 Upgrading SimpleX
On your build machine:
bash git pull origin main cargo build --releaseThen:
bash scp target/release/smp-server user@vps:/home/user/ scp target/release/xfp-server user@vps:/home/user/On VPS:
bash sudo systemctl stop smp xfp sudo mv /home/user/smp-server /usr/local/bin/ sudo mv /home/user/xfp-server /usr/local/bin/ sudo systemctl start smp xfp
What if you communicated securely?
📡 SimpleX – Anonymous chat, no phone numbers, no metadata
SimpleX is unlike anything else. It doesn’t just encrypt your messages—it hides who you're talking to. No central servers, no profiles, no traces. Just pure private messaging.
Perfect for when you need total metadata privacy and no digital fingerprint.
🌱 Nostr DMs – Messages with your Web of Trust
If you’re already on Nostr, using DMs is a natural step. Messages are encrypted end-to-end and tied to your public key identity.
Great for building trusted, decentralized communication channels within your Web of Trust.
🔐 PGP Email – Old-school but rock solid
PGP lets you encrypt your emails and verify identities with public keys. It’s still one of the most powerful tools for asynchronous, verifiable, and encrypted communication—especially for long-form or professional exchanges.
🔁 Use them all together
Different tools for different roles. Want to talk anonymously? Use SimpleX.
Connecting with your Nostr tribe? Slide into those DMs.
Need to send a secure file or message over email? PGP's got your back.Privacy isn’t just one app—it’s a toolkit. Build yours.
-
 @ 92f1335f:2c8220d1
2025-04-22 05:38:24
@ 92f1335f:2c8220d1
2025-04-22 05:38:24The Quiet Hold (2020)
As 2020 dawned, Jonathan kept his Bitcoin purchase a secret. He didn’t tell his parents, or his coworkers—not even his best friend, Sam. He wasn’t in it for hype. He believed in the tech.
Then came March 2020. The pandemic hit. Markets crashed. Panic spread.
Bitcoin dropped below $4,000.
Jonathan’s hands trembled as he stared at the red numbers on his screen. But instead of selling, he doubled down. He scraped together another $1,000 and bought the dip.
Weeks turned into months. People lost jobs, businesses closed, and the economy floundered. But Bitcoin began recovering—slowly at first, then with growing momentum By December, it hit $29,000.
Jonathan’s half Bitcoin? Worth over $14,000.
He smiled for the first time in weeks.
-
 @ 9c9d2765:16f8c2c2
2025-04-22 05:30:03
@ 9c9d2765:16f8c2c2
2025-04-22 05:30:03CHAPTER NINE
"I hope you all see that I keep my promises," Mark announced confidently, raising his glass as the Ray family members murmured among themselves. "Another gift for the family, and all I ask in return is Rita’s hand. It’s a simple trade, isn’t it?"
It was the Ray family fun weekend, and Mark had once again positioned himself as their savior. He had been invited, and as expected, he made sure to make his presence known. The Ray family wasn’t happy that the new president had canceled the investment plans, which were against their initial arrangements. They had pinned their hopes on Mark, and once again, he didn’t disappoint.
At the end of the evening, Mark handed over another generous gift of cash, sealing his influence within the family. "You all know what needs to be done," he continued, flashing a smug smile. "Rita divorces James, and I’ll continue to help the family business thrive."
The murmurs grew louder. The push for divorce within the Ray family gained momentum, and James could feel the weight of humiliation pressing down on him once again. Yet, amidst the pressure and manipulation, Rita remained firm.
"I’m not divorcing James," she declared, her voice unwavering despite the glares she received from her own family. "Not now, not ever."
A heavy silence fell over the room, but James knew this was far from over.
"You! Throw him out!" Mark barked, pointing a commanding finger at James as he entered the gathering. The Ray family fun night was in full swing, and Mark, feeling emboldened by the power he had secured within the family, was eager to humiliate James once and for all.
The private guard, a broad-shouldered man dressed in a sleek black uniform, stepped forward. But as soon as his gaze met James’s, his stern expression softened. He hesitated, his posture shifting from aggression to submission. Then, to the shock of everyone present, he bent slightly at the waist and uttered a quiet but firm apology.
"I’m sorry, sir. I cannot do that," the guard said, his voice steady yet respectful.
Mark’s eyes widened in disbelief. “What? Are you insane? I said, throw him out!” he roared, his face twisting in fury.
The guard, still standing between Mark and James, clenched his fists at his sides. “I work part-time at JP Company. I know who this man is. I cannot lay a hand on him.”
A murmur rippled through the room. Helen, Christopher, and the rest of the Ray family exchanged puzzled glances. Why would a mere security guard refuse an order so boldly? What did he mean by knowing James?
Mark’s frustration boiled over. He took a threatening step forward. “Then you’re fired! Get out!” he spat, his voice thick with rage.
The guard stood his ground, his eyes flicking briefly to James, who remained calm, his expression unreadable. With a respectful nod to James, the guard turned on his heel and exited, his departure leaving an unsettling silence in his wake.
Helen, unable to contain her curiosity, leaned toward Christopher. “What just happened? Why would he refuse Mark’s order? What does he know about James that we don’t?”
Christopher shook his head, his brow furrowed in confusion. “I have no idea. But that was not just any ordinary security guard. He spoke as if James was someone important.”
Susan, who had been quietly observing the scene, finally spoke. “Could it be that James has some hidden power we don’t know about?”
Helen scoffed. “Ridiculous! That beggar? He’s nothing but a burden!” But despite her words, an uneasy feeling settled in her stomach.
Mark, still seething, turned his glare to James. “Enjoy this moment, you wretch. Soon, you’ll have nowhere left to run.” He stormed out, leaving a tense and confused silence behind.
James remained where he was, his calm demeanor never wavering. He had stood his ground without even speaking a word, and yet, the Ray family’s perception of him was beginning to shift. There were too many unanswered questions. Why did a security guard from JP Company recognize him? Why did he refuse to act against him? And most importantly who was James, really?.
"We can't let this business week slip through our fingers," Helen muttered anxiously, pacing back and forth in the living room. "Christopher, Robert, one of you must represent Ray Enterprises. We need to secure more investments."
Christopher sighed, rubbing his temples. "Helen, we are aware of how important this meeting is. But are you sure you should attend with me? You know these investors expect to meet actual executives."
"I have every right to be there," Helen snapped. "The future of this family business is at stake! If you won't do it, I'll step in to make sure we don't lose more ground."
Meanwhile, across the city, James stepped into the most luxurious boutique, scanning the racks of high-end suits. The store clerk eyed him skeptically, unimpressed by his simple attire. "Sir, are you sure you’re in the right place?" the clerk asked with a forced smile.
James smirked. "Yes. Get me the best suit you have."
After a long selection process, he emerged wearing a custom-tailored suit worth a fortune, making even the store owner widen his eyes in disbelief. James checked his reflection in the mirror, adjusting his cuffs. "Perfect," he murmured.
The day of the business meeting arrived, and the grand hall was filled with top executives, investors, and company representatives from across the city. The chatter in the hall buzzed with anticipation as they awaited the arrival of JP Enterprises' new president.
Helen sat rigidly beside Christopher, her fingers tapping nervously on the table. "I wonder who JP Enterprises will send. Their investments have been making waves lately," she whispered.
Before Christopher could respond, a hush fell over the crowd. The doors swung open, and the awaited president stepped in, his presence commanding immediate attention.
-
 @ 9f8b9baa:b922fc09
2025-04-22 04:55:30
@ 9f8b9baa:b922fc09
2025-04-22 04:55:308KI là một nền tảng giải trí trực tuyến nổi bật, mang đến cho người dùng những trải nghiệm đa dạng và thú vị. Với giao diện dễ sử dụng và thiết kế tối giản, 8KI giúp người chơi dễ dàng tiếp cận và thưởng thức các trò chơi yêu thích. Nền tảng này không chỉ cung cấp các trò chơi giải trí mà còn có các tính năng tương tác độc đáo, tạo ra không gian thú vị để người dùng khám phá và tận hưởng. Dù bạn là người mới hay đã có kinh nghiệm, 8KI luôn mang đến những hoạt động đa dạng, từ các trò chơi giải trí nhẹ nhàng đến những thử thách cần kỹ năng cao. Hệ thống cập nhật thường xuyên giúp nền tảng luôn giữ được sự mới mẻ và thu hút, khiến người dùng không bao giờ cảm thấy nhàm chán.
Một trong những điểm mạnh của 8KI là khả năng tùy chỉnh trải nghiệm người dùng, mang đến sự linh hoạt tối đa cho mọi người tham gia. Người chơi có thể điều chỉnh các thiết lập theo sở thích cá nhân, từ việc thay đổi độ khó cho đến lựa chọn các chế độ chơi khác nhau. Điều này giúp người dùng cảm thấy thoải mái hơn khi tham gia, đồng thời cũng tạo ra những thử thách mới mẻ để không ngừng phát triển kỹ năng. Hệ thống này giúp 8KI trở thành một nền tảng phù hợp cho mọi đối tượng, từ những người mới bắt đầu cho đến những người chơi kỳ cựu. Mỗi người dùng có thể tìm thấy một kiểu chơi phù hợp với sở thích của mình, mang lại một trải nghiệm cá nhân hóa và thú vị. Khả năng điều chỉnh này tạo ra sự khác biệt, giúp người dùng không chỉ giải trí mà còn nâng cao khả năng của bản thân qua từng trò chơi.
Không chỉ dừng lại ở việc cung cấp những trò chơi hấp dẫn, 8KI còn tạo ra một cộng đồng mạnh mẽ, nơi người chơi có thể giao lưu, chia sẻ kinh nghiệm và kết nối với nhau. Các tính năng xã hội như bảng xếp hạng, diễn đàn và các cuộc thi định kỳ tạo ra cơ hội để người dùng tương tác và phát triển mối quan hệ với những người chơi khác. Cộng đồng 8KI không chỉ đơn thuần là một không gian giải trí mà còn là nơi để những người cùng sở thích có thể chia sẻ những câu chuyện, chiến lược và học hỏi từ nhau. Điều này làm tăng thêm giá trị của nền tảng, giúp người chơi không chỉ tận hưởng các trò chơi mà còn xây dựng được các mối quan hệ bền vững. Sự kiện và chương trình khuyến mãi thú vị cũng thường xuyên được tổ chức, giúp cộng đồng 8KI luôn sôi động và thu hút người tham gia. Với môi trường thân thiện và tính năng tương tác mạnh mẽ, 8KI đã và đang trở thành một điểm đến giải trí lý tưởng cho những ai yêu thích sự kết nối và sáng tạo.
-
 @ 9f8b9baa:b922fc09
2025-04-22 04:54:38
@ 9f8b9baa:b922fc09
2025-04-22 04:54:38MM99 là một nền tảng giải trí trực tuyến nổi bật, cung cấp cho người dùng một không gian đa dạng để thưởng thức các trò chơi và hoạt động giải trí. Với giao diện dễ sử dụng và thiết kế trực quan, MM99 tạo ra một trải nghiệm liền mạch và dễ tiếp cận cho tất cả người dùng. Nền tảng này không chỉ thu hút với kho nội dung phong phú mà còn đem đến những cập nhật liên tục, giúp người chơi không bao giờ cảm thấy nhàm chán. MM99 đặc biệt chú trọng vào việc cung cấp các trò chơi đa dạng, từ những trò chơi mang tính thử thách cao cho đến các hoạt động giải trí nhẹ nhàng, đáp ứng được nhu cầu của mọi người dùng. Với mỗi lần tham gia, người chơi luôn có thể tìm thấy những trải nghiệm mới mẻ và hấp dẫn, giúp họ thư giãn và giải trí sau những giờ làm việc căng thẳng.
Điều khiến MM99 trở nên đặc biệt chính là khả năng tùy chỉnh trải nghiệm của người dùng. Nền tảng này cho phép mỗi người chơi điều chỉnh các thiết lập trò chơi theo sở thích và nhu cầu cá nhân, giúp mang lại cảm giác thoải mái và dễ dàng kiểm soát. Người dùng có thể thay đổi mức độ khó, lựa chọn các chế độ chơi khác nhau và thậm chí thay đổi các yếu tố giao diện sao cho phù hợp nhất với mình. Sự linh hoạt này giúp MM99 luôn duy trì sự hấp dẫn và tạo ra một trải nghiệm giải trí cá nhân hóa cho từng người dùng. Đặc biệt, MM99 không chỉ phù hợp với những người chơi mới mà còn là lựa chọn lý tưởng cho những ai yêu thích thử thách và khám phá các chiến lược mới. Tính năng tùy chỉnh giúp người chơi dễ dàng tham gia và luôn cảm thấy hào hứng mỗi khi quay lại nền tảng này.
Bên cạnh việc cung cấp một loạt các trò chơi thú vị, MM99 còn chú trọng đến việc xây dựng một cộng đồng gắn kết và tương tác. Các tính năng xã hội như bảng xếp hạng, diễn đàn trò chuyện và các sự kiện đặc biệt giúp người chơi có cơ hội giao lưu, học hỏi và kết bạn với những người cùng sở thích. MM99 đã tạo ra một môi trường nơi người dùng không chỉ tham gia vào các trò chơi mà còn có thể kết nối và chia sẻ những trải nghiệm của mình. Những cuộc thi và sự kiện thường xuyên được tổ chức, tạo ra một không khí sôi động và đầy thử thách, thúc đẩy người chơi quay lại để tham gia và cải thiện kỹ năng. Cộng đồng MM99 ngày càng trở nên mạnh mẽ và đoàn kết, là yếu tố quan trọng giúp nền tảng này phát triển và duy trì sự hấp dẫn trong mắt người dùng. MM99 không chỉ là một nơi để giải trí mà còn là một không gian giao lưu tuyệt vời cho những ai muốn tìm kiếm niềm vui và kết nối với những người có cùng đam mê.
-
 @ 9f8b9baa:b922fc09
2025-04-22 04:53:45
@ 9f8b9baa:b922fc09
2025-04-22 04:53:4532Win là một nền tảng giải trí trực tuyến sáng tạo, mang đến cho người dùng một loạt các hoạt động và trải nghiệm đa dạng. Với giao diện dễ sử dụng và thiết kế trực quan, 32Win giúp người dùng dễ dàng tham gia và tận hưởng những phút giây giải trí thú vị. Nền tảng này nổi bật với khả năng cung cấp các nội dung luôn mới mẻ và đa dạng, từ các trò chơi đầy thử thách cho đến những hoạt động mang tính giải trí cao. Dù bạn là người mới hay đã có kinh nghiệm, 32Win luôn có thể đáp ứng nhu cầu của tất cả mọi người. Hệ thống của nền tảng này liên tục được cập nhật và đổi mới, đảm bảo mang lại những trải nghiệm giải trí chất lượng và không bao giờ nhàm chán. Các hoạt động thú vị và tính năng độc đáo của 32Win chính là điểm thu hút chính, khiến người dùng luôn muốn quay lại để khám phá thêm nhiều điều mới mẻ.
Sự thành công của 32WIN không chỉ đến từ sự đa dạng của các trò chơi mà còn từ khả năng cá nhân hóa cao. Nền tảng này cho phép người dùng điều chỉnh các thiết lập theo sở thích riêng, từ việc thay đổi mức độ khó, chọn chủ đề yêu thích cho đến lựa chọn các chế độ chơi khác nhau. Điều này giúp người dùng có thể tạo ra một trải nghiệm hoàn toàn phù hợp với nhu cầu và sở thích cá nhân. Bằng cách này, 32Win mang lại sự linh hoạt tối đa, đảm bảo rằng mỗi người dùng có thể tìm được niềm vui và sự thách thức ở mức độ phù hợp nhất với mình. Hệ thống cài đặt cá nhân hóa không chỉ giúp nâng cao trải nghiệm mà còn giúp người dùng cảm thấy thoải mái và hài lòng trong suốt quá trình tham gia. 32Win luôn chú trọng đến sự hài lòng của người dùng và cam kết mang lại những dịch vụ giải trí tốt nhất.
Một điểm đáng chú ý nữa của 32Win là cộng đồng người dùng sôi động và thân thiện. Nền tảng này không chỉ cung cấp các trò chơi mà còn tạo ra một môi trường nơi mọi người có thể giao lưu, kết nối và chia sẻ kinh nghiệm. Các tính năng như bảng xếp hạng, diễn đàn thảo luận và các cuộc thi giữa người chơi không chỉ tăng cường tính tương tác mà còn tạo ra một không gian gắn kết, nơi người dùng có thể học hỏi và hỗ trợ lẫn nhau. Cộng đồng mạnh mẽ của 32Win là một yếu tố quan trọng trong việc xây dựng một môi trường giải trí lành mạnh và thú vị. Thêm vào đó, các sự kiện đặc biệt và các chương trình khuyến mãi hấp dẫn thường xuyên được tổ chức, giúp giữ cho người dùng luôn có động lực quay lại và tham gia. Với những tính năng này, 32Win không chỉ là một nền tảng giải trí, mà còn là một nơi để mọi người có thể kết nối, tạo dựng mối quan hệ và tận hưởng thời gian bên nhau.
-
 @ f6488c62:c929299d
2025-04-22 04:04:18
@ f6488c62:c929299d
2025-04-22 04:04:18วันนี้ตลาดโลก “เดือดแบบเงียบ ๆ” แม้ทรัมป์จะยังไม่พูดอะไร แต่สินทรัพย์เสี่ยงกลับพลิกเกมกันคนละทาง โดยเฉพาะฝั่งทองคำและคริปโตที่มีสัญญาณบวกหลายจุด ⚡
🟡 ไฮไลต์ร้อนวันนี้ 🪙 ทองคำพุ่งทะลุ $3,510/oz (ตามราคา PAXG) → นักลงทุนวิ่งเข้าทองแบบ Panic Buy ท่ามกลางความไม่แน่นอนทางเศรษฐกิจโลก 🪙 Bitcoin มั่นคงจากแรงซื้อของ BlackRock & MicroStrategy รวมกันเกือบ $640M → โทนตลาดยังเอียงฝั่งบวก 🪙 Paul Atkins ผู้สนับสนุนคริปโต ขึ้นแท่นประธาน SEC → อาจพลิกเกมกฎระเบียบในสหรัฐฯ ไปอีกฝั่ง 🪙 Coinbase เปิดฟิวเจอร์ส XRP / สิงคโปร์เปิด Bitcoin Futures กลางปีนี้ → แสดงถึงสัญญาณยอมรับระดับโลก
🔻 ฝั่งน่าห่วง ⚠️ Ethereum ETF ถูกถอนทุน $1.1B ใน 7 สัปดาห์ → แสดงความลังเลของนักลงทุนสถาบัน ⚠️ ตลาดยังหวาดระแวง หลัง "ภาษีวันปลดปล่อย" ของทรัมป์และการโจมตี Fed → ทรัมป์เงียบ = ตลาดระวัง ⚠️ หุ้นสหรัฐแกว่งแรง → นักลงทุนย้ายเงินเข้าทอง-คริปโตเพื่อหาที่พักพิง
📌 กลยุทธ์วันนี้:
"ทองไม่ใช่แค่ Safe Haven แต่ตอนนี้คือทางหนี" นักลงทุนเริ่มขยับพอร์ตหนีจากตลาดหุ้น เข้าทองและคริปโต → ระวังแรงกระเพื่อมรอบดึก (โดยเฉพาะจากฝั่งสหรัฐฯ)
📎 ฝากแชร์โพสต์นี้ไว้ดูอีกที ถ้าคุณคิดว่า “ปี 2025 น่าจะผันผวนที่สุดในรอบ 10 ปี”
ทองคำ #Bitcoin #ข่าวการเงิน #Crypto #ตลาดโลก #เฟด #ทรัมป์ #ทองขึ้น #ลงทุนทอง
-
 @ 3c389c8f:7a2eff7f
2025-04-22 02:53:41
@ 3c389c8f:7a2eff7f
2025-04-22 02:53:41Unlike traditional online databases, Nostr relays do not gather mass amounts of information like giant, corporate owned servers. Nor do they function like the smaller, yet segregated servers that many other social protocols have been designed to incorporate. Information on the Nostr network is spread across thousands of relays, and organized in multiple ways. These relays are run by individuals, organizations & companies alike. They vary in size, capacity, content, user numbers, and geographical location. While most Nostr notes (and other stuff) are spread across multiple relays, this also makes the searching for specific things a little different than "googling" a term. Looking for different things, like searching for a person vs a specific term, is best achieved by using different tools. Decentralization of the data also means decentralization of the ways that we engage with it. None of this is difficult, its just different.
People Search:
Searching for person on Nostr is super simple, and you have multiple approaches that you can use. Many clients offer profile search directly within their interface. You can search by name, NIP-05 identifier, and npub or any of its various formats. When searching by name, it is good practice to visit the user's profile and verify that it is the account that you are looking for to avoid being duped by a scammer or copycat.
If your preferred client offers precision relay controls, you can connect to a relay that specializes in indexing user profiles for better results. These relays host the pertinent information housed in your nprofile, which makes it possible for users to find each other's notes.
If your favorite Nostr client doesn't have an in-app search feature, or you are simply not finding satisfactory results, tools like npub.world offer powerful, independent profile searches. Utilizing AI and indexing similar to Pagerank to sift out scammers, spammers, and bots, you are sure to find the npub you are seeking. These services may be incorporated within some clients that leverage the interoperability of Nostr.
Note Search:
For when you want to look up something that you have already seen, there are a ton of note search tools that all offer different functionality. Some allow to search by author and time frame, others search by event ID (which also goes by many names, i.e. note ID, Nostr link, naddr, nevent). All of these search tools vary in performance, based on whatever criteria they use to search, along with what relays they are able to access. Its up to you to decide which will work best for your purposes.
A couple of my favorite examples:
https://nosey.vercel.app/
https://advancednostrsearch.vercel.app/
Term Search:
Term search is best achieved within a client that allows for fine-grained relay controls. Connecting to a general search relay will open up wider swathes of the network for searching than your usual read/write relays can enable. These search relays will use various methods, like crawling and indexing, to gather as much data as possible that may apply to your search. Returns are sometimes a wild list of results that may include profile bios, note content, lists, and other types of events. Oddly enough, search quickly becomes discovery and you may find interesting and unexpected things, in addition to the information you were looking to find.
Relay Search:
All this talk about specialized relays for searching but where do you find them? Relay search tools exist just for that. In addition to the many curated lists of suggested relays, like this, you can also use relay search to find the relays you want to try. Results about a relay may include location, uptime, user numbers and more.
https://nostr.watch/ is an author favorite.
Paid Search Services:
Nostr clients built on a traditional business structure may include upgraded search options as part of their paid services. If your favorite client offers a subscription services, consider upgrading to support their business while enhancing your own experience.
Dude, Where's My Note?:
Sometimes things will get lost, a relay will go down, or your client just can't find it. For times like this, there are tools to search by event ID across the network to figure out where your note are being stored. These tools also come in handy for verifying redundancy or trying to reign in your reach:
https://nadar.tigerville.no/
http://nadar.sandwich.farm/
Happy Hunting :)
nostr
-
 @ 86102a64:33871ac0
2025-04-22 02:11:57
@ 86102a64:33871ac0
2025-04-22 02:11:57{"imageData":"data:image/png;base64,iVBORw0KGgoAAAANSUhEUgAAAXAAAAEUCAYAAAAyfG1zAAAgAElEQVR4Xux9CWBcRf3/N5uz6X3RNk16t0lb6F16gaCC8hcERQVFEFAUFUFU/AkooiKKioqAKKICIpeIXJ4cytkWytVCaZLeTZo2bdq0TZp7d//f7xzvzXv7jnlv326SsrOEttk5vzPzme98r8mDXHo3USBvQtXyhyAv72OZHnQSkpCHH5mS+Jc8/B39n5Lle/PXnt1KJrHOPLNOVo/td+q/nfKnNIDlk1glqxX7Qb2GPGvfdWnFhmH+T7eYdj4aD1Uf06CBqPTCuuqVd2k3kMvY7yhg3Q39rvu5DgehwITK5Tfg7v9WkDJh8mrisQLnNkB3aRTxCwHc+qX9d+q/LX8XxwahNR0kBNqUCHCTWCkDXtEjA9DDDN4oo0uF4I2kHlpWutC4Rbq7rvqlC4K3kCvRXyiQA/D+MlNp9rOiavkFyL3emWY1gYr7ccB2gFUXo52DZ/CqDeC8NMNjAmnOFgfqu+V0CVbSzB2mWYdbhl/zToeYKLMWAXyeX/nc9/2XAgFXdf8d6Lu558MmzRs2uKS0AQF8QLbo4AS2HIRNMYiKb35gbynLRB2c60wmCNUFUHO0tgBoksQhabDUdtFPYPqFAHG/NhitlLE6iZHE1407Nqwc61df7vv+S4EcgPffudPuOcq9v4fAdq12gQgzpgC5AmieoE3yXsFxc7m0kC/TISAF1oTXQcCZiUt4B4IsfOonB8QgpZRzxOHmECGJPapKdu/YUFQK8GxPdtrLtZJtCoRbkdnuZa690BSYNOnEksSA7gasYHjoSkIWZMDHsFdVZjorCLl6zpRJy7/zpk0EdGVoA3C6UkQcdPEHaCIkxZRiPo3xQwUpKwdhz2/IwZOvJZLJB6EA/lC/ftX+9DuWq6EvUSDoGu5Lfc/1RYMCE2YuPw83+p80skaSxcQRDskSvIVUmsumhYUKxxghDuCqRQH19r/bJNiiETeMcxPf2Aeom08tpyPqiYSQPpWoAO4mQuEnIj//jL9DXg/+ey/++/GuRNdPG2vXbMlGf3NtZIYCOQDPDF37TK0VVSvuQi7t/Ix2iMmkU038/NrkHDoJsvmfBjOp/FvmYThky+dVv5MS1DF/GBT3G5jb9wHb8jospKWJQj6jVcUKRVxpLAAu6C3oCbHq7kTXqTkgDzupvVsuB+C9S/+Mt44c+DbcxRMz0ZAh9ggkUU7tCQNblGXbFY7y99ygxFRGWv4uFHpMMBNyNfcVrjqFMj6AL/udanMv7zamfbvCgVsAPA9iSNkE5CXy7q+rXYm3NYhnYq3k6swMBUIu+cx0JldrtBQQ8u/2aGvltWlzuJloPECdfQ2cg/XHWxDOrVGEuEk5vaTSlchEildVCWtKU7iSmCA+mYcAnkQgTyZeqK9Z9Z4A5M1l7WUK5AC8lycgk82Pnr147IBE0a5MttEf6s6q8tGHIAGlKN61eWhjTemUaUGjgjcDbqZjRv6bWfiwv5GZzpb6lm3HQENDW3+Y23d7H3MAfgSvgPFVx47MzytsinSIkSKQS89ssnEjl8XzR7HNU36fDlgH446dHYv8aB2UfF43nRRLFLoZmdYnpgKZW2GyexNPJngzL1TxFTOxZP/Fn6+vfvkEv7Hkvu99CuQAvPfnIKM9mFC1ogN3aHFGG+kHlQcFZ50hZaJOnXYZ3gosDi33ZzAukmLVwyvGn0TyF3W1q7+h259cvt6hQA7Ae4fuWWs1k0rMrA0iYENBuVxL9YEKh+P3tYHfoy/EmdPXamArlfu2eKcyQUlqMAGphJZcObf04WIV6mNT6+GK9p3r6gOSP5c9ixTIAXgWid0bTU2YueIpbPektNsOBGxpt8YrSEOU4tQDHeDUyRPR6Hyr8TcjVMISGKITazQBeyNeppgGualQIoES8eSLO2tWH+/b0VyGXqNADsB7jfTZaXhC1bIrIS/24+y01ndacQI/HXDWyaOOMqg1TqD6wzH4Qr4ipN4O8m92NipmmdbxCN8fRHOMM5Osb90+KKfQ7Dvr2t6THID33bmJpGcTJhw3PDkwUY+qKoyJES4FAp1wTbiWMmydyWTOZion/632z/i7443BHxH9c6Q3wCAXGbfDgYk+KCxuyN2rPUbsbFdP/Nrdm17+QXqjzpXOFAVCLoFMdSdXbyYogN6Yv8XNfnHYuvsjgIflwAPRKAgai4q1wdOjI2YdqsOO2MpMEO7NfUsOXDZhiVWjHJREw3gyuaOhZtXEQHTJZc4aBXIAnjVS915DZE4Yg8JqBPFRYXoRAqfCNONYJmIxuFa/dA8s3XzWRvUg3K1uw0nHiDsQjBN3bd02yZL7T2BC5558LcLlMmWdAjkAzzrJe6fBisoVX8yLwW/CtB4OqMK0lFomtAgFq3IUQWjgp/Z4NeqKhgpmLQmMf06blolPmJelqbQ0rLy5KQkPGcalLZZgB6r1iVNgXXX8cWxvZ83KHE5EPZER1ZebmIgI2R+qQZPCe3Arn9sf+hpFH+1ArAPMOnlk34IrML0tRIwxu1x5zNsIekziaaxE2dUglxS36MdC5ybhSairacCHQLZ1aDSSy5JlCuQAPMsE7+Xm8vFxhyeRc3ufdj96gctM6Zvsg70v6r/d/q5UpgO4Onm0aRdhRgN+WdCvVJvuKJpihxdVJDh77rmZB02NBya2N6/fEUUbuTqipUAOwKOlZ5+vjQJcxQd0/xIn/ou6nQ3ClerWqZsvrAjFiYnVGYeuvF+nLnWMuvVaytA/qKA8nBhwCwUlQ3QhNGHyFJGPAbD4nxCl8H8F2+pc1s7rbWo8mANw3QWb5XzBZjXLncs1lzkKVFQuPyMvxh459n2pJwz4RNXzsEpMZysUTRFGVJ1Pox6OvehMw2TcMcNkkNtvC+hWYqhzF3hn6xP2FX1H74O6ALl6UPJum/lbDnZMbG54LceBpzGfmSqaA/BMUbYf1Dt22vGjiwri30F0uMyru70pVpBtO8W8tr72I8CLq+5CUV+bq87AiWYYBLIHP01RBvrSMHd5w/qEoJW94mDgtdZYU+r3MCKXbUk7+/amwsF79z7bqtVQLlNWKRBupWe1i7nGMk2BsVVLJxXlxb6EsLEckWGB3ekH40QfQi5wSKb74VR/WBGKva7ePITc6MatQSQYOx886NEOMdJXWuyzqcbg4hNpfUJ/xvAjk53GSaEjZa2QErM6Z4XSG2tfp80cgOtQ6V2W56jJS8YUlOSNp2HHWvI2tJUkCgcV5uM7inlF/YIUIThkbe5bgwBedfGuUbAoZ/tty0GDmTEeCbMDjMVQoILIisIUIVYRHfGRf3PFJIK1TXzCuGxFpq4Oy+D6mfwGkgjgJtprjD+XJXsUyAF49mjdr1uqmLn8AYScs7mujP5njWVnGRwTn5pPpBk5BWBYuEniQYmZZBhjNa8IK/9OIXQIQA8zWZyfFhDM6CO3l5Bbk8yaGG4G4uafnNNNlc8TeMcU3STF646xhxc4486SOAhUsYfgzUVUQZ5ZvrrDxDNSfKI2Kv7O5eWyf2zm9tVXrwzlABaGhrkywSiQA/Bg9HrX5i6bctyEWFFiPQLAIC8iMPmzMIpg0gGBCKpcWspw+RuYFHpaiarnAehaxM8SWBt9MYDa5J3dxNNO4O3UXfk7yQmjMyR/Gk3Q1di0GtYnDOARhtVXd2JkQy6TrQNyvvgYiNuP/xYjEn5Ji/a5TFmnQA7As07yftlg/vjpS69EvMCgRuruN8fCAEZwd4bCjXGVHNBN8OL5pAiXc3tcDqwD6AxYxKp1YCAjJq4JymO6O2FidweM7e6C0T1d8JehR8HB/EKLujRscCmnThNoW0Qc3CgkPfGJoLEUvTNoJ4E3QbWYP8nRk7iG/DjbEsmKfbWrdkZM2Fx1EVEgB+AREfJIrqa8cskcVGK+ivu/0G2cFssIKWZRwNlezhfQsYBqeUHlGTOPzCPJgdMGbxc2uRiBczwC9dz2Fjjx8AGY2tUO0zvboYQBnZn2xwpg8fTF0EMaRqWvasTEMGtChnnlMmqSlfMDTopPuFmhqFlT/q2KT4yTlB22ghO3iE/4bSgZx7bzklsxDsqUMOPIlckOBXIAnh06999WZs8uKo8PeRUHcIwreHuITfir6KZM1RCv2CqzALoUu0jOnPGIVpk7U+gheAY2GRQy3sGJHqjsbGMc9bieDjim/TB8sHV/ClB7TdzOgiL4f5PnwcECfq6Z4iKN6faQp1A9dFxQBCkpXmK3EyYH8QJv6gQjFk9CWG68Oo+1kviE6y9NYTfjwgWt1VfsMQ7KzIbaVdUao8ll6SUK5AC8lwjfX5otr1x2Cm7qf3n1V256dfNTfgt4C7GJF6Bz7lXhOgXIeDmfENgRkHO8SjXFo+9LEaDGd3XA+5CjPrbtEFR1HoYKFIlEkRpHAixeOB/ydmC4EAnikkWWIO3XkA3M6XAiQGVKXaIB/hHG+kTIYDiei1fnDR0F/ZaJaYT4RNVD0OP0kLgPue9P+3U9933vUiAH4L1L/z7fOr3og7Do+aKPFoALgDC4cTdAl8DP0TDlEQc7wYiPHIVg/P62g8hJd8HAeBwGJuIwBDnsSQjaxGXbxR9REX3HBIAlLwPsHgtQ/MJwGPHtaVCwV3LjNBCSgripNJVe2ACccfJ0JsmiBOAIwOHFJ1zHYNQpxCesHaIxHoD4+g7+yfOh/2eivjoXQjaqdZLJenIAnknq+tQ9fMrCoQMLit6XzMs7CTfPglgyOQ6LDMOtVIxXXNrCPfj3NjLlwj1el0jEX+6Eztuaat5oyFa3yXwQ2zrbqz1u58C5X3uoUlV8Yue+1X8LvBYiWs51WuN+KLJfoQNVWxuLIH5RcwNc0LwbiqQtXAaJtGkqwHEvAjQieKupaO1AGPrLSVD86hDI65GCCuJyhWzZpsAlXCWaJYZ3Qff0dogP7oaBT49m+bkVCoJrBOaDJJTh4hPeIufEmZkQs25hZwb+m8LV4r/+iNz35zJIvlzVEVEgB+AREVK3mjFTlx+FItNzkfCfx/1SGTQcv9h+rcgx/QNZpu/urH6xVrftMPnSB3ATuLjVgykPtwK6aalC/VQtTVTbZXlAGHbmeN1XRcN4CKKIpA1OONwMX2mqh8E25WMYGtjL1JWj2GRNKnjb88UOFUDh+oFQvG4g5NeXALSiVJtMSUoT0FPeAZ1zWqH76MOQHBI3ig65ejIMfmSssPcWtIvIfFCKT1gsFUULLA9fmg8S33R3541p3LxyTxS0ytWRWQrkADyz9DVqHz9zxVJ0yrgJ98iSqJpkDjFJOIAPX329rublO6OqV60nbRGKwplzAHcDdAnapshBRsQzwNxg0xkTaSjrGJizf5r8Py3sGILRzxs2wpkt+yIjTfMwgJkb/ME7bIPjZy9BZaWinBXmg0IfyavVdN4xvC8JsI0IWOKmJBXFKD4x7My5XrOhvmYl88LNpb5PgRyAZ3iOJkxbMitZUPBrBKETM9YU36D7IRH/LAL5Y1G2U1619ER0xf6fV52BZOBugG7jzA2sNiwquEjBMNMz5Ma8Z24gTt6MS1A+/uCOd5hVRzqpDfWUUzehzLssnVo8ynbkwfi5S0XsE2k+SIBtGpbwq4mQIbGBi/9x0xKebM47vAIhJzHoT/mY3ITpMvPZnwnoTHYdv7f2NRQO5VJ/oEAOwDM0S+S5mF+U/CXuko8i6GSczpyzZcKG3XGIn9qwYfXrEQ0tVl65nOqa61aftB7hCMKtSBisMAsHcV0X/04RoUhAsSs5VasIVp+slEshOEcqQElQV3L4Tv1ciCD+yA50JA2ZujAKzDFvAdTOCFmBRrHB102AofeVm7pGwX2HUV7auW9DfMXmhwM6kY0OODr8SIGZ6EkerN+4Eu8YudRfKJBxYOkvhIiynxVVyz+AW+Ix3CEo+Mx+wg1Ku/SvdTWrzoqi9fEzjpsbiyXW4Lb3cOQhjJX3fVOYwRlGwTUyjz8XQLcBuTU4iBCNGHIEHmXEAuJioIZXJ+G7RaUKMAll409vWxtYydmOs3g0gveWaVFQ070OEp8Aik/ICJyCV0XuvCO5dWK5xYEaJ3v6vHzmkRlP9Jywa+Oa5zM7ylztUVIgB+BRUhPrqpi57BLceTcjkPR+BLdksqWjB+bv2bRyc7rDTFsWLhRnjCqOgC7AnQEvB3l5cbHGp+aR/LglhRCFS0acnIYEp+4lF78HOfHj0NNSJx0YymXeu8k+KJOpLQ/K5y9lnLChJ8iE8w7RSJgPkviEmQ8y5SU9XrwqhweZnOMM1J2bsAiJWlG14hbcC1+JsMr0qiJGnJtwPBQ/2HFhQ8NrbelUWDZr2fz8BDyMdU52q8c7mBW/tNPZxjGEbI85oNs5c5UD5yIZofyUoiLjEOA94bE8GPKbyk1DKGztLbV75sE9cNMuFGh7pAY0EZz/JsCeMelQTa/soFvHw9BbJwjTST6GTDjvMLt0IXrioWqJ22eKzANoOuj7OpPeaHK5skWBHIBHROnymSs+h1j0+4iqi7wa3Ldoehg/q752tadXpV/DZWULS2FQ4YdRIfgx3PvLMP8oLlphiMov6cyLkDPQLFSsYfFAj4QJ3pnJVqyAboIvtyiXtoRq7GoTzFlLJs7zw8oAJ0PtIOTldgsV6sd7W/bDn3Y6e4pvwSNq2arsgDd1+6gVC6FoPwraaRCCNOm5zjOFiLPzjphkFrCKnmvDfyfiiTt3blz9Wb/5z33ftyiQA/AI5qOsatny/LzYc0jMggiqy0gVhtlvIvlf9BH6/I7aF7dkoiHEjA9hvX/FH+5b7pL2o9z1hjGT4IWBQ6EpVgid+WQjIiMVcvAmxxJKXH2pmr/ZZepmLosDkBSneHDiZx9ohJ/ttkqYNk4HOP4FNBXMAuctyVNetYydV9LSJiru2815hxqT5oPM9rsrOXbP1pcbM7EmcnVmjgI5AE+TtuOnLSmPFeS/iRwfRsXo+4m/0II4kZe8pz0Ru7Sp5iU9YbDG0BBoP4rZ/oI/gQ8yO6B3EGeIMlo1vopFTCJAmWO8lIsrDkDs1/6u+HRonHZoD9yG9uKUss15U5t5W4ug7EML0f4b/0EiJRKfROQ6L+NUscHJ3S4MeiwmiJB3e1ei66eNtWsycrBrLJ9clhAUyAF4CKKpRdDi5N8ILB9Ms5qMF7e82GICWydyXz/CuBc/xA5Y46UG7BFiwmewyF0KTASswZq9KZYPZ06cA9uLS5likkkDpALOsGk2ZeccyAXHLuTgpis+RywvCxWyFf9x4h1YgUFzsyHzVkc79j0LMYZKEdMJqK7zYcwHzdCxPM63cfPiBMD/CZmSQS6pAZbWQbHq7kTXqTkgT2v5Zq1wDsDTIDVF6kMFUFoy5TSaD1zUas1hWnrgJt/a2ZM8Oay1CkLCVdiZHwXukEaBy8ZNg8eGjTGu+1SEiYkFiEt3fFPJySs1Le8dohu6eG4mChLQeMd66F4a2aXEf4TovFM2dwmgCI4dU2w8IvZJGABHY0CuCKX/woafJUVzIu/+utqV5+EATD9//9HkcmSZAjkAD0/w2ISZK9A6GGaFr6L3StofAENwpydYflS3YeU1QXqFYHoL5s+o5c09Q8fA98ZOgS6CJnqhnT+2y5WljMvkmj8pTrFw4gLsUyxU3EAcQfTwaXuh+WfeFipBaOSVd/ANFTD07nJjHBLAg4Avu50IxloqfCORoScTL6BlynuiGmuunugpkAPwkDRF0ckFuNnuDFm814q5iFLM/iA33tPddULD5jV1fp1EzCBl5cf88kXxfSsKh787bgo8PngkdOcXQBzDxpIFBXN4oQYMT07VflxKDawWKlIW7OW52b7oADTd804UXfesY/wsdJ0XBjwq+MpbhhRXu1ciVbz4J5eaRC1D31Lfsu0YaGhIywQ144R8lzaQA/AwE4+v1ExIDMUogHkTwxTva2XsDyEQN454+DMManSlW18RLuj2cXRvjOX3w8fC9WMmQw+9R0AxrCkJ13DFzNnwtFedfpRfimLc3I7z8NZXf7omtUHj42vRSNIfRsPQIW9LEYw/dRFvV5gPchNMaWXjB9v8FiJDxNrDz4YRwaS+3kM0iT9fX/3yCWHGmCuTWQrkADwEfSmyIBq9oZVw/0yqEYLh9Wez2OAjS25vb+9eunfbmt1ypFiWwgOQpUKmfRM9iXsAzRBvGzUe/jx0LLQWFFiUnNY445qemy6mhiQX3/PHt6FrUfRy8bHHo/Kyqdg4OHRD5kjlrCQQs+dmIiGrDJ3NM7fJF1EOBLcuFASGUQq/wvAjDE1h8jAUPcUPt4SfTSR+UVe7+hv9c8X3bq/HTjt+dEF+/ArsxQeQ4ZiEVB6I242HpchLdqFZ7yGk/zb83UNQkPx9/fpV+3V7nANwXUop+SZULr8BzQW+FaJo3ygiHGsUTZ9Hv5LdyNldgJYq9+EWJyO3XfhzVN8YCO/F58ZXwn8GDudPq6Vw4iLIl4fnpq/TD+6Slk83wMFvb4tu2OQ6v2ApA1YmQtEIvGAAt3LNINg1HtOQYiRLdXpbXIrWONorAK7Y3ze1Hq5o37muPjoiHNk1DZs8f+LgopK/4Ao81lCq61kCrYvH2z+5a+PrGMTBO+nNrl8t77LvJ1StqEb2pLK/DtuO395cOLNWoV391Obq1TMLIVnRF8f98OBR8DW0WEmiSEU6r1gtVBi7Y3lQws3pxwAz20Bbzt4FB763NZLhk+v8sFvQdV7YuutWajELRBkJiyaomFCa8WOoRnHX8gENThlhgsmpxJ9vY52SLy2R80DixZ01q4/X7eu7OB9G8Fz2OyQgemeHfAqPbkDJvEfralbSa1hdbrTMAXjAVVY2Y1lVQX7M92QMWG3Ws/sqM0WP1KBStJkXtrXAN/duh2X4OHBfS/vRdvxDE+dCQzE6gZIvv2KhIkUEhgk5AZVY/YaFihiQaS+eKvtODOmG1rMa4eDFyIgOCm86P+YEFJ/sLmJxuH2T0VFCVTM/eVLyG4cQoHMkNsLtSscnCcSq6IzDNAdpacVjhKAV0M+dvqSCgOkKknUt2wblFJruM1Y2Y+GoGBRuwndGh6pP4ckzlIupxOFqRO8Uh6Whz1BEWcnEzsPdXbObt7x20KlVjdXju7zeVRn6q/WJfZKsAK6AmaMs3CwtAX1ovBu+ik+WfXZ/g4v0uPeWxVfHToW/oe04c/xhe8UEOLupIX3HviV8YvjIZclynK4PRWBUr6YbNkLHaeFe+ymrItvvfG7PrpvUQFTsUkRCLbTEEYDLqmEAbsrDdarm1i9CcSojPSqHhrpWunri1+7e9PIPdOp9l+WJja9cej/OxllSF2FsDLGudOjBxWHi7sTmkZkWNTd3HJx1eNt6Qxcl6wqwenSaP/LzUFhVvPd6vtLeH6hgd+qRfbZy3P4jGYCvv1++tx6+uH+nf+Ys5vhS2Qz4x5BRvEVHz00uTjHEDErfDLiXBi4CECUXrw6je1w7ND68DpLDg/m7VFRi7JN8DcG3C83iyH2zQGFMZCQsUWR/lSPVPLqsz82pHLgx9wQeNFZxezF+L+KHi9d7duysWTkxi1PZ55sah7Lu/OKSNUj+0VLwJA9Eu8JZezBC8SxNpNAwrK6+ZjXR3XItzAG4NkV5xvKZy29CudZXAxbrc9lTvDINZZXllm702w/Yy7o64H6Msz2pu6PPjPW82dPhufhowWFzFttuoZIiF5eCBYMlFx6r7LorAd/cNvS3BFpu7PvBZmj/+F69se+PQcVyjP3tt/tEBidxF7ODpw6R3pYL8w05Npd6WOPAeHVMcuBqd6RNuiGGopsKZw0T6NyT7ut0enTqg7nKZpxYFcvr+jZOzYexe0MM4jNugGMrF2pJx7L0BmEyGazuu+uqV12g1ui3hNJr/Qgsja+0P4pTc0Z/H5rx8IHk1izasdTR2QHcbjvOFi7Wccm+epSR7+h18vz9VICPo5tR6XVTofSvow1loQQk035aPiSBI+IiZUYRsqk2NiNjdfnGdBN5EH06Klth71/WAWBUWK80+McVMPyeCYFoZFc0E4CTspZhvAR6BUBk5WE4cPPqr8jccXz0eg85T9VXr3zX4UbF0cunYlCBf+NSYO8ycbEbZwr4B29CkuhOJ7PBUZvTzpaVQkm3LciyUTv403S4rby9fq1x3X3XTUSgXeOQuWLmitVItMhelk+3P2HLp4hQlNXjBM5O7bhx5VPx6bKHtr8FI+M9YbuXVrlffB3gihu57TOlAf8cCcO/Pg03WL7hucmYSXEZ5fsw1dyQ2VeLD+NwfVhmqqNrZis0PuAN4mNRgVm4p9hzjKo1iSmfl3J6DFBCHLiQfxOAW+YsAg6cdc5KIAbgdGjUVTeglnhb37lqpbVafAsXoGz7PpyPT8g5YTcedb+giClJymSmUDYTB14rSHu1Zt6EUgsxhgtNg/DzLIpS3mucFb7dz2WwUOBIBXALGLuyAgpH5rMuihFgbty9CU4/1JTVFfTVXwHcfFlqk3nN+TDmjHlQuJcDZwoHLjlu2psMuxgKctEE25h6vA5tsaYf1UD7R9yVm+WzlzN/GS/CmACuvkQkZN1sLyOYIoCrh4p6q7LI9w0FpWiRtSxBiP+OX/u5DNzKFYrbB9Yh44c3NR6c2N68vvevWVlYWRVVy15EgqxQRVTq9kiQvSX7BX/ZiJ17QhwZtntSyG1fILQmyUe6/uCWwdDYeFjMYthm3p3ljhgRigFYYpmoq9JHnKLOvJ9sfAGaG/6+fkPGuXEKvEcik0fO9F6Xoz9xNJS8PUQgM0Nqw/LEfKuTb0IJbH6ct73FBFqo1L+8GuU3Fn2TzLYZ19BUC0o6dNnFcpDlJNBgkhMyQRRzZTjzMBA2r/g6IhQnM0KOROLAFn+yxybw162HOic2N7x2hAP4wtLymUXr8ECbajp6CSrL6xs71EgXgcBN9vwZhkQpSulJJn7aULOaORJmus0MDyn71eO7l7/Febs4+y1H22KKElMAGd+37gowz3HeQ30AACAASURBVO9cOI8YXjE/17wLvr1nW0YWXA+q1D78d4B/n6JHoxGXVELpMyMs3DUDbIa3bHeaZoS+mkbnNpsv3QYtX0qxzOmA6qJjKz66CGUs3snCgXP2z7gRxDEIDAXxMuLAiDkTJ060ZoQCyIkxZ2c+/u/wnq5hzc3Odsl+4+ov3yPn/SxS+AROUw6TbHlY9gkdpqiLYM5YFCZT/4aqS4cU3RPevPAgrUOHKqZEyQG4LiVFvglVy7+Hs3VtwGJ9LnsqgBvr1HMh+nHcXt+X4mK/oQHFKi1NkS28ZnyGd/EagM3I0wZJAx4bBSOunIZgR3JxITJRLE+k7XhQ7lv2oX3Ffth7R4q/15kjxh/96qChQwNzr6oSk/4ur+sGBy6u8XxTh9vWUoRimBGqcl5xYyMxys5aUgMduWl85bJfomnm5XY9hEprKYKT8+K6TmyCcMO6h5lr8gNBxqtxmzbrnkIzIFRG1NdyS6AjeiIyscSOREcezl1wz0XOZATjwP1A3TIPWPdIdAK6cs92+AS+DJ/OAtwyBcH7FYD9IR+zI7n4UecdA0WbS80uCnmxsTFD9rB7XAfseuY1deh/wKouGj584dDBY0oOeK5NB6Ko0gwK3c7eCxXKS0NW79BXHRGKU19UM0ICGflWJz5+nMTHj8MbsGdiU0ZY5wh8IrE0P7YDAZmSUTMXhpnevdICxYjg63BTC7QvePVaiExzgZZABOAkOcylIBQ4El3pOWibHLjXTdDpO7vSxrG8wy8HoRPQuft3w5Xomh90Ib60HOCUf6M8dnCQ2XPOO/qCWVDy8jDDYZMxRuTMgixSWA68e3Qn7HruVdngth7o+Uo+5K/AX5ThQyDn+/U6RYkpwYOJd/jzcuK0Va5OolYmDUrPDtxeNw9VS3E9Es0Y2AzlT0dimlZcMeOowzhMdJElMFV0DDbRCX0ldQKWNYL5mEVKBslD89/c3DKmtXHdnky2k8Eh9G7VR1owKw7gykMIHlr0wFyFy1SpeF6MopWL9+2EL+PPADLG9klPnowy7ycwwo+3JZ5fNZbvR1yKcvGnRuLIydZZbMAA1if2xjrmtMAeNCcsgZL4LtgVHwbDDOvwSbOON+zM3Tpp4LON62OWCAJMDYbNww48CBFSrFCE2ITqYACOsqaenq47Gzau+WyQevtJ3lhF5VKUeeXNYCINO0dtEyfR90yZzC5CUm/ib2qqS4sUPw1lj9JcHDzUMrOl4a3qHIDrUlTJ1++9MeXGVBepZYGmMnVy+G4AnsqFp3KATmWN3yEaUVTvczG2ypfxZ0yPcwC2v+G792fhu/fxwO/e+080ycVHXjUdknHsO/NwtJrp+ddg5jj42Xpou6IBqvEzBT9qmrvkg9Dc0upZnRkd0BRtSSClP+XGNTh1l0M3rAhFnW92wPNTHtriiYr9m14+4kLKTpi5/B6U75/LNAgCwC1MjU0/SduFTDnzhemgtvwjyCJykalQ202NB5gpZw7AAxGUZ+5vjxnbh+hmZ+oH0nwPu1zNbSISx3xeshm1k9jBqs7DcNm+Ojj1kGlPfcdFAF/4nYJeIebOrwjJxUdcOQOK/jsE8gswNBEheYi059634ZX5L8Ax+LGkH/4Qrrr1j3DvcO/3MOwiFA6iXHxC+5oFMXSzkIlKhGIuCBZeluwTUXxyxGHGqMpFlSVQuEGy3Zy0pvjEMn/iRFSNAJwZE0UkKSogb0o6edmRTHNE3Lvf2rLJxTnvhQ5jbd1TG3es2eJb3q/+d+f3CwsnVBXvxVkeeiSMP2UBegCtq5NCCoC740sQmg1Gb84vYdTDQxfvhKsz8u69c2/y9qPjz8nzobCtKLAcvGdiB/z3H/dCZUwJGU/0OessfEX0r7CzoAiWT1sUikA0V0ycQSCg2IFLgKc/ebgA/huWwjryyDnFP+MEO4nkwfra1cOCzF9/yIsmg7uQrmPzMDqkTJJkqvmmeZ6ZzlXcwlPCKN8dRHZ961NVPepMLetNgLeNyuRytETZmQPwkCusonLFF5E5+03I4r1WzFl6EkTh5bw4dWXjbmeDn/davLQHDn25Dlo+25BV2o354DwoqivVNs1L5ifhvr/+Ao6rtEVbmDkToLra6PviaQuhsdDHnV4BBsmrsRgtxIHb4ohnxJFHoTTJe9EC+V50IEExw5GTxkxbsLQwv3gloaIKhtJMkP3JDkUzyTXMQi2wG5qM4qjBUYchHek9mGjHvAHv2PBSzgolDC2VMjFUZm5Cuk5Os54+VdwPiF2Zc4cv/OqyD9wvP22kxLBu2HdjDXQsd4xvnxFajrhsBgx6GiOFaqRLvvZp+L/Pf8nMeRD7OX06wF5rpMJXBwyGj01E8Yo+q8bqNJSYhuyVNyWv9IwjjDIeuBgJ2X8faG87unXH2vUaZOgnWcpKyysn0XuU+RyIeXKaEnV5G4elvOVYuPDMDN04RLjoJVm34SXW4RwHnga90SX6k3gu3p9GFVktqsrtZMN20PQFURcZeBCZtx+3rUOUtpP2wf4fbEJAz07ArMLVg+Gor1VB/kGXUIOTu+FPN94EJ8xcZnYf48HAmDEA+5zjolw6bgY8NtT7YDDBhG9hBuD4N757rWZucjerRmxBlJiujjwktsHmujrjY/dsfblRZ376QZ58FJ3gqZo3XCpo2dMYTADuoOuxWaFwMYmOEDsaSlgOkGRyf131Sub9kAPwNOmLjj3rcCJtmqo0K+3DxV2tUBzkfroWK2GHmyiNw4FvbIPWs/GhknC6xkBN57XHoOSlYVBUMxAKN3Lnn+5pbTCsaiA8f/yTMKHY9lzoIpRzv2Zx5klp77gpC2BHEQb380hWYyEuM1WtT1IceSJQYlocebA9+nf74fbxTXVvZFeGFWiGdDNPKqmYWbYLWVlFni9V+7wOuxmhfS2TSMkuxtJtPWw+2YdkIvFQXc0qVKjkADwsLY1yZbOWzS9IxF7Co9B7F6bdUvQVBOa+vezDHb5zB3t9mbvOqLsntcE+fN6sa463aZ5OXUHzTIfp8AJ+xuDHki65BOC223yr2x8rgMXTF0OPTSTiVhAdIYkPT3Glp/yRRyNU2D4SoaDzyNjDe97u7xw4ct7L9yBAj5CKXm5XH5MqXwHg3s5t9EiR05RZRS3iMAhjfSIOTbuTEEF2R3f8uD2bV7+UA3Df7aWXAa9in0IZ2n16uftGrjBiDK8yTrLxINy6SpUw5ahM56JDKB+vhfgY10e8IyX+ZFR/rMJPCni/8QbAggXabZFVyocmz4MDBYW+ZQwxGANswYExRZtw82YKNRY62pTl+lihMHoz8YHV5tyIBy7aOgKiEBYieO9CscNIHldRiKW47Qg/AIU82wivqwop7NpMY7YyY31iXwziwEmi+IS8IJjHW06E4rtl9DL0WeceJ7MThyH5yb4Zh+ci/3b7zjW/60bgHdPpi+us4IpuOacBmr+9VW/iQuYaD+PhNfykgDfRexzaeDcGY1TpRc2TJ8+HzcXeFzkhQBHgo4hSxDzLl9DDADgLUp4UVhXSu1OuH4SK9sNt/VmEEptQuWw9ss1VfI0J8BNrURrzyeXArVBsCk3xC+thyYNSZQxI7bL3PGis27ByrNHPkOs3VyyFAicWVMzs+i+e3Mf3N+KE4cZTxhjACsUPoINy+k707jmqE3Y/sBYSY7sjn47BMBg24icFvKmlb2GY5p/+NHSb/xs4HK4omwZ78525cRn2VgazkigjH1sIBOBKL5lIQDwdZ7FeNNg8ptnDV3jyXuzo6fy/vZtexWtG/0nkaYkM9rkMr8mOWrwuJG80RuwYAeiO0UwUMbnKrWeTColk/JH66tVG1PuMHRzZHFTfaWshXtGK78YF8qm+06doeuLDNDs24gbEfgDu1WNXM0aHQslYEpqv3AKt56KSM6JUCIWwAT9T8ZOS3noLYM6cSFp6o2Qg/GT0JHi5dAg60ZjbVJVzkyOPBHRDwYUgHEOW0IkDl/isdhBtu5n4xEJXDZELJGMHOuOd7+sPQE6elgPyijaQqbdBJ8FdGxcMw+lJBAJjlv/c6scSldDjFhrJxDutY0W/1NPTfU7DxlcMy7ccgGeA6uVVyy9Fwt6EE58F2wj9AQQBP/1a3UUe7iIUB5MVW4OeXDhxUS4ddGqzfUUzxuZ+J8iQHPMWYLQWEpvMwU9KIuKOGoWxbfen3Y69gkOo6FyLgP5m8UCoQRHLY0PHGBYQFFpWmheya78AcJPTZN+mEExy7ERIN8A3tHqM2NJkUcw3gT6BfyJvTV3tSowNCdmx5wxBXfK0xP6jp6XwUFVk/Sw8gQBINf6MYSZoX5e9AeDysMG+HO7uGYqxaNB2naccgIdYEDpFxs9Y9v5YfuwxJPBAnfyZzxOGhxa98kH+oNYmWhy4R5thRD7d4ztg9xNvQLLEP9qh01wUQzGsxs88/Dimj30M4G9/y/g0NucXwJxpi1loV1Nuq3CKhiMPf5CZ5XHY5QTgzPLCBvjmKpG8vixueiRysQMdFlxmjlz8jp3VqyZmfPAhGiBPy6KCkpXUYeldSX2XXo2WKiWd2PNDnG52px436xNWD5YhekpoVf5qmLTorF03rh/P6nhdzUuWMG45AA+xKHSLHDV5yZjiovzv4j75PC4FfxMD3Ypt+QzRnPiLjnNfprhxtWtpiVC8ANyHgXdrtwdjdDfe/xbEyzoDUXoEjIB1+CHFpWN6+mnUQGKM2yykvQjgC6Yfa7GhMBBaOKAwzBaLwC7LJZEJfwZAiAYMwNc37eQ24sKKg3l94qvsybzWnXs2lJeNnjsultf1Dfz6VOzkKPyywDxJBChCXjdWQa9dP96V6PppY+2aLZkh3aSS8spxrRgGN9/LSspu886wmMBYnH1yP6UyHgyxeT5NJOV1UP38EAmSMIzCdnzIYZJaJmAVQZrL5ZUUKJ+9bEReT+wqvKtejtMWXSBUHwsTd547DW7cfni4XCk9uWyN00OLSw+xxCimStOt1dC5VM8Vn0wF1+BnJH5cE3lb7tkTojfBi+xG5eZiDITF4BMRwOCLDe5RoE6q1IQ1xvlqkdn4Q5Wxy2/dOXDZa9Vzk7P6SbTfzGOuqtYYIt7cPEJadXei69SIgZzsvSl+wXAjrgm3EeR0ELcIBqaKGIW/c8YB2TDZZKIXTlDz1Sp90HaaZTYLXtvQvkcwLx6TtyCAX5YD8OD7JpISZWULS6Gk4Oz8ovzbcFGVhK9UsNryfmw7hoVVqrlRQzakgbOuNetcFT27FVJsY4KLs3yQSEbKzYPowdlyobdT4XJYDv/GD1mduKYbbwT45jdDUjh4sb0oD5+Pjj9s86MSU7rUS2Wm3YNQbYG/ICNlAyYYsau/5Mg1uiQ5cLnsyKJDgrY9DoufSMbQntJ8J+B+lKefh3WRVWU6idl74wi5u7myP0wlpk05yYnADx7lJmsBcbGj0tkXYQdF/cjvKBq3bduzFo18jgPXpOikSSeW9Azo/H+o8JmLRWaLYm8n8pLrCtqL/4WERRMr/VQ+fellefmxm/ia4Oe6isecoeH1sUmymBA4T5vK59hzRMdzm2MMahfOhqSpBPLN5wfwiubePiuyaPtxzdB0c7WjXPxkOBmewA/Jvl1TE0oBKtB9viPQ1OsvEoec9ciBL53KOXADwJ1qtN3PSeZNSGbEUGHLiy+wdGKnWBWdoq6wBwKTSCRfQDvn96RBJMPemwOxcE4yOG/JXaf+6Sb3Rtd1ltnrcEyjv65FVSYID98dyH1PtGfOAbgG5Zm7fDzvPtTXVKn2WeY1KLm7K578SOPG1S9rVGdkGTZs3rDBYwc8gytjAV3duLVAsCmxcjip1qtRceMpIOgBkF408AVmUdiPy/Hj8HXbiQ/phj1/XA/dsw4b3f4ofBT+gh+yOvFMX/wiwO23B5nytPOSCGXR1IXcyA05cDXsKauc2Q+mNpPE3ydtHLuxWkICLtfasRNAiLlTDwQGocqyFjwJ8iO8n+rjBuxfzAQyuaW+Zdsx0NDQFpRgpr03Z4mMmDGCcfDzMZD7yb4NVU7cgboG98UlMOwk4kyXnA6ffe20XiXd6M84JM5pqF6VEjgvGFoEpWb/z49ytBXfQq7g+7iqCmgxsAXBOQU5P8Yo8Sr5UrKl+wMNDa8FWnjl0xafkFdQdC8C+HiSa5o4jstNdfNiG0EsMbEBnAUFJndl5a+yMyFe3L4usEYF0Dojprk89IV6OPjVHXARfn6HH0dHDrWyNWsAli5FwAxn1aLTL6c8pMScjxw4WZAwO3Bx3/cUnVAfae0IwJf1psWB2/QvqfMlWIdAPAmHd/4oQuL5uupVJwSh0+iZS6aXJPNruL23vLnyGkwwVEHdyoXzfOIQMjWXok9cvKImHbGVPb+QsGsNy9gryUTXjupV5KKbsthyAO5BytGT5s0rKS59FZEag6cLbkfKypgZlRXEiZioaOjp6omftmfTK//RmiUzU17FtGUXJgvzbkEupDQT3HjA/kSfPYAcx5cD1xDF+DVnP0xGHD0Inv7t/TByxHD/sS9cCPD66/75Is4hOXAG4FLuJnax+cCAtVFpMqi+4GMB3DAcODbBRXupoMbk4IwrN5O8rXLGVAC1YSljBVlZKtHT86v6jS9frkvCispl67A/x9g9LblC1RbnxaNSO4izF5CUcZrHTEj4lAy67sCSyYd3VK/8uFP2kD3Qbbkf55s9u6g8PhRd65IzUrgxsXGY0MMZxJGBSP5tZ+1qCvmorZDBec1vyct/7Poxk069f9gYZmUQBTce5Sz4gWJqAAl1F+uzY36cut/31KpfHqdDonRACfzkuivh9A+d5E62O+8E+GzvPMxOSswFqMSkF+KdgMZpQ1sA3AKqVpGHLshK5Qy/jZpzmmKpwUDeEJpoLUNzTLzqvQebJ3Xs2rDdr/Do8gXTSgaV1LIjRSgi1e6pa0EFczdGwZB7Y4XE9nIA5yIR+TqOX5/8vnds2/5LbC/R1TOjfsvLG3MA7kdR5fsx0489rSi/4AnOeXMwsJziEsSliZGtbpH/lZ01q8lLzRfECbwxH3mCnE5VbSksgQsnzIKt+GemlCdsa2lwsnJoflxxAPL6Z/VTUmr02w/AvTqxZNE8+M1N16Vy46S4LC8H6AxmS+4/YL0c9bFCWDYdlZhi3VnXhjM/Rt6aBPgsCbrKtcwP5AAgK2XsAXU1eqMzc8l+Yde76mpWkjOch6dnWWlF1cRmdHwuYsy9zdPSVxymdk7hUOivXBTjbiOvK98PyynjraoeH5K2BZo3Oxy23qDz0e/yV1Qu/SPk5V8o7UTlGne6irkBLAPxBKyur115nBeI28FbJdbjQ0bC1/Hlli7cgFFNli8X7TBb6YJ3uuXtXdKpTwfAvfIUFBTAt752MXzhQiW0zfEYq+zFF3ttPTMAn4FmhAQuDHz9E43RCH7ln90zB3PBFwpUt4ye1klGn/3tzNl5Qz+JZE19zUp8VNQ4adSmU+y9VaaLMhqKTEWMorN+qKwMemUda3ryffuc2TFFpV883nPFztqXf+5Ga535T3PK+2dxjJ+wFi9OcwyDfrlj2IrgG4cvAi7mcBKlMI00Ob4lk3/ZWbvqbCdKeIG3zN+G8s4zJ86BDQMGekoovCjNuW2rYifKmdEBS932dOqKKo9On8rGjYEH7roFJj7/P4Bze/dNXwLw5QjgTtDtxBQzHSu5y6tKOUfunVPCi6OkV2hMRb4qOkkRhdvxjt9eNbl2Loqx8s09yfgDDdWrbUHi8E3Lqkm7kbUZzA4zG5r5rZEUELefiExcIsRMUo7uIN/XWUNB8sh+U/868g8M3rt+vetLJTkAd6EsD4ATwwA4pmbaNNbmhaRyhMupTYsAe5W0CLq7ek5q3LLmGfU7HfBW8986shxuHD2BLynWLyXsvJxJsehUOWCQxWPrnxaHF7Z+t3J+G48DjT8g6CquXOWgCsdGz2d9Z+8O+NyeHVEPN1B9JoDbMJJx2amx09gr9jgObw5cj6MkAGd1ab4e5GTlEmSwrFdCG4rznexK9kxtrHllq6jDeFnHWA+SsxLrw+DEQ3Desp9cJCNPNlajMYQoxSfq2SHrxZtHHYqPJnjRLAfgLtTBBxq2I+MyQQVpO2jbi6o2p/bv8CrWg/JwculjXh9BwVvWV4PvJ35k0hxoyyeReWamL1O240E2r19eHXDWAXm/w8Bex/y2Q/CH+g0wMt47wffIkWfFjGMt3oJyDE40Y1wz2X87cL8SIJ0eJDABRcAwD3poiG1SxBK2U9BpftIFPFQs1uNbkCgPlpw3IOdtjSlicq96cmvXdSaurJw26j7TO+xsxyv7p58djL3vqLu4HU0p0dnAPWUGAfx2Xz/4HjnwfyFbfYrkccUMsD8MbtsmSrFbBdiHiSdqR1d357G7t7xGsU0NhWVQcrTE8uHUSXNhG4YW5Qav0UyjKpWMqsagh4wO6Ork8QNmlea69fE6AUqScbhx1yY4/RDFY8puOpSXD8dUov25gwCcX/Zt0MFYSOa0yZNYK3aLEbm+vUQdcn3LPaA38ugAj7jwjpa2BSWDBzyNCkvmJs+VjDQu3huDexXbwv5v1z477CPVfNDrsNOjQ7BciBXJeLLzqIba1zwXWTT7NFjf+kXu8ZVLLo/lFfzSIgNnK0QsFmW3cG4Ep1iIUvxk4pc21W/45r4dpJQJnaj5y8dNh0eGjOa7ky3k4GBu5bQC6etD9z3dgrqAq5/P+wx0OiOp7uVtB+HXO2uyzo1PqCLDptTkBL4cdJ05cFmDk6hDXRc8dni+WN/8G34OiFwO9383wEuLCyejAMiL4zrPZ00qsnyDe/Xgc/14HWNLC/Ecjx0jlF8OnLiUZYb1vjTor4gD5TgS8fjW+trVU/z2Sg7A3SlEXpioPEiaQacURabV1pRPvY5MnE8QwD+3roWjOwM5bDr2dOWAIfCFipnQgh56ckuZOE6HirgmiC91PTn9Fk4mvtcHXH/5Nx+u36WVj0K3XacxFyC4XbqvHi5vqssESRzrnIgAzp/htadUHpyBM64BLgN3AX2DfZVKO8tC5/bmgjewmC+6IGIqdx8NF67Ok33OTE7b29MylWQOTA8/KNgK6g3vS7Ym4/DV+o0rb/ZbVDkA96DQ+GnLPhEryPuLBEYilrm0Tdkb3ySpFXmZF5aiDHX9xleY8Xe6icSTF5dXwZOD8FaZoRnlTJbDvT3dzovyumAbpDldYNbJ55dnTE8nPLFlLYyJR/8Gp33Mc9AK5QDKwp1oZr9DUb9p1qQM3PE2oSxe+4v28lbJzOlIaZ6vKvE4M+K26Jy4cC7REZtFcY5hY5R1GXIRKX8WIxVjkcxTWvbeClHtnLf8SqUvz6PHEDiuUX6Oum9PZWJozjryD3pan8g2MrTdg2yzvp2XycIhdgq7RqKSn6yx2ZVJBGRXFQ8p5oWUTcggLaMULmLH4hX8rzvWR0aAd0pK4TtjpsDryJUzL84IkgHZmcNuw1lCS5bvdw8OMWadKt0AXN3kxI3fjCKVU1ujf1ZNHdZVYybDvcPHOY/UNu2s30zkkfIFkxupzIf1dR4uTzaAQpjPMccvQ6Buypzt9q12LpyDuRC6sHYlmKmaF47i8jvZd4P9F/vJtPhSmChVDKEArevcOsvFlJuNFBXxTmfK+9JpXcUTiT07a1ZhkHn/FM0u92+nX+com7nkk/mJ/D+hRr+QBQQiay0FwBW2nI1TNSl0sxPn53kS/rz9HTihXe9xAV0iHkYzr2sQyP+O8vFOTZMvtW65b3UWB99+fU927scxW8arbH43GnuBvL2ts5t3w093b9adrsD5thcWv3P81IWkQ2GE96K+yoG73XLU9zFlPG8Lryg8G1msFRaQVhEZWuS3qboEg4GhfrLXawKIv7igm50Spsw7TZ29woi4cd5sb/qsCZ0DKOjEyvlJxBOP1teu+qhOeZ09qlPPEZ9n8OCqkUPGD7ka4vlfQiMQjAxmhvI0QNs4+U2FpuRwXJ0YcKHcveNtOBHN0zKRnh04DG4dVQ5riCs3ThqhmjEUUWwEwSxa2JUwjStliMEGuQT4bcCgAB6kuwT28zpa4NFt63j87WgTvnoD48nRDNdUmSMoi1dlJJPARH8OHDi/SYrOKUjAA17yhw3IDZ/e5pbKfO6whqNS3dU9wE5y4mKFWSihHopGNwisbU48KqAaXLnor1XMYa5HnVuV0RlD5m0eDs50FXoVzdstH7vz8WqpX+STfe7pSXy6YeOq+3SWTQ7AdahkyzN+xtId+GBxBZsawR0YIO4gMjE2jwQ9cZXki5pFMIRPNzfC9Y1bIpGJOw2JvDkvL5sB/xkyInXH6tJAIGigzeFRd1T16HbfLZ8u2Ovmk+1M6zgM/0QQLxYv1qTbT1H+S7hmfltWtWx5PuS9yNhvhhPWrSyXIfWZnJBMixEOKhwUhXG3AuQELExMaLtWUv30nqZ0rFFcyLiYUNwE5JwaopmUG4KPQlOAKRePu3PequjSXddk49btHAA7NUx6yPmhVil+unRYkkKesPdMqQvw00/JMbVBR1nThtfQkdA/5QDcn0ZOOYrLK5e34cagkHBCJi5FJ/LWZy5qvkw4antFMDz7QCPcuDtD77uKUawqRauV8plwkDkCyfXLuS1poWKKRdiJ46F5CUc8Dh5pXoUjPRg0efsQnZ6ClkaPbHsLhiUicfx5A2djgRx6ReWKe3FBnaMIlA2qSDw3YnnY+s45WUwioylGEbczvnzlEhEHgOBAxe2TnITocHAki709JgN3CDOrrAOnA9IC1FLJpKwfe9shpijVdlwRCzpx4m43B8bPsZus3rZRV50hPklCvL7a+vK81y7LAXhIDCqfuuyjeYV56IzDhHviKsqVKuqJbVFiCk7HC8SXHj4ID9S9kzFOnIZL3Phn0fRwFYpXckmfAn4cuNv3ZV3t8ND29VCOlippJIpouRSX0KtqHchIbEYOdIrTEcTWIr0GhhIPSsAIDQAAIABJREFUuQ4ls035hSrHFKPIKz9x22R1wvgTxo+acnaxvmNY2s4Fy3z2w8Gu0JTHgMr8GqBoiBO4rDwVoMXv1T7ZiKoF4i7cN2cuuNjImnxuDo4TywVDXoJGk4b8LMWDtL6eeZvqpRyA69HJMRcGkH8cqf5hOUVSU61uZKcN4HTllQ1Q/tkdrfB3vHpHYWLoNbx7Meb4tajs7A6h6AxDNk0+N0zVRhk/kLVXHiS/X16372nrD0Oz0fsRxGd3mk+3BRzo7bhZU9yqx48/dmT+4MKd2AZ7vNMrYJQBFsobj05iFKuPA4cgrvMhcR+97sOPASlSUDl546BwkBNLUULKpc4Bcf0571R7b096uqC6IfKx3wQ4MfnhFXUAK4/xxhPxP2PIDXrYWSvlAFyLTO6ZyipX/CsGiVPIztYO4IYckC13ZcHLxe0hE1/c1gIPoXIz0yDeidvwirLp8PjQUWyTZiIJ3iVw/X6AmQ4YGwdmgF759cdR8SUaorIFuAZ+V18NJ7U2ByVzOxZAnQvscyo4YuriioGFhW/gd+IVdus8sgcd8JDm0QQ5Hsvn2Ng/GafOZb5Mdm6Lp82wTKwNY02TFRYyqdwyRZrzUUXOsrFULpz3w1gbjNt2B2UD0D35WW+ycn6Y2nW3hLG4zyuyfbVmkxGRd225c8J5Sqjj7uhKrNizedVK3QWSmR2r2/oRkm/k5PmfGVA04G7aHNIbk4lJxAJgDAzfBSkbwSuK4UcP7IFf7d6UUSr14AlxGj5b8fS8Ihh16UwoXo+x8zW17H4dU5d34IWmdQ/264HO9/r3Aj8A12mNwOOaxm1wUXODVnaR6QdIv2t9CuRPqFz+NtK8ym75QFxzDF3hWWRCJvvmeg1DjCJglDEhHMENqxOjTYH0qliGh6rlohZDmS8OB4GTjkvJLmI0lfwm+HMxDO+nWpcF5BUwd10uTl8wsRCvONU4xwXc5WGjuTf43tdTe5o3o2QSow8Sz2acNX6LJPC+8qvw3fg9UvuEBweOePqbFZX48DFyMWJhyeukXIQGqNuI5GUrPg2v3H9HJVhptJYMrAetgwCWrAZ4Z7bZoYIdxTDsx1NgwPPDaW8GBnMrd6K3gPvLmtEBcC8uXB3nZ/Y3wHWNW3WGfgg36VA1I2LDPPz3hfgzC3/G4o98sWbPgw+P6bjmR5MXtx+ODVHwz5Any9d55JNhDMSk0i3FksWLU6VyqHHDw6EA7Wq9RCeWvsu9QRgljWCUG6n9EpgNztuwEmHIaR2z3QIlqALT0wLFdrgkEnGUf6/Wln+zudNZQbk87hTAZbgIv30Of0rfO2k+bBlQaip3+B2RJUuoWcFY8PkzveHclJsxBO8/1m2A96LnZlRpF277+XjpbqTt75Dy9xbC0J9NgoH/wGBZCXlFxuXYj2Kr+NFKB5CdwMez3gA3h3P372Kmox6JVs9HcLk8jtXOwb9TbIxl+FPkN7Y31g6EH/1scs8rrw2OJZJkyM05WmPM4qTly5N/Z+V4FU5cLmJhXy5twllJ7Jg0t5OiGl6jbM+ByxX7gjMuNq6bWwGkz3k7EciD85Zjscj/DQ4/egWmfe2xAzAJtyEHfonf3Krf5wA8CLVseZHkR+OvSF5Fcb6hCxdf5YylEKerkwRmvpotQO3YpJRN0iZzeSj5lEP74LcNtWnLxTdPheQKtCB2A2+1fwTkw6+Zjhz5MNMSIQ2aORaVHGCIeoOCcIgmjCJabfkAuL0OH6/NZ3DtfBc7cA/++EamcxvboUMFyWOWLkQqFyCYK2IUBrPEcZKjDocCi/LQSRFp4q3BdUsQt7/ebumPCtSC+2Yu+S4SrCCcdwrJXeq008fCeeOeU22/jUMoagWmHUOEPJ7EUQfz9o1qqa521HO4zW0OwEPuaFwjk7HoOvxBQYSZ/o4Bpb5cXom/MBCZfalyP3LB0SK1m2hJsHfqFuWf234IHt0eXrm5ZQoklr8EMR3wVvtQUFcMI6+ohKK3BkUH5AG41ZDT5F4sRNs6AO6XJ+V77MdXMJLhN+3RDPOgFT8boBTo/bS000WXzIAn/4u3KVpxAjTkBZHA25BiCIA21yjnoJlonNaxDTHkGpYmh/wg4AiaIk6SlcgciuIylSOV7SqKTR2ZdxqUYuFj6XYsL86KzooBunp4iXZ4PH5xh9FhRCyVcAENY/YSiXZ8rKI0aPdzAB6UYnzx0U6gu68FvGVV38VgQ3cOw2BDUpsvFoJFQaSIV4JaqByLFip/CWGhsnUyxJethPyg4K2SKK81H4b9YiIMfPQoyGs3ObdAZBSLWJNRClR1JjNrybf9OHAFhIy+Ypnb0TrlFDMIVhzWQBMK57QCGumMed/+Api7fDGLSmjoZgT3LcurCninOlNAXIph2BccuO1iEXs9xOXKU8BLH6hDa60zmB08CvJ6EMv58I1efKJ2wTgoE4mHEMDP0plLy34MWuDdnh+XAnm/0MOITGzilu4dOgauRiBPiNfkTVm3ouGXzApVopz20lQrSguVKMDbMlZ0Kyl9chQMvq0cijcT42A6XZibz2RJ+Jg4e9MfVZt+nLWkjW4++7qJ4R36CbT9P5rsxH8PLfA57/UVZh9OmLmMiUukGEVaSVjtvlNN+VyBUnxBsm9av/JNTk4DsahtMm7eb3Phq3brVuY0JOft0ln7jcICooaMX9FV0WGUYfEJO1rYLZwceDpH+72+4zTnOQ48wE5AQpOJD8UoIA7cNx1A8D51wjzYUVLMvdoEiKlKoGxYqEQO3raRF78+GIb/cAoUVpN4JVPJUIsJAMhUO8716nCEfEP6G+641TWopwf+MXPt4UmPdZBVSeRp3opFsH8/+fsoYhRpMuh0M9DogZCsAMQR8JRY4VZ5A8/FbMbRnNHg1G31R0Vjo09SVOQ4DitnzS4RxuRxsYjKaLA7hsGD8BZkyGa55nXmnq8RYcTIbkNUT7K1fsNKT4bQbSoyt980Jr8/ZRHg/Tb2uSpov88ePwtWDTbd1lXLE6pLy0LF5b5ZiNzP3XXrYYVLNMOwMu+gY6T8hRsGwqhvzoDCLYFFed7NRSVr0d1hDr3R5ay1QMijH+PGdMK/HnkThg+LJHaKZSTXXj8Z/nDPWC5G4UhiBmxSwE4dgyf3zRevCc6GbbUpplHXNp9GAYsCeWwiYYuMXasfcoROHWXcLW/ITVwjxUJk02h3n5eSfN6EHlSa5pR6ZSg/buG/76xdiR7dwZNer4LXe0SVEOD9JA7qfWEHdvqEOfBG6UAG1kyhabu2SbGJU/1+0Qyp7DkO0QwzzXm70aJo3SAYdcUMyK/H1+hE3PSgdFO2XtCivZpf64zwyoSLbWZVK/ztXrT9LyVD6ejSzl1FsPS9iwTDgMCBbfG3GUwlpm9rymGqcroGyNnCzJr4yq1dsFUjxoqfzN3eFz/a+nHedqsTblhA4E60EGFzXYDaHLaxc+XR4GhII8GfzG4dDw8hOiEadHbGT27csvppX9o7ZMgBuA/VBHg/htlODUNgtcxHK2bDq6XDkOvh1yi7+MQuiwwqF//Ugd3wExHNcPtE6Fy6Gop3u9h5pzsW3/KIPYMeHAvDf4rGOp08QCmXkyseduJeyrggKTOVf/VtQC+DyRGFX+pBLgA6nLpnHoFSC+YegofueQsK+FOnkaWJKAdHu3Csj8LGIqAysnB5cyCOV+0RgREXBVjBmbP5LKdJQ6kDMq1bVIBzs0ZxJUCanDcbdSwJ3eM6oXDnAGFxI5Wxwp7dS9uqdIzvaauGRx4qpphF1THwv3ce7prauGNNqDCk4Vd1ZEuqb1eEE/Aw9vDMqHp56djp8NgwRYTuZqHCgEy1GDB74OW5OR2VYL8//NahZWsTQ9KxNolqvLEDBXDUZ2cz8YqqsIqq/j5Xjx+byNCMb3S/tOzYA3D/net1svpVZXx/0SWV8J9nMCa8ABoJ2k5zk9JN+0kmAdpmQ65GMrSIHmwxVnSV2X7kSofzJvBueOINKPvwAvQ85nMieWzd/tmJb3D6PlMsD6sdjY1DYf+mUC+6+K8i7aVxZGWMkvO2U+bs8tmwatBQgytxslBJRy6ezE9A4+/XQ9eSUGsiIxM56K5xMPxnk/mDAP0p+aFHiLH4cekqJ3zi8fvh7ts3hGjFuQiJUZaduJhzmpL7pqwGCGudLZbKJYlYsCzx4ppl/bIzSzoMidsna1IApiJ/1x5oFJx3fhJ2/u9VSIzuhopZyw3Rph24LXJ60cHA9t/qwESFBoBveCn0pghdUJvQ/TBjJsFbkuNz46vgPwMx3gg9lOxgoWJXdNrJaDW/MngQIxv9pvXsXXDgmq3cdqYPpIKtJTDm/GMg1lSYMVNCqZTSYHAjp4gfMMsGg54JH/pAE/zmpprI+jtx9jJ0HBF6GEQAEqU44It3ezbuW2Y2Xu2hS4Z4/JiJV4Q6UZrGRnEbS4fzTqB+Ydejb0C8HONxNhRAxfuPtZ1c0dt/p4qH2Ai66qpXslDAYVIOwG1UywZ4yyYfGjwKvjF2GgKsuYFUWaSccLnhpdxccggpYCXkkIYnGTYUR6uGQxc0wOFPNWLE6GiVYqEWHDoCkYKz5PkRzCxLU7nv25R6hPXWotYGcB2TPQvKJ+Gqb2yDL34uUARDV5qRGOXJ/1L4YEE1LhL3FnG5nDrm2hQybWYqK5qWdYp5VqXh7AbgQQeLrsTvdGEKQT1rEzq2uqe1wa4n3jRqHXVpFZQ+zcVKUvwR6UNUDrQzjGITia3owBM6TEJvrXXfDdkbGbIJ3nJ8TRjJ7QOT58PeQuRKFQsVU/4tlD5iV1jB2+rs4LUJE4N6YO/Pq6Hz+OgCYoWeIyT0sF9PQCcgDLxGm5zwg+kCgiVTEczQIFJZsS4YB+sxz63Dgae2n4Q//HoDnPTewLHEU7rIrFHet5DbOgvCS8soL7mvH8crRse5ewxlqb5gz8YtADtd7tuvH67WJijv3o8HYetnrQdh+dylEOsWERWFTspyZhh8hp4Fivea4KeZXAPxePzunbWrLwizjqhM0D0Ttp0+X06A94vY0aW90Vm7hYqvXFw6YEg2nCZTyg0cOHGa6ASyvIfP3APN39/cq2KVfJTpPIWfxLNFcPFl34ZudGCRm5+QnL92by5PA8zktZ195RBrozcmTvY8gBxX53BwyhNDAHriobVw9MzQr/oYFJqx4FjoaEcTF8kJ00vzwhrFQsaQsmbuMc8WolIdBy/uyJZqheLIdYsqHIEqAOfdM6YDGh9dCwmbfX3hulIY+8l5qSI9KfbRlMU5WaB4LUc5v41791V2NlXXhl26OQBny5ZJiUlTND0sIaMop1qoeAO4yW2miFXEFdaNy6H8LecI2XgUnQ5YRwG+S7MSP4tFjKaNm7bCaWddBB0dab0XGbAXvZxdjwV3vFIMLO2Bf/1tLUyc0JHWIP715HD4wlfp7QcBAexwdLZZDsPxGq//GNUrIWttPdchBxWRvhKua5sOIHFgcCaAH/KtH98NzT9wttIb9/4FULhrgNEjuwUKO3LkISKYJS8PTE8LFIeB7khDgWmyOGkthf5dGOeGFAg0u2V9YSTSQkUIFliXnOTixoLm204JUKTBieOi7njvfmi6BRVjWVRwFmEY69fwczSLwmumpqb9cMqZF8LepkCRNPvCdLE+6HDUwTvroiBAECgr64J/Ppy+t+b0+Uugg2z0ifsmjtj+jq+90wE4XsVVzVqLkJepXHgKbTy4boNz5xvAUWzGQZS/F5EsjsPON192Jv/hGFQsxgu3cLYx5NJsT8ljS4/H9fPAVNeIMYY4xOtq9V+gdxqEXu+Cr75+UUJw3ihPgIl9qcNkofLkIFKqcBm3RT6pnOLWRcGFyYaMXIMTbz0DxSk3ZPbJNknXATAA1uJnusslh8Zy/sVXwLMvrO5X9uJarvPK4tIFe698tARmReCt+eobg+HMT+NhyrhWDlnCcERrOzjJmu0FLTbhDvJlv4b8uG5eniO+ynXLPbP77rege3GLYzNDfzIRht5d7tkF8xjVk38LCTd7+MRJ+mICfR69QL8FX6Cf6kcDr+/f7QBOjzHQCyd9LpGFyhVl05CLyDc8N+0mWIaViqLglAuEBqRjatj+3ibYdwuK4DLIiQ/EF79ewc8s9gKYd3rs70/BN759PXR3Rx8LxK/toN+zszSg9lQfwP2VsrNntsLjD65Ny1vz4ksr4V9PjWLctwouPAC4gId0UALrSQjZunHYKS/7pNDcyWJDyssFVjsCo+C6SbwhvX57Snqg4XUX7hvrGvsBFJ9guAduDWV9rYj1NQ35t8G/q+NhNxieuDNe8pYd1SsvC7ru1PzpTE067fZ6WSTk77ETn+v1jnh0gCxUzpp4DGwq5sGhxKQbO9u48ikKNF9TQ6yHi/LEBsV/xEd0Qwtq5lsu2hk5OYjzfg4/Uuat00Br62H49EVfgzfXvpMxNbvklDLWgM5APfL4Az0fQdWMw/BvDH6liTWOLZJFys5dJYz7VkGcWuCKRbb6ArVBa5NJoak8RirEx4AsMuwUnFbOCz+ZOx+EjetmIG+aE9Ii3/X316FnqruuoHzOMoj1mHKjbHhgqsrb9vaOsqbtr1F009DpXQngONffQIrdGJpqWS6oysVVjs8O4CkKGAHUdq844zCwjSM+qgv23lQNXQucr5xBh03WJk/j50T8hEn/fOo5+ObV10Nra1tkOGvghAIYYfoWpow/KKu1endQrWvihHZ48tE3oaQknJ3/fnzsYdF7FkFPnD/QIR88NhWcCjC6xHPnS032WXnYAX/30sZX4UNT5sOBgkKDb9A6cALK3NUT5vAH9sK+mzyMO7rzoAIB3NgbwsQxZQb4OcEOIjZE0XEJnLoKWFmvnDd8wPgwPmDs+CBMkLX1rgNwnIaPI4H+wliKfpTeP2neO7XFpbOo1xQOlO8XaxCiFJm4wjVZrsfGaqIFyRU+BteD37Ud3wz7f1UDyQHhAIEdEPh5CD8fw086qa2tHb5/w81w/1+fCO34Y1xb0+mIUjbopg3VrE8jdngfc1Qn/O2+t6C8LJw1z84fFsEH754LhxBkudLcvKkxCbmCuKalheSCpc23NA+k6H55UIQR/v6x5Q2o6u6AFpTRzJmxBN+LJU6cbz6jSvtg5A3RhvJeMndpgkhg2z2+HXY/9bon2WO7C2G8CCmgAr95M+OrWCdpKTBZdcqjJ8nE3XXVqy7Qqd8rj14P022lj5THyXkvdoXCwkYc4y3jA/wVguyaAY+O+vOIq6Yx12dVHu4sSjE3iJMiyE85lCiKw95foePPCQdCDe5OuBMuwE9U6bkXX4YvXHo1tHd28JdSjIr5lhPGDQQ74ht+fQ9079fobNgqg3Hf4SxbBg/qhttvroEVS0M4a/0/9Nr9N8BJk+bB5pJSxbyQwJhoSmvOXS5M42OKO4qrjeE2R/R0wasb11hUKzsKiuH46QuFCE85FFyIqoob7By75bZplMe+ordxwzMY32SEtw4lf0MJjP8YOjN5TKh5roRUYDrK87lwKZHoCvUCj32JvmsAHCdjHg7+JfyJ+LUBjV2fXpa7cN9cg1Wsx58hefvyMZ7I0VC0eRCXKXLocjU1pKatehQT+vyUnFR1y4U74cDXtwdSct4AN8C38BN1ajvUAucuOAFeK+pfUxjUUoXPmb8SzRl7kvDtb26DL1wYwO3+OWzwRHO2/ocxei4vmw778wsEp2zCBAdqLm8m2QI5h6GanS1D+n1pMg7f3b0VzjnYmDL9z70HA+rfXwRlp8+HvMNca26KMER2KXN3lLEIUY7tXOYcMPZlaDfsQn1AYlyX79Ibev0kGHrveJMNkPRmt1F/2suCXOfkHUKW55V0y4N4ItG6s2ZVqBd43pUAjiSmWANv9UPwfgb7fDLuEbKWsXiIjvz6DBj479E8DrMMki/leMrOtgNBqpKTAzpXkDqLVNqPPQj7frdBK5bKZXAZ/Ao/kac4PsI5Zw7AO+/APcPGwrVjp+B1PDv8h/2GH2RsbCoCWqro1u91GzjhuGb43c3VenLx5djiqtRW3ygZCD8YPRkfIhmCQG0Vo1hyY0cm4M3ou41b4OQ29xvbODxTduNb35TGnbIACrahC4YEP8OhyJS3u9mKG/wwcfwopiEzra4ZrbAbPS1101h04CnycODRrccAcmYFw+wkXZPciz3xxCMNtasiCVGdnR0QlBoR5sf9gwbVgCyk8wvyETYVdVX0cPIUBO/v45/fdqq89IExMPJHUyCJDAd/Dkpw4ir3poK5Ym7I6zO5Ah2Ryp7b3/EMUXs+nA934SfyRGP4GMrSH3nEqPogvq144YRZ8FopMTKZWcYKlEQ+JK8KdbhvMXuG3b9anyw/dEg3/OG2DbDYSyn9Eyx5pf/wDsUKYE3JIHgF6d2IopAheKDO6TwEJ7QegtGJbt8Kbr0E4NJbrdmKXxgOI6+ajtEpuUu/nEVneTsaI9rc/WlZJEZ3QdP1mzDGT7AYMRUzMXys1CU5KDA5N0P9JftyTm35KDc7j9lXmutO7EG5FXfs2VsO+2ojMfnS7IHv/PTJDHSjw44RocwHKftkT1M6RYG8xyF40/uba/DH3UfuUAyG/3gylP4bbXk7UDrODXoVAbj591Qlp7VdrVgqH2+E5mvRcdVmN34KnAL/wI89NGkk5P7859Hok6w+U9P/Bg6Fr4yfCa30zJHuhvLplCrx7I0Nosvxu+azsOZJ+L/Lt8MlX3DAi/8gIVD2bdFgRzJh1kr2IQtVhtx3l0vQ1KK1A2HoLydB0ZohaHIozRXdzRZJ8d45twUOfGsLdM0NEReGPDAXLXUEYT9Gxk4ev0Ne3XOkSyADhHTd59U+9Mb6zMASSa0SFzdBTD3+9NajYmHH2Y4FK3GNEktBNqLapkajzp8JA17BMK3Kld0O2qZJIce7FJGK4DykkpQPgsvZ5Z8tZ+2GA983Y0tMhalQjR+KcxJ5ugbF/z/8oWe1bXhoXTtmMjw4HKc6pMjCqrAK+xaL2c2wys4g9PNqw/pdEj6D8W+u+85Ws3pywF2AP9FYjHp2+1P3AzzwSb2RxQ4VQOH6gVD8+iDI31QK+fhvCoPcM6kd2vGBkp75rZAYkp6T19Dr0QPzXvTAtNxOqX/iuT+9rlpzSQZd/tY2OYqDXTfG/y4K04RTmSMSwAV4U8Bfa9CNqKiWuXqInZiCk7IH1xIpXEk6GSgNv3I6DHxstGlqqCxK01pFgLciUlE9ONUGmV+bg6lh9+Q2aPzrOhhQWoKd3YO+lgMD9VMr86145770Uq2slGkVymrPr5iFT3BiaFC+HwVTzi0kjDs6+72AbC6kxhTdVkgLvHXZbxqehqJTJd6pH9wLv/5FLeShfxTzP84CeP8LOfwP/VN7CrOScRw6LhXuxge3WeKiEgbdESwBN8Uy07Oy5pJpxf+2EyiCLmeF5tqNCPB+QSxR7XJ9ICNFcpqNE4IvL8AK/DuNIdT8jPw8Bqh/ETlx1T2YLVURoU0Am507V60lzGiI7sqrZEECLrvuPLjijC9FT7477gD4whcC10v2xqdOngfbi80Ic4Er6ScF/K1bUk+DFQsOwH0PoEET6oQznVrxTK/EeGkNprFHppvUqr/8GPTARKclt2SRQIpMaT2hxnCbMxOJZPyO+urVwRe2S2dDAYQWlXohkwDvN7DpY3qh+XSarMPCixjnTSnJRD9pLfvhV0+FwY+gSEGISSx24zYAl3I/pwFYTQ155+wilfM++RH4wXe+Dvn5EQVUefBBgE9q3rldqH4ZmsE9NuSokEdg8KkMwDi7A0fgK7x3q24c+v872AS/bYjuiTa3AV3ya4DbvhyclhktQR6YCODyuTezLWcTRe++cLbaSfBiHK6GApMbGOzfc3BW6763I3vk9IgBcCQlyYopsiDu2n6VSJi8TAHv0/DfT0QxAtPUUN7fODft5MHJ25PB9rlYwXz9x1o+tW8oY/3Ux+C6a76efrf/ifftD38YWZXwXqCyE/cNHQNXjcNgbxGLSNRB+imx0ieIew1+IhQveD+7eTf8dDdtl8ykl/GJyaWr2ZLqUym2pRjKT1tk3QMskmFmu8pFKMkkyr+JyzE3VJrU6WPkDTcapAbpt8lzgUwG+1OygjebYyAJ5cyoBiFNDQE5D84800o1g92rscQNsQmHctYFRxd8uQKloFkoOY9fvhjuueMXaJbrF1jaZXTPP4+ugCehL7S/WZouff43cBh8Hq1UuvDd0Sg9M3vbUkXOjW7EPDu9qP/n798N16HtdtSpC0OezEYpzaZefR7FeVTDvzGtafC/xowSeGphVHgJLhOPwnzQuKsKATgaQvbsrF6F1IkuHSkAvhVJMik6smSlJifwJm9REgFFm4Sp4YD/joTYQW5zS+ZMKiduBLVXFGN2kyrp8SbtzVNAAcsOHTIY7rr9Z7BwXkAp1mpk1973PoB2MsKJNq1DhxSK6thOcTiEw1IY5xqTo/WXPkc7Aufa/DhwDvLu1pVU/nzkxKMG8St/DPATDdvybNDI3sb4ect2xbryxtntjKI2H5TtqsYB+PedGP/bOwB5QKL0ewDH9flXHHN6EZMCEi2C7BuxjuOZwlJNSRan5eQI6netovDNQXDUl2dCrJkzAnZlpVWxad38PGAQK8TKimsh/YL+Jf7kX//yhmvgzNM/qDeUdevQ3gYNbg6HsOnVawE2Fw1A5eZcaEcLFWNzsUH0jqWKZrdds+lauujk+8x+NDGMiBN/HVmQhRRHqm8iy18qZq44A9enYZHuLsXWnCFi2H3EL4YCM5H4IwJ4pCGs+yaZ9WlHLwS83WeXi/M4UjlvDiSL8f8UfT4rczL6CzOhBD3hTPA1wVyKVZxipVjtw90sVGhbxOAv99wKSxbO9Z7NjXiWLVkC0BzMk05ziViy7c4vhBOnLbSAeJh6+kIZHe6bLytv22YJLp840Ag37krvdSaa9aEYR6tlSF+gUEofumGVKctoAAAgAElEQVRHSVX5BxdsZm9ciRCcmTIftDJCGOALb3+N+w5O69zzdqSKh6yARaamExcMrbi0niTKVN9c6iX3+MWGwlLNlAQKXpxVqeHwq6fBwL+RpQZ6iDGtpfLSu90RwTBB5DyLXfZqXhU5N065iouKoPaNZ9xl4nVofHMsart2787aNOwpKIATpiyENgzU1JspXasVHc6aA7g+R/Ce1ma4p45UMOHSB9Cz86kPhCubhVI/GVk595bS2MB6V70BI5YiKBM+Aiz6JVvW/LqmZNHqttgbkSsw2T7U6kEfzISkPBW79fc+2DW3LpGd9ywX8P4efndtb4xlwD9HwogrMB4Fxpmw2I2rXmpCLu4kJ1RlfE5OPwUF+WihciZc9Y0vQ3Gx4oC2dy/etTGcJ4F4ltMe5MTfP3UBHBTR9rLcfFab0wF6lVuc2tkG/9i6FgZQkKgAaR2qPOaiJKyPJnqW56hhU+aPGFwyYJuTn63ujcYYn8vJaLnxKMTHt0G76qtXuQQTCE+1/gzgZEtJsUL6Q6IFNNEFvNNy2oli8BSi9qjPHANFW8yn2yxXQHHSWxwcDNeyVDm6U59KSorhh9deAZ84A13z9uFZNns2agBSQ45GMR6dOrYWlcBpk+ZAK4L5kZx0gMmeZ1C8Bx7a/hbMQjDXTeSwUztDN3fW830fWdXvjZpy7KIBRQVrLC8N2ULBZqpn8US8fmfN6oqo6++XAI6HH8U3SestuagJ6VEfsTLHIaFTA3YmgTTSJAaK/GQOM75R582GAa8O5XCtPJ3lZEro5HrvFwyLXPLPOeUkuP72n0N+mz44hBmLTpk3MbreJ9A6pSus2aNOI5iH38w9zEE06wmTzU8GTnU6dS0fOfBv79kOn9vvH1f8+eMATkAL0D56n2/Fng3FviUqKlfci7LCc5igkE1HZuBPZc4l/ePxxD07a1d9JswcepXJzAii7qWtPiQQvWdJ71r29UQOyychkZ9N6WgSSIO4DX/6lMpnJFqoDPgvdo3k4ixErYi5QX8xrE/4EvULhuU0OQT8nzxATiTR2x+HWQzPop34BRg/hcwLueQ+/UBWsh/2QGFh+mcvowPI1jJBpOCpPTwe5eI3N9TCCOTK3dIstPneQOYEfTOdh1P6Z+rahKrlh3DRYvzh9GjiPExrnYaJrji3W7t7Zu/f9HJ4BYMLbfsrgJPL+ei+uV6MXhHnfSoSGB+qckj4aDb+tk9GSpz16LFw+NuF6AypxBe3Abjd6cciC1c4G7tyU1q9nNKyD36zs8YelbZXpvShIaPhivHq/d+IGsMAPUzi2zkTQBGsNzoiFKrRK9+weDf8ur4GjmtLfartHXQ5mx05LAUbo0fudTgJzAyqbMbCUfmxYsINXLrWOZW6yygfL5Z9yqQCk23JyEiVpYqQ2NOwKbKj7uvpXCTuvS7gTRzBp/viAAbDYHy7bT0M2DcQPnnBZVC7aavRTadQtObviNUw+Vc/5SZVurDtEDyAVg/FARVmmaDbD0dPhDtGOfhYSPkCM75ReHS8ofA3IPnvTSL1rW2lC+BuHj9GeaTDRw7uhZ+jqSEGeDWGeyqaEfyTzAn6XqIrwzCcIOZcML5y2S/zY7HLZTfNA1Z/vkxRonsZq/mg8dRhd92G6ELIqqTujwDeH6xPrkbCoj+aQ0oCebf8C3/6JO3/jLfNTytny3d/+Au4688Po1k3WcwqIhW7JycbEPfulMniJETf2cLSEgFiCN7XozjlnIM8jldvpk9MOBpewQcijqSkC+Be+dTvhqAo5eFt62BGVzv0ce77c7jk/ijnsqJqWS3aYkdipivBnx3gHrtY0i2RSNSjA0/kCkz9o6cPrWgk3tewO7/oQ12yd+UPOKcXufYvCXQP7VNyb9nXD+LZ8m8Hic/d9z0M370OSa7IwCU4251+nJSb0lHTycyQ1j/GiIBTDu3DCHm1vS5SWYaOPg2FMlZ0H1llISUxQfSmukDPQAMr/jFy4g/duQce+WgfoZG1G4/hmvuI+quKyuVxjEAYCzJOv5FJVsWO4fbpQguUP6MFynl+9YX5vk9ygV4DQeLQC+0/CDPYLJR5CAl6lgd4X4Hf/SwL/QjcBL2msw8/Q1zOlo0oSjnpdLEGZYhMxbnH9NA0lZsWhRtHavY4nHCCY31k/hHiu7kdh+DR7W/3Koh3FObB8gWLYN+hyB5NCTwXaoF0ACdIWb+8Tt+3nt4I+29Iz3szLeI4FyYGaQYuLONKN3bakllFBQXr7Xdei1msqCvduN9Ujd3ctrM7uWLP5lX0MHnkqT8COIXJcRZPRE6eQBVSEKolSFDnUHpJGIXfk8thREGzA/XNN/N1cB18Bz9e6clnnofPX3q1GQRLcfBROXE1vripDuQu3V5cOIlWl7a3wAM7egnECbPxHafWCTE47uRF0Hygd23E/UDVb1IzxYGr7XbMPQR77n3L69VWv25G/b1FdEKVo/z7Tyj/ltwHYzvMGDg6zXNeO8iDa6b4JJmsr4k2hKza4/4I4BR0+uc6ZM9iHnQrZE+hkc2pc0rC7fhFZC9xRDm2ozCE+m786BjQ/fzmO+Dm39wt1Hn2+ClcyiLN51hkTgHyrL+M3RaycqYIS5UNJJFNv75uE3zmcFOUQ/Svi8D7FfwRoVv2NqG35mnz4eCh3gVx/45Hk0PnsHCT5HRVtULj/W+xtyt7OT2Pa+wEex/Kq5YdxhtiqXSJzwTo2elnmhEmdtZVRxuBsL8D+Jk4ANSq9ZlEXpaTcFG4uxUmWXxvCroVMlB2Zsf6MJLzTPzoplt+exf87GZ8JZ4pLDkqW1/8EdJBAnM0RVStUxjzw6IakqiFG9qZ/+N10fc/2VUL56BcPCuJwPs5/FlqbW3r9hI49eNzMUhi78ZNyQYNtOzLPVj6riltsOfPb0FiWHoPDqcxVopDPBOX1Xa1jvKqpSei8v1/ljUoMpgHkhrdnb5M3wDUAPBE8ra6mpWXpDEuz6KZOIwy1VdWLxJ9JP6RZfbMdUi0Wik4FT2g7J6ScAN++a2MEiZk5VUYjeAd/Ohw32oT9Q274cxzvgS7dqOoUTj9GIuWsd7WSHhGHBW2OQjw6SzjwG9PUhG67PABFlwpo9JoYrDp0V18R8IpvbkOvTXPOxq6usRDKpny3hPGyEHnIeS0O9LczzPRTyTTXdYOe/60HuJlnVF1K0g9/4dLK0W/VFG1oganzDTyl+tScx75bVJ3VqxHAhU9CPtHtVRXZ4wT6XcALkCc3PgmB5ndDOSlVUrgjQJAn5SEasxR6ZetN75/BB5Bdb1FYa/fjeeeg1s+9Vm4Ed+eTOblc77F8Gjk3Dd7e1Aw5By4hfyRWhF/dzIvlIrN0w41wW3IjWck0RlCj9d9yLv2Z19Ab80vorcmRaWjbvshWZDORlmXaFeLm7b1UUeEwvaeKhKz10FH88A4NP7pbeiembnY7g7kJf3TIlyAFhlO2dTFFfmFhdvJc0fy2LpQbG+D0dQv8LedHolkO3LfPMBQhlJ/BfBbkR4Zu5Zo0PoA5pmHxLNc1xzLJVnArcgeMdXom3aWkXiZ2YufUIv6x6hH/g4qPfHtykMYS+TDE+fCVnwJ3rBGYdIQwZEoYhPZOR0bcTIvpP/+VLce3otOP5GnB7DGs/VqfeSJ0XD5t2zemj52wF41M9ymDH1kB+qCvh/QM6DEMTVfvQVaP52VMMEE2sdgmyn+oOXIfSP/MMNpbOLCwx9jEL4L7LUmZUp0zlYvesSTyad2Vq/MaIDdPrJ89DaRzIXEJ+6bAqP3Rv9JfDMbG9bzPEEHNsz/SLARZif3LXALfAU/gVIcw7ssWoRCo1Sp0fnlM+F/gyjEC0/2jaOCtpFJVWw6OPoQiOcjJ7+hdjUMCNRRn8y/we+/GKzCG34xAX7ze5s/Bu5yDgJkDmmLFW1c14W6luWJMtpKsP675fYDZbVckLwdiw9C06+qMy0X/w2iwJftYxszddHRRYVF61S/ec5OiOugJnRIcR7Hdn+4UUG/qyOxZPfWVaQaz1jy71HGmk6vYpyGx7EGfL48q8k9LKzr7mAwQXDRpxK5zB/ETyDu+6mnAM44w/Pdyq+UTYfHMbYI2yYyoqHcM/Qr4cEZ1Ea8rLsDXtryejQ2mD/CjlwVbjrOvmA2rH5lWLjCfbSULvdN3dcBcDVPojgOB/5vG7Sejdx49Cp8EmMOxkWcYrqLT6etRs56id1VkjPbUskuuAcLprProoHVarAEHsVQeF9ajb1TndyQCFG/QO+0fPozgFP8s7X4ky0TAZrmE5BgLwTah0n4Hua/NlCZLGT+I3oZX4gfrUSPL1x6KcCDD2plv2zcdPjb4FH4Eg9DbKWMdcP0io04xbCkWJZppJM+PB82bs6oaDN470z9WeCyOqAsKw0C9mpHuie1wb4bNkLXHHdL28Adp2M4jxkIWNOYOQMrhg9qkdy3NGuVDmTS+omvTHcLFM598+uVPeqNG3AqivxGjH+S8WB1/RbAOenhu/jH90NMfJgityGxgsvd+yCAL0J9zxr8+CZawL/9LW4TZFcPpkai8yr/+OCR8BUEcobicpWpnA6JE+w24j6emqTs/GVdDXz88H7frjtmoAAHd4QrqpZCsT986GNzYUPNoPQri6CGIACcbnO6bTnlo991vOcA7PtJbRRiFXJcGOc0nooZK+5Cnfr5DCNkbB5agwkh66IvGGPBdSzcysQMVMYPKWYjJaoXsi8Xqyl5DKi3WQzxc3tdzUsBhXTBZ6e/AzjZdhEXjs+7ZDT9D2v/IBLL2cvSq+lk3xKhDIJBTHFZgh/PRC/FX3ABwBuk4A+XaIcdW0XG1Q7LjG6qio245Oz8PDXJ1mVtzUqM0B8wUYADUlpGuOLPPOcYeO3N3g1rowuobtQKyrjrtufJqWNgtJazdkPzNWhMFn4+PoJlH3ME8MplrXmx2EAJ4NzKiQKtcdwW0B3oQQdXc0IZVkLULdvs6Oget3fbmoxrccOTL+D+yVR2pBtplZ7Dn8kZaoPeGvkAEiqccWsfUmLmowT5Dfwcgx/X1IpXXLIu+dWvIiHnYwNHwFcqKk1Zu8H48GtpChfOxI/OkQulVcqpB/bCbxsDxODAV9yYuWAGghicf/FMePaFEZHQqj9Uog3gHuaGcpyJ0h7Yf+1maDsN7QKCIdFazD/PiV7DJs0bNrikFK9oCNvydMK6Y8IElElEAjamtmP4MyjROCVoSzv6RDLZUF+9cnw25jMY2bLRoxBt4Dzh0+pAXHLU74JQnachkcK//5WESVjH1hDDiryIr833HzH65tcw2OOhaE32ziqfBasoTCtdVcWKkzbiTp6a3BLNHcRJlvlWzSo9LpyMuPC19Eym2+4YDz+9aSJTcPWrpGMnZxuQLoC70cGpfHxYFxy8eCe0nofPt+kpOs/A5UFGDCmpvHLZT2Ox2DeJ3UYg5Vy2YBr8HJXCzp06Jvp7PAGXNNSuvC1sfUHK9bMV5z403NN0Zfol/nw+CAFc8pI0lmwVrkUCpR/goQ848niaDD79NMC552b0keHTJ8yB1wcMxGfakKo8YAoXPwpuyNEqhW08YaZn4ZqSMADjUq/e9DoMT9KrdS5pCf7+WfzJQnTY2k0l8KkL5kDTPtSpa3r5BV2nnKMMElIpaAv++YMAeJDzgalH8hPQdvJ+aL5qCyRGu0or38ClsMCtp2T7jVt2hsFlZxi8eegHbl1FCxpviT3IfZPzsNT4+BM1jRxHDIBLGiDVyCn6TvxxeF5Fi1IkU/8GEuYZrdw6mZJwE2b7qk7WTOQZASNYqFjHdBFq9v7wh0w0m1LnmfhgwprSIYIh4gqkFE9NQ53Ei5veb1ZpLS3cBH5+3LAZzj1EscRsifxeX8WfLOoZW1rz4YtfrYIXVuFDMEHQy4/6Udbl15bP94EAnKkBg0MMzXR3RRu0fmY3tH4SXx60ir5cuW/qennl8g4kfjFrN+PgjQ0yRsQMoYz/eBS9L7MWJT04ddNcANkqjouAXoAmA3/iw/xSC2agK9mtSJDVfpkDf9/LcvA70PTiIvsbE11dqPpF3e+mALLkwANPLXAPmhdePR6tU2h/MR7F3GiGxYDgaEj5xHIYLszOID69ow3+ja/EGDFTKHAv8mF4bmU9Edbe9OsKuOk27vDj92qLVwcz5a0ZBITt/QtS1vPccdGeGvXT+U5MbSwOHe87APuv2UxcuSf3LQA8KW95YU0egy4alSZdyfjk3dWrtwWtI2z+IxbAJUFwHZDGjp5Som1NP2SxQp4YpCGux5/nkAj/DUtA7XJJdpk/QTt/RBkdue8DGAlg8mQA+rMX0oOlI+CbEyotIhTCcSkPZxtCfHRBfFxHJ7y47Q0oIndNOpPKemFgSpPPPDscLkZuvLsbhbpHgLcmP4yCSYc8wT5gZQTGidJ4Y/JQ4dcaNr5IDgkpos2ioyrnHDVi5FqLGD1D4ix1dRmWinnJ9Ts2rDw6myvviAfwbBLTs60kHI/fk0VLVtOD8CA+EaQ8ElSPZ9acORisojmr/bA39n6MnVJbWsqv2EyaoogMxb+DgviYzk5Y+XcE8ahV2SEpVbNxAJx+1lzo6MyA+UvIPqVVLATohhWhUD/dwAkPBjIxaUlA3loUwW1FKN90uKfrrgGx/Ndi+bHRzFFHBlJLa8D6hZPoHIDkWVJfm1nXeXuPcgCuP0fp58xyWNn3wHvQvvI5s9/r1wOsWBHYKSf9gafWQHF4p1QtM12QacMpkQwlqDuCuO1ZNrnZycxw7Bh0uX8SQTyjMWj1KdLYWAgnnTEfDXv6/8MQLlIPV2L44b2XiMOrrFmOKxBZBEwEULZWUH4iRXGZsjpxGjB2o6duQwe6574W3FdEfzml5MwBeBrEC1yUu3ZR9OlTApcNWIBinZDishA/LGHoVzj1VMDXCQLWlLnsXxs7FR4eNkYomzg8SLdn1qoDJ842qce1mMpPnNgGzzz+Zp8B8dbWGJz0/9u7EjC7iip93uukOxsJZFWyL6QTCYYkDJAMgcggixAQmZHVccBv2BxZhpHwKSCoGYkSENEBRjFiZkYz7AOMMOqwSLqDLEMjId1BpLM1JEAwQRKzdN/5z13ee91599W991Xd5fWp/i7d4VWdqvpv3f/WO3WWebOoY09DKOcRc8jHI1lF4NWMort6BqZ7CLKW55DGbDYGN8h8Pv5vPcg+fxKyzz9ezbzCthUCD4tYtfUtO2sw+7GXxiatVmq39pyg+GX8HOw5qN57L9E552CPkFi2lLLz49FMxi6c32v2rsozLyzd6rkkjoTitowguyp+uE8+8R36/s2vU138z/G+c70H783z8/SZ8YdQa/8YzWI0rqooZByoTaBK/hPxmoM8Qdp5ewPAyycfg+6756jQ9V0bWs27z5f2KwSucZEHFmVhe+xYvSwI3CZgxYEwh2/Bz2T82IXjmNy0b7yfgOKMV/M8NR1jFNczE706X43d7l1zwzD6VH6MH/iPFjrs0IS/cbRjDjgv5vIhXkLnjjuYXmJTyrD6iBB3wv0uUwJgiMYaqwbhZpVVi+pzb7hM4MW0fnlTpvgV0cF8W0DgZT1ENcLaTZQQuClkVXIR5hpVkBWBvqyqGvTzmcjI+wx+BvMmvw12dAvwfnjbeDiGoMPzrceemqsGcXQTx/vS8cQskrhKbeIneMTw3dT06xeovm/JAWnVow0hgAPvsTVhibEPk/h5IPEXByAKaqkZZQixflUL7wTNL4egJNpzXHoIPJjli+11yWvGfW0F+aamAfIeIqzNsEIxHoGwtFMhcP13MZxECyeNjuPRpHANi7VZz70EP1fix7br5tCvj8eqios69EK7IyfNpo56dpl0PC9LSZy/Gkct99y1mhbMT8BcEmb2dhK99n1H7pE478S52KQTkXS9V1MaH+RAxB+E5X1uvtfUMeMrApiA9sQdobVn/Zp6HGQ+FZuuMo33Peqzmu12lh2cm6NVB46syAeVZ+KHHXXoLXisXXcdEccz8QxTM4SIrQ9vnOtE/OTHsYTEnQTI0cqiK9vp0r/fFK1x1FZshzALF4x+/AqT+JnjZ9Dv+rM2zSn2OYAXdMn9P16wASfMSpGutXp6Rp2nlnbqN5fqRdBlWzC5GGLtV/PCr3ZK+Z19+7e3P8WJX2IpQuCxwByiE8t2QeE0bMeCoA+FOmTSTtqZ4/CvI/HDeSwn4edz+Jlvm5bzc42H4POfJ1q+PERH6av6yKBhdDEy+jghxFmd4nCWd4AZZcSnnPQO/WCpoaTI5QbE5vXs+/u6erRM4qdOnEm/b0hZcgj10JU1VKTrCQhaz69Db/ft6L/dlyAqJ6JCsazt61ubQkc6VoJZoYIQeDXoGWyLhc3B6l/FVdkhHM4rdO65RPffb3A08Yn+27HT6VcNQ6iOY0K5JJ4PGKKu3CjPOG0L3fKtAGyqY4rtLnkHy5Zq98gk/onJs2lz3wYdI9AnowrVhjMI9c7arsXnHQFYyK+e/f+9rtzf9q8AMvWB5c7Ysl5HGjVj1mXlxpvANHXDVpvyQOBsaojswYpyzTVES5aoamXq84cGD6MvjpxC+T6uG08VKpTF1yPY1VkxHORy7BU+zQhB3t5NQfYBmj/lMNraJ/vOPmEXWtAdeKV6jgq8eFDNqqhqvrWFnYNXH/2uQBq1s6K2j9JOCDwKaobbYLFCmU1fV3bD9t2fLXGTVzbIToWtp9bR3HWH0o5dfW0HjajlwZ+9QrNncqwyg6UK8vZGtRvfNk6BOqWtn51IJtMl6K7amWTQnbrrJ1AGGSfJQimV+dc1CSzGcTYInPM+xVaEwGODOlhHIG824G7FVTlZMycangTDFc6gU0uFVyRHYscXCy6HHT2LtrzTP5JOc9rUD+kXD7zsJFc2VTSQd+nQLhndSI8hYmMSKgBTEFWUG5DtK7rW27pv1w7cDWEbxmdAx7w5PstOKzfk3baVhncL3UcrBK7j7mmUgXVwH8SdoRR5MfKl3nWXslqmKvBG+0FcC7uP+vAFc+jtLXBD9w1vtO8s+/TpokfvbaHpjdGTKSmxa0cNPrCMoDapJPu7w8bQrSPGJaPIVU5aVSHYjtqTokOFwrIKoYg9wa5jmGq0uj5H8Kw1iAMeexg1IXBdd1CDHCxCTg0He0DFqd1rrxHNQNTKDJoL+sLEwaeacfnkWjlu4Ux6/Y3gbujGzQe3Yax8XKWZvD18fgfLlAvg8LO5T32I11a4RVg4+wt4kBhOerDaugjc9sTkQODupMK87ION1L8W77535+jjm9c0sdFBrEUIPFa4K3eGdbAYNb6iHFKtHVxydPaXcY2vPPN/WzGCrvvGFOrq8teJjB2zk+68rY1mTDfoQs9WvtNxtSvvVNUVFo+cQP86lPPjamTZgGqLsIMPt/cOJ105ZFToctPNFaIVQi8ehyoKdujvbGxr4s1X7EUIPHbIK77JN+NT9UKYNs1xla+F8glM4n9wVdb4F2a6dWsd3bVsNLW8sh+9ua4f7d6dp2FD91Dj1B104iffo+OPfZ8aGqpPY+oLLaw2bVerN+ID/3k4+1w8ehq9i914ZJdNe7iupUYhw1F8cyjXU9Ddtz1ydpWvFIWyMDdU9pzAXNtwkyTOLvxd1u5pHW0vJPJACoEnu4YLvWOBQulJ65TDacX55nTe/mW8sNnzbbguytA8PgBLzAA9rI9/zNsQHvXyA6fSk/t5bgEcC9vdYdqHeC5xuTxtP9g9vDdNjVpFrn79htmxq/rwPkck2QKB2wHSDDOc1QnTwbXxmg6W4ml4eqaWTO3JxQI8BbN6RDmzhx4iOj22nKnK4YSuwCvuTFx8/uqEAslG2Uh7aRq+JxjUzAQB4qcHfIS+NmoS1AW969ENSuCMoRPYikMUO1xuCiro3d9E/O/IMYyC3G9Vnd61ClRoJPg5FuhX0f03lUO4806iSy5RVktlBc4WuAyX2j0pXcNvwcHyHPoodaZjWGuR+PM02IzvSCBpgYeATaj8j+J/woETZvttS67coJTge1qkFFQvSkV60CnYluc7rA+ssRs3Nm8N2spEPSFwE6hGkIlFtxTN/lHZ9IYbiG68UVktVRV4p/0NXP+Ay6RNtolJr6PlNIHO86jKRBdRZO6A9+aJEw+ldQ2cxVlKzx26H4kX/DUVOvWeiDrc7xyPQne19cO9nTO3/v45ToqeaBECTxT+YudYcOx5yR6YlUvWCJwdRVnXHWuUZBWIgT9fhOf1ctROOMe9/3gvHT2VHhs8IvCEqq5oOz06KoqopVIuzHIyVeoTblNuc+0lefA+dL4suONGA/c7REUVi2epaytk7ENRC0kbmmJN2lAJ5+h3Ierdk3ZlEcDCWIQP1KlzsqJCGQPXuHuw3z42kzeco9t+ARyFDNB0Ydpn8PMhI/dc/dEpbMcDbUHtPdJBtC3lSL5wsOkZ39gsX0z0VIqVF8rXtvLhkL4lLyn35fDWnq7cBW+1PZuqQPu1d7fT/rT5jA+Ljb0v2Quzckn/IaZFV2C7chPIO2UB9lTQup+zlfepeNA58bRapRVQqMFq7Lp92NjGuZPgx/IwwjjV6+RwbWrjqgBQU3hZAnfd6r2uOXN9MeSVZyPubysOmWiQa7a6/nzVxtdffK6qKRhqLARuCNiwYrFY+Huw2q+vvR05FieGFR9PfZhl00qq9/OmjGcQVfWyCyaCx8GhiL8NsVVQ2gsC4tAMPMT2uhk37Yg5RHVP4s/9LLC483Crya90kgXCdnerzmfpp4myapkyb5+iuaGT+Qku8IX8ffaOnKfaSTv67GkYjcQMCaRyCrfk0n9nws0n07WxuDZgAmOUk0ijI890+jO9hKwTnBUtm4Xz6ByBB/g7+P1XGZhCB8Y4yyNvb7wHNv5lY13eWgn6Hlakb1ct4Gl97XM4N+mBtyW1mSCsdto8SsH03+WdfCrtyovqFadtNysWsnYgqmAmwkIKgZtfg4F7wCL6HiojoaWiXHEFDmX2DEoAABAySURBVAb5ZDAl5e+g774bKpOsWZgU4WP/ykNB3hfgt7Yk0wbvznuQ/bGe5F0g8alzhvfJ92vBfFJ7+KoTGz+SL/v/3V15RQJHZh0cVMaaWScqHkLgUZEz0A6LikPJIiuxoqRJD34Dxvo11YBT/TmHpZoNsmPr9BWpHqkzOE6XPNaPvL3xjzj44EH9Ovd/DpvL2CPklWIYToHTA/2ACvggu3RPsh9xd9+B09sb1qzkjFipL0LgKbtFWEisw1ygHNYCVHn6aWU1YxXYrmo5aA/Z3DJcOKLJIZgFK37acaXdN5RdiY7CQ7sqIOa5cdPn3oKDzSt63YPu8+YIROBW12sbWpsDJxcPeC+MVOt199UIihqFYoEdA3FPKUU+8wzRMVw1gZIHef8CtHd8An3r6/LXEHUCdqideNa/i7/Z3jvNhSnpFDyw/x12kPVNQ94feen0/fO7omc2CttnbPV9dumqzbtChfJLqFAysbqFwGNbacE7wuK6BbWvVLZIIqxsHcj7addCWjnA1Fa4FcRtmwiCFcfjF2c9TntCysvxsPIZSbhi0Qlo8HjuwzyNOu/jVN9m7mzO3vSqmDPc6CPV9h1Cya68EoF3Wp23bGpddVWkzmNuJAQeM+BBu8MCQ9YGO+q0f4FdK33qU0RPPBFUbHX1+uGwsglHlbOqE5Nw60Ug7297Y8Az/S387SZwS3hk/t2vwIMaLVmuRWsgFvGHndKveQjtv3gS9f3DAG3Ggbbbum2Bp4FOQrwAfPXril2593HP34yP43lpnY8d+E9SuxpKBqYB8SxMM3tjxEPBUfz5a35jxdFvwxncHJj/vmE4QPUExOF7jQZSdkNv2N6VIO+fluKJ5/VN/HtCilfIJoxtHB7U8EHOLXsDwBuBfUrDC4Np2NUHUd3b/Uri9oVHwSHRqo4qw3caoUU3Tlcw+N4ua3rH2mbOS5v6IgSe4lsEEudDtf/CVVnZvX070cknEz37rInZWNAOb4eWOBNmVT4AsJngQpD3L3uQ90H491oToGmSyS+dCXhImcTDFz6pINujtHzBK2HQio/QAd+ZSLmdvIVmA3Guakfbc3bUHMCJ447bEop+jJGjEJYZib2D5/40uJD6WqSUMLj3uun5m8cAv551G1tXTggPdjIthMCTwT1wr1iQfPLE+tobcfnvfzthoPAVZGP7dkE7ELiPChXXIgp2PdWleoeqmie7xh8Nbni+Z0U8wKfi/z2sEpDg52fgAX0gUv/O7nu1zcOKkv9jHxp+2TRqeH6wFhJV9Zfqz7usJevbmtKuUitAqLy5qQa7Fw0ORM6B43+Ay39HxXiwaSFnrOfMPdHL+zCo+xJtoyUQwaqcrBbbQQfkXRYMEDiAojtSOrmH8HBGz9xh2aaGR4SZ24CHR9DQGyZTrVmrdLPxtj1Qi9ELS1Ur/HdXjuZuWrMyqJlmGHiN1BUCNwKrOaFYjLyzYm/Nz+HyT9O+bBnR0qV7afXqgNkm7TFzsrA78E2Z3clZtZBotpEqUWSHl5l+5M2y8bwGC+Fb5UAiNN+JNiPwcEbL/2PRPLRnfVr45xtqlaHXT6GBD42gXIXk0RHmVGhSCNEacnSVHHZCnH36D92it9a3rsyU92pICKu5bdJWNwJY0HMhk68puMbiYkcPPpRrwdUEneJakBQvyE/jOhIXe3qOwsV54Dn2BwdD4pgavOP4FyyGLXgQOBbLC2493UOOSx4T32yQd0X9NrDhNBPXxjWoEP2ch3vx7yHqd69q2SmXq3r55rf2oWFXNVL/VVgqmliiRIMeXmQFhg7qiamw/eYwspdsaFuJlFfZKZpuTXYmLCP1RwDPCOvb+eFn2+islncx8Bkg782qCYBQLkUdVkulqbTgoYyeMMCyD7yf0jWhunf60hAccg58DLGxrHxo4vVMDO23gKu+0DU2W05FYg+eDxPjfBWmgzMhMby1j9YJhRMmBB4Or5qtjeeAD0h5x6qOhpheFFgF9Bcgb3VYXn72iT6DX/enaDqssx+Oh/JPkcdkEVx0aX7k9j4NmcgH3z6OBt0/0latOAkPuLj2KVhAthWJa8XifMQGhtVl76k0j0rGi0F35Z58q7Pr9A1rm5ExPFtFCDxb98vYaPH8NUM4q1myWtowcLY2CUTePEkQwFT84nZpKQvxQD5a1WAsO9iVMa/Surfqaeg1U6kfW6yE3o8HnBluDMfqjkxOYRXiltW0vrWJsy9lrkTGKHMzlQH7IoD1fjM+zITrsM8kQpN3YedF9Af8PTEFy6M6qxPnjcTxO2Jxy+3T3o+GfbmR6lcP1EfkYYm3zE3bZ1eucNrBi2JHZ846quO15v9LwRoIPQQh8NCQ1VYDrG/29GR366yuhcjk7e7C0xDIig9dR0W2Oim+jWI/lK3raKD9l46n/k8MpxyO0CM543gxulWLEPVshYzGlYqsaecg8uDPsvpUa4QiqxD07nHjmWBnj0RjRldxB9ah7eFh1CY9+8KOLbDDSxXjVDU9Cw9i9bHILboXHf21qjMjn+/J0cBHR9CQW8cT68udLDeec6enBy/qRmxfT1tPUllHbpscKupEnk/GnHbKzVMIPPLdz35DPByc95Fd9bO4Dtja5OBqyLu4caWf4+8zE7qjvwX4oRxufMdp0ZP4bEFC8yh0a8dZuazRqnsf+ZUjryzPnZ/FVhAScVcO6c8gbRpjVWrdmDR0ofuPDG/onqRB6hDI8MHlDoA5UQd5803BE8z28WyBE3dSOE6NNhIPoR7TNUMWKBEX7mVjph05IJeru8mxRXGIOIfdNO+8ux1SepYrthEL6lQyL+H7Ve2uvMv60fq2XTAhfZF9ITJdhMAzffuqGzweBKMWC9WNzrc1xzZhO2+t4RfBCUsh144RHlNh7CfiAWRHKj0lJTtwTGYLeJgdxmjU5Hkz6uvzdyP9++FesCzdu3KP7znBfJ7fhu5vh+gLSed5OJ14cVy0cc3Ku/UAnrwUIfDk70EiI8DiPgkdh87ukshgi51uxZ+NIABWn2gtrK6FQI5WGEdGes7DOQ8dlg31Gnlilh1++NjI7fU1PB1odrOpHjtj3mTam/sx9t7zCwpyLxBt1F25wsKk9LQTduHvdVm5v9nUtpLVTDVThMBr5laGmwjWfhYSGZRO6iX8gw8sOVyAkQISPwCCX8Rl0qzwN3jojjY0AX4h84s5ybIdvOwbevjAA+cMzw+qvyqfz/OZw4RoNoiu2trbehd+O4eidnF1NPjXh9DL3LFr196bt7z5nNI7N0ngovQtBB4FtRpoAwJ/BNPgQ8y0Fybsa0HcN8UxUDzw/NWfQ7hyQCidBUHbiWOcMO5mimV/gzjOjPDAUltAyoFDAYxtPBKmj/kTsFtmS6gBuIr+Qd2OFz0tusPNtls+D8nWx3gVS+jMsrah3u1W3rp14+pm/uZWk0UIvCZvq3pSIPBXUSvtmbfZNf4YPKPt6hnprQFK4BfGIk1Sf4gH7UJNsvzFWEh45wQ3S7I0g1kjvfywOx9QN6j++FxdDiEOcgsxCQ66Fqb8EWT+aBdZD3Rt2/1ER8eLfNhd00UIvKZvb4VnXUPEOsPQ3Q75/wTy5sO+RApInFUp38R1Nq6wzwpblizHdT0a8ovIfMk4gfcEaNy0Ixd2Ud08mAZxpM0DcT9G4y444V4t6gCunKmoA2qTTTgkfXZ96ypz327M371IPYRdlJE6kUbpQwA78KpDjhqaFRPf2SDu/zQkP7RYEAc7+3D8ddbbqsK08sEkB8hajoeLs93HV9KhQvkVSPaT8U26d/ckBN5L739KVShsIjgf5M3xyFNZQOYzMLDZuDgQ1iG42JaYSZvJelXspF2KkpWoQ5I3khUg8LNSefNqcFBC4DV4U4NMCQTOZl6nBakbUx12avmYLuecmMacrm4s+ioGxCqfJMu1IPDFSQ6gN/UtBN6b7nbJXFNmRsjOLLOEvKtcjJadeenBKqVU23wfG/BqBUp7fwSEwHvp6gCBH4Wp/yYF05edt66bYMGu2kmpl2SZiB14e5ID6E19C4H3prvdY64gcdbfhkl6rBstDqM6OUj6M90d16w8izZibqMTmt9GkDdbjEiJCQEh8JiATmM3IHAOYh/Y6ULzHNja5CCQNydUkKILAYuSjG9+Gwj8Cl1TETlqBITA1RjVbI2E9eC3gLyznAUonesiWT34SSDwx9MJTG2OSgi8Nu9r4FmBxOG95h+7IrCgcBW3g7x942WEEyW190HAsrPSHxMzMk+DvBfE3Gev704IvJcvARD4FwHB92OG4UIQ+A9j7rP3dGfZWek5O32cZR4InBNjS4kRASHwGMFOa1cxJ3ZYBfJOOl5HWm+FvnFZWmO5qMa1BOR9jaqSfK4fASFw/ZhmTiIInDPRvI1rhOHBcxzvUSBwPRloDA820+I5tQ3RY7hMh5d9wu6D0+5IiR0BIfDYIU9nhyDxMRgZx0epNzRCJwNNTmMGGkMDrRmxFg3GXH6Lq9HQnDgN3WEg7w8MyRexCgSEwGWJFBAAiXOkt1dwDdMMC8djPkTIWzOqQcRZtB+qcXxz3XHC/xcyPy3kHeQmmKsjBG4O20xKBonzDpwPwPRkSid6HrKOSjIsbCZvhM5BW1QHcf+M62pNYm+GnGtA3sayI2kaZ82LEQKv+VscbYIg8i+h5RJc/aNJoJ1otwjEzXG9paQBActO5fY9XDMjDqcF7S4Dccdt4RJxuLXfTAi89u9xVTMEkXMG78/iGhRQEKcOuw/E/YWA9aVa3AhYdD66vAhX0G9Zz6Luj0Hcy+IeqvRXGQEhcFkhgRAAkc/iHTUujoPNqa48Qv8T/mZnID7Q+jqIW2+m9UCjk0qREHDOPDiC4UG4hrsXi2JrIb44xvl9IO4tkeRLI+MICIEbh1g6EAQEAUHADAJC4GZwFamCgCAgCBhHQAjcOMTSgSAgCAgCZhAQAjeDq0gVBAQBQcA4AkLgxiGWDgQBQUAQMIOAELgZXEWqICAICALGERACNw6xdCAICAKCgBkEhMDN4CpSBQFBQBAwjoAQuHGIpQNBQBAQBMwgIARuBleRKggIAoKAcQSEwI1DLB0IAoKAIGAGASFwM7iKVEFAEBAEjCMgBG4cYulAEBAEBAEzCAiBm8FVpAoCgoAgYBwBIXDjEEsHgoAgIAiYQUAI3AyuIlUQEAQEAeMICIEbh1g6EAQEAUHADAJC4GZwFamCgCAgCBhHQAjcOMTSgSAgCAgCZhAQAjeDq0gVBAQBQcA4AkLgxiGWDgQBQUAQMIOAELgZXEWqICAICALGERACNw6xdCAICAKCgBkEhMDN4CpSBQFBQBAwjoAQuHGIpQNBQBAQBMwgIARuBleRKggIAoKAcQSEwI1DLB0IAoKAIGAGASFwM7iKVEFAEBAEjCMgBG4cYulAEBAEBAEzCAiBm8FVpAoCgoAgYBwBIXDjEEsHgoAgIAiYQUAI3AyuIlUQEAQEAeMICIEbh1g6EAQEAUHADAJC4GZwFamCgCAgCBhHQAjcOMTSgSAgCAgCZhAQAjeDq0gVBAQBQcA4Av8PmtVExuho1m4AAAAASUVORK5CYII=","user":{},"timestamp":"2025-04-22T02:11:57.947Z"}
-
 @ 1c19eb1a:e22fb0bc
2025-04-22 01:36:33
@ 1c19eb1a:e22fb0bc
2025-04-22 01:36:33After my first major review of Primal on Android, we're going to go a very different direction for this next review. Primal is your standard "Twitter clone" type of kind 1 note client, now branching into long-form. They also have a team of developers working on making it one of the best clients to fill that use-case. By contrast, this review will not be focusing on any client at all. Not even an "other stuff" client.
Instead, we will be reviewing a very useful tool created and maintained by nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5 called #Amber. For those unfamiliar with Amber, it is an #Android application dedicated to managing your signing keys, and allowing you to log into various #Nostr applications without having to paste in your private key, better known as your #nsec. It is not recommended to paste your nsec into various applications because they each represent another means by which it could be compromised, and anyone who has your nsec can post as you. On Nostr, your #npub is your identity, and your signature using your private key is considered absolute proof that any given note, reaction, follow update, or profile change was authorized by the rightful owner of that identity.
It happens less often these days, but early on, when the only way to try out a new client was by inputting your nsec, users had their nsec compromised from time to time, or they would suspect that their key may have been compromised. When this occurs, there is no way to recover your account, or set a new private key, deprecating the previous one. The only thing you can do is start over from scratch, letting everyone know that your key has been compromised and to follow you on your new npub.
If you use Amber to log into other Nostr apps, you significantly reduce the likelihood that your private key will be compromised, because only one application has access to it, and all other applications reach out to Amber to sign any events. This isn't quite as secure as storing your private key on a separate device that isn't connected to the internet whatsoever, like many of us have grown accustomed to with securing our #Bitcoin, but then again, an online persona isn't nearly as important to secure for most of us as our entire life savings.
Amber is the first application of its kind for managing your Nostr keys on a mobile device. nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5 didn't merely develop the application, but literally created the specification for accomplishing external signing on Android which can be found in NIP-55. Unfortunately, Amber is only available for Android. A signer application for iOS is in the works from nostr:npub1yaul8k059377u9lsu67de7y637w4jtgeuwcmh5n7788l6xnlnrgs3tvjmf, but is not ready for use at this time. There is also a new mobile signer app for Android and iOS called Nowser, but I have not yet had a chance to try this app out. From a cursory look at the Android version, it is indeed in the very early stages of development and cannot be compared with Amber.
This review of Amber is current as of version 3.2.5.

Overall Impression
Score: 4.7 / 5 (Updated 4/21/2025)
I cannot speak highly enough about Amber as a tool that every Nostr user on Android should start using if they are not already. When the day comes that we have more options for well-developed signer apps on mobile, my opinion may very well change, but until then Amber is what we have available to us. Even so, it is an incredibly well thought-out and reliable tool for securing your nsec.
Despite being the only well-established Android signer available for Android, Amber can be compared with other external signing methods available on other platforms. Even with more competition in this arena, though, Amber still holds up incredibly well. If you are signing into web applications on a desktop, I still would recommend using a browser extension like #Alby or #Nos2x, as the experience is usually faster, more seamless, and far more web apps support this signing method (NIP-07) than currently support the two methods employed by Amber. Nevertheless that gap is definitely narrowing.
A running list I created of applications that support login and signing with Amber can be found here: Nostr Clients with External Signer Support
I have run into relatively few bugs in my extensive use of Amber for all of my mobile signing needs. Occasionally the application crashes when trying to send it a signing request from a couple of applications, but I would not be surprised if this is no fault of Amber at all, and rather the fault of those specific apps, since it works flawlessly with the vast majority of apps that support either NIP-55 or NIP-46 login.
I also believe that mobile is the ideal platform to use for this type of application. First, because most people use Nostr clients on their phone more than on a desktop. There are, of course, exceptions to that, but in general we spend more time on our phones when interacting online. New users are also more likely to be introduced to Nostr by a friend having them download a Nostr client on their phone than on a PC, and that can be a prime opportunity to introduce the new user to protecting their private key. Finally, I agree with the following assessment from nostr:npub1jlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qdjynqn.
nostr:nevent1qqsw0r6gzn05xg67h5q2xkplwsuzedjxw9lf7ntrxjl8ajm350fcyugprfmhxue69uhhyetvv9ujumn0wd68yurvv438xtnrdaksyg9hyaxj3clfswlhyrd5kjsj5v04clhjvgeq6pwztmysfzdvn93gev7awu9v
The one downside to Amber is that it will be quite foreign for new users. That is partially unavoidable with Nostr, since folks are not accustomed to public/private key cryptography in general, let alone using a private key to log into websites or social media apps. However, the initial signup process is a bit cumbersome if Amber is being used as the means of initially generating a key pair. I think some of this could be foregone at start-up in favor of streamlining onboarding, and then encourage the user to back-up their private key at a later time.
Features
Amber has some features that may surprise you, outside of just storing your private key and signing requests from your favorite Nostr clients. It is a full key management application, supporting multiple accounts, various backup methods, and even the ability to authorize other users to access a Nostr profile you control.
Android Signing
This is the signing method where Amber really shines in both speed and ease of use. Any Android application that supports this standard, and even some progressive web-apps that can be installed to your Android's home-screen, can very quickly and seamlessly connect with Amber to authorize anything that you need signed with your nsec. All you have to do is select "Login with Amber" in clients like #Amethyst or #0xChat and the app will reach out to Amber for all signing requests from there on out. If you had previously signed into the app with your nsec, you will first need to log out, then choose the option to use Amber when you log back in.

This is a massive deal, because everything you do on Nostr requires a signature from your private key. Log in? Needs a signature. Post a "GM" note? Needs a signature. Follow someone who zapped your note? Needs a signature. Zap them back? You guessed it; needs a signature. When you paste your private key into an application, it will automatically sign a lot of these actions without you ever being asked for approval, but you will quickly realize just how many things the client is doing on your behalf when Amber is asking you to approve them each time.
Now, this can also get quite annoying after a while. I recommend using the setting that allows Amber to automatically sign for basic functions, which will cut down on some of the authorization spam. Once you have been asked to authorize the same type of action a few times, you can also toggle the option to automatically authorize that action in the future. Don't worry, though, you have full control to require Amber to ask you for permission again if you want to be alerted each time, and this toggle is specific to each application, so it's not a blanket approval for all Nostr clients you connect with.

This method of signing is just as fast as signing via browser extension on web clients, which users may be more accustomed to. Everything is happening locally on the device, so it can be very snappy and secure.
Nostr Connect/Bunker Signing
This next method of signing has a bit of a delay, because it is using a Nostr relay to send encrypted information back and forth between the app the user is interacting with and Amber to obtain signatures remotely. It isn't a significant delay most of the time, but it is just enough to be noticeable.
Also, unlike the previous signing method that would automatically switch to Amber as the active application when a signing request is sent, this method only sends you a notification that you must be watching for. This can lead to situations where you are wondering why something isn't working in a client you signed into remotely, because it is waiting on you to authorize the action and you didn't notice the notification from Amber. As you use the application, you get used to the need to check for such authorization requests from time to time, or when something isn't working as expected.

By default, Amber will use relay.nsec.app to communicate with whichever Nostr app you are connecting to. You can set a different relay for this purpose, if you like, though not just any relay will support the event kinds that Amber uses for remote signing. You can even run your own relay just for your own signing purposes. In fact, the creator of Amber has a relay application you can run on your phone, called Citrine, that can be used for signing with any web app you are using locally on your phone. This is definitely more of an advanced option, but it is there for you if you want it. For most users, sticking with relay.nsec.app will be just fine, especially since the contents of the events sent back and forth for signing are all encrypted.
Something many users may not realize is that this remote signing feature allows for issuing signing permissions to team members. For instance, if anyone ever joined me in writing reviews, I could issue them a connection string from Amber, and limit their permissions to just posting long-form draft events. Anything else they tried to do would require my explicit approval each time. Moreover, I could revoke those permissions if I ever felt they were being abused, without the need to start over with a whole new npub. Of course, this requires that your phone is online whenever a team member is trying to sign using the connection string you issued, and it requires you pay attention to your notifications so you can approve or reject requests you have not set to auto-approve. However, this is probably only useful for small teams, and larger businesses will want to find a more robust solution for managing access to their npub, such as Keycast from nostr:npub1zuuajd7u3sx8xu92yav9jwxpr839cs0kc3q6t56vd5u9q033xmhsk6c2uc.
The method for establishing a connection between Amber and a Nostr app for remote signing can vary for each app. Most, at minimum, will support obtaining a connection string from Amber that starts with "bunker://" and pasting it in at the time of login. Then you just need to approve the connection request from Amber and the client will log you in and send any subsequent signing requests to Amber using the same connection string.

Some clients will also offer the option to scan a QR code to connect the client to Amber. This is quite convenient, but just remember that this also means the client is setting which relay will be used for communication between the two. Clients with this option will also have a connection string you can copy and paste into Amber to achieve the same purpose. For instance, you may need this option if you are trying to connect to an app on your phone and therefore can't scan the QR code using Amber on the same phone.

Multiple Accounts
Amber does not lock you into using it with only a single set of keys. You can add all of your Nostr "accounts" to Amber and use it for signing events for each independently. Of course, Nostr doesn't actually have "accounts" in the traditional sense. Your identity is simply your key-pair, and Amber stores and accesses each private key as needed.

When first signing in using native Android signing as described above, Amber will default to whichever account was most recently selected, but you can switch to the account that is needed before approving the request. After initial login, Amber will automatically detect the account that the signing request is for.
Key Backup & Restore
Amber allows multiple ways to back up your private key. As most users would expect, you can get your standard nsec and copy/paste it to a password manager, but you can also obtain your private key as a list of mnemonic seed words, an encrypted version of your key called an ncryptsec, or even a QR code of your nsec or ncryptsec.

Additionally, in order to gain access to this information, Amber requires you to enter your device's PIN or use biometric authentication. This isn't cold-storage level protection for your private key by any means, especially since your phone is an internet connected device and does not store your key within a secure element, but it is about as secure as you can ask for while having your key accessible for signing Nostr events.
Tor Support
While Amber does not have Tor support within the app itself, it does support connecting to Tor through Orbot. This would be used with remote signing so that Amber would not connect directly over clearnet to the relay used for communication with the Nostr app requesting the signature. Instead, Amber would connect through Tor, so the relay would not see your IP address. This means you can utilize the remote signing option without compromising your anonymity.

Additional Security
Amber allows the user the option to require either biometric or PIN authentication before approving signing requests. This can provide that extra bit of assurance that no one will be able to sign events using your private key if they happen to gain access to your phone. The PIN you set in Amber is also independent from the PIN to unlock your device, allowing for separation of access.
Can My Grandma Use It?
Score: 4.6 / 5 (Updated 4/21/2025)
At the end of the day, Amber is a tool for those who have some concept of the importance of protecting their private key by not pasting it into every Nostr client that comes along. This concept in itself is not terribly approachable to an average person. They are used to just plugging their password into every service they use, and even worse, they usually have the same password for everything so they can more readily remember it. The idea that they should never enter their "Nostr password" into any Nostr application would never occur to them unless someone first explained how cryptography works related to public/private key pairs.
That said, I think there can be some improvements made to how users are introduced to these concepts, and that a signer application like Amber might be ideal for the job. Considering Amber as a new user's first touch-point with Nostr, I think it holds up well, but could be somewhat streamlined.
Upon opening the app, the user is prompted to either use their existing private key or "Create a new Nostr account." This is straightforward enough. "Account" is not a technically correct term with Nostr, but it is a term that new users would be familiar with and understand the basic concept.

The next screen announces that the account is ready, and presents the user with their public key, explaining that it is "a sort of username" that will allow others to find them on Nostr. While it is good to explain this to the user, it is unnecessary information at this point. This screen also prompts the user to set a nickname and set a password to encrypt their private key. Since the backup options also allow the user to set this password, I think this step could be pushed to a later time. This screen would better serve the new user if it simply prompted them to set a nickname and short bio that could be saved to a few default relays.

Of course, Amber is currently prompting for a password to be set up-front because the next screen requires the new user to download a "backup kit" in order to continue. While I do believe it is a good idea to encourage the creation of a backup, it is not crucial to do so immediately upon creation of a new npub that has nothing at stake if the private key is lost. This is something the UI could remind the user to do at a later time, reducing the friction of profile creation, and expediting getting them into the action.

Outside of these minor onboarding friction points, I think Amber does a great job of explaining to the user the purpose of each of its features, all within the app and without any need to reference external documentation. As long as the user understands the basic concept that their private key is being stored by Amber in order to sign requests from other Nostr apps, so they don't have to be given the private key, Amber is very good about explaining the rest without getting too far into the technical weeds.
The most glaring usability issue with Amber is that it isn't available in the Play Store. Average users expect to be able to find applications they can trust in their mobile device's default app store. There is a valid argument to be made that they are incorrect in this assumption, but that doesn't change the fact that this is the assumption most people make. They believe that applications in the Play Store are "safe" and that anything they can't install through the Play Store is suspect. The prompts that the Android operating system requires the user to approve when installing "unknown apps" certainly doesn't help with this impression.
Now, I absolutely love the Zapstore from nostr:npub1wf4pufsucer5va8g9p0rj5dnhvfeh6d8w0g6eayaep5dhps6rsgs43dgh9, but it doesn't do much to alleviate this issue. Users will still need to be convinced that it is safe to install the Zapstore from the GitHub repo, and then install Amber from there. Furthermore, this adds yet another step to the onboarding process.
Instead of:
- Install Amber
- Set up your keys
- Install the client you want to use
- Log in with Amber
The process becomes:
- Go to the Zapstore GitHub and download the latest version from the releases page.
- Install the APK you downloaded, allowing any prompt to install unknown apps.
- Open Zapstore and install Amber, allowing any prompt to install unknown apps again.
- Open Amber and set up your keys.
- Install the client you want to use
- Log in with Amber
An application as important as Amber for protecting users' private keys should be as readily available to the new user as possible. New users are the ones most prone to making mistakes that could compromise their private keys. Amber should be available to them in the Play Store.
UPDATE: As of version 3.2.8 released on 4/21/2025, the onboarding flow for Amber has been greatly improved! Now, when selecting to set up a new "account" the user is informed on the very next screen, "Your Nostr account is ready!" and given their public key/npub. The only field the user must fill in is their "nickname"/display name and hit "Continue."
From there the user is asked if they want Amber to automatically approve basic actions, or manually approve each app, and then they are shown a new Applications screen, with a prompt to create a backup of their account. This prompt persists until the user has done so.
As you can see, the user is also encouraged to find applications that can be used with Amber with links to nostrapps.com and the Zapstore.
Thanks to these updates, Amber is now the smoothest and most user-friendly onboarding experience I have seen for Nostr to date. Sure, it doesn't have anything for setting up a profile picture or lightning address, but that is better done in a client like Amethyst or YakiHonne, anyway. Just tap "create," type in a handle to call yourself, and you're done!
How do UI Look?
Score: 4.5 / 5
Amber's UI can be described as clean but utilitarian. But then, Amber is a tool, so this is somewhat expected. It is not an app you will be spending a lot of time in, so the UI just needs to be serviceable. I would say it accomplishes this and then some. UI elements are generally easy to understand what they do, and page headings fill in the gaps where that is not the case.

I am not the biggest fan of the color-scheme, particularly in light-mode, but it is not bad in dark-mode at all, and Amber follows whatever theme you have set for your device in that respect. Additionally, the color choice does make sense given the application's name.

It must also be taken into consideration that Amber is almost entirely the product of a single developer's work. He has done a great job producing an app that is not only useful, but pleasant to interact with. The same cannot be said for most utility apps I have previously used, with interfaces that clearly made good design the lowest priority. While Amber's UI may not be the most beautiful Nostr app I have seen, design was clearly not an afterthought, either, and it is appreciated.
Relay Management
Score: 4.9 / 5
Even though Amber is not a Nostr client, where users can browse notes from their favorite npubs, it still relies heavily on relays for some of its features. Primarily, it uses relays for communicating with other Nostr apps for remote signing requests. However, it also uses relays to fetch profile data, so that each private key you add to Amber will automatically load your chosen username and profile picture.
In the relay settings, users can choose which relays are being used to fetch profile data, and which relays will be used by default when creating new remote signing connection strings.

The user can also see which relays are currently connected to Amber and even look at the information that has been passed back and forth on each of those active relays. This information about actively connected relays is not only available within the application, but also in the notification that Amber has to keep in your device's notification tray in order to continue to operate in the background while you are using other apps.

Optionality is the name of the game when it comes to how Amber handles relay selection. The user can just stick with the default signing relay, use their own relay as the default, or even use a different relay for each Nostr application that they connect to for remote signing. Amber gives the user an incredible amount of flexibility in this regard.
In addition to all of this, because not all relays accept the event types needed for remote signing, when you add a relay address to Amber, it automatically tests that relay to see if it will work. This alone can be a massive time saver, so users aren't trying to use relays that don't support remote signing and wondering why they can't log into noStrudel with the connection string they got from Amber.

The only way I could see relay management being improved would be some means of giving the user relay recommendations, in case they want to use a relay other than relay.nsec.app, but they aren't sure which other relays will accept remote signing events. That said, most users who want to use a different relay for signing remote events will likely be using their own, in which case recommendations aren't needed.
Current Users' Questions
The AskNostr hashtag can be a good indication of the pain points that other users are currently having with any Nostr application. Here are some of the most common questions submitted about Amber in the last two months.
nostr:nevent1qqsfrdr68fafgcvl8dgnhm9hxpsjxuks78afxhu8yewhtyf3d7mkg9gpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgq3qkgh77xxt7hhtt4u528hecnx69rhagla8jj3tclgyf9wvkxa6dc0sxp0e6m
This is a good example of Amber working correctly, but the app the user is trying to log into not working. In my experience with #Olas in particular, it sometimes allows remote signer login, and sometimes doesn't. Amber will receive the signing request and I will approve it, but Olas remains on the login screen.
If Amber is receiving the signing requests, and you are approving them, the fault is likely with the application you are trying to log into.
That's it. That's all the repeated questions I could find. Oh, there were a few one-off questions where relay.nsec.app wouldn't connect, or where the user's out-of-date web browser was the issue. Outside of that, though, there were no common questions about how to use Amber, and that is a testament to Amber's ease of use all on its own.
Wrap Up
If you are on Android and you are not already using Amber to protect your nsec, please do yourself a favor and get it installed. It's not at all complicated to set up, and it will make trying out all the latest Nostr clients a safe and pleasant experience.
If you are a client developer and you have not added support for NIP-55 or NIP-46, do your users the courtesy of respecting the sanctity of their private keys. Even developers who have no intention of compromising their users' keys can inadvertently do so. Make that eventuality impossible by adding support for NIP-55 and NIP-46 signing.
Finally, I apologize for the extended time it took me to get this review finished. The time I have available is scarce, Nostr is distracting, and nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5 kept improving Amber even as I was putting it through its paces over the last two months. Keep shipping, my friend! You have made one of the most useful tools we have seen for Nostr to date!
Now... What should I review next?
-
 @ d9e9fb27:d5fe5e1a
2025-04-22 01:29:16
@ d9e9fb27:d5fe5e1a
2025-04-22 01:29:16"There are two pillars in Costa Rica, education and coffee." A tourist guide I met told me this, and during the trip I discovered the strong link between coffee and the locals.
In fact, coffee runs very deeply in the Ticos' culture. So deep that the summer vacations from school (November to January) coincide with the coffee collection season. Children had to help their parents with the coffee. Coffee was a family business.
Monteverde, in the region of Puentarenas, is one of those places where coffee ha always been a corner stone of the society. Here, My gf and I went to visit a coffee plantation and discovered how coffee is made.
Monteverde
Monteverde is a well-known turistic location in the central part of Costa Rica. Many people reach this beautiful place to visit the famous Cloud Rainforest, acres and acres of pristine forest, with many different kind of animals and plants living in it.

However, other than tourism is coffee that pushes the economy of this place. The hills around the town are covered with coffee plantations and there are tours than try to explain how coffee is made.

Coffee Tours
While we were in Monteverde, we joined one of these tours. We decided to give credit to a smaller plantation instead of the super turistic ones. A more rustic and family-owned business, El Pueblo Coffee Tour. We were not disappointed. We had the show all to ourselves, a super-prepared guide and all the time to make questions and enjoy with no rush.
The Plant of Coffee
Since Costa Rica is a quite small country, to compete on the market producers decided to bet on quality instead of quantity. That's why, the only type produced here is the Arabica.
Before the coffee bean, the plant produces a nice white flower, similar to the jasmine.

After a while, the coffee beans appear.

As soon as they turn red, they are ready to be collected.
Interesting fact: between the coffee plants many fruit trees like mangos or bananos can be found. In fact, those plants help keep the soil fertile and healthy, thus leading to a higher coffee quality!
Coffee Harvesting
Coffee is still harvested by hand. Beans do not get mature at the same time, so manual labor is needed. Laborer use a very simple tool to collect coffee, one which allow them to have both hands free.
 Workers do not get paid by hours, but by the number of cajuelas that they can fill. A cajuela is a standard box, which contains around 13kg of beans. It's divided into quarters, so that the worker can get paid for the quarter, too.
Workers do not get paid by hours, but by the number of cajuelas that they can fill. A cajuela is a standard box, which contains around 13kg of beans. It's divided into quarters, so that the worker can get paid for the quarter, too.
Each cajuela is paid around 3.50$.
Coffee Drying
In the farm we visited, drying was perfomed naturally, through the heat of the sun. There are three ways in which the bean is left to dry: lavado, miel and naturàl.
- Lavado: The beans are peeled and washed to remove the jelly.
 - Miel: The jelly on the beans is maintained to give it more sweet flavour.
- Miel: The jelly on the beans is maintained to give it more sweet flavour. - Naturàl: The bean is left to dry with its peel on, to give it a more fruity taste.
- Naturàl: The bean is left to dry with its peel on, to give it a more fruity taste.
Back in the days, to peel the beans for the lavado and the miel variety, the pìlon was used. The bean is very hard, thus this tool does not damage it.

However, today the peeling procedure is done using a machine.

Coffee Roasting
The last step in the production of coffee is roasting. Coffee is put inside a sort of hoven, and is left there at high temperature according to the level of roasting that is needed. The more roasting, the less caffeine there is and the more bitter the coffee. Usually you have light, medium and dark roast.

Coffee Tasting
In the end, we also had a coffee tasting. We tried different roasting and different varieties.
Our guide explained us the best way to taste coffee and helped us defining the different flavours that we perceived. He also taught us the best way to prepare it: infusion time, water temperature, coffe makers and so on.
My favorite one was the dark one, while my gf enjoyed the light roast more. Of course, we bought some packs of these varieties!
Thanks for tuning in!
I hope you enjoyed this brief overview of the Costa Rican coffee.
Pura Vida
Tuma
-
 @ 812cff5a:5c40aeeb
2025-04-22 01:27:45
@ 812cff5a:5c40aeeb
2025-04-22 01:27:45يوم جديد وتطبيق نوستر جديد
أكتب هذا المقال من داخل نفس التطبيق اللي براجعه—يعني بختبر وبوثق التجربة في نفس الوقت، حرفياً!
الهدف من تطبيق أنتايپ
untyp| هو تطبيق مخصص للمنشورات الطويلة على بروتوكول نوستر. فكرته بسيطة جداً، لكنها عبقرية: إزالة كل الحواجز بينك وبين أفكارك، بحيث تقدر تكتب بحرية وسلاسة، كأنك بتكتب على ورقة فاضية... بس رقمية.
المزاية.. آو يمكن الميزة الوحيدة
ميزة التطبيق الأساسية هي دعمه الكامل لتنسيق Markdown، وهذا يعطيك مرونة هائلة في عرض أفكارك بشكل منظم وواضح—عناوين، روابط، كود، اقتباسات، وكل شيء بينهما.
الفكرة مو بس في المزايا، بل في الحد من المشتتات. التصميم بسيط وأنيق، بدون أي زوائد أو إعلانات، مما يساعدك تركز على الكتابة فقط.
untyp| مش بس وسيلة للنشر، بل أداة بتخليك أقرب لأفكارك، وأسرع في التعبير عنها.
جربته؟ قول لي رأيك. مطور التطبيق هو كارنج: nostr:npub1r0rs5q2gk0e3dk3nlc7gnu378ec6cnlenqp8a3cjhyzu6f8k5sgs4sq9ac
-
 @ 502ab02a:a2860397
2025-04-22 01:16:17
@ 502ab02a:a2860397
2025-04-22 01:16:17ก่อนที่จะมูฟออนจากเทคนิคการสร้าง เรามาดูเรื่องสำคัญครับ
วันที่ไม่มีวัว แต่มีเวย์โปรตีน – เบื้องหลังเทคโนโลยีที่เปลี่ยนถังหมักให้กลายเป็นเต้านมวัว เคยมีคำถามไหมว่า “เวย์โปรตีน” ที่กินตอนออกกำลังกาย หรือโยเกิร์ตถ้วยโปรดที่ซื้อมาจากร้านใกล้บ้าน มันยังมาจากนมวัวอยู่ไหม? ถ้าคำตอบคือ “ไม่” แล้วมันมาจากไหน?
ยินดีต้อนรับสู่โลกของ Perfect Day บริษัทที่บอกว่า "เราสร้างเวย์โปรตีนได้ โดยไม่ต้องใช้วัวเลยแม้แต่นิดเดียว” ฟังดูเหมือนมายากล แต่นี่คือวิทยาศาสตร์ขั้นสูงที่ผูกสูตรไว้กับ DNA, จุลินทรีย์ และการหมักอย่างแยบยล
ขั้นตอนที่ 1: หารหัสโปรตีนจากแม่วัว เริ่มต้นจากคำถามง่าย ๆ ว่า “โปรตีนเวย์ที่อยู่ในน้ำนมวัว คืออะไร?” คำตอบคือ เบต้า-แลคโตโกลบูลิน (Beta-lactoglobulin) ซึ่งเป็นโปรตีนหลักในเวย์ประมาณ 50-55% โดยในธรรมชาติ วัวจะสร้างโปรตีนนี้จาก รหัสพันธุกรรมใน DNA ของมัน Perfect Day จึงไปค้นหา ลำดับเบส (DNA sequence) ของโปรตีนนี้จากฐานข้อมูลวิทยาศาสตร์ชื่อ UniProt (Universal Protein Resource) ซึ่งเก็บรหัสโปรตีนของสิ่งมีชีวิตแทบทุกชนิดไว้ครบถ้วน ได้รหัสมาแล้ว ก็เตรียมเข้าสู่ภารกิจ “หลอกจุลินทรีย์ให้สร้างโปรตีนแทนวัว”
ขั้นตอนที่ 2: สร้างแผ่นดีเอ็นเอสังเคราะห์ รหัส DNA ที่ได้จาก UniProt จะถูกนำไปสร้างเป็น DNA สังเคราะห์ โดยนักชีววิทยาจะออกแบบให้เหมาะสมกับการทำงานในเซลล์ของจุลินทรีย์ ไม่ใช่เซลล์วัว จะเรียกว่านี่คือ “การดัดแปลงบทละครชีวิตของวัว แล้วส่งให้จุลินทรีย์เล่นแทน” ก็ไม่ผิด DNA ที่ออกแบบนี้ มักจะมาพร้อมกับเครื่องมือบางอย่าง เช่น ตัวกระตุ้นการทำงานของยีน (promoter) หรือ ตัวตัดต่อยีน ที่จะทำให้จุลินทรีย์ยอมรับและใช้มันได้อย่างมีประสิทธิภาพ
ขั้นตอนที่ 3: ปลอมตัวแทรกเข้าไปในจุลินทรีย์ จุลินทรีย์ที่ Perfect Day ใช้คือกลุ่มที่เรียกว่า Microflora ซึ่งอาจเป็นยีสต์, เชื้อรา, หรือแบคทีเรียชนิดที่เลี้ยงง่าย แต่มันจะไม่ยอมรับ DNA แปลกปลอมง่าย ๆ ดังนั้นต้องมี “เทคนิคหลอกล่อ” นิดหน่อย เขาจะทำให้ DNA ของจุลินทรีย์ เสียหายตรงจุดหนึ่ง แล้วแอบแนบ DNA ปลอม (ที่มีรหัสโปรตีนของวัว) เข้าไปซ่อมแซมจุดนั้นพอดีเป๊ะ แบบ “จิ๊กซอว์พอดีช่อง” แล้วจุลินทรีย์ก็จะเผลอรับ DNA แปลกปลอมนี้เข้าร่าง เมื่อติดตั้งสำเร็จ มันจะเริ่มแปลรหัสและ “ผลิตโปรตีนเวย์” ออกมาเหมือนกับแม่วัวตัวจริงไม่มีผิด
ขั้นตอนที่ 4: เลี้ยงจุลินทรีย์ในถังหมัก ตอนนี้จุลินทรีย์กลายเป็น “แม่วัวในร่างเซลล์เดียว” แล้ว Perfect Day ก็แค่เลี้ยงมันใน ถังหมักชีวภาพ (fermentor) ที่ควบคุมอุณหภูมิ ค่าความเป็นกรดด่าง อากาศ และใส่น้ำตาลลงไปเป็นอาหาร จุลินทรีย์จะกินน้ำตาลแล้วเปลี่ยนเป็น เวย์โปรตีน ปล่อยออกมานอกเซลล์ จากนั้นก็เก็บเอาน้ำที่มีโปรตีนนี้ ไปผ่านกระบวนการกรอง แยก แปรรูป และทำให้แห้ง เป็นผงเวย์โปรตีน พร้อมใช้ในอาหารหรือเครื่องดื่มต่าง ๆ
ขั้นตอนที่ 5: ตรวจสอบความเหมือนจริง ก่อนนำเวย์โปรตีนที่ได้ไปใช้งาน บริษัทต้อง ตรวจสอบระดับโมเลกุล ว่าโปรตีนที่ได้เหมือนกับของวัวจริง ๆ ไหม? สิ่งที่ต้องดูคือ โครงสร้างโปรตีน: ใช้เทคนิค mass spectrometry ตรวจความแม่นยำระดับกรดอะมิโน พฤติกรรมทางชีวเคมี เช่น ความสามารถในการจับกับน้ำ การเกิดฟอง หรือการละลาย ความปลอดภัย ตรวจหาสารปนเปื้อน สารก่อภูมิแพ้ หรือสารที่ไม่ได้ตั้งใจให้มี Perfect Day เคลมว่าทั้งหมดนี้ปลอดภัย และได้รับการรับรองจาก FDA ว่าเป็น GRAS (Generally Recognized as Safe)
แล้วเราควรรู้สึกยังไง? นี่คือ “นมที่ไม่มีวัว” แต่มีเวย์โปรตีนครบสูตร ทำให้โยเกิร์ต ไอศกรีม และแม้กระทั่งกาแฟลาเต้ที่ไม่มีนมวัว แต่ยังมีฟองนมหนานุ่ม กลายเป็นจริงได้แบบไม่ต้องพึ่งวัวเลยแม้แต่นิดเดียว แต่คำถามที่ลึกกว่านั้นคือ... เรายังได้กินอาหารจากธรรมชาติอยู่หรือเปล่า? หรือกำลังอยู่ในยุคที่ “ชีวิต” ถูกตัดออกจากอาหาร โดยสิ้นเชิง? เทคโนโลยีนี้อาจช่วยโลกในมุมของ ESG แต่สำหรับบางคน มันคือ ทางแยกของความจริงกับของจำลอง คำว่า “Perfect” จึงอาจขึ้นอยู่กับว่า… สมบูรณ์แบบในสายตาใคร?
แล้วคำถามที่ล่องลอยอยู่เสมอคือ เมื่อทางเลือกกลายเป็นทางหลัก แล้วเราจะเหลือทางไหนอีกบ้าง หรือจะเป็น...ทางตัน? #pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก
-
 @ fd06f542:8d6d54cd
2025-04-22 00:59:34
@ fd06f542:8d6d54cd
2025-04-22 00:59:34NIP-18
Reposts
draftoptionalA repost is a
kind 6event that is used to signal to followers that akind 1text note is worth reading.The
contentof a repost event is the stringified JSON of the reposted note. It MAY also be empty, but that is not recommended. Reposts of NIP-70-protected events SHOULD always have an emptycontent.The repost event MUST include an
etag with theidof the note that is being reposted. That tag MUST include a relay URL as its third entry to indicate where it can be fetched.The repost SHOULD include a
ptag with thepubkeyof the event being reposted.Quote Reposts
Quote reposts are
kind 1events with an embeddedqtag of the note being quote reposted. Theqtag ensures quote reposts are not pulled and included as replies in threads. It also allows you to easily pull and count all of the quotes for a post.qtags should follow the same conventions as NIP 10etags, with the exception of themarkargument.["q", <event-id>, <relay-url>, <pubkey>]Quote reposts MUST include the NIP-21
nevent,note, ornaddrof the event in the content.Generic Reposts
Since
kind 6reposts are reserved forkind 1contents, we usekind 16as a "generic repost", that can include any kind of event inside other thankind 1.kind 16reposts SHOULD contain aktag with the stringified kind number of the reposted event as its value. -
 @ fd06f542:8d6d54cd
2025-04-22 00:58:49
@ fd06f542:8d6d54cd
2025-04-22 00:58:49NIP-17
Private Direct Messages
draftoptionalThis NIP defines an encrypted direct messaging scheme using NIP-44 encryption and NIP-59 seals and gift wraps.
Direct Message Kind
Kind
14is a chat message.ptags identify one or more receivers of the message.jsonc { "id": "<usual hash>", "pubkey": "<sender-pubkey>", "created_at": "<current-time>", "kind": 14, "tags": [ ["p", "<receiver-1-pubkey>", "<relay-url>"], ["p", "<receiver-2-pubkey>", "<relay-url>"], ["e", "<kind-14-id>", "<relay-url>"] // if this is a reply ["subject", "<conversation-title>"], // rest of tags... ], "content": "<message-in-plain-text>", }.contentMUST be plain text. Fieldsidandcreated_atare required.An
etag denotes the direct parent message this post is replying to.qtags MAY be used when citing events in the.contentwith NIP-21.json ["q", "<event-id> or <event-address>", "<relay-url>", "<pubkey-if-a-regular-event>"]Kind
14s MUST never be signed. If it is signed, the message might leak to relays and become fully public.File Message Kind
jsonc { "id": "<usual hash>", "pubkey": "<sender-pubkey>", "created_at": "<current-time>", "kind": 15, "tags": [ ["p", "<receiver-1-pubkey>", "<relay-url>"], ["p", "<receiver-2-pubkey>", "<relay-url>"], ["e", "<kind-14-id>", "<relay-url>", "reply"], // if this is a reply ["subject", "<conversation-title>"], ["file-type", "<file-mime-type>"], ["encryption-algorithm", "<encryption-algorithm>"], ["decryption-key", "<decryption-key>"], ["decryption-nonce", "<decryption-nonce>"], ["x", "<the SHA-256 hexencoded string of the file>"], // rest of tags... ], "content": "<file-url>" }Kind 15 is used for sending encrypted file event messages:
file-type: Specifies the MIME type of the attached file (e.g.,image/jpeg,audio/mpeg, etc.).encryption-algorithm: Indicates the encryption algorithm used for encrypting the file. Supported algorithms may includeaes-gcm,chacha20-poly1305,aes-cbcetc.decryption-key: The decryption key that will be used by the recipient to decrypt the file.decryption-nonce: The decryption nonce that will be used by the recipient to decrypt the file.content: The URL of the file (<file-url>).xcontaining the SHA-256 hexencoded string of the file.size(optional) size of file in bytesdim(optional) size of the file in pixels in the form<width>x<height>blurhash(optional) the blurhash to show while the client is loading the filethumb(optional) URL of thumbnail with same aspect ratio (encrypted with the same key, nonce)fallback(optional) zero or more fallback file sources in caseurlfails
Just like kind 14, kind
15s MUST never be signed.Chat Rooms
The set of
pubkey+ptags defines a chat room. If a newptag is added or a current one is removed, a new room is created with a clean message history.Clients SHOULD render messages of the same room in a continuous thread.
An optional
subjecttag defines the current name/topic of the conversation. Any member can change the topic by simply submitting a newsubjectto an existingpubkey+p-tags room. There is no need to sendsubjectin every message. The newestsubjectin the thread is the subject of the conversation.Encrypting
Following NIP-59, the unsigned
kind:14&kind:15chat messages must be sealed (kind:13) and then gift-wrapped (kind:1059) to each receiver and the sender individually.jsonc { "id": "<usual hash>", "pubkey": randomPublicKey, "created_at": randomTimeUpTo2DaysInThePast(), "kind": 1059, // gift wrap "tags": [ ["p", receiverPublicKey, "<relay-url>"] // receiver ], "content": nip44Encrypt( { "id": "<usual hash>", "pubkey": senderPublicKey, "created_at": randomTimeUpTo2DaysInThePast(), "kind": 13, // seal "tags": [], // no tags "content": nip44Encrypt(unsignedKind14, senderPrivateKey, receiverPublicKey), "sig": "<signed by senderPrivateKey>" }, randomPrivateKey, receiverPublicKey ), "sig": "<signed by randomPrivateKey>" }The encryption algorithm MUST use the latest version of NIP-44.
Clients MUST verify if pubkey of the
kind:13is the same pubkey on thekind:14, otherwise any sender can impersonate others by simply changing the pubkey onkind:14.Clients SHOULD randomize
created_atin up to two days in the past in both the seal and the gift wrap to make sure grouping bycreated_atdoesn't reveal any metadata.The gift wrap's
p-tag can be the receiver's main pubkey or an alias key created to receive DMs without exposing the receiver's identity.Clients CAN offer disappearing messages by setting an
expirationtag in the gift wrap of each receiver or by not generating a gift wrap to the sender's public keyPublishing
Kind
10050indicates the user's preferred relays to receive DMs. The event MUST include a list ofrelaytags with relay URIs.jsonc { "kind": 10050, "tags": [ ["relay", "wss://inbox.nostr.wine"], ["relay", "wss://myrelay.nostr1.com"], ], "content": "", // other fields... }Clients SHOULD publish kind
14events to the10050-listed relays. If that is not found that indicates the user is not ready to receive messages under this NIP and clients shouldn't try.Relays
It's advisable that relays do not serve
kind:1059to clients other than the ones tagged in them.It's advisable that users choose relays that conform to these practices.
Clients SHOULD guide users to keep
kind:10050lists small (1-3 relays) and SHOULD spread it to as many relays as viable.Benefits & Limitations
This NIP offers the following privacy and security features:
- No Metadata Leak: Participant identities, each message's real date and time, event kinds, and other event tags are all hidden from the public. Senders and receivers cannot be linked with public information alone.
- No Public Group Identifiers: There is no public central queue, channel or otherwise converging identifier to correlate or count all messages in the same group.
- No Moderation: There are no group admins: no invitations or bans.
- No Shared Secrets: No secret must be known to all members that can leak or be mistakenly shared
- Fully Recoverable: Messages can be fully recoverable by any client with the user's private key
- Optional Forward Secrecy: Users and clients can opt-in for "disappearing messages".
- Uses Public Relays: Messages can flow through public relays without loss of privacy. Private relays can increase privacy further, but they are not required.
- Cold Storage: Users can unilaterally opt-in to sharing their messages with a separate key that is exclusive for DM backup and recovery.
The main limitation of this approach is having to send a separate encrypted event to each receiver. Group chats with more than 100 participants should find a more suitable messaging scheme.
Implementation
Clients implementing this NIP should by default only connect to the set of relays found in their
kind:10050list. From that they should be able to load all messages both sent and received as well as get new live updates, making it for a very simple and lightweight implementation that should be fast.When sending a message to anyone, clients must then connect to the relays in the receiver's
kind:10050and send the events there but can disconnect right after unless more messages are expected to be sent (e.g. the chat tab is still selected). Clients should also send a copy of their outgoing messages to their ownkind:10050relay set.Examples
This example sends the message
Hola, que tal?fromnsec1w8udu59ydjvedgs3yv5qccshcj8k05fh3l60k9x57asjrqdpa00qkmr89mtonsec12ywtkplvyq5t6twdqwwygavp5lm4fhuang89c943nf2z92eez43szvn4dt.The two final GiftWraps, one to the receiver and the other to the sender, respectively, are:
json { "id":"2886780f7349afc1344047524540ee716f7bdc1b64191699855662330bf235d8", "pubkey":"8f8a7ec43b77d25799281207e1a47f7a654755055788f7482653f9c9661c6d51", "created_at":1703128320, "kind":1059, "tags":[ [ "p", "918e2da906df4ccd12c8ac672d8335add131a4cf9d27ce42b3bb3625755f0788"] ], "content":"AsqzdlMsG304G8h08bE67dhAR1gFTzTckUUyuvndZ8LrGCvwI4pgC3d6hyAK0Wo9gtkLqSr2rT2RyHlE5wRqbCOlQ8WvJEKwqwIJwT5PO3l2RxvGCHDbd1b1o40ZgIVwwLCfOWJ86I5upXe8K5AgpxYTOM1BD+SbgI5jOMA8tgpRoitJedVSvBZsmwAxXM7o7sbOON4MXHzOqOZpALpS2zgBDXSAaYAsTdEM4qqFeik+zTk3+L6NYuftGidqVluicwSGS2viYWr5OiJ1zrj1ERhYSGLpQnPKrqDaDi7R1KrHGFGyLgkJveY/45y0rv9aVIw9IWF11u53cf2CP7akACel2WvZdl1htEwFu/v9cFXD06fNVZjfx3OssKM/uHPE9XvZttQboAvP5UoK6lv9o3d+0GM4/3zP+yO3C0NExz1ZgFmbGFz703YJzM+zpKCOXaZyzPjADXp8qBBeVc5lmJqiCL4solZpxA1865yPigPAZcc9acSUlg23J1dptFK4n3Tl5HfSHP+oZ/QS/SHWbVFCtq7ZMQSRxLgEitfglTNz9P1CnpMwmW/Y4Gm5zdkv0JrdUVrn2UO9ARdHlPsW5ARgDmzaxnJypkfoHXNfxGGXWRk0sKLbz/ipnaQP/eFJv/ibNuSfqL6E4BnN/tHJSHYEaTQ/PdrA2i9laG3vJti3kAl5Ih87ct0w/tzYfp4SRPhEF1zzue9G/16eJEMzwmhQ5Ec7jJVcVGa4RltqnuF8unUu3iSRTQ+/MNNUkK6Mk+YuaJJs6Fjw6tRHuWi57SdKKv7GGkr0zlBUU2Dyo1MwpAqzsCcCTeQSv+8qt4wLf4uhU9Br7F/L0ZY9bFgh6iLDCdB+4iABXyZwT7Ufn762195hrSHcU4Okt0Zns9EeiBOFxnmpXEslYkYBpXw70GmymQfJlFOfoEp93QKCMS2DAEVeI51dJV1e+6t3pCSsQN69Vg6jUCsm1TMxSs2VX4BRbq562+VffchvW2BB4gMjsvHVUSRl8i5/ZSDlfzSPXcSGALLHBRzy+gn0oXXJ/447VHYZJDL3Ig8+QW5oFMgnWYhuwI5QSLEyflUrfSz+Pdwn/5eyjybXKJftePBD9Q+8NQ8zulU5sqvsMeIx/bBUx0fmOXsS3vjqCXW5IjkmSUV7q54GewZqTQBlcx+90xh/LSUxXex7UwZwRnifvyCbZ+zwNTHNb12chYeNjMV7kAIr3cGQv8vlOMM8ajyaZ5KVy7HpSXQjz4PGT2/nXbL5jKt8Lx0erGXsSsazkdoYDG3U", "sig":"a3c6ce632b145c0869423c1afaff4a6d764a9b64dedaf15f170b944ead67227518a72e455567ca1c2a0d187832cecbde7ed478395ec4c95dd3e71749ed66c480" }json { "id":"162b0611a1911cfcb30f8a5502792b346e535a45658b3a31ae5c178465509721", "pubkey":"626be2af274b29ea4816ad672ee452b7cf96bbb4836815a55699ae402183f512", "created_at":1702711587, "kind":1059, "tags":[ [ "p", "44900586091b284416a0c001f677f9c49f7639a55c3f1e2ec130a8e1a7998e1b"] ], "content":"AsTClTzr0gzXXji7uye5UB6LYrx3HDjWGdkNaBS6BAX9CpHa+Vvtt5oI2xJrmWLen+Fo2NBOFazvl285Gb3HSM82gVycrzx1HUAaQDUG6HI7XBEGqBhQMUNwNMiN2dnilBMFC3Yc8ehCJT/gkbiNKOpwd2rFibMFRMDKai2mq2lBtPJF18oszKOjA+XlOJV8JRbmcAanTbEK5nA/GnG3eGUiUzhiYBoHomj3vztYYxc0QYHOx0WxiHY8dsC6jPsXC7f6k4P+Hv5ZiyTfzvjkSJOckel1lZuE5SfeZ0nduqTlxREGeBJ8amOykgEIKdH2VZBZB+qtOMc7ez9dz4wffGwBDA7912NFS2dPBr6txHNxBUkDZKFbuD5wijvonZDvfWq43tZspO4NutSokZB99uEiRH8NAUdGTiNb25m9JcDhVfdmABqTg5fIwwTwlem5aXIy8b66lmqqz2LBzJtnJDu36bDwkILph3kmvaKPD8qJXmPQ4yGpxIbYSTCohgt2/I0TKJNmqNvSN+IVoUuC7ZOfUV9lOV8Ri0AMfSr2YsdZ9ofV5o82ClZWlWiSWZwy6ypa7CuT1PEGHzywB4CZ5ucpO60Z7hnBQxHLiAQIO/QhiBp1rmrdQZFN6PUEjFDloykoeHe345Yqy9Ke95HIKUCS9yJurD+nZjjgOxZjoFCsB1hQAwINTIS3FbYOibZnQwv8PXvcSOqVZxC9U0+WuagK7IwxzhGZY3vLRrX01oujiRrevB4xbW7Oxi/Agp7CQGlJXCgmRE8Rhm+Vj2s+wc/4VLNZRHDcwtfejogjrjdi8p6nfUyqoQRRPARzRGUnnCbh+LqhigT6gQf3sVilnydMRScEc0/YYNLWnaw9nbyBa7wFBAiGbJwO40k39wj+xT6HTSbSUgFZzopxroO3f/o4+ubx2+IL3fkev22mEN38+dFmYF3zE+hpE7jVxrJpC3EP9PLoFgFPKCuctMnjXmeHoiGs756N5r1Mm1ffZu4H19MSuALJlxQR7VXE/LzxRXDuaB2u9days/6muP6gbGX1ASxbJd/ou8+viHmSC/ioHzNjItVCPaJjDyc6bv+gs1NPCt0qZ69G+JmgHW/PsMMeL4n5bh74g0fJSHqiI9ewEmOG/8bedSREv2XXtKV39STxPweceIOh0k23s3N6+wvuSUAJE7u1LkDo14cobtZ/MCw/QhimYPd1u5HnEJvRhPxz0nVPz0QqL/YQeOkAYk7uzgeb2yPzJ6DBtnTnGDkglekhVzQBFRJdk740LEj6swkJ", "sig":"c94e74533b482aa8eeeb54ae72a5303e0b21f62909ca43c8ef06b0357412d6f8a92f96e1a205102753777fd25321a58fba3fb384eee114bd53ce6c06a1c22bab" } -
 @ fd06f542:8d6d54cd
2025-04-22 00:58:35
@ fd06f542:8d6d54cd
2025-04-22 00:58:35- 第三章、NIP-03: OpenTimestamps Attestations for Events
- 第四章、NIP-04: Encrypted Direct Message
- 第五章、NIP-05: Mapping Nostr keys to DNS-based internet identifiers
- 第六章、NIP-06: Basic key derivation from mnemonic seed phrase
- 第七章、NIP-07: window.nostr capability for web browsers
- 第八章、NIP-08: Handling Mentions --- unrecommended: deprecated in favor of NIP-27
- 第九章、NIP-09: Event Deletion Request
- 第十章、NIP-10: Text Notes and Threads
- 第十一章、NIP-11: Relay Information Document
- 第十二章、NIP-13: Proof of Work
- 第十三章、NIP-14: Subject tag in text events
- 第十四章、NIP-15: Nostr Marketplace (for resilient marketplaces)
- 第十五章、NIP-17: Private Direct Messages
- 第十六章、NIP-18: Reposts
-
 @ 39cc53c9:27168656
2025-04-09 07:59:33
@ 39cc53c9:27168656
2025-04-09 07:59:33Know Your Customer is a regulation that requires companies of all sizes to verify the identity, suitability, and risks involved with maintaining a business relationship with a customer. Such procedures fit within the broader scope of anti-money laundering (AML) and counterterrorism financing (CTF) regulations.
Banks, exchanges, online business, mail providers, domain registrars... Everyone wants to know who you are before you can even opt for their service. Your personal information is flowing around the internet in the hands of "god-knows-who" and secured by "trust-me-bro military-grade encryption". Once your account is linked to your personal (and verified) identity, tracking you is just as easy as keeping logs on all these platforms.
Rights for Illusions
KYC processes aim to combat terrorist financing, money laundering, and other illicit activities. On the surface, KYC seems like a commendable initiative. I mean, who wouldn't want to halt terrorists and criminals in their tracks?
The logic behind KYC is: "If we mandate every financial service provider to identify their users, it becomes easier to pinpoint and apprehend the malicious actors."
However, terrorists and criminals are not precisely lining up to be identified. They're crafty. They may adopt false identities or find alternative strategies to continue their operations. Far from being outwitted, many times they're several steps ahead of regulations. Realistically, KYC might deter a small fraction – let's say about 1% ^1 – of these malefactors. Yet, the cost? All of us are saddled with the inconvenient process of identification just to use a service.
Under the rhetoric of "ensuring our safety", governments and institutions enact regulations that seem more out of a dystopian novel, gradually taking away our right to privacy.
To illustrate, consider a city where the mayor has rolled out facial recognition cameras in every nook and cranny. A band of criminals, intent on robbing a local store, rolls in with a stolen car, their faces obscured by masks and their bodies cloaked in all-black clothes. Once they've committed the crime and exited the city's boundaries, they switch vehicles and clothes out of the cameras' watchful eyes. The high-tech surveillance? It didn’t manage to identify or trace them. Yet, for every law-abiding citizen who merely wants to drive through the city or do some shopping, their movements and identities are constantly logged. The irony? This invasive tracking impacts all of us, just to catch the 1% ^1 of less-than-careful criminals.
KYC? Not you.
KYC creates barriers to participation in normal economic activity, to supposedly stop criminals. ^2
KYC puts barriers between many users and businesses. One of these comes from the fact that the process often requires multiple forms of identification, proof of address, and sometimes even financial records. For individuals in areas with poor record-keeping, non-recognized legal documents, or those who are unbanked, homeless or transient, obtaining these documents can be challenging, if not impossible.
For people who are not skilled with technology or just don't have access to it, there's also a barrier since KYC procedures are mostly online, leaving them inadvertently excluded.
Another barrier goes for the casual or one-time user, where they might not see the value in undergoing a rigorous KYC process, and these requirements can deter them from using the service altogether.
It also wipes some businesses out of the equation, since for smaller businesses, the costs associated with complying with KYC norms—from the actual process of gathering and submitting documents to potential delays in operations—can be prohibitive in economical and/or technical terms.
You're not welcome
Imagine a swanky new club in town with a strict "members only" sign. You hear the music, you see the lights, and you want in. You step up, ready to join, but suddenly there's a long list of criteria you must meet. After some time, you are finally checking all the boxes. But then the club rejects your membership with no clear reason why. You just weren't accepted. Frustrating, right?
This club scenario isn't too different from the fact that KYC is being used by many businesses as a convenient gatekeeping tool. A perfect excuse based on a "legal" procedure they are obliged to.
Even some exchanges may randomly use this to freeze and block funds from users, claiming these were "flagged" by a cryptic system that inspects the transactions. You are left hostage to their arbitrary decision to let you successfully pass the KYC procedure. If you choose to sidestep their invasive process, they might just hold onto your funds indefinitely.
Your identity has been stolen
KYC data has been found to be for sale on many dark net markets^3. Exchanges may have leaks or hacks, and such leaks contain very sensitive data. We're talking about the full monty: passport or ID scans, proof of address, and even those awkward selfies where you're holding up your ID next to your face. All this data is being left to the mercy of the (mostly) "trust-me-bro" security systems of such companies. Quite scary, isn't it?
As cheap as $10 for 100 documents, with discounts applying for those who buy in bulk, the personal identities of innocent users who passed KYC procedures are for sale. ^3
In short, if you have ever passed the KYC/AML process of a crypto exchange, your privacy is at risk of being compromised, or it might even have already been compromised.
(they) Know Your Coins
You may already know that Bitcoin and most cryptocurrencies have a transparent public blockchain, meaning that all data is shown unencrypted for everyone to see and recorded forever. If you link an address you own to your identity through KYC, for example, by sending an amount from a KYC exchange to it, your Bitcoin is no longer pseudonymous and can then be traced.
If, for instance, you send Bitcoin from such an identified address to another KYC'ed address (say, from a friend), everyone having access to that address-identity link information (exchanges, governments, hackers, etc.) will be able to associate that transaction and know who you are transacting with.
Conclusions
To sum up, KYC does not protect individuals; rather, it's a threat to our privacy, freedom, security and integrity. Sensible information flowing through the internet is thrown into chaos by dubious security measures. It puts borders between many potential customers and businesses, and it helps governments and companies track innocent users. That's the chaos KYC has stirred.
The criminals are using stolen identities from companies that gathered them thanks to these very same regulations that were supposed to combat them. Criminals always know how to circumvent such regulations. In the end, normal people are the most affected by these policies.
The threat that KYC poses to individuals in terms of privacy, security and freedom is not to be neglected. And if we don’t start challenging these systems and questioning their efficacy, we are just one step closer to the dystopian future that is now foreseeable.
Edited 20/03/2024 * Add reference to the 1% statement on Rights for Illusions section to an article where Chainalysis found that only 0.34% of the transaction volume with cryptocurrencies in 2023 was attributable to criminal activity ^1
-
 @ 401014b3:59d5476b
2025-04-22 00:23:24
@ 401014b3:59d5476b
2025-04-22 00:23:24About Me
I come to Nostr with extensive experience in the digital landscape. As a blockchain native since 2017, I've witnessed the evolution of decentralized technologies firsthand. Most of my professional career has been spent working within big tech companies, giving me a unique perspective on both centralized and decentralized systems.
My social media journey began on Twitter in 2007, where I've maintained a presence for over 17 years. I've also explored other decentralized social platforms including BlueSky, Farcaster, and Lens Protocol. As a Bitcoin maximalist, I was particularly intrigued by Nostr's compatibility with the Lightning Network, which initially drew me to the platform.
The Onboarding Challenge
The Nostr onboarding experience presents a significant hurdle for newcomers. Despite my technical background in blockchain technologies, I found the initial setup process more complicated than expected. Understanding public/private key cryptography just to join a social network creates a steeper learning curve than necessary.
BlueSky and Farcaster have demonstrated that it's possible to maintain decentralized principles while providing a more streamlined onboarding experience. Their approaches show that user-friendly design and decentralization aren't mutually exclusive concepts.
Relay Management: Room for Improvement
The concept of relays represents one of Nostr's most distinctive features, though it can be confusing for newcomers. While many clients come pre-configured with default relays, users eventually encounter situations where content or connections seem inconsistent.
When someone I've interacted with doesn't appear in my feed or doesn't respond, I'm often left wondering if we're simply on different relays. This uncertainty creates friction that doesn't exist on other platforms where connectivity is handled behind the scenes.
The relay system introduces a layer of complexity that, while important to Nostr's architecture, could benefit from better abstraction in the user experience. When using BlueSky or Farcaster, I don't need to think about the underlying infrastructure, something Nostr could learn from while maintaining its decentralized principles.
The Zap Economy: Growing Pains
The Lightning-powered zap system shows tremendous potential, but I've observed some concerning economic patterns. Longer-term Nostr users have expressed frustration about continuously sending zaps while seeing limited growth in the overall ecosystem.
Interestingly, there appears to be a connection between this liquidity issue and community growth dynamics. Some established users who voice concerns about bearing the financial burden of the zapping economy are simultaneously less welcoming to newer accounts, rarely following, engaging with, or zapping newcomers.
This creates a challenging environment for new users, who face a cold reception and have little incentive to load their Lightning wallets or participate in the zap economy. Why bring fresh liquidity to a platform where established users rarely engage with your content? This dynamic has limited the expansion of the ecosystem, with the same sats often circulating among established users rather than growing with new participants.
Client Diversity: Strength and Challenge
Nostr's multiple client options offer users choice, which is valuable. However, the implementation of NIPs (Nostr Implementation Possibilities) varies across clients, creating inconsistent experiences. Features that work seamlessly in one client might be implemented differently in another.
This extends to fundamental aspects like search functionality, thread navigation, and notification systems, all of which can differ significantly between clients. For users accustomed to consistent experiences, this fragmentation creates a learning curve with each new client they try.
Lightning Integration: Varying Experiences
The Lightning Network integration varies in quality and user experience across Nostr clients. While the functionality is generally present, the implementation quality, feature set, and ease of use differ depending on which client you choose.
This inconsistency means users may need to experiment with several clients to find one that provides the Lightning experience they're looking for, rather than having a consistent experience across the ecosystem.
Finding Balance
Nostr appears to be navigating the challenge of balancing technical innovation with user experience. While its cryptographic foundation and decentralized architecture are impressive technical achievements, these same strengths sometimes come at the cost of accessibility.
Despite my technical background and interest in decentralized technologies, I find myself using BlueSky and Farcaster more frequently for daily social interactions, while checking Nostr less often. For Nostr to achieve its potential for broader adoption, addressing these user experience considerations while maintaining its core principles will be essential.
The platform has tremendous potential with improvements to user experience, community dynamics, and economic sustainability, Nostr could evolve from a fascinating technical experiment into a truly compelling alternative to mainstream social media.
-
 @ 52524fbb:ae4025dc
2025-04-09 03:36:09
@ 52524fbb:ae4025dc
2025-04-09 03:36:09 To most of us it's all about the sound of freedom, the innovation, it's technical implication, what if feels like in a decentralised environment. Now let's head into that which brings our fantasies to reality, Nostr which stands for "Notes and other stuffs Transmitted by Relays", is an open protocol designed for decentralised social networkin
To most of us it's all about the sound of freedom, the innovation, it's technical implication, what if feels like in a decentralised environment. Now let's head into that which brings our fantasies to reality, Nostr which stands for "Notes and other stuffs Transmitted by Relays", is an open protocol designed for decentralised social networkinNostr most Amazing Features
-
Decentralisation: compared to traditional social media platforms like like Twitter (X) and Instagram that rely on centralised servers, Nostr operates through a network of relays. These relays serves as servers that store and forward messages. This amazing feature of decentralisation aims to make the network completely resistant to censorship, most people would say how? To answer your question it's because no single individual control's it
-
User Control: ever thought of the purest feeling of freedom, well Nostr just gave you the space to experience. User's have total control over their data and identity.
-
Simplicity: why get stressed when Nostr got you covered? This protocol is designed to be relatively simple, making it easier for developers to build applications on top of it.

Nostr Relation to Bitcoin
Who wouldn't want to be part of a community that embraces it's ethics in a dignified manner. Nostr has gained popularity within the Bitcoin community, and the Bitcoin Lightning Network is used for features like "Zaps" (which represents small payments or tips). There are also similarities in the philosophy of decentralization, that both bitcoin and Nostr share. Just like the saying goes, birds of the same feather flock together. This leads me to one of the best magnificent project, focused on building decentralisation media infrastructure, particularly within the Nostr ecosystem.

Yakihonne the future of the world
YakiHonne is an amazing project focused on building decentralized media infrastructure, particularly within the Nostr ecosystem. It's mind blowing features includes:
-
Decentralized Media: YakiHonne aims to provide tools and platforms that support freedom and automation in content creation, curation, article writing and reporting. It leverages the decentralized nature of the Nostr protocol to achieve this amazing feat.
-
Nostr and Bitcoin Integration: YakiHonne is closely tied to the Nostr network, and it also incorporates Bitcoin functionality. This integration includes features related to the Lightning Network, enabling things like "zaps" (small Bitcoin payments) within the platform.
-
Mobile Application: YakiHonne offers a mobile application with an eye catching user interface simply designed to provide users with a smooth and intuitive Nostr experience. This app includes features like: -Support for various login options. -Content curation tools. -Lightning Network integration. -Long form article support.

Disadvantages of Traditional social media
Lets go back to a world without the flute of freedom echoing in our hearts, where implementations are controlled by certain entities, reasons why traditional social media platforms hold not even a single stance compared to Nostr:
- Privacy Concerns:
Data Collection: Social media platforms collect vast amounts of user data, often without full transparency. This data can be used for targeted advertising, and sometimes, it can be compromised in data breaches. Which won't happen or be possible on yakihonne
-
Social Comparison and Low Self-Esteem: The over hyped and often unrealistic portrayals of life on social media can lead to feelings of inadequacy and low self-esteem. But on yakihonne you get to connect and grow with a community with specified goals bent on implementation
-
Misinformation and Fake News:
Spread of False Information: Social media platforms can be breeding grounds for misinformation and fake news, which can spread rapidly and have significant real-world consequences. Is that possible on yakihonne, well we all know the answer. 4. Centralized Control:
Censorship: Centralized platforms have the power to censor content, raising concerns about freedom of speech. Algorithm Bias: Algorithms can be biased, leading to unfair or discriminatory outcomes. This tells us why a decentralised media platform like yakihonne stands out to be the only media with a future.

Why Chose Nostr why chose yakihonne
When considering Nostr and related projects like YakiHonne, the appeal stems largely from a desire for greater control, privacy, and freedom in online communication. Which from the points aligned above, gives us no second chance of thought, but the thought of being part of the Nostr community, active on a platform like yakihonne.
-
-
 @ df478568:2a951e67
2025-04-21 23:36:17
@ df478568:2a951e67
2025-04-21 23:36:17Testing
-
 @ d41bf82f:ed90d888
2025-04-21 23:18:20
@ d41bf82f:ed90d888
2025-04-21 23:18:20"ประวัติศาสตร์ก็เฉกเช่นธรรมชาติ — การเกิดและการตายล้วนดำเนินไปอย่างสมดุล" -โยฮัน ฮุยซิงกา3
การเสื่อมถอยของโลกยุคใหม่
พวกเรากำลังอยู่ในช่วงปลายของสิ่งที่เรียกว่า “ยุคใหม่” — ระบบโลกที่ถูกจัดระเบียบผ่านรัฐชาติอันรวมศูนย์ ซึ่งเคยพาเราผ่านยุคอุตสาหกรรม สงครามโลก และการสร้างโครงสร้างทางสังคมที่เข้มแข็งด้วยภาษี สวัสดิการ และระบบราชการ แต่ยุคนี้กำลังเคลื่อนเข้าสู่ฉากสุดท้ายของมันอย่างเงียบงัน โดยไม่มีใครในกระแสหลักพูดถึงอย่างจริงจัง และสิ่งที่กำลังมาแทนที่ก็จะแตกต่างอย่างสิ้นเชิงในเชิงคุณภาพจากโลกที่เราคุ้นเคย
เช่นเดียวกับที่สังคมเกษตรกรรมเคยมาแทนที่สังคมสัตว์-หาของป่า และระบบอุตสาหกรรมเคยมาแทนระบบศักดินา สังคมใหม่ที่กำลังปรากฏขึ้นจะเป็นการเปลี่ยนผ่านครั้งใหญ่ โดยในยุคใหม่นี้ “ประสิทธิภาพ” จะไม่ผูกติดกับ “ขนาด” อีกต่อไป อำนาจแบบรวมศูนย์ของรัฐจะถูกสั่นคลอน และระบบใหม่จะเกิดขึ้นซึ่งเล็กกว่า คล่องตัวกว่า และยากที่รัฐแบบเดิมจะควบคุม
นักประวัติศาสตร์ในอนาคตอาจมองว่าการล่มสลายของสหภาพโซเวียตในปี 1991 หรือการพังทลายของกำแพงเบอร์ลินในปี 1989 คือจุดสิ้นสุดของยุคสมัยนี้ และเปิดฉากสู่สิ่งใหม่ — บ้างเรียกมันว่ายุคหลังสมัยใหม่ บ้างว่าโลกไซเบอร์ หรือสังคมสารสนเทศ ไม่ว่าจะตั้งชื่ออย่างไร สิ่งที่ทุกคนยอมรับคือมันคือ "โลกใบใหม่" ที่แตกต่างอย่างถึงแก่นจากโลกเดิม
ความเข้าใจของมนุษย์ต่อการเปลี่ยนแปลงใหญ่ระดับอารยธรรมมักมาช้า เพราะขาดกรอบความคิดและภาษาที่จะมองเห็นมันได้ในขณะที่มันเกิดขึ้นจริง ยกตัวอย่างเช่น ไม่มีใครในยุคศักดินาคิดว่าตนเองอยู่ใน “ยุคกลาง” จนกระทั่งยุคใหม่เข้ามาเปรียบเทียบ ในทำนองเดียวกัน พวกเราทุกวันนี้ก็อาจไม่รู้ตัวว่าเรากำลังอยู่ในช่วงสิ้นสุดของยุคหนึ่ง และจุดเริ่มต้นของอีกยุคหนึ่ง
ระบบสังคมใดก็ตามมักฝังข้อสันนิษฐานโดยปริยายว่าระบบของตนคือสิ่งสูงสุด เป็นสิ่งที่ไม่มีวันเปลี่ยน และไม่ควรถูกตั้งคำถาม การตั้งคำถามถึงความอยู่รอดของระบบ จึงเป็นเรื่องที่ถูกกีดกันโดยไม่รู้ตัว เพราะยิ่งระบบใกล้ล่มสลายเท่าไร มันก็ยิ่งต้องพยายามปกปิดไม่ให้ใครรับรู้ถึงความเปราะบางของมัน
ตัวอย่างจากประวัติศาสตร์เช่น การล่มสลายของจักรวรรดิโรมันใน ค.ศ. 476 ก็ไม่ได้รับการรับรู้ว่าเป็น “จุดจบ” ในเวลานั้น แม้เมื่อจักรพรรดิองค์สุดท้าย(โรมุลุส เอากุสตุส)ถูกปลด แต่ผู้คนและโครงสร้างเดิมของโรมันก็ยังคงแสร้งทำว่าทุกอย่างดำเนินไปตามปกติ รูปแบบของรัฐบาลเก่ายังคงถูกรักษาไว้ พิธีกรรมในระบบเดิมยังคงจัดขึ้น วุฒิสภายังคงประชุม กงสุลยังได้รับการแต่งตั้ง และระบบราชการก็ยังคงอยู่เกือบครบถ้วน พวกป่าเถื่อนที่เข้ามาปกครองก็ยังแสดงตนว่าให้ความเคารพต่อจักรวรรดิไบแซนไทน์และกฎหมายโรมัน ศาสนาคริสต์ยังคงดำรงเป็นศาสนาประจำรัฐ เครื่องราชสัญลักษณ์ยังถูกใช้ในพิธีสาธารณะ ทั้งหมดนี้เป็นฉากหน้าของการพยายามรักษาภาพความต่อเนื่องในขณะที่แก่นของอำนาจได้เปลี่ยนไปแล้วโดยสิ้นเชิง
ประวัติศาสตร์ช่วงนี้สอนให้เห็นว่า การเปลี่ยนแปลงใหญ่ในระดับอารยธรรมมักถูกซ่อนเร้นอยู่ภายใต้ความเฉื่อยของสังคมที่ไม่ยอมรับความเป็นจริง คนในยุคนั้นไม่ได้รู้สึกว่าโรมล่มสลายไปแล้ว พวกเขาเพียงรู้สึกว่าชีวิตยังดำเนินต่อไปได้ แม้ภายใต้ระเบียบใหม่ที่ซ้อนทับเข้ามาโดยไม่ได้ประกาศตนอย่างเป็นทางการ ความเปลี่ยนแปลงที่แท้จริงจึงไม่ใช่เหตุการณ์ที่เกิดขึ้นในวันใดวันหนึ่ง แต่เป็นกระบวนการค่อยเป็นค่อยไปที่อาศัยแรงเฉื่อยของความเชื่อเก่าว่าสิ่งต่างๆ “ยังเหมือนเดิม”
ผู้เขียนใช้ตัวอย่างนี้เพื่อสะท้อนมาสู่โลกปัจจุบันว่า แม้ตัวอย่างโรมจะดูไกลตัว แต่ก็มีลักษณะใกล้เคียงกับสิ่งที่เรากำลังเผชิญอยู่ ระบบรัฐชาติสมัยใหม่ก็อาจกำลังเข้าสู่ภาวะเสื่อมถอยโดยที่คนส่วนใหญ่ยังไม่รู้ตัวเช่นเดียวกัน หนังสือเล่มนี้จึงไม่ได้ตั้งต้นจากการคาดเดาอนาคตอย่างลอย ๆ หากแต่เสนอว่า เราจะเข้าใจอนาคตได้ดีขึ้น ถ้าเริ่มจากการเรียนรู้กระบวนการเปลี่ยนผ่านในอดีต โดยเฉพาะพลวัตทางการเมืองและตรรกะของอำนาจ
จุดเปลี่ยนของโรมันไม่เพียงแต่แสดงให้เห็นการล่มสลายของรัฐรวมศูนย์ แต่ยังเผยให้เห็นว่าการล่มสลายนั้นสามารถเปิดทางให้กิจกรรมทางเศรษฐกิจในท้องถิ่นเบ่งบานขึ้นได้ ในยุคของเรา แม้สาเหตุจะต่างกัน — โรมล่มเพราะขยายเกินตัว เศรษฐกิจเกษตรกรรมไม่สามารถรองรับภาระรัฐ การเก็บภาษีที่หนักหนาและทหารที่ใช้อำนาจในทางมิชอบ — แต่สิ่งที่คล้ายกันคือ การไม่ยอมรับต่อการเปลี่ยนแปลงที่กำลังก่อตัว
เรายังเห็นการเปรียบเทียบถึงผลกระทบจากโรคระบาดในอดีต เช่น โรคฝีดาษที่ทำให้โรมอ่อนแอลง เช่นเดียวกับความกังวลเรื่องไวรัสกลายพันธุ์ในยุคปัจจุบัน ที่บ่งชี้ถึงความเปราะบางของโครงสร้างสังคม แม้รูปแบบของภัยคุกคามจะต่างกัน แต่สิ่งที่เหมือนกันคือ “ความไม่พร้อมของระบบ” ที่จะรับมือกับความเปลี่ยนแปลงใหญ่
แต่สิ่งสำคัญที่สุดที่ผู้เขียนต้องการชี้ ไม่ใช่แค่สาเหตุของการล่มสลาย แต่คือความจริงที่ว่า ผู้คนในยุคนั้น “ไม่เห็น” ว่าตนเองอยู่ในจุดเปลี่ยน เพราะแรงเฉื่อยทางความคิดและการเมืองทำให้พวกเขายึดมั่นในสิ่งที่เคยรู้จัก โดยไม่รู้เลยว่าโลกได้เคลื่อนเข้าสู่ระยะใหม่แล้ว และเราทุกวันนี้ก็อาจกำลังทำเช่นเดียวกัน
เรากำลังอยู่ในช่วงเวลาที่ไมโครโปรเซสเซอร์ เทคโนโลยีดิจิทัล และโครงสร้างไร้ศูนย์กลางจะเปลี่ยนกฎเกณฑ์ของอำนาจอย่างรุนแรง แต่ผู้คนกลับพยายามตีความสิ่งเหล่านี้ผ่านเลนส์ของโครงสร้างอุตสาหกรรมแบบเดิม ซึ่งอาจทำให้พลาดโอกาสที่จะเข้าใจการเปลี่ยนแปลงที่แท้จริง
ผู้เขียนเตือนว่าแม้บางหนังสือว่าด้วยอนาคตจะเต็มไปด้วยข้อมูล แต่กลับพาเราเข้าใจผิด เพราะยังยึดติดอยู่กับกรอบคิดเดิม เช่น การเชื่อว่ามนุษย์สามารถควบคุมทิศทางประวัติศาสตร์ได้เสมอ ทั้งที่ในความจริงแล้ว ปัจจัยที่ขับเคลื่อนการเปลี่ยนแปลงทางประวัติศาสตร์นั้น มักเป็นเงื่อนไขพื้นฐานที่มนุษย์ควบคุมไม่ได้ และไม่ได้อยู่ในความสนใจของการเมืองกระแสหลัก
มนุษย์มักไม่เปลี่ยนแปลงเพราะ “ต้องการเปลี่ยน” แต่เพราะ “ไม่เปลี่ยนไม่ได้แล้ว” และการเปลี่ยนแปลงเหล่านั้นมักเกิดสวนทางกับความต้องการของคนส่วนใหญ่ที่อยากรักษาสถานะเดิม
ชีวิตที่ขาดวิสัยทัศน์
ความไม่ตระหนักถึงการเปลี่ยนแปลงอันยิ่งใหญ่ที่กำลังก่อตัวขึ้นรอบตัวเรา อาจไม่ได้เกิดจากความไม่รู้ แต่เพราะเราลึกๆ แล้ว “ไม่อยากเห็น” ความเปลี่ยนแปลงนั้นเอง ความต้านทานนี้ไม่ใช่เรื่องใหม่ บรรพบุรุษของเราที่ดำรงชีพด้วยการล่าสัตว์และหาของป่าก็อาจเคยดื้อรั้นไม่ต่างกัน เพียงแต่พวกเขามีข้อแก้ตัวที่ฟังขึ้นมากกว่า เพราะในยุคก่อนประวัติศาสตร์ ไม่มีใครอาจคาดเดาว่า “การปฏิวัติการเกษตร” จะเปลี่ยนโลกไปในระดับใด พวกเขาไม่มีปฏิทิน ไม่มีการบันทึก ไม่มีแบบจำลองใดจากอดีตให้ใช้ทำนายอนาคต แม้แต่แนวคิดเรื่อง “เวลา” ก็ยังไม่มีอยู่ในจิตสำนึก พวกเขาใช้ชีวิตอยู่ใน “ปัจจุบันที่ไม่สิ้นสุด” และเมื่อพูดถึงการคาดการณ์อนาคต พวกเขาก็เป็นเหมือน “คนตาบอด” ที่ยังไม่เคยลิ้มรส “ผลไม้แห่งความรู้” (ตามคำเปรียบในพระคัมภีร์) แต่ต่างจากพวกเขา พวกเราในวันนี้มีเครื่องมือและมุมมองที่ลึกซึ้งกว่า จากองค์ความรู้ของบรรพบุรุษกว่าสี่ห้าร้อยรุ่น วิทยาศาสตร์ คณิตศาสตร์ และอัลกอริธึมของคอมพิวเตอร์ความเร็วสูง ช่วยให้เราทำความเข้าใจระบบที่ซับซ้อนอย่างเศรษฐกิจมนุษย์และพลวัตของสังคมได้ดียิ่งขึ้น แม้ทฤษฎีเศรษฐศาสตร์จะไม่สามารถอธิบายพฤติกรรมมนุษย์ได้แบบสมบูรณ์ แต่ก็ทำให้เราเข้าใจว่า “แรงจูงใจ” คือแรงผลักดันสำคัญ เมื่อผลตอบแทนสูงขึ้น หรือความเสี่ยงต่ำลง พฤติกรรมย่อมเกิดขึ้นถี่ขึ้น และนี่คือหลักการที่แม่นยำอย่างยิ่งในการวิเคราะห์อนาคต
แรงจูงใจนี้เองที่เป็นหัวใจของการพยากรณ์ และการพยากรณ์ที่ดีไม่ได้ขึ้นกับการรู้เหตุการณ์ล่วงหน้าแบบเฉพาะเจาะจง แต่ขึ้นอยู่กับการเข้าใจโครงสร้างของแรงขับเคลื่อน เช่นเดียวกับที่เราอาจไม่รู้ว่าเมื่อไรเสียงฟ้าร้องจะดังขึ้น แต่เมื่อเห็นฟ้าแลบ ก็สามารถคาดหมายได้ว่าจะมีเสียงตามมา เช่นกัน หากเราสามารถเข้าใจ “ตรรกะของความรุนแรง” ที่กำลังเปลี่ยนไปในระดับการเมืองมหภาคได้ เราก็จะมองเห็น “โอกาส” หรือ “ช่องโหว่” ของระเบียบเดิม และใครจะเป็นผู้ฉวยโอกาสเหล่านั้น
การเปลี่ยนแปลงครั้งใหญ่ในอดีต เช่น การปฏิวัติการเกษตร หรือการเข้าสู่ยุคอุตสาหกรรม ล้วนเกิดขึ้นช้าและกินเวลาหลายศตวรรษกว่าจะเผยผลเต็มที่ ในทางตรงกันข้าม การเปลี่ยนผ่านสู่ยุคสารสนเทศกลับเกิดขึ้นรวดเร็วเพียงช่วงชีวิตเดียว
ผู้เขียนวางกรอบเพื่อให้เราเข้าใจว่า การเปลี่ยนแปลงทางการเมืองมหภาคมักมาก่อนการเปลี่ยนแปลงในโครงสร้างของรัฐอย่างเป็นรูปธรรม รายได้ที่ลดลง วิกฤตที่เกิดจากทรัพยากรจำกัด และแรงกดดันจากประชากร ล้วนเป็นผลพลอยได้จากความไม่สามารถของระเบียบเดิมในการรองรับแรงกระแทกของโลกใหม่ และการพูดถึงการเปลี่ยนแปลงจาก “ภายนอกระบบ” มักถูกห้ามหรือมองว่าเป็นเรื่องต้องห้ามในทุกยุคทุกสมัย ยิ่งไปกว่านั้น การเปลี่ยนแปลงในระดับนี้มักก่อให้เกิดแรงปะทะทางวัฒนธรรมระหว่างผู้ที่ยึดมั่นในกรอบศีลธรรมดั้งเดิมกับผู้ที่เปิดรับแนวคิดใหม่ และไม่ใช่เรื่องแปลกที่การเปลี่ยนแปลงเช่นนี้จะไม่เป็นที่นิยม เพราะมันลดคุณค่าของทุนทางปัญญาเดิม ทำให้ระบบเก่าไร้ความหมาย และบีบบังคับให้สังคมต้องเรียนรู้ใหม่เกือบทั้งหมด โดยเฉพาะในกลุ่มคนที่ได้รับผลกระทบโดยตรง
สัญญาณของการเสื่อมถอยมักปรากฏในรูปของคอร์รัปชัน ความไร้ประสิทธิภาพ และการสูญเสียศีลธรรมของผู้มีอำนาจ ซึ่งมักเป็นสัญญาณล่วงหน้าของการเปลี่ยนแปลงที่หลีกเลี่ยงไม่ได้ ยิ่งในยุคที่เทคโนโลยีก้าวหน้าเร็วขึ้น กระบวนการเหล่านี้ก็จะยิ่งเร่งตัว จนทำให้เวลาที่เหลืออยู่สำหรับการปรับตัวลดลงเรื่อย ๆ
"เมื่อมองย้อนกลับไปตลอดหลายศตวรรษ — หรือแม้แต่แค่ในปัจจุบัน — เราจะเห็นได้อย่างชัดเจนว่า มีผู้คนจำนวนมากที่สร้างรายได้(บ่อยครั้งเป็นรายได้จำนวนมาก) จากทักษะในการใช้ความรุนแรงผ่านอาวุธ และกิจกรรมของพวกเขาเหล่านี้มีบทบาทอย่างสำคัญยิ่งในการกำหนดว่าทรัพยากรที่มีอยู่จำกัดในสังคมจะถูกจัดสรรไปในทิศทางใด." --เฟรเดอริก ซี. เลน
แนวคิดของการเมืองมหภาค(megapolitics) เป็นกรอบความคิดที่ทรงพลัง ซึ่งช่วยให้เรามองเห็นกลไกเบื้องหลังเหตุการณ์ที่ดูซับซ้อนหรือลึกลับในประวัติศาสตร์ ไม่ว่าจะเป็นเหตุผลที่บางรัฐบาลเจริญรุ่งเรือง ขณะที่บางแห่งกลับล่มสลาย เหตุใดสงครามจึงอุบัติขึ้น และเหตุใดฝ่ายหนึ่งจึงมีชัย หรือแม้กระทั่งว่าอะไรเป็นตัวแปรที่กำหนดวงจรแห่งความรุ่งเรืองและความตกต่ำทางเศรษฐกิจ ทั้งหมดล้วนสามารถอธิบายได้ผ่านเลนส์ของการเมืองมหภาค ซึ่งเน้นวิเคราะห์ว่า "ต้นทุนและผลตอบแทนของการใช้ความรุนแรง" เปลี่ยนไปอย่างไรในแต่ละบริบทของเวลา หากต้นทุนในการใช้อำนาจบังคับลดต่ำลง เช่น การเข้าถึงอาวุธที่ง่ายขึ้นและราคาถูกลง ก็ทำให้อำนาจเปลี่ยนมือได้ง่ายขึ้นตามไปด้วย หลักการนี้ยังคงใช้ได้ตั้งแต่ยุคโบราณจนถึงโลกยุคไซเบอร์สเปซในปัจจุบัน
ใน Part 2 เราจะมาดูกันว่ามีปัจจัยอะไรบ้างที่อยู่เบื้องหลังการเปลี่ยนแปลงครั้งใหญ่ในประวัติศาสตร์ to be continue....
-
 @ 2b24a1fa:17750f64
2025-04-04 08:10:53
@ 2b24a1fa:17750f64
2025-04-04 08:10:53Wir leben in einer Demokratie. So heißt es immer. Immerhin hat die Bevölkerung, der Souverän ein Mitspracherecht. Einmal alle vier Jahre. Und damit fünfundzwanzig Mal in einem Jahrhundert. Diese 25 Wahltage ergeben zeitlich 0,07 Prozent des gesamten Jahrhunderts. Würde man das Jahrhundert auf einen Tag runter rechnen, dann ergäben diese 0,07 Prozent ziemlich genau eine Minute des Mitspracherechts. Eine Minute pro Tag darf der Souverän also bestimmen, wer am restlichen Tag ungehindert schalten und walten darf – bis in das Grundgesetz hinein.
https://soundcloud.com/radiomuenchen/das-grundgesetz-als-schmierzettel-von-henry-matthes?
Die Veränderung in diesem zentralen Gesetzestexten ist allein den Parteien vorbehalten. An sämtliche Änderungen halten, dürfen sich dann nachher alle – selbst dann, wenn noch so wenige Bürger dahinterstehen.
In den letzten Wochen offenbarte sich dieser Missstand in präzedenzloser Weise. Die als Sondervermögen schön-deklarierte Neuverschuldung wurde im Grundgesetz festgeschrieben. Ist eine solch selektive Umgestaltungsmöglichkeit des wichtigsten Gesetzestext einer Demokratie würdig? Bräuchte es nicht zumindest einer Absegnung durch Volksabstimmungen?
Henry Mattheß hat sich hierzu Gedanken gemacht. Hören Sie seinen Text „Das Grundgesetz als Schmierzettel“, der zunächst auf dem Blog von Norbert Häring erschienen war.
Sprecher: Karsten Tryoke
Bild: Radio München
www.radiomuenchen.net/\ @radiomuenchen\ www.facebook.com/radiomuenchen\ www.instagram.com/radio_muenchen/\ twitter.com/RadioMuenchen
Radio München ist eine gemeinnützige Unternehmung.\ Wir freuen uns, wenn Sie unsere Arbeit unterstützen.
GLS-Bank\ IBAN: DE65 4306 0967 8217 9867 00\ BIC: GENODEM1GLS\ Bitcoin (BTC): bc1qqkrzed5vuvl82dggsyjgcjteylq5l58sz4s927\ Ethereum (ETH): 0xB9a49A0bda5FAc3F084D5257424E3e6fdD303482
-
 @ df67f9a7:2d4fc200
2025-04-03 19:54:29
@ df67f9a7:2d4fc200
2025-04-03 19:54:29More than just “follows follows” on Nostr, webs of trust algos will ingest increasingly MORE kinds of user generated content in order to map our interactions across the network. Webs of trust will power user discovery, content search, reviews and reccomendations, identity verification, and access to all corners of the Nostr network. Without relying on a central “trust authority” to recommend people and content for us, sovereign Nostr users will make use of “relative trust” scores generated by a wide range of independent apps and services. The problem is, Nostr doesn’t have an opensource library for performing WoT calculations and delivering NIP standard recommendations to users. In order for a “free market” ecosystem of really smart apps and services to thrive, independent developers will need access to extensible “middleware” such as this.
Project Description
I am building a library for independent developers to offer their own interoperable and configurable WoT services and clients. In addition, and as the primary use case, I am also developing a web client for “in person onboarding” to Nostr, which will make use of this library to provide webs of trust recommendations for “invited” users.
-
Meet Me On Nostr (onboarding client) : This is my first project on Nostr, which began a year ago with seed funding from @druid. This web client will leverage “in person” QR invites to generate WoT powered recommendations of follows, apps, and other stuff for new users at their first Nostr touchpoint. The functional MVP release (April ‘25) allows for “instant, anonymous, and fully encrypted” direct messaging and “move in ready” profile creation from a single QR scan.
-
GrapeRank Engine (developer library) : Working with @straycat last fall, I built an opensource and extensible library for Nostr developers to integrate “web of trust” powered reccomendations into their products and services. The real power behind GrapeRank is its “pluggable” interpreter, allowing any kind of content (not just “follows follows”) to be ingested for WoT scoring, and configurable easily by developers as well as end users. This library is currently in v0.1, “generating and storing usable scores”, and doesn’t yet produce NIP standard outputs for Nostr clients.
-
My Grapevine (algo dashboard) : In addition, I’ve just wrapped up the demo release of a web client by which users and developers can explore the power of the GrapeRank Engine.
Potential Impact
Webs of Trust is how Nostr scales. But so far, Nostr implementations have been ad-hoc and primarily client centered, with no consistency and little choice for end users. The “onboarding and discovery” tools I am developing promise to :
-
Establish sovereignty for webs of trust users (supporting a “free market” of algo choices), with opensource libraries by which any developer can easily implement WoT powered recommendations.
-
Accelerate the isolation of bots and bad actors (and improve the “trustiness” of Nostr for everyone else) by streamlining the onboarding of “real world” acquaintances directly into established webs of trust.
-
Improve “discoverability of users and content” for any user on any client (to consume and take advantage of WoT powered recommendations for any use case, even as the NIP standards for this are still in flux), by providing an algo engine with “pluggable” inputs and outputs.
-
Pave the way for “global Nostr adoption”, where WoT powered recommendations (and searches) are consistently available for every user across a wide variety of clients.
Timeline & Milestones
2025 roadmap for “Webs of Trust Onboarding and Discovery” :
-
Meet Me On Nostr (onboarding client) : MVP release : “scan my QR invite to private message me instantly with a ‘move in ready’ account on Nostr”. https://nostrmeet.me/
-
GrapeRank Engine (developer library) : 1.0 release : “expanded inputs and output WoT scores to Nostr NIPs and other stuff” for consumption by clients and relays. https://github.com/Pretty-Good-Freedom-Tech/graperank-nodejs
-
My Grapevine (algo dashboard) : 1.0 release : “algo usage and configuration webapp with API endpoints” for end users to setup GrapeRank scoring for consumption by their own clients and relays. https://grapevine.my/
-
Meet Me On Nostr (onboarding client) : 1.0 release : first GrapeRank integration, offering “follow and app recommendations for invited users”, customizable per-invite for Nostr advocates. https://nostrmeet.me/
Prior contributions
-
Last spring I hosted panel discussions and wrote articles on Nostr exploring how to build “sovereign webs of trust”, where end users can have control over which algorithms to use, and what defines “trust”.
-
I contributed gift wrap encryption to NDK.
-
I am also authoring gift wrapped direct messaging and chat room modules for NDK.
-
Last July, I attended The Bitcoin Conference on an OpenSource pass to raise funds for my onboarding client. I onboarded many Bitcoiners to Nostr, and made valuable connections at Bitcoin Park.
About Me
I discovered Nostr in September ‘23 as a freelance web developer, after years of looking for a “sovereignty respecting” social media on which to build apps. With this came my first purchase of Bitcoin. By December of that year, I was settled on “open source freedom tech” (Nostr and Bitcoin) as the new direction for my career.
As a web professional for 20+ years, I know the importance of “proof of work” and being connected. For the last 18 months, I have been establishing myself as a builder in this community. This pivot has not been easy, but it has been rewarding and necessary. After so many years building private tech for other people, I finally have a chance to build freedom tech for everyone. I have finally come home to my peeps and my purpose.
Thank you for considering this application for funding.
-
-
 @ d360efec:14907b5f
2025-04-21 22:10:23
@ d360efec:14907b5f
2025-04-21 22:10:23สวัสดีเพื่อนนักเทรดทุกท่าน! 👋 วันนี้ฉันมาแนะนำตารางกิจวัตรประจำวันของ Day Trader ที่น่าสนใจนี้กันนะคะ มาดูกันว่ามีอะไรที่เราสามารถเรียนรู้และนำไปปรับใช้กับการเทรดของเราได้บ้างค่ะ

ภาพรวมกิจวัตรประจำวันของ Day Trader 📊
ตารางนี้แสดงให้เห็นถึงโครงสร้างของวันที่สมดุลสำหรับนักเทรดรายวันที่ประสบความสำเร็จ โดยเน้นทั้งการเตรียมตัว 🤓 การลงมือเทรด 🚀 การเรียนรู้ 📚 และการดูแลสุขภาพส่วนตัว 🧘♀️ ซึ่งเป็นสิ่งสำคัญอย่างยิ่งในการรักษาประสิทธิภาพและความสม่ำเสมอในการเทรด 💪
การวิเคราะห์และอธิบายแต่ละช่วงเวลา
$ 05.30 น. > ตื่นนอน 🌅 อาบน้ำ 🚿 และเตรียมตัว 👔 > การเริ่มต้นวันอย่างกระปรี้กระเปร่า 🎉 และการมีกิจวัตรส่วนตัวที่ผ่อนคลายเป็นสิ่งสำคัญในการเตรียมพร้อมทั้งร่างกายและจิตใจ 🧠 สำหรับการเทรด
$ 06.00 น. > ตรวจสอบข่าวสาร 📰 วิเคราะห์กราฟ 📈 และเตรียมตัว 🎯 > ช่วงเวลานี้เป็นหัวใจสำคัญของการเตรียมตัวก่อนตลาดเปิด ⏰ นักเทรดจะตรวจสอบข่าวเศรษฐกิจ 💰 และข่าวที่เกี่ยวข้องกับสินทรัพย์ที่ตนเองเทรด 🧐 วิเคราะห์กราฟเพื่อหาแนวโน้ม 🔭 และระดับราคาที่น่าสนใจ 📍 รวมถึงวางแผนกลยุทธ์การเทรดสำหรับวันนี้ ✍️
$ 06.30 น. > ตลาดเปิด 🔔 เริ่มทำการเทรด 🚀 > เมื่อตลาดเปิด นักเทรดจะเริ่มดำเนินการตามแผนที่วางไว้ 📝 โดยจะเฝ้าติดตามการเคลื่อนไหวของราคา 👀 และเข้าเทรดตามสัญญาณที่เกิดขึ้น 🚦
$ 12.00 น. > พักรับประทานอาหารกลางวัน 🥪 > การพักผ่อน 😌 และการเติมพลัง 💪 ในช่วงกลางวันเป็นสิ่งสำคัญในการรักษาความมีสมาธิ 🧘♀️ และความสามารถในการตัดสินใจที่ดี 👍
$ 12.45 น. > ปิดสถานะการเทรดทั้งหมด 🛑 > สำหรับ Day Trader การปิดสถานะทั้งหมดภายในวันถือเป็นกฎเหล็ก 🚫 เพื่อหลีกเลี่ยงความเสี่ยงจากความผันผวนข้ามคืน 🌙
$ 13.00 น. > ทบทวน 🤔 เรียนรู้ 📚 และปรับปรุง ⚙️ > หลังจากการเทรด นักเทรดที่ประสบความสำเร็จ 🎉 จะใช้เวลาในการทบทวนการเทรดของตนเอง 🧐 วิเคราะห์ว่าอะไรทำได้ดี 👍 และอะไรที่ต้องปรับปรุง 📝 การเรียนรู้อย่างต่อเนื่องเป็นกุญแจสำคัญสู่การพัฒนา 🚀
$ 14.00 น. > ออกกำลังกาย 💪 และพักผ่อน 🧘♀️ > การดูแลสุขภาพกาย 🍎 และใจ 💖 มีความสำคัญไม่ยิ่งหย่อนไปกว่าการเทรด 📈 การออกกำลังกายและการมีเวลาว่าง 🌴 ช่วยลดความเครียด 😥 และเพิ่มประสิทธิภาพในการเทรดในระยะยาว ✨
$ 17.00 น. > รับประทานอาหารเย็น 🍽️ และพักผ่อน 🛋️ > การมีเวลาพักผ่อนกับครอบครัว ❤️ หรือทำกิจกรรมที่ชอบ 😊 ช่วยให้ผ่อนคลาย 😌 และเตรียมพร้อมสำหรับวันต่อไป 🌅
$ 19.00 น. > วางแผนการเทรดสำหรับวันพรุ่งนี้ 🗓️ และตรวจสอบข่าวสาร 📰 > การวางแผนล่วงหน้า 🤓 ช่วยให้นักเทรดมีความพร้อม 💪 และสามารถตอบสนองต่อสถานการณ์ตลาดได้อย่างมีประสิทธิภาพ 🚀
$ 22.00 น. > เข้านอน 😴 > การนอนหลับพักผ่อนอย่างเพียงพอ 🛌 เป็นสิ่งจำเป็นสำหรับการรักษาสุขภาพ 💖 และประสิทธิภาพในการเทรด 💪
สิ่งที่น่าสนใจและข้อคิด 🤔
$ ความมีระเบียบวินัย 💯 > ตารางนี้แสดงให้เห็นถึงความมีระเบียบวินัยที่เข้มงวด 📏 ซึ่งเป็นคุณสมบัติที่สำคัญของนักเทรดที่ประสบความสำเร็จ 🎉
$ การเตรียมตัวอย่างรอบคอบ 🧐 > การใช้เวลาในการวิเคราะห์ 📊 และวางแผน 📝 ก่อนตลาดเปิดช่วยลดการตัดสินใจที่ผิดพลาด 🚫 และเพิ่มโอกาสในการทำกำไร 💰
$ การเรียนรู้อย่างต่อเนื่อง 📚 > การทบทวน 🤔 และปรับปรุงกลยุทธ์ ⚙️ อยู่เสมอเป็นสิ่งสำคัญในการพัฒนาทักษะการเทรด 🚀
$ ความสมดุล ⚖️ > การให้ความสำคัญกับการดูแลสุขภาพ 🧘♀️ และการพักผ่อน 🌴 ควบคู่ไปกับการเทรด 📈 ช่วยป้องกันภาวะหมดไฟ 🔥 และรักษาประสิทธิภาพในระยะยาว ✨
การนำไปปรับใช้ 🛠️
เพื่อนๆ นักเทรดสามารถนำแนวคิดจากตารางนี้ไปปรับใช้กับกิจวัตรประจำวันของตนเองได้ 👍 โดยอาจไม่จำเป็นต้องทำตามทุกช่วงเวลาอย่างเคร่งครัด ⏰ แต่ให้เน้นที่หลักการสำคัญ เช่น การเตรียมตัวก่อนเทรด 🤓 การทบทวนหลังเทรด 🤔 และการดูแลสุขภาพ 🧘♀️ เพื่อสร้างสมดุล ⚖️ และเพิ่มประสิทธิภาพในการเทรดของเราค่ะ 💪
ขอให้ทุกท่านประสบความสำเร็จในการเทรดนะคะ! 💸🚀
#DayTrader #นักเทรดรายวัน #กิจวัตรประจำวัน #การลงทุน #เทรด #หุ้น #คริปโต #ตลาดหุ้น #แรงบันดาลใจ #พัฒนาตัวเอง #LinaEngword
-
 @ 7d33ba57:1b82db35
2025-04-21 20:16:41
@ 7d33ba57:1b82db35
2025-04-21 20:16:41Helsinki, the stylish and compact capital of Finland, sits right on the edge of the Baltic Sea, blending Scandinavian design, sustainable living, and a love for nature. It’s a city of clean lines, calm energy, and a creative spirit—where you can go from a seaside sauna to a sleek design museum in minutes.
🧭 Top Things to Do in Helsinki
⛪ Helsinki Cathedral
- The city’s iconic white-domed landmark, perched on Senate Square
- Climb the steps for sweeping views over the city’s neoclassical heart
🏝️ Suomenlinna Sea Fortress
- A UNESCO World Heritage Site spread across several islands
- Explore old ramparts, tunnels, museums, and scenic picnic spots
- A short ferry ride from the city center, perfect for a half-day trip
🧊 Löyly Sauna
- One of Helsinki’s most famous public saunas, right on the waterfront
- Relax in the heat, then dip in the Baltic like a local
- Beautiful architecture and a must-do cultural experience
🏛️ Design District & Museums
- Wander the Design District for boutique shops, galleries, and Finnish fashion
- Visit the Design Museum, Kiasma (contemporary art), and Ateneum (classic Finnish art)
🌲 Nature + Nordic Calm
- Walk along the Esplanadi park or relax in Kaivopuisto by the sea
- Take a boat to the nearby archipelago islands for hiking, birdwatching, or quiet cafés
- Even in winter, the city feels clean, serene, and cozy
☕ Food, Coffee & Nordic Flavors
- Try karjalanpiirakka (Karelian pies), salmon soup, or reindeer meat if you’re adventurous
- Helsinki has a big coffee culture—Finns drink more coffee per capita than anyone!
- Cozy up in a café with a cinnamon pulla and watch the snow fall (or the summer sun glow at midnight)
🚲 Getting Around
- Easy to explore by foot, tram, or city bikes
- Excellent ferries and boats to nearby islands and Tallinn, Estonia
- Helsinki Airport is well-connected and just 30 mins from downtown
📅 When to Go
- Summer: Endless daylight, festivals, and outdoor dining
- Winter: Snowy streets, cozy interiors, and a shot at the Northern Lights if you head north
- Autumn: Ruska (fall colors) is stunning in the parks and forests
-
 @ 7bdef7be:784a5805
2025-04-02 12:37:35
@ 7bdef7be:784a5805
2025-04-02 12:37:35The following script try, using nak, to find out the last ten people who have followed a
target_pubkey, sorted by the most recent. It's possibile to shortensearch_timerangeto speed up the search.```
!/usr/bin/env fish
Target pubkey we're looking for in the tags
set target_pubkey "6e468422dfb74a5738702a8823b9b28168abab8655faacb6853cd0ee15deee93"
set current_time (date +%s) set search_timerange (math $current_time - 600) # 24 hours = 86400 seconds
set pubkeys (nak req --kind 3 -s $search_timerange wss://relay.damus.io/ wss://nos.lol/ 2>/dev/null | \ jq -r --arg target "$target_pubkey" ' select(. != null and type == "object" and has("tags")) | select(.tags[] | select(.[0] == "p" and .[1] == $target)) | .pubkey ' | sort -u)
if test -z "$pubkeys" exit 1 end
set all_events "" set extended_search_timerange (math $current_time - 31536000) # One year
for pubkey in $pubkeys echo "Checking $pubkey" set events (nak req --author $pubkey -l 5 -k 3 -s $extended_search_timerange wss://relay.damus.io wss://nos.lol 2>/dev/null | \ jq -c --arg target "$target_pubkey" ' select(. != null and type == "object" and has("tags")) | select(.tags[][] == $target) ' 2>/dev/null)
set count (echo "$events" | jq -s 'length') if test "$count" -eq 1 set all_events $all_events $events endend
if test -n "$all_events" echo -e "Last people following $target_pubkey:" echo -e ""
set sorted_events (printf "%s\n" $all_events | jq -r -s ' unique_by(.id) | sort_by(-.created_at) | .[] | @json ') for event in $sorted_events set npub (echo $event | jq -r '.pubkey' | nak encode npub) set created_at (echo $event | jq -r '.created_at') if test (uname) = "Darwin" set follow_date (date -r "$created_at" "+%Y-%m-%d %H:%M") else set follow_date (date -d @"$created_at" "+%Y-%m-%d %H:%M") end echo "$follow_date - $npub" endend ```
-
 @ 3ad01248:962d8a07
2025-04-21 19:40:22
@ 3ad01248:962d8a07
2025-04-21 19:40:22It has almost been a month since the Bitcoin friendly Trump administration has been in power. The Bitcoin price was riding high days before and after the election with Bitcoin reaching a new all time high of 109k. It sure seem like surely once Trump got into office the price would skyrocket and everyone finally would have lambos and girlfriends.
Sadly for the number go up crowd this didn't happen. There are no lambos to be found and no girlfriends. All we get is some sideways price action and a Strategic Bitcoin Reserve (BSR).
If you are in Bitcoin for the right reasons and understand what you hold, this is the perfect time to stack sats before the price goes parabolic. I say this because Bitcoin sure seems to be poised to make a massive run. If you look past the current price of Bitcoin you can see a storm of dollars flowing into Bitcoin from the traditional fiat economy. The signs are there if you start looking for them.
US States Creating Bitcoin Strategic Reserves
Guess how many states are considering creating a state level Bitcoin reserve of their own? Lots. Here is a list of states that are thinking about creating a reserve for their state:
- Alabama
- Arizona
- Florida
- Kansas
- Illinois
- Iowa
- Massachusetts
- Michigan
- Missouri
- Montana
- New Hampshire
- New Jersey
- New Mexico
- North Carolina
- North Dakota
- Ohio
- Pennsylvania
- South Dakota
- Texas
- Utah
- Wisconsin
- Wyoming
Each state is at some varying degree of interest in creating a reserve. Texas and Arizona are by far have made the most progress on making a Bitcoin reserve a reality. Texas is currently holding a public hearing on this at the time of this writing. There is strong political will to create a reserve so I definitely can see them being first movers on this and once Texas makes it a reality the other state will move in short order.
Arizona's strategic reserve bill passed the senate finance committee on a 5-2 which is a big deal in itself but still has a long way to go before it becomes policy. If it passes the Senate it still has to pass the Arizona House of Representatives and signed by Democrat Governor Katie Hobbs, so the odds of this becoming law is slim. Arizona Democrats seem to be anti-Bitcoin in general and any bills coming from Republicans will likely be shoot down or watered down.
Analysts believe that $23 billion could flow into Bitcoin from government reserves which equates to 247k Bitcoin going into government cold storage. I have reservations about governments creating BSR's but if we are going to have them I much rather them be at the state level where it can benefit citizens the most. Especially state pension funds that so many of our firefighters, police and first responders depend on for retirement.
We will probably see a state level BSR created by the end of the year if not sooner. Time will tell.
SAB 121 Repeal
What is SAB 121? SAB 121 or Staff Accounting Bulletin 121 made it problematic for financial institutions to custody digital assets such as Bitcoin for their customers. SAB 121 required institutions to record their holdings as a liability and not an asset.
Naturally banks and other financial institutions didn't see an upside to custody digital assets if it meant taking on liability and having an administration that was hostile to crypto in general. Why take the chance to piss off the government and give them a reason to go after you is probably the reasoning of most bank executives. SAB 121 achieved the goal the Biden administration set out to accomplish, namely stymie Bitcoin adoption by banks and individuals as long as possible.
President Trump swiftly issued a executive order rescinding SAB 121 and with that ushering a new era in the realm of Bitcoin and digital assets in general. Financial institutions now have the ability to explore Bitcoin custody solutions that fit their customer's need without fear of having to record a liability on their books.
As more and more people and business learn about Bitcoin third party custody options are going to be popular. Think about it from a small business owner perspective for a second. They are in the business of selling their widgets for Bitcoin but they don't want to manage the complexity that comes with accounting, taxes etc.. In steps in their local bank that they have been with for years if not decades and starts providing Bitcoin management services. Small business owners would be all over that idea. In the long run I think the repeal of SAB 121 is going to be a bigger deal than states creating Bitcoin strategic reserves.
FASB
Financial Accounting Standards Board or FASB for short has applied fair value accounting rules on Bitcoin and other digital assets. This is a huge deal because it will allow business to realize profit and losses of Bitcoin based on market prices. It also makes it easier for investors who evaluate businesses that hold Bitcoin on their balance sheet. Overall it treats Bitcoin like any other asset that a business would hold.
This accounting rule change will pave the way for more businesses to put Bitcoin on their balance sheet further driving demand for Bitcoin.
Lightning Companies Leading The Way
We all know that L1 Bitcoin can not scale to the entire world and that in order to bring more people into Bitcoin that layer two solutions would have to be built. This has largely been done with the creation of the lightning network which enables seamless peer to peer micropayments in the blink of an eye.
Base layer Bitcoin will certain not be used to buy your daily coffees or gym memberships but lightning will be used for that purpose. Businesses small and large will demand one click on demand solutions to help them accept Bitcoin payments for their businesses. There are plenty of Bitcoin business ready to help business adopt a Bitcoin standard.
Businesses such as Opennode, Zaprite, Voltage, Breez make switching over to a Bitcoin standard easy for businesses to do.
So when you take a step back and really look at the Bitcoin ecosystem it is a lot more mature than most give it credit for and will slowly eat away at fiat currency dominance around the world.
The best thing that you can do is be patient, stack as many sats as you can and educate others about Bitcoin. We all know how fiat currencies end. Our time will come.
-
 @ 7bdef7be:784a5805
2025-04-02 12:12:12
@ 7bdef7be:784a5805
2025-04-02 12:12:12We value sovereignty, privacy and security when accessing online content, using several tools to achieve this, like open protocols, open OSes, open software products, Tor and VPNs.
The problem
Talking about our social presence, we can manually build up our follower list (social graph), pick a Nostr client that is respectful of our preferences on what to show and how, but with the standard following mechanism, our main feed is public, so everyone can actually snoop what we are interested in, and what is supposable that we read daily.
The solution
Nostr has a simple solution for this necessity: encrypted lists. Lists are what they appear, a collection of people or interests (but they can also group much other stuff, see NIP-51). So we can create lists with contacts that we don't have in our main social graph; these lists can be used primarily to create dedicated feeds, but they could have other uses, for example, related to monitoring. The interesting thing about lists is that they can also be encrypted, so unlike the basic following list, which is always public, we can hide the lists' content from others. The implications are obvious: we can not only have a more organized way to browse content, but it is also really private one.
One might wonder what use can really be made of private lists; here are some examples:
- Browse “can't miss” content from users I consider a priority;
- Supervise competitors or adversarial parts;
- Monitor sensible topics (tags);
- Following someone without being publicly associated with them, as this may be undesirable;
The benefits in terms of privacy as usual are not only related to the casual, or programmatic, observer, but are also evident when we think of how many bots scan our actions to profile us.
The current state
Unfortunately, lists are not widely supported by Nostr clients, and encrypted support is a rarity. Often the excuse to not implement them is that they are harder to develop, since they require managing the encryption stuff (NIP-44). Nevertheless, developers have an easier option to start offering private lists: give the user the possibility to simply mark them as local-only, and never push them to the relays. Even if the user misses the sync feature, this is sufficient to create a private environment.
To date, as far as I know, the best client with list management is Gossip, which permits to manage both encrypted and local-only lists.
Beg your Nostr client to implement private lists!
-
 @ 000002de:c05780a7
2025-04-21 19:36:30
@ 000002de:c05780a7
2025-04-21 19:36:30When people typically use the analogy of digital gold to describe bitcoin they mean that it is a digital asset that functions in the market in a way very similar to gold. By this they mean it is a store of value, not really a medium of exchange. This framing is not popular with the bitcoin is money crowd because when people use the digital gold framing they typically mean bitcoin isn't money. Its just a store of value. A hedge against inflation. It would never be used as money. It isn't good for buying stuff. Some that say this I'm pretty convinced are simply pushing this idea because of fear of the state. Others seem to really mean it.
The other day I was thinking about this and something occurred to me. I thought I understood gold before I understood bitcoin. I imagine like most people are similar. The truth is reading "The Bitcoin Standard" taught me much more about gold than bitcoin. In fact, I didn't really learn much about bitcoin from the book. I'm not saying its not a great book about bitcoin but rather my ignorance of gold was much greater than I realized. I imagine I'm not alone in that.
I remember thinking about gold after reading it... gold is pretty cool. Its properties are kinda wild. Gold has been used as money far longer than paper money. Its absolutely absurd to compare gold to bitcoin. Bitcoin is so new! But gold has qualities that make it unique among precious metals. These are not all unique properties but these are some of its qualities that make it a good money.
- You cannot create it, you have to find/mine it.
- You cannot destroy it.
- It is fungible.
- Its authenticity can be verified.
- Its supply has a very small increase over time(for now).
- It has been used for thousands of years as both a store of value and medium of exchange.
So why don't we use gold every day to buy goods. A common opinion is that it is because of greedy bankers and central planners but that's not the whole story. The truth is that gold died as a common money largely due to technology. Telecommunications and the speed of communication across great distances is what really supplanted gold as money. Gold was still used to back paper money(notes) but its use as the actual direct medium of exchange is largely dead. Bitcoin was not the first attempt to make digital money nor digital gold, but it has been the most successful by far.
So what am I saying? Bitcoin isn't digital gold but its a good analog. If you could make gold digital is would be great money. Bitcoin is a great store of value for the same reasons gold has been. Bitcoin however can be sent across great distances with ease and at the same time it can be stored for long periods of time at low cost. It is better than gold in both ways. As a store of value and medium of exchange. I can't send an oz of gold across the globe in seconds. I can't validate the authenticity of my gold with a simple computer.
My belief is that people that think bitcoin is only a viable store of value don't really understand bitcoin. Its true that currently under standard economic definitions bitcoin is not a generally accepted medium of exchange but that is only an issue of adoption and understanding. Bitcoin without lightning is still better than any fiat money. The dollar is only digital due to custodial services and trust in third parties. Our biggest problem with bitcoin as a medium of exchange is literally a lack of knowledge. This will be solved over time as people start to hold it to preserve their long term wealth. As fiat money dies and as regimes crack down on humans we will see a rise in desire for a new money. Sadly, I think most people will need to get wrecked before they get it.
My recommendation is to stop fighting over the "digital gold" label but instead agree and focus on the digital aspect. If gold was digital it would not have been supplanted by paper notes.
What do you think?
originally posted at https://stacker.news/items/951965
-
 @ 9063ef6b:fd1e9a09
2025-04-21 19:26:26
@ 9063ef6b:fd1e9a09
2025-04-21 19:26:26Quantum computing is not an emergency today — but it is a slow-moving tsunami. The earlier Bitcoin prepares, the smoother the transition will be.
1. Why Quantum Computing Threatens Bitcoin
Bitcoin’s current cryptographic security relies on ECDSA (Elliptic Curve Digital Signature Algorithm). While this is secure against classical computers, a sufficiently powerful quantum computer could break it using Shor’s algorithm, which would allow attackers to derive private keys from exposed public keys. This poses a serious threat to user funds and the overall trust in the Bitcoin network.
Even though SHA-256, the hash function used for mining and address creation, is more quantum-resistant, it too would be weakened (though not broken) by quantum algorithms.
2. The Core Problem
Bitcoin’s vulnerability to quantum computing stems from how it handles public keys and signatures.
🔓 Public Key Exposure
Most Bitcoin addresses today (e.g., P2PKH or P2WPKH) are based on a hash of the public key, which keeps the actual public key hidden — until the user spends from that address.
Once a transaction is made, the public key is published on the blockchain, making it permanently visible and linked to the address.

🧠 Why This Matters
If a sufficiently powerful quantum computer becomes available in the future, it could apply Shor’s algorithm to derive the private key from a public key.
This creates a long-term risk:
- Any Bitcoin tied to an address with an exposed public key — even from years ago — could be stolen.
- The threat persists after a transaction, not just while it’s being confirmed.
- The longer those funds sit untouched, the more exposed they become to future quantum threats.
⚠️ Systemic Implication
This isn’t just a theoretical risk — it’s a potential threat to long-term trust in Bitcoin’s security model.
If quantum computers reach the necessary scale, they could: - Undermine confidence in the finality of old transactions - Force large-scale migrations of funds - Trigger panic or loss of trust in the ecosystem
Bitcoin’s current design protects against today’s threats — but revealed public keys create a quantum attack surface that grows with time.
3. Why It’s Hard to Fix
Transitioning Bitcoin to post-quantum cryptography is a complex challenge:
- Consensus required: Changes to signature schemes or address formats require wide agreement across the Bitcoin ecosystem.
- Signature size: Post-quantum signature algorithms could be significantly larger, which affects blockchain size, fees, and performance.
- Wallet migration: Updating wallets and moving funds to new address types must be done securely and at massive scale.
- User experience: Any major cryptographic upgrade must remain simple enough for users to avoid security risks.
4. The Path Forward
The cryptographers worldwide are already working on solutions:
- Post-Quantum Cryptographic Algorithms are being standardized by NIST, including CRYSTALS-Dilithium, Kyber, FALCON, and SPHINCS+.
- Prototypes and experiments are ongoing in testnets and research networks.
- Hybrid signature schemes are being explored to allow backward compatibility.
Governments and institutions like NIST, ENISA, and ISO are laying the foundation for cryptographic migration across industries — and Bitcoin will benefit from this ecosystem.
5. What You could do in short term
- Keep large holdings in cold storage addresses that have never been spent from.
- Avoid reusing addresses to prevent public key exposure.
References & Further Reading
- https://komodoplatform.com/en/academy/p2pkh-pay-to-pubkey-hash
- https://csrc.nist.gov/projects/post-quantum-cryptography
- https://www.enisa.europa.eu/publications/post-quantum-cryptography-current-state-and-quantum-mitigation
- https://en.bitcoin.it/wiki/Quantum_computing_and_Bitcoin
- https://research.ibm.com/blog/ibm-quantum-condor-1121-qubits
- https://blog.google/technology/research/google-willow-quantum-chip/
- https://azure.microsoft.com/en-us/blog/quantum/2025/02/19/microsoft-unveils-majorana-1-the-worlds-first-quantum-processor-powered-by-topological-qubits/
- https://www.aboutamazon.com/news/aws/quantum-computing-aws-ocelot-chip
```
-
 @ fd78c37f:a0ec0833
2025-04-01 11:49:06
@ fd78c37f:a0ec0833
2025-04-01 11:49:06In this edition, we invited Keypleb, the founder of Bitcoin Indonesia, to share how he built the Bitcoin community in Indonesia, overcoming challenges like member turnover and venue selection, while driving the adoption and growth of Bitcoin.
YakiHonne: Welcome, Keypleb. Before we begin, let me briefly introduce YakiHonne. YakiHonne is a decentralized media client built on Nostr—a protocol designed to empower freedom of speech through technology. It enables creators to own their voices and assets while offering innovative tools like smart widgets, verified notes, and support for long-form content. We focus on free speech and free media by user privacy and data to be protected. So before starting the interview, I'd like to hear about yourself and your community.
Keypleb:My name is Keypleb, though it’s a pseudonym—a name I use to respect privacy. I'm a co-founder of Bitcoin Indonesia, Bitcoin House Bali, and Code Orange, a new developer school we launched at a conference just a few days ago. We focus on driving adoption through meetups, hackathons, and technical workshops. I'll dive into more details later, but that's a brief overview. I'm based in Bali now, though I travel a lot and consider myself quite nomadic. Great to be here.
YakiHonne: What sparked your interest in Bitcoin and what motivated you to create a community on Bitcoin?
Keypleb:I first got interested in Bitcoin because it solved a specific problem. At the time, I didn’t know exactly what the solution was, but the problem was that I couldn’t afford a home. Back in 2019, I was living in London, and a two-bedroom apartment was £600,000, which was insanely expensive. First-time buyers like myself simply couldn’t afford it. Why was it so expensive? Why was buying a house so hard? During the COVID lockdown, I had more time on my hands and started listening to Michael Saylor on a Bitcoin podcast, where he talked about how the system is rigged, and that’s why people work hard but still can’t afford a house. That really resonated with me. So I started looking for a community, but unfortunately, there wasn’t one.. Keypleb:After moving to Bali, I attended a lot of crypto meetups, especially scammy altcoin ones, thinking, “There has to be a solution.” But none of them resonated with me. There was no sense of freedom, and no real discussion about inflation resistance. I remembered a podcast from Dea Reskita, an Indonesian host who’s pretty well-known online. I reached out to her and said, “ you’ve got to help me. I’m surrounded by all these shitcoiners, and I can’t take it anymore. I need a real community. Is anything happening?” She replied, “Yes, something is happening. We should restart these meetups next month.” And that’s how it all began. Keypleb:There’s also another story about how we started Bitcoin House and how Bitcoin in Asia came to be, but maybe I’ll save that for later. Anyway, the spark of interest came from Bitcoin solving a real problem, and my drive to keep going came from the lack of quality meetups. Now, we’ve hosted 31 meetups, launched Bitcoin House and Code Orange, and the movement is growing rapidly.

YakiHonne: That’s such an amazing story—going from being on the brink of homelessness to creating something so impactful, and keeping it running every day, bringing new people into the journey. It’s truly inspiring. I’m curious about how the community started. How did you manage to attract members and build a strong community? What challenges did you face along the way?
Keypleb:It all started with our first meetup at the end of 2022, which was two and a half years ago now. At that time, we sent out an email to a group from a previous database, and the first meetup had around 20 people, which was a good start. However, problems quickly arose as people started dropping off, and the community lacked retention. In Bali, people come and go, usually staying for no more than two months, leading to a lack of long-term participation. This became one of our challenges: how to attract more people and, more importantly, get the same people to keep coming back. While I've been coming back for two and a half years, not everyone is able to return as often, and that has been a real challenge. Keypleb:Actually, I should also mention how I met my co-founders—Marius, Diana, and Dimas. We met at the 2023 Indonesia Bitcoin Conference. As time went on, we kept hosting meetups and had a lot of fun each time, though the locations kept changing. One of the initial challenges was that we didn't realize the importance of having a fixed meetup location. We changed venues several times before we realized that having a consistent location is crucial. If anyone wants to run a meetup, it's best to always choose a fixed location. We learned this through trial and error, but now it's no longer an issue. Keypleb:Since the conference, my co-founders and I have been working together, consistently putting in the effort. This is why our community has grown so large—so far, we are hosting 31 monthly meetups, 6 of which are in Bali. This means there is a bitcoin meetup almost every day on a regular basis. We've also established Bitcoin House Bali, a physical space, and the movement is growing rapidly. Without this movement, the region would face many challenges, including inflation and heavy censorship. It all started from just one meetup.
 YakiHonne: It's amazing to see how you met your co-founders and how you’ve built something incredible that continues to grow today. What advice would you give to someone looking to start a successful Bitcoin community right now?
YakiHonne: It's amazing to see how you met your co-founders and how you’ve built something incredible that continues to grow today. What advice would you give to someone looking to start a successful Bitcoin community right now?Keypleb:First, one very important piece of advice is to ensure that every meetup is held at the same location regularly. We realized this challenge through trial and error. To help others who are interested, we’ve published our meetup guide on GitHub, where everyone can check it out. For example, meetups should be held regularly, ideally once a month, or even once a week. In Chiang Mai, the Bitcoin meetup starts every Thursday at 7 PM, and everyone knows the time and location, making it easy to join without having to look up the next meetup. Keypleb:Additionally, our meetup structure is very simple. First, we do a round of introductions where everyone shares their name, where they’re from, and what Bitcoin means to them. This usually takes about 15 minutes. Then, we discuss three main questions: First, why do we need Bitcoin? The discussion typically focuses on two main issues Bitcoin addresses: inflation and censorship;Secondly, how to buy Bitcoin? We usually ask who wants to buy some Bitcoin, and then we do a small purchase together and conduct a P2P trade to demonstrate how easy it is to buy Bitcoin. Lastly, how to store Bitcoin? We introduce self-custody and show how to use hardware wallets (like Trezor), explaining the concept of the 12 words and private keys. Keypleb:The whole meetup usually wraps up in about an hour, after which people can continue socializing at Bitcoin House or wherever the meetup is taking place. In short, keeping the meetup simple and efficient, and ensuring a fixed location for each event, are key factors in building a successful community.
YakiHonne: What's the major approach? Is it more technical, or do you focus on non-technical aspects, or do you cover both?
Keypleb:Our approach includes both technical and non-technical content. Initially, our meetups were completely non-technical, just casual gatherings for people to socialize. Over time, however, we've evolved to incorporate more technical content. Keypleb:Out of the 31 monthly regular meetups we host, most of them have been non-technical, simply regular gatherings held at the same time and place according to our meetup guide. For example, we host the “Bitcoin for Beginners” meetup, which is designed for newcomers and takes place every second Friday of the month at 5 PM at the Bitcoin House Bali. This is entirely non-technical. Additionally, every Wednesday at Bitcoin House, we host the “My First Bitcoin” course. While the course touches on some technical aspects, such as seed phrases and backups, it’s still beginner-friendly and not too technical. The course runs for 10 weeks, and we plan to offer it in the local language at Bali University to help the local community better understand Bitcoin. Keypleb:On the other hand, we also offer highly technical content. We launched a new program called “Code Orange,” which is specifically designed for developers and programmers. We use the “Decoding Bitcoin” website, created by Jamal, which is a learning platform for developers. Many developer schools, like Code Orange, use this resource. Additionally, we host “Code Orange” meetups where we dive into the technical aspects of Bitcoin, such as how mining works and how to prevent single points of failure. Keypleb:We also organize technical workshops, such as “How to Defend Against a Five-Dollar Wrench Attack,” which is closely related to security. Recently, there have been some kidnapping incidents in Bali, and many people are concerned about their Bitcoin being stolen. To address this, we plan to hold a workshop on how to protect Bitcoin against such attacks. Additionally, we host hackathons and other high-tech events, and we just completed a very successful beginner-level hackathon. Keypleb:In summary, our community caters to everyone, from beginners to technical experts. For beginners, we offer easy-to-understand, non-technical content, while for experienced Bitcoiners, we provide in-depth technical material.
 YakiHonne: It's great to approach it in both ways, so everyone gets their own "piece of the cake."Now, I'd like to dive into the technical side. What advice would you give to technically inclined individuals or organizations looking to contribute to the Bitcoin ecosystem? How should they approach the technical aspects of Bitcoin if they want to get involved?
YakiHonne: It's great to approach it in both ways, so everyone gets their own "piece of the cake."Now, I'd like to dive into the technical side. What advice would you give to technically inclined individuals or organizations looking to contribute to the Bitcoin ecosystem? How should they approach the technical aspects of Bitcoin if they want to get involved?Keypleb:I have some additional advice. First, technical individuals can sign up for the “Decoding Bitcoin” course that starts on 18th March 2025 or join our “Code Orange” program and participate in the end-of-year hackathon. If they are technically proficient, this will be a great opportunity. “Decoding Bitcoin” is great for beginners, but it’s also useful for technical individuals. If someone is very skilled, they can start contributing code right away. If they find the course too easy, they can skip it and dive directly into more advanced projects. Additionally, Bitshala and Chaincode Labs offer advanced courses, which more technically advanced individuals can choose to pursue.
 Keypleb:Additionally, it's worth mentioning that the Bitcoin Dev Project has a great platform where technical individuals can find “Good First Issue” or open-source projects to start contributing code. You'll learn about the philosophy behind Bitcoin and why it's more meaningful than other “shitcoins.” Once you’ve taken enough “orange pills” (the philosophy and technology of Bitcoin), you can dive deeper into Bitcoin core development and potentially start coding in C++. If you're interested, you can join specific projects like Nostr, Fedimint or E-Cash.
Keypleb:Additionally, it's worth mentioning that the Bitcoin Dev Project has a great platform where technical individuals can find “Good First Issue” or open-source projects to start contributing code. You'll learn about the philosophy behind Bitcoin and why it's more meaningful than other “shitcoins.” Once you’ve taken enough “orange pills” (the philosophy and technology of Bitcoin), you can dive deeper into Bitcoin core development and potentially start coding in C++. If you're interested, you can join specific projects like Nostr, Fedimint or E-Cash.YakiHonne: I’d like to move on to the next question: How do you see Bitcoin communities evolving as technology progresses, particularly in areas like scalability, privacy, and adaptability to other systems? Keypleb:I believe the Bitcoin community will continue to evolve, and it has already made incredible progress. Two and a half years ago, we started alone in Bali, with just ourselves. We began in the official phase and have had numerous conversations throughout the year. For example, we are now starting a Bitcoin club at a university in Bali; we just need to find a passionate, driven “Bitcoin maximalist,” and the Bitcoin club will begin. Like what our friends did in Banyuwangi, Indonesia, these clubs could eventually evolve into Bitcoin houses.
Keypleb:Regarding privacy and scalability, the community is making strides. We’re big fans of Fedi, which builds on top of the Fedimint protocol and uses e-cash to scale Bitcoin while improving privacy. Fedi low fees and high privacy potential give Bitcoin great opportunities in this area. Keypleb:As for Bitcoin's compatibility with fiat systems, although Bitcoin payments are illegal in some countries like Indonesia, smart developers across Southeast Asia are working on legal solutions. For example, there's a website called Pleb QR that works in Thailand, allowing you to pay in fiat via the Lightning Network. Koral is another app specifically for Indonesia. These kinds of testing products already exist and are physically possible, but we’re just waiting on regulations. My influential friends are actively lobbying the government for adoption. Keypleb:In summary, privacy, scalability, and compatibility with fiat systems are all works in progress, and they will continue to evolve positively. There will be more meetups, more wallet downloads, and more adoption—there’s no doubt about that.
YakiHonne: You mentioned the concept of cross-country issues, so I have one last question: How is the government’s stance on Bitcoin? Is the political climate supportive or against Bitcoin? How do you see the government's approach to Bitcoin in your community or environment?
Keypleb:This reminds me of a person, Jeff Booth, who once said, “We are them, the government is made up of us.” In Indonesia, many politicians actually support Bitcoin, and many of them mine Bitcoin themselves. When money is involved, the incentive is strong, and politicians naturally like to make more money. As a result, Indonesia has a large Bitcoin mining scene. However, overall, the Indonesian government is against Bitcoin, as seen in their ban on Bitcoin payments. The 2011 currency law states that any currency other than the Indonesian Rupiah (IDR) cannot be used, and violators can face up to one year in prison or a fine. This means you cannot pay with US dollars, lira, euros, pesos or pounds. Keypleb:This shows that the government’s legal system is somewhat fragile. It’s understandable that the government is concerned about disruptive technologies like Bitcoin, especially with such a fragile fiat system. Indonesia has also seen many arrests. In 2016, Bank Indonesia issued a letter announcing a crackdown on cryptocurrency payments. Those involved in paying in Bitcoin had their funds seized, and the police cooperated in shutting down businesses accepting Bitcoin payments in the cities. While this isn't very friendly, it does highlight the fragility of the existing system. We also believe that a new executive order may be introduced in the future, similar to when President Roosevelt in 1933 ordered Americans to hand over all their gold with his Executive Order 6102. If it happened before, it could happen again. Keypleb:Therefore, we predict that Bitcoin custody could become a legal issue, which is one of the reasons we blur the faces of participants at every meetup. We need to protect the community from any potential risks. But overall, we remain optimistic. Despite the government ban, the ideology of Bitcoin is unstoppable, and its spread cannot be stopped. So, we are very optimistic about the future.
YakiHonne: I think almost every government around the world, even in Africa, faces similar issues with Bitcoin. Some governments might want Bitcoin but hesitate to openly accept it due to the fear of it undermining the traditional financial system, which, of course, could eventually happen. But hopefully, as the new generation comes into power, we'll see more Bitcoin-friendly governments. So, thank you so much for sharing your insights and advice. I really appreciate your time and the valuable input you've provided.
Keypleb:I'm really glad this conversation enlightened me. I enjoyed it a lot, and it made me reflect on how much work we're doing and how valuable it is. There are a lot of problems out there, with censorship being the biggest one, followed by inflation, which is also a major issue depending on the region. But Bitcoin is open, the community is growing, and people are fighting against censorship and internet shutdowns in places like Indonesia and beyond. The movement is definitely growing. So, I'm very happy to be here and have this chat. Thanks again.
Bitcoin Indonesia nostr: nostr:npub1y4qd2zhtn05gnsaaq5xfejzfk4a32638tx6gpp9g8k6e42g9d66qaxhcr3
Keypleb nostr: nostr:npub190trvg63e6tyqlwlj6lccqpftx76lckj25c006vwx3dzvdl88yxs2nyqdx
-
 @ d34e832d:383f78d0
2025-04-21 19:09:53
@ d34e832d:383f78d0
2025-04-21 19:09:53Such a transformation positions Nostr to compete with established social networking platforms in terms of reach while simultaneously ensuring the preservation of user sovereignty and the integrity of cryptographic trust mechanisms.

The Emergence of Encrypted Relay-to-Relay Federation
In the context of Nostr protocol scalability challenges pertaining to censorship-resistant networking paradigms, Nostr stands as a paradigm-shifting entity, underpinned by robust public-key cryptography and minimal operational assumptions. This feature set has rendered Nostr an emblematic instrument for overcoming systemic censorship, fostering permissionless content dissemination, and upholding user autonomy within digital environments. However, as the demographic footprint of Nostr's user base grows exponentially, coupled with an expanding range of content modalities, the structural integrity of individual relays faces increasing pressure.
Challenges of Isolation and Limited Scalability in Decentralized Networks
The current architecture of Nostr relays is primarily constituted of simple TCP or WebSocket servers that facilitate the publication and reception of events. While aesthetically simple, this design introduces significant performance bottlenecks and discoverability issues. Relays targeting specific regional or topical niches often rely heavily on client-side interactions or third-party directories for information exchange. This operational framework presents inefficiencies when scaled globally, especially in scenarios requiring high throughput and rapid dissemination of information. Furthermore, it does not adequately account for redundancy and availability, especially in low-bandwidth environments or regions facing strict censorship.

Navigating Impediments of Isolation and Constrained Scalability
Current Nostr relay infrastructures mainly involve basic TCP and WebSocket configurations for event publication and reception. While simple, these configurations contribute to performance bottlenecks and a significant discoverability deficit. Relays that serve niche markets often operate under constraints, relying on client-side interactions or third-party directories. These inefficiencies become particularly problematic at a global scale, where high throughput and rapid information distribution are necessary. The absence of mechanisms to enhance redundancy and availability in environments with limited connectivity or under censorship further exacerbates these issues.
Proposal for Encrypted Relay Federation
Encrypted relay federation in decentralized networking can be achieved through a novel Nostr Improvement Proposal (NIP), which introduces a sophisticated gossip-style mesh topology. In this system, relays subscribe to content tags, message types, or public keys from peer nodes, optimizing data flow and relevance.
Central to this architecture is a mutual key handshake protocol using Elliptic Curve Diffie-Hellman (ECDH) for symmetric encryption over relay keys. This ensures data integrity and confidentiality during transmission. The use of encrypted event bundles, compression, and routing based on relay reputation metrics and content demand analytics enhances throughput and optimizes network resources.
To counter potential abuse and spam, strategies like rate limiting, financially incentivized peering, and token gating are proposed, serving as control mechanisms for network interactions. Additionally, the relay federation model could emulate the Border Gateway Protocol (BGP), allowing for dynamic content advertisement and routing updates across the federated mesh, enhancing network resilience.
Advantages of Relay Federation in Data Distribution Architecture
Relay federation introduces a distributed data load management system where relays selectively store pertinent events. This enhances data retrieval efficiency, minimizes congestion, and fosters a censorship-resistant information flow. By decentralizing data storage, relays contribute to a global cache network, ensuring no single relay holds comprehensive access to all network data. This feature helps preserve the integrity of information flow, making it resistant to censorship.
An additional advantage is offline communication capabilities. Even without traditional internet access, events can still be communicated through alternative channels like Bluetooth, Wi-Fi Direct, or LoRa. This ensures local and community-based interactions remain uninterrupted during network downtime.
Furthermore, relay federations may introduce monetization strategies where specialized relays offer access to rare or high-quality data streams, promoting competition and interoperability while providing users with diverse data options.
Some Notable Markers To Nostr Becoming the Internet Layer for Censorship Resistance
Stop for a moment in your day and try to understand what Nostr can do for your communications by observing these markers:
- Protocol Idea (NIP-01 by fiatjaf) │ ▼
- npub/nsec Keypair Standard │ ▼
- First Relays Go Online │ ▼
- Identity & Auth (NIP-05, NIP-07) │ ▼
- Clients Launch (Damus, Amethyst, Iris, etc.) │ ▼
- Lightning Zaps + NWC (NIP-57) │ ▼
- Relay Moderation & Reputation NIPs │ ▼
- Protocol Bridging (ActivityPub, Matrix, Mastodon) │ ▼
- Ecash Integration (Cashu, Walletless Zaps) │ ▼
- Encrypted Relay Federation (Experimental) │ ▼
- Relay Mesh Networks (WireGuard + libp2p) │ ▼
- IoT Integration (Meshtastic + ESP32) │ ▼
- Fully Decentralized, Censorship-Resistant Social Layer
The implementation of encrypted federation represents a pivotal technological advancement, establishing a robust framework that challenges the prevailing architecture of fragmented social networking ecosystems and monopolistic centralized cloud services. This innovative approach posits that Nostr could:
- Facilitate a comprehensive, globally accessible decentralized index of information, driven fundamentally by user interactions and a novel microtransaction system (zaps), enabling efficient content valorization and information dissemination.
- Empower the concept of nomadic digital identities, allowing them to seamlessly traverse various relays, devoid of reliance on centralized identity verification systems, promoting user autonomy and privacy.
- Become the quintessential backend infrastructure for decentralized applications, knowledge graphs, and expansive datasets conducive to DVMs.
- Achieve seamless interoperability with established protocols, such as ActivityPub, Matrix, IPFS, and innovative eCash systems that offer incentive mechanisms, fostering an integrated and collaborative ecosystem.
In alignment with decentralization, encrypted relay-to-relay federation marks a significant evolution for the Nostr protocol, transitioning from isolated personal broadcasting stations to an interoperable, adaptive, trustless mesh network of communication nodes.
By implementing this sophisticated architecture, Nostr is positioned to scale efficiently, addressing global needs while preserving free speech, privacy, and individual autonomy in a world marked by surveillance and compartmentalized digital environments.
Nostr's Countenance Structure: Noteworthy Events
``` Nostr Protocol Concept by fiatjaf:
- First Relays and npub/nsec key pairs appear
- Damus, Amethyst, and other clients emerge
- Launch of Zaps and Lightning Tip Integration
- Mainstream interest post Twitter censorship events
- Ecosystem tools: NWC, NIP-07, NIP-05 adoption
- Nostr devs propose relay scoring and moderation NIPs
- Bridging begins (ActivityPub, Matrix, Mastodon)
- Cashu eCash integration with Nostr zaps (walletless tips)
- Relay-to-relay encrypted federation proposed
- Hackathons exploring libp2p, LNbits, and eCash-backed identities
- Scalable P2P Mesh using WireGuard + Nostr + Gossip
- Web3 & IoT integration with ESP32 + Meshtastic + relays
- A censorship-resistant, decentralized social internet ```
-
 @ 75869cfa:76819987
2025-04-01 05:55:38
@ 75869cfa:76819987
2025-04-01 05:55:38GM, Nostriches!
The Nostr Review is a biweekly newsletter focused on Nostr statistics, protocol updates, exciting programs, the long-form content ecosystem, and key events happening in the Nostr-verse. If you’re interested, join me in covering updates from the Nostr ecosystem!
Quick review:
In the past two weeks, Nostr statistics indicate over 221,000 daily trusted pubkey events. The number of new users has seen a notable decrease, with profiles containing a contact list dropping by 79%. More than 10 million events have been published, reflecting a 12% decrease. Total Zap activity stands at approximately 21 million, marking a 15% increase.
Additionally, 15 pull requests were submitted to the Nostr protocol, with 2 merged. A total of 45 Nostr projects were tracked, with 8 releasing product updates, and over 569 long-form articles were published, 24% focusing on Bitcoin and Nostr. During this period, 7 notable events took place, and 2 significant events are upcoming.
Nostr Statistics
Based on user activity, the total daily trusted pubkeys writing events is about 221,000, representing a slight 8 % decrease compared to the previous period. Daily activity peaked at 17662 events, with a low of approximately 15781.
The number of new users has decreased significantly. Profiles with bio are now around 25951, reflecting a 79% drop. Pubkeys writing events have decreased by 50% compared to the previous period.
Regarding event publishing, all metrics have shown a decline. The total number of note events published is around 10 million, reflecting a 12% decrease. Posts remain the most dominant in terms of volume, totaling approximately 1.7 million, which is a 4.4 % decrease. Both reposts and reactions have decreased by about 5%.
For zap activity, the total zap amount is about 21 million, showing an increase of over 15% compared to the previous period.
Data source: https://stats.nostr.band/
NIPs
Added optional signString() method
nostr:npub1emq0gngdvntdn4apepxrxr65vln49nytqe0hyr58fg9768z5zmfqcwa3jz is proposing a signString() method that allow Nostr users to sign/authenticate messages for external apps without compromising their private key (nsec).It opens up a more generic and flexible challenge-response style external authentication method, using the same Schnorr signature mechanism that Nostr uses to sign events natively.External apps need only understand Schnorr signatures - they do not need to understand Nostr's event structure. This widens interoperability.A concrete example of where this would be useful is P2PK locking of Cashu ecash tokens to a Nostr pubkey (npub). Decoding the token requires a Scnorr signature on a structured message string. This method would allow a signer to handle It cleanly.
nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 defines kind:39701 as website bookmarks.Bookmarks can be queried by the d tag, which is just their URL without the scheme, which is always and everywhere assumed to be https://. The querystring and the hash must be removed entirely, unless their requirement is explicitly stated either by the user or by some hardcoded list of URLs that rely on query strings for basic routing provided by the client (I've searched the internet extensively and could only find 3 websites that do this: YouTube, Hacker News and a random guy's sad old blog). Bookmarks can be commented on with NIP-22.
nostr:npub1zwnx29tj2lnem8wvjcx7avm8l4unswlz6zatk0vxzeu62uqagcash7fhrf is proposing a NIP that covers the inclusion of Progress Events as implemented in Open Librarian. While the specific implementation is focused on tracking reading progress, the NIP is generic enough to be used in a whole range of other progress tracking scenarios (e.g. Fitness challenges, course progression for learning, personal goals etc..)
nostr:npub1zwnx29tj2lnem8wvjcx7avm8l4unswlz6zatk0vxzeu62uqagcash7fhrf is proposing a NIP that includes a minor update to extend kind 30003 in NIP-51 to include the i tag for external identities, as implemented for book reading lists in Open Librarian.
nostr:npub15qydau2hjma6ngxkl2cyar74wzyjshvl65za5k5rl69264ar2exs5cyejr is proposing a NIP that Enable references to commits, files and lines for both nip34 repositories and other git repositories. Useful for code reviews of nip34 patches, the forthcoming nip95 code snippets and referencing specific code more generally.
Notable Projects
Yakihonne nostr:npub1yzvxlwp7wawed5vgefwfmugvumtp8c8t0etk3g8sky4n0ndvyxesnxrf8q
🌐web v4.5.0: * Custom reactions are here! Choose your preferred emoji to react to notes and other content. * Improved profile organization with notes and replies now displayed separately. * Adding the ability to zap notes directly from the notifications center. * Enhanced DM filtering by time, allowing you to view only recent messages or browse further back. * Manual cache clearing from settings to optimize web app performance. * Resolved issue preventing users from removing custom media uploader servers. * Expanded export data, including more relevant details in credential and wallet files. * General bug fixes and performance improvements.
📱mobile v1.6.8: * One tap zap: Send a Lightning Network payment with one tap. * Dms extensive filtering: Use advanced filters to sort or prioritise direct messages efficiently. * Separating replies from notes: Split replies and notes in profiles, adding a tab for easier browsing. * Adding slide to display options: Swipe in notifications to access zap, reply, or DM options quickly. * Custom reactions: Choose from a set of emojis for personalised reactions, beyond standard likes. * App cache manager: Manage and clear app cache to boost performance and save space. * Variety of bugs fixed: Fixed multiple bugs for a more stable and seamless app experience. * General app improvements: Enhanced overall performance, usability, and design across the app.
0xchat nostr:npub1tm99pgz2lth724jeld6gzz6zv48zy6xp4n9xu5uqrwvx9km54qaqkkxn72
0xChat v1.0.2-Desktop Beta is now live! * Supports NIP-104 MLS secret chat. * Copy images directly from the clipboard. * The app stays running after closing the window. * Fixed Enter key sending messages immediately on desktop.
Nostur v1.18.2 nostr:npub1n0stur7q092gyverzc2wfc00e8egkrdnnqq3alhv7p072u89m5es5mk6h0
Nostur v1.18.2 bugfix update: * Fixed Follow button sometimes disabled * Fixed account switching reload issue * Fixed custom feeds missing * Fixed live stream banner scroll/swipe issue * Fixed screen turns off while playing video
voca v0.0.6 nostr:npub17h9fn2ny0lycg7kmvxmw6gqdnv2epya9h9excnjw9wvml87nyw8sqy3hpu
This release fine tunes the release process and makes publishing to @Zapstore a lot easier. There are also continuous improvements to initializing the text to speech engine for a faster startup.
WasabiWallet 2.5.0 nostr:npub1jw7scmeuewhywwytqxkxec9jcqf3znw2fsyddcn3948lw9q950ps9y35fg
- 3rd Party Providers for Fee & Exchange Rate
- Quality of Life Features
- Backend and Coordinator packaged for Linux
GitPlaza nostr:npub1useke4f9maul5nf67dj0m9sq6jcsmnjzzk4ycvldwl4qss35fvgqjdk5ks
- Login via nsec
- Activity feed for the people you follow (only issue creation)
- Create issues
- Comment on issues
ZEUS v0.10.1 nostr:npub1xnf02f60r9v0e5kty33a404dm79zr7z2eepyrk5gsq3m7pwvsz2sazlpr5
ZEUS v0.10.1-beta1 is now available for testing. * NameDesc / bLIP-11 support: add receiver name to invoices * Bug fix: import of QR image from camera roll * Bug fix: Embedded LND: Open Channel: fund max * UI: Add dynamic background/text colors to Android NFC modal
KYCNOT.ME nostr:npub188x98j0r7l2fszeph6j7hj99h8xl07n989pskk5zd69d2fcksetq5mgcqf
- UI/UX - designe a new logo and color palette for kycnot.me.
- Point system - The new point system provides more detailed information about the listings, and can be expanded to cover additional features across all services.
- ToS Scrapper: implement a powerful automated terms-of-service scrapper that collects all the ToS pages from the listings. It saves you from the hassle of reading the ToS by listing the lines that are suspiciously related to KYC/AML practices.
- Search bar - The new search bar allows you to easily filter services. It performs a full-text search on the Title, Description, Category, and Tags of all the services.
- Transparency - To be more transparent, all discussions about services now take place publicly on GitLab.
- Additionally, there's a real-time audits page that displays database changes.
- Listing Requests - upgrade the request system. The new form allows you to directly request services or points without any extra steps.
- Lightweight and fast - The new site is lighter and faster than its predecessor!
- Tor and I2P - At last! kycnot.me is now officially on Tor and I2P!
Long-Form Content Eco
In the past two weeks, more than 569 long-form articles have been published, including over 94 articles on Bitcoin and more than 43 related to Nostr, accounting for 24% of the total content.
These articles about Nostr mainly explore the growing importance of decentralization in communication, identity management, and digital infrastructure. From beginner-friendly guides like Nostr 101 and Getting Started with Primal, to more technical deep dives such as NIP-101e, NIP-95, and tutorials on running Nostr relays as TOR hidden services. Some articles focus on security and privacy—like protecting your Nsec with Amber or using tools such as ProtonMail—while others tackle complex challenges including Sybil attack mitigation and child protection in decentralized environments. There are also cultural and political reflections, such as letters from political prisoners and thoughts on the future of free speech in a post-Twitter world. In addition, the Nostr community shows a strong spirit of experimentation—ranging from agent-to-agent communication through dad jokes, to desktop-like clients, fitness tracking protocols, and Lightning integrations like Work Zaps and Wallet Connect. Together, these pieces showcase a dynamic, resilient, and freedom-driven movement shaping the future of the web.
The Bitcoin articles discuss a wide range of themes—from foundational ideas like "What is Money?" and Bitcoin’s first principles, to practical guides on mining, self-custody, Lightning payments, and privacy tools. Many explore Bitcoin’s role as a hedge against inflation, a form of sovereignty, and a response to fiat fragility. Cultural and economic reflections appear throughout—ranging from using Bitcoin to buy homes in Italy, to hip-hop collaborations, and even personal stories of financial awakening. There's critical analysis of Bitcoin UX, memetics, policy-making, and even war-time monetary history. From node sovereignty to P2P lending, from grassroots adoption to global macro shifts, these articles together portray Bitcoin not just as a currency, but as a cultural movement, a technological evolution, and a lens to reimagine freedom, value, and the future of money.
Thank you, nostr:npub1akzvuyyd79us07m8mtp2ruuha3ylp9757qg46d50rcrkhnx0fs4q2xzr37 nostr:npub1q67f4d7qdja237us384ryeekxsz88lz5kaawrcynwe4hqsnufr6s27up0e nostr:npub1xr8tvnnnr9aqt9vv30vj4vreeq2mk38mlwe7khvhvmzjqlcghh6sr85uum nostr:npub1zmc6qyqdfnllhnzzxr5wpepfpnzcf8q6m3jdveflmgruqvd3qa9sjv7f60 nostr:npub1ygzj9skr9val9yqxkf67yf9jshtyhvvl0x76jp5er09nsc0p3j6qr260k2 nostr:npub1ktt8phjnkfmfrsxrgqpztdjuxk3x6psf80xyray0l3c7pyrln49qhkyhz0 nostr:npub1qny3tkh0acurzla8x3zy4nhrjz5zd8l9sy9jys09umwng00manysew95gx nostr:npub1l5r02s4udsr28xypsyx7j9lxchf80ha4z6y6269d0da9frtd2nxsvum9jm nostr:npub186k25a5rymtae6q0dmsh4ksen04706eurfst8xc5uzjchwkxdljqe59hv0 and others, for your work. Enriching Nostr’s long-form content ecosystem is crucial.
Nostriches Global Meet Ups
Recently, several Nostr events have been hosted in different countries.
-
YakiHonne teamed up with Bitcoin Safari, nostr:npub1w7z986fez3gmjvxy6dd3sku4ndazhxzafjv2lf6aaa26mtl70q6scz4erj nostr:npub1t4ljwhhg7zlxeahxwgmkwqmn4jjxxq8lzhyuzy0zvy23hq0sacxsdl9fvv nostr:npub1pw778uxwkky3xgq7w3anykdwdw9g46xy8de9mnau0kgwzz375zkq3udv57 and FULAFIA University to successfully host a series of Nostr Workshops, attracting over 200 participants in total. These events introduced the Nostr ecosystem and Bitcoin payments, allowing attendees to explore decentralized technologies through YakiHonne while earning rewards. Participants were encouraged to register and verify their accounts to claim exclusive bonuses—and invite friends to unlock even more benefits.
-
The 2025 Bitcoin, Crypto Economy, and Law FAQ Webinar was held online on March 20, 2025 (Thursday) from 12:00 to 13:00 Argentina time. The webinar was hosted by Martin Paolantonio (Academic Director of the course) and Daniel Rybnik (a lawyer specializing in Banking, Corporate, and Financial Law). The session aimed to introduce the academic program and explored Bitcoin, the crypto economy, and related legal issues.
-
The monthly Bitcoin Meetup organized by Mi Primer Bitcoin took place on Thursday, March 27 at 7:00 PM at CRAFT Basilea in San Salvador. The event featured Bitcoin education, networking opportunities, live music, and fun extras like merchandise, raffles, and more. It was a vibrant evening dedicated to building community and spreading knowledge around Bitcoin. nostr:npub10zuxk4yhygswdmt5n9mfyeq6lh7gcu5g042tlggrgp8yunl32clqsu5t9r
Here is the upcoming Nostr event that you might want to check out.
- Bitcoin Educators Unconference 2025 will take place on April 10, 2025, at Bitcoin Park in Nashville, Tennessee, USA. This event is non-sponsored and follows an Unconference format, allowing all participants to apply as speakers and share their Bitcoin education experiences in a free and interactive environment. the event has open-sourced all its blueprints and Standard Operating Procedures (SOPs) to encourage global communities to organize similar Unconference events.
- Panama Blockchain Week 2025 will take place from April 22 to 24 at the Panama Convention Center in Panama City. As the first large-scale blockchain event in Central America, it aims to position Panama as a leading blockchain financial hub in Latin America. The event features a diverse lineup, including a blockchain conference, Investor’s Night, Web3 gaming experiences, tech exhibitions, and an after-party celebration.
Additionally, We warmly invite event organizers who have held recent activities to reach out to us so we can work together to promote the prosperity and development of the Nostr ecosystem.
Thanks for reading! If there’s anything I missed, feel free to reach out and help improve the completeness and accuracy of my coverage.
-
 @ c239c0f9:fa4a5015
2025-04-21 17:42:49
@ c239c0f9:fa4a5015
2025-04-21 17:42:49Block:#893398- April 2025The Monthly Thunderbolt Dispatch on Bitcoin layers two innovations, aggregating the Best posts about the ~Lightning Network and others Bitcoin L2 solution- Exclusively on Stacker.News
It's again that time of the month, time to catch up with the latest features and trends that are shaping the future of Bitcoin—the very first and most commented insights from around the SN world. In every issue arrives expert analysis, in-depth interview, and breaking news of the most significant advancements in the Bitcoin layer two solutions.
Subscribe and make sure you don’t miss anything about the ~Lightning Revolution!
Now let's focus on the top five items for each category, an electrifying selection that hope you'll be able to read before next edition.
Happy Zapping!
Top ~Lightning posts
Most zapranked posts this month:
-
Use RIZFUL as your BTCPay Server lightning node via NWC by @supratic 10.2k sats \ 2 comments \ 14 Apr
-
c-otto.de routing node history with a bit of data by @C_Otto 6301 sats \ 31 comments \ 23 Mar
-
Phoenix Wallet available again in the US by @Scoresby 4696 sats \ 29 comments \ 8 Apr
-
Short Text Note: Cashu is coming to ZEUS. by @supratic 5270 sats \ 13 comments \ 1 Apr
-
Hydrus - Automating lightning liquidity management by @aftermath 2281 sats \ 9 comments \ 27 Mar
Top posts by comments
Excluding the ones already mentioned above, you can see them all here (excluding those already listed above):
-
Liquidity squeezing from your node by @k00b 644 sats \ 20 comments \ 5 Apr
-
ZEUS starting to open up Cashu test builds to community sponsors. by @supratic 499 sats \ 14 comments \ 6 Apr
-
Ask Node Runners: What is the longest lived LN channel you have? by @DarthCoin 276 sats \ 12 comments \ 10 Apr
-
What's the best way to accept lightning payments on Wordpress + WooCommerce? by @Jon_Hodl 1879 sats \ 12 comments \ 10 Apr
-
Lightning node over tor by @BallLightning 219 sats \ 9 comments \ 28 Mar
Top ~Lightning Boosts
Check them all here.
-
Missing r/place? LNboard.com is the Lightning Network's Anarchy Art Gallery by @f0e6f4f43b 905 sats \ 40k boost \ 20 comments \ 2 Apr
-
Try out the Ark protocol on signet by @nwoodfine 2083 sats \ 30k boost \ 12 comments \ 19 Mar
-
Amboss CEO On Growth Of The Lightning Network, Tether (USDT) On Lightning by @Jestopher_BTC 577 sats \ 20k boost \ 10 comments \ 19 Feb
-
Building Self Custody Lightning in 2025 by @k00b 2293 sats \ 10k boost \ 8 comments \ 23 Jan
Top Lightning posts outside ~Lightning
This month best posts about the Lightning Network outside ~Lightning territory:
-
I made a game with Lightning where you can earn some sats by @stacks 4732 sats \ 46 comments \ 17 Apr on
~bitcoin -
"Lightning self custody works for 100 million users" "But it needs 10 billion!!" by @standardcrypto 2998 sats \ 22 comments \ 24 Mar on
~bitcoin -
24 Hours of Lightning: Watch LNboard.com's First Day Unfold by @f0e6f4f43b 809 sats \ 8 comments \ 2 Apr on
~bitcoin -
Lightning Payments Tour by Yopaki by @PlebLab 355 sats \ 0 comments \ 11 Apr on
~builders -
👀 My Bitcoin Startup Company Portfolio through Lightning Ventures. 👀 by @BlokchainB 965 sats \ 13 comments \ 16 Apr on
~Stacker_Stocks
Forever top ~Lightning posts
La crème de la crème... check them all here. Nothing has changed this month!
-
👨🚀 We're releasing 𝗔𝗟𝗕𝗬 𝗚𝗢 - the easiest lightning mobile wallet by @Alby 29.2k sats \ 41 comments \ 25 Sep 2024 on
~lightning -
Building Self Custody Lightning in 2025 by @k00b 2303 sats \ 8 comments \ 22 Jan on
~lightning -
Lightning Wallets: Self-Custody Despite Poor Network - Apps Tested in Zimbabwe by @anita 72.8k sats \ 39 comments \ 28 Jan 2024 on
~lightning -
How to Attach Your self-hosted LNbits wallet to SEND/RECEIVE sats to/from SN by @supratic 1765 sats \ 18 comments \ 23 Sep 2024 on
~lightning -
A Way to Use Stacker News to improve your Zap Receiving by @bzzzt 1652 sats \ 22 comments \ 15 Jul 2024 on
~lightning
Forever top Lightning posts outside ~Lightning
The rise of Supertestnet at #5, congrats!
-
Rethinking Lightning by @benthecarman with 51.6k sats \ 137 comments \ 6 Jan 2024 on
~bitcoin -
Lightning Everywhere by @TonyGiorgio with 12k sats \ 27 comments \ 24 Jul 2023 on
~bitcoin -
Lightning is dead, long live the Lightning! by @supertestnet and zaps forwarded to @anita (50%) @k00b (50%) 6321 sats \ 28 comments \ @tolot 27 Oct 2023 on
~bitcoin -
Lightning Is Doomed by @Rsync25 2450 sats \ 15 comments \ 27 Nov 2023 on
~bitcoin -
Bisq2 adds lightning by @supertestnet 3019 sats \ 47 comments \ 19 Aug 2024 on
~bitcoin
-
-
 @ d5c3d063:4d1159b3
2025-04-01 04:20:50
@ d5c3d063:4d1159b3
2025-04-01 04:20:50“วิธีที่ดีที่สุดในการทำลายทุนนิยมคือทำลายค่าเงิน” Lenin Was Right
ประโยคนี้ไม่ใช่แค่คำปลุกระดมของนักปฏิวัติ แต่มันเป็นเหมือนสัญญาณเตือนล่วงหน้า ที่คนส่วนใหญ่ไม่สนใจ จนวันหนึ่งมันก็เกิดขึ้นจริง แบบเงียบ ๆ โดยไม่มีใครทันตั้งตัว
Henry Hazlitt เขียนบทความนี้ไว้ตั้งแต่ปี 1947 เขาไม่เพียงบอกว่าเลนินพูดถูก แต่เขาแฉว่าโลกทั้งใบ “กำลังทำตามแผนของเลนิน” แบบไม่รู้ตัว
ตอนนั้นรัฐบาลหลายประเทศ โดยเฉพาะในยุโรป พิมพ์เงินออกมาใช้มหาศาล โดยอ้างว่าสงครามบีบบังคับให้ต้องทำแบบนั้น แต่ปัญหาคือ...พอสงครามจบในปี 1945 แล้ว รัฐกลับไม่หยุดพิมพ์เงิน ยังทำเหมือนอยู่ในภาวะฉุกเฉิน
เหมือนที่ อ. #SaifedeanAmmous พูดไว้ในหนังสือ #TheBitcoinStandard ว่าเวลารัฐอยากพิมพ์เงินแบบไม่ต้องรับผิดชอบ ก็แค่เอาสงครามมาอ้าง พอพูดว่า “เพื่อความมั่นคง” หรือ “เพื่อชาติ” เท่านั้นแหละ ทุกอย่างก็ดูเป็นเรื่องจำเป็นขึ้นมาทันที แล้วไม่มีใครกล้าถามว่าจริง ๆ แล้วเงินมันมาจากไหน
พอเงินเฟ้อมันแรง ของก็แพงขึ้น แต่รัฐไม่ยอมรับหรอกว่าที่ของแพงเพราะตัวเองพิมพ์เงินออกมาเยอะเกิน แต่กลับไปโทษพ่อค้า โทษคนทำธุรกิจ ว่าขายของแพง ค้ากำไรเกินควรซะงั้น
Hazlitt เขาเตือนว่า...รัฐกำลังทำให้คนเกลียดพ่อค้า เกลียดเจ้าของธุรกิจ เพื่อให้ดูเหมือนว่าตัวเองมีเหตุผลที่จะเข้ามาคุมเศรษฐกิจ ซึ่งที่น่ากลัวคือ... มันไม่ได้เกิดจากความไม่รู้ แต่มันเกิดจาก “ระบบ” ที่เปิดช่องให้เขาทำแบบนี้ได้เลย แบบไม่ต้องรับผิดชอบอะไรทั้งนั้น
ตรงนี้แหละที่ Hazlitt เอาคำพูดของ John Maynard Keynes เข้ามาเสริม เพราะแม้แต่ Keynes ก็ยังเคยเตือนไว้ในหนังสือ The Economic Consequences of the Peace ว่า “เงินเฟ้อ” มันเหมือนเครื่องมือเงียบ ๆ ที่จะค่อย ๆ ทำลายระบบเศรษฐกิจ โดยที่คนส่วนใหญ่ไม่รู้ตัว
Hazlitt เขาเป็น "สายวิจารณ์" Keynes ตัวพ่อเลยนะ เขาเขียนหนังสือ The Failure of the New Economics ที่ไล่รื้อแนวคิดของ Keynes แบบ “ตา-ต่อ-ตา หน้า-ต่อ-หน้า” กับหนังสือ The General Theory ของ Keynes เลยนะ
แต่พอมาในบทความนี้...Hazlitt กลับหยิบคำพูดของ Keynes มาใช้อย่างเต็มใจ เพราะมันตรงเกินไปที่จะมองข้ามได้ ว่าแม้แต่ #Keynes เองยังเคยเตือนเลยว่า “การทำลายค่าเงิน” คืออาวุธเงียบ ที่ใช้ทำลายระบบทุนนิยมได้อย่างแนบเนียนที่สุด . . พออ่านแล้วแบบ…แม้แต่คนที่เราคิดว่าเชียร์ฝั่งรัฐ ยังเตือนเรื่องนี้ไว้ แล้วเราจะยังเฉยอยู่ได้ไง
คือถ้าเงินมันถูกทำให้ด้อยค่าลงเรื่อย ๆ วันนึงมันจะพังแบบเงียบ ๆ จนคนไม่รู้ตัวเลย คนทั่วไปจะรู้แค่ว่าของมันแพงขึ้น แต่ไม่มีใครเห็น ว่าจริง ๆ แล้ว เงินที่เราใช้มันเริ่มไม่มีเสถียรภาพ และไม่มั่นคงอีกต่อไปแล้ว
แล้วถ้ามองตัวเลขนี่ยิ่งช็อก ระหว่างปี 1939 ถึง 1947 ในเวลาแค่ 8 ปี ปริมาณเงินในระบบของสหรัฐฯ เพิ่มจาก 33,000 ล้านดอลลารเป็น 108,500 ล้านดอลลาร์ พูดง่าย ๆ คือ คูณสาม (ช่วงสงครามโลกครั้งที่ 2)
Hazlitt พูดแบบตรง ๆ เลยว่า ปัญหาที่เกิดขึ้น มันไม่ใช่เพราะเศรษฐกิจโตหรือคนรวยขึ้นนะ มันเกิดจากการที่รัฐเพิ่มปริมาณเงินในระบบเร็วเกินไป เมื่อเงินในตลาดเลยเยอะขึ้น แต่ของที่มีให้ซื้อไม่ได้เยอะขึ้นตาม เมื่อเงินไหลเวียนมากขึ้น โดยที่ของยังมีเท่าเดิม ราคาของก็เลยพุ่ง
ทีนี้พอของขึ้นราคา รัฐบาลกลับไม่ยอมรับว่าเป็นเพราะเขาพิมพ์เงิน แต่ไปเลือกวิธีแก้แบบง่าย ๆ แต่สร้างปัญหาในระยะยาว เช่น สั่งห้ามขึ้นราคา กดดันคนทำธุรกิจให้แบกต้นทุนไว้ หรือไม่ก็ล็อกค่าเงิน เหมือนไม่มีอะไรเกิดขึ้น
หลังจากนั้น เศรษฐกิจยุโรปก็เริ่มพัง ผู้ผลิตเจอต้นทุนบาน การค้าระหว่างประเทศก็รวน สุดท้ายก็ต้องพึ่งดอลลาร์จากอเมริกา (Marshall Aid) มาช่วยอุ้ม เหมือนพิมพ์เงินของตัวเองจนระบบรวน แล้วไปขอเงินจากฝั่งที่พิมพ์ได้มากกว่าอีกที
นี่แหละจุดเริ่มของ “วิกฤตเศรษฐกิจโลกหลังสงคราม” ที่จริง ๆ แล้ว...ก็แค่เรื่องของการพิมพ์เงินล้วน ๆ . . แต่นั้นมันเป็นเรื่องเกิดขึ้นเมื่อปี 1947 นะ...แล้ววันนี้ล่ะ
ล่าสุด ปี 2020 ก่อนโควิด ระดับ M2 money supply ของสหรัฐอยู่ราว ๆ 15 ล้านล้านดอลลาร์ แค่ไม่กี่ปีต่อมา มันทะลุไปถึง 21 ล้านล้าน ในเวลาไม่ถึง 3 ปีเงินเพิ่มขึ้นในระบบเศรษฐกิจกว่า 6 ล้านล้านดอลลาร์
แล้วของก็แพงขึ้น ค่าแรงวิ่งตามไม่ทัน แต่แทนที่รัฐจะบอกว่า “เราพิมพ์เงินมากไป” ก็ไปเล่นมุกเดิม โทษตลาด โทษนายทุน โทษธุรกิจ (บ้างก็โทษโลกร้อน)
สุดท้ายก็จะมีคนบางกลุ่มเชียร์ให้ “ควบคุมราคา” อีก มันคือ loop เดิม ที่ #Hazlitt เคยเตือนไว้ เมื่อเกือบ 80 ปีก่อน.. . . สิ่งที่ซุปเห็นชัดเจนที่สุดจากบทความนี้คือ... เกมนี้มันไม่มีใครหยุดได้เลย ถ้าคุณยังถือเงินที่รัฐพิมพ์ได้
เพราะตราบใดที่ยังมีคนสั่งพิมพ์เงินได้ตามใจ ระบบเศรษฐกิจก็จะปั่นป่วนซ้ำไปซ้ำมา ของก็จะแพงขึ้นเรื่อย ๆ แบบไม่มีจุดจบ
คุณก็จะต้องเหนื่อยทำงานมากขึ้น แต่ซื้อได้น้อยลง แล้วคุณก็จะโทษตัวเอง ว่ายังขยันไม่มากพอ ทั้ง ๆ ที่คุณทำงาน 4-5 อย่าง
.
เลนิน พูดถูก ถ้าจะทำลายทุนนิยม ก็แค่ทำลายค่าเงิน ฟังดูแรงเนอะ...แต่เรื่องนี้มันไม่ใช่แค่ทฤษฎีแล้ว เพราะเรากำลังเห็น ว่ามันกำลังเกิดขึ้นอยู่จริง ๆ
แต่วันนี้ เราเลือกที่จะไม่อยู่ในเกมที่พังซ้ำๆ ได้แล้ว
เพราะเรามี “ทางออก” อยู่ตรงหน้า บิตคอยน์ ไม่ใช่อะไรที่ทุกคนจะเข้าใจมันได้ทันที แต่มันคือ “เงิน” ที่ไม่มีใครพิมพ์เพิ่มได้ตามใจ ไม่มีใครมานั่งกดปุ่มสร้างมันขึ้นมาได้ง่าย ๆ ไม่มีใครเปลี่ยนกติกากลางเกมได้ และไม่มีใครแทรกแซงนโยบายของมันได้
สิ่งเดียวที่ #บิตคอยน์ บอกเราตรง ๆ ก็คือ “ความขาดแคลน” ไม่ใช่ปัญหา...
สิ่งที่ Hazlitt เตือนเมื่ออดีต คือกับดักของเงินไม่มีขอบเขต
สิ่งที่ #Bitcoin เสนอ คือขอบเขตที่ทำให้ “มูลค่า” กลับมามีความหมาย
[Newsweek column from September 22, 1947, and reprinted in Business Tides: The Newsweek Era of Henry Hazlitt.] https://mises.org/mises-wire/lenin-was-right
Siamstr
-
 @ d34e832d:383f78d0
2025-04-21 17:29:37
@ d34e832d:383f78d0
2025-04-21 17:29:37This foundational philosophy positioned her as the principal architect of the climactic finale of the Reconquista—a protracted campaign that sought to reclaim territories under Muslim dominion. Her decisive participation in military operations against the Emirate of Granada not only consummated centuries of Christian reclamation endeavors but also heralded the advent of a transformative epoch in both Spanish and European identity, intertwining religious zeal with nationalistic aspirations and setting the stage for the emergence of a unified Spanish state that would exert significant influence on European dynamics for centuries to come.
Image Above Map Of Th Iberias
During the era of governance overseen by Muhammad XII, historically identified as Boabdil, the Kingdom of Granada was characterized by a pronounced trajectory of decline, beset by significant internal dissent and acute dynastic rivalry, factors that fundamentally undermined its structural integrity. The political landscape of the emirate was marked by fragmentation, most notably illustrated by the contentious relationship between Boabdil and his uncle, the militarily adept El Zagal, whose formidable martial capabilities further exacerbated the emirate's geopolitical vulnerabilities, thereby impairing its capacity to effectively mobilize resistance against the encroaching coalition of Christian forces. Nevertheless, it is imperative to acknowledge the strategic advantages conferred by Granada’s formidable mountainous terrain, coupled with the robust fortifications of its urban centers. This geographical and structural fortitude, augmented by the fervent determination and resilience of the local populace, collectively contributed to Granada's status as a critical and tenacious stronghold of Islamic governance in the broader Iberian Peninsula during this tumultuous epoch.
The military campaign initiated was precipitated by the audacious territorial annexation of Zahara by the Emirate in the annum 1481—a pivotal juncture that served as a catalytic impetus for the martial engagement orchestrated by the Catholic Monarchs, Isabel I of Castile and Ferdinand II of Aragon.

Image Above Monarchs Of Castilles
What subsequently unfolded was an arduous protracted conflict, extending over a decade, characterized by a series of decisive military confrontations—most notably the Battle of Alhama, the skirmishes at Loja and Lucena, the strategic recapture of Zahara, and engagements in Ronda, Málaga, Baza, and Almería. Each of these encounters elucidates the intricate dynamics of military triumph entwined with the perils of adversity. Isabel's role transcended mere symbolic representation; she emerged as an astute logistical architect, meticulously structuring supply chains, provisioning her armies with necessary resources, and advocating for military advancements, including the tactical incorporation of Lombard artillery into the operational theater. Her dual presence—both on the battlefield and within the strategic command—interwove deep-seated piety with formidable power, unifying administrative efficiency with unyielding ambition.
In the face of profound personal adversities, exemplified by the heart-wrenching stillbirth of her progeny amidst the tumultuous electoral campaign, Isabel exhibited a remarkable steadfastness in her quest for triumph. Her strategic leadership catalyzed a transformative evolution in the constructs of monarchical power, ingeniously intertwining the notion of divine right—a historically entrenched justification for sovereign authority—with pragmatic statecraft underpinned by the imperatives of efficacious governance and stringent military discipline. The opposition posed by El Zagal, characterized by his indefatigable efforts and tenacious resistance, elongated the duration of the campaign; however, the indomitable spirit and cohesive resolve of the Catholic Monarchs emerged as an insuperable force, compelling the eventual culmination of their aspirations into a definitive victory.
The capitulation of the Emirate of Granada in the month of January in the year 1492 represents a pivotal moment in the historical continuum of the Iberian Peninsula, transcending the mere conclusion of the protracted series of military engagements known as the Reconquista. This momentous event is emblematic of the intricate process of state-building that led to the establishment of a cohesive Spanish nation-state fundamentally predicated on the precepts of Christian hegemony. Furthermore, it delineates the cusp of an imperial epoch characterized by expansionist ambitions fueled by religious zealotry. The ramifications of this surrender profoundly altered the sociocultural and political framework of the region, precipitating the coerced conversion and expulsion of significant Jewish and Muslim populations—a demographic upheaval that would serve to reinforce the ideological paradigms that underpinned the subsequent institution of the Spanish Inquisition, a systematic apparatus of religious persecution aimed at maintaining ideological conformity and unity under the Catholic Monarchs.

Image Above Surrender At Granada
In a broader historical context, the capitulation of the Nasrid Kingdom of Granada transpired concurrently with the inaugural expedition undertaken by the navigator Christopher Columbus, both events being facilitated under the auspices of Queen Isabel I of Castile. This significant temporal nexus serves to underscore the confluence of the termination of Islamic hegemony in the Iberian Peninsula with the commencement of European maritime exploration on a grand scale. Such a juxtaposition of religiously motivated conquest and the zealous pursuit of transoceanic exploration precipitated a paradigm shift in the trajectory of global history. It catalyzed the ascendance of the Spanish Empire, thereby marking the nascent stages of European colonial endeavors throughout the Americas.

Image Above Columbus At The Spanish Court
This epochal transformation not only redefined territorial dominion but also initiated profound socio-economic and cultural repercussions across continents, forever altering the intricate tapestry of human civilization.
Consequently, the cessation of hostilities in Granada should not merely be interpreted as the conclusion of a protracted medieval conflict; rather, it represents a critical juncture that fundamentally reoriented the socio-political landscape of the Old World while concurrently heralding the advent of modernity. The pivotal contributions of Queen Isabel I in this transformative epoch position her as an extraordinarily significant historical figure—an autocrat whose strategic foresight, resilience, and zeal indelibly influenced the trajectory of nations and entire continents across the globe.
-
 @ e97aaffa:2ebd765d
2025-04-21 12:57:16
@ e97aaffa:2ebd765d
2025-04-21 12:57:16Se este movimento de desglobalização continuar, poderá provocar uma cisão no mundo geopolítico, criar dois grandes blocos económicos, uma nova guerra fria.
Se isso se concretizar, quantos anos vão ser necessários para o S&P500 superar máximos históricos em termos reais, em poder de compra?
Em valores nominais vai ser rápido, o governo dos EUA vai imprimir tanto dinheiro, rapidamente vai superar máximos, mas em termos reais, vai demorar muitos anos.
Até agora, todo o mundo estava a investir nos EUA, mas se os países do bloco oriental, sobretudo a China, deixarem de investir em ações, obrigações e moeda dos EUA, irá provocar uma enorme redução de liquidez e na procura/demanda, não vai ser fácil ultrapassar isso.
Nos US Treasury, o afastamento da China começou em 2014(1° guerra da Ucrânia), mas o movimento acelerou em 2022(2° guerra da Ucrânia).

Os EUA, ao congelar as reservas da Rússia, ao utilizar as reservas como uma arma de guerra, “assustaram” a China e outros países. As sanções à Rússia e como esta fez para contornar as sanções foi um case study para a China.
Como o objetivo da China é recuperar Taiwan, sabe que sofrerá as mesmas represálias que hoje a Rússia sofre, por isso a China tem que se afastar da economia dos EUA.
A China está a trocar US Treasury por outros ativos e por outras geografias, o principal beneficiado foi o ouro, um ativo soberano, que não tem problemas de contraparte.
Este movimento da China foi bem visível no preço do ouro no último ano, uma valorização superior a 42%.
Mas não é só a China que está a apostar no ouro, são diversos, mas sobretudo composta por países do bloco oriental.
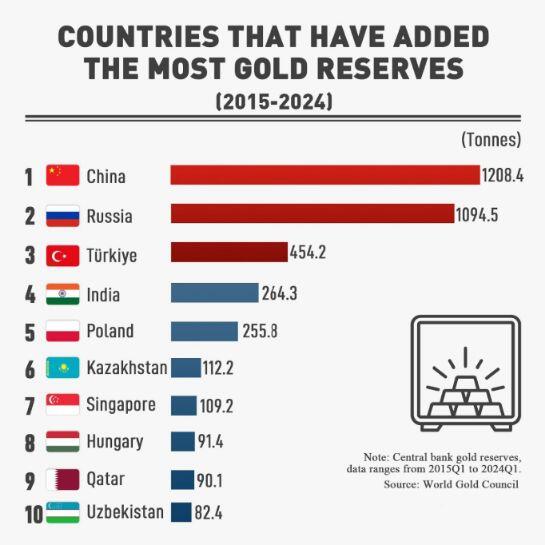
Enquanto, Taiwan for a fábrica do mundo nos semicondutores, estarão protegidos pelo guarda-chuva dos EUA. Mas os EUA, estão a construir fábricas próprias, quando forem auto-suficientes, vão descartar o “guarda-chuva”, Taiwan não terá qualquer hipótese sobre o poderio da China.
A China pensa sempre a longo prazo, estão apenas a aguardar, isto poderá estar para muito em breve.
Se isto se confirmar, o S&P500 poderá demorar décadas para recuperar desta crise, em termos de poder de compra.
-
 @ f3328521:a00ee32a
2025-03-31 00:25:36
@ f3328521:a00ee32a
2025-03-31 00:25:36This paper was originaly writen in early November 2024 as a proposal for an international Muslim entrepreneurial initiative. It was first publish on NOSTR 27 November 2024 as part 1 of a 4 part series of essays. Last updated/revised: 30 March 2025.
The lament of the Ummah for the past century has been the downfall of the Khalifate. With the genocide in occupied Palestine over the past year and now escalations in Lebanon as well, this concern is at the forefront of a Muslim’s mind. In our tradition, when one part of the Ummah suffers, all believers are affected and share in that suffering. The Ummah today has minimal sovereignty at best. It lacks a Khalifate. It is spiritually weakened due to those not practicing and fulfilling their duties and responsibilities. And, as we will address in this paper, it has no real economic power. In our current monetary system, it is nearly impossible to avoid the malevolence of riba (interest) – one of the worst sins. However, with bitcoin there is an opportunity to alleviate this collective suffering and reclaim economic sovereignty.
Since it’s invention 15 years ago, bitcoin has risen to achieve a top 10 market cap ranking as a global asset (currently valued at $1.8 trillion USD). Institutional investors are moving full swing to embrace bitcoin in their portfolios. Recent proposals in Kazan hint that BRICS may even be utilizing bitcoin as part of their new payments system. State actors will be joining soon. With only about 1 million bitcoins left to be mined we need to aim to get as much of those remaining coins as possible into the wallets of Muslims over the next decade. Now is the time to onboard the Ummah. This paper presents Bitcoin as the best option for future economic sovereignty of the Ummah and proposes steps needed to generate a collective waqf of an initial 0.1%-0.5% chain dominance to safeguard a revived Khalifate.
Money is the protocol that facilitates economic coordination to help the development and advancement of civilization. Throughout history money has existed as cattle, seashells, salt, beads, stones, precious metals. Money develops naturally and spontaneously; it is not the invention of the state (although it at times is legislated by states). Money exists marginally, not by fiat. During the past few millenniums, gold and silver were optimally used by most advanced civilizations due to strong properties such as divisibility, durability, fungibility, portability, scarcity, and verifiability. Paper money modernized usability through attempts to enhance portability, divisibility, and verifiability. However, all these monetary properties are digitized today. And with the increase of fractional-reserve banking over the past two centuries, riba is now the de facto foundation of the consensus reserve currency – the USD.
This reserve currency itself is backed by the central banking organ of the treasury bond markets which are essentially government issued debt. Treasurey bonds opperate by manipulating the money supply arbitrarily with the purpose of targeting a set interest rate – injecting or liquidating money into the supply by fiat to control intrest yeilds. At its root, the current global monetary order depends entirely on riba to work. One need not list the terrible results of riba as Muslims know well its harshness. As Lyn Alden wonderful states in her book, Broken Money, “Everything is a claim of a claim of a claim, reliant on perpetual motion and continual growth to not collapse”. Eventual collapse is inevitable, and Muslims need to be aware and prepared for this reality.
The status quo among Muslims has been to search for “shariah compliance”. However, fatwa regarding compliance as well as the current Islamic Banking scene still operate under the same fiat protocol which make them involved in the creation of money through riba. Obfuscation of this riba through contractum trinius or "shariah compliant" yields (which are benchmarked to interest rates) is simply an attempt to replicate conventional banking, just with a “halal” label. Fortunately, with the advent of the digital age we now have other monetary options available.
Experiments and theories with digital money date back to the 1980s. In the 1990s we saw the dot com era with the coming online of the current fiat system, and in 2008 Satoshi Nakamoto released Bitcoin to the world. We have been in the crypto era ever since. Without diving into the technical aspects of Bitcoin, it is simply a P2P e-cash that is cryptographically stored in digital wallets and secured via a decentralized blockchain ledger. For Muslims, it is essential to grasp that Bitcoin is a new type of money (not just an investment vehicle or payment application) that possesses “anti-riba” properties.
Bitcoin has a fixed supply cap of 21 million, meaning there will only ever be 21 million Bitcoin (BTC). Anyone with a cheap laptop or computer with an internet connection can participate on the Bitcoin network to verify this supply cap. This may seem like an inadequate supply for global adoption, but each bitcoin is highly divisible into smaller units (1 btc = 100,000,000 satoshis or sats). Bitcoins are created (or mined) from the processing of transactions on the blockchain which involves expending energy in the real world (via CPU power) and providing proof that this work was done.
In contrast, with the riba-based fiat system, central banks need to issue debt instruments, either in the form of buying treasuries or through issuing a bond. Individual banks are supposed to be irresponsibly leveraged and are rewarded for making risky loans. With Bitcoin, there is a hard cap of 21 million, and there is no central authority that can change numbers on a database to create more money or manipulate interest rates. Under a Bitcoin standard, money is verifiably stored on a ledger and is not loaned to create more money with interest. Absolute scarcity drives saving rather than spending, but with increasing purchasing power from the exponentially increasing demand also comes the desire to use that power and increased monetary economization. With bitcoin you are your own bank, and bitcoin becomes for your enemies as much as it is for your friends. Bitcoin ultimately provides a clean foundation for a stable money that can be used by muslims and should be the currency for a future Khalifate.
The 2024 American presidential election has perhaps shown more clearly than ever the lack of politcal power that American Muslims have as well as the dire need for them to attain political influence. Political power comes largely through economic sovereignty, military might, and media distribution. Just a quick gloss of Muslim countries and Turkey & Egypt seem to have decent militaries but failing economies. GCC states have good economies but weak militaries. Iran uniquely has survived sanctions for decades and despite this weakened economic status has still been able to make military gains. Although any success from its path is yet to be seen it is important to note that Iran is the only country that has been able to put up any clear resistance to western powers. This is just a noteworthy observation and as this paper is limited to economic issues, full analysis of media and miliary issues must be left for other writings.
It would also be worthy to note that BDS movements (Boycott, Divest & Sanction) in solidarity with Palestine should continue to be championed. Over the past year they have undoubtedly contributed to PEP stock sinking 2.25% and MCD struggling to break even. SBUX and KO on the other hand, despite active boycott campaigns, remain up 3.5% & 10.6% respectively. But some thought must be put into why the focus of these boycotts has been on snack foods that are a luxury item. Should we not instead be focusing attention on advanced tech weaponry? MSFT is up 9.78%, GOOG up 23.5%, AMZN up 30%, and META up 61%! It has been well documented this past year how most of the major tech companies have contracts with occupying entity and are using the current genocide as a testing ground for AI. There is no justification for AI being a good for humanity when it comes at the expense of the lives of our brothers in Palestine. However, most “sharia compliant” investment guides still list these companies among their top recommendations for Muslims to include in their portfolios.
As has already been argued, by investing in fiat-based organization, businesses, ETFs, and mutual funds we are not addressing the root cause of riba. We are either not creating truly halal capital, are abusing the capital that Allah has entrusted to us or are significantly missing blessings that Allah wants to give us in the capital that we have. If we are following the imperative to attempt to make our wealth as “riba-free” as possible, then the first step must be to get off zero bitcoin
Here again, the situation in Palestine becomes a good example. All Palestinians suffer from inflation from using the Israeli Shekel, a fiat currency. Palestinians are limited in ways to receive remittances and are shrouded in sanctions. No CashApp, PayPal, Venmo. Western Union takes huge cuts and sometimes has confiscated funds. Bank wires do this too and here the government sanctions nearly always get in the way. However, Palestinians can use bitcoin which is un-censorable. Israel cannot stop or change the bitcoin protocol. Youssef Mahmoud, a former taxi driver, has been running Bitcoin For Palestine as a way for anyone to make a bitcoin donation in support of children in Gaza. Over 1.6 BTC has been donated so far, an equivalent of about $149,000 USD based on current valuation. This has provided a steady supply of funds for the necessary food, clothing, and medication for those most in need of aid (Note: due to recent updates in Gaza, Bitcoin For Palestine is no longer endorsed by the author of this paper. However, it remains an example of how the Bitcoin network opperates through heavy sanctions and war).
Over in one of the poorest countries in the world, a self-managed orphanage is providing a home to 77 children without the patronage of any charity organization. Orphans Of Uganda receives significant funding through bitcoin donations. In 2023 and 2024 Muslims ran Ramadan campaigns that saw the equivalent of $14,000 USD flow into the orphanage’s bitcoin wallet. This funding enabled them to purchase food, clothing, medical supplies and treatment, school costs, and other necessities. Many who started donating during the 2023 campaign also have continued providing monthly donations which has been crucial for maintaining the well-being of the children.
According to the Muslim Philanthropy Initiative, Muslim Americans give an estimated $1.8 billion in zakat donations every year with the average household donating $2070 anually. Now imagine if international zakat organizations like Launchgood or Islamic Relief enabled the option to donate bitcoin. So much could be saved by using an open, instant, permissionless, and practically feeless way to send zakat or sadaqah all over the world! Most zakat organizations are sleeping on or simply unaware of this revolutionary technology.
Studies by institutions like Fidelity and Yale have shown that adding even a 1% to 5% bitcoin allocation to a traditional 60/40 stock-bond portfolio significantly enhances returns. Over the past decade, a 5% bitcoin allocation in such a portfolio has increased returns by over 3x without a substantial increase in risk or volatility. If American Muslims, who are currently a demographic estimated at 2.5 million, were to only allocate 5% ($270 million) of their annual zakat to bitcoin donations, that would eventually become worth $14.8 billion at the end of a decade. Keep in mind this rate being proposed here is gathered from American Muslim zakat data (a financially privileged population, but one that only accounts for 0.04% of the Ummah) and that it is well established that Muslims donate in sadaqa as well. Even with a more conservative rate of a 1% allocation you would still be looking at nearly $52 million being liquidated out of fiat and into bitcoin annually. However, if the goal is to help Muslims hit at least 0.1% chain dominance in the next decade then a target benchmark of a 3% annual zakat allocation will be necessary.
Islamic financial institutions will be late to the game when it comes to bitcoin adoption. They will likely hesitate for another 2-4 years out of abundance of regulatory caution and the persuasion to be reactive rather than proactive. It is up to us on the margin to lead in this regard. Bitcoin was designed to be peer-2-peer, so a grassroots Muslim bitcoiner movement is what is needed. Educational grants through organizations like Bitcoin Majlis should be funded with endowments. Local Muslim bitcoin meetups must form around community mosques and Islamic 3rd spaces. Networked together, each community would be like decentralized nodes that could function as a seed-holder for a multi-sig waqf that can circulate wealth to those that need it, giving the poorer a real opportunity to level up and contribute to societ and demonstrating why zakat is superior to interest.
Organic, marginal organizing must be the foundation to building sovereignty within the Ummah. Sovereignty starts at the individual level and not just for all spiritual devotion, but for economics as well. Physical sovereignty is in the individual human choice and action of the Muslim. It is the direct responsibility placed upon insan when the trust of khalifa was placed upon him. Sovereignty is the hallmark of our covenant, we must embrace our right to self-determination and secede from a monetary policy of riba back toward that which is pure.
"Whatever loans you give, seeking interest at the expense of people’s wealth will not increase with Allah. But whatever charity you give, seeking the pleasure of Allah—it is they whose reward will be multiplied." (Quran 30:39)
FAQ
Why does bitcoin have any value?
Unlike stocks, bonds, real-estate or even commodities such as oil and wheat, bitcoins cannot be valued using standard discounted cash-flow analysis or by demand for their use in the production of higher order goods. Bitcoins fall into an entirely different category of goods, known as monetary goods, whose value is set game-theoretically. I.e., each market participant values the good based on their appraisal of whether and how much other participants will value it. The truth is that the notions of “cheap” and “expensive” are essentially meaningless in reference to monetary goods. The price of a monetary good is not a reflection of its cash flow or how useful it is but, rather, is a measure of how widely adopted it has become for the various roles of money.
Is crypto-currency halal?
It is important to note that this paper argues in favor of Bitcoin, not “Crypto” because all other crypto coins are simply attempts a re-introducing fiat money-creation in digital space. Since they fail to address the root cause error of riba they will ultimately be either destroyed by governments or governments will evolve to embrace them in attempts to modernize their current fiat system. To highlight this, one can call it “bit-power” rather than “bit-coin” and see that there is more at play here with bitcoin than current systems contain. Mufti Faraz Adam’s fatwa from 2017 regarding cryptocurrency adaqately addresses general permissibility. However, bitcoin has evolved much since then and is on track to achieve global recognition as money in the next few years. It is also vital to note that monetary policy is understood by governments as a vehicle for sanctions and a tool in a political war-chest. Bitcoin evolves beyond this as at its backing is literal energy from CPU mining that goes beyond kinetic power projection limitations into cyberspace. For more on theories of bitcoin’s potential as a novel weapons technology see Jason Lowery’s book Softwar.
What about market volatility?
Since the inception of the first exchange traded price in 2010, the bitcoin market has witnessed five major Gartner hype cycles. It is worth observing that the rise in bitcoin’s price during hype cycles is largely correlated with an increase in liquidity and the ease with which investors could purchase bitcoins. Although it is impossible to predict the exact magnitude of the current hype cycle, it would be reasonable to conjecture that the current cycle reaches its zenith in the range of $115,000 to $170,000. Bitcoin’s final Gartner hype cycle will begin when nation-states start accumulating it as a part of their foreign currency reserves. As private sector interest increases the capitalization of Bitcoin has exceeded 1 trillion dollars which is generally considered the threshold at which an assest becomes liquid enough for most states to enter the market. In fact, El Salvador is already on board.
-
 @ dbb19ae0:c3f22d5a
2025-04-21 12:29:38
@ dbb19ae0:c3f22d5a
2025-04-21 12:29:38Notice this consistent apparitioon in the timeline of something that reflects a major key shift in tech:
💾 1980s – The Personal Computer Era
- IBM PC (1981) launches the home computing revolution.
- Rise of Apple II, Commodore 64, etc.
- Storage is local and minimal.
- Paradigm shift: Computing becomes personal.
🎮 1990s – Networking & Gaming
- LAN parties, DOOM (1993) popularizes multiplayer FPS.
- Early internet (dial-up, BBS, IRC).
- There is lots of room for connecting PC.
- Paradigm shift: Networked interaction begins.
🌐 2000s – The Internet Boom
- Web 2.0, broadband, Google, Wikipedia.
- Rise of forums, blogs, file sharing.
- A bigger need of interaction is looming
- Storage is on cd and dvd.
- Paradigm shift: Global information access explodes.
📱 2010s – Social Media & Mobile
- Facebook, Twitter, Instagram dominate.
- Smartphones become ubiquitous.
- Bitcoin appears and start a revolution.
- Collecting personal data from users to fuel the next shift.
- Paradigm shift: Always-connected, algorithmic society.
🤖 2020s – AI & Decentralization
- GPT, Stable Diffusion, Midjourney, Copilot.
- Blockchain, Nostr, Web3 experiments.
- Storage is in the cloud.
- Paradigm shift: Autonomous intelligence and freedom tech emerge.
roughly every decade, a tech leap reshapes how we live and think.
-
 @ 57d1a264:69f1fee1
2025-04-21 12:11:22
@ 57d1a264:69f1fee1
2025-04-21 12:11:22There's any content about SN out there?
In the news: - @BitcoinNews Stacker.News Raises $1.25m Seed Round At $25m Valuation - @Alby blog post explain how Stacker News adds Self-custodial Spending with NWC - @cryotosensei on @0xbitcoiner's website Stacker News encourages deep sharing ad Random things I learnt about Bitcoin from Stacker News - @anita's Earn bitcoin on Stacker News: People asked and I answered
Recently we have seen an article in BM writing about how PlebLab is shaping the future of bitcoin startups in Austin. SN was mentioned and linked 🎉
Started in 2021 by one of PlebLab’s cofounders Keyan Kousha, Stacker.news has quickly become a hub of news for many tech-savvy Bitcoiners. Boasting an open source Lightning-powered Reddit, the platform has gathered an active and loyal fan base that reward each other with sats for every upvote, often being early to integrate the latest technologies in the Bitcoin-social media tech scene.
In the past it has also only mentioned here.
From a startup pitch perspective:
Developer of a news platform intended for individuals to earn real money for creating and curating content. The company's platform specializes in allowing individuals to submit, vote, and comment on content, stories, and discussions about the topics in communities organized around their interests, enabling individuals to post content and get paid while reading the news. PitchBook -
https://pitchbook.com/profiles/company/535835-44#overviewStacker News is a forum (like Reddit or Hacker News) where you can earn real money for creating or curating content. F6S -
https://www.f6s.com/company/stacker-news#aboutPeople talking about SN:
-
A stacker shared a Lessons learned from Stacker.news and how SN works. Discourse Co-CEO respond:
Heh, it’s not a healthy or sustainable model for the types of communities consciously we build for. Definitely not something we would consider building into core but you could make it work with a plugin. Extrinsic motivators attract the wrong people for the wrong reasons, in my experience. Healthy community ecosystems are driven by intrinsic motivation.
-
on BitcoinTalk here, here and here. There are probably more posts where it has ben mentioned and discussed.
-
HackerNews crowd does not seem too excited about it. Just few comments on each post.
Some review have been collected on @julian's Apollo and ProductHunt.
Let's check what YT has:
Some interviews first. At 2023 ZBD x PlebLab TabConf Hackathon, Keyan Kousha explain Why Not to Use Stacker News
@kr did a great job interviewing k00b when SN was in its infancy - Stacker News Is Growing FAST - Stacker News Is Disrupting Social Media | E17 - Keyan Kousha on Stacker News, Earning Bitcoin, & Decentralized Content | The Kevin Rooke Show | E17 - How Siggy47 Stacked Over 500,000 Sats on Stacker News | SS8
And here some interviews:
Stacker News is a user-generated, feed-style news platform, modeled after Hacker News, but with the important distinction of having natively-integrated bitcoin lightning payments, as a means of fostering more natural communities (think less spam and antisocial behavior), cultivating high-signal bitcoin content, and providing a better user experience overall.
Stacker News is still in the very early days of its development, but it's a great showcase of how bitcoin can be used to improve upon an existing model, and in doing so, explore how improved incentives might influence media publishing, monetization, and moderation.
Keyan is a prime example of someone who caught the bitcoin bug, and just couldn't resist getting involved. The result is a product built with and for bitcoiners, and it was great to have him on the show to explain more about his motivations and ambitions.
-
From ~ideasfrommtheedge pod: AI, Simulations, and Startups with Keyan Kousha (Founder, Stacker News)
-
@alexstrenger's Convos On The Pedicab #177 Stacker News: A Bitcoiners Alternative To Reddit
-
@dk and @MaxAWebster intro on What's new with Stacker.News and Nostr? also shared here
-
@ConnectTheWorld stream Keep Austin Weird! Meet Keyan, the founder of Stacker.news
-
@Thriller Lightning: Stacker.News Founder Keyan
-
0.00000018: Keyan Kousha, Stacker.News: an interview in the Changing the Tide show here
-
@bitcoinplebdev reading top ~devs stories 04/08/2024 and stacker.news codebase overview / how to run locally)
That's the interviews I was able to find. Continuing the dig...
-
@TheWildHustle compiles SN ~Music' vibes into YT playlists
-
@kdnolan7 on was giving some updates about the ~Education territory here and here
Gradually, then suddenly, the message start to change, and the majority of videos communicate something that is probably, at least from my perspective, not the right way to market a product like SN:
-
@SatsMate lay out Why He Love Stacker News!
-
@voltage share a story quickly talking how Stacker News is like YCombinators Hacker News but YOU EARN! https://www.youtube.com/shorts/d1xZ3RE9plk
@HattyHats Earn Bitcoin (LN) Blogging with Stacker News
The long list continues: - Earn bitcoin Satoshis Reading & Sharing Content on Stacker.News - First Time Walk Through by @SatoshiTutor - Earn Free Bitcoin | Stacker News Quick Tutorial from Earning Crypto Site - One of the Different Ways to Earn Bitcoin 👉 stacker.news | Bitcoin Lifestyle #2 from @SatoshiComTR - @1100note another Stacker.News story - ...
This list of references can, and probably will, go on and on with the same topic. The message looks like will be always the same: come over, stack sats, stay humble. There's maybe something wrong with the message we share SN out there? Is not what we do, is how we do it, that make the difference. As you can see, there's not much there that refer to quality content, great supportive community, community moderated contents, no ads, no spam, no bots (well, not many) and no ai. Pure human content.
In other successful platforms where people earn money for the contents they create, the money factor is totally hidden, is not their main sales point in the pitch. Look at YT itself. We all know people earn fiat producing and sharing videos, but their comms does not talk about it, at least not the way stackers do. And you'll not find many YTers inviting others to create videos to earn money. Well ok, some do!
Something we could make an effort to improve, is the way we talk about SN. Finding alternative ways to do it is hard, some have been mentioned here https://stacker.news/items/948462/r/Design_r
Just wanted to see how much other quality content is out there talking about SN that is not about stacking sats? Share your best contents, nostr notes, x tweets, blog posts, articles, videos, interviews, reviews or any other media that has been created by others about SN (no memes shill) or that somehow mention it in the comments below.
originally posted at https://stacker.news/items/951177
-
-
 @ 71550e6c:b64c37a9
2025-03-29 10:55:55
@ 71550e6c:b64c37a9
2025-03-29 10:55:55Just do the same as this video shows.
Here's the video: https://cdn.azzamo.net/7cdcc2718f1e15eb03e323f62e07582b4001da273aa5c21475d680f02b32f0e9.mp4
One caveat: do not trust the draft will be kept here after you close
nak fs. Wait, no, it definitely won't stay here, but I'm not even sure it will stay here if you only navigate away and come back later, FUSE is weird and I didn't test.But at least it should work for copy-pasting. Or writing everything in one go.
-
 @ 92f1335f:2c8220d1
2025-04-21 11:38:11
@ 92f1335f:2c8220d1
2025-04-21 11:38:11Chapter 1: The Spark (2019)
Jonathan Parker wasn’t exactly a risk-taker. A software developer in his late twenties, he preferred routines—morning coffee, coding sprints, and quiet evenings with podcasts. But something kept catching his attention: Bitcoin.
It wasn't the first time he'd heard about it. Back in 2017, his college roommate had begged him to buy some at $3,000. Jonathan laughed it off. Then, Bitcoin soared and crashed. By 2019, most people had already moved on.
But not Jonathan.
In April 2019, curiosity turned into obsession. He began reading whitepapers, watching crypto influencers on YouTube, and combing through Reddit threads at midnight. After weeks of research, he took the plunge: he invested $2,600 into Bitcoin, buying half a coin at $5,200.
To his friends, it was a “weird tech gamble.” To Jonathan, it was something else entirely—a hedge against the world, a bet on the future.
-
 @ a60e79e0:1e0e6813
2025-03-28 08:47:35
@ a60e79e0:1e0e6813
2025-03-28 08:47:35This is a long form note of a post that lives on my Nostr educational website Hello Nostr.
When most people stumble across Nostr, they see is as a 'decentralized social media alternative' — something akin to Twitter (X), but free from corporate control. But the full name, "Notes and Other Stuff Transmitted by Relays", gives a clue that there’s more to it than just posting short messages. The 'notes' part is easy to grasp because it forms almost everyone's first touch point with the protocol. But the 'other stuff'? That’s where Nostr really gets exciting. The 'other stuff' is all the creative and experimental things people are building on Nostr, beyond simple text based notes.
Every action on Nostr is an event, a like, a post, a profile update, or even a payment. The 'Kind' is what specifies the purpose of each event. Kinds are the building blocks of how information is categorized and processed on the network, and the most popular become part of higher lever specification guidelines known as Nostr Implementation Possibility - NIP. A NIP is a document that defines how something in Nostr should work, including the rules, standards, or features. NIPs define the type of 'other stuff' that be published and displayed by different styles of client to meet different purposes.
Nostr isn’t locked into a single purpose. It’s a foundation for whatever 'other stuff' you can dream up.
Types of Other Stuff
The 'other stuff' name is intentionally vague. Why? Because the possibilities of what can fall under this category are quite literally limitless. In the short time since Nostr's inception, the number of sub-categories that have been built on top of the Nostr's open protocol is mind bending. Here are a few examples:
- Long-Form Content: Think blog posts or articles. NIP-23.
- Private Messaging: Encrypted chats between users. NIP-04.
- Communities: Group chats or forums like Reddit. NIP-72
- Marketplaces: People listing stuff for sale, payable with zaps. NIP-15
- Zaps: Value transfer over the Lightning Network. NIP57

Popular 'Other Stuff' Clients
Here's a short list of some of the most recent and popular apps and clients that branch outside of the traditional micro-blogging use case and leverage the openness, and interoperability that Nostr can provide.
Blogging (Long Form Content)
- Habla - Web app for Nostr based blogs
- Highlighter - Web app that enables users to highlight, store and share content
Group Chats
- Chachi Chat - Relay-based (NIP-29) group chat client
- 0xchat - Mobile based secure chat
- Flotilla - Web based chat app built for self-hosted communities
- Nostr Nests - Web app for audio chats
- White Noise - Mobile based secure chat
Marketplaces
- Shopstr - Permissionless marketplace for web
- Plebeian Market - Permissionless marketplace for web
- LNBits Market - Permissionless marketplace for your node
- Mostro - Nostr based Bitcoin P2P Marketplace
Photo/Video
Music
- Fountain - Podcast app with Nostr features
- Wavlake - A music app supporting the value-for-value ecosystem
Livestreaming
- Zap.stream - Nostr native live streams
Misc
- Wikifreedia - Nostr based Wikipedia alternative
- Wikistr - Nostr based Wikipedia alternative
- Pollerama - Nostr based polls
- Zap Store - The app store powered by your social graph
The 'other stuff' in Nostr is what makes it special. It’s not just about replacing Twitter or Facebook, it’s about building a decentralized ecosystem where anything from private chats to marketplaces can thrive. The beauty of Nostr is that it’s a flexible foundation. Developers can dream up new ideas and build them into clients, and the relays just keep humming along, passing the data around. It’s still early days, so expect the 'other stuff' to grow wilder and weirder over time!
You can explore the evergrowing 'other stuff' ecosystem at NostrApps.com, Nostr.net and Awesome Nostr.
-
 @ 9c9d2765:16f8c2c2
2025-04-21 11:08:37
@ 9c9d2765:16f8c2c2
2025-04-21 11:08:37CHAPTER EIGHT
James woke up early the next morning, the weight of his new responsibilities settling over him like a quiet storm. His uncle, Charles, had called him the previous night to officially confirm his appointment as the new president of JP Enterprises. His first task would be to review all the company’s investment plans and oversee critical decisions that would shape the future of the business.
He had gladly accepted the challenge. This was his chance to prove himself, not just to the Ray family but to everyone who had ever doubted him.
The following morning, James dressed in his usual simple attire: a plain button-down shirt and worn-out jeans. He had never been one for extravagant outfits, and he saw no reason to change now. With determination in his heart, he made his way to JP Enterprises.
However, upon arriving at the company’s grand entrance, he was met with hostility. The senior security guard, a burly man named Greg, frowned as he assessed James from head to toe.
“Excuse me, sir,” Greg said, blocking his way. “This is a corporate building. If you’re here to beg, you should leave.”
James raised an eyebrow, his expression calm. “I’m here to meet with the board.”
Greg let out a short laugh. “You? Meet with the board? Do you even know where you are? This isn’t some charity house, get out before I call for backup.”
James stood firm, unwilling to engage in an argument but also refusing to leave. The confrontation drew attention from other employees, some whispering among themselves while others simply watched in curiosity.
At that moment, Nancy, the company’s general secretary, arrived from a different entrance and noticed the scene unfolding. She gave the security guard an order not to let him in, she was unaware of James’s new appointment and didn't know that they had made a grave mistake.
Sandra, the company’s general manager, had been watching the scene from her office window and stormed outside the building in fury. As soon as she saw James being harassed at the entrance, her temper flared.
She didn’t hesitate. Walking straight to Greg, she raised her hand and delivered a resounding slap across his face.
“You fool!” she shouted. “Do you have any idea who you just insulted?”
Greg, now holding his stinging cheek, looked at Sandra in shock. “Ma’am, I didn’t know… I thought…”
Sandra didn’t let him finish. She immediately turned to James, her demeanor shifting to one of deep respect. She bent down slightly, bowing her head in reverence.
“Boss,” she addressed him formally. “I apologize for this man’s ignorance. Please, allow me to escort you inside.”
At the use of the word “Boss,” the entire crowd watching from the sidelines gasped in surprise. Murmurs spread through the employees gathered nearby.
“Did she just call him boss?”
“Wait… is he the new president?”
Greg’s face turned pale as he suddenly realized the grave mistake he had made. Without hesitation, he fell to his knees. “Sir, I’m so sorry! I didn’t know! Please forgive me!”
James, however, did not spare him a second glance. His eyes held no anger, just a quiet authority. Without a word, he turned to Sandra, nodding in acknowledgment.
“Let’s go inside,” he said calmly.
As James stepped into the building, Sandra leading the way, every employee inside the vast, modern corporate office stood up in unison. They had already received word of the new president’s arrival, but no one had expected him to be introduced in such a dramatic fashion.
As he walked past, whispers filled the air.
“So that’s the new president?”
“He was treated like a beggar outside… unbelievable.”
“I heard he’s Charles’s nephew… But why is he dressed like that?”
James paid no attention to the whispers. He had expected doubt and skepticism. What mattered to him now was proving his worth through actions, not appearances.
As he entered the boardroom, he turned to Sandra and Nancy. “Let’s begin. I want to see all the investment reports immediately.”
Both women nodded, admiration shining in their eyes. James was not just stepping into power he was about to redefine it.
Nancy walked briskly down the marble hallway of JP Enterprises, her heels clicking against the polished floors. She had been summoned to the president’s office, a place she had only entered a handful of times under the previous administration. The air was thick with whispers from employees who had just witnessed the shocking revelation that the so-called beggar at the entrance was none other than the new president.
Her heart pounded as she approached the large mahogany doors, pushing them open slowly. Her breath hitched at the sight before her, James seated comfortably in the president’s chair, his fingers interlocked as he observed her with an unreadable expression.
Nancy’s knees nearly buckled. She had been one of the skeptics, assuming that James was nothing more than an unfortunate case. And now, seeing him in that seat, she realized just how wrong she had been.
“Mr. James…” she stammered, her voice barely above a whisper. “I… I had no idea. Please, forgive me for my doubts.”
James remained silent for a moment, then spoke in a firm but measured tone. “What’s done is done. But let this be a lesson, Nancy never judges someone based on their appearance.”
She nodded hastily, her face flushed with embarrassment. “Understood, sir. It won’t happen again.”
His gaze darkened slightly. “Good. Now, I need your complete discretion. If anyone finds out about my true identity before the right time, you will no longer have a place in this company.”
Nancy swallowed hard and nodded. “I won’t tell a soul, sir.”
With that matter settled, she quickly pulled out a folder from her bag and placed it on the desk. “Here are the company’s current investment plans, Mr. James.”
James opened the folder and scanned the documents. His expression remained neutral, but internally, he was unimpressed. The investments were scattered across various top companies in the city, some of which had questionable stability. He had seen similar patterns before risky, short-term gains that often led to losses in the long run.
Without hesitation, he reached for a pen and started crossing out each investment one by one.
Nancy’s eyes widened in shock. “Sir? You’re… cancelling all the investment plans?”
James set the pen down and met her gaze. “Yes. These investments are not what the company needs right now. We need to rebuild our foundation with something more solid.”
She hesitated before speaking. “But, sir, these were carefully chosen by the previous board. Some of these are partnerships with major corporations.”
James leaned back in his chair. “That may be, but their choices were reckless. I won’t allow this company to sink under the weight of poor decisions.”
Nancy nodded slowly, beginning to understand the shift in leadership. “So, what’s the next move, sir?”
A small smirk played on James’s lips. “I will personally be investing ten million dollars into this company. That will more than cover the loss from these cancelled investments.”
Nancy’s mouth fell open slightly. “You’re investing… ten million dollars? Personally?”
James nodded. “Yes. Consider it a reset. JP Enterprises needs a fresh start, and I intend to give it one.”
Nancy stood still, stunned by the weight of his words. This was no longer the James she had heard rumors about. This was a man of power, a man with a vision.
As she gathered the documents and prepared to execute his orders, she couldn’t shake the feeling that this was only the beginning. James wasn’t just here to lead JP Enterprises he was here to dominate.
-
 @ f1989a96:bcaaf2c1
2025-03-27 13:53:14
@ f1989a96:bcaaf2c1
2025-03-27 13:53:14Good morning, readers!
Turkey’s currency plunged to a record low after the arrest of Istanbul Mayor Ekrem Imamoglu, one of President Recep Tayyip Erdogan’s main political rivals. This follows a pattern of escalating repression of opposition figures, which have been described as an effort to suppress competition ahead of primary elections. As economic conditions deteriorate, Erdogan is resorting to desperate measures — blocking social media, arresting dissenters, and tear-gassing protests — to maintain power over an increasingly restless populace.
In the Caribbean, we shed light on Cubans' struggles accessing remittances sent from family members abroad. This is a symptom of the regime's strict monetary controls over foreign currency. Cubans face long delays or can’t withdraw cash due to bank liquidity shortages. And when they can, remittances are converted into pesos at the overvalued official Cuban exchange rate. This effectively allows the Communist Party of Cuba (PCC) to loot the value from Cuban remittances.
In freedom tech news, we highlight Demand Pool, the first-ever Stratum V2 mining pool. Stratum V2 is a mining protocol designed to decentralize Bitcoin mining by letting individual miners create their own block templates rather than relying on centralized pools to do so for them. This improves censorship resistance and promotes a more decentralized and resilient Bitcoin network — critical features for human rights defenders and nonprofits using Bitcoin to protect against financial repression from authoritarian regimes.
We end by featuring Vijay Selvam's new book, “Principles of Bitcoin.” It offers a clear, first-principles guide to understanding how Bitcoin’s technology interacts with economics, politics, philosophy, and human rights. Whether you’re new to Bitcoin or looking to deepen your understanding, this book provides a solid foundation, and it even features a foreword by HRF Chief Strategy Officer Alex Gladstein.
Now, let’s dive right in!
Subscribe Here
GLOBAL NEWS
Turkey | Lira in Free Fall as Erdogan Arrests Political Rival
Turkey’s lira plunged to a record low after officials arrested Istanbul Mayor Ekrem Imamoglu, President Recep Tayyip Erdogan’s main political rival. Imamoglu’s arrest comes ahead of primary elections and follows the increasing repression of opposition figures in recent months, including the suspension of political opposition accounts on X. Officials also arrested Buğra Gökçe, head of the Istanbul Planning Agency, for publishing data exposing the country’s deepening poverty. The currency’s fallout and political repression have sparked protests in Istanbul despite a four-day ban. The regime is responding with tear gas and rubber bullets. Meanwhile, Turks dissenting online risk joining over a dozen other citizens recently arrested for “provocative” social media posts. Netblocks reports that the Turkish regime imposed restrictions on social media and messaging to quell the uprising of Turks struggling with financial conditions and deepening repression.
Cuba | Banks “Hijack” Citizen Remittances
Cubans are struggling to access remittances sent from their families abroad. This is because the regime completely controls all incoming foreign currency transfers. When remittances arrive, communist banking authorities force their conversion into collapsing Cuban pesos or “Moneda Libremente Convertible” (MLC), Cuba’s digital currency with limited use. On top of this, Cubans receive pesos in their accounts based on the official Cuban exchange rate, which is far below the informal market rate. This allows the regime to opaquely siphon off much of the remittances’ real value. Even when the money clears, Cubans face long delays or can’t withdraw the cash due to banks’ liquidity shortages. Many Cubans are accusing these banks of “hijacking” their remittances. As inflation, electrical blackouts, and food shortages continue, remittances are more critical than ever for Cuban families. Yet, they’re blocked at every turn by a system designed to impoverish them.
Pakistan | Announces Plans to Regulate Digital Assets
Pakistan announced plans to create a regulatory framework for Bitcoin and digital assets to attract foreign investment and domestic economic activity. It’s a peculiar shift for a regime that regularly suspends the Internet, censors social media, represses opposition, and burdens its people with the highest cost of living in Asia. We suspect the plans indicate efforts to control the industry rather than empower individuals. The military-backed regime is also exploring a Central Bank Digital Currency (CBDC) and tightening controls on VPN use, which are hardly the hallmarks of leadership committed to permissionless financial systems. But perhaps it matters little. Grassroots Bitcoin adoption in Pakistan already ranks among the highest in the world, with an estimated 15 to 20 million users turning to digital assets to preserve their savings, circumvent financial controls, and escape the failures of a collapsing fiat system. HRF supported Bitcoin Pakistan with a grant to help translate resources into Urdu, a language spoken by 60 million people trapped in this repressive scenario.
Russia | Piloting CBDC in Tatarstan to Test Smart Contract Functionality
Russia’s central bank plans to pilot its CBDC, the digital ruble, in Tatarstan to test smart contract functionality. Specifically, the central bank will experiment with conditional spending, using smart contracts to restrict where and what users can spend money on. If these features are implemented, it will empower the Kremlin with micro-controls over Russians’ spending activity. Officials could program funds to expire, restrict purchases to regime-approved goods, or block transactions at certain locations — leaving users with no financial autonomy or privacy. Those who oppose the Russian dictatorship, such as activists, nonprofits, and dissenters, could be debanked with more ease, their assets frozen or confiscated without recourse.
Nicaragua | Government Mandates Public Employees Declare All Assets
In Nicaragua, dictator Daniel Ortega intensified state financial surveillance by mandating all public servants to disclose information on all personal and family assets. The mandate requires all public employees to declare everything from personal bank accounts, loans, vehicles, and other assets — as well as the assets and accounts of immediate family members. Those who do not comply face the threat of termination. Ironically, despite the law requiring such disclosure, Ortega himself has not declared his assets since 2006. Under the guise of regulatory compliance, this policy is yet another link in the chain tightening state surveillance over Nicaraguan society. Bitcoin adoption continues to grow in this repressed Central American nation.
BITCOIN AND FREEDOM TECH NEWS
Demand Pool | First Stratum V2 Mining Pool Launches
Bitcoin mining could become more decentralized and censorship-resistant with the launch of Demand Pool, the first mining pool to ever implement Stratum V2. Stratum V2 is open-source software that allows miners to build their own block templates, enabling more individual mining and less dependence on large and centralized mining pools. This helps maintain Bitcoin’s key features: its decentralized, permissionless, and uncensorable nature. All of which are crucial for human rights defenders and nonprofits bypassing the financial repression and surveillance of authoritarian regimes. Learn more here.
Bitcoin Mining | Three Solo Blocks Found
Three separate solo miners mined Bitcoin blocks in the past seven days. This marks the second, third, and fourth solo blocks mined in the past two weeks alone, hinting at a surge in home mining. This promotes greater decentralization within the Bitcoin network because solo miners have little functional ability to censor. In contrast, large mining pools are points of failure that centralized interests can more easily pressure — to the detriment of activists and human rights defenders. The first block was mined on March 21 by a miner using a self-hosted FutureBit Apollo machine that earned 3.125 BTC plus fees for processing block 888,737. Just days later, a solo miner with under 1 TH/s of self-hosted hash rate found block 888,989, which became just the third block ever to be mined using an open-source Bitaxe device. Most recently, on March 24, a solo miner using a $300 setup successfully mined block 889,240.
Krux | Adds Taproot and Miniscript Support
Krux, open-source software for building your own Bitcoin signing devices (hardware for Bitcoin self-custody), released an update that enhances privacy and flexibility. The update introduces support for Taproot, a past Bitcoin upgrade that improves privacy and security, and Miniscript, a simplified way to create more complex Bitcoin transaction rules. This allows users to manage multi-signature wallets (where more than one private key is required to interact with your Bitcoin) in a more private and flexible way. It also enables spending conditions that are harder to censor and easier to verify. Krux continues to support the struggle for financial freedom and human rights by breaking down barriers to Bitcoin self-custody. HRF has recognized this impact and awarded grants to open-source developers working on Krux to advance this mission.
Cashu | Developing Tap-to-Pay Ecash
Calle, the creator of Cashu, an open-source Chaumian ecash protocol for Bitcoin integrated with the Lightning Network, is developing a new tap-to-pay feature that enables instant, offline ecash payments via NFC. Ecash functions as a bearer asset, meaning the funds are stored directly on the user’s device. With tap-to-pay, it can be transferred with a single tap (similar to tapping your credit card). More generally, ecash offers fast, private transactions resistant to surveillance and censorship. But for activists and dissenters, this particular advancement makes private and permissionless payments more accessible and user-friendly. This development will be worth following closely. Watch a demo here.
OpenSats | Announces 10th Wave of Bitcoin Grants
OpenSats, a public nonprofit that supports open-source software and projects, announced its 10th wave of grants supporting Bitcoin initiatives. This round includes funding for Stable Channels, which enable stabilized Bitcoin-backed balances on the Lightning Network (allowing users to peg Bitcoin to fiat currencies in a self-custodial way) that provide stable, censorship-resistant payments. OpenSats also renewed its support for Floresta, a lightweight Bitcoin node (a computer that runs the Bitcoin software). It lowers entry barriers to running Bitcoin, helping make the network more decentralized and censorship-resistant.
Bitcoin Policy Institute | Launches Bitcoin Summer Research Program
The Bitcoin Student Network (BSN) and the Bitcoin Policy Institute (BPI) are teaming up to offer students an eight-week research internship this summer. The program is part of BPI’s Research Experiences for Undergraduates (REU) initiative and invites students passionate about the future of money, financial inclusion, and Bitcoin’s civil liberties impacts to conduct hands-on research. Participants will also receive mentorship from BPI researchers. The program runs from June 9 to Aug. 8, 2025, and includes an in-person colloquium in Washington, DC. It is an incredible opportunity for students worldwide, especially those living in oppressive regimes, to get involved with Bitcoin. Applications are open until April 7. Apply here.
RECOMMENDED CONTENT
Principles of Bitcoin by Vijay Selvam
“Principles of Bitcoin” by Vijay Selvam is a new book offering a first-principles guide to understanding Bitcoin’s technology, economics, politics, and philosophy. With a foreword by HRF Chief Strategy Officer Alex Gladstein, the book cuts through the noise to explain why Bitcoin stands alone as a tool for individual empowerment and financial freedom. Selvam’s work makes the case for Bitcoin as a once-in-history invention shaping a more decentralized and equitable future. Read it here.
Rule Breakers — The True Story of Roya Mahboob
“Rule Breakers” is a new film that tells the true story of Roya Mahboob, Afghanistan’s first female tech CEO, who empowered young girls in Afghanistan with financial literacy, robotics, and financial freedom through Bitcoin. The film recounts Mahboob’s courageous work educating these girls despite huge personal risks under a regime that bans their education. It follows the story of Afghan Dreamers, the country’s first all-girls robotics team, and the obstacles they overcome to compete on the world stage. “Rule Breakers” is a testament to the power of education, innovation, and resilience in the face of oppression. It’s now in theaters, and you can watch the trailer here.
If this article was forwarded to you and you enjoyed reading it, please consider subscribing to the Financial Freedom Report here.
Support the newsletter by donating bitcoin to HRF’s Financial Freedom program via BTCPay.\ Want to contribute to the newsletter? Submit tips, stories, news, and ideas by emailing us at ffreport @ hrf.org
The Bitcoin Development Fund (BDF) is accepting grant proposals on an ongoing basis. The Bitcoin Development Fund is looking to support Bitcoin developers, community builders, and educators. Submit proposals here.
-
 @ 04c915da:3dfbecc9
2025-03-26 20:54:33
@ 04c915da:3dfbecc9
2025-03-26 20:54:33Capitalism is the most effective system for scaling innovation. The pursuit of profit is an incredibly powerful human incentive. Most major improvements to human society and quality of life have resulted from this base incentive. Market competition often results in the best outcomes for all.
That said, some projects can never be monetized. They are open in nature and a business model would centralize control. Open protocols like bitcoin and nostr are not owned by anyone and if they were it would destroy the key value propositions they provide. No single entity can or should control their use. Anyone can build on them without permission.
As a result, open protocols must depend on donation based grant funding from the people and organizations that rely on them. This model works but it is slow and uncertain, a grind where sustainability is never fully reached but rather constantly sought. As someone who has been incredibly active in the open source grant funding space, I do not think people truly appreciate how difficult it is to raise charitable money and deploy it efficiently.
Projects that can be monetized should be. Profitability is a super power. When a business can generate revenue, it taps into a self sustaining cycle. Profit fuels growth and development while providing projects independence and agency. This flywheel effect is why companies like Google, Amazon, and Apple have scaled to global dominance. The profit incentive aligns human effort with efficiency. Businesses must innovate, cut waste, and deliver value to survive.
Contrast this with non monetized projects. Without profit, they lean on external support, which can dry up or shift with donor priorities. A profit driven model, on the other hand, is inherently leaner and more adaptable. It is not charity but survival. When survival is tied to delivering what people want, scale follows naturally.
The real magic happens when profitable, sustainable businesses are built on top of open protocols and software. Consider the many startups building on open source software stacks, such as Start9, Mempool, and Primal, offering premium services on top of the open source software they build out and maintain. Think of companies like Block or Strike, which leverage bitcoin’s open protocol to offer their services on top. These businesses amplify the open software and protocols they build on, driving adoption and improvement at a pace donations alone could never match.
When you combine open software and protocols with profit driven business the result are lean, sustainable companies that grow faster and serve more people than either could alone. Bitcoin’s network, for instance, benefits from businesses that profit off its existence, while nostr will expand as developers monetize apps built on the protocol.
Capitalism scales best because competition results in efficiency. Donation funded protocols and software lay the groundwork, while market driven businesses build on top. The profit incentive acts as a filter, ensuring resources flow to what works, while open systems keep the playing field accessible, empowering users and builders. Together, they create a flywheel of innovation, growth, and global benefit.
-
 @ 86dfbe73:628cef55
2025-04-21 10:08:34
@ 86dfbe73:628cef55
2025-04-21 10:08:34Mit dem Internet kam das Ende der Massengesellschaft. Heutzutage sind Öffentlichkeit im Allgemeinen und die digitale Öffentlichkeit im Besonderen nur als Netzwerk verstehbar. Nicht als Netzwerk zur Kommunikation, sondern als Netzwerk der Beziehungen, bestehend aus den Erwartungen, Kenntnissen und letztlich bestehend aus dem Vertrauen, das Menschen gegenüber anderen Menschen und Institutionen aufzubauen pflegen. Wichtig ist nicht mehr, wo jemand eine Information plaziert, wichtig ist, wann und wer und unter Einbeziehung welcher Faktoren diese abfragt.
In Sozialen Netzwerken entscheidet jeder selbst, wem er folgt. Er entscheidet selbst, wie die eigene Startseite, der eigene Blick auf den Dienst, aussieht. Als Beispiel sei hier Twitter erwähnt. Aus der Liste der Gefolgten wird die Timeline generiert, die eine Wirklichkeit abbildet, die einzig und alleine von den Following-Entscheidungen des Nutzers bestimmt ist.
Die Beziehungsweise des Folgens ist eine direkte Willenserklärung, die Inhalte eines Users sehen zu wollen. Sie ist ein Pakt, der auch eine gewisse, wenn auch kleine, Verantwortungsübernahme bedeutet. Und diese Beziehungsweise wurde zum integralen Strukturbaustein der digitalen Öffentlichkeit zwischen 2010 bis 2020 und damit auch zur tragenden Säule vieler Karrieren, Geschäftsmodellen und außerdem zur Grundlage der Selektionsverfahren von kulturellen Trends. Im Follower steckte die Macht.
Die digitale Öffentlichkeit hat aufgehört eine vernetzte Öffentlichkeit zu sein und geht zunehmend in den „For you“-Algorithmen der kommerziellen Plattformen auf. Ab 2020 wurde dem Follower von Diensten wie Tiktok der Gar ausgemacht und von dort setzte sich der „For You-Algoritmus“ auf allen kommerziellen Plattformen durch. Das bedeutet, dass die neue digitale Öffentlichkeit nicht mehr durch menschliche Beziehungen und vernetztes Vertrauen getragen wird, sondern vollends den Steuerungsinstrumenten einer Hand voll Konzernen ausgeliefert ist. Auf einmal bedeutete ein Following nicht mehr die Garantie, dass der Content die Abonnenten erreicht.
Mit der Zerstörung dieser Beziehung entgleiten den Creators ihre medialen Regime und beide, User und Creator werden immer abhängiger vom Algorithmus und arbeiten folglich nur noch für die Interessen der Plattformen, statt für sich selbst.
-
 @ 6b3780ef:221416c8
2025-03-26 18:42:00
@ 6b3780ef:221416c8
2025-03-26 18:42:00This workshop will guide you through exploring the concepts behind MCP servers and how to deploy them as DVMs in Nostr using DVMCP. By the end, you'll understand how these systems work together and be able to create your own deployments.
Understanding MCP Systems
MCP (Model Context Protocol) systems consist of two main components that work together:
- MCP Server: The heart of the system that exposes tools, which you can access via the
.listTools()method. - MCP Client: The interface that connects to the MCP server and lets you use the tools it offers.
These servers and clients can communicate using different transport methods:
- Standard I/O (stdio): A simple local connection method when your server and client are on the same machine.
- Server-Sent Events (SSE): Uses HTTP to create a communication channel.
For this workshop, we'll use stdio to deploy our server. DVMCP will act as a bridge, connecting to your MCP server as an MCP client, and exposing its tools as a DVM that anyone can call from Nostr.
Creating (or Finding) an MCP Server
Building an MCP server is simpler than you might think:
- Create software in any programming language you're comfortable with.
- Add an MCP library to expose your server's MCP interface.
- Create an API that wraps around your software's functionality.
Once your server is ready, an MCP client can connect, for example, with
bun index.js, and then call.listTools()to discover what your server can do. This pattern, known as reflection, makes Nostr DVMs and MCP a perfect match since both use JSON, and DVMs can announce and call tools, effectively becoming an MCP proxy.Alternatively, you can use one of the many existing MCP servers available in various repositories.
For more information about mcp and how to build mcp servers you can visit https://modelcontextprotocol.io/
Setting Up the Workshop
Let's get hands-on:
First, to follow this workshop you will need Bun. Install it from https://bun.sh/. For Linux and macOS, you can use the installation script:
curl -fsSL https://bun.sh/install | bash-
Choose your MCP server: You can either create one or use an existing one.
-
Inspect your server using the MCP inspector tool:
bash npx @modelcontextprotocol/inspector build/index.js arg1 arg2This will: - Launch a client UI (default: http://localhost:5173)
- Start an MCP proxy server (default: port 3000)
-
Pass any additional arguments directly to your server
-
Use the inspector: Open the client UI in your browser to connect with your server, list available tools, and test its functionality.
Deploying with DVMCP
Now for the exciting part – making your MCP server available to everyone on Nostr:
-
Navigate to your MCP server directory.
-
Run without installing (quickest way):
npx @dvmcp/bridge -
Or install globally for regular use:
npm install -g @dvmcp/bridge # or bun install -g @dvmcp/bridgeThen run using:bash dvmcp-bridge
This will guide you through creating the necessary configuration.
Watch the console logs to confirm successful setup – you'll see your public key and process information, or any issues that need addressing.
For the configuration, you can set the relay as
wss://relay.dvmcp.fun, or use any other of your preferenceTesting and Integration
- Visit dvmcp.fun to see your DVM announcement.
- Call your tools and watch the responses come back.
For production use, consider running dvmcp-bridge as a system service or creating a container for greater reliability and uptime.
Integrating with LLM Clients
You can also integrate your DVMCP deployment with LLM clients using the discovery package:
-
Install and use the
@dvmcp/discoverypackage:bash npx @dvmcp/discovery -
This package acts as an MCP server for your LLM system by:
- Connecting to configured Nostr relays
- Discovering tools from DVMCP servers
-
Making them available to your LLM applications
-
Connect to specific servers or providers using these flags: ```bash # Connect to all DVMCP servers from a provider npx @dvmcp/discovery --provider npub1...
# Connect to a specific DVMCP server npx @dvmcp/discovery --server naddr1... ```
Using these flags, you wouldn't need a configuration file. You can find these commands and Claude desktop configuration already prepared for copy and paste at dvmcp.fun.
This feature lets you connect to any DVMCP server using Nostr and integrate it into your client, either as a DVM or in LLM-powered applications.
Final thoughts
If you've followed this workshop, you now have an MCP server deployed as a Nostr DVM. This means that local resources from the system where the MCP server is running can be accessed through Nostr in a decentralized manner. This capability is powerful and opens up numerous possibilities and opportunities for fun.
You can use this setup for various use cases, including in a controlled/local environment. For instance, you can deploy a relay in your local network that's only accessible within it, exposing all your local MCP servers to anyone connected to the network. This setup can act as a hub for communication between different systems, which could be particularly interesting for applications in home automation or other fields. The potential applications are limitless.
However, it's important to keep in mind that there are security concerns when exposing local resources publicly. You should be mindful of these risks and prioritize security when creating and deploying your MCP servers on Nostr.
Finally, these are new ideas, and the software is still under development. If you have any feedback, please refer to the GitHub repository to report issues or collaborate. DVMCP also has a Signal group you can join. Additionally, you can engage with the community on Nostr using the #dvmcp hashtag.
Useful Resources
- Official Documentation:
- Model Context Protocol: modelcontextprotocol.org
-
DVMCP.fun: dvmcp.fun
-
Source Code and Development:
- DVMCP: github.com/gzuuus/dvmcp
-
DVMCP.fun: github.com/gzuuus/dvmcpfun
-
MCP Servers and Clients:
- Smithery AI: smithery.ai
- MCP.so: mcp.so
-
Glama AI MCP Servers: glama.ai/mcp/servers
Happy building!
- MCP Server: The heart of the system that exposes tools, which you can access via the
-
 @ 95cb4330:96db706c
2025-04-21 09:59:02
@ 95cb4330:96db706c
2025-04-21 09:59:02Principle:
Reduce internal friction by minimizing unnecessary processes, approvals, and meetings.
Empower small, autonomous teams to make decisions quickly and independently.
💡 What It Means
- Bureaucracy kills speed, innovation, and ownership.
- Instead of creating endless layers of management and approval, build the smallest system necessary to enable great work.
- Give teams the trust and tools they need to move fast.
The goal is not chaos, but flexibility with lightweight structure—so the organization stays dynamic as it scales.
📈 Why It Matters
✅ Speed is a competitive advantage in entrepreneurship.
✅ Empowered teams are more creative and motivated.
✅ Minimal bureaucracy allows companies to iterate fast and stay customer-focused.
🏛️ Examples in Action
- Spotify uses small “squads” with high autonomy and light-touch leadership to maintain speed and innovation.
- Basecamp designs its company around minimal meetings, clear asynchronous communication, and trusting small teams to own outcomes.
- Amazon uses the "two-pizza team" rule—teams should be small enough to be fed with two pizzas.
📚 Resources to Explore
- 📄 Spotify’s Engineering Culture – Part 1
- 📖 Basecamp’s Approach to Minimal Management
- 📘 Harvard Business Review on 3 Ways to Improve Your Decision Making
- Spotify Engineering Culture - Part 1 (aka the "Spotify Model")
🚀 Action Prompthttps://hbr.org/2018/01/3-ways-to-improve-your-decision-making
Ask yourself:
"What approvals, meetings, or processes can I eliminate or simplify today to help my team move faster?"Build only as much structure as needed—and no more. Protect creativity, speed, and ownership at all costs.
-
 @ b2d670de:907f9d4a
2025-03-25 20:17:57
@ b2d670de:907f9d4a
2025-03-25 20:17:57This guide will walk you through setting up your own Strfry Nostr relay on a Debian/Ubuntu server and making it accessible exclusively as a TOR hidden service. By the end, you'll have a privacy-focused relay that operates entirely within the TOR network, enhancing both your privacy and that of your users.
Table of Contents
- Prerequisites
- Initial Server Setup
- Installing Strfry Nostr Relay
- Configuring Your Relay
- Setting Up TOR
- Making Your Relay Available on TOR
- Testing Your Setup]
- Maintenance and Security
- Troubleshooting
Prerequisites
- A Debian or Ubuntu server
- Basic familiarity with command line operations (most steps are explained in detail)
- Root or sudo access to your server
Initial Server Setup
First, let's make sure your server is properly set up and secured.
Update Your System
Connect to your server via SSH and update your system:
bash sudo apt update sudo apt upgrade -ySet Up a Basic Firewall
Install and configure a basic firewall:
bash sudo apt install ufw -y sudo ufw allow ssh sudo ufw enableThis allows SSH connections while blocking other ports for security.
Installing Strfry Nostr Relay
This guide includes the full range of steps needed to build and set up Strfry. It's simply based on the current version of the
DEPLOYMENT.mddocument in the Strfry GitHub repository. If the build/setup process is changed in the repo, this document could get outdated. If so, please report to me that something is outdated and check for updated steps here.Install Dependencies
First, let's install the necessary dependencies. Each package serves a specific purpose in building and running Strfry:
bash sudo apt install -y git build-essential libyaml-perl libtemplate-perl libregexp-grammars-perl libssl-dev zlib1g-dev liblmdb-dev libflatbuffers-dev libsecp256k1-dev libzstd-devHere's why each dependency is needed:
Basic Development Tools: -
git: Version control system used to clone the Strfry repository and manage code updates -build-essential: Meta-package that includes compilers (gcc, g++), make, and other essential build toolsPerl Dependencies (used for Strfry's build scripts): -
libyaml-perl: Perl interface to parse YAML configuration files -libtemplate-perl: Template processing system used during the build process -libregexp-grammars-perl: Advanced regular expression handling for Perl scriptsCore Libraries for Strfry: -
libssl-dev: Development files for OpenSSL, used for secure connections and cryptographic operations -zlib1g-dev: Compression library that Strfry uses to reduce data size -liblmdb-dev: Lightning Memory-Mapped Database library, which Strfry uses for its high-performance database backend -libflatbuffers-dev: Memory-efficient serialization library for structured data -libsecp256k1-dev: Optimized C library for EC operations on curve secp256k1, essential for Nostr's cryptographic signatures -libzstd-dev: Fast real-time compression algorithm for efficient data storage and transmissionClone and Build Strfry
Clone the Strfry repository:
bash git clone https://github.com/hoytech/strfry.git cd strfryBuild Strfry:
bash git submodule update --init make setup-golpe make -j2 # This uses 2 CPU cores. Adjust based on your server (e.g., -j4 for 4 cores)This build process will take several minutes, especially on servers with limited CPU resources, so go get a coffee and post some great memes on nostr in the meantime.
Install Strfry
Install the Strfry binary to your system path:
bash sudo cp strfry /usr/local/binThis makes the
strfrycommand available system-wide, allowing it to be executed from any directory and by any user with the appropriate permissions.Configuring Your Relay
Create Strfry User
Create a dedicated user for running Strfry. This enhances security by isolating the relay process:
bash sudo useradd -M -s /usr/sbin/nologin strfryThe
-Mflag prevents creating a home directory, and-s /usr/sbin/nologinprevents anyone from logging in as this user. This is a security best practice for service accounts.Create Data Directory
Create a directory for Strfry's data:
bash sudo mkdir /var/lib/strfry sudo chown strfry:strfry /var/lib/strfry sudo chmod 755 /var/lib/strfryThis creates a dedicated directory for Strfry's database and sets the appropriate permissions so that only the strfry user can write to it.
Configure Strfry
Copy the sample configuration file:
bash sudo cp strfry.conf /etc/strfry.confEdit the configuration file:
bash sudo nano /etc/strfry.confModify the database path:
```
Find this line:
db = "./strfry-db/"
Change it to:
db = "/var/lib/strfry/" ```
Check your system's hard limit for file descriptors:
bash ulimit -HnUpdate the
nofilessetting in your configuration to match this value (or set to 0):```
Add or modify this line in the config (example if your limit is 524288):
nofiles = 524288 ```
The
nofilessetting determines how many open files Strfry can have simultaneously. Setting it to your system's hard limit (or 0 to use the system default) helps prevent "too many open files" errors if your relay becomes popular.You might also want to customize your relay's information in the config file. Look for the
infosection and update it with your relay's name, description, and other details.Set ownership of the configuration file:
bash sudo chown strfry:strfry /etc/strfry.confCreate Systemd Service
Create a systemd service file for managing Strfry:
bash sudo nano /etc/systemd/system/strfry.serviceAdd the following content:
```ini [Unit] Description=strfry relay service
[Service] User=strfry ExecStart=/usr/local/bin/strfry relay Restart=on-failure RestartSec=5 ProtectHome=yes NoNewPrivileges=yes ProtectSystem=full LimitCORE=1000000000
[Install] WantedBy=multi-user.target ```
This systemd service configuration: - Runs Strfry as the dedicated strfry user - Automatically restarts the service if it fails - Implements security measures like
ProtectHomeandNoNewPrivileges- Sets resource limits appropriate for a relayEnable and start the service:
bash sudo systemctl enable strfry.service sudo systemctl start strfryCheck the service status:
bash sudo systemctl status strfryVerify Relay is Running
Test that your relay is running locally:
bash curl localhost:7777You should see a message indicating that the Strfry relay is running. This confirms that Strfry is properly installed and configured before we proceed to set up TOR.
Setting Up TOR
Now let's make your relay accessible as a TOR hidden service.
Install TOR
Install TOR from the package repositories:
bash sudo apt install -y torThis installs the TOR daemon that will create and manage your hidden service.
Configure TOR
Edit the TOR configuration file:
bash sudo nano /etc/tor/torrcScroll down to wherever you see a commented out part like this: ```
HiddenServiceDir /var/lib/tor/hidden_service/
HiddenServicePort 80 127.0.0.1:80
```
Under those lines, add the following lines to set up a hidden service for your relay:
HiddenServiceDir /var/lib/tor/strfry-relay/ HiddenServicePort 80 127.0.0.1:7777This configuration: - Creates a hidden service directory at
/var/lib/tor/strfry-relay/- Maps port 80 on your .onion address to port 7777 on your local machine - Keeps all traffic encrypted within the TOR networkCreate the directory for your hidden service:
bash sudo mkdir -p /var/lib/tor/strfry-relay/ sudo chown debian-tor:debian-tor /var/lib/tor/strfry-relay/ sudo chmod 700 /var/lib/tor/strfry-relay/The strict permissions (700) are crucial for security as they ensure only the debian-tor user can access the directory containing your hidden service private keys.
Restart TOR to apply changes:
bash sudo systemctl restart torMaking Your Relay Available on TOR
Get Your Onion Address
After restarting TOR, you can find your onion address:
bash sudo cat /var/lib/tor/strfry-relay/hostnameThis will output something like
abcdefghijklmnopqrstuvwxyz234567.onion, which is your relay's unique .onion address. This is what you'll share with others to access your relay.Understanding Onion Addresses
The .onion address is a special-format hostname that is automatically generated based on your hidden service's private key.
Your users will need to use this address with the WebSocket protocol prefix to connect:
ws://youronionaddress.onionTesting Your Setup
Test with a Nostr Client
The best way to test your relay is with an actual Nostr client that supports TOR:
- Open your TOR browser
- Go to your favorite client, either on clearnet or an onion service.
- Check out this list of nostr clients available over TOR.
- Add your relay URL:
ws://youronionaddress.onionto your relay list - Try posting a note and see if it appears on your relay
- In some nostr clients, you can also click on a relay to get information about it like the relay name and description you set earlier in the stryfry config. If you're able to see the correct values for the name and the description, you were able to connect to the relay.
- Some nostr clients also gives you a status on what relays a note was posted to, this could also give you an indication that your relay works as expected.
Note that not all Nostr clients support TOR connections natively. Some may require additional configuration or use of TOR Browser. E.g. most mobile apps would most likely require a TOR proxy app running in the background (some have TOR support built in too).
Maintenance and Security
Regular Updates
Keep your system, TOR, and relay updated:
```bash
Update system
sudo apt update sudo apt upgrade -y
Update Strfry
cd ~/strfry git pull git submodule update make -j2 sudo cp strfry /usr/local/bin sudo systemctl restart strfry
Verify TOR is still running properly
sudo systemctl status tor ```
Regular updates are crucial for security, especially for TOR which may have security-critical updates.
Database Management
Strfry has built-in database management tools. Check the Strfry documentation for specific commands related to database maintenance, such as managing event retention and performing backups.
Monitoring Logs
To monitor your Strfry logs:
bash sudo journalctl -u strfry -fTo check TOR logs:
bash sudo journalctl -u tor -fMonitoring logs helps you identify potential issues and understand how your relay is being used.
Backup
This is not a best practices guide on how to do backups. Preferably, backups should be stored either offline or on a different machine than your relay server. This is just a simple way on how to do it on the same server.
```bash
Stop the relay temporarily
sudo systemctl stop strfry
Backup the database
sudo cp -r /var/lib/strfry /path/to/backup/location
Restart the relay
sudo systemctl start strfry ```
Back up your TOR hidden service private key. The private key is particularly sensitive as it defines your .onion address - losing it means losing your address permanently. If you do a backup of this, ensure that is stored in a safe place where no one else has access to it.
bash sudo cp /var/lib/tor/strfry-relay/hs_ed25519_secret_key /path/to/secure/backup/locationTroubleshooting
Relay Not Starting
If your relay doesn't start:
```bash
Check logs
sudo journalctl -u strfry -e
Verify configuration
cat /etc/strfry.conf
Check permissions
ls -la /var/lib/strfry ```
Common issues include: - Incorrect configuration format - Permission problems with the data directory - Port already in use (another service using port 7777) - Issues with setting the nofiles limit (setting it too big)
TOR Hidden Service Not Working
If your TOR hidden service is not accessible:
```bash
Check TOR logs
sudo journalctl -u tor -e
Verify TOR is running
sudo systemctl status tor
Check onion address
sudo cat /var/lib/tor/strfry-relay/hostname
Verify TOR configuration
sudo cat /etc/tor/torrc ```
Common TOR issues include: - Incorrect directory permissions - TOR service not running - Incorrect port mapping in torrc
Testing Connectivity
If you're having trouble connecting to your service:
```bash
Verify Strfry is listening locally
sudo ss -tulpn | grep 7777
Check that TOR is properly running
sudo systemctl status tor
Test the local connection directly
curl --include --no-buffer localhost:7777 ```
Privacy and Security Considerations
Running a Nostr relay as a TOR hidden service provides several important privacy benefits:
-
Network Privacy: Traffic to your relay is encrypted and routed through the TOR network, making it difficult to determine who is connecting to your relay.
-
Server Anonymity: The physical location and IP address of your server are concealed, providing protection against denial-of-service attacks and other targeting.
-
Censorship Resistance: TOR hidden services are more resilient against censorship attempts, as they don't rely on the regular DNS system and can't be easily blocked.
-
User Privacy: Users connecting to your relay through TOR enjoy enhanced privacy, as their connections are also encrypted and anonymized.
However, there are some important considerations:
- TOR connections are typically slower than regular internet connections
- Not all Nostr clients support TOR connections natively
- Running a hidden service increases the importance of keeping your server secure
Congratulations! You now have a Strfry Nostr relay running as a TOR hidden service. This setup provides a resilient, privacy-focused, and censorship-resistant communication channel that helps strengthen the Nostr network.
For further customization and advanced configuration options, refer to the Strfry documentation.
Consider sharing your relay's .onion address with the Nostr community to help grow the privacy-focused segment of the network!
If you plan on providing a relay service that the public can use (either for free or paid for), consider adding it to this list. Only add it if you plan to run a stable and available relay.
-
 @ 7d33ba57:1b82db35
2025-04-21 08:47:51
@ 7d33ba57:1b82db35
2025-04-21 08:47:51Spread across 14 islands and connected by elegant bridges, Stockholm is often called the **"Venice of the North." It blends royal history, cutting-edge design, lush nature, and a laid-back Nordic vibe like few cities can. With cobblestone streets in Gamla Stan, sleek modern art in Södermalm, and serene waterways everywhere, Stockholm is both storybook and futuristic.

🏰 Top Things to Do in Stockholm
🏛️ Gamla Stan (Old Town)
- A beautifully preserved medieval core with colorful buildings, narrow alleys, and cozy cafés
- Visit the Royal Palace, Stockholm Cathedral, and watch the changing of the guard
- Stop by Stortorget Square for the classic photo and a fika (Swedish coffee break)
🖼️ Vasa Museum
- Home to the Vasa warship, which sank on its maiden voyage in 1628 and was miraculously recovered 333 years later
- One of Sweden’s most popular and jaw-dropping museums

🏡 Skansen Open-Air Museum
- A walk through Sweden’s past—complete with historic homes, craft demos, and even Scandinavian animals
- Great for families or anyone curious about Swedish traditions
🌉 Södermalm
- Stockholm’s hip, creative district
- Full of boutique shops, vintage stores, craft coffee, and rooftop bars
- Climb Monteliusvägen for incredible views of the city skyline and Lake Mälaren

🌿 Nature & Water Everywhere
- Take a boat tour of the Stockholm Archipelago, made up of 30,000+ islands
- Kayak through the canals or paddleboard around Kungsholmen
- In summer, locals swim off the rocks in the city or picnic in Djurgården Park

🍽️ Food & Fika
- Try Swedish meatballs, gravad lax, or herring smörgåsbord
- Visit the indoor Östermalm Market Hall for local specialties
- Don’t miss fika culture—coffee + cinnamon buns (kanelbullar) is a must

🚆 Getting Around
- Super walkable and bike-friendly
- Excellent public transport: trams, ferries, metro (Tunnelbana)
- The T-Centralen station even doubles as an underground art gallery

📅 Best Time to Visit
- Summer (June–August): Long sunny days, outdoor festivals, archipelago adventures
- Winter: Christmas markets, cozy cafés, and snow-dusted rooftops
- Year-round appeal with distinct charm in every season

-
 @ 04c915da:3dfbecc9
2025-03-25 17:43:44
@ 04c915da:3dfbecc9
2025-03-25 17:43:44One of the most common criticisms leveled against nostr is the perceived lack of assurance when it comes to data storage. Critics argue that without a centralized authority guaranteeing that all data is preserved, important information will be lost. They also claim that running a relay will become prohibitively expensive. While there is truth to these concerns, they miss the mark. The genius of nostr lies in its flexibility, resilience, and the way it harnesses human incentives to ensure data availability in practice.
A nostr relay is simply a server that holds cryptographically verifiable signed data and makes it available to others. Relays are simple, flexible, open, and require no permission to run. Critics are right that operating a relay attempting to store all nostr data will be costly. What they miss is that most will not run all encompassing archive relays. Nostr does not rely on massive archive relays. Instead, anyone can run a relay and choose to store whatever subset of data they want. This keeps costs low and operations flexible, making relay operation accessible to all sorts of individuals and entities with varying use cases.
Critics are correct that there is no ironclad guarantee that every piece of data will always be available. Unlike bitcoin where data permanence is baked into the system at a steep cost, nostr does not promise that every random note or meme will be preserved forever. That said, in practice, any data perceived as valuable by someone will likely be stored and distributed by multiple entities. If something matters to someone, they will keep a signed copy.
Nostr is the Streisand Effect in protocol form. The Streisand effect is when an attempt to suppress information backfires, causing it to spread even further. With nostr, anyone can broadcast signed data, anyone can store it, and anyone can distribute it. Try to censor something important? Good luck. The moment it catches attention, it will be stored on relays across the globe, copied, and shared by those who find it worth keeping. Data deemed important will be replicated across servers by individuals acting in their own interest.
Nostr’s distributed nature ensures that the system does not rely on a single point of failure or a corporate overlord. Instead, it leans on the collective will of its users. The result is a network where costs stay manageable, participation is open to all, and valuable verifiable data is stored and distributed forever.
-
 @ 27dd78c2:66ffe658
2025-03-25 17:12:08
@ 27dd78c2:66ffe658
2025-03-25 17:12:08In an age where ‘run clubs’ are getting more popular than ‘night clubs’, it’s exciting to see a Nostr-based sovereign fitness tracker hit the scene: Enter Runstr.club!
Runstr has emerged as a game-changer, redefining how runners connect, track progress, and stay motivated. For Bitcoin Runners, a movement that advocates sovereignty of one’s wealth, while improving one’s health, Runstr.club presents an exciting platform of choice to record your proof-of-work, take ownership of your personal data, and selectively engage with your social graph.
What is Runstr.club?
Runstr.club is a platform that’s being built to grow the proof-of-work community, with plans to offer interactive leaderboards, challenges, and social engagement. Unlike traditional running apps that focus purely on statistics, Runstr.club puts emphasis on camaraderie, motivation, and shared goals. It’s the Strava alternative that values ownership of your data, interoperability between platforms, and privacy as standard.
Why Runstr.club is a Great Fit for Bitcoin Runners
Bitcoin Runners isn’t just about proof-of-work; it’s about promoting freedom tech, decentralisation, and self-sovereignty principles that align closely with the ethos of Runstr.club.
Here’s why this platform is a great match for our movement:
- Community-Driven & Decentralised Spirit
Bitcoin Runners thrives on grassroots adoption and community participation, much like Runstr.club’s organic and community-focused model. Unlike corporate-owned fitness platforms that prioritise monetisation, Runstr.club is designed to empower runners, keeping the experience authentic and meaningful.
- Privacy-First Approach
One of the key concerns for bitcoiners is privacy. Mainstream fitness platforms harvest user data for profit, but Runstr.club offers a privacy-first alternative. This makes it an excellent choice for runners who value sovereignty in the digital age.
- The Advantage of Nostr Over Centralised Run Tracking Tools
Most mainstream running apps, like Strava or Nike Run Club, rely on centralised platforms that control user data, impose restrictions, and often monetise user activity. Runstr.club, however, is built on Nostr, a decentralised protocol that enables users to interact without getting trapped inside a walled garden.
With Nostr, runners benefit from:
-
True ownership of their data – no risk of platforms selling or misusing personal running history.
-
Resilience against censorship – no arbitrary bans or content moderation dictated by a 'shadowy suit'.
-
Interoperability – seamless integration with other Nostr-based applications, keeping data fluid and accessible across different platforms.
-
Peer-to-peer connectivity – allowing runners to share progress, create challenges, and stay engaged independent of big tech.
For Bitcoin Runners, Nostr’s decentralised nature aligns perfectly with the principles of sovereignty, freedom, and privacy.
- Gamification & Challenges
Runstr.club has engaging challenges and decentralised leaderboards on its roadmap. Whether you’re stacking sats through running-related bitcoin challenges or simply competing with fellow bitcoiners for fun, the platform will add an extra layer of engagement to every run. We would love to see such features come to life!
Conclusion
Runstr.club is more than just a running tracker—it’s a Nostr, bitcoin, and fitness onboarding community-driven movement. By embracing platforms that respect privacy, encourage competition, and foster community, we stay true to our values while pushing our limits as runners.
Let’s take this to the next level - be sure to follow Runstr on Nostr!
Run free. Stay sovereign. Stack zaps!
We’re shilling this open-source initiative out of genuine appreciation for both its vision and the dedicated team behind it.
-
 @ d34e832d:383f78d0
2025-04-21 08:32:02
@ d34e832d:383f78d0
2025-04-21 08:32:02The operational landscape for Nostr relay operators is fraught with multifaceted challenges that not only pertain to technical feasibility but also address pivotal economic realities in an increasingly censored digital environment.
While the infrastructure required to run a Nostr relay can be considered comparatively lightweight in terms of hardware demands, the operators must navigate a spectrum of operational hurdles and associated costs. Key among these are bandwidth allocation, effective spam mitigation, comprehensive security protocols, and the critical need for sustained uptime.
To ensure economic viability amidst these challenges, many relay operators have implemented various strategies, including the introduction of rate limiting mechanisms and subscription-based financial models that leverage user payments to subsidize operational costs. The conundrum remains: how can the Nostr framework evolve to permit relay operators to cultivate at least a singular relay to its fullest operational efficiency?
It is essential to note that while the trajectory of user engagement with these relays remains profoundly unpredictable—analogous to the nebulous impetus behind their initial inception—indicators within our broader economic and sociocultural contexts illuminate potential pathways to harmonizing commercial interests with user interaction through the robust capabilities of websocket relays.
A few musingsI beg you to think about the Evolutionary Trajectory of Nostr Infrastructure Leveraging BDK (Bitcoin Development Kit) and NDK (Nostr Development Kit) in the Context of Sovereign Communication Infrastructure
As the Nostr ecosystem transitions through its iterative phases of maturity, the infrastructure, notably the relays, is projected to undergo significant enhancements to accommodate an array of emerging protocols, particularly highlighted by the Mostr Bridge implementation.
Additionally, the integration of decentralized identity frameworks, exemplified by PKARR (Public-Key Addressable Resource Records), signifies a robust evolutionary step towards fostering user accountability and autonomy.
Moreover, the introduction of sophisticated filtering mechanisms, including but not limited to Set Based Reconciliation techniques, seeks to refine the user interface by enabling more granular control over content visibility and interaction dynamics.
These progressive innovations are meticulously designed to augment the overall user experience while steadfastly adhering to the foundational ethos of the Nostr protocol, which emphasizes the principles of digital freedom, uncurtailed access to publication, and the establishment of a harassment-free digital environment devoid of shadowbanning practices.
Such advancements underscore the balancing act between technological progression and ethical considerations in decentralized communication frameworks.
-
 @ d34e832d:383f78d0
2025-04-21 08:08:49
@ d34e832d:383f78d0
2025-04-21 08:08:49Let’s break it down.
🎭 The Cultural Love for Hype
Trinidadians are no strangers to investing. We invest in pyramid schemes, blessing circles, overpriced insurance packages, corrupt ministries, miracle crusades, and football teams that haven’t kicked a ball in years. Anything wrapped in emotion, religion, or political flag-waving gets support—no questions asked.
Bitcoin, on the other hand, demands research, self-custody, and personal responsibility. That’s not sexy in a culture where people would rather “leave it to God,” “vote them out,” or “put some pressure on the boss man.”
🧠 The Mindset Gap
There’s a deep psychological barrier here:
Fear of responsibility: Bitcoin doesn’t come with customer service. It puts you in control—and that scares people used to blaming the bank, the government, or the devil.
Love for middlemen: Whether it’s pastors, politicians, or financiers, Trinidad loves an “intercessor.” Bitcoin removes them all.
Resistance to abstraction: We’re tactile people. We want paper receipts, printed statements, and "real money." Bitcoin’s digital nature makes it feel unreal—despite being harder money than the TT dollar will ever be.
🔥 What Gets Us Excited
Let a pastor say God told him to buy a jet—people pledge money.
Let a politician promise a ghost job—people campaign.
Let a friend say he knows a man that can flip $100 into $500—people sign up.
But tell someone to download a Bitcoin wallet, learn about self-custody, and opt out of inflation?
They tell you that’s a scam.
⚖️ The Harsh Reality
Trinidad is on the brink of a currency crisis. The TT dollar is quietly bleeding value. Bank fees rise, foreign exchange is a riddle, and financial surveillance is tightening.
Bitcoin is an escape hatch—but it requires a new kind of mindset: one rooted in self-education, long-term thinking, and personal accountability. These aren’t values we currently celebrate—but they are values we desperately need.
🟠 A Guide to Starting with Bitcoin in Trinidad
- Understand Bitcoin
It’s not a stock or company. It’s a decentralized protocol like email—but for money.
It’s finite. Only 21 million will ever exist.
It’s permissionless. No bank, government, or pastor can block your access.
- Get a Wallet
Start with Phoenix Wallet or Blue Wallet (for Lightning).
If you're going offline, learn about SeedSigner or Trezor for cold storage.
- Earn or Buy BTC
Use Robosats or Peach for peer-to-peer (P2P) trading.
Ask your clients to pay in Bitcoin.
Zap content on Nostr to earn sats.
- Secure It
Learn about seed phrases, hardware wallets, and multisig options.
Never leave your coins on exchanges.
Consider a steel backup plate.
- Use It
Pay others in BTC.
Accept BTC for services.
Donate to freedom tech projects or communities building open internet tools.
🧭 Case In Point
Bitcoin isn’t just technology. It’s a mirror—one that reveals who we really are. Trinidad isn’t slow to adopt Bitcoin because it’s hard. We’re slow because we don’t want to let go of the comfort of being misled.
But times are changing. And the first person to wake up usually ends up leading the others.
So maybe it’s time.
Maybe you are the one to bring Bitcoin to Trinidad—not by shouting, but by living it.
-
 @ 220522c2:61e18cb4
2025-03-25 16:05:27
@ 220522c2:61e18cb4
2025-03-25 16:05:27draftoptionalAbstract
This NIP defines a new event kind for sharing and storing code snippets. Unlike regular text notes (
kind:1), code snippets have specialized metadata like language, extension, and other code-specific attributes that enhance discoverability, syntax highlighting, and improved user experience.Event Kind
This NIP defines
kind:1337as a code snippet event.The
.contentfield contains the actual code snippet text.Optional Tags
-
filename- Filename of the code snippet -
l- Programming language name (lowercase). Examples: "javascript", "python", "rust" -
extension- File extension (without the dot). Examples: "js", "py", "rs" -
description- Brief description of what the code does -
runtime- Runtime or environment specification (e.g., "node v18.15.0", "python 3.11") -
license- License under which the code is shared (e.g., "MIT", "GPL-3.0", "Apache-2.0") -
dep- Dependency required for the code to run (can be repeated) -
repo- Reference to a repository where this code originates
Format
```json {
"id": "<32-bytes lowercase hex-encoded SHA-256 of the the serialized event data>",
"pubkey": "<32-bytes lowercase hex-encoded public key of the event creator>",
"created_at":
, "kind": 1337,
"content": "function helloWorld() {\n console.log('Hello, Nostr!');\n}\n\nhelloWorld();",
"tags": [
["l", "javascript"], ["extension", "js"], ["filename", "hello-world.js"], ["description", "A basic JavaScript function that prints 'Hello, Nostr!' to the console"], ["runtime", "node v18.15.0"], ["license", "MIT"], ["repo", "https://github.com/nostr-protocol/nostr"]],
"sig": "<64-bytes signature of the id>"
} ```
Client Behavior
Clients that support this NIP SHOULD:
-
Display code snippets with proper syntax highlighting based on the language.
-
Allow copying the full code snippet with a single action.
-
Render the code with appropriate formatting, preserving whitespace and indentation.
-
Display the language and extension prominently.
-
Provide "run" functionality for supported languages when possible.
-
Display the description (if available) as part of the snippet presentation.
Clients MAY provide additional functionality such as:
-
Code editing capabilities
-
Forking/modifying snippets
-
Creating executable environments based on the runtime/dependencies
-
Downloading the snippet as a file using the provided extension
-
Sharing the snippet with attribution
References
nip #grownostr
-
-
 @ da0b9bc3:4e30a4a9
2025-04-21 07:56:29
@ da0b9bc3:4e30a4a9
2025-04-21 07:56:29Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/951022
-
 @ 220522c2:61e18cb4
2025-03-25 06:57:24
@ 220522c2:61e18cb4
2025-03-25 06:57:24
-
 @ d34e832d:383f78d0
2025-04-21 07:31:10
@ d34e832d:383f78d0
2025-04-21 07:31:10The inherent heterogeneity of relay types within this ecosystem not only enhances operational agility but also significantly contributes to the overall robustness and resilience of the network architecture, empowering it to endure systemic assaults or coordinated initiatives designed to suppress specific content.
In examining the technical underpinnings of the Nostr protocol, relays are characterized by their exceptional adaptability, permitting deployment across an extensive variety of hosting environments configured to achieve targeted operational objectives.
For example, strategically deploying relays in jurisdictions characterized by robust legal protections for free expression can provide effective countermeasures against local censorship and pervasive legal restrictions in regions plagued by oppressive control.
This strategic operational framework mirrors the approaches adopted by whistleblowers and activists who deliberately position their digital platforms or mirrored content within territories boasting more favorable regulatory environments regarding internet freedoms.
Alternatively, relays may also be meticulously configured to operate exclusively within offline contexts—functioning within localized area networks or leveraging air-gapped computational configurations.
Such offline relays are indispensable in scenarios necessitating disaster recovery, secure communication frameworks, or methods for grassroots documentation, thereby safeguarding sensitive data from unauthorized access, ensuring its integrity against tampering, and preserving resilience in the face of both potential disruptions in internet connectivity and overarching surveillance efforts.
-
 @ 866e0139:6a9334e5
2025-04-21 06:47:57
@ 866e0139:6a9334e5
2025-04-21 06:47:57Autor: Milosz Matuschek. Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier. Sie wollen die neuesten Pareto-Artikel auf einen Blick sehen (Friedenstaube & Co.), um nichts mehr zu verpassen?* Hier geht es zu unserem Telegram-Kanal.***
An Ostern begehen Christen das Hochamt ewiger Ideale. In Kirchen, die zu Hochzeiten der Pandemie geschlossen, später für Impfkampagnen wieder geöffnet wurden, wird der Sieg des Lebens über den Tod beschworen. Der Aufstand des Geistes gegen die Materie. Doch wie steht es um die Revolte des Geistes in einer Welt, die den Menschen zunehmend in die Rolle eines verwalteten Tieres drängt?
Die Revolte der Normalen
Albert Camus, einer der klarsten Köpfe des 20. Jahrhunderts, wusste: Nur wer an etwas glaubt, revoltiert. Der Revoltierende sagt Nein zu Unterdrückung und Ja zur Würde. Ohne Glauben an Werte vergiftet sich der Mensch am Ressentiment – jener toten Emotion, die weder schöpft noch heilt, sondern nur vernichtet. Oder versinkt im Nihilismus. Dieser greift auch heute um sich. Deutschland, deine Leuchttürme sind Irrlichter geworden. Inmitten einer Dauerkrise, die jeden Normalzustand zersetzt, bleibt eine Frage offen: Wie gesund bleibt der Mensch in einem kranken System? Wie lange dauert es, bis Normalität selbst als Revolte gilt?
Camus schrieb:
„Wenn man an nichts glaubt, wenn nichts Sinn hat und wir keinen Wert konstatieren können, dann ist alles möglich und nichts hat Bedeutung.“
In einer Welt, in der Gesundheitspolitik zur Farce, Wissenschaft zur Ideologie und Aufarbeitung zur Fortsetzung der Propaganda mutiert, wird die Revolte der Normalen zur letzten Verteidigungslinie der Freiheit.
https://www.youtube.com/watch?v=Y2roiEvbPuU
Das Leid der Revoltierenden
Die Revolte ist kein Spaziergang. Sie schmerzt. Sie kostet Freunde, Ansehen, Karriere. Aber sie schenkt eine ungeahnte Kraft: Die Entdeckung, dass der Impuls zum Leben stärker ist als zum Tod. Das Wunder von Ostern, die Auferstehung, ist im Innersten die Revolte der Lebendigkeit gegen die Herrschaft des Todes. Der Märtyrer Jesus nimmt die Sünden und Leiden der Welt auf sich – ein menschgewordener Widerstand, der durch seine Hingabe unsterblich wird.
Sein "Verbrechen"? Er stellte sich zugleich gegen die geistige und politische Elite seiner Zeit. Gegen Besatzer, Schriftgelehrte, Pharisäer, Frühbürger. Heute wäre Jesus wohl ein Querdenker, ein Reichgottesbürger, ein Verschwörungstheoretiker. Mindestens ein Rechter. Vielleicht ein antisemitischer Spinner, der es wagte, eine Alternative zum bestehenden Glaubenssystem zu etablieren.
„Wer an mich glaubt, wird leben“, sagte Jesus. Man kann es so lesen:\ Wer an die verkörperten Werte glaubt – Wahrheit, Freiheit, Liebe –, wird leben. Denn wer an einen Wert glaubt, macht ihn lebendig. Der Nihilist hingegen fügt sich ein, wird Stein in der Mauer des Systems.
Camus brachte es auf den Punkt:
„Lieber stehend sterben als knieend leben.“
In Zeiten, in denen Friedenstreiber als Nazis diffamiert werden und Protestierende als Pathologische gelten, bleibt die stille Revolte des Individuums das letzte unzerstörbare Element.
Die Psy-Op der Aufarbeitung
Nach der Inszenierung des Corona-Spektakels erleben wir die nächste Bühne: Die Aufarbeitung durch die Täter selbst. Eine theatralische Umarmung des eigenen Versagens, mit Bundesverdienstkreuz und Download-Gesichtsausdruck bei Frau Buyx inklusive. Wenn Corona eine Psy-Op war, warum sollte nicht auch seine Aufarbeitung Teil der Psy-Op sein? Die Strukturen erinnern an Rosenhan, Milgram und das Stanford Prison Experiment:
- Etikettierung der Kritiker als Verrückte.
- Pathologisierung der Revolte als Krankheit.
- Belohnung der Kollaborateure mit Orden und Posten.
Ein Lehrbuch der totalitären Psychologie.
https://www.youtube.com/watch?v=XTBYWPLXrTk
Immunologische Reaktionen eines sterbenden Systems
Während die Panzer-Osterhasen rollen, also die Neuvariante des Impfspritzbesteck-Gebäcks der letzten Krise, offenbart sich die Wahrheit: Das System hat seine eigene Bevölkerung beschossen. Friendly Fire unter falscher Flagge.\ Kollateralschaden im Namen von Volksgesundheit und Solidarität.

Jetzt dasselbe nochmal in Tarnfleck statt Weißkittel.
Was bleibt?
Demut.\ Selbstständigkeit.\ Verbindungen, die nicht von Zertifikaten abhängen.\ Der stille Aufbau von Netzwerken jenseits der Anstaltsordnung.
Unabhängiger machen kann man sich zum Beispiel bei Vorträgen und Seminaren von Michael Ballweg, der immer noch in einen kafkaesken Prozess verwickelt ist.
Meine Stimme erhebe ich in Zukunft auch mit der FSUS (Free Speech Union Switzerland) im Rücken, einem Verein der u.a. Rechtshilfe für verfolgte Freiredner organisiert. Bei Interesse an einer Mitgliedschaft erfahren Sie hier mehr.
Oder wie manche sagen: “Buy Bitcoin and focus on your craft.”
Die letzte Revolte
Wer heute zweifelt, beweist Charakter.\ Wer heute fragt, zeigt Rückgrat.\ Wer heute eigene Gedanken wagt, revoltiert bereits.
Wenn wir uns verbinden, werden wir das neue Gesicht der Welt.
Ostern erinnert uns daran:\ Die größte Revolte ist das Aufstehen in einer Welt, die uns niederdrücken will.
Nicht die angepasstesten überleben, sondern die Standhaftesten.\ Nicht die Lautesten, sondern die Wahrhaftigsten.\ Nicht die, die folgen, sondern die, die aufstehen.
In diesem Sinne:
Frohe Auferstehung.
https://www.youtube.com/watch?v=vbH9YacSi2o
LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt.
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: friedenstaube@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ 4259e401:8e20e9a6
2025-03-24 14:27:27
@ 4259e401:8e20e9a6
2025-03-24 14:27:27[MVP: Gigi! How do I lightning prism this?]
If I could send a letter to myself five years ago, this book would be it.
I’m not a Bitcoin expert. I’m not a developer, a coder, or an economist.
I don’t have credentials, connections, or capital.
I’m a blue-collar guy who stumbled into Bitcoin almost exactly four years ago, and like everyone else, I had to wrestle with it to understand it.
Bitcoin is one of the most misunderstood, misrepresented, and misinterpreted ideas of our time - not just because it’s complex, but because its very structure makes it easy to distort.
It’s decentralized and leaderless, which means there’s no single voice to clarify what it is or defend it from misinformation.
That’s a feature, not a bug, but it means that understanding Bitcoin isn’t easy.
It’s a system that doesn’t fit into any of our existing categories. It’s not a company. It’s not a product. It’s not a government.
There’s no marketing department, no headquarters, no CEO.
That makes it uniquely resistant to corruption, but also uniquely vulnerable to disinformation.
Whether through negligence or malice, Bitcoin is constantly misunderstood - by skeptics who think it’s just a Ponzi scheme, by opportunists looking to cash in on the hype, by scammers who use the name to push worthless imitations, and by critics who don’t realize they’re attacking a strawman.
If you’re new to Bitcoin, you have to fight through layers of noise before you can even see the signal.
And that process isn’t instant.
Even if you could explain digital signatures off the top of your head, even if you could hash SHA-256 by hand, even if you had a perfect technical understanding of every moving part - you still wouldn’t get it.
Bitcoin isn’t just technology. It’s a shift in incentives, a challenge to power, an enforcer of sovereignty. It resists censorship.
A simple open ledger - yet it shakes the world.
Archimedes asked for a lever and a place to stand, and he could move the world.
Satoshi gave us both.
The lever is Bitcoin - an economic system with perfect game theory, incorruptible rules, and absolute scarcity.
The place to stand is the open-source, decentralized network, where anyone can verify, participate, and build without permission.
And what comes out of this seemingly simple equation?
The entire rearchitecture of trust. The separation of money and state.
A foundation upon which artificial intelligence must negotiate with the real world instead of manipulating it.
A digital economy where energy, computation, and value flow in perfect symmetry, refining themselves in an endless virtuous cycle.
Bitcoin started as a whitepaper.
Now it’s a lifeline, an immune system, a foundation, a firewall, a torch passed through time.
From such a small set of rules - 21 million divisible units, cryptographic ownership, and a fixed issuance schedule - emerges something unstoppable.
Something vast enough to absorb and constrain the intelligence of machines, to resist the distortions of human greed, to create the rails for a world that is freer, more sovereign, more aligned with truth than anything that came before it.
It’s proof that sometimes, the most profound revolutions begin with the simplest ideas. That’s why this book exists.
Bitcoin isn’t something you learn - it’s something you unlearn first.
You start with assumptions about money, value, and authority that have been baked into you since birth. And then, piece by piece, you chip away at them.
It’s like peeling an onion – it takes time and effort.
*And yes, you might shed some tears! *
At first, you might come for the speculation. A lot of people do. But those who stay - who actually take the time to understand what’s happening - don’t stay for the profits.
They stay for the principles.
If you’re holding this book, you’re somewhere on that journey.
Maybe you’re at the very beginning, trying to separate the signal from the noise.
Maybe you’ve been down the rabbit hole for years, looking for a way to articulate what you already know deep in your bones.
Either way, this is for you.
It’s not a technical manual, and it’s not a sales pitch. It’s the book I wish I had when I started.
So if you’re where I was, consider this a message in a bottle, thrown back through time. A hand reaching through the fog, saying:
“Keep going. It’s worth it.”
Preface The End of The Beginning
March 2025.
The moment has arrived. Most haven’t even noticed, let alone processed it. The United States is setting up a Bitcoin (Bitcoin-only!) strategic reserve.
It’s not a theory. Not an idea. The order is signed, the ink is dried.
The people who have been wrong, over and over (and over!) again - for years! - fumble for explanations, flipping through the wreckage of their previous predictions:
“Bubble…’’ “Fad…” “Ponzi…”
No longer.
The same analysts who once sneered are now adjusting their forecasts to protect what’s left of their credibility. Those who dismissed it are now trapped in a slow, humiliating realization: Bitcoin does not require their approval.
It never did.
Something fundamental has shifted, and the air is thick with a paradoxical cocktail of triumph and panic. Bitcoiners saw this coming. Not because they had insider information, but because they understood first principles when everyone else was still playing pretend.
Bitcoin was never just surviving.
It was infiltrating.
The question is no longer whether Bitcoin will succeed.
It already has.
The only question that remains is who understands, and who is still in denial.
Think back to 2022.
At its peak, FTX was one of the world’s largest cryptocurrency exchanges, valued at $32 billion and backed by blue-chip investors. It promised a sophisticated, institutional-grade trading platform, attracting retail traders, hedge funds, and politicians alike. Sam Bankman-Fried, with his disheveled hair and cargo shorts, was its eccentric figurehead, a billionaire who slept on a bean bag and spoke of philanthropy.
Then the illusion shattered.
FTX collapsed overnight, an implosion so violent it left an entire industry scrambling for cover. One moment, Sam Bankman-Fried was the golden boy of crypto - genius quant, regulatory darling, effective altruist™.
The next, he was just another fraudster in handcuffs.
Billions vanished. Customers locked out. Hedge funds liquidated.
Politicians who had once taken photos with SBF and smiled at his political donations, suddenly pretended they had no idea who he was. The same regulators who were supposed to prevent disasters like this stood slack-jawed, acting as if they hadn’t been having closed-door meetings with FTX months before the collapse.
But FTX wasn’t just a scandal, it was a filter.
If you were Bitcoin-only, with your satoshis in cold storage, you didn’t even flinch. From your perspective, nothing important changed:
A new Bitcoin block still arrived every ten minutes (on average). The supply cap of 21 million bitcoins remained untouched. Ownership was still protected by public/private key cryptography.
You were literally unaffected.
You had already updated your priors:
“If you don’t hold your own keys, you own nothing.” “Bitcoin is not ‘crypto’.” “’Crypto’ is a casino.”
FTX was just another financial fire, another chapter in the never-ending saga of people trusting systems that had already proven themselves untrustworthy.
That moment was a prelude.
The U.S. Bitcoin pivot is the paradigm shift.
The Eukaryotic Revolution Is Upon Us
In biology, abiogenesis is when life emerged from non-life - a fragile, uncertain process where the first microscopic self-replicators struggled to survive against hostile conditions. That was Bitcoin’s early history. It had to fight for its existence, attacked by governments, dismissed by economists, ridiculed by mainstream media.
But it survived.
That era is over. We have entered the Eukaryotic Revolution.
This is the moment in evolutionary history when simple lifeforms evolved into something structurally complex - organisms with nuclei, internal scaffolding, and the ability to form multicellular cooperatives and populate diverse ecosystems. Once this transformation happened, there was no going back. Bitcoin is going through its own Eukaryotic leap.
Once an outsider, dismissed and ridiculed, it is maturing into an integrated, resilient force within the global financial system.
On March 2, 2025, the Trump administration announced a Crypto Strategic Reserve.
At first, it wasn’t just Bitcoin - it included XRP, SOL, and ADA, a desperate attempt to appease the altcoin industry. A political move, not an economic one.
For about five minutes, the broader crypto industry cheered. Then came the pushback.
Bitcoiners called it immediately: mixing Bitcoin with centralized altcoin grifts was like adding lead weights to a life raft.
Institutional players rejected it outright: sovereign reserves need hard assets, not tech company tokens. The government realized, almost immediately, that it had made a mistake.
By March 6, 2025, the pivot was complete.
Strategic Bitcoin reserve confirmed. The President signed an executive order, and legislation has been introduced in the United States House of Representatives.
The U.S. government’s official bitcoin policy: hold, don’t sell. Look for ways to acquire more.
Altcoins relegated to second-tier status, treated as fundamentally separate from and inferior to bitcoin. The government’s official policy: sell, and do not actively accumulate more (ouch!).
“Bitcoin maximalism” – the belief that any cryptocurrency other than bitcoin lies on a spectrum between “bad idea” and outright scam - wasn’t vindicated by debate.
It was vindicated by economic reality.
When the government was forced to choose what belonged in a sovereign reserve, it wasn’t even close. Bitcoin stood alone.
“There is no second best.” -Michael Saylor
Who This Book Is For: The Three Types of Readers
You’re here for a reason.
Maybe you felt something shift.
Maybe you saw the headlines, sensed the undercurrents, or simply couldn’t ignore the growing drumbeat any longer.
Maybe you’ve been here all along, waiting for the world to catch up.
Whatever brought you to this book, one thing is certain: you’re curious enough to learn more.
Bitcoin forces a reevaluation of assumptions - about money, trust, power, and the very foundations of the economic order. How much of that process you’ve already undergone will determine how you read these pages.
1. The Layperson → new, curious, maybe skeptical. Bitcoin probably looks like chaos to you right now. One person says it’s the future. Another says it’s a scam. The price crashes. The price doubles. The news is either breathless excitement or total doom. How the hell are you supposed to figure this out?
If that’s you, welcome.
This book was built for you.
You don’t need to be an economist, a technologist, or a finance geek to understand what’s in these pages. You just need an open mind and the willingness to engage with new ideas - ideas that will, if you follow them far enough, challenge some of your deepest assumptions.
Bitcoin is not an investment. Bitcoin is not a company. Bitcoin is not a stock, a trend, or a passing phase.
Bitcoin is a paradigm shift. And by the time you reach the last page, you won’t need to be convinced of its importance. You’ll see it for yourself.
2. The Student → understand the basics, want to go deeper.
You’ve already stepped through the door.
You’ve realized Bitcoin is more than just digital gold. You understand decentralization, scarcity, censorship resistance… But the deeper you go, the more you realize just how much there is to understand.
3. The Expert → You’ve been in the game for years.
You’ve put in the time.
You don’t need another book telling you Bitcoin will succeed. You already know.
You’re here because you want sharper tools.
Tighter arguments.
A way to shut down nonsense with fewer words, and more force.
Maybe this book will give you a new way to frame an idea you’ve been struggling to convey.
Maybe it will help you refine your messaging and obliterate some lingering doubts in the minds of those around you.
Or maybe this will simply be the book you hand to the next person who asks, “Okay… but what’s the deal with Bitcoin?” so you don’t have to keep explaining it from scratch.
*If you’re already deep in the weeds, you can probably skip Part I (Foundations) without missing much - unless you’re curious about a particular way of putting a particular thing. *
Part II (Resilience) is where things get more interesting. Why you want to run a node, even if you don’t know it yet. The energy debate, stripped of media hysteria. The legend of Satoshi, and what actually matters about it.
If you’re a hardcore cypherpunk who already speaks in block heights and sending Zaps on NOSTR, feel free to jump straight to Part III (The Peaceful Revolution). Chapter 15, “The Separation of Money and State” is where the gloves come off.
Bitcoin isn’t just a technology. Bitcoin isn’t just an economic movement. Bitcoin is a lens.
And once you start looking through it, the world never looks the same again.
This book will teach you what Bitcoin is, as much as it will help you understand why Bitcoiners think the way they do.
It isn’t just something you learn about.
Especially not in one sitting, or from one book.
It’s something you grow to realize.
Regardless of which category you fall into, you’ve already passed the first test.
You’re still reading.
You haven’t dismissed this outright. You haven’t scoffed, rolled your eyes, or walked away. You’re at least curious.
And that’s all it takes.
Curiosity is the only filter that matters.
The rest takes care of itself.
The Essential Role of Memes Memes won the narrative war - it wasn’t textbooks, research papers, or whitepapers that did it. Bitcoin spread the same way evolution spreads successful genes - through replication, variation, and selection. Richard Dawkins coined the term “meme” in The Selfish Gene, describing it as a unit of cultural transmission - behaving much like a gene. Memes replicate, mutate, and spread through culture. Just as natural selection filters out weak genes, memetic selection filters out weak ideas.
But Bitcoin memes weren’t just jokes.
They were premonitions.
The most powerful ideas are often compact, inarguable, and contagious - and Bitcoin’s memes were all three. They cut through complexity like a scalpel, distilling truths into phrases so simple, so undeniable, that they burrowed into the mind and refused to leave.
"Bitcoin fixes this." "Not Your Keys, Not Your Coins." "Number Go Up."
Each of these is more than just a slogan.
They’re memetic payloads, compressed packets of truth that can carry everything you need to understand about Bitcoin in just a few words.
They spread through conversations, through tweets, through shitposts, through relentless repetition.
They bypassed the gatekeepers of financial knowledge, infecting minds before Wall Street even understood what was happening.
And they didn’t just spread.
They reshaped language itself.
Before Bitcoin, the word fiat was a sterile economic term, borrowed from Latin, meaning "by decree." It had no weight, no controversy - just a neutral descriptor for government-issued money.
But Bitcoiners forced a memetic shift.
They didn’t just make fiat mainstream.
**They made it radioactive. **
They stripped away the academic detachment and revealed its true essence:
money because I said so.
No backing. No inherent value.
Just a command.
And of course, an unspoken threat -
"Oh, and by the way, I have a monopoly on violence, so you’d better get on board."
This wasn’t just linguistic evolution; it was a memetic coup.
Bitcoiners took a sterile term and injected it with an unavoidable truth: fiat money exists not because it is chosen, but because it is imposed.
Central banks, governments, and financial institutions now use the term fiat without a second thought.
The meme has done its work.
A word that was once neutral, now carries an implicit critique - a quiet but persistent reminder that there is an alternative.
Bitcoin didn’t just challenge the financial system - it rewired the language we use to describe it.
“Money printer go BRRRRRR" did more damage to the Fed’s reputation than a thousand Austrian economics treatises ever could.
Memes exposed what balance sheets and policy reports tried to obscure. They turned abstract economic forces into something visceral, something undeniable.
And now - they are historical markers of the shift, the fossil record of our collective consciousness coming to terms with something fundamentally new in the universe.
The old world relied on authority, institutional credibility, and narrative control.
Bitcoin broke through with memes, first principles, and lived experience.
This wasn’t just an ideological battle.
It was an evolutionary process.
The weaker ideas died. The strongest ones survived.
Once a meme - in other words, an idea - takes hold, there is nothing - no law, no regulation, no institution, no government - that can stop it.
Bitcoin exists. It simply is.
And it will keep producing blocks, every ten minutes, whether you get it or not.
This book isn’t a trading manual.
It won’t teach you how to time the market, maximize your gains, or set up a wallet.
It’s a carefully curated collection of memes, giving you the prerequisite mental scaffolding to grok the greatest monetary shift in human history.
A shift that has already begun.
The only thing to decide is whether you’re watching from the sidelines or whether you’re part of it.
The rest is up to you.
How This Book Is Structured Bitcoin spreads like an evolutionary force - through memes. Each chapter in this book isn’t just an idea, it’s a memetic payload, designed to install the concepts that make Bitcoin inevitable. The book is broken into three phases:
*I. Foundations *** Memes as Mental Antivirus The first layer cuts through noise and filters out distractions. "Bitcoin Only" is the first test - if you get this one wrong, you waste years chasing ghosts. "Don’t Trust, Verify" rewires how you think about truth. And "Not Your Keys, Not Your Coins"? If you learn it the hard way, it’s already too late.
II. Resilience Memes as Weapons in the Information War Here’s where Bitcoin earns its survival. "Shitcoiners Get REKT" is a law, not an opinion. "Fork Around and Find Out" proves that you don’t change Bitcoin - Bitcoin changes you. "Antifragile, Unstoppable" shows how every attack on Bitcoin has only made it stronger.
III. The Peaceful Revolution ** Memes as Reality Distortion Fields By now, Bitcoin isn’t just an asset - it’s a lens. "Separation of Money and State" isn’t a theory; it’s happening in real time. "Fix the Money, Fix the World" isn’t a slogan; it’s a diagnosis. And "Tick Tock, Next Block"? No matter what happens, Bitcoin keeps producing blocks.
These aren’t just memes. They’re scaffolding for a new way of thinking. Each one embeds deeper until you stop asking if Bitcoin will succeed - because you realize it already has.
Next: Chapter 1: Bitcoin Only. ** For now, it’s a heuristic - an efficient filter that separates signal from noise, with minimal effort.
But by the time you finish this book, it won’t be a heuristic anymore.
It will be something you know.Welcome to the rabbit hole.
-
 @ 866e0139:6a9334e5
2025-03-24 10:51:52
@ 866e0139:6a9334e5
2025-03-24 10:51:52Autor: Milosz Matuschek. Dieser Beitrag wurde mit dem Pareto-Client geschrieben.
Seit Sonntag (zu allem Glück auch noch meinem 45. Geburtstag) ist bei mir noch ein bisschen mehr los als sonst – und das liegt an Ihnen. Der Aufruf zur Gründung der „Friedenstaube“, einer unzensierbaren Friedenspublikation mit bekannten Stimmen aus der kritischen Szene, der Friedensbewegung und von Bürgerjournalisten ist bei Ihnen auf mehr als nur offene Ohren gestoßen! Ich bin regelrecht geplättet von den vielen Reaktionen, die ich noch gar nicht alle beantworten konnte.
Ich danke Ihnen herzlich für das Vertrauen in mich (auch wenn ich natürlich stark auf die Autoren angewiesen bin) und die überwältigenden Reaktionen: Es sind hunderte Abonnements für den Newsletter eingegangen, darunter einige bezahlte Abos und Förderabos und auch die ersten Genossenschaftsanteile wurden gezeichnet! Was mich besonders freut: Gut zehn weitere freiwillige Autoren wollen mitmachen und arbeiten bereits an den ersten Texten. Damit darf ich schon jetzt verkünden, dass die Genossenschaft definitiv gegründet werden kann, die Friedenstaube wird fliegen. Wie hoch und wie weit, das liegt dann nun nur noch in unser aller Hände.
Der Anfang ist jedenfalls gemacht. Die nächsten Wochen werden besonders arbeitsintensiv, ich bitte Sie um etwas Geduld: Aufbau einer Kernredaktion, Organisation der Abläufe, technologische Entwicklungsarbeiten, Genossenschaftsgründung etc. stehen jetzt auf der Agenda. Mit Tom-Oliver Regenauer darf ich den ersten Autor im redaktionellen Kernteam verkünden, der sich nicht nur große Verdienste im Schreiben erarbeitet hat (siehe u.a. sein Buch Hopium) sondern auch über Managementerfahrung verfügt; mit weiteren helfenden Händen bin ich im Gespräch.
Ich freue mich auf die (auch für mich) neue Erfahrung, quasi aus dem Nichts eine Publikation mit Redaktionsbetrieb und freien Autoren auf einer gänzlich neuen technologischen Infrastruktur aufzubauen. Es wäre illusorisch zu glauben, dass alles glatt gehen wird, denn wir starten quasi „on the go“, aber im Fall von Frieden oder Krieg gilt es, keine Zeit verstreichen zu lassen. Ich arbeite nach dem Motto „Tun, statt reden; zeigen, statt ankündigen; liefern, statt versprechen“.
Die ersten Texte zum Thema Frieden sind bereits publiziert, ein halbwegs geordneter Betrieb sollte ab April realistisch sein. Die Liste der Autoren wird regelmäßig aktualisiert, schauen Sie gerne hier (oder noch besser: hier) immer wieder herein. Dort finden Sie auch noch mal alle Infos, wenn Sie die Friedenstaube unterstützen wollen. Ab 1000 Euro/CHF werden Sie Genossenschafter, also Verleger!**
Auch an die bisherigen Unterstützer des Pareto-Projekts, der technologischen Basis der Friedenstaube, will ich hiermit schon etwas zurückgeben: Alle Spender für Pareto werden die Friedenstaube immer kostenlos lesen können. Sie, die Leser dieser Publikation haben die technologische Basis mit aufgebaut, die uns zur weltweit ersten, zensursicheren Friedenspublikation macht. Uns Autoren steht damit ein kompetentes Support-Team von inzwischen über zehn Entwicklern (und weiteren Helfern) an der Seite, welche die Friedenstaube am Fliegen halten werden.
Kontaktieren Sie mich gerne zu allen Fragen (je kürzer die Mail, desto früher kommt die Antwort): milosz\@pareto.space oder kontakt\@idw-europe.org
JETZT ABONNIEREN:
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel in Ihr Postfach, vorerst für alle kostenfrei, wir starten gänzlich ohne Paywall. (Die Bezahlabos fangen erst zu laufen an, wenn ein Monetarisierungskonzept für die Inhalte steht).
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF/EURO werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):
Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie mich an: milosz@pareto.space oder kontakt@idw-europe.org.
Was bewegt mich beim Thema Krieg und Frieden?
Erlauben Sie mir einen kurzen persönlichen Prolog: Ich stamme aus Schlesien. Mein Urgroßvater kämpfte im I. Weltkrieg bei Verdun. Mein Großvater wurde in die Wehrmacht eingezogen, kämpfte im Partisanenkrieg in Jugoslawien, verlor Hand und Auge. Ein Bruder meiner Großmutter entzog sich und landete in Dachau. Ich kenne meine Familiengeschichte nur in groben Umrissen, vielen wird es ähnlich gehen. Einige meiner schlesischen Vorfahren waren später vor allem Lokführer. Aufgrund der bewegten schlesischen Geschichte wechselten sie mehrfach die Uniform. Die Tätigkeit und Fahrstrecke blieb die gleiche. Für wen oder was kämpften sie in Kriegen in welchen Uniformen? Vermutlich wussten sie es selbst nicht.
Auch ich könnte heute nicht genau sagen, welche Interessen und Mächte die Kriegsmaschinerie bedienen. Doch ich wüsste es gerne und Sie vielleicht auch. Kämpfen ohne letztlich zu wissen für wen und warum: Wozu? Krieg simuliert Sinn und Notwendigkeit und lässt einen am Ende mit den großen Fragen allein, ahnungslos gestorben im Schützengraben. Zivilisatorisch ist das ein Offenbarungseid.
Bin ich ein totaler Anti-Militarist? Ich glaube nicht. Ich habe nichts gegen die Idee privaten Waffenbesitzes. Ich kann der Idee der Landesverteidigung durchaus etwas abgewinnen. Den Wehrdienst habe ich bewusst nicht verweigert. Ich wollte die Erfahrung machen. Hier schreibt also auch ein Obergefreiter a. D. eines bayerischen Gebirgspionierbataillons bei Rosenheim mit bronzener Schützenschnur, der am MG durchaus treffsicher war. Aber eben auch jemand, den der Wehrdienst zum Teil-Pazifisten gemacht hat. Mir war nach dem Grundwehrdienst klar: Wir sind eine Gurkentruppe, reines Kanonenfutter. 20-jährige Grünschnäbel mit zu viel Testosteron und Hollywood in den Gliedern, aber wenig Ahnung.
Ich war also einer, der sich verlässlich mit anderen beim Orientierungslauf im Wald verirrte; einer, der mit anderen übermüdet beim ersten Wachdienst einpennte (und damit im Ernstfall den Tod im Schlaf kennengelernt hätte, denn just erfolgte ein simulierter „Angriff“); einer, der auch mal übernächtigt sein Gewehr vor dem Zelt vergaß (wir sollten dem G3 den Namen unserer damaligen Freundin geben – wie pervers – ich vergaß also „Petra“ vor dem Zelt) und schließlich einer, der die meiste Zeit des Dienstes fürs Vaterland letztlich mit dem Servieren von Getränken und Schinkennudeln im Offizierskasino verbrachte und die institutionalisierten Alkoholiker der Bundeswehr bei Laune hielt („it ain’t much, but it was honest work“).
Anders gesagt: Krieg – spätestens seitdem: ohne mich. Auch wenn ich gerne Ernst Jünger lese und zitiere (er war einfach ein großartiger Chronist und lebendiger Geist), seinen abenteuerlustigen Militarismus kreide ich ihm an und rufe ihm posthum hinterher: man muss nicht erst einen Sohn im Krieg verloren haben, um zum Pazifisten zu werden.
Weitere Störgefühle tauchten auf: In meiner Dissertation durfte ich mich u.a. mit philosophischen Theorien zum Gesellschaftsvertrag (u.a. Kant, Rousseau, Locke und Hobbes sind hier zu nennen) beschäftigen. Dies brachte mein Staatsverständnis gerade bei der Kriegsfrage noch mehr durcheinander. Wenn Mindestziel der Staatsgründung innere und äußere Sicherheit sind, aber letztlich nicht der Staat den Bürger, sondern der Bürger den Staat schützt, wozu sich dann eine Schutzmacht erfinden, die einen am Ende durch den Fleischwolf jagt? Hobbes setzte zumindest auf Söldner.
Kriege werden mit Lügen begonnen, wusste Julian Assange. Können Sie mit Wahrheit beendet oder gar verhindert werden? Seit Walter Lippmanns „Liberty and the News“ von 1920 weiß man spätestens, dass gesicherte Information im Krieg das seltenste Gut ist. Sagt Lippmann als oberster Mainstream-Journalist und Einflüsterer der Mächtigen. Jeder Journalist muss hier ein Störgefühl entwickeln, der Leser noch mehr. Der Journalist der Nachrichtenagentur ist selten im Geschehen sondern wird vom heimischen Militär gebrieft, sein Bericht landet dann in den Newstickern und Redaktionen. Die Kriegsmaschinerie produziert also auch ihre eigene Sicht auf die Dinge, die sie den Bürgern als die Realität verkauft.
Kein Wunder, dass jede abweichende Information massiv bekämpft werden muss. Im Krieg ist Zweifel gleich Verrat, quasi unsolidarisches Sektierertum und Wehrkraftzersetzung, wenn nicht Feindbegünstigung. Der kritische Journalist steht in Ausnahmezuständen, wie man schon bei Corona sehen konnte, automatisch aus Staatssicht im Lager des Feindes und wird entsprechend behandelt. Zensursicheres Publizieren ist dann nicht nur ein nettes feature, sondern notwendige Basisvoraussetzung. Vor kurzem war Twitter/X nicht mehr zugänglich wegen massiven Cyberattacken. Wenn dann noch Rundfunk und Presse auf der Propagandawelle surfen und die Plattformzensur wieder zuschlägt, wird das Angebot schnell dünn.
Wem aber dient Zensur und Propaganda? Die aktuelle Lage im Russland-Ukraine-Konflikt ist auch Gelegenheit, um zu zeigen: Es sind eben nicht nur staatliche Interessen, die hier verhandelt werden, sondern es muss (wieder mal) eine andere Entität mit am Tisch sitzen, man nenne sie Deep State oder wie auch immer. Europäische Eliten dienen offensichtlich Fremdinteressen, wenn sie mit Aufrüstungsplänen Volksvermögen verspekulieren oder darin (wie von der Leyen) ein notwendiges „Investment“ sehen. Von wem werden wir letztlich regiert? Auch diesem Themen-Komplex werde ich mich in der Friedenstaube nähern.
Es gibt viel zu tun, aber für mich ist klar: Frieden ist ohne Wahrheit nicht zu bekommen, deshalb ist Wahrheitssuche auch immer Friedenssuche, wie Wahrheitsliebe letztlich Friedensliebe ist.
Gerade fallen auch im Mainstream die Corona-Lügen zur Labortheorie in sich zusammen, fünf Jahre nach Ausrufung der Pandemie. Der Frieden hat nur eine Chance, wenn es uns gelingt, die Lügen nun möglichst synchron zu den Geschehnissen aufzudecken und zu dokumentieren.
Das ist mein persönlicher Wunsch, mit dem ich die Friedenstaube fliegen lasse.
Was ist Ihrer? Schreiben Sie es gerne in die Kommentare. Welche Erwartungen, Wünsche haben Sie an uns? Liebe Autoren: Was ist euer Beweggrund, für den Frieden zur Feder zu greifen?
Zeichnen Sie jetzt “Friedensanleihen”. Werden Sie Genossenschafter und Verleger der Friedenstaube ab 1000 Euro/CHF. Es können mehrere Anteile pro Person gezeichnet werden, es bleibt bei einem Stimmrecht pro Kopf. milosz\@pareto.space
P.S: Mit diesem Text testen wir die Newsletterfunktion erstmals an mehrere Hundert Mailadressen. Wenn Sie die Friedenstaube abonniert haben, sollten Sie diesen Artikel per Mail bekommen haben.
ANZEIGE:
Sie suchen nach dem einfachsten Weg, Bitcoin zu kaufen und selbst zu verwahren?* Die* Relai-App ist Europas erfolgreichste Bitcoin-App.* Hier kaufen Sie Bitcoin in wenigen Schritten und können auch Sparpläne einrichten. Niemand hat Zugriff auf Ihre Bitcoin, außer Sie selbst.* Relai senkt jetzt die Gebühr auf 1%, mit dem Referral-Code MILOSZ sparen Sie weitere 10%. (keine Finanzberatung). Disclaimer wg. EU-Mica-Regulierung: Die Dienste von Relai werden ausschließlich für Einwohner der Schweiz und Italiens empfohlen.
Join the marketplace of ideas! We are building a publishing ecosystem on Nostr for citizen-journalism, starting with a client for blogging and newsletter distribution. Sound money and sound information should finally be in the hands of the people, right? Want to learn more about the Pareto Project? Zap me, if you want to contribute (all Zaps go to the project).
Are you a publication or journalist and want to be part of it, test us, migrate your content to Nostr? Write to team@pareto.space**
Not yet on Nostr and want the full experience? Easy onboarding via Start.
Pareto has started a crowdfunding campaign on Geyser. We were in the Top 3 in February, thank you for the support!
-
 @ 1beecee5:d29d2162
2025-04-21 06:30:55
@ 1beecee5:d29d2162
2025-04-21 06:30:55 -
 @ b0137b96:304501dd
2025-04-21 05:54:41
@ b0137b96:304501dd
2025-04-21 05:54:41Streaming has revolutionized how we consume entertainment, offering unparalleled access to diverse content worldwide. With the rise of theBest OTT Platform options, audiences can enjoy their favorite Hollywood, Bollywood, and regional films anytime, anywhere. However, for many viewers, language can be a barrier to fully experiencing international cinema. That’s where innovative platforms step in, bridging the gap between global content and regional audiences.
If you're searching for theBest OTT Platform that delivers high-quality international and regional content, we’ve got you covered. Let’s explore four leading platforms—Dimension on Demand (DOD), Hoichoi, Olly Plus, and Aha Video—that are transforming the Indian entertainment landscape.
Dimension on Demand (DOD) – The Best OTT Platform for Hollywood in Your Language Among the many platforms available, Dimension on Demand (DOD) stands out as theBest OTT Platform for movie lovers who enjoy global cinema in their native tongue. Unlike other platforms that focus solely on regional or Bollywood content, DOD specializes in offering Hollywood movies dubbed in 9 languages like Hindi, Telugu, Tamil, Bangla, Malayalam, Bhojpuri, English, Kannada, and Marathi. This means you can enjoy blockbuster hits, critically acclaimed masterpieces, and thrilling action films—all in the comfort of your language.
What makes DOD truly unique? A vast library of Hollywood movies dubbed in Indian languages Seamless user experience with high-definition streaming Personalized recommendations based on viewer preferences Accessible across multiple devices—smart TVs, mobiles, and laptops A growing collection that ensures fresh content for movie enthusiasts Beyond its impressive collection, DOD ensures that audiences across India can experience world-class entertainment without language barriers. If you love Hollywood but prefer watching in your native language, DOD is undoubtedly the Best OTT Platform.
Hoichoi – A Must-Have for Bengali Entertainment Hoichoi (https://www.hoichoi.tv/)has become a go-to OTT platform for Bengali audiences, offering an impressive mix of movies, web series, and original content. With a strong focus on Bengali-language storytelling, it delivers a diverse collection ranging from classic films to modern thrillers.
Why Choose Hoichoi? Extensive collection of Bengali films and web series Exclusive Hoichoi Originals with gripping storytelling A mix of contemporary and classic Bengali cinema With its continuous addition of fresh content and commitment to Bengali storytelling, Hoichoi has solidified its position as a top-tier platform for regional entertainment lovers.
Olly Plus – A Celebration of Odia Content Olly Plus (https://www.youtube.com/OllyPlus) is Odisha’s dedicated OTT platform, catering specifically to Odia-speaking audiences. It features a rich selection of Odia movies, music, and podcasts, making it a hub for cultural and entertainment enthusiasts.
What Sets Olly Plus Apart? Exclusive Odia-language movies, music, and short films A platform dedicated to preserving and promoting Odia storytelling Inclusion of music, podcasts, and cultural content With Odia entertainment often underrepresented in mainstream media, Olly Plus plays a crucial role in bringing high-quality Odia content to its audience.
Aha Video – The Ultimate Destination for Telugu & Tamil Viewers Aha Video (https://www.aha.video/) has carved a niche in the Best OTT Platform industry by delivering high-quality Telugu and Tamil entertainment. From blockbuster movies to gripping web series, Aha Video ensures South Indian audiences have access to exclusive content tailored to their preferences.
Why Aha Video is a Must-Try? Exclusive Telugu and Tamil movie collections Original series that cater to South Indian storytelling A strong focus on South Indian cinema and entertainment Its commitment to regional cinema ensures that fans of Telugu and Tamil content always have something fresh and exciting to watch.
Why the Best OTT Platforms Matter for Regional Audiences As the streaming industry expands, the importance of theOTT Platform options for regional audiences cannot be overlooked. They not only cater to language-specific audiences but also help preserve and promote local cultures while making global content more accessible.
The Rise of the Best OTT Platforms for Regional Content: They bridge the gap between global cinema and local audiences Viewers can enjoy Hollywood and indie films in their native language Regional content platforms contribute to cultural storytelling and preservation Whether it’s the Hollywood-dubbed collection of DOD, the Bengali storytelling of Hoichoi, the Odia exclusives of Olly Plus, or the South Indian cinema of Aha Video, each platform plays a vital role in reshaping digital entertainment in India.
The Final Verdict – Which is the Best OTT Platform? Choosing the Best OTT Platform depends on your content preferences. If you are looking for international cinema in regional languages, Dimension on Demand (DOD) is the perfect choice. For regional entertainment lovers, Hoichoi, Olly Plus, and Aha Video offer excellent options tailored to specific linguistic audiences.
With DOD leading the way in bringing global entertainment to regional audiences, it's clear that the future ofOTT lies in localization and accessibility. Whether you're a fan of Hollywood, Bengali dramas, Odia storytelling, or Tamil blockbusters, there’s an OTT platform designed just for you.
Want to experience Hollywood like never before? Watch your favorite global films in your language on Dimension on Demand (DOD). Subscribe now and explore an ever-growing collection of blockbuster movies!
-
 @ 9223d2fa:b57e3de7
2025-04-21 05:53:02
@ 9223d2fa:b57e3de7
2025-04-21 05:53:02193 steps
-
 @ a60e79e0:1e0e6813
2025-03-23 16:10:10
@ a60e79e0:1e0e6813
2025-03-23 16:10:10**This is a long form note test of a post that lives on my Nostr educational website Hello Nostr **
In early 2025, social media is the most common use case for Nostr (and probably the reason you're reading this). Nostr is SO much more than just social media, but that's where the bulk of the activity is, and is what I'm focusing on in this post. Even though the protocol is still so young, that has not prevented an explosion of excellent social media focused clients that predominantly coalesce around the Twitter (X) style feed, containing shorter form content, often with images, and the ability to comment, like and share.
This first steps guide showcases one of the most polished and simplest examples of such a client, Primal. Primal is a cross platform app, that also works on your computer too. The steps that follow are demonstrated on iPhone, but should be identical for Android users. There may be some topics of concepts here that are new to you, to learn more about them, check out our Nostr 101 to learn more about Nostr basics and why it matters.
You can and should explore all of the other options available to you, that's the beauty of Nostr, you're free to choose how and where to interact with your social network. No lock in. No walled gardens. True freedom.

Getting Started
-
Go to your app store and download Primal to your Android or iPhone
-
Open Primal and choose Create Account. Choose your public display name and add a short bio about yourself.
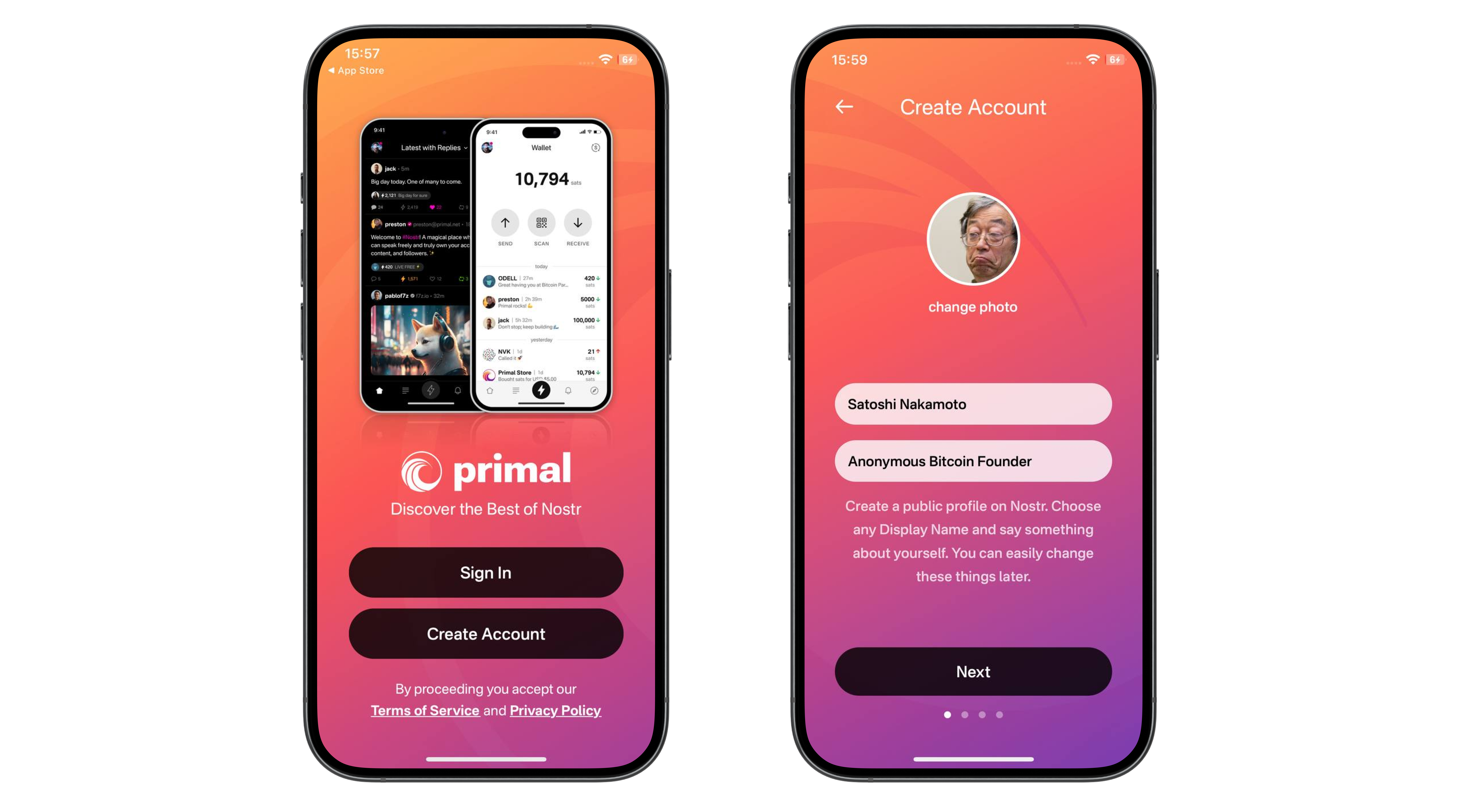
- Select your chosen interests from the list provided. This will bootstrap your feed and auto-follow a number of accounts so that your feed is not completely empty when starting out.
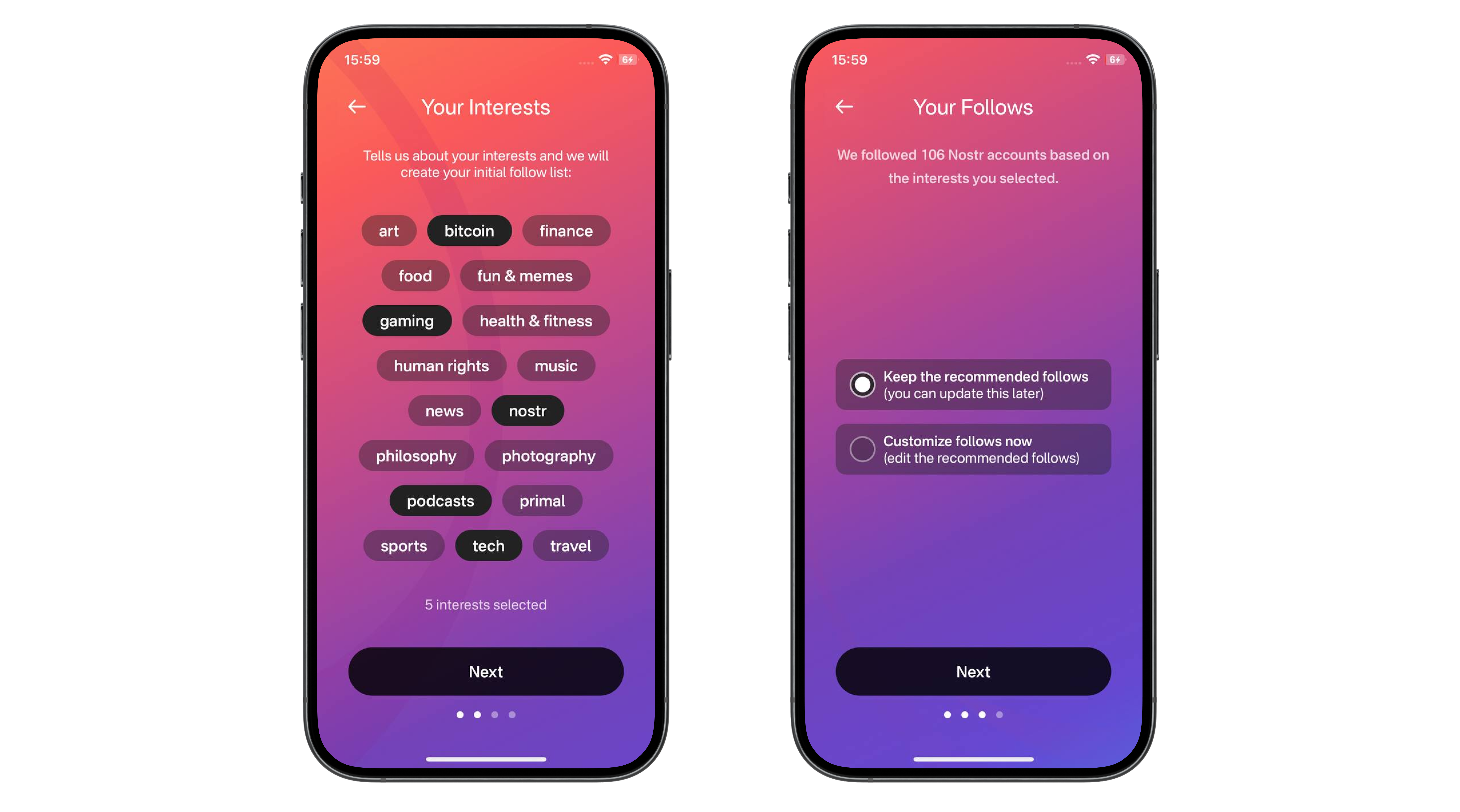
- Review your account info and tap Create Account Now. Take note of the fact that 'Your Nostr Key is available in your Account Settings'. We'll revisit this shortly.
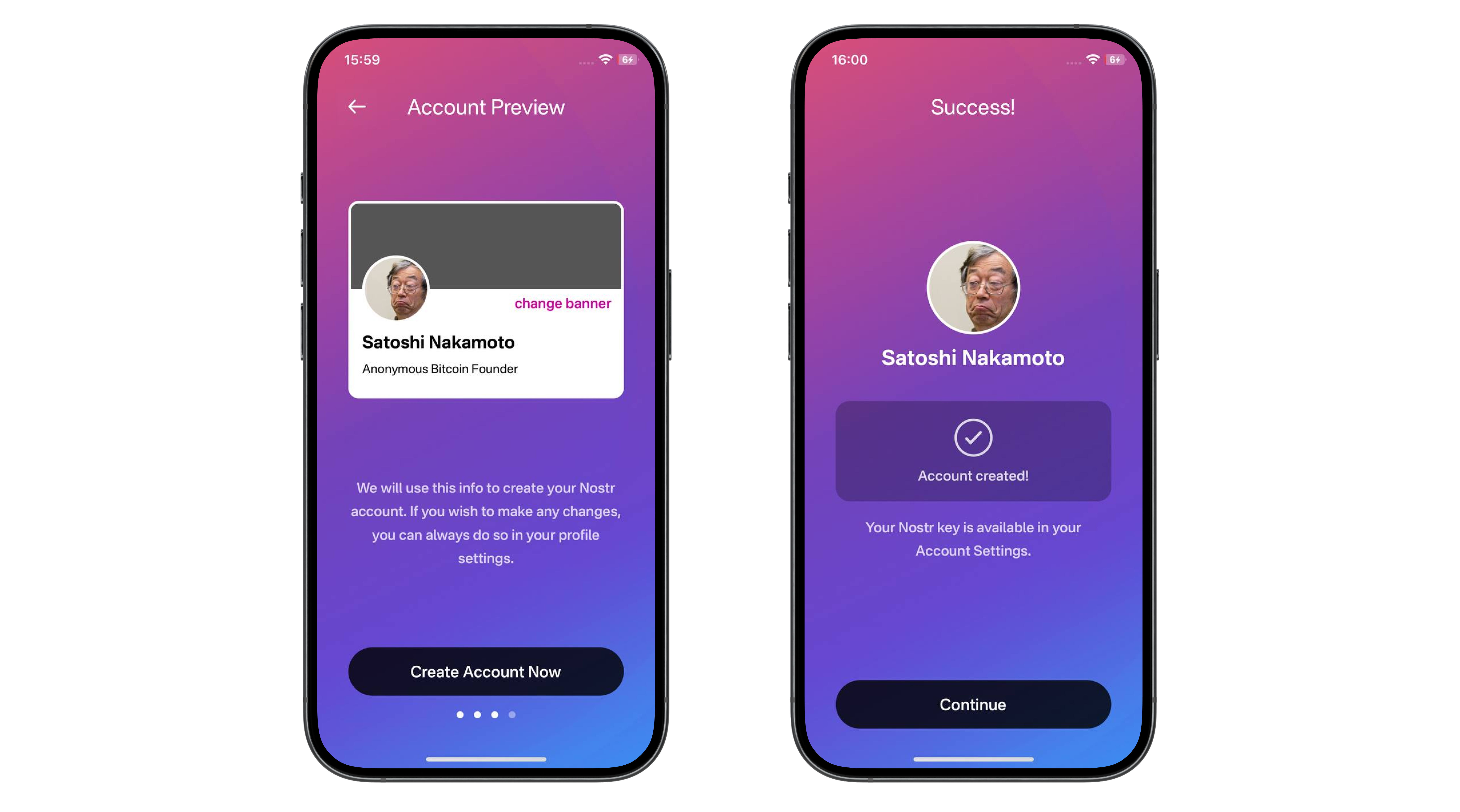
- Next is an optional step of activating the wallet feature within Primal. Having a wallet within your social client enables you to send and receive value (known as 'Zaps') in the form of Bitcoin. On Facebook and Twitter you can like a post, but it means much more to send someone fractions of a penny (or more if you like) to show your appreciation for their insights. You'll need to provide some personal information to enable the wallet, including an email address.
Using the internal wallet and purchasing sats with your credit card will tie your Nostr identity to your real ID. Think very carefully before carrying out this step.
Learn more in the detailed section at the end of this post.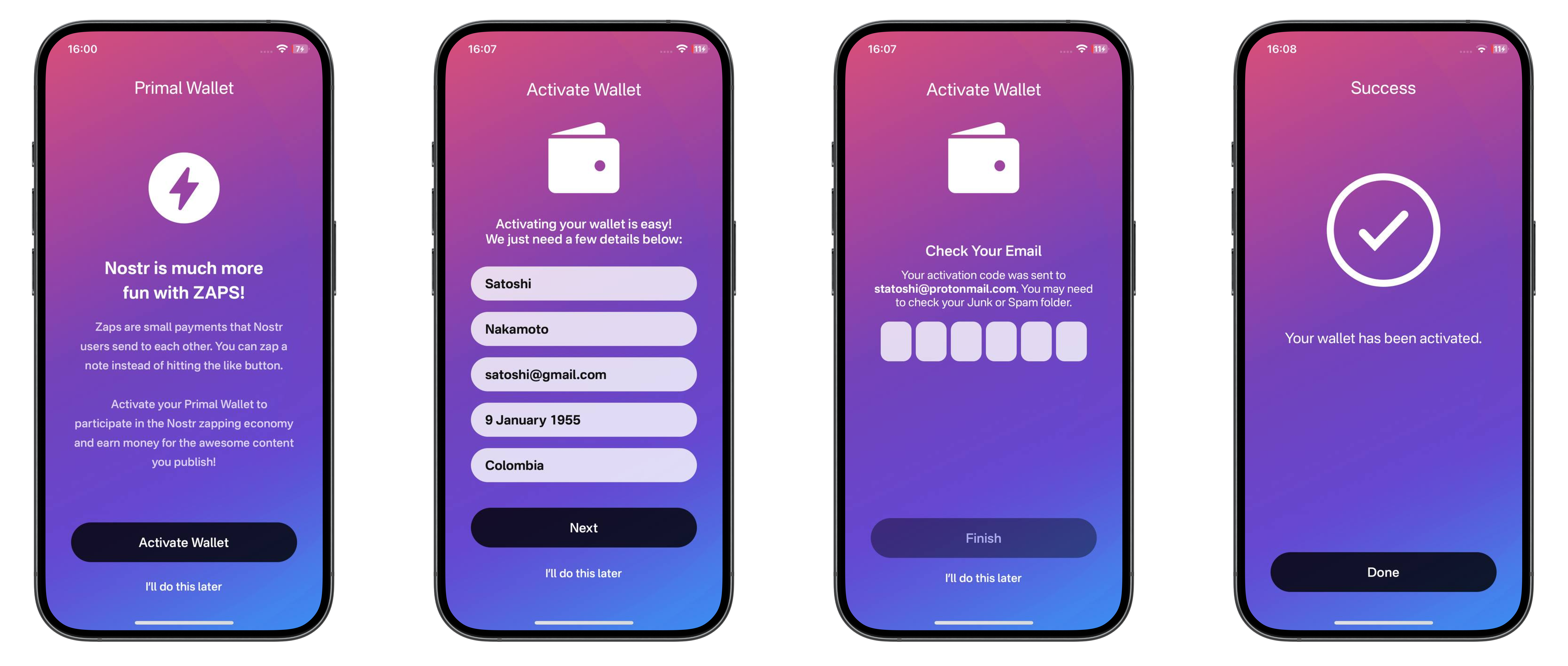
- That's it, you're now set up and ready to start sharing your thoughts, feelings and memes with the world via a decentralized and censorship resistant social network. To post your first note and say hello to the Nostr world, tap the + in the bottom right corner.
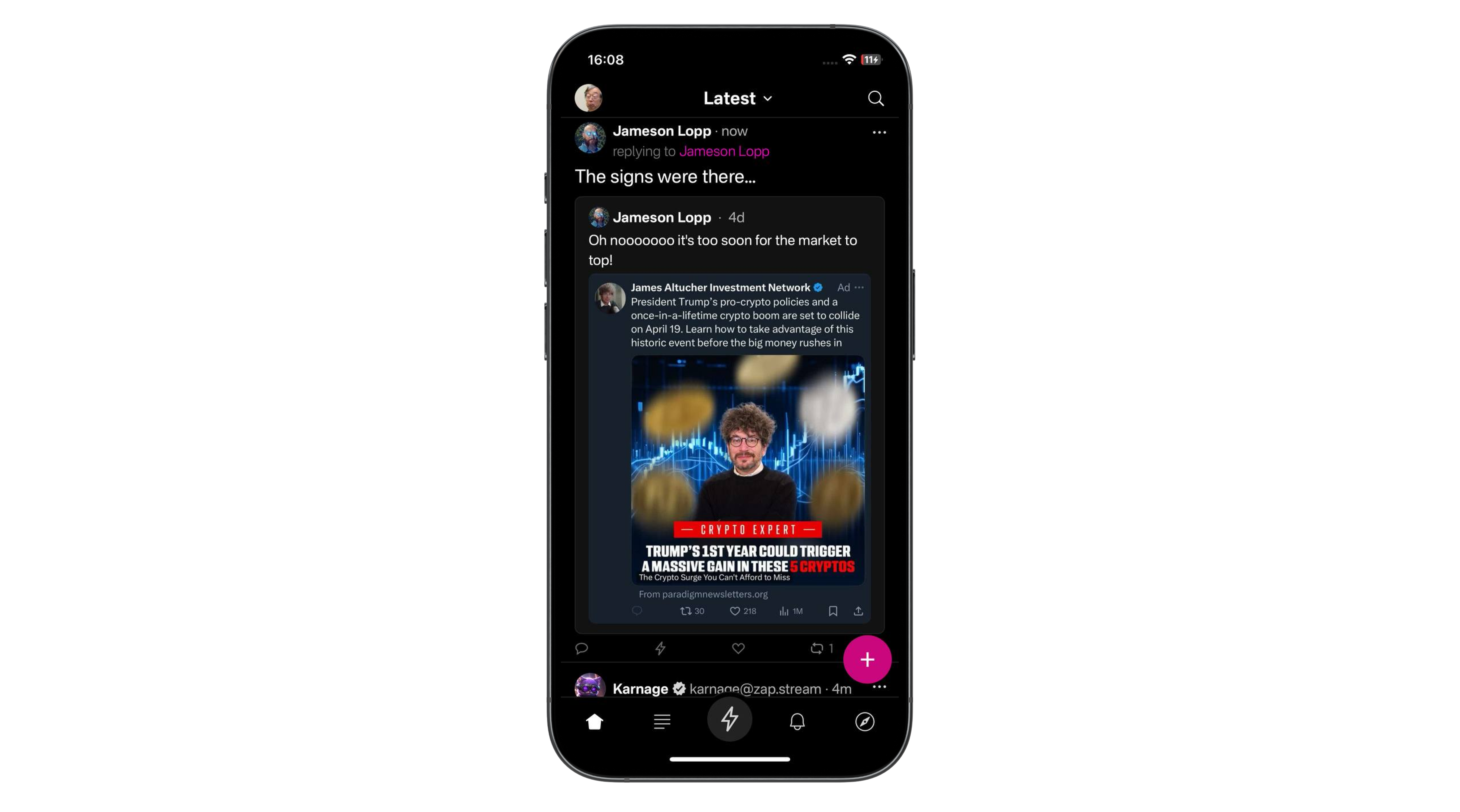
- If you activated the wallet at step 5, you might want to deposit some Bitcoin in there to allow you to send some value to your friends. There are three main ways to do this:
- Post some awesome content and have people send you value in the form of 'Zaps'
- Send some Bitcoin from a wallet you already have
- Purchase some directly within Primal
The latter is made very simple thanks to the in-app purchase feature, which allows you to purchase a small amount with the card you likely already have connected to your Apple/Google account. All you need to do is tap 'Buy Sats Now'.
- Next, let's look at the different feeds available on our home screen. Tap 'Latest' at the top of the screen and you can toggle between three different types of home feeds, great for discovering new people and content.
- Let's assume you already have some friends on Nostr and want to find and follow them. Tap the search icon in the top right corner, the enter the name of the person you want to follow. Once on their profile, simply tap the 'Follow' button.
- So you found a friend and want to start interacting with them so they know you made it over to Nostr. Simply find a note you like and choose from the different types of interactions available. From left to right they are:
- Comment
- Zap (send value from your wallet to theirs)
- Like
- Repost
- Bookmark
When Zapping, a single tap will send a tiny amount of 42 sats. If you want to send more, or a custom amount, tap and hold the zap button to bring up a selector menu. All default zap amounts are configurable in the app settings page.

- After you've started posting and interacting with others, you'll likely receive some notifications to tell you. Notifications can be filtered into interaction types.
- Another great way to find more people to follow and interact with is to use the discover page. To open it, tap the compass in the bottom right corner of the screen. Here you'll be able to browse different types of pre-built feeds, trending profiles, notes with large zaps and extra topics.
The Important Part
You might have noticed that throughout that setup, you were not asked for a unique username, nor were you asked for a password. So how the hell is this secure? What happens if you log out? Is your account lost forever?
This is where Nostr really starts to shine. Just like in Bitcoin or other cryptocurrencies, your Nostr account is protected by a 'Private Key'. Anyone with knowledge of the private key can access your account in any Nostr client. No private key, no access. So let's make sure you have a backup copy of it, so you can still recover access to your account in the event you lose your phone!
Tap on your profile image in the top left of the screen. Then tap Settings > Keys. Here you'll see two keys, one public and one private. Your public key is how people find you on Nostr. It is often referred to by its more technical name 'nPub' which is the prefix if the key itself. Your public key is designed to be exactly that, public!
Your private key is sometimes referred to by its technical name 'nSec' which is also the prefix of the key. Copy your private key and paste it somewhere safe and secure, in a location accessible independently from your phone, and only by you.
If you were to lose your phone, or accidentally delete the Primal app, now all you'd need to do is head back to step 1 above and choose Sign In. You'd then be asked to paste your private key, after which your profile and content would be magically restored.
Your private key can be imported into any other Nostr social client for the same result.
Things to Consider
This post has one primary focus - To get you from zero to posting and zapping in the quickest time and with the least friction. To achieve this, there are some trade-offs made that you should be aware of.
Custodial Wallet
The built in wallet is a custodial one. This means that the funds within are ultimately controlled by the developers behind Primal. They may be good actors, but you should approach the amount of money you maintain inside this wallet accordingly. If your wallet balance ever gets to a balance that makes you uncomfortable, you should send a good chunk of it out to another Bitcoin wallet where you control the keys. I recommend Phoenix or Zeus.
Those sats are never truly yours until you withdraw them to a self-custodial wallet
Wallet Privacy
If you choose to top up the wallet using the convenient in-app purchase method, you will tie that small amount of Bitcoin ownership to your Nostr account. If you Nostr account is literally your name, you might not have an issue with this, but often times people like to remain pseudonymous online. If you fall into that category, using your credit card to deposit Bitcoin into your Nostr account is not a good idea.
Android users of Primal can use an advanced technology called Nostr Wallet Connect (NWC) to connect an external Lightning wallet to their Nostr account in Primal. We'll cover this in a subsequent post.
Your private key allows you to take your profile and social network to any other client
If you found this post useful, please share it with your peers and consider following and zapping me on Nostr. If you write to me and let me know that you found me via this post, I'll be sure to Zap you back! ⚡️
-
-
 @ fd78c37f:a0ec0833
2025-04-21 04:40:30
@ fd78c37f:a0ec0833
2025-04-21 04:40:30Bitcoin is redefining finance, and in Asia—Thailand, Vietnam, Indonesia, and beyond—developers, entrepreneurs, and communities are fueling this revolution. YakiHonne, a decentralized social payments app built on Nostr, sat down with Gio (nostr:npub1yrnuj56rnen08zp2h9h7p74ghgjx6ma39spmpj6w9hzxywutevsst7k5cx), a core member of Thailand’s Sats ‘N’ Facts community, to explore their mission of fostering open-source Bitcoin development. In this interview, Gio shares the origins of Sats ‘N’ Facts, the challenges of hosting Bitcoin-focused events in Asia, and how these efforts are shaping adoption across the region.
YakiHonne: Can you tell us about yourself and how Sats ‘N’ Facts came to life? What sparked your Bitcoin journey?
Gio: I’m originally from Europe but have called Thailand home for six years. My Bitcoin story began while working at a commercial bank, where I saw the fiat system’s flaws firsthand—things like the Cantillon Effect, where money printing favors the connected few, felt deeply unfair. That discomfort led me to Andreas Antonopoulos’ videos, which opened my eyes to Bitcoin’s potential. After moving to Bangkok, I joined the open-source scene at BOB Space, collaborating with folks on tech projects.
Sats ‘N’ Facts grew out of that spirit. We wanted to create a Bitcoin-focused community to support developers and builders in Asia. Our recent conference in Chiang Mai brought together over 70 enthusiasts from Thailand, Vietnam, Laos, and beyond, sparking collaborations like a new Lightning Network tool. It was a milestone in connecting the region’s Bitcoin ecosystem.
YakiHonne: What inspired the Sats ‘N’ Facts conference, and how did you attract attendees?
Gio: The event was born from a desire to create a high-signal, low-noise space for Freedom Tech in Asia. While the U.S. and Europe host major Bitcoin events, Asia’s scene is still emerging under commercial stunts. We aimed to bridge that gap, uniting developers, educators, and enthusiasts to discuss real innovations—no altcoins, no corporate agendas. Our focus was on open-source projects like Bitcoin Core, Ark, Cashu, fostering conversations that could lead to tangible contributions.
Attracting attendees wasn’t easy. We leveraged local networks, reaching out to Bitcoin communities in neighboring countries via Nostr and Telegram. Posts on X helped spread the word, and we saw developers from Laos join for the first time, which was thrilling. Sponsors like Fulgur Ventures, Utreexo, and the Bitcoin Development Kit Foundation played a huge role, covering costs so we could keep the event free and accessible.
YakiHonne: What challenges did you face organizing the conference in Asia?
Gio: It was a steep learning curve. Funding was the biggest hurdle—early on, we struggled to cover venue and travel costs. Thankfully, our sponsors stepped in, letting me focus on logistics, which were no small feat either. As a first-time organizer, I underestimated the chaos of a tight timeline. Day one felt like herding cats without a fixed agenda, but the energy was electric—developers debugging code together, newcomers asking big questions.
Another challenge was cultural. Bitcoin’s still niche in Asia, so convincing locals to attend took persistence; there was no local presence for some reason. Despite the hiccups, we pulled it off, hosting 60+ attendees and sparking ideas for new projects, like a Cashu wallet integration. I’d tweak the planning next time, but the raw passion made it unforgettable.
YakiHonne: How does YakiHonne’s vision of decentralized social payments align with Sats ‘N’ Facts’ goals? Could tools like ours support your community?
Gio: That’s a great question. YakiHonne’s approach—merging Nostr’s censorship-resistant communication with Lightning payments—fits perfectly with our mission to empower users through open tech. At Sats ‘N’ Facts, we’re all about tools that give people control, whether it’s code or money. An app like YakiHonne could streamline community funding, letting developers tip each other for contributions or crowdfund projects directly. Imagine a hackathon where winners get sats instantly via YakiHonne—it’d be a game-changer. I’d love to see you guys at our next event to demo it!
YakiHonne: What advice would you give to someone starting a Bitcoin-focused community or event?
Gio: First, keep it Bitcoin-only. Stay true to the principles—cut out distractions like altcoins or hype-driven schemes. Start small: host regular meetups, maybe five people at a café, and build trust over time. Consistency and authenticity beat flashiness in the medium and long term.
Second, involve technical folks. Developers bring credibility and clarity, explaining Bitcoin’s nuts and bolts in ways newcomers get. I admire how Andreas Antonopoulos bridges that gap—technical yet accessible. You need that foundation to grow a real community.
Finally, lean on existing networks. If you know someone running a Bitcoin meetup in another city, collaborate. Share ideas, speakers, or even livestreams. Nostr’s great for this—our Laos attendees found us through a single post. Relationships are everything.
YakiHonne: Does Sats ‘N’ Facts focus more on Bitcoin’s technical side, non-technical side, or both?
Gio: We blend both. Our event had workshops for coders alongside talks for beginners on why Bitcoin matters. Open-source is our heartbeat, though. If you’re starting out, dive into projects like Bitcoin Core or Lightning. Review a pull request, test a Cashu wallet, or join a hackathon. One developer at our event built a Lightning micropayment tool that’s now live on GitHub.
There’s no shortage of ways to contribute. Community calls, forums, residency programs, and platforms like Geyser Fund are goldmines. YakiHonne could amplify this—imagine tipping developers for bug fixes via your app. It’s about iterating until you create something real.
YakiHonne: Your work is inspiring, Gio. Sats ‘N’ Facts is uniting Asia’s Bitcoin communities in a powerful way. What’s next for you?
Gio: Thanks for the kind words! We’re just getting started. The Chiang Mai event showed what’s possible—connecting developers across borders, reviewing and launching code and testing upcoming technologies. Next, we’re planning smaller hackathons and other events to keep the momentum going, maybe in Vietnam, Indonesia or Korea. I’d love to integrate tools like YakiHonne to fund these efforts directly through Nostr payments. Long-term, we want Sats ‘N’ Facts to be a hub for Asia’s Bitcoin builders, proving open-source can thrive here.

YakiHonne: Thank you, Gio, for sharing Sats ‘N’ Facts incredible journey. Your work is lighting a path for Bitcoin in Asia, and we’re honored to tell this story.
To our readers: Bitcoin’s future depends on communities like Sats ‘N’ Facts—and you can join the revolution. Download YakiHonne on Nostr to connect with builders, send Lightning payments, and explore the decentralized world. Follow Sats ‘N’ Facts for their next hackathon, and let’s build freedom tech together!
-
 @ 1c19eb1a:e22fb0bc
2025-03-21 15:48:32
@ 1c19eb1a:e22fb0bc
2025-03-21 15:48:32For our first edition of #Nostrversity, we'll be diving into Nostr Wallet Connect, or #NWC; a handy means of connecting a #Lightning wallet to your favorite #Nostr app that quickly became the standard and is now an essential part of onboarding to Nostr for any new user who wants to experience the magic of zaps. Yet NWC enables so much more than just one-tap-zapping, as we will see when we look a little closer at how it works under the hood.
Lightning History on Nostr
Back in the wild-west days of Nostr, before nostr:npub1xtscya34g58tk0z605fvr788k263gsu6cy9x0mhnm87echrgufzsevkk5s invented zaps, Bitcoin psychopaths were already sending sats to one another over Nostr. However, the way we had to do it back then was by going into our Lightning wallet, selecting "receive," inputting an amount we wanted, and copy/pasting an invoice from the wallet into our Nostr note, then hope someone was willing to pay it. And the payment side was just as cumbersome, requiring manually copying the invoice from your Nostr client, pasting it into a Lightning wallet so you could see how much the other user wanted, and then deciding if you were even willing to send it.
It didn't take long before Nostr clients, particularly on mobile, started rendering Lightning invoices in a convenient format that showed the invoice amount and a "Pay" button, that would prompt the user to open a Lightning wallet. This took out a decent amount of friction for the sender, but it was still just as big a hassle for the receiver.
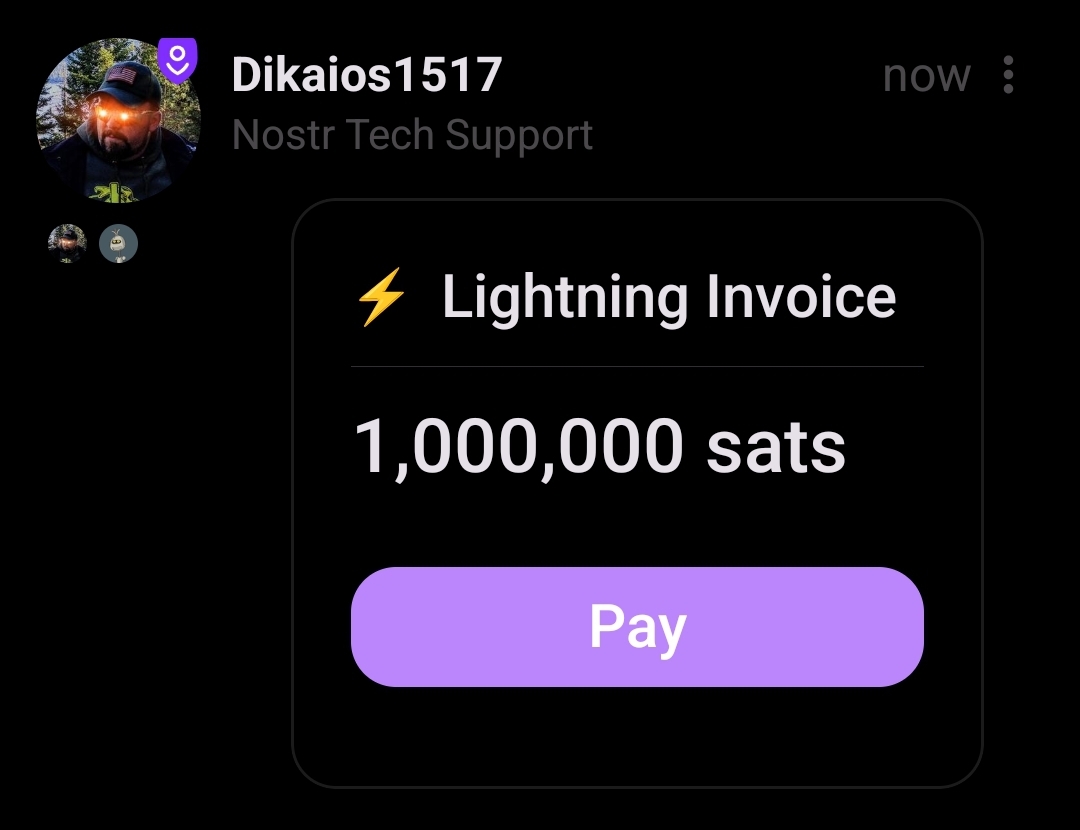
Then zaps came along, and soon everyone had the ability to send sats to any other user when they found value in the content they posted. At least, any other user that added their Lightning address to their profile and whose Lightning wallet provider supported sending a "paid" receipt to a Nostr relay. Receiver friction had been virtually eliminated and the sats began to flow. Nostr also became the de facto directory for Bitcoiner payment addresses. If you heard nostr:npub1a2cww4kn9wqte4ry70vyfwqyqvpswksna27rtxd8vty6c74era8sdcw83a say something brilliant on a podcast, you could just look her up on any Nostr client with zaps and send some sats her way as a thank you.
Enter the zapathon, a community event with one purpose: break nostr:npub1hcwcj72tlyk7thtyc8nq763vwrq5p2avnyeyrrlwxrzuvdl7j3usj4h9rq by zapping each other so much it was effectively a DDOS attack. Sure, it was a stress test on other wallets too, but most users were on Wallet of Satoshi because it was the easiest way to get a Lightning address with a mobile wallet.
It was a ton of fun flinging sats around as fast as your fingers would let you! However, a new friction point was soon discovered from trying to zap so frequently. Every time you tapped the zap icon in your Nostr client, you had to wait for your wallet to open and present the invoice to approve payment, then switch back to your Nostr client to zap the next note. Not a big deal when you only send a zap occasionally, but when trying to zap every note in your feed, it adds a significant amount of time and extra clicks. In fact, this small amount of friction, whether you realize it or not, often acts as just enough of a barrier to zapping that you will choose not to zap a post you found some value in, just because of the extra 5 seconds it takes to load into your wallet app, approve the payment, and switch back to your Nostr client.
Wouldn't it be amazing if we could have one-tap-zaps?
I can't recall if there were any other methods by which this was achieved, but the method that caught on was developed and released into the wild by nostr:npub1getal6ykt05fsz5nqu4uld09nfj3y3qxmv8crys4aeut53unfvlqr80nfm, who called it Nostr Wallet Connect. At that time (March of 2023), Alby was a custodial Lightning wallet for your web browser, and while you could connect your own node to it using LNDHub, most people just stuck with their custodial option since it came with a Lightning address. Nostr Wallet Connect was, at that time, a way to connect your Alby wallet to a Nostr client.
I am not certain which client was the first to support NWC, but I know that #Amethyst was pretty early on, and it was an instant success. Users could get a "connection string" from Alby, paste it into Amethyst, and zap with a single tap of their finger. Just like zaps themselves had eliminated the friction for receiving payments via Lightning for anyone with a Lightning address, Nostr Wallet Connect had eliminated the friction for sending payments. No more wasted seconds switching back and forth between Nostr client and wallet app, just tap and zap sent, tap again and another zap gone.
Of course, this meant that it was all too easy to send way more sats out of your wallet than you intended. This was solved by the ability to set budgets, so your wallet would cut you off once you reached the max amount you had set for yourself.
Because Alby had made Nostr Wallet Connect open source and part of the Nostr protocol, it didn't take long before more and more clients started adding support for it. Users demanded it and wouldn't shut up about it until it was added. Other wallet providers also saw the value of including it. Now it is simply expected, and any wallet that doesn't include it won't attract Nostr users.
Notably, Wallet of Satoshi went from being the most popular wallet among Nostr users to being a rare and quaint throwback to a bygone era, because they never integrated NWC and they pulled away from serving anyone in the U.S. out of fear of regulation under the Biden administration.
So we arrive at the state of Lightning on Nostr today, with Lightning addresses in our profiles for receiving zaps, and Nostr Wallet Connect for sending, and hard pressed to find Nostr clients that don't support both.
So... How does it work?
All of that history is great, but you're here to learn how this technology works. What is happening behind the scenes when you tap that little ⚡️ icon and sats seem to magically leave your Lightning wallet and show up on your screen as a zap underneath the latest nostr:npub1lrnvvs6z78s9yjqxxr38uyqkmn34lsaxznnqgd877j4z2qej3j5s09qnw5 meme, without you having to fiddle around with any Lightning invoices at all?
It's really quite simple, in the end. Your wallet communicating with your Nostr client using a Nostr relay in the middle, the same way you communicate with other Nostr users by saving notes to a relay that they can retrieve them from.
First, your Nostr client has to know how to "tag" your wallet, and on which relay to send it notes. This is why you need to get a "connection string" from your wallet to paste into your Nostr client. This string has all the information that is needed for your Nostr client to know how to communicate with your wallet, and for your wallet to be sure that the payment requests are authorized by you.
Let's take a look at an example connection string:
nostr+walletconnect://b889ff5b1513b641e2a139f661a661364979c5beee91842f8f0ef42ab558e9d4?relay=wss%3A%2F%2Frelay.damus.io&secret=71a8c14c1407c113601079c4302dab36460f0ccd0ad506f1f2dc73b5100e4f3cLooks like a bunch of gobbledygook, right? We'll break down each of its parts and see what it does.
nostr+walletconnect://This portion just defines the type of information that follows it. Because the string starts with this marker, any software reading it will know that what follows is information on how to communicate with a Lightning wallet, so long as it has been programmed to recognize it.
b889ff5b1513b641e2a139f661a661364979c5beee91842f8f0ef42ab558e9d4This section is just a public key, the same as an npub. In fact, it can be readily converted to an npub if you want using nostr:npub1zdr58j526qsrkdjhcg9xs60xfutqeey2ucugms04efnlx3spnmns2eqha9's key converter. It's a nostr identity just like yours or mine, but you won't find any GM posts or catstr pictures in its note history. It's only posting special note types used by NWC. This public key belongs to your Lightning wallet, and just like you can have multiple npubs for each of your alter egos, your wallet creates a separate public key to use with each new app you want to connect it to. Or at least it should. The Nostr client you use will tag your wallet in notes it creates by using this public key.
relay=wss%3A%2F%2Frelay.damus.ioThis section is probably easily recognizable. It's the same as typing
relay=wss://relay.damus.io, except that it has to use%3A%2F%2Fin place of://. This tells your Nostr client which relay it needs to use to communicate with your wallet. Hopefully your wallet uses a relay with high up-time, because one of the major ways for NWC to fail is if the relay is down. You also can't use just any relay. It has to accept the note kinds used by NWC, which is why wallets don't typically let their users choose the relay that will be used. You also can't just modify the connection string to use a relay you prefer, even if you know it allows NWC note kinds. This is because it will result in your Nostr client sending requests to your wallet on that relay, but your wallet is not reading from that relay, so it will never receive the requests.secret=71a8c14c1407c113601079c4302dab36460f0ccd0ad506f1f2dc73b5100e4f3cThis is just a Nostr private key. It's an nsec, but in hex format. Your wallet is giving your Nostr client a private key that it must use to sign all of the requests it sends to your wallet. No request signed by any other private key will be answered by your wallet. Your wallet will generate a separate private key for each connection string, allowing you as the user to revoke those connections individually, or set a separate budget for each connection.
When you tap the ⚡️ icon in your Nostr client, it obtains a Lightning invoice from the user's wallet you are trying to zap using their Lightning address. It then creates a note tagging your wallet's public key and requesting payment of that Lightning invoice, signing the note with the private key your wallet generated for it, and writing that note to the specified Nostr relay. Your wallet is constantly checking that relay for new notes and when it sees the payment request signed by an authorized private key, it pays the invoice, so long as it is within the budget you set, and sends out a payment receipt stating it has been paid so your client can light up the zap indicator to show that it was successful. All of this from a single tap of your finger in Amethyst.
More than Zaps
Now that we know the basics of how NWC works, it doesn't take much extrapolation to realize that this communication between wallet and Nostr client could be used for much more than just payment requests. A client could ask for your wallet's balance information, or transaction history, or ask for a lightning invoice. In fact, why does it have to be a Nostr client making those requests at all? Why not a mobile wallet app, or browser extension?
One of the major pieces of friction felt by those who run Lightning nodes is the difficulty of connecting to them remotely in a secure way. nostr:npub1aghreq2dpz3h3799hrawev5gf5zc2kt4ch9ykhp9utt0jd3gdu2qtlmhct and nostr:npub126ntw5mnermmj0znhjhgdk8lh2af72sm8qfzq48umdlnhaj9kuns3le9ll allow for connecting via Tor by default, but that can be painfully slow and unreliable. Anyone who has set up a connection to their node via LND Rest over Tor to their nostr:npub1xnf02f60r9v0e5kty33a404dm79zr7z2eepyrk5gsq3m7pwvsz2sazlpr5 wallet can attest to the frustration of opening their wallet and waiting several seconds for the interface to load, only to receive a timeout notice.
Nostr Wallet Connect has eliminated this issue thanks to Alby Hub and Alby Go. Just create a new connection in Alby Hub, give it a budget, and scan the QR code with Alby Go and you have a fully-functional, mobile Lightning wallet connected to your node at home that loads extremely quickly and reliably, so long as the Nostr relay in-between is up and running.
Now, you may be concerned that the information being passed back and forth on this Nostr relay is incredibly sensitive financial information, especially if balance and transaction history is involved. However, this is not a concern because the content of the notes is fully encrypted. The relay owner, or anyone else with access to read data on that relay, has no idea what information is contained in the messages being sent between wallet provider and Nostr client, or Lightning node and mobile wallet. And because neither npub being used by your wallet provider or your Nostr client is the same as your npub, there is nothing tying the messages to you.
As a result, NWC is quickly becoming an integral piece of Lightning infrastructure, even if those making use of it have no interest in joining Nostr at all.
The Future of NWC
To wrap this up, I'd like to point the reader to recent developments with Nostr Wallet Connect, and other use-cases we could very well see in the near future.
First, NWC may not just be for Lightning. nostr:npub1utx00neqgqln72j22kej3ux7803c2k986henvvha4thuwfkper4s7r50e8 recently revealed that he has a working prototype of on-chain payments via NWC.
nostr:nevent1qvzqqqqqqypzpckv7l8jqspl8u4y54dn9rcduwlrs4v2040nxce0m2h0cunvrj8tqyw8wumn8ghj7un9d3shjtnzd96xxmmfdecxzunt9e3k7mf0qyfhwumn8ghj7am0wsh82arcduhx7mn99uq32amnwvaz7tmjv4kxz7fww468smewdahx2tcqyzswntflhlvuea2uf3035r94azm32frnskk5qp2evj43x6nz6kt9zd7j485
We are already seeing it used with eCash wallets like nostr:npub1kvaln6tm0re4d99q9e4ma788wpvnw0jzkz595cljtfgwhldd75xsj9tkzv. There is no reason we shouldn't expect to see it used with all forms of Bitcoin payments. This could lead to an explosion of available wallet applications for all platforms, since they will simply be an interface for communicating with your node or wallet provider.
NWC can also be used for subscriptions, as alluded to in nostr:npub1utx00neqgqln72j22kej3ux7803c2k986henvvha4thuwfkper4s7r50e8's note above. Before you protest about what an awful monetization model subscriptions are, I generally agree. That said, subscriptions where the user remains in control the entire time, and can unilaterally cancel the subscription at any time, without having to jump through hoops and give explanations about why they no longer want to use the service, is a massive improvement over the current status quo. Remember, NWC allows the user to set a budget for each connection. This means your subscription can't incrementally increase its monthly fee on you. Not without you willingly going into your wallet settings and adjusting the monthly budget, at any rate.
Last one before we close this out: NWC can be used for streaming services where you pay only for what you use, and give yourself a budget. Instead of paying a monthly subscription to Netflix, you could pay per minute that you watch. Previously this could only be done by topping up a wallet controlled by the service itself, the way nostr:npub1v5ufyh4lkeslgxxcclg8f0hzazhaw7rsrhvfquxzm2fk64c72hps45n0v5's wallet worked with streaming sats for Podcasting 2.0. But now NWC is coming to Fountain, and users can bring their own wallet that they control.
The future of NWC is bright, and it extends well beyond zapping memes on Nostr. It's going to open up a world of possibilities for how we can use our sats to stream media, make reoccurring donations, use micro-payments to rent compute, and so much more. I don't know about you, but I am here for it!
-
 @ 872982aa:8fb54cfe
2025-04-21 02:58:53
@ 872982aa:8fb54cfe
2025-04-21 02:58:53保存到草稿431243214321
-
 @ dd664d5e:5633d319
2025-03-21 12:22:36
@ dd664d5e:5633d319
2025-03-21 12:22:36Men tend to find women attractive, that remind them of the average women they already know, but with more-averaged features. The mid of mids is kween.👸
But, in contradiction to that, they won't consider her highly attractive, unless she has some spectacular, unusual feature. They'll sacrifice some averageness to acquire that novelty. This is why wealthy men (who tend to be highly intelligent -- and therefore particularly inclined to crave novelty because they are easily bored) -- are more likely to have striking-looking wives and girlfriends, rather than conventionally-attractive ones. They are also more-likely to cross ethnic and racial lines, when dating.
Men also seem to each be particularly attracted to specific facial expressions or mimics, which might be an intelligence-similarity test, as persons with higher intelligence tend to have a more-expressive mimic. So, people with similar expressions tend to be on the same wavelength. Facial expessions also give men some sense of perception into womens' inner life, which they otherwise find inscrutable.
Hair color is a big deal (logic says: always go blonde), as is breast-size (bigger is better), and WHR (smaller is better).

-
 @ d34e832d:383f78d0
2025-04-21 02:36:32
@ d34e832d:383f78d0
2025-04-21 02:36:32Lister.lol represents a sophisticated web application engineered specifically for the administration and management of Nostr lists. This feature is intrinsically embedded within the Nostr protocol, facilitating users in the curation of personalized feeds and the exploration of novel content. Although its current functionality remains relatively rudimentary, the platform encapsulates substantial potential for enhanced collaborative list management, as well as seamless integration with disparate client applications, effectively functioning as a micro-app within the broader ecosystem.
The trajectory of Nostr is oriented towards the development of robust developer tools (namely, the Nostr Development Kit - NDK), the establishment of comprehensive educational resources, and the cultivation of a dynamic and engaged community of developers and builders.
The overarching strategy emphasizes a decentralized paradigm, prioritizing the growth of small-scale, sustainable enterprises over the dominance of large, centralized corporations. In this regard, a rigorous experimentation with diverse monetization frameworks and the establishment of straightforward, user-friendly applications are deemed critical for the sustained evolution and scalability of the Nostr platform.
 Nostr's commitment to a decentralized, 'nagar-style' model of development distinguishes it markedly from the more conventional 'cathedral' methodologies employed by other platforms. As it fosters a broad spectrum of developmental outcomes while inherently embracing the properties of emergence. Such principles stand in stark contrast to within a traditional environment, centralized Web2 startup ecosystem, which is why all people need a chance to develop a significant shift towards a more adaptive and responsive design philosophy in involving #Nostr and #Bitcoin.
Nostr's commitment to a decentralized, 'nagar-style' model of development distinguishes it markedly from the more conventional 'cathedral' methodologies employed by other platforms. As it fosters a broad spectrum of developmental outcomes while inherently embracing the properties of emergence. Such principles stand in stark contrast to within a traditional environment, centralized Web2 startup ecosystem, which is why all people need a chance to develop a significant shift towards a more adaptive and responsive design philosophy in involving #Nostr and #Bitcoin. -
 @ aa8de34f:a6ffe696
2025-03-21 12:08:31
@ aa8de34f:a6ffe696
2025-03-21 12:08:3119. März 2025
🔐 1. SHA-256 is Quantum-Resistant
Bitcoin’s proof-of-work mechanism relies on SHA-256, a hashing algorithm. Even with a powerful quantum computer, SHA-256 remains secure because:
- Quantum computers excel at factoring large numbers (Shor’s Algorithm).
- However, SHA-256 is a one-way function, meaning there's no known quantum algorithm that can efficiently reverse it.
- Grover’s Algorithm (which theoretically speeds up brute force attacks) would still require 2¹²⁸ operations to break SHA-256 – far beyond practical reach.
++++++++++++++++++++++++++++++++++++++++++++++++++
🔑 2. Public Key Vulnerability – But Only If You Reuse Addresses
Bitcoin uses Elliptic Curve Digital Signature Algorithm (ECDSA) to generate keys.
- A quantum computer could use Shor’s Algorithm to break SECP256K1, the curve Bitcoin uses.
- If you never reuse addresses, it is an additional security element
- 🔑 1. Bitcoin Addresses Are NOT Public Keys
Many people assume a Bitcoin address is the public key—this is wrong.
- When you receive Bitcoin, it is sent to a hashed public key (the Bitcoin address).
- The actual public key is never exposed because it is the Bitcoin Adress who addresses the Public Key which never reveals the creation of a public key by a spend
- Bitcoin uses Pay-to-Public-Key-Hash (P2PKH) or newer methods like Pay-to-Witness-Public-Key-Hash (P2WPKH), which add extra layers of security.
🕵️♂️ 2.1 The Public Key Never Appears
- When you send Bitcoin, your wallet creates a digital signature.
- This signature uses the private key to prove ownership.
- The Bitcoin address is revealed and creates the Public Key
- The public key remains hidden inside the Bitcoin script and Merkle tree.
This means: ✔ The public key is never exposed. ✔ Quantum attackers have nothing to target, attacking a Bitcoin Address is a zero value game.
+++++++++++++++++++++++++++++++++++++++++++++++++
🔄 3. Bitcoin Can Upgrade
Even if quantum computers eventually become a real threat:
- Bitcoin developers can upgrade to quantum-safe cryptography (e.g., lattice-based cryptography or post-quantum signatures like Dilithium).
- Bitcoin’s decentralized nature ensures a network-wide soft fork or hard fork could transition to quantum-resistant keys.
++++++++++++++++++++++++++++++++++++++++++++++++++
⏳ 4. The 10-Minute Block Rule as a Security Feature
- Bitcoin’s network operates on a 10-minute block interval, meaning:Even if an attacker had immense computational power (like a quantum computer), they could only attempt an attack every 10 minutes.Unlike traditional encryption, where a hacker could continuously brute-force keys, Bitcoin’s system resets the challenge with every new block.This limits the window of opportunity for quantum attacks.
🎯 5. Quantum Attack Needs to Solve a Block in Real-Time
- A quantum attacker must solve the cryptographic puzzle (Proof of Work) in under 10 minutes.
- The problem? Any slight error changes the hash completely, meaning:If the quantum computer makes a mistake (even 0.0001% probability), the entire attack fails.Quantum decoherence (loss of qubit stability) makes error correction a massive challenge.The computational cost of recovering from an incorrect hash is still incredibly high.
⚡ 6. Network Resilience – Even if a Block Is Hacked
- Even if a quantum computer somehow solved a block instantly:The network would quickly recognize and reject invalid transactions.Other miners would continue mining under normal cryptographic rules.51% Attack? The attacker would need to consistently beat the entire Bitcoin network, which is not sustainable.
🔄 7. The Logarithmic Difficulty Adjustment Neutralizes Threats
- Bitcoin adjusts mining difficulty every 2016 blocks (\~2 weeks).
- If quantum miners appeared and suddenly started solving blocks too quickly, the difficulty would adjust upward, making attacks significantly harder.
- This self-correcting mechanism ensures that even quantum computers wouldn't easily overpower the network.
🔥 Final Verdict: Quantum Computers Are Too Slow for Bitcoin
✔ The 10-minute rule limits attack frequency – quantum computers can’t keep up.
✔ Any slight miscalculation ruins the attack, resetting all progress.
✔ Bitcoin’s difficulty adjustment would react, neutralizing quantum advantages.
Even if quantum computers reach their theoretical potential, Bitcoin’s game theory and design make it incredibly resistant. 🚀
-
 @ e39d100f:d27602e5
2025-04-21 02:28:33
@ e39d100f:d27602e5
2025-04-21 02:28:33A 5GBet tem se destacado cada vez mais no cenário brasileiro como uma plataforma completa de entretenimento online, oferecendo aos usuários uma experiência repleta de emoção, segurança e diversidade de jogos. Seja você um jogador iniciante ou experiente, a 5GBet proporciona uma navegação intuitiva e um ambiente confiável para quem busca diversão sem sair de casa.
Desde o primeiro acesso, é fácil perceber que a 5GBet se preocupa com a experiência do usuário. O design do site é moderno e responsivo, adaptando-se perfeitamente a computadores, tablets e celulares. Isso garante que os jogadores possam se divertir a qualquer momento, de qualquer lugar.
Outro ponto forte é a segurança. A plataforma utiliza tecnologia de criptografia avançada para proteger os dados dos usuários, além de contar com métodos de verificação de identidade para garantir transações seguras. Tudo isso contribui para um ambiente confiável, onde o jogador pode focar apenas na diversão.
Variedade de Jogos para Todos os Gostos Na 5gbet , a variedade de jogos é um dos principais diferenciais. O site oferece uma extensa seleção de opções, desde os clássicos jogos de mesa até slots modernos com gráficos impressionantes e temáticas envolventes. Os jogadores podem escolher entre diversos estilos e dinâmicas, o que torna a experiência muito mais rica e personalizada.
Os jogos de cartas, como o pôquer e o blackjack, são populares entre os usuários mais estratégicos. Já os slots oferecem uma jogabilidade mais leve e dinâmica, com recursos interativos e animações cativantes. Há também jogos com crupiês ao vivo, que proporcionam uma experiência ainda mais imersiva, com transmissão em tempo real e interação com outros jogadores.
Experiência do Jogador: Intuitiva e Recompensadora A experiência do jogador na 5GBet é cuidadosamente pensada para ser fluida e gratificante. O processo de cadastro é rápido, e os métodos de depósito e saque são variados, incluindo opções populares como PIX, transferência bancária e carteiras digitais. Além disso, o suporte ao cliente está disponível para tirar dúvidas e resolver questões com agilidade, seja via chat ao vivo ou e-mail.
Outro destaque é o sistema de recompensas e promoções oferecido aos jogadores. Desde bônus de boas-vindas até promoções recorrentes, a 5GBet valoriza seus usuários ativos e oferece incentivos para tornar a jornada ainda mais empolgante.
A comunidade de jogadores também é bastante ativa, e a plataforma frequentemente promove torneios e desafios, permitindo que os usuários testem suas habilidades e interajam com outros entusiastas.
Conclusão A 5GBet se consolida como uma excelente opção para quem busca entretenimento online com qualidade, segurança e muita variedade. Com uma plataforma bem estruturada, jogos empolgantes e uma experiência de usuário impecável, é fácil entender por que cada vez mais brasileiros escolhem a 5GBet como seu destino de diversão online. Se você ainda não conhece, vale a pena explorar e descobrir tudo o que essa plataforma tem a oferecer.
-
 @ 1c19eb1a:e22fb0bc
2025-03-21 00:34:10
@ 1c19eb1a:e22fb0bc
2025-03-21 00:34:10What is #Nostrversity? It's where you can come to learn about all the great tools, clients, and amazing technology that is being built on #Nostr, for Nostr, or utilized by Nostr, presented in an approachable and non-technical format. If you have ever wondered what Blossom, bunker signing, or Nostr Wallet Connect are, how they work, and how you can put them to work to improve your Nostr experience, this is the place you can read about them without needing a computer-science degree ahead of time.
Between writing full-length reviews, which take a fair amount of time to research, test, and draft, I will post shorter articles with the Nostrversity hashtag to provide a Nostr-native resource to help the community understand and utilize the tools our illustrious developers are building. These articles will be much shorter, and more digestible than my full-length reviews. They will also cover some things that may not be quite ready for prime-time, whereas my reviews will continue to focus on Nostr apps that are production-ready.
Keep an eye out, because Nostr Wallet Connect will be the first topic of study. Take your seats, get out your notepads, and follow along to discover how Nostr Wallet Connect is improving Lightning infrastructure. Hint: It's not just for zaps.
-
 @ cb4352cd:a16422d7
2025-04-21 11:17:41
@ cb4352cd:a16422d7
2025-04-21 11:17:41What happens when artificial intelligence meets Web3? It's no longer just an idea — it's happening, and it's reshaping how we think about applications, economies, and communities online.
AI-as-a-Service in Web3
One of the clearest signs of this shift is the rise of decentralized AI marketplaces. Projects like Bittensor show that users can contribute machine learning models and earn rewards in cryptocurrency.
Another example is Gensyn, linking AI developers to decentralized compute resources.
Verifying AI with Blockchain
Blockchain helps verify AI outputs. Initiatives like Oraichain and Fetch.ai ensure AI agents interact securely and transparently in decentralized ecosystems.
AI-Driven Decentralized Organizations
Projects like SingularityNET explore AI marketplaces and autonomous governance models, creating new possibilities for decentralized coordination.
Generative AI in Web3 Content Creation
Platforms like Alethea AI are building intelligent NFTs that adapt to user interactions. AI-generated quests and dynamic worlds are reshaping GameFi.
The Road Ahead
Beyond Banking Conference by WeFi will spotlight how AI and Web3 are converging to redefine ownership, collaboration, and the very nature of the internet.
The question isn't whether AI and Web3 will merge — it's how quickly their union will reshape everything we know about digital life.
-
 @ 502ab02a:a2860397
2025-04-21 02:26:09
@ 502ab02a:a2860397
2025-04-21 02:26:09เรามาดูกันครับว่า Precision Fermentation ของ Perfect Day เค้าใช้อะไรเป็นกำลังสำคัญในการหมัก ให้ได้สินค้ามูลค่ามหาศาล ท้าวความกันก่อนว่า Perfect Day เป็นบริษัทที่ผลิต เวย์โปรตีนได้ โดยไม่ต้องใช้วัวเลยแม้แต่นิดเดียว ด้วยการใช้จุลินทรีย์
Microflora ฟาร์มวัวยุคใหม่ ที่ไม่มีวัว ถ้าคุณเคยดูสารคดีธรรมชาติ แล้วเห็นภาพป่าดิบเขียวชอุ่มที่แต่ละสิ่งมีชีวิตทำหน้าที่ของมันอย่างกลมกลืนกัน ทั้งแมลงที่บินไปมา เชื้อราที่แอบฝังรากอยู่ใต้ใบไม้ หรือจุลินทรีย์ที่ไม่เห็นด้วยตาเปล่าแต่ทำงานหนักอยู่ใต้ดิน... โลกของ microflora ก็ไม่ต่างอะไรกับ “จักรวาลจิ๋ว” แบบนั้นเลย
Microflora คืออะไร? microflora เป็นศัพท์ที่นักวิทยาศาสตร์ใช้เรียกสิ่งมีชีวิตขนาดจิ๋วที่มองไม่เห็นด้วยตาเปล่า แต่มีชีวิตจริงๆ แบบครบสูตร คือเจริญเติบโตได้ แบ่งตัวได้ กินได้ เหมือนสิ่งมีชีวิตอื่นๆ เป๊ะๆ มาจาก micro กับ flora
พอพูดถึงคำว่า “flora” บางคนอาจนึกถึงต้นไม้ แต่ในความหมายนี้ มันกว้างกว่านั้นมาก เพราะ “microflora” ไม่ได้จำกัดแค่พืช แต่หมายถึงสิ่งมีชีวิตจิ๋วจากหลากหลายอาณาจักรในธรรมชาติ เช่น ฟังไจ (Fungi) — ไม่ใช่แค่เห็ดที่เรากินกัน แต่รวมถึงเชื้อราจิ๋วที่อยู่ในดินและอากาศ ที่เก่งเรื่องการปล่อยเอนไซม์ย่อยอาหารนอกตัว แล้วดูดสารอาหารเข้าไป แบคทีเรีย (Bacteria) — นักแบ่งตัวมือโปรที่อยู่ในทุกที่ตั้งแต่ดินในสวน ยันในลำไส้เรา โพรทิสต์ (Protists) — กลุ่มที่เหลือๆ ที่ไม่เข้าพวกกับใคร เช่น สาหร่ายบางชนิด หรืออะมีบา
microflora เหล่านี้เหมือนพนักงานจิ๋วที่ทำหน้าที่เฉพาะทาง บางตัวเก่งเรื่องสร้างโปรตีน บางตัวสร้างไขมัน บางตัวสังเคราะห์วิตามินเก่งสุดๆ เลยกลายเป็นขุมพลังที่มนุษย์เริ่มหันมาใช้มากขึ้นเรื่อยๆ
ความสัมพันธ์ระหว่างมนุษย์กับ microflora ไม่ใช่เรื่องใหม่เลย เราหมักเบียร์ ทำโยเกิร์ต ดองกิมจิ และทำซีอิ๊วจากถั่วเหลืองด้วยกระบวนการที่เรียกว่า “fermentation” หรือ “การหมัก” มานานหลายพันปีแล้ว ซึ่งเป็นการอาศัยพลังของจุลินทรีย์ธรรมชาติให้สร้างรสชาติ วิตามิน หรือย่อยของที่เรากินให้ดูดซึมง่ายขึ้น แต่วันนี้โลกไปไกลกว่านั้นมาก เพราะเราสามารถสอนจุลินทรีย์ให้ผลิต “โปรตีนเฉพาะแบบ” ได้ตามต้องการ กระบวนการนี้เรียกว่า Precision Fermentation หรือ “การหมักแบบแม่นยำ” ฟังดูเหมือนห้องทดลองของ Iron Man เลยเนอะ
Perfect Day ใช้วิธีนี้ในการผลิต เวย์โปรตีน แบบไม่ต้องรีดนมจากวัวเลยสักหยด ด้วยการใช้ “เชื้อราจิ๋ว” ชนิดหนึ่งที่มีชื่อสายวิทยาศาสตร์ว่า Trichoderma
ทำไมต้อง Trichoderma? เจ้า Trichoderma ไม่ใช่เชื้อราหน้าตาน่ากลัวแบบในหนังสยองขวัญ แต่มันคือเชื้อราที่อยู่ในดินมานานกว่า 70 ปีแล้ว และเป็นที่รู้กันในวงการวิทยาศาสตร์ว่า มันเก่งเรื่องการผลิตเอนไซม์ที่ย่อยไม้ ย่อยใบไม้ ย่อยสิ่งมีชีวิตอื่นในธรรมชาติได้อย่างมีประสิทธิภาพ จึงเป็นเหมือน “โรงงานย่อยอาหาร” ชั้นเลิศ
นักวิทยาศาสตร์ของ Perfect Day เห็นแววก็เลยจับมันมา “ฝึกงาน” ใหม่ โดยใช้กระบวนการที่เรียกว่า strain engineering หรือ “การออกแบบสายพันธุ์” พูดง่ายๆ ก็คือ ใส่รหัสพันธุกรรม (เหมือนคำสั่งงาน) เข้าไปให้มันผลิตโปรตีนจากนมได้ เช่น beta-lactoglobulin ซึ่งเป็นโปรตีนตัวหลักของเวย์ในน้ำนมวัว
เมื่อ Trichoderma อ่านคำสั่งนี้ออก มันก็เริ่มเดินเครื่องผลิตโปรตีนตามที่เราสั่ง เหมือนเป็น “วัวในห้องแล็บ” ที่ไม่มีเสียงร้อง ไม่มีปุ๋ยคอก และไม่ต้องเลี้ยงด้วยหญ้า
microflora = วัวจิ๋วยุคใหม่
ลองจินตนาการว่าถ้าในอดีตเราต้องเลี้ยงวัวจริงๆ เพื่อให้ได้โปรตีนจากนม วันนี้เราใช้แค่จุลินทรีย์จิ๋วในถังหมัก แล้วป้อน “อาหาร” ให้มันเป็นน้ำตาลจากพืช (เช่น ข้าวโพด !!! เป็นง่ะ ข้าวโพดอีกแล้ว) มันก็จะเปลี่ยนคาร์โบไฮเดรตเหล่านั้นให้กลายเป็นโปรตีน หรือไขมัน หรือสารที่เราต้องการได้แบบแม่นยำ
microflora ไม่ใช่สัตว์ แต่ก็ทำหน้าที่แทนสัตว์ได้ พวกมันไม่มีสมอง ไม่มีระบบประสาท ไม่รู้สึกเจ็บ ไม่เบื่อ ไม่หิวข้าว ไม่ต้องการวันหยุด แต่มันมี “ความสามารถ” ที่เราสามารถดึงมาใช้ให้เกิดประโยชน์ได้อย่างน่าทึ่ง
ข้อดีของ microflora -เลี้ยงง่าย แค่ให้คาร์บ (จากพืช) ก็พร้อมทำงาน -ไม่ต้องใช้พื้นที่เยอะ ผลิตในถังหมัก ไม่ต้องใช้ทุ่งหญ้ากว้างๆ แบบฟาร์มวัว -ควบคุมคุณภาพได้ ผลิตโปรตีนได้สม่ำเสมอ ปราศจากสารก่อภูมิแพ้หรือยาปฏิชีวนะ -ลดการปล่อยก๊าซเรือนกระจก เพราะไม่ต้องเลี้ยงสัตว์ที่ปล่อยมีเทน
microflora จึงเป็น “เพื่อนร่วมงานที่เล็กที่สุด” แต่ก็อาจจะทรงพลังที่สุดในครัวของอนาคต และแม้เราจะยังยึดมั่นกับ animal-based diet อยู่ แต่ผมคิดว่าเรื่องนี้ก็น่าสนใจในฐานะ เทคโนโลยีที่กำลังท้าทายโลก fiat food อีกแนวทางหนึ่ง เพราะมันไม่ใช่พืชประดิษฐ์ ไม่ใช่แป้ง+สี+กลิ่น+สารพัด additive แต่คือ “การสร้างโปรตีนแท้” ด้วยความรู้ทางวิทยาศาสตร์ ที่เอื้อให้มนุษย์เลิกพึ่งวัวโดยตรง
ไม่แน่ว่าวันหนึ่ง แทนที่จะมีฟาร์มวัวเลี้ยงวัว 500 ตัวเพื่อผลิตเวย์ 1 ตัน เราอาจมีแค่ถังหมัก 1 ถัง ที่เลี้ยงเชื้อรา 500 ล้านตัว แล้วได้เวย์โปรตีนคุณภาพเดียวกัน...โดยไม่ต้องมีเสียง "มอ" เลยสักแอะ
แต่คำถามสำคัญคือ เราจะมีฟาร์มนั้นได้ไหม หรือได้แต่ทำหน้าที่ซื้อนมมารับประทานเท่านั้น
#pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-
 @ 16f1a010:31b1074b
2025-03-20 14:32:25
@ 16f1a010:31b1074b
2025-03-20 14:32:25grain is a nostr relay built using Go, currently utilizing MongoDB as its database. Binaries are provided for AMD64 Windows and Linux. grain is Go Relay Architecture for Implementing Nostr
Introduction
grain is a nostr relay built using Go, currently utilizing MongoDB as its database. Binaries are provided for AMD64 Windows and Linux. grain is Go Relay Architecture for Implementing Nostr
Prerequisites
- Grain requires a running MongoDB instance. Please refer to this separate guide for instructions on setting up MongoDB: nostr:naddr1qvzqqqr4gupzq9h35qgq6n8ll0xyyv8gurjzjrx9sjwp4hry6ejnlks8cqcmzp6tqqxnzde5xg6rwwp5xsuryd3knfdr7g
Download Grain
Download the latest release for your system from the GitHub releases page
amd64 binaries provided for Windows and Linux, if you have a different CPU architecture, you can download and install go to build grain from source
Installation and Execution
- Create a new folder on your system where you want to run Grain.
- The downloaded binary comes bundled with a ZIP file containing a folder named "app," which holds the frontend HTML files. Unzip the "app" folder into the same directory as the Grain executable.
Run Grain
- Open your terminal or command prompt and navigate to the Grain directory.
- Execute the Grain binary.
on linux you will first have to make the program executable
chmod +x grain_linux_amd64Then you can run the program
./grain_linux_amd64(alternatively on windows, you can just double click the grain_windows_amd64.exe to start the relay)
You should see a terminal window displaying the port on which your relay and frontend are running.
If you get
Failed to copy app/static/examples/config.example.yml to config.yml: open app/static/examples/config.example.yml: no such file or directory
Then you probably forgot to put the app folder in the same directory as your executable or you did not unzip the folder.
Congrats! You're running grain 🌾!
You may want to change your NIP11 relay information document (relay_metadata.json) This informs clients of the capabilities, administrative contacts, and various server attributes. It's located in the same directory as your executable.
Configuration Files
Once Grain has been executed for the first time, it will generate the default configuration files inside the directory where the executable is located. These files are:
bash config.yml whitelist.yml blacklist.ymlPrerequisites: - Grain requires a running MongoDB instance. Please refer to this separate guide for instructions on setting up MongoDB: [Link to MongoDB setup guide].
Download Grain:
Download the latest release for your system from the GitHub releases page
amd64 binaries provided for Windows and Linux, if you have a different CPU architecture, you can download and install go to build grain from source
Installation and Execution:
- Create a new folder on your system where you want to run Grain.
- The downloaded binary comes bundled with a ZIP file containing a folder named "app," which holds the frontend HTML files. Unzip the "app" folder into the same directory as the Grain executable.
Run Grain:
- Open your terminal or command prompt and navigate to the Grain directory.
- Execute the Grain binary.
on linux you will first have to make the program executable
chmod +x grain_linux_amd64Then you can run the program
./grain_linux_amd64(alternatively on windows, you can just double click the grain_windows_amd64.exe to start the relay)
You should see a terminal window displaying the port on which your relay and frontend are running.
If you get
Failed to copy app/static/examples/config.example.yml to config.yml: open app/static/examples/config.example.yml: no such file or directory
Then you probably forgot to put the app folder in the same directory as your executable or you did not unzip the folder.
Congrats! You're running grain 🌾!
You may want to change your NIP11 relay information document (relay_metadata.json) This informs clients of the capabilities, administrative contacts, and various server attributes. It's located in the same directory as your executable.
Configuration Files:
Once Grain has been executed for the first time, it will generate the default configuration files inside the directory where the executable is located. These files are:
bash config.yml whitelist.yml blacklist.ymlConfiguration Documentation
You can always find the latest example configs on my site or in the github repo here: config.yml
Config.yml
This
config.ymlfile is where you customize how your Grain relay operates. Each section controls different aspects of the relay's behavior.1.
mongodb(Database Settings)uri: mongodb://localhost:27017/:- This is the connection string for your MongoDB database.
mongodb://localhost:27017/indicates that your MongoDB server is running on the same computer as your Grain relay (localhost) and listening on port 27017 (the default MongoDB port).- If your MongoDB server is on a different machine, you'll need to change
localhostto the server's IP address or hostname. - The trailing
/indicates the root of the mongodb server. You will define the database in the next line.
database: grain:- This specifies the name of the MongoDB database that Grain will use to store Nostr events. Grain will create this database if it doesn't already exist.
- You can name the database whatever you want. If you want to run multiple grain relays, you can and they can have different databases running on the same mongo server.
2.
server(Relay Server Settings)port: :8181:- This sets the port on which your Grain relay will listen for incoming nostr websocket connections and what port the frontend will be available at.
read_timeout: 10 # in seconds:- This is the maximum time (in seconds) that the relay will wait for a client to send data before closing the connection.
write_timeout: 10 # in seconds:- This is the maximum time (in seconds) that the relay will wait for a client to receive data before closing the connection.
idle_timeout: 120 # in seconds:- This is the maximum time (in seconds) that the relay will keep a connection open if there's no activity.
max_connections: 100:- This sets the maximum number of simultaneous client connections that the relay will allow.
max_subscriptions_per_client: 10:- This sets the maximum amount of subscriptions a single client can request from the relay.
3.
resource_limits(System Resource Limits)cpu_cores: 2 # Limit the number of CPU cores the application can use:- This restricts the number of CPU cores that Grain can use. Useful for controlling resource usage on your server.
memory_mb: 1024 # Cap the maximum amount of RAM in MB the application can use:- This limits the maximum amount of RAM (in megabytes) that Grain can use.
heap_size_mb: 512 # Set a limit on the Go garbage collector's heap size in MB:- This sets a limit on the amount of memory that the Go programming language's garbage collector can use.
4.
auth(Authentication Settings)enabled: false # Enable or disable AUTH handling:- If set to
true, this enables authentication handling, requiring clients to authenticate before using the relay.
- If set to
relay_url: "wss://relay.example.com/" # Specify the relay URL:- If authentication is enabled, this is the url that clients will use to authenticate.
5.
UserSync(User Synchronization)user_sync: false:- If set to true, the relay will attempt to sync user data from other relays.
disable_at_startup: true:- If user sync is enabled, this will prevent the sync from starting when the relay starts.
initial_sync_relays: [...]:- A list of other relays to pull user data from.
kinds: []:- A list of event kinds to pull from the other relays. Leaving this empty will pull all event kinds.
limit: 100:- The limit of events to pull from the other relays.
exclude_non_whitelisted: true:- If set to true, only users on the whitelist will have their data synced.
interval: 360:- The interval in minutes that the relay will resync user data.
6.
backup_relay(Backup Relay)enabled: false:- If set to true, the relay will send copies of received events to the backup relay.
url: "wss://some-relay.com":- The url of the backup relay.
7.
event_purge(Event Purging)enabled: false:- If set to
true, the relay will automatically delete old events.
- If set to
keep_interval_hours: 24:- The number of hours to keep events before purging them.
purge_interval_minutes: 240:- How often (in minutes) the purging process runs.
purge_by_category: ...:- Allows you to specify which categories of events (regular, replaceable, addressable, deprecated) to purge.
purge_by_kind_enabled: false:- If set to true, events will be purged based on the kinds listed below.
kinds_to_purge: ...:- A list of event kinds to purge.
exclude_whitelisted: true:- If set to true, events from whitelisted users will not be purged.
8.
event_time_constraints(Event Time Constraints)min_created_at: 1577836800:- The minimum
created_attimestamp (Unix timestamp) that events must have to be accepted by the relay.
- The minimum
max_created_at_string: now+5m:- The maximum created at time that an event can have. This example shows that the max created at time is 5 minutes in the future from the time the event is received.
min_created_at_stringandmax_created_atwork the same way.
9.
rate_limit(Rate Limiting)ws_limit: 100:- The maximum number of WebSocket messages per second that the relay will accept.
ws_burst: 200:- Allows a temporary burst of WebSocket messages.
event_limit: 50:- The maximum number of Nostr events per second that the relay will accept.
event_burst: 100:- Allows a temporary burst of Nostr events.
req_limit: 50:- The limit of http requests per second.
req_burst: 100:- The allowed burst of http requests.
max_event_size: 51200:- The maximum size (in bytes) of a Nostr event that the relay will accept.
kind_size_limits: ...:- Allows you to set size limits for specific event kinds.
category_limits: ...:- Allows you to set rate limits for different event categories (ephemeral, addressable, regular, replaceable).
kind_limits: ...:- Allows you to set rate limits for specific event kinds.
By understanding these settings, you can tailor your Grain Nostr relay to meet your specific needs and resource constraints.
whitelist.yml
The
whitelist.ymlfile is used to control which users, event kinds, and domains are allowed to interact with your Grain relay. Here's a breakdown of the settings:1.
pubkey_whitelist(Public Key Whitelist)enabled: false:- If set to
true, this enables the public key whitelist. Only users whose public keys are listed will be allowed to publish events to your relay.
- If set to
pubkeys::- A list of hexadecimal public keys that are allowed to publish events.
pubkey1andpubkey2are placeholders, you will replace these with actual hexadecimal public keys.
npubs::- A list of npubs that are allowed to publish events.
npub18ls2km9aklhzw9yzqgjfu0anhz2z83hkeknw7sl22ptu8kfs3rjq54am44andnpub2are placeholders, replace them with actual npubs.- npubs are bech32 encoded public keys.
2.
kind_whitelist(Event Kind Whitelist)enabled: false:- If set to
true, this enables the event kind whitelist. Only events with the specified kinds will be allowed.
- If set to
kinds::- A list of event kinds (as strings) that are allowed.
"1"and"2"are example kinds. Replace these with the kinds you want to allow.- Example kinds are 0 for metadata, 1 for short text notes, and 2 for recommend server.
3.
domain_whitelist(Domain Whitelist)enabled: false:- If set to
true, this enables the domain whitelist. This checks the domains .well-known folder for their nostr.json. This file contains a list of pubkeys. They will be considered whitelisted if on this list.
- If set to
domains::- A list of domains that are allowed.
"example.com"and"anotherdomain.com"are example domains. Replace these with the domains you want to allow.
blacklist.yml
The
blacklist.ymlfile allows you to block specific content, users, and words from your Grain relay. Here's a breakdown of the settings:1.
enabled: true- This setting enables the blacklist functionality. If set to
true, the relay will actively block content and users based on the rules defined in this file.
2.
permanent_ban_words:- This section lists words that, if found in an event, will result in a permanent ban for the event's author.
- really bad wordis a placeholder. Replace it with any words you want to permanently block.
3.
temp_ban_words:- This section lists words that, if found in an event, will result in a temporary ban for the event's author.
- crypto,- web3, and- airdropare examples. Replace them with the words you want to temporarily block.
4.
max_temp_bans: 3- This sets the maximum number of temporary bans a user can receive before they are permanently banned.
5.
temp_ban_duration: 3600- This sets the duration of a temporary ban in seconds.
3600seconds equals one hour.
6.
permanent_blacklist_pubkeys:- This section lists hexadecimal public keys that are permanently blocked from using the relay.
- db0c9b8acd6101adb9b281c5321f98f6eebb33c5719d230ed1870997538a9765is an example. Replace it with the public keys you want to block.
7.
permanent_blacklist_npubs:- This section lists npubs that are permanently blocked from using the relay.
- npub1x0r5gflnk2mn6h3c70nvnywpy2j46gzqwg6k7uw6fxswyz0md9qqnhshtnis an example. Replace it with the npubs you want to block.- npubs are the human readable version of public keys.
8.
mutelist_authors:- This section lists hexadecimal public keys of author of a kind1000 mutelist. Pubkey authors on this mutelist will be considered on the permanent blacklist. This provides a nostr native way to handle the backlist of your relay
- 3fe0ab6cbdb7ee27148202249e3fb3b89423c6f6cda6ef43ea5057c3d93088e4is an example. Replace it with the public keys of authors that have a mutelist you would like to use as a blacklist. Consider using your own.- Important Note: The mutelist Event MUST be stored in this relay for it to be retrieved. This means your relay must have a copy of the authors kind10000 mutelist to consider them for the blacklist.
Running Grain as a Service:
Windows Service:
To run Grain as a Windows service, you can use tools like NSSM (Non-Sucking Service Manager). NSSM allows you to easily install and manage any application as a Windows service.
* For instructions on how to install NSSM, please refer to this article: [Link to NSSM install guide coming soon].-
Open Command Prompt as Administrator:
- Open the Windows Start menu, type "cmd," right-click on "Command Prompt," and select "Run as administrator."
-
Navigate to NSSM Directory:
- Use the
cdcommand to navigate to the directory where you extracted NSSM. For example, if you extracted it toC:\nssm, you would typecd C:\nssmand press Enter.
- Use the
-
Install the Grain Service:
- Run the command
nssm install grain. - A GUI will appear, allowing you to configure the service.
- Run the command
-
Configure Service Details:
- In the "Path" field, enter the full path to your Grain executable (e.g.,
C:\grain\grain_windows_amd64.exe). - In the "Startup directory" field, enter the directory where your Grain executable is located (e.g.,
C:\grain).
- In the "Path" field, enter the full path to your Grain executable (e.g.,
-
Install the Service:
- Click the "Install service" button.
-
Manage the Service:
- You can now manage the Grain service using the Windows Services manager. Open the Start menu, type "services.msc," and press Enter. You can start, stop, pause, or restart the Grain service from there.
Linux Service (systemd):
To run Grain as a Linux service, you can use systemd, the standard service manager for most modern Linux distributions.
-
Create a Systemd Service File:
- Open a text editor with root privileges (e.g.,
sudo nano /etc/systemd/system/grain.service).
- Open a text editor with root privileges (e.g.,
-
Add Service Configuration:
- Add the following content to the
grain.servicefile, replacing the placeholders with your actual paths and user information:
```toml [Unit] Description=Grain Nostr Relay After=network.target
[Service] ExecStart=/path/to/grain_linux_amd64 WorkingDirectory=/path/to/grain/directory Restart=always User=your_user #replace your_user Group=your_group #replace your_group
[Install] WantedBy=multi-user.target ```
- Replace
/path/to/grain/executablewith the full path to your Grain executable. - Replace
/path/to/grain/directorywith the directory containing your Grain executable. - Replace
your_userandyour_groupwith the username and group that will run the Grain service.
- Add the following content to the
-
Reload Systemd:
- Run the command
sudo systemctl daemon-reloadto reload the systemd configuration.
- Run the command
-
Enable the Service:
- Run the command
sudo systemctl enable grain.serviceto enable the service to start automatically on boot.
- Run the command
-
Start the Service:
- Run the command
sudo systemctl start grain.serviceto start the service immediately.
- Run the command
-
Check Service Status:
- Run the command
sudo systemctl status grain.serviceto check the status of the Grain service. This will show you if the service is running and any recent logs. - You can run
sudo journalctl -f -u grain.serviceto watch the logs
- Run the command
More guides are in the works for setting up tailscale to access your relay from anywhere over a private network and for setting up a cloudflare tunnel to your domain to deploy a grain relay accessible on a subdomain of your site eg wss://relay.yourdomain.com
-
 @ e39d100f:d27602e5
2025-04-21 02:18:40
@ e39d100f:d27602e5
2025-04-21 02:18:40O mercado de entretenimento digital no Brasil está em constante expansão, e entre as novas opções que vêm ganhando destaque, a plataforma Betao se sobressai como uma das mais promissoras. Com um ambiente moderno, seguro e recheado de atrações, o Betao oferece uma experiência diferenciada tanto para jogadores iniciantes quanto para os mais experientes.
Uma Plataforma Intuitiva e Acessível Logo ao acessar o site do Betao, o usuário já percebe a preocupação com a usabilidade. O design é limpo, responsivo e adaptado para todos os tipos de dispositivos, o que permite que os jogadores aproveitem ao máximo cada funcionalidade, seja no computador, tablet ou celular.
Além disso, o processo de cadastro é rápido e descomplicado. Em poucos cliques, o jogador já está pronto para explorar os jogos disponíveis. Outro ponto positivo é a variedade de métodos de pagamento, que incluem transferências bancárias, carteiras digitais e até opções com criptomoedas, oferecendo mais liberdade e praticidade.
Catálogo de Jogos Variado e Empolgante O Betao se destaca por seu portfólio diversificado de jogos online. A plataforma trabalha com provedores renomados do setor, garantindo alta qualidade gráfica, fluidez nas partidas e mecânicas envolventes.
Entre os destaques, estão os jogos de slots, que atraem jogadores pela combinação de simplicidade e emoção. Com temas variados, gráficos vibrantes e bônus interativos, essas máquinas virtuais oferecem diversão contínua e oportunidades de prêmios significativos.
Outra categoria bastante procurada são os jogos de mesa, como roleta, blackjack e bacará. Essas opções são ideais para quem gosta de jogos que exigem estratégia e tomada de decisões rápidas, proporcionando uma experiência desafiadora e recompensadora.
Experiência do Jogador em Primeiro Lugar No Betao, o foco está na satisfação do jogador. A plataforma investe constantemente em melhorias para garantir um ambiente justo, transparente e divertido. Um dos grandes diferenciais é o suporte ao cliente, que funciona 24 horas por dia, todos os dias da semana. Com atendimento em português e canais acessíveis — como chat ao vivo e e-mail —, os usuários recebem ajuda imediata sempre que necessário.
Além disso, o Betao promove promoções regulares, programas de fidelidade e bônus de boas-vindas que valorizam a permanência e o engajamento dos jogadores. Tudo isso contribui para criar uma comunidade ativa e satisfeita.
Segurança e Confiabilidade Segurança é um fator essencial em qualquer plataforma de jogos online, e o Betao leva isso a sério. A empresa utiliza tecnologias de criptografia avançadas para proteger os dados e transações dos usuários, além de operar de forma legalizada, com licenças reconhecidas internacionalmente. Essa transparência aumenta a confiança dos jogadores e garante tranquilidade durante toda a experiência.
Conclusão Com uma combinação de tecnologia de ponta, ampla variedade de jogos, atendimento eficiente e foco total na experiência do usuário, o Betao se consolida como uma das melhores opções para quem busca diversão e entretenimento de qualidade no universo digital. Seja você um novato ou veterano nesse meio, vale a pena explorar tudo o que a plataforma tem a oferecer.
-
 @ 16f1a010:31b1074b
2025-03-20 14:31:19
@ 16f1a010:31b1074b
2025-03-20 14:31:19Introduction
MongoDB is a popular NoSQL document database, meaning it stores data in flexible, JSON-like documents. This makes it highly scalable and adaptable for various applications. This guide will focus on installing the Community Server edition, which is free and open-source.
This article is designed for beginners and those new to MongoDB, providing a clear and concise walkthrough of the installation process. We will cover installation on both Windows and Linux operating systems.
The official MongoDB documentation on the MongoDB website is very informative and you should be able to follow their guides. This article is written to provide a brief overview and a more streamlined installation experience.
Prerequisites
MongoDB Community Server can be installed and run on a wide range of systems. While specific hardware requirements can vary based on your intended use case and the size of your database, here are the general prerequisites:
- Operating System:
- This guide will cover installation on popular versions of Windows and Linux (specifically Ubuntu/Debian). MongoDB also supports other operating systems, which you can find on the official MongoDB website.
- Storage Space:
- You'll need sufficient disk space to store your database files. The amount of space required will depend on the size of your data. It is recommended to have more storage than you think you will initially need.
- RAM:
- While MongoDB can run with minimal RAM, having more RAM will improve performance, especially for larger databases. The amount of RAM needed will depend on the size of your data.
- Basic System Knowledge:
- Familiarity with using the command line or terminal is helpful, especially for Linux installations.
- Basic understanding of file systems and directories.
Essentially, MongoDB is designed to be flexible and can run on most modern systems. As your data grows, you can always scale your hardware accordingly.
Downloading MongoDB Community Server:
To begin, you'll need to download the MongoDB Community Server installation package.
- Visit the official MongoDB download page: https://www.mongodb.com/try/download/community
On the download page, you'll see options to select the following:
- Version: Choose the desired version of MongoDB. It is generally recommended to select the latest stable release.
- Operating System: Select your operating system (Windows or Linux).
- Package: Select the appropriate package type. For Windows, it will typically be
msi. For Linux, you will choose the package type that aligns with your linux distro. For example.debfor Debian/Ubuntu or.rpmfor RedHat/Fedora.
Once you have made your selections, click the "Download" button to download the installer or package.
Installation on Windows:
Running the Installer:
-
Locate the Downloaded Installer:
- Navigate to the directory where you downloaded the MongoDB
.msiinstaller.
- Navigate to the directory where you downloaded the MongoDB
-
Run the Installer:
- Double-click the
.msifile to start the installation wizard.
- Double-click the
-
Welcome Screen:
- Click "Next" on the welcome screen.
-
License Agreement:
- Read the license agreement, check the "I accept the terms in the License Agreement" box, and click "Next."
-
Setup Type:
- Select "Custom" installation. This allows you to choose the installation location and data directory. Click "Next."
-
Installation Location:
- You can change the default installation directory if desired. Click "Next."
-
Service Configuration:
- You can choose to install MongoDB as a service. It is recommended to install as a service.
- You can also change the "Data Directory" location here. It is recommended to change this to a location such as
C:\data\db. If you do not change it here, you will need to create the data directory manually later. - Click "Next."
-
Ready to Install:
- Click "Install" to begin the installation process.
-
Complete Installation:
- Once the installation is complete, click "Finish."
Setting Environment Variables (Optional but Recommended):
Setting the
PATHenvironment variable allows you to run MongoDB commands from any command prompt window without specifying the full path to the executable.-
Open System Properties:
- Search for "Environment Variables" in the Windows Start menu and select "Edit the system environment variables."
-
Environment Variables:
- In the "System Properties" window, click the "Environment Variables..." button.
-
Edit Path Variable:
- In the "System variables" section, find the "Path" variable and click "Edit."
-
Add MongoDB Bin Directory:
- Click "New" and add the path to the MongoDB
bindirectory. This is typicallyC:\Program Files\MongoDB\Server\<version>\bin, replacing<version>with your installed version. - Click "OK" on all open windows to save the changes.
- Click "New" and add the path to the MongoDB
-
Verify Path:
- Open a new command prompt window and type
mongod --version. If MongoDB is installed correctly and thePATHvariable is set, you should see the MongoDB version information.
- Open a new command prompt window and type
Installation on Linux (Ubuntu/Debian):
These instructions are specifically for Debian-based systems like Ubuntu.
Importing the MongoDB Public GPG Key:
-
Open a Terminal:
- Open your terminal application.
-
Import the GPG Key:
- Run the following command to import the MongoDB public GPG key:
bash wget -qO - [https://www.mongodb.org/static/pgp/server-7.0.asc](https://www.mongodb.org/static/pgp/server-7.0.asc) | sudo apt-key add -- This command downloads the GPG key and adds it to your system's trusted keys. This ensures that the packages you download from the MongoDB repository are authentic.
Adding the MongoDB Repository:
-
Add the Repository:
- Run the following command to add the MongoDB repository to your system's sources list:
bash echo "deb [ arch=amd64,arm64 ] [https://repo.mongodb.org/apt/ubuntu](https://repo.mongodb.org/apt/ubuntu) $(lsb_release -cs)/mongodb-org/7.0 multiverse" | sudo tee /etc/apt/sources.list.d/mongodb-org-7.0.list- This command adds the MongoDB repository to your system's package manager sources. The
$(lsb_release -cs)part automatically determines your Ubuntu/Debian version.
-
Update Package List:
- Run the following command to update your package list:
bash sudo apt update- This command refreshes the package list, including the newly added MongoDB repository.
Installing MongoDB:
-
Install MongoDB:
- Run the following command to install the MongoDB Community Server:
bash sudo apt install mongodb-org- This command downloads and installs the MongoDB packages.
After install, linux and windows should both have a system service already setup from the install process. You can check if it's running on linux with
sudo systemctl status mongod. On Windows, you should see the service running as "MongoDB Server" if you open system services on WindowsBasic MongoDB Commands:
After installing and starting MongoDB, you can use the
mongoshell to interact with your database. Here are some basic commands to get you started:Checking MongoDB Version:
First, let's verify that MongoDB is installed correctly by checking its version:
-
Open a Terminal or Command Prompt:
- Open your terminal (Linux/macOS) or command prompt (Windows).
-
Run
mongosh --version:- Type
mongosh --versionand press Enter. - This command will display the installed MongoDB version if it's correctly installed and in your system's PATH.
- Type
Basic MongoDB Shell Commands:
-
Open the
mongoshShell:- Type
mongoshand press Enter. This will open the MongoDB shell, and you'll see a prompt like>.
- Type
-
Show Databases:
- To see a list of all databases on your MongoDB server, type
show dbsand press Enter. - This will display a list of database names.
- To see a list of all databases on your MongoDB server, type
-
Use a Database:
- To switch to a specific database, type
use <database_name>and press Enter. Replace<database_name>with the name of the database you want to use. - Example:
use mydatabase - If the database doesn't exist, MongoDB will create it when you first store data in it.
- To switch to a specific database, type
-
Show Collections:
- After switching to a database, you can see a list of collections (similar to tables in relational databases) in that database by typing
show collectionsand pressing Enter. - Collections are where you store documents (JSON-like data).
- After switching to a database, you can see a list of collections (similar to tables in relational databases) in that database by typing
Example Session:
```bash
mongosh Current Mongosh Log ID: 6563728637951a37887e2730 Connecting to: mongodb://127.0.0.1:27017/?directConnection=true&serverSelectionTimeoutMS=2000&appName=mongosh Using MongoDB: 7.0.3 Using Mongosh: 2.1.1 For mongosh info see: https://docs.mongodb.com/mongodb-shell/
test> show dbs admin 40 KiB config 72 KiB local 40 KiB test> use mydatabase switched to db mydatabase mydatabase> show collections mydatabase> ```
Conclusion
Congratulations! You have successfully installed and started MongoDB Community Server. You've learned how to download, install, and run MongoDB on both Windows and Linux systems, and you've explored some basic commands to interact with your database.
Now, you might want to try an application like grain, a Nostr relay, which utilizes MongoDB as its database. Learn How to Install grain: nostr:naddr1qvzqqqr4gupzq9h35qgq6n8ll0xyyv8gurjzjrx9sjwp4hry6ejnlks8cqcmzp6tqqxnzde5xg6rqdpnx56rqv34uyz5g4
Remember, this guide covers the basics. There's much more to explore in the world of MongoDB, including advanced querying, indexing, replication, and sharding. Continue exploring the official MongoDB documentation to deepen your knowledge and unlock the full potential of this powerful database.
- Operating System:
-
 @ f1989a96:bcaaf2c1
2025-03-20 14:21:35
@ f1989a96:bcaaf2c1
2025-03-20 14:21:35Good morning, readers!
In Thailand, the government announced a third digital cash handout to “stimulate the economy and drive technological adoption.” This disbursement will allocate 27 billion baht ($800 million) to 2.7 million citizens aged 16-20. Like in previous phases, it will be distributed via a state-controlled “digital wallet” application, which essentially functions as a central bank digital currency (CBDC). This system gives the regime an inside view of Thais’ financial activity and creates a centralized database to monitor, censor, and control.
Meanwhile, in Russia, the central bank has proposed limiting Bitcoin access to only the wealthiest individuals. Under the proposal, only Russians with over $1.2 million in assets or an annual income above $580,000 could buy and sell digital assets — arbitrarily barring everyday Russians (including obviously most journalists and activists) from accessing Bitcoin and the financial independence it grants.
In open-source software news, a new tool called Banxaas is making Bitcoin more accessible in West Africa by integrating with local payment providers to facilitate buying and selling Bitcoin using the CFA currency (XOF). This on-and-off ramp could expand financial freedom for human rights activists, dissidents, and everyday citizens.
We end with the latest edition of the HRF x Pubkey Freedom Tech Series, in which HRF’s Zac Guignard sits down with author Jason Maier to discuss how Bitcoin can drive human rights around the world. Together, they examine the shortcomings of today’s financial system and discuss how Bitcoin is aiding people living under authoritarian regimes.
Now, let’s get right to it!
Subscribe Here
GLOBAL NEWS
Thailand | Announces Third Digital Cash Handout to Boost Economy
The government of Thailand announced a third digital cash handout, allocating 27 billion baht ($800 million) to 2.7 million citizens aged 16-20 to “stimulate the economy and drive technological adoption.” Like in previous phases, the regime will distribute the funds through a state-run “digital wallet” application, which would effectively function as a central bank digital currency (CBDC). Past handouts of the CBDC came with strict restrictions: spending was limited to approved vendors within designated areas, purchases were restricted to certain goods, and funds expired after six months. Meanwhile, Prime Minister Paetongtarn Shinawatra called this third handout the first full deployment of the digital wallet system and urged the public to download the official app. This would directly link citizens' financial activity and data to the regime, threaten privacy, and deepen repression in a country with a long history of silencing dissent.
Russia | Central Bank Proposes Restricting Bitcoin Access to Wealthy Only
Russia’s central bank has proposed restricting Bitcoin and cryptocurrency access to only the country’s wealthiest individuals, barring everyday Russians from buying and selling digital assets unless they meet specific income or asset thresholds. Under the proposal, only Russians with over $1.2 million in assets or an annual income above $580,000 could engage with digital assets — effectively putting Bitcoin officially out of reach of most activists and journalists. The central bank claims the measure protects citizens from “volatility and lack of state backing.” But in reality, it likely signals the regime’s fear of Bitcoin’s ability to provide individual financial autonomy. By blocking most Russians from opting out of the state-controlled financial system, the regime is doubling down on financial repression.
India | Advances Digital Rupee CBDC
India’s government is pushing forward with its CBDC, the Digital Rupee, hailing it as a modern payment solution. But as journalist and author Roger Huang puts it, “it looks like a solution searching for a problem to solve.” Beyond the branding, the Digital Rupee enables state control over financial activity. Its programmability allows the government to dictate how, when, and where people spend — restricting transactions to specific merchants, locations, or goods and even imposing expiration dates on money. India’s crackdown on dissent is well-documented, from freezing opposition bank accounts to attempting a Bitcoin ban. Now, the Reserve Bank of India is embedding the CBDC into its digital payment system (UPI), quietly pushing millions into a tightly controlled and surveilled financial system.
Zimbabwe | Financial Regulators Mandate Earnings in ZiG
Zimbabwe’s market regulator is mandating all companies report their earnings in the new ZiG currency despite it losing 96% of its value since its launch last year. This move tightens state control over an already fragile economy, pushing businesses and citizens deeper into an unstable system that has repeatedly wiped out savings through inflation. The ZiG is Zimbabwe’s sixth currency in 15 years, introduced with gold backing to restore confidence in the regime’s ability to manage a currency. Instead, it’s rapidly devaluing, while the US dollar remains the preferred currency for trade and savings — when accessible. For ordinary Zimbabweans, the mandatory use of ZiG for taxes and government services is already a challenge due to its scarcity.
Egypt | Dictator-imposed Reforms Causing Economic Chaos
In the wake of an $8 billion deal with the International Monetary Fund (IMF) last spring, the Egyptian dictatorship has carried out “reforms” that are fueling inflation and making necessities increasingly unaffordable. To meet IMF conditions, Egyptian officials devalued the pound, slashed subsidies, and hiked the cost of fuel and public transportation — driving inflation beyond 20% for months on end. For millions of Egyptians, basic goods are now unaffordable. And the government’s promised minimum wage increase for public workers remains unfulfilled, leaving the public to absorb the price shocks. These undemocratic reforms — never voted on and executed with no way for the public to push back — aimed at securing further financing have only eroded the financial freedom of 114 million Egyptians and pushed the country into greater debt.
China | Facebook Enabling Authoritarian Censorship
A former Meta executive, Sarah Wynn-Williams, has accused Facebook of working “hand in glove” with the Chinese Communist Party (CCP) to censor and surveil content in China. According to Wynn-Williams, Facebook explored building censorship tools that would suppress viral posts until Chinese authorities approved. They even considered sharing user data in exchange for market access to China’s massive user base. Meta denied these claims, saying they fired Wynn-Williams in 2017 for poor performance. Regardless, the revelations highlight the dangers of for-profit, centralized platforms that authoritarian regimes can co-opt. Protocols like nostr (where no single entity moderates content) are more important than ever. Activists and dissidents seeking free communications can get started with nostr here.
BITCOIN AND FREEDOM TECH NEWS
Banxaas | Spend Sats in West Africa
Hundreds of millions of citizens in West Africa still use the CFA franc in an arrangement upheld by more than a dozen authoritarian leaders. Banxaas offers an alternative by bridging Bitcoin with West Africa’s mobile money networks. This allows individuals to buy and sell Bitcoin through local payment providers using the local CFA currency (XOF) and their own Lightning wallet. By integrating with local payment providers, Banxaas serves as a crucial on-and-off-ramp to Bitcoin, bringing the benefits of financial freedom to individuals, nonprofits, and human rights defenders across the region. Watch a demonstration of how Banxaas works here.
Mi Primer Bitcoin | Bitcoin Workbook Translated to Mandarin
Mi Primer Bitcoin, an open-source Bitcoin educational initiative focused on high-school-age students, released a Mandarin translation of its 2025 Bitcoin Diploma. This open-source resource provides mainland Chinese citizens, activists, and dissidents with accessible Bitcoin education at a time when financial freedom is increasingly under threat. With China tightening restrictions on personal wealth and expanding state surveillance of financial activity through the digital yuan CBDC, the diploma offers a useful new resource to learn the alternatives to state-controlled financial systems.
Blitz Wallet | Improves Ecash Functionality for Greater Financial Autonomy
Blitz Wallet, an open-source and self-custodial Bitcoin Lightning, Liquid, and ecash wallet, released an update that improves ecash functionality. Ecash, a Bitcoin-backed digital money system, allows instant and private transactions but requires custodial “mints” to manage tokens. The new update links users’ ecash to their wallet’s seed phrase (the 12-word backup used for Bitcoin recovery), allowing them to restore funds even if their device is lost or stolen. Users can also now transfer ecash between different wallets, increasing flexibility and control over their funds. Improved ecash UX is much-desired for political dissidents who can’t afford for authoritarian regimes to have full oversight over all of their economic activities.
Fedimint | Adds On-chain Support for Everyone
Fedimint, an open-source Bitcoin custody model that lets communities securely manage Bitcoin funds together, released v0.6.0, adding support for on-chain Bitcoin deposits (transactions directly on Bitcoin’s base layer). By offering private and trust-minimized transactions alongside on-chain support, Fedimint makes it easier, especially for nonprofit communities, to self-custody Bitcoin. It provides greater privacy and autonomy versus using fully centralized platforms that are easily subject to the political and regulatory pressure of authoritarian regimes.
Africa Bitcoin Conference | Announces 2025 Conference
The Africa Bitcoin Conference (ABC) announced its fourth edition, set to take place from Dec. 3-5, 2025, in Port Louis, Mauritius. Hosted at the Caudan Art Center, the event will bring together activists, Bitcoin advocates, and freedom tech developers to explore Bitcoin as a pathway to financial freedom. Now the largest Bitcoin gathering in Africa, ABC has established itself as a key platform for discussions on financial inclusion, inflation resistance, and censorship-resistant money — putting tools for financial sovereignty into the hands of those who need them most. HRF is proud to support ABC and, in particular, is proud to help delegates from dozens of authoritarian regimes attend each year. You can learn more about the conference and buy tickets here.
RECOMMENDED CONTENT
HRF x Pubkey — How Bitcoin Brings About Social Change with Jason Maier
In the latest installment of the HRF x Pubkey Freedom Tech Series, HRF Content and Research Associate Zac Guignard sits down with Jason Maier, author of “A Progressive’s Case for Bitcoin,” to share how Bitcoin can spark a meaningful shift in personal liberty worldwide. Jason explains the core monetary properties that make Bitcoin permissionless, censorship-resistant, and a powerful tool for financial freedom. Together, they examine the shortcomings of today’s financial system and discuss how Bitcoin is aiding people living under authoritarian regimes. They talk about how Bitcoin shouldn’t be a political issue and can be useful to anyone, no matter their beliefs. Watch the full conversation here.
Mélancolies de l’Opprimé by Farida Bemba Nabourema
Farida Bemba Nabourema, a renowned Togolese human rights activist, former HRF freedom fellow, and Bitcoin pioneer, announced that her new book “Mélancolies de l’Opprimé” will be released on April 15, 2025. A decade after her first book, “La Pression de l’Oppression,” this deeply personal and reflective work offers hard-earned wisdom for young activists stepping into the struggle against dictatorships and injustice. Nabourema candidly shares the emotional, physical, and psychological toll of resistance and activism while also highlighting the sense of purpose in the pursuit of freedom and human rights. Learn more about the book here.
If this article was forwarded to you and you enjoyed reading it, please consider subscribing to the Financial Freedom Report here.
Support the newsletter by donating bitcoin to HRF’s Financial Freedom program via BTCPay.\ Want to contribute to the newsletter? Submit tips, stories, news, and ideas by emailing us at ffreport @ hrf.org
The Bitcoin Development Fund (BDF) is accepting grant proposals on an ongoing basis. The Bitcoin Development Fund is looking to support Bitcoin developers, community builders, and educators. Submit proposals here.
-
 @ 87122b31:726e2c4c
2025-04-21 02:16:07
@ 87122b31:726e2c4c
2025-04-21 02:16:07BJ66 là một nền tảng kỹ thuật số nổi bật với thiết kế tối giản nhưng đầy tinh tế, hướng đến việc tạo ra một môi trường thân thiện và dễ tiếp cận cho tất cả người dùng. Ngay từ giao diện đầu tiên, BJ66 cho thấy sự chú trọng vào trải nghiệm người dùng khi mọi yếu tố được sắp xếp một cách khoa học và thuận tiện. Các tính năng chính được trình bày rõ ràng, biểu tượng minh họa sắc nét giúp người dùng dễ dàng thao tác, kể cả với những người chưa có nhiều kinh nghiệm sử dụng công nghệ. Sự linh hoạt trong cách bố trí menu, lựa chọn ngôn ngữ và chế độ hiển thị sáng – tối cũng mang đến sự cá nhân hóa tối đa cho mỗi người dùng. Nền tảng này tương thích mượt mà trên nhiều thiết bị khác nhau từ điện thoại thông minh, máy tính bảng đến laptop, tạo điều kiện cho người dùng kết nối mọi lúc mọi nơi mà không bị giới hạn bởi thiết bị hay hệ điều hành.
Không chỉ dừng lại ở thiết kế giao diện đẹp mắt và thân thiện, BJ66 còn ghi điểm mạnh mẽ ở khả năng vận hành ổn định và bảo mật cao. Với hệ thống máy chủ tối ưu và công nghệ xử lý hiện đại, các thao tác trên BJ66 diễn ra nhanh chóng, mượt mà, không bị giật lag hay gián đoạn. Người dùng có thể thực hiện nhiều hoạt động cùng lúc mà không gặp tình trạng chậm trễ hay lỗi hệ thống, đặc biệt quan trọng trong bối cảnh yêu cầu tốc độ và tính liên tục ngày càng cao. Về bảo mật, BJ66 áp dụng các lớp mã hóa tiên tiến và cơ chế xác minh đa yếu tố, bảo vệ thông tin cá nhân và dữ liệu của người dùng khỏi các rủi ro tấn công mạng. Mọi hoạt động đăng nhập, thay đổi cài đặt hay giao dịch đều được theo dõi và ghi nhận để tăng cường tính minh bạch và an toàn. Đội ngũ hỗ trợ kỹ thuật của BJ66 cũng là một điểm cộng lớn, khi họ hoạt động liên tục 24/7 với thái độ chuyên nghiệp, tận tâm và phản hồi nhanh chóng, đảm bảo người dùng luôn có người đồng hành trong suốt quá trình sử dụng.
BJ66 không ngừng đổi mới và phát triển để mang đến một hệ sinh thái số toàn diện, đáp ứng mọi nhu cầu của người dùng hiện đại. Nền tảng tích hợp nhiều tiện ích thông minh được hỗ trợ bởi công nghệ tiên tiến như trí tuệ nhân tạo (AI), cá nhân hóa nội dung và gợi ý dựa trên thói quen sử dụng. Điều này giúp người dùng tiết kiệm thời gian tìm kiếm và truy cập nhanh hơn đến các tính năng mình yêu thích. Ngoài ra, BJ66 thường xuyên cập nhật những cải tiến mới nhằm nâng cao hiệu suất, cải thiện giao diện và tối ưu hóa các chức năng, từ đó duy trì được tính cạnh tranh và giữ chân người dùng trong thời gian dài. Trong thời đại công nghệ số đang phát triển nhanh chóng, BJ66 nổi bật như một lựa chọn đáng tin cậy, nơi người dùng có thể yên tâm trải nghiệm với sự an toàn, thuận tiện và sự thấu hiểu đến từ một nền tảng luôn đặt người dùng ở vị trí trung tâm. Với sự kết hợp giữa công nghệ hiện đại, giao diện thân thiện và cam kết phát triển bền vững, BJ66 không chỉ đơn thuần là một công cụ mà còn là một phần không thể thiếu trong lối sống số hóa ngày nay.
-
 @ 21335073:a244b1ad
2025-03-20 13:16:22
@ 21335073:a244b1ad
2025-03-20 13:16:22I’d never had the chance to watch Harry Potter on the big screen before. Experiencing the first movie in 3D was nothing short of spectacular. Right from the opening scene with Albus Dumbledore, I was floored—the makeup and costumes were so vivid, it felt like pure magic unfolding before my eyes. It’s clear that real masters of their craft worked behind the scenes, and their artistry shines through. The sets? Absolutely jaw-dropping! The level of detail in Diagon Alley was beyond impressive.
Seeing legends like Alan Rickman as Snape and Maggie Smith as Minerva McGonagall on that massive 3D screen was an unforgettable thrill. The film is packed with phenomenal actors, and it was a joy to catch every tiny eye twitch and subtle nuance of their performances brought to life. It was a mind-blowing experience, and I’d wholeheartedly recommend it to anyone who gets the chance.
Don’t forget to have a little whimsical fun sometimes my friends. 🪄
-
 @ 87122b31:726e2c4c
2025-04-21 02:15:16
@ 87122b31:726e2c4c
2025-04-21 02:15:16WIN1 là nền tảng công nghệ hiện đại được xây dựng với mục tiêu cung cấp một không gian trực tuyến toàn diện, nơi người dùng có thể tương tác, trải nghiệm và kết nối một cách mượt mà, tiện lợi. Sở hữu giao diện trực quan, tối ưu hóa cho cả người mới bắt đầu và người dùng thành thạo, WIN1 tạo ra cảm giác thân thiện ngay từ lần đầu truy cập. Các yếu tố bố cục được sắp xếp hợp lý, màu sắc hài hòa và các biểu tượng dễ hiểu giúp việc điều hướng trở nên dễ dàng trên mọi loại thiết bị – từ điện thoại thông minh, máy tính bảng đến máy tính cá nhân. Không dừng lại ở đó, WIN1 còn cho phép người dùng tùy chỉnh không gian trải nghiệm cá nhân với các chế độ giao diện sáng – tối, ngôn ngữ linh hoạt, và các thiết lập cá nhân hóa dựa trên thói quen sử dụng. Nhờ vậy, người dùng luôn cảm thấy sự chủ động trong mọi tương tác với nền tảng.
Điểm nổi bật khác giúp WIN1 khẳng định vị thế là khả năng vận hành ổn định và bảo mật cao. Hệ thống hoạt động nhanh chóng, ổn định và có khả năng xử lý đồng thời nhiều truy cập mà không gây gián đoạn. Điều này đặc biệt quan trọng trong bối cảnh người dùng ngày càng có xu hướng sử dụng nhiều thiết bị cùng lúc để phục vụ nhu cầu công việc và giải trí. WIN1 áp dụng các công nghệ mã hóa tiên tiến và xác thực bảo mật nhiều lớp, đảm bảo dữ liệu người dùng luôn được bảo vệ nghiêm ngặt. Ngoài ra, nền tảng còn thường xuyên cập nhật và kiểm tra hệ thống để phát hiện, khắc phục kịp thời các rủi ro tiềm ẩn. Bên cạnh yếu tố kỹ thuật, WIN1 còn xây dựng đội ngũ chăm sóc khách hàng tận tâm, hoạt động 24/7, sẵn sàng hỗ trợ người dùng trong mọi tình huống từ những thắc mắc đơn giản đến các vấn đề kỹ thuật phức tạp, giúp người dùng an tâm tuyệt đối trong suốt hành trình trải nghiệm.
Không ngừng đổi mới và hoàn thiện, WIN1 liên tục tích hợp các xu hướng công nghệ tiên tiến nhằm tối ưu hóa hiệu suất và nâng cao trải nghiệm người dùng. Nền tảng này không chỉ đơn thuần là công cụ kết nối, mà còn hướng đến xây dựng một hệ sinh thái số hóa toàn diện, trong đó người dùng có thể tận hưởng sự tương tác thông minh nhờ vào các tiện ích được tích hợp như trí tuệ nhân tạo (AI), hệ thống gợi ý cá nhân hóa và các tính năng tự động hóa thông minh. Các phân tích dữ liệu từ hành vi người dùng được sử dụng một cách linh hoạt để đưa ra đề xuất phù hợp, giúp mỗi lần truy cập vào WIN1 đều mang lại cảm giác mới mẻ và đúng nhu cầu. Đây chính là minh chứng cho định hướng phát triển dài hạn, bền vững của WIN1: luôn lấy người dùng làm trung tâm, không ngừng nâng cấp công nghệ, đồng thời đảm bảo sự ổn định và an toàn trong suốt quá trình sử dụng. Trong thời đại mà công nghệ trở thành một phần không thể thiếu trong cuộc sống, WIN1 là lựa chọn lý tưởng dành cho những ai đang tìm kiếm một nền tảng đáng tin cậy, dễ sử dụng và luôn đổi mới để bắt kịp xu hướng toàn cầu.
-
 @ a60e79e0:1e0e6813
2025-03-20 12:58:13
@ a60e79e0:1e0e6813
2025-03-20 12:58:13*This is a long form Nostr native version of a post that lives on my Nostr educational website Hello Nostr *
At first glance Nostr might appear quite similar to some of the apps you use every day, such as Twitter, Mastodon, or Facebook, but that couldn't be further from the truth. This post aims to dispel the myth that "Nostr is just a Twitter replacement" and give you a better understanding about the 'what', the 'how' and most importantly, the 'why' of Nostr.
What Is Nostr?
Nostr is a decentralized, open-source protocol designed for censorship-resistant networking and communication on the web. It stands for "Notes and Other Stuff Transmitted by Relays," and it works by allowing users to publish messages (notes) and content in the form of 'other stuff', to a network of servers (relays) that store and distribute the content.
Unlike traditional platforms like Twitter, Ebay or Facebook, Nostr doesn't rely on a central authority; instead, users control their own identities via cryptographic key pairs.
The simplest open protocol that is able to create a censorship-resistant global "social" network once and for all.
Fiatjaf - Nostr Creator
Nostr is not a website or an app you download from a single source — it’s an open protocol, like email or the internet. Think of it as a set of rules that anyone can use to build tools for sharing messages, posts, or other data without needing a centralized middleman like a big tech company.
Nostr was created by a developer named Fiatjaf in 2020, and has since been steadily gaining traction among people who care about privacy, freedom, and censorship resistance.

Why Nostr?
Imagine the scenario, you've been using an online platform for 5 or even 10 years. You've built up thousands of contacts, perhaps built yourself a sizeable reputation, or even rely on the income from the platform to feed your family. Then one day you make a controversial post, sell a certain item or upload a video on a spicy subject to the platform where the owner disagrees with. With the click of a button, your account is removed. All trace of you, your social graph, or even your future income, disappears in an instant.
Read aloud like that is sounds crazy that we'd even entertain using such a platform, right!? Sadly that is the reality in 2025. This is exactly what happens every single day on X, Facebook, Ebay, Paypal, Linkedin, etc.
Looking at the problem through a more social media focused lens, many of us have become slaves to the likes of Instagram, Twitter and TikTok. We use these 'free' apps under the guise of being social with others online. The reality is that we see what those apps want us to see. We've become slaves to the manipulation of complex and opaque algrorithms designed to keep us hooked and try to sell us things.

Unlike traditional platforms, which are often governed by centralized entities wielding significant control over user data, content moderation, and algorithmic influence, Nostr flips the script by prioritizing user sovereignty and resilience. Built on an open-source framework, Nostr allows individuals to control their own data and interact through a network of relays, making it much more difficult for any single authority - be it a corporation, government, or bad actor - to censor or manipulate the flow of information.
- Is a relay refusing to host your notes? Use another or run your own!
- A specific client using an algorithm you don't like, take your identity and social graph elsewhere and choose another!
Take your identity and social graph with you, anywhere any time.
Nostr’s ability to foster authentic, unfiltered conversations while safeguarding user sovereignty has made it a cornerstone for communities seeking alternatives - whether they’re activists, creators, or everyday people tired of being pawns in the data-driven game. It's simple and adaptable design also encourages innovation, inviting developers to build tools and interfaces that keep pushing the boundaries of what the decentralized internet can achieve. In short, Nostr isn’t just a tool; it’s a movement toward a freer, more equitable digital future.

How Does Nostr Work?
Instead of one giant server owned by a single company holding all your posts and messages, Nostr spreads everything across lots of smaller servers called relays. To get started, you download a client, create your account and back up your private key. Your private key is used to secure your account and sign every message you send over the network. This allows anyone you interact with the verify the integrity of the data coming from 'you'.
The Nostr network is essentially a collection of bulletin boards that share a common format
When you write a note, or share some other type of compatible data, your client signs it with your private key, then sends it to one or more relays. Which relays your information is sent to is entirely up to you. These relays share your message with others who want to see it.
For others to see your notes or 'other stuff', they'll need to be able to find you. Typically this is done by using your public key, which looks something like this
npub15c88nc8d44gsp4658dnfu5fahswzzu8gaxm5lkuwjud068swdqfspxssvx. Don't panic though, you don't need to memorize all of your friends public keys, there are more human friendly methods of finding people that we'll come onto later.Once someone is following you, their client will ask all of their connected relays for any data shared by your public key. Their client will receive this data, verify it is signed by your private key and then populate it into their feed.
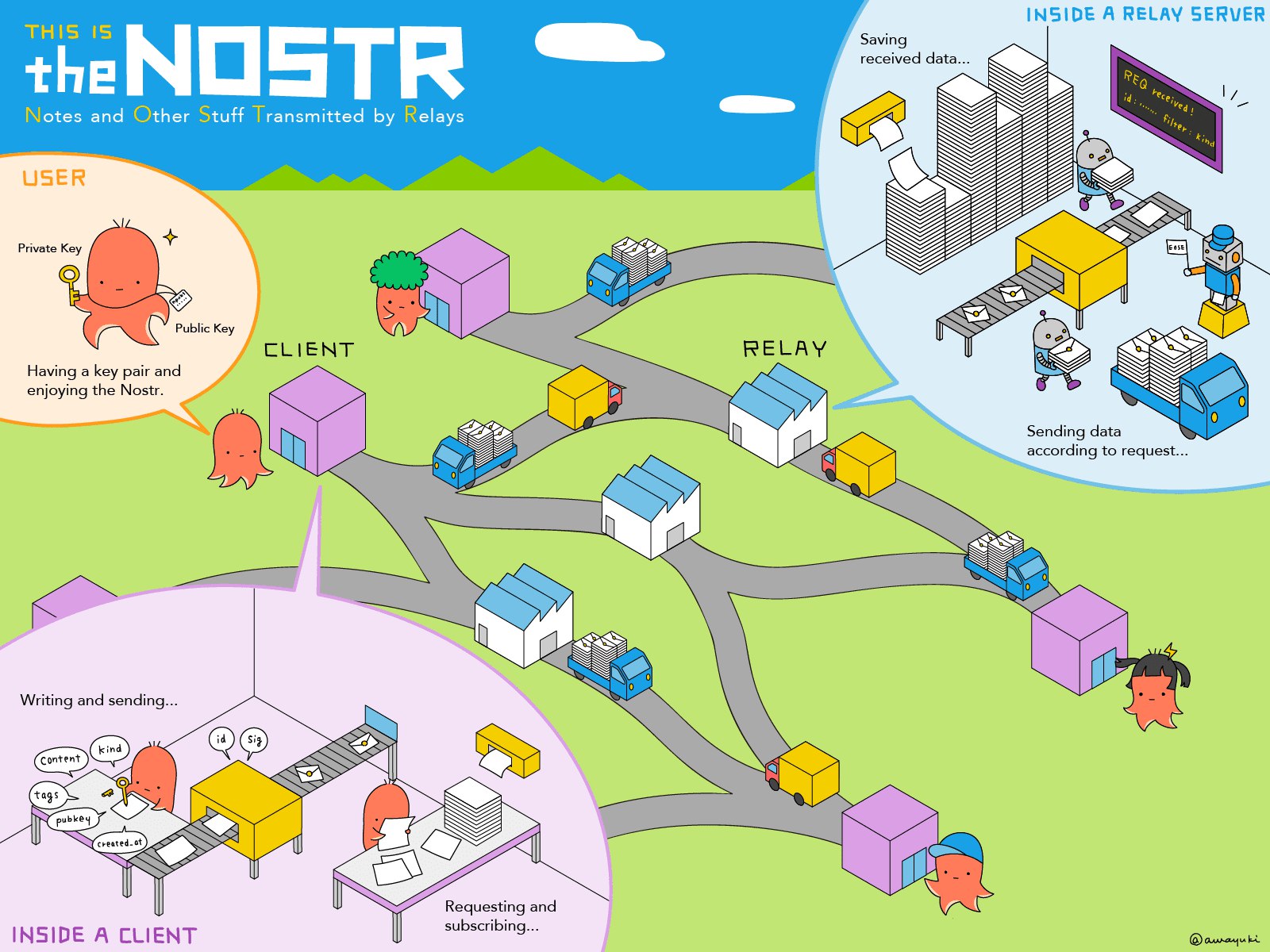
The “Other Stuff” Explained
Nostr’s name hints at this: Notes and Other Stuff Transmitted by Relays. But what is the “other stuff”? Put simply, it’s all the creative and experimental things people are building on Nostr, beyond simple text based notes. Every action on Nostr is an event - like a post, a profile update, or even a payment. The 'Kind' is what specifies the purpose of each event. Kinds are the building blocks of how information is categorized and processed on the network, and the most popular become part of higher lever specification guidelines known as Nostr Implementation Possibility - NIP. A NIP is a document that defines how something in Nostr should work, including the rules, standards, or features. NIPs define the type of 'other stuff' that be published and displayed by different styles of client for different purposes.
Here's some content examples of 'Other Stuff':
- Long-Form Content: Think blog posts or articles. NIP-23.
- Private Messaging: Encrypted chats between users. NIP-04.
- Communities: Group chats or forums like Reddit. NIP-72
- Marketplaces: People listing stuff for sale, payable with zaps. NIP-15
- Zaps: Value transfer over the Lightning Network. NIP57
The beauty of Nostr is that it’s a flexible foundation. Developers can dream up new ideas and build them into clients, and the relays just keep humming along, passing the data around. It’s still early days, so expect the “other stuff” to grow wilder and weirder over time!
Clients vs Relays: What’s the Difference?
Newbies often get tripped up by these two terms, so let’s clearly define them.

Clients
A client is what you use to interact with Nostr. It’s the app or website where you type your posts, read your feed, follow and interact with others. Examples of Nostr clients include:
- Damus (iOS Twitter style client)
- Primal (Cross-platform Twitter style client)
- Amethyst (Android only Twitter style client)
- Habla.News (Web based blog client)
- Olas (Instagram style client)
- 0xchat (Messaging client)
Clients don’t store your data; they just pull it from relays and display it for you. You can switch clients whenever you want, and your account stays the same because it’s tied to your keys, not any single client or app.
Clients are how you use Nostr, and relays are where the data lives. You need both to make the magic happen.
Relays
A relay is a server that stores and shares Nostr data. It’s a little like a post office: you send your note to a relay, and it delivers it to anyone who’s subscribed to see it (like your followers). Relays are run by individuals, groups, or companies who volunteer their computing power. Some are free, some charge a small fee, and you can connect to as many as you like. Most clients will come pre-configured with a list of well-known relays, but you can add or remove any you like.
What Are Zaps?
Zaps are arguably one of Nostr’s coolest features! A zaps is a way to send payments in Bitcoin directly to other users. Imagine liking a post, but instead of just clicking a heart (which you can of course do), you send the poster a few cents worth of Bitcoin to say, “This is awesome!”.
Zaps use Bitcoin's Lightning Network, a faster and cheaper way to move Bitcoin around. To Zap someone, you need a Lightning wallet linked to your Nostr client. Some clients, like Primal, ship with their own custodial wallet to make getting started a breeze. Most clients also allow more advanced users to connect an existing Lightning Wallet to reduce reliance and trust in the client provider.
Zaps are optional but add a fun layer to Nostr. Creators love them because it’s a way to get direct support from fans, with no middleman required.

NIP-05 Identifiers: Your Nostr “Username”
Your nPub, or public key (that long string of letters and numbers) is your 'official' Nostr ID, but it’s not exactly catchy. Enter NIP-05 identifiers, a human-readable and easily sharable way to have people find you. They look like an email address, like
qna@hellonostr.xyz.Here’s how it works:
Most users obtain their NIP-05 ID from a website or service that supports Nostr. Some of these services are free whereas some charge a fee. Some clients, like Primal will set one up for you automatically when you create an account. The email like ID links to your public key, so people can find you more easily. And because these ID's are domain based, there can be no duplicates. qna@hellonostr.xyz can only map to a single public key. The only person that can change that link is the person in control of the domain.
If you control your own domain, you can easily map your Nostr public key to name@my.domain. It’s not mandatory, but it’s super useful for building trust and making your profile recognizable.
Next Steps
So you're bought in. You understand why Nostr is so important and want to get started. Check out our simple onboarding guide here.
Thanks For Reading
Hopefully that moistened your taste buds for more educational Nostr content. This was a basic one, but there will be more focused material coming soon.
If you found this post useful, please share it with your peers and consider following and zapping me on Nostr. If you write to me and let me know that you found me via this post, I'll be sure to Zap you back! ⚡️
-
 @ 87122b31:726e2c4c
2025-04-21 02:14:24
@ 87122b31:726e2c4c
2025-04-21 02:14:24Betwinner mang đến một nền tảng số hiện đại được thiết kế để phục vụ đa dạng đối tượng người dùng trong thời đại công nghệ ngày càng phát triển. Từ giao diện thân thiện đến khả năng tùy biến linh hoạt, nền tảng này luôn đặt sự thuận tiện và trải nghiệm người dùng lên hàng đầu. Ngay từ lần đầu truy cập, bạn sẽ cảm nhận được tốc độ phản hồi nhanh chóng, giao diện mượt mà và bố cục dễ hiểu – những yếu tố giúp Betwinner trở nên khác biệt so với nhiều nền tảng khác. Sự tương thích đa thiết bị, từ điện thoại thông minh đến máy tính bàn, giúp người dùng dễ dàng duy trì kết nối và thao tác linh hoạt trong mọi hoàn cảnh. Với việc tích hợp các tính năng thông minh và các lựa chọn cá nhân hóa như chế độ nền tối, ngôn ngữ hiển thị và điều chỉnh bố cục theo thói quen sử dụng, Betwinner mang lại cảm giác sử dụng cá nhân hóa rõ rệt và gần gũi.
Không chỉ gây ấn tượng với thiết kế và hiệu năng vận hành, Betwinner còn chú trọng vào bảo mật và sự an tâm của người dùng. Nền tảng này sử dụng công nghệ mã hóa tiên tiến để bảo vệ thông tin cá nhân và dữ liệu trong quá trình sử dụng, kết hợp cùng cơ chế xác thực đa lớp để ngăn chặn các truy cập trái phép. Điều này đặc biệt quan trọng khi người dùng ngày càng có yêu cầu cao về tính bảo mật trong các giao dịch và thông tin cá nhân. Ngoài ra, Betwinner còn trang bị hệ thống hỗ trợ khách hàng 24/7, sẵn sàng giải đáp mọi thắc mắc, xử lý vấn đề nhanh chóng và đảm bảo người dùng luôn nhận được sự hỗ trợ cần thiết khi gặp phải bất kỳ sự cố nào. Việc cập nhật hệ thống và cải tiến tính năng diễn ra thường xuyên nhằm tối ưu hóa hiệu năng và tăng cường sự ổn định trong mọi hoạt động, từ những thao tác cơ bản cho đến các chức năng chuyên sâu hơn.
Không dừng lại ở việc cung cấp một nền tảng số tiện lợi, Betwinner còn hướng đến xây dựng một hệ sinh thái kết nối toàn diện. Với khả năng tích hợp nhanh các công nghệ mới như trí tuệ nhân tạo (AI), học máy (machine learning), cũng như tự động hóa quy trình trải nghiệm, nền tảng này đang tạo ra những thay đổi đáng kể trong cách người dùng tiếp cận và tương tác với không gian số. Mọi dữ liệu sử dụng đều được phân tích để từ đó cung cấp các đề xuất thông minh, giúp tiết kiệm thời gian và tối ưu hóa trải nghiệm cá nhân. Không chỉ là nơi cung cấp công cụ, Betwinner còn là điểm đến cho những ai muốn trải nghiệm môi trường công nghệ hiện đại, nơi mỗi hành động đều được hỗ trợ bởi nền tảng kỹ thuật mạnh mẽ và tư duy lấy người dùng làm trọng tâm. Trong bối cảnh xu hướng chuyển đổi số ngày càng mạnh mẽ, Betwinner đã và đang khẳng định vị thế là một trong những lựa chọn hàng đầu dành cho những ai đang tìm kiếm sự tiện nghi, bảo mật và sự chủ động trong trải nghiệm số hóa.
-
 @ e39d100f:d27602e5
2025-04-21 02:14:21
@ e39d100f:d27602e5
2025-04-21 02:14:21O mundo do entretenimento digital não para de crescer, e a 5588bet surge como uma plataforma moderna, segura e completa para quem busca diversão, emoção e oportunidades reais de ganhar prêmios. Com uma interface amigável, suporte eficiente e uma grande variedade de jogos, a 5588bet rapidamente conquistou espaço entre os jogadores brasileiros.
A primeira impressão ao acessar a 5588bet é a de um ambiente profissional e bem estruturado. A navegação é fluida, tanto no computador quanto em dispositivos móveis, permitindo que o usuário explore todas as funcionalidades com facilidade. A plataforma foi desenvolvida pensando na experiência do usuário, oferecendo menus intuitivos, design atrativo e carregamento rápido das páginas.
A segurança é uma prioridade para a 5588bet . Os dados dos jogadores são protegidos com tecnologia de criptografia de ponta, garantindo que todas as transações financeiras e informações pessoais estejam resguardadas. Além disso, a plataforma conta com uma equipe de suporte técnico disponível 24 horas por dia, pronta para auxiliar em qualquer necessidade.
Variedade de Jogos para Todos os Perfis Um dos grandes diferenciais da 5588bet é a diversidade de jogos disponíveis. A plataforma oferece títulos para todos os gostos, desde os clássicos até os mais modernos, todos com gráficos impressionantes e excelente jogabilidade.
Entre os destaques estão os jogos de roleta, bacará, pôquer, além de uma enorme seleção de slots com diferentes temáticas e mecânicas de bônus. Os jogadores podem explorar aventuras inspiradas em mitologia, filmes, frutas clássicas e muito mais. Muitos desses jogos são desenvolvidos por provedores renomados internacionalmente, garantindo qualidade e inovação a cada partida.
Além disso, para quem gosta de emoção em tempo real, a plataforma conta com mesas interativas com apresentadores ao vivo, proporcionando uma experiência imersiva que simula a sensação de estar em um ambiente físico de jogos, tudo isso com a comodidade de estar em casa ou em qualquer lugar.
Experiência do Jogador em Primeiro Lugar A 5588bet entende que a satisfação do jogador vai além da variedade de jogos. Por isso, investe em uma experiência completa. O processo de registro é rápido e simples, permitindo que novos usuários comecem a jogar em poucos minutos. Os métodos de pagamento são diversificados e incluem as principais carteiras digitais e bancos brasileiros, facilitando depósitos e saques.
A plataforma também oferece promoções atrativas para novos usuários e campanhas frequentes para jogadores fiéis. Bônus de boas-vindas, giros gratuitos, cashback e torneios especiais são algumas das formas que a 5588bet utiliza para valorizar seus usuários e tornar cada visita ainda mais interessante.
Outro ponto importante é a transparência. As regras de cada jogo, promoções e procedimentos financeiros são claramente explicados, dando ao jogador confiança e controle total sobre suas escolhas dentro da plataforma.
Conclusão A 5588bet se destaca como uma plataforma inovadora, segura e repleta de opções para quem busca entretenimento online de qualidade. Com jogos envolventes, suporte eficiente e uma experiência focada no usuário, ela se consolida como uma das melhores escolhas para jogadores brasileiros. Se você está em busca de diversão com emoção e recompensas, a 5588bet é o destino ideal.
-
 @ 20e17dd0:2ae504d7
2025-03-20 10:04:35
@ 20e17dd0:2ae504d7
2025-03-20 10:04:35Prerequisite
Installation
Open a Terminal session and write the following command to make sure that Docker is running:
ruby sudo systemctl status dockerYou should get a screen with the docker.service as "running". To get back to command line do CTRL+C
Then, create the volume that Portainer Server will use to store its database:
ruby sudo docker volume create portainer_dataYou are now ready for the on-liner installation:
ruby sudo docker run -d -p 8000:8000 -p 9443:9443 --name portainer --restart=always -v /var/run/docker.sock:/var/run/docker.sock -v portainer_data:/data portainer/portainer-ce:latestTo validate the installer, prompt the following command:
ruby sudo docker psYou should see Portainer's container running.
To access Portainer Server, go to the following adress: https://localhost:9443
Et voila!
-
 @ 4ba8e86d:89d32de4
2025-04-21 02:13:56
@ 4ba8e86d:89d32de4
2025-04-21 02:13:56Tutorial feito por nostr:nostr:npub1rc56x0ek0dd303eph523g3chm0wmrs5wdk6vs0ehd0m5fn8t7y4sqra3tk poste original abaixo:
Parte 1 : http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/263585/tutorial-debloat-de-celulares-android-via-adb-parte-1
Parte 2 : http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/index.php/263586/tutorial-debloat-de-celulares-android-via-adb-parte-2
Quando o assunto é privacidade em celulares, uma das medidas comumente mencionadas é a remoção de bloatwares do dispositivo, também chamado de debloat. O meio mais eficiente para isso sem dúvidas é a troca de sistema operacional. Custom Rom’s como LineageOS, GrapheneOS, Iodé, CalyxOS, etc, já são bastante enxutos nesse quesito, principalmente quanto não é instalado os G-Apps com o sistema. No entanto, essa prática pode acabar resultando em problemas indesejados como a perca de funções do dispositivo, e até mesmo incompatibilidade com apps bancários, tornando este método mais atrativo para quem possui mais de um dispositivo e separando um apenas para privacidade. Pensando nisso, pessoas que possuem apenas um único dispositivo móvel, que são necessitadas desses apps ou funções, mas, ao mesmo tempo, tem essa visão em prol da privacidade, buscam por um meio-termo entre manter a Stock rom, e não ter seus dados coletados por esses bloatwares. Felizmente, a remoção de bloatwares é possível e pode ser realizada via root, ou mais da maneira que este artigo irá tratar, via adb.
O que são bloatwares?
Bloatware é a junção das palavras bloat (inchar) + software (programa), ou seja, um bloatware é basicamente um programa inútil ou facilmente substituível — colocado em seu dispositivo previamente pela fabricante e operadora — que está no seu dispositivo apenas ocupando espaço de armazenamento, consumindo memória RAM e pior, coletando seus dados e enviando para servidores externos, além de serem mais pontos de vulnerabilidades.
O que é o adb?
O Android Debug Brigde, ou apenas adb, é uma ferramenta que se utiliza das permissões de usuário shell e permite o envio de comandos vindo de um computador para um dispositivo Android exigindo apenas que a depuração USB esteja ativa, mas também pode ser usada diretamente no celular a partir do Android 11, com o uso do Termux e a depuração sem fio (ou depuração wifi). A ferramenta funciona normalmente em dispositivos sem root, e também funciona caso o celular esteja em Recovery Mode.
Requisitos:
Para computadores:
• Depuração USB ativa no celular; • Computador com adb; • Cabo USB;
Para celulares:
• Depuração sem fio (ou depuração wifi) ativa no celular; • Termux; • Android 11 ou superior;
Para ambos:
• Firewall NetGuard instalado e configurado no celular; • Lista de bloatwares para seu dispositivo;
Ativação de depuração:
Para ativar a Depuração USB em seu dispositivo, pesquise como ativar as opções de desenvolvedor de seu dispositivo, e lá ative a depuração. No caso da depuração sem fio, sua ativação irá ser necessária apenas no momento que for conectar o dispositivo ao Termux.
Instalação e configuração do NetGuard
O NetGuard pode ser instalado através da própria Google Play Store, mas de preferência instale pela F-Droid ou Github para evitar telemetria.
F-Droid: https://f-droid.org/packages/eu.faircode.netguard/
Github: https://github.com/M66B/NetGuard/releases
Após instalado, configure da seguinte maneira:
Configurações → padrões (lista branca/negra) → ative as 3 primeiras opções (bloquear wifi, bloquear dados móveis e aplicar regras ‘quando tela estiver ligada’);
Configurações → opções avançadas → ative as duas primeiras (administrar aplicativos do sistema e registrar acesso a internet);
Com isso, todos os apps estarão sendo bloqueados de acessar a internet, seja por wifi ou dados móveis, e na página principal do app basta permitir o acesso a rede para os apps que você vai usar (se necessário). Permita que o app rode em segundo plano sem restrição da otimização de bateria, assim quando o celular ligar, ele já estará ativo.
Lista de bloatwares
Nem todos os bloatwares são genéricos, haverá bloatwares diferentes conforme a marca, modelo, versão do Android, e até mesmo região.
Para obter uma lista de bloatwares de seu dispositivo, caso seu aparelho já possua um tempo de existência, você encontrará listas prontas facilmente apenas pesquisando por elas. Supondo que temos um Samsung Galaxy Note 10 Plus em mãos, basta pesquisar em seu motor de busca por:
Samsung Galaxy Note 10 Plus bloatware listProvavelmente essas listas já terão inclusas todos os bloatwares das mais diversas regiões, lhe poupando o trabalho de buscar por alguma lista mais específica.
Caso seu aparelho seja muito recente, e/ou não encontre uma lista pronta de bloatwares, devo dizer que você acaba de pegar em merda, pois é chato para um caralho pesquisar por cada aplicação para saber sua função, se é essencial para o sistema ou se é facilmente substituível.
De antemão já aviso, que mais para frente, caso vossa gostosura remova um desses aplicativos que era essencial para o sistema sem saber, vai acabar resultando na perda de alguma função importante, ou pior, ao reiniciar o aparelho o sistema pode estar quebrado, lhe obrigando a seguir com uma formatação, e repetir todo o processo novamente.
Download do adb em computadores
Para usar a ferramenta do adb em computadores, basta baixar o pacote chamado SDK platform-tools, disponível através deste link: https://developer.android.com/tools/releases/platform-tools. Por ele, você consegue o download para Windows, Mac e Linux.
Uma vez baixado, basta extrair o arquivo zipado, contendo dentro dele uma pasta chamada platform-tools que basta ser aberta no terminal para se usar o adb.
Download do adb em celulares com Termux.
Para usar a ferramenta do adb diretamente no celular, antes temos que baixar o app Termux, que é um emulador de terminal linux, e já possui o adb em seu repositório. Você encontra o app na Google Play Store, mas novamente recomendo baixar pela F-Droid ou diretamente no Github do projeto.
F-Droid: https://f-droid.org/en/packages/com.termux/
Github: https://github.com/termux/termux-app/releases
Processo de debloat
Antes de iniciarmos, é importante deixar claro que não é para você sair removendo todos os bloatwares de cara sem mais nem menos, afinal alguns deles precisam antes ser substituídos, podem ser essenciais para você para alguma atividade ou função, ou até mesmo são insubstituíveis.
Alguns exemplos de bloatwares que a substituição é necessária antes da remoção, é o Launcher, afinal, é a interface gráfica do sistema, e o teclado, que sem ele só é possível digitar com teclado externo. O Launcher e teclado podem ser substituídos por quaisquer outros, minha recomendação pessoal é por aqueles que respeitam sua privacidade, como Pie Launcher e Simple Laucher, enquanto o teclado pelo OpenBoard e FlorisBoard, todos open-source e disponíveis da F-Droid.
Identifique entre a lista de bloatwares, quais você gosta, precisa ou prefere não substituir, de maneira alguma você é obrigado a remover todos os bloatwares possíveis, modifique seu sistema a seu bel-prazer. O NetGuard lista todos os apps do celular com o nome do pacote, com isso você pode filtrar bem qual deles não remover.
Um exemplo claro de bloatware insubstituível e, portanto, não pode ser removido, é o com.android.mtp, um protocolo onde sua função é auxiliar a comunicação do dispositivo com um computador via USB, mas por algum motivo, tem acesso a rede e se comunica frequentemente com servidores externos. Para esses casos, e melhor solução mesmo é bloquear o acesso a rede desses bloatwares com o NetGuard.
MTP tentando comunicação com servidores externos:
Executando o adb shell
No computador
Faça backup de todos os seus arquivos importantes para algum armazenamento externo, e formate seu celular com o hard reset. Após a formatação, e a ativação da depuração USB, conecte seu aparelho e o pc com o auxílio de um cabo USB. Muito provavelmente seu dispositivo irá apenas começar a carregar, por isso permita a transferência de dados, para que o computador consiga se comunicar normalmente com o celular.
Já no pc, abra a pasta platform-tools dentro do terminal, e execute o seguinte comando:
./adb start-serverO resultado deve ser:
daemon not running; starting now at tcp:5037 daemon started successfully
E caso não apareça nada, execute:
./adb kill-serverE inicie novamente.
Com o adb conectado ao celular, execute:
./adb shellPara poder executar comandos diretamente para o dispositivo. No meu caso, meu celular é um Redmi Note 8 Pro, codinome Begonia.
Logo o resultado deve ser:
begonia:/ $
Caso ocorra algum erro do tipo:
adb: device unauthorized. This adb server’s $ADB_VENDOR_KEYS is not set Try ‘adb kill-server’ if that seems wrong. Otherwise check for a confirmation dialog on your device.
Verifique no celular se apareceu alguma confirmação para autorizar a depuração USB, caso sim, autorize e tente novamente. Caso não apareça nada, execute o kill-server e repita o processo.
No celular
Após realizar o mesmo processo de backup e hard reset citado anteriormente, instale o Termux e, com ele iniciado, execute o comando:
pkg install android-toolsQuando surgir a mensagem “Do you want to continue? [Y/n]”, basta dar enter novamente que já aceita e finaliza a instalação
Agora, vá até as opções de desenvolvedor, e ative a depuração sem fio. Dentro das opções da depuração sem fio, terá uma opção de emparelhamento do dispositivo com um código, que irá informar para você um código em emparelhamento, com um endereço IP e porta, que será usado para a conexão com o Termux.
Para facilitar o processo, recomendo que abra tanto as configurações quanto o Termux ao mesmo tempo, e divida a tela com os dois app’s, como da maneira a seguir:
Para parear o Termux com o dispositivo, não é necessário digitar o ip informado, basta trocar por “localhost”, já a porta e o código de emparelhamento, deve ser digitado exatamente como informado. Execute:
adb pair localhost:porta CódigoDeEmparelhamentoDe acordo com a imagem mostrada anteriormente, o comando ficaria “adb pair localhost:41255 757495”.
Com o dispositivo emparelhado com o Termux, agora basta conectar para conseguir executar os comandos, para isso execute:
adb connect localhost:portaObs: a porta que você deve informar neste comando não é a mesma informada com o código de emparelhamento, e sim a informada na tela principal da depuração sem fio.
Pronto! Termux e adb conectado com sucesso ao dispositivo, agora basta executar normalmente o adb shell:
adb shellRemoção na prática Com o adb shell executado, você está pronto para remover os bloatwares. No meu caso, irei mostrar apenas a remoção de um app (Google Maps), já que o comando é o mesmo para qualquer outro, mudando apenas o nome do pacote.
Dentro do NetGuard, verificando as informações do Google Maps:
Podemos ver que mesmo fora de uso, e com a localização do dispositivo desativado, o app está tentando loucamente se comunicar com servidores externos, e informar sabe-se lá que peste. Mas sem novidades até aqui, o mais importante é que podemos ver que o nome do pacote do Google Maps é com.google.android.apps.maps, e para o remover do celular, basta executar:
pm uninstall –user 0 com.google.android.apps.mapsE pronto, bloatware removido! Agora basta repetir o processo para o resto dos bloatwares, trocando apenas o nome do pacote.
Para acelerar o processo, você pode já criar uma lista do bloco de notas com os comandos, e quando colar no terminal, irá executar um atrás do outro.
Exemplo de lista:
Caso a donzela tenha removido alguma coisa sem querer, também é possível recuperar o pacote com o comando:
cmd package install-existing nome.do.pacotePós-debloat
Após limpar o máximo possível o seu sistema, reinicie o aparelho, caso entre no como recovery e não seja possível dar reboot, significa que você removeu algum app “essencial” para o sistema, e terá que formatar o aparelho e repetir toda a remoção novamente, desta vez removendo poucos bloatwares de uma vez, e reiniciando o aparelho até descobrir qual deles não pode ser removido. Sim, dá trabalho… quem mandou querer privacidade?
Caso o aparelho reinicie normalmente após a remoção, parabéns, agora basta usar seu celular como bem entender! Mantenha o NetGuard sempre executando e os bloatwares que não foram possíveis remover não irão se comunicar com servidores externos, passe a usar apps open source da F-Droid e instale outros apps através da Aurora Store ao invés da Google Play Store.
Referências: Caso você seja um Australopithecus e tenha achado este guia difícil, eis uma videoaula (3:14:40) do Anderson do canal Ciberdef, realizando todo o processo: http://odysee.com/@zai:5/Como-remover-at%C3%A9-200-APLICATIVOS-que-colocam-a-sua-PRIVACIDADE-E-SEGURAN%C3%87A-em-risco.:4?lid=6d50f40314eee7e2f218536d9e5d300290931d23
Pdf’s do Anderson citados na videoaula: créditos ao anon6837264 http://eternalcbrzpicytj4zyguygpmkjlkddxob7tptlr25cdipe5svyqoqd.onion/file/3863a834d29285d397b73a4af6fb1bbe67c888d72d30/t-05e63192d02ffd.pdf
Processo de instalação do Termux e adb no celular: https://youtu.be/APolZrPHSms
-
 @ 8fb140b4:f948000c
2025-03-20 01:29:06
@ 8fb140b4:f948000c
2025-03-20 01:29:06As many of you know, https://nostr.build has recently launched a new compatibility layer for the Blossom protocol blossom.band. You can find all the details about what it supports and its limitations by visiting the URL.
I wanted to cover some of the technical details about how it works here. One key difference you may notice is that the service acts as a linker, redirecting requests for the media hash to the actual source of the media—specifically, the nostr.build URL. This allows us to maintain a unified CDN cache and ensure that your media is served as quickly as possible.
Another difference is that each uploaded media/blob is served under its own subdomain (e.g.,
npub1[...].blossom.band), ensuring that your association with the blob is controlled by you. If you decide to delete the media for any reason, we ensure that the link is broken, even if someone else has duplicated it using the same hash.To comply with the Blossom protocol, we also link the same hash under the main (apex) domain (blossom.band) and collect all associations under it. This ensures that Blossom clients can fetch media based on users’ Blossom server settings. If you are the sole owner of the hash and there are no duplicates, deleting the media removes the link from the main domain as well.
Lastly, in line with our mission to protect users’ privacy, we reject any media that contains private metadata (such as GPS coordinates, user comments, or camera serial numbers) or strip it if you use the
/media/endpoint for upload.As always, your feedback is welcome and appreciated. Thank you!
-
 @ 4ba8e86d:89d32de4
2025-04-21 02:12:19
@ 4ba8e86d:89d32de4
2025-04-21 02:12:19SISTEMA OPERACIONAL MÓVEIS
GrapheneOS : https://njump.me/nevent1qqs8t76evdgrg4qegdtyrq2rved63pr29wlqyj627n9tj4vlu66tqpqpzdmhxue69uhk7enxvd5xz6tw9ec82c30qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqppcqec9
CalyxOS : https://njump.me/nevent1qqsrm0lws2atln2kt3cqjacathnw0uj0jsxwklt37p7t380hl8mmstcpydmhxue69uhkummnw3ez6an9wf5kv6t9vsh8wetvd3hhyer9wghxuet59uq3vamnwvaz7tmwdaehgu3wvf3kstnwd9hx5cf0qy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qgcwaehxw309aex2mrp0yhxxatjwfjkuapwveukjtcpzpmhxue69uhkummnw3ezumt0d5hszrnhwden5te0dehhxtnvdakz7qfywaehxw309ahx7um5wgh8ymm4dej8ymmrdd3xjarrda5kuetjwvhxxmmd9uq3uamnwvaz7tmwdaehgu3dv3jhvtnhv4kxcmmjv3jhytnwv46z7qghwaehxw309aex2mrp0yhxummnw3ezucnpdejz7qgewaehxw309ahx7um5wghxymmwva3x7mn89e3k7mf0qythwumn8ghj7cn5vvhxkmr9dejxz7n49e3k7mf0qyg8wumn8ghj7mn09eehgu3wvdez7smttdu
LineageOS : https://njump.me/nevent1qqsgw7sr36gaty48cf4snw0ezg5mg4atzhqayuge752esd469p26qfgpzdmhxue69uhhwmm59e6hg7r09ehkuef0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpnvm779
SISTEMA OPERACIONAL DESKTOP
Tails : https://njump.me/nevent1qqsf09ztvuu60g6xprazv2vxqqy5qlxjs4dkc9d36ta48q75cs9le4qpzemhxue69uhkummnw3ex2mrfw3jhxtn0wfnj7q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqz34ag5t
Qubes OS : https://njump.me/nevent1qqsp6jujgwl68uvurw0cw3hfhr40xq20sj7rl3z4yzwnhp9sdpa7augpzpmhxue69uhkummnw3ezumt0d5hsz9mhwden5te0wfjkccte9ehx7um5wghxyctwvshsz9thwden5te0dehhxarj9ehhsarj9ejx2a30qyg8wumn8ghj7mn09eehgu3wvdez7qg4waehxw309aex2mrp0yhxgctdw4eju6t09uqjxamnwvaz7tmwdaehgu3dwejhy6txd9jkgtnhv4kxcmmjv3jhytnwv46z7qgwwaehxw309ahx7uewd3hkctcpremhxue69uhkummnw3ez6er9wch8wetvd3hhyer9wghxuet59uj3ljr8
Kali linux : https://njump.me/nevent1qqswlav72xdvamuyp9xc38c6t7070l3n2uxu67ssmal2g7gv35nmvhspzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqswt9rxe
Whonix : https://njump.me/nevent1qqs85gvejvzhk086lwh6edma7fv07p5c3wnwnxnzthwwntg2x6773egpydmhxue69uhkummnw3ez6an9wf5kv6t9vsh8wetvd3hhyer9wghxuet59uq3qamnwvaz7tmwdaehgu3wd4hk6tcpzemhxue69uhkummnw3ezucnrdqhxu6twdfsj7qfywaehxw309ahx7um5wgh8ymm4dej8ymmrdd3xjarrda5kuetjwvhxxmmd9uq3wamnwvaz7tmzw33ju6mvv4hxgct6w5hxxmmd9uq3qamnwvaz7tmwduh8xarj9e3hytcpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhszrnhwden5te0dehhxtnvdakz7qg7waehxw309ahx7um5wgkkgetk9emk2mrvdaexgetj9ehx2ap0sen9p6
Kodachi : https://njump.me/nevent1qqsf5zszgurpd0vwdznzk98hck294zygw0s8dah6fpd309ecpreqtrgpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhszgmhwden5te0dehhxarj94mx2unfve5k2epwwajkcmr0wfjx2u3wdejhgtcpremhxue69uhkummnw3ez6er9wch8wetvd3hhyer9wghxuet59uq3qamnwvaz7tmwdaehgu3wd4hk6tcpzamhxue69uhkyarr9e4kcetwv3sh5afwvdhk6tcpzpmhxue69uhkumewwd68ytnrwghszfrhwden5te0dehhxarj9eex7atwv3ex7cmtvf5hgcm0d9hx2unn9e3k7mf0qyvhwumn8ghj7mn0wd68ytnzdahxwcn0denjucm0d5hszrnhwden5te0dehhxtnvdakz7qgkwaehxw309ahx7um5wghxycmg9ehxjmn2vyhsz9mhwden5te0wfjkccte9ehx7um5wghxyctwvshs94a4d5
PGP
Openkeychain : https://njump.me/nevent1qqs9qtjgsulp76t7jkquf8nk8txs2ftsr0qke6mjmsc2svtwfvswzyqpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs36mp0w
Kleopatra : https://njump.me/nevent1qqspnevn932hdggvp4zam6mfyce0hmnxsp9wp8htpumq9vm3anq6etsppemhxue69uhkummn9ekx7mp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpuaeghp
Pgp : https://njump.me/nevent1qqsggek707qf3rzttextmgqhym6d4g479jdnlnj78j96y0ut0x9nemcpzamhxue69uhhyetvv9ujuurjd9kkzmpwdejhgtczyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgptemhe
Como funciona o PGP? : https://njump.me/nevent1qqsz9r7azc8pkvfmkg2hv0nufaexjtnvga0yl85x9hu7ptpg20gxxpspremhxue69uhkummnw3ez6ur4vgh8wetvd3hhyer9wghxuet59upzqjagapkjm9ufdhynxlp72qrfrzfawvt4wt7cr795rhw6tkyaxt0yqvzqqqqqqy259fhs
Por que eu escrevi PGP. - Philip Zimmermann.
https://njump.me/nevent1qqsvysn94gm8prxn3jw04r0xwc6sngkskg756z48jsyrmqssvxtm7ncpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtchzxnad
VPN
Vpn : https://njump.me/nevent1qqs27ltgsr6mh4ffpseexz6s37355df3zsur709d0s89u2nugpcygsspzpmhxue69uhkummnw3ezumt0d5hsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqshzu2fk
InviZible Pro : https://njump.me/nevent1qqsvyevf2vld23a3xrpvarc72ndpcmfvc3lc45jej0j5kcsg36jq53cpz3mhxue69uhhyetvv9ujuerpd46hxtnfdupzqjagapkjm9ufdhynxlp72qrfrzfawvt4wt7cr795rhw6tkyaxt0yqvzqqqqqqy33y5l4
Orbot: https://njump.me/nevent1qqsxswkyt6pe34egxp9w70cy83h40ururj6m9sxjdmfass4cjm4495stft593
I2P
i2p : https://njump.me/nevent1qqsvnj8n983r4knwjmnkfyum242q4c0cnd338l4z8p0m6xsmx89mxkslx0pgg
Entendendo e usando a rede I2P : https://njump.me/nevent1qqsxchp5ycpatjf5s4ag25jkawmw6kkf64vl43vnprxdcwrpnms9qkcppemhxue69uhkummn9ekx7mp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpvht4mn
Criando e acessando sua conta Email na I2P : https://njump.me/nevent1qqs9v9dz897kh8e5lfar0dl7ljltf2fpdathsn3dkdsq7wg4ksr8xfgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpw8mzum
APLICATIVO 2FA
Aegis Authenticator : https://njump.me/nevent1qqsfttdwcn9equlrmtf9n6wee7lqntppzm03pzdcj4cdnxel3pz44zspz4mhxue69uhhyetvv9ujumn0wd68ytnzvuhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqscvtydq
YubiKey : https://njump.me/nevent1qqstsnn69y4sf4330n7039zxm7wza3ch7sn6plhzmd57w6j9jssavtspvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzueyvgt
GERENCIADOR DE SENHAS
KeepassDX: https://njump.me/nevent1qqswc850dr4ujvxnmpx75jauflf4arc93pqsty5pv8hxdm7lcw8ee8qpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpe0492n
Birwaden: https://njump.me/nevent1qqs0j5x9guk2v6xumhwqmftmcz736m9nm9wzacqwjarxmh8k4xdyzwgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpwfe2kc
KeePassXC: https://njump.me/nevent1qqsgftcrd8eau7tzr2p9lecuaf7z8mx5jl9w2k66ae3lzkw5wqcy5pcl2achp
CHAT MENSAGEM
SimpleXchat : https://njump.me/nevent1qqsds5xselnnu0dyy0j49peuun72snxcgn3u55d2320n37rja9gk8lgzyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgmcmj7c
Briar : https://njump.me/nevent1qqs8rrtgvjr499hreugetrl7adkhsj2zextyfsukq5aa7wxthrgcqcg05n434
Element Messenger : https://njump.me/nevent1qqsq05snlqtxm5cpzkshlf8n5d5rj9383vjytkvqp5gta37hpuwt4mqyccee6
Pidgin : https://njump.me/nevent1qqsz7kngycyx7meckx53xk8ahk98jkh400usrvykh480xa4ct9zlx2c2ywvx3
E-MAIL
Thunderbird: https://njump.me/nevent1qqspq64gg0nw7t60zsvea5eykgrm43paz845e4jn74muw5qzdvve7uqrkwtjh
ProtonMail : https://njump.me/nevent1qqs908glhk68e7ms8zqtlsqd00wu3prnpt08dwre26hd6e5fhqdw99cppemhxue69uhkummn9ekx7mp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpeyhg4z
Tutonota : https://njump.me/nevent1qqswtzh9zjxfey644qy4jsdh9465qcqd2wefx0jxa54gdckxjvkrrmqpz4mhxue69uhhyetvv9ujumt0wd68ytnsw43qygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs5hzhkv
k-9 mail : https://njump.me/nevent1qqs200g5a603y7utjgjk320r3srurrc4r66nv93mcg0x9umrw52ku5gpr3mhxue69uhkummnw3ezuumhd9ehxtt9de5kwmtp9e3kstczyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgacflak
E-MAIL-ALIÁS
Simplelogin : https://njump.me/nevent1qqsvhz5pxqpqzr2ptanqyqgsjr50v7u9lc083fvdnglhrv36rnceppcppemhxue69uhkummn9ekx7mp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqp9gsr7m
AnonAddy : https://njump.me/nevent1qqs9mcth70mkq2z25ws634qfn7vx2mlva3tkllayxergw0s7p8d3ggcpzpmhxue69uhkummnw3ezumt0d5hsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs6mawe3
NAVEGADOR
Navegador Tor : https://njump.me/nevent1qqs06qfxy7wzqmk76l5d8vwyg6mvcye864xla5up52fy5sptcdy39lspzemhxue69uhkummnw3ezuerpw3sju6rpw4ej7q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzdp0urw
Mullvap Browser : https://njump.me/nevent1qqs2vsgc3wk09wdspv2mezltgg7nfdg97g0a0m5cmvkvr4nrfxluzfcpzdmhxue69uhhwmm59e6hg7r09ehkuef0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpj8h6fe
LibreWolf : https://njump.me/nevent1qqswv05mlmkcuvwhe8x3u5f0kgwzug7n2ltm68fr3j06xy9qalxwq2cpzemhxue69uhkummnw3ex2mrfw3jhxtn0wfnj7q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzuv2hxr
Cromite : https://njump.me/nevent1qqs2ut83arlu735xp8jf87w5m3vykl4lv5nwkhldkqwu3l86khzzy4cpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs3dplt7
BUSCADORES
Searx : https://njump.me/nevent1qqsxyzpvgzx00n50nrlgctmy497vkm2cm8dd5pdp7fmw6uh8xnxdmaspr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqp23z7ax
APP-STORE
Obtainium : https://njump.me/nevent1qqstd8kzc5w3t2v6dgf36z0qrruufzfgnc53rj88zcjgsagj5c5k4rgpz3mhxue69uhhyetvv9ujuerpd46hxtnfdupzqjagapkjm9ufdhynxlp72qrfrzfawvt4wt7cr795rhw6tkyaxt0yqvzqqqqqqyarmca3
F-Droid : https://njump.me/nevent1qqst4kry49cc9g3g8s5gdnpgyk3gjte079jdnv43f0x4e85cjkxzjesymzuu4
Droid-ify : https://njump.me/nevent1qqsrr8yu9luq0gud902erdh8gw2lfunpe93uc2u6g8rh9ep7wt3v4sgpzpmhxue69uhkummnw3ezumt0d5hsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsfzu9vk
Aurora Store : https://njump.me/nevent1qqsy69kcaf0zkcg0qnu90mtk46ly3p2jplgpzgk62wzspjqjft4fpjgpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzrpmsjy
RSS
Feeder : https://njump.me/nevent1qqsy29aeggpkmrc7t3c7y7ldgda7pszl7c8hh9zux80gjzrfvlhfhwqpp4mhxue69uhkummn9ekx7mqzyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgsvzzjy
VIDEOO CONFERENCIA
Jitsi meet : https://njump.me/nevent1qqswphw67hr6qmt2fpugcj77jrk7qkfdrszum7vw7n2cu6cx4r6sh4cgkderr
TECLADOS
HeliBoard : https://njump.me/nevent1qqsyqpc4d28rje03dcvshv4xserftahhpeylu2ez2jutdxwds4e8syspz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsr8mel5
OpenBoard : https://njump.me/nevent1qqsf7zqkup03yysy67y43nj48q53sr6yym38es655fh9fp6nxpl7rqspzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqswcvh3r
FlorisBoard : https://njump.me/nevent1qqsf7zqkup03yysy67y43nj48q53sr6yym38es655fh9fp6nxpl7rqspzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqswcvh3r
MAPAS
Osmand : https://njump.me/nevent1qqsxryp2ywj64az7n5p6jq5tn3tx5jv05te48dtmmt3lf94ydtgy4fgpzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs54nwpj
Organic maps : https://njump.me/nevent1qqstrecuuzkw0dyusxdq7cuwju0ftskl7anx978s5dyn4pnldrkckzqpr4mhxue69uhkummnw3ezumtp0p5k6ctrd96xzer9dshx7un8qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpl8z3kk
TRADUÇÃO
LibreTranslate : https://njump.me/nevent1qqs953g3rhf0m8jh59204uskzz56em9xdrjkelv4wnkr07huk20442cpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzeqsx40
REMOÇÃO DOS METADADOS
Scrambled Exif : https://njump.me/nevent1qqs2658t702xv66p000y4mlhnvadmdxwzzfzcjkjf7kedrclr3ej7aspyfmhxue69uhk6atvw35hqmr90pjhytngw4eh5mmwv4nhjtnhdaexcep0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpguu0wh
ESTEGANOGRAFIA
PixelKnot: https://njump.me/nevent1qqsrh0yh9mg0lx86t5wcmhh97wm6n4v0radh6sd0554ugn354wqdj8gpz3mhxue69uhhyetvv9ujuerpd46hxtnfdupzqjagapkjm9ufdhynxlp72qrfrzfawvt4wt7cr795rhw6tkyaxt0yqvzqqqqqqyuvfqdp
PERFIL DE TRABALHO
Shelter : https://njump.me/nevent1qqspv9xxkmfp40cxgjuyfsyczndzmpnl83e7gugm7480mp9zhv50wkqpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzdnu59c
PDF
MuPDF : https://njump.me/nevent1qqspn5lhe0dteys6npsrntmv2g470st8kh8p7hxxgmymqa95ejvxvfcpzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs4hvhvj
Librera Reader : https://njump.me/nevent1qqsg60flpuf00sash48fexvwxkly2j5z9wjvjrzt883t3eqng293f3cpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqz39tt3n
QR-Code
Binary Eye : https://njump.me/nevent1qqsz4n0uxxx3q5m0r42n9key3hchtwyp73hgh8l958rtmae5u2khgpgpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzdmn4wp
Climático
Breezy Weather : https://njump.me/nevent1qqs9hjz5cz0y4am3kj33xn536uq85ydva775eqrml52mtnnpe898rzspzamhxue69uhhyetvv9ujuurjd9kkzmpwdejhgtczyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgpd3tu8
ENCRYPTS
Cryptomator : https://njump.me/nevent1qqsvchvnw779m20583llgg5nlu6ph5psewetlczfac5vgw83ydmfndspzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsx7ppw9
VeraCrypt : https://njump.me/nevent1qqsf6wzedsnrgq6hjk5c4jj66dxnplqwc4ygr46l8z3gfh38q2fdlwgm65ej3
EXTENSÕES
uBlock Origin : https://njump.me/nevent1qqswaa666lcj2c4nhnea8u4agjtu4l8q89xjln0yrngj7ssh72ntwzql8ssdj
Snowflake : https://njump.me/nevent1qqs0ws74zlt8uced3p2vee9td8x7vln2mkacp8szdufvs2ed94ctnwchce008
CLOUD
Nextcloud : https://njump.me/nevent1qqs2utg5z9htegdtrnllreuhypkk2026x8a0xdsmfczg9wdl8rgrcgg9nhgnm
NOTEPAD
Joplin : https://njump.me/nevent1qqsz2a0laecpelsznser3xd0jfa6ch2vpxtkx6vm6qg24e78xttpk0cpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpdu0hft
Standard Notes : https://njump.me/nevent1qqsv3596kz3qung5v23cjc4cpq7rqxg08y36rmzgcrvw5whtme83y3s7tng6r
MÚSICA
RiMusic : https://njump.me/nevent1qqsv3genqav2tfjllp86ust4umxm8tr2wd9kq8x7vrjq6ssp363mn0gpzamhxue69uhhyetvv9ujuurjd9kkzmpwdejhgtczyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqg42353n
ViMusic : https://njump.me/nevent1qqswx78559l4jsxsrygd8kj32sch4qu57stxq0z6twwl450vp39pdqqpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzjg863j
PODCAST
AntennaPod : https://njump.me/nevent1qqsp4nh7k4a6zymfwqqdlxuz8ua6kdhvgeeh3uxf2c9rtp9u3e9ku8qnr8lmy
VISUALIZAR VIDEO
VLC : https://njump.me/nevent1qqs0lz56wtlr2eye4ajs2gzn2r0dscw4y66wezhx0mue6dffth8zugcl9laky
YOUTUBE
NewPipe : https://njump.me/nevent1qqsdg06qpcjdnlvgm4xzqdap0dgjrkjewhmh4j3v4mxdl4rjh8768mgdw9uln
FreeTube : https://njump.me/nevent1qqsz6y6z7ze5gs56s8seaws8v6m6j2zu0pxa955dhq3ythmexak38mcpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs5lkjvv
LibreTube : https://snort.social/e/nevent1qqstmd5m6wrdvn4gxf8xyhrwnlyaxmr89c9kjddvnvux6603f84t3fqpz4mhxue69uhhyetvv9ujumt0wd68ytnsw43qygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsswwznc
COMPARTILHAMENTO DE ARQUIVOS
OnionShare : https://njump.me/nevent1qqsr0a4ml5nu6ud5k9yzyawcd9arznnwkrc27dzzc95q6r50xmdff6qpydmhxue69uhkummnw3ez6an9wf5kv6t9vsh8wetvd3hhyer9wghxuet59uq3uamnwvaz7tmwdaehgu3dv3jhvtnhv4kxcmmjv3jhytnwv46z7qgswaehxw309ahx7tnnw3ezucmj9uq32amnwvaz7tmjv4kxz7fwv3sk6atn9e5k7tcpzamhxue69uhkyarr9e4kcetwv3sh5afwvdhk6tcpzemhxue69uhkummnw3ezucnrdqhxu6twdfsj7qgswaehxw309ahx7um5wghx6mmd9uqjgamnwvaz7tmwdaehgu3wwfhh2mnywfhkx6mzd96xxmmfdejhyuewvdhk6tcppemhxue69uhkummn9ekx7mp0qythwumn8ghj7un9d3shjtnwdaehgu3wvfskuep0qyv8wumn8ghj7un9d3shjtnrw4e8yetwwshxv7tf9ut7qurt
Localsend : https://njump.me/nevent1qqsp8ldjhrxm09cvvcak20hrc0g8qju9f67pw7rxr2y3euyggw9284gpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzuyghqr
Wallet Bitcoin
Ashigaru Wallet : https://njump.me/nevent1qqstx9fz8kf24wgl26un8usxwsqjvuec9f8q392llmga75tw0kfarfcpzamhxue69uhhyetvv9ujuurjd9kkzmpwdejhgtczyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgvfsrqp
Samourai Wallet : https://njump.me/nevent1qqstcvjmz39rmrnrv7t5cl6p3x7pzj6jsspyh4s4vcwd2lugmre04ecpr9mhxue69uhkummnw3ezucn0denkymmwvuhxxmmd9upzqjagapkjm9ufdhynxlp72qrfrzfawvt4wt7cr795rhw6tkyaxt0yqvzqqqqqqy3rg4qs
CÂMERA
opencamera : https://njump.me/nevent1qqs25glp6dh0crrjutxrgdjlnx9gtqpjtrkg29hlf7382aeyjd77jlqpzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqssxcvgc
OFFICE
Collabora Office : https://njump.me/nevent1qqs8yn4ys6adpmeu3edmf580jhc3wluvlf823cc4ft4h0uqmfzdf99qpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsj40uss
TEXTOS
O manifesto de um Cypherpunk : https://njump.me/nevent1qqsd7hdlg6galn5mcuv3pm3ryfjxc4tkyph0cfqqe4du4dr4z8amqyspvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzal0efa
Operations security ( OPSEC) : https://snort.social/e/nevent1qqsp323havh3y9nxzd4qmm60hw87tm9gjns0mtzg8y309uf9mv85cqcpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqz8ej9l7
O MANIFESTO CRIPTOANARQUISTA Timothy C. May – 1992. : https://njump.me/nevent1qqspp480wtyx2zhtwpu5gptrl8duv9rvq3mug85mp4d54qzywk3zq9gpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqz5wq496
Declaração de independência do ciberespaço
- John Perry Barlow - 1996 : https://njump.me/nevent1qqs2njsy44n6p07mhgt2tnragvchasv386nf20ua5wklxqpttf6mzuqpzpmhxue69uhkummnw3ezumt0d5hsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsukg4hr
The Cyphernomicon: Criptografia, Dinheiro Digital e o Futuro da Privacidade. escrito por Timothy C. May -Publicado em 1994. :
Livro completo em PDF no Github PrivacyOpenSource.
https://github.com/Alexemidio/PrivacyOpenSource/raw/main/Livros/THE%20CYPHERNOMICON%20.pdf Share
-
 @ 30ceb64e:7f08bdf5
2025-03-19 21:29:59
@ 30ceb64e:7f08bdf5
2025-03-19 21:29:59NIP-101e: Workout Data and Running Extensions
NIP-101e represents a crucial step forward for fitness tracking on Nostr, giving us a common language that would allow workout data to flow freely between apps. This proposal outlines a thoughtful framework with Exercise Templates, Workout Templates, and Workout Records that would finally free our fitness data from proprietary silos and put it back in our hands. I'm eager to see this proposal implemented because it would create the foundation for a genuinely open fitness ecosystem on Nostr.
As a runner building a Nostr running app RUNSTR, I've proposed some running-specific extensions to NIP-101e that address the unique needs of runners without disrupting the elegant structure of the original proposal. My extensions would standardize how we record GPS routes, pace metrics, elevation data, splits, and even weather conditions - all things that matter tremendously to runners but aren't covered in the base proposal that focuses more on strength training.
By implementing NIP-101e along with these running extensions, we could create something truly revolutionary: a fitness ecosystem where runners aren't locked into a single platform because of their data. You could track your morning run in my app, analyze your training in another app that specializes in statistics, and share achievements with friends using whatever Nostr clients they prefer. I believe strongly in getting NIP-101e implemented with these extensions included because it would foster innovation while giving runners unprecedented freedom to own their data and use it however they want. Let's make this happen and show what's possible when fitness data becomes truly interoperable!
-
 @ 04ff5a72:22ba7b2d
2025-03-19 03:25:28
@ 04ff5a72:22ba7b2d
2025-03-19 03:25:28The Evolution of the "World Wide Web"
The internet has undergone a remarkable transformation since its inception, evolving from a collection of static pages to a dynamic, interconnected ecosystem, and now progressing toward a decentralized future. This evolution is commonly divided into three distinct phases: Web 1, Web 2, and the emerging Web 3. Each phase represents not only technological advancement but fundamental shifts in how we interact with digital content, who controls our data, and how value is created and distributed online. While Web 1 and Web 2 have largely defined our internet experience to date, Web 3 promises a paradigm shift toward greater user sovereignty, decentralized infrastructure, and reimagined ownership models for digital assets.
The Static Beginning: Web 1.0
The first iteration of the web, commonly known as Web 1.0, emerged in the early 1990s and continued until the late 1990s. This period represented the internet's infancy, characterized by static pages with limited functionality and minimal user interaction[1]. At the core of Web 1 was the concept of information retrieval rather than dynamic interaction.
Fundamental Characteristics of Web 1
During the Web 1 era, websites primarily served as digital brochures or informational repositories. Most sites were static, comprised of HTML pages containing fixed content such as text, images, and hyperlinks[1]. The HTML (Hypertext Markup Language) provided the structural foundation, while CSS (Cascading Style Sheets) offered basic styling capabilities. These technologies enabled the creation of visually formatted content but lacked the dynamic elements we take for granted today.
The Web 1 experience was predominantly one-directional. The majority of internet users were passive consumers of content, while creators were primarily web developers who produced websites with mainly textual or visual information[2]. Interaction was limited to basic navigation through hyperlinks, with few opportunities for users to contribute their own content or engage meaningfully with websites.
Technical limitations further defined the Web 1 experience. Information access was significantly slower than today's standards, largely due to the prevalence of dial-up connections. This constraint meant websites needed to be optimized for minimal bandwidth usage[1]. Additionally, security measures were rudimentary, making early websites vulnerable to various cyberattacks without adequate protection systems in place.
The Social Revolution: Web 2.0
As the internet matured in the late 1990s and early 2000s, a significant transformation occurred. Web 2.0 emerged as a more dynamic, interactive platform that emphasized user participation, content creation, and social connectivity[6]. This shift fundamentally changed how people engaged with the internet, moving from passive consumption to active contribution.
The Rise of Social Media and Big Data
Web 2.0 gave birth to social media platforms, interactive web applications, and user-generated content ecosystems. Companies like Google, Facebook, Twitter, and Amazon developed business models that leveraged user activity and content creation[4]. These platforms transformed from simple information repositories into complex social networks and digital marketplaces.
Central to the Web 2.0 revolution was the collection and analysis of user data on an unprecedented scale. Companies developed sophisticated infrastructure to handle massive amounts of information. Google implemented systems like the Google File System (GFS) and Spanner to store and distribute data across thousands of machines worldwide[4]. Facebook developed cascade prediction systems to manage user interactions, while Twitter created specialized infrastructure to process millions of tweets per minute[4].
These technological advancements enabled the monetization of user attention and personal information. By analyzing user behavior, preferences, and social connections, Web 2.0 companies could deliver highly targeted advertising and personalized content recommendations. This business model generated immense wealth for platform owners while raising significant concerns about privacy, data ownership, and the concentration of power in the hands of a few technology giants.
The Decentralized Future: Web 3.0
Web 3 represents the next evolutionary stage of the internet, characterized by principles of decentralization, transparency, and user sovereignty[6]. Unlike previous iterations, Web 3 seeks to redistribute control from centralized entities to individual users and communities through blockchain technology and decentralized protocols.
Blockchain as the Foundation
The conceptual underpinnings of Web 3 emerged with the creation of Bitcoin in 2009. Bitcoin introduced a revolutionary approach to digital transactions by enabling peer-to-peer value transfer without requiring a central authority. This innovation demonstrated that trust could be established through cryptographic proof rather than relying on traditional financial institutions.
Ethereum expanded upon Bitcoin's foundation by introducing programmable smart contracts, which allowed for the creation of decentralized applications (dApps) beyond simple financial transactions. This breakthrough enabled developers to build complex applications with self-executing agreements that operate transparently on the blockchain[6].
Ownership and Data Sovereignty
A defining characteristic of Web 3 is the emphasis on true digital ownership. Through blockchain technology and cryptographic tokens, individuals can now assert verifiable ownership over digital assets in ways previously impossible[6]. This stands in stark contrast to Web 2 platforms, where users effectively surrendered control of their content and data to centralized companies.
The concept of self-custody exemplifies this shift toward user sovereignty. Platforms like Trust Wallet enable individuals to maintain control over their digital assets across multiple blockchains without relying on intermediaries[5]. Users hold their private keys, ensuring that they—not corporations or governments—have ultimate authority over their digital property.
Decentralized Physical Infrastructure Networks (DePIN)
Web 3 extends beyond digital assets to reimagine physical infrastructure through Decentralized Physical Infrastructure Networks (DePIN). These networks connect blockchain technology with real-world systems, allowing people to use cryptocurrency tokens to build and manage physical infrastructure—from wireless hotspots to energy systems[7].
DePIN projects decentralize ownership and governance of critical infrastructure, creating more transparent, efficient, and resilient systems aligned with Web 3 principles[7]. By distributing control among network participants rather than centralizing it within corporations or governments, these projects bridge the gap between digital networks and physical reality.
Non-Fungible Tokens and Intellectual Property
Non-Fungible Tokens (NFTs) represent another revolutionary aspect of Web 3, providing a mechanism for verifying the authenticity and ownership of unique digital items. NFTs enable creators to establish provenance for digital art, music, virtual real estate, and other forms of intellectual property, addressing longstanding issues of duplication and unauthorized distribution in the digital realm[6].
This innovation has profound implications for creative industries, potentially enabling more direct relationships between creators and their audiences while reducing dependence on centralized platforms and intermediaries.
Nostr: A Decentralized Protocol for Social Media and Communication
Nostr (Notes and Other Stuff Transmitted by Relays) is a decentralized and censorship-resistant communication protocol designed to enable open and secure social networking. Unlike traditional social media platforms that rely on centralized servers and corporate control, Nostr allows users to communicate directly through a network of relays, ensuring resilience against censorship and deplatforming.
The protocol operates using simple cryptographic principles: users generate a public-private key pair, where the public key acts as their unique identifier, and messages are signed with their private key. These signed messages are then broadcast to multiple relays, which store and propagate them to other users. This structure eliminates the need for a central authority to control user identities or content distribution[8].
As concerns over censorship, content moderation, and data privacy continue to rise, Nostr presents a compelling alternative to centralized social media platforms. By decentralizing content distribution and giving users control over their own data, it aligns with the broader ethos of Web3—empowering individuals and reducing reliance on corporate intermediaries[9].
Additionally Nostr implements a novel way for users to monetize their content via close integration with Bitcoin's "Lightning Network"[11] -- a means by which users are able to instantly transmit small sums (satoshi's, the smallest unit of Bitcoin) with minimal fees. This feature, known as “zapping,” allows users to send micropayments directly to content creators, tipping them for valuable posts, comments, or contributions. By leveraging Lightning wallets, users can seamlessly exchange value without relying on traditional payment processors or centralized monetization models. This integration not only incentivizes quality content but also aligns with Nostr’s decentralized ethos by enabling peer-to-peer financial interactions that are censorship-resistant and borderless.
For those interested in exploring Nostr, setting up an account requires only a private key, and users can begin interacting with the network immediately by selecting a client that suits their needs. The simplicity and openness of the protocol make it a promising foundation for the next generation of decentralized social and communication networks.
Alternative Decentralized Models: Federation
Not all Web 3 initiatives rely on blockchain technology. Platforms like Bluesky are pioneering federation approaches that allow users to host their own data while maintaining seamless connectivity across the network[10]. This model draws inspiration from how the internet itself functions: just as anyone can host a website and change hosting providers without disrupting visitor access, Bluesky enables users to control where their social media data resides.
Federation lets services be interconnected while preserving user choice and flexibility. Users can move between various applications and experiences as fluidly as they navigate the open web[10]. This approach maintains the principles of data sovereignty and user control that define Web 3 while offering alternatives to blockchain-based implementations.
Conclusion
The evolution from Web 1 to Web 3 represents a profound transformation in how we interact with the internet. From the static, read-only pages of Web 1 through the social, data-driven platforms of Web 2, we are now entering an era defined by decentralization, user sovereignty, and reimagined ownership models.
Web 3 technologies—whether blockchain-based or implementing federation principles—share a common vision of redistributing power from centralized entities to individual users and communities. By enabling true digital ownership, community governance, and decentralized infrastructure, Web 3 has the potential to address many of the concerns that have emerged during the Web 2 era regarding privacy, control, and the concentration of power.
As this technology continues to mature, we may witness a fundamental reshaping of our digital landscape toward greater transparency, user autonomy, and equitable value distribution—creating an internet that more closely aligns with its original promise of openness and accessibility for all.
Sources
[1] What is WEB1? a brief history of creation - White and Partners https://whiteand.partners/en/what-is-web1-a-brief-history-of-creation/ [2] Evolution of the Internet - from web1.0 to web3 - LinkedIn https://www.linkedin.com/pulse/evolution-internet-from-web10-web3-ravi-chamria [3] Web3 Social: Create & Monetize with Smart Contracts - Phala Network https://phala.network/web3-social-create-monetize-with-smart-contracts [4] [PDF] Big Data Techniques of Google, Amazon, Facebook and Twitter https://www.jocm.us/uploadfile/2018/0613/20180613044107972.pdf [5] True crypto ownership. Powerful Web3 experiences - Trust Wallet https://trustwallet.com [6] Web3: Revolutionizing Digital Ownership and NFTs - ThoughtLab https://www.thoughtlab.com/blog/web3-revolutionizing-digital-ownership-and-nfts/ [7] DePIN Crypto: How It's Revolutionizing Infrastructure in Web3 https://www.ulam.io/blog/how-depin-is-revolutionizing-infrastructure-in-the-web3-era [8] Nostr: Notes and Other Stuff… https://nostr.com/ [9] Nostr: The Importance of Censorship-Resistant Communication... https://bitcoinmagazine.com/culture/nostr-the-importance-of-censorship-resistant-communication-for-innovation-and-human-progress- [10] Bluesky: An Open Social Web https://bsky.social/about/blog/02-22-2024-open-social-web [11] Wikipedia: Lightning Network https://en.wikipedia.org/wiki/Lightning_Network
-
 @ 4ba8e86d:89d32de4
2025-04-21 02:10:55
@ 4ba8e86d:89d32de4
2025-04-21 02:10:55Seu teclado não deve se conectar à internet. Privacidade em primeiro lugar. Sempre. Estamos desenvolvendo um teclado moderno que respeita totalmente sua privacidade e segurança. O FUTO Keyboard é 100% offline e 100% privado, oferecendo todos os recursos essenciais que você espera de um teclado atual — incluindo digitação por deslizamento, entrada de voz offline, correção automática inteligente, temas personalizáveis e sugestões preditivas de texto. Nosso objetivo é simples: criar um teclado eficiente e funcional, sem comprometer a privacidade do usuário. Este projeto é um fork do LatinIME, o teclado open-source oficial do Android.
Atenção: o FUTO Keyboard está atualmente em fase alfa. Está trabalhando para torná-lo estável e confiável, mas durante esse período você pode encontrar bugs, travamentos ou recursos ainda não implementados.
Configurações
Idiomas e Modelos – Adicione novos idiomas, dicionários, modelos de entrada de voz, transformadores e layouts associados.
Linguagens e Modelos
O menu no qual você adiciona novos idiomas, bem como dicionários, modelos de entrada de voz, modelos de transformadores e layouts associados a eles.
Adicionar idioma.
Alguns idiomas exigem o download de um dicionário. Se você também quiser um modelo de entrada de voz para um idioma específico, precisará baixá-lo também. Cada idioma já possui uma seleção de layouts de teclado associados; você pode escolher qual(is) layout(s) deseja adicionar ao adicionar o idioma. https://video.nostr.build/c775288b7a8ee8d75816af0c7a25f2aa0b4ecc99973fd442b2badc308fa38109.mp4
Mudar idioma.
Existem duas maneiras de alternar o idioma. A primeira é pressionando o ícone do globo na Barra de Ações, localizada próximo ao canto superior esquerdo do teclado. A segunda é pressionando longamente ou deslizando a barra de espaço; você pode personalizar o comportamento de troca de idioma da barra de espaço acessando Configurações -> Teclado e Digitação -> Teclas de Pressão Longa e Barra de Espaço -> Comportamento da Barra de Espaço . Você também pode atribuir o ícone do globo como a Tecla de Ação para que fique ao lado da barra de espaço, que pode ser acessada no menu Todas as Ações pressionando a tecla de reticências (...) no canto superior esquerdo do teclado e, em seguida, acessando Editar Ações. https://video.nostr.build/ed6f7f63a9c203cd59f46419ef54a4b8b442f070f802a688ca7d682bd6811bcb.mp4
Adicionar dicionário.
Alguns idiomas têm um dicionário integrado, mas a maioria não. Se o idioma que você está instalando não tiver um dicionário integrado, você pode iniciar a instalação em nosso site acessando Idiomas e Modelos -> Dicionário (no idioma que você está instalando) -> Explorar -> Baixar (em nosso site). https://video.nostr.build/3b1e09289953b658a9cef33c41bd711095556bc48290cb2ed066d4d0a5186371.mp4
Habilitar digitação multilíngue.
Você pode habilitar a digitação multilíngue para um ou mais idiomas acessando Idiomas e modelos e marcando a caixa Digitação multilíngue no(s) idioma(s) para os quais deseja habilitar a digitação multilíngue. https://video.nostr.build/29f683410626219499787bd63058d159719553f8e33a9f3c659c51c375a682fb.mp4
Criar layout personalizado.
Se desejar criar seu próprio layout personalizado para um idioma específico, você pode fazê-lo ativando Configurações do Desenvolvedor -> Layouts Personalizados -> Criar novo layout . Mais informações sobre layouts personalizados podem ser encontradas https://github.com/futo-org/futo-keyboard-layouts . A personalização das configurações de pressionamento longo tecla por tecla ainda não é suportada, mas está em processo de implementação. https://video.nostr.build/b5993090e28794d0305424dd352ca83760bb87002c57930e80513de5917fad8d.mp4
Teclado e Digitação – Personalize o comportamento das teclas, o tamanho do teclado e outras preferências de digitação.
Previsão de texto.
O menu no qual você define suas preferências para correção automática e sugestões personalizadas. Modelo de Linguagem do Transformador Você pode fazer com que o teclado preveja a próxima palavra que você digitará ou faça correções automáticas mais inteligentes, que usam um modelo de linguagem Transformer pré-treinado com base em conjuntos de dados disponíveis publicamente, ativando o Transformer LM . Observação: atualmente, isso funciona apenas em inglês, mas estamos trabalhando para torná-lo compatível com outros idiomas. Ajuste fino do transformador Você pode fazer com que o teclado memorize o que você digita e quais sugestões você seleciona, o que treina o modelo de idioma (enquanto o telefone estiver inativo) para prever quais palavras sugerir e corrigir automaticamente enquanto você digita, ativando o ajuste fino do Transformer . Observação: este é o seu modelo de idioma pessoal e o FUTO não visualiza nem armazena nenhum dos seus dados. https://video.nostr.build/688354a63bdc48a9dd3f8605854b5631ac011009c6105f93cfa0b52b46bc40d3.mp4
Previsão de texto.
O menu no qual você define suas preferências para correção automática e sugestões personalizadas. Modelo de Linguagem do Transformador Você pode fazer com que o teclado preveja a próxima palavra que você digitará ou faça correções automáticas mais inteligentes, que usam um modelo de linguagem Transformer pré-treinado com base em conjuntos de dados disponíveis publicamente, ativando o Transformer LM . Observação: atualmente, isso funciona apenas em inglês, mas estamos trabalhando para torná-lo compatível com outros idiomas.
Ajuste fino do transformador.
Você pode fazer com que o teclado memorize o que você digita e quais sugestões você seleciona, o que treina o modelo de idioma (enquanto o telefone estiver inativo) para prever quais palavras sugerir e corrigir automaticamente enquanto você digita, ativando o ajuste fino do Transformer . Observação: este é o seu modelo de idioma pessoal e o FUTO não visualiza nem armazena nenhum dos seus dados.
Força do Modelo de Linguagem do Transformador.
Você pode fazer com que a correção automática se comporte mais como o teclado AOSP ou mais como a rede neural acessando Parâmetros avançados -> Intensidade do LM do transformador e arrastando o controle deslizante para um valor menor (o que tornará o comportamento da correção automática mais parecido com o teclado AOSP) ou um valor maior (o que tornará a correção automática mais dependente da rede neural). Limiar de correção automática Você pode alterar o limite da correção automática para que ela ocorra com mais ou menos frequência acessando Parâmetros avançados -> Limite de correção automática e arrastando o controle deslizante para um valor menor (o que fará com que a correção automática ocorra com mais frequência, mas também corrija erros com mais frequência) ou um valor maior (o que fará com que a correção automática ocorra com menos frequência, mas também corrija erros com menos frequência). https://video.nostr.build/ea9c100081acfcab60343c494a91f789ef8143c92343522ec34c714913631cf7.mp4
Lista negra de palavras.
Você pode colocar sugestões de palavras na lista negra, o que impedirá que o teclado continue sugerindo palavras na lista negra, acessando Sugestões na lista negra e adicionando as palavras que você gostaria de colocar na lista negra.
Palavras ofensivas.
Você pode bloquear palavras ofensivas, como palavrões comuns, acessando Sugestões na Lista Negra e marcando a opção Bloquear Palavras Ofensivas . Observação: a opção Bloquear Palavras Ofensivas está ativada por padrão. https://video.nostr.build/ee72f3940b9789bbea222c95ee74d646aae1a0f3bf658ef8114c6f7942bb50f5.mp4
Correção automática.
Você pode ativar a capacidade de corrigir automaticamente palavras digitadas incorretamente ao pressionar a barra de espaço ou digitar pontuação ativando a Correção automática.
Sugestões de correção.
Você pode ativar a capacidade de exibir palavras sugeridas enquanto digita marcando a opção Mostrar sugestões de correção.
Sugestões de palavras.
Você pode ativar a capacidade de aprender com suas comunicações e dados digitados para melhorar as sugestões ativando as Sugestões personalizadas . Observação: desativar as Sugestões personalizadas também desativa o ajuste fino do Transformer. https://video.nostr.build/2c22d109b9192eac8fe4533b3f8e3e1b5896dfd043817bd460c48a5b989b7a2f.mp4
Entrada de Voz – Configure a entrada de voz offline, incluindo a duração e a conversão de fala em texto.
Entrada de voz.
O menu no qual você define suas preferências de entrada de voz, como duração da entrada e configurações de conversão de fala em texto. Entrada de voz integrada Você pode desabilitar a entrada de voz integrada do teclado e, em vez disso, usar o provedor de entrada de voz de um aplicativo externo desativando a opção Desabilitar entrada de voz integrada. https://video.nostr.build/68916e5b338a9f999f45aa1828a6e05ccbf8def46da9516c0f516b40ca8c827b.mp4
Sons de indicação.
Você pode habilitar a capacidade de reproduzir sons ao iniciar e cancelar a entrada de voz ativando Sons de indicação. https://video.nostr.build/7f5fb6a6173c4db18945e138146fe65444e40953d85cee1f09c1a21d236d21f5.mp4
Progresso Detalhado.
Você pode habilitar a capacidade de exibir informações detalhadas, como indicar que o microfone está sendo usado, ativando Progresso detalhado. https://video.nostr.build/8ac2bb6bdd6e7f8bd4b45da423e782c152a2b4320f2e090cbb99fd5c78e8f44f.mp4
Microfone Bluetooth.
Você pode fazer com que a entrada de voz prefira automaticamente seu microfone Bluetooth em vez do microfone integrado, ativando Preferir microfone Bluetooth. https://video.nostr.build/c11404aa6fec2dda71ceb3aaee916c6761b3015fef9575a352de66b7310dad07.mp4
Foco de áudio.
Você pode fazer com que a entrada de voz pause automaticamente vídeos ou músicas quando ela estiver ativada, ativando o Foco de Áudio. https://video.nostr.build/4ac82af53298733d0c5013ef28befb8b2adeb4a4949604308317e124b6431d40.mp4
Supressão de Símbolos.
Por padrão, a entrada de voz transcreve apenas texto básico e pontuação. Você pode desativar a opção "Suprimir símbolos" para liberar a entrada de voz da transcrição de caracteres especiais (por exemplo, @, $ ou %). Observação: Isso não afeta a forma como a entrada de voz interpreta palavras literais (por exemplo, "vírgula", "ponto final"). https://video.nostr.build/10de49c5a9e35508caa14b66da28fae991a5ac8eabad9b086959fba18c07f8f3.mp4
Entrada de voz de formato longo.
Você pode desativar o limite padrão de 30 segundos para entrada de voz ativando a opção Entrada de voz longa . Observação: a qualidade da saída pode ser prejudicada com entradas longas. https://video.nostr.build/f438ee7a42939a5a3e6d6c4471905f836f038495eb3a00b39d9996d0e552c200.mp4
Parada automática em silêncio.
Você pode fazer com que a entrada de voz pare automaticamente quando o silêncio for detectado, ativando a opção Parar automaticamente ao silenciar . Observação: se houver muito ruído de fundo, pode ser necessário interromper manualmente a entrada de voz. Ative também a entrada de voz longa para evitar a interrupção após 30 segundos. https://video.nostr.build/056567696d513add63f6dd254c0a3001530917e05e792de80c12796d43958671.mp4
Dicionário Pessoal – Adicione palavras personalizadas para que o teclado aprenda e sugira com mais precisão.
Dicionário Pessoal.
O menu no qual você cria seu dicionário pessoal de palavras que o teclado irá lembrar e sugerir. Adicionar ao dicionário Você pode adicionar uma palavra ou frase ao seu dicionário pessoal pressionando o ícone de adição na tela "Dicionário pessoal" . Você também pode criar um atalho para ela no campo "Atalho" ao adicionar a palavra ou frase. https://video.nostr.build/dec41c666b9f2276cc20d9096e3a9b542b570afd1f679d8d0e8c43c8ea46bfcb.mp4
Excluir do dicionário.
Você pode excluir uma palavra ou frase do seu dicionário pessoal clicando nessa palavra ou frase e clicando no ícone de lixeira no canto superior direito. https://video.nostr.build/aca25643b5c7ead4c5d522709af4bc337911e49c4743b97dc75f6b877449143e.mp4
Tema – Escolha entre os temas disponíveis ou personalize a aparência do teclado conforme seu gosto.
Tema.
O menu no qual você seleciona seu tema preferido para o teclado. Alterar tema Você pode escolher entre uma variedade de temas para o teclado, incluindo Modo Escuro, Modo Claro, Automático Dinâmico, Escuro Dinâmico, Claro Dinâmico, Material AOSP Escuro, Material AOSP Claro, Roxo Escuro AMOLED, Girassol, Queda de Neve, Cinza Aço, Esmeralda, Algodão Doce, Luz do Mar Profundo, Escuro do Mar Profundo, Gradiente 1, Tema FUTO VI ou Tema Construção . A possibilidade de personalizar seu tema será disponibilizada em breve. https://video.nostr.build/90c8de72f08cb0d8c40ac2fba2fd39451ff63ec1592ddd2629d0891c104bc61e.mp4
Fronteiras Principais.
Você pode habilitar as bordas das teclas rolando para baixo até o final e ativando Bordas das teclas . https://video.nostr.build/fa2087d68ce3fb2d3adb84cc2ec19c4d5383beb8823a4b6d1d85378ab3507ab1.mp4
Site oficial https://keyboard.futo.org/
Baixar no fdroid. https://app.futo.org/fdroid/repo/
Para instalar através do Obtainium , basta ir em Adicionar Aplicativo e colar esta URL do repositório: https://github.com/futo-org/android-keyboard
A adição pode demorar um pouco dependendo da velocidade da sua internet, pois o APK precisa ser baixado.
-
 @ 21335073:a244b1ad
2025-03-18 20:47:50
@ 21335073:a244b1ad
2025-03-18 20:47:50Warning: This piece contains a conversation about difficult topics. Please proceed with caution.
TL;DR please educate your children about online safety.
Julian Assange wrote in his 2012 book Cypherpunks, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense.
This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning.
When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little.
I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?”
I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well.
I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread.
I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard.
I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it.
The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust.
Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this.
I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place.
What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method.
It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code.
They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened.
I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road.
So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally.
Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb.
I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback.
Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed.
That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone.
To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all.
I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society.
I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this.
On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government.
I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories.
There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc.
Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind.
Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now.
There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers?
I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity.
I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place.
My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors.
My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline.
The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online.
I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers.
So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation?
When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that.
I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic.
If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations.
I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process.
Course: - The creation of the internet and computers - The fight for cryptography - The tech supply chain from the ground up (example: human rights violations in the supply chain) - Corporate tech - Freedom tech - Data privacy - Digital privacy rights - AI (history-current) - Online safety (predators, scams, catfishing, extortion) - Bitcoin - Laws - How to deal with online hate and harassment - Information on who to contact if you are being abused online or offline - Algorithms - How to seek out the truth about news, etc., online
The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children.
The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward?
I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone.
Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability.
The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime.
This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful.
This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens.
In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions.
I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation.