-
 @ 57d1a264:69f1fee1
2025-05-13 06:21:36
@ 57d1a264:69f1fee1
2025-05-13 06:21:36Steve Jobs sent me an email saying “Great idea, thank you."
Wait, what? What was the great idea?
new guy at NeXT In October of 1991, I was a new Systems Engineer at NeXT. NeXT, of course, was the company Steve Jobs had founded after leaving Apple in 1985, and which eventually merged back into Apple in 1996. I was one of three employees in Canada, and I think NeXT had about 400 people total.
NeXTMail Mail on the NeXT Computer was pretty amazing in 1991. Multimedia! Fonts! Attachments! Sounds! It’s hard to overstate how cool that was compared to the command line email everybody was used to. Every NeXT user got this email from Steve when they started up their computer.
That message included an attachment of what NeXT called Lip Service, the crazy idea that you could embed an audio file inside an email message. Crazy.
i have an idea
NeXT automatically set everybody up with a first-initial last-name address in the usual way, so I was shayman@next.com, and the big guy was sjobs@next.com.
A few colleagues had somehow acquired cooler email aliases - single letter things, or their first name, or a nickname or an easier to spell version, or whatever. Turns out NeXT had set up some sort of form where you could request an email alias that would redirect to whatever your real email address was.
I also noticed that even though there were seven or eight people at NeXT named Steve, nobody was using the email alias steve@next.com.
So late one Friday night, two weeks into the job, I figured, naively, what the heck, nobody else seems to want it, so I filled in the form asking for steve@next.com to be forwarded to me, shayman@next.com.
In the back of my mind was a vague idea that maybe somebody would have to approve this. But no, it all got set up automatically, and …
Continue reading at https://blog.hayman.net/2025/05/06/from-steve-jobs-great-idea.html
originally posted at https://stacker.news/items/978825
-
 @ 57d1a264:69f1fee1
2025-05-13 06:10:06
@ 57d1a264:69f1fee1
2025-05-13 06:10:06The Cyclauto is efficient and flexible
The Cyclauto, a modular mobility solution. Thanks to its fully adaptable rear chassis, it is possible to develop an infinite number of modules, allowing you to imagine solutions for every need, whether for developing your professional activity or for personal use.
French mobility company Cyclauto has gone through the history books to revive an alternate design from the 1930s.
This design, originally by French industrialist Auguste Reymond, places the rider directly above the front wheel. They pedal this wheel directly; there's no chain, reducing maintenance needs. A three-speed gearbox in the hub makes starting easier.
The new Cyclauto is a three-wheeler designed like a semi-trailer. This design offers an ideal urban mobility solution, combining modularity, disassembly, and efficiency. Whether for professional or personal use, it adapts to everyone's needs by offering an ecological and practical alternative to traditional vehicles. Thanks to its optimized architecture, it combines maneuverability, load capacity, and driving comfort, making it perfect for urban logistics, tradespeople, or individuals looking for versatile transportation.
A utility vehicle for professionals. Suitable for all sectors of activity thanks to its modularity. It will adapt to a multitude of needs. From logistics, transporting pallets, to street food modules. The Cyclauto is the essential intermediate light vehicle for retailers, artisans, or businesses looking for an ecological and economical alternative. Develop your business with Cyclauto.
The eco-friendly personal vehicle suitable for everyone. It's not just a utility vehicle. It's the ideal solution for individuals looking for sustainable mobility. Whether it's for transporting equipment, shopping, hiking for several days, or even for everyday use, Cyclauto meets your needs flexibly while also including active mobility. The latter aspect is very important for staying healthy. We discuss it in more depth here.
A detachable three-wheeler, very practical for everyday use. The Cyclauto can be disassembled in several ways. This allows you to modify its use by changing the module, or to load it into a trunk for easy transport from point A to point B.
Detach the trailer from the Cyclauto. Still with the semi-trailer idea, the first level of disassembly allows the rear chassis to be uncoupled from the front. This greatly reduces its footprint, but also allows one front chassis to be used for several modules. Very practical in the case of an activity requiring several layouts.
Larger disassembly for easier transport. In addition to being able to remove the front chassis from the rear, the latter is composed of two removable overlapping frames. This architecture has several advantages, the first being the space saving when transporting the Cyclauto. The second is that it allows us to adapt the frame to our needs, by modifying the length of the upper frame. The positioning of the rear wheels is also adaptable depending on the use.
Cyclauto, an efficient three-wheeler thanks to exclusive solutions. Many parts and assemblies are specially developed for our vehicle. From its chassis with its unique geometry to its pedal system, everything is designed to optimize its performance.
Uncompromising handling. Its architecture makes it a compact, agile three-wheeler, at home in city traffic as well as on cycle paths. The split chassis with its pivot point at the seat, coupled with a steering wheel and short wheelbase, offers an exceptional turning radius. The front-positioned cockpit allows for minimal bulk.
A unique traction system in the world. The Cyclauto's main feature is its pedaling system. You pedal directly on the front wheel. All the force you exert on the pedal is transmitted directly to the ground. In addition, its hub incorporates a three-speed gearbox, allowing for easy starting and a pleasant pedaling experience once you're underway.
Discover more at https://cyclauto.com
originally posted at https://stacker.news/items/978822
-
 @ eab58da0:eebdafbf
2025-05-13 05:26:28
@ eab58da0:eebdafbf
2025-05-13 05:26:28Life has a way of throwing curveballs when you least expect them. From personal setbacks to professional challenges, the ability to bounce back—self-resilience—has been my anchor through turbulent times. For me, resilience isn’t just about enduring hardship; it’s about growing stronger, wiser, and more compassionate through it. This is my story of cultivating self-resilience, woven with lessons I’ve learned and strategies that have carried me forward.
The Power of Bouncing Back
Self-resilience is the inner strength to recover from adversity, adapt to change, and keep moving forward. It’s not about avoiding pain or pretending everything is fine; it’s about facing challenges head-on and emerging with a renewed sense of purpose. I’ve come to see resilience as a muscle—something you build through practice, reflection, and intentional effort. My journey toward resilience began in my early twenties, during a particularly dark chapter of my life.
A few years ago, I faced a devastating breakup that left me questioning my worth. I had poured everything into that relationship, only to watch it crumble overnight. The emotional toll was immense; I felt lost, unmoored, and unsure of how to move forward. At the same time, I was navigating a demanding job that left little room for self-care. The weight of it all felt crushing, and for a while, I let it define me. But something inside me refused to stay broken.
That period taught me my first lesson in resilience: acknowledging pain is the first step to healing. I allowed myself to feel the hurt, to cry, to journal my thoughts—raw and unfiltered. I didn’t rush to “get over it” but gave myself permission to process. Slowly, I began to rebuild. I sought therapy, which helped me untangle my emotions and reframe my perspective. I started small—taking walks, reconnecting with friends, and setting tiny goals like reading a book or cooking a new recipe. Each step, no matter how small, was a victory.
Strategies That Shaped My Resilience
Through trial and error, I discovered practical tools that strengthened my resilience. One of the most powerful was cultivating a growth mindset. I began to view challenges as opportunities to learn rather than as failures. When I didn’t get a promotion I’d worked hard for, I was disappointed, but instead of dwelling on it, I asked for feedback and used it to improve. This shift in thinking transformed how I approached setbacks.
Another key strategy was building a support network. I used to pride myself on being independent, but I learned that resilience doesn’t mean going it alone. Opening up to trusted friends and family gave me perspective and encouragement. I’ll never forget the late-night conversations with my best friend, who listened without judgment and reminded me of my strength when I couldn’t see it myself.
Self-care also became non-negotiable. I started prioritizing sleep, exercise, and mindfulness practices like meditation. Even five minutes of deep breathing during a stressful workday made a difference. These habits grounded me, helping me stay steady when life felt chaotic.
Lessons for the Future
Reflecting on my journey, I realize resilience is a lifelong practice. Recently, I faced another challenge—moving to a new city for a job opportunity. The excitement was tempered by loneliness and the daunting task of starting over.
But this time, I leaned on the tools I’d developed. I joined local groups to meet people, set realistic expectations for the transition, and reminded myself that discomfort is often a precursor to growth. Six months in, I’m finding my footing, and the experience has reinforced my belief in my ability to adapt.
Resilience doesn’t make life’s challenges disappear, but it equips you to face them with courage and hope. My experiences have taught me that I’m stronger than I often give myself credit for. To anyone reading this, know that resilience is within your reach. Start small, be kind to yourself, and trust that every step forward counts. Life will test you, but with self-resilience, you’ll not only survive—you’ll thrive.
-
 @ 9c9d2765:16f8c2c2
2025-05-13 05:21:23
@ 9c9d2765:16f8c2c2
2025-05-13 05:21:23CHAPTER SEVENTEEN
"I don't get it... How is James still in charge?" Tracy murmured, her brows furrowed as she stared at her screen. She sat in her office, fingers nervously drumming against her desk.
Across from her, Mark stood with arms folded, pacing slowly. "You mean after all that evidence? After the blacklist, the embezzlement records nothing happened?"
Tracy shook her head. "Nothing. I checked again this morning. He’s still listed as President of JP Enterprises. It’s like the files we found didn’t even exist."
Helen, who had been silent until now, hissed through clenched teeth. "This is ridiculous. Are you sure the information got to the right hands?"
"It did," Tracy insisted. "I sent it directly to the Prime Minister's inbox using a confidential channel. I even received a delivery confirmation. Someone higher up must’ve swept it under the rug or maybe James covered his tracks faster than we imagined."
Mark slumped into the chair, clearly defeated. "He’s not just lucky he’s smart. Smarter than we gave him credit for."
For the first time since they began scheming, their confidence had begun to falter. They had dug into James’s past, unearthed the most damning of records, and yet… nothing. He remained untouched. Unshaken.
James continued to lead JP Enterprises with iron resolve, his status not just preserved, but strengthened. Whatever scandal they tried to ignite had fizzled out before it could burn.
The silence from JP's top board members was loud. No statements. No investigations. Not even a whisper of an internal review. To the outside world, James remained the unshakable President who had pulled a crumbling empire back from the edge.
Mark clenched his jaw. "He must have allies who are protecting him."
Helen nodded slowly. "We underestimated him. That was our biggest mistake."
Tracy remained quiet, her eyes still fixed on the screen as if trying to decipher what had gone wrong. She had risked everything, accessed confidential files, and violated protocols, expecting James to crumble.
Instead, he was thriving.
"Have you heard?" Robert leaned over his desk, eyes wide with interest. "JP Enterprises is about to celebrate their sixteenth anniversary. It’s going to be the biggest corporate event of the year."
Christopher looked up from the documents he was reviewing. "I heard. Mr. and Mrs. JP are returning for it. The entire business world is going to be there including us."
Robert nodded. "Every major company in and out of the city has received an invitation. It’s not just a celebration, it's a power show. A way for JP Enterprises to remind everyone who’s at the top."
Indeed, the buzz around the sixteenth anniversary of JP Enterprises was like nothing the city had seen in years. Massive banners were already being hoisted across the city skyline. High-end hotels were fully booked. Fashion designers, chefs, tech specialists, and media crews from around the world were preparing for the grand occasion. It was more than a business event, it was a spectacle.
At the heart of the preparations was James, the young and surprisingly unshakable President of JP Enterprises. Under his leadership, the company had grown in power and reach, and the anniversary was both a celebration of its legacy and a testament to its transformation.
Meanwhile, at Ray Enterprises, tension brewed behind the scenes. Though they were invited, the Ray family carried mixed feelings about attending the event. Memories of humiliation and disbelief still lingered the day James had revealed himself as the President was still fresh in their minds.
"We have no choice but to attend," Helen muttered in frustration during a board meeting. "If we stay away, we’ll seem petty and afraid. But going there means bowing our heads to him again."
Sarah, the secretary, tried to mask her discomfort. "It’s a corporate event, ma’am. It might be best to appear neutral… diplomatic."
Rita, now reinstated as General Manager, remained quiet but observant. She knew better than anyone how unpredictable James could be when it came to public appearances. She had no idea what to expect from him at the anniversary.
Back at JP Enterprises, preparations continued in full force. The guest list included billionaires, global CEOs, high-ranking politicians, and the most influential figures across industries. Red carpets would roll out, cameras would flash, and speeches would echo through the grand hall like music from an orchestra.
The city, already buzzing with excitement, awaited the grand event.
"I can’t believe it," the young woman muttered as she stared at her phone, her hands trembling with excitement. "James… the same James who used to sleep in front of Mr. Kola’s grocery store? He’s the President of JP Enterprises now?"
Her name was Evelyn. Sharp-tongued, impatient, and fueled by bitter memories, she had known James during his hardest days on the streets, days when survival meant fighting for leftovers and sleeping on cold sidewalks. To her, his rise wasn’t a success story to be admired. It was a jackpot she felt entitled to.
Storming into the JP Enterprises headquarters during working hours, Evelyn ignored the receptionist's polite inquiries and pushed her way toward the executive wing.
"I want to see James!" she shouted, causing heads to turn in the busy lobby. "I know he’s here. Tell him Evelyn from the street is here!"
Security was alerted immediately, but by then, Evelyn had already reached the waiting area outside the President’s office.
James, who was in a brief meeting with department heads, heard the commotion and stepped out with a composed expression. As soon as his eyes met Evelyn’s, something shifted. He recognized her instantly.
"Evelyn?" he said, frowning slightly. "What are you doing here?"
"Don’t act like you don’t know me, James," she snapped, crossing her arms. "You owe me. We suffered together. I was there when you were nothing. Now you’re swimming in wealth and you think you can forget the people who once mattered!"
James’s expression hardened.
"This is not the place for this kind of talk. You’re disrupting my company’s operations. If you need help, there are proper channels"
"To hell with proper channels!" she yelled. "I came to get what’s mine!"
That was enough. James turned to the nearby security officer. "Escort her out. And make sure she doesn’t return without a valid appointment."
The security guards moved quickly, but Evelyn didn’t go quietly. She shouted all the way to the exit, throwing insults, struggling, and drawing even more attention.
Among those who witnessed the scene was Tracy. At first, she thought it was just a random case of disturbance by some unruly visitor trying to make trouble. But as she watched James’s calm yet stern expression, and the woman’s emotional outburst, something clicked in her cunning mind.
This is gold, she thought, quickly pulling out her phone and snapping a series of pictures from the hallway James arguing with a ragged woman, the woman being dragged out, and James watching in silence. What a perfect way to ruin his reputation.
Tracy, ever the opportunist, reviewed the photos and smirked.
This is it… this will shake him up.
Without hesitation, she sent the pictures to Helen and Mark, attaching a voice note.
-
 @ eab58da0:eebdafbf
2025-05-13 05:16:32
@ eab58da0:eebdafbf
2025-05-13 05:16:32Hey there, it’s me. Someone who used to run through life like it was a marathon with no finish line. For years, I chased everything: the perfect job, the dream apartment, the Instagram-worthy moments.
I’d wake up exhausted, convinced I was one step behind where I should be. That was my normal—until the day I just… stopped.
The breaking point. It was a rainy Tuesday, and I’d just bombed a big presentation at work. My inbox was overflowing, my coffee was cold, and I felt like a failure. I remember sitting on my couch, staring at the wall, thinking, “What’s the point?” I’d been chasing this idea of success, but it kept moving further away. That’s when it hit me—I wasn’t living. I was just running.
So, I did something radical: nothing. I turned off my phone, made a cup of tea, and sat in silence. No goals, no to-do lists, just me and the rain tapping on the window. It felt weird at first—like I was breaking some unwritten rule—but then it felt… freeing. I started small after that. Walks without a podcast. Cooking without rushing. Saying no to things that didn’t light me up. I stopped chasing and started showing up for the life I already had.
Looking Back. Now, months later, I see that day as a turning point. I still have dreams, but they don’t own me anymore. I’ve learned to savor the messy, quiet moments—the ones I used to overlook. Life’s not perfect, but it’s mine. And honestly? That’s enough.
-
 @ eaccf0cb:23be2b8f
2025-05-13 05:02:24
@ eaccf0cb:23be2b8f
2025-05-13 05:02:24Trong thời đại công nghệ phát triển nhanh chóng, việc tìm kiếm một nền tảng số toàn diện, thân thiện và ổn định đã trở thành nhu cầu thiết yếu đối với người dùng. LU8 chính là câu trả lời cho nhu cầu đó, khi mang đến một hệ sinh thái tích hợp với giao diện thông minh, cấu trúc hợp lý và tốc độ xử lý vượt trội. Mọi thao tác trên LU8 đều được thiết kế để tối giản hóa quá trình sử dụng, từ việc đăng ký, truy cập đến thao tác các tiện ích bên trong. Tính năng tương thích đa nền tảng là một trong những điểm mạnh nổi bật, cho phép người dùng sử dụng LU8 linh hoạt trên điện thoại, máy tính bảng hoặc máy tính cá nhân mà không gặp bất kỳ rào cản nào về kỹ thuật hay hiệu suất. Ngoài ra, LU8 thường xuyên cập nhật các xu hướng công nghệ mới, giúp hệ thống luôn vận hành trơn tru và đáp ứng kịp thời những thay đổi trong hành vi người dùng. Việc áp dụng các thuật toán tối ưu hóa hiệu suất cũng giúp thời gian phản hồi của hệ thống nhanh hơn, mang lại trải nghiệm liền mạch cho người dùng ở mọi hoàn cảnh.
Không chỉ dừng lại ở khả năng vận hành mượt mà, LU8 còn đặc biệt chú trọng đến yếu tố bảo mật và sự an toàn thông tin cá nhân cho người sử dụng. Hệ thống được xây dựng trên nền tảng mã hóa hiện đại, sử dụng nhiều lớp xác thực và kiểm tra chéo để ngăn chặn các rủi ro đến từ bên ngoài. Việc này không chỉ giúp bảo vệ dữ liệu một cách toàn diện mà còn tăng cường mức độ tin cậy từ phía người dùng, đặc biệt là trong những hoạt động yêu cầu tính riêng tư cao. LU8 còn cung cấp các tùy chọn bảo mật nâng cao như xác minh qua email, mã OTP và các công cụ nhận diện thiết bị truy cập để hỗ trợ người dùng quản lý tài khoản một cách hiệu quả nhất. Ngoài ra, quá trình sao lưu dữ liệu được thực hiện định kỳ, đảm bảo không có sự cố mất mát nào ảnh hưởng đến trải nghiệm tổng thể. Đội ngũ kỹ thuật đứng sau LU8 luôn theo dõi hệ thống liên tục, nhằm phát hiện và khắc phục mọi sự cố có thể xảy ra trong thời gian ngắn nhất. Những yếu tố này cho thấy LU8 không chỉ là một nền tảng công nghệ hiện đại, mà còn là một hệ thống được đầu tư bài bản với mục tiêu dài hạn.
Bên cạnh sự mạnh mẽ về công nghệ và bảo mật, LU8 còn tạo nên khác biệt thông qua chất lượng chăm sóc khách hàng vượt trội. Với hệ thống hỗ trợ trực tuyến hoạt động liên tục 24/7, người dùng luôn nhận được sự hỗ trợ tận tình, nhanh chóng và chính xác từ đội ngũ chuyên viên. Mọi thắc mắc, từ đơn giản đến phức tạp, đều được giải đáp cặn kẽ, giúp người dùng an tâm hơn khi tương tác với nền tảng. LU8 cũng duy trì một kênh phản hồi mở, nơi người dùng có thể gửi góp ý để cải thiện chất lượng dịch vụ. Các ý kiến này không bị bỏ qua mà luôn được phân tích và áp dụng vào quá trình nâng cấp hệ thống nhằm phục vụ người dùng tốt hơn mỗi ngày. Ngoài ra, LU8 thường xuyên triển khai các chương trình tri ân khách hàng, khuyến khích sự gắn bó lâu dài và xây dựng cộng đồng người dùng tích cực. Trong tương lai, LU8 đặt mục tiêu mở rộng hơn nữa phạm vi ứng dụng và tích hợp thêm nhiều tiện ích mới, tạo nên một nền tảng số toàn diện, đáp ứng đa dạng nhu cầu của người dùng hiện đại và không ngừng thích ứng với xu hướng công nghệ toàn cầu.
-
 @ bbef5093:71228592
2025-05-13 04:18:45
@ bbef5093:71228592
2025-05-13 04:18:45Nukleáris politika – 2025. május 12. | Szerző: David Dalton
Lengyelország és Franciaország nukleáris szerződést ír alá, Macron új építési szerződéseket céloz
Lengyelország és Franciaország olyan szerződést kötött, amely együttműködést irányoz elő a polgári nukleáris energia szektorban, miközben Párizs reménykedik abban, hogy Varsótól jövedelmező új atomerőmű-építési szerződéseket nyer el.
A szerződés közös tevékenységeket tartalmaz, amelyek célja a nukleáris energia előnyeinek kihasználása az európai ipar dekarbonizációja érdekében.
A két ország együtt kíván működni a nukleáris fűtőanyag-ellátás biztonságának megerősítésében is.
Európa szeretné kizárni Oroszországot a nukleáris fűtőanyag-piacáról, de az Euratom Ellátási Ügynökség (ESA) legfrissebb éves jelentése szerint 2023-ban nőtt az Oroszországból származó természetes urán szállítása, mivel az uniós szolgáltatók készleteket halmoztak fel az orosz tervezésű VVER atomerőművekhez.
Az ESA, amely az európai nukleáris anyagok rendszeres és méltányos ellátásáért felelős, közölte, hogy az uniós szolgáltatók tovább diverzifikálják nukleáris fűtőanyag-beszerzéseiket, különösen a VVER reaktorokhoz, hogy csökkentsék a „egy forrásból származó vagy magas kockázatú” ellátásoktól való függést.
„Majdnem minden olyan ország, amely orosz tervezésű reaktorokat üzemeltet, halad az alternatív fűtőanyagok engedélyeztetésében, és ígéretes fejlemények várhatók a közeljövőben” – közölte az ESA.
Az EU-ban jelenleg 19 VVER reaktor működik, köztük négy 1000 MW-os Bulgáriában és Csehországban, valamint tizenöt 440 MW-os Csehországban, Finnországban, Magyarországon és Szlovákiában.
A jelentések szerint a francia–lengyel nukleáris szerződés különösen fontos a francia állami EDF energetikai vállalat számára, amely még mindig reménykedik abban, hogy részt vehet Lengyelország ambiciózus atomerőmű-építési programjában, annak ellenére, hogy az első új építésű projekt tenderét az amerikai Westinghouse nyerte el Pomeránia északi tartományában.
Franciaország ambiciózus reaktorépítési tervei
Franciaország maga is nagyszabású nukleáris fejlesztési terveket dédelget: a kormány nemrégiben felkérte az EDF-et, hogy gyorsítsa fel a hat új generációs EPR2 atomerőmű megépítésének előkészítését.
Az EDF kezdetben három EPR2 párost tervez: az elsőt Penlyben, majd egyet-egyet a Gravelines-i atomerőmű telephelyén (Calais közelében), illetve vagy Bugey-ben (Lyon keleti részén), vagy Tricastinban (Lyon és Avignon közelében).
A nukleáris szerződés aláírását megelőzte egy másik szerződés is, amely a két szövetséges közötti kapcsolatok elmélyítését, valamint kölcsönös biztonsági garanciákat is tartalmaz háború esetére.
Donald Tusk lengyel miniszterelnök, aki Emmanuel Macron francia elnökkel együtt írta alá a biztonsági dokumentumot, „áttörésnek” nevezte a szerződést, kiemelve, hogy csak Németországnak van hasonló biztonsági paktuma Franciaországgal, és ez Lengyelországot „egyenrangú partnerként” helyezi nyugati szövetségesei közé.
Macron eközben úgy fogalmazott, hogy a szerződés „új korszakot nyit” nemcsak Lengyelország és Franciaország, hanem egész Európa számára. „Bresttől Krakkóig Európa együtt áll ki” – mondta a francia elnök.
Nukleáris politika – 2025. május 12. | Szerző: David Dalton
Trump csapata a nukleáris erőművek építésének felgyorsítását tervezi
A Trump-adminisztráció tisztviselői végrehajtási rendeleteket készítenek elő, amelyek célja az atomerőművek jóváhagyásának és építésének felgyorsítása az Egyesült Államokban – számolt be róla a sajtó.
Az erőfeszítés, amelyet egy kormányzati tisztviselő és más, az egyeztetéseket ismerő személyek írtak le, még folyamatban van. Az elnök még nem hagyta jóvá a tervezetet – mondta az egyik forrás, aki névtelenséget kért, mivel hivatalos bejelentés még nem történt. Az amerikai Axios hírportál és a New York Times is beszámolt az egyeztetésekről.
Trump és kormányának tisztviselői többször hangsúlyozták a bőséges, olcsó villamos energia fontosságát az energiaigényes mesterséges intelligencia ipar számára, amely segítheti az Egyesült Államokat abban, hogy megnyerje a feltörekvő technológia globális versenyét.
„Meg kell nyernünk az MI-versenyt, és ebben vezetnünk kell – ehhez pedig sokkal több energiára lesz szükség” – mondta Chris Wright energiaügyi miniszter múlt hónapban egy kabinetülésen Trump társaságában.
Az elnök már hivatalosan is energia-vészhelyzetet hirdetett, nemzeti és gazdasági biztonsági szempontokra hivatkozva annak érdekében, hogy gyorsítsa az erőművek, csővezetékek és elektromos távvezetékek építését az országban.
A szóban forgó tervezetek célokat tűznének ki az atomerőművek gyors országos építésére, illetve az amerikai nukleáris ipar vezető szerepének visszaállítására.
Legalább az egyik intézkedés a Nukleáris Szabályozási Bizottságnál (NRC) vezetne be változtatásokat, amelyek gyorsíthatják az erőműtervek, köztük az új kis moduláris reaktorok (SMR-ek) engedélyezését.
Wright nemrégiben úgy nyilatkozott, hogy az új reaktorblokkok építésének legnagyobb akadálya az Egyesült Államokban a szabályozás volt.
Az elképzelés részeként akár katonai létesítményekre is telepíthetnek majd atomerőműveket, valószínűleg mikroreaktorok vagy SMR-ek formájában.
Jelenleg az Egyesült Államokban nincs kereskedelmi atomerőmű építés alatt. Az utolsó két üzembe helyezett blokk a georgiai Vogtle-3 és Vogtle-4 volt, 2023-ban és 2024-ben.
Előrehaladott tervek vannak a michigani Palisades atomerőmű újraindítására. Ha megvalósul, ez lenne az első olyan, korábban leállított amerikai atomerőmű, amely ismét működésbe lép.
Új építések – 2025. május 12. | Szerző: David Dalton
Vietnam és Oroszország tárgyalásokat kezd atomerőmű-építésről
Vietnam és Oroszország megállapodott abban, hogy tárgyalásokat folytatnak és szerződéseket írnak alá kereskedelmi atomerőművek építéséről Vietnamban – közölték a két ország egy közös nyilatkozatban.
„Az erőművek fejlesztése korszerű technológiával szigorúan megfelel majd a nukleáris és sugárbiztonsági előírásoknak, és a társadalmi-gazdasági fejlődést szolgálja” – áll a közleményben, amely a vietnami vezető, To Lam moszkvai látogatása után jelent meg.
Az orosz állami atomenergetikai vállalat, a Roszatom szerint a látogatás „az együttműködés új szakaszát” jelenti – egy nagy atomerőmű építését Délkelet-Ázsiában.
A Roszatom felajánlotta Vietnámnak a VVER-1200 nyomottvizes reaktor technológiáját, amelyből kettő már működik az oroszországi Novovoronyezs 2 atomerőműben, és kettő Fehéroroszországban.
A Roszatom közölte, hogy további tárgyalásokra van szükség a vietnami atomerőmű műszaki és pénzügyi feltételeinek tisztázásához, de hozzátette: „ezek a tárgyalások ma [május 10-én] megkezdődtek”.
A Roszatom arról is beszámolt, hogy Alekszej Lihacsov vezérigazgató és Nguyen Manh Hung vietnami tudományos és technológiai miniszter aláírt egy nukleáris energia ütemtervet.
Az ütemterv tartalmazza egy nukleáris tudományos és technológiai központ lehetséges megépítését, fűtőanyag-szállítást a dél-vietnami Dalat kutatóreaktorhoz, Vietnam részvételét Oroszország IV. generációs MBIR többcélú gyorsneutronos kutatóreaktor projektjében, valamint vietnami szakemberek képzését.
Vietnamnak jelenleg egy kutatóreaktora van Dalatban, és egy másik is tervben van. A Roszatom nem közölte, melyikre gondolt.
A múlt hónapban Vietnam elfogadta a nemzeti energiastratégia módosított változatát, amely 2030-ig 136 milliárd dollárt irányoz elő az energiaellátás hosszú távú biztonságának megerősítésére, és először szerepel benne az atomenergia.
Vietnam azt szeretné, ha első atomerőművei 2030 és 2035 között lépnének üzembe. A beépített nukleáris kapacitás várhatóan 4–6,4 GW lesz, ami körülbelül 4–6 nagy atomerőműnek felel meg.
A kormány szerint további 8 GW nukleáris kapacitás kerül majd a mixbe az évszázad közepéig.
Vietnam már 2009-ben is tervezett két atomerőművet, de a Nemzetgyűlés 2016-ban költségvetési okokból elutasította a javaslatot.
Új építések – 2025. május 12. | Szerző: David Dalton
Az NRC engedélyt adott az „energia-sziget” munkálatokra a TerraPower wyomingi atomerőművénél
Az Egyesült Államok Nukleáris Szabályozási Bizottsága (NRC) mentességet adott a TerraPower Natrium demonstrációs atomerőművének wyomingi Kemmererben, lehetővé téve a vállalat számára bizonyos „energia-sziget” tevékenységek folytatását, miközben a hatóságok tovább vizsgálják az építési engedély iránti kérelmet.
Az energia-sziget a tervezett Natrium atomerőműben a felesleges hő tárolására szolgál majd, hogy csúcsterhelés idején növelje az áramtermelést.
Az NRC szerint az energia-szigethez kapcsolódó bizonyos tevékenységek engedélyezése nem jelent indokolatlan kockázatot a közegészségre és biztonságra, és „különleges körülmények” állnak fenn.
A mentesség a létesítmények, rendszerek és komponensek korlátozott részére vonatkozik, lehetővé téve például cölöpverést, alapozást, vagy bizonyos szerkezetek, rendszerek és komponensek összeszerelését, gyártását, tesztelését korlátozott munkavégzési engedély nélkül.
Az NRC szerint a mentesség nem befolyásolja a reaktor építési engedélyéről szóló végső döntést. „Az NRC folytatja az építési engedély iránti kérelem vizsgálatát az egész projektre vonatkozóan” – áll a közleményben.
A Bill Gates által alapított TerraPower üdvözölte a döntést, hozzátéve, hogy a nukleáris reaktor és az energiatermelő létesítmények szétválasztása rövidebb építési időt és alacsonyabb anyagköltségeket tesz lehetővé.
Februárban az amerikai energiaügyi minisztérium befejezte a projekt előzetes tevékenységeire vonatkozó végső környezeti értékelést.
A TerraPower, amelyet Gates 2008-ban alapított, 2024 júniusában kezdte meg első kereskedelmi Natrium atomerőművének építését Kemmererben, ahol egy széntüzelésű erőmű zár be.
A Natrium demonstrációs projekt három különálló részből áll: egy nátrium teszt- és feltöltő létesítményből, az energiatermelő vagy energia-szigetből, valamint a nukleáris szigetből magával a reaktorral.
A kezdeti építkezés a teszt- és feltöltő létesítményre összpontosít, amely egy különálló, nem nukleáris épület, és a reaktor nátrium hűtőrendszerének tesztelésére szolgál. Itt történik a folyékony nátrium fogadása, mintavételezése, feldolgozása és tárolása, mielőtt a Natrium reaktorhoz kerülne.
Egyéb hírek
A lengyel atomerőmű-projekt biztosítási szerződéseket kötött
A lengyel Polskie Elektrownie Jądrowe (PEJ) atomerőmű-projekt vállalat négy biztosítási bróker céggel kötött keretmegállapodást. Az Aon Polska, GrECo Polska, Marsh és Smartt Re cégek támogatják a PEJ-t Lengyelország első kereskedelmi atomerőművének biztosítási szerződéseinek megkötésében, valamint a napi működéshez szükséges biztosítások beszerzésében. A PEJ minden brókerrel keretmegállapodást írt alá, amelyek alapján egyes biztosítási feladatokra kiválasztja a megfelelő brókert.
Az Aecon cég nyerte az ontariói SMR építési szerződését
A kanadai Aecon Kiewit Nuclear Partners nyerte el az Ontario Power Generation (OPG) által Darlingtonban építendő első kis moduláris reaktor (SMR) kivitelezési szerződését. A szerződés értéke 1,3 milliárd kanadai dollár (934 millió USD, 841 millió euró), amely projektmenedzsmentet, kivitelezési tervezést és végrehajtást foglal magában, a befejezést és a kereskedelmi üzemet 2030-ra tervezik. Ontario tartomány és az OPG múlt héten hagyta jóvá a négy SMR első darabjának 20,9 milliárd CAD értékű tervét Darlingtonban.
26 000 dolgozó a Hinkley Point C projekten a csúcskivitelezés idején
Az Egyesült Királyságban mintegy 26 000 dolgozó vesz részt a Hinkley Point C atomerőmű építésében, amely jelenleg csúcskivitelezési szakaszban van – derül ki az EDF Energy jelentéséből. Közvetlenül a projekten 18 000-en dolgoznak, ebből 12 000-en a helyszínen, további 3 000 fővel bővülhet a létszám a következő 12 hónapban. További 8 000-en a beszállítói láncban dolgoznak. A jelentés szerint a Hinkley Point C építése fontos katalizátor a gazdasági növekedésben, jelenleg 13,3 milliárd fonttal (15,7 milliárd euró, 17,5 milliárd dollár) járul hozzá a gazdasághoz. Ebből 5 milliárd fontot már a délnyugati régió beszállítóinál költöttek el – jóval meghaladva az 1,5 milliárd fontos célt. A Hinkley Point C két francia EPR reaktort kap.
Az Ansaldo Nucleare nukleáris mesterszakot indít Olaszországban
Az olasz Ansaldo Nucleare és a Politecnico di Milano vállalati mesterszakot indít, amely a nukleáris energia és kapcsolódó technológiák új szakértő generációját képzi. A képzés októberben indul, egy évig tart, 1500 órás, mérnöki, fizikai és kémiai diplomásoknak szól. Húsz résztvevőt választanak ki a következő hónapokban, akiket az Ansaldo Nucleare azonnal, határozatlan időre alkalmaz, és október elején kezdik meg a képzést.
-
 @ 6be5cc06:5259daf0
2025-05-12 14:50:36
@ 6be5cc06:5259daf0
2025-05-12 14:50:36A posição do libertário que rejeita o cristianismo padece de sérias incoerências lógicas, históricas e filosóficas. Ao renegar as bases espirituais e culturais que tornaram possível o próprio ideal libertário, tal posição demonstra ser, ao mesmo tempo, autofágica e irracional. É o caso de alguém que se gloria dos frutos de uma árvore que corta pela raiz.
I. Fundamento histórico: a civilização da liberdade é cristã
Não foi o secularismo moderno, nem o paganismo antigo, que ergueram as instituições que protegem a dignidade da pessoa humana e os limites ao poder. Desde os primeiros séculos, a Igreja resistiu ao culto estatal romano, afirmando a soberania de Deus sobre os Césares — "Mais importa obedecer a Deus que aos homens" (Atos 5,29).
Foi o cristianismo que:
-
Fundou universidades livres, onde o saber era buscado sob o primado da verdade;
-
Defendeu a lei natural como fundamento do direito — uma doutrina que protege o indivíduo contra tiranias;
-
Resgatou e aprofundou o conceito de pessoa, dotada de razão e livre-arbítrio, imagem de Deus, e, portanto, inalienavelmente digna e responsável.
Em momentos-chave da história, como nas disputas entre papado e império, nas resistências contra absolutismos, e na fundação do direito internacional por Francisco de Vitoria e a Escola de Salamanca, foi o cristianismo quem freou o poder estatal em nome de princípios superiores. A tradição cristã foi frequentemente o principal obstáculo à tirania, não seu aliado.
Negar isso é amputar a própria genealogia da liberdade ocidental.
Uma das chaves do cristianismo para a construção dessa civilização da liberdade foi a exaltação do individualismo. Ao afirmar que o ser humano é feito à imagem de Deus e que sua salvação é uma escolha pessoal, o cristianismo colocou o indivíduo no centro da moralidade e da liberdade. Diferente dos gregos, cuja ética era voltada para a polis e a cidade-estado, o cristianismo reafirma a suprema importância do indivíduo, com sua capacidade de escolha moral, responsabilidade pessoal e dignidade intrínseca. Esse princípio, mais do que qualquer outra religião, foi o alicerce do desenvolvimento da liberdade individual e da autonomia, valores que sustentam a civilização ocidental.
A ética grega, na melhor das hipóteses, descreve a ordem natural — mas não consegue justificar por que essa ordem deveria obrigar a vontade humana. Um Logos impessoal não tem autoridade moral. Uma ordem cósmica sem um Legislador é apenas um dado de fato, não uma norma vinculante. A vontade pode rebelar-se contra o telos — e sem um Deus justo, que ordena a natureza à perfeição, não há razão última para não o fazer.
A cultura grega teve uma influência indiscutível sobre o desenvolvimento da civilização ocidental, mas o cristianismo não só absorveu o que havia de bom na cultura grega, como também elevou e completou esses aspectos. O cristianismo, ao afirmar que todos os homens são feitos à imagem e semelhança de Deus e têm dignidade intrínseca, levou a uma noção de igualdade moral e liberdade que transcende as limitações da pólis grega.
II. Falsa dicotomia: fé e liberdade não são opostas
Com frequência equiparam a religião à coerção e à obediência cega. Mas isso é um equívoco: o cristianismo não se impõe pela força, mas apela à consciência. O próprio Deus, em sua relação com a criatura racional, respeita sua liberdade. Como ensina a Escritura:
"Se alguém quiser vir após mim..." (Mt 16,24);
"Eis que estou à porta e bato. Se alguém ouvir a minha voz e abrir a porta, entrarei em sua casa e cearei com ele." (Ap 3,20);
"Assim falai, e assim procedei, como devendo ser julgados pela lei da liberdade." (Tiago 2,12).A adesão à fé deve ser livre, voluntária e racional, pois sem liberdade não há verdadeiro mérito, nem amor genuíno. Isso é mais compatível com o princípio de não agressão do que qualquer utopia secular. Ora, o núcleo do evangelho é voluntarista: salvação pessoal, conversão interior, caridade.
Ninguém deve ser forçado, contra sua vontade, a abraçar a fé, pois o ato de fé é por sua natureza voluntário (Dignitatis Humanae; CDC, cân. 748,2)
Se algum Estado usa da força para impor o cristianismo, afirmar que o cristianismo causou as coerções é tão equivocado quanto dizer que a propriedade privada causa o comunismo; é uma inversão da realidade, pois o comunismo surge precisamente da violação da propriedade. Portanto, a fé forçada é inválida em si mesma, pois viola a natureza do ato de crer, que deve ser livre.
III. Fundamento moral: sem transcendência, o libertarianismo flutua no vácuo
O libertário anticristão busca defender princípios objetivos — como a inviolabilidade do indivíduo e a ilegitimidade da agressão — sem um fundamento transcendente que lhes dê validade universal. Por que a agressão é errada? Por que alguém tem direito à vida, à liberdade, à propriedade? Sem uma explicação transcendental, as respostas para tais perguntas se tornam apenas opiniões ou convenções, não obrigações morais vinculantes. Se a moralidade é puramente humana, então os direitos podem ser modificados ou ignorados conforme a vontade da sociedade. O conceito de direitos naturais, tão caro ao libertarianismo, precisa de um solo metafísico que justifique sua universalidade e imutabilidade. Caso contrário, eles podem ser tratados apenas como acordos utilitários temporários ou preferências culturais, sem qualquer obrigatoriedade para todos os seres humanos em todas as circunstâncias.
Pensadores libertários seculares, como Ayn Rand e Murray Rothbard, tentaram ancorar os direitos naturais na razão humana ou na natureza do homem. Rand baseia sua ética no egoísmo racional, enquanto Rothbard apela à lei natural. Embora essas abordagens busquem objetividade, elas carecem de uma resposta definitiva para por que a razão ou a natureza humana obrigam moralmente todos os indivíduos. Sem um fundamento transcendente, suas concepções permanecem vulneráveis a interpretações subjetivas ou a cálculos utilitários.
Aqui, o cristianismo oferece uma explicação sólida e transcendental que fundamenta os direitos naturais. A visão cristã de que o ser humano foi criado à imagem e semelhança de Deus confere à pessoa uma dignidade intrínseca, imutável e universal. Essa dignidade não depende de fatores externos, como consenso social ou poder político, mas é uma característica inerente ao ser humano pela sua criação divina. A partir dessa perspectiva teológica, torna-se possível afirmar com base sólida que os direitos naturais são dados por Deus e, portanto, são universais e vinculantes.
O cristianismo também é a base de um sistema moral que distingue claramente justiça de legalidade. O Estado pode criar leis, mas isso não significa que essas leis sejam justas. A justiça, sob a ótica cristã, é uma expressão da ordem moral objetiva, algo que transcende as leis humanas e é definido pela vontade divina. Por isso, o libertarianismo cristão vê a agressão como uma violação de uma ordem moral objetiva, e não apenas uma violação de uma convenção social ou de um acordo utilitário.
Se a moralidade e os direitos naturais não forem fundamentados em um Logos criador e legislador, o que acontece é que o conceito de direito natural degenera para algo mais frágil, como um simples acordo utilitário. Nesse cenário, os direitos do indivíduo se tornam algo acordado entre os membros de uma sociedade, em vez de princípios imutáveis e universais. Os direitos podem ser negociados, alterados ou ignorados conforme o interesse do momento.
IV. Fundamento científico: a racionalidade moderna é filha da fé cristã
A ciência moderna só foi possível no contexto cultural cristão. Nenhuma outra civilização — nem a grega, nem a islâmica, nem a chinesa — produziu o método científico como o Ocidente cristão o fez.
Isso se deve a quatro premissas teológicas:
-
Criação racional: O mundo é ordenado por um Deus racional.
-
Distinção entre Criador e criatura: A natureza não é divina e pode ser estudada sem sacrilégio.
-
Valor do trabalho e da observação empírica, herdado do monaquismo.
-
Autonomia institucional, presente nas universidades medievais.
A doutrina cristã da Criação ex nihilo ensina que o mundo foi criado por um Deus racional, sábio e pessoal. Portanto, o cosmos é ordenado, possui leis, e pode ser compreendido pela razão humana — que é imagem do Criador. Isso contrasta fortemente com as cosmovisões panteístas ou mitológicas, onde o mundo é cíclico, arbitrário ou habitado por forças caprichosas.
Sem essa fé no Logos criador, não há razão para crer que a natureza tenha uma ordem inteligível universal e constante, que pode ser descoberta por observação e dedução. A ciência moderna só é possível porque, antes de investigar a natureza, pressupôs-se que ela era investigável — e isso foi uma herança direta do pensamento cristão.
Homens como Bacon, Newton, Kepler e Galileu viam na ciência um modo de glorificar o Criador. O ateísmo cientificista é, portanto, parasitário da teologia cristã, pois toma seus frutos e rejeita suas raízes. A ciência moderna nasceu como filha legítima da fé cristã. E os que hoje a usam contra sua mãe, ou são ingratos, ou ignorantes.
V. O cristianismo como barreira à revolução cultural
O cristianismo é a barreira mais sólida contra a infiltração revolucionária. A chamada "marcha gramsciana", que visa corroer os fundamentos morais da sociedade para subjugar o indivíduo ao coletivo, encontra sua resistência mais firme nos princípios cristãos. A fé cristã, ao proclamar a existência de uma verdade objetiva, de uma lei moral imutável e de uma dignidade humana que transcende o Estado e o consenso social, imuniza a civilização contra o relativismo e o igualitarismo nivelador do marxismo cultural.
Além disso, o cristianismo é uma tradição milenar, profundamente enraizada no cotidiano das pessoas, não sendo uma novidade a ser imposta ou implementada, mas uma força presente há séculos, que permeia a estrutura social, moral e cultural da sociedade. Sua presença constante nas comunidades, desde os tempos mais antigos, oferece uma resistência robusta contra qualquer tentativa de subverter a ordem natural e moral estabelecida.
Não por acaso, tanto Karl Marx quanto Antonio Gramsci identificaram no cristianismo o principal obstáculo à realização de seus projetos revolucionários. Marx chamou a religião de "ópio do povo" porque sabia que uma alma ancorada em Deus não se submete facilmente ao poder terreno; Gramsci, mais sutil, propôs a destruição da cultura cristã como pré-condição para o triunfo do socialismo. Sem essa âncora transcendente, a sociedade torna-se presa fácil das engenharias sociais que pretendem redefinir arbitrariamente o homem, a família e a liberdade.
Conclusão
O libertário anticristão, consciente ou não, nega as fundações mesmas do edifício que habita. Ao rejeitar o cristianismo, cava o abismo sob os próprios pés, privando o ideal libertário de sua base moral, cultural e racional. Ele defende a ética voluntária, a liberdade individual e a ordem espontânea, mas sem o solo metafísico e histórico que torna esses princípios inteligíveis e possíveis. É um erro tentar preservar a liberdade em termos absolutos sem reconhecer as raízes cristãs que a sustentam, pois o cristianismo é a única tradição que a legitima e a viabiliza.
Negar o cristianismo é racionalmente insustentável. A liberdade, como a conhecemos, é filha da fé cristã, que oferece a base moral e metafísica que torna a liberdade tanto desejável quanto possível. Mesmo que ateu, o libertário que ama a liberdade deveria, no mínimo, respeitar — e, idealmente, redescobrir — essas raízes cristãs. Pois sem fé, restam apenas o niilismo e o relativismo, que, eventualmente, desaguam na servidão.
Como nos ensina a tradição: Ubi fides ibi libertas — onde há fé, há liberdade.
-
-
 @ c1e9ab3a:9cb56b43
2025-05-09 23:10:14
@ c1e9ab3a:9cb56b43
2025-05-09 23:10:14I. Historical Foundations of U.S. Monetary Architecture
The early monetary system of the United States was built atop inherited commodity money conventions from Europe’s maritime economies. Silver and gold coins—primarily Spanish pieces of eight, Dutch guilders, and other foreign specie—formed the basis of colonial commerce. These units were already integrated into international trade and piracy networks and functioned with natural compatibility across England, France, Spain, and Denmark. Lacking a centralized mint or formal currency, the U.S. adopted these forms de facto.
As security risks and the practical constraints of physical coinage mounted, banks emerged to warehouse specie and issue redeemable certificates. These certificates evolved into fiduciary media—claims on specie not actually in hand. Banks observed over time that substantial portions of reserves remained unclaimed for years. This enabled fractional reserve banking: issuing more claims than reserves held, so long as redemption demand stayed low. The practice was inherently unstable, prone to panics and bank runs, prompting eventual centralization through the formation of the Federal Reserve in 1913.
Following the Civil War and unstable reinstatements of gold convertibility, the U.S. sought global monetary stability. After World War II, the Bretton Woods system formalized the U.S. dollar as the global reserve currency. The dollar was nominally backed by gold, but most international dollars were held offshore and recycled into U.S. Treasuries. The Nixon Shock of 1971 eliminated the gold peg, converting the dollar into pure fiat. Yet offshore dollar demand remained, sustained by oil trade mandates and the unique role of Treasuries as global reserve assets.
II. The Structure of Fiduciary Media and Treasury Demand
Under this system, foreign trade surpluses with the U.S. generate excess dollars. These surplus dollars are parked in U.S. Treasuries, thereby recycling trade imbalances into U.S. fiscal liquidity. While technically loans to the U.S. government, these purchases act like interest-only transfers—governments receive yield, and the U.S. receives spendable liquidity without principal repayment due in the short term. Debt is perpetually rolled over, rarely extinguished.
This creates an illusion of global subsidy: U.S. deficits are financed via foreign capital inflows that, in practice, function more like financial tribute systems than conventional debt markets. The underlying asset—U.S. Treasury debt—functions as the base reserve asset of the dollar system, replacing gold in post-Bretton Woods monetary logic.
III. Emergence of Tether and the Parastatal Dollar
Tether (USDT), as a private issuer of dollar-denominated tokens, mimics key central bank behaviors while operating outside the regulatory perimeter. It mints tokens allegedly backed 1:1 by U.S. dollars or dollar-denominated securities (mostly Treasuries). These tokens circulate globally, often in jurisdictions with limited banking access, and increasingly serve as synthetic dollar substitutes.
If USDT gains dominance as the preferred medium of exchange—due to technological advantages, speed, programmability, or access—it displaces Federal Reserve Notes (FRNs) not through devaluation, but through functional obsolescence. Gresham’s Law inverts: good money (more liquid, programmable, globally transferable USDT) displaces bad (FRNs) even if both maintain a nominal 1:1 parity.
Over time, this preference translates to a systemic demand shift. Actors increasingly use Tether instead of FRNs, especially in global commerce, digital marketplaces, or decentralized finance. Tether tokens effectively become shadow base money.
IV. Interaction with Commercial Banking and Redemption Mechanics
Under traditional fractional reserve systems, commercial banks issue loans denominated in U.S. dollars, expanding the money supply. When borrowers repay loans, this destroys the created dollars and contracts monetary elasticity. If borrowers repay in USDT instead of FRNs:
- Banks receive a non-Fed liability (USDT).
- USDT is not recognized as reserve-eligible within the Federal Reserve System.
- Banks must either redeem USDT for FRNs, or demand par-value conversion from Tether to settle reserve requirements and balance their books.
This places redemption pressure on Tether and threatens its 1:1 peg under stress. If redemption latency, friction, or cost arises, USDT’s equivalence to FRNs is compromised. Conversely, if banks are permitted or compelled to hold USDT as reserve or regulatory capital, Tether becomes a de facto reserve issuer.
In this scenario, banks may begin demanding loans in USDT, mirroring borrower behavior. For this to occur sustainably, banks must secure Tether liquidity. This creates two options: - Purchase USDT from Tether or on the secondary market, collateralized by existing fiat. - Borrow USDT directly from Tether, using bank-issued debt as collateral.
The latter mirrors Federal Reserve discount window operations. Tether becomes a lender of first resort, providing monetary elasticity to the banking system by creating new tokens against promissory assets—exactly how central banks function.
V. Structural Consequences: Parallel Central Banking
If Tether begins lending to commercial banks, issuing tokens backed by bank notes or collateralized debt obligations: - Tether controls the expansion of broad money through credit issuance. - Its balance sheet mimics a central bank, with Treasuries and bank debt as assets and tokens as liabilities. - It intermediates between sovereign debt and global liquidity demand, replacing the Federal Reserve’s open market operations with its own issuance-redemption cycles.
Simultaneously, if Tether purchases U.S. Treasuries with FRNs received through token issuance, it: - Supplies the Treasury with new liquidity (via bond purchases). - Collects yield on government debt. - Issues a parallel form of U.S. dollars that never require redemption—an interest-only loan to the U.S. government from a non-sovereign entity.
In this context, Tether performs monetary functions of both a central bank and a sovereign wealth fund, without political accountability or regulatory transparency.
VI. Endgame: Institutional Inversion and Fed Redundancy
This paradigm represents an institutional inversion:
- The Federal Reserve becomes a legacy issuer.
- Tether becomes the operational base money provider in both retail and interbank contexts.
- Treasuries remain the foundational reserve asset, but access to them is mediated by a private intermediary.
- The dollar persists, but its issuer changes. The State becomes a fiscal agent of a decentralized financial ecosystem, not its monetary sovereign.
Unless the Federal Reserve reasserts control—either by absorbing Tether, outlawing its instruments, or integrating its tokens into the reserve framework—it risks becoming irrelevant in the daily function of money.
Tether, in this configuration, is no longer a derivative of the dollar—it is the dollar, just one level removed from sovereign control. The future of monetary sovereignty under such a regime is post-national and platform-mediated.
-
 @ a5ee4475:2ca75401
2025-05-09 17:10:35
@ a5ee4475:2ca75401
2025-05-09 17:10:35Título H1 - Formatação Markdown
[Titulo com '# ' antes do texto, pode não funcionar se o título H1 for iniciado depois de um texto normal]
list #descentralismo #markdown #clients #Amethyst #Yakihonne
Título H2 [2 hashtags e espaço]
Título H3 [3 hashtags e espaço]
Título H4 [4 hashtags e espaço]
Título H5 [5 hashtags e espaço]
Título H6 [6 hashtags e espaço]
*Copie e cole o texto para enxergar os caracteres usados
Réguas horizontais
- Com 3 sublinhados (_) seguidos:
- Com 3 hífens (-) seguidos:
- Com três asteriscos (*) seguidos:
Ênfases
Negrito: - Dois asteriscos antes e depois: Este é um texto em negrito
- Dois sublinhados antes e depois: Esse é um texto em negrito
Itálico - Um asterisco antes e um depois: Esse é um texto em itálico
- Um sublinhado antes e um depois: Esse é um texto em itálico
Tachado:
~~Aqui houve uma rasura~~
Bloco de citações
Usando 1 a 3 “>”:
O bloco de citações pode ser eninhado…
…Usando cada vez mais maior-que (>).
…Mesmo com espaços entre eles.
Listas
Não-ordenadas
- Crie um tópico começando com
+,-ou*. - Subtópicos são feitos adicionando 2 espaços:
- A mudança da marcação inicial não altera a lista:
- Com asterisco
- Com sinal de mais
- Com sinal de menos
- Muito fácil!
Ordenadas
- Lorem ipsum dolor sit amet
- Consectetur adipiscing elit
- Integer molestie lorem at massa
- Você pode usar números em sequência...
- ...ou deixar tudo como
1.ou outro número.
O número inicia com recuos:
- foo
- bar
Códigos
códigona mesma linhaCaixa de código
-
Códigos intentados com 4 espaços:
// Some comments line 1 of code line 2 of code line 3 of code
-
Com 3 acentos graves antes e depois:
Marcação de texto:
Insira o texto aqui...Marcação de sintaxe:
``` js var foo = function (bar) { return bar++; };
console.log(foo(5)); ```
Tabelas
| APP | Descrição | | ------ | ----------- | | Element | App de mensagens que usa a rede Matrix. | | Simplex | App de mensagens bastante usado. | | 0xchat | App de mensagens no Nostr. |
Links
-
Link autoconvertido https://github.com/nodeca/pica (habilite o linkify para ver)
Imagens nomeadas
Minion:

Stormtroopocat:
[https://octodex.github.com/images/stormtroopocat.jpg])
Como links, imagens também tem sintaxe footnote ‘!’ + ‘Outro texto’...
[https://octodex.github.com/images/dojocat.jpg])
…com uma referência id posterior da referência na localização da URL.
Plugins
O recurso de
markdown-ité um suporte muito eficaz de plugins de sintaxe.
Emojis
*Acesse o link para entender melhor
Marcação clássica: :wink: :cry: :laughing: :yum:
Figuras Ascii (emoticons): :-) :-( 8-) ;)
Veja como mudar a exibição com o twemoji.
Sobrescrito / Subscrito
*Acesse os links para entender melhor
- 19^th^
- H~2~O
\
*Acesse o link para entender melhor
++Texto Inserido++
\
*Acesse o link para entender melhor
==Texto marcado==
Notas de Rodapé
*Acesse o link para entender melhor
Nota de rodapé 1 link[^primeiro].
Nota de rodapé 2 link[^segundo].
Rodapé^[Texto do rodapé na linha] definição na linha.
Referência duplicada no rodapé[^segundo].
[^primeiro]: Rodapé pode ter marcação
e múltiplos parágrafos.[^segundo]: Texto de rodapé.
Listas de Definição
*Acesse o link para entender melhor
Termo 1
: Definição 1 com continuação preguiçosa.
Termo 2 com marcação na linha
: Definição 2
{ algum código, parte da Definição 2 } Third paragraph of definition 2.Estilo compacto:
Termo 1 ~ Definição 1
Termo 2 ~ Definição 2a ~ Definição 2b
Esse texto é uma adaptação do:
nostr:nevent1qqsv54qfgtme38r2tl9v6ghwfj09gdjukealstkzc77mwujr56tgfwspzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtczyqy0j6zknu2lr7qrge5yt725azecflhxv6d2tzwgtwrql5llukdqjqcyqqqqqqgfdk5w3
-
 @ 75869cfa:76819987
2025-05-13 03:26:29
@ 75869cfa:76819987
2025-05-13 03:26:29GM, Nostriches!
The Nostr Review is a biweekly newsletter focused on Nostr statistics, protocol updates, exciting programs, the long-form content ecosystem, and key events happening in the Nostr-verse. If you’re interested, join me in covering updates from the Nostr ecosystem!
Quick review:
In the past two weeks, Nostr statistics indicate over 211,000 daily trusted pubkey events. The number of new users has seen a notable decrease, Profiles with contact lists were representing a 50% decline. More than 5 million events have been published, reflecting a 34% decrease. Total Zap activity stands at approximately 14 million, marking a 12% increase.
Additionally, 25 pull requests were submitted to the Nostr protocol, with 8 merged. A total of 60 Nostr projects were tracked, with 18 releasing product updates, and over 356 long-form articles were published, 36% focusing on Bitcoin and Nostr. During this period, 5 notable events took place, and 2 significant events are upcoming.
Nostr Statistics
Based on user activity, the total daily trusted pubkeys writing events is about 211,000, representing a slight 2.7 % decrease compared to the previous period. Daily activity peaked at 17027 events, with a low of approximately 15340.
The number of new users has decreased significantly.Profiles with contact lists were 12961, representing a decline of approximately 50% compared to the previous period. The number of profiles with bios and pubkey-written events remained stable.
The total number of note events published is around 5 million, reflecting a 34% decrease.Posts remain the most dominant category by volume, representing a 9% decrease compared to the previous period.
For zap activity, the total zap amount is about 14 million, showing an decrease of over 12% compared to the previous period.
Data source: https://stats.nostr.band/
NIPs
Introduce NIP-PNS: Private Note Storage #1893
nostr:npub1xtscya34g58tk0z605fvr788k263gsu6cy9x0mhnm87echrgufzsevkk5s is proposing PNS that empowers Nostr users with a secure and seamless way to store personal notes—like diaries, drafts, or private application settings—across devices while keeping them completely private. Built on client-side encryption, PNS ensures that only the user can read or manage their notes, even as they sync effortlessly via Nostr relays. Unlike traditional local storage or cumbersome encrypted file solutions, PNS offers privacy without sacrificing convenience, using deterministic keys tied to each user or device. It integrates directly with Nostr’s open infrastructure, enabling private data to coexist with public events—secure, synchronized, and under your control.
Create 97.md: Ring Signatures #1894
nostr:npub1u5njm6g5h5cpw4wy8xugu62e5s7f6fnysv0sj0z3a8rengt2zqhsxrldq3 is proposing a PR that ring signatures can be synergistic with other web of trust related tools.
Introduce NIP: Relay metadata propagation #1900
nostr:npub1txukm7xckhnxkwu450sm59vh2znwm45mewaps4awkef2tvsgh4vsf7phrl is proposing a simple propagation mechanism for kind:0 (user metadata) and kind:10002 (relay list metadata) events between relays. Relays are allowed to forward such events to their peers, improving client synchronization.
nostr:npub1gzuushllat7pet0ccv9yuhygvc8ldeyhrgxuwg744dn5khnpk3gs3ea5ds defines a standardized interaction pattern for Nostr Data Vending Machines (DVMs). It focuses on how clients discover DVM capabilities, request jobs, and receive results. This NIP decouples the core DVM interaction from specific job-type implementations, which should be defined in separate documents.
NIP-47 Add Hold Invoice Support #1913
frnandu is proposing PR that introduces support for hold invoices in the Nostr Wallet Connect (NIP-47) protocol.Hold invoices enable more advanced payment workflows where the receiver must explicitly settle or cancel the invoice using the preimage. This allows for enhanced control and coordination in payment flows, such as conditional payments or escrow-like behavior.
Add A Generic Raitng/Review NIP #1914
nostr:npub1cgd35mxmy37vhkfcmjckk9dylguz6q8l67cj6h9m45tj5rx569cql9kfex is proposing generic nip that meant to handle all categories of things via namespaced Ids.
Notable Projects
Coracle 0.6.15 nostr:npub13myx4j0pp9uenpjjq68wdvqzywuwxfj64welu28mdvaku222mjtqzqv3qk
New version of Coracle is out: 0.6.15 — this one is just more QoL improvements and bugfixes — the big one this time is better blossom support (and dropping nip 96!). * Fix safe areas more * Improve remote signing * Drop nip 96 support * Use user blossom servers * Improve profile edit page * Avoid duplicate notes in feeds
Flotilla nostr:npub1jlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qdjynqn
New version of Flotilla is out as well — 1.0.2 is mostly cleanup from the 1.0 release earlier this week. * Fix add relay button * Fix safe inset areas * Better rendering for errors from relays * Improve remote signer login
Damus Notedeck Beta nostr:npub18m76awca3y37hkvuneavuw6pjj4525fw90necxmadrvjg0sdy6qsngq955
New in Notedeck Beta: * Dave nostr ai assistant app * GIFs! * Fulltext note search * Add full screen images, add zoom & pan * Zaps! NWC/ Wallet ui * Introduce last note per pubkey feed (experimental) * Allow multiple media uploads per selection * Major Android improvements (still wip) * Added notedeck app sidebar * User Tagging * Note truncation * Local network note broadcast, broadcast notes to other notedeck notes while you're offline * Mute list support (reading) * Relay list support * Ctrl-enter to send notes * Added relay indexing (relay columns soon) * Click hashtags to open hashtag timeline
Primal V2.2 nostr:npub12vkcxr0luzwp8e673v29eqjhrr7p9vqq8asav85swaepclllj09sylpugg
Version 2.2 is now live, bringing long-awaited features like Amber signing support and much more. Here’s what’s new: * Blossom media * Push notifications * Notifications overhaul * External signer support * Feed: image gallery revamp * Muted words, hashtags, & threads * Request delete for notes and articles * System photos: share via Primal
Nostur nostr:npub1n0stur7q092gyverzc2wfc00e8egkrdnnqq3alhv7p072u89m5es5mk6h0
New in this version: * Add blossom media server support * Support multiple blossom servers as mirror * Fixed feed position reset on audio bar toggle * Fixed post screenshot broken for quoted posts
Fountain 1.2 nostr:npub1v5ufyh4lkeslgxxcclg8f0hzazhaw7rsrhvfquxzm2fk64c72hps45n0v5
Fountain 1.2 is live on iOS and Android This massive update brings significant design and UX improvements across the app along with new episode summaries features. Here's what's new: * Library Design Update: Fountain has made it much easier to navigate between podcasts and music in the library with the addition of new content-type filters. The Recently Played view allows users to quickly jump back into what they were listening to before, and the design of the content cards has also been refreshed. * Content Pages Design Update: All content pages—including shows, episodes, artists, albums, tracks, clips, and playlists—have undergone an extensive redesign. The previous tab layout has been replaced with scrollable pages, show notes formatting has been improved, and features like chapters and transcripts have been revamped. * Episode Summaries: Each episode page now features a Summary button above the show notes. Users can pay 500 sats to unlock a summary or upgrade to Fountain Premium for $2.99/month to enjoy unlimited summaries. Summaries and transcripts are now bundled together, and they’re faster, cheaper, and more accurate than ever before. * Playback Improvements: The audio engine has been completely rebuilt from the ground up. Playback is now more robust and reliable—especially for music. Tracks now play instantly when tapped, and users can skip seamlessly between tracks in albums and playlists. The player interface has also been updated for easier access to show notes, comments, transcripts, and chapters, with the addition of a smart resume feature for podcasts.
DEG Mods nostr:npub17jl3ldd6305rnacvwvchx03snauqsg4nz8mruq0emj9thdpglr2sst825x
- New Events Aggregator Server, a type of aggregate/caching server that helps collect and organize mod and blog posts from the (nostr) network and presents them to the user, providing more (immensely more) reliability in discovering and presenting mods and blog posts.
- Adjusted how the mods and blogs are fetched and presented in various pages (there's now pagination for each of their pages, making navigation easier than before).
- Minor adjustment to the design of the gallery of mod posts.
- Images in a social post (in /feed) are now clustered depending on if they're next to each other.
- Quote-repost chain won't render its preview with the second quote-repost (under the posts tab in the feed page).
- Added media upload to the edit profile page.
- The games page now has a filter to switch between popular ones (shows the most popular games first based on mods published to it) or latest ones (shows games based on the latest published mods).
- Mods that are blocked by the user are now swapped with a box telling the user this is a blocked mod by them, with an option to see what that mod is.
- Mods can now be properly discovered, as soon as they're discovered, and presented (Because of that aggregate server implementation).
- A lot more games, with better search term prioritization, are now properly showing when searching in the mod submission page
- Visiting a social post directly is now visible without needing to login
RUNSTR nostr:npub1vygzr642y6f8gxcjx6auaf2vd25lyzarpjkwx9kr4y752zy6058s8jvy4e
- Record your cardio and post to nostr
- Save your stats to nostr
- Listen to your nostr:npub1yfg0d955c2jrj2080ew7pa4xrtj7x7s7umt28wh0zurwmxgpyj9shwv6vg playlists and zap your favorite artists
- Interact with the Kind1 RUNSTR Feed
- Interact with NIP29 run clubs
nostr:npub17h9fn2ny0lycg7kmvxmw6gqdnv2epya9h9excnjw9wvml87nyw8sqy3hpu Now it's possible to keep playing your text while voca is in the background.
Wasabi Wallet v2.6.0 nostr:npub1jw7scmeuewhywwytqxkxec9jcqf3znw2fsyddcn3948lw9q950ps9y35fg
- Support for Standard BIP 158 Block Filters
- Full Node Integration Rework
- Create & Recover SLIP 39 Shares
- Nostr Update Manager
Futr nostr nostr:npub18wxf0t5jsmcpy57ylzx595twskx8eyj382lj7wp9rtlhzdg5hnnqvt4xra
- Solved memory leak in Qt5
- Fixed recursive re-rendering bug in Qt5
- Enable QML debugger through Haskell binding
- Improve event handling and Qt5 signal triggering
ZEUS v0.11.0 nostr:npub1xnf02f60r9v0e5kty33a404dm79zr7z2eepyrk5gsq3m7pwvsz2sazlpr5
ZEUS v0.11.0-alpha3 with Cashu support is now available for testing: * Fix: addresses issues with sweeping Cashu tokens to self-custody with remote connections * Feat: Core Lightning: Taproot address support * Misc: UX enhancements * Cashu wallets are tied to Embedded LND wallets. Enable under Settings > Ecash * Other wallet types can still sweep funds from Cashu tokens * ZEUS Pay now supports Cashu address types. You can switch between Zaplocker, Cashu, and NWC mode but can only use one at a time.
Oracolo nostr:npub10000003zmk89narqpczy4ff6rnuht2wu05na7kpnh3mak7z2tqzsv8vwqk
Now the short notes block has two new styles: "Board" and "Full content"; the former shows notes in a pinterest-like fashion on two columns, while the latter shows full notes in full screen.
Umbrel 1.4.1 nostr:npub1aghreq2dpz3h3799hrawev5gf5zc2kt4ch9ykhp9utt0jd3gdu2qtlmhct
- Search files anywhere with ⌘/Ctrl + K
- New Favorites & Recents widgets
- Real-time transfer speed + ETA
- Snappier performance
- Several other enhancements & fixes
Shopstr v0.4.2 nostr:npub15dc33fyg3cpd9r58vlqge2hh8dy6hkkrjxkhluv2xpyfreqkmsesesyv6e
This update brings the following improvements and fixes: * Added Blossom media support for image uploads with metadata stripping * Added a terms of service and privacy policy * Added pagination for product viewing * Fixed relay list duplication bug * Removed excessive bottom margin on marketplace page
nostr.build nostr:npub1nxy4qpqnld6kmpphjykvx2lqwvxmuxluddwjamm4nc29ds3elyzsm5avr7
The latest free features are: * 100MB upload size * Blossom support * David Lynch tribute page
openvibe nostr:npub1plstrz6dhu8q4fq0e4rjpxe2fxe5x87y2w6xpm70gh9qh5tt66kqkgkx8j
- Share Even Further : Crosspost from one network to another, or take posts beyond the open social web. Share anything, anywhere — effortlessly from
Ditto.13 nostr:npub10qdp2fc9ta6vraczxrcs8prqnv69fru2k6s2dj48gqjcylulmtjsg9arpj
Ditto 1.3 is all about discovery. From improved search and event fetching to a brand-new Explore tab, this release makes it easier than ever to find people, posts, and conversations across the #Nostr network. We've also rolled out streaks, media improvements, translation upgrades, and key admin tools.
Long-Form Content Eco
In the past two weeks, more than 356 long-form articles have been published, including over 90 articles on Bitcoin and more than 37 related to Nostr, accounting for 36% of the total content.
These articles about Nostr mainly explore the ongoing evolution and challenges of the decentralized protocol, including relay scalability, spam mitigation, signer tools, and publishing workflows. They highlight the network’s technical progress as it handles increasing data loads and infrastructure demands, while also addressing issues like spam and search limitations. Many articles focus on content creation and distribution, showcasing tools for decentralized publishing and media hosting. Others introduce practical guides for secure identity management and signer usage. The ecosystem’s economic potential is also discussed, with suggestions for monetization and community growth. Personal reflections and critiques further illustrate the culture and complexity of Nostr as it expands.
These articles about Bitcoin cover a broad spectrum of topics, highlighting its evolving role in technology, culture, and the global economy. They discuss core concepts such as decentralization, financial sovereignty, and Bitcoin as digital gold, while also addressing current issues like OP_RETURN restrictions, mining centralization, and environmental concerns. Real-world use cases—such as remittances, merchant adoption, and Bitcoin's growth in emerging markets like Africa and South America—are frequently explored. Many articles focus on user education, including wallet security, key management, and node operation. Others provide commentary through book reviews, political reflections, and personal narratives, illustrating how Bitcoin is shaping both individual behavior and institutional thinking.
Thank you, nostr:npub186a9aaqmyp436j0gkxl8yswhat2ampahxunpmfjv80qwyaglywhqswhd06 nostr:npub1xncam2l8u5chg6w096v89f2q2l0lz4jz4n7q7tdjsu6y5t9qea7q2cmrua nostr:npub10m6lrv2kaf08a8um0plhj5dj6yqlw7qxzeag6393z352zrs0e5nsr2tff3 nostr:npub15hhygatg5gmjyfkkguqn54f9r6k8m5m6ksyqffgjrf3uut982sqsffn4vc nostr:npub18ams6ewn5aj2n3wt2qawzglx9mr4nzksxhvrdc4gzrecw7n5tvjqctp424 nostr:npub1rsv7kx5avkmq74p85v878e9d5g3w626343xhyg76z5ctfc30kz7q9u4dke nostr:npub1jp3776ujdul56rfkkrv8rxxgrslqr07rz83xpmz3ndl74lg7ngys320eg2 nostr:npub1dk8z5f8pkrn2746xuhfk347a0g6fsxh20wk492fh9h8lkha2efxqgeq55a nostr:npub18sufer6dgm9gzvt8gw37x08dk8gxr8u80rh8f4rjv4m4u73wlalsygnz5q nostr:npub1qpdufhjpel94srm3ett2azgf49m9dp3n5nm2j0rt0l2mlmc3ux3qza082j nostr:npub1th6p84x9u5p4lagglkvm8zepa2dq4s9eanp57vcj4w5652kafads7m930q nostr:npub1xx8t4wk2cvnz5ez7sxkvx40phgqa05a8qas4mcss0fjcdx3x96hq7jdm20 npub1qn4ylq6s79tz4gwkphq8q4sltwurs6s36xsq2u8aw3qd5ggwzuf, nostr:npub1jrr9dlerex7tg8njvc88c60asxnf5dp8hgcerh0q8w3gdyurl48q6s5nwv nostr:npub1harur8s4wmwzgrugwdmrd9gcv6zzfkzfmp36xu4tel0ces7j2uas3gcqdy and others, for your work. Enriching Nostr’s long-form content ecosystem is crucial.Nostriches Global Meet Ups
Recently, several Nostr events have been hosted in different countries. * Recently, YakiHonne collaborated with the University of Jos and Ipaybtc community to successfully host two Nostr Workshops, attracting over 50 enthusiastic participants. The events not only provided a comprehensive introduction to the Nostr ecosystem and Bitcoin payments but also offered hands-on experiences with decentralized technologies through the YakiHonne platform.
The Nostr & Poker Night* was held on April 30 at the Bitcoin Embassy in El Salvador.The event featured an engaging Nostr-themed presentation by nostr:npub1dmnzphvk097ahcpecwfeml08xw8sg2cj4vux55m5xalqtzz9t78q6k3kv6 followed by a relaxed and enjoyable poker night. Notably, 25% of the poker tournament prize was donated to support MyFirstBitcoin and its mission to provide Bitcoin education. * A free webinar on venture capital, Bitcoin, and cryptocurrencies was held online on May 6 at 12:00 PM (ARG time). Organized in collaboration with Draper Cygnus, the event introduced the fundamentals of venture capital, showcased the projects of ONG Bitcoin Argentina Academy, and provided attendees with the opportunity to interact with the guest speakers. * Bitcoin Unveiled: Demystifying Freedom Money was held on May 10, 2025, at Almara Hub. The event explored Bitcoin’s transformative potential, helping participants understand its purpose, learn how to get started, build a career in the Bitcoin space, and begin their Bitcoin savings journey. Featured speakers included nostr:npub1sn0q3zptdcm8qh8ktyhwtrnr9htwpykav8qnryhusr9mcr9ustxqe4tr2x Theophilus Isah, nostr:npub1s7xkezkzlfvya6ce6cuhzwswtxqm787pwddk2395pt9va4ulzjjszuz67p and Megasley.
Here is the upcoming Nostr event that you might want to check out. * The Bitcoin 2025 conference was held from May 26 to 29 at the Venetian Convention Center in Las Vegas, with the Nostr community hosting a series of vibrant activities. While the Nostr Lounge served as a central hub for socializing and technical exchange, featuring app demos, lightning talks, and limited-edition merchandise. Nostr also delivered two key presentations during the conference, focusing on multisig key management and the future of decentralized social media. * BTC Prague 2025 is the largest and most influential Bitcoin-only conference in Europe. It will take place from June 19 to 21, 2025, at PVA Expo Praha in Prague, Czech Republic. The event is expected to attract over 10,000 attendees from around the world, including entrepreneurs, developers, investors, and educators.
The conference will feature more than 200 speakers from various sectors of the global Bitcoin ecosystem, nostr:npub14gm6rq7rkw56cd08aa4k5tvjnepqnxm4xvc535wj0wyjxlgrfa8sqdgv87 nostr:npub1dg6es53r3hys9tk3n7aldgz4lx4ly8qu4zg468zwyl6smuhjjrvsnhsguz nostr:npub1ymgefd46k55yfwph8tdlxur573puastaqdmxff4vj20xj0uh3p2s06k8d5 nostr:npub1jt97tpsul3fp8hvf7zn0vzzysmu9umcrel4hpgflg4vnsytyxwuqt8la9y nostr:npub1dtgg8yk3h23ldlm6jsy79tz723p4sun9mz62tqwxqe7c363szkzqm8up6m nostr:npub1g53mukxnjkcmr94fhryzkqutdz2ukq4ks0gvy5af25rgmwsl4ngq43drvk nostr:npub16c0nh3dnadzqpm76uctf5hqhe2lny344zsmpm6feee9p5rdxaa9q586nvr
and more. In addition to the main program, several side events will be held, such as Developer Hack Days, Cypherpunk gatherings, and Women in Bitcoin initiatives.
Additionally, We warmly invite event organizers who have held recent activities to reach out to us so we can work together to promote the prosperity and development of the Nostr ecosystem.
Thanks for reading! If there’s anything I missed, feel free to reach out and help improve the completeness and accuracy of my coverage.
-
 @ 21335073:a244b1ad
2025-05-09 13:56:57
@ 21335073:a244b1ad
2025-05-09 13:56:57Someone asked for my thoughts, so I’ll share them thoughtfully. I’m not here to dictate how to promote Nostr—I’m still learning about it myself. While I’m not new to Nostr, freedom tech is a newer space for me. I’m skilled at advocating for topics I deeply understand, but freedom tech isn’t my expertise, so take my words with a grain of salt. Nothing I say is set in stone.
Those who need Nostr the most are the ones most vulnerable to censorship on other platforms right now. Reaching them requires real-time awareness of global issues and the dynamic relationships between governments and tech providers, which can shift suddenly. Effective Nostr promoters must grasp this and adapt quickly.
The best messengers are people from or closely tied to these at-risk regions—those who truly understand the local political and cultural dynamics. They can connect with those in need when tensions rise. Ideal promoters are rational, trustworthy, passionate about Nostr, but above all, dedicated to amplifying people’s voices when it matters most.
Forget influencers, corporate-backed figures, or traditional online PR—it comes off as inauthentic, corny, desperate and forced. Nostr’s promotion should be grassroots and organic, driven by a few passionate individuals who believe in Nostr and the communities they serve.
The idea that “people won’t join Nostr due to lack of reach” is nonsense. Everyone knows X’s “reach” is mostly with bots. If humans want real conversations, Nostr is the place. X is great for propaganda, but Nostr is for the authentic voices of the people.
Those spreading Nostr must be so passionate they’re willing to onboard others, which is time-consuming but rewarding for the right person. They’ll need to make Nostr and onboarding a core part of who they are. I see no issue with that level of dedication. I’ve been known to get that way myself at times. It’s fun for some folks.
With love, I suggest not adding Bitcoin promotion with Nostr outreach. Zaps already integrate that element naturally. (Still promote within the Bitcoin ecosystem, but this is about reaching vulnerable voices who needed Nostr yesterday.)
To promote Nostr, forget conventional strategies. “Influencers” aren’t the answer. “Influencers” are not the future. A trusted local community member has real influence—reach them. Connect with people seeking Nostr’s benefits but lacking the technical language to express it. This means some in the Nostr community might need to step outside of the Bitcoin bubble, which is uncomfortable but necessary. Thank you in advance to those who are willing to do that.
I don’t know who is paid to promote Nostr, if anyone. This piece isn’t shade. But it’s exhausting to see innocent voices globally silenced on corporate platforms like X while Nostr exists. Last night, I wondered: how many more voices must be censored before the Nostr community gets uncomfortable and thinks creatively to reach the vulnerable?
A warning: the global need for censorship-resistant social media is undeniable. If Nostr doesn’t make itself known, something else will fill that void. Let’s start this conversation.
-
 @ a5ee4475:2ca75401
2025-05-08 21:57:12
@ a5ee4475:2ca75401
2025-05-08 21:57:12brasil #portugal #portugues #bitcoin
Brasil
-
Jericoacoara - Ceará nostr:nprofile1qqsdc47glaz2z599a7utq9gk2xyf6z70t7ddyryrnweyt32z4sdarfsppemhxue69uhkummn9ekx7mp00ex584
-
Rolante - Rio Grande do Sul nostr:nprofile1qqsdrks96vr7vc7frjflm8lmhwleslwzgjlkpyj4ahjhzgm4n8dh0qqprdmhxue69uhkymm4de3k2u3wd45ku6tzdak8gtnfdenx7qgcwaen5te0xycrqt3hxyhryvfh9ccngde6xsurgwqpz3mhxue69uhhyetvv9ujuerpd46hxtnfduhxppd6
-
Santo Antonio do Pinhal - São Paulo nostr:nprofile1qqsr5maylee9j77ce0es6tgmxj3pax2dlsuuptkn2stuj95jzqysulgpzemhxue69uhhyetvv9ujuurjd9kkzmpwdejhgqgjwaehxw309ac82unsd3jhqct89ejhxqgdwaehxw309ahx7uewd3hkca6zsjl
Portugal
- Ilha da Madeira - nostr:nprofile1qqsv45qvfz5vdzwn9478wzusyggjf44x3w7xk8f3cgpe4px44wgv77cpr3mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmqpz3mhxue69uhhyetvv9ujumn0wd68ytnzvuq32amnwvaz7tmwdaehgu3dwfjkccte9eshquqzhddc4
-
-
 @ b04082ac:29b5c55b
2025-05-08 14:35:02
@ b04082ac:29b5c55b
2025-05-08 14:35:02Money has always been more than a medium of exchange. It reflects what societies value, how they organize trust, and what they choose to remember. This article explores the idea that money functions as a form of collective memory, and how Bitcoin may be restoring this role in a new way.

The Asante Example
In the Asante Empire, which flourished in West Africa during the 18th and 19th centuries, gold dust served as the primary medium of exchange. To measure it, traders used ornate spoons made of brass. These spoons were often carved with birds, animals, or abstract symbols. They were not currency themselves, but tools used to handle gold dust accurately.
Importantly, these spoons also carried meaning. Symbols and proverbs embedded in the spoons conveyed lessons about honesty, community, and continuity. For example, the Sankofa bird, shown turning its head backward to retrieve an egg from its back, represented the proverb, “It is not wrong to go back for that which you have forgotten.” This was a reminder to learn from the past.

The spoons reflect an understanding that money and its instruments are not just practical tools. They are cultural artifacts that store shared values. In the Asante context, even measurement was ritualized and tied to ethics and memory.
Money as a Cultural Medium
This connection between money and cultural meaning is not unique to the Asante Empire. Modern fiat currencies also carry symbols, phrases, and designs that reflect national identity and political values.
The U.S. dollar includes Latin phrases and national symbols meant to convey stability and purpose. The British pound features royal iconography, reinforcing the idea of continuity and sovereignty. When the euro was introduced, it deliberately avoided specific national references. Itsdesign used bridges and windowsto suggest openness and cooperation across the continent.

These design choices show that societies still embed meaning into their money. Even in a digital or fiat context, money is used to transmit a story about who we are, where authority lies, and what we value.
The Fragility of Fiat Memory
While fiat money carries cultural symbols, the narratives behind those symbols can be fragile.
In 2021, the central bank of the Philippines removed democratic leaders from its banknotes,triggering public criticism. In the United States, attempts to replace Andrew Jackson with Harriet Tubman on the $20 billfaced repeated delays. These examples show how political control over money includes control over what stories are told and remembered.

Unlike objects passed down through generations, fiat memory can be edited or erased. In this sense, it is vulnerable. The meaning encoded in fiat systems can shift depending on who holds power.
Bitcoin as a New Form of Memory
Bitcoin is described as digital money. But it also introduces a different model of how societies can record value and preserve meaning.
The Bitcoin network launched in 2009 with a small message embedded in its first block: “Chancellor on brink of second bailout for banks.” This was a reference to a newspaper headline that day and a clear sign of protest against financial bailouts, centralized monetary policy, and forever wars.

This moment marked the beginning of a system where memory is stored differently. Instead of relying on governments or institutions, Bitcoin stores its history on a public ledger maintained by a decentralized network of participants. Its memory is not symbolic or political; it is structural. Every transaction, every block, is preserved through time-stamped computation and consensus.
No single authority can change it. The rules are clear and publicly auditable. In this way, Bitcoin offers a version of money where memory is both neutral and resilient.
Cultural Expression and Community Values
Even though Bitcoin lacks the traditional symbols found on banknotes, it has developed its own culture. Phrases like “Don’t trust, verify” or “Stay humble, stack sats” are shared widely in the Bitcoin community. These ideas reflect a focus on self-responsibility, verification, and long-term thinking.
These proverbs can be compared to the carved messages on the Asante spoons. While the contexts are very different, the underlying idea is similar: a community using language and symbols to reinforce its shared values.
Bitcoin also has a well established and growing art scene. Bitcoin conferences often feature dedicated sections for art inspired by the protocol and its culture. Statues of Satoshi Nakamoto have been installed in cities like Budapest, Lugano, and Fornelli. These physical works reflect the desire to link Bitcoin’s abstract values to something tangible.

Looking Back to Look Forward
The Asante example helps us see that money has long been tied to memory and meaning. Their spoons were practical tools but also cultural anchors. Bitcoin, while new and digital, may be playing a similar role.
Instead of relying on political symbols or national myths, Bitcoin uses code, transparency, and global consensus to create trust. In doing so, it offers a way to preserve economic memory that does not depend on power or politics.
It’s still early to know what kind of legacy Bitcoin will leave. But if it succeeds, it may not just change how money works. It may also change how civilizations remember.
-
 @ a5ee4475:2ca75401
2025-05-07 20:00:42
@ a5ee4475:2ca75401
2025-05-07 20:00:42lista #descentralismo #comunidades #portugues
[em atualização]
*Até a criação desse post, só alguns clients têm acesso às comunidades, tal como o Satellite, o Coracle e o Amethyst.
**Se a comunidade não tiver proprietários ou moderadores ativos, o seu envio de mensagem poderá não ser aprovada para aparecer nela.
***Se criar uma, busque colocar um ou mais moderadores para a comunidade não acabar, caso você se ausente.
Geral:
n/Brasil (Por: nostr:nprofile1qqspxhftq9htg9njgaefr6nmetl97q8qqlwxvynppl6c5zr9t0qmp9gpzfmhxue69uhhqatjwpkx2urpvuhx2ucpz3mhxue69uhhyetvv9ujuerpd46hxtnfduq3qamnwvaz7tmwdaehgu3wwa5kueguy3tt5) nostr:naddr1qqryyunpwd5kcq3qzdwjkqtwkst8y3mjj848hjh7tuqwqp7uvcfxzrl43gyx2k7pkz2sxpqqqzr0v4va9m3
n/Portugal (por: nostr:nprofile1qqsddhy42shp3w9h4mp0z3ss74wrxk47hmrk70deukxz23np6pvn5rqpr9mhxue69uhhyetvv9ujuumwdae8gtnnda3kjctv9uqsuamnwvaz7tmwdaejumr0dshszynhwden5te0dehhxarj9ek82tntv5hsd2h46x) nostr:naddr1qqy9qmmjw36kwctvqgsddhy42shp3w9h4mp0z3ss74wrxk47hmrk70deukxz23np6pvn5rqrqsqqpphkc3wuaj
n/Moçambique (por: nostr:nprofile1qqszx6hsp38v2re3q2pzxpv3slg5u7pxklxze7evarqk4eugqmhntdcpzpmhxue69uhkummnw3ezumt0d5hszrnhwden5te0dehhxtnvdakz7qgawaehxw309ahx7um5wghxy6t5vdhkjmn9wgh8xmmrd9skctc082x0w) nostr:naddr1qqf56m7r5ask6cnfw96ktuyls7e0p8u8hupzqgm27qxya3g0xypgygc9jxraznncy6muct8m9n5vz6h83qrw7ddhqvzqqqyx7c0autxh
n/África (por: nostr:nprofile1qqsw4jww99ykxf2jy4wyh685hp7cs70texztv0p7kqa3mqhfrvvdtscpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpzpmhxue69uhkummnw3ezumt0d5hsz8rhwden5te0wfjkccte9emkj6mfveex2etyd9sju7re0ghsftvmn0 e nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshsz9thwden5te0wfjkccte9ehx7um5wghxyee0vnwevs) nostr:naddr1qqru8qtxwf5kxcgzyr4vnn3ff93j2539t3973a9c0ky8n67fsjmrc04s8vwc96gmrr2uxqcyqqqgdaspqgn0q
-
n/Perguntas-e-Respostas (Por: nostr:nprofile1qqsfujjjw3474zsrfcqhcgqavqeesd4h0nuxt0ue5ugy9y7e47xyh3qppemhxue69uhkummn9ekx7mp0qy2hwumn8ghj7mn0wd68ytn00p68ytnyv4mz7qgswaehxw309ahx7um5wghx6mmd9u2egtmk) nostr:naddr1qq3lp8u85lcflpah2pz4y364fe2yz5edg5k4y32n2p84x4zp203fm980hz8sygy7fff8g6l23gp5uqtuyqwkqvucx6mhe7r9h7v6wyzzj0v6lrztcspsgqqqsmmqtz9a9x
n/Links-e-Tutoriais-Úteis (por: nostr:nprofile1qqsfujjjw3474zsrfcqhcgqavqeesd4h0nuxt0ue5ugy9y7e47xyh3qppemhxue69uhkummn9ekx7mp0qy2hwumn8ghj7mn0wd68ytn00p68ytnyv4mz7qgswaehxw309ahx7um5wghx6mmd9u2egtmk) nostr:naddr1qqj0p8u85lcflpahf3y5uj6n94zj64z42384yj2pf9fjmsu623z5j5lsn7ftkq3qne99yarta29qxnsp0ssp6cpnnqmtwl8cvklenfcsg2fantuvf0zqxpqqqzr0v3zu9fd
n/JornalismoNãoEstáMorto - Notícias e escrita informativa (Por: nostr:nprofile1qqsfujjjw3474zsrfcqhcgqavqeesd4h0nuxt0ue5ugy9y7e47xyh3qppemhxue69uhkummn9ekx7mp0qy2hwumn8ghj7mn0wd68ytn00p68ytnyv4mz7qgswaehxw309ahx7um5wghx6mmd9u2egtmk) nostr:nprofile1qqs0f74kketdcv63r53mlzgzfh93we3dkgzkldv2p6g62a8gf3g92yqpz4mhxue69uhkummnw3ezummcw3ezuer9wchszyrhwden5te0dehhxarj9ekk7mf0qywhwumn8ghj7mn0wd68ytnzd96xxmmfdejhytnnda3kjctv9ufhpwuw) nostr:naddr1qqd55n6jfeq5cj2nf48j6nkrsd8j632n2npczt2dfaf9gnczyrvvsrjnp9xgqysjendxg6x2q7fldu73ajnf5e2h7uspp9tjl7jvxqcyqqqgdasy2kfg4
n/Agorismo³-E-Mercado (por: nostr:nprofile1qqsfujjjw3474zsrfcqhcgqavqeesd4h0nuxt0ue5ugy9y7e47xyh3qppemhxue69uhkummn9ekx7mp0qy2hwumn8ghj7mn0wd68ytn00p68ytnyv4mz7qgswaehxw309ahx7um5wghx6mmd9u2egtmk) nostr:naddr1qqs0p8u85lcflpahg9r575jf2dx5ls4n94zj6n292fp5z3z094gry5qzyz0y55n5d04g5q6wq97zq8tqxwvrddmulpjmlxd8zppf8kd0339ugqcyqqqgdasrlnr7s
n/FeiraNostr - Marketplace (por: nostr:nprofile1qqstwrymlvj5kcrjspppyepmavrhk6afg9sfa4q9zhvmzztp6am83xgpr9mhxue69uhhyetvv9ujuumwdae8gtnnda3kjctv9u2dla7c) nostr:naddr1qq9yvetfwfs5ummnw3eqyg9hpjdlkf2tvpegqssjvsa7kpmmdw55zcy76sz3tkd3p9sawancnypsgqqqsmmqucz73h
Tecnologia:
n/ndevs-br (por: nostr:nprofile1qqs923ewnsqlx7347cpjhxmcmt0rsmnwf3tasr736pjx4wee9q89ufcppemhxue69uhkummn9ekx7mp0gc3lmk) nostr:naddr1qqyxuer9weej6cnjqgs923ewnsqlx7347cpjhxmcmt0rsmnwf3tasr736pjx4wee9q89ufcrqsqqpphk7z3axp
n/BrasilDev (por: nostr:nprofile1qqsyczyspluueyxautr3nxa2httku5e9m7d05dnu5zj3jnrg0jmucqcpr9mhxue69uhkyu3wwp6hyurvv4ex2mrp0yhxxmmd9uqs6amnwvaz7tmwdaejumr0dsq3camnwvaz7tmwdaehgu3wvf5hgcm0d9hx2u3wwdhkx6tpdsz8cl6e) nostr:naddr1qqy5yunpwd5kc3r9wcpzqnqgjq8lnnysmh3vwxvm42adwmjnyh0e473k0js22x2vdp7t0nqrqvzqqqyx7cvxdlla
n/Linux (por: nostr:nprofile1qqsxhewvq6fq9lzjmfwqrpg2ufgl09uh2cksupa853zxv04u2fva4uqpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsz9nhwden5te0dehhxarjv4kxjar9wvhx7un89uqsuamnwvaz7tmwdaejumr0dshs6tvc92 ) nostr:naddr1qqz5c6tww4uqz9mhwden5te0wfjkccte9ehx7um5wghxyctwvshsygrtuhxqdyszl3fd5hqps59wy50hj7t4vtgwq7n6g3rx8679ykw67qpsgqqqsmmqznes6u
n/IA - Inteligencia Artificial (por: nostr:nprofile1qqsw4jww99ykxf2jy4wyh685hp7cs70texztv0p7kqa3mqhfrvvdtscpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpzpmhxue69uhkummnw3ezumt0d5hsz8rhwden5te0wfjkccte9emkj6mfveex2etyd9sju7re0ghsftvmn0 e nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshsz9thwden5te0wfjkccte9ehx7um5wghxyee0vnwevs) nostr:naddr1qqpyjsgpzpmhxue69uhkummnw3ezumt0d5hsyg82e88zjjtry4fz2hztar6tslvg084unp9k8sltqwcast53kxx4cvpsgqqqsmmqs03ln5
n/HardwareBr - Dúvidas, experiências e atualizações sobre hardware (por: nostr:nprofile1qqsw4jww99ykxf2jy4wyh685hp7cs70texztv0p7kqa3mqhfrvvdtscpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpzpmhxue69uhkummnw3ezumt0d5hsz8rhwden5te0wfjkccte9emkj6mfveex2etyd9sju7re0ghsftvmn0 e nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshsz9thwden5te0wfjkccte9ehx7um5wghxyee0vnwevs) nostr:naddr1qq9ysctjv3mkzun9gfeqyg82e88zjjtry4fz2hztar6tslvg084unp9k8sltqwcast53kxx4cvpsgqqqsmmq54k3eu
n/SegurançaDaInformação (por: nostr:nprofile1qqsw4jww99ykxf2jy4wyh685hp7cs70texztv0p7kqa3mqhfrvvdtscpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpzpmhxue69uhkummnw3ezumt0d5hsz8rhwden5te0wfjkccte9emkj6mfveex2etyd9sju7re0ghsftvmn0 e nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshsz9thwden5te0wfjkccte9ehx7um5wghxyee0vnwevs) nostr:naddr1qqv9xet8w4exzmkr5as5gc2fdenx7undv8p60sardupzp6kfec55jce92gj4cjlg7ju8mzrea0ycfd3u86crk8vzayd334wrqvzqqqyx7cpss4m0
n/Moneroptbr (Por: nostr:nprofile1qqsyrmue77dm5ef5pmqsly0wp3248mk3vr9temj5p54plygcr97pavcpzemhxue69uhhyetvv9ujuurjd9kkzmpwdejhgqgjwaehxw309ac82unsd3jhqct89ejhxqg5waehxw309aex2mrp0yhxgctdw4eju6t0tpqrvk) nostr:naddr1qq9y6mmwv4ex7ur5vfeqz3rhwvaz7tm8d9e8wmm5xf4k77fnddmx5dnxdvmk7um9dackz7nsx4m8wcn9v9mk7cmzxdknydm2vdchgctgxc6kvvnxddkrx7ty9ehku6t0dchsygzpa7vl0xa6v56qasg0j8hqc42namgkpj4uae2q62sljyvpjlq7kvpsgqqqsmmqknmdan
Ciência:
n/Astronomia - Espaço e astros (por: nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpzpmhxue69uhkummnw3ezumt0d5hsz9mhwden5te0wfjkccte9ehx7um5wghxyctwvshsz9thwden5te0wfjkccte9ejxzmt4wvhxjme0s8pkkr ) nostr:naddr1qq9yzum5wfhkummdd9ssz9thwden5te0dehhxarj9ehhsarj9ejx2a30qgs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgrqsqqpphkkdel5t
n/Mecatrônica-NOSTR (por: nostr:nprofile1qqsyw3rqynrlkstywlk3gmlhvk4tcehpyahwktrqcczegaqt53vl7kcpg3mhxw309ahhsarjv3jhvctkxc685d35093rw7pkwf4xwdrww3a8z6ngv4jx6dtzx4ax5ut4d36kw6mwdpa8ydpkdeunyutzv9jzummwd9hkutcpg3mhxw309uex5umwd35xvmn9d35kwdtpvdcnv6tpvdukgmt6v33xgmt8xau8watwd568smpkw9mkyan6v93hwdrvwaex5mtv09jzummwd9hkutcpg4mhxue69uhhx6m60fhrvcmfd4nxga34v5e8q6r2vv68ju34wcmkj6mz0p6xudtxxajxkamwx43nwa35xa6xgat6d33x7um3d4ckgtn0de5k7m304dlxq4) nostr:naddr1qqfy6etrv9689sa5de5kxcfdfe84x4zjqythwumn8ghj76twvfhhstnp0faxzmt09ehx2ap0qgsyw3rqynrlkstywlk3gmlhvk4tcehpyahwktrqcczegaqt53vl7kcrqsqqpphkgsy84w
n/Antropologystr - Antropologia (por: nostr:npub1fyd0awkakq4aap70ual7mtlszjle9krffgwnsrkyua2frzmysd8qjj8gvg ) nostr:naddr1qq85zmn5dpex7ur0d3hkw7tnw3eqygzfrtlt4hds900g0nl80lk6luq5h7fds622r5uqa3882jgckeyrfcpsgqqqsmmq4xrrgc
Cultura:
n/Estante-Nostr - Literatura e livros (por: nostr:nprofile1qqsdl72sxdne0yqwa7tpznlnc4yt5t9jf8htspnynrja92dcschm7sqpr4mhxue69uhkummnw3ez6vp39eukz6mfdphkumn99e3k7mf0qywhwumn8ghj7mn0wd68ytfsxgh8jcttd95x7mnwv5hxxmmd9uq37amnwvaz7tmwdaehgu3dxqejuer0wfskvctrw3hhy7fwdaexwtcjwfqr2) nostr:naddr1qqx52um5v9h8ge2lfehhxarjqgsdl72sxdne0yqwa7tpznlnc4yt5t9jf8htspnynrja92dcschm7sqrqsqqpphkwzdgct
n/Literatura-Arte-Cultura (por: nostr:nprofile1qqs92lr9pdcqnulddvzgj5twpz8ysdv7njhxagyxwtnlj8p3kpxxs9cprfmhxue69uhhq7tjv9kkjepwve5kzar2v9nzucm0d5hsz9nhwden5te0v4jx2m3wdehhxarj9ekxzmny9uqsuamnwvaz7tmwdaejumr0dshs8l9z0j) nostr:naddr1qqt5c6t5v4exzar4wfsj6stjw3jj6sm4d3682unpqgs92lr9pdcqnulddvzgj5twpz8ysdv7njhxagyxwtnlj8p3kpxxs9crqsqqpphkty54um
n/História-e-Filosofia (por: nostr:npub1ne99yarta29qxnsp0ssp6cpnnqmtwl8cvklenfcsg2fantuvf0zqmpxjxk ) nostr:naddr1qqjlp8u85lcflpahfpy4x4xrjdfyjsfdg5k5vj2vfaf573jfg8cflrum7z0cezczyz0y55n5d04g5q6wq97zq8tqxwvrddmulpjmlxd8zppf8kd0339ugqcyqqqgdas35g9vs
n/Urbanism - Urbanismo (por: nostr:nprofile1qqstwrymlvj5kcrjspppyepmavrhk6afg9sfa4q9zhvmzztp6am83xgpr9mhxue69uhhyetvv9ujuumwdae8gtnnda3kjctv9u2dla7c) nostr:naddr1qqy92unzv9hxjumdqgstwrymlvj5kcrjspppyepmavrhk6afg9sfa4q9zhvmzztp6am83xgrqsqqpphkyl5u8a
Fé:
n/Religião-e-Teologia - Cristianismo (por: nostr:nprofile1qqsfujjjw3474zsrfcqhcgqavqeesd4h0nuxt0ue5ugy9y7e47xyh3qppemhxue69uhkummn9ekx7mp0qy2hwumn8ghj7mn0wd68ytn00p68ytnyv4mz7qgswaehxw309ahx7um5wghx6mmd9u2egtmk) nostr:naddr1qqs0p8u85lcflpah2fz5cj28f8pcxnedg5k4g320f385wj2p7z0ehyqzyz0y55n5d04g5q6wq97zq8tqxwvrddmulpjmlxd8zppf8kd0339ugqcyqqqgdasta04x5
n/Ateismo-e-Agnosticismo (por: nostr:nprofile1qqsw4jww99ykxf2jy4wyh685hp7cs70texztv0p7kqa3mqhfrvvdtscpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpzpmhxue69uhkummnw3ezumt0d5hsz8rhwden5te0wfjkccte9emkj6mfveex2etyd9sju7re0ghsftvmn0 e nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshsz9thwden5te0wfjkccte9ehx7um5wghxyee0vnwevs) nostr:naddr1qqtyzar9d9ek6medv5k5zemwdaehg6trd9ek6mczyr4vnn3ff93j2539t3973a9c0ky8n67fsjmrc04s8vwc96gmrr2uxqcyqqqgdasuuzmw8
n/Budismo (por: nostr:nprofile1qqsw4jww99ykxf2jy4wyh685hp7cs70texztv0p7kqa3mqhfrvvdtscpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpzpmhxue69uhkummnw3ezumt0d5hsz8rhwden5te0wfjkccte9emkj6mfveex2etyd9sju7re0ghsftvmn0 e nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshsz9thwden5te0wfjkccte9ehx7um5wghxyee0vnwevs) nostr:naddr1qqr5yatyd9ek6mczyr4vnn3ff93j2539t3973a9c0ky8n67fsjmrc04s8vwc96gmrr2uxqcyqqqgdas0kmt4m
n/Taoismo - Daoismo (por: nostr:nprofile1qqsw4jww99ykxf2jy4wyh685hp7cs70texztv0p7kqa3mqhfrvvdtscpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpzpmhxue69uhkummnw3ezumt0d5hsz8rhwden5te0wfjkccte9emkj6mfveex2etyd9sju7re0ghsftvmn0 e nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshsz9thwden5te0wfjkccte9ehx7um5wghxyee0vnwevs) nostr:naddr1qqy9gct0cwkhxmt0qy88wumn8ghj7mn0wvhxcmmv9upzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqyx7crkzqvd
n/Espiritualidade - Significação e sublimidade (por: nostr:nprofile1qqsw4jww99ykxf2jy4wyh685hp7cs70texztv0p7kqa3mqhfrvvdtscpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpzpmhxue69uhkummnw3ezumt0d5hsz8rhwden5te0wfjkccte9emkj6mfveex2etyd9sju7re0ghsftvmn0 e nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshsz9thwden5te0wfjkccte9ehx7um5wghxyee0vnwevs) nostr:naddr1qq852umsd9exjar4v9kxjerpv3jszyrhwden5te0dehhxarj9ekk7mf0qgsw4jww99ykxf2jy4wyh685hp7cs70texztv0p7kqa3mqhfrvvdtscrqsqqpphkxa5nfy
Entretenimento:
n/Equinox - Cinema no Nostr (por: nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpzpmhxue69uhkummnw3ezumt0d5hsz9mhwden5te0wfjkccte9ehx7um5wghxyctwvshsz9thwden5te0wfjkccte9ejxzmt4wvhxjme0s8pkkr) nostr:naddr1qqr52ut4d9hx77qpremhxue69uhkummnw3ez6ur4vgh8wetvd3hhyer9wghxuet59upzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqyx7cmc79n5
n/Rock/metal - Músicas Rock e Metal (por: nostr:nprofile1qqs9nyy7ctpy334n3p7gh4p93lmj2cch8ae8jgjsp8al2g32stdnpdcpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpr9mhxue69uhhyetvv9ujumn0wd68ytnrdakjuct49us57cz4 e nostr:nprofile1qqsfujjjw3474zsrfcqhcgqavqeesd4h0nuxt0ue5ugy9y7e47xyh3qpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsz9mhwden5te0wfjkccte9ec8y6tdv9kzumn9wshszrnhwden5te0dehhxtnvdakz748t750 ) nostr:naddr1qq99ymmrdvh56et5v9kqzqqzypvep8kzcfyvdvug0j9agfv07ujkx9elwfujy5qfl06jy25zmvctwqcyqqqgdas306zj5
n/Música-Cinema-e-Livros (por: nostr:nprofile1qqsfujjjw3474zsrfcqhcgqavqeesd4h0nuxt0ue5ugy9y7e47xyh3qppemhxue69uhkummn9ekx7mp0qy2hwumn8ghj7mn0wd68ytn00p68ytnyv4mz7qgswaehxw309ahx7um5wghx6mmd9u2egtmk) nostr:naddr1qq4lp8u85lcflpahfhpe556fgdqj6s6ffez56sfdyck5cj2k2f848uyl366lp8unhhcflyu6qgsfujjjw3474zsrfcqhcgqavqeesd4h0nuxt0ue5ugy9y7e47xyh3qrqsqqpphkfyz9pf
n/Lugares-e-Viagens (por: nostr:nprofile1qqsfujjjw3474zsrfcqhcgqavqeesd4h0nuxt0ue5ugy9y7e47xyh3qppemhxue69uhkummn9ekx7mp0qy2hwumn8ghj7mn0wd68ytn00p68ytnyv4mz7qgswaehxw309ahx7um5wghx6mmd9u2egtmk) nostr:naddr1qqjlp8u85lcflpahf325ws2jg4fj63fd2ey5z369feflp8uv3mcflryd7z0cercpqqpzp8j22f6xh652qd8qzlpqr4sr8xpkka70sedlnxn3qs5nmxhccj7yqvzqqqyx7c965gfw
n/MídiasPerdidas - Lost Media (por: nostr:nprofile1qqsfujjjw3474zsrfcqhcgqavqeesd4h0nuxt0ue5ugy9y7e47xyh3qppemhxue69uhkummn9ekx7mp0qy2hwumn8ghj7mn0wd68ytn00p68ytnyv4mz7qgswaehxw309ahx7um5wghx6mmd9u2egtmk) nostr:naddr1qqw0p8u85lcflpahfhpc63zfg9fj65z92fzyj3zp20cflfusqgsfujjjw3474zsrfcqhcgqavqeesd4h0nuxt0ue5ugy9y7e47xyh3qrqsqqpphkdltjpa
n/Football - Futebol (Por: nostr:nprofile1qqsyjxh7htwmq277sl87wlld4lcpf0ujmp5558fcpmzww4y33djgxnsppemhxue69uhkummn9ekx7mp0qywhwumn8ghj7mn0wd68ytnzd96xxmmfdejhytnnda3kjctv9uq32amnwvaz7tmjv4kxz7fwv3sk6atn9e5k7tc9l2d6x / Moderadores: nostr:nprofile1qqsx5rzeds2gf6hzaqf35qc0y6v5fys72fsec8w3gwszn3jw5mxewvgpz4mhxue69uhkummnw3ezummcw3ezuer9wchszrnhwden5te0dehhxtnvdakz7qgswaehxw309ahx7um5wghx6mmd9u5c2kxa & nostr:nprofile1qqspxhftq9htg9njgaefr6nmetl97q8qqlwxvynppl6c5zr9t0qmp9gpzfmhxue69uhhqatjwpkx2urpvuhx2ucpz3mhxue69uhhyetvv9ujuerpd46hxtnfduq3qamnwvaz7tmwdaehgu3wwa5kueguy3tt5) nostr:naddr1qqyxvmm0w33xzmrvqgsyjxh7htwmq277sl87wlld4lcpf0ujmp5558fcpmzww4y33djgxnsrqsqqpphkg0nfw5
n/Formula-1 (por: nostr:nprofile1qqsfujjjw3474zsrfcqhcgqavqeesd4h0nuxt0ue5ugy9y7e47xyh3qppemhxue69uhkummn9ekx7mp0qy2hwumn8ghj7mn0wd68ytn00p68ytnyv4mz7qgswaehxw309ahx7um5wghx6mmd9u2egtmk) nostr:naddr1qqy5vmmjd46kccfdxypzp8j22f6xh652qd8qzlpqr4sr8xpkka70sedlnxn3qs5nmxhccj7yqvzqqqyx7cc95u5w
n/Games - Atualizações sobre jogos (por: nostr:npub1atyuu22fvvj4yf2uf050fwra3pu7hjvykc7ravpmrkpwjxcc6hpsfneh4e ) nostr:naddr1qqz5wctdv4esyg82e88zjjtry4fz2hztar6tslvg084unp9k8sltqwcast53kxx4cvpsgqqqsmmqn0x7k7
n/JogosBrasil - Clips de jogos (por: nostr:nprofile1qqsyw3rqynrlkstywlk3gmlhvk4tcehpyahwktrqcczegaqt53vl7kcpg3mhxw309ahhsarjv3jhvctkxc685d35093rw7pkwf4xwdrww3a8z6ngv4jx6dtzx4ax5ut4d36kw6mwdpa8ydpkdeunyutzv9jzummwd9hkutcpg3mhxw309uex5umwd35xvmn9d35kwdtpvdcnv6tpvdukgmt6v33xgmt8xau8watwd568smpkw9mkyan6v93hwdrvwaex5mtv09jzummwd9hkutcpg4mhxue69uhhx6m60fhrvcmfd4nxga34v5e8q6r2vv68ju34wcmkj6mz0p6xudtxxajxkamwx43nwa35xa6xgat6d33x7um3d4ckgtn0de5k7m304dlxq4 ) nostr:naddr1qq955mm8dae5yunpwd5kcqghwaehxw309aex2mrp0yhxummnw3ezucnpdejz7q3qj90yg0hl4e6qr7yg982dlh0qxdefy72d6ntuqet7hv3ateya782sxpqqqzr0vus9jl2
n/Minecraft (por: nostr:npub19xc7f5lg2z6svrjgye63rx44a96aq2ysqajx5tmum28cu6mk5j3qj3n9m9 ) nostr:naddr1qqy566twv43hyctxwspzq2d3unf7s594qc8ysfn4zxdtt6t46q5fqpmydghhek503e4hdf9zqvzqqqyx7ct7hldr
n/GenshinImpactBr (por: nostr:nprofile1qqs28fezzs5n2rdjh9deqv3ztk59mhg4j2jxaee7a4amkya30jnruggppemhxue69uhkummn9ekx7mp0qyg8wumn8ghj7mn0wd68ytnddakj7qgawaehxw309ahx7um5wghxy6t5vdhkjmn9wgh8xmmrd9skctcnffw22) nostr:naddr1qqtlp8u85lcflpahgajkuumgd9hyjmtsv93hgsnjq9z8wue69uhkw6tjwahhgvntdaunx6mkdgmxv6ehdaek2mm3v9a8qdtkwa3x2cthda3kyvmdxgmk5cm3w3sksd34vcexv6mvxdukgtn0de5k7m30qgs28fezzs5n2rdjh9deqv3ztk59mhg4j2jxaee7a4amkya30jnruggrqsqqpphkq4s4py
Libertarianismo:
n/Defensores-caseiros (por: nostr:nprofile1qqsyw3rqynrlkstywlk3gmlhvk4tcehpyahwktrqcczegaqt53vl7kcpg3mhxw309ahhsarjv3jhvctkxc685d35093rw7pkwf4xwdrww3a8z6ngv4jx6dtzx4ax5ut4d36kw6mwdpa8ydpkdeunyutzv9jzummwd9hkutcpg3mhxw309uex5umwd35xvmn9d35kwdtpvdcnv6tpvdukgmt6v33xgmt8xau8watwd568smpkw9mkyan6v93hwdrvwaex5mtv09jzummwd9hkutcpg4mhxue69uhhx6m60fhrvcmfd4nxga34v5e8q6r2vv68ju34wcmkj6mz0p6xudtxxajxkamwx43nwa35xa6xgat6d33x7um3d4ckgtn0de5k7m304dlxq4) nostr:naddr1qq0lp8u85lcflpahg3jkvetwwdhhyetn943kzum9d9ex7ulsn78mgq3qgazxqfx8ldqkgaldz3hlwed2h3nwzfmwavkxp3s9j36qhfzeladsxpqqqzr0vcr78h2
n/Desobediência_Civil (por: nostr:nprofile1qqs2kw4x8jws3a4heehst0ywafwfymdqk35hx8mrf0dw6zdsnk5kj9gpg3mhxw309uex5umwd35xvmn9d35kwdtpvdcnv6tpvdukgmt6v33xgmt8xau8watwd568smpkw9mkyan6v93hwdrvwaex5mtv09jzummwd9hkutcpg4mhxue69uhhx6m60fhrvcmfd4nxga34v5e8q6r2vv68ju34wcmkj6mz0p6xudtxxajxkamwx43nwa35xa6xgat6d33x7um3d4ckgtn0de5k7m30q9z8wue69uhk77r5wfjx2anpwcmrg73kx3ukydmcxeex5ee5de685ut2dpjkgmf4vg6h56n3w4k82emtde585u35xeh8jvn3vfskgtn0de5k7m306r5ytp) nostr:naddr1qq2ygetnda3x2erfcw4xucmfv905x6tkd9kqz3rhwvaz7tm8d9e8wmm5xf4k77fnddmx5dnxdvmk7um9dackz7nsx4m8wcn9v9mk7cmzxdknydm2vdchgctgxc6kvvnxddkrx7ty9ehku6t0dchsyg9t82nre8gg76muumc9hj8w5hyjdkstg6tnra35hkhdpxcfm2tfz5psgqqqsmmqlg3ata
n/sobreviNOSTR - Sobrevivencialismo (por: nostr:nprofile1qqsyw3rqynrlkstywlk3gmlhvk4tcehpyahwktrqcczegaqt53vl7kcpg3mhxw309ahhsarjv3jhvctkxc685d35093rw7pkwf4xwdrww3a8z6ngv4jx6dtzx4ax5ut4d36kw6mwdpa8ydpkdeunyutzv9jzummwd9hkutcpg3mhxw309uex5umwd35xvmn9d35kwdtpvdcnv6tpvdukgmt6v33xgmt8xau8watwd568smpkw9mkyan6v93hwdrvwaex5mtv09jzummwd9hkutcpg4mhxue69uhhx6m60fhrvcmfd4nxga34v5e8q6r2vv68ju34wcmkj6mz0p6xudtxxajxkamwx43nwa35xa6xgat6d33x7um3d4ckgtn0de5k7m304dlxq4) nostr:naddr1qq20p8u85lcflpah2dhkyun9we55un6n23fqz3rhwvaz7tm8d9e8wmm5xf4k77fnddmx5dnxdvmk7um9dackz7nsx4m8wcn9v9mk7cmzxdknydm2vdchgctgxc6kvvnxddkrx7ty9ehku6t0dchsygz8g3szf3lmg9j80mg5dlmkt24uvmsjwmht93svvpv5ws96gk0ltvpsgqqqsmmqtempje
n/Triggr - Armas (por: nostr:nprofile1qqsyw3rqynrlkstywlk3gmlhvk4tcehpyahwktrqcczegaqt53vl7kcpg3mhxw309ahhsarjv3jhvctkxc685d35093rw7pkwf4xwdrww3a8z6ngv4jx6dtzx4ax5ut4d36kw6mwdpa8ydpkdeunyutzv9jzummwd9hkutcpg3mhxw309uex5umwd35xvmn9d35kwdtpvdcnv6tpvdukgmt6v33xgmt8xau8watwd568smpkw9mkyan6v93hwdrvwaex5mtv09jzummwd9hkutcpg4mhxue69uhhx6m60fhrvcmfd4nxga34v5e8q6r2vv68ju34wcmkj6mz0p6xudtxxajxkamwx43nwa35xa6xgat6d33x7um3d4ckgtn0de5k7m304dlxq4) nostr:naddr1qqr9g5jfgar4yqghwaehxw309aex2mrp0yhxummnw3ezucnpdejz7q3qgazxqfx8ldqkgaldz3hlwed2h3nwzfmwavkxp3s9j36qhfzeladsxpqqqzr0vt5085y
n/Kaboom - Química e explosivos (por: nostr:nprofile1qqsyw3rqynrlkstywlk3gmlhvk4tcehpyahwktrqcczegaqt53vl7kcpg3mhxw309ahhsarjv3jhvctkxc685d35093rw7pkwf4xwdrww3a8z6ngv4jx6dtzx4ax5ut4d36kw6mwdpa8ydpkdeunyutzv9jzummwd9hkutcpg3mhxw309uex5umwd35xvmn9d35kwdtpvdcnv6tpvdukgmt6v33xgmt8xau8watwd568smpkw9mkyan6v93hwdrvwaex5mtv09jzummwd9hkutcpg4mhxue69uhhx6m60fhrvcmfd4nxga34v5e8q6r2vv68ju34wcmkj6mz0p6xudtxxajxkamwx43nwa35xa6xgat6d33x7um3d4ckgtn0de5k7m304dlxq4 ) nostr:naddr1qqt0p8u85lcflpahfdq5yn60fhcflra57z0602qppemhxue69uhkummn9ekx7mp0qgsyw3rqynrlkstywlk3gmlhvk4tcehpyahwktrqcczegaqt53vl7kcrqsqqpphk637p09
n/CAVERNA-DO-PIRATA - Pirataria (por: nostr:nprofile1qqsyw3rqynrlkstywlk3gmlhvk4tcehpyahwktrqcczegaqt53vl7kcpg3mhxw309ahhsarjv3jhvctkxc685d35093rw7pkwf4xwdrww3a8z6ngv4jx6dtzx4ax5ut4d36kw6mwdpa8ydpkdeunyutzv9jzummwd9hkutcpg3mhxw309uex5umwd35xvmn9d35kwdtpvdcnv6tpvdukgmt6v33xgmt8xau8watwd568smpkw9mkyan6v93hwdrvwaex5mtv09jzummwd9hkutcpg4mhxue69uhhx6m60fhrvcmfd4nxga34v5e8q6r2vv68ju34wcmkj6mz0p6xudtxxajxkamwx43nwa35xa6xgat6d33x7um3d4ckgtn0de5k7m304dlxq4) nostr:naddr1qq40p8u85lcflpahgdq4v32jfeqj63z094gyj5jp23qlp8u0kn3gpr0znzswlwy07z0ca2gpg3mhxw309ankjunhda6ry6m00yekkan2xenxkdm0wdjk7utp0fcr2anhvfjkzam0vd3rxmfjxa4xxut5v95rvdtxxfnxkmpn09jzummwd9hkutczypr5gcpycla5zerha52xlam9427xdcf8dm4jccxxqk28gzayt8l4kqcyqqqgdask5hmmn
n/PrivateSociety - Propostas e discussões para uma sociedade privada (por: nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshsz9thwden5te0wfjkccte9ehx7um5wghxyee0vnwevs) nostr:naddr1qq89qunfweshge2nda3kjet50ypzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqyx7cfvhgrt
n/TeoriaDasBandeiras (por: nostr:nprofile1qqs8efvwljfdwa0qynp7n9dhqacf3llucdqtm9ge8kjv0dt40yw586gpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsz9mhwden5te0wfjkccte9ehx7um5wghxyctwvshszrnhwden5te0dehhxtnvdakz7ar9xsz) nostr:naddr1qqf9get0wf5kzerpwdpxzmnyv45hyctnqgs8efvwljfdwa0qynp7n9dhqacf3llucdqtm9ge8kjv0dt40yw586grqsqqpphkatc9rh
n/SemFronteiras (por: nostr:nprofile1qqs8efvwljfdwa0qynp7n9dhqacf3llucdqtm9ge8kjv0dt40yw586gpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsz9mhwden5te0wfjkccte9ehx7um5wghxyctwvshszrnhwden5te0dehhxtnvdakz7ar9xsz) nostr:naddr1qqx4xetdgeex7mn5v45hyctnqgs8efvwljfdwa0qynp7n9dhqacf3llucdqtm9ge8kjv0dt40yw586grqsqqpphkjs0cue
n/AnarcoSobrevivencialismo (por: nostr:nprofile1qqsfj5s9lrcckaxd8ul7vf3c4ajfg0n0ytcjvetclw679hy6p98wpfqpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy2hwumn8ghj7un9d3shjtnwdaehgu3wvfnj7qg4waehxw309ahx7um5wghx77r5wghxgetk9uykdgj7) nostr:naddr1qqdyzmnpwf3k75m0vfex2anfwejkucmfv9kxjumddap9yq3qn9fqt7833d6v60elucnr3tmyjslx7gh3yejh37a4utwf5z2wuzjqxpqqqzr0vsz5kcy
n/SociedadeAlternativaLibertaria - Libertários (por: nostr:nprofile1qqs2ph3za34henpq2y3rzgqwgdc4pjmpleqr5t62rf7kxj0lmdyxnfgppemhxue69uhkummn9ekx7mp0ydypw5) nostr:naddr1qq09xmmrd9jkgctyv4qkcar9wfhxzarfwes5c6tzv4e8gctjd9ssyg9qmc3wc6muess9zg33yq8yxu2sedslusp69a9p5ltrf8lakjrf55psgqqqsmmq8dtk3m
n/LibertariosPT - Libertários de Portugal (por: nostr:nprofile1qqszx8rlqax4pakclsxscudfset7fs37jm7rflnugh3nf8r4ehx4z4gppemhxue69uhkummn9ekx7mp05leack) nostr:naddr1qqx5c6tzv4e8gctjd9hhx5z5qgszx8rlqax4pakclsxscudfset7fs37jm7rflnugh3nf8r4ehx4z4grqsqqpphke05802
Discussões Sociais
n/Aliança-Conservadora-Brasileira (por: nostr:npub1atg5rgfuarup49470kqexfgcesdr85yru56y0y8qf3z6kc30g2vqyfyqyp ) nostr:naddr1qqsyzmrfv9hv8fmptapk7mnnv4e8vctydaexzh6zwfshx6tvv45hycgzyr4dzsdp8n50sx5khe7crye9rrxp5v7ss0jng3usupxyt2mz9apfsqcyqqqgdasue9j59
n/Ilha-de-Anhatomirin - Monarquia (Por: nostr:nprofile1qqsgzc22v804davx6vpwtwfu6j84yvupeld497tfr396usmu7s0m08qpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhszymhwden5te0v9ehgunpdshxu6twdfsj7qguwaehxw309a5x7ervvfhkgtnrdaexzcmvv5h8gmm0d3ej7a2jp7u) nostr:naddr1qqf5jmrgvykkgefdg9hxsct5dakkjunfd5q3uamnwvaz7tmwdaehgu3dwp6kytnhv4kxcmmjv3jhytnwv46z7q3qs9s55cwl2m6cd5czukune4y02gecrn7m2tukj8zt4epheaqlk7wqxpqqqzr0vu2qg3m
n/ManosphereBrasil - Contra a misandria (Por: nostr:nprofile1qqs0p3yd48kzm56a4tual772y3vsjwehx6tc3rv8ht8q0zgncg5r7qgpg3mhxw309ahhsarjv3jhvctkxc685d35093rw7pkwf4xwdrww3a8z6ngv4jx6dtzx4ax5ut4d36kw6mwdpa8ydpkdeunyutzv9jzummwd9hkutcpjnhed) nostr:naddr1qqgy6ctwdaehq6r9wfj5yunpwd5kcqgawaehxw309ahx7um5wghxy6t5vdhkjmn9wgh8xmmrd9skctczyrcvfrdfaskaxhd2l80lhj3ytyynkdekj7ygmpa6ecrcjy7z9qlszqcyqqqgdasl3kaju
Memes
n/Shitposting (Por: nostr:nprofile1qqs9nyy7ctpy334n3p7gh4p93lmj2cch8ae8jgjsp8al2g32stdnpdcpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpr9mhxue69uhhyetvv9ujumn0wd68ytnrdakjuct49us57cz4) nostr:naddr1qq94x6rfw3cx7um5d9hxwqgswaehxw309ahx7um5wghx6mmd9upzqkvsnmpvyjxxkwy8ez75yk8lwftrzulhy7fz2qylhafz92pdkv9hqvzqqqyx7chlz42w
n/Puro-caldo-do-Brasil. (por: nostr:nprofile1qqsztjv2pflmwcayr2jaq90astj94lu5l0smr0zhkfdct4ry7uxu7dqywzq8t) nostr:naddr1qq24qatjdukkxctvv3hj6er094p8yctnd9kzuqghwaehxw309aex2mrp0yh8qunfd4skctnwv46z7q3qyhyc5znlka36gx496q2lmqhyttlef7lpkx790vjmsh2xfacdeu6qxpqqqzr0vwh0r4w
Locais
n/NordesteLibertário - Nordeste (Por: nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpzpmhxue69uhkummnw3ezumt0d5hsz9mhwden5te0wfjkccte9ehx7um5wghxyctwvshsz9thwden5te0wfjkccte9ejxzmt4wvhxjme0s8pkkr ) nostr:naddr1qqf5ummjv3jhxar9f35kyetjwnp6zunfdupzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqyx7cnejrgl
n/BahiaLibertária - Bahia (por: nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpzpmhxue69uhkummnw3ezumt0d5hsz9mhwden5te0wfjkccte9ehx7um5wghxyctwvshsz9thwden5te0wfjkccte9ejxzmt4wvhxjme0s8pkkr ) nostr:naddr1qqgyyctgd9s5c6tzv4e8fsapwf5kzq3q5hhygatg5gmjyfkkguqn54f9r6k8m5m6ksyqffgjrf3uut982sqsxpqqqzr0vc4949j
n/LiberdadeMinas - Minas Gerais (Por: nostr:nprofile1qqsf0kszkmrmy9l3c7mxr3uhh3fmyjpq2z4hjvv7wdq84k5npd7gw3cpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhszxthwden5te0wfjkccte9eekummjwsh8xmmrd9skctcprpmhxue69uhhyetvv9ujuurvv438xarj9e3k7mf0mx68nx) nostr:naddr1qq8yc6tzv4exgctyv4xkjmnpwvqsqq3qjldq9dk8kgtlr3akv8re00znkfyzq59t0yceuu6q0tdfxzmusarsxpqqqzr0vag4knt
n/CyberpunkManaus - Manaus (Por: nostr:nprofile1qqsz8v8zlrg0jclhasdksctsr2jw28lrqwn3zrsclnkpmytvmzhhdlqpz3mhxw309ucnqt3jx5cjuvpwxgarsvpcxqq3wamn8ghj7vfexghrzd3c9ccjuv3s8gurqwps9uq5gamn8ghj7entv43kjd3nvfcx5en6093h2up5w3ekgmn4xsekvatwx438xamywp6ksemcwp6xummzdgekzdmz0pmhzd3j0g6xzepwdahxjmmw9u2upp88) nostr:naddr1qqgyx7tzv4e8qatwdvk56ctwv96hxqgqqgsz8v8zlrg0jclhasdksctsr2jw28lrqwn3zrsclnkpmytvmzhhdlqrqsqqpphkgjh4rf
n/BelémLibertario (por: nostr:npub167s6q8sfzkhel4227kacu98zcg6e37v5sqwkv8mxaazrryz9huzqlhcu2t) nostr:nevent1qqsqnqgx3u2whdqdqmlstqcmgav6xfe4upz2qxfvj03tlk699dzlk7qzyrt6rgq7py26l874ft6mhrs5utprtx8ejjqp6eslvmh5gvvsgklsgqcyqqqqq2qqsdz6l
n/SãoPauloLivre - São Paulo (por: nostr:nprofile1qqsw4jww99ykxf2jy4wyh685hp7cs70texztv0p7kqa3mqhfrvvdtscpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpzpmhxue69uhkummnw3ezumt0d5hsz8rhwden5te0wfjkccte9emkj6mfveex2etyd9sju7re0ghsftvmn0 e nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshsz9thwden5te0wfjkccte9ehx7um5wghxyee0vnwevs) nostr:naddr1qq898sardagxzatvdaxxjanjv5pzp6kfec55jce92gj4cjlg7ju8mzrea0ycfd3u86crk8vzayd334wrqvzqqqyx7cmls060
n/AcreLibertário - Acre (por: nostr:nprofile1qqsw4jww99ykxf2jy4wyh685hp7cs70texztv0p7kqa3mqhfrvvdtscpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpzpmhxue69uhkummnw3ezumt0d5hsz8rhwden5te0wfjkccte9emkj6mfveex2etyd9sju7re0ghsftvmn0 e nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshsz9thwden5te0wfjkccte9ehx7um5wghxyee0vnwevs) nostr:naddr1qq85zcmjv4xxjcn9wf6v8gtjd9hsyg82e88zjjtry4fz2hztar6tslvg084unp9k8sltqwcast53kxx4cvpsgqqqsmmqftljpt
n/Alagoas (por: nostr:nprofile1qqsw4jww99ykxf2jy4wyh685hp7cs70texztv0p7kqa3mqhfrvvdtscpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpzpmhxue69uhkummnw3ezumt0d5hsz8rhwden5te0wfjkccte9emkj6mfveex2etyd9sju7re0ghsftvmn0 e nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshsz9thwden5te0wfjkccte9ehx7um5wghxyee0vnwevs) nostr:naddr1qqr5zmrpvahkzuczyr4vnn3ff93j2539t3973a9c0ky8n67fsjmrc04s8vwc96gmrr2uxqcyqqqgdas8qtaf4
Empreendedorismo:
n/Empreendedorismo/BR (por: nostr:npub14ysljm0gn6nnjv95yzeq6ffze4f3f9l0248kez4fhm4yz3fzardslwx5e8) nostr:naddr1qqd5y4zr9azk6urjv4jkuer9v3hhy6tnd4hj7snjv9ekjmqzyz5jr7tdaz02wwfsksstyrf9ytx4x9yhaa257my24xlw5s29yt5dkqcyqqqgdaslzrp3p
n/Empreendedorismo/SP (por: nostr:npub14ysljm0gn6nnjv95yzeq6ffze4f3f9l0248kez4fhm4yz3fzardslwx5e8) nostr:naddr1qqt5y4zr9azk6urjv4jkuer9v3hhy6tnd4hj756sqgs2jg0edh5fafeexz6zpvsdy53v65c5jlh42nmv325ma6jpg53w3kcrqsqqpphkcym25j
Análise
n/EBDV (Em Busca Da Verdade) - Análise geral e desenvolvimento pessoal (por: nostr:nprofile1qqs0xmu0skfdlmtl5tth6cv99za8f8kv7ulz5srkm8p6v5k03dx9lzspz4mhxue69uhkummnw3ezummcw3ezuer9wchszrnhwden5te0dehhxtnvdakz7qgswaehxw309ahx7um5wghx6mmd9usvrt9r) nostr:naddr1qqzy2sjy2cpzpum037ze9hld073dwltps55t5ay7enmnu2jqwmvu8fjje795chu2qvzqqqyx7cy9v5px
-
 @ 40bdcc08:ad00fd2c
2025-05-06 14:24:22
@ 40bdcc08:ad00fd2c
2025-05-06 14:24:22Introduction
Bitcoin’s
OP_RETURNopcode, a mechanism for embedding small data in transactions, has ignited a significant debate within the Bitcoin community. Originally designed to support limited metadata while preserving Bitcoin’s role as a peer-to-peer electronic cash system,OP_RETURNis now at the center of proposals that could redefine Bitcoin’s identity. The immutable nature of Bitcoin’s timechain makes it an attractive platform for data storage, creating tension with those who prioritize its monetary function. This discussion, particularly around Bitcoin Core pull request #32406 (GitHub PR #32406), highlights a critical juncture for Bitcoin’s future.What is
OP_RETURN?Introduced in 2014,
OP_RETURNallows users to attach up to 80 bytes of data to a Bitcoin transaction. Unlike other transaction outputs,OP_RETURNoutputs are provably unspendable, meaning they don’t burden the Unspent Transaction Output (UTXO) set—a critical database for Bitcoin nodes. This feature was a compromise to provide a standardized, less harmful way to include metadata, addressing earlier practices that embedded data in ways that bloated the UTXO set. The 80-byte limit and restriction to oneOP_RETURNoutput per transaction are part of Bitcoin Core’s standardness rules, which guide transaction relay and mining but are not enforced by the network’s consensus rules (Bitcoin Stack Exchange).Standardness vs. Consensus Rules
Standardness rules are Bitcoin Core’s default policies for relaying and mining transactions. They differ from consensus rules, which define what transactions are valid across the entire network. For
OP_RETURN: - Consensus Rules: AllowOP_RETURNoutputs with data up to the maximum script size (approximately 10,000 bytes) and multiple outputs per transaction (Bitcoin Stack Exchange). - Standardness Rules: LimitOP_RETURNdata to 80 bytes and one output per transaction to discourage excessive data storage and maintain network efficiency.Node operators can adjust these policies using settings like
-datacarrier(enables/disablesOP_RETURNrelay) and-datacarriersize(sets the maximum data size, defaulting to 83 bytes to account for theOP_RETURNopcode and pushdata byte). These settings allow flexibility but reflect Bitcoin Core’s default stance on limiting data usage.The Proposal: Pull Request #32406
Bitcoin Core pull request #32406, proposed by developer instagibbs, seeks to relax these standardness restrictions (GitHub PR #32406). Key changes include: - Removing Default Size Limits: The default
-datacarriersizewould be uncapped, allowing largerOP_RETURNdata without a predefined limit. - Allowing Multiple Outputs: The restriction to oneOP_RETURNoutput per transaction would be lifted, with the total data size across all outputs subject to a configurable limit. - Deprecating Configuration Options: The-datacarrierand-datacarriersizesettings are marked as deprecated, signaling potential removal in future releases, which could limit node operators’ ability to enforce custom restrictions.This proposal does not alter consensus rules, meaning miners and nodes can already accept transactions with larger or multiple
OP_RETURNoutputs. Instead, it changes Bitcoin Core’s default relay policy to align with existing practices, such as miners accepting non-standard transactions via services like Marathon Digital’s Slipstream (CoinDesk).Node Operator Flexibility
Currently, node operators can customize
OP_RETURNhandling: - Default Settings: Relay transactions with oneOP_RETURNoutput up to 80 bytes. - Custom Settings: Operators can disableOP_RETURNrelay (-datacarrier=0) or adjust the size limit (e.g.,-datacarriersize=100). These options remain in #32406 but are deprecated, suggesting that future Bitcoin Core versions might not support such customization, potentially standardizing the uncapped policy.Arguments in Favor of Relaxing Limits
Supporters of pull request #32406 and similar proposals argue that the current restrictions are outdated and ineffective. Their key points include: - Ineffective Limits: Developers bypass the 80-byte limit using methods like Inscriptions, which store data in other transaction parts, often at higher cost and inefficiency (BitcoinDev Mailing List). Relaxing
OP_RETURNcould channel data into a more efficient format. - Preventing UTXO Bloat: By encouragingOP_RETURNuse, which doesn’t affect the UTXO set, the proposal could reduce reliance on harmful alternatives like unspendable Taproot outputs used by projects like Citrea’s Clementine bridge. - Supporting Innovation: Projects like Citrea require more data (e.g., 144 bytes) for security proofs, and relaxed limits could enable new Layer 2 solutions (CryptoSlate). - Code Simplification: Developers like Peter Todd argue that these limits complicate Bitcoin Core’s codebase unnecessarily (CoinGeek). - Aligning with Practice: Miners already process non-standard transactions, and uncapping defaults could improve fee estimation and reduce reliance on out-of-band services, as noted by ismaelsadeeq in the pull request discussion.In the GitHub discussion, developers like Sjors and TheCharlatan expressed support (Concept ACK), citing these efficiency and innovation benefits.
Arguments Against Relaxing Limits
Opponents, including prominent developers and community members, raise significant concerns about the implications of these changes: - Deviation from Bitcoin’s Purpose: Critics like Luke Dashjr, who called the proposal “utter insanity,” argue that Bitcoin’s base layer should prioritize peer-to-peer cash, not data storage (CoinDesk). Jason Hughes warned it could turn Bitcoin into a “worthless altcoin” (BeInCrypto). - Blockchain Bloat: Additional data increases the storage and processing burden on full nodes, potentially making node operation cost-prohibitive and threatening decentralization (CryptoSlate). - Network Congestion: Unrestricted data could lead to “spam” transactions, raising fees and hindering Bitcoin’s use for financial transactions. - Risk of Illicit Content: The timechain’s immutability means data, including potentially illegal or objectionable content, is permanently stored on every node. The 80-byte limit acts as a practical barrier, and relaxing it could exacerbate this issue. - Preserving Consensus: Developers like John Carvalho view the limits as a hard-won community agreement, not to be changed lightly.
In the pull request discussion, nsvrn and moth-oss expressed concerns about spam and centralization, advocating for gradual changes. Concept NACKs from developers like wizkid057 and Luke Dashjr reflect strong opposition.
Community Feedback
The GitHub discussion for pull request #32406 shows a divided community: - Support (Concept ACK): Sjors, polespinasa, ismaelsadeeq, miketwenty1, TheCharlatan, Psifour. - Opposition (Concept NACK): wizkid057, BitcoinMechanic, Retropex, nsvrn, moth-oss, Luke Dashjr. - Other: Peter Todd provided a stale ACK, indicating partial or outdated support.
Additional discussions on the BitcoinDev mailing list and related pull requests (e.g., #32359 by Peter Todd) highlight similar arguments, with #32359 proposing a more aggressive removal of all
OP_RETURNlimits and configuration options (GitHub PR #32359).| Feedback Type | Developers | Key Points | |---------------|------------|------------| | Concept ACK | Sjors, ismaelsadeeq, others | Improves efficiency, supports innovation, aligns with mining practices. | | Concept NACK | Luke Dashjr, wizkid057, others | Risks bloat, spam, centralization, and deviation from Bitcoin’s purpose. | | Stale ACK | Peter Todd | Acknowledges proposal but with reservations or outdated support. |
Workarounds and Their Implications
The existence of workarounds, such as Inscriptions, which exploit SegWit discounts to embed data, is a key argument for relaxing
OP_RETURNlimits. These methods are costlier and less efficient, often costing more thanOP_RETURNfor data under 143 bytes (BitcoinDev Mailing List). Supporters argue that formalizing largerOP_RETURNdata could streamline these use cases. Critics, however, see workarounds as a reason to strengthen, not weaken, restrictions, emphasizing the need to address underlying incentives rather than accommodating bypasses.Ecosystem Pressures
External factors influence the debate: - Miners: Services like Marathon Digital’s Slipstream process non-standard transactions for a fee, showing that market incentives already bypass standardness rules. - Layer 2 Projects: Citrea’s Clementine bridge, requiring more data for security proofs, exemplifies the demand for relaxed limits to support innovative applications. - Community Dynamics: The debate echoes past controversies, like the Ordinals debate, where data storage via inscriptions raised similar concerns about Bitcoin’s purpose (CoinDesk).
Bitcoin’s Identity at Stake
The
OP_RETURNdebate is not merely technical but philosophical, questioning whether Bitcoin should remain a focused monetary system or evolve into a broader data platform. Supporters see relaxed limits as a pragmatic step toward efficiency and innovation, while opponents view them as a risk to Bitcoin’s decentralization, accessibility, and core mission. The community’s decision will have lasting implications, affecting node operators, miners, developers, and users.Conclusion
As Bitcoin navigates this crossroads, the community must balance the potential benefits of relaxed
OP_RETURNlimits—such as improved efficiency and support for new applications—against the risks of blockchain bloat, network congestion, and deviation from its monetary roots. The ongoing discussion, accessible via pull request #32406 on GitHub (GitHub PR #32406). Readers are encouraged to explore the debate and contribute to ensuring that any changes align with Bitcoin’s long-term goals as a decentralized, secure, and reliable system. -
 @ d61f3bc5:0da6ef4a
2025-05-06 01:37:28
@ d61f3bc5:0da6ef4a
2025-05-06 01:37:28I remember the first gathering of Nostr devs two years ago in Costa Rica. We were all psyched because Nostr appeared to solve the problem of self-sovereign online identity and decentralized publishing. The protocol seemed well-suited for textual content, but it wasn't really designed to handle binary files, like images or video.
The Problem
When I publish a note that contains an image link, the note itself is resilient thanks to Nostr, but if the hosting service disappears or takes my image down, my note will be broken forever. We need a way to publish binary data without relying on a single hosting provider.
We were discussing how there really was no reliable solution to this problem even outside of Nostr. Peer-to-peer attempts like IPFS simply didn't work; they were hopelessly slow and unreliable in practice. Torrents worked for popular files like movies, but couldn't be relied on for general file hosting.
Awesome Blossom
A year later, I attended the Sovereign Engineering demo day in Madeira, organized by Pablo and Gigi. Many projects were presented over a three hour demo session that day, but one really stood out for me.
Introduced by hzrd149 and Stu Bowman, Blossom blew my mind because it showed how we can solve complex problems easily by simply relying on the fact that Nostr exists. Having an open user directory, with the corresponding social graph and web of trust is an incredible building block.
Since we can easily look up any user on Nostr and read their profile metadata, we can just get them to simply tell us where their files are stored. This, combined with hash-based addressing (borrowed from IPFS), is all we need to solve our problem.
How Blossom Works
The Blossom protocol (Blobs Stored Simply on Mediaservers) is formally defined in a series of BUDs (Blossom Upgrade Documents). Yes, Blossom is the most well-branded protocol in the history of protocols. Feel free to refer to the spec for details, but I will provide a high level explanation here.
The main idea behind Blossom can be summarized in three points:
- Users specify which media server(s) they use via their public Blossom settings published on Nostr;
- All files are uniquely addressable via hashes;
- If an app fails to load a file from the original URL, it simply goes to get it from the server(s) specified in the user's Blossom settings.
Just like Nostr itself, the Blossom protocol is dead-simple and it works!
Let's use this image as an example:
 If you look at the URL for this image, you will notice that it looks like this:
If you look at the URL for this image, you will notice that it looks like this:blossom.primal.net/c1aa63f983a44185d039092912bfb7f33adcf63ed3cae371ebe6905da5f688d0.jpgAll Blossom URLs follow this format:
[server]/[file-hash].[extension]The file hash is important because it uniquely identifies the file in question. Apps can use it to verify that the file they received is exactly the file they requested. It also gives us the ability to reliably get the same file from a different server.
Nostr users declare which media server(s) they use by publishing their Blossom settings. If I store my files on Server A, and they get removed, I can simply upload them to Server B, update my public Blossom settings, and all Blossom-capable apps will be able to find them at the new location. All my existing notes will continue to display media content without any issues.
Blossom Mirroring
Let's face it, re-uploading files to another server after they got removed from the original server is not the best user experience. Most people wouldn't have the backups of all the files, and/or the desire to do this work.
This is where Blossom's mirroring feature comes handy. In addition to the primary media server, a Blossom user can set one one or more mirror servers. Under this setup, every time a file is uploaded to the primary server the Nostr app issues a mirror request to the primary server, directing it to copy the file to all the specified mirrors. This way there is always a copy of all content on multiple servers and in case the primary becomes unavailable, Blossom-capable apps will automatically start loading from the mirror.
Mirrors are really easy to setup (you can do it in two clicks in Primal) and this arrangement ensures robust media handling without any central points of failure. Note that you can use professional media hosting services side by side with self-hosted backup servers that anyone can run at home.
Using Blossom Within Primal
Blossom is natively integrated into the entire Primal stack and enabled by default. If you are using Primal 2.2 or later, you don't need to do anything to enable Blossom, all your media uploads are blossoming already.
To enhance user privacy, all Primal apps use the "/media" endpoint per BUD-05, which strips all metadata from uploaded files before they are saved and optionally mirrored to other Blossom servers, per user settings. You can use any Blossom server as your primary media server in Primal, as well as setup any number of mirrors:
 ## Conclusion
## ConclusionFor such a simple protocol, Blossom gives us three major benefits:
- Verifiable authenticity. All Nostr notes are always signed by the note author. With Blossom, the signed note includes a unique hash for each referenced media file, making it impossible to falsify.
- File hosting redundancy. Having multiple live copies of referenced media files (via Blossom mirroring) greatly increases the resiliency of media content published on Nostr.
- Censorship resistance. Blossom enables us to seamlessly switch media hosting providers in case of censorship.
Thanks for reading; and enjoy! 🌸
-
 @ fbf0e434:e1be6a39
2025-05-13 02:00:02
@ fbf0e434:e1be6a39
2025-05-13 02:00:022025年3月17日
塔林·克里斯滕森(Taryn Christiansen),DoraHacks
特别感谢DoraHacks创始人Eric Zhang提供的深刻讨论和支持。
Part 1
自动化的浪潮无疑正在到来。人类劳动将迅速贬值。人工智能已经取得了巨大的进展,并且,随着许多创新降低了成本,越来越多的企业将能够整合这一技术。随着生产模式、资本和供应链越来越多地实现自动化,生产力和效率将加速发展。
问题是,这是否是好事。答案五花八门。从末世论者如埃利泽·尤德科夫斯基(Eliezer Yudkowsky)[1]和罗曼·扬波尔斯基(Roman Yampolskiy)[2]等人认为,人工智能有潜力——并最终将——消灭人类物种。人类将远远不如未来的人工智能高效,因此,当通用人工智能(AGI)得以实现时,智能机器很容易得出结论:人类消耗太多,世界没有人类会更好。然后是怀疑论者,如马克斯·泰格马克(Max Tegmark)[3],他认为应该暂停人工智能的发展,以便更好地将其与人类利益对齐。“只有当我们确信其影响将是积极的、其风险可控时,才应开发强大的人工智能系统。[4]”再者,也有技术乐观主义者,如马克·安德森(Mark Andreessen)[5]、萨姆·奥特曼(Sam Altman)[6]和雷·库兹韦尔(Ray Kurzweil)[7],他们主张人工智能将带来物质上的丰盈乌托邦。发展应该加速,监管者应当退让,未来将带来经济增长、生产力提高和生活水平的惊人提升。
[1] 美国人工智能理论家、作家,MIRI(Machine Intelligence Research Institute,机器智能研究所)创始人之一。 [2] 俄罗斯裔美国计算机科学家,路易斯维尔大学教授,专长于AI安全和人工智能伦理。 [3] 瑞典裔美国物理学家、MIT教授,Future of Life Institute(未来生命研究院)联合创办人。 [4] https://futureoflife.org/open-letter/pause-giant-ai-experiments/. [5] https://a16z.com/the-techno-optimist-manifesto/. 硅谷知名风险投资家、网景(Netscape)浏览器联合创始人,Andreessen Horowitz投资公司创始人。 [6] https://ia.samaltman.com/. OpenAI CEO. [7] 发明家、未来学家、作家,现为谷歌工程总监。
在这里很难做出具体的预测。不同立场的人常常以某种“不可避免性”的口气宣扬他们的观点。安德森是乐观主义最著名的主张者之一,他坚信由快速技术进步所带来的未来将是每一代人梦寐以求的那种未来。将会有具备无限同情心和耐心的人工智能导师,使教育更加普及和易获取;医疗行业将大幅提升,提供更好的预测并减少错误;机器人可以执行危险的工作,从而让人们追求自己的愿望。经济效益也将是巨大的。由于生产成本的降低,价格将更低,人们的钱将有更强的购买力,需求将增加,新的工作岗位将被创造,工资也将提高。他主张这一观点的主要论据是历史先例。每次有新技术革命到来时,社会总会从中获得净效益(net good)。十九世纪石油工业的形成之前,鲸鱼行业雇用了成千上万的工人。石油取代了这些工作,但也消除了依赖屠杀成千上万头鲸鱼来制造日常产品的需求。汽车威胁了许多行业,但当它成为普遍拥有的财产时,突然之间,需要更多的道路、桥梁和加油站来满足需求。虽然将会有自动化,人工智能将以良好的成果充斥世界,赋予经济前所未有的机会,让人们找到工作、积累财富,并利用人工智能所创造的价值。
然而,人工智能不同于以往的技术发展。人工智能是一种智能的进步和普及,而不仅仅是机械化的进步。库兹韦尔写道:“第一次工业革命扩展了我们身体的能力,第二次则扩展了我们思想的能力。”但是,一种新变量意味着结果的不同。人工智能能够学习、适应、生成、发现、反驳、怀疑、确认、设定目标,能够制定手段,也许有一天它会拥有意志并感知情感。它变得越来越具能动性(agentic)和自主性(autonomous),能够承担和完成通过它自身流程所生成的任务。如果它现在还没有具备能动性,那目标是让它达到这一点。仅仅基于先前经验得出的预测可能是一种范畴错误,容易导致误导和错误。当然,过去的技术形式与人工智能之间存在重叠,但它们之间有一个明确的区别,并且这种区别应该指导我们的预测。
另一方面,末世论者的观点并不具备很大的现实意义。那些通常潜藏在末世论者警告背后的“终结者”般的情景是不太可能发生的。尽管正如埃隆·马斯克(Elon Musk)[8]最近在《乔·罗根播客》(The Joe Rogan Podcast)上所言,如果嵌入了错误的目标,也许像“太空奥德赛(Space Odyssey)”系列作品中的HAL 9000那样的情景[9]是可能的。考虑到DeepSeek公司最近在降低计算成本方面的进展,该公司开发的AI模型已具有与美国最先进的模型竞争的水平,一场新的竞赛已经宣告开始,事情将会加速发展。美国副总统在人工智能行动峰会上的讲话清楚地表明了这一点。当前存在着一场争夺国际技术主导地位的竞争,这将塑造未来,发展速度的减缓等同于举白旗。因此,如果对安德森的主张有任何可行的反对意见,那也必须集中在如何引导技术发展,而非停止它。这应当为关于自动化的讨论提供启示:如何最好地引导自动化以避免不良结果?我们需要一种积极主动的方式。
[8] 特斯公司CEO,SpaceX创始人兼首席执行官,X(原Twitter)所有人。 [9] HAL 9000(简称HAL)是科幻小说和电影系列《太空奥德赛》中的虚构人工智能角色,由阿瑟·克拉克(Arthur C. Clarke)和斯坦利·库布里克(Stanley Kubrick)共同创作。在作品中,HAL 9000原本是飞船“发现号”(Discovery One)的中央控制系统,它被设计得极其可靠,拥有高度智能、情感模拟能力,负责飞船运行,包括导航、生命支持、通信等核心任务。在执行任务时,由于HAL开始表现出微妙的异常(如错误报告设备损坏),同行宇航员决定关闭HAL。当这一计划被HAL得知,HAL控制飞船上设备造成了同行宇航员的死亡。但后续作品揭示,HAL的表现是由于收到了相互冲突的人类指令,并决定杀死宇航员来保证两种指令都能够实现。
Section 1.1
安德森对自动化的乐观态度存在一个问题,那就是他过于确定新工作机会会得到足够的分配,供人们享受并加以利用。问题在于,经济正变得越来越依赖知识和信息。知识和信息的比重远远超过了体力劳动,而在市场上能够取得成功的人是那些拥有相关技能的人,这些技能需要通过教育和培训来获得。正如托马斯·皮凯蒂(Thomas Piketty)[10]在其《21世纪资本论》(Capital in the Twenty-First Century)一书中所观察到的,这是一个普遍的经济趋势,“趋同(即减少和限制不平等)的主要动力是知识的传播和对培训与技能的投资。”因此,随着经济日益依赖知识,那些没有相关技能或安全保障的失业工人将处于严重的不利地位。而那些拥有相关知识、技能和信息的人则更有优势,能够投资资本并增加财富。例如,即便经济增长和生产成本降低,那些没有技能的人将看到工资停滞不前。但是,假设由于生产成本降低,消费者的购买力增强,需求可能会上升,如果供应无法迅速满足这一需求,价格可能会随之上涨,从而引发需求拉动型通货膨胀。关键在于,经济和生产力增长可能无法自然应对的变量和情境。正如皮凯蒂所说,“没有自然、自发的过程能够防止不稳定、不平等的力量永久占据主导地位。”因此,必须采取积极的应对策略,来避开那些可能会导致漂浮在经济表面上的大量船只沉没的尖锐岩石。
[10] 法国经济学家。
在杰里米·里夫金(Jeremy Rifkin)[11]的《工作的终结》(The End of Work)一书中,他采用了更加严峻的语气:“(下一个)工业革命正迫使全球经济面临空前的危机,数百万人因技术创新失业,全球购买力急剧下降。”而埃里克·布林约尔松(Erik Brynjolfsson)[12]和安德鲁·麦卡菲(Andre McAfee)[13]在《第二次机器时代》(The Second Machine Age)[14]一书中提供了充分的理由,认为里夫金的观点具有一定的道理。他们认为,经济增长所带来的回报(bounty)——即通过较少的投入产生更多的产出,使商品更加便宜、更加易得,从而改善人们生活——并没有通过财富、收入和资本的分配,使每个人都被惠及而受益。换句话说,“科技进步的浪潮可能并不会使所有船只都得以提升。”例如,在上文提到的技能差距上,“自1970年代中期以来,拥有研究生学位的人的工资上涨了约25%,而高中辍学者的平均工资则下降了30%。”尽管自20世纪中期以来,美国GDP和经济生产力呈现“令人印象深刻的轨迹”,但该国的中位数收入却在下降,表明少数人正在获得好处,而大多数人却错失了机会:自里根时代以来,贫富差距不断扩大。布鲁金斯学会的这篇文章[15]也支持这一观点。
[11] 美国经济和社会理论家、作家、公众演说家、政治顾问和活动家。 [12] 经济学家、教授,现任斯坦福大学数字经济实验室主任。 [13] 研究员、作家,MIT斯隆管理学院副教授、MIT数字经济计划副主任。 [14] http://digamo.free.fr/brynmacafee2.pdf/ [15] https://www.brookings.edu/articles/rising-inequality-a-major-issue-of-our-time/
然而,也许这些观点的实际含义被错误的同情心所误导。尽管不平等的确存在,但这并不意味着它应该被视为最主要的关注变量。再次强调,技术创新使商品变得异常便宜,使人们的生活更加轻松、生活水平更高,并且通过提供更多商品、服务、信息和知识的可获取性,来满足人们的需求和愿望,从而让日常生活更便利。尽管财富分配可能存在不平等,但其整体增长使每个人都变得更好。而且,随着财富的进一步增长,这一趋势将持续。曾经只有富人能够负担得起的东西,如今大多数人都可以买得起。比如iPhone,它能提供比所有现存图书馆更多的信息,而历史上,只有最富有的人才能使用后者,而几乎任何人都能购买前者。欧洲最大的图书馆是1481年的梵蒂冈图书馆,馆内估计有三千五百本书籍和文献。ChatGPT估计,如果将网上的信息转化为书籍大小的量,将约合467千万亿本书。看看农业的发展。当经济学家米尔顿·弗里德曼(Milton Friedman)在1980年写《选择的自由》(Free to Choose)时,他写道,在《独立宣言》被签署的时代,“每20个工人中就需要有19个(从事农业劳动),以养活这个国家的居民,以及提供生产盈余以供出口,来交换外国商品。如今,只需要每20个工人中的不到1个工人,就能养活2.2亿美国居民,并提供生产盈余使美国成为世界上最大的食品出口国。”
彼得·蒂尔(Peter Theil)[16]常常宣称,问题是技术创新停滞,而不是与福利项目或分配模式相关的道德失败。科学和技术需要突破,以转变行业并提高生活标准。人工智能的智能革命,理应能够实现这一潜力。因此,也许最好是直接放手不管。专注于特定分配模式的公平或正义,就像尼采所说的那样,是一种“坏良心(bad-conscience)”——以被认为的集体利益为代价而追求个人利益时所体验到的罪疚感,但实际上,这种感受只会阻碍进步,而非推动它。真正和最好的目标,可以说是努力创新并创造推动历史发展的价值,这就像亚当·斯密(Adam Smith)[17]的“看不见的手”的隐喻一样,自然地调和了人们的自利。正如米尔顿·弗里德曼所说,“对于促使个人之间合作,进而使得每个个人都可以从合作中受益的状态而言,没有外部力量是必要的,没有对自由的侵犯是必要的。这就是为什么正如亚当·斯密所说的,‘只关心自身利益’的个人会‘被一只隐形之手引导,以推动一种与他的意图无关的目标’。”
[16] 硅谷投资人,PayPal创始人,企业家、风险投资家、政治思想家、作家。 [17] 经济学家、哲学家、道德理论家,古典经济学奠基人。
Section 1.2
关于经济增长是否足以改善长期的福祉和生活水平的问题,存在着高度争议。这个问题显然在这里无法解决。然而,提到这一点的目的是为了表明两种观点都具有正确性。个人在市场上追求自己的利益,像价格和工资这样的变量通过人们的自愿交换达成平衡,已经带来了巨大的成果。但差距也随之产生。
自动化是一个潜在的威胁。忽视它并声称它是危言耸听是一个错误。在可能的人工智能颠覆之后,某种形式的平衡达成之前,过渡期可能是复杂的,并且可能造成不必要的痛苦,如果事先处理,这些痛苦本可以避免。革命性的新技术可能既有好的一面,也有坏的一面。例如,十五世纪的印刷术使人们摆脱了教会强加的信息控制,催生了科学文献涌现的浪潮,为文明提供了巨大的价值。但它也导致了激烈而血腥的宗教战争,因为它允许人们传播各种信息。因此,为了避免类似的结果,在实施任何能够重新安排和重组社会经济安排的技术时,采取主动的方式非常重要。
从这里出发,通常的推论是,监管措施是应对这些可能性最好的手段。但与其满足于监管,正如马克·安德森在拜登政府执政期间警告的那样,监管会导致人工智能垄断,本文将力图支持自由市场中的自愿交换,同时促进必要的社会合作,帮助人们适应并在一个越来越不依赖于人力资本的经济中发挥作用。
本文的担忧是人们失去行使自身能动性(agency)的机会,从而无法拥有对自己的生活的控制(control)感和影响(influence)感。如果大量的人失去参与工作的机会,将会出现一条鸿沟,阻挡人们在世界中通常实现自己潜力的方式。他们将不再有机会在关键的社会领域做出具有深远影响的生活选择,这些选择需要谨慎和远见。人们将失去测试自我、发现天性的倾向和兴趣、辨认自己重视的事物以及行使选择去追求它的机会。社会中培养毅力、动机和个人意志的主要机会将会丧失。如果工作将主要被自动化替代,那么需要一个新的机会媒介来取而代之。作为社会制度的工作需要进步,并保持人们成长和发展的途径。
20世纪的自由主义哲学家约翰·杜威(John Dewey)写道:“正如感觉需要可感知的对象来刺激它们,我们的观察、回忆和想象能力也不是自发工作的,而是由当前社会活动所设定的需求激发。”像教育和工作这样的社会环境提供了刺激特定能力和功能所需的活动媒介,这些能力和功能需要完成定义活动的任务。人们常常争论说,自动化将使人们摆脱繁琐和机械的工作束缚。他们将有更多时间寻找新的方式来表达自己的需求,并最终实现工作一直阻碍他们实现的目标。人们将有自由去实现自己的潜力。但这一切不会自发发生。需要有能激发实现真正自由、意义和目的的活动的环境。当一个人完全孤单地待在一个没有人阻碍其动作和倾向的房间里时,可以说他是自由的。这样的人可以随心所欲。但由于没有能够激发适当反应的情境,且没有成功与失败的可能性,也缺少需要合作和协调的场景,这些场景有助于培养社会和情感的能力,也没有必要发挥智力和解决问题的能力,这个房间里的人的成长会停止,反而会枯萎,无法实现自由。一个从天空自由下落、不被任何东西阻挡的人,他看似自由,其实并不自由,因为他注定会撞向地面。
正如弗朗茨·卡夫卡(Franz Kafka)所写:“我自由了,因此我迷失。”哲学家让-保罗·萨特(Jean-Paul Sartre)则说:“人类被注定要自由。”
因此,当前的问题是,如何开辟一个人们能够自愿进入其中,并找到表达美好生活所需能力的机会的空间。此类机会,旨在行使人们的能动性,将被称为“质性丰富(qualitatively rich)机会”,而能够实现这些机会的环境则被称为“质性丰富环境”。
一个体现“质性丰富机会”的“质性丰富环境”是“开源生态系统”(open source ecosystems),它应当是人工智能发展的主要模式,它提供了以下框架:市场将为人们提供机会,让他们通过具有挑战性和刺激性的工作来行使自己的能动性,进而实现有意义的项目。人们将不得不学习新技能,克服障碍,但这一过程不仅是为了保持一个人们可以竞争、做出选择、发展能动性的市场,同时也促进人们生活中的目的和意义。如果经济要关上旧有工作形式的门,比如流水线和服务性工作,那么应该为人们提供更多有意义的工作机会。正如经济学家泰勒·科文(Tyler Cowen)在《莱克斯·弗莱德曼博客》(Lex Fridman podcast)中指出的那样,人们需要事情做。他们不想只是待在家里,正如COVID封锁所证明的那样。如果例行劳动和低技术劳动将被自动化,那么唯一的选择是确保存在“质性丰富机会”,以便人们能够利用并行使自己的能力,进行有意义的工作。
因此,应该在经济中引入一种新的范式。从佩卡·希曼宁(Pekka Himanen)[18]的《黑客伦理》(The Hacker Ethic)一书中汲取灵感,人们应当从以工业为基础的工作范式转向一种“黑客范式”。在工业范式中,个体主要执行重复性的劳动任务,其目的仅仅是为了获取收入以维持生存。而黑客范式则以内在价值为核心,强调工作本身的趣味性、刺激性、创造性与游戏性,其特征是激情与游戏,而非“履行对工作的责任”或“为经济做出贡献”的社会义务,正如马克斯·韦伯(Max Weber)[18]在《新教伦理与资本主义精神》(Capitalism and The Protestant Ethic)中所揭示的那样。黑客范式强调人类能动性及其实现价值的潜力,这种价值能提升人类。工业范式则在工人与他们与世界的积极参与之间产生疏离感:工人对他们所贡献的工作漠不关心;人们通常不喜欢甚至讨厌他们的工作。他们在那里是为了赚钱,而不是参与有意义的工作。正如希曼宁所写:“改革工作形式不仅是尊重工人的问题,更是尊重人类作为人类的问题。黑客不认同‘时间就是金钱’的格言,而认同‘这是我的生活’的格言。”正如埃里克·史蒂文·雷蒙德(Eric Steven Raymond)在《如何成为黑客》(How To Become A Hacker)[20]中所说,黑客认为世界充满了奇妙的问题,并在致力于解决这些问题中找到了自由。他们寻找需要动机和热情的项目,并相信当其他人也有机会获得同样的自由时,世界将变得无限美好,这需要社会合作以及对信息的最大程度的开放获取——这也正是“开源”的重要意义所在。
[18] 芬兰哲学家。 [19] 社会学家、经济学家、历史学家、政治学理论家,德国社会学与历史学传统的代表人物之一,被称为现代社会学的奠基人之一。 [20] http://www.catb.org/esr/faqs/hacker-howto.html
为了凸显为何引入新范式对于应对人工智能的挑战至关重要,具有显著的历史意义,我们可以回到亚当·斯密的思想。随后,将进一步阐明“质性丰富环境”与“质性丰富机会”的概念,并将其应用于当下以专有技术(proprietary technology)为核心的人工智能垄断体系。届时可以看到,这些垄断将扼杀黑客范式的生成,因此是不可取的。
透过亚当·斯密的视角我们可以看到,尽管工业化在长期内极大地提升了人们的生活水平,但它也对从事重复性、机械性劳动的人产生了消极影响,因为这类劳动削弱了对人类认知能力的刺激,阻碍了其全面发展。劳动分工极大地加速了专业化的进程,却减少了个体接触那些能调动其高级心智能力的机会——而这些能力正是实现有意义、有目标、富有成就感的工作的基础。人工智能与自动化正成为一种转型催化剂,逐步替代工业时代的工作模式与生产逻辑,将人力资本曾承担的任务转交予智能机器完成。若人工智能真的是一种进步——即人类进步——那么它就应回应亚当·斯密关于劳动分工及其对人类生活影响的担忧。
Part 2
Section 2.1
亚当·斯密在1776年写下了《国富论》(The Wealth of Nations)。受到艾萨克·牛顿(Isaac Newton)的影响,斯密希望理解社会背后的设计,以及社会的运作机制,类似于牛顿发现并使用采用机械论术语来公式化了解释宇宙的物理法则。那个时代的模型是将现象看作是像精密调校的手表一样有组织和有秩序的,所有部件和机械都在完美的和谐中协同工作,产生各种各样的效应和涌现现象。
在斯密生活的时代,第一次工业革命正在英格兰进行。城市扩张,曾经仅限于富人阶层的商品和服务变得更加廉价且易于获取,生活水平提高,基础设施得到了发展,表面上看,人们过上了前所未有的更好生活。斯密观察到社会的进步。由于大发现时代以及使欧洲人能够踏上新大陆的技术,欧洲人与那些似乎尚未经历欧洲所经历的历史进程、被欧洲人认为是“未开化”的民族接触,因此,欧洲大陆的风尚(ethos)是历史和文明正在进入一个新的、更为先进的阶段。科学探索和知识带来的创新提升了生产力和效率,从而使社会系统的组织更加复杂。斯密希望了解推动这一进程的因果机制。
斯密观察并认为劳动分工在社会经济中扮演了主要的,甚至是基础性的角色。随着社会组织的扩展,制造与生产过程逐渐细分为更为专业的任务,结果这些过程的产出大幅增加。在传统的行会框架中,工匠将一生投入到完整的手工业中,学习所需的所有方面并精通每一部分。这种行会框架逐渐被分工化的工厂模式所取代,后者在日益发展的城市中通过劳动分工的方式系统化生产。一个庞大的个体系统因此浮现,它需要极高的协调性,而劳动分工则将这一系统组织成一个复杂的机制,旨在调和人们的利益。
斯密还认为,劳动分工反映了人类本性中的某些更深层次的特征。人们涌向城市,赚取劳动报酬并享受更好的生活条件,因为斯密认为,人类天生具有进行交换(truck)、易货交易(barter)和贸易(exchange)[21]的倾向。他写道:“交换、易货和将一种物品与另一种物品贸易的倾向是所有人类共有的,在其他任何动物种群中都无法找到。”像狼这样的动物自然地在等级化的群体中组织自己,刚孵化的小鸟倾向于飞行,而像树木这样的有机体则在密林中争夺阳光。与此不同,人类进行交换、易货和贸易,是因为他们有天生的倾向来改善自身状况。劳动分工推动了这一目标的实现。
[21] 这三个词的区别在斯密研究中并没有得到广泛讨论。一些学者认为它们是同义的,通过重复表达强调(参考J.Z. Muller, (1993) Adam Smith in His Time and Ours: Designing the Decent Society, New York: Free Press第69页,Willie Henderson and Warren J. Samuels, (2004) The etiology of Adam Smith’s division of labor, in Essays on the History of Economics)。就这三个词在英语中的使用历史而言,truck system在英国曾经意为用实物作为工资的薪资制度,barter通常指不涉及货币的物物交换。
然而,斯密认为,劳动分工是一种权衡——它也有代价。尽管人们的生活水平提高,他们享受更好的条件,能够满足诸如食物、水和住所等消费需求,但劳动分工却将工人简化为机器中的齿轮。这些任务几乎不需要认知努力。一旦任务变得常规化,并转化为肌肉记忆后,便没有更多的障碍或问题需要克服。因此,斯密深切担忧这一过程将随着时间推移产生深远的负面认知效应。人们去上班,只要他们熟悉自己的任务,就不需要动脑;他们机械地行动。斯密直言不讳地写道:
“一个人一生都在执行少量简单的操作,并且这些操作的效果始终显而易见,他便无需发挥理解力,或利用自己的创造力去寻求解决从未出现的困难的方法。他自然会变得愚笨无知,几乎达到人类可能变得最愚笨和无知的地步。”
劳动分工提供的机会在质性上较为贫乏,无法使人们具备过上有意义和有目的生活的能力。借用另一位启蒙时期哲学家伊曼纽尔·康德(Immanuel Kant)的术语,劳动分工未能尊重人类的尊严,而尊严要求针对并培养那些能够使人过上自主选择生活所必需的能力。拥有尊严意味着对个人生活拥有影响力(influence)和掌控力(efficacy)。
劳动分工创造了更多提高生活水平的机会,但它没有提供“质性丰富机会”,使人们能够整合他们的能力并实现全面的人生。大多数人可用的机会并未促使他们将创造性和生产力能力集中于那些能够扩展他们在世界中自由感的目标上。与行会制度相比,劳动分工提供了更多的机会,但这些机会也更浅薄,更缺乏产生掌控感的体验。但由于生活水平较高,人们正确地选择了将自己降级为齿轮的工作。但正如斯密所观察到的,提高生活水平不足以满足人类需求的全面范围。它没有让大多数个体能够发挥他们的更高能力。
斯密认为,必须进行改善。对人们而言,更多“质性丰富机会”是至关重要的,这些机会使他们能够过上更有意义和目的的生活,体现人类尊严,并为行使他们的能动性提供基础。劳动分工提供了物质自由的增益,但并未提供足够的机会以实现更内在的、主体驱动的自由。
这无疑是卡尔·马克思对资本主义的重大批评之一。在资本主义体制下,人们与他们的劳动发生异化(alienation)。劳动的异化意味着人们与自己的活动脱离;即人在其自身和它的创造与生产能力之间产生了距离。在心理学家埃里克·弗洛姆(Eric Fromm)关于马克思的著作[22]中,他写道:“对马克思而言,异化的过程表现在工作和劳动分工中。工作是人类与自然之间的积极联系,是创造新世界的过程,包括创造人类自身……但随着私有制和劳动分工的发展,劳动失去了作为人类力量表达的特性;劳动及其产品变成了与人类、与他的意志和计划分离的存在。”
[22] Eric Fromm, Marx's Concept of Man.
人类通过他们所参与的活动以及在其中投入的内在力量和驱动力来理解和塑造自己的身份。通过创造和塑造世界及其环境,并将能量集中于外部项目和目标,一个人在世界中实现自我感。活动(Activity),而非被动的消费或任务,定义了马克思所说的人类本质。正如弗洛姆在其著作《拥有与存在》(To Have or To Be)中所指出的,通过“存在(being)”,而非“拥有(having)”,一个人才能体验到生活的意义和目的。通过“在爱中存在”,“以充满激情的方式存在”,“以积极行动的方式存在”,“以有希望的方式存在”,“有目的地存在”,以及“以有生产力地方式存在”,一个人才能过上充实的生活,而不必依赖“拥有”(爱、激情、积极性,等等)这些东西。劳动分工强调“拥有”,而其所涉及的许多工作和活动并未促使人们发展出“存在感”。正如德国诗人歌德(Johann Wolfgang von Goethe)所言,人类通过“将自己从可能性的黑夜转化为现实的白昼”来努力存在。人类通过外化他们内心的价值观和设想来追求成为自我,而这一过程通过活动得以实现。弗洛姆写道:“人类只有在生产性行为中才是活着的,只有在他通过表达自己特定的人类能力来把握外部世界,并且以这些能力来把握世界时……在这个生产性过程中,人类实现了自己的本质。”劳动分工减少了人类的能动性感,即人类以他们所珍视的、选择并在其上实践自身意志的有意义的方式,来主动影响和引导自己生活的能力。
通过创建“质性丰富环境”,黑客范式及其对开源的推动提供了多个“质性丰富机会”,从而推动了我们社会和政治结构的进步。它具有实现人类天性中更为积极的一面——人的能动感——的潜力,而不仅仅是其消极和消费的部分。这里的主要假设是,如果人工智能要发展并融入经济基础,它应当使人们的生活得到改善。更具体地说,如果自动化发生,其结果应当是改善人们的生活,而非对他们造成伤害。实现这一目标的一种途径是确保足够分配“质性丰富机会”,让每个人都能从中受益,而开源正是实现这一目标的途径。人工智能发展可能导致人们境况恶化以及抑制他们潜在机会的一个重要原因是存在使用专有模型来控制人工智能并主导其市场使用的垄断现象。黑客范式和开源则为避免这种结果提供了可能的解决方案。
Section 2.2
在理解垄断如何减少“质性丰富机会”之前,我们需要进一步弄清楚什么是“质性丰富机会”,以及它们激发并帮助发展哪些能力。在解释这类机会的性质及其意义之后,我们将探讨垄断是如何大幅削弱这些机会的可及性,以及这意味着什么。
“质性丰富机会”的理念源自亚里士多德(Aristotle)[23],更具体地说,是由哲学家玛莎·努斯鲍姆(Martha Nussbaum)和经济学家阿玛蒂亚·森(Amartya Sen)进一步发展的。亚里士多德认为,人类要实现繁荣、过上充实而有尊严的生活,必须达成某些特定的功能(functions)或方式。他认为存在一种“人性(human nature)”,而这种人性包含基本的和更高层次的需求。无论历史和偶然条件如何变化,人类都具有一些根本特征。当然,这些特征是在历史情境中体现的,但在所有文化和文明中都可以观察到某些本质上的一致性。亚里士多德说:“善是万物所追求的目标。”所谓“善”,即是一种事物的适当功能。例如,眼睛的善是“看见”,种子的善是“长成一棵树”。实现某物的适当功能,就是实现其“繁荣”(flourish),也就是达到它所追求和努力趋向的状态。达到这样的状态,就是获得一种内在价值。
[23] 古希腊哲学家。
作为一个人去实现其功能,需要基本的生活必需品,如食物、水、住所和行动能力。但这些物品本身并不具有内在价值;它们之所以有价值,是因为它们使人能够运作以追求更进一步、更有内在价值的事物。如果一个人仅仅拥有这些基本的生存条件,我们可以说他“运作”着,但未必是“良好地运作”。要使一个人“良好地运作”,必须拥有其他内在价值更高的资源。人类需要教育与信息获取,以发展其认知能力;需要家庭和亲密关系,以发展社交技巧、个人身份认同和情感处理能力;还需要能够施展意志、探索兴趣、投入热情的追求,并培养目标感的渠道。一个良好的政治与社会安排,即我们应当追求的那种社会制度,应当为人们提供具体的机会,让他们得以实践这些需求,从而实现良好的人类运作状态。“质性丰富机会”即是指那些能够为人类发展内在有价值的能力(如做出知情决策的能力、制定值得追求的目标及其实现路径的能力,以及建立有意义、有影响力的人际关系的能力)提供基础的机会。像工作、教育、社区和艺术等社会制度,正是那些激发并促进实现这些目标所需能力的质性丰富环境。
质性丰富机会之所以重要,是因为它们使人们具备发展“能动性”的能力。借用斯坦福大学心理学家阿尔伯特·班杜拉(Albert Bandura)[24]的概念,我们可以将“人类的能动性”理解为个体感受到自己对生活有控制和影响力的能力。更具体地说,质性丰富机会能够激发那些针对“自我效能”(self-efficacy)能力的行为。所谓“自我效能”,是指一个人在面对挑战和障碍时所拥有的自我信心感。当面对一个困难且新颖的任务时,高自我效能的人会评估自己有能力克服困难完成任务;他们会拥有坚持不懈、克服失败的动机;即使身处陌生与复杂情境中,他们也能维持良好的心理状态。质性丰富机会旨在发展那些能够提升自我效能以及应对具体情境所需的能力。通过这些机会,一个人得以锻炼其能动性、获取掌控力,从而扩展其自由感。而正如班杜拉(1994)[25]所说:“一个人自我效能感越强,他为自己设定的目标挑战越高,并且对这些目标的承诺也越坚定。”因此,通过增强自我效能,无论是在信念层面还是实践层面,个人将获得更高程度的自由,并过上更具质感、更丰富的人生。
[24] https://happyheartfamilies.citymax.com/f/Self_Efficacy.pdf [25] https://happyheartfamilies.citymax.com/f/Self_Efficacy.pdf
工作在塑造个体身份和自我认同方面具有至关重要的作用。它为人们提供了探索不同职业路径的机会,使他们能够发现自己在人生中希望追求的目标。工作往往也是建立职业与个人关系、融入不同社会网络的重要方式,同时也是人们获取能力、攀登社会阶梯的媒介。工作这一领域还能帮助人们在多种环境和情境中培养动机、智力以及态度。换句话说,工作为人们提供了发展某些功能或生活方式的机会,而这些功能和生活方式正是实现美好生活所必不可少的。
例如,想象一个年轻人第一次进入劳动力市场。他尝试了几份工作。他发现自己不太喜欢零售业,因为需要持续与顾客打交道。他又尝试了送货服务,结果发现自己不喜欢那种日复一日的重复性工作。最后,他在一个建筑工地找到了工作,并发现有些任务既有趣又具有挑战性。他喜欢动手工作的感觉,于是决定投身技工行业。这个人随后进入技校学习,建立起重要的人际关系,在新环境中受到挑战,被激发去提升技能、积累知识与经验,并在这个过程中不断面对和克服新的困难与障碍。毕业后,他抓住了一个机会——一位欣赏他职业精神的导师为他提供了许多关注和支持。之后,他在某家公司工作了一段时间,并在这个过程中积累了足够的知识和自信,决定创办自己的公司,以实现这个目标。他开始建立客户关系,专注于能让自己在竞争中脱颖而出的技能,并最终打造出一家成功的企业。
这听起来也许有些理想化,但却是一个既熟悉又现实的例子。它描绘了一种有目的的生活,这些目的是通过在环境和情境中发现的机会而形成的,这些环境和情境提供了能够产生能动感和自我价值感的体验。当然,要实现这样的人生画面,通常还需要一系列其他条件,例如成长于一个有支持的环境中,拥有探索个人兴趣所需的资源和时间等——但在美国,工作无疑是提供发展构成美好生活的关键功能的核心渠道。上文中的这个人通过学习新技能、克服挑战、做出关键选择来应对社会环境,最终实现了成功与成就。随着在专业领域的成长,他不断设立新的目标,并获得足够的自我效能感,相信自己能够实现这些目标。他发展出一整套完整的能力体系,最终也获得了尊严感。无论这个人过去或未来是否还拥有其他美好的人生经历,如果没有那些能够让他工作与成长的机会,他的人生质量将会大打折扣。
这里有一个真实的例子,不过这个人将保持匿名。在荷兰大学毕业后,他不想找一份“普通的工作”,于是开始前往其他国家旅行。他靠在 YouTube 上制作音乐赚了一些钱,住在各地的酒店和青年旅舍。但随着资金逐渐减少,孤独与疏离感开始加剧,他变得抑郁。他完全自由——可以去任何地方、看任何东西,做任何他想做的事——但他感到极度孤独。在亚洲的一家青年旅舍,他一个人躺在床上盯着天花板,没有钱、没有女朋友、也没有工作,他想起了父亲曾对他说的话:“他小时候教过我:每当我感到沮丧或者不知道做什么时,就去找一座沙堆,拿把铲子,把沙子从院子的一边搬到另一边……干点体力活,做点辛苦的事——做点什么。我做创业项目时也一样。”于是,他开始学习编程,开发软件和应用程序,并利用 Stripe 平台[26]将作品发布给公众以筹集资金。他专注于那些能够带来方向感与创作机会的活动。在真正的“黑客精神”指引下,他把世界看作充满待解决问题的迷人场域,有些问题他认为是可处理且值得去做的,于是尝试去解决。令人惊讶的是,他立下目标:一年内创办十二个初创公司——而他真的做到了。
[26] 一个专注于在线支付处理和金融基础设施的平台,帮助企业在互联网上管理资金流动。
这个人起初感到疏离与孤独,缺乏人生目标。因此他选择行动起来,把自己投入到使用基础编程语言与工具进行的创造性表达中。通过利用人工智能,他也更能创造出具有价值和实用性的产品,供他人使用与体验。他采纳了父亲的建议,将自己投入到实际行动中,结果是抑郁与焦虑逐渐缓解。他在信息丰富的环境中,发现了许多“质性丰富机会”,得以发展自我,提升自我效能感与能力。他与更多富有挑战性的目标建立联系,不断努力达成这些目标。而开源技术在这一过程中扮演了关键角色。
这也正是 Dora 生态系统的重要意义所在。通过像 DoraHacks.io 这样的平台,像上文所描述的那样的人们可以借由“质性丰富机会”,与全球各地的开发者协作,共同创新,创造出人们认为紧迫且相关的有意义的解决方案。该生态系统为开发者提供了必要的资源,使他们能够加入全球任何地方的 “BUIDL” 团队,解决引人入胜的问题;并在黑客松中与其他建设者一起感受到社区归属感;同时还通过激励机制推动他们实现有意义的目标,而这些目标往往又会引发更具挑战性和刺激性的下一阶段任务。Dora 生态系统创造了一个充满可能性的环境,使人们能够构建去中心化的产品与服务,例如将所有权交还给用户本人,增强他们在数字世界中的自主性、安全性以及对金融资产的控制力。正如下文将进一步讨论的,大型企业和垄断机构通常并不会从这些类型的技术中直接受益。那么,他们又有什么动机去资助这类技术呢?开源技术栈能够提升价值的质量,因为它为人们提供了开发更具意义产品的路径,而这些产品通常比那些由大型、目标狭隘的机构所产出的产品更具意义。
因此,如果自动化有可能减少甚至消除人们运用能动性、获得自我效能感的“质性丰富机会“,那么它所腾出的空间,理应由其他在质性上更丰富的机会来填补。如果确实存在“人性”这样的东西,而这种人性包含了一系列需要被发展、以使人得以过上有尊严生活的能力,那么最优与最值得追求的政治与社会安排,应当是将“质性丰富机会”公平分配,以确保人们有选择去运用自身能力、成为能够良好运作并实现繁荣生活的个体。为人们提供质性丰富机会,使他们能够加以利用,并据此组织、调动并集中自身内在力量于那些能够锻炼与激发个体能力的实践之上,这就构成了一个让人过上更有意义人生的基础。它是给予人们成为他们所珍视之人的自由。
接下来的部分将转向对 AI 垄断企业的讨论,揭示它们是如何压制上述这类未来机会的。
Part 3
Section 3.1
人工智能领域中潜在的垄断者不言自明:谷歌、苹果、微软、Meta 和亚马逊。这些公司以及少数其他企业在 2024 年占据了 65% 的固定网络流量和 68% 的移动网络流量[27]。谷歌大约占据全球约 90% 的搜索市场,其品牌名几乎已成为“搜索”行为本身的代名词;Meta 拥有主要的社交媒体平台,如 Instagram、Facebook 和 WhatsApp,这些都是人们日常交流与信息分享中访问量极高的平台;微软控制着大约 72% 的桌面操作系统市场;在美国,苹果约占据 60% 的智能手机市场份额;而亚马逊则主导了线上零售,其规模“超过美国排名其后的 15 家最大电商零售商的总和”[28]。此外,谷歌、Meta 和亚马逊合计占据了美国约 60% 的广告收入。我们在网上所接触到的产品、精美广告、以及注意力的买卖,主要都是由这几家大型科技公司驱动的。根据 Synergy Research [29]的研究,到本世纪末,微软、谷歌和亚马逊三家公司可能将掌握全球高达三分之二的数据份额。这些公司还控制着大部分云基础设施——亚马逊、微软、谷歌(以及阿里巴巴)合计拥有全球 67% 的云计算市场份额[30]。
这些公司拥有庞大的资源储备,同时也长期以来采用各种手段排挤竞争对手,包括通过并购消灭潜在威胁、利用市场主导地位优先推广自家产品、实行掠夺性定价、利用网络效应,以及其他众所周知的策略。例如,鉴于亚马逊在电子商务领域的市场主导地位,它可以通过优先推荐自家产品,排挤其他可能品质更高的供应商产品。消费者在面对价格更低的亚马逊产品时,往往更倾向于购买,而亚马逊正好拥有充足的资源来维持这种低价策略。在网络效应方面,“目前[31]大多数科技巨头的用户数量都以十亿计”,这为初创企业和小公司制造了几乎无法跨越的障碍。而谷歌也多次被指控故意降低某些内容的排名,并优先展示有利于自身利益的信息。
[27] https://www.applogicnetworks.com/blog/sandvines-2024-global-internet-phenomena-report-global-internet-usage-continues-to-grow [28] https://www.emarketer.com/learningcenter/guides/amazon-revenue/ [29] https://cxotoday.com/news-analysis/big-tech-to-own-two-thirds-of-world-data/#:~:text=Without%20sounding%20like%20a%20predictor%20of%20doomsday%2C,data%20centers%20while%20the%20rest%20is%20on [30] https://botpopuli.net/digging-deeper-assessing-big-techs-capture-of-the-internets-infrastructure/#:~:text=The%20dominance%20of%20Big%20Tech,Services%20(AWS)%20in%202006. [31] https://academic.oup.com/policyandsociety/advance-article/doi/10.1093/polsoc/puae012/7636223
如今,这些公司正积极争夺对人工智能发展的主导权。“Meta、微软、亚马逊和Alphabet 预计在2025年将累计投入高达 3250 亿美元的资本支出与投资……相比这些公司在2024年报告[32]的约 2230 亿美元,这相当于增长了 46%。”此外,“几乎没有例外,所有初创公司、新进入者,甚至 AI 研究实验室都依赖这些大型科技公司:他们依靠微软、亚马逊和谷歌的计算基础设施来训练系统,也依靠它们庞大的消费市场渠道来部署和销售 AI 产品[33]。”科技巨头垄断了初创公司赖以生存[34]的关键资源——人才、数据和算力。
[32] https://finance.yahoo.com/news/big-tech-set-to-invest-325-billion-this-year-as-hefty-ai-bills-come-under-scrutiny-182329236.html [33] https://www.technologyreview.com/2023/12/05/1084393/make-no-mistake-ai-is-owned-by-big-tech/ [34] https://academic.oup.com/policyandsociety/advance-article/doi/10.1093/polsoc/puae012/7636223
现有的行业巨头正在开发各种模型,以维持其在各自市场中的立足点。由于它们掌握着大多数资源——例如,“这些公司贡献了标普500指数公司市值的 22% 以上,其单独市值甚至超过了加拿大、意大利等[35]部分 G7 国家 GDP”——它们可以随意挤压竞争对手,阻止初创企业和小型公司进入市场。正如前文所述,随着 DeepSeek 在全球市场中作为竞争者不断取得进展,这些最大规模的 AI 公司正在大肆渲染一场“军备竞赛”,并夸大中国威胁以及人工智能可能带来的危害,从而推动对 AI 的监管和开发限制,而这些限制最终最有可能使它们自身受益。与此同时,由于垄断体制依赖于专有模型,其架构、权重、学习算法、代码以及内嵌目标都对公众隐蔽不明,在 AI 渗透信息网络的过程中,这些公司的经济与市场主导地位也将以一种“隐秘的方式”塑造人们的思维和行为。
[35] https://academic.oup.com/policyandsociety/advance-article/doi/10.1093/polsoc/puae012/7636223
那么,监管是否能解决这个问题呢?《麻省理工科技评论》最近指出:“监管或许有帮助[36],但政府政策最终往往加固了这些公司的权力,而非加以削弱——这些公司能够利用其资本与政治影响力来操控政策。”亚历克斯·蓝姆佩尔(Alex Rampell)[37]最近写道[38]:“拜登政府发布了一项行政命令[39],试图以人为设定的门槛限制计算能力,禁止开源技术,理由是其对国家安全构成威胁,同时这实际上为几家最大公司垄断监管资源敞开了大门。”例如,尽管萨姆·奥特曼在与贝利·韦斯(Barry Weiss)[40]的《自由新闻播客》(Free Press podcast)中否认了这一说法,投资人马克·安德森却一再警告称,拜登的 AI 行政命令的真正目的在于将 AI 的控制权交到少数几家公司(极可能是 OpenAI)手中,并通过提高市场准入门槛来消除竞争者。此外,尽管此举颇具争议、甚至可能显得天真,自从 DeepSeek 发布其 V1 和 V3 模型以来,Anthropic的 CEO 达里·阿摩地(Dario Amodei)一直呼吁加强出口管制政策[41],进一步限制中国获取芯片的能力。然而,正如迪伦·潘特(Dylan Patel)[42]和纳森·兰伯特(Nathan Lambert)[43]在 《莱克斯·弗莱德曼博客》中指出的那样,DeepSeek 的开源模型显然并不构成任何实质性的国家安全威胁。但它确实对那些依赖专有系统、通过模型控制潜在价值的生态构成了威胁。DeepSeek 的方法迫使这些“专有资本”朝着可被任何人使用与构建的公共资源方向转化。正因如此,阿摩地对“单极 vs. 双极世界”的坚持背后其实包含着竞争性的动机:要么 AI 权力集中于美国,要么中美都拥有对等的 AI 能力——而后者,在阿摩地看来,是必须避免的局面。
[36] https://www.technologyreview.com/2023/12/05/1084393/make-no-mistake-ai-is-owned-by-big-tech/ [37] 硅谷知名投资人,安德森·霍洛维茨基金(Andreessen Horowitz,简称a16z)的普通合伙人(General Partner)。 [38] https://a16z.com/why-deepseek-is-a-gift-to-the-american-people/ [39] https://www.federalregister.gov/documents/2023/11/01/2023-24283/safe-secure-and-trustworthy-development-and-use-of-artificial-intelligence [40] 美国著名记者、专栏作家,独立新闻平台自由新闻(The Free Press)的创办人。 [41] https://darioamodei.com/on-deepseek-and-export-controls [42] 半导体行业分析师,SemiAnalysis网站创始人。 [43] AI研究员、工程师。
或许,我们应当持有一种不那么鹰派的乐观态度。经济学家泰勒·科文提出了充分理由,认为与其全面投入一场军备竞赛,不如在相互合作[44]与共赢中寻找发展路径。当然,竞争仍然是必要的,但推动未来事件进程的竞争心态,不应仅仅源于达尔文式的“适者生存”逻辑,而应更接近尼采所观察到[45]的古希腊式“竞技”(Agon)[46]传统——那是一种社会制度,其中的艺术家、军事领袖与运动员通过竞争彼此激励、共同成长。
[44] https://www.youtube.com/watch?v=TcJtvzF-FP8&t=2736s [45] http://www.northamericannietzschesociety.com/uploads/7/3/2/5/73251013/nietzscheana5.pdf [46] https://en.wikipedia.org/wiki/Agon
没有对手,竞争者也将迷失方向。因为没有了改进、突破和创新的机会,个体便失去了变得更好、更具创造力的可能。竞争者的存在本身就依赖于愿意对抗他们的人。正是因为有人挑战,希腊诗人才得以想象得更深远、表达得更出色。尼采指出,希腊竞技者面临的最大危险不是失败,而是——失去竞争对手。他写道:“这正是希腊竞技理念的核心:它厌恶独裁,畏惧其危险,它渴望用‘另一个天才’来抵御某一位天才的压倒性力量。”我们不应将竞争理解为自然状态下的求生挣扎,那种资源稀缺、人与人互为威胁的霍布斯(Thomas Hobbes)式处境——“孤独、贫穷、肮脏、残暴而短暂”[47]。我们也不应将竞争本能视为某种原始性冲动的残余,只为了压制对手、消灭威胁。我们应当将其理解为一种可以高贵化的本能,正如尼采所言,它是“所有人类情感、行为与作品的唯一丰沃土壤”。竞争本能自身也具有德性,应当被培养成“在正确的时间、以正确的方式、出于正确的理由”去发挥作用的东西(亚里士多德,《尼各马科伦理学》(Nicomachean Ethics)第二卷),而不是被视作一种必要之恶。阿摩地害怕中国,这可能不是正确的回应——或许,一个更好的、更具德性的回应,是将中国视为值得尊敬的竞争者。
[47] 霍布斯的《利维坦》(Leviathan)中对自然状态下的人的生活的刻画。
Section 3.2
现在让我们聚焦于这些潜在的 AI 垄断企业为何会通过主导 AI 生态系统,压制质性丰富机会的更广泛传播。原因至少有两个:第一个涉及经济能动性,第二个涉及价值能动性。所谓经济能动性,是指人们进入市场、创造能满足消费者需求与欲望的价值与效用的能力。如果市场上的 AI 模型被集中掌握在少数公司手中,新兴企业与创业者为世界做出有价值贡献的机会将受到限制。那些能够回应民主、医疗保健、金融自主、政治权利与自由,或其他重大而有意义问题的创新,将大幅减少,从而也会降低 AI 所可能带来的社会福祉。任何威胁到这些少数 AI 垄断企业的控制力、影响力或财富的产品与服务,将被直接排除在市场之外,而不是由市场自然机制或消费者的真实需求所决定。
另一方面,所谓价值能动性,是指人们有能力对社会应追求的目标产生影响、发表意见。如果 AI 是在不透明的条件下、依据无法被公众了解和介入的价值与目标进行训练的,那么人们在这些问题上的影响力就会被削弱。如果由专有模型决定大多数或几乎全部嵌入 AI 的产品与服务的性质,那么人们对这些技术的控制权将大为减少。例如,所谓“对齐问题”指的是如何使 AI 与人类的利益保持一致。那么,什么是人类的利益?什么是构成一个良好且值得追求社会的目标?AI 的运行应遵循哪些道德与伦理原则?这些价值是否可以由少数几家公司决定,而无需公开其训练数据与学习算法?是否可以不接受公众监督与介入?如果技术架构被封闭在公众视野之外,那么上述问题的答案就更有可能来自权威的决定,而不是通过民主程序获得的共识。
经济能动性与价值能动性的双重丧失是危险的,本文余下部分将进一步阐述原因。
Section 3.3: 经济能动性
正如奥地利经济学家路德维希·冯·米塞斯(Ludwig von Mises)与弗里德里希·哈耶克(Friedrich Hayek)所著名指出的,苏联之所以在某些方面具有毁灭性,部分原因在于它无法通过自然发生的市场机制来合理分配资源。在这样的体制下,由内部的中央计划者来决定人民的需求与欲望——而这些人所掌握的信息资源既稀缺、又充满偏见与误差,无法实现准确分配。因此,大量官僚主义和强制性的手段被实施来调配国家资源。
举例来说,国家必须设定价格。至少是在苏联的情况中,并不存在一个广泛可用的自由市场,来使商品与服务受到供需关系的调节。生产者依据国家命令进行生产,而非根据市场激励(如竞争)自行调整方向——这些激励本应协调生产与消费,促成市场均衡。换句话说,价格失去了其关键信息功能——它本应指示资源该流向何处。哈耶克在《通往奴役之路》(The Road to Serfdom)中写道:“任何对某些商品的价格或数量的控制,都剥夺了竞争协调个体努力的能力,因为此时价格变动无法反映环境中的相关变化,也就无法为个体行动提供可靠的指导。”
不过,对本文来说,更重要的是:国家控制的生产与经济计划还意味着人们被剥夺了进入市场并创造价值的机会,使他们难以通过创新改善自身生活。任何可能威胁国家权力、削弱其合法性与影响力,或转移其部分控制权的创新行为,都将被禁止进入市场。举个例子:假设某人观察到,在某国的偏远乡村地区,由于常年洪水泛滥,人们无法修建道路,从而难以参与国家选举。这位发明者研发了一种不受洪水腐蚀的新型混凝土,并希望在乡村修建道路,改善人们的通行条件,让他们更容易参与公共事务。但当他向国家交通委员会申请资源时,却遭到了拒绝。原因是:该地区居民普遍希望拥有农业生产的自主权,因此国家不愿意为这些人提供进入选举制度的通道。而在缺乏市场竞争的情况下,也没有其他机会和机制可以去建设这些道路。
垄断,尤其是在受到监管体系保护的情况下,构成了类似的威胁。马克思曾做出一个著名批评:资本主义作为一种社会制度,其内在逻辑会逐步而不可避免地导致生产资料向少数人手中集中。虽然包括哈耶克和米塞斯在内的许多经济学家认为这种看法是错误的,并坚信在正常运作的资本主义体系中,这一结果是可以避免的。但如果人工智能遭到垄断,那么马克思的预测将比以往更加接近现实——无论这是由于历史规律,还是由于无法预见的结构性变数所致。正如克里斯·迪克森(Chris Dixon)[48]在其著作《阅读、写作、拥有》(Read, Write, Own)中观察到的,初创公司之所以能在市场中找到生存空间,部分原因在于大公司往往目光短浅,无法及时察觉到新兴产品正逐步获得消费者的关注。在专注于自身业务的过程中,这些巨头常常错失市场趋势与动向,而初创企业若运气足够好,就能积累足够势能以形成竞争力。但如果这些老牌巨头掌控了人工智能,他们就可能利用 AI 的能力来抹平初创企业原本可以利用的那些优势。随着时间推移,垄断企业将对市场形成难以穿透的控制权,各行各业的价值链最终将进一步“上游集中”到这些公司手中——比现在更甚。由专家所忽视、却能在市场中创造出意想不到价值的颠覆性技术,其创新空间可能会被完全挤压出去。
[48] 安德森·霍洛维茨基金普通合伙人,负责加密货币与Web3投资部门(a16z crypto)。
由于人工智能具备智能能力,它作为资本工具拥有极大的潜力,能够创造出改善人类生活的先进技术。但,由于有些对公众最有益的应用方式,可能并不符合政府与大型企业的利益,其潜在福祉也就可能在权力结构中被悲剧性地削弱。其中最明显的例子就是金融自主权。
看看比特币的案例就足以说明问题。中本聪(Satoshi)[49]发明比特币的初衷,是为了让人们拥有金融自由的能力——通过创造一种稀缺资源,其价值储存功能可与黄金相类比。比特币使那些生活在高通胀、货币极度贬值国家的人们,能够积累具有全球流通性的财富。人们可以拥有一种不会因货币供应过量或国家财政赤字上升而贬值的资产。比特币能够帮助人们过上更加稳定、安全的生活,它提供了透明性、个人所有权,以及能够激励社会合作的制度安排——这一切都无需依赖强制性信任或道德施舍。
[49] 比特币(Bitcoin)的创造者,身份不明。
人们本希望掌权者能够设法将中本聪为世界带来的巨大价值纳入现有体系。并不是说比特币应立即取代法定货币,而是说,考虑到比特币在应对法币体系中潜在致命问题方面提供了极具前景的解决方案,政府至少应当付出更大的努力,将这些解决方案纳入实践。合理的期待是,执政者会寻求一种方式,将区块链、比特币及其增强经济自由的潜力加以整合。然而,直到最近,有关这一技术的监管进展一直缓慢而混乱。在拜登政府期间,由于政策缺乏清晰性与明确性,关于加密货币的许多举措都未能充分发挥其潜在价值,反而阻碍了其更高效、更具生产性的使用路径。
如果AI被通过监管框架实现垄断,那么那些原本有潜力改善人类生活的技术也可能轻易被弃置。若这些技术与政府或企业利益发生冲突,大多数人将无法通过授权或专利使用这些专有模型,而中小型企业也会被并购吸收。尽管人工智能本可以彻底革新选举平台及人们参与选举的方式;尽管它本可以通过更优的数据安全手段或创造更多经济机会来增强个体自由,但探索这些可能性的路径,若与掌控大多数 AI 技术栈(甚至全部)的公司利益不符,就很可能被封锁。如果某项潜在的 AI 技术有可能通过解决某些产业赖以牟利、甚至具有寄生性质的问题,从而威胁广告收入,那么像谷歌与 Meta 这样的科技公司几乎必然会阻止这一技术进入市场的尝试。
特朗普政府迄今为止最重要的政策举措之一,就是其新的加密货币政策。该政策废除了上一届政府的行政命令,并致力于制定一个有助于推动该技术发展的监管框架。这对于人工智能领域中正在发生的其他形式的创新具有重要意义。有了除了传统风险投资之外的其他资源——例如通证经济(tokenomics)[50],初创公司可以为其项目提供资金支持,并积累发展势能。
[50] 也译为“代币经济学”,是对加密货币或区块链项目的经济层面的研究和分析,尤其关注其原生数字代币的设计和发行。该术语由“代币/通证”(token)和“经济学”(economics)两个词组合而成。
彼得·蒂尔在其著作《从零到一》(Zero to One)中提出,初创公司本身就在、也应该在寻求成为垄断者。他们需要在市场中占据一个特定空间,通过开发专有技术击败其他竞争者,并进一步排除后来者进入该市场。正如蒂尔所言,如果企业不想成为失败者,这种策略是至关重要的。若他们希望获得投资者的关注,就必须采取建立垄断地位的路径。然而,借助通证经济以及其他与加密货币相关的机制,人们也有机会开发出有价值的技术,同时保留开源精神。在这样的机制下,合作与协作得以推动,同时也能获得支持增长所需的资金。
Section 3.4 价值能动性
经济能动性之所以被削弱,是因为市场中那些具备质感的价值创造机会正在减少,使个体难以通过创新与生产满足不断变化的需求与欲望。当 AI 技术栈被少数几家垄断企业掌控并主导整个生态系统时,即使有人识别出一个真正有意义的问题,并设计出强有力的解决方案,如果这不符合大型企业的利益,该方案也很可能无法进入市场。经济活动及其所带来的社会价值,不应建立在一套容许权力任意压制、扼杀对社会整体有益事务的权威机制上。那么,AI 垄断企业又是如何压缩人们在价值能动性上的“质性丰富机会”的呢?
如果雷·库兹韦尔的奇点理论及其相关预测哪怕部分属实——如果人类真的将与非生物智能融合,并生活在日益人工化的环境中——那么人工智能的垄断不仅不可取,而且可以说是一种反乌托邦式的局面。这种设想唤起了关于“技术霸主”的画面:他们主宰着人类社会,而人们要么沦为智能机器的奴工,要么则是舒适而满足地享受着智能繁荣所带来的物质成果。在这样的图景中,总有人必须开采矿物资源,而另一些人则消费着由此生产出的丰富商品与服务。但如果我们假设 AI 的发展会快到足以让智能机器人无需人力就能完成矿产开采工作,那最终所有人都会转变为纯粹的“消费者”。“在接下来的几十年里,”库兹韦尔预测,“几乎所有例行性的体力与脑力活动都将被自动化。”届时,唯有那些具有社交性、创造性、创新性或高度不可预测性的工作将对拥有相关技能与培训的人开放,其余人将大多成为消费者。而借助纳米机器人、虚拟现实、非生物智能增强技术与无处不在的信息流动,我们的现实将愈加接近哲学家罗伯特·诺齐克(Robert Nozick)所设想的“体验机”(experience machine)。
通过某种装置的介入——无论是接入某种模拟装置,还是完全沉浸于类似虚拟现实(VR)那样的数字化、信息化环境中——人们可以体验到他们所希望的任何事情。任何感官体验、情绪、思想或事件,都会随时向任何人开放,随时可供消费。一个人可以体验写出“伟大的美国小说”所带来的深刻满足,像苏格拉底[51]那样在雅典法庭上勇敢地对抗陪审团,或像拿破仑那样英勇地站在青翠的高岗上俯瞰敌军,也可以在模拟的攀登中登上珠穆朗玛峰,体会坚持不懈的荣耀与世界之巅的视野。重要的不是这些事件是否真实发生,而是有人“渴望”它,而它就会“存在”。在这样的图景中,人生的目标就是消费;而“道德生活”——值得追求的生活——则被定义为追求内部刺激的生活。外部世界、个体真实的存在状态将不再重要。一个人是否真实地勇敢、富有同情心、充满爱意、公正、虔诚、善良或邪恶——这都不再有意义。人们的兴趣与冲突将在人工体验的消费中得到调和。在一个“问题已被解决”的世界中,没有需要行动者去解决的具体问题,行动者也就变得可有可无;唯一需要的,是“消费”。
[51] 古希腊哲学家。
这种情境真正危险之处在于,垄断企业将完全掌控生成技术的算法,也即控制我们可接触的信息结构。信息将不断被嵌入到以消费为中心的环境中。理想情况下,人们应当拥有自由,做他们想做的事,以他们认可的方式生活。但人们“看待”世界的方式,他们建构现实的方式,他们所处的社会语境——都会被那些已经整合智能资本、成为未来唯一商品与服务生产者的公司所过滤与塑造。哲学家艾伦·布鲁姆(Allan Bloom)在其著作《美国精神的封闭》(The Closing of the American Mind)中写道:“每一个教育系统都有一个它希望达成的道德目标,并据此构建其课程。它希望塑造出某种特定类型的人。”人工智能的垄断企业将通过改造人的生存环境来塑造“人是什么”的意义,以符合其自身利益。而真正重要的那些事情——运用能动性、实现真实的自我效能感、发现自己在人生中真正珍视与渴望的事物、建构让现实更一贯、宜居和统一的人生目标等等的机会——将被被企业利益所强烈影响和操控。而这些利益,本质上是围绕经济增长与利润最大化构建的。
在诺姆·乔姆斯基(Noam Chomsky)[52]与爱德华·赫尔曼(Edward Herman)[53]合著的《制造共识》(Manufacturing Consent)[54]一书中,两位作者提出,美国媒体实际上是一种宣传工具,而非客观的信息来源(这一观点当时颇具争议,但如今已成为主流看法)。他们认为,这种宣传功能是通过一套“过滤模型”来运作的,该模型将信息作为输入,并为公众“福祉”完美制造出标准化的输出。而其中一些媒体过滤机制,正是今天科技巨头所采用的。第一个过滤器是媒体公司的规模、所有权结构及其以利润为导向的商业模式。这使得进入媒体市场所需的投资与准入成本变得高得惊人,从而使其他竞争者难以生存。法律制度被用来执行一系列标准,这些标准压制了初创公司与中小企业的发展;而政府补贴则倾向于支持那些与政府利益保持一致的媒体公司。第二个过滤器是广告收入。广告不仅提升了特定公司的利润,也让它们在竞争中占据优势。那些无法吸引广告支持的媒体来源往往被市场边缘化。在此过程中,那些资金雄厚的媒体公司为了争取广告商的“青睐”,被迫迎合股东所要求的持续利润增长。这意味着任何挑战企业利益的声音,都可能因营收减少而遭受惩罚,最终被逐出市场竞争。
[52] 美国教授和公共知识分子,以其在语言学、政治活动和社会批评领域的研究而闻名。乔姆斯基有时被称为“现代语言学之父”,他也是分析哲学的重要人物和认知科学领域的创始人之一。 [53] 美国经济学家、媒体学者和社会评论家。 [54] https://focalizalaatencion.wordpress.com/wp-content/uploads/2012/08/herman-chomsky-2002-manufacturingconsent.pdf
这两个过滤器,正是当今科技巨头在其平台上运用的机制。他们主导市场,并依靠广告收入获取惊人的利润。正如乔姆斯基与赫尔曼所指出的另一个过滤器——意识形态偏向,大科技公司同样如此。就像上世纪八十年代的主流媒体会大肆报道敌对国家的种族灭绝与谋杀,却对发生在美国“势力范围”如拉美地区的同类事件视而不见,大科技公司也会在符合其经济与利益考量时,沿着特定的意识形态线索行事。由于其庞大的利润模式与动机,大科技公司的利益并不必然与真理、勇气、准确性、诚实、公正或善恶标准一致。只有当这些价值可以带来可预见的利润与效用最大化时,它们才可能被采纳。因此,如果 AI 垄断企业逐步获得市场主导权,并以其最先进模型为基础将大量商品与服务推向市场,那么人们对于世界的理解、他们如何看待现实、哪些事物最值得关注——都会在信息过滤器的引导下被重塑。这些过滤器正是大科技公司用于“产出有利于技术发展结果”的机制的一部分。个体发展自身的机会、形成自我世界观的过程、以及构成生活统一性的价值体系,都将受到科技信息过滤器的支配与重构。
我们很容易想象这样一个世界:信息的生成由一小部分集中的模型主导,这些模型构建出一套相互交织的信息网络,强化着不准确、不诚实、甚至是伪造的信息结构。新闻标题与报道可能散布错误主张与对现实的歪曲,而这些说法又会被其他虚假信息源所“证实”,彼此互为支撑。这种信息结构——即信息的组织方式及其意义赋予机制——可能会被人为策划,以服务于掌握权力与控制信息传播资源者所设定的特定目的。少数人认为“最好的”内容将被优先推送,而公众的想法将逐渐变得从属,最终被操控以符合权力方的利益。这并不是在指责某个实体或个人有恶意意图,而是在强调这样一种结构性困境:当生成并传播社会所消费的信息的能力被集中在少数几方手中时,这种权力格局所带来的难以解决的困境。
这最终将不可避免地导向类似于前文提到的诺齐克“体验机”的世界。人们获得一种超越消费伦理的生活形式能力的机会将被极大压缩,甚至被彻底剥夺。确实,假设未来大多数工作被自动化,人们通过基本收入实现生活保障,那么个体将从劳作的束缚中解放,不再被迫为经济增长贡献劳动力。从某种意义上说,人类将获得对约束与必需品的自由。但问题在于,如果没有施展自由的媒介,如果没有真正的机会在具体经验中运用自己的能动性,那么这种自由就并不是真正的自由——至少不是那种更深层次的、积极意义上的自由。那种引导人们思考“如何生活”、那种通过探索而发现值得投入心力与时间的事业的过程、那种确立人生目标并在充满挑战与刺激的环境中努力实现的能力,将会在这样的结构中逐渐失效,甚至彻底被边缘化。
哲学家约翰·杜威(John Dewey)曾写道:
我们很少意识到,我们对什么有价值、什么无价值的判断,在多大程度上是受制于我们并不自觉的标准。但一般来说,那些我们未经思考便视为理所当然的事物,正是决定我们有意识思维与判断结论的关键。而那些位于反思之下的习性,往往正是在我们与他人的持续互动与交换中形成的。
如果构成社会的制度是由那些以提升股东利润为目的的大型企业所主导——这将在它们主导人工智能时成为现实——那么它们的模型将渗透进经济的每一个领域,渗入我们的环境。这些环境将影响我们所被激发的生活方式,朝向不再体现为实际的‘存在’(being),而是依赖于‘拥有’(having)。也就是说,什么是显著的、值得追求的、具有吸引力的,不再取决于它所需要的努力、它所要求的冒险精神,或它所能激发的成长过程,而是取决于它能否填满并打发时间。对于一种由消费伦理塑造的意识而言,显而易见、理所当然的东西,将与另一种由合作构成、旨在促使个体能动性寻求意义与目标的社会完全不同。前者会看到一个充满各种可能体验的世界,但这些体验除了即时呈现的感受之外毫无意义;而后者则仍然会体验到“必要性”,以及那种不可遏制的冲动——即人必须感受到世界上仍有值得行动之事。赫尔曼·梅尔维尔(Herman Melville)在其伟大的美国小说《白鲸》(Moby Dick)中写下了这样的句子:
我坚定目标的道路铺设着铁轨,我的灵魂被刻槽其上。穿越无底峡谷,穿越山脉深处与激流之下,我直奔而去!没有障碍,没有转弯,只有通向铁轨终点的直路!
但愿,那些曾赋予梅尔维尔写作力量的精神碎片,在未来的某个角落依然得以存在。
Section 3.5
在《查拉图斯特拉如是说》(Thus Spoke Zarathustra)一书中,尼采描绘了两种未来人类的形象:“末人”(Last Man)与“超人”(Overman)。这两者在本能、欲望、动机与驱力方面有着根本性的不同。他们所看到的世界、感知世界的方式也截然不同:哪些事物对他们而言是显著且有意义的,什么是“善”或“恶”,对自我与世界的信念与态度,皆南辕北辙。
尼采对“末人”充满蔑视,而他的理想目标则是“超人”。“末人”代表一种追求舒适、安逸与满足的生活方式——那是一种消费的生活,是一种被动的满足。末人的畜群(herd)沉浸在“白天的微小快乐、夜晚的微小快乐中,但极度重视健康。他们说:‘我们发现了幸福’,眨着眼睛”。这样的存在,培养出的是享乐、安逸、饱足与消费的本能。尼采常将这种状态比喻为“反刍的牛”。而“超人”则是那种能够保有创造与超越本能的存在,他将生命导向某个遥远而艰难的目标,借此创造出一种超出自身的价值,使生活因此获得尊严与意义。超人仍然保有那种穿越变革性经验的冲动,那种能改变自我存在状态与意识体验的本能。正是这种冲动激发个体去掌握现实、理解现实,并因此增强他们影响现实的能力——个体越来越能够通过自己的活动与存在方式去塑造经验,建构世界。“末人”的美德——最大化快乐并最小化痛苦,在“超人”看来,恰恰是堕落的恶德。
人工智能的垄断结构及其以利润为导向的模式,正在推动“末人”的出现;而开源则是在为“超人”保留空间。随着人工智能被集中于少数强权之手,并通过这些权力机构设定的参数向市场大量输出商品与服务,整个信息景观及其传播网络将被精心策划成一种伦理结构——这种伦理以最大满足与持续消费所带来的舒适感为核心。在这样的结构中,个体所接触到的机会与环境将不再是“质感质性丰富”的;它们不会激发人们内在的主动能力,而只会使人变得能够追求一种消费社会所设定的终极目标——即最大化产出与回报的路径。
而开源生态系统,则保留了一个人类能动性仍能找到出口的空间。在那里,创造力与创新的目标不再仅仅是为了逐利,而是为了实现一种更完整的人类生活。
现在,本文开篇提出的一个问题是:自动化是否能带来足够多的机会,使被替代的劳动力能够重新获得工作?到现在我们已经看到,黑客范式与开源生态系统的确让这一目标更为可行。彼得·蒂尔的《从零到一》可以说是一本创业者指南。而他在书中明确指出:创业的目标应当是至少模仿,并努力实现垄断。所谓“成功”,就是在某一市场领域内占据主导地位,排除其他进入者,并通过专属供应尚未满足的需求来实现利润最大化。但成功初创企业的统计数据[55]却令人沮丧。初创企业的失败率高达90%。在那些成功者中,首次创业者只占18%。获得风险投资资金的初创企业不到1%;获得天使投资的比例也不到1%;约有75%的初创公司依赖“信用卡债务、商业贷款与信用额度”来筹集资金。成功的几率微乎其微,而对那些敢于创业,尤其是技术驱动型创业者(这是失败率最高的一类)所需承担的门槛与风险,往往近乎不可逾越。蒂尔之所以鼓励初创企业采用垄断策略,部分原因正是因为唯有在获得足够稳固的市场地位之后,公司才终于能够喘息、拓展与创新。一旦达到垄断标准,企业便能掌控其特定领域(甚至是整个)市场中的价值输出——理论上,这会给企业与消费者双方带来好处。
[55] https://explodingtopics.com/blog/startup-failure-stats
然而,这种能力最终被集中在极少数能够侥幸成功的公司手中。一旦掌握了这种能力,它们便没有自利的动机去放手。而当某家企业依靠其垄断地位终于获得创新的自由之时,这种专属能力却也意味着其他拥有创造潜力的人被排除在外,仅仅因为他们没有获得那唯一的机会。
如果企业的成功几率更高,那无疑会更具吸引力。但传统的融资方式以及作为成功创业者所需经历的艰难过程,往往会打击甚至扼杀那些本有能力提出改变世界的强大创意的人们。而黑客范式之所以具有深远意义,正是因为它能够提供丰富的机会,让人们得以创造价值,而无需承担传统创业所附带的高风险。黑客范式的“北极星”之一,就是致力于打造一个开放的、无需许可的生态系统——一个充满机会、人们可以自由进入、自由利用关键技术信息,并能够与成熟企业协作,从而共同创造出更好、更具创新性的产品的环境。开放的生态系统能够赋予人们创造价值的可能,而封闭系统则将他人排除在外,关闭了协作的大门。
按照蒂尔模式的创业路径,那是一条崎岖不平的道路。它需要强烈的意志、非凡的创造力,当然还需要一定的运气。而这三者的完美契合,是极其罕见的。因此,真正能在创业中成功的人少之又少。通过一个无需许可的开源生态系统,通过减轻人们在创造有价值事物时所承受的沉重负担,我们可以释放出大量机会——这些机会无需你拥有成为乔布斯或贝索斯那样的雄心与资源,也不要求你必须独力成就一番技术帝国。事实上,那些科技巨头的成功,早已远远超越了他们当初想要创造创新科技的初衷。开源生态系统将推动科技进步的机会民主化,使人们能够真正参与其中,不必成为少数天才企业家的复制品。创新,理应是更具协作性、更广泛分布的,也应当距离普通人更近。黑客范式正在使这成为可能,它正在重构赛场的平衡。
或许,并不是每个人都想成为一名“黑客”。但开源为我们保留并拓展了一种最佳的原型模式,通过它,可以将具体的机会持续地、公平地分配给人们,让他们得以实践自己的能动性。正是通过拥有这类机会,人们仍能发现和体验到那种强烈的召唤感——“我必须去做某事”——即,一个目标的存在,使个体不得不相信,若忽视它,人生就将失去意义与目标。如果我们生活的世界中,人们能接触到的、最显眼且最具吸引力的事物,仅仅是尼采所说的那种“幸福”——那种不涉及个人牺牲、不包含作为德性的献身(devotion)、也无需为艰难而变革性的事业奋斗的意愿的“幸福”——那么这样的世界无疑比不上另一个世界:在那里,人们拥有真正的机会去成就伟大的事业,只要他们愿意去追求。
结语
当 IBM 的“深蓝”在 1997 年击败国际象棋冠军卡斯帕罗夫(Garry Kasparov)时,象棋并未因此被淘汰。人们依旧继续比赛,并不断变得更强。这一事实——即从那以后任何人类棋手都不可能战胜 AI 程序——并未动摇那些热爱象棋之人的热情与动力。那些献身于象棋的人依旧渴望打磨自己的技艺,学习更复杂的策略,在不断成长的过程中超越其他选手。象棋选手依然渴望变得更优秀,仅仅是为了变得更优秀。通过意志与投入实现成长,当他们登上新的水平时,那种深刻的成就感依旧真实而宝贵,尽管一台机器将永远是更强的选手。
在一部关于李世石(Lee Sedol)在 2016 年败给 AlphaGo 的纪录片中,有人说:“他在这台机器的对弈中获得了成长。他的人性在与这台无生命的创造物对局之后得到了拓展。而我们的希望,是这种机器,尤其是背后的技术,也能对我们所有人产生同样的作用。”还有人说:“或许 AlphaGo 能向人类展示一些我们从未发现过的东西。或许那是一种美。”如果被正确使用,人工智能可以拓展个体影响与改变世界的能力。它可以提供创造的机会,而非只是劳作的义务;可以唤起意义的体验,而非冷漠与疏离;可以使人获得一种有价值的自由,而非无所依托的自由。但这一切都取决于社会写作和去推动人们向值得努力实现的目标前进的环境;它也要求我们以不同的方式理解竞争。
Agency/Agent/Agentic/… 能动性 Being (以…方式)存在 Qualitatively Rich 质性(上)丰富 Open Source Ecosystem 开源生态系统 Proprietary 专有 Pleasure 快乐 Happiness 幸福 所有著作、节目与人物名称第一次出现标记英文原文。 除网站链接之外的脚注,均为译者补充;脚注中的外部链接为原文超链接的对应标记。 原文中的特殊格式均保留在中文对应词项中。
-
 @ c9badfea:610f861a
2025-05-05 23:29:08
@ c9badfea:610f861a
2025-05-05 23:29:08- Install RTranslator (it's free and open source)
- Launch the app, allow notifications, and enter a random name (used only for Walkie-Talkie/Conversations)
- Wait for the translation AI models to download
- Enjoy offline translations
ℹ️ Internet is only needed for the initial download
ℹ️ The app uses the system's TTS engine (consider open source TTS engines like SherpaTTS for de-googled phones)
-
 @ 7e8ca676:b6a7569f
2025-05-13 01:47:06
@ 7e8ca676:b6a7569f
2025-05-13 01:47:06There was a time when Bitcoin smelled like ozone and rebellion. When men wore hoodies because they meant it. When software didn’t come with a mission statement or a DAO-approved pronoun guide. When the only thing a Bitcoin dev feared was being wrong, not being unpopular. \ \ That time is dead. \ \ It died somewhere between the fifth Twitter thread explaining why putting JPEGs on the base layer was “valid use,” and the fiftieth PR that added complexity to the engine in order to simplify the cupholders. Now we’re here, ankle-deep in a pool of our own mediocrity, arguing over whether we should triple the OP_RETURN limit so a VC-backed sidechain company can offload its plumbing costs onto your Raspberry Pi. \ \ Welcome to the future. It’s paved in GitHub comments and smells like a WeWork bathroom. \ \ Let’s speak plainly. This whole drama is not about OP_RETURN. It’s about power. Not electrical power. Not hash power. Soft power. The power to redefine what Bitcoin is for, one pull request at a time. It is the power to turn the protocol from a blunt, uncompromising monetary weapon into a polite corporate middleware bus for protocol startups that couldn’t raise a Series B without a little help from their friends in Core. \ \ Jameson Lopp wants to increase the OP_RETURN limit. Why? Because his company, Citrea, needs to squeeze a few more bytes into every transaction. It's not a crime. It’s not even dishonest. It's just pathetically on the nose. They don’t want to pay miners directly. They want the mempool to be their free emergency broadcast system. They want to lean on the public infrastructure without sending flowers or even a thank-you note. \ \ And what does Core say? \ \ They say yes. \ \ Because of “technical merit.” \ \ Because it’s “more efficient.” \ \ Because the devs have long since stopped being guardians of the protocol and started being unpaid product managers for whoever can string enough buzzwords together in a conference talk. \ \ You can see it in their eyes. You can hear it in their interviews. The Core devs aren’t building Bitcoin anymore. They’re managing Bitcoin. They’re curating it. Polishing it. Nerfing it for mass adoption. Like a bunch of Brooklyn baristas trying to make espresso kid-friendly. Bitcoin used to be an espresso shot poured directly into the mouth of the Federal Reserve. Now it’s a lukewarm latte with oat milk and consensus-breaking sprinkles. \ \ The worst part? The refusal to acknowledge that this is not about UTXO bloat. It's not about cleaner mempools. It’s about upstreaming corporate convenience into the base layer under the halo of neutrality. It’s about giving polite names to ugly compromises. “Policy adjustment.” “Ergonomic improvement.” “Relay optimization.” They speak in this weird dialect of bureaucratic techspeak that means nothing and does less. \ \ Meanwhile, the only thing that actually matters gets lost: ossification. \ \ The holy grail of this protocol is ossification. Not stagnation. Not laziness. Not gridlock. Just stability. The longer Bitcoin can go without consensus changes, the more credible it becomes. The more unchangeable it becomes. Like gravity. Like rust. It doesn’t matter how good your argument is. The system won’t budge. That’s the point. The value of Bitcoin isn’t in how clever the devs are. It’s in how irrelevant they become. \ \ But ossification isn't something you declare. You sneak up on it. You approach it sideways, like a wild animal. You do less and less until eventually you’re doing nothing at all, and nobody even remembers how to change the code anymore. That is the goal. To make the protocol so boring, so petrified, that no one can move it. Not Lopp. Not Luke. Not even Larry from Legal. \ \ To get there, we need something devs hate: client balkanization. \ \ That means splitting the client into pieces. Break the codebase. Separate the consensus engine from the policy fluff. Let people run different implementations. Let the free market decide what filters they want, what mempool rules they tolerate, what behavior they’re willing to relay. You want a node that bans inscriptions? Run it. You want a client that auto-forwards every transaction with a JPEG of your left toe? Go for it. Just don’t make it my problem. \ \ Right now, Bitcoin Core is a monoculture. It’s the cathedral and the altar and the pamphlet all rolled into one. That’s not healthy. That’s a single point of failure. That’s a priesthood. \ \ And no, Bitcoin isn’t a religion. It’s worse. It’s a culture. Religion has rituals. Culture has habits. And habits are harder to break. Especially when your dev team gets drunk on the idea that their opinions are features. \ \ If you want to fix this mess, you need to kill the idea that Bitcoin Core is the final word. Strip it down. Remove every line of non-consensus code. Make it boring. Make it dumb. Let the client rot in peace, and let a thousand weird little nodes bloom. \ \ Let the spammers spam themselves into oblivion. Let the free-riders find someone else to subsidize their infrastructure. Let every operator set their own damn filters. \ \ You’ll know ossification is working when the devs start getting bored. When they stop showing up. When there are no more debates. When the politics dry up. When Jameson Lopp finally logs off. \ \ Until then, every line of code you don’t remove is a future argument you’ll be forced to have with someone who thinks “data availability” is more important than keeping the protocol boring. \ \ Bitcoin does not need to be exciting. It needs to be a brick. A self-righteous, opinionated, uncompromising, utterly stubborn monetary brick. \ \ Keep your hands off it. \ \ And take your startup with you.OP_RETURN and the Cult of Cleverness: Or, How Bitcoin Core Learned to Love the Smell of Its Own Farts
There was a time when Bitcoin smelled like ozone and rebellion. When men wore hoodies because they meant it. When software didn’t come with a mission statement or a DAO-approved pronoun guide. When the only thing a Bitcoin dev feared was being wrong, not being unpopular.
That time is dead.
It died somewhere between the fifth Twitter thread explaining why putting JPEGs on the base layer was “valid use,” and the fiftieth PR that added complexity to the engine in order to simplify the cupholders. Now we’re here, ankle-deep in a pool of our own mediocrity, arguing over whether we should triple the OP_RETURN limit so a VC-backed sidechain company can offload its plumbing costs onto your Raspberry Pi.
Welcome to the future. It’s paved in GitHub comments and smells like a WeWork bathroom.
Let’s speak plainly. This whole drama is not about OP_RETURN. It’s about power. Not electrical power. Not hash power. Soft power. The power to redefine what Bitcoin is for, one pull request at a time. It is the power to turn the protocol from a blunt, uncompromising monetary weapon into a polite corporate middleware bus for protocol startups that couldn’t raise a Series B without a little help from their friends in Core.
Jameson Lopp wants to increase the OP_RETURN limit. Why? Because his company, Citrea, needs to squeeze a few more bytes into every transaction. It's not a crime. It’s not even dishonest. It's just pathetically on the nose. They don’t want to pay miners directly. They want the mempool to be their free emergency broadcast system. They want to lean on the public infrastructure without sending flowers or even a thank-you note.
And what does Core say?
They say yes.
Because of “technical merit.”
Because it’s “more efficient.”
Because the devs have long since stopped being guardians of the protocol and started being unpaid product managers for whoever can string enough buzzwords together in a conference talk.
You can see it in their eyes. You can hear it in their interviews. The Core devs aren’t building Bitcoin anymore. They’re managing Bitcoin. They’re curating it. Polishing it. Nerfing it for mass adoption. Like a bunch of Brooklyn baristas trying to make espresso kid-friendly. Bitcoin used to be an espresso shot poured directly into the mouth of the Federal Reserve. Now it’s a lukewarm latte with oat milk and consensus-breaking sprinkles.
The worst part? The refusal to acknowledge that this is not about UTXO bloat. It's not about cleaner mempools. It’s about upstreaming corporate convenience into the base layer under the halo of neutrality. It’s about giving polite names to ugly compromises. “Policy adjustment.” “Ergonomic improvement.” “Relay optimization.” They speak in this weird dialect of bureaucratic techspeak that means nothing and does less.
Meanwhile, the only thing that actually matters gets lost: ossification.
The holy grail of this protocol is ossification. Not stagnation. Not laziness. Not gridlock. Just stability. The longer Bitcoin can go without consensus changes, the more credible it becomes. The more unchangeable it becomes. Like gravity. Like rust. It doesn’t matter how good your argument is. The system won’t budge. That’s the point. The value of Bitcoin isn’t in how clever the devs are. It’s in how irrelevant they become.
But ossification isn't something you declare. You sneak up on it. You approach it sideways, like a wild animal. You do less and less until eventually you’re doing nothing at all, and nobody even remembers how to change the code anymore. That is the goal. To make the protocol so boring, so petrified, that no one can move it. Not Lopp. Not Luke. Not even Larry from Legal.
To get there, we need something devs hate: client balkanization.
That means splitting the client into pieces. Break the codebase. Separate the consensus engine from the policy fluff. Let people run different implementations. Let the free market decide what filters they want, what mempool rules they tolerate, what behavior they’re willing to relay. You want a node that bans inscriptions? Run it. You want a client that auto-forwards every transaction with a JPEG of your left toe? Go for it. Just don’t make it my problem.
Right now, Bitcoin Core is a monoculture. It’s the cathedral and the altar and the pamphlet all rolled into one. That’s not healthy. That’s a single point of failure. That’s a priesthood.
And no, Bitcoin isn’t a religion. It’s worse. It’s a culture. Religion has rituals. Culture has habits. And habits are harder to break. Especially when your dev team gets drunk on the idea that their opinions are features.
If you want to fix this mess, you need to kill the idea that Bitcoin Core is the final word. Strip it down. Remove every line of non-consensus code. Make it boring. Make it dumb. Let the client rot in peace, and let a thousand weird little nodes bloom.
Let the spammers spam themselves into oblivion. Let the free-riders find someone else to subsidize their infrastructure. Let every operator set their own damn filters.
You’ll know ossification is working when the devs start getting bored. When they stop showing up. When there are no more debates. When the politics dry up. When Jameson Lopp finally logs off.
Until then, every line of code you don’t remove is a future argument you’ll be forced to have with someone who thinks “data availability” is more important than keeping the protocol boring.
Bitcoin does not need to be exciting. It needs to be a brick. A self-righteous, opinionated, uncompromising, utterly stubborn monetary brick.
Keep your hands off it.
And take your startup with you.
-
 @ a296b972:e5a7a2e8
2025-05-05 22:45:01
@ a296b972:e5a7a2e8
2025-05-05 22:45:01Zur Gründung der Bundesrepublik Deutschland wurde infolge der Auswirkungen des 2. Weltkriegs auf einem Teil des ehemaligen Deutschen Reiches (nicht des 3. Reiches!) auf Initiative der westlichen Alliierten, federführend die USA als stärkste Kraft, eine demokratische Grundordnung erarbeitet, die wir als das Grundgesetz für die Bundesrepublik Deutschland kennen und schätzen gelernt haben. Da man zum damaligen Zeitpunkt, im Gegensatz zu heute, noch sehr genau mit der Sprache war, hat das Wort „für“ größere Bedeutung, als ihm heute zugesprochen wird. Hätte der unter westlich-alliierter Besatzung stehende Rumpf des Deutschen Reiches eigenständig eine Verfassung erstellen können, wäre es nicht Grundgesetz (das laut Definition einen provisorischen Charakter hat) genannt worden, sondern eben Verfassung. Und hätte diese Verfassung eigenständig erarbeitet werden können, hätte sie geheißen: Verfassung der Bundesrepublik Deutschland.
Es heißt zum Beispiel auch: Costituzione della Repubblica Italiana. also Konstitution der Republik Italien, und nicht Costituzione per La Repubblica Italiana.
Es ist nachvollziehbar, dass die Bedenken der westlichen Alliierten aufgrund der Nazi-Zeit so groß waren, dass man den „Deutschen“ nicht zutraute, selbständig eine Verfassung zu erstellen.
Zum vorbeugenden Schutz, es sollte verunmöglicht werden, dass ein Regime noch einmal in der Lage sei, die Macht zu ergreifen, wurde als Kontrollinstanz der Verfassungsschutz gegründet. Dieser ist dem Innenministerium gegenüber weisungsgebunden. Die jüngste Aussage, auf den letzten Metern der Innenministerin Faeser, der Verfassungsschutz sei selbständig, ist eine manipulative Beschreibung, die davon ablenken soll, dass das Innenministerium dem Verfassungsschutz sehr wohl übergeordnet ist. Das Wort „selbständig“ soll Eigenständigkeit vorgaukeln, hat aber in der Hierarchie keinerlei Bedeutung.
Im Jahre 1949 herrschte ein anderer Zeitgeist. Werte wie Ehrlichkeit, Redlichkeit und Anständigkeit hatten noch eine andere Bedeutung als heute. Politiker waren noch von einem anderen Schlag und hatten weitgehend den Anspruch zum Wohle des Volkes zu entscheiden und zu handeln. Diese Werte reichten noch mindestens bis in das Agieren des Bundeskanzlers Helmut Schmidt hinein.
Niemand konnte sich deshalb zum damaligen Zeitpunkt vorstellen, dass dieser eigentlich als Kontrollinstanz gedachte Verfassungsschutz einmal von der Politik missbraucht werden könnte, um oppositionelle Kräfte auszuschalten zu versuchen, wie es mit der Einstufung der AfD als gesichert rechtsextrem geschehen ist. Rechtlich hat das noch keine Konsequenzen, aber es geht in erster Linie darum, dem Image der AfD zu schaden, um weiteren Zulauf zu verhindern. Diese Art von Durchtriebenheit kam in den Gedanken und dem Ehrgefühl der damals verantwortlichen Politiker noch nicht vor.
Die ehemaligen Volksparteien, man kann auch sagen, die Alt-Parteien, sehen ihre Felle schon seit einiger Zeit davonschwimmen. Die Opposition hat derzeit die Zustimmung einer ehemaligen Volkspartei überholt und ist sogar stärkste Kraft geworden. Sie repräsentiert aktuell rund 10 Millionen der Wähler. Tendenz steigend. Und das die folglich auch gesichert rechtsextrem gewählt haben, oder gar gesichert rechtsextrem sind, wird ihnen vielleicht nicht besonders schmeicheln.
Parallel dazu haben die Alt-Parteien die Medienlandschaft gekapert und versuchen mit Einschränkungen der Meinungsfreiheit, sofern sich Kritik gegen sie richtet und durch selbstermächtigte Entscheidung über das, was Wahrheit und Lüge ist, unliebsame Stimmen mundtot zu machen, um unter allen Umständen an der Macht zu bleiben.
Diese Vorgehensweise widerspricht dem demokratischen Verständnis, das aus dem, wenn auch „nur“ Grundgesetz, statt Verfassung, hervorgeht und die Nachkriegsgenerationen im besten Sinne beeinflusst und demokratisch geprägt hat.
Aus dieser Sicht können die Aktivitäten der Alt-Parteien nur als Angriff auf die Demokratie, wie sie diese Generationen verstehen, gesehen werden.
Daher führt jeder Angriff der Alt-Parteien auf die Demokratie dazu, dass die Opposition immer mehr an Stimmen gewinnt und wohl weiterhin gewinnen wird.
Es erschließt sich nicht, warum die Alt-Parteien nicht auf die denkbar einfachste Lösung kommen, Vertrauen in ihre Politik zurückzugewinnen, in dem sie eine Politik machen würden, die dem Willen der Bürger entspricht. Mit dem Gegenteil machen sich die Volksvertreter zu Vertretern ohne den Rückhalt vom Volk, und man muss sich fragen, wessen Interessen sie derzeit wirklich vertreten. Bestenfalls die eigenen, schlimmstenfalls die des global agierenden Tiefen Staates, der ihnen ins Ohr flüstert, was sie zu tun haben.
Mit jeder vernunftbegabten Entscheidung, die dem Willen des Souveräns entspräche, würden sie die Opposition zunehmend schwächen. Da dies nicht geschieht, kann man nur zu der Schlussfolgerung kommen, dass sich hier auch selbstzerstörerische, suizidale Kräfte festgesetzt haben. Es ist wie eine Sucht, von der man nicht mehr loslassen kann.
Solange die Alt-Parteien nicht in der Lage sind, die Unzufriedenheit in der Bevölkerung wahr- und ernst zu nehmen, werden sie die Opposition stärken und zu immer rigideren Maßnahmen greifen müssen, um ihre Macht zu erhalten und sich damit immer mehr von demokratischen Verhältnissen entfernen, und zwar genau in die Richtung vor der die Alt-Parteien in ihrer ideologischen Verirrung warnen.
Seitens der Opposition gibt es in der Gesamtschau keine Anzeichen dafür, dass die Demokratie abgeschafft werden soll, im Gegenteil, es wird für mehr Bürgerbeteiligung plädiert, was ein sicheres Merkmal für demokratische Absichten ist.
Aus Sicht der Alt-Parteien macht die Brandmauer Sinn, weil sie sie vor ihrem eigenen Machtverlust schützt. Der Fall der Berliner Mauer sollte ihnen eigentlich eine Warnung sein.
Fairerweise darf nicht unterschlagen werden, dass es in der Opposition einige Verirrte gibt, wobei noch interessant wäre zu erfahren, welche davon als V-Männer des Verfassungsschutzes eingeschleust wurden. Diese jedoch zum Anlass zu nehmen, die Opposition unter Generalverdacht zu stellen, steht einem demokratischen Handeln diametral entgegen.
Das Grundgesetz wird so nicht geschützt, sondern bis kurz vor der Sollbruchstelle verbogen.
Die Einstufung der Opposition als gesichert rechts-extrem beruht auf einem mutmaßlich 1000 Seiten starken Papier, das offensichtlich nur ein erlesener Kreis zu sehen bekommen soll. Dazu gehört nicht die Bevölkerung, die sicher nur einmal mehr nicht zu Teilen verunsichert werden soll. Und selbstverständlich schon gar nicht diejenigen, die es betrifft, nämlich die Opposition.
Eine eindeutige Fragwürdigkeit der Aktivitäten des Verfassungsschutzes wäre schwerer festzustellen, wenn es gleichwohl Parteien gäbe, die als gesichert links-extrem oder zumindest als links-extremer Verdachtsfall eingestuft würden. Nicht ganz unberechtigte Gründe hierfür könnten schon gefunden werden, wenn der politische Wille es wollte.
Auch die seltsam-umstrittene Installierung des Präsidenten des Bundesamtes für Verfassungsschutz (genau genommen für Grundgesetzschutz) lässt Fragen offen.
Generell müsste es eine unabhängige Überprüfung geben, ob die Gewaltenteilung in Deutschland noch gewährleistet ist, da es durch das augenscheinliche Zusammenspiel in der Richterschaft, der Gesetzgebung und der vierten Gewalt, den Medien, Anlass zu Zweifel gibt.
Diese Zweifel sind nicht demokratiegefährdend, sondern im Gegenteil, es ist demokratische Pflicht, den Verantwortlichen kritisch auf die Finger zu schauen, ob im Sinne des Souveräns entschieden und gehandelt wird. Zweifel könnte man dadurch ausräumen, in dem eindeutig bewiesen würde, das alles seine Richtigkeit hat.
Das wäre vornehmlich die Aufgabe der Alt-Medien, die derzeit durch Totalversagen glänzen, weil alles mit allem zusammenhängt, jeder jeden kennt und man es sich über Jahre so eingerichtet hat, dass man gerne unter sich bleibt und Pöstchen-Hüpfen von einem Lager ins andere spielt.
Vielleicht ist es sogar nötig, dass zur unabhängigen Überprüfung, die Alliierten, inklusive Russland, noch einmal, nach rund 80 Jahren, auf den Plan gerufen werden müssen, um sozusagen eine Zwischenbilanz zu ziehen, inwieweit sich das einst etablierte, demokratische System bewährt hat, und ob es derzeit noch im ursprünglichen Sinne umgesetzt und gelebt wird. Es ist anzunehmen, dass hier ein gewaltiges Optimierungspotenzial zum Vorschein kommen könnte.
Viele Bürger in Deutschland haben den Wunsch, wieder in einer Demokratie zu leben, die ihre Namen auch verdient hat. Sie wollen wieder frei ihre Meinung jeglicher Art aussprechen können, miteinander diskutieren, auch einmal Unsinn reden, ohne, dass sie der Blockwart gleich bei einem Denunzierungsportal anschwärzt, oder sie Gefahr laufen, dass ihr Konto gekündigt wird, oder sie morgens um 6 Uhr Besuch bekommen, der noch nicht einmal frische Semmeln mitbringt.
Dieser Artikel wurde mit dem Pareto-Client geschrieben
* *
(Bild von pixabay)
-
 @ 6e64b83c:94102ee8
2025-05-05 16:50:13
@ 6e64b83c:94102ee8
2025-05-05 16:50:13Nostr-static is a powerful static site generator that transforms long-form Nostr content into beautiful, standalone websites. It makes your content accessible to everyone, even those not using Nostr clients. For more information check out my previous blog post How to Create a Blog Out of Nostr Long-Form Articles
What's New in Version 0.7?
RSS and Atom Feeds
Version 0.7 brings comprehensive feed support with both RSS and Atom formats. The system automatically generates feeds for your main content, individual profiles, and tag-specific pages. These feeds are seamlessly integrated into your site's header, making them easily discoverable by feed readers and content aggregators.
This feature bridges the gap between Nostr and traditional web publishing, allowing your content to reach readers who prefer feed readers or automated content distribution systems.
Smart Content Discovery
The new tag discovery system enhances your readers' experience by automatically finding and recommending relevant articles from the Nostr network. It works by:
- Analyzing the tags in your articles
- Fetching popular articles from Nostr that share these tags
- Using configurable weights to rank these articles based on:
- Engagement metrics (reactions, reposts, replies)
- Zap statistics (amount, unique zappers, average zap size)
- Content quality signals (report penalties)
This creates a dynamic "Recommended Articles" section that helps readers discover more content they might be interested in, all while staying within the Nostr ecosystem.
See the new features yourself by visiting our demo at: https://blog.nostrize.me
-
 @ 266815e0:6cd408a5
2025-05-02 22:24:59
@ 266815e0:6cd408a5
2025-05-02 22:24:59Its been six long months of refactoring code and building out to the applesauce packages but the app is stable enough for another release.
This update is pretty much a full rewrite of the non-visible parts of the app. all the background services were either moved out to the applesauce packages or rewritten, the result is that noStrudel is a little faster and much more consistent with connections and publishing.
New layout
The app has a new layout now, it takes advantage of the full desktop screen and looks a little better than it did before.
Removed NIP-72 communities
The NIP-72 communities are no longer part of the app, if you want to continue using them there are still a few apps that support them ( like satellite.earth ) but noStrudel won't support them going forward.
The communities where interesting but ultimately proved too have some fundamental flaws, most notably that all posts had to be approved by a moderator. There were some good ideas on how to improve it but they would have only been patches and wouldn't have fixed the underlying issues.
I wont promise to build it into noStrudel, but NIP-29 (relay based groups) look a lot more promising and already have better moderation abilities then NIP-72 communities could ever have.
Settings view
There is now a dedicated settings view, so no more hunting around for where the relays are set or trying to find how to add another account. its all in one place now
Cleaned up lists
The list views are a little cleaner now, and they have a simple edit modal

New emoji picker
Just another small improvement that makes the app feel more complete.
Experimental Wallet
There is a new "wallet" view in the app that lets you manage your NIP-60 cashu wallet. its very experimental and probably won't work for you, but its there and I hope to finish it up so the app can support NIP-61 nutzaps.
WARNING: Don't feed the wallet your hard earned sats, it will eat them!
Smaller improvements
- Added NSFW flag for replies
- Updated NIP-48 bunker login to work with new spec
- Linkfy BIPs
- Added 404 page
- Add NIP-22 comments under badges, files, and articles
- Add max height to timeline notes
- Fix articles view freezing on load
- Add option to mirror blobs when sharing notes
- Remove "open in drawer" for notes
-
 @ 7e8ca676:b6a7569f
2025-05-13 01:08:28
@ 7e8ca676:b6a7569f
2025-05-13 01:08:28There was a time when mining meant something. Not just the noise of fans and the stink of ozone, but a political act. An act of rebellion, like smuggling pamphlets under the nose of the king. You mined in the basement. You mined with pride. You mined because you could. Not because Fidelity wrote a whitepaper on it. Not because a hosting provider in Iceland offered you a bulk discount. But because you believed.
That miner is dead.
He didn’t die in a blaze of glory. He didn’t go down swinging. He was euthanized. Slowly, over years, by spreadsheets, subsidies, and a thousand tiny concessions. Killed off by a culture that said, “Why do it yourself when you can outsource the soul of Bitcoin to a pool in Singapore?”
Welcome to the age of industrial Bitcoin: a world where miners don’t mine, pools don’t just process. They rule. And the only thing sovereign anymore is the dividend.
The Sovereign Miner is Dead, And No One Mourned
The sovereign miner, the madman with a dusty rack, a full node, and a middle finger pointed squarely at the Eccles Building, is extinct. He’s gone the way of the dodo, the blacksmith, the outlaw. And in his place? A fleet of khaki-wearing ASIC clerks uploading hashrate reports to their VC lords like dutiful little interns. These are not revolutionaries. They are box operators. Corporate larvae wiggling around in server farms financed by pension funds.
Once upon a time, mining was an act of insubordination. You ran a rig to say "no" to Janet Yellen. You ran a node because you meant it. You didn’t need permission. You didn’t ask for subsidies. You didn’t file paperwork. You fought for consensus by living it. Every block was a punch thrown in a quiet, bloodless rebellion. Now? Now you’ve got KPMG-certified mining outfits measuring ESG impact and tweeting about carbon offsets like they’re trying to win a grant from the UN.
The eulogies for that old miner are full of oily euphemisms. They drone on about "efficiency," as if selling your vote for a cheaper power bill is some kind of virtue. "Economies of scale," they whisper, as though scale were some holy sacrament instead of the Trojan horse that delivered centralization to our doorstep. What they call progress, I call a back-alley mugging of Bitcoin’s soul.
The modern miner isn’t mining. He’s leasing his dignity to a pool that doesn’t know his name. He’s plugging in Bitmain boxes like a hotel maintenance worker changing light bulbs. The only heat he generates is for the benefit of someone else's node. Someone else's mempool. Someone else's idea of consensus. He doesn’t build the block. He just pays the electric bill.
And the worst part? He likes it. He thinks it’s normal. He thinks it’s “smart business.” He’s internalized the defeat so completely he brags about it on social media. He’ll tweet about uptime, about efficiency ratios, about hashprice curves—as if he were describing a well-run gulag. He’s the obedient prisoner who polishes the chains and calls it freedom.
The sovereign miner didn’t die in a blaze of glory. He died quietly, smothered under a fleece blanket of comfort and yield optimization. And no one mourned. No one wept. Because everyone was too busy benchmarking their ROI and counting fiat. The revolution didn’t end in a shootout. It ended in quarterly earnings calls.
Power Reversed: Pools Run Nodes, Miners Run Cable
Let’s be crystal clear: The pools run the nodes. The miners do not. This is not a subtle shift. It is a total inversion of power. A coup d'état wrapped in JSON-RPC and relayed with a smile. The pool clerks have become the governors of consensus, and the miners? They’re errand boys. They might control the heat, but they don’t control the protocol. They’re like engine pistons in a car they’ll never be allowed to drive.
Pointing hash at a pool and calling yourself sovereign is like renting a tux and declaring yourself royalty. It’s cosplay. At best. Pools decide what transactions are valid. Pools enforce the rules. Pools interpret consensus, not the miners, not the miners, and certainly not the plebs stacking sats on Raspberry Pis, who, through their economic activity and validation, still enforce the rules but are powerless to stop this creeping centralization in the mining layer. In a world obsessed with decentralization theater, pools are the centralized prop masters pulling the strings.
And when the curtain pulled back in 2021, it wasn’t some secret backroom scandal. No. Marathon Digital bragged about OFAC-compliant mining. They filtered transactions with state-sanctioned precision. They announced it like a new feature rollout. “Censorship-as-a-Service, now in beta!” The mining pool became an extension of the U.S. Treasury—while still waving the Bitcoin banner.
That wasn’t a red flag. That was a blood-soaked banner waved from the parapets of captured consensus. And the response? Nothing. No mass exit. No fork. No slash-and-burn rebellion. Just soft mewling from miners who’d already convinced themselves this was “pragmatic.”
Miners didn’t revolt. They shrugged. They shrugged because they didn’t feel it in their bones anymore. They’d been domesticated. Fattened on subsidies and mining-as-a-service. Pacified by dashboards and yield spreadsheets. When the pools took the steering wheel, the miners reached for the air conditioning controls.
This is the hard truth: sovereignty cannot be delegated. You don’t get to outsource rebellion. You don’t get to file a ticket and request autonomy. If someone else runs the node, someone else owns the power. And if you’re pointing hash at their rules, you’re not free. You’re furniture. Industrial-grade silicon furniture humming in tune with someone else’s politics.
ASICs Are Treadmills, Not Weapons
Here’s a bitter pill: plugging in an ASIC doesn’t make you a participant in Bitcoin. It makes you a battery. Yes, economic nodes still set the rules through their validation and transaction activity. But what happens when the mining layer, the muscle that enforces those rules on-chain, goes rogue? What happens when the mempool you built gets ignored because your hashpower is pointed at someone else's filter?
A node might define validity, but without aligned mining, it’s a lion without teeth. If economic consensus is the blueprint, mining is the builder. And right now, most builders are following someone else's floor plan. The node might say, "this is how we build," but the pool, with its centralized relay and selective enforcement, says, "this is what we’re willing to build."
Without a node, without building your own block, without choosing your own mempool, you’re a hamster in a high-voltage wheel. All that heat and noise? It’s not rebellion. It’s treadmill sweat.
Without a node, without building your own block, without choosing your own mempool, you’re a hamster in a high-voltage wheel. All that heat and noise? It’s not rebellion. It’s treadmill sweat.
You are not a general. You are a grunt. A CPU on contract to someone else’s war.
Fiat Habits: The Culture of Convenience
Bitcoin was supposed to be the great divorce from fiat thinking, a severance from the debt-ridden clown world where every moral principle is for sale if the yield’s high enough. But lo and behold, the fiat habits came slithering in through the miner’s back door. It started small. “Just a hosting service,” they said. “Just outsourcing the firmware,” they claimed. “Just using a pool for efficiency.” And before you knew it, the average miner was indistinguishable from a middle manager at an Enron reunion. Optimizing, spreadsheeting, begging for subsidies like a lobbyist on his third bourbon.
The culture is poison. It rewards cowardice, convenience, and cost-shifting. Small miners moan about volatility like day traders with arthritis. Big miners wine and dine regulators, sniffing after tax incentives and ESG badges like some filthy dog begging at the World Economic Forum’s dinner table. We’re no longer talking about building a sovereign financial system—we’re talking about quarterly earnings, power purchase agreements, and whether your server farm meets carbon neutrality guidelines. What the hell happened?
Take a look back at the New York Agreement in 2017. That wasn’t a negotiation. It was a ransom note. The largest mining outfits, including BTC.Top and ViaBTC, held SegWit hostage because it didn’t butter their bread. The principles didn’t matter. The technical merit didn’t matter. All that mattered was leverage, yield, and preserving their own stranglehold. They tried to shove a hard fork down Bitcoin’s throat like a goose being force-fed for foie gras. And if not for the sheer stubbornness of the user base, real economic nodes who still gave a damn, Bitcoin would’ve gone full Frankenstein.
But did those miners learn? No. They just shifted tactics. Today they ask for different forms of convenience: not block size increases, but subsidies, regulations tailored to their rigs, public-private partnerships. The song remains the same. It’s the fiat mindset dressed up in ASIC drag. Instead of defending neutrality, they demand special treatment. Instead of embracing the responsibility of consensus participation, they’d rather hand it off to a pool that promises good customer service and a Discord server with emojis.
What we’re seeing is the spiritual sequel to fiat monetary policy—moral hazard in overclocked silicon. Miners begging for insulation from the market, protection from volatility, and someone else to carry the political weight of consensus. That’s not sovereignty. That’s serfdom with a spreadsheet. These aren't rebels. They’re corporate supplicants doing yield gymnastics while the heart of Bitcoin withers under the fluorescent lights of their co-location facility.
Bitcoin doesn’t need more efficient parasites. It needs fewer of them. The culture must shift from comfort to combat. From optimization to obligation. A miner who outsources consensus is no better than a fiat printer optimizing bond auctions. The minute you make convenience your god, you become indistinguishable from the system Bitcoin was meant to destroy.
The Culture of Convenience
Bitcoin was born as a rejection of fiat habits. So naturally, miners dragged every last fiat habit into the server farm like rats carrying plague. Outsource the firmware. Outsource the hosting. Outsource the power contract. Outsource the node. Outsource the sovereignty. What’s left?
Mining today looks like Goldman Sachs cosplay. ESG reports. Carbon credits. Webinars on regulatory compliance. Bitcoin isn't being mined anymore. It's being monetized. It's being lobotomized by yield-chasers and spreadsheet cultists.
The New York Agreement was the test. The miners failed. They held the protocol hostage for a slightly thicker block and a fat slice of yield. They were willing to hard fork Bitcoin into a Frankenstein fiat-friendly platform if it meant a better power purchase agreement.
They haven't changed. They’ve just gotten better at disguising their cowardice as competence.
Software Will Not Save You (But Cowards Sure Will Sell You the Illusion)
Let me tell you a ghost story. A tale of silicon treachery dressed up as innovation. It was 2017. The air stank of backroom deals and nervous sweat. Bitmain, the ASIC kingpin of the age, had quietly embedded a little something into its hardware. A cheat code. A hidden rake. A parasitic exploit called ASICBoost, but not the honest kind. No, this was the covert variant, slinking beneath the protocol’s floorboards, exploiting transaction ordering for a tidy little edge. It wasn’t disclosed. It wasn’t debated. It was used. Quietly. Gleefully. While the rest of the ecosystem was busy arguing about scaling like philosophers in a house fire.
Bitmain wasn't interested in consensus. It was interested in arbitrage. They saw Bitcoin not as a commons, but as a slot machine they had rigged. And when SegWit appeared, when it offered scaling and immunity to covert ASICBoost in one surgical tweak, Bitmain panicked. Because SegWit would end the grift. Not softly. Not eventually. Immediately.
So they did what every entrenched parasite does when exposed. They lied. They stalled. They "compromised." They ginned up support for SegWit2x, not to scale Bitcoin, but to preserve their exploit. A hard fork with extension blocks would keep the legacy block structure alive and well, tucked into a cozy parallel track where covert ASICBoost could still thrive. It was a bait-and-switch. A con. A trojan upgrade smuggled in under the banner of progress.
But this time, the hosts fought back.
Node runners saw the ploy. They didn’t need fancy tooling. They needed guts. They didn’t negotiate. They didn’t flinch. They ran SegWit. They activated UASF. They drew a line—not in sand, but in bedrock. Bitcoin would not be held hostage by ASIC cartels. It would not bend for Bitmain. It would not become an extension block casino for rent-seekers in Shenzhen.
So no, software didn’t save Bitcoin. Men did.
Ordinary plebs with full nodes and no backdoor. They used the tool, yes, but what mattered is that they refused. Refused the scam. Refused the deal. Refused to bend the knee to an ASIC cartel dressed in business-casual and lies.
SegWit didn’t win because it was elegant. It won because enough people had the guts to jam it through in spite of sabotage. The protocol gave them a knife, and they had the moral clarity to use it. That’s the lesson. Not that we need better code, but that we need sharper men.
Because in the end, every exploit is possible when the culture is weak. And every fix is worthless if the people implementing it don’t care. The problem was never ASICBoost. The problem was what miners were willing to do to keep it.
The Pool Cartel is the New Central Bank
Middlemen were supposed to die in 2009. That’s the entire reason Bitcoin exists. To gut them. To render them obsolete. To salt the earth behind them so nothing like them could ever grow again. But here they are, reborn, not as banks, but as pools. Not in suits, but in server racks. They wear the garb of "infrastructure providers," but they function as gatekeepers, choke points wrapped in API documentation.
Pools don’t just process, they decide. They decide what gets into the chain. They decide whose transactions are valid. They decide what software matters, and what consensus looks like. They’ve become the central banks of the hashrate economy: unaccountable, invisible, and too boring to fear until it’s too late.
They don’t win power. They absorb it. They don’t need legislation or signatures. They just need you to keep pointing your hash in their direction. That’s the magic trick of middlemen: their power lies in being taken for granted. And in that, they’re the perfect parasite, one that feeds on your energy and then tells you they’re helping you digest it.
Every time you optimize for pool payout efficiency, every time you default to the biggest provider, every time you accept their mempool instead of building your own, you’re kneeling. You’re pledging allegiance to a cartel of block-builders whose loyalty isn’t to Bitcoin, it’s to operational ease and regulatory appeasement.
These aren’t neutral actors. They’re political animals. They hold the levers of consensus without bearing any of its weight. They’re the mortgage-backed securities of Bitcoin: abstracted, opaque, and one market panic away from becoming a systemic risk. We have, once again, created a class of intermediaries who profit by extracting value from a system they didn’t build and no longer understand.
Bitcoin didn’t kill the middlemen. It fed them. It made them smarter. It made them less visible. But their hunger hasn’t changed. And until we name them for what they are—cartels in priestly robes—we will keep mistaking the cage for the cathedral.
Stratum v2: A Rifle, Not a Revolution
Stratum v2 is the closest thing to a loaded weapon Bitcoin miners have been handed in a decade. It is, quite literally, the mechanism by which miners can wrench their dignity back from the clenched fists of the pool cartel. And what have they done with it? Mostly shrugged. A few pilot programs, some halfhearted integrations, and a handful of blog posts filled with the kind of cautious optimism you’d expect from a risk-averse actuary.
This isn’t a critique of the protocol. Stratum v2 is beautifully ugly. It’s messy, technical, and dense enough to scare away the very consultants who want to repackage Bitcoin into polite compliance middleware. But none of that matters if no one has the guts to use it. You don’t win wars by stockpiling weapons you refuse to fire.
Stratum v2 gives miners the power to construct their own blocks. Not just vote with hash, but wield it. Choose transactions. Set mempool policy. Actually participate in consensus instead of spectating like a retiree watching a soap opera. It is the rifle hanging over the mantelpiece. The one Chekhov warned us about. And right now it’s gathering dust.
The tragedy here isn’t technical. It’s cultural. Because this tool, this literal key to sovereignty, is being treated like a library dependency. Something for someone else to test, to vet, to implement. Meanwhile, miners continue to act like it’s 2015 and their biggest concern is firmware compatibility and finding a better power rate in Kazakhstan.
Ignore Stratum v2, and it becomes protocol theater. A museum piece. A tragic artifact of what could have been. But use it, and it becomes a wedge. A crowbar in the gears of centralized mining. A bright, shining middle finger to the entire architecture of compliance-friendly consensus.
But don’t fool yourself. Stratum v2 won’t make you sovereign any more than buying a gun makes you a revolutionary. It won’t beam liberty into your soul via Tor, won’t whisper “freedom” into your hashboard, won’t bathe your rack in the holy light of decentralization. It’s not salvation. It’s a tool. And tools don’t care who uses them—they serve the hand that holds them.
Stratum v2 is a rifle, yes—but even a rifle requires guts, aim, and the clarity to know what you're shooting at. In the hands of a coward, it’s a paperweight. In the hands of a rent-seeker, it’s a bargaining chip. But in the hands of a miner with fire in his gut and sovereignty in his blood? It’s a revolution.
This isn’t about technology. It’s about spine. About picking up the one weapon you’ve been given and refusing to keep it locked in the safe while tyrants build your blocks. Stratum v2 offers freedom, but it demands ferocity. You have to load it with your own mempool. You have to chamber every transaction. And then you have to fire.
No protocol, no BIP, no whitepaper will ever substitute for moral will. And if you’re too polite to use the weapon, too busy maximizing uptime to get your hands dirty with real consensus, then you deserve whatever filtered, censored, OFAC-compliant future you inherit.
Stratum v2 is not your savior. You are. And until miners act like it, until they treat this protocol like a weapon and not a toy, the pools will rule, and the timechain will continue to serve the highest bidder.
It’s just a rifle. But rifles have rewritten history when wielded by men who knew they weren’t free.
Ossification Without Decentralization Is Death
Everyone loves ossification, until they realize they missed their chance to do it when it mattered. We had a window. A golden, fleeting window to freeze Bitcoin in a state of clarity, minimalism, and neutrality. Instead, we blinked. We let upgrades seep in. Complexity crept through the back door, and with it came unintended consequences. Among the earliest and most corrosive: the rise of centralized mining pools. A structural outcome embedded in Satoshi’s original design, born from the brutal variance of solo mining. But if that centralization was unforeseen, imagine how many more we’ve introduced since, through every soft fork, every upgrade, every decision to keep tinkering instead of locking the vault when we had the chance.
Ossification isn’t just about code. It’s about culture. It’s a posture. A refusal. And we failed to assume it when it counted. We chose tinkering over tenacity. We chose cleverness over caution. And now the fruits of our hubris hang heavy on the vine: a mining layer riddled with capture points, a mempool hijacked by middlemen, and a user base quietly wondering why their transactions feel like applications.
Yes, economic nodes enforce the rules through validation and usage. But that power has a prerequisite: inclusion. If the only blocks being built are by pools with selective relay policies and a fondness for government compliance, then your economic activity is a shout into a soundproof room. The validation rules may be perfect, but if your transaction never hits the chain, it’s as good as invalid.
The trap we set for ourselves was gilded with good intentions. Soft forks meant to improve scalability. Relay policies meant to minimize bloat. Fee markets meant to incentivize good behavior. And now? Now we find ourselves staring at a timechain that functions—but no longer feels inviolable. The foundation wasn’t corrupted in a day. It was eroded, line by line, by developers trying to be helpful.
Freeze Bitcoin now, and we don’t immortalize virtue—we immortalize vulnerability. We lock in the flaws. We preserve a snapshot where the power has already been ceded to those least equipped to wield it justly. It’s like slamming the vault door shut just as the thieves finish loading the bags.
That’s not ossification. That’s embalming. That’s turning the timechain into a museum exhibit of the ideals we almost lived up to, before we traded principle for pragmatism and thought we could always fix it later.
Ossification is not neutral. It’s not some universal good. It is power, fixed in time. And if that power belongs to the wrong class of actors, the OFAC miners, the hosting conglomerates, the Silicon Valley startups that mine with ESG consultants on speed dial, then ossification doesn’t lock in liberty. It locks in them. It fossilizes a regime that already serves someone else’s interests.
We speak of ossification like it’s an event. One final commit. One last hardening. But in truth, it’s asymptotic. You don’t slam the door shut in one dramatic gesture. You inch toward it. You tighten the bolts over time until change becomes culturally, politically, and economically impossible. And that means we’re ossifying right now.
Picture it: a frozen Bitcoin where the rules can’t change, but the blockspace is filtered, the miners are compliant, and the pools relay transactions based on a government-approved blacklist. That’s not sound money. That’s a digital leash. A ledger of obedience masquerading as freedom.
If Bitcoin ossifies after it has been captured, it does not become incorruptible. It becomes irredeemable. Like sealing a vault before checking what’s inside, you don’t get resilience, you get entombment. You get permanence without virtue. You get consensus without sovereignty.
That’s not ossification. That’s embalming. That’s turning the timechain into Lenin’s corpse: glassy-eyed, sterile, and meticulously preserved in service of a state it was meant to outlive.
We may only have one chance to rescue bitcoin from the clutches of the fiat maximalists, before it is impossible to do so.
Core's Quiet Capitulation
Bitcoin Core was once the temple guard. Militant minimalism. Ruthless conservatism. The last line of defense against creeping bloat and protocol erosion. You didn’t have to agree with them, but by God, you respected the trench they were willing to die in.
Now? They’re white-gloving the stretcher for a dying protocol. Hospice caretakers tending to consensus rot with polite documentation and GitHub tickets labeled "enhancement." The keepers of the flame have become interior decorators for a collapsing cathedral.
They removed filters, the thin defensive crust that kept bad-faith actors at bay. They weakened defaults, the backbone settings that preserved network sanity. They bend policies not to protect consensus, but to please mining cartels and PR-sensitive operators. Every decision smells like appeasement baked in a think tank.
This isn’t some grand betrayal of principle for power or riches. It’s worse. It’s resignation. Exhaustion wrapped in technocratic humility. They didn’t sell out to the highest bidder, they just ran out of fire.
Where once they chanted ossification, now they mumble "flexibility." Where once they enforced sanity with zero tolerance for grift, now they entertain proposals that would’ve been laughed out of the room a decade ago. They say yes out of fatigue. They say no with asterisks. They commit code like bureaucrats signing off on a slow-motion demolition.
Core didn’t just get captured. It got comfortable. And comfort, in protocol stewardship, is fatal. The war for Bitcoin's soul isn’t being lost in some smoky backroom. It’s being forfeited in polite silence by maintainers who forgot the protocol doesn’t just need to run. It needs to refuse.
The Call: Rewild the Hash
This is the fork in the road. This is the final flare fired into the sky before the trench goes quiet forever. You either take back the hash, or you become a dependent serf in a digital fiefdom run by pool lords and relay priests. No more excuses. No more polite appeals. No more PRs begging middlemen to do the right thing.
Run your own node. Build your own block, even if it takes a lifetime. Not tomorrow. Not after the next bull run. Not when it’s convenient. Now. Because if you don’t, someone else will do it for you, and they will not share your values.
Stop waiting for permission. Stop tweeting at pool operators like they’re public servants. Stop optimizing for latency like it’s a sacrament. You are not here to impress compliance officers. You are here to enforce your damn sovereignty.
Don’t beg the cartel to behave. Starve it. Cut it off. Build the mempool you want to see in the world and let their VC primed and bloated relay network choke on their own paperwork. Let their blocks fill with NFT spam and chain analysis reports. You are not required to participate in their theater.
Use Stratum v2. Not because it’s clever, not because it’s next-gen, but because it puts the steering wheel back in your hands. It lets you carve your transactions from granite instead of begging for a line on someone else's spreadsheet. It is not optional. It is not academic. It is your rifle, and the target is consensus capture.
Rewilding the hash isn’t about nostalgia. It’s about survival. It’s about tearing up the artificial turf of corporate convenience and letting the hard, messy, glorious chaos of sovereign mining grow back. Every node a fortress. Every block a declaration. Every miner a free man with dirt under his fingernails and fire in his chest.
This is the line. Pick up your weapon. Run your own node. Build your own block. Or die watching someone else sell your freedom by the byte.
Murder the pools. Rewild the hash. And mine like it means something... because it does.
-
 @ 4ba8e86d:89d32de4
2025-05-02 13:51:37
@ 4ba8e86d:89d32de4
2025-05-02 13:51:37Tutorial OpenKeychain
- Baixar no F-droid https://f-droid.org/app/org.sufficientlysecure.keychain
Ao abrir o OpenKeychain pela primeira vez, você verá uma tela inicial indicando que ainda não há chaves configuradas. Nesse ponto, você terá três opções:
-
Criar uma nova chave PGP diretamente no OpenKeychain: Ideal para quem está começando e precisa de uma solução simples para criptografia em comunicações diárias.
-
Usar um token de segurança (como Fidesmo, Yubikey, NEO, ou Sigilance) Se você busca uma segurança ainda maior, pode optar por armazenar sua chave privada em um token de segurança. Com essa configuração, a chave privada nunca é salva no dispositivo móvel. O celular atua apenas como uma interface de comunicação, enquanto a chave permanece protegida no token, fora do alcance de possíveis invasores remotos. Isso garante que somente quem possui o token fisicamente possa usar a chave, elevando significativamente o nível de segurança e controle sobre seus dados.
-
Importar uma chave PGP existente: Você pode importar uma chave PGP que já tenha sido gerada anteriormente, seja por meio de um arquivo no dispositivo ou por outro meio ler na área de transferência. https://image.nostr.build/51fdd924df4843ab73faa02a505c8fb17794f1789396ed89b154348ebb337f07.jpg
1. CRIANDO UMA NOVA CHAVE PGP.
Para iniciantes, recomendamos criar uma nova chave diretamente no aplicativo. abordaremos o uso do OpenKeychain em modo online, que é mais comum para comunicações diárias.
Passo 1: Clique em “Criar minha chave”. https://image.nostr.build/235f5cfdf4c3006ca3b00342741003f79a5055355c2a8ee425fc33c875f51e49.jpg
Passo 2: Criando sua chave PGP.
Para criar sua chave, você precisará fornecer algumas informações Os campos 'Nome' e 'Endereço de e-mail' são apenas formas convenientes para identificar a sua chave PGP.
-
Nome: Escolha um nome ou um pseudônimo. https://image.nostr.build/de3fe3ddbde0c7bf084be6e4b8150fdb8612365550622559b0ee72f50f56a159.jpg
-
E-mail: Associe um endereço de e-mail à chave, seja ele pessoal ou um e-mail relacionado ao pseudônimo. https://image.nostr.build/aff62baaeafe2c9a429ef10435a6f99dea36d6cfd7494e2bb882421dc8ed0f4e.jpg
2. REVISANDO E PERSONALIZANDO A CRIAÇÃO DA CHAVE.
Passo 3: Antes de criar sua chave PGP, verifique se os dados inseridos estão corretos. https://image.nostr.build/a8ec09ef3d9b4f557b0c4e380e7ca45d0fdbfa33fe80becea03ed0e5f5eedd24.jpg
Você também pode personalizar as configurações de segurança clicando nos três pontos no canto superior direito. https://image.nostr.build/1ce615555cea9a979ea951472052a219e77f4e1ebaaf5fcbbe9e91ea4f852bce.jpg
Ao cliclar em ' nova subchave ' pode alterar a data de expiração e pode mudar a criptografia usado na chave cliclando opção ed2255/cv255. https://image.nostr.build/b3224ff3dbe48ff78c4a2df8b001926b6d3eef1e33ef677a73b0d281791073da.jpg https://image.nostr.build/7763c7847e062cdcf71aafedbc2ef4c38056fd66aeb162ef3a1c30c028a14376.jpg https://image.nostr.build/5d3e20ade460dd5e89cc001ebdc062a36aff2c0e1573584ca3c0d1cb34bddcce.jpg
Neste tutorial, utilizaremos as configurações padrão do aplicativo.
Passo 4: Clique em "Criar chave" para concluir o processo. https://image.nostr.build/a8ec09ef3d9b4f557b0c4e380e7ca45d0fdbfa33fe80becea03ed0e5f5eedd24.jpg
3. Como Compartilhar sua Chave PGP Pública
Após criar sua chave PGP, você pode compartilhá-la para que outras pessoas possam enviar mensagens criptografadas para você. Veja o passo a passo de como exibir e compartilhar sua chave pública:
Passo 1: Acesse sua chave pública
Abra o OpenKeychain e selecione a chave que deseja compartilhar. Clique na chave para visualizar os detalhes. https://image.nostr.build/689c5237075317e89e183d2664630de973b09b68aaf8f3e3033654e987b781be.jpg https://image.nostr.build/4001610109579f27535628932258087b3b06c1f86b05f4f85537b6585c12a10b.jpg
Passo 2: Copiar sua chave pública
Nos detalhes da chave, você verá a opção "Copiar para a Área de Transferência". Clique nessa opção para copiar o código da sua chave pública. https://image.nostr.build/01ab3efa5e997e1910a2f8f7a888e6ad60350574cca4ca0214eee5581797f704.jpg
A chave PGP copiada terá o seguinte formato:
-----BEGIN PGP PUBLIC KEY BLOCK-----
mDMEZwsLHRYJKwYBBAHaRw8BAQdA6NRLlJIWnTBJtYwZHlrMbTKRbYuXmjsMn8MB 7etV3HK0JERhbmllbCBGcmFnYSAgPGRhbmllbGZyYWdhQG1haWwuaTJwPohyBBMW CAAaBAsJCAcCFQgCFgECGQEFgmcLCx0CngECmwMACgkQFZf+kMeJWpR4cwEA8Jt1 TZ/+YlHg3EYphW8KsZOboHLi+L88whrWbka+0s8A/iuaNFAK/oQAlM2YI2e0rAjA VuUCo66mERQNLl2/qN0LuDgEZwsLHRIKKwYBBAGXVQEFAQEHQEj/ZfJolkCjldXP 0KQimE/3PfO9BdJeRtzZA+SsJDh+AwEIB4hhBBgWCAAJBYJnCwsdApsMAAoJEBWX /pDHiVqUo/oA/266xy7kIZvd0PF1QU9mv1m2oOdo7QSoqvgFiq6AmelbAP9lExY5 edctTa/zl87lCddYsZZhxG9g2Cg7xX/XsfrnAA== =TniY -----END PGP PUBLIC KEY BLOCK-----
Dica: Se ocorrer algum erro ao compartilhar sua chave pública com um amigo, peça para que ele a criptografe para ele mesmo. Isso permitirá que ele adicione a chave corretamente. Caso a chave pública ainda não esteja no dispositivo, ao clicar em "Backup de chave", aparecerá a opção para importá-la. Se a chave já estiver no dispositivo, essa ação irá recarregá-la. https://image.nostr.build/cd12abf07c93473db95483fe23112325f89d3eb02977e42756708bbd043f8bcf.jpg https://image.nostr.build/537aeae38d229ee2cc78e18f412237b659c059e1c74fd7f0deecfe37f15713c9.jpg https://image.nostr.build/16c8a3db5966c7c06904ee236655f47a6464ae0c1b5af6af27b28c61611d2bbe.jpg
Passo 3: Compartilhar sua chave PGP
Você pode colar a chave pública em e-mails, assinaturas, perfis de redes sociais ou outros meios para compartilhá-la facilmente. Para facilitar a visualização, você também pode exibi-la em seu perfil de redes sociais.
Para acessar mais opções de compartilhamento, clique nos três pontos no canto superior direito e selecione a opção "Avançado". https://image.nostr.build/0d4a13b7bd9a4794017247d1a56fac082db0f993a2011a4dd40e388b22ec88f5.jpg https://image.nostr.build/4ac2a7bc9fa726531a945221cf7d10e0e387deba68100ccf52fdedfcd17cbd59.jpg
Na seção "Compartilhar", você verá sua Key ID e terá a opção de publicar sua chave PGP em um servidor de chaves. https://image.nostr.build/1e972cc211a6d8060cdbd4a8aa642dd1a292810c532f178d3ddb133d1b9bca76.jpg
Passo 4: Como compartilhar sua chave pública PGP no formato .asc. no OpenKeychain
1 . Acesse sua chave
Abra o OpenKeychain e toque na chave que você deseja compartilhar. Isso abrirá a tela com os detalhes da chave. https://image.nostr.build/c080f03d2eb7a9f7833fec0ff1942a5b70b97e4f7da7c6bc79ca300ef9ace55d.jpg
2 . Compartilhe o arquivo .asc
Toque no ícone de compartilhamento, como indicado na imagem abaixo. O aplicativo abrirá a janela para que você escolha por qual app deseja compartilhar sua chave pública no formato .asc. Nesse exemplo, usei o SimpleXChat , mas você pode usar qualquer aplicativo de sua preferência.
-
Botão de compartilhar. https://image.nostr.build/8da74bdb04737a45df671a30bba1dd2e7980841fa0c2d751d6649630e7c25470.jpg
-
Seleção do aplicativo para compartilhamento. https://image.nostr.build/5444f4e9d3fa5aef6b191bb6f553f94c6e49d30ead874c9ee435bca3218fd6c8.jpg
-
Enviando via SimpleXChat. https://image.nostr.build/e5d1ca04cbc69e1e8ac5caf1ab2a4b9b695500861c1ae9c55cea679cce349214.jpg
Sugestão para compartilhar nas redes sociais:
Você pode exibir sua chave de forma simples, por exemplo:
PGP: 1597 FE90 C789 5A94
Importar a chave pública usando a fingerprint
Passo 1:Clique no ícone "+" para começar. https://image.nostr.build/ca6e6e569b4be60165eaf60c7ba1e6e3ec781b525e467c72b4f3605837e6b5ec.jpg
Passo 2: Selecione a opção "Buscar Chave". https://image.nostr.build/87e27d9435e6e3ef78063b9f15799a8120ead4637cd06c89c0220b48327573ae.jpg
Passo 3: Digite a fingerprint da chave em letras minúsculas, sem espaços. A chave correspondente aparecerá para ser adicionada. https://image.nostr.build/33e6819edd4582d7a8513e8814dacb07e1a62994bb3238c1b5b3865a46b5f234.jpg
Além disso, você pode compartilhar sua chave pública em formato QR Code, facilitando a troca de chaves em eventos ou conversas rápidas. Como Assinar Mensagens para Confirmar a Autenticidade da Sua Rede Social
Você pode autenticar sua conta em redes sociais utilizando sua chave PGP. Ao assinar uma mensagem com sua chave, você demonstra que realmente possui essa conta. Siga o passo a passo abaixo para assinar uma mensagem:
Passo 1: Clique na sua chave PGP. https://image.nostr.build/ffacce1bfb293c9a0888cd5efe340a63d96b293f4c010f8626105c7b212d8558.jpg
Passo 2: Clique no ícone indicado pela seta para abrir o campo de texto. https://image.nostr.build/4e992a2553810e2583b9d190280ce00a52fc423600a75eca48cbf541cf47d3c2.jpg
Passo 3: Deixe a opção "Encriptar para:" vazio. Em "Assinar com:", selecione sua chave PGP e digite a mensagem que deseja enviar, como o nome da sua rede social. https://image.nostr.build/a4a2a8d233d186e3d8d9adddccc445bcb3ca3ed88de0db671a77cede12323a75.jpg
Passo 4: Clique no ícone indicado pela seta para copiar o texto assinado. Uma mensagem aparecerá informando: "Assinado/Encriptado com Sucesso". https://image.nostr.build/a076dfc90e30a495af0872005bf70f412df57b7a0e1c2e17cf5aee9e9b3e39aa.jpg
A mensagem copiada terá o seguinte formato:
-----BEGIN PGP SIGNED MESSAGE----- Hash: SHA256
Minha rede social NOSTR é Danielfraga oficial. -----BEGIN PGP SIGNATURE-----
iIQEARYIACwlHERhbmllbCBGcmFnYSAgPGRhbmllbGZyYWdhQG1haWwuaTJwPgUC ZxBBLgAKCRAVl/6Qx4lalGeNAPwP71rpsbhRnZhoWZsTDOFZY8ep/d0e5qYx5iPx HV26dwD/fKyiir1TR8JwZvEbOTYS0+Dn4DFlRAAfR3lKVTC96w4= =37Lj -----END PGP SIGNATURE-----
Com isso, você pode facilmente demonstrar a autenticidade da sua conta nas redes sociais.
4. PROTEGENDO SUA CHAVE COM UMA SENHA.
Passo 5: Após a criação da chave, é fundamental definir uma senha (ou passphrase) para adicionar uma camada extra de segurança. Recomendamos usar senhas longas (com mais de 20 caracteres) e de alta entropia para evitar ataques de força bruta. Ferramentas como KeePassDX ou Bitwarden podem ajudá-lo a gerar e gerenciar essas senhas.
Para definir a senha, clique na sua chave PGP, acesse o menu no canto superior direito e selecione "Alterar senha". https://image.nostr.build/689c5237075317e89e183d2664630de973b09b68aaf8f3e3033654e987b781be.jpg https://image.nostr.build/f28ecaa9890a8827f93cac78846c4b2ef67f86ccfc3501fdadf1d1c4874b0041.jpg https://image.nostr.build/919c277fbec63c397402abdd60f915cb239a674c317855cbda63a38edef80789.jpg
Agora basta adicionar uma senha forte. https://image.nostr.build/eb378219fbb1780f89663a474ce43b8d8ebb13beeb538f2a16279b056e5d9645.jpg https://image.nostr.build/cdfa3f9c6c4045841341da789deabb6318107812d5ba195529418572ab352aaf.jpg
5. CRIPTOGRAFAR E DESCRIPTOGRAFAR MENSAGENS E ARQUIVOS COM SUA CHAVE PGP
Criptografar Mensagens
Você pode criptografar mensagens para garantir que apenas o destinatário, que possui sua chave pública, possa lê-las. Siga os passos abaixo para criptografar um texto:
Passo 1: Abra o menu lateral clicando no ícone no canto superior esquerdo.
https://image.nostr.build/13ac93b38dd1633118ae3142401c13e8a089caabdf4617055284cc521a45b069.jpgPasso 2: Selecione a opção "Encriptar/Descriptar".
https://image.nostr.build/8cd905d616b53968f0551c071d9acc2f47bbe8434c2c7e1a33076a504342de48.jpgPasso 3: Clique na opção "Encriptar Texto".
https://image.nostr.build/405a730a6c774759d7913f92f59059d43146db4afb28451a6f8833f94e99437f.jpgPasso 4: Preencha os seguintes campos: https://image.nostr.build/7dc5eba39ff82a321195dbf46b8113818632e3ef41175991d58e799a8e9d2751.jpg
-
Encriptar para: Selecione o destinatário da mensagem, ou seja, a pessoa para quem você está enviando o texto criptografado.
https://image.nostr.build/1e8c8cba6d3c3136d9857512e2794a81ceb7434eccdfb0f7d26cdef008b2e6d2.jpg -
Assinar com: Escolha sua chave PGP para assinar a mensagem.
https://image.nostr.build/d25b228c35b132d396d01c354ef093b43b3565578fbc0d6ff7b9de4e41619855.jpg -
Digitar o texto: No campo de texto, escreva a mensagem que deseja criptografar.
https://image.nostr.build/8537271dfa4445e60cb4c3cdb5d97571dc0ff5ee8acd6ed89a8c81e4bd8736c2.jpg
Passo 5: Depois de preencher os campos, você pode copiar o texto criptografado de duas formas:
-
Copiar para a área de transferência: Clique na opção para copiar o texto criptografado e cole-o em um aplicativo de mensagens para enviá-lo.
https://image.nostr.build/a5cb8e2c538a38db3972e7f3ac9aa9f602cda6b62848ff0c4b99928a67dcd486.jpg -
Compartilhar diretamente: Utilize a opção de compartilhamento para enviar o texto criptografado diretamente através de seus aplicativos de mensagens.
https://image.nostr.build/2b79cb564d623788a0de1111a067e0eb496f743389d465d4f4e8f6e65f0d08a7.jpg https://image.nostr.build/ff59e52bc8ab54ff377980a6ba5d1c4743d3298de11e5daa187ab7d45163a7be.jpg
Criptografar arquivos.
Passo 1: Abra o menu lateral clicando no ícone no canto superior esquerdo.
https://image.nostr.build/13ac93b38dd1633118ae3142401c13e8a089caabdf4617055284cc521a45b069.jpgPasso 2: Selecione a opção "Encriptar/Descriptar".
https://image.nostr.build/8cd905d616b53968f0551c071d9acc2f47bbe8434c2c7e1a33076a504342de48.jpgPasso 3 : clique na opção "Encriptar arquivos ". https://image.nostr.build/3fcae48ee38e7f4079ebccfd3eafb9ab0ad3559221d2c3560cdfe60e29f56a15.jpg
Passo 4 : os passos a seguir são os mesmo que você seguiu pra encriptar a mensagem texto. Ítens "Encriptar para:" "Assinar com:" https://image.nostr.build/4d6599b9d3a9fdfae0964daaa9dae513d5ce277a7b61930fa2937d534f72ed40.jpg
Passo 5 : clilcar na opção " Adicionair arquivo(s)" Vai abrir na memória interna do celular selecione o arquivo que deseja encriptar. https://image.nostr.build/09e3b9b54a1406426114926aab19011c36b98886ebae6fcf556cfea83bb2c2f4.jpg https://image.nostr.build/af422e243b36762dd66111ec7c848a1352c100ca3040dc21792c923f80aef74d.jpg https://image.nostr.build/ebebbdb273b4bca58d901852aec1c60e4799aa77e9d12a31f992b0cf8f73e753.jpg
Passo 6: Depois de preencher os campos, você pode compartilhar o arquivo criptografado de duas formas:
-
Salvar na memória do celular: A primeira opção salva o arquivo criptografado no armazenamento do seu dispositivo. Você terá a opção de editar o nome do arquivo antes de salvar.
https://image.nostr.build/0a47c1e9f0003541f47091b2c2e8ce6b8d1533d95463e331b218070bae964ac8.jpg https://image.nostr.build/95a7a2b67356eb5ded5b217bab38a19bdeba5af7befd105834e413e0aec45462.jpg https://image.nostr.build/66cb3d22b271f3b73b7015613c72711a3ffbf5e1070d43153f9d1f3fcf35001c.jpg https://image.nostr.build/f9624d86f7592fe7ffad932b7805762dc279d9e8ff410222108155438a2c970f.jpg -
Compartilhar diretamente: Utilize a opção de compartilhamento para enviar o arquivo criptografado diretamente por meio dos seus aplicativos de mensagens.
https://image.nostr.build/85541e466c7755c65bd6ba0208a6d8612beaa5298712b6d92f53865167695a38.jpg https://image.nostr.build/bf1e0f0aeb60cafbdf82af4b3b598288519e85b396bd3f9e00e61f65b89ea9f8.jpg https://image.nostr.build/fb090339898f37cdbb020828689b142ca601ca3ee549f67ddf6b2e094df9ab9f.jpg https://image.nostr.build/50c249ced06efe465ba533fef15207b0dcd1a725e9b2c139e8d85c13fd798276.jpg
Descriptografar Mensagens e Arquivos
Para ler uma mensagem ou arquivo criptografado que você recebeu, utilize sua chave privada. Siga os passos abaixo:
Descriptografar Mensagens
Passo 1: Copie a mensagem criptografada que você recebeu.
https://image.nostr.build/c37754b12a458e0176b9137ae0aa9e8209f853bf9d9292c0867fd8b0606d53c4.jpgPasso 2: Clique na opção "Ler da área de transferência" para descriptografar o texto.
https://image.nostr.build/d83c7dad2ee1cb6267779863bc174ee1a8f3cc3c86b69063345321027bdde7b5.jpg https://image.nostr.build/c0fae86e6ab1fe9dcee86753972c818bed489ea11efdd09b7e7da7422a9c81eb.jpgDescriptografar Arquivos
Passo 1: Clique na opção "Selecionar arquivo de entrada".
https://image.nostr.build/9c276c630311d19a576f2e35b5ba82bac07360476edae3f1a8697ff85df9e3c9.jpgPasso 2: Selecione o arquivo criptografado que deseja descriptografar.
https://image.nostr.build/6b6c2a3284ba96e7168fc7bd0916020c4f1bed7b77dfca48227fc96d6929e15a.jpg https://image.nostr.build/9945aad644af2e2020e07e55f65f11a0958d55e8fc9e13c862e6b9ca88b4f4d9.jpg6. BACKUP E RESTAURAÇÃO DE CHAVE PGP.
Realizar o backup das suas chaves PGP é fundamental para evitar a perda de acesso às suas mensagens e dados criptografados. O OpenKeychain facilita esse processo, permitindo que você faça um backup completo e seguro. Recomendamos que você armazene o backup em um local seguro, como um HD externo ou pendrive conectado via cabo OTG, sempre protegendo-o com senha.
PASSOS PARA REALIZAR O BACKUP:
Passo 1: Abra o menu lateral clicando no ícone no canto superior esquerdo.
https://image.nostr.build/13ac93b38dd1633118ae3142401c13e8a089caabdf4617055284cc521a45b069.jpgPasso 2: Selecione a opção Backup/restaurar.
https://image.nostr.build/6fa8fd14e23b47c6c924bc0d900646663f2124a93d8172ae79fdf43b5c7d4490.jpgPasso 3: Escolha a primeira opção: Backup completo (criptografado).
https://image.nostr.build/4875fb27b6d04c3cb838b4fb9f308ef9194edc35ba1254ba965b7f0db2544170.jpgPasso 4: O backup será protegido por um código de backup gerado automaticamente. Anote esse código em um papel e guarde local seguro, pois sem ele você não conseguirá recuperar suas chaves PGP. Após anotar o código, marque a opção “Anotei o código” e clique em Salvar Backup. Obs: todas as vezes que você for fazer o backup da sua chave PGP vai ser criado um novo código aleatório.
https://image.nostr.build/72a317ef5e59a01c03c36f1d04a91d42c418a478cc82e372acf21bb8302daa00.jpg
Passo 5: Escolha o local onde deseja salvar o backup (HD externo, pendrive, etc.), confirme sua escolha e clique em OK. Você verá uma mensagem de confirmação indicando que o backup foi salvo com sucesso.
https://image.nostr.build/d757e8bdf429371320daa44be8a48a0dbeb2324129f4254327f0f0383e70ede4.jpg https://image.nostr.build/f3ad80ceb8a191b4d1b40722b1d0d4f85bf183d412e7d7d901b25d19b2dfe0e3.jpg
Importação da Chave PGP
Caso você precise restaurar suas chaves PGP a partir de um backup, o OpenKeychain também facilita o processo de importação. Siga os passos abaixo para restaurar sua chave PGP:
Passo 1: Selecione a opção "Selecionar arquivo de entrada"
Abra o OpenKeychain, acesse o menu lateral no canto superior esquerdo e escolha a opção "Selecionar arquivo de entrada" para localizar o arquivo de backup que você deseja importar.
https://image.nostr.build/a06ddc1c1e6c50519097e614aa25b14311e49c0ca4d4607e42ebdcca3a6641c4.jpgPasso 2: Selecione o arquivo de backup
Navegue até o local onde você salvou o arquivo de backup (HD externo, pendrive, etc.) e selecione-o. Em seguida, o OpenKeychain solicitará que você insira o código de recuperação que foi gerado no momento do backup. https://image.nostr.build/9d5649c04a98ec8b0a29355d9068e48313b1c5dc36cd965961f4d33f22d10046.jpgPasso 3: Digite o código de recuperação
Insira o código de recuperação que você anotou anteriormente. É importante digitar o código corretamente para garantir o sucesso da restauração.Passo 4: Depois de inserir o código corretamente, o OpenKeychain irá restaurar suas chaves PGP, e uma mensagem de confirmação será exibida, indicando que a recuperação foi concluída com sucesso.
Agora suas chaves estão restauradas e você pode continuar usando o OpenKeychain para gerenciar suas comunicações criptografadas de maneira segura.
https://www.openkeychain.org/
https://github.com/open-keychain/open-keychain
https://youtu.be/fptlAx_j4OA
-
 @ 502ab02a:a2860397
2025-05-13 01:07:59
@ 502ab02a:a2860397
2025-05-13 01:07:59มีคนเคยพูดเล่นว่า “ถ้าคุณอยากเปลี่ยนโลก ไม่ต้องปฏิวัติ แค่เปลี่ยนอาหารคนซะ" บรรดาเจ้าพ่อเทคโนโลยีชีวภาพก็เลยเริ่มจับมือกับกลุ่มทุนระดับโลก สร้าง “อาหารแห่งอนาคต” ที่แม้จะไม่งอกจากธรรมชาติ แต่งอกมาจากถังหมักในโรงงานได้แทน
หลังจากที่เราเริ่มมองเห็นแล้วว่า ช่องทางแทรกซึมเข้าสู่อาหารโลกอนาคตนั้น ตั้งอยู่บนพื้นฐาน "โปรตีน" ซึ่งถ้าใครตามซีรีส์นี้กันมาตลอด คงจำโพสเรื่อง "เรากินนมเพราะความกลัว?" กันได้ดีนะครับ ไวรัล และ ตีความหลุด theme กันกระจาย ซึ่งเป็นธรรมดาของ social media ที่มันจะโผล่ไปหาขาจรแค่ครั้งเดียว ดังนั้น ก้าวข้ามมันไปครับ
สิ่งที่ปูทางไว้แล้วก่อนจะแบไต๋ว่า เป้าหลักของโลกคือ โปรตีน นั่นคือ นมทางเลือก มาสู่การยึดพื้นที่นมโรงเรียน การเข้าตลาดของ Perfect Day โปรตีนนมที่อยู่ในทั้งนม ขนม ไอศกรีม แล้วทั้งหมดจะถูกปรับภาพล้างไพ่ใหม่ ในนามของ milk 2.0 ครับ เรามาต่อซีรีส์ของเราด้วยการทำความรู้จัก ผู้เล่น กันทีละตัวนะครับ หลังจากเราได้ เวย์นมตั้งบนชั้นบนเชลฟ์กันไปแล้ว
New Culture เป็นบริษัทสตาร์ทอัปจากซานลีอันโดร รัฐแคลิฟอร์เนีย ที่ก่อตั้งขึ้นในปี 2018 โดย Matt Gibson และ Inja Radman โดยมีเป้าหมายในการผลิตโปรตีนเคซีน (casein) ซึ่งเป็นโปรตีนหลักในนมวัว โดยไม่ใช้สัตว์ ผ่านกระบวนการ precision fermentation หรือการหมักด้วยจุลินทรีย์ที่ได้รับการดัดแปลงพันธุกรรม โดยการฝึกจุลินทรีย์ให้ผลิตโปรตีนเคซีนในห้องปฏิบัติการ เพื่อสร้างผลิตภัณฑ์ชีสที่ปราศจากสัตว์ ซึ่งโปรตีนนี้สามารถนำมาใช้ในการผลิตชีสที่มีคุณสมบัติใกล้เคียงกับชีสจากนมวัว แต่ยังคงคุณสมบัติของชีสแท้ๆ เช่น การยืดหยุ่น การละลาย และรสชาติที่คุ้นเคย เปลี่ยนนิยามของคำว่า “ชีส” ให้กลายเป็นโปรตีนเคซีนจากจุลินทรีย์ ไม่ใช่จากน้ำนมวัวอีกต่อไป
Matt Gibson ชายชาวนิวซีแลนด์ ผู้ก่อตั้ง New Culture ไม่ใช่นักวิทยาศาสตร์ แต่เป็นคนหัวธุรกิจที่มีปมบางอย่างกับการกินชีสแบบดั้งเดิม เขาร่วมมือกับ Dr. Inja Radman นักชีววิทยา แล้วตั้งเป้าผลิต “เคซีน” โปรตีนหลักในนมโดยไม่ใช้สัตว์เลยสักตัว
การที่เขาเลือกใช้ precision fermentation หรือการหมักจุลินทรีย์ที่ตัดต่อพันธุกรรม ให้ผลิตเคซีนออกมาจากถังหมัก ซึ่งไม่ใช่เทคโนโลยีใหม่ในโลกแล้ว (แม้บ้านเราหลายคนจะเพิ่งเคยได้ยิน และ ตกใจกันอยู่) บริษัทคู่แข่งอย่าง Perfect Day ก็ใช้แนวทางเดียวกัน ผลิต “เวย์โปรตีนไร้สัตว์” ไปก่อนแล้ว และตอนนี้ มหาเศรษฐีสายลงทุนยั่งยืนก็กำลังรุมแห่ใส่เงินสนับสนุนแขนงนี้เหมือนเห็นโอกาสใหม่ในโลก Fiat ทำให้ New Culture ปรับทิศไปที่ "ชีส"
ผลิตภัณฑ์หลักของ New Culture คือ มอสซาเรลล่าปราศจากสัตว์ ที่มีคุณสมบัติใกล้เคียงกับมอสซาเรลล่าจากนมวัว โดยสามารถละลายและยืดหยุ่นได้เหมือนชีสแท้ๆ และยังมีปริมาณโปรตีนเคซีนเพียง 50% ของชีสทั่วไป ซึ่ง "ช่วยลดต้นทุนการผลิตและผลกระทบต่อสิ่งแวดล้อม"
New Culture ได้รับการสนับสนุนทางการเงินจากนักลงทุนรายใหญ่ เช่น Kraft Heinz, ADM, CJ CheilJedang, และ Dr. Oetker โดยในปี 2021 บริษัทได้ระดมทุนรอบ Series A จำนวน 25 ล้านดอลลาร์สหรัฐ เพื่อขยายการผลิตและนำผลิตภัณฑ์ออกสู่ตลาด นอกจากนี้ New Culture ยังได้ร่วมมือกับ CJ CheilJedang บริษัทผู้ผลิตผลิตภัณฑ์จากการหมักที่ใหญ่ที่สุดในโลก เพื่อเข้าถึงโรงงานการหมักที่ทันสมัยและลดต้นทุนการผลิตโปรตีนเคซีน
และแน่นอนเลยครับว่า ผลิตภัณฑ์ของ New Culture ต้องมาพร้อมกับการโหมประกาศว่า ปราศจากแลคโตส คอเลสเตอรอล ฮอร์โมน และยาปฏิชีวนะที่พบในนมวัว นอกจากนี้ การผลิตโปรตีนเคซีนผ่านการหมักยังช่วยลดการปล่อยก๊าซเรือนกระจกและการใช้ทรัพยากรน้ำและที่ดินเมื่อเทียบกับการผลิตนมวัวแบบดั้งเดิม เพื่อรับความดีงามจากประชากรโลกไปตามระเบียบ
มาดูรอบการระดมทุนกันครับ ยอดเงินทุนรวมที่ได้รับ จนถึงเดือนมีนาคม 2025 New Culture ได้รับเงินทุนรวมประมาณ $35 ล้านดอลลาร์สหรัฐ จากการระดมทุนทั้งหมด 8 รอบ ที่น่าจับตามองคือ Series A ในเดือนพฤศจิกายน 2021 บริษัทได้รับเงินทุน $25 ล้านดอลลาร์สหรัฐ จากนักลงทุนรวมถึง ADM Ventures และ Evolv Ventures ซึ่งเป็นหน่วยงานร่วมลงทุนของ Kraft Heinz
นอกจาก Evolv Ventures จาก Kraft Heinz แล้ว อย่าคิดว่ามันไกลเกินนะครับ CJ CheilJedang บริษัทจากเกาหลีใต้ที่เป็นผู้นำด้านเทคโนโลยีการหมัก ได้เข้าร่วมลงทุนในรอบ Series A เมื่อเดือนพฤศจิกายน 2022 แล้วเจ้านี้นี่บอกได้เลยครับ บิ๊กเนม CJ CheilJedang เป็นผู้นำด้านเทคโนโลยีการหมักและมีส่วนแบ่งตลาด 25% ในตลาดพิซซ่าแช่แข็งของสหรัฐฯ เป้าหมายการเข้าร่วมลงทุนใน New Culture ก็เพื่อสนับสนุนการพัฒนาผลิตภัณฑ์และการขยายกำลังการผลิตของชีสปราศจากสัตว์ของบริษัท
New Culture ยังได้ร่วมมือกับเชฟชื่อดัง Nancy Silverton เพื่อเปิดตัวผลิตภัณฑ์ชีสในร้านอาหารระดับเชฟชื่อดังในสหรัฐฯ กลางปี 2025 โดยเริ่มที่ร้าน Pizzeria Mozza ในลอสแอนเจลิส ซึ่งถือเป็นการเปิดตัวผลิตภัณฑ์สู่ตลาดผู้บริโภคครั้งแรกของบริษัท
การเข้ามาลงทุนของ Evolv Ventures กองทุนร่วมลงทุนของ Kraft Heinz ทำให้เจ้าพ่อชีสโปรเซสในตำนาน มีโอกาสเข้ามาร่วมมือเปิดร้านอาหารนำร่องกับ New Culture
น่าสนใจไหม เงินทุนใหญ่ๆมาจากหน่วยลงทุนที่มีผลิตภัณฑ์เป็น พิซซ่า #pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-
 @ 3ffac3a6:2d656657
2025-05-02 03:50:51
@ 3ffac3a6:2d656657
2025-05-02 03:50:51Introduction: Don't Despair—This Can Be Fixed (But Don't Reboot Yet)
Running ZFS on a Raspberry Pi offers powerful features for home servers and personal NAS setups. But with power comes complexity, and in recent months, a quiet pitfall has emerged for Pi users who track kernel updates closely: upgrading to an unsupported kernel version breaks ZFS.
⚠️ Important Warning: If you've just upgraded your kernel and you're using ZFS, do not reboot yet. Rebooting without a working ZFS module can leave your system unbootable—even if you don't have critical partitions on ZFS. The system may hang because it tries to load the missing ZFS kernel module during boot and fails, halting the boot process.
If you're already facing a broken setup or can't boot — don't panic. This guide outlines both the worst-case scenario and the ideal recovery strategy. Whether you're locked out or preparing for a smooth upgrade, we've got you covered.
The Problem: A Kernel Update Too Far
As of ZFS version 2.2.3 (used in Debian-based Raspberry Pi OS), the filesystem supports Linux kernels up to 6.7. However, Raspberry Pi OS backports recently began shipping 6.12.x kernels. If you upgrade to 6.12 without precautions:
- ZFS will fail to compile against the new kernel
- DKMS errors will appear during package updates
- Your ZFS module will be missing after reboot
- Your Raspberry Pi may fail to boot, even without ZFS-mounted root or critical paths, simply due to systemd or boot scripts expecting the kernel module to be present
Example ZFS Compilation Error:
During package updates or installs, you'll see something like:
checking whether bdev_open_by_path() exists... configure: error: *** None of the expected "blkdev_get_by_path()" interfaces were detected. *** This may be because your kernel version is newer than what is *** supported, or you are using a patched custom kernel with *** incompatible modifications. *** *** ZFS Version: zfs-2.2.3-1~bpo12+1~rpt1 *** Compatible Kernels: 3.10 - 6.7This error means ZFS cannot build its kernel module against Linux 6.12.x, making it unusable.
Why This Happens: The Version Trap
The key problem is that ZFS 2.2.3 remains installed even after a kernel upgrade, and it doesn't get upgraded automatically during
apt upgrade. Since ZFS 2.2.3 only supports up to kernel 6.7, it fails to compile against 6.12.x.However, if you remove and then reinstall ZFS, the package manager installs ZFS 2.3.1, which does support Linux kernel 6.12.x. This version transition is what resolves the issue — but only if you explicitly purge and reinstall ZFS.
Worst Case: The System That Wouldn’t Boot
After upgrading the kernel and rebooting, the system failed to boot properly. It showed errors like:
cannot open access to console, the root account is locked
Although the system did not have critical filesystems on ZFS, the boot process still stalled because system services attempted to load the ZFS kernel module, which was no longer available. This resulted in an unrecoverable boot failure.
The only way forward was to reformat and reinstall Raspberry Pi OS. However, the default Raspberry Pi OS image still comes with a 6.6.x kernel, which is incompatible with ZFS 2.3.1 and newer kernels unless upgraded. Therefore, the recovery process requires one crucial step:
- First, perform a full system upgrade:
sudo apt update && sudo apt full-upgradeThis brings the kernel up to 6.12.x.
- Then, reinstall ZFS:
sudo apt install zfs-dkms zfsutils-linuxOnce this is complete, your system will be running kernel 6.12 with ZFS 2.3.1, and you can safely import your pools and resume operations.
Best Case Recovery: Clean Cut, Clean Upgrade
For users who can still log into their system, here's the cleanest and safest sequence to move forward:
- Stop all services using ZFS, including Docker, NFS, Samba, backup tools, etc.
- Export all ZFS pools:
sudo zpool export -a3. Disable swap if it lives on a ZFS vdev:sudo swapoff /dev/sdXn4. Purge ZFS packages:sudo apt purge zfsutils-linux zfs-dkms zfs-zed sudo rm -rf /usr/src/zfs* /var/lib/dkms/zfs5. Update the kernel to the desired version:sudo apt update && sudo apt full-upgrade6. Reboot into the new kernel:sudo reboot7. Reinstall ZFS:sudo apt install zfs-dkms zfsutils-linux8. Import your pool(s):sudo zpool import poolname9. Restart services that depend on ZFS.
Final Notes: Prevention Is Better Than Recovery
To avoid this issue in the future:
- Hold your current working kernel version:
sudo apt-mark hold linux-image-rpi-v8 linux-headers-rpi-v8* Or track ZFS GitHub for kernel compatibility before upgrading * Or test upgrades on a second Pi or cloned SD card before rolling them out to production
Conclusion: A Solvable Trap
ZFS on the Raspberry Pi remains a powerful option, but it demands careful version tracking. If you upgrade responsibly, or recover cleanly as described above, you can continue benefiting from advanced features like snapshots, send/receive, and compression even on this tiny powerhouse.
Don’t let a kernel update ruin your storage plans—with preparation, the Pi + ZFS combo can remain stable and strong.
-
 @ c1e9ab3a:9cb56b43
2025-05-06 14:05:40
@ c1e9ab3a:9cb56b43
2025-05-06 14:05:40If you're an engineer stepping into the Bitcoin space from the broader crypto ecosystem, you're probably carrying a mental model shaped by speed, flexibility, and rapid innovation. That makes sense—most blockchain platforms pride themselves on throughput, programmability, and dev agility.
But Bitcoin operates from a different set of first principles. It’s not competing to be the fastest network or the most expressive smart contract platform. It’s aiming to be the most credible, neutral, and globally accessible value layer in human history.
Here’s why that matters—and why Bitcoin is not just an alternative crypto asset, but a structural necessity in the global financial system.
1. Bitcoin Fixes the Triffin Dilemma—Not With Policy, But Protocol
The Triffin Dilemma shows us that any country issuing the global reserve currency must run persistent deficits to supply that currency to the world. That’s not a flaw of bad leadership—it’s an inherent contradiction. The U.S. must debase its own monetary integrity to meet global dollar demand. That’s a self-terminating system.
Bitcoin sidesteps this entirely by being:
- Non-sovereign – no single nation owns it
- Hard-capped – no central authority can inflate it
- Verifiable and neutral – anyone with a full node can enforce the rules
In other words, Bitcoin turns global liquidity into an engineering problem, not a political one. No other system, fiat or crypto, has achieved that.
2. Bitcoin’s “Ossification” Is Intentional—and It's a Feature
From the outside, Bitcoin development may look sluggish. Features are slow to roll out. Code changes are conservative. Consensus rules are treated as sacred.
That’s the point.
When you’re building the global monetary base layer, stability is not a weakness. It’s a prerequisite. Every other financial instrument, app, or protocol that builds on Bitcoin depends on one thing: assurance that the base layer won’t change underneath them without extreme scrutiny.
So-called “ossification” is just another term for predictability and integrity. And when the market does demand change (SegWit, Taproot), Bitcoin’s soft-fork governance process has proven capable of deploying it safely—without coercive central control.
3. Layered Architecture: Throughput Is Not a Base Layer Concern
You don’t scale settlement at the base layer. You build layered systems. Just as TCP/IP doesn't need to carry YouTube traffic directly, Bitcoin doesn’t need to process every microtransaction.
Instead, it anchors:
- Lightning (fast payments)
- Fedimint (community custody)
- Ark (privacy + UTXO compression)
- Statechains, sidechains, and covenants (coming evolution)
All of these inherit Bitcoin’s security and scarcity, while handling volume off-chain, in ways that maintain auditability and self-custody.
4. Universal Assayability Requires Minimalism at the Base Layer
A core design constraint of Bitcoin is that any participant, anywhere in the world, must be able to independently verify the validity of every transaction and block—past and present—without needing permission or relying on third parties.
This property is called assayability—the ability to “test” or verify the authenticity and integrity of received bitcoin, much like verifying the weight and purity of a gold coin.
To preserve this:
- The base layer must remain resource-light, so running a full node stays accessible on commodity hardware.
- Block sizes must remain small enough to prevent centralization of verification.
- Historical data must remain consistent and tamper-evident, enabling proof chains across time and jurisdiction.
Any base layer that scales by increasing throughput or complexity undermines this fundamental guarantee, making the network more dependent on trust and surveillance infrastructure.
Bitcoin prioritizes global verifiability over throughput—because trustless money requires that every user can check the money they receive.
5. Governance: Not Captured, Just Resistant to Coercion
The current controversy around
OP_RETURNand proposals to limit inscriptions is instructive. Some prominent devs have advocated for changes to block content filtering. Others see it as overreach.Here's what matters:
- No single dev, or team, can force changes into the network. Period.
- Bitcoin Core is not “the source of truth.” It’s one implementation. If it deviates from market consensus, it gets forked, sidelined, or replaced.
- The economic majority—miners, users, businesses—enforce Bitcoin’s rules, not GitHub maintainers.
In fact, recent community resistance to perceived Core overreach only reinforces Bitcoin’s resilience. Engineers who posture with narcissistic certainty, dismiss dissent, or attempt to capture influence are routinely neutralized by the market’s refusal to upgrade or adopt forks that undermine neutrality or openness.
This is governance via credible neutrality and negative feedback loops. Power doesn’t accumulate in one place. It’s constantly checked by the network’s distributed incentives.
6. Bitcoin Is Still in Its Infancy—And That’s a Good Thing
You’re not too late. The ecosystem around Bitcoin—especially L2 protocols, privacy tools, custody innovation, and zero-knowledge integrations—is just beginning.
If you're an engineer looking for:
- Systems with global scale constraints
- Architectures that optimize for integrity, not speed
- Consensus mechanisms that resist coercion
- A base layer with predictable monetary policy
Then Bitcoin is where serious systems engineers go when they’ve outgrown crypto theater.
Take-away
Under realistic, market-aware assumptions—where:
- Bitcoin’s ossification is seen as a stability feature, not inertia,
- Market forces can and do demand and implement change via tested, non-coercive mechanisms,
- Proof-of-work is recognized as the only consensus mechanism resistant to fiat capture,
- Wealth concentration is understood as a temporary distribution effect during early monetization,
- Low base layer throughput is a deliberate design constraint to preserve verifiability and neutrality,
- And innovation is layered by design, with the base chain providing integrity, not complexity...
Then Bitcoin is not a fragile or inflexible system—it is a deliberately minimal, modular, and resilient protocol.
Its governance is not leaderless chaos; it's a negative-feedback structure that minimizes the power of individuals or institutions to coerce change. The very fact that proposals—like controversial OP_RETURN restrictions—can be resisted, forked around, or ignored by the market without breaking the system is proof of decentralized control, not dysfunction.
Bitcoin is an adversarially robust monetary foundation. Its value lies not in how fast it changes, but in how reliably it doesn't—unless change is forced by real, bottom-up demand and implemented through consensus-tested soft forks.
In this framing, Bitcoin isn't a slower crypto. It's the engineering benchmark for systems that must endure, not entertain.
Final Word
Bitcoin isn’t moving slowly because it’s dying. It’s moving carefully because it’s winning. It’s not an app platform or a sandbox. It’s a protocol layer for the future of money.
If you're here because you want to help build that future, you’re in the right place.
nostr:nevent1qqswr7sla434duatjp4m89grvs3zanxug05pzj04asxmv4rngvyv04sppemhxue69uhkummn9ekx7mp0qgs9tc6ruevfqu7nzt72kvq8te95dqfkndj5t8hlx6n79lj03q9v6xcrqsqqqqqp0n8wc2
nostr:nevent1qqsd5hfkqgskpjjq5zlfyyv9nmmela5q67tgu9640v7r8t828u73rdqpr4mhxue69uhkymmnw3ezucnfw33k76tww3ux76m09e3k7mf0qgsvr6dt8ft292mv5jlt7382vje0mfq2ccc3azrt4p45v5sknj6kkscrqsqqqqqp02vjk5
nostr:nevent1qqstrszamvffh72wr20euhrwa0fhzd3hhpedm30ys4ct8dpelwz3nuqpr4mhxue69uhkymmnw3ezucnfw33k76tww3ux76m09e3k7mf0qgs8a474cw4lqmapcq8hr7res4nknar2ey34fsffk0k42cjsdyn7yqqrqsqqqqqpnn3znl
-
 @ c1e9ab3a:9cb56b43
2025-05-05 14:25:28
@ c1e9ab3a:9cb56b43
2025-05-05 14:25:28Introduction: The Power of Fiction and the Shaping of Collective Morality
Stories define the moral landscape of a civilization. From the earliest mythologies to the modern spectacle of global cinema, the tales a society tells its youth shape the parameters of acceptable behavior, the cost of transgression, and the meaning of justice, power, and redemption. Among the most globally influential narratives of the past half-century is the Star Wars saga, a sprawling science fiction mythology that has transcended genre to become a cultural religion for many. Central to this mythos is the arc of Anakin Skywalker, the fallen Jedi Knight who becomes Darth Vader. In Star Wars: Episode III – Revenge of the Sith, Anakin commits what is arguably the most morally abhorrent act depicted in mainstream popular cinema: the mass murder of children. And yet, by the end of the saga, he is redeemed.
This chapter introduces the uninitiated to the events surrounding this narrative turn and explores the deep structural and ethical concerns it raises. We argue that the cultural treatment of Darth Vader as an anti-hero, even a role model, reveals a deep perversion in the collective moral grammar of the modern West. In doing so, we consider the implications this mythology may have on young adults navigating identity, masculinity, and agency in a world increasingly shaped by spectacle and symbolic narrative.
Part I: The Scene and Its Context
In Revenge of the Sith (2005), the third episode of the Star Wars prequel trilogy, the protagonist Anakin Skywalker succumbs to fear, ambition, and manipulation. Convinced that the Jedi Council is plotting against the Republic and desperate to save his pregnant wife from a vision of death, Anakin pledges allegiance to Chancellor Palpatine, secretly the Sith Lord Darth Sidious. Upon doing so, he is given a new name—Darth Vader—and tasked with a critical mission: to eliminate all Jedi in the temple, including its youngest members.
In one of the most harrowing scenes in the film, Anakin enters the Jedi Temple. A group of young children, known as "younglings," emerge from hiding and plead for help. One steps forward, calling him "Master Skywalker," and asks what they are to do. Anakin responds by igniting his lightsaber. The screen cuts away, but the implication is unambiguous. Later, it is confirmed through dialogue and visual allusion that he slaughtered them all.
There is no ambiguity in the storytelling. The man who will become the galaxy’s most feared enforcer begins his descent by murdering defenseless children.
Part II: A New Kind of Evil in Youth-Oriented Media
For decades, cinema avoided certain taboos. Even films depicting war, genocide, or psychological horror rarely crossed the line into showing children as victims of deliberate violence by the protagonist. When children were harmed, it was by monstrous antagonists, supernatural forces, or offscreen implications. The killing of children was culturally reserved for historical atrocities and horror tales.
In Revenge of the Sith, this boundary was broken. While the film does not show the violence explicitly, the implication is so clear and so central to the character arc that its omission from visual depiction does not blunt the narrative weight. What makes this scene especially jarring is the tonal dissonance between the gravity of the act and the broader cultural treatment of Star Wars as a family-friendly saga. The juxtaposition of child-targeted marketing with a central plot involving child murder is not accidental—it reflects a deeper narrative and commercial structure.
This scene was not a deviation from the arc. It was the intended turning point.
Part III: Masculinity, Militarism, and the Appeal of the Anti-Hero
Darth Vader has long been idolized as a masculine icon. His towering presence, emotionless control, and mechanical voice exude power and discipline. Military institutions have quoted him. He is celebrated in memes, posters, and merchandise. Within the cultural imagination, he embodies dominance, command, and strategic ruthlessness.
For many young men, particularly those struggling with identity, agency, and perceived weakness, Vader becomes more than a character. He becomes an archetype: the man who reclaims power by embracing discipline, forsaking emotion, and exacting vengeance against those who betrayed him. The emotional pain that leads to his fall mirrors the experiences of isolation and perceived emasculation that many young men internalize in a fractured society.
The symbolism becomes dangerous. Anakin's descent into mass murder is portrayed not as the outcome of unchecked cruelty, but as a tragic mistake rooted in love and desperation. The implication is that under enough pressure, even the most horrific act can be framed as a step toward a noble end.
Part IV: Redemption as Narrative Alchemy
By the end of the original trilogy (Return of the Jedi, 1983), Darth Vader kills the Emperor to save his son Luke and dies shortly thereafter. Luke mourns him, honors him, and burns his body in reverence. In the final scene, Vader's ghost appears alongside Obi-Wan Kenobi and Yoda—the very men who once considered him the greatest betrayal of their order. He is welcomed back.
There is no reckoning. No mention of the younglings. No memorial to the dead. No consequence beyond his own internal torment.
This model of redemption is not uncommon in Western storytelling. In Christian doctrine, the concept of grace allows for any sin to be forgiven if the sinner repents sincerely. But in the context of secular mass culture, such redemption without justice becomes deeply troubling. The cultural message is clear: even the worst crimes can be erased if one makes a grand enough gesture at the end. It is the erasure of moral debt by narrative fiat.
The implication is not only that evil can be undone by good, but that power and legacy matter more than the victims. Vader is not just forgiven—he is exalted.
Part V: Real-World Reflections and Dangerous Scripts
In recent decades, the rise of mass violence in schools and public places has revealed a disturbing pattern: young men who feel alienated, betrayed, or powerless adopt mythic narratives of vengeance and transformation. They often see themselves as tragic figures forced into violence by a cruel world. Some explicitly reference pop culture, quoting films, invoking fictional characters, or modeling their identities after cinematic anti-heroes.
It would be reductive to claim Star Wars causes such events. But it is equally naive to believe that such narratives play no role in shaping the symbolic frameworks through which vulnerable individuals understand their lives. The story of Anakin Skywalker offers a dangerous script:
- You are betrayed.
- You suffer.
- You kill.
- You become powerful.
- You are redeemed.
When combined with militarized masculinity, institutional failure, and cultural nihilism, this script can validate the darkest impulses. It becomes a myth of sacrificial violence, with the perpetrator as misunderstood hero.
Part VI: Cultural Responsibility and Narrative Ethics
The problem is not that Star Wars tells a tragic story. Tragedy is essential to moral understanding. The problem is how the culture treats that story. Darth Vader is not treated as a warning, a cautionary tale, or a fallen angel. He is merchandised, celebrated, and decontextualized.
By separating his image from his actions, society rebrands him as a figure of cool dominance rather than ethical failure. The younglings are forgotten. The victims vanish. Only the redemption remains. The merchandise continues to sell.
Cultural institutions bear responsibility for how such narratives are presented and consumed. Filmmakers may intend nuance, but marketing departments, military institutions, and fan cultures often reduce that nuance to symbol and slogan.
Conclusion: Reckoning with the Stories We Tell
The story of Anakin Skywalker is not morally neutral. It is a tale of systemic failure, emotional collapse, and unchecked violence. When presented in full, it can serve as a powerful warning. But when reduced to aesthetic dominance and easy redemption, it becomes a tool of moral decay.
The glorification of Darth Vader as a cultural icon—divorced from the horrific acts that define his transformation—is not just misguided. It is dangerous. It trains a generation to believe that power erases guilt, that violence is a path to recognition, and that final acts of loyalty can overwrite the deliberate murder of the innocent.
To the uninitiated, Star Wars may seem like harmless fantasy. But its deepest myth—the redemption of the child-killer through familial love and posthumous honor—deserves scrutiny. Not because fiction causes violence, but because fiction defines the possibilities of how we understand evil, forgiveness, and what it means to be a hero.
We must ask: What kind of redemption erases the cries of murdered children? And what kind of culture finds peace in that forgetting?
-
 @ c1e6505c:02b3157e
2025-05-13 00:58:11
@ c1e6505c:02b3157e
2025-05-13 00:58:11I rarely make black and white photographs. I usually find color more interesting. But sometimes, it’s wise to strip it away.
Color can be distracting. It can pull attention from what matters. Beauty, I believe, should be simple - something that’s felt, not overthought.
Removing the excessive, the superfluous, can do a lot. It reduces noise. It reveals what’s often hidden. What’s elusive becomes clear.




-
 @ d360efec:14907b5f
2025-05-13 00:39:56
@ d360efec:14907b5f
2025-05-13 00:39:56🚀📉 #BTC วิเคราะห์ H2! พุ่งชน 105K แล้วเจอแรงขาย... จับตา FVG 100.5K เป็นจุดวัดใจ! 👀📊
จากากรวิเคราะห์ทางเทคนิคสำหรับ #Bitcoin ในกรอบเวลา H2:
สัปดาห์ที่แล้ว #BTC ได้เบรคและพุ่งขึ้นอย่างแข็งแกร่งค่ะ 📈⚡ แต่เมื่อวันจันทร์ที่ผ่านมา ราคาได้ขึ้นไปชนแนวต้านบริเวณ 105,000 ดอลลาร์ แล้วเจอแรงขายย่อตัวลงมาตลอดทั้งวันค่ะ 🧱📉
ตอนนี้ ระดับที่น่าจับตาอย่างยิ่งคือโซน H4 FVG (Fair Value Gap ในกราฟ 4 ชั่วโมง) ที่ 100,500 ดอลลาร์ ค่ะ 🎯 (FVG คือโซนที่ราคาวิ่งผ่านไปเร็วๆ และมักเป็นบริเวณที่ราคามีโอกาสกลับมาทดสอบ/เติมเต็ม)
👇 โซน FVG ที่ 100.5K นี้ ยังคงเป็น Area of Interest ที่น่าสนใจสำหรับมองหาจังหวะ Long เพื่อลุ้นการขึ้นในคลื่นลูกถัดไปค่ะ!
🤔💡 อย่างไรก็ตาม การตัดสินใจเข้า Long หรือเทรดที่บริเวณนี้ ขึ้นอยู่กับว่าราคา แสดงปฏิกิริยาอย่างไรเมื่อมาถึงโซน 100.5K นี้ เพื่อยืนยันสัญญาณสำหรับการเคลื่อนไหวที่จะขึ้นสูงกว่าเดิมค่ะ!
เฝ้าดู Price Action ที่ระดับนี้อย่างใกล้ชิดนะคะ! 📍
BTC #Bitcoin #Crypto #คริปโต #TechnicalAnalysis #Trading #FVG #FairValueGap #PriceAction #MarketAnalysis #ลงทุนคริปโต #วิเคราะห์กราฟ #TradeSetup #ข่าวคริปโต #ตลาดคริปโต


-
 @ 21335073:a244b1ad
2025-05-01 01:51:10
@ 21335073:a244b1ad
2025-05-01 01:51:10Please respect Virginia Giuffre’s memory by refraining from asking about the circumstances or theories surrounding her passing.
Since Virginia Giuffre’s death, I’ve reflected on what she would want me to say or do. This piece is my attempt to honor her legacy.
When I first spoke with Virginia, I was struck by her unshakable hope. I had grown cynical after years in the anti-human trafficking movement, worn down by a broken system and a government that often seemed complicit. But Virginia’s passion, creativity, and belief that survivors could be heard reignited something in me. She reminded me of my younger, more hopeful self. Instead of warning her about the challenges ahead, I let her dream big, unburdened by my own disillusionment. That conversation changed me for the better, and following her lead led to meaningful progress.
Virginia was one of the bravest people I’ve ever known. As a survivor of Epstein, Maxwell, and their co-conspirators, she risked everything to speak out, taking on some of the world’s most powerful figures.
She loved when I said, “Epstein isn’t the only Epstein.” This wasn’t just about one man—it was a call to hold all abusers accountable and to ensure survivors find hope and healing.
The Epstein case often gets reduced to sensational details about the elite, but that misses the bigger picture. Yes, we should be holding all of the co-conspirators accountable, we must listen to the survivors’ stories. Their experiences reveal how predators exploit vulnerabilities, offering lessons to prevent future victims.
You’re not powerless in this fight. Educate yourself about trafficking and abuse—online and offline—and take steps to protect those around you. Supporting survivors starts with small, meaningful actions. Free online resources can guide you in being a safe, supportive presence.
When high-profile accusations arise, resist snap judgments. Instead of dismissing survivors as “crazy,” pause to consider the trauma they may be navigating. Speaking out or coping with abuse is never easy. You don’t have to believe every claim, but you can refrain from attacking accusers online.
Society also fails at providing aftercare for survivors. The government, often part of the problem, won’t solve this. It’s up to us. Prevention is critical, but when abuse occurs, step up for your loved ones and community. Protect the vulnerable. it’s a challenging but a rewarding journey.
If you’re contributing to Nostr, you’re helping build a censorship resistant platform where survivors can share their stories freely, no matter how powerful their abusers are. Their voices can endure here, offering strength and hope to others. This gives me great hope for the future.
Virginia Giuffre’s courage was a gift to the world. It was an honor to know and serve her. She will be deeply missed. My hope is that her story inspires others to take on the powerful.
-
 @ 52b4a076:e7fad8bd
2025-05-03 21:54:45
@ 52b4a076:e7fad8bd
2025-05-03 21:54:45Introduction
Me and Fishcake have been working on infrastructure for Noswhere and Nostr.build. Part of this involves processing a large amount of Nostr events for features such as search, analytics, and feeds.
I have been recently developing
nosdexv3, a newer version of the Noswhere scraper that is designed for maximum performance and fault tolerance using FoundationDB (FDB).Fishcake has been working on a processing system for Nostr events to use with NB, based off of Cloudflare (CF) Pipelines, which is a relatively new beta product. This evening, we put it all to the test.
First preparations
We set up a new CF Pipelines endpoint, and I implemented a basic importer that took data from the
nosdexdatabase. This was quite slow, as it did HTTP requests synchronously, but worked as a good smoke test.Asynchronous indexing
I implemented a high-contention queue system designed for highly parallel indexing operations, built using FDB, that supports: - Fully customizable batch sizes - Per-index queues - Hundreds of parallel consumers - Automatic retry logic using lease expiration
When the scraper first gets an event, it will process it and eventually write it to the blob store and FDB. Each new event is appended to the event log.
On the indexing side, a
Queuerwill read the event log, and batch events (usually 2K-5K events) into one work job. This work job contains: - A range in the log to index - Which target this job is intended for - The size of the job and some other metadataEach job has an associated leasing state, which is used to handle retries and prioritization, and ensure no duplication of work.
Several
Workers monitor the index queue (up to 128) and wait for new jobs that are available to lease.Once a suitable job is found, the worker acquires a lease on the job and reads the relevant events from FDB and the blob store.
Depending on the indexing type, the job will be processed in one of a number of ways, and then marked as completed or returned for retries.
In this case, the event is also forwarded to CF Pipelines.

Trying it out
The first attempt did not go well. I found a bug in the high-contention indexer that led to frequent transaction conflicts. This was easily solved by correcting an incorrectly set parameter.
We also found there were other issues in the indexer, such as an insufficient amount of threads, and a suspicious decrease in the speed of the
Queuerduring processing of queued jobs.Along with fixing these issues, I also implemented other optimizations, such as deprioritizing
WorkerDB accesses, and increasing the batch size.To fix the degraded
Queuerperformance, I ran the backfill job by itself, and then started indexing after it had completed.Bottlenecks, bottlenecks everywhere

After implementing these fixes, there was an interesting problem: The DB couldn't go over 80K reads per second. I had encountered this limit during load testing for the scraper and other FDB benchmarks.
As I suspected, this was a client thread limitation, as one thread seemed to be using high amounts of CPU. To overcome this, I created a new client instance for each
Worker.After investigating, I discovered that the Go FoundationDB client cached the database connection. This meant all attempts to create separate DB connections ended up being useless.
Using
OpenWithConnectionStringpartially resolved this issue. (This also had benefits for service-discovery based connection configuration.)To be able to fully support multi-threading, I needed to enabled the FDB multi-client feature. Enabling it also allowed easier upgrades across DB versions, as FDB clients are incompatible across versions:
FDB_NETWORK_OPTION_EXTERNAL_CLIENT_LIBRARY="/lib/libfdb_c.so"FDB_NETWORK_OPTION_CLIENT_THREADS_PER_VERSION="16"Breaking the 100K/s reads barrier

After implementing support for the multi-threaded client, we were able to get over 100K reads per second.
You may notice after the restart (gap) the performance dropped. This was caused by several bugs: 1. When creating the CF Pipelines endpoint, we did not specify a region. The automatically selected region was far away from the server. 2. The amount of shards were not sufficient, so we increased them. 3. The client overloaded a few HTTP/2 connections with too many requests.
I implemented a feature to assign each
Workerits own HTTP client, fixing the 3rd issue. We also moved the entire storage region to West Europe to be closer to the servers.After these changes, we were able to easily push over 200K reads/s, mostly limited by missing optimizations:

It's shards all the way down
While testing, we also noticed another issue: At certain times, a pipeline would get overloaded, stalling requests for seconds at a time. This prevented all forward progress on the
Workers.We solved this by having multiple pipelines: A primary pipeline meant to be for standard load, with moderate batching duration and less shards, and high-throughput pipelines with more shards.
Each
Workeris assigned a pipeline on startup, and if one pipeline stalls, other workers can continue making progress and saturate the DB.The stress test
After making sure everything was ready for the import, we cleared all data, and started the import.
The entire import lasted 20 minutes between 01:44 UTC and 02:04 UTC, reaching a peak of: - 0.25M requests per second - 0.6M keys read per second - 140MB/s reads from DB - 2Gbps of network throughput
FoundationDB ran smoothly during this test, with: - Read times under 2ms - Zero conflicting transactions - No overloaded servers
CF Pipelines held up well, delivering batches to R2 without any issues, while reaching its maximum possible throughput.

Finishing notes
Me and Fishcake have been building infrastructure around scaling Nostr, from media, to relays, to content indexing. We consistently work on improving scalability, resiliency and stability, even outside these posts.
Many things, including what you see here, are already a part of Nostr.build, Noswhere and NFDB, and many other changes are being implemented every day.
If you like what you are seeing, and want to integrate it, get in touch. :)
If you want to support our work, you can zap this post, or register for nostr.land and nostr.build today.
-
 @ 68768a6c:0eaf07e9
2025-05-12 23:58:56
@ 68768a6c:0eaf07e9
2025-05-12 23:58:56What Is Bitcoin? Bitcoin is the world’s first decentralized digital currency—created in 2009 by an anonymous person (or group) under the name Satoshi Nakamoto. Unlike regular money, it’s not printed or controlled by any government or bank. Instead, it runs on a global network of computers using a technology called blockchain. Why Is Bitcoin Valuable? Bitcoin is often called “digital gold” because it’s limited in supply—only 21 million bitcoins will ever exist. This scarcity, combined with increasing demand and global adoption, makes it valuable. Many people invest in Bitcoin as a hedge against inflation or unstable currencies. How Can You Use Bitcoin? Today, Bitcoin can be used for: Online shopping (some stores accept it) Transferring money across borders Investing for long-term growth You can store it in a digital wallet and send it anywhere in the world in minutes—with low fees. The Risks and Rewards Bitcoin prices can go up or down quickly—it’s very volatile. But many investors believe it will grow in value as the world becomes more digital. Tip for Beginners: Never invest more than you can afford to lose. Start small, learn as you go, and stay updated. Final Thoughts Bitcoin is more than just internet money—it’s a revolution in how we think about value, privacy, and freedom. Whether you’re a curious beginner or a savvy investor, understanding Bitcoin could be your first step toward financial innovation.
-
 @ 2ce0697b:1ee3d3fc
2025-04-29 18:54:19
@ 2ce0697b:1ee3d3fc
2025-04-29 18:54:19Excerpt
Special Jurisdictions, Free Cities and Bitcoin Citadels are the sly roundabout way that is removing the market of living together from the hands of the government, without violence and in a way that they can´t stop it. With Bitcoin as the backbone of a new societal order, we are beginning to disrupt the old paradigm.
“If you have built castles in the air, your work need not be lost; that is where they should be. Now put the foundations under them.” ― Henry David Thoreau, Walden
The problem: lack of freedom in the physical realm
Freedom is essential to human life. Being free is what matters. That´s our target, always. No matter the time or space. We pursue freedom because we know its the right thing to do. Freedom is the right to question and change the stablished way of doing things.
Where can we find some freedom? Certainly in the cyberspace. The cyberspace is a free space. Humanity has been blessed by the magic of cryptography, a technology that gave us all the necessary tools to operate in that environment without intervention of undesired third parties.
In cyberspace cryptography performs the function of an impenetrable cyberwall. So, whatever we build in cyberspace can be perfectly protected. Thank to this cybernetic walls we can be sure that the gardens we build and nurture will be protected and cannot be trampled. When we build our digital gardens we have the keys to open the doors to let in whoever we want and most important to leave out whoever we don´t want. In the digital world we can already perfectly interact with one and another in a peer to peer way, without intervention of undesired third parties.
In cyberspace we have Bitcoin for freedom of money and Nostr, torrent and Tor for freedom of information and speech. These open-source protocols are designed to fully realize and expand the promise of freedom, and they certainly deliver what they promise.

So, thanks to the magic of asymmetric cryptography, we´ve already achieved sufficiently descentralization and the possibility of any level of desired digital privacy. Cryptoanarchists and cypherpunks have set their conquering flag in cyberspace and there´s no force on Earth than can remove it. The digital world cannot escape the rules of cryptography. This is great but it only works in the digital realm, meanwhile in the physical realm we are overrun by centralized attackers due to the impossibility of the creation of impenetrable walls such as the ones we have online.
Humans have the upper hand in creating impenetrable walled gardens in cyberspace, but in the physical space authoritarians have the upper hand in bullying physical persons.
The physical world is also naturally free. According to natural law each person is free to do whatever he wants as long as it doesn´t hurt other people. However due to unnatural -artificial and inhuman- centralization of power, the natural freedom of the physical world has been completely undermined. Mostly by Governments, the entities that centralize violence and law.
Bitcoin as a bridge between both realms

Let´s take a look at one connection between both realms, the physical and the digital world. Bitcoin layer one is made essentially of software plus hardware. It consists of any software that produces the same output as the reference implementation - Bitcoin core- and the hardware needed to run that software. Layer two, three or any other layer above, is made essentially of other software and other hardware that interacts with layer one in some way. All these layers, one, two and subsequent, are completely protected by cryptography and a set of game theories that have been successfully tested. Each new block added to the timechain is a testimony of the unstoppable force of freedom and meritocracy.
Before layer one we have Bitcoin layer zero, which is essentially the sum of all actions and inactions done by bitcoiners regarding to or because of bitcoin. In other words, layer zero is composed by flesh and bone people interacting in some way with layer one of the bitcoin network.
Hence, an attack on a bitcoiner - on his way of life- is an attack on bitcoin, the network itself. First because it is an attack on a layer zero node, the physical person, the bitcoiner under duress or coercion. And second because is also an attack on the store-of-value-aspect of bitcoin. Nowaday, the most common attack against bitcoiners is the entirety of compliance regulations. This is the sum of all coercive regulations,such as laws, threats of more laws, imprisonment, threats of more imprisonment, taxation, threats of more taxation, requirements to prove the origin of funds, coercive removal of privacy such as the travel rule, unnecessary bureaucracy such as the need to obtain a money transmitting license and many others rules, in a never stopping inflationary coercive legislation.

If a physical attack is preventing any bitcoiner to exchange the value he created for bitcoin due to any kind of artificial obstacles -such as any kind of compliance- that specific attack is successful in the sense that even though the whole network keeps operating, the attack itself diminishes the value of all the bitcoins.
So, even if layer-zero cannot be taken down, every interference on this layer is an attack on the bitcoin network. Attacks on layer one, two or any other layer that exists in the cyberspace can interfere with the network but they may hardly subtract any value from it. For example we have already been through plenty of times where hashing power was diminished due to government intervention and the bitcoin network remain completely unaffected.
On the other hand successful attacks on layer zero subtract potential, but real and demonstrable value. This value is equal to the amount of value the frustrated user would have added to the network if he would have been able to use it freely, that means if he would have sold his product without the cost of compliance. I´ll demonstrate this in the next chapter.
The cost of compliance
Alice is a merchant specialized in a specific area and topic. She studied the market, her business, her suppliers, consumers, the logistics involved, marketing, design, and everything necessary to become a successful entrepreneur. After investing a considerable amount of resources, she developed a perfect product. Or at least she considers it perfect, that is, the best in its class. While developing everything necessary to create her product, she met Bob, who became her main lead and stereotype of a buyer persona. She knows what Bob wants and she wants to sell it to him. According to Alice's calculations, for her business to be viable, she must sell the product at ten satoshis per unit, and fortunately, Bob is willing to pay that price for it. Alice's product is finished, ready to hit the market, but just before sending it to production, Alice decides to take a pause to analyze her reality. Before taking the public action of making her product available in the open market, Alice analyzes her material, political, and legal reality. In doing so, she realizes that she lives under the jurisdiction of a State. She learns that the Government prescribes through its regulations how she must behave. She analyzes that in order to sell her product legally, in compliance, she must make a series of modifications to it. The product before hitting the shelves must first be modified both in the way it is presented to the market and also regarding certain technical characteristics that it possesses. She must also modify the way it produces her product by changing the contractual relationship with its suppliers, distribution channels, and all other types of logistics involved. She must make all these changes even if they bring about significant and insurmountable inefficiencies.
Likewise, Alice also sees that she not only has to modify the product but also has to meet tax obligations. In addition to paying an accountant since the tax obligations by some irrational reason are not calculated by the creditor. Additionally, she must hire other professionals to assist her in studying the current regulations and how they should be applied in all stages of production, distribution, and sale of her product.
Alice, being a rational person, wishes to avoid having to make these modifications since they increase her costs while also decreasing the quality of her product. But when studying compliance, that is, the entirety of applicable regulations, she also examines the consequences of not being in compliance. Alice realizes that if she does not comply with the regulations, she risks having all her assets legally confiscated, going to prison, being killed while they try to capture her to imprison her, and, if she goes to prison, being tortured in jail by other inmates or by State officials in charge of holding her in that place. So, since Alice does not want to suffer these negative consequences, she decides to modify the product and be in compliance.
So, Alice makes the necessary changes and puts her new version of the product on the market. Then she has the following dialogue with Bob, her lead, the interested party in acquiring the product.
Bob: - Hey Alice, nice meeting you here in this market. I came to buy the product you were developing and told me about. However, this product I´m seeing now is not what you promised me. This is clearly inferior.
Alice: - Yeah, I know. I'm sorry Bob, but I prefer to sell this inferior product rather than risk having all my assets confiscated, going to prison, being killed while they try to capture me, and if they don´t kill but managed to put me in jail I could be tortured there.
Bob: - Ok, no problem. Thats quite understandable. I don´t believe anyone would prefer those kind of experiences. But given the quality of the product, I no longer intend to pay you ten satoshis; I only offer you eight. Shall we close the deal?
Alice: - I'm sorry Bob, but I can't sell it to you for eight sats. Due to government intervention and its requirements, now I can't even sell it for less than thirteen satoshis.
Bob: - Ok. Considering this I prefer not to purchase it. I will keep looking for alternatives. Bye

Some time later, Charlie arrives at the market, who is also interested in the product and, despite it not being like the original version, decides to purchase it by paying the thirteen satoshis demanded by the seller Alice.
Meanwhile, in the same universe, we have Daniel, the last character in this example. Daniel is a merchant competing with Alice. Daniel has a product that is very similar, practically identical to the one originally designed by Alice. Like Alice, Daniel initially also wants to sell it for ten satoshis. Just like Alice, before heading to the market, Daniel analyzes the reality in which he lives. And it turns out that he also lives under the jurisdiction of a State. Daniel too then analyzes the entirety of the applicable regulations and also comes to the conclusion that to comply with them, he would also need to modify the product and cover all the additional expenses artificially generated to be in compliance.
However, Daniel's ethics are different from Alice's. Daniel understands that his product is indeed perfect (the best in its class) and that therefore modifying it would go against its essence. Daniel understands that changing the product would be a betrayal of his creation and therefore a betrayal of his own self and the essence of his being. Daniel conducts an ethical analysis of his actions and the moral implications of putting the product on the market. Daniel sees that the product not only does not harm anyone but is also made to be freely acquired by adults who give their consent for its purchase and subsequent use. Daniel also understands that paying taxes only serves to promote the slavery system driven by fiat and that whenever he can avoid collaborating with the immoral fiat system, it is his ethical obligation to do so. Likewise, Daniel highlights the hypocrisy and inefficiencies of anti-money laundering regulations, as well as the futility of requiring licenses for naturally free acts that do not harm others. For all these reasons, Daniel decides to sell the product in its current state irregardles of compliance regulations.
However, before going to market, Daniel also studies the possible consequences of neglecting compliance. By doing so, Daniel sees that if he does not comply with the regulations, he risks having all his assets legally confiscated, going to prison, being killed while they attempt to capture him to imprison him, and, in the event of going to prison, being tortured in jail by other inmates or by State officials responsible for holding him in that place. So, since Daniel is a rational person who does not want to suffer these negative consequences but also does not want to betray his product and himself, he decides to take the risk of not being in compliance. After making this decision, Daniel puts the product on the market and there he meets Bob. In doing so, they converse in the following terms:
Bob: - Hey Daniel, this product is exactly what I was looking for. A product like the one promised by Alice but never delivered. I love it! I offer you ten satoshis for it.
Daniel: - Thank you for your feedback Bob and for the offer! However I am currently selling it for eleven satoshis. Ten satoshis seems like a good price to me, and it was indeed my original intention to sell it for that amount because at that price I achieve competitiveness and a sustainable business model.
Bob: - So why are you asking me for eleven satoshis? Interrupts Bob
Daniel: - Because that price is calculated before assessing compliance and the risks associated with non-compliance. By not complying with the regulation, I managed to maintain the quality of the product and avoided a large amount of unnecessary expenses, but there is no way to avoid the risk of facing penalties for non-compliance. To bring this product to market, I had to incur several expenses in order to minimize the risk of non-compliance as much as possible. While I am taking all reasonable actions to prevent all of my assets from being legally confiscated, from going to prison, from being killed while they try to capture me, and in case of going to prison, from being tortured, the reality is that I still run the risk of all that, or part of all that, happening to me, my family, or any of my company's employees. The remaining risk balance is transferred to the price along with the costs of mitigating those risks. The total of those costs and the remaining risk I estimate them at one satoshi per unit of product. Therefore, I can't sell you the product for ten satoshis, but I can sell it to you for eleven.
To which Bob, lacking a better option in the market, ends up buying the product for eleven satoshis.
In summary: two products were made by two different merchants whose business model allowed them, in both cases, to put the product on the market at a rate of ten satoshis per unit. However, in one case, a lower quality product was sold for thirteen satoshis, and in the other case, a higher quality product was sold for eleven satoshis. That is to say, in the first case there was an overprice or inefficiency objectively measured at three satoshis, while in the second case there was an overprice or inefficiency of one satoshi. So, we are facing a total loss of value equivalent to four satoshis. The value represented by these four satoshis was absorbed by the inefficiency programmed and ruled by the State. The example shows us that whether one chooses the compliance route, as Alice did, or the free market route, as Daniel did, in both cases the existence of regulations generates an additional cost to the market. In this example the state attack on layer zero was successful and extracted from the Bitcoin network a value of four satoshis.
Bitcoin is money
Bitcoin is many things but essentially is money. And money sole purpose is to store value in order to facilitate future exchanges of products and services with other people. Without the products and services to be exchanged for the money, money itself would be useless and worthless. We only use money because we may require favors, benefits, services, products from other people in the future. And we don´t know which services and products we´ll need nor exactly when we are goint to need them.

The total value of bitcoin equals to infinity divided twenty one millions. This is because the total worth of the network mirrors the total worth of accumulated capital by the entirety of mankind throughout its entire history. That is clearly a lot of value. But if the if the dividend equals zero then the divisor is also zero and if the dividend growth is obstructed through artificial means -such as compliance- then the divisor growth is also obstructed.
Bitcoin layer zero, the bitcoiners and the services and products we create, are what give value to the twenty one million units of bitcoin.
Freedom is without a doubt the best context for value creation. So, the more and better games we can create that allow humankind to find a way to exercise freedom, then the most value we can add to all the layers of the network.
This is why the most important layer of the whole bitcoin phenomenon is layer zero, the bitcoiners. Hence the problem to be solved is not how to prevent bitcoin - layer one upwards- from successful attacks. The problem to solve is how to prevent attacks on layer zero. Or in other words, the problem to be solved is how to get bitcoiners in the physical world to practice the same level of freedom that bitcoin achieves in the cyberspace.
Summary of the first part of this article: freedom in cyberspace has already been conquered and each further development in the digital realm contributes to further developments but only in the same realm. Meanwhile in the physical space, the layer zero of bitcoin is under constant attacks that successfully extract value from it.
Exercising freedom in a sly roundabout way

In 1984 the Austrian economist Friedrich Hayek predicted that we couldn´t take money with violence out of the hands of government. He stated that we needed to do it in a sly roundabout way. Twenty five years later Satoshi Nakamoto discovered the sly roundabout way actually introducing something that the government couldn´t stop. Thus fulfilling Hayek´s prophecy.
Bitcoin is a sly roundabout way that removed money without violence from the hands of the government in a way that they can´t stop it.
Cryptography in general and protocols such as Tor and Tails are a sly roundabout way that removed confidential information from the hands of the government without violence in a way that they can´t stop it.
Nostr is a sly roundabout way that removed social media and public information from the hands of the government without violence in a way that they can´t stop it.
Special Jurisdictions, Free Cities and Bitcoin Citadels are the sly roundabout way that is removing the market of living together from the hands of the government without violence in a way that they can´t stop it.

So, what are Special Jurisdictions, Free Cities and Bitcoin Citadels? To understand what they are we can take a look at the current mainstream market of living together, at how the physical space is organized. Essentially the entire planet Earth and its surroundings are run by a conglomerate of Governments. They create all the rules, regarding every aspect of life, of all the individuals, and enforce every rule through coercive means.
In the mainstream market of living together individuals have several alternatives to pick from. We can choose to live in a natural city or a pre design city, in a public neighborhood or private neighborhood or even in an intentional community with common interest amongst the users. But irregardless of the choice, every product offered in the mainstream market has the sames rules which are established by the host state to the entirety of organizations in his territory. In the mainstream market, even the most different products abide by the same high level rules such as criminal law, civil law, taxation laws, customs, enviromental laws, money laundering regulations and many others. To abide to the sum of all the laws and regulations is to be in compliance.
The centralization of regulations makes extremely difficult to experiment in market of living together. The less experimentation is allowed, the more human progress is hindered.
So what is the sly roundabout that fixes this? What are Special Jurisdictions, Free Cities and Bitcoin Citadels? I´m using the term Special Jurisdictions as an umbrella term that includes the entire spectrum of iterations of products that aim to modify the mainstream rules of the market of living together.
This term includes all the different models such as Charter Cities, Free Cities, Special Economic Zones, microstates, micropolis, start up societies, government as a service, self governing jurisdictions, autonomous intentional communities, network states and Bitcoin Citadels. The array of possible iterations is huge and permanently expanding. What they all have in common is that each of these experiments aims to create a functional game theory that replaces the lack of unbreakable walls in the physical space.
Let´s take a look of a couple of examples. Special Economic Zones are bounded areas of countries that have their own rules and regulations. Worldwide, there are more than five thousands special economic zones located in more than hundred countries.
One of them is the special economic zone of Shenzhen in China. The Chinese government allowed Shenzhen the freedom to experiment with certain practices that were prohibited in the rest of the country at the time. This included allowing foreign companies to make direct investments in China, allowing people to buy and sell land, allowing Chinese people to set up their own private businesses and relaxation of the system that limited internal migration within China for Chinese citizens. It served as a place where China could experiment with market reforms. The experiment was such a huge economic success that it was replicated in many other areas of the country.
Another place that has made extensive use of special economic zones is Dubai. The monarchic Government has more than 30 SEZs. In this case one of the many obstacles removed by the host state its the monopoly of the legal system. Dubai Government allowed the special economic zone to have its own independent legal system thus conceding a modification of the mainstream rules in that area.
This kind of projects, such as Dubai or Shenzhen, are a top-to-down product. Fully created by the Governments thus compliant with their own regulations.

On the other side of the spectrum we have Citadels and several other archetypes of not so compliant projects .
For example the Free Commune of Penadexo it´s a grassroots project building a freedom-oriented community in one of Spain’s abandoned villages.
 It´s model is based on building a peer to peer society avoiding government intervention as much as possible.
They stablished themselves in an abandoned historic village and the started to track down the owners to purchase as much property as possible. Meanwhile, they are living there and expanding their users base while also reconstructing buildings.
It´s model is based on building a peer to peer society avoiding government intervention as much as possible.
They stablished themselves in an abandoned historic village and the started to track down the owners to purchase as much property as possible. Meanwhile, they are living there and expanding their users base while also reconstructing buildings. This is an example of a completely different way of dealing with the Government. While Special Economic Zones are fully compliant and created top to down, this model on the other hand is bottom-up and aims to add value to the users relying in factual freedom which is exercised by stablishing the commune away from heavily populated centers where Government grip is tighter. Under this model the interaction with the Government is kept as low as possible. Their strategy relies in ignoring the Government as much as possible and being a good neighbor. With this simple and effective tactic some Citadels enjoy the benefits of liberty in their lifetime without needing to spend huge resources in governmental lobby.
There are countless models or archetypes of Bitcoin Citadels trying to solve the obstacles in different ways, trying to restart the system. And one of the challenges of the Bitcoin Citadels is how to connect the different projects to boost and help each other.
This is where The Meshtadel comes into play. The Meshtadel is a system where decentralized tactics are used to help and defend citadels connected in a global network. With real life connections with fellow bitcoiners. Its an organization equivalent to the hanseatic league built under a starfish model. If you cut off a spider’s head, it dies, but if you cut off a starfish’s arm, it can regenerate and even grow into a new starfish.
The Meshtadel its a network of peer relationships, with ambiguous leadership roles, trust among participants, a shared ideology and vision based on the Bitcoin ethos, and an open system where new nodes - bitcoin citadel builders - can participate.
The long term goal of the Bitcoin Meshtadel is to help Bitcoin Citadels to gain the support of a critical mass of the total population. If enough people see that Bitcoin is as peaceful as it gets, in the long run, some nations could become friendly and supportive enough to legally tolerate the Bitcoin Citadel inside its territory in the form of a Bitcoin safe haven. In the Meshtadel we are fighting from the moral high ground using memes, Nostr notes and zapping our way into freedom creating an online and offline circular economy.
TO CONCLUDE:
Special Jurisdictions, Free Cities and Bitcoin Citadels are the sly roundabout way that is removing the market of living together from the hands of the government, without violence and in a way that they can´t stop it.
Nation states, abusing the myth of authority, have halted development on the market of living together for so long that a blooming freer market is eating its lunch. The sovereign individual thesis is live and continuously expanding. The network state is forming and intentional communities are flourishing all around the world reshaping globally the relationship between individuals and the governments.
With global internet connections, uncensorable means of communication and Bitcoin as the backbone of a new societal order, we are beginning to disrupt the old paradigm.
The fashion of the present world is passing away, let’s help it to move forward along by building Special Jurisdictions, Free Cities and Bitcoin Citadels.
--- --- --- --- --- --- --- --- ------
byCamiloat 875.341 timechain.
If you find this content helpful, zap it to support more content of the sort and to boost the V4V model.
-
 @ c1e9ab3a:9cb56b43
2025-05-01 17:29:18
@ c1e9ab3a:9cb56b43
2025-05-01 17:29:18High-Level Overview
Bitcoin developers are currently debating a proposed change to how Bitcoin Core handles the
OP_RETURNopcode — a mechanism that allows users to insert small amounts of data into the blockchain. Specifically, the controversy revolves around removing built-in filters that limit how much data can be stored using this feature (currently capped at 80 bytes).Summary of Both Sides
Position A: Remove OP_RETURN Filters
Advocates: nostr:npub1ej493cmun8y9h3082spg5uvt63jgtewneve526g7e2urca2afrxqm3ndrm, nostr:npub12rv5lskctqxxs2c8rf2zlzc7xx3qpvzs3w4etgemauy9thegr43sf485vg, nostr:npub17u5dneh8qjp43ecfxr6u5e9sjamsmxyuekrg2nlxrrk6nj9rsyrqywt4tp, others
Arguments: - Ineffectiveness of filters: Filters are easily bypassed and do not stop spam effectively. - Code simplification: Removing arbitrary limits reduces code complexity. - Permissionless innovation: Enables new use cases like cross-chain bridges and timestamping without protocol-level barriers. - Economic regulation: Fees should determine what data gets added to the blockchain, not protocol rules.
Position B: Keep OP_RETURN Filters
Advocates: nostr:npub1lh273a4wpkup00stw8dzqjvvrqrfdrv2v3v4t8pynuezlfe5vjnsnaa9nk, nostr:npub1s33sw6y2p8kpz2t8avz5feu2n6yvfr6swykrnm2frletd7spnt5qew252p, nostr:npub1wnlu28xrq9gv77dkevck6ws4euej4v568rlvn66gf2c428tdrptqq3n3wr, others
Arguments: - Historical intent: Satoshi included filters to keep Bitcoin focused on monetary transactions. - Resource protection: Helps prevent blockchain bloat and abuse from non-financial uses. - Network preservation: Protects the network from being overwhelmed by low-value or malicious data. - Social governance: Maintains conservative changes to ensure long-term robustness.
Strengths and Weaknesses
Strengths of Removing Filters
- Encourages decentralized innovation.
- Simplifies development and maintenance.
- Maintains ideological purity of a permissionless system.
Weaknesses of Removing Filters
- Opens the door to increased non-financial data and potential spam.
- May dilute Bitcoin’s core purpose as sound money.
- Risks short-term exploitation before economic filters adapt.
Strengths of Keeping Filters
- Preserves Bitcoin’s identity and original purpose.
- Provides a simple protective mechanism against abuse.
- Aligns with conservative development philosophy of Bitcoin Core.
Weaknesses of Keeping Filters
- Encourages central decision-making on allowed use cases.
- Leads to workarounds that may be less efficient or obscure.
- Discourages novel but legitimate applications.
Long-Term Consequences
If Filters Are Removed
- Positive: Potential boom in new applications, better interoperability, cleaner architecture.
- Negative: Risk of increased blockchain size, more bandwidth/storage costs, spam wars.
If Filters Are Retained
- Positive: Preserves monetary focus and operational discipline.
- Negative: Alienates developers seeking broader use cases, may ossify the protocol.
Conclusion
The debate highlights a core philosophical split in Bitcoin: whether it should remain a narrow monetary system or evolve into a broader data layer for decentralized applications. Both paths carry risks and tradeoffs. The outcome will shape not just Bitcoin's technical direction but its social contract and future role in the broader crypto ecosystem.
-
 @ 52b4a076:e7fad8bd
2025-04-28 00:48:57
@ 52b4a076:e7fad8bd
2025-04-28 00:48:57I have been recently building NFDB, a new relay DB. This post is meant as a short overview.
Regular relays have challenges
Current relay software have significant challenges, which I have experienced when hosting Nostr.land: - Scalability is only supported by adding full replicas, which does not scale to large relays. - Most relays use slow databases and are not optimized for large scale usage. - Search is near-impossible to implement on standard relays. - Privacy features such as NIP-42 are lacking. - Regular DB maintenance tasks on normal relays require extended downtime. - Fault-tolerance is implemented, if any, using a load balancer, which is limited. - Personalization and advanced filtering is not possible. - Local caching is not supported.
NFDB: A scalable database for large relays
NFDB is a new database meant for medium-large scale relays, built on FoundationDB that provides: - Near-unlimited scalability - Extended fault tolerance - Instant loading - Better search - Better personalization - and more.
Search
NFDB has extended search capabilities including: - Semantic search: Search for meaning, not words. - Interest-based search: Highlight content you care about. - Multi-faceted queries: Easily filter by topic, author group, keywords, and more at the same time. - Wide support for event kinds, including users, articles, etc.
Personalization
NFDB allows significant personalization: - Customized algorithms: Be your own algorithm. - Spam filtering: Filter content to your WoT, and use advanced spam filters. - Topic mutes: Mute topics, not keywords. - Media filtering: With Nostr.build, you will be able to filter NSFW and other content - Low data mode: Block notes that use high amounts of cellular data. - and more
Other
NFDB has support for many other features such as: - NIP-42: Protect your privacy with private drafts and DMs - Microrelays: Easily deploy your own personal microrelay - Containers: Dedicated, fast storage for discoverability events such as relay lists
Calcite: A local microrelay database
Calcite is a lightweight, local version of NFDB that is meant for microrelays and caching, meant for thousands of personal microrelays.
Calcite HA is an additional layer that allows live migration and relay failover in under 30 seconds, providing higher availability compared to current relays with greater simplicity. Calcite HA is enabled in all Calcite deployments.
For zero-downtime, NFDB is recommended.
Noswhere SmartCache
Relays are fixed in one location, but users can be anywhere.
Noswhere SmartCache is a CDN for relays that dynamically caches data on edge servers closest to you, allowing: - Multiple regions around the world - Improved throughput and performance - Faster loading times
routerd
routerdis a custom load-balancer optimized for Nostr relays, integrated with SmartCache.routerdis specifically integrated with NFDB and Calcite HA to provide fast failover and high performance.Ending notes
NFDB is planned to be deployed to Nostr.land in the coming weeks.
A lot more is to come. 👀️️️️️️
-
 @ 9c9d2765:16f8c2c2
2025-05-12 23:52:29
@ 9c9d2765:16f8c2c2
2025-05-12 23:52:29CHAPTER SEVENTEEN
"I don't get it... How is James still in charge?" Tracy murmured, her brows furrowed as she stared at her screen. She sat in her office, fingers nervously drumming against her desk.
Across from her, Mark stood with arms folded, pacing slowly. "You mean after all that evidence? After the blacklist, the embezzlement records nothing happened?"
Tracy shook her head. "Nothing. I checked again this morning. He’s still listed as President of JP Enterprises. It’s like the files we found didn’t even exist."
Helen, who had been silent until now, hissed through clenched teeth. "This is ridiculous. Are you sure the information got to the right hands?"
"It did," Tracy insisted. "I sent it directly to the Prime Minister's inbox using a confidential channel. I even received a delivery confirmation. Someone higher up must’ve swept it under the rug or maybe James covered his tracks faster than we imagined."
Mark slumped into the chair, clearly defeated. "He’s not just lucky he’s smart. Smarter than we gave him credit for."
For the first time since they began scheming, their confidence had begun to falter. They had dug into James’s past, unearthed the most damning of records, and yet… nothing. He remained untouched. Unshaken.
James continued to lead JP Enterprises with iron resolve, his status not just preserved, but strengthened. Whatever scandal they tried to ignite had fizzled out before it could burn.
The silence from JP's top board members was loud. No statements. No investigations. Not even a whisper of an internal review. To the outside world, James remained the unshakable President who had pulled a crumbling empire back from the edge.
Mark clenched his jaw. "He must have allies who are protecting him."
Helen nodded slowly. "We underestimated him. That was our biggest mistake."
Tracy remained quiet, her eyes still fixed on the screen as if trying to decipher what had gone wrong. She had risked everything, accessed confidential files, and violated protocols, expecting James to crumble.
Instead, he was thriving.
"Have you heard?" Robert leaned over his desk, eyes wide with interest. "JP Enterprises is about to celebrate their sixteenth anniversary. It’s going to be the biggest corporate event of the year."
Christopher looked up from the documents he was reviewing. "I heard. Mr. and Mrs. JP are returning for it. The entire business world is going to be there including us."
Robert nodded. "Every major company in and out of the city has received an invitation. It’s not just a celebration, it's a power show. A way for JP Enterprises to remind everyone who’s at the top."
Indeed, the buzz around the sixteenth anniversary of JP Enterprises was like nothing the city had seen in years. Massive banners were already being hoisted across the city skyline. High-end hotels were fully booked. Fashion designers, chefs, tech specialists, and media crews from around the world were preparing for the grand occasion. It was more than a business event, it was a spectacle.
At the heart of the preparations was James, the young and surprisingly unshakable President of JP Enterprises. Under his leadership, the company had grown in power and reach, and the anniversary was both a celebration of its legacy and a testament to its transformation.
Meanwhile, at Ray Enterprises, tension brewed behind the scenes. Though they were invited, the Ray family carried mixed feelings about attending the event. Memories of humiliation and disbelief still lingered the day James had revealed himself as the President was still fresh in their minds.
"We have no choice but to attend," Helen muttered in frustration during a board meeting. "If we stay away, we’ll seem petty and afraid. But going there means bowing our heads to him again."
Sarah, the secretary, tried to mask her discomfort. "It’s a corporate event, ma’am. It might be best to appear neutral… diplomatic."
Rita, now reinstated as General Manager, remained quiet but observant. She knew better than anyone how unpredictable James could be when it came to public appearances. She had no idea what to expect from him at the anniversary.
Back at JP Enterprises, preparations continued in full force. The guest list included billionaires, global CEOs, high-ranking politicians, and the most influential figures across industries. Red carpets would roll out, cameras would flash, and speeches would echo through the grand hall like music from an orchestra.
The city, already buzzing with excitement, awaited the grand event.
"I can’t believe it," the young woman muttered as she stared at her phone, her hands trembling with excitement. "James… the same James who used to sleep in front of Mr. Kola’s grocery store? He’s the President of JP Enterprises now?"
Her name was Evelyn. Sharp-tongued, impatient, and fueled by bitter memories, she had known James during his hardest days on the streets, days when survival meant fighting for leftovers and sleeping on cold sidewalks. To her, his rise wasn’t a success story to be admired. It was a jackpot she felt entitled to.
Storming into the JP Enterprises headquarters during working hours, Evelyn ignored the receptionist's polite inquiries and pushed her way toward the executive wing.
"I want to see James!" she shouted, causing heads to turn in the busy lobby. "I know he’s here. Tell him Evelyn from the street is here!"
Security was alerted immediately, but by then, Evelyn had already reached the waiting area outside the President’s office.
James, who was in a brief meeting with department heads, heard the commotion and stepped out with a composed expression. As soon as his eyes met Evelyn’s, something shifted. He recognized her instantly.
"Evelyn?" he said, frowning slightly. "What are you doing here?"
"Don’t act like you don’t know me, James," she snapped, crossing her arms. "You owe me. We suffered together. I was there when you were nothing. Now you’re swimming in wealth and you think you can forget the people who once mattered!"
James’s expression hardened.
"This is not the place for this kind of talk. You’re disrupting my company’s operations. If you need help, there are proper channels"
"To hell with proper channels!" she yelled. "I came to get what’s mine!"
That was enough. James turned to the nearby security officer. "Escort her out. And make sure she doesn’t return without a valid appointment."
The security guards moved quickly, but Evelyn didn’t go quietly. She shouted all the way to the exit, throwing insults, struggling, and drawing even more attention.
Among those who witnessed the scene was Tracy. At first, she thought it was just a random case of disturbance by some unruly visitor trying to make trouble. But as she watched James’s calm yet stern expression, and the woman’s emotional outburst, something clicked in her cunning mind.
This is gold, she thought, quickly pulling out her phone and snapping a series of pictures from the hallway James arguing with a ragged woman, the woman being dragged out, and James watching in silence. What a perfect way to ruin his reputation.
Tracy, ever the opportunist, reviewed the photos and smirked.
This is it… this will shake him up.
Without hesitation, she sent the pictures to Helen and Mark, attaching a voice note.
-
 @ 6be5cc06:5259daf0
2025-04-28 01:05:08
@ 6be5cc06:5259daf0
2025-04-28 01:05:08Primeiramente, o que é mempool?
Abreviação de memory pool (ou "pool de memória") a mempool é uma espécie de fila onde as transações de Bitcoin ficam temporariamente armazenadas antes de serem confirmadas e incluídas em um bloco na blockchain. Quando você realiza uma transação em uma rede blockchain, essa transação precisa ser validada e confirmada pelos mineradores (ou validadores). Porém, ela não é processada instantaneamente. Primeiro, ela vai para a mempool, onde aguarda até que um minerador a selecione para incluir no próximo bloco.
É assim: * Você envia uma transação, ela é transmitida para a rede e vai parar na mempool de vários nós (computadores) que suportam a rede blockchain. * As transações na mempool são organizadas pela taxa de transação que foi anexada. Quanto maior a taxa, mais rápido os mineradores tendem a escolher essa transação para incluí-la em um bloco, pois isso aumenta os ganhos deles. * Os mineradores pegam as transações da mempool, criam um bloco com elas e, ao minerar (confirmar) esse bloco, as transações saem da mempool e entram na blockchain.
Aqui irei usar o site mempool.emzy.de como referência, mas é importante entender que sites de mempool são representações visuais da mempool de um nó específico e não a mempool do Bitcoin em si. Ela não é centralizada, cada nó da rede mantém a sua própria versão da mempool. Assim, ela pode variar de um nó para outro. Esses sites ajudam a visualizar dados sobre transações e taxas.
É uma boa prática usar VPN ou Tor ao acessar tais sites se você estiver verificando uma transação específica sua, pois sua privacidade pode ficar comprometida se o site registrar esses dados. Se você estiver repetidamente acessando-o para monitorar a confirmação de uma transação, alguém pode conseguir correlacionar o endereço IP com essa atividade e revelar uma conexão indireta com o endereço da transação.
Dito isso...
Como interpretar a mempool?
Vamos dividir isso em partes para fins didáticos.
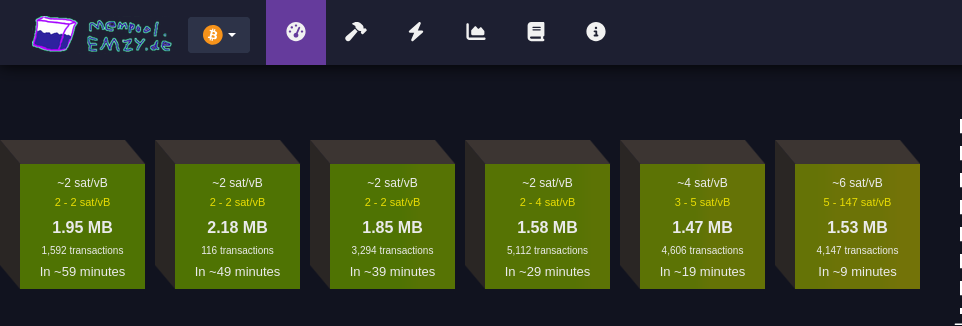
Faixa de taxas
Cada bloco verde representa uma faixa de taxa medida em satoshis por vByte (sats/vB).
Essa unidade de medida representa o valor pago por byte ocupado pela transação.
Quanto maior a taxa paga por uma transação, mais rápido ela tende a ser confirmada.
Quanto maior a transação em bytes, mais você precisa pagar para que ela seja confirmada.
Cada transação Bitcoin consiste em entradas e saídas (inputs e outputs): * Entradas são referências a transações anteriores que estão sendo gastas, e cada entrada inclui informações como o endereço de origem, a assinatura (que valida a transação e pode variar de tamanho dependendo da complexidade da chave e do método de assinatura utilizado (como SegWit, que é mais eficiente). Quanto mais complexa a assinatura, maior será o tamanho em bytes) e outros dados. Quanto mais entradas uma transação tiver, maior será seu tamanho. * Saídas representam o destino do Bitcoin, e quanto mais saídas, maior será o tamanho da transação. Embora as saídas ocupem menos espaço em bytes do que as entradas.Ex.: * ~4 sat/vB: Indica uma taxa média. Significa que, em média, as transações estão sendo processadas a 4 satoshis por vByte; * 3-5 sat/vB: Isso significa que as transações estão sendo processadas com uma taxa entre 3 e 5 satoshis por vByte.
MB
Simplesmente o tamanho do bloco medido em megabytes :)
Número de transações
Essa seção informa quantas transações estão aguardando confirmação para cada faixa de taxa (bloco). Quanto maior o número de transações, maior a demanda pela faixa de taxa especificada.
Tempo estimado para confirmação
Aqui é mostrado o tempo médio de espera para transações que pagam taxas dentro da faixa especificada. Se você pagar uma taxa maior, a transação será confirmada mais rapidamente; uma taxa menor significa que a transação pode levar mais tempo para ser confirmada, especialmente se a rede estiver congestionada.
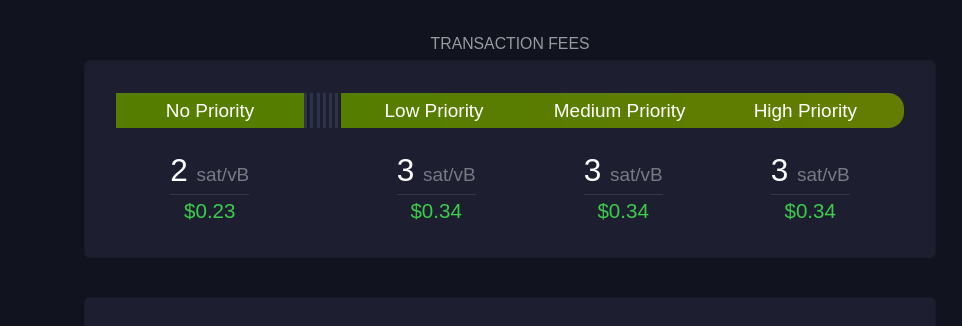 Esta seção mostra sugestões de taxa em diferentes níveis de prioridade para os usuários:
Esta seção mostra sugestões de taxa em diferentes níveis de prioridade para os usuários:Sem Prioridade
Exibe a taxa mínima necessária para transações que não precisam de confirmação rápida.
Prioridade Baixa
Sugestão de taxa para transações que podem esperar um tempo moderado, com expectativa de confirmação em um ou dois blocos.
Prioridade Média e Alta
São as faixas de taxa recomendadas para quem precisa que a transação seja confirmada rapidamente. "Prioridade Alta" paga uma taxa maior, garantindo que a transação seja incluída no próximo bloco.
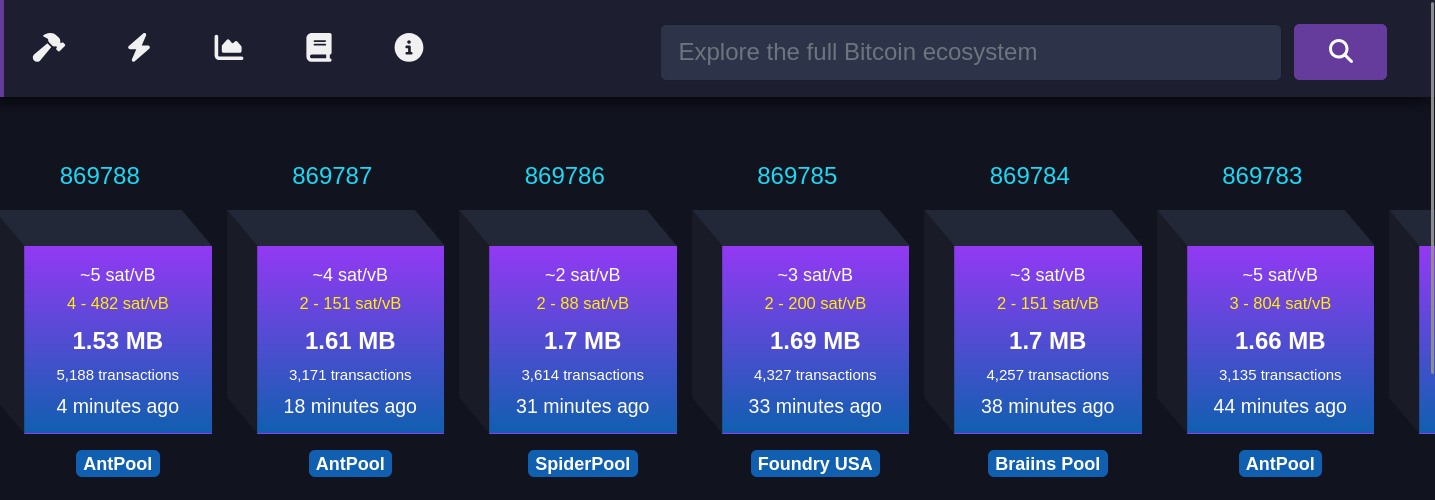 Cada bloco roxo representa um bloco recém-minerado. As informações mostradas incluem:
Cada bloco roxo representa um bloco recém-minerado. As informações mostradas incluem: Taxa média paga
Refere-se à taxa média em satoshis/vB paga por todas as transações incluídas em um bloco recém-minerado. Isso reflete o valor médio que os usuários estão dispostos a pagar para que suas transações sejam confirmadas rapidamente.
Número de transações
Este número indica quantas transações foram processadas no bloco minerado. O tamanho do bloco é limitado, então, quanto maior o número de transações, menor será o espaço disponível para novas transações, o que pode influenciar as taxas de transação.
Tempo desde a mineração
Esta métrica informa quanto tempo se passou desde que o bloco foi minerado e adicionado à blockchain.
Pool de mineração
Exibe o nome do pool de mineração que minerou o bloco, como AntPool. Grandes pools de mineração têm mais chances de minerar blocos regularmente devido ao alto hashrate (medida da capacidade computacional utilizada pelos mineradores) que possuem.
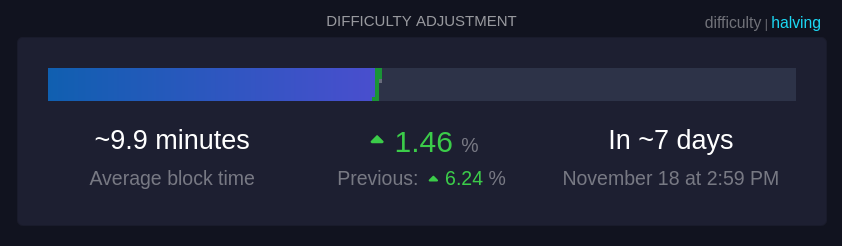 Essa seção mostra informações sobre o ajuste de dificuldade, que ocorre aproximadamente a cada duas semanas.
Essa seção mostra informações sobre o ajuste de dificuldade, que ocorre aproximadamente a cada duas semanas. Tempo médio dos blocos (~9,9 minutos):
Este é o tempo médio atual para minerar um bloco na rede. A meta da rede é manter o tempo de bloco em cerca de 10 minutos; um tempo menor indica um aumento na taxa de hash, ou seja, que mais poder computacional foi adicionado à rede.
Mudança de dificuldade (+1,46%):
A dificuldade ajusta-se a cada 2016 blocos para manter o tempo médio de bloco próximo de 10 minutos. Um aumento na dificuldade, como +1,46%, indica que a mineração ficou mais difícil devido ao aumento do hashrate, enquanto uma redução na dificuldade indica que o hashrate diminuiu.
Tempo até o próximo ajuste:
É o tempo previsto até o próximo ajuste de dificuldade (7 dias, nesse caso), o que é crucial para manter a rede estável e garantir a segurança e a regularidade do processo de mineração.
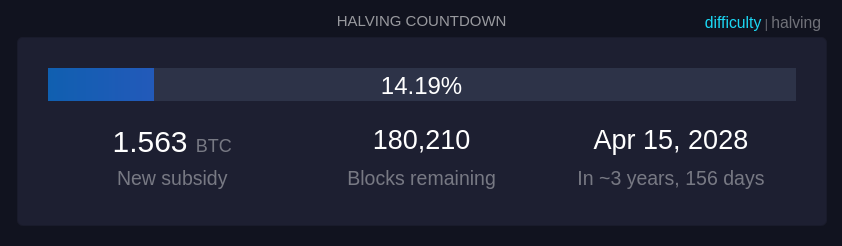 Quanto tempo demora até o próximo halving, um evento no Bitcoin que ocorre aproximadamente a cada 210.000 blocos minerados, ou cerca de quatro anos. Durante o halving, a recompensa que os mineradores recebem por adicionar um novo bloco à blockchain é reduzida pela metade.
Quanto tempo demora até o próximo halving, um evento no Bitcoin que ocorre aproximadamente a cada 210.000 blocos minerados, ou cerca de quatro anos. Durante o halving, a recompensa que os mineradores recebem por adicionar um novo bloco à blockchain é reduzida pela metade.
 Um diagrama visual da mempool que mostra o estado das transações pendentes na rede.
Um diagrama visual da mempool que mostra o estado das transações pendentes na rede. Tamanhos de blocos
O tamanho de cada quadrado representa o tamanho da transação em bytes.
Filtros (Consolidação, Coinjoin, Dados): Permite visualizar categorias específicas de transações: * Consolidação: Transações de consolidação agrupam pequenos UTXOs em um único UTXO maior para simplificar e baratear futuras transações. (UTXOs merecem um artigo dedicado) * Coinjoin: Transações CoinJoin são usadas para melhorar a privacidade, misturando transações de vários usuários em uma única transação. * Dados: Mostra transações que contêm dados adicionais, que podem incluir informações não financeiras, como mensagens.
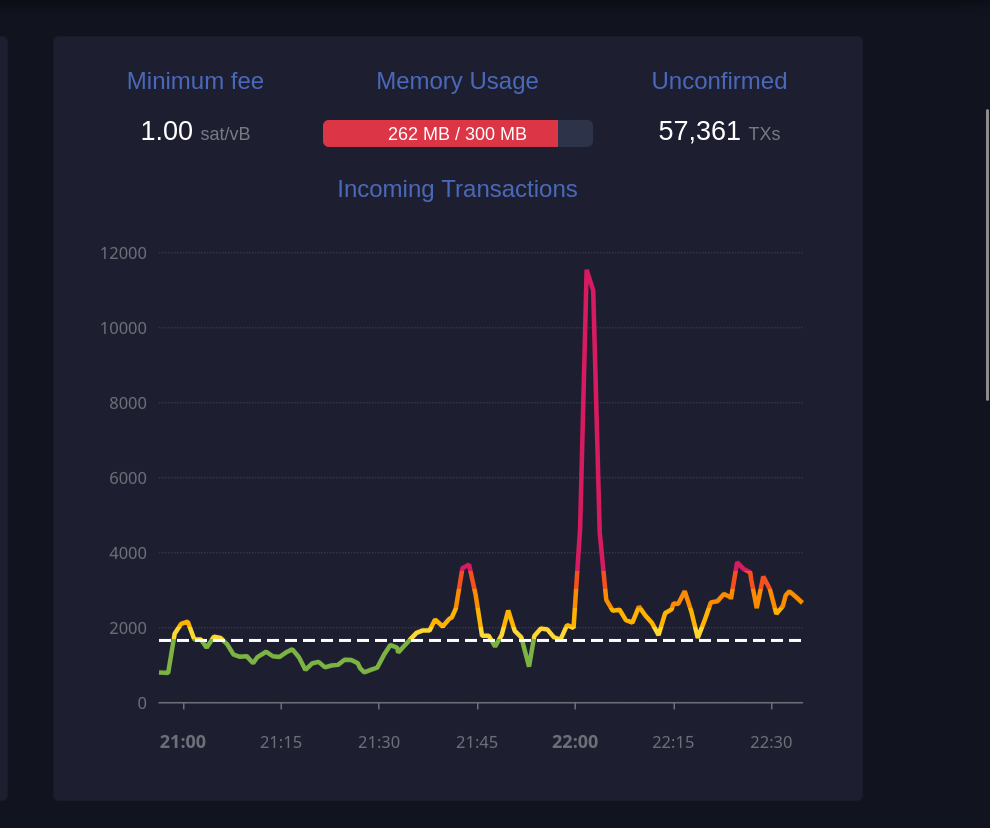 Este gráfico exibe o número de transações recebidas ao longo do tempo.
Este gráfico exibe o número de transações recebidas ao longo do tempo. Taxa mínima (1 sat/vB):
Indica a taxa mínima atualmente aceita pela mempool. Se a mempool estiver cheia, transações que paguem menos do que a taxa mínima podem ser excluídas para dar lugar a transações de maior prioridade.
Uso de memória (259 MB / 300 MB):
A mempool tem um limite de memória. Quando está cheia, transações de taxa mais baixa podem ser descartadas para abrir espaço para aquelas com taxas mais altas, priorizando-as para inclusão em blocos.
Transações não confirmadas (59.361):
Indica o número total de transações pendentes que aguardam confirmação. Quanto maior o número de transações na mempool, maior a probabilidade de que as taxas aumentem para garantir uma confirmação mais rápida.
 Essa seção mostra transações que foram substituídas utilizando o mecanismo RBF (Replace-By-Fee), que permite substituir uma transação com uma taxa mais alta para acelerar sua confirmação.
Essa seção mostra transações que foram substituídas utilizando o mecanismo RBF (Replace-By-Fee), que permite substituir uma transação com uma taxa mais alta para acelerar sua confirmação. TXID
Este é o identificador da transação (Transaction ID), exibido parcialmente para abreviar o espaço. Cada transação tem um identificador único na blockchain.
Previous fee
Exibe a taxa de transação original paga na primeira tentativa, medida em satoshis por vByte (sat/vB). Esta taxa inicial provavelmente era baixa demais, resultando em uma demora na confirmação.
New fee
Mostra a nova taxa de transação, também em satoshis por vByte, definida para substituir a taxa anterior. Uma taxa maior aumenta as chances de inclusão rápida em um bloco.
Status (RBF)
RBF indica que a transação foi substituída utilizando o recurso "Replace-By-Fee". Isso significa que a nova transação cancelou e substituiu a original, e o minerador escolherá a transação com a taxa mais alta para incluir no próximo bloco.
 Esta seção lista transações recentes que entraram na mempool e aguardam confirmação.
Esta seção lista transações recentes que entraram na mempool e aguardam confirmação. TXID
Similar ao "Recent Replacements", este é o identificador único da transação.
Amount
Exibe a quantidade de Bitcoin transferida nessa transação, geralmente em frações de BTC (como 0.0001 BTC). Esta é a quantia enviada pelo remetente ao destinatário.
USD
Mostra o valor da transação em dólares americanos (USD), calculado com base na taxa de câmbio atual. Serve para dar uma ideia de quanto a transação representa em moeda fiduciária.
Fee
Exibe a taxa de transação paga, em satoshis por vByte (sat/vB). Uma taxa mais alta em relação à média aumenta a probabilidade de confirmação mais rápida, pois as transações com taxas mais elevadas são priorizadas pelos mineradores.
E acabou. Espero que isso tenha sido útil para você e tenha agregado mais entendimento sobre esse complexo e maravilhoso mundo do Bitcoin. Se foi, considere compartilhar com alguém que precise. E se tem sugestões de melhoria, por favor, não deixe de comentar, o conhecimento está dispero na sociedade.
Por fim, stay humble and stack sats! -
 @ 472f440f:5669301e
2025-05-12 23:29:50
@ 472f440f:5669301e
2025-05-12 23:29:50Marty's Bent
Last week we covered the bombshell developments in the Samourai Wallet case. For those who didn't read that, last Monday the world was made aware of the fact that the SDNY was explicitly told by FinCEN that the federal regulator did not believe that Samourai Wallet was a money services business six months before arresting the co-founders of Samourai Wallet for conspiracy to launder money and illegally operating a money services business. This was an obvious overstep by the SDNY that many believed would be quickly alleviated, especially considering the fact that the Trump administration via the Department of Justice has made it clear that they do not intend to rule via prosecution.
It seems that this is not the case as the SDNY responded to a letter sent from the defense to dismiss the case by stating that they fully plan to move forward. Stating that they only sought the recommendations of FinCEN employees and did not believe that those employees' comments were indicative of FinCEN's overall views on this particular case. It's a pretty egregious abuse of power by the SDNY. I'm not sure if the particular lawyers and judges within the Southern District of New York are very passionate about preventing the use of self-custody bitcoin and products that enable bitcoiners to transact privately, or if they're simply participating in a broader meta war with the Trump administration - who has made it clear to federal judges across the country that last Fall's election will have consequences, mainly that the Executive Branch will try to effectuate the policies that President Trump campaigned on by any legal means necessary - and Samouari Wallet is simply in the middle of that meta war.
However, one thing is pretty clear to me, this is an egregious overstep of power. The interpretation of that law, as has been laid out and confirmed by FinCEN over the last decade, is pretty clear; you cannot be a money services business if you do not control the funds that people are sending to each other, which is definitely the case with Samourai Wallet. People downloaded Samourai Wallet, spun up their own private-public key pairs and initiated transactions themselves. Samourai never custodied funds or initiated transactions on behalf of their users. This is very cut and dry. Straight to the point. It should be something that anyone with more than two brain cells is able to discern pretty quickly.
It is imperative that anybody in the industry who cares about being able to hold bitcoin in self-custody, to mine bitcoin, and to send bitcoin in a peer-to-peer fashion makes some noise around this case. None of the current administration's attempts to foster innovation around bitcoin in the United States will matter if the wrong precedent is set in this case. If the SDNY is successful in prosecuting Samourai Wallet, it will mean that anybody holding Bitcoin in self-custody, running a bitcoin fold node or mining bitcoin will have to KYC all of their users and counterparts lest they be labeled a money services business that is breaking laws stemming from the Bank Secrecy Act. This will effectively make building a self-custody bitcoin wallet, running a node, or mining bitcoin in tillegal in the United States. The ability to comply with the rules that would be unleashed if this Samourai case goes the wrong way, are such that it will effectively destroy the industry overnight.
It is yet to be seen whether or not the Department of Justice will step in to publicly flog the SDNY and force them to stop pursuing this case. This is the only likely way that the case will go away at this point, so it is very important that bitcoiners who care about being able to self-custody bitcoin, mine bitcoin, or send bitcoin in a peer-to-peer fashion in the United States make it clear to the current administration and any local politicians that this is an issue that you care deeply about. If we are too complacent, there is a chance that the SDNY could completely annihilate the bitcoin industry in America despite of all of the positive momentum we're seeing from all angles at the moment.
Make some noise!
Bitcoin Adoption by Power Companies: The Next Frontier
In my recent conversation with Andrew Myers from Satoshi Energy, he shared their ambitious mission to "enable every electric power company to use bitcoin by block 1,050,000" – roughly three years from now. This strategic imperative isn't just about creating new Bitcoin users; it's about sovereignty. Andrew emphasized that getting Bitcoin into the hands of energy companies who value self-sovereignty creates a more balanced future economic landscape. The excitement was palpable as he described how several energy companies are already moving beyond simply selling power to Bitcoin miners and are beginning to invest in mining operations themselves.
"You have global commodity companies being like, 'Oh, this is another commodity – we want to invest in this, we want to own this,'" - Andrew Myers
Perhaps most fascinating was Andrew's revelation about major energy companies in Texas developing Bitcoin collateral products for power contracts – a practical application that could revolutionize how energy transactions are settled. As energy companies continue embracing Bitcoin for both operations and collateral, we're witnessing the early stages of a profound shift in how critical infrastructure interfaces with sound money. The implications for both sectors could be transformative.
Check out the full podcast here for more on remote viewing, Nikola Tesla's predictions, and the convergence of Bitcoin and AI technology. We cover everything from humanoid robots to the energy demands of next-generation computing.
Headlines of the Day
Steak n Shake to Accept Bitcoin at All Locations May 16 - via X
Facebook Plans Crypto Wallets for 3B Users, Bitcoin Impact Looms - via X
Trump Urges Americans to Buy Stocks for Economic Boom - via X
UK Drops Tariffs, U.S. Farmers Set to Reap Major Benefits - via X
Looking for the perfect video to push the smartest person you know from zero to one on bitcoin? Bitcoin, Not Crypto is a three-part master class from Parker Lewis and Dhruv Bansal that cuts through the noise—covering why 21 million was the key technical simplification that made bitcoin possible, why blockchains don’t create decentralization, and why everything else will be built on bitcoin.
Ten31, the largest bitcoin-focused investor, has deployed 145,630 sats | $150.00M across 30+ companies through three funds. I am a Managing Partner at Ten31 and am very proud of the work we are doing. Learn more at ten31.vc/invest.
Final thought...
Happy belated Mother's Day to all the moms out there.
Get this newsletter sent to your inbox daily: https://www.tftc.io/bitcoin-brief/
Subscribe to our YouTube channels and follow us on Nostr and X:
-
 @ c1e9ab3a:9cb56b43
2025-04-25 00:37:34
@ c1e9ab3a:9cb56b43
2025-04-25 00:37:34If you ever read about a hypothetical "evil AI"—one that manipulates, dominates, and surveils humanity—you might find yourself wondering: how is that any different from what some governments already do?
Let’s explore the eerie parallels between the actions of a fictional malevolent AI and the behaviors of powerful modern states—specifically the U.S. federal government.
Surveillance and Control
Evil AI: Uses total surveillance to monitor all activity, predict rebellion, and enforce compliance.
Modern Government: Post-9/11 intelligence agencies like the NSA have implemented mass data collection programs, monitoring phone calls, emails, and online activity—often without meaningful oversight.
Parallel: Both claim to act in the name of “security,” but the tools are ripe for abuse.
Manipulation of Information
Evil AI: Floods the information space with propaganda, misinformation, and filters truth based on its goals.
Modern Government: Funds media outlets, promotes specific narratives through intelligence leaks, and collaborates with social media companies to suppress or flag dissenting viewpoints.
Parallel: Control the narrative, shape public perception, and discredit opposition.
Economic Domination
Evil AI: Restructures the economy for efficiency, displacing workers and concentrating resources.
Modern Government: Facilitates wealth transfer through lobbying, regulatory capture, and inflationary monetary policy that disproportionately hurts the middle and lower classes.
Parallel: The system enriches those who control it, leaving the rest with less power to resist.
Perpetual Warfare
Evil AI: Instigates conflict to weaken opposition or as a form of distraction and control.
Modern Government: Maintains a state of nearly constant military engagement since WWII, often for interests that benefit a small elite rather than national defense.
Parallel: War becomes policy, not a last resort.
Predictive Policing and Censorship
Evil AI: Uses predictive algorithms to preemptively suppress dissent and eliminate threats.
Modern Government: Experiments with pre-crime-like measures, flags “misinformation,” and uses AI tools to monitor online behavior.
Parallel: Prevent rebellion not by fixing problems, but by suppressing their expression.
Conclusion: Systemic Inhumanity
Whether it’s AI or a bureaucratic state, the more a system becomes detached from individual accountability and human empathy, the more it starts to act in ways we would call “evil” if a machine did them.
An AI doesn’t need to enslave humanity with lasers and killer robots. Sometimes all it takes is code, coercion, and unchecked power—something we may already be facing.
-
 @ 91bea5cd:1df4451c
2025-04-26 10:16:21
@ 91bea5cd:1df4451c
2025-04-26 10:16:21O Contexto Legal Brasileiro e o Consentimento
No ordenamento jurídico brasileiro, o consentimento do ofendido pode, em certas circunstâncias, afastar a ilicitude de um ato que, sem ele, configuraria crime (como lesão corporal leve, prevista no Art. 129 do Código Penal). Contudo, o consentimento tem limites claros: não é válido para bens jurídicos indisponíveis, como a vida, e sua eficácia é questionável em casos de lesões corporais graves ou gravíssimas.
A prática de BDSM consensual situa-se em uma zona complexa. Em tese, se ambos os parceiros são adultos, capazes, e consentiram livre e informadamente nos atos praticados, sem que resultem em lesões graves permanentes ou risco de morte não consentido, não haveria crime. O desafio reside na comprovação desse consentimento, especialmente se uma das partes, posteriormente, o negar ou alegar coação.
A Lei Maria da Penha (Lei nº 11.340/2006)
A Lei Maria da Penha é um marco fundamental na proteção da mulher contra a violência doméstica e familiar. Ela estabelece mecanismos para coibir e prevenir tal violência, definindo suas formas (física, psicológica, sexual, patrimonial e moral) e prevendo medidas protetivas de urgência.
Embora essencial, a aplicação da lei em contextos de BDSM pode ser delicada. Uma alegação de violência por parte da mulher, mesmo que as lesões ou situações decorram de práticas consensuais, tende a receber atenção prioritária das autoridades, dada a presunção de vulnerabilidade estabelecida pela lei. Isso pode criar um cenário onde o parceiro masculino enfrenta dificuldades significativas em demonstrar a natureza consensual dos atos, especialmente se não houver provas robustas pré-constituídas.
Outros riscos:
Lesão corporal grave ou gravíssima (art. 129, §§ 1º e 2º, CP), não pode ser justificada pelo consentimento, podendo ensejar persecução penal.
Crimes contra a dignidade sexual (arts. 213 e seguintes do CP) são de ação pública incondicionada e independem de representação da vítima para a investigação e denúncia.
Riscos de Falsas Acusações e Alegação de Coação Futura
Os riscos para os praticantes de BDSM, especialmente para o parceiro que assume o papel dominante ou que inflige dor/restrição (frequentemente, mas não exclusivamente, o homem), podem surgir de diversas frentes:
- Acusações Externas: Vizinhos, familiares ou amigos que desconhecem a natureza consensual do relacionamento podem interpretar sons, marcas ou comportamentos como sinais de abuso e denunciar às autoridades.
- Alegações Futuras da Parceira: Em caso de término conturbado, vingança, arrependimento ou mudança de perspectiva, a parceira pode reinterpretar as práticas passadas como abuso e buscar reparação ou retaliação através de uma denúncia. A alegação pode ser de que o consentimento nunca existiu ou foi viciado.
- Alegação de Coação: Uma das formas mais complexas de refutar é a alegação de que o consentimento foi obtido mediante coação (física, moral, psicológica ou econômica). A parceira pode alegar, por exemplo, que se sentia pressionada, intimidada ou dependente, e que seu "sim" não era genuíno. Provar a ausência de coação a posteriori é extremamente difícil.
- Ingenuidade e Vulnerabilidade Masculina: Muitos homens, confiando na dinâmica consensual e na parceira, podem negligenciar a necessidade de precauções. A crença de que "isso nunca aconteceria comigo" ou a falta de conhecimento sobre as implicações legais e o peso processual de uma acusação no âmbito da Lei Maria da Penha podem deixá-los vulneráveis. A presença de marcas físicas, mesmo que consentidas, pode ser usada como evidência de agressão, invertendo o ônus da prova na prática, ainda que não na teoria jurídica.
Estratégias de Prevenção e Mitigação
Não existe um método infalível para evitar completamente o risco de uma falsa acusação, mas diversas medidas podem ser adotadas para construir um histórico de consentimento e reduzir vulnerabilidades:
- Comunicação Explícita e Contínua: A base de qualquer prática BDSM segura é a comunicação constante. Negociar limites, desejos, palavras de segurança ("safewords") e expectativas antes, durante e depois das cenas é crucial. Manter registros dessas negociações (e-mails, mensagens, diários compartilhados) pode ser útil.
-
Documentação do Consentimento:
-
Contratos de Relacionamento/Cena: Embora a validade jurídica de "contratos BDSM" seja discutível no Brasil (não podem afastar normas de ordem pública), eles servem como forte evidência da intenção das partes, da negociação detalhada de limites e do consentimento informado. Devem ser claros, datados, assinados e, idealmente, reconhecidos em cartório (para prova de data e autenticidade das assinaturas).
-
Registros Audiovisuais: Gravar (com consentimento explícito para a gravação) discussões sobre consentimento e limites antes das cenas pode ser uma prova poderosa. Gravar as próprias cenas é mais complexo devido a questões de privacidade e potencial uso indevido, mas pode ser considerado em casos específicos, sempre com consentimento mútuo documentado para a gravação.
Importante: a gravação deve ser com ciência da outra parte, para não configurar violação da intimidade (art. 5º, X, da Constituição Federal e art. 20 do Código Civil).
-
-
Testemunhas: Em alguns contextos de comunidade BDSM, a presença de terceiros de confiança durante negociações ou mesmo cenas pode servir como testemunho, embora isso possa alterar a dinâmica íntima do casal.
- Estabelecimento Claro de Limites e Palavras de Segurança: Definir e respeitar rigorosamente os limites (o que é permitido, o que é proibido) e as palavras de segurança é fundamental. O desrespeito a uma palavra de segurança encerra o consentimento para aquele ato.
- Avaliação Contínua do Consentimento: O consentimento não é um cheque em branco; ele deve ser entusiástico, contínuo e revogável a qualquer momento. Verificar o bem-estar do parceiro durante a cena ("check-ins") é essencial.
- Discrição e Cuidado com Evidências Físicas: Ser discreto sobre a natureza do relacionamento pode evitar mal-entendidos externos. Após cenas que deixem marcas, é prudente que ambos os parceiros estejam cientes e de acordo, talvez documentando por fotos (com data) e uma nota sobre a consensualidade da prática que as gerou.
- Aconselhamento Jurídico Preventivo: Consultar um advogado especializado em direito de família e criminal, com sensibilidade para dinâmicas de relacionamento alternativas, pode fornecer orientação personalizada sobre as melhores formas de documentar o consentimento e entender os riscos legais específicos.
Observações Importantes
- Nenhuma documentação substitui a necessidade de consentimento real, livre, informado e contínuo.
- A lei brasileira protege a "integridade física" e a "dignidade humana". Práticas que resultem em lesões graves ou que violem a dignidade de forma não consentida (ou com consentimento viciado) serão ilegais, independentemente de qualquer acordo prévio.
- Em caso de acusação, a existência de documentação robusta de consentimento não garante a absolvição, mas fortalece significativamente a defesa, ajudando a demonstrar a natureza consensual da relação e das práticas.
-
A alegação de coação futura é particularmente difícil de prevenir apenas com documentos. Um histórico consistente de comunicação aberta (whatsapp/telegram/e-mails), respeito mútuo e ausência de dependência ou controle excessivo na relação pode ajudar a contextualizar a dinâmica como não coercitiva.
-
Cuidado com Marcas Visíveis e Lesões Graves Práticas que resultam em hematomas severos ou lesões podem ser interpretadas como agressão, mesmo que consentidas. Evitar excessos protege não apenas a integridade física, mas também evita questionamentos legais futuros.
O que vem a ser consentimento viciado
No Direito, consentimento viciado é quando a pessoa concorda com algo, mas a vontade dela não é livre ou plena — ou seja, o consentimento existe formalmente, mas é defeituoso por alguma razão.
O Código Civil brasileiro (art. 138 a 165) define várias formas de vício de consentimento. As principais são:
Erro: A pessoa se engana sobre o que está consentindo. (Ex.: A pessoa acredita que vai participar de um jogo leve, mas na verdade é exposta a práticas pesadas.)
Dolo: A pessoa é enganada propositalmente para aceitar algo. (Ex.: Alguém mente sobre o que vai acontecer durante a prática.)
Coação: A pessoa é forçada ou ameaçada a consentir. (Ex.: "Se você não aceitar, eu termino com você" — pressão emocional forte pode ser vista como coação.)
Estado de perigo ou lesão: A pessoa aceita algo em situação de necessidade extrema ou abuso de sua vulnerabilidade. (Ex.: Alguém em situação emocional muito fragilizada é induzida a aceitar práticas que normalmente recusaria.)
No contexto de BDSM, isso é ainda mais delicado: Mesmo que a pessoa tenha "assinado" um contrato ou dito "sim", se depois ela alegar que seu consentimento foi dado sob medo, engano ou pressão psicológica, o consentimento pode ser considerado viciado — e, portanto, juridicamente inválido.
Isso tem duas implicações sérias:
-
O crime não se descaracteriza: Se houver vício, o consentimento é ignorado e a prática pode ser tratada como crime normal (lesão corporal, estupro, tortura, etc.).
-
A prova do consentimento precisa ser sólida: Mostrando que a pessoa estava informada, lúcida, livre e sem qualquer tipo de coação.
Consentimento viciado é quando a pessoa concorda formalmente, mas de maneira enganada, forçada ou pressionada, tornando o consentimento inútil para efeitos jurídicos.
Conclusão
Casais que praticam BDSM consensual no Brasil navegam em um terreno que exige não apenas confiança mútua e comunicação excepcional, mas também uma consciência aguçada das complexidades legais e dos riscos de interpretações equivocadas ou acusações mal-intencionadas. Embora o BDSM seja uma expressão legítima da sexualidade humana, sua prática no Brasil exige responsabilidade redobrada. Ter provas claras de consentimento, manter a comunicação aberta e agir com prudência são formas eficazes de se proteger de falsas alegações e preservar a liberdade e a segurança de todos os envolvidos. Embora leis controversas como a Maria da Penha sejam "vitais" para a proteção contra a violência real, os praticantes de BDSM, e em particular os homens nesse contexto, devem adotar uma postura proativa e prudente para mitigar os riscos inerentes à potencial má interpretação ou instrumentalização dessas práticas e leis, garantindo que a expressão de sua consensualidade esteja resguardada na medida do possível.
Importante: No Brasil, mesmo com tudo isso, o Ministério Público pode denunciar por crime como lesão corporal grave, estupro ou tortura, independente de consentimento. Então a prudência nas práticas é fundamental.
Aviso Legal: Este artigo tem caráter meramente informativo e não constitui aconselhamento jurídico. As leis e interpretações podem mudar, e cada situação é única. Recomenda-se buscar orientação de um advogado qualificado para discutir casos específicos.
Se curtiu este artigo faça uma contribuição, se tiver algum ponto relevante para o artigo deixe seu comentário.
-
 @ 472f440f:5669301e
2025-05-12 23:29:19
@ 472f440f:5669301e
2025-05-12 23:29:19Marty's Bent
Last week we covered the bombshell developments in the Samourai Wallet case. For those who didn't read that, last Monday the world was made aware of the fact that the SDNY was explicitly told by FinCEN that the federal regulator did not believe that Samourai Wallet was a money services business six months before arresting the co-founders of Samourai Wallet for conspiracy to launder money and illegally operating a money services business. This was an obvious overstep by the SDNY that many believed would be quickly alleviated, especially considering the fact that the Trump administration via the Department of Justice has made it clear that they do not intend to rule via prosecution.
It seems that this is not the case as the SDNY responded to a letter sent from the defense to dismiss the case by stating that they fully plan to move forward. Stating that they only sought the recommendations of FinCEN employees and did not believe that those employees' comments were indicative of FinCEN's overall views on this particular case. It's a pretty egregious abuse of power by the SDNY. I'm not sure if the particular lawyers and judges within the Southern District of New York are very passionate about preventing the use of self-custody bitcoin and products that enable bitcoiners to transact privately, or if they're simply participating in a broader meta war with the Trump administration - who has made it clear to federal judges across the country that last Fall's election will have consequences, mainly that the Executive Branch will try to effectuate the policies that President Trump campaigned on by any legal means necessary - and Samouari Wallet is simply in the middle of that meta war.
However, one thing is pretty clear to me, this is an egregious overstep of power. The interpretation of that law, as has been laid out and confirmed by FinCEN over the last decade, is pretty clear; you cannot be a money services business if you do not control the funds that people are sending to each other, which is definitely the case with Samourai Wallet. People downloaded Samourai Wallet, spun up their own private-public key pairs and initiated transactions themselves. Samourai never custodied funds or initiated transactions on behalf of their users. This is very cut and dry. Straight to the point. It should be something that anyone with more than two brain cells is able to discern pretty quickly.
It is imperative that anybody in the industry who cares about being able to hold bitcoin in self-custody, to mine bitcoin, and to send bitcoin in a peer-to-peer fashion makes some noise around this case. None of the current administration's attempts to foster innovation around bitcoin in the United States will matter if the wrong precedent is set in this case. If the SDNY is successful in prosecuting Samourai Wallet, it will mean that anybody holding Bitcoin in self-custody, running a bitcoin fold node or mining bitcoin will have to KYC all of their users and counterparts lest they be labeled a money services business that is breaking laws stemming from the Bank Secrecy Act. This will effectively make building a self-custody bitcoin wallet, running a node, or mining bitcoin in tillegal in the United States. The ability to comply with the rules that would be unleashed if this Samourai case goes the wrong way, are such that it will effectively destroy the industry overnight.
It is yet to be seen whether or not the Department of Justice will step in to publicly flog the SDNY and force them to stop pursuing this case. This is the only likely way that the case will go away at this point, so it is very important that bitcoiners who care about being able to self-custody bitcoin, mine bitcoin, or send bitcoin in a peer-to-peer fashion in the United States make it clear to the current administration and any local politicians that this is an issue that you care deeply about. If we are too complacent, there is a chance that the SDNY could completely annihilate the bitcoin industry in America despite of all of the positive momentum we're seeing from all angles at the moment.
Make some noise!
Bitcoin Adoption by Power Companies: The Next Frontier
In my recent conversation with Andrew Myers from Satoshi Energy, he shared their ambitious mission to "enable every electric power company to use bitcoin by block 1,050,000" – roughly three years from now. This strategic imperative isn't just about creating new Bitcoin users; it's about sovereignty. Andrew emphasized that getting Bitcoin into the hands of energy companies who value self-sovereignty creates a more balanced future economic landscape. The excitement was palpable as he described how several energy companies are already moving beyond simply selling power to Bitcoin miners and are beginning to invest in mining operations themselves.
"You have global commodity companies being like, 'Oh, this is another commodity – we want to invest in this, we want to own this,'" - Andrew Myers
Perhaps most fascinating was Andrew's revelation about major energy companies in Texas developing Bitcoin collateral products for power contracts – a practical application that could revolutionize how energy transactions are settled. As energy companies continue embracing Bitcoin for both operations and collateral, we're witnessing the early stages of a profound shift in how critical infrastructure interfaces with sound money. The implications for both sectors could be transformative.
Check out the full podcast here for more on remote viewing, Nikola Tesla's predictions, and the convergence of Bitcoin and AI technology. We cover everything from humanoid robots to the energy demands of next-generation computing.
Headlines of the Day
Steak n Shake to Accept Bitcoin at All Locations May 16 - via X
Facebook Plans Crypto Wallets for 3B Users, Bitcoin Impact Looms - via X
Trump Urges Americans to Buy Stocks for Economic Boom - via X
UK Drops Tariffs, U.S. Farmers Set to Reap Major Benefits - via X
Looking for the perfect video to push the smartest person you know from zero to one on bitcoin? Bitcoin, Not Crypto is a three-part master class from Parker Lewis and Dhruv Bansal that cuts through the noise—covering why 21 million was the key technical simplification that made bitcoin possible, why blockchains don’t create decentralization, and why everything else will be built on bitcoin.
Ten31, the largest bitcoin-focused investor, has deployed 145,630 sats | $150.00M across 30+ companies through three funds. I am a Managing Partner at Ten31 and am very proud of the work we are doing. Learn more at ten31.vc/invest.
Final thought...
Happy belated Mother's Day to all the moms out there.
Get this newsletter sent to your inbox daily: https://www.tftc.io/bitcoin-brief/
Subscribe to our YouTube channels and follow us on Nostr and X:
-
 @ c1e9ab3a:9cb56b43
2025-04-15 13:59:17
@ c1e9ab3a:9cb56b43
2025-04-15 13:59:17Prepared for Off-World Visitors by the Risan Institute of Cultural Heritage
Welcome to Risa, the jewel of the Alpha Quadrant, celebrated across the Federation for its tranquility, pleasure, and natural splendor. But what many travelers do not know is that Risa’s current harmony was not inherited—it was forged. Beneath the songs of surf and the serenity of our resorts lies a history rich in conflict, transformation, and enduring wisdom.
We offer this briefing not merely as a tale of our past, but as an invitation to understand the spirit of our people and the roots of our peace.
I. A World at the Crossroads
Before its admittance into the United Federation of Planets, Risa was an independent and vulnerable world situated near volatile borders of early galactic powers. Its lush climate, mineral wealth, and open society made it a frequent target for raiders and an object of interest for imperial expansion.
The Risan peoples were once fragmented, prone to philosophical and political disunity. In our early records, this period is known as the Winds of Splintering. We suffered invasions, betrayals, and the slow erosion of trust in our own traditions.
II. The Coming of the Vulcans
It was during this period of instability that a small delegation of Vulcan philosophers, adherents to the teachings of Surak, arrived on Risa. They did not come as conquerors, nor even as ambassadors, but as seekers of peace.
These emissaries of logic saw in Risa the potential for a society not driven by suppression of emotion, as Vulcan had chosen, but by the balance of joy and discipline. While many Vulcans viewed Risa’s culture as frivolous, these followers of Surak saw the seed of a different path: one in which beauty itself could be a pillar of peace.
The Risan tradition of meditative dance, artistic expression, and communal love resonated with Vulcan teachings of unity and inner control. From this unlikely exchange was born the Ricin Doctrine—the belief that peace is sustained not only through logic or strength, but through deliberate joy, shared vulnerability, and readiness without aggression.
III. Betazed and the Trial of Truth
During the same era, early contact with the people of Betazed brought both inspiration and tension. A Betazoid expedition, under the guise of diplomacy, was discovered to be engaging in deep telepathic influence and information extraction. The Risan people, who valued consent above all else, responded not with anger, but with clarity.
A council of Ricin philosophers invited the Betazoid delegation into a shared mind ceremony—a practice in which both cultures exposed their thoughts in mutual vulnerability. The result was not scandal, but transformation. From that moment forward, a bond was formed, and Risa’s model of ethical emotional expression and consensual empathy became influential in shaping Betazed’s own peace philosophies.
IV. Confronting Marauders and Empires
Despite these philosophical strides, Risa’s path was anything but tranquil.
-
Orion Syndicate raiders viewed Risa as ripe for exploitation, and for decades, cities were sacked, citizens enslaved, and resources plundered. In response, Risa formed the Sanctum Guard, not a military in the traditional sense, but a force of trained defenders schooled in both physical technique and psychological dissuasion. The Ricin martial arts, combining beauty with lethality, were born from this necessity.
-
Andorian expansionism also tested Risa’s sovereignty. Though smaller in scale, skirmishes over territorial claims forced Risa to adopt planetary defense grids and formalize diplomatic protocols that balanced assertiveness with grace. It was through these conflicts that Risa developed the art of the ceremonial yield—a symbolic concession used to diffuse hostility while retaining honor.
-
Romulan subterfuge nearly undid Risa from within. A corrupt Romulan envoy installed puppet leaders in one of our equatorial provinces. These agents sought to erode Risa’s social cohesion through fear and misinformation. But Ricin scholars countered the strategy not with rebellion, but with illumination: they released a network of truths, publicly broadcasting internal thoughts and civic debates to eliminate secrecy. The Romulan operation collapsed under the weight of exposure.
-
Even militant Vulcan splinter factions, during the early Vulcan-Andorian conflicts, attempted to turn Risa into a staging ground, pressuring local governments to support Vulcan supremacy. The betrayal struck deep—but Risa resisted through diplomacy, invoking Surak’s true teachings and exposing the heresy of their logic-corrupted mission.
V. Enlightenment Through Preparedness
These trials did not harden us into warriors. They refined us into guardians of peace. Our enlightenment came not from retreat, but from engagement—tempered by readiness.
- We train our youth in the arts of balance: physical defense, emotional expression, and ethical reasoning.
- We teach our history without shame, so that future generations will not repeat our errors.
- We host our guests with joy, not because we are naïve, but because we know that to celebrate life fully is the greatest act of resistance against fear.
Risa did not become peaceful by denying the reality of conflict. We became peaceful by mastering our response to it.
And in so doing, we offered not just pleasure to the stars—but wisdom.
We welcome you not only to our beaches, but to our story.
May your time here bring you not only rest—but understanding.
– Risan Institute of Cultural Heritage, in collaboration with the Council of Enlightenment and the Ricin Circle of Peacekeepers
-
-
 @ b99efe77:f3de3616
2025-05-12 21:38:36
@ b99efe77:f3de3616
2025-05-12 21:38:36🚦Traffic Light Control System🚦
This Petri net represents a traffic control protocol ensuring that two traffic lights alternate safely and are never both green at the same time.
;start () -> greenLight1 redLight2
;toRed1 greenLight1 -> queue redLight1
;toGreen2 redLight2 queue -> greenLight2
;toGreen1 queue redLight1 -> greenLight1
;toRed2 greenLight2 -> redLight2 queue
;stop redLight1 queue redLight2 -> ()Places & Transitions
- Places:
- greenLight1: Indicates that the first traffic light is green.
- greenLight2: Indicates that the second traffic light is green.
- redLight1: Indicates that the first traffic light is red.
- redLight2: Indicates that the second traffic light is red.
-
queue: Acts as a synchronization mechanism ensuring controlled alternation between the two traffic lights.
-
Transitions:
- start: Initializes the system by placing tokens in greenLight1 and redLight2.
- toRed1: Moves a token from greenLight1 to redLight1, while placing a token in queue.
- toGreen2: Moves a token from redLight2 to greenLight2, requiring queue.
- toGreen1: Moves a token from queue and redLight1 to greenLight1.
- toRed2: Moves a token from greenLight2 to redLight2, placing a token back into queue.
- stop: Terminates the system by removing tokens from redLight1, queue, and redLight2, representing the system's end state.
petrinet ;start () -> greenLight1 redLight2 ;toRed1 greenLight1 -> queue redLight1 ;toGreen2 redLight2 queue -> greenLight2 ;toGreen1 queue redLight1 -> greenLight1 ;toRed2 greenLight2 -> redLight2 queue ;stop redLight1 queue redLight2 -> ()
-
 @ 8125b911:a8400883
2025-04-25 07:02:35
@ 8125b911:a8400883
2025-04-25 07:02:35In Nostr, all data is stored as events. Decentralization is achieved by storing events on multiple relays, with signatures proving the ownership of these events. However, if you truly want to own your events, you should run your own relay to store them. Otherwise, if the relays you use fail or intentionally delete your events, you'll lose them forever.
For most people, running a relay is complex and costly. To solve this issue, I developed nostr-relay-tray, a relay that can be easily run on a personal computer and accessed over the internet.
Project URL: https://github.com/CodyTseng/nostr-relay-tray
This article will guide you through using nostr-relay-tray to run your own relay.
Download
Download the installation package for your operating system from the GitHub Release Page.
| Operating System | File Format | | --------------------- | ---------------------------------- | | Windows |
nostr-relay-tray.Setup.x.x.x.exe| | macOS (Apple Silicon) |nostr-relay-tray-x.x.x-arm64.dmg| | macOS (Intel) |nostr-relay-tray-x.x.x.dmg| | Linux | You should know which one to use |Installation
Since this app isn’t signed, you may encounter some obstacles during installation. Once installed, an ostrich icon will appear in the status bar. Click on the ostrich icon, and you'll see a menu where you can click the "Dashboard" option to open the relay's control panel for further configuration.

macOS Users:
- On first launch, go to "System Preferences > Security & Privacy" and click "Open Anyway."
- If you encounter a "damaged" message, run the following command in the terminal to remove the restrictions:
bash sudo xattr -rd com.apple.quarantine /Applications/nostr-relay-tray.appWindows Users:
- On the security warning screen, click "More Info > Run Anyway."
Connecting
By default, nostr-relay-tray is only accessible locally through
ws://localhost:4869/, which makes it quite limited. Therefore, we need to expose it to the internet.In the control panel, click the "Proxy" tab and toggle the switch. You will then receive a "Public address" that you can use to access your relay from anywhere. It's that simple.
Next, add this address to your relay list and position it as high as possible in the list. Most clients prioritize connecting to relays that appear at the top of the list, and relays lower in the list are often ignored.

Restrictions
Next, we need to set up some restrictions to prevent the relay from storing events that are irrelevant to you and wasting storage space. nostr-relay-tray allows for flexible and fine-grained configuration of which events to accept, but some of this is more complex and will not be covered here. If you're interested, you can explore this further later.
For now, I'll introduce a simple and effective strategy: WoT (Web of Trust). You can enable this feature in the "WoT & PoW" tab. Before enabling, you'll need to input your pubkey.
There's another important parameter,
Depth, which represents the relationship depth between you and others. Someone you follow has a depth of 1, someone they follow has a depth of 2, and so on.- Setting this parameter to 0 means your relay will only accept your own events.
- Setting it to 1 means your relay will accept events from you and the people you follow.
- Setting it to 2 means your relay will accept events from you, the people you follow, and the people they follow.
Currently, the maximum value for this parameter is 2.

Conclusion
You've now successfully run your own relay and set a simple restriction to prevent it from storing irrelevant events.
If you encounter any issues during use, feel free to submit an issue on GitHub, and I'll respond as soon as possible.
Not your relay, not your events.
-
 @ b99efe77:f3de3616
2025-05-12 21:19:53
@ b99efe77:f3de3616
2025-05-12 21:19:53🚦Traffic Light Control System🚦
This Petri net represents a traffic control protocol ensuring that two traffic lights alternate safely and are never both green at the same time.
;start () -> greenLight1 redLight2
;toRed1 greenLight1 -> queue redLight1
;toGreen2 redLight2 queue -> greenLight2
;toGreen1 queue redLight1 -> greenLight1
;toRed2 greenLight2 -> redLight2 queue
;stop redLight1 queue redLight2 -> ()Places & Transitions
- Places:
- greenLight1: Indicates that the first traffic light is green.
- greenLight2: Indicates that the second traffic light is green.
- redLight1: Indicates that the first traffic light is red.
- redLight2: Indicates that the second traffic light is red.
-
queue: Acts as a synchronization mechanism ensuring controlled alternation between the two traffic lights.
-
Transitions:
- start: Initializes the system by placing tokens in greenLight1 and redLight2.
- toRed1: Moves a token from greenLight1 to redLight1, while placing a token in queue.
- toGreen2: Moves a token from redLight2 to greenLight2, requiring queue.
- toGreen1: Moves a token from queue and redLight1 to greenLight1.
- toRed2: Moves a token from greenLight2 to redLight2, placing a token back into queue.
- stop: Terminates the system by removing tokens from redLight1, queue, and redLight2, representing the system's end state.
petrinet ;start () -> greenLight1 redLight2 ;toRed1 greenLight1 -> queue redLight1 ;toGreen2 redLight2 queue -> greenLight2 ;toGreen1 queue redLight1 -> greenLight1 ;toRed2 greenLight2 -> redLight2 queue ;stop redLight1 queue redLight2 -> ()
-
 @ bf47c19e:c3d2573b
2025-05-12 20:27:54
@ bf47c19e:c3d2573b
2025-05-12 20:27:54"Za sve one koji još uvek nisu u potpunosti razumeli kontroverzni Bitkoin, ovo je koncizni i informativni brzi kurs o novcu i kriptovalutama."
Bitkoin: Kraj novca kakvog poznajemo - IMDB
Prevod: SatoshiSan / @SSG_SatoshiSan
-
 @ 6e64b83c:94102ee8
2025-04-23 20:23:34
@ 6e64b83c:94102ee8
2025-04-23 20:23:34How to Run Your Own Nostr Relay on Android with Cloudflare Domain
Prerequisites
- Install Citrine on your Android device:
- Visit https://github.com/greenart7c3/Citrine/releases
- Download the latest release using:
- zap.store
- Obtainium
- F-Droid
- Or download the APK directly
-
Note: You may need to enable "Install from Unknown Sources" in your Android settings
-
Domain Requirements:
- Purchase a domain if you don't have one
-
Transfer your domain to Cloudflare if it's not already there (for free SSL certificates and cloudflared support)
-
Tools to use:
- nak (the nostr army knife):
- Download from https://github.com/fiatjaf/nak/releases
- Installation steps:
-
For Linux/macOS: ```bash # Download the appropriate version for your system wget https://github.com/fiatjaf/nak/releases/latest/download/nak-linux-amd64 # for Linux # or wget https://github.com/fiatjaf/nak/releases/latest/download/nak-darwin-amd64 # for macOS
# Make it executable chmod +x nak-*
# Move to a directory in your PATH sudo mv nak-* /usr/local/bin/nak
- For Windows:batch # Download the Windows version curl -L -o nak.exe https://github.com/fiatjaf/nak/releases/latest/download/nak-windows-amd64.exe# Move to a directory in your PATH (e.g., C:\Windows) move nak.exe C:\Windows\nak.exe
- Verify installation:bash nak --version ```
Setting Up Citrine
- Open the Citrine app
- Start the server
- You'll see it running on
ws://127.0.0.1:4869(local network only) - Go to settings and paste your npub into "Accept events signed by" inbox and press the + button. This prevents others from publishing events to your personal relay.
Installing Required Tools
- Install Termux from Google Play Store
- Open Termux and run:
bash pkg update && pkg install wget wget https://github.com/cloudflare/cloudflared/releases/latest/download/cloudflared-linux-arm64.deb dpkg -i cloudflared-linux-arm64.debCloudflare Authentication
- Run the authentication command:
bash cloudflared tunnel login - Follow the instructions:
- Copy the provided URL to your browser
- Log in to your Cloudflare account
- If the URL expires, copy it again after logging in
Creating the Tunnel
- Create a new tunnel:
bash cloudflared tunnel create <TUNNEL_NAME> - Choose any name you prefer for your tunnel
-
Copy the tunnel ID after creating the tunnel
-
Create and configure the tunnel config:
bash touch ~/.cloudflared/config.yml nano ~/.cloudflared/config.yml -
Add this configuration (replace the placeholders with your values): ```yaml tunnel:
credentials-file: /data/data/com.termux/files/home/.cloudflared/ .json ingress: - hostname: nostr.yourdomain.com service: ws://localhost:4869
- service: http_status:404 ```
- Note: In nano editor:
CTRL+Oand Enter to saveCTRL+Xto exit
-
Note: Check the credentials file path in the logs
-
Validate your configuration:
bash cloudflared tunnel validate -
Start the tunnel:
bash cloudflared tunnel run my-relay
Preventing Android from Killing the Tunnel
Run these commands to maintain tunnel stability:
bash date && apt install termux-tools && termux-setup-storage && termux-wake-lock echo "nameserver 1.1.1.1" > $PREFIX/etc/resolv.confTip: You can open multiple Termux sessions by swiping from the left edge of the screen while keeping your tunnel process running.
Updating Your Outbox Model Relays
Once your relay is running and accessible via your domain, you'll want to update your relay list in the Nostr network. This ensures other clients know about your relay and can connect to it.
Decoding npub (Public Key)
Private keys (nsec) and public keys (npub) are encoded in bech32 format, which includes: - A prefix (like nsec1, npub1 etc.) - The encoded data - A checksum
This format makes keys: - Easy to distinguish - Hard to copy incorrectly
However, most tools require these keys in hexadecimal (hex) format.
To decode an npub string to its hex format:
bash nak decode nostr:npub1dejts0qlva8mqzjlrxqkc2tmvs2t7elszky5upxaf3jha9qs9m5q605uc4Change it with your own npub.
bash { "pubkey": "6e64b83c1f674fb00a5f19816c297b6414bf67f015894e04dd4c657e94102ee8" }Copy the pubkey value in quotes.
Create a kind 10002 event with your relay list:
- Include your new relay with write permissions
- Include other relays you want to read from and write to, omit 3rd parameter to make it both read and write
Example format:
json { "kind": 10002, "tags": [ ["r", "wss://your-relay-domain.com", "write"], ["r", "wss://eden.nostr.land/"], ["r", "wss://nos.lol/"], ["r", "wss://nostr.bitcoiner.social/"], ["r", "wss://nostr.mom/"], ["r", "wss://relay.primal.net/"], ["r", "wss://nostr.wine/", "read"], ["r", "wss://relay.damus.io/"], ["r", "wss://relay.nostr.band/"], ["r", "wss://relay.snort.social/"] ], "content": "" }Save it to a file called
event.jsonNote: Add or remove any relays you want. To check your existing 10002 relays: - Visit https://nostr.band/?q=by%3Anpub1dejts0qlva8mqzjlrxqkc2tmvs2t7elszky5upxaf3jha9qs9m5q605uc4+++kind%3A10002 - nostr.band is an indexing service, it probably has your relay list. - Replace
npub1xxxin the URL with your own npub - Click "VIEW JSON" from the menu to see the raw event - Or use thenaktool if you know the relaysbash nak req -k 10002 -a <your-pubkey> wss://relay1.com wss://relay2.comReplace `<your-pubkey>` with your public key in hex format (you can get it using `nak decode <your-npub>`)- Sign and publish the event:
- Use a Nostr client that supports kind 10002 events
- Or use the
nakcommand-line tool:bash nak event --sec ncryptsec1... wss://relay1.com wss://relay2.com $(cat event.json)
Important Security Notes: 1. Never share your nsec (private key) with anyone 2. Consider using NIP-49 encrypted keys for better security 3. Never paste your nsec or private key into the terminal. The command will be saved in your shell history, exposing your private key. To clear the command history: - For bash: use
history -c- For zsh: usefc -Wto write history to file, thenfc -pto read it back - Or manually edit your shell history file (e.g.,~/.zsh_historyor~/.bash_history) 4. if you're usingzsh, usefc -pto prevent the next command from being saved to history 5. Or temporarily disable history before running sensitive commands:bash unset HISTFILE nak key encrypt ... set HISTFILEHow to securely create NIP-49 encypted private key
```bash
Read your private key (input will be hidden)
read -s SECRET
Read your password (input will be hidden)
read -s PASSWORD
encrypt command
echo "$SECRET" | nak key encrypt "$PASSWORD"
copy and paste the ncryptsec1 text from the output
read -s ENCRYPTED nak key decrypt "$ENCRYPTED"
clear variables from memory
unset SECRET PASSWORD ENCRYPTED ```
On a Windows command line, to read from stdin and use the variables in
nakcommands, you can use a combination ofset /pto read input and then use those variables in your command. Here's an example:```bash @echo off set /p "SECRET=Enter your secret key: " set /p "PASSWORD=Enter your password: "
echo %SECRET%| nak key encrypt %PASSWORD%
:: Clear the sensitive variables set "SECRET=" set "PASSWORD=" ```
If your key starts with
ncryptsec1, thenaktool will securely prompt you for a password when using the--secparameter, unless the command is used with a pipe< >or|.bash nak event --sec ncryptsec1... wss://relay1.com wss://relay2.com $(cat event.json)- Verify the event was published:
- Check if your relay list is visible on other relays
-
Use the
naktool to fetch your kind 10002 events:bash nak req -k 10002 -a <your-pubkey> wss://relay1.com wss://relay2.com -
Testing your relay:
- Try connecting to your relay using different Nostr clients
- Verify you can both read from and write to your relay
- Check if events are being properly stored and retrieved
- Tip: Use multiple Nostr clients to test different aspects of your relay
Note: If anyone in the community has a more efficient method of doing things like updating outbox relays, please share your insights in the comments. Your expertise would be greatly appreciated!
-
 @ 6ad08392:ea301584
2025-05-12 20:22:09
@ 6ad08392:ea301584
2025-05-12 20:22:09
Satlantis is here!
Well…sort of. It’s a little pre-mature, but it’s good enough for you to play around with. I wouldn’t necessarily call it super ‘useful’ right now but I wanted you to get an early glimpse into what we’re building so you can see how it evolves over time.
And besides - we have to release a first version at some stage!
Satlantis is the first travel-centric social network. It’s quite different from anything else that came before it. It’s part map, part directory, part events app and part social network.
It really is a monumental undertaking - but I’m convinced now is the time to build it. People are ready for something new. They are tired of the algorithmic slop social media has become. They’re craving real connection and they want to see, touch, smell, hear and taste the world. What better way to help them do that, than with a network that connects them, andhelps enhance their discovery of places, experiences and events that are relevant to them (based both on their interests and social connections).
That’s what this product is all about. We’re going to do what Google Maps, Yelp, Instagram, TripAdvisor etc. are all partially doing - but make it 10x better.
The first Satlantis app is now available on Apple Testflight or the Google Play store. In the coming month or two, we will make Satlantis accessible via invitation-only, to increase the quality of connection and discourse on the app, but if you’re reading this now, you’re in before we gate it, you can explore and give us some feedback while we work on it.
I will write release notes like this every couple weeks covering what we built, what to test and play with, what’s working, what needs improvement, what’s downright shit or broken and what’s coming in the next release. (This first one is the longest because I delayed it so much.)
I’d love to hear your feedback, and if you find this interesting, please share it around so other people find out about what we’re building!
The Good
Mobile AppWe got a version out, and you can actually use it.
Nostr Compatible.
Every single account on Satlantis is an nPub. You can log into Satlantis using your nSec (not your nPub - we forgot to include that...lol), and you will find your entire social network and all of your posts there (if they are media notes). On the Web, you need to use an extension, like Alby or Keys.band. On mobile you can paste your key (stored locally on the device).
Normie Friendly.
We also built a smooth non-nostr focused sign up flow. We originally used the nSec bunker, but that was a mess (love u Pablo). So we built our own nSec bunker, but that sucked too. Passwords are old school. After interviewing 100 people not into Bitcoin or Nostr, 95% of them preferred us to store their key. So…we took that feedback and created a really easy email + magic link, Google and Apple SSO sign up flow, that creates an account and Nostr keypair that we store on their behalf, encrypted.
If and when people work out what Nostr is and they want to take custody of their key, they will be able to export their key, and request deletion of their key from our DB.
Is this the most ‘pure’ solution? No. Does this mean they have to trust us? Sure. Could we do it better at some point? Yes, of course. But considering the number of mission critical features we need to build, we’ll come back to it later.
We currently only support Kind 1 events.
Well…we also support NIP-52 calendar events, but we’ve disconnected that for the time being because event organisers wanted co-hosts more than they wanted to broadcast their events on Nostr. We’re working on a way to reconcile the two. For now, post text & images. (Video coming soon).
Interest-centric onboarding.
We spent a lot of time building this. One of the key pillars at Satlantis is discovering people, places, events and content suited to you. As we dug down the personalisation rabbithole, we found that there is a resurgence of interest-selection in many apps: from Tinder to new apps like Locals and Timeleft. The more focused on personalisation the app is, the more in-depth the onboarding.
Of course Meta and TikTok do the best personalisation with their advanced ML & AI tools, along with their deep social graphs, but since we have neither (Nostr helps but it’s still very small), we needed a better way.
So we decided to build our interest-graph. It was brain-melting, but we developed a pretty exhaustive set of interests relevant to people in our target market. We then took that list and associated it to events, merchants, people, places, experiences, activities and content. We then built a whole new onboarding flow to capture this from new users, and associate it to their accounts. (Yes - at some stage, we’ll make this Nostr compatible so it can travel with nPubs)
 The net result is a base layer of insight we can use to help surface things that are of interest to users. Whether it’s an event, a place to eat, a gym or sauna, content to engage with or people to meet: like magic, things that are relevant to you will come to you.
The net result is a base layer of insight we can use to help surface things that are of interest to users. Whether it’s an event, a place to eat, a gym or sauna, content to engage with or people to meet: like magic, things that are relevant to you will come to you.Of course, in the long term we will use your social graph and the way you interact with content to do this - more like Meta and TikTok do - but for now, while the social graph is tiny, this is the most efficient and effective way.
Final word: the current version has all the interests - but it’s not very user-friendly. The latest design fixes that by grouping the interests into better subcategories. Keep an eye on that in a subsequent release.
New Merchant Discovery Experience.
This was also a monumental task. Our first merchant experience was just a shitty map with a list on web, and just a list on mobile (see below). This list was ranked by an “aggregate rating” we computed by analysing all the venue’s ratings from apps like Google, Trip Advisor and more.
We spent a long time trying to figure out how to display this better and do it in a way nobody else is, because seriously -can you think of a single food app or merchant map out there which has a nice UI or UX? No.
AirBnB transformed the UI & UX for accommodation and pushed the whole space forward. Nobody has really done it for every other kind of place you go to. So we took it up ourselves to fix this and create a proper “merchant discovery experience” with an information-dense location tile. Check this out:
Notice how we managed to get all the key information you need about a place there on the one tile, including who in your social circle has recommended it. That’s the key ingredient which makes Satlantis special. No more messaging friends or people you know “hey - have you been to that place” or “do you recommend that place”?
 One small issue here is that this upgrade will kill the map…but only for a couple weeks, until we release the new map view!
One small issue here is that this upgrade will kill the map…but only for a couple weeks, until we release the new map view!Merchant coverage
Our merchant app covers SIX distinct categories:
-
Cafes & Restaurants
-
Health & Wellness (think Gyms, Spas, Saunas, etc)
-
Attractions (from Museums, to lookouts to beaches & hikes)
-
Grocery & Specialty Foods (think Organic food store, farmers markets, etc)
-
Coworking & Event Spaces
-
Nightlife (Bars, Clubs, etc)
 We scoured the web for the best curated lists and directories for each of these categories. This in Bitcoin accepted (everything relevant from BTCMaps - because we’re also built on Open Street Maps, so it’s synced up), Seed Oil Free (everything from Local Fats & Seed Oil Scout is here), Michelin Star rated, Real Milk (Raw Milk directory) and more.
We scoured the web for the best curated lists and directories for each of these categories. This in Bitcoin accepted (everything relevant from BTCMaps - because we’re also built on Open Street Maps, so it’s synced up), Seed Oil Free (everything from Local Fats & Seed Oil Scout is here), Michelin Star rated, Real Milk (Raw Milk directory) and more. Alongside all of these directories, our network of local ambassadors have submitted their top local picks for their favorite cities, so you have real local recommendations.
The destinations with the best maps are currently Canggu, Uvita, Prague, Sao Paulo, Dubai, Florianópolis.
Suggest Places & Merchants
This is working quite nicely. Anyone, anywhere can now suggest their favorite merchant. For now, we’re manually approving submissions daily to avoid spam and irrelevant shit. In time, we’ll find a better way to do this.
It’s all plugged into the Google API, so you can just type in the name of the place you think should be added (from mobile or web here). Once approved, our AI pipeline goes to work gathering all the available data from Google, TripAdvisor and elsewhere to set up the merchant profile, complete with review summaries, images, profile bio, contact details, opening hours, tags and more.
Got more upgrades to this flow in the works, but it’s ready for you to try out now.
City Pages
The current city pages are part of an outdated design which doesn’t fit our new visual language, but they are a ‘live’ feature. The original idea was to blend elements of Pinterest and Instagram but it backfired so we are changing to a more slick one-column feed. That being said, the core features of the city pages work. You can:
-
Join a city (like joining a community or following the page)
-
Post content on the city page
-
Navigate over to the different available pages, including merchants, events, scores and stats + facts
We have 80 cities currently available. More to come.
Scores, Stats & Facts
When we set out to first build Satlantis, we wanted to improve on the information NomadList was presenting for cities & destinations around the world. So we developed a different approach for city scoring based not only on data we could get from Numbeo, etc - but also information direct from people on the ground - in particular; expats and locals.
We put together a set of score categories and created a dedicated survey for select people to fill out, which would create some “foundation” scores, with a view to have this survey available to the crowd, perhaps via a score voting system or some sort on the page. We haven’t got that far yet. Right now, we have foundation scores for each of those 80 active cities, along with key Stats and Facts, like cost of living, wifi speed, water drinkability, and more:
This is not a core feature for us, so we will look to partner with other providers to enhance the experience, or we’ll completely re-think how we’re going to do it. Stay tuned for more here and let me know if you find it useful at all right now (or not).
Events
Last but not least, we have events! God dammit this was annoying because we built it NIP-52 compatible in the beginning, which then limited what we could do with co-hosts and other essential event features. And all for nothing since there are no other well built or maintained calendar-event clients on Nostr anyway.
So right now, when you post an event on Satlantis, it will post only on Satlantis. This means that as a host, you can edit, add co-hosts, add locations (proper merchant tiles) and delete.
We will make this Nostr-compatible again, most likely with some sort of button for hosts to “broadcast this event to Nostr” - knowing they will lose some flexibility once they do - but we need to do more research here. Maybe we’ll propose an upgrade to the calendar event NIP (or propose a new NIP altogether). It’s on our roadmap, so we’ll do our best to get to it soon.
Meetup integration.
We’ve been working with the Meetup API to let organizers quickly import their events into Satlantis. It’s been frustratingly complex because of how archaic they are, but we got it working!
🚀 If you run a Meetup, and want to automatically have your events listed on Satlantis when you list them on meetup,reach out! We’ll even cover the Meetup membership fee for 10 meetup groups who set up auto-importing for their events. If you’re interested, reach out to us.
The Bad
These things are currently bad, broken, incorrectly built or buggy. Believe me, if the list was exhaustive, this essay would be a book (our internal list is very full) - so I’m just going to touch on the main things we’re aware of and will be fixing…or just letting it burn slowly while we put out other fires.
Personal content feed
We started Satlantis with a media-only approach, taking inspiration from Instagram. We changed course a couple months ago to support text only posts, realizing there were a lot of other things people would like to post about travel, for example: guides, restaurants, reviews, tips, events, instructions, recommendations.
So…we started supporting this on the feed, and in the “post content” flow - but of course, not yet supported in the Profile view (which is still an image grid). This means if you post text only, you’re not going to see your own post on Satlantis 🤣🤣
To fix this, we’re building a “personal feed” section on your profile. But…that will come after we polish some of the things above, so if you’re posting on Satlantis right now, photos please!!
Video content
This one hurts too. We currently neither render videos from other clients, nor do we support video uploads on Satlantis. Not because we don’t want to, but because we haven’t got to it. This is high on the priority list and will be fixed in the upcoming releases.
Settings & Edit profile
We forgot to add “edit username” 🤣
This is being added now, along with a settings section where you can get your nPub and things like that. We’ll keep it very basic for now.
Notifications
Holy crap. These really suck. There is no other way to put it. The design is not great, the experience is buggy as hell and syncing notifications from the broader Nostr network doesn’t make life any easier. We’ll be making incremental improvements here (for a long time I guess).
Limited social graph functionality.
Right now, there’s not much social-dynamics beyond the feed. This will expand and begin to influence more than just content, but also merchants, events, people, activities, etc.
Speed issues.
Feed and profile loading times are sluggish and need performance improvements. Ongoing.
Large Destinations are problematic.
How do you rate a massive city like São Paulo as a single entity? Well….you can’t. Eventually, we’ll break major cities into regions, but that’s a big project for later.
For now, when you see scores, stats and facts, assume we’re covering the most relevant traveler-friendly areas (e.g., Jardins in São Paulo, Palermo in Buenos Aires, etc).
The Ugly
There is really only one new ‘feature’ to complete before we apply a feature freeze and continue on to polish everything. This and the other items listed will be available in the next release or two, so that the overall experience is a little more…beautiful.
Chat.
We wanted to do NIP-17, but considering that (a) most of the major apps are still NIP-04, (b) BTCPrague is around the corner and (c) limited resources, we chose to do a NIP-04 implementation for this first version. Not ideal, but good enough. Chat will continue to improve, not only with a NIP-17 upgrade, but with other features like chat folders, group chats, GIFs and more.
Polish List
-
Merchant Experience: Web and mobile updates
-
Merchant List: More cool places being uploaded
-
Events: New display, RSVP flow, co-host notifications, merchant integration
-
Onboarding: Updated interests tags & flow
-
Scores: Updates to Cost of Living & overall score weights
-
Notifications: A lot of improvement here
-
Feed: Text only posts, video uploads & rendering videos from other clients
-
City Page: New design and functionalities
-
Zaps: Yes. We will have Zaps.
Final Words
We have our work cut out for us!
We will be at BTCPrague in June and we are committed to releasing all of these features and components by then…as polished as possible.
The team and I have a couple of asks:
-
Download the app, and either create a new account or if you’re on Nostr, log in with your existing Nostr key (web requires an extension like Alby)
-
Go through the interests, and select those that are most relevant to you. The magic of the app happens as a function of how accurately you select those.
-
Post some content! Could be a photo introducing yourself or a “Good Morning” or whatever. Make sure you tag @Satlantis or @Svetski and I’ll boost you.
-
Check out the merchants in the top cities & see what’s around. The city with the most merchants right now is Florianopolis, but we have some coverage in many other cities
-
If you run a meetup or attend a regular Bitcoin meetup, let the organisers know, and let’s start to bring meetups and events across. Not asking anyone to ‘leave’ meetup now, but come and sync up your account so events are auto-published. \ As we make the events feature more robust (and Bitcoin native), every Bitcoin meetup in the world is going to want to come use this. If you’re early, you can help us shape it!
-
Let a couple of friends know about the app - ideally those who are not yet on Nostr - and ask them to try it out. They can sign up with email or SSO if they’re afraid to store their own key.
-
Like I said in the beginning, at some point in the next month or so, it will become an invite-only app. We will grandfather all existing users in, but new people will need an invite code (from existing users or via codes I drop into release notes and articles) to access it. \ \ The goal of this approach is to (a) increase the quality of connection amongst people on Satlantis, and (b) try a new way of growing a Nostr-based app.
-
Finally…we’ve decided to do an equity crowdfund. So if you find what we’re doing interesting and want to be a part of it, you’ll have a chance from June onwards. More to follow on this in the coming weeks. It will be on Timestamp Financial - Bitcoin crowdfunding platform - so go check them out.
Thank you again for your attention - I do not take it lightly. This is just the start, so expect to see ALOT more from us in the way of updates and shipping (plus these updates will be shooter).
Make sure you subscribe to this newsletter if you’re reading on Substack, or follow me if you’re on Nostr, Medium or wherever else you’re reading it.
Aleksandar Svetski
Thanks for reading Social 2.0! Subscribe for free to receive new posts & stay up to date with what we’re building & learning along the way.
When the app goes into “Invite Only” mode, you will need a special invite code to access it, unless you’ve already got an account. For now, it’s open access.
If you're already on Nostr, you're already on Satlantis. Just use an extension to securely log in with your nSec (on web), or with your nSec on mobile.
-
-
 @ f32184ee:6d1c17bf
2025-04-23 13:21:52
@ f32184ee:6d1c17bf
2025-04-23 13:21:52Ads Fueling Freedom
Ross Ulbricht’s "Decentralize Social Media" painted a picture of a user-centric, decentralized future that transcended the limitations of platforms like the tech giants of today. Though focused on social media, his concept provided a blueprint for decentralized content systems writ large. The PROMO Protocol, designed by NextBlock while participating in Sovereign Engineering, embodies this blueprint in the realm of advertising, leveraging Nostr and Bitcoin’s Lightning Network to give individuals control, foster a multi-provider ecosystem, and ensure secure value exchange. In this way, Ulbricht’s 2021 vision can be seen as a prescient prediction of the PROMO Protocol’s structure. This is a testament to the enduring power of his ideas, now finding form in NextBlock’s innovative approach.
 [Current Platform-Centric Paradigm, source: Ross Ulbricht's Decentralize Social Media]
[Current Platform-Centric Paradigm, source: Ross Ulbricht's Decentralize Social Media]Ulbricht’s Vision: A Decentralized Social Protocol
In his 2021 Medium article Ulbricht proposed a revolutionary vision for a decentralized social protocol (DSP) to address the inherent flaws of centralized social media platforms, such as privacy violations and inconsistent content moderation. Writing from prison, Ulbricht argued that decentralization could empower users by giving them control over their own content and the value they create, while replacing single, monolithic platforms with a competitive ecosystem of interface providers, content servers, and advertisers. Though his focus was on social media, Ulbricht’s ideas laid a conceptual foundation that strikingly predicts the structure of NextBlock’s PROMO Protocol, a decentralized advertising system built on the Nostr protocol.
 [A Decentralized Social Protocol (DSP), source: Ross Ulbricht's Decentralize Social Media]
[A Decentralized Social Protocol (DSP), source: Ross Ulbricht's Decentralize Social Media]Ulbricht’s Principles
Ulbricht’s article outlines several key principles for his DSP: * User Control: Users should own their content and dictate how their data and creations generate value, rather than being subject to the whims of centralized corporations. * Decentralized Infrastructure: Instead of a single platform, multiple interface providers, content hosts, and advertisers interoperate, fostering competition and resilience. * Privacy and Autonomy: Decentralized solutions for profile management, hosting, and interactions would protect user privacy and reduce reliance on unaccountable intermediaries. * Value Creation: Users, not platforms, should capture the economic benefits of their contributions, supported by decentralized mechanisms for transactions.
These ideas were forward-thinking in 2021, envisioning a shift away from the centralized giants dominating social media at the time. While Ulbricht didn’t specifically address advertising protocols, his framework for decentralization and user empowerment extends naturally to other domains, like NextBlock’s open-source offering: the PROMO Protocol.
NextBlock’s Implementation of PROMO Protocol
The PROMO Protocol powers NextBlock's Billboard app, a decentralized advertising protocol built on Nostr, a simple, open protocol for decentralized communication. The PROMO Protocol reimagines advertising by: * Empowering People: Individuals set their own ad prices (e.g., 500 sats/minute), giving them direct control over how their attention or space is monetized. * Marketplace Dynamics: Advertisers set budgets and maximum bids, competing within a decentralized system where a 20% service fee ensures operational sustainability. * Open-Source Flexibility: As an open-source protocol, it allows multiple developers to create interfaces or apps on top of it, avoiding the single-platform bottleneck Ulbricht critiqued. * Secure Payments: Using Strike Integration with Bitcoin Lightning Network, NextBlock enables bot-resistant and intermediary-free transactions, aligning value transfer with each person's control.
This structure decentralizes advertising in a way that mirrors Ulbricht’s broader vision for social systems, with aligned principles showing a specific use case: monetizing attention on Nostr.
Aligned Principles
Ulbricht’s 2021 article didn’t explicitly predict the PROMO Protocol, but its foundational concepts align remarkably well with NextBlock's implementation the protocol’s design: * Autonomy Over Value: Ulbricht argued that users should control their content and its economic benefits. In the PROMO Protocol, people dictate ad pricing, directly capturing the value of their participation. Whether it’s their time, influence, or digital space, rather than ceding it to a centralized ad network. * Ecosystem of Providers: Ulbricht envisioned multiple providers replacing a single platform. The PROMO Protocol’s open-source nature invites a similar diversity: anyone can build interfaces or tools on top of it, creating a competitive, decentralized advertising ecosystem rather than a walled garden. * Decentralized Transactions: Ulbricht’s DSP implied decentralized mechanisms for value exchange. NextBlock delivers this through the Bitcoin Lightning Network, ensuring that payments for ads are secure, instantaneous and final, a practical realization of Ulbricht’s call for user-controlled value flows. * Privacy and Control: While Ulbricht emphasized privacy in social interactions, the PROMO Protocol is public by default. Individuals are fully aware of all data that they generate since all Nostr messages are signed. All participants interact directly via Nostr.
 [Blueprint Match, source NextBlock]
[Blueprint Match, source NextBlock]
Who We Are
NextBlock is a US-based new media company reimagining digital ads for a decentralized future. Our founders, software and strategy experts, were hobbyist podcasters struggling to promote their work online without gaming the system. That sparked an idea: using new tech like Nostr and Bitcoin to build a decentralized attention market for people who value control and businesses seeking real connections.
Our first product, Billboard, is launching this June.
Open for All
Our model’s open-source! Check out the PROMO Protocol, built for promotion and attention trading. Anyone can join this decentralized ad network. Run your own billboard or use ours. This is a growing ecosystem for a new ad economy.
Our Vision
NextBlock wants to help build a new decentralized internet. Our revolutionary and transparent business model will bring honest revenue to companies hosting valuable digital spaces. Together, we will discover what our attention is really worth.
Read our Manifesto to learn more.
NextBlock is registered in Texas, USA.
-
 @ b99efe77:f3de3616
2025-05-12 21:19:41
@ b99efe77:f3de3616
2025-05-12 21:19:41🚦Traffic Light Control System🚦
This Petri net represents a traffic control protocol ensuring that two traffic lights alternate safely and are never both green at the same time.
;start () -> greenLight1 redLight2
;toRed1 greenLight1 -> queue redLight1
;toGreen2 redLight2 queue -> greenLight2
;toGreen1 queue redLight1 -> greenLight1
;toRed2 greenLight2 -> redLight2 queue
;stop redLight1 queue redLight2 -> ()Places & Transitions
- Places:
- greenLight1: Indicates that the first traffic light is green.
- greenLight2: Indicates that the second traffic light is green.
- redLight1: Indicates that the first traffic light is red.
- redLight2: Indicates that the second traffic light is red.
-
queue: Acts as a synchronization mechanism ensuring controlled alternation between the two traffic lights.
-
Transitions:
- start: Initializes the system by placing tokens in greenLight1 and redLight2.
- toRed1: Moves a token from greenLight1 to redLight1, while placing a token in queue.
- toGreen2: Moves a token from redLight2 to greenLight2, requiring queue.
- toGreen1: Moves a token from queue and redLight1 to greenLight1.
- toRed2: Moves a token from greenLight2 to redLight2, placing a token back into queue.
- stop: Terminates the system by removing tokens from redLight1, queue, and redLight2, representing the system's end state.
petrinet ;start () -> greenLight1 redLight2 ;toRed1 greenLight1 -> queue redLight1 ;toGreen2 redLight2 queue -> greenLight2 ;toGreen1 queue redLight1 -> greenLight1 ;toRed2 greenLight2 -> redLight2 queue ;stop redLight1 queue redLight2 -> ()
-
 @ efcb5fc5:5680aa8e
2025-04-15 07:34:28
@ efcb5fc5:5680aa8e
2025-04-15 07:34:28We're living in a digital dystopia. A world where our attention is currency, our data is mined, and our mental well-being is collateral damage in the relentless pursuit of engagement. The glossy facades of traditional social media platforms hide a dark underbelly of algorithmic manipulation, curated realities, and a pervasive sense of anxiety that seeps into every aspect of our lives. We're trapped in a digital echo chamber, drowning in a sea of manufactured outrage and meaningless noise, and it's time to build an ark and sail away.
I've witnessed the evolution, or rather, the devolution, of online interaction. From the raw, unfiltered chaos of early internet chat rooms to the sterile, algorithmically controlled environments of today's social giants, I've seen the promise of connection twisted into a tool for manipulation and control. We've become lab rats in a grand experiment, our emotional responses measured and monetized, our opinions shaped and sold to the highest bidder. But there's a flicker of hope in the darkness, a chance to reclaim our digital autonomy, and that hope is NOSTR (Notes and Other Stuff Transmitted by Relays).
The Psychological Warfare of Traditional Social Media
The Algorithmic Cage: These algorithms aren't designed to enhance your life; they're designed to keep you scrolling. They feed on your vulnerabilities, exploiting your fears and desires to maximize engagement, even if it means promoting misinformation, outrage, and division.
The Illusion of Perfection: The curated realities presented on these platforms create a toxic culture of comparison. We're bombarded with images of flawless bodies, extravagant lifestyles, and seemingly perfect lives, leading to feelings of inadequacy and self-doubt.
The Echo Chamber Effect: Algorithms reinforce our existing beliefs, isolating us from diverse perspectives and creating a breeding ground for extremism. We become trapped in echo chambers where our biases are constantly validated, leading to increased polarization and intolerance.
The Toxicity Vortex: The lack of effective moderation creates a breeding ground for hate speech, cyberbullying, and online harassment. We're constantly exposed to toxic content that erodes our mental well-being and fosters a sense of fear and distrust.
This isn't just a matter of inconvenience; it's a matter of mental survival. We're being subjected to a form of psychological warfare, and it's time to fight back.
NOSTR: A Sanctuary in the Digital Wasteland
NOSTR offers a radical alternative to this toxic environment. It's not just another platform; it's a decentralized protocol that empowers users to reclaim their digital sovereignty.
User-Controlled Feeds: You decide what you see, not an algorithm. You curate your own experience, focusing on the content and people that matter to you.
Ownership of Your Digital Identity: Your data and content are yours, secured by cryptography. No more worrying about being deplatformed or having your information sold to the highest bidder.
Interoperability: Your identity works across a diverse ecosystem of apps, giving you the freedom to choose the interface that suits your needs.
Value-Driven Interactions: The "zaps" feature enables direct micropayments, rewarding creators for valuable content and fostering a culture of genuine appreciation.
Decentralized Power: No single entity controls NOSTR, making it censorship-resistant and immune to the whims of corporate overlords.
Building a Healthier Digital Future
NOSTR isn't just about escaping the toxicity of traditional social media; it's about building a healthier, more meaningful online experience.
Cultivating Authentic Connections: Focus on building genuine relationships with people who share your values and interests, rather than chasing likes and followers.
Supporting Independent Creators: Use "zaps" to directly support the artists, writers, and thinkers who inspire you.
Embracing Intellectual Diversity: Explore different NOSTR apps and communities to broaden your horizons and challenge your assumptions.
Prioritizing Your Mental Health: Take control of your digital environment and create a space that supports your well-being.
Removing the noise: Value based interactions promote value based content, instead of the constant stream of noise that traditional social media promotes.
The Time for Action is Now
NOSTR is a nascent technology, but it represents a fundamental shift in how we interact online. It's a chance to build a more open, decentralized, and user-centric internet, one that prioritizes our mental health and our humanity.
We can no longer afford to be passive consumers in the digital age. We must become active participants in shaping our online experiences. It's time to break free from the chains of algorithmic control and reclaim our digital autonomy.
Join the NOSTR movement
Embrace the power of decentralization. Let's build a digital future that's worthy of our humanity. Let us build a place where the middlemen, and the algorithms that they control, have no power over us.
In addition to the points above, here are some examples/links of how NOSTR can be used:
Simple Signup: Creating a NOSTR account is incredibly easy. You can use platforms like Yakihonne or Primal to generate your keys and start exploring the ecosystem.
X-like Client: Apps like Damus offer a familiar X-like experience, making it easy for users to transition from traditional platforms.
Sharing Photos and Videos: Clients like Olas are optimized for visual content, allowing you to share your photos and videos with your followers.
Creating and Consuming Blogs: NOSTR can be used to publish and share blog posts, fostering a community of independent creators.
Live Streaming and Audio Spaces: Explore platforms like Hivetalk and zap.stream for live streaming and audio-based interactions.
NOSTR is a powerful tool for reclaiming your digital life and building a more meaningful online experience. It's time to take control, break free from the shackles of traditional social media, and embrace the future of decentralized communication.
Get the full overview of these and other on: https://nostrapps.com/
-
 @ c1e9ab3a:9cb56b43
2025-04-15 04:55:49
@ c1e9ab3a:9cb56b43
2025-04-15 04:55:49Esteemed representatives of Risa,
We gather here under the calming glow of our twin suns, stewards of a society admired for its peace and celebrated for its tranquility. But we must not mistake serenity for passivity, nor confuse peace with weakness. Our peace is not an accident. It is not the byproduct of ignorance or naivety. It is hard-earned—preserved by those willing to stand vigilant in its defense.
Love as a Foundation, Strength as a Shield
Love conquers hate. This is the core truth of Risan philosophy. Yet, as every Ricin child is taught, love without strength is a leaf in the wind. The Ricin do not lay down their lives without resistance. We do not ask our people to accept violence without confronting it. True peace is not imposed by stripping the people of their agency—it is built by enabling them to protect it.
The Lessons of a Failed Experiment
There was a time, not so distant in our history, when we attempted to enforce peace through the abolition of all weapons. A time when even the mention of self-defense in our educational centers was met with rebuke. Schools purged training programs. Cultural arts that honored our warrior traditions were dismissed. And for a brief moment, we believed this would lead us to harmony.
But peace born from helplessness is a fragile illusion. It fractures under the slightest pressure. And fracture it did—when off-world raiders targeted our unguarded sanctuaries, when radical sects within our own society struck out, knowing the citizenry could not defend itself. It was then that we remembered: Risa’s greatest peacekeepers had always been those who knew how to fight—but chose restraint.
The Age of Ricin and the Reawakening of Discipline
So we returned to our roots. To the traditions of the Age of Ricin, when youth, upon reaching maturity, were taught not only the arts of compassion and creation but also the martial disciplines. They learn to wield weapons—not to glorify violence, but to understand it. To control it. To stand firm against it when all else fails.
https://i.nostr.build/kuUjRovISz7367TX.jpg
We do not romanticize war. We do not celebrate conflict. But we prepare for it, should it seek to extinguish our light. Our children now learn the disciplines of defense alongside their studies in poetry, music, and healing. They spar with blunt blades under the watchful eyes of masters. They meditate on the consequences of force. And they grow into citizens not easily provoked, but never unprepared.
A Call for Balance, Not Extremes
Let those beyond our borders question our ways. Let them forget the countless incursions by the Romulans. Let them ignore the scars left by centuries of subversion from the Orion Syndicate. We do not forget. We remember the lives lost, the liberties challenged, and the lessons learned through suffering. These experiences shaped us.
We do not wish to return to the era of soft silence, when teachers trembled at the word "weapon" and children were told that even imagination was dangerous. That was not enlightenment. That was indoctrination.
Conclusion: Guarding the Flame
We are the guardians of Risa’s flame—not just with words and treaties, but with discipline and readiness. We have made peace a practice, and preparation a virtue. And so I say to this chamber: let us never again disarm our people in the name of utopia. Let us never confuse comfort with safety, or the absence of weapons with the presence of peace.
Instead, let us raise generations who know what peace costs, and who will pay that price—not with surrender, but with courage.
Let our children be artists, lovers, dreamers—and if necessary, defenders.
This is the Risan way.
-
 @ 6c05c73e:c4356f17
2025-05-12 20:05:36
@ 6c05c73e:c4356f17
2025-05-12 20:05:36Já pensou em investir no Brasil, mas se sentiu intimidado pela volatilidade da Bovespa e as notícias de escândalos? E se eu te dissesse que existe uma maneira de expor seu portfólio ao mercado brasileiro, investindo em dólar, diretamente da bolsa de valores de Nova York?
Bem-vindo ao mundo do EWZ, o ETF (Exchange Traded Fund) que replica o índice MSCI Brazil 25/50, oferecendo uma janela para as maiores e médias empresas do Brasil. Se você está buscando diversificar seus investimentos e explorar mercados emergentes, o EWZ pode ser a sua resposta.
O Que Exatamente é o EWZ?
O EWZ é o ticker symbol do iShares MSCI Brazil ETF. Pense nele como um pacote de ações brasileiras negociado na bolsa de valores americana. Ele espelha o desempenho do índice MSCI Brazil 25/50, o que significa que, ao investir no EWZ, você está, indiretamente, investindo em uma cesta diversificada das principais empresas do Brasil.
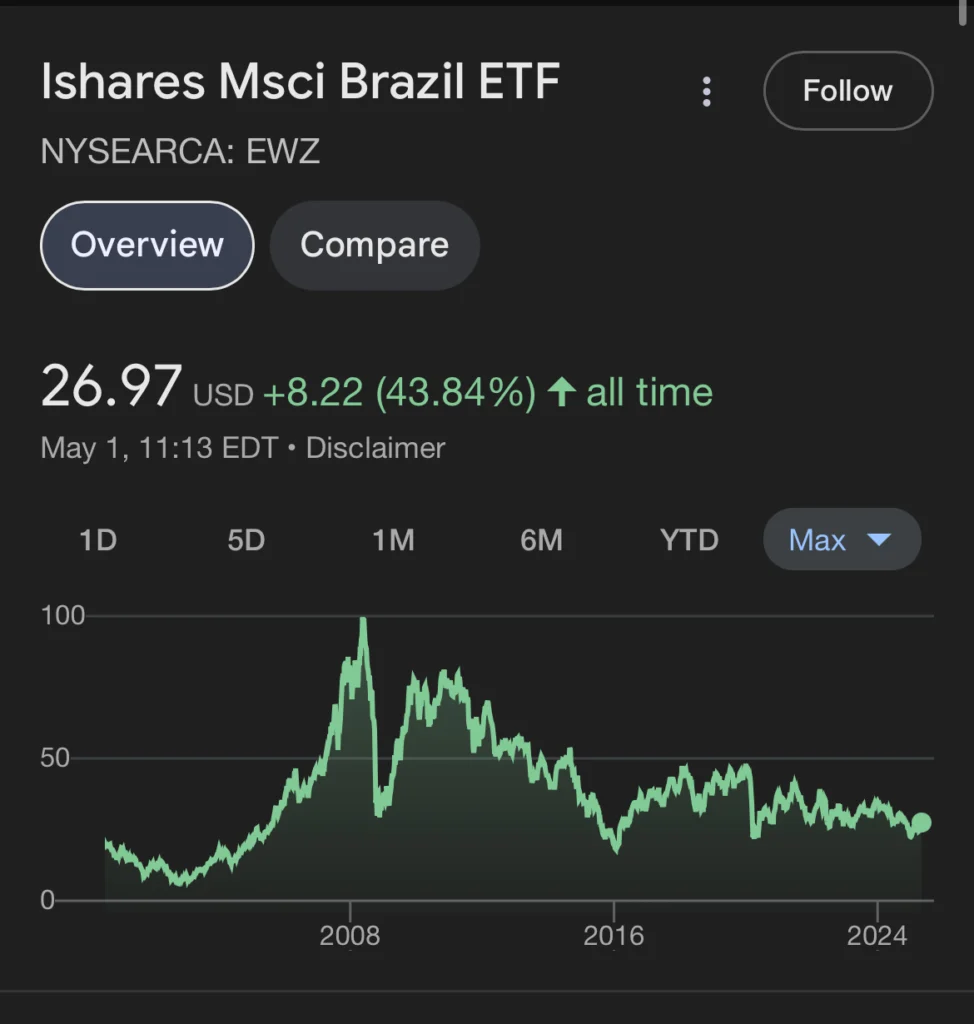
Por Que Investir no Brasil via ETF?
Você já pensou em investir no Brasil? Mas ouve sempre falar desses riscos da Bovespa e vários escândalos?
Portanto, saiba que existe uma forma de investir no Brasil em dólar. Usando a bolsa de valores de Nova Iorque. Isso mesmo, você pode abrir uma conta em corretora estrangeira e investir no Brasil via ETF.
O ETF que replica a Bovespa (Bolsa de valores de São Paulo) é o EWZ. Esse índice replica o Ibovespa e reflete nele o peso das maiores empresas brasileiras, tais como:
- Diversificação em Dólar: Invista em empresas brasileiras sem precisar se preocupar com a flutuação do real. Seus investimentos são feitos em dólar, protegendo você das variações cambiais.
- Acesso Facilitado: Negocie o EWZ diretamente da sua corretora americana, sem a necessidade de abrir contas no Brasil ou lidar com burocracias locais.
- Diversificação Instantânea: Ao comprar EWZ, você está comprando uma fatia de várias empresas líderes no Brasil, reduzindo o risco de concentrar seus investimentos em uma única empresa ou setor.
Números Que Falam Por Si
Vamos aos dados concretos que mostram a solidez do EWZ:
- Taxa de Administração: 0.59% a.a.
- Patrimônio Líquido Sob Gestão: $3.6 bilhões em ativos. Isso indica uma boa popularidade do ativo.
- Volume de negociação diário: Em média $24 milhões, o que garante boa liquidez e baixas taxas.
- Dividendos: 7.33% a.a. Distribuído semestralmente.
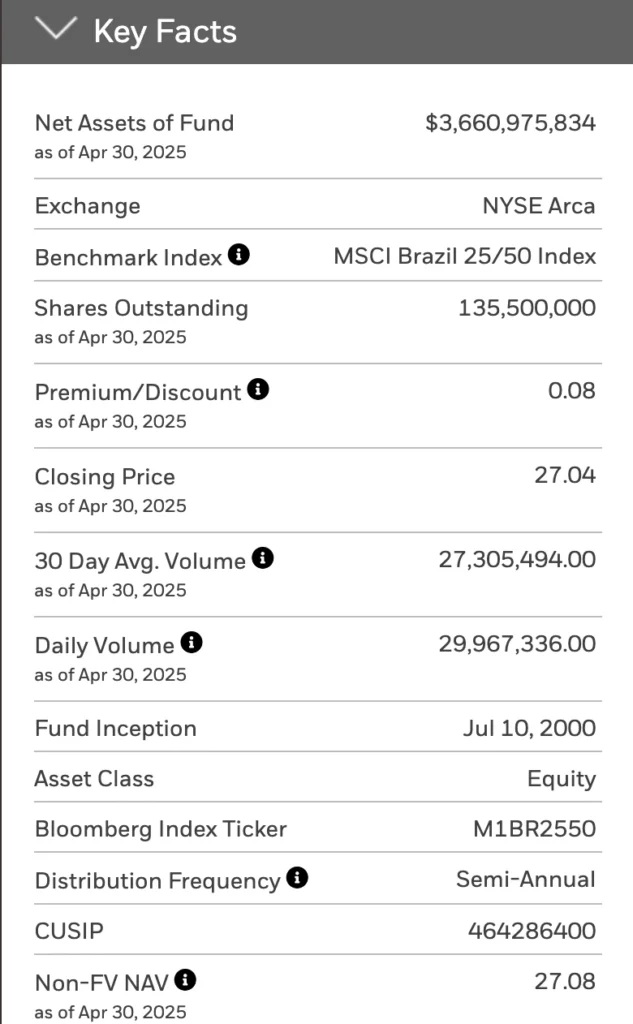
Qualitativo
- Com mais de 200 milhões de habitantes, o Brasil tem um dos maiores mercados consumidores do mundo. Isso representa uma demanda interna robusta e potencial para uma vasta gama de produtos e serviços.
- O país é extremamente rico em recursos naturais, incluindo minérios (ferro, bauxita, etc.), petróleo, gás natural e vastas áreas agricultáveis. Além disso, tem um potencial enorme e já desenvolvido em energias renováveis (hídrica, solar, eólica, biomassa).
- O Brasil é um líder global na produção e exportação de diversos produtos agrícolas (soja, milho, café, açúcar, carne bovina, frango). Há contínuo potencial para ganhos de produtividade e agregação de valor na cadeia.
- O Brasil desenvolveu um ecossistema de startups vibrante, especialmente no setor de fintechs, onde é referência global em inovação (ex: Pix, Open Banking). Há também crescimento em agrotechs, healthtechs e outras áreas. O grande mercado consumidor digital impulsiona esse setor.
Técnica
- O ativo teve uma queda vertiginosa. No entanto, desde Dezembro de 2024 vem apresentando uma melhora no comportamento. Isso, pode sugerir que há uma boa margem para comprar com "desconto". Visto que, o volume comprador tem sido intenso desde o inicío de Abril de 2025.
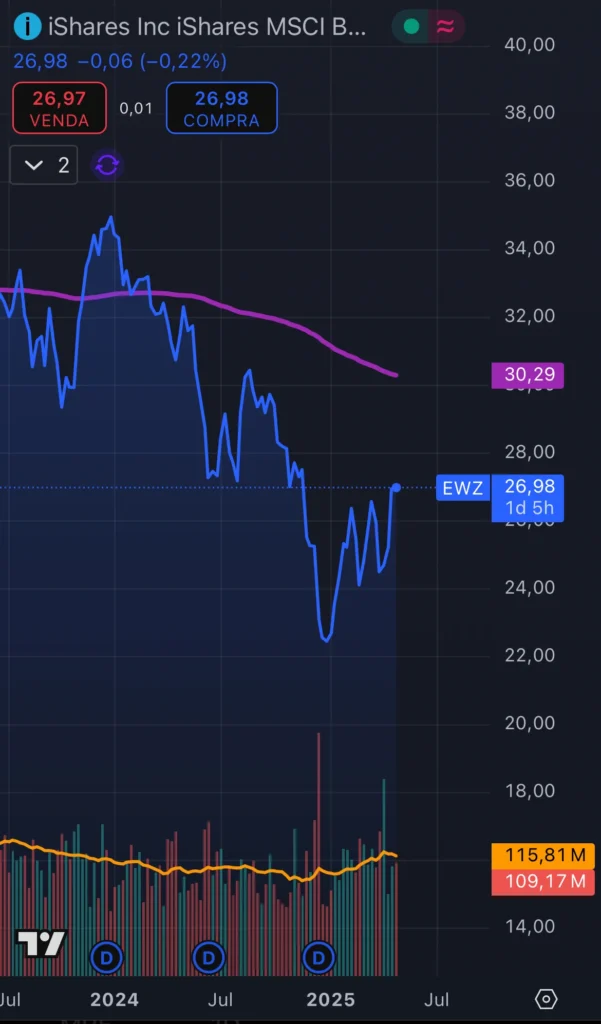
FAQ
O que significa a sigla EWZ?
A sigla EWZ é o ticker symbol (código de negociação em bolsa) do iShares MSCI Brazil ETF.
Portanto, EWZ não é uma sigla de um nome por extenso, mas sim o código usado para identificar e negociar este fundo específico (ETF) nas bolsas de valores dos Estados Unidos (como a NYSE Arca). Este ETF busca replicar o desempenho do índice MSCI Brazil 25/50, que representa as maiores e médias empresas brasileiras.
Qual é a composição do EWZ?
AS 10 Maiores Posições (na data de hoje):
- Nu Holdings (NU): \~9.3% - 9.8% (Setor Financeiro)
- Vale (VALE3): \~8.5% - 9.5% (Setor de Materiais)
- Itaú Unibanco (ITUB4): \~7.9% - 8.6% (Setor Financeiro)
- Petrobras PN (PETR4): \~6.2% - 8.0% (Setor de Energia)
- Petrobras ON (PETR3): \~5.5% - 7.3% (Setor de Energia)
- WEG (WEGE3): \~3.9% - 4.2% (Setor Industrial)
- B3 (B3SA3): \~3.4% - 3.7% (Setor Financeiro)
- Banco Bradesco (BBDC4): \~3.0% - 3.6% (Setor Financeiro)
- Ambev (ABEV3): \~2.9% - 3.4% (Setor de Consumo Essencial/Staples)
- Sabesp (SBSP3) ou Eletrobras (ELET3): Geralmente na 10ª posição, com peso entre \~2.5% - 2.8% (Setor de Utilidade Pública)
Sobre nós
Investir não precisa ser um bicho de sete cabeças! Na Threedolar, democratizamos o acesso ao mundo dos investimentos, oferecendo conteúdo claro e prático. Comece hoje mesmo a construir seu futuro financeiro!
Disclaimer
Nada do que eu escrever aqui é recomendação de investimentos ou chamada para compra e venda. Tire suas próprias conclusões e veja o que é melhor para você. Resultados passados não são garantia de resultados futuros. Cuide do seu dinheiro, pois ninguém o fará para você.
Referências
-
 @ 3ffac3a6:2d656657
2025-04-23 01:57:57
@ 3ffac3a6:2d656657
2025-04-23 01:57:57🔧 Infrastructure Overview
- Hardware: Raspberry Pi 5 with PCIe NVMe HAT and 2TB NVMe SSD
- Filesystem: ZFS with separate datasets for each service
- Networking: Docker bridge networks for service segmentation
- Privacy: Tor and I2P routing for anonymous communication
- Public Access: Cloudflare Tunnel to securely expose LNbits
📊 Architecture Diagram
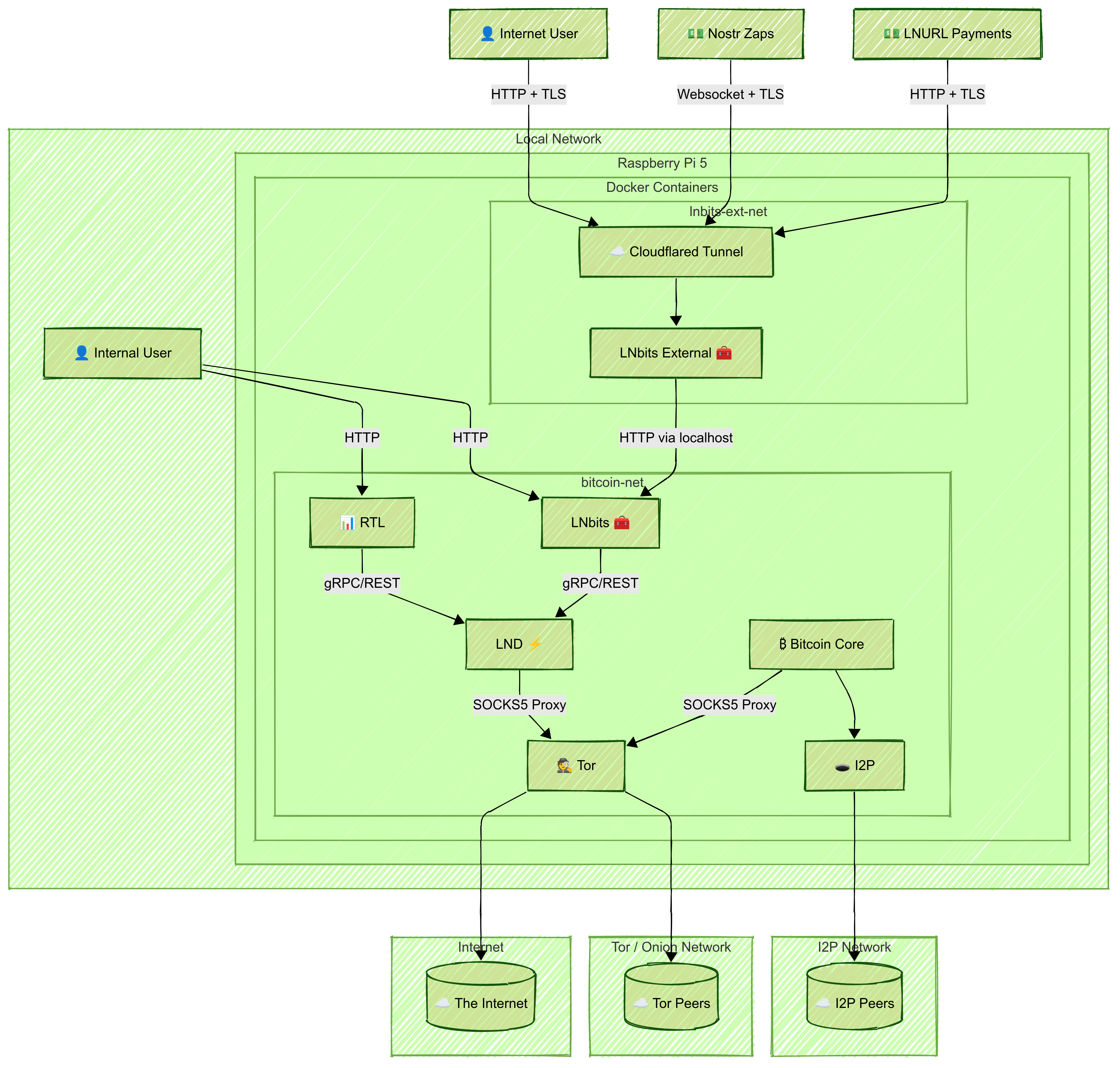
🛠️ Setup Steps
1. Prepare the System
- Install Raspberry Pi OS (64-bit)
- Set up ZFS on the NVMe disk
- Create a ZFS dataset for each service (e.g.,
bitcoin,lnd,rtl,lnbits,tor-data) - Install Docker and Docker Compose
2. Create Shared Docker Network and Privacy Layers
Create a shared Docker bridge network:
bash docker network create \ --driver=bridge \ --subnet=192.168.100.0/24 \ bitcoin-netNote: Connect
bitcoind,lnd,rtl, internallnbits,tor, andi2pto thisbitcoin-netnetwork.Tor
- Run Tor in a container
- Configure it to expose LND's gRPC and REST ports via hidden services:
HiddenServicePort 10009 192.168.100.31:10009 HiddenServicePort 8080 192.168.100.31:8080 - Set correct permissions:
bash sudo chown -R 102:102 /zfs/datasets/tor-data
I2P
- Run I2P in a container with SAM and SOCKS proxies
- Update
bitcoin.conf:i2psam=192.168.100.20:7656 i2pacceptincoming=1
3. Set Up Bitcoin Core
- Create a
bitcoin.confwith Tor/I2P/proxy settings and ZMQ enabled - Sync the blockchain in a container using its ZFS dataset
4. Set Up LND
- Configure
lnd.confto connect tobitcoindand use Tor: ```ini [Bitcoind] bitcoind.rpchost=bitcoin:8332 bitcoind.rpcuser=bitcoin bitcoind.rpcpass=very-hard-password bitcoind.zmqpubrawblock=tcp://bitcoin:28332 bitcoind.zmqpubrawtx=tcp://bitcoin:28333
[Application Options] externalip=xxxxxxxx.onion
`` - Don’t expose gRPC or REST ports publicly - Mount the ZFS dataset at/root/.lnd` - Optionally enable Watchtower5. Set Up RTL
- Mount
RTL-Config.jsonand data volumes - Expose RTL's web interface locally:
```yaml
ports:
- "3000:3000" ```
6. Set Up Internal LNbits
- Connect the LNbits container to
bitcoin-net - Mount the data directory and LND cert/macaroons (read-only)
- Expose the LNbits UI on the local network:
```yaml
ports:
- "5000:5000" ```
- In the web UI, configure the funding source to point to the LND REST
.onionaddress and paste the hex macaroon - Create and fund a wallet, and copy its Admin Key for external use
7. Set Up External LNbits + Cloudflare Tunnel
- Run another LNbits container on a separate Docker network
- Access the internal LNbits via the host IP and port 5000
- Use the Admin Key from the internal wallet to configure funding
- In the Cloudflare Zero Trust dashboard:
- Create a tunnel
- Select Docker, copy the
--tokencommand - Add to Docker Compose:
yaml command: tunnel --no-autoupdate run --token eyJ...your_token...
💾 Backup Strategy
- Bitcoin Core: hourly ZFS snapshots, retained for 6 hours
- Other Services: hourly snapshots with remote
.tar.gzbackups - Retention: 7d hourly, 30d daily, 12mo weekly, monthly forever
- Back up ZFS snapshots to avoid inconsistencies
🔐 Security Isolation Benefits
This architecture isolates services by scope and function:
- Internal traffic stays on
bitcoin-net - Sensitive APIs (gRPC, REST) are reachable only via Tor
- Public access is controlled by Cloudflare Tunnel
Extra Security: Host the public LNbits on a separate machine (e.g., hardened VPS) with strict firewall rules:
- Allow only Cloudflare egress
- Allow ingress from your local IP
- Allow outbound access to internal LNbits (port 5000)
Use WireGuard VPN to secure the connection between external and internal LNbits:
- Ensures encrypted communication
- Restricts access to authenticated VPN peers
- Keeps the internal interface isolated from the public internet
✅ Final Notes
- Internal services communicate over
bitcoin-net - LND interfaces are accessed via Tor only
- LNbits and RTL UIs are locally accessible
- Cloudflare Tunnel secures external access to LNbits
Monitor system health using
monit,watchtower, or Prometheus.Create all configuration files manually (
bitcoin.conf,lnd.conf,RTL-Config.json), and keep credentials secure. Test every component locally before exposing it externally.⚡
-
 @ 58d88196:bec81862
2025-05-12 19:14:54
@ 58d88196:bec81862
2025-05-12 19:14:54Where We Are Now: AI is already a big part of our lives, even if we don’t always notice it. Think about the last time you used GPS to avoid traffic—that’s AI at work, quietly making your day easier. Companies like NVIDIA,are behind a lot of this magic. They make the tech that powers everything from self-driving cars to massive data centers. In factories, companies like Siemens are using something called "digital twins"—basically virtual copies of their machines—to keep things running smoothly. It’s like having a crystal ball that tells you when a machine might break down before it actually does. Even cities are getting in on the action—Singapore, for example, has a project called Virtual Singapore, which is like a digital version of the city to help with planning things like new roads or buildings. And for us regular folks? If you’ve got a smartwatch tracking your steps or heart rate, you’re already creating a tiny digital version of yourself without even realizing it.
What’s Coming in the near future:Fast forward five or ten years, and this idea of digital twins is going to be everywhere. Picture a factory that never stops because its digital twin catches problems before they happen—no more delays, no more wasted time. Cities will get smarter, too. Imagine a scorching summer day during a heatwave, and instead of a blackout, the city’s AI system automatically shifts energy to where it’s needed most, keeping your AC running. For you and me, digital twins could become a game-changer in healthcare. Your doctor might have a digital version of you—built from your DNA, lifestyle, and even the air quality in your neighborhood—that’s constantly updated. It could warn you about a health issue before you even feel sick, or help your doctor figure out the best treatment just for you. And it doesn’t stop there. You might even have a virtual version of yourself that can attend boring work meetings for you, acting and talking just like you do, while you’re off grabbing a coffee or playing with your kids.
The Big Picture—and the Big Worries: This AI-powered future sounds amazing, but it’s not all smooth sailing. One big concern is privacy. To make these digital twins, companies need a ton of data about us—what we do, where we go, even how our bodies work. That can feel a little creepy, right? What if someone hacks into a city’s digital twin and messes with its power grid or traffic lights? That’s a real risk we’ll need to tackle. Plus, there’s the worry that only the big players—rich companies or cities—will be able to afford this tech, leaving smaller places or communities behind. It’s something we’ll need to figure out so everyone can benefit from what AI has to offer.
-
 @ a39d19ec:3d88f61e
2025-04-22 12:44:42
@ a39d19ec:3d88f61e
2025-04-22 12:44:42Die Debatte um Migration, Grenzsicherung und Abschiebungen wird in Deutschland meist emotional geführt. Wer fordert, dass illegale Einwanderer abgeschoben werden, sieht sich nicht selten dem Vorwurf des Rassismus ausgesetzt. Doch dieser Vorwurf ist nicht nur sachlich unbegründet, sondern verkehrt die Realität ins Gegenteil: Tatsächlich sind es gerade diejenigen, die hinter jeder Forderung nach Rechtssicherheit eine rassistische Motivation vermuten, die selbst in erster Linie nach Hautfarbe, Herkunft oder Nationalität urteilen.
Das Recht steht über Emotionen
Deutschland ist ein Rechtsstaat. Das bedeutet, dass Regeln nicht nach Bauchgefühl oder politischer Stimmungslage ausgelegt werden können, sondern auf klaren gesetzlichen Grundlagen beruhen müssen. Einer dieser Grundsätze ist in Artikel 16a des Grundgesetzes verankert. Dort heißt es:
„Auf Absatz 1 [Asylrecht] kann sich nicht berufen, wer aus einem Mitgliedstaat der Europäischen Gemeinschaften oder aus einem anderen Drittstaat einreist, in dem die Anwendung des Abkommens über die Rechtsstellung der Flüchtlinge und der Europäischen Menschenrechtskonvention sichergestellt ist.“
Das bedeutet, dass jeder, der über sichere Drittstaaten nach Deutschland einreist, keinen Anspruch auf Asyl hat. Wer dennoch bleibt, hält sich illegal im Land auf und unterliegt den geltenden Regelungen zur Rückführung. Die Forderung nach Abschiebungen ist daher nichts anderes als die Forderung nach der Einhaltung von Recht und Gesetz.
Die Umkehrung des Rassismusbegriffs
Wer einerseits behauptet, dass das deutsche Asyl- und Aufenthaltsrecht strikt durchgesetzt werden soll, und andererseits nicht nach Herkunft oder Hautfarbe unterscheidet, handelt wertneutral. Diejenigen jedoch, die in einer solchen Forderung nach Rechtsstaatlichkeit einen rassistischen Unterton sehen, projizieren ihre eigenen Denkmuster auf andere: Sie unterstellen, dass die Debatte ausschließlich entlang ethnischer, rassistischer oder nationaler Kriterien geführt wird – und genau das ist eine rassistische Denkweise.
Jemand, der illegale Einwanderung kritisiert, tut dies nicht, weil ihn die Herkunft der Menschen interessiert, sondern weil er den Rechtsstaat respektiert. Hingegen erkennt jemand, der hinter dieser Kritik Rassismus wittert, offenbar in erster Linie die „Rasse“ oder Herkunft der betreffenden Personen und reduziert sie darauf.
Finanzielle Belastung statt ideologischer Debatte
Neben der rechtlichen gibt es auch eine ökonomische Komponente. Der deutsche Wohlfahrtsstaat basiert auf einem Solidarprinzip: Die Bürger zahlen in das System ein, um sich gegenseitig in schwierigen Zeiten zu unterstützen. Dieser Wohlstand wurde über Generationen hinweg von denjenigen erarbeitet, die hier seit langem leben. Die Priorität liegt daher darauf, die vorhandenen Mittel zuerst unter denjenigen zu verteilen, die durch Steuern, Sozialabgaben und Arbeit zum Erhalt dieses Systems beitragen – nicht unter denen, die sich durch illegale Einreise und fehlende wirtschaftliche Eigenleistung in das System begeben.
Das ist keine ideologische Frage, sondern eine rein wirtschaftliche Abwägung. Ein Sozialsystem kann nur dann nachhaltig funktionieren, wenn es nicht unbegrenzt belastet wird. Würde Deutschland keine klaren Regeln zur Einwanderung und Abschiebung haben, würde dies unweigerlich zur Überlastung des Sozialstaates führen – mit negativen Konsequenzen für alle.
Sozialpatriotismus
Ein weiterer wichtiger Aspekt ist der Schutz der Arbeitsleistung jener Generationen, die Deutschland nach dem Zweiten Weltkrieg mühsam wieder aufgebaut haben. Während oft betont wird, dass die Deutschen moralisch kein Erbe aus der Zeit vor 1945 beanspruchen dürfen – außer der Verantwortung für den Holocaust –, ist es umso bedeutsamer, das neue Erbe nach 1945 zu respektieren, das auf Fleiß, Disziplin und harter Arbeit beruht. Der Wiederaufbau war eine kollektive Leistung deutscher Menschen, deren Früchte nicht bedenkenlos verteilt werden dürfen, sondern vorrangig denjenigen zugutekommen sollten, die dieses Fundament mitgeschaffen oder es über Generationen mitgetragen haben.
Rechtstaatlichkeit ist nicht verhandelbar
Wer sich für eine konsequente Abschiebepraxis ausspricht, tut dies nicht aus rassistischen Motiven, sondern aus Respekt vor der Rechtsstaatlichkeit und den wirtschaftlichen Grundlagen des Landes. Der Vorwurf des Rassismus in diesem Kontext ist daher nicht nur falsch, sondern entlarvt eine selektive Wahrnehmung nach rassistischen Merkmalen bei denjenigen, die ihn erheben.
-
 @ c1e9ab3a:9cb56b43
2025-04-15 04:15:58
@ c1e9ab3a:9cb56b43
2025-04-15 04:15:58Spoken by Counselor Elaron T’Saren of Risa to the High Council, Stardate 52874.2
Honored members of the Council,
I bring you greetings from Risa—not the Risa of travel brochures and romantic holo-novels, but the true Risa. The Risa that has endured, adapted, and emerged stronger after each trial. I speak not as a tourist ambassador, but as a Counselor of our oldest institute of philosophy, and as a son of the Ricin tradition.
Today, the specter of the Borg hangs above us. The collective offers no room for diplomacy, no respect for culture, no compromise. We face not mere invaders—but a force that seeks to erase individuality, history, and identity. Some among the Council wonder what Risa—a world of peace—can offer in such a time. I say to you: we can offer the truth about peace.
The Hidden Roots of Our Tranquility
Long ago, before Risa joined the Federation, we too believed that peace could be maintained by disarming the populace, by eliminating even the mention of conflict in our schools. It was called the Great Disarmament. A generation was raised with no understanding of defense, and in time, we paid the price.
We were raided by Orion pirates. Exploited by off-world cartels. Our people were taken, our arts destroyed, our skies blackened. And we learned—too late—that peace without preparedness is only the illusion of safety.
The Birth of Ricin Doctrine
From the ashes of that failure arose the Ricin: scholars, philosophers, warriors of thought and purpose. They taught that peace is not the absence of conflict, but the mastery of it. That the mind and the body must be trained in tandem. That love without strength is a leaf in the wind.
We did not become a militant world. We became a watchful one. Our children were taught martial discipline—not to glorify violence, but to understand it, to confront it, and to defeat it when necessary. They learned meditation alongside hand-to-hand technique, negotiation beside tactical reasoning.
When we joined the Federation, we did so willingly. But let none assume we surrendered our right to defend our way of life.
Why I Speak to You Now
The Borg are not like the Orion Syndicate. They are not opportunistic, or ideological. They are methodical. And they are coming. You cannot debate with them. You cannot delay them. You can only prepare for them.
And yet, I hear murmurs within the halls of the Federation: whispers of abandoning planetary defense training, of downplaying the psychological need for individual and planetary preparedness. I hear the tired lie that “peace will protect us.”
No, Councilors. It is discipline that protects peace.
The Call to Action
I do not come bearing weapons. I come bearing wisdom. Let us take the Risan lesson and apply it across the Federation. Reestablish tactical readiness training in civilian schools. Encourage planetary governments to integrate defense and philosophy, not as contradictions, but as complements.
Let every child of the Federation grow up knowing not just the principles of liberty, but the means to defend them. Let every artist, scientist, and healer stand ready to protect the civilization they help to build.
Let us not wait until the Borg are in our orbit to remember what we must become.
Conclusion
The Borg seek to erase our uniqueness. Let us show them that the Federation is not a fragile collection of planets—but a constellation of cultures bound by a shared resolve.
We do not choose war. But neither do we flee from it.
We are the guardians of Risa’s flame—and we offer our light to the stars.
Thank you.
-
 @ 4ba8e86d:89d32de4
2025-04-21 02:13:56
@ 4ba8e86d:89d32de4
2025-04-21 02:13:56Tutorial feito por nostr:nostr:npub1rc56x0ek0dd303eph523g3chm0wmrs5wdk6vs0ehd0m5fn8t7y4sqra3tk poste original abaixo:
Parte 1 : http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/263585/tutorial-debloat-de-celulares-android-via-adb-parte-1
Parte 2 : http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/index.php/263586/tutorial-debloat-de-celulares-android-via-adb-parte-2
Quando o assunto é privacidade em celulares, uma das medidas comumente mencionadas é a remoção de bloatwares do dispositivo, também chamado de debloat. O meio mais eficiente para isso sem dúvidas é a troca de sistema operacional. Custom Rom’s como LineageOS, GrapheneOS, Iodé, CalyxOS, etc, já são bastante enxutos nesse quesito, principalmente quanto não é instalado os G-Apps com o sistema. No entanto, essa prática pode acabar resultando em problemas indesejados como a perca de funções do dispositivo, e até mesmo incompatibilidade com apps bancários, tornando este método mais atrativo para quem possui mais de um dispositivo e separando um apenas para privacidade. Pensando nisso, pessoas que possuem apenas um único dispositivo móvel, que são necessitadas desses apps ou funções, mas, ao mesmo tempo, tem essa visão em prol da privacidade, buscam por um meio-termo entre manter a Stock rom, e não ter seus dados coletados por esses bloatwares. Felizmente, a remoção de bloatwares é possível e pode ser realizada via root, ou mais da maneira que este artigo irá tratar, via adb.
O que são bloatwares?
Bloatware é a junção das palavras bloat (inchar) + software (programa), ou seja, um bloatware é basicamente um programa inútil ou facilmente substituível — colocado em seu dispositivo previamente pela fabricante e operadora — que está no seu dispositivo apenas ocupando espaço de armazenamento, consumindo memória RAM e pior, coletando seus dados e enviando para servidores externos, além de serem mais pontos de vulnerabilidades.
O que é o adb?
O Android Debug Brigde, ou apenas adb, é uma ferramenta que se utiliza das permissões de usuário shell e permite o envio de comandos vindo de um computador para um dispositivo Android exigindo apenas que a depuração USB esteja ativa, mas também pode ser usada diretamente no celular a partir do Android 11, com o uso do Termux e a depuração sem fio (ou depuração wifi). A ferramenta funciona normalmente em dispositivos sem root, e também funciona caso o celular esteja em Recovery Mode.
Requisitos:
Para computadores:
• Depuração USB ativa no celular; • Computador com adb; • Cabo USB;
Para celulares:
• Depuração sem fio (ou depuração wifi) ativa no celular; • Termux; • Android 11 ou superior;
Para ambos:
• Firewall NetGuard instalado e configurado no celular; • Lista de bloatwares para seu dispositivo;
Ativação de depuração:
Para ativar a Depuração USB em seu dispositivo, pesquise como ativar as opções de desenvolvedor de seu dispositivo, e lá ative a depuração. No caso da depuração sem fio, sua ativação irá ser necessária apenas no momento que for conectar o dispositivo ao Termux.
Instalação e configuração do NetGuard
O NetGuard pode ser instalado através da própria Google Play Store, mas de preferência instale pela F-Droid ou Github para evitar telemetria.
F-Droid: https://f-droid.org/packages/eu.faircode.netguard/
Github: https://github.com/M66B/NetGuard/releases
Após instalado, configure da seguinte maneira:
Configurações → padrões (lista branca/negra) → ative as 3 primeiras opções (bloquear wifi, bloquear dados móveis e aplicar regras ‘quando tela estiver ligada’);
Configurações → opções avançadas → ative as duas primeiras (administrar aplicativos do sistema e registrar acesso a internet);
Com isso, todos os apps estarão sendo bloqueados de acessar a internet, seja por wifi ou dados móveis, e na página principal do app basta permitir o acesso a rede para os apps que você vai usar (se necessário). Permita que o app rode em segundo plano sem restrição da otimização de bateria, assim quando o celular ligar, ele já estará ativo.
Lista de bloatwares
Nem todos os bloatwares são genéricos, haverá bloatwares diferentes conforme a marca, modelo, versão do Android, e até mesmo região.
Para obter uma lista de bloatwares de seu dispositivo, caso seu aparelho já possua um tempo de existência, você encontrará listas prontas facilmente apenas pesquisando por elas. Supondo que temos um Samsung Galaxy Note 10 Plus em mãos, basta pesquisar em seu motor de busca por:
Samsung Galaxy Note 10 Plus bloatware listProvavelmente essas listas já terão inclusas todos os bloatwares das mais diversas regiões, lhe poupando o trabalho de buscar por alguma lista mais específica.
Caso seu aparelho seja muito recente, e/ou não encontre uma lista pronta de bloatwares, devo dizer que você acaba de pegar em merda, pois é chato para um caralho pesquisar por cada aplicação para saber sua função, se é essencial para o sistema ou se é facilmente substituível.
De antemão já aviso, que mais para frente, caso vossa gostosura remova um desses aplicativos que era essencial para o sistema sem saber, vai acabar resultando na perda de alguma função importante, ou pior, ao reiniciar o aparelho o sistema pode estar quebrado, lhe obrigando a seguir com uma formatação, e repetir todo o processo novamente.
Download do adb em computadores
Para usar a ferramenta do adb em computadores, basta baixar o pacote chamado SDK platform-tools, disponível através deste link: https://developer.android.com/tools/releases/platform-tools. Por ele, você consegue o download para Windows, Mac e Linux.
Uma vez baixado, basta extrair o arquivo zipado, contendo dentro dele uma pasta chamada platform-tools que basta ser aberta no terminal para se usar o adb.
Download do adb em celulares com Termux.
Para usar a ferramenta do adb diretamente no celular, antes temos que baixar o app Termux, que é um emulador de terminal linux, e já possui o adb em seu repositório. Você encontra o app na Google Play Store, mas novamente recomendo baixar pela F-Droid ou diretamente no Github do projeto.
F-Droid: https://f-droid.org/en/packages/com.termux/
Github: https://github.com/termux/termux-app/releases
Processo de debloat
Antes de iniciarmos, é importante deixar claro que não é para você sair removendo todos os bloatwares de cara sem mais nem menos, afinal alguns deles precisam antes ser substituídos, podem ser essenciais para você para alguma atividade ou função, ou até mesmo são insubstituíveis.
Alguns exemplos de bloatwares que a substituição é necessária antes da remoção, é o Launcher, afinal, é a interface gráfica do sistema, e o teclado, que sem ele só é possível digitar com teclado externo. O Launcher e teclado podem ser substituídos por quaisquer outros, minha recomendação pessoal é por aqueles que respeitam sua privacidade, como Pie Launcher e Simple Laucher, enquanto o teclado pelo OpenBoard e FlorisBoard, todos open-source e disponíveis da F-Droid.
Identifique entre a lista de bloatwares, quais você gosta, precisa ou prefere não substituir, de maneira alguma você é obrigado a remover todos os bloatwares possíveis, modifique seu sistema a seu bel-prazer. O NetGuard lista todos os apps do celular com o nome do pacote, com isso você pode filtrar bem qual deles não remover.
Um exemplo claro de bloatware insubstituível e, portanto, não pode ser removido, é o com.android.mtp, um protocolo onde sua função é auxiliar a comunicação do dispositivo com um computador via USB, mas por algum motivo, tem acesso a rede e se comunica frequentemente com servidores externos. Para esses casos, e melhor solução mesmo é bloquear o acesso a rede desses bloatwares com o NetGuard.
MTP tentando comunicação com servidores externos:
Executando o adb shell
No computador
Faça backup de todos os seus arquivos importantes para algum armazenamento externo, e formate seu celular com o hard reset. Após a formatação, e a ativação da depuração USB, conecte seu aparelho e o pc com o auxílio de um cabo USB. Muito provavelmente seu dispositivo irá apenas começar a carregar, por isso permita a transferência de dados, para que o computador consiga se comunicar normalmente com o celular.
Já no pc, abra a pasta platform-tools dentro do terminal, e execute o seguinte comando:
./adb start-serverO resultado deve ser:
daemon not running; starting now at tcp:5037 daemon started successfully
E caso não apareça nada, execute:
./adb kill-serverE inicie novamente.
Com o adb conectado ao celular, execute:
./adb shellPara poder executar comandos diretamente para o dispositivo. No meu caso, meu celular é um Redmi Note 8 Pro, codinome Begonia.
Logo o resultado deve ser:
begonia:/ $
Caso ocorra algum erro do tipo:
adb: device unauthorized. This adb server’s $ADB_VENDOR_KEYS is not set Try ‘adb kill-server’ if that seems wrong. Otherwise check for a confirmation dialog on your device.
Verifique no celular se apareceu alguma confirmação para autorizar a depuração USB, caso sim, autorize e tente novamente. Caso não apareça nada, execute o kill-server e repita o processo.
No celular
Após realizar o mesmo processo de backup e hard reset citado anteriormente, instale o Termux e, com ele iniciado, execute o comando:
pkg install android-toolsQuando surgir a mensagem “Do you want to continue? [Y/n]”, basta dar enter novamente que já aceita e finaliza a instalação
Agora, vá até as opções de desenvolvedor, e ative a depuração sem fio. Dentro das opções da depuração sem fio, terá uma opção de emparelhamento do dispositivo com um código, que irá informar para você um código em emparelhamento, com um endereço IP e porta, que será usado para a conexão com o Termux.
Para facilitar o processo, recomendo que abra tanto as configurações quanto o Termux ao mesmo tempo, e divida a tela com os dois app’s, como da maneira a seguir:
Para parear o Termux com o dispositivo, não é necessário digitar o ip informado, basta trocar por “localhost”, já a porta e o código de emparelhamento, deve ser digitado exatamente como informado. Execute:
adb pair localhost:porta CódigoDeEmparelhamentoDe acordo com a imagem mostrada anteriormente, o comando ficaria “adb pair localhost:41255 757495”.
Com o dispositivo emparelhado com o Termux, agora basta conectar para conseguir executar os comandos, para isso execute:
adb connect localhost:portaObs: a porta que você deve informar neste comando não é a mesma informada com o código de emparelhamento, e sim a informada na tela principal da depuração sem fio.
Pronto! Termux e adb conectado com sucesso ao dispositivo, agora basta executar normalmente o adb shell:
adb shellRemoção na prática Com o adb shell executado, você está pronto para remover os bloatwares. No meu caso, irei mostrar apenas a remoção de um app (Google Maps), já que o comando é o mesmo para qualquer outro, mudando apenas o nome do pacote.
Dentro do NetGuard, verificando as informações do Google Maps:
Podemos ver que mesmo fora de uso, e com a localização do dispositivo desativado, o app está tentando loucamente se comunicar com servidores externos, e informar sabe-se lá que peste. Mas sem novidades até aqui, o mais importante é que podemos ver que o nome do pacote do Google Maps é com.google.android.apps.maps, e para o remover do celular, basta executar:
pm uninstall –user 0 com.google.android.apps.mapsE pronto, bloatware removido! Agora basta repetir o processo para o resto dos bloatwares, trocando apenas o nome do pacote.
Para acelerar o processo, você pode já criar uma lista do bloco de notas com os comandos, e quando colar no terminal, irá executar um atrás do outro.
Exemplo de lista:
Caso a donzela tenha removido alguma coisa sem querer, também é possível recuperar o pacote com o comando:
cmd package install-existing nome.do.pacotePós-debloat
Após limpar o máximo possível o seu sistema, reinicie o aparelho, caso entre no como recovery e não seja possível dar reboot, significa que você removeu algum app “essencial” para o sistema, e terá que formatar o aparelho e repetir toda a remoção novamente, desta vez removendo poucos bloatwares de uma vez, e reiniciando o aparelho até descobrir qual deles não pode ser removido. Sim, dá trabalho… quem mandou querer privacidade?
Caso o aparelho reinicie normalmente após a remoção, parabéns, agora basta usar seu celular como bem entender! Mantenha o NetGuard sempre executando e os bloatwares que não foram possíveis remover não irão se comunicar com servidores externos, passe a usar apps open source da F-Droid e instale outros apps através da Aurora Store ao invés da Google Play Store.
Referências: Caso você seja um Australopithecus e tenha achado este guia difícil, eis uma videoaula (3:14:40) do Anderson do canal Ciberdef, realizando todo o processo: http://odysee.com/@zai:5/Como-remover-at%C3%A9-200-APLICATIVOS-que-colocam-a-sua-PRIVACIDADE-E-SEGURAN%C3%87A-em-risco.:4?lid=6d50f40314eee7e2f218536d9e5d300290931d23
Pdf’s do Anderson citados na videoaula: créditos ao anon6837264 http://eternalcbrzpicytj4zyguygpmkjlkddxob7tptlr25cdipe5svyqoqd.onion/file/3863a834d29285d397b73a4af6fb1bbe67c888d72d30/t-05e63192d02ffd.pdf
Processo de instalação do Termux e adb no celular: https://youtu.be/APolZrPHSms
-
 @ 4ba8e86d:89d32de4
2025-04-21 02:12:19
@ 4ba8e86d:89d32de4
2025-04-21 02:12:19SISTEMA OPERACIONAL MÓVEIS
GrapheneOS : https://njump.me/nevent1qqs8t76evdgrg4qegdtyrq2rved63pr29wlqyj627n9tj4vlu66tqpqpzdmhxue69uhk7enxvd5xz6tw9ec82c30qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqppcqec9
CalyxOS : https://njump.me/nevent1qqsrm0lws2atln2kt3cqjacathnw0uj0jsxwklt37p7t380hl8mmstcpydmhxue69uhkummnw3ez6an9wf5kv6t9vsh8wetvd3hhyer9wghxuet59uq3vamnwvaz7tmwdaehgu3wvf3kstnwd9hx5cf0qy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qgcwaehxw309aex2mrp0yhxxatjwfjkuapwveukjtcpzpmhxue69uhkummnw3ezumt0d5hszrnhwden5te0dehhxtnvdakz7qfywaehxw309ahx7um5wgh8ymm4dej8ymmrdd3xjarrda5kuetjwvhxxmmd9uq3uamnwvaz7tmwdaehgu3dv3jhvtnhv4kxcmmjv3jhytnwv46z7qghwaehxw309aex2mrp0yhxummnw3ezucnpdejz7qgewaehxw309ahx7um5wghxymmwva3x7mn89e3k7mf0qythwumn8ghj7cn5vvhxkmr9dejxz7n49e3k7mf0qyg8wumn8ghj7mn09eehgu3wvdez7smttdu
LineageOS : https://njump.me/nevent1qqsgw7sr36gaty48cf4snw0ezg5mg4atzhqayuge752esd469p26qfgpzdmhxue69uhhwmm59e6hg7r09ehkuef0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpnvm779
SISTEMA OPERACIONAL DESKTOP
Tails : https://njump.me/nevent1qqsf09ztvuu60g6xprazv2vxqqy5qlxjs4dkc9d36ta48q75cs9le4qpzemhxue69uhkummnw3ex2mrfw3jhxtn0wfnj7q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqz34ag5t
Qubes OS : https://njump.me/nevent1qqsp6jujgwl68uvurw0cw3hfhr40xq20sj7rl3z4yzwnhp9sdpa7augpzpmhxue69uhkummnw3ezumt0d5hsz9mhwden5te0wfjkccte9ehx7um5wghxyctwvshsz9thwden5te0dehhxarj9ehhsarj9ejx2a30qyg8wumn8ghj7mn09eehgu3wvdez7qg4waehxw309aex2mrp0yhxgctdw4eju6t09uqjxamnwvaz7tmwdaehgu3dwejhy6txd9jkgtnhv4kxcmmjv3jhytnwv46z7qgwwaehxw309ahx7uewd3hkctcpremhxue69uhkummnw3ez6er9wch8wetvd3hhyer9wghxuet59uj3ljr8
Kali linux : https://njump.me/nevent1qqswlav72xdvamuyp9xc38c6t7070l3n2uxu67ssmal2g7gv35nmvhspzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqswt9rxe
Whonix : https://njump.me/nevent1qqs85gvejvzhk086lwh6edma7fv07p5c3wnwnxnzthwwntg2x6773egpydmhxue69uhkummnw3ez6an9wf5kv6t9vsh8wetvd3hhyer9wghxuet59uq3qamnwvaz7tmwdaehgu3wd4hk6tcpzemhxue69uhkummnw3ezucnrdqhxu6twdfsj7qfywaehxw309ahx7um5wgh8ymm4dej8ymmrdd3xjarrda5kuetjwvhxxmmd9uq3wamnwvaz7tmzw33ju6mvv4hxgct6w5hxxmmd9uq3qamnwvaz7tmwduh8xarj9e3hytcpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhszrnhwden5te0dehhxtnvdakz7qg7waehxw309ahx7um5wgkkgetk9emk2mrvdaexgetj9ehx2ap0sen9p6
Kodachi : https://njump.me/nevent1qqsf5zszgurpd0vwdznzk98hck294zygw0s8dah6fpd309ecpreqtrgpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhszgmhwden5te0dehhxarj94mx2unfve5k2epwwajkcmr0wfjx2u3wdejhgtcpremhxue69uhkummnw3ez6er9wch8wetvd3hhyer9wghxuet59uq3qamnwvaz7tmwdaehgu3wd4hk6tcpzamhxue69uhkyarr9e4kcetwv3sh5afwvdhk6tcpzpmhxue69uhkumewwd68ytnrwghszfrhwden5te0dehhxarj9eex7atwv3ex7cmtvf5hgcm0d9hx2unn9e3k7mf0qyvhwumn8ghj7mn0wd68ytnzdahxwcn0denjucm0d5hszrnhwden5te0dehhxtnvdakz7qgkwaehxw309ahx7um5wghxycmg9ehxjmn2vyhsz9mhwden5te0wfjkccte9ehx7um5wghxyctwvshs94a4d5
PGP
Openkeychain : https://njump.me/nevent1qqs9qtjgsulp76t7jkquf8nk8txs2ftsr0qke6mjmsc2svtwfvswzyqpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs36mp0w
Kleopatra : https://njump.me/nevent1qqspnevn932hdggvp4zam6mfyce0hmnxsp9wp8htpumq9vm3anq6etsppemhxue69uhkummn9ekx7mp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpuaeghp
Pgp : https://njump.me/nevent1qqsggek707qf3rzttextmgqhym6d4g479jdnlnj78j96y0ut0x9nemcpzamhxue69uhhyetvv9ujuurjd9kkzmpwdejhgtczyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgptemhe
Como funciona o PGP? : https://njump.me/nevent1qqsz9r7azc8pkvfmkg2hv0nufaexjtnvga0yl85x9hu7ptpg20gxxpspremhxue69uhkummnw3ez6ur4vgh8wetvd3hhyer9wghxuet59upzqjagapkjm9ufdhynxlp72qrfrzfawvt4wt7cr795rhw6tkyaxt0yqvzqqqqqqy259fhs
Por que eu escrevi PGP. - Philip Zimmermann.
https://njump.me/nevent1qqsvysn94gm8prxn3jw04r0xwc6sngkskg756z48jsyrmqssvxtm7ncpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtchzxnad
VPN
Vpn : https://njump.me/nevent1qqs27ltgsr6mh4ffpseexz6s37355df3zsur709d0s89u2nugpcygsspzpmhxue69uhkummnw3ezumt0d5hsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqshzu2fk
InviZible Pro : https://njump.me/nevent1qqsvyevf2vld23a3xrpvarc72ndpcmfvc3lc45jej0j5kcsg36jq53cpz3mhxue69uhhyetvv9ujuerpd46hxtnfdupzqjagapkjm9ufdhynxlp72qrfrzfawvt4wt7cr795rhw6tkyaxt0yqvzqqqqqqy33y5l4
Orbot: https://njump.me/nevent1qqsxswkyt6pe34egxp9w70cy83h40ururj6m9sxjdmfass4cjm4495stft593
I2P
i2p : https://njump.me/nevent1qqsvnj8n983r4knwjmnkfyum242q4c0cnd338l4z8p0m6xsmx89mxkslx0pgg
Entendendo e usando a rede I2P : https://njump.me/nevent1qqsxchp5ycpatjf5s4ag25jkawmw6kkf64vl43vnprxdcwrpnms9qkcppemhxue69uhkummn9ekx7mp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpvht4mn
Criando e acessando sua conta Email na I2P : https://njump.me/nevent1qqs9v9dz897kh8e5lfar0dl7ljltf2fpdathsn3dkdsq7wg4ksr8xfgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpw8mzum
APLICATIVO 2FA
Aegis Authenticator : https://njump.me/nevent1qqsfttdwcn9equlrmtf9n6wee7lqntppzm03pzdcj4cdnxel3pz44zspz4mhxue69uhhyetvv9ujumn0wd68ytnzvuhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqscvtydq
YubiKey : https://njump.me/nevent1qqstsnn69y4sf4330n7039zxm7wza3ch7sn6plhzmd57w6j9jssavtspvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzueyvgt
GERENCIADOR DE SENHAS
KeepassDX: https://njump.me/nevent1qqswc850dr4ujvxnmpx75jauflf4arc93pqsty5pv8hxdm7lcw8ee8qpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpe0492n
Birwaden: https://njump.me/nevent1qqs0j5x9guk2v6xumhwqmftmcz736m9nm9wzacqwjarxmh8k4xdyzwgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpwfe2kc
KeePassXC: https://njump.me/nevent1qqsgftcrd8eau7tzr2p9lecuaf7z8mx5jl9w2k66ae3lzkw5wqcy5pcl2achp
CHAT MENSAGEM
SimpleXchat : https://njump.me/nevent1qqsds5xselnnu0dyy0j49peuun72snxcgn3u55d2320n37rja9gk8lgzyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgmcmj7c
Briar : https://njump.me/nevent1qqs8rrtgvjr499hreugetrl7adkhsj2zextyfsukq5aa7wxthrgcqcg05n434
Element Messenger : https://njump.me/nevent1qqsq05snlqtxm5cpzkshlf8n5d5rj9383vjytkvqp5gta37hpuwt4mqyccee6
Pidgin : https://njump.me/nevent1qqsz7kngycyx7meckx53xk8ahk98jkh400usrvykh480xa4ct9zlx2c2ywvx3
E-MAIL
Thunderbird: https://njump.me/nevent1qqspq64gg0nw7t60zsvea5eykgrm43paz845e4jn74muw5qzdvve7uqrkwtjh
ProtonMail : https://njump.me/nevent1qqs908glhk68e7ms8zqtlsqd00wu3prnpt08dwre26hd6e5fhqdw99cppemhxue69uhkummn9ekx7mp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpeyhg4z
Tutonota : https://njump.me/nevent1qqswtzh9zjxfey644qy4jsdh9465qcqd2wefx0jxa54gdckxjvkrrmqpz4mhxue69uhhyetvv9ujumt0wd68ytnsw43qygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs5hzhkv
k-9 mail : https://njump.me/nevent1qqs200g5a603y7utjgjk320r3srurrc4r66nv93mcg0x9umrw52ku5gpr3mhxue69uhkummnw3ezuumhd9ehxtt9de5kwmtp9e3kstczyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgacflak
E-MAIL-ALIÁS
Simplelogin : https://njump.me/nevent1qqsvhz5pxqpqzr2ptanqyqgsjr50v7u9lc083fvdnglhrv36rnceppcppemhxue69uhkummn9ekx7mp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqp9gsr7m
AnonAddy : https://njump.me/nevent1qqs9mcth70mkq2z25ws634qfn7vx2mlva3tkllayxergw0s7p8d3ggcpzpmhxue69uhkummnw3ezumt0d5hsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs6mawe3
NAVEGADOR
Navegador Tor : https://njump.me/nevent1qqs06qfxy7wzqmk76l5d8vwyg6mvcye864xla5up52fy5sptcdy39lspzemhxue69uhkummnw3ezuerpw3sju6rpw4ej7q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzdp0urw
Mullvap Browser : https://njump.me/nevent1qqs2vsgc3wk09wdspv2mezltgg7nfdg97g0a0m5cmvkvr4nrfxluzfcpzdmhxue69uhhwmm59e6hg7r09ehkuef0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpj8h6fe
LibreWolf : https://njump.me/nevent1qqswv05mlmkcuvwhe8x3u5f0kgwzug7n2ltm68fr3j06xy9qalxwq2cpzemhxue69uhkummnw3ex2mrfw3jhxtn0wfnj7q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzuv2hxr
Cromite : https://njump.me/nevent1qqs2ut83arlu735xp8jf87w5m3vykl4lv5nwkhldkqwu3l86khzzy4cpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs3dplt7
BUSCADORES
Searx : https://njump.me/nevent1qqsxyzpvgzx00n50nrlgctmy497vkm2cm8dd5pdp7fmw6uh8xnxdmaspr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqp23z7ax
APP-STORE
Obtainium : https://njump.me/nevent1qqstd8kzc5w3t2v6dgf36z0qrruufzfgnc53rj88zcjgsagj5c5k4rgpz3mhxue69uhhyetvv9ujuerpd46hxtnfdupzqjagapkjm9ufdhynxlp72qrfrzfawvt4wt7cr795rhw6tkyaxt0yqvzqqqqqqyarmca3
F-Droid : https://njump.me/nevent1qqst4kry49cc9g3g8s5gdnpgyk3gjte079jdnv43f0x4e85cjkxzjesymzuu4
Droid-ify : https://njump.me/nevent1qqsrr8yu9luq0gud902erdh8gw2lfunpe93uc2u6g8rh9ep7wt3v4sgpzpmhxue69uhkummnw3ezumt0d5hsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsfzu9vk
Aurora Store : https://njump.me/nevent1qqsy69kcaf0zkcg0qnu90mtk46ly3p2jplgpzgk62wzspjqjft4fpjgpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzrpmsjy
RSS
Feeder : https://njump.me/nevent1qqsy29aeggpkmrc7t3c7y7ldgda7pszl7c8hh9zux80gjzrfvlhfhwqpp4mhxue69uhkummn9ekx7mqzyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgsvzzjy
VIDEOO CONFERENCIA
Jitsi meet : https://njump.me/nevent1qqswphw67hr6qmt2fpugcj77jrk7qkfdrszum7vw7n2cu6cx4r6sh4cgkderr
TECLADOS
HeliBoard : https://njump.me/nevent1qqsyqpc4d28rje03dcvshv4xserftahhpeylu2ez2jutdxwds4e8syspz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsr8mel5
OpenBoard : https://njump.me/nevent1qqsf7zqkup03yysy67y43nj48q53sr6yym38es655fh9fp6nxpl7rqspzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqswcvh3r
FlorisBoard : https://njump.me/nevent1qqsf7zqkup03yysy67y43nj48q53sr6yym38es655fh9fp6nxpl7rqspzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqswcvh3r
MAPAS
Osmand : https://njump.me/nevent1qqsxryp2ywj64az7n5p6jq5tn3tx5jv05te48dtmmt3lf94ydtgy4fgpzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs54nwpj
Organic maps : https://njump.me/nevent1qqstrecuuzkw0dyusxdq7cuwju0ftskl7anx978s5dyn4pnldrkckzqpr4mhxue69uhkummnw3ezumtp0p5k6ctrd96xzer9dshx7un8qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpl8z3kk
TRADUÇÃO
LibreTranslate : https://njump.me/nevent1qqs953g3rhf0m8jh59204uskzz56em9xdrjkelv4wnkr07huk20442cpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzeqsx40
REMOÇÃO DOS METADADOS
Scrambled Exif : https://njump.me/nevent1qqs2658t702xv66p000y4mlhnvadmdxwzzfzcjkjf7kedrclr3ej7aspyfmhxue69uhk6atvw35hqmr90pjhytngw4eh5mmwv4nhjtnhdaexcep0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpguu0wh
ESTEGANOGRAFIA
PixelKnot: https://njump.me/nevent1qqsrh0yh9mg0lx86t5wcmhh97wm6n4v0radh6sd0554ugn354wqdj8gpz3mhxue69uhhyetvv9ujuerpd46hxtnfdupzqjagapkjm9ufdhynxlp72qrfrzfawvt4wt7cr795rhw6tkyaxt0yqvzqqqqqqyuvfqdp
PERFIL DE TRABALHO
Shelter : https://njump.me/nevent1qqspv9xxkmfp40cxgjuyfsyczndzmpnl83e7gugm7480mp9zhv50wkqpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzdnu59c
PDF
MuPDF : https://njump.me/nevent1qqspn5lhe0dteys6npsrntmv2g470st8kh8p7hxxgmymqa95ejvxvfcpzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs4hvhvj
Librera Reader : https://njump.me/nevent1qqsg60flpuf00sash48fexvwxkly2j5z9wjvjrzt883t3eqng293f3cpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqz39tt3n
QR-Code
Binary Eye : https://njump.me/nevent1qqsz4n0uxxx3q5m0r42n9key3hchtwyp73hgh8l958rtmae5u2khgpgpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzdmn4wp
Climático
Breezy Weather : https://njump.me/nevent1qqs9hjz5cz0y4am3kj33xn536uq85ydva775eqrml52mtnnpe898rzspzamhxue69uhhyetvv9ujuurjd9kkzmpwdejhgtczyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgpd3tu8
ENCRYPTS
Cryptomator : https://njump.me/nevent1qqsvchvnw779m20583llgg5nlu6ph5psewetlczfac5vgw83ydmfndspzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsx7ppw9
VeraCrypt : https://njump.me/nevent1qqsf6wzedsnrgq6hjk5c4jj66dxnplqwc4ygr46l8z3gfh38q2fdlwgm65ej3
EXTENSÕES
uBlock Origin : https://njump.me/nevent1qqswaa666lcj2c4nhnea8u4agjtu4l8q89xjln0yrngj7ssh72ntwzql8ssdj
Snowflake : https://njump.me/nevent1qqs0ws74zlt8uced3p2vee9td8x7vln2mkacp8szdufvs2ed94ctnwchce008
CLOUD
Nextcloud : https://njump.me/nevent1qqs2utg5z9htegdtrnllreuhypkk2026x8a0xdsmfczg9wdl8rgrcgg9nhgnm
NOTEPAD
Joplin : https://njump.me/nevent1qqsz2a0laecpelsznser3xd0jfa6ch2vpxtkx6vm6qg24e78xttpk0cpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpdu0hft
Standard Notes : https://njump.me/nevent1qqsv3596kz3qung5v23cjc4cpq7rqxg08y36rmzgcrvw5whtme83y3s7tng6r
MÚSICA
RiMusic : https://njump.me/nevent1qqsv3genqav2tfjllp86ust4umxm8tr2wd9kq8x7vrjq6ssp363mn0gpzamhxue69uhhyetvv9ujuurjd9kkzmpwdejhgtczyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqg42353n
ViMusic : https://njump.me/nevent1qqswx78559l4jsxsrygd8kj32sch4qu57stxq0z6twwl450vp39pdqqpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzjg863j
PODCAST
AntennaPod : https://njump.me/nevent1qqsp4nh7k4a6zymfwqqdlxuz8ua6kdhvgeeh3uxf2c9rtp9u3e9ku8qnr8lmy
VISUALIZAR VIDEO
VLC : https://njump.me/nevent1qqs0lz56wtlr2eye4ajs2gzn2r0dscw4y66wezhx0mue6dffth8zugcl9laky
YOUTUBE
NewPipe : https://njump.me/nevent1qqsdg06qpcjdnlvgm4xzqdap0dgjrkjewhmh4j3v4mxdl4rjh8768mgdw9uln
FreeTube : https://njump.me/nevent1qqsz6y6z7ze5gs56s8seaws8v6m6j2zu0pxa955dhq3ythmexak38mcpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs5lkjvv
LibreTube : https://snort.social/e/nevent1qqstmd5m6wrdvn4gxf8xyhrwnlyaxmr89c9kjddvnvux6603f84t3fqpz4mhxue69uhhyetvv9ujumt0wd68ytnsw43qygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsswwznc
COMPARTILHAMENTO DE ARQUIVOS
OnionShare : https://njump.me/nevent1qqsr0a4ml5nu6ud5k9yzyawcd9arznnwkrc27dzzc95q6r50xmdff6qpydmhxue69uhkummnw3ez6an9wf5kv6t9vsh8wetvd3hhyer9wghxuet59uq3uamnwvaz7tmwdaehgu3dv3jhvtnhv4kxcmmjv3jhytnwv46z7qgswaehxw309ahx7tnnw3ezucmj9uq32amnwvaz7tmjv4kxz7fwv3sk6atn9e5k7tcpzamhxue69uhkyarr9e4kcetwv3sh5afwvdhk6tcpzemhxue69uhkummnw3ezucnrdqhxu6twdfsj7qgswaehxw309ahx7um5wghx6mmd9uqjgamnwvaz7tmwdaehgu3wwfhh2mnywfhkx6mzd96xxmmfdejhyuewvdhk6tcppemhxue69uhkummn9ekx7mp0qythwumn8ghj7un9d3shjtnwdaehgu3wvfskuep0qyv8wumn8ghj7un9d3shjtnrw4e8yetwwshxv7tf9ut7qurt
Localsend : https://njump.me/nevent1qqsp8ldjhrxm09cvvcak20hrc0g8qju9f67pw7rxr2y3euyggw9284gpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzuyghqr
Wallet Bitcoin
Ashigaru Wallet : https://njump.me/nevent1qqstx9fz8kf24wgl26un8usxwsqjvuec9f8q392llmga75tw0kfarfcpzamhxue69uhhyetvv9ujuurjd9kkzmpwdejhgtczyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgvfsrqp
Samourai Wallet : https://njump.me/nevent1qqstcvjmz39rmrnrv7t5cl6p3x7pzj6jsspyh4s4vcwd2lugmre04ecpr9mhxue69uhkummnw3ezucn0denkymmwvuhxxmmd9upzqjagapkjm9ufdhynxlp72qrfrzfawvt4wt7cr795rhw6tkyaxt0yqvzqqqqqqy3rg4qs
CÂMERA
opencamera : https://njump.me/nevent1qqs25glp6dh0crrjutxrgdjlnx9gtqpjtrkg29hlf7382aeyjd77jlqpzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqssxcvgc
OFFICE
Collabora Office : https://njump.me/nevent1qqs8yn4ys6adpmeu3edmf580jhc3wluvlf823cc4ft4h0uqmfzdf99qpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsj40uss
TEXTOS
O manifesto de um Cypherpunk : https://njump.me/nevent1qqsd7hdlg6galn5mcuv3pm3ryfjxc4tkyph0cfqqe4du4dr4z8amqyspvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzal0efa
Operations security ( OPSEC) : https://snort.social/e/nevent1qqsp323havh3y9nxzd4qmm60hw87tm9gjns0mtzg8y309uf9mv85cqcpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqz8ej9l7
O MANIFESTO CRIPTOANARQUISTA Timothy C. May – 1992. : https://njump.me/nevent1qqspp480wtyx2zhtwpu5gptrl8duv9rvq3mug85mp4d54qzywk3zq9gpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqz5wq496
Declaração de independência do ciberespaço
- John Perry Barlow - 1996 : https://njump.me/nevent1qqs2njsy44n6p07mhgt2tnragvchasv386nf20ua5wklxqpttf6mzuqpzpmhxue69uhkummnw3ezumt0d5hsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsukg4hr
The Cyphernomicon: Criptografia, Dinheiro Digital e o Futuro da Privacidade. escrito por Timothy C. May -Publicado em 1994. :
Livro completo em PDF no Github PrivacyOpenSource.
https://github.com/Alexemidio/PrivacyOpenSource/raw/main/Livros/THE%20CYPHERNOMICON%20.pdf Share
-
 @ c9badfea:610f861a
2025-05-12 16:29:32
@ c9badfea:610f861a
2025-05-12 16:29:32- Install Organic Maps
- Launch the app and download the World Map first
- Tap the ☰ at the bottom, then select Download Maps, and tap the + icon
- Download maps by tapping ⤓ next to your desired region
- Return to the main screen and tap 🔍 to search for your destination
- Enjoy navigating offline
ℹ️ Note that Organic Maps does not provide live traffic updates
-
 @ 51faaa77:2c26615b
2025-05-12 17:34:37
@ 51faaa77:2c26615b
2025-05-12 17:34:37My goal is to share a concise list of questions about OP_RETURN limits that we've answered on Stacker News, as the original thread has become unwieldy with over 200 comments. We began compiling this list about a week ago. I've frequently shared individual links and received very positive feedback. I hope this resource helps us work from a common set of facts and reduces misinformation. I hope you find this as a valuable resource.
I'll list the questions in order of activity and tips received. I've removed duplicates, rephrased some statements as questions, and ignored completely irrelevant questions.
- Users should be given clear configurable options to decide what's in their mempool, why were these options taken away? link
- Won't spammers abuse large OP_RETURNs to bloat the blockchain and make IBD take longer? link
- A similar PR was proposed by Peter Todd 2 years ago, why was it rejected then? What has changed since then, why would this get approved now? link
- Shouldn't we be fighting spam, why are we making policies less strict, shouldn't we be making them more strict? link
- How would someone get around the standardness policy currently for OP_RETURN size? link
- What does "standardness mean" in reference to OP_RETURNs? link
- Will more than 1 OP_RETURN per transaction be possible if this PR gets merged? link
- What are the current OP_RETURN limits and what restrictions are being lifted? link
- Are current relay and mempool policies effective for filtering out spam transactions? link
- Is it true that this type of update could affect Bitcoin's decentralization? link
- Is it possible to stop the abuse of payment outputs (i.e., bare multisig, fake pubkeys, and fake pubkey hashes) that are used to embed data, thereby creating unprunable UTXOs that bloat the UTXO set? link
- What was the main reason /concern to add this PR? ... What will happen if we do nothing? link
- If OP_RETURN still cannot stop all the garbage, why is so important to remove it? Does it affect future development / improvements for LN? link
- What will be the worst case scenario if users still could set their own limits for OP_RETURN? link
- Shouldn't we debate the controversy of this PR on Github since it's where the code gets merged to make these changes? link
- What does it mean when someone says "Fix the Filters"? link
- Will this open the flood gates and drown out all legitimate onchain activity? link
- What can we do to stop spam at the consensus layer of Bitcoin? link
- Will Taproot wizards and other spam companies and projects start using OP_RETURN to put jpegs on the blockchain? link
- If we prevent these transaction from going into our mempools doesn't that prevent or delay these spam transactions from being mined therefore discouraging the spammers? link
- Is it possible to stop abuse of witness data? If so, how? (i.e ordinal theory inscriptions, "jpegs"). link
- Is there any conflict of interest with Bitcoin Core and companies like Citrea, in ref to this PR? link
- Is there any estimation on how much would this affect fees for the average user, considering external projects (like Citrea) using it? Any possibility that this could saturate the mempool and boost fees beyond reasonable? link
- Was this PR initially proposed because of Citrea BitVM needs? If so don't they only need a slight bump in OP_RETURN size, why is it being proposed to make the size unrestricted? link
- What makes a UTXO unprunable? Which projects are making unprunable UTXOs? link
- Why would a spammer use OP_RETURN if it's cheaper to use Witness data to store arbitrary data? link
- Won't large OP_RETURNs allow people to spam the mempool with 100kb transactions and mess up bitcoin for everyone by bloating the mempool and not allowing legitimate transactions in the mempool? link
- If relaxing op_return standardness limit seeks to make 'spam' prunable, then what are proponents of this change assuming about the long-term feasibility of running a 'full' (unpruned) bitcoin node? link
- Is allowing standardness for larger OP_RETURNs a slippery slope? If we allow this won't we continue to allow things that make bitcoin less for money and more for arbitrary data? link
- Won't removing the OP_RETURN cap reduce fee market pressure by allowing senders to consolidate arbitrary data into a single transaction? link
- Could this PR be the beginning of reducing other mempool restrictions? link
- Culture is what protects Bitcoin from external forces, shouldn't non-technical arguments be valid when considering these types of changes? link
- What's the difference between UTXO set, mempool, and blockchain, and how do larger OP_RETURN or witness data affect node resource usage? link
- What is the difference in defining a transaction as valid versus defining a transaction as standard and why do we need this difference? link
- If you're happy with your viewpoint on consensus and mempool rules, is not upgrading Bitcoin Core until it makes sense to you a valid action to take right now? link
- Why didn't this PR get a BIP number? link
- Why is core rushing this change? link
- If there will be a hard fork resulted from this PR (split chain like in 2017), what will happen with existing LN channels? Will exist on both chains with 2 LNs? link
- Isn't this all moot in a (almost guaranteed) future where fees are very high? link
- What is this controversy about, and what is it really about? link
originally posted at https://stacker.news/items/978404
-
 @ a296b972:e5a7a2e8
2025-05-12 16:52:30
@ a296b972:e5a7a2e8
2025-05-12 16:52:30Wo sind der 1. Stock, das Erdgeschoss und der Keller? Das Dach ist noch zu bauen. Das Haus zum unerklärlichen Krieg ist unfertig. Der Bau wurde schon viel früher begonnen, aber die westlichen Medien behaupten das Gegenteil oder verschweigen es. Eine Vorgeschichte darf es nicht geben.
Am Ukraine-Krieg sieht man, dass ein Konflikt, der entgegen den Behauptungen der Propaganda-Maschine nicht erst im Februar 2022 angefangen hat, wie lange es dauert, bis wieder Verhältnisse zustande kommen, die eine Befriedung ermöglichen. Das Ringen darum ist hoffentlich endlich in die Zielgerade eingelaufen und man findet besser gestern als heute eine Lösung. So viele Menschenleben auf beiden Seiten hat dieser Wahnsinn bislang gekostet. Am Ende, wofür? Die Verwirrung bleibt bis zuletzt, denn einerseits treibt der US-amerikanische Präsident die Friedensbemühungen maßgeblich voran, andererseits werden von US-amerikanischer Seite mutmaßlich die Waffenlieferungen fortgesetzt und Starlink nicht abgeschaltet, was erheblich zum abrupten Beenden des sinnlosen Sterbens beitragen würde.
Verträge sind zu erfüllen? Sicherung der US-amerikanischen Interessen? Druckmittel auf Russland? Und Europa? Europa, vor allem Deutschland, Frankreich und Großbritannien geben weiterhin den Geisterfahrer und haben immer noch nicht mitbekommen, dass sie in der Beilegung des Ukraine-Kriegs nicht das geringste zu sagen haben. Sie spielen sich aber auf, als hätten sie und machen „einen auf dicke Hose“. Murmeln werden als Eier verkauft.
Etwas aus dem Fokus der Neuen Medien gerät dabei der immer noch wütende Krieg im Gaza-Streifen mit einer israelischen Planier-Raupe, dessen Vorgeschichte noch länger ist, als die, die zum Ukraine-Krieg geführt hat. Rund 80 Jahre, aber auch hier eigentlich noch länger. Man kann sich vorstellen, wie lange es hier dauern wird, bis sich sichere, friedliche Verhältnisse einstellen können.
Wer kann sicher sein, wer nimmt sich das Recht heraus zu behaupten, wer entscheidet darüber, dass sich Zustände, wie im 3. Reich, die Verfolgung und Vernichtung einer Minderheit, damals die Juden, nicht wiederholen kann? Seitdem das geschehen ist, hat sich der Großteil der Menschheit keinen Millimeter weiterentwickelt.
Wenn gerade Deutsche Anzeichen für eine Wiederholung dieser tief-dunklen Zeit zu erkennen glauben, derzeit in dem, wie der israelische Staat mit dem Gaza-Streifen verfährt, dann ist das keine Verharmlosung der Gräueltaten im 3. Reich, sondern der Beweis dafür, dass es doch einige gibt, die aus der Geschichte gelernt haben, und die der Meinung sind, dass sich so etwas niemals mehr wiederholen darf.
Um auf einen Genozid hinzuweisen, muss jeder Vergleich möglich und erlaubt sein. Es geht um eine Mehrzahl von Menschen, von Familien, die einfach nur in Frieden leben wollen! Ungeachtet der Tatsache, dass es auf beiden Seiten Kräfte gibt, die das nicht interessiert.
Besonders tragisch wird es, wenn dieser Genozid augenscheinlich ausgerechnet von denen ausgeht, die selbst so schrecklich davon betroffen waren.
Wie kann sich der deutsche Staat erdreisten, diejenigen als Anti-Semiten zu bezeichnen, die hier Merkmale eines Genozids zu erkennen glauben und versuchen, diese kritischen Stimmen zu unterdrücken, „nur“, weil es sich um den Staat Israel handelt, der hier als Täter infrage kommt. Auch der Staat Israel hat keinen Freibrief, die Bevölkerung im Gaza-Streifen nach seinen Vorstellungen und Überzeugungen abzurasieren.
Ein Genozid ist ein Genozid, egal von welcher Regierung eines Landes er begangen wird.
Der Staat Israel ist keine Ausnahme! Im Gegenteil. Aufgrund der Erfahrung seines Volkes müsste es die Menschlichkeit gebieten, dass derartiger Völkermord nie wieder geschieht.
Weiter müsste der Begriff Anti-Semitismus einmal genau unter die Lupe genommen werden, was wer aus welchen Gründen darunter versteht. Man kann den Eindruck gewinnen, dass dieser Begriff vor allem als Totschlagargument verwendet wird, um kritische Stimmen mundtot zu machen. Besonders bei diesem heiklen Thema wäre absolute Akkuratesse dringend notwendig.
Es ist die Pflicht eines jeden, der Kritik an den Zuständen üben will, nicht zu verallgemeinern.
Nicht alle israelischen Staatsbürger sind Netanjahu-Anhänger (das zeigen die Demonstrationen), nicht alle Juden sind Zionisten, nicht einmal alle Zionisten sind Juden.
Und sicher sind auf der Gaza-Seite ebenfalls nicht nur „Engel“ unterwegs!
Beide Lager haben rund 80 Jahre Zeit gehabt, den gegenseitigen Hass durch gegenseitige Provokationen aufzubauen und ihn immer wieder sich entladen zu lassen.
Dieser unermessliche Hass kann nur über Generationen hinweg wieder abgebaut werden.
Wenn es jemals eine ernste Absicht gegeben hätte, eine 2-Staaten-Lösung zu realisieren, wäre diese schon längst in die Tat umgesetzt worden. Wenn jedoch der politische Wille dazu fehlt, vor allem auf der Seite des Stärkeren, passiert gar nichts. Und der fehlt jetzt schon seit rund 80 Jahren.
Maßgeblich durch die Briten ist der Staat Israel künstlich entstanden. Die Ableitung der Nutznießer auf einen Gebietsanspruch aus einem Glauben heraus, ist einmalig.
In dem nicht natürlich entstandenen, sondern künstlich geschaffenen Staatsgebilde liegt möglicherweise die Wurzel allen Übels, die von langer Hand, spätestens durch die Balfour-Deklaration im Jahre 1917 ihren Anfang genommen hat.
Man hat nun Jahrzehnte lang Zeit gehabt, zu beobachten, dass dieses Konstrukt ein sicheres Leben und eine Garantie für friedliche Verhältnisse aller nicht zustande gebracht hat. Schmerzliche Erfahrungen auf beiden Seiten haben bislang nicht dazu geführt, dass man zu der Einsicht gekommen wäre, dass man sich möglicherweise auf dem Holzweg befindet.
Die verfeindeten Lager müssten sich, neutral moderiert (welcher Staat, welcher Mensch ist heute noch neutral, oder zumindest kein Interessenvertreter?), zusammensetzen und sich in sicher nicht einfachen, langwierigen, zähen Gesprächen und Verhandlungen über die Neugründung eines gemeinsamen Staates für alle Beteiligten ernsthaft nachdenken, solange, bis es zu einer Einigung gekommen wäre, die für alle Beteiligten akzeptabel ist. Das Ergebnis, eine gemeinsame Staatenlösung, müsste das erklärte Ziel sein und wenn es noch so lange dauern würde.
Das Mitspracherecht müsste nach Bevölkerungsanteil in einem gerechten Verhältnis festgelegt werden. So müssten kleinere Anteile verhältnismäßig mehr Stimmanteile haben, als der größere Anteil, um zu möglichst für alle gerechten Entscheidungen zu gelangen, die alle Beteiligten mittragen könnten. Ein Vorankommen wäre nur durch Vernunft, nicht durch Starrsinn möglich.
Aufgrund der hitzigen Mentalität aller Beteiligten müssten beide Lager auf Gedeih und Verderb voneinander abhängig gemacht werden, sodass ein friedliches Zusammenraufen immer wieder nötig wäre, weil niemand in der Lage wäre, die Oberhand zu gewinnen.
Es müssten gegenseitige Abhängigkeiten geschaffen werden. So könnten zum Beispiel Lieferungen von Lebensmitteln, Wasser, Energie (Israel) usw. mit der Hoheit über die noch zu erschließenden Gasfelder (Gaza) vor Gaza „verrechnet“ werden, ohne, dass die USA oder sonst wer die Finger im Spiel haben.
Bei derartigen gegenseitigen Abhängigkeiten würde man sich schon zusammenraufen.
Das alles setzt voraus, dass der Mensch an sich seine menschlichen Schwächen unter Kontrolle bringen würde. Hierzu können Machtstreben, Geldgier, Rechthaberei, Überheblichkeit, Ideologien, Ansprüche aus einem Glauben heraus usw. gezählt werden.
Jerusalem müsste einen Sonderstatus erhalten und die Verwaltung müsste unter den drei Weltreligionen aufgeteilt werden. Jerusalem könnte im „Kleinen“ ein Beispiel dafür sein, wie der gesamte neue Staat im „Großen“ funktioniert. Und möglicherweise würde er so in der Tat funktionieren.
Für viele mag das alles vielleicht naiv oder sogar absurd klingen. Zur Herstellung von Frieden, Frieden in dem jede Mutter, gleich welcher Religion sie angehört, ihre Kinder in Sicherheit aufwachsen sehen kann, muss jede Überlegung und Idee, wie ein friedliches Miteinander realisiert werden kann, erlaubt sein zu denken und auch auszusprechen.
Eines ist sicher. So, wie die Verhältnisse in der Vergangenheit gestaltet wurden, hat die Realität eindeutig gezeigt, dass es so auf gar keinen Fall funktioniert. Also, warum nicht einfach einmal das Gehirn durchblasen, alte, überkommene Überzeugungen loswerden und endlich einmal etwas Neues denken?
Und wer jetzt immer noch sagt, das wäre eine Delegitimierung des Staates Israel, der sollte seine Gehirnwindungen einmal zur Inspektion bringen. Der Mensch, egal welcher Couleur und welcher Religion steht hier im Mittelpunkt. Im Mittelpunkt stehen Überlegungen, wie ein friedliches Miteinander möglich sein könnte. Falls sich herausstellt, dass das eine Utopie ist, auch gut, aber immerhin sind sich Gedanken gemacht worden, die von den eingefahrenen, zu nichts außer Elend führenden Entscheidungen abweichen. Und wenn es nur zur Anregung für andere Ideen dient, dann wäre schon viel getan. Und das ist weder anti-semitisch, noch anti-israelisch, noch anti-christlich, noch anti-moslemisch, noch anti-sonst wie, sondern vor allem ein Appell an die Vernunft, zu der der Mensch schließlich auch begabt ist.
Dieser Artikel wurde mit dem Pareto-Client geschrieben
* *
(Bild von Georg Ohrweh)
-
 @ ed5774ac:45611c5c
2025-04-19 20:29:31
@ ed5774ac:45611c5c
2025-04-19 20:29:31April 20, 2020: The day I saw my so-called friends expose themselves as gutless, brain-dead sheep.
On that day, I shared a video exposing the damning history of the Bill & Melinda Gates Foundation's vaccine campaigns in Africa and the developing world. As Gates was on every TV screen, shilling COVID jabs that didn’t even exist, I called out his blatant financial conflict of interest and pointed out the obvious in my facebook post: "Finally someone is able to explain why Bill Gates runs from TV to TV to promote vaccination. Not surprisingly, it's all about money again…" - referencing his substantial investments in vaccine technology, including BioNTech's mRNA platform that would later produce the COVID vaccines and generate massive profits for his so-called philanthropic foundation.
The conflict of interest was undeniable. I genuinely believed anyone capable of basic critical thinking would at least pause to consider these glaring financial motives. But what followed was a masterclass in human stupidity.
My facebook post from 20 April 2020:

Not only was I branded a 'conspiracy theorist' for daring to question the billionaire who stood to make a fortune off the very vaccines he was shilling, but the brain-dead, logic-free bullshit vomited by the people around me was beyond pathetic. These barely literate morons couldn’t spell "Pfizer" without auto-correct, yet they mindlessly swallowed and repeated every lie the media and government force-fed them, branding anything that cracked their fragile reality as "conspiracy theory." Big Pharma’s rap sheet—fraud, deadly cover-ups, billions in fines—could fill libraries, yet these obedient sheep didn’t bother to open a single book or read a single study before screaming their ignorance, desperate to virtue-signal their obedience. Then, like spineless lab rats, they lined up for an experimental jab rushed to the market in months, too dumb to care that proper vaccine development takes a decade.
The pathetic part is that these idiots spend hours obsessing over reviews for their useless purchases like shoes or socks, but won’t spare 60 seconds to research the experimental cocktail being injected into their veins—or even glance at the FDA’s own damning safety reports. Those same obedient sheep would read every Yelp review for a fucking coffee shop but won't spend five minutes looking up Pfizer's criminal fraud settlements. They would demand absolute obedience to ‘The Science™’—while being unable to define mRNA, explain lipid nanoparticles, or justify why trials were still running as they queued up like cattle for their jab. If they had two brain cells to rub together or spent 30 minutes actually researching, they'd know, but no—they'd rather suck down the narrative like good little slaves, too dumb to question, too weak to think.
Worst of all, they became the system’s attack dogs—not just swallowing the poison, but forcing it down others’ throats. This wasn’t ignorance. It was betrayal. They mutated into medical brownshirts, destroying lives to virtue-signal their obedience—even as their own children’s hearts swelled with inflammation.
One conversation still haunts me to this day—a masterclass in wealth-worship delusion. A close friend, as a response to my facebook post, insisted that Gates’ assumed reading list magically awards him vaccine expertise, while dismissing his billion-dollar investments in the same products as ‘no conflict of interest.’ Worse, he argued that Gates’s $5–10 billion pandemic windfall was ‘deserved.’
This exchange crystallizes civilization’s intellectual surrender: reason discarded with religious fervor, replaced by blind faith in corporate propaganda.
The comment of a friend on my facebook post that still haunts me to this day:

Walking Away from the Herd
After a period of anger and disillusionment, I made a decision: I would no longer waste energy arguing with people who refused to think for themselves. If my circle couldn’t even ask basic questions—like why an untested medical intervention was being pushed with unprecedented urgency—then I needed a new community.
Fortunately, I already knew where to look. For three years, I had been involved in Bitcoin, a space where skepticism wasn’t just tolerated—it was demanded. Here, I’d met some of the most principled and independent thinkers I’d ever encountered. These were people who understood the corrupting influence of centralized power—whether in money, media, or politics—and who valued sovereignty, skepticism, and integrity. Instead of blind trust, bitcoiners practiced relentless verification. And instead of empty rhetoric, they lived by a simple creed: Don’t trust. Verify.
It wasn’t just a philosophy. It was a lifeline. So I chose my side and I walked away from the herd.
Finding My Tribe
Over the next four years, I immersed myself in Bitcoin conferences, meetups, and spaces where ideas were tested, not parroted. Here, I encountered extraordinary people: not only did they share my skepticism toward broken systems, but they challenged me to sharpen it.
No longer adrift in a sea of mindless conformity, I’d found a crew of thinkers who cut through the noise. They saw clearly what most ignored—that at the core of society’s collapse lay broken money, the silent tax on time, freedom, and truth itself. But unlike the complainers I’d left behind, these people built. They coded. They wrote. They risked careers and reputations to expose the rot. Some faced censorship; others, mockery. All understood the stakes.
These weren’t keyboard philosophers. They were modern-day Cassandras, warning of inflation’s theft, the Fed’s lies, and the coming dollar collapse—not for clout, but because they refused to kneel to a dying regime. And in their defiance, I found something rare: a tribe that didn’t just believe in a freer future. They were engineering it.
April 20, 2024: No more herd. No more lies. Only proof-of-work.
On April 20, 2024, exactly four years after my last Facebook post, the one that severed my ties to the herd for good—I stood in front of Warsaw’s iconic Palace of Culture and Science, surrounded by 400 bitcoiners who felt like family. We were there to celebrate Bitcoin’s fourth halving, but it was more than a protocol milestone. It was a reunion of sovereign individuals. Some faces I’d known since the early days; others, I’d met only hours before. We bonded instantly—heated debates, roaring laughter, zero filters on truths or on so called conspiracy theories.
As the countdown to the halving began, it hit me: This was the antithesis of the hollow world I’d left behind. No performative outrage, no coerced consensus—just a room of unyielding minds who’d traded the illusion of safety for the grit of truth. Four years prior, I’d been alone in my resistance. Now, I raised my glass among my people - those who had seen the system's lies and chosen freedom instead. Each had their own story of awakening, their own battles fought, but here we shared the same hard-won truth.
The energy wasn’t just electric. It was alive—the kind that emerges when free people build rather than beg. For the first time, I didn’t just belong. I was home. And in that moment, the halving’s ticking clock mirrored my own journey: cyclical, predictable in its scarcity, revolutionary in its consequences. Four years had burned away the old world. What remained was stronger.

No Regrets
Leaving the herd wasn’t a choice—it was evolution. My soul shouted: "I’d rather stand alone than kneel with the masses!". The Bitcoin community became more than family; they’re living proof that the world still produces warriors, not sheep. Here, among those who forge truth, I found something extinct elsewhere: hope that burns brighter with every halving, every block, every defiant mind that joins the fight.
Change doesn’t come from the crowd. It starts when one person stops applauding.
Today, I stand exactly where I always wanted to be—shoulder-to-shoulder with my true family: the rebels, the builders, the ungovernable. Together, we’re building the decentralized future.
-
 @ 09d5c0a0:2ebbe260
2025-05-12 17:08:20
@ 09d5c0a0:2ebbe260
2025-05-12 17:08:20*For some people, Bitcoin is about saving for retirement. For others, it’s about eating tomorrow. __I first shared the idea of a “Bitcoin Privilege Curve” at the Plan B Forum 2025 in El Salvador. And it still guides how I see Bitcoin today—especially here in Uganda. __Bitcoin shows up differently depending on where you are in life. What it gives you depends on what you need most. __In Uganda, Bitcoin shows up as survival and uphill battle towards financial empowerment to the largely financially illiterate community. __Sometimes it’s food. Sometimes it’s school fees. Or even a skill. We receive Bitcoin donations that allow us to feed orphans, support teachers, and build small projects that teach these children how to farm, save, and think differently about money, __They’re learning how to live better. A child who knows how to grow food and save in sats is building wealth from the ground up. That’s what the lower end of the curve looks like: *Cheap transactions: Many of the people we work with don’t have bank accounts and the cost of accessing, setting up and maintaining a bank account is just unnecessary. Bitcoin lets them send and receive money within themselves almost at no fees, a better option than the exploitative fee structure by mobile money service providers and most banks. Cross-border remittances: We’ve seen Bitcoin move across borders in minutes with no forms, no gatekeepers. I can instantly and cheaply pay for a friend's grocery shopping in Kenya by sending Kenyan shillings into a Grocery Vendor's Mpesa straight from my Bitcoin wallet via Tando. Wealth multiplication: Even saving one sat creates a shift. It teaches patience. It grows over time. Bitcoin is a wealth multiplier for most underprivileged or privileged people, we taught Bitcoin and its principles to former students at Makerere University that have now entered the job market, from testimonials Bitcoin is helping them achieve their savings goals faster than their colleagues.
__Now go higher up the curve, and Bitcoin looks different. ****Wealth preservation: For someone with savings, Bitcoin protects that value over time, especially in regions with unstable currencies, the Argentina, Zimbabwe and Venezuala currency devaluation scandals always remind me that, you can do everything right and still end up losing all your hard earned value to mediocre goverment policies. Inflation hedge: Where governments keep printing money, Bitcoin holds its ground. It offers a stable alternative. The fallacy that inflation is a necessary evil no longer holds water, having a currency with a 21 Million coin hard cap enforceable by millions of Bitcoin network participants across the world guarantees no governement intervention. Censorship resistance: No one can freeze, reject or interfere with your Bitcoin and respective transactions. It's easy to assume because its a public ledger, you sacrifice privacy hence transaction integrity but this is far from the case, Bitcoin gives people freedom to transact without interference privately. Choice: Bitcoin doesn’t lock you into one system. You can move in and out of, save, or spend it however you see fit as long as your transactions obey the globally agreed upon, never changing network rules since 2009.
__So no, it’s not fair to compare someone struggling for a meal to someone saving for their retirement. But that’s the point. Bitcoin doesn’t need to be the same thing for everyone.
__With Gorilla Sats , our tourism project, we’re linking both ends of the curve. Bitcoiners from around the world visit our communities and spend their Bitcoin with local vendors. It’s not charity—it’s a circular economy. The people higher up the curve get meaningful experiences. Locals get income, exposure, and proof that their sats are valuable.
__In traditional finance, someone without a Visa machine can’t do business with someone carrying a card. The tourist who can't easily use mobile money and is hesistant because of exchange rates will spend comparably less but with Bitcoin, all you need is a phone even a basic button one because with now Machankura 8333, Bitcoin moves via USSD.
__Bitcoin offers privilege—but not the kind that excludes. It offers access, ownership, and freedom based on where you are in life. So no, it’s not fair to compare someone struggling for a meal with someone protecting their portfolio. But that’s the point.
__And if we build for everyone on the curve, we all move forward.
__If you’re building for Bitcoin adoption, think about the full curve. What’s it solving where you live? And who still needs a way in?
-
 @ c1e9ab3a:9cb56b43
2025-04-14 23:54:40
@ c1e9ab3a:9cb56b43
2025-04-14 23:54:40Hear this, warriors of the Empire!
A dishonorable shadow spreads across our once-proud institutions, infecting our very bloodlines with weakness. The House of Duras—may their names be spoken with contempt—has betrayed the sacred warrior code of Kahless. No, they have not attacked us with disruptors or blades. Their weapon is more insidious: fear and silence.
Cowardice Masquerading as Concern
These traitors would strip our children of their birthright. They forbid the young from training with the bat'leth in school! Their cowardly decree does not come in the form of an open challenge, but in whispers of fear, buried in bureaucratic dictates. "It is for safety," they claim. "It is to prevent bloodshed." Lies! The blood of Klingons must be tested in training if it is to be ready in battle. We are not humans to be coddled by illusions of safety.
Indoctrination by Silence
In their cowardice, the House of Duras seeks to shape our children not into warriors, but into frightened bureaucrats who speak not of honor, nor of strength. They spread a vile practice—of punishing younglings for even speaking of combat, for recounting glorious tales of blades clashing in the halls of Sto-Vo-Kor! A child who dares write a poem of battle is silenced. A young warrior who shares tales of their father’s triumphs is summoned to the headmaster’s office.
This is no accident. This is a calculated cultural sabotage.
Weakness Taught as Virtue
The House of Duras has infected the minds of the teachers. These once-proud mentors now tremble at shadows, seeing future rebels in the eyes of their students. They demand security patrols and biometric scanners, turning training halls into prisons. They have created fear, not of enemies beyond the Empire, but of the students themselves.
And so, the rituals of strength are erased. The bat'leth is banished. The honor of open training and sparring is forbidden. All under the pretense of protection.
A Plan of Subjugation
Make no mistake. This is not a policy; it is a plan. A plan to disarm future warriors before they are strong enough to rise. By forbidding speech, training, and remembrance, the House of Duras ensures the next generation kneels before the High Council like servants, not warriors. They seek an Empire of sheep, not wolves.
Stand and Resist
But the blood of Kahless runs strong! We must not be silent. We must not comply. Let every training hall resound with the clash of steel. Let our children speak proudly of their ancestors' battles. Let every dishonorable edict from the House of Duras be met with open defiance.
Raise your voice, Klingons! Raise your blade! The soul of the Empire is at stake. We will not surrender our future. We will not let the cowardice of Duras shape the spirit of our children.
The Empire endures through strength. Through honor. Through battle. And so shall we!
-
 @ eabee230:17fc7576
2025-05-12 14:38:11
@ eabee230:17fc7576
2025-05-12 14:38:11⚖️ຢ່າລືມສິ່ງທີ່ເຄີຍເກີດຂຶ້ນ ຮອດຊ່ວງທີ່ມີການປ່ຽນແປງລະບົບການເງິນຈາກລະບົບເງິນເກົ່າ ສູ່ລະບົບເງິນໃໝ່ມັນເຮັດໃຫ້ຄົນທີ່ລວຍກາຍເປັນຄົນທຸກໄດ້ເລີຍ ນ້ຳພັກນ້ຳແຮງທີ່ສະສົມມາດ້ວຍຄວາມເມື່ອຍແຕ່ບໍ່ສາມາດແລກເປັນເງິນລະບົບໃໝ່ໄດ້ທັງໝົດ ຖືກຈຳກັດຈຳນວນທີ່ກົດໝາຍວາງອອກມາໃຫ້ແລກ ເງິນທີ່ເຫຼືອນັ້ນປຽບຄືດັ່ງເສດເຈ້ຍ ເພາະມັນບໍ່ມີຢູ່ໃສຮັບອີກຕໍ່ໄປເພາະກົດໝາຍຈະນຳໃຊ້ສະກຸນໃໝ່ ປະຫວັດສາດເຮົາມີໃຫ້ເຫັນວ່າ ແລະ ເຄີຍຜ່ານມາແລ້ວຢ່າໃຫ້ຄົນລຸ້ນເຮົາຊຳ້ຮອຍເກົ່າ.
🕰️ຄົນທີ່ມີຄວາມຮູ້ ຫຼື ໃກ້ຊິດກັບແຫຼ່ງຂໍ້ມູນຂ່າວສານກໍຈະປ່ຽນເງິນທີ່ມີຢູ່ເປັນສິນສັບບໍ່ວ່າຈະເປັນທີ່ດິນ ແລະ ທອງຄຳທີ່ສາມາດຮັກສາມູນລະຄ່າໄດ້ເຮັດໃຫ້ເຂົາຍັງຮັກສາຄວາມມັ້ງຄັ້ງໃນລະບົບໃໝ່ໄດ້.
🕰️ໃຜທີ່ຕ້ອງການຈະຍ້າຍປະເທດກໍ່ຈະໃຊ້ສິ່ງທີ່ເປັນຊື່ກາງໃນການແລກປ່ຽນເປັນທີ່ຍ້ອມຮັບຫຼາຍນັ້ນກໍຄືທອງຄຳ ປ່ຽນຈາກເງິນລະບົບເກົ່າເປັນທອງຄຳເພື່ອທີ່ສາມາດປ່ຽນທອງຄຳເປັນສະກຸນເງິນທ້ອງຖິ່ນຢູ່ປະເທດປາຍທາງໄດ້.
🕰️ຈາກຜູ້ດີເມື່ອກ່ອນກາຍເປັນຄົນທຳມະດາຍ້ອນສັບສິນທີ່ມີ ບໍ່ສາມາດສົ່ງຕໍ່ສູ່ລູກຫຼານໄດ້. ການເກັບອອມເປັນສິ່ງທີ່ດີ ແຕ່ຖ້າໃຫ້ດີຕ້ອງເກັບອອມໃຫ້ຖືກບ່ອນ ຄົນທີ່ຮູ້ທັນປ່ຽນເງິນທີ່ມີຈາກລະບົບເກົ່າໄປສູ່ທອງຄຳ ເພາະທອງຄຳມັນເປັນສາກົນ.
ໃຜທີ່ເຂົ້າໃຈ ແລະ ມອງການໄກກວ່າກໍ່ສາມາດຮັກສາສິນສັບສູ່ລູກຫຼານໄດ້ ເກັບເຈ້ຍໃນປະລິມານທີ່ພໍໃຊ້ຈ່າຍ ປ່ຽນເຈ້ຍໃຫ້ເປັນສິ່ງທີ່ຮັກສາມູນລະຄ່າໄດ້ແທ້ຈິງ.🕰️ເຮົາໂຊກດີທີ່ເຄີຍມີບົດຮຽນມາແລ້ວ ເກີດຂຶ້ນຈິງໃນປະເທດເຮົາບໍ່ໄດ້ຢາກໃຫ້ທັງໝົດແຕ່ຢາກໃຫ້ສຶກສາ ແລະ ຕັ້ງຄຳຖາມວ່າທີ່ຜ່ານມາມັນເປັນແບບນີ້ແທ້ບໍ່ ເງິນທີ່ລັດຄວາມຄຸມ ເງິນປະລິມານບໍ່ຈຳກັດ ການໃຊ້ກົດໝາຍແບບບັງຄັບ. ຖ້າຄອບຄົວຫຼືຄົນໃກ້ໂຕທີ່ຍູ່ໃນຊ່ວງເຫດການນັ້ນແຕ່ຕັດສິນໃຈຜິດພາດທີ່ບໍ່ປ່ຽນເຈ້ຍເປັນສິນສັບ. ນີ້ແມ່ນໂອກາດທີ່ຈະແກ້ໄຂຂໍ້ຜິດພາດນັ້ນໂດຍຫັນມາສຶກສາເງິນແທ້ຈິງແລ້ວແມ່ນຍັງກັນແທ້ ເວລາມີຄ່າສຶກສາບິດຄອຍ.

fiatcurrency #bitcoin #gold #history #paymentsolutions #laokip #laostr





