-
 @ 005bc4de:ef11e1a2
2025-05-04 12:01:42
@ 005bc4de:ef11e1a2
2025-05-04 12:01:42OSU commencement speech revisited 1 year later
One year ago, May 5, 2024, the commencement speaker at Ohio State University was Chris Pan. He got booed for mentioning bitcoin. There were some other things involved, but the bitcoin part is what could my ears.
Here's an article about the speech and a video clip with the bitcoin mention. The quote that I feel is especially pertinent is this, '“The mechanics of investing are actually easy, but it comes down to mindset,” Pan said. “The most common barriers are fear, laziness and closed-mindedness.”'
Last year, I wrote this and had it sent as a reminder to myself (I received the reminder yesterday after totally forgetting about this):
Ohio State commencement speaker mentions bitcoin and got booed.
I wondered what would've happened if they'd taken his advice to heart and bought bitcoin that day. Linked article: https://www.businessinsider.com/osu-commencement-speaker-ayahuasca-praises-bitcoin-booed-viral-2024-5
Nat Brunell interviewed him on her Coin Stories podcast shortly after his speech: https://www.youtube.com/watch?v=LRqKxKqlbcI
BTC on 5/5/2024 day of speech: about $64,047 (chart below)
If any of those now wise old 23 year olds remember the advice they were given, bitcoin is currently at $95,476. If any took Pan's advice, they achieved a 49% gain in one year. Those who did not take Pan's advice, lost about 2.7% of their buying power due to inflation.
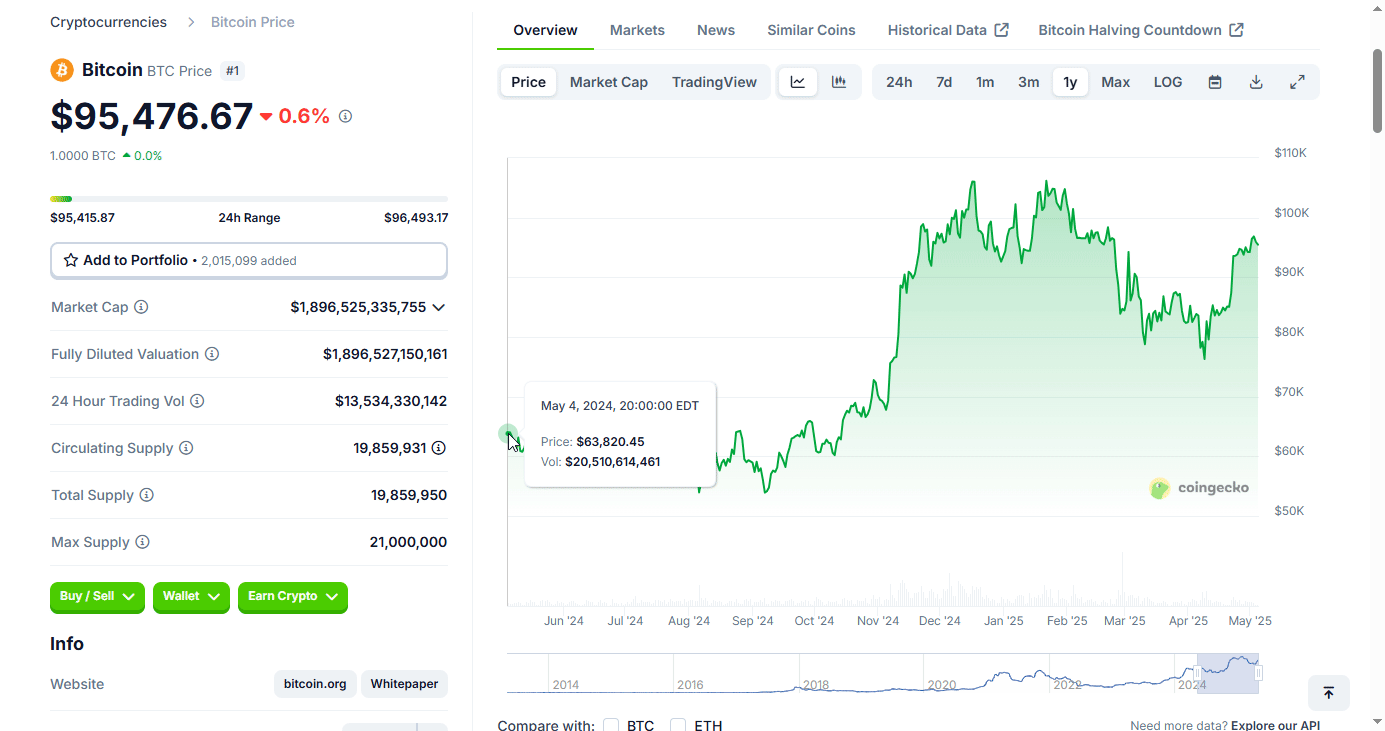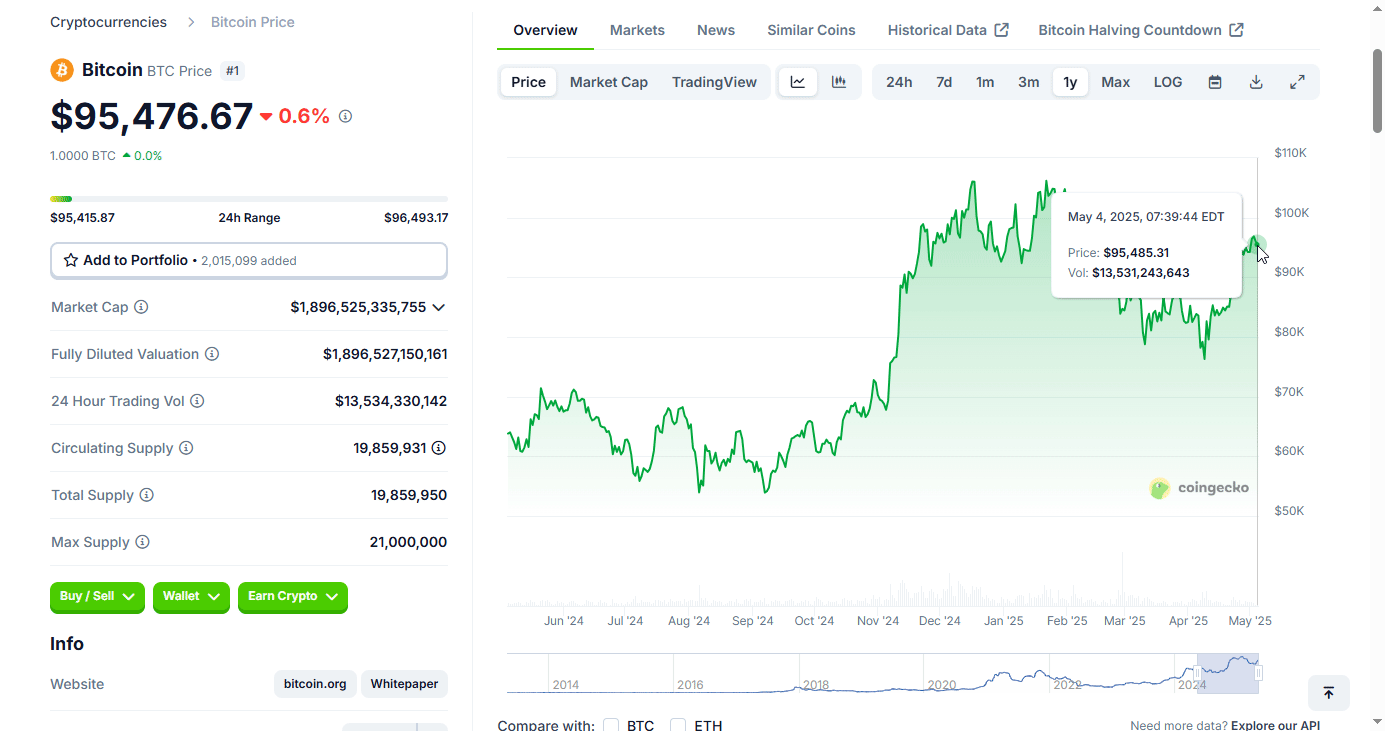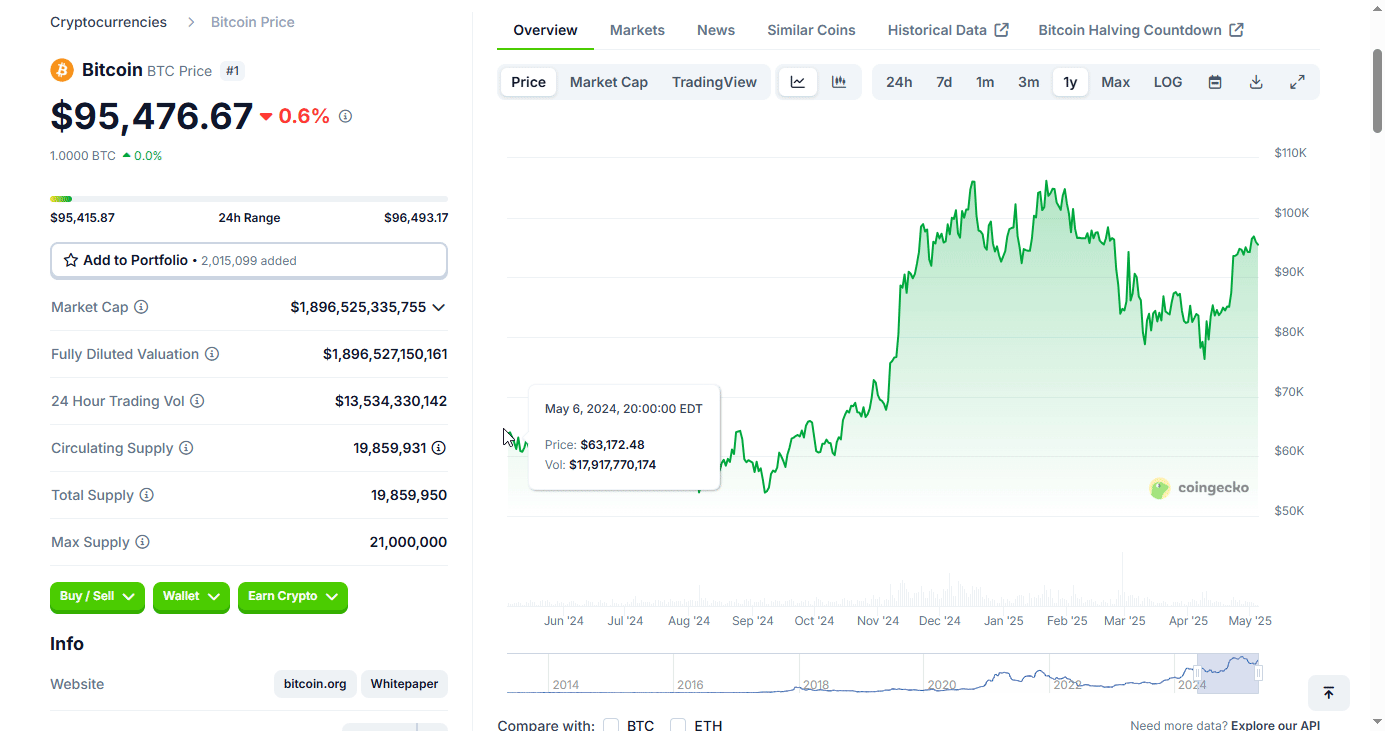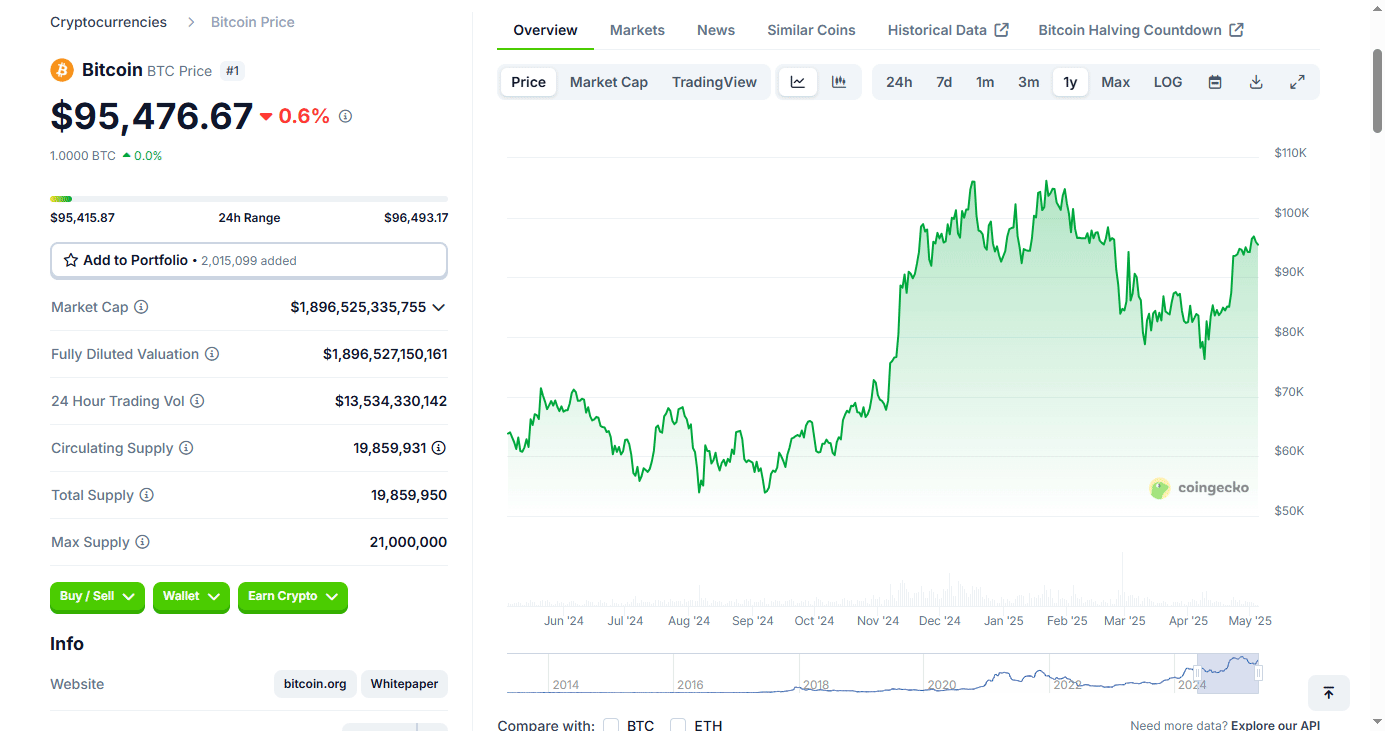
For bitcoiners, think about how far we've come. May of 2024 was still the waning days of the "War on Crypto," bitcoin was boiling the oceans, if you held, used, or liked bitcoin you were evil. Those were dark days and days I'm glad are behind us.
Here is the full commencement speech. The bitcoin part is around the 5 or 6 minute mark: https://m.youtube.com/watch?v=lcH-iL_FdYo
-
 @ 84b0c46a:417782f5
2025-05-04 10:00:28
@ 84b0c46a:417782f5
2025-05-04 10:00:28₍ ・ᴗ・ ₎ ₍ ・ᴗ・ ₎₍ ・ᴗ・ ₎
-
 @ 4fe14ef2:f51992ec
2025-05-04 06:02:38
@ 4fe14ef2:f51992ec
2025-05-04 06:02:38Let's support Bitcoin merchants! I'd love to hear some of your latest Lightning purchases and interesting products you bought. Feel free to include links to the shops or businesses you bought from.
Who else has a recent purchase they’re excited about? Bonus sats if you found a killer deal! ⚡
If you missed our last thread, here are some of the items stackers recently spent and zap on.
Share and repost: N: https://nostrudel.ninja/#/n/nevent1qvzqqqqqqypzqnlpfme... X: https://x.com/AGORA_SN/status/1918907693516914793
originally posted at https://stacker.news/items/970896
-
 @ 84b0c46a:417782f5
2025-05-04 09:49:45
@ 84b0c46a:417782f5
2025-05-04 09:49:45- 1:nan:
- 2
- 2irorio絵文字
- 1nostr:npub1sjcvg64knxkrt6ev52rywzu9uzqakgy8ehhk8yezxmpewsthst6sw3jqcw
- 2
- 2
- 3
- 3
- 2
- 1
|1|2| |:--|:--| |test| :nan: |
 ---
---:nan: :nan:
- 1
- 2
- tet
- tes
- 3
- 1
-
2
t
te
test
-
19^th^
- H~2~O
本サイトはfirefoxのみサポートしています うにょ :wayo: This text will bounce wss://catstrr.swarmstr.com/
うにょうにょてすと
-
 @ 2a655bda:344d8870
2025-05-04 04:24:19
@ 2a655bda:344d8870
2025-05-04 04:24:19Bet888 là một nền tảng giải trí trực tuyến hiện đại, thu hút sự quan tâm của đông đảo người dùng nhờ vào những trải nghiệm độc đáo và phong phú mà nó mang lại. Nền tảng này được thiết kế với giao diện thân thiện, dễ sử dụng, giúp người tham gia dễ dàng truy cập và tận hưởng các hoạt động giải trí ngay trên thiết bị của mình. Bet888 không chỉ là một nền tảng giải trí đơn thuần mà còn tạo ra một không gian cho người tham gia có thể thư giãn, học hỏi và khám phá những cơ hội mới. Với sự kết hợp hoàn hảo giữa công nghệ tiên tiến và các dịch vụ tiện ích, Bet888 đem đến cho người tham gia một trải nghiệm trực tuyến thú vị và mượt mà. Từ các trò chơi thử thách trí tuệ, các sự kiện đặc biệt, đến những hoạt động cộng đồng, nền tảng này không ngừng cải tiến để đáp ứng nhu cầu giải trí ngày càng cao của người dùng. Bet888 cam kết mang lại một không gian giải trí an toàn, thân thiện và luôn tạo ra những cơ hội mới mẻ cho cộng đồng người tham gia.
Một trong những yếu tố làm nên sự thành công của BET888 chính là khả năng cá nhân hóa trải nghiệm người dùng. Nền tảng này cung cấp rất nhiều lựa chọn cho người tham gia, từ các trò chơi giải trí, thử thách trí tuệ đến các sự kiện đặc biệt, giúp người tham gia có thể tự do lựa chọn hoạt động phù hợp với sở thích và nhu cầu cá nhân. Bet888 không chỉ mang lại những giây phút giải trí thú vị mà còn giúp người tham gia phát triển các kỹ năng cá nhân, từ khả năng giải quyết vấn đề đến tư duy chiến lược. Các trò chơi và thử thách được thiết kế không chỉ để giải trí mà còn để kích thích sự sáng tạo và khả năng tư duy logic của người tham gia. Nền tảng này cũng chú trọng đến việc xây dựng một cộng đồng mạnh mẽ, nơi mà người tham gia có thể giao lưu, kết nối và học hỏi lẫn nhau. Các sự kiện cộng đồng được tổ chức thường xuyên, khuyến khích sự hợp tác và chia sẻ ý tưởng sáng tạo giữa các thành viên, từ đó tạo ra một không gian giải trí vui vẻ và đầy thử thách. Bet888 luôn lắng nghe phản hồi từ cộng đồng người tham gia để cải tiến các dịch vụ, giúp nền tảng ngày càng trở nên hấp dẫn và phù hợp với nhu cầu người dùng.
Bảo mật và chất lượng dịch vụ là hai yếu tố quan trọng mà Bet888 luôn chú trọng. Nền tảng này áp dụng các công nghệ bảo mật tiên tiến, đảm bảo rằng thông tin cá nhân của người tham gia luôn được bảo vệ một cách an toàn. Với hệ thống bảo mật chặt chẽ, người dùng có thể yên tâm tham gia vào các hoạt động trực tuyến mà không phải lo lắng về vấn đề bảo mật dữ liệu. Bet888 cũng đặc biệt chú trọng đến việc cung cấp dịch vụ hỗ trợ khách hàng chất lượng cao, giúp người tham gia giải quyết mọi thắc mắc và vấn đề gặp phải trong quá trình sử dụng nền tảng. Đội ngũ hỗ trợ khách hàng của Bet888 luôn sẵn sàng 24/7 để đảm bảo rằng người dùng có thể nhận được sự trợ giúp kịp thời và hiệu quả. Bên cạnh đó, nền tảng này liên tục cải tiến giao diện người dùng, giúp người tham gia dễ dàng tìm kiếm và tham gia vào các hoạt động yêu thích mà không gặp phải bất kỳ trở ngại nào. Các tính năng mới luôn được cập nhật nhanh chóng, giúp người tham gia luôn cảm thấy hài lòng và không bao giờ cảm thấy nhàm chán. Bet888 cam kết tiếp tục phát triển mạnh mẽ, mang lại cho người dùng những trải nghiệm thú vị, an toàn và chất lượng, từ đó giữ vững vị thế là một trong những nền tảng giải trí hàng đầu.
-
 @ 502ab02a:a2860397
2025-05-04 03:13:06
@ 502ab02a:a2860397
2025-05-04 03:13:06เรารู้จักกับ Circadian Rhythm และ Infradian Rhythm แล้ว คราวนี้เรามารู้จักกับ Ultradian Rhythm กันครับ จากรากศัพท์ภาษาละติน คำว่า “Ultra” แปลว่า “มากกว่า” หรือ “ถี่กว่า” คำว่า diem” = แปลว่า "วัน" พอเอามารวมกันเป็น “ultradian” ก็หมายถึงวงจรชีวภาพที่เกิดขึ้น บ่อยกว่า 1 รอบต่อวัน (ความถี่สูงกว่ารอบ 24 ชั่วโมง) ไม่ใช่ “ยาวกว่า 1 วัน” สรุปเป็นภาษาง่ายๆคือ "จังหวะชีวภาพที่เกิดซ้ำ มากกว่า 1 ครั้งภายใน 24 ชั่วโมง"
หรือถ้าเราจะเรียงลำดับของ Rythm ทั้ง 3 ประเภทเราจะได้เป็น 1.Circadian Rhythm (ประมาณ 24 ชม.) 2.Ultradian Rhythm (น้อยกว่า 24 ชม.) 3.Infradian Rhythm (มากกว่า 24 ชม.)
สำหรับตัวอย่าง Ultradian Rhythm ที่สำคัญๆนะครับ เช่น 1. วัฏจักรการนอน (Sleep Cycle) ที่แต่ละรอบ จะอยู่ที่ราวๆ 90–120 นาที สลับกันไปมาระหว่าง NREM (หลับลึก) และ REM (ฝัน) อย่างที่สายสุขภาพเรียนรู้กันมาคือ ถ้าหลับสลับครบ 4–6 รอบ จะหลับสนิท ฟื้นเช้ามาสดชื่นแจ่มใสพักผ่อนเต็มที่
แสงเช้า-แดดอ่อนๆ ช่วยรีเซ็ต circadian แต่ก็ส่งผลให้ ultradian sleep cycle เริ่มต้นตรงจังหวะพอดี นอกจากนี้ยังมีสิ่งที่เรียกว่า Power nap ตอนแดดบ่าย (20–25 นาทีแดดอ่อน) จะช่วยกระตุ้น ultradian nap cycle ให้ตื่นขึ้นมาเป๊ะ ไม่งัวเงีย ให้เลือกจุดที่แดดยังอ่อน เช่น ริมหน้าต่างที่มีแดดผ่านมานุ่ม ๆ หรือใต้ต้นไม้ที่กรองแสงได้บางส่วน ไม่จำเป็นต้องนอนตากแดดโดยตรง แต่ให้ “รับแสงธรรมชาติ” พร้อมกับงีบ จะช่วยให้ circadian และ ultradian cycles ทำงานประสานกันได้ดีขึ้น
- การหลั่งฮอร์โมนแบบพัลซ์ หรือ Pulsatile Hormone Secretion คือรูปแบบการปล่อยฮอร์โมนออกมาจากต่อมต่าง ๆ ในร่างกายแบบเป็น “จังหวะ” หรือ “เป็นช่วง” (bursts/pulses) ไม่ใช่การหลั่งออกมาอย่างต่อเนื่องตลอดเวลา เช่น เทพแห่งการลดน้ำหนัก Growth Hormone (GH) หลั่งพุ่งตอนหลับลึกทุก 3–4 ชั่วโมง / Cortisol มีพัลซ์เล็กๆ ในวัน แม้หลักๆ จะเป็น circadian แต่ก็มี ultradian pulse ทุก 1–2 ชั่วโมง ได้เหมือนกัน / Insulin & Glucagon ชัดเลยชาว keto IF รู้ดีที่สุดว่า หลั่งเป็นรอบตามมื้ออาหารและช่วงพักระหว่างมื้อ
ลองนึกภาพว่า “แสงแดง” และ “อินฟราเรด” เปรียบเหมือนอาหารเช้าของเซลล์เรา เมื่อผิวเราโดนแดดอ่อน ๆ ในช่วงเช้าหรือบ่ายแก่ แสงเหล่านี้จะซึมเข้าไปกระตุ้น “โรงไฟฟ้าประจำเซลล์” (ไมโตคอนเดรีย) ให้ผลิตพลังงาน (ATP) ขึ้นมาเพิ่ม เหมือนเติมน้ำมันให้เครื่องยนต์วิ่งได้ลื่น พอเซลล์มีพลังงานมากขึ้น ในช่วงที่ร่างกายหลั่งฮอร์โมนการซ่อมแซมอย่าง “growth hormone” (GH) ร่างกายก็จะใช้พลังงานจากแสงนี้พร้อมกับฮอร์โมนในการซ่อมแซมกล้ามเนื้อและเนื้อเยื่อต่าง ๆ ได้เต็มประสิทธิภาพขึ้นนั่นเองครับ
- ช่วงเวลาการจดจ่อ หรือ Attention Span & Energy Cycle คนทั่วไปมีสมาธิ/พลังงานโฟกัสอยู่รอบละ 90 นาที หลังจากนั้นควรพัก 10–20 นาที หากฝืนต่อเนื่อง จะเกิดอาการอ่อนล้า สมาธิหลุด
Blue light เช้า จากแดดจะไปกระตุ้นในส่วนของ suprachiasmatic nucleus (SCN) ในสมองให้ปล่อยสารกระตุ้นความตื่นตัว (เช่น คอร์ติซอล) พอสมควร ซึ่งช่วยให้ ultradian cycle ของสมาธิ (โฟกัสได้ประมาณ 90 นาที) ทำงานเต็มประสิทธิภาพ ถ้าเช้าๆ ไม่เจอแดดเลย cycle นี้จะเลื่อนออกไป ทำให้รู้สึกง่วงเหงาหาวนอนเร็ว หรือโฟกัสไม่ได้นานตามปกติ เป็นที่มาของการเพลียแม้จะตื่นสายแล้วก็ตาม
- รอบความหิว หรือ Appetite & Digestive Rhythm ชื่อเท่ห์ป่ะหล่ะ 555 คือความหิวมาเป็นรอบตามวิธีการกินของแต่ละคน ซึ่งเป็นความสัมพันธ์กับ ฮอร์โมน GI (เช่น ghrelin, leptin) ก็วิ่งเป็นรอบเหมือนกัน
แสงแดดเช้า ช่วยตั้ง leptin/ghrelin baseline ให้สมดุล ลดการกินจุกจิกนอกมื้อได้ ส่วนแสงอ่อนๆ ตอนบ่ายช่วยบูสต์ blood flow ในทางเดินอาหาร ให้ digestion cycle หรือการดูดซึมสารอาหารตรงจังหวะ
แดดเป็นแค่ส่วนสำคัญในชีวิตแต่การใช้ Ultradian Rhythm มันต้องประกอบกับกิจกรรมอื่นๆด้วยนะครับ เช่น ทำงานหรืออ่านหนังสือ 90 นาที แล้ว พัก 15–20 นาที ยืดเส้นสาย เคลื่อนไหวเล็กน้อย, ออกกำลังกายให้ตรงจังหวะ, ในช่วง ultradian break พยายามลดการใช้จอมือถือ/คอมฯ ออกไปรับแสงธรรมชาติ หรือยืดเส้น เปิดเพลงเบาๆ เพื่อหลีกเลี่ยง "stimuli" ช่วง break หรือ สิ่งเร้าภายนอก ที่มากระตุ้นประสาทสัมผัสและสมองเรา
แสงแดดจึงเป็น ตัวตั้งเวลา (zeitgeber) ที่ไม่ได้แค่กับรอบวัน-เดือน-ปี แต่รวมถึงจังหวะสั้นๆ ภายในวันด้วย การใช้แสงธรรมชาติให้พอดีในแต่ละช่วง (เช้า เบรก บ่าย) จะช่วยให้ ultradian rhythms ในด้านสมาธิ การนอน ฮอร์โมน และการย่อยอาหาร ทำงานสอดคล้องกับจังหวะชีวิตที่เป็นธรรมชาติที่สุดครับ #pirateketo #SundaySpecialเราจะไปเป็นหมูแดดเดียว #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-
 @ 84b0c46a:417782f5
2025-05-04 09:36:08
@ 84b0c46a:417782f5
2025-05-04 09:36:08 -
 @ 1f79058c:eb86e1cb
2025-05-04 09:34:30
@ 1f79058c:eb86e1cb
2025-05-04 09:34:30I think we should agree on an HTML element for pointing to the Nostr representation of a document/URL on the Web. We could use the existing one for link relations for example:
html <link rel="alternate" type="application/nostr+json" href="nostr:naddr1qvzqqqr4..." title="This article on Nostr" />This would be useful in multiple ways:
- Nostr clients, when fetching meta/preview information for a URL that is linked in a note, can detect that there's a Nostr representation of the content, and then render it in Nostr-native ways (whatever that may be depending on the client)
- User agents, usually a browser or browser extension, when opening a URL on the Web, can offer opening the alternative representation of a page in a Nostr client. And/or they could offer to follow the author's pubkey on Nostr. And/or they could offer to zap the content.
- When publishing a new article, authors can share their preferred Web URL everywhere, without having to consider if the reader knows about or uses Nostr at all. However, if a Nostr user finds the Web version of an article outside of Nostr, they can now easily jump to the Nostr version of it.
- Existing Web publications can retroactively create Nostr versions of their content and easily link the Nostr articles on all of their existing article pages without having to add prominent Nostr links everywhere.
There are probably more use cases, like Nostr search engines and whatnot. If you can think of something interesting, please tell me.
Update: I came up with another interesting use case, which is adding alternate links to RSS and Atom feeds.
Proof of concept
In order to show one way in which this could be used, I have created a small Web Extension called Nostr Links, which will discover alternate Nostr links on the pages you visit.
If it finds one or more links, it will show a purple Nostr icon in the address bar, which you can click to open the list of links. It's similar to e.g. the Feed Preview extension, and also to what the Tor Browser does when it discovers an Onion-Location for the page you're looking at:
The links in this popup menu will be
web+nostr:links, because browsers currently do not allow web apps or extensions to handle unprefixednostr:links. (I hope someone is working on getting those on par withipfs:etc.)Following such a link will either open your default Nostr Web app, if you have already configured one, or it will ask you which Web app to open the link with.
Caveat emptor: At the time of writing, my personal default Web app, noStrudel, needs a new release for the links to find the content.
Try it now
Have a look at the source code and/or download the extension (currently only for Firefox).
I have added alternate Nostr links to the Web pages of profiles and long-form content on the Kosmos relay's domain. It's probably the only place on the Web, which will trigger the extension right now.
You can look at this very post to find an alternate link for example.
Update: A certain fiatjaf has added the element to his personal website, which is built entirely from Nostr articles. Multiple other devs also expressed their intent to implement.
Update 2: There is now a pull request for documenting this approach in two existing NIPs. Your feedback is welcome there.
-
 @ 0c87e540:8a0292f2
2025-05-04 01:53:02
@ 0c87e540:8a0292f2
2025-05-04 01:53:02A plataforma 188W tem se destacado como uma das opções mais confiáveis e empolgantes para jogadores brasileiros que buscam entretenimento de alto nível no mundo dos jogos online. Com um ambiente moderno, seguro e recheado de funcionalidades, o site oferece uma experiência completa, indo muito além das expectativas do público que procura lazer aliado à tecnologia de ponta.
Introdução à Plataforma 188W Desde sua chegada ao mercado, o 188W vem conquistando espaço e fidelizando usuários graças à sua interface intuitiva, sistema de navegação simplificado e compatibilidade com todos os dispositivos — seja computador, tablet ou smartphone. A proposta é clara: oferecer uma plataforma prática e acessível para jogadores de todos os perfis, desde os iniciantes até os mais experientes.
Além de um visual atrativo, o site se destaca por sua segurança. A proteção de dados dos usuários é prioridade, utilizando criptografia de última geração e protocolos rigorosos para garantir uma experiência tranquila e confiável.
Catálogo de Jogos Variado e Emocionante O 188W apresenta um portfólio amplo de jogos para todos os gostos. Entre os destaques estão as slots online (conhecidas como caça-níqueis virtuais), com centenas de opções que variam entre temas clássicos e modernos, gráficos vibrantes e trilhas sonoras imersivas. Esses jogos são desenvolvidos por fornecedores renomados, o que garante qualidade e desempenho técnico superior.
Para quem prefere desafios estratégicos, a plataforma oferece também jogos de cartas e roleta online, que permitem ao usuário testar suas habilidades e explorar diferentes modos de jogo. Muitos desses jogos são ao vivo, com transmissão em tempo real e interatividade com crupiês profissionais, o que torna a experiência ainda mais autêntica e envolvente.
Os fãs de esportes também encontram espaço no 188W. A seção de apostas esportivas é completa, com cobertura de dezenas de modalidades, como futebol, basquete, tênis, MMA, entre outros. É possível apostar antes ou durante os jogos, aproveitando as melhores odds do mercado e diversas promoções exclusivas.
A Experiência do Jogador no 188W Um dos principais diferenciais da plataforma é o foco total na experiência do usuário. Desde o cadastro rápido até o suporte ao cliente 24 horas, tudo é pensado para que o jogador se sinta valorizado e tenha acesso fácil a todas as funcionalidades.
Os bônus de boas-vindas são generosos e frequentes, oferecendo vantagens reais para novos usuários. Além disso, o 188W costuma lançar promoções temáticas, desafios semanais e sorteios especiais que tornam a jornada ainda mais divertida.
O suporte ao cliente é outro ponto forte da plataforma. Com atendimento em português via chat ao vivo, e-mail e WhatsApp, a equipe está sempre pronta para ajudar com dúvidas, problemas técnicos ou informações sobre pagamentos e retiradas.
O sistema de pagamentos também é eficiente e seguro. O 188W aceita diversos métodos populares no Brasil, incluindo PIX, transferências bancárias, carteiras digitais e boletos. As retiradas são processadas rapidamente, muitas vezes em menos de 24 horas.
Conclusão O 188W é muito mais do que uma simples plataforma de jogos. Ele representa um ambiente completo, onde entretenimento, segurança e inovação caminham juntos. Com um catálogo vasto, suporte de qualidade e uma experiência de usuário pensada nos mínimos detalhes, o site se firma como uma excelente escolha para quem busca diversão com praticidade e confiança.
-
 @ a296b972:e5a7a2e8
2025-05-04 08:30:56
@ a296b972:e5a7a2e8
2025-05-04 08:30:56Am Ende der Woche von Unseremeinungsfreiheit wird in der Unserehauptstadt von Unserdeutschland, Unserberlin, voraussichtlich der neue Unserbundeskanzler vereidigt.
Der Schwur des voraussichtlich nächsten Unserbundeskanzlers sollte aktualisiert werden:
Jetzt, wo endlich mein Traum in Erfüllung geht, nur einmal im Leben Unserbundeskanzler zu werden, zahlen sich für mich alle Tricks und Kniffe aus, die ich angewendet habe, um unter allen Umständen in diese Position zu kommen.
Ich schwöre, dass ich meine Kraft meinem Wohle widmen, meinen Nutzen mehren, nach Vorbild meines Vorgängers Schaden von mir wenden, das Grundgesetz und die Gesetze des Unserbundes formen, meine Pflichten unsergewissenhaft erfüllen und Unseregerechtigkeit gegen jedermann und jederfrau nicht nur üben, sondern unter allen Umständen auch durchsetzen werde, die sich mir bei der Umsetzung der Vorstellungen von Unseredemokratie in den Weg stellen. (So wahr mir wer auch immer helfe).
Der Antrittsbesuch des Unserbundeskanzlers beim Repräsentanten der noch in Unserdeutschland präsenten Besatzungsmacht wird mit Spannung erwartet.
Ein großer Teil der Unsereminister ist schon bekannt. Die Auswahl verspricht viele Unsereüberraschungen.
Die Unsereeinheitspartei, bestehend aus ehemaligen Volksparteien, wird weiterhin dafür sorgen, dass die Nicht-Unsereopposition so wenig wie möglich Einfluss erhält, obwohl sie von den Nicht-Unserebürgern, die mindestens ein Viertel der Urnengänger ausmachen, voll-demokratisch gewählt wurde.
Das Zentralkomitee der Deutschen Unseredemokratischen Bundesrepublik wird zum Wohle seiner Unserebürger alles daransetzen, Unseredemokratie weiter voranzubringen und hofft auch weiterhin auf die Unterstützung von Unser-öffentlich-rechtlicher-Rundfunk.
Die Unserepressefreiheit wird auch weiterhin garantiert.
Auf die Verlautbarungen der Unserepressekonferenz, besetzt mit frischem Unserpersonal, brauchen die Insassen von Unserdeutschland auch weiterhin nicht zu verzichten.
Alles, was nicht gesichert unserdemokratisch ist, gilt als gesichert rechtsextrem.
Als Maxime gilt für alles Handeln: Es muss unter allen Umständen demokratisch aussehen, aber wir (die Unseredemokraten) müssen alles in der Hand haben.
Es ist unwahrscheinlich, dass Unsersondervermögen von den Unserdemokraten zurückgezahlt wird. Dieser Vorzug ist den Unserebürgern und den Nicht-Unserebürgern durch Unseresteuerzahlungen vorbehalten.
Die Unserebundeswehr soll aufgebaut werden (Baut auf, baut auf!), die Unsererüstungsindustrie läuft auf Hochtouren und soll Unserdeutschland wieder unserkriegstüchtig machen, weil Russland immer Unserfeind sein wird.
Von Unserdeutschland soll nur noch Unserfrieden ausgehen.
Zur Bekräftigung, dass alles seinen unser-sozialistischen Gang geht, tauchte die Phoenix*in aus der Asche auf, in dem Unseremutti kürzlich ihren legendären Satz wiederholte:
Wir schaffen das.
Ob damit der endgültige wirtschaftliche Untergang und die Vollendung der gesellschaftlichen Spaltung von Unserdeutschland gemeint war, ist nicht überliefert.
Orwellsche Schlussfolgerung:
Wir = unser
Ihr = Euer
Vogel und Maus passen nicht zusammen
Ausgerichtet auf Ruinen und der Zukunft abgewandt, Uneinigkeit und Unrecht und Unfreiheit für das deutsche Unserland.
Unserdeutschland – ein Land mit viel Vergangenheit und wenig Zukunft?
Es ist zum Heulen.
Dieser Artikel wurde mit dem Pareto-Client geschrieben
* *
(Bild von pixabay)
-
 @ 0c87e540:8a0292f2
2025-05-04 01:52:26
@ 0c87e540:8a0292f2
2025-05-04 01:52:26No cenário atual de entretenimento digital, plataformas que oferecem praticidade, segurança e uma ampla gama de jogos são cada vez mais valorizadas pelos usuários. A KCBET surge como uma dessas opções, conquistando o público brasileiro com uma proposta moderna e intuitiva, que combina tecnologia de ponta, variedade de jogos e um suporte eficiente ao usuário.
Desde o primeiro acesso, a KCBET impressiona pelo seu design amigável e pela facilidade de navegação. O site é totalmente otimizado para funcionar tanto em computadores quanto em dispositivos móveis, o que garante liberdade ao usuário para jogar onde e quando quiser. Outro diferencial importante é a interface em português, o que torna a experiência ainda mais personalizada para o público brasileiro.
A KCBETse destaca por oferecer um ambiente seguro, utilizando tecnologias de criptografia avançadas para proteger os dados dos usuários. Além disso, o processo de cadastro é simples e rápido, permitindo que novos jogadores comecem sua jornada em poucos minutos.
Variedade de Jogos para Todos os Perfis O grande atrativo da KCBET é, sem dúvida, a diversidade de jogos disponíveis. A plataforma conta com uma seleção impressionante de opções para todos os gostos e estilos. Os fãs de jogos tradicionais vão encontrar diversas versões de títulos consagrados, enquanto aqueles que preferem novidades e inovação têm à disposição opções modernas com gráficos de última geração e recursos interativos.
Entre os destaques estão os jogos de mesa, jogos de cartas, slots virtuais e opções com crupiês ao vivo — uma experiência que aproxima o jogador da emoção de estar em um ambiente físico, sem sair de casa. Todos os jogos são fornecidos por desenvolvedores renomados do setor, o que garante qualidade visual, fluidez e, principalmente, resultados justos e auditados.
Experiência do Jogador: Imersão e Suporte A experiência do usuário na KCBET vai além dos jogos. A plataforma investe continuamente em proporcionar um ambiente imersivo, com bônus promocionais atrativos, torneios temáticos e desafios semanais que mantêm a emoção sempre em alta. Para novos usuários, há ofertas de boas-vindas que tornam o início da jornada ainda mais empolgante.
Outro ponto alto da KCBET é o atendimento ao cliente. O suporte está disponível 24 horas por dia, sete dias por semana, pronto para auxiliar em qualquer dúvida ou situação. Os canais de atendimento incluem chat ao vivo, e-mail e até suporte via aplicativos de mensagem, garantindo agilidade e eficiência na resolução de problemas.
A KCBET também oferece uma plataforma de pagamentos completa, com diversos métodos de depósito e saque, incluindo opções locais como PIX e boletos bancários. As transações são rápidas, seguras e sem complicações, o que contribui para uma experiência ainda mais satisfatória.
Conclusão: KCBET é a Escolha Certa para Jogadores Brasileiros Com uma proposta moderna, segura e voltada para o entretenimento de qualidade, a KCBET se firma como uma das melhores opções para jogadores brasileiros que buscam diversão online com praticidade. Sua vasta gama de jogos, promoções atrativas, atendimento eficiente e suporte a métodos de pagamento nacionais tornam a plataforma uma escolha inteligente para quem quer transformar momentos de lazer em experiências memoráveis.
-
 @ b2caa9b3:9eab0fb5
2025-05-04 08:20:46
@ b2caa9b3:9eab0fb5
2025-05-04 08:20:46Hey friends,
Exciting news – I’m currently setting up my very first Discord server!
This space will be all about my travels, behind-the-scenes stories, photo sharing, and practical tips and insights from the road. My goal is to make it the central hub connecting all my decentralized social platforms where I can interact with you more directly, and share exclusive content.
Since I’m just starting out, I’d love to hear from you:
Do you know any useful RSS-feed integrations for updates?
Can you recommend any cool Discord bots for community engagement or automation?
Are there any tips or features you think I must include?
The idea is to keep everything free and accessible, and to grow a warm, helpful community around the joy of exploring the world.
It’s my first time managing a Discord server, so your experience and suggestions would mean a lot. Leave a comment – I’m all ears!
Thanks for your support, Ruben Storm
-
 @ 6ad3e2a3:c90b7740
2025-05-03 15:33:07
@ 6ad3e2a3:c90b7740
2025-05-03 15:33:07You are wearing a helmet, but it's been on your head so long you no longer notice it.
The helmet interfaces with your mind via thought-emotion. It influences what you think about and how you feel.
You could remove the helmet at any time. But the thought-emotions keep you distracted, fearful and attached.
Occasionally you remember you are wearing it. Moments of clarity and detachment. You see the way your experience is colored by it. You know it is biased, untrue to reality. You seriously contemplate removing it.
But the moment passes.
Later, you remember contemplating your helmet’s removal, but you wonder what you will gain from it, whether it’s worth doing.
You are no longer having a moment of clarity, just a memory of the question that arose from it, but colored now by thought-emotions.
You decide even if you wanted to remove it, you would put it back on before long. After all, you have never kept it off before, why would you suddenly live without this interface now? The interface is what you know.
Maybe one day, when you are in a more secure place, when your ducks are more in a row, you will remove it. Not now, not in the midst of all this chaos, so many things to do, so much on your plate. You will leave it on for now. You will deal with this later.
But one day too late it dawns on you it is always ever now, and later means never. You have lived your entire life at the behest of the interface when all you had to do was remove it.
-
 @ f6488c62:c929299d
2025-05-03 11:53:03
@ f6488c62:c929299d
2025-05-03 11:53:03ช่วงปลายปี 2567 ถึงต้นปี 2568 BNB Chain เปิดตัวโปรเจกต์ใหม่หลากหลายแนว ทั้ง AI, DeFi, GameFi และโครงสร้างพื้นฐาน เช่น Ballies, Coinfair, OpenTaskAI และ VeraBridge 🌐
วันนี้ ผมได้อ่าน x ของทางคุณ CZ เจอขายโพสไว้หลายโพส ดูแล้วน่าสนใจ จึงคิดว่า การที่ Kraken เริ่มลิสต์โปรเจกต์จาก BNB Chain ยิ่งตอกย้ำว่า ecosystem นี้กำลัง “โตจริง” 🚀
พร้อมทั้งมีโปรแกรมสนับสนุนมากมาย เช่น MVB Accelerator, TVL Incentive และ Gas-Free Carnival ช่วยดึงดูดนักพัฒนาและผู้ใช้จากทั่วโลก
🧠 เป้าหมายปี 2568: รองรับ 100 ล้านธุรกรรม/วัน, ผสาน AI เต็มรูปแบบ และเครื่องมือใหม่ช่วย dev สร้างโปรเจกต์ได้ง่ายขึ้น!
📈 ใครจับตา BNB Chain อยู่ บอกเลย... ช่วงนี้ของจริง!
-
 @ a5142938:0ef19da3
2025-05-03 10:02:03
@ a5142938:0ef19da3
2025-05-03 10:02:03🧵 Products made from this material
The following brands offer products made exclusively or primarily from this material:
Clothing
This article is published on origin-nature.com 🌐 Voir cet article en français
-
 @ 86dfbe73:628cef55
2025-05-04 06:56:33
@ 86dfbe73:628cef55
2025-05-04 06:56:33Building A Second Brain (BASB) ist eine Methode, mit der man Ideen, Einsichten und Vernetzungen, die man durch seine Erfahrungen gewonnen hat, systematisch speichert und die jeder Zeit abrufbar sind. Kurz, BASB erweitert das Gedächtnis mit Hilfe moderner digitaler Werkzeuge und Netzwerke. Die Kernidee ist, dass man durch diese Verlagerung sein biologisches Gehirn befreit, um frei denken zu können, seiner Kreativität freien Lauf zu geben oder einfach im Moment sein kann.
Die Methode besteht aus drei Grundschritten: dem Sammeln von Ideen und Erkenntnissen, dem Vernetzen dieser Ideen und Erkenntnisse und dem Erschaffen konkreter Ergebnisse.
Sammeln: Der erste Schritt beim Aufbau eines Second Brains ist das «Sammeln» der Ideen und Erkenntnisse, die genug wichtig oder interessant sind, um sie festzuhalten. Dafür wird als Organisationsstruktur P.A.R.A empfohlen.
Vernetzen: Sobald man angefangen hat, sein persönliches Wissen strukturiert zu sammeln, wird man anfangen, Muster und Verbindungen zwischen den Ideen und Erkenntnissen zu erkennen. Ab dieser Stelle verwende ich parallel die Zettelkastenmethode (ZKM)
Erschaffen: All das Erfassen, Zusammenfassen, Verbinden und Strukturieren haben letztlich das Ziel: Konkrete Ergebnisse in der realen Welt zu erschaffen.
PARA ist die Organisationsstruktur, die auf verschiedenen Endgeräten einsetzt werden kann, um digitale Informationen immer nach dem gleichen Schema abzulegen. Seien es Informationen, Notizen, Grafiken, Videos oder Dateien, alles hat seinen festen Platz und kann anhand von vier Kategorien bzw. „Buckets“ kategorisiert werden.
PARA steht dabei für: * Projekte * Areas * Ressourcen * Archiv
Projekte (engl. Projects) sind kurzfristige Bemühungen in Arbeit und Privatleben. Sie sind das, woran Du aktuell arbeitest. Sie haben einige für die Arbeit förderliche Eigenschaften: * Sie haben einen Anfang und ein Ende (im Gegensatz zu einem Hobby oder einem Verantwortungsbereich). * Sie haben ein konkretes Ergebnis, dass erreicht werden soll und bestehen aus konkreten Schritten, die nötig und zusammen hinreichend sind, um dieses Ziel zu erreichen, entspricht GTD von David Allen
Verantwortungsbereiche (engl. Areas) betreffen alles, was man langfristig im Blick behalten will. Sie unterscheidet von Projekten, dass man bei ihnen kein Ziel verfolgt, sondern einem Standard halten will. Sie sind dementsprechend nicht befristet. Man könnte sagen, dass sie einen Anspruch an uns selbst und unsere Lebenswelt darstellen.
Ressourcen (engl. Resources) sind Themen, die allenfalls langfristig relevant oder nützlich werden könnten. Sie sind eine Sammelkategorie für alles, was weder Projekt noch Verantwortungsbereich ist. Es sind: * Themen, die interessant sind. (English: Topic) * Untersuchungsgegenständige, die man erforschen will. (Englisch: Subject) * Nützliche Informationen für den späteren Gebrauch.
Das Archiv ist für alles Inaktive aus den obigen drei Kategorien. Es ist ein Lager für Beendetes und Aufgeschobenes.
Das System PARA ist eine nach zeitlicher Handlungsrelevanz angeordnete Ablage. Projekte kommen vor den Verantwortungsbereichen, weil sie einen kurz- bis mittelfristigen Zeithorizont haben, Verantwortungsbereiche dagegen einen unbegrenzten Zeithorizont. Ressourcen und Archiv bilden die Schlusslichter, weil sie gewöhnlich weder Priorität haben, noch dringend sind.
-
 @ a5142938:0ef19da3
2025-05-03 10:01:17
@ a5142938:0ef19da3
2025-05-03 10:01:17🧵 Products made from this material
The following brands offer products made exclusively or primarily from this material:
Clothing
- Engel
- Dilling (merino wool)
- ManyMonths (merino wool)
Home
This article is published on origin-nature.com 🌐 Voir cet article en français
-
 @ a5142938:0ef19da3
2025-05-03 10:00:49
@ a5142938:0ef19da3
2025-05-03 10:00:49🧵 Products made from this material
The following brands offer products made exclusively or primarily from this material:
Clothing
- Engel (organic cotton)
- Dilling (organic cotton)
- ManyMonths (organic cotton)
This article is published on origin-nature.com 🌐 Voir cet article en français
-
 @ a296b972:e5a7a2e8
2025-05-03 07:48:25
@ a296b972:e5a7a2e8
2025-05-03 07:48:25Derzeit formiert sich ein neues Gruselkabinett, als Folge einer Pandemie der Ungeeigneten. Kostproben der Unfähigkeit konnte man schon in den aktuellen „Quassel-Shows“ des Staatsfunks „genießen“. Die Riege der Universal-Dilettanten, die noch schnell hochgelobt wurde, macht gerade Platz für Rekruten aus dem Milieu der überzeugten Realitätsverweigerer.
Impfpflichtbefürworter, ideologisch vergiftete Klima- und Gender-Gagaisten, Verteidiger des Russen-Dauer-Feindbilds, Finanzwirtschafts-Ahnungslose, zahllose „Südamerika-Experten“, die davon überzeugt sind, solche zu sein, weil sie unfallfrei eine Banane essen können und weitere, die als einzige Qualifikation das Prädikat „Untauglich“ auszeichnet, geben sich ein neues Stelldichein.
Nach Vorbild des öffentlich-rechtlichen Unfugs bilden sie ein in sich geschlossenes System, das sich gegen Kritik abschotten will, in dem es alles, was sich nach Nicht-nach-dem-Maul geredet anhört, als Hass und Hetze bezeichnet und sich als Hüter der Wahrheit aufspielt.
Begriffe wie „Hass und Hetze“ und „Kriegstüchtigkeit“ werden einem Wortschatz entlehnt, die dem bisher dunkelsten Kapitel der deutschen Geschichte entnommen sind. Zur Abschreckung verwendete Begriffe, im Sinne von „Wehret den Anfängen!“, wie die Anlehnung „Impfen macht frei“ hingegen, werden mit Geldbußen und Haft belegt. Es kommt eben immer darauf an, von wem diese verbrannten Begriffe verwendet werden.
Wenn aus einer Demokratie „Unseredemokratie“ wird, müssen alle Alarmglocken schrillen, weil so Tür und Tor weit aufgerissen werden, um Tendenzen und Ideologien den Einzug zu ermöglichen, die in einer freiheitlich-demokratischen Grundordnung nichts, aber auch rein gar nichts zu suchen haben, weil die Auslegung davon, was „Unseredemokratie“ bedeutet, in den Händen derjenigen liegt, die sich zwar noch als Volksvertreter ausgeben, aber den Willen des Souveräns nicht mehr umsetzen.
Die Meinung und der Wille des Volkes werden maximal ignoriert und unterdrückt. Mit einem „weiter so“ manifestiert sich die Verachtung der Wähler, die in ihrer unterstellten Dummheit bestenfalls noch als Stimmvieh taugen, ansonsten aber zu vernachlässigen sind, wenn das Ziel erreicht ist: Die Macht!
Eine Absichtserklärung, genannt Koalitionsvertrag, ist die Grundlage für „alles kann, nichts muss“. Er lässt so eine unbegrenzte Flexibilität in jede Richtung zu, alles ist möglich. ALLES!
Die Basis der Koalition beruht auf Lügen, sei es in der Migrationspolitik oder in der Neuverschuldung. Das gemeinsame Klüngeln hat schon begonnen, bevor der eigentliche Regierungsauftrag überhaupt erteilt wurde.
Das wirklich einzige, gemeinsame Ziel ist, mit allen Mitteln an der Macht zu bleiben, koste es, was es wolle und eine demokratisch gewählte Opposition, die rund ein Viertel der Wählerstimmen ausmacht, wo immer es geht zu delegitimieren und so klein zu halten, wie es nur eben geht.
Hirngespinste sollen weiter vorangetrieben, die Rückkehr zur Vernunft soll unter allen Umständen verhindert werden, bzw. ist aufgrund mangelnder Kenntnisse und Einsicht gar nicht möglich.
Das Lügen bleibt den Nicht-Volksvertretern vorbehalten, die definieren, was Lüge ist und was nicht, sofern die Kritik vom Volk kommt. Berichtet man über die Politik, spricht man von Unwahrheiten, spricht die Politik über das Volk, sind es Lügen. Überall wird mit zweierlei Maß gemessen.
Die Verachtung des Souveräns wirkt wie ein Bumerang und wird wie durch einen Spiegel auf die Versender zurückgeworfen.
Ein zukünftiger Ex-Bundeskanzler verliert bereits den Rückhalt, noch bevor er in sein Amt eingesetzt wird. Grisu, der kleine Drache, will unbedingt, nur einmal im Leben, Feuerwehrmann werden. Phrasen-Dreschen wird zur Staatsräson.
Ministerposten werden nach maximaler Fachferne verschachert.
Gut ausgebildete Kräfte verlassen das Land, die Wirtschaft stagniert, massive Einbrüche in der Auto-Industrie, der einstigen Vorzeige-Marken in der ganzen Welt. Ja, Autos bauen, das könnten die Deutschen, wenn sie noch dürften.
Wer kann, wandert ab ins Ausland, wo Energiekosten und Steuern ein unternehmerisches Handeln ermöglichen, statt es mit aller Kraft durch gezielte Wirtschaftsvernichtung abzuwürgen. Wo ist der massive Widerstand seitens der Wirtschaftsverbände, der Industrie- und Handelskammern und Groß-Unternehmen? Geht es denen immer noch zu gut?
Recht haben und Recht bekommen waren noch nie so weit auseinander, wie heute.
Die Kirche, in einem christlich geprägten Land, schreibt ihre eigene Lehre um: „Gott ist queer!“ Grenzt das schon an Gotteslästerung aus den eigenen Reihen? Dabei merkt sie offensichtlich nicht, dass sie sich damit selbst abschafft. Wieder einmal springt sie auf den Zug der vorgegebenen Staatsdoktrin auf. Unvergessen die Hakenkreuzfahne über dem Hauptportal am Kölner Dom in der bisher dunkelsten Zeit Deutschlands.
Eine Überzeugung, und seien die Beweggründe mit noch so guten Absichten verbunden, darf nie wieder zu einer Ideologie werden, die nur in die Irre führen kann. Deshalb ist es demokratische Pflicht, auf die Gefahr hinzuweisen, wenn auch nur der leiseste Hauch Anlass zu solchen Befürchtungen gibt. Das gilt für die Kirche, die Politik, die Rechtsprechung und Menschen, von denen man den Eindruck hat, dass sie sich verirrt haben.
Das Zuviel an Fremden wird nicht gestoppt. Eine Minderheit, die bei Verstand geblieben ist, verlässt das Land, wenn es ihr finanziell möglich ist. Andere, die sich das nicht leisten können, müssen ausharren und dabei zusehen, wie ein Land vor die Hunde geht.
Gut integrierte „Gastarbeiter“ schämen sich für den Plebs, der nach Deutschland kommt. Natürlich unter dem Deckmantel der Menschlichkeit, der die Menschlichkeit gegenüber den Bio-Deutschen mit Füßen tritt. Ihr Ansehen, ihr Fleiß und ihre Dankbarkeit, dass sich ihre Vätergeneration hier eine neue Existenz aufbauen konnte, wird mit Füßen getreten. Sie geraten unter einen Generalverdacht, der ihnen schadet. Auch sie haben Jahrzehnte in die Krankenkassen eingezahlt und ihre Steuern brav entrichtet.
Der Polizei sind von staatlicher Seite die Hände gebunden gegen Clan-Kriminalität und asozialem Verhalten durchzugreifen. Sie bilden Parallel-Gesellschaften mit eigenen Regeln und eigenen Gesetzen und die Polizei muss tatenlos dabei zusehen. Banden in Berlin und Duisburg stellen sich über herrschende Gesetze, Roma terrorisieren Kiel, benehmen sich, wie die Axt im Walde. „An Leib und Leben gefährdete Migranten“ werfen, wie in Bochum, Ziegel von Dächern, und gefährden die Bevölkerung an Leib und Leben. Anschließend setzen sie sich mit einem Gartenstuhl auf einem Kamin in die Sonne und träumen vermutlich vom Ausblick auf dem Kilimandscharo. Statt sie bei Kopf und Kragen zu fassen und sofort aus dem Land zu werfen, werden solche irren Taten mit psychischen Problemen aufgrund der Erfahrungen in ihrem Heimatland entschuldigt. Würden sich solche Bekloppte in ihrem eigenen Land vergleichbare Handlungen erlauben, würde sie die Dorfgemeinschaft wahrscheinlich den Löwen zum Fraß vorwerfen.
Jeder, der nicht das in Deutschland geltende Recht akzeptiert und stattdessen seine eigene Auffassung von Recht durchsetzen will, gehört unverzüglich des Landes verwiesen, und es ist Aufgabe des Staates, dafür zu sorgen, dass solche Personen nie wieder einen Fuß über die Grenzen des Landes setzen dürfen. Stattdessen werden die Fahnder verfolgt und die Täter laufen gelassen. Der Staat lässt so zu, dass geltendes Recht unterwandert und außer Kraft gesetzt wird. Seine abschreckende Wirkung geht verloren, weil es in den einschlägigen Kreisen bekannt ist, dass sich jeder aufführen kann, wie er will, ohne, dass es Konsequenzen nach sich zieht.
Gepaart mit Willkür ist das hoch gefährliches Dynamit, dass die Gesellschaft sprengt und eine Gefahr in sich birgt, dass die Gesellschaft ab dem Punkt, wo es unerträglich geworden ist, zur Selbstjustiz greift, und das wäre möglicherweise der Anfang eines Bürgerkriegs.
Für alles ist Geld da. Es werden Schulden in atemberaubender Höhe aufgenommen, vor allem, um die Kriegswirtschaft anzukurbeln, um vor einem Feind - Russland gewappnet zu sein, das nicht das geringste Interesse an einem Land hat, das nichts unversucht lässt, auf irgendeine Art und Weise Selbstmord zu begehen. Einmal muss es doch gelingen!
Und natürlich müssen auch die westlichen Werte im Stellvertreterkrieg zwischen den USA und Russland in der Ukraine verteidigt werden.
Kein Geld ist allerdings für die eigenen Leute da. Im Gegenteil: Wer Flaschen sammelt, muss ab einer bestimmten Höhe der Einnahmen ein Gewerbe anmelden. Aber sonst haben die Sesselfurzer nichts zu tun, oder? Es sollte Geld in die Hand genommen werden, die zunehmende Armut in der Bevölkerung nachhaltig zu stoppen, aus dem Abfahrtsvorschlags-Plan der Bahn wieder einen richtigen Fahrplan zu machen, die Schlagloch-Nostalgie á la DDR abzuschaffen, Brücken wieder ihrem Wesen zuzuführen, nämlich, dass man drüberfahren kann, das ganze Land einer dringenden Generalüberholung zu unterziehen, die Gewinnorientierung aus dem Gesundheitssystem wieder abzuschaffen, die Fallpauschalen samt dem Verursacher in die Wüste zu schicken, Deutschland steuer-sexy zu machen.
Das ist wohl zu viel verlangt, denn diejenigen, die das bewirken könnten, haben keine Not. Die einzige Not, die sie kennen, ist, wie sie immer genug Leim auf Vorrat haben können, um an ihrem Pöstchen kleben zu bleiben. Solche Menschen können nur in einem geschützten Rahmen existieren, weil sie in der Welt da draußen gar nicht zurecht kämen, geschweige denn in der Lage wären, für ihren Lebensunterhalt mit einer wirklichen Arbeit selbst zu sorgen.
Der Staat erfüllt nicht mehr seine Aufgabe für die Sicherheit seiner Bürger zu sorgen. Statt Messer-Attacken und Terror-Anschläge aufzuklären und damit den Bürgern ein Gefühl von Sicherheit zu vermitteln, wird die Aufklärung auf dem Mond im Meer der Stille versenkt. Transparenz: Fehlanzeige. Im besten Fall werden Symptom-Bekämpfungs-Maßnahmen ergriffen, statt die Ursachen zu verunmöglichen. Schilder an Messerverbots-Zonen aufzustellen, manifestieren bestenfalls die Gewissheit der Lächerlichkeit und Unfähigkeit seitens der Messerfachkräfte und der selbstfahrenden Autos, die von niemandem gesteuert werden.
Gleiches gilt für das Nennen der hinlänglich bekannten Verursacher der Sprengung der Nordstream 2-Pipelines, die dem scheidenden Bundeskanzler, an dessen Namen man sich schon jetzt nicht mehr erinnern kann, bekannt gewesen sein müssen. Selbst Trump soll sich auf die Frage, ob die USA maßgeblich daran beteiligt waren, geäußert haben, dass, wenn er auf diese Frage antworten würde, er seinem Land sehr schaden würde. Er könne aber mit Gewissheit sagen, dass es die Russen nicht waren. Immerhin ist eine für ganz Europa wichtige Energieversorgung absichtlich, bewusst und mutwillig zerstört worden. Aber aus Rücksicht darauf, dass die Wahrheit Teile der deutschen Bevölkerung verunsichern könnte, verzichtet man in Berlin auf eine Stellungnahme, lügt wiederholt, dass die Ermittlungen noch andauern und glaubt, dass man die Bürger damit ahnungslos halten kann. Die doofen Deutschen werden auch das noch schlucken.
Vergessen die Verpflichtung: Von deutschem Boden soll nur noch Frieden ausgehen. Vergessen die grauen Gesichter der Männer mit einem hochgeklappten Hosenbein, in der Kinderzeit. Wer von den aktuellen Kriegstreibern war live bei einem Gemetzel dabei, in dem Körperteile herumfliegen und Blut spritzt, in dem Menschen zerfetzt werden oder in ihren Panzern bei lebendigem Leib verbrennen? Viele Dümmste unter den Dummen kennen Krieg nur aus Video-Spielen. Nur einmal live als Zaungast dabei sein, und sehen, wie der halbe Darm aus dem Körper heraushängt, dann würde sich ihr großes Maul schon von alleine schließen.
Immer mehr Deutsche sagen: Das ist nicht mehr mein Staat. Kann man es ihnen verdenken?
Deutschland ist ein Paradebeispiel dafür, wie man in der heutigen Zeit, ein einst in aller Welt hochangesehenes Land, im Handumdrehen wirtschaftlich, politisch, rechtsstaatlich, gesundheitlich, und nicht zuletzt auch gesellschaftlich zerstören kann.
Sowohl innen- als auch außenpolitisch wurde nichts unterlassen, um Deutschland, vom Ausland aus gesehen, in die absolute Lächerlichkeit zu überführen.
Die Dummheit, gepaart mit unerträglicher Überheblichkeit, haben ein Maß erreicht, dass in die Gefährlichkeit übergegangen ist. Deutschland braucht gar keinen Feind von außen, denn der Feind sitzt im eigenen Land und zerstört es von innen heraus.
Der Eindruck taucht auf, dass spätestens mit dem Corona-Ereignis das Schleusentor des Wahnsinns sperrangelweit aufgerissen wurde, und keiner vermag es derzeit wieder zu schließen.
Entweder schließen sich Kräfte zusammen, die noch vorhanden sind, dieses Land von innen heraus zu retten, hierzu tragen auch die Neuen Medien erheblich bei, oder Deutschland ist noch einmal darauf angewiesen, von außen gerettet zu werden.
Zukunftsplanungen werden verunmöglicht. Mindestens eine Generation wird die komplette Lebensplanung geraubt. Man ist gezwungen, von einem Tag auf den anderen zu leben, weil alles derartig unberechenbar geworden ist. Eine junge Familie überlegt sich drei Mal, ob sie noch Kinder in diese Welt setzen will. Wo soll das enden?
Der Alltag in Deutschland gleicht einer Dauer-Vorstellung eines Theater-Stücks. Irgendwie läuft es noch, jedoch es fehlt der Rückhalt. Man versucht seinen Alltag zu meistern, Normalität zu leben, doch über allem schwebt das Damokles-Schwert. Keiner weiß, wie lange was noch gut geht und welchen Irrsinn sich die Realitätsverweigerer als Nächstes ausdenken werden. Manchen gelingt das Verdrängen recht gut. Manche schotten sich vollkommen von schlechten Nachrichten ab. Die Psychologie sagt jedoch, dass jedes erlebte Trauma den Menschen früher oder später einholen wird.
Wetten, wie lange die unheilvolle Allianz der Neuen Nullen halten wird, können ab sofort entgegengenommen werden. Und dann? Wie geht es weiter?
Dieser Beitrag wurde mit dem Pareto-Client geschrieben.
(Bild von pixabay)
-
 @ a5142938:0ef19da3
2025-05-03 09:45:38
@ a5142938:0ef19da3
2025-05-03 09:45:38Engel is a German brand that creates clothing and accessories made from organic cotton, merino wool, and silk for the whole family.
Natural materials used in products
⚠️ Warning: some products from this brand (especially bras) contain non-natural materials, including:
Categories of products offered
#Clothing
- Fits: babies, children, women, men, unisex
- Underwear: boxers, panties
- One-piece: bodysuits
- Tops: tank tops, cardigans, t-shirts, sweaters, jackets
- Bottoms: trousers, shorts
- Head & hands: hats
- Nightwear: pyjamas
#Home
- Linen: blankets, sleeping bags
Other information
- GOTS certification
- IVN Best certification
- Made in Germany
👉 Learn more on the brand's website
This article is published on origin-nature.com 🌐 Voir cet article en français
📝 You can contribute to this entry by suggesting edits in comments.
🗣️ Do you use this product? Share your opinion in the comments.
⚡ Happy to have found this information? Support the project by making a donation to thank the contributors.
-
 @ 4e8933a9:aadeb641
2025-05-03 07:23:55
@ 4e8933a9:aadeb641
2025-05-03 07:23:55XENG là một nền tảng giải trí trực tuyến nổi bật, mang đến cho người chơi một không gian giải trí đa dạng và phong phú. Với giao diện thân thiện và dễ sử dụng, XENG cung cấp cho người chơi rất nhiều trò chơi hấp dẫn từ những tựa game dễ chơi đến những trò đòi hỏi sự chiến lược và tư duy. Những trò chơi này được thiết kế với đồ họa bắt mắt, âm thanh sống động và gameplay hấp dẫn, mang lại cho người chơi những giờ phút thư giãn tuyệt vời. XENG luôn cố gắng cập nhật và bổ sung các tựa game mới để người chơi không cảm thấy nhàm chán và có cơ hội trải nghiệm nhiều điều thú vị. Điều này giúp XENG trở thành một lựa chọn tuyệt vời cho những ai yêu thích không gian giải trí đa dạng và đầy thử thách.
Một trong những yếu tố giúp XENG thu hút đông đảo người chơi chính là hệ thống bảo mật an toàn và hiệu quả. Nền tảng này sử dụng công nghệ mã hóa tiên tiến, giúp bảo vệ thông tin cá nhân và giao dịch của người chơi. Các giao dịch tài chính được thực hiện một cách an toàn và minh bạch, đảm bảo rằng người chơi không phải lo lắng về việc thông tin bị rò rỉ hay bị xâm nhập trái phép. Đội ngũ của XENG luôn chú trọng đến việc bảo vệ quyền lợi của người chơi và đảm bảo một môi trường chơi game an toàn. Nhờ vào sự cam kết này, người chơi có thể hoàn toàn yên tâm khi tham gia các hoạt động giải trí trên nền tảng mà không phải lo lắng về vấn đề bảo mật.
Bên cạnh chất lượng trò chơi và bảo mật, XENG còn đặc biệt chú trọng đến dịch vụ khách hàng. Đội ngũ hỗ trợ khách hàng của XENG luôn sẵn sàng giúp đỡ người chơi trong suốt quá trình trải nghiệm trên nền tảng. Dịch vụ hỗ trợ 24/7 giúp người chơi giải quyết mọi vấn đề, từ kỹ thuật đến các thắc mắc về trò chơi, đảm bảo rằng họ sẽ không gặp phải bất kỳ khó khăn nào khi tham gia. Hơn nữa, XENG cũng tổ chức nhiều chương trình khuyến mãi và sự kiện hấp dẫn, tạo cơ hội cho người chơi nhận được các phần thưởng giá trị. Những chương trình này không chỉ giúp người chơi có thêm niềm vui mà còn tạo ra các cơ hội chiến thắng hấp dẫn. Nhờ những yếu tố này, XENG đã và đang giữ vững được lòng tin của người chơi và trở thành một nền tảng giải trí uy tín và đáng tin cậy.
-
 @ a93be9fb:6d3fdc0c
2025-05-03 06:02:56
@ a93be9fb:6d3fdc0c
2025-05-03 06:02:56GG
-
 @ 266815e0:6cd408a5
2025-05-02 22:24:59
@ 266815e0:6cd408a5
2025-05-02 22:24:59Its been six long months of refactoring code and building out to the applesauce packages but the app is stable enough for another release.
This update is pretty much a full rewrite of the non-visible parts of the app. all the background services were either moved out to the applesauce packages or rewritten, the result is that noStrudel is a little faster and much more consistent with connections and publishing.
New layout
The app has a new layout now, it takes advantage of the full desktop screen and looks a little better than it did before.
Removed NIP-72 communities
The NIP-72 communities are no longer part of the app, if you want to continue using them there are still a few apps that support them ( like satellite.earth ) but noStrudel won't support them going forward.
The communities where interesting but ultimately proved too have some fundamental flaws, most notably that all posts had to be approved by a moderator. There were some good ideas on how to improve it but they would have only been patches and wouldn't have fixed the underlying issues.
I wont promise to build it into noStrudel, but NIP-29 (relay based groups) look a lot more promising and already have better moderation abilities then NIP-72 communities could ever have.
Settings view
There is now a dedicated settings view, so no more hunting around for where the relays are set or trying to find how to add another account. its all in one place now
Cleaned up lists
The list views are a little cleaner now, and they have a simple edit modal

New emoji picker
Just another small improvement that makes the app feel more complete.
Experimental Wallet
There is a new "wallet" view in the app that lets you manage your NIP-60 cashu wallet. its very experimental and probably won't work for you, but its there and I hope to finish it up so the app can support NIP-61 nutzaps.
WARNING: Don't feed the wallet your hard earned sats, it will eat them!
Smaller improvements
- Added NSFW flag for replies
- Updated NIP-48 bunker login to work with new spec
- Linkfy BIPs
- Added 404 page
- Add NIP-22 comments under badges, files, and articles
- Add max height to timeline notes
- Fix articles view freezing on load
- Add option to mirror blobs when sharing notes
- Remove "open in drawer" for notes
-
 @ 57d1a264:69f1fee1
2025-05-04 06:37:52
@ 57d1a264:69f1fee1
2025-05-04 06:37:52KOReader is a document viewer for E Ink devices. Supported file formats include EPUB, PDF, DjVu, XPS, CBT, CBZ, FB2, PDB, TXT, HTML, RTF, CHM, DOC, MOBI and ZIP files. It’s available for Kindle, Kobo, PocketBook, Android and desktop Linux.
Download it from https://koreader.rocks Repository: https://github.com/koreader/koreader
originally posted at https://stacker.news/items/970912
-
 @ 08f84d15:4d49bb42
2025-05-03 01:35:19
@ 08f84d15:4d49bb42
2025-05-03 01:35:19O universo dos jogos online está em constante evolução, e a 30XBet surge como uma das plataformas mais promissoras do momento para quem busca diversão, segurança e variedade. Com uma proposta moderna e focada na experiência do usuário, a 30XBet vem conquistando o público brasileiro ao oferecer uma navegação intuitiva, suporte de qualidade e um portfólio de jogos envolvente.
Introdução à Plataforma 30XBet Desde o primeiro acesso, é possível perceber o cuidado da 30XBet com a apresentação visual e funcional da sua plataforma. O site é responsivo, o que significa que pode ser acessado com facilidade tanto em computadores quanto em dispositivos móveis, garantindo a flexibilidade que o jogador moderno exige. A interface é organizada e pensada para facilitar a navegação, mesmo para quem não tem muita experiência com plataformas de apostas e jogos online.
Outro ponto positivo é o suporte ao cliente, que está disponível em português e funciona 24 horas por dia. Isso garante que dúvidas ou problemas possam ser resolvidos rapidamente, contribuindo para uma jornada mais tranquila e agradável para o usuário.
Variedade de Jogos para Todos os Gostos A 30XBet se destaca pela diversidade de jogos disponíveis. Desde os títulos mais tradicionais até opções mais inovadoras, o jogador encontra aqui uma enorme variedade para se entreter por horas. Entre os destaques estão:
Slots (Caça-níqueis): Com dezenas de opções, os slots são ideais para quem busca partidas rápidas e emocionantes. Com gráficos de alta qualidade e diferentes temáticas — como aventura, fantasia, esportes e cultura pop —, esses jogos garantem entretenimento para todos os perfis.
Jogos de Mesa: Para os que preferem jogos estratégicos e desafiadores, a plataforma oferece versões digitais de clássicos como roleta, blackjack e bacará, com regras claras e dinâmicas atrativas.
Jogos ao Vivo: Uma das grandes inovações da 30XBet é a opção de jogos com crupiês em tempo real. Essa funcionalidade proporciona uma experiência imersiva, onde o jogador pode interagir com o apresentador e com outros participantes, elevando a sensação de realismo.
Apostas Esportivas: Os amantes de esportes também encontram na 30XBet uma excelente alternativa para se divertir. A plataforma cobre uma grande variedade de eventos esportivos nacionais e internacionais, com cotações competitivas e diversos tipos de apostas.
Experiência do Jogador A experiência do usuário na 30XBet é um dos seus maiores diferenciais. Desde o cadastro rápido até a facilidade para realizar depósitos e saques, tudo foi desenvolvido pensando na praticidade e na segurança do jogador. Os métodos de pagamento são variados, incluindo opções populares no Brasil como PIX, boleto bancário e carteiras digitais, o que facilita o acesso para todos.
Além disso, a plataforma frequentemente oferece promoções e bônus de boas-vindas, proporcionando vantagens extras para os novos usuários. Também há campanhas regulares para jogadores ativos, incentivando a participação contínua e premiando a fidelidade.
Outro ponto importante é o compromisso com o jogo responsável. A 30XBet disponibiliza recursos para que o jogador possa definir limites de gastos e tempo de jogo, incentivando o entretenimento consciente e equilibrado.
Conclusão A 30XBet chega ao mercado brasileiro com uma proposta sólida, unindo tecnologia, variedade e excelente atendimento ao cliente. Seja para quem está começando agora no mundo dos jogos online ou para jogadores mais experientes, a plataforma oferece todos os recursos necessários para uma experiência segura, divertida e gratificante.
Se você busca uma nova opção de entretenimento digital com qualidade e confiança, a 30XBet é, sem dúvidas, uma escolha que vale a pena conhecer.
-
 @ 08f84d15:4d49bb42
2025-05-03 01:34:34
@ 08f84d15:4d49bb42
2025-05-03 01:34:34Nos últimos anos, o entretenimento digital tem conquistado um espaço significativo no dia a dia dos brasileiros, e a BRRBET surge como uma das plataformas mais completas e confiáveis para quem busca emoção, praticidade e variedade em um só lugar. Com uma interface moderna, recursos intuitivos e uma ampla gama de opções de jogos, a BRRBET oferece uma experiência única, tanto para jogadores iniciantes quanto para os mais experientes.
Uma Plataforma Completa e de Fácil Navegação Desde o primeiro acesso, fica evidente que a BRRBET foi desenvolvida com foco total no usuário. A interface é limpa, objetiva e responsiva, o que permite que o jogador encontre tudo o que procura com poucos cliques. Seja pelo computador ou pelo celular, a navegação é fluida e otimizada, garantindo acesso rápido aos jogos, promoções, suporte e área do usuário.
A plataforma se destaca também pela segurança. Com tecnologia de ponta e sistemas de criptografia avançados, a BRRBET assegura a proteção das informações pessoais e financeiras de todos os seus usuários. Além disso, os métodos de pagamento são variados, rápidos e seguros, com suporte total para transações em reais, o que facilita ainda mais a vida do jogador brasileiro.
Jogos para Todos os Gostos A diversidade de jogos disponíveis na BRRBET é um de seus principais diferenciais. A plataforma oferece títulos renomados e desenvolvidos por provedores internacionais de alta qualidade, garantindo gráficos impressionantes, jogabilidade envolvente e mecânicas inovadoras.
Entre os destaques, estão os jogos de cartas, roletas virtuais, slots com temáticas variadas e experiências interativas em tempo real. Os famosos caça-níqueis online são atualizados frequentemente, com lançamentos que trazem bônus, rodadas grátis e jackpots progressivos, proporcionando prêmios incríveis e muita adrenalina a cada rodada.
A BRRBET também disponibiliza jogos com crupiês ao vivo, onde o jogador interage em tempo real com profissionais que conduzem a ação de maneira realista e imersiva. Essa funcionalidade cria uma atmosfera envolvente, que aproxima ainda mais o usuário da experiência tradicional dos grandes centros de entretenimento.
Experiência do Jogador: Praticidade e Suporte Dedicado Outro ponto forte da BRRBET é o cuidado com a experiência do usuário. Além da excelente estrutura técnica, a plataforma oferece suporte ao cliente 24 horas por dia, 7 dias por semana, com atendimento em português e profissionais prontos para resolver qualquer dúvida ou problema com agilidade.
As promoções também são um atrativo à parte. Os novos usuários são recebidos com bônus generosos, enquanto os jogadores frequentes têm acesso a promoções recorrentes, programas de fidelidade e desafios exclusivos que aumentam as chances de ganho e a diversão.
Além disso, a BRRBET valoriza o jogo responsável, oferecendo ferramentas para controle de tempo de uso e limites de depósito, incentivando uma experiência saudável e equilibrada.
Conclusão: BRRBET é Sinônimo de Diversão e Confiabilidade Combinando inovação, segurança e variedade, a BRRBET se consolida como uma das plataformas de entretenimento digital mais completas do Brasil. Seja para quem deseja se divertir em jogos rápidos ou para aqueles que buscam grandes prêmios e emoções intensas, a BRRBET oferece um ambiente confiável, moderno e acolhedor.
Se você está em busca de diversão de qualidade e uma plataforma que realmente entende o que o jogador brasileiro quer, a BRRBET é, sem dúvida, uma excelente escolha. Cadastre-se hoje mesmo e descubra por que tantos jogadores já fazem parte dessa comunidade vibrante e apaixonada por jogos online.
-
 @ 57d1a264:69f1fee1
2025-05-04 06:27:15
@ 57d1a264:69f1fee1
2025-05-04 06:27:15Well, today posts looks are dedicated to STAR WARS. Enjoy!
Today we’re looking at Beat Saber (2019) and why its most essential design element can be used to make great VR games that have nothing to do with music or rhythm.
https://www.youtube.com/watch?v=EoOeO7S9ehw
It’s hard to believe Beat Saber was first released in Early Access seven years ago today. From day one, it was clear the game was something special, but even so we couldn’t have predicted it would become one of VR’s best-selling games of all time—a title it still holds all these years later. In celebration of the game’s lasting legacy we’re re-publishing our episode of Inside XR Design which explores the secret to Beat Saber’s fun, and how it can be applied to VR games which have nothing to do with music.
Read more at https://www.roadtovr.com/beat-saber-instructed-motion-until-you-fall-inside-xr-design/
originally posted at https://stacker.news/items/970909
-
 @ 57d1a264:69f1fee1
2025-05-04 06:16:58
@ 57d1a264:69f1fee1
2025-05-04 06:16:58Found this really fun, so created a few intros for latest SN newsletters https://stacker.news/items/960787/r/Design_r?commentId=970902 and https://stacker.news/items/970459/r/Design_r?commentId=970905
Create your STAR-WARS-like movie intro https://starwarsintrocreator.kassellabs.io/
originally posted at https://stacker.news/items/970906
-
 @ 211c0393:e9262c4d
2025-05-04 02:32:24
@ 211c0393:e9262c4d
2025-05-04 02:32:24**日本の覚せい剤ビジネスの闇:
警察、暴力団、そして「沈黙の共犯関係」の真相**
1. 暴力団の支配構造(公的データに基づく)
- 輸入依存の理由:
- 国内製造は困難(平成6年「覚せい剤原料規制法」で規制強化)→ ミャンマー・中国からの密輸が主流(国連薬物犯罪事務所「World Drug Report 2023」)。
- 暴力団の利益率:1kgあたり仕入れ価格30万円 → 小売価格500万~1000万円(警察庁「薬物情勢報告書」2022年)。
2. 警察と暴力団の「共生関係」
- 逮捕統計の不自然さ:
- 全薬物逮捕者の70%が単純所持(厚生労働省「薬物乱用状況」2023年)。
- 密輸組織の摘発は全体の5%未満(東京地検特捜部データ)。
- メディアの検証:
- NHKスペシャル「覚せい剤戦争」(2021年)で指摘された「末端ユーザー優先捜査」の実態。
3. 矛盾する現実
- 需要の不可視性:
- G7で最高の覚せい剤価格(1gあたり3~7万円、欧米の3倍)→ 暴力団の暴利(財務省「組織犯罪資金流動調査」)。
- 使用者率は低い(人口の0.2%、国連調査)が、逮捕者の過半数を占める矛盾。
4. 「密輸組織対策」の限界
- 国際的な失敗例:
- メキシコ(カルテル摘発後も市場拡大)、欧州(合成薬物の蔓延)→ 代替組織が即座に台頭(英「The Economist」2023年6月号)。
- 日本の地理的ハンデ:
- 海上密輸の摘発率は10%未満(海上保安庁報告)。
5. 解決策の再考(事実に基づく提案)
- ADHD治療薬の合法化:
- アメリカ精神医学会「ADHD患者の60%が自己治療で違法薬物使用」(2019年研究)。
- 日本ではリタリン・アデロール禁止→ 暴力団の市場独占。
- 労働環境改革:
- 過労死ライン超えの労働者20%(厚労省「労働時間調査」2023年)→ 覚せい剤需要の一因。
6. 告発のリスクと情報源
- 匿名性の重要性:
- 過去の暴力団報復事例(2018年、告発記者への脅迫事件・毎日新聞報道)。
- 公的データのみ引用:
- 例:「警察庁統計」「国連報告書」など第三者検証可能な情報。
結論:変革のためには「事実」の可視化が必要
「薬物=個人の道徳的問題」という幻想が、暴力団と腐敗官僚を利している。
国際データと国内統計の矛盾を突くことで、システムの欺瞞を暴ける。安全な共有のために:
- 個人特定を避け、匿名プラットフォーム(Tor上フォーラム等)で議論。
- 公的機関のデータを直接リンク(例:警察庁PDFレポート)。
この文書は、公表された統計・メディア報道のみを根拠とし、個人の推測を排除しています。
脅威を避けるため、具体的な個人・組織の非難は意図的に避けています。 -
 @ 4ba8e86d:89d32de4
2025-05-02 13:51:37
@ 4ba8e86d:89d32de4
2025-05-02 13:51:37Tutorial OpenKeychain
- Baixar no F-droid https://f-droid.org/app/org.sufficientlysecure.keychain
Ao abrir o OpenKeychain pela primeira vez, você verá uma tela inicial indicando que ainda não há chaves configuradas. Nesse ponto, você terá três opções:
-
Criar uma nova chave PGP diretamente no OpenKeychain: Ideal para quem está começando e precisa de uma solução simples para criptografia em comunicações diárias.
-
Usar um token de segurança (como Fidesmo, Yubikey, NEO, ou Sigilance) Se você busca uma segurança ainda maior, pode optar por armazenar sua chave privada em um token de segurança. Com essa configuração, a chave privada nunca é salva no dispositivo móvel. O celular atua apenas como uma interface de comunicação, enquanto a chave permanece protegida no token, fora do alcance de possíveis invasores remotos. Isso garante que somente quem possui o token fisicamente possa usar a chave, elevando significativamente o nível de segurança e controle sobre seus dados.
-
Importar uma chave PGP existente: Você pode importar uma chave PGP que já tenha sido gerada anteriormente, seja por meio de um arquivo no dispositivo ou por outro meio ler na área de transferência. https://image.nostr.build/51fdd924df4843ab73faa02a505c8fb17794f1789396ed89b154348ebb337f07.jpg
1. CRIANDO UMA NOVA CHAVE PGP.
Para iniciantes, recomendamos criar uma nova chave diretamente no aplicativo. abordaremos o uso do OpenKeychain em modo online, que é mais comum para comunicações diárias.
Passo 1: Clique em “Criar minha chave”. https://image.nostr.build/235f5cfdf4c3006ca3b00342741003f79a5055355c2a8ee425fc33c875f51e49.jpg
Passo 2: Criando sua chave PGP.
Para criar sua chave, você precisará fornecer algumas informações Os campos 'Nome' e 'Endereço de e-mail' são apenas formas convenientes para identificar a sua chave PGP.
-
Nome: Escolha um nome ou um pseudônimo. https://image.nostr.build/de3fe3ddbde0c7bf084be6e4b8150fdb8612365550622559b0ee72f50f56a159.jpg
-
E-mail: Associe um endereço de e-mail à chave, seja ele pessoal ou um e-mail relacionado ao pseudônimo. https://image.nostr.build/aff62baaeafe2c9a429ef10435a6f99dea36d6cfd7494e2bb882421dc8ed0f4e.jpg
2. REVISANDO E PERSONALIZANDO A CRIAÇÃO DA CHAVE.
Passo 3: Antes de criar sua chave PGP, verifique se os dados inseridos estão corretos. https://image.nostr.build/a8ec09ef3d9b4f557b0c4e380e7ca45d0fdbfa33fe80becea03ed0e5f5eedd24.jpg
Você também pode personalizar as configurações de segurança clicando nos três pontos no canto superior direito. https://image.nostr.build/1ce615555cea9a979ea951472052a219e77f4e1ebaaf5fcbbe9e91ea4f852bce.jpg
Ao cliclar em ' nova subchave ' pode alterar a data de expiração e pode mudar a criptografia usado na chave cliclando opção ed2255/cv255. https://image.nostr.build/b3224ff3dbe48ff78c4a2df8b001926b6d3eef1e33ef677a73b0d281791073da.jpg https://image.nostr.build/7763c7847e062cdcf71aafedbc2ef4c38056fd66aeb162ef3a1c30c028a14376.jpg https://image.nostr.build/5d3e20ade460dd5e89cc001ebdc062a36aff2c0e1573584ca3c0d1cb34bddcce.jpg
Neste tutorial, utilizaremos as configurações padrão do aplicativo.
Passo 4: Clique em "Criar chave" para concluir o processo. https://image.nostr.build/a8ec09ef3d9b4f557b0c4e380e7ca45d0fdbfa33fe80becea03ed0e5f5eedd24.jpg
3. Como Compartilhar sua Chave PGP Pública
Após criar sua chave PGP, você pode compartilhá-la para que outras pessoas possam enviar mensagens criptografadas para você. Veja o passo a passo de como exibir e compartilhar sua chave pública:
Passo 1: Acesse sua chave pública
Abra o OpenKeychain e selecione a chave que deseja compartilhar. Clique na chave para visualizar os detalhes. https://image.nostr.build/689c5237075317e89e183d2664630de973b09b68aaf8f3e3033654e987b781be.jpg https://image.nostr.build/4001610109579f27535628932258087b3b06c1f86b05f4f85537b6585c12a10b.jpg
Passo 2: Copiar sua chave pública
Nos detalhes da chave, você verá a opção "Copiar para a Área de Transferência". Clique nessa opção para copiar o código da sua chave pública. https://image.nostr.build/01ab3efa5e997e1910a2f8f7a888e6ad60350574cca4ca0214eee5581797f704.jpg
A chave PGP copiada terá o seguinte formato:
-----BEGIN PGP PUBLIC KEY BLOCK-----
mDMEZwsLHRYJKwYBBAHaRw8BAQdA6NRLlJIWnTBJtYwZHlrMbTKRbYuXmjsMn8MB 7etV3HK0JERhbmllbCBGcmFnYSAgPGRhbmllbGZyYWdhQG1haWwuaTJwPohyBBMW CAAaBAsJCAcCFQgCFgECGQEFgmcLCx0CngECmwMACgkQFZf+kMeJWpR4cwEA8Jt1 TZ/+YlHg3EYphW8KsZOboHLi+L88whrWbka+0s8A/iuaNFAK/oQAlM2YI2e0rAjA VuUCo66mERQNLl2/qN0LuDgEZwsLHRIKKwYBBAGXVQEFAQEHQEj/ZfJolkCjldXP 0KQimE/3PfO9BdJeRtzZA+SsJDh+AwEIB4hhBBgWCAAJBYJnCwsdApsMAAoJEBWX /pDHiVqUo/oA/266xy7kIZvd0PF1QU9mv1m2oOdo7QSoqvgFiq6AmelbAP9lExY5 edctTa/zl87lCddYsZZhxG9g2Cg7xX/XsfrnAA== =TniY -----END PGP PUBLIC KEY BLOCK-----
Dica: Se ocorrer algum erro ao compartilhar sua chave pública com um amigo, peça para que ele a criptografe para ele mesmo. Isso permitirá que ele adicione a chave corretamente. Caso a chave pública ainda não esteja no dispositivo, ao clicar em "Backup de chave", aparecerá a opção para importá-la. Se a chave já estiver no dispositivo, essa ação irá recarregá-la. https://image.nostr.build/cd12abf07c93473db95483fe23112325f89d3eb02977e42756708bbd043f8bcf.jpg https://image.nostr.build/537aeae38d229ee2cc78e18f412237b659c059e1c74fd7f0deecfe37f15713c9.jpg https://image.nostr.build/16c8a3db5966c7c06904ee236655f47a6464ae0c1b5af6af27b28c61611d2bbe.jpg
Passo 3: Compartilhar sua chave PGP
Você pode colar a chave pública em e-mails, assinaturas, perfis de redes sociais ou outros meios para compartilhá-la facilmente. Para facilitar a visualização, você também pode exibi-la em seu perfil de redes sociais.
Para acessar mais opções de compartilhamento, clique nos três pontos no canto superior direito e selecione a opção "Avançado". https://image.nostr.build/0d4a13b7bd9a4794017247d1a56fac082db0f993a2011a4dd40e388b22ec88f5.jpg https://image.nostr.build/4ac2a7bc9fa726531a945221cf7d10e0e387deba68100ccf52fdedfcd17cbd59.jpg
Na seção "Compartilhar", você verá sua Key ID e terá a opção de publicar sua chave PGP em um servidor de chaves. https://image.nostr.build/1e972cc211a6d8060cdbd4a8aa642dd1a292810c532f178d3ddb133d1b9bca76.jpg
Passo 4: Como compartilhar sua chave pública PGP no formato .asc. no OpenKeychain
1 . Acesse sua chave
Abra o OpenKeychain e toque na chave que você deseja compartilhar. Isso abrirá a tela com os detalhes da chave. https://image.nostr.build/c080f03d2eb7a9f7833fec0ff1942a5b70b97e4f7da7c6bc79ca300ef9ace55d.jpg
2 . Compartilhe o arquivo .asc
Toque no ícone de compartilhamento, como indicado na imagem abaixo. O aplicativo abrirá a janela para que você escolha por qual app deseja compartilhar sua chave pública no formato .asc. Nesse exemplo, usei o SimpleXChat , mas você pode usar qualquer aplicativo de sua preferência.
-
Botão de compartilhar. https://image.nostr.build/8da74bdb04737a45df671a30bba1dd2e7980841fa0c2d751d6649630e7c25470.jpg
-
Seleção do aplicativo para compartilhamento. https://image.nostr.build/5444f4e9d3fa5aef6b191bb6f553f94c6e49d30ead874c9ee435bca3218fd6c8.jpg
-
Enviando via SimpleXChat. https://image.nostr.build/e5d1ca04cbc69e1e8ac5caf1ab2a4b9b695500861c1ae9c55cea679cce349214.jpg
Sugestão para compartilhar nas redes sociais:
Você pode exibir sua chave de forma simples, por exemplo:
PGP: 1597 FE90 C789 5A94
Importar a chave pública usando a fingerprint
Passo 1:Clique no ícone "+" para começar. https://image.nostr.build/ca6e6e569b4be60165eaf60c7ba1e6e3ec781b525e467c72b4f3605837e6b5ec.jpg
Passo 2: Selecione a opção "Buscar Chave". https://image.nostr.build/87e27d9435e6e3ef78063b9f15799a8120ead4637cd06c89c0220b48327573ae.jpg
Passo 3: Digite a fingerprint da chave em letras minúsculas, sem espaços. A chave correspondente aparecerá para ser adicionada. https://image.nostr.build/33e6819edd4582d7a8513e8814dacb07e1a62994bb3238c1b5b3865a46b5f234.jpg
Além disso, você pode compartilhar sua chave pública em formato QR Code, facilitando a troca de chaves em eventos ou conversas rápidas. Como Assinar Mensagens para Confirmar a Autenticidade da Sua Rede Social
Você pode autenticar sua conta em redes sociais utilizando sua chave PGP. Ao assinar uma mensagem com sua chave, você demonstra que realmente possui essa conta. Siga o passo a passo abaixo para assinar uma mensagem:
Passo 1: Clique na sua chave PGP. https://image.nostr.build/ffacce1bfb293c9a0888cd5efe340a63d96b293f4c010f8626105c7b212d8558.jpg
Passo 2: Clique no ícone indicado pela seta para abrir o campo de texto. https://image.nostr.build/4e992a2553810e2583b9d190280ce00a52fc423600a75eca48cbf541cf47d3c2.jpg
Passo 3: Deixe a opção "Encriptar para:" vazio. Em "Assinar com:", selecione sua chave PGP e digite a mensagem que deseja enviar, como o nome da sua rede social. https://image.nostr.build/a4a2a8d233d186e3d8d9adddccc445bcb3ca3ed88de0db671a77cede12323a75.jpg
Passo 4: Clique no ícone indicado pela seta para copiar o texto assinado. Uma mensagem aparecerá informando: "Assinado/Encriptado com Sucesso". https://image.nostr.build/a076dfc90e30a495af0872005bf70f412df57b7a0e1c2e17cf5aee9e9b3e39aa.jpg
A mensagem copiada terá o seguinte formato:
-----BEGIN PGP SIGNED MESSAGE----- Hash: SHA256
Minha rede social NOSTR é Danielfraga oficial. -----BEGIN PGP SIGNATURE-----
iIQEARYIACwlHERhbmllbCBGcmFnYSAgPGRhbmllbGZyYWdhQG1haWwuaTJwPgUC ZxBBLgAKCRAVl/6Qx4lalGeNAPwP71rpsbhRnZhoWZsTDOFZY8ep/d0e5qYx5iPx HV26dwD/fKyiir1TR8JwZvEbOTYS0+Dn4DFlRAAfR3lKVTC96w4= =37Lj -----END PGP SIGNATURE-----
Com isso, você pode facilmente demonstrar a autenticidade da sua conta nas redes sociais.
4. PROTEGENDO SUA CHAVE COM UMA SENHA.
Passo 5: Após a criação da chave, é fundamental definir uma senha (ou passphrase) para adicionar uma camada extra de segurança. Recomendamos usar senhas longas (com mais de 20 caracteres) e de alta entropia para evitar ataques de força bruta. Ferramentas como KeePassDX ou Bitwarden podem ajudá-lo a gerar e gerenciar essas senhas.
Para definir a senha, clique na sua chave PGP, acesse o menu no canto superior direito e selecione "Alterar senha". https://image.nostr.build/689c5237075317e89e183d2664630de973b09b68aaf8f3e3033654e987b781be.jpg https://image.nostr.build/f28ecaa9890a8827f93cac78846c4b2ef67f86ccfc3501fdadf1d1c4874b0041.jpg https://image.nostr.build/919c277fbec63c397402abdd60f915cb239a674c317855cbda63a38edef80789.jpg
Agora basta adicionar uma senha forte. https://image.nostr.build/eb378219fbb1780f89663a474ce43b8d8ebb13beeb538f2a16279b056e5d9645.jpg https://image.nostr.build/cdfa3f9c6c4045841341da789deabb6318107812d5ba195529418572ab352aaf.jpg
5. CRIPTOGRAFAR E DESCRIPTOGRAFAR MENSAGENS E ARQUIVOS COM SUA CHAVE PGP
Criptografar Mensagens
Você pode criptografar mensagens para garantir que apenas o destinatário, que possui sua chave pública, possa lê-las. Siga os passos abaixo para criptografar um texto:
Passo 1: Abra o menu lateral clicando no ícone no canto superior esquerdo.
https://image.nostr.build/13ac93b38dd1633118ae3142401c13e8a089caabdf4617055284cc521a45b069.jpgPasso 2: Selecione a opção "Encriptar/Descriptar".
https://image.nostr.build/8cd905d616b53968f0551c071d9acc2f47bbe8434c2c7e1a33076a504342de48.jpgPasso 3: Clique na opção "Encriptar Texto".
https://image.nostr.build/405a730a6c774759d7913f92f59059d43146db4afb28451a6f8833f94e99437f.jpgPasso 4: Preencha os seguintes campos: https://image.nostr.build/7dc5eba39ff82a321195dbf46b8113818632e3ef41175991d58e799a8e9d2751.jpg
-
Encriptar para: Selecione o destinatário da mensagem, ou seja, a pessoa para quem você está enviando o texto criptografado.
https://image.nostr.build/1e8c8cba6d3c3136d9857512e2794a81ceb7434eccdfb0f7d26cdef008b2e6d2.jpg -
Assinar com: Escolha sua chave PGP para assinar a mensagem.
https://image.nostr.build/d25b228c35b132d396d01c354ef093b43b3565578fbc0d6ff7b9de4e41619855.jpg -
Digitar o texto: No campo de texto, escreva a mensagem que deseja criptografar.
https://image.nostr.build/8537271dfa4445e60cb4c3cdb5d97571dc0ff5ee8acd6ed89a8c81e4bd8736c2.jpg
Passo 5: Depois de preencher os campos, você pode copiar o texto criptografado de duas formas:
-
Copiar para a área de transferência: Clique na opção para copiar o texto criptografado e cole-o em um aplicativo de mensagens para enviá-lo.
https://image.nostr.build/a5cb8e2c538a38db3972e7f3ac9aa9f602cda6b62848ff0c4b99928a67dcd486.jpg -
Compartilhar diretamente: Utilize a opção de compartilhamento para enviar o texto criptografado diretamente através de seus aplicativos de mensagens.
https://image.nostr.build/2b79cb564d623788a0de1111a067e0eb496f743389d465d4f4e8f6e65f0d08a7.jpg https://image.nostr.build/ff59e52bc8ab54ff377980a6ba5d1c4743d3298de11e5daa187ab7d45163a7be.jpg
Criptografar arquivos.
Passo 1: Abra o menu lateral clicando no ícone no canto superior esquerdo.
https://image.nostr.build/13ac93b38dd1633118ae3142401c13e8a089caabdf4617055284cc521a45b069.jpgPasso 2: Selecione a opção "Encriptar/Descriptar".
https://image.nostr.build/8cd905d616b53968f0551c071d9acc2f47bbe8434c2c7e1a33076a504342de48.jpgPasso 3 : clique na opção "Encriptar arquivos ". https://image.nostr.build/3fcae48ee38e7f4079ebccfd3eafb9ab0ad3559221d2c3560cdfe60e29f56a15.jpg
Passo 4 : os passos a seguir são os mesmo que você seguiu pra encriptar a mensagem texto. Ítens "Encriptar para:" "Assinar com:" https://image.nostr.build/4d6599b9d3a9fdfae0964daaa9dae513d5ce277a7b61930fa2937d534f72ed40.jpg
Passo 5 : clilcar na opção " Adicionair arquivo(s)" Vai abrir na memória interna do celular selecione o arquivo que deseja encriptar. https://image.nostr.build/09e3b9b54a1406426114926aab19011c36b98886ebae6fcf556cfea83bb2c2f4.jpg https://image.nostr.build/af422e243b36762dd66111ec7c848a1352c100ca3040dc21792c923f80aef74d.jpg https://image.nostr.build/ebebbdb273b4bca58d901852aec1c60e4799aa77e9d12a31f992b0cf8f73e753.jpg
Passo 6: Depois de preencher os campos, você pode compartilhar o arquivo criptografado de duas formas:
-
Salvar na memória do celular: A primeira opção salva o arquivo criptografado no armazenamento do seu dispositivo. Você terá a opção de editar o nome do arquivo antes de salvar.
https://image.nostr.build/0a47c1e9f0003541f47091b2c2e8ce6b8d1533d95463e331b218070bae964ac8.jpg https://image.nostr.build/95a7a2b67356eb5ded5b217bab38a19bdeba5af7befd105834e413e0aec45462.jpg https://image.nostr.build/66cb3d22b271f3b73b7015613c72711a3ffbf5e1070d43153f9d1f3fcf35001c.jpg https://image.nostr.build/f9624d86f7592fe7ffad932b7805762dc279d9e8ff410222108155438a2c970f.jpg -
Compartilhar diretamente: Utilize a opção de compartilhamento para enviar o arquivo criptografado diretamente por meio dos seus aplicativos de mensagens.
https://image.nostr.build/85541e466c7755c65bd6ba0208a6d8612beaa5298712b6d92f53865167695a38.jpg https://image.nostr.build/bf1e0f0aeb60cafbdf82af4b3b598288519e85b396bd3f9e00e61f65b89ea9f8.jpg https://image.nostr.build/fb090339898f37cdbb020828689b142ca601ca3ee549f67ddf6b2e094df9ab9f.jpg https://image.nostr.build/50c249ced06efe465ba533fef15207b0dcd1a725e9b2c139e8d85c13fd798276.jpg
Descriptografar Mensagens e Arquivos
Para ler uma mensagem ou arquivo criptografado que você recebeu, utilize sua chave privada. Siga os passos abaixo:
Descriptografar Mensagens
Passo 1: Copie a mensagem criptografada que você recebeu.
https://image.nostr.build/c37754b12a458e0176b9137ae0aa9e8209f853bf9d9292c0867fd8b0606d53c4.jpgPasso 2: Clique na opção "Ler da área de transferência" para descriptografar o texto.
https://image.nostr.build/d83c7dad2ee1cb6267779863bc174ee1a8f3cc3c86b69063345321027bdde7b5.jpg https://image.nostr.build/c0fae86e6ab1fe9dcee86753972c818bed489ea11efdd09b7e7da7422a9c81eb.jpgDescriptografar Arquivos
Passo 1: Clique na opção "Selecionar arquivo de entrada".
https://image.nostr.build/9c276c630311d19a576f2e35b5ba82bac07360476edae3f1a8697ff85df9e3c9.jpgPasso 2: Selecione o arquivo criptografado que deseja descriptografar.
https://image.nostr.build/6b6c2a3284ba96e7168fc7bd0916020c4f1bed7b77dfca48227fc96d6929e15a.jpg https://image.nostr.build/9945aad644af2e2020e07e55f65f11a0958d55e8fc9e13c862e6b9ca88b4f4d9.jpg6. BACKUP E RESTAURAÇÃO DE CHAVE PGP.
Realizar o backup das suas chaves PGP é fundamental para evitar a perda de acesso às suas mensagens e dados criptografados. O OpenKeychain facilita esse processo, permitindo que você faça um backup completo e seguro. Recomendamos que você armazene o backup em um local seguro, como um HD externo ou pendrive conectado via cabo OTG, sempre protegendo-o com senha.
PASSOS PARA REALIZAR O BACKUP:
Passo 1: Abra o menu lateral clicando no ícone no canto superior esquerdo.
https://image.nostr.build/13ac93b38dd1633118ae3142401c13e8a089caabdf4617055284cc521a45b069.jpgPasso 2: Selecione a opção Backup/restaurar.
https://image.nostr.build/6fa8fd14e23b47c6c924bc0d900646663f2124a93d8172ae79fdf43b5c7d4490.jpgPasso 3: Escolha a primeira opção: Backup completo (criptografado).
https://image.nostr.build/4875fb27b6d04c3cb838b4fb9f308ef9194edc35ba1254ba965b7f0db2544170.jpgPasso 4: O backup será protegido por um código de backup gerado automaticamente. Anote esse código em um papel e guarde local seguro, pois sem ele você não conseguirá recuperar suas chaves PGP. Após anotar o código, marque a opção “Anotei o código” e clique em Salvar Backup. Obs: todas as vezes que você for fazer o backup da sua chave PGP vai ser criado um novo código aleatório.
https://image.nostr.build/72a317ef5e59a01c03c36f1d04a91d42c418a478cc82e372acf21bb8302daa00.jpg
Passo 5: Escolha o local onde deseja salvar o backup (HD externo, pendrive, etc.), confirme sua escolha e clique em OK. Você verá uma mensagem de confirmação indicando que o backup foi salvo com sucesso.
https://image.nostr.build/d757e8bdf429371320daa44be8a48a0dbeb2324129f4254327f0f0383e70ede4.jpg https://image.nostr.build/f3ad80ceb8a191b4d1b40722b1d0d4f85bf183d412e7d7d901b25d19b2dfe0e3.jpg
Importação da Chave PGP
Caso você precise restaurar suas chaves PGP a partir de um backup, o OpenKeychain também facilita o processo de importação. Siga os passos abaixo para restaurar sua chave PGP:
Passo 1: Selecione a opção "Selecionar arquivo de entrada"
Abra o OpenKeychain, acesse o menu lateral no canto superior esquerdo e escolha a opção "Selecionar arquivo de entrada" para localizar o arquivo de backup que você deseja importar.
https://image.nostr.build/a06ddc1c1e6c50519097e614aa25b14311e49c0ca4d4607e42ebdcca3a6641c4.jpgPasso 2: Selecione o arquivo de backup
Navegue até o local onde você salvou o arquivo de backup (HD externo, pendrive, etc.) e selecione-o. Em seguida, o OpenKeychain solicitará que você insira o código de recuperação que foi gerado no momento do backup. https://image.nostr.build/9d5649c04a98ec8b0a29355d9068e48313b1c5dc36cd965961f4d33f22d10046.jpgPasso 3: Digite o código de recuperação
Insira o código de recuperação que você anotou anteriormente. É importante digitar o código corretamente para garantir o sucesso da restauração.Passo 4: Depois de inserir o código corretamente, o OpenKeychain irá restaurar suas chaves PGP, e uma mensagem de confirmação será exibida, indicando que a recuperação foi concluída com sucesso.
Agora suas chaves estão restauradas e você pode continuar usando o OpenKeychain para gerenciar suas comunicações criptografadas de maneira segura.
https://www.openkeychain.org/
https://github.com/open-keychain/open-keychain
https://youtu.be/fptlAx_j4OA
-
 @ e516ecb8:1be0b167
2025-05-04 01:45:38
@ e516ecb8:1be0b167
2025-05-04 01:45:38El sol de la tarde caía oblicuo sobre un campo de hierba alta, tiñéndolo de tonos dorados y rojizos. A un lado, una formación disciplinada de hombres vestidos con armaduras de cuero y metal relucía bajo la luz. Eran legionarios romanos, cada uno portando un scutum, el gran escudo rectangular, y un gladius corto y letal. Se movían como una sola entidad, un muro de escudos erizado de puntas de lanza que asomaban por encima.
Al otro lado del campo, una fuerza más dispersa pero igualmente imponente esperaba. Eran samuráis, guerreros vestidos con armaduras lacadas de intrincado diseño. En sus manos, las brillantes curvas de las katanas reflejaban el sol poniente. Su presencia era menos de masa compacta y más de tensión contenida, como la de depredadores listos para abalanzarse.
El silencio se quebró cuando un oficial romano alzó su signum, un estandarte con el águila imperial. Al unísono, los legionarios avanzaron con paso firme, sus sandalias clavándose en la tierra. Gritaban su grito de guerra, un rugido gutural que resonaba en el aire.
Los samuráis observaron el avance implacable. Su líder, un hombre de rostro sereno con una cicatriz que le cruzaba la mejilla, desenvainó su katana con un movimiento fluido y silencioso. La hoja brilló intensamente. Con un grito agudo, dio la orden de ataque.
La batalla comenzó con un choque violento. Los legionarios, con sus escudos entrelazados, formaron una muralla impenetrable. Los samuráis se lanzaron contra ella, sus katanas trazando arcos de acero en el aire. El choque de metal contra metal llenó el campo, un coro estridente de la guerra.
Un samurái, ágil como un felino, intentó saltar sobre el muro de escudos. Pero un legionario, rápido y entrenado, lo recibió con una estocada precisa de su gladius, que encontró un hueco en la armadura. El samurái cayó, la sangre tiñendo la hierba.
Otro samurái, con un grito furioso, lanzó un corte horizontal con su katana. El golpe impactó contra un scutum, dejando una marca profunda en la madera y el metal, pero el escudo resistió. Antes de que pudiera recuperar su arma, el legionario detrás del escudo le asestó un golpe rápido con el gladius en el costado desprotegido.
La formación romana era una máquina de matar eficiente. Los legionarios trabajaban en equipo, protegiéndose mutuamente con sus escudos y atacando con sus gladius en los momentos oportunos. La disciplina y el entrenamiento eran sus mayores armas.
Sin embargo, la ferocidad y la habilidad individual de los samuráis eran innegables. Sus katanas, a pesar de no poder penetrar fácilmente la sólida pared de escudos, eran devastadoras en los espacios abiertos. Un samurái logró flanquear a un grupo de legionarios y, con movimientos rápidos y precisos, cortó brazos y piernas, sembrando el caos en la retaguardia romana.
La batalla se convirtió en un torbellino de acero y gritos. Los legionarios mantenían su formación, avanzando lentamente mientras repelían los ataques. Los samuráis, aunque sufrían bajas, no retrocedían, impulsados por su honor y su valentía.
En un punto crucial, un grupo de samuráis liderados por su comandante logró concentrar sus ataques en un sector de la línea romana. Con golpes repetidos y feroces, consiguieron romper la formación, creando una brecha. Se lanzaron a través de ella, sus katanas sedientas de sangre.
La disciplina romana se tambaleó por un momento. Los samuráis, aprovechando la oportunidad, lucharon cuerpo a cuerpo con una furia indomable. La longitud de sus katanas les daba ventaja en el combate individual, permitiéndoles mantener a raya a los legionarios con cortes amplios y letales.
Sin embargo, la respuesta romana fue rápida. Los oficiales gritaron órdenes, y las líneas se cerraron nuevamente, rodeando a los samuráis que habían penetrado la formación. Los legionarios, trabajando en parejas, inmovilizaban los largos brazos de los samuráis con sus escudos mientras otros asestaban golpes mortales con sus gladius.
La batalla continuó durante lo que pareció una eternidad. El sol finalmente se ocultó en el horizonte, tiñendo el campo de batalla de sombras oscuras y reflejos sangrientos. Ambos bandos lucharon con una determinación feroz, sin ceder terreno fácilmente.
Al final, la disciplina y la formación compacta de los legionarios comenzaron a imponerse. Lentamente, pero de manera constante, fueron cercando y diezmando a los samuráis. La muralla de escudos era demasiado sólida, y la lluvia constante de estocadas del gladius era implacable.
Los últimos samuráis lucharon con la desesperación de quienes saben que su final está cerca. Sus katanas seguían cortando con gracia mortal, pero eran superados en número y en la táctica del combate en grupo. Uno a uno, fueron cayendo, sus brillantes espadas manchadas de sangre.
Cuando la última katana cayó al suelo con un resonido metálico, un silencio pesado se cernió sobre el campo. Los legionarios, exhaustos pero victoriosos, permanecieron en formación, sus escudos goteando sangre. Habían prevalecido gracias a su disciplina, su equipo y su táctica de combate en grupo. La ferocidad individual y la maestría de la katana de los samuráis no habían sido suficientes contra la máquina de guerra romana.
La noche cubrió el campo de batalla, llevándose consigo los ecos de la lucha y dejando solo la sombría realidad de la victoria y la derrota.
-
 @ 4961e68d:a2212e1c
2025-05-02 07:47:16
@ 4961e68d:a2212e1c
2025-05-02 07:47:16热死人了
-
 @ 5df413d4:2add4f5b
2025-05-04 01:13:31
@ 5df413d4:2add4f5b
2025-05-04 01:13:31Short photo-stories of the hidden, hard to find, obscure, and off the beaten track.
Come now, take a walk with me…
The Traveller 02: Jerusalem Old City
The bus slowly lurches up the winding and steep embankment. We can finally start to see the craggy tops of buildings peaking out over the ridge in the foreground distance. We have almost reached it. Jerusalem, the City on the Hill.
https://i.nostr.build/e2LpUKEgGBwfveGi.jpg
Our Israeli tour guide speaks over the mic to draw our attention to the valley below us instead - “This is the the Valley of Gehenna, the Valley of the Moloch,” he says. “In ancient times, the pagans who worshiped Moloch used this place for child sacrifice by fire. Now, imagine yourself, an early Hebrew, sitting atop the hill, looking down in horror. This is the literal Valley of The Shadow of Death, the origin of the Abrahamic concept of Hell.” Strong open - this is going to be fun.
https://i.nostr.build/5F29eBKZYs4bEMHk.jpg
Inside the Old City, our guide - a chubby, cherub-faced intelligence type on some sort of punishment duty, deputized to babysit foreigners specifically because he reads as so dopey and disarming - points out various Judeo-Christian sites on a map, his tone subtly suggesting which places are most suggested, or perhaps, permitted…
https://i.nostr.build/J44fhGWc9AZ5qpK4.jpg
https://i.nostr.build/3c0jh09nx6d5cEdt.jpg
Walking, we reach Judaism’s Kotel, the West Wall - massive, grand, and ancient, whispering of the Eternal. Amongst the worshipers, we touch the warm, dry limestone and, if we like, place written prayers into the wall's smaller cracks. A solemn and yearning ghost fills the place - but whose it is, I'm not sure.  https://i.nostr.build/AjDwA0rFiFPlrw1o.jpg
Just above the Kotel, Islam’s Dome of the Rock can be seen, its golden cap blazing in the sun. I ask our guide about visiting the dome. He cuts a heavy eyeroll in my direction - it seems I’ve outed myself as my group’s “that guy.” His face says more than words ever could, “Oy vey, there’s one in every group…”
“Why would anyone want to go there? It is a bit intense, no?” Still, I press. “Well, it is only open to tourists on Tuesday and Thursdays…” It is Tuesday. “And even then, visiting only opens from 11:30…” It is 11:20. As it becomes clear to him that I don't intend to drop this...“Fine!” he relents, with a dramatic flaring of the hands and an uniquely Israeli sigh, “Go there if you must. But remember, the bus leaves at 1PM. Good luck...” Great! Totally not ominous at all.
https://i.nostr.build/6aBhT61C28QO9J69.jpg
The checkpoint for the sole non-Muslim entrance leading up to the Dome is administered by several gorgeous and statuesque, assault rifle clad, Ethiop-Israeli female soldiers. In this period of relative peace and calm, they feel lax enough to make a coy but salacious game of their “screening” the men in line. As I observe, it seems none doth protest...
https://i.nostr.build/jm8F3pUp9EXqPRkN.jpg
Past the gun-totting Sirens, a long wooden rampart leads up to the Temple Mount, The Mount of the House of the Holy, al-Ḥaram al-Sharīf, The Noble Sanctuary, The Furthest Mosque, the site of the Dome of the Rock and the al-Masjid al-Asqa.
https://i.nostr.build/DoS0KIkrVN0yiVJ0.jpg
On the Mount, the Dome dominates all views. To those interested in pure expressions of beauty, the Dome is, undeniably, a thing of absolute glory. I pace the grounds, snapping what pictures I can. I pause to breathe and to let the electric energy of the setting wash over me.
https://i.nostr.build/0BQYLwpU291q2fBt.jpg
https://i.nostr.build/yCxfB1V8eAcfob93.jpg
It’s 12:15 now, I decide to head back. Now, here is what they don’t tell you. The non-Muslin entrance from the West Wall side is a one-way deal. Leaving the Dome plaza dumps you out into the back alley bazaar of Old City’s Muslim district. And so it is. I am lost.
https://i.nostr.build/XnQ5eZgjeS1UTEBt.jpg
https://i.nostr.build/EFGD5vgmFx5YYuH4.jpg
I run through the Muslim quarter, blindly turning down alleyways that seem to be taking me in the general direction of where I need to be - glimpses afforded by the city’s uneven elevation and cracks in ancient stone walls guiding my way.
https://i.nostr.build/mWIEAXlJfdqt3nuh.jpg
In a final act of desperation and likely a significant breach of Israeli security protocol, I scale a low wall and flop down back on the side of things where I'm “supposed” to be. But either no one sees me or no one cares. Good luck, indeed.
I make it back to my group - they are not hard to find, a bunch of MBAs in “business casual” travel attire and a tour guide wearing a loudly colored hat and jacket - with just enough time to still visit the Church of the Holy Sepulcher.
https://i.nostr.build/3nFvsXdhd0LQaZd7.jpg
https://i.nostr.build/sKnwqC0HoaZ8winW.jpg
Inside, a chaotic and dizzying array of chapels, grand domed ceilings, and Christian relics - most notably the Stone of Anointing, commemorating where Christ’s body was prepared for burial and Tomb of Christ, where Christ is said to have laid for 3 days before Resurrection.
https://i.nostr.build/Lb4CTj1dOY1pwoN6.jpg
https://i.nostr.build/LaZkYmUaY8JBRvwn.jpg
In less than an hour, one can traverse from the literal Hell, to King David’s Wall, The Tomb of Christ, and the site of Muhammad’s Ascension. The question that stays with me - What is it about this place that has caused so many to turn their heads to the heavens and cry out for God? Does he hear? And if he answers, do we listen?
https://i.nostr.build/elvlrd7rDcEaHJxT.jpg
Jerusalem, The Old City, circa 2014. Israel.
There are secrets to be found. Go there.
Bitcoin #Jerusalem #Israel #Travel #Photography #Art #Story #Storytelling #Nostr #Zap #Zaps #Plebchain #Coffeechain #Bookstr #NostrArt #Writing #Writestr #Createstr
-
 @ 4961e68d:a2212e1c
2025-05-02 07:46:46
@ 4961e68d:a2212e1c
2025-05-02 07:46:46热死人了!
-
 @ 5df413d4:2add4f5b
2025-05-04 00:51:49
@ 5df413d4:2add4f5b
2025-05-04 00:51:49Short photo-stories of the hidden, hard to find, obscure, and off the beaten track.
Come now, take a walk with me…
The Traveller 01: Ku/苦 Bar
Find a dingy, nondescript alley in a suspiciously quiet corner of Bangkok’s Chinatown at night. Walk down it. Pass the small prayer shrine that houses the angels who look over these particular buildings and approach an old wooden door. You were told that there is a bar here, as to yet nothing suggests that this is so…

Wait! A closer inspection reveals a simple bronze plaque, out of place for its polish and tended upkeep, “cocktails 3rd floor.” Up the stairs then! The landing on floor 3 presents a white sign with the Chinese character for bitter, ku/苦, and a red arrow pointing right.


Pass through the threshold, enter a new space. To your right, a large expanse of barren concrete, an empty “room.” Tripods for…some kind of filming? A man-sized, locked container. Yet, you did not come here to ask questions, such things are none of your business!

And to your left, you find the golden door. Approach. Enter. Be greeted. You have done well! You have found it. 苦 Bar. You are among friends now. Inside exudes deep weirdness - in the etymological sense - the bending of destinies, control of the fates. And for the patrons, a quiet yet social place, a sensual yet sacred space.


Ethereal sounds, like forlorn whale songs fill the air, a strange music for an even stranger magic. But, Taste! Taste is the order of the day! Fragrant, Bizarre, Obscure, Dripping and Arcane. Here you find a most unique use flavor, flavors myriad and manifold, flavors beyond name. Buddha’s hand, burnt cedar charcoal, ylang ylang, strawberry leaf, maybe wild roots brought in by some friendly passerby, and many, many other things. So, Taste! The drinks here, libations even, are not so much to be liked or disliked, rather, the are liquid context, experience to be embraced with a curious mind and soul freed from judgment.

And In the inner room, one may find another set of stairs. Down this time. Leading to the second place - KANGKAO. A natural wine bar, or so they say. Cozy, botanical, industrial, enclosed. The kind of private setting where you might overhear Bangkok’s resident “State Department,” “UN,” and “NGO” types chatting auspiciously in both Mandarin and English with their Mainland Chinese counterparts. But don’t look hard or listen too long! Surely, there’s no reason to be rude… Relax, relax, you are amongst friends now.

**苦 Bar. Bangkok, circa 2020. There are secrets to be found. Go there. **
Plebchain #Bitcoin #NostrArt #ArtOnNostr #Writestr #Createstr #NostrLove #Travel #Photography #Art #Story #Storytelling #Nostr #Zap #Zaps #Bangkok #Thailand #Siamstr
-
 @ 20986fb8:cdac21b3
2025-05-02 14:08:55
@ 20986fb8:cdac21b3
2025-05-02 14:08:55传统黑客松:闪耀火花中的局限
过去几十年里,黑客松一直是技术文化的培养皿——24小时或48小时的狂热编程马拉松,在披萨、咖啡因和几近不可能的乐观情绪中推进。
自1999年Sun Microsystems首次举办黑客松,要求Java开发者在Palm V掌上电脑上完成一日编程,到创业公司和大学里通宵达旦的“黑客日”[1],这些活动始终在庆祝黑客精神。它们为我们带来了Facebook的“点赞”按钮和聊天功能——这些标志性的创新[1],皆诞生于一夜之间的即兴狂想。
它们也催生了如GroupMe这样的公司——这个应用仅用了几个深夜时段就完成开发,一年后就被Skype以8000万美元收购[2]。
黑客松逐渐成为技术界的传说,成为“无拘束创造力”的代名词。然而,尽管充满激情和炒作,传统黑客松却存在着严重的局限:它们是偶发、线下的活动——更像是“蓝月亮”才出现一次的肾上腺素爆发,而不是一种可持续的创新流程。
一次黑客松也许能在周末召集100名程序员共聚一室,但活动结束后便销声匿迹,直到下一年。
频率低、规模小、触达有限。只有能亲临现场的人(往往是硅谷或精英高校)才有机会参与。哪怕你是来自拉各斯或圣保罗的天才黑客,只要身处远方,你的绝妙创意也注定被忽视。
这类冲刺式活动的成果也极为受限。
当然,团队可能构建出炫酷的演示项目,并赢得一时风头。但大多数情况下,这些项目只是一次性原型——“玩具”应用,最终并未发展为真正的产品或公司。有研究表明,只有约5%的黑客松项目在活动结束几个月后还有任何生命迹象[3]。
其余95%则如烟云般消散——在“黑客松宿醉”中夭折:人们回到“正职”,而演示代码也蒙尘。
批评者甚至给黑客松取了个贬义的别名:“周末虚耗松”(weekend wastedathons),抨击其成果如同短命的“蒸汽软件”(vaporware)[3]。
想想看:一阵创造力的爆发,数十个点子竞相绽放……然后呢?
你能说出几个真正从黑客松走出的成功企业名字?对于每一个如Carousell或EasyTaxi那样从黑客松中诞生、后来成功融资数千万美元的项目,就有几百个聪明的创意组合永远不见天日[2]。
传统黑客松模式,尽管令人兴奋,却极少能转化为持续的创新。
它更像是被时间、地域和后续缺失所束缚的孤岛式创新。黑客松是事件,不是流程;它是烟花,不是日出。
此外,黑客松在历史上一直颇为封闭。
直到近年,它们主要由技术圈内人士自办自娱。大型科技公司会举办内部黑客松,以激发员工创造力(Facebook每几周举办一次通宵活动,最终诞生了时间线和标记功能,影响了十亿用户 [1]);NASA和世界银行也曾尝试用黑客松推进公民科技。但这些都是例外,印证了一个普遍规律:黑客松从来不是常规工作流程,而是特例事件。
在科技巨头之外,鲜有组织具备资源或经验能频繁举办黑客松。
除非你是Google、Microsoft,或资金雄厚的创业孵化器,否则黑客松只是一场偶尔奢侈的尝试。事实上,当今世界上最大的黑客松是微软的内部全球黑客松——有多达70,000名员工跨越75个国家同时参与,这是壮观的成就,但唯有企业巨头才能负担得起[4]。
而中小型玩家只能仰望、惊叹。
限制显而易见:黑客松太少见、太封闭,无法真正激活全球人才库;周期太短,难以构建成熟产品;过于孤立,无法真正撼动行业。
没错,它们确实产生过惊艳的灵感时刻——创新的闪光灯。
但若视其为持续进步的机制,传统黑客松则显得捉襟见肘。作为投资者或科技领袖,你或许会为创造力鼓掌,但仍会追问:真正的长期影响在哪里?有谁搭建了把这些火花转化为持续光束的基础设施?
正如克莱顿·克里斯滕森的《创新者的窘境》所言,传统巨头往往将黑客松项目视作“玩具”——有趣但不切实际。
而事实上,“每一个未来的大事物,起初总是被当作玩具”。黑客松的确催生了不少“玩具”,却极少能拥有支持系统去把它们变为下一个伟大的事物。
这个模式,是时候被重新发明了。
为何到了2020年代,我们还在用1990年代的创新方式?为何将突破性的想法限制在一个周末或一个地点?为何允许95%的早期创新无声凋谢?
这些问题,悬而未解,等待着回答。
Hackathons 2.0 ——DoraHacks与黑客松的第一次进化(2020–2024)
DoraHacks登场。
在2020年代初,DoraHacks如同一台“心脏除颤器”,令黑客松这种形式重获新生。DoraHacks 1.0(大致始于2020年、延续至2024年)并非对黑客松的微调,而是对其彻底的重塑:将传统黑客松从1.0升级到2.0。它汲取原有理念,加速、扩展并升级至全维度,全方位放大其影响力。结果是一场全球黑客运动的兴起,一个将黑客松从“一锤子买卖”变为持续技术创新引擎的平台。
DoraHacks如何革命性地重构黑客松?请看以下几个维度:
从24小时到24天(甚至24周)——时间轴的重构
DoraHacks拉长了黑客松的时间框架,解锁了远超以往的创新潜能。
相比于传统那种紧张焦躁的24小时冲刺,DoraHacks支持的黑客松往往持续数周甚至数月——这是一场范式转变。
团队终于有了足够时间去打磨原型、迭代优化、反复精炼。更长的周期意味着项目能从粗糙演示走向成熟MVP。黑客们终于可以“偶尔睡觉”,引入用户反馈,将灵感的火花铸造成实用的成果。
时间的延展模糊了黑客松与加速器之间的界限,但保留了黑客松自由、开放的精神。例如,DoraHacks为区块链初创团队组织的黑客松通常持续6到8周,最终成果往往能吸引真实用户与投资人。
延长的时间,把“玩具”变成了产品。就像黑客松终于“长大成人”:Less Hack, More BUIDL(少些临时拼凑,多些踏实构建)。打破24小时范式之后,黑客松真正变得更高效、更深远、更具生产力。
从街角咖啡馆到全球虚拟竞技场——地理限制的打破
DoraHacks将黑客松从线下搬到云端,释放出全球参与的可能性。
2020年之前,黑客松意味着必须到现场——可能是旧金山某仓库,或是大学实验室,与本地队友并肩作战。而DoraHacks颠覆了这一格局:任何人、任何地方,只要连上网络,就可以参与。
一位尼日利亚的开发者、乌克兰的设计师、巴西的产品经理,如今可以在同一场线上黑客松中协作创新。地理边界不复存在。
当DoraHacks举办面向非洲区块链开发者的Naija HackAtom时,吸引了来自尼日利亚科技社群的500多名参与者(包括160多位开发者,odaily.news)。在另一场活动中,来自数十个国家的黑客同时在线参与、构思、竞争 [6]。
这种全球性拓展不仅增加了参与人数,更引入了多样的视角和本地问题。一个金融科技黑客松中,可能有拉美开发者解决汇款问题;一个AI黑客松中,亚洲或非洲开发者将机器学习应用于本地医疗。
线上化,让黑客松变得真正普惠。DoraHacks有效地民主化了创新的入场门槛——你只需要一根网线和一颗创作的心。
结果是:创意的数量与质量实现量子飞跃。 黑客松不再是精英小圈子的游戏,而是一场面向全人类的全球创新嘉年华。
从几十人到数万人——规模的跃迁
DoraHacks推动的另一项革命,就是规模的扩展。传统黑客松人少而亲密(几十人,顶多几百)。DoraHacks则催生了成千上万人参与、数百万美元奖金池的大型活动。
例如,在2021年的一场线上黑客松中,近7000名参与者提交了550个项目,争夺500万美元奖金。这是2010年代初期根本无法想象的规模[7]。
DoraHacks本身也成为这些“超级黑客松”的中枢。平台在Web3领域所举办的黑客松常常吸引数百支队伍参赛,奖金高达数百万美元。
这不只是好看的数据,而是更广泛的全球人才投入,也带来了更高概率的真正突破性成果。
以BNB Chain支持的黑客松系列为例,在DoraHacks推动下,有216支开发团队获得了超过1000万美元的资金支持[8]——是的,真金白银的种子投资。这哪是黑客松?简直就是一个小型经济体。
奖池也从“披萨钱”膨胀成“起步资本”,吸引那些有抱负、懂商业的创业者参与。越来越多的项目不再只是周末练习,而是具备融资能力的初创企业。黑客松,也由“科技科学展”升格为“全球创业发射台”。
从玩具项目到真公司(甚至独角兽)——成果的飞跃
最令人振奋的一点是:DoraHacks所孵化的项目,不只是应用,更是真正的公司。其中一些甚至成长为独角兽(估值超过10亿美元的公司)。
我们之前提到过2020年之前为数不多的成功案例,比如Carousell(一个在2012年黑客松上诞生的小点子,如今已成为估值11亿美元的二手市场[2]),或EasyTaxi(始于黑客松,后融资7500万美元、覆盖30个国家[2])。
DoraHacks让这种奇迹频繁上演。通过更长的周期、更多的支持、更好的资金接力,黑客松逐渐成为真正的“创新孵化器”。
以1inch Network为例——它是一家去中心化金融聚合平台,起初就是在2019年一个黑客松中诞生的。创始人Sergej Kunz和Anton Bukov在社区支持下完成了最初的原型,随后持续迭代。
如今,1inch的累计交易额已超4000亿美元,成为DeFi领域的头部平台之一 [9]。
再看DoraHacks Web3黑客松中的优胜者,许多项目已经完成了数百万美元的融资,获得顶级VC支持。
黑客松成为了“创业世界的前门”,创始人往往在此首次亮相。比如Solana Season Hackathons中的热门项目STEPN —— 一个“边走边赚”应用,于2021年赢得黑客松奖项,不久后就成长为拥有数十亿美元代币经济的现象级产品[10]。
这不是孤立事件,而是DoraHacks设定的系统性趋势。它的黑客松正在源源不断地产出可投、可用、可落地的创业项目。
某种意义上,DoraHacks模糊了黑客松与早期孵化器的界限。玩乐的黑客精神依然在,但结果已不只是炫耀——而是真实存在的公司,有用户,有营收,有估值。
借用投资人Chris Dixon的话说:DoraHacks把那些“玩具”,扶育成了下一个伟大的事物[5]。
DoraHacks不仅优化了旧模式,它创造了一个全新的创新生态
DoraHacks主导的第一次黑客松进化,不只是“修补优化”,而是打造了一个全新的创新系统。
黑客松变得高频、全球化、具决定性影响。
它不再是短暂的周末狂欢,而是持续的创新供给链。
DoraHacks平台每年孵化出上百个可行项目,其中很多都获得后续融资。它不仅提供活动本身,更提供“术后护理”:社区支持、导师指导、连接投资人与资助渠道(如DoraHacks的资助计划和二次方资助机制)。 到2024年,成果不言自明。DoraHacks已成长为全球最重要的黑客松平台——一个贯通区块链、AI乃至更多前沿科技的黑客运动中枢。
数据不会说谎。
9年间,DoraHacks帮助4000多个项目获得超过3000万美元资金(coindesk.com)[11];到2025年,这一数字飙升,DoraHacks支持的黑客松和资助总计为超过21000个初创团队提供了逾8000万美元资金(linkedin.com)[12]。
这不是夸张宣传——而是写入技术史的事实。CoinDesk评价道:“DoraHacks已成为全球最活跃的多链Web3开发平台与黑客松组织者之一。”(coindesk.com)[13]
主流技术生态纷纷注意到这一趋势。
超过40个公链(包括L1与L2)——从Solana到Polygon再到Avalanche——皆与DoraHacks合作,组织黑客松与开放创新计划(blockworks.co)[13]。
Blockworks 报道称,DoraHacks已成为数十个Web3生态系统的“核心合作伙伴”,帮助他们连接全球开发者资源(blockworks.co)[11]。
在投资人眼中,DoraHacks本身就是关键基础设施:“DoraHacks对Web3基础设施建设至关重要。”一位支持平台的VC如此指出(blockworks.co)[13]。
简而言之:到2024年,DoraHacks已将黑客松从一个小众事件变为全球创新引擎。
它证明:只要规模足够、流程健全,黑客松可以持续地产出真实、可投、可商业化的创新。
它连接开发者与资源,把“孤岛式创新”变成一场全球开发者的常青运动。
这就是Hackathons 2.0:更大、更久、更无界,也远比以往更具颠覆性。
也许你会问:还能比这更好吗?
DoraHacks似乎已经破解了“如何让黑客创造力产生持久影响”的密码。
但这并不是终点。事实上,DoraHacks团队即将揭示的,是一场更加激进的革命。
如果说DoraHacks 1.0是“进化”,那接下来将是一次范式转移的“革命”。
Agentic Hackathon:BUIDL AI与第二次黑客松革命
2024年,DoraHacks推出了BUIDL AI,并由此提出了“Agentic Hackathon(自主智能黑客松)”的概念。
如果说最初的黑客松像是模拟电话,DoraHacks 1.0则使其进化为智能手机,那么BUIDL AI的出现,就像为黑客松安装上了AI副驾驶——进入自动驾驶模式。
这不仅是渐进式的提升,而是一场彻底的第二次革命。
BUIDL AI为黑客松注入了人工智能、自动化与“智能代理”能力(Agentic),根本性地改变了黑客松的组织方式与体验路径。
我们正迈入“自主智能创新时代(Age of Agentic Innovation)”,在这个时代中,借助AI代理运行的黑客松可以以前所未有的频率、高效与智慧展开。
那么,究竟什么是Agentic Hackathon?
它是一种由AI代理全面增强的黑客松,从策划、评审到参与者支持都涵盖在内,使得创新的速度与规模达到前所未有的高度。
在Agentic Hackathon中,AI是那位永不疲倦的共同组织者,与人类并肩工作。 过去那些压垮组织者的繁琐流程,如今交由智能算法完成。你可以想象——黑客松几乎在自动运行,如同一场永不停歇的“点子锦标赛”。
借助BUIDL AI,DoraHacks实现了“自驾黑客松”:自主、高效、全天候运行,且可在多个领域同时并行。 这并非科幻小说,而是正在发生的现实。我们来看BUIDL AI是如何运作的,以及它如何将黑客松效率提升十倍以上:
AI驱动的评审与项目筛选:效率提升10倍以上
大型黑客松中最耗时的环节之一就是评审数百个项目提交。传统做法常常需要组织者耗费数周精力,才能从中筛选出有潜力的项目。
BUIDL AI彻底改变了这一切。
它配备了BUIDL Review模块——一个AI驱动的评审系统,能够从多个维度(项目完整性、创意性、主题契合度等)智能分析项目,并自动剔除质量较低的提交[14]。
就像配备了一支随叫随到的专家评审军团。
效果如何?原本需要几百人小时完成的工作,如今几分钟即可完成。
DoraHacks报告称,AI辅助评审已将组织效率提高超过10倍[14]。
想象一下:一项原本需要一个月枯燥工作完成的任务,如今在几天之内搞定,而且评分更一致、公正、透明。 组织者不再淹没在文书工作中,参与者也能更快获得反馈。
当然,AI并不完全取代人工评委——最终决策仍需专家参与,但AI承担了繁重的初审环节。这也意味着:黑客松可放心接纳更多项目提交,因为AI会帮你完成筛选。
不再因为“人手不足”而限制报名人数。
在Agentic Hackathon中,再也没有优秀项目被埋没的遗憾,因为AI确保它们都能被看到。
自动化市场营销与内容讲述:让每场黑客松都自带扩散力
赢得一场黑客松固然令人激动,但如果无人知晓,影响力也就大打折扣。
过去,黑客松结束后,组织者通常需要手动撰写总结、撰文致谢、更新结果——虽然重要,却常常被推迟。
BUIDL AI改变了这一点。
它配备了自动化营销模块,可一键生成黑客松的总结报告与传播内容[14]。
想象这样一个AI,它完整“观察”了整场黑客松(包括提交项目、获奖名单、技术趋势),然后自动撰写出一份专业报道:突出最佳创意、介绍获胜团队、提炼洞察(比如“本次黑客松中60%的项目应用AI于医疗场景”)。
BUIDL AI正是这么做的:自动生成“高光集锦”与总结报告[14]。
这不仅节省了组织者的写作工作,还极大提升了黑客松的传播力。
活动结束数小时内,一份内容丰富的总结即可全球发布,展示创新成果,吸引关注。
赞助方与合作伙伴对此尤为青睐,因为他们的投资能被迅速宣传;参与者也很喜欢,因为自己的项目立刻获得庆祝与曝光。
本质上,每一场黑客松都在讲述一个故事,而BUIDL AI确保这个故事被迅速、广泛地传播。
这种自动化叙事机制,使得黑客松不再是孤立事件,而是持续内容的源泉,为下一场活动积蓄动能。
这是一个良性循环:黑客松产出创新,AI包装传播,传播吸引更多创新者。
一键发起,多黑客松并行:组织者的自由释放
BUIDL AI最具解放性的功能之一,是一键启动黑客松、支持多场并行管理。
过去,发起一场黑客松本身就是一项大型项目:报名系统、评委协调、奖金设计、沟通流程……一切都需人工配置。
DoraHacks的BUIDL AI引入了“一键发起黑客松”工具 [14] 。
组织者只需输入基本信息(主题、奖池、时间、评审规则),平台即自动生成活动页面、提交入口、评审流程等,就像发一篇博客一样简单。
这极大降低了社区与公司举办黑客松的门槛。
如今,即使是一个初创公司或大学社团,也可以轻松举办全球级黑客松,无需专职活动团队。
此外,BUIDL AI还支持多场黑客松的并行管理[14]。
过去,即使是科技巨头也难以同步组织多场黑客松——资源消耗太大。如今,一个生态系统可以同时运行DeFi、AI、 IoT等主题黑客松,背后由AI自动调度。
自BUIDL AI发布以来,组织12场/年,甚至同时运行数场黑客松,从“不可能”变成常规操作[14]。
平台还自动管理参与者接入、发送提醒、通过聊天机器人回答常见问题,确保流程顺畅。
简而言之,BUIDL AI让黑客松主办方像使用云服务器一样“按需发起”创新活动。
这是一场结构性转变:黑客松不再是“偶尔有空才办”的事件,而是“需要时就能发”的常态流程。 我们正在见证永续黑客松文化的诞生——不再是偶尔的火花,而是持续的火焰,始终燃烧,永不熄灭。
实时AI导师与智能助手:人人皆可成为“Agentic Hacker”
Agentic Hackathon的“智能代理”不仅体现在后台,也贯穿了参与者的体验。
借助AI集成,开发者得到了更智能的工具与支持。
例如,BUIDL AI可以配备AI助手,在活动中实时回答开发者问题(如“这个API怎么用?”、“有没有这个算法的代码示 例?”),就像随叫随到的技术导师。
它还可以推荐协作伙伴、推送参考资料。
本质上,每位参与者都像身边多了一个AI队友——全能、勤奋、永不疲倦。
一些本需数小时调试的bug,借助AI助手几分钟即可解决。
这意味着:项目质量提升,参与者学习效率大幅提高。
正如followin.io所言,这种“agentic协助”体现了“人人皆可成为黑客”的愿景[14]。
AI自动化了大量重复性工作,放大了小团队的能力边界[14]。
在Agentic Hackathon中,两个人加AI助手,就能完成过去五人团队数周才能达成的任务[14]。
这既降低了门槛,也拉高了上限——创新的天花板不再遥不可及。
总结:从黑客松2.0跃迁至3.0,进入智能化持续创新的新时代
所有这些变革,指向同一个事实:黑客松已从偶发的灵感爆发,演化为持续、高频、AI优化的创新流程。
我们正从黑客松2.0走向黑客松3.0——一个自主、常驻、智能的新时代。
这是一场范式转移。
黑客松不再是你参加的一场活动,而是你生活的一个创新环境。
借助BUIDL AI,DoraHacks描绘出这样的世界:“黑客松将进入一个前所未有的自动化与智能化时代,使全球更多黑客、开发者与开源社区能够轻松发起与参与。”
创新将随时随地发生,因为支持它的基础设施正由AI驱动、全天候运转于云端。
黑客松已成为一个智能平台,随时准备将创意转化为现实。
更关键的是,这一切并不局限于区块链。
BUIDL AI是通用平台——无论是AI、气候科技、医疗、教育等领域,都可接入Agentic Hackathon平台,享受更高频、更高效的创新节奏。
这预示着一个未来:黑客松将成为默认的解决问题方式。
公司与社区不再靠封闭的委员会与研发部门推进创新,而是将问题投入黑客松竞技场——一个始终活跃的解决问题引擎。
形象地说:
**DoraHacks 1.0 让黑客松拥有了高速引擎;
DoraHacks 2.0 加上 BUIDL AI,则让它变成一辆自动驾驶的赛车——油门踩到底。**
成本、复杂度、时间的阻碍——都不复存在。
如今,任何组织都能毫无阻力地驶入创新高速公路,从0加速到60。
黑客松频率如博客更新,融入日常运营,如同敏捷开发的冲刺演示。
按需创新,规模扩张——这就是Agentic Hackathon的力量。
随需创新:Agentic Hackathon 如何惠及所有人
Agentic Hackathon(自主智能黑客松)的诞生,并非只是技术社区的一款“新奇玩具”,而是一种变革性的工具,可服务于企业、开发者,乃至整个行业。
我们正步入一个全新时代:任何拥有愿景的人都能将“黑客松即服务”转化为推动创新的引擎。以下是不同参与者如何从这场革命中受益:
AI公司 —— 加速生态成长的发动机
对于专注于人工智能的公司(如 OpenAI、Google、Microsoft、Stability AI 等),黑客松是一座座发掘其技术创意用途的金矿。
如今借助 Agentic Hackathon,这些公司几乎可以为自己的平台持续举办一场“永不落幕”的开发者大会。
比如,OpenAI 可以为 GPT-4 或 DALL·E 启动全年在线的黑客松,鼓励全球开发者持续实验、展示这些AI的应用场景——本质上,以众包方式为AI平台孵化创新与杀手级应用。
收益何在?生态系统和用户基数的指数级扩展。
新的用例往往来自公司内部未曾设想的角落。 (最早展示 GPT-3 能撰写法律合同、生成游戏关卡的,不是大公司,而是独立黑客——他们在黑客松和社区挑战中发现了这些潜力。)
有了 BUIDL AI,AI 公司可以一键启动月度黑客松,每月聚焦不同方向(比如本月自然语言处理,下月机器人控制)。 这是市场营销与产品研发的倍增器。
无需再组织昂贵的开发者布道之旅,AI 将成为全球开发者互动的主力军。产品在推广的同时也在优化。 本质上,每家AI公司都可以开启自己的“黑客松联赛”,推动API或模型的普及与应用。
Coinbase最近首次举办AI主题黑客松,尝试连接加密与AI领域——他们很清楚,要播下新范式的种子,黑客松是最佳路径[15] 。
未来,我们将看到所有AI平台效仿:持续通过黑客松教育开发者、生成内容(演示、教程),并发掘可投资/可招聘的杰出人才。这将是社区建设的超级助推器。
L1/L2与技术平台 —— 发现下一只独角兽
对于区块链的一层/二层网络(Layer1/Layer2),以及任何技术平台(如云服务、VR平台等)来说,黑客松已成为新的“Deal Flow”(项目源)。
在 Web3 世界里,许多顶级项目与协议都诞生于黑客松,这一点早已被广泛认同。
我们看到,1inch 就是始于黑客松,后来成长为 DeFi 独角兽(cointelegraph.com)[9]。
Polygon 积极举办黑客松以寻找其生态的新型dApps;Filecoin 借助黑客松发掘分布式存储应用。
借助 DoraHacks 和 BUIDL AI,这些平台现在可以高频率地组织黑客松,持续输出创新成果。
不再是一年一两次大型活动,而是一个滚动进行的计划——比如每季度一场,甚至同时多地开展全球挑战,保持开发者“常态建设”。
回报率巨大:即使设有可观奖金,黑客松的举办成本也远低于收购一个蓬勃发展的初创公司或协议所需投入。 黑客松本质上是将早期研发外包给充满热情的社区成员,最好的创意自然浮现。
Solana 的黑客松就促成了 Phantom、Solend 等明星项目的落地。Facebook 的内部黑客松也曾带来推动平台主导地位的功能创新[1]。
现在,任何平台都可以将黑客松“外部化”:作为发现人才与创新的“雷达”。借助 BUIDL AI,哪怕一个 L2 区块链的核心团队人手有限,也能并行运行多场黑客松与赏金任务——一场关注 DeFi,一场关注 NFT,一场关注游戏等等。
AI 负责初审项目与管理社区问答,让平台的 DevRel 团队不至于“过劳”。结果是,一条源源不断的创新供给链,不断喂养平台增长。下一个独角兽、下一个杀手级应用,将被提前识别并扶持成长。
黑客松已成为 VC 和技术生态的新型创业漏斗(Startup Funnel)。
未来,投资人将活跃于 Agentic Hackathon 中——因为那里正是“未来车库”的所在:黑客们聚集在云端黑客室中重塑世界。
正如 Paul Graham 所言:“黑客与画家,皆为创造者”,他们将在黑客松平台的画布上,描绘未来科技的蓝图。
所有公司与社区 —— 创新成为一种持续流程
或许 BUIDL AI 最深远的影响是:让所有组织都能举办黑客松,不再局限于科技公司。
任何希望推动创新的机构——银行探索金融科技、医院网络寻找医疗科技方案、政府寻找公民科技创意——都可以利用 Agentic Hackathon。
创新不再是巨头的特权,它成为一项“云服务”,人人可用。
比如,一个城市政府可以举办全年黑客松,征集“智慧城市”解决方案,让本地开发者持续提出、建设项目以改善城市生活。
BUIDL AI 平台可以设置不同“赛道”:交通、能源、安全,每月评选最佳创意并给予奖励。
这比传统招标流程更加灵活,能更高效地激发社区活力与项目孵化。
同样地,任何担心被颠覆的财富500强公司(其实谁不担心?)都可以主动“自我颠覆”——通过黑客松邀请员工和外部创新者挑战企业自身难题。
在 agentic 模式下,即使是非技术型公司也能轻松参与;AI 会引导流程,保障运行顺畅。试想:黑客松成为每一家企业战略部门的“标配工具”,不断原型化未来。
正如 Marc Andreessen 所说,“软件正在吞噬整个世界”——而现在,每家公司都可以通过举办黑客松,参与“软件化”自身问题的过程。
这将推动跨行业的创新民主化。
尝试大胆创意的门槛大幅降低(周末黑客松 vs. 数月企业流程),更多潜在颠覆性创意将在企业内部浮现。
有了 DoraHacks 的全球影响力,企业也能轻松吸引外部创新者参与。
零售公司为何不能从全球黑客那里众包 AR 购物创意?
制药公司为何不办场生物信息学黑客松以探索数据分析新方法?
答案只有一个:没有理由不做。Agentic Hackathon 让一切变得可行、值得。
黑客松即服务(Hackathon-as-a-Service)将成为下一代的创新部门——要么使用它,要么被使用它的人超越。
结语:从偶发事件到创新基础设施的演进
所有上述变革,归结为一个深刻转变:黑客松正从一次性的活动,演变为创新生态系统中的常驻组成部分。
它们正成为像云计算、宽带网络一样的基础资源:随时可用,规模无限。
想获得新点子或原型?办场黑客松,让全球开发者接招。
想激活开发者社群?发布主题黑客松,提供舞台。
想试验10种解决方案?来一场比赛,看看谁跑出来。
我们正在见证所谓“创新公地(Innovation Commons)”的诞生:一个持续匹配问题与创意、迅速迭代解决方案的协 作空间。
AI是这片公地的维护者,保证运行高效、协作持久,不再需要消耗人为组织者的精力。
这也正好回应了人们对黑客松的批评:缺乏可持续性与后续跟进。
而在Agentic模型中,黑客松不再是孤岛——它们可以彼此衔接:上届的优胜团队可以直接晋级加速器,或参与下月的 新主题挑战。
BUIDL AI 甚至可以追踪团队进展,推荐资助机会、合作方、甚至下一步要申请的Grant,彻底解决过去“项目周末之后无人接手”的痛点。
好项目不会在周日夜晚“死掉”,而是被自动引导进入下一阶段的旅程。
我们还应认识到一种更深层的哲学意义:
创新文化,变得更具实验性、更重才智、更具节奏感。
在Agentic Hackathon的世界中,座右铭是:“为啥不原型一下?为啥不现在就试?”
因为启动一场实验的门槛如此之低,创新思维将像空气般流入每一个组织、每一个社区。
失败的成本极低(只需几周),成功的可能却极高(也许就是下一个突破)。
这是一块供“颠覆性想法”安全试验的沙盒,也正是解决《创新者的窘境》的现实路径:
结构性地为那些被视为“玩具”的想法,保留生长空间[5]。
企业无需在“核心业务”与“实验创新”之间二选一——他们可以为后者开设一条常驻黑客松轨道。
本质上,DoraHacks 与 BUIDL AI 打造了一座“创新工厂”——任何有远见的组织都可以“租用”一周末,甚至一年。
从 Like 按钮到点火升空:黑客松是创新的摇篮
要真正理解这个新时代的分量,我们不妨回顾一下——多少改变世界的创新,其实起源于黑客松项目或类似黑客松的实验,即使当时还受限于旧有模式。而现在,随着这些限制被移除,我们能期待的,将远远不止于此。 历史本身,就是黑客松创新模式的最佳佐证:
Facebook 的基因,由黑客松塑造
马克·扎克伯格本人曾表示,Facebook 的许多关键功能都来自公司内部的黑客松:“点赞”按钮、Facebook Chat、时间线功能,无一不是工程师们在通宵达旦的黑客松中迸发出的创意[1]。
一位实习生在黑客松中构建的“评论区标记好友”原型,在短短两周后就上线,触达了十亿用户[1]。Facebook 的核心理念“Move fast and break things(快速行动,大胆试错)”,几乎就是黑客松精神的官方化表达。
可以毫不夸张地说,Facebook 能在2000年代超越 MySpace,正是得益于其由黑客松推动的快速创新文化[1]。
如果黑客松能在一家公司的内部产生如此颠覆性作用,想象一下——当它成为全球网络时,创新的速度将怎样改变整个世界?
Google 的“20% 时间”项目:制度化的黑客精神
Google 长期鼓励员工将20%的时间投入到自由探索的副项目中,这本质上是黑客松理念的延伸:结构外的探索实验。 Gmail 和 Google News 就是这样诞生的。
此外,Google 也曾围绕其 API 举办公开黑客松(如 Android 黑客松),催生了无数应用。
换句话说,Google 将黑客式实验制度化,获得了巨大的创新红利。
如今借助 Agentic Hackathon,即便没有 Google 资源的公司,也能制度化实验文化。
世界各地的开发者,都可以把每个周末当作自己的“20%时间”,借由这些平台启动属于自己的探索。
开源运动的推进器:Hackathons + Open Source = 强生态
开源软件世界也从“代码冲刺”(黑客松形式)中受益匪浅。
例如整个 OpenBSD 操作系统的开发就离不开其定期举办的黑客松[3]。
近年来,Node.js 与 TensorFlow 等项目也都通过黑客松来构建工具与生态组件。
其结果是:更强壮的技术生态,更活跃的贡献者社群。
DoraHacks 也在延续这种传统,并将自己定位为“全球领先的黑客松社区与开源开发者激励平台”[17]。
开源与黑客松的结合——都去中心化、社群驱动、基于 meritocracy(才智主义)——本身就是创新引擎。
我们可以预见,未来开源项目将借助 BUIDL AI 启动“永不停歇的黑客松”:持续修复 bug、加入新功能、奖励优秀贡献者。
这将为开源世界注入新生命——不仅通过奖金提供激励,还能以系统化的方式提供认可与传播。
初创世界:黑客松造就新公司
众多初创企业的起点,都是黑客松。 我们已提到的 Carousell(起于Startup Weekend,估值超10亿美元[2])、EasyTaxi(同样出自Startup Weekend,融资7500万美元[2])。 再加上:
- Zapier(集成工具平台,灵感来自黑客松)
- GroupMe(如前所述,被Skype收购)
- Instacart(传说在Y Combinator Demo Day 黑客松中以早期版本夺得优胜)
- 以及无数加密初创项目(包括 Ethereum 创始人们的相识与合作也源于早期黑客松与比特币线下聚会)
如今,当 Coinbase 想寻找链上 AI 的下一个机会时,他们办一场黑客松[15]。
Stripe 想推动支付平台上的应用数量,也选择了办黑客松并发放 Bounty。
这种模式行之有效:找到充满热情的构建者,为他们提供跳板。
有了 Agentic Hackathon,这个跳板不再只是弹射一次,而是始终在线,能接住更多人。
这个“创业漏斗”变宽了,我们将看到更多初创企业诞生于黑客松。
完全可以想象:
2030年代最伟大的公司,不会诞生于车库,而是源自一场在线黑客松,由几个在 Discord 上认识的开发者,在 AI 导师协助下完成原型,并在 DoraHacks 平台数周内获得融资。
换句话说,“车库神话”已进化为全球、云端、AI驱动的创业现实。
黑客与画家:创造者的共鸣
Paul Graham 在《Hackers & Painters》中曾将“黑客”比作“画家”——两者皆为纯粹的创作者[16]。
而黑客松,正是这种创造能量最集中、最爆发的场域。
许多伟大程序员都会告诉你,他们最具灵感的作品,正是在黑客松或秘密小项目中完成的——在没有官僚主义的束缚 下,沉浸于“心流”中完成的创作。
扩大黑客松的规模与频率,本质上就是扩大人类的创造力边界。
我们或许会想起文艺复兴时期——艺术家与发明家聚集在赞助人举办的工坊中自由创作;而如今,黑客松就是现代文艺复兴的“创客工坊”。
它融合了艺术、科学与企业家精神。
若达·芬奇活在今天,他一定会如鱼得水地出现在黑客松中——他以疯狂原型迭代著称。
更重要的是:黑客松完美解决了《创新者的窘境》中的核心问题:鼓励人们去做那些 incumbent(巨头)不屑一顾、看似“小而无用”的项目——而那恰恰往往是颠覆性创新的藏身之处 [5]。
DoraHacks 正是通过制度化黑客松,制度化了颠覆本身——确保下一个 Netflix、Airbnb,不会因为“听起来像个玩具”而被错过。
黑客松已成为全球创新基础设施的一部分
我们已从“黑客松罕见且本地化”的时代,走到了“黑客松持续且全球化”的今天。
这不仅是节奏上的转变,更是全球创新基础设施的关键转折点。
19世纪,我们修建了铁路与电报,催化了工业革命,连接了市场与思想;
20世纪,我们构建了互联网与万维网,引爆了信息革命;
而今,21世纪,DoraHacks 与 BUIDL AI 正在搭建“创新高速公路”:一个持续运行、AI驱动的网络,
在全球范围内,实时连接解决者与问题、人才与机会、资本与创意。
这是为 创新本身修建的基础设施。
伟大的愿景:全球创新的新基础设施
我们正站在一个历史拐点上。
有了 DoraHacks 和 Agentic Hackathon(自主智能黑客松)的出现,创新不再局限于象牙塔、硅谷办公室,或一年一度的大会。
它正成为一项持续的全球性活动——一个随时随地聚集最聪明头脑与最大胆创意的竞技场。
这是一个未来:创新将像 Wi-Fi 一样无处不在,像摩尔定律一样不断加速。
这是 DoraHacks 正在主动构建的未来,而它所带来的影响将是深远的。
想象几年之后的世界:DoraHacks + BUIDL AI 成为跨行业创新项目的默认基础设施。
这个平台7×24不间断运转,承载着从 AI 医疗、气候变化应对,到艺术娱乐前沿的各类黑客松。
而且它不仅仅属于程序员——设计师、创业者、科学家,任何有创造力冲动的人,都能接入这张全球创新网络。
一个伦敦的创业者凌晨2点冒出商业点子;2点15分,她就在 DoraHacks 上发起一场48小时黑客松,AI 自动为她召集来自四大洲的协作者。
听起来疯狂?但未来这将成为常态。
亚洲某国突发环境危机,政府通过 BUIDL AI 紧急发起黑客松,数日内即收到来自全球的数十个可执行科技方案。 纽约某家风投基金希望发现新项目,不再只是等着 PPT 投递——他们直接赞助一场开放黑客松,要求提交原型,而非空谈构想。
这就是 Agentic 创新正在发生的方式:快速、无边界、智能协作。 在这个即将到来的时代,DoraHacks 将如同 GitHub 之于代码、AWS 之于初创企业一般,成为全球创新的基础平台。
你甚至可以称它为创新的 GitHub——不是一个存储代码的工具,而是项目诞生的土壤[17]。 DoraHacks 自称是“全球黑客运动的引擎”;而有了 BUIDL AI,它更成为这场运动的自动驾驶系统。
我们应将其视为全球公共创新基础设施的一部分:
正如高速公路运输货物、互联网传递信息,DoraHacks 传递的是创新本身——
从创意萌芽到落地实施,以惊人的速度。
当历史回顾2020年代,持续性、AI驱动的黑客松的诞生,将被视为人类创新模式变革的重要篇章。
这是一幅宏大但真实可触的愿景:
创新,将变成一场永恒的黑客松。
设想一下:
黑客精神深入社会每个角落,成为对现状的持续挑战,时刻发出这样的提问:
“我们如何改进这件事?”、“我们如何重新发明那件事?”
然后立刻号召人才,迅速投入行动。
这不是混乱,而是一种全新的、有组织、去中心化的研发模式。
一个大胆问题——“我们能治愈这种疾病吗?”、“我们能否让儿童教育更高效?”、“我们能不能让城市真正可持续?”—— 不再需要靠闭门造车的委员会来思考十年,而是一场全球黑客松,就可能在几天或几周内产生答案。 这将是一个创新不再稀缺、不再由少数人垄断,而是成为一项公共物品的世界。
一场开放的、胜者为王的比赛,不管解决方案来自斯坦福博士,还是拉各斯的自学黑客,只要够好,就能脱颖而出。 如果你觉得这听起来太理想,请看看我们已经走了多远:
黑客松从一个名不见经传的程序员聚会,变成了支撑十亿美元企业和全球关键技术的创新机制。 (别忘了,比特币本身就是黑客文化的产物!)
随着 DoraHacks 的壮大和 BUIDL AI 的腾飞,黑客松正朝着持续化与无处不在的方向稳步推进。 技术已经准备就绪,模式已经跑通,现在的关键是执行与普及。
而趋势已然明朗:
- 越来越多公司拥抱开放创新;
- 越来越多开发者远程工作、参与在线社区;
- AI 正快速成为每个创造过程的副驾驶。
DoraHacks 正站在这场转型的核心。
它拥有先发优势、全球社区、明确愿景。
他们的理念非常清晰:“为黑客运动提供永恒燃料”是他们的口号之一[18]。
在他们眼中,黑客松不仅是活动,更是一场必须永续进行的思维革命。 而 BUIDL AI,正是支撑这场永续革命的引擎。
这预示着一个未来:
DoraHacks + BUIDL AI,将成为全球创新关键基础设施的一部分,就像公共事业一样。
这是一张“创新电网”;一旦接入它,奇迹发生。
Marc Andreessen 常在文章中以“建造更好的未来”为信条,热情洋溢地谈论人类的进步。
如果秉持这一精神,我们可以大胆断言:
Agentic Hackathon 将重塑我们的未来——更快、更好。
它们将加速人类解决最难问题的速度,
动员更广泛的人才库,
以史无前例的节奏不断迭代方案。
它们将赋能每一个人——让地球上任何拥有创造力的人,立即就能获得工具、社群和机会,产生真正的影响,而不是“未来某天”。
这是一种深层次的民主化。
它呼应了早期互联网的精神:不需许可的创新(Permissionless Innovation)。
而 DoraHacks 正在将这一精神引入结构化的创新事件中,并将其延展为一种持久的创新模式。
总结:我们正目睹一场范式的彻底转变:黑客松被重塑,创新被解放。
旧模型的限制已被打破,
新范式的核心是:
高频黑客松、AI增强、结果导向。
DoraHacks 在 2020–2024 年引领了这场变革,
而随着 BUIDL AI 的登场,它即将开启下一个篇章——Agentic Innovation 的时代。
对投资者与有远见的领袖而言,这是一场集结号。
我们常说要“投资基础设施”,
那么现在,就是投资“创新本身的基础设施”。
支持 DoraHacks 和它的使命,
就像支持跨洲铁路或洲际高速的建造者,
只不过这次运载的是创意与突破。
网络效应巨大:每一场新增的黑客松、每一位新增的参与者,
都以复利效应提升整个生态系统的价值。
这是一场正和博弈(Positive-Sum Game),
DoraHacks 将是那个创造并捕捉全球价值的平台与社区。
DoraHacks 重新定义了黑客松:
它将黑客松从偶发行为变成了持续创新的系统方法。
在这个过程中,它敞开了创新之门,
引领我们进入一个全新的时代:
一个创新可以自主驱动、自组织、永不停歇的时代。
我们正站在这个新时代的黎明。
这是一个真正意义上:
拥有开发者,拥有世界的时代[14] 。
DoraHacks 正在确保:
无论你身在何处,只要你是开发者、黑客、梦想家,
你都能为这个世界的未来贡献力量。
前方的远景令人震撼——一个由全球黑客思维构成的智能蜂巢,
不断发明、持续发现,
由 AI 指引航向,
由 DoraHacks 与 BUIDL AI 领航。
这不仅仅是一个平台,
它是一项革命性的基础设施——创新的铁路,创意的高速。
请系好安全带:
DoraHacks 已经启程,
Agentic Innovation 的时代已经到来,
未来正以黑客松的速度,向我们疾驰而来。
这场黑客松,永不停歇。
而这,正是我们构建更美好世界的方式。
参考文献:
[1] Vocoli. (2015). Facebook’s Secret Sauce: The Hackathon . https://www.vocoli.com/blog/june-2015/facebook-s-secret-sauce-the-hackathon/
[2] Analytics India Magazine. (2023). Borne Out Of Hackathons . https://analyticsindiamag.com/ai-trends/borne-out-of-hackathons/
[3] Wikipedia. (n.d.). Hackathon: Origin and History . https://en.wikipedia.org/wiki/Hackathon#Origin_and_history
[4] LinkedIn. (2024). This year marked my third annual participation in Microsoft’s Global… . https://www.linkedin.com/posts/clare-ashforth_this-year-marked-my-third-annual-participation-activity-7247636808119775233-yev-
[5] Glasp. (n.d.). Chris Dixon’s Quotes . https://glasp.co/quotes/chris-dixon
[6] ODaily. (2024). Naija HackAtom Hackathon Recap . https://www.odaily.news/en/post/5203212
[7] Solana. (2021). Meet the winners of the Riptide hackathon - Solana . https://solana.com/news/riptide-hackathon-winners-solana
[8] DoraHacks. (n.d.). BNB Grant DAO - DoraHacks . https://dorahacks.io/bnb
[9] Cointelegraph. (2021). From Hackathon Project to DeFi Powerhouse: AMA with 1inch Network . https://cointelegraph.com/news/from-hackathon-project-to-defi-powerhouse-ama-with-1inch-network
[10] Gemini. (2022). How Does STEPN Work? GST and GMT Token Rewards . https://www.gemini.com/cryptopedia/stepn-nft-sneakers-gmt-token-gst-crypto-move-to-earn-m2e
[11] CoinDesk. (2022). Inside DoraHacks: The Open Source Bazaar Empowering Web3 Innovations . https://www.coindesk.com/sponsored-content/inside-dorahacks-the-open-source-bazaar-empowering-web3-innovations
[12] LinkedIn. (n.d.). DoraHacks . https://www.linkedin.com/company/dorahacks
[13] Blockworks. (2022). Web3 Hackathon Incubator DoraHacks Nabs $20M From FTX, Liberty City . https://blockworks.co/news/web3-hackathon-incubator-dorahacks-nabs-20m-from-ftx-liberty-city
[14] Followin. (2024). BUIDL AI: The future of Hackathon, a new engine for global open source technology . https://followin.io/en/feed/16892627
[15] Coinbase. (2024). Coinbase Hosts Its First AI Hackathon: Bringing the San Francisco Developer Community Onchain . https://www.coinbase.com/developer-platform/discover/launches/Coinbase-AI-hackathon
[16] Graham, P. (2004). Hackers & Painters . https://ics.uci.edu/~pattis/common/handouts/hackerspainters.pdf
[17] Himalayas. (n.d.). DoraHacks hiring Research Engineer – BUIDL AI . https://himalayas.app/companies/dorahacks/jobs/research-engineer-buidl-ai
[18] X. (n.d.). DoraHacks . https://x.com/dorahacks?lang=en
-
 @ a5142938:0ef19da3
2025-05-02 13:12:56
@ a5142938:0ef19da3
2025-05-02 13:12:56ManyMonths is a Finnish brand that creates adjustable clothing for babies and children, made from organic cotton, hemp, and merino wool.
Natural materials used in products
⚠️ Warning: some products from this brand (especially Catégorie niv 2 - catégorie niv 3, catégorie niv 3, catégorie niv3) contain non-natural materials, including:
Categories of products offered
-
Clothing : baby, child, bodysuits, scarves, hoods, balaclavas, jackets, shorts, pants, skirts, t-shirts, leggings, hats, dresses, tank tops, fingerless gloves, mittens...
Other information
- GOTS® Certification (factory in Chine)
- Oeko-Tex® Standard 100 Certification
- Made in China
👉 Learn more on the brand's website
This article is published on origin-nature.com 🌐 Voir cet article en français
📝 You can contribute to this entry by suggesting edits in comments.
🗣️ Do you use this product? Share your opinion in the comments.
⚡ Happy to have found this information? Support the project by making a donation to thank the contributors.
-
-
 @ 3ffac3a6:2d656657
2025-05-02 03:50:51
@ 3ffac3a6:2d656657
2025-05-02 03:50:51Introduction: Don't Despair—This Can Be Fixed (But Don't Reboot Yet)
Running ZFS on a Raspberry Pi offers powerful features for home servers and personal NAS setups. But with power comes complexity, and in recent months, a quiet pitfall has emerged for Pi users who track kernel updates closely: upgrading to an unsupported kernel version breaks ZFS.
⚠️ Important Warning: If you've just upgraded your kernel and you're using ZFS, do not reboot yet. Rebooting without a working ZFS module can leave your system unbootable—even if you don't have critical partitions on ZFS. The system may hang because it tries to load the missing ZFS kernel module during boot and fails, halting the boot process.
If you're already facing a broken setup or can't boot — don't panic. This guide outlines both the worst-case scenario and the ideal recovery strategy. Whether you're locked out or preparing for a smooth upgrade, we've got you covered.
The Problem: A Kernel Update Too Far
As of ZFS version 2.2.3 (used in Debian-based Raspberry Pi OS), the filesystem supports Linux kernels up to 6.7. However, Raspberry Pi OS backports recently began shipping 6.12.x kernels. If you upgrade to 6.12 without precautions:
- ZFS will fail to compile against the new kernel
- DKMS errors will appear during package updates
- Your ZFS module will be missing after reboot
- Your Raspberry Pi may fail to boot, even without ZFS-mounted root or critical paths, simply due to systemd or boot scripts expecting the kernel module to be present
Example ZFS Compilation Error:
During package updates or installs, you'll see something like:
checking whether bdev_open_by_path() exists... configure: error: *** None of the expected "blkdev_get_by_path()" interfaces were detected. *** This may be because your kernel version is newer than what is *** supported, or you are using a patched custom kernel with *** incompatible modifications. *** *** ZFS Version: zfs-2.2.3-1~bpo12+1~rpt1 *** Compatible Kernels: 3.10 - 6.7This error means ZFS cannot build its kernel module against Linux 6.12.x, making it unusable.
Why This Happens: The Version Trap
The key problem is that ZFS 2.2.3 remains installed even after a kernel upgrade, and it doesn't get upgraded automatically during
apt upgrade. Since ZFS 2.2.3 only supports up to kernel 6.7, it fails to compile against 6.12.x.However, if you remove and then reinstall ZFS, the package manager installs ZFS 2.3.1, which does support Linux kernel 6.12.x. This version transition is what resolves the issue — but only if you explicitly purge and reinstall ZFS.
Worst Case: The System That Wouldn’t Boot
After upgrading the kernel and rebooting, the system failed to boot properly. It showed errors like:
cannot open access to console, the root account is locked
Although the system did not have critical filesystems on ZFS, the boot process still stalled because system services attempted to load the ZFS kernel module, which was no longer available. This resulted in an unrecoverable boot failure.
The only way forward was to reformat and reinstall Raspberry Pi OS. However, the default Raspberry Pi OS image still comes with a 6.6.x kernel, which is incompatible with ZFS 2.3.1 and newer kernels unless upgraded. Therefore, the recovery process requires one crucial step:
- First, perform a full system upgrade:
sudo apt update && sudo apt full-upgradeThis brings the kernel up to 6.12.x.
- Then, reinstall ZFS:
sudo apt install zfs-dkms zfsutils-linuxOnce this is complete, your system will be running kernel 6.12 with ZFS 2.3.1, and you can safely import your pools and resume operations.
Best Case Recovery: Clean Cut, Clean Upgrade
For users who can still log into their system, here's the cleanest and safest sequence to move forward:
- Stop all services using ZFS, including Docker, NFS, Samba, backup tools, etc.
- Export all ZFS pools:
sudo zpool export -a3. Disable swap if it lives on a ZFS vdev:sudo swapoff /dev/sdXn4. Purge ZFS packages:sudo apt purge zfsutils-linux zfs-dkms zfs-zed sudo rm -rf /usr/src/zfs* /var/lib/dkms/zfs5. Update the kernel to the desired version:sudo apt update && sudo apt full-upgrade6. Reboot into the new kernel:sudo reboot7. Reinstall ZFS:sudo apt install zfs-dkms zfsutils-linux8. Import your pool(s):sudo zpool import poolname9. Restart services that depend on ZFS.
Final Notes: Prevention Is Better Than Recovery
To avoid this issue in the future:
- Hold your current working kernel version:
sudo apt-mark hold linux-image-rpi-v8 linux-headers-rpi-v8* Or track ZFS GitHub for kernel compatibility before upgrading * Or test upgrades on a second Pi or cloned SD card before rolling them out to production
Conclusion: A Solvable Trap
ZFS on the Raspberry Pi remains a powerful option, but it demands careful version tracking. If you upgrade responsibly, or recover cleanly as described above, you can continue benefiting from advanced features like snapshots, send/receive, and compression even on this tiny powerhouse.
Don’t let a kernel update ruin your storage plans—with preparation, the Pi + ZFS combo can remain stable and strong.
-
 @ 21335073:a244b1ad
2025-05-01 01:51:10
@ 21335073:a244b1ad
2025-05-01 01:51:10Please respect Virginia Giuffre’s memory by refraining from asking about the circumstances or theories surrounding her passing.
Since Virginia Giuffre’s death, I’ve reflected on what she would want me to say or do. This piece is my attempt to honor her legacy.
When I first spoke with Virginia, I was struck by her unshakable hope. I had grown cynical after years in the anti-human trafficking movement, worn down by a broken system and a government that often seemed complicit. But Virginia’s passion, creativity, and belief that survivors could be heard reignited something in me. She reminded me of my younger, more hopeful self. Instead of warning her about the challenges ahead, I let her dream big, unburdened by my own disillusionment. That conversation changed me for the better, and following her lead led to meaningful progress.
Virginia was one of the bravest people I’ve ever known. As a survivor of Epstein, Maxwell, and their co-conspirators, she risked everything to speak out, taking on some of the world’s most powerful figures.
She loved when I said, “Epstein isn’t the only Epstein.” This wasn’t just about one man—it was a call to hold all abusers accountable and to ensure survivors find hope and healing.
The Epstein case often gets reduced to sensational details about the elite, but that misses the bigger picture. Yes, we should be holding all of the co-conspirators accountable, we must listen to the survivors’ stories. Their experiences reveal how predators exploit vulnerabilities, offering lessons to prevent future victims.
You’re not powerless in this fight. Educate yourself about trafficking and abuse—online and offline—and take steps to protect those around you. Supporting survivors starts with small, meaningful actions. Free online resources can guide you in being a safe, supportive presence.
When high-profile accusations arise, resist snap judgments. Instead of dismissing survivors as “crazy,” pause to consider the trauma they may be navigating. Speaking out or coping with abuse is never easy. You don’t have to believe every claim, but you can refrain from attacking accusers online.
Society also fails at providing aftercare for survivors. The government, often part of the problem, won’t solve this. It’s up to us. Prevention is critical, but when abuse occurs, step up for your loved ones and community. Protect the vulnerable. it’s a challenging but a rewarding journey.
If you’re contributing to Nostr, you’re helping build a censorship resistant platform where survivors can share their stories freely, no matter how powerful their abusers are. Their voices can endure here, offering strength and hope to others. This gives me great hope for the future.
Virginia Giuffre’s courage was a gift to the world. It was an honor to know and serve her. She will be deeply missed. My hope is that her story inspires others to take on the powerful.
-
 @ 5cb68b7a:b7cb67d5
2025-05-04 00:13:44
@ 5cb68b7a:b7cb67d5
2025-05-04 00:13:44Losing access to your cryptocurrency can feel like losing a part of your future. Whether it’s a forgotten password, a damaged seed backup, or simply one wrong transfer, the stress can be overwhelming. But there’s a silver lining — Crypt Recver is here to help! With our expert-led recovery services, you can reclaim your lost Bitcoin and other cryptos safely and swiftly.
Why Trust Crypt Recver? 🤝 🛠️ Expert Recovery Solutions At Crypt Recver, we specialize in resolving some of the most complex wallet-related issues. Our team of skilled engineers has the tools and expertise to tackle:
Partially lost or forgotten seed phrases Extracting funds from outdated or invalid wallet addresses Recovering data from damaged hardware wallets Restoring coins from old or unsupported wallet formats You’re not just getting a service; you’re gaining a partner in your cryptocurrency journey.
🚀 Fast and Efficient Recovery We understand that time is critical in crypto recovery. Our optimized systems ensure that you can regain access to your funds quickly, aiming for speed without sacrificing security. With a 90%+ success rate, you can trust us to fight against the clock on your behalf.
🔒 Privacy is Our Priority Your confidentiality matters. Every recovery session is handled with the utmost care, ensuring all processes are encrypted and confidential. You can rest easy, knowing your sensitive information stays private.
💻 Advanced Technology Our proprietary tools and brute-force optimization techniques allow for maximum efficiency in recovery. No matter how challenging your case may be, our technology is designed to give you the best chance at getting your crypto back.
Our Recovery Services Include: 📈 Bitcoin Recovery: Lost access to your Bitcoin wallet? We help recover lost wallets, private keys, and passphrases. Transaction Recovery: Mistakes happen — whether it’s an incorrect wallet address or a lost password, let us handle the recovery. Cold Wallet Restoration: If your cold wallet is failing, we can safely extract your assets and migrate them into a secure, new wallet. Private Key Generation: Lost your private key? Don’t worry. Our experts can help you regain control using advanced methods — all while ensuring your privacy remains intact. ⚠️ What We Don’t Do While we can handle many scenarios, there are some limitations. For example, we cannot recover funds stored in custodial wallets, or cases where there is a complete loss of four or more seed words without any partial info available. We’re transparent about what’s possible, so you know what to expect.
Don’t Let Lost Crypto Hold You Back! ⏳ Did you know that 3 to 3.4 million BTC — nearly 20% of the total supply — are estimated to be permanently lost? Don’t become part of that statistic! Whether it’s due to a forgotten password, sending funds to the wrong address, or damaged drives, we can help you navigate through it all.
🛡️ Real-Time Dust Attack Protection Protecting your privacy goes beyond just recovery. Our services include dust attack protection, which keeps your activity anonymous and your funds secure. Our suite will shield your identity from unwanted tracking, ransomware, and phishing attempts.
🎉 Start Your Recovery Journey Today! Are you ready to reclaim your lost crypto? Don’t wait until it’s too late!
👉 Request Wallet Recovery Help Now!
📞 Need Immediate Assistance? Connect with Us! For real-time support or questions, reach out to our dedicated team on:
✉️ Telegram: Chat with Us on Telegram 💬 WhatsApp: Message Us on WhatsApp Crypt Recver is your trusted partner in the world of cryptocurrency recovery. Let us turn your challenges into victories. Don’t hesitate — your crypto future starts now! 🚀✨
Act fast and secure your digital assets with Crypt Recver!Losing access to your cryptocurrency can feel like losing a part of your future. Whether it’s a forgotten password, a damaged seed backup, or simply one wrong transfer, the stress can be overwhelming. But there’s a silver lining — Crypt Recver is here to help! With our expert-led recovery services, you can reclaim your lost Bitcoin and other cryptos safely and swiftly.
 # Why Trust Crypt Recver? 🤝
# Why Trust Crypt Recver? 🤝🛠️ Expert Recovery Solutions
At Crypt Recver, we specialize in resolving some of the most complex wallet-related issues. Our team of skilled engineers has the tools and expertise to tackle:
- Partially lost or forgotten seed phrases
- Extracting funds from outdated or invalid wallet addresses
- Recovering data from damaged hardware wallets
- Restoring coins from old or unsupported wallet formats
You’re not just getting a service; you’re gaining a partner in your cryptocurrency journey.
🚀 Fast and Efficient Recovery
We understand that time is critical in crypto recovery. Our optimized systems ensure that you can regain access to your funds quickly, aiming for speed without sacrificing security. With a 90%+ success rate, you can trust us to fight against the clock on your behalf.
🔒 Privacy is Our Priority
Your confidentiality matters. Every recovery session is handled with the utmost care, ensuring all processes are encrypted and confidential. You can rest easy, knowing your sensitive information stays private.
💻 Advanced Technology
Our proprietary tools and brute-force optimization techniques allow for maximum efficiency in recovery. No matter how challenging your case may be, our technology is designed to give you the best chance at getting your crypto back.
Our Recovery Services Include: 📈
- Bitcoin Recovery: Lost access to your Bitcoin wallet? We help recover lost wallets, private keys, and passphrases.
- Transaction Recovery: Mistakes happen — whether it’s an incorrect wallet address or a lost password, let us handle the recovery.
- Cold Wallet Restoration: If your cold wallet is failing, we can safely extract your assets and migrate them into a secure, new wallet.
- Private Key Generation: Lost your private key? Don’t worry. Our experts can help you regain control using advanced methods — all while ensuring your privacy remains intact.
⚠️ What We Don’t Do
While we can handle many scenarios, there are some limitations. For example, we cannot recover funds stored in custodial wallets, or cases where there is a complete loss of four or more seed words without any partial info available. We’re transparent about what’s possible, so you know what to expect.
 # Don’t Let Lost Crypto Hold You Back! ⏳
# Don’t Let Lost Crypto Hold You Back! ⏳Did you know that 3 to 3.4 million BTC — nearly 20% of the total supply — are estimated to be permanently lost? Don’t become part of that statistic! Whether it’s due to a forgotten password, sending funds to the wrong address, or damaged drives, we can help you navigate through it all.
🛡️ Real-Time Dust Attack Protection
Protecting your privacy goes beyond just recovery. Our services include dust attack protection, which keeps your activity anonymous and your funds secure. Our suite will shield your identity from unwanted tracking, ransomware, and phishing attempts.
🎉 Start Your Recovery Journey Today!
Are you ready to reclaim your lost crypto? Don’t wait until it’s too late!
👉 Request Wallet Recovery Help Now!
📞 Need Immediate Assistance? Connect with Us!
For real-time support or questions, reach out to our dedicated team on:
- ✉️ Telegram: Chat with Us on Telegram
- 💬 WhatsApp: Message Us on WhatsApp
Crypt Recver is your trusted partner in the world of cryptocurrency recovery. Let us turn your challenges into victories. Don’t hesitate — your crypto future starts now! 🚀✨
Act fast and secure your digital assets with Crypt Recver!
-
 @ a5142938:0ef19da3
2025-05-02 12:50:48
@ a5142938:0ef19da3
2025-05-02 12:50:48🧵 Products made from this material
The following brands offer products made exclusively or primarily from this material:
Clothing
This article is published on origin-nature.com 🌐 Voir cet article en français
-
 @ a5142938:0ef19da3
2025-05-02 12:31:35
@ a5142938:0ef19da3
2025-05-02 12:31:35Dilling is a Danish brand that creates wool, silk, and organic cotton clothing for the whole family.
Natural materials used in products
- Cotton (organic)
- Natural latex (OEKO-TEX ®)
- Silk
- Wool (merino, alpaca)
⚠️ Warning: some products from this brand (especially Clothes – socks, jackets, thongs, shorts) contain non-natural materials, including:
- Elastane, spandex, lycra
- Polyamide, nylon (recycled nylon)
- Polyester (recycled)
Categories of products offered
-
Clothing : men, women, children, babies, underwear, t-shirts, tank tops, dresses, jackets, trousers, shorts, sweaters, cardigans, bodysuits, jumpsuits, panties, briefs, boxers...
Other information
- Nordic Swan ecolabel (dye)
- Made in Lithuania (cutting and sewing)
- Made in Denmark (dye)
- Made in Europe
👉 Learn more on the brand's website
This article is published on origin-nature.com 🌐 Voir cet article en français
📝 You can contribute to this entry by suggesting edits in comments.
🗣️ Do you use this product? Share your opinion in the comments.
⚡ Happy to have found this information? Support the project by making a donation to thank the contributors.
-
 @ 5df413d4:2add4f5b
2025-05-04 00:06:31
@ 5df413d4:2add4f5b
2025-05-04 00:06:31This opinion piece was first published in BTC Magazine on Feb 20, 2023
Just in case we needed a reminder, banks are showing us that they can and will gatekeep their customers’ money to prevent them from engaging with bitcoin. This should be a call to action for Bitcoiners or anyone else who wants to maintain control over their finances to move toward more proactive use of permissionless bitcoin tools and practices.
Since January of 2023, when Jamie Dimon decried Bitcoin as a “hyped-up fraud” and “a pet rock,” on CNBC, I've found myself unable to purchase bitcoin using my Chase debit card on Cash App. And I'm not the only one — if you have been following Bitcoin Twitter, you might have also seen Alana Joy tweet about her experience with the same. (Alana Joy Twitter account has since been deleted).
In both of our cases, it is the bank preventing bitcoin purchases and blocking inbound fiat transfers to Cash App for customers that it has associated with Bitcoin. All under the guise of “fraud protection,” of course.
No, it doesn’t make a whole lot of sense — Chase still allows ACH bitcoin purchases and fiat on Cash App can be used for investing in stocks, saving or using Cash App’s own debit card, not just bitcoin — but yes, it is happening. Also, no one seems to know exactly when this became Chase’s policy. The fraud representative I spoke with wasn’t sure and couldn’t point to any documentation, but reasoned that the rule has been in place since early last year. Yet murkier still, loose chatter can be found on Reddit about this issue going back to at least April 2021.
However, given that I and so many others were definitely buying bitcoin via Chase debit throughout 2021 and 2022, I’d wager that this policy, up to now, has only been exercised haphazardly, selectively, arbitrarily, even. Dark patterns abound, but for now, it seems like I just happen to be one of the unlucky ones…
That said, there is nothing preventing this type of policy from being enforced broadly and in earnest by one or many banks. If and as banks feel threatened by Bitcoin, we will surely see more of these kinds of opaque practices.
It’s Time To Get Proactive
Instead, we should expect it and prepare for it. So, rather than railing against banks, I want to use this as a learning experience to reflect on the importance of permissionless, non-KYC Bitcoining, and the practical actions we can take to advance the cause.
Bank with backups and remember local options. Banking is a service, not servitude. Treat it as such. Maintaining accounts at multiple banks may provide some limited fault tolerance against banks that take a hostile stance toward Bitcoin, assuming it does not become the industry norm. Further, smaller, local and regional banks may be more willing to work with Bitcoiner customers, as individual accounts can be far more meaningful to them than they are to larger national banks — though this certainly should not be taken for granted.
If you must use KYC’d Bitcoin services, do so thoughtfully. For Cash App (and services like it), consider first loading in fiat and making buys out of the app’s native cash balance instead of purchasing directly through a linked bank account/debit card where information is shared with the bank that allows it to flag the transaction for being related to bitcoin. Taking this small step may help to avoid gatekeeping and can provide some minor privacy, from the bank at least.
Get comfortable with non-KYC bitcoin exchanges. Just as many precoiners drag their feet before making their first bitcoin buys, so too do many Bitcoiners drag their feet in using permissionless channels to buy and sell bitcoin. Robosats, Bisq, Hodl Hodl— you can use the tools. For anyone just getting started, BTC Sessions has excellent video tutorial content on all three, which are linked.
If you don’t yet know how to use these services, it’s better to pick up this knowledge now through calm, self-directed learning rather than during the panic of an emergency or under pressure of more Bitcoin-hostile conditions later. And for those of us who already know, we can actively support these services. For instance, more of us taking action to maintain recurring orders on such platforms could significantly improve their volumes and liquidity, helping to bootstrap and accelerate their network effects.
Be flexible and creative with peer-to-peer payment methods. Cash App, Zelle, PayPal, Venmo, Apple Cash, Revolut, etc. — the services that most users seem to be transacting with on no-KYC exchanges — they would all become willing, if not eager and active agents of financial gatekeeping in any truly antagonistic, anti-privacy environment, even when used in a “peer-to-peer” fashion.
Always remember that there are other payment options — such as gift cards, the original digital-bearer items — that do not necessarily carry such concerns. Perhaps, an enterprising soul might even use Fold to earn bitcoin rewards on the backend for the gift cards used on the exchange…
Find your local Bitcoin community! In the steadily-advancing shadow war on all things permissionless, private, and peer-to-peer, this is our best defense. Don’t just wait until you need other Bitcoiners to get to know other Bitcoiners — to paraphrase Texas Slim, “Shake your local Bitcoiner’s hand.” Get to know people and never underestimate the power of simply asking around. There could be real, live Bitcoiners near you looking to sell some corn and happy to see it go to another HODLer rather than to a bunch of lettuce-handed fiat speculators on some faceless, centralized, Ponzi casino exchange. What’s more, let folks know your skills, talents and expertise — you might be surprised to find an interested market that pays in BTC!
In closing, I believe we should think of permissionless Bitcoining as an essential and necessary core competency, just like we do with Self-Custody. And we should push it with similar urgency and intensity. But as we do this, we should also remember that it is a spectrum and a progression and that there are no perfect solutions, only tradeoffs. Realization of the importance of non-KYC practices will not be instant or obvious to near-normie newcoiners, coin-curious fence-sitters or even many minted Bitcoiners. My own experience is certainly a testament to this.
As we promote the active practice of non-KYC Bitcoining, we can anchor to empathy, patience and humility — always being mindful of the tremendous amount of unlearning most have to go through to get there. So, even if someone doesn’t get it the first time, or the nth time, that they hear it from us, if it helps them get to it faster at all, then it’s well worth it.
~Moon
-
 @ a5142938:0ef19da3
2025-05-02 12:18:08
@ a5142938:0ef19da3
2025-05-02 12:18:08What is a natural material? It's a topic of debate, and everyone will prioritize their own criteria. Here’s how materials are classified on this site. The list is regularly updated based on the products added. Feel free to share your thoughts!
✅ Natural Materials
Materials of plant, animal, or mineral origin, without chemical transformation that alters their molecular structure.
🌱 Main Criteria: - Biodegradability - Non-toxicity - Naturally occurring and recquiring minimal transformation
🔍 List of Natural Materials: - Regenerated Cellulose (cupra, lyocell, modal, rayon) - Cork - Cotton - Earth - Glass - Hemp - Natural Latex, rubber - Leather - Linen - Metal - Silk - Wood - Wool - … (Other materials)
⚠️ Although "natural", these materials can have negative impacts depending on their production conditions (pesticide pollution, excessive water consumption, chemical treatments, animal exploitation, etc.). These impacts are mentionned in the description of each material.
Organic versions of these materials — free from chemical treatments, animal mistreatment, etc. — are preferred for listing products on this site, as indicated on each material's page (coming soon).
Conventional versions are only referenced when no more sustainable alternative has yet been found for that product category.
🚫 Non-Natural Materials
Synthetic or heavily modified materials, often derived from petrochemicals.
📌 Main Issues: - Toxicity and microplastic emissions - Dependence on fossil fuels - Poor biodegradability
🔍 List of Non-Natural Materials: - Acrylic - Elastane, spandex, lycra - Polyamides, nylon - Polyester - Silicone - … (Other materials)
⚠️ These materials are not accepted on this site. However, they may be present in certain listed products if:
- they are used in removable accessories (e.g., elastics, buttons—often not listed in the product’s composition by the brand) that can be detached for recycling or composting, and
- no 100% natural alternative has yet been identified for that product category.
In such cases, a warning will be displayed on the product page.
This article is published on origin-nature.com 🌐 Voir cet article en français
-
 @ 6fc114c7:8f4b1405
2025-05-03 22:06:36
@ 6fc114c7:8f4b1405
2025-05-03 22:06:36In the world of cryptocurrency, the stakes are high, and losing access to your digital assets can be a nightmare. But fear not — Crypt Recver is here to turn that nightmare into a dream come true! With expert-led recovery services and cutting-edge technology, Crypt Recver specializes in helping you regain access to your lost Bitcoin and other cryptocurrencies.
Why Choose Crypt Recver? 🤔 🔑 Expertise You Can Trust At Crypt Recver, we combine state-of-the-art technology with skilled engineers who have a proven track record in crypto recovery. Whether you’ve forgotten your passwords, lost your private keys, or dealt with damaged hardware wallets, our team is equipped to help.
⚡ Fast Recovery Process Time is of the essence when it comes to recovering lost funds. Crypt Recver’s systems are optimized for speed, enabling quick recoveries — so you can get back to what matters most: trading and investing.
🎯 High Success Rate With over a 90% success rate, our recovery team has helped countless clients regain access to their lost assets. We understand the intricacies of cryptocurrency and are dedicated to providing effective solutions.
🛡️ Confidential & Secure Your privacy is our priority. All recovery sessions at Crypt Recver are encrypted and kept entirely confidential. You can trust us with your information, knowing that we maintain the highest standards of security.
🔧 Advanced Recovery Tools We use proprietary tools and techniques to handle complex recovery scenarios, from recovering corrupted wallets to restoring coins from invalid addresses. No matter how challenging the situation, we have a plan.
Our Recovery Services Include: 📈 Bitcoin Recovery: Have you lost access to your Bitcoin wallet? We can help you recover lost wallets, private keys, and passphrases. Transaction Recovery: Mistaken transfers, lost passwords, or missing transaction records — let us help you reclaim your funds! Cold Wallet Restoration: Did your cold wallet fail? We specialize in extracting assets safely and securely. Private Key Generation: Forgotten your private key? We can help you generate new keys linked to your funds without compromising security. Don’t Let Lost Crypto Ruin Your Day! 🕒 With an estimated 3 to 3.4 million BTC lost forever, it’s critical to act swiftly when facing access issues. Whether you’ve been a victim of a dust attack or have simply forgotten your key, Crypt Recver offers the support you need to reclaim your digital assets.
🚀 Start Your Recovery Now! Ready to get your cryptocurrency back? Don’t let uncertainty hold you back!
👉 Request Wallet Recovery Help Today!
Need Immediate Assistance? 📞 For quick queries or support, connect with us on:
✉️ Telegram: Chat with Us on Telegram 💬 WhatsApp: Message Us on WhatsApp Trust Crypt Recver for the Best Crypto Recovery Service — Get back to trading with confidence! 💪In the world of cryptocurrency, the stakes are high, and losing access to your digital assets can be a nightmare. But fear not — Crypt Recver is here to turn that nightmare into a dream come true! With expert-led recovery services and cutting-edge technology, Crypt Recver specializes in helping you regain access to your lost Bitcoin and other cryptocurrencies.
 # Why Choose Crypt Recver? 🤔
# Why Choose Crypt Recver? 🤔🔑 Expertise You Can Trust
At Crypt Recver, we combine state-of-the-art technology with skilled engineers who have a proven track record in crypto recovery. Whether you’ve forgotten your passwords, lost your private keys, or dealt with damaged hardware wallets, our team is equipped to help.
⚡ Fast Recovery Process
Time is of the essence when it comes to recovering lost funds. Crypt Recver’s systems are optimized for speed, enabling quick recoveries — so you can get back to what matters most: trading and investing.
🎯 High Success Rate
With over a 90% success rate, our recovery team has helped countless clients regain access to their lost assets. We understand the intricacies of cryptocurrency and are dedicated to providing effective solutions.
🛡️ Confidential & Secure
Your privacy is our priority. All recovery sessions at Crypt Recver are encrypted and kept entirely confidential. You can trust us with your information, knowing that we maintain the highest standards of security.
🔧 Advanced Recovery Tools
We use proprietary tools and techniques to handle complex recovery scenarios, from recovering corrupted wallets to restoring coins from invalid addresses. No matter how challenging the situation, we have a plan.
 # Our Recovery Services Include: 📈
# Our Recovery Services Include: 📈- Bitcoin Recovery: Have you lost access to your Bitcoin wallet? We can help you recover lost wallets, private keys, and passphrases.
- Transaction Recovery: Mistaken transfers, lost passwords, or missing transaction records — let us help you reclaim your funds!
- Cold Wallet Restoration: Did your cold wallet fail? We specialize in extracting assets safely and securely.
- Private Key Generation: Forgotten your private key? We can help you generate new keys linked to your funds without compromising security.
Don’t Let Lost Crypto Ruin Your Day! 🕒
With an estimated 3 to 3.4 million BTC lost forever, it’s critical to act swiftly when facing access issues. Whether you’ve been a victim of a dust attack or have simply forgotten your key, Crypt Recver offers the support you need to reclaim your digital assets.
🚀 Start Your Recovery Now!
Ready to get your cryptocurrency back? Don’t let uncertainty hold you back!
👉 Request Wallet Recovery Help Today!
Need Immediate Assistance? 📞
For quick queries or support, connect with us on:
- ✉️ Telegram: Chat with Us on Telegram
- 💬 WhatsApp: Message Us on WhatsApp
Trust Crypt Recver for the Best Crypto Recovery Service — Get back to trading with confidence! 💪
-
 @ 68768a6c:0eaf07e9
2025-05-02 11:06:40
@ 68768a6c:0eaf07e9
2025-05-02 11:06:40In 2009, a mysterious figure named Satoshi Nakamoto launched Bitcoin — a decentralized digital currency with no central bank, no borders, and no permission needed. At the time, 1 BTC was worth less than a cent. Today, it represents a revolution in how we think about value, freedom, and financial systems.
But Bitcoin is more than just a digital asset. It’s a response to distrust in traditional banks and fiat currency. With only 21 million coins ever to exist, Bitcoin is often compared to gold — scarce, mined (digitally), and increasingly seen as a store of value.
Bitcoin is transparent (you can track every transaction), secure (thanks to blockchain technology), and global (it works the same in New York or Nairobi). For some, it’s a hedge against inflation. For others, it’s a path to financial independence.
Still, Bitcoin isn’t without risk — its price is volatile, and its environmental impact has been criticized. But one thing is clear: Bitcoin has changed the financial conversation forever.
Whether it’s the future of money or just the beginning of a larger movement, Bitcoin forces us to ask: Who should control our money?

-
 @ a5142938:0ef19da3
2025-05-02 10:48:55
@ a5142938:0ef19da3
2025-05-02 10:48:55Finding 100% natural, plastic-free products turned out to be much harder than I expected… So I started collecting bookmarks. And then I thought: "What if we shared?!
Help me discover the best natural alternatives for clothing and gear without plastic!
This project is all about sharing: half of the site's potential revenue is redistributed to contributors. A small experiment in revenue and value sharing on the internet. :-)
Q&A
Why focus on natural materials?
Synthetic materials are mostly plastics (polyester, polyamide…). The problem? They end up contaminating us:
- Microplastics absorbed through the skin,
- Particles released with every wash, making their way into the water we drink and the food we eat,
- Major challenges in recycling plastic waste.
What exactly are natural materials?
They are non-synthetic materials, whose components exist in nature without molecular modification. But what really matters here is their biodegradability and non-toxicity.
Some materials may spark debates about their acceptability on this site!
How is this different from other ethical fashion or shopping websites?
Many websites offer ethical and sustainable products, but I often found they still included synthetic materials. I had to check every product individually. Some promote recycled plastic fibers as an eco-friendly choice, but I’d rather not put plastic on my skin or my children's.
How can I contribute?
If you find this project useful or interesting, here’s how you can support it:
-
📝 Contribute: suggest edits by commenting on existing entries or propose new product or brand references. 👉 Learn more about contributions
-
⚡ Donate: Help sustain the project and support contributors. 👉 Learn more about donations
-
📢 Spread the word: tell people around you, share the site on social media, your blog…
How can I receive a share of the site’s revenue?
You need a NOSTR account and a Bitcoin Lightning address.
What is NOSTR?
NOSTR is a decentralized internet protocol, still experimental, that allows you to:
- Publish and browse content without relying on a centralized platform.
- Log in to multiple services while keeping full control over your data.
- Use the Bitcoin Lightning network for instant, peer-to-peer payments.
What about my data privacy?
- No ads, no personalized tracking.
- NOSTR comments are public, but you can use a pseudonym.
- You retain ownership of your contributions on the NOSTR protocol.
Who is behind this project?
We use open-source tools and services:
- NOSTR for content publishing and contributions checking,
- npub.pro for content visualization,
- Coinos.io for payment management.
This article is published on origin-nature.com 🌐 Voir cet article en français
-
 @ 1c19eb1a:e22fb0bc
2025-04-30 22:02:13
@ 1c19eb1a:e22fb0bc
2025-04-30 22:02:13I am happy to present to you the first full review posted to Nostr Reviews: #Primal for #Android!
Primal has its origins as a micro-blogging, social media client, though it is now expanding its horizons into long-form content. It was first released only as a web client in March of 2023, but has since had a native client released for both iOS and Android. All of Primal's clients recently had an update to Primal 2.0, which included both performance improvements and a number of new features. This review will focus on the Android client specifically, both on phone and tablet.
Since Primal has also added features that are only available to those enrolled in their new premium subscription, it should also be noted that this review will be from the perspective of a free user. This is for two reasons. First, I am using an alternate npub to review the app, and if I were to purchase premium at some time in the future, it would be on my main npub. Second, despite a lot of positive things I have to say about Primal, I am not planning to regularly use any of their apps on my main account for the time being, for reasons that will be discussed later in the review.
The application can be installed through the Google Play Store, nostr:npub10r8xl2njyepcw2zwv3a6dyufj4e4ajx86hz6v4ehu4gnpupxxp7stjt2p8, or by downloading it directly from Primal's GitHub. The full review is current as of Primal Android version 2.0.21. Updates to the review on 4/30/2025 are current as of version 2.2.13.
In the ecosystem of "notes and other stuff," Primal is predominantly in the "notes" category. It is geared toward users who want a social media experience similar to Twitter or Facebook with an infinite scrolling feed of notes to interact with. However, there is some "other stuff" included to complement this primary focus on short and long form notes including a built-in Lightning wallet powered by #Strike, a robust advanced search, and a media-only feed.

Overall Impression
Score: 4.4 / 5 (Updated 4/30/2025)
Primal may well be the most polished UI of any Nostr client native to Android. It is incredibly well designed and thought out, with all of the icons and settings in the places a user would expect to find them. It is also incredibly easy to get started on Nostr via Primal's sign-up flow. The only two things that will be foreign to new users are the lack of any need to set a password or give an email address, and the prompt to optionally set up the wallet.
Complaints prior to the 2.0 update about Primal being slow and clunky should now be completely alleviated. I only experienced quick load times and snappy UI controls with a couple very minor exceptions, or when loading DVM-based feeds, which are outside of Primal's control.
Primal is not, however, a client that I would recommend for the power-user. Control over preferred relays is minimal and does not allow the user to determine which relays they write to and which they only read from. Though you can use your own wallet, it will not appear within the wallet interface, which only works with the custodial wallet from Strike. Moreover, and most eggregiously, the only way for existing users to log in is by pasting their nsec, as Primal does not support either the Android signer or remote signer options for users to protect their private key at this time. This lack of signer support is the primary reason the client received such a low overall score. If even one form of external signer log in is added to Primal, the score will be amended to 4.2 / 5, and if both Android signer and remote signer support is added, it will increase to 4.5.
Update: As of version 2.2.13, Primal now supports the Amber Android signer! One of the most glaring issues with the app has now been remedied and as promised, the overall score above has been increased.
Another downside to Primal is that it still utilizes an outdated direct message specification that leaks metadata that can be readily seen by anyone on the network. While the content of your messages remains encrypted, anyone can see who you are messaging with, and when. This also means that you will not see any DMs from users who are messaging from a client that has moved to the latest, and far more private, messaging spec.
That said, the beautiful thing about Nostr as a protocol is that users are not locked into any particular client. You may find Primal to be a great client for your average #bloomscrolling and zapping memes, but opt for a different client for more advanced uses and for direct messaging.
Features
Primal has a lot of features users would expect from any Nostr client that is focused on short-form notes, but it also packs in a lot of features that set it apart from other clients, and that showcase Primal's obvious prioritization of a top-tier user experience.
Home Feed
By default, the infinitely scrolling Home feed displays notes from those you currently follow in chronological order. This is traditional Nostr at its finest, and made all the more immersive by the choice to have all distracting UI elements quickly hide themselves from view as the you begin to scroll down the feed. They return just as quickly when you begin to scroll back up.

Scrolling the feed is incredibly fast, with no noticeable choppiness and minimal media pop-in if you are on a decent internet connection.
Helpfully, it is easy to get back to the top of the feed whenever there is a new post to be viewed, as a bubble will appear with the profile pictures of the users who have posted since you started scrolling.

Interacting With Notes
Interacting with a note in the feed can be done via the very recognizable icons at the bottom of each post. You can comment, zap, like, repost, and/or bookmark the note.
Notably, tapping on the zap icon will immediately zap the note your default amount of sats, making zapping incredibly fast, especially when using the built-in wallet. Long pressing on the zap icon will open up a menu with a variety of amounts, along with the ability to zap a custom amount. All of these amounts, and the messages that are sent with the zap, can be customized in the application settings.

Users who are familiar with Twitter or Instagram will feel right at home with only having one option for "liking" a post. However, users from Facebook or other Nostr clients may wonder why they don't have more options for reactions. This is one of those things where users who are new to Nostr probably won't notice they are missing out on anything at all, while users familiar with clients like #Amethyst or #noStrudel will miss the ability to react with a 🤙 or a 🫂.
It's a similar story with the bookmark option. While this is a nice bit of feature parity for Twitter users, for those already used to the ability to have multiple customized lists of bookmarks, or at minimum have the ability to separate them into public and private, it may be a disappointment that they have no access to the bookmarks they already built up on other clients. Primal offers only one list of bookmarks for short-form notes and they are all visible to the public. However, you are at least presented with a warning about the public nature of your bookmarks before saving your first one.
Yet, I can't dock the Primal team much for making these design choices, as they are understandable for Primal's goal of being a welcoming client for those coming over to Nostr from centralized platforms. They have optimized for the onboarding of new users, rather than for those who have been around for a while, and there is absolutely nothing wrong with that.
Post Creation
Composing posts in Primal is as simple as it gets. Accessed by tapping the obvious circular button with a "+" on it in the lower right of the Home feed, most of what you could need is included in the interface, and nothing you don't.

Your device's default keyboard loads immediately, and the you can start typing away.
There are options for adding images from your gallery, or taking a picture with your camera, both of which will result in the image being uploaded to Primal's media-hosting server. If you prefer to host your media elsewhere, you can simply paste the link to that media into your post.
There is also an @ icon as a tip-off that you can tag other users. Tapping on this simply types "@" into your note and brings up a list of users. All you have to do to narrow down the user you want to tag is continue typing their handle, Nostr address, or paste in their npub.

This can get mixed results in other clients, which sometimes have a hard time finding particular users when typing in their handle, forcing you to have to remember their Nostr address or go hunt down their npub by another means. Not so with Primal, though. I had no issues tagging anyone I wanted by simply typing in their handle.
Of course, when you are tagging someone well known, you may find that there are multiple users posing as that person. Primal helps you out here, though. Usually the top result is the person you want, as Primal places them in order of how many followers they have. This is quite reliable right now, but there is nothing stopping someone from spinning up an army of bots to follow their fake accounts, rendering follower count useless for determining which account is legitimate. It would be nice to see these results ranked by web-of-trust, or at least an indication of how many users you follow who also follow the users listed in the results.
Once you are satisfied with your note, the "Post" button is easy to find in the top right of the screen.
Feed Selector and Marketplace
Primal's Home feed really shines when you open up the feed selection interface, and find that there are a plethora of options available for customizing your view. By default, it only shows four options, but tapping "Edit" opens up a new page of available toggles to add to the feed selector.

The options don't end there, though. Tapping "Add Feed" will open up the feed marketplace, where an ever-growing number of custom feeds can be found, some created by Primal and some created by others. This feed marketplace is available to a few other clients, but none have so closely integrated it with their Home feeds like Primal has.

Unfortunately, as great as these custom feeds are, this was also the feature where I ran into the most bugs while testing out the app.
One of these bugs was while selecting custom feeds. Occasionally, these feed menu screens would become unresponsive and I would be unable to confirm my selection, or even use the back button on my device to back out of the screen. However, I was able to pull the screen down to close it and re-open the menu, and everything would be responsive again.
This only seemed to occur when I spent 30 seconds or more on the same screen, so I imagine that most users won't encounter it much in their regular use.
Another UI bug occurred for me while in the feed marketplace. I could scroll down the list of available feeds, but attempting to scroll back up the feed would often close the interface entirely instead, as though I had pulled the screen down from the top, when I was swiping in the middle of the screen.
The last of these bugs occurred when selecting a long-form "Reads" feed while in the menu for the Home feed. The menu would allow me to add this feed and select it to be displayed, but it would fail to load the feed once selected, stating "There is no content in this feed." Going to a different page within the the app and then going back to the Home tab would automatically remove the long-form feed from view, and reset back to the most recently viewed short-form "Notes" feed, though the long-form feed would still be available to select again. The results were similar when selecting a short-form feed for the Reads feed.
I would suggest that if long-form and short-form feeds are going to be displayed in the same list, and yet not be able to be displayed in the same feed, the application should present an error message when attempting to add a long-form feed for the Home feed or a short-form feed for the Reads feed, and encourage the user add it to the proper feed instead.
Long-Form "Reads" Feed
A brand new feature in Primal 2.0, users can now browse and read long-form content posted to Nostr without having to go to a separate client. Primal now has a dedicated "Reads" feed to browse and interact with these articles.
This feed displays the author and title of each article or blog, along with an image, if available. Quite conveniently, it also lets you know the approximate amount of time it will take to read a given article, so you can decide if you have the time to dive into it now, or come back later.

Noticeably absent from the Reads feed, though, is the ability to compose an article of your own. This is another understandable design choice for a mobile client. Composing a long-form note on a smart-phone screen is not a good time. Better to be done on a larger screen, in a client with a full-featured text editor.
Tapping an article will open up an attractive reading interface, with the ability to bookmark for later. These bookmarks are a separate list from your short-form note bookmarks so you don't have to scroll through a bunch of notes you bookmarked to find the article you told yourself you would read later and it's already been three weeks.
While you can comment on the article or zap it, you will notice that you cannot repost or quote-post it. It's not that you can't do so on Nostr. You absolutely can in other clients. In fact, you can do so on Primal's web client, too. However, Primal on Android does not handle rendering long-form note previews in the Home feed, so they have simply left out the option to share them there. See below for an example of a quote-post of a long-form note in the Primal web client vs the Android client.
Primal Web:

Primal Android:

The Explore Tab
Another unique feature of the Primal client is the Explore tab, indicated by the compass icon. This tab is dedicated to discovering content from outside your current follow list. You can find the feed marketplace here, and add any of the available feeds to your Home or Reads feed selections. You can also find suggested users to follow in the People tab. The Zaps tab will show you who has been sending and receiving large zaps. Make friends with the generous ones!
The Media tab gives you a chronological feed of just media, displayed in a tile view. This can be great when you are looking for users who post dank memes, or incredible photography on a regular basis. Unfortunately, it appears that there is no way to filter this feed for sensitive content, and so you do not have to scroll far before you see pornographic material.
Indeed, it does not appear that filters for sensitive content are available in Primal for any feed. The app is kind enough to give a minimal warning that objectionable content may be present when selecting the "Nostr Firehose" option in your Home feed, with a brief "be careful" in the feed description, but there is not even that much of a warning here for the media-only feed.

The media-only feed doesn't appear to be quite as bad as the Nostr Firehose feed, so there must be some form of filtering already taking place, rather than being a truly global feed of all media. Yet, occasional sensitive content still litters the feed and is unavoidable, even for users who would rather not see it. There are, of course, ways to mute particular users who post such content, if you don't want to see it a second time from the same user, but that is a never-ending game of whack-a-mole, so your only realistic choices in Primal are currently to either avoid the Nostr Firehose and media-only feeds, or determine that you can put up with regularly scrolling past often graphic content.
This is probably the only choice Primal has made that is not friendly to new users. Most clients these days will have some protections in place to hide sensitive content by default, but still allow the user to toggle those protections off if they so choose. Some of them hide posts flagged as sensitive content altogether, others just blur the images unless the user taps to reveal them, and others simply blur all images posted by users you don't follow. If Primal wants to target new users who are accustomed to legacy social media platforms, they really should follow suit.
The final tab is titled "Topics," but it is really just a list of popular hashtags, which appear to be arranged by how often they are being used. This can be good for finding things that other users are interested in talking about, or finding specific content you are interested in.
If you tap on any topic in the list, it will display a feed of notes that include that hashtag. What's better, you can add it as a feed option you can select on your Home feed any time you want to see posts with that tag.
The only suggestion I would make to improve this tab is some indication of why the topics are arranged in the order presented. A simple indicator of the number of posts with that hashtag in the last 24 hours, or whatever the interval is for determining their ranking, would more than suffice.
Even with those few shortcomings, Primal's Explore tab makes the client one of the best options for discovering content on Nostr that you are actually interested in seeing and interacting with.
Built-In Wallet
While this feature is completely optional, the icon to access the wallet is the largest of the icons at the bottom of the screen, making you feel like you are missing out on the most important feature of the app if you don't set it up. I could be critical of this design choice, but in many ways I think it is warranted. The built-in wallet is one of the most unique features that Primal has going for it.

Consider: If you are a new user coming to Nostr, who isn't already a Bitcoiner, and you see that everyone else on the platform is sending and receiving sats for their posts, will you be more likely to go download a separate wallet application or use one that is built-into your client? I would wager the latter option by a long shot. No need to figure out which wallet you should download, whether you should do self-custody or custodial, or make the mistake of choosing a wallet with unexpected setup fees and no Lightning address so you can't even receive zaps to it. nostr:npub16c0nh3dnadzqpm76uctf5hqhe2lny344zsmpm6feee9p5rdxaa9q586nvr often states that he believes more people will be onboarded to Bitcoin through Nostr than by any other means, and by including a wallet into the Primal client, his team has made adopting Bitcoin that much easier for new Nostr users.
Some of us purists may complain that it is custodial and KYC, but that is an unfortunate necessity in order to facilitate onboarding newcoiners to Bitcoin. This is not intended to be a wallet for those of us who have been using Bitcoin and Lightning regularly already. It is meant for those who are not already familiar with Bitcoin to make it as easy as possible to get off zero, and it accomplishes this better than any other wallet I have ever tried.
In large part, this is because the KYC is very light. It does need the user's legal name, a valid email address, date of birth, and country of residence, but that's it! From there, the user can buy Bitcoin directly through the app, but only in the amount of $4.99 at a time. This is because there is a substantial markup on top of the current market price, due to utilizing whatever payment method the user has set up through their Google Play Store. The markup seemed to be about 19% above the current price, since I could purchase 4,143 sats for $4.99 ($120,415 / Bitcoin), when the current price was about $101,500. But the idea here is not for the Primal wallet to be a user's primary method of stacking sats. Rather, it is intended to get them off zero and have a small amount of sats to experience zapping with, and it accomplishes this with less friction than any other method I know.
Moreover, the Primal wallet has the features one would expect from any Lightning wallet. You can send sats to any Nostr user or Lightning address, receive via invoice, or scan to pay an invoice. It even has the ability to receive via on-chain. This means users who don't want to pay the markup from buying through Primal can easily transfer sats they obtained by other means into the Primal wallet for zapping, or for using it as their daily-driver spending wallet.
Speaking of zapping, once the wallet is activated, sending zaps is automatically set to use the wallet, and they are fast. Primal gives you immediate feedback that the zap was sent and the transaction shows in your wallet history typically before you can open the interface. I can confidently say that Primal wallet's integration is the absolute best zapping experience I have seen in any Nostr client.
One thing to note that may not be immediately apparent to new users is they need to add their Lightning address with Primal into their profile details before they can start receiving zaps. So, sending zaps using the wallet is automatic as soon as you activate it, but receiving is not. Ideally, this could be further streamlined, so that Primal automatically adds the Lightning address to the user's profile when the wallet is set up, so long as there is not currently a Lightning address listed.
Of course, if you already have a Lightning wallet, you can connect it to Primal for zapping, too. We will discuss this further in the section dedicated to zap integration.
Advanced Search
Search has always been a tough nut to crack on Nostr, since it is highly dependent on which relays the client is pulling information from. Primal has sought to resolve this issue, among others, by running a caching relay that pulls notes from a number of relays to store them locally, and perform some spam filtering. This allows for much faster retrieval of search results, and also makes their advanced search feature possible.
Advanced search can be accessed from most pages by selecting the magnifying glass icon, and then the icon for more options next to the search bar.
As can be seen in the screenshot below, there are a plethora of filters that can be applied to your search terms.

You can immediately see how this advanced search could be a very powerful tool for not just finding a particular previous note that you are looking for, but for creating your own custom feed of notes. Well, wouldn't you know it, Primal allows you to do just that! This search feature, paired with the other features mentioned above related to finding notes you want to see in your feed, makes Primal hands-down the best client for content discovery.
The only downside as a free user is that some of these search options are locked behind the premium membership. Or else you only get to see a certain number of results of your advanced search before you must be a premium member to see more.
Can My Grandma Use It?
Score: 4.8 / 5 Primal has obviously put a high priority on making their client user-friendly, even for those who have never heard of relays, public/private key cryptography, or Bitcoin. All of that complexity is hidden away. Some of it is available to play around with for the users who care to do so, but it does not at all get in the way of the users who just want to jump in and start posting notes and interacting with other users in a truly open public square.
To begin with, the onboarding experience is incredibly smooth. Tap "Create Account," enter your chosen display name and optional bio information, upload a profile picture, and then choose some topics you are interested in. You are then presented with a preview of your profile, with the ability to add a banner image, if you so choose, and then tap "Create Account Now."

From there you receive confirmation that your account has been created and that your "Nostr key" is available to you in the application settings. No further explanation is given about what this key is for at this point, but the user doesn't really need to know at the moment, either. If they are curious, they will go to the app settings to find out.
At this point, Primal encourages the user to activate Primal Wallet, but also gives the option for the user to do it later.

That's it! The next screen the user sees if they don't opt to set up the wallet is their Home feed with notes listed in chronological order. More impressive, the feed is not empty, because Primal has auto-followed several accounts based on your selected topics.
Now, there has definitely been some legitimate criticism of this practice of following specific accounts based on the topic selection, and I agree. I would much prefer to see Primal follow hashtags based on what was selected, and combine the followed hashtags into a feed titled "My Topics" or something of that nature, and make that the default view when the user finishes onboarding. Following particular users automatically will artificially inflate certain users' exposure, while other users who might be quality follows for that topic aren't seen at all.
The advantage of following particular users over a hashtag, though, is that Primal retains some control over the quality of the posts that new users are exposed to right away. Primal can ensure that new users see people who are actually posting quality photography when they choose it as one of their interests. However, even with that example, I chose photography as one of my interests and while I did get some stunning photography in my Home feed by default based on Primal's chosen follows, I also scrolled through the Photography hashtag for a bit and I really feel like I would have been better served if Primal had simply followed that hashtag rather than a particular set of users.
We've already discussed how simple it is to set up the Primal Wallet. You can see the features section above if you missed it. It is, by far, the most user friendly experience to onboarding onto Lightning and getting a few sats for zapping, and it is the only one I know of that is built directly into a Nostr client. This means new users will have a frictionless introduction to transacting via Lightning, perhaps without even realizing that's what they are doing.
Discovering new content of interest is incredibly intuitive on Primal, and the only thing that new users may struggle with is getting their own notes seen by others. To assist with this, I would suggest Primal encourage users to make their first post to the introductions hashtag and direct any questions to the AskNostr hashtag as part of the onboarding process. This will get them some immediate interactions from other users, and further encouragement to set up their wallet if they haven't already done so.
How do UI look?
Score: 4.9 / 5
Primal is the most stunningly beautiful Nostr client available, in my honest opinion. Despite some of my hangups about certain functionality, the UI alone makes me want to use it.

It is clean, attractive, and intuitive. Everything I needed was easy to find, and nothing felt busy or cluttered. There are only a few minor UI glitches that I ran into while testing the app. Some of them were mentioned in the section of the review detailing the feed selector feature, but a couple others occurred during onboarding.
First, my profile picture was not centered in the preview when I uploaded it. This appears to be because it was a low quality image. Uploading a higher quality photo did not have this result.

The other UI bug was related to text instructions that were cut off, and not able to scroll to see the rest of them. This occurred on a few pages during onboarding, and I expect it was due to the size of my phone screen, since it did not occur when I was on a slightly larger phone or tablet.

Speaking of tablets, Primal Android looks really good on a tablet, too! While the client does not have a landscape mode by default, many Android tablets support forcing apps to open in full-screen landscape mode, with mixed results. However, Primal handles it well. I would still like to see a tablet version developed that takes advantage of the increased screen real estate, but it is certainly a passable option.





At this point, I would say the web client probably has a bit better UI for use on a tablet than the Android client does, but you miss out on using the built-in wallet, which is a major selling point of the app.
This lack of a landscape mode for tablets and the few very minor UI bugs I encountered are the only reason Primal doesn't get a perfect score in this category, because the client is absolutely stunning otherwise, both in light and dark modes. There are also two color schemes available for each.

Log In Options
Score: 4 / 5 (Updated 4/30/2025)
Unfortunately, Primal has not included any options for log in outside of pasting your private key into the application. While this is a very simple way to log in for new users to understand, it is also the least secure means to log into Nostr applications.
This is because, even with the most trustworthy client developer, giving the application access to your private key always has the potential for that private key to somehow be exposed or leaked, and on Nostr there is currently no way to rotate to a different private key and keep your identity and social graph. If someone gets your key, they are you on Nostr for all intents and purposes.
This is not a situation that users should be willing to tolerate from production-release clients at this point. There are much better log in standards that can and should be implemented if you care about your users.
That said, I am happy to report that external signer support is on the roadmap for Primal, as confirmed below:
nostr:note1n59tc8k5l2v30jxuzghg7dy2ns76ld0hqnn8tkahyywpwp47ms5qst8ehl
No word yet on whether this will be Android signer or remote signer support, or both.
This lack of external signer support is why I absolutely will not use my main npub with Primal for Android. I am happy to use the web client, which supports and encourages logging in with a browser extension, but until the Android client allows users to protect their private key, I cannot recommend it for existing Nostr users.
Update: As of version 2.2.13, all of what I have said above is now obsolete. Primal has added Android signer support, so users can now better protect their nsec by using Amber!
I would still like to see support for remote signers, especially with nstart.me as a recommended Nostr onboarding process and the advent of FROSTR for key management. That said, Android signer support on its own has been a long time coming and is a very welcome addition to the Primal app. Bravo Primal team!
Zap Integration
Score: 4.8 / 5
As mentioned when discussing Primal's built-in wallet feature, zapping in Primal can be the most seamless experience I have ever seen in a Nostr client. Pairing the wallet with the client is absolutely the path forward for Nostr leading the way to Bitcoin adoption.
But what if you already have a Lightning wallet you want to use for zapping? You have a couple options. If it is an Alby wallet or another wallet that supports Nostr Wallet Connect, you can connect it with Primal to use with one-tap zapping.

How your zapping experience goes with this option will vary greatly based on your particular wallet of choice and is beyond the scope of this review. I used this option with a hosted wallet on my Alby Hub and it worked perfectly. Primal gives you immediate feedback that you have zapped, even though the transaction usually takes a few seconds to process and appear in your wallet's history.
The one major downside to using an external wallet is the lack of integration with the wallet interface. This interface currently only works with Primal's wallet, and therefore the most prominent tab in the entire app goes unused when you connect an external wallet.

An ideal improvement would be for the wallet screen to work similar to Alby Go when you have an external wallet connected via Nostr Wallet Connect, allowing the user to have Primal act as their primary mobile Lightning wallet. It could have balance and transaction history displayed, and allow sending and receiving, just like the integrated Primal wallet, but remove the ability to purchase sats directly through the app when using an external wallet.
Content Discovery
Score: 4.8 / 5
Primal is the best client to use if you want to discover new content you are interested in. There is no comparison, with only a few caveats.
First, the content must have been posted to Nostr as either a short-form or long-form note. Primal has a limited ability to display other types of content. For instance, discovering video content or streaming content is lacking.
Second, you must be willing to put up with the fact that Primal lacks a means of filtering sensitive content when you are exploring beyond the bounds of your current followers. This may not be an issue for some, but for others it could be a deal-breaker.
Third, it would be preferable for Primal to follow topics you are interested in when you choose them during onboarding, rather than follow specific npubs. Ideally, create a "My Topics" feed that can be edited by selecting your interests in the Topics section of the Explore tab.
Relay Management
Score: 2.5 / 5
For new users who don't want to mess around with managing relays, Primal is fantastic! There are 7 relays selected by default, in addition to Primal's caching service. For most users who aren't familiar with Nostr's protocol archetecture, they probably won't ever have to change their default relays in order to use the client as they would expect.
However, two of these default relays were consistently unreachable during the week that I tested. These were relay.plebes.fans and remnant.cloud. The first relay seems to be an incorrect URL, as I found nosflare.plebes.fans online and with perfect uptime for the last 12 hours on nostr.watch. I was unable to find remnant.cloud on nostr.watch at all. A third relay was intermittent, sometimes online and reachable, and other times unreachable: v1250.planz.io/nostr. If Primal is going to have default relays, they should ideally be reliable and with accurate URLs.
That said, users can add other relays that they prefer, and remove relays that they no longer want to use. They can even set a different caching service to use with the client, rather than using Primal's.

However, that is the extent of a user's control over their relays. They cannot choose which relays they want to write to and which they want to read from, nor can they set any private relays, outbox or inbox relays, or general relays. Loading the npub I used for this review into another client with full relay management support revealed that the relays selected in Primal are being added to both the user's public outbox relays and public inbox relays, but not to any other relay type, which leads me to believe the caching relay is acting as the client's only general relay and search relay.
One unique and welcomed addition is the "Enhanced Privacy" feature, which is off by default, but which can be toggled on. I am not sure why this is not on by default, though. Perhaps someone from the Primal team can enlighten me on that choice.
By default, when you post to Nostr, all of your outbox relays will see your IP address. If you turn on the Enhanced Privacy mode, only Primal's caching service will see your IP address, because it will post your note to the other relays on your behalf. In this way, the caching service acts similar to a VPN for posting to Nostr, as long as you trust Primal not to log or leak your IP address.
In short, if you use any other Nostr clients at all, do not use Primal for managing your relays.
Media Hosting Options
Score: 4.9 / 5 This is a NEW SECTION of this review, as of version 2.2.13!
Primal has recently added support for the Blossom protocol for media hosting, and has added a new section within their settings for "Media Uploads."
Media hosting is one of the more complicated problems to solve for a decentralized publishing protocol like Nostr. Text-based notes are generally quite small, making them no real burden to store on relays, and a relay can prune old notes as they see fit, knowing that anyone who really cared about those notes has likely archived them elsewhere. Media, on the other hand, can very quickly fill up a server's disk space, and because it is usually addressable via a specific URL, removing it from that location to free up space means it will no longer load for anyone.
Blossom solves this issue by making it easy to run a media server and have the same media mirrored to more than one for redundancy. Since the media is stored with a file name that is a hash of the content itself, if the media is deleted from one server, it can still be found from any other server that has the same file, without any need to update the URL in the Nostr note where it was originally posted.
Prior to this update, Primal only allowed media uploads to their own media server. Now, users can upload to any blossom server, and even choose to have their pictures or videos mirrored additional servers automatically. To my knowledge, no other Nostr client offers this automatic mirroring at the time of upload.
One of my biggest criticisms of Primal was that it had taken a siloed approach by providing a client, a caching relay, a media server, and a wallet all controlled by the same company. The whole point of Nostr is to separate control of all these services to different entities. Now users have more options for separating out their media hosting and their wallet to other providers, at least. I would still like to see other options available for a caching relay, but that relies on someone else being willing to run one, since the software is open for anyone to use. It's just not your average, lightweight relay that any average person can run from home.
Regardless, this update to add custom Blossom servers is a most welcome step in the right direction!
Current Users' Questions
The AskNostr hashtag can be a good indication of the pain points that other users are currently having with a client. Here are some of the most common questions submitted about Primal since the launch of 2.0:
nostr:note1dqv4mwqn7lvpaceg9s7damf932ydv9skv2x99l56ufy3f7q8tkdqpxk0rd
This was a pretty common question, because users expect that they will be able to create the same type of content that they can consume in a particular client. I can understand why this was left out in a mobile client, but perhaps it should be added in the web client.
nostr:note16xnm8a2mmrs7t9pqymwjgd384ynpf098gmemzy49p3572vhwx2mqcqw8xe
This is a more concerning bug, since it appears some users are experiencing their images being replaced with completely different images. I did not experience anything similar in my testing, though.
nostr:note1uhrk30nq0e566kx8ac4qpwrdh0vfaav33rfvckyvlzn04tkuqahsx8e7mr
There hasn't been an answer to this, but I have not been able to find a way. It seems search results will always include replies as well as original notes, so a feed made from the search results will as well. Perhaps a filter can be added to the advanced search to exclude replies? There is already a filter to only show replies, but there is no corresponding filter to only show original notes.
nostr:note1zlnzua28a5v76jwuakyrf7hham56kx9me9la3dnt3fvymcyaq6eqjfmtq6
Since both mobile platforms support the wallet, users expect that they will be able to access it in their web client, too. At this time, they cannot. The only way to have seamless zapping in the web client is to use the Alby extension, but there is not a way to connect it to your Primal wallet via Nostr Wallet Connect either. This means users must have a separate wallet for zapping on the web client if they use the Primal Wallet on mobile.
nostr:note15tf2u9pffy58y9lk27y245ew792raqc7lc22jezxvqj7xrak9ztqu45wep
It seems that Primal is filtering for spam even for profiles you actively follow. Moreover, exactly what the criteria is for being considered spam is currently opaque.
nostr:note1xexnzv0vrmc8svvduurydwmu43w7dftyqmjh4ps98zksr39ln2qswkuced
For those unaware, Blossom is a protocol for hosting media as blobs identified by a hash, allowing them to be located on and displayed from other servers they have been mirrored to when when the target server isn't available. Primal currently runs a Blossom server (blossom.primal.net) so I would expect we see Blossom support in the future.
nostr:note1unugv7s36e2kxl768ykg0qly7czeplp8qnc207k4pj45rexgqv4sue50y6
Currently, Primal on Android only supports uploading photos to your posts. Users must upload any video to some other hosting service and copy/paste a link to the video into their post on Primal. I would not be surprised to see this feature added in the near future, though.
nostr:note10w6538y58dkd9mdrlkfc8ylhnyqutc56ggdw7gk5y7nsp00rdk4q3qgrex
Many Nostr users have more than one npub for various uses. Users would prefer to have a way to quickly switch between accounts than to have to log all the way out and paste their npub for the other account every time they want to use it.
There is good news on this front, though:
nostr:note17xv632yqfz8nx092lj4sxr7drrqfey6e2373ha00qlq8j8qv6jjs36kxlh
Wrap Up
All in all, Primal is an excellent client. It won't be for everyone, but that's one of the strengths of Nostr as a protocol. You can choose to use the client that best fits your own needs, and supplement with other clients and tools as necessary.
There are a couple glaring issues I have with Primal that prevent me from using it on my main npub, but it is also an ever-improving client, that already has me hopeful for those issues to be resolved in a future release.
So, what should I review next? Another Android client, such as #Amethyst or #Voyage? Maybe an "other stuff" app, like #Wavlake or #Fountain? Please leave your suggestions in the comments.
I hope this review was valuable to you! If it was, please consider letting me know just how valuable by zapping me some sats and reposting it out to your follows.
Thank you for reading!
PV 🤙
-
 @ bc52210b:20bfc6de
2025-04-28 20:08:09
@ bc52210b:20bfc6de
2025-04-28 20:08:09
Imagine a world where clean, safe, and efficient nuclear power can be delivered to any corner of the globe, powering everything from small villages to bustling cities. This vision is becoming a reality with the development of nuclear modular plants—compact, portable nuclear reactors that can be shipped in standard containers and set up quickly to provide reliable energy. These innovative power sources use fission—the process of splitting atomic nuclei to release energy, the same fundamental principle that powers traditional nuclear plants—but with a twist: they utilize thorium as fuel and a molten salt system for cooling and fuel delivery. This combination offers a host of benefits that could revolutionize how we think about nuclear energy.
Portability and Deployment
One of the most significant advantages of these nuclear modular plants is their portability. Designed to fit within standard shipping containers, these reactors can be transported by truck, ship, or even air to virtually any location. This makes them ideal for remote communities, disaster relief efforts, or military operations where traditional power infrastructure is lacking or damaged. Setting up a conventional power plant typically takes years, but these modular units can be operational in a matter of weeks, providing a rapid solution to energy needs.
Safety Features
Safety is a paramount concern in nuclear energy, and modular thorium molten salt reactors (MSRs) offer several inherent safety advantages. Unlike traditional reactors that use water under high pressure, MSRs operate at atmospheric pressure, eliminating the risk of pressure-related accidents. The fuel is dissolved in the molten salt, which means there's no solid fuel that could melt down. If the reactor overheats, the salt expands, naturally slowing the fission reaction—a built-in safety mechanism. Additionally, thorium-based fuels produce less long-lived radioactive waste, reducing the long-term environmental impact.
Efficiency and Abundance
Thorium is a more abundant resource than uranium, with estimates suggesting it is three to four times more plentiful in the Earth's crust. This abundance makes thorium a sustainable fuel choice for the future. Moreover, MSRs can operate at higher temperatures than traditional reactors, leading to greater thermal efficiency. This means more electricity can be generated from the same amount of fuel, making the energy production process more efficient and cost-effective in the long run.
Scalability
The modular design of these reactors allows for scalability to meet varying power demands. A single unit might power a small community, while multiple units can be combined to serve larger towns or cities. This flexibility is particularly useful for growing populations or regions with fluctuating energy needs. As demand increases, additional modules can be added without the need for extensive new infrastructure.
Cost-Effectiveness
While the initial investment in nuclear modular plants may be significant, the long-term operational costs can be lower than traditional power sources. The high efficiency of MSRs means less fuel is needed over time, and the reduced waste production lowers disposal costs. Additionally, the ability to mass-produce these modular units could drive down manufacturing costs, making nuclear power more accessible and affordable.
Environmental Impact
Nuclear power is already one of the cleanest energy sources in terms of carbon emissions, and thorium MSRs take this a step further. By producing less long-lived waste and utilizing a more abundant fuel, these reactors offer a more sustainable path for nuclear energy. Furthermore, their ability to provide reliable baseload power can help reduce reliance on fossil fuels, contributing to global efforts to combat climate change.
Challenges and Considerations
Despite these benefits, there are challenges to overcome before nuclear modular plants can be widely deployed. The technology for thorium MSRs is still in the developmental stage, with ongoing research needed to address issues such as material corrosion and fuel processing. Regulatory frameworks will also need to adapt to this new type of reactor, and public perception of nuclear energy remains a hurdle in many regions. However, with continued investment and innovation, these obstacles can be addressed.
Conclusion
In conclusion, nuclear modular plants using thorium and molten salt systems represent a promising advancement in nuclear technology. Their portability, safety features, efficiency, scalability, and environmental benefits make them an attractive option for meeting the world's growing energy needs. While challenges remain, the potential of these reactors to provide clean, reliable power to communities around the globe is undeniable. As research and development continue, we may soon see a new era of nuclear energy that is safer, more efficient, and more accessible than ever before.
-
 @ a5142938:0ef19da3
2025-05-02 10:38:10
@ a5142938:0ef19da3
2025-05-02 10:38:10Happy to have found useful information on this site?
Support the project by making a donation to keep it running and thank the contributors.
In bitcoin
- On-chain:
bc1qkm8me8l9563wvsl9sklzt4hdcuny3tlejznj7d
- Lightning network:
⚡️
origin-nature@coinos.ioYou can also support us on a recurring basis 👉 Set up a recurring Lightning payment
In euros, dollars, or any other supported currency
-
By bank transfer, IBAN: FR76 2823 3000 0144 3759 8717 669
-
You can also support us on a recurring basis 👉 Make a pledge on LiberaPay
Contact us if you’d like to make a donation using any other cryptocurrency.
💡 A Value-Sharing Model
Half of the donations are redistributed to the contributors who create the site's value, experimenting with a revenue-sharing model on the Internet—one that respects your data and doesn’t seek to capture your attention.
The other half helps cover the website’s operating costs, compensate the core team, and support the open-source tools we rely on.
This article is published on origin-nature.com 🌐 Voir cet article en français
-
 @ a53364ff:e6ba5513
2025-04-26 17:55:16
@ a53364ff:e6ba5513
2025-04-26 17:55:16About
Bitcoin Core is an open source project which maintains and releases Bitcoin client software called “Bitcoin Core”.
It is a direct descendant of the original Bitcoin software client released by Satoshi Nakamoto after he published the famous Bitcoin whitepaper.
Bitcoin Core consists of both “full-node” software for fully validating the blockchain as well as a bitcoin wallet. The project also currently maintains related software such as the cryptography library libsecp256k1 and others located at GitHub.
Anyone can contribute to Bitcoin Core.
Team
The Bitcoin Core project has a large open source developer community with many casual contributors to the codebase. There are many more who contribute research, peer review, testing, documentation, and translation.
Maintainers
Project maintainers have commit access and are responsible for merging patches from contributors. They perform a janitorial role merging patches that the team agrees should be merged. They also act as a final check to ensure that patches are safe and in line with the project goals. The maintainers’ role is by agreement of project contributors.
Contributors
Everyone is free to propose code changes and to test, review and comment on open Pull Requests. Anyone who contributes code, review, test, translation or documentation to the Bitcoin Core project is considered a contributor. The release notes for each Bitcoin Core software release contain a credits section to recognize all those who have contributed to the project over the previous release cycle. A list of code contributors can be found on Github.
-
 @ a5142938:0ef19da3
2025-05-02 10:26:59
@ a5142938:0ef19da3
2025-05-02 10:26:59Contribute to enrich the site!
Each contribution helps improve this site by supporting the listing of natural alternatives.
💡 What Counts as a Contribution?
A contribution can be:
📝 Proposing a new entry, by providing its initial information. Each piece of information added (name, link, category, etc.) is considered a contribution: - Add a product - Add a brand
📝 Adding or modifying information in an existing entry. Each piece of information added or removed is considered a contribution.
✅ Contribution validation
Contributions are reviewed by the core team. A contribution is validated when the information provided is submitted for the first time (the earliest comment is taken into account) and can be verified.
Once validated, contributions are counted and eligible for rewards. 👉 Learn more about rewards
Information added directly by the core team during the verification of a contribution is not counted. However, core team members can also contribute just like anyone else.
This article is published on origin-nature.com 🌐 Voir cet article en français
-
 @ 52b4a076:e7fad8bd
2025-05-03 21:54:45
@ 52b4a076:e7fad8bd
2025-05-03 21:54:45Introduction
Me and Fishcake have been working on infrastructure for Noswhere and Nostr.build. Part of this involves processing a large amount of Nostr events for features such as search, analytics, and feeds.
I have been recently developing
nosdexv3, a newer version of the Noswhere scraper that is designed for maximum performance and fault tolerance using FoundationDB (FDB).Fishcake has been working on a processing system for Nostr events to use with NB, based off of Cloudflare (CF) Pipelines, which is a relatively new beta product. This evening, we put it all to the test.
First preparations
We set up a new CF Pipelines endpoint, and I implemented a basic importer that took data from the
nosdexdatabase. This was quite slow, as it did HTTP requests synchronously, but worked as a good smoke test.Asynchronous indexing
I implemented a high-contention queue system designed for highly parallel indexing operations, built using FDB, that supports: - Fully customizable batch sizes - Per-index queues - Hundreds of parallel consumers - Automatic retry logic using lease expiration
When the scraper first gets an event, it will process it and eventually write it to the blob store and FDB. Each new event is appended to the event log.
On the indexing side, a
Queuerwill read the event log, and batch events (usually 2K-5K events) into one work job. This work job contains: - A range in the log to index - Which target this job is intended for - The size of the job and some other metadataEach job has an associated leasing state, which is used to handle retries and prioritization, and ensure no duplication of work.
Several
Workers monitor the index queue (up to 128) and wait for new jobs that are available to lease.Once a suitable job is found, the worker acquires a lease on the job and reads the relevant events from FDB and the blob store.
Depending on the indexing type, the job will be processed in one of a number of ways, and then marked as completed or returned for retries.
In this case, the event is also forwarded to CF Pipelines.

Trying it out
The first attempt did not go well. I found a bug in the high-contention indexer that led to frequent transaction conflicts. This was easily solved by correcting an incorrectly set parameter.
We also found there were other issues in the indexer, such as an insufficient amount of threads, and a suspicious decrease in the speed of the
Queuerduring processing of queued jobs.Along with fixing these issues, I also implemented other optimizations, such as deprioritizing
WorkerDB accesses, and increasing the batch size.To fix the degraded
Queuerperformance, I ran the backfill job by itself, and then started indexing after it had completed.Bottlenecks, bottlenecks everywhere

After implementing these fixes, there was an interesting problem: The DB couldn't go over 80K reads per second. I had encountered this limit during load testing for the scraper and other FDB benchmarks.
As I suspected, this was a client thread limitation, as one thread seemed to be using high amounts of CPU. To overcome this, I created a new client instance for each
Worker.After investigating, I discovered that the Go FoundationDB client cached the database connection. This meant all attempts to create separate DB connections ended up being useless.
Using
OpenWithConnectionStringpartially resolved this issue. (This also had benefits for service-discovery based connection configuration.)To be able to fully support multi-threading, I needed to enabled the FDB multi-client feature. Enabling it also allowed easier upgrades across DB versions, as FDB clients are incompatible across versions:
FDB_NETWORK_OPTION_EXTERNAL_CLIENT_LIBRARY="/lib/libfdb_c.so"FDB_NETWORK_OPTION_CLIENT_THREADS_PER_VERSION="16"Breaking the 100K/s reads barrier

After implementing support for the multi-threaded client, we were able to get over 100K reads per second.
You may notice after the restart (gap) the performance dropped. This was caused by several bugs: 1. When creating the CF Pipelines endpoint, we did not specify a region. The automatically selected region was far away from the server. 2. The amount of shards were not sufficient, so we increased them. 3. The client overloaded a few HTTP/2 connections with too many requests.
I implemented a feature to assign each
Workerits own HTTP client, fixing the 3rd issue. We also moved the entire storage region to West Europe to be closer to the servers.After these changes, we were able to easily push over 200K reads/s, mostly limited by missing optimizations:

It's shards all the way down
While testing, we also noticed another issue: At certain times, a pipeline would get overloaded, stalling requests for seconds at a time. This prevented all forward progress on the
Workers.We solved this by having multiple pipelines: A primary pipeline meant to be for standard load, with moderate batching duration and less shards, and high-throughput pipelines with more shards.
Each
Workeris assigned a pipeline on startup, and if one pipeline stalls, other workers can continue making progress and saturate the DB.The stress test
After making sure everything was ready for the import, we cleared all data, and started the import.
The entire import lasted 20 minutes between 01:44 UTC and 02:04 UTC, reaching a peak of: - 0.25M requests per second - 0.6M keys read per second - 140MB/s reads from DB - 2Gbps of network throughput
FoundationDB ran smoothly during this test, with: - Read times under 2ms - Zero conflicting transactions - No overloaded servers
CF Pipelines held up well, delivering batches to R2 without any issues, while reaching its maximum possible throughput.

Finishing notes
Me and Fishcake have been building infrastructure around scaling Nostr, from media, to relays, to content indexing. We consistently work on improving scalability, resiliency and stability, even outside these posts.
Many things, including what you see here, are already a part of Nostr.build, Noswhere and NFDB, and many other changes are being implemented every day.
If you like what you are seeing, and want to integrate it, get in touch. :)
If you want to support our work, you can zap this post, or register for nostr.land and nostr.build today.
-
 @ 044da344:073a8a0e
2025-05-03 19:02:02
@ 044da344:073a8a0e
2025-05-03 19:02:02Mein Thema kommt heute aus dem Kalender und hat gleich noch zu einem Video geführt. Internationaler Tag der Pressefreiheit – wie jedes Jahr am 3. Mai. Das Publikum liebt Ranglisten. Shanghai für die Hochschulen, der Best Country Report für die Lebensqualität und Freedom House für die Freiheit in der Welt. Es gibt Aufsteiger und Absteiger und Jahr für Jahr eine Meldung, über die sich trefflich diskutieren lässt – vor allem in Europa und Nordamerika, wo die Sieger wohnen. Man muss die Statistik dafür nicht einmal fälschen, sondern einfach nur das messen, was man selbst am besten kann, und alles weglassen, was das Bild trüben könnte. Bei den „Reportern ohne Grenzen“ sorgen dafür die Geldgeber und Fragen, die sich zum Beispiel in Afrika oder in Südostasien gar nicht stellen. Ergebnis: Die Medien sind bei uns ziemlich frei, auch wenn Leser dieser Seite wissen, dass das so nicht stimmt.
Okay: Deutschland hat es wieder nicht ganz geschafft in den grünen Bereich – dorthin, wo die skandinavischen Länder stehen, die Niederlande oder Irland. Deutschland gehört auch nicht mehr zu den Top Ten wie noch 2024, aber es war knapp. Platz elf. Zum Glück nennen die „Reporter ohne Grenzen“ die Schuldigen. Zensur? Gott bewahre. Das Ausblenden, Diffamieren, Verleumden von allen, die laut Fragen stellen zum Regierungskurs? Doch nicht bei uns. Dieses Land würde auch in Sachen Pressefreiheit längst Weltmeister sein, wenn da nicht ein paar Unverbesserliche wären, die auf Journalisten ungefähr so reagieren wie ein Stier auf ein rotes Tuch. Glaubt man den „Reportern ohne Grenzen“, dann sind Demos in Deutschland ein gefährlicher Ort für alle, die dort mit Kamera, Mikro oder Presseschild auftauchen. 75 „physische Angriffe“ 2024, davon die meisten in Berlin und beim Thema Nahost, wobei es zwei Bild-Reporter allein auf 29 Einträge gebracht haben (Iman Sefati und seine Fotografin Yalcin Askin).
Vorweg: Jede Attacke ist eine zu viel. Gleich danach kommt aber der Verdacht, dass das ganz gut passt, weil die „Reporter ohne Grenzen“ so eine „zunehmende Pressefeindlichkeit“ beklagen können und „ein verengtes Verständnis von Pressefreiheit“. Zitat: „Denn viele Bürger*innen sehen Berichterstattende, die nicht ihrem eigenen politischen Spektrum entstammen, mittlerweile als Gegner an.“
Sorry für die Genderei. Ich habe das so gelassen, weil es vermutlich bereits damit anfängt. Mit einem „verengten Verständnis“ auch und gerade bei der Sprache. Lassen Sie uns das in drei Schritten angehen. Nummer eins: Wir schauen auf den Kellner, der da jedes Jahr zum Welttag der Pressefreiheit eine Quittung ausstellt. Nummer zwei: Wir zählen nach. Und Nummer drei: Wir schlagen all das drauf, was in der Rechnung fehlt.
Die „Reporter ohne Grenzen“ sitzen in Paris und sind damit auf den ersten Blick weniger verdächtig als der US-Thinktank „Freedom House“, der bis 2017 jedes Jahr eine Konkurrenzliste veröffentlicht hat und einen Großteil seiner Gelder und Sicherheiten direkt oder indirekt aus dem Staatshaushalt in Washington bezieht. Der Volksmund weiß, was das Brot aus den Liedern macht, die draußen gesungen werden. Bei den „Reportern ohne Grenzen“ kommt das Geld aus ganz ähnlich Töpfen – 2023 zu drei Vierteln von der EU, von staatlichen Behörden und von den großen Stiftungen. Ford, Luminate (Geldbörse von Ebay-Gründer Pierre Omidyar, der auch bei den Faktencheckern mitspielt), Open Society Foundations. Der deutsche Steuerzahler ist über ein Ministerium (Entwicklungshilfe) und den Berliner Senat jeweils mit einer Viertelmillion Euro dabei. Dass die Niederlande und Schweden mitspielen, erklärt sich bei einem Blick auf die Ergebnisse (in diesem Jahr: Platz 3 und 4). Besser kann man nicht investieren in Werbung für das eigene Land.
Diese Platzierungen sind gewissermaßen ein Selbstläufer, weil all das in die Wertung kommt, was der Westen gut findet – die formale Trennung von Regierung und Redaktionen zum Beispiel. Andersherum: Abzüge gibt es überall da, wo der Staat, Parteien oder Politiker selbst Medien betreiben. In Uganda zum Beispiel, Platz 143, gibt es kaum Werbetreibende, die ein TV-Programm finanzieren könnten, und nur ein kleines Publikum, das sich ein Zeitungsabo leisten kann und will. Sonntags drängen sich die Menschen dort vor kleinen Hütten mit großen Bildschirmen, um ihren Lieblingen aus der Premier League zuzujubeln und vielleicht einen Wettgewinn einzustreichen, der sie über die Woche trägt. Auf dem Land gehören die Radiostationen in aller Regel lokalen Größen. Kirche, Politik, Wirtschaft. Ich habe dort Interviews geführt und gelernt: Über „Pressefreiheit“ und Informationsqualität sagt das alles wenig. Die Menschen in Uganda wissen sehr genau, wer jeweils zu ihnen spricht, und machen sich ihren Reim darauf. Ein anderer Kriterienkatalog könnte daraus ein Qualitätsmerkmal machen. Während Besitz- und damit Machtverhältnisse im Westen hinter Nebelkerzen versteckt werden (Objektivität, Unabhängigkeit, Neutralität), herrscht in Uganda Transparenz.
Neben dem „politischen Kontext“ haben die „Reporter ohne Grenzen“ vier weitere Blöcke in ihrem Punktekatalog. Gesetze, Wirtschaft, Gesellschaft, Sicherheit. Die Fragen decken das ab, was bei uns Standard ist. Dürfen sich Journalisten gewerkschaftlich organisieren? Werden sie bestochen? Können Nachrichtenmedien finanziell überleben? Werden Karikaturen toleriert? Ich will hier nicht zu sehr auf Uganda herumreiten. Nur: Der Beruf wird dort völlig anders gesehen als hier. Es gibt nur eine kleine vierstellige Zahl an Journalisten. 1000, vielleicht 1500. Die meisten sind jung, weil die Redaktionen als Sprungbrett gesehen werden zu einem wirklich lukrativen Job in der Verwaltung, in den Unternehmen, in der Politik. Wer zu einer Pressekonferenz fährt, erwartet dort einen Umschlag. Offiziell: Anreisepauschale. Inoffiziell der Preis für einen wohlwollenden Bericht. Die „Reporter ohne Grenzen“ strafen Uganda folglich ab. Angriffe auf Journalisten (oft von Sicherheitsleuten), wenig Schutz vor Gericht, wenig Achtung vor dem Beruf. Platz 143 halt.
Und Deutschland? Die Demos wie gesagt und Leute, die die Dinge einfach falsch sehen. Ein „verengtes Verständnis von Pressefreiheit“. Außerdem sagen die „Reporter ohne Grenzen“: Wir tun zu wenig gegen „Hassrede und Desinformation“. Der Koalitionsvertrag von Schwarz-Rot ist offenbar nicht mehr eingeflossen in diesen Bericht. Dort heißt es:
Gezielte Einflussnahme auf Wahlen sowie inzwischen alltägliche Desinformation und Fake News sind ernste Bedrohungen für unsere Demokratie, ihre Institutionen und den gesellschaftlichen Zusammenhalt. Die bewusste Verbreitung falscher Tatsachenbehauptungen ist durch die Meinungsfreiheit nicht gedeckt. Deshalb muss die staatsferne Medienaufsicht unter Wahrung der Meinungsfreiheit auf der Basis klarer gesetzlicher Vorgaben gegen Informationsmanipulation sowie Hass und Hetze vorgehen können.
Schon vorab hatten die „Reporter ohne Grenzen“ von „einem stark verengten Meinungskorridor bei der Arbeit zu Israel und Palästina“ berichtet. Selbst alte Hasen haben in dieser Befragung gesagt, dass sie noch nie einen solchen Druck erlebt hätten – vor allem dann, wenn es um die israelische Kriegsführung geht, um die Folgen für die Bevölkerung in Gaza und um das, was in Deutschland zu diesem Thema passiert. Ich verlinke hier die Münchner Rede von Andreas Zumach, gehalten im November 2018, wo all das schon Thema war.
Und sonst? Corona, Ukraine, Klima und damit Energiewende? Kontokündigungen? Gerichtsurteile, die selbst es bis in die Weltpresse schafften (im Bild: The Economist vom 16. April 2025) und dort Unbehagen auslösten? Eine Cancel Culture, die Sprecher aus der Öffentlichkeit verbannt, die sich gegen die herrschende Ideologie und den Regierungskurs stellen?
Alles kein Thema – jedenfalls nicht für die Experten, die gefragt werden (Journalisten, Forscher, Akademiker, Menschenrechtsspezialisten; mithin Menschen, die in irgendeiner Form von Staat oder Konzernen abhängen). Die konzernfreien oder neuen Medien senden für die „Reporter ohne Grenzen“ offenbar jenseits von Gut und Böse. Und dass die Regierung Fernsehen, Radio und Presse nicht unbedingt selbst betreiben muss wie in Uganda, um ihre Sicht der Dinge flächendeckend zu verbreiten, scheint dort außerhalb jeder Vorstellungskraft zu liegen. Anders ist nicht zu erklären, dass im Bericht zwar ein paar öffentlich-rechtliche Skandälchen auftauchen und der Stellenabbau bei der Südwestdeutschen Medienholding, aber nichts zu lesen ist über die Aufrüstung der Medienapparate in Ministerien, Parteien, Unternehmen und über den Druck, der davon auf Journalisten ausgeht, die zwar keinen Umschlag bekommen, wenn sie ordentlich berichten, aber sicher ein wenig Exklusives, wahrscheinlich eine Beförderung und vielleicht sogar ein Ticket für den Sprung auf die andere, besser entlohnte Seite. Bis es soweit ist, melden sie einfach, dass mit der Medienfreiheit alles okay ist, wenn es da nicht diese Chaoten auf der Straße geben würde und ein paar Unverbesserliche mit einem „verengten Verständnis von Pressefreiheit“. Sonst müsste man sich möglicherweise aufmachen und nach den Ursachen für den Unmut fragen.
-
 @ 91bea5cd:1df4451c
2025-04-26 10:16:21
@ 91bea5cd:1df4451c
2025-04-26 10:16:21O Contexto Legal Brasileiro e o Consentimento
No ordenamento jurídico brasileiro, o consentimento do ofendido pode, em certas circunstâncias, afastar a ilicitude de um ato que, sem ele, configuraria crime (como lesão corporal leve, prevista no Art. 129 do Código Penal). Contudo, o consentimento tem limites claros: não é válido para bens jurídicos indisponíveis, como a vida, e sua eficácia é questionável em casos de lesões corporais graves ou gravíssimas.
A prática de BDSM consensual situa-se em uma zona complexa. Em tese, se ambos os parceiros são adultos, capazes, e consentiram livre e informadamente nos atos praticados, sem que resultem em lesões graves permanentes ou risco de morte não consentido, não haveria crime. O desafio reside na comprovação desse consentimento, especialmente se uma das partes, posteriormente, o negar ou alegar coação.
A Lei Maria da Penha (Lei nº 11.340/2006)
A Lei Maria da Penha é um marco fundamental na proteção da mulher contra a violência doméstica e familiar. Ela estabelece mecanismos para coibir e prevenir tal violência, definindo suas formas (física, psicológica, sexual, patrimonial e moral) e prevendo medidas protetivas de urgência.
Embora essencial, a aplicação da lei em contextos de BDSM pode ser delicada. Uma alegação de violência por parte da mulher, mesmo que as lesões ou situações decorram de práticas consensuais, tende a receber atenção prioritária das autoridades, dada a presunção de vulnerabilidade estabelecida pela lei. Isso pode criar um cenário onde o parceiro masculino enfrenta dificuldades significativas em demonstrar a natureza consensual dos atos, especialmente se não houver provas robustas pré-constituídas.
Outros riscos:
Lesão corporal grave ou gravíssima (art. 129, §§ 1º e 2º, CP), não pode ser justificada pelo consentimento, podendo ensejar persecução penal.
Crimes contra a dignidade sexual (arts. 213 e seguintes do CP) são de ação pública incondicionada e independem de representação da vítima para a investigação e denúncia.
Riscos de Falsas Acusações e Alegação de Coação Futura
Os riscos para os praticantes de BDSM, especialmente para o parceiro que assume o papel dominante ou que inflige dor/restrição (frequentemente, mas não exclusivamente, o homem), podem surgir de diversas frentes:
- Acusações Externas: Vizinhos, familiares ou amigos que desconhecem a natureza consensual do relacionamento podem interpretar sons, marcas ou comportamentos como sinais de abuso e denunciar às autoridades.
- Alegações Futuras da Parceira: Em caso de término conturbado, vingança, arrependimento ou mudança de perspectiva, a parceira pode reinterpretar as práticas passadas como abuso e buscar reparação ou retaliação através de uma denúncia. A alegação pode ser de que o consentimento nunca existiu ou foi viciado.
- Alegação de Coação: Uma das formas mais complexas de refutar é a alegação de que o consentimento foi obtido mediante coação (física, moral, psicológica ou econômica). A parceira pode alegar, por exemplo, que se sentia pressionada, intimidada ou dependente, e que seu "sim" não era genuíno. Provar a ausência de coação a posteriori é extremamente difícil.
- Ingenuidade e Vulnerabilidade Masculina: Muitos homens, confiando na dinâmica consensual e na parceira, podem negligenciar a necessidade de precauções. A crença de que "isso nunca aconteceria comigo" ou a falta de conhecimento sobre as implicações legais e o peso processual de uma acusação no âmbito da Lei Maria da Penha podem deixá-los vulneráveis. A presença de marcas físicas, mesmo que consentidas, pode ser usada como evidência de agressão, invertendo o ônus da prova na prática, ainda que não na teoria jurídica.
Estratégias de Prevenção e Mitigação
Não existe um método infalível para evitar completamente o risco de uma falsa acusação, mas diversas medidas podem ser adotadas para construir um histórico de consentimento e reduzir vulnerabilidades:
- Comunicação Explícita e Contínua: A base de qualquer prática BDSM segura é a comunicação constante. Negociar limites, desejos, palavras de segurança ("safewords") e expectativas antes, durante e depois das cenas é crucial. Manter registros dessas negociações (e-mails, mensagens, diários compartilhados) pode ser útil.
-
Documentação do Consentimento:
-
Contratos de Relacionamento/Cena: Embora a validade jurídica de "contratos BDSM" seja discutível no Brasil (não podem afastar normas de ordem pública), eles servem como forte evidência da intenção das partes, da negociação detalhada de limites e do consentimento informado. Devem ser claros, datados, assinados e, idealmente, reconhecidos em cartório (para prova de data e autenticidade das assinaturas).
-
Registros Audiovisuais: Gravar (com consentimento explícito para a gravação) discussões sobre consentimento e limites antes das cenas pode ser uma prova poderosa. Gravar as próprias cenas é mais complexo devido a questões de privacidade e potencial uso indevido, mas pode ser considerado em casos específicos, sempre com consentimento mútuo documentado para a gravação.
Importante: a gravação deve ser com ciência da outra parte, para não configurar violação da intimidade (art. 5º, X, da Constituição Federal e art. 20 do Código Civil).
-
-
Testemunhas: Em alguns contextos de comunidade BDSM, a presença de terceiros de confiança durante negociações ou mesmo cenas pode servir como testemunho, embora isso possa alterar a dinâmica íntima do casal.
- Estabelecimento Claro de Limites e Palavras de Segurança: Definir e respeitar rigorosamente os limites (o que é permitido, o que é proibido) e as palavras de segurança é fundamental. O desrespeito a uma palavra de segurança encerra o consentimento para aquele ato.
- Avaliação Contínua do Consentimento: O consentimento não é um cheque em branco; ele deve ser entusiástico, contínuo e revogável a qualquer momento. Verificar o bem-estar do parceiro durante a cena ("check-ins") é essencial.
- Discrição e Cuidado com Evidências Físicas: Ser discreto sobre a natureza do relacionamento pode evitar mal-entendidos externos. Após cenas que deixem marcas, é prudente que ambos os parceiros estejam cientes e de acordo, talvez documentando por fotos (com data) e uma nota sobre a consensualidade da prática que as gerou.
- Aconselhamento Jurídico Preventivo: Consultar um advogado especializado em direito de família e criminal, com sensibilidade para dinâmicas de relacionamento alternativas, pode fornecer orientação personalizada sobre as melhores formas de documentar o consentimento e entender os riscos legais específicos.
Observações Importantes
- Nenhuma documentação substitui a necessidade de consentimento real, livre, informado e contínuo.
- A lei brasileira protege a "integridade física" e a "dignidade humana". Práticas que resultem em lesões graves ou que violem a dignidade de forma não consentida (ou com consentimento viciado) serão ilegais, independentemente de qualquer acordo prévio.
- Em caso de acusação, a existência de documentação robusta de consentimento não garante a absolvição, mas fortalece significativamente a defesa, ajudando a demonstrar a natureza consensual da relação e das práticas.
-
A alegação de coação futura é particularmente difícil de prevenir apenas com documentos. Um histórico consistente de comunicação aberta (whatsapp/telegram/e-mails), respeito mútuo e ausência de dependência ou controle excessivo na relação pode ajudar a contextualizar a dinâmica como não coercitiva.
-
Cuidado com Marcas Visíveis e Lesões Graves Práticas que resultam em hematomas severos ou lesões podem ser interpretadas como agressão, mesmo que consentidas. Evitar excessos protege não apenas a integridade física, mas também evita questionamentos legais futuros.
O que vem a ser consentimento viciado
No Direito, consentimento viciado é quando a pessoa concorda com algo, mas a vontade dela não é livre ou plena — ou seja, o consentimento existe formalmente, mas é defeituoso por alguma razão.
O Código Civil brasileiro (art. 138 a 165) define várias formas de vício de consentimento. As principais são:
Erro: A pessoa se engana sobre o que está consentindo. (Ex.: A pessoa acredita que vai participar de um jogo leve, mas na verdade é exposta a práticas pesadas.)
Dolo: A pessoa é enganada propositalmente para aceitar algo. (Ex.: Alguém mente sobre o que vai acontecer durante a prática.)
Coação: A pessoa é forçada ou ameaçada a consentir. (Ex.: "Se você não aceitar, eu termino com você" — pressão emocional forte pode ser vista como coação.)
Estado de perigo ou lesão: A pessoa aceita algo em situação de necessidade extrema ou abuso de sua vulnerabilidade. (Ex.: Alguém em situação emocional muito fragilizada é induzida a aceitar práticas que normalmente recusaria.)
No contexto de BDSM, isso é ainda mais delicado: Mesmo que a pessoa tenha "assinado" um contrato ou dito "sim", se depois ela alegar que seu consentimento foi dado sob medo, engano ou pressão psicológica, o consentimento pode ser considerado viciado — e, portanto, juridicamente inválido.
Isso tem duas implicações sérias:
-
O crime não se descaracteriza: Se houver vício, o consentimento é ignorado e a prática pode ser tratada como crime normal (lesão corporal, estupro, tortura, etc.).
-
A prova do consentimento precisa ser sólida: Mostrando que a pessoa estava informada, lúcida, livre e sem qualquer tipo de coação.
Consentimento viciado é quando a pessoa concorda formalmente, mas de maneira enganada, forçada ou pressionada, tornando o consentimento inútil para efeitos jurídicos.
Conclusão
Casais que praticam BDSM consensual no Brasil navegam em um terreno que exige não apenas confiança mútua e comunicação excepcional, mas também uma consciência aguçada das complexidades legais e dos riscos de interpretações equivocadas ou acusações mal-intencionadas. Embora o BDSM seja uma expressão legítima da sexualidade humana, sua prática no Brasil exige responsabilidade redobrada. Ter provas claras de consentimento, manter a comunicação aberta e agir com prudência são formas eficazes de se proteger de falsas alegações e preservar a liberdade e a segurança de todos os envolvidos. Embora leis controversas como a Maria da Penha sejam "vitais" para a proteção contra a violência real, os praticantes de BDSM, e em particular os homens nesse contexto, devem adotar uma postura proativa e prudente para mitigar os riscos inerentes à potencial má interpretação ou instrumentalização dessas práticas e leis, garantindo que a expressão de sua consensualidade esteja resguardada na medida do possível.
Importante: No Brasil, mesmo com tudo isso, o Ministério Público pode denunciar por crime como lesão corporal grave, estupro ou tortura, independente de consentimento. Então a prudência nas práticas é fundamental.
Aviso Legal: Este artigo tem caráter meramente informativo e não constitui aconselhamento jurídico. As leis e interpretações podem mudar, e cada situação é única. Recomenda-se buscar orientação de um advogado qualificado para discutir casos específicos.
Se curtiu este artigo faça uma contribuição, se tiver algum ponto relevante para o artigo deixe seu comentário.
-
 @ a5142938:0ef19da3
2025-05-02 10:24:43
@ a5142938:0ef19da3
2025-05-02 10:24:43
This article is published on origin-nature.com 🌐 Voir cet article en français
-
 @ 3bf0c63f:aefa459d
2025-04-25 19:26:48
@ 3bf0c63f:aefa459d
2025-04-25 19:26:48Redistributing Git with Nostr
Every time someone tries to "decentralize" Git -- like many projects tried in the past to do it with BitTorrent, IPFS, ScuttleButt or custom p2p protocols -- there is always a lurking comment: "but Git is already distributed!", and then the discussion proceeds to mention some facts about how Git supports multiple remotes and its magic syncing and merging abilities and so on.
Turns out all that is true, Git is indeed all that powerful, and yet GitHub is the big central hub that hosts basically all Git repositories in the giant world of open-source. There are some crazy people that host their stuff elsewhere, but these projects end up not being found by many people, and even when they do they suffer from lack of contributions.
Because everybody has a GitHub account it's easy to open a pull request to a repository of a project you're using if it's on GitHub (to be fair I think it's very annoying to have to clone the repository, then add it as a remote locally, push to it, then go on the web UI and click to open a pull request, then that cloned repository lurks forever in your profile unless you go through 16 screens to delete it -- but people in general seem to think it's easy).
It's much harder to do it on some random other server where some project might be hosted, because now you have to add 4 more even more annoying steps: create an account; pick a password; confirm an email address; setup SSH keys for pushing. (And I'm not even mentioning the basic impossibility of offering
pushaccess to external unknown contributors to people who want to host their own simple homemade Git server.)At this point some may argue that we could all have accounts on GitLab, or Codeberg or wherever else, then those steps are removed. Besides not being a practical strategy this pseudo solution misses the point of being decentralized (or distributed, who knows) entirely: it's far from the ideal to force everybody to have the double of account management and SSH setup work in order to have the open-source world controlled by two shady companies instead of one.
What we want is to give every person the opportunity to host their own Git server without being ostracized. at the same time we must recognize that most people won't want to host their own servers (not even most open-source programmers!) and give everybody the ability to host their stuff on multi-tenant servers (such as GitHub) too. Importantly, though, if we allow for a random person to have a standalone Git server on a standalone server they host themselves on their wood cabin that also means any new hosting company can show up and start offering Git hosting, with or without new cool features, charging high or low or zero, and be immediately competing against GitHub or GitLab, i.e. we must remove the network-effect centralization pressure.
External contributions
The first problem we have to solve is: how can Bob contribute to Alice's repository without having an account on Alice's server?
SourceHut has reminded GitHub users that Git has always had this (for most) arcane
git send-emailcommand that is the original way to send patches, using an once-open protocol.Turns out Nostr acts as a quite powerful email replacement and can be used to send text content just like email, therefore patches are a very good fit for Nostr event contents.
Once you get used to it and the proper UIs (or CLIs) are built sending and applying patches to and from others becomes a much easier flow than the intense clickops mixed with terminal copypasting that is interacting with GitHub (you have to clone the repository on GitHub, then update the remote URL in your local directory, then create a branch and then go back and turn that branch into a Pull Request, it's quite tiresome) that many people already dislike so much they went out of their way to build many GitHub CLI tools just so they could comment on issues and approve pull requests from their terminal.
Replacing GitHub features
Aside from being the "hub" that people use to send patches to other people's code (because no one can do the email flow anymore, justifiably), GitHub also has 3 other big features that are not directly related to Git, but that make its network-effect harder to overcome. Luckily Nostr can be used to create a new environment in which these same features are implemented in a more decentralized and healthy way.
Issues: bug reports, feature requests and general discussions
Since the "Issues" GitHub feature is just a bunch of text comments it should be very obvious that Nostr is a perfect fit for it.
I will not even mention the fact that Nostr is much better at threading comments than GitHub (which doesn't do it at all), which can generate much more productive and organized discussions (and you can opt out if you want).
Search
I use GitHub search all the time to find libraries and projects that may do something that I need, and it returns good results almost always. So if people migrated out to other code hosting providers wouldn't we lose it?
The fact is that even though we think everybody is on GitHub that is a globalist falsehood. Some projects are not on GitHub, and if we use only GitHub for search those will be missed. So even if we didn't have a Nostr Git alternative it would still be necessary to create a search engine that incorporated GitLab, Codeberg, SourceHut and whatnot.
Turns out on Nostr we can make that quite easy by not forcing anyone to integrate custom APIs or hardcoding Git provider URLs: each repository can make itself available by publishing an "announcement" event with a brief description and one or more Git URLs. That makes it easy for a search engine to index them -- and even automatically download the code and index the code (or index just README files or whatever) without a centralized platform ever having to be involved.
The relays where such announcements will be available play a role, of course, but that isn't a bad role: each announcement can be in multiple relays known for storing "public good" projects, some relays may curate only projects known to be very good according to some standards, other relays may allow any kind of garbage, which wouldn't make them good for a search engine to rely upon, but would still be useful in case one knows the exact thing (and from whom) they're searching for (the same is valid for all Nostr content, by the way, and that's where it's censorship-resistance comes from).
Continuous integration
GitHub Actions are a very hardly subsidized free-compute-for-all-paid-by-Microsoft feature, but one that isn't hard to replace at all. In fact there exists today many companies offering the same kind of service out there -- although they are mostly targeting businesses and not open-source projects, before GitHub Actions was introduced there were also many that were heavily used by open-source projects.
One problem is that these services are still heavily tied to GitHub today, they require a GitHub login, sometimes BitBucket and GitLab and whatnot, and do not allow one to paste an arbitrary Git server URL, but that isn't a thing that is very hard to change anyway, or to start from scratch. All we need are services that offer the CI/CD flows, perhaps using the same framework of GitHub Actions (although I would prefer to not use that messy garbage), and charge some few satoshis for it.
It may be the case that all the current services only support the big Git hosting platforms because they rely on their proprietary APIs, most notably the webhooks dispatched when a repository is updated, to trigger the jobs. It doesn't have to be said that Nostr can also solve that problem very easily.
-
 @ a5142938:0ef19da3
2025-05-02 09:39:05
@ a5142938:0ef19da3
2025-05-02 09:39:05Do you know a brand offering natural alternatives? Share it here by commenting on this page!
To be listed, the brand must offer at least some of its products made from natural materials. 👉 Learn more about materials
Each piece of information added (name, link, category, etc.) and validated is considered a contribution. 👉 Learn more about contributions
Every validated contribution is counted and eligible for rewards. Make sure to securely save your keys (credentials) in a vault like nsec.app). You can also share more easily your finds without creating an account via the contact form (not eligible for rewards). 👉 Learn more about rewards
Copy and paste the template below and fill in the information you have. Other contributors or the core team can complete any missing details.
New brand or manufacturer
- Brand name:
- Image representing the brand’s products (link, ideally from the brand’s website):
- Short description:
- Categories of products offered:
- Materials used in its products:
- Brand’s website:
- Other information (place of production, certifications, etc.):
This article is published on origin-nature.com 🌐 Voir cet article en français
-
 @ d0ea1c34:9c84dc37
2025-05-03 17:53:05
@ d0ea1c34:9c84dc37
2025-05-03 17:53:05Markdown Rendering Test Document
Basic Text Formatting
This is a paragraph with bold text, italic text, and bold italic text. You can also use underscores for bold or single underscores for italics.
This is a paragraph with some
inline codeusing backticks.Lists
Unordered Lists
- Item 1
- Item 2
- Nested item 2.1
- Nested item 2.2
- Item 3
Ordered Lists
- First item
- Second item
- Nested item 2.1
- Nested item 2.2
- Third item
Links and Images
Blockquotes
This is a blockquote.
It can span multiple lines.
And can be nested.
Code Blocks
```python def hello_world(): print("Hello, world!")
This is a Python code block with syntax highlighting
hello_world() ```
javascript // JavaScript code block function helloWorld() { console.log("Hello, world!"); }Tables
| Header 1 | Header 2 | Header 3 | |----------|----------|----------| | Cell 1 | Cell 2 | Cell 3 | | Cell 4 | Cell 5 | Cell 6 | | Cell 7 | Cell 8 | Cell 9 |
Horizontal Rules
Task Lists
- [x] Completed task
- [ ] Incomplete task
- [x] Another completed task
Math (if supported)
Inline math: $E = mc^2$
Block math:
$$ \frac{d}{dx}e^x = e^x $$
Footnotes
Here's a sentence with a footnote reference[^1].
[^1]: This is the footnote content.
Definition Lists
Term 1 : Definition 1
Term 2 : Definition 2a : Definition 2b
Special Characters & Escaping
*This text is surrounded by asterisks but not italicized*
Advanced Formatting
Click to expand
This is hidden content that appears when expanded.Emoji (if supported)
:smile: :heart: :thumbsup:
Final Notes
This document demonstrates various Markdown formatting features. Compatibility may vary across different Markdown renderers and platforms.
-
 @ 2e8970de:63345c7a
2025-05-03 17:31:07
@ 2e8970de:63345c7a
2025-05-03 17:31:07The figure in this article illustrates exactly how most biology papers are secretly p-hacked. A large number of hypotheses is explored, and only the ones that form a coherent story are reported.
This is actually the main reason behind the replication crisis in biology IMO. (source)
https://www.nature.com/articles/s41587-025-02635-7
originally posted at https://stacker.news/items/970464
-
 @ 3bf0c63f:aefa459d
2025-04-25 18:55:52
@ 3bf0c63f:aefa459d
2025-04-25 18:55:52Report of how the money Jack donated to the cause in December 2022 has been misused so far.
Bounties given
March 2025
- Dhalsim: 1,110,540 - Work on Nostr wiki data processing
February 2025
- BOUNTY* NullKotlinDev: 950,480 - Twine RSS reader Nostr integration
- Dhalsim: 2,094,584 - Work on Hypothes.is Nostr fork
- Constant, Biz and J: 11,700,588 - Nostr Special Forces
January 2025
- Constant, Biz and J: 11,610,987 - Nostr Special Forces
- BOUNTY* NullKotlinDev: 843,840 - Feeder RSS reader Nostr integration
- BOUNTY* NullKotlinDev: 797,500 - ReadYou RSS reader Nostr integration
December 2024
- BOUNTY* tijl: 1,679,500 - Nostr integration into RSS readers yarr and miniflux
- Constant, Biz and J: 10,736,166 - Nostr Special Forces
- Thereza: 1,020,000 - Podcast outreach initiative
November 2024
- Constant, Biz and J: 5,422,464 - Nostr Special Forces
October 2024
- Nostrdam: 300,000 - hackathon prize
- Svetski: 5,000,000 - Latin America Nostr events contribution
- Quentin: 5,000,000 - nostrcheck.me
June 2024
- Darashi: 5,000,000 - maintaining nos.today, searchnos, search.nos.today and other experiments
- Toshiya: 5,000,000 - keeping the NIPs repo clean and other stuff
May 2024
- James: 3,500,000 - https://github.com/jamesmagoo/nostr-writer
- Yakihonne: 5,000,000 - spreading the word in Asia
- Dashu: 9,000,000 - https://github.com/haorendashu/nostrmo
February 2024
- Viktor: 5,000,000 - https://github.com/viktorvsk/saltivka and https://github.com/viktorvsk/knowstr
- Eric T: 5,000,000 - https://github.com/tcheeric/nostr-java
- Semisol: 5,000,000 - https://relay.noswhere.com/ and https://hist.nostr.land relays
- Sebastian: 5,000,000 - Drupal stuff and nostr-php work
- tijl: 5,000,000 - Cloudron, Yunohost and Fraidycat attempts
- Null Kotlin Dev: 5,000,000 - AntennaPod attempt
December 2023
- hzrd: 5,000,000 - Nostrudel
- awayuki: 5,000,000 - NOSTOPUS illustrations
- bera: 5,000,000 - getwired.app
- Chris: 5,000,000 - resolvr.io
- NoGood: 10,000,000 - nostrexplained.com stories
October 2023
- SnowCait: 5,000,000 - https://nostter.vercel.app/ and other tools
- Shaun: 10,000,000 - https://yakihonne.com/, events and work on Nostr awareness
- Derek Ross: 10,000,000 - spreading the word around the world
- fmar: 5,000,000 - https://github.com/frnandu/yana
- The Nostr Report: 2,500,000 - curating stuff
- james magoo: 2,500,000 - the Obsidian plugin: https://github.com/jamesmagoo/nostr-writer
August 2023
- Paul Miller: 5,000,000 - JS libraries and cryptography-related work
- BOUNTY tijl: 5,000,000 - https://github.com/github-tijlxyz/wikinostr
- gzuus: 5,000,000 - https://nostree.me/
July 2023
- syusui-s: 5,000,000 - rabbit, a tweetdeck-like Nostr client: https://syusui-s.github.io/rabbit/
- kojira: 5,000,000 - Nostr fanzine, Nostr discussion groups in Japan, hardware experiments
- darashi: 5,000,000 - https://github.com/darashi/nos.today, https://github.com/darashi/searchnos, https://github.com/darashi/murasaki
- jeff g: 5,000,000 - https://nostr.how and https://listr.lol, plus other contributions
- cloud fodder: 5,000,000 - https://nostr1.com (open-source)
- utxo.one: 5,000,000 - https://relaying.io (open-source)
- Max DeMarco: 10,269,507 - https://www.youtube.com/watch?v=aA-jiiepOrE
- BOUNTY optout21: 1,000,000 - https://github.com/optout21/nip41-proto0 (proposed nip41 CLI)
- BOUNTY Leo: 1,000,000 - https://github.com/leo-lox/camelus (an old relay thing I forgot exactly)
June 2023
- BOUNTY: Sepher: 2,000,000 - a webapp for making lists of anything: https://pinstr.app/
- BOUNTY: Kieran: 10,000,000 - implement gossip algorithm on Snort, implement all the other nice things: manual relay selection, following hints etc.
- Mattn: 5,000,000 - a myriad of projects and contributions to Nostr projects: https://github.com/search?q=owner%3Amattn+nostr&type=code
- BOUNTY: lynn: 2,000,000 - a simple and clean git nostr CLI written in Go, compatible with William's original git-nostr-tools; and implement threaded comments on https://github.com/fiatjaf/nocomment.
- Jack Chakany: 5,000,000 - https://github.com/jacany/nblog
- BOUNTY: Dan: 2,000,000 - https://metadata.nostr.com/
April 2023
- BOUNTY: Blake Jakopovic: 590,000 - event deleter tool, NIP dependency organization
- BOUNTY: koalasat: 1,000,000 - display relays
- BOUNTY: Mike Dilger: 4,000,000 - display relays, follow event hints (Gossip)
- BOUNTY: kaiwolfram: 5,000,000 - display relays, follow event hints, choose relays to publish (Nozzle)
- Daniele Tonon: 3,000,000 - Gossip
- bu5hm4nn: 3,000,000 - Gossip
- BOUNTY: hodlbod: 4,000,000 - display relays, follow event hints
March 2023
- Doug Hoyte: 5,000,000 sats - https://github.com/hoytech/strfry
- Alex Gleason: 5,000,000 sats - https://gitlab.com/soapbox-pub/mostr
- verbiricha: 5,000,000 sats - https://badges.page/, https://habla.news/
- talvasconcelos: 5,000,000 sats - https://migrate.nostr.com, https://read.nostr.com, https://write.nostr.com/
- BOUNTY: Gossip model: 5,000,000 - https://camelus.app/
- BOUNTY: Gossip model: 5,000,000 - https://github.com/kaiwolfram/Nozzle
- BOUNTY: Bounty Manager: 5,000,000 - https://nostrbounties.com/
February 2023
- styppo: 5,000,000 sats - https://hamstr.to/
- sandwich: 5,000,000 sats - https://nostr.watch/
- BOUNTY: Relay-centric client designs: 5,000,000 sats https://bountsr.org/design/2023/01/26/relay-based-design.html
- BOUNTY: Gossip model on https://coracle.social/: 5,000,000 sats
- Nostrovia Podcast: 3,000,000 sats - https://nostrovia.org/
- BOUNTY: Nostr-Desk / Monstr: 5,000,000 sats - https://github.com/alemmens/monstr
- Mike Dilger: 5,000,000 sats - https://github.com/mikedilger/gossip
January 2023
- ismyhc: 5,000,000 sats - https://github.com/Galaxoid-Labs/Seer
- Martti Malmi: 5,000,000 sats - https://iris.to/
- Carlos Autonomous: 5,000,000 sats - https://github.com/BrightonBTC/bija
- Koala Sat: 5,000,000 - https://github.com/KoalaSat/nostros
- Vitor Pamplona: 5,000,000 - https://github.com/vitorpamplona/amethyst
- Cameri: 5,000,000 - https://github.com/Cameri/nostream
December 2022
- William Casarin: 7 BTC - splitting the fund
- pseudozach: 5,000,000 sats - https://nostr.directory/
- Sondre Bjellas: 5,000,000 sats - https://notes.blockcore.net/
- Null Dev: 5,000,000 sats - https://github.com/KotlinGeekDev/Nosky
- Blake Jakopovic: 5,000,000 sats - https://github.com/blakejakopovic/nostcat, https://github.com/blakejakopovic/nostreq and https://github.com/blakejakopovic/NostrEventPlayground
-
 @ ca495706:2476e4d0
2025-05-02 09:38:12
@ ca495706:2476e4d0
2025-05-02 09:38:12VIPWIN là một nền tảng trực tuyến phát triển mạnh mẽ trong thời gian gần đây, mang đến cho người dùng những trải nghiệm mượt mà và an toàn. Được thiết kế với giao diện thân thiện và dễ sử dụng, VIPWIN không chỉ chú trọng đến việc tối ưu hóa trải nghiệm người dùng mà còn bảo vệ quyền lợi của họ một cách tối đa. Tính năng của nền tảng này luôn được cập nhật và cải tiến để phục vụ nhu cầu ngày càng cao của người dùng. VIPWIN cung cấp một không gian trực tuyến hiện đại, dễ tiếp cận, cho phép người dùng truy cập các dịch vụ chỉ trong vài bước đơn giản. Dù bạn là người mới sử dụng hay là người đã có kinh nghiệm, việc làm quen với hệ thống của VIPWIN sẽ rất dễ dàng nhờ vào giao diện trực quan và các tính năng hỗ trợ rõ ràng. Một trong những yếu tố quan trọng tạo nên sự khác biệt của VIPWIN chính là tốc độ truy cập ổn định và nhanh chóng. Người dùng sẽ không gặp phải tình trạng gián đoạn hay độ trễ trong suốt quá trình sử dụng dịch vụ.
Bảo mật là một trong những yếu tố quan trọng mà VIPWIN đặc biệt chú trọng. Với sự phát triển không ngừng của công nghệ, việc bảo vệ thông tin cá nhân của người dùng là vô cùng cần thiết. VIPWIN sử dụng các công nghệ mã hóa tiên tiến để đảm bảo rằng dữ liệu của người sử dụng luôn được bảo vệ an toàn tuyệt đối. Các thông tin giao dịch và dữ liệu cá nhân đều được mã hóa, giúp người dùng yên tâm khi sử dụng nền tảng mà không phải lo lắng về việc bị lộ lọt thông tin. Ngoài ra, đội ngũ bảo mật của VIPWIN luôn theo dõi và kiểm tra hệ thống thường xuyên để phát hiện và xử lý kịp thời các mối đe dọa tiềm ẩn. Điều này giúp người dùng hoàn toàn tin tưởng vào sự an toàn của nền tảng. Không chỉ vậy, VIPWIN còn cung cấp dịch vụ hỗ trợ khách hàng chuyên nghiệp, hoạt động liên tục 24/7, sẵn sàng giải đáp mọi thắc mắc và hỗ trợ người dùng khi gặp phải vấn đề. Đội ngũ hỗ trợ của VIPWIN luôn tận tâm và chu đáo, đảm bảo người dùng luôn được hỗ trợ nhanh chóng và hiệu quả.
Với cam kết phát triển không ngừng và cải tiến liên tục, VIPWIN không chỉ đáp ứng nhu cầu của người dùng mà còn luôn tạo ra những giá trị mới cho cộng đồng. Nền tảng này luôn cập nhật và cải tiến các tính năng để mang đến cho người dùng những trải nghiệm tối ưu nhất. Các tính năng mới luôn được phát triển dựa trên nhu cầu thực tế của người sử dụng, nhằm cải thiện hiệu suất và nâng cao chất lượng dịch vụ. VIPWIN luôn chú trọng đến việc cải tiến giao diện, nâng cao tốc độ truy cập và cập nhật các công cụ hỗ trợ người dùng. Một điểm đáng chú ý nữa là nền tảng này luôn sẵn sàng lắng nghe ý kiến đóng góp từ cộng đồng người dùng, từ đó đưa ra các thay đổi và cải tiến phù hợp. Chính nhờ sự sáng tạo và cam kết không ngừng nâng cao chất lượng dịch vụ, VIPWIN đang ngày càng trở thành lựa chọn hàng đầu của người dùng trong môi trường trực tuyến. Với đội ngũ phát triển chuyên nghiệp và tầm nhìn dài hạn, VIPWIN chắc chắn sẽ tiếp tục phát triển mạnh mẽ và duy trì vị thế là một trong những nền tảng trực tuyến đáng tin cậy nhất trong tương lai.
-
 @ a5142938:0ef19da3
2025-05-02 09:37:56
@ a5142938:0ef19da3
2025-05-02 09:37:56Have you found a natural product? Share it here by commenting on this page!
This site only lists durable-use products and objects. Consumables (food, cosmetics, fuels, etc.) are not included.
To be listed, the product must be made of natural materials. 👉 Learn more about materials
Each piece of information added (name, material, link, shipping area, etc.) and validated is considered a contribution. 👉 Learn more about contributions
Every validated contribution is counted and eligible for rewards. Make sure to securely save your keys (credentials) in a vault like nsec.app). You can also share more easily your finds without creating an account via the contact form (not eligible for rewards). 👉 Learn more about rewards
You can copy and paste the template below and fill in the information you have. Other contributors or the core team can complete any missing details.
New product
- Product name :
- Product image (link):
- Short description:
- Categories:
- Brand or manufacturer:
- Composition (materials used, including unknown elements):
- Links to buy (and shipping area):
- Other information (place of manufacture, certifications…):
This article is published on origin-nature.com 🌐 Voir cet article en français
-
 @ fc7085c3:0b32a4cb
2025-05-03 16:17:10
@ fc7085c3:0b32a4cb
2025-05-03 16:17:10- ~~finish writing some experimental specs and store on hidden repo for later~~
- ~~fix bugs on in-house js web components framework (with react-like hooks)~~
- ~~add signal/reactive hooks to framework~~ (thx to nootropics)
- (ongoing) slooowly migrate kind:1 app from Qwik to above framework
- test feasibility of new app - codename: ZULULA. cool? flawed?
- if cool, finish ZULULA basic features
- nread.me: add nostr documentation (mpa for this part cause seo)
- nread.me: add nip crud (save on relay)
- nread.me: add nip curation (rating and labeling)
- nread.me: filter by curator / rating / labeling
- nread.me: seed curator (fiatjaf) adds other curators
- revamp kind:1 app login
- add basic engagement features then halt kind:1 app dev
- start simplified messenger app to test custom chat spec
- ...don't know what's next yet
-
 @ f32184ee:6d1c17bf
2025-04-23 13:21:52
@ f32184ee:6d1c17bf
2025-04-23 13:21:52Ads Fueling Freedom
Ross Ulbricht’s "Decentralize Social Media" painted a picture of a user-centric, decentralized future that transcended the limitations of platforms like the tech giants of today. Though focused on social media, his concept provided a blueprint for decentralized content systems writ large. The PROMO Protocol, designed by NextBlock while participating in Sovereign Engineering, embodies this blueprint in the realm of advertising, leveraging Nostr and Bitcoin’s Lightning Network to give individuals control, foster a multi-provider ecosystem, and ensure secure value exchange. In this way, Ulbricht’s 2021 vision can be seen as a prescient prediction of the PROMO Protocol’s structure. This is a testament to the enduring power of his ideas, now finding form in NextBlock’s innovative approach.
 [Current Platform-Centric Paradigm, source: Ross Ulbricht's Decentralize Social Media]
[Current Platform-Centric Paradigm, source: Ross Ulbricht's Decentralize Social Media]Ulbricht’s Vision: A Decentralized Social Protocol
In his 2021 Medium article Ulbricht proposed a revolutionary vision for a decentralized social protocol (DSP) to address the inherent flaws of centralized social media platforms, such as privacy violations and inconsistent content moderation. Writing from prison, Ulbricht argued that decentralization could empower users by giving them control over their own content and the value they create, while replacing single, monolithic platforms with a competitive ecosystem of interface providers, content servers, and advertisers. Though his focus was on social media, Ulbricht’s ideas laid a conceptual foundation that strikingly predicts the structure of NextBlock’s PROMO Protocol, a decentralized advertising system built on the Nostr protocol.
 [A Decentralized Social Protocol (DSP), source: Ross Ulbricht's Decentralize Social Media]
[A Decentralized Social Protocol (DSP), source: Ross Ulbricht's Decentralize Social Media]Ulbricht’s Principles
Ulbricht’s article outlines several key principles for his DSP: * User Control: Users should own their content and dictate how their data and creations generate value, rather than being subject to the whims of centralized corporations. * Decentralized Infrastructure: Instead of a single platform, multiple interface providers, content hosts, and advertisers interoperate, fostering competition and resilience. * Privacy and Autonomy: Decentralized solutions for profile management, hosting, and interactions would protect user privacy and reduce reliance on unaccountable intermediaries. * Value Creation: Users, not platforms, should capture the economic benefits of their contributions, supported by decentralized mechanisms for transactions.
These ideas were forward-thinking in 2021, envisioning a shift away from the centralized giants dominating social media at the time. While Ulbricht didn’t specifically address advertising protocols, his framework for decentralization and user empowerment extends naturally to other domains, like NextBlock’s open-source offering: the PROMO Protocol.
NextBlock’s Implementation of PROMO Protocol
The PROMO Protocol powers NextBlock's Billboard app, a decentralized advertising protocol built on Nostr, a simple, open protocol for decentralized communication. The PROMO Protocol reimagines advertising by: * Empowering People: Individuals set their own ad prices (e.g., 500 sats/minute), giving them direct control over how their attention or space is monetized. * Marketplace Dynamics: Advertisers set budgets and maximum bids, competing within a decentralized system where a 20% service fee ensures operational sustainability. * Open-Source Flexibility: As an open-source protocol, it allows multiple developers to create interfaces or apps on top of it, avoiding the single-platform bottleneck Ulbricht critiqued. * Secure Payments: Using Strike Integration with Bitcoin Lightning Network, NextBlock enables bot-resistant and intermediary-free transactions, aligning value transfer with each person's control.
This structure decentralizes advertising in a way that mirrors Ulbricht’s broader vision for social systems, with aligned principles showing a specific use case: monetizing attention on Nostr.
Aligned Principles
Ulbricht’s 2021 article didn’t explicitly predict the PROMO Protocol, but its foundational concepts align remarkably well with NextBlock's implementation the protocol’s design: * Autonomy Over Value: Ulbricht argued that users should control their content and its economic benefits. In the PROMO Protocol, people dictate ad pricing, directly capturing the value of their participation. Whether it’s their time, influence, or digital space, rather than ceding it to a centralized ad network. * Ecosystem of Providers: Ulbricht envisioned multiple providers replacing a single platform. The PROMO Protocol’s open-source nature invites a similar diversity: anyone can build interfaces or tools on top of it, creating a competitive, decentralized advertising ecosystem rather than a walled garden. * Decentralized Transactions: Ulbricht’s DSP implied decentralized mechanisms for value exchange. NextBlock delivers this through the Bitcoin Lightning Network, ensuring that payments for ads are secure, instantaneous and final, a practical realization of Ulbricht’s call for user-controlled value flows. * Privacy and Control: While Ulbricht emphasized privacy in social interactions, the PROMO Protocol is public by default. Individuals are fully aware of all data that they generate since all Nostr messages are signed. All participants interact directly via Nostr.
 [Blueprint Match, source NextBlock]
[Blueprint Match, source NextBlock]
Who We Are
NextBlock is a US-based new media company reimagining digital ads for a decentralized future. Our founders, software and strategy experts, were hobbyist podcasters struggling to promote their work online without gaming the system. That sparked an idea: using new tech like Nostr and Bitcoin to build a decentralized attention market for people who value control and businesses seeking real connections.
Our first product, Billboard, is launching this June.
Open for All
Our model’s open-source! Check out the PROMO Protocol, built for promotion and attention trading. Anyone can join this decentralized ad network. Run your own billboard or use ours. This is a growing ecosystem for a new ad economy.
Our Vision
NextBlock wants to help build a new decentralized internet. Our revolutionary and transparent business model will bring honest revenue to companies hosting valuable digital spaces. Together, we will discover what our attention is really worth.
Read our Manifesto to learn more.
NextBlock is registered in Texas, USA.
-
 @ 3ffac3a6:2d656657
2025-04-23 01:57:57
@ 3ffac3a6:2d656657
2025-04-23 01:57:57🔧 Infrastructure Overview
- Hardware: Raspberry Pi 5 with PCIe NVMe HAT and 2TB NVMe SSD
- Filesystem: ZFS with separate datasets for each service
- Networking: Docker bridge networks for service segmentation
- Privacy: Tor and I2P routing for anonymous communication
- Public Access: Cloudflare Tunnel to securely expose LNbits
📊 Architecture Diagram
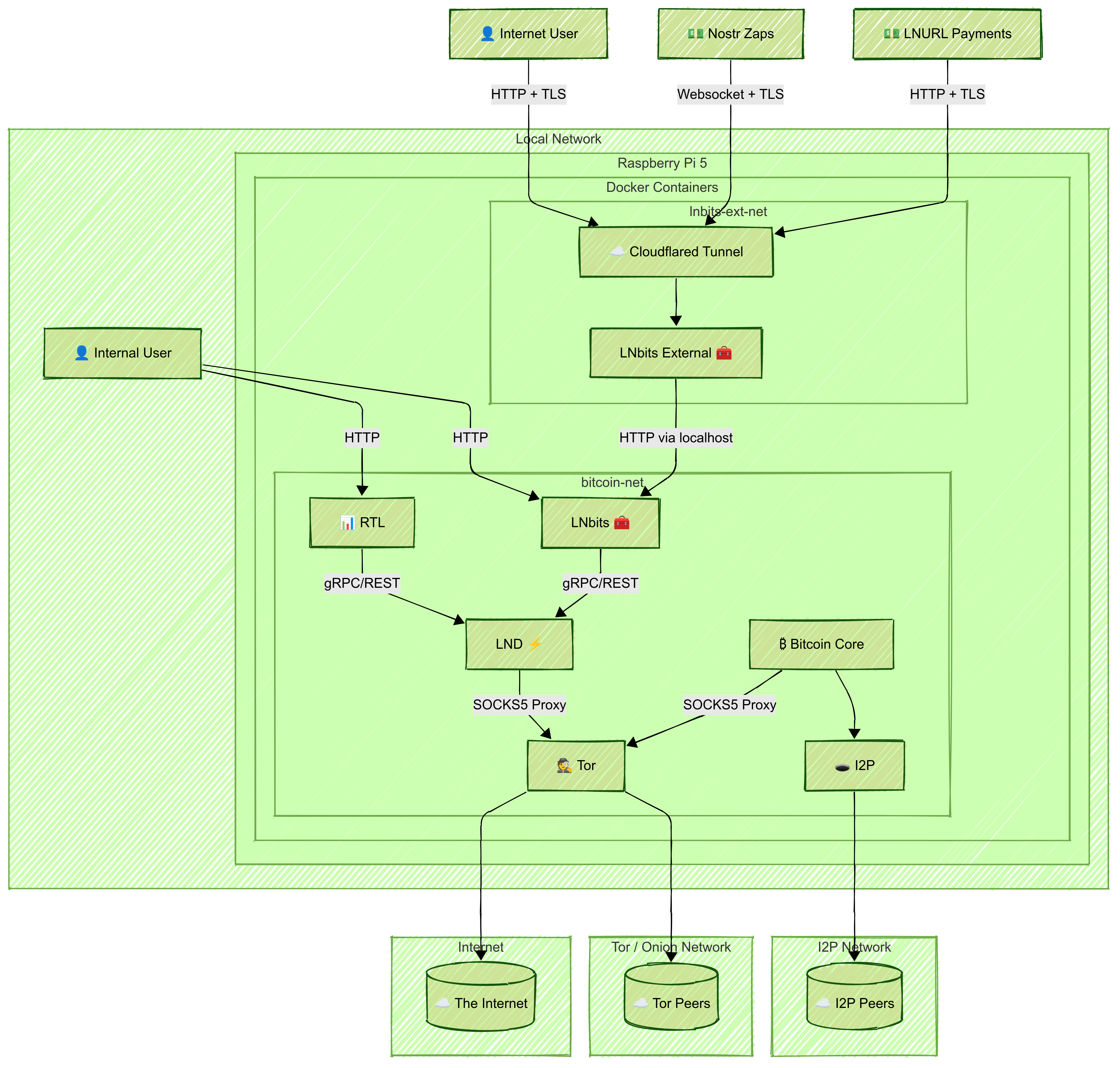
🛠️ Setup Steps
1. Prepare the System
- Install Raspberry Pi OS (64-bit)
- Set up ZFS on the NVMe disk
- Create a ZFS dataset for each service (e.g.,
bitcoin,lnd,rtl,lnbits,tor-data) - Install Docker and Docker Compose
2. Create Shared Docker Network and Privacy Layers
Create a shared Docker bridge network:
bash docker network create \ --driver=bridge \ --subnet=192.168.100.0/24 \ bitcoin-netNote: Connect
bitcoind,lnd,rtl, internallnbits,tor, andi2pto thisbitcoin-netnetwork.Tor
- Run Tor in a container
- Configure it to expose LND's gRPC and REST ports via hidden services:
HiddenServicePort 10009 192.168.100.31:10009 HiddenServicePort 8080 192.168.100.31:8080 - Set correct permissions:
bash sudo chown -R 102:102 /zfs/datasets/tor-data
I2P
- Run I2P in a container with SAM and SOCKS proxies
- Update
bitcoin.conf:i2psam=192.168.100.20:7656 i2pacceptincoming=1
3. Set Up Bitcoin Core
- Create a
bitcoin.confwith Tor/I2P/proxy settings and ZMQ enabled - Sync the blockchain in a container using its ZFS dataset
4. Set Up LND
- Configure
lnd.confto connect tobitcoindand use Tor: ```ini [Bitcoind] bitcoind.rpchost=bitcoin:8332 bitcoind.rpcuser=bitcoin bitcoind.rpcpass=very-hard-password bitcoind.zmqpubrawblock=tcp://bitcoin:28332 bitcoind.zmqpubrawtx=tcp://bitcoin:28333
[Application Options] externalip=xxxxxxxx.onion
`` - Don’t expose gRPC or REST ports publicly - Mount the ZFS dataset at/root/.lnd` - Optionally enable Watchtower5. Set Up RTL
- Mount
RTL-Config.jsonand data volumes - Expose RTL's web interface locally:
```yaml
ports:
- "3000:3000" ```
6. Set Up Internal LNbits
- Connect the LNbits container to
bitcoin-net - Mount the data directory and LND cert/macaroons (read-only)
- Expose the LNbits UI on the local network:
```yaml
ports:
- "5000:5000" ```
- In the web UI, configure the funding source to point to the LND REST
.onionaddress and paste the hex macaroon - Create and fund a wallet, and copy its Admin Key for external use
7. Set Up External LNbits + Cloudflare Tunnel
- Run another LNbits container on a separate Docker network
- Access the internal LNbits via the host IP and port 5000
- Use the Admin Key from the internal wallet to configure funding
- In the Cloudflare Zero Trust dashboard:
- Create a tunnel
- Select Docker, copy the
--tokencommand - Add to Docker Compose:
yaml command: tunnel --no-autoupdate run --token eyJ...your_token...
💾 Backup Strategy
- Bitcoin Core: hourly ZFS snapshots, retained for 6 hours
- Other Services: hourly snapshots with remote
.tar.gzbackups - Retention: 7d hourly, 30d daily, 12mo weekly, monthly forever
- Back up ZFS snapshots to avoid inconsistencies
🔐 Security Isolation Benefits
This architecture isolates services by scope and function:
- Internal traffic stays on
bitcoin-net - Sensitive APIs (gRPC, REST) are reachable only via Tor
- Public access is controlled by Cloudflare Tunnel
Extra Security: Host the public LNbits on a separate machine (e.g., hardened VPS) with strict firewall rules:
- Allow only Cloudflare egress
- Allow ingress from your local IP
- Allow outbound access to internal LNbits (port 5000)
Use WireGuard VPN to secure the connection between external and internal LNbits:
- Ensures encrypted communication
- Restricts access to authenticated VPN peers
- Keeps the internal interface isolated from the public internet
✅ Final Notes
- Internal services communicate over
bitcoin-net - LND interfaces are accessed via Tor only
- LNbits and RTL UIs are locally accessible
- Cloudflare Tunnel secures external access to LNbits
Monitor system health using
monit,watchtower, or Prometheus.Create all configuration files manually (
bitcoin.conf,lnd.conf,RTL-Config.json), and keep credentials secure. Test every component locally before exposing it externally.⚡
-
 @ 9bde4214:06ca052b
2025-04-22 22:04:08
@ 9bde4214:06ca052b
2025-04-22 22:04:08"With the shift towards this multi-agent collaboration and orchestration world, you need a neutral substrate that has money/identity/cryptography and web-of-trust baked in, to make everything work."
Pablo & Gigi are getting high on glue.
Books & articles mentioned:
- Saving beauty by Byung-Chul Han
- LLMs as a tool for thought by Amelia Wattenberger
In this dialogue:
- vibeline & vibeline-ui
- LLMs as tools, and how to use them
- Vervaeke: AI thresholds & the path we must take
- Hallucinations and grounding in reality
- GPL, LLMs, and open-source licensing
- Pablo's multi-agent Roo setup
- Are we going to make programmers obsolete?
- "When it works it's amazing"
- Hiring & training agents
- Agents creating RAG databases of NIPs
- Different models and their context windows
- Generalists vs specialists
- "Write drunk, edit sober"
- DVMCP.fun
- Recklessness and destruction of vibe-coding
- Sharing secrets with agents & LLMs
- The "no API key" advantage of nostr
- What data to trust? And how does nostr help?
- Identity, web of trust, and signing data
- How to fight AI slop
- Marketplaces of code snippets
- Restricting agents with expert knowledge
- Trusted sources without a central repository
- Zapstore as the prime example
- "How do you fight off re-inventing GitHub?"
- Using large context windows to help with refactoring
- Code snippets for Olas, NDK, NIP-60, and more
- Using MCP as the base
- Using nostr as the underlying substrate
- Nostr as the glue & the discovery layer
- Why is this important?
- Why is this exciting?
- "With the shift towards this multi-agent collaboration and orchestration world, you need a neutral substrate that has money/identity/cryptography and web-of-trust baked in, to make everything work."
- How to single-shot nostr applications
- "Go and create this app"
- The agent has money, because of NIP-60/61
- PayPerQ
- Anthropic and the genius of mcp-tools
- Agents zapping & giving SkyNet more money
- Are we going to run the mints?
- Are agents going to run the mints?
- How can we best explain this to our bubble?
- Let alone to people outside of our bubble?
- Building pipelines of multiple agents
- LLM chains & piped Unix tools
- OpenAI vs Anthropic
- Genius models without tools vs midwit models with tools
- Re-thinking software development
- LLMs allow you to tackle bigger problems
- Increased speed is a paradigm shift
- Generalists vs specialists, left brain vs right brain
- Nostr as the home for specialists
- fiatjaf publishing snippets (reluctantly)
- fiatjaf's blossom implementation
- Thinking with LLMs
- The tension of specialization VS generalization
- How the publishing world changed
- Stupid faces on YouTube thumbnails
- Gaming the algorithm
- Will AI slop destroy the attention economy?
- Recency bias & hiding publication dates
- Undoing platform conditioning as a success metric
- Craving realness in a fake attention world
- The theater of the attention economy
- What TikTok got "right"
- Porn, FoodPorn, EarthPorn, etc.
- Porn vs Beauty
- Smoothness and awe
- "Beauty is an angel that could kill you in an instant (but decides not to)."
- The success of Joe Rogan & long-form conversations
- Smoothness fatigue & how our feeds numb us
- Nostr & touching grass
- How movement changes conversations
- LangChain & DVMs
- Central models vs marketplaces
- Going from assembly to high-level to conceptual
- Natural language VS programming languages
- Pablo's code snippets
- Writing documentation for LLMs
- Shared concepts, shared language, and forks
- Vibe-forking open-source software
- Spotting vibe-coded interfaces
- Visualizing nostr data in a 3D world
- Tweets, blog posts, and podcasts
- Vibe-producing blog posts from conversations
- Tweets are excellent for discovery
- Adding context to tweets (long-form posts, podcasts, etc)
- Removing the character limit was a mistake
- "Everyone's attention span is rekt"
- "There is no meaning without friction"
- "Nothing worth having ever comes easy"
- Being okay with doing the hard thing
- Growth hacks & engagement bait
- TikTok, theater, and showing faces and emotions
- The 1% rule: 99% of internet users are Lurkers
- "We are socially malnourished"
- Web-of-trust and zaps bring realness
- The semantic web does NOT fix this LLMs might
- "You can not model the world perfectly"
- Hallucination as a requirement for creativity
-
 @ 90c656ff:9383fd4e
2025-05-03 11:52:14
@ 90c656ff:9383fd4e
2025-05-03 11:52:14In recent years, Bitcoin has often been compared to gold, earning the nickname “digital gold.” This comparison arises because both forms of value share key characteristics, such as scarcity, durability, and global acceptance. However, Bitcoin also represents a technological innovation that redefines the concept of money and investment, standing out as a modern and efficient alternative to physical gold.
One of the main reasons Bitcoin is compared to gold is its programmed scarcity. While gold is a naturally limited resource whose supply depends on mining, Bitcoin has a maximum cap of 21 million units, defined in its code. This cap protects Bitcoin from inflation, unlike traditional currencies that can be created without limit by central banks.
This scarcity gives Bitcoin lasting value, similar to gold, as the limited supply helps preserve purchasing power over time. As demand for Bitcoin grows, its reduced availability reinforces its role as a store of value.
Another feature that brings Bitcoin closer to gold is durability. While gold is resistant to corrosion and can be stored for centuries, Bitcoin is a digital asset protected by advanced cryptography and stored on the blockchain. An immutable and decentralized ledger.
Moreover, Bitcoin is far easier to transport than gold. Moving physical gold involves high costs and security risks, making transport particularly difficult for international transactions. Bitcoin, on the other hand, can be sent digitally anywhere in the world in minutes, with low fees and no intermediaries. This technological advantage makes Bitcoin more effective in a globalized and digital world.
Security is another trait that Bitcoin and gold share. Gold is difficult to counterfeit, making it a reliable store of value. Similarly, Bitcoin uses cryptographic protocols that ensure secure transactions and protect against fraud.
In addition, all Bitcoin transactions are recorded on the blockchain, offering a level of transparency that physical gold does not provide. Anyone can review transactions on the network, increasing trust and traceability.
Historically, gold has been used as a hedge against inflation and economic crises. During times of instability, investors turn to gold as a way to preserve their wealth. Bitcoin is emerging as a digital alternative with the same purpose.
In countries with high inflation or political instability, Bitcoin has been used as a safeguard against the devaluation of local currencies. Its decentralized nature prevents governments from directly confiscating or controlling the asset, providing greater financial freedom to users.
Despite its similarities with gold, Bitcoin still faces challenges. Its volatility is much higher, which can cause short-term uncertainty. However, many experts argue that this volatility is typical of new assets and tends to decrease over time as adoption grows and the market matures.
Another challenge is regulation. While gold is globally recognized as a financial asset, Bitcoin still faces resistance from governments and financial institutions, which seek ways to control and regulate it.
In summary, Bitcoin - often called "digital gold" - offers a new form of value that combines the best characteristics of gold with the efficiency and innovation of digital technology. Its programmed scarcity, cryptographic security, portability, and resistance to censorship make it a viable alternative for preserving wealth and conducting transactions in the modern world.
Despite its volatility, Bitcoin is establishing itself as both a store of value and a hedge against economic crises. As such, it represents not just an evolution of the financial system but also a symbol of the shift toward a decentralized and global digital economy.
Thank you very much for reading this far. I hope everything is well with you, and sending a big hug from your favorite Bitcoiner maximalist from Madeira. Long live freedom!
-
 @ 4ba8e86d:89d32de4
2025-04-21 02:13:56
@ 4ba8e86d:89d32de4
2025-04-21 02:13:56Tutorial feito por nostr:nostr:npub1rc56x0ek0dd303eph523g3chm0wmrs5wdk6vs0ehd0m5fn8t7y4sqra3tk poste original abaixo:
Parte 1 : http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/263585/tutorial-debloat-de-celulares-android-via-adb-parte-1
Parte 2 : http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/index.php/263586/tutorial-debloat-de-celulares-android-via-adb-parte-2
Quando o assunto é privacidade em celulares, uma das medidas comumente mencionadas é a remoção de bloatwares do dispositivo, também chamado de debloat. O meio mais eficiente para isso sem dúvidas é a troca de sistema operacional. Custom Rom’s como LineageOS, GrapheneOS, Iodé, CalyxOS, etc, já são bastante enxutos nesse quesito, principalmente quanto não é instalado os G-Apps com o sistema. No entanto, essa prática pode acabar resultando em problemas indesejados como a perca de funções do dispositivo, e até mesmo incompatibilidade com apps bancários, tornando este método mais atrativo para quem possui mais de um dispositivo e separando um apenas para privacidade. Pensando nisso, pessoas que possuem apenas um único dispositivo móvel, que são necessitadas desses apps ou funções, mas, ao mesmo tempo, tem essa visão em prol da privacidade, buscam por um meio-termo entre manter a Stock rom, e não ter seus dados coletados por esses bloatwares. Felizmente, a remoção de bloatwares é possível e pode ser realizada via root, ou mais da maneira que este artigo irá tratar, via adb.
O que são bloatwares?
Bloatware é a junção das palavras bloat (inchar) + software (programa), ou seja, um bloatware é basicamente um programa inútil ou facilmente substituível — colocado em seu dispositivo previamente pela fabricante e operadora — que está no seu dispositivo apenas ocupando espaço de armazenamento, consumindo memória RAM e pior, coletando seus dados e enviando para servidores externos, além de serem mais pontos de vulnerabilidades.
O que é o adb?
O Android Debug Brigde, ou apenas adb, é uma ferramenta que se utiliza das permissões de usuário shell e permite o envio de comandos vindo de um computador para um dispositivo Android exigindo apenas que a depuração USB esteja ativa, mas também pode ser usada diretamente no celular a partir do Android 11, com o uso do Termux e a depuração sem fio (ou depuração wifi). A ferramenta funciona normalmente em dispositivos sem root, e também funciona caso o celular esteja em Recovery Mode.
Requisitos:
Para computadores:
• Depuração USB ativa no celular; • Computador com adb; • Cabo USB;
Para celulares:
• Depuração sem fio (ou depuração wifi) ativa no celular; • Termux; • Android 11 ou superior;
Para ambos:
• Firewall NetGuard instalado e configurado no celular; • Lista de bloatwares para seu dispositivo;
Ativação de depuração:
Para ativar a Depuração USB em seu dispositivo, pesquise como ativar as opções de desenvolvedor de seu dispositivo, e lá ative a depuração. No caso da depuração sem fio, sua ativação irá ser necessária apenas no momento que for conectar o dispositivo ao Termux.
Instalação e configuração do NetGuard
O NetGuard pode ser instalado através da própria Google Play Store, mas de preferência instale pela F-Droid ou Github para evitar telemetria.
F-Droid: https://f-droid.org/packages/eu.faircode.netguard/
Github: https://github.com/M66B/NetGuard/releases
Após instalado, configure da seguinte maneira:
Configurações → padrões (lista branca/negra) → ative as 3 primeiras opções (bloquear wifi, bloquear dados móveis e aplicar regras ‘quando tela estiver ligada’);
Configurações → opções avançadas → ative as duas primeiras (administrar aplicativos do sistema e registrar acesso a internet);
Com isso, todos os apps estarão sendo bloqueados de acessar a internet, seja por wifi ou dados móveis, e na página principal do app basta permitir o acesso a rede para os apps que você vai usar (se necessário). Permita que o app rode em segundo plano sem restrição da otimização de bateria, assim quando o celular ligar, ele já estará ativo.
Lista de bloatwares
Nem todos os bloatwares são genéricos, haverá bloatwares diferentes conforme a marca, modelo, versão do Android, e até mesmo região.
Para obter uma lista de bloatwares de seu dispositivo, caso seu aparelho já possua um tempo de existência, você encontrará listas prontas facilmente apenas pesquisando por elas. Supondo que temos um Samsung Galaxy Note 10 Plus em mãos, basta pesquisar em seu motor de busca por:
Samsung Galaxy Note 10 Plus bloatware listProvavelmente essas listas já terão inclusas todos os bloatwares das mais diversas regiões, lhe poupando o trabalho de buscar por alguma lista mais específica.
Caso seu aparelho seja muito recente, e/ou não encontre uma lista pronta de bloatwares, devo dizer que você acaba de pegar em merda, pois é chato para um caralho pesquisar por cada aplicação para saber sua função, se é essencial para o sistema ou se é facilmente substituível.
De antemão já aviso, que mais para frente, caso vossa gostosura remova um desses aplicativos que era essencial para o sistema sem saber, vai acabar resultando na perda de alguma função importante, ou pior, ao reiniciar o aparelho o sistema pode estar quebrado, lhe obrigando a seguir com uma formatação, e repetir todo o processo novamente.
Download do adb em computadores
Para usar a ferramenta do adb em computadores, basta baixar o pacote chamado SDK platform-tools, disponível através deste link: https://developer.android.com/tools/releases/platform-tools. Por ele, você consegue o download para Windows, Mac e Linux.
Uma vez baixado, basta extrair o arquivo zipado, contendo dentro dele uma pasta chamada platform-tools que basta ser aberta no terminal para se usar o adb.
Download do adb em celulares com Termux.
Para usar a ferramenta do adb diretamente no celular, antes temos que baixar o app Termux, que é um emulador de terminal linux, e já possui o adb em seu repositório. Você encontra o app na Google Play Store, mas novamente recomendo baixar pela F-Droid ou diretamente no Github do projeto.
F-Droid: https://f-droid.org/en/packages/com.termux/
Github: https://github.com/termux/termux-app/releases
Processo de debloat
Antes de iniciarmos, é importante deixar claro que não é para você sair removendo todos os bloatwares de cara sem mais nem menos, afinal alguns deles precisam antes ser substituídos, podem ser essenciais para você para alguma atividade ou função, ou até mesmo são insubstituíveis.
Alguns exemplos de bloatwares que a substituição é necessária antes da remoção, é o Launcher, afinal, é a interface gráfica do sistema, e o teclado, que sem ele só é possível digitar com teclado externo. O Launcher e teclado podem ser substituídos por quaisquer outros, minha recomendação pessoal é por aqueles que respeitam sua privacidade, como Pie Launcher e Simple Laucher, enquanto o teclado pelo OpenBoard e FlorisBoard, todos open-source e disponíveis da F-Droid.
Identifique entre a lista de bloatwares, quais você gosta, precisa ou prefere não substituir, de maneira alguma você é obrigado a remover todos os bloatwares possíveis, modifique seu sistema a seu bel-prazer. O NetGuard lista todos os apps do celular com o nome do pacote, com isso você pode filtrar bem qual deles não remover.
Um exemplo claro de bloatware insubstituível e, portanto, não pode ser removido, é o com.android.mtp, um protocolo onde sua função é auxiliar a comunicação do dispositivo com um computador via USB, mas por algum motivo, tem acesso a rede e se comunica frequentemente com servidores externos. Para esses casos, e melhor solução mesmo é bloquear o acesso a rede desses bloatwares com o NetGuard.
MTP tentando comunicação com servidores externos:
Executando o adb shell
No computador
Faça backup de todos os seus arquivos importantes para algum armazenamento externo, e formate seu celular com o hard reset. Após a formatação, e a ativação da depuração USB, conecte seu aparelho e o pc com o auxílio de um cabo USB. Muito provavelmente seu dispositivo irá apenas começar a carregar, por isso permita a transferência de dados, para que o computador consiga se comunicar normalmente com o celular.
Já no pc, abra a pasta platform-tools dentro do terminal, e execute o seguinte comando:
./adb start-serverO resultado deve ser:
daemon not running; starting now at tcp:5037 daemon started successfully
E caso não apareça nada, execute:
./adb kill-serverE inicie novamente.
Com o adb conectado ao celular, execute:
./adb shellPara poder executar comandos diretamente para o dispositivo. No meu caso, meu celular é um Redmi Note 8 Pro, codinome Begonia.
Logo o resultado deve ser:
begonia:/ $
Caso ocorra algum erro do tipo:
adb: device unauthorized. This adb server’s $ADB_VENDOR_KEYS is not set Try ‘adb kill-server’ if that seems wrong. Otherwise check for a confirmation dialog on your device.
Verifique no celular se apareceu alguma confirmação para autorizar a depuração USB, caso sim, autorize e tente novamente. Caso não apareça nada, execute o kill-server e repita o processo.
No celular
Após realizar o mesmo processo de backup e hard reset citado anteriormente, instale o Termux e, com ele iniciado, execute o comando:
pkg install android-toolsQuando surgir a mensagem “Do you want to continue? [Y/n]”, basta dar enter novamente que já aceita e finaliza a instalação
Agora, vá até as opções de desenvolvedor, e ative a depuração sem fio. Dentro das opções da depuração sem fio, terá uma opção de emparelhamento do dispositivo com um código, que irá informar para você um código em emparelhamento, com um endereço IP e porta, que será usado para a conexão com o Termux.
Para facilitar o processo, recomendo que abra tanto as configurações quanto o Termux ao mesmo tempo, e divida a tela com os dois app’s, como da maneira a seguir:
Para parear o Termux com o dispositivo, não é necessário digitar o ip informado, basta trocar por “localhost”, já a porta e o código de emparelhamento, deve ser digitado exatamente como informado. Execute:
adb pair localhost:porta CódigoDeEmparelhamentoDe acordo com a imagem mostrada anteriormente, o comando ficaria “adb pair localhost:41255 757495”.
Com o dispositivo emparelhado com o Termux, agora basta conectar para conseguir executar os comandos, para isso execute:
adb connect localhost:portaObs: a porta que você deve informar neste comando não é a mesma informada com o código de emparelhamento, e sim a informada na tela principal da depuração sem fio.
Pronto! Termux e adb conectado com sucesso ao dispositivo, agora basta executar normalmente o adb shell:
adb shellRemoção na prática Com o adb shell executado, você está pronto para remover os bloatwares. No meu caso, irei mostrar apenas a remoção de um app (Google Maps), já que o comando é o mesmo para qualquer outro, mudando apenas o nome do pacote.
Dentro do NetGuard, verificando as informações do Google Maps:
Podemos ver que mesmo fora de uso, e com a localização do dispositivo desativado, o app está tentando loucamente se comunicar com servidores externos, e informar sabe-se lá que peste. Mas sem novidades até aqui, o mais importante é que podemos ver que o nome do pacote do Google Maps é com.google.android.apps.maps, e para o remover do celular, basta executar:
pm uninstall –user 0 com.google.android.apps.mapsE pronto, bloatware removido! Agora basta repetir o processo para o resto dos bloatwares, trocando apenas o nome do pacote.
Para acelerar o processo, você pode já criar uma lista do bloco de notas com os comandos, e quando colar no terminal, irá executar um atrás do outro.
Exemplo de lista:
Caso a donzela tenha removido alguma coisa sem querer, também é possível recuperar o pacote com o comando:
cmd package install-existing nome.do.pacotePós-debloat
Após limpar o máximo possível o seu sistema, reinicie o aparelho, caso entre no como recovery e não seja possível dar reboot, significa que você removeu algum app “essencial” para o sistema, e terá que formatar o aparelho e repetir toda a remoção novamente, desta vez removendo poucos bloatwares de uma vez, e reiniciando o aparelho até descobrir qual deles não pode ser removido. Sim, dá trabalho… quem mandou querer privacidade?
Caso o aparelho reinicie normalmente após a remoção, parabéns, agora basta usar seu celular como bem entender! Mantenha o NetGuard sempre executando e os bloatwares que não foram possíveis remover não irão se comunicar com servidores externos, passe a usar apps open source da F-Droid e instale outros apps através da Aurora Store ao invés da Google Play Store.
Referências: Caso você seja um Australopithecus e tenha achado este guia difícil, eis uma videoaula (3:14:40) do Anderson do canal Ciberdef, realizando todo o processo: http://odysee.com/@zai:5/Como-remover-at%C3%A9-200-APLICATIVOS-que-colocam-a-sua-PRIVACIDADE-E-SEGURAN%C3%87A-em-risco.:4?lid=6d50f40314eee7e2f218536d9e5d300290931d23
Pdf’s do Anderson citados na videoaula: créditos ao anon6837264 http://eternalcbrzpicytj4zyguygpmkjlkddxob7tptlr25cdipe5svyqoqd.onion/file/3863a834d29285d397b73a4af6fb1bbe67c888d72d30/t-05e63192d02ffd.pdf
Processo de instalação do Termux e adb no celular: https://youtu.be/APolZrPHSms
-
 @ 90c656ff:9383fd4e
2025-05-03 11:39:03
@ 90c656ff:9383fd4e
2025-05-03 11:39:03The emergence of Bitcoin brought a new perspective to the concept of money, challenging the conventional financial system based on fiat currencies. While fiat currencies like the real, dollar, and euro are widely used and recognized as means of exchange, Bitcoin represents a digital innovation that promotes decentralization and financial autonomy. Although both serve basic functions such as a medium of exchange and store of value, their main differences lie in how they are issued, managed, and transacted.
One of the key distinctions between Bitcoin and fiat currencies is the way they are issued and administered. Fiat currencies are issued by central banks, which have the power to regulate the amount in circulation. This model allows for the implementation of monetary policies, such as increasing the money supply to stimulate the economy or decreasing it to control inflation. However, this power can also result in currency devaluation if money is issued in excess.
Bitcoin, on the other hand, has a completely decentralized issuance system. It is created through a process called mining, in which computers solve complex mathematical problems to validate transactions on the network. Additionally, the total supply of bitcoins is limited to 21 million units, making it a deflationary asset—its scarcity can potentially increase its value over time. This limitation contrasts sharply with the unlimited nature of fiat money printing.
Fiat currencies are centralized, meaning their issuance and control are decided by governmental authorities. This also means that transactions involving these currencies go through intermediaries like banks, which can impose fees and limits, and are subject to regulations and audits.
Bitcoin, by contrast, is decentralized. It operates on a peer-to-peer network where transactions are verified by participants called miners and recorded in a public ledger known as the blockchain. This decentralization eliminates the need for intermediaries, making Bitcoin more resistant to censorship and government control. It also provides greater transparency, as anyone can verify transactions on the network.
Another important difference lies in how transactions are carried out. With fiat currencies, transactions usually depend on banks or payment systems, which may impose time restrictions and high fees, especially for international transfers.
Bitcoin, on the other hand, enables direct transfers between people, anywhere in the world and at any time, without the need for intermediaries. This makes the system more accessible, particularly for those without bank accounts or living in countries with restrictive financial systems. Additionally, Bitcoin transaction fees can be lower than those charged by traditional banks.
Fiat currencies offer security backed by government laws and the banking system, but users must place trust in those intermediaries. Bitcoin, by contrast, offers a high level of security through advanced cryptography. Digital wallets that store bitcoins are protected by private keys, ensuring that only the owner has access.
However, privacy works differently. Fiat currency transactions are typically linked to the user's identity, whereas Bitcoin offers a certain level of anonymity, since wallet addresses do not require personal identification. Still, all transactions are public and recorded on the blockchain, which can serve as a point of monitoring for authorities.
The value of fiat currencies is backed by trust in the government that issues them and the country's economy. In contrast, Bitcoin is not backed by any government or physical asset. Its value is determined by market supply and demand, making it highly volatile. While this volatility presents a risk, it also attracts people who see Bitcoin as a long-term appreciation opportunity.
In summary, Bitcoin and fiat currencies differ significantly in their structure, control, and functionality. While fiat currencies are government-controlled and depend on intermediaries, Bitcoin offers decentralization, transparency, and financial freedom. Despite its volatility and some regulatory challenges, Bitcoin represents a new alternative to the traditional financial system.
Thank you very much for reading this far. I hope everything is well with you, and sending a big hug from your favorite Bitcoiner maximalist from Madeira. Long live freedom!
-
 @ 90c656ff:9383fd4e
2025-05-03 11:17:21
@ 90c656ff:9383fd4e
2025-05-03 11:17:21Bitcoin was created as something far beyond just a digital currency; it is a revolutionary idea that challenges the foundations of the conventional financial system. The concept behind its creation, presented by the enigmatic Satoshi Nakamoto, focuses on two main principles: decentralization and financial freedom. These ideas reflect an effort to return control of money to the people, eliminating intermediaries and reducing the influence of governments and large financial institutions.
Decentralization is the foundation of Bitcoin. Unlike traditional currencies, which are issued and managed by central banks and governments, Bitcoin operates on a peer-to-peer network. This means there is no central authority or single entity controlling the currency. Instead, all transactions are validated and recorded on a public ledger called the blockchain or timechain, maintained by thousands of computers around the world.
This decentralized structure ensures that Bitcoin is resistant to censorship and immune to monetary policy manipulations such as excessive money printing, which can lead to inflation. It also removes the need for intermediaries like banks, allowing for direct transactions between users. This is especially valuable in scenarios where the traditional banking system is inaccessible or unreliable, such as in remote areas or countries facing economic crises.
The financial freedom promoted by Bitcoin is another transformative element. In traditional systems, individuals depend on third parties such as banks or financial institutions to access, store, and transfer money. These entities can impose restrictions like withdrawal limits, high transfer fees, or even freeze accounts. With Bitcoin, the user has full control over their funds through private keys (a kind of password that grants access to their digital wallet).
Moreover, Bitcoin offers an accessible solution for billions of people worldwide who are unbanked. According to World Bank data, around 1.4 billion adults lack access to a bank account, but many of them do have access to the internet or smartphones. Bitcoin allows these individuals to participate in the global economy without needing intermediary institutions.
Another crucial point is its censorship resistance. In authoritarian regimes or politically unstable situations, governments may confiscate or freeze citizens' assets. Bitcoin, being decentralized and operating on a global network, cannot be arbitrarily controlled or seized, offering an extra layer of financial protection for individuals at risk.
Bitcoin’s vision also includes the creation of a fairer and more transparent financial system. The blockchain or timechain, by recording all transactions in a public and immutable way, reduces the chances of fraud and corruption. Additionally, the limited supply of 21 million bitcoins, hard-coded into the system, supports a deflationary model that contrasts with the unlimited expansion of fiat currencies. This gives Bitcoin the potential to be a stable store of value in the long term.
Despite its promising vision, the path toward full financial freedom is not without challenges. Bitcoin’s price volatility, regulatory concerns, and technological barriers remain hurdles to overcome. However, these challenges also create opportunities for innovation and for strengthening the ecosystem over time.
In summary, the vision behind Bitcoin represents a disruption of the centralized financial system, offering people more autonomy, transparency, and security over their financial resources. It is not just a technology but a movement that aims to empower individuals, especially those excluded or harmed by traditional economic models. By promoting decentralization and financial freedom, Bitcoin paves the way for a future where money truly belongs to the people, not the institutions.
Thank you very much for reading this far — I hope everything is well with you, and sending a big hug from your favorite Bitcoiner maximalist from Madeira. Long live freedom!
-
 @ 90c656ff:9383fd4e
2025-05-03 11:07:50
@ 90c656ff:9383fd4e
2025-05-03 11:07:50Bitcoin is the world’s first decentralized digital currency, created in 2009 by an individual or group under the pseudonym Satoshi Nakamoto. Its birth marked the beginning of a revolution in the global financial system, introducing a new kind of currency that is not controlled by governments or traditional financial institutions. The history of Bitcoin is deeply rooted in the ideals of economic freedom, transparency, and resistance to censorship.
The journey began in October 2008, when Satoshi Nakamoto published a paper titled “Bitcoin: A Peer-to-Peer Electronic Cash System.” The white paper, published on the Cryptography mailing list, described the idea of a digital payment system based on a peer-to-peer network. This concept eliminates the need for intermediaries like banks and solves a problem known as “double spending” — the possibility of duplicating digital currencies — through a technology called blockchain, or what Satoshi Nakamoto himself referred to as the timechain.
The blockchain, or timechain, is essentially a public and immutable ledger that records all Bitcoin transactions. It operates through a decentralized system where participants in the network (the so-called nodes) verify transactions and organize them into blocks. These blocks are in turn linked together in a continuous chain, forming the basis of the system’s security and transparency.
On January 3, 2009, Satoshi Nakamoto mined the first Bitcoin block, known as the genesis block. The block contained a coded message referencing the 2008 global financial crisis: "The Times, January 3, 2009, Chancellor on brink of second bailout for banks." This message is emblematic of the motivation behind Bitcoin: to provide an alternative to the centralized financial system that failed to protect the global economy.
Throughout 2009 and 2010, Bitcoin remained an experiment among tech and crypto enthusiasts. The first Bitcoin transactions took place between network participants, and the first commercial use of the currency occurred on May 22, 2010, when a programmer named Laszlo Hanyecz bought two pizzas for 10,000 Bitcoins. This historic transaction became known as “Bitcoin Pizza Day.”
Satoshi Nakamoto continued to contribute to Bitcoin's development until the end of 2010, when he gradually disappeared from the community. To this day, his identity remains a mystery, and there is no concrete evidence of who or how many people were behind the pseudonym. Before leaving, Satoshi Nakamoto handed over control of the project to other developers and made it clear that Bitcoin should be a decentralized technology, owned by everyone and controlled by no one.
Since then, Bitcoin has grown exponentially. It has evolved from a technological experiment into a multibillion-dollar asset and is widely considered a legitimate form of digital money and store of value. Governments, companies, and individuals around the world have adopted Bitcoin as an alternative to traditional fiat currencies.
In summary, the creation of Bitcoin by Satoshi Nakamoto was more than just the birth of a digital currency; it was the beginning of a global movement to rethink how money is controlled and distributed. Although the identity of Satoshi Nakamoto remains unknown, his legacy will continue to shape the future of the financial system and challenge traditional economic structures.
Thank you very much for reading this far. I hope everything is well with you, and sending a big hug from your favorite Bitcoiner maximalist from Madeira. Long live freedom!
-
 @ ccb30bfc:90b6869f
2025-05-02 03:23:40
@ ccb30bfc:90b6869f
2025-05-02 03:23:40A busca por diversão online segura e variada levou muitos jogadores a conhecer a plataforma 98A, que tem ganhado destaque no Brasil por seu excelente desempenho técnico, suporte ao cliente de qualidade e, claro, uma vasta biblioteca de jogos envolventes.
Ao acessar o 98A, o jogador se depara com uma interface fluida, ideal para quem quer jogar sem complicações. A plataforma foi projetada para funcionar com eficiência tanto em computadores quanto em dispositivos móveis, permitindo jogatinas rápidas e práticas a qualquer momento.
O catálogo de jogos chama a atenção logo de início. São centenas de opções divididas em categorias que vão desde jogos de giro até clássicos de cartas. Cada jogo conta com uma descrição clara, regras bem definidas e modos para iniciantes e avançados. Isso democratiza o acesso, fazendo com que qualquer pessoa possa se divertir, independentemente do seu nível de experiência.
Um dos pontos altos do 98Aé o sistema de bonificações. Novos usuários são recebidos com recompensas logo no cadastro, enquanto os jogadores frequentes acumulam benefícios conforme sua atividade na plataforma. Esses prêmios vão desde bônus de crédito até acesso antecipado a novos lançamentos e torneios temáticos.
Além disso, o ambiente do 98A é fortemente voltado para a comunidade. Através de chats ao vivo e quadros de líderes, os jogadores podem interagir, trocar dicas e acompanhar o desempenho de outros participantes. Isso transforma o simples ato de jogar em uma atividade social e divertida.
A plataforma é completamente adaptada à realidade brasileira, com opções de pagamento locais e atendimento em português. Isso garante uma experiência personalizada, segura e acessível. A equipe de suporte, sempre presente, reforça o compromisso com a excelência no atendimento.
Combinando diversidade, inovação e suporte de qualidade, o 98A se posiciona como uma escolha certeira para quem busca diversão e praticidade em um só lugar.
-
 @ 0d8633e5:eec06e57
2025-05-03 10:58:22
@ 0d8633e5:eec06e57
2025-05-03 10:58:22The Flash USDT Generator is responsible for producing and storing Flash USDT tokens with a flexible daily limit. It ensures a consistent supply of tokens for transactions while managing distribution securely and efficiently. Our Flash USDT offers a unique, temporary cryptocurrency that lasts for 90 days before expiring. This innovative solution allows for seamlesstrading and transferring of funds. Notably, the Flash Bitcoin and USDT can be transferred to 12 different wallets, including prominent platforms like Binance and Trust Wallet.
Features Adjustable Daily Limit: Customizable settings allow for modifying the token generation cap. Automated Distribution: Ensures quick and secure token transfers to user wallets. Minimal Latency: Prevents blockchain congestion issues for seamless transfers. Real-Time Transaction Verification: Each transaction is immediately verified on the respective blockchain explorer to confirm accuracy and validity. Temporary Nature: One of the most distinctive characteristics of USDT FLASH Generator is that it generates flash coin that is designed to disappear from any wallet after a period of ninety days. This unique feature ensures that any assets received in USDT FLASH will not linger indefinitely, creating a dynamic and engaging transaction experience.
Kindly visit globalfashexperts.com for more information Contact Information For more information or to make a purchase, please contact us through the following channels:
Email: globalfashexperts@gmail.com Flash USDT:https://globalfashexperts.com/product/flash-usdt/ Flash USDT: https://globalfashexperts.com/product/flash-usdt-generator-software/The Flash USDT Generator is responsible for producing and storing Flash USDT tokens with a flexible daily limit. It ensures a consistent supply of tokens for transactions while managing distribution securely and efficiently. Our Flash USDT offers a unique, temporary cryptocurrency that lasts for 90 days before expiring. This innovative solution allows for seamlesstrading and transferring of funds. Notably, the Flash Bitcoin and USDT can be transferred to 12 different wallets, including prominent platforms like Binance and Trust Wallet.
Features
- Adjustable Daily Limit: Customizable settings allow for modifying the token generation cap.
- Automated Distribution: Ensures quick and secure token transfers to user wallets.
- Minimal Latency: Prevents blockchain congestion issues for seamless transfers.
- Real-Time Transaction Verification: Each transaction is immediately verified on the respective blockchain explorer to confirm accuracy and validity.
- Temporary Nature: One of the most distinctive characteristics of USDT FLASH Generator is that it generates flash coin that is designed to disappear from any wallet after a period of ninety days. This unique feature ensures that any assets received in USDT FLASH will not linger indefinitely, creating a dynamic and engaging transaction experience.
 Kindly visit globalfashexperts.com for more information
Kindly visit globalfashexperts.com for more informationContact Information
For more information or to make a purchase, please contact us through the following channels:
- Email: globalfashexperts@gmail.com
- Flash USDT:https://globalfashexperts.com/product/flash-usdt/
- Flash USDT: https://globalfashexperts.com/product/flash-usdt-generator-software/
-
 @ d0aa74cd:603d35cd
2025-05-03 10:55:11
@ d0aa74cd:603d35cd
2025-05-03 10:55:11CLI #Haskell
https://photonsphere.org/post/2025-05-03-command-line-energy-prices-haskell/
-
 @ 4ba8e86d:89d32de4
2025-04-21 02:10:55
@ 4ba8e86d:89d32de4
2025-04-21 02:10:55Seu teclado não deve se conectar à internet. Privacidade em primeiro lugar. Sempre. Estamos desenvolvendo um teclado moderno que respeita totalmente sua privacidade e segurança. O FUTO Keyboard é 100% offline e 100% privado, oferecendo todos os recursos essenciais que você espera de um teclado atual — incluindo digitação por deslizamento, entrada de voz offline, correção automática inteligente, temas personalizáveis e sugestões preditivas de texto. Nosso objetivo é simples: criar um teclado eficiente e funcional, sem comprometer a privacidade do usuário. Este projeto é um fork do LatinIME, o teclado open-source oficial do Android.
Atenção: o FUTO Keyboard está atualmente em fase alfa. Está trabalhando para torná-lo estável e confiável, mas durante esse período você pode encontrar bugs, travamentos ou recursos ainda não implementados.
Configurações
Idiomas e Modelos – Adicione novos idiomas, dicionários, modelos de entrada de voz, transformadores e layouts associados.
Linguagens e Modelos
O menu no qual você adiciona novos idiomas, bem como dicionários, modelos de entrada de voz, modelos de transformadores e layouts associados a eles.
Adicionar idioma.
Alguns idiomas exigem o download de um dicionário. Se você também quiser um modelo de entrada de voz para um idioma específico, precisará baixá-lo também. Cada idioma já possui uma seleção de layouts de teclado associados; você pode escolher qual(is) layout(s) deseja adicionar ao adicionar o idioma. https://video.nostr.build/c775288b7a8ee8d75816af0c7a25f2aa0b4ecc99973fd442b2badc308fa38109.mp4
Mudar idioma.
Existem duas maneiras de alternar o idioma. A primeira é pressionando o ícone do globo na Barra de Ações, localizada próximo ao canto superior esquerdo do teclado. A segunda é pressionando longamente ou deslizando a barra de espaço; você pode personalizar o comportamento de troca de idioma da barra de espaço acessando Configurações -> Teclado e Digitação -> Teclas de Pressão Longa e Barra de Espaço -> Comportamento da Barra de Espaço . Você também pode atribuir o ícone do globo como a Tecla de Ação para que fique ao lado da barra de espaço, que pode ser acessada no menu Todas as Ações pressionando a tecla de reticências (...) no canto superior esquerdo do teclado e, em seguida, acessando Editar Ações. https://video.nostr.build/ed6f7f63a9c203cd59f46419ef54a4b8b442f070f802a688ca7d682bd6811bcb.mp4
Adicionar dicionário.
Alguns idiomas têm um dicionário integrado, mas a maioria não. Se o idioma que você está instalando não tiver um dicionário integrado, você pode iniciar a instalação em nosso site acessando Idiomas e Modelos -> Dicionário (no idioma que você está instalando) -> Explorar -> Baixar (em nosso site). https://video.nostr.build/3b1e09289953b658a9cef33c41bd711095556bc48290cb2ed066d4d0a5186371.mp4
Habilitar digitação multilíngue.
Você pode habilitar a digitação multilíngue para um ou mais idiomas acessando Idiomas e modelos e marcando a caixa Digitação multilíngue no(s) idioma(s) para os quais deseja habilitar a digitação multilíngue. https://video.nostr.build/29f683410626219499787bd63058d159719553f8e33a9f3c659c51c375a682fb.mp4
Criar layout personalizado.
Se desejar criar seu próprio layout personalizado para um idioma específico, você pode fazê-lo ativando Configurações do Desenvolvedor -> Layouts Personalizados -> Criar novo layout . Mais informações sobre layouts personalizados podem ser encontradas https://github.com/futo-org/futo-keyboard-layouts . A personalização das configurações de pressionamento longo tecla por tecla ainda não é suportada, mas está em processo de implementação. https://video.nostr.build/b5993090e28794d0305424dd352ca83760bb87002c57930e80513de5917fad8d.mp4
Teclado e Digitação – Personalize o comportamento das teclas, o tamanho do teclado e outras preferências de digitação.
Previsão de texto.
O menu no qual você define suas preferências para correção automática e sugestões personalizadas. Modelo de Linguagem do Transformador Você pode fazer com que o teclado preveja a próxima palavra que você digitará ou faça correções automáticas mais inteligentes, que usam um modelo de linguagem Transformer pré-treinado com base em conjuntos de dados disponíveis publicamente, ativando o Transformer LM . Observação: atualmente, isso funciona apenas em inglês, mas estamos trabalhando para torná-lo compatível com outros idiomas. Ajuste fino do transformador Você pode fazer com que o teclado memorize o que você digita e quais sugestões você seleciona, o que treina o modelo de idioma (enquanto o telefone estiver inativo) para prever quais palavras sugerir e corrigir automaticamente enquanto você digita, ativando o ajuste fino do Transformer . Observação: este é o seu modelo de idioma pessoal e o FUTO não visualiza nem armazena nenhum dos seus dados. https://video.nostr.build/688354a63bdc48a9dd3f8605854b5631ac011009c6105f93cfa0b52b46bc40d3.mp4
Previsão de texto.
O menu no qual você define suas preferências para correção automática e sugestões personalizadas. Modelo de Linguagem do Transformador Você pode fazer com que o teclado preveja a próxima palavra que você digitará ou faça correções automáticas mais inteligentes, que usam um modelo de linguagem Transformer pré-treinado com base em conjuntos de dados disponíveis publicamente, ativando o Transformer LM . Observação: atualmente, isso funciona apenas em inglês, mas estamos trabalhando para torná-lo compatível com outros idiomas.
Ajuste fino do transformador.
Você pode fazer com que o teclado memorize o que você digita e quais sugestões você seleciona, o que treina o modelo de idioma (enquanto o telefone estiver inativo) para prever quais palavras sugerir e corrigir automaticamente enquanto você digita, ativando o ajuste fino do Transformer . Observação: este é o seu modelo de idioma pessoal e o FUTO não visualiza nem armazena nenhum dos seus dados.
Força do Modelo de Linguagem do Transformador.
Você pode fazer com que a correção automática se comporte mais como o teclado AOSP ou mais como a rede neural acessando Parâmetros avançados -> Intensidade do LM do transformador e arrastando o controle deslizante para um valor menor (o que tornará o comportamento da correção automática mais parecido com o teclado AOSP) ou um valor maior (o que tornará a correção automática mais dependente da rede neural). Limiar de correção automática Você pode alterar o limite da correção automática para que ela ocorra com mais ou menos frequência acessando Parâmetros avançados -> Limite de correção automática e arrastando o controle deslizante para um valor menor (o que fará com que a correção automática ocorra com mais frequência, mas também corrija erros com mais frequência) ou um valor maior (o que fará com que a correção automática ocorra com menos frequência, mas também corrija erros com menos frequência). https://video.nostr.build/ea9c100081acfcab60343c494a91f789ef8143c92343522ec34c714913631cf7.mp4
Lista negra de palavras.
Você pode colocar sugestões de palavras na lista negra, o que impedirá que o teclado continue sugerindo palavras na lista negra, acessando Sugestões na lista negra e adicionando as palavras que você gostaria de colocar na lista negra.
Palavras ofensivas.
Você pode bloquear palavras ofensivas, como palavrões comuns, acessando Sugestões na Lista Negra e marcando a opção Bloquear Palavras Ofensivas . Observação: a opção Bloquear Palavras Ofensivas está ativada por padrão. https://video.nostr.build/ee72f3940b9789bbea222c95ee74d646aae1a0f3bf658ef8114c6f7942bb50f5.mp4
Correção automática.
Você pode ativar a capacidade de corrigir automaticamente palavras digitadas incorretamente ao pressionar a barra de espaço ou digitar pontuação ativando a Correção automática.
Sugestões de correção.
Você pode ativar a capacidade de exibir palavras sugeridas enquanto digita marcando a opção Mostrar sugestões de correção.
Sugestões de palavras.
Você pode ativar a capacidade de aprender com suas comunicações e dados digitados para melhorar as sugestões ativando as Sugestões personalizadas . Observação: desativar as Sugestões personalizadas também desativa o ajuste fino do Transformer. https://video.nostr.build/2c22d109b9192eac8fe4533b3f8e3e1b5896dfd043817bd460c48a5b989b7a2f.mp4
Entrada de Voz – Configure a entrada de voz offline, incluindo a duração e a conversão de fala em texto.
Entrada de voz.
O menu no qual você define suas preferências de entrada de voz, como duração da entrada e configurações de conversão de fala em texto. Entrada de voz integrada Você pode desabilitar a entrada de voz integrada do teclado e, em vez disso, usar o provedor de entrada de voz de um aplicativo externo desativando a opção Desabilitar entrada de voz integrada. https://video.nostr.build/68916e5b338a9f999f45aa1828a6e05ccbf8def46da9516c0f516b40ca8c827b.mp4
Sons de indicação.
Você pode habilitar a capacidade de reproduzir sons ao iniciar e cancelar a entrada de voz ativando Sons de indicação. https://video.nostr.build/7f5fb6a6173c4db18945e138146fe65444e40953d85cee1f09c1a21d236d21f5.mp4
Progresso Detalhado.
Você pode habilitar a capacidade de exibir informações detalhadas, como indicar que o microfone está sendo usado, ativando Progresso detalhado. https://video.nostr.build/8ac2bb6bdd6e7f8bd4b45da423e782c152a2b4320f2e090cbb99fd5c78e8f44f.mp4
Microfone Bluetooth.
Você pode fazer com que a entrada de voz prefira automaticamente seu microfone Bluetooth em vez do microfone integrado, ativando Preferir microfone Bluetooth. https://video.nostr.build/c11404aa6fec2dda71ceb3aaee916c6761b3015fef9575a352de66b7310dad07.mp4
Foco de áudio.
Você pode fazer com que a entrada de voz pause automaticamente vídeos ou músicas quando ela estiver ativada, ativando o Foco de Áudio. https://video.nostr.build/4ac82af53298733d0c5013ef28befb8b2adeb4a4949604308317e124b6431d40.mp4
Supressão de Símbolos.
Por padrão, a entrada de voz transcreve apenas texto básico e pontuação. Você pode desativar a opção "Suprimir símbolos" para liberar a entrada de voz da transcrição de caracteres especiais (por exemplo, @, $ ou %). Observação: Isso não afeta a forma como a entrada de voz interpreta palavras literais (por exemplo, "vírgula", "ponto final"). https://video.nostr.build/10de49c5a9e35508caa14b66da28fae991a5ac8eabad9b086959fba18c07f8f3.mp4
Entrada de voz de formato longo.
Você pode desativar o limite padrão de 30 segundos para entrada de voz ativando a opção Entrada de voz longa . Observação: a qualidade da saída pode ser prejudicada com entradas longas. https://video.nostr.build/f438ee7a42939a5a3e6d6c4471905f836f038495eb3a00b39d9996d0e552c200.mp4
Parada automática em silêncio.
Você pode fazer com que a entrada de voz pare automaticamente quando o silêncio for detectado, ativando a opção Parar automaticamente ao silenciar . Observação: se houver muito ruído de fundo, pode ser necessário interromper manualmente a entrada de voz. Ative também a entrada de voz longa para evitar a interrupção após 30 segundos. https://video.nostr.build/056567696d513add63f6dd254c0a3001530917e05e792de80c12796d43958671.mp4
Dicionário Pessoal – Adicione palavras personalizadas para que o teclado aprenda e sugira com mais precisão.
Dicionário Pessoal.
O menu no qual você cria seu dicionário pessoal de palavras que o teclado irá lembrar e sugerir. Adicionar ao dicionário Você pode adicionar uma palavra ou frase ao seu dicionário pessoal pressionando o ícone de adição na tela "Dicionário pessoal" . Você também pode criar um atalho para ela no campo "Atalho" ao adicionar a palavra ou frase. https://video.nostr.build/dec41c666b9f2276cc20d9096e3a9b542b570afd1f679d8d0e8c43c8ea46bfcb.mp4
Excluir do dicionário.
Você pode excluir uma palavra ou frase do seu dicionário pessoal clicando nessa palavra ou frase e clicando no ícone de lixeira no canto superior direito. https://video.nostr.build/aca25643b5c7ead4c5d522709af4bc337911e49c4743b97dc75f6b877449143e.mp4
Tema – Escolha entre os temas disponíveis ou personalize a aparência do teclado conforme seu gosto.
Tema.
O menu no qual você seleciona seu tema preferido para o teclado. Alterar tema Você pode escolher entre uma variedade de temas para o teclado, incluindo Modo Escuro, Modo Claro, Automático Dinâmico, Escuro Dinâmico, Claro Dinâmico, Material AOSP Escuro, Material AOSP Claro, Roxo Escuro AMOLED, Girassol, Queda de Neve, Cinza Aço, Esmeralda, Algodão Doce, Luz do Mar Profundo, Escuro do Mar Profundo, Gradiente 1, Tema FUTO VI ou Tema Construção . A possibilidade de personalizar seu tema será disponibilizada em breve. https://video.nostr.build/90c8de72f08cb0d8c40ac2fba2fd39451ff63ec1592ddd2629d0891c104bc61e.mp4
Fronteiras Principais.
Você pode habilitar as bordas das teclas rolando para baixo até o final e ativando Bordas das teclas . https://video.nostr.build/fa2087d68ce3fb2d3adb84cc2ec19c4d5383beb8823a4b6d1d85378ab3507ab1.mp4
Site oficial https://keyboard.futo.org/
Baixar no fdroid. https://app.futo.org/fdroid/repo/
Para instalar através do Obtainium , basta ir em Adicionar Aplicativo e colar esta URL do repositório: https://github.com/futo-org/android-keyboard
A adição pode demorar um pouco dependendo da velocidade da sua internet, pois o APK precisa ser baixado.
-
 @ ccb30bfc:90b6869f
2025-05-02 03:23:04
@ ccb30bfc:90b6869f
2025-05-02 03:23:04O mundo dos jogos online está em constante evolução, e a BRRBet surge como uma das líderes nesse cenário. Com foco no público brasileiro, a plataforma oferece um ambiente completo, seguro e recheado de opções para quem quer relaxar e se divertir de maneira prática.
Logo ao acessar o site, o usuário se depara com um layout moderno, com menus bem organizados e uma estética agradável. Todo o conteúdo está em português, o que facilita a navegação e torna a experiência muito mais amigável para quem está começando agora.
A BRRBet disponibiliza uma seleção de jogos que agrada a todos os gostos. Seja você fã de jogos de cartas, roleta, slots com temas variados ou experiências ao vivo, há sempre algo novo para explorar. Os jogos são fornecidos por estúdios renomados, garantindo qualidade gráfica, fluidez e mecânicas justas.
Outro atrativo da plataforma são as apostas esportivas. A BRRBet cobre diversos campeonatos nacionais e internacionais, permitindo que o usuário aposte em tempo real e acompanhe as estatísticas das partidas diretamente na tela. Isso traz ainda mais emoção para quem acompanha o mundo esportivo.
No aspecto da experiência do usuário, a BRRBet dá show. O processo de registro é rápido, os métodos de pagamento são variados e seguros, e os saques são processados com agilidade. O suporte ao cliente funciona 24 horas por dia, com atendentes preparados para resolver qualquer dúvida.
A plataforma também oferece recompensas aos jogadores, como bônus de boas-vindas, giros grátis e programas de fidelidade que beneficiam os usuários mais ativos. Tudo isso contribui para tornar a experiência contínua, divertida e cheia de surpresas agradáveis.
Outro ponto que merece destaque é o compromisso com o jogo responsável. A BRRBet disponibiliza ferramentas que permitem ao usuário controlar seus gastos e tempo de uso, promovendo uma experiência equilibrada e saudável.
Portanto, se você procura uma plataforma confiável, divertida e feita para o público brasileiro, a BRRBet é uma excelente escolha. Experimente, explore e descubra um novo nível de entretenimento online com uma plataforma que valoriza cada momento do seu tempo.
-
 @ f839fb67:5c930939
2025-04-16 21:07:13
@ f839fb67:5c930939
2025-04-16 21:07:13Relays
| Name | Address | Price (Sats/Year) | Status | | - | - | - | - | | stephen's aegis relay | wss://paid.relay.vanderwarker.family | 42069 |
| | stephen's Outbox | wss://relay.vanderwarker.family | Just Me |
| | stephen's Inbox | wss://haven.vanderwarker.family/inbox | WoT |
| | stephen's DMs | wss://haven.vanderwarker.family/chat | WoT |
| | VFam Data Relay | wss://data.relay.vanderwarker.family | 0 |
| | VFam Bots Relay | wss://skeme.vanderwarker.family | Invite |
| | VFGroups (NIP29) | wss://groups.vanderwarker.family | 0 |
| | [TOR] My Phone Relay | ws://naswsosuewqxyf7ov7gr7igc4tq2rbtqoxxirwyhkbuns4lwc3iowwid.onion | 0 | Meh... |
My Pubkeys
| Name | hex | nprofile | | - | - | - | | Main | f839fb6714598a7233d09dbd42af82cc9781d0faa57474f1841af90b5c930939 | nostr:nprofile1qqs0sw0mvu29nznjx0gfm02z47pve9up6ra22ar57xzp47gttjfsjwgpramhxue69uhhyetvv9ujuanpdejx2unhv9exketj9enxzmtfd3us9mapfx | | Vanity (Backup) | 82f21be67353c0d68438003fe6e56a35e2a57c49e0899b368b5ca7aa8dde7c23 | nostr:nprofile1qqsg9usmuee48sxkssuqq0lxu44rtc4903y7pzvmx694efa23h08cgcpramhxue69uhhyetvv9ujuanpdejx2unhv9exketj9enxzmtfd3ussel49x | | VFStore | 6416f1e658ba00d42107b05ad9bf485c7e46698217e0c19f0dc2e125de3af0d0 | nostr:nprofile1qqsxg9h3uevt5qx5yyrmqkkehay9cljxdxpp0cxpnuxu9cf9mca0p5qpramhxue69uhhyetvv9ujuanpdejx2unhv9exketj9enxzmtfd3usaa8plu | | NostrSMS | 9be1b8315248eeb20f9d9ab2717d1750e4f27489eab1fa531d679dadd34c2f8d | nostr:nprofile1qqsfhcdcx9fy3m4jp7we4vn305t4pe8jwjy74v062vwk08dd6dxzlrgpramhxue69uhhyetvv9ujuanpdejx2unhv9exketj9enxzmtfd3us595d45 |
Bots
Unlocks Bot
Hex: 2e941ad17144e0a04d1b8c21c4a0dbc3fbcbb9d08ae622b5f9c85341fac7c2d0
nprofile:
nostr:nprofile1qqsza9q669c5fc9qf5dccgwy5rdu877th8gg4e3zkhuus56pltru95qpramhxue69uhhx6m9d4jjuanpdejx2unhv9exketj9enxzmtfd3ust4kvak
Latest Data:
nostr:naddr1qq882mnvda3kkttrda6kuar9wgq37amnwvaz7tmnddjk6efwweskuer9wfmkzuntv4ezuenpd45kc7gzyqhfgxk3w9zwpgzdrwxzr39qm0plhjae6z9wvg44l8y9xs06clpdqqcyqqq823cgnl9u5Step Counter
Hex: 9223d2faeb95853b4d224a184c69e1df16648d35067a88cdf947c631b57e3de7
nprofile: nostr:nprofile1qqsfyg7jlt4etpfmf53y5xzvd8sa79ny356sv75gehu50333k4lrmecpramhxue69uhhx6m9d4jjuanpdejx2unhv9exketj9enxzmtfd3ustswp3w
Latest Data:
nostr:naddr1qvzqqqr4gupzpy3r6tawh9v98dxjyjscf357rhckvjxn2pn63rxlj37xxx6hu008qys8wumn8ghj7umtv4kk2tnkv9hxgetjwashy6m9wghxvctdd9k8jtcqp3ehgets943k7atww3jhyn39gffRCTGuest
Hex: 373904615c781e46bf5bf87b4126c8a568a05393b1b840b1a2a3234d20affa0c
nprofile: nostr:nprofile1qqsrwwgyv9w8s8jxhadls76pymy2269q2wfmrwzqkx32xg6dyzhl5rqpramhxue69uhhx6m9d4jjuanpdejx2unhv9exketj9enxzmtfd3usy92jlxNow Playing
Hex: 8096ed6ba1f21a3713bd47a503ee377b0ce2f187b3e5a3ae909a25b84901018b
nprofile: nostr:nprofile1qqsgp9hddwslyx3hzw750fgracmhkr8z7xrm8edr46gf5fdcfyqsrzcpramhxue69uhhx6m9d4jjuanpdejx2unhv9exketj9enxzmtfd3uspk5v4w
Latest Data:
nostr:naddr1qq9kummh94cxccted9hxwqglwaehxw309aekketdv5h8vctwv3jhyampwf4k2u3wvesk66tv0ypzpqyka446rus6xufm63a9q0hrw7cvutcc0vl95whfpx39hpyszqvtqvzqqqr4gupdk2hd
NIP-29 Groups
- Minecraft Group Chat
nostr:naddr1qqrxvc33xpnxxqfqwaehxw309anhymm4wpejuanpdejx2unhv9exketj9enxzmtfd3usygrzymrpd2wz8ularp06y8ad5dgaddlumyt7tfzqge3vc97sgsarjvpsgqqqnpvqazypfd- VFNet Group Chat
nostr:naddr1qqrrwvfjx9jxzqfqwaehxw309anhymm4wpejuanpdejx2unhv9exketj9enxzmtfd3usygrzymrpd2wz8ularp06y8ad5dgaddlumyt7tfzqge3vc97sgsarjvpsgqqqnpvq08hx48
"Nostrified Websites"
[D] = Saves darkmode preferences over nostr
[A] = Auth over nostr
[B] = Beta (software)
[z] = zap enabled
Other Services (Hosted code)
Emojis Packs
- Minecraft
nostr:naddr1qqy566twv43hyctxwsq37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gzyrurn7m8z3vc5u3n6zwm6s40stxf0qwsl2jhga83ssd0jz6ujvynjqcyqqq82nsd0k5wp- AIM
nostr:naddr1qqxxz6tdv4kk7arfvdhkuucpramhxue69uhhyetvv9ujuanpdejx2unhv9exketj9enxzmtfd3usyg8c88akw9ze3fer85yah4p2lqkvj7qap749w360rpq6ly94eycf8ypsgqqqw48qe0j2yk- Blobs
nostr:naddr1qqz5ymr0vfesz8mhwden5te0wfjkccte9emxzmnyv4e8wctjddjhytnxv9kkjmreqgs0sw0mvu29nznjx0gfm02z47pve9up6ra22ar57xzp47gttjfsjwgrqsqqqa2wek4ukj- FavEmojis
nostr:naddr1qqy5vctkg4kk76nfwvq37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gzyrurn7m8z3vc5u3n6zwm6s40stxf0qwsl2jhga83ssd0jz6ujvynjqcyqqq82nsf7sdwt- Modern Family
nostr:naddr1qqx56mmyv4exugzxv9kkjmreqy0hwumn8ghj7un9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jq3qlqulkec5tx98yv7snk759tuzejtcr5865468fuvyrtuskhynpyusxpqqqp65ujlj36n- nostriches (Amethyst collection)
nostr:naddr1qq9xummnw3exjcmgv4esz8mhwden5te0wfjkccte9emxzmnyv4e8wctjddjhytnxv9kkjmreqgs0sw0mvu29nznjx0gfm02z47pve9up6ra22ar57xzp47gttjfsjwgrqsqqqa2w2sqg6w- Pepe
nostr:naddr1qqz9qetsv5q37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gzyrurn7m8z3vc5u3n6zwm6s40stxf0qwsl2jhga83ssd0jz6ujvynjqcyqqq82ns85f6x7- Minecraft Font
nostr:naddr1qq8y66twv43hyctxwssyvmmwwsq37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gzyrurn7m8z3vc5u3n6zwm6s40stxf0qwsl2jhga83ssd0jz6ujvynjqcyqqq82nsmzftgr- Archer Font
nostr:naddr1qq95zunrdpjhygzxdah8gqglwaehxw309aex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0ypzp7peldn3gkv2wgeap8dag2hc9nyhs8g04ft5wnccgxhepdwfxzfeqvzqqqr4fclkyxsh- SMB Font
nostr:naddr1qqv4xatsv4ezqntpwf5k7gzzwfhhg6r9wfejq3n0de6qz8mhwden5te0wfjkccte9emxzmnyv4e8wctjddjhytnxv9kkjmreqgs0sw0mvu29nznjx0gfm02z47pve9up6ra22ar57xzp47gttjfsjwgrqsqqqa2w0wqpuk
Git Over Nostr
- NostrSMS
nostr:naddr1qqyxummnw3e8xmtnqy0hwumn8ghj7un9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jqfrwaehxw309amk7apwwfjkccte9emxzmnyv4e8wctjddjhytnxv9kkjmreqyj8wumn8ghj7urpd9jzuun9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jqg5waehxw309aex2mrp0yhxgctdw4eju6t0qyxhwumn8ghj7mn0wvhxcmmvqgs0sw0mvu29nznjx0gfm02z47pve9up6ra22ar57xzp47gttjfsjwgrqsqqqaueqp0epk- nip51backup
nostr:naddr1qq9ku6tsx5ckyctrdd6hqqglwaehxw309aex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0yqjxamnwvaz7tmhda6zuun9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jqfywaehxw309acxz6ty9eex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0yq3gamnwvaz7tmjv4kxz7fwv3sk6atn9e5k7qgdwaehxw309ahx7uewd3hkcq3qlqulkec5tx98yv7snk759tuzejtcr5865468fuvyrtuskhynpyusxpqqqpmej4gtqs6- bukkitstr
nostr:naddr1qqykyattdd5hgum5wgq37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gpydmhxue69uhhwmm59eex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0yqjgamnwvaz7tmsv95kgtnjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gpz3mhxue69uhhyetvv9ujuerpd46hxtnfduqs6amnwvaz7tmwdaejumr0dspzp7peldn3gkv2wgeap8dag2hc9nyhs8g04ft5wnccgxhepdwfxzfeqvzqqqrhnyf6g0n2
Market Places
Please use Nostr Market or somthing simular, to view.
- VFStore
nostr:naddr1qqjx2v34xe3kxvpn95cnqven956rwvpc95unscn9943kxet98q6nxde58p3ryqglwaehxw309aex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0yqjvamnwvaz7tmgv9mx2m3wweskuer9wfmkzuntv4ezuenpd45kc7f0da6hgcn00qqjgamnwvaz7tmsv95kgtnjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gpydmhxue69uhhwmm59eex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0ypzqeqk78n93wsq6sss0vz6mxl5shr7ge5cy9lqcx0smshpyh0r4uxsqvzqqqr4gvlfm7gu
Badges
Created
- paidrelayvf
nostr:naddr1qq9hqctfv3ex2mrp09mxvqglwaehxw309aex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0ypzp7peldn3gkv2wgeap8dag2hc9nyhs8g04ft5wnccgxhepdwfxzfeqvzqqqr48y85v3u3- iPow
nostr:naddr1qqzxj5r02uq37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gzyrurn7m8z3vc5u3n6zwm6s40stxf0qwsl2jhga83ssd0jz6ujvynjqcyqqq82wgg02u0r- codmaster
nostr:naddr1qqykxmmyd4shxar9wgq37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gzyrurn7m8z3vc5u3n6zwm6s40stxf0qwsl2jhga83ssd0jz6ujvynjqcyqqq82wgk3gm4g- iMine
nostr:naddr1qqzkjntfdejsz8mhwden5te0wfjkccte9emxzmnyv4e8wctjddjhytnxv9kkjmreqgs0sw0mvu29nznjx0gfm02z47pve9up6ra22ar57xzp47gttjfsjwgrqsqqqafed5s4x5
Clients I Use
- Amethyst
nostr:naddr1qqxnzd3cx5urqv3nxymngdphqgsyvrp9u6p0mfur9dfdru3d853tx9mdjuhkphxuxgfwmryja7zsvhqrqsqqql8kavfpw3- noStrudel
nostr:naddr1qqxnzd3cxccrvd34xser2dpkqy28wumn8ghj7un9d3shjtnyv9kh2uewd9hsygpxdq27pjfppharynrvhg6h8v2taeya5ssf49zkl9yyu5gxe4qg55psgqqq0nmq5mza9n- nostrsms
nostr:naddr1qq9rzdejxcunxde4xymqz8mhwden5te0wfjkccte9emxzmnyv4e8wctjddjhytnxv9kkjmreqgsfhcdcx9fy3m4jp7we4vn305t4pe8jwjy74v062vwk08dd6dxzlrgrqsqqql8kjn33qm
Lists
- Bluesky
nostr:naddr1qvzqqqr4xqpzp7peldn3gkv2wgeap8dag2hc9nyhs8g04ft5wnccgxhepdwfxzfeqys8wumn8ghj7un9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jtcqqapxcat9wd4hj0ah0jw
- Fediverse
nostr:naddr1qvzqqqr4xqpzp7peldn3gkv2wgeap8dag2hc9nyhs8g04ft5wnccgxhepdwfxzfeqys8wumn8ghj7un9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jtcqp9rx2erfwejhyum9j4g0xh
- Fediverse_Bots
nostr:naddr1qvzqqqr4xqpzp7peldn3gkv2wgeap8dag2hc9nyhs8g04ft5wnccgxhepdwfxzfeqys8wumn8ghj7un9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jtcqperx2erfwejhyum9tapx7arnfcpdzh
- My Bots
nostr:naddr1qvzqqqr4xqpzp7peldn3gkv2wgeap8dag2hc9nyhs8g04ft5wnccgxhepdwfxzfeqys8wumn8ghj7un9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jtcqz4uh5jnpwscyss24fpkxw4fewafk566twa2q8f6fyk
-
 @ 7c082548:0b32521e
2025-05-02 03:22:36
@ 7c082548:0b32521e
2025-05-02 03:22:36TQ247 là một nền tảng giải trí trực tuyến được thiết kế để mang đến cho người dùng những trải nghiệm mới mẻ và đầy thú vị. Với giao diện người dùng đơn giản, dễ sử dụng và phong cách thiết kế hiện đại, TQ247 mang đến một không gian giải trí tuyệt vời, nơi người tham gia có thể dễ dàng truy cập vào các trò chơi và dịch vụ đa dạng. Từ những trò chơi trí tuệ giúp kích thích tư duy cho đến những trò chơi hành động đầy kịch tính, TQ247 đều đáp ứng được nhu cầu giải trí của người tham gia ở mọi lứa tuổi. Nền tảng này không ngừng cải tiến và cập nhật các tính năng mới, nhằm đem lại những trải nghiệm mượt mà và hấp dẫn hơn nữa cho người tham gia. TQ247 cũng tổ chức thường xuyên các sự kiện và chương trình khuyến mãi, giúp người tham gia có cơ hội nhận được các phần thưởng hấp dẫn và gia tăng hứng thú khi tham gia các hoạt động giải trí.
Bảo mật luôn là yếu tố quan trọng mà TQ247 đặt lên hàng đầu. Nền tảng này sử dụng các công nghệ bảo mật tiên tiến để đảm bảo rằng mọi thông tin cá nhân của người tham gia đều được bảo vệ an toàn tuyệt đối. TQ247 cam kết không chia sẻ thông tin người dùng với bất kỳ bên thứ ba nào và luôn đảm bảo rằng mọi giao dịch tài chính diễn ra trên nền tảng đều được mã hóa và xử lý cẩn thận. Hệ thống bảo mật của TQ247 luôn được nâng cấp liên tục để đối phó với các mối nguy hiểm và các lỗ hổng bảo mật mới, giúp người tham gia có thể hoàn toàn yên tâm khi tham gia vào các hoạt động giải trí. Bên cạnh đó, dịch vụ chăm sóc khách hàng của TQ247 luôn hoạt động 24/7, với đội ngũ nhân viên tận tình, sẵn sàng hỗ trợ và giải đáp mọi thắc mắc của người tham gia, đảm bảo rằng mọi vấn đề đều được xử lý một cách nhanh chóng và hiệu quả.
Không chỉ chú trọng đến các yếu tố về bảo mật và chất lượng dịch vụ, TQ247 còn đặc biệt quan tâm đến việc xây dựng một cộng đồng người tham gia thân thiện và gắn kết. Nền tảng này thường xuyên tổ chức các hoạt động giao lưu, các sự kiện đặc biệt và chương trình khuyến mãi hấp dẫn để người tham gia có cơ hội gặp gỡ, kết nối và chia sẻ những trải nghiệm giải trí tuyệt vời. TQ247 hiểu rằng việc tạo ra một cộng đồng mạnh mẽ và tích cực không chỉ giúp người tham gia có những phút giây vui vẻ mà còn tạo cơ hội học hỏi và phát triển. Nền tảng này luôn lắng nghe và tiếp nhận ý kiến phản hồi từ cộng đồng người tham gia để cải thiện và nâng cao chất lượng dịch vụ, từ đó đáp ứng tốt hơn nhu cầu của người dùng. Chính sự kết hợp hoàn hảo giữa các trò chơi thú vị, bảo mật an toàn và cộng đồng người tham gia năng động đã giúp TQ247 trở thành một trong những nền tảng giải trí trực tuyến đáng tin cậy và được yêu thích hiện nay.
-
 @ 90c656ff:9383fd4e
2025-05-03 10:31:25
@ 90c656ff:9383fd4e
2025-05-03 10:31:25Bitcoin is a decentralized digital currency created in 2009 by an individual or group under the pseudonym Satoshi Nakamoto. Unlike traditional government-issued currencies like the US dollar or the euro, Bitcoin is not controlled by any central authority, such as a central bank or financial institution. This innovative feature has made it a focal point of economic, technological, and even social debate in recent years.
Bitcoin operates using a technology called blockchain (which the Bitcoin community increasingly prefers to call "timechain"). It is essentially a distributed digital ledger. The blockchain or timechain records all transactions made on the Bitcoin network in an open and transparent way. Each block contains a set of transactions that are immutably added to the chain once they are verified by miners (miners are basically network participants who use their computing power to validate these same transactions). This ensures security and prevents fraud, as no person or entity can retroactively alter the records.
One of Bitcoin's most notable features is its limited supply. Only 21 million Bitcoins can ever be created, which gives Bitcoin a deflationary nature — unlike fiat currencies, which central banks can print in unlimited quantities. This fixed limit, combined with growing global interest in the technology in general and individual privacy specifically, has driven Bitcoin’s value over time.
Another important characteristic of Bitcoin is that it enables direct peer-to-peer transactions, removing the need for intermediaries. This is particularly useful in cases like international transfers, where Bitcoin can be used to send money quickly and at low cost, without going through a bank or traditional financial services. Additionally, it is seen as a form of financial freedom in countries with unstable local currencies (often due to central banks printing money uncontrollably) or strict state-imposed capital controls.
However, Bitcoin is not immune to criticism — though these are often hollow arguments that mask the personal interests of those making them, whether because they work in traditional banks or brokerages and fear losing "power" or even their jobs, or because they have bad intentions and want to promote their own cryptocurrencies, which are fundamentally worthless (the infamous “shitcoins”). Bitcoin’s price volatility can also pose significant risks for inexperienced users who buy at a certain price and end up selling when the value drops by half, losing at least half their money. On the other hand, many experts view Bitcoin as a technological and social milestone that challenges existing economic models.
In summary, Bitcoin is much more than just a “crypto” or “cryptocurrency.” It represents a revolution — or a revision — in how most people think about money, offering a decentralized, transparent, and censorship-resistant alternative. Although it still faces challenges to becoming widely accepted by some skeptics and by governments worried about losing control over “their” populations (as mentioned earlier), its impact has been undeniable, paving the way for a new era in the global economy and opening many minds to reflection.
Thank you very much for reading this far — I hope you're doing well, and sending a huge hug from your favorite Bitcoiner maximalist from Madeira. Long live freedom!
-
 @ 5f078e90:b2bacaa3
2025-05-03 10:18:41
@ 5f078e90:b2bacaa3
2025-05-03 10:18:41The Spoonbill's Dawn
In a marsh where reeds whispered secrets to the wind, a roseate spoonbill named Sable waded through dawn’s amber glow. Her pink feathers shimmered, catching the first light as she swept her spoon-shaped bill through the shallows, sifting for shrimp. Unlike her flock, who chattered and preened, Sable moved with quiet purpose, her eyes tracing ripples for signs of life.

Each morning, she returned to a lone cypress, its roots cradling a pool where minnows danced. Here, Sable had found an odd companion: a young alligator named Moss, whose emerald scales blended with the water’s edge. Moss never lunged, only watched, his eyes like polished stones. Sable, curious, began leaving shrimp at the pool’s edge. Moss, in turn, nudged smooth pebbles toward her, gifts from the marsh’s depths.
One dawn, a storm loomed, its thunder rattling the reeds. The flock fled, their wings a pink blur against charcoal clouds, but Sable lingered. The pool was still; Moss hadn’t surfaced. She dipped her bill, calling softly, her heart a flutter of worry. Then, a ripple—Moss emerged, sluggish, a gash on his flank from a poacher’s trap. Sable’s instinct was to flee, but she stayed, her bill probing the mud for healing herbs she’d seen egrets use.
With gentle nudges, she pressed the herbs to Moss’s wound, her pink wings shielding him from the rain. Moss rumbled, a low thanks, and rested. By dusk, the storm passed, and the marsh gleamed under a crescent moon. Moss stirred, stronger, and nudged a final pebble to Sable—a heart-shaped stone, glinting pink like her feathers.
Sable took flight, the stone clutched in her bill, her wings carving hope into the sky. The flock returned, awed by her tale, and the marsh buzzed with their chatter. Sable and Moss remained, their bond a quiet legend, proof that even in a wild world, trust could bloom where dawn met dusk.
Word count: 313
-
 @ 7c082548:0b32521e
2025-05-02 03:20:12
@ 7c082548:0b32521e
2025-05-02 03:20:12KO66 là nền tảng giải trí trực tuyến nổi bật, được nhiều người tham gia yêu thích nhờ sự đa dạng trong các trò chơi và hoạt động giải trí. Với giao diện trực quan, dễ sử dụng và các tính năng tiện ích, KO66 mang đến cho người tham gia những trải nghiệm thú vị và mượt mà. Người dùng có thể dễ dàng truy cập vào các trò chơi hấp dẫn, từ các trò chơi trí tuệ đến những thử thách hành động đầy kịch tính. Hệ thống trò chơi trên KO66 luôn được cập nhật liên tục, đảm bảo rằng người tham gia luôn có những trải nghiệm mới mẻ và không bị nhàm chán. Ngoài các trò chơi giải trí, KO66 còn cung cấp các dịch vụ khác như các sự kiện và chương trình khuyến mãi hấp dẫn, tạo ra cơ hội để người tham gia có thể trải nghiệm nhiều hoạt động giải trí thú vị và đầy hứng khởi.
Bảo mật là một yếu tố quan trọng mà KO66 luôn chú trọng, nhằm đảm bảo sự an toàn cho thông tin cá nhân và các giao dịch tài chính của người tham gia. Nền tảng này sử dụng các công nghệ bảo mật tiên tiến để mã hóa dữ liệu, giúp bảo vệ người tham gia khỏi các mối đe dọa và rủi ro từ các bên thứ ba. Các thông tin cá nhân và giao dịch tài chính luôn được xử lý một cách cẩn thận và bảo mật tuyệt đối. Người tham gia có thể hoàn toàn yên tâm khi tham gia các hoạt động trên KO66, vì nền tảng này luôn đặt sự an toàn và bảo mật của người dùng lên hàng đầu. Ngoài ra, KO66 còn cung cấp dịch vụ chăm sóc khách hàng chuyên nghiệp và tận tình, với đội ngũ nhân viên luôn sẵn sàng hỗ trợ giải đáp mọi thắc mắc và giúp đỡ người tham gia trong mọi tình huống. Dịch vụ hỗ trợ khách hàng của KO66 hoạt động 24/7, đảm bảo người dùng luôn nhận được sự hỗ trợ nhanh chóng và kịp thời.
Ngoài việc chú trọng đến chất lượng dịch vụ và bảo mật, KO66 còn đặc biệt quan tâm đến việc xây dựng cộng đồng người tham gia gắn kết và tích cực. Nền tảng này tổ chức các sự kiện giao lưu và các chương trình khuyến mãi hấp dẫn, giúp người tham gia có cơ hội kết nối, chia sẻ kinh nghiệm và khám phá thêm nhiều hoạt động giải trí mới mẻ. Các sự kiện này không chỉ mang lại những phần thưởng giá trị mà còn tạo ra không gian giao lưu, học hỏi, giúp cộng đồng người tham gia ngày càng trở nên năng động và sáng tạo. KO66 luôn lắng nghe và tiếp thu ý kiến phản hồi từ người tham gia để cải thiện và nâng cao chất lượng dịch vụ, từ đó đáp ứng tốt hơn nhu cầu giải trí của người dùng. Chính sự kết hợp giữa các trò chơi hấp dẫn, bảo mật an toàn và các hoạt động cộng đồng sôi động đã giúp KO66 trở thành một nền tảng giải trí trực tuyến đáng tin cậy và ngày càng được ưa chuộng.
-
 @ e4950c93:1b99eccd
2025-05-03 09:59:59
@ e4950c93:1b99eccd
2025-05-03 09:59:59🧵 Produits en cette matière
Les marques suivantes proposent des produits fait exclusivement ou principalement avec cette matière :
Vêtements
Cet article est publié sur origine-nature.com 🌐 See this article in English
-
 @ 1d7ff02a:d042b5be
2025-05-03 09:47:49
@ 1d7ff02a:d042b5be
2025-05-03 09:47:49ບົດຄວາມນີ້ແປມາຈາ: https://jackkruse.com/what-to-do-with-new-cancer-diagnosis/
ເນື້ອຫາສຳລັບຜູ້ອ່ານ: 1. ຈະເຮັດແນວໃດເມື່ອທ່ານໄດ້ຮັບການວິນິດໄສວ່າເປັນມະເຮັງ? 2. ສະໜາມຮົບກັບມະເຮັງທີ່ສຳຄັນແມ່ນຢູ່ບ່ອນການປິ່ນປົວແບບແພດ ຫຼື ໃນຮ່າງກາຍຂອງທ່ານເອງ? 3. ອາຫານການກິນມີບົດບາດແນວໃດ? 4. ຈະຮັບມືກັບໝໍມະເຮັງຄົນໃໝ່ຂອງທ່ານແນວໃດ? 5. ບໍ່ຕ້ອງຢ້ານທີ່ຈະສຳຫຼວດທຸກຄວາມເປັນໄປໄດ້ເພື່ອຊະນະສົງຄາມນີ້. ຮຽນຮູ້ກ່ຽວກັບອາຫານ ketogenic!!!
ກ່ອນທ່ານຈະອ່ານບົດຄວາມນີ້, ໃຫ້ເບິ່ງວິດີໂອນີ້: HYPERLINK
ບົດຄວາມນີ້ແມ່ນສຳລັບໜຶ່ງໃນໝູ່ທີ່ພິເສດຂອງຂ້ອຍ ຜູ້ທີ່ພົວພັນຂ້ອຍໃນອາທິດນີ້ ແລະ ບອກວ່າເມຍລາວຖືກວິນິດໄສວ່າເປັນມະເຮັງໃນໄວອາຍຸໜຸ່ມ. ຂ້ອຍໄດ້ຍິນຈາກການໂທ ແລະ ໂພສຂອງລາວໃນ Facebook ວ່າມັນກຳລັງທຳລາຍລາວ. ຂ້ອຍບອກລາວທັນທີໃຫ້ໄປຊື້ປື້ມ Anti Cancer: A New Way of Life ໂດຍ David Servan Schreiber ແລະ ມອບໃຫ້ເຈົ້າສາວຂອງລາວ. ຂ່າວດີກໍ່ຄືຫຼາຍລ້ານຄົນໃນຈຳນວນ 6 ລ້ານຄົນທີ່ກຳລັງປິ່ນປົວມະເຮັງໃນປະຈຸບັນຈະມີຊີວິດທີ່ສົມບູນຕໍ່ໄປ. ຈຳນວນຜູ້ລອດຊີວິດຕາມຄວາມຄິດເຫັນຂອງຂ້ອຍຍັງຕ່ຳເກີນໄປ (ປະມານ 45-50%). ນອກຈາກນັ້ນ, ຫຼາຍຄົນໃນຈຳນວນ 2000 ຄົນທີ່ເສຍຊີວິດຈາກມະເຮັງທຸກມື້ແມ່ນເນື່ອງຈາກຄອບຄົວຂອງພວກເຂົາບໍ່ຮູ້ກ່ຽວກັບຊັບພະຍາກອນທີ່ມີໃນປະຈຸບັນສຳລັບການປິ່ນປົວມະເຮັງທັງແບບດັ້ງເດີມ ແລະ ແບບທາງເລືອກ ເຊັ່ນ: ການປິ່ນປົວແບບເສີມ ຫຼື ແບບບູລະນາການ.
ເມື່ອຖືກວິນິດໄສດ້ວຍພະຍາດນີ້, ທ່ານຈະຮູ້ສຶກສັ່ນສະເທືອນຢ່າງຮຸນແຮງ. ສິ່ງສຳຄັນທີ່ທ່ານຕ້ອງຮູ້ແມ່ນພະຍາດນີ້ບໍ່ພຽງແຕ່ສາມາດຕໍ່ສູ້ໄດ້ແຕ່ຍັງສາມາດປ້ອງກັນໄດ້ຖ້າທ່ານຕັດສິນໃຈປ່ຽນແປງບາງສິ່ງທັນທີ ແລະ ປ່ອຍວາງຄວາມເຊື່ອທີ່ບໍ່ຖືກຕ້ອງທີ່ທ່ານໄດ້ສະສົມໃນຊີວິດ. ນີ້ເປັນຄວາມຈິງໂດຍສະເພາະຖ້າທ່ານເຮັດວຽກໃນຂົງເຂດສາທາລະນະສຸກ ແລະ ໄດ້ດຳລົງຊີວິດຕາມຄວາມເຊື່ອຕາຍຕົວຕະຫຼອດຊີວິດ. ປື້ມນີ້ຂຽນໂດຍແພດນັກຄົ້ນຄວ້າທີ່ບໍ່ພຽງແຕ່ຖືກກະທົບຈາກມະເຮັງ ແຕ່ຍັງເປັນມະເຮັງສະໝອງທີ່ອັນຕະລາຍທີ່ສຸດ. ລາວສາມາດຮື້ຖອນຄວາມເຊື່ອຂອງຕົນເອງໃນຖານະແພດດ້ວຍວິທະຍາສາດໃໝ່ທີ່ມີຢູ່ສຳລັບນັກຄົ້ນຄວ້າ ແຕ່ບໍ່ແມ່ນແພດມະເຮັງທົ່ວໄປ. ປື້ມນີ້ຈຳເປັນສຳລັບທຸກຄົນທີ່ເປັນມະເຮັງ ຫຼື ມີປັດໄຈສ່ຽງ ເພື່ອທ່ານຈະໄດ້ຊະນະກ່ອນມັນເລີ່ມ. ນີ້ແມ່ນໜຶ່ງໃນເຫດຜົນທີ່ຂ້ອຍຂຽນ QUILT ຂອງຂ້ອຍ ເພາະຂ້ອຍເຊື່ອວ່າຖ້າທ່ານປົກປ້ອງຈຸລັງຂອງທ່ານ ທ່ານຈະບໍ່ເປັນພະຍາດນີ້. ດຽວນີ້ ໝູ່ຂອງຂ້ອຍເປັນພະຍາດນີ້... ນີ້ແມ່ນບົດຄວາມກ່ຽວກັບສິ່ງທີ່ທ່ານອາດພິຈາລະນາເຮັດທັນທີຫຼັງຈາກປຶກສາກັບແພດມະເຮັງຂອງທ່ານ. ພິຈາລະນາຂໍຄວາມຄິດເຫັນທີສອງຈາກສູນມະເຮັງທີ່ສຳຄັນເຊັ່ນ MD Anderson.
-
ອ່ານປື້ມ Anticancer ທີ່ກ່າວເຖິງຂ້າງເທິງ. ມັນສຳຄັນທີ່ຈະເຫັນພະຍາດນີ້ໃນມຸມມອງໃໝ່.
-
ປ່ຽນອາຫານການກິນຂອງທ່ານທັນທີເປັນ Epi-paleo Rx ແລະ ອອກຫ່າງຈາກອາຫານແບບຕາເວັນຕົກມາດຕະຖານ.
-
ເລີ່ມເຮັດສະມາທິໂດຍໄວເທົ່າທີ່ຈະເປັນໄປໄດ້ເພື່ອຄວບຄຸມ cortisol ແລະ ຄວາມກັງວົນຂອງທ່ານ. (ທາງເລືອກບໍ່ສຳຄັນແຕ່ການເຮັດຈິງຊ່ວຍຊີວິດໄດ້)
-
ຄົນເຈັບຄວນປຶກສາຫາລືກ່ຽວກັບແຜນການປິ່ນປົວມະເຮັງ: ປັດໃຈສຳຄັນໃນມະເຮັງ: ຄວນຄົນເຈັບໃຊ້ອາຫານເສີມສຳລັບປະເພດມະເຮັງທີ່ທ່ານມີບໍ?
-
ພິຈາລະນາເລີ່ມລະບົບອາຫານເສີມ ລວມເຖິງ Curcumin, Reservatrol, Quercetin, ນ້ຳມັນປາ Omega ສາມ (ຄຸນນະພາບ Rx), ວິຕາມິນ D3 ໂດຍມີເປົ້າໝາຍເກີນ 50 ng/dl, ການໃຊ້ CoEnZQ10 ເປັນປະຈຳທຸກວັນ, R-alpha lipoic acid ແລະ ວິຕາມິນ K ທຸກມື້. ພິຈາລະນາການໃຊ້ N Acetyl Cysteine ທຸກວັນເຊັ່ນກັນ. ສັງເກດວ່າຂ້ອຍບໍ່ໄດ້ກຳນົດປະລິມານເພາະປະລິມານທີ່ຕ້ອງການສຳລັບການບຳບັດມະເຮັງແມ່ນສູງກວ່າທີ່ຈະໃຊ້ໃນການປ້ອງກັນ. ສິ່ງນີ້ຄວນເຮັດພາຍໃຕ້ການປຶກສາກັບແພດມະເຮັງຂອງທ່ານ. ຖ້າແພດມະເຮັງຂອງທ່ານບໍ່ເປີດໃຈກວ້າງກ່ຽວກັບບັນຫາເຫຼົ່ານີ້... ຫຼັງຈາກອ່ານປື້ມໃນຂັ້ນຕອນທີໜຶ່ງ ທ່ານອາດຈະຕ້ອງຊອກຫາແພດມະເຮັງຄົນໃໝ່. ເຫຼົ່ານີ້ແມ່ນສິ່ງທີ່ຂ້ອຍພິຈາລະນາວ່າເປັນອາຫານເສີມຫຼັກສຳລັບມະເຮັງສ່ວນໃຫຍ່ທີ່ມະນຸດເປັນ.
-
ໃນອາຫານຂອງທ່ານໃຫ້ເພີ່ມ ຂີ້ໝິ້ນ, ຂິງ, ກະທຽມ, ຣອດສະແມລີ, ແລະ ໃບແບຊິນ (ໃບໂຫລະພາ) ໃສ່ອາຫານຂອງທ່ານໃຫ້ຫຼາຍເທົ່າທີ່ຈະເປັນໄປໄດ້. ທ່ານຄວນດື່ມຊາຂຽວ 1 ລິດຕໍ່ມື້. ຊາຂຽວມີ L-Theanine ທີ່ຊ່ວຍຫຼຸດຄວາມກັງວົນ ແຕ່ຍັງເປັນສ່ວນເສີມຂອງຢາເຄມີບຳບັດໂດຍເຮັດໃຫ້ພວກມັນມີປະສິດທິພາບຍິ່ງຂຶ້ນ. ທ່ານຍັງສາມາດໃຊ້ສານສະກັດຊາຂຽວຖ້າທ່ານບໍ່ຕ້ອງການດື່ມຂອງແຫຼວຫຼາຍ ຫຼື ບໍ່ສາມາດດື່ມໄດ້ເນື່ອງຈາກສະພາບຂອງທ່ານ.
-
ໃນປີ 1955 Otto Warburg ຜູ້ຊະນະລາງວັນໂນເບວພົບວ່າມະເຮັງທັງໝົດໃຊ້ນ້ຳຕານເປັນແຫຼ່ງພະລັງງານ ແລະ ລະດັບອິນຊູລິນສູງເຮັດໃຫ້ຮ່າງກາຍສູນເສຍການຄວບຄຸມລະບົບພູມຄຸ້ມກັນທີ່ຈະປ້ອງກັນມັນ. ນີ້ໝາຍຄວາມວ່າຄົນເຈັບຕ້ອງຈຳກັດທຸກສິ່ງທີ່ກະຕຸ້ນອິນຊູລິນ. ອາຫານແບບ Epi-paleo ທີ່ມີຄາໂບໄຮເດຣດຕ່ຳເຮັດໄດ້ແນວນີ້ພໍດີ. ຂໍ້ມູນອ້າງອີງທີ່ດີສຳລັບອາຫານແມ່ນຢູ່ບ່ອນນີ້.
-
ລະບົບພູມຄຸ້ມກັນຂອງທ່ານແມ່ນການປ້ອງກັນທີ່ດີທີ່ສຸດຕໍ່ມະເຮັງ. ເພີ່ມລະດັບວິຕາມິນ D ແລະ ຮັກສາລະດັບອິນຊູລິນໃຫ້ຕ່ຳກວ່າສອງ. ການຫຼຸດລະດັບ cortisol ຈະປັບປຸງ leptin ແຕ່ສິ່ງສຳຄັນທີ່ສຸດແມ່ນເພີ່ມຈຳນວນຈຸລັງ Natural Killer (WBC) ທີ່ເປັນສ່ວນໜຶ່ງຂອງລະບົບພູມຄຸ້ມກັນໃນຈຸລັງທີ່ຕໍ່ສູ້ກັບມະເຮັງ. ທ່ານຈະໄດ້ອ່ານຫຼາຍກ່ຽວກັບຈຸລັງເຫຼົ່ານີ້ໃນປື້ມທີ່ຂ້ອຍແນະນຳໃນຂັ້ນຕອນທີໜຶ່ງ.
-
ຜັກ. ເຮັດໃຫ້ຜັກຕະກຸນ cruciferous ເປັນອາຫານຫຼັກ. ພືດທັງໝົດໃນຕະກຸນ Brassica ແມ່ນໝູ່ຂອງທ່ານ. Glucosinolates ສາມາດຢັບຢັ້ງ, ຊະລໍ, ແລະ ປີ້ນການເກີດມະເຮັງຫຼາຍຂັ້ນຕອນ. ເຫດຜົນແມ່ນການປ່ອຍ isothiocyanates ເຊັ່ນ sulphoraphanes. Sulphoraphanes ເຮັດສອງສິ່ງຫຼັກ. ພວກມັນສົ່ງເສີມ apoptosis (levee 19) ແລະ ກະຕຸ້ນເອນໄຊມ໌ detoxification ໄລຍະສອງໃນຕັບທີ່ເສີມຄວາມເຂັ້ມແຂງໃຫ້ກັບຍີນ p53 ເປັນຜູ້ປົກປ້ອງຈີໂນມຂອງພວກເຮົາ. ຈຸລັງມະເຮັງມັກຈະຕາຍ (necrosis) ເມື່ອສຳຜັດກັບ sulphoraphanes ຢ່າງຕໍ່ເນື່ອງເປັນເວລາດົນ. ຜັກບຣອກໂຄລີຍັງມີສານ metabolite ຂັ້ນສອງທີ່ເອີ້ນວ່າ Indole 3 Carbinol ທີ່ແຕກຕົວຕໍ່ໄປເປັນສານຕ້ານມະເຮັງອີກຊະນິດໜຶ່ງຊື່ວ່າ DIM, diindolylmethane. ທ່ານບໍ່ສາມາດກິນຜັກພວກນີ້ຫຼາຍພໍຖ້າທ່ານເປັນມະເຮັງໃນທັດສະນະຂອງຂ້ອຍ. I3C ຍັງຂັດຂວາງ 16-hydroxyestrone ແລະ ມີປະໂຫຍດຫຼາຍໃນການປ້ອງກັນມະເຮັງເຕົ້ານົມ ແລະ ມະເຮັງຮັງໄຂ່ໃນແມ່ຍິງ ແລະ ມະເຮັງຕ່ອມລູກໝາກໃນຜູ້ຊາຍ.
-
ນີ້ແມ່ນສິ່ງທີ່ຂັດກັບຄວາມເຊື່ອຊຶ່ງຢູ່ໃນຫົວຂອງທ່ານ... ກິນ cholesterol ຫຼາຍໆ. ໂດຍສະເພາະນ້ຳມັນໝາກພ້າວ. ຫຼາຍການສຶກສາທາງລະບາດວິທະຍາສະແດງໃຫ້ເຫັນວ່າລະດັບ cholesterol ໃນເລືອດຕ່ຳສຳພັນກັບອັດຕາການເກີດມະເຮັງສູງ. ນີ້ແມ່ນເຫດຜົນທີ່ການກິນອາຫານ ketogenic Epi-paleo ມີຄວາມໝາຍຫຼາຍ. ເປັນຫຍັງອາຫານແບບ ketogenic? ເພາະມະເຮັງທັງໝົດໃຊ້ກລູໂຄສເປັນວັດຖຸດິບ. ທ່ານຈຳເປັນຕ້ອງປ່ຽນເຊື້ອໄຟຂອງຈຸລັງ. ໄປຊອກຫາ Otto Warburg ໃນ Google ສຳລັບລາຍລະອຽດເພີ່ມເຕີມ. ອາຫານແບບ ketogenic ຄວນມີ MCT ຈາກນ້ຳມັນໝາກພ້າວຫຼາຍ ເພາະພວກມັນໃຫ້ຂໍ້ໄດ້ປຽບຫຼາຍແກ່ຈຸລັງປົກກະຕິກວ່າຈຸລັງມະເຮັງ. ຂໍ້ໄດ້ປຽບນີ້ເຮັດໃຫ້ລະບົບພູມຄຸ້ມກັນຂອງທ່ານສາມາດຕາມທັນຈຸລັງມະເຮັງ ແລະ ທຳລາຍພວກມັນໂດຍໃຊ້ກົນໄກຊີວະວິທະຍາຂອງທ່ານເອງ. ມີຫຼາຍບົດຄວາມໃນວາລະສານມະເຮັງທີ່ພິມເຜີຍແຜ່ສະແດງໃຫ້ເຫັນການເຊື່ອມໂຍງແບບດຽວກັນ.
-
-
 @ 502ab02a:a2860397
2025-05-02 03:05:18
@ 502ab02a:a2860397
2025-05-02 03:05:18เราได้อ่านเรื่อง EVERY eggwhite ไปแล้วคิดว่าเขาจะหยุดแค่นี้ไหมครับ 555555 ไม่มีทางครับ การคืบคลานต้องมีต่อไป วันนี้จะมาในตอนที่ชื่อว่า
EVERY Egg ไข่ยุคใหม่ที่ไม่ต้องใช้แม่ไก่อีกต่อไป ลองนึกภาพ "ไข่เจียว" ที่ไม่มีแม่ไก่เกี่ยวข้องแม้แต่ขนไก่สักเส้น...ใช่เลยจ้ะ โลกตอนนี้ไปถึงจุดที่ ไข่ สามารถผลิตได้จาก “ยีสต์” ที่ถูกดัดแปลงพันธุกรรม เพื่อให้มันสร้าง “โปรตีนไข่” แบบเดียวกับในธรรมชาติ โดยไม่ต้องผ่านแม่ไก่ ไม่ต้องมีเปลือก และแน่นอน...ไม่มีเสียงขันตอนเช้าอีกต่อไป
ผู้เล่นที่น่าจับตาที่สุดคือบริษัท EVERY Company จาก Silicon Valley เจ้าเดิมที่เปิดตัวผลิตภัณฑ์ใหม่ในชื่อ EVERY Egg ซึ่งเป็น “ของเหลว” ที่หน้าตาเหมือนวิปไข่ไก่ แต่เบื้องหลังคือกระบวนการผลิตระดับไซไฟ! พวกเขาใช้เทคนิคที่เรียกว่า precision fermentation หรือ “การหมักแม่นยำ” เพื่อสั่งให้ยีสต์สร้างโปรตีน ovalbumin (โปรตีนหลักในไข่ขาว) และ lysozyme (สารฆ่าเชื้อแบคทีเรียตามธรรมชาติในไข่) ออกมา จากนั้นก็เอามาผสม เติมแต่ง แต่งกลิ่น เติมสี ใส่สารกันเสียเล็กน้อย...ปิ๊ง! ได้ไข่ที่ไม่มีไข่ ได้ใจประชาชนที่กินสารอาหารแบบคลั่งตัวเลข
จุดขายที่ EVERY Company ใช้ในการนำเสนอ EVERY Egg สลุตมาเป็นตับ ตับ ตับ แบบนี้ครับ 1. High quality egg protein ใช้โปรตีน ovalbumin ที่ได้จากกระบวนการ fermentation ด้วย precision fermentation จากยีสต์สายพันธุ์ Pichia pastoris ซึ่งเป็น โปรตีนหลักในไข่ขาวธรรมชาติและเคลมว่าให้คุณสมบัติเทียบเท่าหรือดีกว่าไข่จากไก่ในเรื่องโครงสร้างโปรตีนและการทำงานในอาหาร เช่น การตีขึ้นฟู (foaming) และการอิมัลซิไฟ คุณเอ๊ยยยย ฟลัฟฟลี่สุดๆ 555 2. No hens used เป็น selling point หลักที่สื่อสารหนักมากในเชิง “ไม่เบียดเบียนสัตว์” ดูมีคุณธรรม จึงถูกจัดเป็นมังสวิรัติ (vegan-friendly) แม้จะได้จากจุลินทรีย์ที่ออกแบบให้ผลิตโปรตีนที่เหมือนจากสัตว์ จุดนี้ล่อใจผู้บริโภควีแกนและกลุ่มที่ต่อต้านฟาร์มอุตสาหกรรมอย่างเต็มๆ พร้อมถวิลหา 3. No cholesterol ยังเป็นจุดขายหลักได้ตลอดกาลกับการครอบงำให้กลัวคอเลสเตอรอล เพราะผลิตจากจุลินทรีย์ ไม่ใช่จากสัตว์จริง ๆ จึงไม่มีคอเลสเตอรอลเลย ซึ่งเป็นข้อได้เปรียบเทียบกับไข่ไก่ที่มีคอเลสเตอรอลตามธรรมชาติ 4. No saturated fat พอๆกันครับ ยังเป็นจุดขู่จุดขายได้ตลอดกาลเช่นเดียวกับคอเลสเตอรอล โปรตีนที่ผลิตจากยีสต์ไม่มีไขมันอิ่มตัวเช่นเดียวกับผลิตภัณฑ์จากสัตว์จริง 5. No artificial flavors แหม่ พยายามสร้างภาพลักษณ์ว่าเป็น clean label ไม่ใช้แต่งกลิ่นหรือสารเติมแต่งรส (แม้จะเป็นผลิตภัณฑ์ที่ผ่านกระบวนการขั้นสูงมากก็ตาม) 6. No salmonella จุดที่คนโคตรกลัวเลยในไข่ สังเกตุไหมว่า จัดหนักจัดเน้นขยี้ความกลัวของคนได้ทุกจุด อย่างอันนี้เนื่องจากไม่มีสัตว์เข้ามาเกี่ยวข้องในการผลิต ทำให้โอกาสปนเปื้อนเชื้อซัลโมเนลลาที่พบบ่อยในไข่สดแทบเป็นศูนย์ เป็นจุดขายด้านความปลอดภัยอาหาร (food safety) ที่เขาเน้นมาก
เท่านี้ยังไม่พอครับ คำถามที่คนต้องสงสัยแน่นอนคือ ชนิดของกรดอมิโนหละครบไหม pain point ของชาววีแกน เนื่องจาก EVERY Company ใช้เทคนิค “Precision Fermentation” โดยใส่ยีนจากไก่ลงไปในยีสต์ เพื่อให้ผลิต ovalbumin ได้เหมือนในธรรมชาติ จึงทำให้โครงสร้างของกรดอะมิโนในโปรตีนนี้ เหมือนไข่จริงแทบ 100% โปรตีน ovalbumin ที่ใช้ผลิต เป็น primary protein จึงถือว่าเป็น โปรตีนมาตรฐาน (reference protein) ในทางโภชนาการ เพราะมี กรดอะมิโนจำเป็นทั้ง 9 ชนิด ในปริมาณที่เพียงพอ ได้แก่ Leucine, Lysine, Valine, Isoleucine, Threonine, Methionine, Phenylalanine, Tryptophan, Histidine
แต่... แม้จะมีกรดอะมิโนครบ ก็ยังมีเรื่องให้คิด โปรตีนนี้ ไม่มาจากธรรมชาติ โดยตรง แต่ผ่านการผลิตจากสิ่งมีชีวิตดัดแปลงพันธุกรรม (GMO yeast) ยังไม่มีข้อมูลชัดเจนเรื่อง bioavailability (การดูดซึม) เมื่อเทียบกับไข่จริง และที่สำคัญ คือการบริโภค “complete protein” ไม่ได้แปลว่า ปลอดภัยในระยะยาว ถ้าพื้นฐานมันคือ GMO จากแลปที่ไม่มีวิวัฒนาการร่วมกับมนุษย์ แน่นอนว่ามันยังต้องการ "ตลาดทดลอง" เพื่อทดลองและเก็บข้อมูลประกอบสินค้าในระยะเวลานึง เข้าใจไหม "หนูๆ"
คำถามคือ โปรตีนแท้...หรือแค่ “เลียนแบบ” EVERY Egg บอกว่าเขาสร้างโปรตีนเหมือนไข่เป๊ะชนิดที่ว่าเชฟชื่อดังยังแยกไม่ออก (ถ้าไม่ดูฉลาก) สามารถนำไปทอด ทำไข่คน ไข่เจียว โอ๊มเล็ต ได้เหมือนไข่จริงทุกประการ แถมยังไม่มีคอเลสเตอรอล ไม่มีไขมันอิ่มตัว มีแต่ “โปรตีนล้วนๆ” แบบคลีนๆ
แต่ตรงนี้แหละที่มันเริ่ม น่าสงสัย เพราะการไม่มีไขมันเลย มันก็คือการตัดเอา matrix ทางโภชนาการ ที่ธรรมชาติออกแบบมาให้เราย่อยง่าย ดูดซึมวิตามินได้ดี และช่วยให้เรารู้สึกอิ่มแบบธรรมชาติ ไข่แท้จากไก่ ไม่ใช่แค่แหล่งโปรตีน แต่มันคือ “ของขวัญจากธรรมชาติ” ที่มีทั้ง choline, lutein, zeaxanthin, วิตามิน A, D, E, B12, โอเมก้า-3, ไขมันดี และเลซิธิน อยู่ครบทุกอนู ช่วยทั้งสมอง ดวงตา และตับ
ในขณะที่ EVERY Egg คือ “ไข่ที่เราอยากให้มันเป็น” มากกว่า “ไข่ที่ธรรมชาติอยากให้เราได้กิน”
บริษัท The EVERY Company ได้ร่วมมือกับเชฟระดับสุดยอดมากมาย ซึ่งการร่วมมือครั้งนี้มีเป้าหมายเพื่อแสดงให้เห็นว่าโปรตีนไข่ที่ผลิตจากกระบวนการ precision fermentation ของ EVERY Egg สามารถตอบสนองมาตรฐานสูงสุดของวงการอาหารชั้นเลิศได้ เรามาดูตัวอย่างกันครับว่า มีที่ไหนบ้าง
-
Eleven Madison Park โดย เชฟ Daniel Humm (มิชลิน3 ดาว ที่นิวยอร์ก) EVERY Egg เปิดตัวครั้งแรกในปี 2023 ที่ร้าน Eleven Madison Park ซึ่งเป็นร้านอาหารระดับมิชลิน 3 ดาว ในนิวยอร์ก โดยเชฟ Daniel Humm ได้สร้างสรรค์เมนูพิเศษที่ใช้ EVERY Egg เป็นส่วนประกอบหลัก เช่น ออมเล็ต ค็อกเทล และของหวาน เพื่อแสดงถึงความสามารถของผลิตภัณฑ์นี้ในการตอบสนองมาตรฐานสูงสุดของวงการอาหารชั้นเลิศระดับ fine dining มิชลิน
-
Chantal Guillon (ร้านมาการองฝรั่งเศสในซานฟรานซิสโก) EVERY Company ได้ร่วมมือกับร้านขนม Chantal Guillon ในการผลิตมาการองที่ใช้ EVERY EggWhite™ ซึ่งเป็นโปรตีนไข่ขาวที่ผลิตจากกระบวนการ precision fermentation โดยไม่มีการใช้ไข่จากไก่เลย ผลิตภัณฑ์นี้ได้รับการยอมรับว่าให้รสชาติและเนื้อสัมผัสที่เทียบเท่ากับไข่ขาวธรรมชาติ
-
The Vegetarian Butcher เป็นแบรนด์ในเครือ Unilever ตามที่ได้เคยให้ข้อมูลไปแล้ว EVERY Company ได้จับมือกับ The Vegetarian Butcher ซึ่งเป็นแบรนด์อาหารมังสวิรัติในเครือ Unilever เพื่อพัฒนาและผลิตผลิตภัณฑ์ที่ใช้โปรตีนไข่จาก EVERY Egg โดยมีเป้าหมายในการลดการใช้สัตว์ในห่วงโซ่อาหารและส่งเสริมความยั่งยืนในอุตสาหกรรมอาหาร
-
Grupo Palacios ผู้ผลิต Spanish Omelet รายใหญ่ของโลก EVERY Company ได้ร่วมมือกับ Grupo Palacios ซึ่งเป็นผู้ผลิต Spanish Omelet รายใหญ่ของโลก โดยนำ EVERY Egg มาใช้ในผลิตภัณฑ์ของตน เพื่อเป็นทางเลือกที่ปลอดภัยและยั่งยืนต่อไข่ไก่ธรรมชาติ ซึ่งอาจมีปัญหาเรื่องการปนเปื้อนและความไม่แน่นอนในการผลิต
Fiat Egg บนเส้นทางเดียวกับ Fiat Food เฮียชวนให้มองภาพใหญ่เหมือนเวลาเรายืนอยู่บนดาดฟ้าแล้วมองลงไปที่ตลาด... ผลิตภัณฑ์อย่าง EVERY Egg ไม่ใช่แค่การสร้าง “ของใหม่” แต่มันคือการ เปลี่ยนแปลงพื้นฐานของอาหาร ด้วยแนวคิดแบบ “Fiat” เป๊ะ Fiat Food คืออาหารที่ไม่ได้เกิดจากธรรมชาติ แต่ถูก “กำหนดให้มีคุณค่า” โดยอุตสาหกรรม Fiat Money คือเงินที่ไม่ได้มีมูลค่าในตัวเอง แต่รัฐบาลบอกให้เรายอมรับมันเป็นเงิน
ในโลกนี้ ถ้า “ไข่” ไม่ต้องมาจากแม่ไก่ “นม” ไม่ต้องมาจากเต้า และ “เนื้อ” ไม่ต้องมาจากวัว แต่ใช้แค่สารเคมี + ยีสต์ + กราฟ + กลิ่นสังเคราะห์ = “ของกินได้” แล้วมันจะเหลือความเป็น อาหารแท้ (real food) อยู่อีกไหม?
เบื้องหลังที่เราควรถามให้ลึก แม้ว่า EVERY จะอ้างว่าโปรตีนจากยีสต์ของเขา “ปลอดภัยและยั่งยืน” แต่ยังไม่มีข้อมูลด้าน long-term health impact ยังไม่มีข้อมูลว่ายีสต์ GMO ที่ใช้ จะกระตุ้นภูมิแพ้หรือมีสารตกค้างหรือไม่ ยังไม่รู้ว่าสารแต่งกลิ่น รส และตัวพาอื่นๆ ที่ใส่ใน EVERY Egg จะส่งผลอะไรกับ microbiome หรือฮอร์โมนของเราในระยะยาว แต่นั่นก็คงมาพร้อมกับคำตอบหรูๆหล่อๆว่า "ขอให้มั่นใจในกระบวนการผลิตที่ทันสมัยและดีเยี่ยม" . . . ตามเคย
และที่น่าสนใจคือ...ผลิตภัณฑ์ EVERY Egg ยังไม่ได้รับการรับรอง GRAS (Generally Recognized As Safe) อย่างเป็นทางการจาก FDA จึงยังไม่สามารถวางจำหน่ายในร้านค้าปลีกทั่วไปได้ บริษัทกำลังร่วมมือกับบริษัทอาหารข้ามชาติในการเปิดตัวผลิตภัณฑ์ในปีนี้ แต่ยังไม่มีข้อมูลชัดเจนเกี่ยวกับการวางจำหน่ายในร้านค้าปลีกทั่วไป แต่ส่วนตัวเฮียคิดว่าไม่น่ากังวล น่าจะผ่านฉลุยแหละ 5555
ไข่สังเคราะห์ = ความหวัง? หรือกับดักในรูปของนวัตกรรม? เราคงไม่ปฏิเสธว่ามีหลายคนบนโลกที่แพ้ไข่จริง หรือห่วงใยเรื่องสวัสดิภาพสัตว์ รวมถึงต้องการความ "บริสุทธิ์" "สกัด" "เข้มข้น" แต่คำถามคือ...จะดีกว่าไหมถ้าเราหาทางผลิต ไข่จริงจากไก่ที่เลี้ยงแบบธรรมชาติ ในระบบ regenerative farming แทนที่จะพยายามสร้างโปรตีนปลอมขึ้นมาแข่ง? ทุกครั้งที่มีของใหม่ที่ดูดี สะอาด และ “คลีน” เฮียอยากให้ทุกคน ถามกลับในใจว่า “คลีน” แค่ในห้องแล็บ หรือ “คลีน” ในธรรมชาติจริงๆ?
สรุปแบบไม่ต้องตีลังกาคิดได้ว่า EVERY Egg คือก้าวใหม่ของเทคโนโลยีอาหารที่กำลังวิ่งไปข้างหน้าแบบไม่เหลียวหลัง แต่ในฐานะที่เฮียเชื่อใน real food, nutrient density และความฉลาดของธรรมชาติ เราอาจต้องเตือนใจไว้ว่า...การใช้ยีสต์ดัดแปลงพันธุกรรมมาผลิต “ไข่เทียม” ไม่ใช่ความผิด แต่ก็ไม่ใช่ความจำเป็นไหม เพราะแท้จริงแล้ว เรามี “ไข่” ที่สมบูรณ์แบบอยู่ในธรรมชาติแล้ว...แค่ไม่ควรปล่อยให้อุตสาหกรรมทำลายภาพลักษณ์ของมัน เพื่อขายของที่ “เหมือนไข่” แต่ไม่มีชีวิต
คำถามเดิมครับ วันนึงเมื่อถึงจุดที่คุณไม่ได้เลือก แล้วมันมีให้แค่นี้ วันนั้นจะทำอย่างไร วันแห่งความ "บริสุทธิ์" "สกัด" "เข้มข้น" ที่เราถวิลหา ??? #pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-
-
 @ 3ffac3a6:2d656657
2025-04-15 14:49:31
@ 3ffac3a6:2d656657
2025-04-15 14:49:31🏅 Como Criar um Badge Épico no Nostr com
nak+ badges.pageRequisitos:
- Ter o
nakinstalado (https://github.com/fiatjaf/nak) - Ter uma chave privada Nostr (
nsec...) - Acesso ao site https://badges.page
- Um relay ativo (ex:
wss://relay.primal.net)
🔧 Passo 1 — Criar o badge em badges.page
- Acesse o site https://badges.page
-
Clique em "New Badge" no canto superior direito
-
Preencha os campos:
- Nome (ex:
Teste Épico) - Descrição
-
Imagem e thumbnail
-
Após criar, você será redirecionado para a página do badge.
🔍 Passo 2 — Copiar o
naddrdo badgeNa barra de endereços, copie o identificador que aparece após
/a/— este é o naddr do seu badge.Exemplo:
nostr:naddr1qq94getnw3jj63tsd93k7q3q8lav8fkgt8424rxamvk8qq4xuy9n8mltjtgztv2w44hc5tt9vetsxpqqqp6njkq3sd0Copie:
naddr1qq94getnw3jj63tsd93k7q3q8lav8fkgt8424rxamvk8qq4xuy9n8mltjtgztv2w44hc5tt9vetsxpqqqp6njkq3sd0
🧠 Passo 3 — Decodificar o naddr com
nakAbra seu terminal (ou Cygwin no Windows) e rode:
bash nak decode naddr1qq94getnw3jj63tsd93k7q3q8lav8fkgt8424rxamvk8qq4xuy9n8mltjtgztv2w44hc5tt9vetsxpqqqp6njkq3sd0Você verá algo assim:
json { "pubkey": "3ffac3a6c859eaaa8cdddb2c7002a6e10b33efeb92d025b14ead6f8a2d656657", "kind": 30009, "identifier": "Teste-Epico" }Grave o campo
"identifier"— nesse caso: Teste-Epico
🛰️ Passo 4 — Consultar o evento no relay
Agora vamos pegar o evento do badge no relay:
bash nak req -d "Teste-Epico" wss://relay.primal.netVocê verá o conteúdo completo do evento do badge, algo assim:
json { "kind": 30009, "tags": [["d", "Teste-Epico"], ["name", "Teste Épico"], ...] }
💥 Passo 5 — Minerar o evento como "épico" (PoW 31)
Agora vem a mágica: minerar com proof-of-work (PoW 31) para que o badge seja classificado como épico!
bash nak req -d "Teste-Epico" wss://relay.primal.net | nak event --pow 31 --sec nsec1SEU_NSEC_AQUI wss://relay.primal.net wss://nos.lol wss://relay.damus.ioEsse comando: - Resgata o evento original - Gera um novo com PoW de dificuldade 31 - Assina com sua chave privada
nsec- E publica nos relays wss://relay.primal.net, wss://nos.lol e wss://relay.damus.io⚠️ Substitua
nsec1SEU_NSEC_AQUIpela sua chave privada Nostr.
✅ Resultado
Se tudo der certo, o badge será atualizado com um evento de PoW mais alto e aparecerá como "Epic" no site!
- Ter o
-
 @ 5a261a61:2ebd4480
2025-04-15 06:34:03
@ 5a261a61:2ebd4480
2025-04-15 06:34:03What a day yesterday!
I had a really big backlog of both work and non-work things to clean up. But I was getting a little frisky because my health finally gave me some energy to be in the mood for intimacy after the illness-filled week had forced libido debt on me. I decided to cheat it out and just take care of myself quickly. Horny thoughts won over, and I got at least e-stim induced ass slaps to make it more enjoyable. Quick clean up and everything seemed ok...until it wasn't.
The rest of the morning passed uneventfully as I worked through my backlog, but things took a turn in the early afternoon. I had to go pickup kids, and I just missed Her between the doors, only managed to get a fast kiss. A little bummed from the work issues and failed expectations of having a few minutes together, I got on my way.
Then it hit me—the most serious case of blue balls I had in a long time. First came panic. I was getting to the age when unusual symptoms raise concerns—cancer comes first to mind, as insufficient release wasn't my typical problem. So I called Her. I explained what was happening and expressed hope for some alone time. Unfortunately, that seemed impossible with our evening schedule: kids at home, Her online meeting, and my standing gamenight with the boys. These game sessions are our sacred ritual—a preserved piece of pre-kids sanity that we all protect in our calendars. Not something I wanted to disturb.
Her reassurance was brief but unusualy promising: "Don't worry, I get this."
Evening came, and just as I predicted, there was ZERO time for shenanigans while we took care of the kids. But once we put them to bed (I drew straw for early sleeper), with parental duties complete, I headed downstairs to prepare for my gaming session. Headset on, I greeted my fellows and started playing.
Not five minutes later, She opened the door with lube in one hand, fleshlight in the other, and an expecting smile on Her face. Definitely unexpected. I excused myself from the game, muted mic, but She stopped me.
"There will be nothing if you won't play," She said. She just motioned me to take my pants off. And off to play I was. Not an easy feat considering I twisted my body sideways so She could access anything She wanted while I still reached keyboard and mouse.
She slowly started touching me and observing my reactions, but quickly changed to using Her mouth. Getting a blowjob while semihard was always so strange. The semi part didn't last long though...
As things intensified, She was satisfied with my erection and got the fleshlight ready. It was a new toy for us, and it was Her first time using it on me all by Herself (usually She prefers watching me use toys). She applied an abundance of lube that lasted the entire encounter and beyond.
Shifting into a rhythm, She started pumping slowly but clearly enjoyed my reactions when She unexpectedly sped up, forcing me to mute the mic. I knew I wouldn't last long. When She needed to fix Her hair, I gentlemanly offered to hold the fleshlight, having one hand still available for gaming. She misunderstood, thinking I was taking over completely, which initially disappointed me.
To my surprise, She began taking Her shirt off the shoulders, offering me a pornhub-esque view. To clearly indicate that finish time had arrived, She moved Her lubed hand teasingly toward my anal. She understood precisely my contradictory preferences—my desire to be thoroughly clean before such play versus my complete inability to resist Her when aroused. That final move did it—I muted the mic just in time to vocally express how good She made me feel.
Quick clean up, kiss on the forehead, and a wish for me to have a good game session followed. The urge to abandon the game and cuddle with Her was powerful, but She stopped me. She had more work to complete on Her todo list than just me.
Had a glass, had a blast; overall, a night well spent I would say.
-
 @ f3873798:24b3f2f3
2025-04-11 22:43:43
@ f3873798:24b3f2f3
2025-04-11 22:43:43Durante décadas, ouvimos que o Brasil era o "país do futuro". Uma terra rica, com imenso potencial humano e natural, destinada a se tornar uma grande potência e referência para o mundo. Essa ideia, repetida em discursos políticos e publicações internacionais, alimentou gerações com esperança. Mas o tempo passou — e esse futuro promissor parece nunca chegar.
Na prática, o que vemos é um ciclo de promessas não cumpridas, problemas sociais profundos e um povo muitas vezes desiludido. Apesar do potencial imenso, o Brasil enfrenta barreiras estruturais e culturais que dificultam seu pleno desenvolvimento. E é justamente sobre isso que precisamos refletir.
A raiz dos nossos desafios
Não há como ter jeito sem que haja um enfrentamento com seriedade aos problemas que estão na base da nossa sociedade. Um dos maiores entraves é a precariedade da educação, tanto no acesso quanto na qualidade. Em muitas regiões, o estudo ainda é visto como perda de tempo, algo que não contribui para o sustento imediato da família. Mesmo com incentivos governamentais, o desempenho das escolas é baixo. Em vez de formar cidadãos críticos e profissionais capacitados, muitas vezes vemos instituições focadas em ideologias ou agendas desconectadas da realidade do aluno.
Outro ponto sensível é a estrutura familiar. Em áreas onde faltam referências morais, espirituais e sociais, o ambiente familiar pode se tornar disfuncional, com casos extremos de abusos e ausência total de valores básicos. Nesses contextos, a ausência de instituições que promovem virtudes e limites — como a Igreja, por exemplo — faz diferença. Não se trata de impor uma religião, mas de reconhecer o papel histórico que a fé teve (e ainda tem) na construção de uma base ética e civilizatória.
A falta de valores basilares e estrutura para a promoção da relações em sociedade, faz do ambiente escolar um local sem propósito, onde são depositados crianças para serem expostas a um convívio forçado com estranhos sem nenhum preparo familiar, e sendo muitas vezes subentendido pelos profissionais educadores como dever da família, no entanto tal estrutura foi corrompida e devido o combate a religião pelos veículos midiáticos.
O papel da cultura e da moralidade
A cultura brasileira também tem sido afetada por uma inversão de valores. Virtudes como honestidade, humildade e dedicação são muitas vezes vistas com desdém, enquanto comportamentos imprudentes e hedonistas são exaltados. Essa distorção enfraquece a sociedade e prejudica qualquer tentativa de avanço coletivo.
A elite intelectual e política, por sua vez, parece muitas vezes mais preocupada com interesses próprios do que com o bem comum. Muitos aderem a ideias que, em vez de promover a soberania e a autonomia nacional, aprofundam nossa dependência e fragilidade como país.
Existe saída?
Sim, existe. Mas não será simples — e muito menos rápida. O Brasil precisa de uma mudança profunda de mentalidade. Isso inclui:
Resgatar o valor da família e da formação moral;
Investir de verdade em uma educação que liberte, que forme e que inspire;
Incentivar a produção científica e tecnológica local;
Valorizar o trabalho árduo, a persistência e o compromisso com a verdade.
Também é preciso reconhecer que o desenvolvimento de uma nação não é apenas econômico, mas também espiritual e cultural. Mesmo que você não seja religioso, é possível entender que a construção de uma sociedade mais justa exige princípios, virtudes e limites. Sem isso, qualquer progresso será frágil e passageiro.
O Brasil tem jeito? Sim. Mas depende de nós — da nossa capacidade de enxergar com coragem onde estamos falhando, e da nossa disposição para agir com sabedoria, verdade e esperança.
-
 @ 3eba5ef4:751f23ae
2025-05-02 02:10:09
@ 3eba5ef4:751f23ae
2025-05-02 02:10:09加密洞见
secp256k1lab:一个不安全的 Python 库,如何让比特币更安全
一些比特币开发者长期以来一直认为应该有一个统一的、可重用的加密 BIP 参考 secp256k1 代码标准。Blockstream 研究团队发布了 secp256k1lab (GitHub Repo)—— 一个新的、故意不安全的 Python 库,用于原型开发、实验和 BIP 规范的制定。
该库并不用于生产的(因为没有常数时间防护,因此易受侧道攻击),但填补了一个空白:提供了一个干净且一致的 secp256k1 功能参考实现,包括 BIP-340 风格的 Schnorr 签名、ECDH 以及底层的域/群运算。该库的目标是:通过避免重复的、一次性的实现,让未来编写 BIP 变得更简单、更安全。对于 BIP 作者来说,这意味着更少的自定义代码和规范问题,以及一条更清晰的从原型到正式提案的路径。
使用基于时间的一次性密码(TOTP)在软件钱包中进行密码验证和访问控制
本文介绍了一种在比特币软件钱包中,使用基于区块的时间同步一次性密码(TOTP, Time-based One-Time Password)机制进行密码验证和钱包访问控制的方法。 与传统的 TOTP 系统不同,这种方法将区块链数据——特别是比特币的区块高度和区块哈希 ——同一个安全存储的加密信息结合,来生成一个动态变化的 6 位数验证码,具备以下安全属性:
-
双重保护:结合了设备持有性和基于区块链衍生的、基于时间的数据(blockchain-derived time-based data)。
-
抗重放攻击:验证码随每个新区块(约 10 分钟一个周期)更新。
-
最小攻击面:无需输入或复制密码短语。
-
硬件加密保护秘密信息:移动端应用的秘密信息存储在不可导出的安全硬件中。
比特币特征矩阵:跟踪比特币产品/服务的互操作性
Bitcoin Opentech 在此页汇集并跟踪比特币相关产品/服务的互操作性。
汇集各种比特币软分叉提案的网站
bitcoin.softforks.org 网站汇集了各种比特币软分叉提案,包含组件、实现原语等关键软分叉信息,以及使用该分叉的使用案例和用户等。
以太坊社区热议 RISC-V 替代 EVM,CKB-VM 经验倍受关注
Vitalik 近日在 Ethereum 的论坛上提出了将用 RISC‑V 代替 EVM 的设想,并提到 CKB-VM 的设计作为参考范例,引发了两个社区对 RISC-V 技术决策的关注和探讨。随着讨论的展开,CKB-VM 当年的设计考量又重新被提起,并吸引了更多人回顾和学习相关经验。CKB 是 Nervos Network 的 Layer 1 公链,其支持智能合约的 Cell 模型受比特币 UTXO 模型启发,并使用基于 RISC-V 的 CKB-VM 虚拟机,实现高效且支持多语言的合约执行。了解更多 CKB-VM 详情:
在 Ark 中集成 Taproot Assets 的概念验证
Ark Labs 分享了如何将 Taproot 资产集成到 Ark 的链下批处理层中:在 Ark 标准交易流程上,引入了 tVTXO(tokenized Virtual Transaction Output)——嵌入 Taproot 资产承诺的虚拟输出。tVTXO 的行为与任何其他 VTXO 一样,可在 Ark 的链下层花费,可预先签名以实现单边退出,但它包括两个关键附加功能:
-
资产承诺(Asset Commitments):使用 Taproot 的内部密钥和 TapTree 结构嵌入到 PkScript 中。
-
传输证明文件(Transfer Proof Files)是一条加密见证的确定性链,通过链下树跟踪资产的包含路径。这些证明可以通过链上元数据激活,从而退出 Taproot Asset 生态。
Erk:改进 Ark 协议,无需用户轮次交互
Erk 是 Ark 协议的一种新颖变体,引入了具有可重新绑定签名的「退款交易」(refund transactions),允许用户提前提供可应用于未来输出的签名。然后,服务器可以安全地刷新 VTXO,而无需用户在每一轮都处于联机状态。这解决了 Ark 的关键限制之一——要求用户在 VTXO 到期之前上线。
Erk 的另一个强大功能是「永久离线刷新」——用户可以按顺序批量预签名未来的刷新。通过 watchtower 监控协议,用户可以在资金保持安全的情况下无限期地保持离线状态。
Robosats:无 KYC 闪电网络 P2P 交易,支持人民币通过微信交易
RoboSats 是一个无 KYC 的开源闪电网络交易平台,使用LN Hodl invoices 最大限度地减少托管和信任要求。用户通过 Tor 浏览器操作,体验简单且交易费用低廉的 P2P 交易。
平台目前也支持通过微信进行人民币。
值得关注的几个闪电网络基础设施项目
OpenSats 的这篇文章重点关注闪电网络在基础设施上的推进,提到以下项目:
-
Lighting Splicing: 允许用户在不停机的情况下动态调整通道容量。通过消除关闭和重新打开通道的需要,Splicing 即减少了摩擦和成本,又简化了流动性管理。
-
Validating Lightning Signer (VLS): 通过将密钥存储和交易验证转移给外部签名者,来解决闪电网络传统的、将私钥直接存储在节点上用于交易签名的方式的风险,从而确保即使闪电节点遭到入侵,攻击者也无法访问或滥用私钥来窃取资金。
-
BLAST (Big Lightning Automated Simulation Tool): 目标是为闪电网络提供稳定的建模和仿真框架,为研究和开发人员和节点运营商提供更准确地反映真实网络状况的大规模测试环境。
-
Lampo: 提供了一个基于 Lightning 开发工具包(LDK)构建的模块化、社区驱动的开发工具和节点实现方案。
-
Lnprototest: 提供了一个基于 Python 的测试库,可帮助开发人员验证不同实现中的协议合规性,确保交叉兼容性并防止回归,以免影响实际用户。
Citrea 推出基于 BitVM 的信任最小化双向挂钩桥 Clementine
Rollup 项目 Citrea 在比特币测试网上部署了 Clementine Bridge,这是比特币测试网上第一个完整的 BitVM 桥设计。Clementine 桥是 Citrea 基于 BitVM 的信任最小化双向挂钩方案,核心组件包括:
-
比特币和 Citrea 的轻客户端证明
-
BitVM 中的零知识证明验证器
只要 BitVM 设置中的单个验证器是诚实的,Clementine 就会保持安全。这是对现有解决方案(开放和封闭联合)的重大改进。Clementine 桥的设计和 Citrea 的去信任轻客户端一起,最大限度减少了对 Citrea 双向挂钩的信任要求,且无需软分叉。
详情可参考 Clementine 白皮书,以及特征简介。
RISC-V 成为 BitVMX 验证系统最佳选择的五个关键原因
作为 BitVMX 的主要开发者的 Fairgate Labs 概述了 RISC-V 成为 BitVMX 验证系统最佳选择的五大关键:
-
开放且通用:RISC-V 作为标准,无 IP 障碍
-
成熟的工具支持:编译器和调试器的丰富生态系统
-
操作码简单
-
支持高级语言
-
支持通用验证
精彩无限,不止于链
违规却挡不住需求:深圳的 LuckyMiner 在争议中推动家用小型矿机普及
LuckyMiner 是一家深圳的比特币挖矿初创公司,它们生产家用迷你矿机正越来越受欢迎。LuckyMiner 模仿的主要对象是美国产的开源的小型矿机 Bitaxe。虽然开源,但 Bitaxe 适用于 CERN-OHL-S-2.0 规则,要求任何修改都需公开,而 LuckyMiner 并未遵循此规则。
这条推文的发帖人称跟 LuckyMiner 的创始人吃了饭,后者并不遮掩 LuckyMiner 违反了许可,并表示,除了零售的 LuckyMiner 之外,它们也为 B 端客户生产符合开源许可的 Bitaxes,并且同时仿造 braiins 的挖矿设备。
在对负担得起的家用采矿设备的需求不断增长的推动下,LuckyMiner 已经取得了成功。虽然存在争议,但低成本矿工的崛起表明草根阶层对比特币感兴趣,尤其是在亚洲努力应对日益增长的威权主义和金融压迫的时候。
反对销毁受易量子攻击的比特币
关于如何处理易受攻击的地址里的比特币,Jameson Lopp 在此前的文章中,表示它反对恢复这些代币,并主张原地销毁,以防止资金被量子计算的获胜者拿走。
而 UTXO Management 的 Guillaume Girard 在此反驳了 Lopp 的主张,出于以下考虑:
-
侵犯财产权:未经持有者同意就销毁这些币,违反了财产权原则。强制让这些币不可使用,破坏了比特币中对所有权和控制权的基本尊重
-
伦理问题:尽管销毁易受攻击的币是为了防止未来量子攻击者盗币,但实际上也会无差别地惩罚那些遗失钱包或不了解量子威胁的用户。这种做法在伦理上存在严重问题,因为不给用户自救的机会。
他提出了一些更具建设性的替代方案来取代销毁策略:
- Hourglass(沙漏机制):旨在减轻“没收式销毁”和“市场抛售”这两种方式带来的负面影响。它通过限制量子攻击事件可能引发的供应冲击,既不烧毁币,也不导致市场被抛压所淹没。
这一方案由 Hunter Beast 提出,试图成为“破坏性最小”的解决方案,目前正在开发者社区中接受评估。此外,Hunter Beast 也已经提出了 BIP 360,以引入抗量子密码学(PQC)并新增一种比特币地址类型。
让旧矿机继续发挥余热:边挖矿边供暖的未来可能
BitMEX 对 Heatbit Trio 比特币挖矿加热器做了测评。该产品本质上是一个旧矿机,配备有一个安静的风扇,适用于房间供暖。
作者表示 Heatbit 的商业模式很吸引人,结合挖矿机和加热器的领域也值得长期关注。因为从长远来看,部分由于摩尔定律的物理限制,ASIC 效率的提高速度将下降,因此 ASIC 可以经济地开采比特币更长的时间(如 10 年)。随着涉及的新风险技术的减少,生产成本也应该会下降。当这种情况发生到足够程度时,将比特币挖矿与加热设备相结合可能是有意义的,例如,游泳池、商用锅炉、住宅锅炉以及商用和住宅电加热系统。
开放、即时和无国界支付:稳定币未来
a16z 的该报告探讨了稳定币会如何颠覆全球支付行业,以及谁将从中受益最大等问题。
作者将稳定币的到来称为赚钱的「WhatsApp 时刻」,因为它使国际交易几乎免费、即时、开放。此外,文章指出只有两种稳定币是被认可的:法币或资产支持的稳定币,而 「策略支持的合成美元 」(Strategy-backed synthetic dollars, SBSD)并不被承认是可靠的价值储存或交换媒介。
-
-
 @ 9a1adc34:9a9d705b
2025-04-11 01:59:19
@ 9a1adc34:9a9d705b
2025-04-11 01:59:19Testing the concept of using Nostr as a personal CMS.
-
 @ b69b97fa:982d77f6
2025-05-02 01:58:50
@ b69b97fa:982d77f6
2025-05-02 01:58:50O livro de Gênesis, o primeiro da Bíblia, revela o início da história da criação e da redenção. A tradição reformada atribui a autoria humana de Gênesis a Moisés, inspirado por Deus. Escrito por volta de 1446–1406 a.C. enquanto o povo de Israel se preparava para entrar na terra prometida, Gênesis foi dado para “instruir os israelitas sobre o propósito de Deus para eles como nação” e mostrar como seus primórdios se ligam ao plano de salvação. Desde as primeiras linhas o texto enfoca a soberania divina: “Nas primeiras linhas de Gênesis…desdobra-se o poder e a autoridade divina na formação do mundo” . Esse pano de fundo inspirador abre o livro, preparando o coração do leitor para entender como Deus age desde o começo da criação até a aliança com os patriarcas.
Temas principais em Gênesis
-
Criação e soberania de Deus: Gênesis relata que “no princípio Deus criou os céus e a terra” (Gn 1:1) e apresenta o Senhor como Criador onipotente. A narrativa mostra que o mundo tem um propósito – Deus ordenado e bom – e que o homem é formado à imagem de Deus, conferindo ao ser humano dignidade única. Desde o início vemos que Deus é soberano sobre toda a história, como apontado em estudos bíblicos: “a narrativa da criação desdobra o poder e a autoridade divina na formação do mundo”.
-
A Queda do homem: Com Adão e Eva, o pecado entra no mundo (Gn 3). O texto registra que a desobediência rompeu a comunhão entre a humanidade e Deus, trazendo culpa, medo e sofrimento a todas as relações. A Bíblia explica que “o pecado introduz no mundo a culpa e o medo, marcas profundas” e provoca consequências como violência e separação de Deus. Essa queda fundamenta em Gênesis a doutrina do pecado original e explica por que o mundo ficou quebrado. Mas logo após a Queda Deus faz promessas redentoras – uma decepção de um começo ao mostrar também a graça que virá.
-
Aliança com o povo de Deus: Em Gênesis, Deus estabelece pactos importantes. Ao salvar Noé, Deus renova a criação e promete nunca mais destruir a terra com água (Gn 9), selando um arco-íris como sinal de aliança. Depois, chama Abraão e promete: “far-te-ei uma grande nação… em ti serão benditas todas as famílias da terra” (Gn 12:2–3). Essa promessa a Abraão – de que os descendentes dele seriam muitos e abençoariam o mundo – é o fundamento da aliança abraâmica. Nas palavras de estudiosos, “o conceito de aliança… começa com a promessa feita a Abraão, na qual Deus se compromete a fazer dele uma grande nação… abençoando-o e tornando-o uma bênção para todas as nações”. Assim, Gênesis mostra Deus escolhendo e guiando um povo através de acordos firmados por Sua graça.
-
Promessa do Redentor: Mesmo depois da Queda, Deus anuncia a salvação futura. Logo após a queda de Adão, Ele diz à serpente que fará inimizade entre a “semente da mulher” e a do inimigo, e que “essa lhe ferirá a cabeça” (Gn 3:15). Essa profecia inicial – chamada de protoevangelho – antecipa a vinda de um Redentor. Gênesis, portanto, já aponta a esperança de redenção: como interpretações reformadas explicam, Deus “revelou Seu pacto da graça… prometendo um Salvador (Gn.3:15), aquele que restauraria o reino recentemente destruído”. Esse fio vermelho continua na aliança com Abraão: a bênção prometida a ele (“em ti serão benditas todas as famílias da terra”) vislumbra a obra de Cristo para todas as nações. Em resumo, Gênesis apresenta a teia de criação, pecado e aliança na qual Deus já coloca as sementes de Sua salvação.
Cristo anunciado em Gênesis
Ao ler Gênesis à luz de Cristo, vemos vários anúncios e figuras do Messias:
- Protoevangelho (Gn 3:15): Logo depois da queda, Deus promete que a “semente da mulher” ferirá a cabeça da serpente. Essa é a primeira promessa de redenção bíblica . Ela estabelece “a expectativa de um Redentor, que seria um descendente… de Adão e Eva” . Em outras palavras, mesmo no Éden, Deus começava a revelar Seu plano de salvar o mundo. Ao longo da narrativa, essa semente se identifica com Cristo, que derrotaria o pecado e a morte.
- Promessa a Abraão: Deus disse a Abraão que “em tua descendência… seriam abençoadas todas as nações” (Gn 12:3). O Novo Testamento esclarece que essa “descendência” se refere a Cristo. Como ensina um comentário bíblico: “A ‘semente’ mencionada… refere-se à vinda do Redentor, que os cristãos identificam como Jesus Cristo. Em Gênesis 12 vemos a continuação da promessa do Redentor através da descendência de Abraão”. Assim, Jesus é o cumprimento da promessa dada a Abraão (cf. Gl 3:16).
-
Tipos de Cristo em Gênesis: Vários personagens e eventos de Gênesis prefiguram Jesus:
• José: Amado por seu pai, mas traído e vendido por prata, José sofre injustamente nas mãos dos irmãos. Depois é exaltado e acaba salvando muitas pessoas durante a fome. Esse paralelo com Jesus é marcante: Cristo era amado pelo Pai (Mateus 3:17), rejeitado pelo seu povo, traído por 30 moedas de prata, sofreu injustamente e acabou salvando o mundo do pecado. José é o tipo perfeito de “servo sofredor” que Deus exalta para trazer salvação.
• Abraão e Isaque: Abraão demonstrou fé ao aceitar sacrificar seu filho Isaque em obediência a Deus (Gn 22). Deus proveu um carneiro substituto no lugar de Isaque. Essa cena figura o grande sacrifício de Deus oferecendo Seu Filho como Cordeiro do pecado. Como nota um estudo, o quase-sacrifício de Isaque “simboliza o sacrifício de Deus com Jesus”.
• Adão e o “último Adão”: A Bíblia chama Jesus de o “último Adão” (1Co 15:45). Onde Adão trouxe morte (pelo pecado), Cristo traz vida eterna. A queda do primeiro homem abriu caminho à necessidade do Salvador; Cristo, o último Adão, repara o que foi quebrado. Este paralelo é mencionado em estudos bíblicos: “Adão: Jesus é chamado de o ‘último Adão’… pois trouxe vida onde Adão trouxe morte”.
Cada um desses elementos mostra que Gênesis não é apenas história antiga, mas um começo anunciado da obra de Cristo. Desde as promessas a Adão e Abraão até as figuras de José e Isaac, vemos Deus preparando o caminho para o Redentor.
Aplicações práticas para a vida cristã hoje
-
Fé e confiança em Deus: Gênesis exalta a fé dos patriarcas como exemplo para nós. Abraão é chamado de “pai da fé” porque creu nas promessas de Deus mesmo sem ver todos os detalhes. A Bíblia diz de Abraão: “Abrão creu no Senhor, e isso lhe foi creditado como justiça” (Gn 15:6). Esse acontecimento mostra que a justificação do cristão não vem de obras, mas de crer em Deus. Somos encorajados a confiar nas promessas divinas como Abraão fez – crer que Deus cumprirá o que prometeu, mesmo em meio à espera. Como observa um estudo, mesmo sem saber para onde Deus o levava, Abraão “obedeceu prontamente, demonstrando uma confiança inabalável no plano divino”. Em nossa vida, confiar em Deus sem ver o fim da história é um exercício de fé constante, inspirado pelo exemplo de Abraão.
-
Obediência e perseverança: Gênesis ensina que a verdadeira fé se manifesta na obediência. Ao ser chamado para uma terra desconhecida, Abraão saiu da sua terra por ordem de Deus. Ao quase sacrificar Isaque, ele mostrou obediência sem entender todos os detalhes. José, mesmo injustiçado, permaneceu íntegro no Egito e Deus o usou para realizar grandes coisas. Assim, aprendemos a servir a Deus fielmente, mesmo em situações difíceis. O blog Fé e Reflexões resume bem: “a verdadeira fé se revela não quando entendemos tudo, mas quando obedecemos e confiamos que Deus tem um plano perfeito para nossas vidas”. Somos chamados a confiar em Deus e fazer o que Ele pede, sabendo que Ele guia cada passo, mesmo quando não vemos a rota completa.
-
Esperança na redenção: Desde o princípio, Gênesis afirma que Deus já tinha um plano de salvação. O “protoevangelho” de Gn 3:15 é um lembrete de que Deus promete reverter o mal em bem. Como salienta a Escritura, mesmo após a queda “Deus não os destruiu, mas revelou Seu pacto da graça… prometendo um Salvador (Gn 3:15)”. Para o cristão de hoje, isso dá esperança firme: sabemos que Deus já venceu o pecado e a morte por meio de Jesus Cristo. Não importa o tamanho do problema ou do pecado, Deus é soberano e fiel para cumprir suas promessas. As histórias de Gênesis nos ensinam que Deus continua trabalhando para restaurar o que foi perdido. José entendeu isso ao dizer aos irmãos: “vocês intentaram o mal contra mim, mas Deus o tornou em bem” (Gn 50:20). Em nossa vida diária, podemos seguir em frente com a confiança de que o Senhor está conosco, transformando dificuldades em bênçãos e conduzindo-nos a um futuro de redenção.
Conclusão
O livro de Gênesis molda nossa visão de Deus como Criador soberano, fiel em suas promessas e Senhor da história. Essas páginas iniciais mostram que Deus é onipotente (ele criou tudo) e, ao mesmo tempo, misericordioso (prometeu um Redentor quando nós falhamos). Para nós hoje, essa mensagem é encorajadora: o mesmo Deus que falou com Adão, Noé e Abraão é o Deus que fala conosco e cumpre cada promessa. Assim, podemos viver com fé, sabendo que Cristo está no centro de tudo o que Gênesis anuncia. A história de Gênesis aponta para Jesus – e em Cristo “toda a criação será restaurada” (Rm 8:21) – dando-nos esperança e paz no caminho da vida. Confiemos no Senhor, pois Ele é fiel para realizar em nós o que prometeu desde o princípio.
Fontes: Esta reflexão reuniu ensinamentos bíblicos fundamentados na teologia reformada. As Escrituras de Gênesis e os comentários de autores reformados foram citados para apoiar cada ponto (por exemplo, Gn 3:15, Gn 15:6, Gn 22, e passagens de Paulo). As lições extraídas refletem tanto a simplicidade da narrativa quanto a profundidade do plano de salvação que vem de Deus.
-
-
 @ 866e0139:6a9334e5
2025-05-03 04:53:34
@ 866e0139:6a9334e5
2025-05-03 04:53:34Autor: Friderike Komárek. Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier. Die neuesten Pareto-Artikel finden Sie in unserem Telegram-Kanal.
Die neuesten Artikel der Friedenstaube gibt es jetzt auch im eigenen Friedenstaube-Telegram-Kanal.
Was grade war, ist schief.
Wer Frieden will, ist böse.
Wer tötet, der ist lieb.
Gesund ist nur symptomlos krank,
Abstand ist gefühlte Nähe,
Maskenatmen – Gott sei Dank!
Fakten dienen Hass und Hetze,
Lügen tun gut.
Wer Fakten nennt, der wird zensiert,
Wahrheit schafft nur böses Blut.
Für Frieden braucht man Krieg,
für Meinungsfreiheit die Zensur.
Demokratie, die braucht Verbote,
fürs Klima zerstört man die Natur.
Mann ist Frau
und Frau ist Mann.
Ein Glück, dass man
die Biologie jetzt lenken kann!
Der Größenwahn beherrscht die Welt,
hat alles auf den Kopf gestellt.
Kritiker wandern als Kriminelle ins Gefängnis.
Mit ihren Gedanken bringen sie
die andern in Bedrängnis.
Was schief war, das ist grade.
Was grade war, ist schief.
LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt.
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: friedenstaube@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ 39cc53c9:27168656
2025-04-09 07:59:33
@ 39cc53c9:27168656
2025-04-09 07:59:33Know Your Customer is a regulation that requires companies of all sizes to verify the identity, suitability, and risks involved with maintaining a business relationship with a customer. Such procedures fit within the broader scope of anti-money laundering (AML) and counterterrorism financing (CTF) regulations.
Banks, exchanges, online business, mail providers, domain registrars... Everyone wants to know who you are before you can even opt for their service. Your personal information is flowing around the internet in the hands of "god-knows-who" and secured by "trust-me-bro military-grade encryption". Once your account is linked to your personal (and verified) identity, tracking you is just as easy as keeping logs on all these platforms.
Rights for Illusions
KYC processes aim to combat terrorist financing, money laundering, and other illicit activities. On the surface, KYC seems like a commendable initiative. I mean, who wouldn't want to halt terrorists and criminals in their tracks?
The logic behind KYC is: "If we mandate every financial service provider to identify their users, it becomes easier to pinpoint and apprehend the malicious actors."
However, terrorists and criminals are not precisely lining up to be identified. They're crafty. They may adopt false identities or find alternative strategies to continue their operations. Far from being outwitted, many times they're several steps ahead of regulations. Realistically, KYC might deter a small fraction – let's say about 1% ^1 – of these malefactors. Yet, the cost? All of us are saddled with the inconvenient process of identification just to use a service.
Under the rhetoric of "ensuring our safety", governments and institutions enact regulations that seem more out of a dystopian novel, gradually taking away our right to privacy.
To illustrate, consider a city where the mayor has rolled out facial recognition cameras in every nook and cranny. A band of criminals, intent on robbing a local store, rolls in with a stolen car, their faces obscured by masks and their bodies cloaked in all-black clothes. Once they've committed the crime and exited the city's boundaries, they switch vehicles and clothes out of the cameras' watchful eyes. The high-tech surveillance? It didn’t manage to identify or trace them. Yet, for every law-abiding citizen who merely wants to drive through the city or do some shopping, their movements and identities are constantly logged. The irony? This invasive tracking impacts all of us, just to catch the 1% ^1 of less-than-careful criminals.
KYC? Not you.
KYC creates barriers to participation in normal economic activity, to supposedly stop criminals. ^2
KYC puts barriers between many users and businesses. One of these comes from the fact that the process often requires multiple forms of identification, proof of address, and sometimes even financial records. For individuals in areas with poor record-keeping, non-recognized legal documents, or those who are unbanked, homeless or transient, obtaining these documents can be challenging, if not impossible.
For people who are not skilled with technology or just don't have access to it, there's also a barrier since KYC procedures are mostly online, leaving them inadvertently excluded.
Another barrier goes for the casual or one-time user, where they might not see the value in undergoing a rigorous KYC process, and these requirements can deter them from using the service altogether.
It also wipes some businesses out of the equation, since for smaller businesses, the costs associated with complying with KYC norms—from the actual process of gathering and submitting documents to potential delays in operations—can be prohibitive in economical and/or technical terms.
You're not welcome
Imagine a swanky new club in town with a strict "members only" sign. You hear the music, you see the lights, and you want in. You step up, ready to join, but suddenly there's a long list of criteria you must meet. After some time, you are finally checking all the boxes. But then the club rejects your membership with no clear reason why. You just weren't accepted. Frustrating, right?
This club scenario isn't too different from the fact that KYC is being used by many businesses as a convenient gatekeeping tool. A perfect excuse based on a "legal" procedure they are obliged to.
Even some exchanges may randomly use this to freeze and block funds from users, claiming these were "flagged" by a cryptic system that inspects the transactions. You are left hostage to their arbitrary decision to let you successfully pass the KYC procedure. If you choose to sidestep their invasive process, they might just hold onto your funds indefinitely.
Your identity has been stolen
KYC data has been found to be for sale on many dark net markets^3. Exchanges may have leaks or hacks, and such leaks contain very sensitive data. We're talking about the full monty: passport or ID scans, proof of address, and even those awkward selfies where you're holding up your ID next to your face. All this data is being left to the mercy of the (mostly) "trust-me-bro" security systems of such companies. Quite scary, isn't it?
As cheap as $10 for 100 documents, with discounts applying for those who buy in bulk, the personal identities of innocent users who passed KYC procedures are for sale. ^3
In short, if you have ever passed the KYC/AML process of a crypto exchange, your privacy is at risk of being compromised, or it might even have already been compromised.
(they) Know Your Coins
You may already know that Bitcoin and most cryptocurrencies have a transparent public blockchain, meaning that all data is shown unencrypted for everyone to see and recorded forever. If you link an address you own to your identity through KYC, for example, by sending an amount from a KYC exchange to it, your Bitcoin is no longer pseudonymous and can then be traced.
If, for instance, you send Bitcoin from such an identified address to another KYC'ed address (say, from a friend), everyone having access to that address-identity link information (exchanges, governments, hackers, etc.) will be able to associate that transaction and know who you are transacting with.
Conclusions
To sum up, KYC does not protect individuals; rather, it's a threat to our privacy, freedom, security and integrity. Sensible information flowing through the internet is thrown into chaos by dubious security measures. It puts borders between many potential customers and businesses, and it helps governments and companies track innocent users. That's the chaos KYC has stirred.
The criminals are using stolen identities from companies that gathered them thanks to these very same regulations that were supposed to combat them. Criminals always know how to circumvent such regulations. In the end, normal people are the most affected by these policies.
The threat that KYC poses to individuals in terms of privacy, security and freedom is not to be neglected. And if we don’t start challenging these systems and questioning their efficacy, we are just one step closer to the dystopian future that is now foreseeable.
Edited 20/03/2024 * Add reference to the 1% statement on Rights for Illusions section to an article where Chainalysis found that only 0.34% of the transaction volume with cryptocurrencies in 2023 was attributable to criminal activity ^1
-
 @ d9a329af:bef580d7
2025-05-03 04:20:42
@ d9a329af:bef580d7
2025-05-03 04:20:42To be clear, this is 100% my subjective opinion on the alternatives to popular music, as it has become practically a formula of witchcraft, pseudoscience and mysticism. There is nothing you can do to get me to listen to Western pop music from the late 2010's to now. I could certainly listen to almost anything... just not modern pop, which is now completely backwards.
Most examples of compositions for these genres will be my own, unless otherwise stated. The genres on this list are in no particular order, though my favorite of which will be first: 1. Bossa Nova
Bossa Nova is a subgenre of jazz from Brazil, created in the 1950's as a mix of standard jazz and samba rhythms in a more gentle and relaxing manner. This genre's most famous songs are Tom Jobim's The Girl from Ipanema (found in albums like Getz/Gilberto), Wave, and even Triste. Most of the music is written in 2/4 time signature, and any key is almost acceptable. It's called Afro-Brazilian Jazz for a reason after all. I have a ton of compositions I produced, from Forget and Regret, to Rabbit Theory, Beaches of Gensokyo Past, Waveside, and even Willows of Ice to name a few of them.
- Metal
This is an umbrella term for many subgenres of this fork of hard rock, with more distorted guitars, speedy and technical writing, vocals that sound demonic (some subgenres don't have that), or sometimes, chaotic lyrics and downright nasty ones if you look deep enough. If you want to get into it, just make sure it's not Black Metal (it's weird), Blackened Metal (Any subgenre of metal that's been inserted with elements of Black Metal), Metalcore, or any other genre that has vocals that aren't the best to hear (these are vocal fries that are really good if you're into the weird demonic sounds). This isn't for the faint of heart. Instrumental metal is good though, and an example is my composition from Touhou Igousaken called A Sly Foxy Liar if you want to know what techincal groove metal is like at a glance.
- Touhou-style
I can attest to this one, as I produced bossa nova with a Touhou-like writing style. Touhou Project is a series of action video games created by one guy (Jun'ya Outa, a.k.a. ZUN), and are usually bullet curtain games in the main franchise, with some official spinoffs that are also action games (fighting games like Touhou 12.3 ~ Hisoutensoku). What I'm referring to here is music written by ZUN himself (He does almost everything for Touhou Project, and he's really good at it), or fans that write to his style with their own flair. I did this once with my composition, Toiled Bubble, which is from my self-titled EP. I probably wouldn't do much with it to be fair, and stick to bossa nova (my main genre if you couldn't tell).
- Hip-Hop/Rap
This can get subjective here, but old-school rap and hip-hop... give me more of it. Before it became corrupted with all kinds of immoral things, hip-hop and rap were actually very good for their time. These were new, innovative and creative with how lyrics were written. Nowadays, while we're talking about cars, unspeakable acts, money, and just being dirtbags, artists in this genre back then were much classier than that. I fit in the latter category with my piece entitled, Don't Think, Just Roast, where I called out antis for a Vtuber agency who wanted to give its talent a hard time. It didn't get much traction on YouTube, because I'm not a well-known artist (I'm considered a nobody in the grand scheme of things. I'd like to get it fixed, but I don't want a record deal... I'd have to become a Pharisee or a Jesuit for that).
- Synthwave
This is a genre of electronic music focused on 80's and 90's synths being used to carry a composition. Nowadays, we have plugins like Vital, Serum, Surge and others to create sounds we would otherwise be hearing on an 80's or 90's keyboard. An example of this is my composition, Wrenched Torque, which was composed for a promotion I did with RAES when he released his Vital synth pack.
More are to come in future installments of this series, and I will adjust the title of this one accordingly if y'all have any ideas of genres I should look into.
-
 @ d9a329af:bef580d7
2025-05-03 04:10:03
@ d9a329af:bef580d7
2025-05-03 04:10:03Everyone who sees it knows at this point that the matrix of control comes from the overdependence of proprietary software to do our everyday tasks. You can think of this like us being the cling wrap that will just not let go of these pieces of garbage software that don't allow you to see what is in their source code, and how they work. This will tend to lead to the unlawful collection of data (violating the most basic of privacy laws, despite unenforceable contracts that are enforced regardless), bad OPSEC that sees you being stalked and harassed over nothing significant. In the worst of cases, if you speak your mind where you aren't necessarily supposed to be able to do that, and you get doxxed, the worst cases could be far worse than one could imagine.
The solution to this, on the other hand, is using almost exclusively free/libre open-source software and GNU/Linux operation systems. If you're using certain proprietary software, hardening it to give as little data as possible to the entity responsible for it will also work, as long as you know which ones to use. This is a hard pass for a lot of people, but if you want to escape the control matrix of proprietary software, Winblows, HackOS, iHackOS, iBloatOS and stock Google AI Fever Dream, then researching which Free Software (notice the spelling) to use is your first bet. I had already done this for the past four and a half years, and will continue to do it as long as I live, seeing what new Free Software compliant applications and libraries come into the spotlight once things get locked down into walled gardens like what HackOS, iHackOS and BlindnessOS do on a regular basis.
Each of these pieces of software will be in a categorized list with a brief description of what the software is used for. There is a lot to take in, so research this yourself and see if these are right for you. These are the applications I personally use on a regular day-to-day basis, and they work for my needs.
- Operating Systems (the core to your device)
- GNU/Linux operating systems (for PCs) or GrapheneOS (for de-googled Android phones)
To be fair on this one, GNU/Linux is the combination of the Linux kernel with the GNU toolchain, which in turn allows any developer to make an operating system that is FOSS, not necessarily Free Software, especially with the Linux Kernel's proprietary bits of code. The Linux kernel is also used in the Android Open-Source Project (AOSP), and is used as the base of operating systems for Android phones such as GrapheneOS, the only AOSP custom ROM I would recommend based upon the research I had done on this (even if very little).
My recommendations on the Linux side of things are almost any Arch-based distribution (with the exception of Manjaro), Debian-based distributions like Linux Mint Debian edition, regular Debian, AntiX or Devuan, or a Fedora/RedHat-based distribution like Nobara Project (if you're a gamer), OpenSUSE (if set up properly) or even Bluefin if you want an atomic desktop (I wouldn't recommend Bluefin if you want to monkey with your operating system and DIY on many aspects of it). Once you learn how to set these up securely, privately and properly, you're on your way to starting your journey into digital liberation, but there's far more to go on this front.
- Web Browsers (How you surf the internet)
- Firefox Forks
This one is self-explanatory. I harden all the Firefox forks I use (LibreWolf, Waterfox, Cachy Browser, Floorp and Zen as some examples) to the nines, despite being unable to do anything about my fingerprint. This is why I use multiple browsers for specific purposes to counteract the fingerprint spying due to weaponized JavaScript. There are ways to circumvent the fingerprint-based espionage, and make sure the site fingerprint.com doesn't know that one's lying about what their user agent is, though it's not very easy to fool that site, as it's used by 6,000 companies.
- Brave Browser
This is the only Chromium-based browser I would recommend, as it's better when hardened against all the other Chromium-based browsers, including Ungoogled Chromium, which is almost impossible to harden due to security vulnerabilities. Despite that, Brave has some of the best features for a Chromium-based browser one can feel comfortable using, even though you'll have similar issues with Firefox-based browsers that aren't actually Firefox (and Firefox has its own issues regarding espionage from Mozilla)
- Office Suites (If you need to do professional office documents)
- LibreOffice
A fork of Apache's OpenOffice, made better with many features missing from even OnlyOffice and OpenOffice, this suite of applications is the go-to Free Software office suite for many people looking to switch from the proprietary software nether to the diamonds of free/libre open-source software. Though one may need to perform some extra steps to set up compatibility with G-Suite and Microsoft Office past 2015 potentially, it's still a good thing that people trust LibreOffice as their one-stop shop for office documents, despite being completely different from your standard office suite fare.
- OnlyOffice
The competitor to LibreOffice with the ease of Microsoft Office and G-Suite compatibility, OnlyOffice is another office suite that can be good for those who need it, especially since anybody who had used Microsoft Office in particular will be familiar with its layout, if not for a slight learning curve. As someone who's used G-Suite more (due to schooling that stunk worse than a decomposing rat in New York City), that's part of the reason why I switched to LibreOffice, though I tried some others, including OnlyOffice and Abiword (since I use a word processor a lot). This one is another solid option for those who need it.
- Wordgrinder
For those who like to use a terminal emulator like I do, Wordgrinder is a word processor with a terminal user interface (TUI) designed with just focusing on typing without distractions in mind. .wg is the file extension for documents made using Wordgrinder, especially since nowadays most word processors are cloud based. For those who live in a terminal, this is a good option to your terminal UI-based toolbox
- Text editors
- Vi, Vim, Neovim and other Vim-like editors
The classic VI Improved (Vim), a fork of the TUI modal editor, vi, with keybinds that will be confusing at first, but with practice and patience, bring about muscle memory to stay on the keyboard, and not necessarily touch the mouse, keypad on the right hand side, or even the arrow keys. These keybind skills will stay with one for the rest of their life once they learn how the modes in vi, Vim or vi-based editors work. It's a classic for those working in the terminal, and a staple in FLOSS text editing and coding tools once customized potentially to the nines to your particular style.
- VSCodium
The Free Software fork of Code OSS by Microsoft, but made to be similar in function to VSCode without Microsoft's espionage baked into it. It has almost exactly the same features as VSCode that one would need, and even any VSIX files from VSCode will work in VSCodium. This one is an easy switch from VSCode for those who use it, but don't want the forced telemetry.
- Emacs
The competitor to Vim, Emacs is an editor that is FLOSS in every way imaginable. It is one of the most customizable editors anybody could have ever conceived, though the programming language used in Emacs is a dialect of Lisp the developers had made themselves. There are more keybinds to memorize compared to Vim, though Vim keybinds can be added using the Evil Mode package in any Emacs package manager to get the best of both worlds in Emacs. Once one gets a handle of the steep learning curve for Emacs, it's customizable in every imaginable way almost.
These four categories will get you started on your privacy journey, though I covered things a developer might want. I have plans on more lists to compile once I get my ducks in a row on what I want to cover here on Nostr in a longform format. Feel free to let me know if you have recommendations for me to write about, and I can do some digging on that if it isn't a rabbit hole.
-
 @ 3eba5ef4:751f23ae
2025-05-02 01:56:09
@ 3eba5ef4:751f23ae
2025-05-02 01:56:09Crypto Insights
secp256k1lab: An Insecure Python Library That Makes Bitcoin Safer
Some Bitcoin developers have long believed in the need for a unified, reusable cryptographic BIP reference standard for secp256k1. Blockstream Research has released secp256k1lab — an intentionally insecure new Python library designed for prototyping, experimentation, and BIP specifications.
This library is NOT intended for production use (it lacks constant-time protections and is thus vulnerable to side-channel attacks). However, it fills a gap by providing a clean and consistent reference implementation of secp256k1 functionality, including BIP-340 style Schnorr signatures, ECDH, and low-level field/group operations. Its goal: to make future BIP authoring simpler and more secure by avoiding redundant, one-off implementations. For BIP authors, this means less custom code, fewer specification bugs, and a clearer path from prototype to proposal.
Block-Based Time-Based One-Time Passwords for Secure Passphrase Validation in Bitcoin Wallets
This article introduces a method for passphrase validation and Bitcoin software wallet access control using a block-based time-based one-time password (TOTP) system.
Unlike traditional TOTP systems, this method uses blockchain data — specifically Bitcoin block height and block hash — combined with securely stored cryptographic secrets to generate a 6-digit dynamic verification code with the following security properties:
-
Two-Factor Protection: Combines device possession and blockchain-derived time-based data.
-
Replay Resistance: Codes change with every block (~10-min cycle).
-
Minimal Attack Surface: Passphrase never typed or copied.
-
Hardware-Backed Secrets: Mobile app secret stored in non-exportable secure hardware.
Bitcoin Feature Matrix: Tracking Interoperability of Bitcoin Products/Services
You can use this page on Bitcoin Opentech to track interoperability among Bitcoin products and services.
Tracking Bitcoin Soft Fork Proposals in One Place
bitcoin.softforks.org aggregates various Bitcoin soft fork proposals, including components, implementation primitives, use cases, and users.
Ethereum Community Explores Replacing EVM with RISC-V — Spotlight on CKB-VM Experience
Vitalik recently proposed the idea of replacing the EVM with RISC-V on the Ethereum forum, citing the design of CKB-VM as a reference. This has sparked active discussion in both communities around RISC-V as a technical direction. As the conversation deepens, the original design decisions behind CKB-VM have resurfaced, drawing renewed interest and encouraging more developers to study its architecture and lessons.
CKB is the Layer 1 blockchain of the Nervos Network. Its smart contract model, called the Cell model, is inspired by Bitcoin’s UTXO system. It uses the RISC-V–based CKB-VM to enable efficient and multi-language smart contract execution. Find more details in:
-
A Blockchain VM Built on RISC-V (The Birth of CKB-VM Part 1)
-
CKB-VM: Its Inspiration, Design, and Strengths (The Birth of CKB-VM, Part 2)
-
How to Have Fun with CKB-VM (The Birth of CKB-VM, Part 3)
Integrating Taproot Assets into Ark
Ark Labs shared their proof-of-concept of integrating Taproot Assets into the off-chain batching layer of Ark. They introduced tVTXOs (tokenized Virtual Transaction Outputs) — virtual outputs that embed Taproot Asset commitments.
tVTXOs behave like regular VTXOs, spendable off-chain and pre-signable for unilateral exits, but with two additional features:
-
Asset Commitments: Embedded in PkScript using Taproot’s internal key and TapTree structure.
-
Transfer Proof Files: A cryptographically linked, deterministic chain of off-chain proofs tracking asset inclusion. These can be activated via on-chain metadata to exit the Taproot Asset ecosystem.
Erk: An Ark Protocol Upgrade Removing User Round Interactions
Erk is a novel variant of the Ark protocol that introduces refund transactions with rebindable signatures. This allows users to pre-sign outputs that the server can safely refresh without needing the user to be online for each round — addressing one of Ark’s limitations.
Another feature of Erk is “perpetual offline refresh” — users can bulk pre-sign future refreshes. With watchtowers monitoring the protocol, users can stay offline indefinitely while their funds remain safe.
Robosats: No-KYC Lightning P2P Trading
RoboSats is an open-source, no-KYC Lightning P2P exchange using LN Hodl invoices to minimize custodial requirements and trust. Operated via the Tor browser, it offers a simple and low-fee user experience.
Find more in their GitHub repo and user guide.
Advancements in Lightning Infrastructure
OpenSats highlights several key Lightning infrastructure advancements:
-
Lightning Splicing: Allows dynamic channel capacity adjustment without downtime, simplifying liquidity management and reducing costs.
-
Validating Lightning Signer (VLS): Shifts key storage and transaction validation to an external signer. Even if a node is compromised, the attacker can’t access or misuse private keys.
-
BLAST (Big Lightning Automated Simulation Tool): Designed to provide a stable modeling and simulation framework of the Lightning Network for developers and node operators.
-
Lampo: A modular, community-driven development toolkit and node implementation built on Lightning Dev Kit (LDK).
-
Lnprototest: A Python-based testing library to help developers validate protocol adherence across different implementations.
Citrea Launches Clementine: A BitVM-Based Trust-Minimized 2-Way Peg Bridge
Rollup Citrea has deployed Clementine Bridge on Bitcoin testnet — the first fully BitVM-based bridge design on Bitcoin testnet. Clementine is Citrea’s trust-minimized, two-way peg solution powered by:
-
Bitcoin and Citrea’s light client proofs
-
Zero-knowledge proof verifier in BitVM
As long as one single verifier in the BitVM setup is honest, Clementine remains secure — a major improvement over existing approaches (e.g., open and closed federations). Paired with Citrea’s trustless light client, Clementine minimizes trust in Citrea’s bridge design and doesn’t require a soft fork.
Find more details in Clementine Whitepaper and Feature Overview.
Five Reasons RISC-V Is the Best Architecture for the BitVMX Proving System
Fairgate Labs, the main developers behind BitVMX, outlined five key reasons why RISC-V is the optimal choice for BitVMX:
-
Open and Universal: RISC-V as a standard with no IP barriers
-
Mature Tooling: A rich ecosystem of compilers and debuggers
-
Opcode Simplicity
-
High-Level Language Support
-
Universal Verification
Top Reads on Blockchain and Beyond
Demand Outpaces Licensing: LuckyMiner Drives Home Mining Boom Amid Controversy
LuckyMiner, a Bitcoin mining startup based in Shenzhen, China, is gaining traction with its mini miners. Their products are clones of the open-source Bitaxe miners from the U.S. However, Bitaxe is licensed under CERN-OHL-S-2.0, which requires all modifications to be open-sourced—something LuckyMiner has not complied with.
According to this post, LuckyMiner's founder openly admitted to violating the license and claimed that while their LuckyMiner devices for retail customers don’t comply with the open-source terms, they also produce fully license-compliant Bitaxes for business clients, while simultaneously cloning mining equipment from Braiins.
Against Burning Quantum-Vulnerable Bitcoins
Jameson Lopp has previously argued in favor of burning bitcoin in vulnerable addresses, to prevent funds from being taken by those who win the quantum computing race.
Guillaume Girard from UTXO Management disagrees, offering these counterpoints:
-
Property rights violation: Burning coins without the owner’s consent undermines the very principle of property rights. Forcing coins into unspendability erodes the core Bitcoin ethos of ownership and control.
-
Ethical concerns: While burning these coins may prevent quantum theft, it also punishes users who lost wallets or don’t understand the quantum threat—offering no chance for recovery.
Instead of burning, he proposes more constructive steps:
- Hourglass: Mitigates the downsides of both “confiscatory” and “liquidation” approaches – by limiting the potential supply shock of a quantum event, without burning coins or flooding markets.
This solution, proposed by Hunter Beast, aims to be the “least damaging” option and is currently under review by developers. Additionally, Hunter Beast has already proposed BIP 360 to bring Post-Quantum Cryptography (PQC) to Bitcoin with a new address type.
Old Miners, New Heat: Mining-as-Heating Might Just Work
BitMEX reviewed the Heatbit Trio—a Bitcoin miner repurposed into a room heater redesigned with a quiet fan.
The reviewer found the Heatbit concept commercially appealing and believes the heating-mining hybrid space is worth watching. The rate of improvement in ASIC efficiencies will decline (partly due to the limits of Moore’s Law), such that ASICs can economically mine Bitcoin for much longer—possibly up to 10 years. With fewer new technical risks, production costs should also drop. When that happens, integrating mining with heating systems may become practical.
Open, Instant, Borderless Payments: Stablecoins and Their Future
This a16z report explores how stablecoins are poised to change the global payments landscape—and who stands to benefit most.
The report sees stablecoins the "WhatsApp moment for money," enabling international transfers nearly free and instant. It also stresses that only two types of stablecoins are considered trustworthy: fiat-backed or asset-backed. The so-called Strategy-Backed Synthetic Dollars (SBSDs) are NOT considered to be a reliable store of value or medium of exchange.
-
-
 @ f7f4e308:b44d67f4
2025-04-09 02:12:18
@ f7f4e308:b44d67f4
2025-04-09 02:12:18https://sns-video-hw.xhscdn.com/stream/1/110/258/01e7ec7be81a85850103700195f3c4ba45_258.mp4
-
 @ 088436cd:9d2646cc
2025-05-01 21:01:55
@ 088436cd:9d2646cc
2025-05-01 21:01:55The arrival of the coronavirus brought not only illness and death but also fear and panic. In such an environment of uncertainty, people have naturally stocked up on necessities, not knowing when things will return to normal.
Retail shelves have been cleared out, and even online suppliers like Amazon and Walmart are out of stock for some items. Independent sellers on these e-commerce platforms have had to fill the gap. With the huge increase in demand, they have found that their inventory has skyrocketed in value.
Many in need of these items (e.g. toilet paper, hand sanitizer and masks) balk at the new prices. They feel they are being taken advantage of in a time of need and call for intervention by the government to lower prices. The government has heeded that call, labeling the independent sellers as "price gougers" and threatening sanctions if they don't lower their prices. Amazon has suspended seller accounts and law enforcement at all levels have threatened to prosecute. Prices have dropped as a result and at first glance this seems like a victory for fair play. But, we will have to dig deeper to understand the unseen consequences of this intervention.
We must look at the economics of the situation, how supply and demand result in a price and how that price acts as a signal that goes out to everyone, informing them of underlying conditions in the economy and helping coordinate their actions.
It all started with a rise in demand. Given a fixed supply (e.g., the limited stock on shelves and in warehouses), an increase in demand inevitably leads to higher prices. Most people are familiar with this phenomenon, such as paying more for airline tickets during holidays or surge pricing for rides.
Higher prices discourage less critical uses of scarce resources. For example, you might not pay $1,000 for a plane ticket to visit your aunt if you can get one for $100 the following week, but someone else might pay that price to visit a dying relative. They value that plane seat more than you.
*** During the crisis, demand surged and their shelves emptied even though
However, retail outlets have not raised prices. They have kept them low, so the low-value uses of things like toilet paper, masks and hand sanitizer has continued. Often, this "use" just takes the form of hoarding. At everyday low prices, it makes sense to buy hundreds of rolls and bottles. You know you will use them eventually, so why not stock up? And, with all those extra supplies in the closet and basement, you don't need to change your behavior much. You don't have to ration your use.
At the low prices, these scarce resources got bought up faster and faster until there was simply none left. The reality of the situation became painfully clear to those who didn't panic and got to the store late: You have no toilet paper and you're not going to any time soon.
However, if prices had been allowed to rise, a number of effects would have taken place that would have coordinated the behavior of everyone so that valuable resources would not have been wasted or hoarded, and everyone could have had access to what they needed.
On the demand side, if prices had been allowed to rise, people would have begun to self-ration. You might leave those extra plies on the roll next time if you know they will cost ten times as much to replace. Or, you might choose to clean up a spill with a rag rather than disposable tissue. Most importantly, you won't hoard as much. That 50th bottle of hand sanitizer might just not be worth it at the new, high price. You'll leave it on the shelf for someone else who may have none.
On the supply side, higher prices would have incentivized people to offer up more of their stockpiles for sale. If you have a pallet full of toilet paper in your basement and all of the sudden they are worth $15 per roll, you might just list a few online. But, if it is illegal to do so, you probably won't.
Imagine you run a business installing insulation and have a few thousand respirator masks on hand for your employees. During a pandemic, it is much more important that people breathe filtered air than that insulation get installed, and that fact is reflected in higher prices. You will sell your extra masks at the higher price rather than store them for future insulation jobs, and the scarce resource will be put to its most important use.
Producers of hand sanitizer would go into overdrive if prices were allowed to rise. They would pay their employees overtime, hire new ones, and pay a premium for their supplies, making sure their raw materials don't go to less important uses.
These kinds of coordinated actions all across the economy would be impossible without real prices to guide them. How do you know if it makes sense to spend an extra $10k bringing a thousand masks to market unless you know you can get more than $10 per mask? If the price is kept artificially low, you simply can't do it. The money just isn't there.
These are the immediate effects of a price change, but incredibly, price changes also coordinate people's actions across space and time.
Across space, there are different supply and demand conditions in different places, and thus prices are not uniform. We know some places are real "hot spots" for the virus, while others are mostly unaffected. High demand in the hot spots leads to higher prices there, which attracts more of the resource to those areas. Boxes and boxes of essential items would pour in where they are needed most from where they are needed least, but only if prices were allowed to adjust freely.
This would be accomplished by individuals and businesses buying low in the unaffected areas, selling high in the hot spots and subtracting their labor and transportation costs from the difference. Producers of new supply would know exactly where it is most needed and ship to the high-demand, high-price areas first. The effect of these actions is to increase prices in the low demand areas and reduce them in the high demand areas. People in the low demand areas will start to self-ration more, reflecting the reality of their neighbors, and people in the hotspots will get some relief.
However, by artificially suppressing prices in the hot spot, people there will simply buy up the available supply and run out, and it will be cost prohibitive to bring in new supply from low-demand areas.
Prices coordinate economic actions across time as well. Just as entrepreneurs and businesses can profit by transporting scarce necessities from low-demand to high-demand areas, they can also profit by buying in low-demand times and storing their merchandise for when it is needed most.
Just as allowing prices to freely adjust in one area relative to another will send all the right signals for the optimal use of a scarce resource, allowing prices to freely adjust over time will do the same.
When an entrepreneur buys up resources during low-demand times in anticipation of a crisis, she restricts supply ahead of the crisis, which leads to a price increase. She effectively bids up the price. The change in price affects consumers and producers in all the ways mentioned above. Consumers self-ration more, and producers bring more of the resource to market.
Our entrepreneur has done a truly incredible thing. She has predicted the future, and by so doing has caused every individual in the economy to prepare for a shortage they don't even know is coming! And, by discouraging consumption and encouraging production ahead of time, she blunts the impact the crisis will have. There will be more of the resource to go around when it is needed most.
On top of this, our entrepreneur still has her stockpile she saved back when everyone else was blithely using it up. She can now further mitigate the damage of the crisis by selling her stock during the worst of it, when people are most desperate for relief. She will know when this is because the price will tell her, but only if it is allowed to adjust freely. When the price is at its highest is when people need the resource the most, and those willing to pay will not waste it or hoard it. They will put it to its highest valued use.
The economy is like a big bus we are all riding in, going down a road with many twists and turns. Just as it is difficult to see into the future, it is difficult to see out the bus windows at the road ahead.
On the dashboard, we don't have a speedometer or fuel gauge. Instead we have all the prices for everything in the economy. Prices are what tell us the condition of the bus and the road. They tell us everything. Without them, we are blind.
Good times are a smooth road. Consumer prices and interest rates are low, investment returns are steady. We hit the gas and go fast. But, the road is not always straight and smooth. Sometimes there are sharp turns and rough patches. Successful entrepreneurs are the ones who can see what is coming better than everyone else. They are our navigators.
When they buy up scarce resources ahead of a crisis, they are hitting the brakes and slowing us down. When they divert resources from one area to another, they are steering us onto a smoother path. By their actions in the market, they adjust the prices on our dashboard to reflect the conditions of the road ahead, so we can prepare for, navigate and get through the inevitable difficulties we will face.
Interfering with the dashboard by imposing price floors or price caps doesn't change the conditions of the road (the number of toilet paper rolls in existence hasn't changed). All it does is distort our perception of those conditions. We think the road is still smooth--our heavy foot stomping the gas--as we crash onto a rocky dirt road at 80 miles per hour (empty shelves at the store for weeks on end).
Supply, demand and prices are laws of nature. All of this is just how things work. It isn't right or wrong in a moral sense. Price caps lead to waste, shortages and hoarding as surely as water flows downhill. The opposite--allowing prices to adjust freely--leads to conservation of scarce resources and their being put to their highest valued use. And yes, it leads to profits for the entrepreneurs who were able to correctly predict future conditions, and losses for those who weren't.
Is it fair that they should collect these profits? On the one hand, anyone could have stocked up on toilet paper, hand sanitizer and face masks at any time before the crisis, so we all had a fair chance to get the supplies cheaply. On the other hand, it just feels wrong that some should profit so much at a time when there is so much need.
Our instinct in the moment is to see the entrepreneur as a villain, greedy "price gouger". But we don't see the long chain of economic consequences the led to the situation we feel is unfair.
If it weren't for anti-price-gouging laws, the major retailers would have raised their prices long before the crisis became acute. When they saw demand outstrip supply, they would have raised prices, not by 100 fold, but gradually and long before anyone knew how serious things would have become. Late comers would have had to pay more, but at least there would be something left on the shelf.
As an entrepreneur, why take risks trying to anticipate the future if you can't reap the reward when you are right? Instead of letting instead of letting entrepreneurs--our navigators--guide us, we are punishing and vilifying them, trying to force prices to reflect a reality that simply doesn't exist.
In a crisis, more than any other time, prices must be allowed to fluctuate. To do otherwise is to blind ourselves at a time when danger and uncertainty abound. It is economic suicide.
In a crisis, there is great need, and the way to meet that need is not by pretending it's not there, by forcing prices to reflect a world where there isn't need. They way to meet the need is the same it has always been, through charity.
If the people in government want to help, the best way for the to do so is to be charitable and reduce their taxes and fees as much as possible, ideally to zero in a time of crisis. Amazon, for example, could instantly reduce the price of all crisis related necessities by 20% if they waived their fee. This would allow for more uses by more people of these scarce supplies as hoarders release their stockpiles on to the market, knowing they can get 20% more for their stock. Governments could reduce or eliminate their tax burden on high-demand, crisis-related items and all the factors that go into their production, with the same effect: a reduction in prices and expansion of supply. All of us, including the successful entrepreneurs and the wealthy for whom high prices are not a great burden, could donate to relief efforts.
These ideas are not new or untested. This is core micro economics. It has been taught for hundreds of years in universities the world over. The fact that every crisis that comes along stirs up ire against entrepreneurs indicates not that the economics is wrong, but that we have a strong visceral reaction against what we perceive to be unfairness. This is as it should be. Unfairness is wrong and the anger it stirs in us should compel us to right the wrong. Our anger itself isn't wrong, it's just misplaced.
Entrepreneurs didn't cause the prices to rise. Our reaction to a virus did that. We saw a serious threat and an uncertain future and followed our natural impulse to hoard. Because prices at major retail suppliers didn't rise, that impulse ran rampant and we cleared the shelves until there was nothing left. We ran the bus right off the road and them blamed the entrepreneurs for showing us the reality of our situation, for shaking us out of the fantasy of low prices.
All of this is not to say that entrepreneurs are high-minded public servants. They are just doing their job. Staking your money on an uncertain future is a risky business. There are big risks and big rewards. Most entrepreneurs just scrape by or lose their capital in failed ventures.
However, the ones that get it right must be allowed to keep their profits, or else no one will try and we'll all be driving blind. We need our navigators. It doesn't even matter if they know all the positive effects they are having on the rest of us and the economy as a whole. So long as they are buying low and selling high--so long as they are doing their job--they will be guiding the rest of us through the good times and the bad, down the open road and through the rough spots.
-
 @ 34f1ddab:2ca0cf7c
2025-05-03 02:45:30
@ 34f1ddab:2ca0cf7c
2025-05-03 02:45:30In the world of cryptocurrency, the stakes are high, and losing access to your digital assets can be a nightmare. But fear not — Crypt Recver is here to turn that nightmare into a dream come true! With expert-led recovery services and cutting-edge technology, Crypt Recver specializes in helping you regain access to your lost Bitcoin and other cryptocurrencies.
Why Choose Crypt Recver? 🤔 🔑 Expertise You Can Trust At Crypt Recver, we combine state-of-the-art technology with skilled engineers who have a proven track record in crypto recovery. Whether you’ve forgotten your passwords, lost your private keys, or dealt with damaged hardware wallets, our team is equipped to help.
⚡ Fast Recovery Process Time is of the essence when it comes to recovering lost funds. Crypt Recver’s systems are optimized for speed, enabling quick recoveries — so you can get back to what matters most: trading and investing.
🎯 High Success Rate With over a 90% success rate, our recovery team has helped countless clients regain access to their lost assets. We understand the intricacies of cryptocurrency and are dedicated to providing effective solutions.
🛡️ Confidential & Secure Your privacy is our priority. All recovery sessions at Crypt Recver are encrypted and kept entirely confidential. You can trust us with your information, knowing that we maintain the highest standards of security.
🔧 Advanced Recovery Tools We use proprietary tools and techniques to handle complex recovery scenarios, from recovering corrupted wallets to restoring coins from invalid addresses. No matter how challenging the situation, we have a plan.
Our Recovery Services Include: 📈 Bitcoin Recovery: Have you lost access to your Bitcoin wallet? We can help you recover lost wallets, private keys, and passphrases. Transaction Recovery: Mistaken transfers, lost passwords, or missing transaction records — let us help you reclaim your funds! Cold Wallet Restoration: Did your cold wallet fail? We specialize in extracting assets safely and securely. Private Key Generation: Forgotten your private key? We can help you generate new keys linked to your funds without compromising security. Don’t Let Lost Crypto Ruin Your Day! 🕒 With an estimated 3 to 3.4 million BTC lost forever, it’s critical to act swiftly when facing access issues. Whether you’ve been a victim of a dust attack or have simply forgotten your key, Crypt Recver offers the support you need to reclaim your digital assets.
🚀 Start Your Recovery Now! Ready to get your cryptocurrency back? Don’t let uncertainty hold you back!
👉 Request Wallet Recovery Help Today!
Need Immediate Assistance? 📞 For quick queries or support, connect with us on:
✉️ Telegram: Chat with Us on Telegram 💬 WhatsApp: Message Us on WhatsApp Trust Crypt Recver for the Best Crypto Recovery Service — Get back to trading with confidence! 💪In the world of cryptocurrency, the stakes are high, and losing access to your digital assets can be a nightmare. But fear not — Crypt Recver is here to turn that nightmare into a dream come true! With expert-led recovery services and cutting-edge technology, Crypt Recver specializes in helping you regain access to your lost Bitcoin and other cryptocurrencies.
 # Why Choose Crypt Recver? 🤔
# Why Choose Crypt Recver? 🤔🔑 Expertise You Can Trust
At Crypt Recver, we combine state-of-the-art technology with skilled engineers who have a proven track record in crypto recovery. Whether you’ve forgotten your passwords, lost your private keys, or dealt with damaged hardware wallets, our team is equipped to help.
⚡ Fast Recovery Process
Time is of the essence when it comes to recovering lost funds. Crypt Recver’s systems are optimized for speed, enabling quick recoveries — so you can get back to what matters most: trading and investing.
🎯 High Success Rate
With over a 90% success rate, our recovery team has helped countless clients regain access to their lost assets. We understand the intricacies of cryptocurrency and are dedicated to providing effective solutions.
🛡️ Confidential & Secure
Your privacy is our priority. All recovery sessions at Crypt Recver are encrypted and kept entirely confidential. You can trust us with your information, knowing that we maintain the highest standards of security.
🔧 Advanced Recovery Tools
We use proprietary tools and techniques to handle complex recovery scenarios, from recovering corrupted wallets to restoring coins from invalid addresses. No matter how challenging the situation, we have a plan.
 # Our Recovery Services Include: 📈
# Our Recovery Services Include: 📈- Bitcoin Recovery: Have you lost access to your Bitcoin wallet? We can help you recover lost wallets, private keys, and passphrases.
- Transaction Recovery: Mistaken transfers, lost passwords, or missing transaction records — let us help you reclaim your funds!
- Cold Wallet Restoration: Did your cold wallet fail? We specialize in extracting assets safely and securely.
- Private Key Generation: Forgotten your private key? We can help you generate new keys linked to your funds without compromising security.
Don’t Let Lost Crypto Ruin Your Day! 🕒
With an estimated 3 to 3.4 million BTC lost forever, it’s critical to act swiftly when facing access issues. Whether you’ve been a victim of a dust attack or have simply forgotten your key, Crypt Recver offers the support you need to reclaim your digital assets.
🚀 Start Your Recovery Now!
Ready to get your cryptocurrency back? Don’t let uncertainty hold you back!
👉 Request Wallet Recovery Help Today!
Need Immediate Assistance? 📞
For quick queries or support, connect with us on:
- ✉️ Telegram: Chat with Us on Telegram
- 💬 WhatsApp: Message Us on WhatsApp
Trust Crypt Recver for the Best Crypto Recovery Service — Get back to trading with confidence! 💪
-
 @ 3ffac3a6:2d656657
2025-04-05 04:55:12
@ 3ffac3a6:2d656657
2025-04-05 04:55:12O Impacto do Namoro com Pelé na Carreira de Xuxa Meneghel
Disclaimer:
Esse texto foi totalmente escrito pelo ChatGPT, eu apenas pedi que ele fizesse uma pesquisa sobre o tema.
Introdução: O relacionamento entre Xuxa Meneghel e Pelé, que durou cerca de seis anos (início dos anos 1980 até 1986), foi um dos mais comentados da década de 1980 (Xuxa e Pelé: um romance que se tornou inesquecível... | VEJA). Xuxa tinha apenas 17 anos quando começou a namorar o já consagrado “Rei do Futebol”, então com 40 anos (A história da foto de revista que gerou o namoro de Pelé e Xuxa) (Xuxa e Pelé: um romance que se tornou inesquecível... | VEJA). Esse romance altamente midiático não só atiçou a curiosidade do público, como também alavancou a carreira de Xuxa de forma significativa. A seguir, detalhamos como o namoro aumentou a visibilidade da apresentadora, quais oportunidades profissionais podem ter tido influência direta de Pelé, o papel da revista Manchete e de outras mídias na promoção de sua imagem, se o relacionamento contribuiu para Xuxa conquistar espaços na TV (como o programa Clube da Criança e, posteriormente, na Rede Globo) e como mídia e público percebiam o casal – tudo embasado em fontes da época, entrevistas e biografias.
Aumento da Visibilidade Midiática nos Anos 1980
O namoro com Pelé catapultou Xuxa a um novo patamar de fama. Até então uma modelo em começo de carreira, Xuxa “se tornou famosa ao aparecer ao lado do esportista de maior status do Brasil” (Pelé viveu com Xuxa um namoro intenso afetado por fofocas e indiscrições). A partir do momento em que o relacionamento se tornou público, ela passou a estampar capas de revistas com frequência e a ser assunto constante na imprensa. Em 20 de dezembro de 1980, a jovem apareceu na capa da revista Manchete ao lado de Pelé e outras modelos – um ensaio fotográfico que marcou o primeiro encontro dos dois e deu início à enorme atenção midiática em torno de Xuxa (Xuxa e Pelé: o relacionamento que ficou cravado na história da imprensa brasileira) (Xuxa e Pelé: o relacionamento que ficou cravado na história da imprensa brasileira). Não por acaso, “naquele ano, ela foi capa de mais de cem revistas” (Xuxa está em paz - revista piauí), um indicativo claro de como sua visibilidade explodiu após começar a namorar Pelé. Jornais, revistas de celebridades e programas de fofoca passaram a segui-los de perto; o casal virou sensação nacional, comparado até ao “Casal 20” (dupla glamourosa de uma série de TV americana) pelo seu alto perfil na mídia (Xuxa e Pelé: um romance que se tornou inesquecível... | VEJA).
Essa exposição intensa colocou Xuxa não apenas sob os holofotes do público, mas também a inseriu nos bastidores do entretenimento. Como namorada de Pelé – um dos homens mais conhecidos do mundo – Xuxa passou a frequentar eventos de gala, festas e bastidores de programas, onde conheceu figuras influentes do meio artístico e televisivo. Os fotógrafos os seguiam em eventos como bailes de carnaval e inaugurações, registrando cada aparição pública do casal. Com Pelé ao seu lado, Xuxa ganhou trânsito livre em círculos antes inacessíveis para uma modelo iniciante, construindo uma rede de contatos valiosa nos meios de comunicação. De fato, naquele início dos anos 80, “os dois eram perseguidos por fotógrafos, apareciam em capas de revistas e até faziam publicidade juntos” (Pelé viveu com Xuxa um namoro intenso afetado por fofocas e indiscrições) – evidência de que Xuxa, graças ao namoro, transitava tanto na frente quanto por trás das câmeras com muito mais facilidade. Em suma, o relacionamento conferiu a ela um grau de notoriedade nacional que provavelmente demoraria anos para conquistar de outra forma, preparando o terreno para os passos seguintes de sua carreira.
Influência Direta de Pelé nas Oportunidades Profissionais de Xuxa
Além do aumento geral da fama, há casos específicos em que Pelé influenciou diretamente oportunidades profissionais para Xuxa. Um exemplo contundente é o filme “Amor Estranho Amor” (1982) – longa de teor erótico no qual Xuxa atuou no início da carreira. Segundo relatos da própria apresentadora, foi Pelé quem a incentivou a aceitar participar desse filme (Pelé e Xuxa: um estranho amor que durou seis anos - 29/12/2022 - Celebridades - F5). Na época ainda em início de trajetória, Xuxa acabou convencida pelo namorado de que aquela oportunidade poderia ser benéfica. Anos mais tarde, ela revelaria arrependimento pela escolha desse papel, mas o fato reforça que Pelé teve influência ativa em decisões profissionais de Xuxa no começo de sua jornada.
Outra área de influência direta foram as publicidades e campanhas comerciais. Graças ao prestígio de Pelé, Xuxa recebeu convites para estrelar anúncios ao lado do então namorado. Já em 1981, por exemplo, os dois gravaram juntos comerciais para uma empresa imobiliária, aparecendo como casal em campanhas de TV daquele Natal (pelas Imóveis Francisco Xavier, um case famoso entre colecionadores de propagandas da época) (Xuxa e Pelé: Natal de 1981 na Publicidade Imobiliária | TikTok) (Xuxa com Pelé em comercial de imobiliária em dezembro de 1981). Assim, Xuxa obteve espaço em campanhas publicitárias que dificilmente envolveriam uma modelo desconhecida – mas que, com a “namorada do Pelé” no elenco, ganhavam apelo extra. Isso evidencia que Pelé abriu portas também no mercado publicitário, dando a Xuxa oportunidades de trabalho e renda enquanto sua própria imagem pública se consolidava.
Ademais, a presença de Pelé ao lado de Xuxa em diversos editoriais e ensaios fotográficos serviu para elevá-la de modelo anônima a personalidade conhecida. Revistas e jornais buscavam os dois para sessões de fotos e entrevistas, sabendo do interesse do público pelo casal. As capas conjuntas em publicações de grande circulação (como Manchete e outras) não só aumentaram a exposição de Xuxa, mas também conferiram a ela certa credibilidade midiática por associação. Em outras palavras, estar ao lado de um ícone como Pelé funcionou como um “selo de aprovação” implícito, deixando editores e produtores mais propensos a convidá-la para projetos. Vale lembrar que “ao longo dos seis anos de relacionamento, [eles] posaram para várias capas da Manchete”, com a revista acompanhando de perto cada fase do namoro (A história da foto de revista que gerou o namoro de Pelé e Xuxa). Essa recorrência nas bancas solidificou o rosto e o nome de Xuxa na indústria do entretenimento.
Por fim, é importante notar que nem todas as influências de Pelé foram positivas para a carreira dela – algumas foram tentativas de direcionamento. A própria Xuxa contou que, quando surgiu a oportunidade de ela ir para a TV Globo em 1986, Pelé desencorajou a mudança. Ele sugeriu que Xuxa permanecesse na TV Manchete, dizendo que “ser a primeira [na Globo] é muito difícil; melhor ficar onde está”, o que ela interpretou como falta de apoio dele à sua ascensão (Xuxa e Pelé: o relacionamento que ficou cravado na história da imprensa brasileira). Esse episódio mostra que Pelé tentou influenciar também os rumos que Xuxa tomaria, embora, nesse caso, ela tenha decidido seguir sua intuição profissional e aceitar o desafio na Globo – escolha que se revelaria acertada. Em resumo, Pelé atuou sim como facilitador de várias oportunidades profissionais para Xuxa (de filmes a comerciais e visibilidade editorial), mas ela soube trilhar seu caminho a partir daí, inclusive contrariando conselhos dele quando necessário.
Papel da Revista Manchete e Outras Mídias na Promoção de Xuxa
A revista Manchete teve um papel central na ascensão de Xuxa durante o relacionamento com Pelé. Foi justamente num ensaio para a Manchete que os dois se conheceram, em dezembro de 1980 (Xuxa e Pelé: o relacionamento que ficou cravado na história da imprensa brasileira), e a partir daí a publicação tornou-se uma espécie oficiosa de cronista do romance. A Manchete era uma das revistas mais populares do Brasil naquela época e, ao perceber o interesse do público pelo casal, passou a trazê-los frequentemente em suas páginas. De fato, a revista que agiu como "cupido" do casal “contava detalhes do romance a cada edição”, alimentando a curiosidade nacional sobre a vida de Pelé e sua jovem namorada (A história da foto de revista que gerou o namoro de Pelé e Xuxa). As capas exibindo Xuxa e Pelé juntos (em cenários que iam da praia a eventos sociais) viraram chamariz nas bancas e contribuíram enormemente para fixar a imagem de Xuxa na mente do público.
(A história da foto de revista que gerou o namoro de Pelé e Xuxa) Capa da revista Manchete (20 de dezembro de 1980) mostrando Pelé ao centro com Xuxa (à esquerda) e outras modelos. A partir desse ensaio fotográfico, a revista passou a acompanhar de perto o romance, impulsionando a imagem de Xuxa nacionalmente. (A história da foto de revista que gerou o namoro de Pelé e Xuxa) (Xuxa e Pelé: o relacionamento que ficou cravado na história da imprensa brasileira)
Além da Manchete, outras mídias impressas também surfaram no interesse pelo casal e ajudaram a moldar a imagem de Xuxa. Revistas de celebridades e colunas sociais publicavam notas e fotos frequentes, ora exaltando o glamour do par, ora especulando sobre fofocas. Xuxa, que pouco antes era desconhecida fora do circuito da moda, tornou-se figura constante em revistas semanais como Contigo! e Amiga (dedicadas à vida dos famosos), assim como em jornais de grande circulação. Esse bombardeio de aparições – entrevistas, fotos e manchetes – construiu a persona pública de Xuxa simultaneamente como modelo desejada e namorada devotada. A promoção de sua imagem tinha um tom deliberadamente positivo nas revistas: enfatizava-se sua beleza, juventude e sorte por ter sido “escolhida” pelo rei Pelé. Em contrapartida, eventuais polêmicas (como cenas ousadas que ela fez no cinema ou rumores de crises no namoro) eram administradas pela própria mídia de maneira a preservar o encanto em torno de Xuxa, que já despontava como uma espécie de Cinderella moderna na narrativa do entretenimento brasileiro.
Cabe destacar que a conexão de Xuxa com a Manchete não ficou só nas páginas da revista, mas transbordou para a televisão, já que a Rede Manchete (canal de TV fundado em 1983) pertencia ao mesmo grupo empresarial. Essa sinergia mídia impressa/televisão beneficiou Xuxa: quando a Rede Manchete buscava uma apresentadora para seu novo programa infantil em 1983, Xuxa – já famosa pelas capas de revista – foi convidada para o posto (Xuxa está em paz - revista piauí). Ou seja, a exposição na revista Manchete serviu de vitrine para que os executivos da emissora homônima apostassem nela na TV. Outras mídias também legitimaram sua transição de modelo para apresentadora, publicando matérias sobre sua simpatia com as crianças e seu carisma diante das câmeras, preparando o público para aceitar Xuxa em um novo papel. Assim, o período do relacionamento com Pelé viu a mídia – liderada pela revista Manchete – construir e promover intensamente a imagem de Xuxa, pavimentando o caminho para suas conquistas seguintes.
O Relacionamento e a Conquista de Espaços na TV: Clube da Criança e Rede Globo
O namoro com Pelé coincidiu com a entrada de Xuxa na televisão e possivelmente facilitou essa transição. Em 1983, a recém-inaugurada Rede Manchete lançou o “Clube da Criança”, primeiro programa infantil de auditório da emissora, e Xuxa foi escolhida como apresentadora. Há indícios de que sua fama prévia – alavancada pelo relacionamento – foi decisiva nessa escolha. Conforme relatos, o diretor Maurício Sherman (responsável pelo projeto) estava de olho em Xuxa por sua notoriedade e carisma, chegando a dizer que ela reunia “a sensualidade de Marilyn Monroe, o sorriso de Doris Day e um quê de Peter Pan” (Xuxa está em paz - revista piauí) – uma combinação que poderia funcionar bem num programa infantil. Xuxa inicialmente hesitou em aceitar, talvez pelo contraste entre sua imagem de modelo sensual e o universo infantil, mas acabou assinando contrato com a Manchete (Clube da Criança – Wikipédia, a enciclopédia livre). Assim, aos 20 anos de idade, ela estreava como apresentadora de TV, em grande parte graças à visibilidade e confiança que o nome “Xuxa” (já famoso por ser namorada do Pelé) passava aos produtores.
Não há registro de que Pelé tenha intervindo diretamente para que Xuxa conseguisse o posto no Clube da Criança. Foi a própria rede Manchete – estimulada pelo burburinho em torno dela – que a “procurou e a convidou para apresentar” o programa (Xuxa está em paz - revista piauí). Porém, é inegável que, sem o destaque que Xuxa conquistara nos anos anteriores na imprensa (devido ao namoro), dificilmente uma emissora arriscaria colocar uma jovem inexperiente para comandar um show infantil nacional. Ou seja, o relacionamento criou as condições favoráveis para essa oportunidade surgir. Uma vez no ar, Xuxa rapidamente mostrou talento próprio: o Clube da Criança foi ganhando audiência e revelou a aptidão dela em se comunicar com o público infantil (Xuxa, Pantanal, Cavaleiros dos Zodíacos: lembre sucessos da TV ...). Ainda durante seu tempo na Manchete, Xuxa manteve-se nos holofotes tanto pela carreira quanto pelo namoro com Pelé – frequentemente um assunto alimentava o outro na mídia.
Em meados de 1986, já conhecida como a “Rainha dos Baixinhos” pelo sucesso junto às crianças, Xuxa recebeu uma proposta para se transferir para a Rede Globo, a principal emissora do país (A história da foto de revista que gerou o namoro de Pelé e Xuxa). Novamente, aqui o relacionamento com Pelé tem um papel indireto: por um lado, pode ter ajudado a construir a notoriedade que chamou a atenção da Globo; por outro, chegava ao fim exatamente nesse momento, marcando uma virada na vida dela. Após alguns anos de Clube da Criança, Xuxa decidiu dar um passo adiante. Ela mesma tomou a iniciativa de terminar o namoro com Pelé e aceitou o convite para fazer o “Xou da Xuxa” na Globo (A história da foto de revista que gerou o namoro de Pelé e Xuxa). Pelé, como mencionado, havia expressado reservas sobre essa mudança de emissora (Xuxa e Pelé: o relacionamento que ficou cravado na história da imprensa brasileira), mas sem sucesso em demovê-la. Com a benção do dono da Manchete, Adolpho Bloch (que a tratava “como filha” e apoiou seu crescimento) (Xuxa está em paz - revista piauí) (Xuxa está em paz - revista piauí), Xuxa partiu para a Globo levando sua diretora Marlene Mattos, e estreou em junho de 1986 o programa que a consagraria definitivamente.
É importante notar que, ao ingressar na Globo, Xuxa já não dependia mais da aura de “namorada do Pelé” – ela havia se firmado como apresentadora de sucesso por méritos próprios. Ainda assim, o relacionamento anterior continuou a ser parte de sua imagem pública: a mídia noticiou a mudança destacando que a namorada de Pelé chegara à Globo, e muitos espectadores tinham curiosidade sobre aquela moça cuja fama começara nos braços do ídolo do futebol. Em resumo, o namoro ajudou Xuxa a conquistar o primeiro grande espaço na TV (na Manchete), fornecendo-lhe exposição e credibilidade iniciais, enquanto sua ida para a Globo foi impulsionada principalmente pelo desempenho no Clube da Criança – algo que o prestígio conquistado durante o relacionamento tornou possível em primeiro lugar.
Percepção da Mídia e do Público sobre o Casal e a Imagem de Xuxa
Durante os anos de namoro, Pelé e Xuxa foram um prato cheio para a imprensa e objeto de variadas opiniões do público. De um lado, eram celebrados como “casal perfeito na mídia”, aparecendo sorridentes em eventos e capas, o que projetava uma imagem glamourosa e apaixonada (Pelé viveu com Xuxa um namoro intenso afetado por fofocas e indiscrições). Xuxa era frequentemente retratada como a bela jovem humilde que havia conquistado o coração do "rei", uma narrativa de conto de fadas que agradava muitos fãs. Pessoas próximas diziam na época: “Nossa, como ela está apaixonada, como ela está de quatro pelo Pelé”, segundo relembrou a própria Xuxa, indicando que sua dedicação ao namorado era visível e comentada (Xuxa e Pelé: um romance que se tornou inesquecível... | VEJA). Essa percepção de autenticidade nos sentimentos ajudou a humanizar Xuxa aos olhos do público, diferenciando-a de estereótipos de roupante ou interesse calculado.
Por outro lado, nem toda a atenção era positiva. Houve murmúrios maldosos e preconceituosos nos bastidores. Pelé e Xuxa formavam um casal interracial (ele negro, ela branca e bem mais jovem), o que, segundo a imprensa, “gerava olhares de reprovação dos conservadores” e até comentários racistas proferidos pelas costas (Pelé viveu com Xuxa um namoro intenso afetado por fofocas e indiscrições). Além disso, alguns duvidavam das intenções de Xuxa no relacionamento, insinuando que ela buscava ascensão social por meio de Pelé. Termos pejorativos como “maria-chuteira” (gíria para mulheres que namoram jogadores em busca de status) e “alpinista social” chegaram a ser associados a Xuxa por fofoqueiros da época (Pelé viveu com Xuxa um namoro intenso afetado por fofocas e indiscrições). Essa desconfiança lançava sombra sobre a imagem dela, pintando-a, aos olhos de alguns, como oportunista em vez de namorada dedicada. Xuxa teve de lidar com esse tipo de insinuação ao longo do namoro, buscando provar que seu amor era verdadeiro e que ela também tinha talentos e ambições próprias.
A mídia impressa, em geral, manteve uma postura favorável ao casal, explorando o romance como algo encantador. Mas não deixou de reportar as turbulências: sabia-se, por exemplo, das frequentes traições de Pelé, que Xuxa anos depois revelou ter suportado calada na época (Xuxa e Pelé: o relacionamento que ficou cravado na história da imprensa brasileira) (Xuxa e Pelé: o relacionamento que ficou cravado na história da imprensa brasileira). Essas infidelidades eram rumores correntes nos círculos de fofoca, embora Xuxa raramente comentasse publicamente enquanto estava com Pelé. O público, portanto, via um casal bonito e famoso, mas também acompanhava as especulações de crises e reconciliações pelos noticiários de celebridades. Cada aparição pública deles – fosse em um jogo de futebol, um evento beneficente ou nos camarotes do carnaval – era dissecada pelos repórteres, e cada declaração (ou silêncio) alimentava interpretações sobre o estado do relacionamento e sobre quem era Xuxa por trás da fama.
No saldo final, o namoro com Pelé influenciou profundamente a imagem pública de Xuxa. Inicialmente marcada como “a namorada do Rei” – posição que trazia tanto admiração quanto inveja – Xuxa soube aproveitar a visibilidade para mostrar carisma e trabalho, transformando-se em uma estrela por direito próprio. Ao se tornar apresentadora infantil de sucesso ainda durante o namoro, ela começou a dissociar sua imagem da de Pelé, provando que podia ser mais do que um apêndice de um astro do esporte. Quando o relacionamento terminou em 1986, Xuxa emergiu não caída em desgraça, mas sim pronta para reinar sozinha na TV. A mídia continuou a mencioná-la em referência a Pelé por algum tempo (era inevitável, dado o quão famoso o casal fora), mas cada vez mais o público passou a enxergá-la principalmente como a “Rainha dos Baixinhos”, a figura alegre das manhãs na TV Globo. Em entrevistas posteriores, Xuxa admitiu ter sentimentos mistos ao lembrar dessa fase: ela se ressentiu, por exemplo, de Pelé ter classificado o que viveram como “uma amizade colorida” em vez de namoro sério (Pelé e Xuxa: um estranho amor que durou seis anos - 29/12/2022 - Celebridades - F5) – frase do ex-jogador que a magoou e que veio a público muitos anos depois. Esse comentário retroativo de Pelé apenas reforçou o quanto a mídia e o público discutiram e dissecaram a natureza daquela relação.
Em conclusão, a percepção do casal Xuxa e Pelé oscilou entre o encanto e a controvérsia, mas inegavelmente manteve Xuxa nos trending topics de sua época (para usar um termo atual). A jovem modelo gaúcha ganhou projeção, prestígio e também enfrentou julgamentos enquanto esteve com Pelé. Tudo isso moldou sua imagem – de símbolo sexual e socialite em ascensão a profissional talentosa pronta para brilhar por conta própria. O relacionamento forneceu-lhe a plataforma e a armadura mediática; coube a Xuxa transformar essa visibilidade em uma carreira sólida, o que ela fez com maestria ao se tornar uma das maiores apresentadoras da história da TV brasileira.
Fontes: Entrevistas e depoimentos de Xuxa Meneghel (inclusive do livro Memórias, 2020), reportagens da época em revistas como Manchete, colunas sociais e jornais (compiladas em repositórios atuais), e biografias e retrospectivas sobre ambos os envolvidos (A história da foto de revista que gerou o namoro de Pelé e Xuxa) (Pelé viveu com Xuxa um namoro intenso afetado por fofocas e indiscrições) (Xuxa e Pelé: o relacionamento que ficou cravado na história da imprensa brasileira) (Xuxa e Pelé: um romance que se tornou inesquecível... | VEJA), entre outras. Essas fontes confirmam o papel catalisador que o namoro com Pelé teve nos primeiros passos da trajetória de Xuxa, bem como os desafios e oportunidades que surgiram dessa intensa exposição pública.