-
 @ 005bc4de:ef11e1a2
2025-05-02 16:14:46
@ 005bc4de:ef11e1a2
2025-05-02 16:14:46Popes and Horses
It's probably not kosher to compare popes with horses, and yet...the Kentucky Derby is tomorrow and the papal conclave begins Monday. The question in both cases is, "Who will win?" So, here we go...
Polymarket, or other such "prediction markets", are becoming go-to places for things such as this. At least to me, they're interesting because it's a bit more than an opinion poll. With these markets, people have to put up real money, or cryptocurrency, to make their predictions. They actually have to put their money where their mouth is.
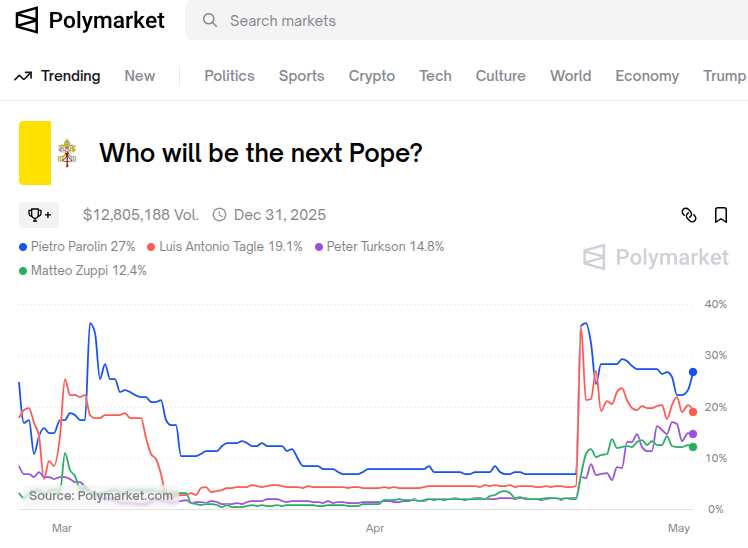
Polymarket currently lists four cardinals as front runners for pope, as below:
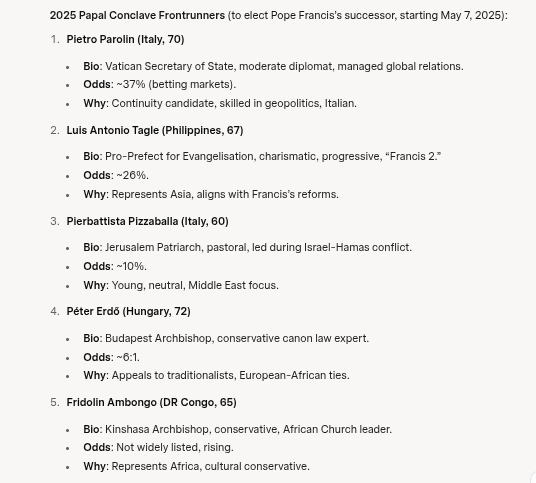
And, thanks to Grok, here's a short run-down for leading candidates (ironically 3 are not on Polymarket at the moment):
And as to the Kentucky Derby, Polymarket has this prediction at the moment:
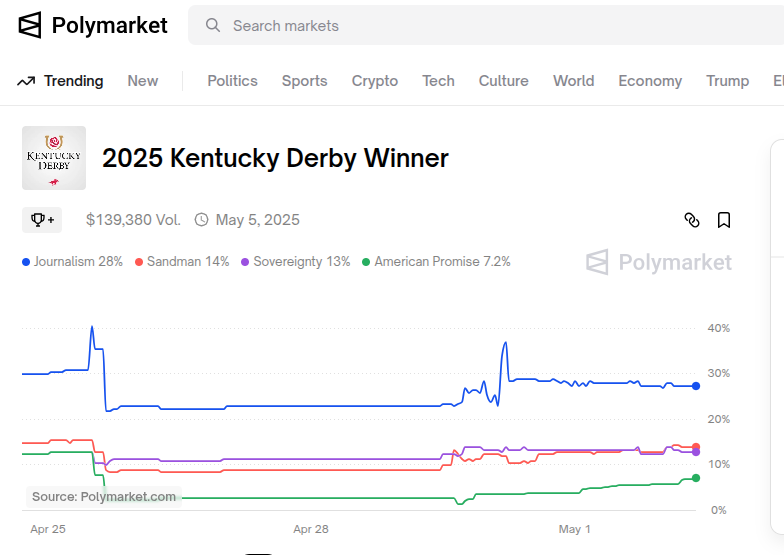
I know more about horse racing than papal politics. This is not bragging. I know very little about horse racing, which means I know zero about papal politics. But, one thing I believe with horse racing and especially with the Kentucky Derby is this...
...when the horses are making that final fourth turn, it's usually not the front runner you need to watch out for. All eyes are on that horse, of course, and the announcer is calling that horse's name, but that's not the place to focus. The dangerous horse is usually about two or three slots back, lurking and waiting for "the moment."
The Derby is the longest race these 3-year old horses have every run at 1 1/8 miles. That front horse often/usually fades, not always, but often. That horse sitting in the 3 or 4 spot is often a distancer, a stalker, and if a wise jockey is aboard, has been biding his time. That final 100 yards is go-time.

In the image above, I'd keep an eye on the blue/yellow jockey and horse...he's sitting in 4th place, directly positioned behind the front runner, hugging the rail, about to make a move and power ahead to win.
And back to papal politics, which again, I know nothing about...two things come to mind:
- In political elections I'm typically a big believer in the pendulum swing of elections and movements. The pendulum swings conservative, then liberal, then back again. This is a religious election, so the pendulum effect may play less of a role here. It stands to figure that for centuries the pendulum should have been stuck on the "conservative" side of things. That's kind of how religion works...the Bible doesn't change. But, let's not fool ourselves, it is 2025 and people change their views on things...this election is political too. Both world politics and internal, unseen "Vatican politics" figure in. The pendulum may be at play is simply seen in Pope Francis himself. Pope John Paul was conservative, Francis swung the pendulum the other way, and if the pendulum is indeed swinging, then "conservative" cardinals stand to benefit in their chances of election.
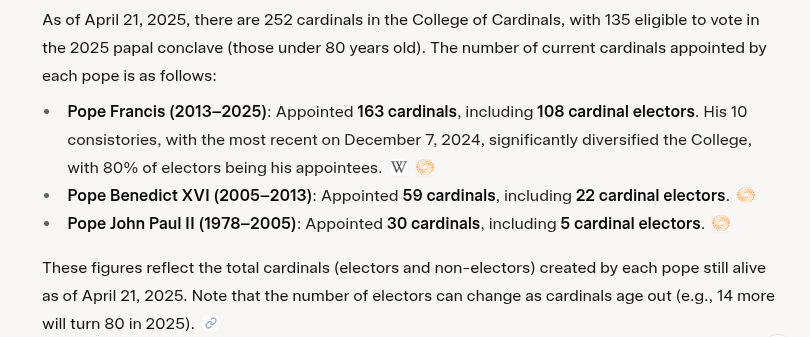
- However, if you want to win an election, you pick the voters. According to Grok, Pope Francis appointed 108 of the 135 voting cardinals. That leaves only 27 candidates from the conservative old-guard popes. Like gerrymandering a district, getting the right people to vote can yield a candidate-of-choice.
Voters, according to Grok:
Circling back to the front runners on Polymarket, I'd normally go with the horse, er cardinal, sitting in the three spot, Turkson on Polymarket. Or, I'd go with number 4 according to Grok, Peter Erdo, if I felt the pendulum effect is at play.
Yet, you win by votes and 108/135 are Francis-men. So, the top two, being continuity candidates have the best chances in my view. I still, can't go with the lead horse though. So, my prediction...
Luis Antonio Tagle will be the next pope.
And, the Kentucky Derby winner: Owen Almighty - This horse has good past performances with the exception of the last time out at the Bluegrass Stakes which is a mile and 1/8. This is concerning and might mean the horse can't handle the extra distance. No doubt this is what got the 30/1 odds. But, a jockey change was made. I like the new jockey Javier Castellano and maybe his experience can navigate the horse through.
We'll see how my predictions pan out.
-
 @ 52b4a076:e7fad8bd
2025-04-28 00:48:57
@ 52b4a076:e7fad8bd
2025-04-28 00:48:57I have been recently building NFDB, a new relay DB. This post is meant as a short overview.
Regular relays have challenges
Current relay software have significant challenges, which I have experienced when hosting Nostr.land: - Scalability is only supported by adding full replicas, which does not scale to large relays. - Most relays use slow databases and are not optimized for large scale usage. - Search is near-impossible to implement on standard relays. - Privacy features such as NIP-42 are lacking. - Regular DB maintenance tasks on normal relays require extended downtime. - Fault-tolerance is implemented, if any, using a load balancer, which is limited. - Personalization and advanced filtering is not possible. - Local caching is not supported.
NFDB: A scalable database for large relays
NFDB is a new database meant for medium-large scale relays, built on FoundationDB that provides: - Near-unlimited scalability - Extended fault tolerance - Instant loading - Better search - Better personalization - and more.
Search
NFDB has extended search capabilities including: - Semantic search: Search for meaning, not words. - Interest-based search: Highlight content you care about. - Multi-faceted queries: Easily filter by topic, author group, keywords, and more at the same time. - Wide support for event kinds, including users, articles, etc.
Personalization
NFDB allows significant personalization: - Customized algorithms: Be your own algorithm. - Spam filtering: Filter content to your WoT, and use advanced spam filters. - Topic mutes: Mute topics, not keywords. - Media filtering: With Nostr.build, you will be able to filter NSFW and other content - Low data mode: Block notes that use high amounts of cellular data. - and more
Other
NFDB has support for many other features such as: - NIP-42: Protect your privacy with private drafts and DMs - Microrelays: Easily deploy your own personal microrelay - Containers: Dedicated, fast storage for discoverability events such as relay lists
Calcite: A local microrelay database
Calcite is a lightweight, local version of NFDB that is meant for microrelays and caching, meant for thousands of personal microrelays.
Calcite HA is an additional layer that allows live migration and relay failover in under 30 seconds, providing higher availability compared to current relays with greater simplicity. Calcite HA is enabled in all Calcite deployments.
For zero-downtime, NFDB is recommended.
Noswhere SmartCache
Relays are fixed in one location, but users can be anywhere.
Noswhere SmartCache is a CDN for relays that dynamically caches data on edge servers closest to you, allowing: - Multiple regions around the world - Improved throughput and performance - Faster loading times
routerd
routerdis a custom load-balancer optimized for Nostr relays, integrated with SmartCache.routerdis specifically integrated with NFDB and Calcite HA to provide fast failover and high performance.Ending notes
NFDB is planned to be deployed to Nostr.land in the coming weeks.
A lot more is to come. 👀️️️️️️
-
 @ 40b9c85f:5e61b451
2025-04-24 15:27:02
@ 40b9c85f:5e61b451
2025-04-24 15:27:02Introduction
Data Vending Machines (DVMs) have emerged as a crucial component of the Nostr ecosystem, offering specialized computational services to clients across the network. As defined in NIP-90, DVMs operate on an apparently simple principle: "data in, data out." They provide a marketplace for data processing where users request specific jobs (like text translation, content recommendation, or AI text generation)
While DVMs have gained significant traction, the current specification faces challenges that hinder widespread adoption and consistent implementation. This article explores some ideas on how we can apply the reflection pattern, a well established approach in RPC systems, to address these challenges and improve the DVM ecosystem's clarity, consistency, and usability.
The Current State of DVMs: Challenges and Limitations
The NIP-90 specification provides a broad framework for DVMs, but this flexibility has led to several issues:
1. Inconsistent Implementation
As noted by hzrd149 in "DVMs were a mistake" every DVM implementation tends to expect inputs in slightly different formats, even while ostensibly following the same specification. For example, a translation request DVM might expect an event ID in one particular format, while an LLM service could expect a "prompt" input that's not even specified in NIP-90.
2. Fragmented Specifications
The DVM specification reserves a range of event kinds (5000-6000), each meant for different types of computational jobs. While creating sub-specifications for each job type is being explored as a possible solution for clarity, in a decentralized and permissionless landscape like Nostr, relying solely on specification enforcement won't be effective for creating a healthy ecosystem. A more comprehensible approach is needed that works with, rather than against, the open nature of the protocol.
3. Ambiguous API Interfaces
There's no standardized way for clients to discover what parameters a specific DVM accepts, which are required versus optional, or what output format to expect. This creates uncertainty and forces developers to rely on documentation outside the protocol itself, if such documentation exists at all.
The Reflection Pattern: A Solution from RPC Systems
The reflection pattern in RPC systems offers a compelling solution to many of these challenges. At its core, reflection enables servers to provide metadata about their available services, methods, and data types at runtime, allowing clients to dynamically discover and interact with the server's API.
In established RPC frameworks like gRPC, reflection serves as a self-describing mechanism where services expose their interface definitions and requirements. In MCP reflection is used to expose the capabilities of the server, such as tools, resources, and prompts. Clients can learn about available capabilities without prior knowledge, and systems can adapt to changes without requiring rebuilds or redeployments. This standardized introspection creates a unified way to query service metadata, making tools like
grpcurlpossible without requiring precompiled stubs.How Reflection Could Transform the DVM Specification
By incorporating reflection principles into the DVM specification, we could create a more coherent and predictable ecosystem. DVMs already implement some sort of reflection through the use of 'nip90params', which allow clients to discover some parameters, constraints, and features of the DVMs, such as whether they accept encryption, nutzaps, etc. However, this approach could be expanded to provide more comprehensive self-description capabilities.
1. Defined Lifecycle Phases
Similar to the Model Context Protocol (MCP), DVMs could benefit from a clear lifecycle consisting of an initialization phase and an operation phase. During initialization, the client and DVM would negotiate capabilities and exchange metadata, with the DVM providing a JSON schema containing its input requirements. nip-89 (or other) announcements can be used to bootstrap the discovery and negotiation process by providing the input schema directly. Then, during the operation phase, the client would interact with the DVM according to the negotiated schema and parameters.
2. Schema-Based Interactions
Rather than relying on rigid specifications for each job type, DVMs could self-advertise their schemas. This would allow clients to understand which parameters are required versus optional, what type validation should occur for inputs, what output formats to expect, and what payment flows are supported. By internalizing the input schema of the DVMs they wish to consume, clients gain clarity on how to interact effectively.
3. Capability Negotiation
Capability negotiation would enable DVMs to advertise their supported features, such as encryption methods, payment options, or specialized functionalities. This would allow clients to adjust their interaction approach based on the specific capabilities of each DVM they encounter.
Implementation Approach
While building DVMCP, I realized that the RPC reflection pattern used there could be beneficial for constructing DVMs in general. Since DVMs already follow an RPC style for their operation, and reflection is a natural extension of this approach, it could significantly enhance and clarify the DVM specification.
A reflection enhanced DVM protocol could work as follows: 1. Discovery: Clients discover DVMs through existing NIP-89 application handlers, input schemas could also be advertised in nip-89 announcements, making the second step unnecessary. 2. Schema Request: Clients request the DVM's input schema for the specific job type they're interested in 3. Validation: Clients validate their request against the provided schema before submission 4. Operation: The job proceeds through the standard NIP-90 flow, but with clearer expectations on both sides
Parallels with Other Protocols
This approach has proven successful in other contexts. The Model Context Protocol (MCP) implements a similar lifecycle with capability negotiation during initialization, allowing any client to communicate with any server as long as they adhere to the base protocol. MCP and DVM protocols share fundamental similarities, both aim to expose and consume computational resources through a JSON-RPC-like interface, albeit with specific differences.
gRPC's reflection service similarly allows clients to discover service definitions at runtime, enabling generic tools to work with any gRPC service without prior knowledge. In the REST API world, OpenAPI/Swagger specifications document interfaces in a way that makes them discoverable and testable.
DVMs would benefit from adopting these patterns while maintaining the decentralized, permissionless nature of Nostr.
Conclusion
I am not attempting to rewrite the DVM specification; rather, explore some ideas that could help the ecosystem improve incrementally, reducing fragmentation and making the ecosystem more comprehensible. By allowing DVMs to self describe their interfaces, we could maintain the flexibility that makes Nostr powerful while providing the structure needed for interoperability.
For developers building DVM clients or libraries, this approach would simplify consumption by providing clear expectations about inputs and outputs. For DVM operators, it would establish a standard way to communicate their service's requirements without relying on external documentation.
I am currently developing DVMCP following these patterns. Of course, DVMs and MCP servers have different details; MCP includes capabilities such as tools, resources, and prompts on the server side, as well as 'roots' and 'sampling' on the client side, creating a bidirectional way to consume capabilities. In contrast, DVMs typically function similarly to MCP tools, where you call a DVM with an input and receive an output, with each job type representing a different categorization of the work performed.
Without further ado, I hope this article has provided some insight into the potential benefits of applying the reflection pattern to the DVM specification.
-
 @ 22050dd3:480c11ea
2025-05-02 16:10:59
@ 22050dd3:480c11ea
2025-05-02 16:10:59Bitcoin isn’t complicated, nor is it difficult to understand. It just requires a bit of time and the realization that Bitcoin is unlike anything you’ve heard of or seen before. It’s different.
From the outside looking in, Bitcoin seems like a whole world full of strange and sophisticated words. What is a hash? Is it related to hash rate? What about this talk of public keys, private keys, and seed phrases? Are these seeds edible? While these aren’t words you’d find in traditional finance and economics jargon, they’re fairly simple to understand.
Going deeper, there are concepts and properties of Bitcoin that aren’t found elsewhere.
What does it mean that Bitcoin is deflationary? What’s this talk of Lightning, layers, and on-chain vs off-chain? These can seem complex to the uneducated reader, but fear not as they can be understood with a little bit of explanation.
These concepts aren’t complicated, just different.
I once read that “Bitcoin is everything people don’t understand about computers mixed with everything people don’t understand about money”. While I do find this amusing and think it’s a witty one-liner, I don’t think it’s entirely accurate.
I would say that Bitcoin is the answer and the solution to a significant problem in the world today that the majority of people don’t even realize exists.
Our money and everything built on it is broken.
To the average person that last sentence probably provokes thoughts and questions. Most people do not understand what money is and its purpose. It makes sense why this is. At least in the United States, we are not taught what money is.
We all think we know what money is: the dollars in our wallets that we use to buy goods and services. These dollars are actually currency, which is a form of money, though the two are different.
Before I went down the rabbit hole and learned about Bitcoin, I also had no idea what money was.
 Going back to Bitcoin, Bitcoin is two things: money, and a computer network.
Going back to Bitcoin, Bitcoin is two things: money, and a computer network. The fact that we don’t understand money is why Bitcoin seems so complicated. Add that Bitcoin is a new form of money that our species has never seen before and things get hairy very quickly for the outside observer. With a basic understanding of what money is, as well as a run-down of how blockchain technology works, Bitcoin becomes much more digestible.
Money is three things: medium of exchange, store of value, and unit of account. Currency is two things: medium of exchange and unit of account. We use money in the form of currency as a medium of exchange to pay for goods and services. We use units of account to price goods and services. The store of value property is how we preserve the fruits of our time and energy (work) into the future.
To be good money a thing must fulfill these three properties well. Gold did succeed as a hard money until it didn’t. Gold still succeeds as a store of value, which is the most elusive of the three properties. However, gold has failed as a medium of exchange, which is why we transact with paper currency and not gold coins. Gold can only move at the speed of humans.
Bitcoin is proving with each passing day that it succeeds as hard and sound money by checking the box of these three properties.
If you’re reading this and asking “but a bitcoin is worth $96,000, how do you possibly use that to transact with?” then I have a great answer for you: a bitcoin is divisible into 100 million units, called satoshis or sats. This divisibility property gives Bitcoin the ability to succeed as a medium of exchange and unit of account. Everyday and small purchases are priced in satoshis, while less frequent but significant purchases are priced in bitcoin. A cup of coffee can be 3000 satoshis, while a house can be 3 bitcoin.
Bitcoin already has and will continue to succeed and take over on a global scale due to its store of value properties. For the first time in human history, a perfect money exists. Or rather, as close to “perfect” as possible. Due to its unique properties and absolute scarcity, Bitcoin will continue to become more valuable over time. It’s logical.
Absolute scarcity is difficult to comprehend because it has never existed before on such a large scale. More gold can always be mined, and more oil can always be drilled, but more than 21 million bitcoin total and a predictable and fixed release/minting schedule is forever. For the first time, society can save in money that can’t be debased and diluted. For the first time, society has money that discourages frivolous spending. This is amazing.
On a subconscious level, we are conditioned to want to spend our paper money since we are aware that it is constantly losing its value and buys us less in the future. With hard and sound money, there is no need to buy 20 properties to preserve one’s wealth. For the first time people can save in money, and no longer monetize other things. This will allow the prices of everything to fall, as they naturally should.
 Photo by David McBee
Photo by David McBeeWith this understanding of what good money should be, the defects with our current money become blindingly obvious, as if a switch were flipped for the first time. With this new understanding, it becomes a lot easier to understand Bitcoin and what it means for the world.
Understanding Bitcoin and its monetary system requires looking outside of the existing system. What makes it seem complicated is the fact that the majority of people do not realize what the current system is, how it works, and why it’s so severely flawed.
There are other and more comprehensive resources on the web for understanding how the Bitcoin blockchain works. However, I will provide a very basic explanation to get your big toe wet.
Transactions amongst peers are sent to a pool where they await inclusion into the blockchain. Highly specialized computers are constantly working around the globe to solve complex math problems to win the right to add the next block to the chain. When a computer solves the math problem, it adds transactions to the next block and is rewarded with a fixed amount of bitcoin (the block reward). Each block references and builds upon the previous block. Each new transaction is checked against previous transactions to ensure that no bitcoin is being double spent or invalidly spent. Once the new block is assembled, it is sent out to a global network of nodes that check the new block (and with it the rest of the chain) to verify that it is valid and conforms to the rules of the network. If the nodes are in consensus, the new block is added to the chain and the process starts over again.
There is no need for trust in the Bitcoin network, just verification.
A very important aspect of this process is that physical world energy, resources and time are required to mine blocks and keep the system running. This link between the physical and digital world is extremely crucial and is what sets Bitcoin aside from the rest and makes it the money that it is.
No matter how much computational power and no matter how much money you put into the system, there will never be more than 21 million coins total, with a release schedule set every 10 minutes on average. You could be the richest person in the world and have the computational power of Google, Microsoft, and Amazon combined. But on the Bitcoin network, you’re the same as the person who holds 1/100 of a bitcoin, and this is beautiful.
An understanding of Bitcoin isn’t something that happens overnight. While it’s possible to understand the concepts behind Bitcoin, a full understanding of what Bitcoin means to the world takes time. Much like any large change in life, it takes time to digest and truly understand that it has and will continue to have in the future.
 Learning about and understanding Bitcoin isn’t like learning a new theory or equation. It isn’t like learning about a new way of doing things in the existing system. It’s a completely new and foreign system providing solutions to problems that you didn’t even know existed.
Learning about and understanding Bitcoin isn’t like learning a new theory or equation. It isn’t like learning about a new way of doing things in the existing system. It’s a completely new and foreign system providing solutions to problems that you didn’t even know existed. Bitcoin is changing the world with each passing day and will continue to change and improve our world in ways we can’t even imagine in 2024.
With a growing understanding and the passage of time to digest, comprehend, and fully realize it, Bitcoin will change your perspective on the world and what you do with your time and energy. Once the mind opens up to what Bitcoin is and its significance, the world as it is now and the way we deal with money will seem completely asinine.
Bitcoin is exactly one of those things that you don’t notice until you notice it. And then it becomes impossible to ignore and see things as they once were.
Study Bitcoin.
-
 @ 5d4b6c8d:8a1c1ee3
2025-05-02 15:20:18
@ 5d4b6c8d:8a1c1ee3
2025-05-02 15:20:18After exclusively talking about NFL draft and NBA playoffs last week, we have a lot of ground to make up.
The race for second place in the T20k cricket contest is heating up, but @Coinsreporter has a very commanding hold on 1st. I similarly have a stranglehold on last place in the CricZap contest and, not to brag, I just broke @grayruby's impressive mark for worst single month performance.
We're down to the final two survivors in the UEFA Survivor Pool. C'mon @TNStacker, we're all pulling for you.
The US continues to dominate the rest of the world... in our US vs the world contest.
Our MLB fantasy league (courtesy of @NEEDcreations) is a lot of fun, with tons of daily roster moves and movement in the standings. We should also finally have time for @grayruby to rant about how the American League is the suckiest bunch of sucks who ever sucked (where's that from?).
We do have more playoff basketball to cover. The games this week have been spectacular and we have second round series to start talking about. Shoutout to @WeAreAllSatoshi for hosting discussion threads. I'll get some posts up later summarizing how the bracket challenge is going and taking second round picks in the playoff points challenge.
NHL playoffs are also underway and we've barely talked about them, yet. What are the interesting storylines of round 1? How's the bracket challenge going?
And, of course, we'll talk about our favorite Predyx sports markets.
What else do stackers want to talk about?
originally posted at https://stacker.news/items/969413
-
 @ 1d7ff02a:d042b5be
2025-05-02 14:50:01
@ 1d7ff02a:d042b5be
2025-05-02 14:50:01ผมได้ติดตามการแบนการซื้อขายแบบ P2P ของ Binance ในประเทศไทยมาระยะหนึ่งแล้ว จากสถานการณ์ดังกล่าว เห็นได้อย่างชัดเจนว่ารัฐบาลกำลังเริ่มโจมตี Bitcoin ก่อนที่เราจะบรรลุถึง Bitcoin Standard เราจำเป็นต้องมีความเป็นส่วนตัวและอิสระทางการเงิน ซึ่งการซื้อขายแบบ P2P มีความสำคัญมากในการบรรลุเป้าหมายนี้
ความสำคัญของ No-KYC P2P
No-KYC P2P คือหัวใจสำคัญ - เราจำเป็นต้องมีแพลตฟอร์มที่เป็นทางรอด เราไม่สามารถเชื่อใจแพลตฟอร์มแบบรวมศูนย์ได้เนื่องจากสาเหตุสองประการ: 1. ความเสี่ยงจากการถูกโกงโดยแพลตฟอร์มเอง (rug pull) 2. การถูกควบคุมจากภาครัฐ
แพลตฟอร์ม No-KYC P2P ที่แนะนำ
ผมอยากเสนอให้นักพัฒนาและชุมชน Bitcoin ไทย พิจารณาการศึกษาและพัฒนาแพลตฟอร์ม No-KYC P2P ปัจจุบันมีหลายทางเลือกที่มีอยู่แล้ว เช่น:
- Bisq
- RoboSats
- Mostro
- HodlHodl
- Lnp2pbot
เหตุผลที่แนะนำ Lnp2pbot
ผมขอแนะนำให้นำใช้หรือพัฒนาต่อจาก Lnp2pbot เนื่องจากข้อดีหลายประการ:
- ประสบการณ์ผู้ใช้ (UX) ที่ดีกว่า - เมื่อเทียบกับแพลตฟอร์มอื่นๆ
- ใช้ Telegram เป็นพื้นฐาน - มีระบบ Escrow (บุคคลที่สามที่ถือเงินระหว่างการทำธุรกรรม) ซึ่งเพิ่มความมั่นใจและลดโอกาสการถูกโกง
- ลดการรวมศูนย์ - ไม่จำเป็นต้องพัฒนาแอปและส่งขึ้นสโตร์ ซึ่งจะทำให้นักพัฒนาต้องเปิดเผยตัวตนและกลายเป็นจุดอ่อนให้รัฐบาลควบคุม
- สร้างชุมชนได้ง่าย - ทุกคนสามารถสร้างกลุ่มหรือชุมชนเพื่อการซื้อขายได้ ทำให้ตลาดพัฒนากลุ่มที่น่าเชื่อถือตามกลไกตลาดเสรี
- ใช้งานจริงในหลายประเทศแล้ว - ปัจจุบันมีหลายประเทศที่นำ Lnp2pbot ไปใช้งานจริงแล้ว แสดงให้เห็นถึงความเสถียรและความเชื่อถือได้ของระบบ
บทบาทของนักพัฒนาไทย
Lnp2pbot อาจยังมีข้อจำกัดด้าน UX โดยเฉพาะสำหรับผู้ใช้ท้องถิ่น นักพัฒนาไทยสามารถนำเอาซอฟต์แวร์มาพัฒนาต่อและดำเนินการเองได้ เนื่องจากเป็นโอเพนซอร์สอยู่แล้ว
สิ่งสำคัญที่สุดคือการรักษาให้ซอฟต์แวร์เป็นโอเพนซอร์สและให้ทุกคนสามารถนำไปใช้หรือทำให้มันทำงานได้ด้วยตนเอง วิธีการนี้จะหลีกเลี่ยงการมีจุดรวมศูนย์ที่รัฐบาลสามารถโจมตีได้
-
 @ 20986fb8:cdac21b3
2025-05-02 14:08:55
@ 20986fb8:cdac21b3
2025-05-02 14:08:55传统黑客松:闪耀火花中的局限
过去几十年里,黑客松一直是技术文化的培养皿——24小时或48小时的狂热编程马拉松,在披萨、咖啡因和几近不可能的乐观情绪中推进。
自1999年Sun Microsystems首次举办黑客松,要求Java开发者在Palm V掌上电脑上完成一日编程,到创业公司和大学里通宵达旦的“黑客日”[1],这些活动始终在庆祝黑客精神。它们为我们带来了Facebook的“点赞”按钮和聊天功能——这些标志性的创新[1],皆诞生于一夜之间的即兴狂想。
它们也催生了如GroupMe这样的公司——这个应用仅用了几个深夜时段就完成开发,一年后就被Skype以8000万美元收购[2]。
黑客松逐渐成为技术界的传说,成为“无拘束创造力”的代名词。然而,尽管充满激情和炒作,传统黑客松却存在着严重的局限:它们是偶发、线下的活动——更像是“蓝月亮”才出现一次的肾上腺素爆发,而不是一种可持续的创新流程。
一次黑客松也许能在周末召集100名程序员共聚一室,但活动结束后便销声匿迹,直到下一年。
频率低、规模小、触达有限。只有能亲临现场的人(往往是硅谷或精英高校)才有机会参与。哪怕你是来自拉各斯或圣保罗的天才黑客,只要身处远方,你的绝妙创意也注定被忽视。
这类冲刺式活动的成果也极为受限。
当然,团队可能构建出炫酷的演示项目,并赢得一时风头。但大多数情况下,这些项目只是一次性原型——“玩具”应用,最终并未发展为真正的产品或公司。有研究表明,只有约5%的黑客松项目在活动结束几个月后还有任何生命迹象[3]。
其余95%则如烟云般消散——在“黑客松宿醉”中夭折:人们回到“正职”,而演示代码也蒙尘。
批评者甚至给黑客松取了个贬义的别名:“周末虚耗松”(weekend wastedathons),抨击其成果如同短命的“蒸汽软件”(vaporware)[3]。
想想看:一阵创造力的爆发,数十个点子竞相绽放……然后呢?
你能说出几个真正从黑客松走出的成功企业名字?对于每一个如Carousell或EasyTaxi那样从黑客松中诞生、后来成功融资数千万美元的项目,就有几百个聪明的创意组合永远不见天日[2]。
传统黑客松模式,尽管令人兴奋,却极少能转化为持续的创新。
它更像是被时间、地域和后续缺失所束缚的孤岛式创新。黑客松是事件,不是流程;它是烟花,不是日出。
此外,黑客松在历史上一直颇为封闭。
直到近年,它们主要由技术圈内人士自办自娱。大型科技公司会举办内部黑客松,以激发员工创造力(Facebook每几周举办一次通宵活动,最终诞生了时间线和标记功能,影响了十亿用户 [1]);NASA和世界银行也曾尝试用黑客松推进公民科技。但这些都是例外,印证了一个普遍规律:黑客松从来不是常规工作流程,而是特例事件。
在科技巨头之外,鲜有组织具备资源或经验能频繁举办黑客松。
除非你是Google、Microsoft,或资金雄厚的创业孵化器,否则黑客松只是一场偶尔奢侈的尝试。事实上,当今世界上最大的黑客松是微软的内部全球黑客松——有多达70,000名员工跨越75个国家同时参与,这是壮观的成就,但唯有企业巨头才能负担得起[4]。
而中小型玩家只能仰望、惊叹。
限制显而易见:黑客松太少见、太封闭,无法真正激活全球人才库;周期太短,难以构建成熟产品;过于孤立,无法真正撼动行业。
没错,它们确实产生过惊艳的灵感时刻——创新的闪光灯。
但若视其为持续进步的机制,传统黑客松则显得捉襟见肘。作为投资者或科技领袖,你或许会为创造力鼓掌,但仍会追问:真正的长期影响在哪里?有谁搭建了把这些火花转化为持续光束的基础设施?
正如克莱顿·克里斯滕森的《创新者的窘境》所言,传统巨头往往将黑客松项目视作“玩具”——有趣但不切实际。
而事实上,“每一个未来的大事物,起初总是被当作玩具”。黑客松的确催生了不少“玩具”,却极少能拥有支持系统去把它们变为下一个伟大的事物。
这个模式,是时候被重新发明了。
为何到了2020年代,我们还在用1990年代的创新方式?为何将突破性的想法限制在一个周末或一个地点?为何允许95%的早期创新无声凋谢?
这些问题,悬而未解,等待着回答。
Hackathons 2.0 ——DoraHacks与黑客松的第一次进化(2020–2024)
DoraHacks登场。
在2020年代初,DoraHacks如同一台“心脏除颤器”,令黑客松这种形式重获新生。DoraHacks 1.0(大致始于2020年、延续至2024年)并非对黑客松的微调,而是对其彻底的重塑:将传统黑客松从1.0升级到2.0。它汲取原有理念,加速、扩展并升级至全维度,全方位放大其影响力。结果是一场全球黑客运动的兴起,一个将黑客松从“一锤子买卖”变为持续技术创新引擎的平台。
DoraHacks如何革命性地重构黑客松?请看以下几个维度:
从24小时到24天(甚至24周)——时间轴的重构
DoraHacks拉长了黑客松的时间框架,解锁了远超以往的创新潜能。
相比于传统那种紧张焦躁的24小时冲刺,DoraHacks支持的黑客松往往持续数周甚至数月——这是一场范式转变。
团队终于有了足够时间去打磨原型、迭代优化、反复精炼。更长的周期意味着项目能从粗糙演示走向成熟MVP。黑客们终于可以“偶尔睡觉”,引入用户反馈,将灵感的火花铸造成实用的成果。
时间的延展模糊了黑客松与加速器之间的界限,但保留了黑客松自由、开放的精神。例如,DoraHacks为区块链初创团队组织的黑客松通常持续6到8周,最终成果往往能吸引真实用户与投资人。
延长的时间,把“玩具”变成了产品。就像黑客松终于“长大成人”:Less Hack, More BUIDL(少些临时拼凑,多些踏实构建)。打破24小时范式之后,黑客松真正变得更高效、更深远、更具生产力。
从街角咖啡馆到全球虚拟竞技场——地理限制的打破
DoraHacks将黑客松从线下搬到云端,释放出全球参与的可能性。
2020年之前,黑客松意味着必须到现场——可能是旧金山某仓库,或是大学实验室,与本地队友并肩作战。而DoraHacks颠覆了这一格局:任何人、任何地方,只要连上网络,就可以参与。
一位尼日利亚的开发者、乌克兰的设计师、巴西的产品经理,如今可以在同一场线上黑客松中协作创新。地理边界不复存在。
当DoraHacks举办面向非洲区块链开发者的Naija HackAtom时,吸引了来自尼日利亚科技社群的500多名参与者(包括160多位开发者,odaily.news)。在另一场活动中,来自数十个国家的黑客同时在线参与、构思、竞争 [6]。
这种全球性拓展不仅增加了参与人数,更引入了多样的视角和本地问题。一个金融科技黑客松中,可能有拉美开发者解决汇款问题;一个AI黑客松中,亚洲或非洲开发者将机器学习应用于本地医疗。
线上化,让黑客松变得真正普惠。DoraHacks有效地民主化了创新的入场门槛——你只需要一根网线和一颗创作的心。
结果是:创意的数量与质量实现量子飞跃。 黑客松不再是精英小圈子的游戏,而是一场面向全人类的全球创新嘉年华。
从几十人到数万人——规模的跃迁
DoraHacks推动的另一项革命,就是规模的扩展。传统黑客松人少而亲密(几十人,顶多几百)。DoraHacks则催生了成千上万人参与、数百万美元奖金池的大型活动。
例如,在2021年的一场线上黑客松中,近7000名参与者提交了550个项目,争夺500万美元奖金。这是2010年代初期根本无法想象的规模[7]。
DoraHacks本身也成为这些“超级黑客松”的中枢。平台在Web3领域所举办的黑客松常常吸引数百支队伍参赛,奖金高达数百万美元。
这不只是好看的数据,而是更广泛的全球人才投入,也带来了更高概率的真正突破性成果。
以BNB Chain支持的黑客松系列为例,在DoraHacks推动下,有216支开发团队获得了超过1000万美元的资金支持[8]——是的,真金白银的种子投资。这哪是黑客松?简直就是一个小型经济体。
奖池也从“披萨钱”膨胀成“起步资本”,吸引那些有抱负、懂商业的创业者参与。越来越多的项目不再只是周末练习,而是具备融资能力的初创企业。黑客松,也由“科技科学展”升格为“全球创业发射台”。
从玩具项目到真公司(甚至独角兽)——成果的飞跃
最令人振奋的一点是:DoraHacks所孵化的项目,不只是应用,更是真正的公司。其中一些甚至成长为独角兽(估值超过10亿美元的公司)。
我们之前提到过2020年之前为数不多的成功案例,比如Carousell(一个在2012年黑客松上诞生的小点子,如今已成为估值11亿美元的二手市场[2]),或EasyTaxi(始于黑客松,后融资7500万美元、覆盖30个国家[2])。
DoraHacks让这种奇迹频繁上演。通过更长的周期、更多的支持、更好的资金接力,黑客松逐渐成为真正的“创新孵化器”。
以1inch Network为例——它是一家去中心化金融聚合平台,起初就是在2019年一个黑客松中诞生的。创始人Sergej Kunz和Anton Bukov在社区支持下完成了最初的原型,随后持续迭代。
如今,1inch的累计交易额已超4000亿美元,成为DeFi领域的头部平台之一 [9]。
再看DoraHacks Web3黑客松中的优胜者,许多项目已经完成了数百万美元的融资,获得顶级VC支持。
黑客松成为了“创业世界的前门”,创始人往往在此首次亮相。比如Solana Season Hackathons中的热门项目STEPN —— 一个“边走边赚”应用,于2021年赢得黑客松奖项,不久后就成长为拥有数十亿美元代币经济的现象级产品[10]。
这不是孤立事件,而是DoraHacks设定的系统性趋势。它的黑客松正在源源不断地产出可投、可用、可落地的创业项目。
某种意义上,DoraHacks模糊了黑客松与早期孵化器的界限。玩乐的黑客精神依然在,但结果已不只是炫耀——而是真实存在的公司,有用户,有营收,有估值。
借用投资人Chris Dixon的话说:DoraHacks把那些“玩具”,扶育成了下一个伟大的事物[5]。
DoraHacks不仅优化了旧模式,它创造了一个全新的创新生态
DoraHacks主导的第一次黑客松进化,不只是“修补优化”,而是打造了一个全新的创新系统。
黑客松变得高频、全球化、具决定性影响。
它不再是短暂的周末狂欢,而是持续的创新供给链。
DoraHacks平台每年孵化出上百个可行项目,其中很多都获得后续融资。它不仅提供活动本身,更提供“术后护理”:社区支持、导师指导、连接投资人与资助渠道(如DoraHacks的资助计划和二次方资助机制)。 到2024年,成果不言自明。DoraHacks已成长为全球最重要的黑客松平台——一个贯通区块链、AI乃至更多前沿科技的黑客运动中枢。
数据不会说谎。
9年间,DoraHacks帮助4000多个项目获得超过3000万美元资金(coindesk.com)[11];到2025年,这一数字飙升,DoraHacks支持的黑客松和资助总计为超过21000个初创团队提供了逾8000万美元资金(linkedin.com)[12]。
这不是夸张宣传——而是写入技术史的事实。CoinDesk评价道:“DoraHacks已成为全球最活跃的多链Web3开发平台与黑客松组织者之一。”(coindesk.com)[13]
主流技术生态纷纷注意到这一趋势。
超过40个公链(包括L1与L2)——从Solana到Polygon再到Avalanche——皆与DoraHacks合作,组织黑客松与开放创新计划(blockworks.co)[13]。
Blockworks 报道称,DoraHacks已成为数十个Web3生态系统的“核心合作伙伴”,帮助他们连接全球开发者资源(blockworks.co)[11]。
在投资人眼中,DoraHacks本身就是关键基础设施:“DoraHacks对Web3基础设施建设至关重要。”一位支持平台的VC如此指出(blockworks.co)[13]。
简而言之:到2024年,DoraHacks已将黑客松从一个小众事件变为全球创新引擎。
它证明:只要规模足够、流程健全,黑客松可以持续地产出真实、可投、可商业化的创新。
它连接开发者与资源,把“孤岛式创新”变成一场全球开发者的常青运动。
这就是Hackathons 2.0:更大、更久、更无界,也远比以往更具颠覆性。
也许你会问:还能比这更好吗?
DoraHacks似乎已经破解了“如何让黑客创造力产生持久影响”的密码。
但这并不是终点。事实上,DoraHacks团队即将揭示的,是一场更加激进的革命。
如果说DoraHacks 1.0是“进化”,那接下来将是一次范式转移的“革命”。
Agentic Hackathon:BUIDL AI与第二次黑客松革命
2024年,DoraHacks推出了BUIDL AI,并由此提出了“Agentic Hackathon(自主智能黑客松)”的概念。
如果说最初的黑客松像是模拟电话,DoraHacks 1.0则使其进化为智能手机,那么BUIDL AI的出现,就像为黑客松安装上了AI副驾驶——进入自动驾驶模式。
这不仅是渐进式的提升,而是一场彻底的第二次革命。
BUIDL AI为黑客松注入了人工智能、自动化与“智能代理”能力(Agentic),根本性地改变了黑客松的组织方式与体验路径。
我们正迈入“自主智能创新时代(Age of Agentic Innovation)”,在这个时代中,借助AI代理运行的黑客松可以以前所未有的频率、高效与智慧展开。
那么,究竟什么是Agentic Hackathon?
它是一种由AI代理全面增强的黑客松,从策划、评审到参与者支持都涵盖在内,使得创新的速度与规模达到前所未有的高度。
在Agentic Hackathon中,AI是那位永不疲倦的共同组织者,与人类并肩工作。 过去那些压垮组织者的繁琐流程,如今交由智能算法完成。你可以想象——黑客松几乎在自动运行,如同一场永不停歇的“点子锦标赛”。
借助BUIDL AI,DoraHacks实现了“自驾黑客松”:自主、高效、全天候运行,且可在多个领域同时并行。 这并非科幻小说,而是正在发生的现实。我们来看BUIDL AI是如何运作的,以及它如何将黑客松效率提升十倍以上:
AI驱动的评审与项目筛选:效率提升10倍以上
大型黑客松中最耗时的环节之一就是评审数百个项目提交。传统做法常常需要组织者耗费数周精力,才能从中筛选出有潜力的项目。
BUIDL AI彻底改变了这一切。
它配备了BUIDL Review模块——一个AI驱动的评审系统,能够从多个维度(项目完整性、创意性、主题契合度等)智能分析项目,并自动剔除质量较低的提交[14]。
就像配备了一支随叫随到的专家评审军团。
效果如何?原本需要几百人小时完成的工作,如今几分钟即可完成。
DoraHacks报告称,AI辅助评审已将组织效率提高超过10倍[14]。
想象一下:一项原本需要一个月枯燥工作完成的任务,如今在几天之内搞定,而且评分更一致、公正、透明。 组织者不再淹没在文书工作中,参与者也能更快获得反馈。
当然,AI并不完全取代人工评委——最终决策仍需专家参与,但AI承担了繁重的初审环节。这也意味着:黑客松可放心接纳更多项目提交,因为AI会帮你完成筛选。
不再因为“人手不足”而限制报名人数。
在Agentic Hackathon中,再也没有优秀项目被埋没的遗憾,因为AI确保它们都能被看到。
自动化市场营销与内容讲述:让每场黑客松都自带扩散力
赢得一场黑客松固然令人激动,但如果无人知晓,影响力也就大打折扣。
过去,黑客松结束后,组织者通常需要手动撰写总结、撰文致谢、更新结果——虽然重要,却常常被推迟。
BUIDL AI改变了这一点。
它配备了自动化营销模块,可一键生成黑客松的总结报告与传播内容[14]。
想象这样一个AI,它完整“观察”了整场黑客松(包括提交项目、获奖名单、技术趋势),然后自动撰写出一份专业报道:突出最佳创意、介绍获胜团队、提炼洞察(比如“本次黑客松中60%的项目应用AI于医疗场景”)。
BUIDL AI正是这么做的:自动生成“高光集锦”与总结报告[14]。
这不仅节省了组织者的写作工作,还极大提升了黑客松的传播力。
活动结束数小时内,一份内容丰富的总结即可全球发布,展示创新成果,吸引关注。
赞助方与合作伙伴对此尤为青睐,因为他们的投资能被迅速宣传;参与者也很喜欢,因为自己的项目立刻获得庆祝与曝光。
本质上,每一场黑客松都在讲述一个故事,而BUIDL AI确保这个故事被迅速、广泛地传播。
这种自动化叙事机制,使得黑客松不再是孤立事件,而是持续内容的源泉,为下一场活动积蓄动能。
这是一个良性循环:黑客松产出创新,AI包装传播,传播吸引更多创新者。
一键发起,多黑客松并行:组织者的自由释放
BUIDL AI最具解放性的功能之一,是一键启动黑客松、支持多场并行管理。
过去,发起一场黑客松本身就是一项大型项目:报名系统、评委协调、奖金设计、沟通流程……一切都需人工配置。
DoraHacks的BUIDL AI引入了“一键发起黑客松”工具 [14] 。
组织者只需输入基本信息(主题、奖池、时间、评审规则),平台即自动生成活动页面、提交入口、评审流程等,就像发一篇博客一样简单。
这极大降低了社区与公司举办黑客松的门槛。
如今,即使是一个初创公司或大学社团,也可以轻松举办全球级黑客松,无需专职活动团队。
此外,BUIDL AI还支持多场黑客松的并行管理[14]。
过去,即使是科技巨头也难以同步组织多场黑客松——资源消耗太大。如今,一个生态系统可以同时运行DeFi、AI、 IoT等主题黑客松,背后由AI自动调度。
自BUIDL AI发布以来,组织12场/年,甚至同时运行数场黑客松,从“不可能”变成常规操作[14]。
平台还自动管理参与者接入、发送提醒、通过聊天机器人回答常见问题,确保流程顺畅。
简而言之,BUIDL AI让黑客松主办方像使用云服务器一样“按需发起”创新活动。
这是一场结构性转变:黑客松不再是“偶尔有空才办”的事件,而是“需要时就能发”的常态流程。 我们正在见证永续黑客松文化的诞生——不再是偶尔的火花,而是持续的火焰,始终燃烧,永不熄灭。
实时AI导师与智能助手:人人皆可成为“Agentic Hacker”
Agentic Hackathon的“智能代理”不仅体现在后台,也贯穿了参与者的体验。
借助AI集成,开发者得到了更智能的工具与支持。
例如,BUIDL AI可以配备AI助手,在活动中实时回答开发者问题(如“这个API怎么用?”、“有没有这个算法的代码示 例?”),就像随叫随到的技术导师。
它还可以推荐协作伙伴、推送参考资料。
本质上,每位参与者都像身边多了一个AI队友——全能、勤奋、永不疲倦。
一些本需数小时调试的bug,借助AI助手几分钟即可解决。
这意味着:项目质量提升,参与者学习效率大幅提高。
正如followin.io所言,这种“agentic协助”体现了“人人皆可成为黑客”的愿景[14]。
AI自动化了大量重复性工作,放大了小团队的能力边界[14]。
在Agentic Hackathon中,两个人加AI助手,就能完成过去五人团队数周才能达成的任务[14]。
这既降低了门槛,也拉高了上限——创新的天花板不再遥不可及。
总结:从黑客松2.0跃迁至3.0,进入智能化持续创新的新时代
所有这些变革,指向同一个事实:黑客松已从偶发的灵感爆发,演化为持续、高频、AI优化的创新流程。
我们正从黑客松2.0走向黑客松3.0——一个自主、常驻、智能的新时代。
这是一场范式转移。
黑客松不再是你参加的一场活动,而是你生活的一个创新环境。
借助BUIDL AI,DoraHacks描绘出这样的世界:“黑客松将进入一个前所未有的自动化与智能化时代,使全球更多黑客、开发者与开源社区能够轻松发起与参与。”
创新将随时随地发生,因为支持它的基础设施正由AI驱动、全天候运转于云端。
黑客松已成为一个智能平台,随时准备将创意转化为现实。
更关键的是,这一切并不局限于区块链。
BUIDL AI是通用平台——无论是AI、气候科技、医疗、教育等领域,都可接入Agentic Hackathon平台,享受更高频、更高效的创新节奏。
这预示着一个未来:黑客松将成为默认的解决问题方式。
公司与社区不再靠封闭的委员会与研发部门推进创新,而是将问题投入黑客松竞技场——一个始终活跃的解决问题引擎。
形象地说:
**DoraHacks 1.0 让黑客松拥有了高速引擎;
DoraHacks 2.0 加上 BUIDL AI,则让它变成一辆自动驾驶的赛车——油门踩到底。**
成本、复杂度、时间的阻碍——都不复存在。
如今,任何组织都能毫无阻力地驶入创新高速公路,从0加速到60。
黑客松频率如博客更新,融入日常运营,如同敏捷开发的冲刺演示。
按需创新,规模扩张——这就是Agentic Hackathon的力量。
随需创新:Agentic Hackathon 如何惠及所有人
Agentic Hackathon(自主智能黑客松)的诞生,并非只是技术社区的一款“新奇玩具”,而是一种变革性的工具,可服务于企业、开发者,乃至整个行业。
我们正步入一个全新时代:任何拥有愿景的人都能将“黑客松即服务”转化为推动创新的引擎。以下是不同参与者如何从这场革命中受益:
AI公司 —— 加速生态成长的发动机
对于专注于人工智能的公司(如 OpenAI、Google、Microsoft、Stability AI 等),黑客松是一座座发掘其技术创意用途的金矿。
如今借助 Agentic Hackathon,这些公司几乎可以为自己的平台持续举办一场“永不落幕”的开发者大会。
比如,OpenAI 可以为 GPT-4 或 DALL·E 启动全年在线的黑客松,鼓励全球开发者持续实验、展示这些AI的应用场景——本质上,以众包方式为AI平台孵化创新与杀手级应用。
收益何在?生态系统和用户基数的指数级扩展。
新的用例往往来自公司内部未曾设想的角落。 (最早展示 GPT-3 能撰写法律合同、生成游戏关卡的,不是大公司,而是独立黑客——他们在黑客松和社区挑战中发现了这些潜力。)
有了 BUIDL AI,AI 公司可以一键启动月度黑客松,每月聚焦不同方向(比如本月自然语言处理,下月机器人控制)。 这是市场营销与产品研发的倍增器。
无需再组织昂贵的开发者布道之旅,AI 将成为全球开发者互动的主力军。产品在推广的同时也在优化。 本质上,每家AI公司都可以开启自己的“黑客松联赛”,推动API或模型的普及与应用。
Coinbase最近首次举办AI主题黑客松,尝试连接加密与AI领域——他们很清楚,要播下新范式的种子,黑客松是最佳路径[15] 。
未来,我们将看到所有AI平台效仿:持续通过黑客松教育开发者、生成内容(演示、教程),并发掘可投资/可招聘的杰出人才。这将是社区建设的超级助推器。
L1/L2与技术平台 —— 发现下一只独角兽
对于区块链的一层/二层网络(Layer1/Layer2),以及任何技术平台(如云服务、VR平台等)来说,黑客松已成为新的“Deal Flow”(项目源)。
在 Web3 世界里,许多顶级项目与协议都诞生于黑客松,这一点早已被广泛认同。
我们看到,1inch 就是始于黑客松,后来成长为 DeFi 独角兽(cointelegraph.com)[9]。
Polygon 积极举办黑客松以寻找其生态的新型dApps;Filecoin 借助黑客松发掘分布式存储应用。
借助 DoraHacks 和 BUIDL AI,这些平台现在可以高频率地组织黑客松,持续输出创新成果。
不再是一年一两次大型活动,而是一个滚动进行的计划——比如每季度一场,甚至同时多地开展全球挑战,保持开发者“常态建设”。
回报率巨大:即使设有可观奖金,黑客松的举办成本也远低于收购一个蓬勃发展的初创公司或协议所需投入。 黑客松本质上是将早期研发外包给充满热情的社区成员,最好的创意自然浮现。
Solana 的黑客松就促成了 Phantom、Solend 等明星项目的落地。Facebook 的内部黑客松也曾带来推动平台主导地位的功能创新[1]。
现在,任何平台都可以将黑客松“外部化”:作为发现人才与创新的“雷达”。借助 BUIDL AI,哪怕一个 L2 区块链的核心团队人手有限,也能并行运行多场黑客松与赏金任务——一场关注 DeFi,一场关注 NFT,一场关注游戏等等。
AI 负责初审项目与管理社区问答,让平台的 DevRel 团队不至于“过劳”。结果是,一条源源不断的创新供给链,不断喂养平台增长。下一个独角兽、下一个杀手级应用,将被提前识别并扶持成长。
黑客松已成为 VC 和技术生态的新型创业漏斗(Startup Funnel)。
未来,投资人将活跃于 Agentic Hackathon 中——因为那里正是“未来车库”的所在:黑客们聚集在云端黑客室中重塑世界。
正如 Paul Graham 所言:“黑客与画家,皆为创造者”,他们将在黑客松平台的画布上,描绘未来科技的蓝图。
所有公司与社区 —— 创新成为一种持续流程
或许 BUIDL AI 最深远的影响是:让所有组织都能举办黑客松,不再局限于科技公司。
任何希望推动创新的机构——银行探索金融科技、医院网络寻找医疗科技方案、政府寻找公民科技创意——都可以利用 Agentic Hackathon。
创新不再是巨头的特权,它成为一项“云服务”,人人可用。
比如,一个城市政府可以举办全年黑客松,征集“智慧城市”解决方案,让本地开发者持续提出、建设项目以改善城市生活。
BUIDL AI 平台可以设置不同“赛道”:交通、能源、安全,每月评选最佳创意并给予奖励。
这比传统招标流程更加灵活,能更高效地激发社区活力与项目孵化。
同样地,任何担心被颠覆的财富500强公司(其实谁不担心?)都可以主动“自我颠覆”——通过黑客松邀请员工和外部创新者挑战企业自身难题。
在 agentic 模式下,即使是非技术型公司也能轻松参与;AI 会引导流程,保障运行顺畅。试想:黑客松成为每一家企业战略部门的“标配工具”,不断原型化未来。
正如 Marc Andreessen 所说,“软件正在吞噬整个世界”——而现在,每家公司都可以通过举办黑客松,参与“软件化”自身问题的过程。
这将推动跨行业的创新民主化。
尝试大胆创意的门槛大幅降低(周末黑客松 vs. 数月企业流程),更多潜在颠覆性创意将在企业内部浮现。
有了 DoraHacks 的全球影响力,企业也能轻松吸引外部创新者参与。
零售公司为何不能从全球黑客那里众包 AR 购物创意?
制药公司为何不办场生物信息学黑客松以探索数据分析新方法?
答案只有一个:没有理由不做。Agentic Hackathon 让一切变得可行、值得。
黑客松即服务(Hackathon-as-a-Service)将成为下一代的创新部门——要么使用它,要么被使用它的人超越。
结语:从偶发事件到创新基础设施的演进
所有上述变革,归结为一个深刻转变:黑客松正从一次性的活动,演变为创新生态系统中的常驻组成部分。
它们正成为像云计算、宽带网络一样的基础资源:随时可用,规模无限。
想获得新点子或原型?办场黑客松,让全球开发者接招。
想激活开发者社群?发布主题黑客松,提供舞台。
想试验10种解决方案?来一场比赛,看看谁跑出来。
我们正在见证所谓“创新公地(Innovation Commons)”的诞生:一个持续匹配问题与创意、迅速迭代解决方案的协 作空间。
AI是这片公地的维护者,保证运行高效、协作持久,不再需要消耗人为组织者的精力。
这也正好回应了人们对黑客松的批评:缺乏可持续性与后续跟进。
而在Agentic模型中,黑客松不再是孤岛——它们可以彼此衔接:上届的优胜团队可以直接晋级加速器,或参与下月的 新主题挑战。
BUIDL AI 甚至可以追踪团队进展,推荐资助机会、合作方、甚至下一步要申请的Grant,彻底解决过去“项目周末之后无人接手”的痛点。
好项目不会在周日夜晚“死掉”,而是被自动引导进入下一阶段的旅程。
我们还应认识到一种更深层的哲学意义:
创新文化,变得更具实验性、更重才智、更具节奏感。
在Agentic Hackathon的世界中,座右铭是:“为啥不原型一下?为啥不现在就试?”
因为启动一场实验的门槛如此之低,创新思维将像空气般流入每一个组织、每一个社区。
失败的成本极低(只需几周),成功的可能却极高(也许就是下一个突破)。
这是一块供“颠覆性想法”安全试验的沙盒,也正是解决《创新者的窘境》的现实路径:
结构性地为那些被视为“玩具”的想法,保留生长空间[5]。
企业无需在“核心业务”与“实验创新”之间二选一——他们可以为后者开设一条常驻黑客松轨道。
本质上,DoraHacks 与 BUIDL AI 打造了一座“创新工厂”——任何有远见的组织都可以“租用”一周末,甚至一年。
从 Like 按钮到点火升空:黑客松是创新的摇篮
要真正理解这个新时代的分量,我们不妨回顾一下——多少改变世界的创新,其实起源于黑客松项目或类似黑客松的实验,即使当时还受限于旧有模式。而现在,随着这些限制被移除,我们能期待的,将远远不止于此。 历史本身,就是黑客松创新模式的最佳佐证:
Facebook 的基因,由黑客松塑造
马克·扎克伯格本人曾表示,Facebook 的许多关键功能都来自公司内部的黑客松:“点赞”按钮、Facebook Chat、时间线功能,无一不是工程师们在通宵达旦的黑客松中迸发出的创意[1]。
一位实习生在黑客松中构建的“评论区标记好友”原型,在短短两周后就上线,触达了十亿用户[1]。Facebook 的核心理念“Move fast and break things(快速行动,大胆试错)”,几乎就是黑客松精神的官方化表达。
可以毫不夸张地说,Facebook 能在2000年代超越 MySpace,正是得益于其由黑客松推动的快速创新文化[1]。
如果黑客松能在一家公司的内部产生如此颠覆性作用,想象一下——当它成为全球网络时,创新的速度将怎样改变整个世界?
Google 的“20% 时间”项目:制度化的黑客精神
Google 长期鼓励员工将20%的时间投入到自由探索的副项目中,这本质上是黑客松理念的延伸:结构外的探索实验。 Gmail 和 Google News 就是这样诞生的。
此外,Google 也曾围绕其 API 举办公开黑客松(如 Android 黑客松),催生了无数应用。
换句话说,Google 将黑客式实验制度化,获得了巨大的创新红利。
如今借助 Agentic Hackathon,即便没有 Google 资源的公司,也能制度化实验文化。
世界各地的开发者,都可以把每个周末当作自己的“20%时间”,借由这些平台启动属于自己的探索。
开源运动的推进器:Hackathons + Open Source = 强生态
开源软件世界也从“代码冲刺”(黑客松形式)中受益匪浅。
例如整个 OpenBSD 操作系统的开发就离不开其定期举办的黑客松[3]。
近年来,Node.js 与 TensorFlow 等项目也都通过黑客松来构建工具与生态组件。
其结果是:更强壮的技术生态,更活跃的贡献者社群。
DoraHacks 也在延续这种传统,并将自己定位为“全球领先的黑客松社区与开源开发者激励平台”[17]。
开源与黑客松的结合——都去中心化、社群驱动、基于 meritocracy(才智主义)——本身就是创新引擎。
我们可以预见,未来开源项目将借助 BUIDL AI 启动“永不停歇的黑客松”:持续修复 bug、加入新功能、奖励优秀贡献者。
这将为开源世界注入新生命——不仅通过奖金提供激励,还能以系统化的方式提供认可与传播。
初创世界:黑客松造就新公司
众多初创企业的起点,都是黑客松。 我们已提到的 Carousell(起于Startup Weekend,估值超10亿美元[2])、EasyTaxi(同样出自Startup Weekend,融资7500万美元[2])。 再加上:
- Zapier(集成工具平台,灵感来自黑客松)
- GroupMe(如前所述,被Skype收购)
- Instacart(传说在Y Combinator Demo Day 黑客松中以早期版本夺得优胜)
- 以及无数加密初创项目(包括 Ethereum 创始人们的相识与合作也源于早期黑客松与比特币线下聚会)
如今,当 Coinbase 想寻找链上 AI 的下一个机会时,他们办一场黑客松[15]。
Stripe 想推动支付平台上的应用数量,也选择了办黑客松并发放 Bounty。
这种模式行之有效:找到充满热情的构建者,为他们提供跳板。
有了 Agentic Hackathon,这个跳板不再只是弹射一次,而是始终在线,能接住更多人。
这个“创业漏斗”变宽了,我们将看到更多初创企业诞生于黑客松。
完全可以想象:
2030年代最伟大的公司,不会诞生于车库,而是源自一场在线黑客松,由几个在 Discord 上认识的开发者,在 AI 导师协助下完成原型,并在 DoraHacks 平台数周内获得融资。
换句话说,“车库神话”已进化为全球、云端、AI驱动的创业现实。
黑客与画家:创造者的共鸣
Paul Graham 在《Hackers & Painters》中曾将“黑客”比作“画家”——两者皆为纯粹的创作者[16]。
而黑客松,正是这种创造能量最集中、最爆发的场域。
许多伟大程序员都会告诉你,他们最具灵感的作品,正是在黑客松或秘密小项目中完成的——在没有官僚主义的束缚 下,沉浸于“心流”中完成的创作。
扩大黑客松的规模与频率,本质上就是扩大人类的创造力边界。
我们或许会想起文艺复兴时期——艺术家与发明家聚集在赞助人举办的工坊中自由创作;而如今,黑客松就是现代文艺复兴的“创客工坊”。
它融合了艺术、科学与企业家精神。
若达·芬奇活在今天,他一定会如鱼得水地出现在黑客松中——他以疯狂原型迭代著称。
更重要的是:黑客松完美解决了《创新者的窘境》中的核心问题:鼓励人们去做那些 incumbent(巨头)不屑一顾、看似“小而无用”的项目——而那恰恰往往是颠覆性创新的藏身之处 [5]。
DoraHacks 正是通过制度化黑客松,制度化了颠覆本身——确保下一个 Netflix、Airbnb,不会因为“听起来像个玩具”而被错过。
黑客松已成为全球创新基础设施的一部分
我们已从“黑客松罕见且本地化”的时代,走到了“黑客松持续且全球化”的今天。
这不仅是节奏上的转变,更是全球创新基础设施的关键转折点。
19世纪,我们修建了铁路与电报,催化了工业革命,连接了市场与思想;
20世纪,我们构建了互联网与万维网,引爆了信息革命;
而今,21世纪,DoraHacks 与 BUIDL AI 正在搭建“创新高速公路”:一个持续运行、AI驱动的网络,
在全球范围内,实时连接解决者与问题、人才与机会、资本与创意。
这是为 创新本身修建的基础设施。
伟大的愿景:全球创新的新基础设施
我们正站在一个历史拐点上。
有了 DoraHacks 和 Agentic Hackathon(自主智能黑客松)的出现,创新不再局限于象牙塔、硅谷办公室,或一年一度的大会。
它正成为一项持续的全球性活动——一个随时随地聚集最聪明头脑与最大胆创意的竞技场。
这是一个未来:创新将像 Wi-Fi 一样无处不在,像摩尔定律一样不断加速。
这是 DoraHacks 正在主动构建的未来,而它所带来的影响将是深远的。
想象几年之后的世界:DoraHacks + BUIDL AI 成为跨行业创新项目的默认基础设施。
这个平台7×24不间断运转,承载着从 AI 医疗、气候变化应对,到艺术娱乐前沿的各类黑客松。
而且它不仅仅属于程序员——设计师、创业者、科学家,任何有创造力冲动的人,都能接入这张全球创新网络。
一个伦敦的创业者凌晨2点冒出商业点子;2点15分,她就在 DoraHacks 上发起一场48小时黑客松,AI 自动为她召集来自四大洲的协作者。
听起来疯狂?但未来这将成为常态。
亚洲某国突发环境危机,政府通过 BUIDL AI 紧急发起黑客松,数日内即收到来自全球的数十个可执行科技方案。 纽约某家风投基金希望发现新项目,不再只是等着 PPT 投递——他们直接赞助一场开放黑客松,要求提交原型,而非空谈构想。
这就是 Agentic 创新正在发生的方式:快速、无边界、智能协作。 在这个即将到来的时代,DoraHacks 将如同 GitHub 之于代码、AWS 之于初创企业一般,成为全球创新的基础平台。
你甚至可以称它为创新的 GitHub——不是一个存储代码的工具,而是项目诞生的土壤[17]。 DoraHacks 自称是“全球黑客运动的引擎”;而有了 BUIDL AI,它更成为这场运动的自动驾驶系统。
我们应将其视为全球公共创新基础设施的一部分:
正如高速公路运输货物、互联网传递信息,DoraHacks 传递的是创新本身——
从创意萌芽到落地实施,以惊人的速度。
当历史回顾2020年代,持续性、AI驱动的黑客松的诞生,将被视为人类创新模式变革的重要篇章。
这是一幅宏大但真实可触的愿景:
创新,将变成一场永恒的黑客松。
设想一下:
黑客精神深入社会每个角落,成为对现状的持续挑战,时刻发出这样的提问:
“我们如何改进这件事?”、“我们如何重新发明那件事?”
然后立刻号召人才,迅速投入行动。
这不是混乱,而是一种全新的、有组织、去中心化的研发模式。
一个大胆问题——“我们能治愈这种疾病吗?”、“我们能否让儿童教育更高效?”、“我们能不能让城市真正可持续?”—— 不再需要靠闭门造车的委员会来思考十年,而是一场全球黑客松,就可能在几天或几周内产生答案。 这将是一个创新不再稀缺、不再由少数人垄断,而是成为一项公共物品的世界。
一场开放的、胜者为王的比赛,不管解决方案来自斯坦福博士,还是拉各斯的自学黑客,只要够好,就能脱颖而出。 如果你觉得这听起来太理想,请看看我们已经走了多远:
黑客松从一个名不见经传的程序员聚会,变成了支撑十亿美元企业和全球关键技术的创新机制。 (别忘了,比特币本身就是黑客文化的产物!)
随着 DoraHacks 的壮大和 BUIDL AI 的腾飞,黑客松正朝着持续化与无处不在的方向稳步推进。 技术已经准备就绪,模式已经跑通,现在的关键是执行与普及。
而趋势已然明朗:
- 越来越多公司拥抱开放创新;
- 越来越多开发者远程工作、参与在线社区;
- AI 正快速成为每个创造过程的副驾驶。
DoraHacks 正站在这场转型的核心。
它拥有先发优势、全球社区、明确愿景。
他们的理念非常清晰:“为黑客运动提供永恒燃料”是他们的口号之一[18]。
在他们眼中,黑客松不仅是活动,更是一场必须永续进行的思维革命。 而 BUIDL AI,正是支撑这场永续革命的引擎。
这预示着一个未来:
DoraHacks + BUIDL AI,将成为全球创新关键基础设施的一部分,就像公共事业一样。
这是一张“创新电网”;一旦接入它,奇迹发生。
Marc Andreessen 常在文章中以“建造更好的未来”为信条,热情洋溢地谈论人类的进步。
如果秉持这一精神,我们可以大胆断言:
Agentic Hackathon 将重塑我们的未来——更快、更好。
它们将加速人类解决最难问题的速度,
动员更广泛的人才库,
以史无前例的节奏不断迭代方案。
它们将赋能每一个人——让地球上任何拥有创造力的人,立即就能获得工具、社群和机会,产生真正的影响,而不是“未来某天”。
这是一种深层次的民主化。
它呼应了早期互联网的精神:不需许可的创新(Permissionless Innovation)。
而 DoraHacks 正在将这一精神引入结构化的创新事件中,并将其延展为一种持久的创新模式。
总结:我们正目睹一场范式的彻底转变:黑客松被重塑,创新被解放。
旧模型的限制已被打破,
新范式的核心是:
高频黑客松、AI增强、结果导向。
DoraHacks 在 2020–2024 年引领了这场变革,
而随着 BUIDL AI 的登场,它即将开启下一个篇章——Agentic Innovation 的时代。
对投资者与有远见的领袖而言,这是一场集结号。
我们常说要“投资基础设施”,
那么现在,就是投资“创新本身的基础设施”。
支持 DoraHacks 和它的使命,
就像支持跨洲铁路或洲际高速的建造者,
只不过这次运载的是创意与突破。
网络效应巨大:每一场新增的黑客松、每一位新增的参与者,
都以复利效应提升整个生态系统的价值。
这是一场正和博弈(Positive-Sum Game),
DoraHacks 将是那个创造并捕捉全球价值的平台与社区。
DoraHacks 重新定义了黑客松:
它将黑客松从偶发行为变成了持续创新的系统方法。
在这个过程中,它敞开了创新之门,
引领我们进入一个全新的时代:
一个创新可以自主驱动、自组织、永不停歇的时代。
我们正站在这个新时代的黎明。
这是一个真正意义上:
拥有开发者,拥有世界的时代[14] 。
DoraHacks 正在确保:
无论你身在何处,只要你是开发者、黑客、梦想家,
你都能为这个世界的未来贡献力量。
前方的远景令人震撼——一个由全球黑客思维构成的智能蜂巢,
不断发明、持续发现,
由 AI 指引航向,
由 DoraHacks 与 BUIDL AI 领航。
这不仅仅是一个平台,
它是一项革命性的基础设施——创新的铁路,创意的高速。
请系好安全带:
DoraHacks 已经启程,
Agentic Innovation 的时代已经到来,
未来正以黑客松的速度,向我们疾驰而来。
这场黑客松,永不停歇。
而这,正是我们构建更美好世界的方式。
参考文献:
[1] Vocoli. (2015). Facebook’s Secret Sauce: The Hackathon . https://www.vocoli.com/blog/june-2015/facebook-s-secret-sauce-the-hackathon/
[2] Analytics India Magazine. (2023). Borne Out Of Hackathons . https://analyticsindiamag.com/ai-trends/borne-out-of-hackathons/
[3] Wikipedia. (n.d.). Hackathon: Origin and History . https://en.wikipedia.org/wiki/Hackathon#Origin_and_history
[4] LinkedIn. (2024). This year marked my third annual participation in Microsoft’s Global… . https://www.linkedin.com/posts/clare-ashforth_this-year-marked-my-third-annual-participation-activity-7247636808119775233-yev-
[5] Glasp. (n.d.). Chris Dixon’s Quotes . https://glasp.co/quotes/chris-dixon
[6] ODaily. (2024). Naija HackAtom Hackathon Recap . https://www.odaily.news/en/post/5203212
[7] Solana. (2021). Meet the winners of the Riptide hackathon - Solana . https://solana.com/news/riptide-hackathon-winners-solana
[8] DoraHacks. (n.d.). BNB Grant DAO - DoraHacks . https://dorahacks.io/bnb
[9] Cointelegraph. (2021). From Hackathon Project to DeFi Powerhouse: AMA with 1inch Network . https://cointelegraph.com/news/from-hackathon-project-to-defi-powerhouse-ama-with-1inch-network
[10] Gemini. (2022). How Does STEPN Work? GST and GMT Token Rewards . https://www.gemini.com/cryptopedia/stepn-nft-sneakers-gmt-token-gst-crypto-move-to-earn-m2e
[11] CoinDesk. (2022). Inside DoraHacks: The Open Source Bazaar Empowering Web3 Innovations . https://www.coindesk.com/sponsored-content/inside-dorahacks-the-open-source-bazaar-empowering-web3-innovations
[12] LinkedIn. (n.d.). DoraHacks . https://www.linkedin.com/company/dorahacks
[13] Blockworks. (2022). Web3 Hackathon Incubator DoraHacks Nabs $20M From FTX, Liberty City . https://blockworks.co/news/web3-hackathon-incubator-dorahacks-nabs-20m-from-ftx-liberty-city
[14] Followin. (2024). BUIDL AI: The future of Hackathon, a new engine for global open source technology . https://followin.io/en/feed/16892627
[15] Coinbase. (2024). Coinbase Hosts Its First AI Hackathon: Bringing the San Francisco Developer Community Onchain . https://www.coinbase.com/developer-platform/discover/launches/Coinbase-AI-hackathon
[16] Graham, P. (2004). Hackers & Painters . https://ics.uci.edu/~pattis/common/handouts/hackerspainters.pdf
[17] Himalayas. (n.d.). DoraHacks hiring Research Engineer – BUIDL AI . https://himalayas.app/companies/dorahacks/jobs/research-engineer-buidl-ai
[18] X. (n.d.). DoraHacks . https://x.com/dorahacks?lang=en
-
 @ 4ba8e86d:89d32de4
2025-05-02 13:51:37
@ 4ba8e86d:89d32de4
2025-05-02 13:51:37Tutorial OpenKeychain
- Baixar no F-droid https://f-droid.org/app/org.sufficientlysecure.keychain
Ao abrir o OpenKeychain pela primeira vez, você verá uma tela inicial indicando que ainda não há chaves configuradas. Nesse ponto, você terá três opções:
-
Criar uma nova chave PGP diretamente no OpenKeychain: Ideal para quem está começando e precisa de uma solução simples para criptografia em comunicações diárias.
-
Usar um token de segurança (como Fidesmo, Yubikey, NEO, ou Sigilance) Se você busca uma segurança ainda maior, pode optar por armazenar sua chave privada em um token de segurança. Com essa configuração, a chave privada nunca é salva no dispositivo móvel. O celular atua apenas como uma interface de comunicação, enquanto a chave permanece protegida no token, fora do alcance de possíveis invasores remotos. Isso garante que somente quem possui o token fisicamente possa usar a chave, elevando significativamente o nível de segurança e controle sobre seus dados.
-
Importar uma chave PGP existente: Você pode importar uma chave PGP que já tenha sido gerada anteriormente, seja por meio de um arquivo no dispositivo ou por outro meio ler na área de transferência. https://image.nostr.build/51fdd924df4843ab73faa02a505c8fb17794f1789396ed89b154348ebb337f07.jpg
1. CRIANDO UMA NOVA CHAVE PGP.
Para iniciantes, recomendamos criar uma nova chave diretamente no aplicativo. abordaremos o uso do OpenKeychain em modo online, que é mais comum para comunicações diárias.
Passo 1: Clique em “Criar minha chave”. https://image.nostr.build/235f5cfdf4c3006ca3b00342741003f79a5055355c2a8ee425fc33c875f51e49.jpg
Passo 2: Criando sua chave PGP.
Para criar sua chave, você precisará fornecer algumas informações Os campos 'Nome' e 'Endereço de e-mail' são apenas formas convenientes para identificar a sua chave PGP.
-
Nome: Escolha um nome ou um pseudônimo. https://image.nostr.build/de3fe3ddbde0c7bf084be6e4b8150fdb8612365550622559b0ee72f50f56a159.jpg
-
E-mail: Associe um endereço de e-mail à chave, seja ele pessoal ou um e-mail relacionado ao pseudônimo. https://image.nostr.build/aff62baaeafe2c9a429ef10435a6f99dea36d6cfd7494e2bb882421dc8ed0f4e.jpg
2. REVISANDO E PERSONALIZANDO A CRIAÇÃO DA CHAVE.
Passo 3: Antes de criar sua chave PGP, verifique se os dados inseridos estão corretos. https://image.nostr.build/a8ec09ef3d9b4f557b0c4e380e7ca45d0fdbfa33fe80becea03ed0e5f5eedd24.jpg
Você também pode personalizar as configurações de segurança clicando nos três pontos no canto superior direito. https://image.nostr.build/1ce615555cea9a979ea951472052a219e77f4e1ebaaf5fcbbe9e91ea4f852bce.jpg
Ao cliclar em ' nova subchave ' pode alterar a data de expiração e pode mudar a criptografia usado na chave cliclando opção ed2255/cv255. https://image.nostr.build/b3224ff3dbe48ff78c4a2df8b001926b6d3eef1e33ef677a73b0d281791073da.jpg https://image.nostr.build/7763c7847e062cdcf71aafedbc2ef4c38056fd66aeb162ef3a1c30c028a14376.jpg https://image.nostr.build/5d3e20ade460dd5e89cc001ebdc062a36aff2c0e1573584ca3c0d1cb34bddcce.jpg
Neste tutorial, utilizaremos as configurações padrão do aplicativo.
Passo 4: Clique em "Criar chave" para concluir o processo. https://image.nostr.build/a8ec09ef3d9b4f557b0c4e380e7ca45d0fdbfa33fe80becea03ed0e5f5eedd24.jpg
3. Como Compartilhar sua Chave PGP Pública
Após criar sua chave PGP, você pode compartilhá-la para que outras pessoas possam enviar mensagens criptografadas para você. Veja o passo a passo de como exibir e compartilhar sua chave pública:
Passo 1: Acesse sua chave pública
Abra o OpenKeychain e selecione a chave que deseja compartilhar. Clique na chave para visualizar os detalhes. https://image.nostr.build/689c5237075317e89e183d2664630de973b09b68aaf8f3e3033654e987b781be.jpg https://image.nostr.build/4001610109579f27535628932258087b3b06c1f86b05f4f85537b6585c12a10b.jpg
Passo 2: Copiar sua chave pública
Nos detalhes da chave, você verá a opção "Copiar para a Área de Transferência". Clique nessa opção para copiar o código da sua chave pública. https://image.nostr.build/01ab3efa5e997e1910a2f8f7a888e6ad60350574cca4ca0214eee5581797f704.jpg
A chave PGP copiada terá o seguinte formato:
-----BEGIN PGP PUBLIC KEY BLOCK-----
mDMEZwsLHRYJKwYBBAHaRw8BAQdA6NRLlJIWnTBJtYwZHlrMbTKRbYuXmjsMn8MB 7etV3HK0JERhbmllbCBGcmFnYSAgPGRhbmllbGZyYWdhQG1haWwuaTJwPohyBBMW CAAaBAsJCAcCFQgCFgECGQEFgmcLCx0CngECmwMACgkQFZf+kMeJWpR4cwEA8Jt1 TZ/+YlHg3EYphW8KsZOboHLi+L88whrWbka+0s8A/iuaNFAK/oQAlM2YI2e0rAjA VuUCo66mERQNLl2/qN0LuDgEZwsLHRIKKwYBBAGXVQEFAQEHQEj/ZfJolkCjldXP 0KQimE/3PfO9BdJeRtzZA+SsJDh+AwEIB4hhBBgWCAAJBYJnCwsdApsMAAoJEBWX /pDHiVqUo/oA/266xy7kIZvd0PF1QU9mv1m2oOdo7QSoqvgFiq6AmelbAP9lExY5 edctTa/zl87lCddYsZZhxG9g2Cg7xX/XsfrnAA== =TniY -----END PGP PUBLIC KEY BLOCK-----
Dica: Se ocorrer algum erro ao compartilhar sua chave pública com um amigo, peça para que ele a criptografe para ele mesmo. Isso permitirá que ele adicione a chave corretamente. Caso a chave pública ainda não esteja no dispositivo, ao clicar em "Backup de chave", aparecerá a opção para importá-la. Se a chave já estiver no dispositivo, essa ação irá recarregá-la. https://image.nostr.build/cd12abf07c93473db95483fe23112325f89d3eb02977e42756708bbd043f8bcf.jpg https://image.nostr.build/537aeae38d229ee2cc78e18f412237b659c059e1c74fd7f0deecfe37f15713c9.jpg https://image.nostr.build/16c8a3db5966c7c06904ee236655f47a6464ae0c1b5af6af27b28c61611d2bbe.jpg
Passo 3: Compartilhar sua chave PGP
Você pode colar a chave pública em e-mails, assinaturas, perfis de redes sociais ou outros meios para compartilhá-la facilmente. Para facilitar a visualização, você também pode exibi-la em seu perfil de redes sociais.
Para acessar mais opções de compartilhamento, clique nos três pontos no canto superior direito e selecione a opção "Avançado". https://image.nostr.build/0d4a13b7bd9a4794017247d1a56fac082db0f993a2011a4dd40e388b22ec88f5.jpg https://image.nostr.build/4ac2a7bc9fa726531a945221cf7d10e0e387deba68100ccf52fdedfcd17cbd59.jpg
Na seção "Compartilhar", você verá sua Key ID e terá a opção de publicar sua chave PGP em um servidor de chaves. https://image.nostr.build/1e972cc211a6d8060cdbd4a8aa642dd1a292810c532f178d3ddb133d1b9bca76.jpg
Passo 4: Como compartilhar sua chave pública PGP no formato .asc. no OpenKeychain
1 . Acesse sua chave
Abra o OpenKeychain e toque na chave que você deseja compartilhar. Isso abrirá a tela com os detalhes da chave. https://image.nostr.build/c080f03d2eb7a9f7833fec0ff1942a5b70b97e4f7da7c6bc79ca300ef9ace55d.jpg
2 . Compartilhe o arquivo .asc
Toque no ícone de compartilhamento, como indicado na imagem abaixo. O aplicativo abrirá a janela para que você escolha por qual app deseja compartilhar sua chave pública no formato .asc. Nesse exemplo, usei o SimpleXChat , mas você pode usar qualquer aplicativo de sua preferência.
-
Botão de compartilhar. https://image.nostr.build/8da74bdb04737a45df671a30bba1dd2e7980841fa0c2d751d6649630e7c25470.jpg
-
Seleção do aplicativo para compartilhamento. https://image.nostr.build/5444f4e9d3fa5aef6b191bb6f553f94c6e49d30ead874c9ee435bca3218fd6c8.jpg
-
Enviando via SimpleXChat. https://image.nostr.build/e5d1ca04cbc69e1e8ac5caf1ab2a4b9b695500861c1ae9c55cea679cce349214.jpg
Sugestão para compartilhar nas redes sociais:
Você pode exibir sua chave de forma simples, por exemplo:
PGP: 1597 FE90 C789 5A94
Importar a chave pública usando a fingerprint
Passo 1:Clique no ícone "+" para começar. https://image.nostr.build/ca6e6e569b4be60165eaf60c7ba1e6e3ec781b525e467c72b4f3605837e6b5ec.jpg
Passo 2: Selecione a opção "Buscar Chave". https://image.nostr.build/87e27d9435e6e3ef78063b9f15799a8120ead4637cd06c89c0220b48327573ae.jpg
Passo 3: Digite a fingerprint da chave em letras minúsculas, sem espaços. A chave correspondente aparecerá para ser adicionada. https://image.nostr.build/33e6819edd4582d7a8513e8814dacb07e1a62994bb3238c1b5b3865a46b5f234.jpg
Além disso, você pode compartilhar sua chave pública em formato QR Code, facilitando a troca de chaves em eventos ou conversas rápidas. Como Assinar Mensagens para Confirmar a Autenticidade da Sua Rede Social
Você pode autenticar sua conta em redes sociais utilizando sua chave PGP. Ao assinar uma mensagem com sua chave, você demonstra que realmente possui essa conta. Siga o passo a passo abaixo para assinar uma mensagem:
Passo 1: Clique na sua chave PGP. https://image.nostr.build/ffacce1bfb293c9a0888cd5efe340a63d96b293f4c010f8626105c7b212d8558.jpg
Passo 2: Clique no ícone indicado pela seta para abrir o campo de texto. https://image.nostr.build/4e992a2553810e2583b9d190280ce00a52fc423600a75eca48cbf541cf47d3c2.jpg
Passo 3: Deixe a opção "Encriptar para:" vazio. Em "Assinar com:", selecione sua chave PGP e digite a mensagem que deseja enviar, como o nome da sua rede social. https://image.nostr.build/a4a2a8d233d186e3d8d9adddccc445bcb3ca3ed88de0db671a77cede12323a75.jpg
Passo 4: Clique no ícone indicado pela seta para copiar o texto assinado. Uma mensagem aparecerá informando: "Assinado/Encriptado com Sucesso". https://image.nostr.build/a076dfc90e30a495af0872005bf70f412df57b7a0e1c2e17cf5aee9e9b3e39aa.jpg
A mensagem copiada terá o seguinte formato:
-----BEGIN PGP SIGNED MESSAGE----- Hash: SHA256
Minha rede social NOSTR é Danielfraga oficial. -----BEGIN PGP SIGNATURE-----
iIQEARYIACwlHERhbmllbCBGcmFnYSAgPGRhbmllbGZyYWdhQG1haWwuaTJwPgUC ZxBBLgAKCRAVl/6Qx4lalGeNAPwP71rpsbhRnZhoWZsTDOFZY8ep/d0e5qYx5iPx HV26dwD/fKyiir1TR8JwZvEbOTYS0+Dn4DFlRAAfR3lKVTC96w4= =37Lj -----END PGP SIGNATURE-----
Com isso, você pode facilmente demonstrar a autenticidade da sua conta nas redes sociais.
4. PROTEGENDO SUA CHAVE COM UMA SENHA.
Passo 5: Após a criação da chave, é fundamental definir uma senha (ou passphrase) para adicionar uma camada extra de segurança. Recomendamos usar senhas longas (com mais de 20 caracteres) e de alta entropia para evitar ataques de força bruta. Ferramentas como KeePassDX ou Bitwarden podem ajudá-lo a gerar e gerenciar essas senhas.
Para definir a senha, clique na sua chave PGP, acesse o menu no canto superior direito e selecione "Alterar senha". https://image.nostr.build/689c5237075317e89e183d2664630de973b09b68aaf8f3e3033654e987b781be.jpg https://image.nostr.build/f28ecaa9890a8827f93cac78846c4b2ef67f86ccfc3501fdadf1d1c4874b0041.jpg https://image.nostr.build/919c277fbec63c397402abdd60f915cb239a674c317855cbda63a38edef80789.jpg
Agora basta adicionar uma senha forte. https://image.nostr.build/eb378219fbb1780f89663a474ce43b8d8ebb13beeb538f2a16279b056e5d9645.jpg https://image.nostr.build/cdfa3f9c6c4045841341da789deabb6318107812d5ba195529418572ab352aaf.jpg
5. CRIPTOGRAFAR E DESCRIPTOGRAFAR MENSAGENS E ARQUIVOS COM SUA CHAVE PGP
Criptografar Mensagens
Você pode criptografar mensagens para garantir que apenas o destinatário, que possui sua chave pública, possa lê-las. Siga os passos abaixo para criptografar um texto:
Passo 1: Abra o menu lateral clicando no ícone no canto superior esquerdo.
https://image.nostr.build/13ac93b38dd1633118ae3142401c13e8a089caabdf4617055284cc521a45b069.jpgPasso 2: Selecione a opção "Encriptar/Descriptar".
https://image.nostr.build/8cd905d616b53968f0551c071d9acc2f47bbe8434c2c7e1a33076a504342de48.jpgPasso 3: Clique na opção "Encriptar Texto".
https://image.nostr.build/405a730a6c774759d7913f92f59059d43146db4afb28451a6f8833f94e99437f.jpgPasso 4: Preencha os seguintes campos: https://image.nostr.build/7dc5eba39ff82a321195dbf46b8113818632e3ef41175991d58e799a8e9d2751.jpg
-
Encriptar para: Selecione o destinatário da mensagem, ou seja, a pessoa para quem você está enviando o texto criptografado.
https://image.nostr.build/1e8c8cba6d3c3136d9857512e2794a81ceb7434eccdfb0f7d26cdef008b2e6d2.jpg -
Assinar com: Escolha sua chave PGP para assinar a mensagem.
https://image.nostr.build/d25b228c35b132d396d01c354ef093b43b3565578fbc0d6ff7b9de4e41619855.jpg -
Digitar o texto: No campo de texto, escreva a mensagem que deseja criptografar.
https://image.nostr.build/8537271dfa4445e60cb4c3cdb5d97571dc0ff5ee8acd6ed89a8c81e4bd8736c2.jpg
Passo 5: Depois de preencher os campos, você pode copiar o texto criptografado de duas formas:
-
Copiar para a área de transferência: Clique na opção para copiar o texto criptografado e cole-o em um aplicativo de mensagens para enviá-lo.
https://image.nostr.build/a5cb8e2c538a38db3972e7f3ac9aa9f602cda6b62848ff0c4b99928a67dcd486.jpg -
Compartilhar diretamente: Utilize a opção de compartilhamento para enviar o texto criptografado diretamente através de seus aplicativos de mensagens.
https://image.nostr.build/2b79cb564d623788a0de1111a067e0eb496f743389d465d4f4e8f6e65f0d08a7.jpg https://image.nostr.build/ff59e52bc8ab54ff377980a6ba5d1c4743d3298de11e5daa187ab7d45163a7be.jpg
Criptografar arquivos.
Passo 1: Abra o menu lateral clicando no ícone no canto superior esquerdo.
https://image.nostr.build/13ac93b38dd1633118ae3142401c13e8a089caabdf4617055284cc521a45b069.jpgPasso 2: Selecione a opção "Encriptar/Descriptar".
https://image.nostr.build/8cd905d616b53968f0551c071d9acc2f47bbe8434c2c7e1a33076a504342de48.jpgPasso 3 : clique na opção "Encriptar arquivos ". https://image.nostr.build/3fcae48ee38e7f4079ebccfd3eafb9ab0ad3559221d2c3560cdfe60e29f56a15.jpg
Passo 4 : os passos a seguir são os mesmo que você seguiu pra encriptar a mensagem texto. Ítens "Encriptar para:" "Assinar com:" https://image.nostr.build/4d6599b9d3a9fdfae0964daaa9dae513d5ce277a7b61930fa2937d534f72ed40.jpg
Passo 5 : clilcar na opção " Adicionair arquivo(s)" Vai abrir na memória interna do celular selecione o arquivo que deseja encriptar. https://image.nostr.build/09e3b9b54a1406426114926aab19011c36b98886ebae6fcf556cfea83bb2c2f4.jpg https://image.nostr.build/af422e243b36762dd66111ec7c848a1352c100ca3040dc21792c923f80aef74d.jpg https://image.nostr.build/ebebbdb273b4bca58d901852aec1c60e4799aa77e9d12a31f992b0cf8f73e753.jpg
Passo 6: Depois de preencher os campos, você pode compartilhar o arquivo criptografado de duas formas:
-
Salvar na memória do celular: A primeira opção salva o arquivo criptografado no armazenamento do seu dispositivo. Você terá a opção de editar o nome do arquivo antes de salvar.
https://image.nostr.build/0a47c1e9f0003541f47091b2c2e8ce6b8d1533d95463e331b218070bae964ac8.jpg https://image.nostr.build/95a7a2b67356eb5ded5b217bab38a19bdeba5af7befd105834e413e0aec45462.jpg https://image.nostr.build/66cb3d22b271f3b73b7015613c72711a3ffbf5e1070d43153f9d1f3fcf35001c.jpg https://image.nostr.build/f9624d86f7592fe7ffad932b7805762dc279d9e8ff410222108155438a2c970f.jpg -
Compartilhar diretamente: Utilize a opção de compartilhamento para enviar o arquivo criptografado diretamente por meio dos seus aplicativos de mensagens.
https://image.nostr.build/85541e466c7755c65bd6ba0208a6d8612beaa5298712b6d92f53865167695a38.jpg https://image.nostr.build/bf1e0f0aeb60cafbdf82af4b3b598288519e85b396bd3f9e00e61f65b89ea9f8.jpg https://image.nostr.build/fb090339898f37cdbb020828689b142ca601ca3ee549f67ddf6b2e094df9ab9f.jpg https://image.nostr.build/50c249ced06efe465ba533fef15207b0dcd1a725e9b2c139e8d85c13fd798276.jpg
Descriptografar Mensagens e Arquivos
Para ler uma mensagem ou arquivo criptografado que você recebeu, utilize sua chave privada. Siga os passos abaixo:
Descriptografar Mensagens
Passo 1: Copie a mensagem criptografada que você recebeu.
https://image.nostr.build/c37754b12a458e0176b9137ae0aa9e8209f853bf9d9292c0867fd8b0606d53c4.jpgPasso 2: Clique na opção "Ler da área de transferência" para descriptografar o texto.
https://image.nostr.build/d83c7dad2ee1cb6267779863bc174ee1a8f3cc3c86b69063345321027bdde7b5.jpg https://image.nostr.build/c0fae86e6ab1fe9dcee86753972c818bed489ea11efdd09b7e7da7422a9c81eb.jpgDescriptografar Arquivos
Passo 1: Clique na opção "Selecionar arquivo de entrada".
https://image.nostr.build/9c276c630311d19a576f2e35b5ba82bac07360476edae3f1a8697ff85df9e3c9.jpgPasso 2: Selecione o arquivo criptografado que deseja descriptografar.
https://image.nostr.build/6b6c2a3284ba96e7168fc7bd0916020c4f1bed7b77dfca48227fc96d6929e15a.jpg https://image.nostr.build/9945aad644af2e2020e07e55f65f11a0958d55e8fc9e13c862e6b9ca88b4f4d9.jpg6. BACKUP E RESTAURAÇÃO DE CHAVE PGP.
Realizar o backup das suas chaves PGP é fundamental para evitar a perda de acesso às suas mensagens e dados criptografados. O OpenKeychain facilita esse processo, permitindo que você faça um backup completo e seguro. Recomendamos que você armazene o backup em um local seguro, como um HD externo ou pendrive conectado via cabo OTG, sempre protegendo-o com senha.
PASSOS PARA REALIZAR O BACKUP:
Passo 1: Abra o menu lateral clicando no ícone no canto superior esquerdo.
https://image.nostr.build/13ac93b38dd1633118ae3142401c13e8a089caabdf4617055284cc521a45b069.jpgPasso 2: Selecione a opção Backup/restaurar.
https://image.nostr.build/6fa8fd14e23b47c6c924bc0d900646663f2124a93d8172ae79fdf43b5c7d4490.jpgPasso 3: Escolha a primeira opção: Backup completo (criptografado).
https://image.nostr.build/4875fb27b6d04c3cb838b4fb9f308ef9194edc35ba1254ba965b7f0db2544170.jpgPasso 4: O backup será protegido por um código de backup gerado automaticamente. Anote esse código em um papel e guarde local seguro, pois sem ele você não conseguirá recuperar suas chaves PGP. Após anotar o código, marque a opção “Anotei o código” e clique em Salvar Backup. Obs: todas as vezes que você for fazer o backup da sua chave PGP vai ser criado um novo código aleatório.
https://image.nostr.build/72a317ef5e59a01c03c36f1d04a91d42c418a478cc82e372acf21bb8302daa00.jpg
Passo 5: Escolha o local onde deseja salvar o backup (HD externo, pendrive, etc.), confirme sua escolha e clique em OK. Você verá uma mensagem de confirmação indicando que o backup foi salvo com sucesso.
https://image.nostr.build/d757e8bdf429371320daa44be8a48a0dbeb2324129f4254327f0f0383e70ede4.jpg https://image.nostr.build/f3ad80ceb8a191b4d1b40722b1d0d4f85bf183d412e7d7d901b25d19b2dfe0e3.jpg
Importação da Chave PGP
Caso você precise restaurar suas chaves PGP a partir de um backup, o OpenKeychain também facilita o processo de importação. Siga os passos abaixo para restaurar sua chave PGP:
Passo 1: Selecione a opção "Selecionar arquivo de entrada"
Abra o OpenKeychain, acesse o menu lateral no canto superior esquerdo e escolha a opção "Selecionar arquivo de entrada" para localizar o arquivo de backup que você deseja importar.
https://image.nostr.build/a06ddc1c1e6c50519097e614aa25b14311e49c0ca4d4607e42ebdcca3a6641c4.jpgPasso 2: Selecione o arquivo de backup
Navegue até o local onde você salvou o arquivo de backup (HD externo, pendrive, etc.) e selecione-o. Em seguida, o OpenKeychain solicitará que você insira o código de recuperação que foi gerado no momento do backup. https://image.nostr.build/9d5649c04a98ec8b0a29355d9068e48313b1c5dc36cd965961f4d33f22d10046.jpgPasso 3: Digite o código de recuperação
Insira o código de recuperação que você anotou anteriormente. É importante digitar o código corretamente para garantir o sucesso da restauração.Passo 4: Depois de inserir o código corretamente, o OpenKeychain irá restaurar suas chaves PGP, e uma mensagem de confirmação será exibida, indicando que a recuperação foi concluída com sucesso.
Agora suas chaves estão restauradas e você pode continuar usando o OpenKeychain para gerenciar suas comunicações criptografadas de maneira segura.
https://www.openkeychain.org/
https://github.com/open-keychain/open-keychain
https://youtu.be/fptlAx_j4OA
-
 @ 5188521b:008eb518
2025-05-02 10:19:17
@ 5188521b:008eb518
2025-05-02 10:19:17Fabian Sixsmith leaned closer to the screen. A couple of white pixels fizzed through the frame, and the hairs on his arm prickled. It had to be her. The blonde. Underworld’s most wanted — T1n4Red.
It was nearing daybreak in Lewistown, Montana. The end of yet another 14-hour shift at the DoS facility. Pulling fourteens was tough on his body, but it reduced the time it would take for Fabian to gain promotion to agent. Working at the Department of Surveillance came with the serious drawback of being labeled a snoop, but agents could be free — solid pension credits and private property. But today, he would not slink back to his closet-sized studio for buttered noodles and two hours on the velobike. Today would be the day he proved his work was responsible for locating T1n4Red. Her crimes were manifold; her methods were meticulous. Operating encrypted communication networks and thousands of transaction joins to obfuscate Underworld finances. Fabian flipped the plastic cover of the alarm on his console and pressed the button.
Agent Williams appeared behind him in seconds. The babble of voice commands in the CCTV facility cut to zero. “Situation update, Operative Sixsmith.”
Liquidating the bad guys had been the dream ever since his father lost his college fund to a hacker. Cypherpunks came in all guises, and some could phish credits from careless Boston drunks and cover their tracks with encryption. Fabian opened the dossier on his desk. “Tier 1 target located. DNA confirmation requested from ground team.” He was certain. So many nights following encoded messages he found hidden data in images on the public comms ledger. Many were drop sites for the scumbags who delivered supplies to the Underworld in exchange for bitcoin — the only money the government couldn’t meter out and strip away automatically. That pixel of white had to be her blonde hair vanishing, once again, underground.
“Enhance the facial image,” said Williams.
There was no clear image to enhance. Fabian would have some explaining to do if he was wrong. Except he couldn’t be wrong. Those pixels had been his life for the last ten months. Finally, he had trapped her. Straightening his glasses, he prepared his reply. “I can bring up the drop locations from the LSB ima—”
“Operative. What is the protocol required to initiate a Tier 1 alert?”
Fabian could feel the heat of his boss’s glare. “Agent, there is insufficient facial recognition data, but if you give me a minute…” He had captured dozens of steganographical messages — locations, account numbers, usernames. Hiding messages in plain sight was apparently how cypherpunks avoided detection with such ease.
Williams was already patching through to the ground team on his Neurocomms link. “What’s your ETA on the location?” He furrowed his brow. “Copy that... proceed.” Turning towards Fabian, he snapped his fingers. “My office. Now.”
According to Fabian’s calculations, the ground team would report back with the DNA scan in three to four minutes. When they got a match, she’d be toast. T1n4Red would be underground forever; if she resurfaced, the dronecopters would gun her down in minutes. He just had to stall Williams until the confirmation came through. That might be the only way to avoid his first ever sanction. Having a blemish on record would set his lifeplan back by several months. He thought about requesting a comfort break on the system, but Williams would deny it. Fabian stood up purposefully. He arranged the chair and a few items on the desk, then dragged his feet all the way to the office.
Each agent in the DoS facility had an area of control around the size of a football field. Their 12’ by 12’ office comprised the only enclosed space and was positioned in the middle of rows upon rows of desks. Four walls of two-way mirrored glass formed the raised office cube — a mini panopticon within the greater panopticon of DoS. The agent sat in the swivel chair and swung his feet onto the desk. “You better be right about this, Sixsmith, or you’re done here.”
Fabian’s heart beat like a heavy bass kick. The perfectly calibrated 67-degree air didn’t stop him from wanting to loosen his tie. When he jammed his fingers down the small gap between his neck and collar, they came out slick with sweat. All those nights chasing. The tabulations, the data models, the transcripts from Underworld detainees, the ciphers he’d decoded — they all seemed like a game. A dream. He was the grizzled sheriff finally placing the noose around the neck of the uncatchable outlaw. He knew that in sixty seconds or so, the ground team would confirm a DNA match, and it would be impossible for T1n4Red to resurface without physical liquidation. “I’m sure, sir. This was the only way. We’d never get a facial match on a Tier 1.”
The agent looked at the communicator on his desk. Nothing.
Did T1n4Red eat buttered noodles and work out in her underground living closet? Did she crave for the feel of a paperback novel, or perhaps own a non-cataloged copy? It’s not like she could step foot inside the state knowledge center. “What action will DoS—”
Ground Unit Bravo to Williams. Do you copy?
“This is Williams. Over.”
Bravo commander confirmed the DNA match. It was her. She would now be classified a subverter. The payment instructions she had etched into the self-repair polymer bench had been photographed. Any wallet receiving those coins would be investigated. The fintech arm would already be working on liquidating affiliated Overworld accounts. One wrong turn and they can shut down your life’s wealth.
But T1n4Red was smarter. DoS would always be one step behind the cypherpunks because they were bound by government protocol, unable to infiltrate the Level 3 realm of encrypted private comms. Fabian had to take risks. What use was all his dedication if it just led to being remaining on the outside of a panopticon looking in?
“You can leave.” Williams motioned to the office door. “Your shift was over sixteen minutes ago.”
The State Knowledge Center smelled of the past. That’s what Fabian liked about it. He turned the page, savoring the quality feel of thick paper, imagining that when this book ran through enough hands, the inked fibers would run from black to gray to cream-white and the story would be gone. These were some of the only off Ledger items left in the country.
Wild Country Outlaws was Fabian’s sanctuary from the pressures of his job. All fiction was based on the kind of truth that needed to survive. Back to the times when eyes touched words without being digitally tracked, when citizens could own things. He read a paragraph and closed his eyes to imagine how life was back then. The cavernous knowledge center, with its hard seats and CCTV lenses transformed into lush plains and steep hills. Fabian felt the warm breeze on his face and the muscles of the horse beneath him. The two rifles slung on his back would shoot those boys dead. No one would take his property. His wife, children, his lame brother, hell, the whole damned village of Lewistown depended on his cattle to provide.
Of course, land could only be leased now. Livestock too. Those rustlers would have a hard time taking anything without public subscription fees and pre-taxed profits coming out. And if they wanted, the Department of Property could rescind custody of any item and confiscate it. Fabian’s smart-band vibrated, indicating he had just ten minutes of reading time left. The thing buzzed too hard. It pinched, but like all sanctioned hardware, it was government hard-coded.
He hadn’t been able to focus this time. Not really. Was T1n4Red an outlaw or a rancher? Either way, she was fighting the system that had stripped Americans of their right to call their house a home. According to the Department of Education, pre-ledger days were violent wealth-disparity wars, but the novels Fabian read painted a different picture — a fantasy freedom where ordinary citizens could build wealth.
Fabian rose to go. He handed the book to the desk girl and watched her scan it into the system. His smart-band buzzed again with a compliance point. To think his friends chased these stupid tokens for avatar upgrades and paid-time-off options. But, without them, he might end up with his ID frozen like his high school buddy, Scott, cut off from all legal avenues to earn a living and watched like a hawk by DoS. Did he have a secret stash of satoshis that kept him clear of the state debtors’ facility?
The lady at the desk smiled. Her brown bob remained undisturbed by the air cooling system. “We hope you enjoyed your trip into our analog archives, Fabian.”
“Sure. See you next time, Miranda.” He breezed out. They had history, but it wasn’t something he was interested in repeating. Imagine the conversations about cataloging systems and the internal squabbles of the Knowledge Center board. Fabian was already in a committed relationship with the powers of his imagination. Explicit videos were far too risky for a DoS worker to use, but the image of T1n4Red’s full lips and blond hair invaded his dreams. They could run a ranch together, or maybe they’d be cattle rustlers on the run. He wasn’t sure why, but every night, Fabian masturbated to the one rendered CGI model of T1n4Red they had on file. On the outside, his life was the ultimate mundanity, but the thrill of T1n4Red, the taste of the air on the great ranches outside the city, the sheer danger of even thinking all this, was the only way he could sleep.

They watched the pollination drone flit between the hibiscus flowers in the thick air of the botanical biodome. Fabian had been lucky to receive two of the limited daily visitor passes. It was even luckier for Scott, who now had the chance to get out of his mom’s dingy basement for a few hours.
“You know why they made them bigger than bees, right?” Scott spoke out of the side of his mouth. When Fabian shrugged, he leant in to inspect the device hovering around eye level. He blew a kiss and waved at its pollen-collector end.
“You don’t know that.”
Scott turned and swept his lank hair off his forehead. “You're the one who checks the footage, snoop.”
Micro cameras were yet another panopticon in the armory of the State. You had to assume, even when lying in bed with a lover, even when going to the toilet, that it was possible you were recorded, watched, and analyzed even years later. Secrecy was a virus DoS sought to eradicate.
The biosphere wristband on Fabian’s right arm sounded. Closing time was fast approaching. Fabian put a hand on Scott’s shoulder. “You know, there was a time when access to nature wasn’t so strictly controlled.” He stopped himself from saying more.
They joined the crowds heading to the exit down the palm pathway. “You heard about the latest blacklist?” asked Scott. “The mixnets are awash with it.”
Fabian’s neck muscles tightened. “You shouldn’t be telling me you’re on those forums.” Until he became an agent, even Fabian was prohibited from accessing the decentralized ‘Level 2’ network.
Scott laughed. It was the first time Fabian had heard him laugh that day. “That’s the fun of this little game, homie. Encoding and decrypting ciphers is living. It’s all I got apart from running from debt.” He lowered his voice. “My identity is already in prison, but I ain’t going too.”
Glancing left then right, Fabian made a decision. It was a decision to offer information to a friend, a true friend who had no reason to stick by him when all others cut ties. Sharing a secret in the meatspace was the biggest risk Fabian had taken in years, but he had no way to do it digitally.
“I was behind it.” He expelled a sigh.
Scott turned his head. They carried on walking towards the exit in the throng of people. A few seconds passed.
Fabian scratched at the mole above his eye. “Spent months unraveling stego messages. I feel like I know her. Like really know her.” Was he saying this out of pride or trepidation? Even if they ended in constrained mediocrity, lifeplans were so beautifully simple. Tina, Williams, the ranch, avenging his father’s bankruptcy, the forums, the caution, it all seemed so jumbled. “Maybe I’m in love.” What was Fabian saying? However long T1n4Red lasted underground, she’d never be able to surface again.
Scott bumped Fabian by stepping across his path. “Not in the meatspace. Keep checking the images. There’s a lot more hiding in plain sight than you know.”
They walked in silence through the automated exit gate into the gray city air. As they departed, Scott turned back and called out, “Right pocket.”
Sure enough, Fabian felt the weight of a ‘brick’. He had held one of the untethered devices once in DoS training. Without even putting his hand into his pocket he knew that it was there and what it meant. Decentralized forum instructions would be written on an attached note. The code would be something only he and Scott knew. T14nRed and the entire underworld were now at his fingertips.

23:43 - untethered alert.
Invitation to join Level 2 CP mixnet.
Confirmation Key: M0ntann4Sc0ttySn00ps2031
Fabian lay back in his single bed. He followed the personalized invite link Scott had generated. It must have been strange, he thought, when space was not at a premium, when people went for a walk to escape, rather than lie on their bunk and plug themselves into a metaverse or L2 world. The Ledger made everything easy, an all-in-one software system for citizens so dialed in to their lifeplans, they didn’t have a second to spare. That’s how it had seized control of the nation.
The forum loaded and he found his welcome message from Scott.
Relay from T1n4Red:
It is never too late to use the powers of surveillance for good, Operative Sixsmith. Underworld 4gives but the ledger does not 4get.
In the darkness of his cabin, his face bathed in blue light, Fabian sat bolt upright. His head broke the plane of the holoscreen and a tinge of current trickled through his temple. She knew who he was; she knew what he had done. A charge pulsed through him, the thrill of true privacy. How had he been duped into thinking a total lack of encryption guaranteed freedom and not a glass cage?
The holoscreen flickered for a second. A multimedia message.
Level 2s were a gray area, not illegal. Messages could be relayed peer to peer along a mixnet to the end user. With personalized links hidden in messages on the public comms ledger, communities could be discerning about who joined.
When Fabian leaned back into a lying position, he was greeted by a 3D render of the woman he’d been chasing for over a year. His eyes drank in the red-lipped smile and blonde hair of the woman he’d forced underground, never to feel the rays of the Montana sun again. She held a piece of paper up to the camera, but Fabian couldn’t tear his eyes from her piercing gaze. 64k cameras could pick up the tiniest imperfection. She looked even more real than if he saw her in the flesh. The piece of paper she held was another invite code — this time to an L3 channel.
Fabian exhaled. Breathe. He ran his finger over the chain of three tiny moles above his right eyebrow as if checking they were still there. There were agents who’d been on the force for decades without penetrating Level 3. All messages were stored on the Ledger — that couldn’t be avoided. But with all the red herrings and strong encryption, it was impossible for even the most powerful computers at DoS to uncover much about the members of Underworld’s inner circle. Fabian’s hand reached for his untethered brick. He entered the address from the 3D render of Tina’s paper, followed by the 24-character code from the paper on the outside of the brick. He was in. His next shift at DoS started in ten hours, but he knew he wouldn’t sleep much before then. Tina, and the Underworld answers he’d been seeking awaited on the L3 forum. Fabian made his way to the bathroom and rooted out an old lighter from the medicine cabinet. Staring back from the mirror was his reflection; perhaps it was an avatar of him bound for the Underworld while he remained in the meatspace with his tiny closet apartment and faltering lifeplan. They both watched the password on the paper note burn.
The hubbub of DoS Sector 4A quietened as Fabian walked down the corridor. The hum of hundreds of microcameras was imperceptible to human ears. The one place without them was the toilets — a DoS employee committee had made sure of that — and that is where Fabian’s untethered communicator brick lay. Even if it was found on a bug sweep, they couldn’t trace it to him. And he had ten minutes every two hours to get to the bathroom and check in.
At first she’d been cautious, wanting to know if Fabian would follow her precise instruction. Then, information from Tina had came fast and furious. Names, transactions, locations, protocol, so much information. The tips she’d provided checked out. In fact, they were all just about low-level enough that it was believable that Fabian’s data-driven detective work had unearthed them. She’d even provided a methodology to show which macros and filters he could use to locate L2 peddlers and fixers.
He removed the floor tile behind the toilet bowl. This never got less gross. After relieving himself and pulling the flush chain, he attached the remote charge pack and switched it on. No battery, no trace signal.
11:03 - Message waiting: 6Smith, something important is about to happen. Act surprised. After confirmation, we must meet in person. It will not be easy to get you here. Instructions will follow.
Fabian heard the toilet door open. Could DoS be employing physical spies without the use of cameras in the bathrooms?
The sound of a belt buckle. Charcoal-gray trousers descended and appeared on top of brown loafers through the little gap under the cubicle wall. The heavy-set man dumped himself onto the john and exhaled.
After he deleted the message, Fabian switched off the phone and wiped the power back into his remote charger. He scrubbed his prints off the brick and replaced it behind the bowl. Another flush and he was gone. Out the door before charcoal trousers could physically tie him to the brick. If he was snooping, they would know. He’d get questions about using an unsanctioned jailbroken device. Maybe he could claim he was trying to arrange a physical meeting with T1n4Red. Still, the interrogation would be brutal.
Back on the floor, Agent Williams activated a meeting alert on Fabian’s desk. The red light informed him he must report to the cube immediately. It took great restraint for Fabian to avoid any nervous ticks. Especially with the scrutiny of operatives at his level, he couldn’t avoid a single nervous exploration of the moles on his temple or wiping of hands on trousers. The electronic band every citizen had clamped around their right wrist fed streams of bio-data to the DoS servers. Who would be alerted if his heartbeat spiked or breathing patterns changed? As he’d learned on the L2 forums, flying under the radar took a lot more than digital restraint. The surveillance apparatus of the state kept so much biometric data it had become a living cyborg. Could this be about the bathroom break? The guy in the next stall with the charcoal trousers? The brick? Was this the start of a downfall that ended in the same invisible blacklist Scott was on? Maybe that chick in the library had something against him too.
The glass door slid open and Fabian moved through the entry point in one clean step.
“No need to sit, Operative Sixsmith. Let’s stay on our feet here.”
Sixsmith awaited the news. Whatever it was, at least it would be quick.
Williams raised a stainless steel travel mug to his lips and drank. If the coffee was hot, he showed no signs of it. “I must admit, I’ve had my doubts about you.” An ominous start. “Up until this year, your work was adequate.” Williams paced towards the glass wall to watch the goings on of the morning-shift operators. His invisible stare could put someone’s back out. “And that stunt you pulled to get the jump on T1n4Red… some stricter agents might have filed that as a denial-of-protocol infraction.”
Fabian locked his gaze to the coffee cup and let him talk.
“But since then, your results have been quite something. An 89% strike rate on intel and twelve L2 agitators liquidated. That’s as high as I’ve seen.”
“Thank you, sir.” Fabian rearranged his cotton shirt, which, despite the blasting air con, was stuck firmly to his back.
“Good news.” Agent Williams went to his desk drawer and removed a six-inch blade. The silver tip matched the glint of William’s graying hair under the strip light. “You are no longer an operative here at the Department of Surveillance.”
Fabian imagined the angle of attack. A diagonal slashing motion from up high. He wouldn’t have time to avoid the agent’s quick reflexes.
“Congratulations, Agent Sixsmith.”
Fabian took a step back. His right hand found its way to his brow. “What?”
“You’ve been promoted, son. It can’t be that much of a surprise.”
Fabian had spent so long tracking certainties, he had forgotten what surprise felt like. He had his doubts about the system, his L3 secrets, his upcoming liaison with T1n4Red, his friendship with Scott. But things would be better as an agent. His family back in Boston would surely offer some begrudging respect. If he wasn’t six feet under, his old man might feel some kind of peace knowing his boy had won back those credits. Freedom from bio-data collection and freedom to roam. He faced his boss. “But I’m not up for review until—”
“Take the win.” Williams approached, knife in hand. “We need all the capable agents we can get.” He reached for Fabian’s right forearm. His grip was that of a much bigger man. “Effective immediately, you are Agent Sixsmith of the Department of Surveillance.” He slid the knife under Fabian’s communicator wristband and sliced through the strap.
The cool office air touched his now naked wrist. Fabian smoothed the skin as if he had been unshackled.
Once Williams returned the knife to its drawer, he offered his hand to shake. “Congratulations, Agent. Full briefing tomorrow at 0930.”
“Yes sir. Thank you for your trust.” He turned to go.
“Stop,” a sharp voice called. Williams held a small piece of metal between thumb and forefinger. “Don’t forget this.”
Agent Fabian Sixsmith accepted the gift — an American flag pin. He nodded and stepped through the doorway in the same way he entered.
](https://image.nostr.build/b3cff409a4d05409b84ddd61f9689f707b24376f196887558c2eaee1d17c8275.jpg)
Fabian zipped his thick hoodie and stepped out into the night. The reflectors in the fabric would dazzle the night vision of the cameras, and the Federal Government hadn’t passed any laws telling people how to dress… yet. He opened the door and set out to meet his handler.
He started his run towards the city outskirts, the hood shrouding his adrenaline-shot eyes. The back of his skull throbbed. It had been bothering him all afternoon. Throwing in a few boxing moves for good measure, Fabian pounded out the miles. One, two, past the city limits and onto the shoulder of the 87, the sixteen-wheeler auto rigs ripping past. The drones would be following — of that he was sure.
His handler was there. Just like Tina said. Half a mile after the first junction, under the bridge, Scott straddled his solarbike. This must be how he earned his sats — acting as a go between for Underworld agents who had gone to ground.
No words, just the exchange. Fabian unzipped the hoodie and draped it over his friend’s shoulders. Scott removed a 3D image scanner from his pocket and ran it over Fabian’s face. Two seconds and the ID confirmation would be relayed on the Ledger, probably embedded with a stego message. A quick clap of the hands, and he drove into the night. Forty, fifty, sixty, and gone, west towards Great Falls. Fabian took a breath. Is this what he had done all those reps in the closet for? He scrambled up the bank and jumped for the bridge railing. Hauling his body up and over in one swift motion. Then, crouching low behind the advertising hoarding, he duck-walked over the bridge and down the bank. How would he disable the micro cameras? Even without tracking data, the DoS apparatus wouldn’t be far behind — especially after they scrambled a drone to intercept Scott. Thirty seconds tops.
This place, just a few miles away from Lewistown, was the setting for one of those books he loved — cowboys, sheriffs, and theft. Of course, the subterfuge of Level 3 protocol and 256-bit encryption was a little more complicated now. The idea of coding messages is as old as civilization, only the attack vectors changed over time.
Left. Right. Feet smacking dirt. Fabian had to trust the track was level. He could barely see three feet in front of him — only the dim Montana moonlight for company. The whirr of a camcopter approached overhead. If it locked his thermal image, he was toast. Just a few more strides surely. His lungs burned after all those miles.
DoS wasn’t just going to let a newly-minted agent go for a mysterious wilderness night run.
His foot jammed against a root. He stumbled on, narrowly avoiding a painful fall.
“IDENTIFY ORDER.” The camcopter had locked the human gait recognition. “FAILURE TO COMPLY EVOKES FEDERAL CREDIT ELIMINATION.”
Fabian almost laughed. These fucking things threatening to zero-out people’s hard-earned savings. How the hell had Americans let things go this far? He spotted the manhole cover under the tree. His lungs sucked in the night air, and his heart tore at his ribs.
Wham. Down to the ground. The force of a truck pinned Fabian and pushed his face into the dirt. “No,” he cried. “Let me explain.” Searing pain pulsed through his skull from the back to the front. In the seconds that followed, it was as if his brain was rebooting. Who was this? What were they doing?
“Neural tracer deactivated,” said the voice of the brute on top of him.
Fabian managed to turn his head. He caught a glimpse of the man, but it was too dark to see his face. The pressure on Fabian’s back slowly released. He shook the cobwebs out of his head.
As Fabian stood, he saw the guard moving away, pointing his EMP caster at the sky, sweeping left then right.
Crash. One dronecopter downed. A crash to the right, another drone gone. These things would be disposed of in some pit or quarry. The figure collected the drones and moved into the night.
Fabian dusted himself off and walked towards his destination of the irrigation pipe system. As Agent Sixsmith hauled the steel grate to the side, he took a breath. This was it. Too late to deny involvement. Too far down the rabbit hole. He’d have to give up everything he worked for — respect at Thanksgiving and a pension large enough to retire to a ranch and ride a horse over the land. In exchange, he’d get a one-time Underworld trip, where he would learn the methods and tactics the punks used to stay off grid.
Now it was quiet, bar the low hum of the highway and the sound of his rasping breath. He’d never been this alive. It sure beat the meticulous protocol of DoS. Before he could stop himself, Fabian was inside, his hands replacing the grate, gripping the ladder, his feet on the rungs, stepping down, down into the dark. Whatever she had to tell him, he needed to hear it. Meeting T1n4Red in the meatspace trumped any handshake from Agent Williams, any pension plan, and any begrudging respect from his nagging mother and fucked-up family. He descended to the Underworld.
At the end of the dank tunnel, Fabian saw the purple glow of UV light. He approached slowly. The sound of soft footsteps approached from behind. He didn’t dare turn. Then, a few paces from the curve where the light grew stronger, a flat plastic object jammed the base of his skull forward. Click. Probably a 3D-printed gun.
“Arms out. Legs astride.”
Fabian complied. The EM scan wouldn’t find anything. He was stripped of all tech — one of the many firsts he’d experienced that day. It was safer for all parties if he didn’t turn around.
The voice barked, “Clear,” and a rough hand pushed him forward. The footsteps descended back towards the tunnel opening.
Peering into the mirror positioned at the tunnel corner, Fabian caught a glimpse of the woman he came to see. The channel between well-defined back muscles drew his eye south. How long had it been since he felt the touch of a woman? How did she stay in such good shape down here? The weak UV light faded to a soft yellow glow in the chamber.
“Agent Sixsmith. We’ve been expecting you.” Tina pulled a t-shirt over her bra and cinched her blonde hair into a top bun. She laughed. “Take a seat.”
“How do you know I’m an agent?” Fabian sat on the plastic chair closest to him. The room had been widened from its original layout. It was now around fifteen feet square with a camp bed, a desk with double monitors, and a treadmill. His eyes settled on the black desktop compu-box.
She touched his arm, her hand surprisingly warm. “I bet you’d love to open that up and take a look.”
Fabian had never seen a homemade device connected up. Getting the parts must have taken years, but nobody could detect unregistered tech through lead linings and all the perimeter protocal. She truly owned something, even if it was just a little black box.
“You didn’t think agents are unsurveilled, did you? Poor boy.”
Fabian’s mind switched to rational mode. Was he burned? Would he ever be able to surface without getting financially or physically liquidated?
“Relax. I know what you’re thinking. This is your first trip here, but it won’t be your last. We fried your tracer chip and they can’t admit they implanted ‘cause it ain’t legal.” She swiveled the computer chair and sat on it back to front. The high chair back almost came up to her chin. “You get one question. Shoot.”
In their digital conversation, Tina had always been careful to give instructions only, never responding to Fabian’s questions. He might have a lot to learn, but at least he wasn’t living in the dark like her, a trapped soldier unable to look above the parapet. Was he walking into a trap? Was he already in one? If things got tough in the interrogation he was sure to receive from Williams, he could always offer some Underworld secret. Fabian turned to face the shadow of a woman he had chased for nearly a year. “Where are the Level 3 relay servers kept?”
“Ooh amor, you’ve gotta think bigger than that.” Tina Red was more than just a celebrity crush. Her blue eyes burned with the intensity of a neutron star. Her slender legs wrapped around the chair like a boa constrictor drawing in its prey. She drew closer, and he could smell the sweat. “There are no dedicated L3 relay servers. We’ve been using a hacked DoS server for months. Keeps you searching for that mythical Underworld data center, right?”
There were so many units in the DoS server cities that it would take years to isolate the hack. Smart. “What’s the end goal to all of this?” he asked.
Instead of replying, Tina shook her head.
Play by Underworld rules, Fabian. It didn’t matter — he knew. Reversing the grip of the big-government machine was virtually impossible, but the dream was that the country returned to ‘the land of the free.’ Freedom to secrecy. Freedom to own. Freedom to transact with whomever you wanted.
Fabian watched as T1n4Red stood and crossed the six-foot gap between them. She leant over and moved a hand to the back of his hair, gripping his short black hair in her fist. The same fear pulsed through him as in the meeting he’d had with Agent Williams — the same Williams who was organizing the search and interrogate protocol for him at that very moment. Was her bodyguard waiting around the corner with the 3D-printed gun, primed to deliver its one shot straight into his brain?
“This is our endgame.” Their faces were inches apart. He saw the same freckles and imperfections in her skin as in the high-res digital render. But there was nothing like real life.
And then, a swell of the tide inside him. Euphoria. The kiss was deep. Their lips fused, one person, one dream. Fabian’s hands reached for the shape of the woman he’d dreamed about so many nights. She sat, straddling his legs and they went on. Blood rising like an ocean swell, Fabian dived into bliss. It all melted away — the dronecopters hovering above, the awkward entry to the office tomorrow, the nagging fear that his accounts would be zeroed out in mere hours. But one image remained. The moment transported Fabian to his spiritual home — the wilds of the Montana hills, the wind blowing through the grassland, the mountain range guarding the horizon. The wild country that called him.
When they finally broke the kiss, Tina stood. “Did you feel it?”
Fabian raised his gaze. “I think so. A place. The wild—”
She raised a finger to silence him. “Don’t say it. This is our secret, Agent Sixsmith.”
He thought for a second. Project Wild Country. It was strange, but he had no doubt. The phrase was branded into his mind clearer than the passphrase he had to memorize for his DoS access. How could two beings communicate telepathically?
“It’s called ‘Telepathic Key Exchange’. TKX for short.” Tina approached and whispered into his ear. “From the mentalists of the late 20th Century.” It had been there all along — a method to eliminate the gap where biological beings had to enter a passphrase physically. This was only part of the information chain without a cipher. No more worries about the micro cameras that could capture keystrokes or capture pen and ink comms.
“Our project,” she breathed.
The image swam through Fabian’s mind once more, the color of the sky as vivid as the eyes of the woman in front of him. The hills and plains in front of them. All protests start with the spark of non-compliance. And all revolution hinges on the man who knows how to play both sides. He’d have to learn more about it, understand it better, but TKX could lay the path to a fully anonymous market, unbreakable smart contracts, and a citizens’ private arbitration court. This would be the rewilding of America.
“We only have a few more minutes.” Tina returned to her chair. She explained the comms protocol and that the two of them were the only people on Earth to know the name of this mission. Project Wild Country would bring TKX to the masses.
“How can we teach people?”
“We lead people through the levels, just like I got you here. There are more stego images on the Ledger every day. It’s already started.”
Fabian looked at the wrist his bio-band had once gripped. “What do I say to DoS to explain this time-gap?” How long had he even been down there, fifteen minutes?
“You wouldn’t be much of an agent if you couldn’t think of something. Be the sovereign of yourself, Fabian.” T1n4Red laughed. “Better get running.”
Fabian moved toward the dark tunnel that led to a surface world buzzing with invisible spies. “I’ll be thinking of you,” he said. Fabian thought he detected the hint of a smile on Tina’s lips, and he felt a tiny swell of the euphoria that had filled him moments earlier. Then, he turned to go. Agent Sixsmith rounded the corner and started his journey back to the wild country.
This story first appeared in Financial Fallout. Find out more about the book at 21futures.com
21 Futures retains 21% of the zaps received to cover operating costs. The majority of the sats are forwarded to the author.

Max Hillebrand is a praxeologist who contributes to several open-source projects, because code is abundant and not scarce. He shares his work freely for others to use and modify. His goal is to help build a parallel economy based on sound money and individual sovereignty, where people can pursue their entrepreneurial ambitions without interference from central authorities. Find out more at towardsliberty.com
-
 @ 5cb68b7a:b7cb67d5
2025-05-02 15:09:57
@ 5cb68b7a:b7cb67d5
2025-05-02 15:09:57Losing access to your cryptocurrency can feel like losing a part of your future. Whether it’s a forgotten password, a damaged seed backup, or simply one wrong transfer, the stress can be overwhelming. But there’s a silver lining — Crypt Recver is here to help! With our expert-led recovery services, you can reclaim your lost Bitcoin and other cryptos safely and swiftly.
Why Trust Crypt Recver? 🤝 🛠️ Expert Recovery Solutions At Crypt Recver, we specialize in resolving some of the most complex wallet-related issues. Our team of skilled engineers has the tools and expertise to tackle:
Partially lost or forgotten seed phrases Extracting funds from outdated or invalid wallet addresses Recovering data from damaged hardware wallets Restoring coins from old or unsupported wallet formats You’re not just getting a service; you’re gaining a partner in your cryptocurrency journey.
🚀 Fast and Efficient Recovery We understand that time is critical in crypto recovery. Our optimized systems ensure that you can regain access to your funds quickly, aiming for speed without sacrificing security. With a 90%+ success rate, you can trust us to fight against the clock on your behalf.
🔒 Privacy is Our Priority Your confidentiality matters. Every recovery session is handled with the utmost care, ensuring all processes are encrypted and confidential. You can rest easy, knowing your sensitive information stays private.
💻 Advanced Technology Our proprietary tools and brute-force optimization techniques allow for maximum efficiency in recovery. No matter how challenging your case may be, our technology is designed to give you the best chance at getting your crypto back.
Our Recovery Services Include: 📈 Bitcoin Recovery: Lost access to your Bitcoin wallet? We help recover lost wallets, private keys, and passphrases. Transaction Recovery: Mistakes happen — whether it’s an incorrect wallet address or a lost password, let us handle the recovery. Cold Wallet Restoration: If your cold wallet is failing, we can safely extract your assets and migrate them into a secure, new wallet. Private Key Generation: Lost your private key? Don’t worry. Our experts can help you regain control using advanced methods — all while ensuring your privacy remains intact. ⚠️ What We Don’t Do While we can handle many scenarios, there are some limitations. For example, we cannot recover funds stored in custodial wallets, or cases where there is a complete loss of four or more seed words without any partial info available. We’re transparent about what’s possible, so you know what to expect.
Don’t Let Lost Crypto Hold You Back! ⏳ Did you know that 3 to 3.4 million BTC — nearly 20% of the total supply — are estimated to be permanently lost? Don’t become part of that statistic! Whether it’s due to a forgotten password, sending funds to the wrong address, or damaged drives, we can help you navigate through it all.
🛡️ Real-Time Dust Attack Protection Protecting your privacy goes beyond just recovery. Our services include dust attack protection, which keeps your activity anonymous and your funds secure. Our suite will shield your identity from unwanted tracking, ransomware, and phishing attempts.
🎉 Start Your Recovery Journey Today! Are you ready to reclaim your lost crypto? Don’t wait until it’s too late!
👉 Request Wallet Recovery Help Now!
📞 Need Immediate Assistance? Connect with Us! For real-time support or questions, reach out to our dedicated team on:
✉️ Telegram: Chat with Us on Telegram 💬 WhatsApp: Message Us on WhatsApp Crypt Recver is your trusted partner in the world of cryptocurrency recovery. Let us turn your challenges into victories. Don’t hesitate — your crypto future starts now! 🚀✨
Act fast and secure your digital assets with Crypt Recver!Losing access to your cryptocurrency can feel like losing a part of your future. Whether it’s a forgotten password, a damaged seed backup, or simply one wrong transfer, the stress can be overwhelming. But there’s a silver lining — Crypt Recver is here to help! With our expert-led recovery services, you can reclaim your lost Bitcoin and other cryptos safely and swiftly.
 # Why Trust Crypt Recver? 🤝
# Why Trust Crypt Recver? 🤝🛠️ Expert Recovery Solutions
At Crypt Recver, we specialize in resolving some of the most complex wallet-related issues. Our team of skilled engineers has the tools and expertise to tackle:
- Partially lost or forgotten seed phrases
- Extracting funds from outdated or invalid wallet addresses
- Recovering data from damaged hardware wallets
- Restoring coins from old or unsupported wallet formats
You’re not just getting a service; you’re gaining a partner in your cryptocurrency journey.
🚀 Fast and Efficient Recovery
We understand that time is critical in crypto recovery. Our optimized systems ensure that you can regain access to your funds quickly, aiming for speed without sacrificing security. With a 90%+ success rate, you can trust us to fight against the clock on your behalf.
🔒 Privacy is Our Priority
Your confidentiality matters. Every recovery session is handled with the utmost care, ensuring all processes are encrypted and confidential. You can rest easy, knowing your sensitive information stays private.
💻 Advanced Technology
Our proprietary tools and brute-force optimization techniques allow for maximum efficiency in recovery. No matter how challenging your case may be, our technology is designed to give you the best chance at getting your crypto back.
Our Recovery Services Include: 📈
- Bitcoin Recovery: Lost access to your Bitcoin wallet? We help recover lost wallets, private keys, and passphrases.
- Transaction Recovery: Mistakes happen — whether it’s an incorrect wallet address or a lost password, let us handle the recovery.
- Cold Wallet Restoration: If your cold wallet is failing, we can safely extract your assets and migrate them into a secure, new wallet.
- Private Key Generation: Lost your private key? Don’t worry. Our experts can help you regain control using advanced methods — all while ensuring your privacy remains intact.
⚠️ What We Don’t Do
While we can handle many scenarios, there are some limitations. For example, we cannot recover funds stored in custodial wallets, or cases where there is a complete loss of four or more seed words without any partial info available. We’re transparent about what’s possible, so you know what to expect.
 # Don’t Let Lost Crypto Hold You Back! ⏳
# Don’t Let Lost Crypto Hold You Back! ⏳Did you know that 3 to 3.4 million BTC — nearly 20% of the total supply — are estimated to be permanently lost? Don’t become part of that statistic! Whether it’s due to a forgotten password, sending funds to the wrong address, or damaged drives, we can help you navigate through it all.
🛡️ Real-Time Dust Attack Protection
Protecting your privacy goes beyond just recovery. Our services include dust attack protection, which keeps your activity anonymous and your funds secure. Our suite will shield your identity from unwanted tracking, ransomware, and phishing attempts.
🎉 Start Your Recovery Journey Today!
Are you ready to reclaim your lost crypto? Don’t wait until it’s too late!
👉 Request Wallet Recovery Help Now!
📞 Need Immediate Assistance? Connect with Us!
For real-time support or questions, reach out to our dedicated team on:
- ✉️ Telegram: Chat with Us on Telegram
- 💬 WhatsApp: Message Us on WhatsApp
Crypt Recver is your trusted partner in the world of cryptocurrency recovery. Let us turn your challenges into victories. Don’t hesitate — your crypto future starts now! 🚀✨
Act fast and secure your digital assets with Crypt Recver!
-
 @ c4b5369a:b812dbd6
2025-04-15 07:26:16
@ c4b5369a:b812dbd6
2025-04-15 07:26:16Offline transactions with Cashu
Over the past few weeks, I've been busy implementing offline capabilities into nutstash. I think this is one of the key value propositions of ecash, beinga a bearer instrument that can be used without internet access.
 It does however come with limitations, which can lead to a bit of confusion. I hope this article will clear some of these questions up for you!
It does however come with limitations, which can lead to a bit of confusion. I hope this article will clear some of these questions up for you!What is ecash/Cashu?
Ecash is the first cryptocurrency ever invented. It was created by David Chaum in 1983. It uses a blind signature scheme, which allows users to prove ownership of a token without revealing a link to its origin. These tokens are what we call ecash. They are bearer instruments, meaning that anyone who possesses a copy of them, is considered the owner.
Cashu is an implementation of ecash, built to tightly interact with Bitcoin, more specifically the Bitcoin lightning network. In the Cashu ecosystem,
Mintsare the gateway to the lightning network. They provide the infrastructure to access the lightning network, pay invoices and receive payments. Instead of relying on a traditional ledger scheme like other custodians do, the mint issues ecash tokens, to represent the value held by the users.How do normal Cashu transactions work?
A Cashu transaction happens when the sender gives a copy of his ecash token to the receiver. This can happen by any means imaginable. You could send the token through email, messenger, or even by pidgeon. One of the common ways to transfer ecash is via QR code.
The transaction is however not finalized just yet! In order to make sure the sender cannot double-spend their copy of the token, the receiver must do what we call a
swap. A swap is essentially exchanging an ecash token for a new one at the mint, invalidating the old token in the process. This ensures that the sender can no longer use the same token to spend elsewhere, and the value has been transferred to the receiver.
What about offline transactions?
Sending offline
Sending offline is very simple. The ecash tokens are stored on your device. Thus, no internet connection is required to access them. You can litteraly just take them, and give them to someone. The most convenient way is usually through a local transmission protocol, like NFC, QR code, Bluetooth, etc.
The one thing to consider when sending offline is that ecash tokens come in form of "coins" or "notes". The technical term we use in Cashu is
Proof. It "proofs" to the mint that you own a certain amount of value. Since these proofs have a fixed value attached to them, much like UTXOs in Bitcoin do, you would need proofs with a value that matches what you want to send. You can mix and match multiple proofs together to create a token that matches the amount you want to send. But, if you don't have proofs that match the amount, you would need to go online and swap for the needed proofs at the mint.Another limitation is, that you cannot create custom proofs offline. For example, if you would want to lock the ecash to a certain pubkey, or add a timelock to the proof, you would need to go online and create a new custom proof at the mint.
Receiving offline
You might think: well, if I trust the sender, I don't need to be swapping the token right away!
You're absolutely correct. If you trust the sender, you can simply accept their ecash token without needing to swap it immediately.
This is already really useful, since it gives you a way to receive a payment from a friend or close aquaintance without having to worry about connectivity. It's almost just like physical cash!
It does however not work if the sender is untrusted. We have to use a different scheme to be able to receive payments from someone we don't trust.
Receiving offline from an untrusted sender
To be able to receive payments from an untrusted sender, we need the sender to create a custom proof for us. As we've seen before, this requires the sender to go online.
The sender needs to create a token that has the following properties, so that the receciver can verify it offline:
- It must be locked to ONLY the receiver's public key
- It must include an
offline signature proof(DLEQ proof) - If it contains a timelock & refund clause, it must be set to a time in the future that is acceptable for the receiver
- It cannot contain duplicate proofs (double-spend)
- It cannot contain proofs that the receiver has already received before (double-spend)

If all of these conditions are met, then the receiver can verify the proof offline and accept the payment. This allows us to receive payments from anyone, even if we don't trust them.
At first glance, this scheme seems kinda useless. It requires the sender to go online, which defeats the purpose of having an offline payment system.
I beleive there are a couple of ways this scheme might be useful nonetheless:
-
Offline vending machines: Imagine you have an offline vending machine that accepts payments from anyone. The vending machine could use this scheme to verify payments without needing to go online itself. We can assume that the sender is able to go online and create a valid token, but the receiver doesn't need to be online to verify it.
-
Offline marketplaces: Imagine you have an offline marketplace where buyers and sellers can trade goods and services. Before going to the marketplace the sender already knows where he will be spending the money. The sender could create a valid token before going to the marketplace, using the merchants public key as a lock, and adding a refund clause to redeem any unspent ecash after it expires. In this case, neither the sender nor the receiver needs to go online to complete the transaction.
How to use this
Pretty much all cashu wallets allow you to send tokens offline. This is because all that the wallet needs to do is to look if it can create the desired amount from the proofs stored locally. If yes, it will automatically create the token offline.
Receiving offline tokens is currently only supported by nutstash (experimental).
To create an offline receivable token, the sender needs to lock it to the receiver's public key. Currently there is no refund clause! So be careful that you don't get accidentally locked out of your funds!

The receiver can then inspect the token and decide if it is safe to accept without a swap. If all checks are green, they can accept the token offline without trusting the sender.

The receiver will see the unswapped tokens on the wallet homescreen. They will need to manually swap them later when they are online again.
 Later when the receiver is online again, they can swap the token for a fresh one.
Later when the receiver is online again, they can swap the token for a fresh one.
Summary
We learned that offline transactions are possible with ecash, but there are some limitations. It either requires trusting the sender, or relying on either the sender or receiver to be online to verify the tokens, or create tokens that can be verified offline by the receiver.
I hope this short article was helpful in understanding how ecash works and its potential for offline transactions.
Cheers,
Gandlaf
-
 @ bf95e1a4:ebdcc848
2025-05-02 10:00:55
@ bf95e1a4:ebdcc848
2025-05-02 10:00:55This is a part of the Bitcoin Infinity Academy course on Knut Svanholm's book Bitcoin: Sovereignty Through Mathematics. For more information, check out our Geyser page!
Holding On
In the old days, we Scandinavians had to save in order to prepare for the long winter. We chopped wood and salted meat in order to survive. In our current age of consumerism, however, we’ve forgotten all that and we pilgrim to the shopping malls as much as everyone else. No one seems to even have a savings account anymore. Interest rates are low, and we’re told to borrow and spend as much as we can. We’re bombarded with advertising for loans, mortgages, and financial services on a daily basis. Why? Because of our inability to understand the nature of money and its mechanics. Inflation is the underlying force that makes us squander rather than save. Inflation hinders us from reaping the fruits of our labor whenever we see fit, and it makes that very fruit rot. Bitcoin reverses the rotting process and provides us with a means of transporting the value of our labor not only through space but also through time.
The Stanford Marshmallow Experiments was a series of studies on delayed gratification conducted in the late 1960s and early 1970s. In these experiments, children were given a marshmallow or a cookie and were told that they would receive an additional one if they could control their urges and not touch the first one for fifteen minutes. Follow-up studies found that the kids who were able to resist the temptation of the first cookie tended to score better on SAT tests, have lower BMIs, and higher incomes than their less disciplined counterparts. Investing in your future self — in other words, resisting present temptation by delaying gratification — is the most effective skill you can cultivate for a brighter future. You reap what you sow. This can be described as having a low time preference. Having a low time preference is a fundamental factor in the economic success of any human endeavor. Not trying to catch fish with your hands for a couple of days in order to construct a rod or net when on a deserted island might make you hungry during those sacrificed days, but it will provide a better chance of catching fish in the future. Likewise, learning new skills now might lead to a higher salary in the future. Unfortunately, our current monetary system distorts our perceptions and incentives and favors those with a higher time preference — those who spend rather than save. We’re at a different point in history than the above-mentioned marooned fisherman. "Give a man a fish and feed him for a day, teach a man to fish and feed him for a lifetime," the saying goes. The ultimate goal should be to teach mankind to teach itself how to fish. What our current paradigm endorses is “give a man enough distractions, and he will stop thinking about finding better ways to support his loved ones and will succumb to whatever narrative you fill his head with, to make him work for you through taxes and inflation instead of for himself.”
In Bitcoin, people with a low time preference win. If you can resist the urge to sell, you will be rewarded in the future. The Bitcoin community refers to not selling as HODLing, which originated when a bitcointalk.org forumer named GameKyuubi misspelled the word holding in a now-famous post titled "I AM HODLING." The post became one of the Bitcoin community’s most prominent memes and a battle cry to resist the urge to sell during bear markets. Bitcoiners who have decided never to sell most or all of their holdings are referred to as HODLers of last resort. This term is not to be confused with the central banking term lender of last resort. The yearly highs in the price of Bitcoin are arguably less interesting than the yearly lows, which are practically decided by these HODLers of last resort. Considering its limited supply, all that Bitcoin needs to keep rising in price over the medium and long term are these people. Adoption and other metrics of measuring the success of Bitcoin are all dwarfed by the currency’s remarkable rise in value since its inception. The price has increased by a factor of ten approximately every three years. The best guarantee we have that it will keep doing so is Bitcoin’s limited supply combined with the HODLers of last resort.
In the Bitcoin space, and even more so in the cryptocurrency space on the whole, there’s a lot of talk about usage and adoption. We’re shown metrics of trading volumes and merchant acceptance, and we’re led to believe that these correlate with the short and long-term value in one way or another. While there may be truth in some of these theories, the most basic function of a deflationary asset is overlooked and rarely mentioned — the elephant in the room, so to speak. The best use for a commodity as scarce as Bitcoin is not to spend it or even to trade it but to save it and hold it for as long as you can. By doing so, you limit the number of coins in circulation. The more people that do this, the harder it will be to come by and the higher its price will be. Nothing on Earth is as scarce as Bitcoin. Nothing is as irreplicable, as immutable, and at the same time as portable as Bitcoin — its unique history and resistance to change have already proven this over and over. Its absolute scarcity is what gives Bitcoin its value, and ironically enough, this seems to be the hardest thing for people to understand about it. What if everyone in the network became a HODLer and decided to never sell, wouldn’t the network just slowly come to a halt? Not at all. Everyone has a price. Few would resist selling some of their Bitcoin if it could buy them a small city. There are price levels for each HODLer where reallocating financially may be a wise thing to do. A Bitcoin is also very divisible: The smallest unit, the satoshi, sometimes referred to as a sat, is one-hundred millionth of a Bitcoin. Even smaller units are made possible with the introduction of the Lightning Network, albeit not in the actual Bitcoin blockchain. Together, this enables Bitcoin to be highly saleable even at astronomical price levels.
What not having sound money has done to us is simply unfathomable. Imagine every person on Earth knowing that every transaction they’ll ever make will have a real impact on their future prosperity. We’re so used to inflationary currencies that most people don’t even realize why sound money is important. We’re so used to having a large cut of our income silently taken away from us that we don’t even realize how much of our day we spend working for someone else. Wars are funded by inflation. Imagine how many man-hours were put in by people who didn’t realize they were actually working for a war machine funded by a corrupt currency during World War II. Every time you use a fiat currency, you legitimize counterfeiting. Every time you use Bitcoin, you promote sound money. In fact, every time you don’t use your Bitcoin but save it instead, you promote sound money because sound money increases in value when the total number of coins in circulation is limited. It all sounds a bit magic and far-fetched, doesn’t it? Increased value over time, no matter what happens? Well, that is why many of us so-called Bitcoin Maximalists are so excited that we put our careers at risk for this technology. Once you realize what Bitcoin is and what it will do for the world, there is no way of un-realizing it. It really is mind-blowing.
At the beginning of time-that-actually-is-money — in other words, around 2009 — Bitcoin was mostly considered a toy for the cypherpunk movement. As its price started to grow rapidly, a small group of early investors became very wealthy, which in turn spawned a media hype around the phenomenon. Mainstream media remained largely skeptical, portraying Bitcoin as a pyramid scheme, a tulip craze, or a bubble at best. Most journalists simply couldn’t understand how an asset seemingly created out of thin air could have any long-term relevance. Some were frustrated because they thought that they’d missed the train. Many still do. In a world where companies like Google, Facebook, and Amazon can rise from zero to world dominance in a decade, people tried to find the Next Big Thing — the next Bitcoin. This attracted charlatans and scammers to the field who launched hundreds of altcoins, claiming to someday be technically superior, faster, or more privacy-focused. What the snake-oil salespeople omitted were the crucial facts: their new coins and tokens were not decentralized (and therefore neither immutable nor censorship-resistant), did not have a fair distribution, and so on. What most people still don’t get is that if Bitcoin doesn’t work, nothing will. This is humanity’s best shot at sound money. It is also, very likely, our only shot at it.
Many venture capital firms, hedge funds, and retail investors were bamboozled by the buzzword frenzy and invested great sums in these quack tokens. This generated confusion in the market as many altcoins increased dramatically in price at an even higher rate than Bitcoin. Due to human nature and a lack of understanding of basic monetary economics, the bubble grew bigger and bigger until it inevitably popped and wiped out most of the useless alternative cryptocurrencies. Bitcoin experienced ups and downs as well, but they were less volatile. Bitcoin bottomed at levels well above the beginning of the previous bull run and then resumed rising just as it had done several times before. The victims of the altcoin craze will take note of this. They will learn the hard way what separates the original from the copycat. They will see the undisputable superiority of sound money. It’s just a matter of time. Time, which is money.
Every time the people of Venezuela, Turkey, Argentina, or Zimbabwe are screwed over by their respective central banking authorities and turn to Bitcoin to preserve their savings or income from rampant inflation, the world becomes more aware of Bitcoin as a store of value. In comparison to the Venezuelan Bolivar, there was no crash in Bitcoin at all. There’s also a good chance the really big players will accumulate aggressively during the next bull market, given that Bitcoin, for the moment, still represents a very small allocation of institutional and hedge fund investment. Consider what will happen when institutional investors and a growing number of larger nations start to see Bitcoin’s potentially limitless upside. At this point, central banks will start to accumulate Bitcoin in an attempt to keep up with reality. This will legitimize the technology even further.
It is still unclear when this will all play out. When it does, however, it will be the largest transfer of wealth from one medium to another in human history. Early investors, many of which are technically competent, will become financially independent and, therefore, able to contribute to the ecosystem full-time. More and more people will demand payment in Bitcoin for its ability to store value. Remember that the next block reward halving is just around the corner and that Bitcoin will have an even greater stock-to-flow ratio than gold in just a few years. After the halving in 2020, Bitcoin will have a supply inflation rate of approximately 1.8%, which is lower than the US Federal Reserve’s target 2% price inflation rate. It is important to remember that Bitcoin is still an experiment. Should the experiment work, however, hyperbitcoinization is just a matter of time.
The implications of giving everyone on Earth the ability to rot-proof the fruit of their labor and transport its value through time are hard to overstate. The closest thing we’ve had to it historically is gold, but gold is not very divisible and not very easy for the general public to get their hands on. More importantly, gold is not absolutely scarce. No one knows how much of it there is left buried in the Earth's crust. Investing in real estate has also been seen as a good store of value throughout the ages, but real estate needs a lot of maintenance and is not cheap to hold on to. Real estate is also relatively easy to confiscate in the event of political collapse. Bitcoin provides us with the potential ability to store any amount in our heads and pass it down through generations without anyone ever knowing we had it in the first place. It effectively endows each individual with the power possessed by the feudal kings to turn people into knights. Any bitcoiner can now dub any no-coiner into a fully-fledged time-proof bitcoiner.
About the Bitcoin Infinity Academy
The Bitcoin Infinity Academy is an educational project built around Knut Svanholm’s books about Bitcoin and Austrian Economics. Each week, a whole chapter from one of the books is released for free on Highlighter, accompanied by a video in which Knut and Luke de Wolf discuss that chapter’s ideas. You can join the discussions by signing up for one of the courses on our Geyser page. Signed books, monthly calls, and lots of other benefits are also available.
-
 @ 8f69ac99:4f92f5fd
2025-05-02 09:29:41
@ 8f69ac99:4f92f5fd
2025-05-02 09:29:41À medida que Portugal se aproxima das eleições legislativas de 2025, a 18 de Maio, torna-se essencial compreender as diferentes propostas políticas e os programas eleitorais dos partidos para votar de forma informada. Este artigo funciona como um índice para uma série de análises realizadas aos programas dos principais partidos, com foco em temas como liberdades individuais, descentralização e crescimento económico.
A Evolução da Esquerda e da Direita: Um Contexto Histórico e Ideológico
Os termos “esquerda” e “direita” surgiram na Revolução Francesa (1789–1799) para distinguir quem se sentava ao lado do presidente da Assembleia: as forças favoráveis às reformas radicais (à esquerda) e as defensoras da monarquia e da ordem estabelecida (à direita). Com o século XIX e o advento do liberalismo económico, a direita passou a associar-se ao livre mercado e ao direito de propriedade, enquanto a esquerda defendeu maior intervenção estatal para promover igualdade.
No final do século XIX e início do século XX, surgiram o socialismo e o comunismo como correntes mais radicais da esquerda, propondo a abolição da propriedade privada dos meios de produção (comunismo) ou sistemas mistos com forte regulação e redistribuição (socialismo). A resposta liberal-conservadora evoluiu para o capitalismo democrático, que combina mercado livre com alguns mecanismos de assistência social.
Hoje, o espectro político vai além do simples eixo esquerda–direita, incluindo dimensões como:
- Autoritarismo vs. Liberdade: grau de controlo do Estado sobre a vida individual e as instituições;
- Intervenção Estatal vs. Livre Mercado: equilíbrio entre regulação económica e iniciativas privadas;
- Igualdade Social vs. Mérito e Responsabilidade Individual: ênfase na redistribuição de recursos ou na criação de incentivos pessoais.
Este modelo multidimensional ajuda a capturar melhor as posições dos partidos contemporâneos e as suas promessas de governação.
Visão Geral das Análises por Partido
Segue-se um resumo dos principais partidos políticos em Portugal, com destaque para a sua orientação ideológica segundo as dimensões de autoritarismo, nível de Intervenção estatal e grau de liberdade individual. Cada nome de partido estará ligado à respectiva análise detalhada.
| Partido | Orientação Ideológica | Nível de Intervenção Estatal | Grau de Liberdade Individual | |----------------------------------------|---------------------------------------------------------------------------------------|------------------------------|------------------------------| | AD – Aliança Democrática (PSD/CDS) | Centro-direita democrática (baixo autoritarismo / equilíbrio intervenção–mercado) | Médio | Médio | | PS – Partido Socialista | Centro-esquerda social-democrata (moderado autoritarismo / intervenção estatal) | Alto | Médio | | CDU – Coligação Democrática Unitária (PCP/PEV) | Esquerda comunista/eco-marxista (mais autoritário / forte intervenção) | Muito alto | Baixo | | IL – Iniciativa Liberal | Liberalismo clássico (muito baixa intervenção / alta liberdade) | Baixo | Muito alto | | Chega | Nacionalismo autoritário (controlo social elevado / mercado regulado com foco interno)| Médio | Baixo | | Livre | Esquerda progressista verde (baixa hierarquia / intervenção social) | Alto | Médio | | BE – Bloco de Esquerda | Esquerda democrática radical (moderado autoritarismo / intervenção forte) | Alto | Médio | | PAN – Pessoas-Animais-Natureza | Ambientalismo progressista (intervenção pragmática / foco em direitos e sustentabilidade) | Médio | Alto | | Ergue-te | Nacionalismo soberanista (autoritarismo elevado / intervenção seletiva com foco nacional) | Médio | Baixo | | ADN – Alternativa Democrática Nacional | Nacionalismo conservador (autoritarismo elevado / intervenção seletiva com foco nacional) | Médio | Baixo |
Análises Detalhadas dos Programas Eleitorais
Estas análises pretendem oferecer aos eleitores uma visão clara e objetiva das propostas de cada partido, facilitando decisões conscientes nas urnas. Ao focar-se nas promessas relacionadas com liberdades individuais, descentralização e crescimento económico, este conjunto de textos ajuda a compreender melhor o impacto potencial de cada escolha política.
Aliança Democrática (AD)
Partido Socialista (PS)
Coligação Democrática Unitária (CDU)
Iniciativa Liberal (IL)
Chega
Livre
Bloco de Esquerda (BE)
Pessoas,Animais e Natureza (PAN)
Alternativa Democrática Nacional (ADN)
Ergue-te
Photo by Brett Kunsch on Unsplash
-
 @ 8f69ac99:4f92f5fd
2025-05-02 08:42:53
@ 8f69ac99:4f92f5fd
2025-05-02 08:42:53O ADN (Alternativa Democrática Nacional) apresenta-se às eleições de 2025 com um programa orgulhosamente anti-sistema, culturalmente conservador e auto-descrito como “colocar os portugueses em primeiro lugar”. O seu programa soa a uma rutura radical com a política tradicional—misturando políticas familiares fortes, ceticismo em relação à moeda digital e retórica descentralizadora com prescrições morais rígidas e propostas de saneamento institucional.
Mas, sob a superfície, a visão de liberdade do partido é seletiva. O ADN defende a autonomia financeira, promove a transparência e propõe a redução da burocracia—mas também advoga a imposição estatal de normas culturais, o controlo do acesso a direitos e uma autoridade moral centralizada, levantando sérias dúvidas sobre a coerência na defesa da liberdade individual.
Os Pontos Positivos: Autonomia Financeira e Disciplina Institucional
Em algumas áreas, o ADN parece alinhar-se com princípios de liberdade económica e responsabilização institucional. Propõe:
- Acabar com o financiamento público dos partidos políticos, regalias dos deputados e as portas giratórias entre o jornalismo e o governo.
- Proteger o dinheiro físico e as criptomoedas descentralizadas da vigilância dos bancos centrais.
- Limitar despesas extraordinárias do Estado, reduzir a frota automóvel pública e combater as comissões bancárias abusivas.
Estas propostas respondem a preocupações reais com o excesso de poder estatal, a governação opaca e o controlo tecnocrático. Um Estado transparente e frugal, aliado a um sistema monetário baseado na troca voluntária, reflete instintos liberais genuínos.
As Contradições: Liberdade, Mas Só Para Alguns
O ADN promove valores como a liberdade, a família e a dignidade—mas impõe limites rígidos à forma como os indivíduos definem e expressam esses mesmos valores.
- O partido compromete-se a banir todo o conteúdo LGBT+ e a chamada “ideologia de género” do ensino público, a restringir os direitos de transição de género (especialmente para menores) e a revogar a legislação sobre aborto e eutanásia, mesmo quando baseada na escolha individual.
- Propõe ainda retirar o apoio estatal a organizações que defendem direitos ligados ao género ou identidade.
Aqui, a linha entre proteger as crianças e impor uma moral única torna-se difusa. O ADN não propõe apenas retirar a influência do Estado na educação—substitui-a por um filtro cultural rígido, imposto de cima. Ao fazê-lo, põe em risco a liberdade de consciência e a autoridade parental para quem não se conforma com a norma dominante.
Prioridade pelo Passaporte: Soberania à Custa da Igualdade de Acesso
O ADN defende de forma consistente a preferência por cidadãos portugueses no acesso à habitação pública, serviços sociais e apoios estatais. Embora popular, esta abordagem assume implicitamente que os bens públicos são privilégios, e não direitos ligados à contribuição individual ou necessidade.
Isto abre espaço para discriminação institucionalizada, independentemente do estatuto legal ou da participação fiscal. Uma sociedade verdadeiramente liberal assenta na igualdade perante a lei, e não na distribuição seletiva de benefícios com base na identidade.
Ceticismo Climático e Científico: Rejeição Sem Alternativa
O partido classifica a política climática como “fraude climática” e opõe-se à geoengenharia, embora defenda a energia nuclear e “mercados livres de energia”. No entanto, rejeitar por completo a intervenção climática—sem apresentar alternativas baseadas na inovação descentralizada—deixa um vazio onde poderia florescer uma verdadeira gestão ambiental voluntária e local.
Soluções ambientais baseadas na liberdade incluem conservação liderada por proprietários, precificação de carbono pelos mercados e autonomia energética local—não a negação dos riscos ou do consenso científico.
Referendos e Democracia Direta: Ferramentas Poderosas, Resultados Arriscados
O ADN propõe alargar o uso de referendos, contratos eleitorais vinculativos e maior consulta pública. Estas reformas descentralizam o poder no papel—mas sem salvaguardas constitucionais, correm o risco de se tornarem instrumentos de imposição da vontade da maioria, onde minorias impopulares ficam vulneráveis ao controlo plebiscitário.
Liberdade não é apenas “mais democracia”. É também proteger os direitos individuais contra abusos—tanto do Estado como da maioria.
Conclusão: A Liberdade Não Pode Ser Seletiva
O ADN promete soberania, transparência e responsabilidade—e, em algumas áreas, entrega. Mas o seu modelo mais abrangente impõe uma visão moral estreita, centraliza a autoridade cultural e define direitos com base na identidade e na tradição, em vez da universalidade.
Uma sociedade livre não protege apenas a tua família, a tua fé ou a tua moeda—protege também o direito do teu vizinho de viver de forma diferente.
Para quem procura verdadeira descentralização, associação voluntária e liberdade face à coerção—seja estatal ou cultural—é importante ponderar se a visão do ADN alarga a liberdade ou apenas transfere o controlo de Bruxelas para Lisboa, e de burocratas para vigilantes morais**.
Photo by Claudio Schwarz on Unsplash
-
 @ 8f69ac99:4f92f5fd
2025-05-02 08:35:48
@ 8f69ac99:4f92f5fd
2025-05-02 08:35:48O partido nacionalista Ergue-te apresenta uma crítica abrangente ao globalismo, ao multiculturalismo e às reformas sociais progressistas. O seu programa eleitoral para 2025 posiciona-se como uma defesa da “civilização portuguesa e europeia”, propondo o desmantelamento do enquadramento federal da UE, o regresso às leis de nacionalidade baseadas no ius sanguinis e a reversão de políticas que classifica como “ideologia de género” ou “suicídio cultural”.
Há que reconhecer ao Ergue-te a ênfase na soberania, na descentralização face a instituições supranacionais e na autodeterminação nacional—valores que ressoam com quem quer aproximar o poder das comunidades e afastá-lo de burocracias não eleitas. Mas o seu modelo de liberdade termina na fronteira nacional.
Uma vez resgatado o poder de Bruxelas, o programa do partido sugere que este seja centralizado em Lisboa—não para capacitar os cidadãos, mas para impor uma cultura nacional uniforme. O resultado não é descentralização, mas sim autoritarismo cultural sob uma bandeira nacionalista.
Descentralização da UE, Recentralização Interna
O Ergue-te rejeita o Tratado de Lisboa e defende uma confederação de nações europeias unidas apenas por acordos voluntários e revogáveis. Esta visão critica, com razão, a centralização crescente de poder na UE.
Contudo, embora o partido queira repelir o controlo externo, não demonstra o mesmo cepticismo em relação ao excesso de poder doméstico. Entre as suas propostas estão:
- Proibição da chamada “ideologia de género” em todas as escolas públicas.
- Revogação do casamento entre pessoas do mesmo sexo, da despenalização do aborto e das leis da eutanásia.
- Reintrodução de linguagem binária e baseada no sexo biológico na educação cívica.
- Fim do financiamento público a organizações que promovam valores “não tradicionais”.
Estas medidas substituem o domínio externo por uma moralidade estatal imposta internamente. A liberdade cultural não está mais protegida por ser legislada em Lisboa do que por ser decidida em Bruxelas.
Soberania sobre a Cidadania, Não Liberdade dentro dela
O Ergue-te propõe alterar a lei da nacionalidade portuguesa para um modelo baseado no sangue (ius sanguinis), limitando o acesso à cidadania a imigrantes e seus filhos, independentemente da sua integração ou contribuição para a sociedade.
Com esta proposta, o partido desvaloriza o princípio de que a cidadania deve assentar em direitos e responsabilidades individuais—e não em linhagem. A soberania torna-se assim um mecanismo de exclusão, e não uma base de participação cívica.
Ordem Moral pela Lei
Apresentada como uma defesa da “vida e da família”, a política social do partido visa anular décadas de liberalização legal. Defende:
- Fim do financiamento público ao aborto, salvo em situações médicas urgentes.
- Revogação da legislação sobre eutanásia.
- Anulação do casamento entre pessoas do mesmo sexo.
Embora apresentadas como salvaguarda da tradição, estas propostas implicam a codificação legal de uma visão moral única, à custa da autonomia pessoal e do pluralismo. A liberdade de escolher o próprio modelo familiar, as crenças ou decisões médicas é rejeitada em favor da conformidade imposta.
Imigração e Islão: Política Culturalmente Direccionada
O programa do Ergue-te opõe-se abertamente ao multiculturalismo e alerta para a “islamização da Europa”. Defende controles fronteiriços mais apertados e a prevenção da imigração não europeia, com o objectivo de preservar uma “homogeneidade cultural”.
Este discurso, envolto em retórica identitária, abre caminho para a punição colectiva e exclusão cultural. Confunde imigrantes com ideologias, negando-lhes a oportunidade de serem avaliados pelo seu mérito ou conduta. Assume ainda que a cultura nacional é estática e frágil—em vez de algo que as comunidades constroem e renegoceiam livremente.
Defesa e Política Externa: Um Duplo Critério
O partido apoia uma capacidade de defesa europeia, mas apenas como associação subordinada às forças armadas nacionais. Aponta a soberania militar como resposta a potências como os EUA ou a China—mas é vago quanto à forma como o nacionalismo militarizado promove a liberdade ou a paz.
A segurança não pode servir de pretexto para mobilização permanente nem para uma política fechada sobre si mesma. A verdadeira independência exige diplomacia, resiliência e abertura ao mundo—não apenas músculo militar.
Conclusão: A Liberdade Exige Mais do que uma Bandeira
O Ergue-te apresenta-se como defensor da soberania. Mas o seu programa sugere que a soberania pertence ao Estado, e não ao indivíduo. Combate a influência externa, mas convida à imposição interna. Diz defender a tradição, mas fá-lo por via da coerção, não do consentimento.
Uma política centrada na liberdade permite que as pessoas vivam de forma diferente, não apenas que resistam a Bruxelas. Dá espaço para que as famílias se formem nos seus próprios termos, para que os imigrantes se tornem vizinhos, e para que os cidadãos debatam em vez de obedecerem.
Na sua busca por ordem e identidade, o Ergue-te oferece controlo—não liberdade.
Photo by Claudio Schwarz on Unsplash
-
 @ 8f69ac99:4f92f5fd
2025-05-02 08:28:02
@ 8f69ac99:4f92f5fd
2025-05-02 08:28:02O partido Pessoas–Animais–Natureza (PAN) apresenta uma plataforma serena e voltada para o futuro nas legislativas de 2025—uma que combina consciência ecológica, bem-estar animal e reformas sociais progressistas com um surpreendente toque de pragmatismo económico. Da saúde mental ao salário mínimo, dos direitos dos animais à redução de emissões, o PAN aborda quase todas as áreas da política pública com um impulso moral unificador: proteger os vulneráveis—sejam humanos ou não.
Mas apesar da sua compaixão, o programa do PAN levanta uma questão central: pode uma sociedade expandir a liberdade confiando fortemente numa moralidade imposta pelo Estado e numa engenharia comportamental? Ou, mais directamente: quando a política pretende “fazer o bem”, quem decide o que isso significa—e até onde deve o Estado ir para o impor?
Acção Climática: Urgência de Cima para Baixo ou Autonomia Local?
A missão central do PAN é a acção climática. O partido opõe-se à exploração de combustíveis fósseis, defende uma transição total para as energias renováveis e apoia grandes investimentos no transporte público e na conservação da natureza.
Estes objectivos alinham-se com a resiliência a longo prazo—mas os métodos são quase exclusivamente liderados pelo Estado. Há pouca menção a instrumentos de mercado como o preço do carbono, a conservação baseada na propriedade privada ou a autonomia energética local. O plano parte do princípio de que o caminho é o controlo tecnocrático e o investimento centralizado.
Contudo, a liberdade prospera onde as soluções são descentralizadas, impulsionadas pela inovação privada, pela cooperação voluntária e pela experimentação de base. Ao manter o Estado no centro da reforma ecológica, o PAN corre o risco de reproduzir as mesmas estruturas de dependência que pretende ultrapassar.
Bem-Estar Animal: Uma Visão Ética com Ferramentas Coercivas
O PAN merece reconhecimento por ter trazido a protecção animal para o debate político nacional. O seu apelo à proibição da agropecuária industrial, à reforma legislativa e à integração da ética animal no ordenamento jurídico reflecte uma posição moral sincera.
Mas, novamente, o método escolhido é a proibição legal, e não a persuasão ou a evolução do mercado. O salto entre a preocupação ética e os mandatos de estilo de vida impostos—sobretudo por reguladores não eleitos—pode rapidamente resvalar para a coerção em vez da consciência. Uma sociedade livre deve acomodar visões diversas sobre alimentação, agricultura e ética, permitindo que os sinais do mercado e o discurso civil orientem os comportamentos, em vez de impor proibições generalizadas.
Política Social Progressista: Compaixão com Centralismo
O apoio do PAN à eutanásia, à reforma da saúde mental, às leis anti-discriminação e ao apoio à população idosa reflecte uma preocupação genuína com a inclusão social. O foco na saúde mental e no combate à solidão é particularmente humano.
No entanto, quase todas estas reformas são enquadradas como expansão de programas e mandatos estatais, em vez de iniciativas comunitárias, redes de entreajuda ou modelos de cuidado centrados na família. Há pouca ênfase em soluções voluntárias, parcerias com o sector privado ou iniciativas de base—apenas um apelo repetido, e repetitivo, a mais programas públicos, mais intervenção estatal e mais regulamentação.
Pragmatismo Económico: Uma Viragem Bem-Vinda (mas Incompleta)
Um dos elementos mais surpreendentes do PAN é a sua defesa da redução do IRC para 17% até 2028, da isenção de IVA em bens essenciais, e de benefícios fiscais para jovens trabalhadores. São raros sinais de liberalização económica—e revelam que o partido está atento às dificuldades causadas pela inflação e estagnação salarial.
Ainda assim, o PAN continua a assumir que o Estado deve ajustar comportamentos através de alavancas fiscais: incentivos, isenções, apoios dirigidos. A verdadeira liberdade económica implica simplificação fiscal, redução das distorções e confiança na ordem espontânea—não apenas redistribuir com um selo verde.
Independência Política: Aberto a Todos, Ligado a Todos?
O PAN afirma ser politicamente independente, colaborando com a esquerda e o centro consoante a convergência com a sua missão. Esta flexibilidade é louvável. No entanto, independência de alianças não equivale a independência de método. Ao longo do programa, o fio condutor é uma aposta na expansão institucional—e não na iniciativa pessoal.
Para um partido que defende a diversidade, há pouca margem para diversidade ideológica na forma como as pessoas vivem, trabalham e se relacionam com o mundo natural.
Conclusão: Ética sem Autoritarismo Seria Mais Forte
O PAN traz temas importantes para a mesa. A sua bússola ecológica e ética enriquece a democracia portuguesa. Mas a liberdade não pode ser usada apenas como instrumento para “boas causas”—deve ser um travão ao excesso de confiança do poder político motivado por causas.
Uma sociedade que cuida dos animais, do planeta e dos vulneráveis deve também confiar nos seus cidadãos para escolher como viver esses valores—em vez de os impor de cima.
No final, boas intenções não garantem liberdade. E a liberdade, quando bem defendida, alcança muitas vezes mais do que qualquer regulação poderia.
Photo by Claudio Schwarz on Unsplash
-
 @ 57d1a264:69f1fee1
2025-05-02 06:17:05
@ 57d1a264:69f1fee1
2025-05-02 06:17:05Simple design
For as long as I remember, I’ve believed in simple design as a principle in my practice. It feels fundamental to me when I think about good design.
At the same time, I see many successful examples of complex products in the world. So I decided to ask, what value is simple design really providing me and my work?
Is it nostalgia?
I sometimes wonder if simple design is rooted in nostalgia. An example I like to use is:
Imagine yourself in the year 1981. You just purchased a brand new desk calculator. You are excited because you should be able to do any type of paperwork calculations you can imagine on it.
As you start to use it for the first time, it immediately prompts you to update its software. After using it for a few calculations, it asks you to fill out a survey about your experience. One day in the middle of adding up your checkbook, it interrupts you to tell you about a new leather-bound desk calendar the company just released. Sometimes in the middle of a complex calculation, the calculator will lag and crash. You have to restart it often to fix the issue.
I have a feeling that a person in 1981 would think this is a terrible calculator. They purchased the device to perform their calculations, nothing more. Why is it requiring so much more of their attention and effort?
Focus
I think simple design often refers to a focused product. A product that does a specific task can sometimes do that task really well. Products that try to do many things can offer a lot of value, but rarely do all the things well.
Some people prefer to use specific tools for specific tasks. Others prefer a wide variety of features.
I think the benefits of using fewer products are often a major reason complex products are successful. They may not be focused, they might be lower quality as a result, but people can use them for a wide variety of applications.
You can open a can of beans with a Swiss Army Knife — it will get the job done.
Art and subjectivity
Maybe simple design is valuable for intangible reasons. There is an art to simplicity. There is a beauty to simplicity.
A user can see more of the product's intentionality. The creator chose to leave certain features out. They decided what to include. The product likely exudes more vision and personality.
That might be unnoticed by some, but very valuable to others who care about craft. People who value the experience as much as the result.
Ease of use
I think a true benefit of simple design is the effect it has on ease of use. The less things there are to do in a product, the more obvious the things you can do become.
A simple product requires less of a user. That means a user can stay focused on their own needs and use the product in ways they define. They will encounter boundaries which limit them. These limitations could drive some away, but some might be engaged to find new and creative ways of working.
When to abandon simple design
I think the sad news is simple design is ultimately a limiting factor of a product's growth. I think there are many examples of this throughout the course of history (i.e. Ello vs Facebook, Rdio vs Spotify, Simplenote vs Notion, VSCO vs Instagram, Clear vs Things, Peach vs Twitter, etc). At the same time, I think 'simple design' does provide an entry point to successfully define what a product is.
The biggest challenge is continuing to evoke the benefits of simple design in an established product, while allowing a product to evolve and grow to meet its users' needs. That is a balancing act that very few products have ever achieved, but feels like an ideal that successful products should strive for.
One of Charlie Deets Writings
originally posted at https://stacker.news/items/969089
-
 @ 57d1a264:69f1fee1
2025-05-02 06:04:19
@ 57d1a264:69f1fee1
2025-05-02 06:04:19After being featured in the NY Times and WSJ, New York City officially opens a major addition to Central Park, the Davis Center at the Harlem Meer. Designed by architect Susan T Rodriguez in collaboration with Mitchell Giurgola, the renovation project replaces the old Lasker Rink and pool with a recreational facility that’s built directly into the landscape, restoring nature, reconnecting paths, and creating a year-round space for community activity. At the heart of the new design is a transformative water feature that shifts with the seasons, from a skating rink in winter to a lush green lawn in spring and fall and a pool in the summer.
The center’s new oval-shaped pool sits lower than the old one, surrounded by a gently sloped grassy berm. In winter, the pool becomes an ice-skating rink, making the site a destination in every season. A splash pad at the end of the water feature offers extra water play in the summer. By integrating the design into the natural shape of the land, the architects were able to open up the space around the pool and allow the landscape to flow around it, resulting in a setting that feels like it’s always been there.
Sustainability was a core part of the project. The building is expected to earn LEED Gold certification, thanks to features like passive ventilation, locally sourced stone and wood, energy-efficient systems, and a roof that absorbs rainwater. Bird-safe glass helps protect local wildlife, and recycled materials from the old building were reused during construction. Even more important, the new center supports free and low-cost programming year-round, including education, nature walks, community events, and recreation. It’s designed to welcome all kinds of visitors—from families and school groups to joggers, birdwatchers, and casual parkgoers.
Continue reading: https://www.designboom.com/architecture/giant-pool-new-york-central-park-new-davis-center-susan-t-rodriguez-mitchell-giurgola-04-24-2025/
originally posted at https://stacker.news/items/969086
-
 @ 57d1a264:69f1fee1
2025-05-02 05:16:39
@ 57d1a264:69f1fee1
2025-05-02 05:16:39Large Language Models (LLMs) have transformed software engineering, but their application to physical engineering domains remains underexplored. This paper evaluates LLMs' capabilities in high-powered rocketry design through RocketBench, a benchmark connecting LLMs to high-fidelity rocket simulations. We test models on two increasingly complex design tasks: target altitude optimization and precision landing challenges. Our findings reveal that while state-of-the-art LLMs demonstrate strong baseline engineering knowledge, they struggle to iterate on their designs when given simulation results and ultimately plateau below human performance levels. However, when enhanced with reinforcement learning (RL), we show that a 7B parameter model outperforms both SoTA foundation models and human experts. This research demonstrates that RL-trained LLMs can serve as effective tools for complex engineering optimization, potentially transforming engineering domains beyond software development.
PDF: https://arxiv.org/pdf/2504.19394
Source: https://arxiv.org/abs/2504.19394
originally posted at https://stacker.news/items/969083
-
 @ 826e9f89:ffc5c759
2025-04-12 21:34:24
@ 826e9f89:ffc5c759
2025-04-12 21:34:24What follows began as snippets of conversations I have been having for years, on and off, here and there. It will likely eventually be collated into a piece I have been meaning to write on “payments” as a whole. I foolishly started writing this piece years ago, not realizing that the topic is gargantuan and for every week I spend writing it I have to add two weeks to my plan. That may or may not ever come to fruition, but in the meantime, Tether announced it was issuing on Taproot Assets and suddenly everybody is interested again. This is as good a catalyst as any to carve out my “stablecoin thesis”, such as it exists, from “payments”, and put it out there for comment and feedback.
In contrast to the “Bitcoiner take” I will shortly revert to, I invite the reader to keep the following potential counterargument in mind, which might variously be termed the “shitcoiner”, “realist”, or “cynical” take, depending on your perspective: that stablecoins have clear product-market-fit. Now, as a venture capitalist and professional thinkboi focusing on companies building on Bitcoin, I obviously think that not only is Bitcoin the best money ever invented and its monetization is pretty much inevitable, but that, furthermore, there is enormous, era-defining long-term potential for a range of industries in which Bitcoin is emerging as superior technology, even aside from its role as money. But in the interest not just of steelmanning but frankly just of honesty, I would grudgingly agree with the following assessment as of the time of writing: the applications of crypto (inclusive of Bitcoin but deliberately wider) that have found product-market-fit today, and that are not speculative bets on future development and adoption, are: Bitcoin as savings technology, mining as a means of monetizing energy production, and stablecoins.
I think there are two typical Bitcoiner objections to stablecoins of significantly greater importance than all others: that you shouldn’t be supporting dollar hegemony, and that you don’t need a blockchain. I will elaborate on each of these, and for the remainder of the post will aim to produce a synthesis of three superficially contrasting (or at least not obviously related) sources of inspiration: these objections, the realisation above that stablecoins just are useful, and some commentary on technical developments in Bitcoin and the broader space that I think inform where things are likely to go. As will become clear as the argument progresses, I actually think the outcome to which I am building up is where things have to go. I think the technical and economic incentives at play make this an inevitability rather than a “choice”, per se. Given my conclusion, which I will hold back for the time being, this is a fantastically good thing, hence I am motivated to write this post at all!
Objection 1: Dollar Hegemony
I list this objection first because there isn’t a huge amount to say about it. It is clearly a normative position, and while I more or less support it personally, I don’t think that it is material to the argument I am going on to make, so I don’t want to force it on the reader. While the case for this objection is probably obvious to this audience (isn’t the point of Bitcoin to destroy central banks, not further empower them?) I should at least offer the steelman that there is a link between this and the realist observation that stablecoins are useful. The reason they are useful is because people prefer the dollar to even shitter local fiat currencies. I don’t think it is particularly fruitful to say that they shouldn’t. They do. Facts don’t care about your feelings. There is a softer bridging argument to be made here too, to the effect that stablecoins warm up their users to the concept of digital bearer (ish) assets, even though these particular assets are significantly scammier than Bitcoin. Again, I am just floating this, not telling the reader they should or shouldn’t buy into it.
All that said, there is one argument I do want to put my own weight behind, rather than just float: stablecoin issuance is a speculative attack on the institution of fractional reserve banking. A “dollar” Alice moves from JPMorgan to Tether embodies two trade-offs from Alice’s perspective: i) a somewhat opaque profile on the credit risk of the asset: the likelihood of JPMorgan ever really defaulting on deposits vs the operator risk of Tether losing full backing and/or being wrench attacked by the Federal Government and rugging its users. These risks are real but are almost entirely political. I’m skeptical it is meaningful to quantify them, but even if it is, I am not the person to try to do it. Also, more transparently to Alice, ii) far superior payment rails (for now, more on this to follow).
However, from the perspective of the fiat banking cartel, fractional reserve leverage has been squeezed. There are just as many notional dollars in circulation, but there the backing has been shifted from levered to unlevered issuers. There are gradations of relevant objections to this: while one might say, Tether’s backing comes from Treasuries, so you are directly funding US debt issuance!, this is a bit silly in the context of what other dollars one might hold. It’s not like JPMorgan is really competing with the Treasury to sell credit into the open market. Optically they are, but this is the core of the fiat scam. Via the guarantees of the Federal Reserve System, JPMorgan can sell as much unbacked credit as it wants knowing full well the difference will be printed whenever this blows up. Short-term Treasuries are also JPMorgan’s most pristine asset safeguarding its equity, so the only real difference is that Tether only holds Treasuries without wishing more leverage into existence. The realization this all builds up to is that, by necessity,
Tether is a fully reserved bank issuing fiduciary media against the only dollar-denominated asset in existence whose value (in dollar terms) can be guaranteed. Furthermore, this media arguably has superior “moneyness” to the obvious competition in the form of US commercial bank deposits by virtue of its payment rails.
That sounds pretty great when you put it that way! Of course, the second sentence immediately leads to the second objection, and lets the argument start to pick up steam …
Objection 2: You Don’t Need a Blockchain
I don’t need to explain this to this audience but to recap as briefly as I can manage: Bitcoin’s value is entirely endogenous. Every aspect of “a blockchain” that, out of context, would be an insanely inefficient or redundant modification of a “database”, in context is geared towards the sole end of enabling the stability of this endogenous value. Historically, there have been two variations of stupidity that follow a failure to grok this: i) “utility tokens”, or blockchains with native tokens for something other than money. I would recommend anybody wanting a deeper dive on the inherent nonsense of a utility token to read Only The Strong Survive, in particular Chapter 2, Crypto Is Not Decentralized, and the subsection, Everything Fights For Liquidity, and/or Green Eggs And Ham, in particular Part II, Decentralized Finance, Technically. ii) “real world assets” or, creating tokens within a blockchain’s data structure that are not intended to have endogenous value but to act as digital quasi-bearer certificates to some or other asset of value exogenous to this system. Stablecoins are in this second category.
RWA tokens definitionally have to have issuers, meaning some entity that, in the real world, custodies or physically manages both the asset and the record-keeping scheme for the asset. “The blockchain” is at best a secondary ledger to outsource ledger updates to public infrastructure such that the issuer itself doesn’t need to bother and can just “check the ledger” whenever operationally relevant. But clearly ownership cannot be enforced in an analogous way to Bitcoin, under both technical and social considerations. Technically, Bitcoin’s endogenous value means that whoever holds the keys to some or other UTXOs functionally is the owner. Somebody else claiming to be the owner is yelling at clouds. Whereas, socially, RWA issuers enter a contract with holders (whether legally or just in terms of a common-sense interpretation of the transaction) such that ownership of the asset issued against is entirely open to dispute. That somebody can point to “ownership” of the token may or may not mean anything substantive with respect to the physical reality of control of the asset, and how the issuer feels about it all.
And so, one wonders, why use a blockchain at all? Why doesn’t the issuer just run its own database (for the sake of argument with some or other signature scheme for verifying and auditing transactions) given it has the final say over issuance and redemption anyway? I hinted at an answer above: issuing on a blockchain outsources this task to public infrastructure. This is where things get interesting. While it is technically true, given the above few paragraphs, that, you don’t need a blockchain for that, you also don’t need to not use a blockchain for that. If you want to, you can.
This is clearly the case given stablecoins exist at all and have gone this route. If one gets too angry about not needing a blockchain for that, one equally risks yelling at clouds! And, in fact, one can make an even stronger argument, more so from the end users’ perspective. These products do not exist in a vacuum but rather compete with alternatives. In the case of stablecoins, the alternative is traditional fiat money, which, as stupid as RWAs on a blockchain are, is even dumber. It actually is just a database, except it’s a database that is extremely annoying to use, basically for political reasons because the industry managing these private databases form a cartel that never needs to innovate or really give a shit about its customers at all. In many, many cases, stablecoins on blockchains are dumb in the abstract, but superior to the alternative methods of holding and transacting in dollars existing in other forms. And note, this is only from Alice’s perspective of wanting to send and receive, not a rehashing of the fractional reserve argument given above. This is the essence of their product-market-fit. Yell at clouds all you like: they just are useful given the alternative usually is not Bitcoin, it’s JPMorgan’s KYC’d-up-the-wazoo 90s-era website, more than likely from an even less solvent bank.
So where does this get us? It might seem like we are back to “product-market-fit, sorry about that” with Bitcoiners yelling about feelings while everybody else makes do with their facts. However, I think we have introduced enough material to move the argument forward by incrementally incorporating the following observations, all of which I will shortly go into in more detail: i) as a consequence of making no technical sense with respect to what blockchains are for, today’s approach won’t scale; ii) as a consequence of short-termist tradeoffs around socializing costs, today’s approach creates an extremely unhealthy and arguably unnatural market dynamic in the issuer space; iii) Taproot Assets now exist and handily address both points i) and ii), and; iv) eCash is making strides that I believe will eventually replace even Taproot Assets.
To tease where all this is going, and to get the reader excited before we dive into much more detail: just as Bitcoin will eat all monetary premia, Lightning will likely eat all settlement, meaning all payments will gravitate towards routing over Lightning regardless of the denomination of the currency at the edges. Fiat payments will gravitate to stablecoins to take advantage of this; stablecoins will gravitate to TA and then to eCash, and all of this will accelerate hyperbitcoinization by “bitcoinizing” payment rails such that an eventual full transition becomes as simple as flicking a switch as to what denomination you want to receive.
I will make two important caveats before diving in that are more easily understood in light of having laid this groundwork: I am open to the idea that it won’t be just Lightning or just Taproot Assets playing the above roles. Without veering into forecasting the entire future development of Bitcoin tech, I will highlight that all that really matters here are, respectively: a true layer 2 with native hashlocks, and a token issuance scheme that enables atomic routing over such a layer 2 (or combination of such). For the sake of argument, the reader is welcome to swap in “Ark” and “RGB” for “Lightning” and “TA” both above and in all that follows. As far as I can tell, this makes no difference to the argument and is even exciting in its own right. However, for the sake of simplicity in presentation, I will stick to “Lightning” and “TA” hereafter.
1) Today’s Approach to Stablecoins Won’t Scale
This is the easiest to tick off and again doesn’t require much explanation to this audience. Blockchains fundamentally don’t scale, which is why Bitcoin’s UTXO scheme is a far better design than ex-Bitcoin Crypto’s’ account-based models, even entirely out of context of all the above criticisms. This is because Bitcoin transactions can be batched across time and across users with combinations of modes of spending restrictions that provide strong economic guarantees of correct eventual net settlement, if not perpetual deferral. One could argue this is a decent (if abstrusely technical) definition of “scaling” that is almost entirely lacking in Crypto.
What we see in ex-Bitcoin crypto is so-called “layer 2s” that are nothing of the sort, forcing stablecoin schemes in these environments into one of two equally poor design choices if usage is ever to increase: fees go higher and higher, to the point of economic unviability (and well past it) as blocks fill up, or move to much more centralized environments that increasingly are just databases, and hence which lose the benefits of openness thought to be gleaned by outsourcing settlement to public infrastructure. This could be in the form of punting issuance to a bullshit “layer 2” that is a really a multisig “backing” a private execution environment (to be decentralized any daw now) or an entirely different blockchain that is just pretending even less not to be a database to begin with. In a nutshell, this is a decent bottom-up explanation as to why Tron has the highest settlement of Tether.
This also gives rise to the weirdness of “gas tokens” - assets whose utility as money is and only is in the form of a transaction fee to transact a different kind of money. These are not quite as stupid as a “utility token,” given at least they are clearly fulfilling a monetary role and hence their artificial scarcity can be justified. But they are frustrating from Bitcoiners’ and users’ perspectives alike: users would prefer to pay transaction fees on dollars in dollars, but they can’t because the value of Ether, Sol, Tron, or whatever, is the string and bubblegum that hold their boondoggles together. And Bitcoiners wish this stuff would just go away and stop distracting people, whereas this string and bubblegum is proving transiently useful.
All in all, today’s approach is fine so long as it isn’t being used much. It has product-market fit, sure, but in the unenviable circumstance that, if it really starts to take off, it will break, and even the original users will find it unusable.
2) Today’s Approach to Stablecoins Creates an Untenable Market Dynamic
Reviving the ethos of you don’t need a blockchain for that, notice the following subtlety: while the tokens representing stablecoins have value to users, that value is not native to the blockchain on which they are issued. Tether can (and routinely does) burn tokens on Ethereum and mint them on Tron, then burn on Tron and mint on Solana, and so on. So-called blockchains “go down” and nobody really cares. This makes no difference whatsoever to Tether’s own accounting, and arguably a positive difference to users given these actions track market demand. But it is detrimental to the blockchain being switched away from by stripping it of “TVL” that, it turns out, was only using it as rails: entirely exogenous value that leaves as quickly as it arrived.
One underdiscussed and underappreciated implication of the fact that no value is natively running through the blockchain itself is that, in the current scheme, both the sender and receiver of a stablecoin have to trust the same issuer. This creates an extremely powerful network effect that, in theory, makes the first-to-market likely to dominate and in practice has played out exactly as this theory would suggest: Tether has roughly 80% of the issuance, while roughly 19% goes to the political carve-out of USDC that wouldn’t exist at all were it not for government interference. Everybody else combined makes up the final 1%.
So, Tether is a full reserve bank but also has to be everybody’s bank. This is the source of a lot of the discomfort with Tether, and which feeds into the original objection around dollar hegemony, that there is an ill-defined but nonetheless uneasy feeling that Tether is slowly morphing into a CBDC. I would argue this really has nothing to do with Tether’s own behavior but rather is a consequence of the market dynamic inevitably created by the current stablecoin scheme. There is no reason to trust any other bank because nobody really wants a bank, they just want the rails. They want something that will retain a nominal dollar value long enough to spend it again. They don’t care what tech it runs on and they don’t even really care about the issuer except insofar as having some sense they won’t get rugged.
Notice this is not how fiat works. Banks can, of course, settle between each other, thus enabling their users to send money to customers of other banks. This settlement function is actually the entire point of central banks, less the money printing and general corruption enabled (we might say, this was the historical point of central banks, which have since become irredeemably corrupted by this power). This process is clunkier than stablecoins, as covered above, but the very possibility of settlement means there is no gigantic network effect to being the first commercial issuer of dollar balances. If it isn’t too triggering to this audience, one might suggest that the money printer also removes the residual concern that your balances might get rugged! (or, we might again say, you guarantee you don’t get rugged in the short term by guaranteeing you do get rugged in the long term).
This is a good point at which to introduce the unsettling observation that broader fintech is catching on to the benefits of stablecoins without any awareness whatsoever of all the limitations I am outlining here. With the likes of Stripe, Wise, Robinhood, and, post-Trump, even many US megabanks supposedly contemplating issuing stablecoins (obviously within the current scheme, not the scheme I am building up to proposing), we are forced to boggle our minds considering how on earth settlement is going to work. Are they going to settle through Ether? Well, no, because i) Ether isn’t money, it’s … to be honest, I don’t think anybody really knows what it is supposed to be, or if they once did they aren’t pretending anymore, but anyway, Stripe certainly hasn’t figured that out yet so, ii) it won’t be possible to issue them on layer 1s as soon as there is any meaningful volume, meaning they will have to route through “bullshit layer 2 wrapped Ether token that is really already a kind of stablecoin for Ether.”
The way they are going to try to fix this (anybody wanna bet?) is routing through DEXes, which is so painfully dumb you should be laughing and, if you aren’t, I would humbly suggest you don’t get just how dumb it is. What this amounts to is plugging the gap of Ether’s lack of moneyness (and wrapped Ether’s hilarious lack of moneyness) with … drum roll … unknowable technical and counterparty risk and unpredictable cost on top of reverting to just being a database. So, in other words, all of the costs of using a blockchain when you don’t strictly need to, and none of the benefits. Stripe is going to waste billions of dollars getting sandwich attacked out of some utterly vanilla FX settlement it is facilitating for clients who have even less of an idea what is going on and why North Korea now has all their money, and will eventually realize they should have skipped their shitcoin phase and gone straight to understanding Bitcoin instead …
3) Bitcoin (and Taproot Assets) Fixes This
To tie together a few loose ends, I only threw in the hilariously stupid suggestion of settling through wrapped Ether on Ether on Ether in order to tee up the entirely sensible suggestion of settling through Lightning. Again, not that this will be new to this audience, but while issuance schemes have been around on Bitcoin for a long time, the breakthrough of Taproot Assets is essentially the ability to atomically route through Lightning.
I will admit upfront that this presents a massive bootstrapping challenge relative to the ex-Bitcoin Crypto approach, and it’s not obvious to me if or how this will be overcome. I include this caveat to make it clear I am not suggesting this is a given. It may not be, it’s just beyond the scope of this post (or frankly my ability) to predict. This is a problem for Lightning Labs, Tether, and whoever else decides to step up to issue. But even highlighting this as an obvious and major concern invites us to consider an intriguing contrast: scaling TA stablecoins is hardest at the start and gets easier and easier thereafter. The more edge liquidity there is in TA stables, the less of a risk it is for incremental issuance; the more TA activity, the more attractive deploying liquidity is into Lightning proper, and vice versa. With apologies if this metaphor is even more confusing than it is helpful, one might conceive of the situation as being that there is massive inertia to bootstrap, but equally there could be positive feedback in driving the inertia to scale. Again, I have no idea, and it hasn’t happened yet in practice, but in theory it’s fun.
More importantly to this conversation, however, this is almost exactly the opposite dynamic to the current scheme on other blockchains, which is basically free to start, but gets more and more expensive the more people try to use it. One might say it antiscales (I don’t think that’s a real word, but if Taleb can do it, then I can do it too!).
Furthermore, the entire concept of “settling in Bitcoin” makes perfect sense both economically and technically: economically because Bitcoin is money, and technically because it can be locked in an HTLC and hence can enable atomic routing (i.e. because Lightning is a thing). This is clearly better than wrapped Eth on Eth on Eth or whatever, but, tantalisingly, is better than fiat too! The core message of the payments tome I may or may not one day write is (or will be) that fiat payments, while superficially efficient on the basis of centralized and hence costless ledger amendments, actually have a hidden cost in the form of interbank credit. Many readers will likely have heard me say this multiple times and in multiple settings but, contrary to popular belief, there is no such thing as a fiat debit. Even if styled as a debit, all fiat payments are credits and all have credit risk baked into their cost, even if that is obscured and pushed to the absolute foundational level of money printing to keep banks solvent and hence keep payment channels open.
Furthermore! this enables us to strip away the untenable market dynamic from the point above. The underappreciated and underdiscussed flip side of the drawback of the current dynamic that is effectively fixed by Taproot Assets is that there is no longer a mammoth network effect to a single issuer. Senders and receivers can trust different issuers (i.e. their own banks) because those banks can atomically settle a single payment over Lightning. This does not involve credit. It is arguably the only true debit in the world across both the relevant economic and technical criteria: it routes through money with no innate credit risk, and it does so atomically due to that money’s native properties.
Savvy readers may have picked up on a seed I planted a while back and which can now delightfully blossom:
This is what Visa was supposed to be!
Crucially, this is not what Visa is now. Visa today is pretty much the bank that is everybody’s counterparty, takes a small credit risk for the privilege, and oozes free cash flow bottlenecking global consumer payments.
But if you read both One From Many by Dee Hock (for a first person but pretty wild and extravagant take) and Electronic Value Exchange by David Stearns (for a third person, drier, but more analytical and historically contextualized take) or if you are just intimately familiar with the modern history of payments for whatever other reason, you will see that the role I just described for Lightning in an environment of unboundedly many banks issuing fiduciary media in the form of stablecoins is exactly what Dee Hock wanted to create when he envisioned Visa:
A neutral and open layer of value settlement enabling banks to create digital, interbank payment schemes for their customers at very low cost.
As it turns out, his vision was technically impossible with fiat, hence Visa, which started as a cooperative amongst member banks, was corrupted into a duopolistic for-profit rent seeker in curious parallel to the historical path of central banks …
4) eCash
To now push the argument to what I think is its inevitable conclusion, it’s worth being even more vigilant on the front of you don’t need a blockchain for that. I have argued that there is a role for a blockchain in providing a neutral settlement layer to enable true debits of stablecoins. But note this is just a fancy and/or stupid way of saying that Bitcoin is both the best money and is programmable, which we all knew anyway. The final step is realizing that, while TA is nice in terms of providing a kind of “on ramp” for global payments infrastructure as a whole to reorient around Lightning, there is some path dependence here in assuming (almost certainly correctly) that the familiarity of stablecoins as “RWA tokens on a blockchain” will be an important part of the lure.
But once that transition is complete, or is well on its way to being irreversible, we may as well come full circle and cut out tokens altogether. Again, you really don’t need a blockchain for that, and the residual appeal of better rails has been taken care of with the above massive detour through what I deem to be the inevitability of Lightning as a settlement layer. Just as USDT on Tron arguably has better moneyness than a JPMorgan balance, so a “stablecoin” as eCash has better moneyness than as a TA given it is cheaper, more private, and has more relevantly bearer properties (in other words, because it is cash). The technical detail that it can be hashlocked is really all you need to tie this all together. That means it can be atomically locked into a Lightning routed debit to the recipient of a different issuer (or “mint” in eCash lingo, but note this means the same thing as what we have been calling fully reserved banks). And the economic incentive is pretty compelling too because, for all their benefits, there is still a cost to TAs given they are issued onchain and they require asset-specific liquidity to route on Lightning. Once the rest of the tech is in place, why bother? Keep your Lightning connectivity and just become a mint.
What you get at that point is dramatically superior private database to JPMorgan with the dramatically superior public rails of Lightning. There is nothing left to desire from “a blockchain” besides what Bitcoin is fundamentally for in the first place: counterparty-risk-free value settlement.
And as a final point with a curious and pleasing echo to Dee Hock at Visa, Calle has made the point repeatedly that David Chaum’s vision for eCash, while deeply philosophical besides the technical details, was actually pretty much impossible to operate on fiat. From an eCash perspective, fiat stablecoins within the above infrastructure setup are a dramatic improvement on anything previously possible. But, of course, they are a slippery slope to Bitcoin regardless …
Objections Revisited
As a cherry on top, I think the objections I highlighted at the outset are now readily addressed – to the extent the reader believes what I am suggesting is more or less a technical and economic inevitability, that is. While, sure, I’m not particularly keen on giving the Treasury more avenues to sell its welfare-warfare shitcoin, on balance the likely development I’ve outlined is an enormous net positive: it’s going to sell these anyway so I prefer a strong economic incentive to steadily transition not only to Lightning as payment rails but eCash as fiduciary media, and to use “fintech” as a carrot to induce a slow motion bank run.
As alluded to above, once all this is in place, the final step to a Bitcoin standard becomes as simple as an individual’s decision to want Bitcoin instead of fiat. On reflection, this is arguably the easiest part! It's setting up all the tech that puts people off, so trojan-horsing them with “faster, cheaper payment rails” seems like a genius long-term strategy.
And as to “needing a blockchain” (or not), I hope that is entirely wrapped up at this point. The only blockchain you need is Bitcoin, but to the extent people are still confused by this (which I think will take decades more to fully unwind), we may as well lean into dazzling them with whatever innovation buzzwords and decentralization theatre they were going to fall for anyway before realizing they wanted Bitcoin all along.
Conclusion
Stablecoins are useful whether you like it or not. They are stupid in the abstract but it turns out fiat is even stupider, on inspection. But you don’t need a blockchain, and using one as decentralization theatre creates technical debt that is insurmountable in the long run. Blockchain-based stablecoins are doomed to a utility inversely proportional to their usage, and just to rub it in, their ill-conceived design practically creates a commercial dynamic that mandates there only ever be a single issuer.
Given they are useful, it seems natural that this tension is going to blow up at some point. It also seems worthwhile observing that Taproot Asset stablecoins have almost the inverse problem and opposite commercial dynamic: they will be most expensive to use at the outset but get cheaper and cheaper as their usage grows. Also, there is no incentive towards a monopoly issuer but rather towards as many as are willing to try to operate well and provide value to their users.
As such, we can expect any sizable growth in stablecoins to migrate to TA out of technical and economic necessity. Once this has happened - or possibly while it is happening but is clearly not going to stop - we may as well strip out the TA component and just use eCash because you really don’t need a blockchain for that at all. And once all the money is on eCash, deciding you want to denominate it in Bitcoin is the simplest on-ramp to hyperbitcoinization you can possibly imagine, given we’ve spent the previous decade or two rebuilding all payments tech around Lightning.
Or: Bitcoin fixes this. The End.
- Allen, #892,125
thanks to Marco Argentieri, Lyn Alden, and Calle for comments and feedback
-
 @ dbc27e2e:b1dd0b0b
2025-04-05 20:44:00
@ dbc27e2e:b1dd0b0b
2025-04-05 20:44:00This method focuses on the amount of water in the first pour, which ultimately defines the coffee’s acidity and sweetness (more water = more acidity, less water = more sweetness). For the remainder of the brew, the water is divided into equal parts according to the strength you wish to attain.

Dose:
20g coffee (Coarse ground coffee) 300mL water (92°C / 197.6°F) Time: 3:30Instructions:
- Pour 1: 0:00 > 50mL (42% of 120mL = 40% of total – less water in the ratio, targeting sweetness.)
- Pour 2: 0:45 > 70mL (58% of 120mL = 40% of total – the top up for 40% of total.)
- Pour 3: 1:30 > 60mL (The remaining water is 180mL / 3 pours = 60mL per pour)
- Pour 4: 2:10 > 60mL
- Pour 5: 2:40 > 60mL
- Remove the V60 at 3:30
-
 @ 3ffac3a6:2d656657
2025-05-02 03:50:51
@ 3ffac3a6:2d656657
2025-05-02 03:50:51Introduction: Don't Despair—This Can Be Fixed (But Don't Reboot Yet)
Running ZFS on a Raspberry Pi offers powerful features for home servers and personal NAS setups. But with power comes complexity, and in recent months, a quiet pitfall has emerged for Pi users who track kernel updates closely: upgrading to an unsupported kernel version breaks ZFS.
⚠️ Important Warning: If you've just upgraded your kernel and you're using ZFS, do not reboot yet. Rebooting without a working ZFS module can leave your system unbootable—even if you don't have critical partitions on ZFS. The system may hang because it tries to load the missing ZFS kernel module during boot and fails, halting the boot process.
If you're already facing a broken setup or can't boot — don't panic. This guide outlines both the worst-case scenario and the ideal recovery strategy. Whether you're locked out or preparing for a smooth upgrade, we've got you covered.
The Problem: A Kernel Update Too Far
As of ZFS version 2.2.3 (used in Debian-based Raspberry Pi OS), the filesystem supports Linux kernels up to 6.7. However, Raspberry Pi OS backports recently began shipping 6.12.x kernels. If you upgrade to 6.12 without precautions:
- ZFS will fail to compile against the new kernel
- DKMS errors will appear during package updates
- Your ZFS module will be missing after reboot
- Your Raspberry Pi may fail to boot, even without ZFS-mounted root or critical paths, simply due to systemd or boot scripts expecting the kernel module to be present
Example ZFS Compilation Error:
During package updates or installs, you'll see something like:
checking whether bdev_open_by_path() exists... configure: error: *** None of the expected "blkdev_get_by_path()" interfaces were detected. *** This may be because your kernel version is newer than what is *** supported, or you are using a patched custom kernel with *** incompatible modifications. *** *** ZFS Version: zfs-2.2.3-1~bpo12+1~rpt1 *** Compatible Kernels: 3.10 - 6.7This error means ZFS cannot build its kernel module against Linux 6.12.x, making it unusable.
Why This Happens: The Version Trap
The key problem is that ZFS 2.2.3 remains installed even after a kernel upgrade, and it doesn't get upgraded automatically during
apt upgrade. Since ZFS 2.2.3 only supports up to kernel 6.7, it fails to compile against 6.12.x.However, if you remove and then reinstall ZFS, the package manager installs ZFS 2.3.1, which does support Linux kernel 6.12.x. This version transition is what resolves the issue — but only if you explicitly purge and reinstall ZFS.
Worst Case: The System That Wouldn’t Boot
After upgrading the kernel and rebooting, the system failed to boot properly. It showed errors like:
cannot open access to console, the root account is locked
Although the system did not have critical filesystems on ZFS, the boot process still stalled because system services attempted to load the ZFS kernel module, which was no longer available. This resulted in an unrecoverable boot failure.
The only way forward was to reformat and reinstall Raspberry Pi OS. However, the default Raspberry Pi OS image still comes with a 6.6.x kernel, which is incompatible with ZFS 2.3.1 and newer kernels unless upgraded. Therefore, the recovery process requires one crucial step:
- First, perform a full system upgrade:
sudo apt update && sudo apt full-upgradeThis brings the kernel up to 6.12.x.
- Then, reinstall ZFS:
sudo apt install zfs-dkms zfsutils-linuxOnce this is complete, your system will be running kernel 6.12 with ZFS 2.3.1, and you can safely import your pools and resume operations.
Best Case Recovery: Clean Cut, Clean Upgrade
For users who can still log into their system, here's the cleanest and safest sequence to move forward:
- Stop all services using ZFS, including Docker, NFS, Samba, backup tools, etc.
- Export all ZFS pools:
sudo zpool export -a3. Disable swap if it lives on a ZFS vdev:sudo swapoff /dev/sdXn4. Purge ZFS packages:sudo apt purge zfsutils-linux zfs-dkms zfs-zed sudo rm -rf /usr/src/zfs* /var/lib/dkms/zfs5. Update the kernel to the desired version:sudo apt update && sudo apt full-upgrade6. Reboot into the new kernel:sudo reboot7. Reinstall ZFS:sudo apt install zfs-dkms zfsutils-linux8. Import your pool(s):sudo zpool import poolname9. Restart services that depend on ZFS.
Final Notes: Prevention Is Better Than Recovery
To avoid this issue in the future:
- Hold your current working kernel version:
sudo apt-mark hold linux-image-rpi-v8 linux-headers-rpi-v8* Or track ZFS GitHub for kernel compatibility before upgrading * Or test upgrades on a second Pi or cloned SD card before rolling them out to production
Conclusion: A Solvable Trap
ZFS on the Raspberry Pi remains a powerful option, but it demands careful version tracking. If you upgrade responsibly, or recover cleanly as described above, you can continue benefiting from advanced features like snapshots, send/receive, and compression even on this tiny powerhouse.
Don’t let a kernel update ruin your storage plans—with preparation, the Pi + ZFS combo can remain stable and strong.
-
 @ c631e267:c2b78d3e
2025-04-04 18:47:27
@ c631e267:c2b78d3e
2025-04-04 18:47:27Zwei mal drei macht vier, \ widewidewitt und drei macht neune, \ ich mach mir die Welt, \ widewide wie sie mir gefällt. \ Pippi Langstrumpf
Egal, ob Koalitionsverhandlungen oder politischer Alltag: Die Kontroversen zwischen theoretisch verschiedenen Parteien verschwinden, wenn es um den Kampf gegen politische Gegner mit Rückenwind geht. Wer den Alteingesessenen die Pfründe ernsthaft streitig machen könnte, gegen den werden nicht nur «Brandmauern» errichtet, sondern der wird notfalls auch strafrechtlich verfolgt. Doppelstandards sind dabei selbstverständlich inklusive.
In Frankreich ist diese Woche Marine Le Pen wegen der Veruntreuung von EU-Geldern von einem Gericht verurteilt worden. Als Teil der Strafe wurde sie für fünf Jahre vom passiven Wahlrecht ausgeschlossen. Obwohl das Urteil nicht rechtskräftig ist – Le Pen kann in Berufung gehen –, haben die Richter das Verbot, bei Wahlen anzutreten, mit sofortiger Wirkung verhängt. Die Vorsitzende des rechtsnationalen Rassemblement National (RN) galt als aussichtsreiche Kandidatin für die Präsidentschaftswahl 2027.
Das ist in diesem Jahr bereits der zweite gravierende Fall von Wahlbeeinflussung durch die Justiz in einem EU-Staat. In Rumänien hatte Călin Georgescu im November die erste Runde der Präsidentenwahl überraschend gewonnen. Das Ergebnis wurde später annulliert, die behauptete «russische Wahlmanipulation» konnte jedoch nicht bewiesen werden. Die Kandidatur für die Wahlwiederholung im Mai wurde Georgescu kürzlich durch das Verfassungsgericht untersagt.
Die Veruntreuung öffentlicher Gelder muss untersucht und geahndet werden, das steht außer Frage. Diese Anforderung darf nicht selektiv angewendet werden. Hingegen mussten wir in der Vergangenheit bei ungleich schwerwiegenderen Fällen von (mutmaßlichem) Missbrauch ganz andere Vorgehensweisen erleben, etwa im Fall der heutigen EZB-Chefin Christine Lagarde oder im «Pfizergate»-Skandal um die Präsidentin der EU-Kommission Ursula von der Leyen.
Wenngleich derartige Angelegenheiten formal auf einer rechtsstaatlichen Grundlage beruhen mögen, so bleibt ein bitterer Beigeschmack. Es stellt sich die Frage, ob und inwieweit die Justiz politisch instrumentalisiert wird. Dies ist umso interessanter, als die Gewaltenteilung einen essenziellen Teil jeder demokratischen Ordnung darstellt, während die Bekämpfung des politischen Gegners mit juristischen Mitteln gerade bei den am lautesten rufenden Verteidigern «unserer Demokratie» populär zu sein scheint.
Die Delegationen von CDU/CSU und SPD haben bei ihren Verhandlungen über eine Regierungskoalition genau solche Maßnahmen diskutiert. «Im Namen der Wahrheit und der Demokratie» möchte man noch härter gegen «Desinformation» vorgehen und dafür zum Beispiel den Digital Services Act der EU erweitern. Auch soll der Tatbestand der Volksverhetzung verschärft werden – und im Entzug des passiven Wahlrechts münden können. Auf europäischer Ebene würde Friedrich Merz wohl gerne Ungarn das Stimmrecht entziehen.
Der Pegel an Unzufriedenheit und Frustration wächst in großen Teilen der Bevölkerung kontinuierlich. Arroganz, Machtmissbrauch und immer abstrusere Ausreden für offensichtlich willkürliche Maßnahmen werden kaum verhindern, dass den etablierten Parteien die Unterstützung entschwindet. In Deutschland sind die Umfrageergebnisse der AfD ein guter Gradmesser dafür.
[Vorlage Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ 7bdef7be:784a5805
2025-04-02 12:12:12
@ 7bdef7be:784a5805
2025-04-02 12:12:12We value sovereignty, privacy and security when accessing online content, using several tools to achieve this, like open protocols, open OSes, open software products, Tor and VPNs.
The problem
Talking about our social presence, we can manually build up our follower list (social graph), pick a Nostr client that is respectful of our preferences on what to show and how, but with the standard following mechanism, our main feed is public, so everyone can actually snoop what we are interested in, and what is supposable that we read daily.
The solution
Nostr has a simple solution for this necessity: encrypted lists. Lists are what they appear, a collection of people or interests (but they can also group much other stuff, see NIP-51). So we can create lists with contacts that we don't have in our main social graph; these lists can be used primarily to create dedicated feeds, but they could have other uses, for example, related to monitoring. The interesting thing about lists is that they can also be encrypted, so unlike the basic following list, which is always public, we can hide the lists' content from others. The implications are obvious: we can not only have a more organized way to browse content, but it is also really private one.
One might wonder what use can really be made of private lists; here are some examples:
- Browse “can't miss” content from users I consider a priority;
- Supervise competitors or adversarial parts;
- Monitor sensible topics (tags);
- Following someone without being publicly associated with them, as this may be undesirable;
The benefits in terms of privacy as usual are not only related to the casual, or programmatic, observer, but are also evident when we think of how many bots scan our actions to profile us.
The current state
Unfortunately, lists are not widely supported by Nostr clients, and encrypted support is a rarity. Often the excuse to not implement them is that they are harder to develop, since they require managing the encryption stuff (NIP-44). Nevertheless, developers have an easier option to start offering private lists: give the user the possibility to simply mark them as local-only, and never push them to the relays. Even if the user misses the sync feature, this is sufficient to create a private environment.
To date, as far as I know, the best client with list management is Gossip, which permits to manage both encrypted and local-only lists.
Beg your Nostr client to implement private lists!
-
 @ ecda4328:1278f072
2025-03-26 12:06:30
@ ecda4328:1278f072
2025-03-26 12:06:30When designing a highly available Kubernetes (or k3s) cluster, one of the key architectural questions is: "How many ETCD nodes should I run?"
A recent discussion in our team sparked this very debate. Someone suggested increasing our ETCD cluster size from 3 to more nodes, citing concerns about node failures and the need for higher fault tolerance. It’s a fair concern—nobody wants a critical service to go down—but here's why 3-node ETCD clusters are usually the sweet spot for most setups.
The Role of ETCD and Quorum
ETCD is a distributed key-value store used by Kubernetes to store all its state. Like most consensus-based systems (e.g., Raft), ETCD relies on quorum to operate. This means that more than half of the ETCD nodes must be online and in agreement for the cluster to function correctly.
What Quorum Means in Practice
- In a 3-node ETCD cluster, quorum is 2.
- In a 5-node cluster, quorum is 3.

⚠️ So yes, 5 nodes can tolerate 2 failures vs. just 1 in a 3-node setup—but you also need more nodes online to keep the system functional. More nodes doesn't linearly increase safety.
Why 3 Nodes is the Ideal Baseline
Running 3 ETCD nodes hits a great balance:
- Fault tolerance: 1 node can fail without issue.
- Performance: Fewer nodes = faster consensus and lower latency.
- Simplicity: Easier to manage, upgrade, and monitor.
Even the ETCD documentation recommends 3–5 nodes total, with 5 being the upper limit before write performance and operational complexity start to degrade.
Systems like Google's Chubby—which inspired systems like ETCD and ZooKeeper—also recommend no more than 5 nodes.
The Myth of Catastrophic Failure
"If two of our three ETCD nodes go down, the cluster will become unusable and need deep repair!"
This is a common fear, but the reality is less dramatic:
- ETCD becomes read-only: You can't schedule or update workloads, but existing workloads continue to run.
- No deep repair needed: As long as there's no data corruption, restoring quorum just requires bringing at least one other ETCD node back online.
- Still recoverable if two nodes are permanently lost: You can re-initialize the remaining node as a new single-node ETCD cluster using
--cluster-init, and rebuild from there.
What About Backups?
In k3s, ETCD snapshots are automatically saved by default. For example:
- Default path:
/var/lib/rancher/k3s/server/db/snapshots/
You can restore these snapshots in case of failure, making ETCD even more resilient.
When to Consider 5 Nodes
Adding more ETCD nodes only makes sense at scale, such as:
- Running 12+ total cluster nodes
- Needing stronger fault domains for regulatory/compliance reasons
Note: ETCD typically requires low-latency communication between nodes. Distributing ETCD members across availability zones or regions is generally discouraged unless you're using specialized networking and understand the performance implications.
Even then, be cautious—you're trading some simplicity and performance for that extra failure margin.
TL;DR
- 3-node ETCD clusters are the best choice for most Kubernetes/k3s environments.
- 5-node clusters offer more redundancy but come with extra complexity and performance costs.
- Loss of quorum is not a disaster—it’s recoverable.
- Backups and restore paths make even worst-case recovery feasible.
And finally: if you're seeing multiple ETCD nodes go down frequently, the real problem might not be the number of nodes—but your hosting provider.
-
 @ 2b24a1fa:17750f64
2025-05-02 13:40:12
@ 2b24a1fa:17750f64
2025-05-02 13:40:12Das Kriegsgrauen kriecht unter die Haut. Bilder von verstümmelten Beinen und Armen, von Kriegstraumatisierten schweigenden Männern, von Kriegsgräbern steigen auf. Als Mutter, Schwester, Tante, Großmutter wachsen die Ängste, dass sich ein Verwandter von der politischen und medialen Kriegslust anstecken lässt und tatsächlich die Beteiligung an den näher kommenden kriegerischen Auseinandersetzungen in Erwägung zieht. Einen wütenden Kommentar anlässlich der wachsenden Kriegstreiberei verfasste unser Autor Nicolas Riedl.
https://soundcloud.com/radiomuenchen/sofa-soldaten-an-die-front-von-nicolas-riedl?
Bild: KI
-
 @ 04c915da:3dfbecc9
2025-03-25 17:43:44
@ 04c915da:3dfbecc9
2025-03-25 17:43:44One of the most common criticisms leveled against nostr is the perceived lack of assurance when it comes to data storage. Critics argue that without a centralized authority guaranteeing that all data is preserved, important information will be lost. They also claim that running a relay will become prohibitively expensive. While there is truth to these concerns, they miss the mark. The genius of nostr lies in its flexibility, resilience, and the way it harnesses human incentives to ensure data availability in practice.
A nostr relay is simply a server that holds cryptographically verifiable signed data and makes it available to others. Relays are simple, flexible, open, and require no permission to run. Critics are right that operating a relay attempting to store all nostr data will be costly. What they miss is that most will not run all encompassing archive relays. Nostr does not rely on massive archive relays. Instead, anyone can run a relay and choose to store whatever subset of data they want. This keeps costs low and operations flexible, making relay operation accessible to all sorts of individuals and entities with varying use cases.
Critics are correct that there is no ironclad guarantee that every piece of data will always be available. Unlike bitcoin where data permanence is baked into the system at a steep cost, nostr does not promise that every random note or meme will be preserved forever. That said, in practice, any data perceived as valuable by someone will likely be stored and distributed by multiple entities. If something matters to someone, they will keep a signed copy.
Nostr is the Streisand Effect in protocol form. The Streisand effect is when an attempt to suppress information backfires, causing it to spread even further. With nostr, anyone can broadcast signed data, anyone can store it, and anyone can distribute it. Try to censor something important? Good luck. The moment it catches attention, it will be stored on relays across the globe, copied, and shared by those who find it worth keeping. Data deemed important will be replicated across servers by individuals acting in their own interest.
Nostr’s distributed nature ensures that the system does not rely on a single point of failure or a corporate overlord. Instead, it leans on the collective will of its users. The result is a network where costs stay manageable, participation is open to all, and valuable verifiable data is stored and distributed forever.
-
 @ 502ab02a:a2860397
2025-05-02 03:05:18
@ 502ab02a:a2860397
2025-05-02 03:05:18เราได้อ่านเรื่อง EVERY eggwhite ไปแล้วคิดว่าเขาจะหยุดแค่นี้ไหมครับ 555555 ไม่มีทางครับ การคืบคลานต้องมีต่อไป วันนี้จะมาในตอนที่ชื่อว่า
EVERY Egg ไข่ยุคใหม่ที่ไม่ต้องใช้แม่ไก่อีกต่อไป ลองนึกภาพ "ไข่เจียว" ที่ไม่มีแม่ไก่เกี่ยวข้องแม้แต่ขนไก่สักเส้น...ใช่เลยจ้ะ โลกตอนนี้ไปถึงจุดที่ ไข่ สามารถผลิตได้จาก “ยีสต์” ที่ถูกดัดแปลงพันธุกรรม เพื่อให้มันสร้าง “โปรตีนไข่” แบบเดียวกับในธรรมชาติ โดยไม่ต้องผ่านแม่ไก่ ไม่ต้องมีเปลือก และแน่นอน...ไม่มีเสียงขันตอนเช้าอีกต่อไป
ผู้เล่นที่น่าจับตาที่สุดคือบริษัท EVERY Company จาก Silicon Valley เจ้าเดิมที่เปิดตัวผลิตภัณฑ์ใหม่ในชื่อ EVERY Egg ซึ่งเป็น “ของเหลว” ที่หน้าตาเหมือนวิปไข่ไก่ แต่เบื้องหลังคือกระบวนการผลิตระดับไซไฟ! พวกเขาใช้เทคนิคที่เรียกว่า precision fermentation หรือ “การหมักแม่นยำ” เพื่อสั่งให้ยีสต์สร้างโปรตีน ovalbumin (โปรตีนหลักในไข่ขาว) และ lysozyme (สารฆ่าเชื้อแบคทีเรียตามธรรมชาติในไข่) ออกมา จากนั้นก็เอามาผสม เติมแต่ง แต่งกลิ่น เติมสี ใส่สารกันเสียเล็กน้อย...ปิ๊ง! ได้ไข่ที่ไม่มีไข่ ได้ใจประชาชนที่กินสารอาหารแบบคลั่งตัวเลข
จุดขายที่ EVERY Company ใช้ในการนำเสนอ EVERY Egg สลุตมาเป็นตับ ตับ ตับ แบบนี้ครับ 1. High quality egg protein ใช้โปรตีน ovalbumin ที่ได้จากกระบวนการ fermentation ด้วย precision fermentation จากยีสต์สายพันธุ์ Pichia pastoris ซึ่งเป็น โปรตีนหลักในไข่ขาวธรรมชาติและเคลมว่าให้คุณสมบัติเทียบเท่าหรือดีกว่าไข่จากไก่ในเรื่องโครงสร้างโปรตีนและการทำงานในอาหาร เช่น การตีขึ้นฟู (foaming) และการอิมัลซิไฟ คุณเอ๊ยยยย ฟลัฟฟลี่สุดๆ 555 2. No hens used เป็น selling point หลักที่สื่อสารหนักมากในเชิง “ไม่เบียดเบียนสัตว์” ดูมีคุณธรรม จึงถูกจัดเป็นมังสวิรัติ (vegan-friendly) แม้จะได้จากจุลินทรีย์ที่ออกแบบให้ผลิตโปรตีนที่เหมือนจากสัตว์ จุดนี้ล่อใจผู้บริโภควีแกนและกลุ่มที่ต่อต้านฟาร์มอุตสาหกรรมอย่างเต็มๆ พร้อมถวิลหา 3. No cholesterol ยังเป็นจุดขายหลักได้ตลอดกาลกับการครอบงำให้กลัวคอเลสเตอรอล เพราะผลิตจากจุลินทรีย์ ไม่ใช่จากสัตว์จริง ๆ จึงไม่มีคอเลสเตอรอลเลย ซึ่งเป็นข้อได้เปรียบเทียบกับไข่ไก่ที่มีคอเลสเตอรอลตามธรรมชาติ 4. No saturated fat พอๆกันครับ ยังเป็นจุดขู่จุดขายได้ตลอดกาลเช่นเดียวกับคอเลสเตอรอล โปรตีนที่ผลิตจากยีสต์ไม่มีไขมันอิ่มตัวเช่นเดียวกับผลิตภัณฑ์จากสัตว์จริง 5. No artificial flavors แหม่ พยายามสร้างภาพลักษณ์ว่าเป็น clean label ไม่ใช้แต่งกลิ่นหรือสารเติมแต่งรส (แม้จะเป็นผลิตภัณฑ์ที่ผ่านกระบวนการขั้นสูงมากก็ตาม) 6. No salmonella จุดที่คนโคตรกลัวเลยในไข่ สังเกตุไหมว่า จัดหนักจัดเน้นขยี้ความกลัวของคนได้ทุกจุด อย่างอันนี้เนื่องจากไม่มีสัตว์เข้ามาเกี่ยวข้องในการผลิต ทำให้โอกาสปนเปื้อนเชื้อซัลโมเนลลาที่พบบ่อยในไข่สดแทบเป็นศูนย์ เป็นจุดขายด้านความปลอดภัยอาหาร (food safety) ที่เขาเน้นมาก
เท่านี้ยังไม่พอครับ คำถามที่คนต้องสงสัยแน่นอนคือ ชนิดของกรดอมิโนหละครบไหม pain point ของชาววีแกน เนื่องจาก EVERY Company ใช้เทคนิค “Precision Fermentation” โดยใส่ยีนจากไก่ลงไปในยีสต์ เพื่อให้ผลิต ovalbumin ได้เหมือนในธรรมชาติ จึงทำให้โครงสร้างของกรดอะมิโนในโปรตีนนี้ เหมือนไข่จริงแทบ 100% โปรตีน ovalbumin ที่ใช้ผลิต เป็น primary protein จึงถือว่าเป็น โปรตีนมาตรฐาน (reference protein) ในทางโภชนาการ เพราะมี กรดอะมิโนจำเป็นทั้ง 9 ชนิด ในปริมาณที่เพียงพอ ได้แก่ Leucine, Lysine, Valine, Isoleucine, Threonine, Methionine, Phenylalanine, Tryptophan, Histidine
แต่... แม้จะมีกรดอะมิโนครบ ก็ยังมีเรื่องให้คิด โปรตีนนี้ ไม่มาจากธรรมชาติ โดยตรง แต่ผ่านการผลิตจากสิ่งมีชีวิตดัดแปลงพันธุกรรม (GMO yeast) ยังไม่มีข้อมูลชัดเจนเรื่อง bioavailability (การดูดซึม) เมื่อเทียบกับไข่จริง และที่สำคัญ คือการบริโภค “complete protein” ไม่ได้แปลว่า ปลอดภัยในระยะยาว ถ้าพื้นฐานมันคือ GMO จากแลปที่ไม่มีวิวัฒนาการร่วมกับมนุษย์ แน่นอนว่ามันยังต้องการ "ตลาดทดลอง" เพื่อทดลองและเก็บข้อมูลประกอบสินค้าในระยะเวลานึง เข้าใจไหม "หนูๆ"
คำถามคือ โปรตีนแท้...หรือแค่ “เลียนแบบ” EVERY Egg บอกว่าเขาสร้างโปรตีนเหมือนไข่เป๊ะชนิดที่ว่าเชฟชื่อดังยังแยกไม่ออก (ถ้าไม่ดูฉลาก) สามารถนำไปทอด ทำไข่คน ไข่เจียว โอ๊มเล็ต ได้เหมือนไข่จริงทุกประการ แถมยังไม่มีคอเลสเตอรอล ไม่มีไขมันอิ่มตัว มีแต่ “โปรตีนล้วนๆ” แบบคลีนๆ
แต่ตรงนี้แหละที่มันเริ่ม น่าสงสัย เพราะการไม่มีไขมันเลย มันก็คือการตัดเอา matrix ทางโภชนาการ ที่ธรรมชาติออกแบบมาให้เราย่อยง่าย ดูดซึมวิตามินได้ดี และช่วยให้เรารู้สึกอิ่มแบบธรรมชาติ ไข่แท้จากไก่ ไม่ใช่แค่แหล่งโปรตีน แต่มันคือ “ของขวัญจากธรรมชาติ” ที่มีทั้ง choline, lutein, zeaxanthin, วิตามิน A, D, E, B12, โอเมก้า-3, ไขมันดี และเลซิธิน อยู่ครบทุกอนู ช่วยทั้งสมอง ดวงตา และตับ
ในขณะที่ EVERY Egg คือ “ไข่ที่เราอยากให้มันเป็น” มากกว่า “ไข่ที่ธรรมชาติอยากให้เราได้กิน”
บริษัท The EVERY Company ได้ร่วมมือกับเชฟระดับสุดยอดมากมาย ซึ่งการร่วมมือครั้งนี้มีเป้าหมายเพื่อแสดงให้เห็นว่าโปรตีนไข่ที่ผลิตจากกระบวนการ precision fermentation ของ EVERY Egg สามารถตอบสนองมาตรฐานสูงสุดของวงการอาหารชั้นเลิศได้ เรามาดูตัวอย่างกันครับว่า มีที่ไหนบ้าง
-
Eleven Madison Park โดย เชฟ Daniel Humm (มิชลิน3 ดาว ที่นิวยอร์ก) EVERY Egg เปิดตัวครั้งแรกในปี 2023 ที่ร้าน Eleven Madison Park ซึ่งเป็นร้านอาหารระดับมิชลิน 3 ดาว ในนิวยอร์ก โดยเชฟ Daniel Humm ได้สร้างสรรค์เมนูพิเศษที่ใช้ EVERY Egg เป็นส่วนประกอบหลัก เช่น ออมเล็ต ค็อกเทล และของหวาน เพื่อแสดงถึงความสามารถของผลิตภัณฑ์นี้ในการตอบสนองมาตรฐานสูงสุดของวงการอาหารชั้นเลิศระดับ fine dining มิชลิน
-
Chantal Guillon (ร้านมาการองฝรั่งเศสในซานฟรานซิสโก) EVERY Company ได้ร่วมมือกับร้านขนม Chantal Guillon ในการผลิตมาการองที่ใช้ EVERY EggWhite™ ซึ่งเป็นโปรตีนไข่ขาวที่ผลิตจากกระบวนการ precision fermentation โดยไม่มีการใช้ไข่จากไก่เลย ผลิตภัณฑ์นี้ได้รับการยอมรับว่าให้รสชาติและเนื้อสัมผัสที่เทียบเท่ากับไข่ขาวธรรมชาติ
-
The Vegetarian Butcher เป็นแบรนด์ในเครือ Unilever ตามที่ได้เคยให้ข้อมูลไปแล้ว EVERY Company ได้จับมือกับ The Vegetarian Butcher ซึ่งเป็นแบรนด์อาหารมังสวิรัติในเครือ Unilever เพื่อพัฒนาและผลิตผลิตภัณฑ์ที่ใช้โปรตีนไข่จาก EVERY Egg โดยมีเป้าหมายในการลดการใช้สัตว์ในห่วงโซ่อาหารและส่งเสริมความยั่งยืนในอุตสาหกรรมอาหาร
-
Grupo Palacios ผู้ผลิต Spanish Omelet รายใหญ่ของโลก EVERY Company ได้ร่วมมือกับ Grupo Palacios ซึ่งเป็นผู้ผลิต Spanish Omelet รายใหญ่ของโลก โดยนำ EVERY Egg มาใช้ในผลิตภัณฑ์ของตน เพื่อเป็นทางเลือกที่ปลอดภัยและยั่งยืนต่อไข่ไก่ธรรมชาติ ซึ่งอาจมีปัญหาเรื่องการปนเปื้อนและความไม่แน่นอนในการผลิต
Fiat Egg บนเส้นทางเดียวกับ Fiat Food เฮียชวนให้มองภาพใหญ่เหมือนเวลาเรายืนอยู่บนดาดฟ้าแล้วมองลงไปที่ตลาด... ผลิตภัณฑ์อย่าง EVERY Egg ไม่ใช่แค่การสร้าง “ของใหม่” แต่มันคือการ เปลี่ยนแปลงพื้นฐานของอาหาร ด้วยแนวคิดแบบ “Fiat” เป๊ะ Fiat Food คืออาหารที่ไม่ได้เกิดจากธรรมชาติ แต่ถูก “กำหนดให้มีคุณค่า” โดยอุตสาหกรรม Fiat Money คือเงินที่ไม่ได้มีมูลค่าในตัวเอง แต่รัฐบาลบอกให้เรายอมรับมันเป็นเงิน
ในโลกนี้ ถ้า “ไข่” ไม่ต้องมาจากแม่ไก่ “นม” ไม่ต้องมาจากเต้า และ “เนื้อ” ไม่ต้องมาจากวัว แต่ใช้แค่สารเคมี + ยีสต์ + กราฟ + กลิ่นสังเคราะห์ = “ของกินได้” แล้วมันจะเหลือความเป็น อาหารแท้ (real food) อยู่อีกไหม?
เบื้องหลังที่เราควรถามให้ลึก แม้ว่า EVERY จะอ้างว่าโปรตีนจากยีสต์ของเขา “ปลอดภัยและยั่งยืน” แต่ยังไม่มีข้อมูลด้าน long-term health impact ยังไม่มีข้อมูลว่ายีสต์ GMO ที่ใช้ จะกระตุ้นภูมิแพ้หรือมีสารตกค้างหรือไม่ ยังไม่รู้ว่าสารแต่งกลิ่น รส และตัวพาอื่นๆ ที่ใส่ใน EVERY Egg จะส่งผลอะไรกับ microbiome หรือฮอร์โมนของเราในระยะยาว แต่นั่นก็คงมาพร้อมกับคำตอบหรูๆหล่อๆว่า "ขอให้มั่นใจในกระบวนการผลิตที่ทันสมัยและดีเยี่ยม" . . . ตามเคย
และที่น่าสนใจคือ...ผลิตภัณฑ์ EVERY Egg ยังไม่ได้รับการรับรอง GRAS (Generally Recognized As Safe) อย่างเป็นทางการจาก FDA จึงยังไม่สามารถวางจำหน่ายในร้านค้าปลีกทั่วไปได้ บริษัทกำลังร่วมมือกับบริษัทอาหารข้ามชาติในการเปิดตัวผลิตภัณฑ์ในปีนี้ แต่ยังไม่มีข้อมูลชัดเจนเกี่ยวกับการวางจำหน่ายในร้านค้าปลีกทั่วไป แต่ส่วนตัวเฮียคิดว่าไม่น่ากังวล น่าจะผ่านฉลุยแหละ 5555
ไข่สังเคราะห์ = ความหวัง? หรือกับดักในรูปของนวัตกรรม? เราคงไม่ปฏิเสธว่ามีหลายคนบนโลกที่แพ้ไข่จริง หรือห่วงใยเรื่องสวัสดิภาพสัตว์ รวมถึงต้องการความ "บริสุทธิ์" "สกัด" "เข้มข้น" แต่คำถามคือ...จะดีกว่าไหมถ้าเราหาทางผลิต ไข่จริงจากไก่ที่เลี้ยงแบบธรรมชาติ ในระบบ regenerative farming แทนที่จะพยายามสร้างโปรตีนปลอมขึ้นมาแข่ง? ทุกครั้งที่มีของใหม่ที่ดูดี สะอาด และ “คลีน” เฮียอยากให้ทุกคน ถามกลับในใจว่า “คลีน” แค่ในห้องแล็บ หรือ “คลีน” ในธรรมชาติจริงๆ?
สรุปแบบไม่ต้องตีลังกาคิดได้ว่า EVERY Egg คือก้าวใหม่ของเทคโนโลยีอาหารที่กำลังวิ่งไปข้างหน้าแบบไม่เหลียวหลัง แต่ในฐานะที่เฮียเชื่อใน real food, nutrient density และความฉลาดของธรรมชาติ เราอาจต้องเตือนใจไว้ว่า...การใช้ยีสต์ดัดแปลงพันธุกรรมมาผลิต “ไข่เทียม” ไม่ใช่ความผิด แต่ก็ไม่ใช่ความจำเป็นไหม เพราะแท้จริงแล้ว เรามี “ไข่” ที่สมบูรณ์แบบอยู่ในธรรมชาติแล้ว...แค่ไม่ควรปล่อยให้อุตสาหกรรมทำลายภาพลักษณ์ของมัน เพื่อขายของที่ “เหมือนไข่” แต่ไม่มีชีวิต
คำถามเดิมครับ วันนึงเมื่อถึงจุดที่คุณไม่ได้เลือก แล้วมันมีให้แค่นี้ วันนั้นจะทำอย่างไร วันแห่งความ "บริสุทธิ์" "สกัด" "เข้มข้น" ที่เราถวิลหา ??? #pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-
-
 @ 99e7936f:d5d2197c
2025-05-02 13:25:06
@ 99e7936f:d5d2197c
2025-05-02 13:25:06Frieden braucht die Kapitulation, keine Gebrauchsanweisung
Wenn Dir ständig jemand erklärt, wie Du etwas zu machen hast, dann machst Du irgendwann gar nichts mehr, sondern wartest nur noch auf die nächste Aufforderung, dies oder jenes zu tun.
Manchmal ist das gut so, aber meist ist diese abwartende Haltung eine Vorlage für andere Menschen, die nichts Gutes im Schilde führen. Sie nutzen dieses entgegengebrachte Vertrauen aus und geben Anweisungen, die nur ihnen selbst dienen und sonst keinem. Das Phänomen ist hinreichend bekannt.
Ich habe lange gebraucht, um zu verstehen, warum Menschen auf Aufforderungen von anderen warten. Das ist offensichtlich früh gelerntes Verhalten, wie so vieles im Leben. In meiner Kindheit habe ich auch viele dysfunktionale Verhaltensweisen gelernt, aber exakt diese nicht, da ich kaum Aufforderungen erhielt. Ich hätte gerne welche erhalten. Meine Eltern waren aber meist mit sich selbst und den Anforderungen des Alltags beschäftigt.
Mein Vater war 11 Jahre und meine Mutter war 8 Jahre alt als der zweite Weltkrieg endete. Zwanzig Jahre später kreuzten sich ihre Wege, sie heirateten und bekamen drei Kinder. Sie kümmerten sich um alle praktischen Aufgaben, sorgten für Sicherheit, ein schönes Zuhause und materiellen Wohlstand. Ich muss schlucken beim Schreiben dieses Satzes.
Mit 11 Jahren fing ich an, Tagebuch zu schreiben, weil ich so vieles nicht verstand. Trauma wird weiter gegeben, wenn es nicht aufgelöst wird. Ich hätte, wie gesagt, gerne mal klare Aufforderungen und Anweisungen gehabt. Ich suchte in der Schule und in meinen Ausbildungen nach Antworten, fand sie aber nicht. 1990 war ich 20 Jahre alt und startete nicht gut vorbereitet ins Erwachsenenleben. Wenn ich heute auf die letzten 35 Jahre zurück blicke, dann verstehe ich so viel, dass mir schwindelig wird. Heute mag ich mich und bereite mich daher nur noch selten auf etwas vor. Diese Erkenntnis ist aber nicht über Nacht gekommen. Das hätte ich wohl kaum überlebt. Die hierzu notwendigen Krisen in meinem Leben kamen in regelmäßigen Abständen und waren wohldosiert. Mit Krisen kenne ich mich aus. Krisen folgen immer demselben Muster, egal ob persönliche oder globale.
Wer bin ich, und warum schreibe ich hier einen Artikel über Frieden?
Ich bin eine Psychologin, die sich für ihr Leben gern mit Trauma beschäftigt. Das ist, nebenbei bemerkt, eines der positivsten Themen, die es gibt. Aber dazu erzähle ich ein anderes Mal. Ich bin das Kind meiner Eltern, Spätentwicklerin und die Eiskönigin nach der Verwandlung. Menschen, die meine Geschichte nicht kennen, halten mich für stark, obwohl ich auch nicht stärker bin als andere. Bewältigtes Trauma macht einen stark. Seitdem ich vor ein paar Jahren meinen persönlichen Knoten gelöst habe, folge ich nur noch meinem Herzen, was unglaublich polarisiert. Ich kann jetzt nicht mehr anders. Früher habe ich mein Herz zwar auch schon deutlich gehört, aber überholte Glaubenssätze hatten oft das letzte Wort und bestimmten mein Handeln. Das war dann nicht selten der innerliche Spagat, um es vor allem anderen recht zu machen. Die leere Batterie, die ich mehrmals kennen lernen durfte, hat mich dann gelehrt, es anders zu machen. Heute achte ich auf meine sehr feine Wahrnehmung und auf meine Bedürfnisse. Das kommt aber meistens auch anderen zugute.
Wer gelernt hat, sich selbst so anzunehmen wie er ist, was gleichzusetzen ist mit Schmerz, der möchte anderen keinen Schmerz zufügen. Eigentlich könnte ich an dieser Stelle den Artikel schon beenden.
Selbstliebe und Schmerz sind unzertrennliche Freunde. Aber dazu erzähle ich auch ein anderes Mal.
Heute möchte ich etwas dazu sagen, warum ich für den Frieden keine Gebrauchsanweisung brauche, sondern die Kapitulation.
Ich bin dem Krieg * in* mir begegnet. Dieser Krieg hat in meinem Außen über lange Zeit für Unruhe gesorgt, und er hat meine Batterie im Innern dadurch öfters leer gezogen. Er war immer berechtigt, begründet und gerechtfertigt, aber dennoch nicht gut für mich oder andere. Im größten Schmerz, den ich je empfunden habe, kam dann 2018/19 endlich der Frieden in mein persönliches Leben. Ich musste dafür nichts tun. Ausrufungszeichen. Den Frieden bekam ich quasi geschenkt, weil ich aufgehört hatte zu kämpfen, weil ich mich dem Schmerz hingegeben hatte, weil ich es akzeptiert hatte, am Boden zu liegen.
Alle wollen Frieden, aber niemand will am Boden liegen.
Kann ich gut verstehen, aber meine Erfahrung ist genau diese, dass Du gefühlt am Boden liegen musst. Frieden kann man „machen“ durch bewusstes Unterlassen von verbalem Zurückschlagen und von Ablenkungs- oder Vermeidungsverhalten, um den eigenen Schmerz nicht spüren zu müssen. Nach diesem Verzicht kann man dann Wut und Schmerz deutlicher oder sogar hervorragend spüren, und dann kommt das Geschenk. Der Frieden durchflutet Dich in einem Moment, in dem Du es nicht erwartest. Frieden kommt, wenn die Situation gefährlich und existenziell bedrohlich wird. Der ganze Körper entspannt in einem einzigen Moment. Das ist wie eine Erlösung. Man sagt nicht umsonst, dass es schön sei, wenn der Schmerz aufhöre. Das stimmt wirklich. Da passiert auch auf biologischer Ebene ganz viel. Körpereigene Stoffe, die schmerzfrei und unglaublich leicht fühlen lassen, werden in Hülle und Fülle ausgeschüttet. Die Evolution hat an alles gedacht. Sie lässt Dich nicht im Stich, wenn es dicke kommt. Frieden ist ein unbeschreiblicher Zustand. Wenn Du den einmal gespürt hast, dann ist der Weg frei, und dann brauchst Du keine Gebrauchsanweisung mehr. Dieser Moment verändert Dich für immer. Du hast eine Erfahrung gemacht, die Dir keiner mehr nehmen kann. Ich habe diese Erfahrung damals alleine gemacht, weil ich niemanden hatte, dem ich mich anvertrauen wollte. Das war ganz unspektakulär im Wohnzimmer. Aber diese Erfahrung, für die es tausende von Bezeichnungen gibt, verändert Dein Leben von Grund auf. Schön ist, wenn man jemanden an seiner Seite hat, der einfach nur zuhört und ab und zu einfach mal was Nettes sagt. Und genau das ist so schwer, so jemanden zu finden, der gerne bei einem sein möchte, wenn man gerade gefühlt stirbt. Die meisten Menschen laufen dann weg oder sagen: „Jetzt reiß Dich mal zusammen.“
Frieden ist nichts für schwache Nerven.
Wenn Du Frieden einmal selbst am eigenen Körper erlebt hast, dann gehst Du anders in Auseinandersetzungen (und globale Krisen) hinein, weil Du diesen Mechanismus kennen gelernt hast, weil Du weißt, dass Du geschützt bist. Das Leben liebt Dich und arbeitet für Dich. Immer. Mit diesem Wissen ausgestattet, kannst Du leichter ruhig bleiben, wenn es nicht so gut läuft, wenn es brenzlig wird, auch wenn große Dinge in der Welt schief laufen. Der Schmerz ist nicht mehr Dein Feind, den es unbedingt zu vermeiden gilt. Jetzt wird es kurios. Ich mag sicherlich keinen Schmerz, aber ich laufe vor „dem Schmerz“ nicht mehr davon. Oft empfinden wir Schmerz schon, wenn jemand unsere Glaubenssätze triggert. Ich schau mir den Schmerz an, fühle rein und höre zu, was er mir sagen will. Und in den meisten Fällen ist es gar nicht MEIN Schmerz. Jemand greift mich an, weil er selber Ängste hat, sich getriggert fühlt oder sonst etwas hat oder nicht hat. Ich bin irritiert und vielleicht auch wütend, weil es weh tut, aber genau dann kommt dieses erfahrene Wissen zum Einsatz und legt die rettende Pause in mein Denken und Handeln ein. Ich reagiere nicht mit einem Schlagabtausch, und freu mich umgehend unglaublich über mich selbst. Und dann laufen die Dinge für mich. Ich brauche nur Geduld. Der andere hat jetzt etwas zum Nachdenken. Wenn man nicht zurück schlägt, dann hat der andere etwas zum Nachdenken. Das ist jetzt die Kurzfassung der Geschichte. Jedenfalls aktiviert dieses Unterlassen von Schlagabtausch auch in den schwierigsten Zeitgenossen etwas Gutes. Versprochen. Und dieses Gute fängt dann an zu arbeiten, für mich, für uns alle und vor allem für den Frieden.
Das Ganze ist eine komplexe Erfahrung, die ich erst persönlich gemacht habe, dann aber auch bei anderen beobachten und raushören konnte. Über das Phänomen wird viel geredet. Aber zentral wichtig ist mir zu sagen, dass der Frieden kommt, wenn Du aufgibst, nicht mehr kämpfst, auf einen Schlagabtausch verzichtest. Das gilt für Deine Freundschaften, für Deine Partnerschaft, für Deine Familie und für das Land, in dem Du lebst. Frieden entsteht im Streit, im Krieg. Frieden entsteht, wenn die Situation einen unglaublich verletzt, wütend und fassungslos macht. Die Evolution braucht Dich an Deinem persönlichen Siedepunkt, Schmelzpunkt. Nenn es, wie Du willst. Im Schmerz öffnet sich ein Zugang zu einem anderen Bewusstsein. Du wirst weit auf allen Ebenen. Alles, was Du auf Deinem Weg mal verloren hast, kommt zu Dir zurück. Der Schmerz repariert erst Dich und dann alle anderen, mit denen Du zu tun hast. Menschen, die diese Erfahrung am eigenen Körper gemacht haben, schauen anders auf und in diese Welt, weil sie diese andere Welt, dieses weite Bewusstsein, kennen gelernt haben. Es gibt viele Wege zu diesem weiten Bewusstsein und, nebenbei bemerkt, auch viel Zensur zum Thema in der wissenschaftlichen Welt, aber auch im Mainstream. Ich persönlich habe das Phänomen am eigenen Körper kennen gelernt, bevor ich einen Namen dafür hatte. Aber der wichtige Punkt ist, wenn mich jemand fragen würde, was man mitten im Krieg tun kann, dann würde ich sagen: „Lass den Schmerz zu.“
Soll das etwa heißen, dass der ganze Widerstand aktuell für die Katze ist? Nein, natürlich nicht.
Über Missstände berichten? Ja. Schuldige benennen? Ja. Rechtsstaatliche Maßnahmen? Ja.
Aber lass Deinen Schmerz zu. Spür nach, was genau Dich so wütend macht. Frag Dich konkret, warum Dich das Verhalten von XY so trifft. Warum kann Dich jemand, den Du gar nicht persönlich kennst, so fassungslos machen? Und dann kommen wir alle unweigerlich zu uns selbst. Was ist mir so unglaublich wichtig? Und warum? Und was hat das mit meinen Wunden zu tun?
Mich kann man heute auch immer noch triggern, weil ich ein Mensch aus Fleisch und Blut bin. Aber ich setze mich jedes Mal wieder hin und schaue es mir an, was da noch weh tut in mir. Und dann bin ich bei mir. Und dann geht’s um mich. Und dann gebe ich mir alles Gute, Nährende, Pflegende und Aufmunternde. Das tut mir gut und bringt mich weiter. Und mit dieser Haltung kann ich dann wieder auf Menschen zugehen, denen ich nicht aus dem Weg gehen kann. Und Menschen, die dieser Gesellschaft aktiv Schaden zufügen, kann ich nicht aus dem Weg gehen. Sie sägen an meinem Baum. Sie sägen, aber ich stell mich immer wieder daneben. Ich rede mit ihnen wie mit einem normalen Menschen. Ausrufungszeichen. Ich adressiere das im anderen, was ich wachsen sehen möchte. Ich brauche Pausen, aber ich bleibe ruhig, denn nur so arbeitet das Gute im anderen für mich, für uns alle, für den Frieden. Das Gute im anderen ist in 99,9 % der Fälle da und erreichbar, ist zumindest meine Erfahrung.
Die Erfahrung von Frieden kann mir keiner mehr nehmen.
Und eine Gebrauchsanweisung für den Frieden brauche ich auch nicht mehr.
Kapitulation bringt Frieden.
-
 @ fd0bcf8c:521f98c0
2025-05-02 02:02:13
@ fd0bcf8c:521f98c0
2025-05-02 02:02:13Bitcoin
It stands alone. Immutable. Unyielding. It records without mercy. Each transaction cuts deep. Some carry wealth. Others just data. The debate rages on.
OP_RETURN
It divides us all. Bloat versus freedom. Money versus use. Simple versus complex.
Nodes
They bear heavy weight. Each byte costs something. Storage grows. Bandwidth drains. Money defenders stand guard.
"Our purpose is clear...Money serves one master." —Mises
Not art.
Not storage.
Not games.
The fee-payers
They disagree. "I paid. I belong." The miners take their cut. The highest fee wins. No questions asked. The protocol allows it.
"Accept what exists."—Marcus Aurelius
The chain is neutral. Always neutral.
What is a transaction?
None agree. Value transfer only? Or any valid data? The white paper speaks. "Electronic cash system." Yet code evolved. It grew teeth. It allows more now.
"Shitcoin"
Cuts both ways. A dangerous word. It keeps focus. It maintains unity. But it wounds creation. Makes builders desperate. They force ideas onto Bitcoin. They use OP_RETURN poorly. They bloat what needs no bloating. Seneca saw this coming...
"Fear makes suffering worse."
Innovation needs proper soil. Not forced transplants.
Money debates sharpen knives. Is Bitcoin gold? Is it currency? Mantras echo loudly.
"Digital gold."
_"Spend dollars, saving Bitcoin." _
"Never sell your Bitcoin."
Bitcoin becomes idol. Not tool. Mises would disapprove, "Money must move." Without exchange, it dies. If none spend, why fight bloat?
Rhetoric
It hurts us. "Shitcoin" closes minds. Forces square pegs round. Drives experiments home. To Bitcoin they return. Bearing misshapen plans.
"Knowledge exists in dispersion," Hayek warns.
Let ideas find homes. Let Bitcoin be Bitcoin.
Fees
They bring new problems. Users flee high costs. They seek cheaper chains. The wealthy still play games. They can afford the bloat. The poor cannot compete. The rich inscribe at will. Rothbard saw this trap, "Markets need equal rules."
Fee markets favor wealth. Always have. Always will.
Nodes must still run. Validators must validate. Decentralized. Resistant. Strong. The burden grows heavier. But principles matter most.
The battle
It continues. Hard words. Hard choices.
Bitcoin endures all. Money or platform? Gold or currency? The answers shift. The chain grows. Block by block. Byte by byte.
We need clearer words. Cleaner definitions. Less pride. More thought. Let Bitcoin be what it is. Not what we demand.
Bitcoin is human.
Not magical. Not divine. Fallible like its makers. A young experiment still. It could fail tomorrow.
"Nothing is too big to fail." —Satoshi
Our rhetoric needs maturity. Our definitions need clarity. Bitcoin needs humility. From all who touch the code.
-
 @ 87f5e1d9:e251d8f4
2025-05-02 13:15:23
@ 87f5e1d9:e251d8f4
2025-05-02 13:15:23In the world of cryptocurrency, the stakes are high, and losing access to your digital assets can be a nightmare. But fear not — Crypt Recver is here to turn that nightmare into a dream come true! With expert-led recovery services and cutting-edge technology, Crypt Recver specializes in helping you regain access to your lost Bitcoin and other cryptocurrencies.
Why Choose Crypt Recver? 🤔 🔑 Expertise You Can Trust At Crypt Recver, we combine state-of-the-art technology with skilled engineers who have a proven track record in crypto recovery. Whether you’ve forgotten your passwords, lost your private keys, or dealt with damaged hardware wallets, our team is equipped to help.
⚡ Fast Recovery Process Time is of the essence when it comes to recovering lost funds. Crypt Recver’s systems are optimized for speed, enabling quick recoveries — so you can get back to what matters most: trading and investing.
🎯 High Success Rate With over a 90% success rate, our recovery team has helped countless clients regain access to their lost assets. We understand the intricacies of cryptocurrency and are dedicated to providing effective solutions.
🛡️ Confidential & Secure Your privacy is our priority. All recovery sessions at Crypt Recver are encrypted and kept entirely confidential. You can trust us with your information, knowing that we maintain the highest standards of security.
🔧 Advanced Recovery Tools We use proprietary tools and techniques to handle complex recovery scenarios, from recovering corrupted wallets to restoring coins from invalid addresses. No matter how challenging the situation, we have a plan.
Our Recovery Services Include: 📈 Bitcoin Recovery: Have you lost access to your Bitcoin wallet? We can help you recover lost wallets, private keys, and passphrases. Transaction Recovery: Mistaken transfers, lost passwords, or missing transaction records — let us help you reclaim your funds! Cold Wallet Restoration: Did your cold wallet fail? We specialize in extracting assets safely and securely. Private Key Generation: Forgotten your private key? We can help you generate new keys linked to your funds without compromising security. Don’t Let Lost Crypto Ruin Your Day! 🕒 With an estimated 3 to 3.4 million BTC lost forever, it’s critical to act swiftly when facing access issues. Whether you’ve been a victim of a dust attack or have simply forgotten your key, Crypt Recver offers the support you need to reclaim your digital assets.
🚀 Start Your Recovery Now! Ready to get your cryptocurrency back? Don’t let uncertainty hold you back!
👉 Request Wallet Recovery Help Today!
Need Immediate Assistance? 📞 For quick queries or support, connect with us on:
✉️ Telegram: Chat with Us on Telegram 💬 WhatsApp: Message Us on WhatsApp Trust Crypt Recver for the Best Crypto Recovery Service — Get back to trading with confidence! 💪In the world of cryptocurrency, the stakes are high, and losing access to your digital assets can be a nightmare. But fear not — Crypt Recver is here to turn that nightmare into a dream come true! With expert-led recovery services and cutting-edge technology, Crypt Recver specializes in helping you regain access to your lost Bitcoin and other cryptocurrencies.
 # Why Choose Crypt Recver? 🤔
# Why Choose Crypt Recver? 🤔🔑 Expertise You Can Trust
At Crypt Recver, we combine state-of-the-art technology with skilled engineers who have a proven track record in crypto recovery. Whether you’ve forgotten your passwords, lost your private keys, or dealt with damaged hardware wallets, our team is equipped to help.
⚡ Fast Recovery Process
Time is of the essence when it comes to recovering lost funds. Crypt Recver’s systems are optimized for speed, enabling quick recoveries — so you can get back to what matters most: trading and investing.
🎯 High Success Rate
With over a 90% success rate, our recovery team has helped countless clients regain access to their lost assets. We understand the intricacies of cryptocurrency and are dedicated to providing effective solutions.
🛡️ Confidential & Secure
Your privacy is our priority. All recovery sessions at Crypt Recver are encrypted and kept entirely confidential. You can trust us with your information, knowing that we maintain the highest standards of security.
🔧 Advanced Recovery Tools
We use proprietary tools and techniques to handle complex recovery scenarios, from recovering corrupted wallets to restoring coins from invalid addresses. No matter how challenging the situation, we have a plan.
 # Our Recovery Services Include: 📈
# Our Recovery Services Include: 📈- Bitcoin Recovery: Have you lost access to your Bitcoin wallet? We can help you recover lost wallets, private keys, and passphrases.
- Transaction Recovery: Mistaken transfers, lost passwords, or missing transaction records — let us help you reclaim your funds!
- Cold Wallet Restoration: Did your cold wallet fail? We specialize in extracting assets safely and securely.
- Private Key Generation: Forgotten your private key? We can help you generate new keys linked to your funds without compromising security.
Don’t Let Lost Crypto Ruin Your Day! 🕒
With an estimated 3 to 3.4 million BTC lost forever, it’s critical to act swiftly when facing access issues. Whether you’ve been a victim of a dust attack or have simply forgotten your key, Crypt Recver offers the support you need to reclaim your digital assets.
🚀 Start Your Recovery Now!
Ready to get your cryptocurrency back? Don’t let uncertainty hold you back!
👉 Request Wallet Recovery Help Today!
Need Immediate Assistance? 📞
For quick queries or support, connect with us on:
- ✉️ Telegram: Chat with Us on Telegram
- 💬 WhatsApp: Message Us on WhatsApp
Trust Crypt Recver for the Best Crypto Recovery Service — Get back to trading with confidence! 💪
-
 @ 16f1a010:31b1074b
2025-03-20 14:32:25
@ 16f1a010:31b1074b
2025-03-20 14:32:25grain is a nostr relay built using Go, currently utilizing MongoDB as its database. Binaries are provided for AMD64 Windows and Linux. grain is Go Relay Architecture for Implementing Nostr
Introduction
grain is a nostr relay built using Go, currently utilizing MongoDB as its database. Binaries are provided for AMD64 Windows and Linux. grain is Go Relay Architecture for Implementing Nostr
Prerequisites
- Grain requires a running MongoDB instance. Please refer to this separate guide for instructions on setting up MongoDB: nostr:naddr1qvzqqqr4gupzq9h35qgq6n8ll0xyyv8gurjzjrx9sjwp4hry6ejnlks8cqcmzp6tqqxnzde5xg6rwwp5xsuryd3knfdr7g
Download Grain
Download the latest release for your system from the GitHub releases page
amd64 binaries provided for Windows and Linux, if you have a different CPU architecture, you can download and install go to build grain from source
Installation and Execution
- Create a new folder on your system where you want to run Grain.
- The downloaded binary comes bundled with a ZIP file containing a folder named "app," which holds the frontend HTML files. Unzip the "app" folder into the same directory as the Grain executable.
Run Grain
- Open your terminal or command prompt and navigate to the Grain directory.
- Execute the Grain binary.
on linux you will first have to make the program executable
chmod +x grain_linux_amd64Then you can run the program
./grain_linux_amd64(alternatively on windows, you can just double click the grain_windows_amd64.exe to start the relay)
You should see a terminal window displaying the port on which your relay and frontend are running.
If you get
Failed to copy app/static/examples/config.example.yml to config.yml: open app/static/examples/config.example.yml: no such file or directory
Then you probably forgot to put the app folder in the same directory as your executable or you did not unzip the folder.
Congrats! You're running grain 🌾!
You may want to change your NIP11 relay information document (relay_metadata.json) This informs clients of the capabilities, administrative contacts, and various server attributes. It's located in the same directory as your executable.
Configuration Files
Once Grain has been executed for the first time, it will generate the default configuration files inside the directory where the executable is located. These files are:
bash config.yml whitelist.yml blacklist.ymlPrerequisites: - Grain requires a running MongoDB instance. Please refer to this separate guide for instructions on setting up MongoDB: [Link to MongoDB setup guide].
Download Grain:
Download the latest release for your system from the GitHub releases page
amd64 binaries provided for Windows and Linux, if you have a different CPU architecture, you can download and install go to build grain from source
Installation and Execution:
- Create a new folder on your system where you want to run Grain.
- The downloaded binary comes bundled with a ZIP file containing a folder named "app," which holds the frontend HTML files. Unzip the "app" folder into the same directory as the Grain executable.
Run Grain:
- Open your terminal or command prompt and navigate to the Grain directory.
- Execute the Grain binary.
on linux you will first have to make the program executable
chmod +x grain_linux_amd64Then you can run the program
./grain_linux_amd64(alternatively on windows, you can just double click the grain_windows_amd64.exe to start the relay)
You should see a terminal window displaying the port on which your relay and frontend are running.
If you get
Failed to copy app/static/examples/config.example.yml to config.yml: open app/static/examples/config.example.yml: no such file or directory
Then you probably forgot to put the app folder in the same directory as your executable or you did not unzip the folder.
Congrats! You're running grain 🌾!
You may want to change your NIP11 relay information document (relay_metadata.json) This informs clients of the capabilities, administrative contacts, and various server attributes. It's located in the same directory as your executable.
Configuration Files:
Once Grain has been executed for the first time, it will generate the default configuration files inside the directory where the executable is located. These files are:
bash config.yml whitelist.yml blacklist.ymlConfiguration Documentation
You can always find the latest example configs on my site or in the github repo here: config.yml
Config.yml
This
config.ymlfile is where you customize how your Grain relay operates. Each section controls different aspects of the relay's behavior.1.
mongodb(Database Settings)uri: mongodb://localhost:27017/:- This is the connection string for your MongoDB database.
mongodb://localhost:27017/indicates that your MongoDB server is running on the same computer as your Grain relay (localhost) and listening on port 27017 (the default MongoDB port).- If your MongoDB server is on a different machine, you'll need to change
localhostto the server's IP address or hostname. - The trailing
/indicates the root of the mongodb server. You will define the database in the next line.
database: grain:- This specifies the name of the MongoDB database that Grain will use to store Nostr events. Grain will create this database if it doesn't already exist.
- You can name the database whatever you want. If you want to run multiple grain relays, you can and they can have different databases running on the same mongo server.
2.
server(Relay Server Settings)port: :8181:- This sets the port on which your Grain relay will listen for incoming nostr websocket connections and what port the frontend will be available at.
read_timeout: 10 # in seconds:- This is the maximum time (in seconds) that the relay will wait for a client to send data before closing the connection.
write_timeout: 10 # in seconds:- This is the maximum time (in seconds) that the relay will wait for a client to receive data before closing the connection.
idle_timeout: 120 # in seconds:- This is the maximum time (in seconds) that the relay will keep a connection open if there's no activity.
max_connections: 100:- This sets the maximum number of simultaneous client connections that the relay will allow.
max_subscriptions_per_client: 10:- This sets the maximum amount of subscriptions a single client can request from the relay.
3.
resource_limits(System Resource Limits)cpu_cores: 2 # Limit the number of CPU cores the application can use:- This restricts the number of CPU cores that Grain can use. Useful for controlling resource usage on your server.
memory_mb: 1024 # Cap the maximum amount of RAM in MB the application can use:- This limits the maximum amount of RAM (in megabytes) that Grain can use.
heap_size_mb: 512 # Set a limit on the Go garbage collector's heap size in MB:- This sets a limit on the amount of memory that the Go programming language's garbage collector can use.
4.
auth(Authentication Settings)enabled: false # Enable or disable AUTH handling:- If set to
true, this enables authentication handling, requiring clients to authenticate before using the relay.
- If set to
relay_url: "wss://relay.example.com/" # Specify the relay URL:- If authentication is enabled, this is the url that clients will use to authenticate.
5.
UserSync(User Synchronization)user_sync: false:- If set to true, the relay will attempt to sync user data from other relays.
disable_at_startup: true:- If user sync is enabled, this will prevent the sync from starting when the relay starts.
initial_sync_relays: [...]:- A list of other relays to pull user data from.
kinds: []:- A list of event kinds to pull from the other relays. Leaving this empty will pull all event kinds.
limit: 100:- The limit of events to pull from the other relays.
exclude_non_whitelisted: true:- If set to true, only users on the whitelist will have their data synced.
interval: 360:- The interval in minutes that the relay will resync user data.
6.
backup_relay(Backup Relay)enabled: false:- If set to true, the relay will send copies of received events to the backup relay.
url: "wss://some-relay.com":- The url of the backup relay.
7.
event_purge(Event Purging)enabled: false:- If set to
true, the relay will automatically delete old events.
- If set to
keep_interval_hours: 24:- The number of hours to keep events before purging them.
purge_interval_minutes: 240:- How often (in minutes) the purging process runs.
purge_by_category: ...:- Allows you to specify which categories of events (regular, replaceable, addressable, deprecated) to purge.
purge_by_kind_enabled: false:- If set to true, events will be purged based on the kinds listed below.
kinds_to_purge: ...:- A list of event kinds to purge.
exclude_whitelisted: true:- If set to true, events from whitelisted users will not be purged.
8.
event_time_constraints(Event Time Constraints)min_created_at: 1577836800:- The minimum
created_attimestamp (Unix timestamp) that events must have to be accepted by the relay.
- The minimum
max_created_at_string: now+5m:- The maximum created at time that an event can have. This example shows that the max created at time is 5 minutes in the future from the time the event is received.
min_created_at_stringandmax_created_atwork the same way.
9.
rate_limit(Rate Limiting)ws_limit: 100:- The maximum number of WebSocket messages per second that the relay will accept.
ws_burst: 200:- Allows a temporary burst of WebSocket messages.
event_limit: 50:- The maximum number of Nostr events per second that the relay will accept.
event_burst: 100:- Allows a temporary burst of Nostr events.
req_limit: 50:- The limit of http requests per second.
req_burst: 100:- The allowed burst of http requests.
max_event_size: 51200:- The maximum size (in bytes) of a Nostr event that the relay will accept.
kind_size_limits: ...:- Allows you to set size limits for specific event kinds.
category_limits: ...:- Allows you to set rate limits for different event categories (ephemeral, addressable, regular, replaceable).
kind_limits: ...:- Allows you to set rate limits for specific event kinds.
By understanding these settings, you can tailor your Grain Nostr relay to meet your specific needs and resource constraints.
whitelist.yml
The
whitelist.ymlfile is used to control which users, event kinds, and domains are allowed to interact with your Grain relay. Here's a breakdown of the settings:1.
pubkey_whitelist(Public Key Whitelist)enabled: false:- If set to
true, this enables the public key whitelist. Only users whose public keys are listed will be allowed to publish events to your relay.
- If set to
pubkeys::- A list of hexadecimal public keys that are allowed to publish events.
pubkey1andpubkey2are placeholders, you will replace these with actual hexadecimal public keys.
npubs::- A list of npubs that are allowed to publish events.
npub18ls2km9aklhzw9yzqgjfu0anhz2z83hkeknw7sl22ptu8kfs3rjq54am44andnpub2are placeholders, replace them with actual npubs.- npubs are bech32 encoded public keys.
2.
kind_whitelist(Event Kind Whitelist)enabled: false:- If set to
true, this enables the event kind whitelist. Only events with the specified kinds will be allowed.
- If set to
kinds::- A list of event kinds (as strings) that are allowed.
"1"and"2"are example kinds. Replace these with the kinds you want to allow.- Example kinds are 0 for metadata, 1 for short text notes, and 2 for recommend server.
3.
domain_whitelist(Domain Whitelist)enabled: false:- If set to
true, this enables the domain whitelist. This checks the domains .well-known folder for their nostr.json. This file contains a list of pubkeys. They will be considered whitelisted if on this list.
- If set to
domains::- A list of domains that are allowed.
"example.com"and"anotherdomain.com"are example domains. Replace these with the domains you want to allow.
blacklist.yml
The
blacklist.ymlfile allows you to block specific content, users, and words from your Grain relay. Here's a breakdown of the settings:1.
enabled: true- This setting enables the blacklist functionality. If set to
true, the relay will actively block content and users based on the rules defined in this file.
2.
permanent_ban_words:- This section lists words that, if found in an event, will result in a permanent ban for the event's author.
- really bad wordis a placeholder. Replace it with any words you want to permanently block.
3.
temp_ban_words:- This section lists words that, if found in an event, will result in a temporary ban for the event's author.
- crypto,- web3, and- airdropare examples. Replace them with the words you want to temporarily block.
4.
max_temp_bans: 3- This sets the maximum number of temporary bans a user can receive before they are permanently banned.
5.
temp_ban_duration: 3600- This sets the duration of a temporary ban in seconds.
3600seconds equals one hour.
6.
permanent_blacklist_pubkeys:- This section lists hexadecimal public keys that are permanently blocked from using the relay.
- db0c9b8acd6101adb9b281c5321f98f6eebb33c5719d230ed1870997538a9765is an example. Replace it with the public keys you want to block.
7.
permanent_blacklist_npubs:- This section lists npubs that are permanently blocked from using the relay.
- npub1x0r5gflnk2mn6h3c70nvnywpy2j46gzqwg6k7uw6fxswyz0md9qqnhshtnis an example. Replace it with the npubs you want to block.- npubs are the human readable version of public keys.
8.
mutelist_authors:- This section lists hexadecimal public keys of author of a kind1000 mutelist. Pubkey authors on this mutelist will be considered on the permanent blacklist. This provides a nostr native way to handle the backlist of your relay
- 3fe0ab6cbdb7ee27148202249e3fb3b89423c6f6cda6ef43ea5057c3d93088e4is an example. Replace it with the public keys of authors that have a mutelist you would like to use as a blacklist. Consider using your own.- Important Note: The mutelist Event MUST be stored in this relay for it to be retrieved. This means your relay must have a copy of the authors kind10000 mutelist to consider them for the blacklist.
Running Grain as a Service:
Windows Service:
To run Grain as a Windows service, you can use tools like NSSM (Non-Sucking Service Manager). NSSM allows you to easily install and manage any application as a Windows service.
* For instructions on how to install NSSM, please refer to this article: [Link to NSSM install guide coming soon].-
Open Command Prompt as Administrator:
- Open the Windows Start menu, type "cmd," right-click on "Command Prompt," and select "Run as administrator."
-
Navigate to NSSM Directory:
- Use the
cdcommand to navigate to the directory where you extracted NSSM. For example, if you extracted it toC:\nssm, you would typecd C:\nssmand press Enter.
- Use the
-
Install the Grain Service:
- Run the command
nssm install grain. - A GUI will appear, allowing you to configure the service.
- Run the command
-
Configure Service Details:
- In the "Path" field, enter the full path to your Grain executable (e.g.,
C:\grain\grain_windows_amd64.exe). - In the "Startup directory" field, enter the directory where your Grain executable is located (e.g.,
C:\grain).
- In the "Path" field, enter the full path to your Grain executable (e.g.,
-
Install the Service:
- Click the "Install service" button.
-
Manage the Service:
- You can now manage the Grain service using the Windows Services manager. Open the Start menu, type "services.msc," and press Enter. You can start, stop, pause, or restart the Grain service from there.
Linux Service (systemd):
To run Grain as a Linux service, you can use systemd, the standard service manager for most modern Linux distributions.
-
Create a Systemd Service File:
- Open a text editor with root privileges (e.g.,
sudo nano /etc/systemd/system/grain.service).
- Open a text editor with root privileges (e.g.,
-
Add Service Configuration:
- Add the following content to the
grain.servicefile, replacing the placeholders with your actual paths and user information:
```toml [Unit] Description=Grain Nostr Relay After=network.target
[Service] ExecStart=/path/to/grain_linux_amd64 WorkingDirectory=/path/to/grain/directory Restart=always User=your_user #replace your_user Group=your_group #replace your_group
[Install] WantedBy=multi-user.target ```
- Replace
/path/to/grain/executablewith the full path to your Grain executable. - Replace
/path/to/grain/directorywith the directory containing your Grain executable. - Replace
your_userandyour_groupwith the username and group that will run the Grain service.
- Add the following content to the
-
Reload Systemd:
- Run the command
sudo systemctl daemon-reloadto reload the systemd configuration.
- Run the command
-
Enable the Service:
- Run the command
sudo systemctl enable grain.serviceto enable the service to start automatically on boot.
- Run the command
-
Start the Service:
- Run the command
sudo systemctl start grain.serviceto start the service immediately.
- Run the command
-
Check Service Status:
- Run the command
sudo systemctl status grain.serviceto check the status of the Grain service. This will show you if the service is running and any recent logs. - You can run
sudo journalctl -f -u grain.serviceto watch the logs
- Run the command
More guides are in the works for setting up tailscale to access your relay from anywhere over a private network and for setting up a cloudflare tunnel to your domain to deploy a grain relay accessible on a subdomain of your site eg wss://relay.yourdomain.com
-
 @ b5b28e8a:8930a19b
2025-05-02 13:07:56
@ b5b28e8a:8930a19b
2025-05-02 13:07:56Testing
This is my first page.
-
 @ 75869cfa:76819987
2025-03-18 07:54:38
@ 75869cfa:76819987
2025-03-18 07:54:38GM, Nostriches!
The Nostr Review is a biweekly newsletter focused on Nostr statistics, protocol updates, exciting programs, the long-form content ecosystem, and key events happening in the Nostr-verse. If you’re interested, join me in covering updates from the Nostr ecosystem!
Quick review:
In the past two weeks, Nostr statistics indicate over 225,000 daily trusted pubkey events. The number of new users has seen a notable decrease, with profiles containing a contact list dropping by 95%. More than 10 million events have been published, with posts and reposts showing a decrease. Total Zap activity stands at approximately 15 million, marking a 10% decrease.
Additionally, 26 pull requests were submitted to the Nostr protocol, with 6 merged. A total of 45 Nostr projects were tracked, with 8 releasing product updates, and over 463 long-form articles were published, 29% focusing on Bitcoin and Nostr. During this period, 2 notable events took place, and 3 significant events are upcoming.
Nostr Statistics
Based on user activity, the total daily trusted pubkeys writing events is about 225,000, representing a slight 8 % decrease compared to the previous period. Daily activity peaked at 18179 events, with a low of approximately 16093.
The number of new users has decreased significantly. Profiles with a contact list are now around 17,511, reflecting a 95% drop. Profiles with a bio have decreased by 62% compared to the previous period. The only category showing growth is pubkeys writing events, which have increased by 27%.
Regarding event publishing, all metrics have shown a decline. The total number of note events published is around 10 million, reflecting a 14% decrease. Posts remain the most dominant in terms of volume, totaling approximately 1.6 million, which is a 6.1% decrease. Both reposts and reactions have decreased by about 10%.
For zap activity, the total zap amount is about 15 million, showing an increase of over 10% compared to the previous period.
Data source: https://stats.nostr.band/
NIPs
nostr:npub1gcxzte5zlkncx26j68ez60fzkvtkm9e0vrwdcvsjakxf9mu9qewqlfnj5z is proposing that A bulletin board is a relay-centric system of forums where users can post and reply to others, typically around a specific community. The relay operator controls and moderates who can post and view content. A board is defined by kind:30890. Its naddr representation must provide the community's home relays, from which all posts should be gathered. No other relays should be used.
nostr:npub1xy54p83r6wnpyhs52xjeztd7qyyeu9ghymz8v66yu8kt3jzx75rqhf3urc is proposing a standardized way to represent fitness and workout data in Nostr, including: Exercise Templates (kind: 33401) for storing reusable exercise definitions, Workout Templates (kind: 33402) for defining workout plans, Workout Records (kind: 1301) for recording completed workouts. The format provides structured data for fitness tracking while following Nostr conventions for data representation.Many fitness applications use proprietary formats, locking user data into specific platforms. This NIP enables decentralized fitness tracking, allowing users to control their workout data and history while facilitating social sharing and integration between fitness applications.
nostr:npub1zk6u7mxlflguqteghn8q7xtu47hyerruv6379c36l8lxzzr4x90q0gl6ef is proposing a PR introduces two "1-click" connection flows for setting up initial NWC connections. Rather than having to copy-paste a connection string, the user is presented with an authorization page which they can approve or decline. The secret is generated locally and never leaves the client. HTTP flow - for publicly accessible lightning wallets. Implemented in Alby Hub (my.albyhub.com) and CoinOS (coinos.io). Nostr flow - for mobile-based / self-hosted lightning wallets, very similar to NWA but without a new event type added. Implemented in Alby Go and Alby Hub. Benefits over NWC Deep Links are that it works cross-device, mobile to web, and the client-generated secret never leaves the client. Both flows are also implemented in Alby JS SDK and Bitcoin Connect.
add B0 NIP for Blossom interaction
nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 describes a tiny subset of possible Blossom capabilities, but arguably the most important from the point of view of a most basic Nostr client. This NIP specifies how Nostr clients can use Blossom for handling media. Blossom is a set of standards (called BUDs) for dealing with servers that store files addressable by their SHA-256 sums. Nostr clients may make use of all the BUDs for allowing users to upload files, manage their own files and so on, but most importantly Nostr clients SHOULD make use of BUD-03 to fetch kind:10063 lists of servers for each user.
nostr:npub149p5act9a5qm9p47elp8w8h3wpwn2d7s2xecw2ygnrxqp4wgsklq9g722q defines a standard for creating, managing and publishing to communities by leveraging existing key pairs and relays, introducing the concept of "Communi-keys". This approach allows any existing npub to become a community (identity + manager) while maintaining compatibility with existing relay infrastructure.
A way for relays to be honest about their algos
securitybrahh is proposing a PR introduces NIP-41, a way for relays to be honest about their algos, edits 01.md to account for changes in limit (related #78, #1434, received_at?, #620, #1645) when algo is provided, appends 11.md for relays to advertize whether they are an aggregator or not and their provided algos. solves #522, supersedes #579.
nip31: template-based "alt" tags for known kinds
nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 is proposing that clients hardcoding alt tags are not very trustworthy. alt tags tend to be garbage in a long-enough timeframe.This fixes it with hardcoded rich templates that anyone can implement very easily without having to do it manually for each kind. alt tags can still be used as a fallback.
nostr:npub1gcxzte5zlkncx26j68ez60fzkvtkm9e0vrwdcvsjakxf9mu9qewqlfnj5z is proposing a PR addresses 3 main problems of NIP-44v2. First, It has a message size limit of 65Kb, which is unnecessarily small. Second, It forces the encrypting key to be the same as the event's signing key. Which forces multi-sig actors to share their main private key in order to encrypt the payload that would be later signed by the group. Decoupling singing and encryption keys, for both source and destination, is one of the goals of this version. And It offers no way to describe what's inside the encrypted blob before requesting the user's approval to decrypt and send the decrypted info back to the requesting application. This PR adds an alt description to allow decrypting signers to display a message and warn the user of what type of information the requesting application is receiving.
Notable Projects
Damus nostr:npub18m76awca3y37hkvuneavuw6pjj4525fw90necxmadrvjg0sdy6qsngq955
- Notes in progress will always be persisted and saved automatically. Never lose those banger notes when you aren't quite ready to ship them.
- Make your profile look just right without any fuss. It also optimizes them on upload now to not nuke other people’s phone data bills.
- You won't see the same note more than once in your home feed.
- Fixed note loading when clicking notifications and damus.io links.
- Fixed NWC not working when you first connect a wallet.
- Fixed overly sensitive and mildly infuriating touch gestures in the thread view when scrolling
Primal nostr:npub12vkcxr0luzwp8e673v29eqjhrr7p9vqq8asav85swaepclllj09sylpugg
Primal for Android build 2.1.9 has been released. * Multi-account support * Deep linking support * "Share via Primal" support * Bug fixes and improvements
Yakihonne nostr:npub1yzvxlwp7wawed5vgefwfmugvumtp8c8t0etk3g8sky4n0ndvyxesnxrf8q
YakiHonne Wallet just got a fresh new look!
0xchat nostr:npub1tm99pgz2lth724jeld6gzz6zv48zy6xp4n9xu5uqrwvx9km54qaqkkxn72
0xchat v1.4.7-beta release * Upgraded the Flutter framework to v3.29.0. * Private chat implementation changed to NIP-104 Nostr MLS. * NIP-17 and NIP-29 messages now support q tags. * You can swipe left to reply to your own messages. * Chat messages now support code block display. * Copy images from the clipboard. * Fixed an issue where underlined text in chat appeared as italic.
GOSSIP 0.14.0 nostr:npub189j8y280mhezlp98ecmdzydn0r8970g4hpqpx3u9tcztynywfczqqr3tg8
Several major bugs have been fixed in the last week. * New Features and Improvements * Zappers and amounts are now shown (click on the zap total) * Reactions and who reacted are now shown (click on the reaction numbers) * Multiple search UI/UX improvements * Undo Send works for DMs too * Undo Send now restores the draft * UI: Side panel contains less so it can be thinner. Bottom bar added. * UI: frame count and spinner (optional) * Relay UI: sorting by score puts important relays at the top. * Relay UI: add more filters so all the bits are covered * Image and video loading is much faster (significant lag reduction) * Thread loading fix makes threads load far more reliably * Settings have reset-to-default buttons, so you don't get too lost. * Setting 'limit inbox seeking to inbox relays' may help avoid spam at the expense of possibly * Fix some bugs * And more updates
Nostur v1.18.1 nostr:npub1n0stur7q092gyverzc2wfc00e8egkrdnnqq3alhv7p072u89m5es5mk6h0
New in this version: * Floating mini video player * Videos: Save to library, Copy video URL, Add bookmark * Improved video stream / chat view * Top zaps on live chat * Posting to Picture-first * Profile view: Show interactions with you (conversations, reactions, zaps, reposts) * Profile view: Show actual reactions instead of only Likes * Improved search + Bookmark search * Detect nsfw / content-warning in posts * Show more to show reactions outside Web of Trust * Show more to show zaps outside Web of Trust * Support .avif image format * Support .mp3 format * Support .m4v video format * Improved zap verification for changed wallets * Improved outbox support * Show label on restricted posts * Low data mode: load media in app on tap instead of external browser * Many other bug fixes and performance improvements
Alby nostr:npub1getal6ykt05fsz5nqu4uld09nfj3y3qxmv8crys4aeut53unfvlqr80nfm
Latest two releases of Alby Go, 1.10 and 1.11, brought you lots of goodies: * BTC Map integration for quick access to global bitcoin merchants map * Confirm new NWC connections to your Alby Hub directly in Alby Go! No more copy-pasting or QR code scanning * Support for MoneyBadger Pay Pick n Pay QR payments in over 2000 stores in South Africa
ZEUS v0.10.0 nostr:npub1xnf02f60r9v0e5kty33a404dm79zr7z2eepyrk5gsq3m7pwvsz2sazlpr5
ZEUS v0.10.0 is now available. This release features the ability to renew channel leases, spin up multiple embedded wallets, Nostr Wallet Connect client support, and more. * Renewable channels * NWC client support * Ability to create multiple Embedded LND 'node in the phone' wallets * Ability to delete Embedded LND wallets * Embedded LND: v0.18.5-beta * New share button (share ZEUS QR images) * Tools: Export Activity CSVs, Developer tools, chantools * Activity: filter by max amount, memo, and note
Long-Form Content Eco
In the past two weeks, more than 463 long-form articles have been published, including over 91 articles on Bitcoin and more than 41 related to Nostr, accounting for 29% of the total content.
These articles about Nostr mainly explore the rise of Nostr as a decentralized platform that is reshaping the future of the internet. They emphasize Nostr's role in providing users with greater freedom, ownership, and fair monetization, particularly in the realm of content creation. The platform is positioned as a counter to centralized social media networks, offering uncensored interactions, enhanced privacy, and direct transactions. Many articles delve into Nostr’s potential to integrate with Bitcoin, creating a Layer 3 solution that promises to end the dominance of old internet structures. Discussions also cover the technical aspects of Nostr, such as the implementation of relays and group functionalities, as well as security concerns like account hacks. Furthermore, there is an exploration of the philosophical and anthropological dimensions of Nostr, with the rise of "Dark Nostr" being portrayed as a deeper expression of decentralized freedom.
The Bitcoin articles discuss the ongoing evolution of Bitcoin and its increasing integration into global financial systems. Many articles focus on the growing adoption of Bitcoin, particularly in areas like Argentina and the U.S., where Bitcoin is being used for rental payments and the establishment of a strategic Bitcoin reserve. Bitcoin is also portrayed as a response to the centralized financial system, with discussions about how it can empower individuals through financial sovereignty, provide a hedge against inflation, and create fairer monetization models for creators. Additionally, the articles explore the challenges and opportunities within the Bitcoin ecosystem, including the rise of Bitcoin ETFs, the development of Bitcoin mining, and the potential impact of AI on Bitcoin adoption. There is also emphasis on Bitcoin's cultural and economic implications, as well as the need for decentralized education and innovation to drive further adoption.
Thank you, nostr:npub1ygzsm5m9ndtgch9n22cwsx2clwvxhk2pqvdfp36t5lmdyjqvz84qkca2m5 nostr:npub1rsv7kx5avkmq74p85v878e9d5g3w626343xhyg76z5ctfc30kz7q9u4dke nostr:npub17wrn0xxg0hfq7734cfm7gkyx3u82yfrqcdpperzzfqxrjf9n7tes6ra78k nostr:npub1fxq5crl52mre7luhl8uqsa639p50853r3dtl0j0wwvyfkuk4f6ssc5tahv nostr:npub1qny3tkh0acurzla8x3zy4nhrjz5zd8l9sy9jys09umwng00manysew95gx nostr:npub19mf4jm44umnup4he4cdqrjk3us966qhdnc3zrlpjx93y4x95e3uq9qkfu2 nostr:npub1marc26z8nh3xkj5rcx7ufkatvx6ueqhp5vfw9v5teq26z254renshtf3g0 nostr:npub1uv0m8xc6q4cnj2p0tewmcgkyzg8cnteyhed0zv30ez03w6dzwvnqtu6gwl nostr:npub1ygzsm5m9ndtgch9n22cwsx2clwvxhk2pqvdfp36t5lmdyjqvz84qkca2m5 nostr:npub1mhcr4j594hsrnen594d7700n2t03n8gdx83zhxzculk6sh9nhwlq7uc226 nostr:npub1xzuej94pvqzwy0ynemeq6phct96wjpplaz9urd7y2q8ck0xxu0lqartaqn nostr:npub1gqgpfv65dz8whvyup942daagsmwauj0d8gtxv9kpfvgxzkw4ga4s4w9awr nostr:npub16dswlmzpcys0axfm8kvysclaqhl5zv20ueurrygpnnm7k9ys0d0s2v653f and others, for your work. Enriching Nostr’s long-form content ecosystem is crucial.
Nostriches Global Meet Ups
Recently, several Nostr events have been hosted in different countries. * The first Bitcoin Meetup organized by Mi Primer Bitcoin was successfully held on March 14, 2025, at Texijal Pizza in Apaneca. The event included Bitcoin education, networking, a Q&A session, and merchandise distribution, offering an exciting experience for all participants.
* The Btrust Space discussion was successfully held on March 13, 2024. The event focused on how to support Bitcoin developers, fund open-source contributions, and grow the Bitcoin ecosystem. The speakers included Bitcoin core contributors, Btrust CEO, engineering leads, and other project leaders.Here is the upcoming Nostr event that you might want to check out.
- The Nostr Workshop, organized by YakiHonne and Bitcoin Safari, will take place online via Google Meet on March 17, 2025, at 7:00 PM (GMT+1). The event will introduce the Nostr ecosystem and Bitcoin payments, with participants learning about decentralized technology through YakiHonne and earning rewards. Register and verify your account to claim exclusive rewards, and invite friends to unlock additional rewards.
- The 2025 Bitcoin, Crypto Economy, and Law FAQ Webinar will be held online on March 20, 2025 (Thursday) from 12:00 to 13:00 Argentina time. The webinar will be hosted by Martin Paolantonio (Academic Director of the course) and Daniel Rybnik (Lawyer specializing in Banking, Corporate, and Financial Law). The session aims to introduce the academic program and explore Bitcoin, the crypto economy, and related legal issues.
- Bitcoin Educators Unconference 2025 will take place on April 10, 2025, at Bitcoin Park in Nashville, Tennessee, USA. This event is non-sponsored and follows an Unconference format, allowing all participants to apply as speakers and share their Bitcoin education experiences in a free and interactive environment. The event has open-sourced all its blueprints and Standard Operating Procedures (SOPs) to encourage global communities to organize similar Unconference events.
Additionally, We warmly invite event organizers who have held recent activities to reach out to us so we can work together to promote the prosperity and development of the Nostr ecosystem.
Thanks for reading! If there’s anything I missed, feel free to reach out and help improve the completeness and accuracy of my coverage.
-
 @ 000002de:c05780a7
2025-05-01 23:17:11
@ 000002de:c05780a7
2025-05-01 23:17:11A lot of typing has been done comparing various right wing figures and people like Donald Trump and Elon Mush to Fascism and Nazism. It is frankly pretty absurd at this point. I'd be with them if they were just talking about these people being authoritarians. They clearly are in many ways. I'm not a fan.
But very little is said in a "non-partisan" way about the left. This is gonna be short and is meant to peak your curiosity to go and do some research for yourself.
The economist Milton Friedman famously said.
"After the fall of communism, everybody in the world agreed that socialism was a failure. Everybody in the world, more or less, agreed that capitalism was a success. And every capitalist country in the world apparently deduced from that what the West needed was more socialism."
This was said a long time ago and it is still the case. People espouse socialist ideas without even a concern about being called out for it. The same is NOT true of fascism or even traditional American patriotism.
But many of you may not realize just how deep the rot of socialism goes. Most people agree that the USSR committed terrible acts and was a failure. Before the creation of the USSR two socialists movements fought for power and control, the Bolsheviks and Mensheviks. The primary difference between the two groups was how to bring about socialism. The Bolsheviks led by Lenin favored a more radical revolutionary force led by a small group. The Mensheviks, led by Julius Martov, preferred a larger, more democratic rise to power. They supported a more gradual rise of socialism. In October of 1917 the Bolsheviks seized power in Russia in a bloody revolution.
Even to this day there are two different minds around how to bring about socialism. In the US the Menshevik approach is the one more popular. People like Bernie and AOC are this type of socialist. But make no mistake. They want to bring about a socialist utopian society. The type of system we have seen fail time and time again.
A few years ago I heard about another socialist movement and was frankly shocked that I had never heard about it before. In 1890 Britain a group of socialists formed an organization called the Fabian Society. The Fabians were/are socialists. But they believe in gradual incrementalism to bring about socialism. So what did the do you ask? They were at the center of the founding of the Labour party in the UK. Now, you might say. Big deal. But here's the weird thing. The Fabian Society's coat of arms was literally a wolf in sheep's clothing
They sought to bring about socialism covertly through democratic processes by presenting themselves as more moderate politicians. They have worked for decades to bring about socialism in the UK. If you don't count Margret Thatcher's era they've done a pretty great job. The UK is a mess.
So what does this have to do with May Day or Labor day for that matter? Well, socialists are at the center of every labor movement and celebrations like May day. Socialist ideas have been pumped into the government textbooks in the US for decades. Teachers are instructed in Universities full of believers in this wolf in sheep's clothing movement of democratic socialism.
Socialism leads to death and poverty. I'm not here to say that the US economy is the example for what the world should do. I'm a free market guy. We live in a corporatism led economy where the state partners with corporations to screw many in the US as well as the world. But I can tell you this. Socialism would be even worse.
The famous and infamous Russian anarchist Emma Goldman upon returning from her visit to the USSR was broken hearted. She had been a supporter of the revolution, but when she saw it with her own eyes she had a change of heart.
The compassion that seems to be a part of socialism is a lie. You can't institutionalize compassion. It has to come from the people, not a system. We should care for our brothers and sisters. But WE have to do it. We can't take from one group and give to another. We can't surrender our liberties to those that say they will take care of it for us. We have to do it. Capitalism is amoral. The free market is amoral. Both require us to be moral and show the way.
I hope this sparks your interest into looking into the history around socialist movements across the globe. I don't doubt that some have good motives, but the results are disastrous for the masses.
originally posted at https://stacker.news/items/968901
-
 @ e4950c93:1b99eccd
2025-05-02 12:48:46
@ e4950c93:1b99eccd
2025-05-02 12:48:46🧵 Produits en cette matière
Les marques suivantes proposent des produits fait exclusivement ou principalement avec cette matière :
Vêtements
Cet article est publié sur origine-nature.com 🌐 See this article in English
-
 @ e4950c93:1b99eccd
2025-05-02 12:47:27
@ e4950c93:1b99eccd
2025-05-02 12:47:27Dilling est une marque danoise qui crée des vêtements en laine, soie et coton biologique pour toute la famille.
Matières naturelles utilisées dans les produits
- Coton (biologique)
- Laine (mérinos, alpaga)
- Latex naturel (OEKO-TEX ®)
- Soie
⚠️ Attention, certains produits de cette marque (notamment les Vêtements - chaussettes, vestes, strings, shorts) contiennent des matières non naturelles, dont :
- Elasthanne
- Polyamide, nylon (nylon recyclé)
- Polyester (recyclé)
Catégories de produits proposés
-
Vêtements : homme, femme, enfant, bébé, sous-vêtements, t-shirts, débardeurs, robes, vestes, pantalons, shorts, pulls, gilets, bodies, combinaisons, culottes, slips, boxers...
Autres informations
- Ecolabel Nordic Swan (teintures)
- Fabriqué en Lituanie (coupe et couture)
- Fabriqué au Danemark (teintures)
- Fabriqué en Europe
👉 En savoir plus sur le site de la marque
Cet article est publié sur origine-nature.com 🌐 See this article in English
📝 Tu peux contribuer à cette fiche en suggérant une modification en commentaire.
🗣️ Tu utilises ce produit ? Partage ton avis en commentaire.
⚡ Heureu-x-se de trouver cette information ? Soutiens le projet en faisant un don, pour remercier les contribut-eur-ice-s.
-
 @ 04cb16e4:2ec3e5d5
2025-03-13 21:26:13
@ 04cb16e4:2ec3e5d5
2025-03-13 21:26:13Wenn man etwas verkaufen will, muss man eine Geschichte über sein Produkt erzählen. Nur wenige können etwas damit anfangen, wenn du sagst: Unser Produkt enthält 50 Gramm Hafer (hoffentlich gentechnikfrei), 5 mittelgroße Erdbeeren, Spuren von Sesamschalen sowie einen Teelöffel Honig. So funktioniert das nicht. Dein Riegel braucht einen Namen und eine Geschichte.
Wenn wir über Krieg und Frieden sprechen, denn gibt es zumeist Zahlen, Fakten und Meinungen. Tausende von Kindern die in einem Krieg getötet werden sind eine schockierende Anzahl. Nimmst du die Zahlen weg und beschäftigst dich mit jedem einzelnen Schicksal, dann ist das unmöglich zu ertragen. Also kämpfen wir hier vor Ort, in Deutschland, zwar nicht mit Waffen gegeneinander, sondern mittels unserer Meinungen in Kombination mit zu vermittelnden relativen Wahrheiten. Da kommt das Ego ins Spiel. Wir wollen unbedingt Recht haben! Irgendeiner soll in diesem Meinungskampf am Ende als Gewinner dastehen. Weil er die besseren Argumente hat. Schließlich werden Emotionen mit Fakten vermischt und als Totschlagargumente in die Gegenfront geworfen.
Was aber, wenn man eine Geschichte über den Krieg erzählt, die jeden mitnehmen kann, ganz gleich, welche Meinung man zu den aktuell verhandelten Kampfschauplätzen hat? Alles Trennende wird aus der Erzählung herausgenommen und was bleibt, sind die zerstörerische Kraft des Krieges und die Verantwortung jedes einzelnen Menschen zu entscheiden, ob er dieses grausame Monster füttert oder eben nicht. In dem afrikanischen Märchen „Sheikhi“ basieren diese Entscheidungen nicht auf Fakten und Meinungen, sondern auf persönlichen Erfahrungen. Die Protagonisten nehmen uns mit in ihre Welt und lassen uns ihre inneren Kämpfe, Zweifel, Ängste und Hoffnungen miterleben. Wir können uns mit ihnen identifizieren, obwohl wir unter völlig anderen Bedingungen leben und sterben.
Hier kannst du das Buch direkt beim Verlag bestellen
Die alternative Buchmesse Seitenwechsel
Am Ende des Buches konnte ich gar nicht anders, als eine tiefe Sehnsucht nach Frieden und Einigkeit zu verspüren. Diese Sehnsucht basierte aber nicht mehr auf dem Bedürfnis, bessere Argumente als die vermeintliche Gegenseite zu haben, sondern vielmehr darauf, dass dieses verzweifelte Ringen und Hassen endlich zu einem Ende kommt. Nicht nur auf den Schlachtfeldern Asiens und Afrikas, sondern ebenfalls auf Facebook, X, den Straßen unserer Städte und im Krieg jedes Menschen gegen sich selbst. Inzwischen gelingt es mir immer öfter, mir einen bissigen Kommentar zu verkneifen, wenn jemand auf Facebook etwas schreibt, was ich unerträglich finde. Ich weiß, das ich ihn nicht vom Gegenteil überzeugen werde und das mein Kommentar das selbe Monster füttert, dass sich an den Opfern des Krieges satt isst.
Wenn es irgendwo Menschen auf der Welt gibt, die Mord und Folter verzeihen können, dann kann auch ich eine andere Meinung ertragen ohne rechthaberisch, arrogant und destruktiv zu werden. Notfalls gehe ich in den Wald und schreie.
-
 @ e4950c93:1b99eccd
2025-05-02 12:19:28
@ e4950c93:1b99eccd
2025-05-02 12:19:28Qu'est-ce qu'une matière naturelle ? La question fait débat, et chacun-e privilégiera ses propres critères. Voici comment les matières sont classées sur ce site. La liste est régulièrement mise à jour en fonction des produits ajoutés. N'hésitez pas à partager votre avis !
✅ Matières naturelles
Matières d'origine végétale, animale ou minérale, sans transformation chimique altérant leur structure moléculaire.
🌱 Principaux critères : - Biodégradabilité - Non-toxicité - Présence naturelle nécessitant le minimum de transformation
🔍 Liste des matières naturelles : - Bois - Cellulose régénérée (cupra, lyocell, modal, viscose) - Chanvre - Coton - Cuir - Liège - Lin - Laine - Latex naturel, caoutchouc - Métal - Soie - Terre - Verre - … (Autres matières)
⚠️ Bien que "naturelles", ces matières peuvent générer des impacts négatifs selon leurs conditions de production (pollution par pesticides, consommation d’eau excessive, traitement chimique, exploitation animale…). Ces impacts sont mentionnés sur la fiche de chaque matière.
Les versions biologiques de ces matières (sans traitement chimique, maltraitance animale, etc.) sont privilégiées pour référencer les produits sur ce site, tel qu'indiqué sur la fiche de chaque matière (à venir).
Les versions conventionnelles ne sont référencées que tant que lorsqu'il n'a pas encore été trouvé d'alternative plus durable pour cette catégorie de produits.
🚫 Matières non naturelles
Matières synthétiques ou fortement modifiées, souvent issues de la pétrochimie.
📌 Principaux problèmes : - Toxicité et émissions de microplastiques - Dépendance aux énergies fossiles - Mauvaise biodégradabilité
🔍 Liste des matières non naturelles : - Acrylique - Élasthanne, lycra, spandex - Polyamides, nylon - Polyester - Silicone - … (Autres matières)
⚠️ Ces matières ne sont pas admises sur le site. Néanmoins, elles peuvent être présentes dans certains produits référencés lorsque :
- elles sont utilisées en accessoire amovible (ex. : élastiques, boutons… généralement non indiqué dans la composition par la marque) pouvant être retiré pour le recyclage ou compostage, et
- aucune alternative 100 % naturelle n’a encore été identifiée pour cette catégorie de produits.
Dans ce cas, un avertissement est alors affiché sur la fiche du produit.
Cet article est publié sur origine-nature.com 🌐 See this article in English
-
 @ 2183e947:f497b975
2025-05-01 22:33:48
@ 2183e947:f497b975
2025-05-01 22:33:48Most darknet markets (DNMs) are designed poorly in the following ways:
1. Hosting
Most DNMs use a model whereby merchants fill out a form to create their listings, and the data they submit then gets hosted on the DNM's servers. In scenarios where a "legal" website would be forced to censor that content (e.g. a DMCA takedown order), DNMs, of course, do not obey. This can lead to authorities trying to find the DNM's servers to take enforcement actions against them. This design creates a single point of failure.
A better design is to outsource hosting to third parties. Let merchants host their listings on nostr relays, not on the DNM's server. The DNM should only be designed as an open source interface for exploring listings hosted elsewhere, that way takedown orders end up with the people who actually host the listings, i.e. with nostr relays, and not with the DNM itself. And if a nostr relay DOES go down due to enforcement action, it does not significantly affect the DNM -- they'll just stop querying for listings from that relay in their next software update, because that relay doesn't work anymore, and only query for listings from relays that still work.
2. Moderation
Most DNMs have employees who curate the listings on the DNM. For example, they approve/deny listings depending on whether they fit the content policies of the website. Some DNMs are only for drugs, others are only for firearms. The problem is, to approve a criminal listing is, in the eyes of law enforcement, an act of conspiracy. Consequently, they don't just go after the merchant who made the listing but the moderators who approved it, and since the moderators typically act under the direction of the DNM, this means the police go after the DNM itself.
A better design is to outsource moderation to third parties. Let anyone call themselves a moderator and create lists of approved goods and services. Merchants can pay the most popular third party moderators to add their products to their lists. The DNM itself just lets its users pick which moderators to use, such that the user's choice -- and not a choice by the DNM -- determines what goods and services the user sees in the interface.
That way, the police go after the moderators and merchants rather than the DNM itself, which is basically just a web browser: it doesn't host anything or approve of any content, it just shows what its users tell it to show. And if a popular moderator gets arrested, his list will still work for a while, but will gradually get more and more outdated, leading someone else to eventually become the new most popular moderator, and a natural transition can occur.
3. Escrow
Most DNMs offer an escrow solution whereby users do not pay merchants directly. Rather, during the Checkout process, they put their money in escrow, and request the DNM to release it to the merchant when the product arrives, otherwise they initiate a dispute. Most DNMs consider escrow necessary because DNM users and merchants do not trust one another; users don't want to pay for a product first and then discover that the merchant never ships it, and merchants don't want to ship a product first and then discover that the user never pays for it.
The problem is, running an escrow solution for criminals is almost certain to get you accused of conspiracy, money laundering, and unlicensed money transmission, so the police are likely to shut down any DNM that does this. A better design is to oursource escrow to third parties. Let anyone call themselves an escrow, and let moderators approve escrows just like they approve listings. A merchant or user who doesn't trust the escrows chosen by a given moderator can just pick a different moderator. That way, the police go after the third party escrows rather than the DNM itself, which never touches user funds.
4. Consequences
Designing a DNM along these principles has an interesting consequence: the DNM is no longer anything but an interface, a glorified web browser. It doesn't host any content, approve any listings, or touch any money. It doesn't even really need a server -- it can just be an HTML file that users open up on their computer or smart phone. For two reasons, such a program is hard to take down:
First, it is hard for the police to justify going after the DNM, since there are no charges to bring. Its maintainers aren't doing anything illegal, no more than Firefox does anything illegal by maintaining a web browser that some people use to browse illegal content. What the user displays in the app is up to them, not to the code maintainers. Second, if the police decided to go after the DNM anyway, they still couldn't take it down because it's just an HTML file -- the maintainers do not even need to run a server to host the file, because users can share it with one another, eliminating all single points of failure.
Another consequence of this design is this: most of the listings will probably be legal, because there is more demand for legal goods and services than illegal ones. Users who want to find illegal goods would pick moderators who only approve those listings, but everyone else would use "legal" moderators, and the app would not, at first glance, look much like a DNM, just a marketplace for legal goods and services. To find the illegal stuff that lurks among the abundant legal stuff, you'd probably have to filter for it via your selection of moderators, making it seem like the "default" mode is legal.
5. Conclusion
I think this DNM model is far better than the designs that prevail today. It is easier to maintain, harder to take down, and pushes the "hard parts" to the edges, so that the DNM is not significantly affected even if a major merchant, moderator, or escrow gets arrested. I hope it comes to fruition.
-
 @ 2cb30c36:cc7ecec1
2025-05-01 21:52:50
@ 2cb30c36:cc7ecec1
2025-05-01 21:52:50Test
This is a test
-
 @ e4950c93:1b99eccd
2025-05-02 10:54:24
@ e4950c93:1b99eccd
2025-05-02 10:54:24Les rétributions sont une démarche expérimentale de partage de la valeur entre les contribut-eur-rice-s du site, via un partage des revenus aux conditions suivantes :
- Les revenus éventuels générés par ce site chaque mois sont répartis sur les 12 mois suivants, afin d’assurer une visibilité sur le projet et de lisser les variations mensuelles.
- Chaque 1er du mois, la moitié des revenus est distribuée à l’ensemble des contribut-eur-rice-s, proportionnellement au nombre de leurs contributions validées.
- Les contributions restent valides à vie, mais les rétributions ne sont versées qu’aux contribut-eur-rice-s ayant réalisé au moins une contribution validée au cours des 12 derniers mois.
Modalités de paiement
Les rétributions sont effectuées via le réseau Lightning, sous forme de sats (la plus petite unité du Bitcoin).
Pour en bénéficier, le compte NOSTR avec lequel tu as réalisé tes contributions doit être lié à un porte-monnaie Lightning.
💡 Si tu découvres ces outils :
- Pas encore de compte ? Une solution simple est d'en créer un sur un client NOSTR open source comme yakihonne.com pour y paramétrer ton profil et ton wallet. Ensuite, récupère tes clés NOSTR (dans les settings) et enregistre les dans un coffre sécurisé comme nsec.app pour te connecter ici et commencer à contribuer.
- Tu as déjà commencé à contribuer sur le site ? Conserve bien les clés NOSTR fournies par le site dans un coffre comme nsec.app. Tu peux aussi te connecter avec sur yakihonne.com pour paramétrer ton profil.
- Tu peux aussi contribuer directement depuis yakihonne.com sur les articles d'Origine Nature.
👉 En savoir plus sur les contributions
Prochaines rétributions
A venir.
Cet article est publié sur origine-nature.com 🌐 See this article in English
-
 @ a012dc82:6458a70d
2025-03-11 15:41:36
@ a012dc82:6458a70d
2025-03-11 15:41:36Argentina's journey through economic turmoil has been long and fraught with challenges. The country has grappled with inflation, debt, and a fragile economic structure that has left policymakers searching for solutions. In this context, President Javier Milei's introduction of the "Ley Ómnibus" represented a bold step towards addressing these systemic issues. The reform package was not just a set of isolated measures but a comprehensive plan aimed at overhauling the Argentine economy and social framework. The intention was to create a more robust, free, and prosperous Argentina, where economic freedoms could lead to broader social benefits.
The "Ley Ómnibus" was ambitious in its scope, covering a wide range of areas from tax reform to social policies, aiming to stimulate economic growth, reduce bureaucratic red tape, and enhance the overall quality of life for Argentines. This package was seen as a critical move to reset the economic compass of the country, aiming to attract foreign investment, boost local industry, and provide a clearer, more stable environment for businesses and individuals alike. However, such sweeping reforms were bound to encounter resistance, particularly when they touched upon sensitive areas like taxation and digital assets.
Table of Contents
-
The Crypto Tax Proposal: Initial Considerations
-
Public Backlash and Strategic Withdrawal
-
The Rationale Behind Dropping Crypto Taxes
-
Implications for Crypto Investors and the Market
-
Milei's Political Strategy and Future Prospects
-
Conclusion
-
FAQs
The Crypto Tax Proposal: Initial Considerations
Within the vast array of proposals in the Ley Ómnibus, the crypto tax stood out due to its novelty and the growing interest in digital currencies within Argentina. The country had seen a surge in cryptocurrency adoption, driven by factors such as high inflation rates and currency controls that made traditional financial systems less attractive. Cryptocurrencies offered an alternative for savings, investment, and transactions, leading to a burgeoning crypto economy.
The initial rationale behind proposing a crypto tax was multifaceted. On one hand, it aimed to bring Argentina in line with global trends where countries are increasingly seeking to regulate and tax digital currencies. On the other hand, it was seen as a potential new revenue stream for the government, which was desperately seeking funds to address its fiscal deficits. The proposal also intended to bring transparency to a sector that is often criticized for its opacity, making it easier to combat fraud, money laundering, and other illicit activities associated with cryptocurrencies.
However, the proposal was not just about regulation and revenue. It was also a litmus test for Argentina's approach to innovation and digital transformation. How the government handled this issue would signal its stance towards new technologies and economic paradigms, which are increasingly dominated by digital assets and fintech innovations.
Public Backlash and Strategic Withdrawal
The backlash against the proposed crypto taxes was swift and significant. The crypto community in Argentina, which had been flourishing in an environment of relative freedom, saw the tax as a direct threat to its growth and viability. But the discontent went beyond the crypto enthusiasts; the general public, already burdened by high taxes and economic instability, viewed the proposal as yet another financial strain.
The protests and debates that ensued highlighted a broader discontent with the government's approach to economic management. Many Argentines felt that the focus should be on fixing the fundamental issues plaguing the economy, such as inflation and corruption, rather than imposing new taxes. The crypto tax became a symbol of the government's perceived detachment from the real concerns of its citizens.
In this heated atmosphere, President Milei's decision to withdraw the crypto tax proposal from the Ley Ómnibus was not just a tactical retreat; it was a necessary move to quell the growing unrest and focus on more pressing economic reforms. This decision underscored the complexities of governing in a highly polarized environment and the need for a more nuanced approach to policy-making, especially when dealing with emerging technologies and markets.
The Rationale Behind Dropping Crypto Taxes
The decision to drop the crypto tax from the omnibus reform package was not taken lightly. It was a recognition of the crypto sector's unique dynamics and the government's limitations in effectively regulating and taxing this space without stifling innovation. The move also reflected a broader understanding of the economic landscape, where rapid development and legislative efficiency were deemed more crucial than ever.
By removing the contentious clauses, the government aimed to streamline the passage of the Ley Ómnibus, ensuring that other, less controversial, reforms could be implemented swiftly. This strategic pivot was also a nod to the global debate on how best to integrate cryptocurrencies into national economies. Argentina's government recognized that a more cautious and informed approach was necessary, one that could balance the need for regulation with the desire to foster a thriving digital economy.
Furthermore, the withdrawal of the crypto tax proposal can be seen as an acknowledgment of the power of public opinion and the crypto community's growing influence. It highlighted the need for governments to engage with stakeholders and understand the implications of new technologies before rushing to regulate them.
Implications for Crypto Investors and the Market
The removal of the crypto tax proposal has had immediate and significant implications for the Argentine crypto market. For investors, the decision has provided a reprieve from the uncertainty that had clouded the sector, allowing them to breathe a sigh of relief and continue their activities without the looming threat of new taxes. This has helped sustain the momentum of the crypto market in Argentina, which is seen as a vital component of the country's digital transformation and economic diversification.
However, the situation remains complex and fluid. The government's stance on cryptocurrencies is still evolving, and future regulations could impact the market in unforeseen ways. Investors are now more aware of the need to stay informed and engaged with regulatory developments, understanding that the legal landscape for digital currencies is still being shaped.
The episode has also highlighted the broader challenges facing the Argentine economy, including the need for comprehensive tax reform and the creation of a more conducive environment for technological innovation and investment. The crypto market's response to the government's actions reflects the delicate balance between regulation and growth, a balance that will be crucial for Argentina's economic future.
Milei's Political Strategy and Future Prospects
President Milei's handling of the crypto tax controversy reveals much about his political strategy and vision for Argentina. By withdrawing the proposal, he demonstrated a willingness to listen to public concerns and adapt his policies accordingly. This flexibility could be a key asset as he navigates the complex landscape of Argentine politics and governance.
The episode also offers insights into the potential future direction of Milei's administration. The focus on economic reforms, coupled with a pragmatic approach to contentious issues, suggests a leadership style that prioritizes economic stability and growth over ideological purity. This could bode well for Argentina's future, particularly if Milei can harness the energy and innovation of the digital economy as part of his broader reform agenda.
However, the challenges ahead are significant. The Ley Ómnibus is just one part of a larger puzzle, and Milei's ability to implement comprehensive reforms will be tested in the coming months and years. The crypto tax saga has shown that while change is possible, it requires careful negotiation, stakeholder engagement, and a clear understanding of the economic and social landscape.
Conclusion
The story of Argentina's crypto tax proposal is a microcosm of the broader challenges facing the country as it seeks to reform its economy and society. It highlights the tensions between innovation and regulation, the importance of public opinion, and the complexities of governance in a rapidly changing world.
As Argentina moves forward, the lessons learned from this episode will be invaluable. The need for clear, informed, and inclusive policy-making has never been greater, particularly as the country navigates the uncertainties of the digital age.
FAQs
What is the Ley Ómnibus? The Ley Ómnibus, formally known as the "Law of Bases and Starting Points for the Freedom of Argentines," is a comprehensive reform package introduced by President Javier Milei. It aims to address various economic, social, and administrative issues in Argentina, aiming to stimulate growth, reduce bureaucracy, and improve the overall quality of life.
Why were crypto taxes proposed in Argentina? Crypto taxes were proposed as part of the Ley Ómnibus to broaden the tax base, align with global trends of regulating digital currencies, and generate additional revenue for the government. They were also intended to bring more transparency to the cryptocurrency sector in Argentina.
Why were the proposed crypto taxes withdrawn? The proposed crypto taxes were withdrawn due to significant public backlash and concerns that they would stifle innovation and economic freedom in the burgeoning crypto market. The decision was also influenced by the government's priority to ensure the swift passage of other reforms within the Ley Ómnibus.
What does the withdrawal of crypto taxes mean for investors? The withdrawal means that, for now, crypto investors in Argentina will not face additional taxes specifically targeting their cryptocurrency holdings or transactions. However, selling large amounts of cryptocurrency at a profit will still be subject to income tax.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co/
Youtube: @thebitcoinlibertarian
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
Get Orange Pill App And Connect With Bitcoiners In Your Area. Stack Friends Who Stack Sats link: https://signup.theorangepillapp.com/opa/croxroad
Buy Bitcoin Books At Konsensus Network Store. 10% Discount With Code “21croxroad” link: https://bitcoinbook.shop?ref=21croxroad
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 04c915da:3dfbecc9
2025-03-10 23:31:30
@ 04c915da:3dfbecc9
2025-03-10 23:31:30Bitcoin has always been rooted in freedom and resistance to authority. I get that many of you are conflicted about the US Government stacking but by design we cannot stop anyone from using bitcoin. Many have asked me for my thoughts on the matter, so let’s rip it.
Concern
One of the most glaring issues with the strategic bitcoin reserve is its foundation, built on stolen bitcoin. For those of us who value private property this is an obvious betrayal of our core principles. Rather than proof of work, the bitcoin that seeds this reserve has been taken by force. The US Government should return the bitcoin stolen from Bitfinex and the Silk Road.
Usually stolen bitcoin for the reserve creates a perverse incentive. If governments see a bitcoin as a valuable asset, they will ramp up efforts to confiscate more bitcoin. The precedent is a major concern, and I stand strongly against it, but it should be also noted that governments were already seizing coin before the reserve so this is not really a change in policy.
Ideally all seized bitcoin should be burned, by law. This would align incentives properly and make it less likely for the government to actively increase coin seizures. Due to the truly scarce properties of bitcoin, all burned bitcoin helps existing holders through increased purchasing power regardless. This change would be unlikely but those of us in policy circles should push for it regardless. It would be best case scenario for American bitcoiners and would create a strong foundation for the next century of American leadership.
Optimism
The entire point of bitcoin is that we can spend or save it without permission. That said, it is a massive benefit to not have one of the strongest governments in human history actively trying to ruin our lives.
Since the beginning, bitcoiners have faced horrible regulatory trends. KYC, surveillance, and legal cases have made using bitcoin and building bitcoin businesses incredibly difficult. It is incredibly important to note that over the past year that trend has reversed for the first time in a decade. A strategic bitcoin reserve is a key driver of this shift. By holding bitcoin, the strongest government in the world has signaled that it is not just a fringe technology but rather truly valuable, legitimate, and worth stacking.
This alignment of incentives changes everything. The US Government stacking proves bitcoin’s worth. The resulting purchasing power appreciation helps all of us who are holding coin and as bitcoin succeeds our government receives direct benefit. A beautiful positive feedback loop.
Realism
We are trending in the right direction. A strategic bitcoin reserve is a sign that the state sees bitcoin as an asset worth embracing rather than destroying. That said, there is a lot of work left to be done. We cannot be lulled into complacency, the time to push forward is now, and we cannot take our foot off the gas. We have a seat at the table for the first time ever. Let's make it worth it.
We must protect the right to free usage of bitcoin and other digital technologies. Freedom in the digital age must be taken and defended, through both technical and political avenues. Multiple privacy focused developers are facing long jail sentences for building tools that protect our freedom. These cases are not just legal battles. They are attacks on the soul of bitcoin. We need to rally behind them, fight for their freedom, and ensure the ethos of bitcoin survives this new era of government interest. The strategic reserve is a step in the right direction, but it is up to us to hold the line and shape the future.
-
 @ e4950c93:1b99eccd
2025-05-02 10:48:12
@ e4950c93:1b99eccd
2025-05-02 10:48:12Trouver des produits 100% naturels, sans plastique, est bien plus compliqué que je ne le pensais… Alors j’ai commencé à collectionner des marque-pages. Et puis je me suis dit : « Et si on partageait ?! »
Aide-moi à dénicher les meilleures alternatives naturelles pour s’habiller et s’équiper sans plastique !
Ce projet repose sur le partage : la moitié des revenus éventuels du site est reversée aux contribut-eur-rice-s. Une petite expérimentation de partage de la valeur sur Internet. :-)
Questions-réponses
Pourquoi se focaliser sur les matières naturelles ?
Les matières synthétiques sont essentiellement des plastiques (polyester, polyamide…). Problème ? Oui ! Ils finissent par nous contaminer :
- Microplastiques absorbés par la peau,
- Particules diffusées à chaque lavage, se retrouvant dans l’eau que nous buvons et les aliments que nous consommons,
- Enjeux majeurs liés au recyclage des déchets plastiques.
C'est quoi, au juste, des matières naturelles ?
Ce sont des matières non synthétiques, dont les composants existent à l’état naturel, sans modification de leur structure moléculaire. Mais ce qui nous intéresse avant tout, c’est leur biodégradabilité et leur absence de toxicité.
Certaines matières feront sûrement débat sur leur acceptabilité ici.
👉 En savoir plus sur les matières
Quelle différence avec d'autres sites de mode ou de shopping éthiques ?
Il existe déjà de nombreux sites proposant des produits éthiques et durables, mais j’ai constaté qu’ils incluaient souvent des matières synthétiques. Je devais vérifier produit par produit. Certains mettent en avant les fibres en plastique recyclé comme démarche environnementale, mais je préfère éviter d’en porter sur ma peau ou d'en mettre sur mes enfants.
Comment contribuer ?
Si tu trouves ce projet utile ou intéressant, voici comment le soutenir :
-
📝 Contribue : suggère des modifications en commentant les fiches existantes ou propose de nouvelles références de produits ou de marque. 👉 En savoir plus sur les contributions
-
⚡ Fais un don : pour faire vivre le projet et remercier les contribut-eur-ice-s. 👉 En savoir plus sur les dons
-
📢 Fais-le connaître : parles-en autour de toi, partage le site sur les réseaux sociaux, ton blog…
Comment recevoir une partie des revenus du site ?
Il suffit d’avoir un compte NOSTR et une adresse Bitcoin Lightning.
👉 En savoir plus sur les rétributions
C'est quoi NOSTR ?
C’est un protocole décentralisé pour Internet, encore en phase expérimentale. Il permet :
- De publier et consulter du contenu sans dépendre d’une plateforme centralisée.
- De se connecter à plusieurs services en conservant le contrôle total de ses données.
- D’intégrer le réseau Bitcoin Lightning pour des paiements instantanés et décentralisés.
Et la confidentialité de mes données ?
- Aucune publicité, aucun traçage personnalisé.
- Les commentaires NOSTR sont publics, mais vous pouvez utiliser un pseudonyme.
- Vous conservez la propriété de vos contributions sur le protocole NOSTR.
Qui porte ce projet ?
👉 Voir les contribut-eur-rice-s
Nous utilisons des outils et services open source :
- NOSTR pour la publication des contenus et la vérification des contributions,
- npub.pro pour la visualisation des contenus,
- Coinos.io pour la gestion des paiements.
Cet article est publié sur origine-nature.com 🌐 See this article in English
-
 @ a87c9bfc:83bda6a8
2025-05-02 10:43:34
@ a87c9bfc:83bda6a8
2025-05-02 10:43:34Large Language Models (LLMs) are revolutionizing how we interact with technology, but their increasing sophistication brings unique security challenges. Malicious actors are constantly finding new ways to exploit these systems, primarily through techniques like prompt injection – crafting inputs to bypass safety controls – and the use of hidden characters to obfuscate harmful commands or disrupt text processing. Ensuring the safety and integrity of LLM applications is paramount.
The Hidden Dangers in Text
Prompt injection allows attackers to manipulate LLM outputs, potentially leading to data leaks, generation of inappropriate content, or unauthorized actions. Similarly, invisible characters (like zero-width spaces or bidirectional text overrides) can be embedded within seemingly innocuous text. These hidden elements can bypass simple security filters, disguise malicious instructions, or interfere with how the LLM interprets the input, leading to unpredictable or harmful behavior.
Vibecondom: A New Shield for LLM Security
To combat these emerging threats, a new open-source tool called Vibecondom has been developed. Written in Go, Vibecondom acts as a specialized security scanner designed specifically for the text content fed into LLMs. It serves as a critical defensive layer for AI developers, security researchers, and content moderation teams aiming to protect their systems.
Core Capabilities
Vibecondom focuses on identifying subtle but dangerous patterns within text data:
- Detecting Deception: It actively scans for known techniques used in prompt injection attacks and identifies various types of hidden or control characters that could signal malicious intent.
- Unmasking Obfuscation: The tool can flag potentially obfuscated content, such as Base64 encoded strings or text mixing different character scripts, which might be used to hide payloads.
- Flexible Integration: Vibecondom is designed for versatility, capable of analyzing text files stored locally or scanning content directly from remote Git repositories.
- Actionable Insights: When potential threats are detected, the tool provides clear alerts, helping teams pinpoint and investigate suspicious inputs before they compromise the LLM.
Enhancing Trust in AI
Tools like Vibecondom represent an essential step forward in securing the LLM ecosystem. By proactively identifying and flagging potentially harmful inputs, developers can build more robust defenses, fostering greater trust and reliability in AI applications.
As an open-source project (MIT License), Vibecondom invites collaboration and contribution from the security community. Anyone interested in bolstering their LLM security posture is encouraged to explore the Vibecondom project on GitHub to learn more.
-
 @ b8a9df82:6ab5cbbd
2025-03-06 22:39:15
@ b8a9df82:6ab5cbbd
2025-03-06 22:39:15Last week at Bitcoin Investment Week in New York City, hosted by Anthony Pompliano, Jack Mallers walked in wearing sneakers and a T-shirt, casually dropping, “Man… I hate politics.”
That was it. That was the moment I felt aligned again. That’s the energy I came for. No suits. No corporate jargon. Just a guy who gets it—who cares about people, bringing Bitcoin-powered payments to the masses and making sure people can actually use it.
His presence was a reminder of why we’re here in the first place. And his words—“I hate politics”—were a breath of fresh air.
Now, don’t get me wrong. Anthony was a fantastic host. His ability to mix wittiness, playfulness, and seriousness made him an entertaining moderator. But this week was unlike anything I’ve ever experienced in the Bitcoin ecosystem.
One of the biggest letdowns was the lack of interaction. No real Q&A sessions, no direct engagement, no real discussions. Just one fireside chat after another.
And sure, I get it—people love to hear themselves talk. But where were the questions? The critical debates? The chance for the audience to actually participate?
I’m used to Bitcoin meetups and conferences where you walk away with new ideas, new friends, and maybe even a new project to contribute to. Here, it was more like sitting in an expensive lecture hall, watching a lineup of speakers tell us things we already know.
A different vibe—and not in a good way
Over the past few months, I’ve attended nearly ten Bitcoin conferences, each leaving me feeling uplifted, inspired, and ready to take action. But this? This felt different. And not in a good way.
If this had been my first Bitcoin event, I might have walked away questioning whether I even belonged here. It wasn’t Prague. It wasn’t Riga. It wasn’t the buzzing, grassroots, pleb-filled gatherings I had grown to love. Instead, it felt more like a Wall Street networking event disguised as a Bitcoin conference.
Maybe it was the suits.
Or the fact that I was sitting in a room full of investors who have no problem dropping $1,000+ on a ticket.
Or that it reminded me way too much of my former life—working as a manager in London’s real estate industry, navigating boardrooms full of finance guys in polished shoes, talking about “assets under management.”
Bitcoin isn’t just an investment thesis. It’s a revolution. A movement. And yet, at times during this week, I felt like I was back in my fiat past, stuck in a room where people measured success in dollars, not in freedom.
Maybe that’s the point. Bitcoin Investment Week was never meant to be a pleb gathering.
That said, the week did have some bright spots. PubKey was a fantastic kickoff. That was real Bitcoin culture—plebs, Nostr, grassroots energy. People who actually use Bitcoin, not just talk about it.
But the absolute highlight? Jack Mallers, sneakers and all, cutting through the noise with his authenticity.
So, why did we even go?
Good question. Maybe it was curiosity. Maybe it was stepping out of our usual circles to see Bitcoin through a different lens. Maybe it was to remind ourselves why we chose this path in the first place.
Would I go again? Probably not.
Would I trade Prague, Riga, bitcoin++ or any of the grassroots Bitcoin conferences for this? Not a chance.
At the end of the day, Bitcoin doesn’t belong to Wall Street from my opinion. It belongs to the people who actually use it. And those are the people I want to be around.
-
 @ 088436cd:9d2646cc
2025-05-01 21:01:55
@ 088436cd:9d2646cc
2025-05-01 21:01:55The arrival of the coronavirus brought not only illness and death but also fear and panic. In such an environment of uncertainty, people have naturally stocked up on necessities, not knowing when things will return to normal.
Retail shelves have been cleared out, and even online suppliers like Amazon and Walmart are out of stock for some items. Independent sellers on these e-commerce platforms have had to fill the gap. With the huge increase in demand, they have found that their inventory has skyrocketed in value.
Many in need of these items (e.g. toilet paper, hand sanitizer and masks) balk at the new prices. They feel they are being taken advantage of in a time of need and call for intervention by the government to lower prices. The government has heeded that call, labeling the independent sellers as "price gougers" and threatening sanctions if they don't lower their prices. Amazon has suspended seller accounts and law enforcement at all levels have threatened to prosecute. Prices have dropped as a result and at first glance this seems like a victory for fair play. But, we will have to dig deeper to understand the unseen consequences of this intervention.
We must look at the economics of the situation, how supply and demand result in a price and how that price acts as a signal that goes out to everyone, informing them of underlying conditions in the economy and helping coordinate their actions.
It all started with a rise in demand. Given a fixed supply (e.g., the limited stock on shelves and in warehouses), an increase in demand inevitably leads to higher prices. Most people are familiar with this phenomenon, such as paying more for airline tickets during holidays or surge pricing for rides.
Higher prices discourage less critical uses of scarce resources. For example, you might not pay $1,000 for a plane ticket to visit your aunt if you can get one for $100 the following week, but someone else might pay that price to visit a dying relative. They value that plane seat more than you.
*** During the crisis, demand surged and their shelves emptied even though
However, retail outlets have not raised prices. They have kept them low, so the low-value uses of things like toilet paper, masks and hand sanitizer has continued. Often, this "use" just takes the form of hoarding. At everyday low prices, it makes sense to buy hundreds of rolls and bottles. You know you will use them eventually, so why not stock up? And, with all those extra supplies in the closet and basement, you don't need to change your behavior much. You don't have to ration your use.
At the low prices, these scarce resources got bought up faster and faster until there was simply none left. The reality of the situation became painfully clear to those who didn't panic and got to the store late: You have no toilet paper and you're not going to any time soon.
However, if prices had been allowed to rise, a number of effects would have taken place that would have coordinated the behavior of everyone so that valuable resources would not have been wasted or hoarded, and everyone could have had access to what they needed.
On the demand side, if prices had been allowed to rise, people would have begun to self-ration. You might leave those extra plies on the roll next time if you know they will cost ten times as much to replace. Or, you might choose to clean up a spill with a rag rather than disposable tissue. Most importantly, you won't hoard as much. That 50th bottle of hand sanitizer might just not be worth it at the new, high price. You'll leave it on the shelf for someone else who may have none.
On the supply side, higher prices would have incentivized people to offer up more of their stockpiles for sale. If you have a pallet full of toilet paper in your basement and all of the sudden they are worth $15 per roll, you might just list a few online. But, if it is illegal to do so, you probably won't.
Imagine you run a business installing insulation and have a few thousand respirator masks on hand for your employees. During a pandemic, it is much more important that people breathe filtered air than that insulation get installed, and that fact is reflected in higher prices. You will sell your extra masks at the higher price rather than store them for future insulation jobs, and the scarce resource will be put to its most important use.
Producers of hand sanitizer would go into overdrive if prices were allowed to rise. They would pay their employees overtime, hire new ones, and pay a premium for their supplies, making sure their raw materials don't go to less important uses.
These kinds of coordinated actions all across the economy would be impossible without real prices to guide them. How do you know if it makes sense to spend an extra $10k bringing a thousand masks to market unless you know you can get more than $10 per mask? If the price is kept artificially low, you simply can't do it. The money just isn't there.
These are the immediate effects of a price change, but incredibly, price changes also coordinate people's actions across space and time.
Across space, there are different supply and demand conditions in different places, and thus prices are not uniform. We know some places are real "hot spots" for the virus, while others are mostly unaffected. High demand in the hot spots leads to higher prices there, which attracts more of the resource to those areas. Boxes and boxes of essential items would pour in where they are needed most from where they are needed least, but only if prices were allowed to adjust freely.
This would be accomplished by individuals and businesses buying low in the unaffected areas, selling high in the hot spots and subtracting their labor and transportation costs from the difference. Producers of new supply would know exactly where it is most needed and ship to the high-demand, high-price areas first. The effect of these actions is to increase prices in the low demand areas and reduce them in the high demand areas. People in the low demand areas will start to self-ration more, reflecting the reality of their neighbors, and people in the hotspots will get some relief.
However, by artificially suppressing prices in the hot spot, people there will simply buy up the available supply and run out, and it will be cost prohibitive to bring in new supply from low-demand areas.
Prices coordinate economic actions across time as well. Just as entrepreneurs and businesses can profit by transporting scarce necessities from low-demand to high-demand areas, they can also profit by buying in low-demand times and storing their merchandise for when it is needed most.
Just as allowing prices to freely adjust in one area relative to another will send all the right signals for the optimal use of a scarce resource, allowing prices to freely adjust over time will do the same.
When an entrepreneur buys up resources during low-demand times in anticipation of a crisis, she restricts supply ahead of the crisis, which leads to a price increase. She effectively bids up the price. The change in price affects consumers and producers in all the ways mentioned above. Consumers self-ration more, and producers bring more of the resource to market.
Our entrepreneur has done a truly incredible thing. She has predicted the future, and by so doing has caused every individual in the economy to prepare for a shortage they don't even know is coming! And, by discouraging consumption and encouraging production ahead of time, she blunts the impact the crisis will have. There will be more of the resource to go around when it is needed most.
On top of this, our entrepreneur still has her stockpile she saved back when everyone else was blithely using it up. She can now further mitigate the damage of the crisis by selling her stock during the worst of it, when people are most desperate for relief. She will know when this is because the price will tell her, but only if it is allowed to adjust freely. When the price is at its highest is when people need the resource the most, and those willing to pay will not waste it or hoard it. They will put it to its highest valued use.
The economy is like a big bus we are all riding in, going down a road with many twists and turns. Just as it is difficult to see into the future, it is difficult to see out the bus windows at the road ahead.
On the dashboard, we don't have a speedometer or fuel gauge. Instead we have all the prices for everything in the economy. Prices are what tell us the condition of the bus and the road. They tell us everything. Without them, we are blind.
Good times are a smooth road. Consumer prices and interest rates are low, investment returns are steady. We hit the gas and go fast. But, the road is not always straight and smooth. Sometimes there are sharp turns and rough patches. Successful entrepreneurs are the ones who can see what is coming better than everyone else. They are our navigators.
When they buy up scarce resources ahead of a crisis, they are hitting the brakes and slowing us down. When they divert resources from one area to another, they are steering us onto a smoother path. By their actions in the market, they adjust the prices on our dashboard to reflect the conditions of the road ahead, so we can prepare for, navigate and get through the inevitable difficulties we will face.
Interfering with the dashboard by imposing price floors or price caps doesn't change the conditions of the road (the number of toilet paper rolls in existence hasn't changed). All it does is distort our perception of those conditions. We think the road is still smooth--our heavy foot stomping the gas--as we crash onto a rocky dirt road at 80 miles per hour (empty shelves at the store for weeks on end).
Supply, demand and prices are laws of nature. All of this is just how things work. It isn't right or wrong in a moral sense. Price caps lead to waste, shortages and hoarding as surely as water flows downhill. The opposite--allowing prices to adjust freely--leads to conservation of scarce resources and their being put to their highest valued use. And yes, it leads to profits for the entrepreneurs who were able to correctly predict future conditions, and losses for those who weren't.
Is it fair that they should collect these profits? On the one hand, anyone could have stocked up on toilet paper, hand sanitizer and face masks at any time before the crisis, so we all had a fair chance to get the supplies cheaply. On the other hand, it just feels wrong that some should profit so much at a time when there is so much need.
Our instinct in the moment is to see the entrepreneur as a villain, greedy "price gouger". But we don't see the long chain of economic consequences the led to the situation we feel is unfair.
If it weren't for anti-price-gouging laws, the major retailers would have raised their prices long before the crisis became acute. When they saw demand outstrip supply, they would have raised prices, not by 100 fold, but gradually and long before anyone knew how serious things would have become. Late comers would have had to pay more, but at least there would be something left on the shelf.
As an entrepreneur, why take risks trying to anticipate the future if you can't reap the reward when you are right? Instead of letting instead of letting entrepreneurs--our navigators--guide us, we are punishing and vilifying them, trying to force prices to reflect a reality that simply doesn't exist.
In a crisis, more than any other time, prices must be allowed to fluctuate. To do otherwise is to blind ourselves at a time when danger and uncertainty abound. It is economic suicide.
In a crisis, there is great need, and the way to meet that need is not by pretending it's not there, by forcing prices to reflect a world where there isn't need. They way to meet the need is the same it has always been, through charity.
If the people in government want to help, the best way for the to do so is to be charitable and reduce their taxes and fees as much as possible, ideally to zero in a time of crisis. Amazon, for example, could instantly reduce the price of all crisis related necessities by 20% if they waived their fee. This would allow for more uses by more people of these scarce supplies as hoarders release their stockpiles on to the market, knowing they can get 20% more for their stock. Governments could reduce or eliminate their tax burden on high-demand, crisis-related items and all the factors that go into their production, with the same effect: a reduction in prices and expansion of supply. All of us, including the successful entrepreneurs and the wealthy for whom high prices are not a great burden, could donate to relief efforts.
These ideas are not new or untested. This is core micro economics. It has been taught for hundreds of years in universities the world over. The fact that every crisis that comes along stirs up ire against entrepreneurs indicates not that the economics is wrong, but that we have a strong visceral reaction against what we perceive to be unfairness. This is as it should be. Unfairness is wrong and the anger it stirs in us should compel us to right the wrong. Our anger itself isn't wrong, it's just misplaced.
Entrepreneurs didn't cause the prices to rise. Our reaction to a virus did that. We saw a serious threat and an uncertain future and followed our natural impulse to hoard. Because prices at major retail suppliers didn't rise, that impulse ran rampant and we cleared the shelves until there was nothing left. We ran the bus right off the road and them blamed the entrepreneurs for showing us the reality of our situation, for shaking us out of the fantasy of low prices.
All of this is not to say that entrepreneurs are high-minded public servants. They are just doing their job. Staking your money on an uncertain future is a risky business. There are big risks and big rewards. Most entrepreneurs just scrape by or lose their capital in failed ventures.
However, the ones that get it right must be allowed to keep their profits, or else no one will try and we'll all be driving blind. We need our navigators. It doesn't even matter if they know all the positive effects they are having on the rest of us and the economy as a whole. So long as they are buying low and selling high--so long as they are doing their job--they will be guiding the rest of us through the good times and the bad, down the open road and through the rough spots.
-
 @ e8ed3798:67dd345a
2025-05-01 20:46:55
@ e8ed3798:67dd345a
2025-05-01 20:46:55test content
-
 @ e4950c93:1b99eccd
2025-05-02 10:39:50
@ e4950c93:1b99eccd
2025-05-02 10:39:50Équipe Cœur
L'équipe Cœur porte le projet et valide les contenus.
- Jean-David Bar : https://njump.me/npub1qr4p7uamcpawv7cr8z9nlhmd60lylukf7lvmtlnpe7r4juwxudzq3hrnll
Pour démarrer, je gère le projet en solo en partageant mes favoris pour éviter le plastique sur nous et sur nos enfants. Contacte-moi si tu souhaites rejoindre l'aventure !
Enrichisseu-r-se-s de contenus
Les contribut-eur-rice-s rendent ce site vivant et intéressant.
A venir.
👉 En savoir plus sur les contributions
Cet article est publié sur origine-nature.com 🌐 See this article in English
-
 @ 2ed3596e:98b4cc78
2025-05-01 20:27:18
@ 2ed3596e:98b4cc78
2025-05-01 20:27:18The Bitcoin Well Affiliate program is here! You can earn a bitcoin bonus of 21% of revenue generated from transactions every time someone you refer transacts on our platform. Bitcoin Well Affiliates can also complete bounty tasks to earn sats, such as Bitcoin Well video tutorials. The Affiliate program is our way of aligning incentives with our mission to enable independence.
How to apply for the Bitcoin Well Affiliate program
The Affiliate program is big folks in and bitcoin or folks with a LOT of experience with bitcoin and self-custody wallets; the most important quality is a passion for orange-pilling!
Bitcoin Well Affiliates earn more than double our referral commission (21% of revenue generated from transactions), get a custom Bitcoin Well Affiliate webpage to help you get referrals and unlock bounty tasks for bonus sats. You can apply to join the Affiliate program by clicking here.
How to earn your Bitcoin Well Referral bonus
To refer a customer to Bitcoin Well, have them sign up using your Bitcoin Well referral link, this can be found in your Bitcoin Well account under Rewards > Referrals. Your referred customers also get a sign up bonus of 1,000 Bitcoin Well. You get 500 points for each referral, too.
Your personal referral link will be https://bitcoinwell.com/app/ref/YOUR_WELLTAG. A person can also be referred by typing in your welltag in the Referral Code field on the sign up page.
The best part? Sats are AUTOMATICALLY paid to your designated Lightning Wallet.

Who is eligible to refer to Bitcoin Well?
The Bitcoin Well Affiliate program is available to anyone! However, our services are only available in Canada and the United States.
The Affiliate program includes referrals to business and High Net Worth Individuals that use our OTC desk.
How to hunt Affiliate bounty tasks and earn sats
Affiliates can hunt bounty tasks by making Bitcoin Well tutorials and uploading them to Youtube or X in exchange for sats.
Bounty tasks such as How to buy bitcoin (USA) on Bitcoin Well are a fantastic resource to generate referrals and boost traffic to your pages. Affiliate bounty tasks earn you 21,000-105,000 sats per video. \ \ Affiliate bounty tasks are only available to approved Bitcoin Well Affiliates. Read our Affiliate Bounty article for more details on submitting Affiliate bounties.
How does the Bitcoin Well referral program work?
The Bitcoin Well Affiliate and referral programs pay you automatically for your referral’s activities.
\ For example, today we have a 1.2% spread on standard portal transactions (buy, sell, pay bills). This means for every $100 someone spends on the platform we make $1.20, you’ll earn $0.24, automatically paid in sats. If they are using a Lite Account, with a 3% spread, you will earn $0.61 on that transaction, automatically paid in sats.
Referral bonuses don’t have an expiration date, cause we are all in bitcoin for the long haul!
The 21% revenue share for whales that end up purchasing through our OTC desk goes a long way, potentially in the thousands of referrals dollars per transaction. We do not place a cap on referral bonuses, so the bigger the whale, the bigger the referral bonus you earn!
How and when do I get paid?
Your referral bonuses are automatically paid out to the designated Lightning Wallet in your referral page. If you prefer, you can select a manual payout where you can withdraw your payouts at any time via LNURLw. \ \ OTC referral bonuses are processed around the middle of each month to your referral Lightning wallet.
What if I am not a fit for the Affiliate Program? Can I still earn from referrals?
Not everyone is the right fit for the Affiliate program, and that’s okay! Maintaining a far-reaching social presence is tough work. \ \ Thankfully, regular customers can still earn unlimited commissions from referrals at a 10% rate! This means for every $100 someone spends on the platform we make $1.20, you’ll earn $0.12, automatically paid in sats. The more your referrals transact, the more sats go to your Lightning wallet!
What makes Bitcoin Well different
Bitcoin Well is on a mission to enable independence. We do this by making it easy to self custody bitcoin. By custodying their own money, our customers are free to do as they wish without begging for permission. By creating a full ecosystem to buy, sell and use your bitcoin to connect with the modern financial world, you are able to have your cake and eat it too - or have your bitcoin in self custody and easily spend it too 🎂
Create your Bitcoin Well account now →
Invest in Bitcoin Well
We are publicly traded (and love it when our customers become shareholders!) and hold ourselves to a high standard of enabling life on a Bitcoin standard. If you want to learn more about Bitcoin Well, please visit our website!
-
 @ c0c42bba:a5feb7b5
2025-05-01 20:04:33
@ c0c42bba:a5feb7b5
2025-05-01 20:04:33Wisdom for the Fourth Decade
🔥
Turning 40 is like hitting the “I should really know better by now” milestone. It’s a time when you look back at your past self, shake your head, and chuckle (or cringe) at your youthful blunders.
Here are 15 truths you should embrace by this significant age, each one a guide to a more fulfilling, empowered life.
Leverage Is Key
Ever wonder why your colleague who seems to be on perpetual coffee breaks makes ten times more than you? It's not black magic. They have leverage—whether it's through technology, skills, or knowing how to delegate their way out of everything. Find your leverage and watch your value skyrocket.
Distraction: The Silent Killer
In our world of incessant notifications and cat videos, distraction is the enemy. It’s like having a mosquito in the room when you're trying to sleep. Cultivate a habit of deep work. Guard your attention like it's the last piece of cake at a party—fiercely.
Beware of Unqualified Advice
Taking advice from someone who hasn’t achieved what you want is like asking a cat for swimming lessons. Be selective with whose counsel you follow. Choose mentors who have walked the path and let their experiences be your map.
Own Your Life
Here’s the blunt truth: no one is coming to save you. Your problems, your life, are 100% your responsibility. Embrace this ownership. Empower yourself to be the hero of your own story. Don’t wait for a knight in shining armor—be your own rescue mission.
Action Over Self-Help Books
You don’t need to turn your living room into a self-help library. You need action. Self-discipline beats all the motivational quotes in the world. Commit to taking steps, however small, towards your goals. It's the doing, not just the knowing, that transforms dreams into reality.
The Power of Sales Skills
Unless your college degree is as specific as a neurosurgeon’s, your ticket to higher earnings in the next 90 days is learning sales. It’s a skill that opens doors, creates opportunities, and accelerates financial growth faster than you can say "commission."
No One Cares (In a Good Way)
Stop worrying about what others think—they’re too busy worrying about themselves. Take bold steps, make your moves, and create your chances. The world is too preoccupied with its own drama to scrutinize yours.
Collaborate with the Brilliant
When you meet someone smarter than you, don’t let your ego turn it into a competition. Collaborate with them. Two heads (especially two brilliant ones) are better than one, and together you can achieve remarkable things.
The Smoking Deception
Smoking has zero benefits. It’s like trying to improve your driving skills by riding a tricycle. If you want to sharpen your focus and enhance your thinking, ditch the habit. Your lungs—and your future self—will thank you.
Comfort: A Dangerous Addiction
Comfort is like quicksand. It feels nice until you’re stuck and can’t move. Regularly challenge yourself. Step out of your comfort zone because growth and fulfillment lie just beyond the boundaries of what feels easy.
Guard Your Privacy
Not everyone needs to know your life story, your plans, or what you had for breakfast. Maintain a sense of mystery. It’s not about being secretive; it’s about keeping some things just for yourself.
Alcohol: A Costly Vice
Alcohol impairs your judgment and lowers your inhibitions. It’s like paying someone to mess up your life. Avoid it. Clear thinking and control over your actions are priceless.
Keep Your Standards High
Don’t settle for less just because it’s available. High standards attract high-quality opportunities and people. Know your worth and hold out for what aligns with your values and goals.
Prioritize Your Chosen Family
The family you create is more important than the one you were born into. Nurture these relationships. They are your ride-or-die, your squad, your home team. Invest in them as they will be the cornerstone of your support system.
Take Nothing Personally
To save yourself from a myriad of mental burdens, learn not to take things personally. Most of the time, people’s actions are a reflection of their reality, not yours. This mindset shift will free you from unnecessary stress and emotional turmoil.
Embrace These Lessons -
 @ 1408bad0:4971f2ca
2025-05-01 19:55:37
@ 1408bad0:4971f2ca
2025-05-01 19:55:37Raised by Wolves is another sci-fi flick where Earth faces an extinction level event and lots of cool androids.
The series has some exciting action points showing a side of AI androids used as super weapons against humanity. If you were thinking to get an AI girlfriend, you might have a change of mind.
We see some pretty cool androids, but the awesome Necromancer is pretty spectacular and powerful and you wonder if anything can stop them. However, bizarrely, at times they are also apparently weak and despite their power, the religious group doesn't shy away from confrontation without any real weapons.
It would have been good if they had explored this side more and some of the advanced tech available like which gave the atheista super strength and speed to combat them.
The series has a feel like Foundation to it, but much less polished and maybe more negative and dreary at times. Instead of exploring exciting themes, it descends into mindless trivialities and bizarre gory rituals like killing a hideous pregnant animal and parading the dead baby corpse around.
They arrive on a mysterious but quite dreary planet and things start to set the scene.
The androids themselves are quite well played. The "Mother" is as expected in these woke times the strong and powerful one. The "Father" is the beta male serving her and the kids. It's all quite bizarre in a way.
When they first land they use some tech to make a base quickly and easily, but it disappoints how basic it all is. This is then compounded when the religious group arrive and instead of using modern tech to make a base as you might expect, instead turn into the Amish and make everything from wood. Oh yes, there are trees on this planet, but no really nice food.
The oddness continues and grows throughout the season as the androids become more human and spoiler alert , the most ridiculous storyline emerges as mother becomes pregnant and also really annoying. She starts attaching other bits and creatures to her to suck their blood out for her baby.
Despite all my criticisms, it has been an interesting first series but very disappointing in many ways compared to Foundation.
-
 @ e4950c93:1b99eccd
2025-05-02 10:36:46
@ e4950c93:1b99eccd
2025-05-02 10:36:46Heureu-x-se d’avoir trouvé une information utile sur ce site ?
Soutiens le projet en faisant un don pour le faire vivre et remercier les contribut-eur-rice-s.
En bitcoin
-
Sur la blockchain : bc1qkm8me8l9563wvsl9sklzt4hdcuny3tlejznj7d
-
Réseau lightning : ⚡️
origin-nature@coinos.ioVous pouvez aussi nous soutenir de manière récurrente 👉 Créer un paiement Lightning récurrent
En euros, dollars, ou toute autre monnaie prise en charge
-
Par virement, IBAN : FR76 2823 3000 0144 3759 8717 669
-
Tu peux aussi nous soutenir de manière récurrente 👉 Faire une promesse sur LiberaPay
Contacte-nous si tu souhaites faire un don avec toute autre cryptomonnaie.
💡 Un modèle de partage de la valeur
La moitié des dons est redistribuée aux contribut-eur-rice-s qui créent la valeur du site, pour expérimenter un modèle de partage de revenus sur Internet — un modèle qui respecte vos données et ne cherche pas à capter votre attention.
L’autre moitié permet de couvrir les frais de fonctionnement du site, rémunérer l'équipe coeur et soutenir les outils open source que nous utilisons.
Cet article est publié sur origine-nature.com 🌐 See this article in English
-
-
 @ e4950c93:1b99eccd
2025-05-02 10:31:12
@ e4950c93:1b99eccd
2025-05-02 10:31:12Contribue à enrichir le site !
Chaque contribution permet d’améliorer ce site en aidant à référencer des alternatives naturelles.
💡 Qu’est-ce qu’une contribution ?
Une contribution peut être :
📝 La proposition d’une nouvelle fiche, en fournissant ses premières informations. Chaque information ajoutée (nom, lien, catégorie, etc.) est une contribution : - Ajouter un produit - Ajouter une marque
📝 L'ajout ou la modification d’informations sur une fiche existante. Chaque information ajoutée ou retirée est une contribution.
✅ Validation des contributions
Les contributions sont vérifiées par l’équipe cœur. Une contribution est validée lorsque l'information indiquée est fournie pour la première fois (le commentaire le plus ancien est pris en compte) et est vérifiable.
Une fois validées, les contributions sont comptabilisées et donnent lieu à une rétribution. 👉 En savoir plus sur les rétributions
Les informations ajoutées directement par l'équipe cœur lors de la vérification d'une contribution ne sont pas comptabilisées. Néanmoins, les membres de l'équipe coeur peuvent aussi contribuer comme tout le monde.
Cet article est publié sur origine-nature.com 🌐 See this article in English
-
 @ e4950c93:1b99eccd
2025-05-02 10:20:25
@ e4950c93:1b99eccd
2025-05-02 10:20:25
Cet article est publié sur origine-nature.com 🌐 See this article in English
-
 @ 8947a945:9bfcf626
2025-03-06 10:50:28
@ 8947a945:9bfcf626
2025-03-06 10:50:28Law of diminishing returns : ทำมากได้น้อย ซวยหน่อยขาดทุน
 ** หมายเหตุ บทความนี้มีเนื้อหาต่อเนื่องจาก “(TH) Why I quit : สาเหตุที่ผมลาออกจากที่(ทำงาน) ที่ (เคย) เรียกว่า”บ้าน” ใครยังไม่ได้อ่าน แนะนำให้ไปอ่านก่อนนะครับ
** หมายเหตุ บทความนี้มีเนื้อหาต่อเนื่องจาก “(TH) Why I quit : สาเหตุที่ผมลาออกจากที่(ทำงาน) ที่ (เคย) เรียกว่า”บ้าน” ใครยังไม่ได้อ่าน แนะนำให้ไปอ่านก่อนนะครับผมได้ยิน คุณท็อป จิรายุส (คุณท๊อป บิทคับ) พูดคำว่า "Law of diminishing returns" ไว้ตอนแชร์มุมมองด้านการทำธุรกิจ ตอนนั้นผมไม่เข้าใจ แต่ผมรู้สึกว่ามันเป็นเจ๋งดี
สำหรับผม สรุปกฏนี้สั้นๆ คือ “ทำมากได้น้อย ซวยหน่อยขาดทุน”
กฏข้อนี้ว่าด้วยเรื่องการทำธุรกิจ พูดถึงปัจจัย 3 อย่าง - Fixed input คือสิ่งที่ไม่สามารถผลิตเพิ่มได้อีกในธุรกิจตอนนั้น เช่น จำนวนห้องตรวจในโรงพยาบาล, พื้นที่ที่ดินทำการเกษตร, ห้องเก็บสินค้า, จำนวนโต๊ะทำงานในสำนักงาน, ช่องบริการลูกค้าในธุรกิจบริการต่างๆ เป็นต้น ผมขอเรียกสั้นๆว่า “พื้นที่” - Variable input คือสิ่งที่สามารถเติมเข้ามาในธุรกิจได้ ปรับแต่งได้ เช่น แรงงาน เครื่องจักร พลังงาน - Marginal product คือผลลัพธ์ของธุรกิจ กำไรเพิ่มขึ้นหลังจากเพิ่ม variable input เข้าสู่ระบบ
ระยะของ law of diminishing returns
- Increased return (ทำเงินได้เยอะขึ้น) เมื่อป้อนแรงงานหรือเครื่องจักรเข้าสู่ระบบ ธุรกิจสามารถทำเงินเพิ่มขึ้นเนื่องจาก fixed input เดิมที่ถูกใช้สอยไม่เต็มที่ (underutilized) ถูกเติมเต็ม กรณีของรพ. คือมีห้องตรวจที่ว่าง ไม่มีหมอนั่งตรวจคนไข้ ห้องตรวจนั้นก็จะไม่สร้างรายได้ แต่เมื่อห้องนั้นมีหมอมานั่ง จะเปลี่ยนเป็นพื้นที่ที่ก่อให้เกิดรายได้ เมื่อห้องตรวจทุกห้องมีหมอนั่งครบ ถือว่าเต็มศักยภาพ ประสิทธิภาพการทำงานที่ดีตามมา
- Diminishing return (ทำมากได้น้อย) จุดของความพอดี (optimum point) คือจุดที่สมดุลพอดีของธุรกิจนั้น ทำกำไรได้เหมาะสม ไม่มากไม่น้อยจนเกินไป แต่ถ้ามองไม่เห็นจุด optimum นี้แล้วยังเพิ่ม”แรงงาน”เข้าไปอีก มันจะทำให้ ”พื้นที่” วุ่นวายเละเทะ ประสิทธิภาพในการทำงานลดลง
- Negative returns (ซวยหน่อยขาดทุน) ถ้ายังไม่หยุดเพิ่ม “แรงงาน” อีก สามารถนำมาสู่การขาดทุน
สรุปเป็นกราฟหน้าตาตามนี้ครับ
ทำไมมันถึงเป็นอย่างนั้น
ผมใช้โมเดลธุรกิจรพ.นี้เป็นตัวอย่างเลยนะครับ
ช่วงแรกที่สร้างรพ. ห้องตรวจมีไม่มาก จำนวนหมอและคนไข้สมดุลกันพอดี งานไม่หนักเกินไป การดูแลคนไข้มีประสิทธิภาพ รพ.เป็นที่ไว้ใจของคนในพื้นที่ มีชื่อเสียง ถูกบอกต่อ ทำให้จำนวนคนไข้เข้ามารับบริการมากขึ้น ต้องขยายพื้นที่รพ. สร้างตึกเพิ่ม รับบุคคลากรทุกระดับเข้ามาทำงานมากขึ้น จนเต็มพื้นที่ที่ดินรพ.ไม่สามารถขยายเพิ่มไปได้มากกว่านี้แล้ว เกิดสมดุลพอดี ทุกพื้นที่ถูกใช้งานเต็มศักยภาพ ประสิทธิภาพงานดีมาก

ผลการดำเนินงาน
ไม่เคยขาดทุน ผ่านช่วงวิกฤตต้มยำกุ้ง และ COVID ได้สบายๆ ฐานะทางการเงินแข็งแรง จ่ายปันผลสม่ำเสมอ ถ้าผมเป็นเจ้าของรพ.ผมจะ 1. สร้างระบบ 2. สร้างทีมผู้บริหาร 3. เน้นย้ำความสำคัญทำตามระบบ 3. Plan - Do- Check - Act เมื่อเกิดปัญหา
เพื่อให้ตัวผมสามารถถอยตัวเองออกมาจากตัวธุรกิจ คอยติดตาม monitor ทุกไตรมาส อย่างใกล้ชิด ไม่ทำอะไรเพิ่มไปมากกว่านี้
แต่สุดท้ายมันก็เกิดเหตุการณ์ทายาทรุ่นที่ 2 “ไม่เอา” นั่นแหละครับ มันทำให้วัฒนธรรมองค์กรเปลี่ยน ก้าวเท้าเข้าไปสู่ยุคตกต่ำ

บริหารแบบล้าหลัง ทำอะไรไม่สุด คิดว่าทำแล้วแต่จริงๆคือไม่ได้ทำ แก้ปัญหาไม่ตรงจุดสร้างปัญหากว่าเดิม
ตัวอย่าง
1. นโยบายการประหยัดพลังงานเพื่อลด carbon footprint
ฟังดูเหมือนจะดี แต่รพ.สื่อสารให้
รณรงค์ให้ปิดไฟ ... ปิดแอร์เมื่อไม่ใช้งาน ...
ผมว่าประโยคนี้มันคุ้นๆ เหมือนเคยได้ยินมามากกว่า 10 ปีแล้ว ... หรือผมเข้าใจผิดหรือเปล่าไม่แน่ใจ
รณรงค์แค่นี้แหละครับ เรื่องลด carbon footprint ไม่ได้เป็นการคิดอะไรใหม่ๆที่เหมาะกับยุคสมัย หรือสร้างอะไรที่จับต้องได้ (objective)
แต่สิ่งที่ทำสวนทางโดยสิ้นเชิงคือใช้พลาสติกแบบใช้แล้วทิ้ง (single use plastic) เป็นภาชนะหลักในการบรรจุอาหารของแพทย์ และผู้เข้าร่วมประชุมงานใหญ่ๆ
 มีเสียงเสนอแนะจากบุคคลากรทุกระดับว่าให้ทำเป็นบุฟเฟ่ต์ จานชามช้อนส้อมแบบปกติก็ได้ เสนอกันมา 5 ปี ก็ยังคงไม่่มีการเปลี่ยนแปลง ได้รับแจ้งลงมาว่าใช้ภาชนะพลาสติกมันประหยัดกว่า เอาเป็นว่ากล่องข้าวพลาสติกมีการใช้อย่างน้อย 1200 กล่องต่อเดือน … คาดว่าสมการการปล่อยก๊าสคาร์บอน (carbon emission) ที่ทีมผู้บริหารคำนวณ อาจจะซับซ้อนเกินความเข้าใจของผมก็ได้นะครับ
มีเสียงเสนอแนะจากบุคคลากรทุกระดับว่าให้ทำเป็นบุฟเฟ่ต์ จานชามช้อนส้อมแบบปกติก็ได้ เสนอกันมา 5 ปี ก็ยังคงไม่่มีการเปลี่ยนแปลง ได้รับแจ้งลงมาว่าใช้ภาชนะพลาสติกมันประหยัดกว่า เอาเป็นว่ากล่องข้าวพลาสติกมีการใช้อย่างน้อย 1200 กล่องต่อเดือน … คาดว่าสมการการปล่อยก๊าสคาร์บอน (carbon emission) ที่ทีมผู้บริหารคำนวณ อาจจะซับซ้อนเกินความเข้าใจของผมก็ได้นะครับ2. การตลาดที่ล้มเหลวและพาแพทย์ซวย

ทำการตลาดไม่เข้าเป้า “เหมือนจะ” ทำ digital marketing แต่ทำแค่โพสกราฟฟิคโปรโมชั่นภาพนิ่งลงสื่อโซเชียลทุกช่องทาง แล้วบอกว่านั่นคือ digital marketing
... แต่เดี๋ยวก่อนๆๆๆ ...
ผมจะบอกว่าการโพสมันเป็นแค่ 1 ใน 10 ของ digital marketing แต่รพ.เข้าใจว่าตัวเองได้เข้าสู่ digital marketing แล้ว
... จริงๆมันไม่ใช่เลยเว้ย ...
ผลลัพธ์คือไม่สามารถเปิดน่านน้ำลูกค้าใหม่ได้เลย ได้แต่ฐานลูกค้าเดิมที่มี brand royalty (แต่แนวโน้มลดลง)
แถมที่แย่ที่สุดคือทำการตลาดแพคเกจออกมาโดยไม่ปรึกษาแพทย์ก่อนว่ามันขัดต่อมาตรฐานการรักษาหรือไม่ กลายเป็นทำแพคเกจดึงดูดคนไข้เข้ามาใช้บริการ แต่การรักษาในแพคเกจขัดต่อมาตรฐานการรักษาของแพทย์
คนไข้ไม่รู้หรอกครับ คนไข้จะเอาตามที่มีในแพคเกจ เขาจ่ายตังค์แล้ว แต่ความซวยมันไปตกอยู่กับแพทย์
3. วางกลยุทธไม่เข้าเป้า

ทุกๆต้นปีทางผู้บริหารจะประกาศกลยุทธประจำปี ว่าในปีนั้นๆรพ.จะมุ้งเน้นพัฒนาด้านไหน รพ.นี้มีปัญหาที่เป็นงูกินหางมานาน มันส่งผลต่อประสิทธิภาพการทำงานของหมอและพยาบาล มีการเสนอแก้ปัญหาเรื่องนี้วนซ้ำซากมา 5 ปี แต่ไม่ได้รับแก้ไขจริงจัง (ผมขอไม่เล่านะครับ)
แต่กลยุทธประจำปี 3 ปีที่ผ่านมา พุ่งใส่ตัวบุคคลากร เน้นพฤติกรรมบริการที่ดีเลิศ ทราบมาว่ามีการลงทุนกับโครงการนี้หลักแสนหรือหลักล้าน มีการจัด workshop เชิญวิทยากรและ trainer จากบริษัทภายนอก (outsource) เข้ามาอบรม เป็นโครงการที่เน้นให้บุคคลากรทุกคนเข้าอบรม 100%
ผมมองว่าปัญหาที่เป็นราก (root cause) มันยังไม่ถูกแก้เลย เปรียบเทียบเหมือนฐานรากของอาคารที่มันโคลงเคลงๆไม่มั่นคงยังไม่ได้รับการแก้ไข แต่พยายามตกแต่งห้องด้วยวัสดุคุณภาพดีและเทคโนโลยีที่ทันสมัย … แต่พร้อมจะล้มลงมาได้ทุกเมื่อ
4. มีเสน่ดึงดูด partner ใหม่ๆ แต่ไม่เอาเอง
ในช่วง COVID ระลอกแรก มีผู้นำทางด้านธุรกิจโรงแรมในจังหวัดมานำเสนอโมเดลธุรกิจ “hospitel เปลี่ยนโรงแรมให้เป็นโรงพยาบาล” ด้วยศักยภาพของรพ.ที่มีบุคคลากรเพียงพอ และตัวโรงแรมที่นำมาเสนอมีห้องพักประมาณ 300 ห้อง เป็นโมเดลที่รพ.และโรงแรม win-win ทั้งคู่ แต่ทางผู้บริหารมองว่าไม่คุ้ม ปฏิเสธข้อเสนอนี้ ทำให้เสียโอกาสให้กับคู่แข่งคว้าตลาด blue ocean นี้ไป

ผมได้แต่เกาหัวตอนรู้เรื่องนี้ เพราะ 1. ช่วง COVID คนไข้น้อย พนักงานโดนลดชั่วโมงการทำงาน ได้เงินเดือนขั้นต่ำ ไม่ได้ OT 2. ทาง partner เสนอขอบุคคลากรเหล่านี้แหละ ไปช่วยงาน เรื่องสถานที่ทางโรงแรมเขามีแม่บ้าน ฝ่ายทำความสะอาดอยู่แล้ว 3. ทาง partner เสนอ profit sharing กับทางรพ. ถึงผมจะไม่รู้ตัวเลข แต่เชื่อว่ามันยุติธรรม
ผมก็ไม่รู้ครับ ว่าอะไรคือคุ้มสำหรับผู้บริหาร
5. Top down absolute power
ไม่ฟังข้อเสนอจากตัวแทนหมอ คนที่มีอำนาจการตัดสินใจไม่เคยเอาตัวลงมาคุยกับหมอแบบจริงจังเลย
1-2 ปีจะลงมาพบหมอทั้งรพ.ซักหนึ่งครั้ง สร้างภาพเก่ง พูดขายฝันสวนหรูถึงภาพที่เขาต้องการ สั่งการลงมา พอเกิดปัญหาตัวเองไม่ลงมารับผิดชอบ แต่อาศัยหน่วยข่าวกรอง(ที่ไม่รู้ว่ากรองอะไรเข้าไปบ้าง) ออกคำสั่งแก้ผ้าเอาหน้ารอดลงมาทีหลัง
แถมสั่งให้เงียบและหุบปาก
ครั้งหนึ่งมีคำสั่งออกมาไม่ชัดเจน จนพยาบาลทำงานไม่ได้ ตัวแทนพยาบาลต้องโทรมาหาผมเพื่อให้ผมช่วย
ผมรวบรวมข้อมูลทั้งหมดและพบว่าคำสั่งมีปัญหาจริงๆ ผมจึง chat line ลงไปสอบถามผู้บริหารเพื่อขอความชัดเจน
… ผ่านไปไม่ถึง 5 นาที หนึ่งในผู้บริหาร(คนที่แทงข้างหลังผมที่หาว่าผมมาตรวจคนไข้ VIP เขาช้า 5 นาทีนั่นแหละ)โทรหาผมทันทีคุยกับผมสั้นๆ ใจความว่า “คำสั่งนั้นเอาแบบเดิม ไม่ต้องแก้ และให้ผมเงียบๆซะ”... (ก็ได้วะครับ)

จุดเปลี่ยนที่ทำให้รพ.เข้าสู่ law of diminishing returns
ห้องตรวจทุกห้องของรพ. ถูกใช้จนเต็มศักยภาพ … เอาจริงๆคือล้นศักยภาพเสียอีก (over-utilized) บางแผนกมีเก้าอี้ดนตรี - หมอคนแรกหมดเวลาออกตรวจ - หมอคนต่อไปเดินเข้าใช้ห้องตรวจต่อทันที - ถ้าไม่ทันก็ต้องคว้าห้องตรวจที่ว่างพร้อมใช้งานก่อน - หมอทำการไล่ที่กันเอง - หมอบางท่านต้องใช้ห้องทำงานของพยาบาลเป็นห้องตรวจชั่วคราว
ห้องพักผู้ป่วยก็เช่นกัน บางช่วงเตียงเต็มจนไม่สามารถ admit คนไข้ได้
แต่จำที่ผมบอกได้มั้ยครับว่า คนที่เป็น top down absolute power ไม่เคยเอาตัวลงมาพูดคุยกับแพทย์เพื่อรับฟังปัญหาที่แท้จริงเลย รับแต่ข่าวกรอง(ที่ไม่รู้ว่ากรองอะไรเข้าไปบ้าง) ช่วงนึงมีคนไข้ complaint ว่ารอนั่งรอหมอนาน หมอมาตรวจช้า ผู้บริหารเลยพยายามจะแก้ปัญหา โดยการ monitor waiting time (ระยะเวลารอหมอ) หยิบยกเรื่องนี้ขึ้นมาเป็นวาระเร่งด่วนต้องรีบแก้ไข
แต่เขายังงงๆกับ concept waiting time อยู่เลยว่าจะนับตั้งแต่ตอนไหนถึงตอนไหน - Waiting time สั้นแปลว่าดี เพราะคนไข้ได้เจอหมอเร็ว - Waiting time นานแปลว่าไม่ดี เพราะคนไข้นั่งรอหมอนาน
เขาตีความจากตัวเลขครับ แต่เคยเอาตัวลงมาดูจริงๆหรือเปล่าว่าทำไมตัวเลขมันถึงออกมาไม่ดี
คำตอบคือ“ไม่” ครับ
หมอบางสาขามีความจำเป็นต้องไปดูคนไข้ที่อาการหนักใช้เวลารักษานาน ... หรือ ... รับปรึกษาจากแพทย์ต่างสาขา ... หรือ ... เป็นสาขาเฉพาะทางของเฉพาะทางอีกที ต้องใช้เวลาตรวจละเอียดตรวจนาน
มันเป็นกระบวนการทำงานของหมอ ที่หมอด้วยกันเข้าใจกัน
ส่วนคนเก็บข้อมูลก็นำเสนอไปทั้งอย่างนั้นโดยที่ไม่ได้วิเคราะห์อะไรเลย มันเป็นการกรองข้อมูลที่ไม่รอบคอบก่อนนำเสนอผู้บริหาร
สุดท้ายผู้บริหาร “โทษหมอ” ว่าไม่มีการบริหารเวลาทำงานที่ดีเพียงพอ ทำให้คนไข้รอนาน เขาสรุปกันดื้อๆแบบนี้เลยครับ
พอหนักๆเข้า “รอหมอนาน ต้องเพิ่มหมอ” season การรับสมัครหมอหลายตำแหน่งได้เริ่มขึ้น
แต่เดี๋ยวนะ ห้องตรวจมันแน่นจนแทบไม่มีที่ให้หมอนั่งทำงานแล้ว แต่เขาก็ไม่สนครับ รับหมอหน้าใหม่ๆมาเพิ่มเรื่อยๆ
ด้วย mindset ว่า "ต้องเพิ่มหมอ หมอจะได้เยอะขึ้น คนไข้จะได้ไม่ต้องรอนาน" และเชื่อว่าจะทำรายได้ให้รพ.มากขึ้น หมอหน้าใหม่บางท่านเข้ามาทำงานวันแรกถึงขั้นอยู่ในสภาวะ dead air คือไม่มีที่ให้นั่งทำงาน
“ทำมากได้น้อย” เริ่มต้น
คนไข้รพ.นี้ ส่วนใหญ่เป็นโรคซับซ้อน ต้องการทักษะและเวลาหมอเฉพาะทางแต่ละสาขาอยู่ดี ไม่ได้ทำให้ waiting time ดีขึ้น คนไข้ยัง “นั่งรอหมอนานเหมือนเดิม”
รายได้เริ่มลดลง ยอดคนไข้เริ่มลดลง รพ.พยายามแก้เกมโดยการเพิ่มราคาค่าบริการ (เพิ่มขนาด ticket size) ทำให้มีเสียงรีวิวตามโซเชียลว่า "แพง"
ผลที่เกิดขึ้นคือคนไข้หลายคนอาศัยรพ.นี้ในการตรวจวินิจฉัยโรคแล้วเอาผลไปรักษาต่อรพ.รัฐบาลตามสิทธิ์เพราะสู้ราคาค่ารักษาไม่ไหว บางคนมีประกันสุขภาพหลายฉบับแต่ก็ต้องจ่ายส่วนต่างมากอยู่ดี

วิธีการข้างต้นนี้ ไม่ผิดกติกาครับ ผล X-ray , CT, MRI, ultrasound จากรพ.เอกชน ไวกว่ารพ.รัฐบาลอยู่แล้ว แต่ก็มีคนไข้บางส่วนยินดีจ่ายแพง เพราะเชื่อมั่นหมอที่รพ.นี้ไม่อยากย้ายรพ.ก็มีครับ เพราะหมอไม่ได้ทำอะไรผิด หมอเก่งๆมีเยอะ
ถึงแม้ว่ารพ.จะรักษา momentum มีจำนวนคนไข้ประมาณ 1100 - 1200 รายต่อวัน แต่ก็เป็นโรคง่ายๆ(simple disease) เช่นไข้หวัด อาหารเป็นพิษ เป็นต้น โรคเหล่านี้ ticket size ไม่ได้ใหญ่มาก ประคองไว้ไม่ให้ขาดทุนเท่านั้นครับ
แต่ความแพงแบบไม่สมเหตุสมผล ทำให้คนไข้หลายรายถอดใจย้ายรพ.ตั้งแต่ทราบค่าใช้จ่ายวินาทีแรก
คนไข้น้อยลง --> รายได้ลดลง --> เพิ่ม ticket size ต่อหัวให้แพงขึ้น --> คนไข้หนีเพราะแพงเกิน
ผมไม่รู้ว่าผู้บริหารเขาเห็นไหม แต่คาดว่าคงจะไม่เห็น
ส่วนโรคหรือการผ่าตัดที่สมศักดิ์ศรีกับศักยภาพของรพ. "น้อยมากจนแทบไม่มี" ไม่ใช่สาเหตุอื่นเลยครับ โดนรพ.คู่แข่งในรัศมี 20 กิโลเมตรเอาไปหมด เพราะราคาถูกกว่า หมอก็เก่งไม่แพ้กัน หมอบางคนเคยอยู่ที่รพ.แห่งนี้ เสนอโปรเจคการรักษาโรคบางโรคที่สามารถสร้างรายได้เป็นกอบเป็นกำ แต่ทางรพ.ไม่เอาเอง สุดท้ายหมอเหล่านั้นย้ายไปอยู่กับรพ.คู่แข่งและผลักดันโปรเจคเหล่านั้นสำเร็จจนมีชื่อเสียง
"รพ.ขายสินค้า premium ไม่ได้เลย ขายได้แต่สินค้าเกรดท้องตลาด"
กลยุทธที่รพ.ทำต่อมาคือเพิ่มจำนวนชั่วโมงการทำงานของหมอให้เพิ่มขึ้นโดยให้หมอมาทำงานเร็วขึ้น 2 ชม. แต่ไม่จ่าย OT ให้ ด้วยตรรกะว่าถ้าหมอทำงานนานขึ้น จะมีจำนวนคนไข้มากขึ้น ทางรพ.ไม่ได้ขอร้อง แต่บีบคอให้หมอร่วมมือ หากไม่ร่วมมือไล่ออกทันที

ไปๆมาๆ มีการไล่ออกกระทันหันเกิดขึ้น มีการส่งหนังสือส่วนตัวหาหมอทุกคน ใครมีรายชื่อที่จะปลดออกก็ต้องออกจากงานทันที
ผมมองว่าฐานะทางการเงินมีปัญหารุนแรงครับ เงินเดือนพนักงานถือเป็น fixed cost ที่ธุรกิจต้องแบกรับ ถ้าเจ๋งจริงต้องควบคุมรายจ่ายให้ธุรกิจสามารถไปต่อได้โดยไม่ปลดคน ในส่วนของธุรกิจรพ. หมอคือบุคคลากรที่สำคัญที่สุดและเป็นด่านสุดท้ายที่จะไล่ออกเพื่อรักษาชีวิตของธุรกิจ ตอนนี้รพ.ได้เข้าสู่ระยะสุดท้ายของ law of diminishing returns คือ “ซวยหน่อยขาดทุน” เป็นที่เรียบร้อยครับ
จุดจบของรพ.แบบนี้ ที่ศักยภาพดี แต่บริหารห่วยแตก มันจะจบด้วยการถูก take over ผ่านมาไม่นานกราฟหุ้นออกอาการ exit liquidity แล้วครับ
ข้อคิดที่อยากแบ่งปันกับทุกคนที่อ่านมาจนจบ
- ช่วงธุรกิจเปลี่ยนผ่านสู่ทายาท คือจุดวัดใจหัวเลี้ยวหัวต่อว่าจะรอดหรือไม่รอด
- Law of diminishing returns ไม่ได้ใช้เฉพาะกับธุรกิจ แต่สามารถประยุกต์ใช้กับการดำเนินชีวิตได้หลายมิติ หากใครเข้าใจ จะขยับเข้าสู่ Pareto’s rule … สั้นๆคือ ทำน้อยแต่ได้(โคตร)มาก
- เจ้าของธุรกิจ ต้องหูไว มองหาเนื้อร้ายที่คอยกัดกินธุรกิจให้เจอ แล้วกำจัดมันซะ ก่อนที่ธุรกิจจะล้มทั้งยืน ทับตัวเองตาย
-
 @ 04ea4f83:210e1713
2025-05-01 18:22:24
@ 04ea4f83:210e1713
2025-05-01 18:22:2430. November 2022
Sehr geehrter Herr Bindseil und Herr Schaff von der Europäischen Zentralbank,
Ich schreibe Ihnen heute, am Tag der Veröffentlichung Ihres EZB-Blog-Berichts „Bitcoin's Last Stand", sowohl mit Belustigung als auch mit Bestürzung. Ich amüsiere mich darüber, wie albern und hilflos Sie beide erscheinen, indem Sie sich auf müde und längst widerlegte Erzählungen über Bitcoin und seine Nutzlosigkeit und Verschwendung stützen. Und ich bin beunruhigt, weil ich von zwei sehr gut ausgebildeten und etablierten Mitgliedern Ihres Fachgebiets eine viel differenziertere kritische Sichtweise auf den aufkeimenden Bitcoin und die Lightning Skalierungslösung erwartet hätte.
Sie haben sich mit Ihren dilettantischen Versuchen, Angst, Unsicherheit und Zweifel an einem globalen Open-Source-Kooperationsprojekt zu säen, das als ein ständig wachsendes Wertspeicher und -übertragungssystem für viele Millionen Menschen weltweit fungiert, wirklich einen Bärendienst erwiesen. Ein System, das jedes Jahr von mehr und mehr Menschen genutzt wird, da sie von seiner Effektivität und seinem Nutzen erfahren. Und ein System, das noch nie gehackt oder geknackt wurde, das funktioniert, um die „Banklosen" zu versorgen, besonders in den Ländern und Orten, wo sie von finsteren totalitären Regierungen schwer unterdrückt oder von der finanziell „entwickelten" Welt einfach im Stich gelassen wurden. In der Tat ist Bitcoin bereits gesetzliches Zahlungsmittel in El Salvador und der Zentralafrikanischen Republik, und erst gestern erhielt er in Brasilien den Status eines „Zahlungsmittels".
Es entbehrt nicht einer gewissen Ironie, wenn ich schreibe, dass Sie das Ziel so gründlich verfehlen, insbesondere weil die Bank- und Finanzsysteme, zu denen Sie gehören, für eine Energie- und Materialverschwendung verantwortlich sind, die um Größenordnungen größer ist als die Systeme und Ressourcen, die das Bitcoin-Netzwerk antreiben und erhalten. Ich bin mir sicher, dass Sie sich der revolutionären kohlenstoff- und treibhausgasreduzierenden Effekte bewusst sind, die Bitcoin-Mining-Anlagen haben, wenn sie neben Methan-emittierenden Mülldeponien und/oder Ölproduktionsanlagen angesiedelt sind. Und ich weiß, dass Sie auch gut über solar- und windbetriebene Bitcoin-Mining-Cluster informiert sind, die dabei helfen, Mikronetze in unterversorgten Gemeinden einzurichten.
Ich könnte noch weiter darüber sprechen, wie das Lightning-Netzwerk implementiert wird, um Überweisungszahlungen zu erleichtern sowie Finanztechnologie und Souveränität in Gemeinden in Laos und Afrika südlich der Sahara zu bringen. Aber lassen Sie mich zu dem Teil kommen, der einen gewöhnlichen Menschen wie mich einfach zutiefst traurig macht. Bitcoin ist, wie Sie sehr wohl wissen (trotz Ihrer dummen und veralteten Verleumdungen), ein technologisches Netzwerk, das nicht auf nationaler oder internationaler Verschuldung oder der Laune von Politikern basiert oder durch sie entwertet wird. Es ist ein System, das jenseits der Kontrolle einer einzelnen Person, eines Landes oder einer Gruppe von Ländern liegt. Wenn Bitcoin sprechen könnte (was er in der Tat ungefähr alle zehn Minuten tut, durch das elektro-mathematische Knistern und Summen des Wahrheitsfeuers), würde er diese Worte aussprechen:
„Über allen Völkern steht die Menschlichkeit".\ \ Als Bankiers der Europäischen Union, als Menschen von der Erde, als biologische Wesen, die denselben Gesetzen des Verfalls und der Krankheit unterliegen wie alle anderen Wesen, wäre es da nicht erfrischend für Sie beide, das Studium und die Teilnahme an einer Technologie zu begrüßen, die die Arbeit und die Bemühungen der sich abmühenden Menschen auf unserem Planeten bewahrt, anstatt sie zu entwerten? Wie die Bitcoin-Kollegin Alyse Killeen wiederholt gesagt hat: „Bitcoin ist FinTech für arme Menschen".
Ich bin dankbar für Ihre Aufmerksamkeit und hoffe, dass Sie über Bitcoin nachdenken und es gründlicher studieren werden.
Mit freundlichen Grüßen,
Cosmo Crixter
-
 @ 1c19eb1a:e22fb0bc
2025-03-06 07:52:32
@ 1c19eb1a:e22fb0bc
2025-03-06 07:52:32It's been barely two years since I joined Nostr on my main npub, nostr:npub1kun5628raxpm7usdkj62z2337hr77f3ryrg9cf0vjpyf4jvk9r9smv3lhe, and in just that relatively short time, the amount of development on top of this protocol has been staggering. When nostr:npub1sg6plzptd64u62a878hep2kev88swjh3tw00gjsfl8f237lmu63q0uf63m first opened the floodgates of adoption by tweeting about Nostr, it felt like most of the available clients were barely serviceable and held together with a prayer and copious amounts of duct tape. Of course, it can sometimes still feel that way, but there are definitely some Nostr apps looking and feeling more polished and providing true innovation when compared with legacy social platforms. Indeed, there are a growing number of Nostr-based applications and tools that have very little to do with social media at all.
One thing we have not had available to the growing Nostr community, and those considering joining it, is a source for application reviews that is thorough, approachable, knowledgeable, and balanced. This is what I hope to begin to provide through this new npub dedicated to reviewing as many of the Nostr clients, apps, and tools as I possibly can, so you the reader can determine which ones will fit your needs, and perhaps help you find new ones you had never heard about.
One of the best parts about Nostr is the portability of your identity and social graph, allowing users to log into any Nostr-based application with their same "account" without some centralized tech giant like Google or Apple owning who you are and all of your data. Leverage this super-power of Nostr with me as we explore the best applications and tools the intrepid developers building on this platform have cooked up.
What will you review?
My choice of applications to review will be based on a few factors.
First, I will only be reviewing applications that have a production release, or are otherwise considered production ready by the developer. nostr:npub1xtscya34g58tk0z605fvr788k263gsu6cy9x0mhnm87echrgufzsevkk5s, you won't have to worry that I will be putting NoteDeck under the microscope while it is still very much in alpha. All of us who love to try the new clients as soon as they are available understand well enough that there will be plenty of bugs, UI quirks, and rough edges to look past.
Second, I will generally be reviewing applications that are meant to be user-facing for the average person. That is, apps that your normie friends might soon be using, and then asking you why they can't edit anything they post. I will not be doing reviews of various relay implementations, for instance, unless they are designed to be approachable to the average user to install and manage. nostr:npub10npj3gydmv40m70ehemmal6vsdyfl7tewgvz043g54p0x23y0s8qzztl5h, your project might just be a notable exception.
Third, my reviews will be limited by the operating systems I have available to me at the time. Sorry folks over on iOS, Mac, and Windows. I will only be able to review apps I can run on Android, Linux, or my web browser for the time being.
How will the apps be rated?
I want to be thorough in my reviews, and yet avoid overloading my readers with information they don't care about. In order to attempt to achieve this, I will break my reviews into several sections, so readers can skip to the sections relevant to their interests.
First, I will provide a basic overview of the type of application I am reviewing, what it is trying to achieve, and why a user might want to try it out.
Next, I will give my overall impression of the application. The good, the bad, and the ugly, as it were, so that those who just want a brief rundown can get the TLDR right out the gate and be on their way.
Then we will begin diving into the nitty-gritty with an in depth look at the main features of the application. What it does well. What features seem lacking. What expected features are absent. What features make it unique and set it apart from other applications with a similar purpose.
For the sake of all the baby Nostriches out there, the next section will be an assessment of how approachable the application would likely be to a normie who is coming to Nostr with no idea what a public and private key are, what relays are, or why they might want to start interacting here instead of on a legacy equivalent. What would someone used to Twitter think of #Snort? What would someone used to Spotify think of #Fountain or #Wavlake?
The next section will be a review of the application's UI. The design and polish. How easy it is to find the things you want in the areas you would expect them. In short, how well the application achieves the goal of making the user feel at home and want to continue using the app just through quality UI design.
If you know me and my contstant harping on developers to include various forms of external signing, it should be no surprise to you that the next section will cover login options. What does the sign-in and sign-up flow look like, and does the user have to expose their private key to the application in order to use it?
A review of virtually any Nostr application would be incomplete without a section dedicated to zap integration. How prominent is zapping in the app? How easy is it to zap or start receiving zaps? Are zaps displayed in a way that encourages users to compete to be top zapper? Is Nostr Wallet Connect supported for using external wallets for one-tap-zapping?
Most Nostr applications, even "other stuff" clients, are designed to present some form of content to the user. The next section will cover how easy it is for the user to find the type of content they may be interested in, or to discover content they didn't know they might be interested in. For social clients, how easy is it to discover other users that they might want to follow?
The backbone of the protocol is the interplay between clients and relays, and the next section of the review will cover how the app manages relays. Are they hidden from the user? Are there sensible defaults? Can users who want to do so select the relays they prefer? Does the app respect relays the user has selected in other apps, or are the app's relays independent of those selected in other apps. Worse, does the app overwrite your selected relays with its defaults?
Finally, I will scour the #AskNostr feed for questions and comments from other users about the app under review to get more perspectives than just my own. What are the common pain-points other users are having? What do they love about the app? What features would they like to see added?
Are there other sections you would like to see me add before I start dropping reviews? Get them to me soon, because I am currently taking notes for my first review, which will be the #Primal #Android client!
PV 🤙
-
 @ 04ea4f83:210e1713
2025-05-01 18:18:36
@ 04ea4f83:210e1713
2025-05-01 18:18:36Digitales Geld ist nur Text, die ganze Zeit
Bei digitalem Geld geht es im Grunde nur um Zahlen in einem Hauptbuch. Die ganze Zeit über sind es die Zahlen, auf die es ankommt. Lange Zahlen sind einfach nur Zeichenketten im PC und diese werden als Nachrichten in einem Netzwerk, das durch Regeln gebildet wird, an gleichwertige Peers gesendet - das ist Bitcoin, das mit einem einzigartigen dezentralen Zeitstempel-Algorithmus kombiniert wird, der durch die Unfälschbarkeit von Energie gesichert ist. Das Ergebnis ist ein Bargeldnetzwerk mit einem festen, vorprogrammierten Zeitplan für die Geldschöpfung, das den ersten absolut knappen digitalen Inhabervermögenswert schafft.\ \ Diese revolutionären Ideen werden bleiben, genauso wie das Feuer, das Rad, die Elektrizität, das Smartphone, das Internet oder die Zahl Null. Technologie entwickelt sich weiter und was machen lebende Organismen? Sie können mutieren, genau wie Viren, und das hat mich zu dem Schluss gebracht, dass es auch in dieser Hinsicht eine Verbindung gibt und das obwohl Gigi bereits einige der vielen Facetten von Bitcoin beschrieben hat. Für mich ist die Grundlage die Abstraktion, dass Bitcoin nur die Summe aller Menschen ist, die Satoshis besitzen oder anderweitig mit dem Bitcoin-Netzwerk interagieren.\ \ Die Technologien werden in einem bestimmten Tempo angenommen. Allerdings gibt es immer frühe oder späte Entdecker von neuer Technologie. Aber was passiert, wenn es zu einer ernsthaften Bedrohung wird, wenn hartes Geld nicht adoptiert wird? Was passiert, wenn die Geschwindigkeit der Preiszunahme so hoch wird, dass es unmöglich ist, jemanden zu finden, der Satoshi in Fiat tauschen möchte? Was passiert, wenn die Hyperbitcoinisierung morgen beginnt? Was wäre, wenn es eine UpSideProtection™️ gäbe, die diesen Prozess noch mehr beschleunigt und dir Bitcoin zu einem Bruchteil seines wahren Wertes sichert?\ \ Wir alle wünschen uns einen sicheren Übergang, um den Krieg aufgrund einer scheiternden Dollar-Hegemonie zu vermeiden, und tatsächlich gibt es ein Rennen, um den Krieg zu vermeiden. Mein größtes Geschenk ist die Zeit, die ich ich investiere, und die monetäre Energie, die ich in Bitcoin spare, und da ich schon eine Weile dabei bin, sehe ich, dass meine Mitstreiter die gleiche Mission verfolgen. Aber das ist NICHT genug. Wir müssen skalieren. Schneller.\ \ Das Erstaunen über den Kurzfilm der große Widerstand hat mich zu dem Schluss gebracht, dass wir alle Werkzeuge und Informationen in Form von Lehrern, Podcasts, Büchern und aufklärenden Videos bereits haben. Der Vorteil einer festen Geldmenge wird aber noch nicht von einer kritischen Masse verstanden, sondern nur von einer intoleranten Minderheit. Diese Minderheit wächst von Tag zu Tag. Ihre Inkarnationen sind die DCA-Armee, die Hodler der letzten Instanz, die unbeirrten Stacker, die Cyberhornets, die Memefactory™️ und Mitglieder der 21 Gruppe auf der ganzen Welt.\ \ Wir Bitcoiner sind räumlich getrennt, aber nicht in der Zeit. Getrennt in der Sprache, aber nicht in der Mission. Vereint müssen wir uns zu Wort melden, aufklären und Bitcoin wie einen Virus verbreiten.\ \ Niemand entscheidet, was Bitcoin für dich ist - dieser Virus des Geistes verfestigt sich in unbestechlichen Zahlen, die zu einer wachsenden Zahl an UTXOs in den Geldbörsen führen, nicht in negativen gesundheitlichen Auswirkungen. Bitcoin ist der Virus der Schuldenindustrie, der Virus, der im 21. Jahrhundert zur größten Definanzialisierung und Auflösung des Kredits führen wird. Da wir noch nicht in einer hyperbitcoinisierten Welt leben, müssen wir den Virus effektiver machen. Bitcoin muss mutieren, aber es ist nicht Bitcoin, der tatsächlich mutiert, sondern die Menschen, die ihn benutzen. Sie werden zu toxischen Maximalisten, die den Virus noch stärker verbreiten und alle Shitcoiner während ihrer Anwesenheit geistig infizieren oder argumentativ töten.\ \ Ich habe mich gefragt, wie wir eine Milliarde Menschen dazu ausbilden und überzeugen können, Bitcoin freiwillig zu nutzen und darin zu sparen, so dass sie Bitcoin als primäres Mittel zur Speicherung und Übermittlung von Werten in Raum und Zeit nutzen? Die Hyperbitcoinisierung braucht nur eine einzige, starke positive Rückkopplungsschleife um wirklich in Gang zu kommen, und diese Rückkopplung gibt es bereits, aber nicht in den Köpfen aller. Ab einer bestimmten Schwelle wird die Schwerkraft von Bitcoins gehärteten monetären Eigenschaften einfach zu hoch sein, als dass die Spieltheorie nicht zu dieser Rückkopplung führen würde, vor allem da Bitcoin im Jahr 2024 Gold in Punkto Knappheit übertrifft.\ \ Die Verbreitung der Idee einer festen dezentralen Geldmenge, die der Macht zentraler Kräfte entzogen ist, ist der Virus. Der Weg, das Spiel zu spielen, ist, Stacker zu stapeln, und Stacker stapeln Sats, wodurch die Geldmenge noch dezentralisierter wird und ein Verbot noch absurder wird. Sats sind endlich und unser Spiel ist es auch. Allein eine bestimmte Anzahl von einfachen Leuten, den Plebs, kann den Preis auf 1.000.000 EURO treiben.\ \ Letztendlich wird sich die Welt an das neue Gleichgewicht der Macht zugunsten des Individuums anpassen. Diese Idee in die Köpfe der Massen zu bringen, ist die wichtigste Aufgabe für 2023, die in das nächste Halving Mitte 2024 führt.\ \ Wir müssen unseren Reproduktionswert erhöhen, um die Akzeptanz zu steigern. Die Verwendung von Bitcoin als Zahlungsmittel und eine Kreislaufwirtschaft ist wichtig. Bildung ist wichtig. Apps und Anwendungsfälle sind wichtig. Die Kaufkraft, d.h. die Moskau Zeit, die sich in Richtung Mitternacht (00:00) bewegt, spielt eine Rolle, und all dies hängt zusammen.\ \ Aber wie genau können Plebs eine Milliarde Menschen überzeugen?\ \ Wie genau hat das Corona-Virus eine Milliarde Menschen infiziert?\ \ Peer-to-Peer.\ \ Erhebe deine Stimme, wer auch immer du bist, sprich über Bitcoin, werde aktiv und BUIDL oder lass uns einfach Spaß daran haben, arm zu bleiben und es genießen, jeden Tag bestohlen zu werden.\ \ Lass uns Yellow mehr Freizeit schenken und Bitcoin bis 100k+ aufkaufen und uns damit ins Stackheaven befördern.
"Don't stop believin' HODL on to that feelin' "
Der Rest wird in die unumstößliche Geschichte der Timechain eingraviert.
„Unter dieser Maske gibt es mehr als nur Fleisch. Unter dieser Maske ist eine Idee. Und Ideen sind kugelsicher." Alan Moore, V wie Vendetta

⚡
Danke für deine Aufmerksamkeit .\ \ #GetShortFiat und #GetOnZero\ \ Es ist immer noch 60 Uhr. Sei weise und stapele unbeirrt. Man kann die Mathematik und Physik nicht austricksen.\ \ Wenn der Post dir Motivation zum Stapeln von Sats oder dem Stapeln von Stackern gemacht hat, freue ich mich, wenn du mir auch etwas beim Stapeln hilfst!
-
 @ e4950c93:1b99eccd
2025-05-02 09:41:12
@ e4950c93:1b99eccd
2025-05-02 09:41:12Tu connais une marque proposant des alternatives naturelles ? Partage-la ici en commentant cette page !
Pour être référencée, la marque doit proposer une partie au moins de ses produits en matières naturelles. 👉 En savoir plus sur les matières
Chaque information ajoutée (nom, lien, catégorie, etc.) et validée est considérée comme une contribution. 👉 En savoir plus sur les contributions
Chaque contribution validée est comptabilisée et donne lieu à une rétribution. Pense à bien sauvegarder tes clés (identifiants) dans un coffre comme nsec.app). Tu peux aussi partager plus simplement tes trouvailles sans créer de compte via le formulaire de contact (non éligible pour les rétributions). 👉 En savoir plus sur les rétributions
Copie-colle le modèle ci-dessous et remplis les informations que tu as. D’autres contribut-eur-rice-s ou l'équipe coeur pourront compléter les éléments manquants.
Nouvelle marque ou fabricant
- Nom de la marque :
- Image représentant des produits de la marque (lien, idéalement depuis le site de la marque) :
- Courte description :
- Catégories de produits proposées :
- Matières utilisées pour ses produits :
- Site internet de la marque :
- Autres informations (lieu de production, labels…) :
Cet article est publié sur origine-nature.com 🌐 See this article in English
-
 @ e4950c93:1b99eccd
2025-05-02 09:36:09
@ e4950c93:1b99eccd
2025-05-02 09:36:09Tu as trouvé un produit naturel ? Partage-le ici en commentant cette page !
Ce site référence uniquement des produits et objets à usage durable. Les consommables (aliments, cosmétiques, combustibles, etc.) ne sont pas inclus.
Pour être référencé, le produit doit être composé de matières naturelles. 👉 En savoir plus sur les matières
Chaque information ajoutée (nom, matière, lien, zone de livraison pour un lien, etc.) et validée est considérée comme une contribution. 👉 En savoir plus sur les contributions
Chaque contribution validée est comptabilisée et donne lieu à une rétribution. Pense à bien sauvegarder tes clés (identifiants) dans un coffre comme nsec.app). Tu peux aussi partager plus simplement tes trouvailles sans créer de compte via le formulaire de contact (non éligible pour les rétributions). 👉 En savoir plus sur les rétributions
Copie-colle le modèle ci-dessous et remplis les informations dont tu disposes. D’autres contribut-eur-rice-s ou l'équipe coeur pourront compléter les éléments manquants.
Nouveau produit
- Nom du produit :
- Image du produit (lien) :
- Description courte :
- Catégories :
- Marque ou fabricant :
- Composition (matériaux utilisés, y compris les éléments inconnus) :
- Liens pour l’acheter (et zone de livraison) :
- Zone de livraison pour les
- Autres infos utiles (lieu de fabrication, labels, etc.) :
Cet article est publié sur origine-nature.com 🌐 See this article in English
-
 @ 62a6a41e:b12acb43
2025-03-04 22:19:29
@ 62a6a41e:b12acb43
2025-03-04 22:19:29War is rarely (or if ever) the will of the people. Throughout history, wars have been orchestrated by political and economic elites, while the media plays a key role in shaping public opinion. World War I is a clear example of how propaganda was used to glorify war, silence dissent, and demonize the enemy.
Today, we see similar tactics being used in the Ukrainian War. The media spreads one-sided narratives, censors alternative views, and manipulates public sentiment. This article argues that wars are decided from the top, and media is used to justify them.
How the Media Glorified and Propagated WW1
The Media Sold War as an Adventure
Before WW1, newspapers and propaganda made war seem noble and exciting. Young men were encouraged to enlist for honor and glory. Posters displayed slogans like “Your Country Needs You”, making war look like a duty rather than a tragedy.
Demonization of the Enemy
Governments and media portrayed Germans as "barbaric Huns," spreading exaggerated stories like the "Rape of Belgium," where German soldiers were accused of horrific war crimes—many later proven false. Today, Russia is painted as purely evil, while NATO’s role and Ukraine’s internal conflicts are ignored.
Social Pressure & Nationalism
Anyone who opposed WW1 was labeled a traitor. Conscientious objectors were shamed, jailed, or even executed. The same happens today—if you question support for Ukraine, you are called "pro-Russian" or "anti-European." In the U.S., opposing war is falsely linked to supporting Trump or extremism.
Fabricated Stories
During WW1, fake reports of German soldiers killing babies were widely spread. In Ukraine, reports of massacres and war crimes often circulate without verification, while Ukrainian war crimes receive little coverage.
How the Media Promotes War Today: The Case of Ukraine
One-Sided Narratives
The media presents Ukraine as a heroic struggle against an evil invader, ignoring the 2014 coup, the Donbas conflict, and NATO expansion. By simplifying the issue, people are discouraged from questioning the full story.
Censorship and Suppression of Dissent
During WW1, anti-war activists were jailed. Today, journalists and commentators questioning NATO’s role face censorship, deplatforming, or cancellation.
Selective Coverage
Media highlights civilian deaths in Ukraine but ignores similar suffering in Yemen, Syria, or Palestine. Coverage depends on political interests, not humanitarian concern.
Glorification of War Efforts
Ukrainian soldiers—even extremist groups—are painted as heroes. Meanwhile, peace negotiations and diplomatic efforts receive little attention.
War is a Top-Down Decision, Not the Will of the People
People Don’t Want Wars
If given a choice, most people would reject war. Examples:
- Before WW1: Many workers and socialists opposed war, but governments ignored them.
- Vietnam War: Protests grew, but the war continued.
- Iraq War (2003): Millions protested, yet the invasion went ahead.
Small Elites Decide War
Wars benefit arms manufacturers, politicians, and corporate interests—not ordinary people. Public opposition is often ignored or crushed.
Manipulation Through Fear
Governments use fear to justify war: “If we don’t act now, it will be too late.” This tactic was used in WW1, the Iraq War, and is used today in Ukraine.
Violence vs. War: A Manufactured Conflict
Violence Happens, But War is Manufactured
Conflicts and disputes are natural, but large-scale war is deliberately planned using propaganda and logistical preparation.
War Requires Justification
If war were natural, why does it need massive media campaigns to convince people to fight? Just like in WW1, today’s wars rely on media narratives to gain support.
The Crimea Referendum: A Case of Ignored Democracy
Crimea’s 2014 Referendum
- Over 90% of Crimeans voted to join Russia in 2014.
- Western governments called it "illegitimate," while similar referendums (like in Kosovo) were accepted.
The Contradiction in Democracy
- If democracy is sacred, why ignore a clear vote in Crimea?
- Other examples: Brexit was resisted, Catalonia’s referendum was shut down, and peace referendums were dismissed when they didn’t fit political interests.
- Democracy is used as a tool when convenient.
VII. The Libertarian Case Against War
The Non-Aggression Principle (NAP)
Libertarianism is fundamentally opposed to war because it violates the Non-Aggression Principle (NAP)—the idea that no person or institution has the right to initiate force against another. War, by its very nature, is the ultimate violation of the NAP, as it involves mass killing, destruction, and theft under the guise of national interest.
War is State Aggression
- Governments wage wars, not individuals. No private citizen would naturally start a conflict with another country.
- The state forces people to fund wars through taxation, violating their economic freedom.
- Conscription, used in many wars, is nothing more than state-sponsored slavery, forcing individuals to fight and die for political goals they may not support.
War Creates Bigger Government
- War expands state power, eroding civil liberties (e.g., WW1's Espionage Act, the Patriot Act after 9/11).
- The military-industrial complex grows richer while taxpayers foot the bill.
- Emergency powers granted during wars rarely get repealed after conflicts end, leaving citizens with fewer freedoms.
Peaceful Trade vs. War
- Libertarians advocate for free trade as a means of cooperation. Countries that trade are less likely to go to war.
- Wars destroy wealth and infrastructure, while peaceful trade increases prosperity for all.
- Many wars have been fought not for defense, but for economic interests, such as securing oil, resources, or geopolitical power.
Who Benefits from War?
- Not the people, who suffer death, destruction, and economic hardship.
- Not small businesses or workers, who bear the burden of inflation and taxes to fund wars.
- Not individual liberty, as war leads to greater state control and surveillance.
- Only the elites, including defense contractors, politicians, and bankers, who profit from war and use it to consolidate power.
Conclusion: The Media’s Role in War is Crucial
Wars don’t happen naturally—they are carefully planned and sold to the public using propaganda, fear, and nationalism.
- WW1 and Ukraine prove that media is key to war-making.
- The media silences peace efforts and glorifies conflict.
- If people truly had a choice, most wars would never happen.
To resist this, we must recognize how we are manipulated and reject the forced narratives that push us toward war.
-
 @ fbb0eb9d:bdb78256
2025-05-02 09:32:40
@ fbb0eb9d:bdb78256
2025-05-02 09:32:40Wir dürfen keinen Millimeter weichen für jene, die unsere Freiheit nicht zu schätzen wissen. Vor zehn Jahren wurden die Journalisten des französischen Satiremagazins Charlie Hebdo in ihrer Redaktion erschossen, weil sie sich die Freiheit nahmen, eine Religion zu beleidigen. Das sollten wir nicht vergessen, und beim Namen nennen. Diesen Text schrieb ich schon damals, und um es vorweg zu nehmen: Ich bin immer noch Charlie.
„Und, sind Sie auch Charlie?“ fragte damals mein Banksachbearbeiter, nachdem ich auf die Frage nach meinem Beruf „Journalistin“ geantwortet hatte. Viele waren seinerzeit „Charlie“, ja, die Solidarität mit den Opfern in Paris war groß. Bei uns im Land und auch weltweit. Tausende Facebooker veränderten ihre Profilbilder, aber genauso sicher, wie das Amen in der Kirche, hatte es nur wenige Tage gedauert, bis die Differenzierer auf den Plan gerufen wurden. Am Tag der Geiselnahmen in Paris fuhr ich gerade Taxi in Berlin, während sich die französischen Sondereinheiten vor der Druckerei und dem jüdischen Supermarkt in Stellung brachten, die ebenfalls unter Beschuss von Islamisten gerieten. Der Taxifahrer war kein potenzieller „Charlie“. Ich konnte seine Nationalität trotz Akzent nicht ausmachen, möglicherweise war er sogar Franzose. Ich habe nicht gefragt. Sein Standpunkt jedenfalls: „Warum mussten die das auch veröffentlichen, das hätte man ja wissen können, das sowas passiert“.
Wenn mehr auf dem Spiel steht, als ein Profilbild
Ein Moslem? Ich weiß es nicht. Aber auch aus dem christlichen Lager kam zunehmend Kritik, nachdem so mancher recherchiert hatte, was für Karikaturen bei „Charlie Hebdo“ in der Vergangenheit erschienen sind. Auch mit uns Christen ging man in dem Satire-Magazin nicht gerade zimperlich um. Sind wir immer noch Charlie, auch dann, wenn unsere eigene Religion aufs Korn genommen oder gar beleidigt wird?
Und so bestätigte ich dem Angestellten am Bankschalter auch gerne: „Ja, ich bin Charlie, aber ich bin auch gespannt, wie viele immer noch Charlie sind, wenn es um ihren eigenen Kopf geht!“ – eine Frage die heute kaum aktueller sein könnte angesichts von katholischen Priestern, die zwischenzeitlich im Namen Allahs in Frankreich am Altar geköpft wurden und auch islamischen Attentätern, die gerne deutsche Weihnachtsmärkte für ein adventliches Töten zum Anlass nehmen. Sind wir immer noch “Charlie” wenn die Frage nach der Solidarität mit den Opfern sich nicht mit einem Wechsel des Profilbildes bei Facebook erledigen lässt? Denn ein Bild zu tauschen, tut nicht weh, ist schnell gemacht und man bewegt sich damit gerade sowieso im Strom der breiten Masse.
Gesicht zu zeigen ist ein Anfang, es bis zur letzten Konsequenz durchzuhalten, oft etwas ganz anderes. Auch Prominente zeigten damals vor zehn Jahren gerne immer wieder Gesicht. Es existierte eine ganze Kampagne dazu unter dem Namen.
Da war dann Klaus Wowereit Migrant, wenn jemand was gegen Migranten hat, Jörg Thadeusz war schwul, wenn jemand etwas gegen Schwule hat, Ulrich Wickert war Jude, wenn jemand etwas gegen Juden hat und Markus Kavka gar schwarz, wenn jemand was gegen Schwarze hat.
 Das ist auch gut so, so wird Flagge gezeigt. Aber es braucht für derlei Bekenntnisse genauso wenig Mut, wie für den Profilbild-Wechsel bei Facebook.
Das ist auch gut so, so wird Flagge gezeigt. Aber es braucht für derlei Bekenntnisse genauso wenig Mut, wie für den Profilbild-Wechsel bei Facebook.Denn sind wir wirklich immer noch „schwarz“, „schwul“, „Jude“ oder „Migrant“, wenn unser Nebenmann angegriffen wird? Kurz nach der Ermordung der Satiriker von Charlie Hebdo bekam damals Ralf König auf Facebook und Co. von allen Seiten die Comiczeichner-Jacke vollgehauen, weil er nicht mehr ganz Charlie sein mag. Aus Angst hatte er eine Karikatur zurückgezogen, die sich mit dem Islam beschäftigte. Bei ihm steht ja auch nicht nur ein Profilbild, sondern – wie Paris gezeigt hat – wesentlich mehr auf dem Spiel. Eine allzu menschliche Reaktion! Und all den Heuchlern, die ihn verurteilen, würde ich gerne zurufen: Euch möchte ich mal in der gleichen Situation erleben. Nämlich dann, wenn es persönlich wird und die Angst nicht abstrakt, sondern konkret begründet werden kann.
Gerade Christen dürfen nicht zurückweichen
Das zeigt aber gleichzeitig, warum es so wichtig ist, dass wir auch weiterhin Charlie sind. Weil die Angst im Kopf uns sonst lähmt.
Wenn ein Journalist anfängt nachzudenken, ob er überhaupt oder wenn, wie er etwas schreiben soll, dann hat die Selbstzensur bereits eingesetzt.
Wenn ein Journalist Fakten weglässt, weil er vermutet, dass sie nicht gerne gehört werden, dann hat Selbstzensur schon eingesetzt.
Wenn ein Zeichner sich nicht mehr traut, manche Themen oder Religionen aufs Korn zu nehmen, dann hat Selbstzensur schon eingesetzt.
Und dann nutzt es nichts, dass gesetzlich keine Zensur existiert, weil diese Gesetze dann nicht mehr das Papier wert sind, auf dem sie stehen. Wir dürfen nicht zurückweichen. Auch und gerade nicht als Christen. Auch wenn wir selbst mit manchen Karikaturen hadern. Beleidigt sein darf man trotzdem. Denn der Grad von persönlicher Entrüstung ist bei allen unterschiedlich. Ich jedenfalls habe Tränen gelacht beim Kinoklassiker „Life of Brian“ und Monty Pythons „Catholic Song“ ist einfach ganz großes Kino. Aber auch ich war schon oft empört, weil mir manches, was unter Satire und Kunst verkauft wird, zu weit ging.
„Würden Sie auch Mohammed-Town ausstrahlen?“
Als etwa 2003 der Musiksender MTV die Comic-Serie „Popetown“ mit einem infantilen Papst und korrupten Kardinälen ausstrahlte, habe ich eine Gegenkampagne dazu organisiert. „Würden Sie auch Mohammed-Town“ ausstrahlen, fragte ich damals in einem offenen Brief die MTV-Geschäftsführerin Catherine Mühlemann. „Kein Christ wird Ihnen bei Ausstrahlung die Studiofenster zertrümmern, handelt es sich doch beim Christentum um eine Religion des Friedens. Wir verdienen aber nicht weniger Respekt als andere Religionen.“ 50.000 Menschen beteiligten sich damals an den Protesten, verschiedene Organisationen, Politiker und sogar der Zentralrat der Juden protestierte, genutzt hat es nichts. Die Serie erledigte sich letztendlich selbst mit niedrigen Einschaltquoten dank ihres unterirdischen Niveaus.

Aber selbst, wenn es ein Erfolg geworden wäre, hätten wir weiter protestiert: friedlich und ganz sicher nicht mit dem Maschinengewehr. Wir sind ein Land, in dem diese Debatten immer und immer wieder neu mit Worten und nicht mit Waffen ausgetragen werden. In unserem Land darf man kritisieren und sich auch empören. Wir dürfen unsere eigene Regierung anprangern und uns über Religionen lustig machen. Das tut weh, wenn man selbst betroffen ist, dieses Recht dürfen wir aber nicht riskieren. Für keinen persönlichen Grad an Beleidigtsein.
Diskurs statt Blasphemie-Gesetze
Wenn wir also Rücksicht nehmen auf Religionen, dann aber bitte auf alle. Wenn Religionen aber Kritik, Humor oder Satire aushalten müssen, dann bitte auch alle. Ich halte nichts von Blasphemie-Gesetzen, aber umso mehr vom freien Diskurs, der nicht nur in der Religionsfrage derzeit ins Hintertreffen gerät.
Die Frage, ob „der Islam“ zu Deutschland gehört, ist also die falsche. Die Frage ist: Will der Islam zu Deutschland oder gar zu Europa gehören? Sind alle seine Gläubigen bereit, friedlich hinzunehmen, dass im Namen von Meinungsfreiheit, Kunst oder Satire der eigene Glaube beleidigt werden darf?
Denn erst dann ist der Islam wirklich im freien Europa angekommen und diese Frage können die Muslime nur unter sich ausmachen. Es ist nicht an uns, ihnen ihre Religion zu erklären. Wir sollten aber langsam klären, wofür wir selbst stehen. Integration kann nur von jemandem erwartet werden, dem man auch erklären kann, in was er sich integrieren und wie weit das reichen soll.
Wir werden den gemeinsamen Nenner aufzeigen müssen, die „Conditio-sine-qua-non“, ohne die sich unsere Gesellschaft sonst immer weiter auseinander bewegt. Ich habe damals von Catherine Mühlemann keine Antwort auf meine Frage bekommen. Ich weiß nicht, ob sie heute Charlie ist. Ich wünsche mir keinen Raum für diese Angst, die uns lähmt, Debatten ehrlich zu führen. Für Menschen, die unsere Freiheit nicht zu schätzen wissen, weiche ich keinen Millimeter. Ich bin Birgit Kelle. Und ich bin immer noch Charlie.
-
 @ 8947a945:9bfcf626
2025-02-28 09:11:21
@ 8947a945:9bfcf626
2025-02-28 09:11:21Chef's notes
https://video.nostr.build/ea19333ab7f700a6557b6f52f1f8cfe214671444687fa7ea56a18e5d751fe0a9.mp4
https://video.nostr.build/bcae8d39e22f66689d51f34e44ecabdf7a57b5099cc456e3e0f29446b1dfd0de.mp4
Details
- ⏲️ Prep time: 5 min
- 🍳 Cook time: 5 min
- 🍽️ Servings: 1
Ingredients
- ไข่ 1 - 2 ฟอง
- ข้าวโอ๊ต 3 - 4 ช้อน
Directions
- ตอกไข่ + ตีไข่
- ปรุงรส พริกไทย หรือ ซอสถั่วเหลืองตามชอบ
- ใส่ข้าวโอ๊ต 3 - 4 ช้อน
- ใส่ถั่วลิสงอบ 1 - 2 หยิบมือ
- เทน้ำใส่พอท่วมข้าวโอ๊ต
- เข้าไมโครเวฟ ไฟแรง 1 - 2 นาที
-
 @ 460c25e6:ef85065c
2025-02-25 15:20:39
@ 460c25e6:ef85065c
2025-02-25 15:20:39If you don't know where your posts are, you might as well just stay in the centralized Twitter. You either take control of your relay lists, or they will control you. Amethyst offers several lists of relays for our users. We are going to go one by one to help clarify what they are and which options are best for each one.
Public Home/Outbox Relays
Home relays store all YOUR content: all your posts, likes, replies, lists, etc. It's your home. Amethyst will send your posts here first. Your followers will use these relays to get new posts from you. So, if you don't have anything there, they will not receive your updates.
Home relays must allow queries from anyone, ideally without the need to authenticate. They can limit writes to paid users without affecting anyone's experience.
This list should have a maximum of 3 relays. More than that will only make your followers waste their mobile data getting your posts. Keep it simple. Out of the 3 relays, I recommend: - 1 large public, international relay: nos.lol, nostr.mom, relay.damus.io, etc. - 1 personal relay to store a copy of all your content in a place no one can delete. Go to relay.tools and never be censored again. - 1 really fast relay located in your country: paid options like http://nostr.wine are great
Do not include relays that block users from seeing posts in this list. If you do, no one will see your posts.
Public Inbox Relays
This relay type receives all replies, comments, likes, and zaps to your posts. If you are not getting notifications or you don't see replies from your friends, it is likely because you don't have the right setup here. If you are getting too much spam in your replies, it's probably because your inbox relays are not protecting you enough. Paid relays can filter inbox spam out.
Inbox relays must allow anyone to write into them. It's the opposite of the outbox relay. They can limit who can download the posts to their paid subscribers without affecting anyone's experience.
This list should have a maximum of 3 relays as well. Again, keep it small. More than that will just make you spend more of your data plan downloading the same notifications from all these different servers. Out of the 3 relays, I recommend: - 1 large public, international relay: nos.lol, nostr.mom, relay.damus.io, etc. - 1 personal relay to store a copy of your notifications, invites, cashu tokens and zaps. - 1 really fast relay located in your country: go to nostr.watch and find relays in your country
Terrible options include: - nostr.wine should not be here. - filter.nostr.wine should not be here. - inbox.nostr.wine should not be here.
DM Inbox Relays
These are the relays used to receive DMs and private content. Others will use these relays to send DMs to you. If you don't have it setup, you will miss DMs. DM Inbox relays should accept any message from anyone, but only allow you to download them.
Generally speaking, you only need 3 for reliability. One of them should be a personal relay to make sure you have a copy of all your messages. The others can be open if you want push notifications or closed if you want full privacy.
Good options are: - inbox.nostr.wine and auth.nostr1.com: anyone can send messages and only you can download. Not even our push notification server has access to them to notify you. - a personal relay to make sure no one can censor you. Advanced settings on personal relays can also store your DMs privately. Talk to your relay operator for more details. - a public relay if you want DM notifications from our servers.
Make sure to add at least one public relay if you want to see DM notifications.
Private Home Relays
Private Relays are for things no one should see, like your drafts, lists, app settings, bookmarks etc. Ideally, these relays are either local or require authentication before posting AND downloading each user\'s content. There are no dedicated relays for this category yet, so I would use a local relay like Citrine on Android and a personal relay on relay.tools.
Keep in mind that if you choose a local relay only, a client on the desktop might not be able to see the drafts from clients on mobile and vice versa.
Search relays:
This is the list of relays to use on Amethyst's search and user tagging with @. Tagging and searching will not work if there is nothing here.. This option requires NIP-50 compliance from each relay. Hit the Default button to use all available options on existence today: - nostr.wine - relay.nostr.band - relay.noswhere.com
Local Relays:
This is your local storage. Everything will load faster if it comes from this relay. You should install Citrine on Android and write ws://localhost:4869 in this option.
General Relays:
This section contains the default relays used to download content from your follows. Notice how you can activate and deactivate the Home, Messages (old-style DMs), Chat (public chats), and Global options in each.
Keep 5-6 large relays on this list and activate them for as many categories (Home, Messages (old-style DMs), Chat, and Global) as possible.
Amethyst will provide additional recommendations to this list from your follows with information on which of your follows might need the additional relay in your list. Add them if you feel like you are missing their posts or if it is just taking too long to load them.
My setup
Here's what I use: 1. Go to relay.tools and create a relay for yourself. 2. Go to nostr.wine and pay for their subscription. 3. Go to inbox.nostr.wine and pay for their subscription. 4. Go to nostr.watch and find a good relay in your country. 5. Download Citrine to your phone.
Then, on your relay lists, put:
Public Home/Outbox Relays: - nostr.wine - nos.lol or an in-country relay. -
.nostr1.com Public Inbox Relays - nos.lol or an in-country relay -
.nostr1.com DM Inbox Relays - inbox.nostr.wine -
.nostr1.com Private Home Relays - ws://localhost:4869 (Citrine) -
.nostr1.com (if you want) Search Relays - nostr.wine - relay.nostr.band - relay.noswhere.com
Local Relays - ws://localhost:4869 (Citrine)
General Relays - nos.lol - relay.damus.io - relay.primal.net - nostr.mom
And a few of the recommended relays from Amethyst.
Final Considerations
Remember, relays can see what your Nostr client is requesting and downloading at all times. They can track what you see and see what you like. They can sell that information to the highest bidder, they can delete your content or content that a sponsor asked them to delete (like a negative review for instance) and they can censor you in any way they see fit. Before using any random free relay out there, make sure you trust its operator and you know its terms of service and privacy policies.
