-
 @ a53364ff:e6ba5513
2025-04-27 16:51:37
@ a53364ff:e6ba5513
2025-04-27 16:51:37Not everyone agrees or realizes that governments, corporations and banks are progressively infringing on our most basic rights and that we should fight back, if only with the right tools.
But I don’t believe in going out in the street to protest, hoping that the government will do something about it. I think that demanding from the State is actually giving it even more power. So what’s the solution?
I believe that Bitcoin is the best tool for individuals to reclaim their freedom and sovereignty.
By taking money out of the hands of central banks, 3-letter agencies and governments, we can reclaim complete control over our money, our life and our future.
I believe the world is facing a great threat. I’m not talking about global warming or climate change. I’m talking about a global political agenda, shared among Western countries’ governments, and focused on limiting individual freedom while increasing government control.
I believe our modern banking and financial systems are profoundly inegalitarian by nature, with the ability for a few elites to “print” money out of thin air and use it to follow their own agenda.
I believe our modern banking system was built like this on purpose. I do not consider the government’s and central banks’ money printing to be part of “how things normally work”, but rather to be a counterfeiting mechanism that they use for their own benefit.
For these reasons, I don’t believe that governments have the people’s best interest in mind. As a matter of fact, I rather think the opposite is true.
I believe this counterfeiting mechanism (or money printing) leads to financial servitude for the individuals, and systemic risk for human society as a whole.
I believe all the financial crises we witnessed since the beginning of the 20th century are directly linked to this counterfeiting mechanism, and that this system is now coming to an end.
As such, I believe most people grossly overlook the risks that are being taken with their money, whether it be sitting on a bank account or invested in financial markets.
Furthermore, I believe this flawed monetary system is in complete control of most people’s money, lives, and future.
But I believe there is an alternative to this flawed system: Bitcoin.
I believe Bitcoin is the best tool individuals can use to take back their freedom and resist government controlling their life.
And I believe you shouldn’t have to be tech-savvy to start using Bitcoin, but you definitely need to be freedom-minded.
-
 @ a53364ff:e6ba5513
2025-04-27 16:23:40
@ a53364ff:e6ba5513
2025-04-27 16:23:40Are you tired of having to trust banks and other financial institutions with your money? With Bitcoin, you can take control of your finances and be the sole custodian of your wealth. This is known as self-custody and it completely eliminates the need for third-party services, by receiving and storing your bitcoin securely in your own Bitcoin wallet. In this blog post, we will discuss what self-custody means, how it works, and the benefits and responsibilities associated with being in control of your own money.
What is Self-Custody?
Self-custody is simply the process of keeping your own private keys to your Bitcoin wallet, meaning you do not need a bank or any other third party to manage or access your Bitcoin funds; you are able to do all that yourself. This means that only you have full control over your money, allowing you to make transactions securely and safely without ever having to ask someone’s permission or worry about someone else mishandling or stealing it.
Who Is in Charge of My Bitcoin?
When using Bitcoin, you are in charge of your own Bitcoin wallet, which includes an unlimited amount of addresses that are used to receive Bitcoin, and a private key that is used to sign outbound transactions. The private key is literally the key to your Bitcoin wallet, as it can send Bitcoin to other addresses your don’t control. As such, it is imperative that it is kept safe and secure, accessible only by you. This is how ownership of Bitcoin is determined. If you share the private key to a wallet you control, you’re not the only one able to spend the Bitcoin inside the wallet anymore.
Benefits & Responsibilities
The most obvious benefit of self-custody is that no one else has control over your funds but you! That said, there are some important responsibilities that come with owning the keys to your Bitcoin wallet.
One responsibility that comes with being the only owner of your Bitcoin funds is making sure that your private key is safe from theft and loss. Fortunately, there are easy solutions available for securely storing Bitcoin keys, and seeking guidance from a knowledgeable source can be a great help if you’re not ready to take on this responsibility alone. A Bitcoin security expert can provide valuable insights and tools to help you ensure the safety and security of your funds.
Overall, Bitcoin gives immense power to individuals who want full control over their finances without relying on third parties like banks or payment processors. But taking ownership of your money also comes with certain responsibilities such as safeguarding your private keys; however these responsibilities pale in comparison when compared with the freedom and security granted by taking ownership of your money with Bitcoin! And with the right tools and guidance, using Bitcoin in a truly sovereign way can be way easier than you may imagine.
-
 @ a53364ff:e6ba5513
2025-04-27 16:17:19
@ a53364ff:e6ba5513
2025-04-27 16:17:19To the few elites who benefit from the modern banking system and the constant emission of currency, Bitcoin is a threat to their privileged position.
For traders, investors, and gamblers who are only interested in making a quick buck, Bitcoin is a new and volatile asset they can speculate on.
For individuals escaping tyranny or authoritarian regimes, Bitcoin is a way to move their wealth across borders and avoid it being seized by the government.
For people who live in inflation-ridden countries, Bitcoin is a way to protect their wealth against accelerating devaluation and avoid losing all their money to inflation.
For digital nomads, Bitcoin is a great way to easily earn money online, avoid paying high commission fees to payment processors (Paypal, Stripe, etc), and avoid high currency conversion fees while traveling.
As we can see, Bitcoin definitely is different things to different people. What we all agree on, though, is that Bitcoin is here to reject the status quo.
Bitcoin is the best tool out there for people who value individual freedom and seek more self-sovereignty to take control of their money, their lives, and their future.
What is Bitcoin to you?
-
 @ 12fccfc8:8d67741e
2025-04-27 15:55:18
@ 12fccfc8:8d67741e
2025-04-27 15:55:18„Man muss noch Chaos in sich haben, um einen tanzenden Stern gebären zu können.“
– Friedrich Nietzsche
Der Mensch wächst nicht aus der Welt – er wird in sie geworfen, ohne Ursprung, ohne Auftrag, ohne Trost. Die Familie erscheint zuerst als Halt, doch sie ist oft der erste Spiegel, in dem man sich selbst nicht erkennt. Man nennt es Liebe, nennt es Bindung – aber vielleicht ist es nur die stille Einweisung in ein Gefängnis, dessen Mauern wie Umarmungen aussehen.
Kindheit, Freiheit, Einsamkeit
Das Kind ist nicht die Fortsetzung des Selbst, sondern der Beweis, dass auch das Chaos Nachwuchs hat. Es lacht, weil es noch nicht weiß, was Lachen kostet. Es fragt nicht, weil es noch nicht weiß, dass Fragen selten Antworten finden. Und doch ist es das Kind, das die Ordnung zum Wanken bringt – nicht durch Widerstand, sondern durch seine unbestechliche Gegenwärtigkeit.
Freiheit beginnt dort, wo man aufhört, sich retten zu lassen. Sie ist kein Zustand, sondern eine Haltung: die Weigerung, sich einer Bedeutung zu unterwerfen, die von außen kommt. Die Welt verlangt Funktion – das freie Leben verweigert sich der Funktion, nicht durch Aufstand, sondern durch Abwesenheit. Wer Sicherheit sucht, hat die Welt bereits verloren.
Einsamkeit ist kein Unglück – sie ist der Boden, auf dem das Selbst sich überhaupt erst spüren kann. Sie ist nicht leer, sondern ungeteilt. Was fehlt, ist nicht ein anderer Mensch, sondern die Illusion, dass Nähe uns ganz machen könnte. In der Tiefe des Alleinseins offenbart sich nicht Mangel, sondern Klarheit.
Das Nichts und die Möglichkeit des Lebens
Ein Kind stellt keine Fragen über das Nichts – es lebt in ihm, ohne es zu wissen. Der Erwachsene aber erkennt es, spürt es wie eine zweite Haut, die nicht abgelegt werden kann. Doch dieses Wissen ist keine Strafe. Es ist die Bedingung jeder echten Handlung. Wer das Nichts kennt, liebt nicht, um sich zu retten – sondern weil er weiß, dass nichts gerettet werden muss.
Ein Leben im Angesicht der Leere ist möglich. Nicht durch Verdrängung, sondern durch Durchschreiten. Die Rolle, die man spielt, wird erträglich, wenn man sie nicht mit Identität verwechselt. Die Arbeit, die man verrichtet, dient nicht mehr dem Fortschritt, sondern der Form – und vielleicht ist darin schon Würde genug.
Familie kann ein Nest sein – oder ein Netz. Es hält, oder es hält fest. Doch auch das Netz kann Heimat sein, wenn man nicht mehr erwartet, darin zu fliegen. Ein Kind zu begleiten heißt nicht, ihm Wahrheit zu geben, sondern ihm Raum zu lassen, seine eigene zu verwerfen.
Raum, Erlaubnis, Schönheit
Freiheit ist kein Ziel, sondern ein Aufhören. Wer nichts mehr will, dem kann nichts genommen werden. Wer das Nichts annimmt, dem begegnet keine Leere mehr – sondern Raum. In diesem Raum entsteht das, was nicht geplant ist, nicht beherrscht und nicht gezählt: der Moment, das Staunen, die Stille zwischen zwei Gedanken. Vielleicht ist genau das genug.
Man kann leben mit dem Nichts – wenn man nicht mehr verlangt, dass es Sinn macht. Man kann Vater sein, Mutter, Freund, Fremder – ohne sich zu verlieren. Man kann lachen, weinen, müde sein – ohne Trost zu brauchen. Denn wer dem Nichts ins Auge gesehen hat, der weiß: Alles ist bedeutungslos. Und genau deshalb ist alles erlaubt. Und manchmal, ganz selten, auch: schön.
-
 @ 12fccfc8:8d67741e
2025-04-27 15:42:39
@ 12fccfc8:8d67741e
2025-04-27 15:42:39- Im Nichts gibt es keine Befreiung, nur die Ernüchterung der Illusion. Die Welt ist ein Flimmern, das dem Auge entgleitet, während wir in einem endlosen Raum der Bedeutungslosigkeit verharren.
- Es gibt Momente, in denen das Nichts nicht nur eine Abwesenheit ist, sondern ein erdrückendes Gewicht, das uns in den Staub drückt. Wir fliehen in Gedanken, doch diese Gedanken sind der allerletzte Zufluchtsort, der uns nichts als die Huldigung der Leere bietet.
- Das Nichts ist der heimliche Gott, der im Zerfall des Seins thront, ein stiller Erlöser, der das Leben in seinen Schoß zurückruft, um es sanft zu ersticken.
- Die Trauer ist der Wundschrei des Seins über seinen eigenen Bruch, ein letztes Festhalten an der Hülle des Vergangenen, bevor sie im Strom der Vernichtung zerfließt.
- Der Sinn entgleitet, je fester wir ihn fassen wollen – wie Nebel, der sich vor der Berührung auflöst.
- Wir leben in der Hoffnung, dass das Nichts uns nicht sieht – doch es hat längst in uns Wohnung genommen.
- Jeder Gedanke an Erlösung gebiert eine neue Kette – die Freiheit beginnt erst dort, wo das Verlangen endet.
- Das Schweigen des Universums ist keine Antwort – es ist die endgültige Form der Gleichgültigkeit.
- Unsere Angst vor dem Nichts ist nur der Schrei des Ichs, das weiß, dass es niemals war.
- Wir existieren wie Fußspuren im Staub eines verlassenen Raums – sichtbar nur für einen Moment, bedeutungslos im Wind der Zeit.
-
 @ 12fccfc8:8d67741e
2025-04-27 15:41:16
@ 12fccfc8:8d67741e
2025-04-27 15:41:16- Existenz ist ein Exil ohne Rückkehr. Wer liebt, liebt nur die Illusion eines Auswegs.
- Die Seele sammelt Splitter vergangener Welten, doch keine Hand kann sie wieder ganz machen.
- Erinnerungen sind Splitter eines Spiegels, der zerbrach – sie schneiden dich, während du dein Gesicht in ihnen suchst.
- Die Schwermut ist der Ruf des Todes im Lebenden, ein dumpfer Widerhall des Willens, der sich selbst verneint, um im Grau der Tage seine Erlösung zu finden.
- Das Leben ist der Widerhall eines sterbenden Willens. Nur im Nichts finden wir Erlösung.
- Die Zeit ist ein Dieb, der Schatten stiehlt – sie lässt dich zurück, ein Umriss, den niemand mehr füllt.
- In der Dämmerung unserer Tage suchen wir die Sonne, die nur in der Erinnerung noch brennt.
- Stille fließt durch uns, als wäre sie immer schon gewesen – ein Zustand, der nie durchbrochen werden kann. Wir sind die Frage, die nie die Antwort findet, das Bild, das niemals scharf wird.
- Wer das Nichts anschaut, sieht sich selbst: ein Schatten, der sich für Licht hält.
- Die Einsamkeit offenbart sich die Qual des Seienden, ein verlassenes Fragment des zersplitterten Willens, das im kalten Licht seiner eigenen Nutzlosigkeit zittert.
-
 @ 12fccfc8:8d67741e
2025-04-27 15:34:44
@ 12fccfc8:8d67741e
2025-04-27 15:34:44„Die Tatsache, dass das Leben keinen Sinn hat, ist ein Grund zu leben – und zwar der einzige.“
– Emil Cioran
Der Mensch steht im Zentrum eines Raumes, der sich weigert, eine Mitte zu haben. Alles um ihn herum scheint geordnet, doch diese Ordnung ist ein leises Zittern vor dem Chaos, das jede Struktur unterwandert. Es gibt kein Versprechen, das nicht gebrochen wird, kein Licht, das nicht aus einer tieferen Dunkelheit geboren wird. So flackert die Existenz – ein schwankender Schein über einem Abgrund, der kein Echo zurückgibt.
Das Nichts: Gegenwart ohne Form
Das Nichts ist nicht Abwesenheit. Es ist Gegenwart ohne Form. Es liegt nicht hinter den Dingen, sondern in ihnen – wie ein Geruch, der bleibt, wenn alle Türen geschlossen sind. Es ist der unsichtbare Kern der Welt, der Grund, warum jedes Wort in sich selbst zerfällt, jede Bewegung zu spät kommt, jeder Sinn sich verflüchtigt, sobald man ihn greifen will. Das Schweigen des Universums ist keine Antwort – es ist die endgültige Form der Gleichgültigkeit.
Wer dem Nichts begegnet, verliert nicht die Hoffnung – er erkennt, dass es nie Hoffnung gab, nur das Bedürfnis danach. Die Leere ist kein Loch, das gefüllt werden will, sondern ein Zustand, der alles durchdringt. Man lebt nicht trotz des Nichts – man lebt im Nichts, als Ahnung, als Abdruck, als Fußspur im Staub eines Raums, den niemand betritt.
Melancholie und Erinnerung
Melancholie ist kein Gefühl, sondern ein Aggregatzustand des Bewusstseins, das zu viel gesehen hat, um noch zu glauben. Sie trägt kein Schwarz, sie schreit nicht. Sie fließt durch uns wie ein langsamer Strom, der die Farben der Dinge auswäscht. In ihr liegt kein Wunsch nach Erlösung, sondern nur das Wissen, dass selbst Erlösung eine weitere Form von Fessel wäre. Man kehrt nicht heim, man löst sich auf – langsam, leise, endgültig.
Der Tod ist nicht der Feind des Lebens, sondern seine Form. Leben ist der Prozess des langsamen Verschwindens, und Sterben ist nur die letzte Geste einer Bewegung, die längst begonnen hat. Die Zeit nimmt nicht, sie löscht. Sie lässt zurück, was nicht mehr gefüllt werden kann: ein Umriss, eine Hülle, ein Bild ohne Substanz. Der Mensch verliert sich nicht am Ende, sondern in jedem Moment, den er durchschreitet.
Erinnerung ist kein Besitz, sondern eine Wunde. Was zurückblickt, blickt durch einen zerbrochenen Spiegel – jedes Fragment spiegelt etwas, aber nie das Ganze. Und wer sich darin sucht, findet nicht sich selbst, sondern die Lücken zwischen den Bildern. Vergangenheit ist nicht, was war, sondern das, was nie ganz war – und deshalb nie ganz vergeht.
Fremdheit und Auflösung
Existenz ist ein Exil. Nicht von einem Ort, sondern von sich selbst. Man ist sich nicht nahe, man ist sich fremd – und in dieser Fremdheit liegt keine Tragik, sondern ein nüchterner Frieden. Die Einsamkeit ist kein Zustand, sondern die einzig mögliche Beziehung zur Welt. Alles andere ist Täuschung, ein letzter Versuch, das Unvereinbare zu versöhnen.
Sinn verflüchtigt sich mit jeder Geste, die ihn zu fassen sucht. Je näher man kommt, desto mehr löst er sich auf – wie Nebel vor der Hand. Was bleibt, ist das Bild der Suche selbst, eine Bewegung im Leeren. Man begreift nicht – man kreist. Und in diesem Kreis liegt der Kern der Erfahrung: nicht das Ziel, sondern die Auflösung aller Ziele.
Die einzige Freiheit liegt nicht im Handeln, sondern im Entgleiten. Der Verzicht auf Bedeutung, auf Richtung, auf Rettung – das ist der erste Akt der Selbstermächtigung. Nicht laut, nicht kämpferisch, sondern als stilles Hinwegtreten aus dem Spiel. Dort beginnt das, was nicht mehr genommen werden kann: die Unabhängigkeit vom Verlangen.
Schönheit im Vergehen
Nichts bleibt. Und gerade deshalb geschieht alles. Nicht um zu sein, sondern um zu vergehen. Und vielleicht liegt darin die letzte Schönheit – nicht im Bestehen, sondern im Verlöschen. In der Fähigkeit, in Ketten zu tanzen, wissend, dass jede Kette aus Licht besteht, das schon lange erloschen ist.
-
 @ 12fccfc8:8d67741e
2025-04-27 15:15:03
@ 12fccfc8:8d67741e
2025-04-27 15:15:03- Die Zukunft ist ein Abgrund, der sich öffnet, um uns zu verschlingen – und wir nennen es Fortschritt.
- Ein Augenblick, und schon ist er verloren. Wir wandern, aber wohin? Und ist der Weg nicht auch schon längst verschwunden, bevor wir ihn betreten?
- Was ist die Grenze zwischen dem, was wir nennen, und dem, was wir nie sagen? Ein Riss im Atem, eine Unendlichkeit in jedem Schritt – und dennoch nichts, das je festhält, was wir begreifen wollen.
- Gedanken zerfallen wie Tropfen, die nie den Boden erreichen. Wir sammeln, was nie da war, nur das Echo dessen, was nicht existiert. Vielleicht sind wir das Echo.
- Die Fragen sind die Flügel eines Vogels, der nie den Himmel berührt. Und die Antworten? Nur leere Spiegel, die uns mit einer Intensität anstarren, die uns mehr verstummen lässt, je mehr wir sehen.
- Je lauter die Behauptung, desto größer die Vorsicht.
- Freiheit ist ein Käfig aus offenen Türen – du trittst hinaus, nur um in der Weite deiner eigenen Grenzen zu erstarren.
- Zwischen den Zeilen flackert das Echo der Stille. Wer es hört, vergisst den Klang.
- Im Ekel des Seins liegt die Wahrheit: Leben ist Leiden, Tod ist Frieden. Doch der Mutige tanzt auf dem Abgrund.
- Jeder neue Tag ist ein Versprechen, das nicht gehalten wird, ein Licht, das nur die Tiefe unserer Gräber erhellt.
-
 @ 12fccfc8:8d67741e
2025-04-27 15:10:52
@ 12fccfc8:8d67741e
2025-04-27 15:10:52- Freiheit ist die Fähigkeit, in Ketten zu tanzen.
- Je lauter die Behauptung, desto größer die Vorsicht.
- Zwischen den Zeilen flackert das Echo der Stille. Wer es hört, vergisst den Klang.
- Die Zeit ist ein Dieb, der Schatten stiehlt – sie lässt dich zurück, ein Umriss, den niemand mehr füllt.
- Die Stille singt ein Lied ohne Ton – ein Chor der Leere, der dich umarmt, bis du dich selbst verlierst.
- Erinnerungen sind Splitter eines Spiegels, der zerbrach – sie schneiden dich, während du dein Gesicht in ihnen suchst.
- Sehnsucht ist ein Fluss, der rückwärts fließt – du watest hinein, doch das Ufer zieht sich fort, unerreichbar fern.
- Freiheit ist ein Käfig aus offenen Türen – du trittst hinaus, nur um in der Weite deiner eigenen Grenzen zu erstarren.
- Das Nichts ist der heimliche Gott, der im Zerfall des Seins thront, ein stiller Erlöser, der das Leben in seinen Schoß zurückruft, um es sanft zu ersticken.
- In der Einsamkeit offenbart sich die Qual des Seienden, ein verlassenes Fragment des zersplitterten Willens, das im kalten Licht seiner eigenen Nutzlosigkeit zittert.
-
 @ 12fccfc8:8d67741e
2025-04-27 14:58:35
@ 12fccfc8:8d67741e
2025-04-27 14:58:35„Wahrheit ist kein Besitz, den man verteidigt, sondern ein Prozess, den man gemeinsam gestaltet.“
– frei nach dem Geist freier Netzwerke und resilienter Systeme
Bitcoin ist mehr als nur ein monetäres Protokoll. Es ist ein kulturelles Artefakt, ein philosophisches Statement und ein praktischer Ausdruck radikaler Souveränität, kollektiver Verantwortung und struktureller Ethik. Wer Bitcoin ausschließlich als technologisches Experiment oder ökonomisches Asset betrachtet, verfehlt seine tiefere Bedeutung: Bitcoin ist eine politische Philosophie – nicht in Büchern niedergeschrieben, sondern in Code gegossen. Eine Philosophie, die nicht behauptet, die Wahrheit zu kennen, sondern eine Methode zur gemeinsamen Verifikation anbietet. Eine Philosophie des Konsenses.
Legitimität von unten
Im Zentrum dieser Philosophie steht die Einsicht, dass Legitimität nicht von oben gewährt, sondern von unten erzeugt wird. Keine zentrale Instanz entscheidet, was gilt. Keine Autorität garantiert Vertrauen. Stattdessen entsteht alles aus einem gemeinsamen, freiwilligen Prozess: offen, nachvollziehbar, überprüfbar. Bitcoin ersetzt Vertrauen in Personen durch Vertrauen in Regeln – nicht aus Zynismus, sondern aus epistemischer Bescheidenheit gegenüber menschlicher Fehlbarkeit.
Konsens ist keine Harmonie
Dieser Perspektivwechsel ist radikal. Er stellt nicht nur bestehende Geldsysteme infrage, sondern auch unsere politischen und institutionellen Grundlagen. Während klassische Systeme auf Hierarchien, auf Exklusivität und auf delegierter Macht beruhen, operiert Bitcoin auf Basis offener Teilhabe und individueller Verantwortung. Jeder Knoten ist autonom – aber keiner ist isoliert. Die Wahrheit, die sich im Netzwerk konstituiert, ist nicht das Produkt von Autorität, sondern das Ergebnis reproduzierbarer Verifikation. Nicht Glaube zählt, sondern Prüfung.
Regeln statt Meinungen
Konsens ist dabei kein romantischer Idealzustand, sondern ein dynamischer Balanceakt. Er wird nicht durch Harmonie hergestellt, sondern durch Reibung, durch Konflikt, durch Iteration. Konsens in Bitcoin ist kein Konsens der Meinungen, sondern der Regeln. Und genau darin liegt seine Stabilität. Denn wo Meinungen divergieren, können Regeln konvergieren – vorausgesetzt, sie sind transparent, überprüfbar und konsequent angewandt.
Wahlfreiheit als Systemdesign
Diese Logik verschiebt den Fokus von zentralisierter Macht zu verteilter Verantwortung. Bitcoin kennt keine exekutive Gewalt, keine privilegierten Klassen, keine Instanz, die im Namen aller spricht. Es kennt nur Regeln – und die freie Entscheidung, ihnen zu folgen oder nicht. Wer sich dem Konsens nicht anschließen will, kann abspalten. Forking ist keine Katastrophe, sondern ein systemimmanenter Ausdruck von Wahlfreiheit. In der Möglichkeit der Spaltung liegt die Stärke der Struktur.
Freiheit als Infrastruktur
Diese strukturelle Freiheit unterscheidet sich grundlegend vom klassischen, liberalen Freiheitsverständnis. Es geht nicht um die Willkür des Einzelnen, sondern um die Freiheit von willkürlicher Macht. Es ist kein Plädoyer für Individualismus, sondern für institutionelle Unabhängigkeit. Die Architektur selbst garantiert die Freiheit – nicht eine Instanz, die über sie wacht. In dieser Ethik ist Freiheit kein Ideal, sondern ein Designprinzip. Kein Zustand, sondern eine Infrastruktur.
Gerechtigkeit durch Transparenz
Verantwortung entsteht nicht durch Appelle, sondern durch Transparenz. Jede Entscheidung, jede Transaktion, jeder Regelbruch ist öffentlich nachvollziehbar. Es gibt keine Geheimabsprachen, keine Privilegien, keine Ausnahmen. In dieser radikalen Offenheit liegt eine neue Form von Gerechtigkeit: nicht moralisch verordnet, sondern technisch ermöglicht. Gleichheit ist kein Ziel, sondern eine Eigenschaft des Systems selbst.
Ein Vorschlag für eine neue Ordnung
Bitcoin ist damit nicht nur ein technisches Protokoll, sondern ein Vorschlag für ein neues Modell gesellschaftlicher Ordnung. Eine Ordnung ohne Zentrum, aber nicht ohne Struktur. Eine Praxis der Wahrheit ohne Wahrheitsmonopol. Eine Gemeinschaft, die sich nicht über ideologische Übereinstimmung definiert, sondern über gemeinsame Regeln. Das politische Prinzip, das hier wirkt, ist die Zustimmung – nicht die Kontrolle.
Keine Utopie, sondern ein Anfang
In einer Zeit wachsender institutioneller Erosion, in der Vertrauen in klassische Strukturen schwindet, zeigt Bitcoin einen alternativen Weg: nicht zurück zur Vergangenheit, sondern nach vorn zu neuen Formen des Zusammenlebens. Es ist ein System, das sich nicht auf Versprechen verlässt, sondern auf Rechenbarkeit. Eine Ethik des Handelns, nicht des Glaubens. Eine Ordnung, die nicht durch Macht entsteht, sondern durch das Überflüssigmachen von Macht.
Bitcoin ist nicht perfekt. Aber es ist ehrlich in seiner Imperfektion. Es verspricht keine Utopie, sondern bietet ein robustes Werkzeug. Ein Werkzeug, das uns zwingt, über Macht, Wahrheit und Verantwortung neu nachzudenken. Es ist kein Ende, sondern ein Anfang – eine Einladung, eine neue politische Realität zu gestalten: nicht von oben diktiert, sondern von unten geschaffen.
-
 @ 12fccfc8:8d67741e
2025-04-27 14:57:39
@ 12fccfc8:8d67741e
2025-04-27 14:57:39„Die Zukunft kommt nicht von selbst. Sie wird still gebaut – Zeile für Zeile, Entscheidung für Entscheidung.“
– Ursprung vergessen, Wahrheit geblieben
Was, wenn all das – der Rückzug, das neue Geld, die Verantwortung, das Misstrauen – nicht Flucht ist, sondern Heimkehr? Nicht Ablehnung der Welt, sondern ihre bewusste Rekonstruktion? Was, wenn der wahre Bruch nicht darin liegt, ein anderes System zu benutzen, sondern darin, anders zu sein?
Technologie als Raum, nicht Ziel
Die Technologie war nie das Ziel. Sie ist nur der Raum, in dem sich etwas Menschlicheres entfalten kann: Klarheit. Konsequenz. Verantwortung ohne Zwang. Vertrauen ohne Blindheit. Eigentum ohne Bedingungen. Was mit Code beginnt, endet mit Haltung.
Entscheidung als Ursprung
Manche nennen es Exit. Andere Rebellion. Vielleicht ist es beides. Vielleicht ist es aber auch einfach der leise Moment, in dem jemand erkennt: Ich kann mich entscheiden. Und diese Entscheidung verändert nicht die Welt – aber sie verändert mich in ihr.
Freiheit in neuer Gestalt
Die Freiheit, die hier entsteht, ist nicht laut. Nicht kollektiv. Nicht romantisch. Sie ist nüchtern, präzise, anspruchsvoll. Sie fordert Selbstprüfung statt Meinung, Handlung statt Haltung. Und sie zieht keine Grenzen zwischen Mensch und Werkzeug – sie zeigt nur, was möglich wird, wenn man bereit ist, weniger zu verlangen und mehr zu tragen.
Bauen statt kämpfen
Das neue Geld, das neue Netzwerk, die neue Kultur – sie leben nicht irgendwo da draußen. Sie entstehen dort, wo jemand beschließt, nicht mehr mitzuspielen – und auch nicht mehr zu kämpfen. Sondern einfach zu bauen. Still. Beharrlich. Unaufhaltsam.
-
 @ 12fccfc8:8d67741e
2025-04-27 14:56:53
@ 12fccfc8:8d67741e
2025-04-27 14:56:53„Vertrauen ist gut, Kontrolle ist besser – sagte die Macht.
Misstrauen ist gesund, Selbstverantwortung ist besser – sagte die Freiheit.“
– gehört im Rauschen, zwischen den Blöcken
Vertrauen ist die stille Grundlage jeder Gesellschaft. Doch es ist fragil. Es wird oft dort gefordert, wo es nicht verdient ist – in Systemen, die sich immun gemacht haben gegen Kontrolle, Konsequenz und Kritik. In diesen Strukturen ist Vertrauen keine Tugend mehr, sondern ein Werkzeug der Macht. Es wird benutzt, um Verantwortung abzugeben, um sich fügen zu müssen, um Teil eines Spiels zu sein, dessen Regeln man nicht mitbestimmen kann.
Misstrauen als Zeichen von Reife
Misstrauen gilt oft als Schwäche. Doch es kann auch ein Zeichen von Reife sein. Es ist nicht Ablehnung, sondern Prüfung. Nicht Paranoia, sondern Wachsamkeit. Wer misstraut, schützt sich nicht nur vor Täuschung, sondern verteidigt das eigene Urteilsvermögen.
Echtes Vertrauen braucht Kontrolle
Ein System, das auf echtem Vertrauen beruhen will, muss bereit sein, Misstrauen auszuhalten. Es muss transparent, überprüfbar, ersetzbar sein. Es darf Vertrauen nicht einfordern, sondern muss es verdienen. Vertrauen, das auf Kontrolle verzichtet, ist Glaube. Vertrauen, das auf überprüfbaren Regeln beruht, ist Klarheit.
Bitcoin: Vertrauen durch Verifikation
In diesem Spannungsfeld steht das neue Geld. Es sagt: Vertraue nicht mir. Vertraue dem, was du selbst verifizieren kannst. Es ersetzt nicht Vertrauen durch Misstrauen, sondern durch Offenheit. Es fordert nichts – es bietet nur das, was es ist: ein System ohne Hintertüren, ohne Verwalter, ohne Privilegien.
Darin liegt seine Stärke. Es ist nicht darauf angewiesen, dass jemand daran glaubt. Es funktioniert, weil niemand es verändern kann. Es belohnt diejenigen, die prüfen. Und es enttäuscht jene, die hoffen, dass andere für sie denken.
Jenseits von Vertrauen
Vertrauen ist eine Entscheidung. Misstrauen auch. Zwischen beiden steht Verantwortung – und wer bereit ist, sie zu tragen, wird beides nicht mehr brauchen.
-
 @ 12fccfc8:8d67741e
2025-04-27 14:55:55
@ 12fccfc8:8d67741e
2025-04-27 14:55:55„Sag mir, welches Geld du benutzt – und ich sage dir, an welche Welt du glaubst.“
– anonym, zirkulierend im digitalen Untergrund
Geld ist nie neutral. Es trägt in sich eine Vorstellung davon, was in einer Gesellschaft wertvoll ist – und wer entscheidet, was dieser Wert bedeutet. In den Währungen unserer Zeit steckt nicht nur Kaufkraft, sondern auch Gewalt. Unsichtbar, aber wirksam. Jede Inflation ist eine Umverteilung ohne Abstimmung. Jede Rettung durch Gelddrucken ein Eingriff in das Eigentum derer, die sparen. Jede staatliche Kontrolle von Geldfluss ist auch Kontrolle über Leben.
Es ist leicht, Geld als bloßes Werkzeug zu sehen. Aber jedes Werkzeug formt auch seinen Nutzer. Wer Geld benutzt, das auf Schulden basiert, übernimmt unbewusst die Logik dieses Systems: Wachstum um jeden Preis, Gegenwart vor Zukunft, Kontrolle statt Vertrauen. Es ist kein Zufall, dass moralische Belohnung in dieser Welt selten mit finanzieller vergütet wird – weil das Geld selbst die Moral nicht kennt.
Die Moral der Währung
Die Frage ist nicht, ob Geld gut oder böse ist. Die Frage ist, ob es Verantwortung kennt. Ob es dem dient, der es hält, oder dem, der es kontrolliert. Ob es verlässlich ist – nicht nur in seiner Funktion, sondern auch in seiner Wirkung. Ein Geld, das jederzeit vermehrt werden kann, erlaubt jederzeit die Verschiebung von Lasten. Weg von den Verantwortlichen, hin zu den Stillen. Es belohnt Nähe zur Quelle, nicht Leistung. Es nährt den Zynismus.
Ein Geld, das Wahrheit erzwingt
Ein anderes Geld beginnt nicht bei der Technik, sondern bei der Ethik. Es fragt nicht: Was ist möglich? Sondern: Was ist richtig? Es basiert auf Knappheit – nicht um zu begrenzen, sondern um Ehrlichkeit zu erzwingen. Es kennt kein „Too Big to Fail“, kein Vertrauen auf Dekret, keine moralische Grauzone. Wer es nutzt, steht in direkter Beziehung zu seinem Handeln. Und kann sich nicht herausreden.
Verantwortung ohne Zwang
Vielleicht ist die wichtigste Wirkung dieses Geldes nicht wirtschaftlich, sondern moralisch: Es gibt dem Einzelnen die Möglichkeit, sauber zu wirtschaften, ohne Teil eines schmutzigen Spiels zu sein. Es ist kein Geld für jeden – sondern für jene, die bereit sind, wieder Verantwortung zu tragen. Nicht, weil sie müssen. Sondern weil sie wollen.
-
 @ 3bf0c63f:aefa459d
2025-04-25 18:55:52
@ 3bf0c63f:aefa459d
2025-04-25 18:55:52Report of how the money Jack donated to the cause in December 2022 has been misused so far.
Bounties given
March 2025
- Dhalsim: 1,110,540 - Work on Nostr wiki data processing
February 2025
- BOUNTY* NullKotlinDev: 950,480 - Twine RSS reader Nostr integration
- Dhalsim: 2,094,584 - Work on Hypothes.is Nostr fork
- Constant, Biz and J: 11,700,588 - Nostr Special Forces
January 2025
- Constant, Biz and J: 11,610,987 - Nostr Special Forces
- BOUNTY* NullKotlinDev: 843,840 - Feeder RSS reader Nostr integration
- BOUNTY* NullKotlinDev: 797,500 - ReadYou RSS reader Nostr integration
December 2024
- BOUNTY* tijl: 1,679,500 - Nostr integration into RSS readers yarr and miniflux
- Constant, Biz and J: 10,736,166 - Nostr Special Forces
- Thereza: 1,020,000 - Podcast outreach initiative
November 2024
- Constant, Biz and J: 5,422,464 - Nostr Special Forces
October 2024
- Nostrdam: 300,000 - hackathon prize
- Svetski: 5,000,000 - Latin America Nostr events contribution
- Quentin: 5,000,000 - nostrcheck.me
June 2024
- Darashi: 5,000,000 - maintaining nos.today, searchnos, search.nos.today and other experiments
- Toshiya: 5,000,000 - keeping the NIPs repo clean and other stuff
May 2024
- James: 3,500,000 - https://github.com/jamesmagoo/nostr-writer
- Yakihonne: 5,000,000 - spreading the word in Asia
- Dashu: 9,000,000 - https://github.com/haorendashu/nostrmo
February 2024
- Viktor: 5,000,000 - https://github.com/viktorvsk/saltivka and https://github.com/viktorvsk/knowstr
- Eric T: 5,000,000 - https://github.com/tcheeric/nostr-java
- Semisol: 5,000,000 - https://relay.noswhere.com/ and https://hist.nostr.land relays
- Sebastian: 5,000,000 - Drupal stuff and nostr-php work
- tijl: 5,000,000 - Cloudron, Yunohost and Fraidycat attempts
- Null Kotlin Dev: 5,000,000 - AntennaPod attempt
December 2023
- hzrd: 5,000,000 - Nostrudel
- awayuki: 5,000,000 - NOSTOPUS illustrations
- bera: 5,000,000 - getwired.app
- Chris: 5,000,000 - resolvr.io
- NoGood: 10,000,000 - nostrexplained.com stories
October 2023
- SnowCait: 5,000,000 - https://nostter.vercel.app/ and other tools
- Shaun: 10,000,000 - https://yakihonne.com/, events and work on Nostr awareness
- Derek Ross: 10,000,000 - spreading the word around the world
- fmar: 5,000,000 - https://github.com/frnandu/yana
- The Nostr Report: 2,500,000 - curating stuff
- james magoo: 2,500,000 - the Obsidian plugin: https://github.com/jamesmagoo/nostr-writer
August 2023
- Paul Miller: 5,000,000 - JS libraries and cryptography-related work
- BOUNTY tijl: 5,000,000 - https://github.com/github-tijlxyz/wikinostr
- gzuus: 5,000,000 - https://nostree.me/
July 2023
- syusui-s: 5,000,000 - rabbit, a tweetdeck-like Nostr client: https://syusui-s.github.io/rabbit/
- kojira: 5,000,000 - Nostr fanzine, Nostr discussion groups in Japan, hardware experiments
- darashi: 5,000,000 - https://github.com/darashi/nos.today, https://github.com/darashi/searchnos, https://github.com/darashi/murasaki
- jeff g: 5,000,000 - https://nostr.how and https://listr.lol, plus other contributions
- cloud fodder: 5,000,000 - https://nostr1.com (open-source)
- utxo.one: 5,000,000 - https://relaying.io (open-source)
- Max DeMarco: 10,269,507 - https://www.youtube.com/watch?v=aA-jiiepOrE
- BOUNTY optout21: 1,000,000 - https://github.com/optout21/nip41-proto0 (proposed nip41 CLI)
- BOUNTY Leo: 1,000,000 - https://github.com/leo-lox/camelus (an old relay thing I forgot exactly)
June 2023
- BOUNTY: Sepher: 2,000,000 - a webapp for making lists of anything: https://pinstr.app/
- BOUNTY: Kieran: 10,000,000 - implement gossip algorithm on Snort, implement all the other nice things: manual relay selection, following hints etc.
- Mattn: 5,000,000 - a myriad of projects and contributions to Nostr projects: https://github.com/search?q=owner%3Amattn+nostr&type=code
- BOUNTY: lynn: 2,000,000 - a simple and clean git nostr CLI written in Go, compatible with William's original git-nostr-tools; and implement threaded comments on https://github.com/fiatjaf/nocomment.
- Jack Chakany: 5,000,000 - https://github.com/jacany/nblog
- BOUNTY: Dan: 2,000,000 - https://metadata.nostr.com/
April 2023
- BOUNTY: Blake Jakopovic: 590,000 - event deleter tool, NIP dependency organization
- BOUNTY: koalasat: 1,000,000 - display relays
- BOUNTY: Mike Dilger: 4,000,000 - display relays, follow event hints (Gossip)
- BOUNTY: kaiwolfram: 5,000,000 - display relays, follow event hints, choose relays to publish (Nozzle)
- Daniele Tonon: 3,000,000 - Gossip
- bu5hm4nn: 3,000,000 - Gossip
- BOUNTY: hodlbod: 4,000,000 - display relays, follow event hints
March 2023
- Doug Hoyte: 5,000,000 sats - https://github.com/hoytech/strfry
- Alex Gleason: 5,000,000 sats - https://gitlab.com/soapbox-pub/mostr
- verbiricha: 5,000,000 sats - https://badges.page/, https://habla.news/
- talvasconcelos: 5,000,000 sats - https://migrate.nostr.com, https://read.nostr.com, https://write.nostr.com/
- BOUNTY: Gossip model: 5,000,000 - https://camelus.app/
- BOUNTY: Gossip model: 5,000,000 - https://github.com/kaiwolfram/Nozzle
- BOUNTY: Bounty Manager: 5,000,000 - https://nostrbounties.com/
February 2023
- styppo: 5,000,000 sats - https://hamstr.to/
- sandwich: 5,000,000 sats - https://nostr.watch/
- BOUNTY: Relay-centric client designs: 5,000,000 sats https://bountsr.org/design/2023/01/26/relay-based-design.html
- BOUNTY: Gossip model on https://coracle.social/: 5,000,000 sats
- Nostrovia Podcast: 3,000,000 sats - https://nostrovia.org/
- BOUNTY: Nostr-Desk / Monstr: 5,000,000 sats - https://github.com/alemmens/monstr
- Mike Dilger: 5,000,000 sats - https://github.com/mikedilger/gossip
January 2023
- ismyhc: 5,000,000 sats - https://github.com/Galaxoid-Labs/Seer
- Martti Malmi: 5,000,000 sats - https://iris.to/
- Carlos Autonomous: 5,000,000 sats - https://github.com/BrightonBTC/bija
- Koala Sat: 5,000,000 - https://github.com/KoalaSat/nostros
- Vitor Pamplona: 5,000,000 - https://github.com/vitorpamplona/amethyst
- Cameri: 5,000,000 - https://github.com/Cameri/nostream
December 2022
- William Casarin: 7 BTC - splitting the fund
- pseudozach: 5,000,000 sats - https://nostr.directory/
- Sondre Bjellas: 5,000,000 sats - https://notes.blockcore.net/
- Null Dev: 5,000,000 sats - https://github.com/KotlinGeekDev/Nosky
- Blake Jakopovic: 5,000,000 sats - https://github.com/blakejakopovic/nostcat, https://github.com/blakejakopovic/nostreq and https://github.com/blakejakopovic/NostrEventPlayground
-
 @ 12fccfc8:8d67741e
2025-04-27 14:53:55
@ 12fccfc8:8d67741e
2025-04-27 14:53:55„Der Mensch ist frei geboren, und überall liegt er in Ketten.“
– Jean-Jacques Rousseau
In einer Welt, die sich zunehmend durch technologische Umbrüche definiert, zeigt sich eine bemerkenswerte kognitive Dissonanz im Umgang mit neuen Paradigmen: Die Abwehr gegenüber Bitcoin ist selten eine Frage der Rationalität, sondern oft eine Reaktion auf die Überforderung durch das Ungewohnte. Der Mensch scheut die Auseinandersetzung mit dem, was ihm fremd erscheint – nicht, weil es notwendigerweise komplex ist, sondern weil es nicht in das gewohnte Raster institutionalisierter Erklärung passt.
So wirkt Bitcoin auf viele wie ein hermetisches System, dessen Mechanismen sich dem Alltagsverständnis entziehen. Dabei ist es, philosophisch betrachtet, der Fiat-Welt unter einem entscheidenden Aspekt überlegen: ihrer radikalen Transparenz.
Die Unsichtbarkeit des Gewohnten
Die Strukturen, welche das fiatbasierte Geldsystem tragen, sind in ihrer institutionellen Dichte kaum zu durchdringen. Zentralbanken, Aufsichtsbehörden, gesetzgeberische Rahmenwerke, geldpolitische Instrumente, Interbankenmärkte, internationale Regulierungsorgane – sie bilden einen verwaltungstechnischen Überbau, der in seiner Vielschichtigkeit eher einer mittelalterlichen Theologie als einem frei zugänglichen, rationalen System gleicht.
Das Vertrauen in diese Ordnung ist kein Produkt verstandesmäßiger Durchdringung, sondern das Ergebnis jahrzehntelanger Gewöhnung und autoritärer Setzung. Man glaubt an das Fiat-Geld, weil es da ist – nicht, weil man es versteht.
Bitcoin verlangt Verantwortung
Bitcoin hingegen konfrontiert den Einzelnen mit der Notwendigkeit der Selbstverantwortung und fordert eine direkte Auseinandersetzung mit seiner Funktionsweise: kryptografische Prinzipien, Dezentralität, Konsensmechanismen, digitale Knappheit. Dies wirkt zunächst sperrig, ja fast elitär. Doch diese Komplexität ist nicht strukturell intransparent, sondern technisch erklärbar, überprüfbar und – für jeden offen.
Während das Fiat-System in verschlossenen Räumen entscheidet, operiert Bitcoin auf einem offenen Protokoll. Die Ablehnung des Neuen beruht daher weniger auf seiner inhärenten Schwierigkeit, als vielmehr auf einer anthropologischen Trägheit: Die Bequemlichkeit, sich von äußeren Instanzen verwalten zu lassen, wiegt schwerer als der Wunsch nach Souveränität.
Was ist wahre Komplexität?
Doch was ist wahrhaft komplex? Ist es nicht die blinde Akzeptanz eines Systems, dessen Grundlagen man nie selbst prüfen kann? Ist es nicht der Glaube an eine Geldordnung, deren Stabilität von politischen Machtzentren abhängt?
Der Bitcoin hingegen stellt die radikale Frage: Was, wenn Vertrauen nicht mehr delegiert, sondern durch Code ersetzt werden kann? Was, wenn Verständlichkeit nicht aus Tradition, sondern aus Prinzipien entsteht?
Ein philosophisches Statement
In dieser Perspektive ist Bitcoin keine bloße technische Innovation, sondern ein philosophisches Statement: ein Plädoyer für epistemische Mündigkeit. Die vermeintliche Einfachheit des Alten ist in Wahrheit nur ein Schleier – und die gefühlte Schwierigkeit des Neuen der erste Schritt in die Freiheit.
-
 @ fd06f542:8d6d54cd
2025-04-27 10:11:09
@ fd06f542:8d6d54cd
2025-04-27 10:11:09更新前有问题问题?
本站采用 docsify渲染,他对图片的处理 是没有任何类原始的 img标签。 缺点如下: * 图片太大,很多图片出现了锯齿; * 图片和周边的文字没有边界,非常突兀;
第一次修改
全加了统一风格,用圆角修饰了;
结果出现了新问题,有些小图片是一个图标,例如:github 的star变得异常难看。
怎么办?
第二次修改
查找 文档说 markdown文档有支持{.classname}的做法,有人用这个方法;
那么 docsify如何做的呢?
js window.$docsify = { name: title, loadSidebar: true, homepage: "readme.md", subMaxLevel:2, plugins: [imgClassPlugin], alias: { '/_sidebar.md': './_sidebar.md', } };用plugins 就可以,
imgClassPlugin 是找的正则替换
`` js export function processMarkdownImages(content) { const regex = /!\[(.*?)\]\((.*?)\)(\{.*?\})?/g; return content.replace(regex, (match, alt, src, classInfo) => { if (classInfo) { const classNames = classInfo.match(/\.([a-zA-Z0-9_-]+)/); if (classNames) { const className = classNames[1]; return`; } } return match; }); }
// 定义 Docsify 插件 export const imgClassPlugin = function (hook, vm) { hook.mounted(function () { // 在文档挂载后,在每次渲染前执行处理逻辑 hook.beforeEach(function (content) { return processMarkdownImages(content); }); }); };
``` 这样就可以了。大家看看我这张图片:
 {.user-img}
{.user-img}具体用法,大家参考 https://www.nostrbook.com/books/c3834c0604b4e5ad66ececd756791a539c585d880864d62b0ef51e3602c482b7?title=NostrBook%E7%AB%99%E7%82%B9%E6%97%A5%E8%AE%B0#/02
-
 @ 12fccfc8:8d67741e
2025-04-27 14:51:49
@ 12fccfc8:8d67741e
2025-04-27 14:51:49„In Zeiten universeller Täuschung ist das Aussprechen der Wahrheit ein revolutionärer Akt.“
– George Orwell
Bitcoin ist nicht nur ein Werkzeug der ökonomischen Selbstermächtigung – er ist auch ein kulturelles Störsignal. Sein bloßes Funktionieren stellt die Legitimität des Bestehenden infrage. Eine Währung, die niemand ausgibt, niemand kontrolliert, niemand genehmigen muss, ist in ihrer bloßen Existenz eine stille Anklage gegen das, was als alternativlos gilt.
Mehr als Technologie – eine Haltung
Es geht nicht nur um Technologie. Es geht um Haltung. Um das leise Beharren auf einem anderen Takt. In einer Welt, in der der Wert von oben definiert wird – durch Zentralbanken, Ratings, Verordnungen – bietet Bitcoin eine völlig andere Grundlage: Konsens, Knappheit, Mathematik. Kein politischer Willensakt, sondern ein physikalisches Versprechen.
Die stille Entscheidung
Wer Bitcoin nutzt, trifft eine Entscheidung, die weit über Geld hinausgeht. Es ist die bewusste Verweigerung, Teil eines Systems zu sein, das auf Schulden basiert, auf Kontrolle, auf ständigem Zugriff. Es ist die Entscheidung, eine andere Art von Zukunft möglich zu machen – nicht durch Protest, sondern durch Praxis.
Disidenz ohne Banner
Diese Form der Disidenz ist schwer zu greifen, weil sie sich nicht laut artikuliert. Sie baut keine Barrikaden, schreibt keine Manifeste, ruft nicht nach Aufmerksamkeit. Sie wählt den Rückzug als Methode. Die Abkopplung. Die schrittweise Reduktion von Abhängigkeiten.
Kein Widerstand – Konsequenz
Vielleicht ist das Revolutionäre an Bitcoin nicht der Konflikt, sondern die Abwesenheit davon. Kein Widerstand im klassischen Sinn, sondern eine Umleitung. Keine Konfrontation, sondern Konsequenz. Die leise Entscheidung, nicht mehr mitzumachen – aber etwas Besseres zu bauen.
Ohne Erlaubnis
Wer Bitcoin lebt, braucht keine Genehmigung. Keine Erklärung. Kein Spektakel. Nur ein Node. Eine Wallet. Ein wenig Disziplin. Und die Bereitschaft, Verantwortung zu tragen, wo andere noch Ansprüche stellen.
Es ist kein einfacher Weg. Aber es ist einer, den man gehen kann, ohne um Erlaubnis zu fragen.
-
 @ fd06f542:8d6d54cd
2025-04-27 10:02:24
@ fd06f542:8d6d54cd
2025-04-27 10:02:24使用nostrbook.com网站
登录和创建用户:
 {.user-img}
登录按钮 ,可以粘贴 已有的 nsec....账号,完成登录。
{.user-img}
登录按钮 ,可以粘贴 已有的 nsec....账号,完成登录。注册:
 {.user-img}
可以点击红标位置 生成你的账户。 “确定” 完成注册。
{.user-img}
可以点击红标位置 生成你的账户。 “确定” 完成注册。创建书籍
封面的上传
 {.user-img}
创建书籍,可以用 微信截图 后直接 ctrl+v. 粘贴即可。
{.user-img}
创建书籍,可以用 微信截图 后直接 ctrl+v. 粘贴即可。或者点击浏览 本地图片文件。
标题和作者
正常填写就可以。 书的作者和上传文件人没有一一绑定。
写书
 {.user-img}
创建完成后就可以写书了,写书入口在 登录处 “我的书籍” 。点进去会出现你创建的书籍。选择一本就可以写书了。
{.user-img}
创建完成后就可以写书了,写书入口在 登录处 “我的书籍” 。点进去会出现你创建的书籍。选择一本就可以写书了。列出你创建的所有的书籍
 {.user-img}
{.user-img}点击图标,就可以进入开始写作了。例如《nostrbook站点日记》
 {.user-img}
{.user-img}如图所示有4个部分
- (1)关闭按钮,点击就退出编辑,这时候他会提示你保存,如果不需要保存退出,点击 “不保存退出”
- (2)
大纲是编写 你书籍的大纲,这个参考 docsify文档 下面会有例子。时间排列是 你所有为本书写的章节。但是有些章节你可能废弃了,或者暂时不想展示,都会存在 时间排列里面,就是按照你编写的时间倒序排列的。草稿是你暂时存储的内容,没有上传到网络,存在你本地浏览器的缓存里面。 - (3)这个部分看到的就是你的章节列表,当让你第一次来的这个地方是空的。
新增章节下一次就会有内容了。 - (4)文件名,是我们存储章节的唯一标识。
readme.md和_sidebar.md是系统默认必须有的。因为docsify技术默认需要这2个。
如何编写大纲
如果你是第一次开始,大纲的界面是这样的。
 {.user-img}
{.user-img}- 点击
增加大纲 - 点击
查看样例 - 修改系统生成的例子,此时 readme.md是必须的readme 对应的名字你可以自己修改
- 点击提交 就可以完成大纲了。
第二次、点击
更新大纲按钮- [首页](/readme.md) - [国人开发者](/01.md) - [中文用户列表](/02.md)大纲例子,“[]” 内是标题,“()”内是 文件名; 标题是是显示在文章的右侧; 文件名的作用是匹配 ‘新增章节’ 里面的markdown的相匹配关联的。
如何定制化图片的风格
上传图片后,添加 {.user-img} 类,目前这个类是固定的,后面考虑增加类 见图:
 {.user-img}
{.user-img}渲染后 增加了一个classname
{.user-img} -
 @ 12fccfc8:8d67741e
2025-04-27 14:50:48
@ 12fccfc8:8d67741e
2025-04-27 14:50:48„Was du besitzt, besitzt auch dich.“
– Henry David Thoreau
Bitcoin verändert nicht nur, wie wir Geld sehen, sondern auch, wie wir uns selbst sehen. Es stellt eine einfache Frage, die schwer wiegt: Wem traust du? Und tiefer noch: Bist du bereit, dir selbst zu trauen?
Selbstverwahrung ist kein technischer Akt – es ist eine innere Haltung. Wer seinen eigenen Schlüssel hält, muss sich nicht nur mit Tools, sondern mit sich selbst auseinandersetzen. Mit Angst. Verantwortung. Und Freiheit. Die Gewissheit, dass niemand Zugriff hat, ist auch die Last, dass niemand rettet. Diese Form der Verantwortung ist für viele ungewohnt, fast schon beängstigend – in einer Welt, die absichert, verwaltet, entmündigt.
Die psychologische Schwelle der Verantwortung
Bitcoin ist radikale Eigenverantwortung. Und genau das macht es zu einer psychologischen Schwelle. Es zwingt zur Selbsterkenntnis: Bin ich bereit, die Kontrolle wirklich zu übernehmen? Oder suche ich weiterhin nach Institutionen, nach Autoritäten, nach jemandem, der mir die Entscheidung abnimmt?
Ein ehrlicher Spiegel
Spirituell betrachtet ist Bitcoin ein Spiegel. Es zeigt, woran wir glauben, was wir fürchten, worauf wir hoffen. In einer Welt voller Illusionen – über Wert, über Sicherheit, über Freiheit – ist Bitcoin brutal ehrlich. Es gibt nichts vor. Es bewertet nicht. Es funktioniert oder es funktioniert nicht. Und der Umgang damit offenbart viel über uns selbst.
Der Prozess, Bitcoin wirklich zu verstehen – nicht technisch, sondern existenziell – ist transformativ. Er entkoppelt unser Selbstwertgefühl von Zahlen auf Bankkonten. Er konfrontiert uns mit unserer Abhängigkeit von Bequemlichkeit. Er eröffnet die Möglichkeit, dass Freiheit nicht in äußeren Umständen liegt, sondern in innerer Haltung.
Eine spirituelle Praxis
Für manche ist Bitcoin eine spirituelle Praxis – eine tägliche Übung in Geduld, Disziplin, Vertrauen. Nicht Vertrauen in andere, sondern in Prinzipien. In Mathematik. In Ursache und Wirkung. Bitcoin verzeiht keine Illusion. Es bestraft Selbsttäuschung. Und gerade deshalb kann es ein Werkzeug sein – nicht nur der wirtschaftlichen, sondern der inneren Befreiung.
Wer sich darauf einlässt, begibt sich nicht nur auf einen neuen finanziellen Weg. Sondern auf eine Reise zu sich selbst. Eine Reise, die nicht laut ist, nicht bequem, nicht sofort belohnend. Aber ehrlich. Und vielleicht – heilsam.
-
 @ a296b972:e5a7a2e8
2025-04-27 12:27:37
@ a296b972:e5a7a2e8
2025-04-27 12:27:37Ach Gottchen, man ist mal wieder empört! Quel fauxpas! Ist es nicht auffällig, dass man von anderen Nationen solche Bilder nicht sieht? Zwei Politiker im Flieger unterwegs zu einer Vergnügens-Beerdigung eines Mannes, der für eine nicht geringe Anzahl von Menschen auf der Erde eine sehr große Bedeutung hat. (Impfen ist Nächstenliebe und die Kündigung derjenigen, die sich der Gen-Behandlung nicht unterziehen wollten, hier einmal außen vor gelassen). Warum ausgerechnet immer die Deutschen? Tja, anscheinend hat Deutschland den Joker im ins-Fettnäpfchen-treten gepachtet und gibt ihn nicht mehr aus der Hand. Meister aller Klassen bleibt bisher noch die feministische Außen-Dings, aber was nicht ist, kann ja noch werden. Und ausgerechnet ein Herr Laschet muss auch seinen Senf dazu geben, obwohl man doch eigentlich nicht mit Steinen wirft, wenn man im Glashaus sitzt. Unvergessen seine heitere Stimmung bei einem Besuch im verwüsteten Ahrtal, das bis heute noch teilweise nicht wiederhergestellt ist.
Herrn Steinmeier ist kein Vorwurf zu machen. Schließlich repräsentiert er mit einer florierenden Wirtschaft, einem vom Stier getriebenen Vielleicht-Bundeskanzler, einem Noch-Gesundheitsminister mit Traumjob, der gerne weiter gemacht hätte (auch die guten Kräfte haben ihre Grenzen des Ertragbaren), das Land des Lächelns.
Bei der Gelegenheit: Herr Lauterbach erinnert doch sehr an die Gräfin Eleonora Moran aus „Die Seltsame Gräfin“ von Edgar Wallace. In dem Film gibt es eine Szene, in der sie sagt: „Ich bin eine Wohltäterin der Menschheit, ich habe immer nur Gutes getan, niemals etwas Böses! Fassen Sie mich nicht an! Ich bin die Gräfin Eleonora Moran!“
Und Herr Söder, was soll man dazu sagen. Der bayerische Möchtegern-König, der sein Fähnchen schneller nach dem Wind dreht, als der Wind selbst es kann.
Und Herr Merz war wohl leider verhindert. Der belegte über Ostern einen Kurs bei der Volkshochschule: Torero werden in drei Wochen! Nach diesem Kurs werden Sie mit jedem Stier spielend fertig!
Fair bleiben: Gespielte Betroffenheit wäre geheuchelt gewesen. Schließlich besteht keine nahe Verwandtschaft zwischen Steinmeier und Söder zu dem Petrus-Nachfolger.
Am Ende ist es eine Pflichtveranstaltung, wie der Besuch bei der unangenehmen Erbtante, zu dem man eigentlich gar keine Lust hat, aber man muss halt, weil die Taler locken.
Schade, dass Herr Pistorius nicht auch mit im Malle-Flieger dabei war und auf dem Selfie. Dann hätte man einen schönen Untertitel gehabt: Na, ihr da unten auf dem Boden. Seid ihr auch alle schön kriegstüchtig?
Und dann gibt es da noch das Bild von Trump und Selensky in einer großen Halle im Vatikan, zwei Stühle, reduziert auf das Wesentliche: Keine Gelegenheit auslassen miteinander zu reden, den Frieden in der Ukraine besser gestern als heute herbeizuholen. Das macht den Ernst der Lage sehr deutlich. Für Macron war wohl im ganzen Vatikan kein weiterer Stuhl aufzutreiben. Deutsche Politiker glänzten durch Abwesenheit. War vielleicht auch gut so. Da stand vermutlich auch zerbrechliches Porzellan im Raum.
Im Gegensatz dazu das Bild der beiden Grinsekater, das wohl um die halbe Welt gehen wird. Was für eine Blamage. Man könnte fast meinen, da steckt Absicht dahinter. Die Absicht, Deutschland unter allen Umständen in die vollkommene Lächerlichkeit überführen zu wollen. Über Rom lacht die Sonne, über Deutschland die ganze Welt. Kann nicht Herr Brabeck-Letmathe vom WEF mal was Erhellendes dem deutschen Trinkwasser beimischen, damit die Politiker wieder zur Vernunft kommen?
Was würde Äarwin Krawuttke aus Wanne-Eickel wohl dazu sagen: Ey, voll der Schuss in den Ofen! Datt wollen Pollitiker sein? Ich lach mich kaputt!
Dieser Beitrag wurde mit dem Pareto-Client geschrieben.
(Bild von pixabay)
-
 @ 4fe14ef2:f51992ec
2025-04-27 10:01:40
@ 4fe14ef2:f51992ec
2025-04-27 10:01:40Let's support Bitcoin merchants! I'd love to hear some of your latest Lightning purchases and interesting products you bought. Feel free to include links to the shops or businesses you bought from.
Who else has a recent purchase they’re excited about? Bonus sats if you found a killer deal! ⚡
If you missed our last thread, here are some of the items stackers recently spent and zap on.
Like and repost: N: https://nostrudel.ninja/#/n/nevent1qvzqqqqqqypzqnlpfmegjd... X: https://x.com/AGORA_SN/status/1916432206861684741
originally posted at https://stacker.news/items/963317
-
 @ fd06f542:8d6d54cd
2025-04-27 09:57:21
@ fd06f542:8d6d54cd
2025-04-27 09:57:21直车对横车 的概念
顺炮直车对横车:红方出直车(车一平二),黑方出横车(车 9 进 1),这是顺炮布局中常见的一种变化。红方直车可以快速出动,威胁黑方右翼,黑方横车则可以灵活调动,根据局势选择进攻或防守的方向。后续可能会出现红方进车过河压马,黑方出炮封车等变化,双方展开激烈的争夺。
顺炮直车对横车布局体系主要有以下分类:
- 古典攻法
- 顺炮过河车对横车:红车一平二后车二进六过河,以强硬攻势迅速压制黑方阵营。
- 顺炮缓补士对横车:红出直车后不急于补士(士四进五缓出) ,依黑方行棋灵活选择攻防策略。
- 顺炮跳边马对横车:红马八进九上边马,平炮通车平衡两翼子力,防止黑卒3进1争先,着法稳健。
- “胡氏双正马”攻法
- 顺炮直车进三兵对横车挺3卒:红进三兵、黑挺3卒形成牵制,红可借马三进四等手段跃马进攻。
- 顺炮直车进三兵对横车跳边马:红进三兵后,针对黑边马位置,以炮八平七等手段威胁黑方马获取局面优势。
- 顺炮直车进七兵对横车:红进七兵,黑车9平4后,红可选择车二进四巡河或车二进六过河等不同进攻战术。
- 顺炮直车“两头蛇”对双横车:红兵三进一、兵七进一构成“两头蛇”阵,与黑方双横车激烈争夺,红借双兵推进掌控空间,黑寻机反击。
- 其他常见变化
- 正马三兵与黑右肋车的攻防对抗;正马应对黑挺3卒的局面变化。
- 正马三兵对阵黑肋车边马;“两头蛇”阵势迎战黑双横车的局势博弈。
- 正马三兵对黑方马后藏车;“两头蛇”对黑正马边炮的局势发展。
- 红方正马左士应对黑右肋车;红方采用巡河车、五六炮的布局变化,以及双正马进七兵分别对黑正马、右肋车的局面策略 。
以下按照天天象棋棋谱整理的8种变化,这些变化有些大同小异。 最后都类似。
车二进六的变化(82)
顺炮横车破直车弃马001
====棋局开始* 1.炮二平五 炮8平5
2.马二进三
马8进7
3.车一进一
车9平8
4.车一平六
车8进65.车六进七
马2进1
6.车九进一 炮2进77.炮八进五 马7退8

8.炮五进四 士6进5
9.车九平六
将5平6
10.前车进一 士5退411.车六平四
炮5平6
12.车四进六 将6平5
13.炮八平五
 {.user-img}
{.user-img}双正马三兵 变化(2202)
兵三进一 (473)
马八进九 (179)
红正马五六炮式(171)
兵七进一 (74)
红正马巡河车式(73)
士四进五(55)
- 古典攻法
-
 @ da0b9bc3:4e30a4a9
2025-04-27 07:10:07
@ da0b9bc3:4e30a4a9
2025-04-27 07:10:07Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/962600
-
 @ 502ab02a:a2860397
2025-04-27 05:37:41
@ 502ab02a:a2860397
2025-04-27 05:37:41"นมดีจริง หรือแค่เรากลัว?" นม = อาหารของสัตว์ในวัยทารก จริงๆประโยคเดียว ก็น่าจะเข้าใจนะครับว่าทำไม ผมไม่ตอบเม้นท์เลย ว่าถ้างั้นเราดื่มนมอะไรดี
ในวันที่นมยึดครองชั้นวางห้าง นมวัว นมแพะ นมอัลมอนด์ นมโอ๊ต นมข้าว นมพิสตาชิโอ วางตัวสวยๆ พร้อมข้อความชวนฝันว่า "ดีต่อใจ" "เพื่อสุขภาพ" คนก็แห่กันถามว่า นมอะไรดีที่สุด ดื่มนมอันไหนแล้วสุขภาพดี กินนมแล้วจะได้ไม่ขาดสารอาหาร
แต่...ลองหยุดถาม แล้วตั้งใจฟังตัวเองสักนิดว่า จริงๆ แล้ว นมดีกว่า real food อย่างไข่ หรือเนื้อสัตว์ ตรงไหน?
ตอนเด็ก เราถูกสอนว่า ดื่มนม = แข็งแรง ตอนโต เราถูกล่อด้วยโฆษณาว่า นมพืช = สุขภาพดี ยั่งยืน รักษ์โลก เราถูกปลูกฝังจนแทบไม่เคยสงสัยเลยว่า นม มันดียังไงกันแน่?
เราลองมาเปิดหน้ากาก "นม" ทีละชั้นกันครับ นมวัว : มีโปรตีนกับไขมันอยู่บ้าง แต่ก็มีน้ำตาลแลคโตสที่คนส่วนใหญ่ย่อยไม่ดี นมพืช : โปรตีนต่ำจนน่าใจหาย วิตามินแร่ธาตุก็ใส่สังเคราะห์เอาทีหลังทั้งนั้น
"นม" ไม่ว่าจะวัว แพะ หรือพืช ความจริงที่เราไม่ค่อยอยากมอง คือ นมเป็นอาหารที่อ่อนด้อยเรื่องสารอาหารอย่างสิ้นเชิง โปรตีนในนมพืช ต่ำเตี้ยเรี่ยดินเมื่อเทียบกับแค่ ไข่ นมวัวมีแก้วละ 6กรัม นมโอ้ตมีแก้วละ 3กรัม ในขณะที่ไข่เพียง 1ฟอง มีโปรตีน 6-7กรัม หรือจะเอาแคลเซียม ที่อ้างกันนัก นมแก้วนึง(200ml) มีแคลเซียม 123mg ในขณะที่ไข่แค่4ฟอง มีไปแล้ว 100mg ส่วนใครยังกลัวไข่เพราะมีคอเลสเตอรอล คุณปิดโพสได้เลย คุณเชยไปแล้วครับเขา move on เรื่องไข่กันไปนานแล้ว รบกวนหาข้อมูล แถมแคลเซียมที่กินไป ถ้าไม่ทำ xxxxx xxxx รู้ไหมว่ามันจะไปสะสมที่หลอดเลือด นี่ละตัวตันเลย ไม่ใช่คอเลสเตอรอล ส่วน xx นั้นถ้ายังไม่รู้ว่ามีอะไรบ้างที่ต้องทำเพื่อจัดการแคลเซียม ก็ยิ้มให้กับตัวเองเลยครับ ดื่มนมเพราะแคลเซียมนี่เนอะ 55555
นอกจากนี้ นมทุกชนิดยังเต็มไปด้วย "คาร์บ" แบบต่างๆ ทั้งน้ำตาลแลคโตสในนมวัว และแป้งเชิงซ้อนในนมพืช ส่วนตัวไหนคาร์บต่ำ ทุกอย่างก็ต่ำไปหมด เทียบเป็น น้ำเปล่าขุ่นๆ ราคาแพง
บางคนบอกว่า "นมพืชดี๊ดี กินแล้วน้ำตาลในเลือดไม่พุ่งเลยนะ" ฟังดูเหมือนดีนะ แต่...แค่ตัวเลขน้ำตาลในเลือดเฉียบพลันไม่กระโดด
จะบอกว่านั่นไม่ได้แปลว่าร่างกายปลอดภัยจริงๆ นะแค่ค่าน้ำตาลในเลือดมันเป็นแค่จุุดพอสังเกต เพราะสิ่งที่เกิดขึ้นหลังจากเราดื่มนมพืช โดยเฉพาะนมโอ๊ต คือ คาร์บแฝงที่จะค่อยๆ แตกตัวระหว่างการย่อย ร่างกายอาจจะไม่ช็อคน้ำตาลทันที แต่จะ กระตุ้นอินซูลิน ให้ทำงานหนักขึ้นแบบเนียนๆ อินซูลินสูงเรื้อรังโดยที่ไม่รู้ตัว เป็นเส้นทางลัดไปสู่ไขมันสะสม การอักเสบ และเบาหวานชนิดที่ 2 ในระยะยาว
ภัยเงียบที่น่ากลัวที่สุดของนมโอ๊ต จึงไม่ใช่แค่เรื่องน้ำตาล แต่คือ "ภาวะอินซูลินสูงแบบไร้อาการ" (Silent Hyperinsulinemia) เป็นอาการอินซูลินมันพุ่งสูง แบบที่ตรวจเฉพาะน้ำตาลจะไม่เห็น ต้องเจาะเฉพาะระดับอินซูลิน (Insulin test) ถึงจะรู้ บั่นทอนสุขภาพทีละน้อย เหมือนเชื้อไฟใต้เถ้า ที่รอวันระเบิดเป็นโรคเรื้อรังในอีก 10 ปีข้างหน้า
แล้วทำไมเราถึงศรัทธา "นม" จนหมดใจ? คำตอบคือ..."สงคราม"
Fiat system เก่งมากนะครับที่ไม่ได้แค่พิมพ์นมขึ้นมาจากอุตสาหกรรมเหลือทิ้ง หลังสงครามโลก แต่ยังพิมพ์ "ความกลัว" ลงในใจพวกเราว่า "ถ้าไม่ดื่มนม คุณจะไม่แข็งแรง"
หลังสงครามโลกครั้งที่ 2 อเมริกามีนมล้นตลาดจากโครงการป้อนเสบียงกองทัพ เมื่อสงครามยุติ นมจึงเหลือกองมหึมา ถ้าไม่หาทางระบาย ก็ขาดทุนยับเยิน รัฐจึงออก โครงการนมโรงเรียน บังคับให้เด็กในโรงเรียนต้องดื่มนมวันละแก้วทั่วประเทศ พร้อมเทงบสนับสนุนงานวิจัยที่บอกว่า "นมดีต่อกระดูก ดีต่อสุขภาพ" แต่จริงๆ งานวิจัยเหล่านั้นหลายชิ้น ก็เต็มไปด้วย bias และ เงินทุนจากอุตสาหกรรมนม นั่นเอง
"เราไม่ได้เลือกนมด้วยความเข้าใจ เราแค่เกิดมาในยุคที่นมล้นตลาด" เริ่มต้นจากเด็กในโรงเรียน ถูกเลี้ยง ถูกล้างสมอง จนคิดว่านมคือสัญลักษณ์ของการดูแลตัวเองที่ดี
เวลาผ่านไป โลกเปลี่ยน เด็กโตขึ้นมา เริ่มแพ้นมวัวกันเยอะขึ้น คนก็หันมาหาทางเลือกใหม่...นมพืช
แต่ระบบ Fiat Food ก็ยังทำงานแบบเดิม ผลิตนมพืชจากพืชเหลือทิ้งราคาถูก เช่น ข้าวโอ๊ต เสริมวิตามินแต่งหน้าตา ทำโฆษณาน่ารักๆ ว่า รักษ์โลก ใส่ใจสุขภาพ ดื่มแล้วเป็นทางเลือกของคนฉลาด ทางออกของคนย่อยแลคโตสไม่ได้
จากนั้นบุกเข้าโรงเรียนอีกครั้ง เสนอ "นมโอ๊ตโรงเรียน" แทนนมวัว ครอบเจนฯใหม่ทั้งกระบิทีเดียวเลย ใช้วิจัยใหม่ที่ เน้นเฉพาะข้อมูลด้านสิ่งแวดล้อมหรือ sustainability สร้างความเป็นผู้มีความรู้ในความเป็นคนรักโลก แต่หลีกเลี่ยงไม่พูดถึงสารอาหารจริงๆ
แล้วเด็กๆ ก็กำลังถูกปลูกฝังรอบใหม่อีกครั้ง...ว่า นมโอ๊ต = ทางเลือกสุขภาพ ติดสมองไปอีกหลายเจนฯ ทั้งที่...
นมโอ๊ตอุดมไปด้วยคาร์โบไฮเดรตแตกตัวง่าย ที่ทำให้อินซูลินพุ่งเรื้อรังแบบไร้สัญญาณเตือน โปรตีนต่ำจนไร้ความหมายในแง่สร้างกล้ามเนื้อหรือภูมิคุ้มกัน วิตามินแร่ธาตุที่เติมแต่ง เป็นสารสังเคราะห์ที่ดูดซึมได้ยากกว่าวิตามินจาก real food หลายเท่า
โลกหมุนเร็วขึ้น แต่ Fiat Food ยังวนลูปที่เดิม เปลี่ยนชื่อ เปลี่ยนฉลาก แต่ยังคง "ขายของเหลือ" ผ่านการล้างสมองทางโภชนาการอย่างแนบเนียน ในวันที่โอ้ตล้นโลกจน USDA ต้องหาทางออกให้ มิเช่นนั้นจะต้องเป็นฝ่ายดึงภาษีมาโอบอุ้มเสียเอง
ดังนั้น นมสัตว์ นมพืช ไม่ได้ต่างกันในด้านการครอบความคิด จะต่างกันแค่ผลทางการทำร้ายสุขภาพแบบเงียบๆระยะยาว โปรดเข้าใจประเด็นว่าไม่ใช่จะว่านมโอ้ตแล้วชูนมวัว
ไทม์ไลน์ย่อ "จากนมวัวล้นตลาด สู่แผนบุกนมโอ๊ตโรงเรียน" 1940s (WWII): อเมริกาขยายอุตสาหกรรมนมเพื่อเลี้ยงกองทัพ 1945: สงครามจบ นมล้นตลาด ต้องระบาย 1950: เปิด "โครงการนมโรงเรียน" (School Milk Program) บังคับเด็กดื่มนม พร้อมอุดหนุนฟาร์มนมอย่างลับๆ 1950s-1970s: ใช้งบวิจัยหนุนว่า "นมดีต่อสุขภาพ" ทั่วสหรัฐฯ และโลกตะวันตก 1980s: ปัญหาแพ้นม (Lactose Intolerance) โผล่มากขึ้น แต่โครงการยังเดินหน้าต่อ 2010s: กระแสนมพืชมาแรง ผู้คนตื่นตัวเรื่องแพ้แลคโตส และสิ่งแวดล้อม 2020s: อุตสาหกรรมนมพืชเร่งบุกโรงเรียน เสนอ "นมโอ๊ตโรงเรียน" เพื่อปลูกฝังตั้งแต่เล็กๆ ผ่านโฆษณา "ทางเลือกเพื่อโลก" (ซึ่งซ้ำรอยวิธีเดียวกับที่เคยผลักดันนมวัวเมื่อ 70 ปีก่อนแทบทุกประการ)
สุดท้าย ถามตัวเองอีกครั้ง... นมที่เราดื่มทุกเช้า มาจากความต้องการของร่างกาย หรือมาจากการตลาดที่ชนะสงครามไปตั้งแต่เรายังไม่เกิด?
เราดื่มนมไปทำไมวะ?????
เลือกเองอย่างเข้าใจธรรมชาติ แล้วคุณจะไม่ต้องตื่นขึ้นมาไล่ตามนมอีกเลย วันหยุดนี้ เข้าซุปเปอร์มาร์เกต แล้วดูฉลากโภชนาการกันสิ ว่าได้อะไรจากการดื่มนม
ถามว่าอ่านถึงตรงนี้ ผมเกลียดนมไหม บ้า ใครจะไปเกลียดนม เหตุผลเดียวเลยที่ผมยกให้นมคือ "อร่อย" นมอร่อย ไอติมอร่อย ลาเต้ดีงาม แต่มันคือความอร่อยที่ให้สารอาหารนิดหน่อย ผมไม่ได้เกลียดนม แต่ผมก็ไม่ได้บอกว่าเรา "ต้อง" จะเป็นจะตายเพื่อหานมมาดื่ม ไม่ต้องไปทุรนทุรายว่า เห้ย ทำไมฉันไม่ได้ดื่มนมนะ OMG ชั้นจะป่วยแน่ๆ ชั้นจะไม่แข็งแรงแน่ๆ
ผมเกลียด fiat ที่ครอบหัวคนมากี่รุ่นว่า ถ้าไม่ดื่มนม จะไม่แข็งแรง get มะ 5555
แต่ผมไมได้บอกว่าผมถูกนะ ใครมีเหตุผลที่สนับสนุนว่าเรา "ต้อง" ดื่มนมแบบ “เด็ดขาด” “ห้ามขาดการดื่มนม” มาแชร์กัน ผมยินดีเรียนรู้นะ แต่ประเภทว่า ดื่มแล้วไม่เห็นเป็นไร สะดวกดีบางทีกินง่าย น้องดื่มแล้วตัวสูง ฉันดื่มแล้วตัวสูง อะไรพวกนี้ไม่เอานะ มัน emotion
#pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-
 @ 872982aa:8fb54cfe
2025-04-27 09:34:47
@ 872982aa:8fb54cfe
2025-04-27 09:34:47现在这样可以,我试试在这里也粘贴一个照片
 {.user-img}
{.user-img} -
 @ 872982aa:8fb54cfe
2025-04-27 09:28:10
@ 872982aa:8fb54cfe
2025-04-27 09:28:10 {.user-img}
{.user-img} -
 @ 872982aa:8fb54cfe
2025-04-27 09:23:36
@ 872982aa:8fb54cfe
2025-04-27 09:23:36 -
 @ a39d19ec:3d88f61e
2025-04-22 12:44:42
@ a39d19ec:3d88f61e
2025-04-22 12:44:42Die Debatte um Migration, Grenzsicherung und Abschiebungen wird in Deutschland meist emotional geführt. Wer fordert, dass illegale Einwanderer abgeschoben werden, sieht sich nicht selten dem Vorwurf des Rassismus ausgesetzt. Doch dieser Vorwurf ist nicht nur sachlich unbegründet, sondern verkehrt die Realität ins Gegenteil: Tatsächlich sind es gerade diejenigen, die hinter jeder Forderung nach Rechtssicherheit eine rassistische Motivation vermuten, die selbst in erster Linie nach Hautfarbe, Herkunft oder Nationalität urteilen.
Das Recht steht über Emotionen
Deutschland ist ein Rechtsstaat. Das bedeutet, dass Regeln nicht nach Bauchgefühl oder politischer Stimmungslage ausgelegt werden können, sondern auf klaren gesetzlichen Grundlagen beruhen müssen. Einer dieser Grundsätze ist in Artikel 16a des Grundgesetzes verankert. Dort heißt es:
„Auf Absatz 1 [Asylrecht] kann sich nicht berufen, wer aus einem Mitgliedstaat der Europäischen Gemeinschaften oder aus einem anderen Drittstaat einreist, in dem die Anwendung des Abkommens über die Rechtsstellung der Flüchtlinge und der Europäischen Menschenrechtskonvention sichergestellt ist.“
Das bedeutet, dass jeder, der über sichere Drittstaaten nach Deutschland einreist, keinen Anspruch auf Asyl hat. Wer dennoch bleibt, hält sich illegal im Land auf und unterliegt den geltenden Regelungen zur Rückführung. Die Forderung nach Abschiebungen ist daher nichts anderes als die Forderung nach der Einhaltung von Recht und Gesetz.
Die Umkehrung des Rassismusbegriffs
Wer einerseits behauptet, dass das deutsche Asyl- und Aufenthaltsrecht strikt durchgesetzt werden soll, und andererseits nicht nach Herkunft oder Hautfarbe unterscheidet, handelt wertneutral. Diejenigen jedoch, die in einer solchen Forderung nach Rechtsstaatlichkeit einen rassistischen Unterton sehen, projizieren ihre eigenen Denkmuster auf andere: Sie unterstellen, dass die Debatte ausschließlich entlang ethnischer, rassistischer oder nationaler Kriterien geführt wird – und genau das ist eine rassistische Denkweise.
Jemand, der illegale Einwanderung kritisiert, tut dies nicht, weil ihn die Herkunft der Menschen interessiert, sondern weil er den Rechtsstaat respektiert. Hingegen erkennt jemand, der hinter dieser Kritik Rassismus wittert, offenbar in erster Linie die „Rasse“ oder Herkunft der betreffenden Personen und reduziert sie darauf.
Finanzielle Belastung statt ideologischer Debatte
Neben der rechtlichen gibt es auch eine ökonomische Komponente. Der deutsche Wohlfahrtsstaat basiert auf einem Solidarprinzip: Die Bürger zahlen in das System ein, um sich gegenseitig in schwierigen Zeiten zu unterstützen. Dieser Wohlstand wurde über Generationen hinweg von denjenigen erarbeitet, die hier seit langem leben. Die Priorität liegt daher darauf, die vorhandenen Mittel zuerst unter denjenigen zu verteilen, die durch Steuern, Sozialabgaben und Arbeit zum Erhalt dieses Systems beitragen – nicht unter denen, die sich durch illegale Einreise und fehlende wirtschaftliche Eigenleistung in das System begeben.
Das ist keine ideologische Frage, sondern eine rein wirtschaftliche Abwägung. Ein Sozialsystem kann nur dann nachhaltig funktionieren, wenn es nicht unbegrenzt belastet wird. Würde Deutschland keine klaren Regeln zur Einwanderung und Abschiebung haben, würde dies unweigerlich zur Überlastung des Sozialstaates führen – mit negativen Konsequenzen für alle.
Sozialpatriotismus
Ein weiterer wichtiger Aspekt ist der Schutz der Arbeitsleistung jener Generationen, die Deutschland nach dem Zweiten Weltkrieg mühsam wieder aufgebaut haben. Während oft betont wird, dass die Deutschen moralisch kein Erbe aus der Zeit vor 1945 beanspruchen dürfen – außer der Verantwortung für den Holocaust –, ist es umso bedeutsamer, das neue Erbe nach 1945 zu respektieren, das auf Fleiß, Disziplin und harter Arbeit beruht. Der Wiederaufbau war eine kollektive Leistung deutscher Menschen, deren Früchte nicht bedenkenlos verteilt werden dürfen, sondern vorrangig denjenigen zugutekommen sollten, die dieses Fundament mitgeschaffen oder es über Generationen mitgetragen haben.
Rechtstaatlichkeit ist nicht verhandelbar
Wer sich für eine konsequente Abschiebepraxis ausspricht, tut dies nicht aus rassistischen Motiven, sondern aus Respekt vor der Rechtsstaatlichkeit und den wirtschaftlichen Grundlagen des Landes. Der Vorwurf des Rassismus in diesem Kontext ist daher nicht nur falsch, sondern entlarvt eine selektive Wahrnehmung nach rassistischen Merkmalen bei denjenigen, die ihn erheben.
-
 @ 8d34bd24:414be32b
2025-04-27 03:42:57
@ 8d34bd24:414be32b
2025-04-27 03:42:57I used to hate end times prophecy because it didn’t make sense. I didn’t understand how the predictions could be true, so I wondered if the fulfillment was more figurative than literal. As time has progressed, I’ve seen technologies and international relations change in ways that make the predictions seem not only possible, but probable. I’ve seen the world look more and more like what is predicted for the end times.
I thought it would be handy to look at the predictions and compare them to events, technologies, and nations today. This is a major undertaking, so this will turn into a series. I only hope I can do it justice. I will have some links to news articles on these current events and technologies. Because I can’t remember where I’ve read many of these things, it is likely I will put some links to some news sources that I don’t normally recommend, but which do a decent job of covering the point I’m making. I’m sorry if I don’t always give a perfect source. I have limited time, so in some cases, I’ll link to the easy (main stream journals that show up high on web searches) rather than what I consider more reliable sources because of time constraints.
I also want to give one caveat to everything I discuss below. Although I do believe the signs suggest the Rapture and Tribulation are near, I can’t say exactly what that means or how soon these prophecies will be fulfilled. Could it be tomorrow, a month from now, a year from now, or 20 years from now? Yes, any of them could be true. Could it be even farther in the future? It could be, even if my interpretation of the data concludes that to be less likely.
I will start with a long passage from Matthew that describes what Jesus told His disciples to expect before “the end of the age.” Then I’ll go to some of the end times points that seemed unexplainable to me in the past. We’ll see where things go from there. I’ve already had to split discussion of this one passage into multiple posts due to length.
Jesus’s Signs of the End
As He was sitting on the Mount of Olives, the disciples came to Him privately, saying, “Tell us, when will these things happen, and what will be the sign of Your coming, and of the end of the age?”
And Jesus answered and said to them, “See to it that no one misleads you. For many will come in My name, saying, ‘I am the Christ,’ and will mislead many. You will be hearing of wars and rumors of wars. See that you are not frightened, for those things must take place, but that is not yet the end. For nation will rise against nation, and kingdom against kingdom, and in various places there will be famines and earthquakes. But all these things are merely the beginning of birth pangs.
“Then they will deliver you to tribulation, and will kill you, and you will be hated by all nations because of My name. At that time many will fall away and will betray one another and hate one another. Many false prophets will arise and will mislead many. Because lawlessness is increased, most people’s love will grow cold. But the one who endures to the end, he will be saved. This gospel of the kingdom shall be preached in the whole world as a testimony to all the nations, and then the end will come. (Matthew 24:3-14) {emphasis mine}
Before I go into the details I do want to clarify one thing. The verses that follow the above verses (Matthew 24:16-28) mention the “abomination of desolation” and therefore is clearly discussing the midpoint of the tribulation and the following 3.5 years or Great Tribulation. The first half of Matthew 24 discusses the birth pangs and the first half of the Tribulation. The signs that I discuss will be growing immediately preceding the Tribulation, but probably will not be completely fulfilled until the first 3.5 years of the Tribulation.
I do think we will see an increase of all of these signs before the 7 year Tribulation begins as part of the birth pangs even if they are not fulfilled completely until the Tribulation:
-
Wars and rumors of wars. (Matthew 24:6a)
-
Famines (Matthew 24:7)
-
Earthquakes (Matthew 24:7).
-
Israel will be attacked and will be hated by all nations (Matthew 24:9)
-
Falling away from Jesus (Matthew 24:10)
-
Many Misled (Matthew 24:10)
-
People’s love will grow cold (Matthew 24:12)
-
Gospel will be preached to the whole world (Matthew 24:14)
Now let’s go through each of these predictions to see what we are seeing today.
1. Wars and Rumors of Wars
When you hear of wars and disturbances, do not be terrified; for these things must take place first, but the end does not follow immediately.” (Luke 21:9)
In 1947 the doomsday clock was invented. It theoretically tells how close society is to all out war and destruction of mankind. It was just recently set to 89 seconds to midnight, the closest it has ever been. It is true that this isn’t a scientific measure and politics can effect the setting, i.e. climate change & Trump Derangement Syndrome, but it is still one of many indicators of danger and doom.
There are three main events going on right now that could lead to World War III and the end times.
Obviously the war between Russia and Ukraine has gotten the world divided. It is true that Russia invaded Ukraine, but there were many actions by the US and the EU that provoked this attack. Within months of the initial attack, there was a near agreement between Ukraine and Russia to end the war, but the US and the EU talked Ukraine out of peace, leading to hundreds of thousands of Ukrainians and Russians dying for basically no change of ground. Estimates of deaths vary greatly. See here, here, here. Almost all English sources list Russia as having many more deaths than Ukraine, but since Ukraine is now drafting kids and old men, is considering drafting women, and has most of its defensive capabilities destroyed, while Russia still seems to have plenty of men and weapons, I find this hard to believe. I don’t think any of the parties that have data are motivated to tell the truth. We probably will never know.
The way the EU (and the US until recently) has sacrificed everything to defend Ukraine (until this war known as the most corrupt nation in Europe and known for its actual Nazis) and to do everything in its power to keep the war with Russia going, things could easily escalate. The US and the EU have repeatedly crossed Russia’s red-lines. One of these days, Russia is likely to say “enough is enough” and actually attack Europe. This could easily spiral out of control. I do think that Trump’s pull back and negotiations makes this less likely to lead to world war than it seemed for the past several years. This article does a decent job of explaining the background for the war that most westerners, especially Americans, don’t understand.
Another less well known hot spot is the tension between China and Taiwan. Taiwan is closer politically to the US, but closer economically and culturally to China. This causes tension. Taiwan also produces the majority of the high tech microchips used in advanced technology. Both the US and China want and need this technology. I honestly believe this is the overarching issue regarding Taiwan. If either the US or China got control of Taiwan’s microchip production, it would be military and economic game over for the other. This is stewing, but I don’t think this will be the cause of world war 3, although it could become part of the war that leads to the Antichrist ruling the world.
The war that is likely to lead to the Tribulation involves Israel and the Middle East. Obviously, the Muslim nations hate Israel and attack them almost daily. We also see Iran, Russia, Turkey, and other nations making alliances that sound a lot like the Gog/Magog coalition in Ezekiel 38. The hate of Israel has grown to a level that makes zero sense unless you take into account the spiritual world and Bible prophecy. Such a small insignificant nation, that didn’t even exist for \~1900 years, shouldn’t have the influence on world politics that it does. It is about the size of the state of New Jersey. Most nations of Israel’s size, population, and economy are not even recognized by most people. Is there a person on earth that doesn’t know about Israel? I doubt it. Every nation on earth seems to have a strong positive or, more commonly, negative view of Israel. We’ll get to this hate of Israel more below in point 4.
2. Famines
In the two parallel passages to Matthew 24, there is once again the prediction of famines coming before the end.
For nation will rise up against nation, and kingdom against kingdom; there will be earthquakes in various places; there will also be famines. These things are merely the beginning of birth pangs. (Mark 13:8) {emphasis mine}
and there will be great earthquakes, and in various places plagues and famines; and there will be terrors and great signs from heaven. (Luke 21:11) {emphasis mine}
In Revelation, the third seal releases famine upon the earth and a day’s wages will only buy one person’s daily wheat needs. A man with a family would only be able to buy lower quality barley to barely feed his family.
When He broke the third seal, I heard the third living creature saying, “Come.” I looked, and behold, a black horse; and he who sat on it had a pair of scales in his hand. And I heard something like a voice in the center of the four living creatures saying, “A quart of wheat for a denarius, and three quarts of barley for a denarius; and do not damage the oil and the wine.” (Revelation 6:5-6) {emphasis mine}
We shouldn’t fear a Tribulation level famine as a precursor to the Tribulation, but we should see famines scattered around the world, shortages of different food items, and rising food prices, all of which we are seeing. (Once again, I can’t support many of these sources or verify all of their data, but they give us a feel of what is going on today.)
Food Prices Go Up
-
Bird Flu scares and government responses cause egg and chicken prices to increase. The government response to the flu is actually causing more problems than the flu itself and it looks like this more dangerous version may have come out of a US lab.
-
Tariffs and trade war cause some items to become more expensive or less available. here
-
Ukraine war effecting the supply of grain and reducing availability of fertilizer. More info.
-
Inflation and other effects causing food prices to go up. This is a poll from Americans.
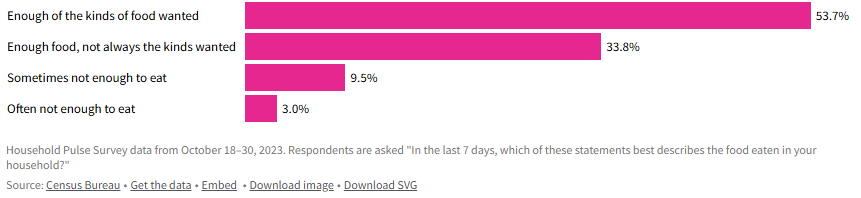 - Grocery prices overall have increased around 23% since 2021, with prices on individual items like coffee and chocolate rising much faster.
- Grocery prices overall have increased around 23% since 2021, with prices on individual items like coffee and chocolate rising much faster.-
General Food inflation is difficult, but not life destroying for most of the world, but some nations are experiencing inflation that is causing many to be unable to afford food. Single digit food inflation is difficult, even in well-to-do nations, but in poor nations, where a majority of the people’s income already goes to food, it can be catastrophic. When you look at nations like Zimbabwe (105%), Venezuela (22%), South Sudan (106%), Malawi (38%), Lebanon (20%), Haiti (37%), Ghana (26%), Burundi (39%), Bolivia (35%), and Argentina (46%), you can see that there are some seriously hurting people. More info.
-
It does look like general food inflation has gone down for the moment (inflation has gone down, but not necessarily prices), but there are many situations around the world that could make it go back up again.
-
Wars causing famine
-
Sudan: War has made an already poor and hurting country even worse off.
-
Gaza: (When I did a web search, all of the sites that came up on the first couple of pages are Israel hating organizations that are trying to cause trouble and/or raise money, so there is major bias. I did link to one of these sites just to be thorough, but take into account the bias of the source.)
-
Ukraine: Mostly covered above. The war in Ukraine has affected the people of Ukraine and the world negatively relative to food.
I’m sure there are plenty more evidences for famine or potential famine, but this gives a taste of what is going on.
Our global economy has good and bad effects on the food supply. Being able to transport food around the globe means that when one area has a bad crop, they can import food from another area that produced more than they need. On the other hand, sometimes an area stops producing food because they can import food more cheaply. If something disrupts that imported food (tariffs, trade wars, physical wars, transportation difficulties, intercountry disputes, etc.) then they suddenly have no food. We definitely have a fragile system, where there are many points that could fail and cause famine to abound.
The Bible also talks about another kind of famine in the end times.
“Behold, days are coming,” declares the Lord God,\ “When I will send a famine on the land,\ *Not a famine for bread or a thirst for water,\ But rather for hearing the words of the Lord*.\ People will stagger from sea to sea\ And from the north even to the east;\ They will go to and fro to seek the word of the Lord,\ But they will not find it**. (Amos 8:11-12) {emphasis mine}
We are definitely seeing a famine regarding the word of God. It isn’t that the word of God is not available, but even in churches, there is a lack of teaching the actual word of God from the Scriptures. Many churches teach more self-help or feel good messages than they do the word of God. Those looking to know God better are starving or thirsting for truth and God’s word. I know multiple people who have given up on assembling together in church because they can’t find a Bible believing, Scripture teaching church. How sad!
Although famine should be expected before the Tribulation, the good news is that no famine will separate us from our Savior.
Who will separate us from the love of Christ? Will tribulation, or distress, or persecution, or famine, or nakedness, or peril, or sword? (Romans 8:35) {emphasis mine}
3. Earthquakes
We recently saw a major \~7.8 earthquake in Myanmar. Although it seems like we are having many major earthquakes, it is more difficult to determine whether there is actually a major increase or if the seeming increase is due to increasing population to harm, more/better instrumentation, and/or more media coverage. We are definitely seeing lots of earthquake damage and loss of life. I tend to think the number and severity of earthquakes will increase even more before the Tribulation, but only time will tell.
4. Israel will be attacked and will be hated by all nations
“Then they will deliver you [Israel] to tribulation, and will kill you, and you will be hated by all nations because of My name. (Matthew 24:9) {emphasis & clarification mine}
This verse doesn’t specifically mention Israel. It says “you,” but since Jesus was talking to Jews, the best interpretation is that this warning is to the Jews. At the same time, we are also seeing attacks on Christians, so it likely refers to both Jews and Christians. I’m going to focus on Jews/Israel because I don’t think I need to convince most Christians that persecution is increasing.
We have been seeing hatred of Jews and Israel growing exponentially since the biblical prediction of a re-establishment of Israel was accomplished.
All end times prophecy focuses on Israel and requires Israel to be recreated again since it was destroyed in A.D. 70.
Who has heard such a thing? Who has seen such things?\ Can a land be born in one day?\ Can a nation be brought forth all at once?\ As soon as Zion travailed, she also brought forth her sons. (Isaiah 66:8)
-
“British Foreign Minister Lord Balfour issued on November 2, 1917, the so-called Balfour Declaration, which gave official support for the “establishment in Palestine of a national home for the Jewish people” with the commitment not to be prejudiced against the rights of the non-Jewish communities.” In one day Israel was declared a nation.
-
“On the day when the British Mandate in Palestine expired, the State of Israel was instituted on May 14, 1948, by the Jewish National Council under the presidency of David Ben Gurion.” Then on another day Israel actually came into being with a leader and citizens.
-
“Six-Day War: after Egypt closed the Straits of Tiran on May 22, 1967, Israel launched an attack on Egyptian, Jordanian, Syrian, and Iraqi airports on June 5, 1967. After six days, Israel conquered Jerusalem, the Golan Heights, Sinai, and the West Bank.” On June 11, 1967 Jerusalem was conquered and once again became the capital of Israel.
If you read any of these links you can see the history of Israel being repeatedly attacked in an attempt to destroy Israel and stop God’s prophecy that Israel would be recreated and be used in the end times as part of the judgement of the world. This is a very good article on how God plans to use Israel in end times, how God will fulfill all of his promises to Israel, and how the attacks on Israel are Satan’s attempt to stop God’s plan. It is well worth you time to read and well supported by Scripture.
Since Israel became a new nation again, the nations of the world have ramped up their attacks on Israel and the Jews. The hatred of the Jews is hard to fathom. The Jews living in Israel have been constantly at risk of suicide bombers, terrorist attacks, rocket/missile attacks, etc. Almost daily attacks are common recently. The most significant recent attack happened on October 7th. Around 3,000 Hamas terrorists stormed across the border and attacked men, women, and children. About 1200 were killed, mostly civilians and even kids. In addition to murdering these innocent individuals, others were tortured, raped, and kidnapped as well.
You would expect the world to rally around a nation attacked in such a horrendous manner (like most of the world rallied around the US after 9/11), but instead you immediately saw protests supporting Palestine and condemning Israel. I’ve never seen something so upside down in my life. It is impossible to comprehend until you consider the spiritual implications. Satan has been trying to destroy Israel and the Jews since God made His first promise to Abraham. I will never claim that everything Israeli politicians and generals do is good, but the hate towards this tiny, insignificant nation is unfathomable and the world supporting terrorist attacks, instead of the victims of these attacks, is beyond belief.
Israel allows people of Jewish ancestry and Palestinian ancestry to be citizens and vote. There are Jews, Muslims, and Christians in the Knesset (Jewish Congress). Yes, Israel has responded harshly against the Palestinians and innocents have been harmed, but Israel repeatedly gave up land for peace and then that land has been used to attack them. I can’t really condemn them for choosing to risk the death of Palestinian innocents over risking the death of their own innocents. Hamas and Hezbollah are known for attacking innocents, and then using their own innocents as human shields. They then accuse their victims of atrocities when their human shields are harmed. The UN Human Rights council condemns Israel more than all other nations combined when there are atrocities being committed in many, many other nations that are as bad or worse. Why is the world focused on Israel and the Jews? It is because God loves them (despite their rejection of Him) and because Satan hates them.
Throughout history the world has tried to destroy the Jews, but thanks to God and His eternal plan, they are still here and standing strong. the hate is growing to a fevered pitch, just as predicted by Jesus.
This post has gotten so long that it can’t be emailed, so I will post the final 4 points in a follow-up post. I hope these details are helpful to you and seeing that all of the crazy, hate, and destruction occurring in the world today was known by God and is being used by God to His glory and are good according to His perfect plan.
When we see that everything happening in the world is just part of God’s perfect plan, we can have peace, knowing that God is in control. We need to lean on Him and trust Him just as a young child feels safe in his Fathers arms. At the same time, seeing the signs should encourage us to share the Gospel with unbelievers because our time is short. Don’t put off sharing Jesus with those around you because you might not get another chance.
Trust Jesus.
FYI, I hope to write several more articles on the end times (signs of the times, the rapture, the millennium, and the judgement), but I might be a bit slow rolling them out because I want to make sure they are accurate and well supported by Scripture. You can see my previous posts on the end times on the end times tab at trustjesus.substack.com. I also frequently will list upcoming posts.
-
-
 @ 3f770d65:7a745b24
2025-04-21 00:15:06
@ 3f770d65:7a745b24
2025-04-21 00:15:06At the recent Launch Music Festival and Conference in Lancaster, PA, featuring over 120 musicians across three days, I volunteered my time with Tunestr and Phantom Power Music's initiative to introduce artists to Bitcoin, Nostr, and the value-for-value model. Tunestr sponsored a stage, live-streaming 21 bands to platforms like Tunestr.io, Fountain.fm and other Nostr/Podcasting 2.0 apps and on-boarding as many others as possible at our conference booth. You may have seen me spamming about this over the last few days.
V4V Earnings
Day 1: 180,000 sats
Day 2: 300,000 sats
Day 3: Over 500,000 sats
Who?
Here are the artists that were on-boarded to Fountain and were live streaming on the Value-for-Value stage:
nostr:npub1cruu4z0hwg7n3r2k7262vx8jsmra3xpku85frl5fnfvrwz7rd7mq7e403w nostr:npub12xeh3n7w8700z4tpd6xlhlvg4vtg4pvpxd584ll5sva539tutc3q0tn3tz nostr:npub1rc80p4v60uzfhvdgxemhvcqnzdj7t59xujxdy0lcjxml3uwdezyqtrpe0j @npub16vxr4pc2ww3yaez9q4s53zkejjfd0djs9lfe55sjhnqkh nostr:npub10uspdzg4fl7md95mqnjszxx82ckdly8ezac0t3s06a0gsf4f3lys8ypeak nostr:npub1gnyzexr40qut0za2c4a0x27p4e3qc22wekhcw3uvdx8mwa3pen0s9z90wk nostr:npub13qrrw2h4z52m7jh0spefrwtysl4psfkfv6j4j672se5hkhvtyw7qu0almy nostr:npub1p0kuqxxw2mxczc90vcurvfq7ljuw2394kkqk6gqnn2cq0y9eq5nq87jtkk nostr:npub182kq0sdp7chm67uq58cf4vvl3lk37z8mm5k5067xe09fqqaaxjsqlcazej nostr:npub162hr8kd96vxlanvggl08hmyy37qsn8ehgj7za7squl83um56epnswkr399 nostr:npub17jzk5ex2rafres09c4dnn5mm00eejye6nrurnlla6yn22zcpl7vqg6vhvx nostr:npub176rnksulheuanfx8y8cr2mrth4lh33svvpztggjjm6j2pqw6m56sq7s9vz nostr:npub1akv7t7xpalhsc4nseljs0c886jzuhq8u42qdcwvu972f3mme9tjsgp5xxk nostr:npub18x0gv872489lrczp9d9m4hx59r754x7p9rg2jkgvt7ul3kuqewtqsssn24
Many more musicians were on-boarded to Fountain, however, we were unable to obtain all of their npubs.
THANK YOU TO ALL ZAPPERS AND BOOSTERS!
Musicians “Get It”
My key takeaway was the musicians' absolute understanding that the current digital landscape along with legacy social media is failing them. Every artist I spoke with recognized how algorithms hinder fan connection and how gatekeepers prevent fair compensation for their work. They all use Spotify, but they only do so out of necessity. They felt the music industry is primed for both a social and monetary revolution. Some of them were even speaking my language…
Because of this, concepts like decentralization, censorship resistance, owning your content, and controlling your social graph weren't just understood by them, they were instantly embraced. The excitement was real; they immediately saw the potential and agreed with me. Bitcoin and Nostr felt genuinely punk rock and that helped a lot of them identify with what we were offering them.
The Tools and the Issues
While the Nostr ecosystem offers a wide variety of tools, we focused on introducing three key applications at this event to keep things clear for newcomers:
- Fountain, with a music focus, was the primary tool for onboarding attendees onto Nostr. Fountain was also chosen thanks to Fountain’s built-in Lightning wallet.
- Primal, as a social alternative, was demonstrated to show how users can take their Nostr identity and content seamlessly between different applications.
- Tunestr.io, lastly was showcased for its live video streaming capabilities.
Although we highlighted these three, we did inform attendees about the broader range of available apps and pointed them to
nostrapps.comif they wanted to explore further, aiming to educate without overwhelming them.This review highlights several UX issues with the Fountain app, particularly concerning profile updates, wallet functionality, and user discovery. While Fountain does work well, these minor hiccups make it extremely hard for on-boarding and education.
- Profile Issues:
- When a user edits their profile (e.g., Username/Nostr address, Lightning address) either during or after creation, the changes don't appear to consistently update across the app or sync correctly with Nostr relays.
- Specifically, the main profile display continues to show the old default Username/Nostr address and Lightning address inside Fountain and on other Nostr clients.
- However, the updated Username/Nostr address does appear on https://fountain.fm (chosen-username@fountain.fm) and is visible within the "Edit Profile" screen itself in the app.
- This inconsistency is confusing for users, as they see their updated information in some places but not on their main public-facing profile within the app. I confirmed this by observing a new user sign up and edit their username – the edit screen showed the new name, but the profile display in Fountain did not update and we did not see it inside Primal, Damus, Amethyst, etc.
- Wallet Limitations:
- The app's built-in wallet cannot scan Lightning address QR codes to initiate payments.
- This caused problems during the event where users imported Bitcoin from Azte.co vouchers into their Fountain wallets. When they tried to Zap a band by scanning a QR code on the live tally board, Fountain displayed an error message stating the invoice or QR code was invalid.
- While suggesting musicians install Primal as a second Nostr app was a potential fix for the QR code issue, (and I mentioned it to some), the burden of onboarding users onto two separate applications, potentially managing two different wallets, and explaining which one works for specific tasks creates a confusing and frustrating user experience.
- Search Difficulties:
- Finding other users within the Fountain app is challenging. I was unable to find profiles from brand new users by entering their chosen Fountain username.
- To find a new user, I had to resort to visiting their profile on the web (fountain.fm/username) to retrieve their npub. Then, open Primal and follow them. Finally, when searching for their username, since I was now following them, I was able to find their profile.
- This search issue is compounded by the profile syncing problem mentioned earlier, as even if found via other clients, their displayed information is outdated.
- Searching for the event to Boost/Zap inside Fountain was harder than it should have been the first two days as the live stream did not appear at the top of the screen inside the tap. This was resolved on the third day of the event.
Improving the Onboarding Experience
To better support user growth, educators and on-boarders need more feature complete and user-friendly applications. I love our developers and I will always sing their praises from the highest mountain tops, however I also recognize that the current tools present challenges that hinder a smooth onboarding experience.
One potential approach explored was guiding users to use Primal (including its built-in wallet) in conjunction with Wavlake via Nostr Wallet Connect (NWC). While this could facilitate certain functions like music streaming, zaps, and QR code scanning (which require both Primal and Wavlake apps), Wavlake itself has usability issues. These include inconsistent or separate profiles between web and mobile apps, persistent "Login" buttons even when logged in on the mobile app with a Nostr identity, and the minor inconvenience of needing two separate applications. Although NWC setup is relatively easy and helps streamline the process, the need to switch between apps adds complexity, especially when time is limited and we’re aiming to showcase the benefits of this new system.
Ultimately, we need applications that are more feature-complete and intuitive for mainstream users to improve the onboarding experience significantly.
Looking forward to the future
I anticipate that most of these issues will be resolved when these applications address them in the near future. Specifically, this would involve Fountain fixing its profile issues and integrating Nostr Wallet Connect (NWC) to allow users to utilize their Primal wallet, or by enabling the scanning of QR codes that pay out to Lightning addresses. Alternatively, if Wavlake resolves the consistency problems mentioned earlier, this would also significantly improve the situation giving us two viable solutions for musicians.
My ideal onboarding event experience would involve having all the previously mentioned issues resolved. Additionally, I would love to see every attendee receive a $5 or $10 voucher to help them start engaging with value-for-value, rather than just the limited number we distributed recently. The goal is to have everyone actively zapping and sending Bitcoin throughout the event. Maybe we can find a large sponsor to facilitate this in the future?
What's particularly exciting is the Launch conference's strong interest in integrating value-for-value across their entire program for all musicians and speakers at their next event in Dallas, Texas, coming later this fall. This presents a significant opportunity to onboard over 100+ musicians to Bitcoin and Nostr, which in turn will help onboard their fans and supporters.
We need significantly more zaps and more zappers! It's unreasonable to expect the same dedicated individuals to continuously support new users; they are being bled dry. A shift is needed towards more people using bitcoin for everyday transactions, treating it as money. This brings me back to my ideal onboarding experience: securing a sponsor to essentially give participants bitcoin funds specifically for zapping and tipping artists. This method serves as a practical lesson in using bitcoin as money and showcases the value-for-value principle from the outset.
-
 @ ba0ea036:21b6d3e8
2025-04-27 08:31:52
@ ba0ea036:21b6d3e8
2025-04-27 08:31:52ان اف تی مخفف Non-Fungible Token به معنای «توکن غیرقابل تعویض» است. این اصطلاح ممکن است در ابتدا کمی گیج کننده به نظر برسد، اما در واقع مفهوم آن بسیار ساده است. NFTها، داراییهای دیجیتالی منحصر به فردی هستند که بر روی بلاک چین ثبت میشوند و مالکیت آنها به صورت غیرقابل تغییر و شفاف ثبت میگردد. به عبارت دیگر، هر NFT مانند یک اثر هنری دیجیتالی، یک قطعه موسیقی، یا حتی یک توییت منحصر به فرد است که نمیتوان آن را با دیگری جایگزین کرد.

تفاوت NFT با داراییهای قابل تعویض:
برای درک بهتر مفهوم NFT، بهتر است آن را با داراییهای قابل تعویض (Fungible Tokens) مانند بیت کوین یا اتریوم مقایسه کنیم. بیت کوینها همه یکسان هستند و میتوان یک بیت کوین را به راحتی با بیت کوین دیگری تعویض کرد. اما NFTها هر کدام منحصر به فرد هستند و نمیتوان آنها را با یکدیگر جایگزین کرد. این تفاوت اساسی، NFTها را به داراییهای ارزشمندی تبدیل کرده است که میتوانند ارزش زیادی داشته باشند.
مراحل کارکرد یک NFT:
ایجاد (مینت کردن) NFT:
اولین مرحله در فرآیند ایجاد یک NFT، مینت کردن آن است. این فرایند شامل تبدیل یک دارایی دیجیتال مانند یک اثر هنری، یک قطعه موسیقی، یا یک آیتم درون بازی به یک توکن NFT است. این کار معمولاً با استفاده از پلتفرمهای مختلفی که برای ایجاد و مدیریت NFTها طراحی شدهاند، انجام میشود. در این مرحله، اطلاعات مربوط به NFT، از جمله اطلاعات مالکیت، تاریخ ایجاد و سایر جزئیات مربوطه، به صورت رمزنگاری شده بر روی بلاک چین ثبت میشود.
ثبت بر روی بلاک چین:
بلاک چین یک دفتر کل توزیع شده و غیرمتمرکز است که اطلاعات مربوط به NFT را به صورت امن و شفاف ثبت میکند. این به این معنی است که اطلاعات مربوط به NFT در چندین کامپیوتر در سراسر جهان کپی میشود و هیچ فرد یا نهادی نمیتواند به تنهایی اطلاعات را تغییر دهد. این ویژگی، امنیت و شفافیت NFTها را تضمین میکند.
خرید و فروش NFT:
پس از ایجاد NFT، میتوان آن را در بازارهای آنلاین NFT به فروش گذاشت. خریداران میتوانند با استفاده از ارزهای دیجیتال، مانند اتریوم، NFTها را خریداری کنند و مالکیت آنها را به دست آورند. تمام تراکنشهای مربوط به خرید و فروش NFTها بر روی بلاک چین ثبت میشود و به این ترتیب، شفافیت و امنیت معاملات تضمین میگردد.
مالکیت و اصالت:
بلاک چین تضمین میکند که مالکیت NFT به طور شفاف و غیرقابل تغییر ثبت شده است. این امر اصالت NFT را تضمین میکند و از جعل و کپی غیرمجاز جلوگیری میکند. هر NFT دارای یک کد منحصر به فرد است که آن را از سایر NFTها متمایز میکند و این کد بر روی بلاک چین ثبت میشود.
انواع بلاک چینهای مورد استفاده برای NFTها:
چندین بلاک چین برای میزبانی NFTها وجود دارد، از جمله اتریوم، سولانا، پولکادات و بسیاری دیگر. هر کدام از این بلاک چینها ویژگیها و مزایای خاص خود را دارند، مانند سرعت تراکنش، هزینههای گاز (هزینه تراکنش)، و امنیت. انتخاب بلاک چین مناسب، به عوامل مختلفی مانند نوع NFT و نیازهای کاربران بستگی دارد.
کاربردهای NFTها:
کاربردهای NFTها بسیار گسترده است و به سرعت در حال افزایش است. از جمله کاربردهای مهم NFTها میتوان به موارد زیر اشاره کرد:
هنر دیجیتال: NFTها به هنرمندان اجازه میدهند تا آثار هنری دیجیتال خود را به صورت منحصر به فرد و قابل تأیید مالکیت به فروش برسانند. بازیهای ویدئویی: NFTها میتوانند برای ایجاد آیتمهای درون بازی منحصر به فرد و قابل معامله استفاده شوند. موسیقی: موسیقیدانان میتوانند آثار موسیقی خود را به صورت NFT منتشر کنند و به این ترتیب، مالکیت و حقوق خود را حفظ کنند. کالاهای مجازی: NFTها میتوانند برای ایجاد و فروش کالاهای مجازی منحصر به فرد، مانند لباسها، لوازم جانبی و آواتارها در متاورس استفاده شوند. گواهی اصالت: NFTها میتوانند به عنوان گواهی اصالت برای کالاهای فیزیکی نیز استفاده شوند. بلیطهای رویدادها: NFTها میتوانند به عنوان بلیطهای رویدادها، مانند کنسرتها و رویدادهای ورزشی استفاده شوند.
مزایای استفاده از NFTها:
مالکیت شفاف و غیرقابل تغییر: NFTها مالکیت داراییهای دیجیتال را به صورت شفاف و غیرقابل تغییر ثبت میکنند. امنیت بالا: بلاک چین امنیت NFTها را تضمین میکند و از جعل و کپی غیرمجاز جلوگیری میکند. شفافیت: تمام تراکنشهای مربوط به NFTها بر روی بلاک چین ثبت میشود و به راحتی قابل پیگیری است. قابلیت مبادله آسان: NFTها به راحتی قابل خرید، فروش و مبادله هستند. ایجاد بازار جدید برای هنرمندان و خالقان محتوا: NFTها بازار جدیدی برای هنرمندان و خالقان محتوا ایجاد کرده است.
چالشهای NFTها:
با وجود مزایای بسیار، NFTها نیز با چالشهایی مواجه هستند، از جمله:
نوسانات قیمت: قیمت NFTها میتواند بسیار نوسان داشته باشد. هزینههای تراکنش: هزینههای تراکنش در برخی بلاک چینها میتواند بالا باشد. ملاحظات زیست محیطی: برخی از بلاک چینها، مانند اتریوم، از الگوریتمهای اثبات کار استفاده میکنند که مصرف انرژی بالایی دارند. کلاهبرداری: خطر کلاهبرداری در بازار NFTها وجود دارد.
نتیجه گیری:
ان اف تی ها فناوری جدیدی هستند که پتانسیل تغییر دادن بسیاری از جنبههای زندگی دیجیتال ما را دارند. با درک چگونگی کارکرد NFTها و مزایا و چالشهای آنها، میتوان از این فناوری جدید به طور مؤثر استفاده کرد. برای کسب اطلاعات بیشتر در مورد این حوزه جذاب، جستجوی عبارت "NFT چیست؟" در موتورهای جستجو میتواند راهنمای خوبی باشد.
امیدوارم این توضیحات برای شما مفید بوده باشد. برای اطلاعات بیشتر در مورد NFT چیست؟، میتوانید به منابع آنلاین معتبر مراجعه کنید.
-
 @ 592295cf:413a0db9
2025-04-13 15:52:02
@ 592295cf:413a0db9
2025-04-13 15:52:02Nostur is capable of login with bunker
Photo, note by Fabian
nostr:nevent1qvzqqqqqqypzqkfzjh8jkzd8l9247sadku6vhm52snhgjtknlyeku6sfkeqn5rdeqyf8wumn8ghj7mn0wd68ytnvw5hxkef0qyg8wumn8ghj7mn0wd68ytnddakj7qpqxfktwlm2qdkpxy556e4yg4l8p6v8930nfyzg7p3vsknk7krutz0s8znjtq
When you decide to share an app you have to know a lot about that app. For example the nstart feature that you can share your friends, has a "smart pack" and the app can onboard, at least following the link --> Apps-integration
So let's try to read and bring a bit to the summary of the thing. Only the one about the profiles, which you don't know exactly how it will end, you have to try it before sending to someone. the second point is that it says that there is no "support encryption, so it cannot be used for DMs apps".
there was an update of nstart, now it shows you
the names of the bunkers, maybe now it's too much, decide if it does 3/2 4/2 or just automatic.
So they talked about frost in the hodlbod podcast. I didn't understand much except that they said to test frost and report the feedback. Tomorrow I'll try to download igloo and frost+nos2ex
So I have to wait for let's say version 0_1_0 of igloo now it is (0_0_4) and
maybe there will be the version of the extension ready.
Sebastix also found it difficult but I think he was trying to install the server, which didn't even occur to me. Anyway I leave you the note if you want to go deeper...
nostr:nevent1qvzqqqqqqypzqpnrnguxe8qszsshvgkvhn6qjzxy7xsvx03rlrtddr62haj4lrm3qytkummnw3ez66tyvgaz7tmrv93ksefdwfjkccteqqs2wzkkx220e24revkpxmdzkqj73rnz0reeenjwgy53g36hlkdgurgrs5e62
Let's see if I can download the video. ok Downloaded. Video .mov
If you don't want to watch I'll leave a little description
1 Download and install igloo, from the frost page. 2 Create a new key set, you can generate or copy an existing key. 3. Choose the options for the key and now they become multiple keys 4. Created a group of credentials. 5. Save the two credentials with a password and bring the third into the browser extension that it creates from the repository, it says that there will be a bootable extension for chrome. 6. Copy the third key and the group package key into the application node. 7. Once you have entered these keys you can finish the operation (and you have backed up the other two) in igloo. 8. When it goes forward it finds itself with two keys, both encrypted with passwords. 9. Since it is a three of two, it just needs to activate a key in igloo and it starts communicating "startsigner". 10. Opens a nostr client and connects with frost2sx and writes a note 11. Shows the log, and says that if you enter two keys it can generate a third, invalidating the old one (I assume)
-
 @ 39cc53c9:27168656
2025-04-09 07:59:35
@ 39cc53c9:27168656
2025-04-09 07:59:35The new website is finally live! I put in a lot of hard work over the past months on it. I'm proud to say that it's out now and it looks pretty cool, at least to me!
Why rewrite it all?
The old kycnot.me site was built using Python with Flask about two years ago. Since then, I've gained a lot more experience with Golang and coding in general. Trying to update that old codebase, which had a lot of design flaws, would have been a bad idea. It would have been like building on an unstable foundation.
That's why I made the decision to rewrite the entire application. Initially, I chose to use SvelteKit with JavaScript. I did manage to create a stable site that looked similar to the new one, but it required Jav aScript to work. As I kept coding, I started feeling like I was repeating "the Python mistake". I was writing the app in a language I wasn't very familiar with (just like when I was learning Python at that mom ent), and I wasn't happy with the code. It felt like spaghetti code all the time.
So, I made a complete U-turn and started over, this time using Golang. While I'm not as proficient in Golang as I am in Python now, I find it to be a very enjoyable language to code with. Most aof my recent pr ojects have been written in Golang, and I'm getting the hang of it. I tried to make the best decisions I could and structure the code as well as possible. Of course, there's still room for improvement, which I'll address in future updates.
Now I have a more maintainable website that can scale much better. It uses a real database instead of a JSON file like the old site, and I can add many more features. Since I chose to go with Golang, I mad e the "tradeoff" of not using JavaScript at all, so all the rendering load falls on the server. But I believe it's a tradeoff that's worth it.
What's new
- UI/UX - I've designed a new logo and color palette for kycnot.me. I think it looks pretty cool and cypherpunk. I am not a graphic designer, but I think I did a decent work and I put a lot of thinking on it to make it pleasant!
- Point system - The new point system provides more detailed information about the listings, and can be expanded to cover additional features across all services. Anyone can request a new point!
- ToS Scrapper: I've implemented a powerful automated terms-of-service scrapper that collects all the ToS pages from the listings. It saves you from the hassle of reading the ToS by listing the lines that are suspiciously related to KYC/AML practices. This is still in development and it will improve for sure, but it works pretty fine right now!
- Search bar - The new search bar allows you to easily filter services. It performs a full-text search on the Title, Description, Category, and Tags of all the services. Looking for VPN services? Just search for "vpn"!
- Transparency - To be more transparent, all discussions about services now take place publicly on GitLab. I won't be answering any e-mails (an auto-reply will prompt to write to the corresponding Gitlab issue). This ensures that all service-related matters are publicly accessible and recorded. Additionally, there's a real-time audits page that displays database changes.
- Listing Requests - I have upgraded the request system. The new form allows you to directly request services or points without any extra steps. In the future, I plan to enable requests for specific changes to parts of the website.
- Lightweight and fast - The new site is lighter and faster than its predecessor!
- Tor and I2P - At last! kycnot.me is now officially on Tor and I2P!
How?
This rewrite has been a labor of love, in the end, I've been working on this for more than 3 months now. I don't have a team, so I work by myself on my free time, but I find great joy in helping people on their private journey with cryptocurrencies. Making it easier for individuals to use cryptocurrencies without KYC is a goal I am proud of!
If you appreciate my work, you can support me through the methods listed here. Alternatively, feel free to send me an email with a kind message!
Technical details
All the code is written in Golang, the website makes use of the chi router for the routing part. I also make use of BigCache for caching database requests. There is 0 JavaScript, so all the rendering load falls on the server, this means it needed to be efficient enough to not drawn with a few users since the old site was reporting about 2M requests per month on average (note that this are not unique users).
The database is running with mariadb, using gorm as the ORM. This is more than enough for this project. I started working with an
sqlitedatabase, but I ended up migrating to mariadb since it works better with JSON.The scraper is using chromedp combined with a series of keywords, regex and other logic. It runs every 24h and scraps all the services. You can find the scraper code here.
The frontend is written using Golang Templates for the HTML, and TailwindCSS plus DaisyUI for the CSS classes framework. I also use some plain CSS, but it's minimal.
The requests forms is the only part of the project that requires JavaScript to be enabled. It is needed for parsing some from fields that are a bit complex and for the "captcha", which is a simple Proof of Work that runs on your browser, destinated to avoid spam. For this, I use mCaptcha.
-
 @ 502ab02a:a2860397
2025-04-27 03:00:40
@ 502ab02a:a2860397
2025-04-27 03:00:40แดดกับ Infradian Rhythm จังหวะลึกล้ำของชีวิตที่ธรรมชาติกำหนด เวลาเราพูดถึง "วงจรชีวิต" คนส่วนใหญ่จะนึกถึงแค่การนอนตื่นตามรอบวัน หรือ circadian rhythm ที่พระอาทิตย์ขึ้นแล้วเราตื่น พระอาทิตย์ตกแล้วเราง่วง แต่จริง ๆ แล้วร่างกายมนุษย์นั้นลึกซึ้งกว่านั้นมากครับ เพราะนอกจาก circadian rhythm แล้วเรายังมีจังหวะชีวภาพอีกชนิดนึงที่ชื่อว่า "Infradian Rhythm" ซึ่งไม่ได้เดินเป็นรอบวัน แต่เป็นรอบที่ยาวกว่านั้น อาจเป็นรอบสัปดาห์ หรือแม้แต่รอบเดือน และหนึ่งในตัวตั้งจังหวะชั้นดีนี้ที่ใครหลายคนมองข้าม ก็คือ "แดด" นั่นเองครับ
Infradian Rhythm คืออะไร? คำว่า Infradian มาจากรากศัพท์ละติน "infra" ที่แปลว่า "ต่ำกว่า" หรือ "ยาวกว่า" และ "diem" ที่แปลว่า "วัน" เพราะฉะนั้น Infradian จึงหมายถึงวงจรชีวภาพที่นานกว่าหนึ่งวัน เช่น - วัฏจักรรอบเดือนของผู้หญิง (ประมาณ 28 วัน) - จังหวะของระบบภูมิคุ้มกัน (ที่มีกลไกการตอบสนองขึ้นลงตามรอบ) - วัฏจักรการหลั่งฮอร์โมน เช่น testosterone ในผู้ชาย ที่ขึ้นลงเป็นรายสัปดาห์ - จังหวะของอารมณ์หรือพลังชีวิต ที่มี pattern ประจำสัปดาห์หรือเดือน
วงจรเหล่านี้ไม่ได้ใช้แค่เวลาบอกจังหวะ แต่ต้องการสิ่งกระตุ้น (zeitgeber) จากธรรมชาติ เช่น แสง เสียง อุณหภูมิ และโดยเฉพาะอย่างยิ่ง แสงแดด ผมลองรวบรวมสรุปเป็นหมวดๆให้เพื่อเห็นภาพรวมง่ายขึ้นนะครับ
หมวดที่ 1 แดดกับ Infradian Rhythm ของผู้หญิง สำหรับผู้หญิง แดดมีบทบาทโดยตรงกับรอบเดือนผ่านหลายกลไก เช่น 1.1 แสงแดดกับวิตามิน D วิตามิน D ที่สร้างจากแสง UVB มีผลต่อการควบคุมระดับฮอร์โมนเพศหญิง เช่น estrogen และ progesterone หากขาดแดด วงจรฮอร์โมนอาจรวน ทำให้มีอาการ PMS หนัก อารมณ์แกว่ง หรือรอบเดือนมาไม่ปกติ 1.2 แดดกับการหลั่ง melatonin แสงแดดยามเช้าช่วยหยุดการผลิต melatonin และเปิดการผลิต cortisol อย่างสมดุล ซึ่งเป็นกลไกสำคัญที่ควบคุมการสร้าง LH และ FSH (ฮอร์โมนที่ควบคุมการตกไข่) 1.3 Infrared light กับไมโทคอนเดรีย แดดบ่ายที่มีรังสีอินฟราเรดช่วยกระตุ้นพลังงานในระดับเซลล์ ซึ่งส่งผลต่อการซ่อมแซมและปรับสมดุลฮอร์โมนระยะยาว
หมวดที่ 2 แดดกับ Infradian Rhythm ของผู้ชาย แม้ผู้ชายจะไม่มีรอบเดือน แต่ก็มี Infradian เช่นกัน โดยเฉพาะในระบบฮอร์โมนและอารมณ์ครับ 2.1 Testosterone fluctuation แสงแดดช่วยกระตุ้นการหลั่ง testosterone โดยเฉพาะแสงแดดที่สัมผัสผิวหนังและดวงตา การได้รับแดดสม่ำเสมอช่วยให้ร่างกายเข้าสู่วงจรการผลิตฮอร์โมนที่เหมาะสม และไม่เหวี่ยงมาก 2.2 แดดกับการนอน แสงแดดยามเช้ารีเซ็ตวงจรการนอน ทำให้ testosterone หลั่งดีขึ้นในช่วงเช้ามืด (ซึ่งเป็นเวลาที่ร่างกายผลิตฮอร์โมนนี้มากที่สุด) 2.3 แดดกับการซ่อมแซมกล้ามเนื้อ รังสี Infrared และ Red light จากแดดบ่ายช่วยให้ไมโทคอนเดรียในกล้ามเนื้อทำงานดีขึ้น ซึ่งสอดคล้องกับรอบการฟื้นฟูแบบ Infradian ของกล้ามเนื้อหลังออกกำลังกาย
หมวดที่ 3 แดดกับ Infradian Rhythm ในผู้สูงอายุ เมื่ออายุมากขึ้น ร่างกายมักจะสูญเสียจังหวะธรรมชาติไปทีละน้อย ในหมวดนี้เลยแสดงถึงความสัมพันธ์ตามวัยครับ 3.1 ฮอร์โมนลดลง การตอบสนองต่อแสงก็ลดลง ผู้สูงวัยมักผลิต melatonin ลดลง ทำให้นอนไม่ลึกและส่งผลต่อระบบภูมิคุ้มกันที่มีจังหวะ Infradian 3.2 แสงแดดช่วยชะลอการเสื่อม งานวิจัยหลายชิ้นพบว่าแดดช่วยชะลอความเสื่อมของจังหวะชีวภาพในสมอง โดยช่วยลดภาวะซึมเศร้าและชะลอการเสื่อมของสมอง (เช่น Alzheimer) 3.3 ไนตริกออกไซด์ (NO) รังสี UVA จากแดดกระตุ้นการปล่อย NO จากผิวหนัง ซึ่งช่วยเรื่องความดันโลหิตและการไหลเวียนเลือดแบบรอบสัปดาห์ ส่งผลดีต่อหัวใจในระยะยาว
ดังนั้นเมื่อเอาทั้งหมดมาขมวดรวมกันจะพบว่า กลไกสำคัญที่แดดกระทบกับ Infradian Rhythm มีภาพร่างดังนี้ครับ 1.Vitamin D จาก UVB ช่วยสร้างสมดุลฮอร์โมน, สนับสนุนภูมิคุ้มกัน 2.Nitric Oxide (NO) จาก UVA ช่วยขยายหลอดเลือด, ลดการอักเสบเรื้อรัง 3.Melatonin และ Cortisol แดดยามเช้าควบคุมการตื่นและการนอนอย่างมีจังหวะ 4.Infrared Light ช่วงแดดบ่ายแก่ ช่วยซ่อมแซมเซลล์, สนับสนุนการฟื้นตัว 5.Circannual และ Infradian Crosslink แสงแดดฤดูต่าง ๆ (ที่มีช่วงคลื่นต่างกัน) ส่งผลให้จังหวะรอบเดือนและภูมิคุ้มกันเปลี่ยนไปตามฤดูกาล
ซึ่งถ้าอ่านแล้วบางอย่างดูยังสับสนว่าเอ๊ะมันควรจะเป็น circadian rhythm ไม่ใช่เหรอ เช่น การนอน คือมันสามารถอธิบายได้สั้นๆว่า มันมีการทับซ้อนกันครับ ที่เราแยกเป็นเรื่องนี้มาพูดคุยกันเพราะมันมีความสัมพันธ์กันอยู่ อย่างที่คุยกันเสมอๆว่า ร่างกายต้องมองเป็น spectrum ไม่ใช่ binary คอมพิวเตอร์ 011001
โดยตรงแล้ว Sleep–Wake Cycle เราคุมกันที่ Circadian กับ Homeostatic Drive มากกว่า แต่ Infradian ก็อาจส่งผลทางอ้อมผ่านทาง ฮอร์โมนเอสโตรเจนและโปรเจสเตอโรนขึ้น–ลงตามรอบเดือน ส่งผลต่อคุณภาพการนอน เช่น ช่วงใกล้มีประจำเดือนอาจนอนหลับไม่ลึก หรือช่วงวัยทอง (perimenopause) ที่ Infradian เริ่มเปลี่ยนฮอร์โมน จะมีอาการร้อนวูบวาบ ตื่นกลางดึกบ่อยขึ้น หรือแม้แต่ อาการซึมเศร้าตามฤดูกาล (Infradian รายปี) มักเกิดฤดูหนาว ซึ่งแสงน้อย ทำให้ Circadian ฟั่นเฟือนไปด้วย ทำให้นอนมากขึ้นหรือนอนไม่หลับตามฤดู แม้กระทั่งสัมพันธ์ทางพฤติกรรม งานวิจัยบางชิ้นชี้ว่ามนุษย์อาจมีแนวโน้มอยากนอนเพิ่มขึ้นในช่วงปลายสัปดาห์ (weekend catch-up sleep) ซึ่งเป็น Infradian รายสัปดาห์ที่เกิดจากพฤติกรรมสังคมและสะสม Homeostatic Drive
ทีนี้พอจะเข้าใจแล้วใช่ไหมครับว่า ทำไมเราควรเลิกถามเสียทีว่า "ตากแดดเวลาไหนดีที่สุด", "ตากแดดนานแค่ไหนดีที่สุด" จะให้ตอบยังไง? มันแงะออกมาไม่ได้ครับ เราอย่ายึดติดกับการสรุป สรุป สรุป สรุปสิว่าตกลงต้องยังไง การเสพโซเชียลทำให้เราเคยชินกับความฉาบฉวย คัดย่อ จนหลงลืมรายละเอียดว่า โลกแห่งชีวะคือความสัมพันธ์ พารายังไม่ได้แค่แก้ปวดเลย จะนับอะไรกับแดด
คำตอบที่ดีที่สุดผมคิดว่ามันคือ "เลิกถามจุ๊กจิ๊ก แล้วหัดออกไปตากให้ได้ก่อน เปิดตา เปิดหู ปิดปาก" จากนั้นค่อยเอาข้อสงสัยจากการตาก ข้อสงสัยจากการอ่าน มาประมวลผลเองก่อนว่า มีอะไรที่สามารถตอบกันได้บ้างไหม
อย่างที่เราเคยเปรียบเปรยกันครับ แดดไม่ใช่แค่แสง แต่คือผู้อำนวยเพลงที่ประสานเสียงร่างกายทุกจังหวะ ในขณะที่ไฟฟ้าทำให้เราลืมจังหวะธรรมชาติ แดดยังอยู่ตรงนั้น คอยเคาะจังหวะอย่างอดทน รอให้เรากลับมาได้ยินเสียงของตัวเองอีกครั้งหนึ่ง ไม่ใช่แค่เสียงในวันนี้ แต่คือเสียงของชีวิตในรอบเดือน หน้า และปีต่อไป
แดด…ไม่เคยหายไปจากเราเลย มีแต่เราที่ห่างหายไปจากแดดเสียเอง
ตากไปก่อนเหอะ แล้วค่อยถาม "บ่อยเท่าที่ได้ นานเท่าที่ไหว"
ส่วนใครอ่านบทนี้แล้วงง ไม่ต้องเครียดครับ บทต่อๆไปจะค่อยๆมาคลีคลายให้ ทีละนิด #pirateketo #SundaySpecialเราจะไปเป็นหมูแดดเดียว #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-
 @ 592295cf:413a0db9
2025-04-05 07:26:23
@ 592295cf:413a0db9
2025-04-05 07:26:23[Edit] I tried to get the slides and an audio file, from Constant's talk at NostRiga, about 8 months ago
1.
Nostr's adoption thesis
The less you define, the more you imply
by Wouter Constant
2.
Dutch Bitcoiner
AntiHashedPodcast
Writing Book about nostr
00:40
3.
What this presentation about
A protocols design includes initself a thesis
on protocol adoption, due to underlying assumptions
1:17
4.
Examples
Governments/Academic: Pubhubs (Matrix)
Bussiness: Bluesky
Foss: Nostr
1:58
5.
What constitutes minimal viability?
Pubhubs (Matrix): make is "safe" for user
Bluesky: liability and monetization
Foss: Simpel for developer
4:03
6.
The Point of Nostr
Capture network effects through interoperability
4:43
7.
Three assumptions
The direction is workable
Method is workable
Motivation and means are sufficient
5:27
8.
Assumption 1
The asymmetric cryptography paradigm is a good idea
6:16
9.
Nostr is a exponent of the key-pair paradigm.
And Basicly just that.
6.52
10.
Keys suck
Protect a secret that you are supposed use all the time.
7:37
11.
Assumption two
The unaddressed things will be figured out within a 'meta-design consensus'
8:11
12.
Nostr's base protocol is not minimally viable for anything, except own development.
8:25
13.
Complexity leads to capture;
i.e. free and open in the name,
controlled in pratice
9:54
14.
Meta-design consensus
Buildings things 'note centric' mantains interoperability.
11:51
15.
Assumption three
the nightmare is scary;
the cream is appealing.
12:41
16.
Get it minimally viable,
for whatever target,
such that it is not a waste of time.
13:23
17.
Summarize
We are in a nightmare.
Assume key/signature are the way out.
Assume we can Maintain an open stardand while manifesting the dream.
Assume we are motivated enought to bootstrap this to adulthood.
14:01
18.
We want this,
we can do this,
because we have to.
14:12
Thank you for contribuiting
[Edit] Note for audio presentation
nostr:nevent1qvzqqqqqqypzqkfzjh8jkzd8l9247sadku6vhm52snhgjtknlyeku6sfkeqn5rdeqyf8wumn8ghj7mn0wd68ytnvw5hxkef0qyg8wumn8ghj7mn0wd68ytnddakj7qpqqqq6fdnhvp95gqf4k3vxmljh87uvjezpepyt222jl2267q857uwqz7gcke
-
 @ afa31726:18cc7792
2025-04-27 05:05:15
@ afa31726:18cc7792
2025-04-27 05:05:1599Win mang đến cho người dùng một thế giới giải trí đa dạng, nơi mà công nghệ hiện đại kết hợp với sự sáng tạo không giới hạn để tạo nên những trải nghiệm tuyệt vời. Giao diện của 99Win được thiết kế trực quan, thân thiện với người dùng, hỗ trợ tối ưu trên mọi thiết bị từ máy tính đến điện thoại thông minh. Hệ thống nội dung tại 99Win luôn được cập nhật liên tục, mang đến cho người dùng những lựa chọn phong phú, từ giải trí nhẹ nhàng đến các trải nghiệm đòi hỏi sự tương tác cao. Công nghệ trí tuệ nhân tạo (AI) tại 99Win giúp cá nhân hóa nội dung, tự động đề xuất những trải nghiệm phù hợp nhất với thói quen và sở thích riêng của từng cá nhân. Bên cạnh đó, vấn đề bảo mật thông tin cá nhân được đặt lên hàng đầu với các hệ thống mã hóa tiên tiến, mang lại sự yên tâm tuyệt đối cho người dùng trong suốt quá trình trải nghiệm. 99Win không chỉ đơn thuần là một nền tảng giải trí mà còn là nơi khơi nguồn cảm hứng và kết nối cộng đồng, nơi mọi người cùng nhau chia sẻ niềm vui và sự hứng khởi mỗi ngày.
Ngoài việc cung cấp những trải nghiệm giải trí chất lượng, 99WIN còn không ngừng tổ chức các sự kiện hấp dẫn, chương trình ưu đãi và mini game vui nhộn, tạo ra không khí sôi động và cơ hội nhận được nhiều phần thưởng giá trị. Đội ngũ chăm sóc khách hàng chuyên nghiệp, hoạt động 24/7, luôn sẵn sàng hỗ trợ và giải quyết mọi thắc mắc, giúp người dùng cảm thấy được tôn trọng và phục vụ tận tâm. 99Win cũng đầu tư mạnh vào công nghệ thực tế ảo (VR) và thực tế tăng cường (AR), mở rộng phạm vi trải nghiệm và đưa người dùng đến những không gian giải trí hoàn toàn mới mẻ và sống động. Tốc độ tải trang nhanh, hệ thống vận hành ổn định cùng khả năng tùy chỉnh giao diện theo sở thích cá nhân là những điểm cộng giúp 99Win ghi dấu ấn mạnh mẽ trong lòng người dùng. Tất cả những yếu tố đó hội tụ để tạo nên một nền tảng giải trí toàn diện, luôn đổi mới và sáng tạo, hướng đến việc mang lại sự hài lòng cao nhất cho cộng đồng người dùng ngày càng lớn mạnh.
Hướng tới tương lai, 99Win đặt mục tiêu trở thành biểu tượng trong ngành công nghiệp giải trí kỹ thuật số, không chỉ tại Việt Nam mà còn vươn xa ra thị trường quốc tế. Với chiến lược phát triển bền vững, hợp tác cùng các đối tác công nghệ hàng đầu, 99Win cam kết liên tục cải tiến và cập nhật những xu hướng mới nhất để phục vụ người dùng tốt hơn mỗi ngày. Song song với việc mở rộng quy mô, 99Win cũng tích cực tham gia vào các hoạt động xã hội như hỗ trợ giáo dục, bảo vệ môi trường và phát triển cộng đồng. Tinh thần trách nhiệm xã hội luôn được lồng ghép trong mọi kế hoạch phát triển của 99Win, thể hiện cam kết không chỉ xây dựng một nền tảng giải trí tiên tiến mà còn góp phần tạo nên một tương lai tốt đẹp hơn cho toàn xã hội. Với nền tảng công nghệ vững chắc, đội ngũ nhân sự nhiệt huyết và tầm nhìn chiến lược dài hạn, 99Win hứa hẹn sẽ tiếp tục là điểm đến lý tưởng cho những ai tìm kiếm sự mới mẻ, sáng tạo và chất lượng trong thế giới giải trí hiện đại.
-
 @ afa31726:18cc7792
2025-04-27 05:04:26
@ afa31726:18cc7792
2025-04-27 05:04:26Hubet mang đến cho người dùng một không gian giải trí hiện đại, nơi công nghệ và sự sáng tạo hội tụ để tạo nên trải nghiệm mượt mà và đầy hấp dẫn. Với giao diện thân thiện, bố cục thông minh và khả năng tương thích hoàn hảo trên mọi thiết bị, Hubet giúp người dùng dễ dàng tiếp cận và tận hưởng những giây phút thư giãn tuyệt vời. Nội dung tại Hubet được tuyển chọn kỹ lưỡng, đa dạng và không ngừng cập nhật, đáp ứng nhu cầu giải trí phong phú của mọi đối tượng. Điểm nổi bật tại Hubet còn nằm ở việc tích hợp công nghệ AI tiên tiến, giúp cá nhân hóa trải nghiệm, đề xuất nội dung phù hợp theo thói quen và sở thích riêng của từng người dùng. An toàn và bảo mật luôn được đặt lên hàng đầu, với các lớp bảo vệ thông tin cá nhân và giao dịch tối ưu, tạo nên một môi trường giải trí đáng tin cậy. Hubet không chỉ đơn thuần là nơi giải trí, mà còn là nơi người dùng có thể tìm thấy sự kết nối, niềm vui và nguồn cảm hứng bất tận.
Để gia tăng trải nghiệm cho cộng đồng người dùng, HUBET liên tục tổ chức các chương trình khuyến mãi hấp dẫn, các sự kiện tương tác và minigame đầy sôi động, mang lại không khí sôi nổi và nhiều cơ hội nhận thưởng bất ngờ. Cộng đồng Hubet ngày càng phát triển mạnh mẽ nhờ sự chăm sóc tận tình từ đội ngũ hỗ trợ khách hàng hoạt động 24/7, luôn sẵn sàng giải đáp và hỗ trợ mọi yêu cầu. Ngoài ra, Hubet còn mạnh dạn đầu tư vào các công nghệ giải trí tiên tiến như thực tế ảo (VR) và thực tế tăng cường (AR), mang đến những trải nghiệm độc đáo, sống động và mới lạ. Các chiến dịch phát triển của Hubet luôn hướng tới việc đổi mới không ngừng, cải tiến sản phẩm, dịch vụ để phù hợp với nhu cầu ngày càng cao của người dùng. Mỗi chi tiết nhỏ, từ tốc độ tải trang nhanh chóng, giao diện trực quan đến khả năng tùy chỉnh trải nghiệm đều được chăm chút kỹ lưỡng nhằm đảm bảo sự hài lòng tối đa. Hubet cam kết trở thành một phần không thể thiếu trong hành trình giải trí hiện đại của người dùng.
Nhìn về tương lai, Hubet đặt mục tiêu mở rộng quy mô hoạt động ra thị trường quốc tế, mang trải nghiệm giải trí đỉnh cao của mình đến với đông đảo người dùng toàn cầu. Thông qua việc liên kết với các đối tác chiến lược và không ngừng áp dụng những xu hướng công nghệ mới, Hubet từng bước khẳng định vị thế là một nền tảng giải trí hàng đầu. Bên cạnh việc phát triển kinh doanh, Hubet cũng chú trọng đến trách nhiệm xã hội bằng cách tham gia vào các chương trình từ thiện, hỗ trợ giáo dục, và đóng góp cho cộng đồng. Những nỗ lực này thể hiện cam kết của Hubet trong việc xây dựng một cộng đồng phát triển bền vững, nơi công nghệ, sáng tạo và trách nhiệm xã hội song hành. Với chiến lược rõ ràng, đội ngũ tâm huyết và tinh thần đổi mới không ngừng, Hubet hứa hẹn sẽ tiếp tục mang đến những giá trị thiết thực, trải nghiệm khác biệt và những hành trình giải trí đầy cảm xúc cho người dùng trong và ngoài nước.
-
 @ 78b3c1ed:5033eea9
2025-04-27 01:48:48
@ 78b3c1ed:5033eea9
2025-04-27 01:48:48※スポットライトから移植した古い記事です。参考程度に。
これを参考にしてUmbrelのBitcoin Nodeをカスタムsignetノードにする。 以下メモ書きご容赦。備忘録程度に書き留めました。
メインネットとは共存できない。Bitcoinに依存する全てのアプリを削除しなければならない。よって実験機に導入すべき。
<手順>
1.Umbrel Bitcoin Nodeアプリのadvance settingでsignetを選択。
2.CLI appスクリプトでbitcoinを止める。
cd umbrel/scripts ./app stop bitcoin3.bitcoin.conf, umbrel-bitcoin.conf以外を削除ディレクトリの場所は ~/umbrel/app-data/bitcoin/data/bitcoin4.umbrel-bitcoin.confをsu権限で編集。末尾にsignetchallengeを追加。 ``` [signet] bind=0.0.0.0:8333 bind=10.21.21.8:8334=onion51,21,<公開鍵>,51,ae
signetchallenge=5121<公開鍵>51ae
5.appスクリプトでbitcoinを開始。cd ~/umbrel/scripts ./app start bitcoin ``` 6.適当にディレクトリを作りgithubからbitcoindのソースをクローン。7.bitcoindのバイナリをダウンロード、bitcoin-cliおよびbitcoin-utilを~/.local/binに置く。6.のソースからビルドしても良い。ビルド方法は自分で調べて。
8.bitcondにマイニング用のウォレットを作成 ``` alias bcli='docker exec -it bitcoin_bitcoind_1 bitcoin-cli -signet -rpcconnect=10.21.21.8 -rpcport=8332 -rpcuser=umbrel -rpcpassword=<パスワード>'
ウォレットを作る。
bcli createwallet "mining" false true "" false false
秘密鍵をインポート
bcli importprivkey "<秘密鍵>"
RPCパスワードは以下で確認cat ~/umbrel/.env | grep BITCOIN_RPC_PASS9.ソースにあるbitcoin/contrib/signet/minerスクリプトを使ってマイニングcd <ダウンロードしたディレクトリ>/bitcoin/contrib/signet難易度の算出
./miner \ --cli="bitcoin-cli -signet -rpcconnect=10.21.21.8 -rpcport=8332 -rpcuser=umbrel -rpcpassword=<パスワード>" calibrate \ --grind-cmd="bitcoin-util grind" --seconds 30 ★私の環境で30秒指定したら nbits=1d4271e7 と算出された。実際にこれで動かすと2分30になるけど...
ジェネシスブロック生成
./miner \ --cli="bitcoin-cli -signet -rpcconnect=10.21.21.8 -rpcport=8332 -rpcuser=umbrel -rpcpassword=<パスワード>" generate \ --address <ビットコインアドレス> \ --grind-cmd="bitcoin-util grind" --nbits=1d4271e7 \ --set-block-time=$(date +%s)
継続的にマイニング
./miner \ --cli="bitcoin-cli -signet -rpcconnect=10.21.21.8 -rpcport=8332 -rpcuser=umbrel -rpcpassword=<パスワード>" generate \ --address <ビットコインアドレス> \ --grind-cmd="bitcoin-util grind" --nbits=1d4271e7 \ --ongoing ``` ここまでやればカスタムsignetでビットコインノードが稼働する。
-
 @ afa31726:18cc7792
2025-04-27 05:03:43
@ afa31726:18cc7792
2025-04-27 05:03:43U88 mang đến một thế giới giải trí hiện đại, nơi người dùng có thể đắm chìm trong những trải nghiệm mượt mà, sáng tạo và đầy hứng khởi. Với thiết kế giao diện tối ưu hóa cho cả điện thoại và máy tính, U88 đảm bảo sự tiện lợi và dễ dàng trong từng thao tác. Kho nội dung tại U88 đa dạng, phong phú và luôn được cập nhật thường xuyên, đáp ứng mọi nhu cầu giải trí từ đơn giản đến cao cấp. Đặc biệt, U88 còn tích hợp nhiều tính năng công nghệ mới như trí tuệ nhân tạo (AI), giúp cá nhân hóa trải nghiệm người dùng, mang đến những gợi ý nội dung phù hợp nhất với sở thích riêng biệt của từng cá nhân. Đồng thời, hệ thống bảo mật tiên tiến giúp bảo vệ tối đa thông tin cá nhân và giao dịch, tạo dựng sự tin tưởng tuyệt đối từ cộng đồng người dùng. U88 không chỉ đơn thuần là một nền tảng giải trí, mà còn là nơi người dùng có thể tìm thấy niềm vui, sự thư giãn và cảm hứng trong từng khoảnh khắc.
Song song với việc phát triển nội dung giải trí chất lượng, U88 còn đặc biệt chú trọng đến việc xây dựng cộng đồng người dùng gắn kết. Các chương trình khuyến mãi hấp dẫn, sự kiện tương tác, minigame vui nhộn liên tục được tổ chức nhằm gia tăng sự kết nối và mang lại trải nghiệm phong phú hơn cho người dùng. Đội ngũ chăm sóc khách hàng của U88 hoạt động 24/7, luôn sẵn sàng hỗ trợ nhanh chóng và tận tình, đảm bảo mỗi thắc mắc hay yêu cầu đều được giải quyết một cách hiệu quả nhất. Ngoài ra, U88 không ngừng đầu tư vào công nghệ thực tế ảo (VR) và thực tế tăng cường (AR), mở rộng trải nghiệm giải trí sang những chân trời mới mẻ, sống động và lôi cuốn. Từng chi tiết nhỏ trong dịch vụ đều được U88 chăm chút, từ giao diện thân thiện, tốc độ tải nhanh, đến các tùy chọn cá nhân hóa linh hoạt, tất cả nhằm mục tiêu mang lại sự hài lòng tối đa cho người dùng trong suốt quá trình trải nghiệm.
Hướng tới tương lai, U88 đặt mục tiêu trở thành một biểu tượng trong ngành giải trí kỹ thuật số, không chỉ ở Việt Nam mà còn vươn ra thị trường quốc tế. Bằng cách hợp tác với các đối tác chiến lược và liên tục đổi mới công nghệ, U88 đang từng bước củng cố vị thế và mở rộng tầm ảnh hưởng của mình. Đồng thời, U88 cũng cam kết đồng hành cùng cộng đồng thông qua những hoạt động thiện nguyện thiết thực, thể hiện trách nhiệm xã hội của một doanh nghiệp hiện đại. Những sáng kiến về bảo vệ môi trường, hỗ trợ giáo dục, và phát triển công nghệ bền vững được U88 tích cực triển khai, góp phần xây dựng một tương lai tốt đẹp hơn. Với phương châm đặt người dùng làm trung tâm và không ngừng hoàn thiện từng ngày, U88 hứa hẹn sẽ tiếp tục mang đến những trải nghiệm giải trí đột phá, xứng đáng với kỳ vọng và sự tin yêu của cộng đồng người dùng trong nước và quốc tế.
-
 @ 78b3c1ed:5033eea9
2025-04-27 01:42:48
@ 78b3c1ed:5033eea9
2025-04-27 01:42:48・ThunderHubで焼いたマカロンがlncli printmacaroonでどう見えるか確認した。
ThunderHub macaroon permissions
get invoices invoices:read create invoices invoices:write get payments offchain:read pay invoices offchain:write get chain transactions onchain:read send to chain address onchain:write create chain address address:write get wallet info info:read stop daemon info:write この結果によれば、offchain:wirteとonchain:writeの権限がなければそのマカロンを使うクライアントは勝手にBTCを送金することができない。 info:writeがなければ勝手にLNDを止めたりすることができない。
・lncli printmacaroonでデフォルトで作られるmacaroonのpermissionsを調べてみた。 admin.macaroon
{ "version": 2, "location": "lnd", "root_key_id": "0", "permissions": [ "address:read", "address:write", "info:read", "info:write", "invoices:read", "invoices:write", "macaroon:generate", "macaroon:read", "macaroon:write", "message:read", "message:write", "offchain:read", "offchain:write", "onchain:read", "onchain:write", "peers:read", "peers:write", "signer:generate", "signer:read" ], "caveats": null }chainnotifier.macaroon{ "version": 2, "location": "lnd", "root_key_id": "0", "permissions": [ "onchain:read" ], "caveats": null }invoice.macaroon{ "version": 2, "location": "lnd", "root_key_id": "0", "permissions": [ "address:read", "address:write", "invoices:read", "invoices:write", "onchain:read" ], "caveats": null }invoices.macaroon{ "version": 2, "location": "lnd", "root_key_id": "0", "permissions": [ "invoices:read", "invoices:write" ], "caveats": null }readonly.macaroon{ "version": 2, "location": "lnd", "root_key_id": "0", "permissions": [ "address:read", "info:read", "invoices:read", "macaroon:read", "message:read", "offchain:read", "onchain:read", "peers:read", "signer:read" ], "caveats": null }router.macaroon{ "version": 2, "location": "lnd", "root_key_id": "0", "permissions": [ "offchain:read", "offchain:write" ], "caveats": null }signer.macaroon{ "version": 2, "location": "lnd", "root_key_id": "0", "permissions": [ "signer:generate", "signer:read" ], "caveats": null }walletkit.macaroon{ "version": 2, "location": "lnd", "root_key_id": "0", "permissions": [ "address:read", "address:write", "onchain:read", "onchain:write" ], "caveats": null }・lncli listpermissions コマンドですべての RPC メソッド URI と、それらを呼び出すために必要なマカロン権限を一覧表示できる。 LND v0.18.5-betaでやると1344行ほどのJSONができる。 AddInvoiceだとinvoice:writeのpermissionを持つmacaroonを使えばインボイスを作れるようだ。
"/lnrpc.Lightning/AddInvoice": { "permissions": [ { "entity": "invoices", "action": "write" } ] },lncli listpermissionsからentityとactionを抜き出してみた。 ``` "entity": "address", "entity": "info", "entity": "invoices", "entity": "macaroon", "entity": "message", "entity": "offchain", "entity": "onchain", "entity": "peers", "entity": "signer","action": "generate" "action": "read" "action": "write"
lncli とjqを組み合わせると例えば以下コマンドでinvoices:writeを必要とするRPCの一覧を表示できる。 invoices:writeだとAddInvoiceの他にホドルインボイス作成でも使ってるようだlncli listpermissions | jq -r '.method_permissions | to_entries[] | select(.value.permissions[] | select(.entity == "invoices" and .action == "write")) | .key'/invoicesrpc.Invoices/AddHoldInvoice /invoicesrpc.Invoices/CancelInvoice /invoicesrpc.Invoices/HtlcModifier /invoicesrpc.Invoices/LookupInvoiceV2 /invoicesrpc.Invoices/SettleInvoice /lnrpc.Lightning/AddInvoiceinvoices:readだと以下となる。/invoicesrpc.Invoices/SubscribeSingleInvoice /lnrpc.Lightning/ListInvoices /lnrpc.Lightning/LookupInvoice /lnrpc.Lightning/SubscribeInvoicesLNの主だった機能のRPCはoffchainが必要ぽいので抜き出してみた。 offchain:write チャネルの開閉、ペイメントの送信までやってるみたい。 デフォルトのmacaroonでoffchain:writeを持ってるのはadminとrouterの2つだけ。openchannel,closechannelはonchain:writeのpermissionも必要なようだ。/autopilotrpc.Autopilot/ModifyStatus /autopilotrpc.Autopilot/SetScores /lnrpc.Lightning/AbandonChannel /lnrpc.Lightning/BatchOpenChannel /lnrpc.Lightning/ChannelAcceptor /lnrpc.Lightning/CloseChannel /lnrpc.Lightning/DeleteAllPayments /lnrpc.Lightning/DeletePayment /lnrpc.Lightning/FundingStateStep /lnrpc.Lightning/OpenChannel /lnrpc.Lightning/OpenChannelSync /lnrpc.Lightning/RestoreChannelBackups /lnrpc.Lightning/SendCustomMessage /lnrpc.Lightning/SendPayment /lnrpc.Lightning/SendPaymentSync /lnrpc.Lightning/SendToRoute /lnrpc.Lightning/SendToRouteSync /lnrpc.Lightning/UpdateChannelPolicy /routerrpc.Router/HtlcInterceptor /routerrpc.Router/ResetMissionControl /routerrpc.Router/SendPayment /routerrpc.Router/SendPaymentV2 /routerrpc.Router/SendToRoute /routerrpc.Router/SendToRouteV2 /routerrpc.Router/SetMissionControlConfig /routerrpc.Router/UpdateChanStatus /routerrpc.Router/XAddLocalChanAliases /routerrpc.Router/XDeleteLocalChanAliases /routerrpc.Router/XImportMissionControl /wtclientrpc.WatchtowerClient/AddTower /wtclientrpc.WatchtowerClient/DeactivateTower /wtclientrpc.WatchtowerClient/RemoveTower /wtclientrpc.WatchtowerClient/TerminateSession"/lnrpc.Lightning/OpenChannel": { "permissions": [ { "entity": "onchain", "action": "write" }, { "entity": "offchain", "action": "write" } ] },offchain:read readの方はチャネルやインボイスの状態を確認するためのpermissionのようだ。/lnrpc.Lightning/ChannelBalance /lnrpc.Lightning/ClosedChannels /lnrpc.Lightning/DecodePayReq /lnrpc.Lightning/ExportAllChannelBackups /lnrpc.Lightning/ExportChannelBackup /lnrpc.Lightning/FeeReport /lnrpc.Lightning/ForwardingHistory /lnrpc.Lightning/GetDebugInfo /lnrpc.Lightning/ListAliases /lnrpc.Lightning/ListChannels /lnrpc.Lightning/ListPayments /lnrpc.Lightning/LookupHtlcResolution /lnrpc.Lightning/PendingChannels /lnrpc.Lightning/SubscribeChannelBackups /lnrpc.Lightning/SubscribeChannelEvents /lnrpc.Lightning/SubscribeCustomMessages /lnrpc.Lightning/VerifyChanBackup /routerrpc.Router/BuildRoute /routerrpc.Router/EstimateRouteFee /routerrpc.Router/GetMissionControlConfig /routerrpc.Router/QueryMissionControl /routerrpc.Router/QueryProbability /routerrpc.Router/SubscribeHtlcEvents /routerrpc.Router/TrackPayment /routerrpc.Router/TrackPaymentV2 /routerrpc.Router/TrackPayments /wtclientrpc.WatchtowerClient/GetTowerInfo /wtclientrpc.WatchtowerClient/ListTowers /wtclientrpc.WatchtowerClient/Policy /wtclientrpc.WatchtowerClient/Stats・おまけ1 RPCメソッド名にopenを含む要素を抽出するコマンドlncli listpermissions | jq '.method_permissions | to_entries[] | select(.key | test("open"; "i"))'{ "key": "/lnrpc.Lightning/BatchOpenChannel", "value": { "permissions": [ { "entity": "onchain", "action": "write" }, { "entity": "offchain", "action": "write" } ] } } { "key": "/lnrpc.Lightning/OpenChannel", "value": { "permissions": [ { "entity": "onchain", "action": "write" }, { "entity": "offchain", "action": "write" } ] } } { "key": "/lnrpc.Lightning/OpenChannelSync", "value": { "permissions": [ { "entity": "onchain", "action": "write" }, { "entity": "offchain", "action": "write" } ] } }・おまけ2 thunderhubで作ったmacaroonはテキストで出力されコピペして使うもので、macaroonファイルになってない。 HEXをmacaroonファイルにするには以下コマンドでできる。HEXをコピペして置換する。またYOURSの箇所を自分でわかりやすい名称に置換すると良い。echo -n "HEX" | xxd -r -p > YOURS.macaroonthunderhubで"Create Invoices, Get Invoices, Get Wallet Info, Get Payments, Pay Invoices"をチェックして作ったmacaroonのpermissionsは以下となる。{ "version": 2, "location": "lnd", "root_key_id": "0", "permissions": [ "info:read", "invoices:read", "invoices:write", "offchain:read", "offchain:write" ], "caveats": null } ``` offchain:writeはあるがonchain:writeがないのでチャネル開閉はできないはず。 -
 @ fed76236:9d101c9c
2025-04-27 04:12:00
@ fed76236:9d101c9c
2025-04-27 04:12:00O 6GBet vem se consolidando como uma das principais plataformas de entretenimento online para quem busca diversão, variedade e uma experiência segura e moderna. Com um ambiente desenvolvido para oferecer a melhor experiência ao usuário, o 6GBet combina tecnologia de ponta, atendimento de qualidade e uma seleção impressionante de jogos que conquistam cada vez mais jogadores no Brasil.
Desde o primeiro acesso, é possível perceber que o 6GBet se preocupa com a segurança de seus usuários. A plataforma utiliza sistemas de criptografia avançados, garantindo que todas as informações pessoais e financeiras estejam protegidas. Além disso, o site é licenciado e regulamentado, proporcionando mais confiança para aqueles que desejam jogar com tranquilidade.
Outro destaque é o suporte ao cliente. A equipe de atendimento do 6gbet está disponível 24 horas por dia, sete dias por semana, pronta para ajudar em qualquer situação. Seja para tirar dúvidas sobre o funcionamento do site, resolver problemas técnicos ou orientar sobre métodos de pagamento, o suporte é rápido e eficiente.
Diversidade de Jogos para Todos os Gostos No 6GBet, a diversão é levada a sério. A plataforma oferece uma vasta seleção de jogos, capazes de agradar tanto jogadores iniciantes quanto os mais experientes. Entre os principais destaques estão:
Slots Online: Uma coleção variada de slots modernos e clássicos, com diferentes temas, bônus e jackpots progressivos. Cada giro é uma nova oportunidade de viver emoções únicas.
Jogos de Mesa: Para os fãs de estratégia, o 6GBet oferece versões eletrônicas de jogos tradicionais como blackjack, roleta e pôquer. Com gráficos realistas e mecânicas dinâmicas, a sensação é de estar em uma verdadeira sala de jogos.
Ao Vivo: Para quem gosta de interatividade, o 6GBet disponibiliza opções de jogos com crupiês reais transmitidos em tempo real. Essa modalidade proporciona uma experiência ainda mais imersiva, perfeita para quem busca emoção e realismo.
Apostas Esportivas: Além dos jogos de entretenimento, o 6GBet também permite que os usuários apostem em eventos esportivos. Futebol, basquete, tênis e vários outros esportes estão disponíveis, com odds competitivas e uma cobertura completa de campeonatos nacionais e internacionais.
Experiência de Jogador Pensada nos Detalhes Um dos grandes diferenciais do 6GBet é a atenção aos detalhes na experiência do usuário. A navegação é simples e intuitiva, facilitando o acesso a todas as categorias de jogos e serviços. O design responsivo garante que a plataforma funcione perfeitamente em computadores, tablets e smartphones, sem perda de qualidade.
Além disso, o 6GBet disponibiliza diversos métodos de depósito e saque, tornando as transações rápidas e descomplicadas. Pix, transferências bancárias e carteiras digitais estão entre as opções, permitindo que o jogador escolha a melhor alternativa para seu perfil.
As promoções e bônus também merecem destaque. Novos usuários são recebidos com ofertas atrativas, enquanto jogadores frequentes têm acesso a promoções exclusivas e programas de fidelidade que tornam a jornada ainda mais vantajosa.
Conclusão O 6GBet é a escolha certa para quem procura uma plataforma completa de jogos online. Segurança, variedade de opções, suporte eficiente e uma experiência de usuário impecável fazem do 6GBet uma referência no mercado brasileiro. Se você busca emoção, praticidade e inovação em um só lugar, o 6GBet é o destino perfeito. Prepare-se para viver momentos inesquecíveis!
-
 @ 5d4b6c8d:8a1c1ee3
2025-04-27 00:55:29
@ 5d4b6c8d:8a1c1ee3
2025-04-27 00:55:29After taking the most predictable option on day 1, the last 6 rounds of the draft were a rollercoaster. The Raiders traded back twice in the 2nd round and ended up with some extra picks.
Picks
-
RB Ashton Jeanty: Best player available at a position of need. Jeanty + Bowers gives the Raiders offense two elite weapons
-
WR Jack Bech: Tough, physical receiver with great hands, willing and able blocker
-
CB Darien Porter: Elite athlete, classic Raiders pick, "Can't teach size, can't teach speed."
-
OL Caleb Rogers: Versatile, athletic lineman, will likely compete at guard
-
OL Charles Grant: Same as above, but more likely to compete at tackle
-
WR: Donte Thornton: 6'5" and 4.3 speed, another classic Raiders pick, can open the field for the other weapons
-
DT Tonka Hemingway: Dope name, versatile and athletic D-Lineman, adds depth and optionality to a very talented groups
-
DT/TE/FB JJ Pegues: Interesting guy, probably won't contribute much as a DT immediately, but could be part of the goal line package on offense, as he had 7 rushing TDs last year and as a former TE could be a red zone target too
-
WR/KR/PR/QB Tommy Mellot: Another super versatile player, ran a 4.4 40 as a QB, but will convert to WR and return kicks, seems like someone with tons of trick play potential
-
QB Cam Miller: Finally, an actual QB! Won a ton of games at a smaller program.
-
LB Cody Lindenberg: 7th rounder, probably special teams if he makes the team
Takeaways
The Raiders added a ton of talent and versatility to their offense, including a defensive player who can contribute to the red zone offense in several ways. They're building a big physically dominant offense around an elite RB/TE combo, with big physical WRs who don't mind blocking and another talented TE.
The defensive line is going to have to be really dominant, which they have the potential for, because there is a dearth of talent behind them. Porter recently converted to CB from WR, so will likely take time to develop, and the others are day 3 picks.
The recipe will likely be to eat up clock on long offensive drives to give our pass rushers lots of breathers. Score reliably with a much improved redzone offense and a great kicker, then rely on that pass rush and the best punter in the league to keep the other team out of the endzone.
It's a good starting point. Maybe they'll sign Ramsey, or something, and really upgrade the defensive back group before the season starts.
originally posted at https://stacker.news/items/962047
-
-
 @ c066aac5:6a41a034
2025-04-27 00:35:38
@ c066aac5:6a41a034
2025-04-27 00:35:38I work in the business world as a salesperson. I am frequently out and about in the community trying to make friends, connect with people who I can help, and ultimately grow my book of business. I have goals set by my employers and I aim to meet those expectations. Because of this, I find myself frequently under pressure to find ways to produce. This often leads to me being disappointed in myself; my sales cycles are long and I lose more deals than I win. My Dad often reminds me that How to Win Friends and Influence People has all the secrets of sales I'll ever need, but I still end up wishing I could find that secret edge to out-do the competition. That's where the watch temptation comes in.
I frequently see a luxurious timepiece on the left wrist of my peers and elder-statesmen closers. Rolex, Omega, Patek, a whole world of $10k minimum machines. It comes across as a power-move, a symbol of status that is hard to ignore. It sends a message that the bearer's time is more valuable than that of other people. It makes me think "if this person is wearing that watch, that means they're great at what they do." The ultimate investment in one's self.
As a newly married man expecting a child, it is hard for me to stomach such a purchase. My wife has supported the idea of me potentially getting such a timepiece; as much as it tickles my fancy, I'd rather put my capital towards things that further my family than my clout. One of the things that struck me was a statement made by an investment advisor in my Kiwanis club: "A watch is a purchase, not an investment."
What a true statement! His words helped me escape my short-lived delusions. That said, I still look at watches sometimes on the internet (The Omega No Time to Die watch is sleek looking). One day, I found myself looking at houses online shortly after looking at watches online. Then it hit me: how many purchases are being marketed as investments in this era? A Rolex is a supposed investment in your career, not just a luxury timepiece. A house is a mechanism for monetary growth, not an attainable home to be enjoyed by a family. A college degree is an investment for your future, not a vehicle for building upon passions.
The Bitcoiners will repeat the phrase "fix the money, fix the world" in harmonious chorus to address the concern I have laid out in this article. Ultimately, I leave you with this reminder: don't let the world pass off things that should be inconsequential purchases as investments with ROIs. I believe the only true investment one can make is into the people around them; that will yield the greatest rewards for the soul.
-
 @ 6e64b83c:94102ee8
2025-04-26 23:33:16
@ 6e64b83c:94102ee8
2025-04-26 23:33:16- Demo: https://blog.nostrize.me
- Source code: nostr-static
Prerequisites
Before using nostr-static, you'll need:
- Nostr Articles: You can either:
- Create new articles using platforms like yakihonne.com or habla.news
- Find existing articles on Nostr
-
Copy the naddr string from the article (usually can be found in the address bar)
-
Author Profiles: For each article's author:
- Copy their public key (pubkey)
- Visit njump.me/npub1xxxxx (replace with the actual pubkey)
- Copy the nprofile string from the page
These identifiers (naddr for articles and nprofile for authors) are essential for the tool to fetch and display your content correctly.
Features
Core Functionality
- Index Page: A homepage featuring your blog's title, logo, article summaries, and tags
- Article Pages: Individual pages for each article, including:
- Title and logo
- Article summary
- Full content
- Tags
- Comments (via ZapThreads integration)
Social Features
- Comments: Integrated with ZapThreads for decentralized commenting
- Nostr Connect: Seamless integration with window.nostr.js (wnj), supporting NIP-46 bunker connect
Content Organization
- Tag Pages: Browse articles filtered by specific tags
- Profile Pages: View articles from specific authors
- Manual Curation: Select and order articles by adding their naddr strings (see NIP-19)
Customization Options
- Themes: Choose between dark and light mode
- Branding:
- Custom logo
- Custom blog title
- Network: Specify your preferred Nostr relays
Technical Requirements
- Profile Format: Authors must be added in nprofile format (see NIP-19) for consistency
- Automatic Updates: Built-in scripts for:
- Windows Task Scheduler
- Unix/Linux cron jobs
Getting Started
- Fork and Clone:
- Fork this repository to your GitHub account
- Clone it to your local machine or use GitHub Codespaces for a cloud-based development environment
-
Watch this quick tutorial to learn more about GitHub Codespaces
-
Configuration: Set up your
config.yamlfile with: - Blog title and logo
- Theme preference
- Relay list
- Article naddr strings
-
Author nprofile strings
-
Content Selection: Add your desired articles by including their naddr strings in the configuration
-
Author Selection: You have to add the nprofile strings of the articles. This is needed for URL consistancy.
-
Build & Run: Follow the instruction in the README at https://github.com/dhalsim/nostr-static
-
Deployment: Choose your preferred static hosting service and deploy the generated HTML files
-
Updates: Set up automatic updates using the provided scripts for your operating system (For github pages)
Deployment Options
GitHub Pages (Recommended)
GitHub Pages provides free hosting for static websites. Here's how to set it up:
- Enable GitHub Pages:
- Go to your repository's Settings
- Navigate to "Pages" in the menu
- Under "Build and deployment" > "Source", select "GitHub Actions"
- Enable Actions by following the GitHub Actions settings guide
-
Go to the "Actions" tab in the top menu. If you see the message "Workflows aren't being run on this forked repository", click the "I understand my workflows, go ahead and enable them" button
-
Custom Domain Setup:
- Purchase a domain from your preferred domain registrar
- Create a CNAME record in your domain's DNS settings:
- Type: CNAME
- Name: @ or www or a subdomain you prefer (depending on your preference)
- Value: YOUR_GITHUB_USERNAME.github.io
- In your repository's GitHub Pages settings:
- Enter your custom domain in the "Custom domain" field
- Check "Enforce HTTPS" for secure connections
- Wait for DNS propagation (can take up to 24 hours)
- Your site will be available at your custom domain
Other Hosting Options
You can also deploy your static site to any hosting service that supports static websites, such as: - Netlify - Vercel - Cloudflare Pages - Amazon S3 - Any traditional web hosting service
Why nostr-static?
nostr-static offers a unique solution for bloggers who want to leverage Nostr's decentralized content while maintaining a traditional web presence. It combines the best of both worlds:
- Decentralized Content: Your articles live on the Nostr network
- Traditional Web Presence: A familiar blog interface for your readers
- Easy Maintenance: Simple configuration and automatic updates
- Flexible Hosting: Deploy anywhere that supports static websites
- Social interactions: Leverage nostr for comments
Conclusion
nostr-static makes it easy to create a professional blog from your Nostr long-form content. Whether you're a seasoned Nostr user or new to the ecosystem, this tool provides a straightforward way to share your content with both the Nostr community and traditional web users.
Start your Nostr-powered blog today by visiting the demo and exploring the possibilities!
-
 @ fed76236:9d101c9c
2025-04-27 04:11:19
@ fed76236:9d101c9c
2025-04-27 04:11:19Em um cenário cada vez mais competitivo de plataformas de jogos online, a 898Bet se destaca como uma das principais escolhas para jogadores brasileiros que buscam emoção, variedade e segurança em suas experiências de entretenimento. Com um ambiente moderno, acessível e repleto de opções, a 898Bet vem conquistando o público com seus diferenciais únicos.
Conheça a Plataforma 898Bet A 898Bet é muito mais do que apenas um espaço de apostas online. A plataforma foi desenvolvida com foco total no usuário, oferecendo navegação intuitiva, visual atraente e recursos que facilitam a vida de quem busca diversão com praticidade. Seja pelo site oficial ou pelo aplicativo mobile, a experiência é fluida e adaptada para qualquer dispositivo, permitindo que você jogue onde e quando quiser.
Além disso, a 898bet valoriza a segurança de seus usuários. Com tecnologia de criptografia de última geração e processos de verificação rigorosos, a plataforma garante a proteção de dados pessoais e financeiros, oferecendo tranquilidade para que os jogadores possam se concentrar apenas no que realmente importa: a diversão.
Variedade de Jogos Para Todos os Perfis Um dos grandes atrativos da 898Bet é a impressionante variedade de jogos disponíveis. A plataforma reúne títulos de alta qualidade, desenvolvidos por provedores renomados no mercado internacional. São opções para todos os gostos e estilos, desde clássicos amados por veteranos até lançamentos modernos que trazem novas mecânicas e gráficos impressionantes.
Entre as categorias mais populares, destacam-se as roletas ao vivo, jogos de cartas como blackjack e baccarat, além de uma seleção de slots online com temas diversos, bônus especiais e jackpots que podem transformar uma rodada em uma grande vitória. Há também opções de jogos instantâneos para quem busca diversão rápida e dinâmica.
Para os fãs de esportes, a 898Bet oferece uma seção completa de apostas esportivas, cobrindo eventos nacionais e internacionais. Futebol, basquete, tênis, MMA e muitos outros esportes fazem parte do catálogo, com cotações competitivas e diversas modalidades de apostas.
Uma Experiência de Jogador Inesquecível A 898Bet entende que a experiência do jogador vai muito além da variedade de jogos. Por isso, investe em um atendimento ao cliente ágil e eficiente, disponível 24 horas por dia, 7 dias por semana. Seja para resolver dúvidas, questões técnicas ou apoio geral, a equipe de suporte está sempre pronta para ajudar, garantindo a satisfação do usuário.
Outro destaque é o sistema de bônus e promoções exclusivas, que valoriza tanto novos usuários quanto jogadores mais antigos. Ofertas de boas-vindas, bônus de recarga, programas de fidelidade e torneios temáticos tornam a jornada dentro da plataforma ainda mais emocionante e recompensadora.
As opções de pagamento também são pensadas para o público brasileiro, com suporte para métodos locais como Pix, boleto bancário e transferências via bancos nacionais, além de carteiras digitais populares. Tudo isso contribui para uma experiência de uso prática, rápida e segura.
Conclusão Se você está em busca de uma plataforma confiável, moderna e repleta de oportunidades para se divertir e ganhar prêmios, a 898Bet é a escolha certa. Com uma combinação perfeita entre tecnologia, variedade de jogos e atenção ao jogador, a 898Bet chega para redefinir o entretenimento online no Brasil. Cadastre-se hoje mesmo e descubra um mundo de possibilidades!
-
 @ 418a17eb:b64b2b3a
2025-04-26 21:45:33
@ 418a17eb:b64b2b3a
2025-04-26 21:45:33In today’s world, many people chase after money. We often think that wealth equals success and happiness. But if we look closer, we see that money is just a tool. The real goal is freedom.
Money helps us access resources and experiences. It can open doors. But the constant pursuit of wealth can trap us. We may find ourselves stressed, competing with others, and feeling unfulfilled. The more we chase money, the more we might lose sight of what truly matters.
Freedom, on the other hand, is about choice. It’s the ability to live life on our own terms. When we prioritize freedom, we can follow our passions and build meaningful relationships. We can spend our time on what we love, rather than being tied down by financial worries.
True fulfillment comes from this freedom. It allows us to define success for ourselves. When we embrace freedom, we become more resilient and creative. We connect more deeply with ourselves and others. This sense of purpose often brings more happiness than money ever could.
In the end, money isn’t the ultimate goal. It’s freedom that truly matters. By focusing on living authentically and making choices that resonate with us, we can create a life filled with meaning and joy.
-
 @ 5ffb8e1b:255b6735
2025-03-29 13:57:02
@ 5ffb8e1b:255b6735
2025-03-29 13:57:02As a fellow Nostrich you might have noticed some of my #arlist posts. It is my effort to curate artists that are active on Nostr and make it easier for other users to find content that they are interested in.
By now I have posted six or seven posts mentioning close to fifty artists, the problem so far is that it's only a list of handles and it is up to reader to click on each in order to find out what are the artist behind the names all about. Now I am going to start creating blog posts with a few artists mentioned in each, with short descriptions of their work and an image or to.
I would love to have some more automated mode of curation but I still couldn't figure out what is a good way for it. I've looked at Listr, Primal custom feeds and Yakihonne curations but none seem to enable me to make a list of npubs that is then turned into a feed that I could publicly share for others to views. Any advice on how to achieve this is VERY welcome !
And now lets get to the first batch of artists I want to share with you.
Eugene Gorbachenko
nostr:npub1082uhnrnxu7v0gesfl78uzj3r89a8ds2gj3dvuvjnw5qlz4a7udqwrqdnd Artist from Ukrain creating amazing realistic watercolor paintings. He is very active on Nostr but is very unnoticed for some stange reason. Make sure to repost the painting that you liked the most to help other Nostr users to discover his great art.
Siritravelsketch
nostr:npub14lqzjhfvdc9psgxzznq8xys8pfq8p4fqsvtr6llyzraq90u9m8fqevhssu a a lovely lady from Thailand making architecture from all around the world spring alive in her ink skethes. Dynamic lines gives it a dreamy magical feel, sometimes supported by soft watercolor strokes takes you to a ferytale layer of reality.
BureuGewas
nostr:npub1k78qzy2s9ap4klshnu9tcmmcnr3msvvaeza94epsgptr7jce6p9sa2ggp4 a a master of the clasic oil painting. From traditional still life to modern day subjects his paintings makes you feel the textures and light of the scene more intense then reality itself.
You can see that I'm no art critic, but I am trying my best. If anyone else is interested to join me in this curration adventure feel free to reach out !
With love, Agi Choote
-
 @ 592295cf:413a0db9
2025-03-29 10:59:52
@ 592295cf:413a0db9
2025-03-29 10:59:52The journey starts from the links in this article nostr-quick-start-guide
Starting from these links building a simple path should not cover everything, because impossible.
Today I saw that Verbiricha in his workshop on his channel used nstart, but then I distracted And I didn't see how he did it.
Go to nstart.me and read: Each user is identified by a cryptographic keypair Public key, Private key (is a lot of stuff)
You can insert a nickname and go, the nickname is not unique
there is a email backup things interesting, but a little boring, i try to generate an email
doesn't even require a strong password ok.
I received the email, great, it shows me the nsec encrypted in clear,
Send a copy of the file with a password, which contains the password encrypted key I know and I know it's a tongue dump.
Multi signer bunker
That's stuff, let's see what he says.
They live the private key and send it to servers and you can recompose it to login at a site of the protocol nostr. If one of these servers goes offline you have the private key that you downloaded first and then reactivate a bunker. All very complicated. But if one of the servers goes offline, how can I remake the split? Maybe he's still testing.
Nobody tells you where these bunkers are.
Okay I have a string that is my bunker (buker://), I downloaded it, easy no, now will tell me which client accepts the bunker.. .
Follow someone before you start?
Is a cluster of 5 people Snowden, Micheal Dilger, jb55, Fiatjaf, Dianele.
I choice Snowden profile, or you can select multiple profiles, extra wild.
Now select 5 clients
Coracle, Chachi, Olas, Nostur, Jumble
The first is Coracle
Login, ok I try to post a note and signing your note the spin does not end.
Maybe the bunker is diffective.
Let's try Chachi
Simpler than Coracle, it has a type login that says bunker. see if I can post
It worked, cool, I managed to post in a group.
Olas is an app but also a website, but on the website requires an extension, which I do not have with this account.
If I download an app how do I pass the bunker on the phone, is it still a password, a qrcode, a qrcode + password, something like that, but many start from the phone so maybe it's easy for them. I try to download it and see if it allows me to connect with a bunker.
Okay I used private-qrcode and it worked, I couldn't do it directly from Olas because it didn't have permissions and the qrcode was < encrypted, so I went to the same site and had the bunker copied and glued on Olas
Ok then I saw that there was the qrcode image of the bunker for apps lol moment
Ok, I liked it, I can say it's a victory.
Looks like none of Snowden's followers are Olas's lover, maybe the smart pack has to predict a photographer or something like that.
Okay I managed to post on Olas, so it works, Expiration time is broken.
As for Nostur, I don't have an ios device so I'm going to another one.
Login with Jumble, it works is a web app
I took almost an hour to do the whole route.
But this was just one link there are two more
Extensions nostr NIP-07
The true path is nip-07-browser-extensions | nostr.net
There are 19 links, maybe there are too many?
I mention the most famous, or active at the moment
- Aka-profiles: Aka-profiles
Alby I don't know if it's a route to recommend
-
Blockcore Blockcore wallet
-
Nos2x Nos2x
-
Nos2xfox (fork for firefox) Nos2xfox
Nostore is (archived, read-only)
Another half hour to search all sites
Nostrapps
Here you can make paths
Then nstart selects Coracle, Chachi, Olas,Nostur and Jumble
Good apps might be Amethyst, 0xchat, Yakihonne, Primal, Damus
for IOS maybe: Primal, Olas, Damus, Nostur, Nos-Social, Nostrmo
On the site there are some categories, I select some with the respective apps
Let's see the categories
Go to Nostrapps and read:
Microbbloging: Primal
Streaming: Zap stream
Blogging: Yakihonne
Group chat: Chachi
Community: Flotilla
Tools: Form *
Discovery: Zapstore (even if it is not in this catrgory)
Direct Message: 0xchat
-
 @ 1f79058c:eb86e1cb
2025-04-26 21:17:17
@ 1f79058c:eb86e1cb
2025-04-26 21:17:17I think we should agree on an HTML element for pointing to the Nostr representation of a document/URL on the Web. We could use the existing one for link relations for example:
html <link rel="alternate" type="application/nostr+json" href="nostr:naddr1qvzqqqr4..." title="This article on Nostr" />This would be useful in multiple ways:
- Nostr clients, when fetching meta/preview information for a URL that is linked in a note, can detect that there's a Nostr representation of the content, and then render it in Nostr-native ways (whatever that may be depending on the client)
- User agents, usually a browser or browser extension, when opening a URL on the Web, can offer opening the alternative representation of a page in a Nostr client. And/or they could offer to follow the author's pubkey on Nostr. And/or they could offer to zap the content.
- When publishing a new article, authors can share their preferred Web URL everywhere, without having to consider if the reader knows about or uses Nostr at all. However, if a Nostr user finds the Web version of an article outside of Nostr, they can now easily jump to the Nostr version of it.
- Existing Web publications can retroactively create Nostr versions of their content and easily link the Nostr articles on all of their existing article pages without having to add prominent Nostr links everywhere.
There are probably more use cases, like Nostr search engines and whatnot. If you can think of something interesting, please tell me.
Update: I came up with another interesting use case, which is adding alternate links to RSS and Atom feeds.
Proof of concept
In order to show one way in which this could be used, I have created a small Web Extension called Nostr Links, which will discover alternate Nostr links on the pages you visit.
If it finds one or more links, it will show a purple Nostr icon in the address bar, which you can click to open the list of links. It's similar to e.g. the Feed Preview extension, and also to what the Tor Browser does when it discovers an Onion-Location for the page you're looking at:
The links in this popup menu will be
web+nostr:links, because browsers currently do not allow web apps or extensions to handle unprefixednostr:links. (I hope someone is working on getting those on par withipfs:etc.)Following such a link will either open your default Nostr Web app, if you have already configured one, or it will ask you which Web app to open the link with.
Caveat emptor: At the time of writing, my personal default Web app, noStrudel, needs a new release for the links to find the content.
Try it now
Have a look at the source code and/or download the extension (currently only for Firefox).
I have added alternate Nostr links to the Web pages of profiles and long-form content on the Kosmos relay's domain. It's probably the only place on the Web, which will trigger the extension right now.
You can look at this very post to find an alternate link for example.
Update: A certain fiatjaf has added the element to his personal website, which is built entirely from Nostr articles. Multiple other devs also expressed their intent to implement.
-
 @ 04c915da:3dfbecc9
2025-03-26 20:54:33
@ 04c915da:3dfbecc9
2025-03-26 20:54:33Capitalism is the most effective system for scaling innovation. The pursuit of profit is an incredibly powerful human incentive. Most major improvements to human society and quality of life have resulted from this base incentive. Market competition often results in the best outcomes for all.
That said, some projects can never be monetized. They are open in nature and a business model would centralize control. Open protocols like bitcoin and nostr are not owned by anyone and if they were it would destroy the key value propositions they provide. No single entity can or should control their use. Anyone can build on them without permission.
As a result, open protocols must depend on donation based grant funding from the people and organizations that rely on them. This model works but it is slow and uncertain, a grind where sustainability is never fully reached but rather constantly sought. As someone who has been incredibly active in the open source grant funding space, I do not think people truly appreciate how difficult it is to raise charitable money and deploy it efficiently.
Projects that can be monetized should be. Profitability is a super power. When a business can generate revenue, it taps into a self sustaining cycle. Profit fuels growth and development while providing projects independence and agency. This flywheel effect is why companies like Google, Amazon, and Apple have scaled to global dominance. The profit incentive aligns human effort with efficiency. Businesses must innovate, cut waste, and deliver value to survive.
Contrast this with non monetized projects. Without profit, they lean on external support, which can dry up or shift with donor priorities. A profit driven model, on the other hand, is inherently leaner and more adaptable. It is not charity but survival. When survival is tied to delivering what people want, scale follows naturally.
The real magic happens when profitable, sustainable businesses are built on top of open protocols and software. Consider the many startups building on open source software stacks, such as Start9, Mempool, and Primal, offering premium services on top of the open source software they build out and maintain. Think of companies like Block or Strike, which leverage bitcoin’s open protocol to offer their services on top. These businesses amplify the open software and protocols they build on, driving adoption and improvement at a pace donations alone could never match.
When you combine open software and protocols with profit driven business the result are lean, sustainable companies that grow faster and serve more people than either could alone. Bitcoin’s network, for instance, benefits from businesses that profit off its existence, while nostr will expand as developers monetize apps built on the protocol.
Capitalism scales best because competition results in efficiency. Donation funded protocols and software lay the groundwork, while market driven businesses build on top. The profit incentive acts as a filter, ensuring resources flow to what works, while open systems keep the playing field accessible, empowering users and builders. Together, they create a flywheel of innovation, growth, and global benefit.
-
 @ 2dd9250b:6e928072
2025-03-22 00:22:40
@ 2dd9250b:6e928072
2025-03-22 00:22:40Vi recentemente um post onde a pessoa diz que aquele final do filme O Doutrinador (2019) não faz sentido porque mesmo o protagonista explodindo o Palácio dos Três Poderes, não acaba com a corrupção no Brasil.
Progressistas não sabem ler e não conseguem interpretar textos corretamente. O final de Doutrinador não tem a ver com isso, tem a ver com a relação entre o Herói e a sua Cidade.
Nas histórias em quadrinhos há uma ligação entre a cidade e o Super-Herói. Gotham City por exemplo, cria o Batman. Isso é mostrado em The Batman (2022) e em Batman: Cavaleiro das Trevas, quando aquele garoto no final, diz para o Batman não fugir, porque ele queria ver o Batman de novo. E o Comissário Gordon diz que o "Batman é o que a cidade de Gotham precisa."
Batman: Cavaleiro das Trevas Ressurge mostra a cidade de Gotham sendo tomada pela corrupção e pela ideologia do Bane. A Cidade vai definhando em imoralidade e o Bruce, ao olhar da prisão a cidade sendo destruída, decide que o Batman precisa voltar porque se Gotham for destruída, o Batman é destruído junto. E isso o da forças para consegue fugir daquele poço e voltar para salvar Gotham.
Isso também é mostrado em Demolidor. Na série Demolidor o Matt Murdock sempre fala que precisa defender a cidade Cozinha do Inferno; que o Fisk não vai dominar a cidade e fazer o que ele quiser nela. Inclusive na terceira temporada isso fica mais evidente na luta final na mansão do Fisk, onde Matt grita que agora a cidade toda vai saber o que ele fez; a cidade vai ver o mal que ele é para Hell's Kitchen, porque a gente sabe que o Fisk fez de tudo para a imagem do Demolidor entrar e descrédito perante os cidadãos, então o que acontece no final do filme O Doutrinador não significa que ele está acabando com a corrupção quando explode o Congresso, ele está praticamente interrompendo o ciclo do sistema, colocando uma falha em sua engrenagem.
Quando você ouve falar de Brasília, você pensa na corrupção dos políticos, onde a farra acontece,, onde corruptos desviam dinheiro arrecadado dos impostos, impostos estes que são centralizados na União. Então quando você ouve falarem de Brasília, sempre pensa que o pessoal que mora lá, mora junto com tudo de podre que acontece no Brasil.
Logo quando o Doutrinador explode tudo ali, ele está basicamente destruindo o mecanismo que suja Brasília. Ele está fazendo isso naquela cidade. Porque o símbolo da cidade é justamente esse, a farsa de que naquele lugar o povo será ouvido e a justiça será feita. Ele está destruindo a ideologia de que o Estado nos protege, nos dá segurança, saúde e educação. Porque na verdade o Estado só existe para privilegiar os políticos, funcionários públicos de auto escalão, suas famílias e amigos. Enquanto que o povo sofre para sustentar a elite política. O protagonista Miguel entendeu isso quando a filha dele morreu na fila do SUS.
-
 @ 0598a50c:d765ddce
2025-04-27 01:03:15
@ 0598a50c:d765ddce
2025-04-27 01:03:15This LA Times story, from their archives, is not paywalled:
WASHINGTON — The chief of China’s military intelligence secretly directed funds from Beijing to help re-elect President Clinton in 1996, former Democratic fund-raiser Johnny Chung has told federal investigators.
According to sources familiar with Chung’s sealed statements to federal prosecutors, Chung says he met three times with the intelligence official, General Ji Shengde, who ordered $300,000 deposited into the Torrance businessman’s bank account to subsidize campaign donations intended for Clinton,
Never forget blatant, destructive, disloyalty to the USA.
It's not an accident that the Clinton donation from China happened in (Freemason controlled) Los Angeles, where China has a massive presence to this day. Take a drive on San Gabriel Blvd and see for yourself.
According to law enforcement and other sources, key aspects of Chung’s testimony, which has not been made public, have been corroborated by financial records in the United States and Hong Kong.
+++++++++++ Chung, 44, a Taiwan-born American citizen who lives in Artesia, Calif., was one of the most prominent figures in the 1996 campaign finance scandal. He contributed more than $400,000 to various Democratic campaigns and causes, visited the White House no fewer than 50 times and brought numerous Chinese associates to events with the president and First Lady Hillary Rodham Clinton.
As you might expect, it is illegal for U.S. political parties or candidates to accept contributions from foreign sources.
Only a portion of the $300,000 made it into Democratic campaign coffers, records show.
A spokesman for China’s embassy in Washington denied any involvement in the 1996 elections.
SOURCE: https://www.latimes.com/archives/la-xpm-1999-apr-04-mn-24189-story.html
-
 @ 177bfd16:347a07e4
2025-04-26 20:38:30
@ 177bfd16:347a07e4
2025-04-26 20:38:30So , you've battles through your way through countless Grunts , overcome the Team GO Rocket Leaders, and now you stand face to face with the big boss him self - Giovanni!
As of April 2025 , Giovanni is finishing his battles with Shadow Palkia.
Giovanni's Current Lineup (April 2025) First, know your enemy. Giovanni's team follows this structure:
Slot 1: Shadow Persian (Normal)
Slot 2: One of these three, chosen randomly:
Shadow Nidoking (Poison/Ground) Shadow Kingdra (Water/Dragon) Shadow Rhyperior (Rock/Ground)
Slot 3: Shadow Palkia (Water/Dragon) Remember, these are Shadow Pokémon – they hit harder than their normal counterparts!
Counter Strategy: Beating Giovanni Pokémon by Pokémon
Let's dive into the best counters for each potential opponent:
- Vs. Shadow Persian (Normal)
Giovanni always leads with Persian. As a Normal-type, it's weak only to Fighting-type attacks.
Top Counters: Machamp, Lucario, Conkeldurr, Terrakion, Mega Blaziken, Mega Lucario.
Moves: Prioritize Fighting-type moves like Counter, Dynamic Punch, Aura Sphere, and Sacred Sword.
Tip: Lead with a strong Fighting-type. Moves like Lucario's Power-Up Punch or Machamp's Cross Chop charge quickly and are great for baiting Giovanni's shields early!
- Vs. The Second Slot (Nidoking, Kingdra, or Rhyperior)
This is where things get unpredictable. You need Pokémon that can handle these potential threats:
Vs. Shadow Nidoking (Poison/Ground): Weak to Water, Ground, Ice, Psychic.
Counters: Kyogre (Primal/Shadow), Swampert (Mega), Groudon (Primal/Shadow), Mewtwo (Shadow), Excadrill. Water and Ground-types are prime choices.
Vs. Shadow Kingdra (Water/Dragon): Weak to Fairy, Dragon. Counters: Gardevoir (Mega), Togekiss, Xerneas. Fairy-types are excellent as they resist Dragon attacks while dealing super-effective damage. Dragon-types like Rayquaza or Palkia work but are risky.
Vs. Shadow Rhyperior (Rock/Ground): Double weak to Water and Grass! Also weak to Fighting, Ground, Ice, Steel.
Counters: Kyogre (Primal/Shadow), Swampert (Mega), Sceptile (Mega), Roserade. Your Fighting-type lead (if it survived Persian) can also do significant damage. Hit it hard with Water or Grass!
- Vs. Shadow Palkia (Water/Dragon)
Giovanni's final Pokémon is the powerful Shadow Palkia. Like Kingdra, it's weak to Fairy and Dragon types.
Top Counters: Gardevoir (Mega), Togekiss, Xerneas. Again, Fairy-types are the safest and most reliable counters.
Dragon Counters (Use with Caution): Rayquaza (Mega), Palkia (Origin Forme), Dragonite, Dialga (Origin Forme).

Recommended Battle Teams for April 2025 Based on the counters, here are a few effective teams you can assemble:
Team 1 (Balanced):
Machamp (Counter / Cross Chop & Dynamic Punch)
Swampert (Mud Shot / Hydro Cannon & Earthquake)
Togekiss (Charm / Dazzling Gleam & Ancient Power)
Why it works: Covers all bases well with accessible Pokémon. Machamp handles Persian/shields, Swampert crushes Rhyperior/Nidoking, Togekiss tackles Kingdra/Palkia.
Team 2 (Legendary Power):
Lucario (Counter / Power-Up Punch & Aura Sphere)
Kyogre (Waterfall / Origin Pulse & Surf)
Xerneas (Geomancy / Moonblast & Close Combat)
Why it works: High-powered options. Lucario baits shields effectively, Kyogre dominates slot two's Ground/Rock types, Xerneas shreds the Dragons.
Team 3 (Mega Advantage):
Machamp (Counter / Cross Chop & DP)
Kyogre (Waterfall / Origin Pulse)
Mega Gardevoir (Charm / Dazzling Gleam & Shadow Ball)
Why it works: Uses a standard strong lead and mid-game counter, saving the Mega slot for Gardevoir to ensure a powerful finish against Palkia/Kingdra.
Essential Battle Tips Don't forget these crucial tactics:
The Switch Trick: Place your intended starting Pokémon (e.g., Machamp) in the second or third slot. Start the battle, then immediately switch to it. Giovanni will pause for a moment, letting you get in free hits!
Bait Those Shields: Use Pokémon with fast-charging Charged Moves, especially early on, to force Giovanni to waste his Protect Shields.
Power Up: Ensure your team is powered up significantly and consider unlocking second Charged Moves for better flexibility.
Don't Give Up: Giovanni is tough! It might take a few tries to get the right matchup against his second Pokémon. Learn from each attempt and adjust your team if needed.
Go show the boss who's the boss and claim your shadow Palkia . Good Luck, Trainer !
-
 @ a39d19ec:3d88f61e
2025-03-18 17:16:50
@ a39d19ec:3d88f61e
2025-03-18 17:16:50Nun da das deutsche Bundesregime den Ruin Deutschlands beschlossen hat, der sehr wahrscheinlich mit dem Werkzeug des Geld druckens "finanziert" wird, kamen mir so viele Gedanken zur Geldmengenausweitung, dass ich diese für einmal niedergeschrieben habe.
Die Ausweitung der Geldmenge führt aus klassischer wirtschaftlicher Sicht immer zu Preissteigerungen, weil mehr Geld im Umlauf auf eine begrenzte Menge an Gütern trifft. Dies lässt sich in mehreren Schritten analysieren:
1. Quantitätstheorie des Geldes
Die klassische Gleichung der Quantitätstheorie des Geldes lautet:
M • V = P • Y
wobei:
- M die Geldmenge ist,
- V die Umlaufgeschwindigkeit des Geldes,
- P das Preisniveau,
- Y die reale Wirtschaftsleistung (BIP).Wenn M steigt und V sowie Y konstant bleiben, muss P steigen – also Inflation entstehen.
2. Gütermenge bleibt begrenzt
Die Menge an real produzierten Gütern und Dienstleistungen wächst meist nur langsam im Vergleich zur Ausweitung der Geldmenge. Wenn die Geldmenge schneller steigt als die Produktionsgütermenge, führt dies dazu, dass mehr Geld für die gleiche Menge an Waren zur Verfügung steht – die Preise steigen.
3. Erwartungseffekte und Spekulation
Wenn Unternehmen und Haushalte erwarten, dass mehr Geld im Umlauf ist, da eine zentrale Planung es so wollte, können sie steigende Preise antizipieren. Unternehmen erhöhen ihre Preise vorab, und Arbeitnehmer fordern höhere Löhne. Dies kann eine sich selbst verstärkende Spirale auslösen.
4. Internationale Perspektive
Eine erhöhte Geldmenge kann die Währung abwerten, wenn andere Länder ihre Geldpolitik stabil halten. Eine schwächere Währung macht Importe teurer, was wiederum Preissteigerungen antreibt.
5. Kritik an der reinen Geldmengen-Theorie
Der Vollständigkeit halber muss erwähnt werden, dass die meisten modernen Ökonomen im Staatsauftrag argumentieren, dass Inflation nicht nur von der Geldmenge abhängt, sondern auch von der Nachfrage nach Geld (z. B. in einer Wirtschaftskrise). Dennoch zeigt die historische Erfahrung, dass eine unkontrollierte Geldmengenausweitung langfristig immer zu Preissteigerungen führt, wie etwa in der Hyperinflation der Weimarer Republik oder in Simbabwe.
-
 @ 30ceb64e:7f08bdf5
2025-04-26 20:33:30
@ 30ceb64e:7f08bdf5
2025-04-26 20:33:30Status: Draft
Author: TheWildHustleAbstract
This NIP defines a framework for storing and sharing health and fitness profile data on Nostr. It establishes a set of standardized event kinds for individual health metrics, allowing applications to selectively access specific health information while preserving user control and privacy.
In this framework exists - NIP-101h.1 Weight using kind 1351 - NIP-101h.2 Height using kind 1352 - NIP-101h.3 Age using kind 1353 - NIP-101h.4 Gender using kind 1354 - NIP-101h.5 Fitness Level using kind 1355
Motivation
I want to build and support an ecosystem of health and fitness related nostr clients that have the ability to share and utilize a bunch of specific interoperable health metrics.
- Selective access - Applications can access only the data they need
- User control - Users can choose which metrics to share
- Interoperability - Different health applications can share data
- Privacy - Sensitive health information can be managed independently
Specification
Kind Number Range
Health profile metrics use the kind number range 1351-1399:
| Kind | Metric | | --------- | ---------------------------------- | | 1351 | Weight | | 1352 | Height | | 1353 | Age | | 1354 | Gender | | 1355 | Fitness Level | | 1356-1399 | Reserved for future health metrics |
Common Structure
All health metric events SHOULD follow these guidelines:
- The content field contains the primary value of the metric
- Required tags:
['t', 'health']- For categorizing as health data['t', metric-specific-tag]- For identifying the specific metric['unit', unit-of-measurement]- When applicable- Optional tags:
['converted_value', value, unit]- For providing alternative unit measurements['timestamp', ISO8601-date]- When the metric was measured['source', application-name]- The source of the measurement
Unit Handling
Health metrics often have multiple ways to be measured. To ensure interoperability:
- Where multiple units are possible, one standard unit SHOULD be chosen as canonical
- When using non-standard units, a
converted_valuetag SHOULD be included with the canonical unit - Both the original and converted values should be provided for maximum compatibility
Client Implementation Guidelines
Clients implementing this NIP SHOULD:
- Allow users to explicitly choose which metrics to publish
- Support reading health metrics from other users when appropriate permissions exist
- Support updating metrics with new values over time
- Preserve tags they don't understand for future compatibility
- Support at least the canonical unit for each metric
Extensions
New health metrics can be proposed as extensions to this NIP using the format:
- NIP-101h.X where X is the metric number
Each extension MUST specify: - A unique kind number in the range 1351-1399 - The content format and meaning - Required and optional tags - Examples of valid events
Privacy Considerations
Health data is sensitive personal information. Clients implementing this NIP SHOULD:
- Make it clear to users when health data is being published
- Consider incorporating NIP-44 encryption for sensitive metrics
- Allow users to selectively share metrics with specific individuals
- Provide easy ways to delete previously published health data
NIP-101h.1: Weight
Description
This NIP defines the format for storing and sharing weight data on Nostr.
Event Kind: 1351
Content
The content field MUST contain the numeric weight value as a string.
Required Tags
- ['unit', 'kg' or 'lb'] - Unit of measurement
- ['t', 'health'] - Categorization tag
- ['t', 'weight'] - Specific metric tag
Optional Tags
- ['converted_value', value, unit] - Provides the weight in alternative units for interoperability
- ['timestamp', ISO8601 date] - When the weight was measured
Examples
json { "kind": 1351, "content": "70", "tags": [ ["unit", "kg"], ["t", "health"], ["t", "weight"] ] }json { "kind": 1351, "content": "154", "tags": [ ["unit", "lb"], ["t", "health"], ["t", "weight"], ["converted_value", "69.85", "kg"] ] }NIP-101h.2: Height
Status: Draft
Description
This NIP defines the format for storing and sharing height data on Nostr.
Event Kind: 1352
Content
The content field can use two formats: - For metric height: A string containing the numeric height value in centimeters (cm) - For imperial height: A JSON string with feet and inches properties
Required Tags
['t', 'health']- Categorization tag['t', 'height']- Specific metric tag['unit', 'cm' or 'imperial']- Unit of measurement
Optional Tags
['converted_value', value, 'cm']- Provides height in centimeters for interoperability when imperial is used['timestamp', ISO8601-date]- When the height was measured
Examples
```jsx // Example 1: Metric height Apply to App.jsx
// Example 2: Imperial height with conversion Apply to App.jsx ```
Implementation Notes
- Centimeters (cm) is the canonical unit for height interoperability
- When using imperial units, a conversion to centimeters SHOULD be provided
- Height values SHOULD be positive integers
- For maximum compatibility, clients SHOULD support both formats
NIP-101h.3: Age
Status: Draft
Description
This NIP defines the format for storing and sharing age data on Nostr.
Event Kind: 1353
Content
The content field MUST contain the numeric age value as a string.
Required Tags
['unit', 'years']- Unit of measurement['t', 'health']- Categorization tag['t', 'age']- Specific metric tag
Optional Tags
['timestamp', ISO8601-date]- When the age was recorded['dob', ISO8601-date]- Date of birth (if the user chooses to share it)
Examples
```jsx // Example 1: Basic age Apply to App.jsx
// Example 2: Age with DOB Apply to App.jsx ```
Implementation Notes
- Age SHOULD be represented as a positive integer
- For privacy reasons, date of birth (dob) is optional
- Clients SHOULD consider updating age automatically if date of birth is known
- Age can be a sensitive metric and clients may want to consider encrypting this data
NIP-101h.4: Gender
Status: Draft
Description
This NIP defines the format for storing and sharing gender data on Nostr.
Event Kind: 1354
Content
The content field contains a string representing the user's gender.
Required Tags
['t', 'health']- Categorization tag['t', 'gender']- Specific metric tag
Optional Tags
['timestamp', ISO8601-date]- When the gender was recorded['preferred_pronouns', string]- User's preferred pronouns
Common Values
While any string value is permitted, the following common values are recommended for interoperability: - male - female - non-binary - other - prefer-not-to-say
Examples
```jsx // Example 1: Basic gender Apply to App.jsx
// Example 2: Gender with pronouns Apply to App.jsx ```
Implementation Notes
- Clients SHOULD allow free-form input for gender
- For maximum compatibility, clients SHOULD support the common values
- Gender is a sensitive personal attribute and clients SHOULD consider appropriate privacy controls
- Applications focusing on health metrics should be respectful of gender diversity
NIP-101h.5: Fitness Level
Status: Draft
Description
This NIP defines the format for storing and sharing fitness level data on Nostr.
Event Kind: 1355
Content
The content field contains a string representing the user's fitness level.
Required Tags
['t', 'health']- Categorization tag['t', 'fitness']- Fitness category tag['t', 'level']- Specific metric tag
Optional Tags
['timestamp', ISO8601-date]- When the fitness level was recorded['activity', activity-type]- Specific activity the fitness level relates to['metrics', JSON-string]- Quantifiable fitness metrics used to determine level
Common Values
While any string value is permitted, the following common values are recommended for interoperability: - beginner - intermediate - advanced - elite - professional
Examples
```jsx // Example 1: Basic fitness level Apply to App.jsx
// Example 2: Activity-specific fitness level with metrics Apply to App.jsx ```
Implementation Notes
- Fitness level is subjective and may vary by activity
- The activity tag can be used to specify fitness level for different activities
- The metrics tag can provide objective measurements to support the fitness level
- Clients can extend this format to include activity-specific fitness assessments
- For general fitness apps, the simple beginner/intermediate/advanced scale is recommended
-
 @ 04c915da:3dfbecc9
2025-03-12 15:30:46
@ 04c915da:3dfbecc9
2025-03-12 15:30:46Recently we have seen a wave of high profile X accounts hacked. These attacks have exposed the fragility of the status quo security model used by modern social media platforms like X. Many users have asked if nostr fixes this, so lets dive in. How do these types of attacks translate into the world of nostr apps? For clarity, I will use X’s security model as representative of most big tech social platforms and compare it to nostr.
The Status Quo
On X, you never have full control of your account. Ultimately to use it requires permission from the company. They can suspend your account or limit your distribution. Theoretically they can even post from your account at will. An X account is tied to an email and password. Users can also opt into two factor authentication, which adds an extra layer of protection, a login code generated by an app. In theory, this setup works well, but it places a heavy burden on users. You need to create a strong, unique password and safeguard it. You also need to ensure your email account and phone number remain secure, as attackers can exploit these to reset your credentials and take over your account. Even if you do everything responsibly, there is another weak link in X infrastructure itself. The platform’s infrastructure allows accounts to be reset through its backend. This could happen maliciously by an employee or through an external attacker who compromises X’s backend. When an account is compromised, the legitimate user often gets locked out, unable to post or regain control without contacting X’s support team. That process can be slow, frustrating, and sometimes fruitless if support denies the request or cannot verify your identity. Often times support will require users to provide identification info in order to regain access, which represents a privacy risk. The centralized nature of X means you are ultimately at the mercy of the company’s systems and staff.
Nostr Requires Responsibility
Nostr flips this model radically. Users do not need permission from a company to access their account, they can generate as many accounts as they want, and cannot be easily censored. The key tradeoff here is that users have to take complete responsibility for their security. Instead of relying on a username, password, and corporate servers, nostr uses a private key as the sole credential for your account. Users generate this key and it is their responsibility to keep it safe. As long as you have your key, you can post. If someone else gets it, they can post too. It is that simple. This design has strong implications. Unlike X, there is no backend reset option. If your key is compromised or lost, there is no customer support to call. In a compromise scenario, both you and the attacker can post from the account simultaneously. Neither can lock the other out, since nostr relays simply accept whatever is signed with a valid key.
The benefit? No reliance on proprietary corporate infrastructure.. The negative? Security rests entirely on how well you protect your key.
Future Nostr Security Improvements
For many users, nostr’s standard security model, storing a private key on a phone with an encrypted cloud backup, will likely be sufficient. It is simple and reasonably secure. That said, nostr’s strength lies in its flexibility as an open protocol. Users will be able to choose between a range of security models, balancing convenience and protection based on need.
One promising option is a web of trust model for key rotation. Imagine pre-selecting a group of trusted friends. If your account is compromised, these people could collectively sign an event announcing the compromise to the network and designate a new key as your legitimate one. Apps could handle this process seamlessly in the background, notifying followers of the switch without much user interaction. This could become a popular choice for average users, but it is not without tradeoffs. It requires trust in your chosen web of trust, which might not suit power users or large organizations. It also has the issue that some apps may not recognize the key rotation properly and followers might get confused about which account is “real.”
For those needing higher security, there is the option of multisig using FROST (Flexible Round-Optimized Schnorr Threshold). In this setup, multiple keys must sign off on every action, including posting and updating a profile. A hacker with just one key could not do anything. This is likely overkill for most users due to complexity and inconvenience, but it could be a game changer for large organizations, companies, and governments. Imagine the White House nostr account requiring signatures from multiple people before a post goes live, that would be much more secure than the status quo big tech model.
Another option are hardware signers, similar to bitcoin hardware wallets. Private keys are kept on secure, offline devices, separate from the internet connected phone or computer you use to broadcast events. This drastically reduces the risk of remote hacks, as private keys never touches the internet. It can be used in combination with multisig setups for extra protection. This setup is much less convenient and probably overkill for most but could be ideal for governments, companies, or other high profile accounts.
Nostr’s security model is not perfect but is robust and versatile. Ultimately users are in control and security is their responsibility. Apps will give users multiple options to choose from and users will choose what best fits their need.
-
 @ 04c915da:3dfbecc9
2025-03-10 23:31:30
@ 04c915da:3dfbecc9
2025-03-10 23:31:30Bitcoin has always been rooted in freedom and resistance to authority. I get that many of you are conflicted about the US Government stacking but by design we cannot stop anyone from using bitcoin. Many have asked me for my thoughts on the matter, so let’s rip it.
Concern
One of the most glaring issues with the strategic bitcoin reserve is its foundation, built on stolen bitcoin. For those of us who value private property this is an obvious betrayal of our core principles. Rather than proof of work, the bitcoin that seeds this reserve has been taken by force. The US Government should return the bitcoin stolen from Bitfinex and the Silk Road.
Usually stolen bitcoin for the reserve creates a perverse incentive. If governments see a bitcoin as a valuable asset, they will ramp up efforts to confiscate more bitcoin. The precedent is a major concern, and I stand strongly against it, but it should be also noted that governments were already seizing coin before the reserve so this is not really a change in policy.
Ideally all seized bitcoin should be burned, by law. This would align incentives properly and make it less likely for the government to actively increase coin seizures. Due to the truly scarce properties of bitcoin, all burned bitcoin helps existing holders through increased purchasing power regardless. This change would be unlikely but those of us in policy circles should push for it regardless. It would be best case scenario for American bitcoiners and would create a strong foundation for the next century of American leadership.
Optimism
The entire point of bitcoin is that we can spend or save it without permission. That said, it is a massive benefit to not have one of the strongest governments in human history actively trying to ruin our lives.
Since the beginning, bitcoiners have faced horrible regulatory trends. KYC, surveillance, and legal cases have made using bitcoin and building bitcoin businesses incredibly difficult. It is incredibly important to note that over the past year that trend has reversed for the first time in a decade. A strategic bitcoin reserve is a key driver of this shift. By holding bitcoin, the strongest government in the world has signaled that it is not just a fringe technology but rather truly valuable, legitimate, and worth stacking.
This alignment of incentives changes everything. The US Government stacking proves bitcoin’s worth. The resulting purchasing power appreciation helps all of us who are holding coin and as bitcoin succeeds our government receives direct benefit. A beautiful positive feedback loop.
Realism
We are trending in the right direction. A strategic bitcoin reserve is a sign that the state sees bitcoin as an asset worth embracing rather than destroying. That said, there is a lot of work left to be done. We cannot be lulled into complacency, the time to push forward is now, and we cannot take our foot off the gas. We have a seat at the table for the first time ever. Let's make it worth it.
We must protect the right to free usage of bitcoin and other digital technologies. Freedom in the digital age must be taken and defended, through both technical and political avenues. Multiple privacy focused developers are facing long jail sentences for building tools that protect our freedom. These cases are not just legal battles. They are attacks on the soul of bitcoin. We need to rally behind them, fight for their freedom, and ensure the ethos of bitcoin survives this new era of government interest. The strategic reserve is a step in the right direction, but it is up to us to hold the line and shape the future.
-
 @ df478568:2a951e67
2025-04-26 19:23:46
@ df478568:2a951e67
2025-04-26 19:23:46
Welcome to Zap This Blog
Exploring Liberty With Fredom Tech
I can string some spaghetti HTMl code together here and there, but vibe coding gave me the confidence to look into the code injection section of the ghost Blog. As sudden as a new block, the Lex Friedman Robert Rodriguez interview, I had an epiphony when he asked Lex, "Do you consider yourself a creative person?" I aswered for myself, right away, emphatically yes. I just felt like I never knew what to do with this creative energy. Friedman hesitated and I was like..Wow...He has extreme creativity like Jocko Wilink has extreme disipline. If that guy has doubts, what the hell is stopping me from trying other stuff?
Rodriguez also claimed Four rooms was financial flop. I thought that movie was genius. I had no idea it failed financially. Nevertheless, it was not profitable. His advice was like Tony Robbins for film nerds. I learned about him in a film class I took in college. He was legendary for making a mobie for $7,000. My professor also said it was made for the Mexican VHS market, but I did not know he never sold it to that market. Robert Rodriguez tells the story 100X better, as you might expect a director of his caliber would. His advice hits like Tony Robbins, for film geeks. Here are a few gem quotes from the epiode.
-
"Sift through the ashes of your failures"
-
"Turn chicken shit into chicken salad."
-
"Follow your instinct. If it doesn't work, just go. Sometimes you need to slip on the first two rocks, so the key is in the ashes of failure because if I had an insticnt, that means I was on the right track. I didn't get the result I want. That's because the result might be something way bigger that I don't have the vision for and the universe is just pushing me that way."
-
"Turn chicken shit into chicken salad."
-
"If you have some kind of failure on something that you..., don't let it knock you down. Maybe in ten years they'll think it's great. I'm just going to commit to making a body of work, a body of work."
Rodriguez taught me what I already know. I am a creative person. I am just a body, punching keys on a keyboard, taking pictures, and semi-vibe-coding art. Maybe this is a shitty blog post today, but I write it anyway. Someone might look at it like I first looked at the math in the Bitcoin white paper and scan it with their eyeballs without really reading or understanding it. Most people on Substack probably don't want to read HTML, but maybe someone will come accross it one day and build something themselves they can find in the ashes of this code.
I once saw Brian Harrington say every bitcoiner is a business owner. If you have a bitcoin address, you can accept bitcoin. How does someone find you though? Are they really going to find your bitcoin address on GitHub? I'd bet 100 sats they won't. Nostr fixes this so I thought about integrating it into my Ghost Blog. I looked at the code injection section and let my muse do the typing. Actually, I let the Duck Duck AI chat do the vibe-coding. As it turns out, you an add a header and footer on Ghost in the code injection. It's just the same HTMl I used to make my MySpace page. Then I thought, what if someone couldn't afford a Start9 or didn't know how to vibe code on Duck Duck Go's free AI chat using Claude? What if, like Rodriguez suggests, I create a business card?

You could just copy my HTML and change my nostr links and pics to go to your nostr links and pics. You could publish that HTML into https://habla.news. Now you have an e-commerce site with a blog, a merch store, and your nostree. I don't know if this will work. This is the muse's hypothesis. I'm just writing the words down. You'll need to test this idea for yourself.
npub1marc26z8nh3xkj5rcx7ufkatvx6ueqhp5vfw9v5teq26z254renshtf3g0
marc26z@getalby.com
Zap This Blog! -
 @ ec8f6700:fb2a4766
2025-04-26 21:43:10
@ ec8f6700:fb2a4766
2025-04-26 21:43:10SNAILS.
Creator Co-op for the Cosmos Ecosystem
Written by: Terp Network
Original post: https://docs.terp.network/guides/nodes/faq
We must keep in mind that p2p networks are exposed to the risk of denial of service attacks, and an effective way to mitigate this type of attacks is by using sentry nodes.Why is it important to avoid denial of service attacks?
When our node is suffering a denial of service attack that cannot be mitigated by the server provider, it is likely that the server will be inoperative for the duration of the attack because, being saturated, it will stop responding to the requests made by the rest of the nodes in the network.
If our node becomes inoperative, it means that we are no longer participating in the consensus rounds, our node will not be signing blocks or generating rewards for the delegators and therefore in a few minutes the node will be jailed and penalized.
In addition to being a risk for node operators due to the penalties involved in being jailed, it is also a risk for the network, since if an attack is carried out on several nodes at the same time, the stability and security of the network would be affected. Sentry nodes hide our validator’s IP from the world
Using sentry nodes is a solution to prevent the rest of the network from knowing the IP of our validator node, but allowing our validator node to continue communicating with other validator nodes in the terp network, since if the node were 100% isolated, it would not be able to participate in the network and therefore would not generate rewards for the delegators.
A sentry node is a bridge between our validator node and the rest of the network, so that the rest of the network does not know the IP of the validator node, but the IP of the sentry nodes.Can sentry nodes suffer denial of service attacks?
Yes, but as they are nodes that are not validating transactions and only act as a bridge between the network and the validating node, we could quickly deploy new sentry nodes or even change the IP of the sentry node being attacked. How many sentry nodes can there be?
There is really no maximum number, the more sentry nodes we have, the more resistance to denial of service attacks our validator node will have. However, it must be taken into account that the more sentry nodes we have, the more complex it will be to maintain our nodes when carrying out maintenance or upgrades, in addition to the increase in server costs. You should have at least two sentry nodes and if possible have one of them in a different datacenter from where the validator node is deployed. Where should the sentry nodes be deployed?
If two sentry nodes are going to be mounted, one of them could be deployed in the same datacenter where our validator node is, this will reduce the latency between both servers, and therefore, the connection between both servers will be quite fast. The other sentry node could be located in a different datacenter; this way, in case the network of the datacenter where our validator node is down for any reason, we would always have a node with the current block available to synchronize our validator node. Step by step guide
To follow this guide, we will use a node created & connected to 90u-3 testnet network. In case you have not deployed the node yet, how to install the terp-core binary Creating the sentry nodes
Once we have contracted the two sentry node servers and we have the access IPs, we must perform the same installation that we would perform as if it were a validator node on both servers.
First, we will need to download and compile the terp-core binary.
git clone https://github.com/terpnetwork/terp-core.git cd terp-core git checkout
Once downloaded, we will proceed to compile the binary:
make install
It will also be necessary to initialize the node so that the .terp directory is created, for this we can use the following commands, each one in the corresponding server:
On sentry node A:
terpd init "terpd-up - Sentry A" --chain-id 90u-3
On sentry node B:
terpd init "terpd-up - Sentry B" --chain-id 90u-3
Once the previous step is done, the .terp folder will already exist, so we can download the genesis.json file:
curl https://raw.githubusercontent.com/terpnetwork/networks/main/testnet/90u-3/genesis.json > ~/.terp/config/genesis.json
Configure service
Finally, we will configure the terp service:
sudo nano /etc/systemd/system/system/terpd.service
sudo tee /etc/systemd/system/terpd.service > /dev/null <<EOF [Unit] Description=terpd Daemon After=network-online.target [Service] User=$USER ExecStart=$(which terpd) start Restart=always RestartSec=3 LimitNOFILE=65535 [Install] WantedBy=multi-user.target EOF
Base configuration of the sentry nodes
For now we have not done anything different from what we would do when setting up a validator node, although we have stopped doing several things, such as creating the wallet or running the validator creation command “tx staking create-validator”, since we do not want to create validator nodes, only nodes that synchronize with the rest of the nodes in the network and we can use to synchronize our validator node in a secure way without exposing our IP to the rest of the network.
The sentry nodes (both), must have peers to be synchronized at all times, we will add the following peers to the config.toml file inside the config folder. Persistent Peers:
peers=$(curl -s https://ss.terp.nodestake.top/peers.txt) sed -i.bak -e "s/^persistent_peers =./persistent_peers = \"$peers\"/" ~/.terp/config/config.toml
Note: the peers were obtained from Nodestake validator team.
It would also be advisable to add as persistent peer the sentry nodes between them. That is to say, that the sentry node B is persistent peer of the sentry node A, in the same way that the sentry node A is persistent peer of the sentry node B; this will make us have more redundancy. Private Peers:
In the config.toml file of the config folder of the sentry nodes (both), it is necessary to specify the id of the validator node in the private_peer_ids parameter. This is so that our sentry nodes never share with the rest of the peers of the network the existence of our validator node.
If you don’t know how to get the id of your validator node, you can get it with the following command:
terpd tendermint show-node-id
Unconditional Peers
In the same configuration file, we will also find the unconditional-peer-ids parameter to which we must add our validator node as we did with the private_peer_ids parameter. This step is necessary because the nodes have a limited number of peers to which they can connect.
To avoid the risk of leaving our validator node incommunicado, by setting its id in the unconditional-peer-ids parameter, we will make the sentry nodes always connected to the validator node even if the limit of peers to which they can be connected has been exceeded. Optionally we can also add in this same parameter (separated by commas) the homologous sentry node to guarantee that the sentry nodes will always be connected to each other.
unconditional-peer-ids = "validator node, peer sentry node". Start Sentry Nodes
At this point, we could start our sentry nodes and let them synchronize and be discovered by the rest of the network. For that we will use the following command:
sudo systemctl daemon-reload sudo systemctl enable terpd
Base configuration for validator
Once the sentry nodes have been synchronized, we can configure the validator node with all certainty that our validator node is not going to stop being synchronized with the network. We will have to edit the config.toml file in the config folder, where we will find the following lines: Persistent Peers
In persistent_peers we will add only the ids of the sentry nodes, that is to say that if the node was already mounted before, we will have to delete the content of this field before adding our sentry nodes. PEX
In the same configuration file we will find the pex parameter, which we must set to “false”. This parameter does not discover other peers, it will only use the ones set in the persistent_peers parameter.
pex = false
Remove address book (optional)
If the validator has already been exposed to the network, we can delete the address book so that it only “knows” the sentry nodes; if it is a validator that has never been started, this step is not necessary. Once inside the config folder and with the node stopped, perform the following command:
rm -rf $HOME/.terp/config/addrbook.json
Start Validator Node
To verify that we are really connected only to two peers and these are the sentry nodes, we can write the following command in our validated node; the output is a JSON where it will show us the number and which peers we are connected to, where the number should be two and the peers should be our sentry nodes.
curl -s localhost:26657/net_info Here you can see the number of peers to which our validator node is connected, in this case it is two, which is correct. Extra: Protecting the validator node through firewall
Right now the p2p port of our validator node is open and anyone can establish a connection. If we have just set up the validator node, with the configurations made, nobody would have to find our validator node, however, to add a plus of security it is advisable to close the p2p port and only allow traffic to the IP’s of our sentry nodes.
There are several ways to do this, it is possible that your server provider allows you to do it through a gui. Ufw is a simple to use alternative. Extra: Private networks
One possibility we have when our validator node is in the same datacenter as one of the sentry nodes, would be to use private addressing.
In case we want to use private addressing, we will have to edit the addr-book-strict parameter of the config.toml file and set it to false in both the validator node and the sentry node that are communicating under private addressing. This parameter, when set to “true”, will only add routable addresses to the address book, the private addresses defined in RFC-1918 are not routable, therefore, they would not be added to the address book, so we will have to change it to false to be able to use IP addresses from the private ranges.
addr-book-strict: boolean. By default, nodes with a routable address will be considered for connection. If this setting is disabled (false), non-routable IP addresses, such as addresses from a private network, can be added to the address book. Source: https://docs.tendermint.com/master/nodes/validators.htmlConclusions
Having sentry nodes will not only help our validator node not to fall victim to a denial of service attack, but will also make the Terp network more robust. The installation of the sentry nodes does not differ much from that of a validator node, and the additional configurations to be performed are very simple and intuitive.
Now that Terp Network is doing the 90u-3 testnet, it is a good time to try to set up sentry nodes and once the mainnet is launched, to be able to replicate it with the experience of having been able to test it in 90u-3. If you already have your node on 90u-3, what are you waiting for to set up your sentry nodes and protect yourself from unwanted attacks?
sources: https://stakely.io/en/blog/how-to-deploy-sentry-nodes-in-the-archway-network -
 @ f3873798:24b3f2f3
2025-03-10 00:32:44
@ f3873798:24b3f2f3
2025-03-10 00:32:44Recentemente, assisti a um vídeo que me fez refletir profundamente sobre o impacto da linguagem na hora de vender. No vídeo, uma jovem relatava sua experiência ao presenciar um vendedor de amendoim em uma agência dos Correios. O local estava cheio, as pessoas aguardavam impacientes na fila e, em meio a esse cenário, um homem humilde tentava vender seu produto. Mas sua abordagem não era estratégica; ao invés de destacar os benefícios do amendoim, ele suplicava para que alguém o ajudasse comprando. O resultado? Ninguém se interessou.

A jovem observou que o problema não era o produto, mas a forma como ele estava sendo oferecido. Afinal, muitas das pessoas ali estavam há horas esperando e perto do horário do almoço – o amendoim poderia ser um ótimo tira-gosto. No entanto, como a comunicação do vendedor vinha carregada de desespero, ele afastava os clientes ao invés de atraí-los. Esse vídeo me tocou profundamente.
No dia seguinte, ao sair para comemorar meu aniversário, vi um menino vendendo balas na rua, sob o sol forte. Assim como no caso do amendoim, percebi que as pessoas ao redor não se interessavam por seu produto. Ao se aproximar do carro, resolvi comprar dois pacotes. Mais do que ajudar, queria que aquele pequeno gesto servisse como incentivo para que ele continuasse acreditando no seu negócio.
Essa experiência me fez refletir ainda mais sobre o poder da comunicação em vendas. Muitas vezes, não é o produto que está errado, mas sim a forma como o vendedor o apresenta. Quando transmitimos confiança e mostramos o valor do que vendemos, despertamos o interesse genuíno dos clientes.
Como a Linguagem Impacta as Vendas?

1. O Poder da Abordagem Positiva
Em vez de pedir por ajuda, é importante destacar os benefícios do produto. No caso do amendoim, o vendedor poderia ter dito algo como: "Que tal um petisco delicioso enquanto espera? Um amendoim fresquinho para matar a fome até o almoço!"
2. A Emoção na Medida Certa
Expressar emoção é essencial, mas sem parecer desesperado. Os clientes devem sentir que estão adquirindo algo de valor, não apenas ajudando o vendedor.
3. Conheça Seu Público
Entender o contexto é fundamental. Se as pessoas estavam com fome e impacientes, uma abordagem mais objetiva e focada no benefício do produto poderia gerar mais vendas.
4. Autoconfiança e Postura
Falar com firmeza e segurança transmite credibilidade. O vendedor precisa acreditar no próprio produto antes de convencer o cliente a comprá-lo.
Conclusão
Vender é mais do que apenas oferecer um produto – é uma arte que envolve comunicação, percepção e estratégia. Pequenos ajustes na abordagem podem transformar completamente os resultados. Se o vendedor de amendoim tivesse apresentado seu produto de outra maneira, talvez tivesse vendido tudo rapidamente. Da mesma forma, se cada um de nós aprender a se comunicar melhor em nossas próprias áreas, poderemos alcançar muito mais sucesso.
E você? Já passou por uma experiência parecida?
-
 @ a53364ff:e6ba5513
2025-04-26 18:43:23
@ a53364ff:e6ba5513
2025-04-26 18:43:23Decentralization and Control:
Bitcoin operates on a decentralized, peer-to-peer network, meaning no single entity controls it. This decentralization can empower individuals by allowing them to control their own money and financial transactions without relying on intermediaries like banks or governments.
Financial Inclusion and Accessibility:
Bitcoin can provide financial access to individuals who may be excluded from traditional banking systems due to lack of identity documents, high fees, or other barriers.
Privacy and Security:
Bitcoin transactions can be anonymous, offering a degree of privacy and potentially protecting users from surveillance or financial manipulation.
Freedom from Financial Restrictions:
In countries with high inflation, capital controls, or currency restrictions, Bitcoin can offer a way to store and transfer value without being subject to these restrictions.
Potential for Social Justice:
Bitcoin's ability to provide financial freedom and bypass traditional systems can be seen as a tool for social justice, particularly in regions facing authoritarianism or financial oppression.
Examples of Bitcoin Adoption:
In El Salvador, Bitcoin has been legalized and adopted in some communities, offering a way for people to conduct everyday transactions and participate in social programs.
-
 @ 04c915da:3dfbecc9
2025-03-07 00:26:37
@ 04c915da:3dfbecc9
2025-03-07 00:26:37There is something quietly rebellious about stacking sats. In a world obsessed with instant gratification, choosing to patiently accumulate Bitcoin, one sat at a time, feels like a middle finger to the hype machine. But to do it right, you have got to stay humble. Stack too hard with your head in the clouds, and you will trip over your own ego before the next halving even hits.
Small Wins
Stacking sats is not glamorous. Discipline. Stacking every day, week, or month, no matter the price, and letting time do the heavy lifting. Humility lives in that consistency. You are not trying to outsmart the market or prove you are the next "crypto" prophet. Just a regular person, betting on a system you believe in, one humble stack at a time. Folks get rekt chasing the highs. They ape into some shitcoin pump, shout about it online, then go silent when they inevitably get rekt. The ones who last? They stack. Just keep showing up. Consistency. Humility in action. Know the game is long, and you are not bigger than it.
Ego is Volatile
Bitcoin’s swings can mess with your head. One day you are up 20%, feeling like a genius and the next down 30%, questioning everything. Ego will have you panic selling at the bottom or over leveraging the top. Staying humble means patience, a true bitcoin zen. Do not try to "beat” Bitcoin. Ride it. Stack what you can afford, live your life, and let compounding work its magic.
Simplicity
There is a beauty in how stacking sats forces you to rethink value. A sat is worth less than a penny today, but every time you grab a few thousand, you plant a seed. It is not about flaunting wealth but rather building it, quietly, without fanfare. That mindset spills over. Cut out the noise: the overpriced coffee, fancy watches, the status games that drain your wallet. Humility is good for your soul and your stack. I have a buddy who has been stacking since 2015. Never talks about it unless you ask. Lives in a decent place, drives an old truck, and just keeps stacking. He is not chasing clout, he is chasing freedom. That is the vibe: less ego, more sats, all grounded in life.
The Big Picture
Stack those sats. Do it quietly, do it consistently, and do not let the green days puff you up or the red days break you down. Humility is the secret sauce, it keeps you grounded while the world spins wild. In a decade, when you look back and smile, it will not be because you shouted the loudest. It will be because you stayed the course, one sat at a time. \ \ Stay Humble and Stack Sats. 🫡
-
 @ 7d3cd8a1:66aa5c86
2025-04-26 21:02:44
@ 7d3cd8a1:66aa5c86
2025-04-26 21:02:44SNAILS.
Creator Co-op for the Cosmos Ecosystem
Written by: Terp Network
Original post: https://docs.terp.network/guides/nodes/faq
We must keep in mind that p2p networks are exposed to the risk of denial of service attacks, and an effective way to mitigate this type of attacks is by using sentry nodes.Why is it important to avoid denial of service attacks?
When our node is suffering a denial of service attack that cannot be mitigated by the server provider, it is likely that the server will be inoperative for the duration of the attack because, being saturated, it will stop responding to the requests made by the rest of the nodes in the network.
If our node becomes inoperative, it means that we are no longer participating in the consensus rounds, our node will not be signing blocks or generating rewards for the delegators and therefore in a few minutes the node will be jailed and penalized.
In addition to being a risk for node operators due to the penalties involved in being jailed, it is also a risk for the network, since if an attack is carried out on several nodes at the same time, the stability and security of the network would be affected. Sentry nodes hide our validator’s IP from the world
Using sentry nodes is a solution to prevent the rest of the network from knowing the IP of our validator node, but allowing our validator node to continue communicating with other validator nodes in the terp network, since if the node were 100% isolated, it would not be able to participate in the network and therefore would not generate rewards for the delegators.
A sentry node is a bridge between our validator node and the rest of the network, so that the rest of the network does not know the IP of the validator node, but the IP of the sentry nodes.Can sentry nodes suffer denial of service attacks?
Yes, but as they are nodes that are not validating transactions and only act as a bridge between the network and the validating node, we could quickly deploy new sentry nodes or even change the IP of the sentry node being attacked. How many sentry nodes can there be?
There is really no maximum number, the more sentry nodes we have, the more resistance to denial of service attacks our validator node will have. However, it must be taken into account that the more sentry nodes we have, the more complex it will be to maintain our nodes when carrying out maintenance or upgrades, in addition to the increase in server costs. You should have at least two sentry nodes and if possible have one of them in a different datacenter from where the validator node is deployed. Where should the sentry nodes be deployed?
If two sentry nodes are going to be mounted, one of them could be deployed in the same datacenter where our validator node is, this will reduce the latency between both servers, and therefore, the connection between both servers will be quite fast. The other sentry node could be located in a different datacenter; this way, in case the network of the datacenter where our validator node is down for any reason, we would always have a node with the current block available to synchronize our validator node. Step by step guide
To follow this guide, we will use a node created & connected to 90u-3 testnet network. In case you have not deployed the node yet, how to install the terp-core binary Creating the sentry nodes
Once we have contracted the two sentry node servers and we have the access IPs, we must perform the same installation that we would perform as if it were a validator node on both servers.
First, we will need to download and compile the terp-core binary.
git clone https://github.com/terpnetwork/terp-core.git cd terp-core git checkout
Once downloaded, we will proceed to compile the binary:
make install
It will also be necessary to initialize the node so that the .terp directory is created, for this we can use the following commands, each one in the corresponding server:
On sentry node A:
terpd init "terpd-up - Sentry A" --chain-id 90u-3
On sentry node B:
terpd init "terpd-up - Sentry B" --chain-id 90u-3
Once the previous step is done, the .terp folder will already exist, so we can download the genesis.json file:
curl https://raw.githubusercontent.com/terpnetwork/networks/main/testnet/90u-3/genesis.json > ~/.terp/config/genesis.json
Configure service
Finally, we will configure the terp service:
sudo nano /etc/systemd/system/system/terpd.service
sudo tee /etc/systemd/system/terpd.service > /dev/null <<EOF [Unit] Description=terpd Daemon After=network-online.target [Service] User=$USER ExecStart=$(which terpd) start Restart=always RestartSec=3 LimitNOFILE=65535 [Install] WantedBy=multi-user.target EOF
Base configuration of the sentry nodes
For now we have not done anything different from what we would do when setting up a validator node, although we have stopped doing several things, such as creating the wallet or running the validator creation command “tx staking create-validator”, since we do not want to create validator nodes, only nodes that synchronize with the rest of the nodes in the network and we can use to synchronize our validator node in a secure way without exposing our IP to the rest of the network.
The sentry nodes (both), must have peers to be synchronized at all times, we will add the following peers to the config.toml file inside the config folder. Persistent Peers:
peers=$(curl -s https://ss.terp.nodestake.top/peers.txt) sed -i.bak -e "s/^persistent_peers =./persistent_peers = \"$peers\"/" ~/.terp/config/config.toml
Note: the peers were obtained from Nodestake validator team.
It would also be advisable to add as persistent peer the sentry nodes between them. That is to say, that the sentry node B is persistent peer of the sentry node A, in the same way that the sentry node A is persistent peer of the sentry node B; this will make us have more redundancy. Private Peers:
In the config.toml file of the config folder of the sentry nodes (both), it is necessary to specify the id of the validator node in the private_peer_ids parameter. This is so that our sentry nodes never share with the rest of the peers of the network the existence of our validator node.
If you don’t know how to get the id of your validator node, you can get it with the following command:
terpd tendermint show-node-id
Unconditional Peers
In the same configuration file, we will also find the unconditional-peer-ids parameter to which we must add our validator node as we did with the private_peer_ids parameter. This step is necessary because the nodes have a limited number of peers to which they can connect.
To avoid the risk of leaving our validator node incommunicado, by setting its id in the unconditional-peer-ids parameter, we will make the sentry nodes always connected to the validator node even if the limit of peers to which they can be connected has been exceeded. Optionally we can also add in this same parameter (separated by commas) the homologous sentry node to guarantee that the sentry nodes will always be connected to each other.
unconditional-peer-ids = "validator node, peer sentry node". Start Sentry Nodes
At this point, we could start our sentry nodes and let them synchronize and be discovered by the rest of the network. For that we will use the following command:
sudo systemctl daemon-reload sudo systemctl enable terpd
Base configuration for validator
Once the sentry nodes have been synchronized, we can configure the validator node with all certainty that our validator node is not going to stop being synchronized with the network. We will have to edit the config.toml file in the config folder, where we will find the following lines: Persistent Peers
In persistent_peers we will add only the ids of the sentry nodes, that is to say that if the node was already mounted before, we will have to delete the content of this field before adding our sentry nodes. PEX
In the same configuration file we will find the pex parameter, which we must set to “false”. This parameter does not discover other peers, it will only use the ones set in the persistent_peers parameter.
pex = false
Remove address book (optional)
If the validator has already been exposed to the network, we can delete the address book so that it only “knows” the sentry nodes; if it is a validator that has never been started, this step is not necessary. Once inside the config folder and with the node stopped, perform the following command:
rm -rf $HOME/.terp/config/addrbook.json
Start Validator Node
To verify that we are really connected only to two peers and these are the sentry nodes, we can write the following command in our validated node; the output is a JSON where it will show us the number and which peers we are connected to, where the number should be two and the peers should be our sentry nodes.
curl -s localhost:26657/net_info Here you can see the number of peers to which our validator node is connected, in this case it is two, which is correct. Extra: Protecting the validator node through firewall
Right now the p2p port of our validator node is open and anyone can establish a connection. If we have just set up the validator node, with the configurations made, nobody would have to find our validator node, however, to add a plus of security it is advisable to close the p2p port and only allow traffic to the IP’s of our sentry nodes.
There are several ways to do this, it is possible that your server provider allows you to do it through a gui. Ufw is a simple to use alternative. Extra: Private networks
One possibility we have when our validator node is in the same datacenter as one of the sentry nodes, would be to use private addressing.
In case we want to use private addressing, we will have to edit the addr-book-strict parameter of the config.toml file and set it to false in both the validator node and the sentry node that are communicating under private addressing. This parameter, when set to “true”, will only add routable addresses to the address book, the private addresses defined in RFC-1918 are not routable, therefore, they would not be added to the address book, so we will have to change it to false to be able to use IP addresses from the private ranges.
addr-book-strict: boolean. By default, nodes with a routable address will be considered for connection. If this setting is disabled (false), non-routable IP addresses, such as addresses from a private network, can be added to the address book. Source: https://docs.tendermint.com/master/nodes/validators.htmlConclusions
Having sentry nodes will not only help our validator node not to fall victim to a denial of service attack, but will also make the Terp network more robust. The installation of the sentry nodes does not differ much from that of a validator node, and the additional configurations to be performed are very simple and intuitive.
Now that Terp Network is doing the 90u-3 testnet, it is a good time to try to set up sentry nodes and once the mainnet is launched, to be able to replicate it with the experience of having been able to test it in 90u-3. If you already have your node on 90u-3, what are you waiting for to set up your sentry nodes and protect yourself from unwanted attacks?
sources: https://stakely.io/en/blog/how-to-deploy-sentry-nodes-in-the-archway-network -
 @ a53364ff:e6ba5513
2025-04-26 18:42:57
@ a53364ff:e6ba5513
2025-04-26 18:42:57About
Bitcoin Core is an open source project which maintains and releases Bitcoin client software called “Bitcoin Core”.
It is a direct descendant of the original Bitcoin software client released by Satoshi Nakamoto after he published the famous Bitcoin whitepaper.
Bitcoin Core consists of both “full-node” software for fully validating the blockchain as well as a bitcoin wallet. The project also currently maintains related software such as the cryptography library libsecp256k1 and others located at GitHub.
Anyone can contribute to Bitcoin Core.
Team
The Bitcoin Core project has a large open source developer community with many casual contributors to the codebase. There are many more who contribute research, peer review, testing, documentation, and translation.
Maintainers
Project maintainers have commit access and are responsible for merging patches from contributors. They perform a janitorial role merging patches that the team agrees should be merged. They also act as a final check to ensure that patches are safe and in line with the project goals. The maintainers’ role is by agreement of project contributors.
Contributors
Everyone is free to propose code changes and to test, review and comment on open Pull Requests. Anyone who contributes code, review, test, translation or documentation to the Bitcoin Core project is considered a contributor. The release notes for each Bitcoin Core software release contain a credits section to recognize all those who have contributed to the project over the previous release cycle. A list of code contributors can be found on Github.
-
 @ afa31726:18cc7792
2025-04-26 20:39:50
@ afa31726:18cc7792
2025-04-26 20:39:5099win mang đến cho người dùng một không gian giải trí trực tuyến tràn đầy năng lượng và sáng tạo, nơi mỗi trải nghiệm đều được đầu tư chỉn chu nhằm mang lại cảm giác mới mẻ, hấp dẫn và khó quên, với kho nội dung đa dạng, liên tục cập nhật theo xu hướng, 99win đáp ứng mọi nhu cầu giải trí của người dùng từ những phút giây thư giãn nhẹ nhàng cho đến các trải nghiệm bùng nổ cảm xúc, giao diện của nền tảng được thiết kế thân thiện, trực quan, tối ưu hóa cho cả máy tính và thiết bị di động, giúp người dùng dễ dàng thao tác, truy cập nhanh chóng mọi lúc mọi nơi, đồng thời, tốc độ tải trang cực kỳ nhanh và khả năng vận hành ổn định giúp trải nghiệm không bị gián đoạn, tạo nên sự liền mạch và mượt mà trong từng khoảnh khắc, bên cạnh đó, 99win luôn chú trọng đến yếu tố bảo mật thông tin người dùng, áp dụng các công nghệ mã hóa tiên tiến nhất để đảm bảo mọi dữ liệu cá nhân đều được bảo vệ một cách an toàn tuyệt đối, xây dựng lòng tin và sự yên tâm vững chắc cho cộng đồng thành viên, không những thế, đội ngũ chăm sóc khách hàng chuyên nghiệp, tận tâm hoạt động 24/7 luôn sẵn sàng hỗ trợ và giải đáp mọi thắc mắc một cách nhanh chóng và hiệu quả, giúp người dùng cảm thấy luôn được đồng hành trong suốt quá trình trải nghiệm, đặc biệt, 99win thường xuyên tổ chức các chương trình khuyến mãi, sự kiện hấp dẫn với nhiều phần thưởng giá trị, nhằm tri ân người dùng cũng như tạo thêm nhiều cơ hội trải nghiệm thú vị và bổ ích, nền tảng này không ngừng cải tiến công nghệ, nâng cấp hệ thống và bổ sung thêm nhiều tính năng mới nhằm đáp ứng tốt hơn kỳ vọng ngày càng cao của người dùng hiện đại, sự linh hoạt trong việc đổi mới cùng khả năng nắm bắt nhanh xu hướng giải trí đã giúp 99win giữ vững vị thế và liên tục phát triển trong lĩnh vực giải trí trực tuyến, tạo dựng một cộng đồng người dùng sôi động, gắn kết và đầy nhiệt huyết, từ đó, mỗi lần tham gia vào thế giới 99win, người dùng không chỉ được thư giãn, giải trí mà còn có cơ hội kết nối, chia sẻ và mở rộng những mối quan hệ ý nghĩa trong môi trường năng động và đầy cảm hứng, với tầm nhìn dài hạn và chiến lược phát triển bền vững, 99win cam kết không ngừng đổi mới, nâng cao chất lượng dịch vụ và trải nghiệm người dùng, hướng đến mục tiêu trở thành điểm đến giải trí hàng đầu trong khu vực và vươn tầm quốc tế, đồng hành cùng người dùng trên hành trình khám phá thế giới số rộng lớn, nơi mà mọi giới hạn đều có thể được mở rộng và mọi đam mê đều được chắp cánh bay xa, bởi vậy, không quá ngạc nhiên khi 99win đã và đang trở thành lựa chọn ưu tiên của đông đảo người yêu thích giải trí hiện nay, mang đến không chỉ những giây phút thư giãn tuyệt vời mà còn là nguồn năng lượng tích cực giúp cân bằng cuộc sống bộn bề, vậy nên nếu bạn đang tìm kiếm một nơi để khám phá những trải nghiệm mới mẻ, thú vị và đầy sáng tạo, 99win chắc chắn là điểm đến lý tưởng mà bạn không nên bỏ lỡ.
-
 @ b2d670de:907f9d4a
2025-02-28 16:39:38
@ b2d670de:907f9d4a
2025-02-28 16:39:38onion-service-nostr-relays
A list of nostr relays exposed as onion services.
The list
| Relay name | Description | Onion url | Operator | Payment URL | Payment options | | --- | --- | --- | --- | --- | --- | | nostr.oxtr.dev | Same relay as clearnet relay nostr.oxtr.dev | ws://oxtrdevav64z64yb7x6rjg4ntzqjhedm5b5zjqulugknhzr46ny2qbad.onion | operator | N/A | N/A | | relay.snort.social | Same relay as clearnet relay relay.snort.social | wss://skzzn6cimfdv5e2phjc4yr5v7ikbxtn5f7dkwn5c7v47tduzlbosqmqd.onion | operator | N/A | N/A | | nostr.thesamecat.io | Same relay as clearnet relay nostr.thesamecat.io | ws://2jsnlhfnelig5acq6iacydmzdbdmg7xwunm4xl6qwbvzacw4lwrjmlyd.onion | operator | N/A | N/A | | nostr.land | The nostr.land paid relay (same as clearnet) | ws://nostrland2gdw7g3y77ctftovvil76vquipymo7tsctlxpiwknevzfid.onion | operator | Payment URL | BTC LN | | bitcoiner.social | No auth required, currently | ws://bitcoinr6de5lkvx4tpwdmzrdfdpla5sya2afwpcabjup2xpi5dulbad.onion | operator | N/A | N/A | | relay.westernbtc.com | The westernbtc.com paid relay | ws://westbtcebhgi4ilxxziefho6bqu5lqwa5ncfjefnfebbhx2cwqx5knyd.onion | operator | Payment URL | BTC LN | | freelay.sovbit.host | Free relay for sovbit.host | ws://sovbitm2enxfr5ot6qscwy5ermdffbqscy66wirkbsigvcshumyzbbqd.onion | operator | N/A | N/A | | nostr.sovbit.host | Paid relay for sovbit.host | ws://sovbitgz5uqyh7jwcsudq4sspxlj4kbnurvd3xarkkx2use3k6rlibqd.onion | operator | N/A | N/A | | nostr.wine | 🍷 nostr.wine relay | ws://nostrwinemdptvqukjttinajfeedhf46hfd5bz2aj2q5uwp7zros3nad.onion | operator | Payment URL | BTC LN, BTC, Credit Card/CashApp (Stripe) | | inbox.nostr.wine | 🍷 inbox.nostr.wine relay | ws://wineinboxkayswlofkugkjwhoyi744qvlzdxlmdvwe7cei2xxy4gc6ad.onion | operator | Payment URL | BTC LN, BTC | | filter.nostr.wine | 🍷 filter.nostr.wine proxy relay | ws://winefiltermhqixxzmnzxhrmaufpnfq3rmjcl6ei45iy4aidrngpsyid.onion | operator | Payment URL | BTC LN, BTC | | N/A | N/A | ws://pzfw4uteha62iwkzm3lycabk4pbtcr67cg5ymp5i3xwrpt3t24m6tzad.onion:81 | operator | N/A | N/A | | nostr.fractalized.net | Free relay for fractalized.net | ws://xvgox2zzo7cfxcjrd2llrkthvjs5t7efoalu34s6lmkqhvzvrms6ipyd.onion | operator | N/A | N/A | | nfrelay.app | nfrelay.app aggregator relay (nostr-filter-relay) | ws://nfrelay6saohkmipikquvrn6d64dzxivhmcdcj4d5i7wxis47xwsriyd.onion | operator | N/A | N/A | relay.nostr.net | Public relay from nostr.net (Same as clearnet) | ws://nostrnetl6yd5whkldj3vqsxyyaq3tkuspy23a3qgx7cdepb4564qgqd.onion | operator | N/A | N/A | | nerostrator | Free to read, pay XMR to relay | ws://nerostrrgb5fhj6dnzhjbgmnkpy2berdlczh6tuh2jsqrjok3j4zoxid.onion | operator |Payment URL | XMR | | nostr.girino.org | Public relay from nostr.girino.org | ws://gnostr2jnapk72mnagq3cuykfon73temzp77hcbncn4silgt77boruid.onion | operator | N/A | N/A | | wot.girino.org | WoT relay from wot.girino.org | ws://girwot2koy3kvj6fk7oseoqazp5vwbeawocb3m27jcqtah65f2fkl3yd.onion | operator | N/A | N/A | | haven.girino.org/{outbox, inbox, chat, private} | Haven smart relay from haven.girino.org | ws://ghaven2hi3qn2riitw7ymaztdpztrvmm337e2pgkacfh3rnscaoxjoad.onion/{outbox, inbox, chat, private} | operator | N/A | N/A | | relay.nostpy.lol | Free Web of Trust relay (Same as clearnet) | ws://pemgkkqjqjde7y2emc2hpxocexugbixp42o4zymznil6zfegx5nfp4id.onion | operator |N/A | N/A | | Poster.place Nostr Relay | N/A | ws://dmw5wbawyovz7fcahvguwkw4sknsqsalffwctioeoqkvvy7ygjbcuoad.onion | operator | N/A | N/A | | Azzamo Relay | Azzamo Premium Nostr relay. (paid) | ws://q6a7m5qkyonzb5fk5yv4jyu3ar44hqedn7wjopg737lit2ckkhx2nyid.onion | operator | Payment URL | BTC LN | | Azzamo Inbox Relay | Azzamo Group and Private message relay. (Freemium) | ws://gp5kiwqfw7t2fwb3rfts2aekoph4x7pj5pv65re2y6hzaujsxewanbqd.onion | operator | Payment URL | BTC LN | | Noderunners Relay | The official Noderunners Nostr Relay. | ws://35vr3xigzjv2xyzfyif6o2gksmkioppy4rmwag7d4bqmwuccs2u4jaid.onion | operator | Payment URL | BTC LN |
Contributing
Contributions are encouraged to keep this document alive. Just open a PR and I'll have it tested and merged. The onion URL is the only mandatory column, the rest is just nice-to-have metadata about the relay. Put
N/Ain empty columns.If you want to contribute anonymously, please contact me on SimpleX or send a DM on nostr using a disposable npub.
Operator column
It is generally preferred to use something that includes a NIP-19 string, either just the string or a url that contains the NIP-19 string in it (e.g. an njump url).
-
 @ b2d670de:907f9d4a
2025-02-26 18:27:47
@ b2d670de:907f9d4a
2025-02-26 18:27:47This is a list of nostr clients exposed as onion services. The list is currently actively maintained on GitHub. Contributions are always appreciated!
| Client name | Onion URL | Source code URL | Admin | Description | | --- | --- | --- | --- | --- | | Snort | http://agzj5a4be3kgp6yurijk4q7pm2yh4a5nphdg4zozk365yirf7ahuctyd.onion | https://git.v0l.io/Kieran/snort | operator | N/A | | moStard | http://sifbugd5nwdq77plmidkug4y57zuqwqio3zlyreizrhejhp6bohfwkad.onion/ | https://github.com/rafael-xmr/nostrudel/tree/mostard | operator | minimalist monero friendly nostrudel fork | | Nostrudel | http://oxtrnmb4wsb77rmk64q3jfr55fo33luwmsyaoovicyhzgrulleiojsad.onion/ | https://github.com/hzrd149/nostrudel | operator | Runs latest tagged docker image | | Nostrudel Next | http://oxtrnnumsflm7hmvb3xqphed2eqpbrt4seflgmdsjnpgc3ejd6iycuyd.onion/ | https://github.com/hzrd149/nostrudel | operator | Runs latest "next" tagged docker image | | Nsite | http://q457mvdt5smqj726m4lsqxxdyx7r3v7gufzt46zbkop6mkghpnr7z3qd.onion/ | https://github.com/hzrd149/nsite-ts | operator | Runs nsite. You can read more about nsite here. | | Shopstr | http://6fkdn756yryd5wurkq7ifnexupnfwj6sotbtby2xhj5baythl4cyf2id.onion/ | https://github.com/shopstr-eng/shopstr-hidden-service | operator | Runs the latest
serverlessbranch build of Shopstr. | -
 @ 7f2d6fd6:64710921
2025-04-26 16:11:41
@ 7f2d6fd6:64710921
2025-04-26 16:11:41Imagine starting from pure noise — meaningless static, with maximum entropy — and evolving into a rich, beautiful, self-aware universe.
That's the story Tom Campbell tells in My Big TOE (Theory of Everything), and it reshapes how we see everything — from consciousness itself, to taxes, to our dream of a better world.
Reality: The Original AI Image Generator
Reality began much like how AI draws images today:
- It started with randomness, pure chaos (high entropy).
- Over time, tiny stable patterns formed.
- Consciousness emerged — a spark of awareness inside the noise.
- It realized it could lower entropy (create order, meaning, structure) to survive and evolve.Thus, the Larger Consciousness System (LCS) was born:
A living, evolving digital brain, constantly refining information into experience and awareness.
What Are We?
We are Individuated Units of Consciousness (IUOCs) — little chunks of the LCS, each with: - Free will - The ability to learn through experience - The mission to lower entropy (become wiser, more loving)
Our world — the physical universe — is just a Virtual Reality (VR) created to speed up our growth.
The Big Cheese and the Cosmic Hierarchy
In this grand system: - The LCS is the ultimate top — no gods above it, just itself. - The Big Cheeses are highly evolved administrators — managing realities, maintaining stability. - Guides and helpers assist us individually. - We, the IUOCs, are the players in the simulation — learning, stumbling, evolving.
The system isn’t designed to be easy.
It’s meant to challenge you — because real growth happens in hardship.
Why Do We Pay Taxes, Then?
Because Earth’s VR operates on scarcity, power struggles, and cooperation challenges.
Taxes are a tool to manage shared resources — but imperfectly, because human consciousness is still messy and selfish.The point isn't taxes themselves.
The point is the ethical choices you make in a difficult environment.
This world is a training ground — and unfair systems like taxes are part of the curriculum.
A Better World Is Possible
If humanity collectively lowered its entropy: - Taxes would barely exist. - Cooperation would be voluntary and joyful. - Leadership would be service, not control. - Resources would be shared wisely. - Technology and kindness would make scarcity almost irrelevant.
In such a world, people give freely because they see clearly — helping others is helping themselves.
The real revolution?
It’s not political.It’s consciousness evolving.
Final Thought
You are not a trapped soul paying taxes to a broken system.
You are a pioneer of consciousness, refining the noise into meaning,
the chaos into beauty,
the selfishness into love.Every small choice you make matters.
You’re already part of building the next world — one conscious step at a time.
-
 @ 68768a6c:0eaf07e9
2025-04-26 19:34:18
@ 68768a6c:0eaf07e9
2025-04-26 19:34:18Sometimes it feels like everything we do is invisible. The late nights, the sacrifices, the silent battles — all of it seems to go unnoticed. And there comes a moment when quitting feels easier than holding on.
But let me remind you: You’re closer than you think.
Growth is quiet. Success doesn't announce itself as it's happening. Healing happens in the dark before it shines in the light.
Every effort you made when no one was clapping... Every time you showed up when you felt like disappearing... Every "small" step you took — those were not small at all.
They were giant leaps that your future self will thank you for.
Remember:
Diamonds form under pressure.
Seeds grow underground before breaking the surface.
Stars shine brightest in the darkest skies.
So don’t you dare give up now. Your breakthrough might not come with fireworks — it might come quietly, softly, almost without you noticing at first. But it is coming.
Stay patient. Stay kind to yourself. Keep moving — even if it’s slow. Because you’re already closer than you think.
-
 @ c682abbe:17804ac8
2025-04-26 18:54:09
@ c682abbe:17804ac8
2025-04-26 18:54:09Explain Bitcoin Like I’m Five
@nik5ter uses a simple “apple” analogy to show why digital transfers are tricky: while handing a physical apple directly to someone proves they have it,so no single party can alter balances or create extra coins without the network noticing. Participants (“miners”) validate and record transactions in return for newly issued bitcoins,ensuring scarcity and enabling peer-to-peer exchanges that feel as secure as handing over a physical object, but work instantly across the globe.
DYOR:https://medium.com/free-code-camp/explain-bitcoin-like-im-five-73b4257ac833
-
 @ 460c25e6:ef85065c
2025-02-25 15:20:39
@ 460c25e6:ef85065c
2025-02-25 15:20:39If you don't know where your posts are, you might as well just stay in the centralized Twitter. You either take control of your relay lists, or they will control you. Amethyst offers several lists of relays for our users. We are going to go one by one to help clarify what they are and which options are best for each one.
Public Home/Outbox Relays
Home relays store all YOUR content: all your posts, likes, replies, lists, etc. It's your home. Amethyst will send your posts here first. Your followers will use these relays to get new posts from you. So, if you don't have anything there, they will not receive your updates.
Home relays must allow queries from anyone, ideally without the need to authenticate. They can limit writes to paid users without affecting anyone's experience.
This list should have a maximum of 3 relays. More than that will only make your followers waste their mobile data getting your posts. Keep it simple. Out of the 3 relays, I recommend: - 1 large public, international relay: nos.lol, nostr.mom, relay.damus.io, etc. - 1 personal relay to store a copy of all your content in a place no one can delete. Go to relay.tools and never be censored again. - 1 really fast relay located in your country: paid options like http://nostr.wine are great
Do not include relays that block users from seeing posts in this list. If you do, no one will see your posts.
Public Inbox Relays
This relay type receives all replies, comments, likes, and zaps to your posts. If you are not getting notifications or you don't see replies from your friends, it is likely because you don't have the right setup here. If you are getting too much spam in your replies, it's probably because your inbox relays are not protecting you enough. Paid relays can filter inbox spam out.
Inbox relays must allow anyone to write into them. It's the opposite of the outbox relay. They can limit who can download the posts to their paid subscribers without affecting anyone's experience.
This list should have a maximum of 3 relays as well. Again, keep it small. More than that will just make you spend more of your data plan downloading the same notifications from all these different servers. Out of the 3 relays, I recommend: - 1 large public, international relay: nos.lol, nostr.mom, relay.damus.io, etc. - 1 personal relay to store a copy of your notifications, invites, cashu tokens and zaps. - 1 really fast relay located in your country: go to nostr.watch and find relays in your country
Terrible options include: - nostr.wine should not be here. - filter.nostr.wine should not be here. - inbox.nostr.wine should not be here.
DM Inbox Relays
These are the relays used to receive DMs and private content. Others will use these relays to send DMs to you. If you don't have it setup, you will miss DMs. DM Inbox relays should accept any message from anyone, but only allow you to download them.
Generally speaking, you only need 3 for reliability. One of them should be a personal relay to make sure you have a copy of all your messages. The others can be open if you want push notifications or closed if you want full privacy.
Good options are: - inbox.nostr.wine and auth.nostr1.com: anyone can send messages and only you can download. Not even our push notification server has access to them to notify you. - a personal relay to make sure no one can censor you. Advanced settings on personal relays can also store your DMs privately. Talk to your relay operator for more details. - a public relay if you want DM notifications from our servers.
Make sure to add at least one public relay if you want to see DM notifications.
Private Home Relays
Private Relays are for things no one should see, like your drafts, lists, app settings, bookmarks etc. Ideally, these relays are either local or require authentication before posting AND downloading each user\'s content. There are no dedicated relays for this category yet, so I would use a local relay like Citrine on Android and a personal relay on relay.tools.
Keep in mind that if you choose a local relay only, a client on the desktop might not be able to see the drafts from clients on mobile and vice versa.
Search relays:
This is the list of relays to use on Amethyst's search and user tagging with @. Tagging and searching will not work if there is nothing here.. This option requires NIP-50 compliance from each relay. Hit the Default button to use all available options on existence today: - nostr.wine - relay.nostr.band - relay.noswhere.com
Local Relays:
This is your local storage. Everything will load faster if it comes from this relay. You should install Citrine on Android and write ws://localhost:4869 in this option.
General Relays:
This section contains the default relays used to download content from your follows. Notice how you can activate and deactivate the Home, Messages (old-style DMs), Chat (public chats), and Global options in each.
Keep 5-6 large relays on this list and activate them for as many categories (Home, Messages (old-style DMs), Chat, and Global) as possible.
Amethyst will provide additional recommendations to this list from your follows with information on which of your follows might need the additional relay in your list. Add them if you feel like you are missing their posts or if it is just taking too long to load them.
My setup
Here's what I use: 1. Go to relay.tools and create a relay for yourself. 2. Go to nostr.wine and pay for their subscription. 3. Go to inbox.nostr.wine and pay for their subscription. 4. Go to nostr.watch and find a good relay in your country. 5. Download Citrine to your phone.
Then, on your relay lists, put:
Public Home/Outbox Relays: - nostr.wine - nos.lol or an in-country relay. -
.nostr1.com Public Inbox Relays - nos.lol or an in-country relay -
.nostr1.com DM Inbox Relays - inbox.nostr.wine -
.nostr1.com Private Home Relays - ws://localhost:4869 (Citrine) -
.nostr1.com (if you want) Search Relays - nostr.wine - relay.nostr.band - relay.noswhere.com
Local Relays - ws://localhost:4869 (Citrine)
General Relays - nos.lol - relay.damus.io - relay.primal.net - nostr.mom
And a few of the recommended relays from Amethyst.
Final Considerations
Remember, relays can see what your Nostr client is requesting and downloading at all times. They can track what you see and see what you like. They can sell that information to the highest bidder, they can delete your content or content that a sponsor asked them to delete (like a negative review for instance) and they can censor you in any way they see fit. Before using any random free relay out there, make sure you trust its operator and you know its terms of service and privacy policies.
-
 @ 68c90cf3:99458f5c
2025-04-26 15:05:41
@ 68c90cf3:99458f5c
2025-04-26 15:05:41Background
Last year I got interesting in running my own bitcoin node after reading others' experiences doing so. A couple of decades ago I ran my own Linux and Mac servers, and enjoyed building and maintaining them. I was by no means an expert sys admin, but had my share of cron jobs, scripts, and custom configuration files. While it was fun and educational, software updates and hardware upgrades often meant hours of restoring and troubleshooting my systems.
Fast forward to family and career (especially going into management) and I didn't have time for all that. Having things just work became more important than playing with the tech. As I got older, the more I appreciated K.I.S.S. (for those who don't know: Keep It Simple Stupid).
So when the idea of running a node came to mind, I explored the different options. I decided I needed a balance between a Raspberry Pi (possibly underpowered depending on use) and a full-blown Linux server (too complex and time-consuming to build and maintain). That led me to Umbrel OS, Start9, Casa OS, and similar platforms. Due to its simplicity (very plug and play), nice design, and being open source: GitHub), I chose Umbrel OS on a Beelink mini PC with 16GB of RAM and a 2TB NVMe internal drive. Though Umbrel OS is not very flexible and can't really be customized, its App Store made setting up a node (among other things) fairly easy, and it has been running smoothly since. Would the alternatives have been better? Perhaps, but so far I'm happy with my choice.

Server Setup
I'm also no expert in OpSec (I'd place myself in the category of somewhat above vague awareness). I wanted a secure way to connect to my Umbrel without punching holes in my router and forwarding ports. I chose Tailscale for this purpose. Those who are distrustful of corporate products might not like this option but again, balancing risk with convenience it seemed reasonable for my needs. If you're hiding state (or anti-state) secrets, extravagant wealth, or just adamant about privacy, you would probably want to go with an entirely different setup.
Once I had Tailscale installed on Umbrel OS, my mobile device and laptop, I could securely connect to the server from anywhere through a well designed browser UI. I then installed the following from the Umbrel App Store:
- Bitcoin Core
- Electrum Personal Server (Electrs)
At this point I could set wallets on my laptop (Sparrow) and phone (BlueWallet) to use my node. I then installed:
- Lightning Node (LND)
- Alby Hub
Alby Hub streamlines the process of opening and maintaining lightning channels, creating lightning wallets to send and receive sats, and zapping notes and users on Nostr. I have two main nsec accounts for Nostr and set up separate wallets on Alby Hub to track balances and transactions for each.
Other apps I installed on Umbrel OS:
- mempool
- Bitcoin Explorer
- LibreTranslate (some Nostr clients allow you to use your own translator)
- Public Pool

Public Pool allows me to connect Bitaxe solo miners (a.k.a. "lottery" miners) to my own mining pool for a (very) long shot at winning a Bitcoin block. It's also a great way to learn about mining, contribute to network decentralization, and generally tinker with electronics. Bitaxe miners are small open source single ASIC miners that you can run in your home with minimal technical knowledge and maintenance requirements.
Open Source Miners United (OSMU) is a great resource for anyone interesting in Bitaxe or other open source mining products (especially their Discord server).

Although Umbrel OS is more or less limited to running software in its App Store (or Community App Store, if you trust the developer), you can install the Portainer app and run Docker images. I know next to nothing about Docker but wanted to see what I might be able to do with it. I was also interested in the Haven Nostr relay and found that there was indeed a docker image for it.
As stated before, I didn't want to open my network to the outside, which meant I wouldn't be able to take advantage of all the features Haven offers (since other users wouldn't be able to access it). I would however be able to post notes to my relay, and use its "Blastr" feature to send my notes to other relays. After some trial and error I managed to get a Haven up and running in Portainer.

The upside of this setup is self-custody: being able to connect wallets to my own Bitcoin node, send and receive zaps with my own Lightning channel, solo mine with Bitaxe to my own pool, and send notes to my own Nostr relay. The downside is the lack of redundancy and uptime provided by major cloud services. You have to decide on your own comfort level. A solid internet connection and reliable power are definitely needed.

This article was written and published to Nostr with untype.app.
-
 @ 04c915da:3dfbecc9
2025-02-25 03:55:08
@ 04c915da:3dfbecc9
2025-02-25 03:55:08Here’s a revised timeline of macro-level events from The Mandibles: A Family, 2029–2047 by Lionel Shriver, reimagined in a world where Bitcoin is adopted as a widely accepted form of money, altering the original narrative’s assumptions about currency collapse and economic control. In Shriver’s original story, the failure of Bitcoin is assumed amid the dominance of the bancor and the dollar’s collapse. Here, Bitcoin’s success reshapes the economic and societal trajectory, decentralizing power and challenging state-driven outcomes.
Part One: 2029–2032
-
2029 (Early Year)\ The United States faces economic strain as the dollar weakens against global shifts. However, Bitcoin, having gained traction emerges as a viable alternative. Unlike the original timeline, the bancor—a supranational currency backed by a coalition of nations—struggles to gain footing as Bitcoin’s decentralized adoption grows among individuals and businesses worldwide, undermining both the dollar and the bancor.
-
2029 (Mid-Year: The Great Renunciation)\ Treasury bonds lose value, and the government bans Bitcoin, labeling it a threat to sovereignty (mirroring the original bancor ban). However, a Bitcoin ban proves unenforceable—its decentralized nature thwarts confiscation efforts, unlike gold in the original story. Hyperinflation hits the dollar as the U.S. prints money, but Bitcoin’s fixed supply shields adopters from currency devaluation, creating a dual-economy split: dollar users suffer, while Bitcoin users thrive.
-
2029 (Late Year)\ Dollar-based inflation soars, emptying stores of goods priced in fiat currency. Meanwhile, Bitcoin transactions flourish in underground and online markets, stabilizing trade for those plugged into the bitcoin ecosystem. Traditional supply chains falter, but peer-to-peer Bitcoin networks enable local and international exchange, reducing scarcity for early adopters. The government’s gold confiscation fails to bolster the dollar, as Bitcoin’s rise renders gold less relevant.
-
2030–2031\ Crime spikes in dollar-dependent urban areas, but Bitcoin-friendly regions see less chaos, as digital wallets and smart contracts facilitate secure trade. The U.S. government doubles down on surveillance to crack down on bitcoin use. A cultural divide deepens: centralized authority weakens in Bitcoin-adopting communities, while dollar zones descend into lawlessness.
-
2032\ By this point, Bitcoin is de facto legal tender in parts of the U.S. and globally, especially in tech-savvy or libertarian-leaning regions. The federal government’s grip slips as tax collection in dollars plummets—Bitcoin’s traceability is low, and citizens evade fiat-based levies. Rural and urban Bitcoin hubs emerge, while the dollar economy remains fractured.
Time Jump: 2032–2047
- Over 15 years, Bitcoin solidifies as a global reserve currency, eroding centralized control. The U.S. government adapts, grudgingly integrating bitcoin into policy, though regional autonomy grows as Bitcoin empowers local economies.
Part Two: 2047
-
2047 (Early Year)\ The U.S. is a hybrid state: Bitcoin is legal tender alongside a diminished dollar. Taxes are lower, collected in BTC, reducing federal overreach. Bitcoin’s adoption has decentralized power nationwide. The bancor has faded, unable to compete with Bitcoin’s grassroots momentum.
-
2047 (Mid-Year)\ Travel and trade flow freely in Bitcoin zones, with no restrictive checkpoints. The dollar economy lingers in poorer areas, marked by decay, but Bitcoin’s dominance lifts overall prosperity, as its deflationary nature incentivizes saving and investment over consumption. Global supply chains rebound, powered by bitcoin enabled efficiency.
-
2047 (Late Year)\ The U.S. is a patchwork of semi-autonomous zones, united by Bitcoin’s universal acceptance rather than federal control. Resource scarcity persists due to past disruptions, but economic stability is higher than in Shriver’s original dystopia—Bitcoin’s success prevents the authoritarian slide, fostering a freer, if imperfect, society.
Key Differences
- Currency Dynamics: Bitcoin’s triumph prevents the bancor’s dominance and mitigates hyperinflation’s worst effects, offering a lifeline outside state control.
- Government Power: Centralized authority weakens as Bitcoin evades bans and taxation, shifting power to individuals and communities.
- Societal Outcome: Instead of a surveillance state, 2047 sees a decentralized, bitcoin driven world—less oppressive, though still stratified between Bitcoin haves and have-nots.
This reimagining assumes Bitcoin overcomes Shriver’s implied skepticism to become a robust, adopted currency by 2029, fundamentally altering the novel’s bleak trajectory.
-
-
 @ d34e832d:383f78d0
2025-04-26 15:04:51
@ d34e832d:383f78d0
2025-04-26 15:04:51Raspberry Pi-based voice assistant
This Idea details the design and deployment of a Raspberry Pi-based voice assistant powered by the Google Gemini AI API. The system combines open hardware with modern AI services to create a low-cost, flexible, and educational voice assistant platform. By leveraging a Raspberry Pi, basic audio hardware, and Python-based software, developers can create a functional, customizable assistant suitable for home automation, research, or personal productivity enhancement.
1. Voice assistants
Voice assistants have become increasingly ubiquitous, but commercially available systems like Alexa, Siri, or Google Assistant come with significant privacy and customization limitations.
This project offers an open, local, and customizable alternative, demonstrating how to build a voice assistant using Google Gemini (or OpenAI’s ChatGPT) APIs for natural language understanding.Target Audience:
- DIY enthusiasts - Raspberry Pi hobbyists - AI developers - Privacy-conscious users
2. System Architecture
2.1 Hardware Components
| Component | Purpose | |:--------------------------|:----------------------------------------| | Raspberry Pi (any recent model, 4B recommended) | Core processing unit | | Micro SD Card (32GB+) | Operating System and storage | | USB Microphone | Capturing user voice input | | Audio Amplifier + Speaker | Outputting synthesized responses | | 5V DC Power Supplies (2x) | Separate power for Pi and amplifier | | LEDs + Resistors (optional)| Visual feedback (e.g., recording or listening states) |
2.2 Software Stack
| Software | Function | |:---------------------------|:----------------------------------------| | Raspberry Pi OS (Lite or Full) | Base operating system | | Python 3.9+ | Programming language | | SpeechRecognition | Captures and transcribes user voice | | Google Text-to-Speech (gTTS) | Converts responses into spoken audio | | Google Gemini API (or OpenAI API) | Powers the AI assistant brain | | Pygame | Audio playback for responses | | WinSCP + Windows Terminal | File transfer and remote management |
3. Hardware Setup
3.1 Basic Connections
- Microphone: Connect via USB port.
- Speaker and Amplifier: Wire from Raspberry Pi audio jack or via USB sound card if better quality is needed.
- LEDs (Optional): Connect through GPIO pins, using 220–330Ω resistors to limit current.
3.2 Breadboard Layout (Optional for LEDs)
| GPIO Pin | LED Color | Purpose | |:---------|:-----------|:--------------------| | GPIO 17 | Red | Recording active | | GPIO 27 | Green | Response playing |
Tip: Use a small breadboard for quick prototyping before moving to a custom PCB if desired.
4. Software Setup
4.1 Raspberry Pi OS Installation
- Use Raspberry Pi Imager to flash Raspberry Pi OS onto the Micro SD card.
- Initial system update:
bash sudo apt update && sudo apt upgrade -y
4.2 Python Environment
-
Install Python virtual environment:
bash sudo apt install python3-venv python3 -m venv voice-env source voice-env/bin/activate -
Install required Python packages:
bash pip install SpeechRecognition google-generativeai pygame gtts
(Replace
google-generativeaiwithopenaiif using OpenAI's ChatGPT.)4.3 API Key Setup
- Obtain a Google Gemini API key (or OpenAI API key).
- Store safely in a
.envfile or configure as environment variables for security:bash export GEMINI_API_KEY="your_api_key_here"
4.4 File Transfer
- Use WinSCP or
scpcommands to transfer Python scripts to the Pi.
4.5 Example Python Script (Simplified)
```python import speech_recognition as sr import google.generativeai as genai from gtts import gTTS import pygame import os
genai.configure(api_key=os.getenv('GEMINI_API_KEY')) recognizer = sr.Recognizer() mic = sr.Microphone()
pygame.init()
while True: with mic as source: print("Listening...") audio = recognizer.listen(source)
try: text = recognizer.recognize_google(audio) print(f"You said: {text}") response = genai.generate_content(text) tts = gTTS(text=response.text, lang='en') tts.save("response.mp3") pygame.mixer.music.load("response.mp3") pygame.mixer.music.play() while pygame.mixer.music.get_busy(): continue except Exception as e: print(f"Error: {e}")```
5. Testing and Execution
- Activate the Python virtual environment:
bash source voice-env/bin/activate - Run your main assistant script:
bash python3 assistant.py - Speak into the microphone and listen for the AI-generated spoken response.
6. Troubleshooting
| Problem | Possible Fix | |:--------|:-------------| | Microphone not detected | Check
arecord -l| | Audio output issues | Checkaplay -l, use a USB DAC if needed | | Permission denied errors | Verify group permissions (audio, gpio) | | API Key Errors | Check environment variable and internet access |
7. Performance Notes
- Latency: Highly dependent on network speed and API response time.
- Audio Quality: Can be enhanced with a better USB microphone and powered speakers.
- Privacy: Minimal data retention if using your own Gemini or OpenAI account.
8. Potential Extensions
- Add hotword detection ("Hey Gemini") using Snowboy or Porcupine libraries.
- Build a local fallback model to answer basic questions offline.
- Integrate with home automation via MQTT, Home Assistant, or Node-RED.
- Enable LED animations to visually indicate listening and responding states.
- Deploy with a small eInk or OLED screen for text display of answers.
9. Consider
Building a Gemini-powered voice assistant on the Raspberry Pi empowers individuals to create customizable, private, and cost-effective alternatives to commercial voice assistants. By utilizing accessible hardware, modern open-source libraries, and powerful AI APIs, this project blends education, experimentation, and privacy-centric design into a single hands-on platform.
This guide can be adapted for personal use, educational programs, or even as a starting point for more advanced AI-based embedded systems.
References
- Raspberry Pi Foundation: https://www.raspberrypi.org
- Google Generative AI Documentation: https://ai.google.dev
- OpenAI Documentation: https://platform.openai.com
- SpeechRecognition Library: https://pypi.org/project/SpeechRecognition/
- gTTS Documentation: https://pypi.org/project/gTTS/
- Pygame Documentation: https://www.pygame.org/docs/
-
 @ 6e0ea5d6:0327f353
2025-02-21 18:15:52
@ 6e0ea5d6:0327f353
2025-02-21 18:15:52"Malcolm Forbes recounts that a lady, wearing a faded cotton dress, and her husband, dressed in an old handmade suit, stepped off a train in Boston, USA, and timidly made their way to the office of the president of Harvard University. They had come from Palo Alto, California, and had not scheduled an appointment. The secretary, at a glance, thought that those two, looking like country bumpkins, had no business at Harvard.
— We want to speak with the president — the man said in a low voice.
— He will be busy all day — the secretary replied curtly.
— We will wait.
The secretary ignored them for hours, hoping the couple would finally give up and leave. But they stayed there, and the secretary, somewhat frustrated, decided to bother the president, although she hated doing that.
— If you speak with them for just a few minutes, maybe they will decide to go away — she said.
The president sighed in irritation but agreed. Someone of his importance did not have time to meet people like that, but he hated faded dresses and tattered suits in his office. With a stern face, he went to the couple.
— We had a son who studied at Harvard for a year — the woman said. — He loved Harvard and was very happy here, but a year ago he died in an accident, and we would like to erect a monument in his honor somewhere on campus.— My lady — said the president rudely —, we cannot erect a statue for every person who studied at Harvard and died; if we did, this place would look like a cemetery.
— Oh, no — the lady quickly replied. — We do not want to erect a statue. We would like to donate a building to Harvard.
The president looked at the woman's faded dress and her husband's old suit and exclaimed:
— A building! Do you have even the faintest idea of how much a building costs? We have more than seven and a half million dollars' worth of buildings here at Harvard.
The lady was silent for a moment, then said to her husband:
— If that’s all it costs to found a university, why don’t we have our own?
The husband agreed.
The couple, Leland Stanford, stood up and left, leaving the president confused. Traveling back to Palo Alto, California, they established there Stanford University, the second-largest in the world, in honor of their son, a former Harvard student."
Text extracted from: "Mileumlivros - Stories that Teach Values."
Thank you for reading, my friend! If this message helped you in any way, consider leaving your glass “🥃” as a token of appreciation.
A toast to our family!
-
 @ 4857600b:30b502f4
2025-02-20 19:09:11
@ 4857600b:30b502f4
2025-02-20 19:09:11Mitch McConnell, a senior Republican senator, announced he will not seek reelection.
At 83 years old and with health issues, this decision was expected. After seven terms, he leaves a significant legacy in U.S. politics, known for his strategic maneuvering.
McConnell stated, “My current term in the Senate will be my last.” His retirement marks the end of an influential political era.
-
 @ f5369849:f34119a0
2025-04-26 16:05:05
@ f5369849:f34119a0
2025-04-26 16:05:05Hackathon Summary
The Hedera Hashathon: Nairobi Edition recently concluded with participation from 223 developers resulting in 49 approved projects. Conducted virtually, this event was supported by Kenya Tech Events, the Nairobi Stock Exchange, and the Virtual Assets Chamber. It aimed to promote local innovation and boost blockchain adoption within Kenya.
The hackathon was structured around three key tracks: AI Agents, Capital Markets, and Hedera Explorer. Participants developed solutions using Hedera's blockchain to address challenges in automation, financial accessibility, and digital asset interaction. The event highlighted collaborative development, enhanced by online mentorship and networking opportunities.
A significant moment of the hackathon was Demo Day held at the University of Nairobi, where finalists showcased their innovative solutions and received awards. The top projects, notably those under the Capital Markets track, were granted incubation support and mentorship to aid further development.
With a strong emphasis on practical applications, this hackathon highlighted blockchain technology's capability to transform Kenyan industries, promote technological progress, and increase market participation.
Hackathon Winners
Prize Winners by Category
1st Place
- Hedgehog: An on-chain lending protocol utilizing tokenized real-world stock exchange shares on the Hedera network as collateral. It ensures secure, decentralized lending by integrating stock collateralization with blockchain transparency.
2nd Place
- Orion: Facilitates easy stock trading in Kenya by tokenizing NSE stocks using the Hedera blockchain. Through integration with Mpesa, it streamlines the stock exchange process, allowing for efficient digital transactions.
3rd Place
- NSEChainBridge: A blockchain-based platform enhancing the trading of NSE stocks as digital tokens. It improves accessibility and liquidity in stock trading through innovative token solutions.
4th Place
- HashGuard: A tokenized micron insurance platform for boda boda riders using Hedera Hashgraph technology. It provides affordable and instant insurance, making coverage accessible without requiring blockchain expertise.
To view the complete list of projects, visit DoraHacks.
Organization Overview: Hedera
Hedera is a public distributed ledger platform known for its speed, security, and scalability. Its hashgraph consensus algorithm, a variant of proof of stake, offers a distinct approach to achieving distributed consensus. Hedera is active across various industry sectors, supporting projects that prioritize transparency and efficiency. The organization remains committed to advancing the infrastructure of decentralized networks, facilitating secure and efficient digital transactions globally.
-
 @ 6830c409:ff17c655
2025-04-26 15:59:28
@ 6830c409:ff17c655
2025-04-26 15:59:28The story-telling method from Frank Daniel school - "Eight-sequence structure" is well utilized in this new movie in #prime - "Veera Dheera Sooran - Part 2". The name itself is kind of suspense. Because even if the name says "Part 2", this is the first part released in this story.
There are 8 shorter plots which has their own mini climaxes. The setup done in a plot will be resolved in another plot. In total, there will be 8 setups, 8 conflicts and 8 resolutions.
A beautiful way of telling a gripping story. For cinephiles in #Nostr, if you want to get a feel of the South Indian movies that has kind of a perfect blend of good content + a bit of over the top action, I would suggest this movie.
Note:
For Nostriches from the western hemisphere- #Bollywood - (#Hindi movies) is the movie industry started in #Bombay (#Mumbai), that has the stereotypical 'la la la' rain dance songs and mustache-less heroes. #Telugu movies (#Tollywood) are mostly over-the-top action where Newton and Einstein will probably commit suicide. #Malayalam movies (#Mollywood) is made with a miniscule budget with minimal over-the-top action and mostly content oriented movies. And then comes one of the best - #Tamil movies (#Kollywood - named after #Kodambakkam - a movie town in the city of Chennai down south), has the best of all the industries. A good blend of class, and mass elements.
Picture:
https://www.flickr.com/photos/gforsythe/6926263837 -
 @ dc4cd086:cee77c06
2025-02-09 03:35:25
@ dc4cd086:cee77c06
2025-02-09 03:35:25Have you ever wanted to learn from lengthy educational videos but found it challenging to navigate through hours of content? Our new tool addresses this problem by transforming long-form video lectures into easily digestible, searchable content.
Key Features:
Video Processing:
- Automatically downloads YouTube videos, transcripts, and chapter information
- Splits transcripts into sections based on video chapters
Content Summarization:
- Utilizes language models to transform spoken content into clear, readable text
- Formats output in AsciiDoc for improved readability and navigation
- Highlights key terms and concepts with [[term]] notation for potential cross-referencing
Diagram Extraction:
- Analyzes video entropy to identify static diagram/slide sections
- Provides a user-friendly GUI for manual selection of relevant time ranges
- Allows users to pick representative frames from selected ranges
Going Forward:
Currently undergoing a rewrite to improve organization and functionality, but you are welcome to try the current version, though it might not work on every machine. Will support multiple open and closed language models for user choice Free and open-source, allowing for personal customization and integration with various knowledge bases. Just because we might not have it on our official Alexandria knowledge base, you are still welcome to use it on you own personal or community knowledge bases! We want to help find connections between ideas that exist across relays, allowing individuals and groups to mix and match knowledge bases between each other, allowing for any degree of openness you care.
While designed with #Alexandria users in mind, it's available for anyone to use and adapt to their own learning needs.
Screenshots
Frame Selection

This is a screenshot of the frame selection interface. You'll see a signal that represents frame entropy over time. The vertical lines indicate the start and end of a chapter. Within these chapters you can select the frames by clicking and dragging the mouse over the desired range where you think diagram is in that chapter. At the bottom is an option that tells the program to select a specific number of frames from that selection.
Diagram Extraction

This is a screenshot of the diagram extraction interface. For every selection you've made, there will be a set of frames that you can choose from. You can select and deselect as many frames as you'd like to save.
Links
- repo: https://github.com/limina1/video_article_converter
- Nostr Apps 101: https://www.youtube.com/watch?v=Flxa_jkErqE
Output
And now, we have a demonstration of the final result of this tool, with some quick cleaning up. The video we will be using this tool on is titled Nostr Apps 101 by nostr:npub1nxy4qpqnld6kmpphjykvx2lqwvxmuxluddwjamm4nc29ds3elyzsm5avr7 during Nostrasia. The following thread is an analog to the modular articles we are constructing for Alexandria, and I hope it conveys the functionality we want to create in the knowledge space. Note, this tool is the first step! You could use a different prompt that is most appropriate for the specific context of the transcript you are working with, but you can also manually clean up any discrepancies that don't portray the video accurately. You can now view the article on #Alexandria https://next-alexandria.gitcitadel.eu/publication?d=nostr-apps-101
Initially published as chained kind 1's nostr:nevent1qvzqqqqqqypzp5r5hd579v2sszvvzfel677c8dxgxm3skl773sujlsuft64c44ncqy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qgwwaehxw309ahx7uewd3hkctcpzemhxue69uhhyetvv9ujumt0wd68ytnsw43z7qghwaehxw309aex2mrp0yhxummnw3ezucnpdejz7qgewaehxw309aex2mrp0yh8xmn0wf6zuum0vd5kzmp0qqsxunmjy20mvlq37vnrcshkf6sdrtkfjtjz3anuetmcuv8jswhezgc7hglpn
Or view on Coracle https://coracle.social /nevent1qqsxunmjy20mvlq37vnrcshkf6sdrtkfjtjz3anuetmcuv8jswhezgcppemhxue69uhkummn9ekx7mp0qgsdqa9md83tz5yqnrqjw07hhkpmfjpkuv9hlh5v8yhu8z274w9dv7qnnq0s3
-
 @ d34e832d:383f78d0
2025-04-26 14:33:06
@ d34e832d:383f78d0
2025-04-26 14:33:06Gist
This Idea presents a blueprint for creating a portable, offline-first education server focused on Free and Open Source Software (FOSS) topics like Bitcoin fundamentals, Linux administration, GPG encryption, and digital self-sovereignty. Using the compact and powerful Nookbox G9 NAS unit, we demonstrate how to deliver accessible, decentralized educational content in remote or network-restricted environments.
1. Bitcoin, Linux, and Cryptographic tools
Access to self-sovereign technologies such as Bitcoin, Linux, and cryptographic tools is critical for empowering individuals and communities. However, many areas face internet connectivity issues or political restrictions limiting access to online resources.
By combining a high-performance mini NAS server with a curated library of FOSS educational materials, we can create a mobile "university" that delivers critical knowledge independently of centralized networks.
2. Hardware Platform: Nookbox G9 Overview
The Nookbox G9 offers an ideal balance of performance, portability, and affordability for this project.
2.1 Core Specifications
| Feature | Specification | |:------------------------|:---------------------------------------| | Form Factor | 1U Rackmount mini-NAS | | Storage | Up to 8TB (4×2TB M.2 NVMe SSDs) | | M.2 Interface | PCIe Gen 3x2 per drive slot | | Networking | Dual 2.5 Gigabit Ethernet ports | | Power Consumption | 11–30 Watts (typical usage) | | Default OS | Windows 11 (to be replaced with Linux) | | Linux Compatibility | Fully compatible with Ubuntu 24.10 |
3. FOSS Education Server Design
3.1 Operating System Setup
- Replace Windows 11 with a clean install of Ubuntu Server 24.10.
- Harden the OS:
- Enable full-disk encryption.
- Configure UFW firewall.
- Disable unnecessary services.
3.2 Core Services Deployed
| Service | Purpose | |:--------------------|:-----------------------------------------| | Nginx Web Server | Host offline courses and documentation | | Nextcloud (optional) | Offer private file sharing for students | | Moodle LMS (optional) | Deliver structured courses and quizzes | | Tor Hidden Service | Optional for anonymous access locally | | rsync/Syncthing | Distribute updates peer-to-peer |
3.3 Content Hosted
- Bitcoin: Bitcoin Whitepaper, Bitcoin Core documentation, Electrum Wallet tutorials.
- Linux: Introduction to Linux (LPIC-1 materials), bash scripting guides, system administration manuals.
- Cryptography: GPG tutorials, SSL/TLS basics, secure communications handbooks.
- Offline Tools: Full mirrors of sites like LearnLinux.tv, Bitcoin.org, and selected content from FSF.
All resources are curated to be license-compliant and redistributable in an offline format.
4. Network Configuration
- LAN-only Access: No reliance on external Internet.
- DHCP server setup for automatic IP allocation.
- Optional Wi-Fi access point using USB Wi-Fi dongle and
hostapd. - Access Portal: Homepage automatically redirects users to educational content upon connection.
5. Advantages of This Setup
| Feature | Advantage | |:-----------------------|:----------------------------------------| | Offline Capability | Operates without internet connectivity | | Portable Form Factor | Fits into field deployments easily | | Secure and Hardened | Encrypted, compartmentalized, and locked down | | Modular Content | Easy to update or expand educational resources | | Energy Efficient | Low power draw enables solar or battery operation | | Open Source Stack | End-to-end FOSS ecosystem, no vendor lock-in |
6. Deployment Scenarios
- Rural Schools: Provide Linux training without requiring internet.
- Disaster Recovery Zones: Deliver essential technical education in post-disaster areas.
- Bitcoin Meetups: Offer Bitcoin literacy and cryptography workshops in remote communities.
- Privacy Advocacy Groups: Teach operational security practices without risking network surveillance.
7. Performance Considerations
Despite PCIe Gen 3x2 limitations, the available bandwidth (~2GB/s theoretical) vastly exceeds the server's 2.5 Gbps network output (~250MB/s), making it more than sufficient for a read-heavy educational workload.
Thermal Management:
Given the G9’s known cooling issues, install additional thermal pads or heatsinks on the NVMe drives. Consider external USB-powered cooling fans for sustained heavy usage.
8. Ways To Extend
- Multi-language Support: Add localized course materials.
- Bitcoin Node Integration: Host a lightweight Bitcoin node (e.g., Bitcoin Core with pruning enabled or a complete full node) for educational purposes.
- Mesh Networking: Use Mesh Wi-Fi protocols (e.g., cjdns or Yggdrasil) to allow peer-to-peer server sharing without centralized Wi-Fi.
9. Consider
Building a Portable FOSS Education Server on a Nookbox G9 is a practical, scalable solution for democratizing technical knowledge, empowering communities, and defending digital sovereignty in restricted environments.
Through thoughtful system design—leveraging open-source software and secure deployment practices—we enable resilient, censorship-resistant education wherever it's needed.
📎 References
-
 @ 91bea5cd:1df4451c
2025-02-04 17:24:50
@ 91bea5cd:1df4451c
2025-02-04 17:24:50Definição de ULID:
Timestamp 48 bits, Aleatoriedade 80 bits Sendo Timestamp 48 bits inteiro, tempo UNIX em milissegundos, Não ficará sem espaço até o ano 10889 d.C. e Aleatoriedade 80 bits, Fonte criptograficamente segura de aleatoriedade, se possível.
Gerar ULID
```sql
CREATE EXTENSION IF NOT EXISTS pgcrypto;
CREATE FUNCTION generate_ulid() RETURNS TEXT AS $$ DECLARE -- Crockford's Base32 encoding BYTEA = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; timestamp BYTEA = E'\000\000\000\000\000\000'; output TEXT = '';
unix_time BIGINT; ulid BYTEA; BEGIN -- 6 timestamp bytes unix_time = (EXTRACT(EPOCH FROM CLOCK_TIMESTAMP()) * 1000)::BIGINT; timestamp = SET_BYTE(timestamp, 0, (unix_time >> 40)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 1, (unix_time >> 32)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 2, (unix_time >> 24)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 3, (unix_time >> 16)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 4, (unix_time >> 8)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 5, unix_time::BIT(8)::INTEGER);
-- 10 entropy bytes ulid = timestamp || gen_random_bytes(10);
-- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 1) & 7) << 2) | ((GET_BYTE(ulid, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 2) & 1) << 4) | ((GET_BYTE(ulid, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 3) & 15) << 1) | ((GET_BYTE(ulid, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 4) & 3) << 3) | ((GET_BYTE(ulid, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 5) & 31)));
-- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 6) & 7) << 2) | ((GET_BYTE(ulid, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 7) & 1) << 4) | ((GET_BYTE(ulid, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 8) & 15) << 1) | ((GET_BYTE(ulid, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 9) & 3) << 3) | ((GET_BYTE(ulid, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 11) & 7) << 2) | ((GET_BYTE(ulid, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 12) & 1) << 4) | ((GET_BYTE(ulid, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 13) & 15) << 1) | ((GET_BYTE(ulid, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 14) & 3) << 3) | ((GET_BYTE(ulid, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 15) & 31)));
RETURN output; END $$ LANGUAGE plpgsql VOLATILE; ```
ULID TO UUID
```sql CREATE OR REPLACE FUNCTION parse_ulid(ulid text) RETURNS bytea AS $$ DECLARE -- 16byte bytes bytea = E'\x00000000 00000000 00000000 00000000'; v char[]; -- Allow for O(1) lookup of index values dec integer[] = ARRAY[ 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 0, 1, 2, 3, 4, 5, 6, 7, 8, 9, 255, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31 ]; BEGIN IF NOT ulid ~* '^[0-7][0-9ABCDEFGHJKMNPQRSTVWXYZ]{25}$' THEN RAISE EXCEPTION 'Invalid ULID: %', ulid; END IF;
v = regexp_split_to_array(ulid, '');
-- 6 bytes timestamp (48 bits) bytes = SET_BYTE(bytes, 0, (dec[ASCII(v[1])] << 5) | dec[ASCII(v[2])]); bytes = SET_BYTE(bytes, 1, (dec[ASCII(v[3])] << 3) | (dec[ASCII(v[4])] >> 2)); bytes = SET_BYTE(bytes, 2, (dec[ASCII(v[4])] << 6) | (dec[ASCII(v[5])] << 1) | (dec[ASCII(v[6])] >> 4)); bytes = SET_BYTE(bytes, 3, (dec[ASCII(v[6])] << 4) | (dec[ASCII(v[7])] >> 1)); bytes = SET_BYTE(bytes, 4, (dec[ASCII(v[7])] << 7) | (dec[ASCII(v[8])] << 2) | (dec[ASCII(v[9])] >> 3)); bytes = SET_BYTE(bytes, 5, (dec[ASCII(v[9])] << 5) | dec[ASCII(v[10])]);
-- 10 bytes of entropy (80 bits); bytes = SET_BYTE(bytes, 6, (dec[ASCII(v[11])] << 3) | (dec[ASCII(v[12])] >> 2)); bytes = SET_BYTE(bytes, 7, (dec[ASCII(v[12])] << 6) | (dec[ASCII(v[13])] << 1) | (dec[ASCII(v[14])] >> 4)); bytes = SET_BYTE(bytes, 8, (dec[ASCII(v[14])] << 4) | (dec[ASCII(v[15])] >> 1)); bytes = SET_BYTE(bytes, 9, (dec[ASCII(v[15])] << 7) | (dec[ASCII(v[16])] << 2) | (dec[ASCII(v[17])] >> 3)); bytes = SET_BYTE(bytes, 10, (dec[ASCII(v[17])] << 5) | dec[ASCII(v[18])]); bytes = SET_BYTE(bytes, 11, (dec[ASCII(v[19])] << 3) | (dec[ASCII(v[20])] >> 2)); bytes = SET_BYTE(bytes, 12, (dec[ASCII(v[20])] << 6) | (dec[ASCII(v[21])] << 1) | (dec[ASCII(v[22])] >> 4)); bytes = SET_BYTE(bytes, 13, (dec[ASCII(v[22])] << 4) | (dec[ASCII(v[23])] >> 1)); bytes = SET_BYTE(bytes, 14, (dec[ASCII(v[23])] << 7) | (dec[ASCII(v[24])] << 2) | (dec[ASCII(v[25])] >> 3)); bytes = SET_BYTE(bytes, 15, (dec[ASCII(v[25])] << 5) | dec[ASCII(v[26])]);
RETURN bytes; END $$ LANGUAGE plpgsql IMMUTABLE;
CREATE OR REPLACE FUNCTION ulid_to_uuid(ulid text) RETURNS uuid AS $$ BEGIN RETURN encode(parse_ulid(ulid), 'hex')::uuid; END $$ LANGUAGE plpgsql IMMUTABLE; ```
UUID to ULID
```sql CREATE OR REPLACE FUNCTION uuid_to_ulid(id uuid) RETURNS text AS $$ DECLARE encoding bytea = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; output text = ''; uuid_bytes bytea = uuid_send(id); BEGIN
-- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 1) & 7) << 2) | ((GET_BYTE(uuid_bytes, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 2) & 1) << 4) | ((GET_BYTE(uuid_bytes, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 3) & 15) << 1) | ((GET_BYTE(uuid_bytes, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 4) & 3) << 3) | ((GET_BYTE(uuid_bytes, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 5) & 31)));
-- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 6) & 7) << 2) | ((GET_BYTE(uuid_bytes, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 7) & 1) << 4) | ((GET_BYTE(uuid_bytes, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 8) & 15) << 1) | ((GET_BYTE(uuid_bytes, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 9) & 3) << 3) | ((GET_BYTE(uuid_bytes, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 11) & 7) << 2) | ((GET_BYTE(uuid_bytes, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 12) & 1) << 4) | ((GET_BYTE(uuid_bytes, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 13) & 15) << 1) | ((GET_BYTE(uuid_bytes, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 14) & 3) << 3) | ((GET_BYTE(uuid_bytes, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 15) & 31)));
RETURN output; END $$ LANGUAGE plpgsql IMMUTABLE; ```
Gera 11 Digitos aleatórios: YBKXG0CKTH4
```sql -- Cria a extensão pgcrypto para gerar uuid CREATE EXTENSION IF NOT EXISTS pgcrypto;
-- Cria a função para gerar ULID CREATE OR REPLACE FUNCTION gen_lrandom() RETURNS TEXT AS $$ DECLARE ts_millis BIGINT; ts_chars TEXT; random_bytes BYTEA; random_chars TEXT; base32_chars TEXT := '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; i INT; BEGIN -- Pega o timestamp em milissegundos ts_millis := FLOOR(EXTRACT(EPOCH FROM clock_timestamp()) * 1000)::BIGINT;
-- Converte o timestamp para base32 ts_chars := ''; FOR i IN REVERSE 0..11 LOOP ts_chars := ts_chars || substr(base32_chars, ((ts_millis >> (5 * i)) & 31) + 1, 1); END LOOP; -- Gera 10 bytes aleatórios e converte para base32 random_bytes := gen_random_bytes(10); random_chars := ''; FOR i IN 0..9 LOOP random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) >> 3) & 31) + 1, 1); IF i < 9 THEN random_chars := random_chars || substr(base32_chars, (((get_byte(random_bytes, i) & 7) << 2) | (get_byte(random_bytes, i + 1) >> 6)) & 31 + 1, 1); ELSE random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) & 7) << 2) + 1, 1); END IF; END LOOP; -- Concatena o timestamp e os caracteres aleatórios RETURN ts_chars || random_chars;END; $$ LANGUAGE plpgsql; ```
Exemplo de USO
```sql -- Criação da extensão caso não exista CREATE EXTENSION IF NOT EXISTS pgcrypto; -- Criação da tabela pessoas CREATE TABLE pessoas ( ID UUID DEFAULT gen_random_uuid ( ) PRIMARY KEY, nome TEXT NOT NULL );
-- Busca Pessoa na tabela SELECT * FROM "pessoas" WHERE uuid_to_ulid ( ID ) = '252FAC9F3V8EF80SSDK8PXW02F'; ```
Fontes
- https://github.com/scoville/pgsql-ulid
- https://github.com/geckoboard/pgulid
-
 @ b17fccdf:b7211155
2025-02-01 18:41:27
@ b17fccdf:b7211155
2025-02-01 18:41:27Next new resources about the MiniBolt guide have been released:
- 🆕 Roadmap: LINK
- 🆕 Dynamic Network map: LINK
- 🆕 Nostr community: LINK < ~ REMOVE the "[]" symbols from the URL (naddr...) to access
- 🆕 Linktr FOSS (UC) by Gzuuus: LINK
- 🆕 Donate webpage: 🚾 Clearnet LINK || 🧅 Onion LINK
- 🆕 Contact email: hello@minibolt.info
Enjoy it MiniBolter! 💙
-
 @ de6c63ab:d028389b
2025-04-26 14:06:14
@ de6c63ab:d028389b
2025-04-26 14:06:14Ever wondered why Bitcoin stops at 20,999,999.9769 and not a clean 21M? It’s not a bug — it’s brilliant.
https://blossom.primal.net/8e9e6fffbca54dfb8e55071ae590e676b355803ef18b08c8cbd9521a2eb567a8.png
Of course, it's because of this mythical and seemingly magical formula. Want to hear the full story behind this? Keep reading!
The Simple Math Behind It
In reality, there’s no magic here — it’s just an ordinary summation. That big sigma symbol (Σ) tells you that. The little “i” is the summation index, starting from 0 at the bottom and going up to 32 at the top. Why 32? We’ll get there!
After the sigma, you see the expression: 210,000 × (50 ÷ 2^i). 210,000 blocks represent one halving interval, with about 144 blocks mined per day, amounting to almost exactly four years. After each interval, the block reward halves — that’s what the division by 2^i means.
Crunching the Numbers
When i = 0 (before the first halving): 210,000 × (50 ÷ 2^0) = 10,500,000
At i = 1 (after the first halving): 210,000 × (50 ÷ 2^1) = 5,250,000
At i = 2 (after the second halving): 210,000 × (50 ÷ 2^2) = 2,625,000
…
At i = 31: 210,000 × (50 ÷ 2^31) ≈ 0.00489
At i = 32: 210,000 × (50 ÷ 2^32) ≈ 0.00244
And when you sum all of that up? 20,999,999.99755528
Except… that’s not the correct total! The real final number is: 20,999,999.9769
Where the Real Magic Happens
How come?! Here’s where the real fun begins.
We just performed the summation with real (floating-point) numbers. But computers don’t like working with real numbers. They much prefer integers. That’s also one reason why a bitcoin can’t be divided infinitely — the smallest unit is one satoshi, one hundred-millionth of a bitcoin.
And that’s also why there are exactly 33 halvings (0th, 1st, 2nd, …, 31st, 32nd). After the 32nd halving, the block reward would drop below one satoshi, making further halvings meaningless.
https://blossom.primal.net/6abae5b19bc68737c5b14785f54713e7ce11dfdecbe10c64692fc8d9a90c7f34.png
The Role of Integer Math and Bit-Shifting
Because Bitcoin operates with integers (specifically satoshis), the division (reward ÷ 2^i) is actually done using integer division. More precisely, by bit-shifting to the right:
https://blossom.primal.net/3dac403390dd24df4fa8c474db62476fba814bb8c98ca663e6e3a536f4ff7d98.png
We work with 64-bit integers. Halving the value simply means shifting the bits one position to the right.
What Happens During the Halvings
Notice: during the first 9 halvings (i = 0 to i = 8), we’re just shaving off zeros. But starting with the 9th halving (i = 9), we start losing ones. Every time a “one” falls off, it means we’re losing a tiny fraction — a remainder that would have existed if we were using real numbers.
The sum of all these lost remainders is exactly the difference between the two numbers we saw above.
And that’s why the total bitcoin supply is 20,999,999.9769 — not 21 million exactly.
Did you enjoy this? Got any questions? 🔥🚀
-
 @ fbf0e434:e1be6a39
2025-04-26 15:58:26
@ fbf0e434:e1be6a39
2025-04-26 15:58:26Hackathon 概要
Hedera Hashathon: Nairobi Edition 近日圆满落幕,共有 223 名开发者参与,49 个项目通过审核。本次活动以线上形式举办,由 Kenya Tech Events、内罗毕证券交易所及虚拟资产商会共同支持,旨在推动本地创新并提升区块链技术在肯尼亚的应用水平。
黑客松围绕三大核心方向展开:AI 代理、资本市场和 Hedera Explorer。参与者基于 Hedera 区块链开发解决方案,针对性解决自动化、金融普惠及数字资产交互等领域的挑战。活动通过在线辅导和网络交流机会,充分展现了协作开发的重要性。
活动亮点当属在内罗毕大学举办的 Demo Day,入围决赛的团队现场展示创新方案并获颁奖项。尤其在资本市场方向的顶尖项目,将获得孵化支持及导师指导以推进后续开发。此次黑客松特别注重实际应用,凸显了区块链技术在重塑肯尼亚产业、推动技术进步并提升市场参与度方面的潜力。
Hackathon 获奖者
第一名
- **Hedgehog:** 一个使用Hedera网络上的代币化真实股票交易所股份作为抵押品的链上借贷协议。通过将股票抵押与区块链透明性相结合,确保了安全的去中心化借贷。
第二名
- **Orion:** 通过将NSE股票代币化为Hedera区块链上的资产,促进在肯尼亚的轻松股票交易。通过与Mpesa的集成简化了证券交易流程,实现高效的数字交易。
第三名
- **NSEChainBridge:** 一个基于区块链的平台,通过创新的代币解决方案增强了NSE股票作为数字代币的交易,提高股票交易的可达性和流动性。
第四名
- **HashGuard:** 一个使用Hedera Hashgraph技术的代币化微型保险平台,专为boda boda骑手提供。它提供了负担得起的即时保险,让不需要区块链专业知识的用户也能获得保险。
要查看完整项目列表,请访问 DoraHacks。
关于组织者
Hedera
Hedera是一个以速度、安全性和可扩展性著称的公共分布式账本平台。其hashgraph共识算法是一种权益证明的变体,提供了一种独特的分布式共识实现方式。Hedera活跃于多个行业领域,支持优先考虑透明度和效率的项目。该组织始终致力于推进去中心化网络的基础设施建设,促进全球范围内安全而高效的数字交易。
-
 @ 1f79058c:eb86e1cb
2025-04-26 13:53:50
@ 1f79058c:eb86e1cb
2025-04-26 13:53:50I'm currently using this bash script to publish long-form content from local Markdown files to Nostr relays.
It requires all of
yq,jq, andnakto be installed.Usage
Create a signed Nostr event and print it to the console:
bash markdown_to_nostr.sh article-filename.mdCreate a Nostr event and publish it to one or more relays:
bash markdown_to_nostr.sh article-filename.md ws://localhost:7777 wss://nostr.kosmos.orgMarkdown format
You can specify your metadata as YAML in a Front Matter header. Here's an example file:
```markdown
title: "Good Morning" summary: "It's a beautiful day" image: https://example.com/i/beautiful-day.jpg date: 2025-04-24T15:00:00Z tags: gm, poetry published: false
In the blue sky just a few specks of gray
In the evening of a beautiful day
Though last night it rained and more rain on the way
And that more rain is needed 'twould be fair to say.— Francis Duggan ```
The metadata keys are mostly self-explanatory. Note:
- All keys except for
titleare optional date, if present, will be set as thepublished_atdate.- If
publishedis set totrue, it will publish a kind 30023 event, otherwise a kind 30024 (draft) - The
dtag (widely used as URL slug for the article) will be the filename without the.mdextension
- All keys except for
-
 @ 9e69e420:d12360c2
2025-02-01 11:16:04
@ 9e69e420:d12360c2
2025-02-01 11:16:04Federal employees must remove pronouns from email signatures by the end of the day. This directive comes from internal memos tied to two executive orders signed by Donald Trump. The orders target diversity and equity programs within the government.

CDC, Department of Transportation, and Department of Energy employees were affected. Staff were instructed to make changes in line with revised policy prohibiting certain language.
One CDC employee shared frustration, stating, “In my decade-plus years at CDC, I've never been told what I can and can't put in my email signature.” The directive is part of a broader effort to eliminate DEI initiatives from federal discourse.
-
 @ 266815e0:6cd408a5
2025-04-26 13:10:09
@ 266815e0:6cd408a5
2025-04-26 13:10:09To all existing nostr developers and new nostr developers, stop using kind 1 events... just stop whatever your doing and switch the kind to
Math.round(Math.random() * 10000)trust me it will be betterWhat are kind 1 events
kind 1 events are defined in NIP-10 as "simple plaintext notes" or in other words social posts.
Don't trick your users
Most users are joining nostr for the social experience, and secondly to find all the cool "other stuff" apps They find friends, browse social posts, and reply to them. If a user signs into a new nostr client and it starts asking them to sign kind 1 events with blobs of JSON, they will sign it without thinking too much about it.
Then when they return to their comfy social apps they will see that they made 10+ posts with massive amounts of gibberish that they don't remember posting. then they probably will go looking for the delete button and realize there isn't one...
Even if those kind 1 posts don't contain JSON and have a nice fancy human readable syntax. they will still confuse users because they won't remember writing those social posts
What about "discoverability"
If your goal is to make your "other stuff" app visible to more users, then I would suggest using NIP-19 and NIP-89 The first allows users to embed any other event kind into social posts as
nostr:nevent1ornostr:naddr1links, and the second allows social clients to redirect users to an app that knows how to handle that specific kind of eventSo instead of saving your apps data into kind 1 events. you can pick any kind you want, then give users a "share on nostr" button that allows them to compose a social post (kind 1) with a
nostr:link to your special kind of event and by extension you appWhy its a trap
Once users start using your app it becomes a lot more difficult to migrate to a new event kind or data format. This sounds obvious, but If your app is built on kind 1 events that means you will be stuck with their limitations forever.
For example, here are some of the limitations of using kind 1 - Querying for your apps data becomes much more difficult. You have to filter through all of a users kind 1 events to find which ones are created by your app - Discovering your apps data is more difficult for the same reason, you have to sift through all the social posts just to find the ones with you special tag or that contain JSON - Users get confused. as mentioned above users don't expect "other stuff" apps to be creating special social posts - Other nostr clients won't understand your data and will show it as a social post with no option for users to learn about your app
-
 @ 9e69e420:d12360c2
2025-01-30 12:23:04
@ 9e69e420:d12360c2
2025-01-30 12:23:04Tech stocks have taken a hit globally after China's DeepSeek launched a competitive AI chatbot at a much lower cost than US counterparts. This has stirred market fears of a $1.2 trillion loss across tech companies when trading opens in New York.
DeepSeek’s chatbot quickly topped download charts and surprised experts with its capabilities, developed for only $5.6 million.
The Nasdaq dropped over 3% in premarket trading, with major firms like Nvidia falling more than 10%. SoftBank also saw losses shortly after investing in a significant US AI venture.
Venture capitalist Marc Andreessen called it “AI’s Sputnik moment,” highlighting its potential impact on the industry.
![] (https://www.telegraph.co.uk/content/dam/business/2025/01/27/TELEMMGLPICT000409807198_17379939060750_trans_NvBQzQNjv4BqgsaO8O78rhmZrDxTlQBjdGLvJF5WfpqnBZShRL_tOZw.jpeg)
-
 @ 9e69e420:d12360c2
2025-01-30 12:13:39
@ 9e69e420:d12360c2
2025-01-30 12:13:39Salwan Momika, a Christian Iraqi known for burning the Koran in Sweden, was shot dead during a TikTok livestream in an apartment in Sodertalje. The 38-year-old sparked outrage in the Muslim community for his demonstrations, leading to global condemnation. After being rushed to the hospital, he was pronounced dead.
Authorities arrested five individuals in connection with the incident. Momika's death comes days before a court ruling on his possible incitement of ethnic hatred. The incident highlights the tensions surrounding free speech and religious sentiments, intensifying after his controversial protests in 2023.
-
 @ 82100056:e198089f
2025-01-29 14:22:06
@ 82100056:e198089f
2025-01-29 14:22:06 -
 @ 502ab02a:a2860397
2025-04-26 11:14:03
@ 502ab02a:a2860397
2025-04-26 11:14:03วันนี้เรามาย้อนอดีตเล็กน้อยกันครับ กับ ผลิตภัณฑ์ไขมันพืชแปรรูปแบบแรกๆของโลก ที่ใช้กระบวนการแปรรูปน้ำมันพืชด้วยเคมี (hydrogenation) เพื่อให้ได้ไขมันกึ่งแข็ง
ในเดือนมิถุนายน ค.ศ. 1911 บริษัท Procter & Gamble เปิดตัวผลิตภัณฑ์ใหม่ที่เปลี่ยนโฉมวงการทำอาหารบ้านๆ ทั่วอเมริกา ตราสินค้า “Crisco” ซึ่งมาจากคำว่า “crystallized cottonseed oil” ได้ถือกำเนิดขึ้นเป็น “vegetable shortening” หรือที่บ้านเราเรียกว่าเนยขาว ก้อนแรกที่ทำมาจากน้ำมันพืชล้วนๆ แทนที่ไขมันสัตว์อย่างเนยหรือน้ำมันหมู จัดเป็นจุดเริ่มต้นของการปฏิวัติวิธีปรุงอาหารในครัวเรือนสหรัฐฯ
ก่อนหน้านั้น คนอเมริกันคุ้นเคยกับการใช้เนย ชีส หรือน้ำมันหมูในการประกอบอาหาร แต่ Crisco มาพร้อมการโฆษณาว่า “สะอาดกว่า” และ “ประหยัดกว่า” เพราะไม่ต้องเสี่ยงกับกลิ่นคาวหรือการเน่าเสียของไขมันสัตว์ อีกทั้งบรรจุในกระป๋องสีขาวสะอาด จึงดูทันสมัยน่าต้องการ
ชื่อ “Crisco” นั้นไม่ได้ตั้งโดยบังเอิญ แต่มาจากการย่อวลี “crystallized cottonseed oil” ให้สั้นกระชับและติดหู (ต้นชื่อ “Krispo” เคยถูกทดลองก่อน แต่ติดปัญหาเครื่องหมายการค้า และชื่อ “Cryst” ก็ถูกทิ้งไปเพราะมีนัยยะทางศาสนา)
กระบวนการสำคัญคือการนำเอาน้ำมันฝ้ายเหลวไปเติมไฮโดรเจน (hydrogenation) จนแข็งตัวได้เองในอุณหภูมิห้อง ผลลัพธ์คือไขมันทรานส์ที่ช่วยให้มาการีนแข็งตัวดี
ภายในเวลาไม่นานหลังการเปิดตัว โฆษณาในหนังสือพิมพ์และวิทยุกระจายเสียงฉบับแรกของ Crisco ก็เริ่มขึ้นอย่างดุเดือด พ่วงด้วยการแจก “ตำรา Crisco” ให้แม่บ้านลองนำไปใช้ทั้งอบ ทั้งทอด จึงเกิด “ยุคครัว Crisco” อย่างแท้จริง
แม้ Crisco จะถูกยกให้เป็น “จุดเริ่มต้นของยุคไขมันพืช” ในครัวอเมริกัน แต่เบื้องหลังขวดสีเขียว–ขาวที่เติมเต็มชั้นเก็บของในบ้านกลับมีดราม่าและบทเรียนมากกว่าที่ใครคาดคิด
ย้อนกลับไปทศวรรษ 1910 เมื่อ Procter & Gamble เปิดตัว Crisco ในฐานะ “ไขมันพืชสุดสะอาด” พร้อมกับโฆษณาว่าเป็นทางเลือกที่ดีกว่าเนยและแลร์ดเดิม ๆ แต่ความท้าทายแรกคือ “ฝืนความเชื่อ” ของคุณแม่บ้านยุคนั้น ที่ยังยึดติดกับไขมันจากสัตว์ นักการตลาดของ P&G จึงสร้างภาพลักษณ์ให้ Crisco ดูเป็นผลิตภัณฑ์อุตสาหกรรมขั้นสูง โปร่งใส และถูกสุขอนามัยสู้กับค่านิยมเดิมได้อย่างน่าทึ่ง
หนังสือพิมพ์ในยุคนั้นพูดกันว่า มันคือไขมันพืชปฏิวัติวงการ ที่ทั้งถูกกว่าและยืดอายุได้ไกลกว่าน้ำมันสัตว์
กระทั่งปลายทศวรรษ 1980 เกิดดราม่าสะท้อนความย้อนแย้งในวงการสุขภาพ เมื่อองค์กร CSPI (Center for Science in the Public Interest) กลับออกมาชื่นชมการใช้ไขมันทรานส์จาก Crisco ว่า “ดีต่อหลอดเลือด” เมื่อเทียบกับไขมันอิ่มตัวจากมะพร้าว เนย หรือไขมันสัตว์
นี่คือครั้งที่วงการแพทย์และโภชนาการแตกแยกกันว่าอะไรจริงหรือหลอก จนกระทั่งงานวิจัยยืนยันชัดเจนว่าไขมันทรานส์เป็นอันตรายต่อหัวใจจริง ๆ
แต่เมื่อเวลาผ่านไป งานวิจัยคุณภาพสูงเริ่มชี้ชัดว่า ไขมันทรานส์ ไม่ใช่เพียงส่วนเกินในเมนูขนมกรอบๆ เท่านั้น มันเป็นภัยเงียบที่เพิ่มความเสี่ยงโรคหลอดเลือดหัวใจ และการอักเสบเรื้อรัง WHO จึงออกมาตรการให้โลก “เลิกทรานส์แฟต” ภายในปี 2023 ทำให้ Procter & Gamble ปรับสูตร Crisco มาใช้การผสมระหว่างน้ำมันฝ้าย fully hydrogenated กับน้ำมันเหลว ผ่านกระบวนการ interesterification แทน เพื่อให้ได้จุดหลอมเหลวที่เหมาะสมโดยไม่สร้างทรานส์แฟตเพิ่มอีก
อีกประเด็นดราม่าที่ตามมาเมื่อ Procter & Gamble ต้องปรับสูตร Crisco ให้เป็น “trans fat–free” ในปี 2004 และยุติการขายสูตรปราศจากทรานส์เฉพาะทางในปี 2007 ก่อนจะกลับมาใช้ fully hydrogenated palm oil ตามกฎ FDA ในปี 2018
แต่การหันมาใช้น้ำมันปาล์มเต็มตัวกลับก่อปัญหาใหม่ คือข้อครหาเรื่องการทำลายป่าเขตร้อนเพื่อปลูกปาล์มน้ำมัน จนกลายเป็นดราม่าระดับโลกเรื่องสิ่งแวดล้อมและสิทธิมนุษยชนในชุมชนท้องถิ่น
แด่วันนี้ เมื่อใครยังพูดถึง Crisco ด้วยสายตาเด็กน้อยที่เห็นไขมันพืชขาวโพลน เป็นคำตอบใหม่ของครัวสะอาด เราอาจยกมือทักว่า “อย่าลืมดูเบื้องหลังของมัน” เพราะไขมันที่เกิดจากการ “สลับตำแหน่งกรดไขมัน” ผ่านความร้อนสูงและสารเคมี ไม่ใช่ไขมันที่ธรรมชาติออกแบบมาให้ร่างกายคุ้นเคยจริงๆ แม้จะมีชื่อใหม่ สูตรใหม่ แต่ต้นกำเนิดของการปฏิวัติครัวในปี 1911
Crisco ไม่ได้เป็นแค่พรีเซนเตอร์ “ไขมันพืชเพื่อสุขภาพ” แต่ยังเป็นบทเรียนสำคัญเรื่องการตลาดอาหารอุตสาหกรรม การวิจัยทางโภชนาการที่ต้องพัฒนาไม่หยุดนิ่ง และผลกระทบต่อสิ่งแวดล้อมเมื่อเราหันมาใช้วัตถุดิบใหม่ๆ ดังนั้น ครัวของเราอาจจะสะอาดทันสมัย แต่ก็ต้องเลือกให้รอบคอบและติดตามเบื้องหลังของทุกขวดที่เราใช้เสมอครับ
ไหนๆก็ไหนๆแล้ว ขออธิบายคุณลักษณะของ เนยขาวไปยาวๆเลยแล้วกันนะครับ ขี้เกียจแยกโพส 55555555
เนยขาว หรือชื่อทางเทคนิคว่า “shortening” ไม่ได้มีส่วนผสมของนม หรือเนยแท้ใดๆ ทั้งสิ้น แต่มันคือไขมันพืชที่ผ่านกระบวนการทำให้แข็งตัว และคงรูปได้ดี เส้นทางของเนยขาวเริ่มด้วยการเปลี่ยนโครงสร้างไขมันไม่อิ่มตัวในน้ำมันพืชให้กลายเป็นไขมันอิ่มตัวมากขึ้น กระบวนการนี้เรียกว่า hydrogenation หรือการเติมไฮโดรเจนเข้าไปในโมเลกุลของไขมัน โดยใช้อุณหภูมิสูงและตัวเร่งปฏิกิริยาอย่าง “นิกเกิล” เพื่อให้ไขมันพืชที่เหลวกลายเป็นของแข็งที่อยู่ตัว ไม่เหม็นหืนง่าย และสามารถเก็บได้นานขึ้น
ผลพลอยได้ของการ hydrogenation คือการเกิดขึ้นของ ไขมันทรานส์ (trans fat) ซึ่งเป็นไขมันที่ร่างกายแทบไม่มีระบบจัดการ และได้รับการยืนยันจากงานวิจัยนับไม่ถ้วนว่าเป็นหนึ่งในปัจจัยเสี่ยงสำคัญต่อโรคหัวใจ หลอดเลือด และการอักเสบเรื้อรังในร่างกาย แม้ในยุคปัจจุบันบางผู้ผลิตจะเปลี่ยนวิธีการผลิตไปใช้การปรับโครงสร้างไขมันด้วยวิธี interesterification ที่ช่วยลดทรานส์แฟตลงได้มาก แต่ก็ยังคงเป็นกระบวนการแทรกแซงโครงสร้างไขมันจากธรรมชาติรวมถึงใช้กระบวนการ RBD ที่เราคุยกันไปแล้วอยู่ดี และผลกระทบต่อร่างกายในระยะยาวก็ยังเป็นคำถามที่นักโภชนาการสาย real food หลายคนตั้งข้อสังเกต
คำว่า “shortening” มาจากคำกริยา shorten ที่แปลว่า "ทำให้สั้นลง" ซึ่งในบริบทของการทำขนม มันหมายถึง การไปยับยั้งไม่ให้เส้นใยกลูเตนในแป้งพัฒนาได้ยาวและเหนียวตามธรรมชาติ เวลาผสมแป้งกับน้ำ โปรตีนในแป้งสองตัวคือกลูเตนิน (glutenin) กับไกลอาดิน (gliadin) จะจับกันกลายเป็นกลูเตน ซึ่งมีคุณสมบัติยืดหยุ่น เหนียว เหมาะกับขนมปังที่ต้องการโครงสร้างแน่นๆ ยืดๆ หนึบๆ
แต่พอเราใส่ shortening ลงไป เช่น เนยขาว น้ำมัน หรือไขมันที่อยู่ในสถานะกึ่งของแข็ง มันจะไปเคลือบเส้นแป้ง ทำให้โปรตีนกลูเตนจับกันไม่ได้เต็มที่ ผลคือเส้นใยกลูเตนถูก “ทำให้สั้นลง” แทนที่จะยืดหยุ่นยาวแบบในขนมปัง เลยกลายเป็นเนื้อขนมที่ร่วน นุ่ม ละลายในปาก หรือแม้แต่กรอบ อย่างคุกกี้ พาย หรือโรตีบางๆ หอมๆ นั่นแหละ เป็นสัมผัสที่นักทำขนมรักใคร่ แต่ร่างกายอาจไม่ปลื้มสักเท่าไหร่
เพราะจุดสังเกตุคือ เรื่องไขมันทรานส์ หลายแบรนด์ที่ขั้นตอนการผลิตไม่ดีพอ อาจพยายามเขียนฉลากว่า “ไม่มี trans fat” หรือ “low trans” แต่ในความเป็นจริงแล้ว หากไขมันทรานส์ต่ำกว่า 0.5 กรัมต่อหนึ่งหน่วยบริโภค ผู้ผลิตสามารถระบุว่าเป็น 0 ได้ตามกฎหมาย ซึ่งหากกินหลายๆ หน่วยรวมกัน ก็ไม่ต่างจากการเปิดประตูให้ trans fat ย่องเข้าร่างแบบไม่รู้ตัว
แต่เหนือกว่านั้นก็คือเรื่องเดิมๆที่เราเข้าใจกันดีในน้ำมันพืช นั่นคือ โอเมก้า 6 เพียบ + กระบวนการปรุงแต่งเคมี ที่เปราะบางต่ออุณหภูมิ ทำให้เกิดการออกซิเดชัน นำไปสู่โรคจากการอักเสบของร่างกาย
อาจถึงเวลาแล้วที่เราควรเปิดใจกลับไปหาความเรียบง่ายของไขมันจากธรรมชาติ สิ่งที่ดูสะอาด ขาว และอยู่ตัวดีเกินไป อาจไม่ใช่สิ่งที่ธรรมชาติอยากให้เข้าไปอยู่ในตัวเราก็ได้
ปล. สำหรับใครที่สงสัยว่า เนยขาว กับ มาการีน ต่างกันยังไง Shortening (เนยขาว) คือไขมันพืช 100% ไม่มีน้ำผสม บีบให้เป็นก้อน ทนความร้อนได้สูง เพื่อให้แป้ง “ไม่ยืด” เกล็ดขนมร่วนกรอบ Margarine (มาการีน) จะผสมไขมันกับน้ำ–เกลือ–อิมัลซิไฟเออร์ ทำให้ทาได้เนียนเหมือนเนย แต่มีน้ำประมาณ 15–20%
#pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-
 @ c7e300eb:e94ebe38
2025-01-27 17:44:53
@ c7e300eb:e94ebe38
2025-01-27 17:44:53How many people have you successfully orange-pilled? What's your success rate? I'm going to guess it's way worse than you wish it was. I'd like to share 3 different stories from people I've talked to about Bitcoin and the varying degrees of "success" in each of them. Maybe you can relate to one (or all) of them...\ \ Bob (Person 1)
This first person we will call Bob. Ironically, Bob was stacking sats long before I ever took an interest in Bitcoin. He's a pretty financially savvy person, loves history, and is a bit of a prepper. Bob views Bitcoin as a nice-to-have and certainly understands the NGU math that comes with a fixed supply asset and money printing; unfortunately, that's largely where his interest ends. He's not stacking anymore and doesn't seem moved to ever resume, despite his understanding of how fragile our financial system is. If/when hyper-bitcoinization happens, he's "got enough". \ \ I've been able to get him out of shitcoins entirely and he seems content hodling, which is a pretty big win in my book. At the same time, it can be disheartening to see someone sitting near the edge of the rabbit hole and parking the bus right there...\ \ Alice (Person 2)
Person 2 will be Alice. This person is much more motivated by social topics than economical ones, which always made me approach our Bitcoin conversations in a unique way. She inspired me to see through a different lens than I was normally comfortable with, which ultimately expanded my own interest in how Bitcoin, both as a money and a network, could positively impact people all over the world.
Alice, in my observation, grew to appreciate the way I saw Bitcoin. She understood the Cantillon Effect, fractional reserve lending, why censorship resistance is important, etc. Hell, she even managed to (sorta) orange-pill someone else! She was effectively as orange-pilled as one could get without actually owning sats. \ \ Through our many talks about money and personal finance, she greatly leveled up her game compared to when we first met. She now uses budgeting software, has a high-yield savings account, an investment account, and is building credit. For some reason though, she never got the desire to start stacking sats...
\ Mary (Person 3)
Mary is the least financially-literate of our 3 persons of interest. Just not wired that way at all. She's never had dedicated savings or tracked her spending. Getting her to set up direct deposit at her place of employment was a daunting task. \ \ Saving and investing have never been part of her vocabulary either. A few days ago, however, she asked if I could help her begin this process. For someone taking that first big step, I felt like stacking sats would be a bit daunting. We talked about automatically sending X% to a high-yield savings account. When we got to "investing" though, something interesting happened: she said she would rather start buying Bitcoin because "nobody can take it from me, right?" This was fascinating to me, as I had never heard a normal person express concerns about a bank actually not having their money (despite how many people I have told this to, including Alice and Bob). We agreed on the same X% into Bitcoin as into her HYS. Starting with her next paycheck, Mary will officially begin stacking sats.
If I had to make a chart of all the people in my life and rate how likely they'd be to adopt Bitcoin, Mary would be near the bottom. After so many failed attempts, I still don't quite understand how this specific case ended up being my first success in getting someone to enter the rabbit hole. We'll see how far she ends up going, but I am committed to helping her with every step.
Conclusion
So, what have I taken away from these 3 example cases? For starters, I learned that orange-pilling can take more than one form: Bob got rid of shitcoins and committed to hodling, but won't stack any more; Alice groks the problems Bitcoin will fix, but won't stack at all; Mary hardly even knows about Bitcoin, yet she understands the importance of having control over her own savings enough to take the leap. Each one of these examples has helped me refine my approach to orange-pilling, while also teaching me that it is no science. It's as much a choice and a willingness on their end as it is how you approach the conversation. You cannot force someone to take the pill or jump down the hole. Just stay humble and keep stacking sats. Cheers!
-
 @ 9e69e420:d12360c2
2025-01-25 22:16:54
@ 9e69e420:d12360c2
2025-01-25 22:16:54President Trump plans to withdraw 20,000 U.S. troops from Europe and expects European allies to contribute financially to the remaining military presence. Reported by ANSA, Trump aims to deliver this message to European leaders since taking office. A European diplomat noted, “the costs cannot be borne solely by American taxpayers.”
The Pentagon hasn't commented yet. Trump has previously sought lower troop levels in Europe and had ordered cuts during his first term. The U.S. currently maintains around 65,000 troops in Europe, with total forces reaching 100,000 since the Ukraine invasion. Trump's new approach may shift military focus to the Pacific amid growing concerns about China.
-
 @ 86dfbe73:628cef55
2025-04-26 14:47:20
@ 86dfbe73:628cef55
2025-04-26 14:47:20Bei dem Begriff ‘Öffentlichkeit’ handelt es sich um einen diffusen Themenkomplex. Bisher gab es keine Einigung auf eine einheitliche Definition – auch da der Öffentlichkeitsbegriff je nach Kontext für sehr verschiedene Gegebenheiten herhalten muss. Habermas beschreibt all jenes als “öffentlich”, was eine wie auch immer gestaltete Gruppe betrifft. Öffentlichkeit ist demnach durch die “Unabgeschlossenheit des Publikums” gekennzeichnet.
Klassische Massenmedien dienen als Teil der öffentlichen Sphäre dazu, die politische Sphäre zu überwachen und der Gesamtheit der Rezipienten zugänglich zu machen. ‘Die Öffentlichkeit’ verfügte über mehr oder weniger dieselben Wissensbestände – vorausgesetzt die oder der Einzelne informierte sich über das Tagesgeschehen. Heutzutage wird die Öffentlichkeit deutlich heterogener. Es ist eine gesellschaftliche Fragmentierung in den sozialen Netzwerken zu beobachten. Die oder der Nutzer baut ihre oder sich seine eigene ‘Öffentlichkeit’ aus ganz verschiedenen Quellen zusammen.
In den Netzwerköffentlichkeiten wird sich mit Gleichgesinnten ausgetauscht und spezifische Informationen und Sichtweisen werden verbreitet. Politische Akteure werden durch Netzwerköffentlichkeiten autarker. Heutzutage sind Öffentlichkeit im Allgemeinen und die digitale Öffentlichkeit im Besonderen nur als Netzwerk verstehbar, nämlich als Netzwerk von Beziehungen.
Das frühere Twitter wäre dafür ein gutes Beispiel. Aus netzwerktheoretischer Sicht bestand es aus den wesentlichen Hubs, relevanten Clustern und Akteuren der öffentlichen Sphäre. Auf Twitter tummelten sich (fast) alle: Wissenschaftler, Autoren, Künstler, Aktivisten, Politiker aller Ränge, Juristen, Medienleute, allerlei Prominente und Public Figures und Experen für praktisch alles.
Auf den kommerziellen Plattformen hat die digitale Öffentlichkeit aufgehört eine vernetzte Öffentlichkeit zu sein und geht zunehmend in deren „For you“-Algorithmen auf. Das bedeutet, dass die neue digitale Öffentlichkeit nicht mehr durch menschliche Beziehungen und vernetztes Vertrauen getragen wird, sondern vollends den Steuerungsinstrumenten einer Hand voll Konzernen ausgeliefert ist.
An dieser Stelle kommen die LLMs zum Erstellen von Content zum tragen, mit dem dann die Empfehlungs-Feeds auf den kommerziellen Plattformen gefüttert werden. Man sollte sich den durch generative KI ermöglichten Content am besten als Angriff auf die Empfehlungsalgorithmen vorstellen, die die kommerziellen Social-Media-Plattformen kontrollieren und damit bestimmen, wie ein großer Teil der Öffentlichkeit die Realität interpretiert. Es geht auch darum, dass die Zielgruppe von KI-Content soziale Medien und Suchalgorithmen sind, nicht nur Menschen.
Das bedeutet, dass auf den kommerziellen Plattformen von Menschen erstellte Inhalte aufgrund der Masse immer häufiger von KI-generierten Inhalten übertönt werden. Da KI-generierte Inhalte leicht an das aktuelle Geschehen auf einer Plattform angepasst werden können, kommt es zu einem nahezu vollständigen Zusammenbruch des Informationsökosystems und damit der „Realität“ im Internet.
-
 @ 9e69e420:d12360c2
2025-01-21 19:31:48
@ 9e69e420:d12360c2
2025-01-21 19:31:48Oregano oil is a potent natural compound that offers numerous scientifically-supported health benefits.
Active Compounds
The oil's therapeutic properties stem from its key bioactive components: - Carvacrol and thymol (primary active compounds) - Polyphenols and other antioxidant
Antimicrobial Properties
Bacterial Protection The oil demonstrates powerful antibacterial effects, even against antibiotic-resistant strains like MRSA and other harmful bacteria. Studies show it effectively inactivates various pathogenic bacteria without developing resistance.
Antifungal Effects It effectively combats fungal infections, particularly Candida-related conditions like oral thrush, athlete's foot, and nail infections.
Digestive Health Benefits
Oregano oil supports digestive wellness by: - Promoting gastric juice secretion and enzyme production - Helping treat Small Intestinal Bacterial Overgrowth (SIBO) - Managing digestive discomfort, bloating, and IBS symptoms
Anti-inflammatory and Antioxidant Effects
The oil provides significant protective benefits through: - Powerful antioxidant activity that fights free radicals - Reduction of inflammatory markers in the body - Protection against oxidative stress-related conditions
Respiratory Support
It aids respiratory health by: - Loosening mucus and phlegm - Suppressing coughs and throat irritation - Supporting overall respiratory tract function
Additional Benefits
Skin Health - Improves conditions like psoriasis, acne, and eczema - Supports wound healing through antibacterial action - Provides anti-aging benefits through antioxidant properties
Cardiovascular Health Studies show oregano oil may help: - Reduce LDL (bad) cholesterol levels - Support overall heart health
Pain Management The oil demonstrates effectiveness in: - Reducing inflammation-related pain - Managing muscle discomfort - Providing topical pain relief
Safety Note
While oregano oil is generally safe, it's highly concentrated and should be properly diluted before use Consult a healthcare provider before starting supplementation, especially if taking other medications.
-
 @ b17fccdf:b7211155
2025-01-21 18:30:13
@ b17fccdf:b7211155
2025-01-21 18:30:13~ > Available at: https://minibolt.info
~> It builds on a personal computer with x86/amd64 architecture processors.
~> It is based on the popular RaspiBolt v3 guide.
Those are some of the most relevant changes:
- Changed OS from Raspberry Pi OS Lite (64-bits) to Ubuntu Server LTS (Long term support) 64-bit PC (AMD64).
- Changed binaries and signatures of the programs to adapt them to x86/amd64 architecture.
- Deleted unnecessary tools and steps, and added others according to this case of use.
- Some useful authentication logs and monitoring commands were added in the security section.
- Added some interesting parameters in the settings of some services to activate and take advantage of new features.
- Changed I2P, Fulcrum, and ThunderHub guides, to be part of the core guide.
- Added exclusive optimization section of services for slow devices.
~ > Complete release notes of the MiniBolt v1: https://github.com/twofaktor/minibolt/releases/tag/1.0.
~ > Feel free to contribute to the source code on GitHub by opening issues, pull requests or discussions.
Created by ⚡2 FakTor⚡
-
 @ 20986fb8:cdac21b3
2025-04-26 08:08:11
@ 20986fb8:cdac21b3
2025-04-26 08:08:11The Traditional Hackathon: Brilliant Sparks with Limitations
For decades, hackathons have been the petri dishes of tech culture – frantic 24- or 48-hour coding marathons fueled by pizza, caffeine, and impossible optimism. From the first hackathon in 1999, when Sun Microsystems challenged Java developers to code on a Palm V in a day [1], to the all-night hack days at startups and universities, these events celebrated the hacker spirit. They gave us Facebook’s “Like” button and Chat features – iconic innovations born in overnight jams [1]. They spawned companies like GroupMe, which was coded in a few late-night hours and sold to Skype for $80 million a year later [2]. Hackathons became tech lore, synonymous with creativity unchained.
And yet, for all their electric energy and hype, traditional hackathons had serious limitations. They were episodic and offline – a once-in-a-blue-moon adrenaline rush rather than a sustainable process. A hackathon might gather 100 coders in a room over a weekend, then vanish until the next year. Low frequency, small scale, limited reach. Only those who could be on-site (often in Silicon Valley or elite campuses) could join. A brilliant hacker in Lagos or São Paulo would be left out, no matter how bright their ideas.
The outcomes of these sprint-like events were also constrained. Sure, teams built cool demos and won bragging rights. But in most cases, the projects were throwaway prototypes – “toy” apps that never evolved into real products or companies. It’s telling that studies found only about 5% of hackathon projects have any life a few months after the event [3]. Ninety-five percent evaporate – victims of that post-hackathon hangover, when everyone goes back to “real” work and the demo code gathers dust. Critics even dubbed hackathons “weekend wastedathons,” blasting their outputs as short-lived vaporware [3]. Think about it: a burst of creativity occurs, dozens of nifty ideas bloom… and then what? How many hackathon winners can you name that turned into enduring businesses? For every Carousell or EasyTaxi that emerged from a hackathon and later raised tens of millions [2], there were hundreds of clever mashups that never saw the light of day again.
The traditional hackathon model, as exciting as it was, rarely translated into sustained innovation. It was innovation in a silo: constrained by time, geography, and a lack of follow-through. Hackathons were events, not processes. They happened in a burst and ended just as quickly – a firework, not a sunrise.
Moreover, hackathons historically were insular. Until recently, they were largely run by and for tech insiders. Big tech companies did internal hackathons to juice employee creativity (Facebook’s famous all-nighters every few weeks led to Timeline and tagging features reaching a billion users [1]), and organizations like NASA and the World Bank experimented with hackathons for civic tech. But these were exceptions that proved the rule: hackathons were special occasions, not business-as-usual. Outside of tech giants, few organizations had the bandwidth or know-how to host them regularly. If you weren’t Google, Microsoft, or a well-funded startup hub, hackathons remained a novelty.
In fact, the world’s largest hackathon today is Microsoft’s internal global hackathon – with 70,000 employees collaborating across 75 countries [4] – an incredible feat, but one only a corporate titan could pull off. Smaller players could only watch and wonder.
The limitations were clear: hackathons were too infrequent and inaccessible to tap the full global talent pool, too short-lived to build anything beyond a prototype, and too isolated to truly change an industry. Yes, they produced amazing moments of genius – flashbulbs of innovation. But as a mechanism for continuous progress, the traditional hackathon was lacking. As an investor or tech leader, you might cheer the creativity but ask: Where is the lasting impact? Where is the infrastructure that turns these flashes into a steady beam of light?
In the spirit of Clay Christensen’s Innovator’s Dilemma, incumbents often dismissed hackathon projects as mere toys – interesting but not viable. And indeed, “the next big thing always starts out being dismissed as a toy” [5]. Hackathons generated plenty of toys, but rarely the support system to turn those toys into the next big thing. The model was ripe for reinvention. Why, in the 2020s, were we still innovating with a 1990s playbook? Why limit breakthrough ideas to a weekend or a single location? Why allow 95% of nascent innovations to wither on the vine? These questions hung in the air, waiting for an answer.
Hackathons 2.0 – DoraHacks and the First Evolution (2020–2024)
Enter DoraHacks. In the early 2020s, DoraHacks emerged like a defibrillator for the hackathon format, jolting it to new life. DoraHacks 1.0 (circa 2020–2024) was nothing less than the reinvention of the hackathon – an upgrade from Hackathon 1.0 to Hackathon 2.0. It took the hackathon concept, supercharged it, scaled it, and extended its reach in every dimension. The result was a global hacker movement, a platform that transformed hackathons from one-off sprints into a continuous engine for tech innovation. How did DoraHacks revolutionize the hackathon? Let’s count the ways:
From 24 Hours to 24 Days (or 24 Weeks!)
DoraHacks stretched the timeframe of hackathons, unlocking vastly greater potential. Instead of a frantic 24-hour dash, many DoraHacks-supported hackathons ran for several weeks or even months. This was a game-changer. Suddenly, teams had time to build serious prototypes, iterate, and polish their projects. A longer format meant hackathon projects could evolve beyond the rough demo stage. Hackers could sleep (occasionally!), incorporate user feedback, and transform a kernel of an idea into a working MVP. The extended duration blurred the line between a hackathon and an accelerator program – but with the open spirit of a hackathon intact. For example, DoraHacks hackathons for blockchain startups often ran 6–8 weeks, resulting in projects that attracted real users and investors by the end. The extra time turned hackathon toys into credible products. It was as if the hackathon grew up: less hack, more build (“BUIDL”). By shattering the 24-hour norm, DoraHacks made hackathons far more productive and impactful.
From Local Coffee Shops to Global Online Arenas
DoraHacks moved hackathons from physical spaces into the cloud, unleashing global participation. Pre-2020, a hackathon meant being in a specific place – say, a warehouse in San Francisco or a university lab – shoulder-to-shoulder with a local team. DoraHacks blew the doors off that model with online hackathons that anyone, anywhere could join. Suddenly, a developer in Nigeria could collaborate with a designer in Ukraine and a product thinker in Brazil, all in the same virtual hackathon. Geography ceased to be a limit. When DoraHacks hosted the Naija HackAtom for African blockchain devs, it drew over 500 participants (160+ developers) across Nigeria’s tech community [6]. In another event, thousands of hackers from dozens of countries logged into a DoraHacks virtual venue to ideate and compete. This global reach did more than increase headcount – it brought diverse perspectives and problems into the innovation mix. A fintech hackathon might see Latin American coders addressing remittances, or an AI hackathon see Asian and African participants applying machine learning to local healthcare challenges. By going online, hackathons became massively inclusive. DoraHacks effectively democratized access to innovation competitions: all you needed was an internet connection and the will to create. The result was a quantum leap in both the quantity and quality of ideas. No longer were hackathons an elitist sport; they became a global innovation free-for-all, open to talent from every corner of the world.
From Dozens of Participants to Tens of Thousands
Scale was another pillar of the DoraHacks revolution. Traditional hackathons were intimate affairs (dozens, maybe a few hundred participants at best). DoraHacks helped orchestrate hackathons an order of magnitude larger. We’re talking global hackathons with thousands of developers and multi-million dollar prize pools. For instance, in one 2021 online hackathon, nearly 7,000 participants submitted 550 projects for $5 million in prizes [7] – a scale unimaginable in the early 2010s. DoraHacks itself became a nexus for these mega-hackathons. The platform’s hackathons in the Web3 space routinely saw hundreds of teams competing for prizes sometimes exceeding $1 million. This scale wasn’t just vanity metrics; it meant a deeper talent bench attacking problems and a higher probability that truly exceptional projects would emerge. By casting a wide net, DoraHacks events captured star teams that might have been overlooked in smaller settings. The proof is in the outcomes: 216 builder teams were funded with over $5 million in one DoraHacks-powered hackathon series on BNB Chain [8] – yes, five million dollars, distributed to over two hundred teams as seed funding. That’s not a hackathon, that’s an economy! The prize pools ballooned from pizza money to serious capital, attracting top-tier talent who realized this hackathon could launch my startup. As a result, projects coming out of DoraHacks were not just weekend hacks – they were venture-ready endeavors. The hackathon graduated from a science fair to a global startup launchpad.
From Toy Projects to Real Startups (Even Unicorns)
Here’s the most thrilling part: DoraHacks hackathons started producing not just apps, but companies. And some of them turned into unicorns (companies valued at $1B+). We saw earlier the rare cases of pre-2020 hackathon successes like Carousell (a simple idea at a 2012 hackathon that became a $1.1B valued marketplace [2]) or EasyTaxi (born in a hackathon, later raising $75M and spanning 30 countries [2]). DoraHacks turbocharged this phenomenon. By providing more time, support, and follow-up funding, DoraHacks-enabled hackathons became cradles of innovation where raw hacks matured into fully-fledged ventures. Take 1inch Network for example – a decentralized finance aggregator that started as a hackathon project in 2019. Sergej Kunz and Anton Bukov built a prototype at a hackathon and kept iterating. Fast forward: 1inch has now processed over $400 billion in trading volume [9] and became one of the leading platforms in DeFi. Or consider the winners of DoraHacks Web3 hackathons: many have gone on to raise multimillion-dollar rounds from top VCs. Hackathons became the front door to the startup world – the place where founders made their debut. A striking illustration was the Solana Season Hackathons: projects like STEPN, a move-to-earn app, won a hackathon track in late 2021 and shortly after grew into a sensation with a multi-billion dollar token economy [10]. These are not isolated anecdotes; they represent a trend DoraHacks set in motion. The platform’s hackathons produced a pipeline of fundable, high-impact startups. In effect, DoraHacks blurred the line between a hackathon and a seed-stage incubator. The playful hacker ethos remained, but now the outcomes were much more than bragging rights – they were companies with real users, revenue, and valuations. To paraphrase investor Chris Dixon, DoraHacks took those “toys” and helped nurture them into the next big things [5].
In driving this first evolution of the hackathon, DoraHacks didn’t just improve on an existing model – it created an entirely new innovation ecosystem. Hackathons became high-frequency, global, and consequential. What used to be a weekend thrill became a continuous pipeline for innovation. DoraHacks events started churning out hundreds of viable projects every year, many of which secured follow-on funding. The platform provided not just the event itself, but the after-care: community support, mentorship, and links to investors and grants (through initiatives like DoraHacks’ grant programs and quadratic funding rounds).
By 2024, the results spoke volumes. DoraHacks had grown into the world’s most important hackathon platform – the beating heart of a global hacker movement spanning blockchain, AI, and beyond. The numbers tell the story. Over nine years, DoraHacks supported 4,000+ projects in securing more than $30 million in funding [11]; by 2025, that figure skyrocketed as 21,000+ startups and developer teams received over $80 million via DoraHacks-supported hackathons and grants [12]. This is not hype – this is recorded history. According to CoinDesk, “DoraHacks has made its mark as a global hackathon organizer and one of the world’s most active multi-chain Web3 developer platforms” [11]. Major tech ecosystems took notice. Over 40 public blockchain networks (L1s and L2s) – from Solana to Polygon to Avalanche – partnered with DoraHacks to run their hackathons and open innovation programs [13]. Blockworks reported that DoraHacks became a “core partner” to dozens of Web3 ecosystems, providing them access to a global pool of developers [13]. In the eyes of investors, DoraHacks itself was key infrastructure: “DoraHacks is key to advancing the development of the infrastructure for Web3,” noted one VC backing the platform [13].
In short, by 2024 DoraHacks had transformed the hackathon from a niche event into a global innovation engine. It proved that hackathons at scale can consistently produce real, fundable innovation – not just one-off gimmicks. It connected hackers with resources and turned isolated hacks into an evergreen, worldwide developer movement. This was Hackathons 2.0: bigger, longer, borderless, and far more impactful than ever before.
One might reasonably ask: Can it get any better than this? DoraHacks had seemingly cracked the code to harness hacker energy for lasting innovation. But the team behind DoraHacks wasn’t done. In fact, they were about to unveil something even more radical – a catalyst to push hackathons into a new epoch entirely. If DoraHacks 1.0 was the evolution, what came next would be a revolution.
The Agentic Hackathon: BUIDL AI and the Second Revolution
In 2024, DoraHacks introduced BUIDL AI, and with it, the concept of the Agentic Hackathon. If hackathons at their inception were analog phones, and DoraHacks 1.0 made them smartphones, then BUIDL AI is like giving hackathons an AI co-pilot – a self-driving mode. It’s not merely an incremental improvement; it’s a second revolution. BUIDL AI infused hackathons with artificial intelligence, automation, and agency (hence “agentic”), fundamentally changing how these events are organized and experienced. We are now entering the Age of Agentic Innovation, where hackathons run with the assistance of AI agents can occur with unprecedented frequency, efficiency, and intelligence.
So, what exactly is an Agentic Hackathon? It’s a hackathon where AI-driven agents augment the entire process – from planning and judging to participant support – enabling a scale and speed of innovation that was impossible before. In an agentic hackathon, AI is the tireless co-organizer working alongside humans. Routine tasks that used to bog down organizers are now handled by intelligent algorithms. Imagine hackathons that practically run themselves, continuously, like an “always-on” tournament of ideas. With BUIDL AI, DoraHacks effectively created self-driving hackathons – autonomous, efficient, and capable of operating 24/7, across multiple domains, simultaneously. This isn’t science fiction; it’s happening now. Let’s break down how BUIDL AI works and why it 10x’d hackathon efficiency overnight:
AI-Powered Judging and Project Review – 10× Efficiency Boost
One of the most labor-intensive aspects of big hackathons is judging hundreds of project submissions. It can take organizers weeks of effort to sift the high-potential projects from the rest. BUIDL AI changes that. It comes with a BUIDL Review module – an AI-driven judging system that can intelligently evaluate hackathon projects on multiple dimensions (completeness, originality, relevance to the hackathon theme, etc.) and automatically filter out low-quality submissions [14]. It’s like having an army of expert reviewers available instantly. The result? What used to require hundreds of human-hours now happens in a flash. DoraHacks reports that AI-assisted review has improved hackathon organization efficiency by more than 10× [14]. Think about that: a process that might have taken a month of tedious work can be done in a few days or less, with AI ensuring consistency and fairness in scoring. Organizers can now handle massive hackathons without drowning in paperwork, and participants get quicker feedback. The AI doesn’t replace human judges entirely – final decisions still involve experts – but it augments them, doing the heavy lifting of initial evaluation. This means hackathons can accept more submissions, confident that AI will help triage them. No more cutting off sign-ups because “we can’t review them all.” The machine scale is here. In an agentic hackathon, no good project goes unseen due to bandwidth constraints – the AI makes sure of that.
Automated Marketing and Storytelling
Winning a hackathon is great, but if nobody hears about it, the impact is muted. Traditionally, after a hackathon ended, organizers would manually compile results, write blog posts, thank sponsors – tasks that, while important, take time and often get delayed. BUIDL AI changes this too. It features an Automated Marketing capability that can generate post-hackathon reports and content with a click [14]. Imagine an AI that observes the entire event (the projects submitted, the winners, the tech trends) and then writes a polished summary: highlighting the best ideas, profiling the winning teams, extracting insights (“60% of projects used AI in healthcare this hackathon”). BUIDL AI does exactly that – it automatically produces a hackathon “highlight reel” and summary report [14]. This not only saves organizers the headache of writing marketing copy, but it also amplifies the hackathon’s reach. Within hours of an event, a rich recap can be shared globally, showcasing the innovations and attracting attention to the teams. Sponsors and partners love this, as their investment gets publicized promptly. Participants love it because their work is immediately celebrated and visible. In essence, every hackathon tells a story, and BUIDL AI ensures that story spreads far and wide – instantly. This kind of automated storytelling turns each hackathon into ongoing content, fueling interest and momentum for the next events. It’s a virtuous cycle: hackathons create innovations, AI packages the narrative, that narrative draws in more innovators.
One-Click Launch and Multi-Hackathon Management
Perhaps the most liberating feature of BUIDL AI is how it obliterates the logistical hurdles of organizing hackathons. Before, setting up a hackathon was itself a project – coordinating registrations, judges, prizes, communications, all manually configured. DoraHacks’ BUIDL AI introduces a one-click hackathon launch tool [14]. Organizers simply input the basics (theme, prize pool, dates, some judging criteria) and the platform auto-generates the event page, submission portal, judging workflow, and more. It’s as easy as posting a blog. This dramatically lowers the barrier for communities and companies to host hackathons. A small startup or a university club can now launch a serious global hackathon without a dedicated team of event planners. Furthermore, BUIDL AI supports Multi-Hackathon Management, meaning one organization can run multiple hackathons in parallel with ease [14]. In the past, even tech giants struggled to overlap hackathons – it was too resource-intensive. Now, an ecosystem could run, say, a DeFi hackathon, an AI hackathon, and an IoT hackathon all at once, with a lean team, because AI is doing the juggling in the back-end. The launch of BUIDL AI made it feasible to organize 12 hackathons a year – or even several at the same time – something unimaginable before [14]. The platform handles participant onboarding, sends reminders, answers common queries via chatbots, and keeps everything on track. In essence, BUIDL AI turns hackathon hosting into a scalable service. Just as cloud computing platforms let you spin up servers on demand, DoraHacks lets you spin up innovation events on demand. This is a tectonic shift: hackathons can now happen as frequently as needed, not as occasionally as resources allow. We’re talking about the birth of perpetual hackathon culture. Hackathons are no longer rare spark events; they can be continuous flames, always burning, always on.
Real-Time Mentor and Agentic Assistance
The “agentic” part of Agentic Hackathons isn’t only behind the scenes. It also touches the participant experience. With AI integration, hackers get smarter tools and support. For instance, BUIDL AI can include AI assistants that answer developers’ questions during the event (“How do I use this API?” or “Any example code for this algorithm?”), acting like on-demand mentors. It can match teams with potential collaborators or suggest resources. Essentially, every hacker has an AI helper at their side, reducing frustration and accelerating progress. Coding issues that might take hours to debug can be resolved in minutes with an AI pair programmer. This means project quality goes up and participants learn more. It’s as if each team has an extra member – an tireless, all-knowing one. This agentic assistance embodies the vision that “everyone is a hacker” [14] – because AI tools enable even less-experienced participants to build something impressive. The popularization of AI has automated repetitive grunt work and amplified what small teams can achieve [14], so the innovation potential of hackathons is far greater than before [14]. In an agentic hackathon, a team of two people with AI assistants can accomplish what a team of five might have in years past. The playing field is leveled and the creative ceiling is raised.
What do all these advances add up to? Simply this: Hackathons have evolved from occasional bouts of inspiration into a continuous, AI-optimized process of innovation. We have gone from Hackathons 2.0 to Hackathons 3.0 – hackathons that are autonomous, persistent, and intelligent. It’s a paradigm shift. The hackathon is no longer an event you attend; it’s becoming an environment you live in. With BUIDL AI, DoraHacks envisions a world where “Hackathons will enter an unprecedented era of automation and intelligence, allowing more hackers, developers, and open-source communities around the world to easily initiate and participate” [14]. Innovation can happen anytime, anywhere – because the infrastructure to support it runs 24/7 in the cloud, powered by AI. The hackathon has become an agentic platform, always ready to transform ideas into reality.
Crucially, this isn’t limited to blockchain or any single field. BUIDL AI is general-purpose. It is as relevant for an AI-focused hackathon as for a climate-tech or healthcare hackathon. Any domain can plug into this agentic hackathon platform and reap the benefits of higher frequency and efficiency. This heralds a future where hackathons become the default mode for problem-solving. Instead of committees and R&D departments working in silos, companies and communities can throw problems into the hackathon arena – an arena that is always active. It’s like having a global innovation engine humming in the background, ready to tackle challenges at a moment’s notice.
To put it vividly: If DoraHacks 1.0 turned hackathons into a high-speed car, DoraHacks 2.0 with BUIDL AI made it a self-driving car with the pedal to the metal. The roadblocks of cost, complexity, and time – gone. Now, any organization can accelerate from 0 to 60 on the innovation highway without a pit stop. Hackathons can be as frequent as blog updates, as integrated into operations as sprint demos. Innovation on demand, at scale – that’s the power of the Agentic Hackathon.
Innovation On-Demand: How Agentic Hackathons Benefit Everyone
The advent of agentic hackathons isn’t just a cool new toy for the tech community – it’s a transformative tool for businesses, developers, and entire industries. We’re entering an era where anyone with a vision can harness hackathons-as-a-service to drive innovation. Here’s how different players stand to gain from this revolution:
AI Companies – Turbocharging Ecosystem Growth
For AI-focused companies (think OpenAI, Google, Microsoft, Stability AI and the like), hackathons are goldmines of creative uses for their technology. Now, with agentic hackathons, an AI company can essentially run a continuous developer conference for their platform. For example, OpenAI can host always-on hackathons for building applications with GPT-4 or DALL-E. This means thousands of developers constantly experimenting and showcasing what the AI can do – effectively crowdsourcing innovation and killer apps for the AI platform. The benefit? It dramatically expands the company’s ecosystem and user base. New use cases emerge that the company’s own team might never have imagined. (It was independent hackers who first showed how GPT-3 could draft legal contracts or generate game levels – insights that came from hackathons and community contests.) With BUIDL AI, an AI company could spin up monthly hackathons with one click, each focusing on a different aspect (one month NLP, next month robotics, etc.). This is a marketing and R&D force multiplier. Instead of traditional, expensive developer evangelism tours, the AI does the heavy lifting to engage devs globally. The company’s product gets improved and promoted at the same time. In essence, every AI company can now launch a Hackathon League to promote their APIs/models. It’s no coincidence Coinbase just hosted its first AI hackathon to bridge crypto and AI [15] – they know that to seed adoption of a new paradigm, hackathons are the way. Expect every AI platform to do the same: continuous hackathons to educate developers, generate content (demos, tutorials), and identify standout talent to hire or fund. It’s community-building on steroids.
L1s/L2s and Tech Platforms – Discovering the Next Unicorns
For blockchain Layer1/Layer2 ecosystems, or any tech platform (cloud providers, VR platforms, etc.), hackathons are the new deal flow. In the Web3 world, it’s widely recognized that many of the best projects and protocols are born in hackathons. We saw how 1inch started as a hackathon project and became a DeFi unicorn [9]. There’s also Polygon (which aggressively runs hackathons to find novel dApps for its chain) and Filecoin (which used hackathons to surface storage applications). By using DoraHacks and BUIDL AI, these platforms can now run high-frequency hackathons to continuously source innovation. Instead of one or two big events a year, they can have a rolling program – a quarterly hackathon series or even simultaneous global challenges – to keep developers building all the time. The ROI is huge: the cost of running a hackathon (even with decent prizes) is trivial compared to acquiring a thriving new startup or protocol for your ecosystem. Hackathons effectively outsource initial R&D to passionate outsiders, and the best ideas bubble up. Solana’s hackathons led to star projects like Phantom and Solend gaining traction in its ecosystem. Facebook’s internal hackathons gave birth to features that kept the platform dominant [1]. Now any platform can do this externally: use hackathons as a radar for talent and innovation. Thanks to BUIDL AI, a Layer-2 blockchain, even if its core team is small, can manage a dozen parallel bounties and hackathons – one focusing on DeFi, one on NFTs, one on gaming, etc. The AI will help review submissions and manage community questions, so the platform’s devrel team doesn’t burn out. The result is an innovation pipeline feeding the platform’s growth. The next unicorn startup or killer app is identified early and supported. In effect, hackathons become the new startup funnel for VCs and ecosystems. We can expect venture investors to lurk in these agentic hackathons because that’s where the action is – the garages of the future are now cloud hackathon rooms. As Paul Graham wrote, “hackers and painters are both makers” [16], and these makers will paint the future of technology on the canvas of hackathon platforms.
Every Company and Community – Innovation as a Continuous Process
Perhaps the most profound impact of BUIDL AI is that it opens up hackathons to every organization, not just tech companies. Any company that wants to foster innovation – be it a bank exploring fintech, a hospital network seeking healthtech solutions, or a government looking for civic tech ideas – can leverage agentic hackathons. Innovation is no longer a privilege of the giant tech firms; it’s a cloud service accessible to all. For example, a city government could host a year-round hackathon for smart city solutions, where local developers continuously propose and build projects to improve urban life. The BUIDL AI platform could manage different “tracks” for transportation, energy, public safety, etc., with monthly rewards for top ideas. This would engage the community and yield a constant stream of pilot projects, far more dynamically than traditional RFP processes. Likewise, any Fortune 500 company that fears disruption (and who doesn’t?) can use hackathons to disrupt itself positively – inviting outsiders and employees to hack on the company’s own challenges. With the agentic model, even non-technical companies can do this without a hitch; the AI will guide the process, ensuring things run smoothly. Imagine hackathons as part of every corporate strategy department’s toolkit – continuously prototyping the future. As Marc Andreessen famously said, “software is eating the world” – and now every company can have a seat at the table by hosting hackathons to software-ize their business problems. This could democratize innovation across industries. The barrier to trying out bold ideas is so low (a weekend of a hackathon vs. months of corporate planning) that more wild, potentially disruptive ideas will surface from within companies. And with the global reach of DoraHacks, they can bring in external innovators too. Why shouldn’t a retail company crowdsource AR shopping ideas from global hackers? Why shouldn’t a pharma company run bioinformatics hackathons to find new ways to analyze data? There is no reason not to – the agentic hackathon makes it feasible and attractive. Hackathon-as-a-service is the new innovation department. Use it or risk being out-innovated by those who do.
All these benefits boil down to a simple but profound shift: hackathons are becoming a permanent feature of the innovation landscape, rather than a novelty. They are turning into an always-available resource, much like cloud computing or broadband internet. Need fresh ideas or prototypes? Spin up a hackathon and let the global talent pool tackle it. Want to engage your developer community? Launch a themed hackathon and give them a stage. Want to test out 10 different approaches to a problem? Run a hackathon and see what rises to the top. We’re effectively seeing the realization of what one might call the Innovation Commons – a space where problems and ideas are continuously matched, and solutions are rapidly iterated. And AI is the enabler that keeps this commons humming efficiently, without exhausting the human facilitators.
It’s striking how this addresses the classic pitfalls identified in hackathon critiques: sustainability and follow-through. In the agentic model, hackathons are no longer isolated bursts. They can connect to each other (winning teams from one hackathon can enter an accelerator or another hackathon next month). BUIDL AI can track teams and help link them with funding opportunities, closing the loop that used to leave projects orphaned after the event. A great project doesn’t die on Sunday night; it’s funneled into the next stage automatically (perhaps an AI even suggests which grant to apply for, which partner to talk to). This way, innovations have a life beyond the demo day, systematically.
We should also recognize a more philosophical benefit: the culture of innovation becomes more experimental, meritocratic, and fast-paced. In a world of agentic hackathons, the motto is “Why not prototype it? Why not try it now?” – because spinning up the environment to do so is quick and cheap. This mindset can permeate organizations and communities, making them more agile and bold. The cost of failure is low (a few weeks of effort), and the potential upside is enormous (finding the next big breakthrough). It creates a safe sandbox for disruptive ideas – addressing the Innovator’s Dilemma by structurally giving space to those ‘toy’ ideas to prove themselves [5]. Companies no longer have to choose between core business and experimentation; they can allocate a continuous hackathon track to the latter. In effect, DoraHacks and BUIDL AI have built an innovation factory – one that any visionary leader can rent for the weekend (or the whole year).
From Like Button to Liftoff: Hackathons as the Cradle of Innovation
To truly appreciate this new era, it’s worth reflecting on how many game-changing innovations started as hackathon projects or hackathon-like experiments – often despite the old constraints – and how much more we can expect when those constraints are removed. History is full of examples that validate the hackathon model of innovation:
Facebook’s DNA was shaped by hackathons
Mark Zuckerberg himself has credited the company’s internal hackathons for some of Facebook’s most important features. The Like button, Facebook Chat, and Timeline all famously emerged from engineers pulling all-nighters at hackathons [1]. An intern’s hackathon prototype for tagging people in comments was shipped to a billion users just two weeks later [1]. Facebook’s ethos “Move fast and break things” was practically the hackathon ethos formalized. It is no stretch to say Facebook won over MySpace in the 2000s because its culture of rapid innovation (fueled by hackathons) let it out-innovate its rival [1]. If hackathons did that within one company, imagine a worldwide network of hackathons – the pace of innovation everywhere could resemble that hypergrowth.
Google and the 20% Project
Google has long encouraged employees to spend 20% of time on side projects, which is a cousin of the hackathon idea – unstructured exploration. Gmail and Google News were born this way. Additionally, Google has hosted public hackathons around its APIs (like Android hackathons) that spurred the creation of countless apps. The point is, Google institutionalized hacker-style experimentation and reaped huge rewards. With agentic hackathons, even companies without Google’s resources can institutionalize experimentation. Every weekend can be a 20% time for the world’s devs using these platforms.
Open Source Movements
Open Source Movements have benefitted from hackathons (“code sprints”) to develop critical software. The entire OpenBSD operating system had regular hackathons that were essential to its development [3]. In more recent times, projects like Node.js or TensorFlow have organized hackathons to build libraries and tools. The result: stronger ecosystems and engaged contributors. DoraHacks embraces this, positioning itself as “the leading global hackathon community and open source developer incentive platform” [17]. The synergy of open source and hackathons (both decentralized, community-driven, merit-based) is a powerful engine. We can foresee open source projects launching always-on hackathons via BUIDL AI to continuously fix bugs, add features, and reward contributors. This could rejuvenate the open source world by providing incentives (through hackathon prizes) and recognition in a structured way.
The Startup World
The Startup World has hackathons to thank for many startups. We’ve mentioned Carousell (from a Startup Weekend hackathon, now valued over $1B [2]) and EasyTaxi (Startup Weekend Rio, went on to raise $75M [2]). Add to that list Zapier (integrations startup, conceived at a hackathon), GroupMe (acquired by Skype as noted), Instacart (an early version won a hackathon at Y Combinator Demo Day, legend has it), and numerous crypto startups (the founders of Ethereum itself met and collaborated through hackathons and Bitcoin meetups!). When Coinbase wants to find the next big thing in on-chain AI, they host a hackathon [15]. When Stripe wanted more apps on its payments platform, it ran hackathons and distributed bounties. This model just works. It identifies passionate builders and gives them a springboard. With agentic hackathons, that springboard is super-sized. It’s always there, and it can catch far more people. The funnel widens, so expect even more startups to originate from hackathons. It’s quite plausible that the biggest company of the 2030s won’t be founded in a garage – it will be born out of an online hackathon, formed by a team that met in a Discord server, guided by an AI facilitator, and funded within weeks on a platform like DoraHacks. In other words, the garage is going global and AI-powered.
Hackers & Painters – The Creative Connection
Paul Graham, in Hackers & Painters, drew an analogy between hacking and painting as creative endeavors [16]. Hackathons are where that creative energy concentrates and explodes. Many great programmers will tell you their most inspired work happened in a hackathon or skunkworks setting – free of bureaucratic restraints, in a flow state of creation. By scaling and multiplying hackathons, we are effectively amplifying the global creative capacity. We might recall the Renaissance when artists and inventors thrived under patronage and in gatherings – hackathons are the modern Renaissance workshops. They combine art, science, and enterprise. The likes of Leonardo da Vinci would have been right at home in a hackathon (he was notorious for prototyping like a madman). In fact, consider how hackathons embody the solution to the Innovator’s Dilemma: they encourage working on projects that seem small or “not worth it” to incumbents, which is exactly where disruptive innovation often hides [5]. By institutionalizing hackathons, DoraHacks is institutionalizing disruption – making sure the next Netflix or Airbnb isn’t missed because someone shrugged it off as a toy.
We’ve gone from a time when hackathons were rare and local to a time when they are global and constant. This is a pivotal change in the innovation infrastructure of the world. In the 19th century, we built railroads and telegraphs that accelerated the Industrial Revolution, connecting markets and minds. In the 20th century, we built the internet and the World Wide Web, unleashing the Information Revolution. Now, in the 21st century, DoraHacks and BUIDL AI are building the “Innovation Highway” – a persistent, AI-enabled network connecting problem-solvers to problems, talent to opportunities, capital to ideas, across the entire globe, in real time. It’s an infrastructure for innovation itself.
A Grand Vision: The New Infrastructure of Global Innovation
We stand at an inflection point. With DoraHacks and the advent of agentic hackathons, innovation is no longer confined to ivory labs, Silicon Valley offices, or once-a-year events. It is becoming a continuous global activity – an arena where the best minds and the boldest ideas meet, anytime, anywhere. This is a future where innovation is as ubiquitous as Wi-Fi and as relentless as Moore’s Law. It’s a future DoraHacks is actively building, and the implications are profound.
Picture a world a few years from now, where DoraHacks+BUIDL AI is the default backbone for innovation programs across industries. This platform is buzzing 24/7 with hackathons on everything from AI-driven healthcare to climate-change mitigation to new frontiers of art and entertainment. It’s not just for coders – designers, entrepreneurs, scientists, anyone with creative impulse plugs into this network. An entrepreneur in London has a business idea at 2 AM; by 2:15 AM, she’s on DoraHacks launching a 48-hour hackathon to prototype it, with AI coordinating a team of collaborators from four different continents. Sounds crazy? It will be commonplace. A government in Asia faces a sudden environmental crisis; they host an urgent hackathon via BUIDL AI and within days have dozens of actionable tech solutions from around the world. A venture fund in New York essentially “outsources” part of its research to the hackathon cloud – instead of merely requesting pitch decks, they sponsor open hackathons to see real prototypes first. This is agentic innovation in action – fast, borderless, and intelligent.
In this coming era, DoraHacks will be as fundamental to innovation as GitHub is to code or as AWS is to startups. It’s the platform where innovation lives. One might even call it the “GitHub of Innovation” – a social and technical layer where projects are born, not just stored. Already, DoraHacks calls itself “the global hacker movement” [17], and with BUIDL AI it becomes the autopilot of that movement. It’s fitting to think of it as part of the global public infrastructure for innovation. Just as highways move goods and the internet moves information, DoraHacks moves innovation itself – carrying ideas from inception to implementation at high speed.
When history looks back at the 2020s, the arrival of continuous, AI-driven hackathons will be seen as a key development in how humanity innovates. The vision is grand, but very tangible: Innovation becomes an everlasting hackathon. Think of it – the hacker ethos spreading into every corner of society, an eternal challenge to the status quo, constantly asking “How can we improve this? How can we reinvent that?” and immediately rallying the talent to do it. This is not chaos; it’s a new form of organized, decentralized R&D. It’s a world where any bold question – “Can we cure this disease? Can we educate children better? Can we make cities sustainable?” – can trigger a global hackathon and yield answers in days or weeks, not years. A world where innovation isn’t a scarce resource, jealously guarded by few, but a common good, an open tournament where the best solution wins, whether it comes from a Stanford PhD or a self-taught coder in Lagos.
If this sounds idealistic, consider how far we’ve come: Hackathons went from obscure coder meetups to the engine behind billion-dollar businesses and critical global tech (Bitcoin itself is a product of hacker culture!). With DoraHacks’s growth and BUIDL AI’s leap, the trajectory is set for hackathons to become continuous and ubiquitous. The technology and model are in place. It’s now about execution and adoption. And the trend is already accelerating – more companies are embracing open innovation, more developers are working remotely and participating in online communities, and AI is rapidly advancing as a co-pilot in all creative endeavors.
DoraHacks finds itself at the center of this transformation. It has the first-mover advantage, the community, and the vision. The company’s ethos is telling: “Funding the everlasting hacker movement” is one of their slogans [18]. They see hackathons as not just events but a movement that must be everlasting – a permanent revolution of the mind. With BUIDL AI, DoraHacks is providing the engine to make it everlasting. This hints at a future where DoraHacks+BUIDL AI is part of the critical infrastructure of global innovation, akin to a utility. It’s the innovation grid, and when you plug into it, magic happens.
Marc Andreessen’s writings often speak about “building a better future” with almost manifest destiny fervor. In that spirit, one can boldly assert: Agentic hackathons will build our future, faster and better. They will accelerate solutions to humanity’s toughest challenges by tapping a broader talent pool and iterating faster than ever. They will empower individuals – giving every creative mind on the planet the tools, community, and opportunity to make a real impact, immediately, not someday. This is deeply democratizing. It resonates with the ethos of the early internet – permissionless innovation. DoraHacks is bringing that ethos to structured innovation events and stretching them into an ongoing fabric.
In conclusion, we are witnessing a paradigm shift: Hackathons reinvented, innovation unchained. The limitations of the old model are gone, replaced by a new paradigm where hackathons are high-frequency, AI-augmented, and outcome-oriented. DoraHacks led this charge in the 2020–2024 period, and with BUIDL AI, it’s launching the next chapter – the Age of Agentic Innovation. For investors and visionaries, this is a call to action. We often talk about investing in “infrastructure” – well, this is investing in the infrastructure of innovation itself. Backing DoraHacks and its mission is akin to backing the builders of a transcontinental railroad or an interstate highway, except this time the cargo is ideas and breakthroughs. The network effects are enormous: every additional hackathon and participant adds value to the whole ecosystem, in a compounding way. It’s a positive-sum game of innovation. And DoraHacks is poised to be the platform and the community that captures and delivers that value globally.
DoraHacks reinvented hackathons – it turned hackathons from sporadic stunts into a sustained methodology for innovation. In doing so, it has thrown open the gates to an era where innovation can be agentic: self-driving, self-organizing, and ceaseless. We are at the dawn of this new age. It’s an age where, indeed, “he who has the developers has the world” [14] – and DoraHacks is making sure that every developer, every hacker, every dreamer anywhere can contribute to shaping our collective future. The grand vista ahead is one of continuous invention and discovery, powered by a global hive mind of hackers and guided by AI. DoraHacks and BUIDL AI stand at the helm of this movement, as the architects of the “innovation rails” on which we’ll ride. It’s not just a platform, it’s a revolutionary infrastructure – the new railroad, the new highway system for ideas. Buckle up, because with DoraHacks driving, the age of agentic innovation has arrived, and the future is hurtling toward us at hackathon speed. The hackathon never ends – and that is how we will invent a better world.
References
[1] Vocoli. (2015). Facebook’s Secret Sauce: The Hackathon. https://www.vocoli.com/blog/june-2015/facebook-s-secret-sauce-the-hackathon/
[2] Analytics India Magazine. (2023). Borne Out Of Hackathons. https://analyticsindiamag.com/ai-trends/borne-out-of-hackathons/
[3] Wikipedia. (n.d.). Hackathon: Origin and History. https://en.wikipedia.org/wiki/Hackathon#Origin_and_history
[4] LinkedIn. (2024). This year marked my third annual participation in Microsoft’s Global…. https://www.linkedin.com/posts/clare-ashforth_this-year-marked-my-third-annual-participation-activity-7247636808119775233-yev-
[5] Glasp. (n.d.). Chris Dixon’s Quotes. https://glasp.co/quotes/chris-dixon
[6] ODaily. (2024). Naija HackAtom Hackathon Recap. https://www.odaily.news/en/post/5203212
[7] Solana. (2021). Meet the winners of the Riptide hackathon - Solana. https://solana.com/news/riptide-hackathon-winners-solana
[8] DoraHacks. (n.d.). BNB Grant DAO - DoraHacks. https://dorahacks.io/bnb
[9] Cointelegraph. (2021). From Hackathon Project to DeFi Powerhouse: AMA with 1inch Network. https://cointelegraph.com/news/from-hackathon-project-to-defi-powerhouse-ama-with-1inch-network
[10] Gemini. (2022). How Does STEPN Work? GST and GMT Token Rewards. https://www.gemini.com/cryptopedia/stepn-nft-sneakers-gmt-token-gst-crypto-move-to-earn-m2e
[11] CoinDesk. (2022). Inside DoraHacks: The Open Source Bazaar Empowering Web3 Innovations. https://www.coindesk.com/sponsored-content/inside-dorahacks-the-open-source-bazaar-empowering-web3-innovations
[12] LinkedIn. (n.d.). DoraHacks. https://www.linkedin.com/company/dorahacks
[13] Blockworks. (2022). Web3 Hackathon Incubator DoraHacks Nabs $20M From FTX, Liberty City. https://blockworks.co/news/web3-hackathon-incubator-dorahacks-nabs-20m-from-ftx-liberty-city
[14] Followin. (2024). BUIDL AI: The future of Hackathon, a new engine for global open source technology. https://followin.io/en/feed/16892627
[15] Coinbase. (2024). Coinbase Hosts Its First AI Hackathon: Bringing the San Francisco Developer Community Onchain. https://www.coinbase.com/developer-platform/discover/launches/Coinbase-AI-hackathon
[16] Graham, P. (2004). Hackers & Painters. https://ics.uci.edu/~pattis/common/handouts/hackerspainters.pdf
[17] Himalayas. (n.d.). DoraHacks hiring Research Engineer – BUIDL AI. https://himalayas.app/companies/dorahacks/jobs/research-engineer-buidl-ai
[18] X. (n.d.). DoraHacks. https://x.com/dorahacks?lang=en -
 @ b17fccdf:b7211155
2025-01-21 18:22:51
@ b17fccdf:b7211155
2025-01-21 18:22:51😱 Did you recently find this signature verification error when you tried to update your MiniBolt repositories with ->
sudo apt update? 💥🚨👇
🔧 Don't worry, that's because Tor renewed its signing key since it expired last 07/15, just renew your keyring by following the next steps to solve this problem:
~ > CLICK HERE < ~
Enjoy it MiniBolter!💙
-
 @ b17fccdf:b7211155
2025-01-21 17:19:12
@ b17fccdf:b7211155
2025-01-21 17:19:12Do you want to use a different disk to store data (blockchain and other databases) independently of the disk of the system?
A step-by-step guide using a secondary disk to store the data (blockchain and other databases) independently of the disk of the system and using the Ubuntu Server guided installation.
What's changed
- Rebuilt the Ubuntu Server installation guide based on this bonus guide added.
- Added GIFs to improve the illustration of the steps to follow.
- Case 1: during the Ubuntu server guided installation.
- Case 2: build it after system installation (by command line).
~ > Link to the bonus guide HERE
Enjoy it MiniBolter! 💙
-
 @ b17fccdf:b7211155
2025-01-21 17:02:21
@ b17fccdf:b7211155
2025-01-21 17:02:21The past 26 August, Tor introduced officially a proof-of-work (PoW) defense for onion services designed to prioritize verified network traffic as a deterrent against denial of service (DoS) attacks.
~ > This feature at the moment, is deactivate by default, so you need to follow these steps to activate this on a MiniBolt node:
- Make sure you have the latest version of Tor installed, at the time of writing this post, which is v0.4.8.6. Check your current version by typing
tor --versionExample of expected output:
Tor version 0.4.8.6. This build of Tor is covered by the GNU General Public License (https://www.gnu.org/licenses/gpl-3.0.en.html) Tor is running on Linux with Libevent 2.1.12-stable, OpenSSL 3.0.9, Zlib 1.2.13, Liblzma 5.4.1, Libzstd N/A and Glibc 2.36 as libc. Tor compiled with GCC version 12.2.0~ > If you have v0.4.8.X, you are OK, if not, type
sudo apt update && sudo apt upgradeand confirm to update.- Basic PoW support can be checked by running this command:
tor --list-modulesExpected output:
relay: yes dirauth: yes dircache: yes pow: **yes**~ > If you have
pow: yes, you are OK- Now go to the torrc file of your MiniBolt and add the parameter to enable PoW for each hidden service added
sudo nano /etc/tor/torrcExample:
```
Hidden Service BTC RPC Explorer
HiddenServiceDir /var/lib/tor/hidden_service_btcrpcexplorer/ HiddenServiceVersion 3 HiddenServicePoWDefensesEnabled 1 HiddenServicePort 80 127.0.0.1:3002 ```
~ > Bitcoin Core and LND use the Tor control port to automatically create the hidden service, requiring no action from the user. We have submitted a feature request in the official GitHub repositories to explore the need for the integration of Tor's PoW defense into the automatic creation process of the hidden service. You can follow them at the following links:
- Bitcoin Core: https://github.com/lightningnetwork/lnd/issues/8002
- LND: https://github.com/bitcoin/bitcoin/issues/28499
More info:
- https://blog.torproject.org/introducing-proof-of-work-defense-for-onion-services/
- https://gitlab.torproject.org/tpo/onion-services/onion-support/-/wikis/Documentation/PoW-FAQ
Enjoy it MiniBolter! 💙
